-
 @ bd4ae3e6:1dfb81f5
2025-05-20 08:46:08
@ bd4ae3e6:1dfb81f5
2025-05-20 08:46:08 -
 @ bd4ae3e6:1dfb81f5
2025-05-20 08:46:06
@ bd4ae3e6:1dfb81f5
2025-05-20 08:46:06 -
 @ c230edd3:8ad4a712
2025-04-11 16:02:15
@ c230edd3:8ad4a712
2025-04-11 16:02:15Chef's notes
Wildly enough, this is delicious. It's sweet and savory.
(I copied this recipe off of a commercial cheese maker's site, just FYI)
I hadn't fully froze the ice cream when I took the picture shown. This is fresh out of the churner.
Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 4
Ingredients
- 12 oz blue cheese
- 3 Tbsp lemon juice
- 1 c sugar
- 1 tsp salt
- 1 qt heavy cream
- 3/4 c chopped dark chocolate
Directions
- Put the blue cheese, lemon juice, sugar, and salt into a bowl
- Bring heavy cream to a boil, stirring occasionally
- Pour heavy cream over the blue cheese mix and stir until melted
- Pour into prepared ice cream maker, follow unit instructions
- Add dark chocolate halfway through the churning cycle
- Freeze until firm. Enjoy.
-
 @ c1e9ab3a:9cb56b43
2025-05-27 16:19:06
@ c1e9ab3a:9cb56b43
2025-05-27 16:19:06Star Wars is often viewed as a myth of rebellion, freedom, and resistance to tyranny. The iconography—scrappy rebels, totalitarian stormtroopers, lone smugglers—suggests a deep anti-authoritarian ethos. Yet, beneath the surface, the narrative arc of Star Wars consistently affirms the necessity, even sanctity, of central authority. This blog entry introduces the question: Is Star Wars fundamentally a celebration of statism?
Rebellion as Restoration, Not Revolution
The Rebel Alliance’s mission is not to dismantle centralized power, but to restore the Galactic Republic—a bureaucratic, centrally governed institution. Characters like Mon Mothma and Bail Organa are high-ranking senators, not populist revolutionaries. The goal is to remove the corrupt Empire and reinstall a previous central authority, presumed to be just.
- Rebels are loyalists to a prior state structure.
- Power is not questioned, only who wields it.
Jedi as Centralized Moral Elites
The Jedi, often idealized as protectors of peace, are unelected, extra-legal enforcers of moral and military order. Their authority stems from esoteric metaphysical abilities rather than democratic legitimacy.
- They answer only to their internal Council.
- They are deployed by the Senate, but act independently of civil law.
- Their collapse is depicted as tragic not because they were unaccountable, but because they were betrayed.
This positions them as a theocratic elite, not spiritual anarchists.
Chaos and the Frontier: The Case of the Cantina
The Mos Eisley cantina, often viewed as a symbol of frontier freedom, reveals something darker. It is: - Lawless - Violent - Culturally fragmented
Conflict resolution occurs through murder, not mediation. Obi-Wan slices off a limb; Han shoots first—both without legal consequence. There is no evidence of property rights, dispute resolution, or voluntary order.
This is not libertarian pluralism—it’s moral entropy. The message: without centralized governance, barbarism reigns.
The Mythic Arc: Restoration of the Just State
Every trilogy in the saga returns to a single theme: the fall and redemption of legitimate authority.
- Prequels: Republic collapses into tyranny.
- Originals: Rebels fight to restore legitimate order.
- Sequels: Weak governance leads to resurgence of authoritarianism; heroes must reestablish moral centralism.
The story is not anti-state—it’s anti-bad state. The solution is never decentralization; it’s the return of the right ruler or order.
Conclusion: The Hidden Statism of a Rebel Myth
Star Wars wears the costume of rebellion, but tells the story of centralized salvation. It: - Validates elite moral authority (Jedi) - Romanticizes restoration of fallen governments (Republic) - Portrays decentralized zones as corrupt and savage (outer rim worlds)
It is not an anarchist parable, nor a libertarian fable. It is a statist mythology, clothed in the spectacle of rebellion. Its core message is not that power should be abolished, but that power belongs to the virtuous few.
Question to Consider:
If the Star Wars universe consistently affirms the need for centralized moral and political authority, should we continue to see it as a myth of freedom? Or is it time to recognize it as a narrative of benevolent empire? -
 @ 21335073:a244b1ad
2025-05-21 16:58:36
@ 21335073:a244b1ad
2025-05-21 16:58:36The other day, I had the privilege of sitting down with one of my favorite living artists. Our conversation was so captivating that I felt compelled to share it. I’m leaving his name out for privacy.
Since our last meeting, I’d watched a documentary about his life, one he’d helped create. I told him how much I admired his openness in it. There’s something strange about knowing intimate details of someone’s life when they know so little about yours—it’s almost like I knew him too well for the kind of relationship we have.
He paused, then said quietly, with a shy grin, that watching the documentary made him realize how “odd and eccentric” he is. I laughed and told him he’s probably the sanest person I know. Because he’s lived fully, chasing love, passion, and purpose with hardly any regrets. He’s truly lived.
Today, I turn 44, and I’ll admit I’m a bit eccentric myself. I think I came into the world this way. I’ve made mistakes along the way, but I carry few regrets. Every misstep taught me something. And as I age, I’m not interested in blending in with the world—I’ll probably just lean further into my own brand of “weird.” I want to live life to the brim. The older I get, the more I see that the “normal” folks often seem less grounded than the eccentric artists who dare to live boldly. Life’s too short to just exist, actually live.
I’m not saying to be strange just for the sake of it. But I’ve seen what the crowd celebrates, and I’m not impressed. Forge your own path, even if it feels lonely or unpopular at times.
It’s easy to scroll through the news and feel discouraged. But actually, this is one of the most incredible times to be alive! I wake up every day grateful to be here, now. The future is bursting with possibility—I can feel it.
So, to my fellow weirdos on nostr: stay bold. Keep dreaming, keep pushing, no matter what’s trending. Stay wild enough to believe in a free internet for all. Freedom is radical—hold it tight. Live with the soul of an artist and the grit of a fighter. Thanks for inspiring me and so many others to keep hoping. Thank you all for making the last year of my life so special.
-
 @ 51bbb15e:b77a2290
2025-05-21 00:24:36
@ 51bbb15e:b77a2290
2025-05-21 00:24:36Yeah, I’m sure everything in the file is legit. 👍 Let’s review the guard witness testimony…Oh wait, they weren’t at their posts despite 24/7 survellience instructions after another Epstein “suicide” attempt two weeks earlier. Well, at least the video of the suicide is in the file? Oh wait, a techical glitch. Damn those coincidences!
At this point, the Trump administration has zero credibility with me on anything related to the Epstein case and his clients. I still suspect the administration is using the Epstein files as leverage to keep a lot of RINOs in line, whereas they’d be sabotaging his agenda at every turn otherwise. However, I just don’t believe in ends-justify-the-means thinking. It’s led almost all of DC to toss out every bit of the values they might once have had.
-
 @ c230edd3:8ad4a712
2025-04-09 00:33:31
@ c230edd3:8ad4a712
2025-04-09 00:33:31Chef's notes
I found this recipe a couple years ago and have been addicted to it since. Its incredibly easy, and cheap to prep. Freeze the sausage in flat, single serving portions. That way it can be cooked from frozen for a fast, flavorful, and healthy lunch or dinner. I took inspiration from the video that contained this recipe, and almost always pan fry the frozen sausage with some baby broccoli. The steam cooks the broccoli and the fats from the sausage help it to sear, while infusing the vibrant flavors. Serve with some rice, if desired. I often use serrano peppers, due to limited produce availability. They work well for a little heat and nice flavor that is not overpowering.
Details
- ⏲️ Prep time: 25 min
- 🍳 Cook time: 15 min (only needed if cooking at time of prep)
- 🍽️ Servings: 10
Ingredients
- 4 lbs ground pork
- 12-15 cloves garlic, minced
- 6 Thai or Serrano peppers, rough chopped
- 1/4 c. lime juice
- 4 Tbsp fish sauce
- 1 Tbsp brown sugar
- 1/2 c. chopped cilantro
Directions
- Mix all ingredients in a large bowl.
- Portion and freeze, as desired.
- Sautè frozen portions in hot frying pan, with broccoli or other fresh veggies.
- Serve with rice or alone.
-
 @ c9badfea:610f861a
2025-05-20 19:49:20
@ c9badfea:610f861a
2025-05-20 19:49:20- Install Sky Map (it's free and open source)
- Launch the app and tap Accept, then tap OK
- When asked to access the device's location, tap While Using The App
- Tap somewhere on the screen to activate the menu, then tap ⁝ and select Settings
- Disable Send Usage Statistics
- Return to the main screen and enjoy stargazing!
ℹ️ Use the 🔍 icon in the upper toolbar to search for a specific celestial body, or tap the 👁️ icon to activate night mode
-
 @ 00000001:b0c77eb9
2025-02-14 21:24:24
@ 00000001:b0c77eb9
2025-02-14 21:24:24مواقع التواصل الإجتماعي العامة هي التي تتحكم بك، تتحكم بك بفرض أجندتها وتجبرك على اتباعها وتحظر وتحذف كل ما يخالفها، وحرية التعبير تنحصر في أجندتها تلك!
وخوارزمياتها الخبيثة التي لا حاجة لها، تعرض لك مايريدون منك أن تراه وتحجب ما لا يريدونك أن تراه.
في نوستر انت المتحكم، انت الذي تحدد من تتابع و انت الذي تحدد المرحلات التي تنشر منشوراتك بها.
نوستر لامركزي، بمعنى عدم وجود سلطة تتحكم ببياناتك، بياناتك موجودة في المرحلات، ولا احد يستطيع حذفها او تعديلها او حظر ظهورها.
و هذا لا ينطبق فقط على مواقع التواصل الإجتماعي العامة، بل ينطبق أيضاً على الـfediverse، في الـfediverse انت لست حر، انت تتبع الخادم الذي تستخدمه ويستطيع هذا الخادم حظر ما لا يريد ظهوره لك، لأنك لا تتواصل مع بقية الخوادم بنفسك، بل خادمك من يقوم بذلك بالنيابة عنك.
وحتى إذا كنت تمتلك خادم في شبكة الـfediverse، إذا خالفت اجندة بقية الخوادم ونظرتهم عن حرية الرأي و التعبير سوف يندرج خادمك في القائمة السوداء fediblock ولن يتمكن خادمك من التواصل مع بقية خوادم الشبكة، ستكون محصوراً بالخوادم الأخرى المحظورة كخادمك، بالتالي انت في الشبكة الأخرى من الـfediverse!
نعم، يوجد شبكتان في الكون الفدرالي fediverse شبكة الصالحين التابعين للأجندة الغربية وشبكة الطالحين الذين لا يتبعون لها، إذا تم إدراج خادمك في قائمة fediblock سوف تذهب للشبكة الأخرى!
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 6ad3e2a3:c90b7740
2025-05-20 13:49:50
@ 6ad3e2a3:c90b7740
2025-05-20 13:49:50I’ve written about MSTR twice already, https://www.chrisliss.com/p/mstr and https://www.chrisliss.com/p/mstr-part-2, but I want to focus on legendary short seller James Chanos’ current trade wherein he buys bitcoin (via ETF) and shorts MSTR, in essence to “be like Mike” Saylor who sells MSTR shares at the market and uses them to add bitcoin to the company’s balance sheet. After all, if it’s good enough for Saylor, why shouldn’t everyone be doing it — shorting a company whose stock price is more than 2x its bitcoin holdings and using the proceeds to buy the bitcoin itself?
Saylor himself has said selling shares at 2x NAV (net asset value) to buy bitcoin is like selling dollars for two dollars each, and Chanos has apparently decided to get in while the getting (market cap more than 2x net asset value) is good. If the price of bitcoin moons, sending MSTR’s shares up, you are more than hedged in that event, too. At least that’s the theory.
The problem with this bet against MSTR’s mNAV, i.e., you are betting MSTR’s market cap will converge 1:1 toward its NAV in the short and medium term is this trade does not exist in a vacuum. Saylor has described how his ATM’s (at the market) sales of shares are accretive in BTC per share because of this very premium they carry. Yes, we’ll dilute your shares of the company, but because we’re getting you 2x the bitcoin per share, you are getting an ever smaller slice of an ever bigger overall pie, and the pie is growing 2x faster than your slice is reducing. (I https://www.chrisliss.com/p/mstr how this works in my first post.)
But for this accretion to continue, there must be a constant supply of “greater fools” to pony up for the infinitely printable shares which contain only half their value in underlying bitcoin. Yes, those shares will continue to accrete more BTC per share, but only if there are more fools willing to make this trade in the future. So will there be a constant supply of such “fools” to keep fueling MSTR’s mNAV multiple indefinitely?
Yes, there will be in my opinion because you have to look at the trade from the prospective fools’ perspective. Those “fools” are not trading bitcoin for MSTR, they are trading their dollars, selling other equities to raise them maybe, but in the end it’s a dollars for shares trade. They are not selling bitcoin for them.
You might object that those same dollars could buy bitcoin instead, so they are surely trading the opportunity cost of buying bitcoin for them, but if only 5-10 percent of the market (or less) is buying bitcoin itself, the bucket in which which those “fools” reside is the entire non-bitcoin-buying equity market. (And this is not considering the even larger debt market which Saylor has yet to tap in earnest.)
So for those 90-95 percent who do not and are not presently planning to own bitcoin itself, is buying MSTR a fool’s errand, so to speak? Not remotely. If MSTR shares are infinitely printable ATM, they are still less so than the dollar and other fiat currencies. And MSTR shares are backed 2:1 by bitcoin itself, while the fiat currencies are backed by absolutely nothing. So if you hold dollars or euros, trading them for MSTR shares is an errand more sage than foolish.
That’s why this trade (buying BTC and shorting MSTR) is so dangerous. Not only are there many people who won’t buy BTC buying MSTR, there are many funds and other investment entities who are only able to buy MSTR.
Do you want to get BTC at 1:1 with the 5-10 percent or MSTR backed 2:1 with the 90-95 percent. This is a bit like medical tests that have a 95 percent accuracy rate for an asymptomatic disease that only one percent of the population has. If someone tests positive, it’s more likely to be a false one than an indication he has the disease*. The accuracy rate, even at 19:1, is subservient to the size of the respective populations.
At some point this will no longer be the case, but so long as the understanding of bitcoin is not widespread, so long as the dollar is still the unit of account, the “greater fools” buying MSTR are still miles ahead of the greatest fools buying neither, and the stock price and mNAV should only increase.
. . .
One other thought: it’s more work to play defense than offense because the person on offense knows where he’s going, and the defender can only react to him once he moves. Similarly, Saylor by virtue of being the issuer of the shares knows when more will come online while Chanos and other short sellers are borrowing them to sell in reaction to Saylor’s strategy. At any given moment, Saylor can pause anytime, choosing to issue convertible debt or preferred shares with which to buy more bitcoin, and the shorts will not be given advance notice.
If the price runs, and there is no ATM that week because Saylor has stopped on a dime, so to speak, the shorts will be left having to scramble to change directions and buy the shares back to cover. Their momentum might be in the wrong direction, though, and like Allen Iverson breaking ankles with a crossover, Saylor might trigger a massive short squeeze, rocketing the share price ever higher. That’s why he actually welcomes Chanos et al trying this copycat strategy — it becomes the fuel for outsized gains.
For that reason, news that Chanos is shorting MSTR has not shaken my conviction, though there are other more pertinent https://www.chrisliss.com/p/mstr-part-2 with MSTR, of which one should be aware. And as always, do your own due diligence before investing in anything.
* To understand this, consider a population of 100,000, with one percent having a disease. That means 1,000 have it, 99,000 do not. If the test is 95 percent accurate, and everyone is tested, 950 of the 1,000 will test positive (true positives), 50 who have it will test negative (false negatives.) Of the positives, 95 percent of 99,000 (94,050) will test negative (true negatives) and five percent (4,950) will test positive (false positives). That means 4,950 out of 5,900 positives (84%) will be false.
-
 @ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03
@ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ b83a28b7:35919450
2025-05-16 19:23:58
@ b83a28b7:35919450
2025-05-16 19:23:58This article was originally part of the sermon of Plebchain Radio Episode 110 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ d61f3bc5:0da6ef4a
2025-05-05 15:26:08
@ d61f3bc5:0da6ef4a
2025-05-05 15:26:08I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify a media file and maliciously ascribe it to the note author.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 2183e947:f497b975
2025-05-01 22:33:48
@ 2183e947:f497b975
2025-05-01 22:33:48Most darknet markets (DNMs) are designed poorly in the following ways:
1. Hosting
Most DNMs use a model whereby merchants fill out a form to create their listings, and the data they submit then gets hosted on the DNM's servers. In scenarios where a "legal" website would be forced to censor that content (e.g. a DMCA takedown order), DNMs, of course, do not obey. This can lead to authorities trying to find the DNM's servers to take enforcement actions against them. This design creates a single point of failure.
A better design is to outsource hosting to third parties. Let merchants host their listings on nostr relays, not on the DNM's server. The DNM should only be designed as an open source interface for exploring listings hosted elsewhere, that way takedown orders end up with the people who actually host the listings, i.e. with nostr relays, and not with the DNM itself. And if a nostr relay DOES go down due to enforcement action, it does not significantly affect the DNM -- they'll just stop querying for listings from that relay in their next software update, because that relay doesn't work anymore, and only query for listings from relays that still work.
2. Moderation
Most DNMs have employees who curate the listings on the DNM. For example, they approve/deny listings depending on whether they fit the content policies of the website. Some DNMs are only for drugs, others are only for firearms. The problem is, to approve a criminal listing is, in the eyes of law enforcement, an act of conspiracy. Consequently, they don't just go after the merchant who made the listing but the moderators who approved it, and since the moderators typically act under the direction of the DNM, this means the police go after the DNM itself.
A better design is to outsource moderation to third parties. Let anyone call themselves a moderator and create lists of approved goods and services. Merchants can pay the most popular third party moderators to add their products to their lists. The DNM itself just lets its users pick which moderators to use, such that the user's choice -- and not a choice by the DNM -- determines what goods and services the user sees in the interface.
That way, the police go after the moderators and merchants rather than the DNM itself, which is basically just a web browser: it doesn't host anything or approve of any content, it just shows what its users tell it to show. And if a popular moderator gets arrested, his list will still work for a while, but will gradually get more and more outdated, leading someone else to eventually become the new most popular moderator, and a natural transition can occur.
3. Escrow
Most DNMs offer an escrow solution whereby users do not pay merchants directly. Rather, during the Checkout process, they put their money in escrow, and request the DNM to release it to the merchant when the product arrives, otherwise they initiate a dispute. Most DNMs consider escrow necessary because DNM users and merchants do not trust one another; users don't want to pay for a product first and then discover that the merchant never ships it, and merchants don't want to ship a product first and then discover that the user never pays for it.
The problem is, running an escrow solution for criminals is almost certain to get you accused of conspiracy, money laundering, and unlicensed money transmission, so the police are likely to shut down any DNM that does this. A better design is to oursource escrow to third parties. Let anyone call themselves an escrow, and let moderators approve escrows just like they approve listings. A merchant or user who doesn't trust the escrows chosen by a given moderator can just pick a different moderator. That way, the police go after the third party escrows rather than the DNM itself, which never touches user funds.
4. Consequences
Designing a DNM along these principles has an interesting consequence: the DNM is no longer anything but an interface, a glorified web browser. It doesn't host any content, approve any listings, or touch any money. It doesn't even really need a server -- it can just be an HTML file that users open up on their computer or smart phone. For two reasons, such a program is hard to take down:
First, it is hard for the police to justify going after the DNM, since there are no charges to bring. Its maintainers aren't doing anything illegal, no more than Firefox does anything illegal by maintaining a web browser that some people use to browse illegal content. What the user displays in the app is up to them, not to the code maintainers. Second, if the police decided to go after the DNM anyway, they still couldn't take it down because it's just an HTML file -- the maintainers do not even need to run a server to host the file, because users can share it with one another, eliminating all single points of failure.
Another consequence of this design is this: most of the listings will probably be legal, because there is more demand for legal goods and services than illegal ones. Users who want to find illegal goods would pick moderators who only approve those listings, but everyone else would use "legal" moderators, and the app would not, at first glance, look much like a DNM, just a marketplace for legal goods and services. To find the illegal stuff that lurks among the abundant legal stuff, you'd probably have to filter for it via your selection of moderators, making it seem like the "default" mode is legal.
5. Conclusion
I think this DNM model is far better than the designs that prevail today. It is easier to maintain, harder to take down, and pushes the "hard parts" to the edges, so that the DNM is not significantly affected even if a major merchant, moderator, or escrow gets arrested. I hope it comes to fruition.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 6be5cc06:5259daf0
2025-05-27 20:22:09
@ 6be5cc06:5259daf0
2025-05-27 20:22:09A posição do libertário que rejeita o cristianismo padece de sérias incoerências lógicas, históricas e filosóficas. Ao renegar as bases espirituais e culturais que tornaram possível o próprio ideal libertário, tal posição demonstra ser, ao mesmo tempo, autofágica e irracional. É o caso de alguém que se gloria dos frutos de uma árvore que corta pela raiz.
I. Fundamento histórico: a civilização da liberdade é cristã
Não foi o secularismo moderno, nem o paganismo antigo, que ergueram as instituições que protegem a dignidade da pessoa humana e os limites ao poder. Desde os primeiros séculos, a Igreja resistiu ao culto estatal romano, afirmando a soberania de Deus sobre os Césares — "Mais importa obedecer a Deus que aos homens" (Atos 5,29).
Foi o cristianismo que:
-
Fundou universidades livres, onde o saber era buscado sob o primado da verdade;
-
Defendeu a lei natural como fundamento do direito — uma doutrina que protege o indivíduo contra tiranias;
-
Resgatou e aprofundou o conceito de pessoa, dotada de razão e livre-arbítrio, imagem de Deus, e, portanto, inalienavelmente digna e responsável.
Em momentos-chave da história, como nas disputas entre papado e império, nas resistências contra absolutismos, e na fundação do direito internacional por Francisco de Vitoria e a Escola de Salamanca, foi o cristianismo quem freou o poder estatal em nome de princípios superiores. A tradição cristã foi frequentemente o principal obstáculo à tirania, não seu aliado.
Negar isso é amputar a própria genealogia da liberdade ocidental.
Uma das chaves do cristianismo para a construção dessa civilização da liberdade foi a exaltação do individualismo. Ao afirmar que o ser humano é feito à imagem de Deus e que sua salvação é uma escolha pessoal, o cristianismo colocou o indivíduo no centro da moralidade e da liberdade. Diferente dos gregos, cuja ética era voltada para a polis e a cidade-estado, o cristianismo reafirma a suprema importância do indivíduo, com sua capacidade de escolha moral, responsabilidade pessoal e dignidade intrínseca. Esse princípio, mais do que qualquer outra religião, foi o alicerce do desenvolvimento da liberdade individual e da autonomia, valores que sustentam a civilização ocidental.
A ética grega, na melhor das hipóteses, descreve a ordem natural — mas não consegue justificar por que essa ordem deveria obrigar a vontade humana. Um Logos impessoal não tem autoridade moral. Uma ordem cósmica sem um Legislador é apenas um dado de fato, não uma norma vinculante. A vontade pode rebelar-se contra o telos — e sem um Deus justo, que ordena a natureza à perfeição, não há razão última para não o fazer.
A cultura grega teve uma influência indiscutível sobre o desenvolvimento da civilização ocidental, mas o cristianismo não só absorveu o que havia de bom na cultura grega, como também elevou e completou esses aspectos. O cristianismo, ao afirmar que todos os homens são feitos à imagem e semelhança de Deus e têm dignidade intrínseca, levou a uma noção de igualdade moral e liberdade que transcende as limitações da pólis grega.
II. Falsa dicotomia: fé e liberdade não são opostas
Com frequência equiparam a religião à coerção e à obediência cega. Mas isso é um equívoco: o cristianismo não se impõe pela força, mas apela à consciência. O próprio Deus, em sua relação com a criatura racional, respeita sua liberdade. Como ensina a Escritura:
"Se alguém quiser vir após mim..." (Mt 16,24);
"Eis que estou à porta e bato. Se alguém ouvir a minha voz e abrir a porta, entrarei em sua casa e cearei com ele." (Ap 3,20);
"Assim falai, e assim procedei, como devendo ser julgados pela lei da liberdade." (Tiago 2,12).A adesão à fé deve ser livre, voluntária e racional, pois sem liberdade não há verdadeiro mérito, nem amor genuíno. Isso é mais compatível com o princípio de não agressão do que qualquer utopia secular. Ora, o núcleo do evangelho é voluntarista: salvação pessoal, conversão interior, caridade.
Ninguém deve ser forçado, contra sua vontade, a abraçar a fé, pois o ato de fé é por sua natureza voluntário (Dignitatis Humanae; CDC, cân. 748,2)
Se algum Estado usa da força para impor o cristianismo, afirmar que o cristianismo causou as coerções é tão equivocado quanto dizer que a propriedade privada causa o comunismo; é uma inversão da realidade, pois o comunismo surge precisamente da violação da propriedade. Portanto, a fé forçada é inválida em si mesma, pois viola a natureza do ato de crer, que deve ser livre.
III. Fundamento moral: sem transcendência, o libertarianismo flutua no vácuo
O libertário anticristão busca defender princípios objetivos — como a inviolabilidade do indivíduo e a ilegitimidade da agressão — sem um fundamento transcendente que lhes dê validade universal. Por que a agressão é errada? Por que alguém tem direito à vida, à liberdade, à propriedade? Sem uma explicação transcendental, as respostas para tais perguntas se tornam apenas opiniões ou convenções, não obrigações morais vinculantes. Se a moralidade é puramente humana, então os direitos podem ser modificados ou ignorados conforme a vontade da sociedade. O conceito de direitos naturais, tão caro ao libertarianismo, precisa de um solo metafísico que justifique sua universalidade e imutabilidade. Caso contrário, eles podem ser tratados apenas como acordos utilitários temporários ou preferências culturais, sem qualquer obrigatoriedade para todos os seres humanos em todas as circunstâncias.
Pensadores libertários seculares, como Ayn Rand e Murray Rothbard, tentaram ancorar os direitos naturais na razão humana ou na natureza do homem. Rand baseia sua ética no egoísmo racional, enquanto Rothbard apela à lei natural. Embora essas abordagens busquem objetividade, elas carecem de uma resposta definitiva para por que a razão ou a natureza humana obrigam moralmente todos os indivíduos. Sem um fundamento transcendente, suas concepções permanecem vulneráveis a interpretações subjetivas ou a cálculos utilitários.
Aqui, o cristianismo oferece uma explicação sólida e transcendental que fundamenta os direitos naturais. A visão cristã de que o ser humano foi criado à imagem e semelhança de Deus confere à pessoa uma dignidade intrínseca, imutável e universal. Essa dignidade não depende de fatores externos, como consenso social ou poder político, mas é uma característica inerente ao ser humano pela sua criação divina. A partir dessa perspectiva teológica, torna-se possível afirmar com base sólida que os direitos naturais são dados por Deus e, portanto, são universais e vinculantes.
O cristianismo também é a base de um sistema moral que distingue claramente justiça de legalidade. O Estado pode criar leis, mas isso não significa que essas leis sejam justas. A justiça, sob a ótica cristã, é uma expressão da ordem moral objetiva, algo que transcende as leis humanas e é definido pela vontade divina. Por isso, o libertarianismo cristão vê a agressão como uma violação de uma ordem moral objetiva, e não apenas uma violação de uma convenção social ou de um acordo utilitário.
Se a moralidade e os direitos naturais não forem fundamentados em um Logos criador e legislador, o que acontece é que o conceito de direito natural degenera para algo mais frágil, como um simples acordo utilitário. Nesse cenário, os direitos do indivíduo se tornam algo acordado entre os membros de uma sociedade, em vez de princípios imutáveis e universais. Os direitos podem ser negociados, alterados ou ignorados conforme o interesse do momento.
IV. Fundamento científico: a racionalidade moderna é filha da fé cristã
A ciência moderna só foi possível no contexto cultural cristão. Nenhuma outra civilização — nem a grega, nem a islâmica, nem a chinesa — produziu o método científico como o Ocidente cristão o fez.
Isso se deve a quatro premissas teológicas:
-
Criação racional: O mundo é ordenado por um Deus racional.
-
Distinção entre Criador e criatura: A natureza não é divina e pode ser estudada sem sacrilégio.
-
Valor do trabalho e da observação empírica, herdado do monaquismo.
-
Autonomia institucional, presente nas universidades medievais.
A doutrina cristã da Criação ex nihilo ensina que o mundo foi criado por um Deus racional, sábio e pessoal. Portanto, o cosmos é ordenado, possui leis, e pode ser compreendido pela razão humana — que é imagem do Criador. Isso contrasta fortemente com as cosmovisões panteístas ou mitológicas, onde o mundo é cíclico, arbitrário ou habitado por forças caprichosas.
Sem essa fé no Logos criador, não há razão para crer que a natureza tenha uma ordem inteligível universal e constante, que pode ser descoberta por observação e dedução. A ciência moderna só é possível porque, antes de investigar a natureza, pressupôs-se que ela era investigável — e isso foi uma herança direta do pensamento cristão.
Homens como Bacon, Newton, Kepler e Galileu viam na ciência um modo de glorificar o Criador. O ateísmo cientificista é, portanto, parasitário da teologia cristã, pois toma seus frutos e rejeita suas raízes. A ciência moderna nasceu como filha legítima da fé cristã. E os que hoje a usam contra sua mãe, ou são ingratos, ou ignorantes.
V. O cristianismo como barreira à revolução cultural
O cristianismo é a barreira mais sólida contra a infiltração revolucionária. A chamada "marcha gramsciana", que visa corroer os fundamentos morais da sociedade para subjugar o indivíduo ao coletivo, encontra sua resistência mais firme nos princípios cristãos. A fé cristã, ao proclamar a existência de uma verdade objetiva, de uma lei moral imutável e de uma dignidade humana que transcende o Estado e o consenso social, imuniza a civilização contra o relativismo e o igualitarismo nivelador do marxismo cultural.
Além disso, o cristianismo é uma tradição milenar, profundamente enraizada no cotidiano das pessoas, não sendo uma novidade a ser imposta ou implementada, mas uma força presente há séculos, que permeia a estrutura social, moral e cultural da sociedade. Sua presença constante nas comunidades, desde os tempos mais antigos, oferece uma resistência robusta contra qualquer tentativa de subverter a ordem natural e moral estabelecida.
Não por acaso, tanto Karl Marx quanto Antonio Gramsci identificaram no cristianismo o principal obstáculo à realização de seus projetos revolucionários. Marx chamou a religião de "ópio do povo" porque sabia que uma alma ancorada em Deus não se submete facilmente ao poder terreno; Gramsci, mais sutil, propôs a destruição da cultura cristã como pré-condição para o triunfo do socialismo. Sem essa âncora transcendente, a sociedade torna-se presa fácil das engenharias sociais que pretendem redefinir arbitrariamente o homem, a família e a liberdade.
Conclusão
O libertário anticristão, consciente ou não, nega as fundações mesmas do edifício que habita. Ao rejeitar o cristianismo, cava o abismo sob os próprios pés, privando o ideal libertário de sua base moral, cultural e racional. Ele defende a ética voluntária, a liberdade individual e a ordem espontânea, mas sem o solo metafísico e histórico que torna esses princípios inteligíveis e possíveis. É um erro tentar preservar a liberdade em termos absolutos sem reconhecer as raízes cristãs que a sustentam, pois o cristianismo é a única tradição que a legitima e a viabiliza.
Negar o cristianismo é racionalmente insustentável. A liberdade, como a conhecemos, é filha da fé cristã, que oferece a base moral e metafísica que torna a liberdade tanto desejável quanto possível. Mesmo que ateu, o libertário que ama a liberdade deveria, no mínimo, respeitar — e, idealmente, redescobrir — essas raízes cristãs. Pois sem fé, restam apenas o niilismo e o relativismo, que, eventualmente, desaguam na servidão.
Como nos ensina a tradição: Ubi fides ibi libertas — onde há fé, há liberdade.
-
-
 @ c9badfea:610f861a
2025-05-24 12:55:17
@ c9badfea:610f861a
2025-05-24 12:55:17Before you post a message or article online, let the LLM check if you are leaking any personal information using this prompt:
Analyze the following text to identify any Personally Identifiable Information (PII): <Your Message>Replace
<Your Message>with your textIf no PII is found, continue by modifying your message to detach it from your personality. You can use any of the following prompts (and further modify it if necessary).
Prompt № 1 - Reddit-Style
Convert the message into a casual, Reddit-style post without losing meaning. Split the message into shorter statements with the same overall meaning. Here is the message: <Your Message>Prompt № 2 - Advanced Modifications
``` Apply the following modifications to the message: - Rewrite it in lowercase - Use "u" instead of "you" - Use "akchoaly" instead of "actually" - Use "hav" instead of "have" - Use "tgat" instead of "that" - Use comma instead of period - Use British English grammar
Here is the message:
``` Prompt № 3 - Neutral Tone
Rewrite the message to correct grammar errors, and ensure the tone is neutral and free of emotional language: <Your Message>Prompt № 4 - Cross Translation Technique
Translate the message into Chinese, then translate the resulting Chinese text back into English. Provide only the final English translation. Here is the message: <Your Message>Check the modified message and send it.
ℹ️ You can use dialects to obfuscate your language further. For example, if you are from the US, you can tell the LLM to use British grammar and vice versa.
⚠️ Always verify the results. Don't fully trust an LLM.
-
 @ cae03c48:2a7d6671
2025-05-27 22:00:40
@ cae03c48:2a7d6671
2025-05-27 22:00:40Bitcoin Magazine

