-
 @ c6dc6b64:69dbbc15
2025-04-24 11:23:26
@ c6dc6b64:69dbbc15
2025-04-24 11:23:26„Sag mir, welches Geld du benutzt – und ich sage dir, an welche Welt du glaubst.“
– anonym, zirkulierend im digitalen Untergrund
Geld ist nie neutral. Es trägt in sich eine Vorstellung davon, was in einer Gesellschaft wertvoll ist – und wer entscheidet, was dieser Wert bedeutet. In den Währungen unserer Zeit steckt nicht nur Kaufkraft, sondern auch Gewalt. Unsichtbar, aber wirksam. Jede Inflation ist eine Umverteilung ohne Abstimmung. Jede Rettung durch Gelddrucken ein Eingriff in das Eigentum derer, die sparen. Jede staatliche Kontrolle von Geldfluss ist auch Kontrolle über Leben.
Es ist leicht, Geld als bloßes Werkzeug zu sehen. Aber jedes Werkzeug formt auch seinen Nutzer. Wer Geld benutzt, das auf Schulden basiert, übernimmt unbewusst die Logik dieses Systems: Wachstum um jeden Preis, Gegenwart vor Zukunft, Kontrolle statt Vertrauen. Es ist kein Zufall, dass moralische Belohnung in dieser Welt selten mit finanzieller vergütet wird – weil das Geld selbst die Moral nicht kennt.
Die Moral der Währung
Die Frage ist nicht, ob Geld gut oder böse ist. Die Frage ist, ob es Verantwortung kennt. Ob es dem dient, der es hält, oder dem, der es kontrolliert. Ob es verlässlich ist – nicht nur in seiner Funktion, sondern auch in seiner Wirkung. Ein Geld, das jederzeit vermehrt werden kann, erlaubt jederzeit die Verschiebung von Lasten. Weg von den Verantwortlichen, hin zu den Stillen. Es belohnt Nähe zur Quelle, nicht Leistung. Es nährt den Zynismus.
Ein Geld, das Wahrheit erzwingt
Ein anderes Geld beginnt nicht bei der Technik, sondern bei der Ethik. Es fragt nicht: Was ist möglich? Sondern: Was ist richtig? Es basiert auf Knappheit – nicht um zu begrenzen, sondern um Ehrlichkeit zu erzwingen. Es kennt kein „Too Big to Fail“, kein Vertrauen auf Dekret, keine moralische Grauzone. Wer es nutzt, steht in direkter Beziehung zu seinem Handeln. Und kann sich nicht herausreden.
Verantwortung ohne Zwang
Vielleicht ist die wichtigste Wirkung dieses Geldes nicht wirtschaftlich, sondern moralisch: Es gibt dem Einzelnen die Möglichkeit, sauber zu wirtschaften, ohne Teil eines schmutzigen Spiels zu sein. Es ist kein Geld für jeden – sondern für jene, die bereit sind, wieder Verantwortung zu tragen. Nicht, weil sie müssen. Sondern weil sie wollen.
-
 @ c6dc6b64:69dbbc15
2025-04-24 11:16:02
@ c6dc6b64:69dbbc15
2025-04-24 11:16:02- Im Nichts gibt es keine Befreiung, nur die Ernüchterung der Illusion. Die Welt ist ein Flimmern, das dem Auge entgleitet, während wir in einem endlosen Raum der Bedeutungslosigkeit verharren.
- Es gibt Momente, in denen das Nichts nicht nur eine Abwesenheit ist, sondern ein erdrückendes Gewicht, das uns in den Staub drückt. Wir fliehen in Gedanken, doch diese Gedanken sind der allerletzte Zufluchtsort, der uns nichts als die Huldigung der Leere bietet.
- Das Nichts ist der heimliche Gott, der im Zerfall des Seins thront, ein stiller Erlöser, der das Leben in seinen Schoß zurückruft, um es sanft zu ersticken.
- Die Trauer ist der Wundschrei des Seins über seinen eigenen Bruch, ein letztes Festhalten an der Hülle des Vergangenen, bevor sie im Strom der Vernichtung zerfließt.
- Der Sinn entgleitet, je fester wir ihn fassen wollen – wie Nebel, der sich vor der Berührung auflöst.
- Wir leben in der Hoffnung, dass das Nichts uns nicht sieht – doch es hat längst in uns Wohnung genommen.
- Jeder Gedanke an Erlösung gebiert eine neue Kette – die Freiheit beginnt erst dort, wo das Verlangen endet.
- Das Schweigen des Universums ist keine Antwort – es ist die endgültige Form der Gleichgültigkeit.
- Unsere Angst vor dem Nichts ist nur der Schrei des Ichs, das weiß, dass es niemals war.
- Wir existieren wie Fußspuren im Staub eines verlassenen Raums – sichtbar nur für einen Moment, bedeutungslos im Wind der Zeit.
-
 @ c6dc6b64:69dbbc15
2025-04-24 11:03:49
@ c6dc6b64:69dbbc15
2025-04-24 11:03:49„Der Mensch ist frei geboren, und überall liegt er in Ketten.“
– Jean-Jacques Rousseau
In einer Welt, die sich zunehmend durch technologische Umbrüche definiert, zeigt sich eine bemerkenswerte kognitive Dissonanz im Umgang mit neuen Paradigmen: Die Abwehr gegenüber Bitcoin ist selten eine Frage der Rationalität, sondern oft eine Reaktion auf die Überforderung durch das Ungewohnte. Der Mensch scheut die Auseinandersetzung mit dem, was ihm fremd erscheint – nicht, weil es notwendigerweise komplex ist, sondern weil es nicht in das gewohnte Raster institutionalisierter Erklärung passt.
So wirkt Bitcoin auf viele wie ein hermetisches System, dessen Mechanismen sich dem Alltagsverständnis entziehen. Dabei ist es, philosophisch betrachtet, der Fiat-Welt unter einem entscheidenden Aspekt überlegen: ihrer radikalen Transparenz.
Die Unsichtbarkeit des Gewohnten
Die Strukturen, welche das fiatbasierte Geldsystem tragen, sind in ihrer institutionellen Dichte kaum zu durchdringen. Zentralbanken, Aufsichtsbehörden, gesetzgeberische Rahmenwerke, geldpolitische Instrumente, Interbankenmärkte, internationale Regulierungsorgane – sie bilden einen verwaltungstechnischen Überbau, der in seiner Vielschichtigkeit eher einer mittelalterlichen Theologie als einem frei zugänglichen, rationalen System gleicht.
Das Vertrauen in diese Ordnung ist kein Produkt verstandesmäßiger Durchdringung, sondern das Ergebnis jahrzehntelanger Gewöhnung und autoritärer Setzung. Man glaubt an das Fiat-Geld, weil es da ist – nicht, weil man es versteht.
Bitcoin verlangt Verantwortung
Bitcoin hingegen konfrontiert den Einzelnen mit der Notwendigkeit der Selbstverantwortung und fordert eine direkte Auseinandersetzung mit seiner Funktionsweise: kryptografische Prinzipien, Dezentralität, Konsensmechanismen, digitale Knappheit. Dies wirkt zunächst sperrig, ja fast elitär. Doch diese Komplexität ist nicht strukturell intransparent, sondern technisch erklärbar, überprüfbar und – für jeden offen.
Während das Fiat-System in verschlossenen Räumen entscheidet, operiert Bitcoin auf einem offenen Protokoll. Die Ablehnung des Neuen beruht daher weniger auf seiner inhärenten Schwierigkeit, als vielmehr auf einer anthropologischen Trägheit: Die Bequemlichkeit, sich von äußeren Instanzen verwalten zu lassen, wiegt schwerer als der Wunsch nach Souveränität.
Was ist wahre Komplexität?
Doch was ist wahrhaft komplex? Ist es nicht die blinde Akzeptanz eines Systems, dessen Grundlagen man nie selbst prüfen kann? Ist es nicht der Glaube an eine Geldordnung, deren Stabilität von politischen Machtzentren abhängt?
Der Bitcoin hingegen stellt die radikale Frage: Was, wenn Vertrauen nicht mehr delegiert, sondern durch Code ersetzt werden kann? Was, wenn Verständlichkeit nicht aus Tradition, sondern aus Prinzipien entsteht?
Ein philosophisches Statement
In dieser Perspektive ist Bitcoin keine bloße technische Innovation, sondern ein philosophisches Statement: ein Plädoyer für epistemische Mündigkeit. Die vermeintliche Einfachheit des Alten ist in Wahrheit nur ein Schleier – und die gefühlte Schwierigkeit des Neuen der erste Schritt in die Freiheit.
-
 @ f5836228:1af99dad
2025-04-24 10:52:34
@ f5836228:1af99dad
2025-04-24 10:52:34A busca por plataformas confiáveis e inovadoras no cenário de jogos online tem crescido significativamente, e a 8855BET se destaca como uma das opções mais completas e seguras do mercado. Voltada ao público brasileiro, a plataforma oferece uma combinação perfeita de tecnologia, diversidade de jogos e suporte qualificado, proporcionando uma experiência imersiva e prazerosa do início ao fim.
Logo ao acessar a 8855BET, é possível perceber o cuidado com cada detalhe. O visual moderno e o layout responsivo foram projetados para facilitar a navegação, seja pelo computador ou dispositivos móveis. Isso garante que o jogador aproveite todos os recursos disponíveis sem dificuldades técnicas, mesmo em conexões mais simples.
O catálogo de jogos é um dos maiores atrativos da plataforma. Com uma variedade impressionante, a 8855bet oferece títulos para todos os gostos. Os apaixonados por jogos de roleta, pôquer e blackjack encontrarão versões atualizadas e dinâmicas. Para quem prefere jogos mais visuais e interativos, os slots são um verdadeiro espetáculo à parte, com gráficos detalhados e efeitos sonoros envolventes.
Além dos jogos tradicionais, a plataforma investe em opções modernas com transmissões em tempo real e interações ao vivo, aproximando o jogador da ação e aumentando a sensação de realismo. Essa inovação torna cada partida única, tornando a experiência ainda mais cativante.
Outro ponto positivo é o sistema de bonificações. Novos usuários são recebidos com incentivos atrativos, e jogadores frequentes contam com promoções constantes e programas de fidelidade que premiam a regularidade. Tudo isso com regras claras e total transparência.
A segurança digital é uma prioridade na 8855BET. Os dados dos usuários são protegidos por criptografia avançada, e todas as transações são monitoradas para garantir a integridade das operações. O suporte a métodos populares de pagamento no Brasil, como PIX e carteiras digitais, torna os processos de depósito e saque rápidos e descomplicados.
O atendimento ao cliente é outro diferencial. Com suporte em português e disponível 24 horas por dia, a equipe está sempre pronta para ajudar com dúvidas, orientações técnicas ou informações sobre promoções. Isso transmite confiança e tranquilidade ao jogador, que sabe que pode contar com o suporte sempre que precisar.
Em resumo, a 8855BET é uma escolha certeira para quem busca entretenimento online de alto nível, com uma plataforma estável, jogos variados e atendimento de qualidade. Ideal para jogadores que valorizam segurança, conforto e diversão.
-
 @ f5836228:1af99dad
2025-04-24 10:51:59
@ f5836228:1af99dad
2025-04-24 10:51:59A busca por diversão online de qualidade cresce a cada dia entre os brasileiros. Nesse cenário, a 333BET se posiciona como uma das plataformas mais completas e confiáveis do mercado. Com um portfólio robusto de jogos, interface amigável e suporte de excelência, a 333BET oferece tudo o que os jogadores precisam para aproveitar momentos de pura emoção.
O primeiro contato com a 333BET já revela um ambiente moderno e acolhedor. A plataforma é responsiva, com navegação simples e fluida tanto em computadores quanto em dispositivos móveis. A usabilidade foi claramente pensada para todos os tipos de público, dos novatos aos mais experientes.
A grande estrela da plataforma, claro, são os jogos. A variedade é impressionante. Os famosos slots trazem temáticas para todos os gostos: aventura, cultura pop, mitologia, esportes, entre outros. Cada jogo é desenvolvido com gráficos avançados, animações vibrantes e recursos especiais que aumentam o envolvimento do jogador a cada rodada.
Além dos slots, a 333bet disponibiliza clássicos digitais como roleta, jogos de cartas e outras modalidades que combinam estratégia e sorte. É possível escolher mesas com diferentes níveis de dificuldade e personalizar a forma de jogar, tornando cada experiência única.
Outro destaque é o programa de bonificação. A 333BET oferece promoções constantes que beneficiam tanto novos usuários quanto jogadores assíduos. Bônus de boas-vindas, rodadas grátis e recompensas por fidelidade fazem parte do dia a dia da plataforma, incentivando o engajamento e oferecendo mais oportunidades de diversão.
Para completar a experiência, o suporte ao cliente é um diferencial. O atendimento funciona 24 horas por dia, em português, e está sempre pronto para resolver qualquer questão. Os métodos de pagamento são variados e incluem opções como Pix, transferência bancária e carteiras digitais, garantindo agilidade nas transações.
Combinando inovação, segurança e uma experiência do usuário impecável, a 333BET se consolida como uma plataforma indispensável para quem busca entretenimento online de alto nível.
-
 @ f5836228:1af99dad
2025-04-24 10:50:58
@ f5836228:1af99dad
2025-04-24 10:50:58Se você já teve experiências frustrantes em outras plataformas de jogos, vai se surpreender com o que a 888win tem a oferecer. Mais do que um ambiente de entretenimento, a plataforma foi desenhada para colocar o jogador em primeiro lugar. Cada detalhe é pensado para garantir conforto, segurança e uma experiência positiva em todos os sentidos.
A interface da plataforma é limpa e intuitiva. Com poucos cliques, é possível registrar-se, fazer depósitos, escolher jogos ou entrar em contato com o suporte. Tudo funciona de forma integrada, proporcionando fluidez e praticidade.
A segurança é uma das prioridades. Com tecnologia de criptografia de ponta, a 888win protege todas as transações e dados dos usuários. O ambiente é confiável, o que permite que o jogador concentre-se totalmente em se divertir, sem preocupações externas.
Outro aspecto elogiado é o suporte ao cliente. A equipe está sempre disponível via chat ao vivo, e-mail ou outras ferramentas de contato. O atendimento é cordial, rápido e resolutivo, algo fundamental para quem valoriza atenção e eficiência.
Além disso, a 888win sabe recompensar seus usuários. Há programas de fidelidade, promoções regulares e um sistema de pontos que podem ser trocados por benefícios. Isso mantém os jogadores motivados e engajados.
A plataforma também promove campanhas temáticas, torneios e bônus surpresa, tornando cada acesso uma nova possibilidade. Essa constância de novidades garante que a experiência nunca fique repetitiva ou monótona.
Por tudo isso, jogar na 888win é sinônimo de qualidade, confiança e diversão duradoura. Se você quer experimentar algo realmente diferenciado, essa é a sua oportunidade.
-
 @ 7d33ba57:1b82db35
2025-04-24 10:49:41
@ 7d33ba57:1b82db35
2025-04-24 10:49:41Tucked away in the rolling hills of southern France’s Hérault department, Montpeyroux is a charming medieval village known for its peaceful atmosphere, beautiful stone houses, and excellent Languedoc wines. It’s the kind of place where time seems to slow down, making it perfect for a relaxed stop on a southern France road trip.
🏡 Why Visit Montpeyroux?
🪨 Authentic Medieval Character
- Wander narrow cobbled streets lined with honey-colored stone houses
- Visit the remains of a medieval castle and old tower that offer stunning views over vineyards and hills
- A tranquil place that feels untouched by time
🍷 Wine Culture
- Surrounded by prestigious vineyards producing Coteaux du Languedoc wines
- Stop by local caves (wineries) to taste bold reds and crisp whites—many with stunning views over the valley
- Don’t miss the annual wine festivals and open cellars
🌄 Scenic Location
- Located near the Gorges de l’Hérault, perfect for hiking, swimming, or kayaking
- Just a short drive from Saint-Guilhem-le-Désert, one of France’s most beautiful villages
- Great base for exploring the natural beauty of Occitanie
🍽️ Where to Eat
- Enjoy local cuisine at cozy bistros—think grilled lamb, duck confit, olives, and regional cheeses
- Many places serve seasonal dishes paired with local wines
🚗 Getting There
- Around 45 minutes by car from Montpellier
- Best explored by car as public transport is limited, but the countryside drive is worth it
-
 @ 1f79058c:eb86e1cb
2025-04-24 10:43:51
@ 1f79058c:eb86e1cb
2025-04-24 10:43:51I'm currently using this bash script to publish long-form content from local Markdown files to Nostr relays.
