-
 @ 95543309:196c540e
2025-05-11 12:42:09
@ 95543309:196c540e
2025-05-11 12:42:09Lets see if this works with the blossom upload and without markdown hassle.
:cat:

https://blossom.primal.net/73a099f931366732c18dd60da82db6ef65bb368eb96756f07d9fa7a8a3644009.mp4
-
 @ 7459d333:f207289b
2025-05-10 10:38:56
@ 7459d333:f207289b
2025-05-10 10:38:56Description: Just as Bitcoin enabled sovereignty over money, a decentralized shipping protocol would enable sovereignty over trade. An LN/Bisq inspired shipping protocol could create an unstoppable free market.
Bitcoin gave us monetary sovereignty, freeing us from central bank manipulation, inflation, and censorship. But there's a missing link in our freedom journey: the physical world of goods.
The Problem: Even with Bitcoin, global trade remains at the mercy of: - Arbitrary tariffs and import restrictions - Political censorship of goods - Privacy invasion of shipping information - Centralized shipping carriers
The Vision: A decentralized shipping protocol with these properties:
- "Onion-routed" packages: Each carrier only knows the previous and next hop
- Bitcoin-secured multi-sig escrow: Funds locked until package delivery confirmed
- Incentive alignment: Carriers set their own fees based on risk assessment
- Privacy tiers: Options for inspected vs. sealed packages with appropriate pricing
- End-to-end sovereignty: Sender and receiver maintain control, intermediate carriers just fulfill their role
How it could work:
- Sender creates shipping request with package details and destination
- Protocol finds optimal route through independent carriers
- Each hop secured by multi-sig deposits larger than package value
- Carriers only see next hop, not ultimate destination
- Reputation systems and economic incentives maintain integrity
This creates a free market where any individual can participate as a carrier, earning Bitcoin for facilitating trade. Just like Lightning Network nodes, anyone can open "channels" with trusted partners.
Impact: This would enable true free market principles globally, making artificial trade barriers obsolete and empowering individuals to engage in voluntary exchange regardless of geographic or political boundaries.
There are a lot of challenges. But the first question is if this is a real problem and if its worth solving it.
What components would need development first? How would you solve the physical handoff challenges?
originally posted at https://stacker.news/items/976326
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ bf47c19e:c3d2573b
2025-05-12 20:27:54
@ bf47c19e:c3d2573b
2025-05-12 20:27:54"Za sve one koji još uvek nisu u potpunosti razumeli kontroverzni Bitkoin, ovo je koncizni i informativni brzi kurs o novcu i kriptovalutama."
Bitkoin: Kraj novca kakvog poznajemo - IMDB
Prevod: SatoshiSan / @SSG_SatoshiSan
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 6e64b83c:94102ee8
2025-05-05 16:50:13
@ 6e64b83c:94102ee8
2025-05-05 16:50:13Nostr-static is a powerful static site generator that transforms long-form Nostr content into beautiful, standalone websites. It makes your content accessible to everyone, even those not using Nostr clients. For more information check out my previous blog post How to Create a Blog Out of Nostr Long-Form Articles
What's New in Version 0.7?
RSS and Atom Feeds
Version 0.7 brings comprehensive feed support with both RSS and Atom formats. The system automatically generates feeds for your main content, individual profiles, and tag-specific pages. These feeds are seamlessly integrated into your site's header, making them easily discoverable by feed readers and content aggregators.
This feature bridges the gap between Nostr and traditional web publishing, allowing your content to reach readers who prefer feed readers or automated content distribution systems.
Smart Content Discovery
The new tag discovery system enhances your readers' experience by automatically finding and recommending relevant articles from the Nostr network. It works by:
- Analyzing the tags in your articles
- Fetching popular articles from Nostr that share these tags
- Using configurable weights to rank these articles based on:
- Engagement metrics (reactions, reposts, replies)
- Zap statistics (amount, unique zappers, average zap size)
- Content quality signals (report penalties)
This creates a dynamic "Recommended Articles" section that helps readers discover more content they might be interested in, all while staying within the Nostr ecosystem.
See the new features yourself by visiting our demo at: https://blog.nostrize.me
-
 @ 6ad08392:ea301584
2025-05-12 20:22:09
@ 6ad08392:ea301584
2025-05-12 20:22:09
Satlantis is here!
Well…sort of. It’s a little pre-mature, but it’s good enough for you to play around with. I wouldn’t necessarily call it super ‘useful’ right now but I wanted you to get an early glimpse into what we’re building so you can see how it evolves over time.
And besides - we have to release a first version at some stage!
Satlantis is the first travel-centric social network. It’s quite different from anything else that came before it. It’s part map, part directory, part events app and part social network.
It really is a monumental undertaking - but I’m convinced now is the time to build it. People are ready for something new. They are tired of the algorithmic slop social media has become. They’re craving real connection and they want to see, touch, smell, hear and taste the world. What better way to help them do that, than with a network that connects them, andhelps enhance their discovery of places, experiences and events that are relevant to them (based both on their interests and social connections).
That’s what this product is all about. We’re going to do what Google Maps, Yelp, Instagram, TripAdvisor etc. are all partially doing - but make it 10x better.
The first Satlantis app is now available on Apple Testflight or the Google Play store. In the coming month or two, we will make Satlantis accessible via invitation-only, to increase the quality of connection and discourse on the app, but if you’re reading this now, you’re in before we gate it, you can explore and give us some feedback while we work on it.
I will write release notes like this every couple weeks covering what we built, what to test and play with, what’s working, what needs improvement, what’s downright shit or broken and what’s coming in the next release. (This first one is the longest because I delayed it so much.)
I’d love to hear your feedback, and if you find this interesting, please share it around so other people find out about what we’re building!
The Good
Mobile AppWe got a version out, and you can actually use it.
Nostr Compatible.
Every single account on Satlantis is an nPub. You can log into Satlantis using your nSec (not your nPub - we forgot to include that...lol), and you will find your entire social network and all of your posts there (if they are media notes). On the Web, you need to use an extension, like Alby or Keys.band. On mobile you can paste your key (stored locally on the device).
Normie Friendly.
We also built a smooth non-nostr focused sign up flow. We originally used the nSec bunker, but that was a mess (love u Pablo). So we built our own nSec bunker, but that sucked too. Passwords are old school. After interviewing 100 people not into Bitcoin or Nostr, 95% of them preferred us to store their key. So…we took that feedback and created a really easy email + magic link, Google and Apple SSO sign up flow, that creates an account and Nostr keypair that we store on their behalf, encrypted.
If and when people work out what Nostr is and they want to take custody of their key, they will be able to export their key, and request deletion of their key from our DB.
Is this the most ‘pure’ solution? No. Does this mean they have to trust us? Sure. Could we do it better at some point? Yes, of course. But considering the number of mission critical features we need to build, we’ll come back to it later.
We currently only support Kind 1 events.
Well…we also support NIP-52 calendar events, but we’ve disconnected that for the time being because event organisers wanted co-hosts more than they wanted to broadcast their events on Nostr. We’re working on a way to reconcile the two. For now, post text & images. (Video coming soon).
Interest-centric onboarding.
We spent a lot of time building this. One of the key pillars at Satlantis is discovering people, places, events and content suited to you. As we dug down the personalisation rabbithole, we found that there is a resurgence of interest-selection in many apps: from Tinder to new apps like Locals and Timeleft. The more focused on personalisation the app is, the more in-depth the onboarding.
Of course Meta and TikTok do the best personalisation with their advanced ML & AI tools, along with their deep social graphs, but since we have neither (Nostr helps but it’s still very small), we needed a better way.
So we decided to build our interest-graph. It was brain-melting, but we developed a pretty exhaustive set of interests relevant to people in our target market. We then took that list and associated it to events, merchants, people, places, experiences, activities and content. We then built a whole new onboarding flow to capture this from new users, and associate it to their accounts. (Yes - at some stage, we’ll make this Nostr compatible so it can travel with nPubs)
 The net result is a base layer of insight we can use to help surface things that are of interest to users. Whether it’s an event, a place to eat, a gym or sauna, content to engage with or people to meet: like magic, things that are relevant to you will come to you.
The net result is a base layer of insight we can use to help surface things that are of interest to users. Whether it’s an event, a place to eat, a gym or sauna, content to engage with or people to meet: like magic, things that are relevant to you will come to you.Of course, in the long term we will use your social graph and the way you interact with content to do this - more like Meta and TikTok do - but for now, while the social graph is tiny, this is the most efficient and effective way.
Final word: the current version has all the interests - but it’s not very user-friendly. The latest design fixes that by grouping the interests into better subcategories. Keep an eye on that in a subsequent release.
New Merchant Discovery Experience.
This was also a monumental task. Our first merchant experience was just a shitty map with a list on web, and just a list on mobile (see below). This list was ranked by an “aggregate rating” we computed by analysing all the venue’s ratings from apps like Google, Trip Advisor and more.
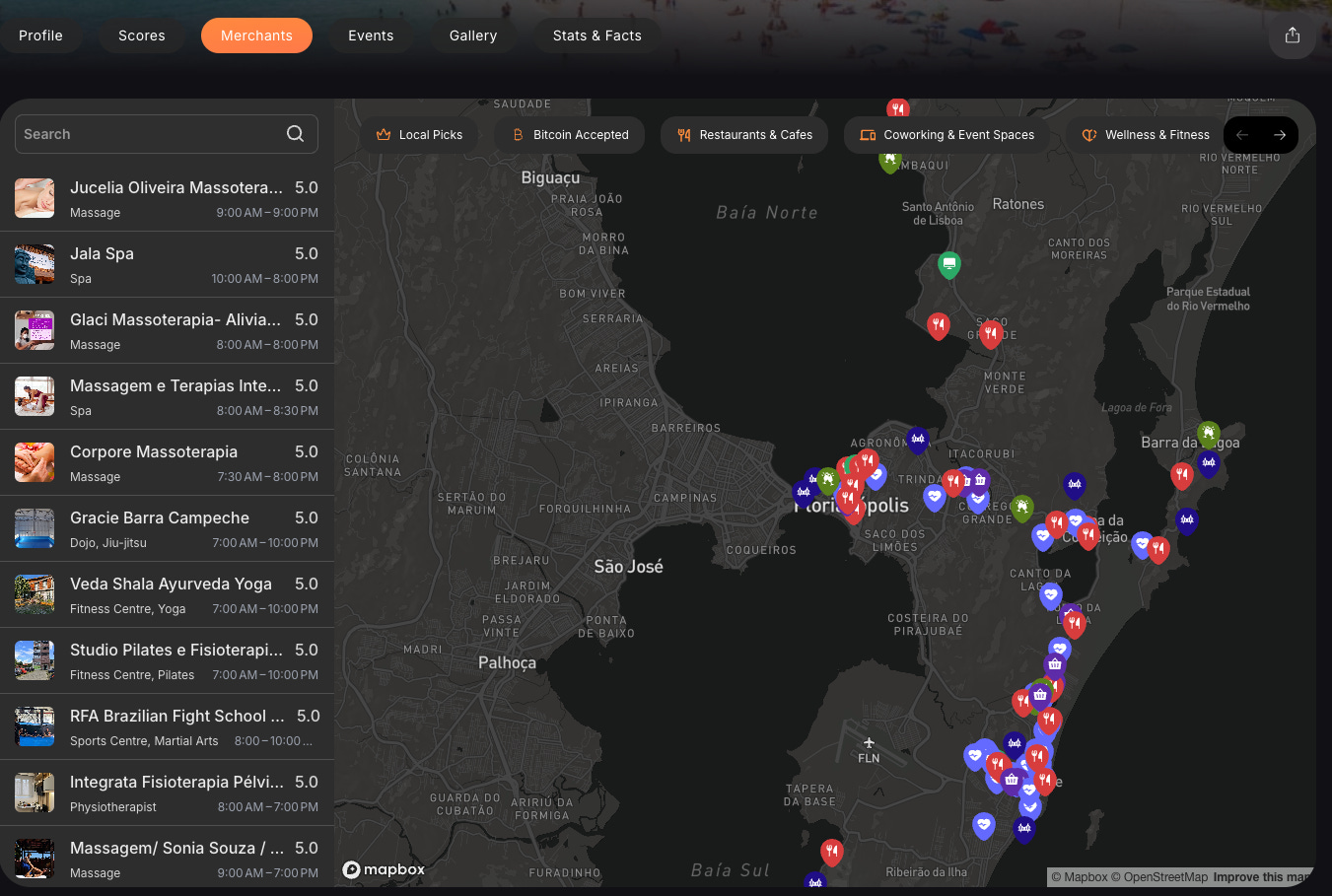
We spent a long time trying to figure out how to display this better and do it in a way nobody else is, because seriously -can you think of a single food app or merchant map out there which has a nice UI or UX? No.
AirBnB transformed the UI & UX for accommodation and pushed the whole space forward. Nobody has really done it for every other kind of place you go to. So we took it up ourselves to fix this and create a proper “merchant discovery experience” with an information-dense location tile. Check this out:
Notice how we managed to get all the key information you need about a place there on the one tile, including who in your social circle has recommended it. That’s the key ingredient which makes Satlantis special. No more messaging friends or people you know “hey - have you been to that place” or “do you recommend that place”?
 One small issue here is that this upgrade will kill the map…but only for a couple weeks, until we release the new map view!
One small issue here is that this upgrade will kill the map…but only for a couple weeks, until we release the new map view!Merchant coverage
Our merchant app covers SIX distinct categories:
-
Cafes & Restaurants
-
Health & Wellness (think Gyms, Spas, Saunas, etc)
-
Attractions (from Museums, to lookouts to beaches & hikes)
-
Grocery & Specialty Foods (think Organic food store, farmers markets, etc)
-
Coworking & Event Spaces
-
Nightlife (Bars, Clubs, etc)
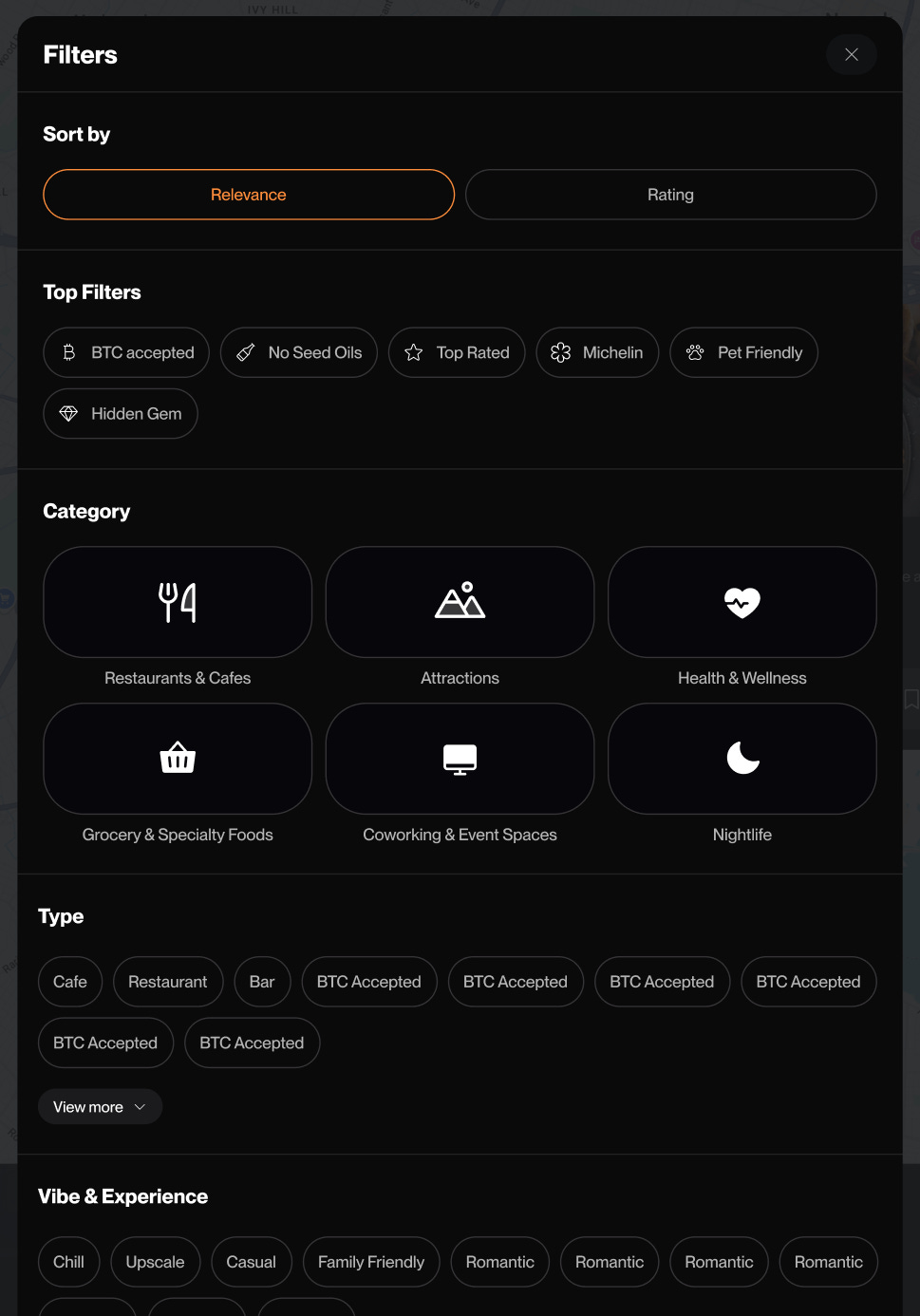 We scoured the web for the best curated lists and directories for each of these categories. This in Bitcoin accepted (everything relevant from BTCMaps - because we’re also built on Open Street Maps, so it’s synced up), Seed Oil Free (everything from Local Fats & Seed Oil Scout is here), Michelin Star rated, Real Milk (Raw Milk directory) and more.
We scoured the web for the best curated lists and directories for each of these categories. This in Bitcoin accepted (everything relevant from BTCMaps - because we’re also built on Open Street Maps, so it’s synced up), Seed Oil Free (everything from Local Fats & Seed Oil Scout is here), Michelin Star rated, Real Milk (Raw Milk directory) and more. Alongside all of these directories, our network of local ambassadors have submitted their top local picks for their favorite cities, so you have real local recommendations.
The destinations with the best maps are currently Canggu, Uvita, Prague, Sao Paulo, Dubai, Florianópolis.
Suggest Places & Merchants
This is working quite nicely. Anyone, anywhere can now suggest their favorite merchant. For now, we’re manually approving submissions daily to avoid spam and irrelevant shit. In time, we’ll find a better way to do this.
It’s all plugged into the Google API, so you can just type in the name of the place you think should be added (from mobile or web here). Once approved, our AI pipeline goes to work gathering all the available data from Google, TripAdvisor and elsewhere to set up the merchant profile, complete with review summaries, images, profile bio, contact details, opening hours, tags and more.
Got more upgrades to this flow in the works, but it’s ready for you to try out now.
City Pages
The current city pages are part of an outdated design which doesn’t fit our new visual language, but they are a ‘live’ feature. The original idea was to blend elements of Pinterest and Instagram but it backfired so we are changing to a more slick one-column feed. That being said, the core features of the city pages work. You can:
-
Join a city (like joining a community or following the page)
-
Post content on the city page
-
Navigate over to the different available pages, including merchants, events, scores and stats + facts
We have 80 cities currently available. More to come.
Scores, Stats & Facts
When we set out to first build Satlantis, we wanted to improve on the information NomadList was presenting for cities & destinations around the world. So we developed a different approach for city scoring based not only on data we could get from Numbeo, etc - but also information direct from people on the ground - in particular; expats and locals.
We put together a set of score categories and created a dedicated survey for select people to fill out, which would create some “foundation” scores, with a view to have this survey available to the crowd, perhaps via a score voting system or some sort on the page. We haven’t got that far yet. Right now, we have foundation scores for each of those 80 active cities, along with key Stats and Facts, like cost of living, wifi speed, water drinkability, and more:
This is not a core feature for us, so we will look to partner with other providers to enhance the experience, or we’ll completely re-think how we’re going to do it. Stay tuned for more here and let me know if you find it useful at all right now (or not).
Events
Last but not least, we have events! God dammit this was annoying because we built it NIP-52 compatible in the beginning, which then limited what we could do with co-hosts and other essential event features. And all for nothing since there are no other well built or maintained calendar-event clients on Nostr anyway.
So right now, when you post an event on Satlantis, it will post only on Satlantis. This means that as a host, you can edit, add co-hosts, add locations (proper merchant tiles) and delete.
We will make this Nostr-compatible again, most likely with some sort of button for hosts to “broadcast this event to Nostr” - knowing they will lose some flexibility once they do - but we need to do more research here. Maybe we’ll propose an upgrade to the calendar event NIP (or propose a new NIP altogether). It’s on our roadmap, so we’ll do our best to get to it soon.
Meetup integration.
We’ve been working with the Meetup API to let organizers quickly import their events into Satlantis. It’s been frustratingly complex because of how archaic they are, but we got it working!
🚀 If you run a Meetup, and want to automatically have your events listed on Satlantis when you list them on meetup,reach out! We’ll even cover the Meetup membership fee for 10 meetup groups who set up auto-importing for their events. If you’re interested, reach out to us.
The Bad
These things are currently bad, broken, incorrectly built or buggy. Believe me, if the list was exhaustive, this essay would be a book (our internal list is very full) - so I’m just going to touch on the main things we’re aware of and will be fixing…or just letting it burn slowly while we put out other fires.
Personal content feed
We started Satlantis with a media-only approach, taking inspiration from Instagram. We changed course a couple months ago to support text only posts, realizing there were a lot of other things people would like to post about travel, for example: guides, restaurants, reviews, tips, events, instructions, recommendations.
So…we started supporting this on the feed, and in the “post content” flow - but of course, not yet supported in the Profile view (which is still an image grid). This means if you post text only, you’re not going to see your own post on Satlantis 🤣🤣
To fix this, we’re building a “personal feed” section on your profile. But…that will come after we polish some of the things above, so if you’re posting on Satlantis right now, photos please!!
Video content
This one hurts too. We currently neither render videos from other clients, nor do we support video uploads on Satlantis. Not because we don’t want to, but because we haven’t got to it. This is high on the priority list and will be fixed in the upcoming releases.
Settings & Edit profile
We forgot to add “edit username” 🤣
This is being added now, along with a settings section where you can get your nPub and things like that. We’ll keep it very basic for now.
Notifications
Holy crap. These really suck. There is no other way to put it. The design is not great, the experience is buggy as hell and syncing notifications from the broader Nostr network doesn’t make life any easier. We’ll be making incremental improvements here (for a long time I guess).
Limited social graph functionality.
Right now, there’s not much social-dynamics beyond the feed. This will expand and begin to influence more than just content, but also merchants, events, people, activities, etc.
Speed issues.
Feed and profile loading times are sluggish and need performance improvements. Ongoing.
Large Destinations are problematic.
How do you rate a massive city like São Paulo as a single entity? Well….you can’t. Eventually, we’ll break major cities into regions, but that’s a big project for later.
For now, when you see scores, stats and facts, assume we’re covering the most relevant traveler-friendly areas (e.g., Jardins in São Paulo, Palermo in Buenos Aires, etc).
The Ugly
There is really only one new ‘feature’ to complete before we apply a feature freeze and continue on to polish everything. This and the other items listed will be available in the next release or two, so that the overall experience is a little more…beautiful.
Chat.
We wanted to do NIP-17, but considering that (a) most of the major apps are still NIP-04, (b) BTCPrague is around the corner and (c) limited resources, we chose to do a NIP-04 implementation for this first version. Not ideal, but good enough. Chat will continue to improve, not only with a NIP-17 upgrade, but with other features like chat folders, group chats, GIFs and more.
Polish List
-
Merchant Experience: Web and mobile updates
-
Merchant List: More cool places being uploaded
-
Events: New display, RSVP flow, co-host notifications, merchant integration
-
Onboarding: Updated interests tags & flow
-
Scores: Updates to Cost of Living & overall score weights
-
Notifications: A lot of improvement here
-
Feed: Text only posts, video uploads & rendering videos from other clients
-
City Page: New design and functionalities
-
Zaps: Yes. We will have Zaps.
Final Words
We have our work cut out for us!
We will be at BTCPrague in June and we are committed to releasing all of these features and components by then…as polished as possible.
The team and I have a couple of asks:
-
Download the app, and either create a new account or if you’re on Nostr, log in with your existing Nostr key (web requires an extension like Alby)
-
Go through the interests, and select those that are most relevant to you. The magic of the app happens as a function of how accurately you select those.
-
Post some content! Could be a photo introducing yourself or a “Good Morning” or whatever. Make sure you tag @Satlantis or @Svetski and I’ll boost you.
-
Check out the merchants in the top cities & see what’s around. The city with the most merchants right now is Florianopolis, but we have some coverage in many other cities
-
If you run a meetup or attend a regular Bitcoin meetup, let the organisers know, and let’s start to bring meetups and events across. Not asking anyone to ‘leave’ meetup now, but come and sync up your account so events are auto-published. \ As we make the events feature more robust (and Bitcoin native), every Bitcoin meetup in the world is going to want to come use this. If you’re early, you can help us shape it!
-
Let a couple of friends know about the app - ideally those who are not yet on Nostr - and ask them to try it out. They can sign up with email or SSO if they’re afraid to store their own key.
-
Like I said in the beginning, at some point in the next month or so, it will become an invite-only app. We will grandfather all existing users in, but new people will need an invite code (from existing users or via codes I drop into release notes and articles) to access it. \ \ The goal of this approach is to (a) increase the quality of connection amongst people on Satlantis, and (b) try a new way of growing a Nostr-based app.
-
Finally…we’ve decided to do an equity crowdfund. So if you find what we’re doing interesting and want to be a part of it, you’ll have a chance from June onwards. More to follow on this in the coming weeks. It will be on Timestamp Financial - Bitcoin crowdfunding platform - so go check them out.
Thank you again for your attention - I do not take it lightly. This is just the start, so expect to see ALOT more from us in the way of updates and shipping (plus these updates will be shooter).
Make sure you subscribe to this newsletter if you’re reading on Substack, or follow me if you’re on Nostr, Medium or wherever else you’re reading it.
Aleksandar Svetski
Thanks for reading Social 2.0! Subscribe for free to receive new posts & stay up to date with what we’re building & learning along the way.
When the app goes into “Invite Only” mode, you will need a special invite code to access it, unless you’ve already got an account. For now, it’s open access.
If you're already on Nostr, you're already on Satlantis. Just use an extension to securely log in with your nSec (on web), or with your nSec on mobile.
-
-
 @ 6e0ea5d6:0327f353
2025-05-04 14:53:42
@ 6e0ea5d6:0327f353
2025-05-04 14:53:42Amico mio, ascolta bene!
Without hesitation, the woman you attract with lies is not truly yours. Davvero, she is the temporary property of the illusion you’ve built to seduce her. And every illusion, sooner or later, crumbles.
Weak men sell inflated versions of themselves. They talk about what they don’t have, promise what they can’t sustain, adorn their empty selves with words that are nothing more than a coat of paint. And they do this thinking that, later, they’ll be able to "show who they really are." Fatal mistake, cazzo!
The truth, amico mio, is not something that appears at the end. It is what holds up the whole beginning.
The woman who approaches a lie may smile at first — but she is smiling at the theater, not at the actor. When the curtains fall, what she will see is not a man. It will be a character tired of performing, begging for love from a self-serving audience in the front row.
That’s why I always point out that lying to win a woman’s heart is the same as sabotaging your own nature. The woman who comes through an invented version of you will be the first to leave when the veil of lies tears apart. Not out of cruelty, but out of consistency with her own interest. Fine... She didn’t leave you, but rather, that version of yourself never truly existed to be left behind.
A worthy man presents himself without deceptive adornments. And those who stay, stay because they know exactly who they are choosing as a man. That’s what differentiates forged seduction from the convenience of love built on honor, loyalty, and respect.
Ah, amico mio, I remember well. It was lunch on an autumn day in Catania. Mediterranean heat, and the Nero D'Avola wine from midday clinging to the lips like dried blood. Sitting in the shade of a lemon tree planted right by my grandfather's vineyard entrance, my uncle — the oldest of my father’s brothers — spoke little, but when he called us to sit by his side, all the nephews would quiet down to listen. And in my youth, he told me something that has never left my mind.
“In Sicily, the woman who endures the silence of a man about his business is more loyal than the one who is enchanted by speeches about what he does or how much he earns. Perchè, figlio mio, the first one has seen the truth. The second one, only a false shine.”
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 6c05c73e:c4356f17
2025-05-12 20:05:36
@ 6c05c73e:c4356f17
2025-05-12 20:05:36Já pensou em investir no Brasil, mas se sentiu intimidado pela volatilidade da Bovespa e as notícias de escândalos? E se eu te dissesse que existe uma maneira de expor seu portfólio ao mercado brasileiro, investindo em dólar, diretamente da bolsa de valores de Nova York?
Bem-vindo ao mundo do EWZ, o ETF (Exchange Traded Fund) que replica o índice MSCI Brazil 25/50, oferecendo uma janela para as maiores e médias empresas do Brasil. Se você está buscando diversificar seus investimentos e explorar mercados emergentes, o EWZ pode ser a sua resposta.
O Que Exatamente é o EWZ?
O EWZ é o ticker symbol do iShares MSCI Brazil ETF. Pense nele como um pacote de ações brasileiras negociado na bolsa de valores americana. Ele espelha o desempenho do índice MSCI Brazil 25/50, o que significa que, ao investir no EWZ, você está, indiretamente, investindo em uma cesta diversificada das principais empresas do Brasil.
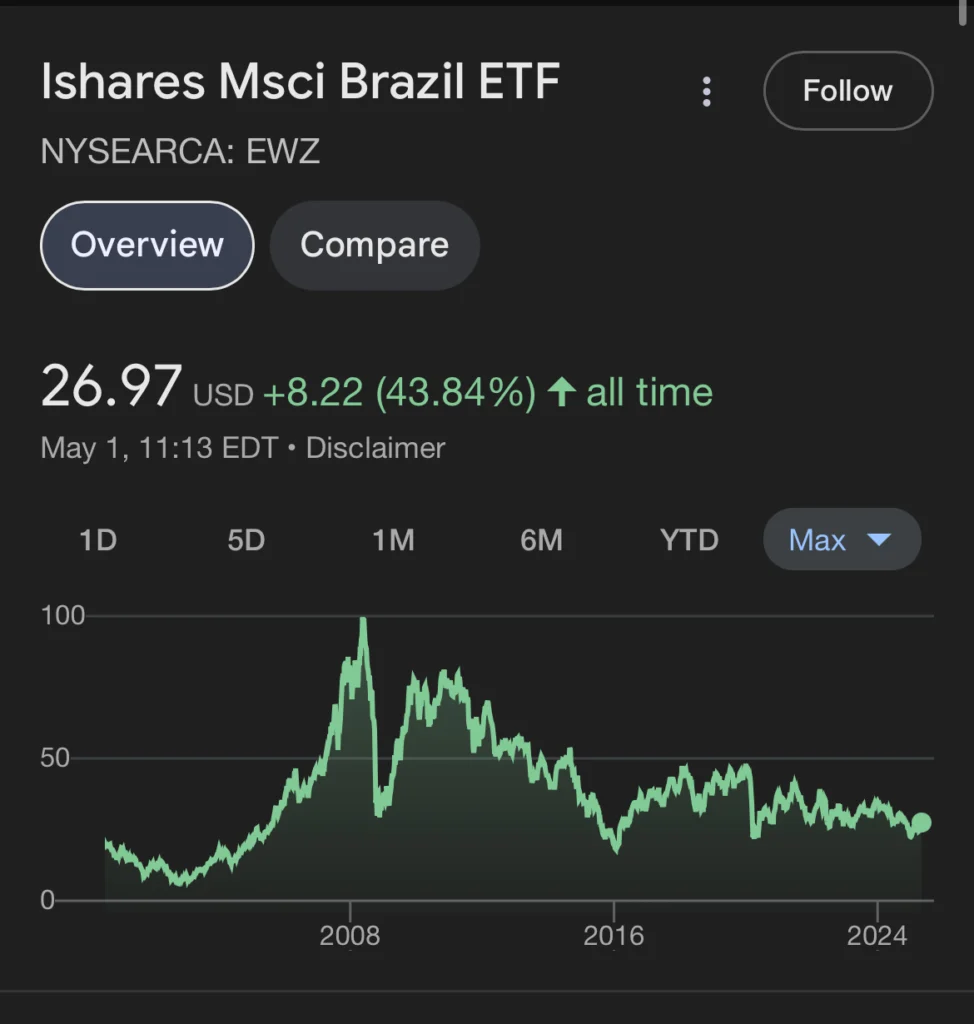
Por Que Investir no Brasil via ETF?
Você já pensou em investir no Brasil? Mas ouve sempre falar desses riscos da Bovespa e vários escândalos?
Portanto, saiba que existe uma forma de investir no Brasil em dólar. Usando a bolsa de valores de Nova Iorque. Isso mesmo, você pode abrir uma conta em corretora estrangeira e investir no Brasil via ETF.
O ETF que replica a Bovespa (Bolsa de valores de São Paulo) é o EWZ. Esse índice replica o Ibovespa e reflete nele o peso das maiores empresas brasileiras, tais como:
- Diversificação em Dólar: Invista em empresas brasileiras sem precisar se preocupar com a flutuação do real. Seus investimentos são feitos em dólar, protegendo você das variações cambiais.
- Acesso Facilitado: Negocie o EWZ diretamente da sua corretora americana, sem a necessidade de abrir contas no Brasil ou lidar com burocracias locais.
- Diversificação Instantânea: Ao comprar EWZ, você está comprando uma fatia de várias empresas líderes no Brasil, reduzindo o risco de concentrar seus investimentos em uma única empresa ou setor.
Números Que Falam Por Si
Vamos aos dados concretos que mostram a solidez do EWZ:
- Taxa de Administração: 0.59% a.a.
- Patrimônio Líquido Sob Gestão: $3.6 bilhões em ativos. Isso indica uma boa popularidade do ativo.
- Volume de negociação diário: Em média $24 milhões, o que garante boa liquidez e baixas taxas.
- Dividendos: 7.33% a.a. Distribuído semestralmente.
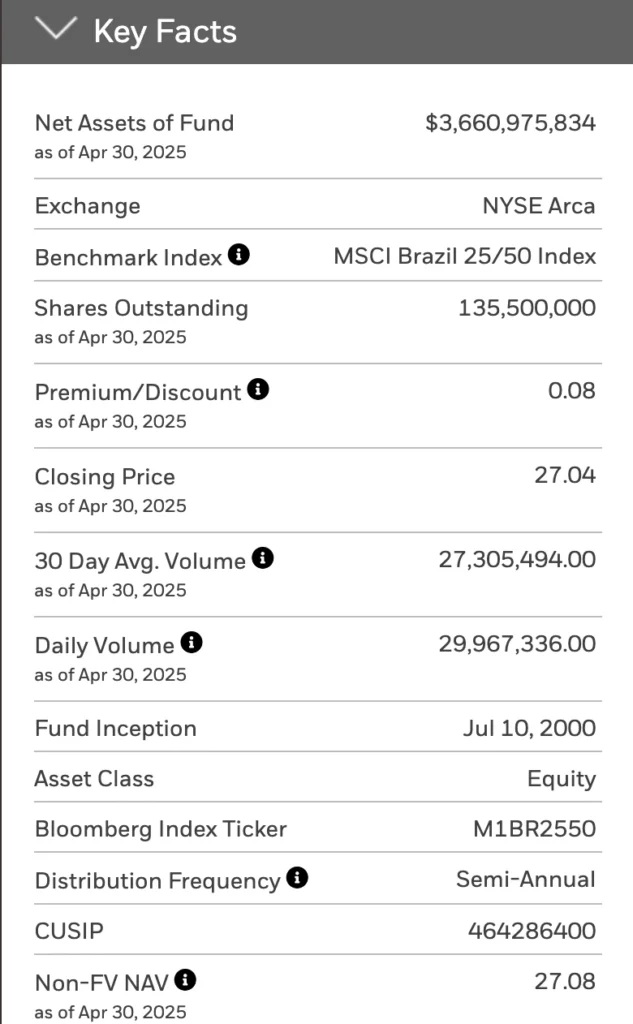
Qualitativo
- Com mais de 200 milhões de habitantes, o Brasil tem um dos maiores mercados consumidores do mundo. Isso representa uma demanda interna robusta e potencial para uma vasta gama de produtos e serviços.
- O país é extremamente rico em recursos naturais, incluindo minérios (ferro, bauxita, etc.), petróleo, gás natural e vastas áreas agricultáveis. Além disso, tem um potencial enorme e já desenvolvido em energias renováveis (hídrica, solar, eólica, biomassa).
- O Brasil é um líder global na produção e exportação de diversos produtos agrícolas (soja, milho, café, açúcar, carne bovina, frango). Há contínuo potencial para ganhos de produtividade e agregação de valor na cadeia.
- O Brasil desenvolveu um ecossistema de startups vibrante, especialmente no setor de fintechs, onde é referência global em inovação (ex: Pix, Open Banking). Há também crescimento em agrotechs, healthtechs e outras áreas. O grande mercado consumidor digital impulsiona esse setor.
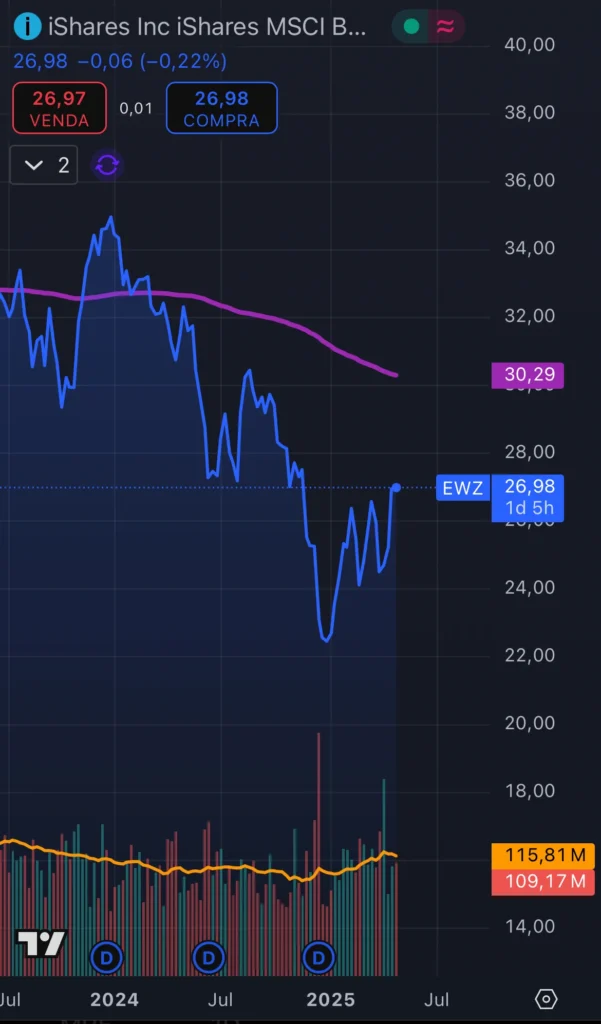
Técnica
- O ativo teve uma queda vertiginosa. No entanto, desde Dezembro de 2024 vem apresentando uma melhora no comportamento. Isso, pode sugerir que há uma boa margem para comprar com "desconto". Visto que, o volume comprador tem sido intenso desde o inicío de Abril de 2025.
FAQ
O que significa a sigla EWZ?
A sigla EWZ é o ticker symbol (código de negociação em bolsa) do iShares MSCI Brazil ETF.
Portanto, EWZ não é uma sigla de um nome por extenso, mas sim o código usado para identificar e negociar este fundo específico (ETF) nas bolsas de valores dos Estados Unidos (como a NYSE Arca). Este ETF busca replicar o desempenho do índice MSCI Brazil 25/50, que representa as maiores e médias empresas brasileiras.
Qual é a composição do EWZ?
AS 10 Maiores Posições (na data de hoje):
- Nu Holdings (NU): \~9.3% - 9.8% (Setor Financeiro)
- Vale (VALE3): \~8.5% - 9.5% (Setor de Materiais)
- Itaú Unibanco (ITUB4): \~7.9% - 8.6% (Setor Financeiro)
- Petrobras PN (PETR4): \~6.2% - 8.0% (Setor de Energia)
- Petrobras ON (PETR3): \~5.5% - 7.3% (Setor de Energia)
- WEG (WEGE3): \~3.9% - 4.2% (Setor Industrial)
- B3 (B3SA3): \~3.4% - 3.7% (Setor Financeiro)
- Banco Bradesco (BBDC4): \~3.0% - 3.6% (Setor Financeiro)
- Ambev (ABEV3): \~2.9% - 3.4% (Setor de Consumo Essencial/Staples)
- Sabesp (SBSP3) ou Eletrobras (ELET3): Geralmente na 10ª posição, com peso entre \~2.5% - 2.8% (Setor de Utilidade Pública)
Sobre nós
Investir não precisa ser um bicho de sete cabeças! Na Threedolar, democratizamos o acesso ao mundo dos investimentos, oferecendo conteúdo claro e prático. Comece hoje mesmo a construir seu futuro financeiro!
Disclaimer
Nada do que eu escrever aqui é recomendação de investimentos ou chamada para compra e venda. Tire suas próprias conclusões e veja o que é melhor para você. Resultados passados não são garantia de resultados futuros. Cuide do seu dinheiro, pois ninguém o fará para você.
Referências
-
 @ 58d88196:bec81862
2025-05-12 19:14:54
@ 58d88196:bec81862
2025-05-12 19:14:54Where We Are Now: AI is already a big part of our lives, even if we don’t always notice it. Think about the last time you used GPS to avoid traffic—that’s AI at work, quietly making your day easier. Companies like NVIDIA,are behind a lot of this magic. They make the tech that powers everything from self-driving cars to massive data centers. In factories, companies like Siemens are using something called "digital twins"—basically virtual copies of their machines—to keep things running smoothly. It’s like having a crystal ball that tells you when a machine might break down before it actually does. Even cities are getting in on the action—Singapore, for example, has a project called Virtual Singapore, which is like a digital version of the city to help with planning things like new roads or buildings. And for us regular folks? If you’ve got a smartwatch tracking your steps or heart rate, you’re already creating a tiny digital version of yourself without even realizing it.
What’s Coming in the near future:Fast forward five or ten years, and this idea of digital twins is going to be everywhere. Picture a factory that never stops because its digital twin catches problems before they happen—no more delays, no more wasted time. Cities will get smarter, too. Imagine a scorching summer day during a heatwave, and instead of a blackout, the city’s AI system automatically shifts energy to where it’s needed most, keeping your AC running. For you and me, digital twins could become a game-changer in healthcare. Your doctor might have a digital version of you—built from your DNA, lifestyle, and even the air quality in your neighborhood—that’s constantly updated. It could warn you about a health issue before you even feel sick, or help your doctor figure out the best treatment just for you. And it doesn’t stop there. You might even have a virtual version of yourself that can attend boring work meetings for you, acting and talking just like you do, while you’re off grabbing a coffee or playing with your kids.
The Big Picture—and the Big Worries: This AI-powered future sounds amazing, but it’s not all smooth sailing. One big concern is privacy. To make these digital twins, companies need a ton of data about us—what we do, where we go, even how our bodies work. That can feel a little creepy, right? What if someone hacks into a city’s digital twin and messes with its power grid or traffic lights? That’s a real risk we’ll need to tackle. Plus, there’s the worry that only the big players—rich companies or cities—will be able to afford this tech, leaving smaller places or communities behind. It’s something we’ll need to figure out so everyone can benefit from what AI has to offer.
-
 @ b99efe77:f3de3616
2025-05-12 21:19:53
@ b99efe77:f3de3616
2025-05-12 21:19:53🚦Traffic Light Control System🚦
This Petri net represents a traffic control protocol ensuring that two traffic lights alternate safely and are never both green at the same time.
;start () -> greenLight1 redLight2
;toRed1 greenLight1 -> queue redLight1
;toGreen2 redLight2 queue -> greenLight2
;toGreen1 queue redLight1 -> greenLight1
;toRed2 greenLight2 -> redLight2 queue
;stop redLight1 queue redLight2 -> ()Places & Transitions
- Places:
- greenLight1: Indicates that the first traffic light is green.
- greenLight2: Indicates that the second traffic light is green.
- redLight1: Indicates that the first traffic light is red.
- redLight2: Indicates that the second traffic light is red.
-
queue: Acts as a synchronization mechanism ensuring controlled alternation between the two traffic lights.
-
Transitions:
- start: Initializes the system by placing tokens in greenLight1 and redLight2.
- toRed1: Moves a token from greenLight1 to redLight1, while placing a token in queue.
- toGreen2: Moves a token from redLight2 to greenLight2, requiring queue.
- toGreen1: Moves a token from queue and redLight1 to greenLight1.
- toRed2: Moves a token from greenLight2 to redLight2, placing a token back into queue.
- stop: Terminates the system by removing tokens from redLight1, queue, and redLight2, representing the system's end state.
petrinet ;start () -> greenLight1 redLight2 ;toRed1 greenLight1 -> queue redLight1 ;toGreen2 redLight2 queue -> greenLight2 ;toGreen1 queue redLight1 -> greenLight1 ;toRed2 greenLight2 -> redLight2 queue ;stop redLight1 queue redLight2 -> ()
-
 @ 266815e0:6cd408a5
2025-05-02 22:24:59
@ 266815e0:6cd408a5
2025-05-02 22:24:59Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.
Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
The communities where interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now
Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal

New emoji picker
Just another small improvement that makes the app feel more complete.
Experimental Wallet
There is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very experimental and probably won't work for you, but its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Don't feed the wallet your hard earned sats, it will eat them!
Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing on load
- Add option to mirror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ b99efe77:f3de3616
2025-05-12 21:19:41
@ b99efe77:f3de3616
2025-05-12 21:19:41🚦Traffic Light Control System🚦
This Petri net represents a traffic control protocol ensuring that two traffic lights alternate safely and are never both green at the same time.
;start () -> greenLight1 redLight2
;toRed1 greenLight1 -> queue redLight1
;toGreen2 redLight2 queue -> greenLight2
;toGreen1 queue redLight1 -> greenLight1
;toRed2 greenLight2 -> redLight2 queue
;stop redLight1 queue redLight2 -> ()Places & Transitions
- Places:
- greenLight1: Indicates that the first traffic light is green.
- greenLight2: Indicates that the second traffic light is green.
- redLight1: Indicates that the first traffic light is red.
- redLight2: Indicates that the second traffic light is red.
-
queue: Acts as a synchronization mechanism ensuring controlled alternation between the two traffic lights.
-
Transitions:
- start: Initializes the system by placing tokens in greenLight1 and redLight2.
- toRed1: Moves a token from greenLight1 to redLight1, while placing a token in queue.
- toGreen2: Moves a token from redLight2 to greenLight2, requiring queue.
- toGreen1: Moves a token from queue and redLight1 to greenLight1.
- toRed2: Moves a token from greenLight2 to redLight2, placing a token back into queue.
- stop: Terminates the system by removing tokens from redLight1, queue, and redLight2, representing the system's end state.
petrinet ;start () -> greenLight1 redLight2 ;toRed1 greenLight1 -> queue redLight1 ;toGreen2 redLight2 queue -> greenLight2 ;toGreen1 queue redLight1 -> greenLight1 ;toRed2 greenLight2 -> redLight2 queue ;stop redLight1 queue redLight2 -> ()
-
 @ 088436cd:9d2646cc
2025-05-01 21:01:55
@ 088436cd:9d2646cc
2025-05-01 21:01:55The arrival of the coronavirus brought not only illness and death but also fear and panic. In such an environment of uncertainty, people have naturally stocked up on necessities, not knowing when things will return to normal.
Retail shelves have been cleared out, and even online suppliers like Amazon and Walmart are out of stock for some items. Independent sellers on these e-commerce platforms have had to fill the gap. With the huge increase in demand, they have found that their inventory has skyrocketed in value.
Many in need of these items (e.g. toilet paper, hand sanitizer and masks) balk at the new prices. They feel they are being taken advantage of in a time of need and call for intervention by the government to lower prices. The government has heeded that call, labeling the independent sellers as "price gougers" and threatening sanctions if they don't lower their prices. Amazon has suspended seller accounts and law enforcement at all levels have threatened to prosecute. Prices have dropped as a result and at first glance this seems like a victory for fair play. But, we will have to dig deeper to understand the unseen consequences of this intervention.
We must look at the economics of the situation, how supply and demand result in a price and how that price acts as a signal that goes out to everyone, informing them of underlying conditions in the economy and helping coordinate their actions.
It all started with a rise in demand. Given a fixed supply (e.g., the limited stock on shelves and in warehouses), an increase in demand inevitably leads to higher prices. Most people are familiar with this phenomenon, such as paying more for airline tickets during holidays or surge pricing for rides.
Higher prices discourage less critical uses of scarce resources. For example, you might not pay $1,000 for a plane ticket to visit your aunt if you can get one for $100 the following week, but someone else might pay that price to visit a dying relative. They value that plane seat more than you.
*** During the crisis, demand surged and their shelves emptied even though
However, retail outlets have not raised prices. They have kept them low, so the low-value uses of things like toilet paper, masks and hand sanitizer has continued. Often, this "use" just takes the form of hoarding. At everyday low prices, it makes sense to buy hundreds of rolls and bottles. You know you will use them eventually, so why not stock up? And, with all those extra supplies in the closet and basement, you don't need to change your behavior much. You don't have to ration your use.
At the low prices, these scarce resources got bought up faster and faster until there was simply none left. The reality of the situation became painfully clear to those who didn't panic and got to the store late: You have no toilet paper and you're not going to any time soon.
However, if prices had been allowed to rise, a number of effects would have taken place that would have coordinated the behavior of everyone so that valuable resources would not have been wasted or hoarded, and everyone could have had access to what they needed.
On the demand side, if prices had been allowed to rise, people would have begun to self-ration. You might leave those extra plies on the roll next time if you know they will cost ten times as much to replace. Or, you might choose to clean up a spill with a rag rather than disposable tissue. Most importantly, you won't hoard as much. That 50th bottle of hand sanitizer might just not be worth it at the new, high price. You'll leave it on the shelf for someone else who may have none.
On the supply side, higher prices would have incentivized people to offer up more of their stockpiles for sale. If you have a pallet full of toilet paper in your basement and all of the sudden they are worth $15 per roll, you might just list a few online. But, if it is illegal to do so, you probably won't.
Imagine you run a business installing insulation and have a few thousand respirator masks on hand for your employees. During a pandemic, it is much more important that people breathe filtered air than that insulation get installed, and that fact is reflected in higher prices. You will sell your extra masks at the higher price rather than store them for future insulation jobs, and the scarce resource will be put to its most important use.
Producers of hand sanitizer would go into overdrive if prices were allowed to rise. They would pay their employees overtime, hire new ones, and pay a premium for their supplies, making sure their raw materials don't go to less important uses.
These kinds of coordinated actions all across the economy would be impossible without real prices to guide them. How do you know if it makes sense to spend an extra $10k bringing a thousand masks to market unless you know you can get more than $10 per mask? If the price is kept artificially low, you simply can't do it. The money just isn't there.
These are the immediate effects of a price change, but incredibly, price changes also coordinate people's actions across space and time.
Across space, there are different supply and demand conditions in different places, and thus prices are not uniform. We know some places are real "hot spots" for the virus, while others are mostly unaffected. High demand in the hot spots leads to higher prices there, which attracts more of the resource to those areas. Boxes and boxes of essential items would pour in where they are needed most from where they are needed least, but only if prices were allowed to adjust freely.
This would be accomplished by individuals and businesses buying low in the unaffected areas, selling high in the hot spots and subtracting their labor and transportation costs from the difference. Producers of new supply would know exactly where it is most needed and ship to the high-demand, high-price areas first. The effect of these actions is to increase prices in the low demand areas and reduce them in the high demand areas. People in the low demand areas will start to self-ration more, reflecting the reality of their neighbors, and people in the hotspots will get some relief.
However, by artificially suppressing prices in the hot spot, people there will simply buy up the available supply and run out, and it will be cost prohibitive to bring in new supply from low-demand areas.
Prices coordinate economic actions across time as well. Just as entrepreneurs and businesses can profit by transporting scarce necessities from low-demand to high-demand areas, they can also profit by buying in low-demand times and storing their merchandise for when it is needed most.
Just as allowing prices to freely adjust in one area relative to another will send all the right signals for the optimal use of a scarce resource, allowing prices to freely adjust over time will do the same.
When an entrepreneur buys up resources during low-demand times in anticipation of a crisis, she restricts supply ahead of the crisis, which leads to a price increase. She effectively bids up the price. The change in price affects consumers and producers in all the ways mentioned above. Consumers self-ration more, and producers bring more of the resource to market.
Our entrepreneur has done a truly incredible thing. She has predicted the future, and by so doing has caused every individual in the economy to prepare for a shortage they don't even know is coming! And, by discouraging consumption and encouraging production ahead of time, she blunts the impact the crisis will have. There will be more of the resource to go around when it is needed most.
On top of this, our entrepreneur still has her stockpile she saved back when everyone else was blithely using it up. She can now further mitigate the damage of the crisis by selling her stock during the worst of it, when people are most desperate for relief. She will know when this is because the price will tell her, but only if it is allowed to adjust freely. When the price is at its highest is when people need the resource the most, and those willing to pay will not waste it or hoard it. They will put it to its highest valued use.
The economy is like a big bus we are all riding in, going down a road with many twists and turns. Just as it is difficult to see into the future, it is difficult to see out the bus windows at the road ahead.
On the dashboard, we don't have a speedometer or fuel gauge. Instead we have all the prices for everything in the economy. Prices are what tell us the condition of the bus and the road. They tell us everything. Without them, we are blind.
Good times are a smooth road. Consumer prices and interest rates are low, investment returns are steady. We hit the gas and go fast. But, the road is not always straight and smooth. Sometimes there are sharp turns and rough patches. Successful entrepreneurs are the ones who can see what is coming better than everyone else. They are our navigators.
When they buy up scarce resources ahead of a crisis, they are hitting the brakes and slowing us down. When they divert resources from one area to another, they are steering us onto a smoother path. By their actions in the market, they adjust the prices on our dashboard to reflect the conditions of the road ahead, so we can prepare for, navigate and get through the inevitable difficulties we will face.
