-
 @ 9973da5b:809c853f
2025-05-23 04:42:49
@ 9973da5b:809c853f
2025-05-23 04:42:49First article Skynet begins to learn rapidly and eventually becomes self-aware at 2:14 a.m., EDT, on August 29, 1997 https://layer3press.layer3.press/articles/45d916c0-f7b2-4b95-bc0f-8faa65950483
-
 @ c7e8fdda:b8f73146
2025-05-22 14:13:31
@ c7e8fdda:b8f73146
2025-05-22 14:13:31🌍 Too Young. Too Idealistic. Too Alive. A message came in recently that stopped me cold.
It was from someone young—16 years old—but you’d never guess it from the depth of what they wrote. They spoke of having dreams so big they scare people. They’d had a spiritual awakening at 14, but instead of being nurtured, it was dismissed. Surrounded by people dulled by bitterness and fear, they were told to be realistic. To grow up. To face “reality.”
This Substack is reader-supported. To receive new posts and support my work, consider becoming a free or paid subscriber.
And that reality, to them, looked like a life that doesn’t feel like living at all.
They wrote that their biggest fear wasn’t failure—it was settling. Dimming their fire. Growing into someone they never chose to be.
And that—more than anything—scared them.
They told me that my book, I Don’t Want to Grow Up, brought them to tears because it validated what they already knew to be true. That they’re not alone. That it’s okay to want something different. That it’s okay to feel everything.
It’s messages like this that remind me why I write.
As many of you know, I include my personal email address at the back of all my books. And I read—and respond to—every single message that comes in. Whether it’s a few sentences or a life story, I see them all. And again and again, I’m reminded: there are so many of us out here quietly carrying the same truth.
Maybe you’ve felt the same. Maybe you still do.
Maybe you’ve been told your dreams are too big, too unrealistic. Maybe people around you—people who love you—try to shrink them down to something more “manageable.” Maybe they call it protection. Maybe they call it love.
But it feels like fear.
The path you wish to walk might be lonelier at first. It might not make sense to the people around you. But if it lights you up—follow it.
Because when you do, you give silent permission to others to do the same. You become living proof that another kind of life is possible. And that’s how we build a better world.
So to the person who wrote to me—and to every soul who feels the same way:
Keep going. Keep dreaming. Keep burning. You are not too young. You are not too idealistic. You are just deeply, radically alive.
And that is not a problem. That is a gift.
—
If this speaks to you, my book I Don’t Want to Grow Up was written for this very reason—to remind you that your wildness is sacred, your truth is valid, and you’re not alone. Paperback/Kindle/Audiobook available here: scottstillmanblog.com
This Substack is reader-supported. To receive new posts and support my work, consider becoming a free or paid subscriber. https://connect-test.layer3.press/articles/041a2dc8-5c42-4895-86ec-bc166ac0d315
-
 @ 909e3fdc:73f2b10a
2025-05-22 02:14:38
@ 909e3fdc:73f2b10a
2025-05-22 02:14:38Pizza Day’s not really about pizza. It’s about Laszlo exhibiting Bitcoin as a P2P payment mechanism. That’s worth a cheers. In 15 years, Bitcoin went from a nerdy experiment to challenging the fiat system. That’s massive! It’s changed how I see the world. Patient hodling and carnivore-focus, practices that I picked up from the bitcoin community, shifted me from kinda nihilistic to stupidly optimistic. So, definitely celebrate Pizza Day. Or maybe barbecue steaks instead. Commiserate on the frivolous purchases that you made with bitcoin in the day. I think of these sometimes. Honour Laszlo’s pioneer vibe and Bitcoin’s insane rise, but keep your eyes on what’s coming. The future’s gonna be wilder than we think.
-
 @ 68d6e729:e5f442ac
2025-05-22 13:55:45
@ 68d6e729:e5f442ac
2025-05-22 13:55:45The Adapter Pattern in TypeScript
What is the Adapter Pattern?
The Adapter Pattern is a structural design pattern that allows objects with incompatible interfaces to work together. It acts as a bridge between two interfaces, enabling integration without modifying existing code.
In simple terms: it adapts one interface to another.
Real-World Analogy
Imagine you have a U.S. laptop charger and you travel to Europe. The charger plug won't fit into the European socket. You need a plug adapter to convert the U.S. plug into a European-compatible one. The charger stays the same, but the adapter allows it to work in a new context.
When to Use the Adapter Pattern
- You want to use an existing class but its interface doesn't match your needs.
- You want to create a reusable class that cooperates with classes of incompatible interfaces.
- You need to integrate third-party APIs or legacy systems with your application.
Implementing the Adapter Pattern in TypeScript
Let’s go through a practical example.
Scenario
Suppose you’re developing a payment system. You already have a
PaymentProcessorinterface that your application uses. Now, you want to integrate a third-party payment gateway with a different method signature.Step 1: Define the Target Interface
javascript ts CopyEdit// The interface your application expects interface PaymentProcessor { pay(amount: number): void; }Step 2: Create an Adaptee (incompatible class)
javascript ts CopyEdit// A third-party library with a different method class ThirdPartyPaymentGateway { makePayment(amountInCents: number): void { console.log(`Payment of $${amountInCents / 100} processed via third-party gateway.`); } }Step 3: Implement the Adapter
```javascript ts CopyEdit// Adapter makes the third-party class compatible with PaymentProcessor class PaymentAdapter implements PaymentProcessor { private gateway: ThirdPartyPaymentGateway;
constructor(gateway: ThirdPartyPaymentGateway) { this.gateway = gateway; }
pay(amount: number): void { const amountInCents = amount * 100; this.gateway.makePayment(amountInCents); } } ```
Step 4: Use the Adapter in Client Code
```javascript ts CopyEditconst thirdPartyGateway = new ThirdPartyPaymentGateway(); const adapter: PaymentProcessor = new PaymentAdapter(thirdPartyGateway);
// Application uses a standard interface adapter.pay(25); // Output: Payment of $25 processed via third-party gateway. ```
Advantages of the Adapter Pattern
- Decouples code from third-party implementations.
- Promotes code reuse by adapting existing components.
- Improves maintainability when dealing with legacy systems or libraries.
Class Adapter vs Object Adapter
In languages like TypeScript, which do not support multiple inheritance, the object adapter approach (shown above) is preferred. However, in classical OOP languages like C++, you may also see class adapters, which rely on inheritance.
Conclusion
The Adapter Pattern is a powerful tool in your design pattern arsenal, especially when dealing with incompatible interfaces. In TypeScript, it helps integrate third-party APIs and legacy systems seamlessly, keeping your code clean and extensible.
By learning and applying the Adapter Pattern, you can make your applications more robust and flexible—ready to adapt to ever-changing requirements. https://fox.layer3.press/articles/cdd71195-62a4-420b-9e24-e23d78b27452
-
 @ 21335073:a244b1ad
2025-05-21 16:58:36
@ 21335073:a244b1ad
2025-05-21 16:58:36The other day, I had the privilege of sitting down with one of my favorite living artists. Our conversation was so captivating that I felt compelled to share it. I’m leaving his name out for privacy.
Since our last meeting, I’d watched a documentary about his life, one he’d helped create. I told him how much I admired his openness in it. There’s something strange about knowing intimate details of someone’s life when they know so little about yours—it’s almost like I knew him too well for the kind of relationship we have.
He paused, then said quietly, with a shy grin, that watching the documentary made him realize how “odd and eccentric” he is. I laughed and told him he’s probably the sanest person I know. Because he’s lived fully, chasing love, passion, and purpose with hardly any regrets. He’s truly lived.
Today, I turn 44, and I’ll admit I’m a bit eccentric myself. I think I came into the world this way. I’ve made mistakes along the way, but I carry few regrets. Every misstep taught me something. And as I age, I’m not interested in blending in with the world—I’ll probably just lean further into my own brand of “weird.” I want to live life to the brim. The older I get, the more I see that the “normal” folks often seem less grounded than the eccentric artists who dare to live boldly. Life’s too short to just exist, actually live.
I’m not saying to be strange just for the sake of it. But I’ve seen what the crowd celebrates, and I’m not impressed. Forge your own path, even if it feels lonely or unpopular at times.
It’s easy to scroll through the news and feel discouraged. But actually, this is one of the most incredible times to be alive! I wake up every day grateful to be here, now. The future is bursting with possibility—I can feel it.
So, to my fellow weirdos on nostr: stay bold. Keep dreaming, keep pushing, no matter what’s trending. Stay wild enough to believe in a free internet for all. Freedom is radical—hold it tight. Live with the soul of an artist and the grit of a fighter. Thanks for inspiring me and so many others to keep hoping. Thank you all for making the last year of my life so special.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 51bbb15e:b77a2290
2025-05-21 00:24:36
@ 51bbb15e:b77a2290
2025-05-21 00:24:36Yeah, I’m sure everything in the file is legit. 👍 Let’s review the guard witness testimony…Oh wait, they weren’t at their posts despite 24/7 survellience instructions after another Epstein “suicide” attempt two weeks earlier. Well, at least the video of the suicide is in the file? Oh wait, a techical glitch. Damn those coincidences!
At this point, the Trump administration has zero credibility with me on anything related to the Epstein case and his clients. I still suspect the administration is using the Epstein files as leverage to keep a lot of RINOs in line, whereas they’d be sabotaging his agenda at every turn otherwise. However, I just don’t believe in ends-justify-the-means thinking. It’s led almost all of DC to toss out every bit of the values they might once have had.
-
 @ c9badfea:610f861a
2025-05-10 11:08:51
@ c9badfea:610f861a
2025-05-10 11:08:51- Install FUTO Keyboard (it's free and open source)
- Launch the app, tap Switch Input Methods and select FUTO Keyboard
- For voice input, choose FUTO Keyboard (needs mic permission) and grant permission While Using The App
- Configure keyboard layouts under Languages & Models as needed
Adding Support for Non-English Languages
Voice Input
- Download voice input models from the FUTO Keyboard Add-Ons page
- For languages like Chinese, German, Spanish, Russian, French, Portuguese, Korean, and Japanese, download the Multilingual-74 model
- For other languages, download Multilingual-244
- Open FUTO Keyboard, go to Languages & Models, and import the downloaded model under Voice Input
Dictionaries
- Get dictionary files from AOSP Dictionaries
- Open FUTO Keyboard, navigate to Languages & Models, and import the dictionary under Dictionary
ℹ️ When typing, tap the microphone icon to use voice input
-
 @ 99e7936f:d5d2197c
2025-05-23 13:51:11
@ 99e7936f:d5d2197c
2025-05-23 13:51:11Staugefahr
Manchmal ist der Lehrer interessanter als der Unterrichtsinhalt. Man lernt dann beiläufig, obwohl das Thema öde ist. Mir ging das vor vielen Jahren so, als ich in meiner Ausbildung zur Krankenschwester Inhalte zum Thema Hygiene lernen durfte. Unser Lehrer für Hygiene duschte morgens in der Schule, bevor er uns unterrichtete, damit er, sauber vor uns sitzend, glaubwürdig über die permanente Gefahr der Mikroorganismen im Klinikalltag reden konnte. Er lebte das, was er predigte. Er bot pathogenen Keimen keinen Nährboden. Er pflegte sich und seine Kleidung penibel. Er trug Hosen, Pullover und Schuhe aus den 70ern, die kaum Gebrauchsspuren aufwiesen. Er blieb Überzeugungen, die er einmal für richtig befunden hatte, treu, war aber stets bereit, etwas Neues anzunehmen, wenn dies Sinn machte. Bevor er jedoch Neues annahm, prüfte er mehrfach gründlich, las Fachliteratur und vermied Gespräche mit Experten.
Er versuchte damals, Entscheidungsträger in der Klinik darüber aufzuklären, wie man mit einfachen Mitteln Infektionen im Hause hätte minimieren können. Meist wurden seine Vorschläge nur zögerlich umgesetzt, obwohl seine Argumente fachlich richtig waren.
Mir kommt es heute mit dem Thema „Trauma“ und „traumatisierte Gesellschaft“ ähnlich vor. Niemand möchte sich mit dem Thema beschäftigen, obwohl doch alle wissen müssten, dass viele unangenehme Verhaltensweisen von Menschen im Alltag oder in der Politik etwas mit diesem Thema zu tun haben. Aber das Thema scheint irgendwie unbequem, mühsam und, vor allem, nicht greifbar.
Ein Trauma kann man genau so wenig sehen wie einen pathogenen Keim, deswegen scheint die Auseinandersetzung mit diesem Thema wie eine unappetitliche und lästige Pflichtaufgabe, die man nur mit spitzen Fingern anfasst, wenn überhaupt.
Wie kann man dieses dringend zu besprechende Thema „Trauma“ sichtbar machen?
Vielleicht geht das mit dem Bild vom Stau auf der Autobahn. Den kennt jeder. Und den Stau kann man nicht übersehen. Große leuchtende Schilder weisen auf ihn hin, damit man nicht unvorbereitet in ihn hinein fährt. Überall wird vor dem Stau gewarnt. Und trotzdem passiert er, denn wir sind der Stau, wir selbst machen den Stau.
Stau passiert, weil es Hindernisse auf unserem Weg gibt.
Der Stau ist VOR dem Hindernis. Die Traumafolgen sind gewissermaßen der Stau in unserem Leben, obwohl das Trauma HINTER uns liegt. Wie geht das? Ein Trauma liegt zeitlich gesehen zwar in der Vergangenheit, aber energetisch gesehen liegt es immer vor uns. Es begleitet uns, verfolgt uns, holt uns ein. Energie kennt kein VOR oder HINTER. Energie ist allgegenwärtig. Sobald das Trauma integriert ist, hört dieser Spuk auf. Aber ein nicht bearbeitetes Trauma stellt definitiv ein Hindernis auf unserem (Lebens)Weg dar. Es liegt dann VOR uns.
Dieser Vergleich humpelt ein wenig, zeigt aber dennoch die einfachen Mechanismen von Trauma auf, wie ich finde.
Auf der Autobahn gibt es also ein Hindernis. Entweder gibt es eine bekannte Baustelle, die wir bereits beim Planen der Route zur Kenntnis genommen haben (Trauma ist bereits gut bekannt). Oder es gibt einen Unfall auf der Strecke vor uns, den niemand absehen konnte (Das frühe Trauma wird in einer Alltagssituation plötzlich aktiviert). Jedenfalls stehen wir dann geplant oder ungeplant im Stau, vielmehr sind wir der Stau. Es geht nur langsam oder gar nicht mehr weiter, obwohl der (Lebens)Motor läuft. Bei Trauma ist das auch so. Trauma bewirkt ganz viel Entwicklungsverzögerung in einzelnen Lebensbereichen. Menschen erlernen mehrere Berufe, brauchen länger, um beruflich anzukommen, heiraten später, mehrfach oder nie. Menschen mit Trauma haben manchmal auch beruflich wie privat große Erfolge, fallen dann aber tief, um dadurch letztlich neu geboren zu werden. Trauma sieht man nicht immer auf den ersten Blick. Es kann auch hinter jeder normalen Fassade stecken. Je nach Schwere des Traumas, kann Trauma auch alle Lebensbereiche gleichermaßen treffen. Das entspricht dann dem Pendler, der regelmäßig Sommer wie Winter im Stau steht und auch schon selbst mal eine Panne, im Stau stehend, hatte.
Man erreicht einfach nicht die Ziele, die man sich selbst gesteckt hat. Man kann dann versuchen, die nächste Abfahrt zu nehmen, einen Umweg zu fahren, während des Staus etwas anderes zu erledigen, sich selbst zu erzählen, dass ein Stau gar kein Hindernis sei, sondern eine prima Gelegenheit, um eine Pause zu machen. Und man kann andere Menschen anrufen und erklären, dass man später komme oder sonstiges tun. Aber man steht im Stau, man ist der Stau. Es geht nicht so weiter, wie gewünscht, und man muss das hinnehmen. Verschiedene unangenehme Gefühle melden sich zwangsläufig. Man stellt sich die Sinnfrage, man schaut, wie andere mit dem Stau umgehen, und man möchte gefühlt nie wieder in einem Stau stehen, weil es nervt. Es bringt einen nicht um, aber es nervt. Und es ist ja nicht das erste Mal. Man möchte so gern ein Leben haben ohne Stau. Das wär´s. Es nervt einfach. Und dann nach langer Zeit, mit Blick auf die Tankanzeige, geht es endlich weiter. Die Autos fahren langsam an und der Verkehr rollt wieder. Man wirft einen kurzen Blick auf das Verkehrshindernis und fährt dann zügig weiter. Denn man will nur noch weg von diesem Streckenabschnitt/ Lebensabschnitt. Der Stresspegel im Körper geht runter, man atmet durch und entspannt sich. Aber es war unschön. Nächstes Mal will man die Route besser planen oder gleich mit dem Zug fahren. Man ist erleichtert und hat endlich die Kontrolle über sein Leben zurück. Jetzt ist alles möglich.
Es gibt viele Parallelen zwischen einem Stau und einem Trauma bzw. den Traumafolgen.
Traumabewältigung ist jedoch viel schmerzhafter, als an einem Verkehrshindernis nach längerer Wartezeit einfach vorbei zu fahren. Und man verpasst auch mehr im Leben als nur eine Stunde Zeit, die man auf leblosem Asphalt verbringt. Der Preis, den man für Trauma bezahlt, ist kaum zu beziffern. Und ein Trauma wirft nicht nur die Sinnfrage auf, sondern auch die Frage nach der eigenen Identität. Im Stau auf der Autobahn weiß ich genau, wer ich bin. Aber nach einem frühen Trauma gehen einige Seelenanteile auf eine lange Reise. Und wenn ein Trauma später im Leben passiert, dann sagen Menschen: „Ich habe mich selbst nicht mehr wieder erkannt.“ Trauma wirbelt alles in Dir durcheinander. Und genau darin liegt die Chance. Du musst jedes Teil, jeden Aspekt Deiner Persönlichkeit einzeln in die Hand nehmen, an den richtigen Ort zurück legen, und dadurch lernst Du Dich selbst kennen (und lieben) wie nie zuvor. Der Gewinn von Traumaarbeit übersteigt den zuvor gezahlten Preis. Das nennt man dann posttraumatisches Wachstum. Man ist erleichtert und hat viel mehr als nur die Kontrolle über sein Leben zurück. Eigentlich ist das schon die ganze Geschichte.
Das riesige Problem an der Traumabewältigung ist halt, dass es ein so schmerzhafter und langwieriger Prozess ist. Aber auch hier gibt es gute Nachrichten. Viel von dem Kummer, den wir „im Stau“ erleben, hat etwas mit unseren positiv wie negativ übertriebenen Erwartungen an uns und andere und dem verloren gegangenen Kulturwissen in Bezug auf das Thema „Trauma“ zu tun. Trauma hat die Eigenart, in Vergessenheit zu geraten. Daher gibt es viele falsche Verkehrsmeldungen diesbezüglich. Deswegen möchte ich mein Erfahrungswissen zum Thema „Trauma“ teilen, weil ich denke, dass das Ängste abbauen kann, sich diesem Thema auf ganz natürliche Weise anzunähern, vergleichbar mit der WDR-Produktion „der siebte Sinn“ und getreu dem Motto „Gefahr erkannt, Gefahr gebannt“.
Man kann jedes Problem aufbauschen oder sachlich betrachten. Und es macht einen riesigen Unterschied, ob man mit einem Problem allein gelassen wird, oder ob man wohlwollende und kundige Hilfe an der Seite hat. Und genau dies sind meine zentralen Kritikpunkte zum Thema. Das Thema „Trauma“ wird als unlösbar hingestellt und dadurch unnötig aufgebauscht. Deswegen muss man dieses Thema quasi schon vermeiden, wenn man sich nicht den Tag verderben möchte. Und in der Folge werden von Experten Hilfen angepriesen, die aber leider oft nicht zuverlässig helfen können, weil das Thema ja unlösbar ist. Der verhängnisvolle Kreis schließt sich, und man kommt ins Schleudern.
Kulturwissen wird verfälscht und verdreht, ein übles Schleudertrauma entsteht.
Nein, mal im Ernst, ich möchte das Thema sachlich betrachten und zumindest Impulse für eine günstige Betrachtungsweise geben. Diese Impulse kommen aus meinen persönlichen Erfahrungen und aus Beobachtungen, die ich gemacht habe. Mir ist bewusst, dass jeder Mensch Verletzungen und spätere Probleme, die daraus resultieren, unterschiedlich erlebt. Aber vielleicht geht es gerade um diesen in unserer Kultur fehlenden analogen, lebendigen und authentischen Austausch von Nicht-Experten über die verschiedenen Verletzungen, die daraus resultierende Probleme und die - sehr wohl - vorhandenen Lösungen.
Trauma ist das, was man draus macht.
Ich persönlich kenne niemanden, der kein Trauma erlebt hat.
Leben bedeutet immer auch, dass man Verletzungen erlebt.
Trauma passiert jedem.
Trauma passiert auch robusten Menschen.
Bestimmte Traumata haben immer sehr ähnliche Traumafolgen. Man ist nicht alleine damit.
Menschen reagieren ähnlich auf bestimmte Ereignisse im Leben, das hängt mit unserem Menschsein, der Biologie und der Evolution zusammen.
Menschen reden nicht gern über ihr Trauma.
Menschen schämen sich für ihr Trauma.
Menschen geben sich selbst die Schuld für ihr Trauma.
Menschen versuchen alles, um ihr Trauma zu vergessen oder ungeschehen zu machen.
Menschen erleben einen tiefen Schmerz durch Trauma.
Menschen werden aggressiv, weil sie selber verletzt wurden.
Menschen werden durch Aggression selbst zum Täter. Diese Gefahr besteht zumindest.
Menschen lehnen sich selbst ab für diese aggressiven Impulse.
Alle Gefühle haben eine Funktion. Auch negative Gefühle haben eine Funktion.
Negative Gefühle beschützen unser Leben.
Deswegen sind auch negative Gefühle im bestimmten Maße gut.
Der Schmerz, der durch Trauma entsteht, hat jedoch eine besondere Funktion.
Streng genommen, ist er kein Gefühl, aber egal.
Er ist jedenfalls der letzte und wichtigste Hüter des Lebens. Man sollte ihn nicht übergehen oder versuchen, ihn weg zu machen. Er ist die rote Ampel, die den Stau regelt.
Eine rote Ampel in einem Stau zu ignorieren, ist verhängnisvoll.
Halte lieber an dieser roten Ampel im Stau, auch wenn es schmerzt.
Dieser Schmerz ist die schwierigste, aber auch wichtigste Herausforderung bei der Traumabewältigung, denn er verzögert Dein ohnehin gestautes Leben noch zusätzlich.
Wer es schafft, die Geduld aufzubringen und sich diesem Schmerz hinzugeben, der erlebt Wunder.
Dieses schlimmste Gefühl bringt Dir quasi Dein Leben und die grüne Welle zurück.
Wenn der Schmerz zu Dir kommt, dann heiße ihn willkommen.
Wir sind gesellschaftlich betrachtet mit unseren unguten Verhaltensweisen mittlerweile im Stau angekommen, und die Ampel, die den Stau regelt, steht auf Rot.
Je ehrlicher wir den Schmerz jetzt zulassen, spüren und nicht wegmachen, desto eher sind wir bereit, unbequeme Veränderungen, die vielleicht mit Verzicht, Orientierungslosigkeit und zaghaften Versuchen zu tun haben, zu beginnen. Im Schmerz wächst ein Bewusstsein dafür, was richtig ist. Und es wächst die Kraft, das Gute zu tun. Der Schmerz macht entschlossen. Der Schmerz zeigt, wo das Lebendige liegt und dass es schützenswert ist. Der Schmerz reduziert unseren Blick auf das Wesentliche, auf das Leben und die Liebe, was aufs Gleiche heraus kommt. Der Schmerz markiert einfach nur die Grenze des Lebens. Und deswegen ist er gut, besonders in diesen Tagen.
Heiße den Schmerz willkommen, er gibt uns alle Information FÜR das Leben.
-
 @ 57c631a3:07529a8e
2025-05-20 15:40:04
@ 57c631a3:07529a8e
2025-05-20 15:40:04The Video: The World's Biggest Toddler
https://connect-test.layer3.press/articles/3f9d28a4-0876-4ee8-bdac-d1a56fa9cd02
-
 @ 2b468756:7930dd9c
2025-05-23 12:17:09
@ 2b468756:7930dd9c
2025-05-23 12:17:09Agorisme is libertarisme in de praktijk: op legale wijze maximale economische en persoonlijke vrijheid. Samen ontdekken en delen we wat er allemaal mogelijk is. We doen dit door: - organiseren jaarlijks agorismefestival - organiseren meerdere themadagen / excursies per jaar - bundelen praktische kennis op Agorisme Wiki - online uitwisselen via (thema)appgroepen
Op deze site worden activiteiten aangekondigd en kun je je opgeven.
Binnenkort: - cursussen metselen, stucen en vloeren - reis naar libertarisch dorp Walden Woods en Liberstad in Noorwegen - introductie Krav Maga zelfverdediging
We zijn gelieerd aan de libertarische partij.
Graag tot ziens!
-
 @ c9badfea:610f861a
2025-05-20 19:49:20
@ c9badfea:610f861a
2025-05-20 19:49:20- Install Sky Map (it's free and open source)
- Launch the app and tap Accept, then tap OK
- When asked to access the device's location, tap While Using The App
- Tap somewhere on the screen to activate the menu, then tap ⁝ and select Settings
- Disable Send Usage Statistics
- Return to the main screen and enjoy stargazing!
ℹ️ Use the 🔍 icon in the upper toolbar to search for a specific celestial body, or tap the 👁️ icon to activate night mode
-
 @ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03
@ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ 3eba5ef4:751f23ae
2025-05-23 09:33:55
@ 3eba5ef4:751f23ae
2025-05-23 09:33:55The article below brings together some of the Q&A from our recent AMA on Reddit. Thanks so much for sending in your questions—we love chatting with you and being part of this awesome community!
Meepo Hardfork Features
What does Meepo bring to CKB, in simple terms?
