-
 @ 90152b7f:04e57401
2025-05-23 23:38:49
@ 90152b7f:04e57401
2025-05-23 23:38:49WikiLeaks The Global Intelligence Files
Released on 2013-03-04 00:00 GMT
| Email-ID | 296467 | | -------- | -------------------------- | | Date | 2007-10-29 20:54:22 | | From | <hrwpress@hrw.org> | | To | <responses@stratfor.com> |
Gaza: Israel's Fuel and Power Cuts Violate Laws of War\ \ For Immediate Release\ \ Gaza: Israel's Fuel and Power Cuts Violate Laws of War\ \ Civilians Should Not Be Penalized for Rocket Attacks by Armed Groups\ \ (New York, October 29, 2007) - Israel's decision to limit fuel and\ electricity to the Gaza Strip in retaliation for unlawful rocket attacks\ by armed groups amounts to collective punishment against the civilian\ population of Gaza, in violation of international law, and will worsen the\ humanitarian crisis there, Human Rights Watch said today.\ \ "Israel may respond to rocket attacks by armed groups to protect its\ population, but only in lawful ways," said Sarah Leah Whitson, director of\ Human Rights Watch's Middle East division. "Because Israel remains an\ occupying power, in light of its continuing restrictions on Gaza, Israel\ must not take measures that harm the civilian population - yet that is\ precisely what cutting fuel or electricity for even short periods will\ do."\ \ On Sunday, the Israeli Defense Ministry ordered the reduction of fuel\ shipments from Israel to Gaza. A government spokesman said the plan was to\ cut the amount of fuel by 5 to 11 percent without affecting the supply of\ industrial fuel for Gaza's only power plant.\ \ According to Palestinian officials, fuel shipments into Gaza yesterday\ fell by more than 30 percent.\ \ In response to the government's decision, a group of 10 Palestinian and\ Israeli human rights groups petitioned the Israeli Supreme Court on\ Sunday, seeking an immediate injunction against the fuel and electricity\ cuts. The court gave the government five days to respond but did not issue\ a temporary injunction. On Monday, the groups requested an urgent hearing\ before the five days expire.\ \ Last Thursday, Defense Minister Ehud Barak approved cutting electricity to\ Gaza for increasing periods in response to ongoing rocket attacks against\ civilian areas in Israel, but the government has not yet implemented the\ order.\ \ The rockets fired by Palestinian armed groups violate the international\ legal prohibition on indiscriminate attacks because they are highly\ inaccurate and cannot be directed at a specific target. Because Hamas\ exercises power inside Gaza, it is responsible for stopping indiscriminate\ attacks even when carried out by other groups, Human Rights Watch said.\ \ On Friday, Israeli Prime Minister Ehud Olmert said that Israel would\ respond strongly to the ongoing attacks without allowing a humanitarian\ crisis. But the UN's top humanitarian official, UN Deputy\ Secretary-General John Holmes, said that a "serious humanitarian crisis"\ in Gaza already exists, and called on Israel to lift the economic blockade\ that it tightened after Hamas seized power in June.\ \ Israel's decision to cut fuel and electricity is the latest move aimed\ ostensibly against Hamas that is affecting the entire population of Gaza.\ In September, the Israeli cabinet declared Gaza "hostile territory" and\ voted to "restrict the passage of various goods to the Gaza Strip and\ reduce the supply of fuel and electricity." Since then, Israel has\ increasingly blocked supplies into Gaza, letting in limited amounts of\ essential foodstuffs, medicine and humanitarian supplies. According to\ Holmes, the number of humanitarian convoys entering Gaza had dropped to\ 1,500 in September from 3,000 in July.\ \ "Cutting fuel and electricity obstructs vital services," Whitson said.\ "Operating rooms, sewage pumps, and water well pumps all need electricity\ to run."\ \ Israel sells to Gaza roughly 60 percent of the electricity consumed by the\ territory's 1.5 million inhabitants. In June 2006, six Israeli missiles\ struck Gaza's only power plant; today, for most residents, electricity is\ available during only limited hours.\ \ Israeli officials said they would cut electricity for 15 minutes after\ each rocket attack and then for increasingly longer periods if the attacks\ persist. Deputy Defense Minister Matan Vilnai said Israel would\ "dramatically reduce" the power it supplied to Gaza over a period of\ weeks.\ \ Cutting fuel or electricity to the civilian population violates a basic\ principle of international humanitarian law, or the laws of war, which\ prohibit a government that has effective control over a territory from\ attacking or withholding objects that are essential to the survival of the\ civilian population. Such an act would also violate Israel's duty as an\ occupying power to safeguard the health and welfare of the population\ under occupation.\ \ Israel withdrew its military forces and settlers from the Gaza Strip in\ 2005. Nonetheless, Israel remains responsible for ensuring the well-being\ of Gaza's population for as long as, and to the extent that, it retains\ effective control over the area. Israel still exercises control over\ Gaza's airspace, sea space and land borders, as well as its electricity,\ water, sewage and telecommunications networks and population registry.\ Israel can and has also reentered Gaza for security operations at will.\ \ Israeli officials state that by declaring Gaza "hostile territory," it is\ no longer obliged under international law to supply utilities to the\ civilian population, but that is a misstatement of the law.\ \ "A mere declaration does not change the facts on the ground that impose on\ Israel the status and obligations of an occupying power," said Whitson.\ \ For more information, please contact:\ \ In New York, Fred Abrahams (English, German): +1-917-385-7333 (mobile)\ \ In Washington, DC, Joe Stork (English): +1-202-299-4925 (mobile)\ \ In Cairo, Gasser Abdel-Razek (Arabic, English): +20-2-2-794-5036 (mobile);\ or +20-10-502-9999 (mobile)
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 86611181:9fc27ad7
2025-05-23 20:31:44
@ 86611181:9fc27ad7
2025-05-23 20:31:44It's time to secure user data in your identity system This post was also published with the Industry Association of Privacy Professionals.
It seems like every day there is a new report of a major personal data breach. In just the past few months, Neiman Marcus, Ticketmaster, Evolve Bank, TeamViewer, Hubspot, and even the IRS have been affected.
The core issue is that user data is commonly spread across multiple systems that are increasingly difficult to fully secure, including database user tables, data warehouses and unstructured documents.
Most enterprises are already running an incredibly secure and hardened identity system to manage customer login and authorization, commonly referred to as a customer identity access management system. Since identity systems manage customer sign-up and sign-in, they typically contain customer names, email addresses, and phone numbers for multifactor authentication. Commercial CIAMs provide extensive logging, threat detection, availability and patch management.
Identity systems are highly secure and already store customers' personally identifiable information, so it stands to reason enterprises should consider identity systems to manage additional PII fields.
Identity systems are designed to store numerous PII fields and mask the fields for other systems. The Liberty Project developed the protocols that became Security Assertion Markup Language 2.0, the architecture at the core of CIAM systems, 20 years ago, when I was its chief technology officer. SAML 2.0 was built so identity data would be fully secure, and opaque tokens would be shared with other systems. Using tokens instead of actual user data is a core feature of identity software that can be used to fully secure user data across applications.
Most modern identity systems support adding additional customer fields, so it is easy to add new fields like Social Security numbers and physical addresses. Almost like a database, some identity systems even support additional tables and images.
A great feature of identity systems is that they often provide a full suite of user interface components for users to register, login and manage their profile fields. Moving fields like Social Security numbers from your database to your identity system means the identity system can fully manage the process of users entering, viewing and editing the field, and your existing application and database become descoped from managing sensitive data.
With sensitive fields fully isolated in an identity system and its user interface components, the identity system can provide for cumbersome and expensive compliance with standards such as the Health Insurance Portability and Accountability Act for medical data and the Payment Card Industry Data Security Standard for payment data, saving the time and effort to achieve similar compliance in your application.
There are, of course, applications that require sensitive data, such as customer service systems and data warehouses. Identity systems use a data distribution standard called System for Cross-domain Identity Management 2.0 to copy user data to other systems. The SCIM is a great standard to help manage compliance such as "right to be forgotten," because it can automatically delete customer data from other systems when a customer record is deleted from the identity system.
When copying customer data from an identity system to another application, consider anonymizing or masking fields. For example, anonymizing a birthdate into an age range when copying a customer record into a data warehouse can descope the data warehouse from containing personal information.
Most enterprises already run an Application Programming Interface Gateway to manage web services between systems. By combining an API Gateway with the identity system's APIs, it becomes very easy to automatically anonymize and mask customer data fields before they are copied into other systems.
A new set of companies including Baffle, Skyflow, and Piiano have introduced services that combine the governance and field management features of an identity system with extensive field masking. Since these systems do not offer the authentication and authorization features of an identity system, it's important to balance the additional features as they introduce an additional threat surface with PII storage and permissions.
PII sprawl is an increasing liability for companies. The most secure, compliant and flexible central data store to manage PII is the existing CIAM and API Gateway infrastructure that enterprises have already deployed.
Move that customer data into your identity system and lock it down. https://peter.layer3.press/articles/3c6912eb-404a-4630-9fe9-fd1bd23cfa64
-
 @ 86611181:9fc27ad7
2025-05-23 20:31:44
@ 86611181:9fc27ad7
2025-05-23 20:31:44With Nostr, Jack is well ahead of what Elon and Zuck have learned about censorship
Mark Zuckerberg’s announcement that he is dropping censorship in the U.S. for Facebook and Instagram was accompanied by a comment that he is going to work with the U.S. government to encourage other countries to not censor content. Upon acquiring Twitter, Elon Musk dropped censorship and soon learned that government mandates from across the world censor content.
In 2024, Brazil blocked Twitter until it complied with censorship demands, France arrested Telegram’s CEO Pavel Durov, the EU censored additional Russian outlets and wrote letters to Twitter mandating more content moderation, and Australia announced it will fine platforms for misinformation.
The current U.S. administration had a heavy censorship hand and had threatened to revoke Section 230 which protects Internet sites from liability about their users’ content. Zuck indicated in his announcement and a letter to Congress in November that Meta felt coerced to comply. Twitter under Jack Dorsey was also coerced to censor, as disclosed in the Twitter Files and Alex Berenson’s amended censorship lawsuit with new insider materials from Twitter.
Western governments did not typically engage in government guidance or mandates on content until after the Brexit and Trump elections in 2016 followed by the Russia-Ukraine war in 2022. Once Western governments realized that they had lost narrative control, they started playing catch up with China, which was well aware from the start of the power of social networks to both disrupt and control narratives.
Due to the secretive nature of government guidance and mandates, Elon and those outside social media organizations had only witnessed basic content moderation. Jack and Zuck had already experienced years of coercive government guidance threatening Section 230 revocation as well as numerous explicit censorship mandates from Western governments.
Zuck’s response was to downrank and de-emphasize political content in early 2021 after the bruising 2020 U.S. election cycle. This was a difficult decision since Facebook made a lot of money from political arguments, as I pointed out in a 2019 article for VentureBeat. Zuck sidestepped government pressure and continued to grow his properties. Correspondingly, despite the volumes of racist and homophobic content on Instagram, there is not much pressure for content moderation from groups like Media Matters and GARM that have targeted X/Twitter.
Jack’s response was to fund Bluesky to shift Twitter to an open protocol like email’s SMTP and the web’s HTTP. Governments can of course censor at the protocol level with firewalls like they currently do for email and web, but by separating the application and protocol layers, Jack recognized that social networks could operate like any other Internet infrastructure that is content neutral. Jack departed Bluesky when the company started massively moderating accounts and content. Jack then discovered Nostr (Notes and Other Stuff Transmitted by Relays), a decentralized messaging protocol initially created by an anonymous developer FiatJeff, much like an anonymous developer Satoshi Nakamoto created Bitcoin.
Nostr is reminiscent of FidoNet, a popular store-and-forward messaging protocol for Bulletin Board Systems (BBS) in the 1980s. Each BBS was fully independent, and each could choose which forum messages to store-and-forward, whether to moderate content, and how long to keep the messages. In addition, FidoNet could store-and-forward private messages between users. UseNet also operated in a similar store-and-forward manner for Internet forums, but did not operate private messages since the Internet already had SMTP.
Nostr developers offer an active ecosystem of both clients and servers offering an interface familiar to social network users, as well as micro apps offering new functionality on top of the protocol. Nostr is decentralized with no central control point and transmits messages across independently operated relays. Just like with current email systems and Nostr predecessors FidoNet and UseNet the independence of the relays create inefficiency. Different users may not see each others’ replies chronologically until the messages transmission has caught up, and not all relays transmit all messages. FidoNet and UseNet were inefficient due to resource constraints such as long distance charges and intermittent connectivity. Nostr and Bitcoin use inefficiency to engineer resilience into the protocol.
A Nostr account can never be “revoked,” however relays are not obligated to carry an account’s messages. Users can easily switch relays or even operate their own. As part of the new generation of decentralized crypto software, Nostr uses a public/private key combination for identity, and you can optionally publish your profile name, e-mail address, and lightning wallet associated with the key. Nostr clients sign messages with your private key when you post, and users know it’s you by your public key. A note of caution: just like with crypto, if your private key gets compromised or lost, it’s like losing or having your Bitcoin private key stolen.
A new administration could easily coerce social media companies. This time, Elon stood in the face of a government onslaught. Zuck followed when the coast was clear. Jack has laid the foundation for the future. https://peter.layer3.press/articles/553ac57f-bb19-4b50-8644-d38d74d1e1e6
-
 @ 21335073:a244b1ad
2025-05-21 16:58:36
@ 21335073:a244b1ad
2025-05-21 16:58:36The other day, I had the privilege of sitting down with one of my favorite living artists. Our conversation was so captivating that I felt compelled to share it. I’m leaving his name out for privacy.
Since our last meeting, I’d watched a documentary about his life, one he’d helped create. I told him how much I admired his openness in it. There’s something strange about knowing intimate details of someone’s life when they know so little about yours—it’s almost like I knew him too well for the kind of relationship we have.
He paused, then said quietly, with a shy grin, that watching the documentary made him realize how “odd and eccentric” he is. I laughed and told him he’s probably the sanest person I know. Because he’s lived fully, chasing love, passion, and purpose with hardly any regrets. He’s truly lived.
Today, I turn 44, and I’ll admit I’m a bit eccentric myself. I think I came into the world this way. I’ve made mistakes along the way, but I carry few regrets. Every misstep taught me something. And as I age, I’m not interested in blending in with the world—I’ll probably just lean further into my own brand of “weird.” I want to live life to the brim. The older I get, the more I see that the “normal” folks often seem less grounded than the eccentric artists who dare to live boldly. Life’s too short to just exist, actually live.
I’m not saying to be strange just for the sake of it. But I’ve seen what the crowd celebrates, and I’m not impressed. Forge your own path, even if it feels lonely or unpopular at times.
It’s easy to scroll through the news and feel discouraged. But actually, this is one of the most incredible times to be alive! I wake up every day grateful to be here, now. The future is bursting with possibility—I can feel it.
So, to my fellow weirdos on nostr: stay bold. Keep dreaming, keep pushing, no matter what’s trending. Stay wild enough to believe in a free internet for all. Freedom is radical—hold it tight. Live with the soul of an artist and the grit of a fighter. Thanks for inspiring me and so many others to keep hoping. Thank you all for making the last year of my life so special.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 611021ea:089a7d0f
2025-05-24 00:00:04
@ 611021ea:089a7d0f
2025-05-24 00:00:04The world of health and fitness data is booming. Users are tracking more aspects of their well-being than ever before, from daily steps and workout intensity to sleep patterns and caloric intake. But for developers looking to build innovative applications on this data, significant hurdles remain: ensuring user privacy, achieving interoperability between different services, and simply managing the complexity of diverse health metrics.
Enter the NIP-101h Health Profile Framework and its companion tools: the HealthNote SDK and the HealthNote API. This ecosystem is designed to empower developers to create next-generation health and fitness applications that are both powerful and privacy-preserving, built on the decentralized and user-centric principles of Nostr.
NIP-101h: A Standardized Language for Health Metrics
At the core of this ecosystem is NIP-101h. It's a Nostr Improvement Proposal that defines a standardized way to represent, store, and share granular health and fitness data. Instead of proprietary data silos, NIP-101h introduces specific Nostr event kinds for individual metrics like weight (kind
1351), height (kind1352), step count (kind1359), and many more.Key features of NIP-101h:
- Granularity: Each piece of health information (e.g., weight, caloric intake) is a distinct Nostr event, allowing for fine-grained control and access.
- User Control: Built on Nostr, the data remains under user control. Users decide what to share, with whom, and on which relays.
- Standardization: Defines common structures for units, timestamps, and metadata, promoting interoperability.
- Extensibility: New metrics can be added as new NIP-101h.X specifications, allowing the framework to evolve.
- Privacy by Design: Encourages the use of NIP-04/NIP-44 for encryption and includes a
consenttag for users to specify data-sharing preferences.
You can explore the full NIP-101h specification and its metric directory in the main project repository.
The HealthNote SDK: Simplifying Client-Side Integration
While NIP-101h provides the "what," the HealthNote SDK provides the "how" for client-side applications. This (currently draft) TypeScript SDK aims to make it trivial for developers to:
- Create & Validate NIP-101h Events: Easily construct well-formed Nostr events for any supported health metric, ensuring they conform to the NIP-101h specification.
- Handle Encryption: Seamlessly integrate with NIP-44 to encrypt sensitive health data before publication.
- Manage Consent: Automatically include appropriate
consenttags (e.g., defaulting toaggregate-only) to respect user preferences. - Publish to Relays: Interact with Nostr relays to publish the user's health data.
- Prepare Data for Analytics: Extract minimal, privacy-preserving "stat-blobs" for use with the HealthNote API.
The SDK's goal is to abstract away the low-level details of Nostr event creation and NIP-101h formatting, letting developers focus on their application's unique features.
The HealthNote API: Powerful Insights, Zero Raw Data Exposure
This is where things get really exciting for developers wanting to build data-driven features. The HealthNote API (detailed in
HealthNote-API.md) is a server-side component designed to provide powerful analytics over aggregated NIP-101h data without ever accessing or exposing individual users' raw, unencrypted metrics.Here's how it achieves this:
- Privacy-Preserving Ingestion: The SDK sends only "stat-blobs" to the API. These blobs contain the numeric value, unit, timestamp, and metric kind, but not the original encrypted content or sensitive user identifiers beyond what's necessary for aggregation.
- Aggregation at its Core: The API's endpoints are designed to return only aggregated data.
GET /trend: Provides time-series data (e.g., average daily step count over the last month).GET /correlate: Computes statistical correlations between two metrics (e.g., does increased activity duration correlate with changes in workout intensity?).GET /distribution: Shows how values for a metric are distributed across the user base.
- Built-in Privacy Techniques:
- k-Anonymity: Ensures that each data point in an aggregated response represents at least 'k' (e.g., 5) distinct users, preventing re-identification.
- Differential Privacy (Optional): Can add statistical noise to query results, further protecting individual data points while preserving overall trends.
- No Raw Data Access for Developers: Developers querying the API receive only these aggregated, anonymized results, perfect for powering charts, dashboards, and trend analysis in their applications.
A Typical Workflow
- A user records a workout in their NIP-101h-compatible fitness app.
- The app uses the HealthNote SDK to create NIP-101h events for metrics like distance, duration, and calories burned. Sensitive data is encrypted.
- The SDK publishes these events to the user's configured Nostr relays.
- The SDK also extracts stat-blobs (e.g.,
{ kind: 1363, value: 5, unit: 'km', ... }) and sends them to the HealthNote API for ingestion, tagged with anaggregate-onlyconsent. - Later, the app (or an authorized third-party service) queries the HealthNote API:
GET /trend?kind=1363&bucket=week&stat=sum. - The API returns a JSON object like:
{"series": [{"date": "2024-W20", "value": 15000}, ...]}showing the total distance run by all consenting users, week by week. This data can directly populate a trend chart.
Benefits for the Ecosystem
- For Users:
- Greater control and ownership of their health data.
- Ability to use a diverse range of interoperable health and fitness apps.
- Confidence that their data can contribute to insights without sacrificing personal privacy.
- For Developers:
- Easier to build sophisticated health and fitness applications without becoming privacy experts or building complex data aggregation pipelines.
- Access to rich, aggregated data for creating compelling user-facing features (trends, benchmarks, correlations).
- Reduced burden of storing and securing sensitive raw health data for analytical purposes.
- Opportunity to participate in an open, interoperable ecosystem.
The Road Ahead
The NIP-101h framework, the HealthNote SDK, and the HealthNote API are foundational pieces for a new generation of health and fitness applications. As these tools mature and gain adoption, we envision a vibrant ecosystem where users can seamlessly move their data between services, and developers can innovate rapidly, all while upholding the highest standards of privacy and user control.
We encourage developers to explore the NIP-101h specifications, experiment with the (upcoming) SDK, and review the HealthNote API design. Your feedback and contributions will be invaluable as we build this privacy-first future for health data.
https://github.com/HealthNoteLabs
-
 @ b83a28b7:35919450
2025-05-16 19:23:58
@ b83a28b7:35919450
2025-05-16 19:23:58This article was originally part of the sermon of Plebchain Radio Episode 110 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ 34f1ddab:2ca0cf7c
2025-05-23 23:15:14
@ 34f1ddab:2ca0cf7c
2025-05-23 23:15:14Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ b0a838f2:34ed3f19
2025-05-23 18:04:16
@ b0a838f2:34ed3f19
2025-05-23 18:04:16- bin - A paste bin that's actually minimalist.
WTFPL/0BSDRust - BinPastes - Minimal pastebin supporting client-side encryption, fulltext search, one-time messages. Intended for one to few users looking for a simple pastebin deployment. (Demo)
Apache-2.0Java - ByteStash - Pastebin and file storage service with a simple web interface. Supports syntax highlighting, optional user authentication and public sharing. (Demo)
GPL-3.0Docker - dpaste - Simple pastebin with multiple text and code option, with short url result easy to remember. (Source Code)
MITDocker/Django - FlashPaper - One-time encrypted zero-knowledge password/secret sharing application focused on simplicity and security. No database or complicated set-up required. (Demo)
MITDocker/PHP - Hemmelig - Share encrypted secrets cross organizations, or as private persons. (Source Code)
MITDocker/Nodejs - lesma - Simple paste app friendly with browser and command line. (Demo, Source Code)
GPL-3.0Rust/Docker - Local Content Share - Store and share text snippets and files within your local network.
MITDocker/Go - not-th.re - Simple paste sharing platform, with client side encryption, featuring the monaco browser-based code editor. (Demo, Source Code)
AGPL-3.0Nodejs/Docker - Opengist - Pastebin powered by Git. (Demo)
AGPL-3.0Docker/Go/Nodejs - paaster - End-to-end encrypted pastebin built with the objective of simplicity. (Source Code)
AGPL-3.0Docker - pacebin - Super-minimal pastebin and file upload service focusing on small executable size, portability, and ease of configuration. (Demo, Source Code)
AGPL-3.0C - Password Pusher - Dead-simple application to securely communicate passwords (or text) over the web. Passwords automatically expire after a certain number of views and/or time has passed. (Source Code)
Apache-2.0Docker/K8S/Ruby - Pastefy - Beautiful, simple and easy to deploy Pastebin with optional client encryption, multitab pastes, an API, a highlighted editor and more. (Source Code, Clients)
MITDocker/K8S/Java - PrivateBin - Minimalist pastebin/discussion board where the server has zero knowledge of hosted data. (Demo, Source Code)
ZlibPHP - rustypaste - A minimal file upload/pastebin service.
MITRust - SnyPy - Open source on-prem code snippet manager. (Demo, Source Code)
MITDocker - Spacebin - Modern Pastebin server written in Go with a JS-free web UI and tons of features. (Demo, Source Code)
Apache-2.0Go/Docker - Sup3rS3cretMes5age - Very simple (to deploy and to use) secret message service using Hashicorp Vault as a secrets storage.
MITGo - Wastebin - Lightweight, minimal and fast pastebin with an SQLite backend. (Demo)
MITRust/Docker - YABin - A pastebin that contains plentiful features while remaining simple. Supports optional E2E encryption, a client-side CLI app, syntax highlighting, minimalistic UI, APIs, keyboard shortcuts, and more. It can even be run in serverless environments. (Demo)
MITNodejs/Docker - ybFeed - Personal micro feed where you can post snippets of text or images.
MITGo/Nodejs/Docker - Yopass - Secure sharing of secrets, passwords and files. (Demo)
Apache-2.0Go/Docker
- bin - A paste bin that's actually minimalist.
-
 @ 6c05c73e:c4356f17
2025-05-23 22:59:35
@ 6c05c73e:c4356f17
2025-05-23 22:59:35Como a grande maioria dos brasileiros. Eu não comecei um negócio porque “queria empreender”. Diferente disso, eu PRECISAVA para poder pagar contas e manter o básico.
Festas, openbar e camisas
Meu primeiro negócio foi na verdade um combo. Eu tinha saído do último trampo e eu gostava de festas. Então, comecei a organizar uma festa mensalmente na casa do meu pai. Eu pagava a água, energia e dava uma grana para ele. Em troca, organizava festa de sábado para domingo open bar.
A fórmula era simples. Criava o evento da festa no facebook, convidava todo mundo que conhecia. Panfletava na cidade e espalhava cartazes nos pontos de ônibus sobre a festa. E, para fechar com chave de ouro. Mulher era OFF até 20:00. Consequência? Os caras vinham e pagavam o ingresso deles e delas. Kkkkk. E, enchia…
Comecei a notar que a galera se vestia mal. E, pensei: "Porque não vestir eles?” Pimba! Comecei a desenha e confeccionar camisas para vender nas festas. E, pimba denovo! Vendeu, tudo! Fiz 2 coleções e mais algumas festas. Até o dia que um menino deu PT de tanto beber e decidi que era hora de tentar outra coisa.
Como assim a Apple não vai vender mais os carregadores?
Isso, foi durante a pandemia. A Apple decidiu vender o telefone e o cabo. E, você que lute com a fonte. Estava difícil achar dinheiro no mercado naqueles tempos e eu pensei. Vou pesquisar no google trends e validar a ideia. Caixa! Tinha mais de 80 pts de busca. Colei em SP, no Brás e comprei literalmente. Todo meu dinheiro de cabo de iphone, carregador e bateria portátil.
Fiquei com R$100 na conta. Para fazer um lanche e pagar pelo uber para voltar para casa. Chegando aqui, eu tirei foto e fiz várias copys. Anunciei no Olx, Mercado Livre e Facebook. Impulsionei os anúncios no OLX, vendi para familiares e amigos, e; vendia até para quem estava na rua. Fiz entrega de bike, a pé, de ônibus e é isso mesmo. Tem que ralar. Para queimar o resto da mercadoria. Deixei com uma loja de eletrônicos e fiz consignado. E, hora da próxima ideia.
Mulheres, doces e TPM
Meu penúltimo negócio veio depois dos cabos. Eu pesquisei na net, negócios online para começar com pouca grana. (Depois que paguei as contas do dia a dia, sobraram R$3mil). E, achei uma pesquisa mostrando que doces. Tinha baixa barreira de entrada e exigia poucos equipamentos. Eu trabalhei em restaurante por muitos anos e sabia como lucrar com aquilo. Além do mais, mulheres consomem mais doce em uma certa época do mês.
Não deu outra, convidei 2 pessoas para serem sócias. Desenvolvemos os produtos, fotografamos e fizemos as copys. Em sequência, precisávamos vender. Então, lá vamos denovo: Ifood, WPP, 99food (na época), Uber eats (na época), Elo7, famílias e amigos e; por fim começamos a vender consignado com alguns restaurantes e lojas. Foi uma época em que aprendi a prospectar clientes de todas as maneiras possíveis.
De novo, minha maior dificuldade era a locomoção para fazer entregas. Só tinha uma bike. Mas, entregávamos. Os primeiros 3 meses foram difíceis demais. Mas, rolou. No fim, nossas maiores vendas vinham de: Ifood, encomendas de festas e consignados. Mas, como nem tudo são flores. Meus dois sócios tomaram outros caminhos e abandonaram o projeto. Galera, está tudo bem com isso. Isso acontece o tempo todo. A vida muda e temos que aprender a aceitar isso. Vida que segue e fui para frente de novo.
Sobre paixões, paciência e acreditar
Estava eu comemorando meu níver de 30 anos, num misto de realizações e pouco realizado. Como assim? Sabe quando você faz um monte de coisas, mas ainda assim. Não sente que é aquilo? Pois então…
Eu amo investimentos, livros, escrever e sempre curti trocar ideia com amigos e família sobre como se desenvolver. Desde que comecei a usar a internet eu criei: Canal no youtube, páginas no IG e FB, pinterest, steemit, blog e até canal no Telegram. Mas, nunca tinha consistente sabe? Tipo assim, vou fazer isso por um ano e plantar 100 sementes aqui. Enfim, inconsistência te derruba meu amigo…Eu voltei a trabalhar com restaurantes e estava doido para mudar de área. Estava exausto de trabalhar e meu wpp não parava de tocar. Fui estudar ADM e Desenvolvimento de sistemas no Senac. Dois anos depois, formei. Consegui trabalho.
