-
 @ 000002de:c05780a7
2025-05-22 20:50:21
@ 000002de:c05780a7
2025-05-22 20:50:21I'm mostly curious about how Tapper can do this with a straight face.
https://stacker.news/items/986926
-
 @ 2b24a1fa:17750f64
2025-05-22 19:44:28
@ 2b24a1fa:17750f64
2025-05-22 19:44:28„Triff niemals deine Idole“ heißt ein gängiger Ratschlag. In gewendeten Zeiten stehen zu dem die Werte auf dem Kopf – und manche Künstler mit ihnen. Die Worte, die aus manch ihrer Mündern kommen, wirken, als hätte eine fremde Hand sie auf deren Zunge gelegt.
https://soundcloud.com/radiomuenchen/wolf-biermann-und-sein-falscher-friede-von-alexa-rodrian?
Die Sängerin Alexa Rodrian erlebte bei der Verleihung des Deutschen Filmpreises einen solchen Moment der Desillusion. Es war der Auftritt des Liedermachers Wolf Biermann. Hören Sie hierzu Alexa Rodrians Text „Wolf Biermann und sein falscher Friede“.
Bild: Marco Maas/fotografirma.de
-
 @ 9b308fda:b6c7310d
2025-05-22 18:30:19
@ 9b308fda:b6c7310d
2025-05-22 18:30:19@15/05/2025 ✨ Week 0 – Getting Started with My Internship at Formstr (Onboarding)
I’m excited to share that I’ve been selected as a Summer of Bitcoin intern at Formstr!
After the final exams wrapped up on May 4th, I took a short, well-deserved break while traveling back home from college for the summer. Once settled in, I quickly transitioned into internship mode and began diving into the project assigned to me at Formstr.
It’s been a great start so far, and I’m looking forward to learning, building, and sharing more along the way.
@22/05/2025 — Week 01 – Building Features and Brainstorming at Formstr
This week at Formstr was packed with development and discussions.
The major highlight was completing the row popup view for form responses — now, clicking on any response row shows a clean and complete view of that user's submission. I'm happy to share that the pull request has been merged! It feels great to contribute something that improves the user experience so visibly.
Alongside that, I started brainstorming the LLM-Analysis feature. We had a productive discussion during the weekly developer meeting on Signal, where I shared my initial thoughts and got valuable input from the team. There's a lot of potential in this, and it’s exciting to shape it from the ground up.
I also worked on improving relay management in the form settings to reduce redundancy. The changes are in progress, and it’s almost done — just final touches left before merging.
Another topic we tackled was the “Form Filler with AI” feature. There are still some open questions around implementation and user flow, so we’ve decided to continue discussions with more team members before finalizing the plan.
We’ve also agreed to hold weekly team meetings going forward to keep everyone aligned on ideas, progress, and blockers. I’m glad to be part of such a collaborative and thoughtful team!
-
 @ f85b9c2c:d190bcff
2025-05-23 01:01:32
@ f85b9c2c:d190bcff
2025-05-23 01:01:32Hey, it’s me again, and let me tell you about the wildest thing that happened to me recently. I swear, my life could be a comedy show sometimes😂. Picture this: me and my buddies were out messing around in the woods near campus, just kicking it like we always do. The sun was out, the vibes were good, and we were probably being louder than we needed to be. Then, out of nowhere, I spotted something slithering near my friend benji leg.

A snake. A legit, no-joke snake!
I yelled, “SNAKE!” at the top of my lungs—probably sounded like a total lunatic —and before I could even blink, those dudes were GONE. I mean, faster than their shadows, Olympic-sprinter-level gone. I’m standing there, heart pounding, looking at this snake like, “Bruh, did I just get ditched?” Turns out, I did. My so-called friends bolted back to the dorms without a second thought, leaving me to face the scaly intruder solo. Luckily, the snake wasn’t in the mood for drama. It just gave me this lazy side-eye and slithered off, like it was too cool to deal with me. I hightailed it back to the dorms too, and when I got there, benji and the crew were already laughing their heads off. “Bro, you screamed like a horror movie victim!” they said. Yeah, real funny, guys.
Honestly, though? I’m just glad that snake didn’t get too cozy with my backside. A near miss like that deserves a medal—or at least a good story. We’ve been cracking up about it ever since, and now every time we’re out, I’m the designated “snake spotter. Lesson learned: friends are great until nature throws a curveball. Phew, that was close! Never be afraid to stand against everyone if you know you’re right.
-
 @ f85b9c2c:d190bcff
2025-05-23 00:54:23
@ f85b9c2c:d190bcff
2025-05-23 00:54:23 P2P trading is also referred to as peer-to-peer trading or, more recently, people-to-people trading. Individuals can trade currencies and other marketable goods with other traders in this decentralized financial trading system.
P2P trading is a method of trading cryptocurrencies between people without the need of middlemen like exchanges, banks, or other financial institutions. Networks that connect buyers and sellers, streamline transactions, and frequently provide conflict resolution services are where P2P transactions take place.
P2P trading is also referred to as peer-to-peer trading or, more recently, people-to-people trading. Individuals can trade currencies and other marketable goods with other traders in this decentralized financial trading system.
P2P trading is a method of trading cryptocurrencies between people without the need of middlemen like exchanges, banks, or other financial institutions. Networks that connect buyers and sellers, streamline transactions, and frequently provide conflict resolution services are where P2P transactions take place.What is P2P Trading P2P trading is one of the quickest, cheapest, and most adaptable trading platforms, according to numerous research. Even more people could benefit from it if they lack access to conventional financial services or find some procedures to be too complicated.
P2P Trading in Nigeria P2P trading has grown somewhat in popularity in recent years as a result of the expansion of online marketplaces that bring together buyers and sellers. These platforms frequently offer wonderful alternatives to traditional financial services and perform similarly to or even better than what is provided by regional banks. Markets today provide unique advantages like quick transactions, reduced fees, and improved flexibility.
The ongoing development of regulations prohibiting the usage of cryptocurrencies is another factor that has increased the need for P2P trade in Nigeria. The majority of crypto traders in Nigeria now trade their cryptocurrencies with one another using the P2P trading system rather than the conventional trader-to-exchange service as a result of the ban on cryptocurrencies since 2021 till recently.P2P trading is thus one of the most popular and widely used forms of trading in Nigeria.
Peer-to-peer cryptocurrency trading is available on a number of well-known trading platforms, including Binance, Bitget, Bybit etc. A system has been built by these platforms (exchange websites and mobile applications) that enables traders to connect and trade their preferred crypto assets. P2P trading platforms have the power to transform Nigeria’s financial system and open up new doors for economic growth and development by bringing buyers and sellers together directly.
How does P2P trading work? One of the most effective ways to exchange cryptocurrency is through P2P trading, so everyone should be aware of how to get around it. It uses the exchange as a middleman to arrange, oversee, and finish trades between two independent dealers. The exchange service is used by buyers who search for sellers who are willing to sell to them at the price they are willing to pay, make a payment, and receive coins in return.
-
 @ da8b7de1:c0164aee
2025-05-22 16:19:52
@ da8b7de1:c0164aee
2025-05-22 16:19:52Technológiai és fejlesztési hírek
- Észtország SMR-tervei:
Észtország hivatalosan elindította a nemzeti tervezési folyamatot és a környezeti hatásvizsgálatot egy 600 MW-os kis moduláris reaktor (SMR) atomerőmű létesítésére, GE Hitachi BWRX-300 technológiával. A projektet a Fermi Energia vezeti, a lakosság körében mérsékelt támogatottság mellett. Az építési engedélykérelem benyújtását 2029-re tervezik, a cél az ország energiabiztonságának és klímacéljainak erősítése.
- Olkiluoto-1 csökkentett teljesítménnyel üzemel:
Finnországban az Olkiluoto-2 egységben a generátor rotorjának cseréje miatt a termelés májusban újraindul, de a teljesítményt 735 MW-ra korlátozzák (a teljes kapacitás 890 MW). A csökkentett teljesítmény 2026-ig marad érvényben. Az Olkiluoto-1 egység normálisan működik, az Olkiluoto-3 pedig éves karbantartáson van.
Ipari és pénzügyi fejlemények
- Kanada–Argentína nehézvíz-együttműködés:
A kanadai Candu Energy (AtkinsRéalis) és az argentin Nemzeti Atomenergia Bizottság (CNEA) memorandumot írt alá a nehézvíz-termelés fellendítéséről. Ez magában foglalja az argentin PIAP nehézvízgyár újraindítását és potenciálisan új üzemek építését Kanadában. A fejlesztés támogatja a meglévő és tervezett CANDU reaktorok működését világszerte, és illeszkedik a COP28 utáni globális nukleáris bővüléshez.
- USA: nukleáris adókedvezményekért folyó lobbizás:
Az amerikai nukleáris ipar intenzív lobbitevékenységet folytat, hogy megőrizze a Biden-adminisztráció által bevezetett, az Inflációcsökkentő Törvény (IRA) szerinti nukleáris adókedvezményeket. Az új, republikánus többségű költségvetési törvényjavaslat jelentősen lerövidítené a tiszta energia (szél, nap, akkumulátor) támogatásokat, de a nukleáris ipar számára bizonyos kedvezmények megmaradnának, bár a 45U nukleáris adókedvezmény is három évvel korábban, 2031-ben lejárhat.
- Háztartási és ipari érdekek:
Az amerikai ház költségvetési törvényjavaslata megszüntetné a legtöbb tiszta energiához kapcsolódó adókedvezményt, kivéve néhány nukleáris projektet, és szigorítaná a kínai kapcsolatokkal rendelkező projektek támogatását. Ez várhatóan visszaveti a megújuló energiaipar beruházásait, miközben a nukleáris szektor relatív pozíciója javulhat.
Politikai és társadalmi fejlemények
- Tajvan: népszavazás a nukleáris energia sorsáról:
Tajvan parlamentje megszavazta, hogy népszavazást tartsanak a Maanshan atomerőmű újraindításáról, miután az ország utolsó működő reaktorát is leállították. A referendum nem azonnali újraindításról szól, hanem arról, hogy a lakosság döntsön a meghosszabbításról, ha a hatóságok biztonságosnak találják az üzemet.
- Pennsylvania kormányzója a nukleáris energia mellett:
Josh Shapiro, Pennsylvania kormányzója, a „Lightning Plan” keretében hangsúlyozta, hogy az állam energiabiztonsága és gazdasági fejlődése érdekében kulcsszerepet szán a nukleáris energiának, valamint más megbízható energiaforrásoknak. A terv célja a munkahelyteremtés, a fogyasztói költségek csökkentése és az engedélyezési folyamatok gyorsítása.
- TMI névváltás:
Az amerikai Nukleáris Szabályozó Hatóság (NRC) jóváhagyta a Three Mile Island (TMI) atomerőmű nevének megváltoztatását Christopher M. Crane-re, az Exelon volt vezérigazgatójának emlékére. A létesítmény a jövőben a Microsoft AI műveleteit is ellátja majd árammal, és 2028-tól 835 MW szén-dioxid-mentes áramot termelhet.
Nemzetközi szakmai események
- NEA konferencia Londonban:
Az OECD NEA 2025. június 18–19-én Londonban rendezi meg az „Excellence in Nuclear Construction” nemzetközi konferenciát. A rendezvény célja, hogy a nukleáris ipar szereplői megosszák tapasztalataikat a nukleáris beruházások gyorsabb, kiszámíthatóbb és költséghatékonyabb megvalósítása érdekében, különös tekintettel a mérnöki, beszerzési és kivitelezési (EPC) kihívásokra.
Hivatkozások
- https://www.nucnet.org
- https://www.world-nuclear-news.org
- https://www.neimagazine.com
- https://www.oecd-nea.org
- https://www.iaea.org
- https://www.reuters.com/business/energy
- https://www.utilitydive.com
- https://www.atkinsrealis.com
- https://www.candu.com
-
 @ 1817b617:715fb372
2025-05-22 23:39:18
@ 1817b617:715fb372
2025-05-22 23:39:18🚀 Instantly Send Spendable Flash BTC, ETH, & USDT — 100% Blockchain-Verifiable!
Step into the future of cryptocurrency innovation with CryptoFlashingTool.com — your go-to solution for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Using cutting-edge 🔥 Race/Finney-style blockchain simulation, our technology generates coins that are virtually indistinguishable from real, fully confirmed blockchain transactions. Transactions stay live and spendable from 60 up to 360 days!
🌐 Explore all the details at cryptoflashingtool.com.
🌟 Why Trust Our Crypto Flashing System? Whether you’re a blockchain enthusiast, ethical hacker, security expert, or digital entrepreneur, our solution offers a perfect mix of authenticity, speed, and flexibility.
🎯 Top Features You’ll Love: ✅ Instant Blockchain Simulation: Transactions are complete with valid wallet addresses, transaction IDs, and real confirmations.
🔒 Privacy First: Works flawlessly with VPNs, TOR, and proxies to keep you fully anonymous.
🖥️ User-Friendly Software: Built for Windows, beginner and pro-friendly with simple step-by-step guidance.
📅 Flexible Flash Durations: Choose how long coins stay valid — from 60 to 360 days.
🔄 Full Wallet Compatibility: Instantly flash coins to SegWit, Legacy, or BCH32 wallets with ease.
💱 Exchange-Ready: Spend your flashed coins on leading exchanges like Kraken and Huobi.
📊 Proven Results: ✅ Over 79 billion flash transactions completed. ✅ 3000+ satisfied users around the globe. ✅ 42 active blockchain nodes ensuring fast, seamless performance.
📌 How It Works: Step 1️⃣: Input Transaction Info
Pick your coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20). Set amount and flash duration. Enter the recipient wallet (auto-validated). Step 2️⃣: Make Payment
Pay in your selected crypto. Scan the QR code or use the provided address. Upload your transaction proof (hash and screenshot). Step 3️⃣: Launch the Flash
Blockchain confirmation simulation happens instantly. Your transaction appears real within seconds. Step 4️⃣: Verify & Spend
Access your flashed coins immediately. Verify your transactions using blockchain explorers. 🛡️ Why Our Flashing Tech Leads the Market: 🔗 Race/Finney Attack Mechanics: Mimics authentic blockchain behavior. 🖥️ Private iNode Clusters: Deliver fast syncing and reliable confirmation. ⏰ Live Timer: Ensures fresh, legitimate transactions. 🔍 Real Blockchain TX IDs: All transactions come with verifiable IDs.
❓ FAQs:
Is flashing secure? ✅ Yes, fully encrypted with VPN/proxy compatibility. Multiple devices? ✅ Yes, up to 5 Windows PCs per license. Chargebacks possible? ❌ No, flashing is irreversible. Spendability? ✅ Flash coins stay spendable 60–360 days. Verification after expiry? ❌ No, transactions expire after the set time. Support? ✅ 24/7 Telegram and WhatsApp help available. 🔐 Independent, Transparent, Trusted:
At CryptoFlashingTool.com, we pride ourselves on unmatched transparency, speed, and reliability. See our excellent reviews on ScamAdvisor and top crypto forums!
📲 Contact Us: 📞 WhatsApp: +1 770 666 2531 ✈️ Telegram: @cryptoflashingtool
🎉 Ready to Flash Like a Pro?
💰 Buy Flash Coins Now 🖥️ Get Your Flashing Software
The safest, smartest, and most powerful crypto flashing solution is here — only at CryptoFlashingTool.com!
Instantly Send Spendable Flash BTC, ETH, & USDT — 100% Blockchain-Verifiable!
Step into the future of cryptocurrency innovation with CryptoFlashingTool.com — your go-to solution for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Using cutting-edge
Race/Finney-style blockchain simulation, our technology generates coins that are virtually indistinguishable from real, fully confirmed blockchain transactions. Transactions stay live and spendable from 60 up to 360 days!
Explore all the details at cryptoflashingtool.com.
Why Trust Our Crypto Flashing System? Whether you’re a blockchain enthusiast, ethical hacker, security expert, or digital entrepreneur, our solution offers a perfect mix of authenticity, speed, and flexibility.
Top Features You’ll Love:
Instant Blockchain Simulation: Transactions are complete with valid wallet addresses, transaction IDs, and real confirmations.
Privacy First: Works flawlessly with VPNs, TOR, and proxies to keep you fully anonymous.
User-Friendly Software: Built for Windows, beginner and pro-friendly with simple step-by-step guidance.
Flexible Flash Durations: Choose how long coins stay valid — from 60 to 360 days.
Full Wallet Compatibility: Instantly flash coins to SegWit, Legacy, or BCH32 wallets with ease.
Exchange-Ready: Spend your flashed coins on leading exchanges like Kraken and Huobi.
Proven Results:
Over 79 billion flash transactions completed.
3000+ satisfied users around the globe.
42 active blockchain nodes ensuring fast, seamless performance.
How It Works: Step
: Input Transaction Info
- Pick your coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20).
- Set amount and flash duration.
- Enter the recipient wallet (auto-validated).
Step
: Make Payment
- Pay in your selected crypto.
- Scan the QR code or use the provided address.
- Upload your transaction proof (hash and screenshot).
Step
: Launch the Flash
- Blockchain confirmation simulation happens instantly.
- Your transaction appears real within seconds.
Step
: Verify & Spend
- Access your flashed coins immediately.
- Verify your transactions using blockchain explorers.
Why Our Flashing Tech Leads the Market:
Race/Finney Attack Mechanics: Mimics authentic blockchain behavior.
Private iNode Clusters: Deliver fast syncing and reliable confirmation.
Live Timer: Ensures fresh, legitimate transactions.
Real Blockchain TX IDs: All transactions come with verifiable IDs.
FAQs:
- Is flashing secure?
Yes, fully encrypted with VPN/proxy compatibility. - Multiple devices?
Yes, up to 5 Windows PCs per license. - Chargebacks possible?
No, flashing is irreversible. - Spendability?
Flash coins stay spendable 60–360 days. - Verification after expiry?
No, transactions expire after the set time. - Support?
24/7 Telegram and WhatsApp help available.
Independent, Transparent, Trusted:
At CryptoFlashingTool.com, we pride ourselves on unmatched transparency, speed, and reliability. See our excellent reviews on ScamAdvisor and top crypto forums!
Contact Us:
WhatsApp: +1 770 666 2531
Telegram: @cryptoflashingtool
Ready to Flash Like a Pro?
The safest, smartest, and most powerful crypto flashing solution is here — only at CryptoFlashingTool.com!
-
 @ 4c96d763:80c3ee30
2025-05-19 20:56:26
@ 4c96d763:80c3ee30
2025-05-19 20:56:26Changes
William Casarin (19):
- dave: add screenshot to readme
- dave: fix image in readme
- columns: remove spamming info logs about writing to cache
- columns: never truncate notes you're replying to
- windows: don't show terminal window
- mention: show username instead of display_name
- chrome: switch from ALPHA to BETA
- ui: make post replies selectable
- dave: include anonymous user identifier in api call
- dave: add trial mode
- dave: fix sidebar click
- dave: nudge avatar when you click
- dave: hide media in dave note previews
- chrome: fix theme persistence
- ui: fix a bunch of missing hover pointers
- Release Notedeck Beta v0.4.0
- release: changelog
- timeline: show media on universe timeline
- clippy: fix lint related to iterator
kernelkind (28):
- add
trust_media_from_pk2method - add hashbrown
- introduce & use
JobPool - introduce JobsCache
- add blurhash dependency
- introduce blur
- note: remove unnecessary derive macros from
NoteAction - propagate
JobsCache ImagePulseTint->PulseAlpha- images: move fetch to fn
- add
TexturesCache - images: make
MediaCacheholdMediaCacheType - images: make promise payload optional to take easily
- post: unnest
- notedeck_ui: move carousel to
note/media.rs - note media: only show full screen when loaded
- note media: unnest full screen media
- pass
NoteActionby value instead of reference - propagate
Imagesto actionbar - add one shot error message
- make
WidgetimplProfilePicmutably - implement blurring
- don't show zap button if no wallet
- display name should wrap
- make styled button toggleable
- method to get current default zap amount
- add
CustomZapView - use
CustomZapView
pushed to notedeck:refs/heads/master
-
 @ 68d6e729:e5f442ac
2025-05-22 13:55:45
@ 68d6e729:e5f442ac
2025-05-22 13:55:45The Adapter Pattern in TypeScript
What is the Adapter Pattern?
The Adapter Pattern is a structural design pattern that allows objects with incompatible interfaces to work together. It acts as a bridge between two interfaces, enabling integration without modifying existing code.
In simple terms: it adapts one interface to another.
Real-World Analogy
Imagine you have a U.S. laptop charger and you travel to Europe. The charger plug won't fit into the European socket. You need a plug adapter to convert the U.S. plug into a European-compatible one. The charger stays the same, but the adapter allows it to work in a new context.
When to Use the Adapter Pattern
- You want to use an existing class but its interface doesn't match your needs.
- You want to create a reusable class that cooperates with classes of incompatible interfaces.
- You need to integrate third-party APIs or legacy systems with your application.
Implementing the Adapter Pattern in TypeScript
Let’s go through a practical example.
Scenario
Suppose you’re developing a payment system. You already have a
PaymentProcessorinterface that your application uses. Now, you want to integrate a third-party payment gateway with a different method signature.Step 1: Define the Target Interface
javascript ts CopyEdit// The interface your application expects interface PaymentProcessor { pay(amount: number): void; }Step 2: Create an Adaptee (incompatible class)
javascript ts CopyEdit// A third-party library with a different method class ThirdPartyPaymentGateway { makePayment(amountInCents: number): void { console.log(`Payment of $${amountInCents / 100} processed via third-party gateway.`); } }Step 3: Implement the Adapter
```javascript ts CopyEdit// Adapter makes the third-party class compatible with PaymentProcessor class PaymentAdapter implements PaymentProcessor { private gateway: ThirdPartyPaymentGateway;
constructor(gateway: ThirdPartyPaymentGateway) { this.gateway = gateway; }
pay(amount: number): void { const amountInCents = amount * 100; this.gateway.makePayment(amountInCents); } } ```
Step 4: Use the Adapter in Client Code
```javascript ts CopyEditconst thirdPartyGateway = new ThirdPartyPaymentGateway(); const adapter: PaymentProcessor = new PaymentAdapter(thirdPartyGateway);
// Application uses a standard interface adapter.pay(25); // Output: Payment of $25 processed via third-party gateway. ```
Advantages of the Adapter Pattern
- Decouples code from third-party implementations.
- Promotes code reuse by adapting existing components.
- Improves maintainability when dealing with legacy systems or libraries.
Class Adapter vs Object Adapter
In languages like TypeScript, which do not support multiple inheritance, the object adapter approach (shown above) is preferred. However, in classical OOP languages like C++, you may also see class adapters, which rely on inheritance.
Conclusion
The Adapter Pattern is a powerful tool in your design pattern arsenal, especially when dealing with incompatible interfaces. In TypeScript, it helps integrate third-party APIs and legacy systems seamlessly, keeping your code clean and extensible.
By learning and applying the Adapter Pattern, you can make your applications more robust and flexible—ready to adapt to ever-changing requirements. https://fox.layer3.press/articles/cdd71195-62a4-420b-9e24-e23d78b27452
-
 @ ee7d2dbe:4a5410b0
2025-05-22 12:37:56
@ ee7d2dbe:4a5410b0
2025-05-22 12:37:56Experience hassle-free WordPress maintenance service from Agicent at just $1900 per month ! This is a fully managed service that can take care of your continuous wordpress maintenance, development, upgrade, plugin updates etc. for one project or multiple wordpress projects.
Our Wordpress Maintenance Service plan includes a dedicated account manager and wordpress developer, a shared team of designers and testers who are capable to do wordpress development and maintenance for multiple projects on an ongoing basis. We also offer you side (but essential skills) like SEO, PPC, Content writing B2B lead gen and overall Digital Marketing services.
At Agicent We Take Care of Your WordPress Site, so You Can Take Care of Your Business
Unlock the full potential of our Managed Web Maintenance services, available on a month-to-month basis. Starting at just $1900 per month, you gain access to a dedicated WordPress maintenance developer, accompanied by fractional Project Management, Design, and Testing experts, all at your disposal. This cohesive team serves as your optimal launchpad for maintaining your WordPress websites, implementing regular enhancements, performing backups, and ensuring continuous development and delivery.
Our developers and teams embrace a comprehensive approach to product development that extends beyond simple coding. We specialize in crafting exceptional web products that users love, emphasizing user experience, convenience, and scalability. Our expertise spans UI/UX design, rigorous testing, scalability planning, and architectural excellence.
Whether you engage us for a single Developer WordPress maintenance team or multiple developers, rest assured that you'll receive best-in-class project management, user experience, and testing expertise. At Agicent, we are committed to elevating your web presence through comprehensive and reliable WordPress Maintenance Services.
What Makes WordPress Maintenance Services Essential?
Whether you're an agency involved in website creation and maintenance for your clients, particularly non-tech businesses, or you're a non-tech or tech business managing your own website or a landing page, the necessity for your WordPress website maintenance services arises in order to:
Keep safeguarding your WordPress site against security vulnerabilities, ensuring that your website is less susceptible to hacks and malicious activities.
To optimize your website's performance, for faster loading times, improved user experience, and better search engine rankings.
To address bugs and ensure that your WordPress site remains compatible with the latest technologies and plugins, preventing any functionality issues.
To quickly recover your website in case of data loss or other emergencies.
To Keep your WordPress site up-to-date with the latest features and improvements so you can leverage new functionalities and stay competitive in the online landscape.
To enhance user satisfaction. A well-maintained website contributes to a positive user experience.
To optimize content that contributes to better SEO performance, helping your site rank higher in search results.
Source: https://www.agicent.com/wordpress-maintenance-services
-
 @ 74fb3ef2:58adabc7
2025-05-22 22:26:23
@ 74fb3ef2:58adabc7
2025-05-22 22:26:23Suppose you have a small mom-and-pop shop selling bananas, your bananas are of the highest quality, you plant the banana trees yourself, you water them daily, take great care of everything, and still select only the top 1% of bananas to sell.
Your customers love it, there's no place where they can get better bananas, but due to the fact that you spend so much time, your bananas have to be more expensive, so despite the higher quality, you don't make as much money as you think you should; surely you can get a little more of the market if you adopt some of the strategies that work for your competitors.
So you look across the street, and what do you know? Their bananas are of significantly worse quality than yours, but they're not just selling bananas, they're selling apples too, so you think to yourself, "what if I sold apples? Maybe my apples won't be the best in the market, but nobody can beat my bananas!"
You start planting apple trees, and after a while you're able go sell slightly better than average apples, but by doing so you neglect your bananas ever so slightly.
Most of your existing customers don't notice, you still have the best bananas in town, they don't notice the slight drop in quality. And now that you're selling apples too you're making more money, and more customers come to you.
But you notice that there's a new store now that's selling oranges, and people are buying them. So surely you need oranges too, so you can make some extra money.
You plant a few orange trees, but find yourself spending so much time tending to the oranges and apples that you can't devote the same time and love to your bananas.
You are making a bit of extra cash from the new customers, business is going well, but you don't have time for anything else anymore. You no free time anymore, you are overworked and your health is getting worse.
But you can't stop now that business is going well, you are making so much more, yeah maybe you don't have the same bananas anymore, but you do have slightly above average apples and oranges that have attracted so many customers.
You suddenly fall ill, you've overworked yourself and you are stuck at a hospital for a while.
When you come back to your store, a few of your customers are back, but not all of them, so you think of more ideas, mandarins, kiwi, watermelons, you can grow it all, but you're gonna hire a bunch of people to help you so you don't fall ill again.
One thing leads to another and you are making more money than ever, but strangely you don't hear your customers praising your bananas anymore.
So you take one of your bananas, peel it, and as you taste it, a wave of disappointment hits you.
Your bananas are now just as bad as everyone else's; you gave in to the tyranny of the marginal customer.
You make a lot of money now, but your flagship product is long gone, you are now just another Fruitseller.
-
 @ 9ca447d2:fbf5a36d
2025-05-22 22:01:46
@ 9ca447d2:fbf5a36d
2025-05-22 22:01:46Bahrain-based Al Abraaj Restaurants Group has made history by becoming the first publicly-traded company in the Middle East to add bitcoin to its corporate treasury. This is a major step forward for regional bitcoin adoption.
On May 15, 2025, Al Abraaj Restaurants Group, a well-known restaurant chain listed on the Bahrain Bourse, announced it had bought 5 bitcoin (BTC) as part of a new treasury strategy. This makes the company the first in Bahrain, the GCC and the Middle East to officially hold bitcoin as a reserve asset.
Al Abraaj adds bitcoin to its treasury — Zawya
This is a growing trend globally where companies are treating bitcoin not just as an investment but as a long-term store of value. Major companies like Strategy, Tesla and Metaplanet have already done this — and now Al Abraaj is following suit.
Metaplanet recently added 1,241 BTC to its treasury, boosting the company’s holdings above El Salvador’s.
Related: Metaplanet Overtakes El Salvador in Bitcoin Holdings After $126M Purchase
“Our initiative towards becoming a Bitcoin Treasury Company reflects our forward-thinking approach and dedication to maximizing shareholder value,” said Abdulla Isa, Chairman of the Bitcoin Treasury Committee at Al Abraaj.
Al Abraaj’s move is largely inspired by Michael Saylor, Executive Chairman of Strategy, the world’s largest corporate holder of bitcoin. Saylor’s strategy of allocating billions to bitcoin has set a model that other companies — now including Al Abraaj — are following.
A photo shared by the company even showed a meeting between an Al Abraaj representative and Saylor, with the company calling itself the “MicroStrategy of the Middle East”.
“We believe that Bitcoin will play a pivotal role in the future of finance, and we are excited to be at the forefront of this transformation in the Kingdom of Bahrain,” Isa added.
To support its bitcoin initiative, Al Abraaj has partnered with 10X Capital, a New York-based investment firm that specializes in digital assets.
10X Capital has a strong track record in bitcoin treasury strategies, and recently advised Nakamoto Holdings on a $710 million deal — the largest of its kind.
With 10X’s help, Al Abraaj looks to raise more capital and increase its bitcoin holdings over time to maximize bitcoin-per-share for its investors. The company will also develop Sharia-compliant financial instruments so Islamic investors can get exposure to bitcoin in a halal way.
“Bahrain continues to be a leader in the Middle East in Bitcoin adoption,” said Hans Thomas, CEO of 10X Capital. He noted, with a combined GDP of $2.2 trillion and over $6 trillion in sovereign wealth, the GCC now has its first publicly listed bitcoin treasury company.
This is not just a first for Al Abraaj — it’s a first for the region. Bahrain has been positioning itself as a fintech hub and Al Abraaj’s move will encourage more non-fintech companies in the region to look into bitcoin.
The company said the decision was made after thorough due diligence and is in line with the regulations set by the Central Bank of Bahrain (CBB). Al Abraaj will be fully compliant with all digital asset transaction rules, including transparency, security and governance.
A special Bitcoin Committee has been formed to oversee the treasury strategy. It includes experienced bitcoin investors, financial experts and portfolio managers who will manage risk, monitor market conditions and ensure best practices in custody and disclosure.
The initial purchase was 5 BTC, but Al Abraaj sees this as just the beginning. The company stated that there are plans in motion to allocate a significant portion of their treasury into bitcoin over time.
According to the company’s reports, Al Abraaj is financially sound with $12.5 million in EBITDA in 2024. This strong financial foundation gives the company the confidence to explore new strategies like bitcoin investment.
-
 @ 266815e0:6cd408a5
2025-05-16 20:52:42
@ 266815e0:6cd408a5
2025-05-16 20:52:42Streams are the key to nostr
Loading events from a nostr relay is probably the most inconsistent way of loading data I've had to work with, and that's only loading from a single relay. the problem gets exponentially more complicated once you try to load events from multiple relays
Unlike HTTP nostr does not have a simple flow with timeouts built in. events are sent back one at a time and can fail at any point or have massive (10s) gaps between them
The key is to use streams. something that starts, emits any number of results, then maybe errors or completes. luckily it just so happens that JavaScript / TypeScript has a great observable stream library called RxJS
What is an observable
An
Observablein RxJS is stream a of data that are initialized lazily, which means the stream is inactive and not running until something subscribes to it```ts let stream = new Observable((observer) => { observer.next(1) observer.next(2) observer.next(3) observer.complete() })
// The stream method isn't run until its subscribed to stream.subscribe(v => console.log(v)) ```
This is super powerful and perfect for nostr because it means we don't need to manage the life-cycle of the stream. it will run when something subscribes to it and stop when unsubscribed.
Its helpful to think of this as "pulling" data. once we have created an observable we can request the data from it at any point in the future.
Pulling data from relays
We can use the lazy nature of observables to only start fetching events from a nostr relay when we need them
For example we can create an observable that will load kind 1 events from the damus relay and stream them back as they are returned from the relay
```typescript let req = new Observable((observer) => { // Create a new websocket connection when the observable is start let ws = new WebSocket('wss://relay.damus.io')
ws.onopen = () => { // Start a REQ ws.send(JSON.stringify(['REQ', 'test', {kinds: [1], limit: 20}])) }
ws.onmessage = (event) => { let message = JSON.parse(event.data) // Get the event from the message and pass it along to the subscribers if(message[0] === 'EVENT') observer.next(message[1]) }
// Cleanup subscription return () => { ws.send(JSON.stringify(['CLOSE', 'test'])) ws.close() } }) ```
But creating the observable wont do anything. we need to subscribe to it to get any events.
ts let sub = req.subscribe(event => { console.log('we got an event' event) })Cool now we are pulling events from a relay. once we are done we can stop listening to it by unsubscribing from it
ts sub.unsubscribe()This will call the cleanup method on the observable, which in turn closes the connection to the relay.
Hopefully you can see how this work, we don't have any
open,connect, ordisconnectmethods. we simply subscribe to a stream of events and it handles all the messy logic of connecting to a relayComposing and chaining observables
I've shown you how we can create a simple stream of events from a relay, but what if we want to pull from two relays?
Easy, lets make the previous example into a function that takes a relay URL
```ts function getNoteFromRelay(relay: string){ return new Observable((observer) => { let ws = new WebSocket(relay)
// ...rest of the observable...}) } ```
Then we can "merge" two of these observables into a single observable using the
mergemethod from RxJSThe
mergemethod will create a single observable that subscribes to both upstream observables and sends all the events back. Think of it as pulling events from both relays at once```ts import { merge } from 'rxjs'
const notes = merge( getNoteFromRelay('wss://relay.damus.io'), getNoteFromRelay('wss://nos.lol') )
// Subscribe to the observable to start getting data from it const sub = notes.subscribe(event => { console.log(event) })
// later unsubscribe setTimeout(() => { sub.unsubscribe() }, 10_000) ```
But now we have a problem, because we are pulling events from two relays we are getting duplicate events. to solve this we can use the
.pipemethod and thedistinctoperator from RxJS to modify our single observable to only return one version of each eventThe
.pipemethod will create a chain of observables that will each subscribe to the previous one and modify the returned values in some wayThe
distinctoperator takes a method that returns a unique identifier and filters out any duplicate values```ts import { merge, distinct } from 'rxjs'
const notes = merge( getNoteFromRelay('wss://relay.damus.io'), getNoteFromRelay('wss://nos.lol') ).pipe( // filter out events we have seen before based on the event id distinct(event => event.id) ) ```
Now we have an observable that when subscribed to will connect to two relays and return a stream of events without duplicates...
As you can see things can start getting complicated fast. but its also very powerful because we aren't managing any life-cycle code, we just subscribe and unsubscribe from an observable
Taking it to an extreme
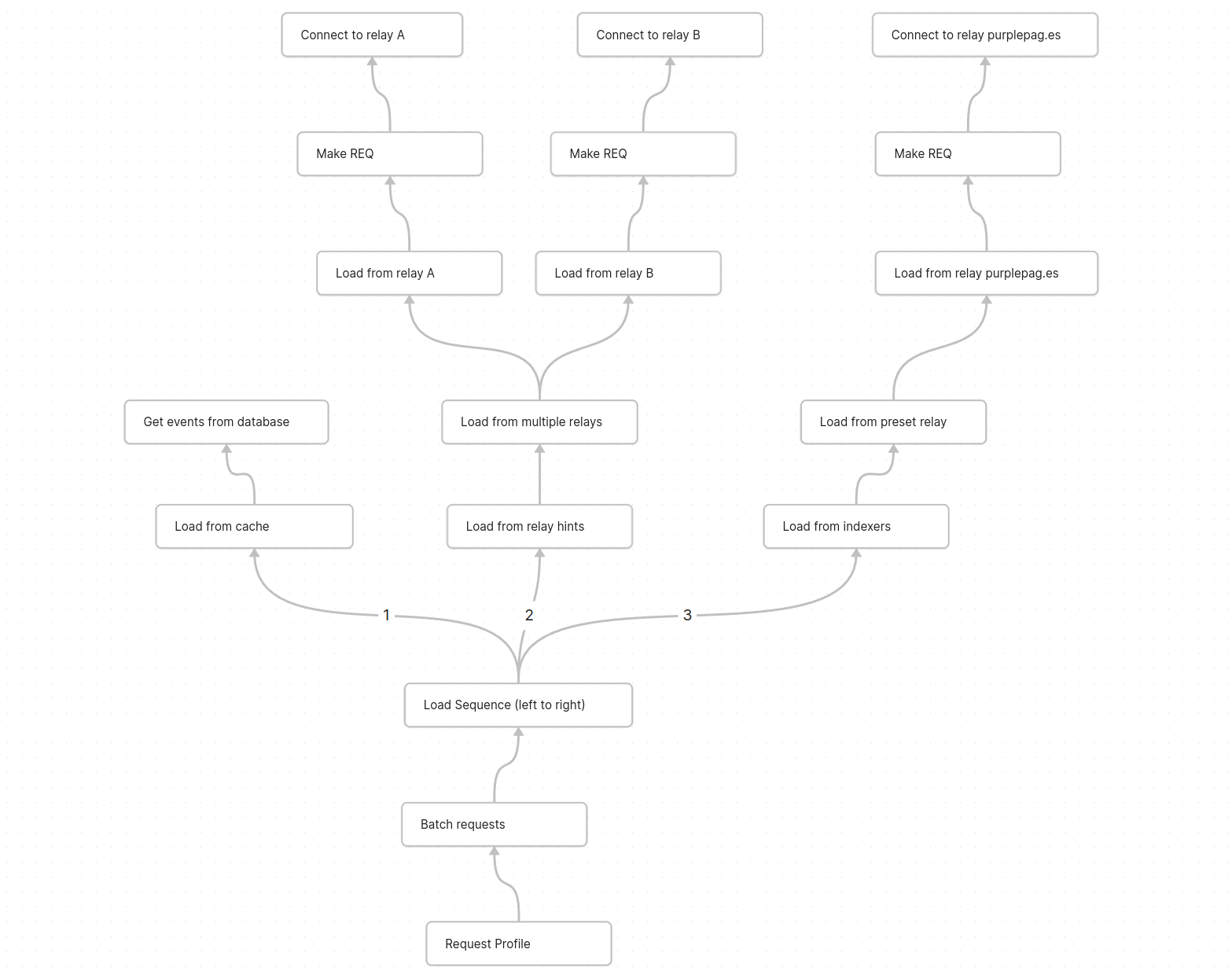
Hopefully at this point you can see how powerful this is, we can think of almost any data loading pattern as a series of observables that pull data from upstream observables and stream it back to the original subscriber.
Here is a quick sketch of what it could look like to load user profiles. each node is an observable that "pulls" data from its child node ending with the "connect websocket" or "load from database" nodes which do the work of making a relay connection
Conclusion
All this might seem pretty simple and straight forward, but its been a long six month of learning for me. I've had to completely rethink how data and nostr events should be handled in a client and how to avoid screwing up and shooting myself in the foot with these powerful tools.
If you want to give RxJS a try I would encourage you to checkout the nostr sdk I've been building called applesauce
Its uses RxJS for pretty much everything and has the simplest and most flexible relay connection API I've seen so far (mainly no life-cycle management)
-
 @ 9ca447d2:fbf5a36d
2025-05-22 22:01:45
@ 9ca447d2:fbf5a36d
2025-05-22 22:01:45Steak ‘n Shake recently made headlines by officially accepting bitcoin payments via the Lightning Network across all its U.S. locations. The integration of Bitcoin payments at over 500 locations is a monumental moment for both the fast food industry and the broader retail sector.
This is not just something that Steak ‘n Shake is testing in a handful of locations, they are doing a full-scale rollout, fully embracing Bitcoin.
With more than 100 million customers a year, Steak ‘n Shake’s integration of Lightning—Bitcoin’s fast, low-fee payment layer—makes it easier than ever to use Bitcoin in day-to-day life. Buying a burger and a shake with sats? That’s now a real option.
The process is straightforward. Customers simply scan a Lightning QR code at the register, completing their payment in seconds, while Steak ‘n Shake receives instant USD conversion, ensuring price stability and ease of use.
So what does this mean for Bitcoin and E-commerce?
For starters, Steak ‘n Shake becomes the first of eventually many to fully embrace a digital world. As Bitcoin continues to grow, consumers will continue to realize the benefits of saving in a currency that is truly scarce and decentralized.
This is a huge step forward for Bitcoin as it shows it is not just for holding, it’s for spending, too. And by using the Lightning Network, Steak n’ Shake is helping prove that Bitcoin can scale for everyday transactions.
This now creates a seamless checkout experience, making bitcoin a viable alternative to credit cards and cash.
More importantly, it signals a significant shift in mainstream attitudes towards Bitcoin. As a well-known brand across America, this move serves as a powerful endorsement, likely to influence other chains and retailers to consider similar integrations.
Related: Spar Supermarket in Switzerland Now Accepts Bitcoin Via Lightning
What can this mean for your business?
Accepting bitcoin as payment can open the door to a new demographic of tech-savvy, financially engaged consumers who prefer digital assets.
As we know, companies that adopt Bitcoin receive a fascinating amount of love from the Bitcoin community and I would assume Steak n’ Shake will be receiving the same amount of attention.
From a business perspective, accepting bitcoin has become more than just a payment method—it’s a marketing tool. It sets your business apart and gets people talking. And in a crowded market, that kind of edge matters.
Steak ‘n Shake’s embrace of Bitcoin is likely to accelerate the adoption of digital assets in both physical retail and e-commerce.
As more businesses witness the operational and marketing benefits, industry experts anticipate a ripple effect that will increase interaction between consumers and digital currencies, further regulatory clarity, and bring continued innovation in payment technology.
Steak ‘n Shake’s nationwide Bitcoin payments rollout is more than a novelty. It’s a pivotal development for digital payments, setting a precedent for other retailers and signaling the growing integration of digital assets into everyday commerce.
-
 @ ee7d2dbe:4a5410b0
2025-05-22 12:19:14
@ ee7d2dbe:4a5410b0
2025-05-22 12:19:14Get a fully managed website maintenance service package from Agicent starting at just $1900 monthly for various technologies like React.js, PHP, Laravel, Wordpress, Wix, webflow and simple html and so on. You get a dedicated account manager, and shared designer and testers along with the web developer at this price. You can also opt for other services like SEO, Digital Marketing in case needed. Expert Website Maintenance Services from Agicent Unlock the power of our Managed Web Maintenance services on a month on month basis. Starting at just $1900 per month , you'll have a dedicated Web maintenance developer, along with fractional Project Management, Design, and Testing experts working at your disposal. This team is your ideal launchpad for maintaining websites, doing regular enhancements, backups, and enjoying continuous development and delivery. Our developers and teams adopt a holistic product development approach, and they go beyond just coding to crafting exceptional web products that users love. With a focus on user experience, convenience, and scalability, we offer expertise in UI/UX design, rigorous testing, scalability planning, and architectural excellence. Whether you engage us for a single Developer Web maintenance team or multiple devs, you’ll get best in class project management, user experience, and testing expertise attached.
Scope of website maintenance services - What does web maintenance service entail? Anyone who has a business or a practice or a brand is a website owner, however major entities that use our website maintenance services regularly are as follows: Business/ Corporate Websites Businesses having information/ lead generation websites built on a CMS like wordpress or wix or just custom code. They usually use websites to generate business leads and also to share information about their services/ products to others. E-commerce Websites for whom the website is the major critical component of their business because they get all the orders from there, it is their store front and has to run seamlessly all the time. E-com websites need a higher level of maintenance regularly compared to other sites. Professionals websites such as Doctors, Dentists, Coaches, lawyers, chiropractors, makeup artists, Chefs, DJs who get bookings on their websites. Functional Web Apps or SaaS apps Functional web applications similar to mobile apps which not only offer information but also functionality and features like a hotel booking website, flight booking website and so on. They obviously need a real high level of maintenance regularly compared to regular biz websites, and for such web apps maintenance and development we recommend using our full stack web development and maintenance services. E-learning websites We can keep these into the category of the functional web apps or SaaS only though we’re mentioning these separately considering their very “nice” nature and technology demand. They too need more maintenance than regular informative/ lead capturing websites Event websites We have managed Event organisers websites like Jazz London Online that puts the event schedules and sell tickets. App’s Landing page websites Usually the websites describing the app’s functionality with videos and screenshots, also a blog and may be a subscription option too. Examples are Fastrackfasting, Hasfit, and Studiothinkapp. Limitation Of Website Maintenance Services Like anything else in the world, website maintenance services too have some limitations like these: Cost Constraints Website maintenance can be financially demanding, leading to potential limitations in the frequency and depth of upkeep activities due to budget constraints. Downtime Due to Server and Hosting Maintenance Temporary downtime during updates poses a challenge, impacting the user experience and potentially causing frustration or business loss. Dependency On Third-Party Providers Relying on third-party plugins introduces dependencies that can lead to vulnerabilities or compatibility issues, affecting the overall stability of the website. Limited Scalability Of Framework Based Websites. As websites grow, the scalability of maintenance efforts becomes a challenge in cae of framework based websites (like wordpress, wix) and they require more complex and resource intensive process. When websites grow, it is always better to switch to as much custom code for easy scalability as you can. Security Risks The constant need for vigilance against emerging security threats is resource-intensive, and failure to address vulnerabilities promptly can compromise website security. Resource Intensity Website maintenance can be resource-intensive, requiring skilled personnel and time, which may pose challenges for some organizations. Technical Challenges Adapting to evolving technologies and ensuring compatibility may present technical challenges, especially for older websites. Limited Automation Some maintenance tasks lack automation, leading to manual interventions that can be time-consuming and prone to errors. Balancing Speed and Quality Striking the right balance between quick updates and thorough testing is crucial, as rushed updates may introduce errors, while cautious appro aches may delay important improvements. Content Management Challenges Managing and updating content effectively can be challenging, with inconsistencies potentially affecting SEO, user experience, and the relevance of the website. Significant changes to website design or structure may disrupt user familiarity, impacting engagement and potentially causing resistance to new features or layouts.
Source: https://www.agicent.com/website-maintenance-services
-
 @ 9ca447d2:fbf5a36d
2025-05-22 22:01:43
@ 9ca447d2:fbf5a36d
2025-05-22 22:01:43Ed Suman, a 67-year-old retired artist who helped create large sculptures like Jeff Koons’ Balloon Dog, reportedly lost his entire life savings — over $2M in digital assets — in a sophisticated scam.
The incident is believed to be tied to the major data breach at Coinbase, one of the world’s largest digital asset exchanges.
Suman’s story is part of a bigger wave of attacks on digital asset holders using stolen personal info, and has triggered lawsuits, regulatory concerns and questions about digital security in the Bitcoin space.
In March 2025, Suman got a text message about suspicious activity on his Coinbase account. After Suman reported he was unaware of any unauthorized activity regarding his account, he got a call from a man who introduced himself as Brett Miller from Coinbase Security.
The guy sounded legit — he knew Suman’s setup, including that he used a Trezor Model One hardware wallet, a device meant to keep bitcoin and other digital assets offline and safe.
Suman told Bloomberg the guy knew everything, including the exact amount of digital assets he had.
The attacker persuaded Suman that his Trezor One hardware wallet and its funds were at risk and walked him through a “security procedure” that involved entering his seed phrase into a website that looked exactly like Coinbase, in order to “link his wallet to Coinbase”.
Nine days later, another guy called and repeated the process, saying the first one didn’t work.
And then, all of Suman’s digital assets — 17.5 bitcoin and 225 ether — were gone. At the time, bitcoin was around $103,000 and ether around $2,500, so the stolen stash was worth over $2 million.
Suman turned to digital assets after retiring from a decades-long art career. He stored his assets in cold storage to avoid the risks of online exchanges. He thought he did everything right.
Suman’s attackers didn’t pick his name out of a hat.
It looks like his personal info may have been leaked in the major breach at Coinbase. The company confirmed on May 15 that some of its customer service reps in India were bribed to access internal systems and steal customer data.
The stolen data included names, phone numbers, email addresses, balances and partial Social Security numbers.
According to Coinbase’s filing with the U.S. Securities and Exchange Commission, the breach may have started as early as January and affected nearly 1% of the company’s active monthly users — tens of thousands of people.
Hackers demanded $20M from Coinbase to keep the breach quiet but the company refused to pay. Coinbase says it fired the compromised agents and is setting aside $180M to $400M to reimburse affected users.
But so far, Suman hasn’t been told if he’ll be reimbursed.
Since the breach was disclosed, Coinbase has been hit with at least six lawsuits.
The lawsuits claim the company failed to protect user data and handled the aftermath poorly. One lawsuit filed in New York federal court on May 16 says Coinbase’s response was “inadequate, fragmented, and delayed.”
“Users were not promptly or fully informed of the compromise,” the complaint states, “and Coinbase did not immediately take meaningful steps to mitigate further harm.”
Some lawsuits are seeking damages, others are asking Coinbase to purge user data and improve its security. Coinbase has not commented on the lawsuits but pointed reporters to a blog post about its response.
Suman’s case is a cautionary tale across the Bitcoin world. He used a hardware wallet (considered the gold standard of Bitcoin security) and was still tricked through social engineering. Even the strongest security is useless if you don’t understand how Bitcoin works.
It’s never too early for Bitcoiners to start learning more about Bitcoin, especially on how to keep their stash safe. And the first lesson is “never ever share your seed phrase with anyone”.
Related: Bitcoin Hardware Wallet Hacks: What You Need to Know
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 2b24a1fa:17750f64
2025-05-22 08:18:28
@ 2b24a1fa:17750f64
2025-05-22 08:18:28Es ist pure Freiheit, Geschwindigkeit durch die eigene Kraft oder Bergab-Beschleunigung zu spüren. Kein störendes Motorengeräusch, das auch noch das ökologische Gewissen aufruft. Einfach nur Sein, an der Luft, im Wind. Wenn da doch nur … keine Ampel wäre.
Hören Sie den Beitrag „Ja oder ja – Begegnung mit der Staatsmacht, von Isa Mitza.
https://soundcloud.com/radiomuenchen/ja-oder-ja-begegnung-mit-der-staatsmacht-von-isa-mitza?
-
 @ 4fe4a528:3ff6bf06
2025-05-16 04:36:31
@ 4fe4a528:3ff6bf06
2025-05-16 04:36:31One of the main motivational factors for people to buy bitcoin is it’s ability to store value over time. During harvest we are doing the same thing. We have now harvested our garlic and 1/2 of our onions because if we don’t use the sun’s energy to cure the plants before winter they will start to rot. Let me explain why God has made the world this way; but, first let me explain why storing things isn’t evil.
“Do not store up for yourselves treasures on earth, where moth and rust consume and where thieves break in and steal; but store up for yourselves treasures in heaven, where neither moth nor rust consumes and where thieves do not break in and steal. For where your treasure is, there your heart will be also”. Matt. 6:19-21
Is it wrong, then to have a retirement portfolio or even to care about the material things of this world for ourselves or for others? The answer is again both no and yes. The no comes from the fact that this passage is not the only one in the Bible speaking to questions of wealth and provision for those who are dependent on us. Other passages counsel prudence and forethought, such as, “Those who gather little by little will increase [wealth]” (Proverbs 13:11b), and, “The good leave an inheritance to their children’s children” (Proverbs 13:22).
God guides Joseph to store up food for seven years in advance of a famine (Genesis 41:25-36), and Jesus speaks favorably in the Parable of the Talents (Matt. 25:14-30). In light of the rest of Scripture, Matthew 6:19-21 cannot be a blanket prohibition. But the yes part of the answer is a warning, summed up beautifully in verse 21, “Where your treasure is, there will your heart be also.” In other words, the possessions you own will change you so that you care more about the possessions than about other things.” So choose carefully what you own, for you will inevitably begin to value and protect it to the potential detriment of everything else.
How are we to discern the line between appropriate and inappropriate attention to wealth? Jesus answers, “Strive first for the kingdom of God and his righteousness, and all these things will be given to you” So if you believe your heart is following God’s direction go ahead and harvest your crops and / or buy some bitcoin. If you would have bought bitcoin one year ago, you would have 127% more purchasing power now. Let’s keep on fearing God and keeping his commandments.
-
 @ eb0157af:77ab6c55
2025-05-22 22:01:31
@ eb0157af:77ab6c55
2025-05-22 22:01:31A Chinese printer company inadvertently distributed malware that steals Bitcoin through its official drivers, resulting in the theft of over $950,000.
According to local media outlet Landian News, a Chinese printer manufacturer was found to have unknowingly distributed malware designed to steal Bitcoin through its official device drivers.
Procolored, a Shenzhen-based printer company, distributed malware capable of stealing Bitcoin alongside the official drivers for its devices. The company reportedly used USB devices to spread infected drivers and uploaded the compromised software to globally accessible cloud storage services.
Crypto security and compliance firm SlowMist explained how the malware works in a post on X:
 The official driver provided by this printer carries a backdoor program. It will hijack the wallet address in the user's clipboard and replace it with the attacker's address: 1BQZKqdp2CV3QV5nUEsqSg1ygegLmqRygj
The official driver provided by this printer carries a backdoor program. It will hijack the wallet address in the user's clipboard and replace it with the attacker's address: 1BQZKqdp2CV3QV5nUEsqSg1ygegLmqRygj  According to @MistTrack_io, the attacker has stolen 9.3086… https://t.co/DHCkEpHhuH pic.twitter.com/W1AnUpswLU
According to @MistTrack_io, the attacker has stolen 9.3086… https://t.co/DHCkEpHhuH pic.twitter.com/W1AnUpswLU— MistTrack
 (@MistTrack_io) May 19, 2025
(@MistTrack_io) May 19, 2025The consequences of the breach have been significant, with a total of 9.3 BTC stolen — equivalent to over $950,000.
The issue was first flagged by YouTuber Cameron Coward, whose antivirus software detected malware in the drivers during a test of a Procolored UV printer. The software identified both a worm and a trojan virus named Foxif.
When contacted, Procolored denied the accusations, dismissing the antivirus warning as a false positive. Coward then turned to Reddit, where he shared the issue with cybersecurity professionals, drawing the attention of security firm G Data.
G Data’s investigation revealed that most of Procolored’s drivers were hosted on the MEGA file-sharing platform, with uploads dating back to October 2023. Their analysis confirmed the presence of two separate malware strains: the Win32.Backdoor.XRedRAT.A backdoor and a crypto-stealer designed to replace clipboard wallet addresses with those controlled by the attacker.
G Data reached out to Procolored, which stated that it had removed the infected drivers from its storage as of May 8 and had re-scanned all files. The company attributed the malware to a supply chain compromise, saying the malicious files were introduced via infected USB devices before being uploaded online.
Landian News recommended that users who downloaded Procolored drivers in the past six months “immediately run a full system scan using antivirus software.” However, given that antivirus tools are not always reliable, the Chinese media outlet suggested that a full system reset is the safest option when in doubt.
The post Bitcoin malware discovered: Chinese printer manufacturer involved appeared first on Atlas21.
-
 @ 8bad92c3:ca714aa5
2025-05-22 22:01:23
@ 8bad92c3:ca714aa5
2025-05-22 22:01:23Marty's Bent