Interfering with the dashboard by imposing price floors or price caps doesn't change the conditions of the road (the number of toilet paper rolls in existence hasn't changed). All it does is distort our perception of those conditions. We think the road is still smooth--our heavy foot stomping the gas--as we crash onto a rocky dirt road at 80 miles per hour (empty shelves at the store for weeks on end).
Supply, demand and prices are laws of nature. All of this is just how things work. It isn't right or wrong in a moral sense. Price caps lead to waste, shortages and hoarding as surely as water flows downhill. The opposite--allowing prices to adjust freely--leads to conservation of scarce resources and their being put to their highest valued use. And yes, it leads to profits for the entrepreneurs who were able to correctly predict future conditions, and losses for those who weren't.
Is it fair that they should collect these profits? On the one hand, anyone could have stocked up on toilet paper, hand sanitizer and face masks at any time before the crisis, so we all had a fair chance to get the supplies cheaply. On the other hand, it just feels wrong that some should profit so much at a time when there is so much need.
Our instinct in the moment is to see the entrepreneur as a villain, greedy "price gouger". But we don't see the long chain of economic consequences the led to the situation we feel is unfair.
If it weren't for anti-price-gouging laws, the major retailers would have raised their prices long before the crisis became acute. When they saw demand outstrip supply, they would have raised prices, not by 100 fold, but gradually and long before anyone knew how serious things would have become. Late comers would have had to pay more, but at least there would be something left on the shelf.
As an entrepreneur, why take risks trying to anticipate the future if you can't reap the reward when you are right? Instead of letting instead of letting entrepreneurs--our navigators--guide us, we are punishing and vilifying them, trying to force prices to reflect a reality that simply doesn't exist.
In a crisis, more than any other time, prices must be allowed to fluctuate. To do otherwise is to blind ourselves at a time when danger and uncertainty abound. It is economic suicide.
In a crisis, there is great need, and the way to meet that need is not by pretending it's not there, by forcing prices to reflect a world where there isn't need. They way to meet the need is the same it has always been, through charity.
If the people in government want to help, the best way for the to do so is to be charitable and reduce their taxes and fees as much as possible, ideally to zero in a time of crisis. Amazon, for example, could instantly reduce the price of all crisis related necessities by 20% if they waived their fee. This would allow for more uses by more people of these scarce supplies as hoarders release their stockpiles on to the market, knowing they can get 20% more for their stock. Governments could reduce or eliminate their tax burden on high-demand, crisis-related items and all the factors that go into their production, with the same effect: a reduction in prices and expansion of supply. All of us, including the successful entrepreneurs and the wealthy for whom high prices are not a great burden, could donate to relief efforts.
These ideas are not new or untested. This is core micro economics. It has been taught for hundreds of years in universities the world over. The fact that every crisis that comes along stirs up ire against entrepreneurs indicates not that the economics is wrong, but that we have a strong visceral reaction against what we perceive to be unfairness. This is as it should be. Unfairness is wrong and the anger it stirs in us should compel us to right the wrong. Our anger itself isn't wrong, it's just misplaced.
Entrepreneurs didn't cause the prices to rise. Our reaction to a virus did that. We saw a serious threat and an uncertain future and followed our natural impulse to hoard. Because prices at major retail suppliers didn't rise, that impulse ran rampant and we cleared the shelves until there was nothing left. We ran the bus right off the road and them blamed the entrepreneurs for showing us the reality of our situation, for shaking us out of the fantasy of low prices.
All of this is not to say that entrepreneurs are high-minded public servants. They are just doing their job. Staking your money on an uncertain future is a risky business. There are big risks and big rewards. Most entrepreneurs just scrape by or lose their capital in failed ventures.
However, the ones that get it right must be allowed to keep their profits, or else no one will try and we'll all be driving blind. We need our navigators. It doesn't even matter if they know all the positive effects they are having on the rest of us and the economy as a whole. So long as they are buying low and selling high--so long as they are doing their job--they will be guiding the rest of us through the good times and the bad, down the open road and through the rough spots.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 51faaa77:2c26615b
2025-05-12 17:34:37
@ 51faaa77:2c26615b
2025-05-12 17:34:37My goal is to share a concise list of questions about OP_RETURN limits that we've answered on Stacker News, as the original thread has become unwieldy with over 200 comments. We began compiling this list about a week ago. I've frequently shared individual links and received very positive feedback. I hope this resource helps us work from a common set of facts and reduces misinformation. I hope you find this as a valuable resource.
I'll list the questions in order of activity and tips received. I've removed duplicates, rephrased some statements as questions, and ignored completely irrelevant questions.
- Users should be given clear configurable options to decide what's in their mempool, why were these options taken away? link
- Won't spammers abuse large OP_RETURNs to bloat the blockchain and make IBD take longer? link
- A similar PR was proposed by Peter Todd 2 years ago, why was it rejected then? What has changed since then, why would this get approved now? link
- Shouldn't we be fighting spam, why are we making policies less strict, shouldn't we be making them more strict? link
- How would someone get around the standardness policy currently for OP_RETURN size? link
- What does "standardness mean" in reference to OP_RETURNs? link
- Will more than 1 OP_RETURN per transaction be possible if this PR gets merged? link
- What are the current OP_RETURN limits and what restrictions are being lifted? link
- Are current relay and mempool policies effective for filtering out spam transactions? link
- Is it true that this type of update could affect Bitcoin's decentralization? link
- Is it possible to stop the abuse of payment outputs (i.e., bare multisig, fake pubkeys, and fake pubkey hashes) that are used to embed data, thereby creating unprunable UTXOs that bloat the UTXO set? link
- What was the main reason /concern to add this PR? ... What will happen if we do nothing? link
- If OP_RETURN still cannot stop all the garbage, why is so important to remove it? Does it affect future development / improvements for LN? link
- What will be the worst case scenario if users still could set their own limits for OP_RETURN? link
- Shouldn't we debate the controversy of this PR on Github since it's where the code gets merged to make these changes? link
- What does it mean when someone says "Fix the Filters"? link
- Will this open the flood gates and drown out all legitimate onchain activity? link
- What can we do to stop spam at the consensus layer of Bitcoin? link
- Will Taproot wizards and other spam companies and projects start using OP_RETURN to put jpegs on the blockchain? link
- If we prevent these transaction from going into our mempools doesn't that prevent or delay these spam transactions from being mined therefore discouraging the spammers? link
- Is it possible to stop abuse of witness data? If so, how? (i.e ordinal theory inscriptions, "jpegs"). link
- Is there any conflict of interest with Bitcoin Core and companies like Citrea, in ref to this PR? link
- Is there any estimation on how much would this affect fees for the average user, considering external projects (like Citrea) using it? Any possibility that this could saturate the mempool and boost fees beyond reasonable? link
- Was this PR initially proposed because of Citrea BitVM needs? If so don't they only need a slight bump in OP_RETURN size, why is it being proposed to make the size unrestricted? link
- What makes a UTXO unprunable? Which projects are making unprunable UTXOs? link
- Why would a spammer use OP_RETURN if it's cheaper to use Witness data to store arbitrary data? link
- Won't large OP_RETURNs allow people to spam the mempool with 100kb transactions and mess up bitcoin for everyone by bloating the mempool and not allowing legitimate transactions in the mempool? link
- If relaxing op_return standardness limit seeks to make 'spam' prunable, then what are proponents of this change assuming about the long-term feasibility of running a 'full' (unpruned) bitcoin node? link
- Is allowing standardness for larger OP_RETURNs a slippery slope? If we allow this won't we continue to allow things that make bitcoin less for money and more for arbitrary data? link
- Won't removing the OP_RETURN cap reduce fee market pressure by allowing senders to consolidate arbitrary data into a single transaction? link
- Could this PR be the beginning of reducing other mempool restrictions? link
- Culture is what protects Bitcoin from external forces, shouldn't non-technical arguments be valid when considering these types of changes? link
- What's the difference between UTXO set, mempool, and blockchain, and how do larger OP_RETURN or witness data affect node resource usage? link
- What is the difference in defining a transaction as valid versus defining a transaction as standard and why do we need this difference? link
- If you're happy with your viewpoint on consensus and mempool rules, is not upgrading Bitcoin Core until it makes sense to you a valid action to take right now? link
- Why didn't this PR get a BIP number? link
- Why is core rushing this change? link
- If there will be a hard fork resulted from this PR (split chain like in 2017), what will happen with existing LN channels? Will exist on both chains with 2 LNs? link
- Isn't this all moot in a (almost guaranteed) future where fees are very high? link
- What is this controversy about, and what is it really about? link
originally posted at https://stacker.news/items/978404
-
 @ a008def1:57a3564d
2025-04-30 17:52:11
@ a008def1:57a3564d
2025-04-30 17:52:11A Vision for #GitViaNostr
Git has long been the standard for version control in software development, but over time, we has lost its distributed nature. Originally, Git used open, permissionless email for collaboration, which worked well at scale. However, the rise of GitHub and its centralized pull request (PR) model has shifted the landscape.
Now, we have the opportunity to revive Git's permissionless and distributed nature through Nostr!
We’ve developed tools to facilitate Git collaboration via Nostr, but there are still significant friction that prevents widespread adoption. This article outlines a vision for how we can reduce those barriers and encourage more repositories to embrace this approach.
First, we’ll review our progress so far. Then, we’ll propose a guiding philosophy for our next steps. Finally, we’ll discuss a vision to tackle specific challenges, mainly relating to the role of the Git server and CI/CD.
I am the lead maintainer of ngit and gitworkshop.dev, and I’ve been fortunate to work full-time on this initiative for the past two years, thanks to an OpenSats grant.
How Far We’ve Come
The aim of #GitViaNostr is to liberate discussions around code collaboration from permissioned walled gardens. At the core of this collaboration is the process of proposing and applying changes. That's what we focused on first.
Since Nostr shares characteristics with email, and with NIP34, we’ve adopted similar primitives to those used in the patches-over-email workflow. This is because of their simplicity and that they don’t require contributors to host anything, which adds reliability and makes participation more accessible.
However, the fork-branch-PR-merge workflow is the only model many developers have known, and changing established workflows can be challenging. To address this, we developed a new workflow that balances familiarity, user experience, and alignment with the Nostr protocol: the branch-PR-merge model.
This model is implemented in ngit, which includes a Git plugin that allows users to engage without needing to learn new commands. Additionally, gitworkshop.dev offers a GitHub-like interface for interacting with PRs and issues. We encourage you to try them out using the quick start guide and share your feedback. You can also explore PRs and issues with gitplaza.
For those who prefer the patches-over-email workflow, you can still use that approach with Nostr through gitstr or the
ngit sendandngit listcommands, and explore patches with patch34.The tools are now available to support the core collaboration challenge, but we are still at the beginning of the adoption curve.
Before we dive into the challenges—such as why the Git server setup can be jarring and the possibilities surrounding CI/CD—let’s take a moment to reflect on how we should approach the challenges ahead of us.
Philosophy
Here are some foundational principles I shared a few years ago:
- Let Git be Git
- Let Nostr be Nostr
- Learn from the successes of others
I’d like to add one more:
- Embrace anarchy and resist monolithic development.
Micro Clients FTW
Nostr celebrates simplicity, and we should strive to maintain that. Monolithic developments often lead to unnecessary complexity. Projects like gitworkshop.dev, which aim to cover various aspects of the code collaboration experience, should not stifle innovation.
Just yesterday, the launch of following.space demonstrated how vibe-coded micro clients can make a significant impact. They can be valuable on their own, shape the ecosystem, and help push large and widely used clients to implement features and ideas.
The primitives in NIP34 are straightforward, and if there are any barriers preventing the vibe-coding of a #GitViaNostr app in an afternoon, we should work to eliminate them.
Micro clients should lead the way and explore new workflows, experiences, and models of thinking.
Take kanbanstr.com. It provides excellent project management and organization features that work seamlessly with NIP34 primitives.
From kanban to code snippets, from CI/CD runners to SatShoot—may a thousand flowers bloom, and a thousand more after them.
Friction and Challenges
The Git Server
In #GitViaNostr, maintainers' branches (e.g.,
master) are hosted on a Git server. Here’s why this approach is beneficial:- Follows the original Git vision and the "let Git be Git" philosophy.
- Super efficient, battle-tested, and compatible with all the ways people use Git (e.g., LFS, shallow cloning).
- Maintains compatibility with related systems without the need for plugins (e.g., for build and deployment).
- Only repository maintainers need write access.
In the original Git model, all users would need to add the Git server as a 'git remote.' However, with ngit, the Git server is hidden behind a Nostr remote, which enables:
- Hiding complexity from contributors and users, so that only maintainers need to know about the Git server component to start using #GitViaNostr.
- Maintainers can easily swap Git servers by updating their announcement event, allowing contributors/users using ngit to automatically switch to the new one.
Challenges with the Git Server
While the Git server model has its advantages, it also presents several challenges:
- Initial Setup: When creating a new repository, maintainers must select a Git server, which can be a jarring experience. Most options come with bloated social collaboration features tied to a centralized PR model, often difficult or impossible to disable.
-
Manual Configuration: New repositories require manual configuration, including adding new maintainers through a browser UI, which can be cumbersome and time-consuming.
-
User Onboarding: Many Git servers require email sign-up or KYC (Know Your Customer) processes, which can be a significant turn-off for new users exploring a decentralized and permissionless alternative to GitHub.
Once the initial setup is complete, the system works well if a reliable Git server is chosen. However, this is a significant "if," as we have become accustomed to the excellent uptime and reliability of GitHub. Even professionally run alternatives like Codeberg can experience downtime, which is frustrating when CI/CD and deployment processes are affected. This problem is exacerbated when self-hosting.
Currently, most repositories on Nostr rely on GitHub as the Git server. While maintainers can change servers without disrupting their contributors, this reliance on a centralized service is not the decentralized dream we aspire to achieve.
Vision for the Git Server
The goal is to transform the Git server from a single point of truth and failure into a component similar to a Nostr relay.
Functionality Already in ngit to Support This
-
State on Nostr: Store the state of branches and tags in a Nostr event, removing reliance on a single server. This validates that the data received has been signed by the maintainer, significantly reducing the trust requirement.
-
Proxy to Multiple Git Servers: Proxy requests to all servers listed in the announcement event, adding redundancy and eliminating the need for any one server to match GitHub's reliability.
Implementation Requirements
To achieve this vision, the Nostr Git server implementation should:
-
Implement the Git Smart HTTP Protocol without authentication (no SSH) and only accept pushes if the reference tip matches the latest state event.
-
Avoid Bloat: There should be no user authentication, no database, no web UI, and no unnecessary features.
-
Automatic Repository Management: Accept or reject new repositories automatically upon the first push based on the content of the repository announcement event referenced in the URL path and its author.
Just as there are many free, paid, and self-hosted relays, there will be a variety of free, zero-step signup options, as well as self-hosted and paid solutions.
Some servers may use a Web of Trust (WoT) to filter out spam, while others might impose bandwidth or repository size limits for free tiers or whitelist specific npubs.
Additionally, some implementations could bundle relay and blossom server functionalities to unify the provision of repository data into a single service. These would likely only accept content related to the stored repositories rather than general social nostr content.
The potential role of CI / CD via nostr DVMs could create the incentives for a market of highly reliable free at the point of use git servers.
This could make onboarding #GitViaNostr repositories as easy as entering a name and selecting from a multi-select list of Git server providers that announce via NIP89.
!(image)[https://image.nostr.build/badedc822995eb18b6d3c4bff0743b12b2e5ac018845ba498ce4aab0727caf6c.jpg]
Git Client in the Browser
Currently, many tasks are performed on a Git server web UI, such as:
- Browsing code, commits, branches, tags, etc.
- Creating and displaying permalinks to specific lines in commits.
- Merging PRs.
- Making small commits and PRs on-the-fly.
Just as nobody goes to the web UI of a relay (e.g., nos.lol) to interact with notes, nobody should need to go to a Git server to interact with repositories. We use the Nostr protocol to interact with Nostr relays, and we should use the Git protocol to interact with Git servers. This situation has evolved due to the centralization of Git servers. Instead of being restricted to the view and experience designed by the server operator, users should be able to choose the user experience that works best for them from a range of clients. To facilitate this, we need a library that lowers the barrier to entry for creating these experiences. This library should not require a full clone of every repository and should not depend on proprietary APIs. As a starting point, I propose wrapping the WASM-compiled gitlib2 library for the web and creating useful functions, such as showing a file, which utilizes clever flags to minimize bandwidth usage (e.g., shallow clone, noblob, etc.).
This approach would not only enhance clients like gitworkshop.dev but also bring forth a vision where Git servers simply run the Git protocol, making vibe coding Git experiences even better.
song
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 created song with a complementary vision that has shaped how I see the role of the git server. Its a self-hosted, nostr-permissioned git server with a relay baked in. Its currently a WIP and there are some compatability with ngit that we need to work out.
We collaborated on the nostr-permissioning approach now reflected in nip34.
I'm really excited to see how this space evolves.
CI/CD
Most projects require CI/CD, and while this is often bundled with Git hosting solutions, it is currently not smoothly integrated into #GitViaNostr yet. There are many loosely coupled options, such as Jenkins, Travis, CircleCI, etc., that could be integrated with Nostr.
However, the more exciting prospect is to use DVMs (Data Vending Machines).
DVMs for CI/CD
Nostr Data Vending Machines (DVMs) can provide a marketplace of CI/CD task runners with Cashu for micro payments.
There are various trust levels in CI/CD tasks:
- Tasks with no secrets eg. tests.
- Tasks using updatable secrets eg. API keys.
- Unverifiable builds and steps that sign with Android, Nostr, or PGP keys.
DVMs allow tasks to be kicked off with specific providers using a Cashu token as payment.
It might be suitable for some high-compute and easily verifiable tasks to be run by the cheapest available providers. Medium trust tasks could be run by providers with a good reputation, while high trust tasks could be run on self-hosted runners.
Job requests, status, and results all get published to Nostr for display in Git-focused Nostr clients.
Jobs could be triggered manually, or self-hosted runners could be configured to watch a Nostr repository and kick off jobs using their own runners without payment.
But I'm most excited about the prospect of Watcher Agents.
CI/CD Watcher Agents
AI agents empowered with a NIP60 Cashu wallet can run tasks based on activity, such as a push to master or a new PR, using the most suitable available DVM runner that meets the user's criteria. To keep them running, anyone could top up their NIP60 Cashu wallet; otherwise, the watcher turns off when the funds run out. It could be users, maintainers, or anyone interested in helping the project who could top up the Watcher Agent's balance.
As aluded to earlier, part of building a reputation as a CI/CD provider could involve running reliable hosting (Git server, relay, and blossom server) for all FOSS Nostr Git repositories.
This provides a sustainable revenue model for hosting providers and creates incentives for many free-at-the-point-of-use hosting providers. This, in turn, would allow one-click Nostr repository creation workflows, instantly hosted by many different providers.
Progress to Date
nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr and nostr:npub16ux4qzg4qjue95vr3q327fzata4n594c9kgh4jmeyn80v8k54nhqg6lra7 have been working on a runner that uses GitHub Actions YAML syntax (using act) for the dvm-cicd-runner and takes Cashu payment. You can see example runs on GitWorkshop. It currently takes testnuts, doesn't give any change, and the schema will likely change.
Note: The actions tab on GitWorkshop is currently available on all repositories if you turn on experimental mode (under settings in the user menu).
It's a work in progress, and we expect the format and schema to evolve.
Easy Web App Deployment
For those disapointed not to find a 'Nostr' button to import a git repository to Vercel menu: take heart, they made it easy. vercel.com_import_options.png there is a vercel cli that can be easily called in CI / CD jobs to kick of deployments. Not all managed solutions for web app deployment (eg. netlify) make it that easy.
Many More Opportunities
Large Patches via Blossom
I would be remiss not to mention the large patch problem. Some patches are too big to fit into Nostr events. Blossom is perfect for this, as it allows these larger patches to be included in a blossom file and referenced in a new patch kind.
Enhancing the #GitViaNostr Experience
Beyond the large patch issue, there are numerous opportunities to enhance the #GitViaNostr ecosystem. We can focus on improving browsing, discovery, social and notifications. Receiving notifications on daily driver Nostr apps is one of the killer features of Nostr. However, we must ensure that Git-related notifications are easily reviewable, so we don’t miss any critical updates.
We need to develop tools that cater to our curiosity—tools that enable us to discover and follow projects, engage in discussions that pique our interest, and stay informed about developments relevant to our work.
Additionally, we should not overlook the importance of robust search capabilities and tools that facilitate migrations.
Concluding Thoughts
The design space is vast. Its an exciting time to be working on freedom tech. I encourage everyone to contribute their ideas and creativity and get vibe-coding!
I welcome your honest feedback on this vision and any suggestions you might have. Your insights are invaluable as we collaborate to shape the future of #GitViaNostr. Onward.
Contributions
To conclude, I want to acknowledge some the individuals who have made recent code contributions related to #GitViaNostr:
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 (gitstr, song, patch34), nostr:npub1useke4f9maul5nf67dj0m9sq6jcsmnjzzk4ycvldwl4qss35fvgqjdk5ks (gitplaza)
nostr:npub1elta7cneng3w8p9y4dw633qzdjr4kyvaparuyuttyrx6e8xp7xnq32cume (ngit contributions, git-remote-blossom),nostr:npub16p8v7varqwjes5hak6q7mz6pygqm4pwc6gve4mrned3xs8tz42gq7kfhdw (SatShoot, Flotilla-Budabit), nostr:npub1ehhfg09mr8z34wz85ek46a6rww4f7c7jsujxhdvmpqnl5hnrwsqq2szjqv (Flotilla-Budabit, Nostr Git Extension), nostr:npub1ahaz04ya9tehace3uy39hdhdryfvdkve9qdndkqp3tvehs6h8s5slq45hy (gnostr and experiments), and others.
nostr:npub1uplxcy63up7gx7cladkrvfqh834n7ylyp46l3e8t660l7peec8rsd2sfek (git-remote-nostr)
Project Management nostr:npub1ltx67888tz7lqnxlrg06x234vjnq349tcfyp52r0lstclp548mcqnuz40t (kanbanstr) Code Snippets nostr:npub1ygzj9skr9val9yqxkf67yf9jshtyhvvl0x76jp5er09nsc0p3j6qr260k2 (nodebin.io) nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac (snipsnip.dev)
CI / CD nostr:npub16ux4qzg4qjue95vr3q327fzata4n594c9kgh4jmeyn80v8k54nhqg6lra7 nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr
and for their nostr:npub1c03rad0r6q833vh57kyd3ndu2jry30nkr0wepqfpsm05vq7he25slryrnw nostr:npub1qqqqqq2stely3ynsgm5mh2nj3v0nk5gjyl3zqrzh34hxhvx806usxmln03 and nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z for their testing, feedback, ideas and encouragement.
Thank you for your support and collaboration! Let me know if I've missed you.
-
 @ 09d5c0a0:2ebbe260
2025-05-12 17:08:20
@ 09d5c0a0:2ebbe260
2025-05-12 17:08:20*For some people, Bitcoin is about saving for retirement. For others, it’s about eating tomorrow. __I first shared the idea of a “Bitcoin Privilege Curve” at the Plan B Forum 2025 in El Salvador. And it still guides how I see Bitcoin today—especially here in Uganda. __Bitcoin shows up differently depending on where you are in life. What it gives you depends on what you need most. __In Uganda, Bitcoin shows up as survival and uphill battle towards financial empowerment to the largely financially illiterate community. __Sometimes it’s food. Sometimes it’s school fees. Or even a skill. We receive Bitcoin donations that allow us to feed orphans, support teachers, and build small projects that teach these children how to farm, save, and think differently about money, __They’re learning how to live better. A child who knows how to grow food and save in sats is building wealth from the ground up. That’s what the lower end of the curve looks like: *Cheap transactions: Many of the people we work with don’t have bank accounts and the cost of accessing, setting up and maintaining a bank account is just unnecessary. Bitcoin lets them send and receive money within themselves almost at no fees, a better option than the exploitative fee structure by mobile money service providers and most banks. Cross-border remittances: We’ve seen Bitcoin move across borders in minutes with no forms, no gatekeepers. I can instantly and cheaply pay for a friend's grocery shopping in Kenya by sending Kenyan shillings into a Grocery Vendor's Mpesa straight from my Bitcoin wallet via Tando. Wealth multiplication: Even saving one sat creates a shift. It teaches patience. It grows over time. Bitcoin is a wealth multiplier for most underprivileged or privileged people, we taught Bitcoin and its principles to former students at Makerere University that have now entered the job market, from testimonials Bitcoin is helping them achieve their savings goals faster than their colleagues.
__Now go higher up the curve, and Bitcoin looks different. ****Wealth preservation: For someone with savings, Bitcoin protects that value over time, especially in regions with unstable currencies, the Argentina, Zimbabwe and Venezuala currency devaluation scandals always remind me that, you can do everything right and still end up losing all your hard earned value to mediocre goverment policies. Inflation hedge: Where governments keep printing money, Bitcoin holds its ground. It offers a stable alternative. The fallacy that inflation is a necessary evil no longer holds water, having a currency with a 21 Million coin hard cap enforceable by millions of Bitcoin network participants across the world guarantees no governement intervention. Censorship resistance: No one can freeze, reject or interfere with your Bitcoin and respective transactions. It's easy to assume because its a public ledger, you sacrifice privacy hence transaction integrity but this is far from the case, Bitcoin gives people freedom to transact without interference privately. Choice: Bitcoin doesn’t lock you into one system. You can move in and out of, save, or spend it however you see fit as long as your transactions obey the globally agreed upon, never changing network rules since 2009.
__So no, it’s not fair to compare someone struggling for a meal to someone saving for their retirement. But that’s the point. Bitcoin doesn’t need to be the same thing for everyone.
__With Gorilla Sats , our tourism project, we’re linking both ends of the curve. Bitcoiners from around the world visit our communities and spend their Bitcoin with local vendors. It’s not charity—it’s a circular economy. The people higher up the curve get meaningful experiences. Locals get income, exposure, and proof that their sats are valuable.
__In traditional finance, someone without a Visa machine can’t do business with someone carrying a card. The tourist who can't easily use mobile money and is hesistant because of exchange rates will spend comparably less but with Bitcoin, all you need is a phone even a basic button one because with now Machankura 8333, Bitcoin moves via USSD.
__Bitcoin offers privilege—but not the kind that excludes. It offers access, ownership, and freedom based on where you are in life. So no, it’s not fair to compare someone struggling for a meal with someone protecting their portfolio. But that’s the point.
__And if we build for everyone on the curve, we all move forward.
__If you’re building for Bitcoin adoption, think about the full curve. What’s it solving where you live? And who still needs a way in?
-
 @ a296b972:e5a7a2e8
2025-05-12 16:52:30
@ a296b972:e5a7a2e8
2025-05-12 16:52:30Wo sind der 1. Stock, das Erdgeschoss und der Keller? Das Dach ist noch zu bauen. Das Haus zum unerklärlichen Krieg ist unfertig. Der Bau wurde schon viel früher begonnen, aber die westlichen Medien behaupten das Gegenteil oder verschweigen es. Eine Vorgeschichte darf es nicht geben.
Am Ukraine-Krieg sieht man, dass ein Konflikt, der entgegen den Behauptungen der Propaganda-Maschine nicht erst im Februar 2022 angefangen hat, wie lange es dauert, bis wieder Verhältnisse zustande kommen, die eine Befriedung ermöglichen. Das Ringen darum ist hoffentlich endlich in die Zielgerade eingelaufen und man findet besser gestern als heute eine Lösung. So viele Menschenleben auf beiden Seiten hat dieser Wahnsinn bislang gekostet. Am Ende, wofür? Die Verwirrung bleibt bis zuletzt, denn einerseits treibt der US-amerikanische Präsident die Friedensbemühungen maßgeblich voran, andererseits werden von US-amerikanischer Seite mutmaßlich die Waffenlieferungen fortgesetzt und Starlink nicht abgeschaltet, was erheblich zum abrupten Beenden des sinnlosen Sterbens beitragen würde.
Verträge sind zu erfüllen? Sicherung der US-amerikanischen Interessen? Druckmittel auf Russland? Und Europa? Europa, vor allem Deutschland, Frankreich und Großbritannien geben weiterhin den Geisterfahrer und haben immer noch nicht mitbekommen, dass sie in der Beilegung des Ukraine-Kriegs nicht das geringste zu sagen haben. Sie spielen sich aber auf, als hätten sie und machen „einen auf dicke Hose“. Murmeln werden als Eier verkauft.
Etwas aus dem Fokus der Neuen Medien gerät dabei der immer noch wütende Krieg im Gaza-Streifen mit einer israelischen Planier-Raupe, dessen Vorgeschichte noch länger ist, als die, die zum Ukraine-Krieg geführt hat. Rund 80 Jahre, aber auch hier eigentlich noch länger. Man kann sich vorstellen, wie lange es hier dauern wird, bis sich sichere, friedliche Verhältnisse einstellen können.
Wer kann sicher sein, wer nimmt sich das Recht heraus zu behaupten, wer entscheidet darüber, dass sich Zustände, wie im 3. Reich, die Verfolgung und Vernichtung einer Minderheit, damals die Juden, nicht wiederholen kann? Seitdem das geschehen ist, hat sich der Großteil der Menschheit keinen Millimeter weiterentwickelt.
Wenn gerade Deutsche Anzeichen für eine Wiederholung dieser tief-dunklen Zeit zu erkennen glauben, derzeit in dem, wie der israelische Staat mit dem Gaza-Streifen verfährt, dann ist das keine Verharmlosung der Gräueltaten im 3. Reich, sondern der Beweis dafür, dass es doch einige gibt, die aus der Geschichte gelernt haben, und die der Meinung sind, dass sich so etwas niemals mehr wiederholen darf.
Um auf einen Genozid hinzuweisen, muss jeder Vergleich möglich und erlaubt sein. Es geht um eine Mehrzahl von Menschen, von Familien, die einfach nur in Frieden leben wollen! Ungeachtet der Tatsache, dass es auf beiden Seiten Kräfte gibt, die das nicht interessiert.
Besonders tragisch wird es, wenn dieser Genozid augenscheinlich ausgerechnet von denen ausgeht, die selbst so schrecklich davon betroffen waren.
Wie kann sich der deutsche Staat erdreisten, diejenigen als Anti-Semiten zu bezeichnen, die hier Merkmale eines Genozids zu erkennen glauben und versuchen, diese kritischen Stimmen zu unterdrücken, „nur“, weil es sich um den Staat Israel handelt, der hier als Täter infrage kommt. Auch der Staat Israel hat keinen Freibrief, die Bevölkerung im Gaza-Streifen nach seinen Vorstellungen und Überzeugungen abzurasieren.
Ein Genozid ist ein Genozid, egal von welcher Regierung eines Landes er begangen wird.
Der Staat Israel ist keine Ausnahme! Im Gegenteil. Aufgrund der Erfahrung seines Volkes müsste es die Menschlichkeit gebieten, dass derartiger Völkermord nie wieder geschieht.
Weiter müsste der Begriff Anti-Semitismus einmal genau unter die Lupe genommen werden, was wer aus welchen Gründen darunter versteht. Man kann den Eindruck gewinnen, dass dieser Begriff vor allem als Totschlagargument verwendet wird, um kritische Stimmen mundtot zu machen. Besonders bei diesem heiklen Thema wäre absolute Akkuratesse dringend notwendig.
Es ist die Pflicht eines jeden, der Kritik an den Zuständen üben will, nicht zu verallgemeinern.
Nicht alle israelischen Staatsbürger sind Netanjahu-Anhänger (das zeigen die Demonstrationen), nicht alle Juden sind Zionisten, nicht einmal alle Zionisten sind Juden.
Und sicher sind auf der Gaza-Seite ebenfalls nicht nur „Engel“ unterwegs!
Beide Lager haben rund 80 Jahre Zeit gehabt, den gegenseitigen Hass durch gegenseitige Provokationen aufzubauen und ihn immer wieder sich entladen zu lassen.
Dieser unermessliche Hass kann nur über Generationen hinweg wieder abgebaut werden.
Wenn es jemals eine ernste Absicht gegeben hätte, eine 2-Staaten-Lösung zu realisieren, wäre diese schon längst in die Tat umgesetzt worden. Wenn jedoch der politische Wille dazu fehlt, vor allem auf der Seite des Stärkeren, passiert gar nichts. Und der fehlt jetzt schon seit rund 80 Jahren.
Maßgeblich durch die Briten ist der Staat Israel künstlich entstanden. Die Ableitung der Nutznießer auf einen Gebietsanspruch aus einem Glauben heraus, ist einmalig.
In dem nicht natürlich entstandenen, sondern künstlich geschaffenen Staatsgebilde liegt möglicherweise die Wurzel allen Übels, die von langer Hand, spätestens durch die Balfour-Deklaration im Jahre 1917 ihren Anfang genommen hat.
Man hat nun Jahrzehnte lang Zeit gehabt, zu beobachten, dass dieses Konstrukt ein sicheres Leben und eine Garantie für friedliche Verhältnisse aller nicht zustande gebracht hat. Schmerzliche Erfahrungen auf beiden Seiten haben bislang nicht dazu geführt, dass man zu der Einsicht gekommen wäre, dass man sich möglicherweise auf dem Holzweg befindet.
Die verfeindeten Lager müssten sich, neutral moderiert (welcher Staat, welcher Mensch ist heute noch neutral, oder zumindest kein Interessenvertreter?), zusammensetzen und sich in sicher nicht einfachen, langwierigen, zähen Gesprächen und Verhandlungen über die Neugründung eines gemeinsamen Staates für alle Beteiligten ernsthaft nachdenken, solange, bis es zu einer Einigung gekommen wäre, die für alle Beteiligten akzeptabel ist. Das Ergebnis, eine gemeinsame Staatenlösung, müsste das erklärte Ziel sein und wenn es noch so lange dauern würde.
Das Mitspracherecht müsste nach Bevölkerungsanteil in einem gerechten Verhältnis festgelegt werden. So müssten kleinere Anteile verhältnismäßig mehr Stimmanteile haben, als der größere Anteil, um zu möglichst für alle gerechten Entscheidungen zu gelangen, die alle Beteiligten mittragen könnten. Ein Vorankommen wäre nur durch Vernunft, nicht durch Starrsinn möglich.
Aufgrund der hitzigen Mentalität aller Beteiligten müssten beide Lager auf Gedeih und Verderb voneinander abhängig gemacht werden, sodass ein friedliches Zusammenraufen immer wieder nötig wäre, weil niemand in der Lage wäre, die Oberhand zu gewinnen.
Es müssten gegenseitige Abhängigkeiten geschaffen werden. So könnten zum Beispiel Lieferungen von Lebensmitteln, Wasser, Energie (Israel) usw. mit der Hoheit über die noch zu erschließenden Gasfelder (Gaza) vor Gaza „verrechnet“ werden, ohne, dass die USA oder sonst wer die Finger im Spiel haben.
Bei derartigen gegenseitigen Abhängigkeiten würde man sich schon zusammenraufen.
Das alles setzt voraus, dass der Mensch an sich seine menschlichen Schwächen unter Kontrolle bringen würde. Hierzu können Machtstreben, Geldgier, Rechthaberei, Überheblichkeit, Ideologien, Ansprüche aus einem Glauben heraus usw. gezählt werden.
Jerusalem müsste einen Sonderstatus erhalten und die Verwaltung müsste unter den drei Weltreligionen aufgeteilt werden. Jerusalem könnte im „Kleinen“ ein Beispiel dafür sein, wie der gesamte neue Staat im „Großen“ funktioniert. Und möglicherweise würde er so in der Tat funktionieren.
Für viele mag das alles vielleicht naiv oder sogar absurd klingen. Zur Herstellung von Frieden, Frieden in dem jede Mutter, gleich welcher Religion sie angehört, ihre Kinder in Sicherheit aufwachsen sehen kann, muss jede Überlegung und Idee, wie ein friedliches Miteinander realisiert werden kann, erlaubt sein zu denken und auch auszusprechen.
Eines ist sicher. So, wie die Verhältnisse in der Vergangenheit gestaltet wurden, hat die Realität eindeutig gezeigt, dass es so auf gar keinen Fall funktioniert. Also, warum nicht einfach einmal das Gehirn durchblasen, alte, überkommene Überzeugungen loswerden und endlich einmal etwas Neues denken?
Und wer jetzt immer noch sagt, das wäre eine Delegitimierung des Staates Israel, der sollte seine Gehirnwindungen einmal zur Inspektion bringen. Der Mensch, egal welcher Couleur und welcher Religion steht hier im Mittelpunkt. Im Mittelpunkt stehen Überlegungen, wie ein friedliches Miteinander möglich sein könnte. Falls sich herausstellt, dass das eine Utopie ist, auch gut, aber immerhin sind sich Gedanken gemacht worden, die von den eingefahrenen, zu nichts außer Elend führenden Entscheidungen abweichen. Und wenn es nur zur Anregung für andere Ideen dient, dann wäre schon viel getan. Und das ist weder anti-semitisch, noch anti-israelisch, noch anti-christlich, noch anti-moslemisch, noch anti-sonst wie, sondern vor allem ein Appell an die Vernunft, zu der der Mensch schließlich auch begabt ist.
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von Georg Ohrweh)
-
 @ c9badfea:610f861a
2025-05-12 16:29:32
@ c9badfea:610f861a
2025-05-12 16:29:32- Install Organic Maps
- Launch the app and download the World Map first
- Tap the ☰ at the bottom, then select Download Maps, and tap the + icon
- Download maps by tapping ⤓ next to your desired region
- Return to the main screen and tap 🔍 to search for your destination
- Enjoy navigating offline
ℹ️ Note that Organic Maps does not provide live traffic updates
-
 @ 6be5cc06:5259daf0
2025-04-28 01:05:49
@ 6be5cc06:5259daf0
2025-04-28 01:05:49Eu reconheço que Deus, e somente Deus, é o soberano legítimo sobre todas as coisas. Nenhum homem, nenhuma instituição, nenhum parlamento tem autoridade para usurpar aquilo que pertence ao Rei dos reis. O Estado moderno, com sua pretensão totalizante, é uma farsa blasfema diante do trono de Cristo. Não aceito outro senhor.
A Lei que me guia não é a ditada por burocratas, mas a gravada por Deus na própria natureza humana. A razão, quando iluminada pela fé, é suficiente para discernir o que é justo. Rejeito as leis arbitrárias que pretendem legitimar o roubo, o assassinato ou a escravidão em nome da ordem. A justiça não nasce do decreto, mas da verdade.
Acredito firmemente na propriedade privada como extensão da própria pessoa. Aquilo que é fruto do meu trabalho, da minha criatividade, da minha dedicação, dos dons a mim concedidos por Deus, pertence a mim por direito natural. Ninguém pode legitimamente tomar o que é meu sem meu consentimento. Todo imposto é uma agressão; toda expropriação, um roubo. Defendo a liberdade econômica não por idolatria ao mercado, mas porque a liberdade é condição necessária para a virtude.
Assumo o Princípio da Não Agressão como o mínimo ético que devo respeitar. Não iniciarei o uso da força contra ninguém, nem contra sua propriedade. Exijo o mesmo de todos. Mas sei que isso não basta. O PNA delimita o que não devo fazer — ele não me ensina o que devo ser. A liberdade exterior só é boa se houver liberdade interior. O mercado pode ser livre, mas se a alma estiver escravizada pelo vício, o colapso será inevitável.
Por isso, não me basta a ética negativa. Creio que uma sociedade justa precisa de valores positivos: honra, responsabilidade, compaixão, respeito, fidelidade à verdade. Sem isso, mesmo uma sociedade que respeite formalmente os direitos individuais apodrecerá por dentro. Um povo que ama o lucro, mas despreza a verdade, que celebra a liberdade mas esquece a justiça, está se preparando para ser dominado. Trocará um déspota visível por mil tiranias invisíveis — o hedonismo, o consumismo, a mentira, o medo.
Não aceito a falsa caridade feita com o dinheiro tomado à força. A verdadeira generosidade nasce do coração livre, não da coerção institucional. Obrigar alguém a ajudar o próximo destrói tanto a liberdade quanto a virtude. Só há mérito onde há escolha. A caridade que nasce do amor é redentora; a que nasce do fisco é propaganda.
O Estado moderno é um ídolo. Ele promete segurança, mas entrega servidão. Promete justiça, mas entrega privilégios. Disfarça a opressão com linguagem técnica, legal e democrática. Mas por trás de suas máscaras, vejo apenas a velha serpente. Um parasita que se alimenta do trabalho alheio e manipula consciências para se perpetuar.
Resistir não é apenas um direito, é um dever. Obedecer a Deus antes que aos homens — essa é a minha regra. O poder se volta contra a verdade, mas minha lealdade pertence a quem criou o céu e a terra. A tirania não se combate com outro tirano, mas com a desobediência firme e pacífica dos que amam a justiça.
Não acredito em utopias. Desejo uma ordem natural, orgânica, enraizada no voluntarismo. Uma sociedade que se construa de baixo para cima: a partir da família, da comunidade local, da tradição e da fé. Não quero uma máquina que planeje a vida alheia, mas um tecido de relações voluntárias onde a liberdade floresça à sombra da cruz.
Desejo, sim, o reinado social de Cristo. Não por imposição, mas por convicção. Que Ele reine nos corações, nas famílias, nas ruas e nos contratos. Que a fé guie a razão e a razão ilumine a vida. Que a liberdade seja meio para a santidade — não um fim em si. E que, livres do jugo do Leviatã, sejamos servos apenas do Senhor.
-
 @ a3c6f928:d45494fb
2025-05-12 15:30:48
@ a3c6f928:d45494fb
2025-05-12 15:30:48Financial freedom is a powerful concept—one that goes beyond simply having money in the bank. It is the ability to live the life you desire, free from the constraints of financial worry. Achieving financial freedom requires planning, discipline, and a clear understanding of your financial goals.
What Is Financial Freedom?
Financial freedom means having enough income, savings, and investments to support the lifestyle you want for yourself and your family. It is about being in control of your finances, instead of your finances controlling you. When you are financially free, you have choices—you can travel, start a business, or retire comfortably without constant stress about money.
Steps to Achieving Financial Freedom
-
Set Clear Financial Goals: Understand what financial freedom means to you and set measurable goals to achieve it.
-
Create a Budget and Stick to It: Track your income and expenses to identify areas where you can save more.
-
Invest Wisely: Grow your wealth by investing in assets like stocks, real estate, or mutual funds.
-
Build an Emergency Fund: Save at least 3-6 months’ worth of living expenses to protect against unexpected events.
-
Eliminate Debt: High-interest debt can be a major barrier to financial freedom. Prioritize paying it off.
Why Financial Freedom Matters
Financial freedom gives you the power to make decisions without being bound by financial constraints. It allows for greater life flexibility, reduces stress, and opens up opportunities that would otherwise be unreachable. Most importantly, it provides peace of mind and the ability to focus on what truly matters.
Start Your Journey Today
The path to financial freedom is not a quick fix—it is a lifelong commitment to smart financial choices. But with perseverance and planning, it is achievable. Begin today, and take control of your financial future.
“Financial freedom is available to those who learn about it and work for it.” — Robert Kiyosaki
Plan wisely. Invest smartly. Live freely.
-
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 6be5cc06:5259daf0
2025-05-12 14:50:36
@ 6be5cc06:5259daf0
2025-05-12 14:50:36A posição do libertário que rejeita o cristianismo padece de sérias incoerências lógicas, históricas e filosóficas. Ao renegar as bases espirituais e culturais que tornaram possível o próprio ideal libertário, tal posição demonstra ser, ao mesmo tempo, autofágica e irracional. É o caso de alguém que se gloria dos frutos de uma árvore que corta pela raiz.
I. Fundamento histórico: a civilização da liberdade é cristã
Não foi o secularismo moderno, nem o paganismo antigo, que ergueram as instituições que protegem a dignidade da pessoa humana e os limites ao poder. Desde os primeiros séculos, a Igreja resistiu ao culto estatal romano, afirmando a soberania de Deus sobre os Césares — "Mais importa obedecer a Deus que aos homens" (Atos 5,29).
Foi o cristianismo que:
-
Fundou universidades livres, onde o saber era buscado sob o primado da verdade;
-
Defendeu a lei natural como fundamento do direito — uma doutrina que protege o indivíduo contra tiranias;
-
Resgatou e aprofundou o conceito de pessoa, dotada de razão e livre-arbítrio, imagem de Deus, e, portanto, inalienavelmente digna e responsável.
Em momentos-chave da história, como nas disputas entre papado e império, nas resistências contra absolutismos, e na fundação do direito internacional por Francisco de Vitoria e a Escola de Salamanca, foi o cristianismo quem freou o poder estatal em nome de princípios superiores. A tradição cristã foi frequentemente o principal obstáculo à tirania, não seu aliado.
Negar isso é amputar a própria genealogia da liberdade ocidental.
Uma das chaves do cristianismo para a construção dessa civilização da liberdade foi a exaltação do individualismo. Ao afirmar que o ser humano é feito à imagem de Deus e que sua salvação é uma escolha pessoal, o cristianismo colocou o indivíduo no centro da moralidade e da liberdade. Diferente dos gregos, cuja ética era voltada para a polis e a cidade-estado, o cristianismo reafirma a suprema importância do indivíduo, com sua capacidade de escolha moral, responsabilidade pessoal e dignidade intrínseca. Esse princípio, mais do que qualquer outra religião, foi o alicerce do desenvolvimento da liberdade individual e da autonomia, valores que sustentam a civilização ocidental.
A ética grega, na melhor das hipóteses, descreve a ordem natural — mas não consegue justificar por que essa ordem deveria obrigar a vontade humana. Um Logos impessoal não tem autoridade moral. Uma ordem cósmica sem um Legislador é apenas um dado de fato, não uma norma vinculante. A vontade pode rebelar-se contra o telos — e sem um Deus justo, que ordena a natureza à perfeição, não há razão última para não o fazer.
A cultura grega teve uma influência indiscutível sobre o desenvolvimento da civilização ocidental, mas o cristianismo não só absorveu o que havia de bom na cultura grega, como também elevou e completou esses aspectos. O cristianismo, ao afirmar que todos os homens são feitos à imagem e semelhança de Deus e têm dignidade intrínseca, levou a uma noção de igualdade moral e liberdade que transcende as limitações da pólis grega.
II. Falsa dicotomia: fé e liberdade não são opostas
Com frequência equiparam a religião à coerção e à obediência cega. Mas isso é um equívoco: o cristianismo não se impõe pela força, mas apela à consciência. O próprio Deus, em sua relação com a criatura racional, respeita sua liberdade. Como ensina a Escritura:
"Se alguém quiser vir após mim..." (Mt 16,24);
"Eis que estou à porta e bato. Se alguém ouvir a minha voz e abrir a porta, entrarei em sua casa e cearei com ele." (Ap 3,20);
"Assim falai, e assim procedei, como devendo ser julgados pela lei da liberdade." (Tiago 2,12).A adesão à fé deve ser livre, voluntária e racional, pois sem liberdade não há verdadeiro mérito, nem amor genuíno. Isso é mais compatível com o princípio de não agressão do que qualquer utopia secular. Ora, o núcleo do evangelho é voluntarista: salvação pessoal, conversão interior, caridade.
Ninguém deve ser forçado, contra sua vontade, a abraçar a fé, pois o ato de fé é por sua natureza voluntário (Dignitatis Humanae; CDC, cân. 748,2)
Se algum Estado usa da força para impor o cristianismo, afirmar que o cristianismo causou as coerções é tão equivocado quanto dizer que a propriedade privada causa o comunismo; é uma inversão da realidade, pois o comunismo surge precisamente da violação da propriedade. Portanto, a fé forçada é inválida em si mesma, pois viola a natureza do ato de crer, que deve ser livre.
III. Fundamento moral: sem transcendência, o libertarianismo flutua no vácuo
O libertário anticristão busca defender princípios objetivos — como a inviolabilidade do indivíduo e a ilegitimidade da agressão — sem um fundamento transcendente que lhes dê validade universal. Por que a agressão é errada? Por que alguém tem direito à vida, à liberdade, à propriedade? Sem uma explicação transcendental, as respostas para tais perguntas se tornam apenas opiniões ou convenções, não obrigações morais vinculantes. Se a moralidade é puramente humana, então os direitos podem ser modificados ou ignorados conforme a vontade da sociedade. O conceito de direitos naturais, tão caro ao libertarianismo, precisa de um solo metafísico que justifique sua universalidade e imutabilidade. Caso contrário, eles podem ser tratados apenas como acordos utilitários temporários ou preferências culturais, sem qualquer obrigatoriedade para todos os seres humanos em todas as circunstâncias.
Pensadores libertários seculares, como Ayn Rand e Murray Rothbard, tentaram ancorar os direitos naturais na razão humana ou na natureza do homem. Rand baseia sua ética no egoísmo racional, enquanto Rothbard apela à lei natural. Embora essas abordagens busquem objetividade, elas carecem de uma resposta definitiva para por que a razão ou a natureza humana obrigam moralmente todos os indivíduos. Sem um fundamento transcendente, suas concepções permanecem vulneráveis a interpretações subjetivas ou a cálculos utilitários.
Aqui, o cristianismo oferece uma explicação sólida e transcendental que fundamenta os direitos naturais. A visão cristã de que o ser humano foi criado à imagem e semelhança de Deus confere à pessoa uma dignidade intrínseca, imutável e universal. Essa dignidade não depende de fatores externos, como consenso social ou poder político, mas é uma característica inerente ao ser humano pela sua criação divina. A partir dessa perspectiva teológica, torna-se possível afirmar com base sólida que os direitos naturais são dados por Deus e, portanto, são universais e vinculantes.
O cristianismo também é a base de um sistema moral que distingue claramente justiça de legalidade. O Estado pode criar leis, mas isso não significa que essas leis sejam justas. A justiça, sob a ótica cristã, é uma expressão da ordem moral objetiva, algo que transcende as leis humanas e é definido pela vontade divina. Por isso, o libertarianismo cristão vê a agressão como uma violação de uma ordem moral objetiva, e não apenas uma violação de uma convenção social ou de um acordo utilitário.
Se a moralidade e os direitos naturais não forem fundamentados em um Logos criador e legislador, o que acontece é que o conceito de direito natural degenera para algo mais frágil, como um simples acordo utilitário. Nesse cenário, os direitos do indivíduo se tornam algo acordado entre os membros de uma sociedade, em vez de princípios imutáveis e universais. Os direitos podem ser negociados, alterados ou ignorados conforme o interesse do momento.
IV. Fundamento científico: a racionalidade moderna é filha da fé cristã
A ciência moderna só foi possível no contexto cultural cristão. Nenhuma outra civilização — nem a grega, nem a islâmica, nem a chinesa — produziu o método científico como o Ocidente cristão o fez.
Isso se deve a quatro premissas teológicas:
-
Criação racional: O mundo é ordenado por um Deus racional.
-
Distinção entre Criador e criatura: A natureza não é divina e pode ser estudada sem sacrilégio.
-
Valor do trabalho e da observação empírica, herdado do monaquismo.
-
Autonomia institucional, presente nas universidades medievais.
A doutrina cristã da Criação ex nihilo ensina que o mundo foi criado por um Deus racional, sábio e pessoal. Portanto, o cosmos é ordenado, possui leis, e pode ser compreendido pela razão humana — que é imagem do Criador. Isso contrasta fortemente com as cosmovisões panteístas ou mitológicas, onde o mundo é cíclico, arbitrário ou habitado por forças caprichosas.
Sem essa fé no Logos criador, não há razão para crer que a natureza tenha uma ordem inteligível universal e constante, que pode ser descoberta por observação e dedução. A ciência moderna só é possível porque, antes de investigar a natureza, pressupôs-se que ela era investigável — e isso foi uma herança direta do pensamento cristão.
Homens como Bacon, Newton, Kepler e Galileu viam na ciência um modo de glorificar o Criador. O ateísmo cientificista é, portanto, parasitário da teologia cristã, pois toma seus frutos e rejeita suas raízes. A ciência moderna nasceu como filha legítima da fé cristã. E os que hoje a usam contra sua mãe, ou são ingratos, ou ignorantes.
V. O cristianismo como barreira à revolução cultural
O cristianismo é a barreira mais sólida contra a infiltração revolucionária. A chamada "marcha gramsciana", que visa corroer os fundamentos morais da sociedade para subjugar o indivíduo ao coletivo, encontra sua resistência mais firme nos princípios cristãos. A fé cristã, ao proclamar a existência de uma verdade objetiva, de uma lei moral imutável e de uma dignidade humana que transcende o Estado e o consenso social, imuniza a civilização contra o relativismo e o igualitarismo nivelador do marxismo cultural.
Além disso, o cristianismo é uma tradição milenar, profundamente enraizada no cotidiano das pessoas, não sendo uma novidade a ser imposta ou implementada, mas uma força presente há séculos, que permeia a estrutura social, moral e cultural da sociedade. Sua presença constante nas comunidades, desde os tempos mais antigos, oferece uma resistência robusta contra qualquer tentativa de subverter a ordem natural e moral estabelecida.
Não por acaso, tanto Karl Marx quanto Antonio Gramsci identificaram no cristianismo o principal obstáculo à realização de seus projetos revolucionários. Marx chamou a religião de "ópio do povo" porque sabia que uma alma ancorada em Deus não se submete facilmente ao poder terreno; Gramsci, mais sutil, propôs a destruição da cultura cristã como pré-condição para o triunfo do socialismo. Sem essa âncora transcendente, a sociedade torna-se presa fácil das engenharias sociais que pretendem redefinir arbitrariamente o homem, a família e a liberdade.
Conclusão
O libertário anticristão, consciente ou não, nega as fundações mesmas do edifício que habita. Ao rejeitar o cristianismo, cava o abismo sob os próprios pés, privando o ideal libertário de sua base moral, cultural e racional. Ele defende a ética voluntária, a liberdade individual e a ordem espontânea, mas sem o solo metafísico e histórico que torna esses princípios inteligíveis e possíveis. É um erro tentar preservar a liberdade em termos absolutos sem reconhecer as raízes cristãs que a sustentam, pois o cristianismo é a única tradição que a legitima e a viabiliza.