E, comecei a pensar em como criar um negócio online, escalável e multilíngue. Passei os próximos 7 meses desenhando e pensando como. Mas, tinha que dar o primeiro passo. Criei um site e fui escrevendo textos. Os primeiros 30 foram aquilo, os próximos 10 melhoraram muito e os 10 a seguir eu fiquei bem satisfeitos. Hoje, tenho o negócio que estava na cabeça desde 2023. Mas, olha o tamanho da volta que o universo me fez dar e aprender para chegar aqui hoje. Dicas? Só 3:
- Você precisa usar a internet para fazer negócio. Em todos os negócios que falei, sempre teve algo online. Não negligencie isso.
- Tem que aprender a vender e se vender.
- Confia em si mesmo e faz sem medo de errar. Porque, advinha? Você vai errar! Mas, vai aprender e melhorar. Tem que persistir…
Por hoje é isso. Tamo junto!
-
 @ b0a838f2:34ed3f19
2025-05-23 17:55:13
@ b0a838f2:34ed3f19
2025-05-23 17:55:13- Evergreen - Highly-scalable software for libraries that helps library patrons find library materials, and helps libraries manage, catalog, and circulate those materials. (Source Code)
GPL-2.0PLpgSQL - Koha - Enterprise-class ILS with modules for acquisitions, circulation, cataloging, label printing, offline circulation for when Internet access is not available, and much more. (Demo, Source Code)
GPL-3.0Perl - RERO ILS - Large-scale ILS that can be run as a service with consortial features, intended primarily for library networks. Includes most standard modules (circulation, acquisitions, cataloging,...) and a web-based public and professional interface. (Demo, Source Code)
AGPL-3.0Python/Docker
- Evergreen - Highly-scalable software for libraries that helps library patrons find library materials, and helps libraries manage, catalog, and circulate those materials. (Source Code)
-
 @ 9bcc5462:eb501d90
2025-04-04 16:02:14
@ 9bcc5462:eb501d90
2025-04-04 16:02:14The story you are about to read is one hundred percent true. It is also my first encounter with a supernatural force.
It was the summer of 2003 and I was visiting my auntie in Nashville as a 16-year-old, pimply-faced teenager. My younger cousins, Alex, Mikey, and Tony were also there. One afternoon, they were all sitting bored outside in the blazing heat, sheltered under the tree on the front lawn. It was a comical sight really, all of them sprawled out lifeless and silent, eaten alive by the unforgiving mosquitos. I ducked inside and asked my aunt if it was okay to borrow her RAV4 to take them to play basketball nearby at Pitts Park. Despite not having a license she handed me the keys and when I went outside to tell the boys we were going to shoot hoops, you’d have thought I said I was taking them to Disney World!
Off we went up and down the rollercoaster-like hills of Tennessee. Yes, I was speeding, and no, we were not wearing seatbelts. (Remember, sixteen, acne, angst, etc.) We arrived at the park and immediately I felt an eerie sensation. I had been there before with my other cousin Kim, but this time was undeniably different. It didn’t matter that the sun was shining above the bright blue sky, I sensed a darkness lingering. And it had nothing to do with the sticky Southern humidity. It was an overwhelming, odd, ineffable sensation. My eyes couldn’t help but focus on the trees behind the court. As if someone or something was watching us.
Nevertheless, after shooting for teams, we began a 2-on-2 immediately. When Mikey and I won, (I towered over them and Mikey was surprisingly pretty good) Tony wasn’t too happy about losing. In frustration, he bounced the basketball with both hands as hard as he could. The ball ended up on the other side of the fences surrounding the court and rolled into the bordering woods. None of the little squirts wanted to retrieve the ball, so as the big cuz I volunteered myself. Nothing to it right? Wrong!
As I walked towards the woods I couldn’t even locate the basketball. I stopped and scanned until I finally saw it, way deep among the trees. “How did it get all the way over there?” I mumbled beneath my breath. Then, while approaching the ball I heard a loud and distinct voice—“Hey!”—I turned around suddenly, but nothing was there. At first I wasn’t afraid, rather I was genuinely confused. It just made no damn sense, there was no one around. I swiveled my head in every direction and once again the deep, gravelly voice called out, “Hey!” This time I knew where it was coming from and crept towards the source until I spotted something in the bushes. I crouched and pushed some branches aside. And that’s when I noticed it. Buried under the shrubs was a tombstone! It stared back at me, weathered, cracked, moss-eaten. I picked my ass up, ran to the ball, scooped it and bolted back to the court.
Little Alex asked if we were going to play a rematch; I said, “Hell no”. After herding them back to the car, we left and never looked back. To this day I remember the voice. I recall the inexplicable feeling of the unknown energy, force, or spirit that was with us. I only recently shared this story with him and now, at 27, he asked why I didn’t tell him sooner. I thought hard about it and answered, “I guess I didn’t want you to get scared and piss yourself.”
-
 @ bf47c19e:c3d2573b
2025-05-23 22:14:37
@ bf47c19e:c3d2573b
2025-05-23 22:14:37Originalni tekst na antenam.net
22.05.2025 / Autor: Ana Nives Radović
Da nema besplatnog ručka sigurno ste čuli svaki put kad bi neko poželio da naglasi da se sve na neki način plaća, iako možda tu cijenu ne primjećujemo odmah. Međutim, kada govorimo o događaju od kojeg je prošlo tačno 15 godina onda o „ručku“ ne govorimo u prenešenom smislu, već o porudžbini pice čija tržišna vrijednost iz godine u godinu dostiže iznos koji je čini najskupljom hranom koja je ikad poručena.
Tog 22. maja 2010. godine čovjek sa Floride pod imenom Laslo Hanjec potrošio je 10.000 bitcoina na dvije velike pice. U to vrijeme, ta količina bitcoina imala je tržišnu vrijednost od oko 41 dolar. Ako uzmemo u obzir da je vrijednost jedne jedinice ove digitalne valute danas nešto više od 111.000 dolara, tih 10.000 bitcoina danas bi značilo vrijednost od 1,11 milijardi dolara.
Nesvakidašnji događaj u digitalnoj i ugostiteljskoj istoriji, nastao zbog znatiželje poručioca koji je želio da se uvjeri da koristeći bitcoin može da plati nešto u stvarnom svijetu, pretvorio se u Bitcoin Pizza Day, kao podsjetnik na trenutak koji je označio prelaz bitcoina iz apstraktnog kriptografskog eksperimenta u nešto što ima stvarnu vrijednost.
Hanjec je bio znatiželjan i pitao se da li se prva, a u to vrijeme i jedina kriptovaluta može iskoristiti za kupovinu nečeg opipljivog. Objavio je ponudu na jednom forumu koja je glasila: 10.000 BTC za dvije pice. Jedan entuzijasta se javio, naručio pice iz restorana Papa John’s i ispisao zanimljivu stranicu istorije digitalne imovine.
Taj inicijalni zabilježeni finansijski dogovor dao je bitcoinu prvu široko prihvaćenu tržišnu vrijednost: 10.000 BTC za 41 dolar, čime je bitcoin napravio svoj prvi korak ka onome što danas mnogi zovu digitalnim zlatom.
Šta je zapravo bitcoin?
Bitcoin je oblik digitalnog novca koji je osmišljen da bude decentralizovan, transparentan i otporan na uticaj centralnih banaka. Kreirao ga je 2009. godine anonimni autor poznat kao Satoši Nakamoto, neposredno nakon globalne finansijske krize 2008. godine. U svojoj suštini, bitcoin je protokol, skup pravila koja sprovodi kompjuterski kod, koji omogućava korisnicima da bez posrednika sigurno razmjenjuju vrijednost putem interneta.
Osnova cijelog sistema je blockchain, distribuisana digitalna knjiga koju održavaju hiljade nezavisnih računara (tzv. čvorova) širom svijeta. Svaka transakcija se bilježi u novi „blok“, koji se potom dodaje u lanac (otud naziv „lanac blokova“, odnosno blockchain). Informacija koja se jednom upiše u blok ne može da se izbriše, niti promijeni, što omogućava više transparentnosti i više povjerenja.
Da bi blockchain mreža u kojoj se sve to odvija zadržala to svojstvo, bitcoin koristi mehanizam konsenzusa nazvan dokaz rada (proof-of-work), što znači da specijalizovani računari koji „rudare“ bitcoin rješavaju kompleksne matematičke probleme kako bi omogućili obavljanje transakcija i pouzdanost mreže.
Deflatorna priroda bitcoina
Najjednostavniji način da se razumije deflatorna priroda bitcoina je da pogledamo cijene izražene u valuti kojoj plaćamo. Sigurno ste u posljednje vrijeme uhvatili sebe da komentarišete da ono što je prije nekoliko godina koštalo 10 eura danas košta 15 ili više. Budući da to ne zapažate kada je u pitanju cijena samo određenog proizvoda ili usluge, već kao sveprisutan trend, shvatate da se radi o tome da je novac izgubio vrijednost. Na primjer, kada je riječ o euru, otkako je Evropska centralna banka počela intenzivno da doštampava novac svake godine, pa je od 2009. kada je program tzv. „kvantitativnog popuštanja“ započet euro zabilježio kumulativnu inflaciju od 42,09% zbog povećane količine sredstava u opticaju.
Međutim, kada je riječ o bitcoinu, njega nikada neće biti više od 21 milion koliko je izdato prvog dana, a to nepromjenjivo pravilo zapisano je i u njegovom kodu. Ova ograničena ponuda oštro se suprotstavlja principima koji važe kod monetarnih institucija, poput centralnih banaka, koje doštampavaju novac, često da bi povećale količinu u opticaju i tako podstakle finansijske tokove, iako novac zbog toga gubi vrijednost. Nasuprot tome, bitcoin se zadržava na iznosu od 21 milion, pa je upravo ta konačnost osnova za njegovu deflatornu prirodu i mogućnost da vremenom dobija na vrijednosti.
Naravno, ovo ne znači da je cijena bitcoina predodređena da samo raste. Ona je zapravo prilično volatilna i oscilacije su česte, posebno ukoliko, na primjer, posmatramo odnos cijena unutar jedne godine ili nekoliko mjeseci, međutim, gledano sa vremenske distance od četiri do pet godina bilo koji uporedni period od nastanka bitcoina do danas upućuje na to da je cijena u međuvremenu porasla. Taj trend će se nastaviti, tako da, kao ni kada je riječ o drugim sredstvima, poput zlata ili nafte, nema mjesta konstatacijama da je „vrijeme niskih cijena prošlo“.
Šta zapravo znači ovaj dan?
Bitcoin Pizza Day je za mnoge prilika da saznaju ponešto novo o bitcoinu, jer tada imaju priliku da o njemu čuju detalje sa raznih strana, jer kako se ovaj događaj popularizuje stvaraju se i nove prilike za učenje. Takođe, ovaj dan od 2021. obilježavaju picerije širom svijeta, u više od 400 gradova iz najmanje 75 zemalja, jer je za mnoge ovo prilika da korisnike bitcoina navedu da potroše djelić svoje imovine na nešto iz njihove ponude. Naravno, taj iznos je danasd zanemarljivo mali, a cijena jedne pice danas je otprilike 0,00021 bitcoina.
No, dok picerije širom svijeta danas na zabavan način pokušavaju da dođu do novih gostiju, ovaj dan je za mnoge vlasnike bitcoina nešto poput opomene da svoje digitalne novčiće ipak ne treba trošiti na nešto potrošno, jer je budućnost nepredvidiva. Bitcoin Pizza Day je dan kada se ideja pretvorila u valutu, kada su linije koda postale sredstvo razmjene.
Prvi let avionom trajao je svega 12 sekundi, a u poređenju sa današnjim transkontinentalnim linijama to djeluje gotovo neuporedivo i čudno, međutim, od nečega je moralo početi. Porudžbina pice plaćene bitcoinom označile su početak razmjene ove vrste, dok se, na primjer, tokom jučerašnjeg dana obim plaćanja bitcoinom premašio 23 milijarde dolara. Nauka i tehnologija nas podsjećaju na to da sve počinje malim, zanemarivim koracima.
-
 @ bf47c19e:c3d2573b
2025-05-23 21:54:43
@ bf47c19e:c3d2573b
2025-05-23 21:54:43Srpski prevod knjige "The Little Bitcoin Book"
Zašto je Bitkoin bitan za vašu slobodu, finansije i budućnost?
Verovatno ste čuli za Bitkoin u vestima ili da o njemu raspravljaju vaši prijatelji ili kolege. Kako to da se cena stalno menja? Da li je Bitkoin dobra investicija? Kako to uopšte ima vrednost? Zašto ljudi stalno govore o tome kao da će promeniti svet?
"Mala knjiga o Bitkoinu" govori o tome šta nije u redu sa današnjim novcem i zašto je Bitkoin izmišljen da obezbedi alternativu trenutnom sistemu. Jednostavnim rečima opisuje šta je Bitkoin, kako funkcioniše, zašto je vredan i kako utiče na individualnu slobodu i mogućnosti ljudi svuda - od Nigerije preko Filipina do Venecuele do Sjedinjenih Država. Ova knjiga takođe uključuje odeljak "Pitanja i odgovori" sa nekim od najčešće postavljanih pitanja o Bitkoinu.
Ako želite da saznate više o ovom novom obliku novca koji i dalje izaziva interesovanje i usvajanje širom sveta, onda je ova knjiga za vas.
-
 @ da8b7de1:c0164aee
2025-05-23 16:08:53
@ da8b7de1:c0164aee
2025-05-23 16:08:53Amerikai Nukleáris Fordulat és Pénzügyi hatások
Donald Trump elnök bejelentette, hogy végrehajtási rendeleteket ír alá a nukleáris energia fellendítésére . Ezek célja az új reaktorok engedélyezési folyamatának egyszerűsítése, az üzemanyag-ellátási láncok megerősítése, valamint a hazai ipar támogatása az orosz és kínai nyersanyagfüggőség csökkentése érdekében. A hír hatására az amerikai és globális nukleáris részvények jelentős emelkedést mutattak: az Uránium Energy 11%, a Centrus Energy 19,6%, az Oklo 16%, a Nano Nuclear 15%, a Nu Power 14,1%, a Global X Uranium ETF pedig 9%-kal erősödött . A növekvő energiaigény, különösen a mesterséges intelligencia által hajtott adatközpontok miatt, tovább növeli a nukleáris energia stratégiai szerepét az USA-ban .
Európai és Nemzetközi Nukleáris Fejlemények
Svédország parlamentje elfogadta az új állami támogatási keretrendszert, amely akár 5 000 MW új nukleáris kapacitás beruházását ösztönzi . Az intézkedés célja az áramárak stabilizálása, az ellátásbiztonság növelése és a zöld átmenet támogatása. A program keveri az állami hiteleket és a piaci árgaranciákat (CfD), a projektek finanszírozásában pedig a magántőke is részt vesz. A törvény 2025. augusztus 1-jén lép hatályba, a végrehajtás azonban még EU-jóváhagyásra vár .
Nukleáris Ellátási Lánc és Iparági Konferencia
Május 20–21-én Varsóban rendezték meg az első World Nuclear Supply Chain Conference-t, amelynek célja a globális nukleáris ellátási lánc megerősítése és bővítése . A konferencián elhangzottak szerint az iparág előtt álló kihívás a kapacitás gyors növelése, hiszen a cél a globális nukleáris kapacitás megháromszorozása 2050-ig. A World Nuclear Association legfrissebb elemzése szerint a következő 15 évben akár 2 billió dollár értékű beruházási lehetőség nyílhat a nemzetközi ellátási láncban . A rendezvényen kiemelték az innováció, a lokalizáció és az iparági együttműködés fontosságát, valamint a szállítási és geopolitikai kihívásokat is.
Új Projektek, Technológiai és Piaci Hírek
Az Egyesült Államokban a Tennessee Valley Authority (TVA) benyújtotta az első hivatalos engedélykérelmet egy BWRX-300 típusú kis moduláris reaktor (SMR) építésére a Clinch River telephelyen . Indiában a nukleáris hatóság jóváhagyta a Mahi Banswara Rajasthan Atomerőmű négy új blokkjának helyszínét . Kínában befejeződött a Haiyang 3 atomerőmű gőzturbinájának fő egységeinek telepítése . Belgiumban és Dániában is újraértékelik a nukleáris energia szerepét, míg Brazília Oroszországgal közös SMR-projektet tervez .
Iparági Trendek és Kilátások
A World Nuclear Association és az International Energy Agency (IEA) szerint a globális nukleáris energiatermelés 2025-ben minden korábbinál magasabb szintet érhet el, köszönhetően az új reaktorok üzembe helyezésének és a stabil, alacsony kibocsátású energiaforrások iránti növekvő igénynek . A nukleáris üzemanyag-ellátási lánc megerősítése, az uránbányászat, az átalakítás és a dúsítás bővítése, valamint a szállítási kapacitás fejlesztése mind kulcsfontosságú tényezők lesznek a következő években .
Hivatkozások
reuters.com
investopedia.com
nucnet.org
world-nuclear-news.org
world-nuclear.org -
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:53:16
@ 6d5c826a:4b27b659
2025-05-23 21:53:16- DefGuard - True enterprise WireGuard with MFA/2FA and SSO. (Source Code)
Apache-2.0Rust - Dockovpn - Out-of-the-box stateless dockerized OpenVPN server which starts in less than 2 seconds. (Source Code)
GPL-2.0Docker - Firezone - WireGuard based VPN Server and Firewall. (Source Code)
Apache-2.0Docker - Gluetun VPN client - VPN client in a thin Docker container for multiple VPN providers, written in Go, and using OpenVPN or Wireguard, DNS over TLS, with a few proxy servers built-in.
MITdocker - Headscale - Self-hostable fork of Tailscale, cross-platform clients, simple to use, built-in (currently experimental) monitoring tools.
BSD-3-ClauseGo - Nebula - A scalable p2p VPN with a focus on performance, simplicity and security.
MITGo - ocserv - Cisco AnyConnect-compatible VPN server. (Source Code)
GPL-2.0C - OpenVPN - Uses a custom security protocol that utilizes SSL/TLS for key exchange. (Source Code)
GPL-2.0C - SoftEther - Multi-protocol software VPN with advanced features. (Source Code)
Apache-2.0C - sshuttle - Poor man's VPN.
LGPL-2.1Python - strongSwan - Complete IPsec implementation for Linux. (Source Code)
GPL-2.0C - WireGuard - Very fast VPN based on elliptic curve and public key crypto. (Source Code)
GPL-2.0C
- DefGuard - True enterprise WireGuard with MFA/2FA and SSO. (Source Code)
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-23 23:37:17
@ 5d4b6c8d:8a1c1ee3
2025-05-23 23:37:17@grayruby loves to blow up the odds of various sports markets at Predyx. Well, the jig is up, because I finally managed to deposit some sats at BetPlay where I can leverage the mismatched odds.
So, I've now locked in guaranteed wins on the 49ers winning the Super Bowl and the Panthers winning the Stanley Cup.
https://stacker.news/items/987847
-
 @ d12614be:8ed99bc6
2025-05-23 13:35:09
@ d12614be:8ed99bc6
2025-05-23 13:35:09Test article 23.05.2025 2
https://drewdru.layer3.press/articles/ddd70871-69c2-41af-ae56-13fea76050e0
-
 @ a296b972:e5a7a2e8
2025-05-23 12:42:10
@ a296b972:e5a7a2e8
2025-05-23 12:42:10Was Rudolf Steiner vor gut 110 Jahren an Informationen zusammengetragen und kommentiert hat, liest sich in großen Abschnitten so, als ob es in der heutigen Zeit geschrieben worden wäre. Man trifft auf eine ganze Reihe von „guten, alten Bekannten“, die auch heute noch maßgeblich an den Strippen ziehen. Deutlich wird, dass ein Krieg nicht aus heiterem Himmel ausbricht, sondern das im Vorfeld schon Kräfte wirken, die auf einen Krieg hinarbeiten. Wie jetzt wieder im Ukraine-Krieg wird diese Vorgeschichte gerne versucht unter den Teppich zu kehren und hochkompetente, sauber recherchierende, akribisch Quellen angebende Journalisten, wie z. B. Frau Gabriele Krone-Schmalz oder Herr Patrik Baab, der sich auf eigene Kosten einen Eindruck von vor Ort verschafft hat, werden versucht mundtot zu machen und mittlerweile gar nicht mehr zu Gesprächen im öffentlich-rechtlichen Rundfunk eingeladen, weil sie die fortlaufende Gehirnwäsche des Ministeriums für Wahrheit und Narrative mit ihren Aussagen gefährden. Andere kommen auf die Sanktionsliste.
Auch heute ist von den „Guten“ und den „Bösen“ die Rede, was darauf schließen lässt, dass man durchaus eingesteht, dass hier geistige Kräfte am Werk sind. Rudolf Steiner kommt auf diese immer wieder zu sprechen. Aus der von ihm gegebenen anthroposophischen Geisteswissenschaft heraus, beleuchtet er die Vorgänge innerhalb der gesamten Menschheitsentwicklung. Mancher stört sich hier an Begriffen, die man heute so nicht mehr verwenden würde. Dabei ist immer zu berücksichtigen, zu welcher Zeit die Vorträge gehalten wurden. Die Anthroposophie von Rudolf Steiner gilt heute bei vielen auch als „umstritten“, aber was ist das heute nicht? Fast könnte man es schon als Auszeichnung sehen, wenn etwas „umstritten“ ist, denn das ist mittlerweile ein Beweis dafür, dass es Ansichten, Meinungen und Einschätzungen gibt, die in einer gesunden Demokratie innerhalb einer Kontroverse zu einem Dialog und Austausch beitragen können, der jedoch leider derzeit weder gewünscht ist, noch gepflegt wird, was an der „Spaltung“ deutlich zu sehen ist. Und auch unter den Anthroposophen hat die „Spaltung“ Einzug gehalten.
Um das aktuelle, viele Bereiche umschließende, gigantische Lügenkonstrukt aufrecht zu erhalten, ist mittlerweile jedes Mittel recht, von der Deutungshoheit der Wahrheit durch systemkonforme Begutachter, bis hin zu infantil-kleingeistigen Kindergartenspielchen, um gegenläufige Meinungen oder Oppositionelle in ihrem Wirken zu behindern.
Der gesunde Hausverstand wird ausgetrocknet, und der Garten des Wahnsinns wird durch immer neue Ideen kranker Geister weiter gegossen, gehegt und gepflegt.
Die Zeitgeschichtlichen Betrachtungen von Rudolf Steiner bestehen aus 3 Bänden aus der GA (Gesamtausgabe):
GA 173 a – Wege zu einer objektiven Urteilsbildung
GA 173 b – Das Karma der Unwahrhaftigkeit
GA 173 c – Die Wirklichkeit okkulter Impulse
Sie bestehen aus niedergeschriebenen Vorträgen und einem sehr umfangreichen Anhang mit näheren Erläuterungen und einer Schilderung der Entstehung dieser drei Bände.
Es bedarf einiger Eingewöhnung in die zur damaligen Zeit verwendete Sprache Rudolf Steiners, der ein Meister im Bilden von Schachtelsätzen war. Der Inhalt jedoch, und auf den kommt es ja an, berührt immer wieder den in allen Menschen vorhandenen Wahrheitssinn.
Hier nur eine kleine Kostprobe, die vielleicht das Interesse wecken kann, sich mit diesem derzeit besonders aktuellen Werk näher zu beschäftigen.
GA 173a, 6. Vortrag, Seite 205 und Seite 206, Dornach, 17. Dezember 1916:
„Viel intimer, viel verborgener liegen die Dinge bei der englischen Politik, die ja ganz beeinflußt ist von dem, was in solcher Weise hinter ihr steckt. Da handelt es sich darum, daß man die Wege findet, um die entsprechenden Menschen an die richtigen Plätze zu befördern. Okkultistische Menschen, im Hintergrunde stehend, sind oftmals – na, verzeihen Sie – Einser, bloße Einser, und bedeuten für sich nichts Besonderes; sie brauchen noch etwas anderes – sie brauchen Nullen. Nullen sind ja nicht Einser, aber (fügt man eine Null zu einer Eins), dann wird gleich eine Zehn daraus. Und wenn man noch mehr Nullen hinzufügt – jede Null ist nur eine Null, aber wenn die Eins irgendwo steckt, dann ist gar mancherlei da, zum Beispiel die Tausend, und wenn man die Eins zudeckt, dann sind (scheinbar) nur die Nullen da; die Nullen brauchen aber nur in der entsprechenden Weise mit den Einsern kombiniert zu sein, und sie brauchen nicht einmal viel zu wissen von der Art, wie sie mit den Einsern kombiniert sind.“
Schildert diese 108 Jahre alte Beschreibung nicht genau das, was sich heute vor unseren Augen abspielt?
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:52:59
@ 6d5c826a:4b27b659
2025-05-23 21:52:59- Ganeti - Cluster virtual server management software tool built on top of KVM and Xen. (Source Code)
BSD-2-ClausePython/Haskell - KVM - Linux kernel virtualization infrastructure. (Source Code)
GPL-2.0/LGPL-2.0C - OpenNebula - Build and manage enterprise clouds for virtualized services, containerized applications and serverless computing. (Source Code)
Apache-2.0C++ - oVirt - Manages virtual machines, storage and virtual networks. (Source Code)
Apache-2.0Java - Packer - A tool for creating identical machine images for multiple platforms from a single source configuration. (Source Code)
MPL-2.0Go - Proxmox VE - Virtualization management solution. (Source Code)
GPL-2.0Perl/Shell - QEMU - QEMU is a generic machine emulator and virtualizer. (Source Code)
LGPL-2.1C - Vagrant - Tool for building complete development environments. (Source Code)
BUSL-1.1Ruby - VirtualBox - Virtualization product from Oracle Corporation. (Source Code)
GPL-3.0/CDDL-1.0C++ - XCP-ng - Virtualization platform based on Xen Source and Citrix® Hypervisor (formerly XenServer). (Source Code)
GPL-2.0C - Xen - Virtual machine monitor for 32/64 bit Intel / AMD (IA 64) and PowerPC 970 architectures. (Source Code)
GPL-2.0C
- Ganeti - Cluster virtual server management software tool built on top of KVM and Xen. (Source Code)
-
 @ eb0157af:77ab6c55
2025-05-23 12:01:07
@ eb0157af:77ab6c55
2025-05-23 12:01:07Banking giants JPMorgan, Bank of America, Citigroup, and Wells Fargo are in talks to develop a unified stablecoin solution.
According to the Wall Street Journal on May 22, some of the largest financial institutions in the United States are exploring the possibility of joining forces to launch a stablecoin.
Subsidiaries of JPMorgan, Bank of America, Citigroup, and Wells Fargo have initiated preliminary discussions for a joint stablecoin issuance, according to sources close to the matter cited by the WSJ. Also at the negotiating table are Early Warning Services, the parent company of the digital payments network Zelle, and the payment network Clearing House.
The talks are reportedly still in the early stages, and any final decision could change depending on regulatory developments and market demand for stablecoins.
Stablecoin regulation
On May 20, the US Senate voted 66 to 32 to advance discussion of the Guiding and Establishing National Innovation for US Stablecoins Act (GENIUS Act), a specific law to regulate stablecoins. The bill outlines a regulatory framework for stablecoin collateralization and mandates compliance with anti-money laundering rules.
David Sacks, White House crypto advisor, expressed optimism about the bill’s bipartisan approval. However, senior Democratic Party officials intend to amend the bill to include a clause preventing former President Donald Trump and other US officials from profiting from stablecoins.
Demand for stablecoins has increased, with total market capitalization rising to $245 billion from $205 billion at the beginning of the year, a 20% increase.
The post Major US banks consider launching a joint stablecoin appeared first on Atlas21.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:52:43
@ 6d5c826a:4b27b659
2025-05-23 21:52:43- Darcs - Cross-platform version control system, like git, mercurial or svn but with a very different approach: focus on changes rather than snapshots. (Source Code)
GPL-2.0Haskell - Fossil - Distributed version control with built-in wiki and bug tracking. (Source Code)
BSD-2-ClauseC - Git - Distributed revision control and source code management (SCM) with an emphasis on speed. (Source Code)
GPL-2.0C - Mercurial - Distributed source control management tool. (Source Code)
GPL-2.0Python/C/Rust - Subversion - Client-server revision control system. (Source Code)
Apache-2.0C
- Darcs - Cross-platform version control system, like git, mercurial or svn but with a very different approach: focus on changes rather than snapshots. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:52:26
@ 6d5c826a:4b27b659
2025-05-23 21:52:26- grml - Bootable Debian Live CD with powerful CLI tools. (Source Code)
GPL-3.0Shell - mitmproxy - A Python tool used for intercepting, viewing and modifying network traffic. Invaluable in troubleshooting certain problems. (Source Code)
MITPython - mtr - Network utility that combines traceroute and ping. (Source Code)
GPL-2.0C - Sysdig - Capture system state and activity from a running Linux instance, then save, filter and analyze. (Source Code)
Apache-2.0Docker/Lua/C - Wireshark - The world's foremost network protocol analyzer. (Source Code)
GPL-2.0C
- grml - Bootable Debian Live CD with powerful CLI tools. (Source Code)
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ 5c26ee8b:a4d229aa
2025-05-23 08:47:45
@ 5c26ee8b:a4d229aa
2025-05-23 08:47:45Generally mentioning God, Allah, by reciting/reading the Quran or performing Salat (compulsory prayer), for instance, brings tranquility to the heart of the believer. The Salat, other than being the first deed a Muslim would be questioned about on Judgement Day, it keeps the person away from the forbidden wrong deeds too. The Salat is sufficient for obtaining God’s provision as he decrees the means for it to reach the person. Wasting or missing performing the Salat or mentioning God (Allah) by reciting/reading the Quran or Tasbieh, can lead to following the desires only and a depressed life as well as punishment in the Thereafter.