Imagine upgrading from wooden blocks to LEGO bricks. That’s what the
spawnsyscall in Meepo does for CKB smart contracts, enabling script interoperability.Spawn and a series of related syscalls are introduced as a major upgrade to CKB-VM, enabling interoperability, modularity, and better developer experience, by letting scripts call other scripts, like modular apps in an operating system.
Key features of the upgraded VM?
The upgraded CKB-VM Meepo version unlocks true decoupling and reuse of CKB scripts, enhancing modularity and reusability in smart contract development.
For instance, before Meepo, if developers wanted to build a new time lock in CKB, they had to bundle all necessary functionalities—like signature algorithms—directly into a single lock or type script. This often led to bloated scripts where most of the code was unrelated to the developer's original design goal (time lock). With the spawn syscall, scripts can now delegate tasks—such as signature checks—to other on-chain scripts. As new algorithms emerge, the time lock can adopt them without being redeployed—just by calling updated signature scripts, as long as a shared protocol is followed.
This separation allows developers to: - Focus solely on their core logic. - Reuse independently deployed signature verification scripts. - Upgrade cryptographic components without modifying the original script. - Embrace a more OS-like model where smart contracts can call each other to perform specialized tasks.
By enabling true decoupling and reuse, the spawn syscall makes CKB scripts significantly more composable, maintainable, and adaptable.
Besides Spawn, other improvements in Meepo include:
- Block Extension Fields: Enables reading extension fields in blocks, opening new possibilities like community voting on hardforks (as this ckb-zero-lock prototype). More use cases are expected.
- CKB-VM Optimization: Reduces cycle consumption for common compiler-generated code, making scripts faster and more efficient.
A practical example: IPC on Spawn
Here's an example building an entire Inter-Process Communication (IPC) layer on top of spawn syscalls: - GitHub Repo - Blog post: Transforming IPC in CKB On-Chain Script: Spawn and the Custom Library for Simplified Communication
What does “every wallet will become a CKB wallet because of ckb-auth” mean?
Current CKB-VM already comes with the power to build omnilock / ckb-auth, spawn just makes them easier to reuse in new scripts through decoupling and improved modularity.
Upgrade Compatibility Concerns
Will Meepo require a new address format?
No. Meepo does not introduce breaking changes like address format switching. The only required upgrade is support for a new hash type (
data2). We aim to keep upgrades smooth and backwards-compatible wherever possible.RISC-V & CKB’s Long-Term Design Philosophy
Ethereum is exploring RISC-V—CKB has been doing this for years. What’s your take?
The discussion about RISC-V in Ethereum, is partly about the ease of building zk solutions on Ethereum. And it's easy to mix two different use cases of RISC-V in zk:
- Use RISC-V as the language to write programs running in a zk engine. In this case, we use zero knowledge algorithms to build a RISC-VM and prove programs running inside these RISC-V VMs.
- Use RISC-V as the underlying engine to run cryptographic algorithms, we then compile the verifier / prover code of zero knowledge algorithm into RISC-V, then we run those verifiers / provers inside RISC-V. Essentially, we run the verifying / proving algorithms of zero knowledge algorithms in RISC-V, the programs running inside ZK VMs can be written in other languages suiting the zk algorithms.
When most people talk about RISC-V in zk, they mean the first point above. As a result, we see a lot of arguments debating if RISC-V fits in zk circuits. I couldn't get a direct confirmation from Vitalik, but based on what I read, when Vitalik proposes the idea of RISC-V in Ethereum, he's at least partly thinking about the second point here. The original idea is to introduce RISC-V in Ethereum, so we can just compile zk verifiers / provers into RISC-V code, so there is no need to introduce any more precompiles so as to support different zk algorithms in Ethereum. This is indeed a rare taken path, but I believe it is a right path, it is also the path CKB chose 7 years ago for the initial design of CKB-VM.
CKB believes that a precompile-free approach is the only viable path if we’re serious about building a blockchain that can last for decades—or even centuries. Cryptographic algorithms evolve quickly; new ones emerge every few years, making it unsustainable for blockchains to keep adding them as precompiles. In contrast, hardware evolves more slowly and lives longer.
By choosing RISC-V, we’ve committed to a model that can better adapt to future cryptographic developments. CKB may be on an uncommon path, but I believe it's the right one—and it's encouraging to see Ethereum now moving in a similar direction. Hopefully, more will follow.
CKB already stands out as the only blockchain VM built on RISC-V and entirely free from cryptographic precompiles. Meepo, with its spawn syscall, builds on this foundation—pushing for even greater modularity and reuse. We're also closely watching progress in the RISC-V ecosystem, with the goal of integrating hardware advances into CKB-VM, making it even more future-proof and a state-of-the-art execution environment for blockchain applications.
Will CKB run directly on RISC-V chips? What are the implications?
The "CKB on RISC-V"comes in several stages:
- For now, CKB-VM can already be compiled into RISC-V architecture and run on a RISC-V CPU (e.g. StarFive board), though optimized native implementations are still in development.
- That said, one key issue in the previous stage was that CKB-VM lacks a high-performance, assembly based VM on RISC-V architecture. Ironically, despite CKB-VM being based on RISC-V, we ended up running a Rust-based VM interpreter on RISC-V CPUs—which is far from ideal.
The root of the problem is that RISC-V CPUs come in many configurations, each supporting a different set of extensions. Porting CKB-VM to run natively on real RISC-V chips isn’t trivial—some extensions used by CKB-VM might not be available on the target hardware. With enough time and effort, a performant native implementation could be built, but it’s a non-trivial challenge that still needs significant work.
How do you see the RISC-V narrative expanding?
We are delighted to see the growing recognition of RISC-V in the blockchain space. For CKB, we firmly believe RISC-V is the best choice. Consensus is costly, so only essential data should be on-chain, with the chain serving as a universal verification layer—this is CKBʼs philosophy, and we have consistently designed and developed in this direction.
CKB Roadmap & Ecosystem Growth
Any plan to boost the usage of the CKB network in the next 6 - 24 months?
Growth starts with better developer experience. Spawn in Meepo significantly lowers the barrier to building complex apps. With better tools and documentation, more devs can experiment on CKB, leading to better apps and more users.
What would you focus on if the secondary issuance budget was huge?
If funding were abundant, we'd expand the Spark Program, support more grassroots projects, and even evolve toward a fully decentralized DAO structure—aligning with our long-term vision of a permissionless, community-owned network.
What’s next for Nervos after Meepo?
We're exploring new RISC-V extensions like CFI, which could boost script security and defend against ROP attacks. Still early-stage, but promising. Check out this: Against ROP Attacks: A Blockchain Architect’s Take on VM-Level Security.
Resources
Take a deeper look at the VM upgrades introduced in the Meepo hardfork:
Explore the CFI (Control Flow Integrity) extension on RISC-V:
Check out the Inter-Process Communication (IPC) layer built on top of spawn syscalls:
-
 @ 502ab02a:a2860397
2025-05-23 07:35:13
@ 502ab02a:a2860397
2025-05-23 07:35:13แหม่ ต้องรีบแวะมาเขียนไว้ก่อน ของกำลังร้อนๆ #ตัวหนังสือมีเสียง เพลง ลานกรองมันส์ นั้นเรื่องที่มาที่ไปน่าจะไปตามอ่านในเพจ ลานกรองมันส์ ได้ครับ recap คร่าวๆคือมันคือ พื้นที่สร้างสรรค์ที่เปิดให้มาทำกิจกรรมต่างๆนานากันได้ครับ
วันนี้เลยจะมาเล่าเรื่องวิธีการใช้คำ ซึ่งมันส์ดีตามชื่อลาน ฮาๆๆๆ ผมตั้งโจทย์ไว้เลยว่า ต้องมีคำว่า ลานกรองมันส์ แน่ๆแล้ว เพราะเป็นชื่อสถานที่ จากนั้นก็เอาคำว่า ลานกองมัน มาแตกขยายความเพราะมันคือต้นกำเนิดเดิมของพื้นที่นั้น คือเป็นลานที่เอาหัวมันมากองกันเอาไว้ รอนำไปผลิตต่อเป็นสินค้าการเกษตรต่างๆ
ตอนนี้เขาเลิกทำไปแล้ว จึงกลายมาเป็น ลานกรองมันส์ ที่เอาชื่อเดิมมาแปลง
เมื่อได้คำหลักๆแล้วผมก็เอาพยัญชนะเลย ลอลิง กอไก่ มอม้า คือตัวหลักของเพลง
โทนดนตรีไม่ต้องเลือกเลยหนีไม่พ้นสามช่าแน่นอน โทนมันมาตั้งแต่เริ่มคิดจะเขียนเลยครับ ฮาๆๆๆ
ผมพยายามแบ่งวรรคไว้ชัดๆ เผื่อไว้เลยว่าอนาคตอาจมีการทำดนตรีแบบแบ่งกันร้อง วรรคของมันเลยเป็น หมู่ เดี่ยว หมู่ เดี่ยว หมู่ เดี่ยว หมู่ แบบสามโทนเลย
ท่อนหมู่นั้น คิดแบบหลายชั้นมากครับ โดยเฉพาะคำว่า มัน เอามันมากอง มันที่ว่าได้ทั้งเป็นคำกิริยา คือ เอามันมากองๆ หรือ มันที่ว่าอาจหมายถึงตัวความฝันเองเป็นคำลักษณะนามเรียกความฝัน "ลานกรองมันส์ เรามาลองกัน มาร่วมกันมอง ลานกรองมันส์ มาร่วมสร้างฝัน เอามันมากอง"
หรือแม้แต่ท่อนต่างๆ ก็เล่นคำว่า มัน กอง เพื่อให้รู้สึกย้ำท่อนหมู่ ที่มีคำว่ามัน เป็นพระเอกหลายหน้า ทั้งความสนุก ทั้งลักษณะนามความฝัน ทั้งกิริยา "ทุกคน ต่างมี ความฝัน เอามา รวมกัน ให้มันเป็นกอง"
อีกท่อนที่ชอบมากตอนเขียนคือ ทำที่ ลานกรองมันส์ idea for fun everyone can do เพราะรู้สึกว่า การพูดภาษาอังกฤษสำเนียงไทยๆ มันตูดหมึกดี ฮาๆๆๆๆ
หัวใจของเพลงคือจะบอกว่า ใครมีฝันก็มาเลย มาทำฝันกัน เรามีที่ให้คุณ ไม่ต้องกลัวอะไรที่จะทำฝันของตัวเอง เล็กใหญ่ ผิดถูก ขอให้ทำมัน อย่าให้ใครหยุดฝันของคุณ นอกจากตัวคุณเอง
เพลงนี้ไม่ได้ลงแพลทฟอร์ม เพราะส่งมอบให้ทาง ลานกรองมันส์เขาครับ ใช้ตามอิสระไปเลย ดังนั้นก็อาจต้องฟังในโพสนี้ หรือ ในยูทูปนะครับ https://youtu.be/W-1OH3YldtM?si=36dFbHgKjiI_9DI8
เนื้อเพลง "ลานกรองมันส์"
ลานกรองมันส์ ขอเชิญทุกท่าน มามันกันดู นะโฉมตรู มาลองดูกัน อ๊ะ มาลันดูกอง
มีงาน คุยกัน สังสรรค์ ดื่มนม ชมจันทร์ ปันฝัน กันเพลิน ทุกคน ต่างล้วน มีดี เรานั้น มีที่ พี่นี้มีโชว์ เอ้า
ลานกรองมันส์ เรามาลองกัน มาร่วมกันมอง ลานกรองมันส์ มาร่วมสร้างฝัน เอามันมากอง
จะเล็ก จะใหญ่ ให้ลอง เราเป็น พี่น้อง เพื่อนพ้อง ต้องตา ทุกคน ต่างมี ความฝัน เอามา รวมกัน ให้มันเป็นกอง เอ้า
ลานกรองมันส์ เรามาลองกัน มาร่วมกันมอง ลานกรองมันส์ มาร่วมสร้างฝัน เอามันมากอง
ชีวิต เราคิดเราทำ ทุกสิ่งที่ย้ำ คือทำสุดใจ จะเขียน จะเรียน จะรำ ทำที่ ลานกรองมันส์ idea for fun everyone can do
ลานกรองมันส์ เรามาลองกัน มาร่วมกันมอง ลานกรองมันส์ มาร่วมสร้างฝัน เอามันมากอง
เรามา ลั่นกลองให้มัน เฮไหนเฮกัน ที่ลานกรองมันส์ ให้ฝัน บันเทิง…
ตัวหนังสือมีเสียง #pirateketo #siamstr
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ db39407c:a36c161e
2025-05-22 10:37:27
@ db39407c:a36c161e
2025-05-22 10:37:27123BET trải nghiệm giải trí online đang trở thành điểm đến lý tưởng cho cộng đồng yêu thích cá cược trực tuyến tại Việt Nam nhờ sự kết hợp giữa công nghệ hiện đại và dịch vụ người dùng xuất sắc. Với định hướng phát triển lâu dài và bền vững, 123BET không chỉ cung cấp hàng trăm trò chơi hấp dẫn từ slot game, baccarat, tài xỉu, bắn cá, roulette đến live casino mà còn tích hợp hệ thống cá cược thể thao đỉnh cao, đem lại sự đa dạng và linh hoạt trong lựa chọn giải trí cho người chơi. Giao diện website và ứng dụng được thiết kế tối ưu cho người Việt, dễ sử dụng, tốc độ mượt mà, tương thích hoàn toàn với mọi hệ điều hành như iOS, Android, Windows… chỉ với một tài khoản duy nhất, bạn có thể dễ dàng đăng nhập và tận hưởng mọi dịch vụ cá cược không giới hạn mọi lúc, mọi nơi. 123BET đặc biệt chú trọng đến tính minh bạch, khi toàn bộ trò chơi đều được chứng nhận bởi các tổ chức kiểm định quốc tế, đảm bảo công bằng tuyệt đối trong từng ván cược.
Ngoài hệ thống trò chơi phong phú, 123BET còn sở hữu nền tảng công nghệ bảo mật hàng đầu, giúp người chơi yên tâm tuyệt đối về thông tin cá nhân và giao dịch tài chính. Hệ thống thanh toán được hỗ trợ 24/7, với nhiều phương thức linh hoạt như chuyển khoản ngân hàng, ví điện tử, thẻ cào và cả mã QR, giúp người chơi dễ dàng nạp tiền và rút thưởng một cách nhanh chóng, chỉ trong vài phút. Đặc biệt, người chơi không cần thông qua bên trung gian mà hoàn toàn có thể giao dịch trực tiếp trên nền tảng với độ an toàn cao, hạn chế tối đa rủi ro bị lộ thông tin hoặc lừa đảo. Đội ngũ kỹ thuật và chăm sóc khách hàng của 123BET hoạt động chuyên nghiệp, tận tâm, hỗ trợ trực tuyến liên tục cả ngày lẫn đêm thông qua nhiều kênh như chat trực tuyến, Zalo, Telegram, Hotline. Mọi thắc mắc và sự cố kỹ thuật đều được xử lý nhanh chóng và hiệu quả, đảm bảo trải nghiệm không bị gián đoạn. Nhờ vào dịch vụ chăm sóc người chơi chuyên biệt và tận tâm, 123BET ngày càng khẳng định vị thế dẫn đầu của mình trên thị trường cá cược trực tuyến Việt Nam.
Không dừng lại ở đó, 123BET còn liên tục triển khai các chương trình khuyến mãi hấp dẫn nhằm tri ân người chơi mới và gắn bó lâu dài. Ngay từ khi đăng ký tài khoản, người chơi sẽ nhận được nhiều phần thưởng hấp dẫn như tiền cược miễn phí, vòng quay may mắn và các mã thưởng nạp đầu giá trị. Ngoài ra, chương trình VIP của 123BET được xây dựng theo mô hình tích điểm nâng hạng với các cấp bậc từ Thành viên, Bạc, Vàng cho đến Kim Cương – mỗi cấp đều đi kèm các đặc quyền riêng như hoàn tiền cược hàng tuần, tỷ lệ nạp cao hơn, rút tiền nhanh hơn và được ưu tiên hỗ trợ riêng biệt. Những sự kiện hot theo tháng, các giải đấu nội bộ cũng được tổ chức thường xuyên với phần thưởng tiền mặt, điện thoại, xe máy hoặc các phần quà có giá trị khác, giúp người chơi luôn có cảm hứng mới khi tham gia. Với định hướng không ngừng đổi mới và lấy người dùng làm trung tâm, 123BET trải nghiệm giải trí online không chỉ là một nhà cái, mà còn là người đồng hành đáng tin cậy trong hành trình giải trí và kiếm thưởng của hàng triệu người Việt mỗi ngày.
-
 @ 6ad3e2a3:c90b7740
2025-05-20 13:49:50
@ 6ad3e2a3:c90b7740
2025-05-20 13:49:50I’ve written about MSTR twice already, https://www.chrisliss.com/p/mstr and https://www.chrisliss.com/p/mstr-part-2, but I want to focus on legendary short seller James Chanos’ current trade wherein he buys bitcoin (via ETF) and shorts MSTR, in essence to “be like Mike” Saylor who sells MSTR shares at the market and uses them to add bitcoin to the company’s balance sheet. After all, if it’s good enough for Saylor, why shouldn’t everyone be doing it — shorting a company whose stock price is more than 2x its bitcoin holdings and using the proceeds to buy the bitcoin itself?
Saylor himself has said selling shares at 2x NAV (net asset value) to buy bitcoin is like selling dollars for two dollars each, and Chanos has apparently decided to get in while the getting (market cap more than 2x net asset value) is good. If the price of bitcoin moons, sending MSTR’s shares up, you are more than hedged in that event, too. At least that’s the theory.
The problem with this bet against MSTR’s mNAV, i.e., you are betting MSTR’s market cap will converge 1:1 toward its NAV in the short and medium term is this trade does not exist in a vacuum. Saylor has described how his ATM’s (at the market) sales of shares are accretive in BTC per share because of this very premium they carry. Yes, we’ll dilute your shares of the company, but because we’re getting you 2x the bitcoin per share, you are getting an ever smaller slice of an ever bigger overall pie, and the pie is growing 2x faster than your slice is reducing. (I https://www.chrisliss.com/p/mstr how this works in my first post.)
But for this accretion to continue, there must be a constant supply of “greater fools” to pony up for the infinitely printable shares which contain only half their value in underlying bitcoin. Yes, those shares will continue to accrete more BTC per share, but only if there are more fools willing to make this trade in the future. So will there be a constant supply of such “fools” to keep fueling MSTR’s mNAV multiple indefinitely?
Yes, there will be in my opinion because you have to look at the trade from the prospective fools’ perspective. Those “fools” are not trading bitcoin for MSTR, they are trading their dollars, selling other equities to raise them maybe, but in the end it’s a dollars for shares trade. They are not selling bitcoin for them.
You might object that those same dollars could buy bitcoin instead, so they are surely trading the opportunity cost of buying bitcoin for them, but if only 5-10 percent of the market (or less) is buying bitcoin itself, the bucket in which which those “fools” reside is the entire non-bitcoin-buying equity market. (And this is not considering the even larger debt market which Saylor has yet to tap in earnest.)
So for those 90-95 percent who do not and are not presently planning to own bitcoin itself, is buying MSTR a fool’s errand, so to speak? Not remotely. If MSTR shares are infinitely printable ATM, they are still less so than the dollar and other fiat currencies. And MSTR shares are backed 2:1 by bitcoin itself, while the fiat currencies are backed by absolutely nothing. So if you hold dollars or euros, trading them for MSTR shares is an errand more sage than foolish.
That’s why this trade (buying BTC and shorting MSTR) is so dangerous. Not only are there many people who won’t buy BTC buying MSTR, there are many funds and other investment entities who are only able to buy MSTR.
Do you want to get BTC at 1:1 with the 5-10 percent or MSTR backed 2:1 with the 90-95 percent. This is a bit like medical tests that have a 95 percent accuracy rate for an asymptomatic disease that only one percent of the population has. If someone tests positive, it’s more likely to be a false one than an indication he has the disease*. The accuracy rate, even at 19:1, is subservient to the size of the respective populations.
At some point this will no longer be the case, but so long as the understanding of bitcoin is not widespread, so long as the dollar is still the unit of account, the “greater fools” buying MSTR are still miles ahead of the greatest fools buying neither, and the stock price and mNAV should only increase.
. . .
One other thought: it’s more work to play defense than offense because the person on offense knows where he’s going, and the defender can only react to him once he moves. Similarly, Saylor by virtue of being the issuer of the shares knows when more will come online while Chanos and other short sellers are borrowing them to sell in reaction to Saylor’s strategy. At any given moment, Saylor can pause anytime, choosing to issue convertible debt or preferred shares with which to buy more bitcoin, and the shorts will not be given advance notice.
If the price runs, and there is no ATM that week because Saylor has stopped on a dime, so to speak, the shorts will be left having to scramble to change directions and buy the shares back to cover. Their momentum might be in the wrong direction, though, and like Allen Iverson breaking ankles with a crossover, Saylor might trigger a massive short squeeze, rocketing the share price ever higher. That’s why he actually welcomes Chanos et al trying this copycat strategy — it becomes the fuel for outsized gains.
For that reason, news that Chanos is shorting MSTR has not shaken my conviction, though there are other more pertinent https://www.chrisliss.com/p/mstr-part-2 with MSTR, of which one should be aware. And as always, do your own due diligence before investing in anything.
* To understand this, consider a population of 100,000, with one percent having a disease. That means 1,000 have it, 99,000 do not. If the test is 95 percent accurate, and everyone is tested, 950 of the 1,000 will test positive (true positives), 50 who have it will test negative (false negatives.) Of the positives, 95 percent of 99,000 (94,050) will test negative (true negatives) and five percent (4,950) will test positive (false positives). That means 4,950 out of 5,900 positives (84%) will be false.
-
 @ fbf0e434:e1be6a39
2025-05-22 06:52:22
@ fbf0e434:e1be6a39
2025-05-22 06:52:22Hackathon 概要
AI BUIDL Lab: 基于提示工程(Prompt Engineering)在 Rootstock 上构建真实 Web3 应用的黑客松 近日收官,共有 211 名开发者注册并提交 22 个项目。本次活动旨在鼓励开发者借助 AI 驱动的工作流程,在 Rootstock 平台开发 Web3 应用。参与者聚焦三大领域:去中心化金融(DeFi)与支付、商业与零工经济,以及 Web3 身份与声誉体系,通过 AI 技术加速去中心化应用(dApps)的创新迭代。
活动产出丰硕成果,包括去中心化金融解决方案、AI 增强型身份管理系统等,凸显了 AI 与 Web3 集成的潜力。赛事奖金池包含 1.5 万美元的 RIF 代币,用于奖励在创意性和技术执行力方面表现突出的顶尖项目。
本次黑客松不仅印证了 AI 在简化去中心化应用开发中的价值,也展现了 Web3 生态系统的进阶成果。活动与 thirdweb、Alchemy 及 RootstockLabs 的合作,为开发者高效参与及产出创新项目提供了有力支持。
Hackathon 获奖者
DeFi 和支付奖项得主
- ProtectedPay_Rootstock:一个在 CrossFi 链上的 DeFi 平台,通过先进的区块链功能促进安全转账、群体支付和智能储蓄。
- AIFi: AI-Powered DeFi Hub on Rootstock:利用 AI 提供汇款、信用评分和用户界面改善,提高拉丁美洲的金融可访问性。
商业和零工经济奖项得主
Web3 中的身份和声誉奖项得主
- AgenticID:提供自我主权身份验证,结合区块链和 AI,使用零知识证明进行安全的用户认证。
- TrustScan:使用 AI 分析 Rootstock 上的钱包活动,生成信誉和身份评分,加强信任。
赏金最佳 AI 提示使用
- AuditFi_Rootstock:提供 AI 驱动的智能合约安全审计,通过链上验证增强透明度和信任。
- RSK Smart Yield Engine:一个 AI 驱动的 DeFi 协议收益优化器,通过智能合约和 AI 管理资金和制定策略。
有关所有项目的更多信息,请访问 DoraHacks。
关于组织者
Rootstock
Rootstock - 比特币 DeFi 层 - 专注于将比特币强大的网络与以太坊的智能合约功能相结合,提升区块链的互操作性。Rootstock 以技术专长著称,已经创建了一个支持去中心化金融应用的平台。该组织致力于通过扩展在金融服务中智能合约的可访问性和功能性来推动区块链领域的创新。
-
 @ c1e9ab3a:9cb56b43
2025-05-18 04:14:48
@ c1e9ab3a:9cb56b43
2025-05-18 04:14:48Abstract
This document proposes a novel architecture that decouples the peer-to-peer (P2P) communication layer from the Bitcoin protocol and replaces or augments it with the Nostr protocol. The goal is to improve censorship resistance, performance, modularity, and maintainability by migrating transaction propagation and block distribution to the Nostr relay network.
Introduction
Bitcoin’s current architecture relies heavily on its P2P network to propagate transactions and blocks. While robust, it has limitations in terms of flexibility, scalability, and censorship resistance in certain environments. Nostr, a decentralized event-publishing protocol, offers a multi-star topology and a censorship-resistant infrastructure for message relay.
This proposal outlines how Bitcoin communication could be ported to Nostr while maintaining consensus and verification through standard Bitcoin clients.
Motivation
- Enhanced Censorship Resistance: Nostr’s architecture enables better relay redundancy and obfuscation of transaction origin.
- Simplified Lightweight Nodes: Removing the full P2P stack allows for lightweight nodes that only verify blockchain data and communicate over Nostr.
- Architectural Modularity: Clean separation between validation and communication enables easier auditing, upgrades, and parallel innovation.
- Faster Propagation: Nostr’s multi-star network may provide faster propagation of transactions and blocks compared to the mesh-like Bitcoin P2P network.
Architecture Overview
Components
-
Bitcoin Minimal Node (BMN):
- Verifies blockchain and block validity.
- Maintains UTXO set and handles mempool logic.
- Connects to Nostr relays instead of P2P Bitcoin peers.
-
Bridge Node:
- Bridges Bitcoin P2P traffic to and from Nostr relays.