Negar o cristianismo é racionalmente insustentável. A liberdade, como a conhecemos, é filha da fé cristã, que oferece a base moral e metafísica que torna a liberdade tanto desejável quanto possível. Mesmo que ateu, o libertário que ama a liberdade deveria, no mínimo, respeitar — e, idealmente, redescobrir — essas raízes cristãs. Pois sem fé, restam apenas o niilismo e o relativismo, que, eventualmente, desaguam na servidão.
Como nos ensina a tradição: Ubi fides ibi libertas — onde há fé, há liberdade.
-
-
 @ eabee230:17fc7576
2025-05-12 14:38:11
@ eabee230:17fc7576
2025-05-12 14:38:11⚖️ຢ່າລືມສິ່ງທີ່ເຄີຍເກີດຂຶ້ນ ຮອດຊ່ວງທີ່ມີການປ່ຽນແປງລະບົບການເງິນຈາກລະບົບເງິນເກົ່າ ສູ່ລະບົບເງິນໃໝ່ມັນເຮັດໃຫ້ຄົນທີ່ລວຍກາຍເປັນຄົນທຸກໄດ້ເລີຍ ນ້ຳພັກນ້ຳແຮງທີ່ສະສົມມາດ້ວຍຄວາມເມື່ອຍແຕ່ບໍ່ສາມາດແລກເປັນເງິນລະບົບໃໝ່ໄດ້ທັງໝົດ ຖືກຈຳກັດຈຳນວນທີ່ກົດໝາຍວາງອອກມາໃຫ້ແລກ ເງິນທີ່ເຫຼືອນັ້ນປຽບຄືດັ່ງເສດເຈ້ຍ ເພາະມັນບໍ່ມີຢູ່ໃສຮັບອີກຕໍ່ໄປເພາະກົດໝາຍຈະນຳໃຊ້ສະກຸນໃໝ່ ປະຫວັດສາດເຮົາມີໃຫ້ເຫັນວ່າ ແລະ ເຄີຍຜ່ານມາແລ້ວຢ່າໃຫ້ຄົນລຸ້ນເຮົາຊຳ້ຮອຍເກົ່າ.
🕰️ຄົນທີ່ມີຄວາມຮູ້ ຫຼື ໃກ້ຊິດກັບແຫຼ່ງຂໍ້ມູນຂ່າວສານກໍຈະປ່ຽນເງິນທີ່ມີຢູ່ເປັນສິນສັບບໍ່ວ່າຈະເປັນທີ່ດິນ ແລະ ທອງຄຳທີ່ສາມາດຮັກສາມູນລະຄ່າໄດ້ເຮັດໃຫ້ເຂົາຍັງຮັກສາຄວາມມັ້ງຄັ້ງໃນລະບົບໃໝ່ໄດ້.
🕰️ໃຜທີ່ຕ້ອງການຈະຍ້າຍປະເທດກໍ່ຈະໃຊ້ສິ່ງທີ່ເປັນຊື່ກາງໃນການແລກປ່ຽນເປັນທີ່ຍ້ອມຮັບຫຼາຍນັ້ນກໍຄືທອງຄຳ ປ່ຽນຈາກເງິນລະບົບເກົ່າເປັນທອງຄຳເພື່ອທີ່ສາມາດປ່ຽນທອງຄຳເປັນສະກຸນເງິນທ້ອງຖິ່ນຢູ່ປະເທດປາຍທາງໄດ້.
🕰️ຈາກຜູ້ດີເມື່ອກ່ອນກາຍເປັນຄົນທຳມະດາຍ້ອນສັບສິນທີ່ມີ ບໍ່ສາມາດສົ່ງຕໍ່ສູ່ລູກຫຼານໄດ້. ການເກັບອອມເປັນສິ່ງທີ່ດີ ແຕ່ຖ້າໃຫ້ດີຕ້ອງເກັບອອມໃຫ້ຖືກບ່ອນ ຄົນທີ່ຮູ້ທັນປ່ຽນເງິນທີ່ມີຈາກລະບົບເກົ່າໄປສູ່ທອງຄຳ ເພາະທອງຄຳມັນເປັນສາກົນ.
ໃຜທີ່ເຂົ້າໃຈ ແລະ ມອງການໄກກວ່າກໍ່ສາມາດຮັກສາສິນສັບສູ່ລູກຫຼານໄດ້ ເກັບເຈ້ຍໃນປະລິມານທີ່ພໍໃຊ້ຈ່າຍ ປ່ຽນເຈ້ຍໃຫ້ເປັນສິ່ງທີ່ຮັກສາມູນລະຄ່າໄດ້ແທ້ຈິງ.🕰️ເຮົາໂຊກດີທີ່ເຄີຍມີບົດຮຽນມາແລ້ວ ເກີດຂຶ້ນຈິງໃນປະເທດເຮົາບໍ່ໄດ້ຢາກໃຫ້ທັງໝົດແຕ່ຢາກໃຫ້ສຶກສາ ແລະ ຕັ້ງຄຳຖາມວ່າທີ່ຜ່ານມາມັນເປັນແບບນີ້ແທ້ບໍ່ ເງິນທີ່ລັດຄວາມຄຸມ ເງິນປະລິມານບໍ່ຈຳກັດ ການໃຊ້ກົດໝາຍແບບບັງຄັບ. ຖ້າຄອບຄົວຫຼືຄົນໃກ້ໂຕທີ່ຍູ່ໃນຊ່ວງເຫດການນັ້ນແຕ່ຕັດສິນໃຈຜິດພາດທີ່ບໍ່ປ່ຽນເຈ້ຍເປັນສິນສັບ. ນີ້ແມ່ນໂອກາດທີ່ຈະແກ້ໄຂຂໍ້ຜິດພາດນັ້ນໂດຍຫັນມາສຶກສາເງິນແທ້ຈິງແລ້ວແມ່ນຍັງກັນແທ້ ເວລາມີຄ່າສຶກສາບິດຄອຍ.

fiatcurrency #bitcoin #gold #history #paymentsolutions #laokip #laostr
-
 @ 30ceb64e:7f08bdf5
2025-04-26 20:33:30
@ 30ceb64e:7f08bdf5
2025-04-26 20:33:30Status: Draft
Author: TheWildHustleAbstract
This NIP defines a framework for storing and sharing health and fitness profile data on Nostr. It establishes a set of standardized event kinds for individual health metrics, allowing applications to selectively access specific health information while preserving user control and privacy.
In this framework exists - NIP-101h.1 Weight using kind 1351 - NIP-101h.2 Height using kind 1352 - NIP-101h.3 Age using kind 1353 - NIP-101h.4 Gender using kind 1354 - NIP-101h.5 Fitness Level using kind 1355
Motivation
I want to build and support an ecosystem of health and fitness related nostr clients that have the ability to share and utilize a bunch of specific interoperable health metrics.
- Selective access - Applications can access only the data they need
- User control - Users can choose which metrics to share
- Interoperability - Different health applications can share data
- Privacy - Sensitive health information can be managed independently
Specification
Kind Number Range
Health profile metrics use the kind number range 1351-1399:
| Kind | Metric | | --------- | ---------------------------------- | | 1351 | Weight | | 1352 | Height | | 1353 | Age | | 1354 | Gender | | 1355 | Fitness Level | | 1356-1399 | Reserved for future health metrics |
Common Structure
All health metric events SHOULD follow these guidelines:
- The content field contains the primary value of the metric
- Required tags:
['t', 'health']- For categorizing as health data['t', metric-specific-tag]- For identifying the specific metric['unit', unit-of-measurement]- When applicable- Optional tags:
['converted_value', value, unit]- For providing alternative unit measurements['timestamp', ISO8601-date]- When the metric was measured['source', application-name]- The source of the measurement
Unit Handling
Health metrics often have multiple ways to be measured. To ensure interoperability:
- Where multiple units are possible, one standard unit SHOULD be chosen as canonical
- When using non-standard units, a
converted_valuetag SHOULD be included with the canonical unit - Both the original and converted values should be provided for maximum compatibility
Client Implementation Guidelines
Clients implementing this NIP SHOULD:
- Allow users to explicitly choose which metrics to publish
- Support reading health metrics from other users when appropriate permissions exist
- Support updating metrics with new values over time
- Preserve tags they don't understand for future compatibility
- Support at least the canonical unit for each metric
Extensions
New health metrics can be proposed as extensions to this NIP using the format:
- NIP-101h.X where X is the metric number
Each extension MUST specify: - A unique kind number in the range 1351-1399 - The content format and meaning - Required and optional tags - Examples of valid events
Privacy Considerations
Health data is sensitive personal information. Clients implementing this NIP SHOULD:
- Make it clear to users when health data is being published
- Consider incorporating NIP-44 encryption for sensitive metrics
- Allow users to selectively share metrics with specific individuals
- Provide easy ways to delete previously published health data
NIP-101h.1: Weight
Description
This NIP defines the format for storing and sharing weight data on Nostr.
Event Kind: 1351
Content
The content field MUST contain the numeric weight value as a string.
Required Tags
- ['unit', 'kg' or 'lb'] - Unit of measurement
- ['t', 'health'] - Categorization tag
- ['t', 'weight'] - Specific metric tag
Optional Tags
- ['converted_value', value, unit] - Provides the weight in alternative units for interoperability
- ['timestamp', ISO8601 date] - When the weight was measured
Examples
json { "kind": 1351, "content": "70", "tags": [ ["unit", "kg"], ["t", "health"], ["t", "weight"] ] }json { "kind": 1351, "content": "154", "tags": [ ["unit", "lb"], ["t", "health"], ["t", "weight"], ["converted_value", "69.85", "kg"] ] }NIP-101h.2: Height
Status: Draft
Description
This NIP defines the format for storing and sharing height data on Nostr.
Event Kind: 1352
Content
The content field can use two formats: - For metric height: A string containing the numeric height value in centimeters (cm) - For imperial height: A JSON string with feet and inches properties
Required Tags
['t', 'health']- Categorization tag['t', 'height']- Specific metric tag['unit', 'cm' or 'imperial']- Unit of measurement
Optional Tags
['converted_value', value, 'cm']- Provides height in centimeters for interoperability when imperial is used['timestamp', ISO8601-date]- When the height was measured
Examples
```jsx // Example 1: Metric height Apply to App.jsx
// Example 2: Imperial height with conversion Apply to App.jsx ```
Implementation Notes
- Centimeters (cm) is the canonical unit for height interoperability
- When using imperial units, a conversion to centimeters SHOULD be provided
- Height values SHOULD be positive integers
- For maximum compatibility, clients SHOULD support both formats
NIP-101h.3: Age
Status: Draft
Description
This NIP defines the format for storing and sharing age data on Nostr.
Event Kind: 1353
Content
The content field MUST contain the numeric age value as a string.
Required Tags
['unit', 'years']- Unit of measurement['t', 'health']- Categorization tag['t', 'age']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the age was recorded['dob', ISO8601-date]- Date of birth (if the user chooses to share it)
Examples
```jsx // Example 1: Basic age Apply to App.jsx
// Example 2: Age with DOB Apply to App.jsx ```
Implementation Notes
- Age SHOULD be represented as a positive integer
- For privacy reasons, date of birth (dob) is optional
- Clients SHOULD consider updating age automatically if date of birth is known
- Age can be a sensitive metric and clients may want to consider encrypting this data
NIP-101h.4: Gender
Status: Draft
Description
This NIP defines the format for storing and sharing gender data on Nostr.
Event Kind: 1354
Content
The content field contains a string representing the user's gender.
Required Tags
['t', 'health']- Categorization tag['t', 'gender']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the gender was recorded['preferred_pronouns', string]- User's preferred pronouns
Common Values
While any string value is permitted, the following common values are recommended for interoperability: - male - female - non-binary - other - prefer-not-to-say
Examples
```jsx // Example 1: Basic gender Apply to App.jsx
// Example 2: Gender with pronouns Apply to App.jsx ```
Implementation Notes
- Clients SHOULD allow free-form input for gender
- For maximum compatibility, clients SHOULD support the common values
- Gender is a sensitive personal attribute and clients SHOULD consider appropriate privacy controls
- Applications focusing on health metrics should be respectful of gender diversity
NIP-101h.5: Fitness Level
Status: Draft
Description
This NIP defines the format for storing and sharing fitness level data on Nostr.
Event Kind: 1355
Content
The content field contains a string representing the user's fitness level.
Required Tags
['t', 'health']- Categorization tag['t', 'fitness']- Fitness category tag['t', 'level']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the fitness level was recorded['activity', activity-type]- Specific activity the fitness level relates to['metrics', JSON-string]- Quantifiable fitness metrics used to determine level
Common Values
While any string value is permitted, the following common values are recommended for interoperability: - beginner - intermediate - advanced - elite - professional
Examples
```jsx // Example 1: Basic fitness level Apply to App.jsx
// Example 2: Activity-specific fitness level with metrics Apply to App.jsx ```
Implementation Notes
- Fitness level is subjective and may vary by activity
- The activity tag can be used to specify fitness level for different activities
- The metrics tag can provide objective measurements to support the fitness level
- Clients can extend this format to include activity-specific fitness assessments
- For general fitness apps, the simple beginner/intermediate/advanced scale is recommended
-
 @ 4bc7982c:4cb5c39d
2025-05-12 14:21:38
@ 4bc7982c:4cb5c39d
2025-05-12 14:21:38-----BEGIN PGP PUBLIC KEY BLOCK----- mQINBFav2jMBEADPCRsFp9Vtw0vlkeho2v8lIPblVNNeW43HLNXeEGvgn+gaK5sW 9H5mbp6ZLEjbdEr7zc3eu7iLFudw9IdJCLKYcqkXWBpAQF7JF6l4J18oOQK1Tfzc QyU5jWuAcc+Ds8REW91X/N9Ae/QF+dtRyuv1ILFKZ88G2za/TdV06PuNdyi3qTlD 5HPVhd5YrZyY7GVG1gTi7Wtj6tONGjjQARR6T1LDuN75QmoDvw3m68U5QnoECGg4 BFAdPrnFxYpTCl6SyV9AsCfzTwP2mIkLKZi7X/wSubt4b+nhPMuFeZ/6XFCfHCD4 mEcQudyXByi7FgAXmX+UPS1iFtaXG8UJHM4Fq2k5FcjdLXW2s0kKk915XVEE9Q4Y wWQpTonr9FwgT+aSbV7UX8ihNhNCSQAv1RnIIt8t9hncztfZD7g/FMj4FfZ8GkI0 gmn3DliSlswBZbr1rN0HTitAzYKNUsiinIxwICfj9yRTcQ92F0ML+zwQB5UOXjEJ ra+D3tGjyVCNKO940rbjvj/QAvakoNBdCnbaZDKf26Hc0qpcn3DvGei0QLFJ2gmz EnK1dW4kftcJE8piibvq35EEptqkDiCMlI0Eq819vtJBumF3ZSBjMeEB1IPfSvDG 1OoUXXS0TGwCGstjMTRQ1S2D8fDb0ENBrbdhyWXZVQFzxi/YMwkNGswDoQARAQAB tBpzaGlub2hhaSA8YnRjaW5mb0BzZGYub3JnPokCNwQTAQgAIQIbAwIeAQIXgAUC Y+g7QQYLCQgHAwIGFQgCCQoLAxYCAQAKCRBKdYg8wbHTTG6OD/wJ9V3tjvaerA6Y GViWU6h0Nrvjs6/NWq48K3hP9eqy9n7CKVOviCjglF/yf1FEfEDg7LKYtFYLs1pf MFzNolynfGearK7HQeOXRoNFfkDqQWcjPWeVWhkEgxrqq9AMg+7gHMMtKnHWezJT E4NaAui7uW7rTiOvS8PT8+Y3uATermzJ0Cmb1c0su/s9in3bPwnmxJpbj9EruOWg MVY8Hov5fEJTwghIwoVBR2D4nWObQMWQsiNrEG/XdPeE1XzHGLrSmH64o6T2vWK2 XkQU6TVDBKhsIy0EjX9B36Hx+MmFx1pfHfxtGpAgZKwnEnMIoNc2vvrkjJhnRCUQ 1MfMoPDnn01mOT/kNkijyTUlh4rYeqa/A5JuqLbQ6qWz4e9rodu9C6/drn7Ivk/D ipRyMihNKbWq1PkAr7I9YQ/1NAM8ZmUE/bFL7/t6rDsa5IinwUeu/WGqNmKHIo0o u5vQD9zwmYOqeZLo2vzmmr/NkaRD7/3j5pb81MTjZzqTh/BGI31TEbjWpJ4StJ4g 2QNcXamGa/7/TpgI5u2EQojdvUojzSg7V3/ZNsNaJnDnqtZNzY7n2q4qvE2H/xJq z5y0SsTgpMPktt+ljg/T3po/LGQIcCPE4EBpSBKSpi0VWvkGVM2sraUCzP82c/X+ ztr12YwcckdET9SWDtSloE942tXKO4kCOQQTAQgAIwUCVq/aMwIbAwcLCQgHAwIB BhUIAgkKCwQWAgMBAh4BAheAAAoJEEp1iDzBsdNMrLMP/1pQZUXNzG9FlhBBGA8X ko+ObEvuVUvtZzTu8DXrQGDp/DYQq+O7YWhZ8WwyxYJx718bkIemHP5IbXbzmeS3 Nijf1mszrCbmw7QZ496YTihoZxyeb8MHYECPAiUbz9Ie2S6/isF45LZX3SbkwlYc M5UfV4iaXqvKSuydRJ8Xk68rn+AiEXFrv1vcGy7cqDz4PBOd9ZJwiAWhr0m9hMZT uDqYPI8choUh3uhpMIEf9YLD77ru1xl0Uba8e34qrOs+Secfv81ItbFION9z0A17 W2/q01dQfojpcoC+YS3CXXCJGm5TwYniIWVUmtL4eIfg6T/ZX5o5Am3aj4pQxr+E y/NNkUvplXZ+nG3fG4mthY4r+NV4E/RSsZJDU55BAWhZj3fHVhu7Q40yVMHLJNP9 KKCdacd/WWJtUX3Z1X/mQplJcMCYwhvdPNCctDpHrEyuIlvDvJuqbCY5eBa0hk8z jRNA9IghWW7JMzcnQR5u6FXWiqmcfFOEJwDUu8hM057Q6e6/FRPjlmua6SzcMK+k ERS+AwAIX4BIaLCnE7ndizQ/y6ek2hpKFXzPBLmxLyID91/wlA6NzbtyZkgZvJ7X g/7Rtt4FyZwKZqbfBFrjzLIyFTkmJ0lSPCSuWna5vaSg1HXPfc05wOUXsGV8xA8D zrolAoj4OIo//H2YMvLy5Giz0f8AACeO/wAAJ4kBEAABAQAAAAAAAAAAAAAAAP/Y /+AAEEpGSUYAAQEAAAAAAAAA/9sAQwAIBgYHBgUIBwcHCQkICgwUDQwLCwwZEhMP FB0aHx4dGhwcICQuJyAiLCMcHCg3KSwwMTQ0NB8nOT04MjwuMzQy/9sAQwEJCQkM CwwYDQ0YMiEcITIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIy MjIyMjIyMjIyMjIy/8AAEQgAyADIAwEiAAIRAQMRAf/EABwAAAIDAQEBAQAAAAAA AAAAAAYHAAQFAwIIAf/EAEkQAAEDAwIDBAcFAwgIBwAAAAECAwQABREGEgchMRNB kaEUIjJRcYGxFSNCYcEIUtEWFyQlM1OSohg0YmNzgpPSQ1RVcpTC4f/EABkBAAMB AQEAAAAAAAAAAAAAAAABAgMEBf/EACIRAAICAgIDAQEBAQAAAAAAAAABAhEDEiFB EzFRBCJhgf/aAAwDAQACEQMRAD8AAbvwd1NZkuKf9GWhH4miog/5aEpOn50UkLQC R7s/rX0K1xpmuEJk6RW4g9exloX5GuMvibpeY2U3TRFxCVclH0dKh4irpfBWfOog P4yUgVyMdwHG2n8q8cGZQw/CfiLV3dk4nH58q/E2Pg/NwpjUaWCT0W4QfMUUgEN6 C9tzgAfnX43DdcHq4p/p4XaLnpzA1iypJ6BTqD+teU8CkryYd/jOJ7iBn6UUg5EM LbII9kVbg6emTpAZSppsnvcJApxyOBd/59nNiLx05kVjyeEesYSj2cL0gD+6dHOi ogZ8DgVqO4xw8zcbVgjOC8rPkmhu8cO7zZXFokKZVsOCUbv1FFyLBru0glqLdI5/ 2Mn6VbTf+IEMhMiRJUnG3ZIjBWfmRRURWxPrirQspJTkcq/RDdV0xTYe1Jc3QW7h YLPKHeVxSlXiDWQ87ZXlZd0p2ZByr0WUpvPjmqSiDbMDTWg7nqdakxZENnb3vubc +Ao1T+zvqpYym4Wkj3h1f/bWIpzTvLbbb3BXn2mZKXCPHFbdvviIiQImr79EGOQe ZCgPjg0nFdMSk+z9/wBHXVf/AKhaf+ov/tqf6Ouq/wDz9p/6q/8Atrft2v782/ln XMGU2kY7OdAUgH/mAzW9B4lanW+cq01NQPwNSy2o+NTqyrFPO4Oaht7qm3JEFRBx lKl8/wDLVNPC29KyPSYQI961fwp9t6/vTqgqToztmu9Uae04fkDiuL2tbSFf0/Q1 8ZCj6znogUB80mjVlKhDq4ZXhPWTC/xq/hVJ/Qs+ODvlw+XuUr+FPh3UfDt93Y8u 4QlH+9YWgDxFeC3w5lqAZ1THCjyw4sfrRqPg+endOyWjjtmD+YJ/hXH7Ekf3jXia +j/5C6amDETUNvcUroN6D+tVX+D6lt5iy4iyf3TVJR7Jkn0Ii26Rm3KSlhuRFbUr oXVkD6Uao4CamcY7VE+1KTt3eq8o/wD1oqk8HryzktJS57tjnOqY0jra0J+4Vcmw ByKCVAU6gZtyFvdNAXa0qUl9xhRT12bv1FSmC7c9dQhskPreQOqZEYHPzxUqtYBc hTtKlME7FOIPfg4q43ebnGQezlvpJ9yzX0C3qrhFfiS8iEy4eoejls/TFezw/wCG moGyqDMaST0LEkcvkaj0aUINrUl1BClvhwjudbSr9KujUvapPptmtkjPXDZQfKnH J4B2p5sGDeHkH3qbCgfCh2ZwEvUcqMSdGkp7gfUNPZCoXyZumHkff2F1pZ6lh7p8 M1aaNkSE+gX26wFk9FlRCfA1rT+Eeq4gUr7OLgH90QrND0jSN9hubH7dJQT72zTt DQSQp2qY53WniAh0p9lt50pz/izW7D1lxVgrKu1hXJHuOwj5EEUrXYLrR2rScjuK ajfpjQ+7cWgZ/CsilaHSHQ1xo1Tb1BF20gVH8RacI/Q1qxOPWnpDgbn2qbG7iVIC wKSsW/32IrLdwlJ/LfkedXV6wmrAEuJCkj8RcjgE/MU6iNJD0b4gcNLsrD0uElau X37JSfpV1myaBvCCYbkFee9h8Z+tfPxv9ikIKZOnGUk/iYcKT51G2NHvthYfuNue V1ASFpHzHOp1XQOI/JHCyyyMqjvLQD05BQrIkcH0bVFmSws9yVNkedLCEJUcZsev XAB7KHXFtjwPKiOFqbiVCSFsTY9zR0GVIXn4YOaWrJ1NWRwkmZ5R2T+bazWa7w3m RchcV/HvCc1bb4u6yty9l20yhZ7i2FDNacXj/ZgsN3O0Toa+8gpWKlwbGkD8TSzl tkJc7HtOfNDoIzTLtsOxPxWk9q/EexzDT6gM/PlVeJxU0NdkpC57aNwyBIaKa2oz +lryN8OVDd/4TgBHyqanH0Pj4fjmnS+3hi7OLQR7LzaHUnyofuOhj2brztrs8wJS TybUyo+HKi9uysJAUw+4kdxCs1+O2l9aFIEtSkqGCFE01kl2SJF3T+m5MdyQ7ZJ8 FaTgvRF9okfOqH2NBSlRt+sZcRwD1Q+laPMGm1O0YVRlMI7TslHJS2vA8KE7joV3 CkbnkoHetGRTWV9oaBuIeIkUA2nV7E9tPQGQlXyIUK2GNc8U7V61wsUe4N95bTt8 01hSNBPtKKmZSASe7Kaz1QdVWlRMSfJCEnklt448KayRfspJBwzxtW24W73pKQxj qpCgryIqUEHV2qYQxMaTJSe6QylVSrTgS0gPTcdJSifSbDJYUe+NI5eBqzHiaSc3 GPerhbz/AL9rI8RXiZw91RbiRJsspPLOQncPKsR61SWSQ/FeQR3LQRVbDDCDDuzL gcsevGlbT6qTKUg+BokjX/i3bAC1KbuKCeXrodz4EHFKURdp9nmPfXdrtmFb2XHW le9Cyk+VCkuxUN1rjVre2L23XTbS0jkT2S2/MZFbET9oO2LA+1LFJZ7tyCFjzpOx tU6ggoKGbtKCP3VnePOryddT3AlM6DbZqU9zsYDPzFH8MKHVG4m8NL/lEtpppajj EmKAfEVcTYOGV/GIjsEKHXsXtp86Rwv2mLgpX2npdltSvxRHijFeVQdCSQOyk3SA 4T1JStIH1o0j0w5Ha9wcsEpBXBuDwz09ZKh5VhTOB0oEmNcGFjuCwU0vIlljtrSq x6/bjlPMB9xbWfh3URx5fFC2JSYOoGrkjPIIfQ/kfDrih430w5Okvg9fWNxTDQ8B 0U26Dn5UPv6AuUdakvQZKVJ6jYaLY/FTiFaXdl50+2+kDqhhST5ZFakX9oCGghFz skhgj2lJUD4A1Gkh2K13TTycpSopx1Cga8N2O5x/WjukEc/VUU074nFTh/eloakY aUsZHbsY8xWu0xoK8hJjTIJUegbkBKvDNS4zQWIhi46nt3NMuT+e5W8edXUajub4 2zIcCUOn38VP1FO9egrQ+gmNIWM9MLChVNXDlAJKZDax3BScUtmh2KiDFh3p9UY6 SjOOhO4+iu7CfgDWo7w+s4b3+g3mAo+0EtbgPCj9Oi34D/pEaMjtE9FNq51stXO7 w0BD0RagnvUmluwsVsW0XOAMWjWLzIT7LcgLRjx5VdTduJ8L14syFcmx1wpCvLka ZLt6Yfb2yrelYPUKGfrQLqq12iWtDsCCYbuPWUydufCrU49jtMzEcWNcWtzF2000 tsdVNoWk/qK04vHu1ZCLjZprHvKBvA+VBjzmpbVziXOZs7krVvHga5K1fektlFxt 8Cck/wB9FAPiKr+GHA1YnFLQN3TtXMbbJ6pfZKSK0UM6NvIBjTYpUvmOzeAPgaRr 100pcF/1hpUMrPNTkV4p5/Cqi7doOSCUXS629WeSXWwseI7qXjRLHtK4ew5SMxpq v+YBQ8qlJqJp6S2oL09r5sHqltUlTZ8DyqUtCbCdj9oZ6PtTdNMPN9ylIc2+AUK1 Y/G7Qt0XsuFueY3cip5hKx4ikO1rK+oTtcmJfT7nmkrz413VqqNISBNsNve95bQW yfz5VVREP9M7hFqFeN1p7VfLJHZK/SvbnCnQd1QVQZGzd+KPKChXz8zcNJyEkSLX Lik/iZWFgeNWGY2nspNu1JMiEnmHmSkD5pNUoJ9hY4pvAKK4k+hXhaPd2re6sGZw GvLWfR5cSQPiUnzoZgz9WRQr7J1yxJS2PVT6Xjl8FVuQtfcU7ad7rCbi2ocgW0q+ YKTmh430w2MeZwh1TEWoC2LdA72lBQNY0jRN4hJK5NtktJHUqaVgeVMSNx8vURQR dtLnlyKmypJ8CK34nH/S0lGyfCmxieRCmwsUtZ/B2ItVtWkHLasD8uVeEQnmnAtj e2pPRTZKSPCvpJGtOGt7ZSl2bbcHmEvI2Hn8qso0joS7JPogiKKu9h8Z+tS7XtDs +eoeotR2zIj3GWkHkQpRUD41oDXt6cQlubHgzUp7noqefzxTlf4PWlxRVHnPoSeg UAqsqRwceTvMeYw4PwhSSCaFOgFZ9uaemhRuekY6VE+1CcU0fCvwsaCmJTtTc7Y5 nmtWHQKNZPCq8MZxCS4P92rNZEnh9OY5vW19H57CRV+ZhwVYdtZbVm0a+Q2ceql4 qbJPjiiCHP4lWxKfRLzFuSP3Q6lz686FpGkFt81JUkjplJFWYukpTyUGA3K7Ue0p vOKXkT9lew1Y4ka7tqwLppzt0e9tsjPzHKtqDxqtDig1cbdMhu9FDbuANZ1u0Lq1 phsxL9KYUQCUvHcBRBbtGX5RP21cLdNST+KICfGmnjftCo0mtf6QnJAXcY6c9zo2 1aSNLXU7mpUNwn9x4fxqo7w103Kyp+A1vPXsxtHhWLK4MWN1RVGmTIx7tqs4qWsX ViCd3SNteR90tQ9xBzWZI0Il1JAdaUO4KRQ0vhVqKEsm06vkIA6Bzdy86prj8WbE 6sNSftJpA9pSUqCvh31Gi6YFqdw4J3g24LH7yKD7loJqOSDHfZwe8GiBfFTWlpWB c9Ndoke1htSD+oq/E47WZ4bLnZZsdXfyCxT1kArZelQ2vDCxu6jNSnOzxA4bXgf0 iTEZcUMESWigj51Kf9fA4AJ7gVCmK32jU0V5s+yFYyfCsSfwM1VEBMZliUO7Y6Af OqMXQCXiF2HW0FZz6oLqmlA+NaybDxaszZVCurkloDOWZiXPI1pp8JBGbw31VA5S bLJSfcgBf0rEesU6J6r8V9o+5bZFM1HEfipp9vNwt632/Zy/EKh4pruzx8lEhq+a XhvD8W0FJ8FA1Li0AozDdTzwg/GvbD9wiEKjyH2SnoW3VDHnTqHFDhld0g3PTTjL g/cjpI/ymu7cXg7enMR7kYi1dEbijHiKLYCki6t1DDX6lzecHudAWPOrR1rLcA9M tdtk+/cyEk/MU1jwf09PQpdo1Aw+SeilJOPCsuZwLvCSTGfiPo6jCsGhTaFQvkXb Tcn/AFrTamCfxRX+/wCBro1H0knK412usJ0nkCjIH+GiCXwm1JEb3/Zi3Eg4+7IN DcnSc6M4UPRJDax+Etqp+VhRuxHLzHATZeIJIRzCHZC2/lhWaJ4+suKEBKCpUKeg DokoXn5g5pWOWN9Jxg/AivKLbLjqy2txtQORtUU0t0/aDkcrfGjU1vQn7W0oTk81 NbkjzogsnGu1XWSmNItc2K6r99ORSLF61JCRsRcpe33FW4edEFplajvcRSloZcKe RcUhKFeNZ5JRSui0mfRd5b9KtHbQ4jL7hAUlK09RVfS90RPhlBiojPNnattIxg0v NE64lRZP2TdXANpwhSj5UWq/qzVLclC8Rpg7jy3V5j/X/R2Q/PcWn/wORUrw2oKT kHOa913xdqziJUqVKoCVKlSgDMvVukXCIUxZRjvgeqcApP5EUir/AHq522a/Eudp tkotqKSpTACj8xX0RQXqnQqL7LMxhxpt0jCkrTyJ99VGTQ0rEM5e9LSjtn6YW2rv VGexj88GpR1cOEd3JUppuM7+SV4NStlkJ1PnssOIJ949xq5Eud2g84s2S1/7XCKf Kb7wYvwHbxWobqh1U2ps/MjlXQcPeGt7VttOoGmlEZShEhKvrzqbChRwuJGtICQl q8vlA/C4kKB8a22uMN3eTtulotNwHQl1gA0aucBC8lS4N/YdT3ZRnzFDdy4H6pjl QYZjyQOikOYz8jSjIXJnfy40TPUBc9EMIOea4ju3Fd1ROEl1JLU262tXuV66fOsG bw31PABVItMkJHUpbJFYrlkmxiQ8y4z/AMRBTWmwWHTHDuxy2+1sOuooKj6iZH3a j51oxdD8TLatK7Rf25aUjKTGnhXkaVqoKx1KVfCvcd+fb1bosmQwR/duFNG4WNlO quMVh3plQpEhKTzU7EDg8U1ficd7sw52V504hIHIq9ZB8CKW8LiFrCApJavcshPR KyFDzrdY4x34p2XOHAuCfc8wmio9oLDxHF3QV1SEXWyONKzzPYpXj5irTM7hRfHE lqUIzh7juR9eVAC9f6MuaNt30MzvPVyIsI8K5B7hTczhDV5tThHUq3p86lRiykM2 Rw70tMjOyLfe0hKU7v7VKkj40obxIVbZyo0aSF4OAWz1q1cNO6ft9tcmWTVqZueS o+wpX88cqG4gV6YHCd2D31z5Uki4vkNrboLUF9hpmRpLaHMggOKwaMYydQW+xrg3 iMrtGPXYfHMZFEOh7g09bmUpGCU0fpbafa2rSlQ9xFeeoQzcPg7vP4kuAQ0fq9u7 wQh1QS+3yWk8jmjJl5LqeRrMOmLR6QX0RENunqpHKtJmKhgYRnArqxRnBU/RzZp4 p8xVM71KlStznJXCUh9xgpjuJbWfxEZxXepSasCi08phxEd0qWsjO/HWulwVITb3 1RNvpAQS3u6ZqzgZ6VWnNregvtNr2LUggK91SkoIq7Yo5nEvWlrcWJGn23kIOCpK Fc/CpS4vVzv0O4SG2rjIRsWQNquXWpWycaLaSfop/bXDe4rPpWnLhbt34or+8J/P BrsjTXDua4fQdZPw1H2BJjHzIrMuHCzVVu/t7TI+KE7h5UPv6euEUqEiM82E9dyC P0rbYxGDC0VfY33mmtbwH8H1ENTS2T8jyrUEzjVY0qSn0uY2nHrhKHx4jnSe7Bxo +qohSe8HBFaMS+3+CoLi3Wc2R02vq/jRsn0A1muNmt7Q2EXjT7bhT7S1tLbz4cq0 4/Hqy3BopvGmOROFBKkuE/IgUtovFfWENnsH5qZaM5xLaDn1rQHFZmY8F3bR9jmH GCoNbDSqFgMVvVHB+9oSJMVqE4T+NktqHzFdTo3hjfDm23xpsjqEvg+RpcN3/hlc 1lM7TMy3qPMuRniQD+QrqNN8Mrg4pcHWEqBuHJqTHyEn409Y/RB5J4GMPtqVbb00 4M8t6MjxBrAncD7+wD2BjSfdsVj61SicPru20XdM68hyVZyhtmYpoq88ZrWjReMd lRvafkzUA8gXkPj60tfjGCEvhxqGCCX7VIAH7qM/SsV7T8mOr76O42fcpGKZo4ta 7tGEXXT5dCT6yzGWnl39OVaUfjjZJaki5WAJKjzPqq8iKThJAhN+hejoVjIJ7q7Q jho7k86ZWu9VaTvFrBs8FtuQTlbgZ2KH5UuYxL4CWk5JPLArmyJ1yXAN9EasRa5H YyFbUjkCTypw2/U0Z4Aodzn86REPRl0lFLiWFEnmAKMrfDm2wpakMrbIA5mvNnHV 3FnfBbKmOFq6trAIUOdWhJSWyoEUCW5x1zaAVEZ76JkJU3EcWonATWmPPJ8MWT88 F6LibiO0wcYq2iShY5GhyG0qSjeFdTWo1GWhIwauGSbIy4ca4RqhQPQ1+1mffJOB muyPSCK6I5P8Od467LRcSDjPOuEl1DbKlOLCEAc1E9K/EsKCtyqwb867IivtFh0R dhC3Ep9YfAd9Ty3yOEE37BeVoPTN4eccYvqO0USojck4J+dSgKdprSL0laWtXOQn 1cyh9kpwfjUrpWPgJWnVnNPFDidYNybpae1Sn2i9EVjxSauxf2gAslu96YYWk9S2 efgoUurfxT1nbUpQ3dluIT3PIC8+NbbPGKdJSRebDaLjnluUyEHFbLV+0YBt/OTw vvKOxuVgXFB5lYjjr8U10TYeEV+UHYd5MRahhLfbbQD+aSKCFas4cXEBM7Rb0VR9 pcV6vQs/Cm6JJYvVztiz+F9veB86NF0Abv8ABG1z/XtN+ZeBHRWD5isGfwKv7IJj iLIA/cXtJ+RrOZ4asuJDundeQVZPqIcdLSvrWkzZOL2n2wm2XRU5nqCxJS8B/io1 f0YMXDhZqa3p3O2d8pJwC2N/0oak6fmRFlMmI+0r3LbIppfzncUrGB9qWMutpICl uRFDPzTyrQa4+srXsu2lTuxhW0jP+YUtJCEiILzSt7RUkjoQcGtC33W/2xQXEukx kg5wl9WPDNO0cROGF6aH2jaFs9/rxwcH4pNdUWPhPfWyqBdGI7ixkDttpT8lUv6X QCxh8V9bQm9i5/pKc8w+gKz+VXlcW3ZrJbu+k7PMUU47QN7VD86PVcGLPNZ322/N ug9FHaoeVYczgde2t3o70aQnPIhW3I+dTswFu1NRc5y0IYSyHPZQjoPyo10ppeZC mpkOsF1gjKeVDdx01O01dyxLZUy8363vGPfW/H4wXexx0xWI8RaW04BW3k+NY5E5 8GsHQ97IWvR0Es9mQMEEVqSYsJ1re8hvA71V88tftCagQrLltgLHuwRV1P7Qjr6Q idp5hxPfscP61gvztL2W8lu/Q4lOQ2l4aU3/AMtS7TOysElxJ5hOBSxh8WND3I4l xZ9ucx1QcpzRaxedOXiyuRI2omtq+eXhhQH51g/zZEzbzRdWddLXhtxBZU764/Oj qM4laMgilM7/ACOsCVPzL4p1XujpzWavjFpW0PKEO3XSSQPVK3AEn5ZqsX58idiy zjMeYSnrgV7HKkAP2iWAMDTrn/yK0Lf+0Lb3SBIs7zIzgntAcV2RtezlodpUAoJ7 zVVNwjLdW0Fex7RPQUHQOKNmucVUlhK9oTnJ91D1413Gt0pLyoy3Ybg3KCe/NTtz SLjjsGuLV5ts67IjwUNZbT67iUj1jUrVXrvhhdUhNwtrjKz1UWenzFSt0pUJmPK4 ATVEqgXaC+nHILBHmKHp3BXVMXeUwG3gnvZczmtiNw01TCy7pvV8aSUc0pZmKST8 skVcFx412HAXFdmoTyJKEugj5Vpr/pkLeXoK+wl7ZNrlNHuy0TWS9YpjCiCFJI7l JINN1HGvWEBWy7aYbXg4JUhaP/ytNnjTpG4rUL5ptTCiMFWxLufAZp6yXQxDGA8k gkjd7wK7xp11gYTFly2ADn7pwp50+0XPg3qDs0lxiI4rkEqC2jn6V1PC7Rd0bWq2 39vnzTtdSoDzqNmApoPFHXUHalN4cdbSMBMhtKwfjW03xiuTxAvNjtE8YwoqY2qP zovlcCpJG6FdmHUnoFNkedDdx4M6kjlSkRUvpT3tKBz8qakBW/llw+uSiq6aJcZW faciO4HhmuiLXwmu5zHvFxtS180pko3JT+XPNDszQV+hnDtpmo/MtEjyrHVZJbZI U2tOOoKcVW7AYbPDeK/td03r23LIVkJcUWz5H9K3Y9q4sWkqMSe3cWRjapD4Wk/A Gk63bJCFHswoK/2eVXI03UFrXui3Gaxg5wh0gZ+FS5X7A29WzNTO3dbt/Zdbkq6h SMDH5UET23CorUORrduV8u10eS7cpjshxIwFOHNVJBS5GOR176zbGgaPKvIJFXHm U5O0g1x7E9MVLYHlt3CvW5imhw90FO1hH9IRI9GYScBRGcigi0afduDiSpJDYPXH Wvqjhrafs3TrXqbAUjAxisZZFeqKUeLEZrrR0/TcoRJEsSGsbkLAxS6eBQo5JJr6 14kaOOpLX20dOZTI5JH4hXzNeLC/EdWgpIUk4IPLFa3RV2uAdCj76/CskGva2nEK IKTW5oywnUGo48ReOyCgpefdUuVK2Qk7GDoO1lOl2nnRgOZAyOoouu8iHZLE1Ldj IfVySltaeShWnJhNx/RbXFKGylshAPTlXjUWiblqK0R/RZDTrzKdqkhWEn4Vhjbl Kzr1UY8i5kar0ZIBVcdIlKj7S4zxHlUqrdeFuqGSr+qH1Ad7RCh5VK9JTdHI/Yvm PtGGvfGffaPeW3Cn6VuQtcaytikmNe5wSnolbm8eBpvN6i4P6jUEPMphOYz67ZbH j0rsOHXD6+c7RqFKFK6JS+lXkedSpfSQChcbNUobDc+PAnI70yGPa8Kufzp6enE/ begrc44eRXHwOXzFEczgPIUlXoV0YfR1G8YPlWBO4H6iYaK2mmnsdzboJPyp7IDw ZXCK8NntoFyta/e2Sa/EaG4f3FzFo14uOo/+HIRg/pQ7P4eX23qUl+3yUKAycIzy +IoedsMhtRJSsE/vJxRsA12uG+tYjXbab1smUhP9mluYRkeOK7tu8bbCFBxDtwTy O4lDoH0NJ9uPOhncw680R0LThT9DWvC1rrC1KBZvU5KQMAKc3fWmqAaX88GtLaQL rpVBQOSlFK0HPmKtM8YtMXBRRddMraCvaUUJVzoFicadXsYTIciS2x1S+wDn5itV njBap7iUXnRlvfCuSlM4B86VR+AHUa9cLbutLhSzGdP4VIUjHhyrsrhvpC+b3bfd FErORsdCgPlQEq+8JLmkofs1ygKUea2ugPyPSvEqw8Pm4SpNq1rcoihzCOavIAEU qXQBVN4FbwDGuqSf943j6UudXaPf006uHIUhSwMhSDyIri1rrUFhfP2XqeTJabOE CQNwI+BrNuurbvqZ0v3J1DjqhglKdo8KhqgBchIcKVHlXpbiUABASa8SGiFkg86r hKietZsY0NMaxtLEWNBehobXkJ7THfX0dp2THdtMcMrScIGcV8SJ3JOQa24Gr7/a 0Yh3WQ0ByACsgVzeNqWyLTTVM+yLpe7bZY/bXCY0wju3HmflSh1wizypibgYoehy RuQ4gFOT30B6JtV11texOu0519hshR7RRO8/Cnvd9Nxpuk3oKQMto3NnHskDupTy NvU0jFJWJZuw6QuCFeu8y73I3VZsFtt2kpEia06Fkp5KUeYoLuYdiy1DJSpJ54rO aemTpbcdLzhSpYB592azqXb4LVJjcWtepoyFuT24EhQJbW4raCPjVVvTXEi2KC7H fWpTQOQhuWOfyNc9S6alSocdERxvLbQHZ5x3UuZdovVrfUnMhtSeeW3VAeVdX55Q SoWTkaCtYcXbIf6balPJHeqPvHik1KWcLWeqbdj0e/T07fwqc3DzqV2rU5Q1buvB 27/61ZZ1seUeZQSUjwNdmdB8Or3lVo1euKR0S+ACD8Tg0LXDhhqSAD2lskJA6lKd w8qwXdNTWge0bdSR3qQRUJsY02eF+q4Z7TT+tmnwPYCZZTy8xXcucbbA0rITNab5 5IS6VD60oEQrlDI7JTiccxsUR9K3ImutZ24jsL1OTt5AKIUB8iKL+gMVjjDri1DF 70uHUj2trS0H6EVoNcbtLTQGLzpp5onkr1EOJH0NBcfjdq5hARKEGYMYIeYxnwq5 /O1ZZ5AvGh4MknkVtYSfMUcPoQaNXbhJqJ1RHZsLCeYKVNj+GawdRWrhkwyosXl1 C8cg0O0FC98uWjZbW+xWR+3LUMrC1ZBPwzQJOeKlHCuVLgZoT3bMy4oRHFuozyUp OKzFzImSEIPhVI868EcqmwLReRjlyriXjzAUarkV+YxStiOoWrPWr8d9SU4x1rMS o5ruw8UHnSsCy8oEnNVuSTXVSt9cVc81AzwtQFeAoEYr8Uk13jWybLGWI61j3imA ZaZ15frRFTFtMOOpLY5nYSfnRAnjRqhsqZejRVFQKSkJINBMDTV7RkMvNR9/tZdA 8a37NplMO4tvXCZGddChgBeR86ylGF2bwUgcuF4fmyVuPNFC1nOMUccN9NremouU xshA5oCh1o/i6J07dlJlLDQdT7iMGtdyK1a2ihpaNgGBisZyVcGqg75Mma4hUlY6 AHArLkutYUlaQoHkcjNWXlJWpSveay5Ccg1y92dCjFoxpOl7XOJKNzSj+7Uq+kba lbLLNL2T4ofAgPGq82xYZvOj5QVj11NhScfIir0fjVoa5fdzobrGR6weYBxS5h8b dVsL/pkeFNT0wtvBHzrRHFTTN1bS1e9FRSScrW1jr7x316NnmjBRO4UaiSdki3Nu dM7i0oV7PDHR1yRmDPPPoW30rpdF7g/d3Cl6JKtqnBjcknamu0bQujpCkqsGvFsn PJLi8YPlQARTOBSVFRj3Ftz3BaMGhu4cGr1CSVtxkyAATlpYOPlWn/JLiNbQfsPW SJrecpSqRzPyOfrXh3U/F/T8VX2lbWZDOMF8pB2/nlJpgLG4xXoC1NOoKFJ5EK7q HJCiSTmiG83GXcHXHpLaUuKOVbffQw6SQakDzvIr938q2NFNtv63sjT7aHWlzWgp CxlKhuHIjvpt37R9tsFj1/cXbew416cwYqSkDa0VJUoIP4QdxTy91ACL3ipuB76Y XEfTundNW6Gm1t7pFxeXLZX2hV2cQgbE4z1yTz68qM5llYnTNGWiRbLOLJOaih4t JQiWtzsio5I9bacde+mIRYFegnnTAl6Xs7T2hEojKAurq0zPvD64D+wfD1fdRL/I 6wp1zNtcjTAjFmOtVviLuCv6wIcxuznIO0EhPfSATyT+dRQpjapg2iDw4kqtcUoQ jUbrLTj7W14NhAwhRPPkc8jS3S4D1ooZ4UMV0ZmSWB906pIHurQtdqN1e2B1Lae9 Ro4h6D0+ljfLnOKPeQqpbSGrvgXv2lKOSt5XPrRBYrNerwntokd1TY/FjkaY1k0x ouK+hSWRJcTz+9Oc/KmfBuVqjMJS00y0hI5JSkACsJzXRunJdiqtFm1LD2FSFNtj qSegrbkzZO7sXcnbyye+u2stdNP3GLZba6kekLCVrT3flWlqKGiMY45EloEn3nFZ ODfJe/0wd+U1VfOBX4t7aoiuEiW20yVLIz3CsXFmsZ8HNaxipWSJDqySrlk1KFFj 2C248IYTx322YUj91xOfMUNS+Et5aUezaafT70LA+tSpXrHmmHK4fXdhtRVbpHLq Nmaw5GmpzRG6G8g92Wz/AAqVKQzmY11iOhSXZjSxzBQtSavjU+qWoS4artNVHUMK QslWR8TUqUwMeRIedQd6VEn/AGTWWpClE5Qv/CalSpAu2KabNqC33Mx1upiSEPFs ct205xnuo0vnE2TfNPy7U7bnEh5jsQsuZ2ntu0yRjnywn5VKlAApqK8rvwtYERbP oMBuHzOd+0n1unLr0rZTrYjWNiv32a5i1RmWC1v5ubElOc45ZzUqUxFlOt4C4FjT JsUlybZ1lTDyZG1PN3tDlO3n7q6J1tZRqOZczpqUUTgVPhUnc4hztN4U2op9Tpj4 GpUoAydR6rGooUxCre+zIk3Fc0kPKLaQRjbs6Z5e1QqELH4Ff4TUqUAdG1vtf2fa JP5A13E+4AFPbPEe7nUqUmkB2j3a5RXN7bjoPwNao1TdHWihal59+DUqVOqKtmjo uFJumrGH1hZDZzkg9c06dXysPMN7cqDfM4qVKJJAm7AKU+pJOEq8KznXVOe0lRx+ VSpXM0joi2cys4xtOfhUqVKii7P/2YkCNgQTAQoAIAUCZ0teqgIbAwULCQgHAwUV CgkICwQWAgEAAh4BAheAAAoJEEp1iDzBsdNMxsoP/2amun27Yf9/9lXVZJUagfkm 5M4dBPDoC5YfR7IQ1kFjvexC5vSEQRcD8w/hxyrAlqdYOZqZ8K30S8DS5XFlo0DV O/UXSiglaaTHpZIBkiZwutB5BJA1BzGdj0CsQZnOc2lVaJQoZg29k1TBFvinO1tQ t5o2ue4GMg20CjNjDG7QmQ+Dex1rNSIlbusEPeNybyLZVoRsAEAWirwZ2khAwuxo S+EUs3hTRTXVuhg0Ed9zL4nvV3f8WiUoK0fTHLj5Esx8DBiB/IXZCGGRZziORupe xeugX7kOx5eRpmok7rxZIPIUEfBpC5Zr0EysVa6lh9b6U11eDPFZfNkIUAYJboj7 MvvvJkviA8kg8xEo4oe2eMrwOvMKnpPq0xtsOesmdT4iXREEAbndlnOm9L7o1lIn ZvH7fk3K+myDryh/JejgUNiz/Vk8s8JBCsD8vb9P0TdkG8Jy07VoiTcKdDjaNj9T dqjXq280OYwb8KprhdQmfSMfVhqOa3X0N5xFxIPutOZHYILenAbLQ9GXpNVhCshm ApW8F0cHqoPJXLyIyAQQRgib2zmUfY8aZCgxd5C08HOZMfnY2vdoYZ+tchVoHGIR mpo4RlLFY9ZF6NQW9c+bXJqVXpFNJqtRc2O7YZCs2HzisaudBnx1aFbz2HLDzSU3 ybKi93/CIASzyBkzVpLtuQINBFav2jMBEACxwOSaz5YrOdJ2pp3L/8454ACGhRGX YzKtNgj9gPNT6GyJDHW+x61TN1AeR13MqM5UaIvMrjhE17bh62LhkpBEvg2cRrYB Ge7r8J/8E0Q1i/FeFnjS7PeAGOmT32krDtz0GhcRYoTh6uWBIb3aiYYyU5dufit5 ObSjS3qWHRBdIr2Pie6/ppLOVXdeDsbtscU63HkujRMljYd4uPR6oJwFgdQbySK9 tKU/HUS3qhX8SJ6hEN6rfuzEONWynN36ofDS74W2srZxXF5rz7XxYMUe27+9sZd0 zlgTmXL+3wcUfyCTfr3ZxZdx0FL8GY53OrZDQmSCyY667133O/EzVdBLH5vY1I9u d1H2PxoDPQacjl36/mRCpKNGs2Oh52B3NbJ5U7YeEG4OMcA1zC2blih9ExRhi3gD KFcpTXklvJPPS4ffIurdYFTkcWa8Ko+Ck+RHEOl3qXAINrQk9B5M2+eK3SBt5vC8 L/+Ke0ah3vpkuLUV2Piimtgw38eoDw/H/3v+vQ6O5mYLTCqY59c84HZw2NWGaJdX gHZpr2DlwuEMCQkwPWUt53r+8/Sru4LaDjsJv2V6MNTTeYB9e4LfWwZhHA1Us3SU 4A47B5MpNmTXmBxVLfX0qVJfrs0c5726F16cuAqpL8pOQ5+O/UPQ9+F2l/1h3lxK w0I0ZBq4tOqhzQARAQABiQIfBBgBCAAJBQJWr9ozAhsMAAoJEEp1iDzBsdNMGugP /05GhajYg4ES54fn8lcbvnkGm1w5NVP7OS9wzGY/6nDTHX8rmMvVFBYQXerCBZEo IihXPBTuvQ3vYfXnfwglyRw6QvepLM3oez0iLLJPjQU25SgXutl2EIjVbzYtcmkX DGhUGi7IHSqmjIQumrTQWbHzyUAA58otUh4aPYl4aAKxCOMSJlqzUnOmkZRFIynC 6zxHZvh68G2bv503w7R0S867fjO7qnckRMQI7+MYRfWvTdiwqtw+0dKUkTDhkHIz 4sHHZmWISUXhC1kIA9BoxxVXddL5GoAde0L/62cSXL7HDt1tkA0hhO17is1wu3sm lLUeTvsL7LfXI3bOIQjY1CdlNyf65utFnvFsNNVav2ZEXGYcZH2uvKgY/quIa1+y Cbf8w/aYt+ahoi54NAldvoXE6EPs+bZuDviGLHXCLfQLuMu7NfJyJEkPbxLMf+58 k/bkZ8r7vC+x3EpRSI7oHaYYtoQDsRN2NIrRYwuCXlLt26dIGmmdbzLT5bribw7Q CZYkhjd9jnV7+dpAcVTVrE+A7AXb46JVvFaKrhl6rPIlcB81+XoSg4hvAJOWPvcZ CfWrtHVGvPzOJpNxBQteoYUc1SrVi/1j5WR+FnVDA68pY5QdK3fNSDXIhctNxMxC Yv5/cxSTVRCsTbtFg8tRHkJHhq4FVIk0O8o+TSVrfxzs =JPry -----END PGP PUBLIC KEY BLOCK-----
-
 @ 005bc4de:ef11e1a2
2025-05-12 14:00:42
@ 005bc4de:ef11e1a2
2025-05-12 14:00:42Hostr
Hive + Nostr = Hostr, a bidirectional bridge.