13:28 Ar-Ra'd
الَّذِينَ آمَنُوا وَتَطْمَئِنُّ قُلُوبُهُمْ بِذِكْرِ اللَّهِ ۗ أَلَا بِذِكْرِ اللَّهِ تَطْمَئِنُّ الْقُلُوبُ
Those who have believed and whose hearts are assured (tranquillised) by the remembrance of Allah. Unquestionably, by the remembrance of Allah hearts are assured (tranquillised)."
29:45 Al-Ankaboot
اتْلُ مَا أُوحِيَ إِلَيْكَ مِنَ الْكِتَابِ وَأَقِمِ الصَّلَاةَ ۖ إِنَّ الصَّلَاةَ تَنْهَىٰ عَنِ الْفَحْشَاءِ وَالْمُنْكَرِ ۗ وَلَذِكْرُ اللَّهِ أَكْبَرُ ۗ وَاللَّهُ يَعْلَمُ مَا تَصْنَعُونَ
Recite, [O Muhammad], what has been revealed to you of the Book and establish prayer. Indeed, prayer prohibits immorality and wrongdoing, and the remembrance of Allah is greater. And Allah knows that which you do.
11:114 Hud
وَأَقِمِ الصَّلَاةَ طَرَفَيِ النَّهَارِ وَزُلَفًا مِنَ اللَّيْلِ ۚ إِنَّ الْحَسَنَاتِ يُذْهِبْنَ السَّيِّئَاتِ ۚ ذَٰلِكَ ذِكْرَىٰ لِلذَّاكِرِينَ
And establish prayer at the two ends of the day and at the approach of the night. Indeed, good deeds do away with misdeeds. That is a reminder for those who remember.
20:132 Taa-Haa
وَأْمُرْ أَهْلَكَ بِالصَّلَاةِ وَاصْطَبِرْ عَلَيْهَا ۖ لَا نَسْأَلُكَ رِزْقًا ۖ نَحْنُ نَرْزُقُكَ ۗ وَالْعَاقِبَةُ لِلتَّقْوَىٰ
And enjoin prayer upon your family [and people] and be steadfast therein. We ask you not for provision; We provide for you, and the [best] outcome is for [those of] righteousness.
20:124 Taa-Haa
وَمَنْ أَعْرَضَ عَنْ ذِكْرِي فَإِنَّ لَهُ مَعِيشَةً ضَنْكًا وَنَحْشُرُهُ يَوْمَ الْقِيَامَةِ أَعْمَىٰ
And whoever turns away from My remembrance - indeed, he will have a depressed life, and We will gather him on the Day of Resurrection blind."
20:125 Taa-Haa
قَالَ رَبِّ لِمَ حَشَرْتَنِي أَعْمَىٰ وَقَدْ كُنْتُ بَصِيرًا
He will say, "My Lord, why have you raised me blind while I was [once] seeing?"
20:126 Taa-Haa
قَالَ كَذَٰلِكَ أَتَتْكَ آيَاتُنَا فَنَسِيتَهَا ۖ وَكَذَٰلِكَ الْيَوْمَ تُنْسَىٰ
[Allah] will say, "Thus did Our signs come to you, and you forgot them; and thus will you this Day be forgotten."
20:127 Taa-Haa
وَكَذَٰلِكَ نَجْزِي مَنْ أَسْرَفَ وَلَمْ يُؤْمِنْ بِآيَاتِ رَبِّهِ ۚ وَلَعَذَابُ الْآخِرَةِ أَشَدُّ وَأَبْقَىٰ
And thus do We recompense he who transgressed and did not believe in the signs of his Lord. And the punishment of the Hereafter is more severe and more enduring.
20:128 Taa-Haa
أَفَلَمْ يَهْدِ لَهُمْ كَمْ أَهْلَكْنَا قَبْلَهُمْ مِنَ الْقُرُونِ يَمْشُونَ فِي مَسَاكِنِهِمْ ۗ إِنَّ فِي ذَٰلِكَ لَآيَاتٍ لِأُولِي النُّهَىٰ
Then, has it not become clear to them how many generations We destroyed before them as they walk among their dwellings? Indeed in that are signs for those of intelligence.
49:17 Al-Hujuraat
يَمُنُّونَ عَلَيْكَ أَنْ أَسْلَمُوا ۖ قُلْ لَا تَمُنُّوا عَلَيَّ إِسْلَامَكُمْ ۖ بَلِ اللَّهُ يَمُنُّ عَلَيْكُمْ أَنْ هَدَاكُمْ لِلْإِيمَانِ إِنْ كُنْتُمْ صَادِقِينَ
They consider it a favor to you that they have accepted Islam. Say, "Do not consider your Islam a favor to me. Rather, Allah has conferred favor upon you that He has guided you to the faith, if you should be truthful."
53:29 An-Najm
فَأَعْرِضْ عَنْ مَنْ تَوَلَّىٰ عَنْ ذِكْرِنَا وَلَمْ يُرِدْ إِلَّا الْحَيَاةَ الدُّنْيَا
So turn away from whoever turns his back on Our message and desires not except the worldly life.
53:30 An-Najm
ذَٰلِكَ مَبْلَغُهُمْ مِنَ الْعِلْمِ ۚ إِنَّ رَبَّكَ هُوَ أَعْلَمُ بِمَنْ ضَلَّ عَنْ سَبِيلِهِ وَهُوَ أَعْلَمُ بِمَنِ اهْتَدَىٰ
That is their sum of knowledge. Indeed, your Lord is most knowing of who strays from His way, and He is most knowing of who is guided.
53:62 An-Najm
فَاسْجُدُوا لِلَّهِ وَاعْبُدُوا ۩
So prostrate to Allah and worship [Him].
-
 @ 3c389c8f:7a2eff7f
2025-05-23 21:35:30
@ 3c389c8f:7a2eff7f
2025-05-23 21:35:30Web:
https://shopstr.store/
https://cypher.space/
https://plebeian.market/
Mobile:
https://www.amethyst.social/
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 3c389c8f:7a2eff7f
2025-05-23 21:27:26
@ 3c389c8f:7a2eff7f
2025-05-23 21:27:26Clients:
https://untype.app
https://habla.news
https://yakihonne.com
https://cypher.space
https://highlighter.com
https://pareto.space/en
https://comet.md/
Plug Ins:
https://github.com/jamesmagoo/nostr-writer
https://threenine.co.uk/products/obstrlish
Content Tagging:
https://labelmachine.org
https://ontolo.social
Blog-like Display and Personal Pages:
https://orocolo.me
https://npub.pro
Personal Notes and Messaging:
https://app.flotilla.social There's an app, too!
https://nosbin.com
RSS Readers:
https://nostrapps.com/noflux
https://nostrapps.com/narr
https://nostrapps.com/feeder
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 6d5c826a:4b27b659
2025-05-23 21:52:06
@ 6d5c826a:4b27b659
2025-05-23 21:52:06- Docker Compose - Define and run multi-container Docker applications. (Source Code)
Apache-2.0Go - Docker Swarm - Manage cluster of Docker Engines. (Source Code)
Apache-2.0Go - Docker - Platform for developers and sysadmins to build, ship, and run distributed applications. (Source Code)
Apache-2.0Go - LXC - Userspace interface for the Linux kernel containment features. (Source Code)
GPL-2.0C - LXD - Container "hypervisor" and a better UX for LXC. (Source Code)
Apache-2.0Go - OpenVZ - Container-based virtualization for Linux. (Source Code)
GPL-2.0C - Podman - Daemonless container engine for developing, managing, and running OCI Containers on your Linux System. Containers can either be run as root or in rootless mode. Simply put:
alias docker=podman. (Source Code)Apache-2.0Go - Portainer Community Edition - Simple management UI for Docker. (Source Code)
ZlibGo - systemd-nspawn - Lightweight, chroot-like, environment to run an OS or command directly under systemd. (Source Code)
GPL-2.0C
- Docker Compose - Define and run multi-container Docker applications. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:49:50
@ 6d5c826a:4b27b659
2025-05-23 21:49:50- Consul - Consul is a tool for service discovery, monitoring and configuration. (Source Code)
MPL-2.0Go - etcd - Distributed K/V-Store, authenticating via SSL PKI and a REST HTTP Api for shared configuration and service discovery. (Source Code)
Apache-2.0Go - ZooKeeper - ZooKeeper is a centralized service for maintaining configuration information, naming, providing distributed synchronization, and providing group services. (Source Code)
Apache-2.0Java/C++
- Consul - Consul is a tool for service discovery, monitoring and configuration. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:49:30
@ 6d5c826a:4b27b659
2025-05-23 21:49:30- DD-WRT - A Linux-based firmware for wireless routers and access points, originally designed for the Linksys WRT54G series. (Source Code)
GPL-2.0C - OpenWrt - A Linux-based router featuring Mesh networking, IPS via snort and AQM among many other features. (Source Code)
GPL-2.0C - OPNsense - An open source FreeBSD-based firewall and router with traffic shaping, load balancing, and virtual private network capabilities. (Source Code)
BSD-2-ClauseC/PHP - pfSense CE - Free network firewall distribution, based on the FreeBSD operating system with a custom kernel and including third party free software packages for additional functionality. (Source Code)
Apache-2.0Shell/PHP/Other
- DD-WRT - A Linux-based firmware for wireless routers and access points, originally designed for the Linksys WRT54G series. (Source Code)
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-23 19:32:28
@ 5d4b6c8d:8a1c1ee3
2025-05-23 19:32:28https://primal.net/e/nevent1qvzqqqqqqypzp6dtxy5uz5yu5vzxdtcv7du9qm9574u5kqcqha58efshkkwz6zmdqqszj207pl0eqkgld9vxknxamged64ch2x2zwhszupkut5v46vafuhg9833px
Some of my colleagues were talking about how they're even more scared of RFK Jr. than they are of Trump. I hope he earns it.
https://stacker.news/items/987685
-
 @ 6d5c826a:4b27b659
2025-05-23 21:49:12
@ 6d5c826a:4b27b659
2025-05-23 21:49:12- Remmina - Feature-rich remote desktop application for linux and other unixes. (Source Code)
GPL-2.0C - Tiger VNC - High-performance, multi-platform VNC client and server. (Source Code)
GPL-2.0C++ - X2go - X2Go is an open source remote desktop software for Linux that uses the NoMachine/NX technology protocol. (Source Code)
GPL-2.0Perl
- Remmina - Feature-rich remote desktop application for linux and other unixes. (Source Code)
-
 @ 2b998b04:86727e47
2025-05-23 01:56:23
@ 2b998b04:86727e47
2025-05-23 01:56:23\> “Huge swathes of people…spend their entire working lives performing tasks they secretly believe do not really need to be performed.”\ \> — David Graeber, Bullshit Jobs
\> “We are in a system that must grow — forever — or it collapses. But technology, by its very nature, is deflationary.”\ \> — Jeff Booth, The Price of Tomorrow
We live in a strange paradox: Technological progress is supposed to make life easier, yet many people feel more overworked and less fulfilled than ever. While artificial intelligence and automation promise unprecedented productivity, it’s not yet clear whether that will mean fewer bullshit jobs — or simply new kinds of them.
What Is a Bullshit Job?
In his landmark book Bullshit Jobs, the late anthropologist David Graeber exposed a haunting truth: millions of jobs exist not because they are needed, but because of economic, political, or psychological inertia. These are roles that even the workers themselves suspect are meaningless — created to serve appearances, maintain hierarchies, or justify budgets.
Think:
-
Middle managers approving other middle managers' reports
-
Employees running meetings to prepare for other meetings
-
Corporate roles invented to interface with poorly implemented AI tools
Bullshit work isn’t the absence of technology. It’s often the outcome of resisting what technology could actually do — in order to preserve jobs, status, or growth targets.
Booth’s Warning: The System is Rigged Against Deflation
In The Price of Tomorrow, entrepreneur Jeff Booth argues that the natural state of a tech-driven economy is deflation — things getting better, cheaper, and faster.
But our global financial system is built on perpetual inflation and debt expansion. Booth writes:
\> “We are using inflationary monetary policy to fight deflationary technological forces.”
Even as AI and automation could eliminate unnecessary jobs and increase abundance, our system requires jobs — or the illusion of them — to keep the economy expanding. So bullshit jobs persist, and even evolve.
AI as a Deflationary Force
AI is rapidly accelerating the deflation Booth described:
-
Tasks that used to take hours now take seconds
-
Whole creative and administrative processes are being streamlined
-
Labor can scale digitally — one tool used globally at near-zero marginal cost
Embraced honestly, this could mean fewer hours, lower costs, and more prosperity. But again, we are not optimized for truth — we are optimized for GDP growth.
So we invent new layers of AI-enhanced bullshit:
-
Prompt engineers writing prompts for other prompt engineers
-
"Human-in-the-loop" validators reviewing AI output they don’t understand
-
Consultants building dashboards that nobody reads
Toward a Post-Bullshit Future
Here’s the real opportunity: If we embrace deflation as a blessing — not a threat — and redesign our systems around truth, efficiency, and abundance, we could:
-
Eliminate meaningless labor
-
Reduce the cost of living dramatically
-
Liberate people to create, heal, build, and rest
This means more than economic reform — it’s a philosophical shift. We must stop equating “employment” with value. That’s where Bitcoin and open-source tools point: toward a world where permissionless value creation is possible without the bloat of gatekeeping institutions.
Final Thought: Tech Won’t Save Us, But Truth Might
Technology, left to its own logic, tends toward freedom, efficiency, and abundance. But our current systems suppress that logic in favor of growth at all costs — even if it means assigning millions of people to do work that doesn’t need doing.
So will AI eliminate bullshit jobs?
It can. But only if we stop pretending we need them.
And for those of us who step outside the wage-work loop, something remarkable happens. We begin using these tools to create actual value — not to impress a boss, but to solve real problems and serve real people.
Recently, I built a tool using AI and automation that helps me cross-post content from Nostr to LinkedIn, Facebook, and X. It wasn’t for a paycheck. It was about leverage — freeing time, expanding reach, and creating a public record of ideas.\ You can check it out here:\ 👉 <https://tinyurl.com/ywxuowl5>
Will it help others? I don’t know yet.\ But it helped me — and that’s the point.
Real value creation doesn’t always begin with a business plan. Sometimes it starts with curiosity, conviction, and the courage to build without permission.
Maybe the future of work isn’t about scaling jobs at all.\ Maybe it’s about reclaiming time — and using these tools to build lives of meaning.
If this resonates — or if you’ve found your own way to reclaim time and create value outside the wage loop — zap me and share your story. Let’s build the post-bullshit economy together. ⚡
-
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 0fa80bd3:ea7325de
2025-04-09 21:19:39
@ 0fa80bd3:ea7325de
2025-04-09 21:19:39DAOs promised decentralization. They offered a system where every member could influence a project's direction, where money and power were transparently distributed, and decisions were made through voting. All of it recorded immutably on the blockchain, free from middlemen.
But something didn’t work out. In practice, most DAOs haven’t evolved into living, self-organizing organisms. They became something else: clubs where participation is unevenly distributed. Leaders remained - only now without formal titles. They hold influence through control over communications, task framing, and community dynamics. Centralization still exists, just wrapped in a new package.
But there's a second, less obvious problem. Crowds can’t create strategy. In DAOs, people vote for what "feels right to the majority." But strategy isn’t about what feels good - it’s about what’s necessary. Difficult, unpopular, yet forward-looking decisions often fail when put to a vote. A founder’s vision is a risk. But in healthy teams, it’s that risk that drives progress. In DAOs, risk is almost always diluted until it becomes something safe and vague.
Instead of empowering leaders, DAOs often neutralize them. This is why many DAOs resemble consensus machines. Everyone talks, debates, and participates, but very little actually gets done. One person says, “Let’s jump,” and five others respond, “Let’s discuss that first.” This dynamic might work for open forums, but not for action.
Decentralization works when there’s trust and delegation, not just voting. Until DAOs develop effective systems for assigning roles, taking ownership, and acting with flexibility, they will keep losing ground to old-fashioned startups led by charismatic founders with a clear vision.
We’ve seen this in many real-world cases. Take MakerDAO, one of the most mature and technically sophisticated DAOs. Its governance token (MKR) holders vote on everything from interest rates to protocol upgrades. While this has allowed for transparency and community involvement, the process is often slow and bureaucratic. Complex proposals stall. Strategic pivots become hard to implement. And in 2023, a controversial proposal to allocate billions to real-world assets passed only narrowly, after months of infighting - highlighting how vision and execution can get stuck in the mud of distributed governance.
On the other hand, Uniswap DAO, responsible for the largest decentralized exchange, raised governance participation only after launching a delegation system where token holders could choose trusted representatives. Still, much of the activity is limited to a small group of active contributors. The vast majority of token holders remain passive. This raises the question: is it really community-led, or just a formalized power structure with lower transparency?
Then there’s ConstitutionDAO, an experiment that went viral. It raised over $40 million in days to try and buy a copy of the U.S. Constitution. But despite the hype, the DAO failed to win the auction. Afterwards, it struggled with refund logistics, communication breakdowns, and confusion over governance. It was a perfect example of collective enthusiasm without infrastructure or planning - proof that a DAO can raise capital fast but still lack cohesion.
Not all efforts have failed. Projects like Gitcoin DAO have made progress by incentivizing small, individual contributions. Their quadratic funding mechanism rewards projects based on the number of contributors, not just the size of donations, helping to elevate grassroots initiatives. But even here, long-term strategy often falls back on a core group of organizers rather than broad community consensus.
The pattern is clear: when the stakes are low or the tasks are modular, DAOs can coordinate well. But when bold moves are needed—when someone has to take responsibility and act under uncertainty DAOs often freeze. In the name of consensus, they lose momentum.
That’s why the organization of the future can’t rely purely on decentralization. It must encourage individual initiative and the ability to take calculated risks. People need to see their contribution not just as a vote, but as a role with clear actions and expected outcomes. When the situation demands, they should be empowered to act first and present the results to the community afterwards allowing for both autonomy and accountability. That’s not a flaw in the system. It’s how real progress happens.
-
 @ 3c389c8f:7a2eff7f
2025-05-23 18:23:28
@ 3c389c8f:7a2eff7f
2025-05-23 18:23:28I've sporadically been trying to spend some time familiarizing myself with Nostr marketplace listings and the clients that support them. I have been pleased with what I have encountered. The clients are simple to use, and people have been receptive to transacting with me. I've sold items to both people whom I consider to be close contacts, as well as to people that I barely know.
My first attempt was close to 2 years ago, when I listed one pound bags of coffee for sale. If I remember correctly, there was only one marketplace client then, and it only had support for extension signing. At the time, my old laptop had just died so I couldn't really interact with my listings through that client. (I have never had much luck with extensions on mobile browsers, so I have never attempted to use one for Nostr.) Instead, I used Amethyst to list my product and exchange messages with potential buyers. The Amethyst approach to handling different Nostr events is brilliant to me. You can do some part of each thing but not all. I view it as great introduction to what Nostr is capable of doing and a gateway to discovering other clients. Marketplace listings on Amethyst are handled in that fashion. You can list products for sale. You can browse and inquire about products listed by your contacts or by a more "global" view, which in the case of Nostr, would be products listed by anyone who publishes their listings to any of the relays that I connect with to read. There is no delete option, should a product sell out, and there is no direct purchase option. All sales need to be negotiated through direct messages. Though it has limited functionality, the system works great for items that will be listed for repeated sale, such as my coffee. If one were to list a one-off item and sell it, the flow to delete the listing would be easy enough. Copy the event ID, visit delete.nostr.com , and remove the product. Should there be a price change, it would be necessary to visit a full marketplace client to edit the listing, though one could easily delete and start over as well. Anyway, much to my surprise I sold more coffee than I had anticipated through that listing. People were eager to try out the feature and support a small business. This was an awesome experience and I see no reason to avoid buying or selling products on Nostr, even if the only client available to you is Amethyst. (Which I think might be the only mobile app with marketplace support.) It is completely manageable.
Later, I tried to list a pair of nearly new shoes. Those did not sell. I have a sneaking suspicion that there were very few people that wore size USw6 shoes using Nostr at the time. Even though no one wanted my shoes, I still ended up having some interesting conversations about different styles of running shoes, boots, and other footwear talk. I can't call the listing a total bust, even though I ended up deleting the listing and donating those shoes to the YWCA. After some number of months watching and reading about development in the Nostr marketplace space, I decided to try again.
This second approach, I started with niche rubber duckies that, for reasons unbeknownst to most, I just happen to have an abundance of. It occurred to me that day that I would most likely be creating most of my listings via mobile app since that is also my main method of taking pictures these days. I could sync or send them, but realistically it's just adding extra steps for me. I listed my ducks with Amethyst (all of which are currently still available, surprise, surprise.). I immediately went to check how the listing renders in the marketplace clients. There are 2 where I can view it, and the listing looks nice, clean, organized in both places. That alone is reason enough to get excited about selling on Nostr. Gone are the days of "this item is cross-posted to blah, blah, blah" lest risk being kicked out of the seller groups on silo'd platforms.
Knowing I can't take it personally that literally no one else on Nostr has an affinity for obscure rubber ducks (that they are willing to admit), I leave my duckies listed and move on. My next listing is for artisan bracelets. Ones that I love to make. I made my mobile listing, checked it across clients and this time I noticed that shopstr.store is collecting my listings into a personal seller profile, like a little shop. I spent some time setting up the description and banner, and now it looks really nice. This is great, since the current site acts as an open and categorized market for all sellers. Maybe someone will see the bracelets while browsing the clothing category and stumble upon the rubber ducky of their dreams in the process. That hasn't happened yet, but I was pretty jazzed to sell a few bracelets right away. Most of the sale and exchange happened via DM, for which I switched to Flotilla because it just handles messaging solidly for me. I made some bracelets, waited a few weeks, then visited Shopstr again to adjust the price. That worked out super well. I noticed that a seller can also list in their preferred currency, which is very cool. Meanwhile, back to my social feed, I can see my listing posted again since there was an edit. While not always the best thing to happen with edits, it is great that it happens with marketplace listings. It removes all the steps of announcing a price reduction, which would be handy for any serious seller. I am very happy with the bracelet experience, and I will keep that listing active and reasonably up to date for as long as any interest arises. Since this has all gone so well, I've opted to continue listing saleable items to Nostr first for a few days to a few weeks prior to marketing them anywhere else.
Looking at my listings on cypher.space, I can see that this client is tailored more towards people who are very passionate about a particular set of things. I might not fall into this category but my listings still look very nice displayed with my writing, transposed poetry, and recipes. I could see this being a great space for truly devotional hobbyists or sellers who are both deeply knowledgeable about their craft and also actively selling. My experience with all 3 of these marketplace-integrated clients had been positive and I would say that if you are considering selling on Nostr, it is worth the effort.
As some sidenotes:
-
I am aware that Shopstr has been built to be self-hosted and anyone interested in selling for the long term should at least consider doing so. This will help reduce the chances of Nostr marketplaces centralizing into just another seller-silo.
-
Plebeian Market is out there, too. From the best I could tell, even though this is a Nostr client, those listings are a different kind than listings made from the other clients referenced here. I like the layout and responsiveness of the site but I opted not to try it out for now. Cross-posting has been the bane of online selling for me for quite some time. If they should migrate to an interoperable listing type (which I think I read may happen in the future), I will happily take that for a spin, too.
-
My only purchase over Nostr marketplaces so far was some vinyls, right around the time I had listed my coffee. It went well, the seller was great to work with, everything arrived in good shape. I have made some other purchases through Nostr contacts, but those were conversations that lead to non-Nostr seller sites. I check the marketplace often, though, for things I may want/need. The listings are changing and expanding rapidly, and I foresee more purchases becoming a part of my regular Nostr experience soon enough.
-
I thought about including screenshots for this, but I would much rather you go check these clients out for yourself.
-
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 9ca447d2:fbf5a36d
2025-05-23 01:01:39
@ 9ca447d2:fbf5a36d
2025-05-23 01:01:39Singapore, May 14, 2025 — NEUTRON, the leading Lightning Network infrastructure provider in Asia, is announcing a new partnership with Cobo, a globally trusted digital asset custody platform.
Through this collaboration, Cobo will integrate Neutron’s Lightning Network API, enabling real-time, cost-effective Bitcoin transactions across its services.
Neutron’s mission is to make the Lightning Network the financial backbone for modern Bitcoin use, bridging traditional finance with Bitcoin’s borderless, decentralized economy.
“We’re thrilled to partner with Cobo, a trusted leader in custodial services, to further accelerate Bitcoin infrastructure across Asia,” said Albert Buu, CEO of Neutron.
“At Neutron, we are committed to providing enterprise businesses with easy and efficient integration into the Lightning Network, enabling next-generation global real-time settlement solutions.
“This partnership will not only drive innovation but also empower businesses across Asia with the fast, secure, and cost-effective benefits of Bitcoin payments.”
Neutron: The Lightning Engine for Bitcoin Adoption
Neutron provides a comprehensive API suite that allows businesses to instantly access the power of the Lightning Network, Bitcoin’s second-layer protocol designed for high-speed, scalable, and low-fee payments.
The integration is part of Neutron’s broader vision to equip forward-thinking institutions with the tools needed to participate in the next generation of Bitcoin utility.
Lightning-Powered Custody for the Next Era of Finance
Cobo’s integration of Neutron’s API gives institutional clients an additional option for BTC settlement, making Lightning Network access more programmable and easier to integrate within their existing systems.
“At Cobo, we’ve built our custody platform to combine uncompromising security with the scalability institutions need to grow,” said Dr. Changhao Jiang, CTO and Co-Founder of Cobo.
“Integrating Neutron’s Lightning Network API allows us to offer real-time, low-cost Bitcoin settlement at scale without compromising on trust or performance. Together, we’re laying the groundwork for faster, more efficient Bitcoin infrastructure across Asia.”
About Neutron
Neutron is Asia’s leading Bitcoin infrastructure company, helping businesses and individuals unlock the power of the Lightning Network, specializing in Lightning-as-a-Service.
nThrough its scalable API platform, mobile app, and lending product, Neutron empowers businesses and individuals to send, receive, save, and build with Bitcoin.
Want to bring Lightning into your product or platform? Reach out to our team at sales@neutron.me or visit us at www.neutron.meAbout Cobo
Cobo is a trusted leader in digital asset custody and wallet infrastructure, providing an all-in-one platform for organizations and developers to easily build, automate, and scale their digital asset businesses securely.
Founded in 2017 by blockchain pioneers and headquartered in Singapore, Cobo is trusted by more than 500 leading digital asset businesses globally, safeguarding billions of dollars in assets.
Today, Cobo offers the industry’s only unified wallet platform that integrates all four digital asset wallet technologies – Custodial Wallets, MPC Wallets, Smart Contract Wallets, and Exchange Wallets.
Committed to the highest security standards and regulatory compliance, Cobo has a zero-incident track record and holds ISO 27001, SOC2 (Type 1 and Type 2) certifications, as well as licenses in multiple jurisdictions.
Recognized for its industry-leading innovations, Cobo has received accolades from prestigious entities such as Hedgeweek and Global Custodian. For more information, please visit www.cobo.com
-
 @ eb0157af:77ab6c55
2025-05-22 22:01:31
@ eb0157af:77ab6c55
2025-05-22 22:01:31A Chinese printer company inadvertently distributed malware that steals Bitcoin through its official drivers, resulting in the theft of over $950,000.
According to local media outlet Landian News, a Chinese printer manufacturer was found to have unknowingly distributed malware designed to steal Bitcoin through its official device drivers.
Procolored, a Shenzhen-based printer company, distributed malware capable of stealing Bitcoin alongside the official drivers for its devices. The company reportedly used USB devices to spread infected drivers and uploaded the compromised software to globally accessible cloud storage services.
Crypto security and compliance firm SlowMist explained how the malware works in a post on X:
 The official driver provided by this printer carries a backdoor program. It will hijack the wallet address in the user's clipboard and replace it with the attacker's address: 1BQZKqdp2CV3QV5nUEsqSg1ygegLmqRygj
The official driver provided by this printer carries a backdoor program. It will hijack the wallet address in the user's clipboard and replace it with the attacker's address: 1BQZKqdp2CV3QV5nUEsqSg1ygegLmqRygj  According to @MistTrack_io, the attacker has stolen 9.3086… https://t.co/DHCkEpHhuH pic.twitter.com/W1AnUpswLU
According to @MistTrack_io, the attacker has stolen 9.3086… https://t.co/DHCkEpHhuH pic.twitter.com/W1AnUpswLU— MistTrack
 (@MistTrack_io) May 19, 2025
(@MistTrack_io) May 19, 2025The consequences of the breach have been significant, with a total of 9.3 BTC stolen — equivalent to over $950,000.