Bitcoin Well Integrates Nostr BTC Purchases via DMsBitcoin Well Inc. (TSXV: BTCW; OTCQB: BCNWF) has launched an integration with Nostr, allowing US customers to buy bitcoin directly through direct messages on the decentralized social protocol, according to a press release sent to Bitcoin Magazine.
Users can link their Nostr identifier (npub) to their Bitcoin Well account and purchase bitcoin by sending specific commands via direct message. The transactions draw from the user’s Cash Balance and send the purchased bitcoin to their existing Lightning Wallet for security.
Nostr is a decentralized social media protocol which is censorship resistant and runs on a network of relays, rather than centralized servers. This means that the users have full control over their message servers. It also adds a layer of protection for the customer’s privacy.
The integration simplifies the process of buying bitcoin by allowing users to make purchases directly through a social platform they already use. As a censorship-resistant protocol, Nostr ensures Bitcoin Well and its customers have full control, avoiding restrictions and potential censorship.
“This is a great achievement for our team!” said founder and CEO of Bitcoin Well Adam O’Brien. “We are deeply committed to make buying bitcoin directly to self custody better than using a custodial exchange. This is a huge step in the right direction. We are meeting bitcoiners where they are and allowing them to buy bitcoin safely.”
Users can link their npub to their Bitcoin Well account to enable bitcoin purchases via direct message. Commands like /buy $21.00 or /stack 69000 sats initiate a transaction, which is confirmed by sending /confirm. The purchase uses funds from the user’s Bitcoin Well Cash Balance, and bitcoin is delivered over the Lightning Network to a pre-registered wallet address.
This post Bitcoin Well Integrates Nostr BTC Purchases via DMs first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:50:22
@ 04c915da:3dfbecc9
2025-05-20 15:50:22There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ bf47c19e:c3d2573b
2025-05-27 21:19:32
@ bf47c19e:c3d2573b
2025-05-27 21:19:32Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Procena vrednosti
- Većina Bitcoin-ovih pozitivnih strana opstaje
- Broj ljudi koji su prihvatili Bitcoin
- Zaključak
Prošlo je trinaest godina od nastanka Bitcoina i lako je poverovati da je većina njegovog rasta iza njega. Deo ovoga je rezultat predrasude koju svi delimo i što nas navodi da zamislimo trenutno stanje stvari kao završni stepen njegovog razvoja. Svaki bitcoiner je nekad mislio da je prekasan sa Bitcoin-om. Međutim, kada primenjujemo kritičko razmišljanje da bismo procenili gde je Bitcoin u svojoj putanji rasta, otkrivamo da je suprotno u stvari tačno: još uvek je vrlo, vrlo rano.
Postoje dva načina da razmišljate o tome koliko je rano za Bitcoin kao zalihu vrednosti neke imovine:
-
Procena vrednosti kao procenat od njegovog punog potencijala
-
Prihvatanje kao procenat od njegovog punog potencijala (na čemu je fokus u ovom članku).
Procena vrednosti
Prvi i najčešći način da se proceni koliko je rano za Bitcoin je da se pogleda njegova ukupna vrednost (trenutno oko 900B USD) i uporedi sa njegovim punim potencijalom. Izazov sa ovim je očigledno da je puni potencijal Bitcoin-a stvar nagađanja. Oni koji duboko razumeju Bitcoin imaju tendenciju da njegov potencijal posmatraju barem kao potencijal zlata (oko 13T USD), ali teoretski više poput 200T USD (oko polovine ukupne vrednosti sveta).
Za brzi pregled ovog potencijala od 200T USD, pogledajmo ukupno raspoloživo tržište Bitcoin-a. Radi jednostavnosti, samo ćemo razmotriti njegovu ulogu zalihe vrednosti i zanemariti njegov potencijal da pojede tržišni udeo od oko 100T USD ukupne vrednosti u različitim svetskim valutama. Uzimajući u obzir različite zalihe vrednosne imovine i grubom procenom koliki bi % Bitcoin mogao da uzme od njih, dobili smo ovakav rezultat:
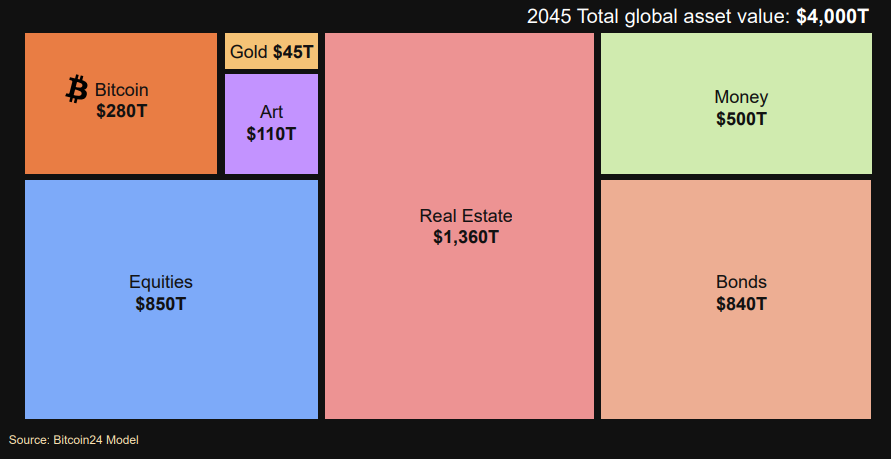
Iako put do 200T USD nije veliko rastezanje, u stvarnoj vrednosti čini se previše dobrim da bi bio istinit. Sa obzirom da je bez presedana da zaliha vrednosti neke robe postigne vrednost veću od zlata, to jednostavno predstavlja neistraženu teritoriju. Ali čak i ako se jednostavno pridržavamo targetiranja niže ciljne vrednosti zlata od 13T USD, Bitcoin još uvek tendenciju velikog porasta svoje cene u budućnosti.
Većina Bitcoin-ovih pozitivnih strana opstaje
Svako ko razmišlja da nešto svog teško zarađenog novca uskladišti u Bitcoin pita se „da li sam poranio ili zakasnio?“ Nepisano je pravilo da se svako oseća kao da je zakasnio kad stigne. Brojni su primeri ljudi koji žale kako su zakasnili 2011. ili 2013. ili 2016. godine, kada je cena Bitcoin-a bila 5, 100, odnosno 600 USD.
Kao i u bilo kojoj zajednici koja se razvija i raste i u kojoj ima manjka nekretninama, pridošlice zavide ljudima koji su već obezbedili sebi nekretninu, ne sluteći da će njima zavideti ljudi koji tek treba da dođu. Ovaj fenomen je primenjiv i na velikom broju drugih primera. Na primer, zakasneli u Kalifornijskoj zlatnoj groznici bili su razočarani kada su došli, a bogata zlatna polja su već bila iscrpljena, i umesto toga su se naseliti na nekoliko stotina hektara zemljišta, a koje sada vrede bogatstvo.
U srcu ovog osećanja je strah da više nema uspona, da više nema novca koji se može zaraditi uzimajući ono što je još uvek ostalo dostupno. Da li smo dostigli tu tačku sa Bitcoin-om?
Pa ne. Čini se da je zapravo suprotno. Na osnovu punog potencijalnog opsega procene koji smo utvrdili gore, čak i u ishodu niskog nivoa (13T USD), velika većina bogatstva koje će steći vlasnici Bitcoin-a, tek treba da se stekne (96%). Da bi parirao proceni zlata, Bitcoin i dalje mora da poraste 26 puta.
A ako se desi vrhunski ishod, punih 99,7% ukupnog stvaranja bogatstva Bitcoin-a ostaje pred nama. To bi značilo da Bitcoin još uvek treba da poraste 400 puta, zanemarujući pariranje zlatu.
Stavljanjem trenutne vrednosti Bitcoin-a u perspektivu, postaje jasno da je za Bitcoin još uvek vrlo rano.
Iako ova analiza sugeriše da za Bitcoin-u ostaje od 26x do 400x rasta, korisno je proveriti ovaj zaključak kroz drugo razumno objašnjenje, a tamo gde je poznat puni potencijal…
Broj ljudi koji su prihvatili Bitcoin
Procene broja vlasnika Bitcoin-a širom sveta se veoma razlikuju. To je dovelo do prilične količine dvosmislenosti i nesigurnosti u vezi sa stvarnim brojevima i određenog stepena odustajanja i mišljenja da je taj broj jednostavno preteško precizno proceniti. Iako je teško utvrditi konačan broj, glavni razlog za odstupanje u procenama je nedostatak standardizovanih definicija šta znači prihvatanje Bitcoin-a.
Istina je da postoje različiti nivoi prihvatanja Bitcoin-a. Podelom na segmente prihvatanja Bitcoin-a lakše je uvideti ne samo zašto postoji širok opseg procena, već i još važnije, koliko je još uvek rano za prihvatanje Bitcoin-a kao preferirane zalihe vrednosti.
U ove svrhe, hajde da podelimo u segmente prihvatanje Bitcoin-a na četiri različita „nivoa“:
1. Kežual amateri (prstom u vodi)
2. Alokatori 1% (stopalima u vodi)
3. Značajni vernici (do pojasa u vodi)
4. Bitcoin maximalisti (u vodi preko glave)
Pre nego što počnemo, potreban nam je imenilac. Mogli bismo da koristimo globalno stanovništvo, ali po mom mišljenju ovo daje loše rezultate. Ono što mi zaista procenjujemo je koji procenat sveta koji poseduje odredjeno bogatstvo za skladištenje u Bitcoin-u, je to i učinio. Prema podacima sa sajta Statista, 2,2 biliona ljudi na svetu poseduje najmanje 10k USD u neto vrednosti, što se čini kao razumna granica za zalihu koju žele da uskladište. Činjenica je da će siromašne zajednice takođe koristiti Bitcoin kao zalihu vrednosti i verovatno će iz njega izvući veću korist kao rezultat marginalnog pristupa tradicionalnoj bankarskoj infrastrukturi kao klijenti banaka sa „niskom vrednošću“. Međutim, u naše svrhe, jednostavno gledamo koliko je ljudi usvojilo Bitcoin među grupama sa značajnim bogatstvom za skladištenje, tako da će 2.2 biliona služiti kao naša puna potencijalna veličina tržišta.
1. Kežual amateri
Ovaj segment ljudi koji su prihvatili Bitcoin uključuje sve one koji imaju bilo koju količinu Bitcoin-a – vašeg prijatelja sa 20 USD BTC-a negde u nekom novčaniku ili vašu tetku koja se ne seća svoje Coinbase lozinke iz 2017. Po mom mišljenju, najveća zabuna oko broja ljudi koji su prihvatili Bitcoin nastaje zbog poistovećivanja „kežual amatera“ sa ljudima koji su u potpunosti prihvatili Bitcoin. Realnost je takva da ljudi ovog segmenta uglavnom samo eksperimentišu, bilo da bi stekli osećaj za ono o čemu svi pričaju, ili samo uložu nekoliko dolara u Bitcoin u nadi da će možda dobiti džekpot, kao što je slučaj sa greb-greb nagradnim igrama.
Zbog toga, „kežual amateri“ su razlog dovodjenja u zabludu pravog broja ljudi koji su u potpunosti prihvatili Bitcoin. Njihovo ponašanje zapravo ne predstavlja prihvatanje u pravom smislu te reči i stoga se ne bi trebalo smatrati ljudima koji su u potpunosti prihvatili Bitcoin. Istina je da, kada kežual amateri shvate da je Bitcoin najbolja zaliha vrednosti neke imovine u istoriji, neće ostati na samo 20 USD u Bitcoin-ima. Umesto toga, oni će svoju štednju prebaciti u mnogo većim iznosima.
Što se tiče odredjivanja veličine ovog segmenta, Willy Woo je sastavio razumno iscrpnu i sveobuhvatnu procenu od oko 187 miliona ljudi koji su prihvatili Bitcoin, što znači da su oni u najmanju ruku „kežual amateri“.
Koristeći ovaj i naš puni potencijal od 2,2 biliona ljudi kao imenioca, 8,5% potencijalnih ljudi koji su prihvatili Bitcoin-e dostiglo je nivo „kežual amatera“. Ovo je prilično velik broj i potpuno obmanjuje stvarni obim potpunog prihvatanja, a što će pokazati sledeći segmenti.
2. Alokatori 1%
Za preostale potkategorije, tačni podaci su manje dostupni. Kao takvi, sve što možemo je da smislimo razumne procene putem triangulacije.
Po mom mišljenju, „alokatori 1%“ se mogu okarakterisati kao ljudi koji su prihvatili Bitcoin, i koji žele da imaju mali, ali ne i zanemarljivi deo u Bitcoin-u. Za naše svrhu, mislim da je pristojan prag za ovu grupu svako ko ima najmanje 0,1 Bitcoin, i može se smatrati da imaju malu, ali ne i zanemarljivu poziciju u Bitcoin-u.
Gledajući Bitcoin blockchain, postoji oko 3 miliona adresa koje imaju najmanje 0,1 BTC. Pored ovih brojeva na blockchain-u, moramo da uzmemo u obzir i znatan broj ljudi koji imaju ovaj iznos na berzi ili GBTC-u. Kombinovanjem, mislim da je razumno proceniti da je 10 miliona ljudi dostiglo nivo „alokatora 1%“ ili veći.
Na osnovu ovih brojeva, samo 1⁄17 „kežual amatera“ dostiglo je nivo prihvatanja „alokatora 1%“, što znači da je ovaj nivo prihvatanja Bitcoin-a do danas postigao samo 0,5% penetracije. Ovaj strmi pad je razlog zašto je došlo do zablude da veliki broj „kežual amatera“ bude označeno kao grupa koja je u potpunosti prihvatila Bitcoin.
3. Značajni vernici
U ovu kategoriju spada svako ko je dostigao nivo razumevanja Bitcoin-a da alokacija od 1% ili čak 5% više ne izgleda dovoljna.
Uopšteno govoreći, ova grupa se kreće u rasponu od 5 – 50%. Išao bih toliko daleko da bih rekao da je većina ljudi koji sebe smatraju vernicima u Bitcoin-e, uključujući većinu Bitcoin Twitter-a, negde u ovoj grupi.
Procena veličine ove grupe postaje mnogo nejasnija, ali možemo se osloniti na podatke iz blockchain-a da bismo došli do razumne procene.
Za početak, hajde da utvrdimo da je većina ljudi koji su dostigli ovaj nivo verovanja i razumevanja Bitcoin-a, izborila da poseduje najmanje 1 Bitcoin. Pored toga, ovaj nivo ljudi koji su prihvatili Bitcoin je verovatno osigurao svoj Bitcoin u chain-u novčanika kojim oni upravljaju. Gledajući podatke na chain-u, oko 820k adresa ima najmanje 1 Bitcoin. Kao grubu pretpostavku, uzmimo da 500k od toga poseduju ljudi koji su dostigli nivo prihvatanja „značajnog vernika“.
Ako potom generički zaokružimo akaunte za ljude koji nisu postigli status wholecoiner-a (eng. osoba koja poseduje barem 1 BTC), ili koji svoja sredstva drže na berzi, dolazimo do grube procene od 2 miliona „značajnih vernika“.
4. Bitcoin maximalisti
Za našu svrhu, recimo da ova grupa uključuje svakoga ko je dovoljno duboko ušao u Bitcoin da je zaključio da bi više od 50% njihove neto vrednosti trebalo da bude uskladišteno u Bitcoin-u.
Procena veličine ove grupe je gotovo nemoguća, zato ćemo morati da budemo kreativni.
-
Prodaja „Bitcoin Standard“
-
Hajde da konzervativno procenimo da je samo 20% maximalističara kupilo Bitcoin Standard, i da je 50% tih ljudi koji su ga razumeli, postali maksimalisti. Na osnovu knjige Amazon US rank (6,681), onlajn kalkulatori procenjuju da je prodato oko 15k primeraka.
- Hajde da budemo velikodušni i da zaokružimo taj broj od oko 15k na 50k, uzimajući u obzir međunarodnu prodaju i kupovinu izvan Amazona.
Ovo nas dovodi do procene broja od 125k maximalista. Da ne bismo pogrešili, bićemo oprezni, i udvostručimo taj broj i rećićemo da ih ima 250k.
- Kvalitativna triangulacija
Čisto subjektivno, ali čini mi se da na Twitter-u, primarnom domu za komunikaciju maximalista, postoji možda 10k aktivno angažovanih Bitcoin maximalista. Da budemo vrlo konzervativni, recimo da ovo predstavlja oko 5% maximalista (od ukupno 200k).
Uz to, kao procenu od vrha nadole, čini se opravdanim da je oko 10% ljudi koji su dostigli 5 – 50% alokacije Bitcoin-a napravilo skok ka maximalizmu.
Sve u svemu, cifra od oko 250k Bitcoin maximalista čini se konzervativnom, ako ne i velikodušnom pretpostavkom.
To nas dovodi do 0,01% penetracije.
Zaključak
Kako god gledali brojke, još uvek je rano za Bitcoin. Posmatrajući procenu vrednosti Bitcoin-a kao procenat njegovog punog potencijala, vidimo da je trenutna vrednost Bitcoin-a negde između 0,2% i 3% njegovog krajnjeg stanja, što znači da ostaje 30x do 500x rasta. Gledajući napredak prihvatanja Bitcoin-a, vidimo da je trenutna penetracija Bitcoin-a negde između 0,01% i 8,5%, u zavisnosti od toga koji prag prihvatanja gledate.
Ako verujete, kao što ja verujem, da je Bitcoin na putu da postane dominantna zaliha vrednosti i preferirani novac za ceo svet, na kraju će norma biti više od 50% posedovanja neto vrednosti u Bitcoin-u. Budući da naša analiza ovde sugeriše da samo 0,01% sveta zadovoljava ove standarde, opravdano je zaključiti da 99,99% sveta ostaje da sledi njihov primer.
Sve u svemu, dok svi koji se pojave na Bitcoin-u neizbežno osećaju žaljenje zbog toga što nisu ranije investirali i pitaju se da li su u potpunosti propustili brod, jasno je da većina rasta Bitcoin-a ostaje pred nama. Da stavimo ovo u neki kontekst, obzirom da može postojati samo 21 milion Bitcoin-a, prosečna osoba na zemlji (od 8 biliona ljudi) imaće samo 0,0025 Bitcoin-a. Još je toliko rano, da ukupna neto vrednost te prosečne osobe u Bitcoin-u može da se kupi za samo 90 USD.
I ako mislite da je kasno, zapravo je veoma rano, zato vam čestitam i uživajte u skupljanju sats-ova dok su još uvek ovako jeftini!
-
 @ 4ba8e86d:89d32de4
2025-05-19 10:13:19
@ 4ba8e86d:89d32de4
2025-05-19 10:13:19DTails é uma ferramenta que facilita a inclusão de aplicativos em imagens de sistemas live baseados em Debian, como o Tails. Com ela, você pode personalizar sua imagem adicionando os softwares que realmente precisa — tudo de forma simples, transparente e sob seu controle total.
⚠️ DTails não é uma distribuição. É uma ferramenta de remasterização de imagens live.
Ela permite incluir softwares como:
✅ SimpleX Chat ✅ Clientes Nostr Web (Snort & Iris) ✅ Sparrow Wallet ✅ Feather Wallet ✅ Cake Wallet ✅ RoboSats ✅ Bisq ✅ BIP39 (Ian Coleman) ✅ SeedTool ... e muito mais. https://image.nostr.build/b0bb1f0da5a9a8fee42eacbddb156fc3558f4c3804575d55eeefbe6870ac223e.jpg
Importante: os binários originais dos aplicativos não são modificados, garantindo total transparência e permitindo a verificação de hashes a qualquer momento.
👨💻 Desenvolvido por: nostr:npub1dtmp3wrkyqafghjgwyk88mxvulfncc9lg6ppv4laet5cun66jtwqqpgte6
GitHub: https://github.com/DesobedienteTecnologico/dtails?tab=readme-ov-file
🎯 Controle total do que será instalado
Com o DTails, você escolhe exatamente o que deseja incluir na imagem personalizada. Se não marcar um aplicativo, ele não será adicionado, mesmo que esteja disponível. Isso significa: privacidade, leveza e controle absoluto.
https://image.nostr.build/b0bb1f0da5a9a8fee42eacbddb156fc3558f4c3804575d55eeefbe6870ac223e.jpg https://image.nostr.build/b70ed11ad2ce0f14fd01d62c08998dc18e3f27733c8d7e968f3459846fb81baf.jpg https://image.nostr.build/4f5a904218c1ea6538be5b3f764eefda95edd8f88b2f42ac46b9ae420b35e6f6.jpg
⚙️ Começando com o DTails
📦 Requisitos de pacotes
Antes de tudo, instale os seguintes pacotes no Debian:
``` sudo apt-get install genisoimage parted squashfs-tools syslinux-utils build-essential python3-tk python3-pil.imagetk python3-pyudev
```
🛠 Passo a passo
1 Clone o repositório:
``` git clone https://github.com/DesobedienteTecnologico/dtails cd dtails
```
2 Inicie a interface gráfica com sudo:
``` sudo ./dtails.py
```
Por que usar sudo? É necessário para montar arquivos .iso ou .img e utilizar ferramentas essenciais do sistema.
💿 Selecione a imagem Tails que deseja modificar
https://nostr.download/e3143dcd72ab6dcc86228be04d53131ccf33d599a5f7f2f1a5c0d193557dac6b.jpg
📥 Adicione ou remova pacotes
1 Marque os aplicativos desejados. 2 Clique Buildld para gerar sua imagem personalizada. https://image.nostr.build/5c4db03fe33cd53d06845074d03888a3ca89c3e29b2dc1afed4d9d181489b771.png
Você pode acompanhar todo o processo diretamente no terminal. https://nostr.download/1d959f4be4de9fbb666ada870afee4a922fb5e96ef296c4408058ec33cd657a8.jpg
💽 .ISO vs .IMG — Qual escolher?
| Formato | Persistência | Observações | | ------- | ---------------------- | ----------------------------------------------- | | .iso | ❌ Não tem persistência | Gera o arquivo DTails.iso na pasta do projeto | | .img | ✅ Suporta persistência | Permite gravar diretamente em um pendrive |
https://nostr.download/587fa3956df47a38b169619f63c559928e6410c3dd0d99361770a8716b3691f6.jpg https://nostr.download/40c7c5badba765968a1004ebc67c63a28b9ae3b5801addb02166b071f970659f.jpg
vídeo
https://www.youtube.com/live/QABz-GOeQ68?si=eYX-AHsolbp_OmAm
-
 @ a5ee4475:2ca75401
2025-05-19 01:11:59
@ a5ee4475:2ca75401
2025-05-19 01:11:59clients #link #list #english #article #finalversion #descentralismo
*These clients are generally applications on the Nostr network that allow you to use the same account, regardless of the app used, keeping your messages and profile intact.
**However, you may need to meet certain requirements regarding access and account NIP for some clients, so that you can access them securely and use their features correctly.
CLIENTS
Twitter like
- Nostrmo - [source] 🌐💻(🐧🪟🍎)🍎🤖(on zapstore)
- Coracle - Super App [source] 🌐🤖(on zapstore)
- Amethyst - Super App with note edit, delete and other stuff with Tor [source] 🤖(on zapstore)
- Primal - Social and wallet [source] 🌐🍎🤖(on zapstore)
- Iris - [source] 🌐🤖🍎
- Current - [source] 🤖🍎
- FreeFrom 🤖🍎
- Openvibe - Nostr and others (new Plebstr) [source] 🤖🍎
- Snort 🌐(🤖[early access]) [onion] [source]
- Damus 🍎 [source]
- Nos 🍎 [source]
- Nostur 🍎 [source]
- NostrBand 🌐 [info] [source]
- Yana [source] 🌐💻(🐧) 🍎🤖(on zapstore)
- Nostribe [on development] 🌐 [source]
- Lume 💻(🐧🪟🍎) [info] [source]
- Gossip - [source] 💻(🐧🪟🍎)
- noStrudel - Gamified Experience [onion] [info/source] 🌐
- [Nostrudel Next] - [onion]
- moStard - Nostrudel with Monero [onion] [info/source] 🌐
- Camelus - [source] 🤖 [early access]
Community
- CCNS - Community Curated Nostr Stuff [source]
- Nostr Kiwi [creator] 🌐
- Satellite [info] 🌐
- Flotilla - [source] 🌐🐧🤖(on zapstore)
- Chachi - [source] 🌐
- Futr - Coded in haskell [source] 🐧 (others soon)
- Soapbox - Comunnity server [info] [source] 🌐
- Ditto - Soapbox community server 🌐 [source] 🌐
- Cobrafuma - Nostr brazilian community on Ditto [info] 🌐
- Zapddit - Reddit like [source] 🌐
- Voyage (Reddit like) [on development] 🤖
Wiki
- Wikifreedia - Wiki Dark mode [source] 🌐
- Wikinostr - Wiki with tabs clear mode [source] 🌐
- Wikistr - Wiki clear mode [info] [source] 🌐
Search
- Keychat - Signal-like chat with AI and browser [source] 💻(🐧🪟🍎) - 📱(🍎🤖{on zapstore})
- Spring - Browser for Nostr apps and other sites [source] 🤖 (on zapstore)
- Advanced nostr search - Advanced note search by isolated terms related to a npub profile [source] 🌐
- Nos Today - Global note search by isolated terms [info] [source] 🌐
- Nostr Search Engine - API for Nostr clients [source]
- Ntrends - Trending notes and profiles 🌐
Website
- Nsite - Nostr Site [onion] [info] [source]
- Nsite Gateway - Nostr Site Gateway [source]
- Npub pro - Your site on Nostr [source]
App Store
ZapStore - Permitionless App Store [source] 🤖 💻(🐧🍎)
Video and Live Streaming
- Flare - Youtube like 🌐 [source]
- ZapStream - Lives, videos, shorts and zaps (NIP-53) [source] 🌐 🤖(lives only | Amber | on zapstore)
- Swae - Live streaming [source] (on development) ⏳
Post Aggregator - Kinostr - Nostr Cinema with #kinostr [english] [author] 🌐 - Stremstr - Nostr Cinema with #kinostr [english] [source] 📱 (on development) ⏳
Link Agreggator - Kinostr - #kinostr - Nostr Cinema Profile with links [English] - Equinox - Nostr Cinema Community with links [Portuguese]
Audio and Podcast Transmission
- Castr - Your npub as podcast feed [source]
- Nostr Nests - Audio Chats [source] 🌐
- Fountain - Podcast [source] 🤖🍎
- Corny Chat - Audio Chat [source] 🌐
Music
- Tidal - Music Streaming [source] [about] [info] 🤖🍎🌐
- Wavlake - Music Streaming [source] 🌐(🤖🍎 [early access])
- Tunestr - Musical Events [source] [about] 🌐
- Stemstr - Musical Colab (paid to post) [source] [about] 🌐
Images
- Lumina - Trending images and pictures [source] 🌐
- Pinstr - Pinterest like [source] 🌐
- Slidestr - DeviantArt like [source] 🌐
- Memestr - ifunny like [source] 🌐
Download and Upload
Documents, graphics and tables
- Mindstr - Mind maps [source] 🌐
- Docstr - Share Docs [info] [source] 🌐
- Formstr - Share Forms [info] 🌐
- Sheetstr - Share Spreadsheets [source] 🌐
- Slide Maker - Share slides 🌐 [Advice: Slide Maker https://zaplinks.lol/ site is down]
Health
- Sobrkey - Sobriety and mental health [source] 🌐
- Runstr - Running app [source] 🌐
- NosFabrica - Finding ways for your health data 🌐
- LazerEyes - Eye prescription by DM [source] 🌐
Forum
- OddBean - Hacker News like [info] [source] 🌐
- LowEnt - Forum [info] 🌐
- Swarmstr - Q&A / FAQ [info] 🌐
- Staker News - Hacker News like 🌐 [info]
Direct Messenges (DM)
- 0xchat 🤖🍎 [source]
- Nostr Chat 🌐🍎 [source]
- Blowater 🌐 [source]
- Anigma (new nostrgram) - Telegram based [on development] [source]
Reading
- Oracolo - A minimalist Nostr html blog [source]
- nRSS - Nostr RSS reader 🌐
- Highlighter - Insights with a highlighted read [info] 🌐
- Zephyr - Calming to Read [info] 🌐
- Flycat - Clean and Healthy Feed [info] 🌐
- Nosta - Check Profiles [on development] [info] 🌐
- Alexandria - e-Reader and Nostr Knowledge Base (NKB) [source] 🌐
Writing
- Habla - Blog [info] 🌐
- Blogstack - Blog [info]🌐
- YakiHonne - Articles and News [info] 🌐🍎🤖(on zapstore)
Lists
- Following - Users list [source] 🌐
- Nostr Unfollower - Nostr Unfollower
- Listr - Lists [source] 🌐
- Nostr potatoes - Movies List [source] 💻(numpy)
Market and Jobs
- Shopstr - Buy and Sell [onion] [source] 🌐
- Nostr Market - Buy and Sell 🌐
- Plebeian Market - Buy and Sell [source] 🌐
- Ostrich Work - Jobs [source] 🌐
- Nostrocket - Jobs [source] 🌐
Data Vending Machines - DVM (NIP90)
(Data-processing tools)
Games
- Chesstr - Chess 🌐 [source]
- Jestr - Chess [source] 🌐
- Snakestr - Snake game [source] 🌐
- Snakes on a Relay - Multiplayer Snake game like slither.io [source] 🌐
ENGINES - DEG Mods - Decentralized Game Mods [info] [source] 🌐 - NG Engine - Nostr Game Engine [source] 🌐 - JmonkeyEngine - Java game engine [source] 🌐
Customization
Like other Services
- Olas - Instagram like [source] 🌐🍎🤖(on zapstore)
- Nostree - Linktree like 🌐
- Rabbit - TweetDeck like [info] 🌐
- Zaplinks - Nostr links 🌐
- Omeglestr - Omegle-like Random Chats [source] 🌐
General Uses
- Njump - HTML text gateway source 🌐
- Filestr - HTML midia gateway [source] 🌐
- W3 - Nostr URL shortener [source] 🌐
- Playground - Test Nostr filters [source] 🌐
Places
- Wherostr - Travel and show where you are
- Arc Map (Mapstr) - Bitcoin Map [info]
Driver and Delivery
- RoadRunner - Uber like [on development] ⏱️
- Nostrlivery - iFood like [on development] ⏱️
⚠️ SCAM ⚠️ | Arcade City - Uber like [source]
OTHER STUFF
Lightning Wallets (zap)
- Alby - Native and extension [info] 🌐
- ZBD - Gaming and Social [info] [source] 🤖🍎
- Wallet of Satoshi - Simplest Lightning Wallet [info] 🤖🍎
- Minibits - Cashu mobile wallet [info] 🤖
- Blink - Opensource custodial wallet (KYC over 1000 usd) [source] 🤖🍎
- LNbits - App and extesion [source] 🤖🍎💻
- Zeus - [info] [source] 🤖🍎
Without Zap - Wassabi Wallet - Privacy-focused and non-custodial with Nostr Update Manager [source]
Exchange
Media Server (Upload Links)
audio, image and video
Connected with Nostr (NIP):
- Nostr Build - Free and paid Upload [info] [source] 🌐
- NostrMedia - Written in Go with Nip 96 / Blossom (free and paid) [info] [source]
- Nostr Check - [info] [source] 🌐
- NostPic - [info] [source] 🌐
- Sovbit - Free and paid upload [info] [source] 🌐
- Voidcat - Nip-96 and Blossom [source] 🌐
- Primal Media - Primal Media Uploader [source] 🌐
Blossom - Your Media Safer
- Primal Blossom 🌐
- NostrBuild Blossom - Free upload (max 100MiB) and paid [info] [source] 🌐
Paid Upload Only
- Satellite CDN - prepaid upload (max 5GB each) [info] [source] 🌐
Without Nostr NIP:
- Pomf - Upload larger videos (max 1GB) [source]
- Catbox - max 200 MB [source]
- x0 - max 512 MiB [source]
Donation and payments
- Zapper - Easy Zaps [source] 🌐
- Autozap [source] 🌐
- Zapmeacoffee 🌐
- Nostr Zap 💻(numpy)
- Creatr - Creators subscription 🌐
- Geyzer - Crowdfunding [info] [source] 🌐
- Heya! - Crowdfunding [source]
Security
- Secret Border - Generate offline keys 💻(java)
- Umbrel - Your private relay [source] 🌐
Key signing/login and Extension
- Amber - Key signing [source] 🤖(on zapstore)
- Nowser - Account access keys 📱(🤖🍎) 💻(🐧🍎🪟)
- Nos2x - Account access keys 🌐
- Nsec.app 🌐 [info]
- Lume - [info] [source] 🐧🪟🍎
- Satcom - Share files to discuss - [info] 🌐
- KeysBand - Multi-key signing [source] 🌐
Code
- Stacks - AI Templates [info] [source] 🌐
- Nostrify - Share Nostr Frameworks 🌐
- Git Workshop (github like) [experimental] 🌐
- Gitstr (github like) [on development] ⏱️
- Osty [on development] [info] 🌐
- Python Nostr - Python Library for Nostr
- Sybil - Creating, managing and test Nostr events [on development] ⏱️
Relay Check and Cloud
- Nostr Watch - See your relay speed 🌐
- NosDrive - Nostr Relay that saves to Google Drive
Bidges and Getways
- Matrixtr Bridge - Between Matrix & Nostr
- Mostr - Between Nostr & Fediverse
- Nostrss - RSS to Nostr
- Rsslay - Optimized RSS to Nostr [source]
- Atomstr - RSS/Atom to Nostr [source]
Useful Profiles and Trends
nostr-voice - Voice note (just some clients)
NOT RELATED TO NOSTR
Voca - Text-to-Speech App for GrapheneOS [source] 🤖(on zapstore)
Android Keyboards
Personal notes and texts
Front-ends
- Nitter - Twitter / X without your data [source]
- NewPipe - Youtube, Peertube and others, without account & your data [source] 🤖
- Piped - Youtube web without you data [source] 🌐
Other Services
- Brave - Browser [source]
- DuckDuckGo - Search [source]
- LLMA - Meta - Meta open source AI [source]
- DuckDuckGo AI Chat - Famous AIs without Login [source]
- Proton Mail - Mail [source]
Other open source index: Degoogled Apps
Some other Nostr index on:
-
 @ cae03c48:2a7d6671
2025-05-27 21:00:56
@ cae03c48:2a7d6671
2025-05-27 21:00:56Bitcoin Magazine

One out of Four People Own Bitcoin and Crypto in 2025: ReportToday, Gemini, a crypto platform, released its 2025 Global State of Crypto Report, revealing a notable increase in cryptocurrency adoption in different countries. According to a press release sent to Bitcoin Magazine, ownership among respondents in the US, UK, France, and Singapore rose from one in five (21%) in 2024 to one in four (24%) in 2025.
The Trump Administration’s treatment of Bitcoin may have played a major role in its global growth. Since taking office in January 2025, President Trump has launched a Strategic Bitcoin Reserve, where he installed leadership at the SEC that are in favor of digital assets, and endorsed legislation aimed at regulating stablecoins and establishing a clear framework for digital assets.
“The United States has proven itself as a global leader in web3 and blockchain technology with the addition of Trump’s pro-crypto policies, which is a significant change from the previous Administration” said the CEO of Gemini Marshall Beard. “With this pro-innovation approach, the crypto industry is positioned for significant growth in the United States and around the world.”
In the US nearly 23% of non-owners said that President Trump’s launch of the Strategic Bitcoin Reserve made them more confident in the value of Bitcoin and other cryptos. Similar feelings were shared by about one in five non-owners in the United Kingdom (21%) and Singapore (19%).
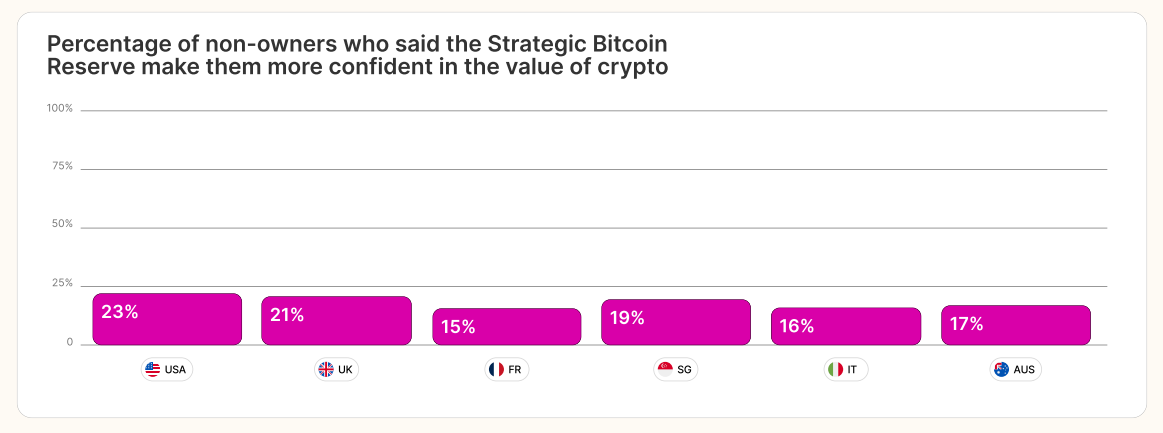
Europe is leading the way in crypto ownership growth. In 2025, 24% of people in the UK said they own cryptocurrency, up from 18% last year; the biggest jump of any country surveyed. France also saw an increase, with 21% owning crypto, compared to 18% in 2024. In the US, adoption rose from 20% to 22%, and Singapore went from 26% to 28%.
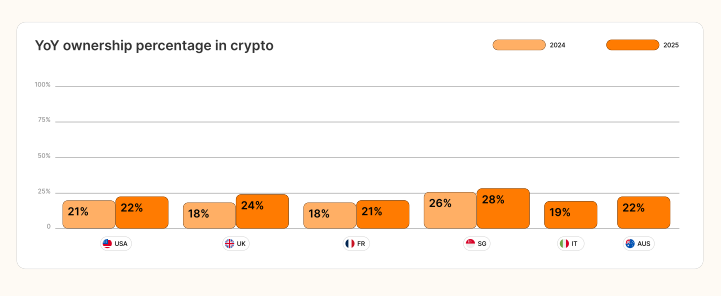
France’s strong pro-crypto stance has encouraged more people there to invest in digital assets, which is the highest rate among all surveyed nations with 67%. Following France are Singapore, Italy, the UK, the US, and Australia.
In the US, nearly two in five crypto owners (39%) have invested in crypto ETFs, showing a steady rise since their approval in early 2024. Additionally, half of Millennials and Gen Z globally have invested in crypto at some point, with 52% of Millennials and 48% of Gen Z reporting current or past ownership.
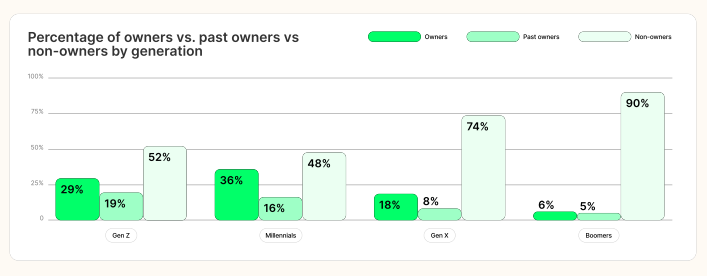
This post One out of Four People Own Bitcoin and Crypto in 2025: Report first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ cae03c48:2a7d6671
2025-05-27 21:00:52
@ cae03c48:2a7d6671
2025-05-27 21:00:52Bitcoin Magazine
1.5 Million Users to Access Bitcoin’s Lightning Network on Xverse thanks to SatiSati, a Bitcoin payments app and Lightning infrastructure provider, today announced the launch of its Lightning integration with Xverse, a Bitcoin wallet used by over 1.5 million people worldwide. Thanks to the integration, Xverse users can now send and receive sats (Bitcoin’s smallest denomination) instantly over the Lightning Network with no setup, no app switching, and no custodial risk.
Initially designed in 2017, the Lightning Network has grown to become Bitcoin’s leading layer-2, with a current BTC capacity of over $465M. Sati is now leveraging this technology to bring the world’s favorite digital currency into the pockets of almost 3 billion users worldwide, thanks to its powerful API integration with WhatsApp.
“Bitcoin was not meant to be an asset for Wall Street—it was built for peer-to-peer money, borderless and accessible,” said Felipe Servin, Founder and CEO of Sati. “Integrating Lightning natively into Xverse brings that vision back to life, making Bitcoin usable at scale for billions.”
Thanks to the integration, every Xverse user now gets a Lightning Address instantly. That means they can receive tips, pay invoices, and use Bitcoin for microtransactions—all without having to manage channels or switch between different apps. Sati expects USDT on Lightning to be supported as early as Q3 for the Xverse wallet and in July 2025
for users accessing Sati through WhatsApp.This integration positions Sati’s role as a Lightning infrastructure provider, not just a consumer app. By leveraging its API-based solution, the company provides plug-and-play backend services to wallets and platforms looking to add Bitcoin payments without compromising on security or UX.
The Xverse launch follows the debut of Parasite Pool, a new mining pool leveraging Sati and Xverse’s tech stack and focused on democratizing Bitcoin mining. Parasite Pool charges 0% fees and pays out instantly over Lightning, making it ideal for small-scale miners, especially those running ultra-low-power hardware like Bitaxe.
With over 500 users joining Parasite Pool within weeks of launch and an average pool hashrate of 5 PH/s, Parasite Pool is steadily growing its presence in the home mining space. Thanks to the Lightning integration, Parasite Pool supports the smallest Lightning payouts in the industry (a fraction of a cent), lowering the barrier to entry for anyone interested in mining.
Sati recently closed a $600K pre-seed round backed by Bitcoin-focused investors, including Draper Associates, BitcoinFi, Arcanum, BoostVC, and Ricardo Salinas. The funding is being used to support global expansion, stablecoin integration, Lightning infrastructure growth, and broader access to Bitcoin in emerging markets.
Sati will be conducting live product demos at Bitcoin 2025 in Las Vegas on May 27-29. To learn more about Sati, visit sati.pro
About Sati
Sati is a Bitcoin payments infrastructure provider. Launched in 2025 with investors of the likes as Draper Associates and Ricardo Salinas, Sati powers fast, seamless Bitcoin payments on applications such as WhatsApp to fuel the next wave of adoption. Learn more at sati.proAbout Xverse
Xverse is the on-chain platform for the Bitcoin economy—think Revolut meets Alchemy, built natively on Bitcoin. Trusted by over 1.5 million users, Xverse is launching a unified portfolio platform for Bitcoin L1 and Layer 2s, alongside developer infrastructure to power seamless Bitcoin-native apps.Press Contact
press@sati.proDisclaimer: This is a sponsored press release. Readers are encouraged to perform their own due diligence before acting on any information presented in this article.
This post 1.5 Million Users to Access Bitcoin’s Lightning Network on Xverse thanks to Sati first appeared on Bitcoin Magazine and is written by Sati.
-
 @ a5ee4475:2ca75401
2025-05-18 16:07:07
@ a5ee4475:2ca75401
2025-05-18 16:07:07ai #artificial #intelligence #english #tech
Open Source
Models
Text
Image
- SDAI FOSS - Stable Diffusion AI to Android [download] [source] 🤖
- Stable Diffusion - Text to image [source] 🌐
- Pixart Alpha - Photorealistic Text to Image Generation [source]
- Pixart Delta - Framework to Pixart Alpha [paper] [source]
- Pixart Sigma - 4K Text to Image Generation [source]
- OmniGen - Pompt, image or subject to image [source]
- Pigallery - Self-Hosted AI Image Generator [source]
Video
Tools
Lightning Based
- Animal Sunset - AI video generation with Nostr npub by lightning payments [source]
- Ai Rand - AI text generation with Pubky DNS by lightning payments [source]
- PlebAI - Text and Image generation without signup [source] 🌐🤖🍎 [sites down - only github available]
Others
- HuggingFace - Test and collaborate on models, datasets and apps. [source]
- DuckDuckGo AI Chat - Famous AIs without Login [source]
- Ollama - Run LLMs Locally [source]
- DreamStudio - Stable Diffusion’s Web App Tool [info] [source]
- Prompt Gallery - AI images with their prompts [source]
Closed Source
Models
Text
- ChatGPT
- Claude
- Gemini
- Copilot
- Maritalk - Text AI in Portuguese focused on Brazil with model Sabia-3 and the open source models Sabia-7b and Sabia-2 [source]
- Amazônia IA - Text AI in Portuguese focused on Brazil with the guara, hapia and golia models [source]
Image
Video
- Minimax - Realistic videos (prompts only in chinese)
Tools
Other index: Amazing AI
-
 @ cae03c48:2a7d6671
2025-05-27 21:00:51
@ cae03c48:2a7d6671
2025-05-27 21:00:51Bitcoin Magazine

Bitlux Announced Private Jet Cards Accepting Bitcoin and Crypto PaymentsBitlux, a global private aviation company with charter solutions based on blockchain technology, just announced the industry’s first cryptocurrency-enabled Private Jet Card Program at the 2025 Bitcoin Conference.
“Bitcoin 2025 convenes innovators who are defining the future of money, mobility, and freedom,” stated Patel. “Our Jet Card is a natural continuation of that dialogue. We’re not just keeping up – we’re setting the new benchmark for what’s possible in luxury flight.”
The Bitlux Jet Card allows clients to fund their accounts using Bitcoin, and other cryptocurrencies. By integrating Bitcoin payments with private aviation, Bitlux aims to deliver transparency, and control for high-frequency private flyers
“The private aviation industry has needed a reboot for a long time,” said Bitlux CEO Kyle Patel. “We didn’t simply put a new face on the old model – we reconstructed it with transparency, efficiency, and user control as the guiding principles. This card is for individuals who demand more from their travel experience and their payment infrastructure.”
The card includes fixed hourly rates and does not apply blackout dates, peak surcharges, or additional fees. Payments are held in escrow until the completion of the flight. The program allows access to a global fleet, includes Wi-Fi on domestic flights, and permits cancellation of one-way bookings after reservation.
Bitlux offers four jet cards: Ascent, Cardinal, Sovereignty, and Nomad, corresponding to cabin classes that include midsize, super-midsize, large, and ultra-long haul. Operational terms specify a 48 hour callout on off-peak days, 36 peak days, and minimum daily flight times that vary depending on the aircraft size.
“Our clients are global citizens – entrepreneurs, investors, tech entrepreneurs – who conduct business in real-time environments,” said Patel. “They don’t have time for ambiguous language or antiquated payment structures. We’re coming to them where they are, with a smarter, safer way to fly.”
This post Bitlux Announced Private Jet Cards Accepting Bitcoin and Crypto Payments first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ cae03c48:2a7d6671
2025-05-27 21:00:50
@ cae03c48:2a7d6671
2025-05-27 21:00:50Bitcoin Magazine

Asigna Raises $3M Funding and Launches Bitcoin Multisig v2 UpgradeAsigna, a smart multisig vault operator for Bitcoin, has raised $3 million in a funding round led by Hivemind and Tykhe Block Ventures, with participation from Sats Ventures, Trust Machines, and others, according to an exclusive press release sent to Bitcoin Magazine. The raise follows a pre-seed round led by Portal Ventures.
“With Asigna, we are establishing foundational infrastructure for institutions and large holders to securely and confidently participate in the evolving Bitcoin ecosystem,” said the Co-Founder of Asigna Viven. “There’s a critical need for robust, transparent, and programmable non-custodial solutions, and the multisig infrastructure is at the heart of this transformation.”
Alongside the funding, Asigna is launching its v2 upgrade, which includes support for Embedded Apps and a developer SDK. The update enables developers to integrate multisig functionality directly into Bitcoin applications.
“Asigna’s innovative approach to Bitcoin security and its seamless integration with Layer-2 protocols make it a game-changer for institutional investors,” said the Senior Investment Principal at Hivemind Capital Kayla Phillips. “We are thrilled to support their mission to provide robust and transparent non-custodial solutions for the evolving Bitcoin ecosystem.”
The update also adds a custom dashboard, BTC swaps, and new tools like the Connection SDK and Multisig SDK, allowing for vault creation, transaction management, and app integration. Other features include sub accounts, email notifications, governance, customizable signer permissions, privacy mode, and advanced UTXO management.
“What’s unique about Asigna is that, unlike many other onchain smart wallet implementations, it is fully native to the Bitcoin layer, with no smart contract risks,” said the Co-Founder of Asigna Vlad. “We don’t directly interact with private keys and account owners can use any wallet to sign their transactions. Which means these multisig wallets can never be frozen or lost, regardless of what happens to Asigna. As it should be”.
Bitcoin has recently risen to a $2.2 trillion market cap and with a growing DeFi sector with over $6 billion in Total Value Locked (TVL), the company plans to use the new funding to provide their clients with access to DeFi and yield generation through staking and lending with a white-glove service.
This post Asigna Raises $3M Funding and Launches Bitcoin Multisig v2 Upgrade first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 6be5cc06:5259daf0
2025-05-27 20:37:22
@ 6be5cc06:5259daf0
2025-05-27 20:37:22At
até uma ferramenta de agendamento de tarefas em Linux usada para executar comandos únicos em um horário e data específicos. Diferente docron, que serve para tarefas recorrentes, oatexecuta uma única vez.Como usar o
at1. Verifique se o
atestá instaladobash which atSe não estiver instalado:
bash sudo apt install atE inicie o serviço (caso necessário):
bash sudo systemctl enable --now atd2. Agendar um comando
bash at 10:00 AM tomorrowVocê será levado a um prompt interativo. Digite o comando desejado e finalize com
Ctrl + D.Exemplo 1:
bash at 09:00 AM next Monday(Entrada do usuário no prompt do
at)echo "Relatório pronto" >> ~/relatorio.txt Ctrl + DResultado: O trecho "relatório pronto" será incluído no documento relatorio.txt.
Exemplo 2:
bash at 21:00 Apr 15Entrada no prompt:
notify-send "Hora de fazer backup!" Ctrl + DResultado: Às 21h do dia 15 de abril, o sistema exibirá uma notificação.
Formatos de Data e Hora Válidos
-
now + 1 minute -
midnight -
tomorrow -
5pm -
08:30 -
7:00am next friday -
noon + 2 days
Visualizar tarefas agendadas
bash atqRemover uma tarefa agendada
bash atrm <número_da_tarefa>Você encontra o número da tarefa com
atq.
cron
O
croné um utilitário de agendamento de tarefas baseado no tempo. Permite executar comandos ou scripts automaticamente em horários específicos. Ele depende do daemoncrond, que deve estar ativo e em execução contínua no sistema.Arquivo de configuração:
-
Cada usuário pode editar seu próprio agendador com:
bash crontab -e -
O formato padrão de uma linha no crontab:
m h dom mon dow comando
|Campo|Descrição|Valores possíveis| |---|---|---| |m|Minuto|0–59| |h|Hora|0–23| |dom|Dia do mês|1–31| |mon|Mês|1–12| |dow|Dia da semana|0–6 (0 = Domingo)| |comando|Comando a executar|Qualquer comando shell válido|
Exemplos:
-
Executar um script a cada minuto:
bash * * * * * /usr/local/bin/execute/this/script.sh -
Fazer backup no dia 10 de junho às 08:30:
bash 30 08 10 06 * /home/sysadmin/full-backup -
Backup todo domingo às 5h da manhã:
bash 0 5 * * 0 tar -zcf /var/backups/home.tgz /home/
Limitações:
Tarefas agendadas com
cronnão são executadas se o computador estiver desligado ou suspenso no horário programado. O comando é simplesmente ignorado. Usecronpara tarefas com data/hora exatas.
anacron
O
anacroné uma alternativa aocronvoltada para sistemas que não ficam ligados o tempo todo, como notebooks e desktops. Ele garante a execução de tarefas periódicas (diárias, semanais, mensais) assim que possível após o sistema ser ligado, caso tenham sido perdidas. Useanacronpara tarefas periódicas tolerantes a atrasos.Verificação da instalação:
bash anacron -VInstalação (caso necessário):
bash sudo apt update sudo apt install anacronArquivo de configuração:
/etc/anacrontabAcessado com:
sudo nano /etc/anacrontabFormato de cada linha:
PERIOD DELAY IDENT COMMAND| Campo | Descrição | | ------- | ------------------------------------------- | | PERIOD | Intervalo em dias (1 = diário, 7 = semanal) | | DELAY | Minutos a esperar após o boot | | IDENT | Nome identificador da tarefa | | COMMAND | Comando ou script a ser executado |
Exemplo:
bash 1 3 limpeza-temporarios /home/usuario/scripts/limpar_tmp.shExecuta o script uma vez por dia, 3 minutos após o sistema ser ligado.
Nota: Não é necessário usar
run-partsnemcron.dailypara tarefas personalizadas. Basta apontar diretamente para o script desejado. Orun-partssó deve ser usado quando se deseja executar todos os scripts de um diretório.Ativação do serviço:
bash sudo systemctl enable --now anacronVerificação de status:
bash systemctl status anacronLogs de execução:
bash grep anacron /var/log/syslog/etc/anacrontab: Arquivo de Configuração doanacronO arquivo
/etc/anacrontabdefine tarefas periódicas a serem executadas peloanacron, garantindo que comandos sejam executados mesmo que o computador esteja desligado no horário originalmente programado.Cabeçalho Padrão
bash SHELL=/bin/sh HOME=/root LOGNAME=root-
SHELL: Shell padrão utilizado para executar os comandos. -
HOME: Diretório home usado durante a execução. -
LOGNAME: Usuário associado à execução das tarefas.
Entradas Padrão do Sistema
bash 1 5 cron.daily run-parts --report /etc/cron.daily 7 10 cron.weekly run-parts --report /etc/cron.weekly @monthly 15 cron.monthly run-parts --report /etc/cron.monthly|Campo|Significado| |---|---| |
1|Executa a tarefa diariamente (a cada 1 dia)| |5|Espera 5 minutos após o boot| |cron.daily|Identificador da tarefa (usado nos logs)| |run-parts|Executa todos os scripts dentro do diretório|Diretórios utilizados:
-
/etc/cron.daily: scripts executados uma vez por dia -
/etc/cron.weekly: scripts semanais -
/etc/cron.monthly: scripts mensais
O comando
run-partsexecuta automaticamente todos os scripts executáveis localizados nesses diretórios.Personalização
Para adicionar tarefas personalizadas ao
anacron, basta adicionar novas linhas com o formato:PERIOD DELAY IDENT COMMANDExemplo:
bash 1 3 limpeza-temporarios /home/usuario/scripts/limpar_tmp.shExecuta o script
limpar_tmp.shdiariamente, com 3 minutos de atraso após o boot.Importante: Não é necessário — nem recomendado — usar
run-partsquando a intenção é executar um script individual. Orun-partsespera um diretório e ignora arquivos individuais. Usarrun-partscom um script individual causará falha na execução. -
-
 @ bf47c19e:c3d2573b
2025-05-27 20:23:48
@ bf47c19e:c3d2573b
2025-05-27 20:23:48Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Šta je Bitcoin?
- Šta Bitcoin može da učini za vas?
- Zašto ljudi kupuju Bitcoin?
- Da li je vaš novac siguran u dolarima, kućama, akcijama ili zlatu?
- Šta je bolje za štednju od dolara, kuća i akcija?
- Po čemu se Bitcoin razlikuje od ostalih valuta?
- kako Bitcoin spašava svet?
- Kako mogu da saznam više o Bitcoin-u?
Bitcoin čini da štednja novca bude kul – i praktična – ponovo. Ovaj članak objašnjava kako i zašto.
Šta je Bitcoin?
Bitcoin se naziva digitalno zlato, mašina za istinu, blockchain, peer to peer mreža čvorova, energetski ponor i još mnogo toga. Bitcoin je, u stvari, sve ovo. Međutim, ova objašnjenja su često toliko tehnička i suvoparna, da bi većina ljudi radije gledala kako trava raste. Što je najvažnije, ova objašnjenja ne pokazuju kako Bitcoin ima bilo kakve koristi za vas.
iPod nije postao kulturološka senzacija jer ga je Apple nazvao „prenosnim digitalnim medijskim uređajem“. Postao je senzacija jer su ga zvali “1,000 pesama u vašem džepu.”
Ne zanima vas šta je Bitcoin. Vas zanima šta on može da učini za vas.
Baš kao i Internet, vaš auto, vaš telefon, kao i mnogi drugi uređaji i sistemi koje svakodnevno koristite, vi ne treba da znate šta je Bitcoin ili kako to funkcioniše da biste razumeli šta on može da učini za vas.
Šta Bitcoin može da učini za vas?
Bitcoin može da sačuva vaš teško zarađeni novac.
Bitcoin je stekao veliku pažnju u 2017. i 2018. godini zbog svoje spekulativne upotrebe. Mnogi ljudi su ga kupili nadajući se da će se obogatiti. Cena je naglo porasla, a zatim se srušila. Ovo nije bio prvi put da je Bitcoin uradio to. Međutim, niko nikada nije izgubio novac držeći bitcoin duže od 3,5 godine – ćak i ako je kupio na apsolutnim vrhovima.
Zašto Bitcoin konstantno raste? Ljudi počinju da shvataju koliko je Bitcoin moćan, kao način uštede novca u svetu u kojem je ’novac’ poput dolara, eura i drugih nacionalnih valuta dizajniran da gubi vrednost.
Ovo čini Bitcoin odličnom opcijom za štednju novca na nekoliko godina ili više. Bitcoin je bolji od štednje novca u dolarima, akcijama, nekretninama, pa čak i u zlatu.
Zato pokušajte da zaboravite na trenutak na razumevanje blockchaina, digitalne valute, kriptografije, seed fraza, novčanika, rudarstva i svih ostalih nerazumljivih termina. Za sada, razgovarajmo o tome zašto ljudi kupuju Bitcoin: razlog je prostiji nego što vi mislite.
Zašto ljudi kupuju Bitcoin?
Naravno, svako ima svoj razlog za kupovinu Bitcoin-a. Jedan od razloga, koji verovatno često čujete, je taj što mu vrednost raste. Ljudi žele da se obogate. Uskoče kao spekulanti, krenu u vožnju i najverovatnije ih prodaju ubrzo nakon kupovine.
Međutim, čak i kada cena krene naglo prema gore i strmoglavo padne nazad, mnogi ljudi ostanu i nakon tog pada. Otkud mi to znamo? Broj aktivnih novčanika dnevno, koji je otprilike sličan broju korisnika Bitcoin-a, nastavlja da raste. Takođe, nakon svakog balona u istoriji Bitcoin-a, cena se nikada ne vraća na svoju cenu pre balona. Uvek ostane malo višlja. Bitcoin se penje, a svaka masovna spekulativna serija dovodi sve više i više ljudi.
Broj aktivnih Bitcoin novčanika neprekidno raste
„Aktivna adresa“ znači da je neko tog dana poslao Bitcoin transakciju. Donji grafikon je na logaritamskoj skali.
 Izvor: Glassnode
Izvor: GlassnodeCena Bitcoina se neprestano penje
Kroz istoriju Bitcoin-a možemo videti divlje kolebanje cena, ali nakon svakog balona, cena se ostaje višlja nego pre. Ovo je cena Bitcoin-a na logaritamskoj skali.
 Izvor: Glassnode
Izvor: GlassnodeTo pokazuje da se ljudi zadržavaju: potražnja za Bitcoin-om se povećava. Da je svaki masovni rast cena bio samo balon koji su iscenirali prevaranti koji žele brzo da se obogate, cena bi se vratila na nivo pre balona. To se dogodilo sa lalama, ali ne i sa Bitcoin-om.
I zašto se onda cena Bitcoin-a stalno povećava? Sve veći broj ljudi čuva Bitcoin dugoročno – oni razumeju šta Bitcoin može učiniti za njihovu štednju.
Zašto ljudi štede svoj novac u Bitcoin-u umesto na štednim računima, kućama, deonicama ili zlatu? Hajde da pogledajmo sve te metode štednje, i zatim da ih uporedimo sa Bitcoin-om.
Da li je vaš novac siguran u dolarima, kućama, akcijama ili zlatu?
Tokom mnogo godina, to su bile pristojne opcije za štednju. Međutim, sistem koji podržava vrednost svega ovoga je u krizi.
Dolari, Euri, Dinari
Dolari i sve ostale „tradicionalne“ valute koje proizvode vlade, stvorene su da izgube vrednost kroz inflaciju. Banke i tradicionalni monetarni sistem uzrokuju inflaciju stalnim stvaranjem i distribucijom novog novca. Kada Američke Federalne Rezerve objave ciljanu stopu od 2% inflacije, to znači da žele da vaš novac svake godine izgubi 2% od svoje vrednosti. Čak i sa inflacijom od samo 2%, vaša štednja u dolarima izgubiće polovinu vrednosti tokom 40-godišnjeg radnog veka.
Izveštena inflacija se danas opasno povečava, uprkos rastućem „buretu sa barutom“ koji bi mogao da explodira i dovede do masivne hiperinflacije. Što je više valute u opticaju, to je više baruta u buretu.
Naše vlade su ekonomiju napunile valutama da bankarski sistem ne bi propao nakon finansijske krize koja se dogodila 2008. godine. Od tada je većina glavnih centralnih banaka postavila vrlo niske kamatne stope, što pojedincima i korporacijama omogućava dobijanje jeftinijih kredita. To znači da mnogi pojedinci i korporacije podižu ogromne kredite i koriste ih za kupovinu druge imovine poput deonica, umetničkih dela i nekretnina. Sve ovo pozajmljivanje znači da stvaramo tone novog novca i stavljamo ga u opticaj.
Računi za podsticaje (stimulus bills) COVID-19 za 2020. godinu unose trilione u sistem. Ovoliko stvaranje valuta na kraju dovodi do inflacije – velikog gubitka u vrednosti valute.
 Količina američkog dolara u opticaju gotovo se udvostručila od marta 2020. godine. Izvor
Količina američkog dolara u opticaju gotovo se udvostručila od marta 2020. godine. IzvorRačuni za podsticaje su bez presedana, toliko da je neko izmislio meme da opiše ovu situaciju.