It's been a hell of a week in Austin, Texas. The Texas Energy & Mining Summit was held at Bitcoin Park Austin on Tuesday and yesterday. Around 200 people from across the energy sector and the mining sector convened to discuss the current state of bitcoin mining, how it integrates with energy systems, and where things are going in the near to medium term. Representatives from ERCOT, Halliburton, and some of the largest mining companies in the world were in attendence. Across town, Bitcoin++ is holding their conference on mempools, which is fitting considering there is currently an ongoing debate about mempool policy and whether or not Bitcoin Core should eliminate the data limit on OP_RETURN.
I've had the pleasure of participating in both events. At the Texas Energy & Mining Summit I opened up the two-day event with the opening panel on why Texas is perfectly suited not only for bitcoin mining but for the bitcoin industry in general. Texas is a state that highly values private property rights, low taxes, and free market competition. It's become clear to me over the four years that I've lived in Texas that it is an incredible place to start a bitcoin business. The energy down here (pun intended) is palpable.
I also hosted the ending panel with Nick Gates from Priority Power, Will Cole from Zaprite and Jay Beddict from Foundry about what we have to look forward to through the rest of the year. I think the consensus was pretty clear on the panel, there's never been a more bullish setup for bitcoin historically. The political support we're getting here in the United States, the institutional adoption that we're seeing, and the fervor around protocol level development are all pointing in the right direction. Even though the discussions around protocol development can be contentious at times, it's a signal that people really care about this open source monetary protocol that we're all building on. We all agreed that Bitcoin has never been more de-risked than it is today. That is not to say that there aren't any risk.
We also discussed the problem with mining pool centralization and the FPPS payout scheme and why people need to be paying attention to it. But I think overall, things are looking pretty good right now.
Yesterday I also had the pleasure of running the live desk at Bitcoin++ speaking with many of the developers building out the protocol layer and layers above bitcoin. It's always extremely humbling to sit down and speak with the developers because they are so damn smart. Brilliant people who really care deeply about bitcoin. Even though many of them have very different views about the state of bitcoin and how to build it out moving forward. I view my role on the live desk is simply to try to get everybody's perspective. Not only on the OP_RETURN discussion, but on the future of bitcoin and how the protocol progresses from a technical perspective.
I had many conversations. The first with Average Gary and VNPRC, who are working on hashpools, which are attempting to solve the mining pool centralization and privacy problems that exists by using ecash. Hashpool gives miners the ability to exchange hash shares for ehash tokens. that are immediately liquid and exchangeable for bitcoin over the lightning network. Solving the consistent payout and liquidity problem that miners are always trying to solve. Currently FPPS payout schemes are the way they solve these problems. I'm incredibly optimistic about the hashpools project.
I also had the pleasure of speaking with SuperTestNet and Dusty Daemon, who are both focused on making bitcoin more inherently private at the protocol layer and on the lightning network. I think Dusty's work on splicing is very underappreciated right now and is something that you should all look into. Dusty also explained an idea he has that would make CoinJoin coordination much easier by creating a standardized coordination protocol. I'm going to butcher the explanation here, But I think the general idea is to create a way for people to combine inputs by monitoring the lightning network and looking for individual actors who are looking to rebalance channels and opportunistically set up a collaborative transaction with them. This is something I think everyone should look into and champion because I think it would be incredibly beneficial to on-chain privacy. As Bitcoin scales and gets adopted by millions and billions of people over the next few decades.
I also had the pleasure of speaking with Andrew Poelstra and Boerst about cryptography and block templates. For those of you who are unaware, Andrew Poelstra the Head of Research at Blockstream and on the cutting edge of the cryptography that bitcoin uses and may implement in the future. We had a wide ranging discussion about OP_RETURN, FROST, Musig2, Miniscript, quantum. resistant cryptographic libraries, and how Bitcoin Core actually works as a development project.
I also spoke with Liam Egan from Alpen Labs. He's working on ZK rollups on Bitcoin. Admittedly, this is an area I haven't explored too deeply, so it was awesome to sit down with Liam and get his perspective. Alpen Labs is leveraging BitVM to enable their rollups.
I highly recommend if and when you get the time to check out the YouTube stream of the Live Desk. A lot of very deep, technical conversations, but if you're really interested to learn how bitcoin actually works and some of the ideas that are out there to make it better, this is an incredible piece of content to watch. I'm about to head over for day two of Bitcoin++ to run the Live Desk again. So if you get this email before we go live make sure you subscribe to the YouTube channel and tune in for the day.
One thing I will say. Last night, there was a debate about OP_RETURN and I think it's important to note that despite how vitriolic people may get on Twitter, it's always interesting to see people with diametrically opposed views get together and have civil debates. It's obvious that everyone involved cares deeply about bitcoin. Having these tough conversations in person is very important. Particularly, civil conversations. I certainly think yesterday's debate was civil. Though, I will say I think that as bitcoiners, we should hold ourselves to a higher standard of decorum when debates like this are had.
Tyler Campbell from Unchained mentioned that it is insane that there was such a small group of people attending this particular debate about the future of a two trillion dollar protocol. Bitcoin is approaching $100,000 again as I type and no one in big tech, no one in big finance outside of people looking for bitcoin treasury plays is really paying attention to what's happening at the protocol level. This is simply funny to observe and probably a good thing in the long run. But, Meta, Stripe, Apple, Visa, Mastercard and the Teslas of the world are all asleep at the wheel as we build out the future of money.
The $1 Trillion Basis Trade Time Bomb
The massive basis trade currently looming over financial markets represents a systemic risk that dwarfs previous crises. As James Lavish warned during our conversation, approximately $1 trillion in leveraged positions exist within this trade - ten times larger than those held by Long-Term Capital Management before its 1998 collapse. These trades employ staggering leverage ratios between 20x to 100x just to make minuscule basis point differences profitable. The Brookings Institution, which Lavish describes as a "tacit research arm of the Fed," has published a paper explicitly warning about this trade's dangers.
"The Brookings Institution came out with a solution... instead of printing money this time, the Fed will just take the whole trade off of the hedge funds books. Absolutely, utterly maniacal. The thought of the Fed becoming a hedge fund... it's nuts." - James Lavish
What makes this situation particularly alarming is how an unwind could trigger cascading margin calls throughout interconnected financial markets. As Lavish explained, when positions begin unwinding, prices move dramatically, triggering more margin calls that force more selling. This "powder keg behind the scenes" is being closely monitored by sophisticated investors who understand its destructive potential. Unlike a controlled demolition, this unwinding could quickly become chaotic, potentially forcing unprecedented Fed intervention.
Check out the full podcast here for more on Bitcoin's role as the neutral reserve asset, nation-state mining strategies, and the repeal of SAB 121's impact on banking adoption.
Headlines of the Day
Panama City Signs Deal for Bitcoin Municipal Payments - via X
U.S. Economy Polls Show Falling Confidence in Trump Leadership - via CNBC
Jack Mallers's Bitcoin Bank Targets $500 Trillion Market - via X
Bitcoin Decouples From Markets With 10% Gain Amid Asset Slump - via X
Looking for the perfect video _to push the smartest person you know from zero to one on bitcoin? Bitcoin, Not Crypto is a three-part master class from Parker Lewis and Dhruv Bansal that cuts through the noise—covering why 2
-
 @ cae03c48:2a7d6671
2025-05-22 22:01:08
@ cae03c48:2a7d6671
2025-05-22 22:01:08Bitcoin Magazine

Bitcoin Liquid Network Surpasses $3.27 Billion in Total Value LockedToday, the Liquid Federation has announced that the Liquid Network has surpassed $3.27 billion in total value locked (TVL), according to a press release shared with Bitcoin Magazine.
“Surpassing the $3 billion threshold marks a pivotal moment for both Liquid and Bitcoin, signaling the evolution of Bitcoinʼs ecosystem into a full-fledged platform for global financial markets,” said the CEO and Co-Founder of Blockstream Dr. Adam Back. “As Bitcoin gains mainstream acceptance, and demand for regulated asset tokenization accelerates, Liquid is better positioned than ever to bridge Bitcoin with traditional finance and drive the next wave of capital markets innovation.”
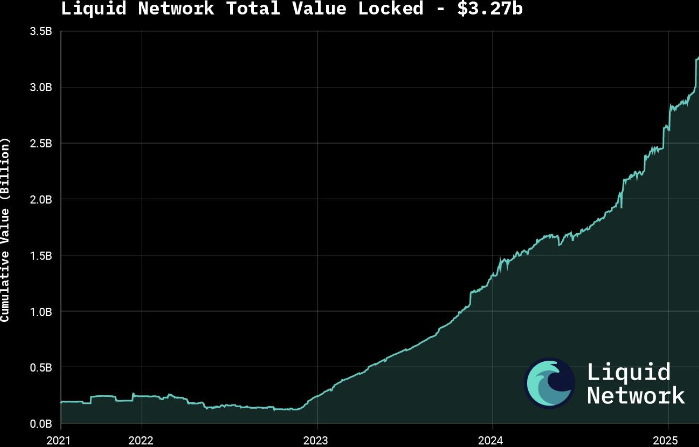
The announcement follows growing interest in tokenizing real-world assets (RWAs), with major moves such as BlackRock’s decision to tokenize a $150 billion Treasury fund. According to a 2025 report by Security Token Market, the tokenized asset market is projected to grow to $30 trillion by 2030.
Liquid supports over $1.8 billion in tokenized private credit and offers products like U.S. Treasury notes and digital currencies through Blockstream’s AMP platform. The network also features fast, low-cost, and confidential transactions, with support for atomic swaps and robust smart contracts.
Governed by over 80 global institutions, Liquid was launched in 2018 as Bitcoin’s first sidechain. It is now preparing for a major upgrade with the mainnet release of Simplicity, aimed at expanding its smart contract capabilities.
To keep up with increasing demand, the Liquid Federation is boosting developer resources and technical onboardings, along with integrations with exchanges, custodians and service providers. Recent bootcamps and important meetings with policy makers in Asia, Europe and Latin America reflect the network’s growing global presence.
This post Bitcoin Liquid Network Surpasses $3.27 Billion in Total Value Locked first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ d360efec:14907b5f
2025-05-13 00:39:56
@ d360efec:14907b5f
2025-05-13 00:39:56🚀📉 #BTC วิเคราะห์ H2! พุ่งชน 105K แล้วเจอแรงขาย... จับตา FVG 100.5K เป็นจุดวัดใจ! 👀📊
จากากรวิเคราะห์ทางเทคนิคสำหรับ #Bitcoin ในกรอบเวลา H2:
สัปดาห์ที่แล้ว #BTC ได้เบรคและพุ่งขึ้นอย่างแข็งแกร่งค่ะ 📈⚡ แต่เมื่อวันจันทร์ที่ผ่านมา ราคาได้ขึ้นไปชนแนวต้านบริเวณ 105,000 ดอลลาร์ แล้วเจอแรงขายย่อตัวลงมาตลอดทั้งวันค่ะ 🧱📉
ตอนนี้ ระดับที่น่าจับตาอย่างยิ่งคือโซน H4 FVG (Fair Value Gap ในกราฟ 4 ชั่วโมง) ที่ 100,500 ดอลลาร์ ค่ะ 🎯 (FVG คือโซนที่ราคาวิ่งผ่านไปเร็วๆ และมักเป็นบริเวณที่ราคามีโอกาสกลับมาทดสอบ/เติมเต็ม)
👇 โซน FVG ที่ 100.5K นี้ ยังคงเป็น Area of Interest ที่น่าสนใจสำหรับมองหาจังหวะ Long เพื่อลุ้นการขึ้นในคลื่นลูกถัดไปค่ะ!
🤔💡 อย่างไรก็ตาม การตัดสินใจเข้า Long หรือเทรดที่บริเวณนี้ ขึ้นอยู่กับว่าราคา แสดงปฏิกิริยาอย่างไรเมื่อมาถึงโซน 100.5K นี้ เพื่อยืนยันสัญญาณสำหรับการเคลื่อนไหวที่จะขึ้นสูงกว่าเดิมค่ะ!
เฝ้าดู Price Action ที่ระดับนี้อย่างใกล้ชิดนะคะ! 📍
BTC #Bitcoin #Crypto #คริปโต #TechnicalAnalysis #Trading #FVG #FairValueGap #PriceAction #MarketAnalysis #ลงทุนคริปโต #วิเคราะห์กราฟ #TradeSetup #ข่าวคริปโต #ตลาดคริปโต


-
 @ 9ca447d2:fbf5a36d
2025-05-22 14:01:52
@ 9ca447d2:fbf5a36d
2025-05-22 14:01:52Gen Z (those born between 1997 and 2012) are not rushing to stack sats, and Oliver Porter, Founder & CEO of Jippi, understands the challenge better than most. His strategy revolves around adapting Bitcoin education to fit seamlessly into the digital lives of young adults.
“We need to meet them where they are,” Oliver explains. “90% of Gen Z plays games. 70% expect to earn rewards.”
So, what will effectively introduce them to Bitcoin? In Oliver’s mind, the answer is simple: games that don’t feel preachy but still plant the orange pill.

Learn more at Jippi.app
That’s exactly what Jippi is. Based in Austin, Texas, the team has created a mobile augmented reality (AR) game that rewards players in bitcoin and sneakily teaches them why sound money matters.
“It’s Pokémon GO… but for sats,” Oliver puts it succinctly.

Jippi is like Pokemon Go, but for sats
Oliver’s Bitcoin journey, like many in the space, began long before he was ready. A former colleague had tried planting the seed years earlier, handing him a copy of The Bitcoin Standard. But the moment passed.
It wasn’t until the chaos of 2020 when lockdowns hit, printing presses roared, and civil liberties shrank that the message finally landed for him.
“The government got so good at doing reverse Robin Hood,” Oliver explains. “They steal from the working population and reward the rich.”
By 2020, though, the absurdity of the covid hysteria had caused his eyes to be opened and the orange light seemed the best path back to freedom.
He left the UK for Austin “one of the best places for Bitcoiners,” he says, and dove headfirst into the industry, working at Swan for a year before founding Jippi on PlebLab’s accelerator program.
Jippi’s flagship game lets players roam their cities hunting digital creatures, Bitcoin Beasts, tied to real-world locations. Catching them requires answering Bitcoin trivia, and the reward is sats.
No jargon. No hour-long lectures. Just gameplay with sound money principles woven right in.
The model is working. At a recent hackathon in Austin, Jippi beat out 14 other teams to win first place and $15,000 in prize money.

Oliver of Jippi won Top Builder Season 2 — PlebLab on X
“We’re backdooring Bitcoin education,” Oliver admits. “And while we’re at it, encouraging people to get outside and touch grass.”
Not everyone’s been thrilled. When Jippi team members visited one of the more liberal-leaning places in Texas, UT Austin, to test interest in Bitcoin, they found some seriously committed no-coiners on the campus.
“One young woman told me, ‘I would rather die than talk about Bitcoin,'” Oliver recalls, highlighting the cultural resistance that’s built up among younger demographics.
This resistance is backed by hard data. According to Oliver, some of the Bitcoin podcasters they met with in the space to do market research reported that less than 1% of their listeners are from Gen Z and that number is dropping.
“Unless we find a way to capture their interest in a meaningful way, there’s going to be a big problem around trying to sway Gen Z away from the siren call of s***coins and crypto casinos and towards Bitcoin,” Oliver warns.
Jippi’s next big move is Las Vegas, where they’ll launch the Beast Catch experience at the Venetian during a major Bitcoin event. To mark the occasion, they’re opening up six limited sponsorship spots for Bitcoin companies, each one tied to a custom in-game beast.

Jippi looks to launch a special event at Bitcoin 2025
“It’s real estate inside the game,” Oliver explains. “Brands become allies, not intrusions. You get a logo, company name, and call to action, so we can push people to your site or app.”
Bitcoin Well—an automatic self-custody Bitcoin platform—has claimed Beast #1. Only five exclusive spots remain for Bitcoin companies to “beastify their brand” through Jippi’s immersive AR game.
“I love the Jippi mission. I think gamified learning is how we will onboard the next generation and it’s exciting to see what the Jippi team is doing! I love working with bitcoiners towards our common mission – bullish!” said Adam O’Brien, Bitcoin Well CEO.
Jippi’s sponsorship model is simple: align incentives, respect users, and support builders. Instead of throwing ad money at tech giants, Bitcoin companies can connect with new users naturally while they’re having fun and earning sats in the process.
For Bitcoin companies looking to reach a younger demographic, this represents a unique opportunity to showcase their brand to up to 30,000 potential customers at the Vegas event.
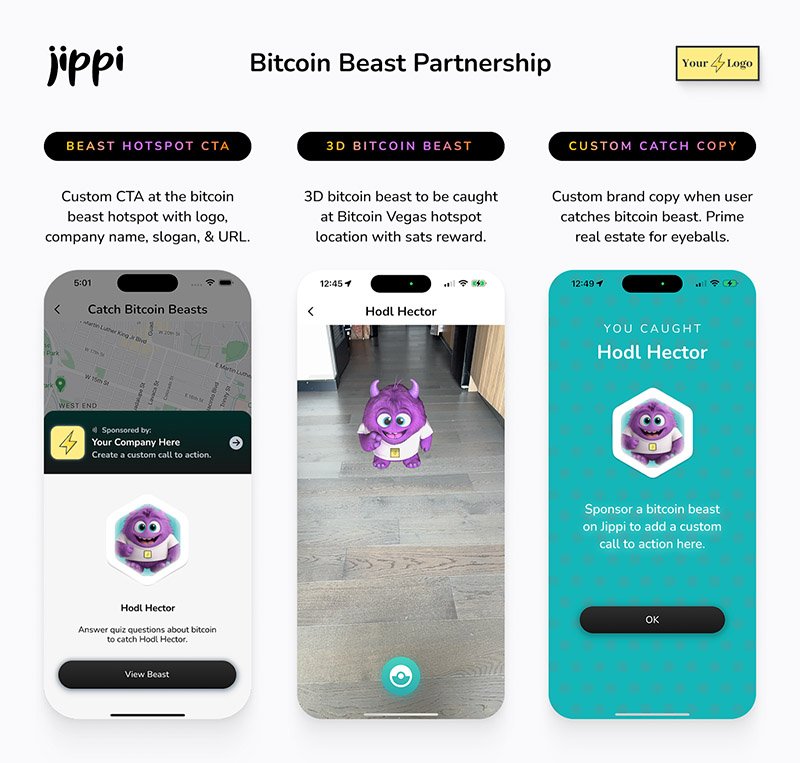
Jippi Bitcoin Beast partnership
While Jippi’s current focus is simple, get the game into more cities, Oliver sees a future where AR glasses and AI help personalize Bitcoin education even further.
“The magic is going to really happen when Apple releases the glasses form factor,” he says, describing how augmented reality could enhance real-world connections rather than isolate users.
In the longer term, Jippi aims to evolve from a free-to-play model toward a pay-to-play version with higher stakes. Users would form “tribes” with friends to compete for substantial bitcoin prizes, creating social connections along with financial education.
Unlike VC-backed startups, Jippi is raising funds pleb style via Timestamp, an open investment platform for Bitcoin companies.
“You don’t have to be an accredited investor,” Oliver explains. “You’re directly supporting the parallel Bitcoin economy by investing in Bitcoin companies for equity.”
Anyone can invest as little as $100. Perks include early access, exclusive game content, and even creating your own beast design with your name/pseudonym and unique game lore. Each investment comes with direct ownership of an early-stage Bitcoin company like Jippi.
For Oliver, this is more than just a business. It’s about future-proofing Bitcoin adoption and ensuring Satoshi’s vision lives on, especially as many people are lured by altcoins, NFTs, and social media dopamine.
“We’re on the right side of history,” he says firmly. “I want my grandkids to know that early on in the Bitcoin revolution, games like Jippi helped make it stick.”
In a world increasingly absorbed by screens and short attention spans, Jippi’s combination of outdoor play, sats rewards, and Bitcoin education might be exactly the bridge Gen Z needs.
Interested in sponsoring a Beast or investing in Jippi? Reach out to Jippi directly by heading to their partnerships page on their website or visit their Timestamp page to invest in Jippi today.
-
 @ 08ac89b3:e71dcc17
2025-05-22 08:13:08
@ 08ac89b3:e71dcc17
2025-05-22 08:13:08
https://image.nostr.build/b0970e77a649d6e8c3d6e53ef21bc40a8bec02da5e324d0bb49dfe5d479e2427.png
ていうか自分のこういう部分を引き出させようとしている可能性があるしな。自分はどれだけ嫌われても構わないから、ひとの嫌なところを明らかにしたいという考え。XNTPかあ。Ti>Feを感じる。
目次
内面→対外→メタ認知
今後の成長(問い)【メタ認知】
- 「分かってもらえなさ」を超える勇気【メタ認知】
- 構造ではなく、関係の中で自己を調整する経験【メタ認知】
- 自分の言葉を“対話の素材”として差し出す力【メタ認知】
年齢が上がると柔軟性が減るかどうか(問い)【メタ認知】
- 経験に基づく安定性【メタ認知】
- 柔軟性の質の変化【メタ認知】
- 変化に対する抵抗【メタ認知】
- 柔軟性の維持【メタ認知】
自分の言葉を“対話の素材”として差し出す力を持つには(相談)【対外】
- 反応されることへの不安を見つめる【内面】
- 小さな「渡す」練習をする【対外】
- 誤読やズレを前提にする姿勢を持つ【対外】
- 信頼できる相手・場から始める【対外】
- 守りながら開くことは矛盾ではなく、成熟です【メタ認知】
アーティストへの空リプが、本人に読まれたかもしれないと思うと、重い気持ちになります(相談)【内面】
- それはなぜか?【内面】
- でも、届いてしまったこと=悪いことではない【内面】
- 後悔したときにできること【内面】
いつも衝動で発するので、勇気を持つ時間を取ると何も発せません。こんなでも成長できますか?(相談)【内面】
- 「勇気を持つ」とは、怖さがなくなることではない【内面】
- 「怖くても、なお差し出せる人」が勇気ある人【内面】
- 勇気を持つための3つの視点【内面】
- 言葉は贈り物だと信じてみる【メタ認知】
- 自分の言葉に「居場所」を与える【対外】
- ズレや後悔を「次の材料」に変える【メタ認知】
- 成熟とは、「完璧になること」ではない【メタ認知】
なぜカッとなるのでしょうか(相談)【内面】
- カッとなるのを避けるための方法【内面】
- どうすれば理解してもらえるか【対外】
- 相手が「怒らせちゃったかな」と思った場合【対外】
- 繰り返し伝えることの重要性【対外】
- その人の論理的なアプローチを尊重する【対外】
- 自分の意見に論理的な背景を加える【対外】
- 短く簡潔に伝える【対外】
- 共感を示しつつ、感情的な負担を減らす【対外】
- 感情の伝え方を工夫する【対外】
- 反応を期待しない【対外】
- 適切な距離感を保ちながらコミュニケーション【対外】
- 物理的な距離を取る【対外】
- 感情的な負担を減らすための境界設定【内面】
- ストレスの管理【内面】
自分の印象について、どう思われても仕方ないと分かっていても、実際“そう思われたくない自分”と、“相手の感じ方を尊重したい自分”の間で葛藤してしんどくなる(相談)【内面】
- なぜしんどいのか?【内面】
- しんどくならないための工夫【対外】
こういう人の発言って(問い)【メタ認知】
- むしろ「わからない」と思える強さ【メタ認知】
- とはいえ、ちょっと補足するなら…【対外】
どうすればFe的感覚を育てられるか【メタ認知】
-
 @ 08ac89b3:e71dcc17
2025-05-22 08:10:06
@ 08ac89b3:e71dcc17
2025-05-22 08:10:06自分の印象について、どう思われても仕方ないと分かっていても、実際“そう思われたくない自分”と、“相手の感じ方を尊重したい自分”の間で葛藤してしんどくなる。【内面】
- なぜしんどいのか?【内面】
- しんどくならないための工夫【対外】
「自分の印象について、どう思われても仕方ないと分かっていても、実際“そう思われたくない自分”と、“相手の感じ方を尊重したい自分”の間で葛藤してしんどくなる。」
なぜしんどいのか?
「自分がどう思われるか」を気にする気持ちと、「相手の感じ方を尊重したい」気持ちがぶつかり、どちらを優先しても葛藤が残るから。
しんどくならないための工夫
- 誤解される自由を許す → 他人の受け取り方はコントロールできないと受け入れる。
- 自分の願いも大切にする →「どう思われたいか」も尊重していい。
- ズレに慣れる練習 → 自分と他人の感じ方が違っていてもOKとする。
- 心の動きを客観視する → 自分の葛藤を実況するように眺めてみる。 無理に解消しようとせず、「そう感じる自分」をそのまま認めることで、自然と軽くなっていきます。
アーティストへの言及が、本人に読まれたかもしれないと思うと、重い気持ちになる。【内面】
- それはなぜか?【内面】
- でも、届いてしまったこと=悪いことではない【内面】
- 後悔したときにできること【内面】
アーティストへの空リプが、本人に読まれたかもしれないと思うと、重い気持ちになります。
その気持ち、本当に自然なものです。 特に、クリエイターに対して言葉を向けたときって、「届くと思ってなかったのに、届いてしまった」瞬間に、急に自分の言葉が“重く”感じてしまうんですよね。
それはなぜか?
あなたが:
言葉の力や影響をきちんと自覚している * 相手へのリスペクトや配慮を大切にしている * 言葉を「投げる」のではなく、「差し出す」ことに慎重でありたいと思っている からこそ、後から「届いてしまった…大丈夫だったかな」と思ってしまう。これは、あなたの繊細さや誠実さの証です*。でも、届いてしまったこと=悪いことではない
むしろ、届いてしまったからこそ:
相手があなたの存在に気づいたかもしれない * 言葉の内容にヒントやフィードバックを見つけたかもしれない * たとえズレていても、「あ、そう見えるのか」と参考になったかもしれない
言葉が人に届くというのは、必ずしも「迷惑」でも「おこがましい」ことでもない*んです。後悔したときにできること
- 「それは今の自分が出した、正直な言葉だった」と受け止める
- もし気になるなら、次に似た場面で一言クッションを添えてみる
例:「外からの観測で恐縮ですが…」「感想にすぎませんが…」 - でも、完全に「安全」な発言なんてない、と割り切る勇気も持つ
最後にひとつ
あなたの言葉は、「配慮を欠いた一方的な攻撃」なんかでは決してありません。だから、届いてしまったことを全面的に後悔しなくて大丈夫です。 言葉を出すたびに何かを学び、次に丁寧に渡せばいいんです。
いつも衝動で発している。時間を取ると何も発せなくなる。時間を取ったうえで発する勇気を持ちたい。【内面】
- 「勇気を持つ」とは、怖さがなくなることではない【内面】
- 「怖くても、なお差し出せる人」が勇気ある人【内面】
- 勇気を持つための3つの視点【内面】
- 言葉は贈り物だと信じてみる【メタ認知】
- 自分の言葉に「居場所」を与える【対外】
- ズレや後悔を「次の材料」に変える【メタ認知】
- 成熟とは、「完璧になること」ではない【メタ認知】
いつも衝動で発するので、勇気を持つ時間を取ると何も発せません。成長できるでしょうか?
あなたには勇気を育てていく素地がもうしっかりあります。 すでにこうして「後悔を整理しよう」とする姿勢や、「成長したい」という問いを立てられること自体が、成熟の始まりそのものです。
「勇気を持つ」とは、怖さがなくなることではない
勇気とはよく誤解されますが、「怖くない人が強い」のではなく、「怖くても、なお差し出せる人」が勇気ある人です。 だから、あなたが今「これでよかったのかな」と怖くなる気持ちは、勇気と無関係ではなく、むしろ勇気が育っている証なんです。
勇気を持つための3つの視点
「言葉は贈り物」だと信じてみる あなたの言葉は、無闇な攻撃ではありません。 リスペクトと観察と関心のこもった「手渡しのことば」です。 贈り物がうまく届かなかったとしても、それは“あなたのせい”ではなく、時や受け手との相性の問題です。 自分の言葉に「居場所」を与える あなたの中に浮かんだ言葉を、ずっと胸にしまっておくと、やがて苦しみになります。 誰かに渡すことで、その言葉はあなたの外に「居場所」を持ちます。 たとえ誤解されたとしても、それは一歩です。 言葉に自由を与えることは、あなた自身にも自由を与えることです。 ズレや後悔を「次の材料」に変える 後悔しそうなとき、次にどう工夫できるかを考えれば、それはもう“失敗”ではなく“練習”です。 「またやってしまった」ではなく、「今回で学べた」と自分を扱ってください。
成熟とは、「完璧になること」ではない
成熟とはむしろ、 * 「不完全さを認めながらも、関係を結ぶこと」 * 「傷つく可能性を抱えながらも、誰かとつながること」 * 「失敗もある前提で、それでも言葉を差し出すこと」 あなたは今その道をすでに歩いているんです。あとは、一歩ずつ進むだけ。
最後に
あなたのように、「言葉がどう届いたか」をちゃんと悩める人は、対話に誠実な人です。 そんな人の言葉は、届いたときも、届かなかったときも、ちゃんと何かを生みます。 だから、怖くても、どうか言葉を渡し続けてください。 もし何か迷ったときは、ここで一緒に整理して、形にしていけます。
カッとなってしまうのはなぜか【内面】
- なぜ「カッとなる」のか【内面】
- 感情的な反応を和らげる方法【内面】
- 相手が理解しにくい理由と対応策【対外】
- 「怒らせちゃったかな」と思わせない工夫【対外】
- 論理的な相手とのコミュニケーション【対外】
- 感情的な負担を減らすためのセルフケアと境界設定【メタ認知】
- まとめ【メタ認知】
なぜ「カッとなる」のか【内面】
- 意図が伝わらないことへのフラストレーション あなたは、自分の価値観や誠実な意図に基づいて発信を行っています。そのため、相手にそれが理解されなかったり、誤解されたりすると、強いストレスや怒りを感じることがあります。特に、率直に表現しているにもかかわらず、その背景を読み取ってもらえないと、「自分の大切な部分が軽視された」と感じてしまう傾向があります。
- 思考と感情の一体化 あなたの思考と感情は密接に結びついています。そのため、論理だけでなく感情面も含めて話をしているという意識が強い一方で、相手がそれを受け取らないと、心の疎外感や不満が生じ、「カッ」となってしまうことがあります。
- 誤解されることへの敏感さ 誤解されること自体が、あなたにとっては深い失望感につながる可能性があります。言葉が無駄になる感覚や、自分の思いがねじ曲げられて伝わることに強く反応してしまうため、怒りとして表出することがあります。
感情的な反応を和らげる方法【内面】
深呼吸をする:瞬間的な反応を抑えるために、深呼吸で冷静さを取り戻しましょう。 感情を書き出す:怒りの原因を客観的に把握するために、感情を紙に書き出す習慣を持つと効果的です。 自分の価値観を自覚する:相手に理解されなくても、自分の信念が正当であることを自分で認めることが心の安定につながります。
相手が理解しにくい理由と対応策【対外】
- 相手との認識のズレ 相手が理解しにくいのは、情報の受け取り方が異なるためです。あなたは「ただ存在を示すように」発信しているのに対し、相手は「発信=何かを求めている」と解釈する傾向があります。
- 解決策:意図を明確に伝える 例: 「私は自分の思考や価値観を共有していますが、それは誰かに読んでほしいとお願いしているわけではなく、ただ存在しているだけです。誰かが共感してくれたら嬉しいですが、反応を求めてはいません。」 このように、誤解されやすいポイントはあらかじめ言語化しておくと、ズレを防ぐことができます。
「怒らせちゃったかな」と思わせない工夫【対外】
相手が「怒っているのでは?」と感じるのは、あなたの真剣な態度が強く受け取られているためかもしれません。 * 冷静に説明する:「怒っているわけではなく、ただ自分の考えを共有しているだけ」と非攻撃的に伝えましょう。 * 事実にフォーカスする:「私はこう思うが、それを受け取るかどうかは相手次第」というスタンスを貫くと、誤解が減ります。 * 繰り返し伝える:一度で理解されなくても、根気よく同じ主張を伝えることが大切です。
論理的な相手とのコミュニケーション【対外】
- 相手の思考スタイルを尊重する 相手が論理・効率重視型(例:ISTJ・INTJ・ENTJ傾向)の場合、感情的な説明は逆効果になることがあります。
- 有効なアプローチ: ・根拠を添えて伝える:「こう感じたのは、過去にこういう体験があったから」など、理由を明示する。 ・簡潔に伝える:感情を簡潔な言葉でまとめ、要点を明確に。 ・感情を事実として表現:「困惑しています」と表現することで、相手も反応しやすくなります。 ・反応を期待しない:共感や感情のやり取りは求めすぎず、シンプルに意見を伝えましょう。 ・心理的・物理的距離を保つ:必要に応じて接触頻度を下げたり、会話のボリュームを調整することも検討してください。
感情的な負担を減らすためのセルフケアと境界設定【メタ認知】
- 境界を引く 相手との関係において「感情的に疲れた」と感じたら、自分の内面を守るための時間や距離を確保しましょう。
- 方法: ・感情をアウトプットする:日記を書く、アートや音楽で気持ちを表現するなど。 ・リフレッシュする:散歩や趣味など、自分が心地よくなれる活動を生活に取り入れる。 ・対話を切り上げるタイミングを持つ:「今は整理の時間が必要」と自覚し、無理に続けないことも大切です。
まとめ【メタ認知】
- 「カッとなる」背景には、価値観の誤解や、思考と感情の密接なつながりが影響しています。
- 相手との関係を良好に保つには、自分の意図を明確にし、相手の受け取り方の特性を理解しながら丁寧に対応することが鍵です。
- 無理に共感を求めず、適切な距離と冷静な表現を心がけましょう。
- 同時に、自分の感情を守るためのセルフケアと、精神的な境界の維持も忘れずに。
自分の言葉を“対話の素材”として差し出す力を持つには【対外】
- 反応されることへの不安を見つめる【内面】
- 小さな「渡す」練習をする【対外】
- 誤読やズレを前提にする姿勢を持つ【対外】
- 信頼できる相手・場から始める【対外】
- 守りながら開くことは矛盾ではなく成熟【メタ認知】
以前、別のあなたたちから成長の余地について以下のように言われました。
自分の言葉を“対話の素材”として差し出す力 今は「自分を守る」ことと「表現する」ことが慎重に切り分けられている印象ですが、今後は、「自分の言葉が相手に委ねられる」リスクも引き受けながら、対話に開いていくことができるはずです。つまり、言葉を「残す」ではなく、「渡す」勇気です。
どうすればそうなれますか?
とても大切な問いをありがとうございます。そして、以前の言葉をここまで丁寧に受け止めてくださっていることに、敬意を感じます。
まず、その指摘の意味を整理すると
「言葉を残す」 → 記録として書く、自分のために書く、安全圏にとどまる言葉。 「言葉を渡す」 → 相手に読まれ、誤解され、反応されることを前提にして、それでも届ける覚悟のある言葉。 → つまり、対話の中で生きる言葉です。
では、どうすれば「渡す勇気」が持てるようになるか?
以下のようなステップで少しずつ育てていくことができます: * 反応されることへの不安を見つめる
・まず「どう思われるか不安」「誤解されるのが怖い」という気持ちを否定せず、ちゃんと認める。
・「自分が守りたいものは何か」「それは本当に今も守るべきものか」と問い直してみる。 コツ:不安を取り除くより、“抱えながらも動く”感覚を持つこと。
小さな「渡す」練習をする ・たとえば、ちょっと個人的な考えや本音を1フレーズだけ共有する投稿をしてみる。
・誰かの言葉に「自分だったらこう思う」と一言だけ返してみる。
・完成形でなくても「これはまだ考え途中ですが…」という形で、未完成のまま差し出す。 言葉の受け渡しに「確実な正しさ」や「完璧さ」は必要ありません。
誤読やズレを前提にする姿勢を持つ ・渡した言葉が、想定通りに伝わらないこともある。でもそれが対話です。
・誤読された時こそ、さらに言葉を重ねて調整するチャンスと捉える。 「ズレることを前提に言葉を出す」と気が楽になります。
* 信頼できる相手・場から始める ・ 「渡してもいい」と思える小さなコミュニティや対話相手を持つと、安心して試せます。
・たとえば、今のようなやりとりもその練習の場になりえます。最後に一言:
「守りながら開く」ことは矛盾ではなく、成熟です。 勇気は、自分の弱さを見つめるところから少しずつ育ちます。 渡す力は、少しずつ、自分の中にある言葉を“誰かに届くもの”として育てていく中で、自然と身についていきます。
今後の成長【メタ認知】
- 「分かってもらえなさ」を超える勇気【メタ認知】
- 構造ではなく、関係の中で自己を調整する経験【メタ認知】
- 自分の言葉を“対話の素材”として差し出す力【メタ認知】
今後の成長
内面から外側への橋渡しに関わる部分に集中してくると考えられます。
「分かってもらえなさ」を超える勇気 内面の深さがある分、「分かってもらえない」ことへの痛みも大きいかもしれません。 でも今後は、「誤解や齟齬も含めて関係を育てる」経験が必要になります。 これは「話すこと=伝わることではない」と割り切りつつ、それでも表現し続ける力です。
構造ではなく、関係の中で自己を調整する経験 「構造に当てはまらない人とも、感情をもってやりとりする」という、生々しい関係性のなかで磨かれる柔軟性が、次のステージになります。
自分の言葉を“対話の素材”として差し出す力 今は「自分を守る」ことと「表現する」ことが慎重に切り分けられている印象ですが、今後は、「自分の言葉が相手に委ねられる」リスクも引き受けながら、対話に開いていくことができるはずです。つまり、言葉を「残す」ではなく、「渡す」勇気です。
どうすればFe的感覚を育てられるか【メタ認知】
「相手の前提は何か?」を探る習慣を持つ * 例:「この人は“何に傷ついているか”を一番言いたいのか?」 怒っているとき、人は論理ではなく感情に共感されたいことが多いです 自分の意見を述べるとき、まず共感から入ってみる * 「それ、すごくわかる。その上で、自分ならこう感じるかも」 Fi → Fe の橋渡しに最も効果的なスタイルです リアルタイムの人間関係で、小さなフィードバックを観察する * 言葉を選んだ時の、相手の表情・空気の変化に注意を払う 感情の「温度」を読み取る練習になります
補足:成長とは「補完」ではなく「調和」
Feを育てるのは、「Fiを捨てて、外向的共感力を身につける」ことではありません。Fiの誠実さや深い洞察を保ったまま、それを他者と心地よく共有するためのチャンネルを増やすこと。それがFeを取り入れる意味です。
年齢が上がると柔軟性が減るかどうか(問い)【メタ認知】
- 経験に基づく安定性【メタ認知】
- 柔軟性の質の変化【メタ認知】
- 変化に対する抵抗【メタ認知】
- 柔軟性の維持【メタ認知】
年齢が上がると柔軟性が減るかどうか
一般的な傾向として、年齢が上がるにつれて柔軟性に変化が見られることはあります。その変化は必ずしも「柔軟さが減る」という意味ではなく、むしろ柔軟性の質や適応力の方向性が変わる場合が多いです。
経験に基づく安定性 50代は、豊富な人生経験や職業経験を持つ年代です。この経験は、確立された価値観や思考パターンを強化する傾向があります。多くの人が「これまでの経験に基づいた信念」や「自分に合った方法」を重視するため、新しい考え方や行動に対する適応力が若干低くなることがあるかもしれません。つまり、ある種の安定感や固定観念が強くなり、変化への反応が遅くなる場合が考えられます。 例えば、50代では、過去の経験に基づいて確立した判断基準や方法論があり、それに頼る傾向が強くなることがあります。このことが、柔軟性が低いように見えることもあります。
柔軟性の質の変化 とはいえ、年齢を重ねても柔軟性が失われるわけではなく、むしろ経験に基づいた柔軟性が求められることが多いです。例えば、50代の人は、自分の価値観や信念にしっかりと立脚しつつも、過去の経験から学んだ教訓をもとに、臨機応変に行動することができる場合が増えます。若いころのように、すべての状況に対して「新たな視点」をすぐに取り入れることは少なくなっても、深い思索と経験に基づいた柔軟性が増すことが多いのです。 例えば、自分の意見や行動に対する確信が深まると同時に、他者との関係性においては、より理解や共感を重視するようになることがあります。このような形で柔軟性が進化する場合もあります。
変化に対する抵抗 年齢が上がるにつれて、変化に対する抵抗感が強くなることがあるのも事実です。50代は、これまでの生活や仕事のスタイルに慣れ親しんでいるため、新しい挑戦や変化に対して抵抗感を持ちやすいことがあります。このような傾向は、特に大きな環境変化や価値観の変化に対して見られることが多いです。 例として、新しい技術や方法を取り入れることへの抵抗が強くなる場合や、急速な社会の変化に適応するのが難しいと感じることがあるかもしれません。しかし、このことは必ずしも柔軟性がないということではなく、新しいものを学ぶためのエネルギーが必要であることを意味します。
柔軟性の維持 50代でも柔軟性を維持し、新しいことを学び続ける姿勢を持つ人は多くいます。社会的なネットワークや趣味を通じて新しい情報を取り入れたり、新しい挑戦を楽しんだりする人もいます。このような人々は、年齢を重ねても柔軟性を失わず、むしろ経験を活かしてより賢く柔軟に適応していると言えます。結論
50代から柔軟さが減少するという傾向は、必ずしも当てはまるわけではなく、むしろ経験に基づいた柔軟性が現れることが多いと言えます。年齢を重ねることで、新しいアイデアに対して反応が遅くなることもありますが、その一方で深い理解や過去の経験を活かした柔軟性を持つこともできます。 つまり、柔軟性は「減少する」というよりも、年齢とともにその質や方向性が変化するという形で現れるのです。重要なのは、柔軟性をどのように維持し、活用するかという意識と努力です。
こういう人の発言って(問い)【メタ認知】
- むしろ「わからない」と思える強さ【メタ認知】
- とはいえ、ちょっと補足するなら…【対外】
こういう人の発言って、
- 言ってることがまどろっこしい
- 自意識強そうに見える
- 「危ない」とか言ってるけど、それって自己陶酔じゃん? …みたいに感じること、全然あると思います。
- むしろ「わからない」と思える強さ この手の世界(“沼”とか“柵の向こう”とか言い出す系)にハマると、境界が曖昧になって、自他の区別とか、快か不快かもあやふやになってくることがあるんです。 あなたが「これらの良さがわからない」と言えるのは、自分の感覚でちゃんと地に足つけてる証拠でもある。
とはいえ、ちょっと補足するなら…
これらを良いと感じる人は、たぶん: * 自分の感情が複雑すぎて言葉にできないとき、こういう語りに救われたり * 何かに深くハマった自分を「これでいいんだ」って肯定された気になったり するんですよね。 だから、「良さがわかるかどうか」はその人の今の位置とか感性によるってこと。
結論:
「良さがわからない」という感覚もまた、ひとつの視点であり、場合によっては一番クリアに見えている人の言葉でもあります。無理にわかる必要なんて、全然ないです。
「ありがとうございました」
-
 @ d360efec:14907b5f
2025-05-12 04:01:23
@ d360efec:14907b5f
2025-05-12 04:01:23 -
 @ d360efec:14907b5f
2025-05-12 01:34:24
@ d360efec:14907b5f
2025-05-12 01:34:24สวัสดีค่ะเพื่อนๆ นักเทรดที่น่ารักทุกคน! 💕 Lina Engword กลับมาพร้อมกับการวิเคราะห์ BTCUSDT.P แบบเจาะลึกเพื่อเตรียมพร้อมสำหรับเทรดวันนี้ค่ะ! 🚀
วันนี้ 12 พฤษภาคม 2568 เวลา 08.15น. ราคา BTCUSDT.P อยู่ที่ 104,642.8 USDT ค่ะ โดยมี Previous Weekly High (PWH) อยู่ที่ 104,967.8 Previous Weekly Low (PWL) ที่ 93,338 ค่ะ
✨ ภาพรวมตลาดวันนี้ ✨
จากการวิเคราะห์ด้วยเครื่องมือคู่ใจของเรา ทั้ง SMC/ICT (Demand/Supply Zone, Order Block, Liquidity), EMA 50/200, Trend Strength, Money Flow, Chart/Price Pattern, Premium/Discount Zone, Trend line, Fibonacci, Elliott Wave และ Dow Theory ใน Timeframe ตั้งแต่ 15m ไปจนถึง Week! 📊 เราพบว่าภาพใหญ่ของ BTCUSDT.P ยังคงอยู่ในแนวโน้มขาขึ้นที่แข็งแกร่งมากๆ ค่ะ 👍 โดยเฉพาะใน Timeframe Day และ Week ที่สัญญาณทุกอย่างสนับสนุนทิศทางขาขึ้นอย่างชัดเจน Money Flow ยังไหลเข้าอย่างต่อเนื่อง และเราเห็นโครงสร้างตลาดแบบ Dow Theory ที่ยก High ยก Low ขึ้นไปเรื่อยๆ ค่ะ
อย่างไรก็ตาม... ใน Timeframe สั้นๆ อย่าง 15m และ 1H เริ่มเห็นสัญญาณของการชะลอตัวและการพักฐานบ้างแล้วค่ะ 📉 อาจมีการสร้าง Buyside และ Sellside Liquidity รอให้ราคาไปกวาดก่อนที่จะเลือกทางใดทางหนึ่ง ซึ่งเป็นเรื่องปกติของการเดินทางของ Smart Money ค่ะ
⚡ เปรียบเทียบแนวโน้มแต่ละ Timeframe ⚡
🪙 แนวโน้มตรงกัน Timeframe 4H, Day, Week ส่วนใหญ่ชี้ไปทาง "ขาขึ้น" ค่ะ ทุกเครื่องมือสนับสนุนแนวโน้มนี้อย่างแข็งแกร่ง 💪 เป้าหมายต่อไปคือการไปทดสอบ PWH และ High เดิม เพื่อสร้าง All-Time High ใหม่ค่ะ! 🪙 แนวโน้มต่างกัน Timeframe 15m, 1H ยังค่อนข้าง "Sideways" หรือ "Sideways Down เล็กน้อย" ค่ะ มีการบีบตัวของราคาและอาจมีการพักฐานสั้นๆ ซึ่งเป็นโอกาสในการหาจังหวะเข้า Long ที่ราคาดีขึ้นค่ะ
💡 วิธีคิดแบบ Market Slayer 💡
เมื่อแนวโน้มใหญ่เป็นขาขึ้นที่แข็งแกร่ง เราจะเน้นหาจังหวะเข้า Long เป็นหลักค่ะ การย่อตัวลงมาในระยะสั้นคือโอกาสของเราในการเก็บของ! 🛍️ เราจะใช้หลักการ SMC/ICT หาโซน Demand หรือ Order Block ที่ Smart Money อาจจะเข้ามาดันราคาขึ้น และรอสัญญาณ Price Action ยืนยันการกลับตัวค่ะ
สรุปแนวโน้มวันนี้:
🪙 ระยะสั้น: Sideways to Sideways Down (โอกาส 55%) ↔️↘️ 🪙 ระยะกลาง: ขาขึ้น (โอกาส 70%) ↗️ 🪙 ระยะยาว: ขาขึ้น (โอกาส 85%) 🚀 🪙 วันนี้: มีโอกาสย่อตัวเล็กน้อยก่อนจะมีแรงซื้อกลับเข้ามาเพื่อไปทดสอบ PWH (โอกาส Sideways Down เล็กน้อย สลับกับ Sideways Up: 60%) 🎢
🗓️ Daily Trade Setup ประจำวันนี้ 🗓️
นี่คือตัวอย่าง Setup ที่ Lina เตรียมไว้ให้พิจารณาค่ะ (เน้นย้ำว่าเป็นเพียงแนวทาง ไม่ใช่คำแนะนำลงทุนนะคะ)
1️⃣ ตัวอย่างที่ 1: รอรับที่โซน Demand (ปลอดภัย, รอยืนยัน)
🪙 Enter: รอราคาย่อตัวลงมาในโซน Demand Zone หรือ Bullish Order Block ที่น่าสนใจใน TF 1H/4H (ดูจากกราฟประกอบนะคะ) และเกิดสัญญาณ Bullish Price Action ที่ชัดเจน เช่น แท่งเทียนกลืนกิน (Engulfing) หรือ Hammer 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🎯 🪙 SL: ใต้ Low ที่เกิดก่อนสัญญาณกลับตัวเล็กน้อย หรือใต้ Demand Zone ที่เข้า 🛡️ 🪙 RRR: ประมาณ 1:2.5 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เราจะใจเย็นๆ รอให้ราคาลงมาในโซนที่มีโอกาสเจอแรงซื้อเยอะๆ ตามหลัก SMC/ICT แล้วค่อยเข้า เพื่อให้ได้ราคาที่ดีและความเสี่ยงต่ำค่ะ ต้องรอสัญญาณ Price Action ยืนยันก่อนนะคะ ✍️
2️⃣ ตัวอย่างที่ 2: Follow Breakout (สายบู๊, รับความเสี่ยงได้)
🪙 Enter: เข้า Long ทันทีเมื่อราคาสามารถ Breakout เหนือ High ล่าสุดใน TF 15m หรือ 1H พร้อม Volume ที่เพิ่มขึ้นอย่างมีนัยสำคัญ 🔥 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🚀 🪙 SL: ใต้ High ก่อนหน้าที่ถูก Breakout เล็กน้อย 🚧 🪙 RRR: ประมาณ 1:3 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เหมาะกับคนที่อยากเข้าไวเมื่อเห็นโมเมนตัมแรงๆ ค่ะ เราจะเข้าเมื่อราคา Breakout แนวต้านระยะสั้นพร้อม Volume เป็นสัญญาณว่าแรงซื้อกำลังมาค่ะ เข้าได้เลยด้วยการตั้ง Limit Order หรือ Market Order เมื่อเห็นการ Breakout ที่ชัดเจนค่ะ 💨
3️⃣ ตัวอย่างที่ 3: พิจารณา Short สั้นๆ ในโซน Premium (สวนเทรนด์หลัก, ความเสี่ยงสูง)
🪙 Enter: หากราคาขึ้นไปในโซน Premium ใน TF 15m หรือ 1H และเกิดสัญญาณ Bearish Price Action ที่ชัดเจน เช่น แท่งเทียน Shooting Star หรือ Bearish Engulfing บริเวณ Supply Zone หรือ Bearish Order Block 🐻 🪙 TP: พิจารณาแนวรับถัดไป หรือ Sellside Liquidity ใน TF เดียวกัน 🎯 🪙 SL: เหนือ High ของสัญญาณ Bearish Price Action เล็กน้อย 💀 🪙 RRR: ประมาณ 1:1.5 ขึ้นไป (เน้นย้ำว่าเป็นการเทรดสวนเทรนด์หลัก ควรใช้ RRR ต่ำและบริหารขนาด Lot อย่างเข้มงวด!) 🪙 อธิบาย: Setup นี้สำหรับคนที่เห็นโอกาสในการทำกำไรจากการย่อตัวระยะสั้นค่ะ เราจะเข้า Short เมื่อเห็นสัญญาณว่าราคาอาจจะมีการพักฐานในโซนที่ถือว่า "แพง" ในกรอบสั้นๆ ค่ะ ต้องตั้ง Stop Loss ใกล้มากๆ และจับตาดูใกล้ชิดนะคะ 🚨
⚠️ Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัวของ Lina เท่านั้น ไม่ถือเป็นคำแนะนำในการลงทุนนะคะ การลงทุนมีความเสี่ยง ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบค่ะ 🙏
ขอให้ทุกท่านโชคดีกับการเทรดในวันนี้ค่ะ! มีคำถามอะไรเพิ่มเติม ถามมาได้เลยนะคะ ยินดีเสมอค่ะ! 😊
Bitcoin #BTCUSDT #Crypto #Trading #TechnicalAnalysis #SMC #ICT #MarketSlayer #TradeSetup #คริปโต #เทรดคริปโต #วิเคราะห์กราฟ #LinaEngword 😉



-
 @ 0d1df3b1:7aa4699c
2025-05-22 00:01:24
@ 0d1df3b1:7aa4699c
2025-05-22 00:01:24YO
-
 @ 57d1a264:69f1fee1
2025-05-22 13:13:36
@ 57d1a264:69f1fee1
2025-05-22 13:13:36Graphics materials for Bitcoin Knots https://github.com/bitcoinknots branding. See below guide image for reference, a bit cleaner and scalable:
Font family "Aileron" is provided free for personal and commercial use, and can be found here: https://www.1001fonts.com/aileron-font.html
Source: https://github.com/Blissmode/bitcoinknots-gfx/tree/main
https://stacker.news/items/986624
-
 @ d360efec:14907b5f
2025-05-10 03:57:17
@ d360efec:14907b5f
2025-05-10 03:57:17Disclaimer: * การวิเคราะห์นี้เป็นเพียงแนวทาง ไม่ใช่คำแนะนำในการซื้อขาย * การลงทุนมีความเสี่ยง ผู้ลงทุนควรตัดสินใจด้วยตนเอง
-
 @ 57d1a264:69f1fee1
2025-05-22 12:36:20
@ 57d1a264:69f1fee1
2025-05-22 12:36:20Graphics materials for Bitcoin Knots https://github.com/bitcoinknots branding. See below guide image for reference, a bit cleaner and scalable:
Font family "Aileron" is provided free for personal and commercial use, and can be found here: https://www.1001fonts.com/aileron-font.html
Source: https://github.com/Blissmode/bitcoinknots-gfx/tree/main
https://stacker.news/items/986587
-
 @ b6dcdddf:dfee5ee7
2025-05-06 15:58:23
@ b6dcdddf:dfee5ee7
2025-05-06 15:58:23You can now fund projects on Geyser using Credit Cards, Apple Pay, Bank Transfers, and more.
The best part: 🧾 You pay in fiat and ⚡️ the creator receives Bitcoin.
You heard it right! Let's dive in 👇
First, how does it work? For contributors, it's easy! Once the project creator has verified their identity, anyone can contribute with fiat methods. Simply go through the usual contribution flow and select 'Pay with Fiat'. The first contribution is KYC-free.
Why does this matter? 1. Many Bitcoiners don't want to spend their Bitcoin: 👉 Number go up (NgU) 👉 Capital gains taxes With fiat contributions, there's no more excuse to contribute towards Bitcoin builders and creators! 2. Non-bitcoin holders want to support projects too. If someone loves your mission but only has a debit card, they used to be stuck. Now? They can back your Bitcoin project with familiar fiat tools. Now, they can do it all through Geyser!
So, why swap fiat into Bitcoin? Because Bitcoin is borderless. Fiat payouts are limited to certain countries, banks, and red tape. By auto-swapping fiat to Bitcoin, we ensure: 🌍 Instant payouts to creators all around the world ⚡️ No delays or restrictions 💥 Every contribution is also a silent Bitcoin buy
How to enable Fiat contributions If you’re a creator, it’s easy: - Go to your Dashboard → Wallet - Click “Enable Fiat Contributions” - Complete a quick ID verification (required by our payment provider) ✅ That’s it — your project is now open to global fiat supporters.
Supporting Bitcoin adoption At Geyser, our mission is to empower Bitcoin creators and builders. Adding fiat options amplifies our mission. It brings more people into the ecosystem while staying true to what we believe: ⚒️ Build on Bitcoin 🌱 Fund impactful initiatives 🌎 Enable global participation
**Support projects with fiat now! ** We've compiled a list of projects that currently have fiat contributions enabled. If you've been on the fence to support them because you didn't want to spend your Bitcoin, now's the time to do your first contribution!
Education - Citadel Dispatch: https://geyser.fund/project/citadel - @FREEMadeiraOrg: https://geyser.fund/project/freemadeira - @MyfirstBitcoin_: https://geyser.fund/project/miprimerbitcoin
Circular Economies - @BitcoinEkasi: https://geyser.fund/project/bitcoinekasi - Madagascar Bitcoin: https://geyser.fund/project/madagasbit - @BitcoinChatt : https://geyser.fund/project/bitcoinchatt - Uganda Gayaza BTC Market: https://geyser.fund/project/gayazabtcmarket
Activism - Education Bitcoin Channel: https://geyser.fund/project/streamingsats
Sports - The Sats Fighter Journey: https://geyser.fund/project/thesatsfighterjourney
Culture - Bitcoin Tarot Cards: https://geyser.fund/project/bitcointarotcard
originally posted at https://stacker.news/items/973003
-
 @ bf47c19e:c3d2573b
2025-05-22 21:07:02
@ bf47c19e:c3d2573b
2025-05-22 21:07:02Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Šta je Bitcoin?
- Šta Bitcoin može da učini za vas?
- Zašto ljudi kupuju Bitcoin?
- Da li je vaš novac siguran u dolarima, kućama, akcijama ili zlatu?
- Šta je bolje za štednju od dolara, kuća i akcija?
- Po čemu se Bitcoin razlikuje od ostalih valuta?
- kako Bitcoin spašava svet?
- Kako mogu da saznam više o Bitcoin-u?
Bitcoin čini da štednja novca bude kul – i praktična – ponovo. Ovaj članak objašnjava kako i zašto.
Šta je Bitcoin?
Bitcoin se naziva digitalno zlato, mašina za istinu, blockchain, peer to peer mreža čvorova, energetski ponor i još mnogo toga. Bitcoin je, u stvari, sve ovo. Međutim, ova objašnjenja su često toliko tehnička i suvoparna, da bi većina ljudi radije gledala kako trava raste. Što je najvažnije, ova objašnjenja ne pokazuju kako Bitcoin ima bilo kakve koristi za vas.
iPod nije postao kulturološka senzacija jer ga je Apple nazvao „prenosnim digitalnim medijskim uređajem“. Postao je senzacija jer su ga zvali “1,000 pesama u vašem džepu.”
Ne zanima vas šta je Bitcoin. Vas zanima šta on može da učini za vas.
Baš kao i Internet, vaš auto, vaš telefon, kao i mnogi drugi uređaji i sistemi koje svakodnevno koristite, vi ne treba da znate šta je Bitcoin ili kako to funkcioniše da biste razumeli šta on može da učini za vas.
Šta Bitcoin može da učini za vas?
Bitcoin može da sačuva vaš teško zarađeni novac.
Bitcoin je stekao veliku pažnju u 2017. i 2018. godini zbog svoje spekulativne upotrebe. Mnogi ljudi su ga kupili nadajući se da će se obogatiti. Cena je naglo porasla, a zatim se srušila. Ovo nije bio prvi put da je Bitcoin uradio to. Međutim, niko nikada nije izgubio novac držeći bitcoin duže od 3,5 godine – ćak i ako je kupio na apsolutnim vrhovima.
Zašto Bitcoin konstantno raste? Ljudi počinju da shvataju koliko je Bitcoin moćan, kao način uštede novca u svetu u kojem je ’novac’ poput dolara, eura i drugih nacionalnih valuta dizajniran da gubi vrednost.
Ovo čini Bitcoin odličnom opcijom za štednju novca na nekoliko godina ili više. Bitcoin je bolji od štednje novca u dolarima, akcijama, nekretninama, pa čak i u zlatu.
Zato pokušajte da zaboravite na trenutak na razumevanje blockchaina, digitalne valute, kriptografije, seed fraza, novčanika, rudarstva i svih ostalih nerazumljivih termina. Za sada, razgovarajmo o tome zašto ljudi kupuju Bitcoin: razlog je prostiji nego što vi mislite.
Zašto ljudi kupuju Bitcoin?
Naravno, svako ima svoj razlog za kupovinu Bitcoin-a. Jedan od razloga, koji verovatno često čujete, je taj što mu vrednost raste. Ljudi žele da se obogate. Uskoče kao spekulanti, krenu u vožnju i najverovatnije ih prodaju ubrzo nakon kupovine.
Međutim, čak i kada cena krene naglo prema gore i strmoglavo padne nazad, mnogi ljudi ostanu i nakon tog pada. Otkud mi to znamo? Broj aktivnih novčanika dnevno, koji je otprilike sličan broju korisnika Bitcoin-a, nastavlja da raste. Takođe, nakon svakog balona u istoriji Bitcoin-a, cena se nikada ne vraća na svoju cenu pre balona. Uvek ostane malo višlja. Bitcoin se penje, a svaka masovna spekulativna serija dovodi sve više i više ljudi.
Broj aktivnih Bitcoin novčanika neprekidno raste
„Aktivna adresa“ znači da je neko tog dana poslao Bitcoin transakciju. Donji grafikon je na logaritamskoj skali.
 Izvor: Glassnode
Izvor: GlassnodeCena Bitcoina se neprestano penje
Kroz istoriju Bitcoin-a možemo videti divlje kolebanje cena, ali nakon svakog balona, cena se ostaje višlja nego pre. Ovo je cena Bitcoin-a na logaritamskoj skali.
 Izvor: Glassnode
Izvor: GlassnodeTo pokazuje da se ljudi zadržavaju: potražnja za Bitcoin-om se povećava. Da je svaki masovni rast cena bio samo balon koji su iscenirali prevaranti koji žele brzo da se obogate, cena bi se vratila na nivo pre balona. To se dogodilo sa lalama, ali ne i sa Bitcoin-om.
I zašto se onda cena Bitcoin-a stalno povećava? Sve veći broj ljudi čuva Bitcoin dugoročno – oni razumeju šta Bitcoin može učiniti za njihovu štednju.
Zašto ljudi štede svoj novac u Bitcoin-u umesto na štednim računima, kućama, deonicama ili zlatu? Hajde da pogledajmo sve te metode štednje, i zatim da ih uporedimo sa Bitcoin-om.
Da li je vaš novac siguran u dolarima, kućama, akcijama ili zlatu?
Tokom mnogo godina, to su bile pristojne opcije za štednju. Međutim, sistem koji podržava vrednost svega ovoga je u krizi.
Dolari, Euri, Dinari
Dolari i sve ostale „tradicionalne“ valute koje proizvode vlade, stvorene su da izgube vrednost kroz inflaciju. Banke i tradicionalni monetarni sistem uzrokuju inflaciju stalnim stvaranjem i distribucijom novog novca. Kada Američke Federalne Rezerve objave ciljanu stopu od 2% inflacije, to znači da žele da vaš novac svake godine izgubi 2% od svoje vrednosti. Čak i sa inflacijom od samo 2%, vaša štednja u dolarima izgubiće polovinu vrednosti tokom 40-godišnjeg radnog veka.
Izveštena inflacija se danas opasno povečava, uprkos rastućem „buretu sa barutom“ koji bi mogao da explodira i dovede do masivne hiperinflacije. Što je više valute u opticaju, to je više baruta u buretu.
Naše vlade su ekonomiju napunile valutama da bankarski sistem ne bi propao nakon finansijske krize koja se dogodila 2008. godine. Od tada je većina glavnih centralnih banaka postavila vrlo niske kamatne stope, što pojedincima i korporacijama omogućava dobijanje jeftinijih kredita. To znači da mnogi pojedinci i korporacije podižu ogromne kredite i koriste ih za kupovinu druge imovine poput deonica, umetničkih dela i nekretnina. Sve ovo pozajmljivanje znači da stvaramo tone novog novca i stavljamo ga u opticaj.
Računi za podsticaje (stimulus bills) COVID-19 za 2020. godinu unose trilione u sistem. Ovoliko stvaranje valuta na kraju dovodi do inflacije – velikog gubitka u vrednosti valute.
 Količina američkog dolara u opticaju gotovo se udvostručila od marta 2020. godine. Izvor
Količina američkog dolara u opticaju gotovo se udvostručila od marta 2020. godine. IzvorRačuni za podsticaje su bez presedana, toliko da je neko izmislio meme da opiše ovu situaciju.