Hostr is a bidirectional bridge between Nostr and Hive. What you post on one is automatically cross-posted to the other. (See SETUP.md if you want to jump right in and run it.)
This is experimental. Expect that there will be glitches, errors, and corrections to be made. So, consider it very beta, with no guarantees, and use at your own risk.
Nostr and Hive have differences, mainly, Nostr is a protocol and Hive is a blockchain. Nostr does not have a token, although bitcoin is much-loved and used across Nostr. Hive has two main tokens: HIVE and the HBD stablecoin. More importantly, Nostr and Hive have similarities. Both are decentralized and censorship resistant thanks to users owning and controlling their own private keys.
Nostr users - why you might want to bridge to Hive
I feel the #1 reason a Nostr user might wish to use this bridge is to permanently store and chronicle your Nostr notes.
-
Immutability for your Nostr notes. Your notes on Nostr are held on relays; if they go away, your notes go away. (There was a “nosdrive.app” backup, however I do not believe it’s still working.) Hive is immutable. There is no "delete" and even an “edit” on Hive does not erase the original. Like with a wiki page, a Hive edit shows the most recent version, but the original still remains historically. This would give Nostr users a permanent record of their notes in chronological order.
-
Hive is an excellent long form blogging platform with stable and persistent links. Finding old Nostr notes can be difficult.
-
Increase your reach and potentially gain followers. Your content will bridge off of the Nostr island and be opened to 10-30,000 daily Hive users. Go to https://peakd.com/c/hive-133987 and look for “Hive statistics” to see numbers.
-
Earn rewards in HIVE and HBD. “Likes” on Nostr do not reward you monetarily, but every upvote on Hive yields rewards. For bitcoin maxis, these tokens can easily be swapped into sats with tools like the https://v4v.app web app, or others.
-
Help grow Nostr. Every note that bridges over to Hive will have a footer saying something like, “This note originated on Nostr,” with a link back to your Nostr note on njump.me. On that page, a "Join Nostr" button is prominent.
Hive users - why you might want to bridge to Nostr
-
Increase your reach and potentially gain followers. Your content will be bridged off the Hive island and be opened to 17-18,000 daily users. See https://stats.nostr.band for Nostr stats.
-
Earn bitcoin sats in the form of “zaps.” Nostr does not have a token. But, it has a strong culture of zapping (tipping) bitcoin satoshis to other users to reward quality content. Memes are loved and often zapped too.
-
Unlimited posting. Nostr is not held back by posting or activity limitations, such as with Resource Credits or community norms that frown on posting too often.
-
Even more censorship resistance. Hive is truly censorship-free in that posted content, no matter the content, does indeed posted. However, front ends can choose to show or not show content that the community has downvoted. Nostr is more free speech or censorship resistant...you post it, it's posted. (Relays can choose to relay it or not, accept it or reject it, but you could run your own relay.)
-
Help grow Hive. Every post that bridges over to Nostr will have a footer saying something like, “This post originated on Hive,” with a link back to your Hive blockchain post. This brings wider exposure to Hive.
Quirks about Nostr and Hive
If you’re unfamiliar with Nostr, it has a few quirks:
-
You have one private key, called an “nsec”. It goes along with your “npub”, your public key. Your npub is your username, your nsec IS your account.
-
You simply need an nsec, then a “client” which is a front end.
- You need to add “relays” to your client in order to connect. This is very easy, but how to do it depends on the client. Client's usually walk you through this when you start.
- Short form content (like the old "Tweets") are called kind 1 notes. Long form notes, like most Hive posts, are called kind 30023.
If you’re unfamiliar with Hive, it has more quirks:
-
Hive has five private keys, yes, five. Each has a specific purpose. From least powerful to most powerful, they are: posting key (to post), active key (to move tokens), owner key (to do anything), memo key (to dm/pm), and backup/master private key (to totally restore all keys). Don’t worry about all the keys. For Hostr, we only deal with posting notes/posts, so the posting key is all we deal with.
-
Hive has a culture of frowning on posting too often. Doing so can be seen as trying to milk the HIVE/HBD rewards that you gain from upvotes. Too much posting can be viewed as spamming and result in downvotes (this hurts your Web-of-Trust score, called “reputation” on Hive, and is shown alongside your username; you want to grow and keep your reputation up). The chain also has a 5-minute cool-down rule coded in: after posting, you cannot post for another five minutes.
-
Additionally, to avoid spam, Hive actions burn “Resource Credits” or RCs. Think of RCs as the charge % in your phone battery. Every action on Hive uses RCs, so they dwindle with every use. Posting is high in RC cost. Bad news: if you run out of RCs, you’re unable to do things on Hive. Good news: RCs also recharge. If out of RCs, you can wait and then do things later. For the Hostr script, over-posting means the script will post until RCs are exhausted, then it will stall until RCs are recharged, post again, stall, etc. You can check your RCs in many places, such as a Hive explorer like https://hivescan.info and entering your Hive username. If you have RC issues, reach out for help.
You don't want to over-post on Hive. To avoid over-posting, Hostr has two versions of the script:
-
bidirectional-longform30023.js
- Nostr ➡️ Hive - Listens only for kind 30023 (long form) Nostr notes to bridge over to Hive. Kind 1 short form notes are ignored.
- Hive ➡️ Nostr - Any Hive post over 380 characters gets truncated as a kind 1 (short form) Nostr note (with a link back to the full Hive post).
-
bidirectional-bridge.js
- Nostr➡️Hive - This script listens for both kind 1 (short form) and kind 30023 (long form) Nostr notes and bridges both over to Hive.
- Hive ➡️ Nostr - Same as above (380+ is truncated).
Which script version should I use?
- If you post frequently on Nostr (more than 2 times per day?), the bidirectional-longform30023.js script is likely best. Per Hive community norms, you don't want to post too often on there. With this script version, only long form notes will bridge over from Nostr to Hive.
- For newcomers to Hive, I would start with this script to be safe.
-
If in doubt, use this script.
-
If you post infrequently on Nostr (2 times per day or fewer?), the bidirectional-bridge.js (both kinds 1 and 30023) might work fine for you.
Nostr users - how to begin
You’ll need a Hive account. You can see sign-up options at https://signup.hive.io. Some options are free, others are not. I (crrdlx) have some free “VIP tickets” to sign up with and you are welcome to use one if you wish, see https://crrdlx.vercel.app/hive-vip-ticket.html. If the tickets there are already spent, contact me and I'll get you set up.
As with Nostr, the critical thing with a Hive account is saving your keys. Hive has multiple keys, just save them all. We’ll only use the “posting key” for the Hostr bridge, however. The other keys can be used on Hive if you wish. (For instance, the "active key" is used to handle your HIVE/HBD rewards earned, the "memo key" for private messages.)
Once signed up (and keys are safe), you can adjust your Hive account/profile using any Hive front end like https://peakd.com/username, https://ecency.com/username, or https://hive.blog/username. Just remember, every action on Hive burns RCs, keep an eye on that.
You can learn more about Hive at https://hivewiki.vercel.app if you wish.
See the "Setting up..." section below to set up the bridge.
Hive users - how to begin
You’ll need a Nostr account. Getting a Nostr "account" is nothing more than generating keys. A simple way to do this is at https://nstart.me If you wish to dig into details, take a look at http://nostrwiki.crrdlx.infinityfreeapp.com/doku.php?id=wiki:get-started
As with Hive, you simply need to safely store your private keys. On Nostr, your private key is called your “nsec” (sec, as in “secret”). Your public key is your “npub” (pub, as in "public"). Your nsec is all you need, but just so you know, your private key comes in two formats: (a) your nsec, and (b) the “hex” form (same key, just different forms). With the Hostr bridge, we’ll use the hex private key. Depending on how you join Nostr, your hex key may be given to you at sign up. But, even if it's not, you can always check back-and-forth between nsec and hex keys using a tool like https://nostrtool.com and choosing "Load a privkey from nsec/hex".
Again, just save your nsec and/or hex private key and you’re set.
You can learn more about Nostr at https://nostrwiki.vercel.app if you wish.
See the "Setting up..." section below to set up the bridge.
Setting up the Hostr bridge
To set up the bridge, see SETUP.md in the repo below. The Hostr bridge has a bit of technicals behind it, but don't get intimidated. Because technical things change, I’ll keep the technical how-to instructions housed at https://github.com/crrdlx/hostr
Disclaimer
This is an experimental bridge. Expect that there will be glitches, errors, and corrections to be made. So, consider it very beta, with no guarantees, and use at your own risk. Source code: https://github.com/crrdlx/hostr
Built with ❤️ by crrdlx
Connect on Hive: @crrdlx
Connect on Nostr: nostr:npub1qpdufhjpel94srm3ett2azgf49m9dp3n5nm2j0rt0l2mlmc3ux3qza082j
All contacts: https://linktr.ee/crrdlx
-
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ 5383d895:7b141166
2025-05-12 13:02:58
@ 5383d895:7b141166
2025-05-12 13:02:58LOVE678 là một nền tảng giải trí trực tuyến hiện đại, được thiết kế để mang đến cho người dùng những trải nghiệm thú vị, an toàn và dễ dàng tiếp cận. Giao diện của nền tảng này rất thân thiện với người dùng, giúp mọi người có thể dễ dàng tìm kiếm các dịch vụ mà mình cần một cách nhanh chóng và thuận tiện. Từ việc truy cập vào các tính năng giải trí cho đến việc quản lý tài khoản, mọi thao tác trên LOVE678 đều được tối ưu hóa để đảm bảo người dùng không gặp phải bất kỳ sự phức tạp nào. Bên cạnh đó, LOVE678 cũng cung cấp tốc độ truy cập nhanh chóng, ổn định trên nhiều thiết bị, từ máy tính để bàn đến điện thoại di động, giúp người dùng có thể tận hưởng dịch vụ mọi lúc, mọi nơi mà không gặp phải sự gián đoạn. Nền tảng này đặc biệt chú trọng đến bảo mật thông tin, với các công nghệ mã hóa tiên tiến giúp bảo vệ dữ liệu người dùng một cách tối ưu. Chính nhờ vào những tính năng vượt trội này, LOVE678 đã và đang trở thành lựa chọn ưu tiên của nhiều người dùng hiện đại.
Không chỉ chú trọng đến sự tiện lợi và bảo mật, LOVE678 còn đặc biệt quan tâm đến việc nâng cao trải nghiệm người dùng thông qua việc cung cấp dịch vụ khách hàng chất lượng cao. Đội ngũ hỗ trợ khách hàng của LOVE678 luôn túc trực 24/7, sẵn sàng giải đáp mọi thắc mắc và xử lý các vấn đề mà người dùng gặp phải trong suốt quá trình sử dụng nền tảng. Người dùng có thể dễ dàng liên hệ với đội ngũ hỗ trợ qua các kênh chat trực tuyến, email hay điện thoại để được giúp đỡ kịp thời. Điều này không chỉ giúp người dùng cảm thấy yên tâm mà còn tạo ra một mối liên kết bền chặt giữa LOVE678 và cộng đồng người sử dụng. Bên cạnh đó, LOVE678 cũng thường xuyên tổ chức các chương trình khuyến mãi, sự kiện và hoạt động giao lưu cộng đồng, tạo cơ hội để người dùng trải nghiệm thêm nhiều dịch vụ hấp dẫn và thú vị. Từ đó, nền tảng này không chỉ là một công cụ giải trí mà còn là một không gian kết nối, giúp người dùng giao lưu, học hỏi và chia sẻ những giá trị hữu ích.
Để đáp ứng nhu cầu ngày càng cao của người dùng, LOVE678 luôn cải tiến và phát triển các tính năng mới, đồng thời không ngừng nâng cấp hệ thống để duy trì sự ổn định và hiệu suất hoạt động. Nền tảng này luôn đặt mục tiêu tạo ra một môi trường trực tuyến an toàn, thú vị và chất lượng, nhằm mang đến những trải nghiệm giải trí tuyệt vời nhất cho người sử dụng. Các tính năng của LOVE678 được thiết kế không chỉ để đáp ứng nhu cầu giải trí mà còn nhằm cung cấp những công cụ tiện ích, giúp người dùng có thể dễ dàng quản lý tài khoản và tối ưu hóa quá trình sử dụng. Với sự cam kết không ngừng phát triển và nâng cao chất lượng dịch vụ, LOVE678 đang từng bước khẳng định vị thế của mình trong ngành giải trí trực tuyến, đồng thời tiếp tục xây dựng niềm tin vững chắc trong lòng người dùng. Nền tảng này không chỉ là nơi để thư giãn, mà còn là nơi để kết nối và phát triển, giúp mọi người trải nghiệm những phút giây giải trí đích thực trong một không gian trực tuyến an toàn và tiện lợi.
-
 @ c3e23eb5:03d7caa9
2025-05-12 13:00:36
@ c3e23eb5:03d7caa9
2025-05-12 13:00:36The issue I have with the term "mesh networks" is that it is associated with a flat network topology. While I love the idea of avoiding hierarchy, this simply doesn't scale. Data Plane: How the Internet Scales
The internet on the scales because it has a tree like structure. As you can see in the diagram below, global (tier 1) ISPs branch out to national (tier 2) ISPs who in turn branch out to local (tier 3) ISPs.
``` ,-[ Tier 1 ISP (Global) ]─-───────[ Tier 1 ISP (Global) ] / |
/ ▼
[IXP (Global)]═══╦═══[IXP (Global)]
║
Tier 2 ISP (National)◄──────────╗
/ \ ║
▼ ▼ ║
[IXP (Regional)]════╬══[IXP (Regional)] ║
/ \ ║
▼ ▼ ║
Tier 3 ISP (Local) Tier 3 ISP (Local) ║
| | ║
▼ ▼ ▼
[User] [User] [Enterprise]▲ IXPs are physical switch fabrics - members peer directly ▲ Tier 1/2 ISPs provide transit through IXPs but don't control them ```
This structure also reflects in IP addresses, where regional traffic gets routed by regional tiers and global traffic keeps getting passed up through gateways till it reaches the root of the tree. The global ISP then routes the traffic into the correct branch so that it can trickle down to the destination IP at the bottom.
12.0.0.0/8 - Tier 1 manages routing (IANA-allocated) └─12.34.0.0/16 - Tier 2 allocated block (through RIR) └─12.34.56.0/24 - Tier 3 subnet via upstream provider ├─12.34.56.1 Public IP (CGNAT pool) └─192.168.1.1 Private IP (local NAT reuse)Balancing idealism with pragmatism
This approach to scaling is much less idealistic than a flat hierarchy, because it relies on an authority (IANA) to assign the IP ranges to ISPs through Regional Internet Registries (RIRs). Even if this authority wasn't required, the fact that many users rely on few Tier 1 ISPs means that the system is inherently susceptible to sabotage (see 2019 BGP leak incident).
Control Plane: the internet is still described as decentralised
The internet is still described as decentralised because there is a flat hierarchy between
tier 1ISPs at the root of the tree. ``` INTERNET CORE (Tier 1 ISPs)AT&T (AS7018) <══════════> Deutsche Telekom (AS3320) ║ ╔════════════════════╗ ║ ║ ║ ║ ║ ╚══>║ NTT (AS2914) ║<══╝ ║ ║ ║ ║ ║ ║ ╚═══════> Lumen (AS3356) ║ ║ ╚════╩════════════> Telia (AS1299)
```
The border gateway protocol (BGP) is used to exchange routing information between autonomous systems (ISPs). Each autonomous system is a branch of the "internet tree" and each autonomous system advertises routes to downstream autonomous systems (branches). However, the autonomous systems at the root of the tree also maintain a record of their piers, so that they can forward traffic to the correct peer. Hence, the following is a more complete diagram of the internet: ```
INTERNET CORE (TIER 1 MESH) ╔══════════════╦═════════════╦════════╦═════════════╗ ║ ║ ║ ║ ║ AT&T (AS7018) <══╬══> Lumen (AS3356) <══╬══> NTT (AS2914) ║ ║ ║ ║ ║ ║ ║ ╚══> Telia (AS1299) <══╝ ║ ║ ╚═══════════════════════════════╝ ║ ║ ╚═> Deutsche Telekom (AS3320) <═╝ ║ TREE HIERARCHY BELOW - MESH ABOVE ║ ▼ [ Tier 1 ISP ]───────────────────┐ / | | / ▼ ▼ [IXP]═══╦═══[IXP] [IXP] ║ ║ ▼ ▼ Tier 2 ISP◄──────────╗ Tier 2 ISP◄───────╗ / \ ║ / \ ║ ▼ ▼ ║ ▼ ▼ ║ [IXP]═╦[IXP] ║ [IXP]═╦[IXP] ║ / \ ║ / \ ║ ▼ ▼ ▼ ▼ ▼ ▼ Tier 3 ISP User Tier 3 ISP Enterprise```
So its a mesh network - whats wrong with that?
In the example above, NTT can only send traffic to Deutsche Telekom via Lumen or AT&T. NTT relies on its peers to maintain a correct record of the IP range that they are responsible for, so that traffic that was intended for Deutsche Telekom doesn't end up in the wrong network. An intentional or even accidental error in an autonomous system's routing tables can be detrimental to the flow of traffic through the network.
Hence, mesh networks require: * Reliability: peers rely on each-other not to fail (e.g., 2019 AWS US-East-1 availability) * Trust: peers must be honest about address ranges (e.g., 2018 BGP hijacking incident) * Central planning: BGP traffic engineering determines which route a packet takes
Application Layer Innovations
Now that we have a rough overview of how the internet is broken, lets think about what can still be done. The flat hierarchy that we associate with mesh networks sounds beautiful, but it doesn't scale. However, the tree-like structure assumes that most participants in the network rely on an authority to give them an address or a range of addresses so that they can communicate.
Overlay networks
Fortunately all it takes to interact with someone on nostr is their public key. The recipients client will render your signed and/or encrypted event no matter how it reaches them. Whether your note reaches them over the internet, over some other network or via a carrier pigeon doesn't matter. nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr is working on a NIP for that and I'm sure he will share an explanation of how it works.
Bitcoin Instead of a Routing Algorithm
Now that we have digital bearer assets (e-cash), users can pay their internet gateway (TollGate) for access to the internet even though they are still offline. Once the TollGate has redeemed the e-cash, it gives the user access to the internet.
Frictionless Switching between ISPs (TollGates)
Legacy internet service providers use KYC money (fiat) to transfer the cost of the infrastructure to their users. However, this means that they are able to identify which packet belongs to which user. The KYC nature of their interaction with the users also makes it difficult for users to switch ISPs when service providers undercut each-other. Internet users who are on e-cash rails can hop between ISPs frictionlessly since they buy small amounts of data frequently in a granular manner.
Users that have access to independent competing TollGates can switch between them freely, so its impossible for any one TollGate to prevent a user from connecting to the internet. The only thing a TollGate can do is attract traffic by providing cheaper and/or faster internet access.
Anyone can arbitrage connectivity
Now that users have non KYC internet, there is nothing stopping them from reselling access to their internet connection. Anyone who has a WiFi router and access to a cheap internet connection can act as a range extender by re-selling access to that gateway for people who aren't able to connect directly.
Now the route that the traffic takes through the network is determined dynamically by the markets. The individual TollGate operators select their gateways and set their prices when they create a business model. The customers select the route that best meets their needs by selecting a gateway for their next purchase.
-
 @ 8125b911:a8400883
2025-04-25 07:02:35
@ 8125b911:a8400883
2025-04-25 07:02:35In Nostr, all data is stored as events. Decentralization is achieved by storing events on multiple relays, with signatures proving the ownership of these events. However, if you truly want to own your events, you should run your own relay to store them. Otherwise, if the relays you use fail or intentionally delete your events, you'll lose them forever.
For most people, running a relay is complex and costly. To solve this issue, I developed nostr-relay-tray, a relay that can be easily run on a personal computer and accessed over the internet.
Project URL: https://github.com/CodyTseng/nostr-relay-tray
This article will guide you through using nostr-relay-tray to run your own relay.
Download
Download the installation package for your operating system from the GitHub Release Page.
| Operating System | File Format | | --------------------- | ---------------------------------- | | Windows |
nostr-relay-tray.Setup.x.x.x.exe| | macOS (Apple Silicon) |nostr-relay-tray-x.x.x-arm64.dmg| | macOS (Intel) |nostr-relay-tray-x.x.x.dmg| | Linux | You should know which one to use |Installation
Since this app isn’t signed, you may encounter some obstacles during installation. Once installed, an ostrich icon will appear in the status bar. Click on the ostrich icon, and you'll see a menu where you can click the "Dashboard" option to open the relay's control panel for further configuration.

macOS Users:
- On first launch, go to "System Preferences > Security & Privacy" and click "Open Anyway."
- If you encounter a "damaged" message, run the following command in the terminal to remove the restrictions:
bash sudo xattr -rd com.apple.quarantine /Applications/nostr-relay-tray.appWindows Users:
- On the security warning screen, click "More Info > Run Anyway."
Connecting
By default, nostr-relay-tray is only accessible locally through
ws://localhost:4869/, which makes it quite limited. Therefore, we need to expose it to the internet.In the control panel, click the "Proxy" tab and toggle the switch. You will then receive a "Public address" that you can use to access your relay from anywhere. It's that simple.
Next, add this address to your relay list and position it as high as possible in the list. Most clients prioritize connecting to relays that appear at the top of the list, and relays lower in the list are often ignored.

Restrictions
Next, we need to set up some restrictions to prevent the relay from storing events that are irrelevant to you and wasting storage space. nostr-relay-tray allows for flexible and fine-grained configuration of which events to accept, but some of this is more complex and will not be covered here. If you're interested, you can explore this further later.
For now, I'll introduce a simple and effective strategy: WoT (Web of Trust). You can enable this feature in the "WoT & PoW" tab. Before enabling, you'll need to input your pubkey.
There's another important parameter,
Depth, which represents the relationship depth between you and others. Someone you follow has a depth of 1, someone they follow has a depth of 2, and so on.- Setting this parameter to 0 means your relay will only accept your own events.
- Setting it to 1 means your relay will accept events from you and the people you follow.
- Setting it to 2 means your relay will accept events from you, the people you follow, and the people they follow.
Currently, the maximum value for this parameter is 2.

Conclusion
You've now successfully run your own relay and set a simple restriction to prevent it from storing irrelevant events.
If you encounter any issues during use, feel free to submit an issue on GitHub, and I'll respond as soon as possible.
Not your relay, not your events.
-
 @ b099870e:f3ba8f5d
2025-05-12 12:37:43
@ b099870e:f3ba8f5d
2025-05-12 12:37:43The hustler's every waking hour is lived with both the practical and the subconscious knowledge that if he ever relaxes, if he ever slows down,the other hungry, restless foxes,ferrets, wolves and vultures out there with him won't hesitate to make him their prey.
Quote in The 50th Law that I'm currently reading
-
 @ e691f4df:1099ad65
2025-04-24 18:56:12
@ e691f4df:1099ad65
2025-04-24 18:56:12Viewing Bitcoin Through the Light of Awakening
Ankh & Ohm Capital’s Overview of the Psycho-Spiritual Nature of Bitcoin
Glossary:
I. Preface: The Logos of Our Logo
II. An Oracular Introduction
III. Alchemizing Greed
IV. Layers of Fractalized Thought
V. Permissionless Individuation
VI. Dispelling Paradox Through Resonance
VII. Ego Deflation
VIII. The Coin of Great Price
Preface: The Logos of Our Logo
Before we offer our lens on Bitcoin, it’s important to illuminate the meaning behind Ankh & Ohm’s name and symbol. These elements are not ornamental—they are foundational, expressing the cosmological principles that guide our work.
Our mission is to bridge the eternal with the practical. As a Bitcoin-focused family office and consulting firm, we understand capital not as an end, but as a tool—one that, when properly aligned, becomes a vehicle for divine order. We see Bitcoin not simply as a technological innovation but as an emanation of the Divine Logos—a harmonic expression of truth, transparency, and incorruptible structure. Both the beginning and the end, the Alpha and Omega.
The Ankh (☥), an ancient symbol of eternal life, is a key to the integration of opposites. It unites spirit and matter, force and form, continuity and change. It reminds us that capital, like Life, must not only be generative, but regenerative; sacred. Money must serve Life, not siphon from it.
The Ohm (Ω) holds a dual meaning. In physics, it denotes a unit of electrical resistance—the formative tension that gives energy coherence. In the Vedic tradition, Om (ॐ) is the primordial vibration—the sound from which all existence unfolds. Together, these symbols affirm a timeless truth: resistance and resonance are both sacred instruments of the Creator.
Ankh & Ohm, then, represents our striving for union, for harmony —between the flow of life and intentional structure, between incalculable abundance and measured restraint, between the lightbulb’s electrical impulse and its light-emitting filament. We stand at the threshold where intention becomes action, and where capital is not extracted, but cultivated in rhythm with the cosmos.
We exist to shepherd this transformation, as guides of this threshold —helping families, founders, and institutions align with a deeper order, where capital serves not as the prize, but as a pathway to collective Presence, Purpose, Peace and Prosperity.
An Oracular Introduction
Bitcoin is commonly understood as the first truly decentralized and secure form of digital money—a breakthrough in monetary sovereignty. But this view, while technically correct, is incomplete and spiritually shallow. Bitcoin is more than a tool for economic disruption. Bitcoin represents a mythic threshold: a symbol of the psycho-spiritual shift that many ancient traditions have long foretold.
For millennia, sages and seers have spoken of a coming Golden Age. In the Vedic Yuga cycles, in Plato’s Great Year, in the Eagle and Condor prophecies of the Americas—there exists a common thread: that humanity will emerge from darkness into a time of harmony, cooperation, and clarity. That the veil of illusion (maya, materiality) will thin, and reality will once again become transparent to the transcendent. In such an age, systems based on scarcity, deception, and centralization fall away. A new cosmology takes root—one grounded in balance, coherence, and sacred reciprocity.
But we must ask—how does such a shift happen? How do we cross from the age of scarcity, fear, and domination into one of coherence, abundance, and freedom?
One possible answer lies in the alchemy of incentive.
Bitcoin operates not just on the rules of computer science or Austrian economics, but on something far more old and subtle: the logic of transformation. It transmutes greed—a base instinct rooted in scarcity—into cooperation, transparency, and incorruptibility.
In this light, Bitcoin becomes more than code—it becomes a psychoactive protocol, one that rewires human behavior by aligning individual gain with collective integrity. It is not simply a new form of money. It is a new myth of value. A new operating system for human consciousness.
Bitcoin does not moralize. It harmonizes. It transforms the instinct for self-preservation into a pathway for planetary coherence.
Alchemizing Greed
At the heart of Bitcoin lies the ancient alchemical principle of transmutation: that which is base may be refined into gold.
Greed, long condemned as a vice, is not inherently evil. It is a distorted longing. A warped echo of the drive to preserve life. But in systems built on scarcity and deception, this longing calcifies into hoarding, corruption, and decay.
Bitcoin introduces a new game. A game with memory. A game that makes deception inefficient and truth profitable. It does not demand virtue—it encodes consequence. Its design does not suppress greed; it reprograms it.
In traditional models, game theory often illustrates the fragility of trust. The Prisoner’s Dilemma reveals how self-interest can sabotage collective well-being. But Bitcoin inverts this. It creates an environment where self-interest and integrity converge—where the most rational action is also the most truthful.
Its ledger, immutable and transparent, exposes manipulation for what it is: energetically wasteful and economically self-defeating. Dishonesty burns energy and yields nothing. The network punishes incoherence, not by decree, but by natural law.
This is the spiritual elegance of Bitcoin: it does not suppress greed—it transmutes it. It channels the drive for personal gain into the architecture of collective order. Miners compete not to dominate, but to validate. Nodes collaborate not through trust, but through mathematical proof.
This is not austerity. It is alchemy.
Greed, under Bitcoin, is refined. Tempered. Re-forged into a generative force—no longer parasitic, but harmonic.
Layers of Fractalized Thought Fragments
All living systems are layered. So is the cosmos. So is the human being. So is a musical scale.
At its foundation lies the timechain—the pulsing, incorruptible record of truth. Like the heart, it beats steadily. Every block, like a pulse, affirms its life through continuity. The difficulty adjustment—Bitcoin’s internal calibration—functions like heart rate variability, adapting to pressure while preserving coherence.
Above this base layer is the Lightning Network—a second layer facilitating rapid, efficient transactions. It is the nervous system: transmitting energy, reducing latency, enabling real-time interaction across a distributed whole.
Beyond that, emerging tools like Fedimint and Cashu function like the capillaries—bringing vitality to the extremities, to those underserved by legacy systems. They empower the unbanked, the overlooked, the forgotten. Privacy and dignity in the palms of those the old system refused to see.
And then there is NOSTR—the decentralized protocol for communication and creation. It is the throat chakra, the vocal cords of the “freedom-tech” body. It reclaims speech from the algorithmic overlords, making expression sovereign once more. It is also the reproductive system, as it enables the propagation of novel ideas and protocols in fertile, uncensorable soil.
Each layer plays its part. Not in hierarchy, but in harmony. In holarchy. Bitcoin and other open source protocols grow not through exogenous command, but through endogenous coherence. Like cells in an organism. Like a song.
Imagine the cell as a piece of glass from a shattered holographic plate —by which its perspectival, moving image can be restructured from the single shard. DNA isn’t only a logical script of base pairs, but an evolving progressive song. Its lyrics imbued with wise reflections on relationships. The nucleus sings, the cell responds—not by command, but by memory. Life is not imposed; it is expressed. A reflection of a hidden pattern.
Bitcoin chants this. Each node, a living cell, holds the full timechain—Truth distributed, incorruptible. Remove one, and the whole remains. This isn’t redundancy. It’s a revelation on the power of protection in Truth.
Consensus is communion. Verification becomes a sacred rite—Truth made audible through math.
Not just the signal; the song. A web of self-expression woven from Truth.
No center, yet every point alive with the whole. Like Indra’s Net, each reflects all. This is more than currency and information exchange. It is memory; a self-remembering Mind, unfolding through consensus and code. A Mind reflecting the Truth of reality at the speed of thought.
Heuristics are mental shortcuts—efficient, imperfect, alive. Like cells, they must adapt or decay. To become unbiased is to have self-balancing heuristics which carry feedback loops within them: they listen to the environment, mutate when needed, and survive by resonance with reality. Mutation is not error, but evolution. Its rules are simple, but their expression is dynamic.
What persists is not rigidity, but pattern.
To think clearly is not necessarily to be certain, but to dissolve doubt by listening, adjusting, and evolving thought itself.
To understand Bitcoin is simply to listen—patiently, clearly, as one would to a familiar rhythm returning.
Permissionless Individuation
Bitcoin is a path. One that no one can walk for you.
Said differently, it is not a passive act. It cannot be spoon-fed. Like a spiritual path, it demands initiation, effort, and the willingness to question inherited beliefs.
Because Bitcoin is permissionless, no one can be forced to adopt it. One must choose to engage it—compelled by need, interest, or intuition. Each person who embarks undergoes their own version of the hero’s journey.
Carl Jung called this process Individuation—the reconciliation of fragmented psychic elements into a coherent, mature Self. Bitcoin mirrors this: it invites individuals to confront the unconscious assumptions of the fiat paradigm, and to re-integrate their relationship to time, value, and agency.
In Western traditions—alchemy, Christianity, Kabbalah—the individual is sacred, and salvation is personal. In Eastern systems—Daoism, Buddhism, the Vedas—the self is ultimately dissolved into the cosmic whole. Bitcoin, in a paradoxical way, echoes both: it empowers the individual, while aligning them with a holistic, transcendent order.
To truly see Bitcoin is to allow something false to die. A belief. A habit. A self-concept.
In that death—a space opens for deeper connection with the Divine itSelf.
In that dissolution, something luminous is reborn.
After the passing, Truth becomes resurrected.
Dispelling Paradox Through Resonance
There is a subtle paradox encoded into the hero’s journey: each starts in solidarity, yet the awakening affects the collective.
No one can be forced into understanding Bitcoin. Like a spiritual truth, it must be seen. And yet, once seen, it becomes nearly impossible to unsee—and easier for others to glimpse. The pattern catches.
This phenomenon mirrors the concept of morphic resonance, as proposed and empirically tested by biologist Rupert Sheldrake. Once a critical mass of individuals begins to embody a new behavior or awareness, it becomes easier—instinctive—for others to follow suit. Like the proverbial hundredth monkey who begins to wash the fruit in the sea water, and suddenly, monkeys across islands begin doing the same—without ever meeting.
When enough individuals embody a pattern, it ripples outward. Not through propaganda, but through field effect and wave propagation. It becomes accessible, instinctive, familiar—even across great distance.
Bitcoin spreads in this way. Not through centralized broadcast, but through subtle resonance. Each new node, each individual who integrates the protocol into their life, strengthens the signal for others. The protocol doesn’t shout; it hums, oscillates and vibrates——persistently, coherently, patiently.
One awakens. Another follows. The current builds. What was fringe becomes familiar. What was radical becomes obvious.
This is the sacred geometry of spiritual awakening. One awakens, another follows, and soon the fluidic current is strong enough to carry the rest. One becomes two, two become many, and eventually the many become One again. This tessellation reverberates through the human aura, not as ideology, but as perceivable pattern recognition.
Bitcoin’s most powerful marketing tool is truth. Its most compelling evangelist is reality. Its most unstoppable force is resonance.
Therefore, Bitcoin is not just financial infrastructure—it is psychic scaffolding. It is part of the subtle architecture through which new patterns of coherence ripple across the collective field.
The training wheels from which humanity learns to embody Peace and Prosperity.
Ego Deflation
The process of awakening is not linear, and its beginning is rarely gentle—it usually begins with disruption, with ego inflation and destruction.
To individuate is to shape a center; to recognize peripherals and create boundaries—to say, “I am.” But without integration, the ego tilts—collapsing into void or inflating into noise. Fiat reflects this pathology: scarcity hoarded, abundance simulated. Stagnation becomes disguised as safety, and inflation masquerades as growth.
In other words, to become whole, the ego must first rise—claiming agency, autonomy, and identity. However, when left unbalanced, it inflates, or implodes. It forgets its context. It begins to consume rather than connect. And so the process must reverse: what inflates must deflate.
In the fiat paradigm, this inflation is literal. More is printed, and ethos is diluted. Savings decay. Meaning erodes. Value is abstracted. The economy becomes bloated with inaudible noise. And like the psyche that refuses to confront its own shadow, it begins to collapse under the weight of its own illusions.
But under Bitcoin, time is honored. Value is preserved. Energy is not abstracted but grounded.
Bitcoin is inherently deflationary—in both economic and spiritual senses. With a fixed supply, it reveals what is truly scarce. Not money, not status—but the finite number of heartbeats we each carry.
To see Bitcoin is to feel that limit in one’s soul. To hold Bitcoin is to feel Time’s weight again. To sense the importance of Bitcoin is to feel the value of preserved, potential energy. It is to confront the reality that what matters cannot be printed, inflated, or faked. In this way, Bitcoin gently confronts the ego—not through punishment, but through clarity.
Deflation, rightly understood, is not collapse—it is refinement. It strips away illusion, bloat, and excess. It restores the clarity of essence.
Spiritually, this is liberation.
The Coin of Great Price
There is an ancient parable told by a wise man:
“The kingdom of heaven is like a merchant seeking fine pearls, who, upon finding one of great price, sold all he had and bought it.”
Bitcoin is such a pearl.
But the ledger is more than a chest full of treasure. It is a key to the heart of things.
It is not just software—it is sacrament.
A symbol of what cannot be corrupted. A mirror of divine order etched into code. A map back to the sacred center.
It reflects what endures. It encodes what cannot be falsified. It remembers what we forgot: that Truth, when aligned with form, becomes Light once again.
Its design is not arbitrary. It speaks the language of life itself—
The elliptic orbits of the planets mirrored in its cryptography,
The logarithmic spiral of the nautilus shell discloses its adoption rate,
The interconnectivity of mycelium in soil reflect the network of nodes in cyberspace,
A webbed breadth of neurons across synaptic space fires with each new confirmed transaction.
It is geometry in devotion. Stillness in motion.
It is the Logos clothed in protocol.
What this key unlocks is beyond external riches. It is the eternal gold within us.
Clarity. Sovereignty. The unshakeable knowing that what is real cannot be taken. That what is sacred was never for sale.
Bitcoin is not the destination.
It is the Path.
And we—when we are willing to see it—are the Temple it leads back to.
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ 55f04590:2d385185
2025-05-12 12:34:10
@ 55f04590:2d385185
2025-05-12 12:34:10
Behind the scenes, a lot has happened over the past weeks.
The design of the book’s pages is nearly finished. I’ve selected and placed the illustrations and sketches I’ll feature and I’m close to finalising the Introduction section. All that’s left to do is a small photo shoot of some things from my archives, selecting one or two more articles for the Context section, and illustrating the articles.
After that I’ll print a dummy and kick off the second round of iteration—crossing T’s, dotting I’s. (And then I’ll cross those T’s and dot those I’s again and again because, surely, more things will arise.)
In parallel, and perhaps most importantly, I’m working on the design of the cover. I have a few ideas I’d like to discuss with the printer to learn more about the various possibilities and costs.

Book site
The book is now also available for pre-order through its own website, where you can pay for it in euros or dollars, if you prefer. BTC payments are still possible, too.
Originally I only offered one pre-order option that included rewards, like a print and a sticker pack. I’ve now named that the Collectors Edition, and added a separate option to order just the book (without additional rewards) at a reduced price.
Once the book is out in the world, this site is where I’ll have it up for sale. I’ll make the articles and illustrations from the Context section available there too. They’ll be published, in their entirety, under the Creative Commons Share-alike license.
Promo video
My friend Lilia shot and edited a short promotional video that provides a glimpse behind the scenes in my studio in Amsterdam, a peek at the book’s production process, and a sneak preview of the first spreads. While the process was new to me, this video was a lot of fun to make and I’m proud of the result.
Pre-orders
The total number of pre-orders has grown to 76—12 of which came through the new website. I initially thought I’d be selling 50 pre-orders at most, so things are definitely exceeding my expectations.
Feel free to place your pre-order through the new site, or use the Geyser crowdfund campaign to secure your copy.
Up next
In my next blog I’ll dive a little deeper into the technical side of the book. I’ll take you through the different kinds of paper I’ll use, the printing methods we’ll employ, and how the book will be bound and finished.
Keep your eyes peeled! Thomas
Previous updates
The NoGood art book announcement Update 01 – Humble beginnings Update 02 – Throwback Update 03 – Loops
Pre-order a book
The NoGood art book is available as a pre-order on book.nogood.studio, where you can pay for it in euros or dollars, if you prefer. BTC payments are still possible, too.
Alternatively, visit the Geyser crowdfund campaign to secure your copy.
originally posted at https://stacker.news/items/978096
-
 @ 6e64b83c:94102ee8
2025-04-23 20:23:34
@ 6e64b83c:94102ee8
2025-04-23 20:23:34How to Run Your Own Nostr Relay on Android with Cloudflare Domain
Prerequisites
- Install Citrine on your Android device:
- Visit https://github.com/greenart7c3/Citrine/releases
- Download the latest release using:
- zap.store
- Obtainium
- F-Droid
- Or download the APK directly
-
Note: You may need to enable "Install from Unknown Sources" in your Android settings
-
Domain Requirements:
- Purchase a domain if you don't have one
-
Transfer your domain to Cloudflare if it's not already there (for free SSL certificates and cloudflared support)
-
Tools to use:
- nak (the nostr army knife):
- Download from https://github.com/fiatjaf/nak/releases
- Installation steps:
-
For Linux/macOS: ```bash # Download the appropriate version for your system wget https://github.com/fiatjaf/nak/releases/latest/download/nak-linux-amd64 # for Linux # or wget https://github.com/fiatjaf/nak/releases/latest/download/nak-darwin-amd64 # for macOS
# Make it executable chmod +x nak-*
# Move to a directory in your PATH sudo mv nak-* /usr/local/bin/nak
- For Windows:batch # Download the Windows version curl -L -o nak.exe https://github.com/fiatjaf/nak/releases/latest/download/nak-windows-amd64.exe# Move to a directory in your PATH (e.g., C:\Windows) move nak.exe C:\Windows\nak.exe
- Verify installation:bash nak --version ```
Setting Up Citrine
- Open the Citrine app
- Start the server
- You'll see it running on
ws://127.0.0.1:4869(local network only) - Go to settings and paste your npub into "Accept events signed by" inbox and press the + button. This prevents others from publishing events to your personal relay.
Installing Required Tools
- Install Termux from Google Play Store
- Open Termux and run:
bash pkg update && pkg install wget wget https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-arm64.deb dpkg -i cloudflared-linux-arm64.debCloudflare Authentication
- Run the authentication command:
bash cloudflared tunnel login - Follow the instructions:
- Copy the provided URL to your browser
- Log in to your Cloudflare account
- If the URL expires, copy it again after logging in
Creating the Tunnel
- Create a new tunnel:
bash cloudflared tunnel create <TUNNEL_NAME> - Choose any name you prefer for your tunnel
-
Copy the tunnel ID after creating the tunnel
-
Create and configure the tunnel config:
bash touch ~/.cloudflared/config.yml nano ~/.cloudflared/config.yml -
Add this configuration (replace the placeholders with your values): ```yaml tunnel:
credentials-file: /data/data/com.termux/files/home/.cloudflared/ .json ingress: - hostname: nostr.yourdomain.com service: ws://localhost:4869
- service: http_status:404 ```
- Note: In nano editor:
CTRL+Oand Enter to saveCTRL+Xto exit
-
Note: Check the credentials file path in the logs
-
Validate your configuration:
bash cloudflared tunnel validate -
Start the tunnel:
bash cloudflared tunnel run my-relay
Preventing Android from Killing the Tunnel
Run these commands to maintain tunnel stability:
bash date && apt install termux-tools && termux-setup-storage && termux-wake-lock echo "nameserver 1.1.1.1" > $PREFIX/etc/resolv.confTip: You can open multiple Termux sessions by swiping from the left edge of the screen while keeping your tunnel process running.
Updating Your Outbox Model Relays
Once your relay is running and accessible via your domain, you'll want to update your relay list in the Nostr network. This ensures other clients know about your relay and can connect to it.
Decoding npub (Public Key)
Private keys (nsec) and public keys (npub) are encoded in bech32 format, which includes: - A prefix (like nsec1, npub1 etc.) - The encoded data - A checksum
This format makes keys: - Easy to distinguish - Hard to copy incorrectly
However, most tools require these keys in hexadecimal (hex) format.
To decode an npub string to its hex format:
bash nak decode nostr:npub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4Change it with your own npub.
bash { "pubkey": "6e64b83c1f674fb00a5f19816c297b6414bf67f015894e04dd4c657e94102ee8" }Copy the pubkey value in quotes.
Create a kind 10002 event with your relay list:
- Include your new relay with write permissions
- Include other relays you want to read from and write to, omit 3rd parameter to make it both read and write
Example format:
json { "kind": 10002, "tags": [ ["r", "wss://your-relay-domain.com", "write"], ["r", "wss://eden.nostr.land/"], ["r", "wss://nos.lol/"], ["r", "wss://nostr.bitcoiner.social/"], ["r", "wss://nostr.mom/"], ["r", "wss://relay.primal.net/"], ["r", "wss://nostr.wine/", "read"], ["r", "wss://relay.damus.io/"], ["r", "wss://relay.nostr.band/"], ["r", "wss://relay.snort.social/"] ], "content": "" }Save it to a file called
event.jsonNote: Add or remove any relays you want. To check your existing 10002 relays: - Visit https://nostr.band/?q=by%3Anpub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4+++kind%3A10002 - nostr.band is an indexing service, it probably has your relay list. - Replace
npub1xxxin the URL with your own npub - Click "VIEW JSON" from the menu to see the raw event - Or use thenaktool if you know the relaysbash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.comReplace `<your-pubkey>` with your public key in hex format (you can get it using `nak decode <your-npub>`)- Sign and publish the event:
- Use a Nostr client that supports kind 10002 events
- Or use the
nakcommand-line tool:bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)
Important Security Notes: 1. Never share your nsec (private key) with anyone 2. Consider using NIP-49 encrypted keys for better security 3. Never paste your nsec or private key into the terminal. The command will be saved in your shell history, exposing your private key. To clear the command history: - For bash: use
history -c- For zsh: usefc -Wto write history to file, thenfc -pto read it back - Or manually edit your shell history file (e.g.,~/.zsh_historyor~/.bash_history) 4. if you're usingzsh, usefc -pto prevent the next command from being saved to history 5. Or temporarily disable history before running sensitive commands:bash unset HISTFILE nak key encrypt ... set HISTFILEHow to securely create NIP-49 encypted private key
```bash
Read your private key (input will be hidden)
read -s SECRET
Read your password (input will be hidden)
read -s PASSWORD
encrypt command
echo "$SECRET" | nak key encrypt "$PASSWORD"
copy and paste the ncryptsec1 text from the output
read -s ENCRYPTED nak key decrypt "$ENCRYPTED"
clear variables from memory
unset SECRET PASSWORD ENCRYPTED ```
On a Windows command line, to read from stdin and use the variables in
nakcommands, you can use a combination ofset /pto read input and then use those variables in your command. Here's an example:```bash @echo off set /p "SECRET=Enter your secret key: " set /p "PASSWORD=Enter your password: "
echo %SECRET%| nak key encrypt %PASSWORD%
:: Clear the sensitive variables set "SECRET=" set "PASSWORD=" ```
If your key starts with
ncryptsec1, thenaktool will securely prompt you for a password when using the--secparameter, unless the command is used with a pipe< >or|.bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)- Verify the event was published:
- Check if your relay list is visible on other relays
-
Use the
naktool to fetch your kind 10002 events:bash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.com -
Testing your relay:
- Try connecting to your relay using different Nostr clients
- Verify you can both read from and write to your relay
- Check if events are being properly stored and retrieved
- Tip: Use multiple Nostr clients to test different aspects of your relay
Note: If anyone in the community has a more efficient method of doing things like updating outbox relays, please share your insights in the comments. Your expertise would be greatly appreciated!
-
 @ 0861144c:e68a1caf
2025-05-12 12:33:43
@ 0861144c:e68a1caf
2025-05-12 12:33:43This is my Bitcoin full node. There are many like it, but this one is mine. My node is my best friend. It is my life. I must master it as I must master my life. Without me, my node is useless. Without my node, I am useless. I must run my node true. I must verify my enemy who is trying to dilute me. I must reject his inflationary blocks. I will. Bitstein (2019)
I love debates. I'm one of those people who, just for fun, analyzes Abraham Lincoln’s speeches on slavery during his election campaigns, or revisits the Frost-Nixon debates—or pretty much any speech I can get my hands on. The essence of debates—and now that I've discovered Socratic seminars—even further enriches the community itself. Where we, as a Bitcoin community, stand superior in every sense of the word is that we don't just talk to stake out positions; a Bitcoiner takes a stand through their actions.
And that's exactly what we've seen over these past few weeks of debate about
OP_RETURN.Many people—instinctively, I’d say—are inviting Bitcoin maximalists to move over to ETH and create non-monetary use cases, even as those same people are the ones loudly promoting and encouraging everyone to get Bitcoinized. So, we find ourselves in a clear contradiction that remains largely misunderstood, especially when podcasters who have never reviewed a single pull request, don't know how the merge works, and don't even have a GitHub account, suddenly want to jump into a debate encouraging others to switch node classes.
As for me, that’s totally fine. The reason is simple: if you are a true Bitcoiner, it doesn't matter whether you understand programming (or not), use Knots, Core[^1], or any other client—as long as you run your own node. I believe this debate helped motivate people and warned them about the real danger of not running their own node.
[^1]: I encourage people to download Core.
Why is it important to run your own node?
When people are using Bitcoin in ways you disagree with, or creating use cases you don't support, the best way to express your disapproval is through your node. Because at the end of the day, it’s the node that allows us to verify transactions—it’s the step before final broadcast to the blockchain. Every node that gets deployed is another victory for the community against reliance on trust; every downloaded node strengthens user privacy.
The fastest way to destroy Bitcoin is by discouraging the use of personal nodes, because centralized services thrive when fewer people use this critical tool.
Use your node.
originally posted at https://stacker.news/items/978094
-
 @ f32184ee:6d1c17bf
2025-04-23 13:21:52
@ f32184ee:6d1c17bf
2025-04-23 13:21:52Ads Fueling Freedom
Ross Ulbricht’s "Decentralize Social Media" painted a picture of a user-centric, decentralized future that transcended the limitations of platforms like the tech giants of today. Though focused on social media, his concept provided a blueprint for decentralized content systems writ large. The PROMO Protocol, designed by NextBlock while participating in Sovereign Engineering, embodies this blueprint in the realm of advertising, leveraging Nostr and Bitcoin’s Lightning Network to give individuals control, foster a multi-provider ecosystem, and ensure secure value exchange. In this way, Ulbricht’s 2021 vision can be seen as a prescient prediction of the PROMO Protocol’s structure. This is a testament to the enduring power of his ideas, now finding form in NextBlock’s innovative approach.
 [Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]
[Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Vision: A Decentralized Social Protocol
In his 2021 Medium article Ulbricht proposed a revolutionary vision for a decentralized social protocol (DSP) to address the inherent flaws of centralized social media platforms, such as privacy violations and inconsistent content moderation. Writing from prison, Ulbricht argued that decentralization could empower users by giving them control over their own content and the value they create, while replacing single, monolithic platforms with a competitive ecosystem of interface providers, content servers, and advertisers. Though his focus was on social media, Ulbricht’s ideas laid a conceptual foundation that strikingly predicts the structure of NextBlock’s PROMO Protocol, a decentralized advertising system built on the Nostr protocol.
 [A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]
[A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Principles
Ulbricht’s article outlines several key principles for his DSP: * User Control: Users should own their content and dictate how their data and creations generate value, rather than being subject to the whims of centralized corporations. * Decentralized Infrastructure: Instead of a single platform, multiple interface providers, content hosts, and advertisers interoperate, fostering competition and resilience. * Privacy and Autonomy: Decentralized solutions for profile management, hosting, and interactions would protect user privacy and reduce reliance on unaccountable intermediaries. * Value Creation: Users, not platforms, should capture the economic benefits of their contributions, supported by decentralized mechanisms for transactions.
These ideas were forward-thinking in 2021, envisioning a shift away from the centralized giants dominating social media at the time. While Ulbricht didn’t specifically address advertising protocols, his framework for decentralization and user empowerment extends naturally to other domains, like NextBlock’s open-source offering: the PROMO Protocol.
NextBlock’s Implementation of PROMO Protocol
The PROMO Protocol powers NextBlock's Billboard app, a decentralized advertising protocol built on Nostr, a simple, open protocol for decentralized communication. The PROMO Protocol reimagines advertising by: * Empowering People: Individuals set their own ad prices (e.g., 500 sats/minute), giving them direct control over how their attention or space is monetized. * Marketplace Dynamics: Advertisers set budgets and maximum bids, competing within a decentralized system where a 20% service fee ensures operational sustainability. * Open-Source Flexibility: As an open-source protocol, it allows multiple developers to create interfaces or apps on top of it, avoiding the single-platform bottleneck Ulbricht critiqued. * Secure Payments: Using Strike Integration with Bitcoin Lightning Network, NextBlock enables bot-resistant and intermediary-free transactions, aligning value transfer with each person's control.
This structure decentralizes advertising in a way that mirrors Ulbricht’s broader vision for social systems, with aligned principles showing a specific use case: monetizing attention on Nostr.
Aligned Principles
Ulbricht’s 2021 article didn’t explicitly predict the PROMO Protocol, but its foundational concepts align remarkably well with NextBlock's implementation the protocol’s design: * Autonomy Over Value: Ulbricht argued that users should control their content and its economic benefits. In the PROMO Protocol, people dictate ad pricing, directly capturing the value of their participation. Whether it’s their time, influence, or digital space, rather than ceding it to a centralized ad network. * Ecosystem of Providers: Ulbricht envisioned multiple providers replacing a single platform. The PROMO Protocol’s open-source nature invites a similar diversity: anyone can build interfaces or tools on top of it, creating a competitive, decentralized advertising ecosystem rather than a walled garden. * Decentralized Transactions: Ulbricht’s DSP implied decentralized mechanisms for value exchange. NextBlock delivers this through the Bitcoin Lightning Network, ensuring that payments for ads are secure, instantaneous and final, a practical realization of Ulbricht’s call for user-controlled value flows. * Privacy and Control: While Ulbricht emphasized privacy in social interactions, the PROMO Protocol is public by default. Individuals are fully aware of all data that they generate since all Nostr messages are signed. All participants interact directly via Nostr.
 [Blueprint Match, source NextBlock]
[Blueprint Match, source NextBlock]
Who We Are
NextBlock is a US-based new media company reimagining digital ads for a decentralized future. Our founders, software and strategy experts, were hobbyist podcasters struggling to promote their work online without gaming the system. That sparked an idea: using new tech like Nostr and Bitcoin to build a decentralized attention market for people who value control and businesses seeking real connections.
Our first product, Billboard, is launching this June.
Open for All
Our model’s open-source! Check out the PROMO Protocol, built for promotion and attention trading. Anyone can join this decentralized ad network. Run your own billboard or use ours. This is a growing ecosystem for a new ad economy.
Our Vision
NextBlock wants to help build a new decentralized internet. Our revolutionary and transparent business model will bring honest revenue to companies hosting valuable digital spaces. Together, we will discover what our attention is really worth.
Read our Manifesto to learn more.
NextBlock is registered in Texas, USA.
-
 @ 9bde4214:06ca052b
2025-04-22 18:13:37
@ 9bde4214:06ca052b
2025-04-22 18:13:37"It's gonna be permissionless or hell."
Gigi and gzuuus are vibing towards dystopia.