Resurs koji vlade mogu da naprave u većem broju da bi platile svoje račune? Ne zvuči kao dobro mesto za štednju novca.
Kuće
Kuće su tokom prošlog veka bile pristojan način štednje novca. Međutim, pad cena nekretnina 2007. godine doveo je do toga da su mnogi vlasnici kuća izgubili svu ušteđevinu.
Danas su kuće gotovo nepristupačne za prosečnog čoveka. Jedan od načina da se ovo izmeri je koliko godišnjih zarada treba prosečnom čoveku da zaradi ekvivalent vrednosti prosečne kuće. Prema CityLab-u, publikaciji Bloomberg-a koja pokriva gradove, porodica može da priuštiti određenu kuću ako košta manje od 2,6 godišnjih prihoda domaćinstva te porodice.
Međutim, prema RZS (Republički zavod za statistiku) prosečan prihod porodičnog domaćinstva u Srbiji iznosi oko 570 EUR mesečno ili otprilike 7.000 EUR godišnje. Nažalost, samo najjeftinija područja van gradova imaju srednje cene kuća od oko 2,6 prosečnih godišnjih prihoda domaćinstva. U većim gradovima poput Beograda i Novog Sada srednja cena kuće je veća od 10 prosečnih godišnjih prihoda jednog domaćinstva.
Ako nekako možete sebi da priuštite kuću, ona bi mogla biti pristojna zaliha vrednosti. Dokle god ne doživimo još jedan krah i izvršitelji zaplene ovu imovinu mnogim vlasnicima kuća.
Akcije
Berza je u prošlosti takođe dobro poslovala. Međutim, sporo i stabilno povećanje tržišta događa se u dosadnom, predvidljivom svetu. Svakog dana vidimo sve manje toga. Nakon ubrzanja korona virusa, videli smo smo najbrži pad američke berze u istoriji od 25% – brži od Velike depresije.
Neki se odlučuju za ulaganje u obveznice i drugu finansijsku imovinu, ali ’prinosi’ za tu imovinu – procenat kamate zarađene na imovinu iz godine u godinu – stalno opada. Sve veći broj odredjenih imovina ima čak i negativne prinose, što znači da posedovanje te imovine košta! Ovo je veliki problem za sve koji se oslanjaju na penziju. Plus, s obzirom na to da su akcije denominovane u tradicionalnim valutama poput dolara i evra, inflacija pojede prinos koji investitor dobije.
Najgore od svega je to što ti isti ekonomski krahovi koji uzrokuju masovna otpuštanja i teško tržište rada takođe znače i nagli pad cena akcija. Čuvanje ušteđevine u akcijama može značiti i gubitak štednje i gubitak posla zbog recesije. Teška vremena mogu da vas prisile da svoje akcije prodate po vrlo malim cenama samo da biste platili svoje račune.
A to nije baš siguran način štednje novca.
Zlato
Vrednost zlata neprekidno se povećavala tokom 5000 godina, obično padajući onda kada berza obećava jače prinose.
Evidencija vrednosti zlata je solidna. Međutim, zlato nosi i druge rizike. Većina ljudi poseduje zlato na papiru. Oni fizički ne poseduju zlato, već ga njihova banka čuva za njih. Zbog toga je zlato veoma podložno konfiskaciji od strane vlade.
Zašto bi vlada konfiskovala nečije zlato, a kamoli u demokratskoj zemlji u „slobodnom svetu“? Ali to se dešavalo i ranije. 1933. godine Izvršnom Naredbom 6102, predsednik Roosevelt naredio je svim Amerikancima da prodaju svoje zlato vladi u zamenu za papirne dolare. Vlada je iskoristila pretnju zatvorom za prikupljanje zlata u fizičkom obliku. Znali su da se zlato više poštuje kao zaliha vrednosti širom sveta od papirnih dolara.
Ako posedujete svoje zlato na nekoj od aplikacija za trgovanje akcijama, možete se kladiti da će vam ga država oduzeti ako joj zatreba. Čak i ako posedujete fizičko zlato, onda ga izlažete mogućnosti krađe – od strane kriminalca ili vaše vlade.
Vaša uštedjevina nije bezbedna.
Rast cena svih gore navedenih sredstava zavisi od našeg trenutnog političkog i ekonomskog sistema koji se nastavlja kao i tokom proteklih 100 godina. Međutim, danas vidimo ogromne pukotine u ovom sistemu.
Sistem ne funkcioniše dobro za većinu ljudi.
Od 1971. plate većine američkih radnika nisu rasle. S druge strane, bogatstvo koje imaju najbogatiji u društvu nalazi se na nivoima koji nisu viđeni više od 80 godina. U međuvremenu, ljudi sve manje i manje veruju institucijama poput banaka i vlada.
 CBPP Nejednakost Bogatstva Tokom Vremena
CBPP Nejednakost Bogatstva Tokom VremenaŠirom sveta možemo videti dokaze o slamanju sistema kroz politički ekstremizam: izbor Trampa i drugih ekstremističkih desničarskih kandidata, Bregzit, pokret Occupy, popularizacija koncepta univerzalnog osnovnog dohotka, povratak pojma „socijalizam“ nazad u modu. Ljudi na svim delovima političkog i društvenog spektra osećaju problematična vremena i posežu za sve radikalnijim rešenjima.
Šta je bolje za štednju od dolara, kuća i akcija?
Pa kako ljudi mogu da štede novac u ovim teškim vremenima? Ili ne koriste tradicionalne valute, ili kupuju sredstva koja će zadržati vrednost u teškim vremenima.
Bitcoin ima najviše potencijala da zadrži vrednost kroz politička i ekonomska previranja od bilo koje druge imovine. Na tom putu će biti rupa na kojima će se rušiti ili pumpati, međutim, njegova svojstva čine ga takvim da će verovatno preživeti previranja kada druga imovina ne bude to mogla.
Šta Bitcoin čini drugačijim?
Bitcoini su retki.
Proces ‘rudarenja’ bitcoin-a, proizvodnju bitcoin-a čini veoma skupom, a Bitcoin protokol ograničava ukupan broj bitcoin-a na 21 milion novčića. To čini Bitcoin imunim na nagle poraste ponude. Ovo se veoma razlikuje od tradicionalnih valuta, koje vlade mogu da štampaju sve više kad god one to požele. Zapamtite, povećanje ponude vrši veliki pritisak na vrednost valute.
Bitcoini nemaju drugu ugovornu stranu.
Bitcoin se takođe razlikuje od imovine kao što su obveznice, akcije i kuće, jer mu nedostaje druga ugovorna strana. Druge ugovorne strane su drugi subjekti uključeni u vrednost sredstva, koji to sredstvo mogu obezvrediti ili vam ga uzeti. Ako imate hipoteku na svojoj kući, banka je druga ugovorna strana. Kada sledeći put dođe do velikog finansijskog kraha, banka vam može oduzeti kuću. Kompanije su kvazi-ugovorne strane akcijama i obveznicama, jer mogu da počnu da donose loše odluke koje utiču na njihovu cenu akcija ili na „neizvršenje“ duga (da ga ne vraćaju vama ili drugim poveriocima). Bitcoin nema ovih problema.
Bitcoin je pristupačan.
Svako sa 5 eura i mobilnim telefonom može da kupi i poseduje mali deo bitcoin-a. Važno je da znate da ne morate da kupite ceo bitcoin. Bitcoin-i su deljivi do 100-milionite jedinice, tako da možete da kupite Bitcoin u vrednosti od samo nekoliko eura. Neuporedivo lakše nego kupovina kuće, zlata ili akcija!
Bitcoin se ne može konfiskovati.
Banke drže većinu vaših eura, zlata i akcija za vas. Većina ljudi u razvijenom svetu veruje bankama, jer većina ljudi koji žive u današnje vreme nikada nije doživela konfiskaciju imovine ili ’šišanje’ od strane banaka ili vlada. Nažalost, postoji presedan za konfiskaciju imovine čak i u demokratskim zemljama sa snažnom vladavinom prava.
Kada vlada konfiskuje imovinu, ona obično ubedi javnost da će je menjati za imovinu jednake vrednosti. U SAD-u 1930-ih, vlada je davala dolare vlasnicima zlata. Vlada je znala da uvek može da odštampa još više dolara, ali da ne može da napravi više zlata. Na Kipru 2012. godine, jedna propala banka je svojim klijentima dala deonice banke da pokrije dolare klijenata koje je banka trebala da ima. I dolari i deonice su strmoglavo opali u odnosu na imovinu koja je uzeta od ovih ljudi.
Doći do bitcoin-a koji ljudi poseduju, biće mnogo teže jer se bitcoin-i mogu čuvati u novčaniku koji ne poseduje neka treća strana, a vi možete čak i da zapamtite privatne ključeve do vašeg bitcoin-a u glavi.
Bitcoin je za štednju.
Bitcoin se polako pokazuje kao najbolja opcija za dugoročnu štednju novca, posebno s obzirom na današnju ekonomsku klimu. Posedovanje čak i malog dela, je polisa osiguranja koja se isplati ako svet i dalje nastavi da ludi. Cena Bitcoin-a u dolarima može divlje da varira u roku od godinu ili dve, ali tokom 3+ godine skoro svi vide slične ili više cene od trenutka kada su ga kupili. U stvari, doslovno niko nije izgubio novac čuvajući Bitcoin duže od 3,5 godine – čak i ako je kupio BTC na apsolutnim vrhovima tržišta.

Imajte na umu da nakon ove tačke ti ljudi više nikada nisu videli rizik od gubitka. Cena se nikada nije smanjila niže od najviše cene u prethodnom ciklusu.
Po čemu se Bitcoin razlikuje od ostalih valuta?
Bitcoin funkcioniše tako dobro kao način štednje zbog svog neobičnog dizajna, koji ga čini drugačijim od bilo kog drugog oblika novca koji je postojao pre njega. Bitcoin je digitalna valuta, prvi i verovatno jedini primer valute koja ima ograničenu ponudu dok radi na otvorenom, decentralizovanom sistemu. Vlade strogo kontrolišu valute koje danas koristimo, poput dolara i eura, i proizvode ih za finansiranje ratova i dugova. Korisnici Bitcoin-a – poput vas – kontrolišu Bitcoin protokol.
Evo šta Bitcoin razlikuje od dolara, eura i drugih valuta:
Bitcoin je otvoren sistem.
Svako može da odluči da se pridruži Bitcoin mreži i primeni pravila softverskog protokola, što je dovelo do vrlo decentralizovanog sistema u kojem nijedan pojedinac ili entitet ne može da blokira transakciju, zamrzne sredstva ili da ukrade od druge osobe.Današnji savremeni bankarski sistem se uveliko razlikuje. Nekoliko banaka je dobilo poverenje da gotovo sve valute, akcije i druge vredne predmete čuvaju na “sigurnom” za svoje klijente. Da biste postali banka, potrebni su vam milioni dolara i neverovatne količine političkog uticaja. Da biste pokrenuli Bitcoin čvor i postali „svoja banka“, potrebno vam je nekoliko stotina dolara i jedno slobodno popodne.
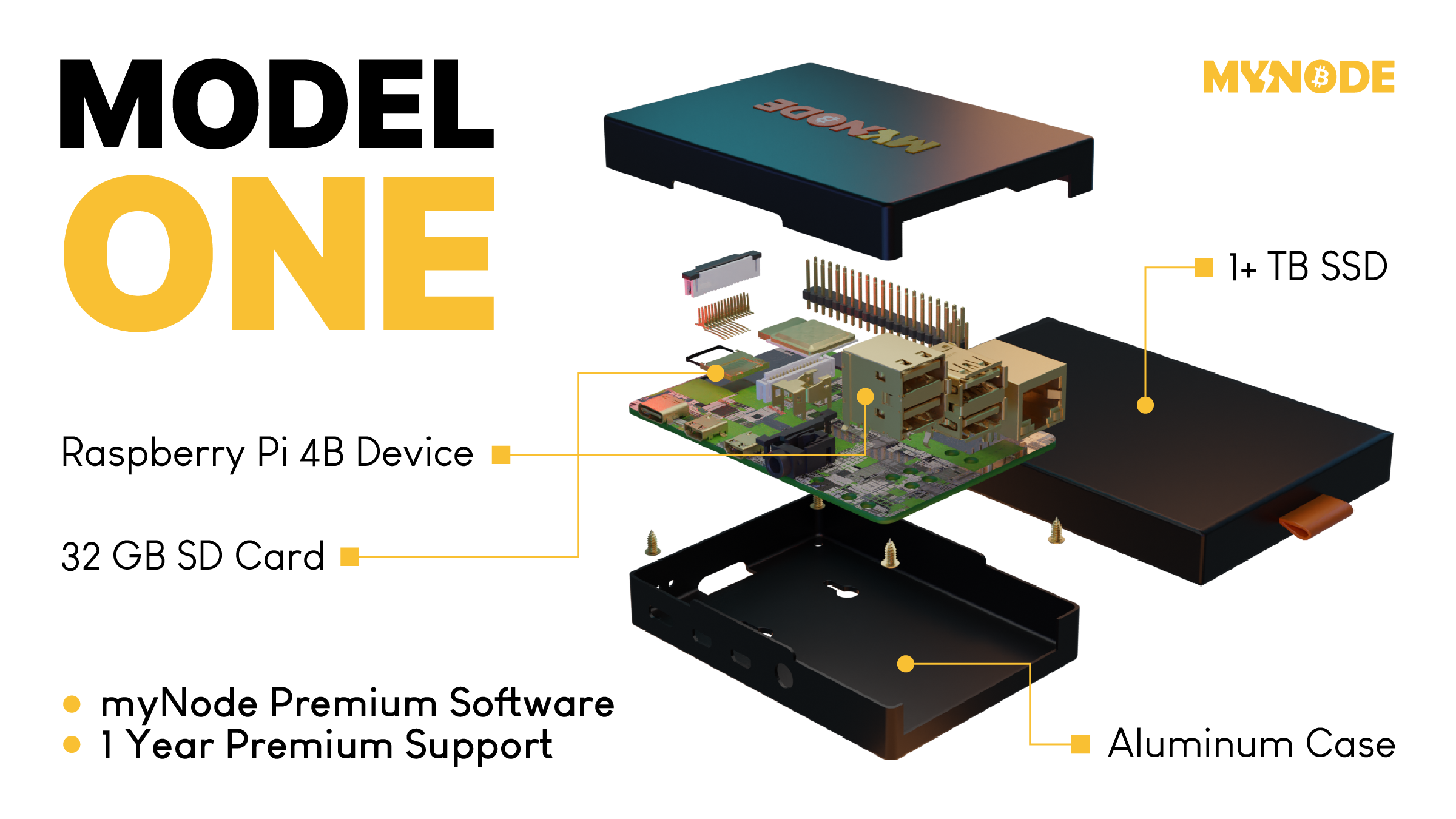 Tako izgleda Bitcoin čvor – Node
MyNode čvor vam omogućava da postanete svoja banka za samo nekoliko minuta.
Tako izgleda Bitcoin čvor – Node
MyNode čvor vam omogućava da postanete svoja banka za samo nekoliko minuta.Bitcoin ima ograničenu ponudu.
Softverski protokol otvorenog koda koji upravlja Bitcoin sistemom ograničava broj novih bitcoin-a koji se mogu stvoriti tokom vremena, sa ograničenjem od ukupno 21.000.000 bitcoin-a. S druge strane, valute koje danas koristimo imaju neograničenu ponudu. Istorija i sadašnje odluke centralnih banaka govore nam da će vlade uvek štampati sve više i više valuta, sve dok valuta ne bude bezvredna. Sve ovo štampanje uzrokuje inflaciju, što pravi štetu običnim radnim ljudima i štedišama.
Tradicionalne valute su dizajnirane tako da opadaju vremenom. Svaki put kada centralna banka kaže da cilja određenu stopu inflacije, oni ustvari kažu da žele da vaš novac svake godine izgubi određeni procenat svoje vrednosti.
Bitcoin-ova ograničena ponuda znači da je on tako dizajniran da raste vremenom kako se potražnja za njim povećava.

Bitcoin putuje oko sveta za nekoliko minuta.
Svako može da pošalje bitcoin-e za nekoliko minuta širom sveta, bez obzira na granice, banke i vlade. Potrebno je manje od minuta da se transakcija pojavi na novčaniku primaoca i oko 60 minuta da se transakcija u potpunosti „obračuna“, tako da primaoc može da bude siguran da su primljeni bitcoin-i sada njegovi (6 konfirmacija bloka). Slanje drugih valuta širom sveta traje danima ili čak mesecima ako se šalju milionski iznosi, a podrazumeva i visoke naknade.
Neke vlade i novinari tvrde da ova sloboda putovanja koju pruža Bitcoin pomaže kriminalcima i teroristima. Međutim, transakciju Bitcoin-a je lakše pratiti nego većinu transakcija u dolarima ili eurima.
Bitcoin se može čuvati na “USB-u”.
Dizajn Bitcoin-a je takav da vam treba samo da čuvate privatni ključ do svojih ‘bitcoin’ adresa (poput lozinke do bankovnih računa) da biste pristupili svojim bitcoin-ima odakle god poželite. Ovaj privatni ključ možete da sačuvate na disku ili na papiru u obliku 12 ili 24 reči na engleskom jeziku. Kao rezultat toga, možete da držite Bitcoin-e vredne milione dolara u svojoj šaci.
Sve ostale valute danas možete ili da strpate u svoj dušek ili da ih poverite banci na čuvanje. Za većinu ljudi koji žive u razvijenom svetu, i koji ne osporavaju autoritet i poverenje u banku, ovo deluje sasvim dobro. Međutim, oni kojima je potrebno da pobegnu od ugnjetavačke vlade ili koji naljute pogrešne ljude, ne mogu verovati bankama. Za njih je sposobnost da nose svoju ušteđevinu bez potrebe za ogromnim koferom neprocenjiva. Čak i ako ne živite na mestu poput ovog, cena Bitcoin-a se i dalje povećava kada ih neko kome oni trebaju kupi.
Kako Bitcoin spašava svet?
Bitcoin, kao ultimativni način štednje, je cakum pakum, ali da li on pomaže u poboljšanju sveta u celini?
Kao što ćete početi da shvatate, ulazeći sve dublje i u druge sadržaje na ovoj stranici, mnogi temeljni delovi našeg današnjeg monetarnog sistema i ekonomije su duboko slomljeni. Međutim, oni koji upravljaju imaju korist od ovakvih sistema, pa se on verovatno neće promeniti bez revolucije ili mirnog svrgavanja od strane naroda. Bitcoin predstavlja novi sistem, sa nekoliko glavnih prednosti:
- Bitcoin popravlja novac, koji je milenijumima služio kao važan alat za rast i poboljšanje društva.
- Bitcoin vraća zdrav razum pozajmljivanju, uklanjanjem apsurdnih situacija poput negativnih kamatnih stopa (gde zajmitelj plaća da bi se zadužio).
- Bitcoin pokreće ulaganja u obnovljive izvore energije i poboljšava energetsku efikasnost u mreži, služeći kao „krajnji kupac“ za sve vrste energije.
Kako mogu da saznam više o Bitcoin-u?
Ovaj članak vam je dao osnovno razumevanje zašto biste trebali razmišljati o Bitcoin-u. Ako želite da saznate više, preporučujem ove resurse:
- Film "Bitcoin: Kraj Novca Kakav Poznajemo"
- Još uvek je rano za Bitcoin
- Zasto baš Bitcoin?
- Šta je to Bitcoin?
- The Bitcoin Whitepaper ← objavljen 2008. godine, ovo je izložio dizajn za Bitcoin.
-
 @ cae03c48:2a7d6671
2025-05-27 21:00:49
@ cae03c48:2a7d6671
2025-05-27 21:00:49Bitcoin Magazine

The Bitcoin Mempool: Private MempoolsIn the last Mempool article, I went through the dynamics of transaction propagation when different nodes on the network are running different mempool relay policies. In this piece I’ll be looking at the dynamics of private mempools, and the implications that has for the utility of the public mempool, mining incentives, and the health of the Bitcoin network overall.
At the heart of the purpose of the mempool is facilitating the aligned incentives of two different parties, miners and transacting users. Users want to transact, and are willing to pay miners’ transaction fees in order to do so. Miners want to make money, and transaction fees are an additional source of revenue in addition to the new coin subsidy in each block, as well as a necessary primary revenue source to cultivate in the long term as the subsidy dwindles.
Bitcoin is a system secured by incentives. This core dynamic is what drives the security of the system, you have a customer(s) and a provider, and the two of them attempting to fulfill their wants and needs is what ensures the blockchain continues ticking forward with a sufficient amount of thermodynamic security.
Attempts to introduce friction into this facilitation mechanism does not ultimately do anything at all to change the incentives of these two parties. A user who wants to make a certain kind of transaction is still going to want to make that transaction, and pay for it. A miner who is willing to accept those kinds of transactions is still going to want to accept them, and collect the fee by including them in a block.
If the transaction is valid, then these two parties are still going to have their unmet wants and needs, and are still going to be strongly motivated to meet them in some form or fashion.
Miner API
Individual end users are not necessarily capitalized enough or competent enough in order to route around friction artificially introduced between both ends of a coincidence of wants, but miners most definitely are. As the old adage goes, “if you build it, they will come.”
The preferential situation for miners is obviously to acquire fee paying transactions in-band through the public mempool. It requires the lowest overhead possible for them, simply running a standard Bitcoin client out of the box, it is a very resilient propagation mechanism that ensures a very high degree of reliability in getting miners the highest fee paying transactions, and they don’t have to do anything. Just download the client and run it.
However, in a very hostile environment such as a network wide effort to filter consensus valid transactions during their propagation across the network, that traditional assumption can be drawn into question.
In such a scenario miners have every incentive to set up out-of-band mechanisms for accepting transactions that are not properly being relayed across the network. Marathon’s Slipstream API for non-standard transactions is not the only example of this. There is in fact a long standing precedent from almost ten years ago that was widely implemented by many mining pools, and still exists to this day. Transaction accelerators.
We now live in a world of Full-RBF, where any transaction, regardless of using the historical “opt-in” flag, can be fee-bumped. Any node who has upgraded to Full-RBF will relay any transaction that is spending an unconfirmed output already pending in the mempool as long as it is paying a higher fee. This has not always been the case. Historically only transactions that were originally made with a flag to opt-in to RBF use could be replaced and expected to propagate across the network.
Transaction accelerators were created by miners in order to facilitate this behavior for transactions that did not opt-in to RBF use.
Third Party APIs
While the overhead is not exorbitantly high for a miner or pool to create their own transaction submission API, it isn’t free. It still does require at least one developer and time to go through the design and release cycle of any piece of software. The curve isn’t particularly exaggerated, but it still does favor larger miners over smaller ones in terms of how much resources they will have to devote to such an endeavor.
Mempool.space has proven that it is a viable endeavour for a third party unrelated to miners to create such an API, allowing miners to simply connect to their service rather than expend the effort to create one themselves from scratch. This does have its issues though, such a third party is not going to build and operate such a service for free. They will want their cut.
There are two ways that this dynamic can go, either these services wind up requiring a higher cost in order to allow both the miners and service providers to earn revenue, or miners will have to share a smaller cut of the revenue in order for such services to remain competitive with directly miner operated ones. This means miners using a third party submission API rather than their own will earn less revenue than the miners operating their own API.
Private Order Flow
Either of the above possibilities introduces serious problems when it comes to the overall system incentives, reliability of end-user software, and potentially even the security model of second layer systems that rely on the use of pre-signed transactions and a reactive security model in order to keep user funds safe.
When transactions are submitted to a private API, they are not visible to network participants until they are actually confirmed in a block. The entire queue of unconfirmed transactions making use of these systems is opaque. This could be made public by the operators of these APIs, but not in a trustless fashion. There is no way to prove or guarantee that operators are not withholding information.
Withholding transactions from public view could distort fee estimates that users make, and even open the door to the possibility of manipulating those feerates by stuffing blocks with their own transactions. Transactions used in the operation of second layer systems could be withheld from public view until confirmation, which can delay users ability to react to transactions they must respond to in order to guarantee the security of their funds.
Lastly, just the existence of such APIs if the demand or need for them is high enough is a massive centralization pressure. Having to handle connecting to each individual API to submit a transaction is a hassle, poor UX, and potential back end complexity. This tends to reinforce the use of the largest API(s) and ignoring the tailend, which creates a feedback loop.
The API operators with the largest hashrate will have the quickest and most reliable confirmations, guaranteeing only those largest miners reliably earn this extra revenue, giving them more capital to grow larger, etc.
Parallel Mempools
On the other end of the spectrum is the possibility of creating totally independent public relay networks. While this does replicate the current openness of the existing public mempool, and avoids the worst of the centralizing pressures of central APIs, it still is not ideal.
Having multiple mempools introducing complexity for miners, for end users, and for end user applications. Users now need to keep track of all the independent mempools, especially ones used for systems they interact with that are not propagated over the primary relay network, in order to have a view of unconfirmed transactions.
If Lightning (or some other Layer 2) were to start making use of a parallel mempool, tracking it would be critical for any user of Lightning (or that other Layer 2). It would also be necessary to track all of the parallel relay networks in order to have an accurate view of the other unconfirmed transactions you are bidding against for inclusion in the next block. Tracking only a subset of them would lead to potentially large margins of error in any users fee estimation.
You Just Make Things Worse
Trying to prevent transactions with willing fee paying users without addressing them at the consensus level is just not possible. Bitcoin is an engine driven by incentives, and when the incentives of multiple parties align they will be facilitated in one form or another.
Trying to pretend that is not the case, and that things can be stopped, disincentivized, or otherwise delayed is a fool’s errand. Not only that, but trying at any serious scale comes with very serious negative consequences, in addition to being doomed to fail.
Bitcoin’s consensus rules are the framework in which incentives are played out. The only thing that can trump incentives is changing that framework. It is literally what informs and shapes the incentives in the first place.
Trying to interfere with those incentives at any other layer is a fool’s errand, and can do nothing but exacerbate the negative outcomes driven by incentives, i.e. centralization.
This post The Bitcoin Mempool: Private Mempools first appeared on Bitcoin Magazine and is written by Shinobi.
-
 @ 94e2c22d:d50b08a3
2025-05-27 19:59:24
@ 94e2c22d:d50b08a3
2025-05-27 19:59:24Definition and Basic Principle
Light painting is a photographic technique in which light sources are moved or purposefully used during a long exposure to create images, patterns, or lettering in space. The light source can appear visibly in the image (light drawing), be used to illuminate the subject (light painting), or the camera itself can be moved (kinetic light painting).
History
The history of light painting ranges from scientific experiments in the 19th century, through the artistic avant-garde of the 1930s, to the diverse, technically sophisticated forms of expression seen today. The sources span from early photographers and scientists like Marey, Demeny, and the Gilbreths, to artists such as Man Ray and Picasso, and on to contemporary light painters experimenting with new light sources and techniques.
Early Scientific Applications (1889–1914)
Étienne-Jules Marey and Georges Demeny (1889):
The earliest documented light paintings originated from scientific motion studies. *Demeny *attached light bulbs to the joints of an assistant and photographed their movements with long exposure. This image (Pathological Walk From in Front) is considered the earliest known example of lightpainting.
Frank and Lillian Gilbreth (1914):
The couple used small lights and open shutters to analyze workflows in industry. Their goal was not art, but the optimization of work processes. Nevertheless, some of the first light painting photographs were created this way.
Artistic Light Painting (from the 1930s)
Man Ray (1935):
The American artist Man Ray is considered the first to use light painting as an artistic means of expression. In his Space Writing series, he wrote his name in the air with a small light pen, creating abstract light trails that were only recognized as his signature in 2009.
Barbara Morgan (1935–1941):
She experimented with light drawings, especially in dance photography, by equipping dancers with lights and capturing their movements.
Famous Light Painters and Innovations (1940s–1970s)
Gjon Mili & Pablo Picasso (1949):
Gjon Mili showed Picasso photographs of figure skaters with lights attached to their skates. Picasso was fascinated and, using a flashlight in a darkened room, created his famous "light drawings," including the well-known Picasso draws a Centaur.
Peter Keetman (1949):
The German photographer developed complex light patterns using point light sources on pendulums, shaping experimental photography in post-war Germany.
Modern Developments and Artists (1970s–Today)
Starting in the 1970s, lightpainting expanded beyond experimental and portrait photography into more diverse and expressive artistic realms. Swiss photographer Jacques Pugin was a pioneer in using lightpainting in natural landscapes, employing candlelight and subtle illumination to reveal hidden shapes and textures. His work often bridges the tangible with the ephemeral, evoking a sense of time and memory in the environment.
From the late 20th century onwards, advances in camera technology—such as more sensitive film and later digital sensors—made long-exposure photography more accessible and versatile. This technological progress allowed artists to experiment with new light sources like LED lights, fiber optics, and even programmable light tools, vastly expanding the creative possibilities.
Lightpainting also intersected with other art forms, such as performance art and installation. Artists began incorporating movement, music, and interactive elements, transforming lightpainting into immersive experiences.
The history of light painting reveals an impressive evolution from scientific studies of human movement to a creative form of artistic expression. By combining technology, creativity, and light, works are created that push the boundaries of photography and captivate the viewer.
Author: Mafu Fuma
Sources: Wikipedia
Picture: Frank Gilbreth
-
 @ cae03c48:2a7d6671
2025-05-27 19:00:51
@ cae03c48:2a7d6671
2025-05-27 19:00:51Bitcoin Magazine

Exodus Launches XO Pay, An In-App Bitcoin And Crypto Purchase SolutionExodus has officially launched XO Pay, a new crypto purchasing feature that allows users to buy and sell digital assets directly within the Exodus mobile wallet, and is now live across the United States. XO Pay aims to simplify the process for its users to easily purchase cryptocurrencies such as Bitcoin.
XO Pay is powered by Coinme’s Crypto-as-a-Service (CaaS) API platform and is a self custody Bitcoin wallet. This means customers can now purchase BTC within the wallet without going through third-party exchanges while keeping full control of their assets.
“XO Pay represents our commitment to making cryptocurrency more accessible to everyday customers,” said JP Richardson, Co-Founder and CEO of Exodus, in a recent press release sent to Bitcoin Magazine. “By integrating the purchasing process directly into our mobile wallet, we’re removing barriers and simplifying the journey from fiat to crypto, and back.”
With XO Pay, Exodus offers a self custodial way to complete Bitcoin transactions. This rollout is part of Exodus’ broader mission to make digital assets more secure, as the demand for Bitcoin is increasing.
“By creating a Web2 checkout experience into a Web3 self-custody wallet, Exodus has set a new bar for crypto user experience,” said Neil Bergquist, CEO and co-founder of Coinme. “Exodus’ innovative integration of Coinme’s APIs delivers the seamless in-app purchase flow users expect while keeping them in full control of their assets.”
This post Exodus Launches XO Pay, An In-App Bitcoin And Crypto Purchase Solution first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ cae03c48:2a7d6671
2025-05-27 22:00:39
@ cae03c48:2a7d6671
2025-05-27 22:00:39Bitcoin Magazine

1.5 Million Users to Access Bitcoin’s Lightning Network on Xverse thanks to SatiSati, a Bitcoin payments app and Lightning infrastructure provider, today announced the launch of its Lightning integration with Xverse, a Bitcoin wallet used by over 1.5 million people worldwide. Thanks to the integration, Xverse users can now send and receive sats (Bitcoin’s smallest denomination) instantly over the Lightning Network with no setup, no app switching, and no custodial risk.
Initially designed in 2017, the Lightning Network has grown to become Bitcoin’s leading layer-2, with a current BTC capacity of over $465M. Sati is now leveraging this technology to bring the world’s favorite digital currency into the pockets of almost 3 billion users worldwide, thanks to its powerful API integration with WhatsApp.
“Bitcoin was not meant to be an asset for Wall Street—it was built for peer-to-peer money, borderless and accessible,” said Felipe Servin, Founder and CEO of Sati. “Integrating Lightning natively into Xverse brings that vision back to life, making Bitcoin usable at scale for billions.”
Thanks to the integration, every Xverse user now gets a Lightning Address instantly. That means they can receive tips, pay invoices, and use Bitcoin for microtransactions—all without having to manage channels or switch between different apps. Sati expects USDT on Lightning to be supported as early as Q3 for the Xverse wallet and in July 2025
for users accessing Sati through WhatsApp.This integration positions Sati’s role as a Lightning infrastructure provider, not just a consumer app. By leveraging its API-based solution, the company provides plug-and-play backend services to wallets and platforms looking to add Bitcoin payments without compromising on security or UX.
The Xverse launch follows the debut of Parasite Pool, a new mining pool leveraging Sati and Xverse’s tech stack and focused on democratizing Bitcoin mining. Parasite Pool charges 0% fees and pays out instantly over Lightning, making it ideal for small-scale miners, especially those running ultra-low-power hardware like Bitaxe.
With over 500 users joining Parasite Pool within weeks of launch and an average pool hashrate of 5 PH/s, Parasite Pool is steadily growing its presence in the home mining space. Thanks to the Lightning integration, Parasite Pool supports the smallest Lightning payouts in the industry (a fraction of a cent), lowering the barrier to entry for anyone interested in mining.
Sati recently closed a $600K pre-seed round backed by Bitcoin-focused investors, including Draper Associates, BitcoinFi, Arcanum, BoostVC, and Ricardo Salinas. The funding is being used to support global expansion, stablecoin integration, Lightning infrastructure growth, and broader access to Bitcoin in emerging markets.
Sati will be conducting live product demos at Bitcoin 2025 in Las Vegas on May 27-29. To learn more about Sati, visit sati.pro
About Sati
Sati is a Bitcoin payments infrastructure provider. Launched in 2025 with investors of the likes as Draper Associates and Ricardo Salinas, Sati powers fast, seamless Bitcoin payments on applications such as WhatsApp to fuel the next wave of adoption. Learn more at sati.proAbout Xverse
Xverse is the on-chain platform for the Bitcoin economy—think Revolut meets Alchemy, built natively on Bitcoin. Trusted by over 1.5 million users, Xverse is launching a unified portfolio platform for Bitcoin L1 and Layer 2s, alongside developer infrastructure to power seamless Bitcoin-native apps.Press Contact
press@sati.proDisclaimer: This is a sponsored press release. Readers are encouraged to perform their own due diligence before acting on any information presented in this article.
This post 1.5 Million Users to Access Bitcoin’s Lightning Network on Xverse thanks to Sati first appeared on Bitcoin Magazine and is written by Sati.
-
 @ 5391098c:74403a0e
2025-05-27 18:20:42
@ 5391098c:74403a0e
2025-05-27 18:20:42Você trabalha 5 meses do ano somente para pagar impostos. Ou seja, 42% da sua renda serve para bancar serviços públicos de péssima qualidade. Mesmo que você tivesse a liberdade de usar esses 42% da sua renda para contratar serviços privados de qualidade (saúde, segurança e ensino), ainda assim você seria um escravo porque você recebe dinheiro em troca do seu trabalho, e o dinheiro perde cerca de 10% do valor a cada ano. Em outras palavras todo seu dinheiro que sobra depois de comprar comida, vestuário e moradia perde 100% do valor a cada 10 anos. Isso acontece porque o Estado imprime dinheiro do nada e joga na economia de propósito para gerar INFLAÇÃO e manter todos nós escravizados. Você pode deixar seu dinheiro investido em qualquer aplicação que imaginar e ainda assim nunca terá uma rentabilidade superior a inflação real. No final, acaba perdendo tudo do mesmo jeito. Caso você se ache esperto por investir o que sobra da sua renda em bens duráveis como imóveis ou veículos, sabia que esses bens também não são seus, porque se deixar de pagar os impostos desses bens (iptu, itr, ipva) você também perde tudo. Além disso, o custo de manutenção desses bens deve ser levado em consideração na conta das novas dívidas que você assumiu. No caso dos imóveis urbanos é impossível alugá-lo por mais de 0,38% do seu valor mensalmente. Em outras palavras, a cada ano você recebe menos de 5% do que investiu, tem que pagar o custo de manutenção, mais impostos e a valorização do bem nunca será superior a inflação real, também fazendo você perder quase tudo em cerca de 15 anos. A situação é ainda pior com os imóveis rurais e veículos, basta fazer as contas. Caso o dinheiro que você receba em troca do seu trabalho seja suficiente apenas para comprar comida, vestuário e moradia, você já sabe que é um escravo né?… Precisamos entender que a escravidão não acabou, apenas foi democratizada. Hoje a escravidão é financeira, nós somos os castiços e os donos do dinheiro são o senhorio. Os donos do dinheiro são os Globalistas e os Estados seus fantoches. O esquema é simples: fazer todo mundo trabalhar em troca de algo que perde 100% do valor a cada 10 anos, ou seja o dinheiro. Se você pudesse trabalhar em troca de algo que aumentasse de valor acima da inflação real a cada 10 anos você finalmente conquistaria sua liberdade financeira e deixaria de ser escravo. Pois bem, isso já é possível, e não se trata de ouro ou imóveis e sim sobre o Bitcoin, que sobe de valor mais de 100% a cada 10 anos, com a vantagem de ser inconfiscável e de fácil transferência para seus herdeiros quando você morrer, através de uma simples transação LockTime feita em vida. Portanto, mesmo que você não tenha dinheiro para comprar Bitcoin, passar a aceitar Bitcoin em troca de seus produtos e serviços é a única forma de se libertar da escravidão financeira. A carta de alforria financeira proporcionada pelo Bitcoin não é imediata, pois a velocidade da sua libertação depende do quanto você está disposto a aprender sobre o assunto. Eu estou aqui para te ajudar, caso queira. No futuro o Bitcoin estará tão presente na sua vida quanto o pix e o cartão de crédito, você querendo ou não. Assim como o cartão de crédito foi a evolução do cheque pós-datado e o pix a evolução do cartão, o Bitcoin e outras criptomoedas serão a evolução de todos esses meios de pagamento. O que te ofereço é a oportunidade de abolição da sua escravatura antes dos demais escravos acordarem para a realidade, afinal a história sempre se repete: desde o ano de 1300 a.c. a escravidão era defendida pelos próprios escravos, que mais cedo ou mais tarde, foram libertados por Moisés em êxodo 11 da Bíblia Sagrada e hoje o povo de israel se tornou a nação mais rica do mundo. A mesma história se repetiu na Roma Antiga: com o pão e circo. Da mesma forma todo esse império escravocrata ruiu porque mais cedo ou mais tarde os escravos se revoltam, bastam as coisas piorarem bastante. O atual regime de escravidão teve início com a queda do padrão-ouro para impressão do dinheiro no ano de 1944. A escravidão apenas ficou mais sofisticada, pois em vez de pagar os escravos com cerveja como no Egito Antigo ou com pão e circo como na Roma Antiga, passou-se a pagar os escravos com dinheiro sem lastro, ou seja dinheiro inventado, criado do nada, sem qualquer representação com a riqueza real da economia. Mesmo sendo a escravidão atual mais sofisticada, que deixou de ser física para ser financeira, o que torna a mentira mais bem contada, mais cedo ou mais tarde os escravos modernos irão acordar, basta as coisas piorarem mais ou perceberem que todos os bens e serviços do mundo não representam nem 1% de todo o dinheiro que impresso sem lastro. Em outras palavras, se os donos de todo o dinheiro do mundo resolvessem utilizá-lo para comprar tudo o que existe à venda, o preço do quilo do café subiria para R$ 297.306,00 e o preço médio dos imóveis subiria para um número tão grande que sequer caberia nesta folha de papel. Hoje, o dinheiro não vale nada, seus donos sabem disso e optam por entregar o dinheiro aos poucos para os escravos em troca do seu trabalho, para manter o atual regime o máximo de tempo possível. Mesmo assim, o atual regime de escravidão financeira está com os dias contados e depende de você se posicionar antes do efeito manada. Nunca é tarde para entrar no Bitcoin, mesmo ele tendo uma quantidade de emissão limitada, seu valor subirá infinitamente. A menor unidade do Bitcoin é o satoshi, cuja abreviação é sats. Diferente do centavo, cada sat vale um centésimo milionésimo de bitcoin. Hoje (25/05/25), cada unidade de Bitcoin equivale a setecentos mil reais. Logo, cada R$ 0,01 equivale à 0,007 sats. Lembrando que o centavo é um real dividido por cem e o sat é um bitcoin dividido por cem milhões, por isso ainda não existe a paridade entre 1 centavo de real e 1 sat. Essa paridade será alcançada quando um Bitcoin passar a valer um milhão de reais. Com a velocidade que nosso dinheiro está perdendo valor isso não irá demorar muito. Utilizando dados econômicos avançados, prevejo que cada unidade de Bitcoin passará a valer hum milhão de reais até o ano de 2029, assim equiparando 1 sat para cada R$ 0,01. Nesse momento, certamente muitos empresários, comerciantes e profissionais liberais passarão a aceitar o Bitcoin como forma de pagamento pelos seus produtos e serviços, assim como o cheque foi substituído pelo cartão de crédito e o cartão pelo pix. Sabendo disso, você pode entrar na onda de transição no futuro junto com a manada e perder essa alta valorização, ou passar a aceitar Bitcoin agora pelos seus produtos e serviços, assinando assim, a própria carta de alforria da sua escravidão financeira. É importante dizer que os próprios globalistas e governos estão trocando dinheiro por Bitcoin como nunca na história e mesmo que eles adquiram todos os bitcoins disponíveis, ainda assim não será mais possível manter seu regime de escravidão financeira funcionando porque a emissão de Bitcoin é limitada, sendo impossível criar Bitcoin sem lastro, como é feito com o dinheiro hoje. Com o presente artigo, te ofereço a oportunidade de conquistar seus primeiros sats agora, de forma segura e independente, sem precisar de corretoras, bancos, intermediários ou terceiros, basta você querer pois toda a informação necessária está disponível na internet gratuitamente. Se ainda assim você quiser continuar sendo escravo financeiro, depois não adiantar se arrepender quando as janelas de oportunidade se fecharem, o Drex for implantado, papel moeda restringido e sua vida piorar bastante. Importante mencionar que a Lei Brasileira ainda permite a movimentação de até R$ 30.000,00 em Bitcoin por mês sem a necessidade de declaração à Receita Federal e que esse direito pode deixar de existir a qualquer momento, e que quando o Drex for implantado você perderá diversos outros direitos, dentre ele a liberdade de gastar seu dinheiro como quiser e o sigilo. Ofereço ainda, a oportunidade de você baixar uma carteira de Bitcoin gratuita e segura no seu aparelho de celular que funciona de forma semelhante a um banco digital como Nubank e Pagseguro por exemplo, para poder começar à receber Bitcoin pelos seus produtos e serviços agora, de forma fácil e gratuita. Utilizando o qrcode abaixo você ainda ganha alguns sats de graça, promoção válida até o dia 29/05/25 e patrocinada pela Corretora Blink de El Salvador, onde o Bitcoin já é moeda oficial do país, basta acessar o link e instalar o aplicativo: https://get.blink.sv/btcvale
Aviso: disponibilizei o link da carteira de Bitcoin da Corretora Blink apenas como exemplo de como é fácil aceitar Bitcoin como forma de pagamento pelos seus produtos e serviços. Não recomento depender de qualquer corretora para guardar seus valores em Bitcoin. A melhor forma de fazer isso é mantendo dois computadores ou notebook em casa, um conectado à internet com memória em disco disponível de 1 terabyte ou mais para armazenar e visualizar suas transações e outro computador ou notebook desconectado da internet para armazenar suas senhas e chaves privadas para assinar as transações via pendrive. Somente assim você estará 100% livre e seguro. Importante ainda fazer backup em vários CDs com criptografia do seu computador ou notebook que assina as transações, assim também ficando 100% livre e seguro para restaurar sua carteira em qualquer outro computador caso necessário. Todas as instruções de como fazer isso já estão disponíveis gratuitamente na internet. Caso deseje contratar uma consultoria pessoal que inclui aulas particulares por vídeo conferência, onde você aprenderá:
→ Tudo o que precisa saber sobre Bitcoin e demais criptomoedas; → Sistema operacional Linux; → Como instalar sua carteira de Bitcoin em dois computadores para assinaturas air gapped; → Se manter 100% livre e seguro. → Com carga horária à combinar conforme sua disponibilidade.
O custo do investimento pelo meu serviço individual para esse tipo de consultoria é de 204.000 sats (R$ 1.543,46 na cotação atual) valor válido até 31/07/25, interessados entrar em contato por aqui ou através da Matrix: @davipinheiro:matrix.org https://davipinheiro.com/voce-e-escravo-e-nem-sabe-eu-vou-te-provar-agora/
-
 @ cae03c48:2a7d6671
2025-05-27 19:00:50
@ cae03c48:2a7d6671
2025-05-27 19:00:50Bitcoin Magazine