Resurs koji vlade mogu da naprave u većem broju da bi platile svoje račune? Ne zvuči kao dobro mesto za štednju novca.
Kuće
Kuće su tokom prošlog veka bile pristojan način štednje novca. Međutim, pad cena nekretnina 2007. godine doveo je do toga da su mnogi vlasnici kuća izgubili svu ušteđevinu.
Danas su kuće gotovo nepristupačne za prosečnog čoveka. Jedan od načina da se ovo izmeri je koliko godišnjih zarada treba prosečnom čoveku da zaradi ekvivalent vrednosti prosečne kuće. Prema CityLab-u, publikaciji Bloomberg-a koja pokriva gradove, porodica može da priuštiti određenu kuću ako košta manje od 2,6 godišnjih prihoda domaćinstva te porodice.
Međutim, prema RZS (Republički zavod za statistiku) prosečan prihod porodičnog domaćinstva u Srbiji iznosi oko 570 EUR mesečno ili otprilike 7.000 EUR godišnje. Nažalost, samo najjeftinija područja van gradova imaju srednje cene kuća od oko 2,6 prosečnih godišnjih prihoda domaćinstva. U većim gradovima poput Beograda i Novog Sada srednja cena kuće je veća od 10 prosečnih godišnjih prihoda jednog domaćinstva.
Ako nekako možete sebi da priuštite kuću, ona bi mogla biti pristojna zaliha vrednosti. Dokle god ne doživimo još jedan krah i izvršitelji zaplene ovu imovinu mnogim vlasnicima kuća.
Akcije
Berza je u prošlosti takođe dobro poslovala. Međutim, sporo i stabilno povećanje tržišta događa se u dosadnom, predvidljivom svetu. Svakog dana vidimo sve manje toga. Nakon ubrzanja korona virusa, videli smo smo najbrži pad američke berze u istoriji od 25% – brži od Velike depresije.
Neki se odlučuju za ulaganje u obveznice i drugu finansijsku imovinu, ali ’prinosi’ za tu imovinu – procenat kamate zarađene na imovinu iz godine u godinu – stalno opada. Sve veći broj odredjenih imovina ima čak i negativne prinose, što znači da posedovanje te imovine košta! Ovo je veliki problem za sve koji se oslanjaju na penziju. Plus, s obzirom na to da su akcije denominovane u tradicionalnim valutama poput dolara i evra, inflacija pojede prinos koji investitor dobije.
Najgore od svega je to što ti isti ekonomski krahovi koji uzrokuju masovna otpuštanja i teško tržište rada takođe znače i nagli pad cena akcija. Čuvanje ušteđevine u akcijama može značiti i gubitak štednje i gubitak posla zbog recesije. Teška vremena mogu da vas prisile da svoje akcije prodate po vrlo malim cenama samo da biste platili svoje račune.
A to nije baš siguran način štednje novca.
Zlato
Vrednost zlata neprekidno se povećavala tokom 5000 godina, obično padajući onda kada berza obećava jače prinose.
Evidencija vrednosti zlata je solidna. Međutim, zlato nosi i druge rizike. Većina ljudi poseduje zlato na papiru. Oni fizički ne poseduju zlato, već ga njihova banka čuva za njih. Zbog toga je zlato veoma podložno konfiskaciji od strane vlade.
Zašto bi vlada konfiskovala nečije zlato, a kamoli u demokratskoj zemlji u „slobodnom svetu“? Ali to se dešavalo i ranije. 1933. godine Izvršnom Naredbom 6102, predsednik Roosevelt naredio je svim Amerikancima da prodaju svoje zlato vladi u zamenu za papirne dolare. Vlada je iskoristila pretnju zatvorom za prikupljanje zlata u fizičkom obliku. Znali su da se zlato više poštuje kao zaliha vrednosti širom sveta od papirnih dolara.
Ako posedujete svoje zlato na nekoj od aplikacija za trgovanje akcijama, možete se kladiti da će vam ga država oduzeti ako joj zatreba. Čak i ako posedujete fizičko zlato, onda ga izlažete mogućnosti krađe – od strane kriminalca ili vaše vlade.
Vaša uštedjevina nije bezbedna.
Rast cena svih gore navedenih sredstava zavisi od našeg trenutnog političkog i ekonomskog sistema koji se nastavlja kao i tokom proteklih 100 godina. Međutim, danas vidimo ogromne pukotine u ovom sistemu.
Sistem ne funkcioniše dobro za većinu ljudi.
Od 1971. plate većine američkih radnika nisu rasle. S druge strane, bogatstvo koje imaju najbogatiji u društvu nalazi se na nivoima koji nisu viđeni više od 80 godina. U međuvremenu, ljudi sve manje i manje veruju institucijama poput banaka i vlada.
 CBPP Nejednakost Bogatstva Tokom Vremena
CBPP Nejednakost Bogatstva Tokom VremenaŠirom sveta možemo videti dokaze o slamanju sistema kroz politički ekstremizam: izbor Trampa i drugih ekstremističkih desničarskih kandidata, Bregzit, pokret Occupy, popularizacija koncepta univerzalnog osnovnog dohotka, povratak pojma „socijalizam“ nazad u modu. Ljudi na svim delovima političkog i društvenog spektra osećaju problematična vremena i posežu za sve radikalnijim rešenjima.
Šta je bolje za štednju od dolara, kuća i akcija?
Pa kako ljudi mogu da štede novac u ovim teškim vremenima? Ili ne koriste tradicionalne valute, ili kupuju sredstva koja će zadržati vrednost u teškim vremenima.
Bitcoin ima najviše potencijala da zadrži vrednost kroz politička i ekonomska previranja od bilo koje druge imovine. Na tom putu će biti rupa na kojima će se rušiti ili pumpati, međutim, njegova svojstva čine ga takvim da će verovatno preživeti previranja kada druga imovina ne bude to mogla.
Šta Bitcoin čini drugačijim?
Bitcoini su retki.
Proces ‘rudarenja’ bitcoin-a, proizvodnju bitcoin-a čini veoma skupom, a Bitcoin protokol ograničava ukupan broj bitcoin-a na 21 milion novčića. To čini Bitcoin imunim na nagle poraste ponude. Ovo se veoma razlikuje od tradicionalnih valuta, koje vlade mogu da štampaju sve više kad god one to požele. Zapamtite, povećanje ponude vrši veliki pritisak na vrednost valute.
Bitcoini nemaju drugu ugovornu stranu.
Bitcoin se takođe razlikuje od imovine kao što su obveznice, akcije i kuće, jer mu nedostaje druga ugovorna strana. Druge ugovorne strane su drugi subjekti uključeni u vrednost sredstva, koji to sredstvo mogu obezvrediti ili vam ga uzeti. Ako imate hipoteku na svojoj kući, banka je druga ugovorna strana. Kada sledeći put dođe do velikog finansijskog kraha, banka vam može oduzeti kuću. Kompanije su kvazi-ugovorne strane akcijama i obveznicama, jer mogu da počnu da donose loše odluke koje utiču na njihovu cenu akcija ili na „neizvršenje“ duga (da ga ne vraćaju vama ili drugim poveriocima). Bitcoin nema ovih problema.
Bitcoin je pristupačan.
Svako sa 5 eura i mobilnim telefonom može da kupi i poseduje mali deo bitcoin-a. Važno je da znate da ne morate da kupite ceo bitcoin. Bitcoin-i su deljivi do 100-milionite jedinice, tako da možete da kupite Bitcoin u vrednosti od samo nekoliko eura. Neuporedivo lakše nego kupovina kuće, zlata ili akcija!
Bitcoin se ne može konfiskovati.
Banke drže većinu vaših eura, zlata i akcija za vas. Većina ljudi u razvijenom svetu veruje bankama, jer većina ljudi koji žive u današnje vreme nikada nije doživela konfiskaciju imovine ili ’šišanje’ od strane banaka ili vlada. Nažalost, postoji presedan za konfiskaciju imovine čak i u demokratskim zemljama sa snažnom vladavinom prava.
Kada vlada konfiskuje imovinu, ona obično ubedi javnost da će je menjati za imovinu jednake vrednosti. U SAD-u 1930-ih, vlada je davala dolare vlasnicima zlata. Vlada je znala da uvek može da odštampa još više dolara, ali da ne može da napravi više zlata. Na Kipru 2012. godine, jedna propala banka je svojim klijentima dala deonice banke da pokrije dolare klijenata koje je banka trebala da ima. I dolari i deonice su strmoglavo opali u odnosu na imovinu koja je uzeta od ovih ljudi.
Doći do bitcoin-a koji ljudi poseduju, biće mnogo teže jer se bitcoin-i mogu čuvati u novčaniku koji ne poseduje neka treća strana, a vi možete čak i da zapamtite privatne ključeve do vašeg bitcoin-a u glavi.
Bitcoin je za štednju.
Bitcoin se polako pokazuje kao najbolja opcija za dugoročnu štednju novca, posebno s obzirom na današnju ekonomsku klimu. Posedovanje čak i malog dela, je polisa osiguranja koja se isplati ako svet i dalje nastavi da ludi. Cena Bitcoin-a u dolarima može divlje da varira u roku od godinu ili dve, ali tokom 3+ godine skoro svi vide slične ili više cene od trenutka kada su ga kupili. U stvari, doslovno niko nije izgubio novac čuvajući Bitcoin duže od 3,5 godine – čak i ako je kupio BTC na apsolutnim vrhovima tržišta.

Imajte na umu da nakon ove tačke ti ljudi više nikada nisu videli rizik od gubitka. Cena se nikada nije smanjila niže od najviše cene u prethodnom ciklusu.
Po čemu se Bitcoin razlikuje od ostalih valuta?
Bitcoin funkcioniše tako dobro kao način štednje zbog svog neobičnog dizajna, koji ga čini drugačijim od bilo kog drugog oblika novca koji je postojao pre njega. Bitcoin je digitalna valuta, prvi i verovatno jedini primer valute koja ima ograničenu ponudu dok radi na otvorenom, decentralizovanom sistemu. Vlade strogo kontrolišu valute koje danas koristimo, poput dolara i eura, i proizvode ih za finansiranje ratova i dugova. Korisnici Bitcoin-a – poput vas – kontrolišu Bitcoin protokol.
Evo šta Bitcoin razlikuje od dolara, eura i drugih valuta:
Bitcoin je otvoren sistem.
Svako može da odluči da se pridruži Bitcoin mreži i primeni pravila softverskog protokola, što je dovelo do vrlo decentralizovanog sistema u kojem nijedan pojedinac ili entitet ne može da blokira transakciju, zamrzne sredstva ili da ukrade od druge osobe.Današnji savremeni bankarski sistem se uveliko razlikuje. Nekoliko banaka je dobilo poverenje da gotovo sve valute, akcije i druge vredne predmete čuvaju na “sigurnom” za svoje klijente. Da biste postali banka, potrebni su vam milioni dolara i neverovatne količine političkog uticaja. Da biste pokrenuli Bitcoin čvor i postali „svoja banka“, potrebno vam je nekoliko stotina dolara i jedno slobodno popodne.
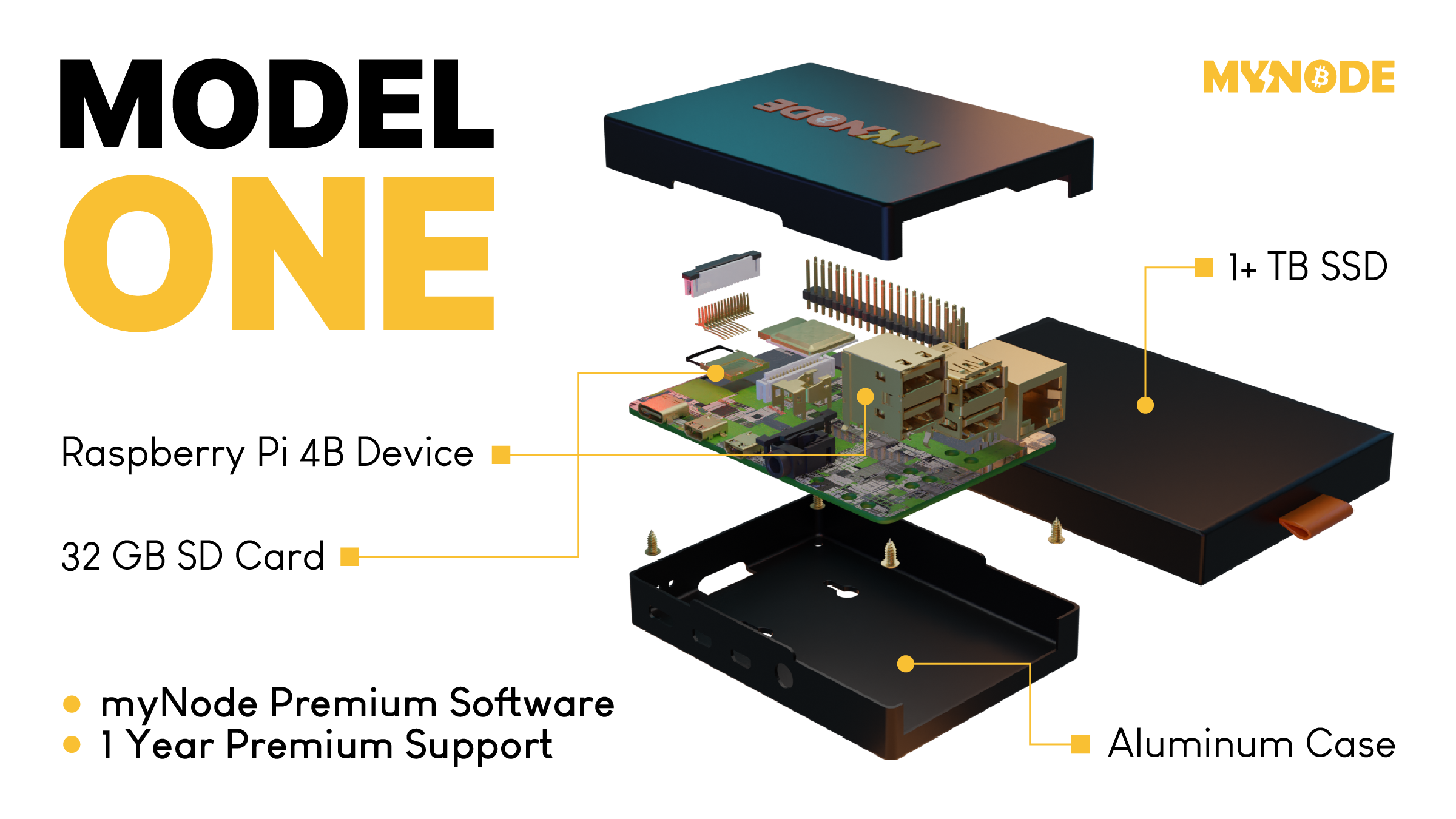 Tako izgleda Bitcoin čvor – Node
MyNode čvor vam omogućava da postanete svoja banka za samo nekoliko minuta.
Tako izgleda Bitcoin čvor – Node
MyNode čvor vam omogućava da postanete svoja banka za samo nekoliko minuta.Bitcoin ima ograničenu ponudu.
Softverski protokol otvorenog koda koji upravlja Bitcoin sistemom ograničava broj novih bitcoin-a koji se mogu stvoriti tokom vremena, sa ograničenjem od ukupno 21.000.000 bitcoin-a. S druge strane, valute koje danas koristimo imaju neograničenu ponudu. Istorija i sadašnje odluke centralnih banaka govore nam da će vlade uvek štampati sve više i više valuta, sve dok valuta ne bude bezvredna. Sve ovo štampanje uzrokuje inflaciju, što pravi štetu običnim radnim ljudima i štedišama.
Tradicionalne valute su dizajnirane tako da opadaju vremenom. Svaki put kada centralna banka kaže da cilja određenu stopu inflacije, oni ustvari kažu da žele da vaš novac svake godine izgubi određeni procenat svoje vrednosti.
Bitcoin-ova ograničena ponuda znači da je on tako dizajniran da raste vremenom kako se potražnja za njim povećava.

Bitcoin putuje oko sveta za nekoliko minuta.
Svako može da pošalje bitcoin-e za nekoliko minuta širom sveta, bez obzira na granice, banke i vlade. Potrebno je manje od minuta da se transakcija pojavi na novčaniku primaoca i oko 60 minuta da se transakcija u potpunosti „obračuna“, tako da primaoc može da bude siguran da su primljeni bitcoin-i sada njegovi (6 konfirmacija bloka). Slanje drugih valuta širom sveta traje danima ili čak mesecima ako se šalju milionski iznosi, a podrazumeva i visoke naknade.
Neke vlade i novinari tvrde da ova sloboda putovanja koju pruža Bitcoin pomaže kriminalcima i teroristima. Međutim, transakciju Bitcoin-a je lakše pratiti nego većinu transakcija u dolarima ili eurima.
Bitcoin se može čuvati na “USB-u”.
Dizajn Bitcoin-a je takav da vam treba samo da čuvate privatni ključ do svojih ‘bitcoin’ adresa (poput lozinke do bankovnih računa) da biste pristupili svojim bitcoin-ima odakle god poželite. Ovaj privatni ključ možete da sačuvate na disku ili na papiru u obliku 12 ili 24 reči na engleskom jeziku. Kao rezultat toga, možete da držite Bitcoin-e vredne milione dolara u svojoj šaci.
Sve ostale valute danas možete ili da strpate u svoj dušek ili da ih poverite banci na čuvanje. Za većinu ljudi koji žive u razvijenom svetu, i koji ne osporavaju autoritet i poverenje u banku, ovo deluje sasvim dobro. Međutim, oni kojima je potrebno da pobegnu od ugnjetavačke vlade ili koji naljute pogrešne ljude, ne mogu verovati bankama. Za njih je sposobnost da nose svoju ušteđevinu bez potrebe za ogromnim koferom neprocenjiva. Čak i ako ne živite na mestu poput ovog, cena Bitcoin-a se i dalje povećava kada ih neko kome oni trebaju kupi.
Kako Bitcoin spašava svet?
Bitcoin, kao ultimativni način štednje, je cakum pakum, ali da li on pomaže u poboljšanju sveta u celini?
Kao što ćete početi da shvatate, ulazeći sve dublje i u druge sadržaje na ovoj stranici, mnogi temeljni delovi našeg današnjeg monetarnog sistema i ekonomije su duboko slomljeni. Međutim, oni koji upravljaju imaju korist od ovakvih sistema, pa se on verovatno neće promeniti bez revolucije ili mirnog svrgavanja od strane naroda. Bitcoin predstavlja novi sistem, sa nekoliko glavnih prednosti:
- Bitcoin popravlja novac, koji je milenijumima služio kao važan alat za rast i poboljšanje društva.
- Bitcoin vraća zdrav razum pozajmljivanju, uklanjanjem apsurdnih situacija poput negativnih kamatnih stopa (gde zajmitelj plaća da bi se zadužio).
- Bitcoin pokreće ulaganja u obnovljive izvore energije i poboljšava energetsku efikasnost u mreži, služeći kao „krajnji kupac“ za sve vrste energije.
Kako mogu da saznam više o Bitcoin-u?
Ovaj članak vam je dao osnovno razumevanje zašto biste trebali razmišljati o Bitcoin-u. Ako želite da saznate više, preporučujem ove resurse:
- Film Bitcoin: Kraj Novca Kakav Poznajemo
- Još uvek je rano za Bitcoin
- Zasto baš Bitcoin?
- Šta je to Bitcoin?
- The Bitcoin Whitepaper ← objavljen 2008. godine, ovo je izložio dizajn za Bitcoin.
-
 @ bf47c19e:c3d2573b
2025-05-22 21:03:52
@ bf47c19e:c3d2573b
2025-05-22 21:03:52Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Šta je finansijski samo-suverenitet?
- Zašto smo prestali da koristimo zlatni standard?
- Šta fali tradicionalnoj valuti i centralnim bankama?
- Kako mogu ljudi da mi ukradu novac ako je u banci?
- Kako ljudi koriste moje finansijske podatke protiv mene?
- Kako ljudi kontrolišu sa kim obavljam transakcije?
- Kako da povratimo svoj finansijski samo-suverenitet?
- Kako Bitcoin funkcioniše?
- Pa onda, zašto Bitcoin?
- Po čemu je Bitcoin bolji od sistema tradicionalnih valuta?
- Kako Bitcoin štiti od Inflacije?
- Kako Bitcoin štiti od Zaplene?
- Kako Bitcoin štiti Privatnost?
- Kako Bitcoin štiti od Cenzure?
- Šta će vlada i banke učiniti sa Bitcoin-om?
- Da li je vrednost Bitcoin-a nestabilna?
- Da li je Bitcoin novac?
- Bitcoin kao Zaliha Vrednosti
- Bitcoin kao Sredstvo Razmene
- Bitcoin kao Obračunska Jedinica
- Bitcoin kao Sistem Kontrole
- Šta je sa „Sledećim Bitcoin-om“?
- Na kraju
Kratki uvod u bezbednost, privatnost i slobodu vašeg novca.
Pre nego što saznate kako morate znati zašto.
Šta je finansijski samo-suverenitet?
Zamislite da u ruci imate zlatni novčić, jedan od najjednostavnijih i najčistijih oblika finansijskog samo-suvereniteta.
Da biste držali taj zlatni novčić, ne morate da se složite sa bilo kojim Uslovima korišćenja ili Politikom privatnosti, da se pridržavate bilo kojih KYC ili AML propisa, da pokažete ličnu kartu, da navedete svoje ime ili jedinstveni matični broj.
Samo ga držite u ruci i njime možete platiti bilo šta, davanjem tog novčića nekom drugom da ga drži u ruci. To je čista sloboda.
Pored slobode onoga što kupujete svojim novčićem, niko ne može magično znati kome plaćate ili koju robu/usluge kupujete tim zlatni novčićem, jer vaša privatnost nije ugrožena sa zlatom.
A pošto imate svoju privatnost, niko ne može znati za vaše transakcije, pa niko ne može da odluči da ograniči ili kontroliše za šta koristite taj zlatni novčić.
Hiljadama godina zlato je bilo globalni standard novca.
Svi su održavali svoj finansijski samo-suverenitet, a privatnost i sloboda svačijeg novca su poštovani.
Zaista je bilo tako jednostavno.
Zašto smo prestali da koristimo zlatni standard?
Trenutni globalni bankarski sistem i sistem tradicionalnih valuta, bankari su vrlo polako implementirali u proteklih 100+ godina.
Udružili su se sa svetskim vladama koje su svima oduzele zlato pod pretnjom nasilja.
Na primer, nakon što je Federalna banka rezervi osnovana u SAD-u 1913. godine, američka vlada je nasilno oduzela svo zlato 1933. godine, prisiljavajući sve da koriste nove centralne banke i sistem novčanica Federalnih rezervi.
 „Dostavite svoje celokupno zlato u naše sefove u zamenu za bezvredni papir, ili ćemo upotrebiti silu nad vama.“
„Dostavite svoje celokupno zlato u naše sefove u zamenu za bezvredni papir, ili ćemo upotrebiti silu nad vama.“Banke su u početku zamenile zlatni standard papirnim priznanicama zvane zlatni sertifikati, ali nakon što je prošlo dovoljno vremena, banke su u osnovi jednostavno prestale da ih otkupljuju za zlato.
Zlatni sertifikati izdavani od banaka (novčanice ili „gotovina“) u tom trenutku bili su samo bezvredni papir, ali zbog vladine pretnje nasiljem, svi su bili primorani da nastave da koriste novčanice Federalnih rezervi.
Od skora, banke koriste digitalnu bazu podataka, u kojoj doslovno mogu stvoriti novac ni iz čega, čak i da ga ne moraju štampati na papiru.
Predsednik Federalnih rezervi priča kako oni „štampaju“ novac.
Oni su učvrstili svoju moć da manipulišu i naduvaju globalnu novčanu masu, nadgledaju finansijske transakcije svih i kontrolišu protok svih tradicionalnih valuta u svom bankarskom sistemu.
Banke sada kontrolišu sve.
Jednom kada su centralni bankari uspešno preuzeli kontrolu nad novčanom masom u svetu, zajedno sa sposobnošću svih da slobodno vrše transakcije i trguju, svet je kolektivno izgubio bezbednost, slobodu i privatnost svog novca.
Šta fali tradicionalnoj valuti i centralnim bankama?
Nakon impelentacije trenutnog globalnog bankarskog sistema i sistema tradicionalnih valuta, svetu nije preostao drugi izbor nego da veruje bankarima i političarima da vode globalni finansijski sistem na pošten način.
„Koren problema tradicionalne valute je potpuno poverenje potrebno za njeno funkcionisanje. Centralnoj banci se mora verovati da neće devalvirati valutu, ali istorija tradicionalnih valuta je puna kršenja tog poverenja. Bankama se mora verovati da čuvaju naš novac i prenose ga elektronskim putem, ali ga daju u talasima kreditnih balona sa malim delićem rezerve. ““ — Satoshi Nakamoto
Istorija zloupotrebe tradicionalnih valuta može se grupisati u 3 kategorije:
• Bezbednost. Loši ljudi kradu vaš novac ili vrednost vašeg novca, ponekad na očigledne načine, ponekad na podle načine.
• Privatnost. Loši ljudi nadgledaju sve vaše privatne finansijske transakcije, i koriste vaše lične finansijske podatke protiv vas.
• Sloboda. Loši ljudi kontrolišu na koji način možete da trošite sopstveni novac, sa kim možete da obavljate transakcije, koliko možete da potrošite itd.
Kako mogu ljudi da mi ukradu novac ako je u banci?
Evo nekoliko primera:
-
Krađa inflacijom: Ovo je primarni način na koji banke kradu vaš novac i jedan od najpodlijih. Kada centralne banke izdaju novi novac, bilo štampanjem na bezvrednom papiru, ili samo dodavanjem knjigovodstvenog unosa u bazu podataka koju kontrolišu, one naduvaju globalnu novčanu masu. Inflacija krade kupovnu moć svih koji drže deo te valute, jednostavno zato što je sada više te valute u opticaju. Zlato se ne može stvoriti, pa su bankari umesto toga izmislili sistem papirnog novca.
-
Krađa zaplenom: Ovo je jedan od načina na koji vlade mogu ukrasti vaš novac. Da li ste ikada čuli za zaplenu imovine? Ako policajac posumnja da je vaša imovina korišćena u krivičnom delu, može je zapleniti, a vi se morate boriti da biste povratili vašu ukradenu imovinu. Ili, drugi primer: Pokušajte da uđete u zemlju sa više od 10.000 USD u džepu, a ne da je prijavite, i pogledajte šta će se dogoditi. Sve je isto: krađa od strane drugih ljudi sa oružjem.
-
Krađa putem oporezivanja: Ovo je još jedan način na koji vam vlade kradu novac. Ne sporim da li je oporezivanje etično ili ne, samo konstatujem činjenicu da vaša vlada može da primora vašu banku da im da vaš novac, a ovo je bezbednostna ranjivost. Da bi novac bio siguran, mora biti nezaplenjiv, a vlade mogu da zaplene vaše bankovne račune.
Kako ljudi koriste moje finansijske podatke protiv mene?
Ako fizičku tradicionalnu valutu predate drugoj osobi, u obliku papirnog novca ili kovanica, relativno je lako zaštititi privatnost svoje transakcije, baš kao što bi bilo da koristite zlatnike.
Međutim, ako koristite kreditne kartice, debitne kartice, bankovne transfere, PayPal, Venmo, LINE Pay, WeChat Pay ili bilo koju drugu mrežu za plaćanje koja je centralno kontrolisana, aktivno pristajete da se odreknete privatnosti podataka svih svojih privatnih finansijskih transakcija i sve ih dajete poverljivoj trećoj strani.
Kada su svi podaci i metapodaci vaših finansijskih transakcija prijavljeni u centralnu bazu podataka, onaj ko ima pristup toj bazi podataka može da koristi vaše podatke protiv vas.
Evo nekoliko osnovnih primera:
- Ako ste kupili robu rizičnog životnog stila poput cigareta, banka može reći vašoj osiguravajućoj kompaniji da poveća vaše osiguranje.
- Ako ste kupili nešto što je ilegalno, poput droga za rekreaciju, vaša banka može reći vašoj vladi da vas zakonski goni.
Ali u slučaju nekih represivnih vlada, oni su to odveli do ekstrema. Oni centralno prikupljaju sve finansijske transakcije i druge podatke svih svojih građana i stvorili su totalitarni Sistem Socijalnih Bodova (eng. Social Credit Score):
 Prepoznavanje lica je jedan od elemenata kineskih napora za praćenje
Prepoznavanje lica je jedan od elemenata kineskih napora za praćenjeZapisi George Orwell-a već su postali stvarnost u Kini zbog sistema tradicionalnih valuta centralne banke i platnih mreža koje su izgrađene na njemu.
Ako mislite da se to neće dogoditi u vašoj zemlji, razmislite ponovo.
To se dešava vrlo polako, ali na kraju će sve svetske vlade primeniti Sistem Socijalnih Bodova, dok je Kina to tek prva učinila.
Kako ljudi kontrolišu sa kim obavljam transakcije?
U prvom primeru sa zlatnim novčićem, kada ga predate nekom drugom kao plaćanje za robu ili uslugu, ne postoji centralizovana evidencija vaše platne transakcije i imate savršenu privatnost.
Međutim, u centralnom bankarskom sistemu, budući da banka ima i znanje o podacima o vašim transakcijama i moć da kontroliše vaša sredstva, oni mogu proceniti niz pravila da bi odlučili da li žele da dozvole vašu transakciju ili da to odbiju, takođe kao i izvršenje te odluke kontrolišući vaša sredstva.
Tako su vlade naoružale tradicionalne valute i centralni bankarski sistem kao Sistem Kontrole nad svojim građanima.
Da rezimiramo: Pošto ste se odrekli bezbednosti i privatnosti svog novca, izgubili ste i svoju finansijsku slobodu.
“Privatnost nije o tome da nešto treba sakriti. Privatnost je o tome da nešto treba zaštititi.” — Edward Snowden
Kako da povratimo svoj finansijski samo-suverenitet?
Pokret Cypherpunk pokrenuli su pojedinci koji su shvatili važnost zaštite privatnosti i slobode pojedinačnih korisnika na Internetu.
Cypherpunk-ovi su verovali da se gore opisani problemi mogu rešiti samo potpuno novim novčanim sistemom, koji poštuje i štiti bezbednost, privatnost i slobodu pojedinca.
Mnogi od Cypherpunk-era pokušali su da izgrade nove etičke sisteme e-gotovine koji bi mogli da zamene tradicionalne valute i centralno bankarstvo.
Bilo je mnogo teških računarskih problema koje je trebalo prevazići u stvaranju tako istinski decentralizovanog sistema, i ako su neki od njih bili blizu cilja, svi su propali.
Odnosno, sve dok jedan pseudonim Cypherpunk-a to konačno nije shvatio 2008. godine: kombinacijom digitalnih potpisa, distribuirane knjige i peer-to-peer mreže, rođen je Bitcoin.
Kako Bitcoin funkcioniše?
Baš kao što ne treba da znate kako Internet funkcioniše da bi gledali slike mačaka na Internetu, razumevanje tehničke složenosti načina na koji Bitcoin radi „ispod haube“ nije neophodno da biste ga koristili i postigli sopstveni finansijski samo-suverenitet.
Važna stvar koju želim da saznate iz ovog članka je da iako većina novih tehnologija u početku ima loše korisničko iskustvo, Bitcoin svesno i vrlo namerno ne žrtvuje svoje osnovne filozofske principe da bi brže pridobio nove korisnike, ili da bi poboljšao korisničko iskustvo.
Najpametniji Cypherpunk-ovi rade na poboljšanju korisničkog iskustva.
Tehnologija će se sa vremenom poboljšavati, baš kao i za Internet.
Pa onda, zašto Bitcoin?
Reći ću vam zašto:
Jer Bitcoin poštuje bezbednost, privatnost i slobodu pojedinca.
Po čemu je Bitcoin bolji od sistema tradicionalnih valuta?
Za početak, Bitcoin nema Uslove korišćenja, Politiku privatnosti i Propise o usklađenosti sa KYC/AML. (Know Your Costumer & Anti-money Laundering)
Bitcoin je uspešan primer implementacije kripto-anarhije, gde su jedina pravila kriptografija, matematika i jak skup konsenzusnih pravila.
To je distribuirani i nepoverljivi sistem zasnovan na finansijskim podsticajima i nijedna osoba ili centralizovani entitet ne može da kontroliše Bitcoin.
Ono što je najvažnije, Bitcoin vam omogućava da odustanete od tradicionalnih valuta, sistema delimičnih rezervi i centralnog bankarstva rešavanjem osnovnih problema poverenja:
- Sigurnost od inflacije korišćenjem fiksnog snabdevanja
- Sigurnost od zaplene korišćenjem ključeva za kontrolu sredstava
- Privatnost plaćanja korišćenjem pseudonimnih identiteta
- Sloboda protiv cenzure korišćenjem peer to peer mreže
Kako Bitcoin štiti od Inflacije?
Jedno od najkritičnijih pravila konsenzusa o Bitcoin-u je da može postojati najviše 21,000,000 Bitcoin-a.
Nakon izdavanja svih Bitcoin-a, nikada više ne može doći do stvaranja novih Bitcoin-a.
Stoga je Bitcoin deflaciona valuta, koja sprečava ljude da ukradu vaš novac ili njegovu vrednost naduvavanjem novčane mase.
 Monetarna Inflacija Bitcoin-a
Monetarna Inflacija Bitcoin-aKako Bitcoin štiti od Zaplene?
Bitcoin se može preneti samo pomoću kriptografskog privatnog ključa koji kontroliše sredstva.
Nijedan bitcoin nikada ne izadje van sistema.
Nijedna vlada, banka ili sudski nalog ne mogu zapleniti ta sredstva.
Jednostavno ne postoji način da se takva odredba ili naredba sprovede od bilo kog „organa vlasti“, jer Bitcoin ne priznaje nijedno „ovlašćenje“ u svom sistemu.
Bitcoin je potpuno samo-suveren sistem i zbog svoje distribuirane prirode ne može se ugasiti.
Postoji zbog sopstvenih zasluga, samo zato što ljudi veruju u to.
Kako Bitcoin štiti Privatnost?
Bitcoin ne traži vaše ime ili druge detalje koji mogu lično da vas identifikuju.
Vaš identitet je kriptografski, a ne vaše stvarno ime.
Dakle, vaš identitet izgleda otprilike kao 1vizSAISbuiKsbt9d8JV8itm5ackk2TorC, a ne kao „Stefan Petrovič“.
Pored toga, niko ne zna ko kontroliše sredstva na datoj Bitcoin adresi, a nova tehnologija se neprestano razvija kako bi se poboljšala privatnost Bitcoin-a.
Kako Bitcoin štiti od Cenzure?
Peer-to-peer Bitcoin mreža je u potpunosti distribuirana.
To znači da ako jedan čvor pokuša da cenzuriše vašu transakciju, neće uspeti ukoliko * svaki * čvor(Node) ne izvrši cenzuru vaše transakcije.
Šta će vlada i banke učiniti sa Bitcoin-om?
Neke zemlje su pokušale da ga regulišu, kontrolišu, isključe itd., ali nijedna od njih nije uspela.
Čini se da uglavnom samo žele da koriste postojeći sistem centralnih banaka da bi kontrolisali kako ljudi trguju tradicionalnim valutama za Bitcoin, i naravno žele da oporezuju Bitcoin na bilo koji mogući način.
Evo nekoliko uobičajenih tvrdnji vlada i banaka o Bitcoin-u:
 Evropska centralna banka kaže da Bitcoin nije valuta i upozorava da je vrlo nestabilna.
Evropska centralna banka kaže da Bitcoin nije valuta i upozorava da je vrlo nestabilna.„Bitcoin, izgleda samo kao prevara“, rekao je gospodin Tramp. „Ne sviđa mi se jer je to još jedna valuta koja se takmiči sa dolarom.“
Da li je vrednost Bitcoin-a nestabilna?
Ako umanjite grafikon cena, videćete da Bitcoin-u neprekidno raste vrednost od kada je stvoren, trgujući sa manje od 0,01 USD i polako se penje na preko 60.000 USD na nedavnom vrhuncu početkom 2021. godine.
 Cena Bitcoina od 2011. godine
Cena Bitcoina od 2011. godineTo je zato što je njegova ponuda fiksna i ljudi cene njegovu nestašicu.
Sa većom potražnjom i fiksnom ponudom, cene vremenom rastu.
Kako godine odmiču, njegova vrednost će se povećavati kako novi korisnici počinju da drže Bitcoin. (U svetu Bitcoina držanju kažemo HODL. Drži bitcoin. Hodl bitcoin.)
Da li je Bitcoin novac?
Da biste odgovorili na pitanje da li je Bitcoin novac ili ne, prvo morate definisati pojam „novac“.
Nažalost, reč „novac“ koristimo da bismo opisali nekoliko vrlo različitih komplikovanih koncepata, koji su svi potpuno odvojeni.
Termin „novac“ se zapravo odnosi na:
- Zaliha Vrednosti (Store of Value)
- Sredstvo Razmene ( Medium of Exchange)
- Obračunska Jedinica (Unit of Account)
- Sistem Kontrole (System Control)
Bitcoin kao Zaliha Vrednosti
Ovaj tweet to savršeno objašnjava:
Sinov prijatelj: “Matt, šta će se dogoditi ako novčić od 1 funte usitnite na pola?”
Dobijaš dva komada bezvrednog metala. Ako zlatnik usitnite na pola, dobićete dva zlatnika, od kojih svaki vredi polovinu onoga što je novčić bio.
Sin: „… isto tako kao sa zlatom jeste sa bitcoinima“.
Bitcoin je potpuno deljiv i deluje kao izvrsna zaliha vrednosti, baš kao što je i zlato već hiljadama godina.
Bitcoin kao Sredstvo Razmene
Bitcoin je dobro služio kao sredstvo razmene za svoje rane korisnike.
Ali skaliranje Bitcoin-a na globalni nivo koji bi mogao da posluži svim ljudima je veliki izazov, jer se osnovna „blockchain“ tehnologija ne skalira na globalni nivo.
Da bi rešio ovaj problem skaliranja, Satoshi je izumeo koncept kanala plaćanja, a u kombinaciji sa malo pomoći drugih briljantnih računarskih naučnika Cipherpunk-a koji su poboljšali koncept tokom poslednjih 10 godina, sada imamo mrežu Lightning, koja omogućava da se Bitcoin koristi kao odlično Sredstvo Razmene, koje se vremenom može proširiti na globalni nivo.
Bitcoin kao Obračunska Jedinica
Najmanja obračunska jedinica Bitcoin-a nazvana je po njenom tvorcu, Satoshi-u.
Jedan Bitcoin je jednak 100.000.000 Satoshi-a.
Na kraju, kako se robe i usluge sve češće razmenjuju za Bitcoin, sve više ljudi će koristiti Bitcoin ili „Sats“ kao obračunsku jedinicu.
Bitcoin kao Sistem Kontrole
Budući da je Bitcoin dizajniran da poštuje i štiti ljudska prava pojedinca, posebno bezbednost, privatnost i slobodu novca; ne bi bio dobar Sistem Kontrole i ne može se koristiti za ugnjetavanje ljudi, kao što se dešava sa tradicionalnim valutama i sistemima centralnog bankarstva koji to trenutno vrlo dobro rade.
Šta je sa „Sledećim Bitcoin-om“?
Kao što može biti samo jedan „globalni“ Internet, tako može biti i samo jedan globalni novac, a stigao je i novi Bitcoin Standard.
Sve ostalo je ili direktna prevara ili gubljenje vremena.
Ako bi neko želeo da vam proda „Sledeće Zlato“, da li biste ga kupili?
Na kraju
Nadam se da vam je ovaj članak pomogao da razumete zašto je Bitcoin stvoren i kako može da pomogne svetu da se oslobodi tradicionalnih valuta i sistema centralnog bankarstva koji je veoma duboko integrisan u naše trenutno društvo.
Evo nekoliko misli koje treba poneti sa sobom:
- Bitcoin nije izmišljen radi zarade, već je izmišljen da bi promenio svet.
- Bitcoin će to učiniti poštujući korisnikovu bezbednost, privatnost i slobodu.
- Bitcoin se već koristi kao novac, na nekoliko načina na koji se novac može koristiti.
- Bitcoin nije nestabilan, njegova vrednost vremenom polako raste (odzumirajte).
- Bitcoin ima mnogo kopija i prevaranata koji će pokušati da vam prodaju svoju kopiju Bitcoin-a. Ne zavaravajte se lažnim Bitcoin-om baš kao što vas ne bi prevarili ni Lažnim Zlatom.
- Bitcoin će postati najveći prenos bogatstva u našem životu, tako da ćete možda želeti da ih uzmete pre nego kasnije.
- Ostanite skromni i skupljajte satošije.
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 4fe4a528:3ff6bf06
2025-05-01 13:36:04
@ 4fe4a528:3ff6bf06
2025-05-01 13:36:04Bitcoin has emerged as a significant player in the financial markets, often drawing comparisons to traditional assets like stocks and gold. Historically, Bitcoin has shown a correlation with the S&P 500, reflecting the broader market trends. However, recent trends indicate a decoupling of Bitcoin from the S&P 500 and a growing correlation with gold. This essay explores the factors contributing to this shift and the implications for investors.
One of the primary reasons for Bitcoin's decoupling from the S&P 500 is the evolving perception of Bitcoin as a store of value rather than a speculative asset. As inflation concerns rise and central banks adopt expansive monetary policies, investors are increasingly looking for assets that can preserve value. Gold has long been regarded as a safe haven during economic uncertainty, and Bitcoin is increasingly being viewed in a similar light. This shift in perception has led to a growing correlation between Bitcoin and gold, as both assets are seen as hedges against inflation and currency devaluation.
Additionally, the increasing institutional adoption of Bitcoin has played a crucial role in its decoupling from traditional equities. Major corporations and institutional investors are now allocating a portion of their portfolios to Bitcoin, viewing it as a digital gold. This institutional interest has provided Bitcoin with a level of legitimacy and stability that was previously lacking, allowing it to operate independently of the stock market's fluctuations. As more institutional players enter the Bitcoin market, the asset's price movements may become less influenced by the broader economic conditions that affect the S&P 500.
Moreover, the unique characteristics of Bitcoin, such as its limited supply and decentralized nature, further differentiate it from traditional equities. Unlike stocks, which can be influenced by company performance and market sentiment, Bitcoin's value is driven by supply and demand dynamics within its own ecosystem. The halving events, which reduce the rate at which new Bitcoins are created, create scarcity and can lead to price appreciation independent of stock market trends.
In conclusion, the decoupling of Bitcoin from the S&P 500 and its coupling with gold can be attributed to a combination of factors, including a shift in perception towards Bitcoin as a store of value, increasing institutional adoption, and its unique characteristics as a digital asset. As investors seek alternatives to traditional assets in an uncertain economic landscape, Bitcoin's role as a hedge against inflation and currency devaluation is likely to strengthen. This evolving relationship between Bitcoin, gold, and traditional equities will continue to shape the investment landscape in the years to come.
Yesterday I fixed my neighbor's computer. He laughed at me for being into Bitcoin. We are still early.
-
 @ 0e9491aa:ef2adadf
2025-05-22 19:01:21
@ 0e9491aa:ef2adadf
2025-05-22 19:01:21
Influencers would have you believe there is an ongoing binance bank run but bitcoin wallet data says otherwise.
- binance wallets are near all time highs
- bitfinex wallets are also trending up
- gemini and coinbase are being hit with massive withdrawals thoughYou should not trust custodians, they can rug you without warning. It is incredibly important you learn how to hold bitcoin yourself, but also consider not blindly trusting influencers with a ref link to shill you.
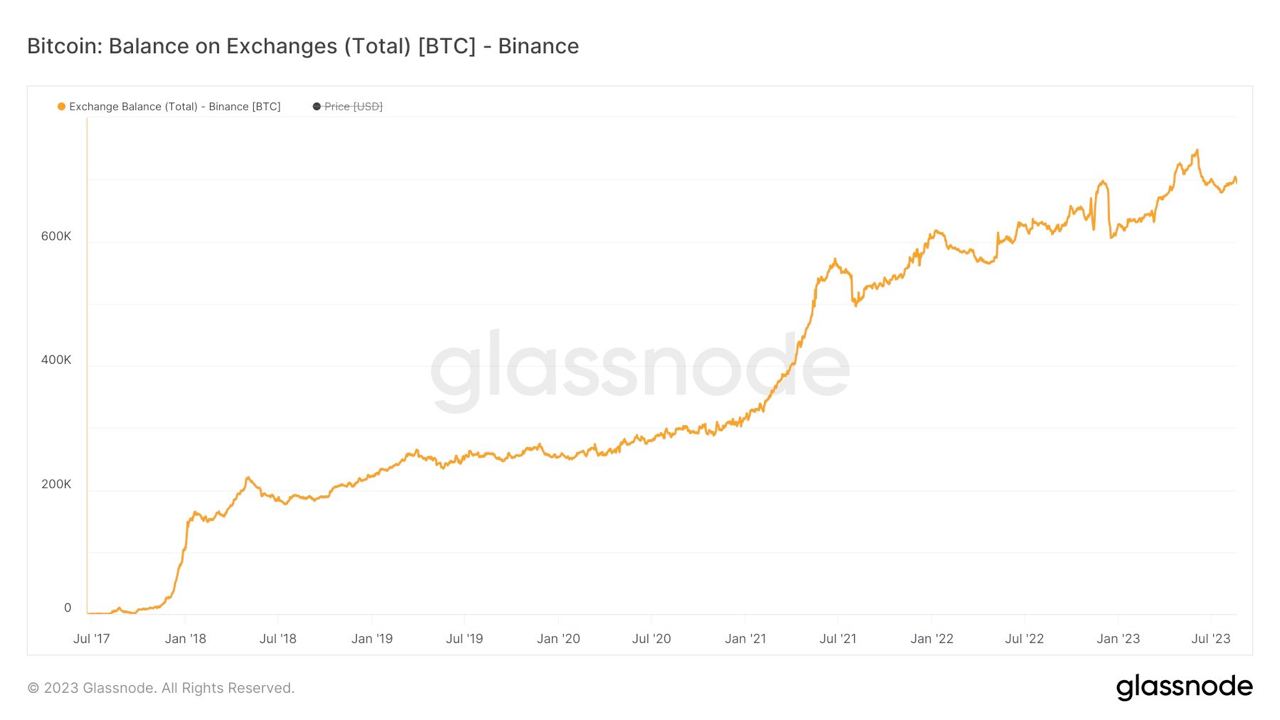
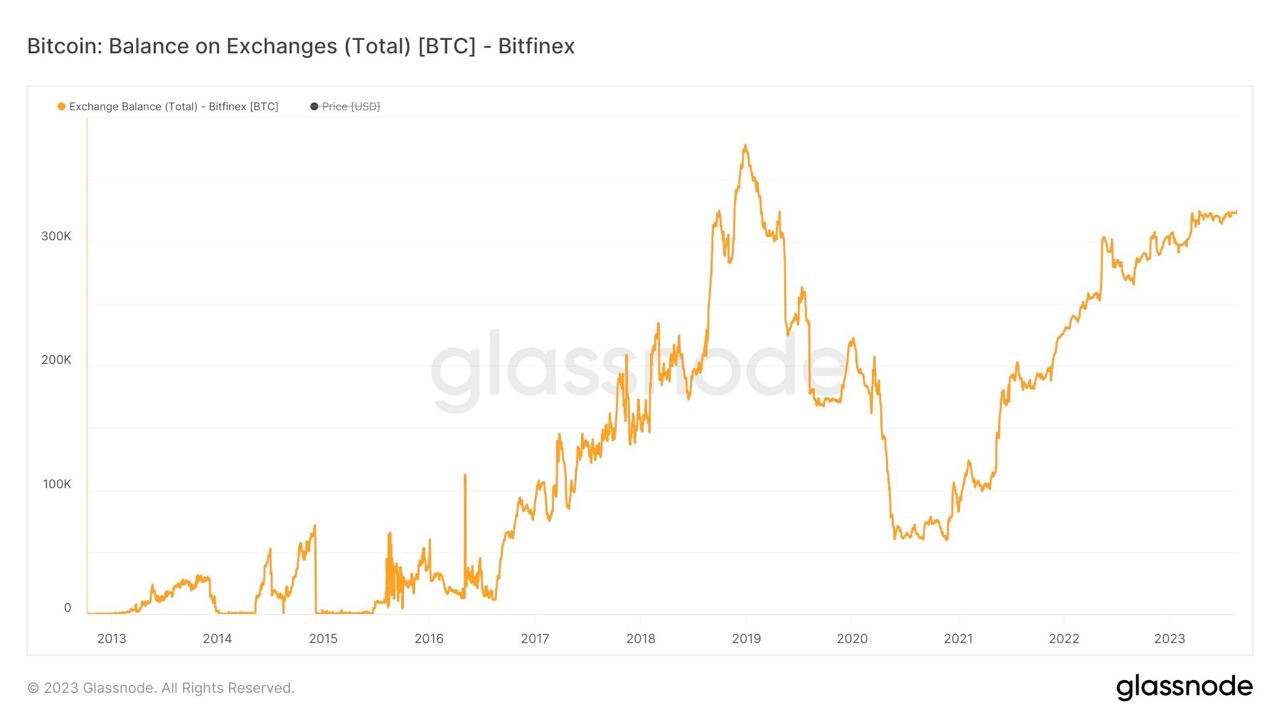
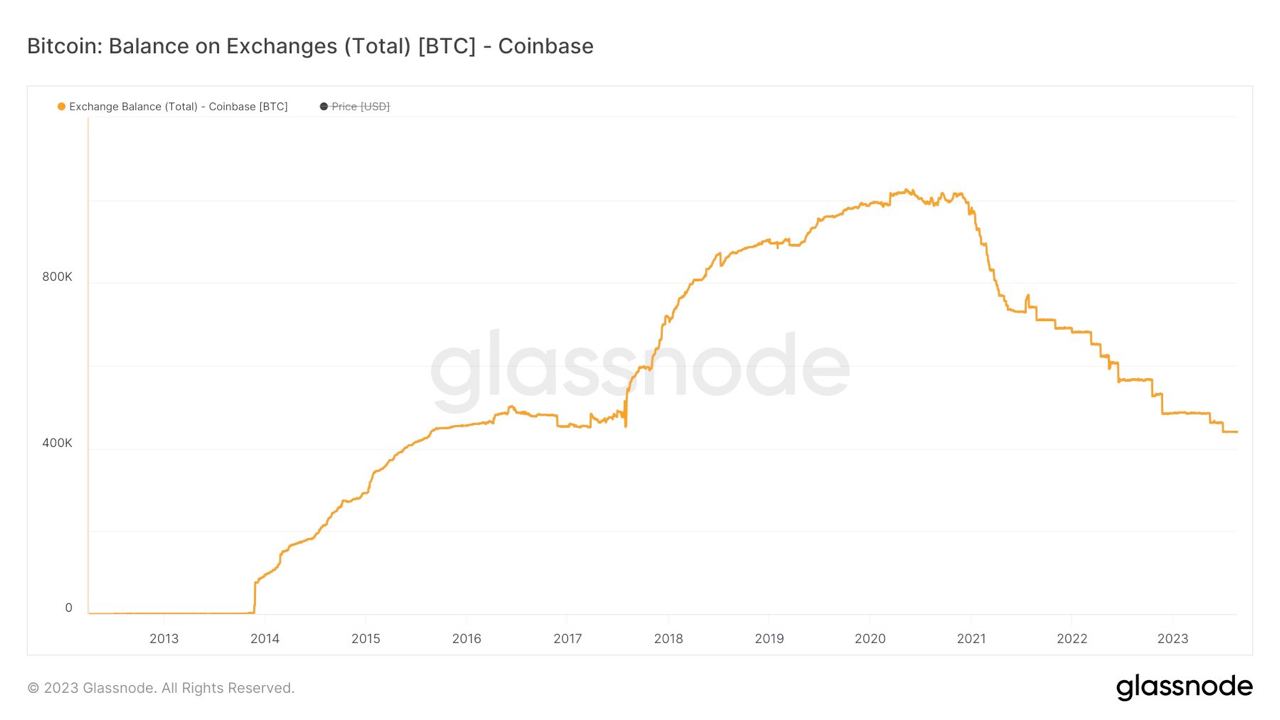
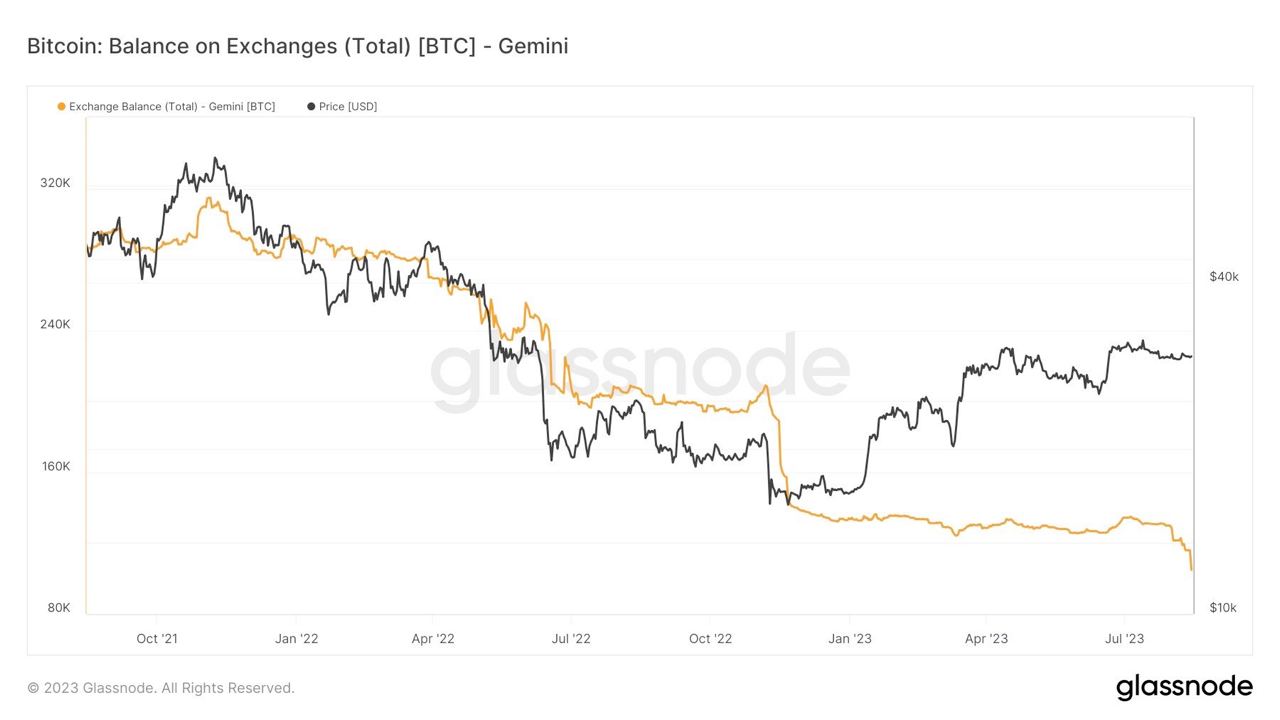
If you found this post helpful support my work with bitcoin.