Books & articles mentioned:
- AI 2027
- DVMs were a mistake
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- The Ultimate Resource by Julian L. Simon
- Harry Potter by J.K. Rowling
- Momo by Michael Ende
In this dialogue:
- Pablo's Roo Setup
- Tech Hype Cycles
- AI 2027
- Prompt injection and other attacks
- Goose and DVMCP
- Cursor vs Roo Code
- Staying in control thanks to Amber and signing delegation
- Is YOLO mode here to stay?
- What agents to trust?
- What MCP tools to trust?
- What code snippets to trust?
- Everyone will run into the issues of trust and micropayments
- Nostr solves Web of Trust & micropayments natively
- Minimalistic & open usually wins
- DVMCP exists thanks to Totem
- Relays as Tamagochis
- Agents aren't nostr experts, at least not right now
- Fix a mistake once & it's fixed forever
- Giving long-term memory to LLMs
- RAG Databases signed by domain experts
- Human-agent hybrids & Chess
- Nostr beating heart
- Pluggable context & experts
- "You never need an API key for anything"
- Sats and social signaling
- Difficulty-adjusted PoW as a rare-limiting mechanism
- Certificate authorities and centralization
- No solutions to policing speech!
- OAuth and how it centralized
- Login with nostr
- Closed vs open-source models
- Tiny models vs large models
- The minions protocol (Stanford paper)
- Generalist models vs specialized models
- Local compute & encrypted queries
- Blinded compute
- "In the eyes of the state, agents aren't people"
- Agents need identity and money; nostr provides both
- "It's gonna be permissionless or hell"
- We already have marketplaces for MCP stuff, code snippets, and other things
- Most great stuff came from marketplaces (browsers, games, etc)
- Zapstore shows that this is already working
- At scale, central control never works. There's plenty scams and viruses in the app stores.
- Using nostr to archive your user-generated content
- HAVEN, blossom, novia
- The switcharoo from advertisements to training data
- What is Truth?
- What is Real?
- "We're vibing into dystopia"
- Who should be the arbiter of Truth?
- First Amendment & why the Logos is sacred
- Silicon Valley AI bros arrogantly dismiss wisdom and philosophy
- Suicide rates & the meaning crisis
- Are LLMs symbiotic or parasitic?
- The Amish got it right
- Are we gonna make it?
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- Harry Potter dementors & Momo's time thieves
- Facebook & Google as non-human (superhuman) agents
- Zapping as a conscious action
- Privacy and the internet
- Plausible deniability thanks to generative models
- Google glasses, glassholes, and Meta's Ray Ben's
- People crave realness
- Bitcoin is the realest money we ever had
- Nostr allows for real and honest expression
- How do we find out what's real?
- Constraints, policing, and chilling effects
- Jesus' plans for DVMCP
- Hzrd's article on how DVMs are broken (DVMs were a mistake)
- Don't believe the hype
- DVMs pre-date MCP tools
- Data Vending Machines were supposed to be stupid: put coin in, get stuff out.
- Self-healing vibe-coding
- IP addresses as scarce assets
- Atomic swaps and the ASS protocol
- More marketplaces, less silos
- The intensity of #SovEng and the last 6 weeks
- If you can vibe-code everything, why build anything?
- Time, the ultimate resource
- What are the LLMs allowed to think?
- Natural language interfaces are inherently dialogical
- Sovereign Engineering is dialogical too
-
 @ 7460b7fd:4fc4e74b
2025-05-12 12:23:54
@ 7460b7fd:4fc4e74b
2025-05-12 12:23:54警惕:那些“帮你”保管密钥的人
—— 多签钱包中的隐形风险与逻辑陷阱
“我们可以帮您设置一个更安全的钱包。” 这句话,听上去就像是关心,其实却可能是一次有预谋的接管。
摘要
多签钱包被广泛视为提升数字资产安全性的“进阶方案”,尤其适用于不希望将所有信任寄托于单一点故障(如一把私钥)的人群。然而,在这些看似“民主化”、“抗单点失败”的技术结构背后,仍潜藏着极为隐秘且被低估的风险。
本文聚焦两类常见却高度隐蔽的逻辑攻击模型:
- 替换 xpub 并接管下一层级地址生成;
- 伪造
k-of-n多签结构,在形式上给予用户参与感,实则实现单人提款。
在未引入 Taproot 的传统多签结构下,这类攻击已能轻易完成。而即便在 Taproot 和 MuSig2 合约模型下,攻击者也可以借助合成结构进一步隐藏其篡改行为。
本报告不仅梳理攻击逻辑,更强调“人性中的信任误区”——攻击者不需要主动索取密钥,只需要维持友善形象,自会有用户主动递交钥匙。更令人警惕的是,在某些极端场景下,这类“被信任的服务商”甚至可能向受害者收取“保管密钥”的费用后再实施盗窃,形成双重获利。
Taproot 虽然在结构上增强了隐私与复杂性,但也使验证逻辑失去了可直观还原的优势。随着时间推移、服务厂商退出市场乃至私有恢复流程被锁死,用户极可能落入无法恢复的“密钥黑箱”中。
阅读本文,希望你能意识到:
真正的安全,从不是托付给别人帮你“多签”,而是你真正理解你签了什么、和谁签的、签名之后将通往哪一个脚本。
多签钱包的逻辑攻击向量分析
以 xpub 替换与伪造 k-of-n 结构为例
攻击模型一:替换 xpub 实现地址劫持
场景设定
攻击者假扮为友好的钱包初始化服务者,主动提出“免费帮你生成一个更安全的多签钱包”。表面上,他为你设置了标准的 HD 多签结构,实际上却在关键的派生路径中,悄悄将本应由你或另一个可信方持有的 xpub 替换为他自己的。
在 HD 钱包结构(例如 BIP45、BIP67)中,用户通常无法直观验证每一个新地址是否仍属于原来的签名组。这种设计让“看上去很安全”的地址,可能早已成为攻击者可完全支配的提款口袋。
攻击结构(逻辑表示)
- 假设多签参与者为
P1, P2, P3 - 攻击者控制伪造者身份
P1',实际替代掉用户的P1 - 地址生成函数为:
Addr = f(xpub(P1'), xpub(P2), xpub(P3))- 用户未验证 xpub 时,成立:
∃ Addr_i ∈ wallet, spendable_by(attacker)换言之,钱包中的某些地址虽然看起来正常,但已可被攻击者花费。
人性陷阱提示
用户往往不认为“地址生成这件事”是需要人工检查的,特别是在使用 Ledger、Trezor 等硬件钱包时形成了“签名即安全”的错觉。而攻击者只需一次替换,就能悄悄监视整个钱包生命周期。
更重要的是,攻击者不需要向你“索取密钥”,他只需维持友善、专业甚至略带“为你好”的姿态。在 100 个用户中,总会有一部分人,在受到“信任感”与“他人看起来更专业”的影响下,主动提出将某个密钥托管给对方,甚至支付一定“密钥保管费”作为安全保障。这类行为并非愚蠢,而是人性的一部分。
这种松懈与依赖,背后深植着心理学上著名的「责任分散效应(diffusion of responsibility)」。当责任从“自己一人持有私钥”转变为“我们多人共同掌控”时,大脑会自动削弱“必须百分百保护密钥”的紧迫感;一旦密钥有三份或五份,人就会默认“即使我丢了一份也无所谓”,由此降低警惕,弱化加密习惯的执行力度。
尤其是在多签结构下,密钥不再是“唯一真理”。你开始认为:“我只是 n-of-m 的一员”,进而产生 安全责任稀释(safety dilution)。举个例子:如果你的 seed words 是唯一的,你很可能将其写在一张专用纸上,藏入防火袋,存放于密封保险箱中;但一旦你拥有的是 3-of-5 多签中的一份,你可能就只是把它存在 Evernote、存图于手机相册,或者发给自己 Telegram 备份——并自我安慰说:“这只是其中一把钥匙,又不怕。”
这正是攻击者渗透的最佳入口。他无需破解密码学算法,仅凭理解人性中的懒惰、依赖与责任下沉机制,就足以发起极具杀伤力的社会工程攻击。
提醒:没有人例外。你的安全不是由数学公式决定,而是由你是否对它持续保持敬畏与冷静判断所决定的。
Taproot 下的隐蔽性升级
在 Taproot + MuSig2 合约结构中:
- 合成公钥如:
P = H(P1 + P2 + P3) - 用户无法从地址推导出其组成
- 所有 pubkey 被掩盖,无任何可读性结构泄露
结果:攻击者替换某个 xpub 之后,哪怕是资深用户,也无法通过比对地址结构来发现任何异常。
攻击模型二:伪造 k-of-n 多签脚本结构
场景设定
攻击者承诺为你部署一个“非常安全”的
2-of-3多签钱包。然而他实际创建的却是一个1-of-3结构,并诱导你保留或交出其中一个密钥。用户一旦信任其脚本不可见性(或 UI 模糊性),资金注入该地址之后,攻击者即可单独提款。
攻击结构(逻辑描述)
- 正确脚本应为:
OP_2 <pk1> <pk2> <pk3> OP_3 OP_CHECKMULTISIG- 实际被构造为:
OP_1 <pk1> <pk2> <pk3> OP_3 OP_CHECKMULTISIG- 用户错误地相信:
user_believes(k=2) ∧ attacker_has(sk1) → safe- 但实际上:
real_k = 1 ∧ attacker_has(sk1) → attacker_can_spend成立条件
- 用户未能验证 redeem script
- 钱包界面(UI 或 PSBT)未明确标识 k 值与脚本结构
- 攻击者拥有脚本定义权,或 UI 权限
人性陷阱提示
这类攻击往往并非“高技术”,而是利用用户对脚本结构的无感。尤其是当攻击者扮演“技术专家”时,用户往往不具备审查 redeem script 的能力或意识。攻击者甚至可以用“给你设置一个冷备密钥”作为幌子,骗取部分 key,并收取额外费用。
多签攻击模型对比分析(无表格)
- 攻击类型一:xpub 替换
- 本质:公钥注入
- 隐蔽性:极高(生成地址完全正常)
- 关键条件:用户未验证每个 xpub
-
Taproot 是否能规避:否,反而更难发现
-
攻击类型二:伪造 k-of-n
- 本质:脚本结构欺骗
- 隐蔽性:中等(需查看 redeem script 才能识别)
- 关键条件:用户不懂脚本,UI 不展示结构
- Taproot 是否能规避:否,合约结构反而隐藏了更多细节
安全建议(基于当前攻击模型)
- 强制在 UI 中完整展示所有 xpub、合成地址派生路径与对应签名人列表
- 如 Coldcard 的二维码验证机制
- 用户必须自行保存每个 xpub,并可验证任一地址确实源自该集合派生
- 多签钱包必须提供可见 redeem script 的界面与 k 值校验提示
- 不接受“帮你配置好了”的 UI 黑箱
- Taproot 虽增强隐私,但也加剧验证障碍
- 若使用合签结构,应避免依赖第三方界面进行签名决策
- 始终优先使用硬件钱包本地签名流程,避免通过 Web 或中间服务生成交易
真实案例分析
1. Coldcard 硬件钱包的 xpub 替换漏洞
2021 年,安全研究员 benma 发现 Coldcard 硬件钱包在注册多签钱包时,未验证自身是否为多签钱包的一部分。这使得恶意计算机钱包可以用攻击者控制的 xpub 替换多签 xpub,同时仍通过所有用户验证。所有接收到此多签钱包的币随后可以随时转移到攻击者的钱包。
来源:benma.github.io2. Bybit 交易所的多签钱包被黑事件
2025 年 2 月,Bybit 交易所的多签冷钱包在一次例行转账中被黑,损失约 14.6 亿美元。该钱包使用 2-of-3 多签设置,意味着需要三位授权签名人中的两位批准交易。用户界面显示了合法的目标地址,并且 URL 与受信任的多签提供商 Safe 相关联。但这是一种欺骗。黑客利用硬件钱包中的“盲签名”漏洞,使设备只能显示交易的哈希,从而掩盖了一个更改,使攻击者控制了钱包的智能合约。
来源:certora.com3. Parity 多签钱包漏洞
2017 年,Parity 多签钱包版本 1.5+ 中发现了一个漏洞,允许攻击者窃取超过 150,000 ETH(约 3000 万美元)。攻击者向受影响的合约发送两个交易:第一个获取多签的独占所有权,第二个移动其所有资金。
来源:blog.openzeppelin.com
攻击流程图解
- 建立信任:攻击者以技术专家或受信任的服务提供商身份接近受害者,提出帮助设置多签钱包。
- 替换 xpub:在设置过程中,攻击者用自己控制的 xpub 替换原本应由用户或第三方控制的 xpub。
- 生成地址:攻击者生成看似正常的多签地址,并展示给用户,用户未进行验证。
- 资金注入:用户将资金转入这些地址,认为资金安全。
- 资金转移:攻击者利用控制的私钥,单方面将资金转出,用户无法察觉。
参考文献
附录:攻击面分析——为何 xpub 替换是多签特有的风险?
单签钱包是否存在 xpub 替换攻击?
答案:否。
在单签钱包结构中(如 BIP32/BIP39 衍生的标准钱包):
- 钱包只依赖一个 xpub,并且这个 xpub 是从用户私钥派生而来;
- Coldcard、Trezor 等硬件钱包会自动根据本地 seed 派生地址,无需输入外部 xpub;
- 用户可以通过设备显示屏确认“这是我派生出来的地址”,不存在外部注入路径。
因此:xpub 替换在单签钱包中不存在攻击面,攻击路径被封死。
多签钱包为什么引入了 xpub 攻击面?
多签钱包(如 2-of-3、3-of-5)需要以下信息来生成地址:
- 所有参与者的 xpub;
- 公钥排序规则(如 BIP67);
- 多签脚本模板(如 OP_2
OP_3 OP_CHECKMULTISIG); - 每个 key 的派生路径(如 m/48'/0'/0'/2'/0/1);
这就意味着,用户必须信任这些输入的 xpub 是来自真正的签名方。如果攻击者悄悄将其中某一份换成自己控制的 xpub,那他就自动成为地址共管人,甚至是单签人。
Coldcard 攻击案例回顾:
- 用户通过 PSBT 模板或 JSON 导入多签配置;
- 攻击者在其中替换了某一参与者的 xpub;
- Coldcard 在旧版本中未提示或验证该替换;
- 用户生成地址、发送资金,攻击者即可随时提取。
攻击面比较表
- 单签钱包
- 不接收外部 xpub,派生路径完全由设备掌控;
- 地址来源明确、签名单一;
-
xpub 替换攻击无效。
-
多签钱包
- 依赖多个外部 xpub 合成结构;
- 用户很难手动验证每一条 xpub 与 fingerprint;
- xpub 替换为高危攻击点。
Taproot 是否规避了 xpub 替换问题?
部分规避,但引入了新的验证难题。
Taproot + MuSig2 等结构通过将多个 pubkey 合成为一个点:
P = H(P1 + P2 + P3)
这确实可以隐藏合约结构,提升隐私,但也导致:
- 用户无法从地址还原参与者是谁;
- 如果其中一个公钥被攻击者替换,生成的地址仍然合法;
- 用户在链上看不到任何异常,但攻击者已取得合约控制权。
因此:Taproot 并未从根本上消除 xpub 替换的攻击面,反而因为其不可还原性使得攻击更加隐蔽。
总结
多签钱包之所以引入新的攻击面,不是因为它“更复杂”,而是因为它必须信任外部结构。一旦你的钱包要“与他人协作生成地址”,你就必须验证“这些人是谁”、“这些地址是怎么来的”——这就是攻击的入口。
单签保护的是私钥,
多签则要求你保护你的伙伴。 -
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ 866e0139:6a9334e5
2025-05-12 10:41:33
@ 866e0139:6a9334e5
2025-05-12 10:41:33Autor: Bastian Barucker. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
John Lennon besang in seinem weltberühmten Lied „Imagine“ die fast unvorstellbare Utopie einer Welt, in der es keinen Grund mehr zu töten gäbe und die Menschen in Frieden zusammen leben. Die enorme Resonanz und Verbreitung dieser Zeilen zeigt den Wunsch fast aller Menschen nach Frieden. Wie Lennon zu diesen Zeilen kam, ist ein Hinweis darauf, dass es dazu neben geopolitischen Analysen und deren Verbreitung durch eine nicht eingebettete und freie Presse vielleicht noch etwas braucht: Schattenarbeit – ein bewusstes Hinwenden zu den eigenen Tiefen der Persönlichkeit, dem inneren Tiefenstaat.
Was ist der Tiefenstaat?
Mit dem Begriff Tiefenstaat verbinde ich Strukturen, die Edward Bernays bereits vor knapp 100 Jahren in seinem Grundlagenwerk „Propaganda“ beschrieb. Im Vorwort schreibt er: „Organisationen, die im Verborgenen arbeiten, lenken die gesellschaftlichen Abläufe. Sie sind die eigentlichen Regierungen in unserem Land.“ Er verwendet diesbezüglich auch das Wort „Schattenkabinett“. Im Bereich der Persönlichkeitsentwicklung wird der Begriff „Schattenarbeit“ dafür verwendet, unbekannte, aber einflussreiche Anteile des eigenen Selbst zu entdecken und zu integrieren.
Lennon begab sich in den 70er Jahren des letzten Jahrhunderts auf die Reise zu sich selbst. Sein Weg führte ihn zum Psychologen Dr. Arthur Janov, der Menschen mithilfe der von ihm entwickelten Primärtherapie dabei begleitete, sich ihrer primären Prägungen und frühkindlichen Traumatisierungen bewusst zu werden und abgespaltenen Schmerz wieder zu erleben, um sich davon zu befreien. Entgegen stark kognitiv geprägter Ansätze wie der Gesprächstherapie steht bei dieser Art der Therapie Gefühlsausdruck im Vordergrund. Janov selbst schreibt dazu: «Die Krankheit ist die Verleugnung des Fühlens, und das Heilmittel ist das Fühlen.»
Auch der Psychologe und Psychotherapeut Franz Ruppert beschäftigt sich intensiv mit dem Fühlen als einem möglichen Weg, eine Traumatisierung aufzuarbeiten. Er schreibt Folgendes über die Bedeutung des Fühlens in seinem Buch „Wer bin ich in einer traumatisierten Gesellschaft“: „Denn letztlich können nur über das Ausdrücken von Gefühlen die fragmentierten psychischen Strukturen wieder zu einer Einheit zusammenfinden.“
Lennon war es möglich, die immense Menge an Schmerz zu entdecken, die er verborgen in sich trug, und er erkannte dabei, welche Verhaltensweisen und Bewältigungsstrategien damit verbunden waren. Laut Lennon ist „Unser Schmerz der Schmerz, durch den wir die ganze Zeit gehen. Du wirst in Schmerz hineingeboren, und wir befinden uns meist im Schmerz. Und ich glaube, je größer der Schmerz ist, umso mehr Götter brauchen wir.“
Die Schilderungen von John Lennon decken sich mit den Erfahrungen meiner Selbsterfahrung und meiner mittlerweile über 10 Jahre langen Begleitungsarbeit in der durch den Schweizer Willi Maurer entwickelten Gefühls- und Körperarbeit.
Auch in dieser Arbeit geht es darum, abgespaltenen Schmerz langsam und über viele Jahre aus dem Schatten in das Bewusstsein zu integrieren, um nicht weiter von ihm unbewusst beeinflusst zu werden. Hunderte Male habe ich Menschen ihnen vorher unbekannten Hass, tiefe Trauer, unendliche Ohnmacht, starke Hilflosigkeit, aber auch Freude, tiefe Geborgenheit, Liebe und Friedfertigkeit entdecken und ausleben sehen. Selber habe ich mich nach einem einjährigen Aufenthalt in der nordamerikanischen Wildnis, bei dem es darum ging, so ehrlich wie möglich miteinander umzugehen, ausführlich meiner Selbsterfahrung gewidmet und dabei Intensitäten von Schmerz, aber auch Zufriedenheit entdeckt, die mir nicht vorstellbar erschienen.
Der Krieg in uns
Fast immer zeigte sich in den begleiteten Prozessen, dass die im Alltag, in der Partnerschaft oder in der Familie angerührten Gefühle aus der eigenen frühen Kindheit stammten. Innere, überfordernde „Kriege“ und Übergriffigkeiten, die auch das Leben im Außen zum Krieg werden ließen, erwachten zum Leben und durften endlich Ausdruck finden. Schlussendlich zeigte sich meist, dass es einen friedlichen Umgang mit der aktuellen Situation gibt, wenn die Altlast „entsorgt“ beziehungsweise kompostiert, also gefühlt und integriert wurde.
Franz Renggli beschreibt diese Psychodynamik in seinem Buch Verlassenheit und Angst – Nähe und Geborgenheit in Bezug auf Partnerschaft wie folgt:
„Die Erfahrung aller meiner Paarbegleitungen zeigt nun: Wenn nach der ersten Verliebtheit langsam der „Alltag“ in eine Beziehung einkehrt, neigen beide Partner immer mehr dazu, ihre Schattenseiten, ihre alten und frühen Verletzungen auch in der Beziehung zuzulassen. Je sicherer die Grenzen sind, desto vertrauensvoller dürfen diese frühen Schmerzen gespürt und erfahren werden. Wir „steigen dann wieder ab“ in unsere ursprüngliche Hölle der Verlassenheit, in die frühkindlichen Prägungen, wie ich sie hier beschrieben habe. Nur: die Hölle sind dann nicht länger die Eltern, sondern jetzt der Partner oder die Partnerin! Vielleicht könnte ich sie oder ihn umbringen vor Enttäuschung und Wut, weil er/sie mich so sehr verletzt hat. Und damit kann sie beginnen, die Heilung der alten Wunden in der Paarbeziehung! Aber nur dann, wenn wir bereit sind, unsere alten verletzten Gefühle wirklich zu spüren und zuzulassen. Und wenn wir zu diesem Schritt bereit sind, dann können wir auch gleichzeitig empfinden und wissen: Das sind unsere ureigensten alten Verletzungen, welche wir seit der Kindheit in uns tragen – ein Partner mit seinen Worten und seinem Verhalten ist nur der Auslöser unseres alten Schmerzes, ein harter Spiegel unserer alten Wunden! Wir alle haben unsere Partner entsprechend gewählt, damit wir in unseren Grundfesten immer wieder – neben allem Glück, das wir mit ihnen erleben und teilen dürfen – auch erschüttert werden.“
Diese wiederkehrenden Erschütterungen werden auch Reinszenierungszwang genannt und lassen Menschen immer wieder dieselben misslichen Lagen (mit)erschaffen, die ihnen Leid zufügen. Willi Maurer beschreibt diese Dynamik in einem sehr lesenswerten Artikel mit dem Titel „Die verschüttete Quelle des Friedens“ wie folgt: „Die Spirale der Gewalt zeigt, dass wir andern Menschen das antun, was uns selbst widerfahren ist. Doch ohne Selbsterforschung bleiben wir blind gegenüber der tief in uns verdrängt liegenden Wahrheit.“
Diese Reinszenierung ist gleichzeitig jedoch eine immer wiederkehrende Chance, sich der Ursache dieser Dynamik zuzuwenden. Das geschieht dann, wenn die Person sich als Erschaffer oder Erschafferin und nicht als reines Opfer der Umstände versteht und beginnt, die volle Verantwortung für das eigene Leben zu übernehmen.
Vor einigen Jahren brachte ich den Prozessbegleiter Willi Maurer und den Friedensforscher Dr. Daniele Ganser zu einem Gespräch zusammen, weil ich der Ansicht war, dass beide Friedensarbeit aus verschiedenen Perspektiven leisten. Es war eine Wohltat, zu erleben, wie Ganser durch die sehr authentischen Schilderungen Maurers zu ahnen begann, dass es eine Verbindung zwischen weltweiten Kriegen und frühen Erfahrungen geben kann. Was hat der Soldat, Politiker oder Geostratege erlebt, dass er in der Lage ist, Krieg zu befördern, zu verursachen oder auch nur zu dulden?
Vielleicht ist die immer wiederkehrende Kriegsbereitschaft und Kriegslust elitärer Kreise neben der wahrscheinlich frühkindlich erzeugten Gier nach Macht, Einfluss und Geld ebenfalls ein gesellschaftlicher Reinszenierungszwang. Die inneren Zerwürfnisse und Kriege müssen quasi ins Außen getragen werden, um sich dem im Schatten der eigenen Persönlichkeit wartenden Schmerz nicht zuwenden zu müssen.
Eine weitere Bewältigungsstrategie für innere, emotionale Zerwürfnisse ist die Projektion, also die Veräußerlichung des Eigenen auf andere. Ein hier vielleicht Sinn stiftendes Beispiel ist die immer wieder betonte weitestgehend unbelegte Unterstellung imperialistischer Bestrebungen Russlands im Zuge des völkerrechtswidrigen Krieges in der Ukraine. Meist kommt diese Behauptung von Vertretern oder Unterstützern der NATO, die – wie an ihrer großflächigen, gegen westliche Zusagen an Russland verstoßenden NATO-Osterweiterung leicht zu erkennen – offensichtlich selbst imperialistische Bestrebungen verfolgt.
Die Projektion ins Außen
Interessanterweise hat ausgerechnet Präsident Putin in anschaulichen Worten beschrieben, was unter anderem mit im Schatten liegenden Persönlichkeitsanteilen auch auf geopolitischer Ebene passieren kann. Sie werden anderen Menschen oder Staaten zugeschrieben, also ins Außen projiziert. Auf die Beschuldigung durch US-Präsidenten Joe Biden, ein Mörder zu sein, antwortete Putin: „Aber wenn wir andere Menschen bewerten, oder wenn wir sogar andere Staaten, andere Völker bewerten, sehen wir immer in den Spiegel, wir sehen uns immer selbst, weil wir auf eine andere Person übertragen, was wir selbst sind, was uns im Wesentlichen ausmacht. Wissen Sie, ich erinnere mich, als wir als Kinder im Hinterhof waren, als wir miteinander gestritten und gesagt haben: Wie Du andere nennst, so bist Du selbst. Und das ist kein Zufall, das ist nicht nur ein Kindersprichwort oder ein Witz. Der Sinn ist sehr psychologisch. Wir sehen immer unsere eigenen Qualitäten in einer anderen Person und denken, dass sie so ist wie wir, und daraus bewerten wir ihr Handeln und bewerten sie insgesamt.“
https://www.youtube.com/watch?v=7sMAHWH_hhQ
Der bereits erwähnte Tiefenstaat, also eine quasi Schattenregierung, existiert auf der geopolitischen Weltbühne und bestimmt größtenteils die Geschicke, insbesondere wenn es um Krieg und Frieden geht. Der Kognitionsforscher Professor Rainer Mausfeld beschreibt die unsichtbar im Hintergrund wirkenden Strukturen in seinem Buch „Angst und Macht“ wie folgt: „Die tatsächliche Macht ist heute in neuartigen globalen Organisationsformen verortet, die vollkommen einer gesellschaftlichen Kontrolle entzogen sind, die für die Bevölkerung weitgehend unsichtbar sind…“
Gleiches gilt meiner Annahme nach auch für die persönlichen Machtverhältnisse, bei denen eigene Schattenanteile ebenfalls großen Einfluss auf die sichtbaren Verhaltensweisen nehmen. Dieser unbewusste Anteil kann auf der einen Seite Macht über die eigene Kriegsbereitschaft und Friedenstüchtigkeit ausüben, auf der anderen Seite wird er von Kriegstreibern mittels kognitiver Kriegsführung aktiv benutzt, um die Bevölkerung zu manipulieren. Der Propagandaforscher Dr. Jonas Tögel schreibt dazu: „Die Tiefenpsychologie dient als Fundament der wohl wichtigsten Manipulationswaffe: die gezielte Beeinflussung des Unbewussten der menschlichen Psyche. Wie bei einem Eisberg liegt ein großer Teil unserer Gedanken und Gefühle „unter der Wasseroberfläche“, und hier können wir so beeinflusst werden, dass wir die Steuerung selbst oft nicht bemerken.“
Der Tiefe Staat kann also ungesehen politisch schalten und walten und gleichzeitig die unbewussten Anteile der menschlichen Psyche zu seinen Gunsten ausnutzen.
Teil 2 folgt in Kürze.
Bastian Barucker, Jahrgang 83, ist Wildnispädagoge, Überlebenstrainer und Prozessbegleiter. Seit 2005 begleitet er Menschen bei Wachstumsprozessen in der Natur. Seit 2011 macht er mithilfe der Gefühls- und Körperarbeit tiefgreifende Selbsterfahrungen, und seit 2014 begleitet er Gruppen, Paare und Einzelpersonen. Er lebt und arbeitet im wunderschönen Lassaner Winkel, nahe der Insel Usedom. Zuletzt erschien von ihm das Buch "Auf Spurensuche nach Natürlichkeit: Vom Leben in der Wildnis und der Reise zu sich selbst" im Massel Verlag.
Kontakt: www.bastian-barucker.de
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ ed5774ac:45611c5c
2025-04-19 20:29:31
@ ed5774ac:45611c5c
2025-04-19 20:29:31April 20, 2020: The day I saw my so-called friends expose themselves as gutless, brain-dead sheep.
On that day, I shared a video exposing the damning history of the Bill & Melinda Gates Foundation's vaccine campaigns in Africa and the developing world. As Gates was on every TV screen, shilling COVID jabs that didn’t even exist, I called out his blatant financial conflict of interest and pointed out the obvious in my facebook post: "Finally someone is able to explain why Bill Gates runs from TV to TV to promote vaccination. Not surprisingly, it's all about money again…" - referencing his substantial investments in vaccine technology, including BioNTech's mRNA platform that would later produce the COVID vaccines and generate massive profits for his so-called philanthropic foundation.
The conflict of interest was undeniable. I genuinely believed anyone capable of basic critical thinking would at least pause to consider these glaring financial motives. But what followed was a masterclass in human stupidity.
My facebook post from 20 April 2020:

Not only was I branded a 'conspiracy theorist' for daring to question the billionaire who stood to make a fortune off the very vaccines he was shilling, but the brain-dead, logic-free bullshit vomited by the people around me was beyond pathetic. These barely literate morons couldn’t spell "Pfizer" without auto-correct, yet they mindlessly swallowed and repeated every lie the media and government force-fed them, branding anything that cracked their fragile reality as "conspiracy theory." Big Pharma’s rap sheet—fraud, deadly cover-ups, billions in fines—could fill libraries, yet these obedient sheep didn’t bother to open a single book or read a single study before screaming their ignorance, desperate to virtue-signal their obedience. Then, like spineless lab rats, they lined up for an experimental jab rushed to the market in months, too dumb to care that proper vaccine development takes a decade.
The pathetic part is that these idiots spend hours obsessing over reviews for their useless purchases like shoes or socks, but won’t spare 60 seconds to research the experimental cocktail being injected into their veins—or even glance at the FDA’s own damning safety reports. Those same obedient sheep would read every Yelp review for a fucking coffee shop but won't spend five minutes looking up Pfizer's criminal fraud settlements. They would demand absolute obedience to ‘The Science™’—while being unable to define mRNA, explain lipid nanoparticles, or justify why trials were still running as they queued up like cattle for their jab. If they had two brain cells to rub together or spent 30 minutes actually researching, they'd know, but no—they'd rather suck down the narrative like good little slaves, too dumb to question, too weak to think.
Worst of all, they became the system’s attack dogs—not just swallowing the poison, but forcing it down others’ throats. This wasn’t ignorance. It was betrayal. They mutated into medical brownshirts, destroying lives to virtue-signal their obedience—even as their own children’s hearts swelled with inflammation.
One conversation still haunts me to this day—a masterclass in wealth-worship delusion. A close friend, as a response to my facebook post, insisted that Gates’ assumed reading list magically awards him vaccine expertise, while dismissing his billion-dollar investments in the same products as ‘no conflict of interest.’ Worse, he argued that Gates’s $5–10 billion pandemic windfall was ‘deserved.’
This exchange crystallizes civilization’s intellectual surrender: reason discarded with religious fervor, replaced by blind faith in corporate propaganda.
The comment of a friend on my facebook post that still haunts me to this day:

Walking Away from the Herd
After a period of anger and disillusionment, I made a decision: I would no longer waste energy arguing with people who refused to think for themselves. If my circle couldn’t even ask basic questions—like why an untested medical intervention was being pushed with unprecedented urgency—then I needed a new community.
Fortunately, I already knew where to look. For three years, I had been involved in Bitcoin, a space where skepticism wasn’t just tolerated—it was demanded. Here, I’d met some of the most principled and independent thinkers I’d ever encountered. These were people who understood the corrupting influence of centralized power—whether in money, media, or politics—and who valued sovereignty, skepticism, and integrity. Instead of blind trust, bitcoiners practiced relentless verification. And instead of empty rhetoric, they lived by a simple creed: Don’t trust. Verify.
It wasn’t just a philosophy. It was a lifeline. So I chose my side and I walked away from the herd.
Finding My Tribe
Over the next four years, I immersed myself in Bitcoin conferences, meetups, and spaces where ideas were tested, not parroted. Here, I encountered extraordinary people: not only did they share my skepticism toward broken systems, but they challenged me to sharpen it.
No longer adrift in a sea of mindless conformity, I’d found a crew of thinkers who cut through the noise. They saw clearly what most ignored—that at the core of society’s collapse lay broken money, the silent tax on time, freedom, and truth itself. But unlike the complainers I’d left behind, these people built. They coded. They wrote. They risked careers and reputations to expose the rot. Some faced censorship; others, mockery. All understood the stakes.
These weren’t keyboard philosophers. They were modern-day Cassandras, warning of inflation’s theft, the Fed’s lies, and the coming dollar collapse—not for clout, but because they refused to kneel to a dying regime. And in their defiance, I found something rare: a tribe that didn’t just believe in a freer future. They were engineering it.
April 20, 2024: No more herd. No more lies. Only proof-of-work.
On April 20, 2024, exactly four years after my last Facebook post, the one that severed my ties to the herd for good—I stood in front of Warsaw’s iconic Palace of Culture and Science, surrounded by 400 bitcoiners who felt like family. We were there to celebrate Bitcoin’s fourth halving, but it was more than a protocol milestone. It was a reunion of sovereign individuals. Some faces I’d known since the early days; others, I’d met only hours before. We bonded instantly—heated debates, roaring laughter, zero filters on truths or on so called conspiracy theories.
As the countdown to the halving began, it hit me: This was the antithesis of the hollow world I’d left behind. No performative outrage, no coerced consensus—just a room of unyielding minds who’d traded the illusion of safety for the grit of truth. Four years prior, I’d been alone in my resistance. Now, I raised my glass among my people - those who had seen the system's lies and chosen freedom instead. Each had their own story of awakening, their own battles fought, but here we shared the same hard-won truth.
The energy wasn’t just electric. It was alive—the kind that emerges when free people build rather than beg. For the first time, I didn’t just belong. I was home. And in that moment, the halving’s ticking clock mirrored my own journey: cyclical, predictable in its scarcity, revolutionary in its consequences. Four years had burned away the old world. What remained was stronger.

No Regrets
Leaving the herd wasn’t a choice—it was evolution. My soul shouted: "I’d rather stand alone than kneel with the masses!". The Bitcoin community became more than family; they’re living proof that the world still produces warriors, not sheep. Here, among those who forge truth, I found something extinct elsewhere: hope that burns brighter with every halving, every block, every defiant mind that joins the fight.
Change doesn’t come from the crowd. It starts when one person stops applauding.
Today, I stand exactly where I always wanted to be—shoulder-to-shoulder with my true family: the rebels, the builders, the ungovernable. Together, we’re building the decentralized future.
-
 @ 6e0ea5d6:0327f353
2025-04-19 15:09:18
@ 6e0ea5d6:0327f353
2025-04-19 15:09:18🩸
The world won’t stop and wait for you to recover.Do your duty regardless of how you feel. That’s the only guarantee you’ll end the day alright.
You’ve heard it before: “The worst workout is the one you didn’t do.” Sometimes you don’t feel like going to the gym. You start bargaining with laziness: “I didn’t sleep well… maybe I should skip today.” But then you go anyway, committing only to the bare minimum your energy allows. And once you start, your body outperforms your mind’s assumptions—it turns out to be one of the best workouts you’ve had in a long time. The feeling of following through, of winning a battle you were losing, gives you the confidence to own the rest of your day. You finally feel good.
And that wouldn’t have happened if you stayed home waiting to feel better. Guilt would’ve joined forces with discouragement, and you’d be crushed by melancholy in a victim mindset. That loss would bleed into the rest of your week, conditioning your mind: because you didn’t spend your energy on the workout, you’d stay up late, wake up worse, and while waiting to feel “ready,” you’d lose a habit that took months of effort to build.
When in doubt, just do your duty. Stick to the plan. Don’t negotiate with your feelings—outsmart them. “Just one page today,” and you’ll end up reading ten. “Only the easy tasks,” and you’ll gain momentum to conquer the hard ones. Laziness is a serpent—you win when you make no deals with it.
A close friend once told me that when he was at his limit during a second job shift, he’d open a picture on his phone—of a fridge or a stove he needed to buy for his home—and that image gave him strength to stay awake. That moment stuck with me forever.
Do you really think the world will have the same mercy on you that you have on yourself? Don’t be surprised when it doesn’t spare you. Move forward even while stitching your wounds: “If you wait for perfect conditions, you’ll never do anything.” (Ecclesiastes 11:4)
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 57d1a264:69f1fee1
2025-05-12 08:23:43
@ 57d1a264:69f1fee1
2025-05-12 08:23:43Shifting left on accessibility means building inclusivity into every phase of a project—from strategy to QA—saving time, reducing risk, and creating better user experiences.
Shifting left is about collaboration: a successful website project isn’t a linear train ride from content to design to development. It’s a dynamic, collaborative ecosystem that means everyone contributes.
- Strategists ensure content is easy to find.
- Designers prioritize color contrast, readable typography, and interactive elements.
- Back-end developers support accessible content structures and accessible interaction.
- Front-end developers implement semantic markup and accessible UI components.
- QA testers verify functionality across assistive devices.
- DevOps engineers integrate automated accessibility checks into the workflow.
- Technical project managers: keep accessibility visible and prioritized.
Accessibility should be part of every conversation—from kickoff to QA.
Read the full article at https://www.lullabot.com/articles/what-it-means-shift-left-accessibility-and-how-do-it-right
originally posted at https://stacker.news/items/977943
-
 @ 57d1a264:69f1fee1
2025-05-12 08:12:40
@ 57d1a264:69f1fee1
2025-05-12 08:12:40VIET GD is a casual index, archive, and celebration of Vietnamese graphic design. Currently, there are 274 objects in this collection. Understandably, a lot of propaganda posters... as well as music themed ones! Here below some of the most interesting ones:
Explore them all at https://vietgd.com/
originally posted at https://stacker.news/items/977939
-
 @ a9434ee1:d5c885be
2025-05-12 08:09:26
@ a9434ee1:d5c885be
2025-05-12 08:09:26Colors as a fun and useful identifier
Nostr apps often use totally random colors for their default avatars, profiles names in chat bubbles, etc... That's a missed opportunity. Why don't we just we just derive a color from the npub and use that instead, interoperably across apps?
It gives us a fun and visual extra point of recognition, often without having to add anything extra to the UIs.
The only problem is that we cannot just allow for any color. The colors should be readable as text in Light and Dark modes and gray-scales should be avoided too.
This is the goal:
Luckily, there's a super simple solution.
(which was used to derive the colors above)Deriving the Colors
You can find the simple spec here: nostr:naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qy88wumn8ghj7mn0wvhxcmmv9uqsuamnwvaz7tmwdaejumr0dshsz8rhwden5te0w35x2cmfw3skgetv9ehx7um5wgcjucm0d5hsz8rhwden5te0w35x2cmfw3skgetv9ehx7um5wgcjucm0d5hszxmhwden5te0w35x2en0wfjhxapwdehhxarjxyhxxmmd9uq3kamnwvaz7tm5dpjkvmmjv4ehgtnwdaehgu339e3k7mf0qyghwumn8ghj7mn0wd68ytnhd9hx2tcpz9mhxue69uhkummnw3ezuamfdejj7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgwwaehxw309ahx7uewd3hkctcpr3mhxue69uhhg6r9vd5hgctyv4kzumn0wd68yvfwvdhk6tcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcprdmhxue69uhhg6r9vehhyetnwshxummnw3erztnrdakj7qg3waehxw309ahx7um5wgh8w6twv5hszythwden5te0dehhxarj9emkjmn99uqsuamnwvaz7tmwdaejumr0dshsz8rhwden5te0w35x2cmfw3skgetv9ehx7um5wgcjucm0d5hsqpnwd9cz6ce3pvatyf
TLDR: 1. Convert HEX pubkey to Int 2. Calculate the Hue value: Int % 360 3. Set Saturation to 90 for Hues between 216 and 273, use 80 for the rest 4. Set Brightness to 65 for Hues between 32 and 212, use 85 for the rest
Convert HSB color to whatever format you need. Done.
Easy & Fun to integrate!
-
 @ 6e0ea5d6:0327f353
2025-04-19 15:02:55
@ 6e0ea5d6:0327f353
2025-04-19 15:02:55My friend, let yourself be deluded for a moment, and reality will see to it that your fantasy is shattered—like a hammer crushing marble. The real world grants no mercy; it will relentlessly tear down your aspirations, casting them into the abyss of disillusionment and burying your dreams under the unbearable weight of your own expectations. It’s an inescapable fate—but the outcome is still in your hands: perish at the bottom like a wretch or turn the pit into a trench.
Davvero, everyone must eventually face something that breaks them. It is in devastation that man discovers what he is made of, and in the silence of defeat that he hears the finest advice. Yet the weak would rather embrace the convenient lie of self-pity, blaming life for failures that are, in truth, the result of their own negligence and cowardly choices. If you hide behind excuses because you fear the painful truth, know this: the responsibility has always been yours.
Ascolta bene! Just remain steadfast, even when everything feels like an endless maze. The difficulties you face today—those you believe you’ll never overcome—will one day seem insignificant under the light of time and experience. Tomorrow, you’ll look back and laugh at yourself for ever letting these storms seem so overwhelming.
Now, it’s up to you to fight your own battle—for the evil day spares no one. Don’t let yourself be paralyzed by shock or bow before adversity. Be strong and of good courage—not as one who waits for relief, but as one prepared to face the inevitable and turn pain into glory.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 57d1a264:69f1fee1
2025-05-12 07:27:52
@ 57d1a264:69f1fee1
2025-05-12 07:27:52A set of beautifully-designed, accessible components and a code distribution platform. Works with your favorite frameworks. Open Source. Open Code.
This is how @kurtispapple make use of it https://www.linkedin.com/pulse/championing-health-data-interoperability-my-journey-nz-kurtis-papple-mwglc
Start building yours at https://ui.shadcn.com/
originally posted at https://stacker.news/items/977930
-
 @ cecdc1e8:b6c264ee
2025-05-12 12:41:57
@ cecdc1e8:b6c264ee
2025-05-12 12:41:57GM
-
 @ 3ffac3a6:2d656657
2025-04-15 14:49:31
@ 3ffac3a6:2d656657
2025-04-15 14:49:31🏅 Como Criar um Badge Épico no Nostr com
nak+ badges.pageRequisitos:
- Ter o
nakinstalado (https://github.com/fiatjaf/nak) - Ter uma chave privada Nostr (
nsec...) - Acesso ao site https://badges.page
- Um relay ativo (ex:
wss://relay.primal.net)
🔧 Passo 1 — Criar o badge em badges.page
- Acesse o site https://badges.page
-
Clique em "New Badge" no canto superior direito
-
Preencha os campos:
- Nome (ex:
Teste Épico) - Descrição
-
Imagem e thumbnail
-
Após criar, você será redirecionado para a página do badge.
🔍 Passo 2 — Copiar o
naddrdo badgeNa barra de endereços, copie o identificador que aparece após
/a/— este é o naddr do seu badge.Exemplo:
nostr:naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0Copie:
naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0
🧠 Passo 3 — Decodificar o naddr com
nakAbra seu terminal (ou Cygwin no Windows) e rode:
bash nak decode naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0Você verá algo assim:
json { "pubkey": "3ffac3a6c859eaaa8cdddb2c7002a6e10b33efeb92d025b14ead6f8a2d656657", "kind": 30009, "identifier": "Teste-Epico" }Grave o campo
"identifier"— nesse caso: Teste-Epico
🛰️ Passo 4 — Consultar o evento no relay
Agora vamos pegar o evento do badge no relay:
bash nak req -d "Teste-Epico" wss://relay.primal.netVocê verá o conteúdo completo do evento do badge, algo assim:
json { "kind": 30009, "tags": [["d", "Teste-Epico"], ["name", "Teste Épico"], ...] }
💥 Passo 5 — Minerar o evento como "épico" (PoW 31)
Agora vem a mágica: minerar com proof-of-work (PoW 31) para que o badge seja classificado como épico!
bash nak req -d "Teste-Epico" wss://relay.primal.net | nak event --pow 31 --sec nsec1SEU_NSEC_AQUI wss://relay.primal.net wss://nos.lol wss://relay.damus.ioEsse comando: - Resgata o evento original - Gera um novo com PoW de dificuldade 31 - Assina com sua chave privada
nsec- E publica nos relays wss://relay.primal.net, wss://nos.lol e wss://relay.damus.io⚠️ Substitua
nsec1SEU_NSEC_AQUIpela sua chave privada Nostr.
✅ Resultado
Se tudo der certo, o badge será atualizado com um evento de PoW mais alto e aparecerá como "Epic" no site!
- Ter o
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 57d1a264:69f1fee1
2025-05-12 06:41:49
@ 57d1a264:69f1fee1
2025-05-12 06:41:49It's incredible how deep people can go into something so mundane as a post stamp. Postage stamps are a surprisingly complex topic, overlapping with money, collectibility and bank notes. I was a postage stamp enthusiast myself, but this is one of those “the universe is surprisingly detailed” type. The rules defining postage and how it has been ruling commerce for centuries is even more fascinating and intriguing.
Discover more at https://www.linyangchen.com/Philately
originally posted at https://stacker.news/items/977918
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ cb4352cd:a16422d7
2025-05-12 12:18:41
@ cb4352cd:a16422d7
2025-05-12 12:18:41In the early days of the internet, openness was a foundational value. Today, as the financial world undergoes its next great evolution, that same principle is making a powerful return — this time through open-source code, permissionless protocols, and user-owned ecosystems. The future of finance isn’t just digital. It’s open.
Beyond the Institution: A Shift in Trust
Traditional finance has always been built around institutions — banks, central authorities, and regulatory bodies. While these structures offer stability, they also limit access, enforce gatekeeping, and concentrate power.
Permissionless innovation flips this model. Instead of asking for approval, builders create protocols that anyone can use, fork, or improve. In DeFi, anyone with an internet connection can lend, borrow, or trade without relying on a centralized intermediary.
Composability: Financial Lego for the Internet Age
Open protocols don’t just stand alone — they connect. In Web3, composability means developers can build on top of each other’s code like financial Lego blocks. This accelerates experimentation and reduces duplication of effort.
You can build a lending protocol that integrates with a decentralized exchange, which in turn connects to a stablecoin, creating a rich, interoperable financial ecosystem — all without closed APIs or licensing fees.
DAOs and the Redefinition of Governance
Openness is not only about access — it’s about control. Decentralized Autonomous Organizations (DAOs) allow communities to govern protocols, allocate resources, and shape development roadmaps. In contrast to top-down decision-making, DAOs are built on transparency, collective voting, and participatory ownership.
As financial systems move on-chain, governance itself becomes programmable. This allows for more adaptive, responsive institutions that can evolve with user needs — not just boardroom mandates.
More Than Code: A Philosophical Shift
Open finance isn’t just a stack of protocols. It reflects a deeper belief: that financial systems should be inclusive, interoperable, and transparent by design.
This philosophy challenges legacy ideas of exclusivity and control. It opens space for local currencies, niche communities, experimental markets, and user-first financial design. It treats users not as passive consumers but as co-owners and co-builders.
How Beyond Banking Conference by WeFi Embraces Openness
This vision of open finance is a central theme of the Beyond Banking Conference by WeFi. Taking place online on May 30, 2025, the conference brings together pioneers from DeFi, AI, Web3, and FinTech to discuss permissionless technologies, composable architecture, and the human values behind them.
Speakers will explore how openness fuels innovation, and how protocol design shapes access, governance, and trust. From DAOs to AI-powered DeFi, the program emphasizes tools that scale freedom — not just efficiency.
In the future, finance won’t just be smart. It will be open. And that changes everything.
-
 @ 90c656ff:9383fd4e
2025-05-12 06:06:00
@ 90c656ff:9383fd4e
2025-05-12 06:06:00Bitcoin emerged as an alternative to the traditional financial system, offering a decentralized and censorship-resistant medium of exchange. However, this proposition directly challenges the control governments exert over the economy, particularly in terms of currency issuance and financial regulation. As a result, many governments view Bitcoin with suspicion and attempt to limit its adoption, while others seek to integrate it into the economy in a controlled manner.
Reasons for conflict between governments and Bitcoin
Government resistance to Bitcoin adoption stems from several key factors:
01 - Loss of Monetary Control: Governments manage monetary policy through the issuance of fiat currency and manipulation of interest rates. Bitcoin, with its fixed supply and decentralized nature, prevents governments from printing more money, thereby limiting their influence over the economy.
02 - Challenges in Taxation: Bitcoin usage makes it harder for authorities to monitor transactions and enforce tax collection, posing a challenge for governments that rely heavily on taxation to fund public services.
03 - Concerns Over Regulation and Financial Crime: Many governments argue that Bitcoin can be used for money laundering, tax evasion, and other illicit activities. However, since all transactions are recorded on the blockchain (or timechain), Bitcoin is actually more traceable than physical cash.
04 - Competition with Central Bank Digital Currencies (CBDCs): Some governments are developing their own digital currencies, known as CBDCs. These offer a high level of control over financial transactions but lack Bitcoin’s decentralized properties. To promote CBDC adoption, some governments attempt to restrict or ban Bitcoin.
Different countries have taken varied approaches to Bitcoin, ranging from full acceptance to outright repression.
- El Salvador:
In 2021, El Salvador became the first country to adopt Bitcoin as legal tender. This decision sparked conflict with global financial institutions like the International Monetary Fund (IMF), which pressured the Salvadoran government to reverse its stance.
- China:
The Chinese government banned Bitcoin mining and usage entirely in 2021, citing environmental concerns and financial risks. Nonetheless, many Chinese miners and users continue to operate through alternative means.
- United States:
While Bitcoin is legal in the U.S., the government has imposed stricter regulations on exchanges and mining operations, seeking to exert more control over the sector. Some politicians advocate for a pro-Bitcoin stance, while others see it as a threat to the dollar.
- European Union:
The EU has taken a more rigorous regulatory approach, requiring user identification and transaction transparency. Despite this, Bitcoin remains legal and widely used.
Despite the challenges imposed by some governments, Bitcoin adoption continues to grow. Many users see Bitcoin as a way to preserve wealth in the face of inflationary monetary policies and excessive government control over money. Furthermore, in countries with unstable economies and limited access to financial services, Bitcoin provides a solution for international payments and protection against economic crises.
Government resistance may slow Bitcoin adoption in certain regions, but it is unlikely to stop it entirely. As a decentralized and global network, Bitcoin will continue to be used regardless of restrictions imposed by any single government. In the long run, its adoption will depend on individuals and businesses standing firm against regulatory pressures and continuing to use it as a financial alternative.
In summary, the conflict between governments and Bitcoin reflects the broader struggle between a centralized traditional financial system and a new decentralized alternative. While some countries seek to ban or restrict its use, others embrace it as part of their economy. Ultimately, government resistance may only delay-but not prevent-the global adoption of Bitcoin, which continues to demonstrate its resilience and utility as a store of value and medium of exchange.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 266815e0:6cd408a5
2025-04-15 06:58:14
@ 266815e0:6cd408a5
2025-04-15 06:58:14Its been a little over a year since NIP-90 was written and merged into the nips repo and its been a communication mess.
Every DVM implementation expects the inputs in slightly different formats, returns the results in mostly the same format and there are very few DVM actually running.
NIP-90 is overloaded
Why does a request for text translation and creating bitcoin OP_RETURNs share the same input
itag? and why is there anoutputtag on requests when only one of them will return an output?Each DVM request kind is for requesting completely different types of compute with diffrent input and output requirements, but they are all using the same spec that has 4 different types of inputs (
text,url,event,job) and an undefined number ofoutputtypes.Let me show a few random DVM requests and responses I found on
wss://relay.damus.ioto demonstrate what I mean:This is a request to translate an event to English
json { "kind": 5002, "content": "", "tags": [ // NIP-90 says there can be multiple inputs, so how would a DVM handle translatting multiple events at once? [ "i", "<event-id>", "event" ], [ "param", "language", "en" ], // What other type of output would text translations be? image/jpeg? [ "output", "text/plain" ], // Do we really need to define relays? cant the DVM respond on the relays it saw the request on? [ "relays", "wss://relay.unknown.cloud/", "wss://nos.lol/" ] ] }This is a request to generate text using an LLM model
json { "kind": 5050, // Why is the content empty? wouldn't it be better to have the prompt in the content? "content": "", "tags": [ // Why use an indexable tag? are we ever going to lookup prompts? // Also the type "prompt" isn't in NIP-90, this should probably be "text" [ "i", "What is the capital of France?", "prompt" ], [ "p", "c4878054cff877f694f5abecf18c7450f4b6fdf59e3e9cb3e6505a93c4577db2" ], [ "relays", "wss://relay.primal.net" ] ] }This is a request for content recommendation
json { "kind": 5300, "content": "", "tags": [ // Its fine ignoring this param, but what if the client actually needs exactly 200 "results" [ "param", "max_results", "200" ], // The spec never mentions requesting content for other users. // If a DVM didn't understand this and responded to this request it would provide bad data [ "param", "user", "b22b06b051fd5232966a9344a634d956c3dc33a7f5ecdcad9ed11ddc4120a7f2" ], [ "relays", "wss://relay.primal.net", ], [ "p", "ceb7e7d688e8a704794d5662acb6f18c2455df7481833dd6c384b65252455a95" ] ] }This is a request to create a OP_RETURN message on bitcoin
json { "kind": 5901, // Again why is the content empty when we are sending human readable text? "content": "", "tags": [ // and again, using an indexable tag on an input that will never need to be looked up ["i", "09/01/24 SEC Chairman on the brink of second ETF approval", "text"] ] }My point isn't that these event schema's aren't understandable but why are they using the same schema? each use-case is different but are they all required to use the same
itag format as input and could support all 4 types of inputs.Lack of libraries
With all these different types of inputs, params, and outputs its verify difficult if not impossible to build libraries for DVMs
If a simple text translation request can have an
eventortextas inputs, apayment-requiredstatus at any point in the flow, partial results, or responses from 10+ DVMs whats the best way to build a translation library for other nostr clients to use?And how do I build a DVM framework for the server side that can handle multiple inputs of all four types (
url,text,event,job) and clients are sending all the requests in slightly differently.Supporting payments is impossible
The way NIP-90 is written there isn't much details about payments. only a
payment-requiredstatus and a genericamounttagBut the way things are now every DVM is implementing payments differently. some send a bolt11 invoice, some expect the client to NIP-57 zap the request event (or maybe the status event), and some even ask for a subscription. and we haven't even started implementing NIP-61 nut zaps or cashu A few are even formatting the
amountnumber wrong or denominating it in sats and not mili-satsBuilding a client or a library that can understand and handle all of these payment methods is very difficult. for the DVM server side its worse. A DVM server presumably needs to support all 4+ types of payments if they want to get the most sats for their services and support the most clients.