The issue was first flagged by YouTuber Cameron Coward, whose antivirus software detected malware in the drivers during a test of a Procolored UV printer. The software identified both a worm and a trojan virus named Foxif.
When contacted, Procolored denied the accusations, dismissing the antivirus warning as a false positive. Coward then turned to Reddit, where he shared the issue with cybersecurity professionals, drawing the attention of security firm G Data.
G Data’s investigation revealed that most of Procolored’s drivers were hosted on the MEGA file-sharing platform, with uploads dating back to October 2023. Their analysis confirmed the presence of two separate malware strains: the Win32.Backdoor.XRedRAT.A backdoor and a crypto-stealer designed to replace clipboard wallet addresses with those controlled by the attacker.
G Data reached out to Procolored, which stated that it had removed the infected drivers from its storage as of May 8 and had re-scanned all files. The company attributed the malware to a supply chain compromise, saying the malicious files were introduced via infected USB devices before being uploaded online.
Landian News recommended that users who downloaded Procolored drivers in the past six months “immediately run a full system scan using antivirus software.” However, given that antivirus tools are not always reliable, the Chinese media outlet suggested that a full system reset is the safest option when in doubt.
The post Bitcoin malware discovered: Chinese printer manufacturer involved appeared first on Atlas21.
-
 @ ecda4328:1278f072
2025-05-23 18:16:24
@ ecda4328:1278f072
2025-05-23 18:16:24And what does it mean to withdraw back to Bitcoin Layer 1?
Disclaimer: This post was written with help from ChatGPT-4o. If you spot any mistakes or have suggestions — feel free to reply or zap in feedback!
Let’s break it down — using three popular setups:
1. Wallet of Satoshi (WoS)
Custodial — you don’t touch Lightning directly
Sending sats:
- You open WoS, paste a Lightning invoice, hit send.
- WoS handles the payment entirely within their system.
- If recipient uses WoS: internal balance update.
- If external: routed via their node.
- You never open channels, construct routes, or sign anything.
Withdrawing to L1:
- You paste a Bitcoin address.
- WoS sends a regular on-chain transaction from their custodial wallet.
- You pay a fee. It’s like a bank withdrawal.
You don’t interact with Lightning directly. Think of it as a trusted 3rd party Lightning “bank”.
2. Phoenix Wallet
Non-custodial — you own keys, Phoenix handles channels
Sending sats:
- You scan a Lightning invoice and hit send.
- Phoenix uses its backend node (ACINQ) to route the payment.
- If needed, it opens a real 2-of-2 multisig channel on-chain automatically.
- You own your keys (12-word seed), Phoenix abstracts the technical parts.
Withdrawing to L1:
- You enter your Bitcoin address.
- Phoenix closes your Lightning channel (cooperatively, if possible).
- Your sats are sent as a real Bitcoin transaction to your address.
You’re using Lightning “for real,” with real Bitcoin channels — but Phoenix smooths out the UX.
3. Your Own Lightning Node
Self-hosted — you control everything
Sending sats:
- You manage your channels manually (or via automation).
- Your node:
- Reads the invoice
- Builds a route using HTLCs
- Sends the payment using conditional logic (preimages, time locks).
- If routing fails: retry or adjust liquidity.
Withdrawing to L1:
- You select and close a channel.
- A channel closing transaction is broadcast:
- Cooperative = fast and cheap
- Force-close = slower, more expensive, and time-locked
- Funds land in your on-chain wallet.
You have full sovereignty — but also full responsibility (liquidity, fees, backups, monitoring).
Core Tech Behind It: HTLCs, Multisig — and No Sidechain
- Lightning channels = 2-of-2 multisig Bitcoin addresses
- Payments = routed via HTLCs (Hashed Time-Locked Contracts)
- HTLCs are off-chain, but enforceable on-chain if needed
- Important:
- The Lightning Network is not a sidechain.
- It doesn't use its own token, consensus, or separate blockchain.
- Every Lightning channel is secured by real Bitcoin on L1.
Lightning = fast, private, off-chain Bitcoin — secured by Bitcoin itself.
Summary Table
| Wallet | Custody | Channel Handling | L1 Withdrawal | HTLC Visibility | User Effort | |--------------------|--------------|------------------------|---------------------|------------------|--------------| | Wallet of Satoshi | Custodial | None | Internal to external| Hidden | Easiest | | Phoenix Wallet | Non-custodial| Auto-managed real LN | Channel close | Abstracted | Low effort | | Own Node | You | Manual | Manual channel close| Full control | High effort |
Bonus: Withdrawing from LN to On-Chain
- WoS: sends sats from their wallet — like PayPal.
- Phoenix: closes a real channel and sends your UTXO on-chain.
- Own node: closes your multisig contract and broadcasts your pre-signed tx.
Bitcoin + Lightning = Sovereign money + Instant payments.
Choose the setup that fits your needs — and remember, you can always level up later.P.S. What happens in Lightning... usually stays in Lightning.
-
 @ bf47c19e:c3d2573b
2025-05-22 21:03:52
@ bf47c19e:c3d2573b
2025-05-22 21:03:52Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Šta je finansijski samo-suverenitet?
- Zašto smo prestali da koristimo zlatni standard?
- Šta fali tradicionalnoj valuti i centralnim bankama?
- Kako mogu ljudi da mi ukradu novac ako je u banci?
- Kako ljudi koriste moje finansijske podatke protiv mene?
- Kako ljudi kontrolišu sa kim obavljam transakcije?
- Kako da povratimo svoj finansijski samo-suverenitet?
- Kako Bitcoin funkcioniše?
- Pa onda, zašto Bitcoin?
- Po čemu je Bitcoin bolji od sistema tradicionalnih valuta?
- Kako Bitcoin štiti od Inflacije?
- Kako Bitcoin štiti od Zaplene?
- Kako Bitcoin štiti Privatnost?
- Kako Bitcoin štiti od Cenzure?
- Šta će vlada i banke učiniti sa Bitcoin-om?
- Da li je vrednost Bitcoin-a nestabilna?
- Da li je Bitcoin novac?
- Bitcoin kao Zaliha Vrednosti
- Bitcoin kao Sredstvo Razmene
- Bitcoin kao Obračunska Jedinica
- Bitcoin kao Sistem Kontrole
- Šta je sa „Sledećim Bitcoin-om“?
- Na kraju
Kratki uvod u bezbednost, privatnost i slobodu vašeg novca.
Pre nego što saznate kako morate znati zašto.
Šta je finansijski samo-suverenitet?
Zamislite da u ruci imate zlatni novčić, jedan od najjednostavnijih i najčistijih oblika finansijskog samo-suvereniteta.
Da biste držali taj zlatni novčić, ne morate da se složite sa bilo kojim Uslovima korišćenja ili Politikom privatnosti, da se pridržavate bilo kojih KYC ili AML propisa, da pokažete ličnu kartu, da navedete svoje ime ili jedinstveni matični broj.
Samo ga držite u ruci i njime možete platiti bilo šta, davanjem tog novčića nekom drugom da ga drži u ruci. To je čista sloboda.
Pored slobode onoga što kupujete svojim novčićem, niko ne može magično znati kome plaćate ili koju robu/usluge kupujete tim zlatni novčićem, jer vaša privatnost nije ugrožena sa zlatom.
A pošto imate svoju privatnost, niko ne može znati za vaše transakcije, pa niko ne može da odluči da ograniči ili kontroliše za šta koristite taj zlatni novčić.
Hiljadama godina zlato je bilo globalni standard novca.
Svi su održavali svoj finansijski samo-suverenitet, a privatnost i sloboda svačijeg novca su poštovani.
Zaista je bilo tako jednostavno.
Zašto smo prestali da koristimo zlatni standard?
Trenutni globalni bankarski sistem i sistem tradicionalnih valuta, bankari su vrlo polako implementirali u proteklih 100+ godina.
Udružili su se sa svetskim vladama koje su svima oduzele zlato pod pretnjom nasilja.
Na primer, nakon što je Federalna banka rezervi osnovana u SAD-u 1913. godine, američka vlada je nasilno oduzela svo zlato 1933. godine, prisiljavajući sve da koriste nove centralne banke i sistem novčanica Federalnih rezervi.
 „Dostavite svoje celokupno zlato u naše sefove u zamenu za bezvredni papir, ili ćemo upotrebiti silu nad vama.“
„Dostavite svoje celokupno zlato u naše sefove u zamenu za bezvredni papir, ili ćemo upotrebiti silu nad vama.“Banke su u početku zamenile zlatni standard papirnim priznanicama zvane zlatni sertifikati, ali nakon što je prošlo dovoljno vremena, banke su u osnovi jednostavno prestale da ih otkupljuju za zlato.
Zlatni sertifikati izdavani od banaka (novčanice ili „gotovina“) u tom trenutku bili su samo bezvredni papir, ali zbog vladine pretnje nasiljem, svi su bili primorani da nastave da koriste novčanice Federalnih rezervi.
Od skora, banke koriste digitalnu bazu podataka, u kojoj doslovno mogu stvoriti novac ni iz čega, čak i da ga ne moraju štampati na papiru.
Predsednik Federalnih rezervi priča kako oni „štampaju“ novac.
Oni su učvrstili svoju moć da manipulišu i naduvaju globalnu novčanu masu, nadgledaju finansijske transakcije svih i kontrolišu protok svih tradicionalnih valuta u svom bankarskom sistemu.
Banke sada kontrolišu sve.
Jednom kada su centralni bankari uspešno preuzeli kontrolu nad novčanom masom u svetu, zajedno sa sposobnošću svih da slobodno vrše transakcije i trguju, svet je kolektivno izgubio bezbednost, slobodu i privatnost svog novca.
Šta fali tradicionalnoj valuti i centralnim bankama?
Nakon impelentacije trenutnog globalnog bankarskog sistema i sistema tradicionalnih valuta, svetu nije preostao drugi izbor nego da veruje bankarima i političarima da vode globalni finansijski sistem na pošten način.
„Koren problema tradicionalne valute je potpuno poverenje potrebno za njeno funkcionisanje. Centralnoj banci se mora verovati da neće devalvirati valutu, ali istorija tradicionalnih valuta je puna kršenja tog poverenja. Bankama se mora verovati da čuvaju naš novac i prenose ga elektronskim putem, ali ga daju u talasima kreditnih balona sa malim delićem rezerve. ““ — Satoshi Nakamoto
Istorija zloupotrebe tradicionalnih valuta može se grupisati u 3 kategorije:
• Bezbednost. Loši ljudi kradu vaš novac ili vrednost vašeg novca, ponekad na očigledne načine, ponekad na podle načine.
• Privatnost. Loši ljudi nadgledaju sve vaše privatne finansijske transakcije, i koriste vaše lične finansijske podatke protiv vas.
• Sloboda. Loši ljudi kontrolišu na koji način možete da trošite sopstveni novac, sa kim možete da obavljate transakcije, koliko možete da potrošite itd.
Kako mogu ljudi da mi ukradu novac ako je u banci?
Evo nekoliko primera:
-
Krađa inflacijom: Ovo je primarni način na koji banke kradu vaš novac i jedan od najpodlijih. Kada centralne banke izdaju novi novac, bilo štampanjem na bezvrednom papiru, ili samo dodavanjem knjigovodstvenog unosa u bazu podataka koju kontrolišu, one naduvaju globalnu novčanu masu. Inflacija krade kupovnu moć svih koji drže deo te valute, jednostavno zato što je sada više te valute u opticaju. Zlato se ne može stvoriti, pa su bankari umesto toga izmislili sistem papirnog novca.
-
Krađa zaplenom: Ovo je jedan od načina na koji vlade mogu ukrasti vaš novac. Da li ste ikada čuli za zaplenu imovine? Ako policajac posumnja da je vaša imovina korišćena u krivičnom delu, može je zapleniti, a vi se morate boriti da biste povratili vašu ukradenu imovinu. Ili, drugi primer: Pokušajte da uđete u zemlju sa više od 10.000 USD u džepu, a ne da je prijavite, i pogledajte šta će se dogoditi. Sve je isto: krađa od strane drugih ljudi sa oružjem.
-
Krađa putem oporezivanja: Ovo je još jedan način na koji vam vlade kradu novac. Ne sporim da li je oporezivanje etično ili ne, samo konstatujem činjenicu da vaša vlada može da primora vašu banku da im da vaš novac, a ovo je bezbednostna ranjivost. Da bi novac bio siguran, mora biti nezaplenjiv, a vlade mogu da zaplene vaše bankovne račune.
Kako ljudi koriste moje finansijske podatke protiv mene?
Ako fizičku tradicionalnu valutu predate drugoj osobi, u obliku papirnog novca ili kovanica, relativno je lako zaštititi privatnost svoje transakcije, baš kao što bi bilo da koristite zlatnike.
Međutim, ako koristite kreditne kartice, debitne kartice, bankovne transfere, PayPal, Venmo, LINE Pay, WeChat Pay ili bilo koju drugu mrežu za plaćanje koja je centralno kontrolisana, aktivno pristajete da se odreknete privatnosti podataka svih svojih privatnih finansijskih transakcija i sve ih dajete poverljivoj trećoj strani.
Kada su svi podaci i metapodaci vaših finansijskih transakcija prijavljeni u centralnu bazu podataka, onaj ko ima pristup toj bazi podataka može da koristi vaše podatke protiv vas.
Evo nekoliko osnovnih primera:
- Ako ste kupili robu rizičnog životnog stila poput cigareta, banka može reći vašoj osiguravajućoj kompaniji da poveća vaše osiguranje.
- Ako ste kupili nešto što je ilegalno, poput droga za rekreaciju, vaša banka može reći vašoj vladi da vas zakonski goni.
Ali u slučaju nekih represivnih vlada, oni su to odveli do ekstrema. Oni centralno prikupljaju sve finansijske transakcije i druge podatke svih svojih građana i stvorili su totalitarni Sistem Socijalnih Bodova (eng. Social Credit Score):
 Prepoznavanje lica je jedan od elemenata kineskih napora za praćenje
Prepoznavanje lica je jedan od elemenata kineskih napora za praćenjeZapisi George Orwell-a već su postali stvarnost u Kini zbog sistema tradicionalnih valuta centralne banke i platnih mreža koje su izgrađene na njemu.
Ako mislite da se to neće dogoditi u vašoj zemlji, razmislite ponovo.
To se dešava vrlo polako, ali na kraju će sve svetske vlade primeniti Sistem Socijalnih Bodova, dok je Kina to tek prva učinila.
Kako ljudi kontrolišu sa kim obavljam transakcije?
U prvom primeru sa zlatnim novčićem, kada ga predate nekom drugom kao plaćanje za robu ili uslugu, ne postoji centralizovana evidencija vaše platne transakcije i imate savršenu privatnost.
Međutim, u centralnom bankarskom sistemu, budući da banka ima i znanje o podacima o vašim transakcijama i moć da kontroliše vaša sredstva, oni mogu proceniti niz pravila da bi odlučili da li žele da dozvole vašu transakciju ili da to odbiju, takođe kao i izvršenje te odluke kontrolišući vaša sredstva.
Tako su vlade naoružale tradicionalne valute i centralni bankarski sistem kao Sistem Kontrole nad svojim građanima.
Da rezimiramo: Pošto ste se odrekli bezbednosti i privatnosti svog novca, izgubili ste i svoju finansijsku slobodu.
“Privatnost nije o tome da nešto treba sakriti. Privatnost je o tome da nešto treba zaštititi.” — Edward Snowden
Kako da povratimo svoj finansijski samo-suverenitet?
Pokret Cypherpunk pokrenuli su pojedinci koji su shvatili važnost zaštite privatnosti i slobode pojedinačnih korisnika na Internetu.
Cypherpunk-ovi su verovali da se gore opisani problemi mogu rešiti samo potpuno novim novčanim sistemom, koji poštuje i štiti bezbednost, privatnost i slobodu pojedinca.
Mnogi od Cypherpunk-era pokušali su da izgrade nove etičke sisteme e-gotovine koji bi mogli da zamene tradicionalne valute i centralno bankarstvo.
Bilo je mnogo teških računarskih problema koje je trebalo prevazići u stvaranju tako istinski decentralizovanog sistema, i ako su neki od njih bili blizu cilja, svi su propali.
Odnosno, sve dok jedan pseudonim Cypherpunk-a to konačno nije shvatio 2008. godine: kombinacijom digitalnih potpisa, distribuirane knjige i peer-to-peer mreže, rođen je Bitcoin.
Kako Bitcoin funkcioniše?
Baš kao što ne treba da znate kako Internet funkcioniše da bi gledali slike mačaka na Internetu, razumevanje tehničke složenosti načina na koji Bitcoin radi „ispod haube“ nije neophodno da biste ga koristili i postigli sopstveni finansijski samo-suverenitet.
Važna stvar koju želim da saznate iz ovog članka je da iako većina novih tehnologija u početku ima loše korisničko iskustvo, Bitcoin svesno i vrlo namerno ne žrtvuje svoje osnovne filozofske principe da bi brže pridobio nove korisnike, ili da bi poboljšao korisničko iskustvo.
Najpametniji Cypherpunk-ovi rade na poboljšanju korisničkog iskustva.
Tehnologija će se sa vremenom poboljšavati, baš kao i za Internet.
Pa onda, zašto Bitcoin?
Reći ću vam zašto:
Jer Bitcoin poštuje bezbednost, privatnost i slobodu pojedinca.
Po čemu je Bitcoin bolji od sistema tradicionalnih valuta?
Za početak, Bitcoin nema Uslove korišćenja, Politiku privatnosti i Propise o usklađenosti sa KYC/AML. (Know Your Costumer & Anti-money Laundering)
Bitcoin je uspešan primer implementacije kripto-anarhije, gde su jedina pravila kriptografija, matematika i jak skup konsenzusnih pravila.
To je distribuirani i nepoverljivi sistem zasnovan na finansijskim podsticajima i nijedna osoba ili centralizovani entitet ne može da kontroliše Bitcoin.
Ono što je najvažnije, Bitcoin vam omogućava da odustanete od tradicionalnih valuta, sistema delimičnih rezervi i centralnog bankarstva rešavanjem osnovnih problema poverenja:
- Sigurnost od inflacije korišćenjem fiksnog snabdevanja
- Sigurnost od zaplene korišćenjem ključeva za kontrolu sredstava
- Privatnost plaćanja korišćenjem pseudonimnih identiteta
- Sloboda protiv cenzure korišćenjem peer to peer mreže
Kako Bitcoin štiti od Inflacije?
Jedno od najkritičnijih pravila konsenzusa o Bitcoin-u je da može postojati najviše 21,000,000 Bitcoin-a.
Nakon izdavanja svih Bitcoin-a, nikada više ne može doći do stvaranja novih Bitcoin-a.
Stoga je Bitcoin deflaciona valuta, koja sprečava ljude da ukradu vaš novac ili njegovu vrednost naduvavanjem novčane mase.
 Monetarna Inflacija Bitcoin-a
Monetarna Inflacija Bitcoin-aKako Bitcoin štiti od Zaplene?
Bitcoin se može preneti samo pomoću kriptografskog privatnog ključa koji kontroliše sredstva.
Nijedan bitcoin nikada ne izadje van sistema.
Nijedna vlada, banka ili sudski nalog ne mogu zapleniti ta sredstva.
Jednostavno ne postoji način da se takva odredba ili naredba sprovede od bilo kog „organa vlasti“, jer Bitcoin ne priznaje nijedno „ovlašćenje“ u svom sistemu.
Bitcoin je potpuno samo-suveren sistem i zbog svoje distribuirane prirode ne može se ugasiti.
Postoji zbog sopstvenih zasluga, samo zato što ljudi veruju u to.
Kako Bitcoin štiti Privatnost?
Bitcoin ne traži vaše ime ili druge detalje koji mogu lično da vas identifikuju.
Vaš identitet je kriptografski, a ne vaše stvarno ime.
Dakle, vaš identitet izgleda otprilike kao 1vizSAISbuiKsbt9d8JV8itm5ackk2TorC, a ne kao „Stefan Petrovič“.
Pored toga, niko ne zna ko kontroliše sredstva na datoj Bitcoin adresi, a nova tehnologija se neprestano razvija kako bi se poboljšala privatnost Bitcoin-a.
Kako Bitcoin štiti od Cenzure?
Peer-to-peer Bitcoin mreža je u potpunosti distribuirana.
To znači da ako jedan čvor pokuša da cenzuriše vašu transakciju, neće uspeti ukoliko * svaki * čvor(Node) ne izvrši cenzuru vaše transakcije.
Šta će vlada i banke učiniti sa Bitcoin-om?
Neke zemlje su pokušale da ga regulišu, kontrolišu, isključe itd., ali nijedna od njih nije uspela.
Čini se da uglavnom samo žele da koriste postojeći sistem centralnih banaka da bi kontrolisali kako ljudi trguju tradicionalnim valutama za Bitcoin, i naravno žele da oporezuju Bitcoin na bilo koji mogući način.
Evo nekoliko uobičajenih tvrdnji vlada i banaka o Bitcoin-u:
 Evropska centralna banka kaže da Bitcoin nije valuta i upozorava da je vrlo nestabilna.
Evropska centralna banka kaže da Bitcoin nije valuta i upozorava da je vrlo nestabilna.„Bitcoin, izgleda samo kao prevara“, rekao je gospodin Tramp. „Ne sviđa mi se jer je to još jedna valuta koja se takmiči sa dolarom.“
Da li je vrednost Bitcoin-a nestabilna?
Ako umanjite grafikon cena, videćete da Bitcoin-u neprekidno raste vrednost od kada je stvoren, trgujući sa manje od 0,01 USD i polako se penje na preko 60.000 USD na nedavnom vrhuncu početkom 2021. godine.
 Cena Bitcoina od 2011. godine
Cena Bitcoina od 2011. godineTo je zato što je njegova ponuda fiksna i ljudi cene njegovu nestašicu.
Sa većom potražnjom i fiksnom ponudom, cene vremenom rastu.
Kako godine odmiču, njegova vrednost će se povećavati kako novi korisnici počinju da drže Bitcoin. (U svetu Bitcoina držanju kažemo HODL. Drži bitcoin. Hodl bitcoin.)
Da li je Bitcoin novac?
Da biste odgovorili na pitanje da li je Bitcoin novac ili ne, prvo morate definisati pojam „novac“.
Nažalost, reč „novac“ koristimo da bismo opisali nekoliko vrlo različitih komplikovanih koncepata, koji su svi potpuno odvojeni.
Termin „novac“ se zapravo odnosi na:
- Zaliha Vrednosti (Store of Value)
- Sredstvo Razmene ( Medium of Exchange)
- Obračunska Jedinica (Unit of Account)
- Sistem Kontrole (System Control)
Bitcoin kao Zaliha Vrednosti
Ovaj tweet to savršeno objašnjava:
Sinov prijatelj: “Matt, šta će se dogoditi ako novčić od 1 funte usitnite na pola?”
Dobijaš dva komada bezvrednog metala. Ako zlatnik usitnite na pola, dobićete dva zlatnika, od kojih svaki vredi polovinu onoga što je novčić bio.
Sin: „… isto tako kao sa zlatom jeste sa bitcoinima“.
Bitcoin je potpuno deljiv i deluje kao izvrsna zaliha vrednosti, baš kao što je i zlato već hiljadama godina.
Bitcoin kao Sredstvo Razmene
Bitcoin je dobro služio kao sredstvo razmene za svoje rane korisnike.
Ali skaliranje Bitcoin-a na globalni nivo koji bi mogao da posluži svim ljudima je veliki izazov, jer se osnovna „blockchain“ tehnologija ne skalira na globalni nivo.
Da bi rešio ovaj problem skaliranja, Satoshi je izumeo koncept kanala plaćanja, a u kombinaciji sa malo pomoći drugih briljantnih računarskih naučnika Cipherpunk-a koji su poboljšali koncept tokom poslednjih 10 godina, sada imamo mrežu Lightning, koja omogućava da se Bitcoin koristi kao odlično Sredstvo Razmene, koje se vremenom može proširiti na globalni nivo.
Bitcoin kao Obračunska Jedinica
Najmanja obračunska jedinica Bitcoin-a nazvana je po njenom tvorcu, Satoshi-u.
Jedan Bitcoin je jednak 100.000.000 Satoshi-a.
Na kraju, kako se robe i usluge sve češće razmenjuju za Bitcoin, sve više ljudi će koristiti Bitcoin ili „Sats“ kao obračunsku jedinicu.
Bitcoin kao Sistem Kontrole
Budući da je Bitcoin dizajniran da poštuje i štiti ljudska prava pojedinca, posebno bezbednost, privatnost i slobodu novca; ne bi bio dobar Sistem Kontrole i ne može se koristiti za ugnjetavanje ljudi, kao što se dešava sa tradicionalnim valutama i sistemima centralnog bankarstva koji to trenutno vrlo dobro rade.
Šta je sa „Sledećim Bitcoin-om“?
Kao što može biti samo jedan „globalni“ Internet, tako može biti i samo jedan globalni novac, a stigao je i novi Bitcoin Standard.
Sve ostalo je ili direktna prevara ili gubljenje vremena.
Ako bi neko želeo da vam proda „Sledeće Zlato“, da li biste ga kupili?
Na kraju
Nadam se da vam je ovaj članak pomogao da razumete zašto je Bitcoin stvoren i kako može da pomogne svetu da se oslobodi tradicionalnih valuta i sistema centralnog bankarstva koji je veoma duboko integrisan u naše trenutno društvo.
Evo nekoliko misli koje treba poneti sa sobom:
- Bitcoin nije izmišljen radi zarade, već je izmišljen da bi promenio svet.
- Bitcoin će to učiniti poštujući korisnikovu bezbednost, privatnost i slobodu.
- Bitcoin se već koristi kao novac, na nekoliko načina na koji se novac može koristiti.
- Bitcoin nije nestabilan, njegova vrednost vremenom polako raste (odzumirajte).
- Bitcoin ima mnogo kopija i prevaranata koji će pokušati da vam prodaju svoju kopiju Bitcoin-a. Ne zavaravajte se lažnim Bitcoin-om baš kao što vas ne bi prevarili ni Lažnim Zlatom.
- Bitcoin će postati najveći prenos bogatstva u našem životu, tako da ćete možda želeti da ih uzmete pre nego kasnije.
- Ostanite skromni i skupljajte satošije.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:48:56
@ 6d5c826a:4b27b659
2025-05-23 21:48:56- ActiveMQ - Java message broker. (Source Code)
Apache-2.0Java - BeanstalkD - A simple, fast work queue. (Source Code)
MITC - Gearman - Fast multi-language queuing/job processing platform. (Source Code)
BSD-3-ClauseC++ - NSQ - A realtime distributed messaging platform. (Source Code)
MPL-2.0Go - ZeroMQ - Lightweight queuing system. (Source Code)
GPL-3.0C++
- ActiveMQ - Java message broker. (Source Code)
-
 @ 866e0139:6a9334e5
2025-05-23 17:57:24
@ 866e0139:6a9334e5
2025-05-23 17:57:24Autor: Caitlin Johnstone. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Ich hörte einem jungen Autor zu, der eine Idee beschrieb, die ihn so sehr begeisterte, dass er die Nacht zuvor nicht schlafen konnte. Und ich erinnerte mich daran, wie ich mich früher – vor Gaza – über das Schreiben freuen konnte. Dieses Gefühl habe ich seit 2023 nicht mehr gespürt.
Ich beklage mich nicht und bemitleide mich auch nicht selbst, ich stelle einfach fest, wie unglaublich düster und finster die Welt in dieser schrecklichen Zeit geworden ist. Es wäre seltsam und ungesund, wenn ich in den letzten anderthalb Jahren Freude an meiner Arbeit gehabt hätte. Diese Dinge sollen sich nicht gut anfühlen. Nicht, wenn man wirklich hinschaut und ehrlich zu sich selbst ist in dem, was man sieht.
Es war die ganze Zeit über so hässlich und so verstörend. Es gibt eigentlich keinen Weg, all diesen Horror umzudeuten oder irgendwie erträglich zu machen. Alles, was man tun kann, ist, an sich selbst zu arbeiten, um genug inneren Raum zu schaffen, um die schlechten Gefühle zuzulassen und sie ganz durchzufühlen, bis sie sich ausgedrückt haben. Lass die Verzweiflung herein. Die Trauer. Die Wut. Den Schmerz. Lass sie deinen Körper vollständig durchfließen, ohne Widerstand, und steh dann auf und schreibe das nächste Stück.
Das ist es, was Schreiben für mich jetzt ist. Es ist nie etwas, worüber ich mich freue, es zu teilen, oder wofür ich von Inspiration erfüllt bin. Wenn überhaupt, dann fühlt es sich eher so an wie: „Okay, hier bitte, es tut mir schrecklich leid, dass ich euch das zeigen muss, Leute.“ Es ist das Starren in die Dunkelheit, in das Blut, in das Gemetzel, in die gequälten Gesichter – und das Aufschreiben dessen, was ich sehe, Tag für Tag.