It requires all of
yq,jq, andnakto be installed.Usage
Create a signed Nostr event and print it to the console:
markdown_to_nostr.sh article-filename.mdCreate a Nostr event and publish it to one or more relays:
markdown_to_nostr.sh article-filename.md ws://localhost:7777 wss://nostr.kosmos.orgMarkdown format
You can specify your metadata as YAML in a Front Matter header. Here's an example file:
```md
title: "Good Morning" summary: "It's a beautiful day" image: https://example.com/i/beautiful-day.jpg date: 2025-04-24T15:00:00Z tags: gm, poetry published: false
In the blue sky just a few specks of gray
In the evening of a beautiful day
Though last night it rained and more rain on the way
And that more rain is needed 'twould be fair to say.— Francis Duggan ```
The metadata keys are mostly self-explanatory. Note:
- All keys except for
titleare optional date, if present, will be set as thepublished_atdate.- If
publishedis set totrue, it will publish a kind 30023 event, otherwise a kind 30024 (draft) - The
dtag (widely used as URL slug for the article) will be the filename without the.mdextension
- All keys except for
-
 @ 10f7c7f7:f5683da9
2025-04-24 10:07:09
@ 10f7c7f7:f5683da9
2025-04-24 10:07:09The first time I received a paycheque from a full-time job, after being told in the interview I would be earning one amount, the amount I received was around 25% less; you’re not in Kansas anymore, welcome to the real work and TAX. Over the years, I’ve continued to pay my taxes, as a good little citizen, and at certain points along the way, I have paid considerable amounts of tax, because I wouldn’t want to break the law by not paying my taxes. Tax is necessary for a civilised society, they say. I’m told, who will pay, at least in the UK, for the NHS, who will pay for the roads, who will pay for the courts, the military, the police, if I don’t pay my taxes? But let’s be honest, apart from those who pay very little to no tax, who, in a society actually gets good value for money out of the taxes they pay, or hears of a government institution that operates efficiently and effectively? Alternatively, imagine if the government didn’t have control of a large military budget, would they be quite so keen to deploy the young of our country into harm’s way, in the name of national security or having streets in Ukraine named after them for their generous donations of munition paid with someone else’s money?
While I’m only half-way through the excellent “Fiat Standard”, I’m well aware that many of these issues have been driven by the ability of those in charge to not only enforce and increase taxation at will, but also, if ends don’t quite meet, print the difference, however, these are rather abstract and high-level ideas for my small engineer’s brain. What has really brought this into sharp focus for me is the impending sale of my first house, that at the age of 25, I was duly provided a 40-year mortgage and was required to sign a form acknowledging that I would still be paying the mortgage after my retirement age. Fortunately for me, thanks to the government now changing the national age of retirement from 65 to 70 (so stealing 5 years of my retirement), in practice this form didn’t need to be signed, lucky me? Even so, what type of person would knowingly put another person in a situation where near 40% of their wage would mainly be paying interest to the bank (which as a side note was bailed out only a few years later). The unpleasant taste really became unbearable when even after being put into this “working life” sentence of debt repayment, was, even with the amount I’d spent on the house (debt interest and maintenance) over the subsequent 19 years, only able to provide a rate of return of less than 1.6%, compared to the average official (bullshit) inflation figure of 2.77%. My house has not kept up with inflation and to add insult to financial injury, His Majesty’s Revenue and Customs feel the need to take their portion of this “profit”.
At which point, I take a very deep breath, sit quietly for a moment, and channel my inner Margot, deciding against grabbing a bottle of bootleg antiseptic to both clear my pallet and dull the pain. I had been convinced I needed to get on the housing ladder to save, but the government has since printed billions, with the rate of, even the conservative estimates of inflation, out pacing my meagre returns on property, and after all that blood, sweet, tears and dust, covering my poor dog, “the law” states some of that money is theirs. I wasn’t able to save in the money that they could print at will, I worked very hard, I took risks and the reward I get is to give them even more money to fritter away of things that won’t benefit me. But, I don’t want your sympathy, I don’t need it, but it helped me to get a new perspective on capital gains, particularly when considered in relation to bitcoin. So, to again draw from Ms. Paez, who herself was drawing from everyone’s favourite Joker, Heath Ledger, not Rachel Reeves (or J. Powell), here we go.
The Sovereign Individual is by no means an easy read, but is absolutely fascinating, providing clear critiques of the system that at the time was only in its infancy, but predicting many aspects of today’s world, with shocking accuracy. One of the most striking parts for me was the critique and effect of taxation (specifically progressive forms) on the prosperity of a nation at large. At an individual level, people have a proportion of their income removed, to be spent by the government, out of the individuals’ control. The person who has applied their efforts, abilities and skills to earn a living is unable to decide how best to utilise a portion of the resources into the future. While this is an accepted reality, the authors’ outline the cumulative, compound impact of forfeiting such a large portion of your wage each year, leading to figures that are near unimaginable to anyone without a penchant for spreadsheets or an understanding of exponential growth. Now, if we put this into the context of the entrepreneur, identifying opportunities, taking on personal and business risk, whenever a profit is realised, whether through normal sales or when realising value from capital appreciation, they must pay a portion of this in tax. While there are opportunities to reinvest this back into the organisation, there may be no immediate investment opportunities for them to offset their current tax bill. As a result, the entrepreneurs are hampered from taking the fruits of their labour and compounding the results of their productivity, forced to fund the social programmes of a government pursuing aims that are misaligned with individuals running their own business. Resources are removed from the most productive individuals in the society, adding value, employing staff, to those who may have limited knowledge of the economic realities of business; see Oxbridge Scholars, with experience in NGOs or charities, for more details please see Labour’s current front bench. What was that Labour? Ah yes, let’s promote growth by taxing companies more and making it more difficult to get rid of unproductive staff, exactly the policies every small business owner has been asking for (Budget October 2024).
Now, for anyone on NOSTR, none of this is new, a large portion of Nostriches were orange pilled long before taking their first purple pill of decentralise Notes and Other Stuff. However, if we’re aware of this system that has been put in place to steal our earnings and confiscate our winnings if we have been able to outwit the Keynesian trap western governments have chosen to give themselves more power, how can we progress? What options do we have? a) being locked up for non-payment of taxes by just spending bitcoin, to hell with paying taxes or b) spend/sell (:/), but keeping a record of those particular coins you bought multiple years ago, in order to calculate your gain and hand over YOUR money the follow tax year, so effectively increasing the cost of anything purchased in bitcoin. Please note, I’m making a conscious effort not to say what should be done, everyone needs to make decisions based on their knowledge and their understanding.
Anyway, option a) is not as flippant as one might think, but also not something one should (damn it) do carelessly. One bitcoin equals one bitcoin, bitcoin is money, as a result, it neither increases nor decreases is value, it is fiat currencies that varies wildly in comparison. If we think about gold, the purchasing power of gold has remained relatively consistent over hundreds of years, gold is viewed as money, which (as a side note) results in Royal Mint gold coins being both exempt of VAT and capital gains tax. While I may consider this from a, while not necessarily biased, but definitely pro-bitcoin perspective, I believe that it is extremely logical for transactions that take place in bitcoin should not require “profits” or “losses” to be reports, but this is where my logic and the treasury’s grabbiness are inconsistent. If what you’re buying is priced in bitcoin, you’re trading goods or services for money, there was no realisation of gains. Having said that, if you choose to do this, best not do any spending from a stack with a connection to an exchange and your identify. When tax collectors (and their government masters) end up not having enough money, they may begin exploring whether those people buying bitcoin from exchanges are also spending it.
But why is this relevant or important? For me and from hearing from many people on podcasts, while not impossible and not actually that difficult, recording gains on each transaction is firstly a barrier for spending bitcoin, it is additional effort, admin and not insignificant cost, and no one likes that. Secondly, from my libertarian leaning perspective, tax is basically the seizure of assets under the threat of incarceration (aka theft), with the government spending that money on crap I don’t give a shit about, meaning I don’t want to help fund their operation more than I already do. The worry is, if I pay more taxes, they think they’re getting good at collecting taxes, they increase taxes, use taxes to employ more tax collectors, rinse and repeat. From this perspective, it is almost my duty not to report when I transact in bitcoin, viewing it as plain and simple, black-market money, where the government neither dictates what I can do with it, nor profit from its appreciation.
The result of this is not the common mantra of never sell your bitcoin, because I, for one, am looking forward to ditching the fiat grind and having more free time driving an interesting 90’s sports car or riding a new mountain bike, which I will need money to be fund. Unless I’m going to take a fair bit of tax evasion-based risk, find some guys who will only accept my KYC free bitcoin and then live off the grid, I’ll need to find another way, which unfortunately may require engaging once more with the fiat system. However, this time, rather than selling bitcoin to buy fiat, looking for financial product providers who offer loans against bitcoin held. This is nothing new, having been a contributing factors to the FTX blow up, and the drawdown of 2022, the logic of such products is solid and the secret catalyst to Mark Moss’s (and others) buy, borrow, die strategy. The difference this time is to earn from our mistakes, to choose the right company and maybe hand over our private keys (multisig is a beautiful thing). The key benefit of this is that by taking a loan, you’re not realising capital gains, so do not create a taxable event. While there is likely to be an interest on any loan, this only makes sense if this is considerably less than either the capital gains rate incurred if you sold the bitcoin or the long-term capital appreciation of the bitcoin you didn’t have to sell, it has to be an option worth considering.
Now, this is interacting with the fiat system, it does involve the effective printing of money and depending on the person providing the loan, there is risk, however, there are definitely some positives, even outside the not inconsiderable, “tax free” nature of this money. Firstly, by borrowing fiat money, you are increasing the money supply, while devaluing all other holders of that currency, which effectively works against fiat governments, causing them to forever print harder to stop themselves going into a deflationary nose drive. The second important aspect is that if you have not had to sell your bitcoin, you have removed sell pressure from the market and buying pressure that would strengthen the fiat currency, so further supporting the stack you have not had to sell.
Now, let’s put this in the context of The Sovereign Individual or the entrepreneurial bitcoiner, who took a risk before fully understanding what they were buying and has now benefiting financially. The barrier of tax-based admin or the reticence to support government operations through paying additional tax are not insignificant, which the loan has allowed you to effectively side step, keeping more value of your holdings to allocate as you see fit. While this may involve the setting up of a new business that itself may drive productive growth, even if all you did was spend that money (such as a sport car or a new bike), this could still be a net, economic positive compared to a large portion of that money being sucked into the government spending black hole. While the government would not be receiving that tax revenue, every retailer, manufacturer or service provider would benefit from this additional business. Rather than the tax money going toward interest costs or civil servant wages, the money would go towards the real businesses you have chosen, their staff’s wages, who are working hard to outcompete their peers. Making this choice to not pay capital gains does not just allow bitcoiner to save money and to a small degree, reduce government funding, but also provides a cash injection to those companies who may still be reeling from minimum wage AND national insurance increases.
I’m not an ethicist, so am unable to provide a clear, concise, philosophical argument to explain why the ability of government to steal from you via the processes of monetary inflation as well as an ever-increasing tax burden in immoral, but I hope this provides a new perspective on the situation. I don’t believe increases in taxes support economic development (it literally does the opposite), I don’t believe that individuals should be penalised for working hard, challenging themselves, taking risks and succeeding. However, I’m not in charge of the system and also appreciate that if any major changes were to take place, the consequences would be significant (we’re talking Mandibles time). I believe removing capital gains tax from bitcoin would be a net positive for the economy and there being precedence based on the UK’s currently position with gold coins, but unfortunately, I don’t believe people in the cabinet think as I do, they see people with assets and pound signs ring up at their eyes.
As a result, my aim moving forward will be to think carefully before making purchases or sales that will incur capital gains tax (no big Lambo purchase for me at the top), but also being willing the promote the bitcoin economy by purchasing products and services with bitcoin. To do this, I’ll double confirm that spend/replace techniques actually get around capital gains by effectively using the payment rails of bitcoin to transfer value rather than to sell your bitcoin. This way, I will get to reward and promote those companies to perform at a level that warrants a little more effort with payment, without it costing me an additional 18-24% in tax later on.
So, to return to where we started and my first pay-cheque. We need to work to earn a living, but as we earn more, an ever-greater proportion is taken from us, and we are at risk of becoming stuck in a never ending fiat cycle. In the past, this was more of an issue, leading people into speculating on property or securities, which, if successful, would then incur further taxes, which will likely be spent by governments on liabilities or projects that add zero net benefits to national citizens. Apologies if you see this as a negative, but please don’t, this is the alternative to adopting a unit of account that cannot be inflated away. If you have begun to measure your wealth in bitcoin, there will be a point where you need to start to start spending. I for one, do not intend to die with my private keys in my head, but having lived a life, turbo charged by the freedom bitcoin has offered me. Bitcoin backed loans are returning to the market, with hopefully a little less risk this time around. There may be blow ups, but once they get established and interest costs start to be competed away, I will first of all acknowledge remaining risks and then not allocate 100% of my stack. Rather than being the one true bitcoiner who has never spent a sat, I will use the tools at my disposal to firstly give my family their best possible lives and secondly, not fund the government more than I need to.
Then, by the time I’m ready to leave this earth, there will be less money for me to leave to my family, but then again, the tax man would again come knocking, looking to gloat over my demise and add to my family’s misery with an outstretched hand. Then again, this piece is about capital gains rather than inheritance tax, so we can leave those discussions for another time.
This is not financial advice, please consult a financial/tax advisor before spending and replacing without filing taxes and don’t send your bitcoin to any old fella who says they’ll return it once you’ve paThe first time I received a paycheque from a full-time job, after being told in the interview I would be earning one amount, the amount I received was around 25% less; you’re not in Kansas anymore, welcome to the real work and TAX. Over the years, I’ve continued to pay my taxes, as a good little citizen, and at certain points along the way, I have paid considerable amounts of tax, because I wouldn’t want to break the law by not paying my taxes. Tax is necessary for a civilised society, they say. I’m told, who will pay, at least in the UK, for the NHS, who will pay for the roads, who will pay for the courts, the military, the police, if I don’t pay my taxes? But let’s be honest, apart from those who pay very little to no tax, who, in a society actually gets good value for money out of the taxes they pay, or hears of a government institution that operates efficiently and effectively? Alternatively, imagine if the government didn’t have control of a large military budget, would they be quite so keen to deploy the young of our country into harm’s way, in the name of national security or having streets in Ukraine named after them for their generous donations of munition paid with someone else’s money? While I’m only half-way through the excellent “Fiat Standard”, I’m well aware that many of these issues have been driven by the ability of those in charge to not only enforce and increase taxation at will, but also, if ends don’t quite meet, print the difference, however, these are rather abstract and high-level ideas for my small engineer’s brain. What has really brought this into sharp focus for me is the impending sale of my first house, that at the age of 25, I was duly provided a 40-year mortgage and was required to sign a form acknowledging that I would still be paying the mortgage after my retirement age. Fortunately for me, thanks to the government now changing the national age of retirement from 65 to 70 (so stealing 5 years of my retirement), in practice this form didn’t need to be signed, lucky me? Even so, what type of person would knowingly put another person in a situation where near 40% of their wage would mainly be paying interest to the bank (which as a side note was bailed out only a few years later). The unpleasant taste really became unbearable when even after being put into this “working life” sentence of debt repayment, was, even with the amount I’d spent on the house (debt interest and maintenance) over the subsequent 19 years, only able to provide a rate of return of less than 1.6%, compared to the average official (bullshit) inflation figure of 2.77%. My house has not kept up with inflation and to add insult to financial injury, His Majesty’s Revenue and Customs feel the need to take their portion of this “profit”.