- Posts new transactions and blocks to Nostr.
- Downloads mempool content and block headers from Nostr.
-
Nostr Relays:
- Accept Bitcoin-specific event kinds (transactions and blocks).
- Store mempool entries and block messages.
- Optionally broadcast fee estimation summaries and tipsets.
Event Format
Proposed reserved Nostr
kindnumbers for Bitcoin content (NIP/BIP TBD):| Nostr Kind | Purpose | |------------|------------------------| | 210000 | Bitcoin Transaction | | 210001 | Bitcoin Block Header | | 210002 | Bitcoin Block | | 210003 | Mempool Fee Estimates | | 210004 | Filter/UTXO summary |
Transaction Lifecycle
- Wallet creates a Bitcoin transaction.
- Wallet sends it to a set of configured Nostr relays.
- Relays accept and cache the transaction (based on fee policies).
- Mining nodes or bridge nodes fetch mempool contents from Nostr.
- Once mined, a block is submitted over Nostr.
- Nodes confirm inclusion and update their UTXO set.
Security Considerations
- Sybil Resistance: Consensus remains based on proof-of-work. The communication path (Nostr) is not involved in consensus.
- Relay Discoverability: Optionally bootstrap via DNS, Bitcoin P2P, or signed relay lists.
- Spam Protection: Relay-side policy, rate limiting, proof-of-work challenges, or Lightning payments.
- Block Authenticity: Nodes must verify all received blocks and reject invalid chains.
Compatibility and Migration
- Fully compatible with current Bitcoin consensus rules.
- Bridge nodes preserve interoperability with legacy full nodes.
- Nodes can run in hybrid mode, fetching from both P2P and Nostr.
Future Work
- Integration with watch-only wallets and SPV clients using verified headers via Nostr.
- Use of Nostr’s social graph for partial trust assumptions and relay reputation.
- Dynamic relay discovery using Nostr itself (relay list events).
Conclusion
This proposal lays out a new architecture for Bitcoin communication using Nostr to replace or augment the P2P network. This improves decentralization, censorship resistance, modularity, and speed, while preserving consensus integrity. It encourages innovation by enabling smaller, purpose-built Bitcoin nodes and offloading networking complexity.
This document may become both a Bitcoin Improvement Proposal (BIP-XXX) and a Nostr Improvement Proposal (NIP-XXX). Event kind range reserved: 210000–219999.
-
 @ a5ee4475:2ca75401
2025-05-15 14:44:45
@ a5ee4475:2ca75401
2025-05-15 14:44:45lista #descentralismo #compilado #portugues
*Algumas destas listas ainda estão sendo trocadas, portanto as versões mais recentes delas só estão visíveis no Amethyst por causa da ferramenta de edição.
Clients do Nostr e Outras Coisas
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
Modelos de IA e Ferramentas
nostr:naddr1qq24xwtyt9v5wjzefe6523j32dy5ga65gagkjqgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guk62czu
Iniciativas de Bitcoin
nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2nvmn5va9x2nrxfd2k5smyf3ux7vesd9znyqxygt4
Profissionais Brasileiros no Nostr
nostr:naddr1qq24qmnkwe6y67zlxgc4sumrxpxxce3kf9fn2qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3q5hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsxpqqqp65wp8uedu
Comunidades em Português no Nostr
nostr:naddr1qq2hwcejv4ykgdf3v9gxykrxfdqk753jxcc4gqg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4gu455fm3
Grupos em Português no Nostr
nostr:nevent1qqs98kldepjmlxngupsyth40n0h5lw7z5ut5w4scvh27alc0w86tevcpzpmhxue69uhkummnw3ezumt0d5hsygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqqqqs3ndneh
Jogos de Código Aberto
Open Source Games nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2kvwp3v4hhvk2sw3j5sm6h23g5wkz5ddzhz8x40v0
Itens Úteis com Esquemas Disponíveis
nostr:naddr1qqgrqvp5vd3kycejxask2efcv4jr2qgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guc43v6c
Formatação de Texto em Markdown
(Amethyst, Yakihone e outros) nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2454m8dfzn26z4f34kvu6fw4rysnrjxfm42wfpe90
Outros Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ 088436cd:9d2646cc
2025-05-01 21:01:55
@ 088436cd:9d2646cc
2025-05-01 21:01:55The arrival of the coronavirus brought not only illness and death but also fear and panic. In such an environment of uncertainty, people have naturally stocked up on necessities, not knowing when things will return to normal.
Retail shelves have been cleared out, and even online suppliers like Amazon and Walmart are out of stock for some items. Independent sellers on these e-commerce platforms have had to fill the gap. With the huge increase in demand, they have found that their inventory has skyrocketed in value.
Many in need of these items (e.g. toilet paper, hand sanitizer and masks) balk at the new prices. They feel they are being taken advantage of in a time of need and call for intervention by the government to lower prices. The government has heeded that call, labeling the independent sellers as "price gougers" and threatening sanctions if they don't lower their prices. Amazon has suspended seller accounts and law enforcement at all levels have threatened to prosecute. Prices have dropped as a result and at first glance this seems like a victory for fair play. But, we will have to dig deeper to understand the unseen consequences of this intervention.
We must look at the economics of the situation, how supply and demand result in a price and how that price acts as a signal that goes out to everyone, informing them of underlying conditions in the economy and helping coordinate their actions.
It all started with a rise in demand. Given a fixed supply (e.g., the limited stock on shelves and in warehouses), an increase in demand inevitably leads to higher prices. Most people are familiar with this phenomenon, such as paying more for airline tickets during holidays or surge pricing for rides.
Higher prices discourage less critical uses of scarce resources. For example, you might not pay $1,000 for a plane ticket to visit your aunt if you can get one for $100 the following week, but someone else might pay that price to visit a dying relative. They value that plane seat more than you.
*** During the crisis, demand surged and their shelves emptied even though
However, retail outlets have not raised prices. They have kept them low, so the low-value uses of things like toilet paper, masks and hand sanitizer has continued. Often, this "use" just takes the form of hoarding. At everyday low prices, it makes sense to buy hundreds of rolls and bottles. You know you will use them eventually, so why not stock up? And, with all those extra supplies in the closet and basement, you don't need to change your behavior much. You don't have to ration your use.
At the low prices, these scarce resources got bought up faster and faster until there was simply none left. The reality of the situation became painfully clear to those who didn't panic and got to the store late: You have no toilet paper and you're not going to any time soon.
However, if prices had been allowed to rise, a number of effects would have taken place that would have coordinated the behavior of everyone so that valuable resources would not have been wasted or hoarded, and everyone could have had access to what they needed.
On the demand side, if prices had been allowed to rise, people would have begun to self-ration. You might leave those extra plies on the roll next time if you know they will cost ten times as much to replace. Or, you might choose to clean up a spill with a rag rather than disposable tissue. Most importantly, you won't hoard as much. That 50th bottle of hand sanitizer might just not be worth it at the new, high price. You'll leave it on the shelf for someone else who may have none.
On the supply side, higher prices would have incentivized people to offer up more of their stockpiles for sale. If you have a pallet full of toilet paper in your basement and all of the sudden they are worth $15 per roll, you might just list a few online. But, if it is illegal to do so, you probably won't.
Imagine you run a business installing insulation and have a few thousand respirator masks on hand for your employees. During a pandemic, it is much more important that people breathe filtered air than that insulation get installed, and that fact is reflected in higher prices. You will sell your extra masks at the higher price rather than store them for future insulation jobs, and the scarce resource will be put to its most important use.
Producers of hand sanitizer would go into overdrive if prices were allowed to rise. They would pay their employees overtime, hire new ones, and pay a premium for their supplies, making sure their raw materials don't go to less important uses.
These kinds of coordinated actions all across the economy would be impossible without real prices to guide them. How do you know if it makes sense to spend an extra $10k bringing a thousand masks to market unless you know you can get more than $10 per mask? If the price is kept artificially low, you simply can't do it. The money just isn't there.
These are the immediate effects of a price change, but incredibly, price changes also coordinate people's actions across space and time.
Across space, there are different supply and demand conditions in different places, and thus prices are not uniform. We know some places are real "hot spots" for the virus, while others are mostly unaffected. High demand in the hot spots leads to higher prices there, which attracts more of the resource to those areas. Boxes and boxes of essential items would pour in where they are needed most from where they are needed least, but only if prices were allowed to adjust freely.
This would be accomplished by individuals and businesses buying low in the unaffected areas, selling high in the hot spots and subtracting their labor and transportation costs from the difference. Producers of new supply would know exactly where it is most needed and ship to the high-demand, high-price areas first. The effect of these actions is to increase prices in the low demand areas and reduce them in the high demand areas. People in the low demand areas will start to self-ration more, reflecting the reality of their neighbors, and people in the hotspots will get some relief.
However, by artificially suppressing prices in the hot spot, people there will simply buy up the available supply and run out, and it will be cost prohibitive to bring in new supply from low-demand areas.
Prices coordinate economic actions across time as well. Just as entrepreneurs and businesses can profit by transporting scarce necessities from low-demand to high-demand areas, they can also profit by buying in low-demand times and storing their merchandise for when it is needed most.
Just as allowing prices to freely adjust in one area relative to another will send all the right signals for the optimal use of a scarce resource, allowing prices to freely adjust over time will do the same.
When an entrepreneur buys up resources during low-demand times in anticipation of a crisis, she restricts supply ahead of the crisis, which leads to a price increase. She effectively bids up the price. The change in price affects consumers and producers in all the ways mentioned above. Consumers self-ration more, and producers bring more of the resource to market.
Our entrepreneur has done a truly incredible thing. She has predicted the future, and by so doing has caused every individual in the economy to prepare for a shortage they don't even know is coming! And, by discouraging consumption and encouraging production ahead of time, she blunts the impact the crisis will have. There will be more of the resource to go around when it is needed most.
On top of this, our entrepreneur still has her stockpile she saved back when everyone else was blithely using it up. She can now further mitigate the damage of the crisis by selling her stock during the worst of it, when people are most desperate for relief. She will know when this is because the price will tell her, but only if it is allowed to adjust freely. When the price is at its highest is when people need the resource the most, and those willing to pay will not waste it or hoard it. They will put it to its highest valued use.
The economy is like a big bus we are all riding in, going down a road with many twists and turns. Just as it is difficult to see into the future, it is difficult to see out the bus windows at the road ahead.
On the dashboard, we don't have a speedometer or fuel gauge. Instead we have all the prices for everything in the economy. Prices are what tell us the condition of the bus and the road. They tell us everything. Without them, we are blind.
Good times are a smooth road. Consumer prices and interest rates are low, investment returns are steady. We hit the gas and go fast. But, the road is not always straight and smooth. Sometimes there are sharp turns and rough patches. Successful entrepreneurs are the ones who can see what is coming better than everyone else. They are our navigators.
When they buy up scarce resources ahead of a crisis, they are hitting the brakes and slowing us down. When they divert resources from one area to another, they are steering us onto a smoother path. By their actions in the market, they adjust the prices on our dashboard to reflect the conditions of the road ahead, so we can prepare for, navigate and get through the inevitable difficulties we will face.
Interfering with the dashboard by imposing price floors or price caps doesn't change the conditions of the road (the number of toilet paper rolls in existence hasn't changed). All it does is distort our perception of those conditions. We think the road is still smooth--our heavy foot stomping the gas--as we crash onto a rocky dirt road at 80 miles per hour (empty shelves at the store for weeks on end).
Supply, demand and prices are laws of nature. All of this is just how things work. It isn't right or wrong in a moral sense. Price caps lead to waste, shortages and hoarding as surely as water flows downhill. The opposite--allowing prices to adjust freely--leads to conservation of scarce resources and their being put to their highest valued use. And yes, it leads to profits for the entrepreneurs who were able to correctly predict future conditions, and losses for those who weren't.
Is it fair that they should collect these profits? On the one hand, anyone could have stocked up on toilet paper, hand sanitizer and face masks at any time before the crisis, so we all had a fair chance to get the supplies cheaply. On the other hand, it just feels wrong that some should profit so much at a time when there is so much need.
Our instinct in the moment is to see the entrepreneur as a villain, greedy "price gouger". But we don't see the long chain of economic consequences the led to the situation we feel is unfair.
If it weren't for anti-price-gouging laws, the major retailers would have raised their prices long before the crisis became acute. When they saw demand outstrip supply, they would have raised prices, not by 100 fold, but gradually and long before anyone knew how serious things would have become. Late comers would have had to pay more, but at least there would be something left on the shelf.
As an entrepreneur, why take risks trying to anticipate the future if you can't reap the reward when you are right? Instead of letting instead of letting entrepreneurs--our navigators--guide us, we are punishing and vilifying them, trying to force prices to reflect a reality that simply doesn't exist.
In a crisis, more than any other time, prices must be allowed to fluctuate. To do otherwise is to blind ourselves at a time when danger and uncertainty abound. It is economic suicide.
In a crisis, there is great need, and the way to meet that need is not by pretending it's not there, by forcing prices to reflect a world where there isn't need. They way to meet the need is the same it has always been, through charity.
If the people in government want to help, the best way for the to do so is to be charitable and reduce their taxes and fees as much as possible, ideally to zero in a time of crisis. Amazon, for example, could instantly reduce the price of all crisis related necessities by 20% if they waived their fee. This would allow for more uses by more people of these scarce supplies as hoarders release their stockpiles on to the market, knowing they can get 20% more for their stock. Governments could reduce or eliminate their tax burden on high-demand, crisis-related items and all the factors that go into their production, with the same effect: a reduction in prices and expansion of supply. All of us, including the successful entrepreneurs and the wealthy for whom high prices are not a great burden, could donate to relief efforts.
These ideas are not new or untested. This is core micro economics. It has been taught for hundreds of years in universities the world over. The fact that every crisis that comes along stirs up ire against entrepreneurs indicates not that the economics is wrong, but that we have a strong visceral reaction against what we perceive to be unfairness. This is as it should be. Unfairness is wrong and the anger it stirs in us should compel us to right the wrong. Our anger itself isn't wrong, it's just misplaced.
Entrepreneurs didn't cause the prices to rise. Our reaction to a virus did that. We saw a serious threat and an uncertain future and followed our natural impulse to hoard. Because prices at major retail suppliers didn't rise, that impulse ran rampant and we cleared the shelves until there was nothing left. We ran the bus right off the road and them blamed the entrepreneurs for showing us the reality of our situation, for shaking us out of the fantasy of low prices.
All of this is not to say that entrepreneurs are high-minded public servants. They are just doing their job. Staking your money on an uncertain future is a risky business. There are big risks and big rewards. Most entrepreneurs just scrape by or lose their capital in failed ventures.
However, the ones that get it right must be allowed to keep their profits, or else no one will try and we'll all be driving blind. We need our navigators. It doesn't even matter if they know all the positive effects they are having on the rest of us and the economy as a whole. So long as they are buying low and selling high--so long as they are doing their job--they will be guiding the rest of us through the good times and the bad, down the open road and through the rough spots.
-
 @ fbf0e434:e1be6a39
2025-05-22 06:41:25
@ fbf0e434:e1be6a39
2025-05-22 06:41:25Hackathon 概要
JAMHacks 9 于 2025 年 5 月 16 日至 18 日在滑铁卢大学举办。作为 JAMHacks 系列的第九届黑客松,该活动汇聚了 170 名高中黑客爱好者,最终评审通过 49 个项目,充分彰显了年轻开发者的技术实力。此次黑客松旨在为高中生打造培育成长的平台,搭配工作坊与互动活动,助力提升技术能力并拓展社交网络。
参与者带来了丰富的项目成果:基于 Pico-8 的创意开发、运用 MongoDB Atlas 的创新应用,以及展示新兴技术应用的生成式 AI 模型项目。活动设置多个奖项类别,包括最佳新手项目、最佳开发者工具、生成式 AI 最佳应用等。奖品涵盖智能手表、无人机、QuillBot 连帽衫,以及其他黑客松的参赛资格。
除技术成果外,JAMHacks 9 同样注重营造趣味互动体验,特别举办扑克之夜、社交派对等活动。此次黑客松成功为年轻开发者搭建了技能提升、创意孵化与专业联结的平台,切实践行其推动科技行业包容性与可及性的愿景。
Hackathon 获奖者
总奖项获奖者
- Mr. Goose:一个有趣的VS Code扩展,为初学者提供提示和鼓励,促进学习而不直接解决问题。
- Guideline:一个基于AR的工具,通过增强现实引导初学电子爱好者进行面包板组装。
- ARmatica:将2D硬件示意图转换为3D AR模型,通过改进可视化增强工程和原型设计过程。
初学者赛道奖项获奖者
- Duedle:一个任务管理应用,利用AI将大型任务分解为可管理的小任务,并提供进度跟踪以提高生产力。
单人赛道奖项获奖者
- Lofied:一个Python应用程序,将Spotify播放列表变为lo-fi版本,具有音乐分离和乐谱生成功能。
女性赛道奖项获奖者
- Doomlings:结合游戏化和教育任务,通过战斗游戏界面提高学生的学习和参与。
Warp 赛道奖项获奖者
Hack Canada 赛道奖项获奖者
- Dionysus:一个用于组织协作活动和参与的平台,提供实时活动管理的统一界面。
MLH 赛道奖项获奖者
- Karma:一个记录和分享积极行动的社交平台,促进自我提升和环境保护,以鼓励社区参与。
- helpidontknowhowtonetworkin.tech:一个使用面部识别和LinkedIn数据的AI驱动网络助手,帮助在活动中建立专业联系。
- SnapCAD:从图像或图纸生成可定制的3D模型,简化工程项目的集成。
PEX Labs 奖项获奖者
- Arctic Explorer:一个Pico-8开放世界游戏,通过探索北极环境促进可持续实践,可以扩展附加小游戏和地图。
查看所有项目 JAMHacks 9。
关于组织者
JAMHacks
JAMHacks 在科技和区块链领域因促进技术爱好者之间的创新与合作而备受认可。该组织擅长举办Hackathon,为开发现实世界挑战的实际解决方案提供了一个平台。JAMHacks 聚焦于技术赋权,已组织多场活动,吸引了来自不同背景的参与者。他们的倡议强调技术技能发展和网络拓展,充分体现了他们致力于推进技术教育和培养一个包容的社区,为有抱负的技术人员和开发者服务。
-
 @ 6e0ea5d6:0327f353
2025-05-20 01:35:20
@ 6e0ea5d6:0327f353
2025-05-20 01:35:20**Ascolta bene! ** A man's sentimental longing, though often disguised in noble language and imagination, is a sickness—not a virtue.
It begins as a slight inclination toward tenderness, cloaked in sweetness. Then it reveals itself as a masked addiction: a constant need to be seen by a woman, validated by her, and reciprocated—as if someone else's affection were the only anchor preventing the shipwreck of his emotions.
The man who understands the weight of leadership seeks no applause, no gratitude, not even romantic love. He knows that his role is not theatrical but structural. He is not measured by the emotion he evokes, but by the stability he ensures. Being a true man is not ornamental. He is not a decorative symbol in the family frame.
We live in an era where male roles have been distorted by an overindulgence in emotion. The man stopped guiding and began asking for direction. His firmness was exchanged for softness, his decisiveness for hesitation. Trying to please, many have given up authority. Trying to love, they’ve begun to bow. A man who begs for validation within his own home is not a leader—he is a guest. And when the patriarch has to ask for a seat at the table he should preside over and sustain, something has already been irreversibly inverted.
Unexamined longing turns into pleading. And all begging is the antechamber of humiliation. A man who never learned to cultivate dignified solitude will inevitably fall to his knees in desperation. And then, he yields. Yields to mediocre presence, to shallow affection, to constant disrespect. He smiles while he bleeds, praises the one who despises him, accepts crumbs and pretends it’s a banquet. All of it, cazzo... just to avoid the horror of being alone.
Davvero, amico mio, for the men who beg for romance, only the consolation of being remembered will remain—not with respect, but with pity and disgust.
The modern world feeds the fragile with illusions, but reality spits them out. Sentimental longing is now celebrated as sensitivity. But every man who nurtures it as an excuse will, sooner or later, pay for it with his dignity.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 3f770d65:7a745b24
2025-05-19 18:09:52
@ 3f770d65:7a745b24
2025-05-19 18:09:52🏌️ Monday, May 26 – Bitcoin Golf Championship & Kickoff Party
Location: Las Vegas, Nevada\ Event: 2nd Annual Bitcoin Golf Championship & Kick Off Party"\ Where: Bali Hai Golf Clubhouse, 5160 S Las Vegas Blvd, Las Vegas, NV 89119\ 🎟️ Get Tickets!
Details:
-
The week tees off in style with the Bitcoin Golf Championship. Swing clubs by day and swing to music by night.
-
Live performances from Nostr-powered acts courtesy of Tunestr, including Ainsley Costello and others.
-
Stop by the Purple Pill Booth hosted by Derek and Tanja, who will be on-boarding golfers and attendees to the decentralized social future with Nostr.
💬 May 27–29 – Bitcoin 2025 Conference at the Las Vegas Convention Center
Location: The Venetian Resort\ Main Attraction for Nostr Fans: The Nostr Lounge\ When: All day, Tuesday through Thursday\ Where: Right outside the Open Source Stage\ 🎟️ Get Tickets!
Come chill at the Nostr Lounge, your home base for all things decentralized social. With seating for \~50, comfy couches, high-tops, and good vibes, it’s the perfect space to meet developers, community leaders, and curious newcomers building the future of censorship-resistant communication.
Bonus: Right across the aisle, you’ll find Shopstr, a decentralized marketplace app built on Nostr. Stop by their booth to explore how peer-to-peer commerce works in a truly open ecosystem.
Daily Highlights at the Lounge:
-
☕️ Hang out casually or sit down for a deeper conversation about the Nostr protocol
-
🔧 1:1 demos from app teams
-
🛍️ Merch available onsite
-
🧠 Impromptu lightning talks
-
🎤 Scheduled Meetups (details below)
🎯 Nostr Lounge Meetups
Wednesday, May 28 @ 1:00 PM
- Damus Meetup: Come meet the team behind Damus, the OG Nostr app for iOS that helped kickstart the social revolution. They'll also be showcasing their new cross-platform app, Notedeck, designed for a more unified Nostr experience across devices. Grab some merch, get a demo, and connect directly with the developers.
Thursday, May 29 @ 1:00 PM
- Primal Meetup: Dive into Primal, the slickest Nostr experience available on web, Android, and iOS. With a built-in wallet, zapping your favorite creators and friends has never been easier. The team will be on-site for hands-on demos, Q\&A, merch giveaways, and deeper discussions on building the social layer of Bitcoin.
🎙️ Nostr Talks at Bitcoin 2025
If you want to hear from the minds building decentralized social, make sure you attend these two official conference sessions:
1. FROSTR Workshop: Multisig Nostr Signing
-
🕚 Time: 11:30 AM – 12:00 PM
-
📅 Date: Wednesday, May 28
-
📍 Location: Developer Zone
-
🎤 Speaker: nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgdwaehxw309ahx7uewd3hkcqpqs9etjgzjglwlaxdhsveq0qksxyh6xpdpn8ajh69ruetrug957r3qf4ggfm (Austin Kelsay) @ Voltage\ A deep-dive into FROST-based multisig key management for Nostr. Geared toward devs and power users interested in key security.
2. Panel: Decentralizing Social Media
-
🕑 Time: 2:00 PM – 2:30 PM
-
📅 Date: Thursday, May 29
-
📍 Location: Genesis Stage
-
🎙️ Moderator: nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqy08wumn8ghj7mn0wd68yttjv4kxz7fwv3jhyettwfhhxuewd4jsqgxnqajr23msx5malhhcz8paa2t0r70gfjpyncsqx56ztyj2nyyvlq00heps - Bitcoin Strategy @ Roxom TV
-
👥 Speakers:
-
nostr:nprofile1qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcppemhxue69uhkummn9ekx7mp0qqsy2ga7trfetvd3j65m3jptqw9k39wtq2mg85xz2w542p5dhg06e5qmhlpep – Early Bitcoin dev, CEO @ Sirius Business Ltd
-
nostr:nprofile1qy2hwumn8ghj7mn0wd68ytndv9kxjm3wdahxcqg5waehxw309ahx7um5wfekzarkvyhxuet5qqsw4v882mfjhq9u63j08kzyhqzqxqc8tgf740p4nxnk9jdv02u37ncdhu7e3 – Analyst & Partner @ Ego Death Capital
Get the big-picture perspective on why decentralized social matters and how Nostr fits into the future of digital communication.
🌃 NOS VEGAS Meetup & Afterparty
Date: Wednesday, May 28\ Time: 7:00 PM – 1:00 AM\ Location: We All Scream Nightclub, 517 Fremont St., Las Vegas, NV 89101\ 🎟️ Get Tickets!
What to Expect:
-
🎶 Live Music Stage – Featuring Ainsley Costello, Sara Jade, Able James, Martin Groom, Bobby Shell, Jessie Lark, and other V4V artists
-
🪩 DJ Party Deck – With sets by nostr:nprofile1qy0hwumn8ghj7cmgdae82uewd45kketyd9kxwetj9e3k7mf6xs6rgqgcwaehxw309ahx7um5wgh85mm694ek2unk9ehhyecqyq7hpmq75krx2zsywntgtpz5yzwjyg2c7sreardcqmcp0m67xrnkwylzzk4 , nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgkwaehxw309anx2etywvhxummnw3ezucnpdejqqg967faye3x6fxgnul77ej23l5aew8yj0x2e4a3tq2mkrgzrcvecfsk8xlu3 , and more DJs throwing down
-
🛰️ Live-streamed via Tunestr
-
🧠 Nostr Education – Talks by nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq37amnwvaz7tmwdaehgu3dwfjkccte9ejx2un9ddex7umn9ekk2tcqyqlhwrt96wnkf2w9edgr4cfruchvwkv26q6asdhz4qg08pm6w3djg3c8m4j , nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqg7waehxw309anx2etywvhxummnw3ezucnpdejz7ur0wp6kcctjqqspywh6ulgc0w3k6mwum97m7jkvtxh0lcjr77p9jtlc7f0d27wlxpslwvhau , nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq3vamnwvaz7tmwdaehgu3wd33xgetk9en82m30qqsgqke57uygxl0m8elstq26c4mq2erz3dvdtgxwswwvhdh0xcs04sc4u9p7d , nostr:nprofile1q9z8wumn8ghj7erzx3jkvmmzw4eny6tvw368wdt8da4kxamrdvek76mrwg6rwdngw94k67t3v36k77tev3kx7vn2xa5kjem9dp4hjepwd3hkxctvqyg8wumn8ghj7mn0wd68ytnhd9hx2qpqyaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgssuy4zk , nostr:nprofile1qy28wue69uhnzvpwxqhrqt33xgmn5dfsx5cqz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqqswavgevxe9gs43vwylumr7h656mu9vxmw4j6qkafc3nefphzpph8ssvcgf8 , and more.