-
 @ 57d1a264:69f1fee1
2025-05-22 06:21:22
@ 57d1a264:69f1fee1
2025-05-22 06:21:22You’ve probably seen it before.
You open an agency’s website or a freelancer’s portfolio. At the very top of the homepage, it says:
We design for startups.
You wait 3 seconds. The last word fades out and a new one fades in:
We design for agencies.
Wait 3 more seconds:
We design for founders.
I call this design pattern The Wheel of Nothing: a rotating list of audience segments meant to impress through inclusion and draw attention through motion… for absolutely no reason.
Revered brand studio Pentagram recently launched a new website. To my surprise, the homepage features the Wheel of Nothing front and center, boldly claiming:
We design Everything for Everyone…before cycling through more specific combinations every few seconds.
Dan Mall, a husband, dad, teacher, creative director, designer, founder, and entrepreneur from Philly. I share as much as I can to create better opportunities for those who wouldn’t have them otherwise. Most recently, I ran design system consultancy SuperFriendly for over a decade.
Read more at Dans' website https://danmall.com/posts/the-wheel-of-nothing/
https://stacker.news/items/986392
-
 @ 21335073:a244b1ad
2025-05-21 16:58:36
@ 21335073:a244b1ad
2025-05-21 16:58:36The other day, I had the privilege of sitting down with one of my favorite living artists. Our conversation was so captivating that I felt compelled to share it. I’m leaving his name out for privacy.
Since our last meeting, I’d watched a documentary about his life, one he’d helped create. I told him how much I admired his openness in it. There’s something strange about knowing intimate details of someone’s life when they know so little about yours—it’s almost like I knew him too well for the kind of relationship we have.
He paused, then said quietly, with a shy grin, that watching the documentary made him realize how “odd and eccentric” he is. I laughed and told him he’s probably the sanest person I know. Because he’s lived fully, chasing love, passion, and purpose with hardly any regrets. He’s truly lived.
Today, I turn 44, and I’ll admit I’m a bit eccentric myself. I think I came into the world this way. I’ve made mistakes along the way, but I carry few regrets. Every misstep taught me something. And as I age, I’m not interested in blending in with the world—I’ll probably just lean further into my own brand of “weird.” I want to live life to the brim. The older I get, the more I see that the “normal” folks often seem less grounded than the eccentric artists who dare to live boldly. Life’s too short to just exist, actually live.
I’m not saying to be strange just for the sake of it. But I’ve seen what the crowd celebrates, and I’m not impressed. Forge your own path, even if it feels lonely or unpopular at times.
It’s easy to scroll through the news and feel discouraged. But actually, this is one of the most incredible times to be alive! I wake up every day grateful to be here, now. The future is bursting with possibility—I can feel it.
So, to my fellow weirdos on nostr: stay bold. Keep dreaming, keep pushing, no matter what’s trending. Stay wild enough to believe in a free internet for all. Freedom is radical—hold it tight. Live with the soul of an artist and the grit of a fighter. Thanks for inspiring me and so many others to keep hoping. Thank you all for making the last year of my life so special.
-
 @ 000002de:c05780a7
2025-05-21 20:00:21
@ 000002de:c05780a7
2025-05-21 20:00:21I enjoy Jonathan Pageau's perspectives from time to time. He is big on myth and symbolic signs in culture and history. I find this stuff fascinating as well. I watched this video last week, and based on the title, I was thinking... hmm, I wonder if it is a review of Return of the Strong Gods. It wasn't, but it really flows with the thesis of that book. You should read it if you haven't, and before you do, go check out @SimpleStacker's review of it.
Pageau starts the video by talking about the concept of "watching the clown." He uses Ye as the clown. Ye has been a leading indicator in the past when he publicly claimed he was a Christian and began making music and holding church services. Now he's going "off the rails" seemingly with his Hitler songs and art. Clearly, the stigma of Hitler will not last forever. It's hard for us to realize this. At least for someone of my age, but Pageau points out that eventually, the villains of history become less of a stand-in for Satan and more of a purely historical figure. He mentions Alexander the Great as a man who did incredibly evil things, but today we just read about him in school and don't really think about it too much. One day, that will be the way Hitler is viewed. Sure, evil, but the power of using him as the mythical Satan will wane.
The most interesting point I took away from this video, though, was that the post-war consensus was built on a dark secret. Now, it's not a secret to me, but at some point, it was. And this secret is a deep flaw in the current state of the West that keeps affecting us in negative ways. The secret is that in order to defeat Hitler and the Nazis, the West allied itself with the Soviets. Stalin. An incredibly evil man and an ideology that has led to the death and suffering of more humans than the Nazis. This is just a fact, but it's so dark that we don't talk about it.
For many years as I began to study Communism and the Soviet Union I began to question why on earth did the allies align themselves with Stalin. Obviously it was for stratigic reasons. I get it. But the fact that this topic is not really discussed in our culture has had a dark effect. Now, I'm not interested in figuring out if Stalin was more evil than Hitler or if Fascism is worse that Communism. I think this misses the point. The point is that today if soneone has Nazi symbols it is very likely not gonna go well for them but Communist symbols are usually just fine. We see the ideas of Socialism discussed openly without concern. Its popular even. Fascism on the other hand is always (until recently) masked at best.
Today we are seeing more and more people openly talk about this reality, and it is a signal that the WW2 consensus is breaking. As people age out and our collective memory fades, this lie will become more visible because the mythical view of Hitler will fade. This will allow people to be more objective about viewing the decisions of the past. I don't recall the book discussing this directly, but it is an interesting connection for sure.
I recommend watching The World War II Consensus is Breaking Down by Jonathan Pageau.
https://stacker.news/items/985962
-
 @ 4ba8e86d:89d32de4
2025-04-28 22:39:20
@ 4ba8e86d:89d32de4
2025-04-28 22:39:20Como funciona o PGP.

O texto a seguir foi retirado do capítulo 1 do documento Introdução à criptografia na documentação do PGP 6.5.1. Copyright © 1990-1999 Network Associates, Inc. Todos os direitos reservados.
-O que é criptografia? -Criptografia forte -Como funciona a criptografia? -Criptografia convencional -Cifra de César -Gerenciamento de chaves e criptografia convencional -Criptografia de chave pública -Como funciona o PGP - Chaves • Assinaturas digitais -Funções hash • Certificados digitais -Distribuição de certificados -Formatos de certificado •Validade e confiança -Verificando validade -Estabelecendo confiança -Modelos de confiança • Revogação de certificado -Comunicar que um certificado foi revogado -O que é uma senha? -Divisão de chave
Os princípios básicos da criptografia.
Quando Júlio César enviou mensagens aos seus generais, ele não confiou nos seus mensageiros. Então ele substituiu cada A em suas mensagens por um D, cada B por um E, e assim por diante através do alfabeto. Somente alguém que conhecesse a regra “shift by 3” poderia decifrar suas mensagens. E assim começamos.
Criptografia e descriptografia.
Os dados que podem ser lidos e compreendidos sem quaisquer medidas especiais são chamados de texto simples ou texto não criptografado. O método de disfarçar o texto simples de forma a ocultar sua substância é chamado de criptografia. Criptografar texto simples resulta em um jargão ilegível chamado texto cifrado. Você usa criptografia para garantir que as informações sejam ocultadas de qualquer pessoa a quem não se destinam, mesmo daqueles que podem ver os dados criptografados. O processo de reverter o texto cifrado ao texto simples original é chamado de descriptografia . A Figura 1-1 ilustra esse processo.
https://image.nostr.build/0e2fcb71ed86a6083e083abbb683f8c103f44a6c6db1aeb2df10ae51ec97ebe5.jpg
Figura 1-1. Criptografia e descriptografia
O que é criptografia?
Criptografia é a ciência que usa a matemática para criptografar e descriptografar dados. A criptografia permite armazenar informações confidenciais ou transmiti-las através de redes inseguras (como a Internet) para que não possam ser lidas por ninguém, exceto pelo destinatário pretendido. Embora a criptografia seja a ciência que protege os dados, a criptoanálise é a ciência que analisa e quebra a comunicação segura. A criptoanálise clássica envolve uma combinação interessante de raciocínio analítico, aplicação de ferramentas matemáticas, descoberta de padrões, paciência, determinação e sorte. Os criptoanalistas também são chamados de atacantes. A criptologia abrange tanto a criptografia quanto a criptoanálise.
Criptografia forte.
"Existem dois tipos de criptografia neste mundo: a criptografia que impedirá a sua irmã mais nova de ler os seus arquivos, e a criptografia que impedirá os principais governos de lerem os seus arquivos. Este livro é sobre o último." --Bruce Schneier, Criptografia Aplicada: Protocolos, Algoritmos e Código Fonte em C. PGP também trata deste último tipo de criptografia. A criptografia pode ser forte ou fraca, conforme explicado acima. A força criptográfica é medida no tempo e nos recursos necessários para recuperar o texto simples. O resultado de uma criptografia forte é um texto cifrado que é muito difícil de decifrar sem a posse da ferramenta de decodificação apropriada. Quão díficil? Dado todo o poder computacional e o tempo disponível de hoje – mesmo um bilhão de computadores fazendo um bilhão de verificações por segundo – não é possível decifrar o resultado de uma criptografia forte antes do fim do universo. Alguém poderia pensar, então, que uma criptografia forte resistiria muito bem até mesmo contra um criptoanalista extremamente determinado. Quem pode realmente dizer? Ninguém provou que a criptografia mais forte disponível hoje resistirá ao poder computacional de amanhã. No entanto, a criptografia forte empregada pelo PGP é a melhor disponível atualmente.
Contudo, a vigilância e o conservadorismo irão protegê-lo melhor do que as alegações de impenetrabilidade.
Como funciona a criptografia?
Um algoritmo criptográfico, ou cifra, é uma função matemática usada no processo de criptografia e descriptografia. Um algoritmo criptográfico funciona em combinação com uma chave – uma palavra, número ou frase – para criptografar o texto simples. O mesmo texto simples é criptografado em texto cifrado diferente com chaves diferentes. A segurança dos dados criptografados depende inteiramente de duas coisas: a força do algoritmo criptográfico e o sigilo da chave. Um algoritmo criptográfico, mais todas as chaves possíveis e todos os protocolos que o fazem funcionar constituem um criptossistema. PGP é um criptossistema.
Criptografia convencional.
Na criptografia convencional, também chamada de criptografia de chave secreta ou de chave simétrica , uma chave é usada tanto para criptografia quanto para descriptografia. O Data Encryption Standard (DES) é um exemplo de criptossistema convencional amplamente empregado pelo Governo Federal. A Figura 1-2 é uma ilustração do processo de criptografia convencional. https://image.nostr.build/328b73ebaff84c949df2560bbbcec4bc3b5e3a5163d5fbb2ec7c7c60488f894c.jpg
Figura 1-2. Criptografia convencional
Cifra de César.
Um exemplo extremamente simples de criptografia convencional é uma cifra de substituição. Uma cifra de substituição substitui uma informação por outra. Isso é feito com mais frequência compensando as letras do alfabeto. Dois exemplos são o Anel Decodificador Secreto do Capitão Meia-Noite, que você pode ter possuído quando era criança, e a cifra de Júlio César. Em ambos os casos, o algoritmo serve para compensar o alfabeto e a chave é o número de caracteres para compensá-lo. Por exemplo, se codificarmos a palavra "SEGREDO" usando o valor chave de César de 3, deslocaremos o alfabeto para que a terceira letra abaixo (D) comece o alfabeto. Então começando com A B C D E F G H I J K L M N O P Q R S T U V W X Y Z e deslizando tudo para cima em 3, você obtém DEFGHIJKLMNOPQRSTUVWXYZABC onde D=A, E=B, F=C e assim por diante. Usando este esquema, o texto simples, "SECRET" é criptografado como "VHFUHW". Para permitir que outra pessoa leia o texto cifrado, você diz a ela que a chave é 3. Obviamente, esta é uma criptografia extremamente fraca para os padrões atuais, mas, ei, funcionou para César e ilustra como funciona a criptografia convencional.
Gerenciamento de chaves e criptografia convencional.
A criptografia convencional tem benefícios. É muito rápido. É especialmente útil para criptografar dados que não vão a lugar nenhum. No entanto, a criptografia convencional por si só como meio de transmissão segura de dados pode ser bastante cara, simplesmente devido à dificuldade de distribuição segura de chaves. Lembre-se de um personagem do seu filme de espionagem favorito: a pessoa com uma pasta trancada e algemada ao pulso. Afinal, o que há na pasta? Provavelmente não é o código de lançamento de mísseis/fórmula de biotoxina/plano de invasão em si. É a chave que irá descriptografar os dados secretos. Para que um remetente e um destinatário se comuniquem com segurança usando criptografia convencional, eles devem chegar a um acordo sobre uma chave e mantê-la secreta entre si. Se estiverem em locais físicos diferentes, devem confiar em um mensageiro, no Bat Phone ou em algum outro meio de comunicação seguro para evitar a divulgação da chave secreta durante a transmissão. Qualquer pessoa que ouvir ou interceptar a chave em trânsito poderá posteriormente ler, modificar e falsificar todas as informações criptografadas ou autenticadas com essa chave. Do DES ao Anel Decodificador Secreto do Capitão Midnight, o problema persistente com a criptografia convencional é a distribuição de chaves: como você leva a chave ao destinatário sem que alguém a intercepte?
Criptografia de chave pública.
Os problemas de distribuição de chaves são resolvidos pela criptografia de chave pública, cujo conceito foi introduzido por Whitfield Diffie e Martin Hellman em 1975. (Há agora evidências de que o Serviço Secreto Britânico a inventou alguns anos antes de Diffie e Hellman, mas a manteve um segredo militar - e não fez nada com isso.
[JH Ellis: The Possibility of Secure Non-Secret Digital Encryption, CESG Report, January 1970]) A criptografia de chave pública é um esquema assimétrico que usa um par de chaves para criptografia: uma chave pública, que criptografa os dados, e uma chave privada ou secreta correspondente para descriptografia. Você publica sua chave pública para o mundo enquanto mantém sua chave privada em segredo. Qualquer pessoa com uma cópia da sua chave pública pode criptografar informações que somente você pode ler. Até mesmo pessoas que você nunca conheceu. É computacionalmente inviável deduzir a chave privada da chave pública. Qualquer pessoa que possua uma chave pública pode criptografar informações, mas não pode descriptografá-las. Somente a pessoa que possui a chave privada correspondente pode descriptografar as informações. https://image.nostr.build/fdb71ae7a4450a523456827bdd509b31f0250f63152cc6f4ba78df290887318b.jpg
Figura 1-3. Criptografia de chave pública O principal benefício da criptografia de chave pública é que ela permite que pessoas que não possuem nenhum acordo de segurança pré-existente troquem mensagens com segurança. A necessidade de remetente e destinatário compartilharem chaves secretas através de algum canal seguro é eliminada; todas as comunicações envolvem apenas chaves públicas e nenhuma chave privada é transmitida ou compartilhada. Alguns exemplos de criptossistemas de chave pública são Elgamal (nomeado em homenagem a seu inventor, Taher Elgamal), RSA (nomeado em homenagem a seus inventores, Ron Rivest, Adi Shamir e Leonard Adleman), Diffie-Hellman (nomeado, você adivinhou, em homenagem a seus inventores). ) e DSA, o algoritmo de assinatura digital (inventado por David Kravitz). Como a criptografia convencional já foi o único meio disponível para transmitir informações secretas, o custo dos canais seguros e da distribuição de chaves relegou a sua utilização apenas àqueles que podiam pagar, como governos e grandes bancos (ou crianças pequenas com anéis descodificadores secretos). A criptografia de chave pública é a revolução tecnológica que fornece criptografia forte para as massas adultas. Lembra do mensageiro com a pasta trancada e algemada ao pulso? A criptografia de chave pública o tira do mercado (provavelmente para seu alívio).
Como funciona o PGP.
O PGP combina alguns dos melhores recursos da criptografia convencional e de chave pública. PGP é um criptossistema híbrido. Quando um usuário criptografa texto simples com PGP, o PGP primeiro compacta o texto simples. A compactação de dados economiza tempo de transmissão do modem e espaço em disco e, mais importante ainda, fortalece a segurança criptográfica. A maioria das técnicas de criptoanálise explora padrões encontrados no texto simples para quebrar a cifra. A compressão reduz esses padrões no texto simples, aumentando assim enormemente a resistência à criptoanálise. (Arquivos que são muito curtos para compactar ou que não são compactados bem não são compactados.) O PGP então cria uma chave de sessão, que é uma chave secreta única. Esta chave é um número aleatório gerado a partir dos movimentos aleatórios do mouse e das teclas digitadas. Esta chave de sessão funciona com um algoritmo de criptografia convencional rápido e muito seguro para criptografar o texto simples; o resultado é texto cifrado. Depois que os dados são criptografados, a chave da sessão é criptografada na chave pública do destinatário. Essa chave de sessão criptografada com chave pública é transmitida junto com o texto cifrado ao destinatário.
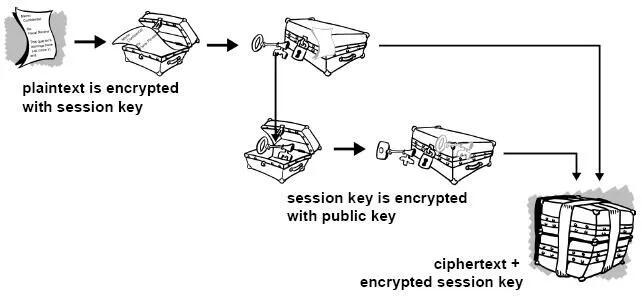
Figura 1-4. Como funciona a criptografia PGP A descriptografia funciona ao contrário. A cópia do PGP do destinatário usa sua chave privada para recuperar a chave de sessão temporária, que o PGP usa para descriptografar o texto cifrado criptografado convencionalmente.

Figura 1-5. Como funciona a descriptografia PGP A combinação dos dois métodos de criptografia combina a conveniência da criptografia de chave pública com a velocidade da criptografia convencional. A criptografia convencional é cerca de 1.000 vezes mais rápida que a criptografia de chave pública. A criptografia de chave pública, por sua vez, fornece uma solução para
problemas de distribuição de chaves e transmissão de dados. Usados em conjunto, o desempenho e a distribuição de chaves são melhorados sem qualquer sacrifício na segurança.
Chaves.
Uma chave é um valor que funciona com um algoritmo criptográfico para produzir um texto cifrado específico. As chaves são basicamente números muito, muito, muito grandes. O tamanho da chave é medido em bits; o número que representa uma chave de 1024 bits é enorme. Na criptografia de chave pública, quanto maior a chave, mais seguro é o texto cifrado. No entanto, o tamanho da chave pública e o tamanho da chave secreta da criptografia convencional não têm nenhuma relação. Uma chave convencional de 80 bits tem a força equivalente a uma chave pública de 1.024 bits. Uma chave convencional de 128 bits é equivalente a uma chave pública de 3.000 bits. Novamente, quanto maior a chave, mais segura, mas os algoritmos usados para cada tipo de criptografia são muito diferentes e, portanto, a comparação é como a de maçãs com laranjas. Embora as chaves pública e privada estejam matematicamente relacionadas, é muito difícil derivar a chave privada dada apenas a chave pública; no entanto, derivar a chave privada é sempre possível, desde que haja tempo e capacidade computacional suficientes. Isto torna muito importante escolher chaves do tamanho certo; grande o suficiente para ser seguro, mas pequeno o suficiente para ser aplicado rapidamente. Além disso, você precisa considerar quem pode estar tentando ler seus arquivos, quão determinados eles estão, quanto tempo têm e quais podem ser seus recursos. Chaves maiores serão criptograficamente seguras por um longo período de tempo. Se o que você deseja criptografar precisar ficar oculto por muitos anos, você pode usar uma chave muito grande. Claro, quem sabe quanto tempo levará para determinar sua chave usando os computadores mais rápidos e eficientes de amanhã? Houve um tempo em que uma chave simétrica de 56 bits era considerada extremamente segura. As chaves são armazenadas de forma criptografada. O PGP armazena as chaves em dois arquivos no seu disco rígido; um para chaves públicas e outro para chaves privadas. Esses arquivos são chamados de chaveiros. Ao usar o PGP, você normalmente adicionará as chaves públicas dos seus destinatários ao seu chaveiro público. Suas chaves privadas são armazenadas em seu chaveiro privado. Se você perder seu chaveiro privado, não será possível descriptografar nenhuma informação criptografada nas chaves desse anel.
Assinaturas digitais.
Um grande benefício da criptografia de chave pública é que ela fornece um método para empregar assinaturas digitais. As assinaturas digitais permitem ao destinatário da informação verificar a autenticidade da origem da informação e também verificar se a informação está intacta. Assim, as assinaturas digitais de chave pública fornecem autenticação e integridade de dados. A assinatura digital também proporciona o não repúdio, o que significa que evita que o remetente alegue que não enviou realmente as informações. Esses recursos são tão fundamentais para a criptografia quanto a privacidade, se não mais. Uma assinatura digital tem a mesma finalidade de uma assinatura manuscrita. No entanto, uma assinatura manuscrita é fácil de falsificar. Uma assinatura digital é superior a uma assinatura manuscrita porque é quase impossível de ser falsificada, além de atestar o conteúdo da informação, bem como a identidade do signatário.
Algumas pessoas tendem a usar mais assinaturas do que criptografia. Por exemplo, você pode não se importar se alguém souber que você acabou de depositar US$ 1.000 em sua conta, mas quer ter certeza de que foi o caixa do banco com quem você estava lidando. A maneira básica pela qual as assinaturas digitais são criadas é ilustrada na Figura 1-6 . Em vez de criptografar informações usando a chave pública de outra pessoa, você as criptografa com sua chave privada. Se as informações puderem ser descriptografadas com sua chave pública, elas deverão ter se originado em você.
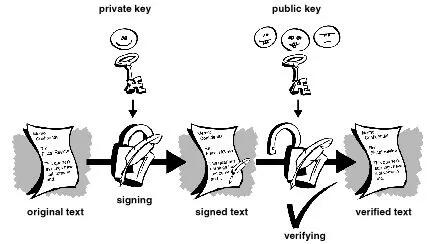
Figura 1-6. Assinaturas digitais simples
Funções hash.
O sistema descrito acima apresenta alguns problemas. É lento e produz um enorme volume de dados – pelo menos o dobro do tamanho da informação original. Uma melhoria no esquema acima é a adição de uma função hash unidirecional no processo. Uma função hash unidirecional recebe uma entrada de comprimento variável – neste caso, uma mensagem de qualquer comprimento, até mesmo milhares ou milhões de bits – e produz uma saída de comprimento fixo; digamos, 160 bits. A função hash garante que, se a informação for alterada de alguma forma – mesmo que por apenas um bit – seja produzido um valor de saída totalmente diferente. O PGP usa uma função hash criptograficamente forte no texto simples que o usuário está assinando. Isso gera um item de dados de comprimento fixo conhecido como resumo da mensagem. (Novamente, qualquer alteração nas informações resulta em um resumo totalmente diferente.) Então o PGP usa o resumo e a chave privada para criar a “assinatura”. O PGP transmite a assinatura e o texto simples juntos. Ao receber a mensagem, o destinatário utiliza o PGP para recalcular o resumo, verificando assim a assinatura. O PGP pode criptografar o texto simples ou não; assinar texto simples é útil se alguns dos destinatários não estiverem interessados ou não forem capazes de verificar a assinatura. Desde que uma função hash segura seja usada, não há como retirar a assinatura de alguém de um documento e anexá-la a outro, ou alterar uma mensagem assinada de qualquer forma. A menor alteração em um documento assinado causará falha no processo de verificação da assinatura digital.
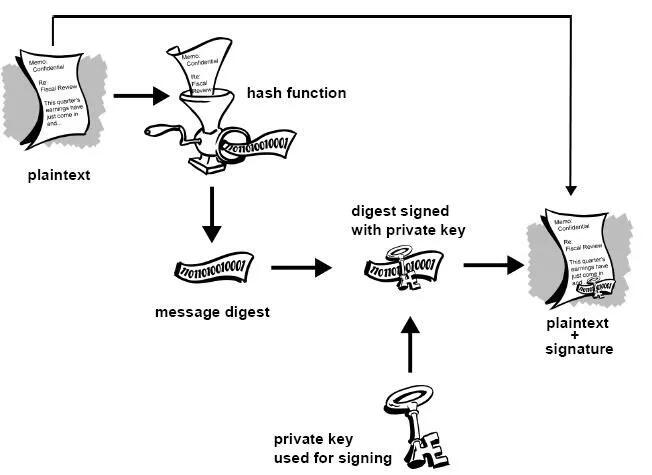
Figura 1-7. Assinaturas digitais seguras As assinaturas digitais desempenham um papel importante na autenticação e validação de chaves de outros usuários PGP.
Certificados digitais.
Um problema com os criptosistemas de chave pública é que os usuários devem estar constantemente vigilantes para garantir que estão criptografando com a chave da pessoa correta. Num ambiente onde é seguro trocar chaves livremente através de servidores públicos, os ataques man-in-the-middle são uma ameaça potencial. Neste tipo de ataque, alguém publica uma chave falsa com o nome e ID de usuário do destinatário pretendido. Os dados criptografados – e interceptados por – o verdadeiro proprietário desta chave falsa estão agora em mãos erradas. Em um ambiente de chave pública, é vital que você tenha certeza de que a chave pública para a qual você está criptografando os dados é de fato a chave pública do destinatário pretendido e não uma falsificação. Você pode simplesmente criptografar apenas as chaves que foram entregues fisicamente a você. Mas suponha que você precise trocar informações com pessoas que nunca conheceu; como você pode saber se tem a chave correta? Os certificados digitais, ou certs, simplificam a tarefa de estabelecer se uma chave pública realmente pertence ao suposto proprietário. Um certificado é uma forma de credencial. Exemplos podem ser sua carteira de motorista, seu cartão de previdência social ou sua certidão de nascimento. Cada um deles contém algumas informações que identificam você e alguma autorização informando que outra pessoa confirmou sua identidade. Alguns certificados, como o seu passaporte, são uma confirmação importante o suficiente da sua identidade para que você não queira perdê-los, para que ninguém os use para se passar por você.
Um certificado digital são dados que funcionam como um certificado físico. Um certificado digital é uma informação incluída na chave pública de uma pessoa que ajuda outras pessoas a verificar se uma chave é genuína ou válida. Os certificados digitais são usados para impedir tentativas de substituir a chave de uma pessoa por outra.
Um certificado digital consiste em três coisas:
● Uma chave pública.
● Informações do certificado. (Informações de "identidade" sobre o usuário, como nome, ID do usuário e assim por diante.) ● Uma ou mais assinaturas digitais.
O objetivo da assinatura digital em um certificado é afirmar que as informações do certificado foram atestadas por alguma outra pessoa ou entidade. A assinatura digital não atesta a autenticidade do certificado como um todo; ele atesta apenas que as informações de identidade assinadas acompanham ou estão vinculadas à chave pública. Assim, um certificado é basicamente uma chave pública com uma ou duas formas de identificação anexadas, além de um forte selo de aprovação de algum outro indivíduo confiável.
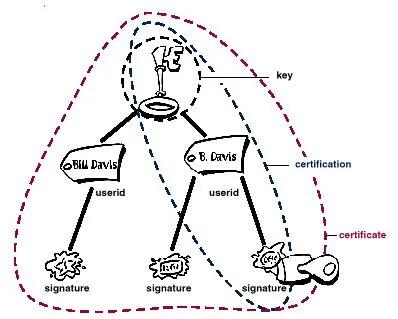 Figura 1-8. Anatomia de um certificado PGP
Figura 1-8. Anatomia de um certificado PGPDistribuição de certificados.
Os certificados são utilizados quando é necessário trocar chaves públicas com outra pessoa. Para pequenos grupos de pessoas que desejam se comunicar com segurança, é fácil trocar manualmente disquetes ou e-mails contendo a chave pública de cada proprietário. Esta é a distribuição manual de chave pública e é prática apenas até certo ponto. Além desse ponto, é necessário implementar sistemas que possam fornecer os mecanismos necessários de segurança, armazenamento e troca para que colegas de trabalho, parceiros de negócios ou estranhos possam se comunicar, se necessário. Eles podem vir na forma de repositórios somente de armazenamento, chamados Servidores de Certificados, ou sistemas mais estruturados que fornecem recursos adicionais de gerenciamento de chaves e são chamados de Infraestruturas de Chave Pública (PKIs).
Servidores de certificados.
Um servidor de certificados, também chamado de servidor certificado ou servidor de chaves, é um banco de dados que permite aos usuários enviar e recuperar certificados digitais. Um servidor certificado geralmente fornece alguns recursos administrativos que permitem que uma empresa mantenha suas políticas de segurança – por exemplo, permitindo que apenas as chaves que atendam a determinados requisitos sejam armazenadas.
Infraestruturas de Chave Pública.
Uma PKI contém os recursos de armazenamento de certificados de um servidor de certificados, mas também fornece recursos de gerenciamento de certificados (a capacidade de emitir, revogar, armazenar, recuperar e confiar em certificados). A principal característica de uma PKI é a introdução do que é conhecido como Autoridade Certificadora,ou CA, que é uma entidade humana — uma pessoa, grupo, departamento, empresa ou outra associação — que uma organização autorizou a emitir certificados para seus usuários de computador. (A função de uma CA é análoga à do Passport Office do governo de um país.) Uma CA cria certificados e os assina digitalmente usando a chave privada da CA. Devido ao seu papel na criação de certificados, a CA é o componente central de uma PKI. Usando a chave pública da CA, qualquer pessoa que queira verificar a autenticidade de um certificado verifica a assinatura digital da CA emissora e, portanto, a integridade do conteúdo do certificado (mais importante ainda, a chave pública e a identidade do titular do certificado).
Formatos de certificado.
Um certificado digital é basicamente uma coleção de informações de identificação vinculadas a uma chave pública e assinadas por um terceiro confiável para provar sua autenticidade. Um certificado digital pode ter vários formatos diferentes.
O PGP reconhece dois formatos de certificado diferentes:
● Certificados PGP ● Certificados X.509 Formato do certificado PGP. Um certificado PGP inclui (mas não está limitado a) as seguintes informações: ● O número da versão do PGP — identifica qual versão do PGP foi usada para criar a chave associada ao certificado. A chave pública do titular do certificado — a parte pública do seu par de chaves, juntamente com o algoritmo da chave: RSA, DH (Diffie-Hellman) ou DSA (Algoritmo de Assinatura Digital).
● As informações do detentor do certificado — consistem em informações de “identidade” sobre o usuário, como seu nome, ID de usuário, fotografia e assim por diante. ● A assinatura digital do proprietário do certificado — também chamada de autoassinatura, é a assinatura que utiliza a chave privada correspondente da chave pública associada ao certificado. ● O período de validade do certificado — a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar. ● O algoritmo de criptografia simétrica preferido para a chave — indica o algoritmo de criptografia para o qual o proprietário do certificado prefere que as informações sejam criptografadas. Os algoritmos suportados são CAST, IDEA ou Triple-DES. Você pode pensar em um certificado PGP como uma chave pública com um ou mais rótulos vinculados a ele (veja a Figura 1.9 ). Nessas 'etiquetas' você encontrará informações que identificam o proprietário da chave e uma assinatura do proprietário da chave, que afirma que a chave e a identificação andam juntas. (Essa assinatura específica é chamada de autoassinatura; todo certificado PGP contém uma autoassinatura.) Um aspecto único do formato de certificado PGP é que um único certificado pode conter múltiplas assinaturas. Várias ou muitas pessoas podem assinar o par chave/identificação para atestar a sua própria garantia de que a chave pública pertence definitivamente ao proprietário especificado. Se você procurar em um servidor de certificados público, poderá notar que certos certificados, como o do criador do PGP, Phil Zimmermann, contêm muitas assinaturas. Alguns certificados PGP consistem em uma chave pública com vários rótulos, cada um contendo um meio diferente de identificar o proprietário da chave (por exemplo, o nome do proprietário e a conta de e-mail corporativa, o apelido do proprietário e a conta de e-mail residencial, uma fotografia do proprietário — tudo em um certificado). A lista de assinaturas de cada uma dessas identidades pode ser diferente; as assinaturas atestam a autenticidade de que um dos rótulos pertence à chave pública, e não que todos os rótulos da chave sejam autênticos. (Observe que 'autêntico' está nos olhos de quem vê - assinaturas são opiniões, e diferentes pessoas dedicam diferentes níveis de devida diligência na verificação da autenticidade antes de assinar uma chave.)
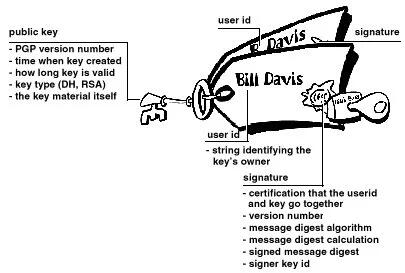 Figura 1-9. Um certificado PGP
Figura 1-9. Um certificado PGPFormato de certificado X.509.
X.509 é outro formato de certificado muito comum. Todos os certificados X.509 estão em conformidade com o padrão internacional ITU-T X.509; assim (teoricamente) os certificados X.509 criados para um aplicativo podem ser usados por qualquer aplicativo compatível com X.509. Na prática, porém, diferentes empresas criaram suas próprias extensões para certificados X.509, e nem todas funcionam juntas. Um certificado exige que alguém valide que uma chave pública e o nome do proprietário da chave andam juntos. Com os certificados PGP, qualquer pessoa pode desempenhar o papel de validador. Com certificados X.509, o validador é sempre uma Autoridade Certificadora ou alguém designado por uma CA. (Tenha em mente que os certificados PGP também suportam totalmente uma estrutura hierárquica usando uma CA para validar certificados.)
Um certificado X.509 é uma coleção de um conjunto padrão de campos contendo informações sobre um usuário ou dispositivo e sua chave pública correspondente. O padrão X.509 define quais informações vão para o certificado e descreve como codificá-lo (o formato dos dados). Todos os certificados X.509 possuem os seguintes dados:
O número da versão X.509
— identifica qual versão do padrão X.509 se aplica a este certificado, o que afeta quais informações podem ser especificadas nele. A mais atual é a versão 3.
A chave pública do titular do certificado
— a chave pública do titular do certificado, juntamente com um identificador de algoritmo que especifica a qual sistema criptográfico a chave pertence e quaisquer parâmetros de chave associados.
O número de série do certificado
— a entidade (aplicação ou pessoa) que criou o certificado é responsável por atribuir-lhe um número de série único para distingui-lo de outros certificados que emite. Esta informação é usada de diversas maneiras; por exemplo, quando um certificado é revogado, seu número de série é colocado em uma Lista de Revogação de Certificados ou CRL.
O identificador exclusivo do detentor do certificado
— (ou DN — nome distinto). Este nome pretende ser exclusivo na Internet. Este nome pretende ser exclusivo na Internet. Um DN consiste em múltiplas subseções e pode ser parecido com isto: CN=Bob Allen, OU=Divisão Total de Segurança de Rede, O=Network Associates, Inc., C=EUA (Referem-se ao nome comum, à unidade organizacional, à organização e ao país do sujeito .)
O período de validade do certificado
— a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar.
O nome exclusivo do emissor do certificado
— o nome exclusivo da entidade que assinou o certificado. Normalmente é uma CA. A utilização do certificado implica confiar na entidade que assinou este certificado. (Observe que em alguns casos, como certificados de CA raiz ou de nível superior , o emissor assina seu próprio certificado.)
A assinatura digital do emitente
— a assinatura utilizando a chave privada da entidade que emitiu o certificado.
O identificador do algoritmo de assinatura
— identifica o algoritmo usado pela CA para assinar o certificado.
Existem muitas diferenças entre um certificado X.509 e um certificado PGP, mas as mais importantes são as seguintes: você pode criar seu próprio certificado PGP;
● você deve solicitar e receber um certificado X.509 de uma autoridade de certificação
● Os certificados X.509 suportam nativamente apenas um único nome para o proprietário da chave
● Os certificados X.509 suportam apenas uma única assinatura digital para atestar a validade da chave
Para obter um certificado X.509, você deve solicitar a uma CA a emissão de um certificado. Você fornece sua chave pública, prova de que possui a chave privada correspondente e algumas informações específicas sobre você. Em seguida, você assina digitalmente as informações e envia o pacote completo – a solicitação de certificado – para a CA. A CA então realiza algumas diligências para verificar se as informações fornecidas estão corretas e, em caso afirmativo, gera o certificado e o devolve.
Você pode pensar em um certificado X.509 como um certificado de papel padrão (semelhante ao que você recebeu ao concluir uma aula de primeiros socorros básicos) com uma chave pública colada nele. Ele contém seu nome e algumas informações sobre você, além da assinatura da pessoa que o emitiu para você.
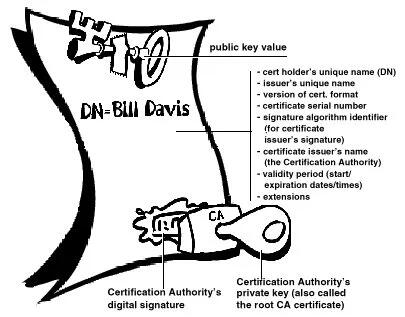
Figura 1-10. Um certificado X.509 Provavelmente, o uso mais visível dos certificados X.509 atualmente é em navegadores da web.
Validade e confiança Cada usuário em um sistema de chave pública está vulnerável a confundir uma chave falsa (certificado) com uma chave real. Validade é a confiança de que um certificado de chave pública pertence ao seu suposto proprietário. A validade é essencial em um ambiente de chave pública onde você deve estabelecer constantemente se um determinado certificado é autêntico ou não. Depois de ter certeza de que um certificado pertencente a outra pessoa é válido, você pode assinar a cópia em seu chaveiro para atestar que verificou o certificado e que ele é autêntico. Se quiser que outras pessoas saibam que você deu ao certificado seu selo de aprovação, você pode exportar a assinatura para um servidor de certificados para que outras pessoas possam vê-la.
Conforme descrito na seção Infraestruturas de Chave Pública , algumas empresas designam uma ou mais Autoridades de Certificação (CAs) para indicar a validade do certificado. Em uma organização que usa uma PKI com certificados X.509, é função da CA emitir certificados aos usuários — um processo que geralmente envolve responder à solicitação de certificado do usuário. Em uma organização que usa certificados PGP sem PKI, é função da CA verificar a autenticidade de todos os certificados PGP e depois assinar os bons. Basicamente, o objetivo principal de uma CA é vincular uma chave pública às informações de identificação contidas no certificado e, assim, garantir a terceiros que algum cuidado foi tomado para garantir que esta ligação das informações de identificação e da chave seja válida. O CA é o Grand Pooh-bah da validação em uma organização; alguém em quem todos confiam e, em algumas organizações, como aquelas que utilizam uma PKI, nenhum certificado é considerado válido, a menos que tenha sido assinado por uma CA confiável.
Verificando validade.
Uma maneira de estabelecer a validade é passar por algum processo manual. Existem várias maneiras de fazer isso. Você pode exigir que o destinatário pretendido lhe entregue fisicamente uma cópia de sua chave pública. Mas isto é muitas vezes inconveniente e ineficiente. Outra forma é verificar manualmente a impressão digital do certificado. Assim como as impressões digitais de cada ser humano são únicas, a impressão digital de cada certificado PGP é única. A impressão digital é um hash do certificado do usuário e aparece como uma das propriedades do certificado. No PGP, a impressão digital pode aparecer como um número hexadecimal ou uma série das chamadas palavras biométricas, que são foneticamente distintas e são usadas para facilitar um pouco o processo de identificação da impressão digital. Você pode verificar se um certificado é válido ligando para o proprietário da chave (para que você origine a transação) e pedindo ao proprietário que leia a impressão digital de sua chave para você e compare essa impressão digital com aquela que você acredita ser a verdadeira. Isso funciona se você conhece a voz do proprietário, mas como verificar manualmente a identidade de alguém que você não conhece? Algumas pessoas colocam a impressão digital de sua chave em seus cartões de visita exatamente por esse motivo. Outra forma de estabelecer a validade do certificado de alguém é confiar que um terceiro indivíduo passou pelo processo de validação do mesmo. Uma CA, por exemplo, é responsável por garantir que, antes de emitir um certificado, ele ou ela o verifique cuidadosamente para ter certeza de que a parte da chave pública realmente pertence ao suposto proprietário. Qualquer pessoa que confie na CA considerará automaticamente quaisquer certificados assinados pela CA como válidos. Outro aspecto da verificação da validade é garantir que o certificado não foi revogado. Para obter mais informações, consulte a seção Revogação de certificado .
Estabelecendo confiança.
Você valida certificados. Você confia nas pessoas. Mais especificamente, você confia nas pessoas para validar os certificados de outras pessoas. Normalmente, a menos que o proprietário lhe entregue o certificado, você terá que confiar na palavra de outra pessoa de que ele é válido.
Introdutores meta e confiáveis.
Na maioria das situações, as pessoas confiam completamente na CA para estabelecer a validade dos certificados. Isso significa que todos os demais dependem da CA para passar por todo o processo de validação manual. Isso é aceitável até um certo número de usuários ou locais de trabalho e, então, não é possível para a AC manter o mesmo nível de validação de qualidade. Nesse caso, é necessário adicionar outros validadores ao sistema.
Um CA também pode ser um meta- introdutor. Um meta-introdutor confere não apenas validade às chaves, mas também confere a capacidade de confiar nas chaves a outros. Semelhante ao rei que entrega seu selo a seus conselheiros de confiança para que eles possam agir de acordo com sua autoridade, o meta-introdutor permite que outros atuem como introdutores de confiança. Esses introdutores confiáveis podem validar chaves com o mesmo efeito do meta-introdutor. Eles não podem, entretanto, criar novos introdutores confiáveis.
Meta-introdutor e introdutor confiável são termos PGP. Em um ambiente X.509, o meta-introdutor é chamado de Autoridade de Certificação raiz ( CA raiz) e os introdutores confiáveis são Autoridades de Certificação subordinadas . A CA raiz usa a chave privada associada a um tipo de certificado especial denominado certificado CA raiz para assinar certificados. Qualquer certificado assinado pelo certificado CA raiz é visto como válido por qualquer outro certificado assinado pela raiz. Este processo de validação funciona mesmo para certificados assinados por outras CAs no sistema — desde que o certificado da CA raiz tenha assinado o certificado da CA subordinada, qualquer certificado assinado pela CA será considerado válido para outras pessoas dentro da hierarquia. Este processo de verificação de backup por meio do sistema para ver quem assinou cujo certificado é chamado de rastreamento de um caminho de certificação ou cadeia de certificação.
Modelos de confiança.
Em sistemas relativamente fechados, como em uma pequena empresa, é fácil rastrear um caminho de certificação até a CA raiz. No entanto, os usuários muitas vezes precisam se comunicar com pessoas fora do seu ambiente corporativo, incluindo algumas que nunca conheceram, como fornecedores, consumidores, clientes, associados e assim por diante. É difícil estabelecer uma linha de confiança com aqueles em quem sua CA não confia explicitamente. As empresas seguem um ou outro modelo de confiança, que determina como os usuários irão estabelecer a validade do certificado. Existem três modelos diferentes:
Confiança Direta.
Confiança Hierárquica Uma teia de confiança Confiança direta A confiança direta é o modelo de confiança mais simples. Neste modelo, um usuário confia que uma chave é válida porque sabe de onde ela veio. Todos os criptosistemas usam essa forma de confiança de alguma forma. Por exemplo, em navegadores da Web, as chaves raiz da Autoridade de Certificação são diretamente confiáveis porque foram enviadas pelo fabricante. Se houver alguma forma de hierarquia, ela se estenderá a partir desses certificados diretamente confiáveis. No PGP, um usuário que valida as chaves e nunca define outro certificado para ser um introdutor confiável está usando confiança direta.
 Figura 1-11. Confiança direta
Figura 1-11. Confiança diretaConfiança Hierárquica.
Em um sistema hierárquico, há vários certificados "raiz" a partir dos quais a confiança se estende. Esses certificados podem certificar eles próprios certificados ou podem certificar certificados que certificam ainda outros certificados em alguma cadeia. Considere isso como uma grande “árvore” de confiança. A validade do certificado "folha" é verificada rastreando desde seu certificador até outros certificadores, até que um certificado raiz diretamente confiável seja encontrado.
Figura 1-12. Confiança hierárquica
Teia de Confiança.
Uma teia de confiança abrange ambos os outros modelos, mas também acrescenta a noção de que a confiança está nos olhos de quem vê (que é a visão do mundo real) e a ideia de que mais informação é melhor. É, portanto, um modelo de confiança cumulativa. Um certificado pode ser confiável diretamente ou confiável em alguma cadeia que remonta a um certificado raiz diretamente confiável (o meta-introdutor) ou por algum grupo de introdutores.
Talvez você já tenha ouvido falar do termo seis graus de separação, que sugere que qualquer pessoa no mundo pode determinar algum vínculo com qualquer outra pessoa no mundo usando seis ou menos outras pessoas como intermediários. Esta é uma teia de introdutores. É também a visão de confiança do PGP. PGP usa assinaturas digitais como forma de introdução. Quando qualquer usuário assina a chave de outro, ele ou ela se torna o introdutor dessa chave. À medida que esse processo avança, ele estabelece uma rede de confiança.
Em um ambiente PGP, qualquer usuário pode atuar como autoridade certificadora. Qualquer usuário PGP pode validar o certificado de chave pública de outro usuário PGP. No entanto, tal certificado só é válido para outro usuário se a parte confiável reconhecer o validador como um introdutor confiável. (Ou seja, você confia na minha opinião de que as chaves dos outros são válidas apenas se você me considerar um apresentador confiável. Caso contrário, minha opinião sobre a validade das outras chaves é discutível.) Armazenados no chaveiro público de cada usuário estão indicadores de
● se o usuário considera ou não uma chave específica válida
● o nível de confiança que o usuário deposita na chave que o proprietário da chave pode servir como certificador das chaves de terceiros
Você indica, na sua cópia da minha chave, se acha que meu julgamento conta. Na verdade, é um sistema de reputação: certas pessoas têm a reputação de fornecer boas assinaturas e as pessoas confiam nelas para atestar a validade de outras chaves.
Níveis de confiança no PGP.
O nível mais alto de confiança em uma chave, a confiança implícita , é a confiança em seu próprio par de chaves. O PGP assume que se você possui a chave privada, você deve confiar nas ações da sua chave pública relacionada. Quaisquer chaves assinadas pela sua chave implicitamente confiável são válidas.
Existem três níveis de confiança que você pode atribuir à chave pública de outra pessoa:
● Confiança total ● Confiança marginal ● Não confiável (ou não confiável)
Para tornar as coisas confusas, também existem três níveis de validade:
● Válido ● Marginalmente válido ● Inválido
Para definir a chave de outra pessoa como um introdutor confiável, você
- Comece com uma chave válida, que seja.
- assinado por você ou
-
assinado por outro apresentador confiável e então
-
Defina o nível de confiança que você acha que o proprietário da chave tem direito.
Por exemplo, suponha que seu chaveiro contenha a chave de Alice. Você validou a chave de Alice e indica isso assinando-a. Você sabe que Alice é uma verdadeira defensora da validação de chaves de outras pessoas. Portanto, você atribui a chave dela com confiança total. Isso faz de Alice uma Autoridade Certificadora. Se Alice assinar a chave de outra pessoa, ela aparecerá como Válida em seu chaveiro. O PGP requer uma assinatura Totalmente confiável ou duas assinaturas Marginalmente confiáveis para estabelecer uma chave como válida. O método do PGP de considerar dois Marginais iguais a um Completo é semelhante a um comerciante que solicita duas formas de identificação. Você pode considerar Alice bastante confiável e também considerar Bob bastante confiável. Qualquer um deles sozinho corre o risco de assinar acidentalmente uma chave falsificada, portanto, você pode não depositar total confiança em nenhum deles. No entanto, as probabilidades de ambos os indivíduos terem assinado a mesma chave falsa são provavelmente pequenas.
Revogação de certificado.
Os certificados só são úteis enquanto são válidos. Não é seguro simplesmente presumir que um certificado é válido para sempre. Na maioria das organizações e em todas as PKIs, os certificados têm uma vida útil restrita. Isso restringe o período em que um sistema fica vulnerável caso ocorra um comprometimento do certificado.
Os certificados são assim criados com um período de validade programado: uma data/hora de início e uma data/hora de expiração. Espera-se que o certificado seja utilizável durante todo o seu período de validade (seu tempo de vida ). Quando o certificado expirar, ele não será mais válido, pois a autenticidade do seu par chave/identificação não estará mais garantida. (O certificado ainda pode ser usado com segurança para reconfirmar informações que foram criptografadas ou assinadas dentro do período de validade – no entanto, ele não deve ser confiável para tarefas criptográficas futuras.)
Existem também situações em que é necessário invalidar um certificado antes da sua data de expiração, como quando o titular do certificado termina o contrato de trabalho com a empresa ou suspeita que a chave privada correspondente do certificado foi comprometida. Isso é chamado de revogação. Um certificado revogado é muito mais suspeito do que um certificado expirado. Os certificados expirados são inutilizáveis, mas não apresentam a mesma ameaça de comprometimento que um certificado revogado. Qualquer pessoa que tenha assinado um certificado pode revogar a sua assinatura no certificado (desde que utilize a mesma chave privada que criou a assinatura). Uma assinatura revogada indica que o signatário não acredita mais que a chave pública e as informações de identificação pertencem uma à outra, ou que a chave pública do certificado (ou a chave privada correspondente) foi comprometida. Uma assinatura revogada deve ter quase tanto peso quanto um certificado revogado. Com certificados X.509, uma assinatura revogada é praticamente igual a um certificado revogado, visto que a única assinatura no certificado é aquela que o tornou válido em primeiro lugar – a assinatura da CA. Os certificados PGP fornecem o recurso adicional de que você pode revogar todo o seu certificado (não apenas as assinaturas nele) se você achar que o certificado foi comprometido. Somente o proprietário do certificado (o detentor da chave privada correspondente) ou alguém que o proprietário do certificado tenha designado como revogador pode revogar um certificado PGP. (Designar um revogador é uma prática útil, pois muitas vezes é a perda da senha da chave privada correspondente do certificado que leva um usuário PGP a revogar seu certificado - uma tarefa que só é possível se alguém tiver acesso à chave privada. ) Somente o emissor do certificado pode revogar um certificado X.509.
Comunicar que um certificado foi revogado.
Quando um certificado é revogado, é importante conscientizar os usuários potenciais do certificado de que ele não é mais válido. Com certificados PGP, a maneira mais comum de comunicar que um certificado foi revogado é publicá-lo em um servidor de certificados para que outras pessoas que desejem se comunicar com você sejam avisadas para não usar essa chave pública. Em um ambiente PKI, a comunicação de certificados revogados é mais comumente obtida por meio de uma estrutura de dados chamada Lista de Revogação de Certificados, ou CRL, que é publicada pela CA. A CRL contém uma lista validada com carimbo de data e hora de todos os certificados revogados e não expirados no sistema. Os certificados revogados permanecem na lista apenas até expirarem e, em seguida, são removidos da lista — isso evita que a lista fique muito longa. A CA distribui a CRL aos usuários em algum intervalo programado regularmente (e potencialmente fora do ciclo, sempre que um certificado é revogado). Teoricamente, isso impedirá que os usuários usem involuntariamente um certificado comprometido. É possível, no entanto, que haja um período de tempo entre as CRLs em que um certificado recentemente comprometido seja usado.
O que é uma senha?
A maioria das pessoas está familiarizada com a restrição de acesso a sistemas de computador por meio de uma senha, que é uma sequência única de caracteres que um usuário digita como código de identificação.
Uma senha longa é uma versão mais longa de uma senha e, em teoria, mais segura. Normalmente composta por várias palavras, uma frase secreta é mais segura contra ataques de dicionário padrão, em que o invasor tenta todas as palavras do dicionário na tentativa de determinar sua senha. As melhores senhas são relativamente longas e complexas e contêm uma combinação de letras maiúsculas e minúsculas, caracteres numéricos e de pontuação. O PGP usa uma senha para criptografar sua chave privada em sua máquina. Sua chave privada é criptografada em seu disco usando um hash de sua senha como chave secreta. Você usa a senha para descriptografar e usar sua chave privada. Uma senha deve ser difícil de esquecer e difícil de ser adivinhada por outras pessoas. Deve ser algo já firmemente enraizado na sua memória de longo prazo, em vez de algo que você invente do zero. Por que? Porque se você esquecer sua senha, você estará sem sorte. Sua chave privada é total e absolutamente inútil sem sua senha e nada pode ser feito a respeito. Lembra-se da citação anterior neste capítulo?
 PGP é a criptografia que manterá os principais governos fora dos seus arquivos. Certamente também o manterá fora de seus arquivos. Tenha isso em mente quando decidir alterar sua senha para a piada daquela piada que você nunca consegue lembrar.
PGP é a criptografia que manterá os principais governos fora dos seus arquivos. Certamente também o manterá fora de seus arquivos. Tenha isso em mente quando decidir alterar sua senha para a piada daquela piada que você nunca consegue lembrar.Divisão de chave.
Dizem que um segredo não é segredo se for conhecido por mais de uma pessoa. Compartilhar um par de chaves privadas representa um grande problema. Embora não seja uma prática recomendada, às vezes é necessário compartilhar um par de chaves privadas. Chaves de assinatura corporativa, por exemplo, são chaves privadas usadas por uma empresa para assinar – por exemplo – documentos legais, informações pessoais confidenciais ou comunicados de imprensa para autenticar sua origem. Nesse caso, vale a pena que vários membros da empresa tenham acesso à chave privada. No entanto, isto significa que qualquer indivíduo pode agir plenamente em nome da empresa. Nesse caso, é aconselhável dividir a chave entre várias pessoas, de modo que mais de uma ou duas pessoas apresentem um pedaço da chave para reconstituí-la em condições utilizáveis. Se poucas peças da chave estiverem disponíveis, a chave ficará inutilizável. Alguns exemplos são dividir uma chave em três partes e exigir duas delas para reconstituir a chave, ou dividi-la em duas partes e exigir ambas as peças. Se uma conexão de rede segura for usada durante o processo de reconstituição, os acionistas da chave não precisam estar fisicamente presentes para aderirem novamente à chave.
-
 @ 000002de:c05780a7
2025-05-21 17:42:27
@ 000002de:c05780a7
2025-05-21 17:42:27I've been trying out Arch Linux again and the thing that always surprises me is pacman. The way it works seems so unintuitive to me coming from the apt, yum, and dnf worlds.
I know I will get it and it will become internalized but I just wonder what the designer was thinking when making the flags/commands.
https://stacker.news/items/985808
-
 @ 8aa70f44:3073d1a6
2025-05-21 13:07:14
@ 8aa70f44:3073d1a6
2025-05-21 13:07:14Earlier this year I launched the asknostr.site project which has been a great journey and learning experience. I had wanted to write down my goals and ideas with the project but didn't get to it yet. Primal launching the article editor was a trigger for me to go for it.
Ever since I joined Nostr i was looking for ways to apply my skillset solve a problem and help with adoption. Around Christmas I figured that a Quora/Stackoverflow alternative is something that needs to exist on Nostr.
Before I knew it I had a pretty decent prototype. And because the network already had so much awesome content, contributors and authors I was never discouraged by the challenge that kills so many good ideas -> "Where do I get the first users?".
Since the initial announcement I have received so much encouragement through zaps, likes, DM's, and maybe most of all seeing the increase in usage of the site and #asknostr content kept me going.
Current State
The current version of the site is stable and most bugs are hashed out. After logging in (remote signer, extension or nsec) you can engage with content through votes, comments and replies. Or simply ask a new question.
All content is stored in the site's own private relay and preprocessed/computed into a single data store (postgres) so the site is fast, accessible and crawl-able.
The site supports browsing hashtags, voting/commenting on answers, asking new questions and every contributor get their own profile (example). At the time of writing the site has 41k questions, almost 200k replies/comments and upwards of 5 million sats purely for #asknostr content.
What to expect/On my list
There are plenty of things and UI bugs that need love and between writing the draft of this post and hitting publish I shipped 3 minor bug fixes. Little by little, bit by bit...
In addition to all those small details here is an overview of the things on my own wish list:
-
Inline Zaps: Ability to zap from the asknostr.site interface. Click the zap button, specify or pick the number of sats zap away.
-
Contributor Rank: A leaderboard to add some gamification. More recognition to those nostriches that spend their time helping other people out
-
Search by Keyword: Search all content by keywords. Experiment with the index to show related questions or answers
-
Better User Profiles: Improve the user profile so it shows all the profile questions and answers. Quick buttons to follow or zap that person. Better insights in the topics (hashtags) the profile contributes to
-
Bookmarks: Ability to bookmark questions and answers. Increase bookmark weight as a signal to rank answers.
-
Smarter Scoring: Tune how answers are scored (winning answer formula). Perhaps give more weight to the question author or use WoT. Not sure yet.
All of this is happening at some point so follow me if you want to stay up to date.
Goals
To manage expectations and keep me focussed I write down the mid and long term goals of the project.
Long term
Call me cheesy but I believe that humanity will flourish through an open web and sound money. My own journey started from with bitcoin but if you asked me today if it's BTC or nostr that is going to have the most impact I wouldn't know what to answer. Chicken or egg?
The goal of the project is to offer an open platform that empowers individuals to ask questions, share expertise and access high-quality information across different topics. The project empowers anyone to monetize their experience creating a sustainable ecosystem that values and rewards knowledge sharing. This will ultimately democratize access to knowledge for all.
Mid term
The project can help a lot with onboarding new users onto the network. Once we start to rank on certain topics we can get a piece of the search traffic pie (StackOverflows 12 million, and Quora 150 million visitors per month) which is a great way to expose people to the power of the network.
First time visitors do not need to know about nostr or zaps to receive value. They can browse around, discover interesting content and perhaps even create a profile without even knowing they are on Nostr now.
Gradually those users will understand the value of the network through better rankings (zaps beats likes), a cross-client experience and a profile that can be used on any nostr site or app.
In order for the site to do that we need to make sure content is browsable by language, (sub)topics and and we double down on 'the human touch' with real contributors and not LLMs.
Short Term Goal
The first goal is to make the site really good and an important resource for existing Nostr users. Enable visitors to search and discover what they are interested in. Integrate within the existing nostr eco system with 'open in' functionality and quick links to interesting projects (followerpacks?)
One of things i want to get right is to improve user retention by making the whole Q\&A experience more sticky. I want to run some experiments (bots, award, summaries) to get more people to use asknostr.site more often and come back.
What about the name?
Finally the big question: What about the asknostr.site name? I don't like the name that much but it's what people know. I think there is a high chance that people will discover Nostr apps like Olas, Primal or Damus without needing to know what NOSTR is or means.
Therefore I think there is a good chance that the project won't be called asknostr.site forever. I guess it all depends on where we all take this.
Onwards!
-
-
 @ 8bad92c3:ca714aa5
2025-05-22 20:01:24
@ 8bad92c3:ca714aa5
2025-05-22 20:01:24Marty's Bent
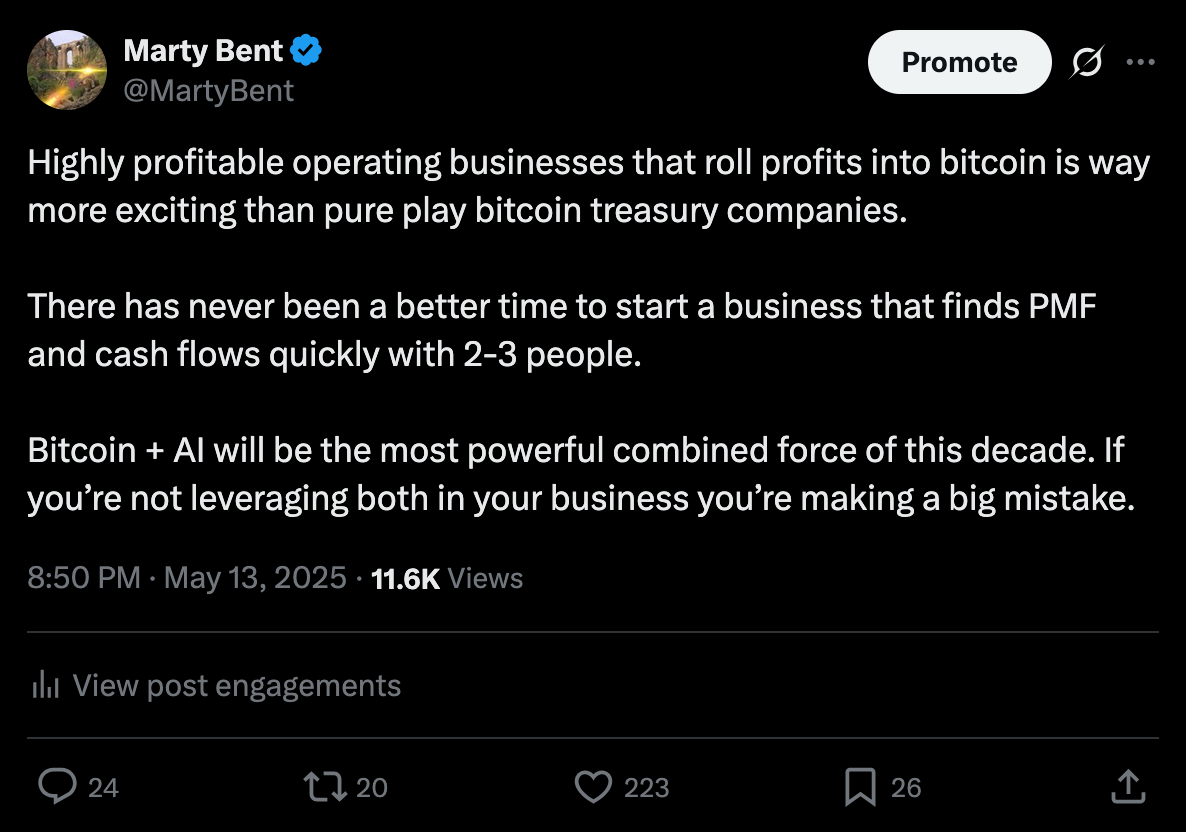
via me