At which point, I take a very deep breath, sit quietly for a moment, and channel my inner Margot, deciding against grabbing a bottle of bootleg antiseptic to both clear my pallet and dull the pain. I had been convinced I needed to get on the housing ladder to save, but the government has since printed billions, with the rate of, even the conservative estimates of inflation, out pacing my meagre returns on property, and after all that blood, sweet, tears and dust, covering my poor dog, “the law” states some of that money is theirs. I wasn’t able to save in the money that they could print at will, I worked very hard, I took risks and the reward I get is to give them even more money to fritter away of things that won’t benefit me. But, I don’t want your sympathy, I don’t need it, but it helped me to get a new perspective on capital gains, particularly when considered in relation to bitcoin. So, to again draw from Ms. Paez, who herself was drawing from everyone’s favourite Joker, Heath Ledger, not Rachel Reeves (or J. Powell), here we go.
The Sovereign Individual is by no means an easy reaD, but is absolutely fascinating, providing clear critiques of the system that at the time was only in its infancy, but predicting many aspects of today’s world, with shocking accuracy. One of the most striking parts for me was the critique and effect of taxation (specifically progressive forms) on the prosperity of a nation at large. At an individual level, people have a proportion of their income removed, to be spent by the government, out of the individuals’ control. The person who has applied their efforts, abilities and skills to earn a living is unable to decide how best to utilise a portion of the resources into the future. While this is an accepted reality, the authors’ outline the cumulative, compound impact of forfeiting such a large portion of your wage each year, leading to figures that are near unimaginable to anyone without a penchant for spreadsheets or an understanding of exponential growth. Now, if we put this into the context of the entrepreneur, identifying opportunities, taking on personal and business risk, whenever a profit is realised, whether through normal sales or when realising value from capital appreciation, they must pay a portion of this in tax. While there are opportunities to reinvest this back into the organisation, there may be no immediate investment opportunities for them to offset their current tax bill. As a result, the entrepreneurs are hampered from taking the fruits of their labour and compounding the results of their productivity, forced to fund the social programmes of a government pursuing aims that are misaligned with individuals running their own business. Resources are removed from the most productive individuals in the society, adding value, employing staff, to those who may have limited knowledge of the economic realities of business; see Oxbridge Scholars, with experience in NGOs or charities, for more details please see Labour’s current front bench. What was that Labour? Ah yes, let’s promote growth by taxing companies more and making it more difficult to get rid of unproductive staff, exactly the policies every small business owner has been asking for (Budget October 2024).
Now, for anyone on NOSTR, none of this is new, a large portion of Nostriches were orange pilled long before taking their first purple pill of decentralise Notes and Other Stuff. However, if we’re aware of this system that has been put in place to steal our earnings and confiscate our winnings if we have been able to outwit the Keynesian trap western governments have chosen to give themselves more power, how can we progress? What options do we have? a) being locked up for non-payment of taxes by just spending bitcoin, to hell with paying taxes or b) spend/sell (:/), but keeping a record of those particular coins you bought multiple years ago, in order to calculate your gain and hand over YOUR money the follow tax year, so effectively increasing the cost of anything purchased in bitcoin. Please note, I’m making a conscious effort not to say what should be done, everyone needs to make decisions based on their knowledge and their understanding.
Anyway, option a) is not as flippant as one might think, but also not something one should (damn it) do carelessly. One bitcoin equals one bitcoin, bitcoin is money, as a result, it neither increases nor decreases is value, it is fiat currencies that varies wildly in comparison. If we think about gold, the purchasing power of gold has remained relatively consistent over hundreds of years, gold is viewed as money, which (as a side note) results in Royal Mint gold coins being both exempt of VAT and capital gains tax. While I may consider this from a, while not necessarily biased, but definitely pro-bitcoin perspective, I believe that it is extremely logical for transactions that take place in bitcoin should not require “profits” or “losses” to be reports, but this is where my logic and the treasury’s grabbiness are inconsistent. If what you’re buying is priced in bitcoin, you’re trading goods or services for money, there was no realisation of gains. Having said that, if you choose to do this, best not do any spending from a stack with a connection to an exchange and your identify. When tax collectors (and their government masters) end up not having enough money, they may begin exploring whether those people buying bitcoin form exchanges are also spending it.
But why is this relevant or important? For me and from hearing from many people on podcasts, while not impossible and not actually that difficult, recording gains on each transaction is firstly a barrier for spending bitcoin, it is additional effort, admin and not insignificant cost, and no one likes that. Secondly, from my libertarian leaning perspective, tax is basically the seizure of assets under the threat of incarceration (aka theft), with the government spending that money on crap I don’t give a shit about, meaning I don’t want to help fund their operation more than I already do. The worry is, if I pay more taxes, they think they’re getting good at collecting taxes, they increase taxes, use taxes to employ more tax collectors, rinse and repeat. From this perspective, it is almost my duty not to report when I transact in bitcoin, viewing it as plain and simple, black-market money, where the government neither dictates what I can do with it, nor profit from its appreciation.
The result of this is not the common mantra of never sell your bitcoin, because I, for one, am looking forward to ditching the fiat grind and having more free time driving an interesting 90’s sports car or riding a new mountain bike, which I will need money to be fund. Unless I’m going to take a fair bit of tax evasion-based risk, find some guys who will only accept my KYC free bitcoin and then live off the grid, I’ll need to find another way, which unfortunately may require engaging once more with the fiat system. However, this time, rather than selling bitcoin to buy fiat, looking for financial product providers who offer loans against bitcoin held. This is nothing new, having been a contributing factors to the FTX blow up, and the drawdown of 2022, the logic of such products is solid and the secret catalyst to Mark Moss’s (and others) buy, borrow, die strategy. The difference this time is to earn from our mistakes, to choose the right company and maybe hand over our private keys (multisig is a beautiful thing). The key benefit of this is that by taking a loan, you’re not realising capital gains, so do not create a taxable event. While there is likely to be an interest on any loan, this only makes sense if this is considerably less than either the capital gains rate incurred if you sold the bitcoin or the long-term capital appreciation of the bitcoin you didn’t have to sell, it has to be an option worth considering.
Now, this is interacting with the fiat system, it does involve the effective printing of money and depending on the person providing the loan, there is risk, however, there are definitely some positives, even outside the not inconsiderable, “tax free” nature of this money. Firstly, by borrowing fiat money, you are increasing the money supply, while devaluing all other holders of that currency, which effectively works against fiat governments, causing them to forever print harder to stop themselves going into a deflationary nose drive. The second important aspect is that if you have not had to sell your bitcoin, you have removed sell pressure from the market and buying pressure that would strengthen the fiat currency, so further supporting the stack you have not had to sell. Now, let’s put this in the context of The Sovereign Individual or the entrepreneurial bitcoiner, who took a risk before fully understanding what they were buying and has now benefiting financially. The barrier of tax-based admin or the reticence to support government operations through paying additional tax are not insignificant, which the loan has allowed you to effectively side step, keeping more value of your holdings to allocate as you see fit. While this may involve the setting up of a new business that itself may drive productive growth, even if all you did was spend that money (such as a sport car or a new bike), this could still be a net, economic positive compared to a large portion of that money being sucked into the government spending black hole. While the government would not be receiving that tax revenue, every retailer, manufacturer or service provider would benefit from this additional business. Rather than the tax money going toward interest costs or civil servant wages, the money would go towards the real businesses you have chosen, their staff’s wages, who are working hard to outcompete their peers. Making this choice to not pay capital gains does not just allow bitcoiner to save money and to a small degree, reduce government funding, but also provides a cash injection to those companies who may still be reeling from minimum wage AND national insurance increases.
I’m not an ethicist, so am unable to provide a clear, concise, philosophical argument to explain why the ability of government to steal from you via the processes of monetary inflation as well as an ever-increasing tax burden in immoral, but I hope this provides a new perspective on the situation. I don’t believe increases in taxes support economic development (it literally does the opposite), I don’t believe that individuals should be penalised for working hard, challenging themselves, taking risks and succeeding. However, I’m not in charge of the system and also appreciate that if any major changes were to take place, the consequences would be significant (we’re talking Mandibles time). I believe removing capital gains tax from bitcoin would be a net positive for the economy and there being precedence based on the UK’s currently position with gold coins, but unfortunately, I don’t believe people in the cabinet think as I do, they see people with assets and pound signs ring up at their eyes.
As a result, my aim moving forward will be to think carefully before making purchases or sales that will incur capital gains tax (no big Lambo purchase for me at the top), but also being willing the promote the bitcoin economy by purchasing products and services with bitcoin. To do this, I’ll double confirm that spend/replace techniques actually get around capital gains by effectively using the payment rails of bitcoin to transfer value rather than to sell your bitcoin. This way, I will get to reward and promote those companies to perform at a level that warrants a little more effort with payment, without it costing me an additional 18-24% in tax later on.
So, to return to where we started and my first pay-cheque. We need to work to earn a living, but as we earn more, an ever-greater proportion is taken from us, and we are at risk of becoming stuck in a never ending fiat cycle. In the past, this was more of an issue, leading people into speculating on property or securities, which, if successful, would then incur further taxes, which will likely be spent by governments on liabilities or projects that add zero net benefits to national citizens. Apologies if you see this as a negative, but please don’t, this is the alternative to adopting a unit of account that cannot be inflated away. If you have begun to measure your wealth in bitcoin, there will be a point where you need to start to start spending. I for one, do not intend to die with my private keys in my head, but having lived a life, turbo charged by the freedom bitcoin has offered me. Bitcoin backed loans are returning to the market, with hopefully a little less risk this time around. There may be blow ups, but once they get established and interest costs start to be competed away, I will first of all acknowledge remaining risks and then not allocate 100% of my stack. Rather than being the one true bitcoiner who has never spent a sat, I will use the tools at my disposal to firstly give my family their best possible lives and secondly, not fund the government more than I need to.
Then, by the time I’m ready to leave this earth, there will be less money for me to leave to my family, but then again, the tax man would again come knocking, looking to gloat over my demise and add to my family’s misery with an outstretched hand. Then again, this piece is about capital gains rather than inheritance tax, so we can leave those discussions for another time.
This is not financial advice, please consult a financial/tax advisor before spending and replacing without filing taxes and don’t send your bitcoin to any old fella who says they’ll return it once you’ve paid off the loan.
-
 @ c6dc6b64:69dbbc15
2025-04-24 10:04:00
@ c6dc6b64:69dbbc15
2025-04-24 10:04:00- Existenz ist ein Exil ohne Rückkehr. Wer liebt, liebt nur die Illusion eines Auswegs.
- Die Seele sammelt Splitter vergangener Welten, doch keine Hand kann sie wieder ganz machen.
- Erinnerungen sind Splitter eines Spiegels, der zerbrach – sie schneiden dich, während du dein Gesicht in ihnen suchst.
- Die Schwermut ist der Ruf des Todes im Lebenden, ein dumpfer Widerhall des Willens, der sich selbst verneint, um im Grau der Tage seine Erlösung zu finden.
- Das Leben ist der Widerhall eines sterbenden Willens. Nur im Nichts finden wir Erlösung.
- Die Zeit ist ein Dieb, der Schatten stiehlt – sie lässt dich zurück, ein Umriss, den niemand mehr füllt.
- In der Dämmerung unserer Tage suchen wir die Sonne, die nur in der Erinnerung noch brennt.
- Stille fließt durch uns, als wäre sie immer schon gewesen – ein Zustand, der nie durchbrochen werden kann. Wir sind die Frage, die nie die Antwort findet, das Bild, das niemals scharf wird.
- Wer das Nichts anschaut, sieht sich selbst: ein Schatten, der sich für Licht hält.
- Die Einsamkeit offenbart sich die Qual des Seienden, ein verlassenes Fragment des zersplitterten Willens, das im kalten Licht seiner eigenen Nutzlosigkeit zittert.
-
 @ c6dc6b64:69dbbc15
2025-04-24 09:58:59
@ c6dc6b64:69dbbc15
2025-04-24 09:58:59„In Zeiten universeller Täuschung ist das Aussprechen der Wahrheit ein revolutionärer Akt.“
– George Orwell
Bitcoin ist nicht nur ein Werkzeug der ökonomischen Selbstermächtigung – er ist auch ein kulturelles Störsignal. Sein bloßes Funktionieren stellt die Legitimität des Bestehenden infrage. Eine Währung, die niemand ausgibt, niemand kontrolliert, niemand genehmigen muss, ist in ihrer bloßen Existenz eine stille Anklage gegen das, was als alternativlos gilt.
Mehr als Technologie – eine Haltung
Es geht nicht nur um Technologie. Es geht um Haltung. Um das leise Beharren auf einem anderen Takt. In einer Welt, in der der Wert von oben definiert wird – durch Zentralbanken, Ratings, Verordnungen – bietet Bitcoin eine völlig andere Grundlage: Konsens, Knappheit, Mathematik. Kein politischer Willensakt, sondern ein physikalisches Versprechen.
Die stille Entscheidung
Wer Bitcoin nutzt, trifft eine Entscheidung, die weit über Geld hinausgeht. Es ist die bewusste Verweigerung, Teil eines Systems zu sein, das auf Schulden basiert, auf Kontrolle, auf ständigem Zugriff. Es ist die Entscheidung, eine andere Art von Zukunft möglich zu machen – nicht durch Protest, sondern durch Praxis.
Disidenz ohne Banner
Diese Form der Disidenz ist schwer zu greifen, weil sie sich nicht laut artikuliert. Sie baut keine Barrikaden, schreibt keine Manifeste, ruft nicht nach Aufmerksamkeit. Sie wählt den Rückzug als Methode. Die Abkopplung. Die schrittweise Reduktion von Abhängigkeiten.
Kein Widerstand – Konsequenz
Vielleicht ist das Revolutionäre an Bitcoin nicht der Konflikt, sondern die Abwesenheit davon. Kein Widerstand im klassischen Sinn, sondern eine Umleitung. Keine Konfrontation, sondern Konsequenz. Die leise Entscheidung, nicht mehr mitzumachen – aber etwas Besseres zu bauen.
Ohne Erlaubnis
Wer Bitcoin lebt, braucht keine Genehmigung. Keine Erklärung. Kein Spektakel. Nur ein Node. Eine Wallet. Ein wenig Disziplin. Und die Bereitschaft, Verantwortung zu tragen, wo andere noch Ansprüche stellen.
Es ist kein einfacher Weg. Aber es ist einer, den man gehen kann, ohne um Erlaubnis zu fragen.
-
 @ c6dc6b64:69dbbc15
2025-04-24 09:48:52
@ c6dc6b64:69dbbc15
2025-04-24 09:48:52- Die Zukunft ist ein Abgrund, der sich öffnet, um uns zu verschlingen – und wir nennen es Fortschritt.
- Ein Augenblick, und schon ist er verloren. Wir wandern, aber wohin? Und ist der Weg nicht auch schon längst verschwunden, bevor wir ihn betreten?
- Was ist die Grenze zwischen dem, was wir nennen, und dem, was wir nie sagen? Ein Riss im Atem, eine Unendlichkeit in jedem Schritt – und dennoch nichts, das je festhält, was wir begreifen wollen.
- Gedanken zerfallen wie Tropfen, die nie den Boden erreichen. Wir sammeln, was nie da war, nur das Echo dessen, was nicht existiert. Vielleicht sind wir das Echo.
- Die Fragen sind die Flügel eines Vogels, der nie den Himmel berührt. Und die Antworten? Nur leere Spiegel, die uns mit einer Intensität anstarren, die uns mehr verstummen lässt, je mehr wir sehen.
- Je lauter die Behauptung, desto größer die Vorsicht.
- Freiheit ist ein Käfig aus offenen Türen – du trittst hinaus, nur um in der Weite deiner eigenen Grenzen zu erstarren.