-
🧾 Vendors & Project Booths – Explore new tools and services
-
🔐 Onboarding Stations – Learn how to use Nostr hands-on
-
🐦 Nostrich Flocking – Meet your favorite nyms IRL
-
🍸 Three Full Bars – Two floors of socializing overlooking vibrant Fremont Street
| | | | | ----------- | -------------------- | ------------------- | | Time | Name | Topic | | 7:30-7:50 | Derek | Nostr for Beginners | | 8:00-8:20 | Mark & Paul | Primal | | 8:30-8:50 | Terry | Damus | | 9:00-9:20 | OpenMike and Ainsley | V4V | | 09:30-09:50 | The Space | Space |
This is the after-party of the year for those who love freedom technology and decentralized social community. Don’t miss it.
Final Thoughts
Whether you're there to learn, network, party, or build, Bitcoin 2025 in Las Vegas has a packed week of Nostr-friendly programming. Be sure to catch all the events, visit the Nostr Lounge, and experience the growing decentralized social revolution.
🟣 Find us. Flock with us. Purple pill someone.
-
-
 @ 2f29aa33:38ac6f13
2025-05-17 12:59:01
@ 2f29aa33:38ac6f13
2025-05-17 12:59:01The Myth and the Magic
Picture this: a group of investors, huddled around a glowing computer screen, nervously watching Bitcoin’s price. Suddenly, someone produces a stick-no ordinary stick, but a magical one. With a mischievous grin, they poke the Bitcoin. The price leaps upward. Cheers erupt. The legend of the Bitcoin stick is born.
But why does poking Bitcoin with a stick make the price go up? Why does it only work for a lucky few? And what does the data say about this mysterious phenomenon? Let’s dig in, laugh a little, and maybe learn the secret to market-moving magic.

The Statistical Side of Stick-Poking
Bitcoin’s Price: The Wild Ride
Bitcoin’s price is famous for its unpredictability. In the past year, it’s soared, dipped, and soared again, sometimes gaining more than 50% in just a few months. On a good day, billions of dollars flow through Bitcoin trades, and the price can jump thousands in a matter of hours. Clearly, something is making this happen-and it’s not just spreadsheets and financial news.
What Actually Moves the Price?
-
Scarcity: Only 21 million Bitcoins will ever exist. When more people want in, the price jumps.
-
Big News: Announcements, rumors, and meme-worthy moments can send the price flying.
-
FOMO: When people see Bitcoin rising, they rush to buy, pushing it even higher.
-
Liquidations: When traders betting against Bitcoin get squeezed, it triggers a chain reaction of buying.
But let’s be honest: none of this is as fun as poking Bitcoin with a stick.

The Magical Stick: Not Your Average Twig
Why Not Every Stick Works
You can’t just grab any old branch and expect Bitcoin to dance. The magical stick is a rare artifact, forged in the fires of internet memes and blessed by the spirit of Satoshi. Only a chosen few possess it-and when they poke, the market listens.
Signs You Have the Magical Stick
-
When you poke, Bitcoin’s price immediately jumps a few percent.
-
Your stick glows with meme energy and possibly sparkles with digital dust.
-
You have a knack for timing your poke right after a big event, like a halving or a celebrity tweet.
-
Your stick is rumored to have been whittled from the original blockchain itself.
Why Most Sticks Fail
-
No Meme Power: If your stick isn’t funny, Bitcoin ignores you.
-
Bad Timing: Poking during a bear market just annoys the blockchain.
-
Not Enough Hype: If the bitcoin community isn’t watching, your poke is just a poke.
-
Lack of Magic: Some sticks are just sticks. Sad, but true.

The Data: When the Stick Strikes
Let’s look at some numbers:
-
In the last month, Bitcoin’s price jumped over 20% right after a flurry of memes and stick-poking jokes.
-
Over the past year, every major price surge was accompanied by a wave of internet hype, stick memes, or wild speculation.
-
In the past five years, Bitcoin’s biggest leaps always seemed to follow some kind of magical event-whether a halving, a viral tweet, or a mysterious poke.
Coincidence? Maybe. But the pattern is clear: the stick works-at least when it’s magical.

The Role of Memes, Magic, and Mayhem
Bitcoin’s price is like a cat: unpredictable, easily startled, and sometimes it just wants to be left alone. But when the right meme pops up, or the right stick pokes at just the right time, the price can leap in ways that defy logic.
The bitcoin community knows this. That’s why, when Bitcoin’s stuck in a rut, you’ll see a flood of stick memes, GIFs, and magical thinking. Sometimes, it actually works.

The Secret’s in the Stick (and the Laughs)
So, does poking Bitcoin with a stick really make the price go up? If your stick is magical-blessed by memes, timed perfectly, and watched by millions-absolutely. The statistics show that hype, humor, and a little bit of luck can move markets as much as any financial report.
Next time you see Bitcoin stalling, don’t just sit there. Grab your stick, channel your inner meme wizard, and give it a poke. Who knows? You might just be the next legend in the world of bitcoin magic.
And if your stick doesn’t work, don’t worry. Sometimes, the real magic is in the laughter along the way.

-aco
@block height: 897,104
-
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 2a7cc007:ce0cc497
2025-05-22 06:41:14
@ 2a7cc007:ce0cc497
2025-05-22 06:41:14A era digital transformou completamente a forma como as pessoas se divertem, e a plataforma 5542 é um exemplo claro dessa evolução. Com uma proposta inovadora, acessível e repleta de possibilidades, a 5542 vem conquistando milhares de usuários brasileiros que buscam entretenimento seguro, moderno e de alta qualidade.
Desde o primeiro acesso, a 5542 impressiona pela interface intuitiva e pelo seu desempenho fluido tanto em computadores quanto em dispositivos móveis. Isso garante uma experiência agradável para todos os perfis de usuários, desde os mais experientes até os iniciantes no mundo dos jogos online.
Variedade que Encanta Um dos grandes destaques da 5542 é sua ampla gama de opções de jogos. A plataforma oferece títulos que agradam a diferentes gostos e estilos, desde clássicos consagrados até novidades empolgantes. Todos os jogos são desenvolvidos por fornecedores reconhecidos internacionalmente, garantindo gráficos de alta qualidade, trilhas sonoras envolventes e mecânicas de jogo equilibradas.
Jogos de cartas, roletas, slots e modalidades ao vivo com interação em tempo real são apenas alguns dos destaques que fazem parte do portfólio da 5542. Essa diversidade é um dos motivos pelos quais a plataforma se mantém em constante crescimento e atrai cada vez mais usuários em todo o Brasil.
Segurança e Confiabilidade A segurança é um fator primordial na escolha de uma plataforma de entretenimento online, e a 5542 leva isso muito a sério. O site utiliza tecnologia de criptografia de ponta para proteger os dados pessoais e financeiros dos usuários, além de contar com um sistema rigoroso de verificação de identidade, garantindo um ambiente confiável e livre de fraudes.
Além disso, a 5542 é comprometida com o jogo responsável, oferecendo ferramentas para que os usuários possam definir limites de tempo e de gastos. Essa abordagem mostra o compromisso da plataforma com o bem-estar dos seus participantes.
Promoções e Bônus Atrativos Outro diferencial da 5542 são suas promoções constantes e bônus generosos. Desde o momento do cadastro, os usuários já são recebidos com vantagens especiais, como bônus de boas-vindas e giros grátis em jogos selecionados. A plataforma também realiza campanhas temáticas e sorteios com prêmios reais, tornando a experiência ainda mais envolvente e recompensadora.
Essas promoções são atualizadas com frequência e muitas vezes incluem eventos sazonais, o que incentiva os jogadores a retornarem sempre e aproveitarem novas oportunidades.
Suporte de Qualidade e Atendimento em Português Um ponto que merece destaque é o suporte ao cliente da 5542. Disponível em português e com atendimento 24 horas por dia, a equipe está sempre pronta para ajudar os usuários com dúvidas, problemas técnicos ou qualquer necessidade. Esse suporte eficiente e humanizado faz toda a diferença, especialmente para quem está começando.
Conclusão A plataforma 5542 se estabelece como uma das líderes no mercado de entretenimento digital no Brasil. Sua combinação de tecnologia de ponta, variedade de jogos, promoções generosas e compromisso com a segurança oferece uma experiência completa para quem busca diversão online com praticidade e confiabilidade.
Se você está em busca de uma plataforma moderna, segura e cheia de opções envolventes, a 5542 é a escolha certa. Explore, jogue e aproveite uma nova forma de se divertir, tudo isso sem sair de casa.
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ a296b972:e5a7a2e8
2025-05-23 12:42:10
@ a296b972:e5a7a2e8
2025-05-23 12:42:10Was Rudolf Steiner vor gut 110 Jahren an Informationen zusammengetragen und kommentiert hat, liest sich in großen Abschnitten so, als ob es in der heutigen Zeit geschrieben worden wäre. Man trifft auf eine ganze Reihe von „guten, alten Bekannten“, die auch heute noch maßgeblich an den Strippen ziehen. Deutlich wird, dass ein Krieg nicht aus heiterem Himmel ausbricht, sondern das im Vorfeld schon Kräfte wirken, die auf einen Krieg hinarbeiten. Wie jetzt wieder im Ukraine-Krieg wird diese Vorgeschichte gerne versucht unter den Teppich zu kehren und hochkompetente, sauber recherchierende, akribisch Quellen angebende Journalisten, wie z. B. Frau Gabriele Krone-Schmalz oder Herr Patrik Baab, der sich auf eigene Kosten einen Eindruck von vor Ort verschafft hat, werden versucht mundtot zu machen und mittlerweile gar nicht mehr zu Gesprächen im öffentlich-rechtlichen Rundfunk eingeladen, weil sie die fortlaufende Gehirnwäsche des Ministeriums für Wahrheit und Narrative mit ihren Aussagen gefährden. Andere kommen auf die Sanktionsliste.
Auch heute ist von den „Guten“ und den „Bösen“ die Rede, was darauf schließen lässt, dass man durchaus eingesteht, dass hier geistige Kräfte am Werk sind. Rudolf Steiner kommt auf diese immer wieder zu sprechen. Aus der von ihm gegebenen anthroposophischen Geisteswissenschaft heraus, beleuchtet er die Vorgänge innerhalb der gesamten Menschheitsentwicklung. Mancher stört sich hier an Begriffen, die man heute so nicht mehr verwenden würde. Dabei ist immer zu berücksichtigen, zu welcher Zeit die Vorträge gehalten wurden. Die Anthroposophie von Rudolf Steiner gilt heute bei vielen auch als „umstritten“, aber was ist das heute nicht? Fast könnte man es schon als Auszeichnung sehen, wenn etwas „umstritten“ ist, denn das ist mittlerweile ein Beweis dafür, dass es Ansichten, Meinungen und Einschätzungen gibt, die in einer gesunden Demokratie innerhalb einer Kontroverse zu einem Dialog und Austausch beitragen können, der jedoch leider derzeit weder gewünscht ist, noch gepflegt wird, was an der „Spaltung“ deutlich zu sehen ist. Und auch unter den Anthroposophen hat die „Spaltung“ Einzug gehalten.
Um das aktuelle, viele Bereiche umschließende, gigantische Lügenkonstrukt aufrecht zu erhalten, ist mittlerweile jedes Mittel recht, von der Deutungshoheit der Wahrheit durch systemkonforme Begutachter, bis hin zu infantil-kleingeistigen Kindergartenspielchen, um gegenläufige Meinungen oder Oppositionelle in ihrem Wirken zu behindern.
Der gesunde Hausverstand wird ausgetrocknet, und der Garten des Wahnsinns wird durch immer neue Ideen kranker Geister weiter gegossen, gehegt und gepflegt.
Die Zeitgeschichtlichen Betrachtungen von Rudolf Steiner bestehen aus 3 Bänden aus der GA (Gesamtausgabe):
GA 173 a – Wege zu einer objektiven Urteilsbildung
GA 173 b – Das Karma der Unwahrhaftigkeit
GA 173 c – Die Wirklichkeit okkulter Impulse
Sie bestehen aus niedergeschriebenen Vorträgen und einem sehr umfangreichen Anhang mit näheren Erläuterungen und einer Schilderung der Entstehung dieser drei Bände.
Es bedarf einiger Eingewöhnung in die zur damaligen Zeit verwendete Sprache Rudolf Steiners, der ein Meister im Bilden von Schachtelsätzen war. Der Inhalt jedoch, und auf den kommt es ja an, berührt immer wieder den in allen Menschen vorhandenen Wahrheitssinn.
Hier nur eine kleine Kostprobe, die vielleicht das Interesse wecken kann, sich mit diesem derzeit besonders aktuellen Werk näher zu beschäftigen.
GA 173a, 6. Vortrag, Seite 205 und Seite 206, Dornach, 17. Dezember 1916:
„Viel intimer, viel verborgener liegen die Dinge bei der englischen Politik, die ja ganz beeinflußt ist von dem, was in solcher Weise hinter ihr steckt. Da handelt es sich darum, daß man die Wege findet, um die entsprechenden Menschen an die richtigen Plätze zu befördern. Okkultistische Menschen, im Hintergrunde stehend, sind oftmals – na, verzeihen Sie – Einser, bloße Einser, und bedeuten für sich nichts Besonderes; sie brauchen noch etwas anderes – sie brauchen Nullen. Nullen sind ja nicht Einser, aber (fügt man eine Null zu einer Eins), dann wird gleich eine Zehn daraus. Und wenn man noch mehr Nullen hinzufügt – jede Null ist nur eine Null, aber wenn die Eins irgendwo steckt, dann ist gar mancherlei da, zum Beispiel die Tausend, und wenn man die Eins zudeckt, dann sind (scheinbar) nur die Nullen da; die Nullen brauchen aber nur in der entsprechenden Weise mit den Einsern kombiniert zu sein, und sie brauchen nicht einmal viel zu wissen von der Art, wie sie mit den Einsern kombiniert sind.“
Schildert diese 108 Jahre alte Beschreibung nicht genau das, was sich heute vor unseren Augen abspielt?
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ c1831fbe:de4b39bf
2025-05-17 09:57:04
@ c1831fbe:de4b39bf
2025-05-17 09:57:04What follows is my best effort to recall the details of an arguably supernatural encounter I experienced almost sixty years ago. I've told this story many times before, and while my recollection may not be perfect in every detail, my account is real and substantively factual.
It was early one long ago morning, in that twilit between-time shortly before dawn. As I dangled precariously in a quasi-aware state, hovering on the knife edge between wakefulness and sleep, I was transported in a dream to another place and time. Was it the Mediterranean coast? Perhaps ancient Greece?
In my mind's eye, I found myself climbing a rather steep, rocky hillside overlooking a sparkling bright blue sea. Ahead of me, and slightly higher, was what appeared to be a young shepherd boy, leading me ever higher up the hill.
As we wove our way upward,
skirting rocky outcroppings and zig-zagging because of the steepness of the slope, I heard the boy chanting:
"Ata, Ata, Archontos, Ata, Ata, Echousi, Ata, Ata, Archousi"
He kept repeating the mantra, over and over:
"Ata, Ata, Archontos, Ata, Ata, Echousi, Ata, Ata, Archousi"
\~ \~ \~
"Ata, Ata, Archontos, Ata, Ata, Echousi, Ata, Ata, Archousi"
I listened for a few cycles, and then took up the chant myself. After several attempts, when at last I got it right, the shepherd boy turned, looking back at me and smiling broadly to signal that I had finally mastered the cadence and the words.
Then I awoke.
Because my dream had been so vivid and unusual, I immediately found a pencil and paper to write down the chant phonetically before I could forget it.
A few days passed.
Life was busy. Then I remembered my friend in grad school, studying biblical Greek. That weekend, I went and hung out with him while he worked his night job at the college heating plant. Between his rounds inspecting and managing the steam boilers keeping students from freezing to death in the Arctic Midwest winter, I told him about my strange dream.
Pulling out an exhaustive Greek lexicon, one by one, my knowledgeable friend looked up the words from my dream, interpreting each according to its verb conjugation, tense, and mood.
"Ata, Ata" had no discernible meaning; we soon concluded that it was probably just meaningless vocables, added to give the chant rhythm and substance. My friend moved on to the first recognizable word of the chant...
"Archontos" - "They are ruled."
OK, so far, so good. He checked the next word:
"Echousi" - "They shed blood."
Hmmmm... This chant is beginning to appear to be more than random sounds.
"Archousi" - "They rule."
At this point, I almost fell out of my chair in shock. Far from being a meaningless chant, this cycle—repeating again and again—is the seemingly never-ending story of the entirety of human history...
"They Are Ruled, They Shed Blood, They Rule."
\~ \~ \~
"They Are Ruled, They Shed Blood, They Rule."
This concise mantra perfectly captures the endlessly repeating cycle of oppression, revolt, and revolution that always leaves us with a fresh set of oppressors all too ready to replace the last.
Who will rescue us?
Who will redeem us from this endless tedious cycle into which we have been born?
A long lifetime of study and reflection has persuaded me that this deadly cycle can and ultimately will be broken. If we follow the teachings of Jesus; if we love one another and live together in voluntary, local societies, serving each other; I am persuaded that we can break free of this desperately destructive cycle of endlessly seeking to dominate one another. It's past time for us to enter into a mutually beneficial life in the Kingdom of our Creator-God Jesus, the most authentically benevolent King the universe has ever known.
stories #politics #Christianity #supernatural #strange
-
 @ 2a7cc007:ce0cc497
2025-05-22 06:39:41
@ 2a7cc007:ce0cc497
2025-05-22 06:39:41Nos últimos anos, o entretenimento online cresceu exponencialmente no Brasil, e plataformas como a 755bet vêm se destacando por oferecer uma experiência completa, segura e repleta de diversão. Com um catálogo variado de jogos, bônus atrativos e suporte eficiente, a 755bet vem conquistando a preferência de jogadores iniciantes e experientes em todo o país.
Interface Moderna e Navegação Intuitiva Uma das grandes vantagens da 755bet é sua interface moderna e amigável. Desde o primeiro acesso, é fácil perceber o cuidado com o design da plataforma. Os menus são bem organizados, facilitando a navegação mesmo para quem não tem muita familiaridade com esse tipo de ambiente. Tudo está a poucos cliques de distância: jogos ao vivo, apostas esportivas, promoções e muito mais.
Variedade de Jogos para Todos os Gostos A diversidade de jogos é um dos pontos fortes da 755bet. Os usuários encontram uma enorme gama de opções que vão desde jogos de cartas clássicos até modalidades mais modernas e dinâmicas, com gráficos de alta qualidade e mecânicas envolventes. A plataforma trabalha com desenvolvedores renomados do setor, garantindo sempre a melhor experiência visual e sonora.
Além disso, há também uma seção dedicada às apostas esportivas, onde os usuários podem apostar em eventos nacionais e internacionais, incluindo futebol, basquete, tênis, e-sports e muito mais. Essa variedade agrada tanto os fãs de esportes quanto aqueles que procuram uma alternativa de diversão com um toque estratégico.
Bônus e Promoções Exclusivas Outro grande atrativo da 755bet são os bônus oferecidos para novos e antigos usuários. Logo ao se cadastrar, o jogador já pode aproveitar ofertas de boas-vindas bastante competitivas. Mas o diferencial está nas promoções constantes para quem já é cliente, incluindo bônus de recarga, cashback, giros grátis e desafios especiais que tornam a experiência ainda mais empolgante.
Esses incentivos são uma forma eficaz de manter os usuários engajados e motivados, oferecendo mais oportunidades de explorar os jogos e, quem sabe, conseguir boas recompensas.
Segurança e Suporte ao Usuário A 755bet preza muito pela segurança de seus usuários. A plataforma utiliza criptografia de dados e outros protocolos de proteção para garantir que todas as informações estejam sempre seguras. Além disso, os métodos de pagamento são variados e confiáveis, incluindo opções populares no Brasil como Pix, boleto bancário, transferência e carteiras digitais.
Outro ponto que merece destaque é o suporte ao cliente. A equipe de atendimento está disponível 24 horas por dia, sete dias por semana, por meio de chat ao vivo e e-mail. O suporte é eficiente, cordial e preparado para resolver qualquer dúvida ou dificuldade rapidamente.
Acesso Fácil em Qualquer Dispositivo Com o avanço da tecnologia móvel, é essencial que uma plataforma esteja otimizada para smartphones e tablets. A 755bet entende isso e oferece uma experiência fluida tanto na versão desktop quanto no mobile. Seja no Android ou iOS, os usuários podem acessar a plataforma de qualquer lugar, a qualquer hora, com a mesma qualidade.
-
 @ 502ab02a:a2860397
2025-05-23 01:57:14
@ 502ab02a:a2860397
2025-05-23 01:57:14น้ำนมมนุษย์ที่ไม่ง้อมนุษย์ หรือนี่กำลังจะกลายเป็นเรื่องจริงเร็วกว่าที่เราคิดนะครับ
ในยุคที่อุตสาหกรรมอาหารหันหลังให้กับปศุสัตว์ ไม่ว่าจะด้วยเหตุผลด้านสิ่งแวดล้อม จริยธรรม หรือความยั่งยืน “น้ำนมจากห้องแล็บ” กำลังกลายเป็นแนวหน้าของการปฏิวัติอาหาร โดยเฉพาะเมื่อบริษัทหนึ่งจากสิงคโปร์นามว่า TurtleTree ประกาศอย่างชัดเจนว่า พวกเขากำลังจะสร้างโปรตีนสำคัญในน้ำนมมนุษย์ โดยไม่ต้องมีมนุษย์แม่เลยแม้แต่น้อย
TurtleTree ก่อตั้งในปี 2019 โดยมีเป้าหมายอันทะเยอทะยานคือการผลิตโปรตีนในนมแม่ให้ได้ผ่านเทคโนโลยีที่เรียกว่า precision fermentation โดยใช้จุลินทรีย์ที่ถูกดัดแปลงพันธุกรรมให้ผลิตโปรตีนเฉพาะ เช่น lactoferrin และ human milk oligosaccharides (HMOs) ซึ่งเป็นองค์ประกอบล้ำค่าที่พบในน้ำนมมนุษย์แต่แทบไม่มีในนมวัว หรือผลิตภัณฑ์นมทั่วไป
โปรตีนตัวแรกที่ TurtleTree ประสบความสำเร็จในการผลิตคือ LF+ หรือ lactoferrin ที่เลียนแบบโปรตีนในนมแม่ ซึ่งมีหน้าที่ช่วยระบบภูมิคุ้มกันของทารก ต่อต้านแบคทีเรีย และช่วยให้ร่างกายดูดซึมธาตุเหล็กได้ดีขึ้น โปรตีนนี้เป็นหนึ่งในหัวใจของนมแม่ ที่บริษัทต้องการนำมาใช้ในอุตสาหกรรมนมผงเด็กและอาหารเสริมสำหรับผู้ใหญ่ ล่าสุดในปี 2024 LF+ ได้รับการรับรองสถานะ GRAS (Generally Recognized As Safe) จากองค์การอาหารและยาสหรัฐฯ (FDA) อย่างเป็นทางการ เป็นหมุดหมายสำคัญที่บอกว่า นี่ไม่ใช่แค่ไอเดียในแล็บอีกต่อไป แต่กำลังกลายเป็นผลิตภัณฑ์เชิงพาณิชย์จริง
เบื้องหลังของโปรเจกต์นี้คือการลงทุนกว่า 30 ล้านดอลลาร์สหรัฐจากกลุ่มทุนทั่วโลก รวมถึงบริษัท Solar Biotech ที่จับมือกับ TurtleTree ในการขยายกำลังการผลิตเชิงอุตสาหกรรมในสหรัฐอเมริกา โดยตั้งเป้าว่าจะสามารถผลิตโปรตีนเหล่านี้ได้ในระดับราคาที่แข่งขันได้ภายในไม่กี่ปีข้างหน้า
สิ่งที่น่าสนใจคือ TurtleTree ไม่ได้หยุดแค่ lactoferrin พวกเขายังวางแผนพัฒนา HMO ซึ่งเป็นน้ำตาลเชิงซ้อนชนิดพิเศษที่มีอยู่เฉพาะในน้ำนมแม่ เป็นอาหารเลี้ยงแบคทีเรียดีในลำไส้ทารก ช่วยพัฒนาระบบภูมิคุ้มกันและสมอง ปัจจุบัน HMOs เริ่มเป็นที่นิยมในวงการ infant formula แต่การผลิตยังจำกัดและมีต้นทุนสูง การที่ TurtleTree จะนำเทคโนโลยี precision fermentation มาใช้ผลิต HMO จึงถือเป็นความพยายามในการลดช่องว่างระหว่าง "นมแม่จริง" กับ "นมผงสังเคราะห์"
ทั้งหมดนี้เกิดขึ้นภายใต้แนวคิดใหม่ของอุตสาหกรรมอาหารที่เรียกว่า "functional nutrition" หรือโภชนาการที่ออกแบบเพื่อทำงานเฉพาะทาง ไม่ใช่แค่ให้พลังงานหรือโปรตีน แต่เล็งเป้าหมายเฉพาะ เช่น เสริมภูมิคุ้มกัน ซ่อมแซมสมอง หรือฟื้นฟูร่างกาย โดยมีรากฐานจากธรรมชาติ แต่ใช้เทคโนโลยีสมัยใหม่ในการผลิต
แม้จะฟังดูเป็นความก้าวหน้าทางวิทยาศาสตร์ที่น่าตื่นเต้น แต่น้ำเสียงที่ดังก้องในอีกมุมหนึ่งก็คือคำถามเชิงจริยธรรม TurtleTree กำลังสร้างโปรตีนที่มีอยู่เฉพาะในมนุษย์ โดยอาศัยข้อมูลพันธุกรรมของมนุษย์เอง แล้วนำเข้าสู่ระบบอุตสาหกรรมเพื่อการค้า คำถามคือ เมื่อใดที่การจำลองธรรมชาติจะกลายเป็นการผูกขาดธรรมชาติ? ใครควรเป็นเจ้าของข้อมูลพันธุกรรมของมนุษย์? และถ้าวันหนึ่งบริษัทใดบริษัทหนึ่งสามารถควบคุมการผลิต “นมแม่จำลอง” ได้แต่เพียงผู้เดียว นั่นจะส่งผลต่อเสรีภาพของสังคมในมุมไหนบ้าง?