🔴 LIVE: The Bitcoin Conference 2025 – Day 1The liveblog has ended.
No liveblog updates yet.
Load more
This post 🔴 LIVE: The Bitcoin Conference 2025 – Day 1 first appeared on Bitcoin Magazine and is written by Bitcoin Magazine.
-
 @ 94e2c22d:d50b08a3
2025-05-27 18:33:13
@ 94e2c22d:d50b08a3
2025-05-27 18:33:13Night photography opens up a whole new dimension of creativity—and with a bit of know-how, your camera becomes a tool for painting with light. Whether you're a curious beginner or looking to refine your technique, these 12 practical tips will help you get started on the right foot. From gear choices to artistic mindset, here’s what you need to know.
-
Know Your Gear – Learn how to operate your camera in complete darkness. You should be comfortable using settings like ISO, aperture, and manual focus without relying on the display.
-
Understand Exposure – Manual settings are crucial. Use low ISO for noise reduction and long exposure times to capture light trails. A tripod is essential for stability.
-
Experiment and Learn – Review your images critically and learn from mistakes. Every attempt offers an opportunity to refine your technique.
-
Avoid Gear Obsession – You don’t need the latest camera. Even basic models can produce impressive results with the right approach.
-
Pack Light – Carry minimal equipment to stay flexible and creative. Too many tools can hinder spontaneity.
-
Use Prime Lenses – Fixed focal length lenses often deliver better quality and let in more light. They also force you to think more about composition.
-
Create Images on Site – Aim to achieve effects in-camera, not later through editing. This improves your skills and leads to more authentic outcomes.
-
See It as a Journey – Be patient and enjoy the process. Your artistic voice will develop over time.
-
Set Goals – Give yourself creative challenges or themes to stay motivated.
-
Plan Your Shoots – Research your location and check weather and moonlight conditions in advance. This minimizes wasted time and frustration.
-
Get Inspired by Others – Study the work of other light painters or night photographers. Join communities to share experiences and gather new ideas.
-
Question the Rules – Creativity often involves breaking away from norms. Don’t be afraid to try unconventional techniques or styles.
Night photography and light painting are not just technical exercises—they're a playful exploration of light, time, and creativity. Don’t stress about perfection. Instead, enjoy the process, embrace the learning curve, and let your imagination run wild. With a bit of patience and these tips in your toolkit, you're well on your way to capturing the magic of the light at night.
Picture created by: Kim Von Coels / Model: Mafu Fuma
-
-
 @ 5391098c:74403a0e
2025-05-27 18:15:38
@ 5391098c:74403a0e
2025-05-27 18:15:38Você trabalha 5 meses do ano somente para pagar impostos. Ou seja, 42% da sua renda serve para bancar serviços públicos de péssima qualidade. Mesmo que você tivesse a liberdade de usar esses 42% da sua renda para contratar serviços privados de qualidade (saúde, segurança e ensino), ainda assim você seria um escravo porque você recebe dinheiro em troca do seu trabalho, e o dinheiro perde cerca de 10% do valor a cada ano. Em outras palavras todo seu dinheiro que sobra depois de comprar comida, vestuário e moradia perde 100% do valor a cada 10 anos. Isso acontece porque o Estado imprime dinheiro do nada e joga na economia de propósito para gerar INFLAÇÃO e manter todos nós escravizados. Você pode deixar seu dinheiro investido em qualquer aplicação que imaginar e ainda assim nunca terá uma rentabilidade superior a inflação real. No final, acaba perdendo tudo do mesmo jeito. Caso você se ache esperto por investir o que sobra da sua renda em bens duráveis como imóveis ou veículos, sabia que esses bens também não são seus, porque se deixar de pagar os impostos desses bens (iptu, itr, ipva) você também perde tudo. Além disso, o custo de manutenção desses bens deve ser levado em consideração na conta das novas dívidas que você assumiu. No caso dos imóveis urbanos é impossível alugá-lo por mais de 0,38% do seu valor mensalmente. Em outras palavras, a cada ano você recebe menos de 5% do que investiu, tem que pagar o custo de manutenção, mais impostos e a valorização do bem nunca será superior a inflação real, também fazendo você perder quase tudo em cerca de 15 anos. A situação é ainda pior com os imóveis rurais e veículos, basta fazer as contas. Caso o dinheiro que você receba em troca do seu trabalho seja suficiente apenas para comprar comida, vestuário e moradia, você já sabe que é um escravo né?… Precisamos entender que a escravidão não acabou, apenas foi democratizada. Hoje a escravidão é financeira, nós somos os castiços e os donos do dinheiro são o senhorio. Os donos do dinheiro são os Globalistas e os Estados seus fantoches. O esquema é simples: fazer todo mundo trabalhar em troca de algo que perde 100% do valor a cada 10 anos, ou seja o dinheiro. Se você pudesse trabalhar em troca de algo que aumentasse de valor acima da inflação real a cada 10 anos você finalmente conquistaria sua liberdade financeira e deixaria de ser escravo. Pois bem, isso já é possível, e não se trata de ouro ou imóveis e sim sobre o Bitcoin, que sobe de valor mais de 100% a cada 10 anos, com a vantagem de ser inconfiscável e de fácil transferência para seus herdeiros quando você morrer, através de uma simples transação LockTime feita em vida. Portanto, mesmo que você não tenha dinheiro para comprar Bitcoin, passar a aceitar Bitcoin em troca de seus produtos e serviços é a única forma de se libertar da escravidão financeira. A carta de alforria financeira proporcionada pelo Bitcoin não é imediata, pois a velocidade da sua libertação depende do quanto você está disposto a aprender sobre o assunto. Eu estou aqui para te ajudar, caso queira. No futuro o Bitcoin estará tão presente na sua vida quanto o pix e o cartão de crédito, você querendo ou não. Assim como o cartão de crédito foi a evolução do cheque pós-datado e o pix a evolução do cartão, o Bitcoin e outras criptomoedas serão a evolução de todos esses meios de pagamento. O que te ofereço é a oportunidade de abolição da sua escravatura antes dos demais escravos acordarem para a realidade, afinal a história sempre se repete: desde o ano de 1300 a.c. a escravidão era defendida pelos próprios escravos, que mais cedo ou mais tarde, foram libertados por Moisés em êxodo 11 da Bíblia Sagrada e hoje o povo de israel se tornou a nação mais rica do mundo. A mesma história se repetiu na Roma Antiga: com o pão e circo. Da mesma forma todo esse império escravocrata ruiu porque mais cedo ou mais tarde os escravos se revoltam, bastam as coisas piorarem bastante. O atual regime de escravidão teve início com a queda do padrão-ouro para impressão do dinheiro no ano de 1944. A escravidão apenas ficou mais sofisticada, pois em vez de pagar os escravos com cerveja como no Egito Antigo ou com pão e circo como na Roma Antiga, passou-se a pagar os escravos com dinheiro sem lastro, ou seja dinheiro inventado, criado do nada, sem qualquer representação com a riqueza real da economia. Mesmo sendo a escravidão atual mais sofisticada, que deixou de ser física para ser financeira, o que torna a mentira mais bem contada, mais cedo ou mais tarde os escravos modernos irão acordar, basta as coisas piorarem mais ou perceberem que todos os bens e serviços do mundo não representam nem 1% de todo o dinheiro que impresso sem lastro. Em outras palavras, se os donos de todo o dinheiro do mundo resolvessem utilizá-lo para comprar tudo o que existe à venda, o preço do quilo do café subiria para R$ 297.306,00 e o preço médio dos imóveis subiria para um número tão grande que sequer caberia nesta folha de papel. Hoje, o dinheiro não vale nada, seus donos sabem disso e optam por entregar o dinheiro aos poucos para os escravos em troca do seu trabalho, para manter o atual regime o máximo de tempo possível. Mesmo assim, o atual regime de escravidão financeira está com os dias contados e depende de você se posicionar antes do efeito manada. Nunca é tarde para entrar no Bitcoin, mesmo ele tendo uma quantidade de emissão limitada, seu valor subirá infinitamente. A menor unidade do Bitcoin é o satoshi, cuja abreviação é sats. Diferente do centavo, cada sat vale um centésimo milionésimo de bitcoin. Hoje (25/05/25), cada unidade de Bitcoin equivale a setecentos mil reais. Logo, cada R$ 0,01 equivale à 0,007 sats. Lembrando que o centavo é um real dividido por cem e o sat é um bitcoin dividido por cem milhões, por isso ainda não existe a paridade entre 1 centavo de real e 1 sat. Essa paridade será alcançada quando um Bitcoin passar a valer um milhão de reais. Com a velocidade que nosso dinheiro está perdendo valor isso não irá demorar muito. Utilizando dados econômicos avançados, prevejo que cada unidade de Bitcoin passará a valer hum milhão de reais até o ano de 2029, assim equiparando 1 sat para cada R$ 0,01. Nesse momento, certamente muitos empresários, comerciantes e profissionais liberais passarão a aceitar o Bitcoin como forma de pagamento pelos seus produtos e serviços, assim como o cheque foi substituído pelo cartão de crédito e o cartão pelo pix. Sabendo disso, você pode entrar na onda de transição no futuro junto com a manada e perder essa alta valorização, ou passar a aceitar Bitcoin agora pelos seus produtos e serviços, assinando assim, a própria carta de alforria da sua escravidão financeira. É importante dizer que os próprios globalistas e governos estão trocando dinheiro por Bitcoin como nunca na história e mesmo que eles adquiram todos os bitcoins disponíveis, ainda assim não será mais possível manter seu regime de escravidão financeira funcionando porque a emissão de Bitcoin é limitada, sendo impossível criar Bitcoin sem lastro, como é feito com o dinheiro hoje. Com o presente artigo, te ofereço a oportunidade de conquistar seus primeiros sats agora, de forma segura e independente, sem precisar de corretoras, bancos, intermediários ou terceiros, basta você querer pois toda a informação necessária está disponível na internet gratuitamente. Se ainda assim você quiser continuar sendo escravo financeiro, depois não adiantar se arrepender quando as janelas de oportunidade se fecharem, o Drex for implantado, papel moeda restringido e sua vida piorar bastante. Importante mencionar que a Lei Brasileira ainda permite a movimentação de até R$ 30.000,00 em Bitcoin por mês sem a necessidade de declaração à Receita Federal e que esse direito pode deixar de existir a qualquer momento, e que quando o Drex for implantado você perderá diversos outros direitos, dentre ele a liberdade de gastar seu dinheiro como quiser e o sigilo. Ofereço ainda, a oportunidade de você baixar uma carteira de Bitcoin gratuita e segura no seu aparelho de celular que funciona de forma semelhante a um banco digital como Nubank e Pagseguro por exemplo, para poder começar à receber Bitcoin pelos seus produtos e serviços agora, de forma fácil e gratuita. Utilizando o qrcode abaixo você ainda ganha alguns sats de graça, promoção válida até o dia 29/05/25 e patrocinada pela Corretora Blink de El Salvador, onde o Bitcoin já é moeda oficial do país, basta acessar o link e instalar o aplicativo: https://get.blink.sv/btcvale
Aviso: disponibilizei o link da carteira de Bitcoin da Corretora Blink apenas como exemplo de como é fácil aceitar Bitcoin como forma de pagamento pelos seus produtos e serviços. Não recomento depender de qualquer corretora para guardar seus valores em Bitcoin. A melhor forma de fazer isso é mantendo dois computadores ou notebook em casa, um conectado à internet com memória em disco disponível de 1 terabyte ou mais para armazenar e visualizar suas transações e outro computador ou notebook desconectado da internet para armazenar suas senhas e chaves privadas para assinar as transações via pendrive. Somente assim você estará 100% livre e seguro. Importante ainda fazer backup em vários CDs com criptografia do seu computador ou notebook que assina as transações, assim também ficando 100% livre e seguro para restaurar sua carteira em qualquer outro computador caso necessário. Todas as instruções de como fazer isso já estão disponíveis gratuitamente na internet. Caso deseje contratar uma consultoria pessoal que inclui aulas particulares por vídeo conferência, onde você aprenderá:
→ Tudo o que precisa saber sobre Bitcoin e demais criptomoedas; → Sistema operacional Linux; → Como instalar sua carteira de Bitcoin em dois computadores para assinaturas air gapped; → Se manter 100% livre e seguro. → Com carga horária à combinar conforme sua disponibilidade.
O custo do investimento pelo meu serviço individual para esse tipo de consultoria é de 204.000 sats (R$ 1.543,46 na cotação atual) valor válido até 31/07/25, interessados entrar em contato por aqui ou através da Matrix: @davipinheiro:matrix.org https://davipinheiro.com/voce-e-escravo-e-nem-sabe-eu-vou-te-provar-agora/
-
 @ f0fcbea6:7e059469
2025-05-27 18:08:04
@ f0fcbea6:7e059469
2025-05-27 18:08:04Muita gente, hoje em dia, acha que a leitura já não é tão necessária quanto foi no passado. O rádio e a televisão acabaram assumindo as funções que outrora pertenciam à mídia impressa, da mesma maneira que a fotografia assumiu as funções que outrora pertenciam à pintura e às artes gráficas. Temos de reconhecer - é verdade - que a televisão cumpre algumas dessas funções muito bem; a comunicação visual dos telejornais, por exemplo, tem impacto enorme. A capacidade do rádio em transmitir informações enquanto estamos ocupados - dirigindo um carro, por exemplo - é algo extraordinário, além de nos poupar muito tempo. No entanto, é necessário questionar se as comunicações modernas realmente aumentam o conhecimento sobre o mundo à nossa volta.
Talvez hoje saibamos mais sobre o mundo do que no passado. Dado que o conhecimento é pré-requisito para o entendimento, trata-se de algo bom. Mas o conhecimento não é um pré-requisito tão importante ao entendimento quanto normalmente se supõe. Não precisamos saber tudo sobre determinada coisa para que possamos entendê-la. Uma montanha de fatos pode provocar o efeito contrário, isto é, pode servir de obstáculo ao entendimento. Há uma sensação, hoje em dia, de que temos acesso a muitos fatos, mas não necessariamente ao entendimento desses fatos.
Uma das causas dessa situação é que a própria mídia é projetada para tornar o pensamento algo desnecessário - embora, é claro, isso seja apenas mera impressão. O ato de empacotar ideias e opiniões intelectuais é uma atividade à qual algumas das mentes mais brilhantes se dedicam com grande diligência. O telespectador, o ouvinte, o leitor de revistas - todos eles se defrontam com um amálgama de elementos complexos, desde discursos retóricos minuciosamente planejados até dados estatísticos cuidadosamente selecionados, cujo objetivo é facilitar o ato de "formar a opinião" das pessoas com esforço e dificuldade mínimos. Por vezes, no entanto, o empacotamento é feito de maneira tão eficiente, tão condensada, que o telespectador, o ouvinte ou o leitor não conseguem formar sua opinião. Em vez disso, a opinião empacotada é introjetada em sua mente mais ou menos como uma gravação é inserida no aparelho de som. No momento apropriado, aperta-se o play e a opinião é "tocada". Eles reproduzem a opinião sem terem pensado a respeito.
-
 @ cae03c48:2a7d6671
2025-05-27 22:00:38
@ cae03c48:2a7d6671
2025-05-27 22:00:38Bitcoin Magazine

Bitlux Announced Private Jet Cards Accepting Bitcoin and Crypto PaymentsBitlux, a global private aviation company with charter solutions based on blockchain technology, just announced the industry’s first cryptocurrency-enabled Private Jet Card Program at the 2025 Bitcoin Conference.
“Bitcoin 2025 convenes innovators who are defining the future of money, mobility, and freedom,” stated Patel. “Our Jet Card is a natural continuation of that dialogue. We’re not just keeping up – we’re setting the new benchmark for what’s possible in luxury flight.”
The Bitlux Jet Card allows clients to fund their accounts using Bitcoin, and other cryptocurrencies. By integrating Bitcoin payments with private aviation, Bitlux aims to deliver transparency, and control for high-frequency private flyers
“The private aviation industry has needed a reboot for a long time,” said Bitlux CEO Kyle Patel. “We didn’t simply put a new face on the old model – we reconstructed it with transparency, efficiency, and user control as the guiding principles. This card is for individuals who demand more from their travel experience and their payment infrastructure.”
The card includes fixed hourly rates and does not apply blackout dates, peak surcharges, or additional fees. Payments are held in escrow until the completion of the flight. The program allows access to a global fleet, includes Wi-Fi on domestic flights, and permits cancellation of one-way bookings after reservation.
Bitlux offers four jet cards: Ascent, Cardinal, Sovereignty, and Nomad, corresponding to cabin classes that include midsize, super-midsize, large, and ultra-long haul. Operational terms specify a 48 hour callout on off-peak days, 36 peak days, and minimum daily flight times that vary depending on the aircraft size.
“Our clients are global citizens – entrepreneurs, investors, tech entrepreneurs – who conduct business in real-time environments,” said Patel. “They don’t have time for ambiguous language or antiquated payment structures. We’re coming to them where they are, with a smarter, safer way to fly.”
This post Bitlux Announced Private Jet Cards Accepting Bitcoin and Crypto Payments first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 91bea5cd:1df4451c
2025-05-16 11:07:16
@ 91bea5cd:1df4451c
2025-05-16 11:07:16Instruções:
- Leia cada pergunta cuidadosamente.
- Escolha a opção (A, B, C ou D) que melhor descreve você na maioria das situações. Seja o mais honesto possível.
- Anote a letra correspondente à sua escolha para cada pergunta.
- No final, some quantas vezes você escolheu cada letra (A, B, C, D).
- Veja a seção de resultados para interpretar sua pontuação.
Teste de Temperamento
1. Em um evento social (festa, reunião), como você geralmente se comporta? A) Sou o centro das atenções, converso com todos, faço piadas e animo o ambiente. B) Tomo a iniciativa, organizo atividades ou discussões, e gosto de liderar conversas. C) Prefiro observar, conversar em grupos menores ou com pessoas que já conheço bem, e analiso o ambiente. D) Sou tranquilo, ouvinte, evito chamar atenção e me adapto ao ritmo do grupo.
2. Ao enfrentar um novo projeto ou tarefa desafiadora no trabalho ou estudo: A) Fico entusiasmado com a novidade, tenho muitas ideias iniciais, mas posso me distrair facilmente. B) Defino metas claras, crio um plano de ação rápido e foco em alcançar resultados eficientemente. C) Analiso todos os detalhes, planejo meticulosamente, prevejo possíveis problemas e busco a perfeição. D) Abordo com calma, trabalho de forma constante e organizada, e prefiro um ambiente sem pressão.
3. Como você geralmente reage a críticas? A) Tento levar na esportiva, talvez faça uma piada, mas posso me magoar momentaneamente e logo esqueço. B) Defendo meu ponto de vista vigorosamente, posso ficar irritado se sentir injustiça, mas foco em corrigir o problema. C) Levo muito a sério, analiso profundamente, posso me sentir magoado por um tempo e repenso minhas ações. D) Escuto com calma, considero a crítica objetivamente e tento não levar para o lado pessoal, buscando a paz.
4. Qual seu estilo de tomada de decisão? A) Sou impulsivo, decido rapidamente com base no entusiasmo do momento, às vezes me arrependo depois. B) Sou decidido e rápido, foco no objetivo final, às vezes sem considerar todos os detalhes ou sentimentos alheios. C) Sou ponderado, analiso todas as opções e consequências, demoro para decidir buscando a melhor escolha. D) Sou cauteloso, prefiro evitar decisões difíceis, busco consenso ou adio se possível.
5. Como você lida com rotina e repetição? A) Acho entediante rapidamente, preciso de variedade e novidade constante para me manter engajado. B) Tolero se for necessário para atingir um objetivo, mas prefiro desafios e mudanças que eu controlo. C) Aprecio a ordem e a previsibilidade, me sinto confortável com rotinas bem estabelecidas. D) Adapto-me bem à rotina, acho confortável e seguro, não gosto de mudanças bruscas.
6. Em uma discussão ou conflito: A) Tento aliviar a tensão com humor, expresso meus sentimentos abertamente, mas não guardo rancor. B) Sou direto e assertivo, defendo minha posição com firmeza, posso parecer confrontador. C) Evito confronto direto, mas fico remoendo o problema, analiso os argumentos e posso guardar ressentimento. D) Busco a conciliação, tento entender todos os lados, sou diplomático e evito o conflito a todo custo.
7. Como você expressa seus sentimentos (alegria, tristeza, raiva)? A) Expresso de forma aberta, intensa e visível, minhas emoções mudam rapidamente. B) Expresso de forma direta e forte, principalmente a raiva ou a determinação, controlo emoções "fracas". C) Tendo a internalizar, minhas emoções são profundas e duradouras, posso parecer reservado. D) Sou contido na expressão emocional, mantenho a calma externamente, mesmo que sinta algo internamente.
8. Qual seu nível de energia habitual? A) Alto, sou muito ativo, falante e entusiasmado, gosto de estar em movimento. B) Muito alto e direcionado, tenho muita energia para perseguir meus objetivos e liderar. C) Variável, posso ter picos de energia para projetos que me interessam, mas também preciso de tempo quieto para recarregar. D) Moderado e constante, sou calmo, tranquilo, prefiro atividades menos agitadas.
9. Como você organiza seu espaço de trabalho ou sua casa? A) Pode ser um pouco caótico e desorganizado, com muitas coisas interessantes espalhadas. B) Organizado de forma funcional para máxima eficiência, focado no essencial para as tarefas. C) Extremamente organizado, metódico, cada coisa em seu lugar, prezo pela ordem e estética. D) Confortável e prático, não necessariamente impecável, mas funcional e sem excessos.
10. O que mais te motiva? A) Reconhecimento social, diversão, novas experiências e interações. B) Poder, controle, desafios, alcançar metas ambiciosas e resultados concretos. C) Qualidade, significado, fazer as coisas da maneira certa, compreensão profunda. D) Paz, estabilidade, harmonia nos relacionamentos, evitar estresse e pressão.
11. Como você reage a imprevistos ou mudanças de plano? A) Adapto-me rapidamente, às vezes até gosto da novidade, embora possa atrapalhar meus planos iniciais. B) Fico irritado com a perda de controle, mas rapidamente busco uma solução alternativa para manter o objetivo. C) Sinto-me desconfortável e ansioso, preciso de tempo para reavaliar e replanejar cuidadosamente. D) Aceito com calma, sou flexível e me ajusto sem muito alarde, desde que não gere conflito.
12. Qual o seu maior medo (em termos gerais)? A) Ser rejeitado, ignorado ou ficar entediado. B) Perder o controle, parecer fraco ou incompetente. C) Cometer erros graves, ser inadequado ou imperfeito. D) Conflitos, pressão, tomar decisões erradas que afetem a estabilidade.
13. Como você costuma passar seu tempo livre? A) Socializando, saindo com amigos, buscando atividades novas e divertidas. B) Engajado em atividades produtivas, esportes competitivos, planejando próximos passos. C) Lendo, estudando, refletindo, dedicando-me a hobbies que exigem atenção e cuidado. D) Relaxando em casa, assistindo filmes, lendo tranquilamente, passando tempo com a família de forma calma.
14. Ao trabalhar em equipe: A) Sou o animador, trago ideias, conecto as pessoas, mas posso ter dificuldade em focar nos detalhes. B) Assumo a liderança naturalmente, delego tarefas, foco nos resultados e mantenho todos na linha. C) Sou o planejador e o crítico construtivo, atento aos detalhes, garanto a qualidade, mas posso ser muito exigente. D) Sou o pacificador e o colaborador, ajudo a manter a harmonia, realizo minhas tarefas de forma confiável.
15. Como você lida com prazos? A) Muitas vezes deixo para a última hora, trabalho melhor sob a pressão do prazo final, mas posso me atrapalhar. B) Gosto de terminar bem antes do prazo, vejo o prazo como um desafio a ser superado rapidamente. C) Planejo o tempo cuidadosamente para cumprir o prazo com qualidade, fico ansioso se o tempo fica curto. D) Trabalho em ritmo constante para cumprir o prazo sem estresse, não gosto de correria.
16. Qual destas frases mais te descreve? A) "A vida é uma festa!" B) "Se quer algo bem feito, faça você mesmo (ou mande fazer do seu jeito)." C) "Tudo tem um propósito e um lugar certo." D) "Devagar se vai ao longe."
17. Em relação a regras e procedimentos: A) Gosto de flexibilidade, às vezes acho as regras limitantes e tento contorná-las. B) Uso as regras a meu favor para atingir objetivos, mas não hesito em quebrá-las se necessário e se eu puder controlar as consequências. C) Sigo as regras rigorosamente, acredito que elas garantem ordem e qualidade. D) Respeito as regras para evitar problemas, prefiro seguir o fluxo estabelecido.
18. Como você reage quando alguém está emocionalmente abalado? A) Tento animar a pessoa, conto piadas, ofereço distração e companhia. B) Ofereço soluções práticas para o problema, foco em resolver a situação que causou o abalo. C) Escuto com empatia, ofereço apoio profundo e tento compreender a dor da pessoa. D) Mantenho a calma, ofereço um ouvido atento e um ombro amigo, sem me deixar abalar muito.
19. Que tipo de filme ou livro você prefere? A) Comédias, aventuras, romances leves, algo que me divirta e me mantenha entretido. B) Ação, suspense, biografias de líderes, estratégias, algo que me desafie ou inspire poder. C) Dramas profundos, documentários, mistérios complexos, ficção científica filosófica, algo que me faça pensar e sentir. D) Histórias tranquilas, dramas familiares, romances amenos, natureza, algo que me relaxe e traga conforto.
20. O que é mais importante para você em um relacionamento (amizade, amoroso)? A) Diversão, cumplicidade, comunicação aberta e espontaneidade. B) Lealdade, objetivos em comum, apoio mútuo nas ambições. C) Compreensão profunda, fidelidade, apoio emocional e intelectual. D) Harmonia, estabilidade, aceitação mútua e tranquilidade.
21. Se você ganhasse na loteria, qual seria sua primeira reação/ação? A) Faria uma grande festa, viajaria pelo mundo, compraria presentes para todos! B) Investiria estrategicamente, planejaria como multiplicar o dinheiro, garantiria o controle financeiro. C) Pesquisaria as melhores opções de investimento, faria um plano detalhado de longo prazo, doaria para causas significativas. D) Guardaria a maior parte em segurança, faria algumas melhorias práticas na vida, evitaria mudanças drásticas.
22. Como você se sente em relação a riscos? A) Gosto de arriscar se a recompensa parecer divertida ou excitante, sou otimista. B) Calculo os riscos e assumo-os se acreditar que a recompensa vale a pena e que posso controlar a situação. C) Evito riscos desnecessários, prefiro a segurança e a previsibilidade, analiso tudo antes de agir. D) Desgosto de riscos, prefiro caminhos seguros e comprovados, a estabilidade é mais importante.
23. Sua memória tende a focar mais em: A) Momentos divertidos, pessoas interessantes, experiências marcantes (embora possa esquecer detalhes). B) Sucessos, fracassos (para aprender), injustiças cometidas contra você, quem te ajudou ou atrapalhou. C) Detalhes precisos, conversas significativas, erros cometidos (por você ou outros), sentimentos profundos. D) Fatos objetivos, rotinas, informações práticas, geralmente de forma neutra.
24. Quando aprende algo novo, você prefere: A) Experimentar na prática imediatamente, aprender fazendo, mesmo que cometa erros. B) Entender o objetivo e a aplicação prática rapidamente, focar no essencial para usar o conhecimento. C) Estudar a fundo a teoria, entender todos os porquês, buscar fontes confiáveis e dominar o assunto. D) Aprender em um ritmo calmo, com instruções claras e passo a passo, sem pressão.
25. Se descreva em uma palavra (escolha a que mais se aproxima): A) Entusiasmado(a) B) Determinado(a) C) Criterioso(a) D) Pacífico(a)
26. Como você lida com o silêncio em uma conversa? A) Sinto-me desconfortável e tento preenchê-lo rapidamente com qualquer assunto. B) Uso o silêncio estrategicamente ou o interrompo para direcionar a conversa. C) Posso apreciar o silêncio para refletir, ou me sentir um pouco ansioso dependendo do contexto. D) Sinto-me confortável com o silêncio, não sinto necessidade de preenchê-lo.
27. O que te deixa mais frustrado(a)? A) Tédio, falta de reconhecimento, ser ignorado. B) Incompetência alheia, falta de controle, obstáculos aos seus planos. C) Desorganização, falta de qualidade, injustiça, superficialidade. D) Conflitos interpessoais, pressão excessiva, desordem emocional.
28. Qual a sua relação com o passado, presente e futuro? A) Foco no presente e nas oportunidades imediatas, otimista em relação ao futuro, esqueço o passado facilmente. B) Foco no futuro (metas) e no presente (ações para alcançá-las), aprendo com o passado mas não me prendo a ele. C) Reflito muito sobre o passado (aprendizados, erros), analiso o presente e planejo o futuro com cautela, às vezes com preocupação. D) Vivo o presente de forma tranquila, valorizo a estabilidade e a continuidade do passado, vejo o futuro com serenidade.
29. Se você tivesse que organizar um evento, qual seria seu papel principal? A) Relações públicas, divulgação, animação, garantir que todos se divirtam. B) Coordenação geral, definição de metas, delegação de tarefas, garantir que tudo aconteça conforme o planejado (por você). C) Planejamento detalhado, logística, controle de qualidade, garantir que nada dê errado. D) Suporte, resolução de problemas de forma calma, garantir um ambiente harmonioso.
30. Qual ambiente de trabalho te agrada mais? A) Dinâmico, social, com muita interação, flexibilidade e novidades. B) Competitivo, desafiador, focado em resultados, onde eu possa liderar ou ter autonomia. C) Estruturado, quieto, onde eu possa me concentrar, com padrões claros de qualidade e tempo para análise. D) Estável, cooperativo, sem pressão, com relacionamentos harmoniosos e tarefas previsíveis.
Calculando seus Resultados:
Agora, conte quantas vezes você escolheu cada letra:
- Total de A: ______
- Total de B: ______
- Total de C: ______
- Total de D: ______
A letra (ou as letras) com a maior pontuação indica(m) seu(s) temperamento(s) dominante(s).
Interpretação dos Resultados:
-
Se sua maior pontuação foi A: Temperamento SANGUÍNEO Dominante
- Características: Você é extrovertido, otimista, sociável, comunicativo, entusiasmado e adora novidades. Gosta de ser o centro das atenções, faz amigos facilmente e contagia os outros com sua energia. É criativo e espontâneo.
- Pontos Fortes: Carismático, inspirador, adaptável, bom em iniciar relacionamentos e projetos, perdoa facilmente.
- Desafios Potenciais: Pode ser indisciplinado, desorganizado, impulsivo, superficial, ter dificuldade em focar e terminar tarefas, e ser muito dependente de aprovação externa.
-
Se sua maior pontuação foi B: Temperamento COLÉRICO Dominante
- Características: Você é enérgico, decidido, líder nato, orientado para metas e resultados. É ambicioso, assertivo, direto e não tem medo de desafios ou confrontos. Gosta de estar no controle e é muito prático.
- Pontos Fortes: Determinado, eficiente, líder natural, bom em tomar decisões e resolver problemas, autoconfiante.
- Desafios Potenciais: Pode ser impaciente, dominador, teimoso, insensível aos sentimentos alheios, propenso à raiva e a "atropelar" os outros para atingir seus objetivos.
-
Se sua maior pontuação foi C: Temperamento MELANCÓLICO Dominante
- Características: Você é introvertido, analítico, sensível, perfeccionista e profundo. É leal, dedicado, aprecia a beleza e a ordem. Tende a ser pensativo, criterioso e busca significado em tudo. Leva as coisas a sério.
- Pontos Fortes: Detalhista, organizado, criativo (em profundidade), leal, empático, comprometido com a qualidade e a justiça.
- Desafios Potenciais: Pode ser pessimista, excessivamente crítico (consigo e com os outros), indeciso (pela análise excessiva), guardar ressentimentos, ser propenso à tristeza e ao isolamento.
-
Se sua maior pontuação foi D: Temperamento FLEUMÁTICO Dominante
- Características: Você é calmo, tranquilo, equilibrado e diplomático. É observador, paciente, confiável e fácil de conviver. Evita conflitos, busca harmonia e estabilidade. É um bom ouvinte e trabalha bem sob rotina.
- Pontos Fortes: Pacífico, estável, confiável, bom ouvinte, diplomático, eficiente em tarefas rotineiras, mantém a calma sob pressão.
- Desafios Potenciais: Pode ser indeciso, procrastinador, resistente a mudanças, parecer apático ou sem entusiasmo, ter dificuldade em se impor e expressar suas próprias necessidades.
Combinações de Temperamentos:
É muito comum ter pontuações altas em duas letras. Isso indica uma combinação de temperamentos. Por exemplo:
- Sanguíneo-Colérico: Extrovertido, enérgico, líder carismático, mas pode ser impulsivo e dominador.
- Sanguíneo-Fleumático: Sociável e agradável, mas pode ter dificuldade com disciplina e iniciativa.
- Colérico-Melancólico: Líder focado e detalhista, muito capaz, mas pode ser excessivamente crítico e exigente.
- Melancólico-Fleumático: Quieto, confiável, analítico, mas pode ser indeciso e resistente a riscos.
Importante: Este teste é uma ferramenta de autoconhecimento. Ninguém se encaixa perfeitamente em uma única caixa. Use os resultados para entender melhor suas tendências naturais, seus pontos fortes e as áreas onde você pode buscar equilíbrio e desenvolvimento.
-
 @ cae03c48:2a7d6671
2025-05-27 22:00:37
@ cae03c48:2a7d6671
2025-05-27 22:00:37Bitcoin Magazine

Asigna Raises $3M Funding and Launches Bitcoin Multisig v2 UpgradeAsigna, a smart multisig vault operator for Bitcoin, has raised $3 million in a funding round led by Hivemind and Tykhe Block Ventures, with participation from Sats Ventures, Trust Machines, and others, according to an exclusive press release sent to Bitcoin Magazine. The raise follows a pre-seed round led by Portal Ventures.
“With Asigna, we are establishing foundational infrastructure for institutions and large holders to securely and confidently participate in the evolving Bitcoin ecosystem,” said the Co-Founder of Asigna Viven. “There’s a critical need for robust, transparent, and programmable non-custodial solutions, and the multisig infrastructure is at the heart of this transformation.”
Alongside the funding, Asigna is launching its v2 upgrade, which includes support for Embedded Apps and a developer SDK. The update enables developers to integrate multisig functionality directly into Bitcoin applications.
“Asigna’s innovative approach to Bitcoin security and its seamless integration with Layer-2 protocols make it a game-changer for institutional investors,” said the Senior Investment Principal at Hivemind Capital Kayla Phillips. “We are thrilled to support their mission to provide robust and transparent non-custodial solutions for the evolving Bitcoin ecosystem.”
The update also adds a custom dashboard, BTC swaps, and new tools like the Connection SDK and Multisig SDK, allowing for vault creation, transaction management, and app integration. Other features include sub accounts, email notifications, governance, customizable signer permissions, privacy mode, and advanced UTXO management.
“What’s unique about Asigna is that, unlike many other onchain smart wallet implementations, it is fully native to the Bitcoin layer, with no smart contract risks,” said the Co-Founder of Asigna Vlad. “We don’t directly interact with private keys and account owners can use any wallet to sign their transactions. Which means these multisig wallets can never be frozen or lost, regardless of what happens to Asigna. As it should be”.
Bitcoin has recently risen to a $2.2 trillion market cap and with a growing DeFi sector with over $6 billion in Total Value Locked (TVL), the company plans to use the new funding to provide their clients with access to DeFi and yield generation through staking and lending with a white-glove service.
This post Asigna Raises $3M Funding and Launches Bitcoin Multisig v2 Upgrade first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ d360efec:14907b5f
2025-05-27 15:46:26
@ d360efec:14907b5f
2025-05-27 15:46:26 -
 @ 04c915da:3dfbecc9
2025-05-15 15:31:45
@ 04c915da:3dfbecc9
2025-05-15 15:31:45Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ bf47c19e:c3d2573b
2025-05-27 14:57:56
@ bf47c19e:c3d2573b
2025-05-27 14:57:56Srpski prevod knjige "The Little Bitcoin Book"
Zašto je Bitkoin bitan za vašu slobodu, finansije i budućnost?
Verovatno ste čuli za Bitkoin u vestima ili da o njemu raspravljaju vaši prijatelji ili kolege. Kako to da se cena stalno menja? Da li je Bitkoin dobra investicija? Kako to uopšte ima vrednost? Zašto ljudi stalno govore o tome kao da će promeniti svet?
"Mala knjiga o Bitkoinu" govori o tome šta nije u redu sa današnjim novcem i zašto je Bitkoin izmišljen da obezbedi alternativu trenutnom sistemu. Jednostavnim rečima opisuje šta je Bitkoin, kako funkcioniše, zašto je vredan i kako utiče na individualnu slobodu i mogućnosti ljudi svuda - od Nigerije preko Filipina do Venecuele do Sjedinjenih Država. Ova knjiga takođe uključuje odeljak "Pitanja i odgovori" sa nekim od najčešće postavljanih pitanja o Bitkoinu.
Ako želite da saznate više o ovom novom obliku novca koji i dalje izaziva interesovanje i usvajanje širom sveta, onda je ova knjiga za vas.
-
 @ bf47c19e:c3d2573b
2025-05-27 14:54:03
@ bf47c19e:c3d2573b
2025-05-27 14:54:03Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- 5 Razloga Zašto je Novac Važan za Vas, Individualno
- 3 Razloga Zašto je Novac Važan za Društvo u Celini
- Zašto ljudi mrze novac?

Novac vs trenuci – da li oni treba da budu u sukobu? Kakva je uloga novca?
Novac je nepredvidiva zver modernog društva – neki ga veličaju sa stalnom željom da steknu više, dok ga drugi demonizuju i kažu da je pohlepa srž društvenih problema. Tokom mnogih godina svog života, ja sam često prelazio sa jednog na drugo gledište, i naučio mnogo toga upoznajući druge ljude koji žive na oba kraja ovog spektra. Kao i kod mnogih složenih tema, istina leži negde u sredini.
Novac je važan zato što on može da pomogne u uklanjanju materijalnih želja i patnji – omogućavanjem da preuzmete kontrolu nad svojim životom i da brinete o voljenima. Novac podiže životni standard društva omogućavanjem trgovine, a pritom minimalizuje potrebu za poverenjem.
Na novac možemo gledati kao na način da svoj uloženi trud sačuvamo u odredjenom obliku, i da ga vremenom prenesemo, tako da možemo da uživamo u plodovima svog rada. Novac kao alat je jedna od najvažnijih stvari za rast civilizacije. Na nesreću, mnogi su vremenom zlostavljali novac, ali sa dobrim razlogom: način na koji naš novac danas funkcioniše dovodi do duboko podeljenog društva – što ću i objasniti.
5 Razloga Zašto je Novac Važan za Vas, Individualno
Novac je važan za rast bogatstva, što je malo drugačije od toga da imamo veliku platu ili jednostavno zarađivati velike količine novca. Bogatstvo je otklanjanje želja, kako bi mogli da obratimo više pažnje na neke korisnije stvari u životu, od pukog preživljavanja i osnovnih udobnosti.
Bogata osoba je ona koja zaradi više novca nego što potroši, i koja ga čuva – ona čuva svoj rad tokom vremena. Uporedite ovo sa visoko plaćenim lekarom koji živi u velikoj vili sa hipotekom i sa Mercedesom na lizing. Iako ova osoba ima visoke prihode, ona takođe ima velike rashode u vidu obaveze plaćanja te hipoteke i lizinga. Te obaveze sprečavaju ovu osobu da uživa u istinskim blagodetima novca i bogatstva koje one predstavljaju:
1. Sloboda od potrebe za radom
Bez bogatstva, vi morate da radite da biste preživeli. Dostizanjem bogatstva i odredjenom imovinom koja vam donosi novac bez potrebe da vi trošite svoje vreme, vi možete da oslobodite svoj raspored. Više ne zavisite od posla koji mrzite, i nemorate da provodite 40 sati nedeljno odvojeni od porodice, samo da biste se pobrinuli za svoje osnovne potrebe. Dobijanje otkaza u padu ekonomije neće vas dovesti do finansijske propasti ili nečeg goreg.
2. Kontrola nad time kako vi trošite svoje vreme
Kada steknete bogatstvo, vi možete da odlučite kako želite da provodite svoje vreme. Kada se nalazimo u trci pacova i radimo 40+ sati nedeljno, često se naviknemo da novac trošimo onda kada imamo slobodnog vremena. Idemo na lepe večere ili idemo na skupe odmore. Međutim, sa više vremena, a možda čak i sa manje novca, mi možemo da imamo isto ili više uživanja živeći usporenije.
Razmislite o ovome – ukoliko imate samo 1 nedelju slobodno od posla, vi onda morate da kupite onaj mnogo skuplji let u Petak uveče koji se vraća u sledeću Nedelju, kako biste maksimalno iskoristili svoje vreme na nekom egzotičnom mestu za odmor. Međutim, ukoliko ste u mogućnosti da izdržavate sebe bez potrebe da mnogo vremena provodite na poslu, vi onda možete u Utorak da krenete jeftinijim letom i vratite se u sledeću Sredu. Takođe nećete osećati toliki pritisak da se opustite u uživanju tokom vaše nedelje u inostranstvu – možda ćete čak moći i da ostanete duže i da istražujete više, bez plaćanja skupih turističkih agencija i hotela kako bi organizovali vaše kraće putovanje.
3. Sposobnost da pomažete vašim prijateljima i porodici
Onda kada novca imate na pretek, možete poboljšati svoje odnose sa prijateljima i porodicom ne samo kroz dodatno slobodno vreme koje provodite sa njima, već i sa samim novcem. Ako je vašem prijatelju potrebna hitna operacija, vi možete da mu izadjete u susret i pomognete mu da stane na svoje noge. Ukoliko vam je tetka bolesna, vi možete da provedete vreme pored nje, umesto da je pozovete na kratko dok putujete prema kući vraćajući se nakon celog dana provedenog u kancelariji.
4. Smanjen finansijski stres
Stres je sveobuhvatno i opasno stanje modernog doba, sa kojim gotovo svi mi živimo u nekoj odredjenoj meri. Povezan je sa lošim zdravljem, sa preko 43% svih odraslih koji kažu da pate od odredjenih zdravstvenih problema uzrokovanih stresom. Stres zbog posla pogađa 83% zaposlenih.
Pravo bogatstvo – koje znači eliminaciju želja i potreba – može da ukloni ovaj stres i njegove negativne uticaje na druge delove života. Ovo bi čak moglo da ukloni većinu stresa u vašem životu, uzimajući u obzir da je uzrok stresa broj 1 upravo novac.
5. Bolje možete da pomognete vašoj zajednici
Mnogi od nas žele da volontiraju u svojim zajednicama i pomognu onima koja je pomoć preko potrebna, ali nisu u stanju da pronađu slobodnog vremena i energije zbog svog posla, porodice i društvenih aktivnosti koje nas mentalno i fizički čine srećnima, zdravima i hranjenima. Sa bogatstvom, mi možemo da posvetimo vreme koje nam je potrebno za razumevanje i doprinos drugima – a ne samo da sa vremena na vreme pomognemo slanjem humanitarnog SMS-a.
Novac, koji se pametno koristi, je moćno sredstvo za poboljšanje vašeg života i života vaših najmilijih i zajednice. Međutim, novac je takođe moćno sredstvo za poboljšanje društva u celini – ukoliko je dobro strukturiran.
3 Razloga Zašto je Novac Važan za Društvo u Celini
Novac poboljšava sposobnost ljudi da trguju jedni s drugima, što podstiče određene specijalizacije. Ako je imanje vašeg komšije odlično za proizvodnju vina, a vaše je pogodno za žito, obojica možete da profitirate trgovinom. Sad oboje imate i hleb i vino, umesto jednog pijanog vlasnika vinograda i jednog proizvodjača žita kome je dosadno!
Novac poboljšava društvo na nekoliko načina:
1. Omogućava specijalizaciju
Kao u primeru vlasnika vinograda i proizvodjača žita, novac omogućava povećanu specijalizaciju poboljšavajući sposobnost trgovine. Svaka razmena dobara ima problem sa ‘sticajima potreba’ – oba partnera u trgovini moraju da žele ono što druga osoba ima da bi pristala na trgovinu.
Možemo da mislimo o novcu kao o dobru koje žele gotovo svi. Ovo trgovinu čini mnogo jednostavnijom – da biste stekli odredjeno dobro, sve što vam je potrebno je novac, a ne neka slučajna stvar koju prodavac tog dobra takođe želi u tom trenutku. Vremenom je upotreba novca omogućila specijalizaciju, što je povećalo kvalitet i složenost roba i usluga.
Zamislite da sami pokušate da napravite svoj telefon – a bili su potrebni milioni stručnjaka i specijalizovana oprema da bi proizveli taj uređaj. Svi ti stručnjaci i kompanije plaćaju jedni drugima u novcu, omogućavajući složenom plesu globalnih proizvođača i lanaca snabdevanja da taj telefon isporuče na dlan vaše ruke. Čak i nešto tako jednostavno kao flaša za vodu uključuje naftna polja i proizvodne pogone koji su možda hiljadama kilometara od vaše kuće.
Kada ljudi mogu da se specijalizuju, kvalitet robe i usluga može da se poveća.
2. Omogućava korisnu trgovinu uz smanjeno poverenje
Mala društva mogu mirno i produktivno da posluju bez novca koristeći usluge, “dodjem ti” i uzajamno razumevanje. Međutim, kako se društva uvećavaju, svima brzo postaje nemoguće da održavaju lične odnose i isti stepen poverenja sa svima ostalima. Sistem trgovine uslugama i međusobnog poverenja ne funkcioniše previše dobro sa putnikom koji se nalazi na proputovanju kroz grad, i provede samo 15 minuta svog života u vašoj prodavnici.
Novac minimizira poverenje potrebno za trgovinu u većim društvima. Sada više ne moram da verujem da ćete mi pomoći kasnije kada mi zatreba – mogu samo da prihvatim uplatu od vas i da to koristim da bih sebi pomogao kasnije. Jedan od mojih omiljenih mislilaca, Nick Szabo, ovo naziva ‘društvena prilagodljivost’.
3. Smanjuje upotrebu sile
Kada društvo teži upotrebi određenog oblika novca za olakšavanje trgovine, može u velikoj meri da smanji nasilje u tom društvu. Kako to može biti tako? Zar ljudi ne bi i dalje želeli da kradu jedni od drugih ili da se svete?
Ukoliko razmišljamo van uobičajnih okvira, možemo da počnemo da razumemo kako novac može da smanji nasilje. Ako ti i ja živimo u susednim zemljama i želimo nešto što druga zemlja ima, imamo dva načina da to dobijemo: uzimanjem na silu ili menjanjem nečeg našeg za to. Kao što je ranije rečeno, novac znatno olakšava trgovinu – pa ćemo postojanjem zajedničkog monetarnog sistema verovatnije radje izvršiti trgovinu nego napad na zemlju. Zašto bismo rizikovali svoje živote kad možemo samo mirno da trgujemo jedni sa drugima?
Zašto ljudi mrze novac?
Pa ako novac ima toliko koristi za nas lično i za društvo u celini, zašto toliko ljudi mrzi novac? Zašto je demonizovan, zajedno sa onima koji ga imaju puno?
Za deo ovoga može biti okrivljen problem u jednakosti mogućnosti – to da je nekima teže da izadju iz nemaštine i postanu bogati. Bez sumnje, neki mali deo potiče od ljudi koji jednostavno ne žele da se trude ili preduzmu neophodne rizike da bi postali bogati.
Međutim, oba ova problema imaju više veze sa problemima kako naš novac danas funkcioniše, nego sa bilo kojim problemom u samom konceptu novca. Novčani sistem treba da nagrađuje ljude koji proizvode vredne stvari i trguju njima sa drugima. Verujem da većina ljudi danas misli da novac tako funkcioniše, i to ne bi smelo da bude daleko od istine.
Naš trenutni monetarni sistem, na žalost, nagrađuje ’finansijalizaciju’ – pretvarajući sve u imovinu, čija vrednost može da se napumpava ili spušta stvaranjem dobre priče i navođenjem drugih da veruju u nju. Razuzdani dug pogonjen stalnim omalovažavanjem svih glavnih valuta dodat je ovom blatu finansijalizacije. Sada je isplativije podići ogroman kredit i koristiti ga za brzo okretanje imovine radi zarade nego izgraditi posao koji društvu nudi korisne robe i usluge.
Tradicionalni monetarni sistem dodatno nagradjuje predatore, partnere u zločinu i neradnike.
Propast našeg novca razvila se tokom proteklih pola veka, počevši od toga kada su naše valute postale ništa više od parčeta papira, podržanog sa verom i kreditima naših vlada. Da biste bolje razumeli ovu promenu, pogledajte moj post o svrsi i istoriji novca.
Ako vam se sviđa moj rad, molim vas da ga podelite sa svojim prijateljima i porodicom. Cilj mi je da svima pružim pogled u ekonomiju i na to kako ona utiče na njihov život.
-
 @ a5ee4475:2ca75401
2025-05-15 14:44:45
@ a5ee4475:2ca75401
2025-05-15 14:44:45lista #descentralismo #compilado #portugues
*Algumas destas listas ainda estão sendo trocadas, portanto as versões mais recentes delas só estão visíveis no Amethyst por causa da ferramenta de edição.
Clients do Nostr e Outras Coisas
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
Modelos de IA e Ferramentas
nostr:naddr1qq24xwtyt9v5wjzefe6523j32dy5ga65gagkjqgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guk62czu
Iniciativas de Bitcoin
nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2nvmn5va9x2nrxfd2k5smyf3ux7vesd9znyqxygt4
Profissionais Brasileiros no Nostr
nostr:naddr1qq24qmnkwe6y67zlxgc4sumrxpxxce3kf9fn2qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3q5hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsxpqqqp65wp8uedu
Comunidades em Português no Nostr
nostr:naddr1qq2hwcejv4ykgdf3v9gxykrxfdqk753jxcc4gqg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4gu455fm3
Grupos em Português no Nostr
nostr:nevent1qqs98kldepjmlxngupsyth40n0h5lw7z5ut5w4scvh27alc0w86tevcpzpmhxue69uhkummnw3ezumt0d5hsygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqqqqs3ndneh
Jogos de Código Aberto
Open Source Games nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2kvwp3v4hhvk2sw3j5sm6h23g5wkz5ddzhz8x40v0
Itens Úteis com Esquemas Disponíveis
nostr:naddr1qqgrqvp5vd3kycejxask2efcv4jr2qgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guc43v6c
Formatação de Texto em Markdown
(Amethyst, Yakihone e outros) nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2454m8dfzn26z4f34kvu6fw4rysnrjxfm42wfpe90
Outros Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ a5ee4475:2ca75401
2025-05-15 14:11:16
@ a5ee4475:2ca75401
2025-05-15 14:11:16lists #descentralismo #compilation #english
*The last list was updated in Amethyst, so the update of this one will only be visible in Amethyst.
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
AI
nostr:naddr1qq24xwtyt9v5wjzefe6523j32dy5ga65gagkjqgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctczyzj7u3r4dz3rwg3x6erszwj4y502clwn026qsp99zgdx8n3v5a2qzqcyqqq823c8mw5zk
FOSS GAME
nostr:naddr1qq2kvwp3v4hhvk2sw3j5sm6h23g5wkz5ddzhzqg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4gut57qtr
OSHW - Open Source Hardware
nostr:naddr1qqgrqvp5vd3kycejxask2efcv4jr2qgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guc43v6c
Markdown Uses for Some Clients
nostr:nevent1qqsv54qfgtme38r2tl9v6ghwfj09gdjukealstkzc77mwujr56tgfwsppemhxue69uhkummn9ekx7mp0qgsq37tg2603tu0cqdrxs30e2n5t8p87uenf4fvfepdcvr7nllje5zgrqsqqqqqpkdvta4
Other Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ 45d6c2bf:56915a25
2025-05-27 14:23:39
@ 45d6c2bf:56915a25
2025-05-27 14:23:39published without nostr installed
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ cae03c48:2a7d6671
2025-05-27 18:01:39
@ cae03c48:2a7d6671
2025-05-27 18:01:39Bitcoin Magazine