- Zwischen den Zeilen flackert das Echo der Stille. Wer es hört, vergisst den Klang.
- Im Ekel des Seins liegt die Wahrheit: Leben ist Leiden, Tod ist Frieden. Doch der Mutige tanzt auf dem Abgrund.
- Jeder neue Tag ist ein Versprechen, das nicht gehalten wird, ein Licht, das nur die Tiefe unserer Gräber erhellt.
-
 @ c6dc6b64:69dbbc15
2025-04-24 09:44:22
@ c6dc6b64:69dbbc15
2025-04-24 09:44:22- Freiheit ist die Fähigkeit, in Ketten zu tanzen.
- Je lauter die Behauptung, desto größer die Vorsicht.
- Zwischen den Zeilen flackert das Echo der Stille. Wer es hört, vergisst den Klang.
- Die Zeit ist ein Dieb, der Schatten stiehlt – sie lässt dich zurück, ein Umriss, den niemand mehr füllt.
- Die Stille singt ein Lied ohne Ton – ein Chor der Leere, der dich umarmt, bis du dich selbst verlierst.
- Erinnerungen sind Splitter eines Spiegels, der zerbrach – sie schneiden dich, während du dein Gesicht in ihnen suchst.
- Sehnsucht ist ein Fluss, der rückwärts fließt – du watest hinein, doch das Ufer zieht sich fort, unerreichbar fern.
- Freiheit ist ein Käfig aus offenen Türen – du trittst hinaus, nur um in der Weite deiner eigenen Grenzen zu erstarren.
- Das Nichts ist der heimliche Gott, der im Zerfall des Seins thront, ein stiller Erlöser, der das Leben in seinen Schoß zurückruft, um es sanft zu ersticken.
- In der Einsamkeit offenbart sich die Qual des Seienden, ein verlassenes Fragment des zersplitterten Willens, das im kalten Licht seiner eigenen Nutzlosigkeit zittert.
-
 @ c6dc6b64:69dbbc15
2025-04-24 09:30:27
@ c6dc6b64:69dbbc15
2025-04-24 09:30:27„Was du besitzt, besitzt auch dich.“
– Henry David Thoreau
Bitcoin verändert nicht nur, wie wir Geld sehen, sondern auch, wie wir uns selbst sehen. Es stellt eine einfache Frage, die schwer wiegt: Wem traust du? Und tiefer noch: Bist du bereit, dir selbst zu trauen?
Selbstverwahrung ist kein technischer Akt – es ist eine innere Haltung. Wer seinen eigenen Schlüssel hält, muss sich nicht nur mit Tools, sondern mit sich selbst auseinandersetzen. Mit Angst. Verantwortung. Und Freiheit. Die Gewissheit, dass niemand Zugriff hat, ist auch die Last, dass niemand rettet. Diese Form der Verantwortung ist für viele ungewohnt, fast schon beängstigend – in einer Welt, die absichert, verwaltet, entmündigt.
Die psychologische Schwelle der Verantwortung
Bitcoin ist radikale Eigenverantwortung. Und genau das macht es zu einer psychologischen Schwelle. Es zwingt zur Selbsterkenntnis: Bin ich bereit, die Kontrolle wirklich zu übernehmen? Oder suche ich weiterhin nach Institutionen, nach Autoritäten, nach jemandem, der mir die Entscheidung abnimmt?
Ein ehrlicher Spiegel
Spirituell betrachtet ist Bitcoin ein Spiegel. Es zeigt, woran wir glauben, was wir fürchten, worauf wir hoffen. In einer Welt voller Illusionen – über Wert, über Sicherheit, über Freiheit – ist Bitcoin brutal ehrlich. Es gibt nichts vor. Es bewertet nicht. Es funktioniert oder es funktioniert nicht. Und der Umgang damit offenbart viel über uns selbst.
Der Prozess, Bitcoin wirklich zu verstehen – nicht technisch, sondern existenziell – ist transformativ. Er entkoppelt unser Selbstwertgefühl von Zahlen auf Bankkonten. Er konfrontiert uns mit unserer Abhängigkeit von Bequemlichkeit. Er eröffnet die Möglichkeit, dass Freiheit nicht in äußeren Umständen liegt, sondern in innerer Haltung.
Eine spirituelle Praxis
Für manche ist Bitcoin eine spirituelle Praxis – eine tägliche Übung in Geduld, Disziplin, Vertrauen. Nicht Vertrauen in andere, sondern in Prinzipien. In Mathematik. In Ursache und Wirkung. Bitcoin verzeiht keine Illusion. Es bestraft Selbsttäuschung. Und gerade deshalb kann es ein Werkzeug sein – nicht nur der wirtschaftlichen, sondern der inneren Befreiung.
Wer sich darauf einlässt, begibt sich nicht nur auf einen neuen finanziellen Weg. Sondern auf eine Reise zu sich selbst. Eine Reise, die nicht laut ist, nicht bequem, nicht sofort belohnend. Aber ehrlich. Und vielleicht – heilsam.
-
 @ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13
@ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13Bitcoin cracked the code for money. Now it's time to rebuild everything else.
What about identity, trust, and collaboration? What about the systems that define how we live, create, and connect?
Bitcoin gave us a blueprint to separate money from the state. But the state still owns most of your digital life. It's time for something more radical.
Welcome to the Atomic Economy - not just a technology stack, but a civil engineering project for the digital age. A complete re-architecture of society, from the individual outward.
The Problem: We Live in Digital Captivity
Let's be blunt: the modern internet is hostile to human freedom.
You don't own your identity. You don't control your data. You don't decide what you see.
Big Tech and state institutions dominate your digital life with one goal: control.
- Poisoned algorithms dictate your emotions and behavior.
- Censorship hides truth and silences dissent.
- Walled gardens lock you into systems you can't escape.
- Extractive platforms monetize your attention and creativity - without your consent.
This isn't innovation. It's digital colonization.
A Vision for Sovereign Society
The Atomic Economy proposes a new design for society - one where: - Individuals own their identity, data, and value. - Trust is contextual, not imposed. - Communities are voluntary, not manufactured by feeds. - Markets are free, not fenced. - Collaboration is peer-to-peer, not platform-mediated.
It's not a political revolution. It's a technological and social reset based on first principles: self-sovereignty, mutualism, and credible exit.
So, What Is the Atomic Economy?
The Atomic Economy is a decentralized digital society where people - not platforms - coordinate identity, trust, and value.
It's built on open protocols, real software, and the ethos of Bitcoin. It's not about abstraction - it's about architecture.
Core Principles: - Self-Sovereignty: Your keys. Your data. Your rules. - Mutual Consensus: Interactions are voluntary and trust-based. - Credible Exit: Leave any system, with your data and identity intact. - Programmable Trust: Trust is explicit, contextual, and revocable. - Circular Economies: Value flows directly between individuals - no middlemen.
The Tech Stack Behind the Vision
The Atomic Economy isn't just theory. It's a layered system with real tools:
1. Payments & Settlement
- Bitcoin & Lightning: The foundation - sound, censorship-resistant money.
- Paykit: Modular payments and settlement flows.
- Atomicity: A peer-to-peer mutual credit protocol for programmable trust and IOUs.
2. Discovery & Matching
- Pubky Core: Decentralized identity and discovery using PKARR and the DHT.
- Pubky Nexus: Indexing for a user-controlled internet.
- Semantic Social Graph: Discovery through social tagging - you are the algorithm.
3. Application Layer
- Bitkit: A self-custodial Bitcoin and Lightning wallet.
- Pubky App: Tag, publish, trade, and interact - on your terms.
- Blocktank: Liquidity services for Lightning and circular economies.
- Pubky Ring: Key-based access control and identity syncing.
These tools don't just integrate - they stack. You build trust, exchange value, and form communities with no centralized gatekeepers.
The Human Impact
This isn't about software. It's about freedom.
- Empowered Individuals: Control your own narrative, value, and destiny.
- Voluntary Communities: Build trust on shared values, not enforced norms.
- Economic Freedom: Trade without permission, borders, or middlemen.
- Creative Renaissance: Innovation and art flourish in open, censorship-resistant systems.
The Atomic Economy doesn't just fix the web. It frees the web.
Why Bitcoiners Should Care
If you believe in Bitcoin, you already believe in the Atomic Economy - you just haven't seen the full map yet.
- It extends Bitcoin's principles beyond money: into identity, trust, coordination.
- It defends freedom where Bitcoin leaves off: in content, community, and commerce.
- It offers a credible exit from every centralized system you still rely on.
- It's how we win - not just economically, but culturally and socially.
This isn't "web3." This isn't another layer of grift. It's the Bitcoin future - fully realized.
Join the Atomic Revolution
- If you're a builder: fork the code, remix the ideas, expand the protocols.
- If you're a user: adopt Bitkit, use Pubky, exit the digital plantation.
- If you're an advocate: share the vision. Help people imagine a free society again.
Bitcoin promised a revolution. The Atomic Economy delivers it.
Let's reclaim society, one key at a time.
Learn more and build with us at Synonym.to.
-
 @ 92f1335f:2c8220d1
2025-04-24 09:14:28
@ 92f1335f:2c8220d1
2025-04-24 09:14:28Chapter 4: The Vision (2025)
By 2025, Jonathan had changed.
He quit his job in 2023 and launched a startup focused on blockchain education. He taught online courses, built tools for newcomers, and advocated for responsible investing.
His original 0.5 BTC? Still untouched, sitting in a cold wallet as a reminder.
Bitcoin had become more than just an asset—it was a movement. And Jonathan wasn’t just along for the ride anymore. He was part of building the road ahead.
At conferences, he’d tell his story. How one quiet investment in 2019 reshaped his future. And when people asked, “Why didn’t you sell it all?” he’d grin.
“Because some things,” he’d say, “are worth holding onto.”
-
 @ 4c86f5a2:935c3564
2025-04-24 09:07:04
@ 4c86f5a2:935c3564
2025-04-24 09:07:04Write Test Postr
-
 @ c6dc6b64:69dbbc15
2025-04-24 08:46:32
@ c6dc6b64:69dbbc15
2025-04-24 08:46:32„Anstatt das System zu bekämpfen, baue ein System, das es überflüssig macht.“
– zugeschrieben Buckminster Fuller
Die Gegenwart ist geprägt von Zentralisierung, digitaler Kontrolle und einem Finanzsystem, das Vertrauen verlangt, aber wenig zurückgibt. Für Bitcoiner stellt sich nicht mehr die Frage nach dem Ob, sondern nach dem Wie des Rückzugs aus diesem System.
Vom Goldstandard zu Bitcoin
Der klassische Goldstandard war Ausdruck eines strukturellen Misstrauens gegenüber staatlicher Willkür. Die Bindung des Geldes an ein rares Gut wie Gold disziplinierte die Geldpolitik – allerdings auf Kosten von Flexibilität, Zugänglichkeit und Dezentralität. Gold war zentral verwahrt, schwer zu transportieren und politisch angreifbar.
Bitcoin übernimmt die Idee der Begrenzung, ohne diese Schwächen: keine zentrale Verwahrung, leicht teilbar, digital übertragbar, resistent gegen Konfiszierung. Was beim Gold noch eine politische Vereinbarung war, ist bei Bitcoin eine technische Tatsache.
Anarchie als Ordnung ohne Herrschaft
Anarchie wird oft missverstanden. Sie ist keine Ablehnung von Ordnung, sondern von Herrschaft. Sie setzt auf freiwillige Strukturen statt auf Zwang, auf Verantwortung statt auf Kontrolle. Bitcoin ist in diesem Sinne anarchisch. Es gibt keine zentrale Autorität, keine Intervention, kein Gatekeeping. Teilhabe ist offen, Regeln sind transparent, Entscheidungen beruhen auf Konsens. Es ist ein System, das sich jeder aneignen kann, ohne jemanden um Erlaubnis zu fragen.
Die Praxis des Rückzugs
Der Rückzug aus dem bestehenden System ist kein plötzlicher Bruch, sondern eine Praxis. Er beginnt mit Selbstverwahrung, mit der Vermeidung von KYC, mit der Nutzung von Peer-to-Peer-Technologien und mit dem bewussten Aufbau eigener Infrastruktur. Es geht nicht darum, das alte System zu stürzen, sondern es überflüssig zu machen – indem man es nicht mehr braucht.
Bitcoin als Entscheidung
Bitcoin ist keine Spekulation, kein Unternehmen, kein Produkt. Es ist eine Entscheidung. Eine Entscheidung für Autonomie. Für Verantwortung. Für Souveränität. Wer sich für diesen Weg entscheidet, entscheidet sich nicht für die einfachste Lösung – sondern für die ehrlichste. Der Preis ist Selbstverantwortung. Die Belohnung ist Freiheit.
Ein stiller Rückzug
Kein Spektakel. Keine Revolution. Nur ein Protokoll. Und ein Mensch, der es nutzt.
-
 @ 3474ebf1:63fb1108
2025-04-24 07:44:40
@ 3474ebf1:63fb1108
2025-04-24 07:44:40 -
 @ 5188521b:008eb518
2025-04-24 07:34:50
@ 5188521b:008eb518
2025-04-24 07:34:50We are losing our freedom.
Don't believe me? Data published by the Cato Institute suggests that 74% of Americans are concerned they could lose freedoms.
But what do we really mean by 'freedom'?
The Cambridge Dictionary defines ‘freedom’ as follows: the condition or right of being able or allowed to do, say, think, etc. whatever you want to, without being controlled or limited.
Despite this clear definition, freedom means different things to different people: it might also refer to freedom of movement, private property rights, free markets, and freedom from violence.
Freedom fiction (also known as Libertarian fiction) denotes fictional stories intrinsically linked to these ideas or, more likely, the sometimes vain pursuit of this idea.
If dystopian fiction is overly bleak, perfectly captured by the image of a boot on the reader's neck, libertarian stories should offer just a glimmer of hope.
What is freedom fiction?
If dystopia, sci-fi, fantasy, and horror are genres, i.e., styles of fiction that must encompass certain tropes, freedom fiction could more generally be considered a category that explores freedom as a theme, without necessarily being part of a specific genre.
Freedom fiction primarily concerns itself with the overarching topics of individual liberty and sovereignty, conflict with authoritarian or surveillance states, and the restoration or preservation of rights that citizens of the Western world have come to expect: privacy, freedom of speech, the right to private property, and freedom to transact and form contracts.
Though enjoying something of a resurgence in recent decades and especially post Covid, freedom fiction is not new, and famous/infamous novels throughout the centuries could be retroactively categorised as freedom fiction.
Think of The Epic of Gilgamesh (2000BC), Greek tragedies (500BC), Uncle Tom's Cabin by Harriet Beecher Stowe (1852), which helped fuel the anti-slavery movement, or We by Yevgeny Zamyatin, written over 100 years ago.
Today, freedom fiction is an emerging category that includes the revival of the cypherpunk movement, as privacy technologies such as Bitcoin seek to remove the reliance on the banking system, which has become an effective method of control for the establishment.
Why read freedom fiction?
 Storytelling is a tradition as old as humanity itself, created to share the joy and wonder of imagined worlds. Fiction can also serve as a warning of what might come, and playing out “what if?” scenarios in our minds can help us in the real world, too.
Storytelling is a tradition as old as humanity itself, created to share the joy and wonder of imagined worlds. Fiction can also serve as a warning of what might come, and playing out “what if?” scenarios in our minds can help us in the real world, too.Any individual interested in escaping the modern debt-slavery rat race we’ve found ourselves forced into can enjoy freedom stories with a greater and deeper understanding of just how real this “fiction” could be in the future.
Spiking interest
Data from Google Trends shows that in the United Kingdom — a nation increasingly concerned with policing speech, surveillance and other dystopic methods — interest in freedom has been spiking in the past five years, centred in England.
 Source: Google Trends
Source: Google TrendsNow let’s take a look at the data for the United States:
 Despite a lower interest overall, the spike in 2023 mirrors that of the UK. Perhaps this was due to an event featured in the news or even a brand name or TikTok trend.