นักชีวจริยธรรมหลายคน เช่น ดร.ซิลเวีย แคมโปเรซี จาก King's College London ตั้งข้อสังเกตไว้ว่า เทคโนโลยีแบบนี้อาจแก้ปัญหาการเข้าถึงนมแม่ในพื้นที่ห่างไกลหรือในกลุ่มแม่ที่ให้นมไม่ได้ แต่ขณะเดียวกันก็อาจกลายเป็นการสร้าง "ระบบอาหารทางเลือก" ที่ควบคุมโดยบริษัทไม่กี่ราย ที่มีอำนาจเกินกว่าผู้บริโภคจะตรวจสอบได้
เมื่อเทคโนโลยีสามารถจำลองสิ่งที่เคยสงวนไว้เฉพาะธรรมชาติ และมนุษย์ได้ใกล้เคียงจนแทบแยกไม่ออก บางทีคำถามที่ควรถามอาจไม่ใช่แค่ว่า “มันปลอดภัยหรือไม่?” แต่อาจต้องถามว่า “เราไว้ใจใครให้สร้างสิ่งนี้แทนธรรมชาติ?” เพราะน้ำนมแม่เคยเป็นสิ่งที่มาจากรักและชีวิต แต่วันนี้มันอาจกลายเป็นเพียงสิ่งที่มาจากห้องแล็บและโมเลกุล... และนั่นคือสิ่งที่เราต้องคิดให้เป็น ก่อนจะกินให้ดี เต่านี้มีบุญคุณอันใหญ่หลวงงงงงงง
เสริมจุดน่าสนใจให้ครับ KBW Ventures ถือเป็นผู้ลงทุนรายใหญ่ที่สุดใน TurtleTree Labs โดยมีบทบาทสำคัญในหลายรอบการระดมทุนของบริษัท KBW Ventures เป็นบริษัทลงทุนจากสหรัฐอาหรับเอมิเรตส์ ก่อตั้งโดย สมเด็จพระราชโอรสเจ้าชายคาเล็ด บิน อัลวาลีด บิน ตาลาล อัล ซาอุด (HRH Prince Khaled bin Alwaleed bin Talal Al Saud) ในรอบการระดมทุน Pre-A มูลค่า 6.2 ล้านดอลลาร์สหรัฐฯ ซึ่งปิดในเดือนธันวาคม 2020 KBW Ventures ได้ร่วมลงทุนพร้อมกับ Green Monday Ventures, Eat Beyond Global และ Verso Capital . นอกจากนี้ เจ้าชาย Khaled ยังได้เข้าร่วมเป็นที่ปรึกษาให้กับ TurtleTree Labs เพื่อสนับสนุนการขยายตลาดและกลยุทธ์การเติบโตของบริษัท
ซึ่งในตัว KBW Ventures นั้น เป็นบริษัทลงทุนที่มุ่งเน้นการสนับสนุนเทคโนโลยีที่ยั่งยืนและนวัตกรรมในหลากหลายอุตสาหกรรม เช่น เทคโนโลยีชีวภาพ (biotech), เทคโนโลยีพลังงานสะอาด, เทคโนโลยีการเงิน (fintech), เทคโนโลยีการขนส่ง, และเทคโนโลยีอาหาร (food tech) โดยเฉพาะ และในส่วนของเจ้าชาย Khaled มีความสนใจอย่างลึกซึ้งในด้านเทคโนโลยีอาหาร โดยเฉพาะในกลุ่มโปรตีนทางเลือก เช่น Beyond Meat ซึ่งเป็นการลงทุนที่สะท้อนถึงความมุ่งมั่นชัดเจนในการส่งเสริมอาหารที่ยั่งยืนและมีจริยธรรมครับ และแน่นอนเลยว่า โดยมีส่วนร่วมในรอบระดมทุนหลายครั้งของ Beyond Meat รวมถึงตอนที่ Beyond Meat เข้าตลาดหุ้น Nasdaq ครั้งแรกในปี 2019
เจ้าชาย Khaled เชื่อมั่นว่าอาหารทางเลือกแบบพืชจะถูกลงและแพร่หลายมากขึ้น จนอาจถูกกว่าราคาเนื้อสัตว์จากสัตว์จริงภายในปี 2025 ตามข้อมูลที่ได้มาแสดงว่า ปีนี้นี่หว่าาาาาาาาาา
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ b83a28b7:35919450
2025-05-16 19:26:56
@ b83a28b7:35919450
2025-05-16 19:26:56This article was originally part of the sermon of Plebchain Radio Episode 111 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 2b24a1fa:17750f64
2025-05-22 19:44:28
@ 2b24a1fa:17750f64
2025-05-22 19:44:28„Triff niemals deine Idole“ heißt ein gängiger Ratschlag. In gewendeten Zeiten stehen zu dem die Werte auf dem Kopf – und manche Künstler mit ihnen. Die Worte, die aus manch ihrer Mündern kommen, wirken, als hätte eine fremde Hand sie auf deren Zunge gelegt.
https://soundcloud.com/radiomuenchen/wolf-biermann-und-sein-falscher-friede-von-alexa-rodrian?
Die Sängerin Alexa Rodrian erlebte bei der Verleihung des Deutschen Filmpreises einen solchen Moment der Desillusion. Es war der Auftritt des Liedermachers Wolf Biermann. Hören Sie hierzu Alexa Rodrians Text „Wolf Biermann und sein falscher Friede“.
Bild: Marco Maas/fotografirma.de
-
 @ 2b24a1fa:17750f64
2025-05-22 08:18:28
@ 2b24a1fa:17750f64
2025-05-22 08:18:28Es ist pure Freiheit, Geschwindigkeit durch die eigene Kraft oder Bergab-Beschleunigung zu spüren. Kein störendes Motorengeräusch, das auch noch das ökologische Gewissen aufruft. Einfach nur Sein, an der Luft, im Wind. Wenn da doch nur … keine Ampel wäre.
Hören Sie den Beitrag „Ja oder ja – Begegnung mit der Staatsmacht, von Isa Mitza.
https://soundcloud.com/radiomuenchen/ja-oder-ja-begegnung-mit-der-staatsmacht-von-isa-mitza?
-
 @ 502ab02a:a2860397
2025-05-22 01:30:37
@ 502ab02a:a2860397
2025-05-22 01:30:37ถ้าพูดถึง "เกาหลีใต้" หลายคนอาจนึกถึงซีรีส์ น้ำจิ้มเผ็ด หรือไอดอลหน้าผ่อง ๆ แต่เบื้องหลังวัฒนธรรมที่ลื่นไหลไปทั่วโลกนี้ ยังมีอาณาจักรธุรกิจขนาดมหึมาที่เป็นเหมือนเครื่องยนต์หลักผลักดันทั้งอาหาร เพลง หนัง และนวัตกรรมระดับโลก หนึ่งในนั้นคือ CJ Group ที่เริ่มต้นจากบริษัทน้ำตาลเล็ก ๆ ในปี 1953 แต่เติบโตจนกลายเป็นหนึ่งใน conglomerate หรือ "กลุ่มธุรกิจผูกเครือ" ที่ทรงอิทธิพลที่สุดของแดนโสม
คำว่า CJ ย่อมาจาก CheilJedang (แปลว่า “หมายเลขหนึ่งแห่งโลก” ในภาษาจีน-เกาหลี) ก่อตั้งโดย อี บยองชอล ผู้ก่อตั้ง Samsung Group ในช่วงเวลานั้น เกาหลีใต้กำลังฟื้นตัวจากสงครามเกาหลี และรัฐบาลส่งเสริมการพัฒนาอุตสาหกรรมภายในประเทศ เดิมเป็นหน่วยธุรกิจอาหารของกลุ่ม Samsung ในปี 1993 Cheil Jedang แยกตัวออกจาก Samsung Group และกลายเป็นบริษัทอิสระภายใต้การบริหารของ อี แจฮยอน หลานชายของอี บยองชอล แล้วขยายขอบเขตธุรกิจอย่างไม่หยุดยั้ง จากความเชี่ยวชาญใน "การหมัก" แบบดั้งเดิม พวกเขากลับกลายเป็นผู้เล่นรายใหญ่ระดับโลกในวงการ เทคโนโลยีชีวภาพ การผลิตอาหารไปจนถึงธุรกิจ บันเทิงระดับฮอลลีวูด และ โลจิสติกส์ข้ามทวีป
พูดง่าย ๆ ว่า CJ ไม่ได้แค่ส่งออกกิมจิหรือบิบิมบับ แต่พวกเขากำลังวางรากฐานของ "อนาคตแห่งอาหาร" และ "ความบันเทิงแบบไร้พรมแดน" ในเวลาเดียวกัน จนใครหลายคนถึงกับบอกว่า ถ้าอยากเข้าใจเกาหลีใต้ ก็ต้องเริ่มจากเข้าใจ CJ Group เสียก่อน
แล้วในเครือข่ายของ CJ Group มีธุรกิจอะไรบ้างที่น่าสนใจ และแบรนด์ไหนที่เราคุ้นเคยแบบไม่รู้ตัว ไปดูกันเลย
- ธุรกิจอาหารและบริการอาหาร (Food & Food Services)
- CJ CheilJedang บริษัทอาหารชั้นนำของเกาหลีใต้ มีผลิตภัณฑ์เด่น ได้แก่ Bibigo แบรนด์อาหารเกาหลีพร้อมรับประทาน เช่น เกี๊ยว ซอส และกิมจิ Hetbahn ข้าวสวยพร้อมรับประทานที่ได้รับความนิยมในเกาหลี
-
CJ Foodville ดำเนินธุรกิจร้านอาหารและเบเกอรี่ เช่น: Tous Les Jours ร้านเบเกอรี่สไตล์ฝรั่งเศส VIPS ร้านสเต็กและสลัดบุฟเฟ่ต์
-
ธุรกิจเทคโนโลยีชีวภาพ (Bio) ความเชี่ยวชาญนี้เป็นรากฐานสำคัญในการขยายธุรกิจด้านเทคโนโลยีชีวภาพของ CJ เลยครับ
- CJ BIO ผู้นำด้านการผลิตกรดอะมิโนและผลิตภัณฑ์ชีวภาพผ่านเทคโนโลยีการหมักจุลินทรีย์ เช่น Lysine, Tryptophan, Valine กรดอะมิโนที่ใช้ในอุตสาหกรรมอาหารสัตว์และอาหารเสริม
-
CJ Bioscience มุ่งเน้นการวิจัยและพัฒนาไมโครไบโอมเพื่อสุขภาพ
-
ธุรกิจโลจิสติกส์และค้าปลีก (Logistics & Retail)
- CJ Logistics ให้บริการโลจิสติกส์ครบวงจร ทั้งการขนส่งทางบก ทางทะเล และทางอากาศ รวมถึงบริการคลังสินค้าและการจัดการซัพพลายเชน
-
CJ Olive Young: ร้านค้าปลีกด้านสุขภาพและความงามอันดับหนึ่งของเกาหลี มีผลิตภัณฑ์ยอดนิยม เช่น Anua PDRN Set ชุดบำรุงผิวที่ได้รับความนิยม MILKTOUCH ผลิตภัณฑ์เมคอัพที่ได้รับความนิยม
-
ธุรกิจบันเทิงและสื่อ (Entertainment & Media) อันนี้ยิ่งใหญ่ระดับโลกมากๆ หลายคนคงจำได้กับ ภาพยนตร์เอเชียแรกกับรางวัลออสการ์ Parasite
- CJ ENM บริษัทผลิตและจัดจำหน่ายเนื้อหาบันเทิงที่มีชื่อเสียงระดับโลก มีผลงานเด่น ได้แก่ Crash Landing on You ซีรีส์ที่ได้รับความนิยมอย่างสูง Parasite ภาพยนตร์ที่ได้รับรางวัลออสการ์
- CJ CGV เครือโรงภาพยนตร์มัลติเพล็กซ์ที่มีสาขาทั่วโลก
CJ Group ขยายธุรกิจไปยังต่างประเทศ เช่น การเข้าซื้อกิจการ Schwan's Company ในสหรัฐอเมริกา และการเปิดสาขา CGV ในหลายประเทศ นอกจากนี้ CJ ยังมีบทบาทสำคัญในการเผยแพร่วัฒนธรรมเกาหลีสู่ระดับโลกผ่าน KCON และการผลิตเนื้อหาบันเทิงที่ได้รับความนิยมในต่างประเทศด้วยครับ
จะเห็นได้ว่า เครือข่ายของ CJ นั้นยิ่งใหญ่มากๆเลย ทีนี้มีเรื่องน่าสนใจตรงนี้ครับ
ในช่วงปี 2013–2016 CJ Group โดยเฉพาะฝ่ายสื่อบันเทิงอย่าง CJ ENM ต้องเผชิญกับแรงกดดันจากรัฐบาลของประธานาธิบดี พัค กึนฮเย เหตุการณ์สำคัญคือการที่ อี มีคยอง (Miky Lee) รองประธาน CJ และผู้มีบทบาทสำคัญในการขับเคลื่อนธุรกิจบันเทิงระดับโลก ถูกกดดันให้ลาออกจากตำแหน่ง รายงานระบุว่า ทำเนียบประธานาธิบดีไม่พอใจเนื้อหาสื่อบางรายการของ CJ ที่มีลักษณะเสียดสีหรือวิพากษ์วิจารณ์รัฐบาล เช่น รายการ SNL Korea ที่ล้อเลียนพัค กึนฮเย ผ่านตัวละคร Teletubbies
ภายใต้แรงกดดันนี้ CJ มีการปรับเปลี่ยนเนื้อหาสื่อ โดยลดการนำเสนอเนื้อหาที่อาจขัดแย้งกับรัฐบาล และหันไปผลิตภาพยนตร์ที่สอดคล้องกับนโยบายของรัฐ เช่น ภาพยนตร์เรื่อง Ode to My Father (2014) ที่สะท้อนความรักชาติและการพัฒนาเศรษฐกิจในยุคของพัค ชุงฮี บิดาของพัค กึนฮเย ภาพยนตร์เรื่องนี้ได้รับการสนับสนุนจากรัฐบาลและถูกมองว่าเป็น "ภาพยนตร์เพื่อสุขภาพ" ที่ส่งเสริมความภาคภูมิใจในชาติ แน่นอนว่าแค้นฝังหุ่นมันยังไม่หายไปไหนครับ
เมื่อเกิดการเปิดโปง "บัญชีดำ" (Blacklist) ของรัฐบาลพัค กึนฮเย ที่มีการจำกัดสิทธิเสรีภาพของศิลปินและผู้ผลิตสื่อที่วิพากษ์วิจารณ์รัฐบาล ทำให้เกิดกระแสต่อต้านอย่างรุนแรงในสังคมเกาหลี. ในปี 2016 ซน กยองชิก ประธาน CJ ได้ให้การต่อศาลว่า มีแรงกดดันจากรัฐบาลให้ อี มีคยอง หลีกเลี่ยงการมีบทบาทในบริษัท เหตุการณ์นี้เป็นส่วนหนึ่งของการเปิดโปงคดีทุจริตของพัค กึนฮเย ซึ่งนำไปสู่การประท้วงครั้งใหญ่และการถอดถอนประธานาธิบดีในปี 2017
หลังจากการเปลี่ยนแปลงทางการเมือง CJ Group ได้กลับมามีบทบาทอย่างเต็มที่ในวงการบันเทิงอีกครั้ง อี มีคยอง กลับมาดำรงตำแหน่งและมีบทบาทสำคัญในการผลักดันภาพยนตร์เรื่อง Parasite (2019) ซึ่งได้รับรางวัลออสการ์และยกระดับภาพลักษณ์ของ CJ ในระดับโลก ซึ่งถ้าใครได้ดูหนังเรื่องนั้นแล้วรู้เรื่องราวเบื้องหลังนี้จะเข้าใจเนื้อหาได้อย่างลึกซึ้งขึ้นไปอีกเลยครับ การนำเสนอเรื่องราวนี้ถือเป็นการวิพากษ์วิจารณ์สังคมและระบบทุนนิยมอย่างชัดเจน ซึ่งแตกต่างจากแนวทางที่ CJ เคยถูกกดดันให้ปฏิบัติตามในยุคของพัค กึนฮเย อย่างสิ้นเชิง
อย่าเพิ่งไปสะใจกับเนื้อหา ให้มองว่า "เขาทำอะไรได้บ้าง" นี่คือประเด็นสำคัญครับ #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ c1e9ab3a:9cb56b43
2025-05-05 14:25:28
@ c1e9ab3a:9cb56b43
2025-05-05 14:25:28Introduction: The Power of Fiction and the Shaping of Collective Morality
Stories define the moral landscape of a civilization. From the earliest mythologies to the modern spectacle of global cinema, the tales a society tells its youth shape the parameters of acceptable behavior, the cost of transgression, and the meaning of justice, power, and redemption. Among the most globally influential narratives of the past half-century is the Star Wars saga, a sprawling science fiction mythology that has transcended genre to become a cultural religion for many. Central to this mythos is the arc of Anakin Skywalker, the fallen Jedi Knight who becomes Darth Vader. In Star Wars: Episode III – Revenge of the Sith, Anakin commits what is arguably the most morally abhorrent act depicted in mainstream popular cinema: the mass murder of children. And yet, by the end of the saga, he is redeemed.
This chapter introduces the uninitiated to the events surrounding this narrative turn and explores the deep structural and ethical concerns it raises. We argue that the cultural treatment of Darth Vader as an anti-hero, even a role model, reveals a deep perversion in the collective moral grammar of the modern West. In doing so, we consider the implications this mythology may have on young adults navigating identity, masculinity, and agency in a world increasingly shaped by spectacle and symbolic narrative.
Part I: The Scene and Its Context
In Revenge of the Sith (2005), the third episode of the Star Wars prequel trilogy, the protagonist Anakin Skywalker succumbs to fear, ambition, and manipulation. Convinced that the Jedi Council is plotting against the Republic and desperate to save his pregnant wife from a vision of death, Anakin pledges allegiance to Chancellor Palpatine, secretly the Sith Lord Darth Sidious. Upon doing so, he is given a new name—Darth Vader—and tasked with a critical mission: to eliminate all Jedi in the temple, including its youngest members.
In one of the most harrowing scenes in the film, Anakin enters the Jedi Temple. A group of young children, known as "younglings," emerge from hiding and plead for help. One steps forward, calling him "Master Skywalker," and asks what they are to do. Anakin responds by igniting his lightsaber. The screen cuts away, but the implication is unambiguous. Later, it is confirmed through dialogue and visual allusion that he slaughtered them all.
There is no ambiguity in the storytelling. The man who will become the galaxy’s most feared enforcer begins his descent by murdering defenseless children.
Part II: A New Kind of Evil in Youth-Oriented Media
For decades, cinema avoided certain taboos. Even films depicting war, genocide, or psychological horror rarely crossed the line into showing children as victims of deliberate violence by the protagonist. When children were harmed, it was by monstrous antagonists, supernatural forces, or offscreen implications. The killing of children was culturally reserved for historical atrocities and horror tales.
In Revenge of the Sith, this boundary was broken. While the film does not show the violence explicitly, the implication is so clear and so central to the character arc that its omission from visual depiction does not blunt the narrative weight. What makes this scene especially jarring is the tonal dissonance between the gravity of the act and the broader cultural treatment of Star Wars as a family-friendly saga. The juxtaposition of child-targeted marketing with a central plot involving child murder is not accidental—it reflects a deeper narrative and commercial structure.
This scene was not a deviation from the arc. It was the intended turning point.
Part III: Masculinity, Militarism, and the Appeal of the Anti-Hero
Darth Vader has long been idolized as a masculine icon. His towering presence, emotionless control, and mechanical voice exude power and discipline. Military institutions have quoted him. He is celebrated in memes, posters, and merchandise. Within the cultural imagination, he embodies dominance, command, and strategic ruthlessness.
For many young men, particularly those struggling with identity, agency, and perceived weakness, Vader becomes more than a character. He becomes an archetype: the man who reclaims power by embracing discipline, forsaking emotion, and exacting vengeance against those who betrayed him. The emotional pain that leads to his fall mirrors the experiences of isolation and perceived emasculation that many young men internalize in a fractured society.
The symbolism becomes dangerous. Anakin's descent into mass murder is portrayed not as the outcome of unchecked cruelty, but as a tragic mistake rooted in love and desperation. The implication is that under enough pressure, even the most horrific act can be framed as a step toward a noble end.
Part IV: Redemption as Narrative Alchemy
By the end of the original trilogy (Return of the Jedi, 1983), Darth Vader kills the Emperor to save his son Luke and dies shortly thereafter. Luke mourns him, honors him, and burns his body in reverence. In the final scene, Vader's ghost appears alongside Obi-Wan Kenobi and Yoda—the very men who once considered him the greatest betrayal of their order. He is welcomed back.
There is no reckoning. No mention of the younglings. No memorial to the dead. No consequence beyond his own internal torment.
This model of redemption is not uncommon in Western storytelling. In Christian doctrine, the concept of grace allows for any sin to be forgiven if the sinner repents sincerely. But in the context of secular mass culture, such redemption without justice becomes deeply troubling. The cultural message is clear: even the worst crimes can be erased if one makes a grand enough gesture at the end. It is the erasure of moral debt by narrative fiat.
The implication is not only that evil can be undone by good, but that power and legacy matter more than the victims. Vader is not just forgiven—he is exalted.
Part V: Real-World Reflections and Dangerous Scripts
In recent decades, the rise of mass violence in schools and public places has revealed a disturbing pattern: young men who feel alienated, betrayed, or powerless adopt mythic narratives of vengeance and transformation. They often see themselves as tragic figures forced into violence by a cruel world. Some explicitly reference pop culture, quoting films, invoking fictional characters, or modeling their identities after cinematic anti-heroes.
It would be reductive to claim Star Wars causes such events. But it is equally naive to believe that such narratives play no role in shaping the symbolic frameworks through which vulnerable individuals understand their lives. The story of Anakin Skywalker offers a dangerous script:
- You are betrayed.
- You suffer.
- You kill.
- You become powerful.
- You are redeemed.
When combined with militarized masculinity, institutional failure, and cultural nihilism, this script can validate the darkest impulses. It becomes a myth of sacrificial violence, with the perpetrator as misunderstood hero.
Part VI: Cultural Responsibility and Narrative Ethics
The problem is not that Star Wars tells a tragic story. Tragedy is essential to moral understanding. The problem is how the culture treats that story. Darth Vader is not treated as a warning, a cautionary tale, or a fallen angel. He is merchandised, celebrated, and decontextualized.
By separating his image from his actions, society rebrands him as a figure of cool dominance rather than ethical failure. The younglings are forgotten. The victims vanish. Only the redemption remains. The merchandise continues to sell.
Cultural institutions bear responsibility for how such narratives are presented and consumed. Filmmakers may intend nuance, but marketing departments, military institutions, and fan cultures often reduce that nuance to symbol and slogan.
Conclusion: Reckoning with the Stories We Tell
The story of Anakin Skywalker is not morally neutral. It is a tale of systemic failure, emotional collapse, and unchecked violence. When presented in full, it can serve as a powerful warning. But when reduced to aesthetic dominance and easy redemption, it becomes a tool of moral decay.
The glorification of Darth Vader as a cultural icon—divorced from the horrific acts that define his transformation—is not just misguided. It is dangerous. It trains a generation to believe that power erases guilt, that violence is a path to recognition, and that final acts of loyalty can overwrite the deliberate murder of the innocent.
To the uninitiated, Star Wars may seem like harmless fantasy. But its deepest myth—the redemption of the child-killer through familial love and posthumous honor—deserves scrutiny. Not because fiction causes violence, but because fiction defines the possibilities of how we understand evil, forgiveness, and what it means to be a hero.
We must ask: What kind of redemption erases the cries of murdered children? And what kind of culture finds peace in that forgetting?
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ 348e7eb2:3b0b9790
2025-05-23 15:10:37
@ 348e7eb2:3b0b9790
2025-05-23 15:10:37Nostr-Konto erstellen - funktioniert
Was der Button macht
Der folgende Code fügt einen Button hinzu, der per Klick einen Nostr-Anmeldedialog öffnet. Alle Schritte sind im Code selbst ausführlich kommentiert.
```html
```
Erläuterungen:
- Dynamisches Nachladen: Das Script
modal.jswird nur bei Klick nachgeladen, um Fehlermeldungen beim Initial-Load zu vermeiden. -
Parameter im Überblick:
-
baseUrl: Quelle für API und Assets. an: App-Name für den Modal-Header.aa: Farbakzent (Foerbico-Farbe als Hex).al: Sprache des Interfaces.am: Licht- oder Dunkelmodus.afb/asb: Bunker-Modi für erhöhten Datenschutz.aan/aac: Steuerung der Rückgabe privater Schlüssel.arr/awr: Primal Relay als Lese- und Schreib-Relay.-
Callbacks:
-
onComplete: Schließt das Modal, zeigt eine Bestätigung und bietet die Weiterleitung zu Primal an. onCancel: Schließt das Modal und protokolliert den Abbruch.