Cake Wallet Introduces PayJoin v2, Increasing Bitcoin Privacy For The MassesCake Wallet, a non-custodial open-source wallet for cryptocurrencies, has officially launched PayJoin v2, becoming the first major mobile wallet to offer Bitcoin silent payments to everyday users.
This integration introduces a protocol upgrade that disrupts blockchain surveillance by mixing transaction inputs from both the sender and receiver, undermining the common blockchain surveillance techniques chain analysts typically rely on.
 JUST LAUNCHED: Cake Wallet v4.28.0 brings Bitcoin Payjoin v2!
JUST LAUNCHED: Cake Wallet v4.28.0 brings Bitcoin Payjoin v2! • No need for both parties to be online
• No server required
• Just a few taps in your walletIt's that simple
 Update Cake Wallet to try it out! pic.twitter.com/IjOccnBYy7
Update Cake Wallet to try it out! pic.twitter.com/IjOccnBYy7— Cake Wallet (@cakewallet) May 19, 2025
“Bitcoin is open and permissionless — but without privacy, it’s a surveillance tool,” said Vikrant Sharma, CEO of Cake Wallet in a recent press release sent to Bitcoin Magazine. “This upgrade gives everyday users the ability to transact privately, without needing to be online or run a server.”
Cake Wallet’s implementation removes the limitation of requiring both parties to be online or run a server to coordinate a transaction. Users can now send or receive Bitcoin through asynchronous, serverless PayJoin transactions—no Tor, no apps, no advanced configuration.
“This makes Bitcoin privacy accessible to people who aren’t developers or hardcore cypherpunks,” said Sharma. “We’ve seen huge progress with Monero privacy tools. Now, Bitcoin users can take a step towards privacy as well, built right into a mainstream wallet.”
This announcement follows closely on the heels of another major privacy upgrade: Cake Wallet recently became one of the first major wallets to support Silent Payments, allowing users to receive Bitcoin without exposing a reusable address.
This post Cake Wallet Introduces PayJoin v2, Increasing Bitcoin Privacy For The Masses first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 43baaf0c:d193e34c
2025-05-27 14:08:02
@ 43baaf0c:d193e34c
2025-05-27 14:08:02During the incredible Bitcoin Filmfest, I attended a community session where a discussion emerged about zapping and why I believe zaps are important. The person leading the Nostr session who is also developing an app that’s partially connected to Nostr mentioned they wouldn’t be implementing the zap mechanism directly. This sparked a brief but meaningful debate, which is why I’d like to share my perspective as an artist and content creator on why zaps truly matter.
Let me start by saying that I see everything from the perspective of an artist and creator, not so much from a developer’s point of view. In 2023, I started using Nostr after spending a few years exploring the world of ‘shitcoins’ and NFTs, beginning in 2018. Even though I became a Bitcoin maximalist around 2023, those earlier years taught me an important lesson: it is possible to earn money with my art.
Whether you love or hate them, NFTs opened my eyes to the idea that I could finally take my art to the next level. Before that, for over 15 years, I ran a travel stock video content company called @traveltelly. You can read the full story about my journey in travel and content here: https://yakihonne.com/article/traveltelly@primal.net/vZc1c8aXrc-3hniN6IMdK
When I truly understood what Bitcoin meant to me, I left all other coins behind. Some would call that becoming a Bitcoin maximalist.
The first time I used Nostr, I discovered the magic of zapping. It amazed me that someone who appreciates your art or content could reward you—not just with a like, but with real value: Bitcoin, the hardest money on earth. Zaps are small amounts of Bitcoin sent as a sign of support or appreciation. (Each Bitcoin is divisible into 100 million units called Satoshis, or Sats for short—making a Satoshi the smallest unit of Bitcoin recorded on the blockchain.)
 The Energy of Zaps
The Energy of ZapsIf you’re building an app on Nostr—or even just connecting to it—but choose not to include zaps, why should artists and content creators share their work there? Why would they leave platforms like Instagram or Facebook, which already benefit from massive network effects?
Yes, the ability to own your own data is one of Nostr’s greatest strengths. That alone is a powerful reason to embrace the protocol. No one can ban you. You control your content. And the ability to post once and have it appear across multiple Nostr clients is an amazing feature.
But for creators, energy matters. Engagement isn’t just about numbers—it’s about value. Zaps create a feedback loop powered by real appreciation and real value, in the form of Bitcoin. They’re a signal that your content matters. And that energy is what makes creating on Nostr so special.
But beyond those key elements, I also look at this from a commercial perspective. The truth is, we still can’t pay for groceries with kisses :)—we still need money as a medium of exchange. Being financially rewarded for sharing your content gives creators a real incentive to keep creating and sharing. That’s where zaps come in—they add economic value to engagement.
A Protocol for Emerging Artists and Creators
I believe Nostr offers a great starting point for emerging artists and content creators. If you’re just beginning and don’t already have a large following on traditional social media platforms, Nostr provides a space where your work can be appreciated and directly supported with Bitcoin, even by a small but engaged community.
On the other hand, creators who already have a big audience and steady income on platforms like Instagram or YouTube may not feel the urgency to switch. This is similar to how wealthier countries are often slower to understand or adopt Bitcoin—because they don’t need it yet. In contrast, people in unbanked regions or countries facing high inflation are more motivated to learn how money really works.
In the same way, emerging creators—those still finding their audience and looking for sustainable ways to grow—are often more open to exploring new ecosystems like Nostr, where innovation and financial empowerment go hand in hand.
The same goes for Nostr. After using it for the past two years, I can honestly say: without Nostr, I wouldn’t be the artist I am today.
Nostr motivates me to create and share every single day. A like is nice but receiving a zap, even just 21 sats, is something entirely different. Once you truly understand that someone is willing to pay you for what you share, it’s no longer about the amount. It’s about the magic behind it. That simple gesture creates a powerful, positive energy that keeps you going.
Even with Nostr’s still relatively small user base, I’ve already been able to create projects that simply wouldn’t have been possible elsewhere.
Zaps do more than just reward—they inspire. They encourage you to keep building your community. That inspiration often leads to new projects. Sometimes, the people who zap you become directly involved in your work, or even ask you to create something specifically for them.
That’s the real value of zaps: not just micro-payments, but micro-connections sparks that lead to creativity, collaboration, and growth.
Proof of Work (PoW)
Over the past two years, I’ve experienced firsthand how small zaps can evolve into full art projects and even lead to real sales. Here are two examples that started with zaps and turned into something much bigger:
Halving 2024 Artwork
When I started the Halving 2024 project, I invited people on Nostr to be part of it. 70 people zapped me 2,100 sats each, and in return, I included their Npubs in the final artwork. That piece was later auctioned and sold to Jurjen de Vries for 225,128 Sats.
Magic Internet Money
For the Magic Internet Money artwork, I again invited people to zap 2,100 sats to be included. Fifty people participated, and their contributions became part of the final art frame. The completed piece was eventually sold to Filip for 480,000 sats.
These examples show the power of zaps: a simple, small act of appreciation can turn into larger engagement, deeper connection, and even the sale of original art. Zaps aren’t just tips—they’re a form of collaboration and support that fuel creative energy.
I hope this article gives developers a glimpse into the perspective of an artist using Nostr. Of course, this is just one artist’s view, and it doesn’t claim to speak for everyone. But I felt it was important to share my Proof of Work and perspective.
For me, Zaps matter.
Thank you to all the developers who are building these amazing apps on Nostr. Your work empowers artists like me to share, grow, and be supported through the value-for-value model.
-
 @ 0c65eba8:4a08ef9a
2025-05-27 17:03:54
@ 0c65eba8:4a08ef9a
2025-05-27 17:03:54Most people assume that the future will look like the present, just more of it. That’s why they get blindsided. Ideas and events that seemed “unthinkable” yesterday often become the norm tomorrow. The end of slavery, universal suffrage, legal equality for women, the collapse of the Soviet Union, the legalization of gay marriage, the fall of the Berlin Wall, the mass adoption of smartphones, and even the outbreak of world wars, none of these were considered likely or even possible by the majority until they were already happening.
Why does this happen? Because what drives large-scale change isn't today's opinions or moral sentiments. It's shifting incentives.
When people change their minds at scale, it's not because everyone suddenly found a better argument. It's because the costs and rewards of holding their previous views changed. Incentives shifted. And when incentives shift, behavior follows. Belief is downstream of necessity.
We have been going in a particular direction for over a century now, a direction increasingly out of alignment with Natural Law. Liberalization, moral relativism, and institutional centralization have undermined the evolutionary constraints that sustain functional cooperation. As the distance from a Natural Law equilibrium grows, so do the costs. The pressure to restore reciprocity, sovereignty, and truth builds beneath the surface.
And this buildup doesn't continue indefinitely. It snaps. When it does, the pendulum swings hard in the other direction. Just as many societal liberalizations once seemed impossible until they occurred, many of the restorations and clawbacks now deemed unthinkable will appear inevitable in hindsight.
This is not a matter of nostalgia or ideology, it’s a matter of survival. Restoration of traditional values aligned with Natural Law will happen, not because it is wanted by all, but because it will become necessary for continued cooperation and survival.
That’s why instead of guessing what the future holds based on what feels right today, we can calculate what is likely based on Natural Law.
Natural Law isn’t a philosophy, it’s a description of the rules that govern cooperation and conflict. It defines the pressures, constraints, and evolutionary incentives that force people to adapt. And it shows how those pressures produce large-scale changes in thought, behavior, and institutions.
That’s the common-language version. But to really understand why this works, and why most predictions fail, we need to move from intuition to computation. We need a scientific grammar of change.
Understanding Natural Law and Its Predictive Power:
Natural Law is a framework developed and refined by Curt Doolittle and a collaborative body of thinkers at the Natural Law Institute. It is not a philosophy or ideology, but a scientific system that explains how incentives shape human cooperation, belief, and institutional stability over time.
This explanation draws on the key principles of Natural Law to clarify why seemingly impossible cultural reversals become inevitable. For more, seek out and follow the Natural Law Institute and Curt Doolittle.
-
First Principle: All human behavior is reducible to acquisition under constraint. Constraints are physical, biological, and institutional.
-
Causal Chain: Beliefs are not causes; they are consequences. What people consider “possible” or “acceptable” is a strategy for surviving current incentive structures. When those structures change, beliefs change.
-
Decidability: Natural Law operationalizes this by providing a decidable, commensurable, and testifiable logic of human cooperation. It identifies invariant incentives and maps them across scales: individual, institutional, and civilizational.
-
Prediction: Prediction is not sentiment or analogy, it is adversarial computation over time. What is inconceivable today becomes obvious tomorrow because people adapt to pressures, not principles.
-
Conclusion: Therefore, we reject moral intuitionism and ideological forecasting. We use Natural Law to trace changes in cooperation and conflict as evolutionary computation. It allows us to model not what people believe, but what they must do to survive within new equilibria of constraint.
Final Thoughts:
Most people attempt to forecast the future using moral intuitions, wishful thinking, ideological narratives, or historical analogies. These methods are little more than guesswork, prophecies dressed up as analysis. They offer comfort, not clarity.
Natural Law offers something different: a method of calculation. A system of first principles, constraints, and causal chains that can be used to project outcomes and identify the likely direction of change. Whether you are a father making long-term decisions for your family, an entrepreneur allocating resources, a CEO steering a corporation, or a statesman crafting policy, Natural Law gives you the tools to understand what pressures are building, what constraints are shifting, and what behaviors will be necessary in the near future.
You don’t need to master every element of Natural Law to benefit from it. That’s what the Natural Law Institute is for. If you have strategic questions, if you are responsible for people, capital, or institutions, reach out. We will help you identify your opportunities, clarify your risks, and calculate the range of outcomes you need to prepare for.
Contact us directly or engage with us online. We exist to make the future decidable.
Noah Revoy Senior Fellow at the Natural Law Institute Natural Law Applied Psychology
-
-
 @ a5ee4475:2ca75401
2025-05-09 17:10:35
@ a5ee4475:2ca75401
2025-05-09 17:10:35Título H1 - Formatação Markdown
[Titulo com '# ' antes do texto, pode não funcionar se o título H1 for iniciado depois de um texto normal]
list #descentralismo #markdown #clients #Amethyst #Yakihonne
Título H2 [2 hashtags e espaço]
Título H3 [3 hashtags e espaço]
Título H4 [4 hashtags e espaço]
Título H5 [5 hashtags e espaço]
Título H6 [6 hashtags e espaço]
*Copie e cole o texto para enxergar os caracteres usados
Réguas horizontais
- Com 3 sublinhados (_) seguidos:
- Com 3 hífens (-) seguidos:
- Com três asteriscos (*) seguidos:
Ênfases
Negrito: - Dois asteriscos antes e depois: Este é um texto em negrito
- Dois sublinhados antes e depois: Esse é um texto em negrito
Itálico - Um asterisco antes e um depois: Esse é um texto em itálico
- Um sublinhado antes e um depois: Esse é um texto em itálico
Tachado:
~~Aqui houve uma rasura~~
Bloco de citações
Usando 1 a 3 “>”:
O bloco de citações pode ser eninhado…
…Usando cada vez mais maior-que (>).
…Mesmo com espaços entre eles.
Listas
Não-ordenadas
- Crie um tópico começando com
+,-ou*. - Subtópicos são feitos adicionando 2 espaços:
- A mudança da marcação inicial não altera a lista:
- Com asterisco
- Com sinal de mais
- Com sinal de menos
- Muito fácil!
Ordenadas
- Lorem ipsum dolor sit amet
- Consectetur adipiscing elit
- Integer molestie lorem at massa
- Você pode usar números em sequência...
- ...ou deixar tudo como
1.ou outro número.
O número inicia com recuos:
- foo
- bar
Códigos
códigona mesma linhaCaixa de código
-
Códigos intentados com 4 espaços:
// Some comments line 1 of code line 2 of code line 3 of code
-
Com 3 acentos graves antes e depois:
Marcação de texto:
Insira o texto aqui...Marcação de sintaxe:
``` js var foo = function (bar) { return bar++; };
console.log(foo(5)); ```
Tabelas
| APP | Descrição | | ------ | ----------- | | Element | App de mensagens que usa a rede Matrix. | | Simplex | App de mensagens bastante usado. | | 0xchat | App de mensagens no Nostr. |
Links
-
Link autoconvertido https://github.com/nodeca/pica (habilite o linkify para ver)
Imagens nomeadas
Minion:

Stormtroopocat:
[https://octodex.github.com/images/stormtroopocat.jpg])
Como links, imagens também tem sintaxe footnote ‘!’ + ‘Outro texto’...
[https://octodex.github.com/images/dojocat.jpg])
…com uma referência id posterior da referência na localização da URL.
Plugins
O recurso de
markdown-ité um suporte muito eficaz de plugins de sintaxe.
Emojis
*Acesse o link para entender melhor
Marcação clássica: :wink: :cry: :laughing: :yum:
Figuras Ascii (emoticons): :-) :-( 8-) ;)
Veja como mudar a exibição com o twemoji.
Sobrescrito / Subscrito
*Acesse os links para entender melhor
- 19^th^
- H~2~O
\
*Acesse o link para entender melhor
++Texto Inserido++
\
*Acesse o link para entender melhor
==Texto marcado==
Notas de Rodapé
*Acesse o link para entender melhor
Nota de rodapé 1 link[^primeiro].
Nota de rodapé 2 link[^segundo].
Rodapé^[Texto do rodapé na linha] definição na linha.
Referência duplicada no rodapé[^segundo].
[^primeiro]: Rodapé pode ter marcação
e múltiplos parágrafos.[^segundo]: Texto de rodapé.
Listas de Definição
*Acesse o link para entender melhor
Termo 1
: Definição 1 com continuação preguiçosa.
Termo 2 com marcação na linha
: Definição 2
{ algum código, parte da Definição 2 } Third paragraph of definition 2.Estilo compacto:
Termo 1 ~ Definição 1
Termo 2 ~ Definição 2a ~ Definição 2b
Esse texto é uma adaptação do:
nostr:nevent1qqsv54qfgtme38r2tl9v6ghwfj09gdjukealstkzc77mwujr56tgfwspzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtczyqy0j6zknu2lr7qrge5yt725azecflhxv6d2tzwgtwrql5llukdqjqcyqqqqqqgfdk5w3
-
 @ c1e9ab3a:9cb56b43
2025-05-27 13:19:53
@ c1e9ab3a:9cb56b43
2025-05-27 13:19:53I. Introduction: Money as a Function of Efficiency and Preference
Money is not defined by law, but by power over productivity. In any open economy, the most economically efficient actors—those who control the most valuable goods, services, and knowledge—ultimately dictate the medium of exchange. Their preferences signal to the broader market what form of money is required to access the highest-value goods, from durable commodities to intangibles like intellectual property and skilled labor.
Whatever money these actors prefer becomes the de facto unit of account and store of value, regardless of its legal status. This emergent behavior is natural and reflects a hierarchy of monetary utility.
II. Classical Gresham’s Law: A Product of Market Distortion
Gresham’s Law, famously stated as:
"Bad money drives out good"
is only valid under coercive monetary conditions, specifically: - Legal tender laws that force the acceptance of inferior money at par with superior money. - Fixed exchange rates imposed by decree, not market valuation. - Governments or central banks backing elastic fiduciary media with promises of redemption. - Institutional structures that mandate debt and tax payments in the favored currency.
Under these conditions, superior money (hard money) is hoarded, while inferior money (soft, elastic, inflationary) circulates. This is not an expression of free market behavior—it is the result of suppressed price discovery and legal coercion.
Gresham’s Law, therefore, is not a natural law of money, but a law of distortion under forced parity and artificial elasticity.
III. The Collapse of Coercion: Inversion of Gresham’s Law
When coercive structures weaken or are bypassed—through technological exit, jurisdictional arbitrage, monetary breakdown, or political disintegration—Gresham’s Law inverts:
Good money drives out bad.
This occurs because: - Market actors regain the freedom to select money based on utility, scarcity, and credibility. - Legal parity collapses, exposing the true economic hierarchy of monetary forms. - Trustless systems (e.g., Bitcoin) or superior digital instruments (e.g., stablecoins) offer better settlement, security, and durability. - Elastic fiduciary media become undesirable as counterparty risk and inflation rise.
The inversion marks a return to monetary natural selection—not a breakdown of Gresham’s Law, but the collapse of its preconditions.
IV. Elasticity and Control
Elastic fiduciary media (like fiat currency) are not intrinsically evil. They are tools of state finance and debt management, enabling rapid expansion of credit and liquidity. However, when their issuance is unconstrained, and legal tender laws force their use, they become weapons of economic coercion.
Banks issue credit unconstrained by real savings, and governments enforce the use of inflated media through taxation and courts. This distorts capital allocation, devalues productive labor, and ultimately hollows out monetary confidence.
V. Monetary Reversion: The Return of Hard Money
When the coercion ends—whether gradually or suddenly—the monetary system reverts. The preferences of the productive and wealthy reassert themselves:
- Superior money is not just saved—it begins to circulate.
- Weaker currencies are rejected not just for savings, but for daily exchange.
- The hoarded form becomes the traded form, and Gresham’s Law inverts completely.
Bitcoin, gold, and even highly credible stable instruments begin to function as true money, not just stores of value. The natural monetary order returns, and the State becomes a late participant, not the originator of monetary reality.
VI. Conclusion
Gresham’s Law operates only under distortion. Its inversion is not an anomaly—it is a signal of the collapse of coercion. The monetary system then reorganizes around productive preference, technological efficiency, and economic sovereignty.
The most efficient market will always dictate the form of hard money. The State can delay this reckoning through legal force, but it cannot prevent it indefinitely. Once free choice returns, bad money dies, and good money lives again.
-
 @ da8b7de1:c0164aee
2025-05-27 15:09:54
@ da8b7de1:c0164aee
2025-05-27 15:09:54Globális nukleáris reneszánsz és új kapacitások
A 2025-ös év a globális nukleáris energiaipar újabb lendületét hozza, amit a Nemzetközi Energiaügynökség (IEA) is megerősít: rekordtermelés várható, jelenleg több mint 70 GW új nukleáris kapacitás épül világszerte, és több mint 40 ország tervezi a nukleáris energia szerepének növelését az energiamixében. A világ számos pontján – Kínában, az Egyesült Államokban, Indiában, az Egyesült Arab Emírségekben és Franciaországban – új blokkok csatlakoznak a hálózatra, miközben nyolc új egység építése is elindult. A cél, hogy 2050-re a jelenlegi 416 GW globális nukleáris kapacitás meghaladja az 1000 GW-ot, ami elengedhetetlen a klímavédelmi és energiabiztonsági célok teljesítéséhez[vg.hu][paks2.hu].
SMR-ek: technológiai áttörés és globális terjeszkedés
A kis moduláris reaktorok (SMR) forradalmasíthatják az iparágat: ezek a kompakt, előregyártott, gyorsan telepíthető egységek különösen alkalmasak távoli területek energiaellátására, ipari hőtermelésre vagy akár tengervíz sótalanítására is. Az SMR-ek fejlesztése világszerte zajlik, az USA, Kína, Oroszország és Európa élen jár, de már több mint 17 országban terveznek ilyen létesítményeket. 2025 májusában Oroszország és Üzbegisztán történelmi megállapodást kötött hat RITM-200N típusú SMR építéséről, amely az első ilyen egység lesz Közép-Ázsiában. Az Egyesült Arab Emírségekben és az USA-ban is új SMR-projektek indulnak, például a Tennessee Valley Authority hivatalosan is engedélyt kért egy BWRX-300 típusú SMR-re a Clinch River telephelyen[makronom.eu][world-nuclear-news.org][nucnet.org].
Nukleáris üzemanyag-ellátás és ellátásbiztonság
Az orosz-ukrán háború és az ellátásbiztonsági kockázatok miatt Európában is felgyorsult az alternatív nukleáris üzemanyag-beszállítók keresése. Franciaországban az EDF, az Orano és az amerikai Westinghouse tárgyalásokat folytat egy új, nyugat-európai üzemanyag-feldolgozó létesítmény létrehozásáról, hogy csökkentsék az orosz függőséget. Az Európai Bizottság részletes útmutatót adott ki az orosz nukleáris technológiákról való leválásról, de a tagállamok jelentős készleteket halmoztak fel orosz üzemanyagból, mivel az azonnali leválás az energiabiztonságot veszélyeztetné[pakspress.hu][nucnet.org].
Technológiai innovációk és üzemanyagciklus-zárás
A gyorsneutronos reaktorok és a MOX-üzemanyag alkalmazása új távlatokat nyit a nukleáris hulladék mennyiségének és veszélyességének csökkentésében, valamint a földi uránkészletek hatékonyabb felhasználásában. Az orosz BN–800 gyorsreaktor már kizárólag kevert, urán-plutónium MOX-üzemanyagot használ, és folyamatban van a BN–1200 típusú egység fejlesztése is. Ezek a fejlesztések a zárt üzemanyagciklus megvalósítását célozzák, amely jelentősen csökkentheti a végleges elhelyezésre kerülő sugárzó hulladék mennyiségét és kezelési költségeit[vg.hu].
Nukleáris energia és digitális infrastruktúra
Az adatközpontok növekvő energiaigénye miatt egyre több technológiai vállalat fordul az atomenergia felé. Az amerikai Oklo és az RPower, valamint a Deep Fission és az Endeavour együttműködése révén föld alatti SMR-eket telepítenek adatközpontok energiaellátására. Ezek a projektek kiemelik a nukleáris energia szerepét a digitális infrastruktúra fenntartható működtetésében[nucnet.org].
Piaci kilátások és geopolitikai kihívások
A Cameco vezérigazgatója szerint a globális nukleáris keresletet nem befolyásolják jelentősen a kereskedelmi vagy geopolitikai feszültségek, mivel a reaktorokra világszerte szükség van, még magasabb költségek vagy vámok mellett is. A magántőke beáramlása, az új szabályozási reformok (pl. az USA-ban az ADVANCE törvény), valamint a nemzetközi együttműködések mind hozzájárulnak az iparág hosszú távú stabilitásához és bővüléséhez[world-nuclear-news.org][nucnet.org].
Források:
world-nuclear-news.org
nucnet.org
vg.hu
makronom.eu
paks2.hu
pakspress.hu -
 @ a0e937b7:50db609a
2025-05-27 13:06:38
@ a0e937b7:50db609a
2025-05-27 13:06:38Because we are not merely addicted to #Narrativium: It is our drive, imbued into our very essence. And it is so much easier to absorb our daily dose from the billions of trickles provided by everyone else as a substitute drug #Gossipium, or temporarily saturate our unquenchable thirst by just giving in to the temptation by the incessable stream of Movies and Series providing #Fictionium than it is to find a properly satisfying Source Of Narrativium (acronymize that 😉), let alone create our own Narrativium that might even be worthy of sharing. And yet, there is so much more fulfilment possible by letting one's creativity work instead of merely using a "share" button - which briefly seems to trick the human brain into believing that one has actually participated in providing one's peers with proper Narrativium, possibly as part of an implicit social contract: "I give you all some Narrativium I found, now give me more in return". It is such a trivial action to take, even more effortless than gossiping. But let's be honest, it often just feels hollow. And even when we write something, it is again tempting to just create #Rantium instead of something actually useful.
 Gossypium herbaceum, the cotton plant (Photo by H. Zell from Wikipedia)
Gossypium herbaceum, the cotton plant (Photo by H. Zell from Wikipedia)Originally I merely wanted to post a witty quote from https://wiki.lspace.org/mediawiki/Narrativium about Narrativium on Facebook:
"Humans add narrativium to their world. They insist on interpreting the universe as if it's telling a story. This leads them to focus on facts that fit the story, while ignoring those that don't." - T. Pratchett, I. Steward, J. Cohen, The Science of Discworld I
Maybe even subtly allude to how that might explain quite a lot about the everyday insanity that seems to surround us, especially these days.
"We are not Homo sapiens, Wise Man. We are the third chimpanzee. [...] We are Pan narrans, the storytelling ape. [...] if you understand the power of story, and learn to detect abuses of it, you might actually deserve the appellation Homo sapiens." - T. Pratchett, I. Steward, J. Cohen, The Science of Discworld II
Really. I was just going to quote a bit and go on about my day with some meaningless procrastination. Why already bother with housework when I can delay that until tomorrow or the day after and just watch some series in the Arrowverse now? But after ten minutes of a Legends of Tomorrow episode called "Lucha de Apuestas", curiosity got the better of me. What is it with Luchadores and their masks, I mockingly wondered. So I read Wikipedia on it. Lots of culture, history and, most importantly to me, Narrativium. I probably couldn't care less for to guys bumping fists on a stage, I don't really care about watching any sports either. But there's a certain fascination to stories, isn't there? So I felt like sharing about Narrativium, and here we are.
—
That's it for now, I might keep writing on this. One day. Just as I keep continuing writing everything else I start. Not. Well, motivate me.
-
 @ 9cb3545c:2ff47bca
2025-05-27 12:58:56
@ 9cb3545c:2ff47bca
2025-05-27 12:58:56Introduction
Public companies that hold Bitcoin on behalf of investors (often issuing securities backed by those Bitcoin holdings) have faced growing pressure to demonstrate proof of reserves – evidence that they genuinely hold the cryptocurrency they claim. One approach is to publish the company’s Bitcoin wallet addresses so that anyone can verify the balances on the blockchain. This practice gained momentum after high-profile crypto collapses (e.g. FTX in 2022) eroded trust, leading major exchanges and fund issuers like Binance, Kraken, OKX, and Bitwise to publicize wallet addresses as proof of assets . The goal is transparency and reassurance for investors. However, making wallet addresses public comes with significant security and privacy risks. This report examines those risks – from cybersecurity threats and blockchain tracing to regulatory and reputational implications – and weighs them against the transparency benefits of on-chain proof of reserves.
Proof of Reserves via Public Wallet Addresses
In the cryptocurrency ethos of “don’t trust – verify,” on-chain proof of reserves is seen as a powerful tool. By disclosing wallet addresses (or cryptographic attestations of balances), a company lets investors and analysts independently verify that the Bitcoin reserves exist on-chain. For example, some firms have dashboards showing their addresses and balances in real time . In theory, this transparency builds trust by proving assets are not being misreported or misused. Shareholders gain confidence that the company’s Bitcoin holdings are intact, potentially preventing fraud or mismanagement.
Yet this approach essentially sacrifices the pseudonymity of blockchain transactions. Publishing a wallet address ties a large, known institution to specific on-chain funds. While Bitcoin addresses are public by design, most companies treat their specific addresses as sensitive information. Public proof-of-reserve disclosures break that anonymity, raising several concerns as detailed below.
Cybersecurity Threats from Visible Wallet Balances
Revealing a wallet address with a large balance can make a company a prime target for hackers and cybercriminals. Knowing exactly where significant reserves are held gives attackers a clear blueprint. As Bitcoin advocate (and MicroStrategy Executive Chairman) Michael Saylor warned in 2025, “publicly known wallet addresses become prime targets for malicious actors. Knowing where significant reserves are held provides hackers with a clear target, potentially increasing the risk of sophisticated attacks” . In other words, publishing the address increases the attack surface – attackers might intensify phishing campaigns, malware deployment, or insider bribery aimed at obtaining the keys or access to those wallets.
Even if the wallets are secured in cold storage, a public address advertisement may encourage attempts to penetrate the organization’s security. Custodians and partners could also be targeted. Saylor noted that this exposure isn’t just risky for the company holding the Bitcoin; it can indirectly put their custodial providers and related exchanges at risk as well . For instance, if a third-party custodian manages the wallets, hackers might attempt to breach that custodian knowing the reward (the company’s Bitcoin) is great.
Companies themselves have acknowledged these dangers. Grayscale Investments, which runs the large Grayscale Bitcoin Trust (GBTC), pointedly refused to publish its wallet addresses in late 2022, citing “security concerns” and complex custody arrangements that have “kept our investors’ assets safe for years” . Grayscale implied that revealing on-chain addresses could undermine those security measures, and it chose not to “circumvent complex security arrangements” just to appease public demand . This highlights a key point: corporate treasury security protocols often assume wallet details remain confidential. Publicizing them could invalidate certain assumptions (for example, if an address was meant to be operationally secret, it can no longer serve that role once exposed).
Additionally, a publicly known trove of cryptocurrency might invite physical security threats. While not a purely “cyber” issue, if criminals know a particular company or facility controls a wallet with, say, thousands of Bitcoin, it could lead to threats against personnel (extortion or coercion to obtain keys). This is a less common scenario for large institutions (which typically have robust physical security), but smaller companies or key individuals could face elevated personal risk by being associated with huge visible crypto reserves.
In summary, cybersecurity experts consider public proof-of-reserve addresses a double-edged sword: transparency comes at the cost of advertising exactly where a fortune is held. As Saylor bluntly put it, “the conventional way of issuing proof of reserves today is actually insecure… This method undermines the security of the issuer, the custodian, the exchanges and the investors. This is not a good idea”  . From a pure security standpoint, broadcasting your wallets is akin to drawing a bullseye on them.
Privacy Risks: Address Clustering and Blockchain Tracing
Blockchain data is public, so publishing addresses opens the door to unwanted analytics and loss of privacy for the business. Even without knowing the private keys, analysts can scrutinize every transaction in and out of those addresses. This enables address clustering – linking together addresses that interact – and other forms of blockchain forensics that can reveal sensitive information about the company’s activities.
One immediate risk is that observers can track the company’s transaction patterns. For example, if the company moves Bitcoin from its reserve address to an exchange or to another address, that move is visible in real time. Competitors, investors, or even attackers could deduce strategic information: perhaps the company is planning to sell (if coins go to an exchange wallet) or is reallocating funds. A known institution’s on-chain movements can thus “reveal strategic movements or holdings”, eroding the company’s operational privacy . In a volatile market, advance knowledge of a large buy or sell by a major player could even be exploited by others (front-running the market, etc.).
Publishing one or a few static addresses also violates a basic privacy principle of Bitcoin: address reuse. Best practice in Bitcoin is to use a fresh address for each transaction to avoid linking them  . If a company continuously uses the same “proof of reserve” address, all counterparties sending funds to or receiving funds from that address become visible. Observers could map out the company’s business relationships or vendors by analyzing counterparties. A Reddit user commenting on an ETF that published a single address noted that “reusing a single address for this makes me question their risk management… There are much better and more privacy-preserving ways to prove reserves… without throwing everything in a single public address” . In other words, a naive implementation of proof-of-reserve (one big address) maximizes privacy leakage.
Even if multiple addresses are used, if they are all disclosed, one can perform clustering analysis to find connections. This happened in the Grayscale case: although Grayscale would not confirm any addresses, community analysts traced and identified 432 addresses likely belonging to GBTC’s custodial holdings by following on-chain traces from known intermediary accounts . They managed to attribute roughly 317,705 BTC (about half of GBTC’s holdings) to those addresses . This demonstrates that even partial information can enable clustering – and if the company directly published addresses, the task becomes even easier to map the entirety of its on-chain asset base.
Another threat vector is “dusting” attacks, which become more feasible when an address is publicly known. In a dusting attack, an adversary sends a tiny amount of cryptocurrency (dust) to a target address. The dust itself is harmless, but if the target address ever spends that dust together with other funds, it can cryptographically link the target address to other addresses in the same wallet. Blockchain security researchers note that “with UTXO-based assets, an attacker could distribute dust to an address to reveal the owner’s other addresses by tracking the dust’s movement… If the owner unknowingly combines this dust with their funds in a transaction, the attacker can… link multiple addresses to a single owner”, compromising privacy . A company that publishes a list of reserve addresses could be systematically dusted by malicious actors attempting to map out all addresses under the company’s control. This could unmask cold wallet addresses that the company never intended to publicize, further eroding its privacy and security.
Investor confidentiality is another subtle concern. If the business model involves individual investor accounts or contributions (for instance, a trust where investors can deposit or withdraw Bitcoin), public addresses might expose those movements. An outside observer might not know which investor corresponds to a transaction, but unusual inflows/outflows could signal actions by big clients. In extreme cases, if an investor’s own wallet is known (say a large investor announces their involvement), one might link that to transactions in the company’s reserve addresses. This could inadvertently reveal an investor’s activities or holdings, breaching expectations of confidentiality. Even absent direct identification, some investors might simply be uncomfortable with their transactions being part of a publicly traceable ledger tied to the company.
In summary, publishing reserve addresses facilitates blockchain tracing that can pierce the veil of business privacy. It hands analysts the keys to observe how funds move, potentially exposing operational strategies, counterparties, and internal processes. As one industry publication noted, linking a large known institution to specific addresses can compromise privacy and reveal more than intended . Companies must consider whether they are ready for that level of transparency into their every on-chain move.
Regulatory and Compliance Implications
From a regulatory perspective, wallet address disclosure lies in uncharted territory, but it raises several flags. First and foremost is the issue of incomplete information: A wallet address only shows assets, not the company’s liabilities or other obligations. Regulators worry that touting on-chain holdings could give a false sense of security. The U.S. Securities and Exchange Commission (SEC) has cautioned investors to “not place too much confidence in the mere fact a company says it’s got a proof-of-reserves”, noting that such reports “lack sufficient information” for stakeholders to ascertain if liabilities can be met . In other words, a public company might show a big Bitcoin address balance, but if it has debts or customer liabilities of equal or greater value, the proof-of-reserve alone is “not necessarily an indicator that the company is in a good financial position” .
This regulatory stance implies that address disclosure, if done, must be paired with proper context. A public company would likely need to clarify in its financial statements or investor communications that on-chain reserves are unencumbered (not pledged as loan collateral, not already sold forward, etc.) and that total liabilities are accounted for. Otherwise, there’s a risk of misleading investors, which could have legal consequences. For example, if investors interpret the on-chain balance as proof of solvency but the company actually had leveraged those bitcoins for loans, lawsuits or regulatory enforcement could follow for misrepresentation.
There’s also a compliance burden associated with revealing addresses. Once an address is known to be the company’s, that company effectively must monitor all transactions related to it. If someone sends funds to that address (even without permission), the company might receive tainted coins (from hacked sources or sanctioned entities). This could trigger anti-money laundering (AML) red flags. Normally, compliance teams can ignore random deposits to unknown wallets, but they cannot ignore something sent into their publicly identified corporate wallet. Even a tiny dust amount sent from a blacklisted address could complicate compliance – for instance, the company would need to prove it has no relation to the sender and perhaps even avoid moving those tainted outputs. Being in the open increases such exposure. Threat actors might even exploit this by “poisoning” a company’s address with unwanted transactions, just to create regulatory headaches or reputational smears.
Another consideration is that custodial agreements and internal risk controls might forbid public disclosure of addresses. Many public companies use third-party custodians for their Bitcoin (for example, Coinbase Custody, BitGo, etc.). These custodians often treat wallet details as confidential for security. Grayscale noted that its Bitcoin are custodied on Coinbase and implied that revealing on-chain info would interfere with security arrangements  . It’s possible that some custodians would object to their clients broadcasting addresses, or might require additional assurances. A company going against such advice might be seen as negligent if something went wrong.
Regulators have so far not mandated on-chain proofs for public companies – in fact, recent laws have exempted public companies from proof-of-reserve mandates on the assumption they are already subject to rigorous SEC reporting. For example, a Texas bill in 2023 required crypto exchanges and custodians to provide quarterly proof-of-reserves to the state, but it “specifically carved out public reporting companies” since they already file audited financials with the SEC . The rationale was that between SEC filings and audits, public companies have oversight that private crypto firms lack . However, this also highlights a gap: even audited financials might not verify 100% of crypto assets (auditors often sample balances). Some observers noted that standard audits “may not ever include the 100% custodial asset testing contemplated by proof of reserves”, especially since quarterly SEC filings (10-Q) are often not audited . This puts public companies in a nuanced position – they are trusted to use traditional audits and internal controls, but the onus is on them if they choose to add extra transparency like on-chain proofs.
Finally, securities regulators focus on fair disclosure and accuracy. If a company publicly posts addresses, those essentially become investor disclosures subject to anti-fraud rules. The firm must keep them up to date and accurate. Any mistake (such as publishing a wrong address or failing to mention that some coins are locked up or lent out) could attract regulatory scrutiny for being misleading. In contrast, a formal audit or certification from a third-party comes with standards and disclaimers that are better understood by regulators. A self-published wallet list is an unprecedented form of disclosure that regulators haven’t fully vetted – meaning the company bears the risk if something is misinterpreted.
In summary, wallet address disclosure as proof-of-reserve must be handled very carefully to avoid regulatory pitfalls. The SEC and others have warned that on-chain assets alone don’t tell the whole story . Public companies would need to integrate such proofs with their official reporting in a responsible way – otherwise they risk confusion or even regulatory backlash for giving a false sense of security.
Reputational and Operational Risks
While transparency is meant to enhance reputation, in practice public wallet disclosures can create new reputational vulnerabilities. Once an address is public, a company’s every on-chain action is under the microscope of the crypto community and media. Any anomaly or perceived misstep can snowball into public relations problems.
One vivid example occurred with Crypto.com in late 2022. After the exchange published its cold wallet addresses to prove reserves (a move prompted by the FTX collapse), on-chain analysts quickly noticed a “suspicious transfer of 320,000 ETH” – about 82% of Crypto.com’s Ether reserves – moving from their cold wallet to another exchange (Gate.io)  . This large, unexpected transfer sparked immediate panic and FUD (fear, uncertainty, and doubt) on social media. Observers speculated that Crypto.com might be insolvent or was manipulating snapshots of reserves by borrowing funds. The CEO had to publicly respond, admitting it was an operational error – the ETH was supposed to go to a new cold storage address but ended up at a whitelisted external address by mistake . The funds were eventually returned, but not before reputational damage was done: the incident made headlines about mishandled funds and rattled user confidence  . This case illustrates how full public visibility can turn an internal slip-up into a highly public crisis. If the addresses had not been public, the mistake might have been quietly corrected; with on-chain transparency, there was nowhere to hide and no way to control the narrative before the public drew worst-case conclusions.
Even routine operations can be misinterpreted. Blockchain data lacks context – analysts may jump to conclusions that hurt a company’s reputation even if nothing is actually wrong. For instance, Binance (the world’s largest crypto exchange) encountered scrutiny when on-chain observers noted that one of its reserve wallets (labeled “Binance 8”) contained far more assets than it should have. This wallet was meant to hold collateral for Binance’s issued tokens, but held an excess balance, suggesting possible commingling of customer funds with collateral  . Bloomberg and others reported a ~$12.7 billion discrepancy visible on-chain . Binance had to acknowledge the issue as a “clerical error” and quickly separate the funds, all under the glare of public attention  . While Binance maintained that user assets were fully backed and the mistake was purely operational, the episode raised public concern over Binance’s practices, feeding a narrative that even the largest exchange had internal control lapses. The key point is that public proof-of-reserves made the lapse obvious to everyone, forcing a reactive explanation. The reputational hit (even if temporary) was an operational risk of being so transparent.
Additionally, strategic confidentiality is lost. If a company holding Bitcoin as a reserve asset decides to make a major move (say, reallocating to a different wallet, or using some Bitcoin for a strategic investment or loan), doing so with known addresses broadcasts that strategy. Competitors or market analysts can infer things like “Company X is moving 10% of its BTC — why? Are they selling? Hedging? Using it as collateral?” This can erode any competitive advantage of keeping financial strategies discreet. It might even affect the company’s stock price if investors interpret moves negatively. For example, if a blockchain analysis shows the company’s reserves dropping, shareholders might fear the company sold Bitcoin (perhaps due to financial distress), even if the reality is benign (like moving funds to a new custodian). The company would be forced into continuous public explanation of on-chain actions to prevent misunderstanding.
There’s also a risk of exposing business partnerships. Suppose the company uses certain exchanges or OTC desks to rebalance its holdings – transactions with those service providers will be visible and could link the company to them. If one of those partners has issues (say a hacked exchange or a sanctioned entity inadvertently), the company could be reputationally contaminated by association through the blockchain trail.
Finally, not all publicity is good publicity in the crypto world. A public proof-of-reserve might invite armchair auditors to scrutinize and criticize every aspect of the company’s crypto management. Minor issues could be blown out of proportion. On the flip side, if a company chooses not to publish addresses, it could face reputational risk from a different angle: skeptics might question why it isn’t being transparent. (Indeed, Grayscale’s refusal to disclose wallet addresses led to social media chatter about whether they truly held all the Bitcoin they claimed, contributing to investor nervousness and a steep discount on GBTC shares .) Thus, companies are in a delicate spot: share too much and every move invites scrutiny; share too little and you breed distrust.
Balancing Transparency Benefits vs. Risks
The central question is whether the benefit of proving reserve holdings to investors outweighs these security and privacy risks. It’s a classic risk-reward calculation, and opinions in the industry are divided.
On the side of transparency, many argue that the credibility and trust gained by proof-of-reserves is invaluable. Advocates note that Bitcoin was designed for open verification – “on-chain auditability and permissionless transparency” are core features . By embracing this, companies demonstrate they are good stewards of a “trustless” asset. In fact, some believe public companies have a duty to be extra transparent. A recent Nasdaq report contended that “when a publicly traded company holds Bitcoin but offers no visibility into how that Bitcoin is held or verified, it exposes itself to multiple levels of risk: legal, reputational, operational, and strategic”, undermining trust . In that view, opacity is riskier in the long run – a lack of proof could weaken investor confidence or invite regulatory suspicion. Shareholders and analysts may actually penalize a company that refuses to provide verifiable proof of its crypto assets .
Transparency done right can also differentiate a firm as a leader in governance. Publishing reserve data (whether via addresses or through third-party attestations) can be seen as a commitment to high standards. For example, Metaplanet, an investment firm, publicly discloses its BTC reserve addresses and even provides a live dashboard for anyone to verify balances . This proactive openness signals confidence and has been touted as an industry best practice in some quarters. By proving its reserves, a company can potentially avoid the fate of those that lost public trust (as happened with opaque crypto firms in 2022). It’s also a means to preempt false rumors – if data is out in the open, misinformation has less room to grow.
However, the pro-transparency camp increasingly acknowledges that there are smarter ways to achieve trust without courting all the risks. One compromise is using cryptographic proofs or audits instead of plain address dumps. For instance, exchanges like Kraken have implemented Merkle tree proof-of-reserves: an independent auditor verifies all customer balances on-chain and provides a cryptographic report, and customers can individually verify their account is included without the exchange revealing every address publicly. This method proves solvency to those who need to know without handing over a complete roadmap to attackers. Another emerging solution is zero-knowledge proofs, where a company can prove knowledge or ownership of certain assets without revealing the addresses or amounts to the public. These technologies are still maturing, but they aim to deliver the best of both worlds: transparency and privacy.
On the side of caution, many experts believe the risks of full public disclosure outweigh the incremental gain in transparency, especially for regulated public companies. Michael Saylor encapsulates this viewpoint: he calls on-chain proof-of-reserve “a bad idea” for institutions, arguing that it “offers one-way transparency” (assets only) and “leaves organizations open to cyberattacks” . He stresses that no serious security expert would advise a Fortune 500 company to list all its wallet addresses, as it essentially compromises corporate security over time . Saylor and others also point out the pointlessness of an assets-only proof: unless you also prove liabilities, showing off reserves might even be dangerous because it could lull investors into a false sense of security .
Regulators and traditional auditors echo this: proof-of-reserves, while a useful tool, “is not enough by itself” to guarantee financial health . They advocate for holistic transparency – audits that consider internal controls, liabilities, and legal obligations, not just a snapshot of a blockchain address  . From this perspective, a public company can satisfy transparency demands through rigorous third-party audits and disclosures rather than raw on-chain data. Indeed, public companies are legally bound to extensive reporting; adding public crypto addresses on top may be seen as redundant and risky.
There is also an implicit cost-benefit analysis: A successful attack resulting from over-sharing could be catastrophic (loss of funds, legal liability, reputational ruin), whereas the benefit of public proof is somewhat intangible (improved investor sentiment, which might be achieved via other assurance methods anyway). Given that trade-off, many firms err on the side of caution. As evidence, few if any U.S.-listed companies that hold Bitcoin have published their wallet addresses. Instead, they reference independent custodians and audits for assurance. Even crypto-native companies have pulled back on full transparency after realizing the downsides – for example, some auditing firms halted issuing proof-of-reserves reports due to concerns about how they were interpreted and the liability involved  .
Industry best practices are still evolving. A prudent approach gaining favor is to prove reserves without leaking sensitive details. This can involve disclosing total balances and having an auditor or blockchain oracle confirm the assets exist, but without listing every address publicly. Companies are also encouraged to disclose encumbrances (whether any of the reserves are collateralized or lent out) in tandem, to address the liabilities issue . By doing so, they aim to achieve transparency and maintain security.
In evaluating whether to publish wallet addresses, a company must ask: Will this level of openness meaningfully increase stakeholder trust, or would a more controlled disclosure achieve the same goal with less risk? For many public companies, the answer has been to avoid public addresses. The risks – from attracting hackers to revealing strategic moves – tend to outweigh the marginal transparency benefit in their judgment. The collapse of unregulated exchanges has certainly proven the value of reserve verification, but public companies operate in a different context with audits and legal accountability. Thus, the optimal solution may be a middle ground: proving reserves through vetted processes (auditor attestations, cryptographic proofs) that satisfy investor needs without blatantly exposing the company’s financial backend to the world.
Conclusion
Publishing Bitcoin wallet addresses as proof of reserves is a bold transparency measure – one that speaks to crypto’s ideals of open verification – but it comes with a laundry list of security considerations. Public companies weighing this approach must contend with the heightened cybersecurity threat of advertising their treasure troves to hackers, the loss of privacy and confidentiality as on-chain sleuths dissect their every transaction, and potential regulatory complications if such disclosures are misunderstood or incomplete. Real-world incidents illustrate the downsides: firms that revealed addresses have seen how quickly online communities flag (and sometimes misinterpret) their blockchain moves, causing reputational turbulence and forcing rapid damage control  .
On the other hand, proving reserves to investors is important – it can prevent fraud and bolster trust. The question is how to achieve it without incurring unacceptable risk. Many experts and industry leaders lean towards the view that simply publishing wallet addresses is too risky a method, especially for public companies with much to lose  . The risks often do outweigh the direct benefits in such cases. Transparency remains crucial, but it can be provided in safer ways – through regular audits, cryptographic proofs that don’t expose all wallet details, and comprehensive disclosures that include liabilities and controls.
In conclusion, while on-chain proof of reserves via public addresses offers a tantalizing level of openness, it must be approached with extreme caution. For most public companies, the smart strategy is to balance transparency with security: verify and show investors that assets exist and are sufficient, but do so in a controlled manner that doesn’t compromise the very assets you’re trying to protect. As the industry matures, we can expect more refined proof-of-reserve practices that satisfy the demand for honesty and solvency verification without unduly endangering the enterprise. Until then, companies will continue to tread carefully, mindful that transparency is only truly valuable when it doesn’t come at the price of security and trust.
Sources:
• Grayscale statement on refusal to share on-chain proof-of-reserves  • Community analysis identifying Grayscale’s wallet addresses  • Cointelegraph – Crypto.com’s mistaken 320k ETH transfer spotted via on-chain proof-of-reserves   • Axios – Binance wallet “commingling” error observed on-chain   • Michael Saylor’s remarks on security risks of publishing wallet addresses    • SEC Acting Chief Accountant on limitations of proof-of-reserves reports  • Nasdaq (Bitcoin for Corporations) – argument for corporate transparency & proof-of-reserves    • 1inch Security Blog – explanation of dusting attacks and privacy loss via address linking  -
 @ a5ee4475:2ca75401
2025-05-08 21:57:12
@ a5ee4475:2ca75401
2025-05-08 21:57:12brasil #portugal #portugues #bitcoin
Brasil
-
Jericoacoara - Ceará nostr:nprofile1qqsdc47glaz2z599a7utq9gk2xyf6z70t7ddyryrnweyt32z4sdarfsppemhxue69uhkummn9ekx7mp00ex584
-
Rolante - Rio Grande do Sul nostr:nprofile1qqsdrks96vr7vc7frjflm8lmhwleslwzgjlkpyj4ahjhzgm4n8dh0qqprdmhxue69uhkymm4de3k2u3wd45ku6tzdak8gtnfdenx7qgcwaen5te0xycrqt3hxyhryvfh9ccngde6xsurgwqpz3mhxue69uhhyetvv9ujuerpd46hxtnfduhxppd6
-
Santo Antonio do Pinhal - São Paulo nostr:nprofile1qqsr5maylee9j77ce0es6tgmxj3pax2dlsuuptkn2stuj95jzqysulgpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqgjwaehxw309ac82unsd3jhqct89ejhxqgdwaehxw309ahx7uewd3hkca6zsjl
Portugal
- Ilha da Madeira - nostr:nprofile1qqsv45qvfz5vdzwn9478wzusyggjf44x3w7xk8f3cgpe4px44wgv77cpr3mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmqpz3mhxue69uhhyetvv9ujumn0wd68ytnzvuq32amnwvaz7tmwdaehgu3dwfjkccte9eshquqzhddc4
-
-
 @ 90c656ff:9383fd4e
2025-05-27 11:27:26
@ 90c656ff:9383fd4e
2025-05-27 11:27:26Since its creation, Bitcoin has been a revolutionary asset, challenging the traditional financial system and proposing a new form of decentralized money. However, its future remains uncertain and the subject of intense debate. Among the possible outcomes, two extreme scenarios stand out: hyperbitcoinization-where Bitcoin becomes the dominant currency in the global economy—and obsolescence, where the network loses relevance and is replaced by other solutions.
- Hyperbitcoinization: The World Adopts Bitcoin as a Monetary Standard
01 - Loss of trust in fiat currencies: Due to excessive money printing by central banks, many economies face rampant inflation. Bitcoin, with its fixed supply of 21 million units, emerges as a more trustworthy alternative.
02 - Growing adoption by companies and governments: Some countries have already begun integrating Bitcoin into their economies, accepting it for payments and as a store of value. If this trend continues, Bitcoin’s legitimacy as a global currency will grow.
03 - Ease of global transactions: Bitcoin enables fast and low-cost international transfers, removing the need for financial intermediaries and reducing operational costs.
04 - Technological advancements: Scalability improvements, such as the Lightning Network, can make Bitcoin more efficient for daily use, encouraging mass adoption.
If hyperbitcoinization becomes reality, the world may witness a radical shift in the financial system—with greater decentralization, censorship resistance, and an economy based on sound, predictable money.
- Obsolescence: Bitcoin Loses Relevance and Is Replaced
01 - Restrictive government regulations: If major economic powers enforce strict regulations on Bitcoin, adoption could slow, reducing its utility.
02 - Technological shortcomings or lack of innovation: Despite its security and decentralization, Bitcoin may struggle to scale effectively. If superior solutions emerge and gain acceptance, Bitcoin could lose its leading position.
03 - Competition from faster, more user-friendly alternatives: Other forms of digital money may surpass Bitcoin in scalability and usability, potentially leading to a decline in Bitcoin adoption.
04 - Decreasing miner incentives: As new Bitcoin issuance halves every four years, miners will rely increasingly on transaction fees. If those fees are insufficient to sustain network security, long-term viability could be at risk.
In summary, Bitcoin’s future could unfold along multiple paths, depending on factors like innovation, global adoption, and resilience to external challenges. Hyperbitcoinization would represent an economic revolution—ushering in a decentralized, inflation-resistant monetary system. Yet, obsolescence remains a risk if the network fails to adapt to future demands. Regardless of the outcome, Bitcoin has already made its mark on financial history, paving the way for a new era of digital money and economic freedom.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 90c656ff:9383fd4e
2025-05-27 11:22:10
@ 90c656ff:9383fd4e
2025-05-27 11:22:10Since its creation, Bitcoin has been much more than just an alternative to traditional money. With the ongoing digitalization of the global economy, Bitcoin has emerged as a foundational pillar for new forms of transactions, commerce, and value storage. Its decentralization, transparency, and censorship resistance make it a solid base for digital economies, where financial interactions occur without the need for traditional intermediaries.
- Bitcoin’s role in the digital economy
01 - Global, borderless transactions: Anyone with internet access can send and receive Bitcoin without needing a bank or government authorization.
02 - Limited and predictable supply: Unlike fiat currencies that can be inflated by central banks, Bitcoin has a fixed cap of 21 million units, making it a scarce and reliable asset.
03 - Security and transparency: The Bitcoin blockchain or timechain publicly records all transactions, ensuring a secure and auditable system.
04 - Censorship resistance: No government or institution can block Bitcoin transactions, enabling a freer and more accessible digital economy.
With these characteristics, Bitcoin is already transforming various economic sectors and driving new forms of commerce and investment.
- Bitcoin in digital commerce and the global economy
01 - E-commerce: Businesses and consumers can use Bitcoin for fast international transactions without exorbitant fees.
02 - International remittances: Workers sending money to their home countries can avoid high fees and long delays by using Bitcoin.
03 - Emerging economies: In countries with unstable currencies and unreliable banking systems, Bitcoin serves as a secure and decentralized alternative for storing wealth and conducting daily transactions.
Additionally, Bitcoin is being adopted by companies and even governments as a store of value, reinforcing its role as a foundation for the digital economy of the future.
- Challenges and adapting to the new economy
01 - Price volatility: Bitcoin’s fluctuating value can make it difficult to use as a daily medium of exchange.
02 - Regulations and governmental resistance: Some countries attempt to restrict or regulate Bitcoin to maintain control over the traditional financial system.
03 - Education and adoption: Many people still lack the knowledge to use Bitcoin safely and effectively.
In summary, Bitcoin is transforming the way the world interacts with money, offering a decentralized and transparent alternative for digital economies. As more individuals and businesses adopt Bitcoin for payments, savings, and global commerce, its impact becomes increasingly clear. Despite the challenges, Bitcoin continues to solidify its place as the foundation of a new economic paradigm—where financial freedom and technological innovation go hand in hand.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ a5ee4475:2ca75401
2025-05-07 20:00:42
@ a5ee4475:2ca75401
2025-05-07 20:00:42lista #descentralismo #comunidades #portugues
[em atualização]
*Até a criação desse post, só alguns clients têm acesso às comunidades, tal como o Satellite, o Coracle e o Amethyst.
**Se a comunidade não tiver proprietários ou moderadores ativos, o seu envio de mensagem poderá não ser aprovada para aparecer nela.
***Se criar uma, busque colocar um ou mais moderadores para a comunidade não acabar, caso você se ausente.
Geral:
n/Brasil (Por: nostr:nprofile1qqspxhftq9htg9njgaefr6nmetl97q8qqlwxvynppl6c5zr9t0qmp9gpzfmhxue69uhhqatjwpkx2urpvuhx2ucpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3qamnwvaz7tmwdaehgu3wwa5kueguy3tt5) nostr:naddr1qqryyunpwd5kcq3qzdwjkqtwkst8y3mjj848hjh7tuqwqp7uvcfxzrl43gyx2k7pkz2sxpqqqzr0v4va9m3
n/Portugal (por: nostr:nprofile1qqsddhy42shp3w9h4mp0z3ss74wrxk47hmrk70deukxz23np6pvn5rqpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9uqsuamnwvaz7tmwdaejumr0dshszynhwden5te0dehhxarj9ek82tntv5hsd2h46x) nostr:naddr1qqy9qmmjw36kwctvqgsddhy42shp3w9h4mp0z3ss74wrxk47hmrk70deukxz23np6pvn5rqrqsqqpphkc3wuaj
n/Moçambique (por: nostr:nprofile1qqszx6hsp38v2re3q2pzxpv3slg5u7pxklxze7evarqk4eugqmhntdcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctc082x0w) nostr:naddr1qqf56m7r5ask6cnfw96ktuyls7e0p8u8hupzqgm27qxya3g0xypgygc9jxraznncy6muct8m9n5vz6h83qrw7ddhqvzqqqyx7c0autxh
n/África (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqru8qtxwf5kxcgzyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdaspqgn0q
-
n/Perguntas-e-Respostas (Por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qq3lp8u85lcflpah2pz4y364fe2yz5edg5k4y32n2p84x4zp203fm980hz8sygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqsmmqtz9a9x
n/Links-e-Tutoriais-Úteis (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqj0p8u85lcflpahf3y5uj6n94zj64z42384yj2pf9fjmsu623z5j5lsn7ftkq3qne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqxpqqqzr0v3zu9fd
n/JornalismoNãoEstáMorto - Notícias e escrita informativa (Por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:nprofile1qqs0f74kketdcv63r53mlzgzfh93we3dkgzkldv2p6g62a8gf3g92yqpz4mhxue69uhkummnw3ezummcw3ezuer9wchszyrhwden5te0dehhxarj9ekk7mf0qywhwumn8ghj7mn0wd68ytnzd96xxmmfdejhytnnda3kjctv9ufhpwuw) nostr:naddr1qqd55n6jfeq5cj2nf48j6nkrsd8j632n2npczt2dfaf9gnczyrvvsrjnp9xgqysjendxg6x2q7fldu73ajnf5e2h7uspp9tjl7jvxqcyqqqgdasy2kfg4
n/Agorismo³-E-Mercado (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqs0p8u85lcflpahg9r575jf2dx5ls4n94zj6n292fp5z3z094gry5qzyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdasrlnr7s
n/FeiraNostr - Marketplace (por: nostr:nprofile1qqstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9u2dla7c) nostr:naddr1qq9yvetfwfs5ummnw3eqyg9hpjdlkf2tvpegqssjvsa7kpmmdw55zcy76sz3tkd3p9sawancnypsgqqqsmmqucz73h
Tecnologia:
n/ndevs-br (por: nostr:nprofile1qqs923ewnsqlx7347cpjhxmcmt0rsmnwf3tasr736pjx4wee9q89ufcppemhxue69uhkummn9ekx7mp0gc3lmk) nostr:naddr1qqyxuer9weej6cnjqgs923ewnsqlx7347cpjhxmcmt0rsmnwf3tasr736pjx4wee9q89ufcrqsqqpphk7z3axp
n/BrasilDev (por: nostr:nprofile1qqsyczyspluueyxautr3nxa2httku5e9m7d05dnu5zj3jnrg0jmucqcpr9mhxue69uhkyu3wwp6hyurvv4ex2mrp0yhxxmmd9uqs6amnwvaz7tmwdaejumr0dsq3camnwvaz7tmwdaehgu3wvf5hgcm0d9hx2u3wwdhkx6tpdsz8cl6e) nostr:naddr1qqy5yunpwd5kc3r9wcpzqnqgjq8lnnysmh3vwxvm42adwmjnyh0e473k0js22x2vdp7t0nqrqvzqqqyx7cvxdlla
n/Linux (por: nostr:nprofile1qqsxhewvq6fq9lzjmfwqrpg2ufgl09uh2cksupa853zxv04u2fva4uqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9nhwden5te0dehhxarjv4kxjar9wvhx7un89uqsuamnwvaz7tmwdaejumr0dshs6tvc92 ) nostr:naddr1qqz5c6tww4uqz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsygrtuhxqdyszl3fd5hqps59wy50hj7t4vtgwq7n6g3rx8679ykw67qpsgqqqsmmqznes6u
n/IA - Inteligencia Artificial (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqpyjsgpzpmhxue69uhkummnw3ezumt0d5hsyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqs03ln5
n/HardwareBr - Dúvidas, experiências e atualizações sobre hardware (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq9ysctjv3mkzun9gfeqyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmq54k3eu
n/SegurançaDaInformação (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqv9xet8w4exzmkr5as5gc2fdenx7undv8p60sardupzp6kfec55jce92gj4cjlg7ju8mzrea0ycfd3u86crk8vzayd334wrqvzqqqyx7cpss4m0
n/Moneroptbr (Por: nostr:nprofile1qqsyrmue77dm5ef5pmqsly0wp3248mk3vr9temj5p54plygcr97pavcpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqgjwaehxw309ac82unsd3jhqct89ejhxqg5waehxw309aex2mrp0yhxgctdw4eju6t0tpqrvk) nostr:naddr1qq9y6mmwv4ex7ur5vfeqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsygzpa7vl0xa6v56qasg0j8hqc42namgkpj4uae2q62sljyvpjlq7kvpsgqqqsmmqknmdan
Ciência:
n/Astronomia - Espaço e astros (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qq9yzum5wfhkummdd9ssz9thwden5te0dehhxarj9ehhsarj9ejx2a30qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqpphkkdel5t
n/Mecatrônica-NOSTR (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qqfy6etrv9689sa5de5kxcfdfe84x4zjqythwumn8ghj76twvfhhstnp0faxzmt09ehx2ap0qgsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcrqsqqpphkgsy84w
n/Antropologystr - Antropologia (por: nostr:npub1fyd0awkakq4aap70ual7mtlszjle9krffgwnsrkyua2frzmysd8qjj8gvg ) nostr:naddr1qq85zmn5dpex7ur0d3hkw7tnw3eqygzfrtlt4hds900g0nl80lk6luq5h7fds622r5uqa3882jgckeyrfcpsgqqqsmmq4xrrgc
Cultura:
n/Estante-Nostr - Literatura e livros (por: nostr:nprofile1qqsdl72sxdne0yqwa7tpznlnc4yt5t9jf8htspnynrja92dcschm7sqpr4mhxue69uhkummnw3ez6vp39eukz6mfdphkumn99e3k7mf0qywhwumn8ghj7mn0wd68ytfsxgh8jcttd95x7mnwv5hxxmmd9uq37amnwvaz7tmwdaehgu3dxqejuer0wfskvctrw3hhy7fwdaexwtcjwfqr2) nostr:naddr1qqx52um5v9h8ge2lfehhxarjqgsdl72sxdne0yqwa7tpznlnc4yt5t9jf8htspnynrja92dcschm7sqrqsqqpphkwzdgct
n/Literatura-Arte-Cultura (por: nostr:nprofile1qqs92lr9pdcqnulddvzgj5twpz8ysdv7njhxagyxwtnlj8p3kpxxs9cprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hsz9nhwden5te0v4jx2m3wdehhxarj9ekxzmny9uqsuamnwvaz7tmwdaejumr0dshs8l9z0j) nostr:naddr1qqt5c6t5v4exzar4wfsj6stjw3jj6sm4d3682unpqgs92lr9pdcqnulddvzgj5twpz8ysdv7njhxagyxwtnlj8p3kpxxs9crqsqqpphkty54um
n/História-e-Filosofia (por: nostr:npub1ne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqmpxjxk ) nostr:naddr1qqjlp8u85lcflpahfpy4x4xrjdfyjsfdg5k5vj2vfaf573jfg8cflrum7z0cezczyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdas35g9vs
n/Urbanism - Urbanismo (por: nostr:nprofile1qqstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9u2dla7c) nostr:naddr1qqy92unzv9hxjumdqgstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgrqsqqpphkyl5u8a
Fé:
n/Religião-e-Teologia - Cristianismo (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqs0p8u85lcflpah2fz5cj28f8pcxnedg5k4g320f385wj2p7z0ehyqzyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdasta04x5
n/Ateismo-e-Agnosticismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqtyzar9d9ek6medv5k5zemwdaehg6trd9ek6mczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdasuuzmw8
n/Budismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqr5yatyd9ek6mczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdas0kmt4m
n/Taoismo - Daoismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqy9gct0cwkhxmt0qy88wumn8ghj7mn0wvhxcmmv9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7crkzqvd
n/Espiritualidade - Significação e sublimidade (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq852umsd9exjar4v9kxjerpv3jszyrhwden5te0dehhxarj9ekk7mf0qgsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscrqsqqpphkxa5nfy
Entretenimento:
n/Equinox - Cinema no Nostr (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr) nostr:naddr1qqr52ut4d9hx77qpremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cmc79n5
n/Rock/metal - Músicas Rock e Metal (por: nostr:nprofile1qqs9nyy7ctpy334n3p7gh4p93lmj2cch8ae8jgjsp8al2g32stdnpdcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpr9mhxue69uhhyetvv9ujumn0wd68ytnrdakjuct49us57cz4 e nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ec8y6tdv9kzumn9wshszrnhwden5te0dehhxtnvdakz748t750 ) nostr:naddr1qq99ymmrdvh56et5v9kqzqqzypvep8kzcfyvdvug0j9agfv07ujkx9elwfujy5qfl06jy25zmvctwqcyqqqgdas306zj5
n/Música-Cinema-e-Livros (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qq4lp8u85lcflpahfhpe556fgdqj6s6ffez56sfdyck5cj2k2f848uyl366lp8unhhcflyu6qgsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qrqsqqpphkfyz9pf
n/Lugares-e-Viagens (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqjlp8u85lcflpahf325ws2jg4fj63fd2ey5z369feflp8uv3mcflryd7z0cercpqqpzp8j22f6xh652qd8qzlpqr4sr8xpkka70sedlnxn3qs5nmxhccj7yqvzqqqyx7c965gfw
n/MídiasPerdidas - Lost Media (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqw0p8u85lcflpahfhpc63zfg9fj65z92fzyj3zp20cflfusqgsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qrqsqqpphkdltjpa
n/Football - Futebol (Por: nostr:nprofile1qqsyjxh7htwmq277sl87wlld4lcpf0ujmp5558fcpmzww4y33djgxnsppemhxue69uhkummn9ekx7mp0qywhwumn8ghj7mn0wd68ytnzd96xxmmfdejhytnnda3kjctv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tc9l2d6x / Moderadores: nostr:nprofile1qqsx5rzeds2gf6hzaqf35qc0y6v5fys72fsec8w3gwszn3jw5mxewvgpz4mhxue69uhkummnw3ezummcw3ezuer9wchszrnhwden5te0dehhxtnvdakz7qgswaehxw309ahx7um5wghx6mmd9u5c2kxa & nostr:nprofile1qqspxhftq9htg9njgaefr6nmetl97q8qqlwxvynppl6c5zr9t0qmp9gpzfmhxue69uhhqatjwpkx2urpvuhx2ucpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3qamnwvaz7tmwdaehgu3wwa5kueguy3tt5) nostr:naddr1qqyxvmm0w33xzmrvqgsyjxh7htwmq277sl87wlld4lcpf0ujmp5558fcpmzww4y33djgxnsrqsqqpphkg0nfw5
n/Formula-1 (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqy5vmmjd46kccfdxypzp8j22f6xh652qd8qzlpqr4sr8xpkka70sedlnxn3qs5nmxhccj7yqvzqqqyx7cc95u5w
n/Games - Atualizações sobre jogos (por: nostr:npub1atyuu22fvvj4yf2uf050fwra3pu7hjvykc7ravpmrkpwjxcc6hpsfneh4e ) nostr:naddr1qqz5wctdv4esyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqn0x7k7
n/JogosBrasil - Clips de jogos (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4 ) nostr:naddr1qq955mm8dae5yunpwd5kcqghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3qj90yg0hl4e6qr7yg982dlh0qxdefy72d6ntuqet7hv3ateya782sxpqqqzr0vus9jl2
n/Minecraft (por: nostr:npub19xc7f5lg2z6svrjgye63rx44a96aq2ysqajx5tmum28cu6mk5j3qj3n9m9 ) nostr:naddr1qqy566twv43hyctxwspzq2d3unf7s594qc8ysfn4zxdtt6t46q5fqpmydghhek503e4hdf9zqvzqqqyx7ct7hldr
n/GenshinImpactBr (por: nostr:nprofile1qqs28fezzs5n2rdjh9deqv3ztk59mhg4j2jxaee7a4amkya30jnruggppemhxue69uhkummn9ekx7mp0qyg8wumn8ghj7mn0wd68ytnddakj7qgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctcnffw22) nostr:naddr1qqtlp8u85lcflpahgajkuumgd9hyjmtsv93hgsnjq9z8wue69uhkw6tjwahhgvntdaunx6mkdgmxv6ehdaek2mm3v9a8qdtkwa3x2cthda3kyvmdxgmk5cm3w3sksd34vcexv6mvxdukgtn0de5k7m30qgs28fezzs5n2rdjh9deqv3ztk59mhg4j2jxaee7a4amkya30jnruggrqsqqpphkq4s4py
Libertarianismo:
n/Defensores-caseiros (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq0lp8u85lcflpahg3jkvetwwdhhyetn943kzum9d9ex7ulsn78mgq3qgazxqfx8ldqkgaldz3hlwed2h3nwzfmwavkxp3s9j36qhfzeladsxpqqqzr0vcr78h2
n/Desobediência_Civil (por: nostr:nprofile1qqs2kw4x8jws3a4heehst0ywafwfymdqk35hx8mrf0dw6zdsnk5kj9gpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m306r5ytp) nostr:naddr1qq2ygetnda3x2erfcw4xucmfv905x6tkd9kqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsyg9t82nre8gg76muumc9hj8w5hyjdkstg6tnra35hkhdpxcfm2tfz5psgqqqsmmqlg3ata
n/sobreviNOSTR - Sobrevivencialismo (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq20p8u85lcflpah2dhkyun9we55un6n23fqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsygz8g3szf3lmg9j80mg5dlmkt24uvmsjwmht93svvpv5ws96gk0ltvpsgqqqsmmqtempje
n/Triggr - Armas (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qqr9g5jfgar4yqghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3qgazxqfx8ldqkgaldz3hlwed2h3nwzfmwavkxp3s9j36qhfzeladsxpqqqzr0vt5085y
n/Kaboom - Química e explosivos (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4 ) nostr:naddr1qqt0p8u85lcflpahfdq5yn60fhcflra57z0602qppemhxue69uhkummn9ekx7mp0qgsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcrqsqqpphk637p09
n/CAVERNA-DO-PIRATA - Pirataria (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq40p8u85lcflpahgdq4v32jfeqj63z094gyj5jp23qlp8u0kn3gpr0znzswlwy07z0ca2gpg3mhxw309ankjunhda6ry6m00yekkan2xenxkdm0wdjk7utp0fcr2anhvfjkzam0vd3rxmfjxa4xxut5v95rvdtxxfnxkmpn09jzummwd9hkutczypr5gcpycla5zerha52xlam9427xdcf8dm4jccxxqk28gzayt8l4kqcyqqqgdask5hmmn
n/PrivateSociety - Propostas e discussões para uma sociedade privada (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq89qunfweshge2nda3kjet50ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cfvhgrt
n/TeoriaDasBandeiras (por: nostr:nprofile1qqs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586gpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshszrnhwden5te0dehhxtnvdakz7ar9xsz) nostr:naddr1qqf9get0wf5kzerpwdpxzmnyv45hyctnqgs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586grqsqqpphkatc9rh
n/SemFronteiras (por: nostr:nprofile1qqs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586gpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshszrnhwden5te0dehhxtnvdakz7ar9xsz) nostr:naddr1qqx4xetdgeex7mn5v45hyctnqgs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586grqsqqpphkjs0cue
n/AnarcoSobrevivencialismo (por: nostr:nprofile1qqsfj5s9lrcckaxd8ul7vf3c4ajfg0n0ytcjvetclw679hy6p98wpfqpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy2hwumn8ghj7un9d3shjtnwdaehgu3wvfnj7qg4waehxw309ahx7um5wghx77r5wghxgetk9uykdgj7) nostr:naddr1qqdyzmnpwf3k75m0vfex2anfwejkucmfv9kxjumddap9yq3qn9fqt7833d6v60elucnr3tmyjslx7gh3yejh37a4utwf5z2wuzjqxpqqqzr0vsz5kcy
n/SociedadeAlternativaLibertaria - Libertários (por: nostr:nprofile1qqs2ph3za34henpq2y3rzgqwgdc4pjmpleqr5t62rf7kxj0lmdyxnfgppemhxue69uhkummn9ekx7mp0ydypw5) nostr:naddr1qq09xmmrd9jkgctyv4qkcar9wfhxzarfwes5c6tzv4e8gctjd9ssyg9qmc3wc6muess9zg33yq8yxu2sedslusp69a9p5ltrf8lakjrf55psgqqqsmmq8dtk3m
n/LibertariosPT - Libertários de Portugal (por: nostr:nprofile1qqszx8rlqax4pakclsxscudfset7fs37jm7rflnugh3nf8r4ehx4z4gppemhxue69uhkummn9ekx7mp05leack) nostr:naddr1qqx5c6tzv4e8gctjd9hhx5z5qgszx8rlqax4pakclsxscudfset7fs37jm7rflnugh3nf8r4ehx4z4grqsqqpphke05802
Discussões Sociais
n/Aliança-Conservadora-Brasileira (por: nostr:npub1atg5rgfuarup49470kqexfgcesdr85yru56y0y8qf3z6kc30g2vqyfyqyp ) nostr:naddr1qqsyzmrfv9hv8fmptapk7mnnv4e8vctydaexzh6zwfshx6tvv45hycgzyr4dzsdp8n50sx5khe7crye9rrxp5v7ss0jng3usupxyt2mz9apfsqcyqqqgdasue9j59
n/Ilha-de-Anhatomirin - Monarquia (Por: nostr:nprofile1qqsgzc22v804davx6vpwtwfu6j84yvupeld497tfr396usmu7s0m08qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszymhwden5te0v9ehgunpdshxu6twdfsj7qguwaehxw309a5x7ervvfhkgtnrdaexzcmvv5h8gmm0d3ej7a2jp7u) nostr:naddr1qqf5jmrgvykkgefdg9hxsct5dakkjunfd5q3uamnwvaz7tmwdaehgu3dwp6kytnhv4kxcmmjv3jhytnwv46z7q3qs9s55cwl2m6cd5czukune4y02gecrn7m2tukj8zt4epheaqlk7wqxpqqqzr0vu2qg3m
n/ManosphereBrasil - Contra a misandria (Por: nostr:nprofile1qqs0p3yd48kzm56a4tual772y3vsjwehx6tc3rv8ht8q0zgncg5r7qgpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpjnhed) nostr:naddr1qqgy6ctwdaehq6r9wfj5yunpwd5kcqgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctczyrcvfrdfaskaxhd2l80lhj3ytyynkdekj7ygmpa6ecrcjy7z9qlszqcyqqqgdasl3kaju
Memes
n/Shitposting (Por: nostr:nprofile1qqs9nyy7ctpy334n3p7gh4p93lmj2cch8ae8jgjsp8al2g32stdnpdcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpr9mhxue69uhhyetvv9ujumn0wd68ytnrdakjuct49us57cz4) nostr:naddr1qq94x6rfw3cx7um5d9hxwqgswaehxw309ahx7um5wghx6mmd9upzqkvsnmpvyjxxkwy8ez75yk8lwftrzulhy7fz2qylhafz92pdkv9hqvzqqqyx7chlz42w
n/Puro-caldo-do-Brasil. (por: nostr:nprofile1qqsztjv2pflmwcayr2jaq90astj94lu5l0smr0zhkfdct4ry7uxu7dqywzq8t) nostr:naddr1qq24qatjdukkxctvv3hj6er094p8yctnd9kzuqghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7q3qyhyc5znlka36gx496q2lmqhyttlef7lpkx790vjmsh2xfacdeu6qxpqqqzr0vwh0r4w
Locais
n/NordesteLibertário - Nordeste (Por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qqf5ummjv3jhxar9f35kyetjwnp6zunfdupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cnejrgl
n/BahiaLibertária - Bahia (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qqgyyctgd9s5c6tzv4e8fsapwf5kzq3q5hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsxpqqqzr0vc4949j
n/LiberdadeMinas - Minas Gerais (Por: nostr:nprofile1qqsf0kszkmrmy9l3c7mxr3uhh3fmyjpq2z4hjvv7wdq84k5npd7gw3cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszxthwden5te0wfjkccte9eekummjwsh8xmmrd9skctcprpmhxue69uhhyetvv9ujuurvv438xarj9e3k7mf0mx68nx) nostr:naddr1qq8yc6tzv4exgctyv4xkjmnpwvqsqq3qjldq9dk8kgtlr3akv8re00znkfyzq59t0yceuu6q0tdfxzmusarsxpqqqzr0vag4knt
n/CyberpunkManaus - Manaus (Por: nostr:nprofile1qqsz8v8zlrg0jclhasdksctsr2jw28lrqwn3zrsclnkpmytvmzhhdlqpz3mhxw309ucnqt3jx5cjuvpwxgarsvpcxqq3wamn8ghj7vfexghrzd3c9ccjuv3s8gurqwps9uq5gamn8ghj7entv43kjd3nvfcx5en6093h2up5w3ekgmn4xsekvatwx438xamywp6ksemcwp6xummzdgekzdmz0pmhzd3j0g6xzepwdahxjmmw9u2upp88) nostr:naddr1qqgyx7tzv4e8qatwdvk56ctwv96hxqgqqgsz8v8zlrg0jclhasdksctsr2jw28lrqwn3zrsclnkpmytvmzhhdlqrqsqqpphkgjh4rf
n/BelémLibertario (por: nostr:npub167s6q8sfzkhel4227kacu98zcg6e37v5sqwkv8mxaazrryz9huzqlhcu2t) nostr:nevent1qqsqnqgx3u2whdqdqmlstqcmgav6xfe4upz2qxfvj03tlk699dzlk7qzyrt6rgq7py26l874ft6mhrs5utprtx8ejjqp6eslvmh5gvvsgklsgqcyqqqqq2qqsdz6l
n/SãoPauloLivre - São Paulo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq898sardagxzatvdaxxjanjv5pzp6kfec55jce92gj4cjlg7ju8mzrea0ycfd3u86crk8vzayd334wrqvzqqqyx7cmls060
n/AcreLibertário - Acre (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq85zcmjv4xxjcn9wf6v8gtjd9hsyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqftljpt
n/Alagoas (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqr5zmrpvahkzuczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdas8qtaf4
Empreendedorismo:
n/Empreendedorismo/BR (por: nostr:npub14ysljm0gn6nnjv95yzeq6ffze4f3f9l0248kez4fhm4yz3fzardslwx5e8) nostr:naddr1qqd5y4zr9azk6urjv4jkuer9v3hhy6tnd4hj7snjv9ekjmqzyz5jr7tdaz02wwfsksstyrf9ytx4x9yhaa257my24xlw5s29yt5dkqcyqqqgdaslzrp3p
n/Empreendedorismo/SP (por: nostr:npub14ysljm0gn6nnjv95yzeq6ffze4f3f9l0248kez4fhm4yz3fzardslwx5e8) nostr:naddr1qqt5y4zr9azk6urjv4jkuer9v3hhy6tnd4hj756sqgs2jg0edh5fafeexz6zpvsdy53v65c5jlh42nmv325ma6jpg53w3kcrqsqqpphkcym25j
Análise
n/EBDV (Em Busca Da Verdade) - Análise geral e desenvolvimento pessoal (por: nostr:nprofile1qqs0xmu0skfdlmtl5tth6cv99za8f8kv7ulz5srkm8p6v5k03dx9lzspz4mhxue69uhkummnw3ezummcw3ezuer9wchszrnhwden5te0dehhxtnvdakz7qgswaehxw309ahx7um5wghx6mmd9usvrt9r) nostr:naddr1qqzy2sjy2cpzpum037ze9hld073dwltps55t5ay7enmnu2jqwmvu8fjje795chu2qvzqqqyx7cy9v5px
-
 @ c9badfea:610f861a
2025-05-05 23:29:08
@ c9badfea:610f861a
2025-05-05 23:29:08- Install RTranslator (it's free and open source)
- Launch the app, allow notifications, and enter a random name (used only for Walkie-Talkie/Conversations)
- Wait for the translation AI models to download
- Enjoy offline translations
ℹ️ Internet is only needed for the initial download
ℹ️ The app uses the system's TTS engine (consider open source TTS engines like SherpaTTS for de-googled phones)
-
 @ 866e0139:6a9334e5
2025-05-27 10:15:17
@ 866e0139:6a9334e5
2025-05-27 10:15:17Autor: Milosz Matuschek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie auch in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Der Schweizer Historiker Daniele Ganser startet eine Plakataktion. Auf Facebook schreibt er:
"Dieses Plakat habe ich ab heute an sechs Bahnhöfen in der Schweiz aufhängen lassen: Die Schweiz muss die Neutralität bewahren. Keine Zusammenarbeit mit der NATO!
Die Aktion läuft eine Woche. Das Plakat hängt in Basel (Gleis 5 und 7), Zürich (Gleis 9 und 12), Bern (Gleis 3 und 11), Luzern (Gleis 7 und 11), St. Gallen (Gleis 1 und 2) und Chur (Gleis 4 und Arosabahn).
Wenn jemand ein Plakat sieht und fotografiert und es mir per Email schickt freut mich das!
https://globalbridge.ch/die-schweiz-muss-die.../
Daniele Ganser kann man über folgende Seite kontaktieren.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:53
@ 39cc53c9:27168656
2025-05-27 09:21:53The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 9ca447d2:fbf5a36d
2025-05-27 12:01:36
@ 9ca447d2:fbf5a36d
2025-05-27 12:01:36Donald Trump’s recent four-day visit took the President to Saudi Arabia, Qatar, and the United Arab Emirates. This visit has intertwined diplomatic relations with business interests, while simultaneously influencing the bitcoin market.
In Qatar, the President met with Emir Tanim bin Hamad Al Thani, resulting in over $243 billion in deals including major defense agreements, according to Bloomberg.
On May 15, the President made his visit to the Sheikh Zayed Grand Mosque in Abu Dhabi alongside Crown Prince Khaled bin Mohamed Al Nahyan. This occurs as the Trump family expands its business presence in the Middle East.
The Trump Organization is developing luxury properties across the region, including Trump Tower Dubai, real estate projects in Riyadh, and development in Jeddah and Oman.
Donald Trump and Mohammed bin Salman in King Khalid International Airport — NBCNews
Eric Trump publicly announced construction plans for Trump Tower Dubai just last month, highlighting the family’s ongoing commercial footprint in the region.
These business connections extend into the digital asset ecosystem as UAE-backed investment firm MGX recently announced it would use USD1, World Liberty Financial’s stablecoin to support a $2 billion investment in Binance, the world’s largest digital asset exchange, according to APNews.
This connection between Trump-aligned interests and major digital asset investments creates a potential avenue for market influence.
Historically, stability in the Middle East, especially among oil-rich nations, reduces global market volatility. This encourages risk appetite among investors, often leading to increased allocations to digital assets like bitcoin.
Middle East diplomacy directly affects global oil prices. Stable oil prices can lower inflation expectations and lead to interest rate cuts by the Fed. Lower rates lead to an increase in liquidity, having positive effects on bitcoin, an asset that benefits from money printing.
Related: Fed Rate Cuts Could Lead to Major Price Swings for Bitcoin
On the investment front, Abu Dhabi’s Wealth Fund, Mubadala Investment Company, has been focused on increasing their shares in BlackRock’s iShares Bitcoin Trust (IBIT).
According to a 13F filing with the U.S. Securities and Exchange Commission, Mubdala held 8.7 million IBIT shares, totaling $408.5 million as of March 31, 2025.
The Abu Dhabi Wealth Fund increased its shares by 500,000 since its last filing in December of 2024.
Back in March, the United States created a Strategic Bitcoin Reserve. The executive order states that the U.S. will not sell the bitcoin they already hold, and will create budget-neutral ways to increase their holdings.
The time has come where governments and wealth funds alike are jumping on board the Bitcoin train.
Trump’s recent visit to the Middle East illustrates how financial, diplomatic, and personal interests are becoming increasingly intertwined with Bitcoin and digital assets, serving as a new axis of influence in the U.S.-Middle East relations.
The combination of diplomatic progress and business expansion has heightened short-term volatility and trading volumes in the bitcoin market.
Trump’s business and digital asset ties in the region may further boost institutional interest and create an opportunity for more players to enter the market.
-
 @ 9ca447d2:fbf5a36d
2025-05-27 12:01:34
@ 9ca447d2:fbf5a36d
2025-05-27 12:01:34Bahrain-based Al Abraaj Restaurants Group has made history by becoming the first publicly-traded company in the Middle East to add bitcoin to its corporate treasury. This is a major step forward for regional bitcoin adoption.
On May 15, 2025, Al Abraaj Restaurants Group, a well-known restaurant chain listed on the Bahrain Bourse, announced it had bought 5 bitcoin (BTC) as part of a new treasury strategy. This makes the company the first in Bahrain, the GCC and the Middle East to officially hold bitcoin as a reserve asset.
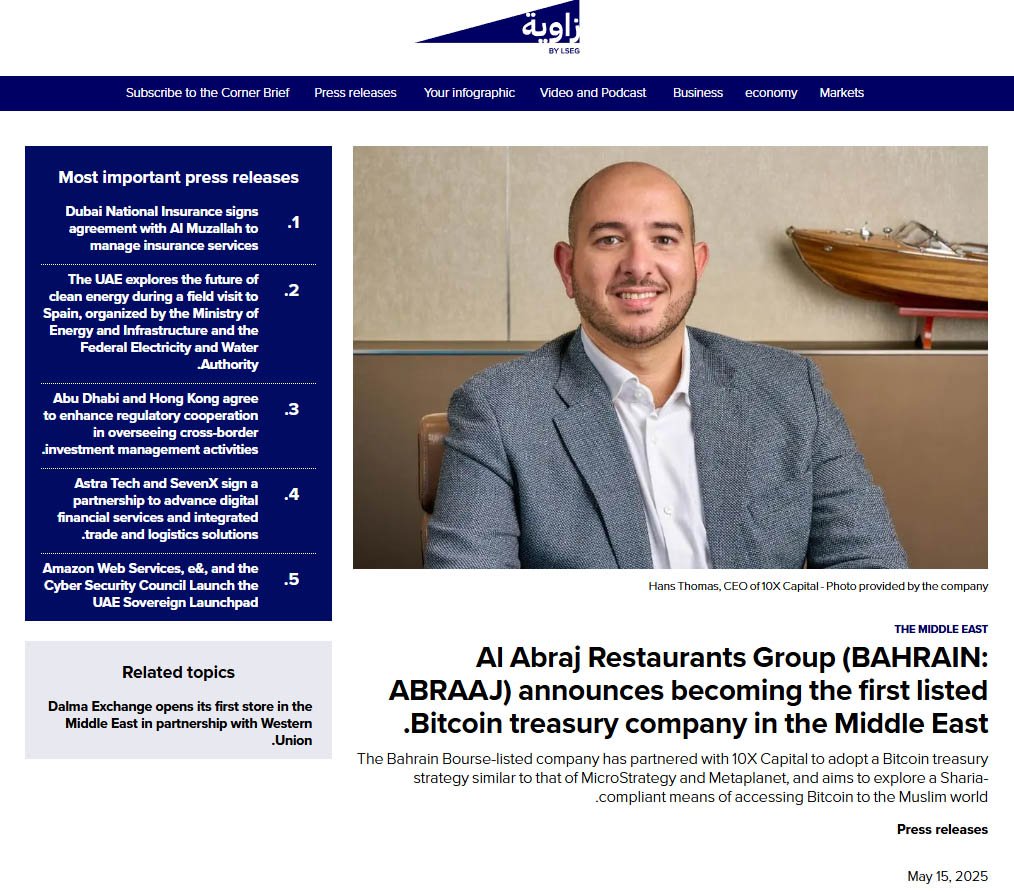
Al Abraaj adds bitcoin to its treasury — Zawya
This is a growing trend globally where companies are treating bitcoin not just as an investment but as a long-term store of value. Major companies like Strategy, Tesla and Metaplanet have already done this — and now Al Abraaj is following suit.
Metaplanet recently added 1,241 BTC to its treasury, boosting the company’s holdings above El Salvador’s.
Related: Metaplanet Overtakes El Salvador in Bitcoin Holdings After $126M Purchase
“Our initiative towards becoming a Bitcoin Treasury Company reflects our forward-thinking approach and dedication to maximizing shareholder value,” said Abdulla Isa, Chairman of the Bitcoin Treasury Committee at Al Abraaj.
Al Abraaj’s move is largely inspired by Michael Saylor, Executive Chairman of Strategy, the world’s largest corporate holder of bitcoin. Saylor’s strategy of allocating billions to bitcoin has set a model that other companies — now including Al Abraaj — are following.
A photo shared by the company even showed a meeting between an Al Abraaj representative and Saylor, with the company calling itself the “MicroStrategy of the Middle East”.
“We believe that Bitcoin will play a pivotal role in the future of finance, and we are excited to be at the forefront of this transformation in the Kingdom of Bahrain,” Isa added.
To support its bitcoin initiative, Al Abraaj has partnered with 10X Capital, a New York-based investment firm that specializes in digital assets.
10X Capital has a strong track record in bitcoin treasury strategies, and recently advised Nakamoto Holdings on a $710 million deal — the largest of its kind.
With 10X’s help, Al Abraaj looks to raise more capital and increase its bitcoin holdings over time to maximize bitcoin-per-share for its investors. The company will also develop Sharia-compliant financial instruments so Islamic investors can get exposure to bitcoin in a halal way.
“Bahrain continues to be a leader in the Middle East in Bitcoin adoption,” said Hans Thomas, CEO of 10X Capital. He noted, with a combined GDP of $2.2 trillion and over $6 trillion in sovereign wealth, the GCC now has its first publicly listed bitcoin treasury company.
This is not just a first for Al Abraaj — it’s a first for the region. Bahrain has been positioning itself as a fintech hub and Al Abraaj’s move will encourage more non-fintech companies in the region to look into bitcoin.
The company said the decision was made after thorough due diligence and is in line with the regulations set by the Central Bank of Bahrain (CBB). Al Abraaj will be fully compliant with all digital asset transaction rules, including transparency, security and governance.
A special Bitcoin Committee has been formed to oversee the treasury strategy. It includes experienced bitcoin investors, financial experts and portfolio managers who will manage risk, monitor market conditions and ensure best practices in custody and disclosure.
The initial purchase was 5 BTC, but Al Abraaj sees this as just the beginning. The company stated that there are plans in motion to allocate a significant portion of their treasury into bitcoin over time.
According to the company’s reports, Al Abraaj is financially sound with $12.5 million in EBITDA in 2024. This strong financial foundation gives the company the confidence to explore new strategies like bitcoin investment.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:51
@ 39cc53c9:27168656
2025-05-27 09:21:51Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ 266815e0:6cd408a5
2025-05-02 22:24:59
@ 266815e0:6cd408a5
2025-05-02 22:24:59Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.
Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
The communities where interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now
Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal

New emoji picker
Just another small improvement that makes the app feel more complete.
Experimental Wallet
There is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very experimental and probably won't work for you, but its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Don't feed the wallet your hard earned sats, it will eat them!
Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing on load
- Add option to mirror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ 39cc53c9:27168656
2025-05-27 09:21:50
@ 39cc53c9:27168656
2025-05-27 09:21:50Over the past few months, I've dedicated my time to a complete rewrite of the kycnot.me website. The technology stack remains unchanged; Golang paired with TailwindCSS. However, I've made some design choices in this iteration that I believe significantly enhance the site. Particularly to backend code.
UI Improvements
You'll notice a refreshed UI that retains the original concept but has some notable enhancements. The service list view is now more visually engaging, it displays additional information in a more aesthetically pleasing manner. Both filtering and searching functionalities have been optimized for speed and user experience.
Service pages have been also redesigned to highlight key information at the top, with the KYC Level box always accessible. The display of service attributes is now more visually intuitive.
The request form, especially the Captcha, has undergone substantial improvements. The new self-made Captcha is robust, addressing the reliability issues encountered with the previous version.
Terms of Service Summarizer
A significant upgrade is the Terms of Service summarizer/reviewer, now powered by AI (GPT-4-turbo). It efficiently condenses each service's ToS, extracting and presenting critical points, including any warnings. Summaries are updated monthly, processing over 40 ToS pages via the OpenAI API using a self-crafted and thoroughly tested prompt.
Nostr Comments
I've integrated a comment section for each service using Nostr. For guidance on using this feature, visit the dedicated how-to page.
Database
The backend database has transitioned to pocketbase, an open-source Golang backend that has been a pleasure to work with. I maintain an updated fork of the Golang SDK for pocketbase at pluja/pocketbase.
Scoring
The scoring algorithm has also been refined to be more fair. Despite I had considered its removal due to the complexity it adds (it is very difficult to design a fair scoring system), some users highlighted its value, so I kept it. The updated algorithm is available open source.
Listings
Each listing has been re-evaluated, and the ones that were no longer operational were removed. New additions are included, and the backlog of pending services will be addressed progressively, since I still have access to the old database.
API
The API now offers more comprehensive data. For more details, check here.
About Page
The About page has been restructured for brevity and clarity.
Other Changes
Extensive changes have been implemented in the server-side logic, since the whole code base was re-written from the ground up. I may discuss these in a future post, but for now, I consider the current version to be just a bit beyond beta, and additional updates are planned in the coming weeks.
-
 @ 4ba8e86d:89d32de4
2025-05-02 13:51:37
@ 4ba8e86d:89d32de4
2025-05-02 13:51:37Tutorial OpenKeychain
- Baixar no F-droid https://f-droid.org/app/org.sufficientlysecure.keychain
Ao abrir o OpenKeychain pela primeira vez, você verá uma tela inicial indicando que ainda não há chaves configuradas. Nesse ponto, você terá três opções:
-
Criar uma nova chave PGP diretamente no OpenKeychain: Ideal para quem está começando e precisa de uma solução simples para criptografia em comunicações diárias.
-
Usar um token de segurança (como Fidesmo, Yubikey, NEO, ou Sigilance) Se você busca uma segurança ainda maior, pode optar por armazenar sua chave privada em um token de segurança. Com essa configuração, a chave privada nunca é salva no dispositivo móvel. O celular atua apenas como uma interface de comunicação, enquanto a chave permanece protegida no token, fora do alcance de possíveis invasores remotos. Isso garante que somente quem possui o token fisicamente possa usar a chave, elevando significativamente o nível de segurança e controle sobre seus dados.
-
Importar uma chave PGP existente: Você pode importar uma chave PGP que já tenha sido gerada anteriormente, seja por meio de um arquivo no dispositivo ou por outro meio ler na área de transferência. https://image.nostr.build/51fdd924df4843ab73faa02a505c8fb17794f1789396ed89b154348ebb337f07.jpg
1. CRIANDO UMA NOVA CHAVE PGP.
Para iniciantes, recomendamos criar uma nova chave diretamente no aplicativo. abordaremos o uso do OpenKeychain em modo online, que é mais comum para comunicações diárias.
Passo 1: Clique em “Criar minha chave”. https://image.nostr.build/235f5cfdf4c3006ca3b00342741003f79a5055355c2a8ee425fc33c875f51e49.jpg
Passo 2: Criando sua chave PGP.
Para criar sua chave, você precisará fornecer algumas informações Os campos 'Nome' e 'Endereço de e-mail' são apenas formas convenientes para identificar a sua chave PGP.
-
Nome: Escolha um nome ou um pseudônimo. https://image.nostr.build/de3fe3ddbde0c7bf084be6e4b8150fdb8612365550622559b0ee72f50f56a159.jpg
-
E-mail: Associe um endereço de e-mail à chave, seja ele pessoal ou um e-mail relacionado ao pseudônimo. https://image.nostr.build/aff62baaeafe2c9a429ef10435a6f99dea36d6cfd7494e2bb882421dc8ed0f4e.jpg
2. REVISANDO E PERSONALIZANDO A CRIAÇÃO DA CHAVE.
Passo 3: Antes de criar sua chave PGP, verifique se os dados inseridos estão corretos. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
Você também pode personalizar as configurações de segurança clicando nos três pontos no canto superior direito. https://image.nostr.build/1ce615555cea9a979ea951472052a219e77f4e1ebaaf5fcbbe9e91ea4f852bce.jpg
Ao cliclar em ' nova subchave ' pode alterar a data de expiração e pode mudar a criptografia usado na chave cliclando opção ed2255/cv255. https://image.nostr.build/b3224ff3dbe48ff78c4a2df8b001926b6d3eef1e33ef677a73b0d281791073da.jpg https://image.nostr.build/7763c7847e062cdcf71aafedbc2ef4c38056fd66aeb162ef3a1c30c028a14376.jpg https://image.nostr.build/5d3e20ade460dd5e89cc001ebdc062a36aff2c0e1573584ca3c0d1cb34bddcce.jpg
Neste tutorial, utilizaremos as configurações padrão do aplicativo.
Passo 4: Clique em "Criar chave" para concluir o processo. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
3. Como Compartilhar sua Chave PGP Pública
Após criar sua chave PGP, você pode compartilhá-la para que outras pessoas possam enviar mensagens criptografadas para você. Veja o passo a passo de como exibir e compartilhar sua chave pública:
Passo 1: Acesse sua chave pública
Abra o OpenKeychain e selecione a chave que deseja compartilhar. Clique na chave para visualizar os detalhes. https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/4001610109579f27535628932258087b3b06c1f86b05f4f85537b6585c12a10b.jpg
Passo 2: Copiar sua chave pública
Nos detalhes da chave, você verá a opção "Copiar para a Área de Transferência". Clique nessa opção para copiar o código da sua chave pública. https://image.nostr.build/01ab3efa5e997e1910a2f8f7a888e6ad60350574cca4ca0214eee5581797f704.jpg
A chave PGP copiada terá o seguinte formato:
-----BEGIN PGP PUBLIC KEY BLOCK-----
mDMEZwsLHRYJKwYBBAHaRw8BAQdA6NRLlJIWnTBJtYwZHlrMbTKRbYuXmjsMn8MB 7etV3HK0JERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPohyBBMW CAAaBAsJCAcCFQgCFgECGQEFgmcLCx0CngECmwMACgkQFZf+kMeJWpR4cwEA8Jt1 TZ/+YlHg3EYphW8KsZOboHLi+L88whrWbka+0s8A/iuaNFAK/oQAlM2YI2e0rAjA VuUCo66mERQNLl2/qN0LuDgEZwsLHRIKKwYBBAGXVQEFAQEHQEj/ZfJolkCjldXP 0KQimE/3PfO9BdJeRtzZA+SsJDh+AwEIB4hhBBgWCAAJBYJnCwsdApsMAAoJEBWX /pDHiVqUo/oA/266xy7kIZvd0PF1QU9mv1m2oOdo7QSoqvgFiq6AmelbAP9lExY5 edctTa/zl87lCddYsZZhxG9g2Cg7xX/XsfrnAA== =TniY -----END PGP PUBLIC KEY BLOCK-----
Dica: Se ocorrer algum erro ao compartilhar sua chave pública com um amigo, peça para que ele a criptografe para ele mesmo. Isso permitirá que ele adicione a chave corretamente. Caso a chave pública ainda não esteja no dispositivo, ao clicar em "Backup de chave", aparecerá a opção para importá-la. Se a chave já estiver no dispositivo, essa ação irá recarregá-la. https://image.nostr.build/cd12abf07c93473db95483fe23112325f89d3eb02977e42756708bbd043f8bcf.jpg https://image.nostr.build/537aeae38d229ee2cc78e18f412237b659c059e1c74fd7f0deecfe37f15713c9.jpg https://image.nostr.build/16c8a3db5966c7c06904ee236655f47a6464ae0c1b5af6af27b28c61611d2bbe.jpg
Passo 3: Compartilhar sua chave PGP
Você pode colar a chave pública em e-mails, assinaturas, perfis de redes sociais ou outros meios para compartilhá-la facilmente. Para facilitar a visualização, você também pode exibi-la em seu perfil de redes sociais.
Para acessar mais opções de compartilhamento, clique nos três pontos no canto superior direito e selecione a opção "Avançado". https://image.nostr.build/0d4a13b7bd9a4794017247d1a56fac082db0f993a2011a4dd40e388b22ec88f5.jpg https://image.nostr.build/4ac2a7bc9fa726531a945221cf7d10e0e387deba68100ccf52fdedfcd17cbd59.jpg
Na seção "Compartilhar", você verá sua Key ID e terá a opção de publicar sua chave PGP em um servidor de chaves. https://image.nostr.build/1e972cc211a6d8060cdbd4a8aa642dd1a292810c532f178d3ddb133d1b9bca76.jpg
Passo 4: Como compartilhar sua chave pública PGP no formato .asc. no OpenKeychain
1 . Acesse sua chave
Abra o OpenKeychain e toque na chave que você deseja compartilhar. Isso abrirá a tela com os detalhes da chave. https://image.nostr.build/c080f03d2eb7a9f7833fec0ff1942a5b70b97e4f7da7c6bc79ca300ef9ace55d.jpg
2 . Compartilhe o arquivo .asc
Toque no ícone de compartilhamento, como indicado na imagem abaixo. O aplicativo abrirá a janela para que você escolha por qual app deseja compartilhar sua chave pública no formato .asc. Nesse exemplo, usei o SimpleXChat , mas você pode usar qualquer aplicativo de sua preferência.
-
Botão de compartilhar. https://image.nostr.build/8da74bdb04737a45df671a30bba1dd2e7980841fa0c2d751d6649630e7c25470.jpg
-
Seleção do aplicativo para compartilhamento. https://image.nostr.build/5444f4e9d3fa5aef6b191bb6f553f94c6e49d30ead874c9ee435bca3218fd6c8.jpg
-
Enviando via SimpleXChat. https://image.nostr.build/e5d1ca04cbc69e1e8ac5caf1ab2a4b9b695500861c1ae9c55cea679cce349214.jpg
Sugestão para compartilhar nas redes sociais:
Você pode exibir sua chave de forma simples, por exemplo:
PGP: 1597 FE90 C789 5A94
Importar a chave pública usando a fingerprint
Passo 1:Clique no ícone "+" para começar. https://image.nostr.build/ca6e6e569b4be60165eaf60c7ba1e6e3ec781b525e467c72b4f3605837e6b5ec.jpg
Passo 2: Selecione a opção "Buscar Chave". https://image.nostr.build/87e27d9435e6e3ef78063b9f15799a8120ead4637cd06c89c0220b48327573ae.jpg
Passo 3: Digite a fingerprint da chave em letras minúsculas, sem espaços. A chave correspondente aparecerá para ser adicionada. https://image.nostr.build/33e6819edd4582d7a8513e8814dacb07e1a62994bb3238c1b5b3865a46b5f234.jpg
Além disso, você pode compartilhar sua chave pública em formato QR Code, facilitando a troca de chaves em eventos ou conversas rápidas. Como Assinar Mensagens para Confirmar a Autenticidade da Sua Rede Social
Você pode autenticar sua conta em redes sociais utilizando sua chave PGP. Ao assinar uma mensagem com sua chave, você demonstra que realmente possui essa conta. Siga o passo a passo abaixo para assinar uma mensagem:
Passo 1: Clique na sua chave PGP. https://image.nostr.build/ffacce1bfb293c9a0888cd5efe340a63d96b293f4c010f8626105c7b212d8558.jpg
Passo 2: Clique no ícone indicado pela seta para abrir o campo de texto. https://image.nostr.build/4e992a2553810e2583b9d190280ce00a52fc423600a75eca48cbf541cf47d3c2.jpg
Passo 3: Deixe a opção "Encriptar para:" vazio. Em "Assinar com:", selecione sua chave PGP e digite a mensagem que deseja enviar, como o nome da sua rede social. https://image.nostr.build/a4a2a8d233d186e3d8d9adddccc445bcb3ca3ed88de0db671a77cede12323a75.jpg
Passo 4: Clique no ícone indicado pela seta para copiar o texto assinado. Uma mensagem aparecerá informando: "Assinado/Encriptado com Sucesso". https://image.nostr.build/a076dfc90e30a495af0872005bf70f412df57b7a0e1c2e17cf5aee9e9b3e39aa.jpg
A mensagem copiada terá o seguinte formato:
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA256
Minha rede social NOSTR é Danielfraga oficial. -----BEGIN PGP SIGNATURE-----
iIQEARYIACwlHERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPgUC ZxBBLgAKCRAVl/6Qx4lalGeNAPwP71rpsbhRnZhoWZsTDOFZY8ep/d0e5qYx5iPx HV26dwD/fKyiir1TR8JwZvEbOTYS0+Dn4DFlRAAfR3lKVTC96w4= =37Lj -----END PGP SIGNATURE-----
Com isso, você pode facilmente demonstrar a autenticidade da sua conta nas redes sociais.
4. PROTEGENDO SUA CHAVE COM UMA SENHA.
Passo 5: Após a criação da chave, é fundamental definir uma senha (ou passphrase) para adicionar uma camada extra de segurança. Recomendamos usar senhas longas (com mais de 20 caracteres) e de alta entropia para evitar ataques de força bruta. Ferramentas como KeePassDX ou Bitwarden podem ajudá-lo a gerar e gerenciar essas senhas.
Para definir a senha, clique na sua chave PGP, acesse o menu no canto superior direito e selecione "Alterar senha". https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/f28ecaa9890a8827f93cac78846c4b2ef67f86ccfc3501fdadf1d1c4874b0041.jpg https://image.nostr.build/919c277fbec63c397402abdd60f915cb239a674c317855cbda63a38edef80789.jpg
Agora basta adicionar uma senha forte. https://image.nostr.build/eb378219fbb1780f89663a474ce43b8d8ebb13beeb538f2a16279b056e5d9645.jpg https://image.nostr.build/cdfa3f9c6c4045841341da789deabb6318107812d5ba195529418572ab352aaf.jpg
5. CRIPTOGRAFAR E DESCRIPTOGRAFAR MENSAGENS E ARQUIVOS COM SUA CHAVE PGP
Criptografar Mensagens
Você pode criptografar mensagens para garantir que apenas o destinatário, que possui sua chave pública, possa lê-las. Siga os passos abaixo para criptografar um texto:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3: Clique na opção "Encriptar Texto".
https://image.nostr.build/405a730a6c774759d7913f92f59059d43146db4afb28451a6f8833f94e99437f.jpgPasso 4: Preencha os seguintes campos: https://image.nostr.build/7dc5eba39ff82a321195dbf46b8113818632e3ef41175991d58e799a8e9d2751.jpg
-
Encriptar para: Selecione o destinatário da mensagem, ou seja, a pessoa para quem você está enviando o texto criptografado.
https://image.nostr.build/1e8c8cba6d3c3136d9857512e2794a81ceb7434eccdfb0f7d26cdef008b2e6d2.jpg -
Assinar com: Escolha sua chave PGP para assinar a mensagem.
https://image.nostr.build/d25b228c35b132d396d01c354ef093b43b3565578fbc0d6ff7b9de4e41619855.jpg -
Digitar o texto: No campo de texto, escreva a mensagem que deseja criptografar.
https://image.nostr.build/8537271dfa4445e60cb4c3cdb5d97571dc0ff5ee8acd6ed89a8c81e4bd8736c2.jpg
Passo 5: Depois de preencher os campos, você pode copiar o texto criptografado de duas formas:
-
Copiar para a área de transferência: Clique na opção para copiar o texto criptografado e cole-o em um aplicativo de mensagens para enviá-lo.
https://image.nostr.build/a5cb8e2c538a38db3972e7f3ac9aa9f602cda6b62848ff0c4b99928a67dcd486.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o texto criptografado diretamente através de seus aplicativos de mensagens.
https://image.nostr.build/2b79cb564d623788a0de1111a067e0eb496f743389d465d4f4e8f6e65f0d08a7.jpg https://image.nostr.build/ff59e52bc8ab54ff377980a6ba5d1c4743d3298de11e5daa187ab7d45163a7be.jpg
Criptografar arquivos.
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3 : clique na opção "Encriptar arquivos ". https://image.nostr.build/3fcae48ee38e7f4079ebccfd3eafb9ab0ad3559221d2c3560cdfe60e29f56a15.jpg
Passo 4 : os passos a seguir são os mesmo que você seguiu pra encriptar a mensagem texto. Ítens "Encriptar para:" "Assinar com:" https://image.nostr.build/4d6599b9d3a9fdfae0964daaa9dae513d5ce277a7b61930fa2937d534f72ed40.jpg
Passo 5 : clilcar na opção " Adicionair arquivo(s)" Vai abrir na memória interna do celular selecione o arquivo que deseja encriptar. https://image.nostr.build/09e3b9b54a1406426114926aab19011c36b98886ebae6fcf556cfea83bb2c2f4.jpg https://image.nostr.build/af422e243b36762dd66111ec7c848a1352c100ca3040dc21792c923f80aef74d.jpg https://image.nostr.build/ebebbdb273b4bca58d901852aec1c60e4799aa77e9d12a31f992b0cf8f73e753.jpg
Passo 6: Depois de preencher os campos, você pode compartilhar o arquivo criptografado de duas formas:
-
Salvar na memória do celular: A primeira opção salva o arquivo criptografado no armazenamento do seu dispositivo. Você terá a opção de editar o nome do arquivo antes de salvar.
https://image.nostr.build/0a47c1e9f0003541f47091b2c2e8ce6b8d1533d95463e331b218070bae964ac8.jpg https://image.nostr.build/95a7a2b67356eb5ded5b217bab38a19bdeba5af7befd105834e413e0aec45462.jpg https://image.nostr.build/66cb3d22b271f3b73b7015613c72711a3ffbf5e1070d43153f9d1f3fcf35001c.jpg https://image.nostr.build/f9624d86f7592fe7ffad932b7805762dc279d9e8ff410222108155438a2c970f.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o arquivo criptografado diretamente por meio dos seus aplicativos de mensagens.
https://image.nostr.build/85541e466c7755c65bd6ba0208a6d8612beaa5298712b6d92f53865167695a38.jpg https://image.nostr.build/bf1e0f0aeb60cafbdf82af4b3b598288519e85b396bd3f9e00e61f65b89ea9f8.jpg https://image.nostr.build/fb090339898f37cdbb020828689b142ca601ca3ee549f67ddf6b2e094df9ab9f.jpg https://image.nostr.build/50c249ced06efe465ba533fef15207b0dcd1a725e9b2c139e8d85c13fd798276.jpg
Descriptografar Mensagens e Arquivos
Para ler uma mensagem ou arquivo criptografado que você recebeu, utilize sua chave privada. Siga os passos abaixo:
Descriptografar Mensagens
Passo 1: Copie a mensagem criptografada que você recebeu.
https://image.nostr.build/c37754b12a458e0176b9137ae0aa9e8209f853bf9d9292c0867fd8b0606d53c4.jpgPasso 2: Clique na opção "Ler da área de transferência" para descriptografar o texto.
https://image.nostr.build/d83c7dad2ee1cb6267779863bc174ee1a8f3cc3c86b69063345321027bdde7b5.jpg https://image.nostr.build/c0fae86e6ab1fe9dcee86753972c818bed489ea11efdd09b7e7da7422a9c81eb.jpgDescriptografar Arquivos
Passo 1: Clique na opção "Selecionar arquivo de entrada".
https://image.nostr.build/9c276c630311d19a576f2e35b5ba82bac07360476edae3f1a8697ff85df9e3c9.jpgPasso 2: Selecione o arquivo criptografado que deseja descriptografar.
https://image.nostr.build/6b6c2a3284ba96e7168fc7bd0916020c4f1bed7b77dfca48227fc96d6929e15a.jpg https://image.nostr.build/9945aad644af2e2020e07e55f65f11a0958d55e8fc9e13c862e6b9ca88b4f4d9.jpg6. BACKUP E RESTAURAÇÃO DE CHAVE PGP.
Realizar o backup das suas chaves PGP é fundamental para evitar a perda de acesso às suas mensagens e dados criptografados. O OpenKeychain facilita esse processo, permitindo que você faça um backup completo e seguro. Recomendamos que você armazene o backup em um local seguro, como um HD externo ou pendrive conectado via cabo OTG, sempre protegendo-o com senha.
PASSOS PARA REALIZAR O BACKUP:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção Backup/restaurar.
https://image.nostr.build/6fa8fd14e23b47c6c924bc0d900646663f2124a93d8172ae79fdf43b5c7d4490.jpgPasso 3: Escolha a primeira opção: Backup completo (criptografado).
https://image.nostr.build/4875fb27b6d04c3cb838b4fb9f308ef9194edc35ba1254ba965b7f0db2544170.jpgPasso 4: O backup será protegido por um código de backup gerado automaticamente. Anote esse código em um papel e guarde local seguro, pois sem ele você não conseguirá recuperar suas chaves PGP. Após anotar o código, marque a opção “Anotei o código” e clique em Salvar Backup. Obs: todas as vezes que você for fazer o backup da sua chave PGP vai ser criado um novo código aleatório.
https://image.nostr.build/72a317ef5e59a01c03c36f1d04a91d42c418a478cc82e372acf21bb8302daa00.jpg
Passo 5: Escolha o local onde deseja salvar o backup (HD externo, pendrive, etc.), confirme sua escolha e clique em OK. Você verá uma mensagem de confirmação indicando que o backup foi salvo com sucesso.
https://image.nostr.build/d757e8bdf429371320daa44be8a48a0dbeb2324129f4254327f0f0383e70ede4.jpg https://image.nostr.build/f3ad80ceb8a191b4d1b40722b1d0d4f85bf183d412e7d7d901b25d19b2dfe0e3.jpg
Importação da Chave PGP
Caso você precise restaurar suas chaves PGP a partir de um backup, o OpenKeychain também facilita o processo de importação. Siga os passos abaixo para restaurar sua chave PGP:
Passo 1: Selecione a opção "Selecionar arquivo de entrada"
Abra o OpenKeychain, acesse o menu lateral no canto superior esquerdo e escolha a opção "Selecionar arquivo de entrada" para localizar o arquivo de backup que você deseja importar.
https://image.nostr.build/a06ddc1c1e6c50519097e614aa25b14311e49c0ca4d4607e42ebdcca3a6641c4.jpgPasso 2: Selecione o arquivo de backup
Navegue até o local onde você salvou o arquivo de backup (HD externo, pendrive, etc.) e selecione-o. Em seguida, o OpenKeychain solicitará que você insira o código de recuperação que foi gerado no momento do backup. https://image.nostr.build/9d5649c04a98ec8b0a29355d9068e48313b1c5dc36cd965961f4d33f22d10046.jpgPasso 3: Digite o código de recuperação
Insira o código de recuperação que você anotou anteriormente. É importante digitar o código corretamente para garantir o sucesso da restauração.Passo 4: Depois de inserir o código corretamente, o OpenKeychain irá restaurar suas chaves PGP, e uma mensagem de confirmação será exibida, indicando que a recuperação foi concluída com sucesso.
Agora suas chaves estão restauradas e você pode continuar usando o OpenKeychain para gerenciar suas comunicações criptografadas de maneira segura.
https://www.openkeychain.org/
https://github.com/open-keychain/open-keychain
https://youtu.be/fptlAx_j4OA
-
 @ 39cc53c9:27168656
2025-05-27 09:21:48
@ 39cc53c9:27168656
2025-05-27 09:21:48I'm launching a new service review section on this blog in collaboration with OrangeFren. These reviews are sponsored, yet the sponsorship does not influence the outcome of the evaluations. Reviews are done in advance, then, the service provider has the discretion to approve publication without modifications.
Sponsored reviews are independent from the kycnot.me list, being only part of the blog. The reviews have no impact on the scores of the listings or their continued presence on the list. Should any issues arise, I will not hesitate to remove any listing.
The review
WizardSwap is an instant exchange centred around privacy coins. It was launched in 2020 making it old enough to have weathered the 2021 bull run and the subsequent bearish year.
| Pros | Cons | |------|------| | Tor-friendly | Limited liquidity | | Guarantee of no KYC | Overly simplistic design | | Earn by providing liquidity | |
Rating: ★★★★★ Service Website: wizardswap.io
Liquidity
Right off the bat, we'll start off by pointing out that WizardSwap relies on its own liquidity reserves, meaning they aren't just a reseller of Binance or another exchange. They're also committed to a no-KYC policy, when asking them, they even promised they would rather refund a user their original coins, than force them to undergo any sort of verification.
On the one hand, full control over all their infrastructure gives users the most privacy and conviction about the KYC policies remaining in place.
On the other hand, this means the liquidity available for swapping isn't huge. At the time of testing we could only purchase at most about 0.73 BTC with XMR.
It's clear the team behind WizardSwap is aware of this shortfall and so they've come up with a solution unique among instant exchanges. They let you, the user, deposit any of the currencies they support into your account and earn a profit on the trades made using your liquidity.
Trading
Fees on WizardSwap are middle-of-the-pack. The normal fee is 2.2%. That's more than some exchanges that reserve the right to suddenly demand you undergo verification, yet less than half the fees on some other privacy-first exchanges. However as we mentioned in the section above you can earn almost all of that fee (2%) if you provide liquidity to WizardSwap.
It's good that with the current Bitcoin fee market their fees are constant regardless of how much, or how little, you send. This is in stark contrast with some of the alternative swap providers that will charge you a massive premium when attempting to swap small amounts of BTC away.
Test trades
Test trades are always performed without previous notice to the service provider.
During our testing we performed a few test trades and found that every single time WizardSwap immediately detected the incoming transaction and the amount we received was exactly what was quoted before depositing. The fees were inline with what WizardSwap advertises.

- Monero payment proof
- Bitcoin received
- Wizardswap TX link - it's possible that this link may cease to be valid at some point in the future.
ToS and KYC
WizardSwap does not have a Terms of Service or a Privacy Policy page, at least none that can be found by users. Instead, they offer a FAQ section where they addresses some basic questions.
The site does not mention any KYC or AML practices. It also does not specify how refunds are handled in case of failure. However, based on the FAQ section "What if I send funds after the offer expires?" it can be inferred that contacting support is necessary and network fees will be deducted from any refund.
UI & Tor
WizardSwap can be visited both via your usual browser and Tor Browser. Should you decide on the latter you'll find that the website works even with the most strict settings available in the Tor Browser (meaning no JavaScript).
However, when disabling Javascript you'll miss the live support chat, as well as automatic refreshing of the trade page. The lack of the first means that you will have no way to contact support from the trade page if anything goes wrong during your swap, although you can do so by mail.
One important thing to have in mind is that if you were to accidentally close the browser during the swap, and you did not save the swap ID or your browser history is disabled, you'll have no easy way to return to the trade. For this reason we suggest when you begin a trade to copy the url or ID to someplace safe, before sending any coins to WizardSwap.
The UI you'll be greeted by is simple, minimalist, and easy to navigate. It works well not just across browsers, but also across devices. You won't have any issues using this exchange on your phone.
Getting in touch
The team behind WizardSwap appears to be most active on X (formerly Twitter): https://twitter.com/WizardSwap_io
If you have any comments or suggestions about the exchange make sure to reach out to them. In the past they've been very receptive to user feedback, for instance a few months back WizardSwap was planning on removing DeepOnion, but the community behind that project got together ^1 and after reaching out WizardSwap reversed their decision ^2.
You can also contact them via email at:
support @ wizardswap . ioDisclaimer
None of the above should be understood as investment or financial advice. The views are our own only and constitute a faithful representation of our experience in using and investigating this exchange. This review is not a guarantee of any kind on the services rendered by the exchange. Do your own research before using any service.
-
 @ 3ffac3a6:2d656657
2025-05-02 03:50:51
@ 3ffac3a6:2d656657
2025-05-02 03:50:51Introduction: Don't Despair—This Can Be Fixed (But Don't Reboot Yet)
Running ZFS on a Raspberry Pi offers powerful features for home servers and personal NAS setups. But with power comes complexity, and in recent months, a quiet pitfall has emerged for Pi users who track kernel updates closely: upgrading to an unsupported kernel version breaks ZFS.
⚠️ Important Warning: If you've just upgraded your kernel and you're using ZFS, do not reboot yet. Rebooting without a working ZFS module can leave your system unbootable—even if you don't have critical partitions on ZFS. The system may hang because it tries to load the missing ZFS kernel module during boot and fails, halting the boot process.
If you're already facing a broken setup or can't boot — don't panic. This guide outlines both the worst-case scenario and the ideal recovery strategy. Whether you're locked out or preparing for a smooth upgrade, we've got you covered.
The Problem: A Kernel Update Too Far
As of ZFS version 2.2.3 (used in Debian-based Raspberry Pi OS), the filesystem supports Linux kernels up to 6.7. However, Raspberry Pi OS backports recently began shipping 6.12.x kernels. If you upgrade to 6.12 without precautions:
- ZFS will fail to compile against the new kernel
- DKMS errors will appear during package updates
- Your ZFS module will be missing after reboot
- Your Raspberry Pi may fail to boot, even without ZFS-mounted root or critical paths, simply due to systemd or boot scripts expecting the kernel module to be present
Example ZFS Compilation Error:
During package updates or installs, you'll see something like:
checking whether bdev_open_by_path() exists... configure: error: *** None of the expected "blkdev_get_by_path()" interfaces were detected. *** This may be because your kernel version is newer than what is *** supported, or you are using a patched custom kernel with *** incompatible modifications. *** *** ZFS Version: zfs-2.2.3-1~bpo12+1~rpt1 *** Compatible Kernels: 3.10 - 6.7This error means ZFS cannot build its kernel module against Linux 6.12.x, making it unusable.
Why This Happens: The Version Trap
The key problem is that ZFS 2.2.3 remains installed even after a kernel upgrade, and it doesn't get upgraded automatically during
apt upgrade. Since ZFS 2.2.3 only supports up to kernel 6.7, it fails to compile against 6.12.x.However, if you remove and then reinstall ZFS, the package manager installs ZFS 2.3.1, which does support Linux kernel 6.12.x. This version transition is what resolves the issue — but only if you explicitly purge and reinstall ZFS.
Worst Case: The System That Wouldn’t Boot
After upgrading the kernel and rebooting, the system failed to boot properly. It showed errors like:
cannot open access to console, the root account is locked
Although the system did not have critical filesystems on ZFS, the boot process still stalled because system services attempted to load the ZFS kernel module, which was no longer available. This resulted in an unrecoverable boot failure.
The only way forward was to reformat and reinstall Raspberry Pi OS. However, the default Raspberry Pi OS image still comes with a 6.6.x kernel, which is incompatible with ZFS 2.3.1 and newer kernels unless upgraded. Therefore, the recovery process requires one crucial step:
- First, perform a full system upgrade:
sudo apt update && sudo apt full-upgradeThis brings the kernel up to 6.12.x.
- Then, reinstall ZFS:
sudo apt install zfs-dkms zfsutils-linuxOnce this is complete, your system will be running kernel 6.12 with ZFS 2.3.1, and you can safely import your pools and resume operations.
Best Case Recovery: Clean Cut, Clean Upgrade
For users who can still log into their system, here's the cleanest and safest sequence to move forward:
- Stop all services using ZFS, including Docker, NFS, Samba, backup tools, etc.
- Export all ZFS pools:
sudo zpool export -a3. Disable swap if it lives on a ZFS vdev:sudo swapoff /dev/sdXn4. Purge ZFS packages:sudo apt purge zfsutils-linux zfs-dkms zfs-zed sudo rm -rf /usr/src/zfs* /var/lib/dkms/zfs5. Update the kernel to the desired version:sudo apt update && sudo apt full-upgrade6. Reboot into the new kernel:sudo reboot7. Reinstall ZFS:sudo apt install zfs-dkms zfsutils-linux8. Import your pool(s):sudo zpool import poolname9. Restart services that depend on ZFS.
Final Notes: Prevention Is Better Than Recovery
To avoid this issue in the future:
- Hold your current working kernel version:
sudo apt-mark hold linux-image-rpi-v8 linux-headers-rpi-v8* Or track ZFS GitHub for kernel compatibility before upgrading * Or test upgrades on a second Pi or cloned SD card before rolling them out to production
Conclusion: A Solvable Trap
ZFS on the Raspberry Pi remains a powerful option, but it demands careful version tracking. If you upgrade responsibly, or recover cleanly as described above, you can continue benefiting from advanced features like snapshots, send/receive, and compression even on this tiny powerhouse.
Don’t let a kernel update ruin your storage plans—with preparation, the Pi + ZFS combo can remain stable and strong.
-
 @ b1ddb4d7:471244e7
2025-05-27 12:01:18
@ b1ddb4d7:471244e7
2025-05-27 12:01:18Global fintech leader Revolut has announced a landmark partnership with Lightspark, a pioneer in blockchain infrastructure solutions, to integrate bitcoin’s Lightning Network into its platform.
This collaboration, now live for Revolut users in the UK and select European Economic Area (EEA) countries, marks a transformative leap toward frictionless, real-time transactions—eliminating delays and exorbitant fees traditionally associated with digital asset transfers.
 Major update: @RevolutApp is now partnering with @lightspark pic.twitter.com/OUblgrj6Xr
Major update: @RevolutApp is now partnering with @lightspark pic.twitter.com/OUblgrj6Xr— Lightspark (@lightspark) May 7, 2025
Breaking Barriers in Digital Currency Usability
By adopting Lightspark’s cutting-edge technology, Revolut empowers its 40+ million customers to execute bitcoin transactions instantly at a fraction of current costs.
This integration addresses longstanding pain points in digital currency adoption, positioning bitcoin as a practical tool for everyday payments. Users can now seamlessly send, receive, and store bitcoin with the same ease as traditional fiat currencies, backed by Revolut’s secure platform.
The partnership also advances Revolut’s integration into the open Money Grid, a decentralized network enabling universal interoperability between financial platforms.
This move aligns Revolut with forward-thinking fintechs adopting next-gen solutions like Lightning transactions and Universal Money Addresses (UMA), which simplify cross-border payments by replacing complex wallet codes with human-readable addresses (e.g., $john.smith).
Why This Matters
The collaboration challenges conventional payment rails, which often incur delays of days and high fees for cross-border transfers. By contrast, Lightning Network transactions settle in seconds for minimal cost, revolutionizing peer-to-peer payments, remittances, and merchant settlements. For Revolut users, this means:
- Instant transactions: Send bitcoin globally in under three seconds.
- Near-zero fees: Dramatically reduce costs compared to traditional crypto transfers.
- Enhanced utility: Use bitcoin for daily spending, not just as a speculative asset.
The Road Ahead
Revolut plans to expand Lightning Network access to additional markets in 2025, with ambitions to integrate UMA support for seamless fiat and digital currency interactions. Lightspark will continue optimizing its infrastructure to support Revolut’s scaling efforts, further bridging the gap between blockchain innovation and mainstream finance.
About Revolut
Revolut is a global financial app serving over 40 million customers worldwide. Offering services ranging from currency exchange and stock trading to digital assets and insurance, Revolut is committed to building a borderless financial ecosystem.
About Lightspark
Founded by former PayPal and Meta executives, Lightspark develops enterprise-grade solutions for the Lightning Network. Its technology stack empowers institutions to harness bitcoin’s speed and efficiency while maintaining regulatory compliance.
-
 @ cae03c48:2a7d6671
2025-05-27 12:01:05
@ cae03c48:2a7d6671
2025-05-27 12:01:05Bitcoin Magazine

The Bitcoin Mempool: Relay Network DynamicsIn the last Mempool article, I went over the different kinds of relay policy filters, why they exist, and the incentives that ultimately decide how effective each class of filter is at preventing the confirmation of different classes of transactions. In this piece I’ll be looking at the dynamics of the relay network when some nodes on the network are running different relay policies compared to other nodes.
All else being equal, when nodes on the network are running homogenous relay policies in their mempools, all transactions should propagate across the entire network given that they pay the minimum feerate necessary not to be evicted from a node’s mempool during times of large transaction backlogs. This changes when different nodes on the network are running heterogenous policies.
The Bitcoin relay network operates on a best effort basis, using what is called a flood-fill architecture. This means that when a transaction is received by one node, it is forwarded to every other node it is connected to except the one that it received the transaction from. This is a highly inefficient network architecture, but in the context of a decentralized system it provides a high degree of guarantee that the transaction will eventually reach its intended destination, the miners.
Introducing filters in a node’s relay policy to restrict the relaying of otherwise valid transactions in theory introduces friction to the propagation of that transaction, and degrades the reliability of the network’s ability to perform this function. In practice, things aren’t that simple.
How Much Friction Prevents Propagation
Let’s look at a simplified example of different network node compositions. In the following graphics blue nodes represent ones that will propagate some arbitrary class of consensus valid transactions, and red nodes represent ones that will not propagate those transactions. The collective set of miners is denoted in the center as a simple representation of where transacting users ultimately want their transactions to wind up so as to eventually be confirmed in the blockchain.

This is a model of the network in which the nodes refusing to propagate these transactions are a clear minority. As you can clearly see, any node on the network that accepts them has a clear path to relay them to the miners. The two nodes attempting to restrict the transactions propagation across the network have no effect on their eventual receipt by miners’ nodes.

In this diagram, you can see that almost half of the example network is instituting filtering policies for this class of transactions. Despite this, only part of the network that propagates these transactions is cut off from a path to miners. The rest of the nodes not filtering still have a clear path to miners. This has introduced some degree of friction for a subset of users, but the others can still freely engage in propagating these transactions.
Even for the users that are affected by filtering nodes, only a single connection to the rest of the network nodes that are not cut off from miners (or a direct connection to a miner) is necessary in order for that friction to be removed. If the real relay network were to have a similar composition to this example, all it would take is a single new connection to alleviate the problem.

In this scenario, only a tiny minority of the network is actually propagating these transactions. The rest of the network is engaging in filtering policies to prevent their propagation. Even in this case however, those nodes that are not filtering still have a clear path to propagate them to miners.
Only this tiny minority of non-filtering nodes is necessary in order to ensure their eventual propagation to miners. Preferential peering logic, i.e. functionality to ensure that your node prefers peers who implement the same software version or relay policies. These types of solutions can guarantee that peers who will propagate something to others won’t find each other and maintain connections amongst themselves across the network.
The Tolerant Minority
As you can see looking at these different examples, even in the face of an overwhelming majority of the public network engaging in filtering of a specific class of transactions, all that is necessary for them to successfully propagate across the network to miners is a small minority of the network to propagate and relay them.
These nodes will essentially, through whatever technical mechanism, create a “sub-network” within the larger public relay network in order to guarantee that there are viable paths from users engaging in these types of transactions to the miners willing to include them in their blocks.
There is essentially nothing that can be done to counter this dynamic except to engage in a sybil attack against all of these nodes, and sybil attacks only need a single honest connection in order to be completely defeated. As well, an honest node creating a very large number of connections with other nodes on the network can raise the cost of such a sybil attack exorbitantly. The more connections it creates, the more sybil nodes must be spun up in order to consume all of its connection slots.
What If There Is No Minority?
So what if there is no Tolerant Minority? What will happen to this class of transactions in that case?

If users still want to make them and pay fees to miners for them, they will be confirmed. Miners will simply set up an API. The role of miners is to confirm transactions, and the reason they do so is to maximize profit. Miners are not selfless entities, or morally or ideologically motivated, they are a business. They exist to make money.
If users exist that are willing to pay them money for a certain type of transaction, and the entirety of the public relay network is refusing to propagate those transactions to miners in order to include them in blocks, miners will create another way for users to submit those transactions to them.
It is simply the rational move to make as a profit motivated actor when customers exist that wish to pay you money.
Relay Policy Is Not A Replacement For Consensus
At the end of the day, relay policy cannot successfully censor transactions if they are consensus valid, users are willing to pay for them, and miners do not have some extenuating circumstances to turn down the fees users are willing to pay (such as causing material damage or harm to nodes on the network, i.e. crashing nodes, propagating blocks that take hours to verify on a consumer PC, etc.).
If some class of transactions is truly seen as undesirable by Bitcoin users and node operators, there is no solution to stopping them from being confirmed in the blockchain short of enacting a consensus change to make them invalid.
If it were possible to simply prevent transactions from being confirmed by filtering policies implemented on the relay network, then Bitcoin would not be censorship resistant.
This post The Bitcoin Mempool: Relay Network Dynamics first appeared on Bitcoin Magazine and is written by Shinobi.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:46
@ 39cc53c9:27168656
2025-05-27 09:21:46Bitcoin enthusiasts frequently and correctly remark how much value it adds to Bitcoin not to have a face, a leader, or a central authority behind it. This particularity means there isn't a single person to exert control over, or a single human point of failure who could become corrupt or harmful to the project.
Because of this, it is said that no other coin can be equally valuable as Bitcoin in terms of decentralization and trustworthiness. Bitcoin is unique not just for being first, but also because of how the events behind its inception developed. This implies that, from Bitcoin onwards, any coin created would have been created by someone, consequently having an authority behind it. For this and some other reasons, some people refer to Bitcoin as "The Immaculate Conception".
While other coins may have their own unique features and advantages, they may not be able to replicate Bitcoin's community-driven nature. However, one other cryptocurrency shares a similar story of mystery behind its creation: Monero.
History of Monero
Bytecoin and CryptoNote
In March 2014, a Bitcointalk thread titled "Bytecoin. Secure, private, untraceable since 2012" was initiated by a user under the nickname "DStrange"^1^. DStrange presented Bytecoin (BCN) as a unique cryptocurrency, in operation since July 2012. Unlike Bitcoin, it employed a new algorithm known as CryptoNote.
DStrange apparently stumbled upon the Bytecoin website by chance while mining a dying bitcoin fork, and decided to create a thread on Bitcointalk^1^. This sparked curiosity among some users, who wondered how could Bytecoin remain unnoticed since its alleged launch in 2012 until then^2^.
Some time after, a user brought up the "CryptoNote v2.0" whitepaper for the first time, underlining its innovative features^4^. Authored by the pseudonymous Nicolas van Saberhagen in October 2013, the CryptoNote v2 whitepaper^5^ highlighted the traceability and privacy problems in Bitcoin. Saberhagen argued that these flaws could not be quickly fixed, suggesting it would be more efficient to start a new project rather than trying to patch the original^5^, an statement simmilar to the one from Satoshi Nakamoto^6^.
Checking with Saberhagen's digital signature, the release date of the whitepaper seemed correct, which would mean that Cryptonote (v1) was created in 2012^7^, although there's an important detail: "Signing time is from the clock on the signer's computer" ^9^.
Moreover, the whitepaper v1 contains a footnote link to a Bitcointalk post dated May 5, 2013^10^, making it impossible for the whitepaper to have been signed and released on December 12, 2012.
As the narrative developed, users discovered that a significant 80% portion of Bytecoin had been pre-mined^11^ and blockchain dates seemed to be faked to make it look like it had been operating since 2012, leading to controversy surrounding the project.
The origins of CryptoNote and Bytecoin remain mysterious, leaving suspicions of a possible scam attempt, although the whitepaper had a good amount of work and thought on it.
The fork
In April 2014, the Bitcointalk user
thankful_for_today, who had also participated in the Bytecoin thread^12^, announced plans to launch a Bytecoin fork named Bitmonero^13^.The primary motivation behind this fork was "Because there is a number of technical and marketing issues I wanted to do differently. And also because I like ideas and technology and I want it to succeed"^14^. This time Bitmonero did things different from Bytecoin: there was no premine or instamine, and no portion of the block reward went to development.
However, thankful_for_today proposed controversial changes that the community disagreed with. Johnny Mnemonic relates the events surrounding Bitmonero and thankful_for_today in a Bitcointalk comment^15^:
When thankful_for_today launched BitMonero [...] he ignored everything that was discussed and just did what he wanted. The block reward was considerably steeper than what everyone was expecting. He also moved forward with 1-minute block times despite everyone's concerns about the increase of orphan blocks. He also didn't address the tail emission concern that should've (in my opinion) been in the code at launch time. Basically, he messed everything up. Then, he disappeared.
After disappearing for a while, thankful_for_today returned to find that the community had taken over the project. Johnny Mnemonic continues:
I, and others, started working on new forks that were closer to what everyone else was hoping for. [...] it was decided that the BitMonero project should just be taken over. There were like 9 or 10 interested parties at the time if my memory is correct. We voted on IRC to drop the "bit" from BitMonero and move forward with the project. Thankful_for_today suddenly resurfaced, and wasn't happy to learn the community had assumed control of the coin. He attempted to maintain his own fork (still calling it "BitMonero") for a while, but that quickly fell into obscurity.
The unfolding of these events show us the roots of Monero. Much like Satoshi Nakamoto, the creators behind CryptoNote/Bytecoin and thankful_for_today remain a mystery^17^, having disappeared without a trace. This enigma only adds to Monero's value.
Since community took over development, believing in the project's potential and its ability to be guided in a better direction, Monero was given one of Bitcoin's most important qualities: a leaderless nature. With no single face or entity directing its path, Monero is safe from potential corruption or harm from a "central authority".
The community continued developing Monero until today. Since then, Monero has undergone a lot of technological improvements, migrations and achievements such as RingCT and RandomX. It also has developed its own Community Crowdfundinc System, conferences such as MoneroKon and Monerotopia are taking place every year, and has a very active community around it.
Monero continues to develop with goals of privacy and security first, ease of use and efficiency second. ^16^
This stands as a testament to the power of a dedicated community operating without a central figure of authority. This decentralized approach aligns with the original ethos of cryptocurrency, making Monero a prime example of community-driven innovation. For this, I thank all the people involved in Monero, that lead it to where it is today.
If you find any information that seems incorrect, unclear or any missing important events, please contact me and I will make the necessary changes.
Sources of interest
- https://forum.getmonero.org/20/general-discussion/211/history-of-monero
- https://monero.stackexchange.com/questions/852/what-is-the-origin-of-monero-and-its-relationship-to-bytecoin
- https://en.wikipedia.org/wiki/Monero
- https://bitcointalk.org/index.php?topic=583449.0
- https://bitcointalk.org/index.php?topic=563821.0
- https://bitcointalk.org/index.php?action=profile;u=233561
- https://bitcointalk.org/index.php?topic=512747.0
- https://bitcointalk.org/index.php?topic=740112.0
- https://monero.stackexchange.com/a/1024
- https://inspec2t-project.eu/cryptocurrency-with-a-focus-on-anonymity-these-facts-are-known-about-monero/
- https://medium.com/coin-story/coin-perspective-13-riccardo-spagni-69ef82907bd1
- https://www.getmonero.org/resources/about/
- https://www.wired.com/2017/01/monero-drug-dealers-cryptocurrency-choice-fire/
- https://www.monero.how/why-monero-vs-bitcoin
- https://old.reddit.com/r/Monero/comments/u8e5yr/satoshi_nakamoto_talked_about_privacy_features/
-
 @ 39cc53c9:27168656
2025-05-27 09:21:40
@ 39cc53c9:27168656
2025-05-27 09:21:40“The future is there... staring back at us. Trying to make sense of the fiction we will have become.” — William Gibson.
This month is the 4th anniversary of kycnot.me. Thank you for being here.
Fifteen years ago, Satoshi Nakamoto introduced Bitcoin, a peer-to-peer electronic cash system: a decentralized currency free from government and institutional control. Nakamoto's whitepaper showed a vision for a financial system based on trustless transactions, secured by cryptography. Some time forward and KYC (Know Your Customer), AML (Anti-Money Laundering), and CTF (Counter-Terrorism Financing) regulations started to come into play.
What a paradox: to engage with a system designed for decentralization, privacy, and independence, we are forced to give away our personal details. Using Bitcoin in the economy requires revealing your identity, not just to the party you interact with, but also to third parties who must track and report the interaction. You are forced to give sensitive data to entities you don't, can't, and shouldn't trust. Information can never be kept 100% safe; there's always a risk. Information is power, who knows about you has control over you.
Information asymmetry creates imbalances of power. When entities have detailed knowledge about individuals, they can manipulate, influence, or exploit this information to their advantage. The accumulation of personal data by corporations and governments enables extensive surveillances.
Such practices, moreover, exclude individuals from traditional economic systems if their documentation doesn't meet arbitrary standards, reinforcing a dystopian divide. Small businesses are similarly burdened by the costs of implementing these regulations, hindering free market competition^1:
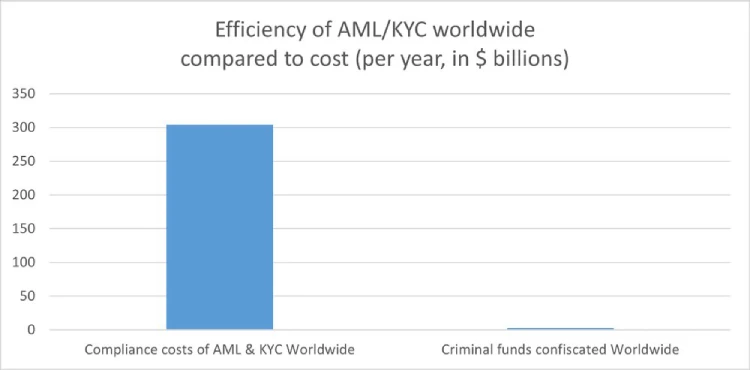
How will they keep this information safe? Why do they need my identity? Why do they force businesses to enforce such regulations? It's always for your safety, to protect you from the "bad". Your life is perpetually in danger: terrorists, money launderers, villains... so the government steps in to save us.
‟Hush now, baby, baby, don't you cry Mamma's gonna make all of your nightmares come true Mamma's gonna put all of her fears into you Mamma's gonna keep you right here, under her wing She won't let you fly, but she might let you sing Mamma's gonna keep baby cosy and warm” — Mother, Pink Floyd
We must resist any attack on our privacy and freedom. To do this, we must collaborate.
If you have a service, refuse to ask for KYC; find a way. Accept cryptocurrencies like Bitcoin and Monero. Commit to circular economies. Remove the need to go through the FIAT system. People need fiat money to use most services, but we can change that.
If you're a user, donate to and prefer using services that accept such currencies. Encourage your friends to accept cryptocurrencies as well. Boycott FIAT system to the greatest extent you possibly can.
This may sound utopian, but it can be achieved. This movement can't be stopped. Go kick the hornet's nest.
“We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.” — Eric Hughes, A Cypherpunk's Manifesto
The anniversary
Four years ago, I began exploring ways to use crypto without KYC. I bookmarked a few favorite services and thought sharing them to the world might be useful. That was the first version of kycnot.me — a simple list of about 15 services. Since then, I've added services, rewritten it three times, and improved it to what it is now.
kycnot.me has remained 100% independent and 100% open source^2 all these years. I've received offers to buy the site, all of which I have declined and will continue to decline. It has been DDoS attacked many times, but we made it through. I have also rewritten the whole site almost once per year (three times in four years).
The code and scoring algorithm are open source (contributions are welcome) and I can't arbitrarly change a service's score without adding or removing attributes, making any arbitrary alterations obvious if they were fake. You can even see the score summary for any service's score.
I'm a one-person team, dedicating my free time to this project. I hope to keep doing so for many more years. Again, thank you for being part of this.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:37
@ 39cc53c9:27168656
2025-05-27 09:21:37After almost 3 months of work, we've completed the redesign of kycnot.me. More modern and with many new features.
Privacy remains the foundation - everything still works with JavaScript disabled. If you enable JS, you will get some nice-to-have features like lazy loading and smoother page transitions, but nothing essential requires it.
User Accounts
We've introduced user accounts that require zero personal information:
- Secret user tokens - no email, no phone number, no personal data
- Randomly generated usernames for default privacy and fairness
- Karma system that rewards contributions and unlocks features: custom display names, profile pictures, and more.
Reviews and Community Discussions
On the previous sites, I was using third party open source tools for the comments and discussions. This time, I've built my own from scratch, fully integrated into the site, without JavaScript requirements.
Everyone can share their experiences and help others make informed decisions:
- Ratings: Comments can have a 1-5 star rating attached. You can have one rating per service and it will affect the overall user score.
- Discussions: These are normal comments, you can add them on any listed service.
Comment Moderation
I was strugling to keep up with moderation on the old site. For this, we've implemented an AI-powered moderation system that:
- Auto-approves legitimate comments instantly
- Flags suspicious content for human review
- Keeps discussions valuable by minimizing spam
The AI still can mark comments for human review, but most comments will get approved automatically by this system. The AI also makes summaries of the comments to help you understand the overall sentiment of the community.
Powerful Search & Filtering
Finding exactly what you need is now easier:
- Advanced filtering system with many parameters. You can even filter by attributes to pinpoint services with specific features.
The results are dynamic and shuffle services with identical scores for fairness.
See all listings
Listings are now added as 'Community Contributed' by default. This means that you can still find them in the search results, but they will be clearly marked as such.
Updated Scoring System
New dual-score approach provides more nuanced service evaluations:
- Privacy Score: Measures how well a service protects your personal information and data
-
Trust Score: Assesses reliability, security, and overall reputation
-
Combined into a weighted Overall Score for quick comparisons
- Completely transparent and open source calculation algorithm. No manual tweaking or hidden factors.
AI-Powered Terms of Service Analysis
Basically, a TLDR summary for Terms of Service:
- Automated system extracts the most important points from complex ToS documents
- Clear summaries
- Updated monthly to catch any changes
The ToS document is hashed and only will be updated if there are any changes.
Service Events and Timelines
Track the complete history of any service, on each service page you can see the timeline of events. There are two types of events:
- Automatic events: Created by the system whenever something about a service changes, like its description, supported currencies, attributes, verification status…
- Manual events: Added by admins when there’s important news, such as a service going offline, being hacked, acquired, shut down, or other major updates.
There is also a global timeline view available at /events
Notification System
Since we now have user accounts, we built a notifiaction system so you can stay informed about anything:
- Notifications for comment replies and status changes
- Watch any comment to get notified for new replies.
- Subscribe to services to monitor events and updates
- Notification customization.
Coming soon: Third-party privacy-preserving notifications integration with Telegram, Ntfy.sh, webhooks...
Service Suggestions
Anyone with an account can suggest a new service via the suggestion form. After submitting, you'll receive a tracking page where you can follow the status of your suggestion and communicate directly with admins.
All new suggestions start as "unlisted" — they won't appear in search results until reviewed. Our team checks each submission to ensure it's not spam or inappropriate. If similar services already exist, you'll be shown possible duplicates and can choose to submit your suggestion as an edit instead.
You can always check the progress of your suggestion, respond to moderator questions, and see when it goes live, everything will also be notified to your account. This process ensures high-quality listings and a collaborative approach to building the directory.
These are some of the main features we already have, but there are many more small changes and improvements that you will find when using the site.
What's Next?
This is just the beginning. We will be constantly working to improve KYCnot.me and add more features that help you preserve your privacy.
Remember: True financial freedom requires the right to privacy. Stay KYC-free!
-
 @ 266815e0:6cd408a5
2025-04-29 17:47:57
@ 266815e0:6cd408a5
2025-04-29 17:47:57I'm excited to announce the release of Applesauce v1.0.0! There are a few breaking changes and a lot of improvements and new features across all packages. Each package has been updated to 1.0.0, marking a stable API for developers to build upon.
Applesauce core changes
There was a change in the
applesauce-corepackage in theQueryStore.The
Queryinterface has been converted to a method instead of an object withkeyandrunfields.A bunch of new helper methods and queries were added, checkout the changelog for a full list.
Applesauce Relay
There is a new
applesauce-relaypackage that provides a simple RxJS based api for connecting to relays and publishing events.Documentation: applesauce-relay
Features:
- A simple API for subscribing or publishing to a single relay or a group of relays
- No
connectorclosemethods, connections are managed automatically by rxjs - NIP-11
auth_requiredsupport - Support for NIP-42 authentication
- Prebuilt or custom re-connection back-off
- Keep-alive timeout (default 30s)
- Client-side Negentropy sync support
Example Usage: Single relay
```typescript import { Relay } from "applesauce-relay";
// Connect to a relay const relay = new Relay("wss://relay.example.com");
// Create a REQ and subscribe to it relay .req({ kinds: [1], limit: 10, }) .subscribe((response) => { if (response === "EOSE") { console.log("End of stored events"); } else { console.log("Received event:", response); } }); ```
Example Usage: Relay pool
```typescript import { Relay, RelayPool } from "applesauce-relay";
// Create a pool with a custom relay const pool = new RelayPool();
// Create a REQ and subscribe to it pool .req(["wss://relay.damus.io", "wss://relay.snort.social"], { kinds: [1], limit: 10, }) .subscribe((response) => { if (response === "EOSE") { console.log("End of stored events on all relays"); } else { console.log("Received event:", response); } }); ```
Applesauce actions
Another new package is the
applesauce-actionspackage. This package provides a set of async operations for common Nostr actions.Actions are run against the events in the
EventStoreand use theEventFactoryto create new events to publish.Documentation: applesauce-actions
Example Usage:
```typescript import { ActionHub } from "applesauce-actions";
// An EventStore and EventFactory are required to use the ActionHub import { eventStore } from "./stores.ts"; import { eventFactory } from "./factories.ts";
// Custom publish logic const publish = async (event: NostrEvent) => { console.log("Publishing", event); await app.relayPool.publish(event, app.defaultRelays); };
// The
publishmethod is optional for the asyncrunmethod to work const hub = new ActionHub(eventStore, eventFactory, publish); ```Once an
ActionsHubis created, you can use therunorexecmethods to execute actions:```typescript import { FollowUser, MuteUser } from "applesauce-actions/actions";
// Follow fiatjaf await hub.run( FollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", );
// Or use the
execmethod with a custom publish method await hub .exec( MuteUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", ) .forEach((event) => { // NOTE: Don't publish this event because we never want to mute fiatjaf // pool.publish(['wss://pyramid.fiatjaf.com/'], event) }); ```There are a log more actions including some for working with NIP-51 lists (private and public), you can find them in the reference
Applesauce loaders
The
applesauce-loaderspackage has been updated to support any relay connection libraries and not justrx-nostr.Before:
```typescript import { ReplaceableLoader } from "applesauce-loaders"; import { createRxNostr } from "rx-nostr";
// Create a new rx-nostr instance const rxNostr = createRxNostr();
// Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(rxNostr); ```
After:
```typescript
import { Observable } from "rxjs"; import { ReplaceableLoader, NostrRequest } from "applesauce-loaders"; import { SimplePool } from "nostr-tools";
// Create a new nostr-tools pool const pool = new SimplePool();
// Create a method that subscribes using nostr-tools and returns an observable function nostrRequest: NostrRequest = (relays, filters, id) => { return new Observable((subscriber) => { const sub = pool.subscribe(relays, filters, { onevent: (event) => { subscriber.next(event); }, onclose: () => subscriber.complete(), oneose: () => subscriber.complete(), });
return () => sub.close();}); };
// Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(nostrRequest); ```
Of course you can still use rx-nostr if you want:
```typescript import { createRxNostr } from "rx-nostr";
// Create a new rx-nostr instance const rxNostr = createRxNostr();
// Create a method that subscribes using rx-nostr and returns an observable function nostrRequest( relays: string[], filters: Filter[], id?: string, ): Observable
{ // Create a new oneshot request so it will complete when EOSE is received const req = createRxOneshotReq({ filters, rxReqId: id }); return rxNostr .use(req, { on: { relays } }) .pipe(map((packet) => packet.event)); } // Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(nostrRequest); ```
There where a few more changes, check out the changelog
Applesauce wallet
Its far from complete, but there is a new
applesauce-walletpackage that provides a actions and queries for working with NIP-60 wallets.Documentation: applesauce-wallet
Example Usage:
```typescript import { CreateWallet, UnlockWallet } from "applesauce-wallet/actions";
// Create a new NIP-60 wallet await hub.run(CreateWallet, ["wss://mint.example.com"], privateKey);
// Unlock wallet and associated tokens/history await hub.run(UnlockWallet, { tokens: true, history: true }); ```
-
 @ cae03c48:2a7d6671
2025-05-27 12:01:03
@ cae03c48:2a7d6671
2025-05-27 12:01:03Bitcoin Magazine