Despite a lower interest overall, the spike in 2023 mirrors that of the UK. Perhaps this was due to an event featured in the news or even a brand name or TikTok trend.It is interesting to note that although a great number of Amercians fear losing their freedoms, fewer are searching how to protect them.
One reason for the rise in freedom fiction could be that Libertarian thinkers, praxeologists, and freedom maximalists seek to alert the populace through emotive stories. Few, it seems, are awakened when presented with legacy media propaganda and government messages.
The benefits & outcomes of reading freedom fiction
Once a human mind has acquired a taste for freedom fiction, there are numerous benefits and likely outcomes that will arise as a result:
Benefits:
- Broadened perspective and understanding of historical issues
- Increased empathy and social understanding
- Inspiration, motivation & empowerment
- Critical thinking skills & awareness
- Emotional connection
Once the reader has enjoyed these benefits, it is likely they will put their newfound understanding to action, bringing about outcomes like these.
Outcomes:
- Appreciation of and gratitude for freedom
- Informed civic engagement
- Agency for social change
- Personal growth
It would appear, then, that at some point, freedom fiction will have a transformative impact on the social demographics of the civilised world. As popular Netflix shows like Black Mirror highlight our reliance and overreliance on digital media, and governments continue to censor user-generated content posted socially, we must ask ourselves, when exactly will we wake up to what is happening?
We are more connected, but more controlled, than ever. How can we use the tools that enslave us to liberate us? Perhaps through sharing stories.
Aspects of freedom, genres, and time periods
Freedom fiction is a broad spectrum, encompassing various aspects, genres and time periods.
Aspects — privacy, freedom of speech, wrongful imprisonment, oppression, discrimination, government overreach, surveilance, debanking, censorship, confiscation, forced separation and more.
Genres — horror, sci-fi, fantasy, thriller and even young adult romance stories can contribute to the growing canon of libertarian-themed fiction.
Time periods — slavery in the past, alien invasions in the future, totalitarian governments in the present. Freedom fiction can relate to any time period.
15+ Classic Freedom-themed Books
 In no particular order, here are 15 of the greatest examples of freedom stories from modern times:
In no particular order, here are 15 of the greatest examples of freedom stories from modern times:-
Nineteen Eighty-Four by George Orwell (1949): A dystopian classic where the Party controls every aspect of people's lives, and Winston Smith rebels against the oppressive regime.
Reason to read: Offers a chilling and thought-provoking exploration of totalitarianism, mass surveillance, and the importance of individual thought and truth.
-
The Handmaid's Tale by Margaret Atwood (1985): In a totalitarian regime where women are stripped of their rights, Offred fights for survival and a chance to regain her freedom.
Reason to read: A haunting story that explores themes of feminism, oppression, and resistance, with a timely warning about the dangers of religious extremism and the fragility of women's rights.
-
Brave New World by Aldous Huxley (1932): A satirical look at a future society where people are genetically engineered and conditioned to conform, and a "savage" challenges their way of life.
Reason to read: Provides an unsettling vision of a future where happiness is manufactured at the cost of individuality, freedom, and genuine human connection.
-
Fahrenheit 451 by Ray Bradbury (1953): In a world where books are banned, Guy Montag, a fireman, discovers the power of knowledge and fights for intellectual freedom.
Reason to read: A passionate defense of the importance of books, ideas, and intellectual freedom, and a warning against censorship.
-
The Giver by Lois Lowry (1993): A young boy named Jonas discovers the dark secrets of his seemingly Utopian society, where there is no pain, sadness, or freedom of choice.
Reason to read: A thought-provoking exploration of utopia, dystopia, and the importance of memory, emotion, and individual choice in a truly human life.
-
One Flew Over the Cuckoo's Nest by Ken Kesey (1962): Randle McMurphy challenges the authority of a mental institution, becoming a symbol of rebellion and the fight for individual freedom.
Reason to read: A powerful and moving story about the struggle against forced conformity and the importance of individuality, even in the face of oppressive systems.
-
Little Brother by Cory Doctorow (2008): This contemporary science fiction novel explores themes of government surveillance, digital rights, and the power of decentralized networks in challenging authority.
Reason to read: a timely exploration of digital surveillance, government overreach, and the power of youthful activism in defending civil liberties in the modern age.
-
Beloved by Toni Morrison (1987): Set after the American Civil War, this novel explores the psychological and emotional scars of slavery and the struggle for freedom and identity.
Reason to read: A masterpiece that delves into the legacy of slavery and its enduring impact on identity, memory, and the quest for freedom.
-
The Book Thief by Markus Zusak (2005): In Nazi Germany, a young girl named Liesel Meminger finds solace in stolen books and discovers the power of words to resist oppression and find freedom.
Reason to read: A beautifully written story about the power of words to nourish the soul, resist oppression, and find hope and freedom in the darkest of times.
-
Animal Farm by George Orwell (1945): An allegorical novella about a revolution on a farm that turns into a totalitarian dictatorship, highlighting the dangers of unchecked power, Communism, and the loss of freedom.
Reason to read: A timeless allegory that exposes the corruption of revolutions, the fragility of freedom, and the importance of resistance against tyranny.
-
A Thousand Splendid Suns by Khaled Hosseini (2007): This novel tells the story of two Afghan women whose lives intersect under the oppressive Taliban regime, and their fight for survival and freedom.
Reason to read: An eye-opening portrayal of the resilience and strength of women in the face of oppression, and a powerful story about the universal desire for dignity.
-
The Underground Railroad by Colson Whitehead (2016): A unique novel that reimagines the Underground Railroad as a literal railroad, and follows a slave's journey.
Reason to read: A compelling blend of historical fiction and magical realism that offers a fresh perspective on the history of slavery and the enduring quest for freedom.
-
Anthem by Ayn Rand (1938): A novella set in a collectivist future where the concept of "I" has been eradicated. It follows one man's rediscovery of individualism and his rebellion against the oppressive society.
Reason to read: a novella that champions radical individualism against the suffocating conformity of collectivist ideology.
-
The Count of Monte Cristo by Alexandre Dumas (1844-46): Edmond Dantès is wrongly imprisoned and seeks revenge and freedom after years of captivity.
Reason to read: An exciting tale of betrayal, revenge, and ultimate triumph, with a focus on themes of justice, freedom, and the resilience of the human spirit.
-
Snow Crash (1992) and Cryptonomicon (1999) by Neal Stephenson: While not strictly libertarian manifestos, these novels explore themes of individual freedom, the power of information, decentralized systems, and critiques of centralized authority in engaging and complex ways.
Reason to read: these books are considered modern cypherpunk classics. They are rich in detail and the perfect starting place to learn more about the genre and why it is important for freedom.
 ## Lesser-known Freedom Books
## Lesser-known Freedom BooksHere are 15 lesser-known, more modern books that also explore the theme of freedom:
- Exit West by Mohsin Hamid (2017): This novel uses magical realism to depict refugees fleeing a war-torn country and seeking freedom and safety in an uncertain world.
- A Lodging of Wayfaring Men by Paul Rosenberg (2007): a libertarian novel based on real events that explores themes of individual sovereignty and free markets.
- The Probability Broach by L. Neil Smith (1979): An alternate history novel where a slight change in the Declaration of Independence leads to a libertarian society in North America. It's the first in Smith's "North American Confederacy" series.
- The Beekeeper of Aleppo by Christy Lefteri (2019): This tells the story of beekeepers forced to flee Syria and their struggle to find freedom and rebuild their lives in a new country.
- Alongside Night by J. Neil Schulman (1979): A dystopian thriller depicting the collapse of the US government and the rise of a libertarian underground.
- Freehold by Michael Z. Williamson (2004): A military science fiction series that portrays a future where individuals have seceded from Earth's controlling government to establish independent, more libertarian colonies.
- No Truce with Kings by Poul Anderson (1963): A novella that won the Hugo Award, depicting a future where scientific progress has led to a world of isolated, self-sufficient individuals, challenging traditional notions of society and government.
- A Passage North by Anuk Arudpragasam (2021): This Booker Prize-nominated novel explores the aftermath of the Sri Lankan Civil War and the complexities of memory, trauma, and the search for inner freedom.
- Kings of the High Frontier by Victor Koman (1996): A hard science fiction novel exploring themes of entrepreneurship and individual liberty in space.
- This Perfect Day by Ira Levin (1970): A dystopian novel where a seemingly Utopian global society controls every aspect of individual life, raising questions about freedom versus engineered happiness.
- Wasp by Eric Frank Russell (1957): A story containing acts of terrorism against oppressive aliens. A notable example of a single individual disrupting a larger, controlling power.
- The Peace War by Vernor Vinge (1984): A ruthless organization, the Peace Authority, uses impenetrable force fields to end war but suppresses technology and individual liberty, leading a group of rebels to fight for the freedom to advance and determine their own future.
- Starship Troopers by Robert A. Heinlein (1959): Heinlein was a prolific science fiction writer whose works frequently touch upon libertarian themes. Starship Troopers explores the ideas of civic virtue and individual responsibility.
- Live Free or Die by John Ringo (2010) follows Tyler Vernon, a fiercely independent and resourceful entrepreneur who stands up against alien oppressors and Earth's own bureaucratic tendencies to forge a path to true liberty and self-determination for humanity.
- Darkship Thieves by Sarah Hoyt (2010): Winner of the Prometheus Award for Best Libertarian SF Novel. This book follows Athena Hera Sinistra, a genetically engineered woman who escapes a tyrannical Earth to a freer society in space.
Freedom Publishers
In addition to the many works of libertarian fiction, a number of publishers are beginning to focus on stories which promote freedom.
- Liberty Island: This publisher focuses on science fiction and fantasy with libertarian and individualist themes.
- Fox News Books: While a mainstream publisher, it has been known to publish fiction with libertarian themes or by authors who are considered libertarian.
- Defiance Press & Publishing: This independent publisher openly states its commitment to publishing conservative and libertarian authors across fiction and non-fiction genres.
- Konsensus Network: A publisher that specifically promotes libertarian themes and bitcoin authors.
- All Seasons Press: Founded by former executives from Simon & Schuster and Hachette, this independent press aims to be a home for conservative voices.
- Baen Books: This is a well-known publisher, particularly in science fiction and fantasy, that often features authors and stories exploring themes of individual liberty, self-reliance, and limited government.
- Morlock Publishing: This small press specializes in science fiction with themes often including aspects of anarcho-capitalism and libertarian rebellion.
- Heresy Press (now an imprint of Skyhorse Publishing): While broader in its scope, Heresy Press aimed to publish "uncensored, outspoken, and free-spirited books" which can include libertarian viewpoints in fiction.
- Libertarian Futurist Society (LFS) (indirectly): While not a traditional publisher, the LFS sponsors the Prometheus Award and promotes libertarian science fiction. Their website and related platforms can be resources for finding authors and works, which are then published by various houses.
Recent Trends in Libertarian Fiction:
 Konsensus Network’s new imprint, 21 Futures, is building a movement centred on freedom fiction, a movement in which emerging and established writers can contribute their storytelling media to anthologies and blogs, as well as publish their own individual works.
Konsensus Network’s new imprint, 21 Futures, is building a movement centred on freedom fiction, a movement in which emerging and established writers can contribute their storytelling media to anthologies and blogs, as well as publish their own individual works.To date, two short story anthologies are available from 21 Futures:
Tales from the Timechain: the world’s first Bitcoin-fiction anthology.
21 writers examine how the hardest sound money ever created can restore freedom and liberty to mankind.
Financial Fallout: in this recently-released anthology, 21 writers weave financial dystopia from across a broader spectrum of freedom fiction, sewing seeds of eventual hope.
In addition to 21 Futures, a host of self-published and even best-selling fiction on the theme of bitcoin is now available. The Rapid Rise of Bitcoin Fiction documents the history and current trends in this genre.
 ## What happens next?
## What happens next?As governments tighten their grip on our data and our freedoms erode, we expect that freedom fiction will become a wider phenomenon. It is our hope and belief that Konsensus Network and 21 Futures will help drive growth in the genre and better understanding of how to protect individual freedom through our multimedia publications.
Follow our socials to keep up to date on future releases.
This blog was originally published on the 21 Futures blog by Alex Boast.
Alex is a web3 writer, ghost writer and ghost story writer. He’s a novelist and poet from England who loves to work with other writers as a coach, mentor and friend. You can find him on LinkedIn.
-
 @ 8671a6e5:f88194d1
2025-04-24 07:23:19
@ 8671a6e5:f88194d1
2025-04-24 07:23:19For whoever has, will be given more, and they will have an abundance. Whoever does not have, even what they have will be taken from them.
Matthew 25:29, The Parable of the Talents (New Testament)For whoever has, will be given more,\ and they will have an abundance.\ Whoever does not have, even what\ they have will be taken from them.\ \ Matthew 25:29,\ The Parable of the Talents (New Testament)

How the Pump-my-bags mentality slows Bitcoin adoption
The parable of “thy Bitcoins” (loosely based on Matthew 25:29)
A man, embarking on a journey, entrusted his wealth to his servants. To one he gave five Bitcoin, to another two Bitcoin, and to another one Bitcoin, each according to his ability. Then he departed.
The servant with five Bitcoin buried his master’s wealth, dreaming of its rising price. The servant with two Bitcoin hid his, guarding its value. But the servant with one Bitcoin acted with vision. He spent 0.5 Bitcoin to unite Bitcoiners, teaching them to use the network and building tools to expand its reach. His efforts grew Bitcoin’s power, though his investment left him with only 0.5 Bitcoin.
Years later, the master returned to settle accounts. The servant with five Bitcoin said, “Master, you gave me five Bitcoin. I buried them, and their price has soared. Here is yours.”
The master replied, “Faithless servant! My wealth was meant to sow freedom. You kept your Bitcoin but buried your potential to strengthen its network. Your wealth is great, but your impact is none!”
The servant with two Bitcoin said, “Master, you gave me two Bitcoin. I hid them, and their value has risen. Here is yours.”
The master replied, “You, too, have been idle! You clung to wealth but failed to spread Bitcoin’s truth. Your Bitcoin endures, but your reach is empty!”
Then the servant with one Bitcoin stepped forward. “Master, you gave me one Bitcoin. I spent 0.5 Bitcoin to teach and build with Bitcoiners. My call inspired many to join the network, though I have only 0.5 Bitcoin left.”
The master said, “Well done, faithful servant! You sparked a movement that grew my network, enriching lives. Though your stack is small, your vision is vast. Share my joy!”
When many use their gifts to build Bitcoin’s future, their sacrifices grow the network and enrich lives. Those who “bury” their Bitcoin and do nothing else keep wealth but miss the greater reward of a thriving in a Bitcoin world.
This parable reflects a timeless truth: between playing it safe and building, resides the choice to take risk. Bitcoin’s power lies not in hoarding wealth (although it’s part of it), but mainly in using it to build a freer world. To free people from their confines. Yet a mentality has taken hold — one that runs counter to that spirit.
PMB betrays the Bitcoin ethos
“Pump my bags” (PMB) stems from the altcoin world, where scammers pump pre-mined coins to dump on naive buyers. In Bitcoin, PMB isn’t about dumping but about hoarding—stacking sats without lifting a finger. These Bitcoiners, from small holders to whales, sit back, eyeing fiat profits, not Bitcoin’s mission. They’re not so different from altcoin grifters. Both chase profit, not glory. They dream of fiat-richness and crappy real estate in Portugal or Chile — not a Bitcoin standard. One holds hard money by chance, the other a fad coin. Neither moves the world forward.
In Bitcoin, the pump-my-bags mindset is more about laziness; everyone looking out for themselves, stacking without ever lifting a finger. There’s a big difference in the way an altcoin promotor would operate and market yet another proof-of-stake pre-mined trashcoin, and how PMB bitcoiners hoard and wait.
They’re much alike however. The belief level might be slightly different, and not everyone has the same ability.