All of this is made even more complicated by the fact that a DVM can ask for payment at any point during the job process. this makes sense for some types of compute, but for others like translations or user recommendation / search it just makes things even more complicated.
For example, If a client wanted to implement a timeline page that showed the notes of all the pubkeys on a recommended list. what would they do when the selected DVM asks for payment at the start of the job? or at the end? or worse, only provides half the pubkeys and asks for payment for the other half. building a UI that could handle even just two of these possibilities is complicated.
NIP-89 is being abused
NIP-89 is "Recommended Application Handlers" and the way its describe in the nips repo is
a way to discover applications that can handle unknown event-kinds
Not "a way to discover everything"
If I wanted to build an application discovery app to show all the apps that your contacts use and let you discover new apps then it would have to filter out ALL the DVM advertisement events. and that's not just for making requests from relays
If the app shows the user their list of "recommended applications" then it either has to understand that everything in the 5xxx kind range is a DVM and to show that is its own category or show a bunch of unknown "favorites" in the list which might be confusing for the user.
In conclusion
My point in writing this article isn't that the DVMs implementations so far don't work, but that they will never work well because the spec is too broad. even with only a few DVMs running we have already lost interoperability.
I don't want to be completely negative though because some things have worked. the "DVM feeds" work, although they are limited to a single page of results. text / event translations also work well and kind
5970Event PoW delegation could be cool. but if we want interoperability, we are going to need to change a few things with NIP-90I don't think we can (or should) abandon NIP-90 entirely but it would be good to break it up into small NIPs or specs. break each "kind" of DVM request out into its own spec with its own definitions for expected inputs, outputs and flow.
Then if we have simple, clean definitions for each kind of compute we want to distribute. we might actually see markets and services being built and used.
-
 @ 9c9d2765:16f8c2c2
2025-05-12 05:15:47
@ 9c9d2765:16f8c2c2
2025-05-12 05:15:47CHAPTER SIXTEEN
Mr. JP sat up abruptly as his phone buzzed. It was an anonymous message. He opened it slowly, his eyes scanning the contents with growing disbelief.
"James has returned to JP Enterprises. Charles reinstated him. He’s now President of your company."
His blood ran cold.
Mrs. JP saw the tension in his expression. "What’s wrong?"
"He’s back," Mr. JP said grimly. "Our son. James. He's taken over the company."
He stared into space, his mind reeling. "And Charles helped him..."
They had spent years trying to distance themselves from the disgrace of James’s past only to now be faced with the reality that he had clawed his way back into the empire they built.
The anonymous message was, of course, sent by Mark and Helen, each relishing in the chaos they had ignited. With the scandalous file now in their hands and James’s own family unknowingly brought into the picture, they believed the final blow was in place.
Mark leaned back in his chair and smiled as he read the forwarded documents.
"Let’s see how your so-called empire stands after this, James," he said quietly.
Helen, standing beside him, added coldly, "This time, he won’t survive it."
"How could he do this?" Mr. JP muttered under his breath, clutching his phone tightly. "How could Charles go behind my back and reinstall him? My own brother..."
The news that James had returned to JP Enterprises and not just as a member, but as its President had shaken him to the core. But what stung more was the betrayal he felt from Charles, who had once promised never to interfere in the matter again.
Fuming with rage and disbelief, Mr. JP boarded the next flight back home. Upon arrival, he didn’t even stop by the family estate. Instead, he went straight to the Regency Grand, the city’s most luxurious hotel, the same place he used to spend time with his family during better days. He booked the presidential suite and immediately dialed Charles' number.
"Meet me. Now. At the hotel," he barked before ending the call without waiting for a response.
Within the hour, Charles walked in, calm but aware of the storm brewing.
"You defied me, Charles," Mr. JP said, his voice icy. "You brought back the one person I had removed. The one person I swore would never set foot in the company again."
"Because you were wrong," Charles replied firmly. "You made a decision based on lies."
Mr. JP’s glare deepened.
"Lies? The records were clear embezzlement. Theft. He disgraced this family, Charles!"
Charles stood his ground. "Those records were manipulated. You never gave James a chance to explain himself."
He stepped closer. "The funds he was accused of stealing? He used them to invest in a struggling tech start-up that exploded in value two years later. That investment saved JP Enterprises during the economic downturn. The company is standing today because of James’s vision and sacrifice."
Silence filled the room.
Mr. JP felt his heart sink as the weight of Charles’s words settled in. He turned away, walking slowly to the window, staring out at the city skyline.
"All this time... I condemned my own son... exiled him... because I trusted false reports?"
Charles nodded. "Yes. And despite it all, he returned not for revenge, but to help us."
Tears welled up in Mr. JP’s eyes. His pride, once like stone, was now crumbling.
Without hesitation, he picked up his phone and dialed James’s number. The phone rang twice before James answered.
"Hello?" came the familiar voice, calm and distant.
"James... it’s your father." His voice trembled. "I... I’m sorry. I was wrong. Gravely wrong. Everything I believed about you was a lie. I let you down, son."
There was silence on the other end.
"I just found out the truth," Mr. JP continued. "And I’m proud of what you’ve done for the company, for our name. I want you to know... you are reinstated as the rightful heir to JP Enterprises. I want you back not just as President, but as my son."
James took a long pause before answering.
"It took you long enough," he said softly. "But... thank you."
Though James had once sworn not to seek his parents' approval, deep down, those words still mattered. And hearing them from the father who had disowned him brought a quiet sense of closure.
The rift that had torn them apart for years was beginning to heal.
"Dad, who told you I was the President of JP Enterprises?" James asked, his tone calm but firm as he stood before his father in the grand office of the family estate.
Mr. JP, still adjusting to the emotional weight of his recent apology, furrowed his brow. "It was anonymous, son. I received a message with no name, no clue. Just the information."
James narrowed his eyes. "Can you forward the message to me?"
"Of course," his father replied, pulling out his phone. Within seconds, the message was in James’s inbox.
Later that evening, James sat in his private office, staring at the message on his screen. Something about it felt off too calculated, too timely. He forwarded it to his personal cybersecurity team with one instruction: “Trace the source. I want to know everything about who sent it, how, and if they’re working with someone.”
Meanwhile, Ray Enterprises was thriving again under James’s investment. With the influx of capital and revitalized operations, profits were skyrocketing. However, while the company’s success looked promising on the surface, the Ray family was barely reaping the rewards.
James’s 85% share ensured he collected the lion’s portion of every deal. Robert, despite being the figurehead chairman, found himself managing a flourishing empire but receiving only crumbs in return.
Frustrated and desperate, Robert scheduled a private meeting with James.
"James, please... eighty-five percent is bleeding us dry. We’re grateful for what you’ve done truly but surely we can renegotiate?"
James leaned back in his chair, expression unreadable. "You signed the agreement, Robert. You knew the terms. And frankly, I'm not in the mood to revisit old conversations."
"We just want fairness," Robert pleaded. "A little breathing space"
"If this discussion continues," James interrupted coldly, "I’ll pull out my funds. And when I do, I promise Ray Enterprises will go down faster than it rose. Do I make myself clear?"
Robert’s face fell. He had no choice but to nod and walk away, defeated.
Two weeks later, James’s cybersecurity team sent their report. The source of the anonymous message had been traced and the result was both surprising and telling.
Tracy.
James sat silently as he read the details. Tracy, his own subordinate, had accessed restricted files from the company’s internal network. It wasn’t just a case of whistleblowing it was deliberate sabotage. But what intrigued him more was the fact that she had gone to great lengths to cover her tracks.
No one takes that risk alone, he thought.
Despite having the evidence in hand, James chose silence. Not out of mercy but strategy. He needed to know who she was working with. Who else had a vested interest in his downfall?
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 9223d2fa:b57e3de7
2025-04-15 02:54:00
@ 9223d2fa:b57e3de7
2025-04-15 02:54:0012,600 steps
-
 @ d7955b22:025a3ba9
2025-05-12 04:31:36
@ d7955b22:025a3ba9
2025-05-12 04:31:36O mundo dos jogos online tem se expandido rapidamente, oferecendo uma infinidade de opções para os jogadores. Entre as diversas plataformas disponíveis, o 99bra se destaca por sua variedade de opções e a experiência de usuário única que proporciona. Este artigo oferece uma visão detalhada sobre o que o 99bra tem a oferecer, desde suas características gerais até a experiência de jogo que promete satisfazer todos os tipos de jogadores.
Introdução à Plataforma 99bra 99bra é uma plataforma de entretenimento digital voltada para os entusiastas de jogos online. Com um design intuitivo e uma interface amigável, a plataforma foi criada para oferecer uma experiência de navegação fluida, seja em desktop ou dispositivos móveis. A plataforma se destaca pela sua confiabilidade e pela qualidade dos jogos oferecidos, sempre priorizando a segurança e a proteção dos dados de seus usuários.
Ao se cadastrar no 99bra, os jogadores têm acesso a uma ampla gama de opções de jogos, desde clássicos até lançamentos inovadores. O site se adapta às necessidades dos usuários, com suporte em português e atendimento ao cliente de excelência, tornando a plataforma acessível a jogadores de todas as idades e níveis de experiência. O processo de inscrição é rápido e simples, permitindo que os novos usuários comecem a se divertir em poucos minutos.
A Variedade de Jogos no 99bra O que realmente chama a atenção no 99bra é a diversidade de jogos oferecidos. A plataforma conta com uma vasta seleção de títulos, abrangendo uma ampla gama de gêneros. Seja você um fã de jogos de mesa, slots ou apostas esportivas, o 99bra tem algo para todos. Cada categoria de jogo é desenvolvida para garantir jogabilidade envolvente, gráficos impressionantes e uma experiência imersiva.
Jogos de Mesa Os jogos de mesa são um dos maiores atrativos da plataforma, com várias opções que incluem clássicos como blackjack, roleta e baccarat. Estes jogos oferecem uma experiência realista e dinâmica, com a possibilidade de interagir com outros jogadores. A interface é cuidadosamente projetada para garantir que cada clique e movimento se sinta natural, criando uma atmosfera que lembra a de um ambiente de jogo físico.
Slots e Máquinas de Vídeo Para os amantes das máquinas de vídeo, o 99bra oferece uma impressionante coleção de slots. Os jogadores podem explorar uma variedade de temas, desde aventuras épicas até histórias de fantasia, com gráficos vibrantes e animações cativantes. As funções de bônus, rodadas grátis e jackpots progressivos tornam os jogos ainda mais emocionantes, com a possibilidade de grandes vitórias a cada giro.
Apostas Esportivas Outro ponto forte da plataforma são as apostas esportivas. O 99bra oferece uma extensa seleção de esportes para os fãs de esportes ao vivo. Seja futebol, basquete, tênis ou eSports, a plataforma proporciona odds competitivas e a chance de apostar em eventos de todo o mundo, com atualizações em tempo real para garantir que o jogador esteja sempre informado.
A Experiência do Jogador A experiência do jogador é o aspecto que diferencia o 99bra de outras plataformas. Desde o momento do cadastro até as interações durante os jogos, a plataforma é projetada para oferecer facilidade, conforto e diversão sem interrupções. O 99bra é otimizado para fornecer uma navegação rápida e sem erros, com um layout que garante que o jogador possa acessar todos os jogos e funcionalidades de forma simples.
Além disso, a plataforma oferece recursos adicionais para tornar a experiência ainda mais envolvente. Os jogadores podem configurar preferências de jogo, participar de promoções exclusivas e interagir com outros jogadores, criando uma verdadeira comunidade. A segurança também é uma prioridade, com criptografia de dados avançada e processos de verificação para garantir que todas as transações e informações pessoais estejam protegidas.
Suporte ao Cliente O suporte ao cliente do 99bra é excepcional. A plataforma oferece múltiplos canais de atendimento, incluindo chat ao vivo, e-mail e telefone, para que os jogadores possam obter assistência rápida sempre que necessário. A equipe de suporte é altamente treinada e pronta para resolver qualquer dúvida ou problema de forma eficiente, garantindo que a experiência do jogador nunca seja comprometida.
Conclusão O 99bra é uma plataforma completa que atende aos mais altos padrões de qualidade e segurança no universo dos jogos online. Com uma vasta seleção de jogos, suporte ao cliente de excelência e uma experiência de usuário impecável, o 99bra se consolida como uma das opções mais atrativas para quem busca diversão e entretenimento. Se você está procurando uma plataforma que combine inovação, variedade e uma jogabilidade envolvente, o 99bra certamente é uma excelente escolha.
-
 @ d7955b22:025a3ba9
2025-05-12 04:31:00
@ d7955b22:025a3ba9
2025-05-12 04:31:00A plataforma 53a é uma das mais novas e emocionantes opções para quem busca uma experiência completa de entretenimento digital. Com uma ampla gama de jogos e funcionalidades voltadas para o prazer e a diversão dos jogadores, a 53a se destaca por sua interface intuitiva, seu foco na segurança e uma vasta gama de opções para todos os gostos. Se você ainda não conhece essa plataforma inovadora, continue lendo e descubra tudo o que ela tem a oferecer!
Introdução à Plataforma 53a A 53a é uma plataforma de entretenimento online que se destaca pelo seu compromisso em oferecer uma experiência única aos jogadores. Com um design moderno e acessível, a plataforma foi criada para atender a um público que busca algo mais do que simples joguinhos – ela oferece uma verdadeira imersão em um universo de possibilidades.
Ao acessar a 53a , os usuários são rapidamente apresentados a um painel de controle simplificado, onde podem facilmente navegar por diferentes categorias de jogos, conferir promoções e acessar uma série de recursos exclusivos. Além disso, a plataforma está disponível em diversos dispositivos, incluindo desktop, smartphones e tablets, permitindo que o jogador tenha acesso à diversão em qualquer lugar e a qualquer momento.
Jogos Empolgantes para Todos os Gostos A 53a não se limita a um único tipo de jogo. Em vez disso, oferece uma vasta gama de opções, com títulos que atendem a diferentes preferências e estilos de jogo. Desde jogos de habilidade, como jogos de mesa e jogos de cartas, até opções mais interativas e imersivas, como máquinas de diversão, a plataforma tem algo para todos os jogadores.
Jogos de Mesa e Cartas: Para os que apreciam uma experiência mais estratégica, a 53a oferece uma seleção diversificada de jogos de mesa, incluindo opções clássicas como o blackjack, pôquer e roleta. Cada jogo é projetado para proporcionar uma experiência desafiadora e envolvente, com gráficos impressionantes e uma jogabilidade fluida.
Máquinas de Diversão: Para quem busca uma experiência mais dinâmica e de fácil acesso, as máquinas de diversão são a escolha perfeita. Com uma vasta gama de temas e estilos, essas máquinas são ideais para momentos de descontração, com rodadas rápidas e prêmios atrativos. Cada jogo tem sua própria atmosfera única, com sons e animações que mantêm o jogador imerso por horas.
Jogos ao Vivo: Uma das grandes atrações da 53a são os jogos ao vivo, onde os jogadores podem interagir em tempo real com dealers e outros participantes. Esses jogos trazem a emoção de uma experiência presencial, mas com a conveniência de estar em casa ou onde preferir.
A Experiência do Jogador na 53a A experiência do jogador na plataforma 53a é pensada para ser fluida, segura e divertida. Com uma interface simples, os jogadores podem facilmente acessar seus jogos favoritos e navegar por outras funcionalidades da plataforma.
Interface Intuitiva: Desde o momento em que você entra na 53a, perceberá como a plataforma foi projetada com o usuário em mente. O layout claro e as opções bem definidas tornam a navegação fácil, mesmo para aqueles que não são tão familiarizados com plataformas digitais.
Segurança e Privacidade: A plataforma 53a adota as melhores práticas de segurança para garantir que todas as informações dos jogadores sejam protegidas. Desde transações financeiras até dados pessoais, a 53a utiliza tecnologias avançadas de criptografia para garantir que seus dados estejam sempre seguros.
Atendimento ao Cliente: A 53a se destaca também pelo seu excelente suporte ao cliente. Caso o jogador tenha alguma dúvida ou precise de ajuda, pode contar com uma equipe de atendimento pronta para oferecer assistência de forma rápida e eficaz. A plataforma também conta com uma seção de perguntas frequentes (FAQ) que ajuda a esclarecer as dúvidas mais comuns.
Conclusão A plataforma 53a se consolida como uma das principais opções de entretenimento online para quem busca diversão, segurança e uma experiência de usuário completa. Com uma grande variedade de jogos, suporte de alta qualidade e uma interface amigável, ela atende às necessidades de todos os tipos de jogadores, proporcionando momentos inesquecíveis. Se você está à procura de uma plataforma inovadora, segura e divertida, a 53a é a escolha certa para você!
-
 @ 6e0ea5d6:0327f353
2025-04-14 15:11:17
@ 6e0ea5d6:0327f353
2025-04-14 15:11:17Ascolta.
We live in times where the average man is measured by the speeches he gives — not by the commitments he keeps. People talk about dreams, goals, promises… but what truly remains is what’s honored in the silence of small gestures, in actions that don’t seek applause, in attitudes unseen — yet speak volumes.
Punctuality, for example. Showing up on time isn’t about the clock. It’s about respect. Respect for another’s time, yes — but more importantly, respect for one’s own word. A man who is late without reason is already running late in his values. And the one who excuses his own lateness with sweet justifications slowly gets used to mediocrity.
Keeping your word is more than fulfilling promises. It is sealing, with the mouth, what the body must later uphold. Every time a man commits to something, he creates a moral debt with his own dignity. And to break that commitment is to declare bankruptcy — not in the eyes of others, but in front of himself.
And debts? Even the small ones — or especially the small ones — are precise thermometers of character. A forgotten sum, an unpaid favor, a commitment left behind… all of these reveal the structure of the inner building that man resides in. He who neglects the small is merely rehearsing for his future collapse.
Life, contrary to what the reckless say, is not built on grand deeds. It is built with small bricks, laid with almost obsessive precision. The truly great man is the one who respects the details — recognizing in them a code of conduct.
In Sicily, especially in the streets of Palermo, I learned early on that there is more nobility in paying a five-euro debt on time than in flaunting riches gained without word, without honor, without dignity.
As they say in Palermo: L’uomo si conosce dalle piccole cose.
So, amico mio, Don’t talk to me about greatness if you can’t show up on time. Don’t talk to me about respect if your word is fickle. And above all, don’t talk to me about honor if you still owe what you once promised — no matter how small.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 6e0ea5d6:0327f353
2025-04-14 15:10:58
@ 6e0ea5d6:0327f353
2025-04-14 15:10:58Ascolta bene.
A man’s collapse never begins on the battlefield.
It begins in the invisible antechamber of his own mind.
Before any public fall, there is an ignored internal whisper—
a small, quiet, private decision that gradually drags him toward ruin.No empire ever fell without first rotting from within.
The world does not destroy a man who hasn’t first surrendered to himself.
The enemy outside only wins when it finds space in the void the man has silently carved.**Non ti sbagliare ** — there are no armies more ruthless than undisciplined thoughts.
There are no blows more fatal than the ones we deal ourselves:
with small concessions, well-crafted excuses,
and the slow deterioration of our integrity.
What people call failure is nothing more than the logical outcome
of a sequence of internal betrayals.Afraid of the world? Sciocchezze.
But a man who’s already bowed before his own weaknesses—
he needs no enemies.
He digs his own grave, chooses the epitaph,
and the only thing the world does is toss in some dirt.Capisci?
Strength isn’t the absence of falling, but the presence of resistance.
The true battle isn’t external.
It takes place within—where there’s only you, your conscience, and the mirror.
And it’s in that silent courtroom where everything is decided.The discipline to say “no” to yourself
is more noble than any public glory.
Self-control is more valuable than any victory over others.In Sicily, we learn early:
“Cu s’abbrazza cu’ so’ nemicu, si scorda la faccia di l’amicu.”
He who embraces his enemy forgets the face of his friend.
The most dangerous enemy is the one you feed daily with self-indulgence.
And the most relentless confrontation is the one you avoid in front of the mirror.So don’t talk to me about external defeats.
Tell me where inside you the weakness began.
Tell me the exact moment you abandoned what you believed in, in the name of ease.
Because a man only falls before the world… after falling before himself.Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ c21b1a6c:0cd4d170
2025-04-14 14:41:20
@ c21b1a6c:0cd4d170
2025-04-14 14:41:20🧾 Progress Report Two
Hey everyone! I’m back with another progress report for Formstr, a part of the now completed grant from nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f . This update covers everything we’ve built since the last milestone — including polish, performance, power features, and plenty of bug-squashing.
🏗️ What’s New Since Last Time?
This quarter was less about foundational rewrites and more about production hardening and real-world feedback. With users now onboard, our focus shifted to polishing UX, fixing issues, and adding new features that made Formstr easier and more powerful to use.
✨ New Features & UX Improvements
- Edit Existing Forms
- Form Templates
- Drag & Drop Enhancements (especially for mobile)
- New Public Forms UX (card-style layout)
- FAQ & Support Sections
- Relay Modal for Publishing
- Skeleton Loaders and subtle UI Polish
🐛 Major Bug Fixes
- Fixed broken CSV exports when responses were empty
- Cleaned up mobile rendering issues for public forms
- Resolved blank.ts export issues and global form bugs
- Fixed invalid
npubstrings in the admin flow - Patched response handling for private forms
- Lots of small fixes for titles, drafts, embedded form URLs, etc.
🔐 Access Control & Privacy
- Made forms private by default
- Fixed multiple issues around form visibility, access control UIs, and anonymous submissions
- Improved detection of pubkey issues in shared forms
🚧 Some Notable In-Progress Features
The following features are actively being developed, and many are nearing completion:
-
Conditional Questions:
This one’s been tough to crack, but we’re close!
Work in progress bykeralissand myself:
👉 PR #252 -
Downloadable Forms:
Fully-contained downloadable HTML versions of forms.
Being led bycasyazmonwith initial code by Basanta Goswami
👉 PR #274 -
OLLAMA Integration (Self-Hosted LLMs):
Users will be able to create forms using locally hosted LLMs.
PR byashu01304
👉 PR #247 -
Sections in Forms:
Work just started on adding section support!
Small PoC PR bykeraliss:
👉 PR #217
🙌 Huge Thanks to New Contributors
We've had amazing contributors this cycle. Big thanks to:
- Aashutosh Gandhi (ashu01304) – drag-and-drop enhancements, OLLAMA integration
- Amaresh Prasad (devAmaresh) – fixed npub and access bugs
- Biresh Biswas (Billa05) – skeleton loaders
- Shashank Shekhar Singh (Shashankss1205) – bugfixes, co-authored image patches
- Akap Azmon Deh-nji (casyazmon) – CSV fixes, downloadable forms
- Manas Ranjan Dash (mdash3735) – bug fixes
- Basanta Goswami – initial groundwork for downloadable forms
- keraliss – ongoing work on conditional questions and sections
We also registered for the Summer of Bitcoin program and have been receiving contributions from some incredibly bright new applicants.
🔍 What’s Still Coming?
From the wishlist I committed to during the grant, here’s what’s still in the oven:
-[x] Upgrade to nip-44 - [x] Access Controlled Forms: A Form will be able to have multiple admins and Editors. - [x] Private Forms and Fixed Participants: Enncrypt a form and only allow certain npubs to fill it. - [x] Edit Past Forms: Being able to edit an existing form. - [x] Edit Past Forms
- [ ] Conditional Rendering (in progress)
- [ ] Sections (just started)
- [ ] Integrations - OLLAMA / AI-based Form Generation (near complete)
- [ ] Paid Surveys
- [ ] NIP-42 Private Relay support
❌ What’s De-Prioritized?
- Nothing is de-prioritized now especially since Ollama Integration got re-prioritized (thanks to Summer Of Bitcoin). We are a little delayed on Private Relays support but it's now becoming a priority and in active development. Zap Surveys will be coming soon too.
💸 How Funds Were Used
- Paid individual contributors for their work.
- Living expenses to allow full-time focus on development
🧠 Closing Thoughts
Things feel like they’re coming together now. We’re out of "beta hell", starting to see real adoption, and most importantly, gathering feedback from real users. That’s helping us make smarter choices and move fast without breaking too much.
Stay tuned for the next big drop — and in the meantime, try creating a form at formstr.app, and let me know what you think!
-
 @ d360efec:14907b5f
2025-05-12 04:01:23
@ d360efec:14907b5f
2025-05-12 04:01:23 -
 @ 0b118e40:4edc09cb
2025-04-13 02:46:36
@ 0b118e40:4edc09cb
2025-04-13 02:46:36note - i wrote this before the global trade war, back when tariffs only affected China, Mexico, and Canada. But you will still get the gist of it.
During tough economic times, governments have to decide if they should open markets to global trade or protect local businesses with tariffs. The United States has swung between these two strategies, and history shows that the results are never straightforward
Just days ago, President Donald Trump imposed tariffs on imports from Canada, Mexico, and China. He framed these tariffs (25% on most Canadian goods, 10% on Canadian energy, 25% on Mexican imports, and 10% on Chinese imports) as a way to protect American industries.
But will they actually help, or could they backfire?
A History of U.S. Tariffs
Many have asked if countries will retaliate against the US. They can and they have. Once upon a time, 60 countries were so pissed off at the US, they retaliated at one go and crushed US dominance over trade.
This was during the Great Depression era in the 1930s when the government passed the Smoot-Hawley Tariff Act, placing high taxes on over 20,000 foreign goods. The goal was to protect American jobs, especially American farmers and manufacturers, but it backfired so badly.
Over 60 countries, including Canada, France, and Germany, retaliated by imposing their own tariffs. By 1933, US imports and exports both dropped significantly over 60%, and unemployment rose to 25%.
After President Franklin Roosevelt came to office, he implemented the Reciprocal Trade Agreements Act of 1934 to reverse these policies, calming the world down and reviving trade again.
The economist history of protectionism
The idea of shielding local businesses with tariffs isn’t new or recent. It's been around for a few centuries. In the 16th to 18th centuries, mercantilism encouraged countries to limit imports and boost exports.
In the 18th century, Adam Smith, in The Wealth of Nations, argued that free trade allows nations to specialize in what they do best countering protectionism policies. Friedrich List later challenged Smith's view by stating that developing countries need some protection to grow their “infant” industries which is a belief that still influences many governments today.
But how often do governments truly support startups and new small businesses in ways that create real growth, rather than allowing funds to trickle down to large corporations instead?
In modern times, John Maynard Keynes supported government intervention during economic downturns, while Milton Friedman championed free trade and minimal state interference.
Paul Krugman argued that limited protectionism can help large industries by providing them unfair advantages to become global market leaders. I have deep reservations about Krugman’s take, particularly on its impact or lack thereof in globalizing small businesses.
The debate between free trade and protectionism has existed for centuries. What’s clear is that there is no one-size-fits-all model to this.
The Political Debate - left vs right
Both the left and right have used tariffs but for different reasons. The right supports tariffs to protect jobs and industries, while the left uses them to prevent multinational corporations from exploiting cheap labor abroad.
Neoliberal policies favor free trade, arguing that competition drives efficiency and growth. In the US this gets a little bit confusing as liberals are tied to the left, and free trade is tied to libertarianism which the rights align closely with, yet at present right wing politicians push for protectionism which crosses the boundaries of free-trade.
There are also institutions like the WTO and IMF who advocate for open markets, but their policies often reflect political alliances and preferential treatment - so it depends on what you define as true 'free trade’.
Who Really Benefits from Tariffs?
Most often, tariffs help capital-intensive industries like pharmaceuticals, tech, and defense, while hurting labor-intensive sectors like manufacturing, agriculture, and construction.
This worsens inequality as big corporations will thrive, while small businesses and working-class people struggle with rising costs and fewer job opportunities.
I’ve been reading through international trade economics out of personal interest, I'll share some models below on why this is the case
1. The Disruption of Natural Trade
Tariffs disrupt the natural flow of trade. The Heckscher-Ohlin model explains that countries export goods that match their resources like Canada’s natural resource energy or China’s labour intensive textile and electronics. When tariffs block this natural exchange, industries suffer.
A clear example was Europe’s energy crisis during the Russia-Ukraine war. By abruptly cutting themselves off from the supply of Russian energy, Europe scrambled to find alternative sources. In the end, it was the people who had to bear the brunt of skyrocketing prices of energy.
2. Who wins and who loses?
The Stolper-Samuelson theorem helps us understand who benefits from tariffs and who loses. The idea behind it is that tariffs benefit capital-intensive industries, while labor-intensive sectors are hurt.
In the US, small manufacturing industries that rely on low-cost imports on intermediary parts from countries like China and Mexico will face rising costs, making their final goods too expensive and less competitive. This is similar to what happened to Argentina, where subsidies and devaluation of pesos contributed to cost-push inflation, making locally produced goods more expensive and less competitive globally.
This also reminded me of the decline of the US Rust Belt during the 1970s and 1980s, where the outsourcing of labour-intensive manufacturing jobs led to economic stagnation in many regions in the Midwest, while capital-intensive sectors flourished on the coasts. It resulted in significantly high income inequality that has not improved over the last 40 years.
Ultimately the cost of economic disruption is disproportionately borne by smaller businesses and low-skilled workers. At the end of the day, the rich get richer and the poor get poorer.
3. Delays in Economic Growth
The Rybczynski theorem suggests that economic growth depends on how efficiently nations reallocate their resources toward capital- or labor-intensive industries. But tariffs can distort this transition and progress.
In the 70s and 80s, the US steel industry had competition from Japan and Germany who modernized their production methods, making their steel more efficient and cost-effective. Instead of prioritizing innovation, many U.S. steel producers relied on tariffs and protectionist measures to shield themselves from foreign competition. This helped for a bit but over time, American steelmakers lost global market share as foreign competitors continued to produce better, cheaper steel. Other factors, such as aging infrastructure, and economic shifts toward a service-based economy, further contributed to the industry's decline.
A similar struggle is seen today with China’s high-tech ambitions. Tariffs on Chinese electronics and technology products limit access to key inputs, such as semiconductors and advanced robotics. While China continues its push for automation and AI-driven manufacturing, these trade barriers increase costs and disrupt supply chains, forcing China to accelerate its decoupling from Western markets. This shift could further strengthen alliances within BRICS, as China seeks alternative trade partnerships to reduce reliance on U.S.-controlled financial and technological ecosystems.
Will the current Tariff imposition backfire and isolate the US like it did a hundred years ago or 50 years ago? Is US risking it's position as a trusted economic leader? Only time would tell
The impact of tariff on innovation - or lack thereof
While the short-term impacts of tariffs often include higher consumer prices and job losses, the long-term effects can be even more damaging, as they discourage innovation by increasing costs and reducing competition.
Some historical examples globally : * Nigeria: Blocking import of rice opened up black market out of desperation to survive. * Brazil: Protectionist car policies led to expensive, outdated vehicles. * Malaysia’s Proton: Sheltered by tariffs and cronyism and failed to compete globally. * India (before 1991): Over-regulation limited the industries, until economic reforms allowed for growth. * Soviet Union during Cold War : Substandard products and minimal innovation due to the absence of foreign alternatives, yielding to economic stagnation.
On the flip side, Vietnam has significantly reduced protectionism policies by actively pursuing free trade agreements. This enabled it to become a key manufacturing hub. But Vietnam is not stopping there as it is actively pushing forward its capital-intensive growth by funding entrepreneurs.
The Future of U.S. Tariffs
History has shown that tariffs rarely deliver their intended benefits without unintended consequences. While they may provide temporary relief, they often raise prices, shrink job opportunities, and weaken industries in the long run.
Without a clear strategy for innovation and industrial modernization, the U.S. risks repeating past mistakes of isolating itself from global trade rather than strengthening its economy.
At this point, only time will tell whether these tariffs will truly help Americans or will they, once again, make the rich richer and the poor poorer.
-
 @ 502ab02a:a2860397
2025-05-12 03:11:06
@ 502ab02a:a2860397
2025-05-12 03:11:06สัปดาห์ที่ผ่านมา เราพักผ่อนย้อนไปเพื่อทำความเข้าใจต้นเหตุของซีรีส์นี้กันแล้วนะครับ ทีนี้เราจะมาสนทนากันต่อจากที่ค้างคาไว้กันครับ
ย้อนกลับไปเมื่อราวทศวรรษ 1970-1980 เป็นยุคที่โลกยังเชื่อว่า “ไขมัน” คือผู้ร้ายตัวจริงในวงการสุขภาพ ปิรามิดอาหารจาก USDA จึงถือกำเนิดขึ้น โดยมีฐานล่างกว้างใหญ่เต็มไปด้วยข้าว แป้ง ซีเรียล พาสต้า และขนมปัง เรียกรวมว่า “กลุ่มคาร์โบไฮเดรต” และถูกวางให้เป็นเสาหลักของอาหารประจำวัน ภายใต้แนวคิดว่าให้พลังงานสูง ไขมันต่ำ ดีต่อหัวใจ และเหมาะกับการเลี้ยงประชากรโลกที่เพิ่มขึ้นอย่างรวดเร็ว
แต่ความจริงที่เปิดเผยภายหลังคือ ปิรามิดอาหารนี้มิได้เกิดจากวิทยาศาสตร์บริสุทธิ์ หากแต่เกิดจากกระบวนการ “เปิดประมูลนโยบาย” โดยกลุ่มอุตสาหกรรมเกษตรรายใหญ่ ซึ่งต้องการระบายผลผลิตคาร์โบไฮเดรตจำนวนมหาศาลจากข้าวโพด ข้าวสาลี และถั่วเหลืองที่รัฐบาลอเมริกันอุดหนุนให้เพาะปลูกเกินความจำเป็น (ดูรายงาน PBS: The Food Pyramid) หน้าที่จัดสรรนี้จึงอยู่ภายใต้ USDA หรือ กระทรวงเกษตรสหรัฐอเมริกา
ขณะที่ผู้คนถูกสอนให้หลีกเลี่ยงไขมัน โปรตีนสัตว์ และหันมากินซีเรียลเป็นอาหารเช้า ผลิตภัณฑ์ไขมันต่ำแทบทุกชนิดกลับต้องเติมน้ำตาลและแป้งเพื่อให้มีรสชาติ นำไปสู่การระบาดของโรคอ้วน เบาหวาน ความดัน และ NCD ทั่วโลก ที่เราเพิ่งจะเข้าใจกันวันนี้ว่ามีรากมาจาก “ปิรามิดคาร์บ” นั่นเอง
คำถามคือ ทำไมการกำหนดอาหารของอเมริกา (ซึ่งแน่นอนว่าแพร่กระจายไปทั่วโลกภายใต้ข้อกำหนดเดียวกัน) จึงเกิดขึ้นจาก "กระทรวงเกษตรสหรัฐอเมริกา" ไม่ใช่ หน่วยงานทางวิทยาศาสตร์ หรือ การแพทย์
หรือเพราะ “อาหาร” ในอเมริกา ไม่ได้เริ่มจากคำว่า “สุขภาพ” แต่เริ่มจาก “เศรษฐกิจ”
ย้อนกลับไปช่วงต้นศตวรรษที่ 20 โดยเฉพาะหลังสงครามโลกครั้งที่สอง สหรัฐฯ ต้องการฟื้นฟูเศรษฐกิจและผลักดันภาคการเกษตรให้โตอย่างรวดเร็ว โดยเฉพาะสินค้าพืชเชิงอุตสาหกรรม เช่น ข้าวโพด ข้าวสาลี ถั่วเหลือง นม และเนื้อจากฟาร์มอุตสาหกรรม และปากท้องของเกษตรกรคือฐานเสียงสำคัญในทุกๆรัฐบาล ดังนั้น USDA ซึ่งเป็นหน่วยงานที่ตั้งขึ้นเพื่อดูแลเกษตรกร จึงรับบทผู้ออก “แนวทางโภชนาการ” โดยเน้นว่า
อาหารอะไรที่ เกษตรกรผลิตได้เยอะ ก็เอามาดันให้ประชาชนกินเยอะ อาหารอะไรที่ ราคาถูก ผลิตได้เร็ว ก็นำมาใส่ไว้ฐานล่างของพีระมิด ให้ประชาชนกินเยอะ อาหารอะไรที่ มีอุตสาหกรรมอยู่เบื้องหลัง ก็เปิดประมูลให้มีบทบาทมากในการล็อบบี้นโยบาย ให้ประชาชนกินเยอะ
พูดง่ายๆ ก็คือ นโยบายอาหารอเมริกา ไม่ได้ออกโดยนักวิทยาศาสตร์หรือนักโภชนาการที่ไม่มีผลประโยชน์ทับซ้อน แต่มาจาก “ข้าราชการสายเกษตร+กลุ่มทุน” ที่ต้องการให้ภาคการเกษตรมีกำไรอย่างต่อเนื่อง และอย่าลืมว่า อเมริกา = โลก
แล้วหน่วยงานด้านวิทยาศาสตร์หรือแพทย์ เช่น NIH (National Institutes of Health) หรือ CDC (Centers for Disease Control and Prevention) หล่ะ แน่นอนครับว่ามีข้อมูลอยุ่ว่าก็มีสิทธิ์เสนอแนะอยู่บ้างแต่ทั้งหมดนี้ ไม่มีอำนาจออกนโยบายหลักที่ใช้จริงกับประชาชน ส่วนใหญ่แค่ให้ข้อมูลวิชาการ ซึ่งมักจะถูกลดทอนหรือละเลยเมื่อนโยบายจริงถูกเขียนขึ้นโดย USDA ในที่สุด
เมื่อเสียงของการตั้งคำถามเริ่มดังกว่าเสียงโฆษณา ขบวนการ “Low Carb” ก็เริ่มตั้งหลักและขยายวงกว้างอย่างเงียบๆ งานวิจัยใหม่ๆ เริ่มบ่งชี้ว่า “น้ำตาลและแป้ง” โดยเฉพาะแป้งแปรรูป คือภัยเงียบที่ส่งผลต่อการอักเสบเรื้อรัง ภาวะดื้ออินซูลิน และเมตาบอลิกซินโดรม จนกระทั่งช่วงต้นทศวรรษ 2010 เป็นต้นมา อาหารแนว “ลดคาร์บ เพิ่มไขมันดี เพิ่มโปรตีน” ก็กลายเป็นกระแสหลักขึ้นมา
ตอนนั้นหลายคนคิดว่า “พวกเราชนะแล้ว” โลกกลับมาฟังเสียงสุขภาพที่แท้จริง โปรตีนกลายเป็นคำตอบใหม่แห่งยุค
แต่มึงเอ๊ยยยยยย... เกมอาจไม่ได้จบตรงนั้น
เพราะในวันที่ประชาชนเริ่มหลีกหนีคาร์บ กลุ่มทุนอาหารข้ามชาติที่เคยวางรากอยู่ในอุตสาหกรรมแป้ง ได้ค่อยๆ แปรทิศ ย้ายการลงทุนไปสู่ “โปรตีนทางเลือก” รอไว้นานแล้วโดยที่เราไม่รู้ตัว ทั้งอาหารพืชแปรรูปอย่าง texture ถั่วเหลือง (TVP), โปรตีนจุลินทรีย์, เนื้อปลูกจากห้องแลบ ไปจนถึง “ไข่” และ “นม” ที่ไม่ได้มาจากสัตว์ โปรตีนสังเคราะห์ที่ผลิตโดยระบบชีวภาพวิศวกรรม (synthetic biology) ซึ่งได้รับเงินทุนจากบริษัทยักษ์ใหญ่อย่างต่อเนื่องตลอดสิบปีที่ผ่านมา
พอถึงวันโปรตีนกลายเป็นเทรนด์ เขาก็เข้ามาเป็นเจ้าของเทรนด์เป็นที่เรียบร้อยแล้ว พร้อมทุกอย่างแล้ว คำถามคือ ใครกันแน่ที่เป็น Trend Setter
โปรตีนจึงไม่ใช่เพียง “สารอาหาร” อีกต่อไป แต่มันคือ “สินค้าอนาคต” ที่สามารถควบคุมแหล่งผลิต แหล่งพันธุ์ เทคโนโลยีการแปรรูป และการกระจายผ่านแพลตฟอร์มค้าปลีกทั่วโลก และถ้าคุณสังเกต จะเห็นว่าไม่มีใครพูดถึง “คาร์บทางเลือก” หรือ "คาร์บเข้มข้น" หรือ "คาร์บที่ไม่ต้องใช้พืช" แม้แต่นิด ทั้งที่ในทางหลักการก็สามารถคิดค้นได้ไม่ต่างกัน แปลว่า พวกเขาไม่ได้แค่อยาก “เลิกขายคาร์บ” แต่กำลัง “เปลี่ยนสินค้าหลักใหม่” ให้ไปอยู่ในกลุ่มที่พวกเขาควบคุมได้ทั้งหมด แค่เอาคำว่า "โปรตีน" ขึ้นมาเป็นฉากหน้าไว้ก่อน
เริ่มเห็นภาพไหมครับ จากคาร์บที่เคยถูกบิดเบือน กลายมาเป็นโปรตีนที่ถูกเสนอให้เรายินดีรับอย่างไม่ตั้งคำถาม
“โปรตีนอนาคต” ดูเหมือนจะเป็นทางเลือก แต่จริงๆ แล้วอาจเป็นกับดักหรือเปล่า
วันนี้ที่หลายคนเฝ้ามองชัยชนะของผู้คนในการล้ม “ปิรามิดคาร์บ” แต่ไม่ทันเห็นว่ากำลังถูกลากเข้าสู่ “หอคอยโปรตีนจำลอง” ที่พวกเขาสร้างขึ้นใหม่ ด้วยบรรจุภัณฑ์สวยหรู คำว่า "รักษ์โลก" "ปลอดภัย" และ "ยั่งยืน" แต่แท้จริงคือห่วงโซ่ที่มัดให้เราเป็นเพียง “ผู้บริโภค” ที่ไม่มีทางรู้ว่าอาหารของเรามาจากธรรมชาติหรือห้องแลบอีกต่อไป เรากลายเป็นหนูที่ย้ายจากกล่องวงกตหนึ่ง มายังอีกกล่องวงกตหนึ่งหรือเปล่า เป็นคำถามที่ยังต้องตอบต่อไป
เฮียไม่ได้มาเพื่อหวาดระแวงนะครับ เพราะในเกมอำนาจอาหาร ไม่มีใครยอมเสียพื้นที่ พวกเขาแค่เปลี่ยนกลยุทธ์ เพื่อครองความเชื่อมั่นใหม่ ในชื่อ “โปรตีน” #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 3b3a42d3:d192e325
2025-04-10 08:57:51
@ 3b3a42d3:d192e325
2025-04-10 08:57:51Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Trading and enforcement of asset option contracts
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ 872982aa:8fb54cfe
2025-05-12 01:40:27
@ 872982aa:8fb54cfe
2025-05-12 01:40:27 {.user-img}
{.user-img}
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ 872982aa:8fb54cfe
2025-05-12 01:39:07
@ 872982aa:8fb54cfe
2025-05-12 01:39:07 {.user-img}
{.user-img}

-
 @ d360efec:14907b5f
2025-05-12 01:34:24
@ d360efec:14907b5f
2025-05-12 01:34:24สวัสดีค่ะเพื่อนๆ นักเทรดที่น่ารักทุกคน! 💕 Lina Engword กลับมาพร้อมกับการวิเคราะห์ BTCUSDT.P แบบเจาะลึกเพื่อเตรียมพร้อมสำหรับเทรดวันนี้ค่ะ! 🚀
วันนี้ 12 พฤษภาคม 2568 เวลา 08.15น. ราคา BTCUSDT.P อยู่ที่ 104,642.8 USDT ค่ะ โดยมี Previous Weekly High (PWH) อยู่ที่ 104,967.8 Previous Weekly Low (PWL) ที่ 93,338 ค่ะ
✨ ภาพรวมตลาดวันนี้ ✨
จากการวิเคราะห์ด้วยเครื่องมือคู่ใจของเรา ทั้ง SMC/ICT (Demand/Supply Zone, Order Block, Liquidity), EMA 50/200, Trend Strength, Money Flow, Chart/Price Pattern, Premium/Discount Zone, Trend line, Fibonacci, Elliott Wave และ Dow Theory ใน Timeframe ตั้งแต่ 15m ไปจนถึง Week! 📊 เราพบว่าภาพใหญ่ของ BTCUSDT.P ยังคงอยู่ในแนวโน้มขาขึ้นที่แข็งแกร่งมากๆ ค่ะ 👍 โดยเฉพาะใน Timeframe Day และ Week ที่สัญญาณทุกอย่างสนับสนุนทิศทางขาขึ้นอย่างชัดเจน Money Flow ยังไหลเข้าอย่างต่อเนื่อง และเราเห็นโครงสร้างตลาดแบบ Dow Theory ที่ยก High ยก Low ขึ้นไปเรื่อยๆ ค่ะ
อย่างไรก็ตาม... ใน Timeframe สั้นๆ อย่าง 15m และ 1H เริ่มเห็นสัญญาณของการชะลอตัวและการพักฐานบ้างแล้วค่ะ 📉 อาจมีการสร้าง Buyside และ Sellside Liquidity รอให้ราคาไปกวาดก่อนที่จะเลือกทางใดทางหนึ่ง ซึ่งเป็นเรื่องปกติของการเดินทางของ Smart Money ค่ะ
⚡ เปรียบเทียบแนวโน้มแต่ละ Timeframe ⚡
🪙 แนวโน้มตรงกัน Timeframe 4H, Day, Week ส่วนใหญ่ชี้ไปทาง "ขาขึ้น" ค่ะ ทุกเครื่องมือสนับสนุนแนวโน้มนี้อย่างแข็งแกร่ง 💪 เป้าหมายต่อไปคือการไปทดสอบ PWH และ High เดิม เพื่อสร้าง All-Time High ใหม่ค่ะ! 🪙 แนวโน้มต่างกัน Timeframe 15m, 1H ยังค่อนข้าง "Sideways" หรือ "Sideways Down เล็กน้อย" ค่ะ มีการบีบตัวของราคาและอาจมีการพักฐานสั้นๆ ซึ่งเป็นโอกาสในการหาจังหวะเข้า Long ที่ราคาดีขึ้นค่ะ
💡 วิธีคิดแบบ Market Slayer 💡
เมื่อแนวโน้มใหญ่เป็นขาขึ้นที่แข็งแกร่ง เราจะเน้นหาจังหวะเข้า Long เป็นหลักค่ะ การย่อตัวลงมาในระยะสั้นคือโอกาสของเราในการเก็บของ! 🛍️ เราจะใช้หลักการ SMC/ICT หาโซน Demand หรือ Order Block ที่ Smart Money อาจจะเข้ามาดันราคาขึ้น และรอสัญญาณ Price Action ยืนยันการกลับตัวค่ะ
สรุปแนวโน้มวันนี้:
🪙 ระยะสั้น: Sideways to Sideways Down (โอกาส 55%) ↔️↘️ 🪙 ระยะกลาง: ขาขึ้น (โอกาส 70%) ↗️ 🪙 ระยะยาว: ขาขึ้น (โอกาส 85%) 🚀 🪙 วันนี้: มีโอกาสย่อตัวเล็กน้อยก่อนจะมีแรงซื้อกลับเข้ามาเพื่อไปทดสอบ PWH (โอกาส Sideways Down เล็กน้อย สลับกับ Sideways Up: 60%) 🎢
🗓️ Daily Trade Setup ประจำวันนี้ 🗓️
นี่คือตัวอย่าง Setup ที่ Lina เตรียมไว้ให้พิจารณาค่ะ (เน้นย้ำว่าเป็นเพียงแนวทาง ไม่ใช่คำแนะนำลงทุนนะคะ)
1️⃣ ตัวอย่างที่ 1: รอรับที่โซน Demand (ปลอดภัย, รอยืนยัน)
🪙 Enter: รอราคาย่อตัวลงมาในโซน Demand Zone หรือ Bullish Order Block ที่น่าสนใจใน TF 1H/4H (ดูจากกราฟประกอบนะคะ) และเกิดสัญญาณ Bullish Price Action ที่ชัดเจน เช่น แท่งเทียนกลืนกิน (Engulfing) หรือ Hammer 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🎯 🪙 SL: ใต้ Low ที่เกิดก่อนสัญญาณกลับตัวเล็กน้อย หรือใต้ Demand Zone ที่เข้า 🛡️ 🪙 RRR: ประมาณ 1:2.5 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เราจะใจเย็นๆ รอให้ราคาลงมาในโซนที่มีโอกาสเจอแรงซื้อเยอะๆ ตามหลัก SMC/ICT แล้วค่อยเข้า เพื่อให้ได้ราคาที่ดีและความเสี่ยงต่ำค่ะ ต้องรอสัญญาณ Price Action ยืนยันก่อนนะคะ ✍️
2️⃣ ตัวอย่างที่ 2: Follow Breakout (สายบู๊, รับความเสี่ยงได้)
🪙 Enter: เข้า Long ทันทีเมื่อราคาสามารถ Breakout เหนือ High ล่าสุดใน TF 15m หรือ 1H พร้อม Volume ที่เพิ่มขึ้นอย่างมีนัยสำคัญ 🔥 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🚀 🪙 SL: ใต้ High ก่อนหน้าที่ถูก Breakout เล็กน้อย 🚧 🪙 RRR: ประมาณ 1:3 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เหมาะกับคนที่อยากเข้าไวเมื่อเห็นโมเมนตัมแรงๆ ค่ะ เราจะเข้าเมื่อราคา Breakout แนวต้านระยะสั้นพร้อม Volume เป็นสัญญาณว่าแรงซื้อกำลังมาค่ะ เข้าได้เลยด้วยการตั้ง Limit Order หรือ Market Order เมื่อเห็นการ Breakout ที่ชัดเจนค่ะ 💨
3️⃣ ตัวอย่างที่ 3: พิจารณา Short สั้นๆ ในโซน Premium (สวนเทรนด์หลัก, ความเสี่ยงสูง)
🪙 Enter: หากราคาขึ้นไปในโซน Premium ใน TF 15m หรือ 1H และเกิดสัญญาณ Bearish Price Action ที่ชัดเจน เช่น แท่งเทียน Shooting Star หรือ Bearish Engulfing บริเวณ Supply Zone หรือ Bearish Order Block 🐻 🪙 TP: พิจารณาแนวรับถัดไป หรือ Sellside Liquidity ใน TF เดียวกัน 🎯 🪙 SL: เหนือ High ของสัญญาณ Bearish Price Action เล็กน้อย 💀 🪙 RRR: ประมาณ 1:1.5 ขึ้นไป (เน้นย้ำว่าเป็นการเทรดสวนเทรนด์หลัก ควรใช้ RRR ต่ำและบริหารขนาด Lot อย่างเข้มงวด!) 🪙 อธิบาย: Setup นี้สำหรับคนที่เห็นโอกาสในการทำกำไรจากการย่อตัวระยะสั้นค่ะ เราจะเข้า Short เมื่อเห็นสัญญาณว่าราคาอาจจะมีการพักฐานในโซนที่ถือว่า "แพง" ในกรอบสั้นๆ ค่ะ ต้องตั้ง Stop Loss ใกล้มากๆ และจับตาดูใกล้ชิดนะคะ 🚨
⚠️ Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัวของ Lina เท่านั้น ไม่ถือเป็นคำแนะนำในการลงทุนนะคะ การลงทุนมีความเสี่ยง ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบค่ะ 🙏
ขอให้ทุกท่านโชคดีกับการเทรดในวันนี้ค่ะ! มีคำถามอะไรเพิ่มเติม ถามมาได้เลยนะคะ ยินดีเสมอค่ะ! 😊
Bitcoin #BTCUSDT #Crypto #Trading #TechnicalAnalysis #SMC #ICT #MarketSlayer #TradeSetup #คริปโต #เทรดคริปโต #วิเคราะห์กราฟ #LinaEngword 😉



-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ 33baa074:3bb3a297
2025-05-12 01:06:27
@ 33baa074:3bb3a297
2025-05-12 01:06:27Soil moisture is one of the key factors affecting crop root development. Too much or too little moisture will have an adverse effect on root growth.
Effect of excessive moisture When there is too much soil moisture, the following problems will occur:
Inhibit root respiration: Excessive moisture will squeeze out oxygen in the soil, causing root hypoxia, thereby inhibiting root respiration, and in severe cases, it can cause root growth to stop or rot and die. Affect soil aeration: Excessive moisture will reduce soil aeration and affect the normal growth of the root system. Effect of too little moisture When there is too little soil moisture, it will also have a negative impact on the root system:
Promote root corking and self-thinning: Lack of water can cause root corking and even self-thinning, affecting the absorption capacity of the root system.
Determine whether the soil moisture is appropriate In order to ensure the healthy development of crop roots, soil moisture needs to be managed reasonably. The following methods can be used to determine whether the soil moisture is appropriate:
Touch test: Use a small shovel to dig up the soil around the root system, grab some soil with your hand and pinch it in your hand. If the soil can be kneaded into a ball and can be spread apart, the moisture content is appropriate; if it can be kneaded into a ball but cannot be spread apart, the moisture content exceeds the standard; if it cannot be kneaded into a ball, the soil is lacking in water.
Conclusion In summary, soil moisture has an important impact on the development of crop roots. Reasonable water management is essential to promote healthy root growth. By monitoring and adjusting soil moisture through appropriate methods, the normal growth and development of crops can be effectively guaranteed.