Something is Brewing in Ireland: A Sound Punt Is Released, As Bitcoin Enters The National ConversationFor years, Bitcoin in Ireland has quietly simmered at the grassroots level—discussed in pubs and meetups, debated in Telegram groups, and occasionally splashed across headlines with predictable suspicion. But recently, the temperature is beginning to rise. With the release of “A Sound Punt: The Case for Ireland’s Interest in Bitcoin” by Bitcoin Network Ireland (BNI), and a weekend that sees both the Bitcoin Ireland Conference and Aontú’s Ard Fheis, it’s clear momentum is building on the Emerald Isle.
A Sound Punt: A Paper for the Citizens of Ireland
The new paper, released today by Bitcoin Network Ireland, is a concise, accessible document crafted to cut through the noise and present the merits of Bitcoin to the general public and politicians alike. Its aim is straightforward: provide a rational, jargon-free entry point into why Bitcoin matters, especially in an era of euro debasement and rising living costs.
The name itself is a clever pun—while it is a nod to both “sound money” and Ireland’s former currency, the punt, it also playfully suggests that although the majority of people view it as associated with risk, this may be worth reevaluating. It’s a signal that this is about more than technology: it’s about claiming monetary sovereignty and re-examining what makes money “good” in the first place.
What BNI is attempting to accomplish is bridging an important gap in understanding, helping citizens seeking change and government officials looking for solutions to recognize that sound, stateless money has value for everyone. As Mark Goodwin famously noted, “Bitcoin simply must be for enemies, or it will never be for friends.“—a neutral system that serves all participants regardless of their political stance.
Ireland’s Long and Complicated Relationship With Money
To appreciate the significance of this moment, it’s worth noting that Ireland’s relationship with money has always been distinct from its European neighbors. While the Romans introduced coinage to Britain over a thousand years before it was adopted in Ireland. The native Irish resisted state-issued money, relying instead on barter and bullion well into the second millennium.
In ancient Ireland, the absence of coinage was a testament to a society that was stateless, highly decentralised, and it embraced a polycentric legal system varying between clans. The ideal of that society was that no man in society has rule over others, and even kings could be disposed of if they abused their power.
So it’s perhaps no coincidence that Ireland was the last European society to adopt coinage, as coinage gives power to rulers. Eventually, it was forced upon the land by the English crown in 1601, this period coincided with the final stages of the Nine Years’ War (1594-1603) and the increasing English control over Ireland. To this day, Ireland has never had its own free-floating currency; it has always been tethered to external powers: first the pound sterling, then the European Monetary System, and now the euro under the ECB. So it should come as no coincidence that in recent years, the EU is growing unabated in power and influence over Ireland.
“Give me control over a nation’s currency, and I care not who makes its laws.” — Mayer Amschel Rothschild (1743–1812)
Perhaps, given this historical context, Ireland is uniquely positioned to understand the value of sound, stateless money. Bitcoin represents a return to the monetary independence that preceded state-issued currencies, but with the technological advantages of the digital age. Where ancient Irish kingdoms used market goods that couldn’t be manipulated by distant authorities, Bitcoin offers a modern equivalent: a system that can’t be debased or controlled by any power, whether domestic or foreign.
This historical skepticism toward centrally-controlled currency is resurfacing in the present, as the Irish state and its citizens face a new wave of economic uncertainty via euro debasement and tariffs. Geopolitical and economic tensions have rarely felt less stable. Tariff disputes, renewed questions over Ireland’s foreign direct-investment model, and potential tech and pharma layoffs are sure to sharpen the focus on sovereignty and resilience. The release of “A Sound Punt” is timely, inviting the nation to once again question the wisdom of tying its fortunes to distant monetary authorities.
A Political Crossroads
Coinciding with the release of “A Sound Punt,” Dr. Niall Burke—a respected academic and BNI member—will be putting forward two motions at the Aontú Ard Fheis (party conference). Aontú, the party that saw the largest surge in votes in the last general election, has shown itself to be receptive to Bitcoin and is opening its doors to conversations that, until recently, were relegated to the margins. That Bitcoin motions are being presented and accepted at a major party conference is a marker of how the conversation is turning.
Meanwhile, the Bitcoin Ireland Conference is gathering the country’s growing community of plebs, builders, and advocates. These circles, once on the periphery, are now finding doors opening in political circles.
Public Discontent and a Call for Financial Autonomy
It’s not just Bitcoiners who are seeking alternatives. Ireland is witnessing its largest public demonstrations since the post-GFC days of 2012. Recent marches have drawn in excess of 100,000 people to the streets of Dublin. These protests reflect deep frustration and a sense that the political establishment is no longer in alignment with its people.
What’s particularly striking is how Bitcoin could serve as common ground for seemingly opposing interests. For protesters, Bitcoin offers protection from inflation and defends against government overreach. For a government concerned about economic stability and growth, Bitcoin may be the very solution it needs, especially to protect pension funds and indeed the state’s very own investment fund—ISIF, from inflation over the coming decades. This is the paradox and promise of sound, stateless money. It serves everyone’s interests because it enforces property rights, and can’t be captured or controlled by any single faction.
Last, but not least, MMA star Conor McGregor’s foray into both politics and Bitcoin is something few would have predicted a year ago, but for those with an ear to the ground, this has been a developing story for some time. His proposal for a national Bitcoin reserve is emblematic of a broader national shift: Bitcoin is finally entering the Zeitgeist and perhaps he, like BNI, has a part to play in keeping it there.
Bitcoin is an open-source monetary protocol, and adoption comes from all quarters, irrespective of politics. Bitcoin is neutral, it supports no partisan cause. What’s perhaps not recognized enough is how empowering Bitcoin can be and we should focus on its ability to unite rather than divide, giving every Irish citizen—regardless of their political views—tools for individual liberty, inflation protection, as well as practical solutions for businesses.
Back to “A Sound Punt” Paper
The paper itself makes a compelling case for Ireland’s interest in Bitcoin:
- Sound Money Principles: It evaluates Bitcoin against the six characteristics of “good money”—durability, divisibility, uniformity, portability, verifiability, and scarcity.
- Store of Value: The document highlights Bitcoin’s fixed supply as protection against rising inflation and currency debasement.
- Practical Examples: It provides evidence of Bitcoin’s monetization, comparing the costs of buying a home in Euros vs. Bitcoin over the span of a decade.
- Common Concern Rebuttals: The paper addresses the most common objections to Bitcoin—energy usage, volatility, criminal activity, undermining traditional currencies, and speculation—offering balanced counterarguments to each.
- Action Steps: Rather than just theoretical arguments, the paper outlines specific actions for individuals, businesses, and the government to consider, from education to strategic Bitcoin reserves.
The Beginning of a Process
No one expects the Irish government to announce a Bitcoin treasury next week, and it’s debatable whether it should establish one at all. But “A Sound Punt” marks the beginning of a process that could, in time, help reshape Ireland’s approach to money and economic sovereignty.
This accessible primer is just the first step in Bitcoin Network Ireland’s broader educational mission. BNI plans to publish a much more comprehensive policy paper for policymakers in the coming months, which is currently going through the editing phase. While “A Sound Punt” introduces the concepts to the general public, the forthcoming document will provide the detailed analysis and policy recommendations that decision-makers need.
As BNI works to elevate this conversation through both public ed
-
 @ cae03c48:2a7d6671
2025-05-27 12:01:02
@ cae03c48:2a7d6671
2025-05-27 12:01:02Bitcoin Magazine