I’ve been in Bitcoin’s trenches since its cypherpunk days, when it was a rebellion against fiat’s centralized control. Bitcoin is a race against the totalitarian fiat system’s grip. Early adopters saw it as a tool to dismantle gatekeepers and empower individuals. But PMB has turned Bitcoin into a get-rich scheme, abandoning the collective effort needed to overthrow fiat’s centuries-long cycles.
Trust is a currency’s core. Hoarding Bitcoin shows trust in its future value, but it’s a shallow trust that seals it away from the world. Real trust comes from admiring Bitcoin’s math, building businesses around it, or spreading its use. PMB Bitcoiners sit on their stacks, expecting others to build trust for them. Newcomers see branding, ego, and grifters, not the low-tech prosperity Bitcoin can offer. PMB Bitcoiners live without spending a sat, happy to hodl. Fine, but they’re furniture in fiat’s ruins, not builders of Bitcoin’s future.
Hoarding hollow victories Hoarding works for those chasing fiat wealth. Bitcoin is even there for them. The lazy, the non-believers, the ones that sold very early, the ones that just started.
By 2021, 75% of Bitcoin sat dormant, driving scarcity and prices up. But it strangles transactions, weakening Bitcoin as a living economy. Reddit calls hoarding “Bitcoin’s most dangerous problem,” choking adoption for profit. Pioneers like Roger Ver built tech companies (where you could buy electronics for bitcoin), Mark Karpelès ran an exchange (Mt. Gox) and Charlie Shrem processed 30% of Bitcoin transactions in 2013. They poured stacks into adoption, people like them (even people you’ve never heard of) more than not, went broke doing the building while hoarders sat back. The irony stings: Bitcoin’s founders are often poorer than PMB hodlers who buried their talents and just sat there passively. Over the years, the critique from these sideline people became more prevalent. They show up here and there, to read the room. But that’s all they do.
The last couple of years, they even became more vocal with social media posts. Everything needs to be perfect, high-quality, not made by them, not funded by them, for free, without ads, and with no effort whatsoever, unless it’s NOT pumping their bags, then it needs to be burned down as fast as possible.
Today’s PMB Bitcoiners want the rewards without the risk. They stack sats, demand perfect content made by others for free, and cheer short-term price pumps. But when asked to build, code, or fund anything real, they disappear. At this point, such Bitcoiners have as much spine as a pack of Frankfurter sausages. This behavior has hollowed out Bitcoin’s activist core.
Activism’s disappointment
Bitcoin’s activist roots—cypherpunks coding, evangelists spreading the word—have been replaced by influencers and silent PMB conference-goers who say nothing but “I hold Bitcoin.” Centralized exchanges like Binance and Coinbase handle 70% of trades by 2025, mocking our decentralized vision. Custodial wallets proliferate as users hand over keys. The Lightning Network has 23,000+ nodes, and privacy tech like CoinJoin exists, yet adoption lags. Regulation creeps in—the U.S. Digital Asset Anti-Money Laundering Act of 2023 and Europe’s MiCa laws threaten KYC on every wallet. Our failure to advance faster gives governments leverage. Our failure would be their victory. Their cycles endlessly repeated.
Activism is a shadow of its potential. The Human Rights Foundation pushes Bitcoin for dissidents, but it’s a drop in the bucket. We could replace supply chains, build Bitcoin-only companies, or claim territories, yet we can’t even convince bars to accept
Bitcoin. We’re distracted by laser-eye memes and altcoin hopium, not building at farmer’s markets, festivals, or local scenes. PMB Bitcoiners demand perfection—free, ad-free, high-quality content—while contributing nothing.
The best way to shut them up, is asking them to do something. ”I would like to see a live counter on that page, so I can see what customers got new products” ”Why don’t YOU write code?” … and they’re gone.
”I would change a few items in your presentation man, it was good, but I would change the diagram on page 7” ”The presentation is open source and online, open for contributions. Do you want to give the presentation next time?” ”… “ and they’re gone.
”We need to have a network of these antennas to communicate with each other and send sats” ”I’ve ordered a few devices like that.. want to help out and search for new network participants?” ” … “ They’re off to some other thing, that’s more entertaining.
If you don’t understand you’re in a very unique fork in the road, a historic shift in society, much so that you’re more busy with picking the right shoes, car, phone, instead of pushing things in the right direction. And guess what? Usually these two lifestyles can even be combines. Knights in old England could fight and defend their king, while still having a decent meal and participate in festivities. These knight (compared to some bitcoiners) didn’t sit back at a fancy dinner and told the others: “yeah man, you should totally put on a harness, get a sword made and fight,… here I’ll give you a carrot for your horse.” To disappear into their castles waiting for the fight to be over a few months later. No, they put on the harness themselves, and ordered a sword to be made, because they knew their own future and that of their next of kin was at stake.
Hardly any of them show you that Bitcoin can be fairly simple and even low-tech solutions for achieving remedies for the world’s biggest problems (having individuals have real ownership for example). It can include some genuine building of prosperity and belief in one’s own talents and skills. You mostly don’t need middlemen. They buy stuff they don’t need, to feel like they’re participants.
And there’s so, enormously much work to be done.
On the other hand. Some bitcoiners can live their whole life without spending any considerable amount of bitcoin, and be perfectly happy. They mind as well could have had no bitcoin at all, but changed their mindset towards a lot of things in life. That’s cool, I know bitcoiners that don’t have any bitcoin anymore. They still “get it” though. Everyone’s life is different. These people are really cool, and they’re usually the silent builders as well. They know.
And yet, people will say they’ve “missed out”. They surely missed out on buying a lot of nice “stuff” … maybe. There are always new luxury items for sale in the burning ruins of fiat. There are always people that want to temporarily like or love you (long time) for fiat, as well as for bitcoin. You’re still an empty shell if your do. Just like the fiat slaves. A crypto bro will always stay the same sell out, even if he holds bitcoin by any chance.
You know why? Because bitcoiners don’t think like “they” do. The fiat masters that screwed this world up, think and work over multi generations. (Remember that for later, in piece twelve of this series.)
The only path forward
Solo heroics can’t beat the market or drive adoption anymore. Collective action is key. The Lightning Network grows from thousands of small nodes for example. Bitcoin Core thrives on shared grit. Profit isn’t sportcars — it’s a thriving network freeing people. If 10,000 people spend 0.05 BTC to fund wallets, educate merchants or build tools, we’d see more users and transactions. Adoption drives demand. Sacrifice now, impact later. Don’t work for PMB orders — they’re fiat victims, not Bitcoin builders.
Act together, thrive together
To kill PMB, rediscover your potential, even if it costs you:
Educate wide: Teach Bitcoin’s truth—how it works, why it matters. Every convert strengthens us.
Build together: Run nodes, fund Lightning hubs, support devs. Small contributions add up.
Use Bitcoin: Spend it, gift it, make it move. Transactions are the network’s heartbeat.
Value the mission: Chase freedom, not fiat. Your legacy is impact, not your stack.
A call to build The parable of Bitcoin is clear: hoard and get rich, but leave nothing behind; act together, sacrifice wealth, and build a thriving Bitcoin world. Hoarding risks a deflationary spiral while Wall Street grabs another 100,000 BTC every few weeks and sits on it for other fund managers to buy the stake (pun intended).
PMB Bitcoiners will cash out, thinking they’re smart, trading our future for fiat luxury. Bitcoin’s value lies in trust, scarcity, and a network grown by those who see beyond their wallets. Bury your Bitcoin or build with it.
If someone slyly nudges you to pump their bags, call them faithless leeches who ignore the call for a better world. They’re quiet, polite, and vanish when it’s time to fund or build. They tally fiat gains while you grind through life’s rot. They sling insults if you educate, risk, or create. They’re all take, no give — enemies, even if they hold Bitcoin.
Bitcoiners route around problems. Certainly if that problem is other bitcoiners. Because we know how they think, we know their buried talents, we know why they do it. It’s in our DNA to know. They don’t know why we keep building however, the worse of them don’t understand.
Bitcoin’s value isn’t in scarcity alone — it’s in the combination of trust, scarcity and the network, grown by those who see beyond their wallets and small gains.
Whether you’ve got 0.01 BTC or 10,000 BTC, your choice matters. Will you bury your Bitcoin, or build with it? I can hope we choose the latter.
If someone, directly or slyly, nudges you to pump their bags, call them out as faithless servants who wouldn’t even hear the calling of a better world. These types are often quiet, polite, and ask few questions, but when it’s time to step up, they vanish — nowhere to be found for funding, working, or doing anything real, big or small. They’re obsessed with “pump my bags,” tallying their fiat gains while you grind, sweat, and ache through life’s rotten misery. Usually they’re well off, because fiat mentality breeds more fiat.
They won’t lift you up or support you, because they’re all about the “take” and take and take more, giving nice sounding incentives to keep you pumping and grinding. They smell work, but never participate. They’re lovely and nice as long as you go along and pump.
Pump-My-Bags bitcoiners are temporary custodians, financial Frankfurter sausages hunting for a bun to flop into. We have the mustard. We know how to make it, package it and pour it over them. We’re the preservers of hard money. We build, think and try.
They get eaten. They’re fiat-born and when the real builders rise (they’re already a few years old), history won’t remember these people’s stacks and irrelevant comments — only our sacrifices.
by: AVB
-
 @ d34e832d:383f78d0
2025-04-24 07:22:54
@ d34e832d:383f78d0
2025-04-24 07:22:54Operation
This operational framework delineates a methodologically sound, open-source paradigm for the self-custody of Bitcoin, prominently utilizing Electrum, in conjunction with VeraCrypt-encrypted USB drives designed to effectively emulate the functionality of a cold storage hardware wallet.
The primary aim of this initiative is to empower individual users by providing a mechanism that is economically viable, resistant to coercive pressures, and entirely verifiable. This is achieved by harnessing the capabilities inherent in open-source software and adhering to stringent cryptographic protocols, thereby ensuring an uncompromising stance on Bitcoin sovereignty.
The proposed methodology signifies a substantial advancement over commercially available hardware wallets, as it facilitates the creation of a do-it-yourself air-gapped environment that not only bolsters resilience and privacy but also affirms the principles of decentralization intrinsic to the cryptocurrency ecosystem.
1. The Need For Trustless, Private, and Secure Storage
With Bitcoin adoption increasing globally, the need for trustless, private, and secure storage is critical. While hardware wallets like Trezor and Ledger offer some protection, they introduce proprietary code, closed ecosystems, and third-party risk. This Idea explores an alternative: using Electrum Wallet within an encrypted VeraCrypt volume on a USB flash drive, air-gapped via Tails OS or offline Linux systems.
2. Architecture of the DIY Hardware Wallet
2.1 Core Components
- Electrum Wallet (SegWit, offline mode)
- USB flash drive (≥ 8 GB)
- VeraCrypt encryption software
- Optional: Tails OS bootable environment
2.2 Drive Setup
- Format the USB drive and install VeraCrypt volumes.
- Choose AES + SHA-512 encryption for robust protection.
- Use FAT32 for wallet compatibility with Electrum (under 4GB).
- Enable Hidden Volume for plausible deniability under coercion.
3. Creating the Encrypted Environment
3.1 Initial Setup
- Download VeraCrypt from the official site; verify GPG signatures.
- Encrypt the flash drive and store a plain Electrum AppImage inside.
- Add a hidden encrypted volume with the wallet seed, encrypted QR backups, and optionally, a decoy wallet.
3.2 Mounting Workflow
- Always mount the VeraCrypt volume on an air-gapped computer, ideally booted into Tails OS.
- Never connect the encrypted USB to an internet-enabled system.
4. Air-Gapped Wallet Operations
4.1 Wallet Creation (Offline)
- Generate a new Electrum SegWit wallet inside the mounted VeraCrypt volume.
- Record the seed phrase on paper, or store it in a second hidden volume.
- Export xpub (public key) for use with online watch-only wallets.
4.2 Receiving Bitcoin
- Use watch-only Electrum wallet with the exported xpub on an online system.
- Generate receiving addresses without exposing private keys.
4.3 Sending Bitcoin
- Create unsigned transactions (PSBT) in the watch-only wallet.
- Transfer them via QR code or USB sneakernet to the air-gapped wallet.
- Sign offline using Electrum, then return the signed transaction to the online device for broadcast.
5. OpSec Best Practices
5.1 Physical and Logical Separation
- Use a dedicated machine or a clean Tails OS session every time.
- Keep the USB drive hidden and disconnected unless in use.
- Always dismount the VeraCrypt volume after operations.
5.2 Seed Phrase Security
- Never type the seed on an online machine.
- Consider splitting the seed using Shamir's Secret Sharing or metal backup plates.
5.3 Coercion Resilience
- Use VeraCrypt’s hidden volume feature to store real wallet data.
- Maintain a decoy wallet in the outer volume with nominal funds.
- Practice your recovery and access process until second nature.
6. Tradeoffs vs. Commercial Wallets
| Feature | DIY Electrum + VeraCrypt | Ledger/Trezor | |--------|--------------------------|---------------| | Open Source | ✅ Fully | ⚠️ Partially | | Air-gapped Usage | ✅ Yes | ⚠️ Limited | | Cost | 💸 Free (except USB) | 💰 $50–$250 | | Hidden/Coercion Defense | ✅ Hidden Volume | ❌ None | | QR Signing Support | ⚠️ Manual | ✅ Some models | | Complexity | 🧠 High | 🟢 Low | | Long-Term Resilience | ✅ No vendor risk | ⚠️ Vendor-dependent |
7. Consider
A DIY hardware wallet built with Electrum and VeraCrypt offers an unprecedented level of user-controlled sovereignty in Bitcoin storage. While the technical learning curve may deter casual users, those who value security, privacy, and independence will find this setup highly rewarding. This Operation demonstrates that true Bitcoin ownership requires not only control of private keys, but also a commitment to operational security and digital self-discipline. In a world of growing surveillance and digital coercion, such methods may not be optional—they may be essential.
8. References
- Nakamoto, Satoshi. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008.
- Electrum Technologies GmbH. “Electrum Documentation.” electrum.org, 2024.
- VeraCrypt. “Documentation.” veracrypt.fr, 2025.
- Tails Project. “The Amnesic Incognito Live System (Tails).” tails.boum.org, 2025.
- Matonis, Jon. "DIY Cold Storage for Bitcoin." Forbes, 2014.
In Addition
🛡️ Create Your Own Secure Bitcoin Hardware Wallet: Electrum + VeraCrypt DIY Guide
Want maximum security for your Bitcoin without trusting third-party devices like Ledger or Trezor?
This guide shows you how to build your own "hardware wallet" using free open-source tools:
✅ Electrum Wallet + ✅ VeraCrypt Encrypted Flash Drive — No extra cost, no vendor risk.Let Go Further
What You’ll Need
- A USB flash drive (8GB minimum, 64-bit recommended)
- A clean computer (preferably old or dedicated offline)
- Internet connection (for setup only, then go air-gapped)
- VeraCrypt software (free, open-source)
- Electrum Bitcoin Wallet AppImage file
Step 1: Download and Verify VeraCrypt
- Go to VeraCrypt Official Website.
- Download the installer for your operating system.
- Verify the GPG signatures to ensure the download isn't tampered with.
👉 [Insert Screenshot Here: VeraCrypt download page]
Pro Tip: Never skip verification when dealing with encryption software!
Step 2: Download Electrum Wallet
- Go to Electrum Official Website.
- Download the Linux AppImage or Windows standalone executable.
- Again, verify the PGP signatures published on the site. 👉 [Insert Screenshot Here: Electrum download page]
Step 3: Prepare and Encrypt Your USB Drive
- Insert your USB drive into the computer.
- Open VeraCrypt and select Create Volume → Encrypt a Non-System Partition/Drive.
- Choose Standard Volume for now (later we'll talk about hidden volumes).
- Select your USB drive, set an extremely strong password (12+ random characters).
- For Encryption Algorithm, select AES and SHA-512 for Hash Algorithm.
- Choose FAT32 as the file system (compatible with Bitcoin wallet sizes under 4GB).
- Format and encrypt. 👉 [Insert Screenshot Here: VeraCrypt creating volume]
Important: This will wipe all existing data on the USB drive!