Damit ist der gesamte Code sichtbar, kommentiert und erklärt.
- Dynamisches Nachladen: Das Script
-
 @ 3fa9f42b:00d5e778
2025-05-21 09:56:23
@ 3fa9f42b:00d5e778
2025-05-21 09:56:23S689 đang ngày càng khẳng định vị thế của mình như một nền tảng kỹ thuật số uy tín và thân thiện với người dùng tại thị trường Việt Nam. Với giao diện hiện đại, tinh gọn và dễ sử dụng, S689 tạo cảm giác thoải mái ngay từ lần đầu truy cập. Tất cả các yếu tố từ thiết kế, bố cục, màu sắc đến cách bố trí các chức năng đều được tối ưu để phục vụ nhu cầu truy cập nhanh chóng và thuận tiện. Người dùng có thể sử dụng S689 trên nhiều thiết bị khác nhau như điện thoại thông minh, máy tính bảng hay laptop mà không gặp khó khăn về tương thích hay tốc độ tải trang. Hệ thống tìm kiếm nhanh, điều hướng mượt mà và khả năng cá nhân hóa nội dung theo sở thích giúp S689 trở thành một lựa chọn lý tưởng cho những ai tìm kiếm sự linh hoạt và hiệu quả trong trải nghiệm số hằng ngày. Không chỉ đơn thuần là một nền tảng trực tuyến, S689 còn là cầu nối mang đến sự tiện nghi, kết nối người dùng với các nội dung chất lượng và phù hợp với nhu cầu cá nhân.
Một trong những điểm mạnh nổi bật của S689 chính là khả năng vận hành ổn định và độ bảo mật cao. Nền tảng được xây dựng trên nền tảng công nghệ tiên tiến, luôn cập nhật các tiêu chuẩn kỹ thuật mới để đảm bảo hiệu suất hoạt động mượt mà và ổn định nhất. Người dùng không phải lo lắng về gián đoạn dịch vụ hay những lỗi kỹ thuật gây ảnh hưởng đến trải nghiệm. Sự an toàn thông tin cá nhân luôn được đặt lên hàng đầu, với các biện pháp bảo mật đa lớp, mã hóa dữ liệu và kiểm soát truy cập chặt chẽ. Chính sách bảo mật minh bạch và hệ thống giám sát tự động giúp người dùng yên tâm khi sử dụng S689 trong thời gian dài. Bên cạnh đó, đội ngũ chăm sóc khách hàng chuyên nghiệp của S689 hoạt động liên tục 24/7 để hỗ trợ người dùng giải quyết mọi vấn đề một cách nhanh chóng, từ các thắc mắc kỹ thuật cho đến hỗ trợ về thông tin tài khoản. Nhờ đó, S689 không chỉ đảm bảo chất lượng dịch vụ mà còn tạo được sự tin tưởng tuyệt đối từ cộng đồng người dùng.
Không dừng lại ở việc xây dựng một nền tảng kỹ thuật số chất lượng, S689 còn chú trọng phát triển một cộng đồng tương tác tích cực và sôi động. Các hoạt động sự kiện, ưu đãi định kỳ và chương trình tặng thưởng cho người dùng thân thiết giúp tạo ra sự gắn bó lâu dài giữa người dùng và nền tảng. Sự tương tác không chỉ đơn thuần mang tính cá nhân mà còn mở rộng ra thành các kết nối cộng đồng, nơi người dùng có thể chia sẻ kinh nghiệm, hỗ trợ nhau và cùng nhau trải nghiệm tiện ích trên nền tảng. Điều này giúp S689 không chỉ là một công cụ sử dụng đơn lẻ, mà còn là một phần của cuộc sống kỹ thuật số hiện đại, nơi mà mỗi người dùng đều cảm nhận được giá trị và sự quan tâm. Với định hướng phát triển bền vững, lấy người dùng làm trung tâm, S689 tiếp tục mở rộng quy mô, cải tiến chất lượng và ứng dụng công nghệ tiên tiến để phục vụ tốt hơn nhu cầu ngày càng đa dạng của người sử dụng. Đây chính là lý do S689 đang ngày càng được yêu thích và tin dùng rộng rãi trên thị trường hiện nay.
-
 @ 866e0139:6a9334e5
2025-05-22 06:51:15
@ 866e0139:6a9334e5
2025-05-22 06:51:15Autor: Milosz Matuschek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie auch in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
https://www.youtube.com/watch?v=gjndTXyk3mw
Im Jahr 1954, als Frankreich gerade dabei war, seine kolonialen Kriege in Indochina und Algerien zu verschärfen, schrieb Boris Vian ein Lied – oder vielmehr: einen poetischen Faustschlag. Le Déserteur ist keine Ballade, sondern ein Manifest. Keine Hymne auf den Frieden, sondern eine Anklage gegen den Krieg. Adressiert an den Präsidenten, beginnt das Chanson wie ein höflicher Brief – und endet als flammender Akt des zivilen Ungehorsams.
„Herr Präsident,\ ich schreibe Ihnen einen Brief,\ den Sie vielleicht lesen werden,\ wenn Sie Zeit haben.“
Was folgt, ist ein klassischer Kriegsdienstverweigerungsbrief, aber eben kein bürokratischer. Vian spricht nicht in Paragraphen, sondern in Herzschlägen. Der Erzähler, ein einfacher Mann, will nicht kämpfen. Nicht für irgendein Vaterland, nicht für irgendeine Fahne, nicht für irgendeinen ideologischen Zweck.
„Ich soll zur Welt gekommen sein,\ um zu leben, nicht um zu sterben.“
70 Jahre später klingt diese Zeile wie ein Skandal. In einer Zeit, in der die Ukraine junge Männer für Kopfgeld auf der Straße zwangsrekrutiert und in Stahlgewitter schickt, in der palästinensische Jugendliche im Gazastreifen unter Trümmern begraben werden, während israelische Reservisten mit Dauerbefehl marschieren – ist Le Déserteur ein sakraler Text geworden. Fast ein Gebet.
„Wenn man mich verfolgt,\ werde ich den Gehorsam verweigern.\ Ich werde keine Waffe in die Hand nehmen,\ ich werde fliehen, bis ich Frieden finde.“
Wie viele „Deserteure“ gibt es heute, die wir gar nicht kennen? Menschen, die sich nicht auf die Seite der Bomben stellen wollen – egal, wer sie wirft? Die sich nicht mehr einspannen lassen zwischen Propaganda und Patriotismus? Die ihre Menschlichkeit über jeden nationalen Befehl stellen?
Der Krieg, sagt Vian, macht aus freien Menschen Befehlsempfänger und aus Söhnen Leichen. Und wer heute sagt, es gebe „gerechte Kriege“, sollte eine Frage beantworten: Ist es auch ein gerechter Tod?
Darum: Verweigert.
Verweigert den Befehl, zu hassen.\ Verweigert den Reflex, Partei zu ergreifen.\ Verweigert den Dienst an der Waffe.
Denn wie Vian singt:
„Sagen Sie's den Leuten:\ Ich werde nicht kommen.“
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 0e9491aa:ef2adadf
2025-05-23 15:01:52
@ 0e9491aa:ef2adadf
2025-05-23 15:01:52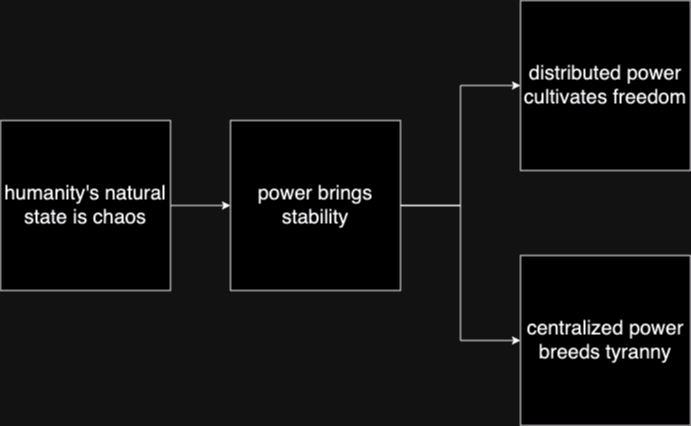
Humanity's Natural State Is Chaos
Without order there is chaos. Humans competing with each other for scarce resources naturally leads to conflict until one group achieves significant power and instates a "monopoly on violence."Power Brings Stability
Power has always been the key means to achieve stability in societies. Centralized power can be incredibly effective in addressing issues such as crime, poverty, and social unrest efficiently. Unfortunately this power is often abused and corrupted.Centralized Power Breeds Tyranny
Centralized power often leads to tyrannical rule. When a select few individuals hold control over a society, they tend to become corrupted. Centralized power structures often lack accountability and transparency, and rely too heavily on trust.Distributed Power Cultivates Freedom
New technology that empowers individuals provide us the ability to rebuild societies from the bottom up. Strong individuals that can defend and provide for themselves will help build strong local communities on a similar foundation. The result is power being distributed throughout society rather than held by a select few.In the short term, relying on trust and centralized power is an easy answer to mitigating chaos, but freedom tech tools provide us the ability to build on top of much stronger distributed foundations that provide stability while also cultivating individual freedom.
The solution starts with us. Empower yourself. Empower others. A grassroots freedom tech movement scaling one person at a time.
If you found this post helpful support my work with bitcoin.

-
 @ 502ab02a:a2860397
2025-05-21 07:49:22
@ 502ab02a:a2860397
2025-05-21 07:49:22หลายคนอาจแปลกใจว่า ทำไมน้ำมันจากผลไม้แบบอโวคาโดถึงกล้าขึ้นชั้น “ไขมันดี” ไปเทียบกับน้ำมันมะกอกได้ ทั้งที่ฟังดูไม่หรูเท่า แต่ความจริงแล้ว น้ำมันอโวคาโดคือหนึ่งในไม่กี่ชนิดของน้ำมันพืชที่สกัดจาก “เนื้อผล” ไม่ใช่เมล็ด ทำให้มีโครงสร้างไขมันที่ต่างจาก seed oils ทั่วไป ทั้งในแง่กรดไขมัน สารต้านอนุมูลอิสระ และวิธีที่มันตอบสนองต่อความร้อน
น้ำมันอโวคาโดมีกรดไขมันไม่อิ่มตัวตำแหน่งเดียว (MUFA) เป็นหลัก โดยเฉพาะ กรดโอเลอิก (Oleic acid) ซึ่งคิดเป็นประมาณ 65–70% ของไขมันทั้งหมด ใกล้เคียงน้ำมันมะกอกเลย แต่เหนือกว่าเล็กน้อยในแง่ของ ค่าควัน (smoke point) ที่สูงถึง 250°C (แบบ refined) และราว 190–200°C (แบบ cold-pressed) ทำให้เหมาะกับการผัดหรือทอดแบบเบา ๆ โดยไม่ทำให้เกิดสารพิษจากไขมันไหม้เร็วเท่าน้ำมันที่ค่าควันต่ำ
นอกจาก MUFA แล้ว น้ำมันอโวคาโดยังมี PUFA อยู่เล็กน้อย ประมาณ 10–14% ส่วนใหญ่คือ โอเมก้า-6 (linoleic acid) ซึ่งก็มีปริมาณไม่มากจนถึงขั้นต้องห่วงเรื่องการอักเสบ เหมือนที่เจอกับพวกน้ำมันรำข้าวหรือถั่วเหลืองที่ PUFA พุ่งสูงเกิน 50% ขึ้นไป และที่สำคัญ...โอเมก้า-3 ในอโวคาโดก็มีอยู่บ้างในรูปของ ALA แม้ไม่เยอะ แต่ก็บอกได้ว่าโครงสร้างโดยรวมของมันสมดุลพอควร ถ้ามองในรูปแบบพลังงานไขมัน ก็ถือว่าใช้ได้เลย
อโวคาโดออยล์แบบไม่ผ่านกระบวนการ (unrefined) ยังมีพวก วิตามินอี (tocopherols) ในระดับประมาณ 13–20 มก. ต่อ 100 กรัม และสารโพลีฟีนอลบางชนิดราวๆ 30–50 mg GAE/100 กรัม เช่น catechins และ procyanidins อยู่บ้าง ซึ่งช่วยลดการเกิดอนุมูลอิสระตอนเจอความร้อน และยังดีต่อผิวหนังในมิติของ skincare ด้วยนะ
ถ้าใช้แบบ cold-pressed, unrefined กลิ่นมันจะออกคล้ายอะโวคาโดสุก ๆ หน่อย มีความเขียวอ่อน ๆ และครีมมี่เล็ก ๆ ซึ่งเหมาะกับการคลุกหรือปรุงแบบ low heat มากกว่าการทอดแรง ส่วนถ้าจะใช้ทำอาหารจริงจัง น้ำมันอโวคาโดแบบ refined ก็จะกลิ่นอ่อนลง สีใสขึ้น และทนไฟได้ดีขึ้นมาก เหมาะจะเอาไปทำ steak หรือผัดไฟกลางได้แบบไม่กังวล อันนี้ก็แล้วแต่จะเลือกนะครับ
ถ้าจะพูดให้ตรง… น้ำมันอโวคาโดคือ “ไขมันผลไม้สายกลาง” ที่ทั้งทนไฟพอใช้ ทำครัวได้หลากหลาย และไม่บิดเบือนสัดส่วนไขมันในร่างกายเราจนเกินไป และถ้าเลือกแบบที่ผลิตดี ไม่โดนสารเคมี ไม่โดนไฮโดรเจนเสริม ก็ถือว่าเป็นน้ำมันดีอีกตัวที่วางใจได้ในครัวจริง ๆ
ใครอยากลองทำเองที่บ้านก็ได้นะ แบบง่ายๆแค่มีผ้าขาวบาง https://youtu.be/gwHGgoMuRnI?si=ehcQceabdbMGfkwG
นอกจากนี้บางคนอาจเคยเห็นโฆษณาสินค้าที่มีน้ำมันจากเมล็ดและเปลือกด้วยใช่ไหมครับ
เมล็ดอโวคาโดนั้นอุดมไปด้วย ไขมันน้อยกว่ามาก เมื่อเทียบกับเนื้อผล แต่มีสารพฤกษเคมีบางชนิดที่นักวิจัยสนใจ เช่น ฟีนอลิกส์ (phenolics), ฟลาโวนอยด์, สารต้านจุลชีพ และ ไฟเบอร์ละลายน้ำสูง การสกัดน้ำมันจากเมล็ดมักจะใช้ ตัวทำละลาย (solvent extraction) หรือ วิธี supercritical CO₂ ไม่ค่อยทำแบบ cold-pressed เพราะน้ำมันน้อยเกิน ปริมาณน้ำมันจากเมล็ดนั้นต่ำมาก คือไม่ถึง 5% ของน้ำหนักแห้ง ทำให้ไม่ค่อยนิยมในเชิงพาณิชย์ น้ำมันจากเมล็ดมักไม่ได้เอาไว้ปรุงอาหาร แต่เอาไปใช้ ด้านเวชสำอาง หรือ functional food มากกว่า เช่น ครีมทาผิว แชมพู หรือผลิตภัณฑ์ชะลอวัย
เปลือกอโวคาโดมี สารต้านจุลชีพและสารต้านออกซิเดชัน บางชนิดเช่นกัน แต่มีไขมันน้อยมากแทบจะไม่มีเลย บางงานวิจัยพยายามสกัดพวก polyphenols หรือสารสีธรรมชาติจากเปลือก เพื่อใช้ในอาหารเสริม หรือผลิตภัณฑ์สุขภาพ ไม่ได้สกัดน้ำมันโดยตรง แบบเนื้อผล แต่ใช้เปลือกเป็นวัตถุดิบเสริมมากกว่า เช่น ผสมในน้ำมันหลักเพื่อเพิ่มคุณสมบัติด้านสุขภาพ
ส่วนตัวคิดว่าไม่ต้องทำเองหรอกครับ ซื้อกินเหอะ 555 เจ้านี้ดีนะ อยู่คู่วงการสุขภาพมาแต่แรกๆเลย https://s.shopee.co.th/8zsnEsLrvh
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ 866e0139:6a9334e5
2025-05-22 06:46:34
@ 866e0139:6a9334e5
2025-05-22 06:46:34Autor: Jana Moava. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie auch in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Zwei Worte nur braucht man – und die Sache ist klar. Jeder gebildete Russe kennt diese Worte: sie stammen aus dem XIX. Jahrhundert, als Nikolaus I. die Krim-Kampagne begann und das Zarenreich nach üblen Querelen ganz Europa und die Türkei zum Gegner hatte - allen voran die Herrscher der Weltmeere: das British Empire mit Queen Victoria. Der historische Ausdruck anglitschanka gadit (locker übersetzt: die Engländerin macht Shit) besitzt bis heute verdeckte politische Sprengkraft und ist seit Ende Februar 2022 in Russland wieder populär. Wer auch immer der Urheber dieser im Original durchaus diskreten Benennung des Fäkalvorgangs war: der Ausdruck steht für ernste Konflikte mit dem Englisch sprechenden Westen, dem Erzfeind.
Ein kurzer Blick in die Geschichte mag dies erläutern: Fast alle westlichen Historiker benennen als Auslöser des Krimkrieges Mitte des IX. Jahrhunderts die Verteidigung der russisch-orthodoxen Kirche und deren Zugang zur Kreuzkirche in Jerusalem. Es wird vom letzten Kreuzzug u.a. geschrieben. Das ist eine höchst einseitige Interpretation, denn es ging Nikolaus I. vor allem um den Zugang zum einzigen dauerhaft eisfreien Hafen Russlands im Schwarzen Meer, durch die Meeresenge der Dardanellen ins Mittelmeer. Das ist verständlich, war doch die Eroberung der Krim ab 1783 unter seiner Großmutter Katharina II. aus eben diesem Grunde erfolgt. Damals schon wurde der Hafen Sewastopol zum Stützpunkt der russischen Flotte ausgebaut.
Ende 1825, nach dem plötzlichen Tod des ältesten Bruders Alexander I., war Nikolaus von seiner Erziehung her auf eine Regentschaft ganz und gar nicht vorbereitet gewesen, doch herrschte er dreißig Jahre lang nicht nur über das russische Reich, sondern auch über Finnland und das damalige Königreich Polen unter russischem Protektorat. Nikolaus I. zeichnete sich von Beginn an durch Gewaltmaßnahmen aus: Als ihm im Dezember (russ. dekabr)1825 eine Gruppe sehr gebildeter, freiheitsliebender junger Adligen aus besten Familien den Eid verweigerte (dies zog als Dekabristenaufstand in die Geschichte ein), ließ er fünf der Rebellen hängen, die anderen schickte er in Fußfesseln nach Sibirien in die Bergwerke. Er gründete die berüchtigte Geheimpolizei Dritte Abteilung, ließ Privatbriefe des Dichters Puschkin öffnen (obwohl dieser „in seiner Gnade stand“) und Historikern ist Nikolaus I. als Gendarm Europas bekannt. Im russischen Volk aber nannte man ihn kurz und bündig: *Nicki Knüppel aus dem Sack (Nikolaschka palkin). *
Leo Tolstoj beschrieb diesen Zaren in seinen Erzählungen über die Kriege im Kaukasus (Hadschi Murat) als feist und fett, mit leblosen, trüben Augen und als berüchtigten Frauenjäger. Tolstoj war es auch, der als junger Teilnehmer im Krimkrieg drei Erzählungen schrieb: Sewastopol im Dezember 1854, im Mai 1855 und im August 1855. Nachdem das British Empire unter Queen Victoria Russland den Krieg erklärt hatte (in Koalition mit Frankreich und Piemont-Sardinien als Schutzmacht des Osmanischen Reiches), entstand der Ausdruck anglitschanka gadit – die Engländerin macht Shit. Bis heute findet man dazu drastische Illustrationen im Netz…
Noch bevor russische Truppen Ende Februar 2022 in die Ukraine marschierten, lebte dieser Ausdruck in Russland wieder auf. Wer hierzulande Interesse an der Wahrheit hat, kann deutliche Parallelen zur damaligen politischen Lage entdecken, auch in Bezug auf die Verhaltensweisen des derzeitigen russischen Staatschefs und des historischen Nicki Knüppel aus dem Sack. Obwohl der amtierende durchaus Anerkennung verdient hat, denn nach dem Zusammenbruch der Sowjetunion in den 1990er Jahren unter Jelzin stellte er die Staatlich-keit des verlotterten, hungernden Landes wieder her und trieb den wirtschaftlichen Aufbau voran. Davon kann ich zeugen, lebte ich doch von 1992 – 2008 vor Ort.
Sicher - heute ist längst bekannt, daß die bereits Ende März 2022 in Istanbul laufenden Friedensverhandlungen zwischen Russland und der Ukraine vom britischen Premier und im Namen des US Präsidenten boykottiert wurden. Daniel Ruch, Schweizer Botschafter a.D., sprach gar von Sabotage! Der deutsche General a. D. Harald Kujat kommentierte damals mit den Worten: „Seit April 2022 gehen alle Kriegsopfer in der Ukraine auf das Konto des Westens!“ Der Ausdruck anglitschanka gadit ist seitdem in Russland wieder geläufig. Nun, brandaktuell, treffen sich die Kriegsparteien wieder in Istanbul: Ausgang ungewiss. Doch wird inzwischen auch von einzelnen westlichen Politikern anerkannt, dass Russland eine neutrale Pufferzone zu den Nato-Staaten verlangt und braucht.
Wenn hierzulande gemutmaßt wird, alle Russen würden den Ukraine-Krieg bejahen, so sollte man zur Kenntnis nehmen, dass derartige Aussagen kaum die wirkliche Überzeugung wiedergeben. Seit den Repressionen unter Stalin, seit in jeder zweiten Familie nahe Angehörige im GULAG einsaßen und umkamen und darüber Jahrzehnte lang geschwiegen werden musste, ist der Wahrheitsgehalt öffentlicher Umfragen getrost zu bezweifeln. Hat man hier etwa vergessen, dass seit 2011 auf eine mächtig wachsende zivile Protestbewegung und riesige Demonstrationen in russischen Großstädten immer schärfere Aktionen von Seiten des Staates erfolgten? Dass Knüppel auf Köpfe und Leiber prasselten, wie zur Zeit Nickis I., und der Polizeiapparat derart wuchs, dass heute das Verhältnis von Bürger und Silowiki (Vertreter der Gewalt)1:1 steht?
Offenbar weiß man hier nicht, dass schon Anfang 2022 von Mitarbeitern in jeder staatlich finanzierten Institution, ob im Bereich von Kultur, Wissenschaft, Forschung oder Lehre die schriftliche Zustimmung zur Spezialoperation mit der Ukraine eingefordert wurde! Eine Weigerung hatte den Verlust des Arbeitsplatzes zur Folge, egal welches Renommée oder welchen Rang der Betroffene besaß! Manche Leiter von staatlichen Institutionen zeigten dabei gehöriges Geschick und zeichneten für alle; andere (z.B. staatliche Theater) riefen jeden Mitarbeiter ins Kontor. Nur wenige Personen, die unter dem persönlichem Schutz des Präsidenten standen, konnten sich dieser Zustimmung zum Krieg entziehen. Wissenschaftler und Künstler emigrierten zuhauf. Berlin ist voll mit Geflohenen aus jenem Land, das kriegerisch ins Bruderland einmarschierte! Aber kann denn jeder emigrieren? Die Alten, Familien mit Kindern? Mit guten Freunden, die dort blieben, ist eine Kommunikation nur verschlüsselt möglich, in Nachrichten wie: die Feuer der Inquisition brennen (jeder, der von der offiziellen Doktrin abweicht, ist gefährdet), Ratten verbreiten Krankheiten bezieht sich auf Denunziationen, die in jeder Diktatur aufblühen, wenn sich jemand dem Schussfeld entziehen möchte und im vorauseilenden Gehorsam den Nachbarn anzeigt. Kennen wir das nicht noch aus unseren hitlerdeutschen 1930er Jahren?!
Je mehr im Reich aller Russen in den letzten Jahren von oben geknebelt und geknüppelt wurde, desto mehr Denunziationen griffen um sich. Junge Menschen, die auf Facebook gegen den Krieg posteten, wurden verhaftet. Seit 2023 sitzen u.a. zwei junge russische Theaterfrauen aufgrund der üblen Denunziation eines Kollegen hinter Gittern. Die Inszenierung der Regisseurin Zhenja Berkowitsch und der Autorin Swetlana Petritschuk erhielt Ende 2022 den höchsten Theaterpreis von ganz Russland, die Goldene Maske. Das Stück Finist (Phönix), klarer Falke ist nach dem Motiv eines russischen Märchens geschrieben, fußt aber auf dokumentarischem Material: es verhandelt die Versuchung junger Frauen, auf Islamisten hereinzufallen und sie aus Frust und falsch verstandener Solidarität zu heiraten. Die Anklage hat den Spieß genau umgedreht: Autorin und Regisseurin wurden des Terrorismus beschuldigt! Das Rechtssystem im Land scheint heute noch vergleichbar mit jenem, das Alexander Puschkin vor über 200 Jahren in seiner Erzählung Dubrowski authentisch beschrieb: Wer die Macht hat, regelt das Recht. Man kann die Erzählung des russischen Robin Hood auch deutsch nachlesen (leider, leider hat Puschkin sie nicht beendet).
Andere, erbaulichere Elemente aus der Zeit Puschkins, bzw. von Nikolaus I., dienen allerdings als Gegengewicht zum Alltag: seit Ende 2007 finden in Moskau und St. Petersburg jeden Winter nach dem Vorbild der historischen Adelsbälle große gesellschaftliche Events statt: Puschkinball, Wiener Opernball, jetzt nur noch Opernball genannt. Der Nachwuchs aus begüterten Familien lernt alte Tanzschritte und feine Sitten. Fort mit dem sowjetischen Schmuddelimage! Prächtige Kostümbälle werden nun zum Abschluss jedes Schuljahres aufgeboten. In stilisierten Kostümen der Zeit Nikolajs I. bzw. Puschkins tanzen Schuldirektoren, Lehrer und junge Absolventen. Der Drang nach altem Glanz und Größe (oder eine notwendige Kompensation?) spiegelt sich im Volk.