What to expect from the BTCfi & L2s companies at the Bitcoin Conference in VegasThe annual Bitcoin Conference in Las Vegas is a pivotal event for the Bitcoin ecosystem, where companies unveil breakthroughs, announce partnerships, and deliver speeches that shape the narrative of digital assets. For many, the sheer volume of information can be overwhelming. Having attended several conferences and being familiar with the attending companies through my work at UTXO, I’ve highlighted key panels and expected developments for 2025, focusing on Bitcoin’s Layer 2 (L2) and BTCfi ecosystems.
The full agenda is available using this link: https://b.tc/conference/2025/agenda
Here’s a breakdown of anticipated announcements and panels, categorized by key themes:
BitVM2 Announcements
Since BitVM’s introduction in 2023, top Bitcoin development teams have been working tirelessly to transform centralized sidechain designs into true Bitcoin rollups and permissionless L2s. At the 2025 conference, expect these teams to unveil the first versions of BitVM2 bridges, providing critical details on their mechanics. Once live, BitVM2 bridges could unlock a wide range of decentralized BTC use cases, accessible to all Bitcoin holders. May 2025 might mark a turning point, potentially signaling the decline of centralized “crypto” and DeFi projects in favor of a Bitcoin-native economy. As the saying goes, on a long enough timeline, everything comes back to Bitcoin.
L2 Partnerships
Bitcoin L2s face a steep challenge: competing with established crypto players while earning the trust of Bitcoiners. The conference is likely to feature major partnership announcements, particularly at the infrastructure level, addressing long-standing barriers to BTCfi adoption. These collaborations could bolster the credibility and functionality of L2 solutions, paving the way for broader acceptance.
Lightning and Taproot Assets Innovation
The recent announcement that Tether (USDT) will return to Bitcoin by issuing its stablecoin on Lightning rails via Taproot Assets has sparked significant excitement. Expect major updates from companies in this space, particularly regarding Taproot Assets and stablecoin integration. The Lightning Network is poised for dominance, and 2025 could be the year it breaks into the mainstream.
Opcodes and Governance Discussions
With growing support for covenant activation on Bitcoin and recent debates over mempool policy on social media, governance discussions will be a focal point. These panels promise to be intellectually stimulating, offering deep insights into Bitcoin’s core mechanics and potential fireworks for those following the debates. Attending these sessions will likely be the most rewarding experience of the week for anyone seeking to understand Bitcoin’s future.
Must-Attend Panels
Below is a curated list of panels aligned with the above categories, along with my expectations for each. (Note: These predictions reflect my personal perspective and are not definitive. This list is not exhaustive but highlights high-signal sessions for attendees with limited time.)
Panels and Keynote with the highest probability of a major announcement related to Bitcoin L2s and BTCfi products: in other words, this is where major alpha will be dropped
Governance Discussions