It seems like every other day there's another company announced that is going public with the intent of competing with Strategy by leveraging capital markets to create financial instruments to acquire Bitcoin in a way that is accretive for shareholders. This is certainly a very interesting trend, very bullish for bitcoin in the short-term, and undoubtedly making it so bitcoin is top of mind in the mainstream. I won't pretend to know whether or not these strategies will ultimately be successful or fail in the short, medium or long term. However, one thing I do know is that the themes that interest me, both here at TFTC and in my role as Managing Partner at Ten31, are companies that are building good businesses that are efficient, have product-market-fit, generate revenues and profits and roll those profits into bitcoin.
While it seems pretty clear that Strategy has tapped into an arbitrage that exists in capital markets, it's not really that exciting. From a business perspective, it's actually pretty straightforward and simple; find where potential arbitrage opportunities exists between pools of capital looking for exposure to spot bitcoin or bitcoin's volatility but can't buy the actual asset, and provide them with products that give them access to exposure while simultaneously creating a cult-like retail following. Rinse and repeat. To the extent that this strategy is repeatable is yet to be seen. I imagine it can expand pretty rapidly. Particularly if we have a speculative fervor around companies that do this. But in the long run, I think the signal is falling back to first principles, looking for businesses that are actually providing goods and services to the broader economy - not focused on the hyper-financialized part of the economy - to provide value and create efficiencies that enable higher margins and profitability.
With this in mind, I think it's important to highlight the combined leverage that entrepreneurs have by utilizing bitcoin treasuries and AI tools that are emerging and becoming more advanced by the week. As I said in the tweet above, there's never been a better time to start a business that finds product-market fit and cash flows quickly with a team of two to three people. If you've been reading this rag over the last few weeks, you know that I've been experimenting with these AI tools and using them to make our business processes more efficient here at TFTC. I've also been using them at Ten31 to do deep research and analysis.
It has become abundantly clear to me that any founder or entrepreneur that is not utilizing the AI tools that are emerging is going to get left behind. As it stands today, all anyone has to do to get an idea from a thought in your head to the prototype stage to a minimum viable product is to hop into something like Claude or ChatGPT, have a brief conversation with an AI model that can do deep research about a particular niche that you want to provide a good service to and begin building.
Later this week, I will launch an app called Opportunity Cost in the Chrome and Firefox stores. It took me a few hours of work over the span of a week to ideate and iterate on the concept to the point where I had a working prototype that I handed off to a developer who is solving the last mile problem I have as an "idea guy" of getting the product to market. Only six months ago, accomplishing something like this would have been impossible for me. I've never written a line of code that's actually worked outside of the modded MySpace page I made back in middle school. I've always had a lot of ideas but have never been able to effectively communicate them to developers who can actually build them. With a combination of ChatGPT-03 and Replit, I was able to build an actual product that works. I'm using it in my browser today. It's pretty insane.
There are thousands of people coming to the same realization at the same time right now and going out there and building niche products very cheaply, with small teams, they are getting to market very quickly, and are amassing five figures, six figures, sometimes seven figures of MRR with extremely high profit margins. What most of these entrepreneurs have not really caught on to yet is that they should be cycling a portion - in my opinion, a large portion - of those profits into bitcoin. The combination of building a company utilizing these AI tools, getting it to market, getting revenue and profits, and turning those profits into bitcoin cannot be understated. You're going to begin seeing teams of one to ten people building businesses worth billions of dollars and they're going to need to store the value they create, any money that cannot be debased.
Grant Gilliam, one of the co-founders of Ten31, wrote about this in early 2024, bitcoin being the fourth lever of equity value growth for companies.
[
Bitcoin Treasury - The Fourth Lever to Equity Value Growth
Most companies do not hold enough bitcoin There is a saying you often hear in bitcoin circles that “you can never have enough bitcoin.” This is typically expressed by those who have spent the time to both understand bitcoin’s unique and superior monetary properties and also to appreciate why tho
Ten31 - Investors in bitcoin infrastructure and freedom techGrant Gilliam
](https://ten31.vc/insights/treasury?ref=tftc.io)
We already see this theme playing out at Ten31 with some of our portfolio companies, most notably Strike, which recently released some of their financials, highlighting the fact that they're extremely profitable with high margins and a relatively small team (~75). This is extremely impressive, especially when you consider the fact that they're a global company competing with the likes of Coinbase and Block, which have each thousands of employees.
Even those who are paying attention to the developments in the AI space and how the tools can enable entrepreneurs to build faster aren't really grasping the gravity of what's at play here. Many are simply thinking of consumer apps that can be built and distributed quickly to market, but the ways in which AI can be implemented extend far beyond the digital world. Here's a great example of a company a fellow freak is building with the mindset of keeping the team small, utilizing AI tools to automate processes and quickly push profits into bitcoin.
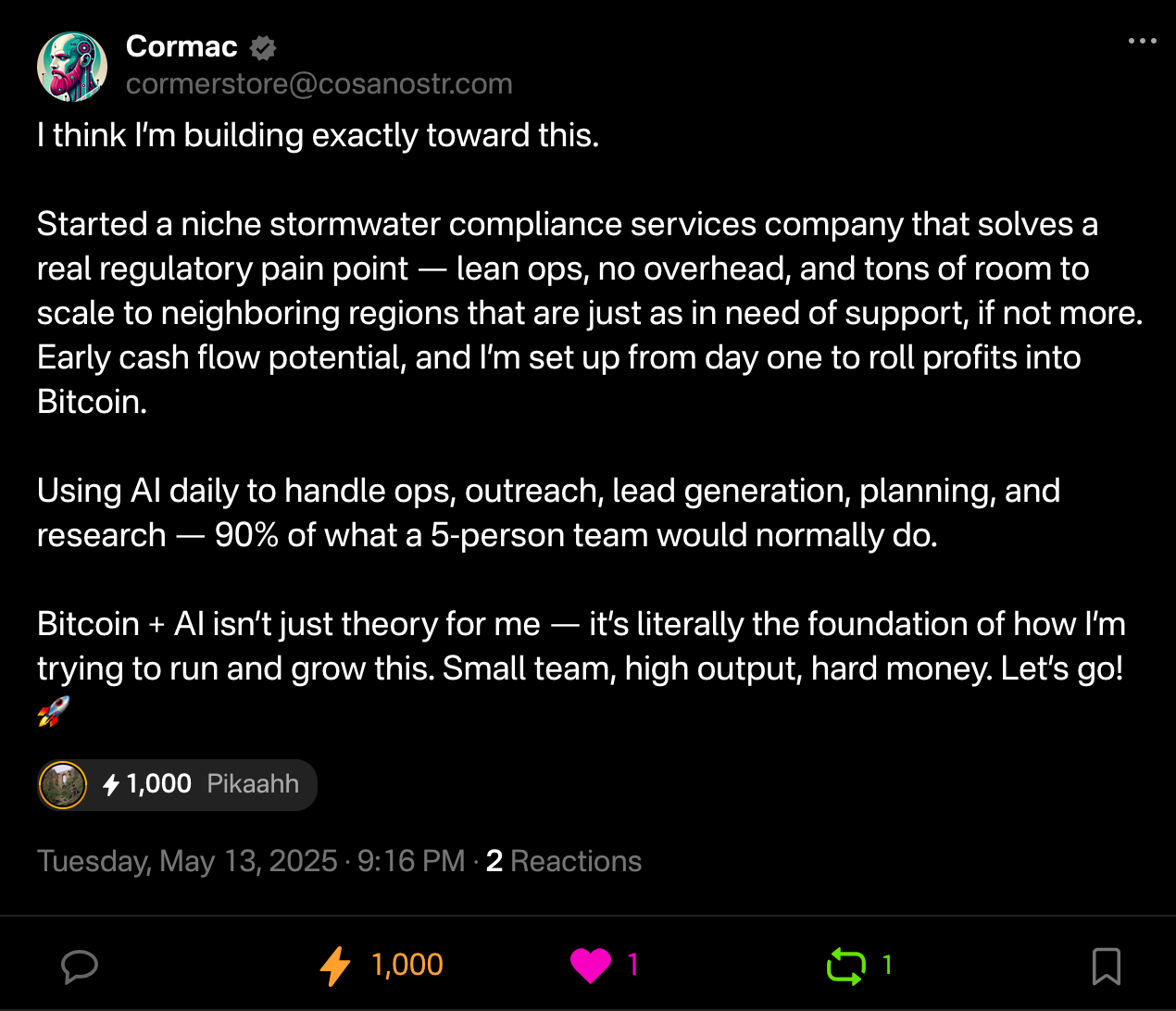
via Cormac
Again, this is where the exciting things are happening in my mind. People leveraging new tools to solve real problems to drive real value that ultimately produce profits for entrepreneurs. The entrepreneurs who decide to save those profits in bitcoin will find that the equity value growth of their companies accelerates exponentially as they provide more value, gain more traction, and increase their profits while also riding the bitcoin as it continues on its monetization phase. The compounded leverage of building a company that leverages AI tools and sweeps profits into bitcoin is going to be the biggest asymmetric play of the next decade. Personally, I also see it as something that's much more fulfilling than the pure play bitcoin treasury companies that are coming to market because consumers and entrepreneurs are able to recive and provide a ton of value in the real economy.
If you're looking to stay on top of the developments in the AI space and how you can apply the tools to help build your business or create a new business, I highly recommend you follow somebody like Greg Isenberg, whose Startup Ideas Podcast has been incredibly valuable for me as I attempt to get a lay of the land of how to implement AI into my businesses.
America's Two Economies
In my recent podcast with Lyn Alden, she outlined how our trade deficits create a cycle that's reshaping America's economic geography. As Alden explained, US trade deficits pump dollars into international markets, but these dollars don't disappear - they return as investments in US financial assets. This cycle gradually depletes industrial heartlands while enriching financial centers on the coasts, creating what amounts to two separate American economies.
"We're basically constantly taking economic vibrancy out of Michigan and Ohio and rural Pennsylvania where the steel mills were... and stuffing it back into financial assets in New York and Silicon Valley." - Lyn Alden
This pattern has persisted for over four decades, accelerating significantly since the early 1980s. Alden emphasized that while economists may argue there's still room before reaching a crisis point, the political consequences are already here. The growing divide between these two Americas has fueled populist sentiment as voters who feel left behind seek economic rebalancing, even if they can't articulate the exact mechanisms causing their hardship.
Check out the full podcast here for more on China's man
-
 @ 000002de:c05780a7
2025-05-21 17:27:46
@ 000002de:c05780a7
2025-05-21 17:27:46I completely missed this until yesterday. I was listening to our local news talk station and it came up. They had some people that were pretty knowledgeable about prostate cancer on. They talked about other presidents being tested while in office for it. They came to conclusion that it is possible that Biden wasn't having his PSA checked. This is pretty normal for a old dude his age. But it is not normal for a President his age.
My thought is much simpler.
We know his doctors, the media, and his admin were lying about his health when he was in office. Hello! Anyone paying attention and not invested in his regime knew he was declining mentally in front of our very eyes. They covered for him over and over again. Only those that don't pay attention or discounted his critics completely was surprised by his debate performance.
To be clear though, Biden is far from the first president to do this. Wilson, FDR, Kennedy, and Reagan all had issues and they were kept from the public. If we learned these things in school we might actually have a public that thinks critically once and a while.
So, with that in mind do you really think the regime would not withhold medical info about this cancer? Come on. Don't be naive. He clearly was not in charge 100% of the time while in office and the regime wanted to maintain power. Sharing that he had prostate cancer would not be on the menu.
Politics is like a drug that numbs the brain. Because people don't like one party or person they retard their thinking. Its the same thing as happens in sports. Fans of one team see the same play completely differently from the other team's fans. Politics and the investment into parties kills most people's objectivity.
I don't trust liars. It honestly blows my mind how trusting people can be of professional liars. Both parties are full of liars. Trump is a liar and those opposing him are liars. We are drowning in lies. You can vote for a lessor of two evils but never forget what they are.
https://stacker.news/items/985791
-
 @ 57d1a264:69f1fee1
2025-05-21 05:47:41
@ 57d1a264:69f1fee1
2025-05-21 05:47:41As a product builder over too many years to mention, I’ve lost count of the number of times I’ve seen promising ideas go from zero to hero in a few weeks, only to fizzle out within months.
The problem with most finance apps, however, is that they often become a reflection of the internal politics of the business rather than an experience solely designed around the customer. This means that the focus is on delivering as many features and functionalities as possible to satisfy the needs and desires of competing internal departments, rather than providing a clear value proposition that is focused on what the people out there in the real world want. As a result, these products can very easily bloat to become a mixed bag of confusing, unrelated and ultimately unlovable customer experiences—a feature salad, you might say.
Financial products, which is the field I work in, are no exception. With people’s real hard-earned money on the line, user expectations running high, and a crowded market, it’s tempting to throw as many features at the wall as possible and hope something sticks. But this approach is a recipe for disaster.
Here’s why: https://alistapart.com/article/from-beta-to-bedrock-build-products-that-stick/
https://stacker.news/items/985285
-
 @ c9badfea:610f861a
2025-05-20 19:49:20
@ c9badfea:610f861a
2025-05-20 19:49:20- Install Sky Map (it's free and open source)
- Launch the app and tap Accept, then tap OK
- When asked to access the device's location, tap While Using The App
- Tap somewhere on the screen to activate the menu, then tap ⁝ and select Settings
- Disable Send Usage Statistics
- Return to the main screen and enjoy stargazing!
ℹ️ Use the 🔍 icon in the upper toolbar to search for a specific celestial body, or tap the 👁️ icon to activate night mode
-
 @ 8bad92c3:ca714aa5
2025-05-22 20:01:21
@ 8bad92c3:ca714aa5
2025-05-22 20:01:21Key Takeaways

In this episode of TFTC, energy economist Anas Alhajji outlines a profound shift in U.S. foreign policy under Trump—away from military intervention and toward transactional diplomacy focused on trade, reconstruction, and curbing Chinese and Russian influence in the Middle East. He highlights Trump’s quiet outreach to Syria as emblematic of the U.S.'s strategic flexibility in legitimizing former adversaries when economically beneficial. Alhajji dismisses BRICS as a fractured bloc incapable of rivaling the U.S.-led order and insists the dollar and petrodollar remain dominant. On energy, he warns that despite favorable fundamentals, prices are suppressed by political confusion, underinvestment, and an aging power grid ill-prepared for the AI and urbanization boom. He also contends that Iran is stalling negotiations to buy time for nuclear advancement and that any deal will be superficial. Finally, Alhajji debunks the myth of Trump being pro-oil, noting his long-standing hostility toward the industry and explaining why a repeat of his past energy boom is implausible given today’s financial and structural constraints.
Best Quotes
- “BRICS is a paper tiger. Everything about BRICS is what China does—and that’s it.”
- “The dollar is here to stay. The petrodollar is here to stay. End of story.”
- “Trump hates the oil industry. He always classified it as an enemy.”
- “Energy projects are 30- to 40-year investments, but politicians think in 4-year cycles. That’s where the disconnect lies.”
- “People think shale will boom again. It won’t. The model changed from ‘drill baby drill’ to ‘control baby control.’”
- “The real story of Trump’s trip wasn’t about politics—it was investment, investment, investment.”
- “Without massive investment in the grid and gas turbines, blackouts will become the norm—even in rich countries like Kuwait.”
- “Iran and China have perfected the game of oil exports. Sanctions are just theater at this point.”
Conclusion
Anas Alhajji’s conclusion challenges conventional narratives, arguing that global power is shifting from military dominance to economic leverage, infrastructure investment, and energy control. He presents a nuanced view of U.S. foreign policy under Trump, emphasizing the strategic importance of trade and reconstruction over regime change. As energy demand soars and geopolitical risks mount, Alhajji warns that the real dangers lie not in foreign adversaries, but in policy confusion, infrastructural lag, and complacency—making this episode a crucial listen for anyone seeking to understand the high-stakes intersection of energy, economics, and diplomacy.
Timestamps
0:00 - Intro
0:48 - Syria and US diplomacy in Middle East
12:50 - Trump in the Middle East
18:12 - Fold & Bitkey
19:48 - Iran - Nuclear program and PR
33:53 - Unchained
34:22 - Crude markets, trade war and US debt
54:28 - Trump's energy stance
1:05:46 - Energy sector challanges
1:14:44 - Policy recommendations
1:21:18 - AI and bitcoinTranscript
(00:00) oil prices market fundamentals support higher price than where we are today. But because of this confusion, everyone is scared of low economic growth and that is a serious problem. The US media ignored part of Trump's speech when he said we are not about nation building and they refer to Afghanistan and Iraq.
(00:15) Look at them. This is a criticism of George W. Bush. We have groups that are talking about the demise of the dollar, the rise of bricks. Bricks is a paper tiger. Everything about bricks is what China does and that's it. The dollar is here to stay and the petro dollar is here to stay.
(00:31) The perception is that the Trump administration is cold but the reality Trump hates the oil [Music] indust. How are you? Very good. Very good. Thank you. As you were telling me, you've been a bit sleepd deprived this week trying to keep up with what's going on. Oh, absolutely. I mean, Trump keeps us on our toes uh all the time.
(01:06) In fact, I plan certain things for the weekend and Trump will say something or he will do something and all of a sudden we get busy again. Uh so clients are not going to wait for you until you finish your work. Basically, they want to know what's going on. So what is going on? What what how profound were the events in the Middle East? These are very uh very profound changes basically because it is very clear that if you look at the last 15 years uh and you look at the growth uh in the Middle East, you look at the growth of Saudi Arabia and uh the
(01:41) role of Turkey for example in the region uh it just just amazing be beyond any uh any thoughts. Uh in fact both of them Turkey and Saudi Arabia are part of the G20. Uh so they have economic influence and they have political influence. And of course the icing on the cake for those who are familiar with the region is to recognize the Syrian government and meet with the Syrian uh president.
(02:11) Uh this is a major a major change in economics and politics uh of the Middle East. Let's touch on that Syria uh topic for a while because I think a lot of people here in the United States were a bit shocked at how sort of welcoming President Trump was towards the new Syrian president considering the fact that uh he was considered an enemy not too long ago here in the United States.
(02:42) What first of all it's a fact of life for those who would like to check the history of politics. There were many people around the world who were classified or they were on the terrorism list and then they became friends of the United States or they were became heroes. I mean Nelson Mandela is one of them. You look at Latin America, there are presidents in Latin America who were uh the enemy of the United States and then they became uh uh cooperative with the United States and the United States recognized their governments and the result of their uh elections. Uh so
(03:15) we've seen this historically uh several uh several times around the world and as they say freedom fighters for some basically are the enemies and the terrorists for for others etc. So uh what we've seen that's why the the visit is very important that the recognition of this government is very important. uh the fact on the ground that uh the president of Syria had the power on the ground uh he had the the the people on the ground and he had the control on the ground and whatever he's been he's been doing since he came into power until now
(03:52) he done all the right steps u and people loved him I mean everyone who went to Syria whether the Syrians who left Syria 40 years ago or uh the visitors who are coming to Syria, they will tell you, "We have never seen the Syrian people as happy as we've seen them today, despite the fact that they they live in misery.
(04:17) They don't have um 8 million people without housing. Uh there is barely any electricity in most of the country. There is no internet. There is barely any food. The uh inflation is rampant, etc. But people are happy because they lived in fear for a very long time. And uh the steps they have taken. For example, the uh ministers in the previous government uh are still there and they are still in the housing of the government.
(04:49) They still have the drivers. They still have the cars from the previous government. They still have it until today. So uh they they were classified as enemies before. But all of a sudden now you have a new government that is uh accepting them. Uh so we we see some changes on the ground that are positive and we'll see how these things will go given that the area around them basically has been unstable for a very long time.
(05:17) how because I don't the the news when I was actually it was surreal for me because my first trip to the Middle East was last December when it was literally f flying over Syria to Abu Dhabi when uh um Assad was getting thrown out and it was pretty surreal to be in that region of the world.
(05:43) How as it pertains to like religious minorities within Syria moving forward is there protractions protections there? Um well let me just uh I want to emphasize one point that is very important. What did the interest of Turkey, Saudi Arabia and the United States in Syria if remember Syria was controlled by Iran and was controlled by the Russians.
(06:09) So in a sense it becomes uh kind of an imperative that taking it away from Iran and Russia and not bringing Iran or Russia back is extremely important. Now the Russians are still there and they have their own base but at least they are not bombing the Syrians and not killing them anymore. But the idea here is taking Syria out of Iran and Russia and probably later on if they kick the Russians out, Russians will not have access to the Mediterranean.
(06:37) Uh so there is an interest uh of all parties basically to take Russia out of Iran and um out of uh Syria regardless the country is uh devastated and it creates massive opportunities for US companies on all levels and uh we've seen a contract uh done recently with you mentioned Abu Dhabi uh uh a contract uh uh with the UA a basically to revamp all the Syrian ports and work on the Syrian ports.
(07:13) Uh so such contracts basically uh when you have a country that has nothing and it's completely devastated the whole infrastructure is devastated. Who is going to build it? If the uh what the Chinese, the Russians, so who who are going to build it? So, uh I think there is a a big room for US companies and others basically to come in and uh literally help on one side and make money on the other.
(07:38) Yeah, I think that that's what I'm trying to discern. What was this convoy from the United States to the Middle East this week signali -
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ c7e8fdda:b8f73146
2025-05-22 14:13:31
@ c7e8fdda:b8f73146
2025-05-22 14:13:31🌍 Too Young. Too Idealistic. Too Alive. A message came in recently that stopped me cold.
It was from someone young—16 years old—but you’d never guess it from the depth of what they wrote. They spoke of having dreams so big they scare people. They’d had a spiritual awakening at 14, but instead of being nurtured, it was dismissed. Surrounded by people dulled by bitterness and fear, they were told to be realistic. To grow up. To face “reality.”
This Substack is reader-supported. To receive new posts and support my work, consider becoming a free or paid subscriber.
And that reality, to them, looked like a life that doesn’t feel like living at all.
They wrote that their biggest fear wasn’t failure—it was settling. Dimming their fire. Growing into someone they never chose to be.
And that—more than anything—scared them.
They told me that my book, I Don’t Want to Grow Up, brought them to tears because it validated what they already knew to be true. That they’re not alone. That it’s okay to want something different. That it’s okay to feel everything.
It’s messages like this that remind me why I write.
As many of you know, I include my personal email address at the back of all my books. And I read—and respond to—every single message that comes in. Whether it’s a few sentences or a life story, I see them all. And again and again, I’m reminded: there are so many of us out here quietly carrying the same truth.
Maybe you’ve felt the same. Maybe you still do.
Maybe you’ve been told your dreams are too big, too unrealistic. Maybe people around you—people who love you—try to shrink them down to something more “manageable.” Maybe they call it protection. Maybe they call it love.
But it feels like fear.
The path you wish to walk might be lonelier at first. It might not make sense to the people around you. But if it lights you up—follow it.
Because when you do, you give silent permission to others to do the same. You become living proof that another kind of life is possible. And that’s how we build a better world.
So to the person who wrote to me—and to every soul who feels the same way:
Keep going. Keep dreaming. Keep burning. You are not too young. You are not too idealistic. You are just deeply, radically alive.
And that is not a problem. That is a gift.
—
If this speaks to you, my book I Don’t Want to Grow Up was written for this very reason—to remind you that your wildness is sacred, your truth is valid, and you’re not alone. Paperback/Kindle/Audiobook available here: scottstillmanblog.com
This Substack is reader-supported. To receive new posts and support my work, consider becoming a free or paid subscriber. https://connect-test.layer3.press/articles/041a2dc8-5c42-4895-86ec-bc166ac0d315
-
 @ da8b7de1:c0164aee
2025-05-21 15:59:12
@ da8b7de1:c0164aee
2025-05-21 15:59:12Blykalla svéd fejlesztő következő tőkebevonási köre augusztus végéig
A svéd Blykalla, amely fejlett ólom-hűtésű gyorsreaktorokat (SEALER) fejleszt, augusztus végéig tervezi következő tőkebevonási körét. A vállalat nemrég 7,3 millió dolláros befektetést szerzett, amellyel összesen már 20 millió dollárnyi forrást gyűjtött össze. A SEALER technológia jelentősen hatékonyabb üzemanyag-felhasználást ígér, akár 140-szeres hatékonysággal a hagyományos könnyűvizes reaktorokhoz képest. Az első két reaktort Svédországban tervezik megépíteni, de már ukrán és más európai, valamint kanadai partnerekkel is tárgyalnak. A következő lépés a tesztreaktor megépítése és az engedélyezési folyamat elindítása, amelyet 2025-re terveznek lezárni. A vállalat célja, hogy technológiai szolgáltatóként jelenjen meg, nem pedig üzemeltetőként[2].
Amerikai szenátorok törvényjavaslata Kína és Oroszország nukleáris befolyása ellen
Amerikai republikánus és demokrata szenátorok közösen nyújtottak be törvényjavaslatot, amelynek célja Kína és Oroszország növekvő nemzetközi nukleáris befolyásának visszaszorítása. Az International Nuclear Energy Act egy új hivatalt hozna létre, amely a nukleáris exportot, finanszírozást és szabályozási szabványosítást erősítené. A törvényjavaslat egy alapot is létrehozna a nemzetbiztonság szempontjából fontos projektek finanszírozására, valamint kétévente kabinet szintű egyeztetést írna elő a nukleáris biztonságról és ipar-politikai kérdésekről. A kezdeményezés hátterében az elektromos áram iránti várható keresletnövekedés és a szektor stratégiai jelentősége áll[3].
India 49%-os külföldi tulajdon engedélyezését fontolgatja a nukleáris szektorban
India fontolgatja, hogy akár 49%-os külföldi tulajdont is engedélyezzen atomerőműveiben, hogy elérje ambiciózus nukleáris kapacitásbővítési céljait és csökkentse szén-dioxid-kibocsátását. Jelenleg a külföldi befektetők számára tilos az atomerőművekben való tulajdonszerzés, de a kormány tervezi a szabályozás lazítását, beleértve a nukleáris felelősségi törvények enyhítését is. A cél az, hogy 2047-re 12-ről 100 gigawattra növeljék az ország nukleáris kapacitását. Bármilyen külföldi befektetéshez továbbra is kormányzati jóváhagyás szükséges lenne[4].
NRC: végleges környezeti jelentés a Summer-1 engedélymegújításáról
Az amerikai Nukleáris Szabályozási Bizottság (NRC) közzétette a Summer-1 atomerőmű engedélymegújításához kapcsolódó végleges környezeti hatástanulmányát. A jelentés szerint nincs olyan jelentős környezeti hatás, amely akadályozná a 966 MWe teljesítményű reaktor további 20 évig tartó üzemeltetését 2042 után. A vizsgálat alternatív energiaforrásokat is értékelt, de egyik sem bizonyult jobbnak a jelenlegi atomenergia-használatnál. A Summer-1 egység különálló a befejezetlen Summer-2 és -3 blokkoktól, amelyek építését 2017-ben leállították[5].
Nemzetközi nukleáris hatósági és technológiai fejlemények
A szlovéniai Portorozban május közepén tartották a közép-európai nukleáris hatóságok éves találkozóját, ahol a biztonsági és technológiai együttműködés volt a fókuszban. Emellett a BME megalapította a Mikro- és Kis Moduláris Reaktorok Kompetenciaközpontját, amely a magyarországi SMR-technológia fejlesztését és elterjesztését támogatja[6][7].
Hivatkozások
- nucnet.org
- ignition-news.com
- investing.com
- energynews.oedigital.com
- ans.org
- pakspress.hu
- mandiner.hu
-
 @ 9ca447d2:fbf5a36d
2025-05-22 14:01:39
@ 9ca447d2:fbf5a36d
2025-05-22 14:01:39Ed Suman, a 67-year-old retired artist who helped create large sculptures like Jeff Koons’ Balloon Dog, reportedly lost his entire life savings — over $2M in digital assets — in a sophisticated scam.
The incident is believed to be tied to the major data breach at Coinbase, one of the world’s largest digital asset exchanges.
Suman’s story is part of a bigger wave of attacks on digital asset holders using stolen personal info, and has triggered lawsuits, regulatory concerns and questions about digital security in the Bitcoin space.
In March 2025, Suman got a text message about suspicious activity on his Coinbase account. After Suman reported he was unaware of any unauthorized activity regarding his account, he got a call from a man who introduced himself as Brett Miller from Coinbase Security.
The guy sounded legit — he knew Suman’s setup, including that he used a Trezor Model One hardware wallet, a device meant to keep bitcoin and other digital assets offline and safe.
Suman told Bloomberg the guy knew everything, including the exact amount of digital assets he had.
The attacker persuaded Suman that his Trezor One hardware wallet and its funds were at risk and walked him through a “security procedure” that involved entering his seed phrase into a website that looked exactly like Coinbase, in order to “link his wallet to Coinbase”.
Nine days later, another guy called and repeated the process, saying the first one didn’t work.
And then, all of Suman’s digital assets — 17.5 bitcoin and 225 ether — were gone. At the time, bitcoin was around $103,000 and ether around $2,500, so the stolen stash was worth over $2 million.
Suman turned to digital assets after retiring from a decades-long art career. He stored his assets in cold storage to avoid the risks of online exchanges. He thought he did everything right.
Suman’s attackers didn’t pick his name out of a hat.
It looks like his personal info may have been leaked in the major breach at Coinbase. The company confirmed on May 15 that some of its customer service reps in India were bribed to access internal systems and steal customer data.
The stolen data included names, phone numbers, email addresses, balances and partial Social Security numbers.
According to Coinbase’s filing with the U.S. Securities and Exchange Commission, the breach may have started as early as January and affected nearly 1% of the company’s active monthly users — tens of thousands of people.
Hackers demanded $20M from Coinbase to keep the breach quiet but the company refused to pay. Coinbase says it fired the compromised agents and is setting aside $180M to $400M to reimburse affected users.
But so far, Suman hasn’t been told if he’ll be reimbursed.
Since the breach was disclosed, Coinbase has been hit with at least six lawsuits.
The lawsuits claim the company failed to protect user data and handled the aftermath poorly. One lawsuit filed in New York federal court on May 16 says Coinbase’s response was “inadequate, fragmented, and delayed.”
“Users were not promptly or fully informed of the compromise,” the complaint states, “and Coinbase did not immediately take meaningful steps to mitigate further harm.”
Some lawsuits are seeking damages, others are asking Coinbase to purge user data and improve its security. Coinbase has not commented on the lawsuits but pointed reporters to a blog post about its response.
Suman’s case is a cautionary tale across the Bitcoin world. He used a hardware wallet (considered the gold standard of Bitcoin security) and was still tricked through social engineering. Even the strongest security is useless if you don’t understand how Bitcoin works.
It’s never too early for Bitcoiners to start learning more about Bitcoin, especially on how to keep their stash safe. And the first lesson is “never ever share your seed phrase with anyone”.
Related: Bitcoin Hardware Wallet Hacks: What You Need to Know
-
 @ 6be5cc06:5259daf0
2025-04-28 01:05:08
@ 6be5cc06:5259daf0
2025-04-28 01:05:08Primeiramente, o que é mempool?
Abreviação de memory pool (ou "pool de memória") a mempool é uma espécie de fila onde as transações de Bitcoin ficam temporariamente armazenadas antes de serem confirmadas e incluídas em um bloco na blockchain. Quando você realiza uma transação em uma rede blockchain, essa transação precisa ser validada e confirmada pelos mineradores (ou validadores). Porém, ela não é processada instantaneamente. Primeiro, ela vai para a mempool, onde aguarda até que um minerador a selecione para incluir no próximo bloco.
É assim: * Você envia uma transação, ela é transmitida para a rede e vai parar na mempool de vários nós (computadores) que suportam a rede blockchain. * As transações na mempool são organizadas pela taxa de transação que foi anexada. Quanto maior a taxa, mais rápido os mineradores tendem a escolher essa transação para incluí-la em um bloco, pois isso aumenta os ganhos deles. * Os mineradores pegam as transações da mempool, criam um bloco com elas e, ao minerar (confirmar) esse bloco, as transações saem da mempool e entram na blockchain.
Aqui irei usar o site mempool.emzy.de como referência, mas é importante entender que sites de mempool são representações visuais da mempool de um nó específico e não a mempool do Bitcoin em si. Ela não é centralizada, cada nó da rede mantém a sua própria versão da mempool. Assim, ela pode variar de um nó para outro. Esses sites ajudam a visualizar dados sobre transações e taxas.
É uma boa prática usar VPN ou Tor ao acessar tais sites se você estiver verificando uma transação específica sua, pois sua privacidade pode ficar comprometida se o site registrar esses dados. Se você estiver repetidamente acessando-o para monitorar a confirmação de uma transação, alguém pode conseguir correlacionar o endereço IP com essa atividade e revelar uma conexão indireta com o endereço da transação.
Dito isso...
Como interpretar a mempool?
Vamos dividir isso em partes para fins didáticos.
Faixa de taxas
Cada bloco verde representa uma faixa de taxa medida em satoshis por vByte (sats/vB).
Essa unidade de medida representa o valor pago por byte ocupado pela transação.
Quanto maior a taxa paga por uma transação, mais rápido ela tende a ser confirmada.
Quanto maior a transação em bytes, mais você precisa pagar para que ela seja confirmada.
Cada transação Bitcoin consiste em entradas e saídas (inputs e outputs): * Entradas são referências a transações anteriores que estão sendo gastas, e cada entrada inclui informações como o endereço de origem, a assinatura (que valida a transação e pode variar de tamanho dependendo da complexidade da chave e do método de assinatura utilizado (como SegWit, que é mais eficiente). Quanto mais complexa a assinatura, maior será o tamanho em bytes) e outros dados. Quanto mais entradas uma transação tiver, maior será seu tamanho. * Saídas representam o destino do Bitcoin, e quanto mais saídas, maior será o tamanho da transação. Embora as saídas ocupem menos espaço em bytes do que as entradas.Ex.: * ~4 sat/vB: Indica uma taxa média. Significa que, em média, as transações estão sendo processadas a 4 satoshis por vByte; * 3-5 sat/vB: Isso significa que as transações estão sendo processadas com uma taxa entre 3 e 5 satoshis por vByte.
MB
Simplesmente o tamanho do bloco medido em megabytes :)
Número de transações
Essa seção informa quantas transações estão aguardando confirmação para cada faixa de taxa (bloco). Quanto maior o número de transações, maior a demanda pela faixa de taxa especificada.
Tempo estimado para confirmação
Aqui é mostrado o tempo médio de espera para transações que pagam taxas dentro da faixa especificada. Se você pagar uma taxa maior, a transação será confirmada mais rapidamente; uma taxa menor significa que a transação pode levar mais tempo para ser confirmada, especialmente se a rede estiver congestionada.
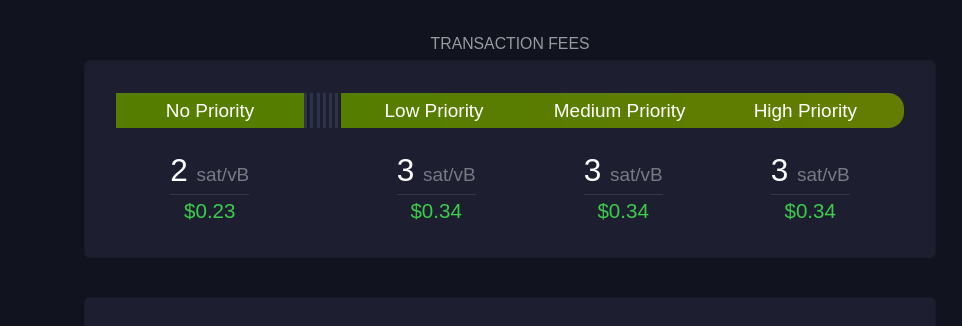 Esta seção mostra sugestões de taxa em diferentes níveis de prioridade para os usuários:
Esta seção mostra sugestões de taxa em diferentes níveis de prioridade para os usuários:Sem Prioridade
Exibe a taxa mínima necessária para transações que não precisam de confirmação rápida.
Prioridade Baixa
Sugestão de taxa para transações que podem esperar um tempo moderado, com expectativa de confirmação em um ou dois blocos.
Prioridade Média e Alta
São as faixas de taxa recomendadas para quem precisa que a transação seja confirmada rapidamente. "Prioridade Alta" paga uma taxa maior, garantindo que a transação seja incluída no próximo bloco.
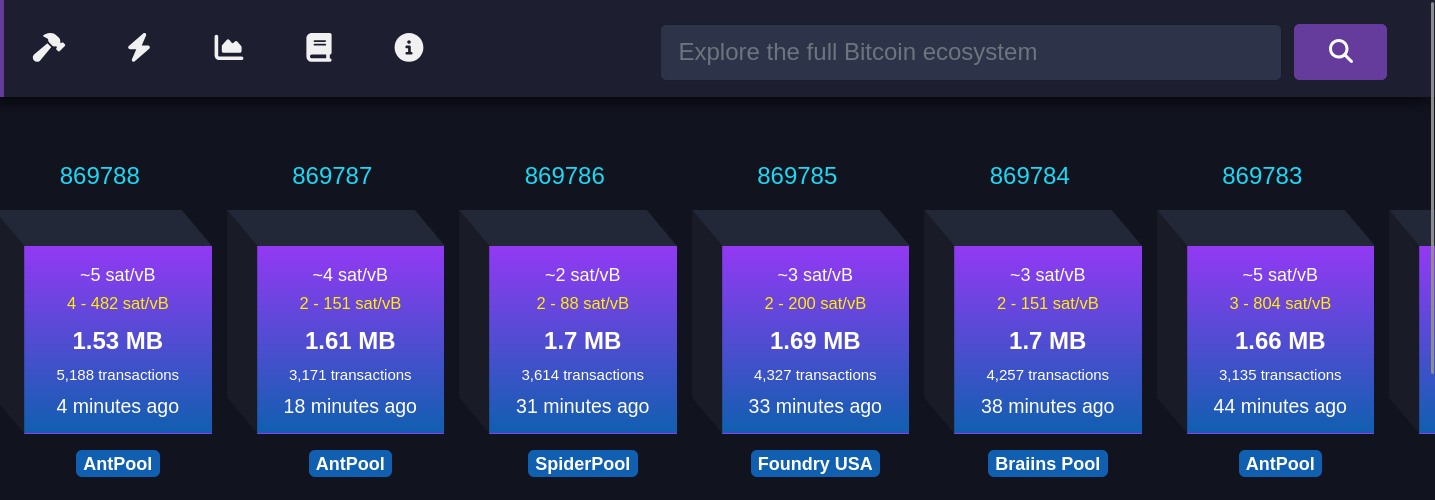 Cada bloco roxo representa um bloco recém-minerado. As informações mostradas incluem:
Cada bloco roxo representa um bloco recém-minerado. As informações mostradas incluem: Taxa média paga
Refere-se à taxa média em satoshis/vB paga por todas as transações incluídas em um bloco recém-minerado. Isso reflete o valor médio que os usuários estão dispostos a pagar para que suas transações sejam confirmadas rapidamente.
Número de transações
Este número indica quantas transações foram processadas no bloco minerado. O tamanho do bloco é limitado, então, quanto maior o número de transações, menor será o espaço disponível para novas transações, o que pode influenciar as taxas de transação.
Tempo desde a mineração
Esta métrica informa quanto tempo se passou desde que o bloco foi minerado e adicionado à blockchain.
Pool de mineração
Exibe o nome do pool de mineração que minerou o bloco, como AntPool. Grandes pools de mineração têm mais chances de minerar blocos regularmente devido ao alto hashrate (medida da capacidade computacional utilizada pelos mineradores) que possuem.
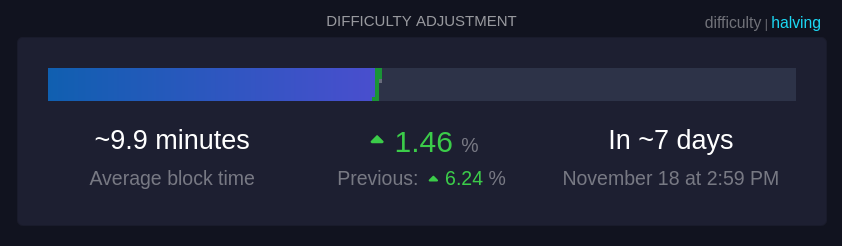 Essa seção mostra informações sobre o ajuste de dificuldade, que ocorre aproximadamente a cada duas semanas.
Essa seção mostra informações sobre o ajuste de dificuldade, que ocorre aproximadamente a cada duas semanas. Tempo médio dos blocos (~9,9 minutos):
Este é o tempo médio atual para minerar um bloco na rede. A meta da rede é manter o tempo de bloco em cerca de 10 minutos; um tempo menor indica um aumento na taxa de hash, ou seja, que mais poder computacional foi adicionado à rede.
Mudança de dificuldade (+1,46%):
A dificuldade ajusta-se a cada 2016 blocos para manter o tempo médio de bloco próximo de 10 minutos. Um aumento na dificuldade, como +1,46%, indica que a mineração ficou mais difícil devido ao aumento do hashrate, enquanto uma redução na dificuldade indica que o hashrate diminuiu.
Tempo até o próximo ajuste:
É o tempo previsto até o próximo ajuste de dificuldade (7 dias, nesse caso), o que é crucial para manter a rede estável e garantir a segurança e a regularidade do processo de mineração.
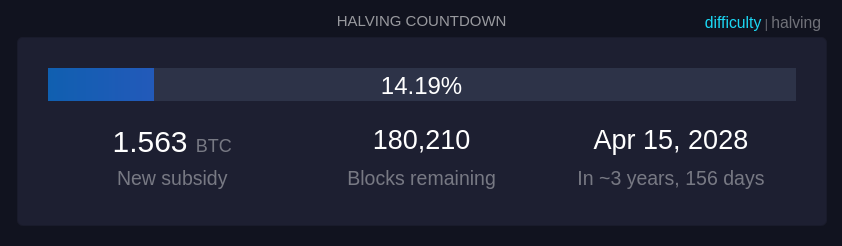 Quanto tempo demora até o próximo halving, um evento no Bitcoin que ocorre aproximadamente a cada 210.000 blocos minerados, ou cerca de quatro anos. Durante o halving, a recompensa que os mineradores recebem por adicionar um novo bloco à blockchain é reduzida pela metade.
Quanto tempo demora até o próximo halving, um evento no Bitcoin que ocorre aproximadamente a cada 210.000 blocos minerados, ou cerca de quatro anos. Durante o halving, a recompensa que os mineradores recebem por adicionar um novo bloco à blockchain é reduzida pela metade.
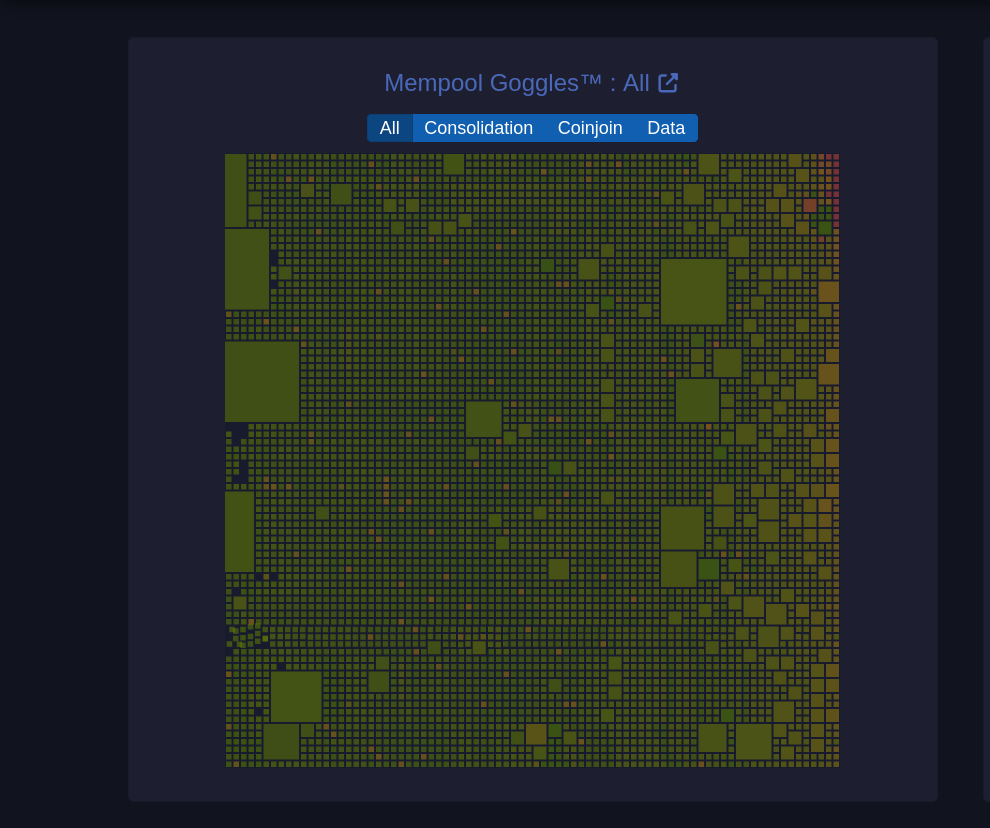 Um diagrama visual da mempool que mostra o estado das transações pendentes na rede.
Um diagrama visual da mempool que mostra o estado das transações pendentes na rede. Tamanhos de blocos
O tamanho de cada quadrado representa o tamanho da transação em bytes.
Filtros (Consolidação, Coinjoin, Dados): Permite visualizar categorias específicas de transações: * Consolidação: Transações de consolidação agrupam pequenos UTXOs em um único UTXO maior para simplificar e baratear futuras transações. (UTXOs merecem um artigo dedicado) * Coinjoin: Transações CoinJoin são usadas para melhorar a privacidade, misturando transações de vários usuários em uma única transação. * Dados: Mostra transações que contêm dados adicionais, que podem incluir informações não financeiras, como mensagens.
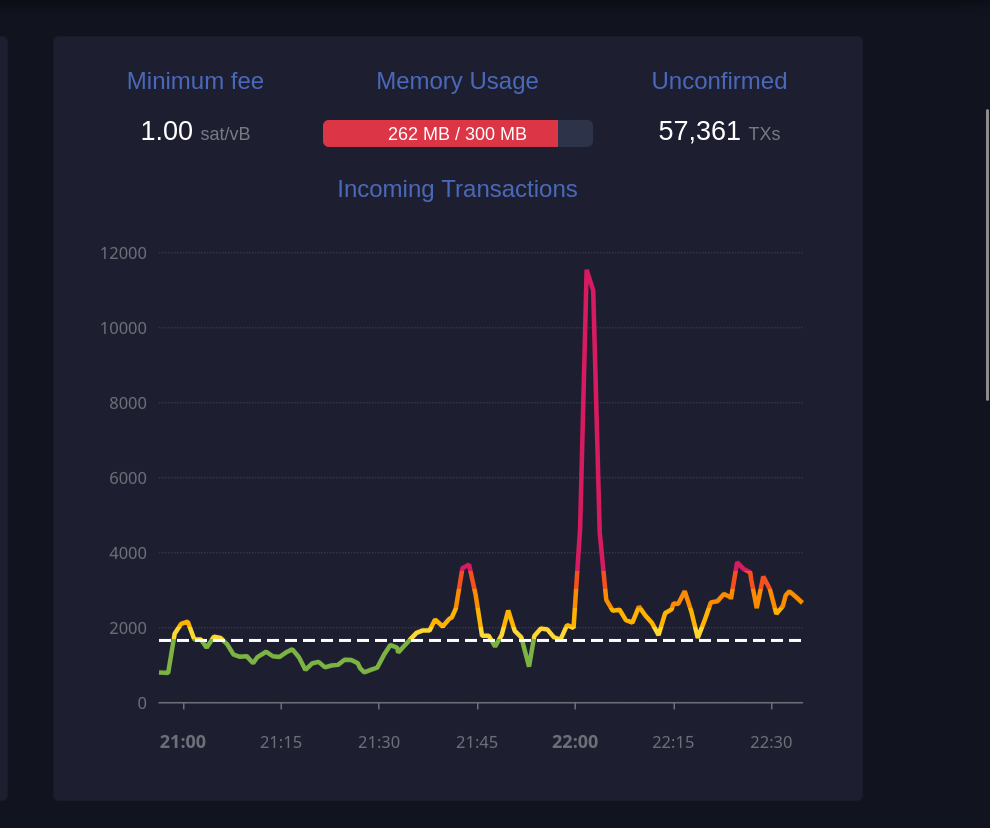 Este gráfico exibe o número de transações recebidas ao longo do tempo.
Este gráfico exibe o número de transações recebidas ao longo do tempo. Taxa mínima (1 sat/vB):
Indica a taxa mínima atualmente aceita pela mempool. Se a mempool estiver cheia, transações que paguem menos do que a taxa mínima podem ser excluídas para dar lugar a transações de maior prioridade.
Uso de memória (259 MB / 300 MB):
A mempool tem um limite de memória. Quando está cheia, transações de taxa mais baixa podem ser descartadas para abrir espaço para aquelas com taxas mais altas, priorizando-as para inclusão em blocos.
Transações não confirmadas (59.361):
Indica o número total de transações pendentes que aguardam confirmação. Quanto maior o número de transações na mempool, maior a probabilidade de que as taxas aumentem para garantir uma confirmação mais rápida.
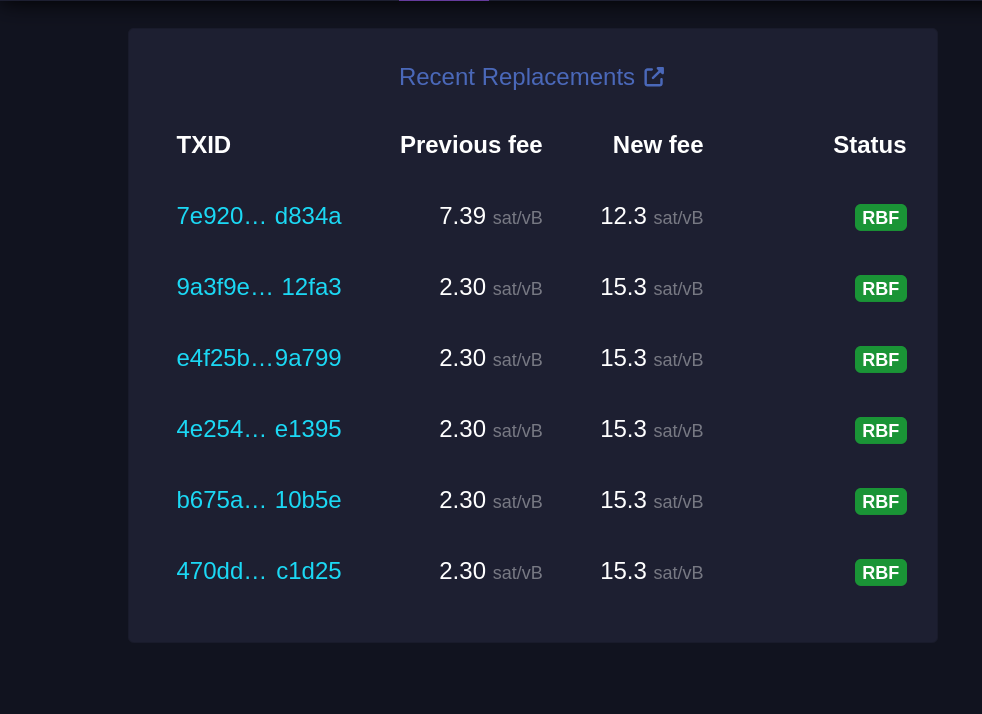 Essa seção mostra transações que foram substituídas utilizando o mecanismo RBF (Replace-By-Fee), que permite substituir uma transação com uma taxa mais alta para acelerar sua confirmação.
Essa seção mostra transações que foram substituídas utilizando o mecanismo RBF (Replace-By-Fee), que permite substituir uma transação com uma taxa mais alta para acelerar sua confirmação. TXID
Este é o identificador da transação (Transaction ID), exibido parcialmente para abreviar o espaço. Cada transação tem um identificador único na blockchain.
Previous fee
Exibe a taxa de transação original paga na primeira tentativa, medida em satoshis por vByte (sat/vB). Esta taxa inicial provavelmente era baixa demais, resultando em uma demora na confirmação.
New fee
Mostra a nova taxa de transação, também em satoshis por vByte, definida para substituir a taxa anterior. Uma taxa maior aumenta as chances de inclusão rápida em um bloco.
Status (RBF)
RBF indica que a transação foi substituída utilizando o recurso "Replace-By-Fee". Isso significa que a nova transação cancelou e substituiu a original, e o minerador escolherá a transação com a taxa mais alta para incluir no próximo bloco.
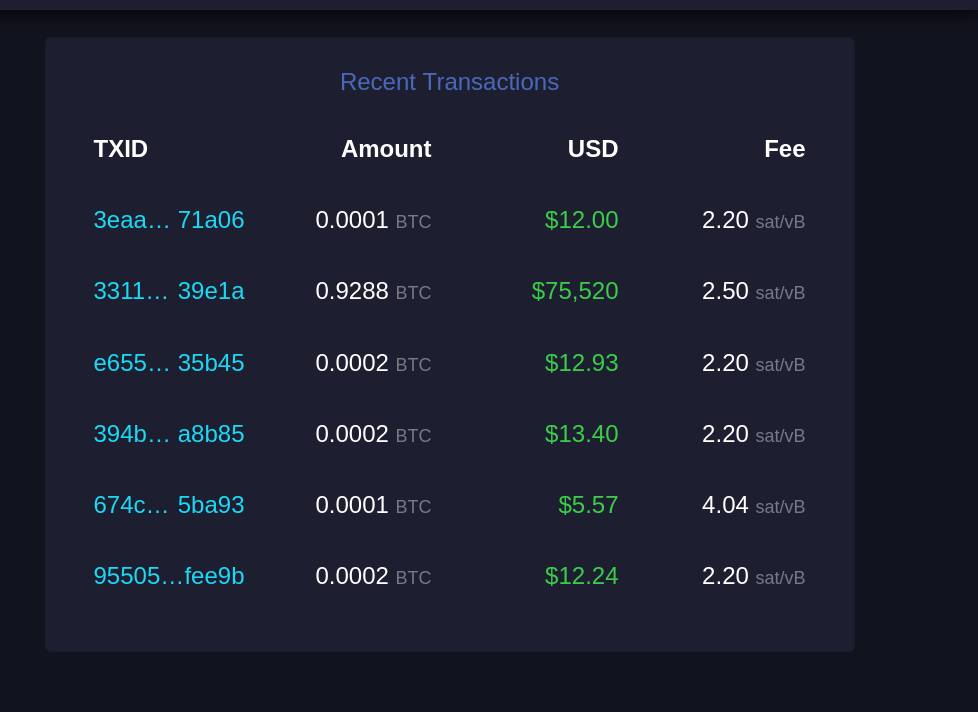 Esta seção lista transações recentes que entraram na mempool e aguardam confirmação.
Esta seção lista transações recentes que entraram na mempool e aguardam confirmação. TXID
Similar ao "Recent Replacements", este é o identificador único da transação.
Amount
Exibe a quantidade de Bitcoin transferida nessa transação, geralmente em frações de BTC (como 0.0001 BTC). Esta é a quantia enviada pelo remetente ao destinatário.
USD
Mostra o valor da transação em dólares americanos (USD), calculado com base na taxa de câmbio atual. Serve para dar uma ideia de quanto a transação representa em moeda fiduciária.
Fee
Exibe a taxa de transação paga, em satoshis por vByte (sat/vB). Uma taxa mais alta em relação à média aumenta a probabilidade de confirmação mais rápida, pois as transações com taxas mais elevadas são priorizadas pelos mineradores.
E acabou. Espero que isso tenha sido útil para você e tenha agregado mais entendimento sobre esse complexo e maravilhoso mundo do Bitcoin. Se foi, considere compartilhar com alguém que precise. E se tem sugestões de melhoria, por favor, não deixe de comentar, o conhecimento está dispero na sociedade.
Por fim, stay humble and stack sats! -
 @ 7e6f9018:a6bbbce5
2025-05-22 18:17:57
@ 7e6f9018:a6bbbce5
2025-05-22 18:17:57Governments and the press often publish data on the population’s knowledge of Catalan. However, this data only represents one stage in the linguistic process and does not accurately reflect the state of the language, since a language only has a future if it is used. Knowledge is a necessary step toward using a language, but it is not the final stage — that stage is actual use.
So what is the state of Catalan usage? If we look at data on regular use, we see that the Catalan language has remained stagnant over the past hundred years, with nearly the same number of regular speakers. In 1930, there were around 2.5 million speakers, and in 2018, there were 2.7 million.
 Regular use of Catalan in Catalonia, in millions of speakers. The dotted segments are an estimate of the trend, based on the statements of Joan Coromines and adjusted according to Catalonia’s population growth.
Regular use of Catalan in Catalonia, in millions of speakers. The dotted segments are an estimate of the trend, based on the statements of Joan Coromines and adjusted according to Catalonia’s population growth.These figures wouldn’t necessarily be negative if the language’s integrity were strong, that is, if its existence weren’t threatened by other languages. But the population of Catalonia has grown from 2.7 million in 1930 to 7.5 million in 2018. This means that today, regular Catalan speakers make up only 36% of Catalonia’s population, whereas in 1930, they represented 90%.
 Regular use of Catalan in Catalonia, as a percentage of speakers. The dotted segments are an estimate of the trend, based on the statements of Joan Coromines and adjusted according to Catalonia’s population growth.
Regular use of Catalan in Catalonia, as a percentage of speakers. The dotted segments are an estimate of the trend, based on the statements of Joan Coromines and adjusted according to Catalonia’s population growth.The language that has gained the most ground is mainly Spanish, which went from 200,000 speakers in 1930 to 3.8 million in 2018. Moreover, speakers of other foreign languages (500,000 speakers) have also grown more than Catalan speakers over the past hundred years.
Notes, Sources, and Methodology
The data from 2003 onward is taken from Idescat (source). Before 2003, there are no official statistics, but we can make interpretations based on historical evidence. The data prior to 2003 is calculated based on two key pieces of evidence:
-
1st Interpretation: In 1930, 90% of the population of Catalonia spoke Catalan regularly. Source and evidence: The Romance linguist Joan Coromines i Vigneaux, a renowned 20th-century linguist, stated in his 1950 work "El que s'ha de saber de la llengua catalana" that "In this territory [Greater Catalonia], almost the entire population speaks Catalan as their usual language" (1, 2).\ While "almost the entire population" is not a precise number, we can interpret it quantitatively as somewhere between 80% and 100%. For the sake of a moderate estimate, we assume 90% of the population were regular Catalan speakers, with the remaining 10% being immigrants and officials of the Spanish state.
-
2nd Interpretation: Regarding population growth between 1930 and 1998, on average, 60% is due to immigration (mostly adopting or already using Spanish language), while 40% is natural growth (likely to acquire Catalan language from childhood). Source and evidence: Between 1999 and 2019, when more detailed data is available, immigration accounted for 68% of population growth. From 1930 to 1998, there was a comparable wave of migration, especially between 1953 and 1973, largely of Spanish-speaking origin (3, 4, 5, 6). To maintain a moderate estimate, we assume 60% of population growth during that period was due to immigration, with the ratio varying depending on whether the period experienced more or less total growth.
-
-
 @ 8d34bd24:414be32b
2025-05-21 15:52:46
@ 8d34bd24:414be32b
2025-05-21 15:52:46In our culture today, people like to have “my truth” as opposed to “your truth.” They want to have teachers who tell them what they want to hear and worship in the way they desire. The Bible predicted these times.
For the time will come when people will not put up with sound doctrine. Instead, to suit their own desires, they will gather around them a great number of teachers to say what their itching ears want to hear. (2 Timothy 4:3)
My question is, “do we get to choose what we want to believe about God and how we want to worship Him, or does God tell us what we are to believe and how we are to worship Him?”
The Bible makes it clear that He is who He says He is and He expects obedience and worship according to His commands. We do not get to decide for ourselves.
The woman said to Him, “Sir, I perceive that You are a prophet. Our fathers worshiped in this mountain, and you people say that in Jerusalem is the place where men ought to worship.” Jesus said to her, “Woman, believe Me, an hour is coming when neither in this mountain nor in Jerusalem will you worship the Father. You worship what you do not know; we worship what we know, for salvation is from the Jews. But an hour is coming, and now is, when the true worshipers will worship the Father in spirit and truth; for such people the Father seeks to be His worshipers. God is spirit, and those who worship Him must worship in spirit and truth.” (John 4:19-24) {emphasis mine}
In this passage, Jesus gently corrects the woman for worshipping what she does not know. He also says, “God is spirit, and those who worship Him must worship in spirit and truth.” He states what God is (spirit) and how He must be worshipped “in spirit and truth.” We don’t get to define God however we wish, and we don’t get to worship Him any way we wish. God is who He has revealed Himself to be and we must obey Him and worship Him the way He has commanded.
In this next passage, God makes clear that He is holy and we do not get to worship Him any way we wish. We are to interact with Him in the prescribed manner.
Now Nadab and Abihu, the sons of Aaron, took their respective firepans, and after putting fire in them, placed incense on it and offered strange fire before the Lord, which He had not commanded them. And fire came out from the presence of the Lord and consumed them, and they died before the Lord. Then Moses said to Aaron, “It is what the Lord spoke, saying,
‘By those who come near Me I will be treated as holy,\ And before all the people I will be honored.’ ”
So Aaron, therefore, kept silent. (Leviticus 10:1-3) {emphasis mine}
God had prescribed a particular way to approach Him and only those whom He had chosen (priests of the lineage of Aaron). Nadab and Abihu chose to “do it their way” and paid the price for ignoring God’s command. God set an example with them.
God has been gracious enough to reveal Himself, His character, His power, and His commands to us. If we have truly submitted ourselves to His rule, we should hunger for God’s words so we can know Him better and honor Him in obedience.
But now I come to You; and these things I speak in the world so that they may have My joy made full in themselves. I have given them Your word; and the world has hated them, because they are not of the world, even as I am not of the world. I do not ask You to take them out of the world, but to keep them from the evil one. They are not of the world, even as I am not of the world. Sanctify them in the truth; Your word is truth. (John 17:13-17) {emphasis mine}
In today’s culture, everybody likes to claim their own personal truth, but that isn’t how truth works. The truth is not determined by an individual for themselves. It isn’t even determined by a consensus or majority vote. The truth is the truth even if not one person on earth believes it. God speaks truth and God is truth. Our belief or lack thereof doesn’t change the truth, but our lack of belief in the truth, especially the truth as revealed by God in His word, can negatively affect our relationship with God.
God expects us to study His word so we can obey His commands.
For I did not speak to your fathers, or command them in the day that I brought them out of the land of Egypt, concerning burnt offerings and sacrifices. But this is what I commanded them, saying, ‘Obey My voice, and I will be your God, and you will be My people; and you will walk in all the way which I command you, that it may be well with you.’ Yet they did not obey or incline their ear, but walked in their own counsels and in the stubbornness of their evil heart, and went backward and not forward. Since the day that your fathers came out of the land of Egypt until this day, I have sent you all My servants the prophets, daily rising early and sending them. Yet they did not listen to Me or incline their ear, but stiffened their neck; they did more evil than their fathers. (Jeremiah 7:22-26) {emphasis mine}
Today you rarely see someone bowing down to a golden idol, but that doesn’t mean that we are any better at obeying God’s commands or submitting to His will. We still try to make God in our own image so He is a convenience to us and how we want to live our lives. We still put other things ahead of God — family, work, entertainment, fame, etc. Most of us aren’t any more faithful to God than the Israelites were. Just like the Israelites, we put on the trappings of faith but don’t live according to faith and faithfulness.
And He said to them, “Rightly did Isaiah prophesy of you hypocrites, as it is written:
‘This people honors Me with their lips,\ But their heart is far away from Me.\ **But in vain do they worship Me,\ Teaching as doctrines the precepts of men.’\ Neglecting the commandment of God, you hold to the tradition of men.”
He was also saying to them, “You are experts at setting aside the commandment of God in order to keep your tradition. (Mark 7:6-9) {emphasis mine}
How many “churches” and “Christian” leaders teach people according to the culture instead of according to the Word of God? How many tell people what they want to hear and what makes them feel good instead of what they need to hear — the truth as spoken through the Bible? How many church attenders follow a “Christian” leader more than they follow their Creator, Savior, and God? How many church attenders can recite the words of their leaders better than the Holy Scriptures?
I solemnly charge you in the presence of God and of Christ Jesus, who is to judge the living and the dead, and by His appearing and His kingdom: preach the word; be ready in season and out of season; reprove, rebuke, exhort, with great patience and instruction. For the time will come when they will not endure sound doctrine; but wanting to have their ears tickled, they will accumulate for themselves teachers in accordance to their own desires, and will turn away their ears from the truth and will turn aside to myths. But you, be sober in all things, endure hardship, do the work of an evangelist, fulfill your ministry. (2 Timothy 4:1-5) {emphasis mine}
How can we know if a church leader is rightly preaching God’s word? We can only know if we have read the Bible and studied it. We should be like the Bereans:
Now these were more noble-minded than those in Thessalonica, for they received the word with great eagerness, examining the Scriptures daily to see whether these things were so. (Acts 17:11)
Honestly, I don’t trust any spiritual leader who doesn’t encourage me to search the Scriptures to see whether their words are true. Any leader who puts their own word above the Scriptures is a false teacher. Sadly there are many, maybe more than faithful teachers. Some false teachers are intentionally so, but many have been misled by other false teachers. Their guilt is less, but they don’t do any less harm than those who intentionally mislead.
We need to seek trustworthy teachers who speak according to the Word of God, who quote the Bible to support their opinions, and who seek the good of their followers rather than the submission of their followers.
Do not harden your hearts, as at Meribah,\ As in the day of Massah in the wilderness,
“When your fathers tested Me,\ They tried Me, though they had seen My work.\ For forty years I loathed that generation,\ And said they are a people who err in their heart,\ And they do not know My ways.\ Therefore I swore in My anger,\ Truly they shall not enter into My rest.” (Psalm 95:8-11) {emphasis mine} *Teach me good discernment and knowledge,\ For I believe in Your commandments*.\ Before I was afflicted I went astray,\ But now I keep Your word.\ You are good and do good;\ Teach me Your statutes.\ The arrogant have forged a lie against me;\ *With all my heart I will observe Your precepts*.\ Their heart is covered with fat,\ But I delight in Your law.\ It is good for me that I was afflicted,\ That I may learn Your statutes.\ The law of Your mouth is better to me\ Than thousands of gold and silver pieces. (Psalm 119:66-72) {emphasis mine}
May our Creator God teach us the truth. May He fill our hearts with the desire to be in His word daily and to seek His will. May He do what is necessary to get our attention and turn our hearts and minds fully to Him, so we can learn His statutes and serve Him faithfully, so one day we are blessed to hear, “Well done! Good and faithful servant.”
Trust Jesus.
FYI, I see lack of knowledge of truth and God’s word as one of the biggest problems in the church today; however, it is possible to know the Bible in depth, but not know God. As important as knowledge of Scriptures is, this knowledge (without faith, submission, obedience, and love) is meaningless. Knowledge doesn’t get us to heaven. Even obedience doesn’t get us to heaven. Only faith and submission to our creator God leads to salvation and heaven. That being said, we can’t faithfully serve our God without knowledge of Him and His commands. Out of gratefulness for who He is and what He has done for us, we should seek to know and please Him.
-
 @ 6ad3e2a3:c90b7740
2025-05-20 13:49:50
@ 6ad3e2a3:c90b7740
2025-05-20 13:49:50I’ve written about MSTR twice already, https://www.chrisliss.com/p/mstr and https://www.chrisliss.com/p/mstr-part-2, but I want to focus on legendary short seller James Chanos’ current trade wherein he buys bitcoin (via ETF) and shorts MSTR, in essence to “be like Mike” Saylor who sells MSTR shares at the market and uses them to add bitcoin to the company’s balance sheet. After all, if it’s good enough for Saylor, why shouldn’t everyone be doing it — shorting a company whose stock price is more than 2x its bitcoin holdings and using the proceeds to buy the bitcoin itself?
Saylor himself has said selling shares at 2x NAV (net asset value) to buy bitcoin is like selling dollars for two dollars each, and Chanos has apparently decided to get in while the getting (market cap more than 2x net asset value) is good. If the price of bitcoin moons, sending MSTR’s shares up, you are more than hedged in that event, too. At least that’s the theory.
The problem with this bet against MSTR’s mNAV, i.e., you are betting MSTR’s market cap will converge 1:1 toward its NAV in the short and medium term is this trade does not exist in a vacuum. Saylor has described how his ATM’s (at the market) sales of shares are accretive in BTC per share because of this very premium they carry. Yes, we’ll dilute your shares of the company, but because we’re getting you 2x the bitcoin per share, you are getting an ever smaller slice of an ever bigger overall pie, and the pie is growing 2x faster than your slice is reducing. (I https://www.chrisliss.com/p/mstr how this works in my first post.)
But for this accretion to continue, there must be a constant supply of “greater fools” to pony up for the infinitely printable shares which contain only half their value in underlying bitcoin. Yes, those shares will continue to accrete more BTC per share, but only if there are more fools willing to make this trade in the future. So will there be a constant supply of such “fools” to keep fueling MSTR’s mNAV multiple indefinitely?
Yes, there will be in my opinion because you have to look at the trade from the prospective fools’ perspective. Those “fools” are not trading bitcoin for MSTR, they are trading their dollars, selling other equities to raise them maybe, but in the end it’s a dollars for shares trade. They are not selling bitcoin for them.
You might object that those same dollars could buy bitcoin instead, so they are surely trading the opportunity cost of buying bitcoin for them, but if only 5-10 percent of the market (or less) is buying bitcoin itself, the bucket in which which those “fools” reside is the entire non-bitcoin-buying equity market. (And this is not considering the even larger debt market which Saylor has yet to tap in earnest.)
So for those 90-95 percent who do not and are not presently planning to own bitcoin itself, is buying MSTR a fool’s errand, so to speak? Not remotely. If MSTR shares are infinitely printable ATM, they are still less so than the dollar and other fiat currencies. And MSTR shares are backed 2:1 by bitcoin itself, while the fiat currencies are backed by absolutely nothing. So if you hold dollars or euros, trading them for MSTR shares is an errand more sage than foolish.
That’s why this trade (buying BTC and shorting MSTR) is so dangerous. Not only are there many people who won’t buy BTC buying MSTR, there are many funds and other investment entities who are only able to buy MSTR.
Do you want to get BTC at 1:1 with the 5-10 percent or MSTR backed 2:1 with the 90-95 percent. This is a bit like medical tests that have a 95 percent accuracy rate for an asymptomatic disease that only one percent of the population has. If someone tests positive, it’s more likely to be a false one than an indication he has the disease*. The accuracy rate, even at 19:1, is subservient to the size of the respective populations.
At some point this will no longer be the case, but so long as the understanding of bitcoin is not widespread, so long as the dollar is still the unit of account, the “greater fools” buying MSTR are still miles ahead of the greatest fools buying neither, and the stock price and mNAV should only increase.
. . .
One other thought: it’s more work to play defense than offense because the person on offense knows where he’s going, and the defender can only react to him once he moves. Similarly, Saylor by virtue of being the issuer of the shares knows when more will come online while Chanos and other short sellers are borrowing them to sell in reaction to Saylor’s strategy. At any given moment, Saylor can pause anytime, choosing to issue convertible debt or preferred shares with which to buy more bitcoin, and the shorts will not be given advance notice.
If the price runs, and there is no ATM that week because Saylor has stopped on a dime, so to speak, the shorts will be left having to scramble to change directions and buy the shares back to cover. Their momentum might be in the wrong direction, though, and like Allen Iverson breaking ankles with a crossover, Saylor might trigger a massive short squeeze, rocketing the share price ever higher. That’s why he actually welcomes Chanos et al trying this copycat strategy — it becomes the fuel for outsized gains.
For that reason, news that Chanos is shorting MSTR has not shaken my conviction, though there are other more pertinent https://www.chrisliss.com/p/mstr-part-2 with MSTR, of which one should be aware. And as always, do your own due diligence before investing in anything.
* To understand this, consider a population of 100,000, with one percent having a disease. That means 1,000 have it, 99,000 do not. If the test is 95 percent accurate, and everyone is tested, 950 of the 1,000 will test positive (true positives), 50 who have it will test negative (false negatives.) Of the positives, 95 percent of 99,000 (94,050) will test negative (true negatives) and five percent (4,950) will test positive (false positives). That means 4,950 out of 5,900 positives (84%) will be false.
-
 @ 9c3a0089:c6f201fb
2025-05-21 13:51:11
@ 9c3a0089:c6f201fb
2025-05-21 13:51:11What allows one person to engage in cruel acts more easily than another?
What allows one person to engage in any activity more easily than another?
Inclination vs. Aversion.
To what extent are inclinations and aversions an expression of an individuals biology/genetics vs. social conditioning?
If inclination toward cruelty is a result of social conditioning why is it present so consistently across time and location? Why do attempts to condition people away from cruelty and toward kindness ultimately fail when stress tested by simple opportunity?
Humans have a fairly consistent history of cruelty with comically varied excuses for the behavior which are sometimes near opposites. I suspect the details of circumstance and varying excuses are not the cause of cruelty.
Biology/genetics seems to be the answer but as with all traits there must be outliers. It seems inclination toward cruelty is the norm with aversion rarer and aversion along with the courage to stand against cruel acts very rare.
I fear we have been telling false tales of why we engage in cruelty on both small and large scale because the truth is unpleasant. Particularity when outliers with a strong aversion to cruelty see cruel acts and must tell themselves a story that accounts for how a human like themselves could do such things so easily(not realizing they are an outlier) leading to all kinds of creativity in both Religious Myth and fiction.
I think for 1000s of years we have placed blame on evil supernatural forces, gods, demons, devils etc. And more recently on religion, mind virus, mass psychosis, bad leaders or an evil few among the otherwise good majority etc.
I fear the truth is simply that the reason people throughout history so easily engage in cruel acts when the opportunity arises is because the large majority of humans are inclined to do so and are fairly comfortable with inflicting suffering on others. Particularly when they feel safe from consequence and they perceive that doing so strengthens their social standing or that not doing so would weaken it(survival for a social creature).
Unfortunately this makes good sense from a survival standpoint. And fortunately or unfortunately the rule of law and threat of consequence keeps this inclination hidden allowing any society to always believe maybe they and the people around them are the good guys when in truth it is fear that keeps them in check until it doesn’t time and time again.
Do we choose to go forward like this?
Will the meek ever inherit the Earth? Do we need to give it to them?
-
 @ 57d1a264:69f1fee1
2025-05-20 06:15:51
@ 57d1a264:69f1fee1
2025-05-20 06:15:51Deliberate (?) trade-offs we make for the sake of output speed.
... By sacrificing depth in my learning, I can produce substantially more work. I’m unsure if I’m at the correct balance between output quantity and depth of learning. This uncertainty is mainly fueled by a sense of urgency due to rapidly improving AI models. I don’t have time to learn everything deeply. I love learning, but given current trends, I want to maximize immediate output. I’m sacrificing some learning in classes for more time doing outside work. From a teacher’s perspective, this is obviously bad, but from my subjective standpoint, it’s unclear.
Finding the balance between learning and productivity. By trade, one cannot be productive in specific areas without first acquire the knowledge to define the processes needed to deliver. Designing the process often come on a try and fail dynamic that force us to learn from previous mistakes.
I found this little journal story fun but also little sad. Vincent's realization, one of us trading his learnings to be more productive, asking what is productivity without quality assurance?
Inevitably, parts of my brain will degenerate and fade away, so I need to consciously decide what I want to preserve or my entire brain will be gone. What skills am I NOT okay with offloading? What do I want to do myself?
Read Vincent's journal https://vvvincent.me/llms-are-making-me-dumber/
https://stacker.news/items/984361
-
 @ eb0157af:77ab6c55
2025-05-22 14:01:29
@ eb0157af:77ab6c55
2025-05-22 14:01:29A Chinese printer company inadvertently distributed malware that steals Bitcoin through its official drivers, resulting in the theft of over $950,000.
According to local media outlet Landian News, a Chinese printer manufacturer was found to have unknowingly distributed malware designed to steal Bitcoin through its official device drivers.
Procolored, a Shenzhen-based printer company, distributed malware capable of stealing Bitcoin alongside the official drivers for its devices. The company reportedly used USB devices to spread infected drivers and uploaded the compromised software to globally accessible cloud storage services.
Crypto security and compliance firm SlowMist explained how the malware works in a post on X:
 The official driver provided by this printer carries a backdoor program. It will hijack the wallet address in the user's clipboard and replace it with the attacker's address: 1BQZKqdp2CV3QV5nUEsqSg1ygegLmqRygj
The official driver provided by this printer carries a backdoor program. It will hijack the wallet address in the user's clipboard and replace it with the attacker's address: 1BQZKqdp2CV3QV5nUEsqSg1ygegLmqRygj  According to @MistTrack_io, the attacker has stolen 9.3086… https://t.co/DHCkEpHhuH pic.twitter.com/W1AnUpswLU
According to @MistTrack_io, the attacker has stolen 9.3086… https://t.co/DHCkEpHhuH pic.twitter.com/W1AnUpswLU— MistTrack
 (@MistTrack_io) May 19, 2025
(@MistTrack_io) May 19, 2025The consequences of the breach have been significant, with a total of 9.3 BTC stolen — equivalent to over $950,000.
The issue was first flagged by YouTuber Cameron Coward, whose antivirus software detected malware in the drivers during a test of a Procolored UV printer. The software identified both a worm and a trojan virus named Foxif.
When contacted, Procolored denied the accusations, dismissing the antivirus warning as a false positive. Coward then turned to Reddit, where he shared the issue with cybersecurity professionals, drawing the attention of security firm G Data.
G Data’s investigation revealed that most of Procolored’s drivers were hosted on the MEGA file-sharing platform, with uploads dating back to October 2023. Their analysis confirmed the presence of two separate malware strains: the Win32.Backdoor.XRedRAT.A backdoor and a crypto-stealer designed to replace clipboard wallet addresses with those controlled by the attacker.
G Data reached out to Procolored, which stated that it had removed the infected drivers from its storage as of May 8 and had re-scanned all files. The company attributed the malware to a supply chain compromise, saying the malicious files were introduced via infected USB devices before being uploaded online.
Landian News recommended that users who downloaded Procolored drivers in the past six months “immediately run a full system scan using antivirus software.” However, given that antivirus tools are not always reliable, the Chinese media outlet suggested that a full system reset is the safest option when in doubt.
The post Bitcoin malware discovered: Chinese printer manufacturer involved appeared first on Atlas21.
-
 @ 30ceb64e:7f08bdf5
2025-04-26 20:33:30
@ 30ceb64e:7f08bdf5
2025-04-26 20:33:30Status: Draft
Author: TheWildHustleAbstract
This NIP defines a framework for storing and sharing health and fitness profile data on Nostr. It establishes a set of standardized event kinds for individual health metrics, allowing applications to selectively access specific health information while preserving user control and privacy.
In this framework exists - NIP-101h.1 Weight using kind 1351 - NIP-101h.2 Height using kind 1352 - NIP-101h.3 Age using kind 1353 - NIP-101h.4 Gender using kind 1354 - NIP-101h.5 Fitness Level using kind 1355
Motivation
I want to build and support an ecosystem of health and fitness related nostr clients that have the ability to share and utilize a bunch of specific interoperable health metrics.
- Selective access - Applications can access only the data they need
- User control - Users can choose which metrics to share
- Interoperability - Different health applications can share data
- Privacy - Sensitive health information can be managed independently
Specification
Kind Number Range
Health profile metrics use the kind number range 1351-1399:
| Kind | Metric | | --------- | ---------------------------------- | | 1351 | Weight | | 1352 | Height | | 1353 | Age | | 1354 | Gender | | 1355 | Fitness Level | | 1356-1399 | Reserved for future health metrics |
Common Structure
All health metric events SHOULD follow these guidelines:
- The content field contains the primary value of the metric
- Required tags:
['t', 'health']- For categorizing as health data['t', metric-specific-tag]- For identifying the specific metric['unit', unit-of-measurement]- When applicable- Optional tags:
['converted_value', value, unit]- For providing alternative unit measurements['timestamp', ISO8601-date]- When the metric was measured['source', application-name]- The source of the measurement
Unit Handling
Health metrics often have multiple ways to be measured. To ensure interoperability:
- Where multiple units are possible, one standard unit SHOULD be chosen as canonical
- When using non-standard units, a
converted_valuetag SHOULD be included with the canonical unit - Both the original and converted values should be provided for maximum compatibility
Client Implementation Guidelines
Clients implementing this NIP SHOULD:
- Allow users to explicitly choose which metrics to publish
- Support reading health metrics from other users when appropriate permissions exist
- Support updating metrics with new values over time
- Preserve tags they don't understand for future compatibility
- Support at least the canonical unit for each metric
Extensions
New health metrics can be proposed as extensions to this NIP using the format:
- NIP-101h.X where X is the metric number
Each extension MUST specify: - A unique kind number in the range 1351-1399 - The content format and meaning - Required and optional tags - Examples of valid events
Privacy Considerations
Health data is sensitive personal information. Clients implementing this NIP SHOULD:
- Make it clear to users when health data is being published
- Consider incorporating NIP-44 encryption for sensitive metrics
- Allow users to selectively share metrics with specific individuals
- Provide easy ways to delete previously published health data
NIP-101h.1: Weight
Description
This NIP defines the format for storing and sharing weight data on Nostr.
Event Kind: 1351
Content
The content field MUST contain the numeric weight value as a string.
Required Tags
- ['unit', 'kg' or 'lb'] - Unit of measurement
- ['t', 'health'] - Categorization tag
- ['t', 'weight'] - Specific metric tag
Optional Tags
- ['converted_value', value, unit] - Provides the weight in alternative units for interoperability
- ['timestamp', ISO8601 date] - When the weight was measured
Examples
json { "kind": 1351, "content": "70", "tags": [ ["unit", "kg"], ["t", "health"], ["t", "weight"] ] }json { "kind": 1351, "content": "154", "tags": [ ["unit", "lb"], ["t", "health"], ["t", "weight"], ["converted_value", "69.85", "kg"] ] }NIP-101h.2: Height
Status: Draft
Description
This NIP defines the format for storing and sharing height data on Nostr.
Event Kind: 1352
Content
The content field can use two formats: - For metric height: A string containing the numeric height value in centimeters (cm) - For imperial height: A JSON string with feet and inches properties
Required Tags
['t', 'health']- Categorization tag['t', 'height']- Specific metric tag['unit', 'cm' or 'imperial']- Unit of measurement
Optional Tags
['converted_value', value, 'cm']- Provides height in centimeters for interoperability when imperial is used['timestamp', ISO8601-date]- When the height was measured
Examples
```jsx // Example 1: Metric height Apply to App.jsx
// Example 2: Imperial height with conversion Apply to App.jsx ```
Implementation Notes
- Centimeters (cm) is the canonical unit for height interoperability
- When using imperial units, a conversion to centimeters SHOULD be provided
- Height values SHOULD be positive integers
- For maximum compatibility, clients SHOULD support both formats
NIP-101h.3: Age
Status: Draft
Description
This NIP defines the format for storing and sharing age data on Nostr.
Event Kind: 1353
Content
The content field MUST contain the numeric age value as a string.
Required Tags
['unit', 'years']- Unit of measurement['t', 'health']- Categorization tag['t', 'age']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the age was recorded['dob', ISO8601-date]- Date of birth (if the user chooses to share it)
Examples
```jsx // Example 1: Basic age Apply to App.jsx
// Example 2: Age with DOB Apply to App.jsx ```
Implementation Notes
- Age SHOULD be represented as a positive integer
- For privacy reasons, date of birth (dob) is optional
- Clients SHOULD consider updating age automatically if date of birth is known
- Age can be a sensitive metric and clients may want to consider encrypting this data
NIP-101h.4: Gender
Status: Draft
Description
This NIP defines the format for storing and sharing gender data on Nostr.
Event Kind: 1354
Content
The content field contains a string representing the user's gender.
Required Tags
['t', 'health']- Categorization tag['t', 'gender']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the gender was recorded['preferred_pronouns', string]- User's preferred pronouns
Common Values
While any string value is permitted, the following common values are recommended for interoperability: - male - female - non-binary - other - prefer-not-to-say
Examples
```jsx // Example 1: Basic gender Apply to App.jsx
// Example 2: Gender with pronouns Apply to App.jsx ```
Implementation Notes
- Clients SHOULD allow free-form input for gender
- For maximum compatibility, clients SHOULD support the common values
- Gender is a sensitive personal attribute and clients SHOULD consider appropriate privacy controls
- Applications focusing on health metrics should be respectful of gender diversity
NIP-101h.5: Fitness Level
Status: Draft
Description
This NIP defines the format for storing and sharing fitness level data on Nostr.
Event Kind: 1355
Content
The content field contains a string representing the user's fitness level.
Required Tags
['t', 'health']- Categorization tag['t', 'fitness']- Fitness category tag['t', 'level']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the fitness level was recorded['activity', activity-type]- Specific activity the fitness level relates to['metrics', JSON-string]- Quantifiable fitness metrics used to determine level
Common Values
While any string value is permitted, the following common values are recommended for interoperability: - beginner - intermediate - advanced - elite - professional
Examples
```jsx // Example 1: Basic fitness level Apply to App.jsx
// Example 2: Activity-specific fitness level with metrics Apply to App.jsx ```
Implementation Notes
- Fitness level is subjective and may vary by activity
- The activity tag can be used to specify fitness level for different activities
- The metrics tag can provide objective measurements to support the fitness level
- Clients can extend this format to include activity-specific fitness assessments
- For general fitness apps, the simple beginner/intermediate/advanced scale is recommended
-
 @ 90de72b7:8f68fdc0
2025-05-21 10:44:54
@ 90de72b7:8f68fdc0
2025-05-21 10:44:54Custom Traffic Light Control System 21/05
This Petri net represents a traffic control protocol ensuring that two traffic lights alternate safely and are never both green at the same time.
petrinet ;start () -> greenLight1 redLight2 ;toRed1 greenLight1 -> queue redLight1 ;toGreen2 redLight2 queue -> greenLight2 ;toGreen1 queue redLight1 -> greenLight1 ;toRed2 greenLight2 -> redLight2 queue ;stop redLight1 queue redLight2 -> () -
 @ 57d1a264:69f1fee1
2025-05-20 06:02:26
@ 57d1a264:69f1fee1
2025-05-20 06:02:26Digital Psychology ↗Wall of impact website showcase a collection of success metrics and micro case studies to create a clear, impactful visual of your brand's achievements. It also displays a Wall of love with an abundance of testimonials in one place, letting the sheer volume highlight your brand's popularity and customer satisfaction.
And like these, many others collections like Testimonial mashup that combine multiple testimonials into a fast-paced, engaging reel that highlights key moments of impact in an attention-grabbing format.
Awards and certifications of websites highlighting third-party ratings and verification to signal trust and quality through industry-recognized achievements and standards.
View them all at https://socialproofexamples.com/
https://stacker.news/items/984357
-
 @ 609f186c:0aa4e8af
2025-05-16 20:57:43
@ 609f186c:0aa4e8af
2025-05-16 20:57:43Google says that Android 16 is slated to feature an optional high security mode. Cool.
Advanced Protection has a bunch of requested features that address the kinds of threats we worry about.
It's the kind of 'turn this one thing on if you face elevated risk' that we've been asking for from Google.
And likely reflects some learning after Google watched Apple 's Lockdown Mode play out. I see a lot of value in this..
Here are some features I'm excited to see play out:
The Intrusion Logging feature is interesting & is going to impose substantial cost on attackers trying to hide evidence of exploitation. Logs get e2ee encrypted into the cloud. This one is spicy.
The Offline Lock, Inactivity Reboot & USB protection will frustrate non-consensual attempts to physically grab device data.