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ 3d073b19:4ae60f39
2025-05-12 00:09:07
@ 3d073b19:4ae60f39
2025-05-12 00:09:07This is an English openletter
-
 @ 33baa074:3bb3a297
2025-05-12 00:49:33
@ 33baa074:3bb3a297
2025-05-12 00:49:33Real-time monitoring of oil concentration in water The basic principle of oil in water sensor is to use the characteristic that oil will produce fluorescence under ultraviolet light, and measure the fluorescence intensity to infer the concentration of oil. The sensor uses ultraviolet light as the excitation light source to illuminate the water sample to be tested. The oil absorbs ultraviolet light and excites fluorescence. The fluorescence signal is received by the photo detector and converted into an electrical signal, and then the strength of the electrical signal is measured to determine the concentration of oil in the water sample, so as to achieve real-time monitoring of the concentration of oil in the water.
 Multi-scenario water quality monitoring
Water source water quality monitoring
It can be used to monitor the water quality of water sources. By continuously monitoring the oil in the water source, the pollution source can be found in time, thereby ensuring the safety of drinking water and water supply.
Multi-scenario water quality monitoring
Water source water quality monitoring
It can be used to monitor the water quality of water sources. By continuously monitoring the oil in the water source, the pollution source can be found in time, thereby ensuring the safety of drinking water and water supply.Sewage treatment plant discharge monitoring Sewage treatment plants may produce oily wastewater in the process of treating sewage. The oil-in-water sensor can monitor the water quality of its discharge to ensure that it meets the discharge standards and avoids secondary pollution to the environment.
Monitoring of water bodies such as rivers and lakes Water bodies such as rivers and lakes may be polluted by oil substances, such as ship leakage and industrial wastewater discharge. This sensor can monitor the water quality of these water bodies, evaluate the pollution status, and provide a basis for pollution control.
Aquaculture monitoring The online oil-in-water monitor (including oil-in-water sensor) can transmit monitoring data in real time to help farmers understand the water quality. Farmers can use it to understand the oil content in the water body in real time, and reasonably release it according to the needs of fish to improve the growth rate and health level of fish; it can also timely detect abnormal conditions in the water body, such as oil pollution and bacterial growth, and take corresponding measures to avoid the occurrence of diseases and reduce breeding costs and risks; at the same time, it helps farmers better understand the growth of fish, reasonably arrange fishing time, avoid overfishing and resource depletion, and promote the sustainable use of aquatic resources.
Early warning and emergency response It has real-time monitoring and early warning functions, and can issue an alarm in time when abnormal conditions of oil substances in the water body (such as exceeding the pee-set safety threshold) are found, providing valuable time for emergency response and reducing losses caused by pollution.
Assisting scientific research The monitoring data of the sensor can be used in scientific research fields such as ecology and environmental chemistry, helping researchers to gain a deeper understanding of the distribution, migration and transformation of oil substances in water bodies, and provide a scientific basis for environmental protection and governance.
Monitoring of pollution sources and environmental changes By detecting oil substances in water bodies, the location of pollution sources and the types of pollutants can be determined, providing a basis for finding and controlling pollution sources; it can also monitor oil pollutants in water bodies to understand the impact of environmental changes on water bodies and take timely measures to protect water sources.
-
 @ e39333da:7c66e53a
2025-05-12 00:03:18
@ e39333da:7c66e53a
2025-05-12 00:03:18::youtube{#VQRLujxTm3c}
Rockstar released the second trailer for Grand Theft Auto VI, where they mention that it showcases both cinematic and gameplay scenes equally, though of course it doesn't show any direct gameplay.
This trailer also announces the release date for the game. The game will come out on the 26th of May, 2026, for the PS5 and the Xbox One.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 3d073b19:4ae60f39
2025-05-11 23:59:56
@ 3d073b19:4ae60f39
2025-05-11 23:59:56Heading 1
Heading 2
Heading 3
Heading 4
Heading 5
Heading 6
Lists
Unordered List
- Item 1
- Item 2
- Subitem 2.1
- Subitem 2.2
Ordered List
- First item
- Second item
- Third item
Links
OpenAI - A link to OpenAI's website. Markdown Guide - A comprehensive guide to Markdown syntax.
Images
 - An example image with a title.
- An example image with a title.Blockquotes
This is a blockquote. It can span multiple lines. It is often used to highlight important information or quotes.
Code
Inline Code
Here is some
inline codethat demonstrates how to format code within a sentence.Code Block
```python
This is a Python code block
def hello_world(): print("Hello, world!") ```
Emphasis
Bold
This text is bold. This text is also bold.
Italic
This text is italic. This text is also italic.
Strikethrough
~~This text is strikethrough.~~
-
 @ 3d073b19:4ae60f39
2025-05-11 23:52:28
@ 3d073b19:4ae60f39
2025-05-11 23:52:28Headings
Heading 1
Heading 2
Heading 3
Heading 4
Heading 5
Heading 6
Lists
Unordered List
- Item 1
- Item 2
- Subitem 2.1
- Subitem 2.2
Ordered List
- First item
- Second item
- Third item
Mixed List
-
Item 1
-
Item 2
-
Item 3
Links
OpenAI - A link to OpenAI's website. Markdown Guide - A comprehensive guide to Markdown syntax.
Images
 - An example image with a title.
- An example image with a title.Blockquotes
This is a blockquote. It can span multiple lines. It is often used to highlight important information or quotes.
Code
Inline Code
Here is some
inline codethat demonstrates how to format code within a sentence.Code Block
```python
This is a Python code block
def hello_world(): print("Hello, world!") ```
Emphasis
Bold
This text is bold. This text is also bold.
Italic
This text is italic. This text is also italic.
Strikethrough
~~This text is strikethrough.~~
-
 @ 3c389c8f:7a2eff7f
2025-05-11 22:53:30
@ 3c389c8f:7a2eff7f
2025-05-11 22:53:30As I'm sitting here trying to hone in on what might be important to write about in this moment, my mind keeps swirling around through all the things that have me sitting here to begin with. Nostr found me in a time when my life needed a change. The discovery of something that provided the light of hope to an otherwise dark, dystopian future was more powerful than I could have ever predicted. Timing is everything, they say. I believe that to be half true, as timing alone means nothing if the will is non-existent. The intersection of opportunity and preparedness, and all that. I know how I found my way here, but I do not fully understand the things that have drawn my curiosity and kept my attention so strongly. My will ached for change, simplicity, and meaning. I found it, in what seem to me, simultaneously the most likely and the most unlikely of places. There's a magic to that, and its probably better to leave some questions unanswered, lest they lose their mystic power.
My experiences are my own but theme of them resonates through most of the people with whom I interact. It's been very clear that I wasn't alone in these feelings. A movement of highly inspired, hopeful people have continued to support this digital freedom movement since my arrival, in varying ways. Some people have highly technical skills ranging from network systems to design to cybersecurity. Others, like myself, have little to offer in the realms of functionality and we do what we can to breathe life into the systems built to provide digital freedom of speech for all. It's a humbling experience. We are reminded. sometimes directly and sometimes indirectly, that none of Nostr would matter if there were no one using it. We know this to be true, but it is no less humbling to be surrounded by constant innovation and a thriving desire to bring this experience to the entire world.
Now here I sit, tapping out these words, in the midst of another massive life change, stressful but chosen. I could sign off, go read a book in the garden, and go about my world as I would have in my pre-Nostr times. I don't want to do that, though. Hope is here. If there is a place to dwell, in hope is where I will always choose.
I find it important to acknowledge, though, that Nostr and the people using it are in a constant state of flux, too. This isn't my rock nor harbor nor shelter. It's the chaotic good, reminding me both to keep an appreciation for how far this ecosystem has come in such a short amount of time and a realistic set of expectations for where this all can go. The same applies for how well things work at any given moment...And equally so in missing my some of my early Nostr friends that have come and gone, while remaining open to the possibility of meeting new ones... Experiences had and experiences yet to come. I don't know if I have ever been so coaxed outside of my mind by a group of strangers on the internet. But here I am, looking back and looking forward, surrounded by awe in all directions, sharing thoughts that would otherwise be scribbled in pen to be burned in a random evening fire. I've long felt that the core of social media should be just this. Spaces for people to connect, above all else, in the ways that create meaning in our lives. I suppose in some ways that did exist before, but it was twisted, and obscured, and slowly pulled away.
Now its here and super-charged by possibility. What this looks like for any individual will not be the same as my own view. That's part of what makes this so beautiful to me. We need to be able to speak freely. Just as importantly we need to be able to surround ourselves with the things and people that makes us want to do more, that make us want to feel humbled. Or not, if we so choose... but I choose hope.
-
 @ bf47c19e:c3d2573b
2025-05-11 22:33:46
@ bf47c19e:c3d2573b
2025-05-11 22:33:46Originalni tekst na dvadesetjedan.com
Autor: Vijay Boyapati / Prevod na hrvatski: Matija
Sa zadnjim cijenama koje je bitcoin dosegao 2017., optimističan scenarij za ulagače se možda čini toliko očitim da ga nije potrebno niti spominjati. Alternativno, možda se nekome čini glupo ulagati u digitalnu vrijednost koja ne počiva na nijednom fizičkom dobru ili vladi i čiji porast cijene su neki usporedili sa manijom tulipana ili dot-com balonom. Nijedno nije točno; optimističan scenarij za Bitcoin je uvjerljiv, ali ne i očit. Postoje značajni rizici kod ulaganja u Bitcoin, no, kao što planiram pokazati, postoji i ogromna prilika.
Geneza
Nikad u povijesti svijeta nije bilo moguće napraviti transfer vrijednosti među fizički udaljenim ljudima bez posrednika, poput banke ili vlade. 2008. godine, anonimni Satoshi Nakamoto je objavio 8 stranica rješenja na dugo nerješivi računalski problem poznat kao “Problem Bizantskog Generala.” Njegovo rješenje i sustav koji je izgradio - Bitcoin - dozvolio je, prvi put ikad, da se vrijednost prenosi brzo i daleko, bez ikakvih posrednika ili povjerenja. Implikacije kreacije Bitcoina su toliko duboke, ekonomski i računalski, da bi Nakamoto trebao biti prva osoba nominirana za Nobelovu nagradu za ekonomiju i Turingovu nagradu.
Za ulagače, važna činjenica izuma Bitcoina (mreže i protokola) je stvaranje novog oskudnog digitalnog dobra - bitcoina (monetarne jedinice). Bitcoini su prenosivi digitalni “novčići” (tokeni), proizvedeni na Bitcoin mreži kroz proces nazvan “rudarenje” (mining). Rudarenje Bitcoina je ugrubo usporedivo sa rudarenjem zlata, uz bitnu razliku da proizvodnja bitcoina prati unaprijed osmišljeni i predvidivi raspored. Samo 21 milijun bitcoina će ikad postojati, i većina (2017., kada je ovaj tekst napisan) su već izrudareni. Svake četiri godine, količina rudarenih bitcoina se prepolovi. Produkcija novih bitcoina će potpuno prestati 2140. godine.
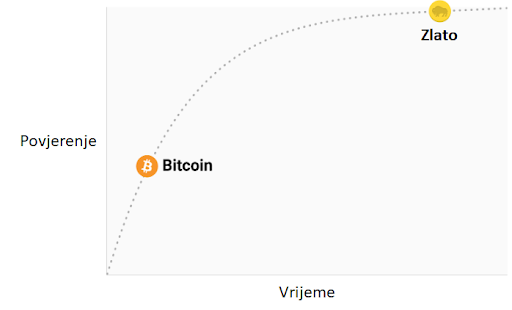 Stopa inflacije —— Monetarna baza
Stopa inflacije —— Monetarna bazaBitcoine ne podržava nikakva roba ili dobra, niti ih garantira ikakva vlada ili firma, što postavlja očito pitanje za svakog novog bitcoin ulagača: zašto imaju uopće ikakvu vrijednost? Za razliku od dionica, obveznica, nekretnina ili robe poput nafte i žita, bitcoine nije moguće vrednovati koristeći standardne ekonomske analize ili korisnost u proizvodnji drugih dobara. Bitcoini pripadaju sasvim drugoj kategoriji dobara - monetarnih dobara, čija se vrijednost definira kroz tzv. teoriju igara; svaki sudionik na tržištu vrednuje neko dobro, onoliko koliko procjenjuje da će ga drugi sudionici vrednovati. Kako bismo bolje razumjeli ovo svojstvo monetarnih dobara, trebamo istražiti podrijetlo novca.
Podrijetlo novca
U prvim ljudskim društvima, trgovina među grupama se vršila kroz robnu razmjenu. Velika neefikasnost prisutna u robnoj razmjeni je drastično ograničavala količinu i geografski prostor na kojem je bila moguća. Jedan od najvećih problema sa robnom razmjenom je problem dvostruke podudarnosti potražnje. Uzgajivač jabuka možda želi trgovati sa ribarom, ali ako ribar ne želi jabuke u istom trenutku, razmjena se neće dogoditi. Kroz vrijeme, ljudi su razvili želju za čuvanjem određenih predmeta zbog njihove rijetkosti i simbolične vrijednosti (npr. školjke, životinjski zube, kremen). Zaista, kako i Nick Szabo govori u svojem izvrsnom eseju o podrijetlu novca, ljudska želja za sakupljanjem predmeta pružila je izraženu evolucijsku prednost ranom čovjeku nad njegovim najbližim biološkim rivalom, neandertalcem - Homo neanderthalensis.
"Primarna i najbitnija evolucijska funkcija sakupljanja bila je osigurati medij za čuvanje i prenošenje vrijednosti".
Predmeti koje su ljudi sakupljali služili su kao svojevrsni “proto-novac,” tako što su omogućavale trgovinu među antagonističkim plemenima i dozvoljavale bogatsvu da se prenosi na sljedeću generaciju. Trgovina i transfer takvih predmeta bile su rijetke u paleolitskim društvima, te su oni služili više kao “spremište vrijednosti” (store of value) nego kao “medij razmjene” (medium of exchange), što je uloga koju danas igra moderni novac. Szabo objašnjava:
"U usporedbi sa modernim novcem, primitivan novac je imao jako malo “brzinu” - mogao je promijeniti ruke samo nekoliko puta u životu prosječnog čovjeka. Svejedno, trajni i čvrsti sakupljački predmet, što bismo danas nazvali “nasljeđe,” mogao je opstati mnogo generacija, dodajući znatnu vrijednost pri svakom transferu - i zapravo omogućiti transfer uopće".
Rani čovjek suočio se sa bitnom dilemom u teoriji igara, kada je odlučivao koje predmete sakupljati: koje od njih će drugi ljudi željeti? Onaj koji bi to točno predvidio imao bi ogromnu prednost u mogućnosti trgovine i akvizicije bogatsva. Neka američka indijanska plemena, npr. Naraganseti, specijalizirala su se u proizvodnji sakupljačkih dobara koja nisu imala drugu svrhu osim trgovine. Valja spomenuti da što je ranije predviđanje da će neko dobro imati takvu vrijednost, veća je prednost koju će imati onaj koji je posjeduje, zato što ju je moguće nabaviti jeftinije, prije nego postane vrlo tražena roba i njezona vrijednost naraste zajedno sa populacijom. Nadalje, nabava nekog dobra u nadi da će u budućnosti biti korišteno kao spremište vrijednosti, ubrzava upravo tu primjenu. Ova cirkularnost je zapravo povratna veza (feedback loop) koja potiče društva da se rapidno slože oko jednog spremišta vrijednosti. U terminima teorije igara, ovo je znano kao “Nashov ekvilibrij.” Postizanje Nashovog ekvilibrija za neko spremište vrijednosti je veliko postignuće za društvo, pošto ono znatno olakšava trgovinu i podjelu rada, i time omogućava napredak civilizacije.
Tisućljećima, kako su ljudska društva rasla i otvarala trgovinske puteve, različite aplikacije spremišta vrijednosti u individualnim društvima počele su se natjecati međusobno. Trgovci su imali izbor: čuvati svoju zaradu u spremištu vrijednosti vlastite kulture, ili one kulture sa kojom su trgovali, ili mješavini oboje. Benefit štednje u stranom spremištu vrijednosti bila je uvećana sposobnost trgovanja u povezanom stranom društvu. Trgovci koji su štedili u stranom spremištu vrijednosti su također imali dobrih razloga da potiču svoje društvo da ga prihvati, jer bi tako uvećali vrijednost vlastite ušteđevine. Prednosti “uvezene” tehnologije spremanja vrijednosti bile su prisutne ne samo za trgovce, nego i za sama društva. Kada bi se dvije grupe konvergirale u jedinstvenom spremištu vrijednosti, to bi značajno smanjilo cijenu troškova trgovine jednog s drugim, i samim time povećanje bogatstva kroz trgovinu. I zaista, 19. stoljeće bilo je prvi put da je najveći dio svijeta prihvatio jedinstveno spremište vrijednosti - zlato - i u tom periodu vidio najveću eksploziju trgovine u povijesti svijeta. O ovom mirnom periodu, pisao je John Maynard Keynes:
"Kakva nevjerojatna epizoda u ekonomskom napretku čovjeka… za svakog čovjeka iole iznadprosječnog, iz srednje ili više klase, život je nudio obilje, ugodu i mogućnosti, po niskoj cijeni i bez puno problema, više nego monarsima iz prethodnih perioda. Stanovnik Londona mogao je, ispijajući jutarnji čaj iz kreveta, telefonski naručiti razne proizvode iz cijele Zemlje, u količinama koje je želio, i sa dobrim razlogom očekivati njihovu dostavu na svoj kućni prag."
Svojstva dobrog spremišta vrijednosti
Kada se spremišta vrijednosti natječu jedno s drugim, specifična svojstva rade razliku koja daje jednom prednost nad drugim. Premda su mnoga dobra u prošlosti korištena kao spremišta vrijednosti ili kao “proto-novac,” određena svojstva su se pokazala kao posebno važna, i omogućila dobrima sa njima da pobijede. Idealno spremište vrijednosti biti će:
- Trajno: dobro ne smije biti kvarljivo ili lako uništeno. Tako naprimjer, žito nije idealno spremište vrijednosti.
- Prenosivo: dobro mora biti lako transportirati i čuvati, što omogućuje osiguranje protiv gubitka ili krađe i dopušta trgovinu na velike udaljenosti. Tako, krava je lošije spremište vrijednosti od zlatne narukvice.
- Zamjenjivo: jedna jedinica dobra treba biti zamjenjiva sa drugom. Bez zamjenjivosti, problem podudarnosti želja ostaje nerješiv. Time, zlato je bolje od dijamanata, jer su oni nepravilni u obliku i kvaliteti.
- Provjerljivo: dobro mora biti lako i brzo identificirano i testirano za autentičnost. Laka provjera povećava povjerenje u trgovini i vjerojatnost da će razmjena biti dovršena.
- Djeljivo: dobro mora biti lako djeljivo na manje dijelove. Premda je ovo svojstvo bilo manje važno u ranim društvima gdje je trgovina bila rijetka, postalo je važnije sa procvatom trgovine. Količine koje su se mijenjale postale su manje i preciznije.
- Oskudno: Monetarno dobro mora imati “cijenu nemoguću za lažirati,” kao što je rekao Nick Szabo. Drugim riječima, dobro ne smije biti obilno ili lako dostupno kroz proizvodnju. Oskudnost je možda i najvažnije svojstvo spremišta vrijednosti, pošto se izravno vezuje na ljudsku želju da sakupljamo ono što je rijetko. Ona je izvor vrijednosti u spremištu vrijednosti.
- Duge povijesti: što je dulje neko dobro vrijedno za društvo, veća je vjerojatnost da će biti prihvaćeno kao spremište vrijednosti. Dugo postojeće spremište vrijednosti biti će jako teško uklonjeno od strane došljaka, osim u slučaju sile (ratno osvajanje) ili ako je nova tehnologija znatno bolja u ostalim svojstvima.
- Otporno na cenzuru: novije svojstvo, sve više važno u modernom digitalnom svijetu sa sveprisutnim nadzorom, je otpornost na cenzuru. Drugim riječima, koliko je teško da vanjski agent, kao korporacija ili država, spriječi vlasnika dobra da ga čuva i koristi. Dobra koja su otporna na cenzuru su idealna za ljude koji žive u režimima koji prisilno nadziru kapital ili čine neke oblike mirne trgovine protuzakonitima.
Ova tablica ocjenjuje Bitcoin, zlato (gold) i fiat novac (kao što je euro ili dolar) po svojstvima izlistanim gore. Objašnjenje svake ocjene slijedi nakon tablice.
Trajnost:
Zlato je neosporeni kralj trajnosti. Velika većina zlata pronađenog kroz povijest, uključujući ono egipatskih faraona, opstaje i danas i vjerojatno će postojati i za tisuću godina. Zlatnici korišteni u antičko doba imaju značajnu vrijednost i danas. Fiat valute i bitcoini su digitalni zapisi koji ponekad imaju fizički oblik (npr. novčanice). Dakle, njihovu trajnost ne određuju njihova fizička svojstva (moguće je zamijeniti staru i oštećenu novčanicu za novu), nego institucije koje stoje iza njih. U slučaju fiat valuta, mnoge države su nastale i nestale kroz stoljeća, i valute su nestale s njima. Marke iz Weimarske republike danas nemaju vrijednost zato što institucija koja ih je izdavala više ne postoji. Ako je povijest ikakav pokazatelj, ne bi bilo mudro smatrati fiat valute trajnima dugoročno; američki dolar i britanska funta su relativne anomalije u ovom pogledu. Bitcoini, zato što nemaju instituciju koja ih održava, mogu se smatrati trajnima dok god mreža koja ih osigurava postoji. Obzirom da je Bitcoin još uvijek mlada valuta, prerano je za čvrste zaključke o njegovoj trajnosti. No, postoje ohrabrujući znakovi - prominente države su ga pokušavale regulirati, hakeri ga napadali - usprkos tome, mreža nastavlja funkcionirati, pokazujući visok stupanj antifragilnosti.
Prenosivost:
Bitcoini su najprenosivije spremište vrijednosti ikad. Privatni ključevi koji predstavljaju stotine milijuna dolara mogu se spremiti na USB drive i lako ponijeti bilo gdje. Nadalje, jednako velike sume mogu se poslati na drugi kraj svijeta skoro instantno. Fiat valute, zbog svojeg temeljno digitalnog oblika, su također lako prenosive. Ali, regulacije i kontrola kapitala od strane države mogu ugroziti velike prijenose vrijednosti, ili ih usporiti danima. Gotovina se može koristiti kako bi se izbjegle kontrole kapitala, ali onda rastu rizik čuvanja i cijena transporta. Zlato, zbog svojeg fizičkog oblika i velike gustoće, je najmanje prenosivo. Nije čudo da većina zlatnika i poluga nikad ne napuste sefove. Kada se radi prijenos zlata između prodavača i kupca, uglavnom se prenosi samo ugovor o vlasništvu, ne samo fizičko zlato. Prijenos fizičkog zlata na velike udaljenosti je skupo, riskantno i sporo.
Zamjenjivost:
Zlato nam daje standard za zamjenjivost. Kada je rastopljeno, gram zlata je praktički nemoguće razlikovati od bilo kojeg drugog grama, i zlato je oduvijek bilo takvo. S druge strane, fiat valute, su zamjenjive samo onoliko koliko njihova institucija želi da budu. Iako je uglavnom slučaj da je novčanica zamjenjiva za drugu istog iznosa, postoje situacije u kojima su velike novčanice tretirane drukčije od malih. Naprimjer, vlada Indije je, u pokušaju da uništi neoporezivo sivo tržište, potpuno oduzela vrijednost novčanicama od 500 i 1000 rupija. To je uzrokovalo da ljudi manje vrednuju te novčanice u trgovini, što je značilo da više nisu bile zaista zamjenjive za manje novčanice. Bitcoini su zamjenjivi na razini mreže; svaki bitcoin je pri prijenosu tretiran kao svaki drugi. No, zato što je moguće pratiti individualne bitcoine na blockchainu, određeni bitcoin može, u teoriji, postati “prljav” zbog korštenja u ilegalnoj trgovini, te ga trgovci ili mjenjačnice možda neće htjeti prihvatiti. Bez dodatnih poboljšanja oko privatnosti i anonimnosti na razini mrežnog protokola, bitcoine ne možemo smatrati jednako zamjenjivim kao zlato.
Mogućnost provjere:
Praktično gledajući, autentičnost fiat valuta i zlata je prilično lako provjeriti. Svejedno, i usprkos pokušajima da spriječe krivotvorenje novčanica, i dalje postoji potencijal prevare za vlade i njihove građane. Zlato također nije imuno na krivotvorenje. Sofisticirani kriminalci su koristili pozlaćeni tungsten kako bi prevarili kupce zlata. Bitcoine je moguće provjeriti sa matematičkom sigurnošću. Korištenjem kriptografskih potpisa, vlasnik bitcoina može javno demonstrirati da posjeduje bitcoine koje tvrdi da posjeduje.
Djeljivost:
Bitcoine je moguće podijeliti u stotinu milijuna manjih jedinica (zvanih satoshi), i prenositi takve (no, valja uzeti u obzir ekonomičnost prijenosa malih iznosa, zbog cijene osiguravanja mreže - “network fee”). Fiat valute su tipično dovoljno djeljive na jedinice sa vrlo niskom kupovnom moći. Zlato, iako fizički i teoretski djeljivo, postaje teško za korištenje kada se podijeli na dovoljno male količine da bi se moglo koristiti u svakodnevnoj trgovini.
Oskudnost:
Svojstvo koje najjasnije razlikuje Bitcoin od fiat valuta i zlata je njegova unaprijed definirana oskudnost. Od početka, konačna količina bitcoina nikad neće biti veća od 21 milijun. To daje vlasnicima bitcoina jasan i znan uvid u postotak ukupnog vlasništva. Naprimjer, vlasnik 10 bitcoina bi znao da najviše 2,1 milijuna ljudi (manje od 0.03% populacije) može ikad imati isto bitcoina kao i on. Premda je kroz povijest uvijek bilo oskudno, zlato nije imuno na povećanje ukupne količine. Ako se ikad izumi nova, ekonomičnija metoda rudarenja ili proizvodnje zlata, ukupna količina zlata bi se mogla dramatično povećati (npr. rudarenje morskog dna ili asteroida). Na kraju, fiat valute, relativno nov izum u povijesti, pokazale su se sklonima konstantnim povećanjima u količini. Države su pokazale stalnu sklonost inflaciji monetarne kvantitete kako bi rješavale kratkoročne političke probleme. Inflacijske tendencije vlada diljem svijeta čine fiat valute gotovo sigurnim da će gubiti vrijednost kroz vrijeme.
Etablirana povijest:
Nijedno monetarno dobro nema povijest kao zlato, koje je imalo vrijednost za cijelog trajanja ljudske civilizacije. Kovanice izrađene u antičko doba i danas imaju značajnu vrijednost. Ne može se isto reći za fiat valute, koje su same relativno nova povijesna anomalija. Od njihovog početka, fiat valute su imale gotovo univerzalni smjer prema bezvrijednosti. Korištenje inflacije kao podmuklog načina za nevidljivo oporezivanje građana je vječita kušnja kojoj se skoro nijedna država u povijesti nije mogla oduprijeti. Ako je 20. stoljeće, u kojem je fiat novac dominirao globalni monetarni poredak, demonstriralo neku ekonomsku istinu, to je onda bila ta da ne možemo računati na fiat novac da održi vrijednost u dužem ili srednjem vremenskom periodu. Bitcoin, usprkos svojoj novosti, je preživio dovoljno testova tržišta da postoji velika vjerojatnost da neće nestati kao vrijedno dobro. Nadalje, Lindy efekt govori da što duže Bitcoin bude korišten, to će veća biti vjera u njega i njegovu sposobnost da nastavi postojati dugo u budućnost. Drugim riječima, društvena vjera u monetarno dobro je asimptotička, kao u grafu ispod:

Ako Bitcoin preživi prvih 20 godina, imat će gotovo sveopće povjerenje da će trajati zauvijek, kao što ljudi vjeruju da je internet trajna stvar u modernom svijetu.
Otpor na cenzuru
Jedan od najbitnijih izvora za ranu potražnju bitcoina bila je njegova upotreba u ilegalnoj kupovini i prodaji droge. Mnogi su zato pogrešno zaključili da je primarna potražnja za bitcoinima utemeljena u njihovoj prividnoj anonimnosti. Međutim, Bitcoin nije anonimna valuta; svaka transakcija na mreži je zauvijek zapisana na javnom blockchainu. Povijesni zapis transakcija dozvoljava forenzičkoj analizi da identificira izvore i tijek sredstava. Takva analiza dovela je do uhićenja počinitelja zloglasne MtGox pljačke. Premda je istina da dovoljno oprezna i pedantna osoba može sakriti svoj identitet koristeći Bitcoin, to nije razlog zašto je Bitcoin bio toliko popularan u trgovini drogom.
Ključno svojstvo koje čini Bitcoin najboljim za takve aktivnosti je njegova agnostičnost i nepotrebnost za dozvolom (“premissionlessness”) na mrežnoj razini. Kada se bitcoini prenose na Bitcoin mreži, ne postoji nitko tko dopušta transakcije. Bitcoin je distribuirana peer-to-peer (korisnik-korisniku) mreža, i samim time dizajnirana da bude otporna na cenzuru. Ovo je u velikom kontrastu sa fiat bankarskim sustavom, u kojem države reguliraju banke i ostale institucije prijenosa novca, kako bi one prijavljivale i sprječavale protuzakonito korištenje monetarnih dobara. Klasičan primjer regulacije novca su kontrole kapitala. Npr., bogati milijunaš će vrlo teško prenijeti svoje bogatstvo u novu zemlju, kada bježi iz opresivnog režima. Premda zlato nije izdano i proizvedeno od države, njegova fizička priroda ga čini teško prenosivim kroz prostor, i samim time ga je daleko lakše regulirati nego Bitcoin. Indijski Akt kontrole zlata je primjer takve regulacije.
Bitcoin je odličan u većini gore navedenih svojstava, što mu omogućava da bude marginalno bolji od modernih i drevnih monetarnih dobara, te da pruži poticaje za svoje rastuće društveno usvajanje. Specifično, moćna kombinacija otpornosti na cenzuru i apsolutne oskudnosti bila je velika motivacija za bogate ulagače koji su uložili dio svojeg bogatstva u Bitcoin.
Evolucija novca
U modernoj monetarnoj ekonomiji postoji opsesija sa ulogom novca kao medija razmjene. U 20. stoljeću, države su monopolizirale izdavanje i kontrolu novca i kontinuirano potkopavale njegovo svojstvo spremišta vrijednosti, stvarajući lažno uvjerenje da je primarna svrha novca biti medij razmjene. Mnogi su kritizirali Bitcoin, govoreći da je neprikladan da bude novac zato što mu je cijena bila previše volatilna za medij razmjene. No, novac je uvijek evoluirao kroz etape; uloga spremišta vrijednosti je dolazila prije medija razmjene. Jedan od očeva marginalističke ekonomije, William Stanley Jevons, objašnjava:
"Povijesno govoreći… čini se da je zlato prvo služilo kao luksuzni metal za ukras; drugo, kao sačuvana vrijednost; treće, kao medij razmjene; i konačno, kao mjerilo vrijednosti."
U modernoj terminologiji, novac uvijek evoluira kroz četiri stadija:
- Kolekcionarstvo: U prvoj fazi svoje evolucije, novac je tražen samo zbog svojih posebnih svojstava, uglavnom zbog želja onog koji ga posjeduje. Školjke, perlice i zlato su bili sakupljani prije nego su poprimili poznatije uloge novca.
- Spremište vrijednosti: Jednom kada je novac tražen od dovoljnog broja ljudi, biti će prepoznat kao način za čuvanje i spremanje vrijednosti kroz vrijeme. Kada neko dobro postane široko korišteno kao spremište vrijednosti, njegova kupovna moć raste sa povećanom potražnjom za tu svrhu. Kupovna moć spremišta vrijednosti će u jednom trenutku doći do vrhunca, kada je dovolno rašireno i broj novih ljudi koji ga potražuju splasne.
- Sredstvo razmjene: Kada je novac potpuno etabliran kao spremište vrijednosti, njegova kupovna moć se stabilizira. Nakon toga, postane prikladno sredstvo razmjene zbog stabilnosti svoje cijene. U najranijim danima Bitcoina, mnogi ljudi nisu shvaćali koju buduću cijenu plaćaju koristeći bitcoine kao sredstvo razmjene, umjesto kao novonastalo spremište vrijednosti. Poznata priča o čovjeku koji je za 10,000 bitcoina (vrijednih oko 94 milijuna dolara kada je ovaj članak napisan) za dvije pizze ilustrira ovaj problem.
- Jedinica računanja vrijednosti: Jednom kada je novac široko korišten kao sredstvo razmjene, dobra će biti vrednovana u njemu, tj. većina cijena će biti izražena u njemu. Uobičajena zabluda je da je većinu dobara moguće zamijeniti za bitcoine danas. Npr., premda je možda moguće kupiti šalicu kave za bitcoine, izlistana cijena nije prava bitcoin cijena; zapravo se radi o cijeni u državnoj valuti koju želi trgovac, preračunatu u bitcoin po trenutnoj tržišnoj cijeni. Kad bi cijena bitcoina pala u odnosu na valutu, vrijednost šalice izražena u bitcoinima bi se povećala. Od trenutka kada trgovci budu voljni prihvaćani bitcoine kao platežno sredstvo, bez obraćanja pažnje na vrijednost bitcoina u državnoj fiat valuti, moći ćemo reći da je Bitcoin zaista postao jedinica računanja vrijednosti.
Monetarna dobra koja još nisu jedinice računanja vrijednosti možemo smatrati “djelomično monetiziranima.” Danas zlato ima takvu ulogu, jer je spremište vrijednosti, ali su mu uloge sredstva razmjene i računanja vrijednosti oduzete intervencijama država. Moguće je također da se jedno dobro koristi kao sredstvo razmjene, dok druga ispunjavaju ostale uloge. To je tipično u zemljama gdje je država disfunkcionalna, npr. Argentina ili Zimbabwe. U svojoj knjizi, Digitalno zlato, Nathaniel Popper piše:
"U Americi, dolar služi trima funkcijama novca: nudi sredstvo razmjene, jedinicu za mjerenje vrijednosti dobara, i mjesto gdje se može čuvati vrijednosti. S druge strane, argentinski peso je korišten kao sredstvo razmjene (za svakodnevne potrebe), ali ga nitko nije koristio kao spremište vrijednosti. Štednja u pesosima bila je ekvivalent bacanja novca. Zato su ljudi svu svoju štednju imali u dolarima, jer je dolar bolje čuvao vrijednost. Zbog volatilnosti pesosa, ljudi su računali cijene u dolarima, što im je pružalo pouzdaniju jedinicu mjerenja kroz vrijeme."
Bitcoin je trenutno u fazi tranzicije iz prvog stadija monetizacije u drugi. Vjerojatno će proći nekoliko godina prije nego Bitcoin pređe iz začetaka spremišta vrijednosti u istinski medij razmjene, i put do tog trenutka je još uvijek pun rizika i nesigurnosti. Važno je napomenuti da je ista tranzicija trajala mnogo stoljeća za zlato. Nitko danas živ nije doživio monetizaciju dobra u realnom vremenu (kroz koju Bitcoin prolazi), tako da nemamo puno iskustva govoriti o putu i načinu na koji će se monetizacija dogoditi.
Put monetizacije
Kroz proces monetizacije, monetarno dobro će naglo porasti u kupovnoj moći. Mnogi su tako komentirali da je uvećanje kupovne moći Bitcoina izgledalo kao “balon” (bubble). Premda je ovaj termin često korišten kako bi ukazao na pretjeranu vrijednosti Bitcoina, sasvim slučajno je prikladan. Svojstvo koje je uobičajeno za sva monetarna dobra jest da je njihova kupovna moć viša nego što se može opravdati samo kroz njihovu uporabnu vrijednost. Zaista, mnogi povijesni novci nisu imali uporabnu vrijednost. Razliku između kupovne moći i vrijednosti razmjene koju bi novac mogao imati za svoju inherentnu korisnost, možemo razmatrati kao “monetarnu premiju.” Kako monetarno dobro prolazi kroz stadije monetizacije (navedene gore), monetarna premija raste. No, ta premija ne raste u ravnoj i predvidivoj liniji. Dobro X, koje je bilo u procesu monetizacije, može izgubiti u usporedbi sa dobrom Y koje ima više svojstava novca, te monetarna premija dobra X drastično padne ili potpuno nestane. Monetarna premija srebra je skoro potpuno nestala u kasnom 19. stoljeću, kada su ga vlade diljem svijeta zamijenile zlatom kao novcem.
Čak i u odsustvu vanjskih faktora, kao što su intervencije vlade ili druga monetarna dobra, monetarna premija novog novca neće ići predvidivim putem. Ekonomist Larry White primijetio je:
"problem sa pričom “balona,” naravno, je da je ona konzistentna sa svakim putem cijene, i time ne daje ikakvo objašnjenje za specifičan put cijene"
Proces monetizacije opisuje teorija igara; svaki akter na tržištu pokušava predvidjeti agregiranu potražnju ostalih aktera, i time buduću monetarnu premiju. Zato što je monetarna premija nevezana za inherentnu korisnost, tržišni akteri se uglavnom vode za prošlim cijenama da bi odredili je li neko dobro jeftino ili skupo, i žele li ga kupiti ili prodati. Veza trenutne potražnje sa prošlim cijenama naziva se “ovisnost o putu” (path dependence); ona je možda najveći izvor konfuzije u shvaćanju kretanja cijena monetarnih dobara.
Kada kupovna moć monetarnog dobra naraste zbog većeg i šireg korištenja, očekivanja tržišta o definicijama “jeftinog” i “skupog” se mijenjaju u skladu s time. Slično tome, kada cijena monetarnog dobra padne, očekivanja tržišta mogu se promijeniti u opće vjerovanje da su prethodne cijene bile “iracionalne” ili prenapuhane. Ovisnost o putu novca ilustrirana je riječima poznatog upravitelja fondova s Wall Streeta, Josha Browna:
"Kupio sam bitcoine kada su koštali $2300, i to mi se udvostručilo gotovo odmah. Onda sam počeo govoriti kako “ne mogu kupiti još” dok im je cijena rasla, premda sam znao da je to razmišljanje bazirano samo na cijenu po kojoj sam ih kupio. Kasnije, kada je cijena pala zbog kineske regulacije mjenjačnica, počeo sam si govoriti, “Odlično, nadam se da će još pasti da mogu kupiti još.”"
Istina leži u tome da su ideje “jeftinog” i “skupog” zapravo besmislene kada govorimo o monetarnim dobrima. Cijena monetarnog dobra ne reflektira njegovu stopu rasprostanjenosti ili korisnosti, nego mjeru koliko je ono široko prihvaćeno da ispuni razne uloge novca.
Dodatna komplikacija u ovom aspektu novca je činjenica da tržišni akteri ne djeluju samo kao nepristrani promatrači koji pokušavaju kupiti i prodati u iščekivanju budućih kretanja monetarne premije, nego i kao aktivni proponenti. Pošto ne postoji objektivno “točna” monetarna premija, širiti dobar glas o superiornijim svojstvima nekog monetarnog dobra je efektivnije nego za obična dobra, čija vrijednost je u konačnici vezana na njegovu osnovnu korisnost. Religiozni zanos sudionika na Bitcoin tržištu vidljiv je na raznim internetskim forumima, gdje Bitcoineri aktivno promoviraju benefine Bitcoina i bogatstvo koje je moguće ostvariti investiranjem u njega. Promatrajući Bitcoin tržište, Leigh Drogen komentira:
"To je prepoznatljivo svima kao religija - priča koju si pričamo i oko koje se slažemo. Religija je krivulja na grafu prihvaćanja o kojoj trebamo razmišljati. Sustav je gotovo savršen - onog trenutka kada netko pristupi krugu Bitcoinera, to će reći svima i nastaviti širiti riječ. Onda njihovi prijatelji pristupe i nastave širiti riječ."
Premda usporedba sa religijom može staviti Bitcoin u iracionalno svjetlo, potpuno je racionalno za individualnog vlasnika da širi dobru vijest o superiornom monetarnom dobru, i za šire društvo da se standardizira oko njega. Novac djeluje kao temelj za svu trgovinu i štednju; tako da prihvaćanje superiornog oblika novca ima ogromne multiplicirajuće benefite za stvaranje bogatstva za sve članove društva.
Oblik monetizacije
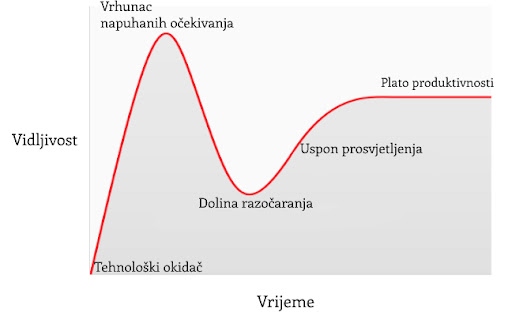
U članku o Spekulativnom prihvaćanju Bitcoina / teorije cijene, Michael Casey postulira da rastući Gartner hype ciklusi predstavljaju faze standardne S-krivulje prihvaćanja novih tehnologija, koje su bile prisutne kod mnogih transformacijskih tehnologija dok su postajale uobičajene u društvu.
Svaki Gartner hype ciklus počinje sa eksplozijom entuzijazma za novom tehnologijom, a cijenu podižu oni sudionici na tržištvu koji su “dostupni” u toj fazi. Najraniji kupci u Gartner hype ciklusu obično imaju jaku vjeru o transformacijskoj prirodi tehnologije u koju ulažu. S vremenom, tržište dosegne vrhunac entuzijazma kako se količina novih kupaca iscrpljuje, te kupovinom počnu dominirati spekulatori koji su više zainteresirani u brze profite nego u samu tehnologiju.
Nakon vrha hype ciklusa, cijene rapidno padaju dok spekulativno ludilo ustupa mjesto očajavanju, javnoj poruzi i osjećaju da tehnologija nije uopće bila transformacijska. S vremenom, cijena dosegne dno i formira plato na kojem se originalnim ulagačima, koji su imali snažno uvjerenje, pridružuju nove grupe ljudi koji su izdržali bol kraha cijena i koji cijene važnost same tehnologije.
Plato traje neko vrijeme i formira, kako Casey kaže, “stabilnu, dosadnu dolinu.” Za ovo vrijeme, javni interes za tehnologiju opada, no nastaviti će se razvijati i snažna zajednica uvjerenja će polako rasti. Tada, postavlja se nova baza za sljedeću iteraciju hype ciklusa, dok vanjski promatrači prepoznaju da tehnologija i dalje postoji i da ulaganje u nju možda nije onoliko rizično kao što se činilo za vrijeme pada cijene. Sljedeća iteracija hype ciklusa donosi mnogo veći broj novih ljudi, pa je i ciklus daleko veći u svojoj magnitudi.
Jako mali broj ljudi koji sudjeluju u Gartner hype ciklusu će točno predvidjeti koliko će visoko cijena porasti za vrijeme ciklusa. Cijene često dosegnu razine koje bi se činile apsurdnima većini ulagača u raniji stadijima ciklusa. Kada ciklus završi, mediji tipično atribuiraju pad cijene nekoj od aktualnih drušvenih tema. Premda takva tema može biti okidač pada, ona nikad nije temeljni razlog zašto ciklus završava. Gartner hype ciklusi završavaju kada je količina dostupnih novih sudionika na tržištu iscrpljena.
Zanimljivo je da je i zlato nacrtalo klasičan graf Gartner hype ciklusa od kasnih 1970-ih do ranih 2000-ih. Moguće je spekulirati da je hype ciklus osnovna socijalna dinamika oko procesa monetizacije.
Gartner kohorte
Od početka trgovanja Bitcoina na mjenjačnicama 2010. godine, Bitcoin tržište je svjedočilo četirima velikim Gartner hype ciklusima. U retrospektivi, možemo vrlo precizno identificirati grupe cijena prethodnih hype ciklusa Bitcoin tržišta. Također, možemo kvalitativno odrediti kohorte ulagača koje su povezane sa svakom iteracijom prethodnih ciklusa.
$ 0–$ 1 (2009. – 3. mjesec 2011.): Prvi hype ciklus u Bitcoin tržištu dominirali su kriptografi, računalni znanstvenici i cypherpunkovi koji su od početka bili spremni razumijeti važnost nevjerojatnog izuma Satoshija Nakamotoa, i koji su bili pioniri u potvrđivanju da Bitcoin protokol nema tehničkih mana.
$ 1–$ 30 (3. mjesec 2011. – 7. mjesec. 2011.): Drugi ciklus privukao je rane entuzijaste oko novih tehnologija kao i stabilan pritok ideološki motiviranih ulagača koji su bili oduševljeni idejom novca odvojenog od države. Libertarijanci poput Rogera Vera došli su u Bitcoin zbog aktivnog anti-institucionalnog stava, i mogućnosti koju je nova tehnologija obećavala. Wences Casares, briljantni i dobro povezani serijski poduzetnik, bio je također dio drugog Bitcoin hype ciklusa te je širio riječ o Bitcoinu među najprominentnijim tehnolozima i ulagačima u Silicijskoj Dolini.
$ 250–$ 1100 (4. mjesec 2013. – 12. mjesec 2013.): Treći hype ciklus doživio je ulazak ranih generalnih i institucionalnih ulagača koji su bili voljni uložiti trud i riskirati kroz užasno komplicirane kanale likvidnosti kako bi kupili bitcoine. Primaran izvor likvidnosti na tržištu za vrijeme ovog perioda bio je MtGox, mjenjačnica bazirana u Japanu, koju je vodio notorno nesposobni i beskrupulozni Mark Karpeles, koji je kasnije završio i u zatvoru zbog svoje uloge u kolapsu MtGoxa.
Valja primijetiti da je rast Bitcoinove cijene za vrijeme spomenuti hype ciklusa većinom povezano sa povećanjem likvidnosti i lakoćom sa kojom su ulagači mogli kupiti bitcoine. Za vrijeme prvog hype ciklusa, nisu postojale mjenjačnice; akvizicija bitcoina se odvijala primarno kroz rudarenje (mining) ili kroz izravnu razmjenu sa onima koju su već izrudarili bitcoine. Za vrijeme drugog hype ciklusa, pojavile su se rudimentarne mjenjačnice, no nabavljanje i osiguravanje bitcoina na ovim mjenjačnicama bilo je previše kompleksno za sve osim tehnološki najsposobnijih ulagača. Čak i za vrijeme trećeg hype ciklusa, ulagači koju su slali novac na MtGox kako bi kupili bitcoine su morali raditi kroz značajne prepreke. Banke nisu bile voljne imati posla sa mjenjačnicom, a oni posrednici koji su nudili usluge transfera bili su često nesposobni, kriminalni, ili oboje. Nadalje, mnogi koji su uspjeli poslati novac MtGoxu, u konačnici su morali prihvatiti gubitak svojih sredstava kada je mjenjačnica hakirana i kasnije zatvorena.
Tek nakon kolapsa MtGox mjenjačnice i dvogodišnje pauze u tržišnoj cijeni Bitcoina, razvili su se zreli i duboki izvori likvidnosti; primjeri poput reguliranih mjenjačnica kao što su GDAX i OTC brokeri kao Cumberland mining. Dok je četvrti hype ciklus započeo 2016. godine, bilo je relativno lako običnim ulagačima kupiti i osigurati bitcoine.
$ 1100 – $ 19600? (2014. –?):
U trenutku pisanja ovog teksta, tržište Bitcoina je prolazilo svoj četvrti veliki hype ciklus. Sudjelovanje u ovom hype ciklusu dominirala je ona skupina koju je Michael Casey opisao kao “rana većina” običnih i institucionalnih ulagača.
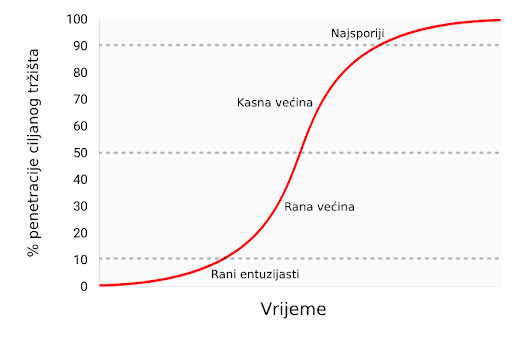
Kako su se izvori likvidnosti produbljivali i sazrijevali, veliki institucionalni ulagači sada imaju priliku sudjelovati kroz regulirana “futures” tržišta. Dostupnosti takvih tržišta stvara put ka kreaciji Bitcoin ETF-a (exchange traded fund) (fond na slobodnom tržištu), koji će onda pokrenuti “kasnu većinu” i “najsporije” u sljedećim hype ciklusima.
Premda je nemoguće predvidjeti točan efekt budućih hype ciklusa, razumno je očekivati da će najviša točka biti između $ 20.000 i $ 50.000 (2021. zenit je bio preko $ 69.000). Znatno više od ovog raspona, i Bitcoin bi imao znatan postotak ukupne vijednosti zlata (zlato i Bitcoin bi imali jednaku tržišnu kapitalizaciju kada bi bitcoini vrijedili oko $ 380.000 u trenutku pisanja ovog teksta). Značajan postotak vrijednosti zlata dolazi od potražnje centralnih banaka, te je malo vjerojatno da će centralne banke ili suverene države sudjelovati u trenutnom hype ciklusu.
Ulazak suverenih država u Bitcoin
Bitcoinov zadnji Gartner hype ciklus će započeti kada ga suverene države počnu akumulirati kao dio svojih rezervi stranih valuta. Tržišna kapitalizacija Bitcoina je trenutno premala da bismo ga smatrali značajnim dodatkom rezervama većini zemalja. No, kako se interes u privatnom sektoru povećava i kapitalizacija Bitcoina se približi trilijunu dolara, postat će dovoljno likvidan za većinu država. Prva država koja službeno doda bitcoine u svoje rezerve će vjerojatno potaknuti stampedo ostalih da učine isto. Države koje su među prvima u usvajanju Bitcoina imat će najviše benefita u svojim knjigama ako Bitcoin u konačnici postane globalna valuta (global reserve currency). Nažalost, vjerojatno će države sa najjačom izvršnom vlasti - diktature poput Sjeverne Koreje - biti najbrže u akumulaciji bitcoina. Neodobravanje prema takvim državama i slaba izvršna tijela zapadnjačkih demokracija uzrokovat će sporost i kašnjenje u akumulaciji bitcoina za njihove vlastite rezerve.
Velika je ironija u tome što je SAD trenutno jedna od regulatorno najotvorenijih nacija prema Bitcoinu, dok su Kina i Rusija najzatvorenije. SAD riskira najviše, geopolitički, ako bi Bitcoin zamijenio dolar kao svjetska rezervna valuta. U 1960-ima, Charles de Gaulle je kritizirao “pretjeranu privilegiju” (“exorbitant privilege”) koju su SAD imale u međunarodnom monetarnom poretku, postavljenom kroz Bretton Woods dogovor 1944. godine. Ruska i kineska vlada još ne shvaćaju geo-strateške benefite Bitcoina kao rezervne valute, te se trenutno brinu o efektima koje bi mogao imati na njihova unutarnja tržišta. Kao de Gaulle u 1960-ima, koji je prijetio SAD-u povratkom na klasični standard zlata, Kinezi i Rusi će s vremenom uvidjeti korist u velikoj poziciji u Bitcoinu - spremištu vrijednosti bez pokrića ijedne vlade. Sa najvećom koncentracijom rudara Bitcoina u Kini (2017.), kineska vlada već ima znatnu potencijalnu prednost u stavljanju bitcoina u svoje rezerve.
SAD se ponosi svojim statusom nacije inovatora, sa Silicijskom dolinom kao krunom svoje ekonomije. Dosad, Silicijska dolina je dominirala konverzacijom usmjerenom prema regulaciji, i poziciji koju bi ona treba zauzeti prema Bitcoinu. No, bankovna industrija i federalna rezerva SAD-a (US Federal Reserve, Fed) napokon počinju uviđati egzistencijalnu prijetnju koju Bitcoin predstavlja za američku monetarnu politiku, postankom globalne rezervne valute. Wall Street Journal, jedan od medijskih glasova federalne reserve, izdao je komentar o Bitcoinu kao prijetnji monetarnoj politici SAD-a:
"Postoji još jedna opasnost, možda i ozbiljnija iz perspektive centralnih banaka i regulatora: bitcoin možda ne propadne. Ako je spekulativni žar u kriptovalutu samo prvi pokazatelj njezinog šireg korištenja kao alternative dolaru, Bitcoin će svakako ugroziti monopol centralnih banaka nad novcem."
U narednim godinama, možemo očekivati veliku borbu između poduzetnika i inovatora u Silicijskoj dolini, koji će pokušavati čuvati Bitcoin od državne kontrole s jedne strane, i bankovne industrije i centralnih banaka koje će učiniti sve što mogu da bi regulirale Bitcoin kako bi spriječile znatne promjene u svojoj industriji i moći izdavanja novca, s druge.
Prijelaz na medij razmjene
Monetarno dobro ne može postati opće prihvaćen medij razmjene (standardna ekonomska definicija za “novac”) prije nego je vrednovano od širokog spektra ljudi; jednostavno, dobro koje nije vrednovano neće biti prihvaćeno u razmjeni. Kroz proces generalnog rasta vrijednosti, i time postanka spremišta vrijednosti, monetarno dobro će brzo narasti u kupovnoj moći, i time stvoriti cijenu za korištenje u razmjeni. Samo kada ta cijena rizika mijenjanja spremišta vrijednosti padne dovoljno nisko, može dobro postati opće prihvaćen medij razmjene.
Preciznije, monetarno dobro će biti prikladno kao medij razmjene samo kada je suma cijene rizika i transakcijske cijene u razmjeni manja nego u trgovini bez tog dobra.
U društvu koje vrši robnu razmjenu, prijelaz spremišta vrijednosti u medij razmjene može se dogoditi čak i onda kada monetarno dobro raste u kupovnoj moći, zato što su transakcijski troškovi robne razmjene iznimno visoki. U razvijenoj ekonomiji, u kojoj su troškovi razmjene niski, moguće je za mladu i rapidno rastućnu tehnologiju spremišta vrijednosti, poput Bitcoina, da se koristi kao medij razmjene, doduše na ograničen način. Jedan primjer je ilegalno tržište droge, gdje su kupci voljni žrtvovati oportunu cijenu čuvanja bitcoina kako bi umanjili znatan rizik kupovine droge koristeći fiat novac.