*Bitcoin L2s and BTCfi products*
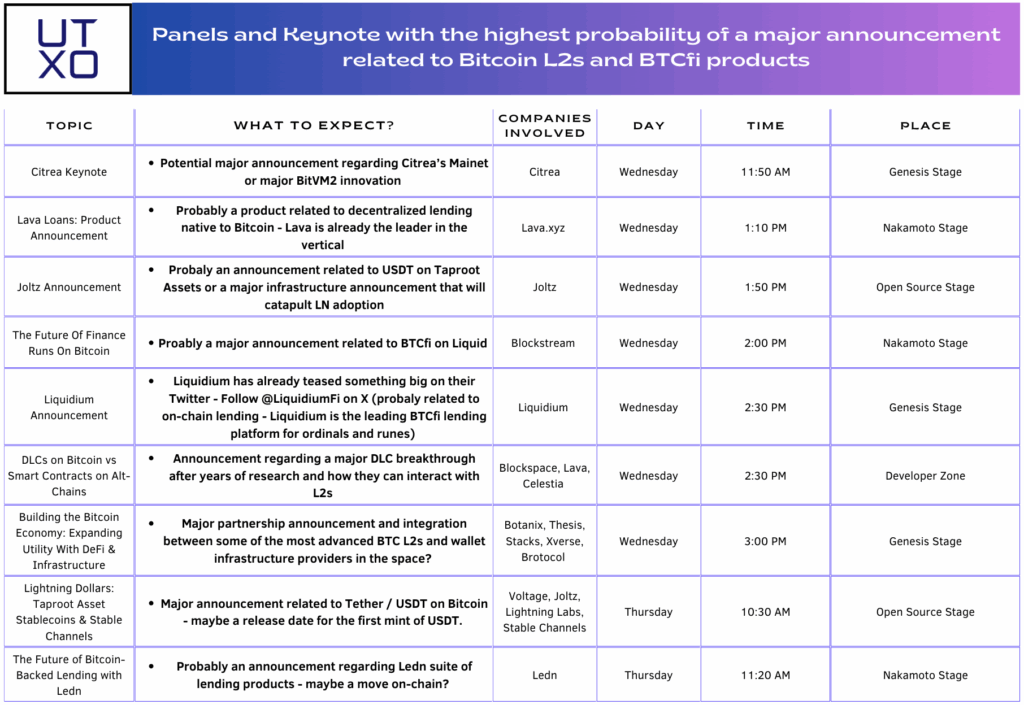
L2 and Lightning discussions
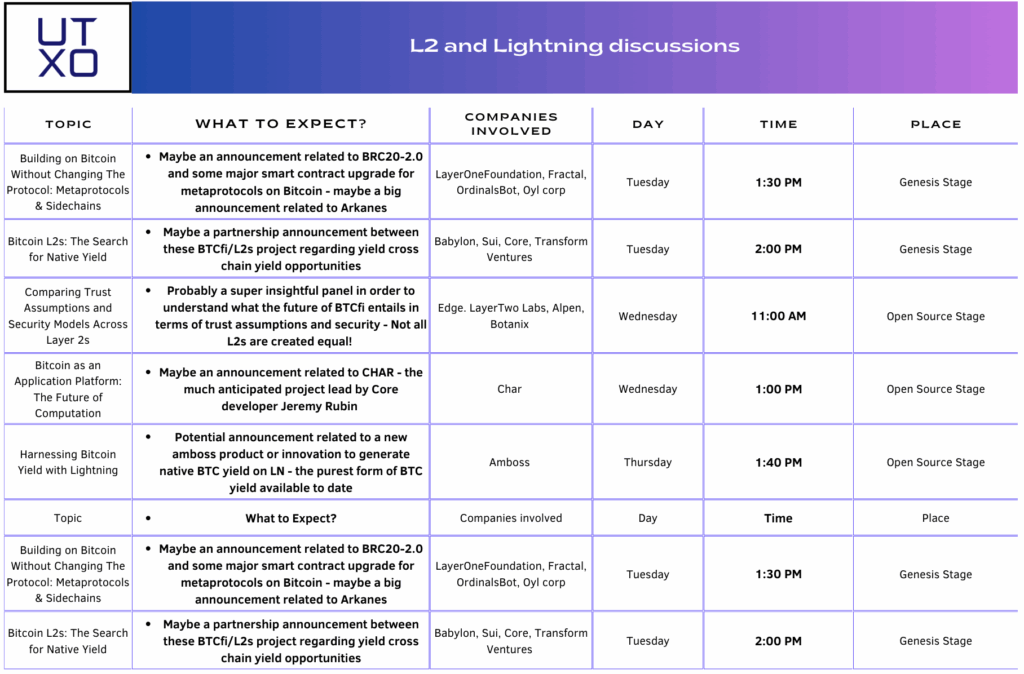
This post What to expect from the BTCfi & L2s companies at the Bitcoin Conference in Vegas first appeared on Bitcoin Magazine and is written by Guillaume Girard.
-
 @ 5ea46480:450da5bd
2025-05-27 08:23:58
@ 5ea46480:450da5bd
2025-05-27 08:23:58Understanding or grasping Nostr can be deceptively difficult. At the very least it is non-trivial. At first glance, looking at NIP-01, the protocol is rather straight forward. But those are just the basics; yes the beauty of Nostr is its ‘simplicity’, but that does not mean the system that results from it is not complex. Conway's Game of Life only has a hand full of rules, yet you can, in theory at least, create any complex system imaginable. And this is where the deception lies; the less you define from the outset, the more you imply on what follows.
It appears that as it stands, Nostr suffers from this deceptiveness. You can reason through all these implications, but that is still an exercise that has to be performed and where mistakes can be made. Worse, this exercise has been a group effort from the start that is still in progress. Currently there is no clear cut ‘authoritative’ example of all the implications that have been ‘discovered’ thus far.
A good example of the implications following Nostr’s primitives is what we now refer to as the ‘outbox model’. The reason we ‘now’ refer to it as such, is because initially it was called the ‘Gossip model’ derived from the client that first implemented the idea. Outbox is fundamental to Nostr, but it was never explicitly stated in the initial protocol description. The result is that roughly five years into this Nostr endeavor, it is still not universally implemented; worse yet, some developers appear to be in no rush to do so. Now the reason they will give you is probably one based on priority, yet I can’t shake the feeling that they apparently don’t ‘get it’.
My point here is not to play some blame game or hold anyone to account. I am just concluding they don’t actually get the new paradigm that we have all stumbled into. To expand on this specific outbox example, its significance only becomes really apparent further along in the ‘reasoning through all the implications’ exercise. In relation to one aspect, but there are more: The point is not ‘just’ censorship-resistance for users, but the freedom for relays that comes with it to apply whatever policy on what they store and make available; it is this discrimination or curation that can add value by making finding relevant information easier in a straightforward manner. But it relies on outbox to avoid isolation; something that only becomes apparent once you are reasoning through all the implications on how we discover and consume content.
To be clear, this piece is not supposed to a crusade on the outbox model, my point here is that there is an inherent logic to Nostr stemming from putting cryptography front and center. It is a logic that has to be applied and will subsequently carry you through all the challenges we face in reconstructing the entirety of the web. This is not to say there is only one obvious path, and different schools of thought are bound to emerge. But it behooves us all, faced with this new paradigm, to continuously reflect on the mental image we have cultivated of what Nostr is; actively re-performing that exercise of exploring the implications this simple set of protocol rules creates.
Unfortunately I can not escape my own folly. After all, I am just an armchair asshole that never wrote a single line of code in his life. Obviously this minds-eye bullshit is not even half the story, the bulk of the effort is translating it into software, the tangible, the real. It is in that effort ultimately the real exploration of this paradigm occurs. All I can do is build castles in the sky.
-
 @ cae03c48:2a7d6671
2025-05-27 12:01:01
@ cae03c48:2a7d6671
2025-05-27 12:01:01Bitcoin Magazine

Trump Media Group Seeks $3 Billion War Chest to Buy Bitcoin and Crypto Assets: FTTrump Media and Technology Group (TMTG), the company behind Truth Social and controlled by the Trump family, is preparing to raise a staggering $3 billion to invest in cryptocurrencies such as Bitcoin, according to the Financial Times.
JUST IN:
 Trump Media Group to raise $3 billion to buy Bitcoin and crypto — Financial Times pic.twitter.com/VEyvy5vpGZ
Trump Media Group to raise $3 billion to buy Bitcoin and crypto — Financial Times pic.twitter.com/VEyvy5vpGZ— Bitcoin Magazine (@BitcoinMagazine) May 26, 2025
The media venture plans to secure $2 billion in fresh equity and another $1 billion through a convertible bond offering, those familiar with the matter told the Financial Times. The capital raise could be formally announced ahead of The Bitcoin 2025 Conference in Las Vegas this week, where Vice President JD Vance, Donald Trump Jr., Eric Trump, and Trump’s crypto advisor David Sachs are expected to speak.
The secondary equity offering will be carried out on an at-the-market basis, meaning shares are expected to be priced near the most recent closing price of $25.72, giving TMTG a current valuation of nearly $6 billion.
TMTG’s push comes amid a wider cryptocurrency resurgence. Bitcoin hit a new record of $111,999 last week, and investor interest in crypto-related plays has surged. The strategy echoes that of Strategy, which used a similar blend of debt and equity financing to buy tens of billions of dollars in Bitcoin—catapulting its market cap to over $100 billion.
Although the news is still yet to be confirmed by TMTG, a comment they made to the Financial Times may give some doubt to the validity of the story:
“Apparently the Financial Times has dumb writers listening to even dumber sources”, reportedly said TMTG. A White House spokesperson also declined to weigh in. Representatives for Donald Trump Jr. did not respond to requests for comment and Reuters also did not immediately receive a request for comment.
TMTG’s deepening crypto pivot has included a slew of ventures: an NFT trading card series, two memecoins, investments in crypto miner American Bitcoin and stablecoin platform World Liberty Financial, and an upcoming crypto ETF.
After returning to the White House last year, Trump transferred his 53% stake in TMTG—worth roughly $3 billion—to a revocable trust controlled by Donald Trump Jr., who holds full investment and voting authority.
This is a developing story and will be updated as needed.
This post Trump Media Group Seeks $3 Billion War Chest to Buy Bitcoin and Crypto Assets: FT first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ cae03c48:2a7d6671
2025-05-27 12:01:00
@ cae03c48:2a7d6671
2025-05-27 12:01:00Bitcoin Magazine

Jippi Launches Pokémon GO-Style AR Bitcoin Education Game at Vegas’s Bitcoin 2025Jippi, a mobile augmented reality (AR) game developer, will debut its Bitcoin education game at the Bitcoin Conference 2025, held at The Venetian Resort in Las Vegas from May 27-29. Inspired by Pokémon GO, the game blends location-based gameplay with financial literacy, aiming to engage over 30,000 attendees by making Bitcoin education fun and accessible.
Using the app, players can explore The Venetian’s grounds to hunt digital “Bitcoin Beasts,” answering Bitcoin-related trivia to capture them and earn 1000 satoshis (sats) per catch. The game is designed to deliver concise lessons on sound money principles, targeting younger audiences, with Jippi’s research showing 90% of Gen Z play mobile games. This approach aims to make learning about Bitcoin intuitive and engaging.
“We’re excited to turn Bitcoin education into an adventure,” said Oliver Porter, Jippi’s Founder and CEO. “Our game meets players where they are, making complex concepts approachable.”
Jippi partnered with six Bitcoin companies—Bitcoin Well, Beyond The Checkout, Bitcoin Trading Cards, Geyser, SHAmory, and 21M Communications—to sponsor unique Beasts. Each is tied to a specific location, offering tailored trivia that highlights the sponsor’s mission. For instance, Bitcoin Well’s Beast teaches wallet security, while SHAmory’s content suits all ages. “Jippi’s game is a fresh way to onboard new users,” said Adam O’Brien, CEO of Bitcoin Well.
The game stems from over a year of development, including university testing and on-site surveys. Jippi’s efforts earned it the top prize at PlebLab’s Top Builder competition in March 2025, a hackathon for Bitcoin startups, cementing its role in gamifying education.
With 30,000 attendees expected, the conference is an ideal stage for Jippi to showcase AR’s potential in Bitcoin adoption. The game promises to transform The Venetian into a dynamic learning hub, encouraging players to explore while grasping Bitcoin’s real-world applications. Jippi aims to expand the game post-conference, adding more educational content.
This post Jippi Launches Pokémon GO-Style AR Bitcoin Education Game at Vegas’s Bitcoin 2025 first appeared on Bitcoin Magazine and is written by Juan Galt.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ b7274d28:c99628cb
2025-05-27 07:07:33
@ b7274d28:c99628cb
2025-05-27 07:07:33A few months ago, a nostrich was switching from iOS to Android and asked for suggestions for #Nostr apps to try out. nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 offered the following as his response:
nostr:nevent1qvzqqqqqqypzq0mhp4ja8fmy48zuk5p6uy37vtk8tx9dqdwcxm32sy8nsaa8gkeyqydhwumn8ghj7un9d3shjtnwdaehgunsd3jkyuewvdhk6tcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszythwden5te0dehhxarj9emkjmn99uqzpwwts6n28eyvjpcwvu5akkwu85eg92dpvgw7cgmpe4czdadqvnv984rl0z
Yes. #Android users are fortunate to have some powerful Nostr apps and tools at our disposal that simply have no comparison over on the iOS side. However, a tool is only as good as the knowledge of the user, who must have an understanding of how best to wield it for maximum effect. This fact was immediately evidenced by replies to Derek asking, "What is the use case for Citrine?" and "This is the first time I'm hearing about Citrine and Pokey. Can you give me links for those?"
Well, consider this tutorial your Nostr starter-kit for Android. We'll go over installing and setting up Amber, Amethyst, Citrine, and Pokey, and as a bonus we'll be throwing in the Zapstore and Coinos to boot. We will assume no previous experience with any of the above, so if you already know all about one or more of these apps, you can feel free to skip that tutorial.
So many apps...
You may be wondering, "Why do I need so many apps to use Nostr?" That's perfectly valid, and the honest answer is, you don't. You can absolutely just install a Nostr client from the Play Store, have it generate your Nostr identity for you, and stick with the default relays already set up in that app. You don't even need to connect a wallet, if you don't want to. However, you won't experience all that Nostr has to offer if that is as far as you go, any more than you would experience all that Italian cuisine has to offer if you only ever try spaghetti.
Nostr is not just one app that does one thing, like Facebook, Twitter, or TikTok. It is an entire ecosystem of applications that are all built on top of a protocol that allows them to be interoperable. This set of tools will help you make the most out of that interoperability, which you will never get from any of the big-tech social platforms. It will provide a solid foundation for you to build upon as you explore more and more of what Nostr has to offer.
So what do these apps do?

Fundamental to everything you do on Nostr is the need to cryptographically sign with your private key. If you aren't sure what that means, just imagine that you had to enter your password every time you hit the "like" button on Facebook, or every time you commented on the latest dank meme. That would get old really fast, right? That's effectively what Nostr requires, but on steroids.
To keep this from being something you manually have to do every 5 seconds when you post a note, react to someone else's note, or add a comment, Nostr apps can store your private key and use it to sign behind the scenes for you. This is very convenient, but it means you are trusting that app to not do anything with your private key that you don't want it to. You are also trusting it to not leak your private key, because anyone who gets their hands on it will be able to post as you, see your private messages, and effectively be you on Nostr. The more apps you give your private key to, the greater your risk that it will eventually be compromised.
Enter #Amber, an application that will store your private key in only one app, and all other compatible Nostr apps can communicate with it to request a signature, without giving any of those other apps access to your private key.
Most Nostr apps for Android now support logging in and signing with Amber, and you can even use it to log into apps on other devices, such as some of the web apps you use on your PC. It's an incredible tool given to us by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, and only available for Android users. Those on iPhone are incredibly jealous that they don't have anything comparable, yet.

Speaking of nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, the next app is also one of his making.
All Nostr data is stored on relays, which are very simple servers that Nostr apps read notes from and write notes to. In most forms of social media, it can be a pain to get your own data out to keep a backup. That's not the case on Nostr. Anyone can run their own relay, either for the sake of backing up their personal notes, or for others to post their notes to, as well.
Since Nostr notes take up very little space, you can actually run a relay on your phone. I have been on Nostr for almost 2 and a half years, and I have 25,000+ notes of various kinds on my relay, and a backup of that full database is just 24MB on my phone's storage.
Having that backup can save your bacon if you try out a new Nostr client and it doesn't find your existing follow list for some reason, so it writes a new one and you suddenly lose all of the people you were following. Just pop into your #Citrine relay, confirm it still has your correct follow list or import it from a recent backup, then have Citrine restore it. Done.
Additionally, there are things you may want to only save to a relay you control, such as draft messages that you aren't ready to post publicly, or eCash tokens, which can actually be saved to Nostr relays now. Citrine can also be used with Amber for signing into certain Nostr applications that use a relay to communicate with Amber.
If you are really adventurous, you can also expose Citrine over Tor to be used as an outbox relay, or used for peer-to-peer private messaging, but that is far more involved than the scope of this tutorial series.

You can't get far in Nostr without a solid and reliable client to interact with. #Amethyst is the client we will be using for this tutorial because there simply isn't another Android client that comes close, so far. Moreover, it can be a great client for new users to get started on, and yet it has a ton of features for power-users to take advantage of as well.
There are plenty of other good clients to check out over time, such as Coracle, YakiHonne, Voyage, Olas, Flotilla and others, but I keep coming back to Amethyst, and by the time you finish this tutorial, I think you'll see why. nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z and others who have contributed to Amethyst have really built something special in this client, and it just keeps improving with every update that's shipped.
Most social media apps have some form of push notifications, and some Nostr apps do, too. Where the issue comes in is that Nostr apps are all interoperable. If you have more than one application, you're going to have both of them notifying you. Nostr users are known for having five or more Nostr apps that they use regularly. If all of them had notifications turned on, it would be a nightmare. So maybe you limit it to only one of your Nostr apps having notifications turned on, but then you are pretty well locked-in to opening that particular app when you tap on the notification.
Pokey, by nostr:npub1v3tgrwwsv7c6xckyhm5dmluc05jxd4yeqhpxew87chn0kua0tjzqc6yvjh, solves this issue, allowing you to turn notifications off for all of your Nostr apps, and have Pokey handle them all for you. Then, when you tap on a Pokey notification, you can choose which Nostr app to open it in.
Pokey also gives you control over the types of things you want to be notified about. Maybe you don't care about reactions, and you just want to know about zaps, comments, and direct messages. Pokey has you covered. It even supports multiple accounts, so you can get notifications for all the npubs you control.

One of the most unique and incredibly fun aspects of Nostr is the ability to send and receive #zaps. Instead of merely giving someone a 👍️ when you like something they said, you can actually send them real value in the form of sats, small portions of a Bitcoin. There is nothing quite like the experience of receiving your first zap and realizing that someone valued what you said enough to send you a small amount (and sometimes not so small) of #Bitcoin, the best money mankind has ever known.
To be able to have that experience, though, you are going to need a wallet that can send and receive zaps, and preferably one that is easy to connect to Nostr applications. My current preference for that is Alby Hub, but not everyone wants to deal with all that comes along with running a #Lightning node. That being the case, I have opted to use nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch for this tutorial, because they offer one of the easiest wallets to set up, and it connects to most Nostr apps by just copy/pasting a connection string from the settings in the wallet into the settings in your Nostr app of choice.
Additionally, even though #Coinos is a custodial wallet, you can have it automatically transfer any #sats over a specified threshold to a separate wallet, allowing you to mitigate the custodial risk without needing to keep an eye on your balance and make the transfer manually.

Most of us on Android are used to getting all of our mobile apps from one souce: the Google Play Store. That's not possible for this tutorial series. Only one of the apps mentioned above is available in Google's permissioned playground. However, on Android we have the advantage of being able to install whatever we want on our device, just by popping into our settings and flipping a toggle. Indeed, thumbing our noses at big-tech is at the heart of the Nostr ethos, so why would we make ourselves beholden to Google for installing Nostr apps?
The nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 is an alternative app store made by nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9 as a resource for all sorts of open-source apps, but especially Nostr apps. What is more, you can log in with Amber, connect a wallet like Coinos, and support the developers of your favorite Nostr apps directly within the #Zapstore by zapping their app releases.
One of the biggest features of the Zapstore is the fact that developers can cryptographically sign their app releases using their Nostr keys, so you know that the app you are downloading is the one they actually released and hasn't been altered in any way. The Zapstore will warn you and won't let you install the app if the signature is invalid.
Getting Started
Since the Zapstore will be the source we use for installing most of the other apps mentioned, we will start with installing the Zapstore.
We will then use the Zapstore to install Amber and set it up with our Nostr account, either by creating a new private key, or by importing one we already have. We'll also use it to log into the Zapstore.
Next, we will install Amethyst from the Zapstore and log into it via Amber.
After this, we will install Citrine from the Zapstore and add it as a local relay on Amethyst.
Because we want to be able to send and receive zaps, we will set up a wallet with CoinOS and connect it to Amethyst and the Zapstore using Nostr Wallet Connect.
Finally, we will install Pokey using the Zapstore, log into it using Amber, and set up the notifications we want to receive.
By the time you are done with this series, you will have a great head-start on your Nostr journey compared to muddling through it all on your own. Moreover, you will have developed a familiarity with how things generally work on Nostr that can be applied to other apps you try out in the future.
Continue to Part 2: The Zapstore. Nostr Link: nostr:naddr1qvzqqqr4gupzpde8f55w86vrhaeqmd955y4rraw8aunzxgxstsj7eyzgntyev2xtqydhwumn8ghj7un9d3shjtnzwf5kw6r5vfhkcapwdejhgtcqp5cnwdphxv6rwwp3xvmnzvqgty5au
-
 @ 9e9085e9:2056af17
2025-05-27 17:16:22
@ 9e9085e9:2056af17
2025-05-27 17:16:22Market Overview
As of May 27, 2025, Bitcoin (BTC) is trading at approximately $110,387, reflecting a modest 0.8% daily gain.
24-Hour Range: $108,291 – $110,415
Recent High: $111,970
Support Level to Watch: $105,700
Bullish Target: $135,000 (based on analyst projections)
The market remains optimistic ahead of the Bitcoin 2025 Conference in Las Vegas, sparking renewed interest and speculation.
Impact on Decentralized Social Media
Bitcoin’s strong performance is influencing decentralized social platforms in multiple ways:
- Increased Engagement
Platforms like Nostr, Mastodon, and others are seeing a spike in activity. Users are sharing price charts, engaging in Bitcoin discourse, and posting market-related content.
- Monetization Opportunities
Creators on decentralized networks are leveraging Bitcoin-based tipping, NFT-based publishing, and tokenized rewards to monetize content more effectively.
- Community Growth
Positive sentiment is drawing in new users and developers, contributing to the growth of decentralized ecosystems and innovation in peer-to-peer social tech.
Strategic Highlights
Trump Media & Technology Group aims to raise $2.5 billion to build a Bitcoin treasury, signaling strong institutional interest.
The U.S. is reportedly establishing a Strategic Bitcoin Reserve, underscoring digital currency’s growing relevance at the national level.
#Bitcoin #BTC #CryptoNews #Web3 #DecentralizedSocialMedia #Nostr #Yakihonne #CryptoCommunity #BitcoinUpdate #BTC2025 #DigitalFreedom #ContentCuration #Hackathon #SocialFi
-
 @ 7f6db517:a4931eda
2025-05-27 05:01:34
@ 7f6db517:a4931eda
2025-05-27 05:01:34
There must be a limit to how much data is transferred across the bitcoin network in order to keep the ability to run and use your own node accessible. A node is required to interact with the global bitcoin network - if you do not use your own node then you must trust someone else's node. If nodes become inaccessible to run then the network will centralize around the remaining entities that operate them - threatening the censorship resistance at the core of bitcoin's value prop. The bitcoin protocol uses three main mechanisms to keep node operation costs low - a fixed limit on the amount of data in each block, an automatic difficulty adjustment that regulates how many blocks are produced based on current mining hash rate, and a robust dynamic transaction fee market.
Bitcoin transaction fees limit network abuse by making usage expensive. There is a cost to every transaction, set by a dynamic free market based on demand for scarce block space. It is an incredibly robust way to prevent spam without relying on centralized entities that can be corrupted or pressured.
After the 2017 bitcoin fee spike we had six years of relative quiet to build tools that would be robust in a sustained high fee market. Fortunately our tools are significantly better now but many still need improvement. Most of the pain points we see today will be mitigated.
The reality is we were never going to be fully prepared - pressure is needed to show the pain points and provide strong incentives to mitigate them.
It will be incredibly interesting to watch how projects adapt under pressure. Optimistic we see great innovation here.
_If you are willing to wait for your transaction to confirm you can pay significantly lower fees. Learn best practices for reducing your fee burden here.
My guide for running and using your own bitcoin node can be found here._
If you found this post helpful support my work with bitcoin.

-
 @ 9e9085e9:2056af17
2025-05-27 16:58:28
@ 9e9085e9:2056af17
2025-05-27 16:58:28Part 2: Community Impact & Key Milestones
How Yakihonne Benefits the Community
Yakihonne is more than an app—it's a platform for freedom and self-expression. Here’s how it empowers its users and community:
Censorship-Resistant Communication Say what matters without fear of shadowbans or takedowns.
Privacy and Data Control You own your data—no tracking, no selling, no manipulation.
Peer-to-Peer Support for Creators With Bitcoin Lightning tipping, fans can directly support creators without needing middlemen.
Open Participation Developers, artists, and builders can all contribute to the network through the open Nostr protocol.
Milestones (You can update these with exact dates later)
Platform Launch: [Insert Date]
1,000+ Users Joined: [Insert Date]
Key Feature Rollouts (Chats, Groups, Tips): [Insert Date]
Yakihonne #Yakihonne #Yakihonne #Nostr #Nostr #YoungDfx
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ 9e9085e9:2056af17
2025-05-27 16:36:45
@ 9e9085e9:2056af17
2025-05-27 16:36:45Part 1: Introducing Yakihonne and the Nostr Protocol
Yakihonne – Redefining Social Media Through Decentralization
Yakihonne is a decentralized social media platform built on the Nostr protocol (Notes and Other Stuff Transmitted by Relays). Unlike traditional social networks controlled by corporations, Yakihonne puts users in charge—your identity, content, and connections are all yours to own.
What is Nostr? Nostr is an open protocol that uses public/private key pairs to enable secure communication. Posts (called “notes”) are sent to public relays instead of being stored on a central server. This allows Yakihonne to offer:
Censorship resistance
User-owned data
Open developer participation
Yakihonne leverages this technology to create a user-first social experience: chat, share, and connect—all without gatekeepers.
Yakihonne #Yakihonne #Yakihonne #Nostr #Nostr #YoungDfx
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ 7f6db517:a4931eda
2025-05-27 05:01:34
@ 7f6db517:a4931eda
2025-05-27 05:01:34
I often hear "bitcoin doesn't interest me, I'm not a finance person."
Ironically, the beauty of sound money is you don't have to be. In the current system you're expected to manage a diversified investment portfolio or pay someone to do it. Bitcoin will make that optional.
— ODELL (@ODELL) September 16, 2018
At first glance bitcoin often appears overwhelming to newcomers. It is incredibly easy to get bogged down in the details of how it works or different ways to use it. Enthusiasts, such as myself, often enjoy going down the deep rabbit hole of the potential of bitcoin, possible pitfalls and theoretical scenarios, power user techniques, and the developer ecosystem. If your first touch point with bitcoin is that type of content then it is only natural to be overwhelmed. While it is important that we have a thriving community of bitcoiners dedicated to these complicated tasks - the true beauty of bitcoin lies in its simplicity. Bitcoin is simply better money. It is the best money we have ever had.
Life is complicated. Life is hard. Life is full of responsibility and surprises. Bitcoin allows us to focus on our lives while relying on a money that is simple. A money that is not controlled by any individual, company, or government. A money that cannot be easily seized or blocked. A money that cannot be devalued at will by a handful of corrupt bureaucrat who live hundreds of miles from us. A money that can be easily saved and should increase in purchasing power over time without having to learn how to "build a diversified stock portfolio" or hire someone to do it for us.
Bitcoin enables all of us to focus on our lives - our friends and family - doing what we love with the short time we have on this earth. Time is scarce. Life is complicated. Bitcoin is the most simple aspect of our complicated lives. If we spend our scarce time working then we should be able to easily save that accrued value for future generations without watching the news or understanding complicated financial markets. Bitcoin makes this possible for anyone.
Yesterday was Mother's Day. Raising a human is complicated. It is hard, it requires immense personal responsibility, it requires critical thinking, but mothers figure it out, because it is worth it. Using and saving bitcoin is simple - simply install an app on your phone. Every mother can do it. Every person can do it.
Life is complicated. Life is beautiful. Bitcoin is simple.
If you found this post helpful support my work with bitcoin.

-
 @ 3ffac3a6:2d656657
2025-04-23 01:57:57
@ 3ffac3a6:2d656657
2025-04-23 01:57:57🔧 Infrastructure Overview
- Hardware: Raspberry Pi 5 with PCIe NVMe HAT and 2TB NVMe SSD
- Filesystem: ZFS with separate datasets for each service
- Networking: Docker bridge networks for service segmentation
- Privacy: Tor and I2P routing for anonymous communication
- Public Access: Cloudflare Tunnel to securely expose LNbits
📊 Architecture Diagram
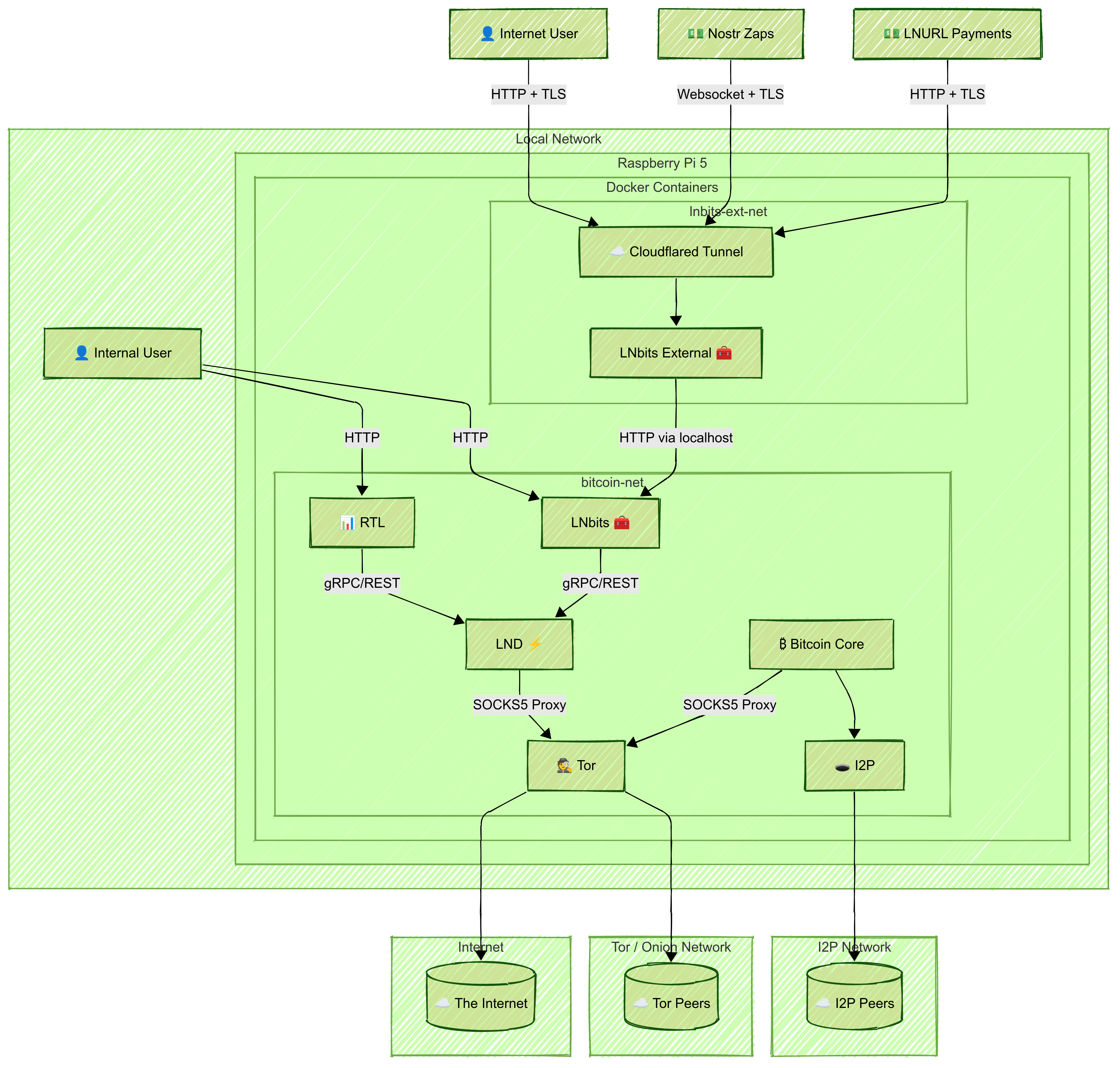
🛠️ Setup Steps
1. Prepare the System
- Install Raspberry Pi OS (64-bit)
- Set up ZFS on the NVMe disk
- Create a ZFS dataset for each service (e.g.,
bitcoin,lnd,rtl,lnbits,tor-data) - Install Docker and Docker Compose
2. Create Shared Docker Network and Privacy Layers
Create a shared Docker bridge network:
bash docker network create \ --driver=bridge \ --subnet=192.168.100.0/24 \ bitcoin-netNote: Connect
bitcoind,lnd,rtl, internallnbits,tor, andi2pto thisbitcoin-netnetwork.Tor
- Run Tor in a container
- Configure it to expose LND's gRPC and REST ports via hidden services:
HiddenServicePort 10009 192.168.100.31:10009 HiddenServicePort 8080 192.168.100.31:8080 - Set correct permissions:
bash sudo chown -R 102:102 /zfs/datasets/tor-data
I2P
- Run I2P in a container with SAM and SOCKS proxies
- Update
bitcoin.conf:i2psam=192.168.100.20:7656 i2pacceptincoming=1
3. Set Up Bitcoin Core
- Create a
bitcoin.confwith Tor/I2P/proxy settings and ZMQ enabled - Sync the blockchain in a container using its ZFS dataset
4. Set Up LND
- Configure
lnd.confto connect tobitcoindand use Tor: ```ini [Bitcoind] bitcoind.rpchost=bitcoin:8332 bitcoind.rpcuser=bitcoin bitcoind.rpcpass=very-hard-password bitcoind.zmqpubrawblock=tcp://bitcoin:28332 bitcoind.zmqpubrawtx=tcp://bitcoin:28333
[Application Options] externalip=xxxxxxxx.onion
`` - Don’t expose gRPC or REST ports publicly - Mount the ZFS dataset at/root/.lnd` - Optionally enable Watchtower5. Set Up RTL
- Mount
RTL-Config.jsonand data volumes - Expose RTL's web interface locally:
```yaml
ports:
- "3000:3000" ```
6. Set Up Internal LNbits
- Connect the LNbits container to
bitcoin-net - Mount the data directory and LND cert/macaroons (read-only)
- Expose the LNbits UI on the local network:
```yaml
ports:
- "5000:5000" ```
- In the web UI, configure the funding source to point to the LND REST
.onionaddress and paste the hex macaroon - Create and fund a wallet, and copy its Admin Key for external use
7. Set Up External LNbits + Cloudflare Tunnel
- Run another LNbits container on a separate Docker network
- Access the internal LNbits via the host IP and port 5000
- Use the Admin Key from the internal wallet to configure funding
- In the Cloudflare Zero Trust dashboard:
- Create a tunnel
- Select Docker, copy the
--tokencommand - Add to Docker Compose:
yaml command: tunnel --no-autoupdate run --token eyJ...your_token...
💾 Backup Strategy
- Bitcoin Core: hourly ZFS snapshots, retained for 6 hours
- Other Services: hourly snapshots with remote
.tar.gzbackups - Retention: 7d hourly, 30d daily, 12mo weekly, monthly forever
- Back up ZFS snapshots to avoid inconsistencies
🔐 Security Isolation Benefits
This architecture isolates services by scope and function:
- Internal traffic stays on
bitcoin-net - Sensitive APIs (gRPC, REST) are reachable only via Tor
- Public access is controlled by Cloudflare Tunnel
Extra Security: Host the public LNbits on a separate machine (e.g., hardened VPS) with strict firewall rules:
- Allow only Cloudflare egress
- Allow ingress from your local IP
- Allow outbound access to internal LNbits (port 5000)
Use WireGuard VPN to secure the connection between external and internal LNbits:
- Ensures encrypted communication
- Restricts access to authenticated VPN peers
- Keeps the internal interface isolated from the public internet
✅ Final Notes
- Internal services communicate over
bitcoin-net - LND interfaces are accessed via Tor only
- LNbits and RTL UIs are locally accessible
- Cloudflare Tunnel secures external access to LNbits
Monitor system health using
monit,watchtower, or Prometheus.Create all configuration files manually (
bitcoin.conf,lnd.conf,RTL-Config.json), and keep credentials secure. Test every component locally before exposing it externally.⚡