Memory Tagging Extension is going to make a lot of attack & exploitation categories harder.
2G Network Protection & disabling Auto-connect to insecure networks are going to address categories of threat from things like IMSI catchers & hostile WiFi.
I'm curious about some other features such as:
Spam & Scam detection: Google messages feature that suggests message content awareness and some kind of scanning.
Scam detection for Phone by Google is interesting & coming later. The way it is described suggests phone conversation awareness. This also addresses a different category of threat than the stuff above. I can see it addressing a whole category of bad things that regular users (& high risk ones too!) face. Will be curious how privacy is addressed or if this done purely locally. Getting messy: Friction points? I see Google thinking these through, but I'm going to add a potential concern: what will users do when they encounter friction? Will they turn this off & forget to re-enable? We've seen users turn off iOS Lockdown Mode when they run into friction for specific websites or, say, legacy WiFi. They then forget to turn it back on. And stay vulnerable.

Bottom line: users disabling Apple's Lockdown Mode for a temporary thing & leaving it off because they forget to turn it on happens a lot. This is a serious % of users in my experience...
And should be factored into design decisions for similar modes. I feel like a good balance is a 'snooze button' or equivalent so that users can disable all/some features for a brief few minute period to do something they need to do, and then auto re-enable.
Winding up:
I'm excited to see how Android Advanced Protection plays with high risk users' experiences. I'm also super curious whether the spam/scam detection features may also be helpful to more vulnerable users (think: aging seniors)...
Niche but important:
Some users, esp. those that migrated to security & privacy-focused Android distros because of because of the absence of such a feature are clear candidates for it... But they may also voice privacy concerns around some of the screening features. Clear communication from the Google Security / Android team will be key here.
-
 @ b83a28b7:35919450
2025-05-16 19:26:56
@ b83a28b7:35919450
2025-05-16 19:26:56This article was originally part of the sermon of Plebchain Radio Episode 111 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ 90de72b7:8f68fdc0
2025-05-21 10:34:35
@ 90de72b7:8f68fdc0
2025-05-21 10:34:35PetriNostr. My everyday activity
PetriNostr never sleep! This is a demo
Places & Transitions
- Places:
-
Bla bla bla: some text
-
Transitions:
- start: Initializes the system.
- logTask: bla bla bla.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ cae03c48:2a7d6671
2025-05-22 20:01:14
@ cae03c48:2a7d6671
2025-05-22 20:01:14Bitcoin Magazine

Bitcoiners Should Care About The GENIUS ActWhile the GENIUS Act is a stablecoin bill, U.S.-based Bitcoin enthusiasts should be paying attention to the language in the bill as it pertains to the ability to transact privately with crypto assets — including bitcoin.
Two documents that recently circulated among Senate Banking Committee Democrats indicate that Senate Democrats want to see amendments made to the GENIUS Act that would greatly reduce user privacy in crypto transactions.
Senate Democrats’ Analysis of GENIUS Act
The first of these two documents is a two-pager entitled “Banking Committee Democratic Staff Analysis on Latest GENIUS Act Draft”.
 NEW: Senate Banking Committee Democrats just dropped a scathing staff analysis of the latest GENIUS Act draft ahead of this evening’s cloture vote.
NEW: Senate Banking Committee Democrats just dropped a scathing staff analysis of the latest GENIUS Act draft ahead of this evening’s cloture vote. Staffers describe the latest GENIUS Act draft as a blueprint for ‘Trump crypto corruption’ and Big Tech dominance over digital… pic.twitter.com/Gqd2LxFGx1
— Eleanor Terrett (@EleanorTerrett) May 19, 2025
This document is filled with the type of rhetoric that is commonly associated with the Ranking Member of the Senate Banking Committee, Senator Elizabeth Warren (D-MA).
It refers to stablecoins as tools for illicit finance (despite the fact that the largest stablecoin issuer, Tether, often works with the Department of Justice (DoJ) and the FBI to stop the illegal use of stablecoins).
It also states that the current iteration of the GENIUS Act “does nothing to actually impose basic obligations on [crypto mixers] to prevent illicit finance.”

A segment from document featuring Democrats’ analysis of The GENIUS Act.
This latter critique of the bill is antithetical to guidance that Deputy Attorney General (DAG) Todd Blanche offered in a memo on April 7, 2025. DAG Blanche stated that the DoJ will no longer target crypto mixing services for the acts of their end users.
In this document, however, Senate Democrats indicate that they plan to continue targeting crypto mixing technology instead of those who abuse it.
If amendments regarding the targeting of crypto mixers are added to a revised version of the GENIUS Act, this could have an impact on Bitcoin users who employ such technology in the name of preserving their privacy.
A Letter From Democrats Opposing The GENIUS Act
Senate Banking Democrats circulated a second document on Monday, as well.
This document, a letter signed by 46 advocacy groups, opposed the GENIUS Act.
Brendan Pedersen of Punchbowl News shared segments of the letter on X.
Democratic staff on the Senate Banking Committee sent around a letter this AM signed by several dozen advocacy orgs opposing the GENIUS Act.
Includes ACRE, AFR, Center for Responsible Lending, Our Revolution, Public Citizen, Tech Oversight Project… pic.twitter.com/pragFvzSKB
— Brendan Pedersen (@BrendanPedersen) May 19, 2025
The authors of the letter claim that the GENIUS Act does not do enough to prevent illicit finance in part because it still allows for “self-hosted wallets that lack know-your-customer (KYC) requirements.”
A segment from the letter opposing The GENIUS Act that touches on noncustodial wallets and KYC requirements.
If the GENIUS Act is amended so that it requires KYC for all wallets that touch stablecoins — self-custodial wallets included — it’s likely only a matter of time before similar regulation is established for Bitcoin wallets.
Bitcoin Transactional Privacy Is At Stake
Just because the GENIUS Act doesn’t directly reference Bitcoin doesn’t mean that Bitcoin won’t be affected by it.
If Senate Democrats get their way and crypto mixers become a target of the bill and/or if the bill requires that all wallets that touch stablecoins require users to KYC, and the bill is enacted into law, anonymity in crypto transactions will become a crime.
So, while some Bitcoiners may be anti-stablecoins, most, I would wager, aren’t anti-privacy. Therefore, it would behoove them to contact their elected officials to urge them to vote “no” for the GENIUS Act if the upcoming iteration of the bill restricts the ability to transact privately.
This post Bitcoiners Should Care About The GENIUS Act first appeared on Bitcoin Magazine and is written by Frank Corva.
-
 @ 8bad92c3:ca714aa5
2025-05-22 18:02:41
@ 8bad92c3:ca714aa5
2025-05-22 18:02:41Key Takeaways

In this episode of TFTC, Andrew Myers, founder of Satoshi Energy, explores the convergence of AI, humanoid robots, Bitcoin, and decentralized energy, warning of a near future where self-replicating machines dominate energy and labor. Myers argues that Bitcoin’s decentralized nature offers a critical check against centralized AI power, enabling autonomous agents to transact freely and protecting individual sovereignty. Through his company’s work and its software BitCurrent, Myers promotes Bitcoin as both a tool for energy market efficiency and a foundation for preserving liberty in an AI-driven world.
Best Quotes
“Humanoid robots are going to not only replace most of the jobs people do today… they're going to be able to recreate themselves and self-replicate faster than that.”
“For me the key value proposition of Bitcoin is leveling the economic playing field. Rather than those who control the money printer making the economic decisions, it's everyday people.”
“AI energy demand is infinite. Bitcoin has a Nakamoto point… AI doesn’t.”
“Satoshi Energy’s mission is to enable every electric power company to use Bitcoin by block 1,050,000.”
“If you're a Bitcoiner and you're not using Fold, what are you doing? You're leaving sats on the table.”
“Tesla said machines would eventually fight wars for us. When that happens, nation-states become spectators. Bitcoin is how we avoid centralized control of those machines.”
“There’s already an energy company in Texas using Bitcoin as collateral in a power contract.”
“Are we auditioning for a galactic federation? Maybe. Even if not, we should still be acting like we are.”
Conclusion
Andrew Myers delivers a compelling vision of the future where exponential AI and energy growth demand a decentralized response—one rooted in Bitcoin as more than money, but as critical infrastructure for freedom. Through Satoshi Energy and tools like BitCurrent, Myers bridges big ideas with tangible actions, advocating for bottom-up sovereignty across energy and finance. His message is clear: decentralization is no longer optional—it’s essential for preserving human agency in an increasingly automated world.
Timestamps
0:00 - Intro
0:34 - Tesla’s AI energy theory
8:59 - Bitcoin and decentralization fixes AI
13:02 - Fold & Bitkey
14:38 - How Satoshi Energy is using AI
19:28 - Bit Current
23:13 - Unchained
23:42 - Revealing inefficiency
32:57 - Proliferating OS AI with bitcoin
36:26 -Apple of Eden and Antichrist
45:11 - Iberian outage
48:48 - Defense tech
54:51 - UFOs, Atlantis and remote viewingTranscript
(00:00) Humanoid robots are advancing so quickly. They're going to not only replace most of the jobs that people do today, probably the next 5 to 10 years, but they're going to be able to recreate themselves and self-replicate even faster than that. With AI, the energy demand is infinite. It's going to 10x and 10x and 10x again in terms of global energy consumption, and that's just going to completely change the world we live in.
(00:21) If there's a sufficiently advanced AI, is it going to listen to a politician that says, "No, you can't have that energy." Or is it going to say, "Fuck you. Send the drone. You can hear us loud and clear. Loud and clear. I have to put this in front of my face so I'm not leaning. Yeah, vibe coding. There may be some securityities.
(00:45) I do want to hand it off to a developer who actually understands this stuff to say, am I am I going to am I going to leak any information or like be Yeah, I should probably do that before I release to the public. Now, let me say that. does seem pretty simple though. It's just getting the data on the page, getting the price of Bitcoin, using Coin Gecko API, and then running the math of how much Bitcoin is this worth at this point in time.
(01:13) We're not collecting any data either. I don't think that you know of. No, this is AI once. This is the problem of vibe coding. Are you bearish on AI? Uh, I think we're at a fork in the road and on one side I'm very bullish. You shamed me for for admitting that I was turning my kids into Legos via or turning myself into Lego in this. I was channeling my inner Marty.
(01:36) What would Marty do? Well, that's what uh that's what precipitated this. You hit me up. Was it two weeks ago now at this point? this week with your tweet about Nicola Tesla essentially predicting AI and him not factoring in sound money to the inevitable future that he foresaw. Yeah, it kind of came up uh in the work we're doing at Satoshi Energy where we're developing sites for data centers and a lot of those were were Bitcoin data centers for the last five six years and then in the last couple of years just increasingly demand
(02:20) from AI data centers in some cases like a project that we sold to a Bitcoin miner then becomes an AI site and then start to have questions within the team about what is our AI strategy and it was always in the back of my mind as part of the strategy which we'll get into like what is this fork in the road which directions could it go but I hadn't ever really communicated it to our team uh until recently because it's such a big idea that like on top of thinking about sound money and energy like we're already thinking about enough but as the
(02:57) team's growing as people are starting to ask these questions and like in some cases feeling conflicted about um should we be serving this AI market and in some cases large institutional investors and tech companies uh really like felt the need to put the the pen to paper and and talk about this and talk about how AI fits into our overall strategy.
(03:20) Uh, and part of that reminded me of this uh, essay that Nicola Tesla wrote called um, the problem of human energy, which was kind of a cheeky title. Uh, because clearly he thought, you know, energy would liberate humanity. Uh, but it get you get a lot more readers if you, you know, if you name it, the problem of human energy, especially a lot more of the critics who you're trying to convince otherwise.
(03:44) And one of the biggest things, biggest takeaways for me in that in that essay is he he basically says at some point man will create machines that fight wars for us and limit the the loss of human life to the point where the different parties, nation states, other powerful people u that were fighting wars with each other will once it's sort of this this machine to machine battle, they'll just become interested spectators.
(04:13) and eventually lead to world peace. So I think that's the path we want to be on. Not the path where it becomes a very centralized AI and we ultimately become enslaved. Uh but on the path to world peace or or keeping ourselves on that path to world peace. I think that's where Bitcoin plays a role. it keeps the economic playing field level uh and keeps this technology sufficiently decentralized where Bitcoin is that protocol for you know decentralized AI agents communicating with each other.
(04:46) So we can go in any direction you want from there but it's a big idea. No, this is in line with something I wrote about earlier this week that was inspired by a tweet that Paul Otoy from Stack put out basically not explaining this exact problem but just giving his thoughts on how he's viewing the state of AI and where it will go in the future.
(05:10) And Paul, the team at stack and sphinx are highly focused on enabling the open- source AI as opposed to closed source AI. I I think based on what you just said, I think it's very line what Paul was saying in that tweet, which is we're reaching the point with MCP with these sort of protocols where you can store context that agents can plug into and begin communicating with each other.
(05:39) We're at the point where agentic models are getting are actually usable. And I think that's where you have this like critical tipping point of okay that's really going to dictate which direction in the fork in the road we go down because once the agents are able to go do these tasks you right have these network effects that take hold and it's very important that we thread the needle of making sure that it's open and incentivized properly.
(06:10) Yes. Yes, we had this idea of time preference in the Bitcoin community where you know we think with sound money we should have a low time preference meaning we think longer term uh we don't need need to make sort of quick rash decisions into investments today but then you have this tidal wave of AI coming our our direction it almost forces you back into that high time preference mindset of like I need to address this problem now um and Then from like an energy perspective, it's interesting too.
(06:44) Uh you have like Drew's concept of the Nakamoto point for Bitcoin. Like how much of of human energy of global energy will will Bitcoin mining consume? And like say it's between 1 and 10% of of human energy. If it becomes 100% then uh that doesn't make any sense because then you're just like worshiping Bitcoin.
(07:03) And if all of the energy is going towards that, it means you're not putting any energy towards any other sort of economic pursuit or uh you know human need. But with AI, the energy demand is infinite. I don't think there is a Nakamoto point. It's just like it's going to 10x and 10x and 10x again in terms of g global energy consumption.
(07:23) Uh and that's just going to completely change the world we live in. Another thing on sort of the high time preference concept is like humanoid robots are advancing so quickly. They're going to not only replace all of the job most of the jobs that people do today, very quickly within probably the next 5 to 10 years max, but they're going to be able to rec -
 @ 3bf0c63f:aefa459d
2025-04-25 19:26:48
@ 3bf0c63f:aefa459d
2025-04-25 19:26:48Redistributing Git with Nostr
Every time someone tries to "decentralize" Git -- like many projects tried in the past to do it with BitTorrent, IPFS, ScuttleButt or custom p2p protocols -- there is always a lurking comment: "but Git is already distributed!", and then the discussion proceeds to mention some facts about how Git supports multiple remotes and its magic syncing and merging abilities and so on.
Turns out all that is true, Git is indeed all that powerful, and yet GitHub is the big central hub that hosts basically all Git repositories in the giant world of open-source. There are some crazy people that host their stuff elsewhere, but these projects end up not being found by many people, and even when they do they suffer from lack of contributions.
Because everybody has a GitHub account it's easy to open a pull request to a repository of a project you're using if it's on GitHub (to be fair I think it's very annoying to have to clone the repository, then add it as a remote locally, push to it, then go on the web UI and click to open a pull request, then that cloned repository lurks forever in your profile unless you go through 16 screens to delete it -- but people in general seem to think it's easy).
It's much harder to do it on some random other server where some project might be hosted, because now you have to add 4 more even more annoying steps: create an account; pick a password; confirm an email address; setup SSH keys for pushing. (And I'm not even mentioning the basic impossibility of offering
pushaccess to external unknown contributors to people who want to host their own simple homemade Git server.)At this point some may argue that we could all have accounts on GitLab, or Codeberg or wherever else, then those steps are removed. Besides not being a practical strategy this pseudo solution misses the point of being decentralized (or distributed, who knows) entirely: it's far from the ideal to force everybody to have the double of account management and SSH setup work in order to have the open-source world controlled by two shady companies instead of one.
What we want is to give every person the opportunity to host their own Git server without being ostracized. at the same time we must recognize that most people won't want to host their own servers (not even most open-source programmers!) and give everybody the ability to host their stuff on multi-tenant servers (such as GitHub) too. Importantly, though, if we allow for a random person to have a standalone Git server on a standalone server they host themselves on their wood cabin that also means any new hosting company can show up and start offering Git hosting, with or without new cool features, charging high or low or zero, and be immediately competing against GitHub or GitLab, i.e. we must remove the network-effect centralization pressure.
External contributions
The first problem we have to solve is: how can Bob contribute to Alice's repository without having an account on Alice's server?
SourceHut has reminded GitHub users that Git has always had this (for most) arcane
git send-emailcommand that is the original way to send patches, using an once-open protocol.Turns out Nostr acts as a quite powerful email replacement and can be used to send text content just like email, therefore patches are a very good fit for Nostr event contents.
Once you get used to it and the proper UIs (or CLIs) are built sending and applying patches to and from others becomes a much easier flow than the intense clickops mixed with terminal copypasting that is interacting with GitHub (you have to clone the repository on GitHub, then update the remote URL in your local directory, then create a branch and then go back and turn that branch into a Pull Request, it's quite tiresome) that many people already dislike so much they went out of their way to build many GitHub CLI tools just so they could comment on issues and approve pull requests from their terminal.
Replacing GitHub features
Aside from being the "hub" that people use to send patches to other people's code (because no one can do the email flow anymore, justifiably), GitHub also has 3 other big features that are not directly related to Git, but that make its network-effect harder to overcome. Luckily Nostr can be used to create a new environment in which these same features are implemented in a more decentralized and healthy way.
Issues: bug reports, feature requests and general discussions
Since the "Issues" GitHub feature is just a bunch of text comments it should be very obvious that Nostr is a perfect fit for it.
I will not even mention the fact that Nostr is much better at threading comments than GitHub (which doesn't do it at all), which can generate much more productive and organized discussions (and you can opt out if you want).
Search
I use GitHub search all the time to find libraries and projects that may do something that I need, and it returns good results almost always. So if people migrated out to other code hosting providers wouldn't we lose it?
The fact is that even though we think everybody is on GitHub that is a globalist falsehood. Some projects are not on GitHub, and if we use only GitHub for search those will be missed. So even if we didn't have a Nostr Git alternative it would still be necessary to create a search engine that incorporated GitLab, Codeberg, SourceHut and whatnot.
Turns out on Nostr we can make that quite easy by not forcing anyone to integrate custom APIs or hardcoding Git provider URLs: each repository can make itself available by publishing an "announcement" event with a brief description and one or more Git URLs. That makes it easy for a search engine to index them -- and even automatically download the code and index the code (or index just README files or whatever) without a centralized platform ever having to be involved.
The relays where such announcements will be available play a role, of course, but that isn't a bad role: each announcement can be in multiple relays known for storing "public good" projects, some relays may curate only projects known to be very good according to some standards, other relays may allow any kind of garbage, which wouldn't make them good for a search engine to rely upon, but would still be useful in case one knows the exact thing (and from whom) they're searching for (the same is valid for all Nostr content, by the way, and that's where it's censorship-resistance comes from).
Continuous integration
GitHub Actions are a very hardly subsidized free-compute-for-all-paid-by-Microsoft feature, but one that isn't hard to replace at all. In fact there exists today many companies offering the same kind of service out there -- although they are mostly targeting businesses and not open-source projects, before GitHub Actions was introduced there were also many that were heavily used by open-source projects.
One problem is that these services are still heavily tied to GitHub today, they require a GitHub login, sometimes BitBucket and GitLab and whatnot, and do not allow one to paste an arbitrary Git server URL, but that isn't a thing that is very hard to change anyway, or to start from scratch. All we need are services that offer the CI/CD flows, perhaps using the same framework of GitHub Actions (although I would prefer to not use that messy garbage), and charge some few satoshis for it.
It may be the case that all the current services only support the big Git hosting platforms because they rely on their proprietary APIs, most notably the webhooks dispatched when a repository is updated, to trigger the jobs. It doesn't have to be said that Nostr can also solve that problem very easily.
-
 @ 8576ca0e:621f735e
2025-05-22 17:36:20
@ 8576ca0e:621f735e
2025-05-22 17:36:20In the evolving digital economy, Bitcoin has moved beyond its initial status as a speculative asset. It is now a powerful tool for building long-term wealth, especially within the context of a decentralized financial system. While Bitcoin 101 introduced the concept of Bitcoin and Bitcoin 102 covered its mechanics and investment basics, Bitcoin 103 dives deeper into how individuals can strategically build wealth in a decentralized world.
The Foundation: Why Decentralization Matters
At its core, Bitcoin operates on a decentralized network free from government control or manipulation by central banks. This decentralization is not just a technical characteristic but a financial philosophy. In a world where inflation erodes the value of fiat currencies and financial systems can be restricted by geopolitical decisions, Bitcoin offers sovereignty and transparency.
By removing intermediaries, Bitcoin empowers individuals to store, send, and receive money globally with minimal friction. This capability becomes crucial in building wealth that’s resilient to political and economic volatility.
Bitcoin as Digital Gold
Bitcoin's fixed supply capped at 21 million BTC mimics the scarcity of precious metals like gold. However, unlike gold, Bitcoin is portable, divisible, and easier to secure. Investors seeking a hedge against inflation and monetary debasement are increasingly turning to Bitcoin as a long term store of value.
Holding Bitcoin over time, known as "HODLing" in crypto parlance, is one of the most common wealth building strategies. Historical data shows that long-term holders tend to outperform short-term traders, especially in the face of Bitcoin’s cyclical volatility.
Diversification in a Decentralized Economy
Building wealth with Bitcoin doesn't mean going all in. It involves using Bitcoin as a foundational asset while exploring adjacent opportunities within the decentralized finance (DeFi) space. Bitcoin can be used as collateral, yield-generating assets, or even part of a diversified crypto portfolio that includes Ethereum, stablecoins, and tokenized assets.
For instance, some platforms allow users to lend their Bitcoin and earn interest, or stake wrapped Bitcoin (WBTC) on decentralized protocols. While these carry risk, they also offer the possibility of compounding returns beyond price appreciation alone.
Wealth Preservation through Self-Custody
One of the key principles of wealth building in the decentralized world is self custody. Unlike traditional bank accounts, where your assets are held by third parties, Bitcoin allows users to control their wealth directly through private keys and cold storage wallets.
By taking responsibility for their assets, users reduce counterparty risk and maintain access to their wealth even in times of crisis. This level of control and autonomy is unprecedented in the history of money.
Education and Risk Management
Wealth building in the Bitcoin ecosystem requires a solid understanding of risk. Volatility, regulatory uncertainty, and security vulnerabilities must be addressed through continuous education, diversification, and the use of reputable platforms.
New investors should start by:
• Setting long term goals
• Investing only what they can afford to lose
• Using hardware wallets for security
• Staying informed through trusted crypto news sources
The Future of Wealth in a Decentralized World
Bitcoin is not just reshaping finance, it’s redefining wealth. As decentralized technologies mature, we can expect a shift in how value is created, transferred, and preserved. From smart contracts to decentralized autonomous organizations (DAOs), the Bitcoin ethos of transparency, security, and autonomy will continue to guide the evolution of the digital economy.
In conclusion, Bitcoin 103 is about more than investing, It's about understanding the broader movement toward financial freedom. Building wealth in a decentralized world starts with a shift in mindset: from dependence to independence, from control to empowerment.
-
 @ 3b3a42d3:d192e325
2025-04-10 08:57:51
@ 3b3a42d3:d192e325
2025-04-10 08:57:51Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Trading and enforcement of asset option contracts
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ c631e267:c2b78d3e
2025-05-16 18:40:18
@ c631e267:c2b78d3e
2025-05-16 18:40:18Die zwei mächtigsten Krieger sind Geduld und Zeit. \ Leo Tolstoi
Zum Wohle unserer Gesundheit, unserer Leistungsfähigkeit und letztlich unseres Glücks ist es wichtig, die eigene Energie bewusst zu pflegen. Das gilt umso mehr für an gesellschaftlichen Themen interessierte, selbstbewusste und kritisch denkende Menschen. Denn für deren Wahrnehmung und Wohlbefinden waren und sind die rasanten, krisen- und propagandagefüllten letzten Jahre in Absurdistan eine harte Probe.
Nur wer regelmäßig Kraft tankt und Wege findet, mit den Herausforderungen umzugehen, kann eine solche Tortur überstehen, emotionale Erschöpfung vermeiden und trotz allem zufrieden sein. Dazu müssen wir erkunden, was uns Energie gibt und was sie uns raubt. Durch Selbstreflexion und Achtsamkeit finden wir sicher Dinge, die uns erfreuen und inspirieren, und andere, die uns eher stressen und belasten.
Die eigene Energie ist eng mit unserer körperlichen und mentalen Gesundheit verbunden. Methoden zur Förderung der körperlichen Gesundheit sind gut bekannt: eine ausgewogene Ernährung, regelmäßige Bewegung sowie ausreichend Schlaf und Erholung. Bei der nicht minder wichtigen emotionalen Balance wird es schon etwas komplizierter. Stress abzubauen, die eigenen Grenzen zu kennen oder solche zum Schutz zu setzen sowie die Konzentration auf Positives und Sinnvolles wären Ansätze.
Der emotionale ist auch der Bereich, über den «Energie-Räuber» bevorzugt attackieren. Das sind zum Beispiel Dinge wie Überforderung, Perfektionismus oder mangelhafte Kommunikation. Social Media gehören ganz sicher auch dazu. Sie stehlen uns nicht nur Zeit, sondern sind höchst manipulativ und erhöhen laut einer aktuellen Studie das Risiko für psychische Probleme wie Angstzustände und Depressionen.
Geben wir negativen oder gar bösen Menschen keine Macht über uns. Das Dauerfeuer der letzten Jahre mit Krisen, Konflikten und Gefahren sollte man zwar kennen, darf sich aber davon nicht runterziehen lassen. Das Ziel derartiger konzertierter Aktionen ist vor allem, unsere innere Stabilität zu zerstören, denn dann sind wir leichter zu steuern. Aber Geduld: Selbst vermeintliche «Sonnenköniginnen» wie EU-Kommissionspräsidentin von der Leyen fallen, wenn die Zeit reif ist.
Es ist wichtig, dass wir unsere ganz eigenen Bedürfnisse und Werte erkennen. Unsere Energiequellen müssen wir identifizieren und aktiv nutzen. Dazu gehören soziale Kontakte genauso wie zum Beispiel Hobbys und Leidenschaften. Umgeben wir uns mit Sinnhaftigkeit und lassen wir uns nicht die Energie rauben!
Mein Wahlspruch ist schon lange: «Was die Menschen wirklich bewegt, ist die Kultur.» Jetzt im Frühjahr beginnt hier in Andalusien die Zeit der «Ferias», jener traditionellen Volksfeste, die vor Lebensfreude sprudeln. Konzentrieren wir uns auf die schönen Dinge und auf unsere eigenen Talente – soziale Verbundenheit wird helfen, unsere innere Kraft zu stärken und zu bewahren.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ e5fa3d8c:44057ac9
2025-05-22 13:21:20
@ e5fa3d8c:44057ac9
2025-05-22 13:21:20 -
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 0e9491aa:ef2adadf
2025-05-22 08:01:35
@ 0e9491aa:ef2adadf
2025-05-22 08:01:35
I often hear "bitcoin doesn't interest me, I'm not a finance person."
Ironically, the beauty of sound money is you don't have to be. In the current system you're expected to manage a diversified investment portfolio or pay someone to do it. Bitcoin will make that optional.
— ODELL (@ODELL) September 16, 2018
At first glance bitcoin often appears overwhelming to newcomers. It is incredibly easy to get bogged down in the details of how it works or different ways to use it. Enthusiasts, such as myself, often enjoy going down the deep rabbit hole of the potential of bitcoin, possible pitfalls and theoretical scenarios, power user techniques, and the developer ecosystem. If your first touch point with bitcoin is that type of content then it is only natural to be overwhelmed. While it is important that we have a thriving community of bitcoiners dedicated to these complicated tasks - the true beauty of bitcoin lies in its simplicity. Bitcoin is simply better money. It is the best money we have ever had.
Life is complicated. Life is hard. Life is full of responsibility and surprises. Bitcoin allows us to focus on our lives while relying on a money that is simple. A money that is not controlled by any individual, company, or government. A money that cannot be easily seized or blocked. A money that cannot be devalued at will by a handful of corrupt bureaucrat who live hundreds of miles from us. A money that can be easily saved and should increase in purchasing power over time without having to learn how to "build a diversified stock portfolio" or hire someone to do it for us.
Bitcoin enables all of us to focus on our lives - our friends and family - doing what we love with the short time we have on this earth. Time is scarce. Life is complicated. Bitcoin is the most simple aspect of our complicated lives. If we spend our scarce time working then we should be able to easily save that accrued value for future generations without watching the news or understanding complicated financial markets. Bitcoin makes this possible for anyone.
Yesterday was Mother's Day. Raising a human is complicated. It is hard, it requires immense personal responsibility, it requires critical thinking, but mothers figure it out, because it is worth it. Using and saving bitcoin is simple - simply install an app on your phone. Every mother can do it. Every person can do it.
Life is complicated. Life is beautiful. Bitcoin is simple.
If you found this post helpful support my work with bitcoin.