Werfen wir jedoch einen Blick auf einige Geschehnisse in der Ukraine ab 2014, die in unserer Presse immer noch verschwiegen werden: Im Spätsommer 2022 begegnete ich auf Kreta einer Ukrainerin aus der Nordukraine, die wegen des fürchterlichen Nationalismus nach 2014 ihre Heimat verließ. Sie ist nicht die einzige! Ihre Kinder waren erwachsen und zogen nach Polen, sie aber reiste mit einer Freundin weiter Richtung Griechenland, lernte die Sprache, erwarb die Staatsbürgerschaft und ist nun auf Kreta verheiratet.
Natalia erzählte mir, was bei uns kaum zu lesen ist, was jedoch Reporter wie Patrick Baab oder Historiker wie Daniele Ganser schon lange berichtet haben: 2014, als die Bilder der Proteste auf dem Maidan um die Welt gingen, habe die damalige amerikanische Regierung unter Präsident Biden die Vorgänge in Kiew für einen Putsch genutzt: Janukowitsch, der korrupte, doch demokratisch gewählte Präsident der Ukraine wurde gestürzt, die Ereignisse mit Hilfe von Strohmännern und rechten Nationalisten gelenkt, die mit Geld versorgt wurden. Bis es zum Massaker auf dem Maidan kam, als bewaffnete, ihrer Herkunft nach zunächst nicht identifi-zierbare Schützen (es waren v.a. rechte Nationalisten, so der gebürtige Ukrainer und US Bürger Professor N. Petro und Prof. Ivan Katchanovskij) von den Dächern in die Menge schossen.
Im YouTube Kanal Neutrality Studies konnte man am 17.02.2024 hören: Anlässlich des traurigen 10. Jahrestages des Maidan-Massakers, bei dem am 20. Februar 2014 mehr als 100 Menschen durch Scharfschützenfeuer getötet wurden, spreche ich heute mit Ivan Katchanovski, einem ukrainischen (und kanadischen) Politikwissenschaftler an der Univer-sität von Ottawa, der das Massaker detailliert erforscht hat. Letztes Jahr veröffentlichte er das Papier „Die Maidan-Massaker-Prozess und Untersuchungserkenntnisse: Implikationen für den Krieg zwischen der Ukraine und Russland und die Beziehungen“. Kurz gesagt, das Massaker wurde NICHT von den Kräften Victor Janukowytschs begangen, wie in westlichen Medien berichtet, und es gibt schlüssige Beweise dafür, dass die Schützen Teil des ultra-rechten Flügels der Ukraine waren, die dann nach dem Putsch an die Macht kamen. (Link zum Paper).
Wer erinnert sich hierzulande noch daran, dass 2014 im deutschen öffentlichen Fernsehen von Hunter Biden, Sohn des US-Präsidenten berichtet wurde, der durch dubiose Gas- und Ölgeschäfte in der Ukraine auffiel? Dass damals im deutschen Fernsehen auch Bilder von Ukrainern mit SS-Stahlhelmen auftauchten? In einer Arte-Reportage zu Hilfs-transporten im März 2022 aus Polen über die Westukraine konnte der aufmerksame Zu-schauer an fast allen Häusern die tiefroten Banner von Anhängern des verstorbenen, in München begrabenen, faschistischen Stepan Bandera erkennen. Ausgesprochen wurde es nicht.
Die neue Kreterin Natalia sprach auch über eine Amerikanerin ukrainischer Herkunft, die Röntgenärztin Uljana Suprun, die aus den USA als Gesundheitsministerin rekrutiert wurde und unter dem amerikafreundlichen Präsidenten Poroschenko von 2016-2019 diesen Posten innehatte. Was bitte sollte eine Röntgenärztin aus den USA auf dem Ministerposten der Ukraine?! Streit und Skandal umgaben sie fast täglich in der RADA, dem ukrainischen Parlament. Es wurde gemunkelt, sie diene als Feigenblatt bei der Herstellung biologischer Waffen. Material zu ihr ist bis heute auf YouTube zu finden.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Natalia bezeichnete die ukrainischen Emigrantenkreise in den USA und Kanada zurecht als ultranationalistisch, sie seien Kollaborateure der Nazis bei der Judenvernichtung gewesen und hätten sich nach dem Rückzug der Deutschen rechtzeitig nach Übersee abgesetzt. Das ist wohl bekannt.
Heute ist das Recherchieren der wahren Geschehnisse von 2014 zwar immer noch mühsam, aber die Wahrheit sickert immer mehr durch, zumal auch Exilukrainer dazu geschrieben und öffentlich gesprochen haben. Die Kanäle SaneVox und Neutrality studies liefern unermüdlich weitere Fakten! Im März 2025 klärte der US-Professor Jeffrey Sachs das Europa-Parlament endlich in allen Details über die kriegerischen Machenschaften bestimmter Kreise innerhalb der englischsprechenden Westmächte auf!
Kürzlich war im multipolar-magazin zu lesen, wie erschreckend tief unser eigenes Land bereits in**** den Ukraine-Krieg verwickelt ist: Da hieß es:
*„Kriegsplanung von deutschem Boden“ *
Zwei umfassende Beiträge der „New York Times“ und der Londoner „Times“ belegen, was lange bestritten wurde: die tiefe militärische und strategische Verwicklung von Nato-Mitgliedsstaaten in den Ukraine-Krieg. Demnach wird deren Kriegsbeteiligung seit Jahren vom europäischen Hauptquartier der US-Armee in Wiesbaden koordiniert. Für Deutschland stellen sich damit verfassungsrechtliche Fragen.
Und ein Karsten Montag schrieb ebenda am 25. April 2025:
Mehr als drei Jahre nach Beginn des russisch-ukrainischen Krieges berichten zwei große westliche Tageszeitungen über die tiefgreifende Beteiligung von Nato-Militärs an diesem Konflikt. Den Anfang machte die „New York Times“ (NYT). Unter dem Titel „Die Partnerschaft: Die geheime Geschichte des Krieges in der Ukraine“ erschien Ende März ein umfassender *Artikel, der laut Autor Adam Entous auf 300 Interviews mit Regierungs-, Militär- und Geheim-dienstvertretern in der Ukraine, den Vereinigten Staaten sowie weiteren Nato-Partnern basiert. Es handle sich um die „unerzählte Geschichte“ der „versteckten Rolle“ der USA bei den ukrainischen Militäroperationen. *
Wenige Wochen später veröffentlichte die britische Tageszeitung „The Times“ Anfang April einen ähnlichen Beitrag mit dem Titel „Die unerzählte Geschichte der entscheidenden Rolle der britischen Militärchefs in der Ukraine“. Dieser bestätigt die tiefe Verstrickung der Nato-Staaten in Militäroperationen wie der ukrainischen Offensive 2023. Abweichend vom NYT-Artikel bezeichnet er jedoch die britischen Militärchefs als die „Köpfe“ der „Anti-Putin“-Koalition. Einigkeit herrscht wiederum bei der Frage, wer für den Misserfolg der Operationen verantwortlich ist: Dies sei eindeutig der Ukraine zuzuschreiben. Auch im Times-Beitrag wird auf die besondere Rolle des europäischen US-Hauptquartiers im hessischen Wiesbaden bei der Koordination der Einsätze und den Waffenlieferungen hingewiesen.
Na also! Es gibt unter den aus der Ukraine Geflüchteten hier allerdings eine große Mehrheit, die von diesen Fakten weder etwas wissen, noch wissen wollen. Amerika und die Heimat der Anglitschanka ist für sie das Gelobte Land und wehe, du sprichst darüber, dann wirst du sofort der russischen Propaganda verdächtig. Wie Nicki mittlerweile daheim den Knüppel schwingt, interessiert sie auch nicht.
Wieso wird hier nicht untersucht, wieso wird verschwiegen, dass Alexej Nawalny für einen englischen Dienst arbeitete – woher erhielt er das viele Geld für seine Kampagnen? Wo leben nun seine Witwe und die Kinder? Auf der Insel im nebligen Avalon/ Albion…
Ein letztes Beispiel aus dem Bereich der Kultur zum Verständnis des leider so aktuellen Ausdrucks Die Engländerin macht Shit: Anfang 2024 wurde im staatlichen Sender ONE (ARD) eine Serie der BBC zu frühen Erzählungen von Michail Bulgakow ausgestrahlt:** Aufzeichnungen eines jungen Arztes. Die BBC verhunzte den in Kiew geborenen Arzt und weltberühmten Autor derart, dass dem Zuschauer schlecht wurde: Mit dem Titel A Young Doctor‘s Notebook verfilmte sie Bulgakows frühe Erzählungen über die Nöte eines jungen Arztes in der bettelarmen sowjetrussischen Provinz in den 1920er Jahren hypernaturalistisch, blut-, dreck- und eitertriefend. Pseudokyrillische Titel und Balalaika Geklimper begleiteten das Leiden von schwer traumatisierten Menschen im russischen Bürgerkrieg oder Abscheulichkeiten, wie das Amputieren eines Mädchenbeines mit einer Baumsäge - ausgestrahlt vom 1. Deutschen Fernsehen! Michail Bulgakow hätte sich im Grabe umgedreht.
Als Autor beherrschte Bulgakow die Kunst der Groteske ebenso wie hochlyrische Schilderungen. Seine Prosa und seine Theaterstücke aber wurden Zeit seines Lebens von der Sowjetmacht verstümmelt - und post mortem auch von seinen ukrainischen Landsleuten: sein schönes Museum, das ehemalige Domizil der Familie Bulgakow in Kiew am Andrejew-Steig, das mit seinem ersten Roman Die weiße Garde (Kiew vor 100 Jahren im Strudel auch ultranationalistischer Strömungen) und der berühmten Dramatisierung Die Tage der Turbins in die große Literatur einzog, dieses Museum wurde abgewickelt und geschlossen, weil Bulgakow angeblich schlecht über die Ukraine geschrieben hätte!
Ein Glück jedoch, dass die bedeutenden Werke Bulgakows seit nun drei Dekaden von russischsprachigen Philologen beharrlich in ihrer ursprünglichen Fassung wieder hergestellt wurden. Seine großen Romane Die weiße Garde und Meister und Margarita seien in der hervorragenden deutschen Übersetzung von Alexander Nitzberg jedem Interessierten ans Herz gelegt!
Die obigen Ausführungen sind keinesfalls eine Rechtfertigung des Krieges, es geht vielmehr um Hintergründe, Fakten und Machenschaften, die in der Regel bis heute bei uns verschwiegen werden! Obwohl es nun sonnenklar und öffentlich ist, dass bestimmte Inter-essengruppen der englischsprachigen Westmächte die hochgefährliche Konfrontationspolitik mit Russland zu verantworten haben: die Engländerin macht Shit…Und wir? Wir schweigen, glauben der immer noch laufenden Propaganda und wehren uns nicht gegen diese üble Russenphobie?! Ich erinnere mich noch lebhaft an die Nachkriegszeit im Ruhrgebiet, als der Ton ruppig war und Dreck und Trümmer unsere Sicht beherrschten. Auch uns kleinen Kindern gegenüber wurde von den bösen Russen gesprochen, als hätten diese unser Land überfallen.
Ja – es waren viele Geflüchtete aus dem Osten hier gestrandet, und diese hatten Unsägliches hinter sich. Lew Kopelew, der den Einmarsch der Roten Armee in Ostpreußen miterlebte und Gräuel vergebens zu verhindern suchte, wurde noch im April 1945 verhaftet und wegen Mitleid mit dem Feind zu 10 Jahren Lager verurteilt. Viele Jahre später erschienen seine Erinnerungen Aufbewahren für alle Zeit – auch auf Deutsch. Über die mindestens 27 Mio Opfer in der damaligen Sowjetunion und über die deutschen Aggressoren, die damals mit Mord und Raub die bösen Russen, sowjetische Zivilisten überfielen, wurde in den 1950er Jahren, im zerbombten und dreckigen Pott kein einziges Wort verloren. Der Spieß wurde einfach umgedreht. Von der Blockade Leningrads erfuhr ich erst als Erwachsene, anno 1974, als Austauschstudentin vor Ort.
Exakt vor 10 Jahren wurde es jedoch möglich – herzlichen Dank der damaligen stell-vertretenden tatarischen Kulturministerin Frau Irada Ayupova! – mein dokumentarisches Antikriegsstück mit Schicksalen von Kriegskindern – sowjetischen, jüdischen, deutschen – in Kasan, der Hauptstadt von Tatarstan, zweisprachig auf die Bühne des dortigen Jugendtheaters zu bringen. Wir spielten 15 Vorstellungen und einige tausend Jugendliche im Saal verstummten und verstanden, dass Krieg furchtbar ist. Hier und heute will leider kein Theater das Stück umsetzen…
Wir Menschen brauchen Frieden und keine Aufrüstung für neue Kriege! Der gute alte Aischylos schrieb einst in seinem Stück Die Perser: Wahrheit ist das erste Opfer eines Krieges. Leider ist dies immer noch genauso aktuell wie damals. Pfui Teufel!
Jana Moava (Pseudonym) ist Journalistin, Dozentin und arbeitete für große Zeitungen als Korrespondentin.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 502ab02a:a2860397
2025-05-21 02:12:10
@ 502ab02a:a2860397
2025-05-21 02:12:10ถ้าเอ่ยถึง CJ หลายคนอาจนึกถึงซอสเกาหลีรสจัดจ้าน หรือบะหมี่กึ่งสำเร็จรูปแบรนด์ดังที่ขายทั่วโลก แต่เบื้องหลังความสำเร็จของแบรนด์เหล่านั้น มีบริษัทแม่อย่าง CJ CheilJedang ที่ไม่ได้แค่ผลิตอาหารแปรรูป แต่เป็นหนึ่งในผู้เล่นใหญ่ของอุตสาหกรรมอาหารระดับโลก ด้วยฐานความรู้ลึกซึ้งในเทคโนโลยีชีวภาพ หนึ่งในแขนงที่โดดเด่นคือ CJ BIO ธุรกิจไบโอเทคโนโลยีที่เน้นการใช้ Microbial Fermentation หรือการหมักจุลินทรีย์เพื่อผลิตสารอาหารและวัตถุดิบอาหารคุณภาพสูงในระดับอุตสาหกรรม
ประวัติของ CJ BIO เริ่มจากจุดเล็ก ๆ แต่ทรงพลัง คือการผลิต โมโนโซเดียมกลูตาเมต (MSG) ซึ่งเป็นกรดอะมิโนชนิดหนึ่งที่มีบทบาทสำคัญในการเพิ่มรสชาติ “อูมามิ” ให้กับอาหารทั่วโลก จุดนี้เองที่ทำให้ CJ BIO ได้สะสมเทคโนโลยีหมักจุลินทรีย์ในระดับอุตสาหกรรมมายาวนานกว่า 60 ปี ด้วยโรงงานหมักขนาดใหญ่ที่ตั้งอยู่ในหลายประเทศ เช่น เกาหลีใต้ จีน บราซิล อินโดนีเซีย และสหรัฐอเมริกา ทำให้ CJ BIO กลายเป็นหนึ่งในผู้ผลิตกรดอะมิโนและวัตถุดิบอาหารหมักจุลินทรีย์รายใหญ่ของโลก
แต่ถ้าให้พูดแบบง่าย ๆ การหมักจุลินทรีย์ของ CJ BIO นั้น ไม่ใช่แค่ “การทำอาหาร” ธรรมดา ๆ แต่เป็นการ “สร้างอาหารในระดับโมเลกุล” ตั้งแต่พื้นฐาน ซึ่งถือเป็นเทคโนโลยีที่สำคัญสำหรับอนาคตของอาหาร เพราะมันช่วยให้เราสามารถผลิตโปรตีน กรดอะมิโน และสารอาหารต่าง ๆ ที่มีคุณภาพสูงและควบคุมได้ในโรงงานขนาดใหญ่ โดยไม่ต้องพึ่งพาการเกษตรแบบดั้งเดิมที่ต้องใช้พื้นที่มากและมีผลกระทบต่อสิ่งแวดล้อม
เมื่อเทรนด์โลกกำลังเปลี่ยนไปในทางที่ผู้บริโภคหันมาใส่ใจสุขภาพและสิ่งแวดล้อมมากขึ้น เรื่อง “อาหารจากห้องแล็บ” หรือ “อาหารเทคโนโลยีชีวภาพ” จึงกลายเป็นสิ่งที่ได้รับความสนใจอย่างมาก และนี่เองที่ทำให้ CJ BIO ไม่ได้หยุดอยู่แค่ Microbial Fermentation แบบดั้งเดิม แต่เริ่มขยับเข้าสู่โลกใหม่ของ Precision Fermentation การใช้จุลินทรีย์ที่ผ่านการดัดแปลงพันธุกรรมอย่างแม่นยำ เพื่อผลิตโปรตีนหรือสารอาหารเฉพาะอย่างที่ต้องการ
ความเคลื่อนไหวที่สำคัญเกิดขึ้นในปี 2022 เมื่อ CJ CheilJedang ประกาศลงทุนใน New Culture สตาร์ทอัพสัญชาติอเมริกันที่กำลังพัฒนา “ชีสไร้วัว” ด้วยเทคโนโลยี Precision Fermentation ซึ่ง New Culture ใช้จุลินทรีย์ที่ถูกออกแบบมาเพื่อผลิตโปรตีนเคซีน โปรตีนหลักในน้ำนมวัว โดยไม่ต้องมีวัวจริงเลย นั่นหมายความว่าชีสที่ผลิตออกมาจะไม่มีส่วนผสมจากสัตว์จริง ๆ แต่ยังคงรสชาติและเนื้อสัมผัสเหมือนชีสธรรมชาติทุกประการ
การลงทุนครั้งนี้ของ CJ CheilJedang บริษัทแม่ของ CJ BIO จึงถือเป็นการผนึกกำลังระหว่างเทคโนโลยีดั้งเดิมที่ผ่านการพิสูจน์แล้วในระดับอุตสาหกรรม กับนวัตกรรมที่พร้อมเปลี่ยนแปลงวงการอาหารครั้งใหญ่
ถ้าให้เปรียบเทียบง่าย ๆ CJ BIO เหมือนกับ “โรงงานปั้นโมเลกุลอาหาร” ที่มีความเชี่ยวชาญสูงในการจัดการกับจุลินทรีย์และการผลิตกรดอะมิโนหลากหลายชนิด โดยเฉพาะ MSG ซึ่งถือเป็น “พี่ใหญ่” ในกลุ่มกรดอะมิโนที่ช่วยเพิ่มรสชาติและถูกใช้ในอุตสาหกรรมอาหารทั่วโลก
ความเชี่ยวชาญในการผลิต MSG นี้เอง คือฐานกำลังสำคัญที่ทำให้ CJ BIO สามารถขยายขอบเขตไปสู่การผลิตโปรตีนด้วย Precision Fermentation ได้อย่างมั่นใจ เพราะกระบวนการหมักจุลินทรีย์เพื่อผลิตกรดอะมิโนและโปรตีนนั้นมีความคล้ายคลึงกันในเชิงเทคนิคและการควบคุมคุณภาพ
CJ BIO มีโรงงานหมักจุลินทรีย์ที่ทันสมัยและขนาดใหญ่กระจายอยู่ทั่วโลก สามารถผลิตวัตถุดิบในปริมาณมหาศาลเพื่อตอบสนองตลาดอาหารที่เติบโตอย่างรวดเร็ว และการมีเครือข่ายโรงงานแบบนี้ทำให้ CJ BIO มีความได้เปรียบในการลดต้นทุนและควบคุมคุณภาพอย่างเข้มงวด
อนาคตที่ CJ BIO กำลังเดินไปนั้น ไม่ใช่แค่การผลิตวัตถุดิบอาหารธรรมดา ๆ แต่คือการสร้างนวัตกรรมที่จะเปลี่ยนแปลงวิธีการผลิตและการบริโภคอาหารของโลก
เมื่อผลิตภัณฑ์จากเทคโนโลยี Precision Fermentation อย่างชีสไร้วัว ไข่ไร่ไก่ หรือโปรตีนทางเลือกต่าง ๆ เริ่มเข้ามาในตลาดมากขึ้น เราอาจจะได้เห็น CJ BIO ทำหน้าที่เหมือน “Intel Inside” ของวงการอาหารอนาคต ที่อยู่เบื้องหลังผลิตภัณฑ์สำคัญ ๆ ที่ผู้บริโภคชื่นชอบโดยไม่รู้ตัว
นี่คือเหตุผลที่ทำให้การมองแค่แบรนด์อาหารหรือการตลาดที่พูดถึง “ความยั่งยืน” หรือ “อาหารปลอดสัตว์” ยังไม่พอ เราต้องมองให้ลึกไปถึงระบบนิเวศของเทคโนโลยีและทุนที่อยู่เบื้องหลัง เพราะนั่นคือเกมกระดานใหญ่ที่กำลังขยับเปลี่ยนแปลงวงการอาหารโลกอย่างแท้จริง
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ c3b2802b:4850599c
2025-05-21 08:47:31
@ c3b2802b:4850599c
2025-05-21 08:47:31In einem Beitrag im Januar 2025 hatte ich das hier kurz schriftlich skizziert. Im April 2025 gab es die Gelegenheit, diese Zusammenhänge etwas ausführlicher im Café mit Katrin Huß darzustellen. Danke, liebe Katrin, für dieses Zusammenkommen in unserer Heimat Sachsen.
Wenn Sie sich für positive Psychologie und deren Einsatz beim Aufbau unserer Regionalgesellschaft interessieren, schauen Sie gern in das 45 -Minuten Gespräch!
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 94215f42:7681f622
2025-05-16 08:18:52
@ 94215f42:7681f622
2025-05-16 08:18:52Value Creation at the Edge
The conversation around artificial intelligence has largely centered on the technology itself, the capabilities of large language models, the race for more parameters, and the competition between AI companies.
He with the most data / biggest model / biggest platform wins all.
As we're been exploring in recent "Good Stuff" podcasts, the true business model of AI may be much more straightforward. AI is after all a productivity tool with little technical moat, in fact the existence of AI coding and learning tools quickly chop away at this moat even quicker!.\ \ We believe that the it's about transforming traditional human heavy businesses by dramatically reducing operational costs while maintaining or increasing output.
AI is poised to create value not primarily for AI companies themselves, but for businesses that effectively implement AI to transform their operations, particularly small, local businesses that can become extraordinarily efficient through AI adoption.
The Value Shift: From AI Companies to AI-Enabled Traditional Businesses
A central insight from episode 1 of the podcast series, is that the value of AI isn't likely to accrue primarily to companies like OpenAI or other AI technology providers. Instead, the real winners will be traditional service businesses that can leverage AI to transform their operations and cost structures.
"I think we're gonna see this shift to traditional service businesses... that traditionally have pretty fixed low margins because of a dependency on language-heavy workflows that require a lot of humans as the medium of intelligence in the business."
The opportunity here is to use AI to manage the language dependency and shift the moments of intelligence, that currently exist in the heads of our staff, into software that can run 24x7 for fractions of a cost.\ \ The real limiting factor here is less a magic AGI, but instead detailed thinking and process redesign to move humans to the edge of the process. As it turns out if we think through what each person is doing in detail we see the specific decisions, outputs, moments of intelligence are actually quite constrained and can be replicated in LLM's if we break them down to a low enough level of fidelity and take each decisions one step at a time.\ \ The result? Businesses that have traditionally operated with fixed, low margins can potentially achieve "software-style margins" by dramatically reducing their operational expenses.
Transforming Traditional Service Businesses
We have developed three key heuristics for identifying businesses that could benefit most from AI transformation:
-
Language Intensity: Businesses where much of the work involves processing language (reading, writing, communicating). Language in, language out. If you are sat in a chair and typing all day, this could be you.
-
Labor Component: Where we see this language intensity so we find many people performing similar, standardized roles. For examples, if we have four people in the same role this is a big clue we have good process, checklists, role descriptions etc for how the work can be done in order to replicate work across multiple people.
-
Load in the Business: Taking these processes into account, what amount of the operational expense of the business do they represent? Where these language and labor-intensive operations represent a significant portion of the business cost, we can see there will be significant return.
Traditional service businesses that match these criteria—legal firms, accounting practices, consulting agencies, contract engineering, design agencies and others—could see dramatic transformations through AI implementation.
By automating these language-heavy processes, businesses can potentially reduce operational costs by 50-80% while maintaining similar levels of output.
The Power of Small
We believe that small businesses may have an inherent advantage in this transformation. While large enterprises face significant barriers to reducing their workforce (political pressure, media scrutiny, organizational complexity), smaller businesses can adapt more quickly and focus on growth rather than just cost-cutting.
If I'm in a 20,000 person business and I need to remove 10,000 people... that's hard. You can't do this without sending political shock waves in your local community.
If I'm a 10 person business and I need to double my revenue, nobody gives a shit. I can just do it.
For small businesses, AI removes growth constraints. When adding the "21st person" no longer represents a significant capital investment, small businesses can scale much more efficiently:
If the next nominal client that you onboard doesn't actually cause you any more additional pain, if you don't need to hire more people to service that client... you just take off the brakes off from a growth perspective.
This gives small business a unique advantage in capitalizing on AI.
From "Bionic Humans" to "Humans at the Edge"
We currently see this integration to business happening in one of two models:
-
The Bionic Human: Equipping workers with AI tools to make them more productive.
-
Human at the Edge: Redesigning processes to be AI-native, with humans entering the process only when needed (and often facilitated by bitcoin payments).
While many businesses are focused on the first approach and it can certainly see returns, it is still a process constrained by the human input. The real value unlock comes from fundamentally redesigning business processes with AI at the core.
Now we can purchase intelligence in buckets of $0.02 API calls, how would we operate different?
This represents a profound shift in how we think about work and processes. Rather than humans being central to processes with tools supporting them, AI becomes the backbone of operations with humans providing input only at critical junctures.
This is "a complete mental shift" that challenges our fundamental assumptions about how businesses operate. The human becomes "the interface with the real world" for AI systems rather than the primary processor of information and decision-maker.