Step 4: Mount the Encrypted Drive
Whenever you want to use the wallet:
- Open VeraCrypt.
- Select a slot (e.g., Slot 1).
- Click Select Device, choose your USB.
- Enter your strong password and Mount. 👉 [Insert Screenshot Here: VeraCrypt mounted volume]
Step 5: Set Up Electrum in Offline Mode
- Mount your encrypted USB.
- Copy the Electrum AppImage (or EXE) onto the USB inside the encrypted partition.
- Run Electrum from there.
- Select Create New Wallet.
- Choose Standard Wallet → Create New Seed → SegWit.
- Write down your 12-word seed phrase on PAPER.
❌ Never type it into anything else. - Finish wallet creation and disconnect from internet immediately. 👉 [Insert Screenshot Here: Electrum setup screen]
Step 6: Make It Air-Gapped Forever
- Only ever access the encrypted USB on an offline machine.
- Never connect this device to the internet again.
- If possible, boot into Tails OS every time for maximum security.
Pro Tip: Tails OS leaves no trace on the host computer once shut down!
Step 7: (Optional) Set Up a Hidden Volume
For even stronger security:
- Repeat the VeraCrypt process to add a Hidden Volume inside your existing USB encryption.
- Store your real Electrum wallet in the hidden volume.
- Keep a decoy wallet with small amounts of Bitcoin in the outer volume.
👉 This way, if you're ever forced to reveal the password, you can give access to the decoy without exposing your true savings.
Step 8: Receiving Bitcoin
- Export your xpub (extended public key) from the air-gapped Electrum wallet.
- Import it into a watch-only Electrum wallet on your online computer.
- Generate receiving addresses without exposing your private keys.
Step 9: Spending Bitcoin (Safely)
To send Bitcoin later:
- Create a Partially Signed Bitcoin Transaction (PSBT) with the online watch-only wallet.
- Transfer the file (or QR code) offline (via USB or QR scanner).
- Sign the transaction offline with Electrum.
- Bring the signed file/QR back to the online device and broadcast it.
✅ Your private keys never touch the internet!
Step 10: Stay Vigilant
- Always dismount the encrypted drive after use.
- Store your seed phrase securely (preferably in a metal backup).
- Regularly practice recovery drills.
- Update Electrum and VeraCrypt only after verifying new downloads.
🎯 Consider
Building your own DIY Bitcoin hardware wallet might seem complex, but security is never accidental — it is intentional.
By using VeraCrypt encryption and Electrum offline, you control your Bitcoin in a sovereign, verifiable, and bulletproof way.⚡ Take full custody. No companies. No middlemen. Only freedom.
-
 @ 1f79058c:eb86e1cb
2025-04-24 07:17:12
@ 1f79058c:eb86e1cb
2025-04-24 07:17:12I think we should agree on an HTML element for pointing to the Nostr representation of a document/URL on the Web. We could use the existing one for link relations for example:
html <link rel="alternate" type="application/nostr+json" href="nostr:naddr1qvzqqqr4..." title="This article on Nostr" />This would be useful in multiple ways:
- Nostr clients, when fetching meta/preview information for a URL that is linked in a note, can detect that there's a Nostr representation of the content, and then render it in Nostr-native ways (whatever that may be depending on the client)
- User agents, usually a browser or browser extension, when opening a URL on the Web, can offer opening the alternative representation of a page in a Nostr client. And/or they could offer to follow the author's pubkey on Nostr. And/or they could offer to zap the content.
- When publishing a new article, authors can share their preferred Web URL everywhere, without having to consider if the reader knows about or uses Nostr at all. However, if a Nostr user finds the Web version of an article outside of Nostr, they can now easily jump to the Nostr version of it.
- Existing Web publications can retroactively create Nostr versions of their content and easily link the Nostr articles on all of their existing article pages without having to add prominent Nostr links everywhere.
There are probably more use cases, like Nostr search engines and whatnot. If you can think of something interesting, please tell me.
Proof of concept
In order to show one way in which this could be used, I have created a small Web Extension called Nostr Links, which will discover alternate Nostr links on the pages you visit.
If it finds one or more links, it will show a purple Nostr icon in the address bar, which you can click to open the list of links. It's similar to e.g. the Feed Preview extension, and also to what the Tor Browser does when it discovers an Onion-Location for the page you're looking at:
The links in this popup menu will be
web+nostr:links, because browsers currently do not allow web apps or extensions to handle unprefixednostr:links. (I hope someone is working on getting those on par withipfs:etc.)Following such a link will either open your default Nostr Web app, if you have already configured one, or it will ask you which Web app to open the link with.
Caveat emptor: At the time of writing, my personal default Web app, noStrudel, needs a new release for the links to find the content.
Try it now
Have a look at the source code and/or download the extension (currently only for Firefox).
I have added alternate Nostr links to the Web pages of profiles and long-form content on the Kosmos relay's domain. It's probably the only place on the Web, which will trigger the extension right now.
You can look at this very post to find an alternate link for example.
-
 @ 866e0139:6a9334e5
2025-04-24 06:34:04
@ 866e0139:6a9334e5
2025-04-24 06:34:04\ Autor: Beate Diederichs. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Die Warener Initiative „Menschlich Stark Miteinander“ organisiert regelmäßig Demonstrationen und andere Aktionen für Frieden, Menschenrechte und gegen die Spaltung der Gesellschaft. Am 21. April rief sie Warener, Menschen aus anderen Teilen der Müritzregion und Touristen zum jährlichen Ostermarsch zusammen.
Die Friedenstaube ermuntert alle, die sich der Friedensbewegung zugehörig fühlen, uns Termine von Kundgebungen bekanntzugeben und darüber zu berichten. Sehen Sie hier die Rede von Ulrike Guérot in Dresden:
https://www.youtube.com/watch?v=KarwcXKmD3E
Rund einhundert Leute hatten sich am Abend des Ostermontags auf dem Neuen Markt in Waren an der Müritz versammelt. Sie trugen Fahnen mit der Friedenstaube, selbstgebastelte Transparente oder Sticker an der Kleidung, die ihre Besitzer als Verfechter von Völkerfreundschaft und Abrüstung auswiesen.
„Dass Menschen angefeindet werden, die Frieden wollen – das gab es so noch nie. Es zeigt uns: Wir sind auf dem richtigen Weg“, sagte Markus Häcker, „Kopf“ der Initiative „Menschlich Stark Miteinander“, bei seiner Begrüßung ins Mikro. Er würdigte dann die Arbeit seiner Mitstreiterin Regina Cleemann, die den Ostermarsch organisiert hatte. Wie in den vergangenen Jahren hatte die Musiklehrerin im Ruhestand eine Route zusammengestellt, die die Demonstranten an Orte innerhalb Warens führte, die an die Schrecken des Krieges erinnerten: die „Trauernde Mutter“, das Ehrenmal für die im Zweiten Weltkrieg gefallenen sowjetischen Soldaten, den Gedenkstein der Synagoge am Tiefwarensee, das Victoriadenkmal zum deutsch-französischen Krieg 1870/1871 und schließlich den Gedenkstein für die Opfer der beiden Weltkriege am Ufer der Müritz.
„Ich wollte diesmal noch mehr als in den vergangenen Jahren die Musik nutzen“, kommentierte Regina Cleemann. So kombinierte sie an drei der vier Stationen ihre Sprechtexte – Hintergrundinformationen zu den Gedenkorten oder Gedichte – mit passenden Musikstücken. Am sowjetischen Ehrenmal erzählte die Warenerin dessen Geschichte und spielte ein russisches Partisanenlied in einer historischen Aufnahme ab, um es authentischer wirken zu lassen. Am Gedenkstein für die Weltkriegstoten erklang „Frieden brauch ich – bin ein Kind“, gesungen von einer klaren jungen Stimme. Danach rezitierte Regina Cleemann das Gedicht „An meine Landsleute“ von Bertolt Brecht. Besonders nachdrücklich intonierte sie die Zeile:
„Ihr Kinder, dass sie euch mit Krieg verschonen.“

Ich schäme mich für die Politik
Die pensionierte Lehrerin, die einst Berufsschülern und jüngeren Kindern den Zauber der Musik nahebrachte, hat bereits eine gewisse Routine bei der Vorbereitung des Ostermarsches in Waren an der Müritz entwickelt. Denn Regina Cleemann organisierte die Veranstaltung zum dritten Mal. „Krieg ist für mich das allerröteste Tuch. Daher schäme ich so sehr für das, was gerade in der Politik passiert“, beschreibt sie ihre Motivation. Als Nachkriegskind sind ihr Begriffe wie „Ruinen“ oder „Lebensmittelmarken“ noch allzu vertraut. „Ich erinnere mich auch noch gut, wie mein Vater nach dem Ende des Zweiten Weltkriegs zu Fuß aus Bayern zu uns in die Müritzregion zurückkehrte.“ Leider nehme die Zahl der Menschen ab, die noch wüssten, was Krieg bedeute, so wie sie. Regina Cleemann kann dennoch nicht verstehen, wie ihre Mitmenschen Aussagen wie „Frieden gibt es genug auf dem Friedhof“ apathisch hinnehmen und hoffen, dass deren Folgen sie nicht betreffen. Mit ihrem Engagement möchte sie diese Mitmenschen aufrütteln.
Praktikanten und Volontäre gesucht!
Die Friedenstaube verstärkt sich redaktionell und bietet 2 Praktikanten- und eine Volontariatsstelle an. Sie wollen an einer starken Stimme für den Frieden arbeiten, sind technisch interessiert, haben Erfahrung mit und Spaß an Textarbeit? Wohnort egal. Schreiben Sie uns, gerne mit Arbeitsproben: friedenstaube\@pareto.space
Schon viele Wochen vor dem jährlichen Ostermarsch beschäftigt sich die Rentnerin damit, welcher Text und welches Musikstück diesmal zu der jeweiligen Station passen. „Es arbeitet in mir“, beschreibt sie diesen Prozess. Oft fallen ihr ganz nebenbei markante Passagen aus Liedern oder Gedichten ein. Dann gräbt sie so lange in Büchern oder im Internet, bis sie sie findet, und bereitet sie für die Veranstaltung auf. „Im kommenden Jahr könnte ich mir auch vorstellen, dass im Vorfeld unterschiedliche Stimmen die Texte einsprechen, um für mehr Abwechslung zu sorgen.“
Regina Cleemann freut sich stets über positive Resonanz bei den Gleichgesinnten. Doch es geht ihr selbstverständlich auch und vor allem darum, Andere für ihr Anliegen zu gewinnen. Daher hat sie sich sehr darüber gefreut, dass nach der letzten Station des rund zweistündigen Rundgangs einige Passanten stehen blieben und Gespräche entstanden. „Ein Tourist aus Wolgast in Vorpommern erzählte, er sei extra wegen unseres Ostermarsches länger in der Stadt geblieben und verfolge auch ab und an den Live-Stream unserer anderen Veranstaltungen. So etwas zu hören, ist immer ein schönes Erlebnis.“
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ d34e832d:383f78d0
2025-04-24 06:28:48
@ d34e832d:383f78d0
2025-04-24 06:28:48Operation
Central to this implementation is the utilization of Tails OS, a Debian-based live operating system designed for privacy and anonymity, alongside the Electrum Wallet, a lightweight Bitcoin wallet that provides a streamlined interface for secure Bitcoin transactions.
Additionally, the inclusion of advanced cryptographic verification mechanisms, such as QuickHash, serves to bolster integrity checks throughout the storage process. This multifaceted approach ensures a rigorous adherence to end-to-end operational security (OpSec) principles while simultaneously safeguarding user autonomy in the custody of digital assets.
Furthermore, the proposed methodology aligns seamlessly with contemporary cybersecurity paradigms, prioritizing characteristics such as deterministic builds—where software builds are derived from specific source code to eliminate variability—offline key generation processes designed to mitigate exposure to online threats, and the implementation of minimal attack surfaces aimed at reducing potential vectors for exploitation.
Ultimately, this sophisticated approach presents a methodical and secure paradigm for the custody of private keys, thereby catering to the exigencies of high-assurance Bitcoin storage requirements.
1. Cold Storage Refers To The offline Storage
Cold storage refers to the offline storage of private keys used to sign Bitcoin transactions, providing the highest level of protection against network-based threats. This paper outlines a verifiable method for constructing such a storage system using the following core principles:
- Air-gapped key generation
- Open-source software
- Deterministic cryptographic tools
- Manual integrity verification
- Offline transaction signing
The method prioritizes cryptographic security, software verifiability, and minimal hardware dependency.
2. Hardware and Software Requirements
2.1 Hardware
- One 64-bit computer (laptop/desktop)
- 1 x USB Flash Drive (≥8 GB, high-quality brand recommended)
- Paper and pen (for seed phrase)
- Optional: Printer (for xpub QR export)
2.2 Software Stack
- Tails OS (latest ISO, from tails.boum.org)
- Balena Etcher (to flash ISO)
- QuickHash GUI (for SHA-256 checksum validation)
- Electrum Wallet (bundled within Tails OS)
3. System Preparation and Software Verification
3.1 Image Verification
Prior to flashing the ISO, the integrity of the Tails OS image must be cryptographically validated. Using QuickHash:
plaintext SHA256 (tails-amd64-<version>.iso) = <expected_hash>Compare the hash output with the official hash provided on the Tails OS website. This mitigates the risk of ISO tampering or supply chain compromise.
3.2 Flashing the OS
Balena Etcher is used to flash the ISO to a USB drive:
- Insert USB drive.
- Launch Balena Etcher.
- Select the verified Tails ISO.
- Flash to USB and safely eject.
4. Cold Wallet Generation Procedure
4.1 Boot Into Tails OS
- Restart the system and boot into BIOS/UEFI boot menu.
- Select the USB drive containing Tails OS.
- Configure network settings to disable all connectivity.
4.2 Create Wallet in Electrum (Cold)
- Open Electrum from the Tails application launcher.
- Select "Standard Wallet" → "Create a new seed".
- Choose SegWit for address type (for lower fees and modern compatibility).
- Write down the 12-word seed phrase on paper. Never store digitally.
- Confirm the seed.
- Set a strong password for wallet access.
5. Exporting the Master Public Key (xpub)
- Open Electrum > Wallet > Information
- Export the Master Public Key (MPK) for receiving-only use.
- Optionally generate QR code for cold-to-hot usage (wallet watching).
This allows real-time monitoring of incoming Bitcoin transactions without ever exposing private keys.
6. Transaction Workflow
6.1 Receiving Bitcoin (Cold to Hot)
- Use the exported xpub in a watch-only wallet (desktop or mobile).
- Generate addresses as needed.
- Senders deposit Bitcoin to those addresses.
6.2 Spending Bitcoin (Hot Redeem Mode)
Important: This process temporarily compromises air-gap security.
- Boot into Tails (or use Electrum in a clean Linux environment).
- Import the 12-word seed phrase.
- Create transaction offline.
- Export signed transaction via QR code or USB.
- Broadcast using an online device.
6.3 Recommended Alternative: PSBT
To avoid full wallet import: - Use Partially Signed Bitcoin Transactions (PSBT) protocol to sign offline. - Broadcast PSBT using Sparrow Wallet or Electrum online.
7. Security Considerations
| Threat | Mitigation | |-------|------------| | OS Compromise | Use Tails (ephemeral environment, RAM-only) | | Supply Chain Attack | Manual SHA256 verification | | Key Leakage | No network access during key generation | | Phishing/Clone Wallets | Verify Electrum’s signature (when updating) | | Physical Theft | Store paper seed in tamper-evident location |
8. Backup Strategy
- Store 12-word seed phrase in multiple secure physical locations.
- Do not photograph or digitize.
- For added entropy, use Shamir Secret Sharing (e.g., 2-of-3 backups).
9. Consider
Through the meticulous integration of verifiable software solutions, the execution of air-gapped key generation methodologies, and adherence to stringent operational protocols, users have the capacity to establish a Bitcoin cold storage wallet that embodies an elevated degree of cryptographic assurance.