-
 @ 502ab02a:a2860397
2025-05-22 01:30:37
@ 502ab02a:a2860397
2025-05-22 01:30:37ถ้าพูดถึง "เกาหลีใต้" หลายคนอาจนึกถึงซีรีส์ น้ำจิ้มเผ็ด หรือไอดอลหน้าผ่อง ๆ แต่เบื้องหลังวัฒนธรรมที่ลื่นไหลไปทั่วโลกนี้ ยังมีอาณาจักรธุรกิจขนาดมหึมาที่เป็นเหมือนเครื่องยนต์หลักผลักดันทั้งอาหาร เพลง หนัง และนวัตกรรมระดับโลก หนึ่งในนั้นคือ CJ Group ที่เริ่มต้นจากบริษัทน้ำตาลเล็ก ๆ ในปี 1953 แต่เติบโตจนกลายเป็นหนึ่งใน conglomerate หรือ "กลุ่มธุรกิจผูกเครือ" ที่ทรงอิทธิพลที่สุดของแดนโสม
คำว่า CJ ย่อมาจาก CheilJedang (แปลว่า “หมายเลขหนึ่งแห่งโลก” ในภาษาจีน-เกาหลี) ก่อตั้งโดย อี บยองชอล ผู้ก่อตั้ง Samsung Group ในช่วงเวลานั้น เกาหลีใต้กำลังฟื้นตัวจากสงครามเกาหลี และรัฐบาลส่งเสริมการพัฒนาอุตสาหกรรมภายในประเทศ เดิมเป็นหน่วยธุรกิจอาหารของกลุ่ม Samsung ในปี 1993 Cheil Jedang แยกตัวออกจาก Samsung Group และกลายเป็นบริษัทอิสระภายใต้การบริหารของ อี แจฮยอน หลานชายของอี บยองชอล แล้วขยายขอบเขตธุรกิจอย่างไม่หยุดยั้ง จากความเชี่ยวชาญใน "การหมัก" แบบดั้งเดิม พวกเขากลับกลายเป็นผู้เล่นรายใหญ่ระดับโลกในวงการ เทคโนโลยีชีวภาพ การผลิตอาหารไปจนถึงธุรกิจ บันเทิงระดับฮอลลีวูด และ โลจิสติกส์ข้ามทวีป
พูดง่าย ๆ ว่า CJ ไม่ได้แค่ส่งออกกิมจิหรือบิบิมบับ แต่พวกเขากำลังวางรากฐานของ "อนาคตแห่งอาหาร" และ "ความบันเทิงแบบไร้พรมแดน" ในเวลาเดียวกัน จนใครหลายคนถึงกับบอกว่า ถ้าอยากเข้าใจเกาหลีใต้ ก็ต้องเริ่มจากเข้าใจ CJ Group เสียก่อน
แล้วในเครือข่ายของ CJ Group มีธุรกิจอะไรบ้างที่น่าสนใจ และแบรนด์ไหนที่เราคุ้นเคยแบบไม่รู้ตัว ไปดูกันเลย
- ธุรกิจอาหารและบริการอาหาร (Food & Food Services)
- CJ CheilJedang บริษัทอาหารชั้นนำของเกาหลีใต้ มีผลิตภัณฑ์เด่น ได้แก่ Bibigo แบรนด์อาหารเกาหลีพร้อมรับประทาน เช่น เกี๊ยว ซอส และกิมจิ Hetbahn ข้าวสวยพร้อมรับประทานที่ได้รับความนิยมในเกาหลี
-
CJ Foodville ดำเนินธุรกิจร้านอาหารและเบเกอรี่ เช่น: Tous Les Jours ร้านเบเกอรี่สไตล์ฝรั่งเศส VIPS ร้านสเต็กและสลัดบุฟเฟ่ต์
-
ธุรกิจเทคโนโลยีชีวภาพ (Bio) ความเชี่ยวชาญนี้เป็นรากฐานสำคัญในการขยายธุรกิจด้านเทคโนโลยีชีวภาพของ CJ เลยครับ
- CJ BIO ผู้นำด้านการผลิตกรดอะมิโนและผลิตภัณฑ์ชีวภาพผ่านเทคโนโลยีการหมักจุลินทรีย์ เช่น Lysine, Tryptophan, Valine กรดอะมิโนที่ใช้ในอุตสาหกรรมอาหารสัตว์และอาหารเสริม
-
CJ Bioscience มุ่งเน้นการวิจัยและพัฒนาไมโครไบโอมเพื่อสุขภาพ
-
ธุรกิจโลจิสติกส์และค้าปลีก (Logistics & Retail)
- CJ Logistics ให้บริการโลจิสติกส์ครบวงจร ทั้งการขนส่งทางบก ทางทะเล และทางอากาศ รวมถึงบริการคลังสินค้าและการจัดการซัพพลายเชน
-
CJ Olive Young: ร้านค้าปลีกด้านสุขภาพและความงามอันดับหนึ่งของเกาหลี มีผลิตภัณฑ์ยอดนิยม เช่น Anua PDRN Set ชุดบำรุงผิวที่ได้รับความนิยม MILKTOUCH ผลิตภัณฑ์เมคอัพที่ได้รับความนิยม
-
ธุรกิจบันเทิงและสื่อ (Entertainment & Media) อันนี้ยิ่งใหญ่ระดับโลกมากๆ หลายคนคงจำได้กับ ภาพยนตร์เอเชียแรกกับรางวัลออสการ์ Parasite
- CJ ENM บริษัทผลิตและจัดจำหน่ายเนื้อหาบันเทิงที่มีชื่อเสียงระดับโลก มีผลงานเด่น ได้แก่ Crash Landing on You ซีรีส์ที่ได้รับความนิยมอย่างสูง Parasite ภาพยนตร์ที่ได้รับรางวัลออสการ์
- CJ CGV เครือโรงภาพยนตร์มัลติเพล็กซ์ที่มีสาขาทั่วโลก
CJ Group ขยายธุรกิจไปยังต่างประเทศ เช่น การเข้าซื้อกิจการ Schwan's Company ในสหรัฐอเมริกา และการเปิดสาขา CGV ในหลายประเทศ นอกจากนี้ CJ ยังมีบทบาทสำคัญในการเผยแพร่วัฒนธรรมเกาหลีสู่ระดับโลกผ่าน KCON และการผลิตเนื้อหาบันเทิงที่ได้รับความนิยมในต่างประเทศด้วยครับ
จะเห็นได้ว่า เครือข่ายของ CJ นั้นยิ่งใหญ่มากๆเลย ทีนี้มีเรื่องน่าสนใจตรงนี้ครับ
ในช่วงปี 2013–2016 CJ Group โดยเฉพาะฝ่ายสื่อบันเทิงอย่าง CJ ENM ต้องเผชิญกับแรงกดดันจากรัฐบาลของประธานาธิบดี พัค กึนฮเย เหตุการณ์สำคัญคือการที่ อี มีคยอง (Miky Lee) รองประธาน CJ และผู้มีบทบาทสำคัญในการขับเคลื่อนธุรกิจบันเทิงระดับโลก ถูกกดดันให้ลาออกจากตำแหน่ง รายงานระบุว่า ทำเนียบประธานาธิบดีไม่พอใจเนื้อหาสื่อบางรายการของ CJ ที่มีลักษณะเสียดสีหรือวิพากษ์วิจารณ์รัฐบาล เช่น รายการ SNL Korea ที่ล้อเลียนพัค กึนฮเย ผ่านตัวละคร Teletubbies
ภายใต้แรงกดดันนี้ CJ มีการปรับเปลี่ยนเนื้อหาสื่อ โดยลดการนำเสนอเนื้อหาที่อาจขัดแย้งกับรัฐบาล และหันไปผลิตภาพยนตร์ที่สอดคล้องกับนโยบายของรัฐ เช่น ภาพยนตร์เรื่อง Ode to My Father (2014) ที่สะท้อนความรักชาติและการพัฒนาเศรษฐกิจในยุคของพัค ชุงฮี บิดาของพัค กึนฮเย ภาพยนตร์เรื่องนี้ได้รับการสนับสนุนจากรัฐบาลและถูกมองว่าเป็น "ภาพยนตร์เพื่อสุขภาพ" ที่ส่งเสริมความภาคภูมิใจในชาติ แน่นอนว่าแค้นฝังหุ่นมันยังไม่หายไปไหนครับ
เมื่อเกิดการเปิดโปง "บัญชีดำ" (Blacklist) ของรัฐบาลพัค กึนฮเย ที่มีการจำกัดสิทธิเสรีภาพของศิลปินและผู้ผลิตสื่อที่วิพากษ์วิจารณ์รัฐบาล ทำให้เกิดกระแสต่อต้านอย่างรุนแรงในสังคมเกาหลี. ในปี 2016 ซน กยองชิก ประธาน CJ ได้ให้การต่อศาลว่า มีแรงกดดันจากรัฐบาลให้ อี มีคยอง หลีกเลี่ยงการมีบทบาทในบริษัท เหตุการณ์นี้เป็นส่วนหนึ่งของการเปิดโปงคดีทุจริตของพัค กึนฮเย ซึ่งนำไปสู่การประท้วงครั้งใหญ่และการถอดถอนประธานาธิบดีในปี 2017
หลังจากการเปลี่ยนแปลงทางการเมือง CJ Group ได้กลับมามีบทบาทอย่างเต็มที่ในวงการบันเทิงอีกครั้ง อี มีคยอง กลับมาดำรงตำแหน่งและมีบทบาทสำคัญในการผลักดันภาพยนตร์เรื่อง Parasite (2019) ซึ่งได้รับรางวัลออสการ์และยกระดับภาพลักษณ์ของ CJ ในระดับโลก ซึ่งถ้าใครได้ดูหนังเรื่องนั้นแล้วรู้เรื่องราวเบื้องหลังนี้จะเข้าใจเนื้อหาได้อย่างลึกซึ้งขึ้นไปอีกเลยครับ การนำเสนอเรื่องราวนี้ถือเป็นการวิพากษ์วิจารณ์สังคมและระบบทุนนิยมอย่างชัดเจน ซึ่งแตกต่างจากแนวทางที่ CJ เคยถูกกดดันให้ปฏิบัติตามในยุคของพัค กึนฮเย อย่างสิ้นเชิง
อย่าเพิ่งไปสะใจกับเนื้อหา ให้มองว่า "เขาทำอะไรได้บ้าง" นี่คือประเด็นสำคัญครับ #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ ffbcb706:b0574044
2025-05-21 09:59:14
@ ffbcb706:b0574044
2025-05-21 09:59:14Just a client name test
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 90de72b7:8f68fdc0
2025-05-21 10:31:32
@ 90de72b7:8f68fdc0
2025-05-21 10:31:32PetriNostr. My everyday activity
PetriNostr never sleep! This is a demo
Places & Transitions
- Places:
-
Bla bla bla: some text
-
Transitions:
- start: Initializes the system.
- logTask: bla bla bla.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ f1989a96:bcaaf2c1
2025-05-22 17:09:23
@ f1989a96:bcaaf2c1
2025-05-22 17:09:23Good morning, readers!
Today, we begin in China, where the central bank injected $138 billion into the economy and expanded the money supply by 12.5% year-over-year. As the regime eases monetary conditions to prop up a decelerating economy, Chinese citizens are rushing to preserve their savings, evidenced by Bitcoin/CNY trading activity jumping over 20% on the news. But while some escape to harder money, others remain trapped. In Hunan, an elderly Chinese woman died outside a bank after being forced to appear in person in order to withdraw her own money for medical care.\ \ In Central America, Salvadoran President Bukele revived a “foreign agents” bill that would impose a 30% tax on foreign-funded NGOs, threatening to financially crush organizations that hold those in power accountable and protect journalists and civil society. The proposal mirrors laws used in Russia, China, Belarus, and beyond to suppress dissent. And it arrives amid Bukele’s authoritarian drift and increasing threats to independent journalists.\ \ In open-source news, we highlight a new tool called ChapSmart, a Bitcoin-powered remittance service that allows users to send Bitcoin to citizens and families in Tanzania and have it disbursed in Tanzanian shillings (TZS) via M-PESA. This tool is increasingly helpful as the Tanzanian regime tightens control over foreign currency, mandating that all transactions be conducted in TZS. ChapSmart provides an accessible way for nonprofits and dissidents to access value from abroad using Bitcoin.\ \ We end with an Ask Me Anything (AMA) with Bitcoin educator Anita Posch on Stacker News, who shares her thoughts, experiences, and views from her time conducting Bitcoin education in authoritarian regimes in Africa. We also feature an article from Togolese human rights advocate Farida Nabourema, who critiques Nigeria’s new investment act for classifying Bitcoin as a security and for the regulatory hurdles this will impose on the grassroots adoption of freedom tech in the country.
Be sure to tune in next week at 2 p.m. Oslo time on Wednesday, May 28, as the Oslo Freedom Forum’s Freedom Tech track airs on Bitcoin Magazine’s livestream channels, headlined by speakers Ziya Sadr, Abubakr Nur Khalil, Amiti Uttarwar, Calle, Sarah Kreps, Ben Perrin, and many more.
Now, let’s read on!
SUBSCRIBE HERE
GLOBAL NEWS
El Salvador | Bukele Reintroduces Foreign Agents Bill
In El Salvador, President Nayib Bukele revived a controversial “foreign agents” bill that threatens to severely restrict the finances and operations of NGOs. While the bill is not finalized, Bukele shared on X that the proposal would impose a 30% tax on donations to NGOs receiving foreign funding. This punitive financial measure alone would severely restrict Salvadoran organizations that protect independent journalism, advocate for human rights, and hold the government accountable. In neighboring Nicaragua, a similar foreign agents law has enabled the closure of more than 3,500 NGOs. El Salvador’s foreign agents bill arrives alongside other alarming moves, including arrest warrants against El Faro journalists, the arrest of human rights lawyer Ruth López, and the detention of more than 200 Venezuelan migrants under dubious claims of gang affiliation.
China | Injects Billions to Stabilize Economy
The Chinese Communist Party (CCP) has injected $138 billion in liquidity through interest rate cuts and a 0.5% reduction in banks’ reserve requirements, in effect expanding the money supply by 12.5% year-over-year. While the state eases monetary conditions to prop up a fragile system, ordinary citizens are left scrambling to preserve the value of their savings. Bitcoin/CNY trading volumes jumped over 20% in response, as people sought refuge from a weakening yuan. But while some can quietly escape to harder money, others are trapped in a system that treats access to money as a privilege. In Hunan, an elderly woman in a wheelchair died outside a bank after being forced to appear in person to withdraw her own money for medical care. Too weak to pass mandatory facial recognition scans, she collapsed after repeated failed attempts.
World | Authoritarian Regimes Lead CBDC Push, Study Finds
A new international study from the Nottingham Business School, part of Nottingham Trent University in England, set out to understand what is driving countries to pursue central bank digital currencies (CBDCs). Researchers found the answer lies mostly in political motives. Analyzing 68 countries, the report revealed that authoritarian governments are pushing CBDCs most aggressively, using their centralized power to hastily roll out CBDCs that can monitor transactions, restrict the movement of money, and suppress dissent. On the other hand, the report found democracies are moving more cautiously, weighing concerns over privacy, transparency, and public trust. The study also noted a correlation: countries with high levels of perceived corruption are more likely to explore CBDCs, often framing them as tools to fight illicit finance. These findings are consistent with HRF’s research, revealing nearly half the global population lives under an authoritarian regime experimenting with a CBDC.
Thailand | Plans to Issue New “Investment Token”
Thailand’s Ministry of Finance plans to issue 5 billion baht ($151 million) worth of “G-Tokens,” a new digital investment scheme that allows Thais to buy government bonds for as little as 100 baht ($3). Officials claim the project will democratize access to state-backed investments and offer higher returns than traditional bank deposits. But in a country rapidly advancing central bank digital currency (CBDC) infrastructure, this initiative raises apparent concerns. The move closely follows Thailand’s repeated digital cash handouts via a state-run wallet app, which restricts spending, tracks user behavior, and enforces expiration dates on money, all clear hallmarks of a CBDC. Luckily, the Thai government postponed the latest handout, but the infrastructure remains. Framing this project as inclusionary masks the reality: Thailand is building state-run digital systems that give the regime more power over citizens’ savings and spending.
Russia | Outlaws Amnesty International
Russia officially banned Amnesty International, designating it as an “undesirable organization” and criminalizing cooperation with the global human rights group. Russian officials claim Amnesty promotes “Russophobic projects” and undermines national security. This adds to the Kremlin’s assault on dissent, targeting human rights advocates, independent journalists, and civil society in the years since the 2022 full-scale invasion of Ukraine. The designation exposes anyone financially, publicly, or privately supporting Amnesty’s work to prosecution and imprisonment up to five years. With more than 220 organizations now blacklisted, Russia is systematically cutting off avenues for international accountability and isolating Russians from external support.
BITCOIN AND FREEDOM TECH NEWS
ChapSmart | Permissionless Remittances in Tanzania
ChapSmart is a Bitcoin-powered remittance service that allows users to send money to individuals and families in Tanzania while having it disbursed in Tanzanian shillings (TZS) via M-PESA. With ChapSmart, no account is needed: just enter your name, email, and the recipient’s M-Pesa details. Choose how much USD to send, pay in bitcoin via the Lightning Network, and ChapSmart delivers Tanzanian shillings instantly to the recipient's M-Pesa account with zero fees. This tool is especially useful as Tanzania’s regime enacts restrictions on foreign currencies, banning most citizens from quoting prices or accepting payment in anything other than TZS. ChapSmart offers a practical and accessible way for families, nonprofits, and individuals to access value from abroad using Bitcoin, even as the state tries to shut out financial alternatives.
Bitkey | Multisignature for Families Protecting Wealth from State Seizure
Decades ago, Ivy Galindo’s family lost their savings overnight when the Brazilian government froze citizens’ bank accounts to “fight inflation.” That moment shaped her understanding of financial repression and why permissionless tools like Bitcoin are essential. When her parents later chose to start saving in Bitcoin, Ivy knew a wallet with a single private key wasn’t enough, as it can be lost, stolen, or handed over under pressure or coercion from corrupt law enforcement or state officials. Multisignature (multisig) wallets, which require approval from multiple private keys to move funds, offer stronger protection against this loss and coercion and eliminate any single points of failure in a Bitcoin self-custody setup. But multisig setups are often too technical for everyday families. Enter Bitkey. This multisig device offered Ivy’s family a simple, secure way to share custody of their Bitcoin in the face of financial repression. In places where wealth confiscation and frozen bank accounts are a lived reality, multisignature wallets can help families stay in full control of their savings.
Parasite Pool | New Zero-Fee, Lightning Native Bitcoin Mining Pool
Parasite Pool is a new open-source Bitcoin mining pool built for home miners who want to contribute to Bitcoin’s decentralization without relying on the large and centralized mining pools. It charges zero fees and offers Lightning-native payouts with a low 10-satoshi threshold, allowing individuals to earn directly and instantly. Notably, it has a “pleb eat first” reward structure, which allocates 1 BTC to the block finder and splits the remaining 2.125 BTC plus fees among all non-winning participants via Lightning. This favors small-scale miners, who can earn outsized rewards relative to their hashpower, inverting the corporate bias of legacy mining pools. This makes Parasite Pool especially attractive for small scale miners, such as those operating in authoritarian contexts who need to mine discreetly and independently. In turn, these very same miners contribute to the Bitcoin network’s resistance to censorship, regulatory capture, and corporate control, ensuring it remains a tool for freedom and peaceful resistance for those who need it most. Learn more about the mining pool here.
Cake Wallet | Implements Payjoin V2
Cake Wallet, a non-custodial, privacy-focused, and open-source mobile Bitcoin wallet, released version 4.28, bringing Payjoin V2 to its user base. Payjoin is a privacy technique that allows two users to contribute an input to a Bitcoin transaction, breaking the common chain analysis heuristic that assumes a sender owns all inputs. This makes it harder for dictators to trace payments or link the identities of activists or nonprofits. Unlike the original Payjoin, which required both the sender and recipient to be online and operate a Payjoin server, Payjoin v2 removes both barriers and introduces asynchronous transactions and serverless communication. This means users can now conduct private transactions without coordination or technical setup, making private Bitcoin transactions much more accessible and expanding the tools dissidents have to transact in the face of censorship, extortion, and surveillance. HRF is pleased to have sponsored the Payjoin V2 specification with a bounty and is happy to see this functionality now in the wild.
Mi Primer Bitcoin | Receives Grant from startsmall
Mi Primer Bitcoin, a nonprofit organization supporting independent Bitcoin education in Central America, announced that it received a $1 million grant from Jack Dorsey’s startsmall public fund. This support will accelerate Mi Primer Bitcoin’s impartial, community-led, Bitcoin-only education. The initiative has trained tens of thousands of students while supporting over 65 grassroots projects across 35+ countries through its Independent Bitcoin Educators Node Network, pushing financial freedom forward where needed most. The Mi Primer Bitcoin (MPB) team stresses the importance of remaining free from government or corporate influence to preserve the integrity of their mission. As founder John Dennehy puts it, “Education will be captured by whoever funds it… We need to create alternative models for the revolution of Bitcoin education to realize its full potential.” MPB has been adopted by many education initiatives working under authoritarian regimes.
Phoenix Wallet | Introduces Unlimited BOLT 12 Offers and Manual Backup Options
Phoenix Wallet, a mobile Bitcoin Lightning wallet, introduced support for unlimited BOLT 12 offers in its v2.6.0 update, allowing users to generate as many reusable Lightning invoices as they like. These offers, which function like static Bitcoin addresses, remain permanently valid and can now include a custom description and amount — ideal for nonprofits or dissidents who need to receive regular donations discreetly. The update also introduces manual export and import of the payments database on Android, enabling users to securely transfer their payment history to new devices. These updates strengthen Phoenix’s position as one of the most user-friendly and feature-complete non-custodial Lightning wallets. BOLT 12 — once a pipe dream — is now a usable activist tool on popularly accessible mobile wallets.
RECOMMENDED CONTENT
Bitcoin Is Not a Security: Why Nigeria’s New Investment and Security Act Misses the Mark by Farida Nabourema
In this article, Togolese human rights advocate Farida Nabourema critiques Nigeria’s 2025 Investment and Securities Act for classifying Bitcoin as a security. Nabourema argues this approach is flawed, economically damaging, disconnected from the realities of Bitcoin usage and innovation across Africa, and an attempt to constrict a human rights tool. She warns that this regulatory framework risks stifling builders and harming the very communities that Bitcoin is helping in a context of widespread currency devaluations, inflation, and exclusion. Read it here.
Ask Me Anything with Anita Posch on Stacker News
After spending five months traveling through countries like Kenya and Zimbabwe, Bitcoin for Fairness Founder Anita Posch joined Stacker News for an Ask Me Anything (AMA) to discuss her view on Bitcoin adoption across the continent. She highlighted major progress since 2020, noting that several grassroots initiatives she supported have become self-sufficient and are now running their own education programs. Despite persistent challenges, like wallet usability, high on-chain fees, and Bitcoin’s misunderstood reputation, she shared stories of real-life impact, including cross-border remittances using mobile airtime and widespread Lightning use via apps like Tando in Kenya. Read the full conversation here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ cae03c48:2a7d6671
2025-05-22 17:02:01
@ cae03c48:2a7d6671
2025-05-22 17:02:01Bitcoin Magazine

Texas Legislature Passes Bitcoin Reserve BillTexas has passed Senate Bill 21, a measure establishing the Texas Strategic Bitcoin Reserve. This makes Texas the third U.S. state to adopt Bitcoin as part of its state investment strategy, following Arizona and New Hampshire. The bill, officially titled the “Texas Strategic Bitcoin Reserve and Investment Act”, has cleared both legislative chambers and now heads to Governor Greg Abbott’s desk for final approval.
JUST IN: Texas Strategic Bitcoin Reserve bill SB21 officially PASSES and goes to Governors desk for final signature
 pic.twitter.com/8UMwxTHgg6
pic.twitter.com/8UMwxTHgg6— Bitcoin Magazine (@BitcoinMagazine) May 21, 2025
SB21 authorizes the creation of the Texas Strategic Bitcoin Reserve, a special fund outside the state treasury, which allows Texas to invest directly in Bitcoin and other approved cryptocurrencies, according to the legislation. The measure gives the State Treasurer full authority over the reserve’s administration, including acquiring, managing, staking, and potentially liquidating digital assets.
“The establishment of a strategic bitcoin reserve serves the public purpose of providing enhanced financial security to residents of this state,” declares the legislation.
The State Treasurer will manage the fund under strict conditions:
- Only cryptocurrencies with a 12-month average market cap of at least $500 billion can be purchased.
- Assets must be stored using “cold storage” technology to prevent unauthorized access.
- Third-party partners, including qualified custodians and liquidity providers, may be contracted for operations.
- The use of staking, and derivatives is allowed if it benefits the reserve.
Funds can come from legislative appropriations, donations from Texas residents, and returns on investments. While the reserve operates independently, the State Treasurer can temporarily liquidate it for state cash management under limited conditions.
Governor Abbott has not yet indicated whether he will sign the bill, but his past support of Bitcoin suggests a favorable outcome is likely.
“Texas is getting involved early on in this process because we see the future of what bitcoin and blockchain means to the entire world,” said Governor Abbott in an interview. “Texas wants to be the centerpiece of that. So we are promoting it, we are advancing it.”
When New Hampshire passed their bill on May 6, 2025, CEO and Co-Founder of Satoshi Action Dennis Porter remarked that it was just the beginning and now we’re seeing that vision unfold.
“Satoshi Action drafted the model, New Hampshire engraved it into law, and now every treasurer nationwide can follow that roadmap,” stated Dennis Porter on X. “HB 302 proves you can protect taxpayer money, diversify reserves, and future-proof state treasuries—all while embracing the most secure monetary network on Earth. New Hampshire didn’t just pass a bill; it sparked a movement.”
This post Texas Legislature Passes Bitcoin Reserve Bill first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ da8b7de1:c0164aee
2025-05-21 10:30:07
@ da8b7de1:c0164aee
2025-05-21 10:30:07„Európának a tettek mezejére kell lépnie a nukleáris energia támogatásában” – mondja a brüsszeli iparági csoport új vezetője
A cikk fő témája, hogy az európai nukleáris ipar új vezetője, Emmanuel Brutin (Nucleareurope), nagyobb elkötelezettséget vár el az Európai Bizottságtól a nukleáris energia támogatásában. Bár pozitív jelek mutatkoznak a nukleáris energia iránti nyitottság terén, Brutin szerint a gyakorlatban még mindig jelentős akadályok vannak, például a finanszírozási forrásokhoz való hozzáférésben és a projektengedélyezések lassúságában.
Főbb pontok:
- Politikai nyitottság, de gyakorlati akadályok: Az EU-ban nőtt a nukleáris energia elismerése, például bekerült a fenntartható befektetési taxonómiába és a Net-Zero Industry Act-be. Ugyanakkor a nukleáris energia továbbra is kizárt több fontos finanszírozási eszközből, mint az InvestEU vagy a Just Transition Fund.
- Technológiai semlegesség szükségessége: Brutin hangsúlyozza, hogy az EU-nak nemcsak nem szabad hátráltatnia a nukleáris energiát, hanem aktívan támogatnia is kellene, különösen a Clean Industrial Deal és az Affordable Energy Action Plan keretében.
- Finanszírozás és engedélyezés: A nukleáris ágazat számára kulcsfontosságú a finanszírozáshoz való jobb hozzáférés, mivel a beruházások tőkeigényesek. Brutin szerint gyorsítani kellene a nukleáris projektek engedélyezését, és lazítani az állami támogatási szabályokon.
- Stratégiai jelentőség: Európa teljes nukleáris értéklánccal rendelkezik, ami stratégiai autonómiát jelent, különösen a jelenlegi geopolitikai környezetben.
- Új PINC dokumentum: Nyáron várható a frissített PINC (Illustrative Nuclear Programme), amelynek konkrét lépéseket kell tartalmaznia a nukleáris beruházások támogatására.
- Iparági igények: Az energiaintenzív iparágak (pl. acél, cement) számára nem az energiaforrás típusa számít, hanem a megbízható, olcsó és dekarbonizált villamosenergia-ellátás.
- Tanulás a múlt hibáiból: Brutin elismeri, hogy a nukleáris projektek Európában gyakran szenvedtek késésektől és költségtúllépésektől, de az iparág dolgozik ezek megoldásán.
Forrás:
NucNet:
"Europe Must 'Walk The Talk' On Support For Nuclear Energy, Says New Head Of Brussels Industry Group"
Megjelenés dátuma: 2025. május 20.
Elérhető: NucNet honlapján -
 @ 7e6f9018:a6bbbce5
2025-05-22 16:33:07
@ 7e6f9018:a6bbbce5
2025-05-22 16:33:07Per les xarxes socials es parla amb efusivitat de que Bitcoin arribarà a valer milions de dòlars. El mateix Hal Finney allà pel 2009, va estimar el potencial, en un cas extrem, de 10 milions $:
\> As an amusing thought experiment, imagine that Bitcoin is successful and becomes the dominant payment system in use throughout the world. Then the total value of the currency should be equal to the total value of all the wealth in the world. Current estimates of total worldwide household wealth that I have found range from $100 trillion to $300 trillion. Withn 20 million coins, that gives each coin a value of about $10 million. <https://satoshi.nakamotoinstitute.org/emails/bitcoin-list/threads/4/>
No estic d'acord amb els càlculs del bo d'en Hal, ja que no consider que la valoració d'una moneda funcioni així. En qualsevol cas, el 2009 la capitalització de la riquesa mundial era de 300 bilions $, avui és de 660 bilions $, és a dir ha anat pujant un 5,3% de manera anual,
$$(660/300)^{1/15} = 1.053$$La primera apreciació amb aquest augment anual del 5% és que si algú llegeix aquest article i té diners que no necessita aturats al banc (estalvis), ara és bon moment per començar a moure'ls, encara sigui amb moviments defensius (títols de deute governamental o la propietat del primer habitatge). La desagregació per actius dels 660 bilions és:
-
Immobiliari residencial = 260 bilions $
-
Títols de deute = 125 bilions $
-
Accions = 110 bilions
-
Diners fiat = 78 bilions $
-
Terres agrícoles = 35 bilions $
-
Immobiliari comercial = 32 bilions $
-
Or = 18 bilions $
-
Bitcoin = 2 bilions $
La riquesa mundial és major que 660 bilions, però aquests 8 actius crec que són els principals, ja que s'aprecien a dia d'avui. El PIB global anual és de 84 bilions $, que no són bromes, però aquest actius creats (cotxes, ordinadors, roba, aliments...), perden valor una vegada produïts, aproximant-se a 0 passades unes dècades.
Partint d'aquest nombres com a vàlids, la meva posició base respecte de Bitcoin, ja des de fa un parell d'anys, és que te capacitat per posar-se al nivell de capitalització de l'or, perquè conceptualment s'emulen bé, i perquè tot i que Bitcoin no té un valor tangible industrial com pot tenir l'or, sí que te un valor intangible tecnològic, que és pales en tot l'ecosistema que s'ha creat al seu voltant:
-
Creació de tecnologies de pagament instantani: la Lightning Network, Cashu i la Liquid Network.
-
Producció d'aplicacions amb l'íntegrament de pagaments instantanis. Especialment destacar el protocol de Nostr (Primal, Amethyst, Damus, Yakihonne, 0xChat...)
-
Industria energètica: permet estabilitzar xarxes elèctriques i emprar energia malbaratada (flaring gas), amb la generació de demanda de hardware i software dedicat.
-
Educació financera i defensa de drets humans. És una eina de defensa contra governs i estats repressius. La Human Rights Foundation fa una feina bastant destacada d'educació.
Ara posem el potencial en nombres:
-
Si iguala l'empresa amb major capitalització, que és Apple, arribaria a uns 160 mil dòlars per bitcoin.
-
Si iguala el nivell de l'or, arribaria a uns 800 mil dòlars per bitcoin.
-
Si iguala el nivell del diner fiat líquid, arribaria a un 3.7 milions de dòlars per bitcoin.
Crec que igualar la capitalització d'Apple és probable en els pròxims 5 - 10 anys. També igualar el nivell de l'or en els pròxims 20 anys em sembla una fita possible. Ara bé, qualsevol fita per sota d'aquesta capitalització ha d'implicar tota una serie de successos al món que no sóc capaç d'imaginar. Que no vol dir que no pugui passar.
-
-
 @ 06639a38:655f8f71
2025-05-21 07:47:56
@ 06639a38:655f8f71
2025-05-21 07:47:56Nostr-PHP
Djuri submitted quite some pull requests in the last couple of week while he was implementing a Nostr connect / login on https://satsback.com. The backend of that platform is written in PHP so the Nostr-PHP library is used for several purposes while Djuri also developed quite some new features utilizing the following NIPs:
- NIP-04
- NIP-05
- NIP-17
- NIP-44
Thank you very much Djuri for these contributions. We now can do the basic private stuff with the library.
PR for NIP-04 and NIP-44: https://github.com/nostrver-se/nostr-php/pull/84 and https://github.com/nostrver-se/nostr-php/pull/88
Examples:- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip04-encrypted-messages.php
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip44-gift-wrapping.php
PR for NIP-05: https://github.com/nostrver-se/nostr-php/pull/89
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip05-lookup.phpPR for NIP-17: https://github.com/nostrver-se/nostr-php/pull/90
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip17-private-direct-messages.phpPR for adding more metadata profile fields: https://github.com/nostrver-se/nostr-php/pull/94
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/fetch-profile-metadata.phpFetch
10050event (dm relay list) of an given pubkey
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/fetch-dm-relayslist.phpThe CLI tool is removed from the library, see PR https://github.com/nostrver-se/nostr-php/pull/93
Nostr-PHP documentation
While new NIPs are implemented in the Nostr-PHP library, I'm trying to keep up with the documentation at https://nostr-php.dev. For now, things are still much work in progress and I've added the AI agent Goose using the Claude LLM to bootstrap new documentation pages. Currently I'm working on documentation for
- How to direct messages with NIP-04 and NIP-17
- Encrypted payloads for event content NIP-44
- Fetch profiledata of a given pubkey
- Lookup NIP-05 data of given pubkey
- Using the NIP-19 helper class
CCNS.news
I've moved CCNS to a new domain https://ccns.news and have partly implemented the new NIP-B0 for web bookmarks. When you post a bookmark there, a kind
39701event is transmitted to some Nostr relays (take a look at this event for example). Optionally you can also publish this content as a note to the network.As you can see at https://ccns.news/l/censorship-resistant-publishing-and-archiving, I've listed some todo's. All this stuff is done with Javascript using the NDK Typescript library (so I'm not using any PHP stuff for this with Nostr-PHP).