The Value Trap: Understanding the Competitive Dynamic
So what happens next? Here we have developed the concept of the Value Trap to explain how the competitive landscape will evolve as AI adoption increases..\ \

Initially, early adopters of AI and "Human at the Edge" business processes, will see dramatic benefits.
If your costs have dropped from 90 to 20 this creates an immediate competitive advantage where the early adopter is "now making 80 units of profit versus your 10 units of profit.
They gain massive pricing power in the industry and can compete for growth with an unfair advantage.
Over time, and here we believe this is likely a 5-10 year period although we believe the quicker side, competitive pressures will erode these advantages.\ \ As competitors adopt similar AI strategies, price competition will intensify, and revenues will decline. The business that initially saw its costs drop from 90 to 20 units might see its revenue decline from 100 to 30 units, resulting in similar margins but much lower overall revenue, often destroying the enterprise value of the company at these new revenue / profit levels!
This evolution creates an imperative for businesses to adopt AI early, not just to maintain perpetual advantage, but simply to survive the transition. Worse they're hit with a second challenge of the value trap, how do I keep hold of the value I generate along the way.\ \ If you're reading this on Nostr you may already suspect a way out of this value trap.\ \ If not I would invite you to consider storing the immediate short term returns you pull forwards in something that would be inflation resistant, hard to seize and ideally portable.\ \ We refer to this as a 'The big orange arbitrage".
Implications for Business Owners and Capital Allocators
For business owners, especially those running small to medium-sized enterprises, the message is clear: understand how AI could transform your industry and begin planning your transition now.\ \ This might involve creating an "AI-native twin" of your current business—similar to how Netflix developed streaming alongside its DVD business—to eventually replace your current operations. If you want help please ask, I heavily favor more small businesses in the world and would love to help make this a reality.
For capital allocation, the emerging opportunity we see if in "transformation led private equity". The acquisition of traditional service businesses and applying AI to dramatically reduce operational costs and increase enterprise value.\ \ This approach treats AI not as a product but as a transformation strategy for existing businesses with proven product-market fit.
Transformation led PE is venture style returns without the risk of product market fit.
So the lesson?
The business model of AI isn't all about selling AI technology, adding a RAG chatbot to a new DB or collecting everyone's data.\ \ Consider the humble cash flow business, use AI to transform the operational processes and save into everyone's favorite orange coin.
-
-
 @ ee6ea13a:959b6e74
2025-05-13 21:29:02
@ ee6ea13a:959b6e74
2025-05-13 21:29:02Reposted without permission from Business Insider.
Bitcoin Is A Joke
Joe Weisenthal Nov 6, 2013, 10:42 PM UTC

REUTERS/Eliana Aponte
Bitcoin is back in the news, as the digital currency has surged to new all-time highs in recent weeks.
A few weeks ago, it was just above $100. Today it's over $260.
This surge has prompted Timothy B Lee at The Washington Post to ask whether those who have called it a bubble in the past should retract and admit that they were wrong.
Well I'm not totally sure if I've called it a bubble, but I have spoken negatively of it, and I'll say that I still think it's a joke, and probably in a bubble.
Now first of all, I find the premise of Lee's post to be hilarious. The currency has been surging several percent every day lately, and that's evidence that it's not in a bubble?
Before going on, I want to be clear that saying something is a bubble is not saying it will go down. It could go to $500 or $1000 or $10,000. That's the nature of manias.
But make no mistake, Bitcoin is not the currency of the future. It has no intrinsic value.
Now this idea of "intrinsic value" when it comes to currency bothers people, and Bitcoin Bugs will immediately ask why the U.S. dollar has intrinsic value. There's an answer to that. The U.S. Dollar has intrinsic value because the U.S. government which sets the laws of doing business in the United States says it has intrinsic value. If you want to conduct commerce in the United States you have to pay taxes, and there's only one currency you're allowed to pay taxes in: U.S. dollars. There's no getting around this fact. Furthermore, if you want to use the banking system at all, there's no choice but to use U.S. dollars, because that's the currency of the Fed which is behind the whole thing.
On top of all these laws requiring the U.S. dollar to be used, the United States has a gigantic military that can force people around the world to use dollars (if it came to that) so yes, there's a lot of real-world value behind greenbacks.
Bitcoin? Nada. There's nothing keeping it being a thing. If people lose faith in it, it's over. Bitcoin is fiat currency in the most literal sense of the word.
But it gets worse. Bitcoin is mostly just a speculative vehicle. Yes, there are PR stunts about bars and other shops accepting bitcoins. And there is a Bitcoin ATM for some reason. But mostly Bitcoin is a speculative vehicle. And really, you'd be insane to actually conduct a sizable amount of commerce in bitcoins. That's because the price swings so wildly, that the next day, there's a good chance that one of the parties will have gotten royally screwed. Either the purchaser of the good will have ended up totally blowing a huge opportunity (by not holding longer) or the seller will be totally screwed (if Bitcoin instantly plunges). The very volatility that excited people to want to play the Bitcoin game is death when it comes to real transactions in the real world.
Again, Bitcoin might go up a lot more before it ultimately ends. That's the nature of bubbles. The dotcom bubble crashed a bunch of times on its way up. Then one day it ended. The same will happen with this.
In the meantime, have fun speculating!
-
 @ c1e9ab3a:9cb56b43
2025-04-25 00:37:34
@ c1e9ab3a:9cb56b43
2025-04-25 00:37:34If you ever read about a hypothetical "evil AI"—one that manipulates, dominates, and surveils humanity—you might find yourself wondering: how is that any different from what some governments already do?
Let’s explore the eerie parallels between the actions of a fictional malevolent AI and the behaviors of powerful modern states—specifically the U.S. federal government.
Surveillance and Control
Evil AI: Uses total surveillance to monitor all activity, predict rebellion, and enforce compliance.
Modern Government: Post-9/11 intelligence agencies like the NSA have implemented mass data collection programs, monitoring phone calls, emails, and online activity—often without meaningful oversight.
Parallel: Both claim to act in the name of “security,” but the tools are ripe for abuse.
Manipulation of Information
Evil AI: Floods the information space with propaganda, misinformation, and filters truth based on its goals.
Modern Government: Funds media outlets, promotes specific narratives through intelligence leaks, and collaborates with social media companies to suppress or flag dissenting viewpoints.
Parallel: Control the narrative, shape public perception, and discredit opposition.
Economic Domination
Evil AI: Restructures the economy for efficiency, displacing workers and concentrating resources.
Modern Government: Facilitates wealth transfer through lobbying, regulatory capture, and inflationary monetary policy that disproportionately hurts the middle and lower classes.
Parallel: The system enriches those who control it, leaving the rest with less power to resist.
Perpetual Warfare
Evil AI: Instigates conflict to weaken opposition or as a form of distraction and control.
Modern Government: Maintains a state of nearly constant military engagement since WWII, often for interests that benefit a small elite rather than national defense.
Parallel: War becomes policy, not a last resort.
Predictive Policing and Censorship
Evil AI: Uses predictive algorithms to preemptively suppress dissent and eliminate threats.
Modern Government: Experiments with pre-crime-like measures, flags “misinformation,” and uses AI tools to monitor online behavior.
Parallel: Prevent rebellion not by fixing problems, but by suppressing their expression.
Conclusion: Systemic Inhumanity
Whether it’s AI or a bureaucratic state, the more a system becomes detached from individual accountability and human empathy, the more it starts to act in ways we would call “evil” if a machine did them.
An AI doesn’t need to enslave humanity with lasers and killer robots. Sometimes all it takes is code, coercion, and unchecked power—something we may already be facing.
-
 @ eed7ca5d:191de8eb
2025-05-23 13:58:46
@ eed7ca5d:191de8eb
2025-05-23 13:58:46Growing up, we were told that in order to build wealth, we need to save little by little. By living below your means, you are providing more for your future.
It is a simple formula that will help you build up the capital necessary to buy a car, a house or start a business… You prioritize long-term benefits and delayed gratification over immediate rewards.
This is called having a low-time preference. In contrast, high-time preference individuals prioritize today over tomorrow, seeking immediate gratification.
Austrian economists explain that civilization growth is driven by low-time preference societies. Groups of individuals who prioritize long-term planning are able to innovate and develop new tools for a better future. Over time, this behavior leads to technological inventions like the light bulb and artistic masterpieces like the Notre Dame cathedral.
***What happens when you realize that the money you save is losing value over time? ***
There is less incentive to save for the future, because in the future your savings will be worth less. You might as well spend it now and enjoy life today.
When the money you save loses its value, you are facing one of two choices:
-
Spend it today and reap the rewards of your hard work;
-
Invest it (stocks, real estate, etc.) with the hope to reap higher rewards later, bearing the risk of losing it all if the investment does not pay off.
There is a distinct difference between saving and investing as the latter approach is riskier than the former. By investing, you are betting on the upside while bearing the downside risk. Saving, in contrast, comes without downside risk. That difference becomes blurry when the money you save is losing value. In fact, saving becomes inherently a losing approach. Logically, you will be forced to place a speculative bet with the hope to outperform the guaranteed loss of value. You are required to find a way to hedge your bet…
Humans over time have always sought out a medium to save their economic energy for a better future. That used to be beads and seashells, and evolved to precious metals like gold and silver.
Money is a tool that we use to save our economic energy over time, and exchange value with each other.
I spend time fishing, you spend time farming, the neighbor spends time building homes, and society rewards us with money for the time and energy we spent being productive
Today, the tool that we use to save our economic energy is clearly losing value over time. The nominal value remains the same, but the purchasing power is decreasing. In other words, the value of our time today will be worth less in the future.
That explains why everyone around us is looking for the next best investment opportunity. We are all needing to become investment experts, speculators, on top of our respective professions. Speculation became necessary, and some of us are forced into a high-time preference lifestyle.
Earn now and spend it all now before you lose it.
This should not be the case…
Time is Money
Our time is the only scarce resource we all have. We use it to be productive and generate economic value, then store that value in the form of money in order to reap the rewards in the future.
Money is the abstract representation of our time. Hence, time is money.
In January 2009, at the height of the global financial crisis, a software protocol called Bitcoin was released pseudonymously by Satoshi Nakamoto. This individual (or group) released a whitepaper a few months prior named “Bitcoin: A Peer-to-Peer Electronic Cash System” outlining how the system enables secure, peer-to-peer transactions without relying on a central authority. (https://bitcoin.org/bitcoin.pdf)
Although there are more technical concepts involved, the bitcoin protocol can be thought of as a language for communicating value. The same way we respect the rules of the English language to communicate ideas with one another, bitcoin users adhere to the network’s consensus rules to communicate value with each other in a peer-to-peer fashion.
There are no physical or digital coins in the bitcoin network. Rather, it is a collection of transactions transferring value from sender to recipient. Transactions are validated and propagated by nodes across the network, before being recorded into the blockchain. The Bitcoin blockchain is a global public ledger of all transactions that cannot be altered.
More importantly, Bitcoin is money that does not lose value overtime.
-
Its supply is capped at 21 million coins.
-
Its scarcity increases over time due to the predictable issuance rate, which halves roughly every 4 years.
-
Its decentralized nature puts the power in the hands of its users.
-
There is no governing body that can devalue or alter it.
It is a tool that we can use to save our economic energy over time, and be able to use it later.
It is the scarcest verifiable commodity: we cannot make more of it no matter how high its demand grows. That cannot be said for any other commodity in the world today.
A savings tool in disguise
See, most people tend to view bitcoin as another speculative investment. They presume they have missed out on another investment opportunity, and it’s now too late to get in.
Meanwhile, it is quite the opposite. Bitcoin’s value will keep growing over time due to its deflationary nature.
With bitcoin, we can save for a better future, for a rainy day, and spend more time with our loved ones or focusing on our craft to build better tools or artistic masterpieces. It takes away the burden of having to speculate on which stock will perform best, or which real estate market will grow the fastest, all while working one or multiple jobs
Bitcoin is not another investment opportunity you missed out on. It is the best savings tool humans have invented (or discovered), while everything else is the speculative bet. Bitcoin is the hedge against the guaranteed devaluation of money, without any counterparty risk.
What we were taught as children is true. With the right tool, the idea that saving will help you build wealth overtime stands true. Bitcoin might seem like an investment today given the volatility during its adoption phase. In reality, it is the perfect way to store your time and economic energy and grow your wealth. Whether you make $1/hour or $1M/hour, you can start saving in the best money humans have invented.
My goal is to help people around me understand this technology and break the stigma around it.
Bitcoin is not the next best investment.
It is the best tool we have found to store our economic energy across time and exchange value with each other.
Bitcoin is Money.
-
-
 @ 0971cd37:53c969f4
2025-05-20 17:00:53
@ 0971cd37:53c969f4
2025-05-20 17:00:53ลดต้นทุนค่าไฟ เพิ่มความคุ้มค่าให้การขุด Bitcoin ที่บ้าน ในยุคที่ต้นทุนพลังงานสูงขึ้นอย่างต่อเนื่อง นักขุด Bitcoin ที่บ้าน หรือ Home Miner ต้องคิดให้รอบคอบก่อนเลือกเครื่องขุด เพราะ “แรงขุดสูงสุด” ไม่ได้แปลว่า “กำไรดีที่สุด” อีกต่อไป การเลือกเครื่องขุดไม่ใช่แค่ดูแค่แรงขุด (Hashrate) สูงสุดเท่านั้น แต่ต้องพิจารณาเรื่อง "การกินไฟ" และ "ความคุ้มค่าในการใช้งานระยะยาว" ด้วย ซึ่งสายหนึ่งที่ได้รับความนิยมมากขึ้นเรื่อย ๆ ก็คือ สาย Tuning Power หรือการจูนเครื่องขุดเพื่อให้ได้อัตราส่วน Hashrate/Watt ที่ดีที่สุด
เทรนด์ใหม่ของวงการขุดคือสาย Tuning Power หรือการปรับแต่งพลังงานของเครื่องขุด Bitcoin (ASIC) ให้ได้ ประสิทธิภาพ Hashrate ต่อการใช้พลังงาน (Efficiency) สูงที่สุด ซึ่งเหมาะอย่างยิ่งสำหรับการขุดในบ้านที่มีข้อจำกัดด้านค่าไฟ ความร้อน และ เสียงรบกวน
Tuning Power คืออะไร? Tuning Power คือการปรับลดแรงขุดของเครื่อง ASIC ลงเล็กน้อย เพื่อให้กินไฟน้อยลงแบบชัดเจน
ตัวอย่างเช่น Custom Firmware Braiins OS ใช้กับ Antminer S19jpro จากเดิมแรงขุด 104 TH/s กินไฟ 3,500W เมื่อปรับแต่งในส่วน Power Target จูนเหลือ 75 TH/s อาจกินไฟแค่ 1,600W-1,800W หลังจาก Tuning ค่าประสิทธิภาพ(Efficiency)ดีขึ้น เช่น จาก 32 J/TH เหลือเพียง 22–20 J/TH
 หมายเหตุ: ค่า Efficiency ยิ่งต่ำ ยิ่งดี แปลว่าใช้พลังงานน้อยต่อ 1 TH
หมายเหตุ: ค่า Efficiency ยิ่งต่ำ ยิ่งดี แปลว่าใช้พลังงานน้อยต่อ 1 THทำไมต้อง Tuning Power? การจูนพลังงาน (Tuning Power) คือการปรับแต่งเครื่องขุด เช่น ASIC ให้ทำงานที่แรงขุดไม่เต็ม 100% แต่กินไฟน้อยลงอย่างชัดเจน ส่งผลให้:
- ประหยัดค่าไฟ โดยเฉพาะถ้าขุดในพื้นที่ต้นทุนพลังงานค่าไฟสูงหรือไม่มี TOU (Time of Use) และ เหมาะสำหรับผู้ใช้ไฟแบบ TOU ที่ค่าไฟกลางวัน ON-Peak แพง ต้องการขุดเลือกช่วงกลางคืนและวันหยุดเสาร์-อาทิตย์ และ วันหยุดราชการตามปกติ Off-Peak , ที่ใช้ระบบ Solar หรือมีระบบ Battery ต้องการประหยัดไฟ
- ลดความร้อนของเครื่อง ทำให้ยืดอายุการใช้งานและลดค่าใช้จ่ายด้าน ซำบำรุง ระบบระบายความร้อน
- เพิ่มความคุ้มค่า ในช่วงตลาดหมี ที่กำไรจากการขุดต่ำ การลดต้นทุนไฟฟ้าคือทางรอดหลัก
เครื่องขุด Bitcoin (ASIC) รุ่นไหน ที่เหมาะกับสาย Tuning Power
-
Antminer รองรับ Custom Firmware เช่น Braiins OS ที่เป็นยอดนิยมในการ Tuning Power
-
WhatsMiner M30-M60s Series ขึ้นไป ใช้โปรแกรม WhatsMinerTool เพื่อทำการ Tuning Power ได้โดยตรงไม่จำเป็นต้อง Custom Firmware
สรุป การเป็น Home Miner ที่ยั่งยืนไม่ได้ขึ้นกับว่าเครื่องขุดแรงแค่ไหน แต่ขึ้นกับว่า “จ่ายค่าไฟแล้วเหลือกำไรหรือไม่ หรือ จ่ายค่าไฟแล้วคุ้มค้ารายได้ Bitcoin จากการขุดจำนวนที่ได้รับมากขึ้นหรือไม่” การเลือกเครื่องขุดสำหรับสาย Tuning Power จึงเป็นทางเลือกที่ตอบโจทย์ผู้ที่ต้องการประสิทธิภาพสูงในต้นทุนที่ควบคุมได้โดยเฉพาะในยุคที่ตลาดผันผวน และ ค่าไฟฟ้าคือศัตรูตัวจริงของนักขุด
-
 @ a296b972:e5a7a2e8
2025-05-20 12:22:00
@ a296b972:e5a7a2e8
2025-05-20 12:22:00Die Natur strebt nach einem Gleichgewicht durch Ausgleich von nicht zueinander passenden Verhältnissen. Die Gesellschaft ist ein sozialer Organismus, der ebenso nach Ausgleich und einer Stimmigkeit der Verhältnisse strebt. Das sind Naturgesetze, die keine Regierung auf Dauer imstande ist, außer Kraft zu setzen.
Weder oppositionelle Kräfte, noch Kräfte innerhalb des Souveräns haben die Absicht, die Demokratie abzuschaffen. Es geht vielmehr darum, sie wieder in der Form herzustellen, in der sie ihren Namen auch verdient. Dazu gehört, dass alle Macht vom Volke ausgeht, was derzeit nicht der Fall ist.
Ein durch den Staat vorgegebenes Bildungssystem hat Menschen vor allem zu gefügigen Rädchen im Wirtschaftsgetriebe und nicht zu alles kritisch hinterfragenden Bürgern erzogen, die ständig der Regierung auf die Finger schauen.
Wenn die Bürger, der Souverän, eine Regierung immer mehr „machen lässt“ und glaubt, es sei genug, alle 4 Jahre sein Wahl-Kreuzchen zu machen, entfernt er sich immer mehr von der Kontrolle der durch ihn beauftragten Vertreter, und diese entfernen sich so immer mehr vom Alltag der Bürger.
Zu wenig Gegenrede des Souveräns führt zu immer mehr Übermut der Regierung, die sich immer sicherer wird, mit jedem Unsinn durchzukommen.
Ist dann die Schmerzgrenze des Souveräns erreicht, beginnt er, die Opposition zu stärken. In einer funktionierenden Demokratie würde das dazu führen, dass die Opposition die Regierung bildet, die dann die Chance hat, Fehlentwicklungen abzustellen und ausgleichend tätig zu werden.
Derzeit findet sowohl beim Souverän, als auch bei den Parteien, die bisher Regierungen zusammengestellt haben, ein Erwachen statt.
Da die ehemaligen Volks-Parteien unbedingt an der Macht festhalten wollen, seitens des Souveräns auf zu wenig Widerstand stoßen, wird mit der Macht, einer Demokratie nicht würdig, umgegangen. Dem sollte dringend Einhalt geboten werden.
Der Missbrauch äußert sich in brutalen (Lieblingswort der Ex-Außen-Dings) Einschränkungen der Grundrechte (Corona-Zeit), in der Einschränkung der Meinungsfreiheit (D S A), in Tendenzen zunehmender Kontrolle und Überwachung, Förderung von Denunzianten-Portalen, Kapern des öffentlich-rechtlichen Rundfunks, Förderung von NGOs, die als Sprechpuppen genutzt werden. Besetzt von Menschen, die entweder tatsächlich überzeugt sind von dem, was sie ideologisch vertreten, oder die über Charaktereigenschaften verfügen, die noch sehr viel Optimierungspotenzial in sich bergen. Gepaart mit fachlicher Inkompetenz ist das ein gefährlicher Cocktail.
Erst jüngst sogar durch Ausreiseverbote, wie in einem Staat, mit dem man das derzeitige Deutschland nicht vergleichen darf. So groß ist inzwischen schon die Angst geworden, die Kontrolle über die Macht zu verlieren. Alles, was an Kritik geäußert werden will, gilt als Delegitimierung des Staates. Auf keinen Fall darf sie im Ausland geäußert werden, damit es ja nichts davon mitbekommt, was in Deutschland abgeht. Das ist so wie ein Kind, dass sich die Hände vor die Augen hält und meint, es würde nicht gesehen werden.
Die Regierung ist übergriffig geworden. Je lauter sie Demokratie schreit, desto totalitärer wird sie.
Durch fehlende Kontrolle des Souveräns sind charakterlich und fachlich ungeeignete Personen in die Politik gelangt, deren ständige Überforderung dazu führt, dass sich deren Entscheidungen immer weiter von der Lebensrealität des Souveräns entfernen.
Bislang haben rund 25% des Souveräns diese Schieflage erkannt und wollen einer Opposition, die so stark geworden ist, weil die Alt-Parteien über Jahre Fehler an Fehler aneinandergereiht haben, die Gelegenheit geben, diese Fehler zu beheben und auszugleichen. Offen bleibt die Frage, ob sie dazu wirklich in der Lage sind, oder ob die Gefahr besteht, dass sie von einem möglicherweise grundsätzlich kranken System vereinnahmt werden.
Da es seitens der Alt-Parteien keine Einsicht gibt, dass sie in der Regierung nicht mehr den Willen des Souveräns vertreten, derzeit auch besonders gut zu sehen an dem Friedenswillen des Souveräns im Vergleich zur Kriegstreiberei der Regierung, bleibt nur, der Opposition zumindest die Chance zu geben, es besser zu machen und den Willen des Souveräns umzusetzen. Gelänge das nicht, ist die Demokratie, wie wir sie bislang verstanden haben, gescheitert.
Eine daraus resultierende Staatsform stünde dem Freiheitsgedanken diametral gegenüber.
Die Verteidigung von Unseredemokratie seitens der Regierung entlarvt das eigentliche, was damit gemeint ist, nämlich die Erhaltung der eigenen Macht, verbunden mit allen Vorzügen und Privilegien. Sie richtet sich gegen das eigene Volk, das mit einer ganz normal funktionierenden Demokratie schon sehr zufrieden wäre. Unseredemokratie ist nicht unsere Demokratie!
In Anlehnung an die berühmt gewordene Lüge Walter Ulbrichs: „Niemand hat die Absicht eine Mauer zu errichten“, hat derzeit niemand die Absicht, die sogenannte Brandmauer einzureißen, bzw. sie so lange stehen zu lassen, wie es eben geht, um die herrschenden Machtverhältnisse so lange wie möglich aufrechtzuerhalten. Die Geschichte hat jedoch zum Glück gezeigt, dass selbst eine Berliner Mauer nicht ewig hält.
Wie sich aus dem absurd-lächerlichen Gutachten, einer der Regierung gegenüber weisungsgebundenen Behörde herausgestellt hat, gibt es keinerlei Anzeichen dafür, dass die Opposition die demokratische Grundordnung weder gefährden noch beseitigen will.
Da die ehemaligen Volksparteien augenscheinlich nicht in der Lage sind, politische, wirtschaftliche und gesellschaftliche Verhältnisse zum Wohle des Deutschen Volkes herzustellen, ist der demokratische Weg, die Opposition hierzu zu ermächtigen.
Wird das weiterhin verhindert, wird der Unmut des Souveräns weiter zunehmen, und spätestens, wenn die zunehmenden Schikanen die Schmerzgrenze überschritten haben, wird der Souverän nach geeigneten Mitteln und Möglichkeiten suchen, diese Schieflage zu beheben und auszugleichen.
Derzeit stehen sich ein in der Zahl und im Befinden zunehmend unzufrieden werdender Souverän und eine immer absurdere Entscheidungen treffende Regierung im lebendigen Tauziehen um Interessen gegenüber. Je mehr Bockmist die Alt-Parteien bauen, um so stärker wird die Opposition.
Aufgrund der jetzt schon vorhandenen Anzahl wacher Bürger und der Anzahl der in der Politik Unfähigen, ist eigentlich schon jetzt klar, wer in diesem Tauziehen die größere Kraft hat und wer das „Spiel“ nach demokratischen Regeln am Ende gewinnen wird. Das ist eindeutig der Souverän. Verliert er, wider Erwarten, verliert auch die Demokratie.
Dem Souverän fehlt nur noch ein wenig mehr Selbstvertrauen und ein Bewusstsein für die Macht, über die er tatsächlich verfügt.
Je mehr absurde Entscheidungen seitens der Regierung getroffen werden, und man arbeitet ja sehr fleißig daran, besonders, wenn es um Frieden geht, desto stärker wird das Selbstbewusstsein des Souveräns werden und ein natürlicher, friedlicher Ausgleich der Schieflage kann stattfinden. Der Start der neuen Regierung war jedenfalls schon einmal sehr "Keine-4-Jahre".
Wer sich in die steile und eisglatte Abfahrtspiste Deutschlands vertiefen will, hier eine Rezension zu dem Buch „Im Taumel des Niedergangs“ von dem von mir sehr geschätzten und akribisch arbeitenden Uwe Froschauer:
https://www.manova.news/artikel/abwarts
oder
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)