Nichts daran ist angenehm oder befriedigend. Es ist einfach das, was man tut, wenn ein Genozid in Echtzeit vor den eigenen Augen stattfindet, mit der Unterstützung der eigenen Gesellschaft. Alles daran ist entsetzlich, und es gibt keinen Weg, das schönzureden – aber man tut, was getan werden muss. So, wie man es täte, wenn es die eigene Familie wäre, die da draußen im Schutt liegt.
Dieser Genozid hat mich für immer verändert. Er hat viele Menschen für immer verändert. Wir werden nie wieder dieselben sein. Die Welt wird nie wieder dieselbe sein. Ganz gleich, was passiert oder wie dieser Albtraum endet – die Dinge werden nie wieder so sein wie zuvor.
Und das sollten sie auch nicht. Der Holocaust von Gaza ist das Ergebnis der Welt, wie sie vor ihm war. Unsere Gesellschaft hat ihn hervorgebracht – und jetzt starrt er uns allen direkt ins Gesicht. Das sind wir. Das ist die Frucht des Baumes, den die westliche Zivilisation bis zu diesem Punkt gepflegt hat.
Jetzt geht es nur noch darum, alles zu tun, was wir können, um den Genozid zu beenden – und sicherzustellen, dass die Welt die richtigen Lehren daraus zieht. Das ist eines der würdigsten Anliegen, denen man sich in diesem Leben widmen kann.
Ich habe noch immer Hoffnung, dass wir eine gesunde Welt haben können. Ich habe noch immer Hoffnung, dass das Schreiben über das, was geschieht, eines Tages wieder Freude bereiten kann. Aber diese Dinge liegen auf der anderen Seite eines langen, schmerzhaften, konfrontierenden Weges, der in den kommenden Jahren vor uns liegt. Es gibt keinen Weg daran vorbei.
Die Welt kann keinen Frieden und kein Glück finden, solange wir uns nicht vollständig damit auseinandergesetzt haben, was wir Gaza angetan haben.
Dieser Text ist die deutsche Übersetzung dieses Substack-Artikels von Caitlin Johnstone.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 04c915da:3dfbecc9
2025-02-25 03:55:08
@ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 91bea5cd:1df4451c
2025-05-23 17:04:49
@ 91bea5cd:1df4451c
2025-05-23 17:04:49Em nota, a prefeitura justificou que essas alterações visam ampliar a segurança das praias, conforto e organização, para os frequentadores e trabalhadores dos locais. No entanto, Orla Rio, concessionária responsável pelos espaços, e o SindRio, sindicato de bares e restaurantes, ficou insatisfeita com as medidas e reforçou que a música ao vivo aumenta em mais de 10% o ticket médio dos estabelecimentos e contribui para manter os empregos, especialmente na baixa temporada.
De acordo com Paes, as medidas visam impedir práticas ilegais para que a orla carioca continue sendo um espaço ativo econômico da cidade: “Certas práticas são inaceitáveis, especialmente por quem tem autorização municipal. Vamos ser mais restritivos e duros. A orla é de todos”.
Saiba quais serão as 16 proibições nas praias do Rio de Janeiro
- Utilização de caixas de som, instrumentos musicais, grupos ou qualquer equipamento sonoro, em qualquer horário. Apenas eventos autorizados terão permissão.
- Venda ou distribuição de bebidas em garrafas de vidro em qualquer ponto da areia ou do calçadão.
- Estruturas comerciais ambulantes sem autorização, como carrocinhas, trailers, food trucks e barracas.
- Comércio ambulante sem permissão, incluindo alimentos em palitos, churrasqueiras, isopores ou bandejas térmicas improvisadas.
- Circulação de ciclomotores e patinetes motorizados no calçadão.
- Escolinhas de esportes ou recreações não autorizadas pelo poder público municipal.
- Ocupação de área pública com estruturas fixas ou móveis de grandes proporções sem autorização.
- Instalação de acampamentos improvisados em qualquer trecho da orla.
- Práticas de comércio abusivo ou enganosas, incluindo abordagens insistentes. Quiosques e barracas devem exibir cardápio, preços e taxas de forma clara.
- Uso de animais para entretenimento, transporte ou comércio.
- Hasteamento ou exibição de bandeiras em mastros ou suportes.
- Fixação de objetos ou amarras em árvores ou vegetação.
- Cercadinhos feitos por ambulantes ou quiosques, que impeçam a livre circulação de pessoas.
- Permanência de carrinhos de transporte de mercadorias ou equipamentos fora dos momentos de carga e descarga.
- Armazenamento de produtos, barracas ou equipamentos enterrados na areia ou depositados na vegetação de restinga.
- Uso de nomes, marcas, logotipos ou slogans em barracas. Apenas a numeração sequencial da prefeitura será permitida.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:48:36
@ 6d5c826a:4b27b659
2025-05-23 21:48:36- aptly - Swiss army knife for Debian repository management. (Source Code)
MITGo - fpm - Versatile multi format package creator. (Source Code)
MITRuby - omnibus-ruby - Easily create full-stack installers for your project across a variety of platforms.
Apache-2.0Ruby - tito - Builds RPMs for git-based projects.
GPL-2.0Python
- aptly - Swiss army knife for Debian repository management. (Source Code)
-
 @ 21335073:a244b1ad
2025-03-12 00:40:25
@ 21335073:a244b1ad
2025-03-12 00:40:25Before I saw those X right-wing political “influencers” parading their Epstein binders in that PR stunt, I’d already posted this on Nostr, an open protocol.
“Today, the world’s attention will likely fixate on Epstein, governmental failures in addressing horrific abuse cases, and the influential figures who perpetrate such acts—yet few will center the victims and survivors in the conversation. The survivors of Epstein went to law enforcement and very little happened. The survivors tried to speak to the corporate press and the corporate press knowingly covered for him. In situations like these social media can serve as one of the only ways for a survivor’s voice to be heard.
It’s becoming increasingly evident that the line between centralized corporate social media and the state is razor-thin, if it exists at all. Time and again, the state shields powerful abusers when it’s politically expedient to do so. In this climate, a survivor attempting to expose someone like Epstein on a corporate tech platform faces an uphill battle—there’s no assurance their voice would even break through. Their story wouldn’t truly belong to them; it’d be at the mercy of the platform, subject to deletion at a whim. Nostr, though, offers a lifeline—a censorship-resistant space where survivors can share their truths, no matter how untouchable the abuser might seem. A survivor could remain anonymous here if they took enough steps.
Nostr holds real promise for amplifying survivor voices. And if you’re here daily, tossing out memes, take heart: you’re helping build a foundation for those who desperately need to be heard.“
That post is untouchable—no CEO, company, employee, or government can delete it. Even if I wanted to, I couldn’t take it down myself. The post will outlive me on the protocol.
The cozy alliance between the state and corporate social media hit me hard during that right-wing X “influencer” PR stunt. Elon owns X. Elon’s a special government employee. X pays those influencers to post. We don’t know who else pays them to post. Those influencers are spurred on by both the government and X to manage the Epstein case narrative. It wasn’t survivors standing there, grinning for photos—it was paid influencers, gatekeepers orchestrating yet another chance to re-exploit the already exploited.
The bond between the state and corporate social media is tight. If the other Epsteins out there are ever to be unmasked, I wouldn’t bet on a survivor’s story staying safe with a corporate tech platform, the government, any social media influencer, or mainstream journalist. Right now, only a protocol can hand survivors the power to truly own their narrative.
I don’t have anything against Elon—I’ve actually been a big supporter. I’m just stating it as I see it. X isn’t censorship resistant and they have an algorithm that they choose not the user. Corporate tech platforms like X can be a better fit for some survivors. X has safety tools and content moderation, making it a solid option for certain individuals. Grok can be a big help for survivors looking for resources or support! As a survivor, you know what works best for you, and safety should always come first—keep that front and center.
That said, a protocol is a game-changer for cases where the powerful are likely to censor. During China's # MeToo movement, survivors faced heavy censorship on social media platforms like Weibo and WeChat, where posts about sexual harassment were quickly removed, and hashtags like # MeToo or "woyeshi" were blocked by government and platform filters. To bypass this, activists turned to blockchain technology encoding their stories—like Yue Xin’s open letter about a Peking University case—into transaction metadata. This made the information tamper-proof and publicly accessible, resisting censorship since blockchain data can’t be easily altered or deleted.
I posted this on X 2/28/25. I wanted to try my first long post on a nostr client. The Epstein cover up is ongoing so it’s still relevant, unfortunately.
If you are a survivor or loved one who is reading this and needs support please reach out to: National Sexual Assault Hotline 24/7 https://rainn.org/
Hours: Available 24 hours
-
 @ 5144fe88:9587d5af
2025-05-23 17:01:37
@ 5144fe88:9587d5af
2025-05-23 17:01:37The recent anomalies in the financial market and the frequent occurrence of world trade wars and hot wars have caused the world's political and economic landscape to fluctuate violently. It always feels like the financial crisis is getting closer and closer.
This is a systematic analysis of the possibility of the current global financial crisis by Manus based on Ray Dalio's latest views, US and Japanese economic and financial data, Buffett's investment behavior, and historical financial crises.
Research shows that the current financial system has many preconditions for a crisis, especially debt levels, market valuations, and investor behavior, which show obvious crisis signals. The probability of a financial crisis in the short term (within 6-12 months) is 30%-40%,
in the medium term (within 1-2 years) is 50%-60%,
in the long term (within 2-3 years) is 60%-70%.
Japan's role as the world's largest holder of overseas assets and the largest creditor of the United States is particularly critical. The sharp appreciation of the yen may be a signal of the return of global safe-haven funds, which will become an important precursor to the outbreak of a financial crisis.
Potential conditions for triggering a financial crisis Conditions that have been met 1. High debt levels: The debt-to-GDP ratio of the United States and Japan has reached a record high. 2. Market overvaluation: The ratio of stock market to GDP hits a record high 3. Abnormal investor behavior: Buffett's cash holdings hit a record high, with net selling for 10 consecutive quarters 4. Monetary policy shift: Japan ends negative interest rates, and the Fed ends the rate hike cycle 5. Market concentration is too high: a few technology stocks dominate market performance
Potential trigger points 1. The Bank of Japan further tightens monetary policy, leading to a sharp appreciation of the yen and the return of overseas funds 2. The US debt crisis worsens, and the proportion of interest expenses continues to rise to unsustainable levels 3. The bursting of the technology bubble leads to a collapse in market confidence 4. The trade war further escalates, disrupting global supply chains and economic growth 5. Japan, as the largest creditor of the United States, reduces its holdings of US debt, causing US debt yields to soar
Analysis of the similarities and differences between the current economic environment and the historical financial crisis Debt level comparison Current debt situation • US government debt to GDP ratio: 124.0% (December 2024) • Japanese government debt to GDP ratio: 216.2% (December 2024), historical high 225.8% (March 2021) • US total debt: 36.21 trillion US dollars (May 2025) • Japanese debt/GDP ratio: more than 250%-263% (Japanese Prime Minister’s statement)
Before the 2008 financial crisis • US government debt to GDP ratio: about 64% (2007) • Japanese government debt to GDP ratio: about 175% (2007)
Before the Internet bubble in 2000 • US government debt to GDP ratio: about 55% (1999) • Japanese government debt to GDP ratio: about 130% (1999)
Key differences • The current US debt-to-GDP ratio is nearly twice that before the 2008 crisis • The current Japanese debt-to-GDP ratio is more than 1.2 times that before the 2008 crisis • Global debt levels are generally higher than historical pre-crisis levels • US interest payments are expected to devour 30% of fiscal revenue (Moody's warning)
Monetary policy and interest rate environment
Current situation • US 10-year Treasury yield: about 4.6% (May 2025) • Bank of Japan policy: end negative interest rates and start a rate hike cycle • Bank of Japan's holdings of government bonds: 52%, plans to reduce purchases to 3 trillion yen per month by January-March 2026 • Fed policy: end the rate hike cycle and prepare to cut interest rates
Before the 2008 financial crisis • US 10-year Treasury yield: about 4.5%-5% (2007) • Fed policy: continuous rate hikes from 2004 to 2006, and rate cuts began in 2007 • Bank of Japan policy: maintain ultra-low interest rates
Key differences • Current US interest rates are similar to those before the 2008 crisis, but debt levels are much higher than then • Japan is in the early stages of ending its loose monetary policy, unlike before historical crises • The size of global central bank balance sheets is far greater than at any time in history
Market valuations and investor behavior Current situation • The ratio of stock market value to the size of the US economy: a record high • Buffett's cash holdings: $347 billion (28% of assets), a record high • Market concentration: US stock growth mainly relies on a few technology giants • Investor sentiment: Technology stocks are enthusiastic, but institutional investors are beginning to be cautious
Before the 2008 financial crisis • Buffett's cash holdings: 25% of assets (2005) • Market concentration: Financial and real estate-related stocks performed strongly • Investor sentiment: The real estate market was overheated and subprime products were widely popular
Before the 2000 Internet bubble • Buffett's cash holdings: increased from 1% to 13% (1998) • Market concentration: Internet stocks were extremely highly valued • Investor sentiment: Tech stocks are in a frenzy
Key differences • Buffett's current cash holdings exceed any pre-crisis level in history • Market valuation indicators have reached a record high, exceeding the levels before the 2000 bubble and the 2008 crisis • The current market concentration is higher than any period in history, and a few technology stocks dominate market performance
Safe-haven fund flows and international relations Current situation • The status of the yen: As a safe-haven currency, the appreciation of the yen may indicate a rise in global risk aversion • Trade relations: The United States has imposed tariffs on Japan, which is expected to reduce Japan's GDP growth by 0.3 percentage points in fiscal 2025 • International debt: Japan is one of the largest creditors of the United States
Before historical crises • Before the 2008 crisis: International capital flows to US real estate and financial products • Before the 2000 bubble: International capital flows to US technology stocks
Key differences • Current trade frictions have intensified and the trend of globalization has weakened • Japan's role as the world's largest holder of overseas assets has become more prominent • International debt dependence is higher than any period in history
-
 @ 9bcc5462:eb501d90
2025-02-24 17:47:28
@ 9bcc5462:eb501d90
2025-02-24 17:47:28Every generation loves to learn. However, our public schooling system has gone as far as it can take us. The abundance of easily accessible information on the internet, coupled with emerging tech like AI, decentralized protocols and bitcoin, means this is our time to innovate our learning infrastructure. A complete overhaul is due along with the development of a pilot program to test new and unconventional models.
Let’s carve a path towards innovation by sparking discussion around this topic. Hence, this blueprint. It is a gauntlet for any person who genuinely wants to become a stakeholder for our country’s future. Entry points are:
- Builders—Startups, developers and investors who will fund and create infrastructure.
- Practitioners—Educators and researchers who will test models.
- Supporters—Parents, donors and community members who want to contribute.
Where Do We Begin?
Let’s think about crafting the main components of a new pilot model. Below are suggested areas of focus:
- DEFINITION
- APPROACH
- PHILOSOPHY
- CULTURE
- PHYSICAL DESIGN
- OPERATIONAL ORGANIZATION
- ACCOUNTABILITY METHODS
- RISKS & CHALLENGES
- STYLE
- STAKEHOLDERS
How It Works
After researching your pedagogical ideas for current and future generations of scholars, it’s time to share your insights. Contribute your viewpoint by structuring a blueprint—one page per section—in the following sequence:
- Definition of your modern learning model with its key principles.
- Description of the core learning approach.
- Philosophy distilled into central concepts that will orient stakeholders.
- Culture your modern learning model aspires to live by.
- Potential challenges, risks and drawbacks.
- Design of physical spaces and rationale.
- Operational framework detailing adult and child learning organization.
- Accountability methods to ensure skill growth and competency.
- Style development and name of your model.
- Skin in the game, sign your model with your first and last name (unite stakeholders).
Perhaps if enough stakeholders come together, we can begin to actualize a more effective and updated way of learning. This is a challenge meant to separate those willing to engage in discourse, planning and laying foundations from those content to complain from the sidelines.
Why Now and Where Does the Money Come From?
After being a public educator for fifteen years, I learned you will not change the system, the system will change you. It’s time to design and build above and apart from the current model. 2025 is when courageous people step up to the plate and discuss our learning infrastructure. Whether it’s contributing out of the box thinking, modernizing curriculum, investing in startups or creating your own venture; there is no greater time than now. And no greater place than in the USA!
(By extension, we also create the opportunity to influence our global allies including our neighbors to the North and South.)
“But how!?” Learning Producers is figuring it out by asking not, “how?” but “who?” Who will unite together to develop our learning infrastructure? If you decide you want to participate and join our efforts, share your blueprint as well. For all stakeholders, this is an investment in an untapped market of a new learning economy.
If not, you’re not alone. Some consider this just rhetoric, idealism, or wishful thinking. Additionally, it is unclear how such actions can be profitable or how such infrastructure building will be funded. Money talks. Bullshit walks, right? In that case, let’s talk, and let’s fine tune our BS detectors. Onward, with this call to action:
- Share your own blueprint online or reach out to Learning Producers, Inc. (Learningproducers.com).
- Conduct research on an ideal location and team to lay foundations on a pilot program at small scale.
- Engage in dialogue with investors interested in developing learning infrastructure for their own children and families.
- Secure stakeholders to develop and test a real world pilot model (real location, real agreements, real timeline, real people).
- Sponsor or donate resources to counter concerns over funding.
Now, we leave you with our blueprint:
PEDAGOGICAL WABI-SABI
We hope you enjoy it.
Sincerely,
Israel Hernandez
Founder of Learning Producers
**[Read or download full blueprint here: https://www.learningproducers.com/blog/pedagogical-wabi-sabiblueprint-for-developing-learning-infrastructure ]
-
 @ 0e9491aa:ef2adadf
2025-05-22 19:01:21
@ 0e9491aa:ef2adadf
2025-05-22 19:01:21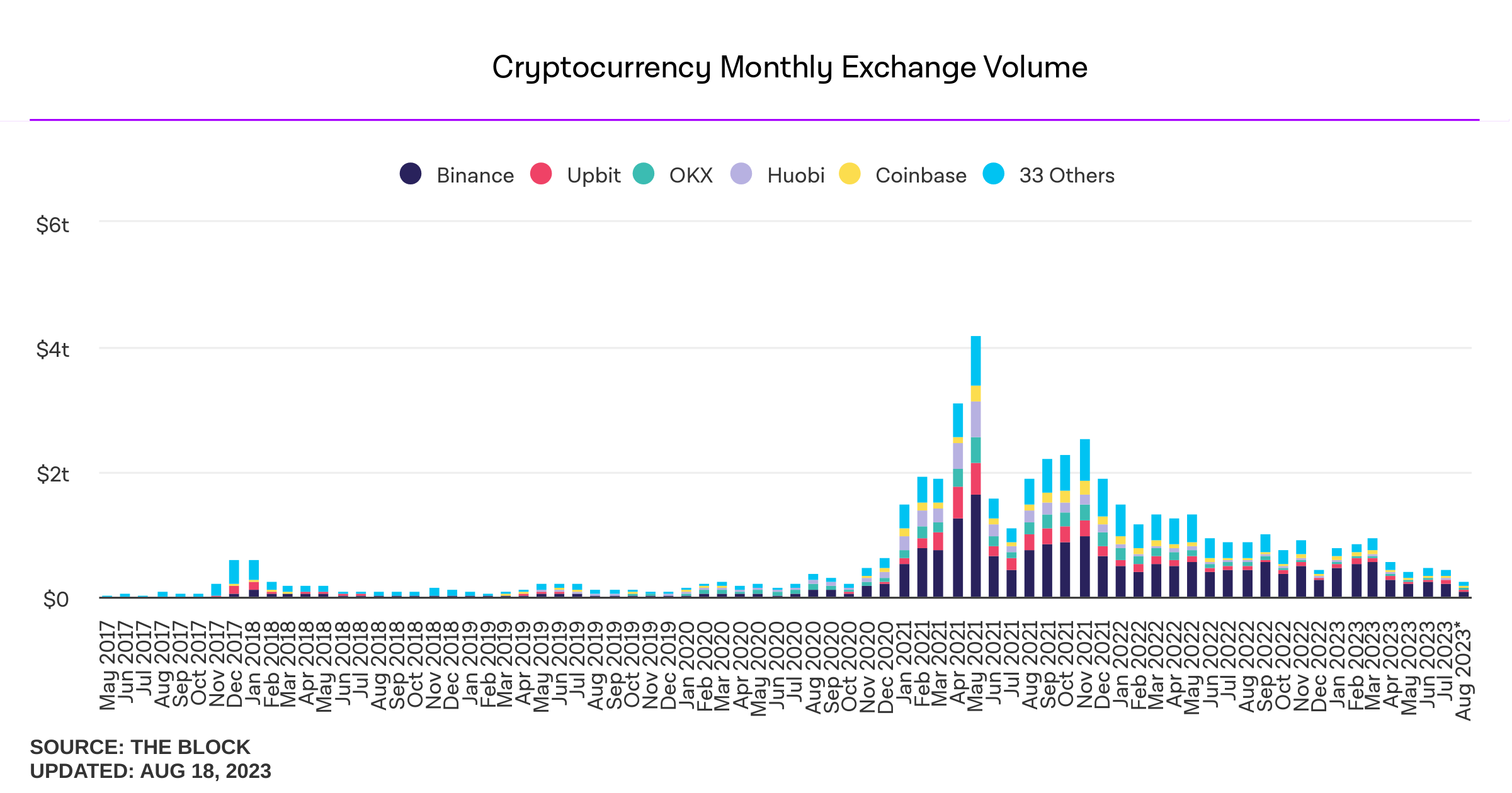
Influencers would have you believe there is an ongoing binance bank run but bitcoin wallet data says otherwise.
- binance wallets are near all time highs
- bitfinex wallets are also trending up
- gemini and coinbase are being hit with massive withdrawals thoughYou should not trust custodians, they can rug you without warning. It is incredibly important you learn how to hold bitcoin yourself, but also consider not blindly trusting influencers with a ref link to shill you.
If you found this post helpful support my work with bitcoin.

-
 @ 94a6a78a:0ddf320e
2025-02-19 21:10:15
@ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables decentralized, censorship-resistant communication. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on users, developers, and relay operators.
If you believe in free speech, decentralization, and an open internet, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, every effort helps build a more robust network.
Here’s how you can get involved and make a difference.
1️⃣ Use Nostr Daily
The simplest and most effective way to contribute to Nostr is by using it regularly. The more active users, the stronger and more valuable the network becomes.
✅ Post, comment, and zap (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ Engage with new users and help them understand how Nostr works.\ ✅ Try different Nostr clients like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience.
Your activity keeps the network alive and helps encourage more developers and relay operators to invest in the ecosystem.
2️⃣ Run Your Own Nostr Relay
Relays are the backbone of Nostr, responsible for distributing messages across the network. The more independent relays exist, the stronger and more censorship-resistant Nostr becomes.
✅ Set up your own relay to help decentralize the network further.\ ✅ Experiment with relay configurations and different performance optimizations.\ ✅ Offer public or private relay services to users looking for high-quality infrastructure.
If you're not technical, you can still support relay operators by subscribing to a paid relay or donating to open-source relay projects.
3️⃣ Support Paid Relays & Infrastructure
Free relays have helped Nostr grow, but they struggle with spam, slow speeds, and sustainability issues. Paid relays help fund better infrastructure, faster message delivery, and a more reliable experience.
✅ Subscribe to a paid relay to help keep it running.\ ✅ Use premium services like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ Donate to relay operators who invest in long-term infrastructure.
By funding Nostr’s decentralized backbone, you help ensure its longevity and reliability.
4️⃣ Zap Developers, Creators & Builders
Many people contribute to Nostr without direct financial compensation—developers who build clients, relay operators, educators, and content creators. You can support them with zaps! ⚡
✅ Find developers working on Nostr projects and send them a zap.\ ✅ Support content creators and educators who spread awareness about Nostr.\ ✅ Encourage builders by donating to open-source projects.
Micro-payments via the Lightning Network make it easy to directly support the people who make Nostr better.
5️⃣ Develop New Nostr Apps & Tools
If you're a developer, you can build on Nostr’s open protocol to create new apps, bots, or tools. Nostr is permissionless, meaning anyone can develop for it.
✅ Create new Nostr clients with unique features and user experiences.\ ✅ Build bots or automation tools that improve engagement and usability.\ ✅ Experiment with decentralized identity, authentication, and encryption to make Nostr even stronger.
With no corporate gatekeepers, your projects can help shape the future of decentralized social media.
6️⃣ Promote & Educate Others About Nostr
Adoption grows when more people understand and use Nostr. You can help by spreading awareness and creating educational content.
✅ Write blogs, guides, and tutorials explaining how to use Nostr.\ ✅ Make videos or social media posts introducing new users to the protocol.\ ✅ Host discussions, Twitter Spaces, or workshops to onboard more people.
The more people understand and trust Nostr, the stronger the ecosystem becomes.
7️⃣ Support Open-Source Nostr Projects
Many Nostr tools and clients are built by volunteers, and open-source projects thrive on community support.
✅ Contribute code to existing Nostr projects on GitHub.\ ✅ Report bugs and suggest features to improve Nostr clients.\ ✅ Donate to developers who keep Nostr free and open for everyone.
If you're not a developer, you can still help with testing, translations, and documentation to make projects more accessible.
🚀 Every Contribution Strengthens Nostr
Whether you:
✔️ Post and engage daily\ ✔️ Zap creators and developers\ ✔️ Run or support relays\ ✔️ Build new apps and tools\ ✔️ Educate and onboard new users
Every action helps make Nostr more resilient, decentralized, and unstoppable.
Nostr isn’t just another social network—it’s a movement toward a free and open internet. If you believe in digital freedom, privacy, and decentralization, now is the time to get involved.
-
 @ cae03c48:2a7d6671
2025-05-23 16:01:05
@ cae03c48:2a7d6671
2025-05-23 16:01:05Bitcoin Magazine

Spark Partners with Breez to Launch Bitcoin-Native SDK for Lightning PaymentsToday, Breez and Spark have announced a new implementation of the Breez SDK, built on Spark’s Bitcoin-native Layer 2 infrastructure. According to a press release sent to Bitcoin Magazine, the update is intended to make it easier for developers to integrate self-custodial Bitcoin Lightning payments into everyday apps and services.
Few companies are as good as @Breez_Tech at putting Bitcoin in people’s hands. We’re incredibly humbled to have them building on Spark.
Learn more → https://t.co/KRPpWJa3os pic.twitter.com/QiCfHbWu9d
— Spark (@buildonspark) May 22, 2025
“This is what the future of Bitcoin looks like — fast, open, and embedded in the apps people use every day. By teaming up with Breez, we’re expanding the ecosystem and giving developers powerful, Bitcoin-native tools to build next-generation payment experiences. Together, we’re building the standard for global, peer-to-peer transactions,” said the creator of Spark Kevin Hurley.
The SDK supports LNURL, Lightning addresses, real-time mobile notifications, and includes bindings for all major programming languages and frameworks. It is designed to allow developers to build directly on Bitcoin without relying on bridges or external consensus. This collaboration gives developers tools to add Bitcoin payment features to apps used for monetization social apps, cross-border remittances, and in-game currencies.
“We need developers to bring Bitcoin into apps people use every day,” said the CEO of Breez Roy Sheinfeld. “That’s why we built the Breez SDK. We’re excited to build on Spark’s revolutionary architecture — giving developers a powerful new Bitcoin-native option and continuing to strengthen Lightning as the common language of Bitcoin.”
Breez will also operate as a Spark Service Provider (SSP), alongside Lightspark, to help support payment facilitation and the growth of Spark’s ecosystem. The new implementation is expected to be released later this year.
“We’re excited to see what developers build with Spark; it’s very exciting to see this come to the world,” said the co-founder and CEO of Lightspark David Marcus.
The Breez SDK is expanding

We’re joining forces with @buildonspark to release a new nodeless implementation of the Breez SDK — giving developers the tools they need to bring Bitcoin payments to everyday apps.
Bitcoin-Native
Powered by Spark’s…— Breez
 (@Breez_Tech) May 22, 2025
(@Breez_Tech) May 22, 2025Yesterday, Magic Eden also partnered with Spark to improve Bitcoin trading by addressing issues like slow transaction times, high fees, and poor user experience. The integration will introduce a native settlement system aimed at making transactions faster and more cost-effective, without using bridges or synthetic assets.
“We’re proud to be betting on BTC DeFi,” said the CEO of Magic Eden Jack Lu. “We’re going to lead the forefront of all Bitcoin DeFi to make BTC fast, fun, and for everyone with Magic Eden as the #1 BTC native app on-chain.”
This post Spark Partners with Breez to Launch Bitcoin-Native SDK for Lightning Payments first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 90152b7f:04e57401
2025-05-23 15:48:58
@ 90152b7f:04e57401
2025-05-23 15:48:58U.S. troops would enforce peace under Army study
The Washington Times - September 10, 2001
by Rowan Scarborough
https://www.ord.io/70787305 (image) https://www.ord.io/74522515 (text)
An elite U.S. Army study center has devised a plan for enforcing a major Israeli-Palestinian peace accord that would require about 20,000 well-armed troops stationed throughout Israel and a newly created Palestinian state. There are no plans by the Bush administration to put American soldiers into the Middle East to police an agreement forged by the longtime warring parties. In fact, Defense Secretary Donald H. Rumsfeld is searching for ways to reduce U.S. peacekeeping efforts abroad, rather than increasing such missions. But a 68-page paper by the Army School of Advanced Military Studies (SAMS) does provide a look at the daunting task any international peacekeeping force would face if the United Nations authorized it, and Israel and the Palestinians ever reached a peace agreement.