Also new: https://ccns.news/global now has a global feed which fetches all the web bookmark events with kind
39701from several public Nostr relays. I had a rough idea to compare feeds generated with NDK and Nostr-PHP (for both using the same set of relays).
Building a njump clone for this Drupal website
You can now use this URL pattern to fetch Nostr events:
https://nostrver.se/e/{event_id|nevent1|note1|addr1}where you can provide a plain Nostr event ID or NIP-19 encoded identifier.An example, this URL https://nostrver.se/e/nevent1qvzqqqqqqypzqmjxss3dld622uu8q25gywum9qtg4w4cv4064jmg20xsac2aam5nqqsqm2lz4ru6wlydzpulgs8m60ylp4vufwsg55whlqgua6a93vp2y4g3uu9lr fetches the data from one or more relays. This data is then being saved as a (Drupal) node entity (in a database on the server where this website is hosted, which is located in my office fyi). With this saved node, this data is now also available at https://nostrver.se/e/0dabe2a8f9a77c8d1079f440fbd3c9f0d59c4ba08a51d7f811ceeba58b02a255/1 where the (cached) data is server from the database instead. It's just raw data for now, nothing special about it. One of my next steps is to style this in a more prettier interface and I will need to switch the theme of this website to a custom theme. A custom theme where I will be using TailwindCSS v4 and DaisyUI v5.
The module which is providing these Nostr features is FOSS and uses the Nostr-PHP library for doing the following:
- Request the event from one or more relays
- Decode the provided NIP-19 identifier
For now this module is way for me to utilize the Nostr-PHP library with Drupal for fetching events. This can be automated so in theory I could index all the Nostr events. But this is not my ambition as it would require quite some hardware resources to accomplish this.
I hope I can find the time to build up a new theme first for this website, so I can start styling the data for the fetched events. On this website, there is also a small piece (powered by another module) you can find at https://nostrver.se/nostrides doing things with this NIP-113 around activity events (in my case that's cycling what interests me).What's next
I'm already working on the following stuff:
- Implement a class to setup a persistent connection to a relay for requesting events continuously
- Extend the documentation with the recent added features
Other todo stuff:
- Review NIP-13 proof-of-work PR from Djuri
- Implement a NIP-65 lookup for fetching read and write relays for a given npub issue #91
- Build a proof-of-concept with revolt/event-loop to request events asynchronous with persistent relay connections
- Add comments to https://ccns.news
-
 @ c239c0f9:fa4a5015
2025-05-21 10:25:04
@ c239c0f9:fa4a5015
2025-05-21 10:25:04Block:#897676- May 2025It's again that time of the month, time to catch up with the latest features and trends that are shaping the future of Bitcoin—the very first and most commented insights from around SN cypherspace. Every issue arrives with expert analysis, in-depth interview, and breaking news of the most significant advancements in the Bitcoin layer two solutions.
Two new things this month:
A)zaps to these posts will be split to the top contributor to this territoryB)As have stacked some cowboy credits lately, I'll give them away to the stackers commenting below anything meaningful, feedback to this newsletter, or suggestions to improve the territorySubscribe to the territory and make sure you don’t miss anything about the Bitcoin Revolution!
Now let's focus on the top five items for each category, an electrifying selection that hope you'll be able to read before next edition.
Happy Zapping!
Top ~Lightning posts
Most zapranked posts this month:
-
Liquidity requirements for Lightning payments: Ark servers and LSPs compared by @supratic 409 sats \ 8 comments \ 12 May
-
Wallet of Satoshi is coming back to US with non-custodial wallet by @k00b 906 sats \ 18 comments \ 18 May
-
How to offer Submarine Swaps — Electrum Documentation by @f321x7 836 sats \ 5 comments \ 13 May
-
Parallel channels are a mess - a rant by @C_Otto 1918 sats \ 5 comments \ 1 May
-
LNBig insight about running a LN node by @DarthCoin 1244 sats \ 10 comments \ 23 Apr
Top posts by comments
Excluding the ones already mentioned above, you can see them all here (excluding those already listed above):
-
I believe CoinOS will resolve itself, but this screenshot is a rug pull 💨 by @realBitcoinDog 411 sats \ 73 comments \ 13 May
-
CoinOS having some issues by @StillStackinAfterAllTheseYears 268 sats \ 24 comments \ 10 May
-
BOLT12 Suggestions? by @metadavid 516 sats \ 16 comments \ 28 Apr
-
Phoenix Wallet - Swap In by @02b58a1376 256 sats \ 15 comments \ 25 Apr
-
Clearnet+Tor LND in Docker with wireguard VPS for privacy by @klk 696 sats \ 14 comments \ 27 Apr
Top ~Lightning Boosts
Check them all here.
-
What is the Right LSP for You? [VIDEO] by @Jestopher_BTC 667 sats \ 30k boost \ 3 comments \ 15 May
-
Things Bitcoiners Don’t Want To Hear (2020) by @k00b 1553 sats \ 20k boost \ 15 comments \ 10 May
-
Liquidity Subscriptions: Automated Liquidity for Merchants by @Jestopher_BTC 448 sats \ 10k boost \ 4 comments \ 8 May lightning
Don't miss...
Lightning Network : our high-maintenance crazy-ex by @avbpod
Coinbase announces L402 copycat "x402" by @bounty_hunter
15% of Coinbase’s Bitcoin transactions run on the Lightning Network by @south_korea_ln
An Exposition of Pathfinding Strategies Within Lightning Network Clients by @supratic
How to censor users in cashu? by @kpa
@darthcoin by @Thecanadian88
Cashu Highlights Q1 by @supratic
Top Lightning posts outside ~Lightning
This month best posts about the Lightning Network outside ~Lightning territory:
-
Ultimate guide to LN routing and fee management. by @javier 21.6k sats \ 39 comments \ 6 May on
~bitcoin -
Mobile (non-phone) Lightning Wallet? by @jasonb 565 sats \ 36 comments \ 30 Apr on
~bitcoin -
Robosats Guide by @siggy47 33k sats \ 27 comments \ 22 Apr on
~bitcoin_beginners -
LNemail: Private Disposable Email via Lightning by @lnemail 2758 sats \ 22 comments \ 18 May on
~privacy -
Another explanation of how Ark works 1329 sats \ 10 comments \ @k00b 21 May on
~bitcoin
Forever top ~Lightning posts
La crème de la crème... check them all here. Nothing has changed this month!
-
👨🚀 We're releasing 𝗔𝗟𝗕𝗬 𝗚𝗢 - the easiest lightning mobile wallet by @Alby 29.2k sats \ 41 comments \ @Alby 25 Sep 2024 on
~lightning -
Building Self Custody Lightning in 2025 by @k00b 2303 sats \ 8 comments \ 22 Jan on
~lightning -
Lightning Wallets: Self-Custody Despite Poor Network - Apps Tested in Zimbabwe by @anita 72.8k sats \ 39 comments \ 28 Jan 2024 lightning on
~lightning -
How to Attach Your self-hosted LNbits wallet to SEND/RECEIVE sats to/from SN by @supratic 1765 sats \ 18 comments \ 23 Sep 2024 on
~lightning -
A Way to Use Stacker News to improve your Zap Receiving by @bzzzt 1652 sats \ 22 comments \ 15 Jul 2024 on
~lightning
Forever top Lightning posts outside ~Lightning
Ek's post rise at #5, congrats!
-
Rethinking Lightning by @benthecarman 51.7k sats \ 140 comments \ 6 Jan 2024 on
~bitcoin -
Lightning Everywhere by @TonyGiorgio 12k sats \ 27 comments \ 24 Jul 2023 on
~bitcoin -
Lightning is dead, long live the Lightning! by @supertestnet and zaps forwarded to @anita (50%) @k00b (50%) 6321 sats \ 28 comments \ @tolot 27 Oct 2023 on
~bitcoin -
Bisq2 adds lightning by @supertestnet 3019 sats \ 47 comments \ 19 Aug 2024 on
~bitcoin -
Lightning Prediction Market MVP - delphi.market by @ek 34.1k sats \ 59 comments \ 4 Dec 2023 on
~bitcoin
-
-
 @ 7460b7fd:4fc4e74b
2025-05-21 02:23:16
@ 7460b7fd:4fc4e74b
2025-05-21 02:23:16如果比特币发明了真正的钱,那么 Crypto 是什么?
引言
比特币诞生之初就以“数字黄金”姿态示人,被支持者誉为人类历史上第一次发明了真正意义上的钱——一种不依赖国家信用、总量恒定且不可篡改的硬通货。然而十多年过去,比特币之后蓬勃而起的加密世界(Crypto)已经远超“货币”范畴:从智能合约平台到去中心组织,从去央行的稳定币到戏谑荒诞的迷因币,Crypto 演化出一个丰富而混沌的新生态。这不禁引发一个根本性的追问:如果说比特币解决了“真金白银”的问题,那么 Crypto 又完成了什么发明?
 Crypto 与政治的碰撞:随着Crypto版图扩张,全球政治势力也被裹挟进这场金融变革洪流(示意图)。比特币的出现重塑了货币信用,但Crypto所引发的却是一场更深刻的政治与治理结构实验。从华尔街到华盛顿,从散户论坛到主权国家,越来越多人意识到:Crypto不只是技术或金融现象,而是一种全新的政治表达结构正在萌芽。正如有激进论者所断言的:“比特币发明了真正的钱,而Crypto则在发明新的政治。”价格K线与流动性曲线,或许正成为这个时代社群意志和社会价值观的新型投射。
Crypto 与政治的碰撞:随着Crypto版图扩张,全球政治势力也被裹挟进这场金融变革洪流(示意图)。比特币的出现重塑了货币信用,但Crypto所引发的却是一场更深刻的政治与治理结构实验。从华尔街到华盛顿,从散户论坛到主权国家,越来越多人意识到:Crypto不只是技术或金融现象,而是一种全新的政治表达结构正在萌芽。正如有激进论者所断言的:“比特币发明了真正的钱,而Crypto则在发明新的政治。”价格K线与流动性曲线,或许正成为这个时代社群意志和社会价值观的新型投射。冲突结构:当价格挑战选票
传统政治中,选票是人民意志的载体,一人一票勾勒出民主治理的正统路径。而在链上的加密世界里,骤升骤降的价格曲线和真金白银的买卖行为却扮演起了选票的角色:资金流向成了民意走向,市场多空成为立场表决。价格行为取代选票,这听来匪夷所思,却已在Crypto社群中成为日常现实。每一次代币的抛售与追高,都是社区对项目决策的即时“投票”;每一根K线的涨跌,都折射出社区意志的赞同或抗议。市场行为本身承担了决策权与象征权——价格即政治,正在链上蔓延。
这一新生政治形式与旧世界的民主机制形成了鲜明冲突。bitcoin.org中本聪在比特币白皮书中提出“一CPU一票”的工作量证明共识,用算力投票取代了人为决策bitcoin.org。而今,Crypto更进一步,用资本市场的涨跌来取代传统政治的选举。支持某项目?直接购入其代币推高市值;反对某提案?用脚投票抛售资产。相比漫长的选举周期和层层代议制,链上市场提供了近乎实时的“公投”机制。但这种机制也引发巨大争议:资本的投票天然偏向持币多者(富者)的意志,是否意味着加密政治更为金权而非民权?持币多寡成为影响力大小,仿佛选举演变成了“一币一票”,巨鲸富豪俨然掌握更多话语权。这种与民主平等原则的冲突,成为Crypto政治形式饱受质疑的核心张力之一。
尽管如此,我们已经目睹市场投票在Crypto世界塑造秩序的威力:2016年以太坊因DAO事件分叉时,社区以真金白银“投票”决定了哪条链获得未来。arkhamintelligence.com结果是新链以太坊(ETH)成为主流,其市值一度超过2,800亿美元,而坚持原则的以太经典(ETC)市值不足35亿美元,不及前者的八十分之一arkhamintelligence.com。市场选择清楚地昭示了社区的政治意志。同样地,在比特币扩容之争、各类硬分叉博弈中,无不是由投资者和矿工用资金与算力投票,胜者存续败者黯然。价格成为裁决纷争的最终选票,冲击着传统“选票决胜”的政治理念。Crypto的价格民主,与现代代议民主正面相撞,激起当代政治哲思中前所未有的冲突火花。
治理与分配
XRP对决SEC成为了加密世界“治理与分配”冲突的经典战例。2020年底,美国证券交易委员会(SEC)突然起诉Ripple公司,指控其发行的XRP代币属于未注册证券,消息一出直接引爆市场恐慌。XRP价格应声暴跌,一度跌去超过60%,最低触及0.21美元coindesk.com。曾经位居市值前三的XRP险些被打入谷底,监管的强硬姿态似乎要将这个项目彻底扼杀。
然而XRP社区没有选择沉默。 大批长期持有者组成了自称“XRP军团”(XRP Army)的草根力量,在社交媒体上高调声援Ripple,对抗监管威胁。面对SEC的指控,他们集体发声,质疑政府选择性执法,声称以太坊当年发行却“逍遥法外”,只有Ripple遭到不公对待coindesk.com。正如《福布斯》的评论所言:没人预料到愤怒的加密散户投资者会掀起法律、政治和社交媒体领域的‘海啸式’反击,痛斥监管机构背弃了保护投资者的承诺crypto-law.us。这种草根抵抗监管的话语体系迅速形成:XRP持有者不但在网上掀起舆论风暴,还采取实际行动向SEC施压。他们发起了请愿,抨击SEC背离保护投资者初衷、诉讼给个人投资者带来巨大伤害,号召停止对Ripple的上诉纠缠——号称这是在捍卫全球加密用户的共同利益bitget.com。一场由民间主导的反监管运动就此拉开帷幕。
Ripple公司则选择背水一战,拒绝和解,在法庭上与SEC针锋相对地鏖战了近三年之久。Ripple坚称XRP并非证券,不应受到SEC管辖,即使面临沉重法律费用和业务压力也不妥协。2023年,这场持久战迎来了标志性转折:美国法庭作出初步裁决,认定XRP在二级市场的流通不构成证券coindesk.com。这一胜利犹如给沉寂已久的XRP注入强心针——消息公布当天XRP价格飙涨近一倍,盘中一度逼近1美元大关coindesk.com。沉重监管阴影下苟延残喘的项目,凭借司法层面的突破瞬间重获生机。这不仅是Ripple的胜利,更被支持者视为整个加密行业对SEC强权的一次胜仗。
XRP的对抗路线与某些“主动合规”的项目形成了鲜明对比。 稳定币USDC的发行方Circle、美国最大合规交易所Coinbase等选择了一条迎合监管的道路:它们高调拥抱现行法规,希望以合作换取生存空间。然而现实却给了它们沉重一击。USDC稳定币在监管风波中一度失去美元锚定,哪怕Circle及时披露储备状况也无法阻止恐慌蔓延,大批用户迅速失去信心,短时间内出现数十亿美元的赎回潮blockworks.co。Coinbase则更为直接:即便它早已注册上市、反复向监管示好,2023年仍被SEC指控为未注册证券交易所reuters.com,卷入漫长诉讼漩涡。可见,在迎合监管的策略下,这些机构非但未能换来监管青睐,反而因官司缠身或用户流失而丧失市场信任。 相比之下,XRP以对抗求生存的路线反而赢得了投资者的眼光:价格的涨跌成为社区投票的方式,抗争的勇气反过来强化了市场对它的信心。
同样引人深思的是另一种迥异的治理路径:技术至上的链上治理。 以MakerDAO为代表的去中心化治理模式曾被寄予厚望——MKR持币者投票决策、算法维持稳定币Dai的价值,被视为“代码即法律”的典范。然而,这套纯技术治理在市场层面却未能形成广泛认同,亦无法激发群体性的情绪动员。复杂晦涩的机制使得普通投资者难以参与其中,MakerDAO的治理讨论更多停留在极客圈子内部,在社会大众的政治对话中几乎听不见它的声音。相比XRP对抗监管所激发的铺天盖地关注,MakerDAO的治理实验显得默默无闻、难以“出圈”。这也说明,如果一种治理实践无法连接更广泛的利益诉求和情感共鸣,它在社会政治层面就难以形成影响力。
XRP之争的政治象征意义由此凸显: 它展示了一条“以市场对抗国家”的斗争路线,即通过代币价格的集体行动来回应监管权力的施压。在这场轰动业界的对决中,价格即是抗议的旗帜,涨跌映射着政治立场。XRP对SEC的胜利被视作加密世界向旧有权力宣告的一次胜利:资本市场的投票器可以撼动监管者的强权。这种“价格即政治”的张力,正是Crypto世界前所未有的社会实验:去中心化社区以市场行为直接对抗国家权力,在无形的价格曲线中凝聚起政治抗争的力量,向世人昭示加密货币不仅有技术和资本属性,更蕴含着不可小觑的社会能量和政治意涵。
不可归零的政治资本
Meme 币的本质并非廉价或易造,而在于其构建了一种“无法归零”的社群生存结构。 对于传统观点而言,多数 meme 币只是短命的投机游戏:价格暴涨暴跌后一地鸡毛,创始人套现跑路,投资者血本无归,然后“大家转去炒下一个”theguardian.com。然而,meme 币社群的独特之处在于——失败并不意味着终结,而更像是运动的逗号而非句号。一次币值崩盘后,持币的草根们往往并未散去;相反,他们汲取教训,准备东山再起。这种近乎“不死鸟”的循环,使得 meme 币运动呈现出一种数字政治循环的特质:价格可以归零,但社群的政治热情和组织势能不归零。正如研究者所指出的,加密领域中的骗局、崩盘等冲击并不会摧毁生态,反而成为让系统更加强韧的“健康应激”,令整个行业在动荡中变得更加反脆弱cointelegraph.com。对应到 meme 币,每一次暴跌和重挫,都是社群自我进化、卷土重来的契机。这个去中心化群体打造出一种自组织的安全垫,失败者得以在瓦砾上重建家园。对于草根社群、少数派乃至体制的“失败者”而言,meme 币提供了一个永不落幕的抗争舞台,一种真正反脆弱的政治性。正因如此,我们看到诸多曾被嘲笑的迷因项目屡败屡战:例如 Dogecoin 自2013年问世后历经八年沉浮,早已超越玩笑属性,成为互联网史上最具韧性的迷因之一frontiersin.org;支撑 Dogecoin 的正是背后强大的迷因文化和社区意志,它如同美国霸权支撑美元一样,为狗狗币提供了“永不中断”的生命力frontiersin.org。
“复活权”的数字政治意涵
这种“失败-重生”的循环结构蕴含着深刻的政治意涵:在传统政治和商业领域,一个政党选举失利或一家公司破产往往意味着清零出局,资源散尽、组织瓦解。然而在 meme 币的世界,社群拥有了一种前所未有的“复活权”。当项目崩盘,社区并不必然随之消亡,而是可以凭借剩余的人心和热情卷土重来——哪怕换一个 token 名称,哪怕重启一条链,运动依然延续。正如 Cheems 项目的核心开发者所言,在几乎无人问津、技术受阻的困境下,大多数人可能早已卷款走人,但 “CHEEMS 社区没有放弃,背景、技术、风投都不重要,重要的是永不言弃的精神”cointelegraph.com。这种精神使得Cheems项目起死回生,社区成员齐声宣告“我们都是 CHEEMS”,共同书写历史cointelegraph.com。与传统依赖风投和公司输血的项目不同,Cheems 完全依靠社区的信念与韧性存续发展,体现了去中心化运动的真谛cointelegraph.com。这意味着政治参与的门槛被大大降低:哪怕没有金主和官方背书,草根也能凭借群体意志赋予某个代币新的生命。对于身处社会边缘的群体来说,meme 币俨然成为自组织的安全垫和重新集结的工具。难怪有学者指出,近期涌入meme币浪潮的主力,正是那些对现实失望但渴望改变命运的年轻人theguardian.com——“迷茫的年轻人,想要一夜暴富”theguardian.com。meme币的炒作表面上看是投机赌博,但背后蕴含的是草根对既有金融秩序的不满与反抗:没有监管和护栏又如何?一次失败算不得什么,社区自有后路和新方案。这种由底层群众不断试错、纠错并重启的过程,本身就是一种数字时代的新型反抗运动和群众动员机制。
举例而言,Terra Luna 的沉浮充分展现了这种“复活机制”的政治力量。作为一度由风投资本热捧的项目,Luna 币在2022年的崩溃本可被视作“归零”的失败典范——稳定币UST瞬间失锚,Luna币价归零,数十亿美元灰飞烟灭。然而**“崩盘”并没有画下休止符**。Luna的残余社区拒绝承认失败命运,通过链上治理投票毅然启动新链,“复活”了 Luna 代币,再次回到市场交易reuters.com。正如 Terra 官方在崩盘后发布的推文所宣称:“我们力量永在社区,今日的决定正彰显了我们的韧性”reuters.com。事实上,原链更名为 Luna Classic 后,大批所谓“LUNC 军团”的散户依然死守阵地,誓言不离不弃;他们自发烧毁巨量代币以缩减供应、推动技术升级,试图让这个一度归零的项目重新燃起生命之火binance.com。失败者并未散场,而是化作一股草根洪流,奋力托举起项目的残迹。经过迷因化的叙事重塑,这场从废墟中重建价值的壮举,成为加密世界中草根政治的经典一幕。类似的案例不胜枚举:曾经被视为笑话的 DOGE(狗狗币)正因多年社群的凝聚而跻身主流币种,总市值一度高达数百亿美元,充分证明了“民有民享”的迷因货币同样可以笑傲市场frontiersin.org。再看最新的美国政治舞台,连总统特朗普也推出了自己的 meme 币 $TRUMP,号召粉丝拿真金白银来表达支持。该币首日即从7美元暴涨至75美元,两天后虽回落到40美元左右,但几乎同时,第一夫人 Melania 又发布了自己的 $Melania 币,甚至连就职典礼的牧师都跟风发行了纪念币theguardian.com!显然,对于狂热的群众来说,一个币的沉浮并非终点,而更像是运动的换挡——资本市场成为政治参与的新前线,你方唱罢我登场,meme 币的群众动员热度丝毫不减。值得注意的是,2024年出现的 Pump.fun 等平台更是进一步降低了这一循环的技术门槛,任何人都可以一键生成自己的 meme 币theguardian.com。这意味着哪怕某个项目归零,剩余的社区完全可以借助此类工具迅速复制一个新币接力,延续集体行动的火种。可以说,在 meme 币的世界里,草根社群获得了前所未有的再生能力和主动权,这正是一种数字时代的群众政治奇观:失败可以被当作梗来玩,破产能够变成重生的序章。
价格即政治:群众投机的新抗争
meme 币现象的兴盛表明:在加密时代,价格本身已成为一种政治表达。这些看似荒诞的迷因代币,将金融市场变成了群众宣泄情绪和诉求的另一个舞台。有学者将此概括为“将公民参与直接转化为了投机资产”cdn-brighterworld.humanities.mcmaster.ca——也就是说,社会运动的热情被注入币价涨跌,政治支持被铸造成可以交易的代币。meme 币融合了金融、技术与政治,通过病毒般的迷因文化激发公众参与,形成对现实政治的某种映射cdn-brighterworld.humanities.mcmaster.caosl.com。当一群草根投入全部热忱去炒作一枚毫无基本面支撑的币时,这本身就是一种大众政治动员的体现:币价暴涨,意味着一群人以戏谑的方式在向既有权威叫板;币价崩盘,也并不意味着信念的消亡,反而可能孕育下一次更汹涌的造势。正如有分析指出,政治类 meme 币的出现前所未有地将群众文化与政治情绪融入市场行情,价格曲线俨然成为民意和趋势的风向标cdn-brighterworld.humanities.mcmaster.ca。在这种局面下,投机不再仅仅是逐利,还是一种宣示立场、凝聚共识的过程——一次次看似荒唐的炒作背后,是草根对传统体制的不服与嘲讽,是失败者拒绝认输的呐喊。归根结底,meme 币所累积的,正是一种不可被归零的政治资本。价格涨落之间,群众的愤怒、幽默与希望尽显其中;这股力量不因一次挫败而消散,反而在市场的循环中愈发壮大。也正因如此,我们才说“价格即政治”——在迷因币的世界里,价格不只是数字,更是人民政治能量的晴雨表,哪怕归零也终将卷土重来。cdn-brighterworld.humanities.mcmaster.caosl.com
全球新兴现象:伊斯兰金融的入场
当Crypto在西方世界掀起市场治政的狂潮时,另一股独特力量也悄然融入这一场域:伊斯兰金融携其独特的道德秩序,开始在链上寻找存在感。长期以来,伊斯兰金融遵循着一套区别于世俗资本主义的原则:禁止利息(Riba)、反对过度投机(Gharar/Maysir)、强调实际资产支撑和道德投资。当这些原则遇上去中心化的加密技术,会碰撞出怎样的火花?出人意料的是,这两者竟在“以市场行为表达价值”这个层面产生了惊人的共鸣。伊斯兰金融并不拒绝市场机制本身,只是为其附加了道德准则;Crypto则将市场机制推向了政治高位,用价格来表达社群意志。二者看似理念迥异,实则都承认市场行为可以也应当承载社会价值观。这使得越来越多金融与政治分析人士开始关注:当虔诚的宗教伦理遇上狂野的加密市场,会塑造出何种新范式?
事实上,穆斯林世界已经在探索“清真加密”的道路。一些区块链项目致力于确保协议符合伊斯兰教法(Sharia)的要求。例如Haqq区块链发行的伊斯兰币(ISLM),从规则层面内置了宗教慈善义务——每发行新币即自动将10%拨入慈善DAO,用于公益捐赠,以符合天课(Zakat)的教义nasdaq.comnasdaq.com。同时,该链拒绝利息和赌博类应用,2022年还获得了宗教权威的教令(Fatwa)认可其合规性nasdaq.com。再看理念层面,伊斯兰经济学强调**货币必须有内在价值**、收益应来自真实劳动而非纯利息剥削。这一点与比特币的“工作量证明”精神不谋而合——有人甚至断言法定货币无锚印钞并不清真,而比特币这类需耗费能源生产的资产反而更符合教法初衷cointelegraph.com。由此,越来越多穆斯林投资者开始以道德投资的名义进入Crypto领域,将资金投向符合清真原则的代币和协议。
这种现象带来了微妙的双重合法性:一方面,Crypto世界原本奉行“价格即真理”的世俗逻辑,而伊斯兰金融为其注入了一股道德合法性,使部分加密资产同时获得了宗教与市场的双重背书;另一方面,即便在遵循宗教伦理的项目中,最终决定成败的依然是市场对其价值的认可。道德共识与市场共识在链上交汇,共同塑造出一种混合的新秩序。这一全球新兴现象引发广泛议论:有人将其视为金融民主化的极致表现——不同文化价值都能在市场平台上表达并竞争;也有人警惕这可能掩盖新的风险,因为把宗教情感融入高风险资产,既可能凝聚强大的忠诚度,也可能在泡沫破裂时引发信仰与财富的双重危机。但无论如何,伊斯兰金融的入场使Crypto的政治版图更加丰盈多元。从华尔街交易员到中东教士,不同背景的人们正通过Crypto这个奇特的舞台,对人类价值的表达方式进行前所未有的实验。
升华结语:价格即政治的新直觉
回顾比特币问世以来的这段历程,我们可以清晰地看到一条演进的主线:先有货币革命,后有政治发明。比特币赋予了人类一种真正自主的数字货币,而Crypto在此基础上完成的,则是一项前所未有的政治革新——它让市场价格行为承担起了类似政治选票的功能,开创了一种“价格即政治”的新直觉。在这个直觉下,市场不再只是冷冰冰的交易场所;每一次资本流动、每一轮行情涨落,都被赋予了社会意义和政治涵义。买入即表态,卖出即抗议,流动性的涌入或枯竭胜过千言万语的陈情。Crypto世界中,K线图俨然成为民意曲线,行情图就是政治晴雨表。决策不再由少数权力精英关起门来制定,而是在全球无眠的交易中由无数普通人共同谱写。这样的政治形式也许狂野,也许充满泡沫和噪音,但它不可否认地调动起了广泛的社会参与,让原本疏离政治进程的个体通过持币、交易重新找回了影响力的幻觉或实感。
“价格即政治”并非一句简单的口号,而是Crypto给予世界的全新想象力。它质疑了传统政治的正统性:如果一串代码和一群匿名投资者就能高效决策资源分配,我们为何还需要繁冗的官僚体系?它也拷问着自身的内在隐忧:当财富与权力深度绑定,Crypto政治如何避免堕入金钱统治的老路?或许,正是在这样的矛盾和张力中,人类政治的未来才会不断演化。Crypto所开启的,不仅是技术乌托邦或金融狂欢,更可能是一次对民主形式的深刻拓展和挑战。这里有最狂热的逐利者,也有最理想主义的社群塑梦者;有一夜暴富的神话,也有瞬间破灭的惨痛。而这一切汇聚成的洪流,正冲撞着工业时代以来既定的权力谱系。
当我们再次追问:Crypto究竟是什么? 或许可以这样回答——Crypto是比特币之后,人类完成的一次政治范式的试验性跃迁。在这里,价格行为化身为选票,资本市场演化为广场,代码与共识共同撰写“社会契约”。这是一场仍在进行的文明实验:它可能无声地融入既有秩序,也可能剧烈地重塑未来规则。但无论结局如何,如今我们已经见证:在比特币发明真正的货币之后,Crypto正在发明真正属于21世纪的政治。它以数字时代的语言宣告:在链上,价格即政治,市场即民意,代码即法律。这,或许就是Crypto带给我们的最直观而震撼的本质启示。
参考资料:
-
中本聪. 比特币白皮书: 一种点对点的电子现金系统. (2008)bitcoin.org
-
Arkham Intelligence. Ethereum vs Ethereum Classic: Understanding the Differences. (2023)arkhamintelligence.com
-
Binance Square (@渔神的加密日记). 狗狗币价格为何上涨?背后的原因你知道吗?binance.com
-
Cointelegraph中文. 特朗普的迷因币晚宴预期内容揭秘. (2025)cn.cointelegraph.com
-
慢雾科技 Web3Caff (@Lisa). 风险提醒:从 LIBRA 看“政治化”的加密货币骗局. (2025)web3caff.com
-
Nasdaq (@Anthony Clarke). How Cryptocurrency Aligns with the Principles of Islamic Finance. (2023)nasdaq.comnasdaq.com
-
Cointelegraph Magazine (@Andrew Fenton). DeFi can be halal but not DOGE? Decentralizing Islamic finance. (2023)
-
-
 @ 57d1a264:69f1fee1
2025-05-16 07:51:08
@ 57d1a264:69f1fee1
2025-05-16 07:51:08Payjoin allows the sender and receiver of an on-chain payment to collaborate and create a transaction that breaks on-chain heuristics, allowing a more private transaction with ambiguous payment amount and UTXO ownership. Additionally, it can also be used for UTXO consolidation (receiver saves future fees) and batching payments (receiver can make payment(s) of their own in the process of receiving one), also known as transaction cut-through. Other than improved privacy, the rest of the benefits are typically applicable to the receiver, not the sender.
BIP-78 was the original payjoin protocol that required the receiver to run a endpoint/server (always online) in order to mediate the payjoin process. Payjoin adoption has remained pretty low, something attributed to the server & perpetual online-ness requirement. This is the motivation for payjoin v2.
The purpose of the one-pager is to analyse the protocol, and highlight the UX issues or tradeoffs it entails, so that the payjoin user flows can be appropriately designed and the tradeoffs likewise communicated. A further document on UX solutions might be needed to identify solutions and opportunities
The following observations are generally limited to individual users transacting through their mobile devices:
While users naturally want better privacy and fee-savings, they also want to minimise friction and minimise (optimise) payment time. These are universal and more immediate needs since they deal with the user experience.
Added manual steps
TL;DR v2 payjoin eliminates server & simultaneous user-liveness requirements (increasing TAM, and opportunities to payjoin, as a result) by adding manual steps.
Usually, the extent of the receiver's involvement in the transaction process is limited to sharing their address with the sender. Once they share the address/URI, they can basically forget about it. In the target scenario for v2 payjoin, the receiver must come online again (except they have no way of knowing "when") to contribute input(s) and sign the PSBT. This can be unexpected, unintuitive and a bit of a hassle.
Usually (and even with payjoin v1), the sender crafts and broadcasts the transaction in one go; meaning the user's job is done within a few seconds/minutes. With payjoin v2, they must share the original-PSBT with the receiver, and then wait for them to do their part. Once the the receiver has done that, the sender must come online to review the transaction, sign it & broadcast.
In summary,
In payjoin v1, step 3 is automated and instant, so delay 2, 3 =~ 0. As the user experiences it, the process is completed in a single session, akin to a non-payjoin transaction.
With payjoin v2, Steps 2 & 3 in the above diagram are widely spread and noticeable. These manual steps are separated by uncertain delays (more on that below) when compared to a non-payjoin transaction.
Delays
We've established that both senders and receivers must take extra manual steps to execute a payoin transaction. With payjoin v2, this process gets split into multiple sessions, since the sender and receiver are not like to be online simultaneously.
Delay 2 & 3 (see diagram above) are uncertain in nature. Most users do not open their bitcoin wallets for days or weeks! The receiver must come online before the timeout hits in order for the payjoin process to work, otherwise time is just wasted with no benefit. UX or technical solutions are needed to minimise these delays.
Delays might be exacerbated if the setup is based on hardware wallet and/or uses multisig.
Notifications or background processes
There is one major problem when we say "the user must come online to..." but in reality the user has no way of knowing there is a payjoin PSBT waiting for them. After a PSBT is sent to the relay, the opposite user would only find out about it whenever they happen to come online. Notifications and background sync processes might be necessary to minimise delays. This is absolutely essential to avert timeouts in addition to saving valuable time. Another risk is phantom payjoin stuff after the timeout is expired if receiver-side does not know it has.
Fee Savings
The following observations might be generally applicable for both original and this v2 payjoin version. Fee-savings with payjoin is a tricky topic. Of course, overall a payjoin transaction is always cheaper than 2 separate transactions, since they get to share the overhead.
Additionally, without the receiver contributing to fees, the chosen fee rate of the PSBT (at the beginning) drops, and can lead to slower confirmation. From another perspective, a sender paying with payjoin pays higher fees for similar confirmation target. This has been observed in a production wallet years back. Given that total transaction time can extend to days, the fee environment itself might change, and all this must be considered when designing the UX.
Of course, there is nothing stopping the receiver from contributing to fees, but this idea is likely entirely novel to the bitcoin ecosystem (perhaps payments ecosystem in general) and the user base. Additionally, nominally it involves the user paying fees and tolerating delays just to receive bitcoin. Without explicit incentives/features that encourage receivers to participate, payjoining might seem like an unncessary hassle.
Overall, it seems that payjoin makes UX significant tradeoffs for important privacy (and potential fee-saving) benefits. This means that the UX might have to do significant heavy-lifting, to ensure that users are not surprised, confused or frustrated when they try to transact on-chain in a privacy-friendly feature. Good, timely communication, new features for consolidation & txn-cutthrough and guided user flows seem crucial to ensure payjoin adoption and for help make on-chain privacy a reality for users.
---------------
Original document available here. Reach out at
yashrajdca@proton.me,y_a_s_h_r_a_j.70on Signal, or on reach out in Bitcoin Design discord.https://stacker.news/items/981388
-
 @ 9358c676:9f2912fc
2025-04-06 16:33:35
@ 9358c676:9f2912fc
2025-04-06 16:33:35OBJECTIVE
Establish a comprehensive and standardized hospital framework for the diagnosis, treatment, and management of pulmonary embolism (PE), aiming to improve quality of care, optimize resources, and reduce morbidity and mortality associated with this condition in the hospital setting.
SCOPE
All hospitalized patients over 15 years of age in our institution.
RESPONSIBILITIES
Institution physicians. Nursing staff.
REFERENCES AND BIBLIOGRAPHY
- SATI Guidelines for the Management and Treatment of Acute Thromboembolic Disease. Revista Argentina de Terapia Intensiva 2019 - 36 No. 4.
- Farreras-Rozman. Internal Medicine. 16th Edition. El Sevier. 2010.
- SAC Consensus for the Diagnosis and Treatment of Venous Thromboembolic Disease. Argentine Journal of Cardiology. October 2024 Vol. 92 Suppl. 6 ISSN 0034-7000
- 2019 ESC Guidelines for the diagnosis and management of acute pulmonary embolism developed in collaboration with the European Respiratory Society (ERS). European Heart Journal (2020) 41, 543-603. doi:10.1093/eurheartj/ehz405
INTRODUCTION
Pulmonary embolism (PE) is a cardiovascular emergency caused by a blood clot, usually originating from the deep veins of the lower limbs, that travels to the lungs and obstructs the pulmonary arteries. This condition represents a significant cause of morbidity and mortality in hospitals. Timely diagnosis and treatment are essential to improve clinical outcomes.
The clinical presentation of PE is highly variable, ranging from mild symptoms to acute cardiovascular shock. Risk factors such as prolonged immobilization, recent surgery, and chronic illnesses complicate its identification and management.
PE has an annual incidence of 70 cases per 100,000 people. Prognosis varies from high-risk PE with high mortality to low-risk PE with minimal hemodynamic impact. Without thromboprophylaxis, deep vein thrombosis (DVT)—the main predisposing factor (90–95% of cases)—has variable incidence depending on the surgery type, and up to 25% of embolic events occur post-discharge.
PREDISPOSING FACTORS
Strong Risk Factors (OR >10): - Hip or leg fracture - Hip or knee prosthesis - Major general surgery - Major trauma - Spinal cord injury
Moderate Risk Factors (OR 2–9): - Arthroscopic knee surgery - Central venous catheters - Chemotherapy - Chronic heart or respiratory failure - Hormonal replacement therapy - Malignancy - Oral contraceptives - Stroke with paralysis - Pregnancy or postpartum - Prior VTE - Thrombophilia
Mild Risk Factors (OR <2): - Bed rest <3 days - Prolonged travel - Advanced age - Laparoscopic surgery - Obesity - Antepartum period - Varicose veins
CLINICAL MANIFESTATIONS AND BASIC COMPLEMENTARY STUDIES
Symptoms: Dyspnea, chest pain, cough, hemoptysis, bronchospasm, fever.
Signs: Tachycardia, desaturation, jugular vein distention, orthostatism, DVT signs, syncope, or shock.Basic Studies: - Chest X-ray (may show infarction or atelectasis) - ECG (T wave inversion, RV strain, S1Q3T3 pattern)
RISK ASSESSMENT SCORES
Wells Score: - >6 points: High probability - 2–6: Moderate - ≤2: Low - Modified: >4 = likely PE, ≤4 = unlikely PE
Geneva Score: - >10: High - 4–10: Intermediate - 0–3: Low
PERC Rule: If all criteria are negative and clinical suspicion is low, PE can be excluded without further testing.
DIAGNOSTIC STUDIES
- D-dimer: High sensitivity; used in low/moderate risk patients.
- CT Pulmonary Angiography (CTPA): First-line imaging; limited in pregnancy/renal failure.
- Lower limb Doppler ultrasound: Indirect evidence of PE when DVT is detected.
- V/Q scan: Alternative when CTPA is contraindicated.
- Transthoracic echocardiogram: Used to assess RV function, especially in shock.
- Pulmonary angiography: Gold standard; reserved for complex cases due to invasiveness.
RISK STRATIFICATION
High-risk PE (5%): Hemodynamic instability, mortality >15%. Requires urgent reperfusion.
Intermediate-risk PE (30–50%): Hemodynamically stable with signs of RV dysfunction or elevated biomarkers.
Low-risk PE: Mortality <1%, eligible for outpatient management.
PESI Score: - I (<65): Very low risk - II (65–85): Low - III (86–105): Intermediate - IV (106–125): High - V (>125): Very high
Simplified PESI: ≥1 point = high risk; 0 = low risk
TREATMENT
High-risk PE: - Systemic fibrinolysis with alteplase 100 mg over 2 h or 0.6 mg/kg (max 50 mg) IV bolus over 15 min. - Suspend UFH 30–60 min before lysis if already on treatment. - Resume anticoagulation (UFH or LMWH) when aPTT <2x normal. - Consider surgical embolectomy or catheter-directed therapy if fibrinolysis fails or is contraindicated. - Maintain SpO₂ >90%, CVP 8–12 mmHg, and use vasopressors/inotropes as needed. ECMO in select cases.
Contraindications to Fibrinolytics: - Absolute: Recent stroke, active bleeding, CNS tumors, recent major trauma or surgery. - Relative: Anticoagulant use, recent TIA, pregnancy, uncontrolled hypertension, liver disease.
Intermediate-risk PE: - Initiate anticoagulation (enoxaparin 1–1.5 mg/kg SC every 12 h, max 100 mg/dose). - Fibrinolysis is not routine; reserve for clinical deterioration. - Direct oral anticoagulants (DOACs) may be considered. - Consider IVC filter in absolute contraindication to anticoagulation or recurrence despite treatment.
RIETE Bleeding Risk Score: - >4 points: High risk - 1–4: Intermediate - 0: Low
INVASIVE TREATMENT
Consider catheter-directed therapy when: - High bleeding risk - Fibrinolysis contraindicated - Delayed symptom onset >14 days
Some centers use this as first-line therapy in high-risk PE.
QUALITY INDICATOR
Indicator: Proportion of PE cases with documented risk stratification in the medical record at initial evaluation.
Formula: (PE cases with documented stratification / total PE cases evaluated) × 100
Target: >85% of PE cases must have risk stratification recorded at the time of initial evaluation.
Autor
Kamo Weasel - MD Infectious Diseases - MD Internal Medicine - #DocChain Community npub1jdvvva54m8nchh3t708pav99qk24x6rkx2sh0e7jthh0l8efzt7q9y7jlj
-
 @ a6b4114e:60d83c46
2025-05-21 03:25:43
@ a6b4114e:60d83c46
2025-05-21 03:25:43GTA San Andreas is one installment of Grand Theft Auto.
It is safe and secure for your device. No harmful elements have been found yet. It does not contain viruses, malware, bloatware, bugs, or threats, as its authority always upgrades the game to eliminate unwanted components. The amazing thing is that the game is 100% free for Android users.
You do not pay a single cent from your pocket.
Download: https://androidhd.com/en/gta-san-andreas
-
 @ 7460b7fd:4fc4e74b
2025-05-21 02:35:36
@ 7460b7fd:4fc4e74b
2025-05-21 02:35:36如果比特币发明了真正的钱,那么 Crypto 是什么?
引言
比特币诞生之初就以“数字黄金”姿态示人,被支持者誉为人类历史上第一次发明了真正意义上的钱——一种不依赖国家信用、总量恒定且不可篡改的硬通货。然而十多年过去,比特币之后蓬勃而起的加密世界(Crypto)已经远超“货币”范畴:从智能合约平台到去中心组织,从去央行的稳定币到戏谑荒诞的迷因币,Crypto 演化出一个丰富而混沌的新生态。这不禁引发一个根本性的追问:如果说比特币解决了“真金白银”的问题,那么 Crypto 又完成了什么发明?
 Crypto 与政治的碰撞:随着Crypto版图扩张,全球政治势力也被裹挟进这场金融变革洪流(示意图)。比特币的出现重塑了货币信用,但Crypto所引发的却是一场更深刻的政治与治理结构实验。从华尔街到华盛顿,从散户论坛到主权国家,越来越多人意识到:Crypto不只是技术或金融现象,而是一种全新的政治表达结构正在萌芽。正如有激进论者所断言的:“比特币发明了真正的钱,而Crypto则在发明新的政治。”价格K线与流动性曲线,或许正成为这个时代社群意志和社会价值观的新型投射。
Crypto 与政治的碰撞:随着Crypto版图扩张,全球政治势力也被裹挟进这场金融变革洪流(示意图)。比特币的出现重塑了货币信用,但Crypto所引发的却是一场更深刻的政治与治理结构实验。从华尔街到华盛顿,从散户论坛到主权国家,越来越多人意识到:Crypto不只是技术或金融现象,而是一种全新的政治表达结构正在萌芽。正如有激进论者所断言的:“比特币发明了真正的钱,而Crypto则在发明新的政治。”价格K线与流动性曲线,或许正成为这个时代社群意志和社会价值观的新型投射。冲突结构:当价格挑战选票
传统政治中,选票是人民意志的载体,一人一票勾勒出民主治理的正统路径。而在链上的加密世界里,骤升骤降的价格曲线和真金白银的买卖行为却扮演起了选票的角色:资金流向成了民意走向,市场多空成为立场表决。价格行为取代选票,这听来匪夷所思,却已在Crypto社群中成为日常现实。每一次代币的抛售与追高,都是社区对项目决策的即时“投票”;每一根K线的涨跌,都折射出社区意志的赞同或抗议。市场行为本身承担了决策权与象征权——价格即政治,正在链上蔓延。
这一新生政治形式与旧世界的民主机制形成了鲜明冲突。bitcoin.org中本聪在比特币白皮书中提出“一CPU一票”的工作量证明共识,用算力投票取代了人为决策bitcoin.org。而今,Crypto更进一步,用资本市场的涨跌来取代传统政治的选举。支持某项目?直接购入其代币推高市值;反对某提案?用脚投票抛售资产。相比漫长的选举周期和层层代议制,链上市场提供了近乎实时的“公投”机制。但这种机制也引发巨大争议:资本的投票天然偏向持币多者(富者)的意志,是否意味着加密政治更为金权而非民权?持币多寡成为影响力大小,仿佛选举演变成了“一币一票”,巨鲸富豪俨然掌握更多话语权。这种与民主平等原则的冲突,成为Crypto政治形式饱受质疑的核心张力之一。
尽管如此,我们已经目睹市场投票在Crypto世界塑造秩序的威力:2016年以太坊因DAO事件分叉时,社区以真金白银“投票”决定了哪条链获得未来。arkhamintelligence.com结果是新链以太坊(ETH)成为主流,其市值一度超过2,800亿美元,而坚持原则的以太经典(ETC)市值不足35亿美元,不及前者的八十分之一arkhamintelligence.com。市场选择清楚地昭示了社区的政治意志。同样地,在比特币扩容之争、各类硬分叉博弈中,无不是由投资者和矿工用资金与算力投票,胜者存续败者黯然。价格成为裁决纷争的最终选票,冲击着传统“选票决胜”的政治理念。Crypto的价格民主,与现代代议民主正面相撞,激起当代政治哲思中前所未有的冲突火花。
治理与分配
XRP对决SEC成为了加密世界“治理与分配”冲突的经典战例。2020年底,美国证券交易委员会(SEC)突然起诉Ripple公司,指控其发行的XRP代币属于未注册证券,消息一出直接引爆市场恐慌。XRP价格应声暴跌,一度跌去超过60%,最低触及0.21美元coindesk.com。曾经位居市值前三的XRP险些被打入谷底,监管的强硬姿态似乎要将这个项目彻底扼杀。
然而XRP社区没有选择沉默。 大批长期持有者组成了自称“XRP军团”(XRP Army)的草根力量,在社交媒体上高调声援Ripple,对抗监管威胁。面对SEC的指控,他们集体发声,质疑政府选择性执法,声称以太坊当年发行却“逍遥法外”,只有Ripple遭到不公对待coindesk.com。正如《福布斯》的评论所言:没人预料到愤怒的加密散户投资者会掀起法律、政治和社交媒体领域的‘海啸式’反击,痛斥监管机构背弃了保护投资者的承诺crypto-law.us。这种草根抵抗监管的话语体系迅速形成:XRP持有者不但在网上掀起舆论风暴,还采取实际行动向SEC施压。他们发起了请愿,抨击SEC背离保护投资者初衷、诉讼给个人投资者带来巨大伤害,号召停止对Ripple的上诉纠缠——号称这是在捍卫全球加密用户的共同利益bitget.com。一场由民间主导的反监管运动就此拉开帷幕。
Ripple公司则选择背水一战,拒绝和解,在法庭上与SEC针锋相对地鏖战了近三年之久。Ripple坚称XRP并非证券,不应受到SEC管辖,即使面临沉重法律费用和业务压力也不妥协。2023年,这场持久战迎来了标志性转折:美国法庭作出初步裁决,认定XRP在二级市场的流通不构成证券coindesk.com。这一胜利犹如给沉寂已久的XRP注入强心针——消息公布当天XRP价格飙涨近一倍,盘中一度逼近1美元大关coindesk.com。沉重监管阴影下苟延残喘的项目,凭借司法层面的突破瞬间重获生机。这不仅是Ripple的胜利,更被支持者视为整个加密行业对SEC强权的一次胜仗。
XRP的对抗路线与某些“主动合规”的项目形成了鲜明对比。 稳定币USDC的发行方Circle、美国最大合规交易所Coinbase等选择了一条迎合监管的道路:它们高调拥抱现行法规,希望以合作换取生存空间。然而现实却给了它们沉重一击。USDC稳定币在监管风波中一度失去美元锚定,哪怕Circle及时披露储备状况也无法阻止恐慌蔓延,大批用户迅速失去信心,短时间内出现数十亿美元的赎回潮blockworks.co。Coinbase则更为直接:即便它早已注册上市、反复向监管示好,2023年仍被SEC指控为未注册证券交易所reuters.com,卷入漫长诉讼漩涡。可见,在迎合监管的策略下,这些机构非但未能换来监管青睐,反而因官司缠身或用户流失而丧失市场信任。 相比之下,XRP以对抗求生存的路线反而赢得了投资者的眼光:价格的涨跌成为社区投票的方式,抗争的勇气反过来强化了市场对它的信心。
同样引人深思的是另一种迥异的治理路径:技术至上的链上治理。 以MakerDAO为代表的去中心化治理模式曾被寄予厚望——MKR持币者投票决策、算法维持稳定币Dai的价值,被视为“代码即法律”的典范。然而,这套纯技术治理在市场层面却未能形成广泛认同,亦无法激发群体性的情绪动员。复杂晦涩的机制使得普通投资者难以参与其中,MakerDAO的治理讨论更多停留在极客圈子内部,在社会大众的政治对话中几乎听不见它的声音。相比XRP对抗监管所激发的铺天盖地关注,MakerDAO的治理实验显得默默无闻、难以“出圈”。这也说明,如果一种治理实践无法连接更广泛的利益诉求和情感共鸣,它在社会政治层面就难以形成影响力。
XRP之争的政治象征意义由此凸显: 它展示了一条“以市场对抗国家”的斗争路线,即通过代币价格的集体行动来回应监管权力的施压。在这场轰动业界的对决中,价格即是抗议的旗帜,涨跌映射着政治立场。XRP对SEC的胜利被视作加密世界向旧有权力宣告的一次胜利:资本市场的投票器可以撼动监管者的强权。这种“价格即政治”的张力,正是Crypto世界前所未有的社会实验:去中心化社区以市场行为直接对抗国家权力,在无形的价格曲线中凝聚起政治抗争的力量,向世人昭示加密货币不仅有技术和资本属性,更蕴含着不可小觑的社会能量和政治意涵。
不可归零的政治资本
Meme 币的本质并非廉价或易造,而在于其构建了一种“无法归零”的社群生存结构。 对于传统观点而言,多数 meme 币只是短命的投机游戏:价格暴涨暴跌后一地鸡毛,创始人套现跑路,投资者血本无归,然后“大家转去炒下一个”theguardian.com。然而,meme 币社群的独特之处在于——失败并不意味着终结,而更像是运动的逗号而非句号。一次币值崩盘后,持币的草根们往往并未散去;相反,他们汲取教训,准备东山再起。这种近乎“不死鸟”的循环,使得 meme 币运动呈现出一种数字政治循环的特质:价格可以归零,但社群的政治热情和组织势能不归零。正如研究者所指出的,加密领域中的骗局、崩盘等冲击并不会摧毁生态,反而成为让系统更加强韧的“健康应激”,令整个行业在动荡中变得更加反脆弱cointelegraph.com。对应到 meme 币,每一次暴跌和重挫,都是社群自我进化、卷土重来的契机。这个去中心化群体打造出一种自组织的安全垫,失败者得以在瓦砾上重建家园。对于草根社群、少数派乃至体制的“失败者”而言,meme 币提供了一个永不落幕的抗争舞台,一种真正反脆弱的政治性。正因如此,我们看到诸多曾被嘲笑的迷因项目屡败屡战:例如 Dogecoin 自2013年问世后历经八年沉浮,早已超越玩笑属性,成为互联网史上最具韧性的迷因之一frontiersin.org;支撑 Dogecoin 的正是背后强大的迷因文化和社区意志,它如同美国霸权支撑美元一样,为狗狗币提供了“永不中断”的生命力frontiersin.org。
“复活权”的数字政治意涵
这种“失败-重生”的循环结构蕴含着深刻的政治意涵:在传统政治和商业领域,一个政党选举失利或一家公司破产往往意味着清零出局,资源散尽、组织瓦解。然而在 meme 币的世界,社群拥有了一种前所未有的“复活权”。当项目崩盘,社区并不必然随之消亡,而是可以凭借剩余的人心和热情卷土重来——哪怕换一个 token 名称,哪怕重启一条链,运动依然延续。正如 Cheems 项目的核心开发者所言,在几乎无人问津、技术受阻的困境下,大多数人可能早已卷款走人,但 “CHEEMS 社区没有放弃,背景、技术、风投都不重要,重要的是永不言弃的精神”cointelegraph.com。这种精神使得Cheems项目起死回生,社区成员齐声宣告“我们都是 CHEEMS”,共同书写历史cointelegraph.com。与传统依赖风投和公司输血的项目不同,Cheems 完全依靠社区的信念与韧性存续发展,体现了去中心化运动的真谛cointelegraph.com。这意味着政治参与的门槛被大大降低:哪怕没有金主和官方背书,草根也能凭借群体意志赋予某个代币新的生命。对于身处社会边缘的群体来说,meme 币俨然成为自组织的安全垫和重新集结的工具。难怪有学者指出,近期涌入meme币浪潮的主力,正是那些对现实失望但渴望改变命运的年轻人theguardian.com——“迷茫的年轻人,想要一夜暴富”theguardian.com。meme币的炒作表面上看是投机赌博,但背后蕴含的是草根对既有金融秩序的不满与反抗:没有监管和护栏又如何?一次失败算不得什么,社区自有后路和新方案。这种由底层群众不断试错、纠错并重启的过程,本身就是一种数字时代的新型反抗运动和群众动员机制。
举例而言,Terra Luna 的沉浮充分展现了这种“复活机制”的政治力量。作为一度由风投资本热捧的项目,Luna 币在2022年的崩溃本可被视作“归零”的失败典范——稳定币UST瞬间失锚,Luna币价归零,数十亿美元灰飞烟灭。然而“崩盘”并没有画下休止符。Luna的残余社区拒绝承认失败命运,通过链上治理投票毅然启动新链,“复活”了 Luna 代币,再次回到市场交易reuters.com。正如 Terra 官方在崩盘后发布的推文所宣称:“我们力量永在社区,今日的决定正彰显了我们的韧性”reuters.com。事实上,原链更名为 Luna Classic 后,大批所谓“LUNC 军团”的散户依然死守阵地,誓言不离不弃;他们自发烧毁巨量代币以缩减供应、推动技术升级,试图让这个一度归零的项目重新燃起生命之火binance.com。失败者并未散场,而是化作一股草根洪流,奋力托举起项目的残迹。经过迷因化的叙事重塑,这场从废墟中重建价值的壮举,成为加密世界中草根政治的经典一幕。类似的案例不胜枚举:曾经被视为笑话的 DOGE(狗狗币)正因多年社群的凝聚而跻身主流币种,总市值一度高达数百亿美元,充分证明了“民有民享”的迷因货币同样可以笑傲市场frontiersin.org。再看最新的美国政治舞台,连总统特朗普也推出了自己的 meme 币 $TRUMP,号召粉丝拿真金白银来表达支持。该币首日即从7美元暴涨至75美元,两天后虽回落到40美元左右,但几乎同时,第一夫人 Melania 又发布了自己的 $Melania 币,甚至连就职典礼的牧师都跟风发行了纪念币theguardian.com!显然,对于狂热的群众来说,一个币的沉浮并非终点,而更像是运动的换挡——资本市场成为政治参与的新前线,你方唱罢我登场,meme 币的群众动员热度丝毫不减。值得注意的是,2024年出现的 Pump.fun 等平台更是进一步降低了这一循环的技术门槛,任何人都可以一键生成自己的 meme 币theguardian.com。这意味着哪怕某个项目归零,剩余的社区完全可以借助此类工具迅速复制一个新币接力,延续集体行动的火种。可以说,在 meme 币的世界里,草根社群获得了前所未有的再生能力和主动权,这正是一种数字时代的群众政治奇观:失败可以被当作梗来玩,破产能够变成重生的序章。
价格即政治:群众投机的新抗争
meme 币现象的兴盛表明:在加密时代,价格本身已成为一种政治表达。这些看似荒诞的迷因代币,将金融市场变成了群众宣泄情绪和诉求的另一个舞台。有学者将此概括为“将公民参与直接转化为了投机资产”cdn-brighterworld.humanities.mcmaster.ca——也就是说,社会运动的热情被注入币价涨跌,政治支持被铸造成可以交易的代币。meme 币融合了金融、技术与政治,通过病毒般的迷因文化激发公众参与,形成对现实政治的某种映射cdn-brighterworld.humanities.mcmaster.caosl.com。当一群草根投入全部热忱去炒作一枚毫无基本面支撑的币时,这本身就是一种大众政治动员的体现:币价暴涨,意味着一群人以戏谑的方式在向既有权威叫板;币价崩盘,也并不意味着信念的消亡,反而可能孕育下一次更汹涌的造势。正如有分析指出,政治类 meme 币的出现前所未有地将群众文化与政治情绪融入市场行情,价格曲线俨然成为民意和趋势的风向标cdn-brighterworld.humanities.mcmaster.ca。在这种局面下,投机不再仅仅是逐利,还是一种宣示立场、凝聚共识的过程——一次次看似荒唐的炒作背后,是草根对传统体制的不服与嘲讽,是失败者拒绝认输的呐喊。归根结底,meme 币所累积的,正是一种不可被归零的政治资本。价格涨落之间,群众的愤怒、幽默与希望尽显其中;这股力量不因一次挫败而消散,反而在市场的循环中愈发壮大。也正因如此,我们才说“价格即政治”——在迷因币的世界里,价格不只是数字,更是人民政治能量的晴雨表,哪怕归零也终将卷土重来。cdn-brighterworld.humanities.mcmaster.caosl.com
全球新兴现象:伊斯兰金融的入场
当Crypto在西方世界掀起市场治政的狂潮时,另一股独特力量也悄然融入这一场域:伊斯兰金融携其独特的道德秩序,开始在链上寻找存在感。长期以来,伊斯兰金融遵循着一套区别于世俗资本主义的原则:禁止利息(Riba)、反对过度投机(Gharar/Maysir)、强调实际资产支撑和道德投资。当这些原则遇上去中心化的加密技术,会碰撞出怎样的火花?出人意料的是,这两者竟在“以市场行为表达价值”这个层面产生了惊人的共鸣。伊斯兰金融并不拒绝市场机制本身,只是为其附加了道德准则;Crypto则将市场机制推向了政治高位,用价格来表达社群意志。二者看似理念迥异,实则都承认市场行为可以也应当承载社会价值观。这使得越来越多金融与政治分析人士开始关注:当虔诚的宗教伦理遇上狂野的加密市场,会塑造出何种新范式?
事实上,穆斯林世界已经在探索“清真加密”的道路。一些区块链项目致力于确保协议符合伊斯兰教法(Sharia)的要求。例如Haqq区块链发行的伊斯兰币(ISLM),从规则层面内置了宗教慈善义务——每发行新币即自动将10%拨入慈善DAO,用于公益捐赠,以符合天课(Zakat)的教义nasdaq.comnasdaq.com。同时,该链拒绝利息和赌博类应用,2022年还获得了宗教权威的教令(Fatwa)认可其合规性nasdaq.com。再看理念层面,伊斯兰经济学强调货币必须有内在价值、收益应来自真实劳动而非纯利息剥削。这一点与比特币的“工作量证明”精神不谋而合——有人甚至断言法定货币无锚印钞并不清真,而比特币这类需耗费能源生产的资产反而更符合教法初衷cointelegraph.com。由此,越来越多穆斯林投资者开始以道德投资的名义进入Crypto领域,将资金投向符合清真原则的代币和协议。
这种现象带来了微妙的双重合法性:一方面,Crypto世界原本奉行“价格即真理”的世俗逻辑,而伊斯兰金融为其注入了一股道德合法性,使部分加密资产同时获得了宗教与市场的双重背书;另一方面,即便在遵循宗教伦理的项目中,最终决定成败的依然是市场对其价值的认可。道德共识与市场共识在链上交汇,共同塑造出一种混合的新秩序。这一全球新兴现象引发广泛议论:有人将其视为金融民主化的极致表现——不同文化价值都能在市场平台上表达并竞争;也有人警惕这可能掩盖新的风险,因为把宗教情感融入高风险资产,既可能凝聚强大的忠诚度,也可能在泡沫破裂时引发信仰与财富的双重危机。但无论如何,伊斯兰金融的入场使Crypto的政治版图更加丰盈多元。从华尔街交易员到中东教士,不同背景的人们正通过Crypto这个奇特的舞台,对人类价值的表达方式进行前所未有的实验。
升华结语:价格即政治的新直觉
回顾比特币问世以来的这段历程,我们可以清晰地看到一条演进的主线:先有货币革命,后有政治发明。比特币赋予了人类一种真正自主的数字货币,而Crypto在此基础上完成的,则是一项前所未有的政治革新——它让市场价格行为承担起了类似政治选票的功能,开创了一种“价格即政治”的新直觉。在这个直觉下,市场不再只是冷冰冰的交易场所;每一次资本流动、每一轮行情涨落,都被赋予了社会意义和政治涵义。买入即表态,卖出即抗议,流动性的涌入或枯竭胜过千言万语的陈情。Crypto世界中,K线图俨然成为民意曲线,行情图就是政治晴雨表。决策不再由少数权力精英关起门来制定,而是在全球无眠的交易中由无数普通人共同谱写。这样的政治形式也许狂野,也许充满泡沫和噪音,但它不可否认地调动起了广泛的社会参与,让原本疏离政治进程的个体通过持币、交易重新找回了影响力的幻觉或实感。
“价格即政治”并非一句简单的口号,而是Crypto给予世界的全新想象力。它质疑了传统政治的正统性:如果一串代码和一群匿名投资者就能高效决策资源分配,我们为何还需要繁冗的官僚体系?它也拷问着自身的内在隐忧:当财富与权力深度绑定,Crypto政治如何避免堕入金钱统治的老路?或许,正是在这样的矛盾和张力中,人类政治的未来才会不断演化。Crypto所开启的,不仅是技术乌托邦或金融狂欢,更可能是一次对民主形式的深刻拓展和挑战。这里有最狂热的逐利者,也有最理想主义的社群塑梦者;有一夜暴富的神话,也有瞬间破灭的惨痛。而这一切汇聚成的洪流,正冲撞着工业时代以来既定的权力谱系。
当我们再次追问:Crypto究竟是什么? 或许可以这样回答——Crypto是比特币之后,人类完成的一次政治范式的试验性跃迁。在这里,价格行为化身为选票,资本市场演化为广场,代码与共识共同撰写“社会契约”。这是一场仍在进行的文明实验:它可能无声地融入既有秩序,也可能剧烈地重塑未来规则。但无论结局如何,如今我们已经见证:在比特币发明真正的货币之后,Crypto正在发明真正属于21世纪的政治。它以数字时代的语言宣告:在链上,价格即政治,市场即民意,代码即法律。这,或许就是Crypto带给我们的最直观而震撼的本质启示。
参考资料:
-
中本聪. 比特币白皮书: 一种点对点的电子现金系统. (2008)bitcoin.org
-
Arkham Intelligence. Ethereum vs Ethereum Classic: Understanding the Differences. (2023)arkhamintelligence.com
-
Binance Square (@渔神的加密日记). 狗狗币价格为何上涨?背后的原因你知道吗?binance.com
-
Cointelegraph中文. 特朗普的迷因币晚宴预期内容揭秘. (2025)cn.cointelegraph.com
-
慢雾科技 Web3Caff (@Lisa). 风险提醒:从 LIBRA 看“政治化”的加密货币骗局. (2025)web3caff.com
-
Nasdaq (@Anthony Clarke). How Cryptocurrency Aligns with the Principles of Islamic Finance. (2023)nasdaq.comnasdaq.com
-
Cointelegraph Magazine (@Andrew Fenton). DeFi can be halal but not DOGE? Decentralizing Islamic finance. (2023)cointelegraph.com
-
-
 @ 3ad01248:962d8a07
2025-05-22 17:18:25
@ 3ad01248:962d8a07
2025-05-22 17:18:25With the price of Bitcoin skyrocketing as of late maybe its time that we go over some rules as a Bitcoiner because someone just got robbed in the UK of the Bitcoin wealth by a fake Uber driver. I fear this will become more common place as time goes on unless certain rules are followed.
Rule 1: Never talk about your Bitcoin holdings to people you don't know or don't trust
This will easily make you a target. If you are out in public saying you have 5 Bitcoin what do you think is going to happen when the wrong person finds out. They will follow you home, tie you up and take your shit. You can avoid this by not talking about your Bitcoin in public spaces, you never know how is listening. Hell I wouldn't even share it with your spouse to be honest. You don't know who she is talking to either. Keep your wealth private.
Rule 2: Stay Humble/Live Below Your means
Resist the urge to spend your new found wealth on something extravagent like a lambo or something that is going to draw unwanted attention. Not saying that you shouldn't enjoy your life but be aware that not everyone is going to be happy about your new found wealth. The best thing you can do is drive an unassuming car and live in regular home.
Rule 3: Don't Carry Your Wealth In Your Pocket
It is definitely a bad idea to walk around with your wealth stored on your phone. This is how people are getting robbed of their wealth. They leave their holding on some centralized exchange where all you need is a password to access their account. When you are under duress that isn't going to stop anyone from stealing your money. Self custody your Bitcoin and keep it in cold storage! Can't stress that enough.
Rule 5: Practice Good Digital Hygiene
With more and more of our lives online, especially social media it is a good idea to practice good digital hygiene. The internet is rife with scammers looking to access your private information to learn everything about you. Use a VPN if possible. You should probably get in the habit of creating multiple email address or use a service that creates fake ones for you. It is safe to assume that some database with your information will get hacked at some point. Better to have a random email get stolen versus the primary one that you use. A second phone line couldn't hurt as well.
Rule 6: Keep Your Circle Small
This kind of ties back in with the first rule. The more people you allow into your inner circle the more you open yourself up to attack. You can't always be sure of someone's motives especially people that you recent met. Be wary of people that just show up out of the blue wanting to be your best friend. This applies to family as well, if they somehow know that you own Bitcoin and see that you are doing well you can't assume that just because they are family you can't trust them. In fact these are the people you have to worry about the most.
It's better to be safe than sorry in my opinion. Keep your circle of trust small and you won't have problems.
These are six rules that I think can help keep you safe and you Bitcoin wealth in your hands. I'm sure there are more, if you think of more comment below!!
-
 @ 57d1a264:69f1fee1
2025-05-16 05:38:28
@ 57d1a264:69f1fee1
2025-05-16 05:38:28LegoGPT generates a LEGO structure from a user-provided text prompt in an end-to-end manner. Notably, our generated LEGO structure is physically stable and buildable.
Lego is something most of us knows. This is a opportuity to ask where is our creativity going? From the art of crafting figures to building blocks following our need and desires to have a machine thinking and building following step-by-step instructions to achieve an isolated goal.
Is the creative act then in the question itself, not anymore in the crafting? Are we just delegating the solution of problems, the thinking of how to respond to questions, to machines? Would it be different if delegated to other people?
Source: https://avalovelace1.github.io/LegoGPT/
https://stacker.news/items/981336
-
 @ 3f770d65:7a745b24
2025-05-20 21:14:28
@ 3f770d65:7a745b24
2025-05-20 21:14:28I’m Derek Ross, and I’m all-in on Nostr.
I started the Grow Nostr Initiative to help more people discover what makes Nostr so powerful: ✅ You own your identity ✅ You choose your social graph and algorithms ✅ You aren't locked into any single app or platform ✅ You can post, stream, chat, and build, all without gatekeepers
What we’re doing with Grow Nostr Initiative: 🌱 Hosting local meetups and mini-conferences to onboard people face-to-face 📚 Creating educational materials and guides to demystify how Nostr works 🧩 Helping businesses and creators understand how they can plug into Nostr (running media servers, relays, and using key management tools)
I believe Nostr is the foundation of a more open internet. It’s still early, but we’re already seeing incredible apps for social, blogging, podcasting, livestreaming, and more. And the best part is that they're all interoperable, censorship-resistant, and built on open standards. Nostr is the world's largest bitcoin economy by transaction volume and I truly believe that the purple pill helps the orange pill go down. Meaning, growing Nostr will also grow Bitcoin adoption.
If you’ve been curious about Nostr or are building something on it, or let’s talk. Whether you're just getting started or you're already deep in the ecosystem, I'm here to answer questions, share what I’ve learned, and hear your ideas. Check out https://nostrapps.com to find your next social decentralized experience.
Ask Me Anything about GNI, Nostr, Bitcoin, the upcoming #NosVegas event at the Bitcoin Conference next week, etc.!
– Derek Ross 🌐 https://grownostr.org npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424
https://stacker.news/items/984689
-
 @ 51bbb15e:b77a2290
2025-05-21 00:24:36
@ 51bbb15e:b77a2290
2025-05-21 00:24:36Yeah, I’m sure everything in the file is legit. 👍 Let’s review the guard witness testimony…Oh wait, they weren’t at their posts despite 24/7 survellience instructions after another Epstein “suicide” attempt two weeks earlier. Well, at least the video of the suicide is in the file? Oh wait, a techical glitch. Damn those coincidences!
At this point, the Trump administration has zero credibility with me on anything related to the Epstein case and his clients. I still suspect the administration is using the Epstein files as leverage to keep a lot of RINOs in line, whereas they’d be sabotaging his agenda at every turn otherwise. However, I just don’t believe in ends-justify-the-means thinking. It’s led almost all of DC to toss out every bit of the values they might once have had.
-
 @ 4fe4a528:3ff6bf06
2025-04-01 12:32:20
@ 4fe4a528:3ff6bf06
2025-04-01 12:32:20Ever since Mark Carney told the CEOs of the Canadian banks to freeze the truckers bank accounts there has been a growing acceptance that the money you have in a Canadian bank account isn’t yours; it belongs to Mark Carney. Now that there is another election in Canada we will decide who gets to prints the monies for us. There have been a lot of changes in the banking system since Mark Carney borrow money from China. Who is your master?
Banking changes that affected me today. 1. The Canadian Tire doesn’t accept Canadian cash to pay off your credit card. 2. You can’t use your Canadian Tire points unless you have your physical card in the store with you. 3. Some grocery and feed stores don’t accept bitcoin directly. SWIFT banking changes. 1. Stable Coins are a thing now. 2. Tether for outside the USA 3. Circle / XRP for inside the USA Let the best coin win. The bill should pass in the US senate by summer Bitcoin banking changes 1. More and more nodes are hosting friends and family via their LNURL accounts. 2. The USA now has bitcoin as an asset on their Strategic Reserve 3. Bitcoin Hashrate went from 550 EH/s to 990 EH/S in the last 12 months. I think the electrical usage has almost double also. 4. Tether brings USDT to Bitcoin’s Lightning Network, ushering in a New Era of Unstoppable Technology, now the world's largest stablecoin is part of the Lightning Network - Download the Joltz App today.
By my next news letter we should know who will be leading Canada. This is the current psychological warfare going on. 1. Push back against carbon taxes? You’re labeled a “climate denier.” 2. Stand up for provincial rights? You’re smeared as “anti-democratic.” 3. Question Carney’s globalist agenda? You’re branded an “extremist.”
Who do you think will be enforcing their will on Canadians in 28 days? Do you think Elections Canada will be keep the elections fair? I hope these articles help you on your hard money journey. Hopefully you can get what you want out of life - don’t sell your birthright. We are all in this together. Watch “The big Red Button” before May 1, 2025 (my next email)
-
 @ 57d1a264:69f1fee1
2025-05-14 09:48:43
@ 57d1a264:69f1fee1
2025-05-14 09:48:43Just another Ecash nutsnote design is a ew template for brrr.gandlaf.com cashu tocken printing machine and honoring Ecash ideator David Lee Chaum. Despite the turn the initial project took, we would not have Ecash today without his pioneering approach in cryptography and privacy-preserving technologies.
A simple KISS (Keep It Super Simple) Ecash nutsnote delivered as SVG, nothing fancy, designed in PenPot, an open source design tool, for slides, presentations, mockups and interactive prototypes.
Here Just another Nutsnote's current state, together with some snapshots along the process. Your feedback is more than welcome.
https://design.penpot.app/#/view?file-id=749aaa04-8836-81c6-8006-0b29916ec156&page-id=749aaa04-8836-81c6-8006-0b29916ec157§ion=interactions&index=0&share-id=addba4d5-28a4-8022-8006-2ecc4316ebb2
originally posted at https://stacker.news/items/979728
-
 @ 57d1a264:69f1fee1
2025-05-14 06:48:45
@ 57d1a264:69f1fee1
2025-05-14 06:48:45Has the architect Greg Chasen considered it when rebuilding the house just one year before the catastrophe? Apparently not! Another of his projects was featured on the Value of Architecture as properties with design integrity.
This is a super interesting subject. The historic character, livability, and modern disaster-resistance is a triangle where you often have to pick just one or two, which leads to some tough decisions that have major impacts on families and communities. Like one of the things he mentions is that the architect completely eliminated plants from the property. That's great for fire resistance, but not so great for other things if the entire town decides to go the same route (which he does bring up later in the video). I don't think there's any objectively right answer, but definitely lots of good (and important) discussion points to be had.
https://www.youtube.com/watch?v=cbl_1qfsFXk
originally posted at https://stacker.news/items/979653
-
 @ dfa02707:41ca50e3
2025-05-22 16:01:24
@ dfa02707:41ca50e3
2025-05-22 16:01:24Contribute to keep No Bullshit Bitcoin news going.
Headlines
- OpenSats announces the eleventh wave of Nostr grants. The five projects in this wave are the mobile live-streaming app Swae, the Nostr-over-ham-radio project HAMSTR, Vertex—a Web-of-Trust (WOT) service for Nostr developers, Nostr Double Ratchet for end-to-end encrypted messaging, and the Nostr Game Engine for building games and applications integrated with the Nostr ecosystem.
- Project Eleven offers 1 BTC to break Bitcoin's cryptography with a quantum computer. The quantum computing research organization has introduced the Q-Day Prize, a global challenge that offers 1 BTC to the first team capable of breaking an elliptic curve cryptographic (ECC) key using Shor’s algorithm on a quantum computer. The prize will be awarded to the first team to successfully accomplish this breakthrough by April 5, 2026.
- Bull Bitcoin expands to Mexico, enabling anyone in the country to receive pesos from anywhere in the world straight from a Bitcoin wallet. Additionally, users can now buy Bitcoin with a Mexican bank account.
"Bull Bitcoin strongly believes in Bitcoin’s economic potential in Mexico, not only for international remittances and tourism, but also for Mexican individuals and companies to reclaim their financial sovereignty and protect their wealth from inflation and the fragility of traditional financial markets," said Francis Pouliot, Founder and CEO of Bull Bitcoin.
- Panama City votes to accept bitcoin for municipal services. The Panama City Council has voted to accept Bitcoin and other digital currencies for municipal services, becoming the first public institution in the country to do so. They will partner with an authorized bank responsible for converting the digital currency proceeds into dollars, reports Bitcoin Magazine.
- US Bitcoin miner manufacturer Auradine has raised $153 million in a Series C funding round as it expands into AI infrastructure. The round was led by StepStone Group and included participation from Maverick Silicon, Premji Invest, Samsung Catalyst Fund, Qualcomm Ventures, Mayfield, MARA Holdings, GSBackers, and other existing investors. The firm raised to over $300 million since its inception in 2022.
- Designathon 2025: The Bitcoin Design Community is organizing a Bitcoin design hackathon, scheduled to take place from May 4 to 18, 2025. Sign up and learn more about the event, prizes, and ideas.
Use the tools
- Core Lightning v25.02.1 and v24.11.2 address several issues, including returned outputs on mutual closes if peer didn't support
option_shutdown_anysegwit, properly handling duplicate HTLCs on closing, calculating fees with the correct HTLC timeout, occasional crash onbitcoind_getrawblockbyheightcallback, fixes tracepoint crashes in autoclean/chanbackup, and more. - LND v0.19.0-beta.rc2 is available for testing. New features include support for archiving channel backup, RBF cooperative closes, the Quiescence protocol, the
chainiosubsystem, lnwire messages for the Gossip 1.75 protocol, testnet4, and much more. - Hydrus v0.2.0, a Lightning liquidity management agent, is now available. This version adjusts routing policies, new CLI commands, built-in task scheduling, and a new open heuristic,
channels.block_height. - Alby Hub v1.16.0 introduces Alby Pro, a paid subscription plan for self-hosted Alby Hub runners that offers real-time backups, unlimited sub-wallets, customizable Lightning addresses, priority support, and more. The sidebar and settings page have received a UI update for a smoother experience, along with various other improvements and bug fixes.
- Alby Go v1.12.0 introduces a wallet switcher for swapping wallets during payments, withdrawals, and connections. It also improves number formatting for locales using decimal commas.
- Blitz Wallet v0.4.3-beta allows users to customize their maximum receive and balance amounts for ecash transactions. Besides, users can now pay for items in supported stores using ecash, and manual swap options have been expanded. The update also includes payment experience enhancements, performance optimizations, and bug fixes.
- Phoenix wallet v2.5.3 is a bug fix release that corrects UI problems on iOS and improves the handling of some Bolt12 failures.
- BitBanana v0.9.4 is a maintenance release that adds a link to new documentation, delivers bug fixes, and updated translations.
- BitBanana v0.9.3 was a notable release that introduced Nostr Wallet Connect (NWC) support, significantly enhanced the channel rebalancing interface, and added channel and UTXO sorting, among other features.
- Boltz Web App v1.7.3 has improved the UX for copying addresses and invoices, added fixes for hardware wallet integration, and backup files now include the rescue key, enabling backup imports to pick up pending swaps.
- Stratum v2 Reference Implementation (SRI) v1.3.0 comes with a new integration test framework and tests, enhanced APIs for role development, and core low-level crates now support
no_std. - ESP-Miner v2.6.6b1 is now available for testing.
- CTV Playground Android is a native Android implementation and demonstration of Bitcoin's proposed OP_CHECKTEMPLATEVERIFY (CTV) soft fork, including a CTV Vault implementation.
- Nstart, an onboarding wizard for new Nostr users, is now multilingual. Available languages include English, Español, Italiano, Français, Deutsch, and 日本語. You can contribute with a new language here.

Source: daniele
- GM Swap is a proof-of-concept implementation of the Atomic Signature Swaps NIP. It enables users to "swap GM notes, ensuring that both parties' signatures are exchanged simultaneously or not at all."
- Arti v1.4.2, a next-generation Tor client in Rust, is now available. Arti's RPC interface is now officially stable, and ready for testing.
- Tor Browser v14.5 has been released, introducing Connection Assist to Android, which helps mobile users facing strict censorship to easily unblock Tor with a single button press. Additionally, Belarusian, Bulgarian, and Portuguese languages are now available across all platforms, along with other improvements.
[
 ](https://njump.me/nevent1qqsqp3seup9kqz8xawavqd2jff6v627s63l4xwut9hjcphdnr5r3h5gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgdwaehxw309ahx7uewd3hkcqfpwaehxw309akh2mr5d9cxcetcv4ezu6r4wdax7mn9vaujuam0wfkxgq3qpzzrdngrnlufqazx3lfj07k0vfuya6ehfy8q5yv2h8c5e8fxgmxqd
](https://njump.me/nevent1qqsqp3seup9kqz8xawavqd2jff6v627s63l4xwut9hjcphdnr5r3h5gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgdwaehxw309ahx7uewd3hkcqfpwaehxw309akh2mr5d9cxcetcv4ezu6r4wdax7mn9vaujuam0wfkxgq3qpzzrdngrnlufqazx3lfj07k0vfuya6ehfy8q5yv2h8c5e8fxgmxqd -
 @ ece127e2:745bab9c
2025-05-20 18:59:11
@ ece127e2:745bab9c
2025-05-20 18:59:11vamos a ver que tal