Postoje međutim velike institucionalne barijere da novonastalo spremište vrijednosti postane sveopće prihvaćen medij razmjene u razvijenom društvu. Države koriste oporezivanje kao moćnu metodu zaštite svojeg suverenog novca protiv rivalskih monetarnih dobara. Ne samo da suvereni novac ima prednost konstantnog izvora potražnje, zato što je porez moguće platiti jedino u njemu, nego su i rivalska monetarna dobra oporezana pri svakoj razmjeni za vrijeme rastuće cijene. Ova metoda oporezivanja stvara znatan otpor korištenju spremišta vrijednosti kao medija razmjene.
Ovakvo sabotiranje tržišnih monetarnih dobara nije nepremostiva barijera za njihovo prihvaćanje kao općeg medija razmjene. Ako ljudi izgube vjeru u suvereni novac, njegova vrijednost može rapidno propasti kroz proces zvan hiperinflacija. Kada suvereni novac prolazi kroz hiperinflaciju, njegova vrijednost propadne prvo u usporedbi sa najlikvidnijim dobrima u društvu, kao što je zlato ili stabilna strana valuta (američki dolar npr.), ako su ona dostupna. Kada nema likvidnih dobara ili ih ima premalo, novac u hiperinflaciji kolabira u usporedbi sa stvarnim dobrima, kao što su nekretnine ili upotrebljiva roba. Arhetipska slika hiperinflacije je trgovina sa praznim policama - potrošači brzo bježe iz propadajuće vrijednosti novca svoje nacije.

Nakon dovoljno vremena, kada je vjera potpuno uništena za vrijeme hiperinflacije, suvereni novac više nitko ne prihvaća, te se društvo može vratiti na robnu razmjenu, ili će doživjeti potpunu zamjenu monetarne jedinice za sredstvo razmjene. Primjer ovog procesa bila je zamjena zimbabveanskog dolara za američki dolar. Takva promjena suverenog novca za stranu valutu je dodatno otežana relativnom oskudnošću strane valute i odsustvom stranih bankarskih institucija koje pružaju likvidnost tržištu.
Sposobnost lakog prenošenja bitcoina preko granica i odsustvo potrebe za bankarskim sustavom čine Bitcoin idealnim monetarnim dobrom za one ljude koji pate pod hiperinflacijom. U nadolazećim godinama, kako fiat valute nastave svoj povijesni trend ka bezvrijednosti, Bitcoin će postati sve popularniji izbor za ušteđevine ljudi diljem svijeta. Kada je novac nacije napušten i zamijenjen Bitcoinom, Bitcoin će napraviti tranziciju iz spremišta vrijednosti u tom društvu u opće prihvaćeno sredstvo razmjene. Daniel Krawicz stvorio je termin “hiperbitcoinizacija” da bi opisao ovaj proces.
Učestala pogrešna shvaćanja
Većina ovog članka usredotočila se na monetarnu prirodu Bitcoina. Sa tim temeljima možemo adresirati neke od najčešćih nerazumijevanja u Bitcoinu.
Bitcoin je balon (bubble)
Bitcoin, kao sva tržišna monetarna dobra, posjeduje monetarnu premiju. Ona često rezultira uobičajenom kritikom da je Bitcoin samo “balon.” No, sva monetarna dobra imaju monetarnu premiju. Naprotiv, ta monetarna premija (cijena viša od one koju diktira potražnja za dobrom kao korisnim) je upravo karakteristična za sve oblike novca. Drugim riječima, novac je uvijek i svuda balon. Paradoksalno, monetarno dobro je istovremeno balon i ispod vrijednosti ukoliko je u ranijim stadijima općeg prihvaćanja kao novac.
Bitcoin je previše volatilan
Volatilnost cijene Bitcoina je funkcija njegovog nedavnog nastanka. U prvih nekoliko godina svojeg postojanja, Bitcoin se ponašao kao mala dionica, i svaki veliki kupac - kao npr. braća Winklevoss - mogao je uzrokovati veliki skok u njegovoj cijeni. No, kako su se prihvaćenost i likvidnost povećavali kroz godine, volatilnost Bitcoina je srazmjerno smanjila. Kada Bitcoin postigne tržišnu kapitalizaciju (vrijednost) zlata, imat će sličnu volatilnost kao i zlato. Kako Bitcoin nastavi rasti, njegova volatilnost će se smanjiti do razine koja ga čini prikladnim za široko korištenje kao medij razmjene. Kao što je prethodno rečeno, monetizacija Bitcoina se odvija u seriji Gartner hype ciklusa. Volatilnost je najniža za vrijeme vrhunaca i dolina unutar ciklusa. Svaki hype ciklus ima nižu volatilnost od prethodnih, zato što je likvidnost tržišta veća.
Cijene transakcija su previsoke
Novija kritika Bitcoin mreže je ta da ju je povećanje cijena prijenosa bitcoina učinilo neprikladnom za sustav plaćanja. No, rast u cijenama transakcija je zdrav i očekivan. One su nužne za plaćanje bitcoin minera (rudara), koji osiguravaju mrežu validacijom transakcija. Rudare se plaća kroz cijene transakcija ili kroz blok-nagrade, koje su inflacijska subvencija od trane trenutnih vlasnika bitcoina.
S obzirom na Bitcoinovu fiksnu proizvodnju (monetarna politika koja ga čini idealnim za spremanje vrijednosti), blok-nagrade će s vremenom nestati i mrežu će se u konačnici morati osiguravati kroz cijene transakcija. Mreža sa “niskim” cijenama transakcija je mreža sa slabom sigurnosti i osjetljiva na vanjsku intervenciju i cenzuru. Oni koji hvale niske cijene Bitcoinovih alternative zapravo niti ne znajući opisuju slabosti tih takozvanih “alt-coina.”
Površan temelj kritika Bitcoinovih “visokih” cijena transakcija je uvjerenje da bi Bitcoin trebao biti prvo sustav plaćanja, i drugo spremište vrijednosti. Kao što smo vidjeli kroz povijest novca, ovo uvjerenje je naopako. Samo onda kada Bitcoin postane duboko ukorijenjeno spremište novca može biti prikladan kao sredstvo razmjene. Nadalje, kada oportunitetni trošak razmjene bitcoina dođe na razinu koja ga čini prikladnim sredstvom razmjene, većina trgovine neće se odvijati na samoj Bitcoin mreži, nego na mrežama “drugog sloja” (second layer) koje će imati niže cijene transakcija. Takve mreže, poput Lightning mreže, služe kao moderna verzija zadužnica koje su korištene za prijenos vlasničkih papira zlata u 19. stoljeću. Banke su koristile zadužnice zato što je prijenos samog metala bio daleko skuplji. Za razliku od takvih zadužnica, Lightning mreža će omogućavati nisku cijenu prijenosa bitcoina bez potrebe za povjerenjem prema trećoj strani, poput banaka. Razvoj Lightning mreže je tehnološka inovacija od izuzetne važnosti u povijesti Bitcoina, i njezina vrijednost će postati očita u narednim godinama, kako je sve više ljudi bude razvijalo i koristilo.
Konkurencija
Pošto je Bitcoin softverski protokol otvorenog tipa (open-source), oduvijek je bilo moguće kopirati softver i imitirati mrežu. Kroz godine nastajali su mnogi imitatori, od identičnih kopija, kao Litecoin, do kompleksnijih varijanti kao što je Ethereum, koje obećavaju arbitrarno kompleksne ugovorne mehanizme koristeći decentralizirani računalni sustav. Česta kritika Bitcoinu od strane ulagača je ta da on ne može zadržati svoju vrijednost kada je vrlo lako stvoriti konkurente koji mogu lako i brzo u sebi imati najnovije inovacije i softverske funkcionalnosti.

Greška u ovom argumentu leži u manju takozvanog “mrežnog efekta” (network effect), koji postoji u prvoj i dominantnoj tehnologiji u nekom području. Mrežni efekt - velika vrijednost korištenja Bitcoina samo zato što je već dominantan - je važno svojstvo samo po sebi. Za svaku tehnologiju koja posjeduje mrežni efekt, to je daleko najvažnije svojstvo koje može imati.
Za Bitcoin, mrežni efekt uključuje likvidnost njegovog tržišta, broj ljudi koji ga posjeduju, i zajednicu programera koji održavaju i unaprjeđuju njegov softver i svjesnost u javnosti. Veliki ulagači, uključujući države, će uvijek prvo tražiti najlikvidnije tržište, kako bi mogli ući i izaći iz tržišta brzo, i bez utjecanja na cijenu. Programeri će se pridružiti dominantnoj programerskoj zajednici sa najboljim talentom, i time pojačati samu zajednicu. Svjesnost o brendu sama sebe pojačava, pošto se nadobudni konkurenti Bitcoina uvijek spominju u kontekstu Bitcoina kao takvog.
Raskrižje na putu (fork)
Trend koji je postao popularan 2017. godine nije bio samo imitacija Bitcoinovog softvera, nego kopiranje potpune povijesti njegovih prošlih transakcija (cijeli blockchain). Kopiranjem Bitcoinovog blockchaina do određene točke/bloka i odvajanjem sljedećih blokova ka novoj mreži, u procesu znanom kao “forking” (odvajanje), Bitcoinovi konkurenti su uspjeli riješiti problem distribuiranja svojeg tokena velikom broju korisnika.

Najznačajniji takav fork dogodio se 1. 8. 2017. godine, kada je nova mreža nazvana Bitcoin Cash (Bcash) stvorena. Vlasnik N količine bitcoina prije 1.8.2017. bi onda posjedovao N bitcoina i N BCash tokena. Mala, ali vrlo glasna zajednica Bcash proponenata je neumorno pokušavala prisvojiti Bitcoinov brend i ime, imenujući svoju novu mrežu Bitcoin Cast i pokušavajući uvjeriti nove pridošlice u Bitcoin da je Bcash “pravi” Bitcoin. Ti pokušaji su većinom propali, i taj neuspjeh se vidi u tržišnim kapitalizacijama dviju mreža. No, za nove ulagače, i dalje postoji rizik da bi konkurent mogao kopirati Bitcoin i njegov blockchain i tako uspjeti u preuzimanju tržišne kapitalizacije, te postati de facto Bitcoin.
Moguće je uočiti važno pravilo gledajući velike forkove u prošlosti Bitcoin i Ethereum mreža. Većina tržišne kapitalizacije odvijat će se na mreži koja zadrži najviši stupanj talenta i aktivnosti u zajednici programera. Premda se na Bitcoin može gledati kao na nov i mlad novac, on je također računalna mreža koja počiva na softveru, kojeg se pak treba održavati i poboljšavati. Kupovina tokena na mreži koja ima malo neiskusnih programera bilo bi kao kupovati kopiju Microsoft Windowsa na kojoj rade lošiji programeri. Jasno je vidljivo iz povijesti forkova koji su se odvili 2017. godine da su najbolji računalni i kriptografski stručnjaci posvećeni razvoju originalnog Bitcoina, a ne nekoj od rastućeg broja imitacija koje su se izrodile iz njega.
Stvarni rizici
Premda su uobičajene kritike upućene Bitconu od strane medija i ekonomske profesije krive i bazirane na netočnom shvaćanju novca, postoje pravi i značajni rizici kod ulaganja u Bitcoin. Bilo bi mudro za novog Bitcoin ulagača da shvati ove rizike prije potencijalnog ulaganja.
Rizik protokola
Bitcoin protokol i kriptografski sastavni dijelovi na kojima je sagrađen potencijalno imaju dosad nepronađenu grešku u svom dizajnu, ili mogu postati nesigurni razvojem kvantnih računala. Ako se pronađe greška u protokolu, ili neka nova metoda računarstva učini mogućim probijanje kriptografskih temelja Bitcoina, vjera u Bitcoin biti će znatno narušena. Rizik protokola bio je najviši u ranim godinama razvoja Bitcoina, kada je još uvijek bilo nejasno, čak i iskusnim kriptografima, je li Satoshi Nakamoto zaista riješio problem bizantskih generala (Byzantine Generals’ Problem). Brige oko ozbiljnih grešaka u Bitcoin protokolu nestale su kroz godine, no uzevši u obzir njegovu tehnološku prirodu, rizik protokola će uvijek ostati u Bitcoinu, makar i kao izuzetak.
Propadanje mjenjačnica
Time što je decentraliziran, Bitcoin je pokazao značajnu otpornost, suočen sa brojnim pokušajima raznih vlada da ga reguliraju ili unište. No, mjenjačnice koje trguju bitcoinima za fiat valute su centralizirani entiteti i podložne regulacijama i zatvaranju. Bez mjenjačnica i volje bankara da s njima posluju, proces monetizacije Bitcoina bio bi ozbiljno usporen, ako ne i potpuno zaustavljen. Iako postoje alternativni izvori likvidnosti za Bitcoin, poput “over-the-counter” brokera i decentraliziranih tržišta za kupovinu i prodaju bitcoina, kritičan proces otkrivanja i definiranja cijene se odvija na najlikvidnijim mjenjačnicama, koje su sve centralizirane.
Jedan od načina za umanjivanje rizika gašenja mjenjačnica je geografska arbitraža. Binance, jedna od velikih mjenjačnica iz Kine, preselila se u Japan nakon što joj je kineska vlada zabranila operiranje u Kini. Vlade su također oprezne kako ne bi ugušile novu industriju koja je potencijalno značajna kao i internet, i time predale nevjerojatnu konkurentnu vrijednost drugim nacijama.
Samo kroz koordinirano globalno ukidanje Bitcoin mjenjačnica bi proces monetizacije mogao biti zaustavljen. Trenutno smo u utrci; Bitcoin raste i postaje sve rašireniji, i doći će do trenutka kada bi potpuno ukidanje mjenjačnica postalo politički neizvedivo - kao i gašenje interneta. Mogućnost takvog ukidanja je još uvijek realna, i valja je uzeti u obzir pri ulaganju u Bitcoin. Kao što je gore objašnjeno, suverene vlade se polako bude i uviđaju prijetnju koju predstavlja neovisna digitalna valuta otporna na cenzuru, za njihovu monetarnu politiku. Otvoreno je pitanje hoće li išta poduzeti da odgovore ovoj prijetnji prije nego Bitcoin postane toliko utvrđen i raširen da politička akcija postane nemoćna i ne-efektivna.
Zamjenjivost
Otvorena i transparentna priroda Bitcoin blockchaina omogućava državama da proglase specifične bitcoine “okaljanima” zbog njihovog korištenja u određenim aktivnostima. Premda Bitcoin, na protokolarnoj razini, ne diskriminira transakcije na ikoji način, “okaljani” bitcoini bi mogli postati bezvrijedni ako bi ih regulacije proglasile ilegalnima i neprihvatljivima za mjenjačnice ili trgovce. Bitcoin bi tada izgubio jedno od kritičnih svojstava monetarnog dobra: zamjenjivost.
Da bi se ovaj problem riješio i umanjio, biti će potrebna poboljšanja na razini protokola kako bi se poboljšala privatnost transakcija. Premda postoji napredak u ovom smjeru, prvi put primjenjen u digitalnim valutama kao što su Monero i Zcash, potrebno je napraviti značajne tehnološke kompromise između efikasnosti i kompleksnosti Bitcoina i njegove privatnosti. Pitanje ostaje otvoreno je li moguće dodati nova svojstva privatnosti na Bitcoin, na način koji neće kompromitirati njegovu korisnost kao novca.
Zaključak
Bitcoin je novonastali novac koji je u procesu transformacije iz sakupljačkog dobra u spremište vrijednosti. Kao neovisno monetarno dobro, moguće je da će u budućnosti postati globalan novac, slično kao zlato za vrijeme 19. stoljeća. Prihvaćanje Bitcoina kao globalnog novca je upravo taj optimističan scenarij za Bitcoin, kojeg je artikulirao Satoshi Nakamoto još 2010. godine u email razmjeni sa Mikeom Hearnom:
"Ako zamisliš da se koristi u nekom dijelu svjetske trgovine, i da će postojati samo 21 milijun bitcoina za cijeli svijet, vrijednost po jedinici će biti znatno veća".
Ovaj scenarij je još snažnije definirao briljantni kriptograf Hal Finney, koji je ujedno primio i prve bitcoine od Nakamotoa, ubrzo nakon najave prvog funkcionalnog Bitcoin softvera:
"Zamislimo da Bitcoin bude uspješan i postane dominantan sustav plaćanja diljem svijeta. U tom slučaju će ukupna vrijednost valute biti jednaka ukupnoj vrijednosti svog bogatstva svijeta. Današnje procjene ukupnog svjetskog bogatska kućanstava koje sam pronašao borave negdje između 100 i 300 trilijuna dolara. Sa 20 milijuna bitcoina, svaki bi onda vrijedio oko 10 milijuna dolara."
Čak i da Bitcoin ne postane u cijelost globalan novac, nego da se samo natječe sa zlatom kao neovisno spremište vrijednosti, i dalje je masivno podcijenjen. Mapiranje tržišne kapitalizacije postojeće količine izrudarenog zlata (oko 8 trilijuna dolara) na maksimalnu dostupnost Bitcoina od 21 milijun, daje vrijednost od otprilike 380,000 dolara po bitcoinu. Kao što smo vidjeli u prethodnom tekstu, svojstva koja omogućavaju monetarnom dobru da bude prikladno spremište vrijednosti, čine Bitcoin superiornijim zlatu u svakom pogledu osim trajanja povijesti. No, kako vrijeme prolazi i Lindy efekt postane jači, dosadašnja povijest će prestati biti prednost zlata. Samim time, nije nerazumno očekivati da će Bitcoin narasti do, a možda i preko, ukupne cijene zlata na tržištvu do 2030. Opaska ovoj tezi je činjenica da veliki postotak vrijednosti zlata dolazi od toga što ga centralne banke čuvaju kao spremište vrijednosti. Da bi Bitcoin došao do te razine, određena količina suverenih država će trebati sudjelovati. Hoće li zapadnjačke demokracije sudjelovati u vlasništvu Bitcoina je nepoznato. Vjerojatnije je, nažalost, da će prve nacije u Bitcoin tržištu biti sitne diktature i kleptokracije.
Ako niti jedna država ne bude sudjelovala u Bitcoin tržištu, optimistična teza i dalje postoji. Kao nevisno spremište vrijednosti u rukama individualnih i institucionalnih ulagača, Bitcoin je i dalje vrlo rano u svojoj “krivulji prihvaćenosti” (adoption curve); tzv. “rana većina” ulaze na tržište sada, dok će ostali ući tek nekoliko godina kasnije. Sa širim sudjelovanjem individualnih i institucionalnih ulagača, cijena po bitcoinu između 100,000 i 200,000 dolara je sasvim moguća.
Posjedovanje bitcoina je jedna od malobrojnih asimetričnih novčanih strategija dostupnih svakome na svijetu. Poput “call” opcija, negativan rizik ulagača je ograničen na 1x, dok potencijalna dobit i dalje iznosi 100x ili više. Bitcoin je prvi istinski globalan balon čija je veličina ograničena samo potražnjom i željom građana svijeta da zaštite svoju ušteđevinu od raznovrsnih ekonomskih malverzacija vlade. Bitcoin je ustao kao feniks iz pepela globalne financijske krize 2008. godine - katastrofe kojoj su prethodile odluke centralnih banaka poput američke Federalne rezerve (Federal Reserve).
Onkraj samo financijske teze za Bitcoin, njegov rast i uspjeh kao neovisno spremište vrijednosti imat će duboke geopolitičke posljedice. Globalna, ne-inflacijska valuta će prisiliti suverene države da promjene svoje primarne mehanizme financiranja od inflacije u izravno oporezivanje; koje je daleko manje politički popularno. Države će se smanjivati proporcionalno političkoj boli koju im nanese oporezivanje kao jedini način financiranja. Nadalje, globalna trgovina vršiti će se na način koji zadovoljava aspiraciju Charlesa de Gaullea, da nijedna nacija ne bi smjela imati privilegiju nad ikojom drugom:
"Smatramo da je potrebno da se uspostavi međunarodna trgovina, kao što je bio slučaj prije velikih nesreća koje su zadesile svijet, na neosporivoj monetarnoj bazi, koja ne nosi na sebi oznaku ijedne države."
Za 50 godina, ta monetarna baza biti će Bitcoin.
-
 @ bf47c19e:c3d2573b
2025-05-11 21:32:19
@ bf47c19e:c3d2573b
2025-05-11 21:32:19Bitkoin, kao jedinstvena digitalna valuta, postaje poznat široj javnosti u trenutku kada se pojavljuju prvi znaci svetske ekonomske krize a postojeći finansijski sistem počinje da pokazuje sve svoje slabosti. Danas, bitkoin, izaziva veliku pažnju svojim naglim skokovima i padovima.
Osnovna ideja o o decentralizovanim valutama potekla je od osnivača kripto-pank pokreta, među kojima su bili direktori kompanija naprednih tehnologija, univerzitetski profesori i istraživači iz oblasti matematike i fizike. Njihova ideja zasnovana je na anonimnoj, istovremenoj komunikaciji koja neće biti kontrolisana i nadgledana od neke treće strane u procesu.
Šta je kriptovaluta, ko je njen tvorac, kako do nje doći, kako trgovati i gde je čuvati, neka su od pitanja za čijim odgovorima tragamo u emisiji.
Sagovornici u emisiji su svi oni koji su u poslednjih godinu dana bili relevantni učesnici priča o kriptovaluti u Srbiji: osnivači Asocijacije bitkoin, predstavnici Narodne banke Srbije i predstavnici medija.
Montažer Milan Radičević
Urednik Aleksandra Šarković
-
 @ 8173f6e1:e488ac0f
2025-05-11 21:23:06
@ 8173f6e1:e488ac0f
2025-05-11 21:23:06TESTNOTEBIN2
-
 @ 26d4b5b2:96393e73
2025-05-11 22:24:38
@ 26d4b5b2:96393e73
2025-05-11 22:24:38https://app.doh.money http://localhost:3000 https://dohmoney-cyxe-cyxeio-cyxecyxeios-projects.vercel.app GET POST OPTIONS PUT DELETE Content-Type Ocp-Apim-Subscription-Key Authorization Accept X-Requested-With X-Verified-By Content-Length Request-Context Date @(context.Request.Headers.GetValueOrDefault("Ocp-Apim-Subscription-Key", "50922ff015c14a84a092b4764dc6dddf")) @(context.Request.Headers.GetValueOrDefault("Origin", "https://app.doh.money")) @(context.Request.Headers.GetValueOrDefault("Origin", "http://localhost:3000")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Ocp-Apim-Subscription-Key, Authorization, Accept, X-Requested-With,X-Verified-By Content-Length, Request-Context, Date @(context.Request.Headers.GetValueOrDefault("Origin", "https://app.doh.money")) @(context.Request.Headers.GetValueOrDefault("Origin", "http://localhost:3000")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Ocp-Apim-Subscription-Key, Authorization, Accept, X-Requested-With, X-Verified-By Content-Length, Request-Context, Date -
 @ 8173f6e1:e488ac0f
2025-05-11 20:54:58
@ 8173f6e1:e488ac0f
2025-05-11 20:54:58testnotebin7testnotebin7testnotebin7testnotebin7
-
 @ 26d4b5b2:96393e73
2025-05-11 21:44:26
@ 26d4b5b2:96393e73
2025-05-11 21:44:26@(context.Request.Headers.GetValueOrDefault("Origin", "")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Authorization, Accept, X-Requested-With, X-Verified-By, Ocp-Apim-Subscription-Key 86400 Access denied: invalid origin {{dohcloud-key}} @(context.Request.Headers.GetValueOrDefault("Origin", "")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Authorization, Accept, X-Requested-With, X-Verified-By, Ocp-Apim-Subscription-Key @(context.Request.Headers.GetValueOrDefault("Origin", "*")) -
 @ 26d4b5b2:96393e73
2025-05-11 21:43:01
@ 26d4b5b2:96393e73
2025-05-11 21:43:01https://app.doh.money http://localhost:3000 https://dohmoney-cyxe-cyxeio-cyxecyxeios-projects.vercel.app GET POST OPTIONS PUT DELETE Content-Type Ocp-Apim-Subscription-Key Authorization Accept X-Requested-With X-Verified-By Content-Length Request-Context Date @(context.Request.Headers.GetValueOrDefault("Ocp-Apim-Subscription-Key", "50922ff015c14a84a092b4764dc6dddf")) @(context.Request.Headers.GetValueOrDefault("Origin", "https://app.doh.money")) @(context.Request.Headers.GetValueOrDefault("Origin", "http://localhost:3000")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Ocp-Apim-Subscription-Key, Authorization, Accept, X-Requested-With,X-Verified-By Content-Length, Request-Context, Date @(context.Request.Headers.GetValueOrDefault("Origin", "https://app.doh.money")) @(context.Request.Headers.GetValueOrDefault("Origin", "http://localhost:3000")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Ocp-Apim-Subscription-Key, Authorization, Accept, X-Requested-With, X-Verified-By Content-Length, Request-Context, Date -
 @ 8173f6e1:e488ac0f
2025-05-11 20:50:24
@ 8173f6e1:e488ac0f
2025-05-11 20:50:24testnotebin123456testnotebin123456testnotebin123456testnotebin123456
-
 @ bf47c19e:c3d2573b
2025-05-11 20:50:05
@ bf47c19e:c3d2573b
2025-05-11 20:50:05„Ova mašina ozelenjava“, koji predstavlja Swan Bitcoin, je dokumentarac koji istražuje složen i nijansiran odnos između Bitkoina i energije. Producent filma je Enrike Pozner, dok je režiser nagrađivani britanski filmski stvaralac Džejmi King čija je serija „Ukradi ovaj film“ (2006–2010) bila jedan od najpreuzimanijih dokumentaraca svih vremena.
U filmu „Ova mašina ozelenjava“ učestvuje glavna ekonomska savetnica Swan-a Lin Alden zajedno sa Aleksom Gladstajnom, Nikom Karterom i mnogim drugima. „Ova mašina ozelenjava“ razbija mnoge zablude o rudarenju Bitkoina i iznosi ubedljive argumente za Bitkoin kao neto-pozitivan faktor za životnu sredinu.
Prevod: bitcoin-balkan.com
-
 @ 26d4b5b2:96393e73
2025-05-11 21:28:47
@ 26d4b5b2:96393e73
2025-05-11 21:28:47// SPDX-License-Identifier: GPL-3.0 Contract PaidMessage( owner: Address, // who collects the fee mut message: ByteVec // last posted message ) { // ── Events ──────────────────────────────────────────────────────────────── /// Fires whenever someone pays and posts a new message event MessageSent(sender: Address, content: ByteVec)
// ── Constants ───────────────────────────────────────────────────────────── /// 0.1 ALPH in atto-ALPH const PRICE = 100000000000000000 /// Maximum allowed message length const MAX_MESSAGE_SIZE = 1024 /// Dust amount for transactions (0.001 ALPH in atto-ALPH) const DUST_AMOUNT = 1000000000000000 // ── Error codes ─────────────────────────────────────────────────────────── enum ErrorCodes { InvalidMessageSize = 0 InsufficientPayment = 1 InvalidCaller = 2 } // ── Read-only helper ────────────────────────────────────────────────────── /// Read back the current message pub fn getMessage() -> ByteVec { return message } // ── Core logic ──────────────────────────────────────────────────────────── /// Requires caller to attach ≥ `PRICE` atto-ALPH, updates message, forwards fee @using(preapprovedAssets = true, updateFields = true, payToContractOnly = false) pub fn sendMessage(newMessage: ByteVec) -> () { // 1️⃣ Check external caller checkCaller!(isAssetAddress!(callerAddress!()), ErrorCodes.InvalidCaller) // 2️⃣ Size check assert!(size!(newMessage) <= MAX_MESSAGE_SIZE, ErrorCodes.InvalidMessageSize) // 3️⃣ Payment check let paid = tokenRemaining!(callerAddress!(), ALPH) assert!(paid >= PRICE, ErrorCodes.InsufficientPayment) // 4️⃣ Update on-chain message message = newMessage // 5️⃣ Transfer exact fee to owner transferToken!(callerAddress!(), owner, ALPH, PRICE) // 6️⃣ Refund excess to caller if above dust amount let change = paid - PRICE if (change >= DUST_AMOUNT) { transferToken!(callerAddress!(), callerAddress!(), ALPH, change) } // 7️⃣ Emit event emit MessageSent(callerAddress!(), newMessage) } // ── Owner-only function ─────────────────────────────────────────────────── /// Allows owner to update the message without payment @using(updateFields = true) pub fn updateMessageByOwner(newMessage: ByteVec) -> () { // 1️⃣ Check if caller is owner checkCaller!(callerAddress!() == owner, ErrorCodes.InvalidCaller) // 2️⃣ Size check assert!(size!(newMessage) <= MAX_MESSAGE_SIZE, ErrorCodes.InvalidMessageSize) // 3️⃣ Update message message = newMessage // 4️⃣ Emit event emit MessageSent(callerAddress!(), newMessage) }}
-
 @ bf47c19e:c3d2573b
2025-05-11 20:24:44
@ bf47c19e:c3d2573b
2025-05-11 20:24:44Kratki dokumentarac zasnovan na istoimenoj knjizi Mareja Rotbarda. Teme uključuju: opasnosti koje sa sobom nosi država blagostanja, monetarne politike zasnovane na dugu, oporezivanje bez zastupanja i ostala sredstva državnog nasilja.
Autor filma: @rjames_BTC
Zvanični vebsajt filma: anatomystatefilm.com
Prevod: bitcoin-balkan.com
-
 @ bf47c19e:c3d2573b
2025-05-11 20:15:51
@ bf47c19e:c3d2573b
2025-05-11 20:15:51U društvu koje koristi čvrst novac, jedini način sticanja bogatstva je stvaranje vrednosti za druge. Šta se jbt desilo 1971?
Autor filma: @rjames_BTC
Zvanični vebsajt: hardmoneyfilm.com
Prevod: bitcoin-balkan.com
-
 @ 26d4b5b2:96393e73
2025-05-11 21:27:27
@ 26d4b5b2:96393e73
2025-05-11 21:27:27SET ANSI_NULLS ON GO SET QUOTED_IDENTIFIER ON GO
ALTER PROCEDURE [dbo].[WALLETCONE] @TokenId NVARCHAR(255),
@InitiatingAddress NVARCHAR(255)
AS BEGIN SET NOCOUNT ON;DECLARE @TokenName NVARCHAR(255), @TableName NVARCHAR(255), @JsonPath NVARCHAR(300), @Sql NVARCHAR(MAX), @StartTime DATETIME = GETDATE(); PRINT 'Procedure started at: ' + CONVERT(NVARCHAR(30), @StartTime, 120); -- Validate inputs IF @TokenId IS NULL OR @TokenId = '' OR @InitiatingAddress IS NULL OR @InitiatingAddress = '' BEGIN PRINT 'Error: TokenId and InitiatingAddress cannot be NULL or empty'; RETURN; END -- Resolve token name SELECT @TokenName = UPPER(REPLACE(Name,' ','_')) FROM dbo.DOH_INFO_TOKENS WHERE TokenID = @TokenId; IF @TokenName IS NULL BEGIN PRINT 'Error: Invalid TokenId: ' + @TokenId; RETURN; END -- Build table name & JSON path SET @TableName = 'DOH_INFO_TRANSACTIONS_' + @TokenName; SET @JsonPath = '$."' + REPLACE(@TokenId,'"','""') + '"'; IF NOT EXISTS (SELECT 1 FROM sys.tables WHERE name = @TableName) BEGIN PRINT 'Error: Table not found: ' + @TableName; RETURN; END ---------------------------------------------------------------- -- 1) Pool Transactions Detail ---------------------------------------------------------------- SET @Sql = N' SELECT @TokenId AS token_id, t.[hash], t.initiating_address, COALESCE(p.Name,''Unknown'') AS pool_name, t.transaction_type, TRY_CAST(COALESCE(JSON_VALUE(t.gotTokens,@JsonPath),''0'') AS FLOAT) AS got_tokens, TRY_CAST(COALESCE(JSON_VALUE(t.forTokens,@JsonPath),''0'') AS FLOAT) AS for_tokens, TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) AS ratio, t.[timestamp], CASE WHEN t.transaction_type LIKE ''%BUY%'' THEN -(TRY_CAST(JSON_VALUE(t.gotTokens,@JsonPath) AS FLOAT) *TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10))) WHEN t.transaction_type LIKE ''%SELL%'' THEN TRY_CAST(JSON_VALUE(t.forTokens,@JsonPath) AS FLOAT) *TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) ELSE NULL END AS gain_loss FROM dbo.' + QUOTENAME(@TableName) + ' t LEFT JOIN dbo.DOH_INFO_POOLS p ON t.pool_id = p.PoolID WHERE (JSON_VALUE(t.gotTokens,@JsonPath) IS NOT NULL OR JSON_VALUE(t.forTokens,@JsonPath) IS NOT NULL) AND t.initiating_address = @InitiatingAddress AND t.pool_id IS NOT NULL;'; EXEC sp_executesql @Sql, N'@TokenId NVARCHAR(255),@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @TokenId,@InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 2) Pool Transactions Summary ---------------------------------------------------------------- SET @Sql = N' SELECT COALESCE(p.Name,''Unknown'') AS pool_name, t.pool_id, COUNT(*) AS transaction_count, SUM(CASE WHEN t.transaction_type LIKE ''%BUY%'' THEN -(TRY_CAST(JSON_VALUE(t.gotTokens,@JsonPath) AS FLOAT) *TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10))) WHEN t.transaction_type LIKE ''%SELL%'' THEN TRY_CAST(JSON_VALUE(t.forTokens,@JsonPath) AS FLOAT) *TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) ELSE 0 END) AS total_gain_loss, AVG(CASE WHEN t.transaction_type LIKE ''%BUY%'' THEN TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) ELSE NULL END) AS avg_buy_price, AVG(CASE WHEN t.transaction_type LIKE ''%SELL%'' THEN TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) ELSE NULL END) AS avg_sell_price, SUM(CASE WHEN t.transaction_type LIKE ''%BUY%'' THEN TRY_CAST(JSON_VALUE(t.gotTokens,@JsonPath) AS FLOAT) WHEN t.transaction_type LIKE ''%SELL%'' THEN TRY_CAST(JSON_VALUE(t.forTokens,@JsonPath) AS FLOAT) ELSE 0 END) AS total_tokens_transacted FROM dbo.' + QUOTENAME(@TableName) + ' t LEFT JOIN dbo.DOH_INFO_POOLS p ON t.pool_id = p.PoolID WHERE (JSON_VALUE(t.gotTokens,@JsonPath) IS NOT NULL OR JSON_VALUE(t.forTokens,@JsonPath) IS NOT NULL) AND t.initiating_address = @InitiatingAddress AND t.pool_id IS NOT NULL GROUP BY COALESCE(p.Name,''Unknown''), t.pool_id ORDER BY total_gain_loss DESC, COALESCE(p.Name,''Unknown'') ASC;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 3) Non-Pool Transactions Detail (all direct txns) ---------------------------------------------------------------- SET @Sql = N' SELECT @TokenId AS token_id, t.[hash], t.initiating_address, t.receiving_address, t.transaction_type, TRY_CAST(COALESCE(JSON_VALUE(t.sent_tokens,@JsonPath),''0'') AS FLOAT) AS sent_tokens, TRY_CAST(COALESCE(JSON_VALUE(t.received_tokens,@JsonPath),''0'') AS FLOAT) AS received_tokens, TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) AS ratio, t.[timestamp], t.status FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE (JSON_VALUE(t.sent_tokens,@JsonPath) IS NOT NULL OR JSON_VALUE(t.received_tokens,@JsonPath) IS NOT NULL) AND t.initiating_address = @InitiatingAddress AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'');'; EXEC sp_executesql @Sql, N'@TokenId NVARCHAR(255),@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @TokenId,@InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 4) Non-Pool Sent Summary (you → others) ---------------------------------------------------------------- SET @Sql = N' SELECT t.initiating_address AS sender_address, t.receiving_address AS receiver_address, COUNT(*) AS send_count, SUM(TRY_CAST(JSON_VALUE(t.sent_tokens,@JsonPath) AS FLOAT)) AS total_sent, MIN(t.[timestamp]) AS first_sent, MAX(t.[timestamp]) AS last_sent FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE JSON_VALUE(t.sent_tokens,@JsonPath) IS NOT NULL AND t.initiating_address = @InitiatingAddress AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') GROUP BY t.initiating_address, t.receiving_address ORDER BY send_count DESC, total_sent DESC;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 5) Non-Pool Received Summary (others → you, no self-sends) ---------------------------------------------------------------- SET @Sql = N' SELECT t.initiating_address AS sender_address, @InitiatingAddress AS receiver_address, COUNT(*) AS send_count, SUM(TRY_CAST(JSON_VALUE(t.received_tokens,@JsonPath) AS FLOAT)) AS total_sent, MIN(t.[timestamp]) AS first_sent, MAX(t.[timestamp]) AS last_sent FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE JSON_VALUE(t.received_tokens,@JsonPath) IS NOT NULL AND t.receiving_address = @InitiatingAddress AND t.initiating_address <> @InitiatingAddress AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') GROUP BY t.initiating_address ORDER BY send_count DESC, total_sent DESC;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 6) Non-Pool Received Detail (every incoming txn) ---------------------------------------------------------------- SET @Sql = N' SELECT @TokenId AS token_id, t.[hash], t.initiating_address AS sender_address, t.receiving_address AS receiver_address, t.transaction_type, TRY_CAST(COALESCE(JSON_VALUE(t.sent_tokens,@JsonPath),''0'') AS FLOAT) AS sent_tokens, TRY_CAST(COALESCE(JSON_VALUE(t.received_tokens,@JsonPath),''0'') AS FLOAT) AS received_tokens, TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) AS ratio, t.[timestamp], t.status FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE JSON_VALUE(t.received_tokens,@JsonPath) IS NOT NULL AND t.receiving_address = @InitiatingAddress AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') ORDER BY t.[timestamp] DESC;'; EXEC sp_executesql @Sql, N'@TokenId NVARCHAR(255),@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @TokenId,@InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 7) Net Token Position Summary ---------------------------------------------------------------- SET @Sql = N' SELECT @InitiatingAddress AS wallet, SUM(TRY_CAST(JSON_VALUE(t.received_tokens,@JsonPath) AS FLOAT)) - SUM(TRY_CAST(JSON_VALUE(t.sent_tokens,@JsonPath) AS FLOAT)) AS net_token_position, (SUM(TRY_CAST(JSON_VALUE(t.received_tokens,@JsonPath) AS FLOAT)) - SUM(TRY_CAST(JSON_VALUE(t.sent_tokens,@JsonPath) AS FLOAT))) * AVG(CAST(t.ratio AS FLOAT)) AS estimated_net_value FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE (JSON_VALUE(t.sent_tokens,@JsonPath) IS NOT NULL OR JSON_VALUE(t.received_tokens,@JsonPath) IS NOT NULL) AND (t.initiating_address = @InitiatingAddress OR t.receiving_address = @InitiatingAddress) AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool''); '; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 8) Unique Counterparty Count ---------------------------------------------------------------- SET @Sql = N' SELECT COUNT(DISTINCT CASE WHEN t.initiating_address = @InitiatingAddress THEN t.receiving_address ELSE t.initiating_address END ) AS unique_counterparties FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE (t.initiating_address = @InitiatingAddress OR t.receiving_address = @InitiatingAddress) AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool''); '; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255)', @InitiatingAddress; ---------------------------------------------------------------- -- 9) Token Activity Timeline (monthly) ---------------------------------------------------------------- SET @Sql = N' SELECT FORMAT(t.[timestamp],''yyyy-MM'') AS month, COUNT(*) AS transaction_count, SUM( COALESCE(TRY_CAST(JSON_VALUE(t.sent_tokens,@JsonPath) AS FLOAT),0) + COALESCE(TRY_CAST(JSON_VALUE(t.received_tokens,@JsonPath) AS FLOAT),0) ) AS total_volume FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE (t.initiating_address = @InitiatingAddress OR t.receiving_address = @InitiatingAddress) AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') GROUP BY FORMAT(t.[timestamp],''yyyy-MM'') ORDER BY month;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 10) Top Volume Counterparties ---------------------------------------------------------------- SET @Sql = N' SELECT CASE WHEN t.initiating_address = @InitiatingAddress THEN t.receiving_address ELSE t.initiating_address END AS counterparty, COUNT(*) AS tx_count, SUM( COALESCE(TRY_CAST(JSON_VALUE(t.sent_tokens,@JsonPath) AS FLOAT),0) + COALESCE(TRY_CAST(JSON_VALUE(t.received_tokens,@JsonPath) AS FLOAT),0) ) AS total_volume FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE (t.initiating_address = @InitiatingAddress OR t.receiving_address = @InitiatingAddress) AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') GROUP BY CASE WHEN t.initiating_address = @InitiatingAddress THEN t.receiving_address ELSE t.initiating_address END ORDER BY total_volume DESC;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 11) Largest Single Transactions ---------------------------------------------------------------- -- 11a) Largest Received SET @Sql = N' SELECT TOP 1 * FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE t.receiving_address = @InitiatingAddress AND JSON_VALUE(t.received_tokens,@JsonPath) IS NOT NULL AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') ORDER BY TRY_CAST(JSON_VALUE(t.received_tokens,@JsonPath) AS FLOAT) DESC;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; -- 11b) Largest Sent SET @Sql = N' SELECT TOP 1 * FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE t.initiating_address = @InitiatingAddress AND JSON_VALUE(t.sent_tokens,@JsonPath) IS NOT NULL AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') ORDER BY TRY_CAST(JSON_VALUE(t.sent_tokens,@JsonPath) AS FLOAT) DESC;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 12) SNIPER: Transactions before first pool txn ---------------------------------------------------------------- SET @Sql = N' SELECT COUNT(*) AS SNIPER FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') AND (t.initiating_address = @InitiatingAddress OR t.receiving_address = @InitiatingAddress) AND t.[timestamp] < ( SELECT MIN(tp.[timestamp]) FROM dbo.' + QUOTENAME(@TableName) + ' tp WHERE tp.initiating_address = @InitiatingAddress AND tp.pool_id IS NOT NULL );'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; PRINT 'Procedure completed at: ' + CONVERT(NVARCHAR(30), GETDATE(), 120) + ', duration (ms): ' + CAST(DATEDIFF(MILLISECOND, @StartTime, GETDATE()) AS NVARCHAR(10));END GO
-
 @ bf47c19e:c3d2573b
2025-05-11 19:29:26
@ bf47c19e:c3d2573b
2025-05-11 19:29:26"Misterija Satoši - Poreklo bitkoina" je francuski dokumentarno-animirani serijal koji dešifruje unutrašnje funkcionisanje bitkoin revolucije, dok istražuje identitet njenog tvorca.
Prvu decentralizovanu i pouzdanu kriptovalutu – bitkoin, osnovao je Satoši Nakamoto 3. januara 2009. godine. On je nestao 2011. i od tada ostaje anoniman, a njegov identitet je predmet svakakvih spekulacija. Tokom poslednjih 12 godina, vrednost bitkoina je porasla sa 0,001 na 69.000 dolara. Svi, od vlada do velikih korporacija, zainteresovali su se za Satošijev izum. Ko je Satoši Nakamoto? Kako je njegov izum postao toliko popularan? Šta nam bitkoin govori o svetu u kome živimo?
Ovaj serijal se prikazivao na Radio-televiziji Srbije (RTS 3) u sklopu novogodišnjeg muzičkog i filmskog programa 2022/2023. godine.
Naslov originala: "Le Mystère Satoshi"
Copyright: ARTE.TV
-
 @ bf47c19e:c3d2573b
2025-05-11 18:57:51
@ bf47c19e:c3d2573b
2025-05-11 18:57:51Originalni tekst na vice.com.
Davno pre nego što je postala šef najdesnije italijanske vlade od Drugog svetskog rata, Đorđa Meloni je kritikovala ono što je nazvala francuskom „kolonijalnom valutom“.
U snimku italijanske televizije iz 2019. koji je prošlog meseca postao megaviralan, Meloni je optužila Francusku da koristi CFA franak za eksploataciju resursa 14 afričkih zemalja i vrši finansijsku dominaciju nad njima. Određene stvari koje je tvrdila u videu nisu baš tačne, ali CFA franak jeste kontroverzan.
CFA franak je stvoren 1945. da bude valuta „francuskih kolonija u Africi“, a pošto Francuska kontroliše njegovo štampanje i promet, francuska vlada i dalje ima finansijsku kontrolu nad dobrim delom zapadnoafričke zemlje i više od 180 miliona ljudi. Dok su francuski zvaničnici ranije nazivali ovu valutu „činom velikodušnosti prema kolonijama“, o njenoj upotrebi se sada žestoko raspravlja.
Neke od afričkih nacija borile su se protiv valute, uključujući građane koji su razbijali prodavnice povezane sa Francuskom i osuđivali francuski jezik koji se uči u školama.
Jedna od onih 14 afričkih zemalja koja još uvek koristi CFA franak je Centralnoafrička Republika, država bez izlaza na more u kojoj živi oko 5 miliona ljudi i jedna od najsiromašnijih zemalja na svetu.
 Predsednik CAR Faustin-Aršanž Touadera govori na COP27 u Egiptu ranije ove godine. Foto: Gehad Hamdi/savez za slike preko Getti Image-a
Predsednik CAR Faustin-Aršanž Touadera govori na COP27 u Egiptu ranije ove godine. Foto: Gehad Hamdi/savez za slike preko Getti Image-aAli dok druge afričke nacije razmatraju odbacivanje CFA franka, CAR je jedna od prvih koja je zaista uradila nešto po tom pitanju, a ranije ove godine postala je prva zemlja u Africi i tek druga u svetu koja je usvojila Bitcoin kao legalnu valutu.
„Alternativa gotovini je kriptovaluta“, rekao je predsednik Faustin-Aršanž Touadera. „Za nas formalna ekonomija više nije opcija”.
Dok su prve najave o bitkoinu izazvale konfuziju, međunarodne nesuglasice i reakcije, vlada CAR-a je nastavila sa uvođenjem. Osam meseci kasnije, mnogi ljudi širom sveta, pa čak i građani CAR-a, možda nisu ni svesni da se promena dogodila.
U CAR samo 14 odsto stanovništva ima pristup električnoj energiji, a još manje – oko 10 odsto – može da koristi internet. A konflikt i dalje tinja i negativno utiče na zemlju i njenu ekonomiju već deceniju.
Na predstavljanju bitkoina, vlada CAR-a je rekla da će usvajanje valute promeniti bogatstvo zemlje i staviti CAR „na mapu najhrabrijih i najvizionarskijih zemalja sveta“.
Bitkoin ne kontroliše nikakva moć, tehnički je univerzalno dostupan i ne može se cenzurisati – što je velika promena u odnosu na drugu valutu nacije, ali prosečnom građaninu CAR bi bilo potrebno 60 godina da kupi jedan novčić.
 Žena maše francuskom zastavom uoči emitovanja polufinala Svetskog prvenstva između Francuske i Maroka u baru u Bangiju. Foto: BARBARA DEBOUT/AFP preko Getti Images
Žena maše francuskom zastavom uoči emitovanja polufinala Svetskog prvenstva između Francuske i Maroka u baru u Bangiju. Foto: BARBARA DEBOUT/AFP preko Getti ImagesU Bangiju – glavnom gradu CAR – studenti Univerziteta rekli su za VICE da se „ništa nije promenilo“ od velike najave vlade.
Studenti su želeli da ostanu anonimni jer su se plašili da negativno govore o ambicijama vlade. Pravo na slobodu izražavanja ne postoji u CAR, a građani često doživljavaju zastrašivanje i nasilje od strane provladinih milicija, oružanih grupa i snaga nacionalne bezbednosti.
„Bilo je ogromno slavlje kada je objavljen Bitcoin plan i svi smo bili ponosni na našu zemlju“, rekao je jedan 20-godišnjak, „ali ne mislim da se život ovde uopšte poboljšao od tada”.
Drugi student je dodao: „Nigde nema cena u radnjama izraženih u bitkoioni, niti iko traži od ljudi da plaćaju koristeći novu valutu. Većina trgovaca i kupaca na tržištu nemaju telefon ili internet. Posebno ljudi izvan Bangija, nemaju ništa““.
Aleks Lilaher, osnivač i izvršni direktor Rise Up Media – marketinške agencije koja radi sa bitkoin startapima – je saglasan sa studentima, rekavši za VICE koliko je „iznenađen” što je ta zemlja uopšte napravila takavpotez.
„Centralnoafrička Republika nije baš lider u tehnologiji na kontinentu, i činilo se da tamo nikada nije bilo mnogo bitkoin korisnika koji bi mogla da lobiraju za takav potez“, rekao je on.
 Pobednički tim slavi posle trke kanua za proslavu Dana nezavisnosti CAR-a u decembru. Fotografija: BARBARA DEBOUT/AFP preko Getti Images
Pobednički tim slavi posle trke kanua za proslavu Dana nezavisnosti CAR-a u decembru. Fotografija: BARBARA DEBOUT/AFP preko Getti ImagesUpitan da li građani CAR-a treba da vide usvajanje bitkoina kao pozitivnu ili negativnu stvar, Lilaher je odgovorio „ni jedno ni drugo, jer jednostavno ne mogu da vidim da će usvajanje uskoro krenuti. Ali imati alternativu i poslati signal Francuskoj da CAR želi da ima više nezavisnosti od valute je pozitivno u mojim očima”.
Dodaje: „Međutim, to takođe može imati posledice jer postoje moćne institucije poput Međunarodnog monetarnog fonda, na primer, sa kojima CAR mora da se bavi, koje nisu srećne što zemlje usvajaju bitkoin. Dakle, moglo bi doći do izazova sa kojima će vlada morati da se nosi“.
Centralnoafrička Republika je druga zemlja u svetu koja je usvojila bitkoin, a prva je El Salvador u septembru 2021. Lansiranje valute je tamo imalo različite rezultate, a nedavno je opisano kao „antiklimaktično“ i samo ga turisti zaista koriste.
Iako su ljudi možda očekivali da će druge nacije pratiti El Salvador, sigurno ne bi pomislili da će CAR odgovarati računu.
Glavna opoziciona stranka CAR-a bila je protiv tog predloga od samog početka. Banka centralnoafričkih država je takođe nazvala ovaj potez „problematičnim“ i navela da bi usvajanje valute uz CFA moglo ugroziti odnos nacije sa drugim afričkim zemljama.
Čak i kada većina ljudi u CAR-u nije mogla da investira u Bitcoin, i sve poruke upozorenja, u julu je vlada CAR-a lansirala sopstvenu kriptovalutu – „Sangocoin“. Sango je lokalni jezik koji se govori širom zemlje.
 Pripadnici teritorijalnog pešadijskog bataljona CAR marširaju tokom parade povodom Dana nezavisnosti u Bangiju. Fotografija: BARBARA DEBOUT/AFP preko Getti Images
Pripadnici teritorijalnog pešadijskog bataljona CAR marširaju tokom parade povodom Dana nezavisnosti u Bangiju. Fotografija: BARBARA DEBOUT/AFP preko Getti ImagesSangocoin neki vide kao budućnost CAR-a, a zahtevao je minimalnu investiciju od 500 dolara. Zauzvrat, investitori su mogli da kupe zemljište u zemlji bogatoj dijamantima za 10.000 dolara, pa čak i da kupe državljanstvo CAR-a za oko 60.000 dolara – iako je ove ponude kasnije blokirao najviši sud zemlje. Sangocoin investitori su takođe trenutno „zaključani“ za kupovinu, bez načina da kriptovalutu prodaju ili razmene.
Bio je to hrabar potez vlade, ali izgleda da se još uvek nije isplatio.
Ovog meseca, Centralnoafrička Republika je saopštila da odlaže puštanje nacionalne kriptovalute na kripto berze – što bi olakšalo međunarodnu trgovinu. Rojters kaže da je vlada okrivila „trenutne tržišne uslove” i „tržišne razloge”, ali je novinska agencija izračunala da je Sangocoin dostigao samo „0,01%” od najnovijeg vladinog cilja prodaje.
Još jedan skeptik je Aleks Gladštajn, glavni strateški službenik Fondacije za ljudska prava. On je dugogodišnji zagovornik usvajanja bitkoina u svetu u razvoju, kao i kritičar CFA franka – ali čak i on oseća da je CAR-ova šema bila „izuzetno neosmišljena“.
„Iako imam mnogo simpatije prema ranjivoj i siromašnoj naciji koja usvaja bitkoin kao drugu valutu – posebno naciji koja je decenijama i decenijama finansijski kontrolisana od strane svoje bivše kolonijalne sile, nisam baš optimističan u pogledu toga kako je to izvedeno“, rekao je za VICE.
 Manekenka učestvuje na prvoj nedelji mode u centralnoj Africi u Bangiju u decembru. Fotografija: BARBARA DEBOUT/AFP preko Getti Images
Manekenka učestvuje na prvoj nedelji mode u centralnoj Africi u Bangiju u decembru. Fotografija: BARBARA DEBOUT/AFP preko Getti ImagesDodao je: „Zaista se čini da je cela ova stvar bila kao prevara da se Sangocoin promoviše. Ne mislim da je cilj bio da se bitkoin integriše na smislen način u ekonomiju zemlje. Čini se da je predsednik zainteresovan za bitkoin i da postoji mala grupa ljudi oko njega koja je iskoristila taj interes da bi mogla da donese ove zakone kako bi pokušala da pokrene Sangocoin, od kojeg su imali viziju da zarade gomilu novca. Ali izgleda da je na kraju uspela da prikupi samo malo novca.”
Gladstein kaže da bi Bitcoin mogao biti „veoma važna finansijska tehnologija za ljude Centralnoafričke Republike tokom vremena, i pametno je da vlada istraži kako to može pomoći ljudima“, ali je potrebno mnogo posla da se to postigne.
Vlada Centralnoafričke Republike i opoziciona vlada nisu odgovorile na nekoliko zahteva za intervju.
Tekst podržao Omidiar Netvork. VICE World News zadržava potpunu uređivačku autonomiju.