Located at Fort Leavenworth, Kan., the School for Advanced Military Studies is both a training ground and a think tank for some of the Army’s brightest officers. Officials say the Army chief of staff, and sometimes the Joint Chiefs of Staff, ask SAMS to develop contingency plans for future military operations. During the 1991 Persian Gulf war, SAMS personnel helped plan the coalition ground attack that avoided a strike up the middle of Iraqi positions and instead executed a “left hook” that routed the enemy in 100 hours.
The cover page for the recent SAMS project said it was done for the Joint Chiefs of Staff. But Maj. Chris Garver, a Fort Leavenworth spokesman, said the study was not requested by Washington. “This was just an academic exercise,” said Maj. Garver. “They were trying to take a current situation and get some training out of it.” The exercise was done by 60 officers dubbed “Jedi Knights,” as all second-year SAMS students are nicknamed.
The SAMS paper attempts to predict events in the first year of a peace-enforcement operation, and sees possible dangers for U.S. troops from both sides. It calls Israel’s armed forces a “500-pound gorilla in Israel. Well armed and trained. Operates in both Gaza . Known to disregard international law to accomplish mission. Very unlikely to fire on American forces. Fratricide a concern especially in air space management.”
Of the Mossad, the Israeli intelligence service, the SAMS officers say: “Wildcard. Ruthless and cunning. Has capability to target U.S. forces and make it look like a Palestinian/Arab act.”
On the Palestinian side, the paper describes their youth as “loose cannons; under no control, sometimes violent.” The study lists five Arab terrorist groups that could target American troops for assassination and hostage-taking. The study recommends “neutrality in word and deed” as one way to protect U.S. soldiers from any attack. It also says Syria, Egypt and Jordan must be warned “we will act decisively in response to external attack.”
It is unlikely either of the three would mount an attack. Of Syria’s military, the report says: “Syrian army quantitatively larger than Israeli Defense Forces, but largely seen as qualitatively inferior. More likely, however, Syrians would provide financial and political support to the Palestinians, as well as increase covert support to terrorism acts through Lebanon.” Of Egypt’s military, the paper says, “Egyptians also maintain a large army but have little to gain by attacking Israel.”
The plan does not specify a full order of battle. An Army source who reviewed the SAMS work said each of a possible three brigades would require about 100 Bradley fighting vehicles, 25 tanks, 12 self-propelled howitzers, Apache attack helicopters, Kiowa Warrior reconnaissance helicopters and Predator spy drones. The report predicts that nonlethal weapons would be used to quell unrest. U.S. European Command, which is headed by NATO’s supreme allied commander, would oversee the peacekeeping operation. Commanders would maintain areas of operation, or AOs, around Nablus, Jerusalem, Hebron and the Gaza strip. The study sets out a list of goals for U.S. troops to accomplish in the first 30 days. They include: “create conditions for development of Palestinian State and security of “; ensure “equal distribution of contract value or equivalent aid” that would help legitimize the peacekeeping force and stimulate economic growth; “promote U.S. investment in Palestine”; “encourage reconciliation between entities based on acceptance of new national identities”; and “build lasting relationship based on new legal borders and not religious-territorial claims.”
Maj. Garver said the officers who completed the exercise will hold major planning jobs once they graduate. “There is an application process” for students, he said. “They screen their records, and there are several tests they go through before they are accepted by the program. The bright planners of the future come out of this program.”
James Phillips, a Middle East analyst at the Heritage Foundation, said it would be a mistake to put peacekeepers in Israel, given the “poor record of previous monitors.” “In general, the Bush administration policy is to discourage a large American presence,” he said. “But it has been rumored that one of the possibilities might be an expanded CIA role.” “It would be a very different environment than Bosnia,” said Mr. Phillips, referring to America’s six-year peacekeeping role in Bosnia-Herzegovina. “The Palestinian Authority is pushing for this as part of its strategy to internationalize the conflict. Bring in the Europeans and Russia and China. But such monitors or peacekeeping forces are not going to be able to bring peace. Only a decision by the Palestinians to stop the violence and restart talks could possibly do that.”
<<https://www.ord.io/70787305>>
<<<https://www.ord.io/74522515>>>
-
 @ da8b7de1:c0164aee
2025-05-22 16:19:52
@ da8b7de1:c0164aee
2025-05-22 16:19:52Technológiai és fejlesztési hírek
- Észtország SMR-tervei:
Észtország hivatalosan elindította a nemzeti tervezési folyamatot és a környezeti hatásvizsgálatot egy 600 MW-os kis moduláris reaktor (SMR) atomerőmű létesítésére, GE Hitachi BWRX-300 technológiával. A projektet a Fermi Energia vezeti, a lakosság körében mérsékelt támogatottság mellett. Az építési engedélykérelem benyújtását 2029-re tervezik, a cél az ország energiabiztonságának és klímacéljainak erősítése.
- Olkiluoto-1 csökkentett teljesítménnyel üzemel:
Finnországban az Olkiluoto-2 egységben a generátor rotorjának cseréje miatt a termelés májusban újraindul, de a teljesítményt 735 MW-ra korlátozzák (a teljes kapacitás 890 MW). A csökkentett teljesítmény 2026-ig marad érvényben. Az Olkiluoto-1 egység normálisan működik, az Olkiluoto-3 pedig éves karbantartáson van.
Ipari és pénzügyi fejlemények
- Kanada–Argentína nehézvíz-együttműködés:
A kanadai Candu Energy (AtkinsRéalis) és az argentin Nemzeti Atomenergia Bizottság (CNEA) memorandumot írt alá a nehézvíz-termelés fellendítéséről. Ez magában foglalja az argentin PIAP nehézvízgyár újraindítását és potenciálisan új üzemek építését Kanadában. A fejlesztés támogatja a meglévő és tervezett CANDU reaktorok működését világszerte, és illeszkedik a COP28 utáni globális nukleáris bővüléshez.
- USA: nukleáris adókedvezményekért folyó lobbizás:
Az amerikai nukleáris ipar intenzív lobbitevékenységet folytat, hogy megőrizze a Biden-adminisztráció által bevezetett, az Inflációcsökkentő Törvény (IRA) szerinti nukleáris adókedvezményeket. Az új, republikánus többségű költségvetési törvényjavaslat jelentősen lerövidítené a tiszta energia (szél, nap, akkumulátor) támogatásokat, de a nukleáris ipar számára bizonyos kedvezmények megmaradnának, bár a 45U nukleáris adókedvezmény is három évvel korábban, 2031-ben lejárhat.
- Háztartási és ipari érdekek:
Az amerikai ház költségvetési törvényjavaslata megszüntetné a legtöbb tiszta energiához kapcsolódó adókedvezményt, kivéve néhány nukleáris projektet, és szigorítaná a kínai kapcsolatokkal rendelkező projektek támogatását. Ez várhatóan visszaveti a megújuló energiaipar beruházásait, miközben a nukleáris szektor relatív pozíciója javulhat.
Politikai és társadalmi fejlemények
- Tajvan: népszavazás a nukleáris energia sorsáról:
Tajvan parlamentje megszavazta, hogy népszavazást tartsanak a Maanshan atomerőmű újraindításáról, miután az ország utolsó működő reaktorát is leállították. A referendum nem azonnali újraindításról szól, hanem arról, hogy a lakosság döntsön a meghosszabbításról, ha a hatóságok biztonságosnak találják az üzemet.
- Pennsylvania kormányzója a nukleáris energia mellett:
Josh Shapiro, Pennsylvania kormányzója, a „Lightning Plan” keretében hangsúlyozta, hogy az állam energiabiztonsága és gazdasági fejlődése érdekében kulcsszerepet szán a nukleáris energiának, valamint más megbízható energiaforrásoknak. A terv célja a munkahelyteremtés, a fogyasztói költségek csökkentése és az engedélyezési folyamatok gyorsítása.
- TMI névváltás:
Az amerikai Nukleáris Szabályozó Hatóság (NRC) jóváhagyta a Three Mile Island (TMI) atomerőmű nevének megváltoztatását Christopher M. Crane-re, az Exelon volt vezérigazgatójának emlékére. A létesítmény a jövőben a Microsoft AI műveleteit is ellátja majd árammal, és 2028-tól 835 MW szén-dioxid-mentes áramot termelhet.
Nemzetközi szakmai események
- NEA konferencia Londonban:
Az OECD NEA 2025. június 18–19-én Londonban rendezi meg az „Excellence in Nuclear Construction” nemzetközi konferenciát. A rendezvény célja, hogy a nukleáris ipar szereplői megosszák tapasztalataikat a nukleáris beruházások gyorsabb, kiszámíthatóbb és költséghatékonyabb megvalósítása érdekében, különös tekintettel a mérnöki, beszerzési és kivitelezési (EPC) kihívásokra.
Hivatkozások
- https://www.nucnet.org
- https://www.world-nuclear-news.org
- https://www.neimagazine.com
- https://www.oecd-nea.org
- https://www.iaea.org
- https://www.reuters.com/business/energy
- https://www.utilitydive.com
- https://www.atkinsrealis.com
- https://www.candu.com
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 6389be64:ef439d32
2025-02-27 21:32:12
@ 6389be64:ef439d32
2025-02-27 21:32:12GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below.
House Democrats’ MEME Act: A Bad Joke?
House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself.
Senate Banking’s First Digital Asset Hearing: The Real Target Is You
Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.”
Bank of America and PayPal Want In on Stablecoins
Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance.
MetaPlanet Buys the Dip
Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats.
UK Expands Crypto Seizure Powers
Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance.
Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk
Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier.
The Bottom Line
The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control.
🎧 Listen to the full episode here: https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks
💰 Support the show by boosting sats on Podcasting 2.0! and I will see you on the other side.
-
 @ 146904a0:890e2a2f
2025-05-23 22:47:55
@ 146904a0:890e2a2f
2025-05-23 22:47:55How Bukele’s bold bitcoin move gained global attention but left the public behind
In a quiet coastal town called El Zonte, where dusty streets meet ocean waves, an amazing experiment began in 2019. A Christian surfer named Mike Peterson arrived with an anonymous bitcoin donation, given with one condition: it must be used only in bitcoin.
This sparked the birth of Bitcoin Beach, a micro-economy powered by Bitcoin, and unknowingly laid the groundwork for the most radical financial experiment ever attempted by a government.
At the Bitcoin 2021 Conference in Miami, El Salvador’s president, Nayib Bukele, appeared via video, making a shocking announcement: his country, El Salvador, would become the first in the world to adopt bitcoin as legal tender.
Just three days later in under five hours, with no public consultation or economic analysis. The Bitcoin Law was approved by El Salvador’s Legislative Assembly—This happened shortly after Bukele had removed the Constitutional Court and Attorney General, effectively eliminating institutional checks.
The government launched its official digital wallet: Chivo Wallet, offering $30 in bitcoin to every citizen who downloaded and registered.
But what was promised as a financial revolution quickly turned chaotic:
-
The app was riddled with technical failures.
-
Thousands of Salvadorans couldn’t access their funds.
-
Identity theft became rampant, with fake accounts created to fraudulently claim the bonus.
Public confidence plummeted, and trust disappeared. For most Salvadorans, bitcoin became a ghost.
According to verified reports:
-
$150M went to a conversion fund ( liquidity for the Chivo wallet)
-
$30M to the Chivo bonus
-
$23.3M to ATMs and infrastructure
-
$2M to marketing and tools
With total cost above $200M USD.
Meanwhile, no audit has ever been released, and most government data is classified.
What did the Salvadoran people get?
-
79% of Salvadorans never used Bitcoin after taking their 30 USD out of the Chivo wallet.
-
Only 10% of businesses accept it
-
Remittances via BTC? Just 1.5% of the total
-
Foreign investment? It actually dropped after the rollout
But yet in El Zonte, where "the bitcoin beach" is located, locals are now being pushed out as land prices soar. A luxury Bitcoin Beach Club is evicting families. The town that started it all is now being sold off—one beach front at a time.
But Bukele won the spotlight
Bitcoin was born as open-source money—neutral, permission-less, and voluntary. No Bitcoiner came to it by force; we each arrived for our own reasons: financial sovereignty, censorship resistance, or simple curiosity. That spirit of freedom stands in sharp contrast to any top-down attempt to impose it on an entire population.
In January 29 2025, El Salvador’s Legislative Assembly hurried through a set of amendments to the 2021 Bitcoin Law. The reform scrapped the mandate that every merchant must accept BTC and removed bitcoin’s status as legal tender, turning it into an optional payment instrument.
Those changes came just days before the IMF approved a US $1.4 billion Extended Fund Facility. The new agreement explicitly required “unwinding” state participation in Chivo and dropping bitcoin as legal tender.
Bukele once framed bitcoin as a symbol of “financial freedom,” yet the 2025 rollback shows the opposite: His government needed Bitcoin’s headline power more than Bitcoin needed state endorsement. True adoption will come, if it comes at all, because Salvadorans choose it—just as millions worldwide already do—not because a decree tells them to.
While the people saw few benefits, Bukele gained international fame. He became the “Bitcoin President,” speaking at conferences, meeting with bitcoin whales, and podcasters, positioning El Salvador as a bitcoin paradise. This is far from reality. The legal tender label is gone, but El Salvador’s citizens remain free to experiment with BTC on their own terms—and many eventually will.
Sources:
-
Bukele: El Señor de los Sueños – Ep. 4\ Produced by: Central Podcast & Radio Ambulante Studios
-
reported by Silvia Biñas and Gabriel Labrador
-
Official transcript: centralpodcast.audio/transcripcion/episodio-4
-
Verified data from FES, Yahoo Finance.
-
-
 @ c7e8fdda:b8f73146
2025-05-22 14:13:31
@ c7e8fdda:b8f73146
2025-05-22 14:13:31🌍 Too Young. Too Idealistic. Too Alive. A message came in recently that stopped me cold.
It was from someone young—16 years old—but you’d never guess it from the depth of what they wrote. They spoke of having dreams so big they scare people. They’d had a spiritual awakening at 14, but instead of being nurtured, it was dismissed. Surrounded by people dulled by bitterness and fear, they were told to be realistic. To grow up. To face “reality.”
This Substack is reader-supported. To receive new posts and support my work, consider becoming a free or paid subscriber.
And that reality, to them, looked like a life that doesn’t feel like living at all.
They wrote that their biggest fear wasn’t failure—it was settling. Dimming their fire. Growing into someone they never chose to be.
And that—more than anything—scared them.
They told me that my book, I Don’t Want to Grow Up, brought them to tears because it validated what they already knew to be true. That they’re not alone. That it’s okay to want something different. That it’s okay to feel everything.
It’s messages like this that remind me why I write.
As many of you know, I include my personal email address at the back of all my books. And I read—and respond to—every single message that comes in. Whether it’s a few sentences or a life story, I see them all. And again and again, I’m reminded: there are so many of us out here quietly carrying the same truth.
Maybe you’ve felt the same. Maybe you still do.
Maybe you’ve been told your dreams are too big, too unrealistic. Maybe people around you—people who love you—try to shrink them down to something more “manageable.” Maybe they call it protection. Maybe they call it love.
But it feels like fear.
The path you wish to walk might be lonelier at first. It might not make sense to the people around you. But if it lights you up—follow it.
Because when you do, you give silent permission to others to do the same. You become living proof that another kind of life is possible. And that’s how we build a better world.
So to the person who wrote to me—and to every soul who feels the same way:
Keep going. Keep dreaming. Keep burning. You are not too young. You are not too idealistic. You are just deeply, radically alive.
And that is not a problem. That is a gift.
—
If this speaks to you, my book I Don’t Want to Grow Up was written for this very reason—to remind you that your wildness is sacred, your truth is valid, and you’re not alone. Paperback/Kindle/Audiobook available here: scottstillmanblog.com
This Substack is reader-supported. To receive new posts and support my work, consider becoming a free or paid subscriber. https://connect-test.layer3.press/articles/041a2dc8-5c42-4895-86ec-bc166ac0d315
-
 @ c1e9ab3a:9cb56b43
2025-05-18 04:14:48
@ c1e9ab3a:9cb56b43
2025-05-18 04:14:48Abstract
This document proposes a novel architecture that decouples the peer-to-peer (P2P) communication layer from the Bitcoin protocol and replaces or augments it with the Nostr protocol. The goal is to improve censorship resistance, performance, modularity, and maintainability by migrating transaction propagation and block distribution to the Nostr relay network.
Introduction
Bitcoin’s current architecture relies heavily on its P2P network to propagate transactions and blocks. While robust, it has limitations in terms of flexibility, scalability, and censorship resistance in certain environments. Nostr, a decentralized event-publishing protocol, offers a multi-star topology and a censorship-resistant infrastructure for message relay.
This proposal outlines how Bitcoin communication could be ported to Nostr while maintaining consensus and verification through standard Bitcoin clients.
Motivation
- Enhanced Censorship Resistance: Nostr’s architecture enables better relay redundancy and obfuscation of transaction origin.
- Simplified Lightweight Nodes: Removing the full P2P stack allows for lightweight nodes that only verify blockchain data and communicate over Nostr.
- Architectural Modularity: Clean separation between validation and communication enables easier auditing, upgrades, and parallel innovation.
- Faster Propagation: Nostr’s multi-star network may provide faster propagation of transactions and blocks compared to the mesh-like Bitcoin P2P network.
Architecture Overview
Components
-
Bitcoin Minimal Node (BMN):
- Verifies blockchain and block validity.
- Maintains UTXO set and handles mempool logic.
- Connects to Nostr relays instead of P2P Bitcoin peers.
-
Bridge Node:
- Bridges Bitcoin P2P traffic to and from Nostr relays.
- Posts new transactions and blocks to Nostr.
- Downloads mempool content and block headers from Nostr.
-
Nostr Relays:
- Accept Bitcoin-specific event kinds (transactions and blocks).
- Store mempool entries and block messages.
- Optionally broadcast fee estimation summaries and tipsets.
Event Format
Proposed reserved Nostr
kindnumbers for Bitcoin content (NIP/BIP TBD):| Nostr Kind | Purpose | |------------|------------------------| | 210000 | Bitcoin Transaction | | 210001 | Bitcoin Block Header | | 210002 | Bitcoin Block | | 210003 | Mempool Fee Estimates | | 210004 | Filter/UTXO summary |
Transaction Lifecycle
- Wallet creates a Bitcoin transaction.
- Wallet sends it to a set of configured Nostr relays.
- Relays accept and cache the transaction (based on fee policies).
- Mining nodes or bridge nodes fetch mempool contents from Nostr.
- Once mined, a block is submitted over Nostr.
- Nodes confirm inclusion and update their UTXO set.
Security Considerations
- Sybil Resistance: Consensus remains based on proof-of-work. The communication path (Nostr) is not involved in consensus.
- Relay Discoverability: Optionally bootstrap via DNS, Bitcoin P2P, or signed relay lists.
- Spam Protection: Relay-side policy, rate limiting, proof-of-work challenges, or Lightning payments.
- Block Authenticity: Nodes must verify all received blocks and reject invalid chains.
Compatibility and Migration
- Fully compatible with current Bitcoin consensus rules.
- Bridge nodes preserve interoperability with legacy full nodes.
- Nodes can run in hybrid mode, fetching from both P2P and Nostr.
Future Work
- Integration with watch-only wallets and SPV clients using verified headers via Nostr.
- Use of Nostr’s social graph for partial trust assumptions and relay reputation.
- Dynamic relay discovery using Nostr itself (relay list events).
Conclusion
This proposal lays out a new architecture for Bitcoin communication using Nostr to replace or augment the P2P network. This improves decentralization, censorship resistance, modularity, and speed, while preserving consensus integrity. It encourages innovation by enabling smaller, purpose-built Bitcoin nodes and offloading networking complexity.
This document may become both a Bitcoin Improvement Proposal (BIP-XXX) and a Nostr Improvement Proposal (NIP-XXX). Event kind range reserved: 210000–219999.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:48:21
@ 6d5c826a:4b27b659
2025-05-23 21:48:21- CapRover - Build your own PaaS in a few minutes. (Demo, Source Code)
Apache-2.0Docker/Nodejs - Coolify - An open-source & self-hostable Heroku / Netlify alternative (and even more). (Source Code)
Apache-2.0Docker - Dokku - An open-source PaaS (alternative to Heroku). (Source Code)
MITDocker/Shell/Go/deb - fx - A tool to help you do Function as a Service with painless on your own servers.
MITGo - Kubero - A self-hosted Heroku PaaS alternative for Kubernetes that implements GitOps. (Demo, Source Code)
GPL-3.0K8S/Nodejs/Go - LocalStack - LocalStack is a fully functional local AWS cloud stack. This includes Lambda for serverless computation. (Source Code)
Apache-2.0Python/Docker/K8S - Nhost - Firebase Alternative with GraphQL. Get a database and backend configured and ready in minutes. (Source Code)
MITDocker/Nodejs/Go - OpenFaaS - Serverless Functions Made Simple for Docker & Kubernetes. (Source Code)
MITGo - Tau - Easily build Cloud Computing Platforms with features like Serverless WebAssembly Functions, Frontend Hosting, CI/CD, Object Storage, K/V Database, and Pub-Sub Messaging. (Source Code)
BSD-3-ClauseGo/Rust/Docker - Trusted-CGI - Lightweight self-hosted lambda/applications/cgi/serverless-functions platform.
MITGo/deb/Docker
- CapRover - Build your own PaaS in a few minutes. (Demo, Source Code)
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ 9ca447d2:fbf5a36d
2025-05-22 14:01:39
@ 9ca447d2:fbf5a36d
2025-05-22 14:01:39Ed Suman, a 67-year-old retired artist who helped create large sculptures like Jeff Koons’ Balloon Dog, reportedly lost his entire life savings — over $2M in digital assets — in a sophisticated scam.
The incident is believed to be tied to the major data breach at Coinbase, one of the world’s largest digital asset exchanges.
Suman’s story is part of a bigger wave of attacks on digital asset holders using stolen personal info, and has triggered lawsuits, regulatory concerns and questions about digital security in the Bitcoin space.
In March 2025, Suman got a text message about suspicious activity on his Coinbase account. After Suman reported he was unaware of any unauthorized activity regarding his account, he got a call from a man who introduced himself as Brett Miller from Coinbase Security.
The guy sounded legit — he knew Suman’s setup, including that he used a Trezor Model One hardware wallet, a device meant to keep bitcoin and other digital assets offline and safe.
Suman told Bloomberg the guy knew everything, including the exact amount of digital assets he had.
The attacker persuaded Suman that his Trezor One hardware wallet and its funds were at risk and walked him through a “security procedure” that involved entering his seed phrase into a website that looked exactly like Coinbase, in order to “link his wallet to Coinbase”.
Nine days later, another guy called and repeated the process, saying the first one didn’t work.
And then, all of Suman’s digital assets — 17.5 bitcoin and 225 ether — were gone. At the time, bitcoin was around $103,000 and ether around $2,500, so the stolen stash was worth over $2 million.
Suman turned to digital assets after retiring from a decades-long art career. He stored his assets in cold storage to avoid the risks of online exchanges. He thought he did everything right.
Suman’s attackers didn’t pick his name out of a hat.
It looks like his personal info may have been leaked in the major breach at Coinbase. The company confirmed on May 15 that some of its customer service reps in India were bribed to access internal systems and steal customer data.
The stolen data included names, phone numbers, email addresses, balances and partial Social Security numbers.
According to Coinbase’s filing with the U.S. Securities and Exchange Commission, the breach may have started as early as January and affected nearly 1% of the company’s active monthly users — tens of thousands of people.
Hackers demanded $20M from Coinbase to keep the breach quiet but the company refused to pay. Coinbase says it fired the compromised agents and is setting aside $180M to $400M to reimburse affected users.
But so far, Suman hasn’t been told if he’ll be reimbursed.
Since the breach was disclosed, Coinbase has been hit with at least six lawsuits.
The lawsuits claim the company failed to protect user data and handled the aftermath poorly. One lawsuit filed in New York federal court on May 16 says Coinbase’s response was “inadequate, fragmented, and delayed.”
“Users were not promptly or fully informed of the compromise,” the complaint states, “and Coinbase did not immediately take meaningful steps to mitigate further harm.”
Some lawsuits are seeking damages, others are asking Coinbase to purge user data and improve its security. Coinbase has not commented on the lawsuits but pointed reporters to a blog post about its response.
Suman’s case is a cautionary tale across the Bitcoin world. He used a hardware wallet (considered the gold standard of Bitcoin security) and was still tricked through social engineering. Even the strongest security is useless if you don’t understand how Bitcoin works.
It’s never too early for Bitcoiners to start learning more about Bitcoin, especially on how to keep their stash safe. And the first lesson is “never ever share your seed phrase with anyone”.
Related: Bitcoin Hardware Wallet Hacks: What You Need to Know
-
 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ eb0157af:77ab6c55
2025-05-22 14:01:29
@ eb0157af:77ab6c55
2025-05-22 14:01:29A Chinese printer company inadvertently distributed malware that steals Bitcoin through its official drivers, resulting in the theft of over $950,000.
According to local media outlet Landian News, a Chinese printer manufacturer was found to have unknowingly distributed malware designed to steal Bitcoin through its official device drivers.
Procolored, a Shenzhen-based printer company, distributed malware capable of stealing Bitcoin alongside the official drivers for its devices. The company reportedly used USB devices to spread infected drivers and uploaded the compromised software to globally accessible cloud storage services.
Crypto security and compliance firm SlowMist explained how the malware works in a post on X:
 The official driver provided by this printer carries a backdoor program. It will hijack the wallet address in the user's clipboard and replace it with the attacker's address: 1BQZKqdp2CV3QV5nUEsqSg1ygegLmqRygj
The official driver provided by this printer carries a backdoor program. It will hijack the wallet address in the user's clipboard and replace it with the attacker's address: 1BQZKqdp2CV3QV5nUEsqSg1ygegLmqRygj  According to @MistTrack_io, the attacker has stolen 9.3086… https://t.co/DHCkEpHhuH pic.twitter.com/W1AnUpswLU
According to @MistTrack_io, the attacker has stolen 9.3086… https://t.co/DHCkEpHhuH pic.twitter.com/W1AnUpswLU— MistTrack
 (@MistTrack_io) May 19, 2025
(@MistTrack_io) May 19, 2025The consequences of the breach have been significant, with a total of 9.3 BTC stolen — equivalent to over $950,000.
The issue was first flagged by YouTuber Cameron Coward, whose antivirus software detected malware in the drivers during a test of a Procolored UV printer. The software identified both a worm and a trojan virus named Foxif.
When contacted, Procolored denied the accusations, dismissing the antivirus warning as a false positive. Coward then turned to Reddit, where he shared the issue with cybersecurity professionals, drawing the attention of security firm G Data.
G Data’s investigation revealed that most of Procolored’s drivers were hosted on the MEGA file-sharing platform, with uploads dating back to October 2023. Their analysis confirmed the presence of two separate malware strains: the Win32.Backdoor.XRedRAT.A backdoor and a crypto-stealer designed to replace clipboard wallet addresses with those controlled by the attacker.
G Data reached out to Procolored, which stated that it had removed the infected drivers from its storage as of May 8 and had re-scanned all files. The company attributed the malware to a supply chain compromise, saying the malicious files were introduced via infected USB devices before being uploaded online.
Landian News recommended that users who downloaded Procolored drivers in the past six months “immediately run a full system scan using antivirus software.” However, given that antivirus tools are not always reliable, the Chinese media outlet suggested that a full system reset is the safest option when in doubt.
The post Bitcoin malware discovered: Chinese printer manufacturer involved appeared first on Atlas21.
-
 @ 87e98bb6:8d6616f4
2025-05-23 15:36:32
@ 87e98bb6:8d6616f4
2025-05-23 15:36:32Use this guide if you want to keep your NixOS on the stable branch, but enable unstable application packages. It took me a while to figure out how to do this, so I wanted to share because it ended up being far easier than most of the vague explanations online made it seem.
I put a sample configuration.nix file at the very bottom to help it make more sense for new users. Remember to keep a backup of your config file, just in case!
If there are any errors please let me know. I am currently running NixOS 24.11.
Steps listed in this guide: 1. Add the unstable channel to NixOS as a secondary channel. 2. Edit the configuration.nix to enable unstable applications. 3. Add "unstable." in front of the application names in the config file (example: unstable.program). This enables the install of unstable versions during the build. 4. Rebuild.
Step 1:
- Open the console. (If you want to see which channels you currently have, type: sudo nix-channel --list)
- Add the unstable channel, type: sudo nix-channel --add https://channels.nixos.org/nixpkgs-unstable unstable
- To update the channels (bring in the possible apps), type: sudo nix-channel --update
More info here: https://nixos.wiki/wiki/Nix_channels
Step 2:
Edit your configuration.nix and add the following around your current config:
``` { config, pkgs, lib, ... }:
let unstable = import
{ config = { allowUnfree = true; }; }; in { #insert normal configuration text here } #remember to close the bracket!```
At this point it would be good to save your config and try a rebuild to make sure there are no errors. If you have errors, make sure your brackets are in the right places and/or not missing. This step will make for less troubleshooting later on if something happens to be in the wrong spot!
Step 3:
Add "unstable." to the start of each application you want to use the unstable version. (Example: unstable.brave)
Step 4:
Rebuild your config, type: sudo nixos-rebuild switch
Example configuration.nix file:
```
Config file for NixOS
{ config, pkgs, lib, ... }:
Enable unstable apps from Nix repository.
let unstable = import
{ config = { allowUnfree = true; }; }; in { #Put your normal config entries here in between the tags. Below is what your applications list needs to look like.
environment.systemPackages = with pkgs; [ appimage-run blender unstable.brave #Just add unstable. before the application name to enable the unstable version. chirp discord ];
} # Don't forget to close bracket at the end of the config file!
``` That should be all. Hope it helps.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:48:04
@ 6d5c826a:4b27b659
2025-05-23 21:48:04- GNS3 - Graphical network simulator that provides a variety of virtual appliances. (Source Code)
GPL-3.0Python - OpenWISP - Open Source Network Management System for OpenWRT based routers and access points. (Demo, Source Code)
GPL-3.0Python - Oxidized - Network device configuration backup tool.
Apache-2.0Ruby - phpIPAM - Open source IP address management with PowerDNS integration. (Source Code)
GPL-3.0PHP - RANCID - Monitor network devices configuration and maintain history of changes. (Source Code)
BSD-3-ClausePerl/Shell - rConfig - Network device configuration management tool. (Source Code)
GPL-3.0PHP
- GNS3 - Graphical network simulator that provides a variety of virtual appliances. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:47:44
@ 6d5c826a:4b27b659
2025-05-23 21:47:44- Adagios - Web based Nagios interface for configuration and monitoring (replacement to the standard interface), and a REST interface. (Source Code)
AGPL-3.0Docker/Python - Alerta - Distributed, scalable and flexible monitoring system. (Source Code)
Apache-2.0Python - Beszel - Lightweight server monitoring platform that includes Docker statistics, historical data, and alert functions. (Source Code)
MITGo - Cacti - Web-based network monitoring and graphing tool. (Source Code)
GPL-2.0PHP - cadvisor - Analyzes resource usage and performance characteristics of running containers.
Apache-2.0Go - checkmk - Comprehensive solution for monitoring of applications, servers, and networks. (Source Code)
GPL-2.0Python/PHP - dashdot - A simple, modern server dashboard for smaller private servers. (Demo)
MITNodejs/Docker - EdMon - A command-line monitoring application helping you to check that your hosts and services are available, with notifications support.
MITJava - eZ Server Monitor - A lightweight and simple dashboard monitor for Linux, available in Web and Bash application. (Source Code)
GPL-3.0PHP/Shell - glances - Open-source, cross-platform real-time monitoring tool with CLI and web dashboard interfaces and many exporting options. (Source Code)
GPL-3.0Python - Healthchecks - Monitoring for cron jobs, background services and scheduled tasks. (Source Code)
BSD-3-ClausePython - Icinga - Nagios fork that has since lapped nagios several times. Comes with the possibility of clustered monitoring. (Source Code)
GPL-2.0C++ - LibreNMS - Fully featured network monitoring system that provides a wealth of features and device support. (Source Code)
GPL-3.0PHP - Linux Dash - A low-overhead monitoring web dashboard for a GNU/Linux machine.
MITNodejs/Go/Python/PHP - Monit - Small utility for managing and monitoring Unix systems. (Source Code)
AGPL-3.0C - Munin - Networked resource monitoring tool. (Source Code)
GPL-2.0Perl/Shell - Naemon - Network monitoring tool based on the Nagios 4 core with performance enhancements and new features. (Source Code)
GPL-2.0C - Nagios - Computer system, network and infrastructure monitoring software application. (Source Code)
GPL-2.0C - Netdata - Distributed, real-time, performance and health monitoring for systems and applications. Runs on Linux, FreeBSD, and MacOS. (Source Code)
GPL-3.0C - NetXMS - Open Source network and infrastructure monitoring and management. (Source Code)
LGPL-3.0/GPL-3.0Java/C++/C - Observium Community Edition - Network monitoring and management platform that provides real-time insight into network health and performance.
QPL-1.0PHP - openITCOCKPIT Community Edition - Monitoring Suite featuring seamless integrations with Naemon, Checkmk, Grafana and more. (Demo, Source Code)
GPL-3.0deb/Docker - Performance Co-Pilot - Lightweight, distributed system performance and analysis framework. (Source Code)
LGPL-2.1/GPL-2.0C - PHP Server Monitor - Open source tool to monitor your servers and websites. (Source Code)
GPL-3.0PHP - PhpSysInfo - A customizable PHP script that displays information about your system nicely. (Source Code)
GPL-2.0PHP - Prometheus - Service monitoring system and time series database. (Source Code)
Apache-2.0Go - Riemann - Flexible and fast events processor allowing complex events/metrics analysis. (Source Code)
EPL-1.0Java - rtop - Interactive, remote system monitoring tool based on SSH.
MITGo - ruptime - Classic system status server.
AGPL-3.0Shell - Scrutiny - Web UI for hard drive S.M.A.R.T monitoring, historical trends & real-world failure thresholds.
MITGo - Sensu - Monitoring tool for ephemeral infrastructure and distributed applications. (Source Code)
MITGo - Status - Simple and lightweight system monitoring tool for small homeservers with a pleasant web interface. (Demo
MITPython - Thruk - Multibackend monitoring web interface with support for Naemon, Nagios, Icinga and Shinken. (Source Code)
GPL-1.0Perl - Wazuh - Unified XDR and SIEM protection for endpoints and cloud workloads. (Source Code)
GPL-2.0C - Zabbix - Enterprise-class software for monitoring of networks and applications. (Source Code)
GPL-2.0C
- Adagios - Web based Nagios interface for configuration and monitoring (replacement to the standard interface), and a REST interface. (Source Code)
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ 10f7c7f7:f5683da9
2025-05-23 15:26:17
@ 10f7c7f7:f5683da9
2025-05-23 15:26:17While I’m going to stand by what I said in my previous piece, minimise capital gains payments, don’t fund the government, get a loan against your bitcoin, but the wheels in my left curve brain have continued to turn, well that, and a few more of my 40PW insights. I mentioned about paying attention to the risks involved in terms of borrowing against your bitcoin, and hopefully ending up paying less in bitcoin at the end of the loan, even if you ultimately sold bitcoin to pay off the loan. However, the idea of losing control of the bitcoin I have spent a good deal of time and effort accumulating being out of my control has led me to reconsider. I also realised I didn’t fully flesh out some other topics that I think are relevant, not least time preference, specifically in relation to what you’re buying. The idea of realising a lump some of capital to live your dreams, buy a house or a cool car may be important, but it may be worth taking a step back and looking at what you’re purchasing. Are you only purchasing those things because you had been able to get this new money “tax free”? If that is the case, and the fiat is burning a hold in your pocket, maybe you’ve just found yourself with the same fiat brained mentality you have been working so hard to escape from while you have sacrificed and saved to stack sats.
While it may no longer be necessary to ask yourself whether a particular product or service is worth selling your bitcoin for because you’ve taken out a loan, it may still be worth asking yourself whether a particular loan fuelled purchase is worth forfeiting control of your keys for? Unlike the foolish 18 year-old, released into a world with their newly preapproved credit card, you need to take a moment and ask yourself:
Is the risk worth it?
Is the purchase worth it?
But also take a moment to consider a number of other things, are there fiat options?
Where in the cycle might you be?
Or if I’m thinking carefully about this, will whatever I’m buying hold its value (experiences may be more difficult to run the numbers on)?
The reason for asking these things, is that if you still have a foot in the fiat world, dealing with a fiat bank account, fiat institutions may still be very willing to provide you with a loan at a lower rate than a bitcoin backed loan. Particularly if you’re planning on using that money to buy a house; if you can qualify for a mortgage, get a mortgage, but if you need cash for a deposit, maybe that is where the bitcoin backed loan may come in. Then, it may be worth thinking about where are you in the bitcoin cycle? No one can answer this, but with the historic data we have, it appears logical that after some type of run up, prices may retrace (Dan Held’s supercycle withstanding).
Matteo Pellegrini with Daniel Prince provided a new perspective on this for me. Rather the riding the bull market gains all the way through to the bear market bottom, what happens if I chose to buy an asset that didn’t lose quite as much fiat value as bitcoin, for example, a Swiss Watch, or a tasteful, more mature sports car? If that was the purchase of choice, they suggested that you could enjoy the car, “the experience” for a year or two, then realise the four door estate was likely always the better option, sell it and be able to buy back as many, if not slightly more bitcoin that you originally sold (not financial, classic car or price prediction advice, I’m not accredited to advise pretty much anything). Having said that, it is a scenario I think worth thinking about when the bitcoin denominated dream car begins to make financial sense.
Then, as we begin to look forward to the near inevitable bear market (they are good for both stacking and grinding), if we’ve decided to take out a loan rather than sell, we then may ultimately need to increase our collateral to maintain loan to value requirements, as well as sell more bitcoin to cover repayments (if that’s the route we’re taking). This then moves us back into the domain of saying, well in actual fact we should just sell our bitcoin when we can get most dollar for it (or the coolest car), with a little extra to cover future taxes, it is probably better to sell near a top than a bottom. The balance between these two rather extreme positions could be to take out a fiat loan to buy the item and maybe sell sufficient bitcoin so you’re able to cover the loan for a period of time (less taxable events to keep track of and also deals with future uncertainty of bitcoin price). In this case, if the loan timeframe is longer than the amount of loan your sale can cover, by the time you need to sell anymore, the price should have recovered from a cycle bottom.
In this scenario, apart from the smaller portion of bitcoin you have had to sell, the majority of your stack can remain in cold storage, the loan you took out will be unsecured (particularly against your bitcoin), but even if it isn’t, the value of what you purchase maintains its value, you can in theory exit the loan at any point by selling the luxury item. Then within this scenario, if you had sold near a top, realised the car gave you a bad back or made you realise you staying humble is more important, sold it, paid off the loan, there may even be a chance you could buy back more bitcoin with the money you had left over from selling your bitcoin to fund the loan.
I have no idea of this could actually work, but to be honest, I’m looking forward to trying it out in the next 6-12 months, although I may keep my daily driver outside of my bitcoin strategy (kids still need a taxi service). Having said that, I think there are some important points to consider in addition to not paying capital gains tax (legally), as well as the opportunities of bitcoin loans. They are still very young products and to quote every trad-fi news outlet, “bitcoin is still a volatile asset”, these thought experiments are still worth working through. To push back on the Uber fiat journalist, Katie Martin, “Bitcoin has no obvious use case”, it does, it can be a store of value to hold or sell, it can be liquid and flexible collateral, but also an asset that moves independently of other assets to balance against fiat liabilities. The idea of being able to release some capital, enjoy the benefits of the capital for a period, before returning that capital to store value feels like a compelling one.
The important thing to remember is that there are a variety of options, whether selling for cash, taking out a bitcoin backed loan, taking out a fiat loan or some combination of each. Saying that, what I would think remains an important question to ask irrespective of the option you go for:
Is what I’m planning on buying, worth selling bitcoin for?
If it cannot pass this first question, maybe it isn’t worth purchasing to start with.
-
 @ 68d6e729:e5f442ac
2025-05-22 13:55:45
@ 68d6e729:e5f442ac
2025-05-22 13:55:45The Adapter Pattern in TypeScript
What is the Adapter Pattern?
The Adapter Pattern is a structural design pattern that allows objects with incompatible interfaces to work together. It acts as a bridge between two interfaces, enabling integration without modifying existing code.
In simple terms: it adapts one interface to another.
Real-World Analogy
Imagine you have a U.S. laptop charger and you travel to Europe. The charger plug won't fit into the European socket. You need a plug adapter to convert the U.S. plug into a European-compatible one. The charger stays the same, but the adapter allows it to work in a new context.
When to Use the Adapter Pattern
- You want to use an existing class but its interface doesn't match your needs.
- You want to create a reusable class that cooperates with classes of incompatible interfaces.
- You need to integrate third-party APIs or legacy systems with your application.
Implementing the Adapter Pattern in TypeScript
Let’s go through a practical example.
Scenario
Suppose you’re developing a payment system. You already have a
PaymentProcessorinterface that your application uses. Now, you want to integrate a third-party payment gateway with a different method signature.Step 1: Define the Target Interface
javascript ts CopyEdit// The interface your application expects interface PaymentProcessor { pay(amount: number): void; }Step 2: Create an Adaptee (incompatible class)
javascript ts CopyEdit// A third-party library with a different method class ThirdPartyPaymentGateway { makePayment(amountInCents: number): void { console.log(`Payment of $${amountInCents / 100} processed via third-party gateway.`); } }Step 3: Implement the Adapter
```javascript ts CopyEdit// Adapter makes the third-party class compatible with PaymentProcessor class PaymentAdapter implements PaymentProcessor { private gateway: ThirdPartyPaymentGateway;
constructor(gateway: ThirdPartyPaymentGateway) { this.gateway = gateway; }
pay(amount: number): void { const amountInCents = amount * 100; this.gateway.makePayment(amountInCents); } } ```
Step 4: Use the Adapter in Client Code
```javascript ts CopyEditconst thirdPartyGateway = new ThirdPartyPaymentGateway(); const adapter: PaymentProcessor = new PaymentAdapter(thirdPartyGateway);
// Application uses a standard interface adapter.pay(25); // Output: Payment of $25 processed via third-party gateway. ```
Advantages of the Adapter Pattern
- Decouples code from third-party implementations.
- Promotes code reuse by adapting existing components.
- Improves maintainability when dealing with legacy systems or libraries.
Class Adapter vs Object Adapter
In languages like TypeScript, which do not support multiple inheritance, the object adapter approach (shown above) is preferred. However, in classical OOP languages like C++, you may also see class adapters, which rely on inheritance.
Conclusion
The Adapter Pattern is a powerful tool in your design pattern arsenal, especially when dealing with incompatible interfaces. In TypeScript, it helps integrate third-party APIs and legacy systems seamlessly, keeping your code clean and extensible.
By learning and applying the Adapter Pattern, you can make your applications more robust and flexible—ready to adapt to ever-changing requirements. https://fox.layer3.press/articles/cdd71195-62a4-420b-9e24-e23d78b27452
-
 @ 6d5c826a:4b27b659
2025-05-23 21:47:22
@ 6d5c826a:4b27b659
2025-05-23 21:47:22- Chocolatey - The package manager for Windows. (Source Code)
Apache-2.0C#/PowerShell - Clonezilla - Partition and disk imaging/cloning program. (Source Code)
GPL-2.0Perl/Shell/Other - DadaMail - Mailing List Manager, written in Perl. (Source Code)
GPL-2.0Perl - Fog - Cloning/imaging solution/rescue suite. (Source Code)
GPL-3.0PHP/Shell - phpList - Newsletter and email marketing software. (Source Code)
AGPL-3.0PHP
- Chocolatey - The package manager for Windows. (Source Code)
-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ 9e69e420:d12360c2
2025-02-01 11:16:04
@ 9e69e420:d12360c2
2025-02-01 11:16:04Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ 6d5c826a:4b27b659
2025-05-23 21:47:03
@ 6d5c826a:4b27b659
2025-05-23 21:47:03- Beats - Single-purpose data shippers that send data from hundreds or thousands of machines and systems to Logstash or Elasticsearch. (Source Code)
Apache-2.0Go - Collectd - System statistics collection daemon. (Source Code)
MITC - Diamond - Daemon that collects system metrics and publishes them to Graphite (and others).
MITPython - Grafana - A Graphite & InfluxDB Dashboard and Graph Editor. (Source Code)
AGPL-3.0Go - Graphite - Scalable graphing server. (Source Code)
Apache-2.0Python - RRDtool - Industry standard, high performance data logging and graphing system for time series data. (Source Code)
GPL-2.0C - Statsd - Daemon that listens for statistics like counters and timers, sent over UDP or TCP, and sends aggregates to one or more pluggable backend services.
MITNodejs - tcollector - Gathers data from local collectors and pushes the data to OpenTSDB. (Source Code)
LGPL-3.0/GPL-3.0Python - Telegraf - Plugin-driven server agent for collecting, processing, aggregating, and writing metrics.
MITGo
- Beats - Single-purpose data shippers that send data from hundreds or thousands of machines and systems to Logstash or Elasticsearch. (Source Code)
-
 @ cae03c48:2a7d6671
2025-05-23 14:01:07
@ cae03c48:2a7d6671
2025-05-23 14:01:07Bitcoin Magazine

KindlyMD, Nakamoto, and Anchorage Digital Form Strategic Bitcoin Treasury AllianceNakamoto Holdings Inc., KindlyMD, Inc., and Anchorage Digital today announced a strategic partnership that will see Anchorage become a trading partner for KindlyMD’s Bitcoin treasury. The partnership will officially take effect upon the close of KindlyMD’s merger with Nakamoto, expected in Q3 2025.
NEW! Anchorage Digital
 @Nakamoto @KindlyMD
@Nakamoto @KindlyMD Today we’re thrilled to announce a strategic partnership with Nakamoto Holdings and $KDLY to accelerate the future of corporate Bitcoin adoption. pic.twitter.com/nQueTyutQH
— Anchorage Digital
 (@Anchorage) May 21, 2025
(@Anchorage) May 21, 2025Anchorage Digital, a U.S. federally chartered digital asset bank, will provide institutional-grade custody, 24/7 trading, and deep liquidity to support the Bitcoin strategy of the combined entity.
“In the not-so-distant-future, the omission of Bitcoin on a balance sheet will be more glaring than its inclusion,” said Nathan McCauley, CEO and Co-Founder of Anchorage Digital. “Until then, companies like Nakamoto-KindlyMD are pioneering a new path forward—one in which Bitcoin is at the heart of corporate strategy.”
The future of corporate treasury strategy is Bitcoin-native. We're here to make it happen. Pumped to be partnering with @Nakamoto and @KindlyMD.@DavidFBailey’s vision continues to open new doors.
— Nathan McCauley
 (@nathanmccauley) May 21, 2025
(@nathanmccauley) May 21, 2025The merger between KindlyMD and Nakamoto is backed by approximately $710 million in financing, including $510 million in PIPE funding—the largest ever PIPE for a public crypto-related deal. The goal is to establish a Bitcoin-native corporate treasury strategy that redefines how capital markets engage with digital assets.
“Our goal is to bring Bitcoin to the center of global capital markets within a compliant, transparent structure,” said David Bailey, Founder and CEO of Nakamoto Holdings Inc. “We are excited to partner with Anchorage Digital to implement our vision with the highest levels of security and battle-tested infrastructure and enable us to deliver sustained value to shareholders.”
This announcement follows a key milestone on May 18, when KindlyMD shareholders approved the proposed merger with Nakamoto. The transaction is now expected to close in Q3 2025, pending SEC review and information statement distribution.
“This milestone brings us one step closer to unlocking Bitcoin’s potential for KindlyMD shareholders,” Bailey said yesterday. “We are grateful that KindlyMD shares our vision for a future in which Bitcoin is a core part of the corporate balance sheet.”
With its Bitcoin-first strategy and strategic alliances, the Nakamoto-KindlyMD partnership is set to accelerate institutional Bitcoin adoption—and with Anchorage Digital’s infrastructure behind it, the foundation is now firmly in place.
“By collaborating with Anchorage Digital, we are implementing our Bitcoin treasury strategy with the utmost standards in safety and security for our shareholders,” stated Tim Pickett, CEO of KindlyMD. “Their institutional-grade platform allows us to confidently hold Bitcoin as a treasury asset as we look to unlock access to Bitcoin and drive value for the long term.”
Disclosure: Nakamoto is in partnership with Bitcoin Magazine’s parent company BTC Inc to build the first global network of Bitcoin treasury companies, where BTC Inc provides certain marketing services to Nakamoto. More information on this can be found here.
This post KindlyMD, Nakamoto, and Anchorage Digital Form Strategic Bitcoin Treasury Alliance first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 9e69e420:d12360c2
2025-01-26 15:26:44
@ 9e69e420:d12360c2
2025-01-26 15:26:44Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards.
While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts.
A report will be prepared within 85 days to recommend which programs to continue or discontinue.
-
 @ e5fa3d8c:44057ac9
2025-05-22 13:21:20
@ e5fa3d8c:44057ac9
2025-05-22 13:21:20 -
 @ 9e69e420:d12360c2
2025-01-25 22:16:54
@ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.”
The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China.
-
 @ 2f29aa33:38ac6f13
2025-05-17 12:59:01
@ 2f29aa33:38ac6f13
2025-05-17 12:59:01The Myth and the Magic
Picture this: a group of investors, huddled around a glowing computer screen, nervously watching Bitcoin’s price. Suddenly, someone produces a stick-no ordinary stick, but a magical one. With a mischievous grin, they poke the Bitcoin. The price leaps upward. Cheers erupt. The legend of the Bitcoin stick is born.
But why does poking Bitcoin with a stick make the price go up? Why does it only work for a lucky few? And what does the data say about this mysterious phenomenon? Let’s dig in, laugh a little, and maybe learn the secret to market-moving magic.

The Statistical Side of Stick-Poking
Bitcoin’s Price: The Wild Ride
Bitcoin’s price is famous for its unpredictability. In the past year, it’s soared, dipped, and soared again, sometimes gaining more than 50% in just a few months. On a good day, billions of dollars flow through Bitcoin trades, and the price can jump thousands in a matter of hours. Clearly, something is making this happen-and it’s not just spreadsheets and financial news.
What Actually Moves the Price?
-
Scarcity: Only 21 million Bitcoins will ever exist. When more people want in, the price jumps.
-
Big News: Announcements, rumors, and meme-worthy moments can send the price flying.
-
FOMO: When people see Bitcoin rising, they rush to buy, pushing it even higher.
-
Liquidations: When traders betting against Bitcoin get squeezed, it triggers a chain reaction of buying.
But let’s be honest: none of this is as fun as poking Bitcoin with a stick.

The Magical Stick: Not Your Average Twig
Why Not Every Stick Works
You can’t just grab any old branch and expect Bitcoin to dance. The magical stick is a rare artifact, forged in the fires of internet memes and blessed by the spirit of Satoshi. Only a chosen few possess it-and when they poke, the market listens.
Signs You Have the Magical Stick
-
When you poke, Bitcoin’s price immediately jumps a few percent.
-
Your stick glows with meme energy and possibly sparkles with digital dust.
-
You have a knack for timing your poke right after a big event, like a halving or a celebrity tweet.
-
Your stick is rumored to have been whittled from the original blockchain itself.
Why Most Sticks Fail
-
No Meme Power: If your stick isn’t funny, Bitcoin ignores you.
-
Bad Timing: Poking during a bear market just annoys the blockchain.
-
Not Enough Hype: If the bitcoin community isn’t watching, your poke is just a poke.
-
Lack of Magic: Some sticks are just sticks. Sad, but true.

The Data: When the Stick Strikes
Let’s look at some numbers:
-
In the last month, Bitcoin’s price jumped over 20% right after a flurry of memes and stick-poking jokes.
-
Over the past year, every major price surge was accompanied by a wave of internet hype, stick memes, or wild speculation.
-
In the past five years, Bitcoin’s biggest leaps always seemed to follow some kind of magical event-whether a halving, a viral tweet, or a mysterious poke.
Coincidence? Maybe. But the pattern is clear: the stick works-at least when it’s magical.

The Role of Memes, Magic, and Mayhem
Bitcoin’s price is like a cat: unpredictable, easily startled, and sometimes it just wants to be left alone. But when the right meme pops up, or the right stick pokes at just the right time, the price can leap in ways that defy logic.
The bitcoin community knows this. That’s why, when Bitcoin’s stuck in a rut, you’ll see a flood of stick memes, GIFs, and magical thinking. Sometimes, it actually works.

The Secret’s in the Stick (and the Laughs)
So, does poking Bitcoin with a stick really make the price go up? If your stick is magical-blessed by memes, timed perfectly, and watched by millions-absolutely. The statistics show that hype, humor, and a little bit of luck can move markets as much as any financial report.
Next time you see Bitcoin stalling, don’t just sit there. Grab your stick, channel your inner meme wizard, and give it a poke. Who knows? You might just be the next legend in the world of bitcoin magic.
And if your stick doesn’t work, don’t worry. Sometimes, the real magic is in the laughter along the way.

-aco
@block height: 897,104
-
-
 @ 6d5c826a:4b27b659
2025-05-23 21:46:46
@ 6d5c826a:4b27b659
2025-05-23 21:46:46- aerc - Terminal MUA with a focus on plaintext and features for developers. (Source Code)
MITGo - Claws Mail - Old school email client (and news reader), based on GTK+. (Source Code)
GPL-3.0C - ImapSync - Simple IMAP migration tool for copying mailboxes to other servers. (Source Code)
NLPLPerl - Mutt - Small but very powerful text-based mail client. (Source Code)
GPL-2.0C - Sylpheed - Still developed predecessor to Claws Mail, lightweight mail client. (Source Code)
GPL-2.0C - Thunderbird - Free email application that's easy to set up and customize. (Source Code)
MPL-2.0C/C++
- aerc - Terminal MUA with a focus on plaintext and features for developers. (Source Code)
-
 @ 0e9491aa:ef2adadf
2025-05-22 08:01:35
@ 0e9491aa:ef2adadf
2025-05-22 08:01:35
I often hear "bitcoin doesn't interest me, I'm not a finance person."
Ironically, the beauty of sound money is you don't have to be. In the current system you're expected to manage a diversified investment portfolio or pay someone to do it. Bitcoin will make that optional.
— ODELL (@ODELL) September 16, 2018
At first glance bitcoin often appears overwhelming to newcomers. It is incredibly easy to get bogged down in the details of how it works or different ways to use it. Enthusiasts, such as myself, often enjoy going down the deep rabbit hole of the potential of bitcoin, possible pitfalls and theoretical scenarios, power user techniques, and the developer ecosystem. If your first touch point with bitcoin is that type of content then it is only natural to be overwhelmed. While it is important that we have a thriving community of bitcoiners dedicated to these complicated tasks - the true beauty of bitcoin lies in its simplicity. Bitcoin is simply better money. It is the best money we have ever had.
Life is complicated. Life is hard. Life is full of responsibility and surprises. Bitcoin allows us to focus on our lives while relying on a money that is simple. A money that is not controlled by any individual, company, or government. A money that cannot be easily seized or blocked. A money that cannot be devalued at will by a handful of corrupt bureaucrat who live hundreds of miles from us. A money that can be easily saved and should increase in purchasing power over time without having to learn how to "build a diversified stock portfolio" or hire someone to do it for us.
Bitcoin enables all of us to focus on our lives - our friends and family - doing what we love with the short time we have on this earth. Time is scarce. Life is complicated. Bitcoin is the most simple aspect of our complicated lives. If we spend our scarce time working then we should be able to easily save that accrued value for future generations without watching the news or understanding complicated financial markets. Bitcoin makes this possible for anyone.
Yesterday was Mother's Day. Raising a human is complicated. It is hard, it requires immense personal responsibility, it requires critical thinking, but mothers figure it out, because it is worth it. Using and saving bitcoin is simple - simply install an app on your phone. Every mother can do it. Every person can do it.
Life is complicated. Life is beautiful. Bitcoin is simple.
If you found this post helpful support my work with bitcoin.

-
 @ 6d5c826a:4b27b659
2025-05-23 21:46:28
@ 6d5c826a:4b27b659
2025-05-23 21:46:28- Fluentd - Data collector for unified logging layer. (Source Code)
Apache-2.0Ruby - Flume - Distributed, reliable, and available service for efficiently collecting, aggregating, and moving large amounts of log data. (Source Code)
Apache-2.0Java - GoAccess - Real-time web log analyzer and interactive viewer that runs in a terminal or through the browser. (Source Code)
MITC - Loki - Log aggregation system designed to store and query logs from all your applications and infrastructure. (Source Code)
AGPL-3.0Go - rsyslog - Rocket-fast system for log processing. (Source Code)
GPL-3.0C
- Fluentd - Data collector for unified logging layer. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:46:11
@ 6d5c826a:4b27b659
2025-05-23 21:46:11- GLPI - Information Resource-Manager with an additional Administration Interface. (Source Code)
GPL-3.0PHP - OCS Inventory NG - Asset management and deployment solution for all devices in your IT Department. (Source Code)
GPL-2.0PHP/Perl - OPSI - Hardware and software inventory, client management, deployment, and patching for Linux and Windows. (Source Code)
GPL-3.0/AGPL-3.0OVF/Python - RackTables - Datacenter and server room asset management like document hardware assets, network addresses, space in racks, networks configuration. (Demo, Source Code)
GPL-2.0PHP - Ralph - Asset management, DCIM and CMDB system for large Data Centers as well as smaller LAN networks. (Demo, Source Code)
Apache-2.0Python/Docker - Snipe IT - Asset & license management software. (Source Code)
AGPL-3.0PHP
- GLPI - Information Resource-Manager with an additional Administration Interface. (Source Code)
-
 @ 502ab02a:a2860397
2025-05-22 01:30:37
@ 502ab02a:a2860397
2025-05-22 01:30:37ถ้าพูดถึง "เกาหลีใต้" หลายคนอาจนึกถึงซีรีส์ น้ำจิ้มเผ็ด หรือไอดอลหน้าผ่อง ๆ แต่เบื้องหลังวัฒนธรรมที่ลื่นไหลไปทั่วโลกนี้ ยังมีอาณาจักรธุรกิจขนาดมหึมาที่เป็นเหมือนเครื่องยนต์หลักผลักดันทั้งอาหาร เพลง หนัง และนวัตกรรมระดับโลก หนึ่งในนั้นคือ CJ Group ที่เริ่มต้นจากบริษัทน้ำตาลเล็ก ๆ ในปี 1953 แต่เติบโตจนกลายเป็นหนึ่งใน conglomerate หรือ "กลุ่มธุรกิจผูกเครือ" ที่ทรงอิทธิพลที่สุดของแดนโสม
คำว่า CJ ย่อมาจาก CheilJedang (แปลว่า “หมายเลขหนึ่งแห่งโลก” ในภาษาจีน-เกาหลี) ก่อตั้งโดย อี บยองชอล ผู้ก่อตั้ง Samsung Group ในช่วงเวลานั้น เกาหลีใต้กำลังฟื้นตัวจากสงครามเกาหลี และรัฐบาลส่งเสริมการพัฒนาอุตสาหกรรมภายในประเทศ เดิมเป็นหน่วยธุรกิจอาหารของกลุ่ม Samsung ในปี 1993 Cheil Jedang แยกตัวออกจาก Samsung Group และกลายเป็นบริษัทอิสระภายใต้การบริหารของ อี แจฮยอน หลานชายของอี บยองชอล แล้วขยายขอบเขตธุรกิจอย่างไม่หยุดยั้ง จากความเชี่ยวชาญใน "การหมัก" แบบดั้งเดิม พวกเขากลับกลายเป็นผู้เล่นรายใหญ่ระดับโลกในวงการ เทคโนโลยีชีวภาพ การผลิตอาหารไปจนถึงธุรกิจ บันเทิงระดับฮอลลีวูด และ โลจิสติกส์ข้ามทวีป
พูดง่าย ๆ ว่า CJ ไม่ได้แค่ส่งออกกิมจิหรือบิบิมบับ แต่พวกเขากำลังวางรากฐานของ "อนาคตแห่งอาหาร" และ "ความบันเทิงแบบไร้พรมแดน" ในเวลาเดียวกัน จนใครหลายคนถึงกับบอกว่า ถ้าอยากเข้าใจเกาหลีใต้ ก็ต้องเริ่มจากเข้าใจ CJ Group เสียก่อน
แล้วในเครือข่ายของ CJ Group มีธุรกิจอะไรบ้างที่น่าสนใจ และแบรนด์ไหนที่เราคุ้นเคยแบบไม่รู้ตัว ไปดูกันเลย
- ธุรกิจอาหารและบริการอาหาร (Food & Food Services)
- CJ CheilJedang บริษัทอาหารชั้นนำของเกาหลีใต้ มีผลิตภัณฑ์เด่น ได้แก่ Bibigo แบรนด์อาหารเกาหลีพร้อมรับประทาน เช่น เกี๊ยว ซอส และกิมจิ Hetbahn ข้าวสวยพร้อมรับประทานที่ได้รับความนิยมในเกาหลี
-
CJ Foodville ดำเนินธุรกิจร้านอาหารและเบเกอรี่ เช่น: Tous Les Jours ร้านเบเกอรี่สไตล์ฝรั่งเศส VIPS ร้านสเต็กและสลัดบุฟเฟ่ต์
-
ธุรกิจเทคโนโลยีชีวภาพ (Bio) ความเชี่ยวชาญนี้เป็นรากฐานสำคัญในการขยายธุรกิจด้านเทคโนโลยีชีวภาพของ CJ เลยครับ
- CJ BIO ผู้นำด้านการผลิตกรดอะมิโนและผลิตภัณฑ์ชีวภาพผ่านเทคโนโลยีการหมักจุลินทรีย์ เช่น Lysine, Tryptophan, Valine กรดอะมิโนที่ใช้ในอุตสาหกรรมอาหารสัตว์และอาหารเสริม
-
CJ Bioscience มุ่งเน้นการวิจัยและพัฒนาไมโครไบโอมเพื่อสุขภาพ
-
ธุรกิจโลจิสติกส์และค้าปลีก (Logistics & Retail)
- CJ Logistics ให้บริการโลจิสติกส์ครบวงจร ทั้งการขนส่งทางบก ทางทะเล และทางอากาศ รวมถึงบริการคลังสินค้าและการจัดการซัพพลายเชน
-
CJ Olive Young: ร้านค้าปลีกด้านสุขภาพและความงามอันดับหนึ่งของเกาหลี มีผลิตภัณฑ์ยอดนิยม เช่น Anua PDRN Set ชุดบำรุงผิวที่ได้รับความนิยม MILKTOUCH ผลิตภัณฑ์เมคอัพที่ได้รับความนิยม
-
ธุรกิจบันเทิงและสื่อ (Entertainment & Media) อันนี้ยิ่งใหญ่ระดับโลกมากๆ หลายคนคงจำได้กับ ภาพยนตร์เอเชียแรกกับรางวัลออสการ์ Parasite
- CJ ENM บริษัทผลิตและจัดจำหน่ายเนื้อหาบันเทิงที่มีชื่อเสียงระดับโลก มีผลงานเด่น ได้แก่ Crash Landing on You ซีรีส์ที่ได้รับความนิยมอย่างสูง Parasite ภาพยนตร์ที่ได้รับรางวัลออสการ์
- CJ CGV เครือโรงภาพยนตร์มัลติเพล็กซ์ที่มีสาขาทั่วโลก
CJ Group ขยายธุรกิจไปยังต่างประเทศ เช่น การเข้าซื้อกิจการ Schwan's Company ในสหรัฐอเมริกา และการเปิดสาขา CGV ในหลายประเทศ นอกจากนี้ CJ ยังมีบทบาทสำคัญในการเผยแพร่วัฒนธรรมเกาหลีสู่ระดับโลกผ่าน KCON และการผลิตเนื้อหาบันเทิงที่ได้รับความนิยมในต่างประเทศด้วยครับ
จะเห็นได้ว่า เครือข่ายของ CJ นั้นยิ่งใหญ่มากๆเลย ทีนี้มีเรื่องน่าสนใจตรงนี้ครับ
ในช่วงปี 2013–2016 CJ Group โดยเฉพาะฝ่ายสื่อบันเทิงอย่าง CJ ENM ต้องเผชิญกับแรงกดดันจากรัฐบาลของประธานาธิบดี พัค กึนฮเย เหตุการณ์สำคัญคือการที่ อี มีคยอง (Miky Lee) รองประธาน CJ และผู้มีบทบาทสำคัญในการขับเคลื่อนธุรกิจบันเทิงระดับโลก ถูกกดดันให้ลาออกจากตำแหน่ง รายงานระบุว่า ทำเนียบประธานาธิบดีไม่พอใจเนื้อหาสื่อบางรายการของ CJ ที่มีลักษณะเสียดสีหรือวิพากษ์วิจารณ์รัฐบาล เช่น รายการ SNL Korea ที่ล้อเลียนพัค กึนฮเย ผ่านตัวละคร Teletubbies
ภายใต้แรงกดดันนี้ CJ มีการปรับเปลี่ยนเนื้อหาสื่อ โดยลดการนำเสนอเนื้อหาที่อาจขัดแย้งกับรัฐบาล และหันไปผลิตภาพยนตร์ที่สอดคล้องกับนโยบายของรัฐ เช่น ภาพยนตร์เรื่อง Ode to My Father (2014) ที่สะท้อนความรักชาติและการพัฒนาเศรษฐกิจในยุคของพัค ชุงฮี บิดาของพัค กึนฮเย ภาพยนตร์เรื่องนี้ได้รับการสนับสนุนจากรัฐบาลและถูกมองว่าเป็น "ภาพยนตร์เพื่อสุขภาพ" ที่ส่งเสริมความภาคภูมิใจในชาติ แน่นอนว่าแค้นฝังหุ่นมันยังไม่หายไปไหนครับ
เมื่อเกิดการเปิดโปง "บัญชีดำ" (Blacklist) ของรัฐบาลพัค กึนฮเย ที่มีการจำกัดสิทธิเสรีภาพของศิลปินและผู้ผลิตสื่อที่วิพากษ์วิจารณ์รัฐบาล ทำให้เกิดกระแสต่อต้านอย่างรุนแรงในสังคมเกาหลี. ในปี 2016 ซน กยองชิก ประธาน CJ ได้ให้การต่อศาลว่า มีแรงกดดันจากรัฐบาลให้ อี มีคยอง หลีกเลี่ยงการมีบทบาทในบริษัท เหตุการณ์นี้เป็นส่วนหนึ่งของการเปิดโปงคดีทุจริตของพัค กึนฮเย ซึ่งนำไปสู่การประท้วงครั้งใหญ่และการถอดถอนประธานาธิบดีในปี 2017
หลังจากการเปลี่ยนแปลงทางการเมือง CJ Group ได้กลับมามีบทบาทอย่างเต็มที่ในวงการบันเทิงอีกครั้ง อี มีคยอง กลับมาดำรงตำแหน่งและมีบทบาทสำคัญในการผลักดันภาพยนตร์เรื่อง Parasite (2019) ซึ่งได้รับรางวัลออสการ์และยกระดับภาพลักษณ์ของ CJ ในระดับโลก ซึ่งถ้าใครได้ดูหนังเรื่องนั้นแล้วรู้เรื่องราวเบื้องหลังนี้จะเข้าใจเนื้อหาได้อย่างลึกซึ้งขึ้นไปอีกเลยครับ การนำเสนอเรื่องราวนี้ถือเป็นการวิพากษ์วิจารณ์สังคมและระบบทุนนิยมอย่างชัดเจน ซึ่งแตกต่างจากแนวทางที่ CJ เคยถูกกดดันให้ปฏิบัติตามในยุคของพัค กึนฮเย อย่างสิ้นเชิง
อย่าเพิ่งไปสะใจกับเนื้อหา ให้มองว่า "เขาทำอะไรได้บ้าง" นี่คือประเด็นสำคัญครับ #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ cae03c48:2a7d6671
2025-05-23 14:01:05
@ cae03c48:2a7d6671
2025-05-23 14:01:05Bitcoin Magazine

How Zeus is Redefining Bitcoin with Cashu Ecash IntegrationThe U.S.-based Bitcoin and Lightning mobile wallet Zeus recently announced an alpha-release integration of Cashu. The move marks the first integration of ecash into a popular Bitcoin wallet, breaking new ground for potential user adoption to Bitcoin.
Cashu is a hot new implementation of Chaumian ecash, a form of digital cash invented by David Chaum in the ’90s that has incredible privacy and scalability properties, with the trade-off of being fundamentally centralized, requiring a significant amount of trust in the issuer.


In a counterintuitive move for Zeus, known as the go-to tool for advanced Lightning users seeking to connect to their home nodes, the integration of Cashu acknowledges a “last mile” challenge Lightning wallets face when delivering Bitcoin to the masses.
“We basically started off as the cypherpunk wallet, right? You got to set up your own Lightning node and connect to it with Zeus. The last two years, we put the node in the phone with one click, you can run it all in a standalone app without a remote node,” Evan Kaloudis, founder and CEO of Zeus, told Bitcoin Magazine.
“Cashu addresses uneconomical self-custody for small bitcoin amounts. On-chain, the dust limit is 546 satoshis, and Layer Two systems like Lightning have costs for channel setup or unilateral exits that aren’t widely discussed,” Evan explained, highlighting a major point of friction in noncustodial Lightning wallets: the need for liquidity and channel management. While these esoteric aspects of the Lightning Network have been mostly abstracted away since its invention in 2016, these fundamental trade-offs continue to manifest even in the most sophisticated and user-friendly wallets.
In the case of both Phoenix and Zeus, two of the most popular noncustodial options in the market, users must pay up to 10,000 sats upfront to gain spending capacity. These fees are necessary to cover the on-chain fees spent to open a channel for the user against the wallet’s liquidity service provider, unlocking a noncustodial experience.
The required up-front fee is difficult to explain and represents a painful onboarding experience for new users who are used to fiat apps giving them money to join instead. The result is the proliferation of custodial Lightning wallets like Wallet of Satoshi (WOS), which gained massive adoption early on by leveraging the global, near-instant settlement power of Bitcoin combined with the excellent user experience centralized wallets can create.
Major developments have been made over seven years after the Lightning Network’s inception, however, and Zeus is pushing the boundaries.
“With Ecash, we make it so easy that anyone can set up a wallet and start participating in our ecosystem, which I really think is going to become more and more prevalent,” Evan explained.
Today, at roughly $100,000 per bitcoin, 1,000 satoshis are equivalent to $1. Transactions of these sizes are known as microtransactions — a popular example are Nostr social media tips known as Zaps. But finding the right tool for this use case is not simple. Self custodied wallets like Phoenix charge transaction fees in the hundreds of satoshis, even with open channels, and on-chain fees often cost the same and are slower to settle. As a result, there’s an entire category of spending that is only served by cheaper alternatives such as custodial lightning wallets like WOS or Blink, but result in significant privacy tradeoffs, often requiring phone numbers from users and in some cases more advanced KYC and IP tracking. Cashu hopes to serve this market with lower privacy costs, the same ease of use, speed and competitive fees.
Digging deeper into the Cashu integration, Evan explained that “for users this means being able to pick and switch between custodians in a single app. For developers this means being able to defer custodial responsibilities to third parties and not have to wire up a new integration when your current custodian halts operations.”
Zaps are satoshi-denominated rewards delivered as “likes” or micro-tips for content in the Nostr social media ecosystem. A Zap can be as small as one satoshi, the smallest amount of bitcoin that can be technically transferred, equivalent today to about a tenth of a penny. “But I think if we look at Nostr and you’re seeing how many people are Zapping and how big a part of that ecosystem it is. It’s like, people are willing to do it,” Evan explained.
“Cashu, while custodial, lets users accumulate small amounts — say, via Nostr Zaps — without needing 6,000 satoshis to open a Lightning channel. Zeus prompts users to upgrade to self-custody as their balance grows,” he concluded, explaining that the wallet will effectively annoy users into self custody, one of several design choices made to mitigate the risks introduced by Cashu.
Ecash
The trade-offs introduced by Cashu challenge the common understanding of custody as an either-or in Bitcoin. Historically you were either a centralized — custodial — exchange, or you were a noncustodial Bitcoin wallet. In the former, you entrust the coins to a third party; in the latter you take personal responsibility for those coins and their corresponding private keys. Cashu changes this paradigm by introducing bitcoin-denominated ecash notes or “nuts,” which are bearer instruments that should be backed by a full bitcoin reserve and Lightning interoperability for instant withdraw.
Similar to fiat cash, you must take control and responsibility over these notes, but there’s also counterparty risk. In the case of Cashu, there are certain things the issuing mint can theoretically do to exploit their users — akin to how a bank can run on a fractional reserve.
The big difference between Cashu or custodial Bitcoin exchanges and fiat currency is that Cashu is open source, is designed around user privacy, and scales very well. It makes the cost of running a mint lower than either alternative, a feature that makes mint competition easier, in theory countering the centralizing network effects of specific mints.
Finally, the user experience of storing Cashu tokens has been attached to known forms of Bitcoin self custody such as the download of 12-words seeds via various mechanisms, though implementations still vary from wallet to wallet and the whole ecosystem is in its early stages.
To further mitigate the custodial risk of Chaumian-style ecash in Bitcoin, the Cashu community has developed various methods for automatically managing custody risk.



“Users can split risk by using multiple mints, switching between them in the user interface. Soon, ZEUS will guide users to select five or six reputable mints, automatically balancing funds to minimize exposure,” Evan explained, referring to a particular approach called automated bank runs. The idea is that as some Cashu mints may hold more of your funds, Zeus de-ranks them and rotates value out to minimize risk.
“I think the idea is going to be that we guide users to pick five or six reputable mints… And from there, users will be able to have the wallet automatically switch between those mints and determine which mint should be receiving the balance depending on the balance of all the mints presently. So you’ll be like, OK. MiniBits has way too much money. Let’s switch the default to one of the mints that doesn’t have a lot. So that way you can sort of mitigate or rather distribute the rug risk there,” Evan explained, adding, “Our Discover Mint feature pulls reviews from bitcoinmints.com, showing vouch counts and user feedback, like mint reliability or longevity,” describing the reputation layer stacked on top of the various other risk management mechanisms.
There is no known way to use Chaumian-style ecash in an entirely noncustodial way. So as long as the custody risk can be minimized, the scaling and privacy upside becomes remarkable.
Microtransactions
One of the opportunities that ecash unlocks is microtransactions, the most popular example of which are Nostr Zaps often in single dollar ranges of value transferred, though it applies to small Lightning transactions as well. This use case triggers an important technical question that predates Bitcoin, do microtransactions actually make economic sense?
There’s a long-standing argu
-
 @ 91bea5cd:1df4451c
2025-02-04 17:15:57
@ 91bea5cd:1df4451c
2025-02-04 17:15:57Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ 0fa80bd3:ea7325de
2025-01-29 05:55:02
@ 0fa80bd3:ea7325de
2025-01-29 05:55:02The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future.
Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs.
There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won.
Our only resource is the will of the people to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root.
So I started asking myself: How do we stop this fragmentation? How do we create a space where people can rebuild their connections when they’re ready? How do we build a self-sustaining network, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—how do we make it spread, even in occupied territory?
In 2009, something historic happened: the internet got its own money. Thanks to Satoshi Nakamoto, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize.
That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became purely digital.
The internet was already a sanctuary for information, a place where people could connect and organize. But with Bitcoin, it evolved. Now, value itself could flow freely, beyond the reach of authorities.
Think about it: when seedlings are grown in controlled environments before being planted outside, they get stronger, survive longer, and bear fruit faster. That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild.
Now, picture the internet as that controlled environment for ideas. Bitcoin? It’s the fertile soil that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless. It can absorb any number of ideas, any number of people, and it doesn’t run out of space.
But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—without surveillance, without censorship, without the constant fear of being erased.
This is where Nostr comes in.
Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. It’s a new kind of city. One that no dictator can seize, no corporation can own, no government can shut down.
It’s built on decentralization, encryption, and individual control. Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them.
In a world where cities fall and governments fail, Nostr is a city that cannot be occupied. A place for ideas, for networks, for freedom. A city that grows stronger the more people build within it.
-
 @ 8d34bd24:414be32b
2025-05-21 15:52:46
@ 8d34bd24:414be32b
2025-05-21 15:52:46In our culture today, people like to have “my truth” as opposed to “your truth.” They want to have teachers who tell them what they want to hear and worship in the way they desire. The Bible predicted these times.
For the time will come when people will not put up with sound doctrine. Instead, to suit their own desires, they will gather around them a great number of teachers to say what their itching ears want to hear. (2 Timothy 4:3)
My question is, “do we get to choose what we want to believe about God and how we want to worship Him, or does God tell us what we are to believe and how we are to worship Him?”
The Bible makes it clear that He is who He says He is and He expects obedience and worship according to His commands. We do not get to decide for ourselves.
The woman said to Him, “Sir, I perceive that You are a prophet. Our fathers worshiped in this mountain, and you people say that in Jerusalem is the place where men ought to worship.” Jesus said to her, “Woman, believe Me, an hour is coming when neither in this mountain nor in Jerusalem will you worship the Father. You worship what you do not know; we worship what we know, for salvation is from the Jews. But an hour is coming, and now is, when the true worshipers will worship the Father in spirit and truth; for such people the Father seeks to be His worshipers. God is spirit, and those who worship Him must worship in spirit and truth.” (John 4:19-24) {emphasis mine}
In this passage, Jesus gently corrects the woman for worshipping what she does not know. He also says, “God is spirit, and those who worship Him must worship in spirit and truth.” He states what God is (spirit) and how He must be worshipped “in spirit and truth.” We don’t get to define God however we wish, and we don’t get to worship Him any way we wish. God is who He has revealed Himself to be and we must obey Him and worship Him the way He has commanded.
In this next passage, God makes clear that He is holy and we do not get to worship Him any way we wish. We are to interact with Him in the prescribed manner.
Now Nadab and Abihu, the sons of Aaron, took their respective firepans, and after putting fire in them, placed incense on it and offered strange fire before the Lord, which He had not commanded them. And fire came out from the presence of the Lord and consumed them, and they died before the Lord. Then Moses said to Aaron, “It is what the Lord spoke, saying,
‘By those who come near Me I will be treated as holy,\ And before all the people I will be honored.’ ”
So Aaron, therefore, kept silent. (Leviticus 10:1-3) {emphasis mine}
God had prescribed a particular way to approach Him and only those whom He had chosen (priests of the lineage of Aaron). Nadab and Abihu chose to “do it their way” and paid the price for ignoring God’s command. God set an example with them.
God has been gracious enough to reveal Himself, His character, His power, and His commands to us. If we have truly submitted ourselves to His rule, we should hunger for God’s words so we can know Him better and honor Him in obedience.
But now I come to You; and these things I speak in the world so that they may have My joy made full in themselves. I have given them Your word; and the world has hated them, because they are not of the world, even as I am not of the world. I do not ask You to take them out of the world, but to keep them from the evil one. They are not of the world, even as I am not of the world. Sanctify them in the truth; Your word is truth. (John 17:13-17) {emphasis mine}
In today’s culture, everybody likes to claim their own personal truth, but that isn’t how truth works. The truth is not determined by an individual for themselves. It isn’t even determined by a consensus or majority vote. The truth is the truth even if not one person on earth believes it. God speaks truth and God is truth. Our belief or lack thereof doesn’t change the truth, but our lack of belief in the truth, especially the truth as revealed by God in His word, can negatively affect our relationship with God.
God expects us to study His word so we can obey His commands.
For I did not speak to your fathers, or command them in the day that I brought them out of the land of Egypt, concerning burnt offerings and sacrifices. But this is what I commanded them, saying, ‘Obey My voice, and I will be your God, and you will be My people; and you will walk in all the way which I command you, that it may be well with you.’ Yet they did not obey or incline their ear, but walked in their own counsels and in the stubbornness of their evil heart, and went backward and not forward. Since the day that your fathers came out of the land of Egypt until this day, I have sent you all My servants the prophets, daily rising early and sending them. Yet they did not listen to Me or incline their ear, but stiffened their neck; they did more evil than their fathers. (Jeremiah 7:22-26) {emphasis mine}
Today you rarely see someone bowing down to a golden idol, but that doesn’t mean that we are any better at obeying God’s commands or submitting to His will. We still try to make God in our own image so He is a convenience to us and how we want to live our lives. We still put other things ahead of God — family, work, entertainment, fame, etc. Most of us aren’t any more faithful to God than the Israelites were. Just like the Israelites, we put on the trappings of faith but don’t live according to faith and faithfulness.
And He said to them, “Rightly did Isaiah prophesy of you hypocrites, as it is written:
‘This people honors Me with their lips,\ But their heart is far away from Me.\ **But in vain do they worship Me,\ Teaching as doctrines the precepts of men.’\ Neglecting the commandment of God, you hold to the tradition of men.”
He was also saying to them, “You are experts at setting aside the commandment of God in order to keep your tradition. (Mark 7:6-9) {emphasis mine}
How many “churches” and “Christian” leaders teach people according to the culture instead of according to the Word of God? How many tell people what they want to hear and what makes them feel good instead of what they need to hear — the truth as spoken through the Bible? How many church attenders follow a “Christian” leader more than they follow their Creator, Savior, and God? How many church attenders can recite the words of their leaders better than the Holy Scriptures?
I solemnly charge you in the presence of God and of Christ Jesus, who is to judge the living and the dead, and by His appearing and His kingdom: preach the word; be ready in season and out of season; reprove, rebuke, exhort, with great patience and instruction. For the time will come when they will not endure sound doctrine; but wanting to have their ears tickled, they will accumulate for themselves teachers in accordance to their own desires, and will turn away their ears from the truth and will turn aside to myths. But you, be sober in all things, endure hardship, do the work of an evangelist, fulfill your ministry. (2 Timothy 4:1-5) {emphasis mine}
How can we know if a church leader is rightly preaching God’s word? We can only know if we have read the Bible and studied it. We should be like the Bereans:
Now these were more noble-minded than those in Thessalonica, for they received the word with great eagerness, examining the Scriptures daily to see whether these things were so. (Acts 17:11)
Honestly, I don’t trust any spiritual leader who doesn’t encourage me to search the Scriptures to see whether their words are true. Any leader who puts their own word above the Scriptures is a false teacher. Sadly there are many, maybe more than faithful teachers. Some false teachers are intentionally so, but many have been misled by other false teachers. Their guilt is less, but they don’t do any less harm than those who intentionally mislead.
We need to seek trustworthy teachers who speak according to the Word of God, who quote the Bible to support their opinions, and who seek the good of their followers rather than the submission of their followers.
Do not harden your hearts, as at Meribah,\ As in the day of Massah in the wilderness,
“When your fathers tested Me,\ They tried Me, though they had seen My work.\ For forty years I loathed that generation,\ And said they are a people who err in their heart,\ And they do not know My ways.\ Therefore I swore in My anger,\ Truly they shall not enter into My rest.” (Psalm 95:8-11) {emphasis mine} *Teach me good discernment and knowledge,\ For I believe in Your commandments*.\ Before I was afflicted I went astray,\ But now I keep Your word.\ You are good and do good;\ Teach me Your statutes.\ The arrogant have forged a lie against me;\ *With all my heart I will observe Your precepts*.\ Their heart is covered with fat,\ But I delight in Your law.\ It is good for me that I was afflicted,\ That I may learn Your statutes.\ The law of Your mouth is better to me\ Than thousands of gold and silver pieces. (Psalm 119:66-72) {emphasis mine}
May our Creator God teach us the truth. May He fill our hearts with the desire to be in His word daily and to seek His will. May He do what is necessary to get our attention and turn our hearts and minds fully to Him, so we can learn His statutes and serve Him faithfully, so one day we are blessed to hear, “Well done! Good and faithful servant.”
Trust Jesus.
FYI, I see lack of knowledge of truth and God’s word as one of the biggest problems in the church today; however, it is possible to know the Bible in depth, but not know God. As important as knowledge of Scriptures is, this knowledge (without faith, submission, obedience, and love) is meaningless. Knowledge doesn’t get us to heaven. Even obedience doesn’t get us to heaven. Only faith and submission to our creator God leads to salvation and heaven. That being said, we can’t faithfully serve our God without knowledge of Him and His commands. Out of gratefulness for who He is and what He has done for us, we should seek to know and please Him.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:45:53
@ 6d5c826a:4b27b659
2025-05-23 21:45:53- BounCA - A personal SSL Key / Certificate Authority web-based tool for creating self-signed certificates. (Source Code)
Apache-2.0Python - easy-rsa - Bash script to build and manage a PKI CA.
GPL-2.0Shell - Fusion Directory - Improve the Management of the services and the company directory based on OpenLDAP. (Source Code)
GPL-2.0PHP - LDAP Account Manager (LAM) - Web frontend for managing entries (e.g. users, groups, DHCP settings) stored in an LDAP directory. (Source Code)
GPL-3.0PHP - Libravatar - Libravatar is a service which delivers your avatar (profile picture) to other websites. (Source Code)
AGPL-3.0Python - Pomerium - An identity and context aware access-proxy inspired by BeyondCorp. (Source Code)
Apache-2.0Docker/Go - Samba - Active Directory and CIFS protocol implementation. (Source Code)
GPL-3.0C - Smallstep Certificates - A private certificate authority (X.509 & SSH) and related tools for secure automated certificate management. (Source Code)
Apache-2.0Go - ZITADEL - Cloud-native Identity & Access Management solution providing a platform for secure authentication, authorization and identity management. (Source Code)
Apache-2.0Go/Docker/K8S
- BounCA - A personal SSL Key / Certificate Authority web-based tool for creating self-signed certificates. (Source Code)
-
 @ cff1720e:15c7e2b2
2025-01-19 17:48:02
@ cff1720e:15c7e2b2
2025-01-19 17:48:02Einleitung\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie roland@pareto.space können sie sogar jederzeit umziehen, egal wohin. Cool, das ist state of the art! Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.

Warum Nostr?
Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz "unserer Demokratie” praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.

Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ Resümee: keine Standards, keine Daten, keine Rechte = keine Zukunft!

\ Wie funktioniert Nostr?
Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum “single point of failure”, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. roland@pareto.space ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ Resümee: ein offener Standard, alle Daten, alle Rechte = große Zukunft!

\ Warum ist Nostr die Zukunft des Internet?
“Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie (Value4Value). OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.

\ Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.
https://nostr.net/ \ https://start.njump.me/
Hier das Interview zum Thema mit Radio Berliner Morgenröte
-
 @ ffbcb706:b0574044
2025-05-21 09:59:14
@ ffbcb706:b0574044
2025-05-21 09:59:14Just a client name test