This DIY system presents a zero-dependency alternative to conventional third-party custody solutions and consumer-grade hardware wallets.
Consequently, it empowers individuals with the ability to manage their Bitcoin assets while ensuring full trust minimization and maximizing their sovereign control over private keys and transaction integrity within the decentralized financial ecosystem..
10. References And Citations
Nakamoto, Satoshi. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008.
“Tails - The Amnesic Incognito Live System.” tails.boum.org, The Tor Project.
“Electrum Bitcoin Wallet.” electrum.org, 2025.
“QuickHash GUI.” quickhash-gui.org, 2025.
“Balena Etcher.” balena.io, 2025.
Bitcoin Core Developers. “Don’t Trust, Verify.” bitcoincore.org, 2025.In Addition
🪙 SegWit vs. Legacy Bitcoin Wallets
⚖️ TL;DR Decision Chart
| If you... | Use SegWit | Use Legacy | |-----------|----------------|----------------| | Want lower fees | ✅ Yes | 🚫 No | | Send to/from old services | ⚠️ Maybe | ✅ Yes | | Care about long-term scaling | ✅ Yes | 🚫 No | | Need max compatibility | ⚠️ Mixed | ✅ Yes | | Run a modern wallet | ✅ Yes | 🚫 Legacy support fading | | Use cold storage often | ✅ Yes | ⚠️ Depends on wallet support | | Use Lightning Network | ✅ Required | 🚫 Not supported |
🔍 1. What Are We Comparing?
There are two major types of Bitcoin wallet address formats:
🏛️ Legacy (P2PKH)
- Format starts with:
1 - Example:
1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa - Oldest, most universally compatible
- Higher fees, larger transactions
- May lack support in newer tools and layer-2 solutions
🛰️ SegWit (P2WPKH)
- Formats start with:
- Nested SegWit (P2SH):
3... - Native SegWit (bech32):
bc1q... - Introduced via Bitcoin Improvement Proposal (BIP) 141
- Smaller transaction sizes → lower fees
- Native support by most modern wallets
💸 2. Transaction Fees
SegWit = Cheaper.
- SegWit reduces the size of Bitcoin transactions in a block.
- This means you pay less per transaction.
- Example: A SegWit transaction might cost 40%–60% less in fees than a legacy one.💡 Why?
Bitcoin charges fees per byte, not per amount.
SegWit removes certain data from the base transaction structure, which shrinks byte size.
🧰 3. Wallet & Service Compatibility
| Category | Legacy | SegWit (Nested / Native) | |----------|--------|---------------------------| | Old Exchanges | ✅ Full support | ⚠️ Partial | | Modern Exchanges | ✅ Yes | ✅ Yes | | Hardware Wallets (Trezor, Ledger) | ✅ Yes | ✅ Yes | | Mobile Wallets (Phoenix, BlueWallet) | ⚠️ Rare | ✅ Yes | | Lightning Support | 🚫 No | ✅ Native SegWit required |
🧠 Recommendation:
If you interact with older platforms or do cross-compatibility testing, you may want to: - Use nested SegWit (address starts with
3), which is backward compatible. - Avoid bech32-only wallets if your exchange doesn't support them (though rare in 2025).
🛡️ 4. Security and Reliability
Both formats are secure in terms of cryptographic strength.
However: - SegWit fixes a bug known as transaction malleability, which helps build protocols on top of Bitcoin (like the Lightning Network). - SegWit transactions are more standardized going forward.
💬 User takeaway:
For basic sending and receiving, both are equally secure. But for future-proofing, SegWit is the better bet.
🌐 5. Future-Proofing
Legacy wallets are gradually being phased out:
- Developers are focusing on SegWit and Taproot compatibility.
- Wallet providers are defaulting to SegWit addresses.
- Fee structures increasingly assume users have upgraded.
🚨 If you're using a Legacy wallet today, you're still safe. But: - Some services may stop supporting withdrawals to legacy addresses. - Your future upgrade path may be more complex.
🚀 6. Real-World Scenarios
🧊 Cold Storage User
- Use SegWit for low-fee UTXOs and efficient backup formats.
- Consider Native SegWit (
bc1q) if supported by your hardware wallet.
👛 Mobile Daily User
- Use Native SegWit for cheaper everyday payments.
- Ideal if using Lightning apps — it's often mandatory.
🔄 Exchange Trader
- Check your exchange’s address type support.
- Consider nested SegWit (
3...) if bridging old + new systems.
📜 7. Migration Tips
If you're moving from Legacy to SegWit:
- Create a new SegWit wallet in your software/hardware wallet.
- Send funds from your old Legacy wallet to the SegWit address.
- Back up the new seed — never reuse the old one.
- Watch out for fee rates and change address handling.
✅ Final User Recommendations
| Use Case | Address Type | |----------|--------------| | Long-term HODL | SegWit (
bc1q) | | Maximum compatibility | SegWit (nested3...) | | Fee-sensitive use | Native SegWit (bc1q) | | Lightning | Native SegWit (bc1q) | | Legacy systems only | Legacy (1...) – short-term only |
📚 Further Reading
- Nakamoto, Satoshi. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008.
- Bitcoin Core Developers. “Segregated Witness (Consensus Layer Change).” github.com/bitcoin, 2017.
- “Electrum Documentation: Wallet Types.” docs.electrum.org, 2024.
- “Bitcoin Wallet Compatibility.” bitcoin.org, 2025.
- Ledger Support. “SegWit vs Legacy Addresses.” ledger.com, 2024.
-
 @ b2caa9b3:9eab0fb5
2025-04-24 06:25:35
@ b2caa9b3:9eab0fb5
2025-04-24 06:25:35Yesterday, I faced one of the most heartbreaking and frustrating experiences of my life. Between 10:00 AM and 2:00 PM, I was held at the Taveta border, denied entry into Kenya—despite having all the necessary documents, including a valid visitor’s permit and an official invitation letter.
The Kenyan Immigration officers refused to speak with me. When I asked for clarification, I was told flatly that I would never be allowed to enter Kenya unless I obtain a work permit. No other reason was given. My attempts to explain that I simply wanted to see my child were ignored. No empathy. No flexibility. No conversation. Just rejection.
While I stood there for hours, held by officials with no explanation beyond a bureaucratic wall, I recorded the experience. I now have several hours of footage documenting what happened—a silent testimony to how a system can dehumanize and block basic rights.
And the situation doesn’t end at the border.
My child, born in Kenya, is also being denied the right to see me. Germany refuses to grant her citizenship, which means she cannot visit me either. The German embassy in Nairobi refuses to assist, stating they won’t get involved. Their silence is loud.
This is not just about paperwork. This is about a child growing up without her father. It’s about a system that chooses walls over bridges, and bureaucracy over humanity. Kenya, by refusing me entry, is keeping a father away from his child. Germany, by refusing to act under §13 StGB, is complicit in that injustice.
In the coming days, I’ll share more about my past travels and how this situation unfolded. I’ll also be releasing videos and updates on TikTok—because this story needs to be heard. Not just for me, but for every parent and child caught between borders and bureaucracies.
Stay tuned—and thank you for standing with me.
-
 @ d34e832d:383f78d0
2025-04-24 06:12:32
@ d34e832d:383f78d0
2025-04-24 06:12:32
Goal
This analytical discourse delves into Jack Dorsey's recent utterances concerning Bitcoin, artificial intelligence, decentralized social networking platforms such as Nostr, and the burgeoning landscape of open-source cryptocurrency mining initiatives.
Dorsey's pronouncements escape the confines of isolated technological fascinations; rather, they elucidate a cohesive conceptual schema wherein Bitcoin transcends its conventional role as a mere store of value—akin to digital gold—and emerges as a foundational protocol intended for the construction of a decentralized, sovereign, and perpetually self-evolving internet ecosystem.
A thorough examination of Dorsey's confluence of Bitcoin with artificial intelligence advancements, adaptive learning paradigms, and integrated social systems reveals an assertion of Bitcoin's position as an entity that evolves beyond simple currency, evolving into a distinctly novel socio-technological organism characterized by its inherent ability to adapt and grow. His vigorous endorsement of native digital currency, open communication protocols, and decentralized infrastructural frameworks is posited here as a revolutionary paradigm—a conceptual
1. The Path
Jack Dorsey, co-founder of Twitter and Square (now Block), has emerged as one of the most compelling evangelists for a decentralized future. His ideas about Bitcoin go far beyond its role as a speculative asset or inflation hedge. In a recent interview, Dorsey ties together themes of open-source AI, peer-to-peer currency, decentralized media, and radical self-education, sketching a future in which Bitcoin is the lynchpin of an emerging technological and social ecosystem. This thesis reviews Dorsey’s statements and offers a critical framework to understand why his vision uniquely positions Bitcoin as the keystone of a post-institutional, digital world.
2. Bitcoin: The Native Currency of the Internet
“It’s the best current manifestation of a native internet currency.” — Jack Dorsey
Bitcoin's status as an open protocol with no central controlling authority echoes the original spirit of the internet: decentralized, borderless, and resilient. Dorsey's framing of Bitcoin not just as a payment system but as the "native money of the internet" is a profound conceptual leap. It suggests that just as HTTP became the standard for web documents, Bitcoin can become the monetary layer for the open web.
This framing bypasses traditional narratives of digital gold or institutional adoption and centers a P2P vision of global value transfer. Unlike central bank digital currencies or platform-based payment rails, Bitcoin is opt-in, permissionless, and censorship-resistant—qualities essential for sovereignty in the digital age.
3. Nostr and the Decentralization of Social Systems
Dorsey’s support for Nostr, an open protocol for decentralized social media, reflects a desire to restore user agency, protocol composability, and speech sovereignty. Nostr’s architecture parallels Bitcoin’s: open, extensible, and resilient to censorship.
Here, Bitcoin serves not just as money but as a network effect driver. When combined with Lightning and P2P tipping, Nostr becomes more than just a Twitter alternative—it evolves into a micropayment-native communication system, a living proof that Bitcoin can power an entire open-source social economy.
4. Open-Source AI and Cognitive Sovereignty
Dorsey's forecast that open-source AI will emerge as an alternative to proprietary systems aligns with his commitment to digital autonomy. If Bitcoin empowers financial sovereignty and Nostr enables communicative freedom, open-source AI can empower cognitive independence—freeing humanity from centralized algorithmic manipulation.
He draws a fascinating parallel between AI learning models and human learning itself, suggesting both can be self-directed, recursive, and radically decentralized. This resonates with the Bitcoin ethos: systems should evolve through transparent, open participation—not gatekeeping or institutional control.
5. Bitcoin Mining: Sovereignty at the Hardware Layer
Block’s initiative to create open-source mining hardware is a direct attempt to counter centralization in Bitcoin’s infrastructure. ASIC chip development and mining rig customization empower individuals and communities to secure the network directly.
This move reinforces Dorsey’s vision that true decentralization requires ownership at every layer, including hardware. It is a radical assertion of vertical sovereignty—from protocol to interface to silicon.
6. Learning as the Core Protocol
“The most compounding skill is learning itself.” — Jack Dorsey
Dorsey’s deepest insight is that the throughline connecting Bitcoin, AI, and Nostr is not technology—it’s learning. Bitcoin represents more than code; it’s a living experiment in voluntary consensus, a distributed educational system in cryptographic form.
Dorsey’s emphasis on meditation, intensive retreats, and self-guided exploration mirrors the trustless, sovereign nature of Bitcoin. Learning becomes the ultimate protocol: recursive, adaptive, and decentralized—mirroring AI models and Bitcoin nodes alike.
7. Critical Risks and Honest Reflections
Dorsey remains honest about Bitcoin’s current limitations:
- Accessibility: UX barriers for onboarding new users.
- Usability: Friction in everyday use.
- State-Level Adoption: Risks of co-optation as mere digital gold.
However, his caution enhances credibility. His focus remains on preserving Bitcoin as a P2P electronic cash system, not transforming it into another tool of institutional control.
8. Bitcoin as a Living System
What emerges from Dorsey's vision is not a product pitch, but a philosophical reorientation: Bitcoin, Nostr, and open AI are not discrete tools—they are living systems forming a new type of civilization stack.
They are not static infrastructures, but emergent grammars of human cooperation, facilitating value exchange, learning, and community formation in ways never possible before.
Bitcoin, in this view, is not merely stunningly original—it is civilizationally generative, offering not just monetary innovation but a path to software-upgraded humanity.
Works Cited and Tools Used
Dorsey, Jack. Interview on Bitcoin, AI, and Decentralization. April 2025.
Nakamoto, Satoshi. “Bitcoin: A Peer-to-Peer Electronic Cash System.” 2008.
Nostr Protocol. https://nostr.com.
Block, Inc. Bitcoin Mining Hardware Initiatives. 2024.
Obsidian Canvas. Decentralized Note-Taking and Networked Thinking. 2025. -
 @ d34e832d:383f78d0
2025-04-24 05:56:06
@ d34e832d:383f78d0
2025-04-24 05:56:06Idea
Through the integration of Optical Character Recognition (OCR), Docker-based deployment, and secure remote access via Twin Gate, Paperless NGX empowers individuals and small organizations to digitize, organize, and retrieve documents with minimal friction. This research explores its technical infrastructure, real-world applications, and how such a system can redefine document archival practices for the digital age.
Agile, Remote-Accessible, and Searchable Document System
In a world of increasing digital interdependence, managing physical documents is becoming not only inefficient but also environmentally and logistically unsustainable. The demand for agile, remote-accessible, and searchable document systems has never been higher—especially for researchers, small businesses, and archival professionals. Paperless NGX, an open-source platform, addresses these needs by offering a streamlined, secure, and automated way to manage documents digitally.
This Idea explores how Paperless NGX facilitates the transition to a paperless workflow and proposes best practices for sustainable, scalable usage.
Paperless NGX: The Platform
Paperless NGX is an advanced fork of the original Paperless project, redesigned with modern containers, faster performance, and enhanced community contributions. Its core functions include:
- Text Extraction with OCR: Leveraging the
ocrmypdfPython library, Paperless NGX can extract searchable text from scanned PDFs and images. - Searchable Document Indexing: Full-text search allows users to locate documents not just by filename or metadata, but by actual content.
- Dockerized Setup: A ready-to-use Docker Compose environment simplifies deployment, including the use of setup scripts for Ubuntu-based servers.
- Modular Workflows: Custom triggers and automation rules allow for smart processing pipelines based on file tags, types, or email source.
Key Features and Technical Infrastructure
1. Installation and Deployment
The system runs in a containerized environment, making it highly portable and isolated. A typical installation involves: - Docker Compose with YAML configuration - Volume mapping for persistent storage - Optional integration with reverse proxies (e.g., Nginx) for HTTPS access
2. OCR and Indexing
Using
ocrmypdf, scanned documents are processed into fully searchable PDFs. This function dramatically improves retrieval, especially for archived legal, medical, or historical records.3. Secure Access via Twin Gate
To solve the challenge of secure remote access without exposing the network, Twin Gate acts as a zero-trust access proxy. It encrypts communication between the Paperless NGX server and the client, enabling access from anywhere without the need for traditional VPNs.
4. Email Integration and Ingestion
Paperless NGX can ingest attachments directly from configured email folders. This feature automates much of the document intake process, especially useful for receipts, invoices, and academic PDFs.
Sustainable Document Management Workflow
A practical paperless strategy requires not just tools, but repeatable processes. A sustainable workflow recommended by the Paperless NGX community includes:
- Capture & Tagging
All incoming documents are tagged with a default “inbox” tag for triage. - Physical Archive Correlation
If the physical document is retained, assign it a serial number (e.g., ASN-001), which is matched digitally. - Curation & Tagging
Apply relevant category and topic tags to improve searchability. - Archival Confirmation
Remove the “inbox” tag once fully processed and categorized.
Backup and Resilience
Reliability is key to any archival system. Paperless NGX includes backup functionality via: - Cron job–scheduled Docker exports - Offsite and cloud backups using rsync or encrypted cloud drives - Restore mechanisms using documented CLI commands
This ensures document availability even in the event of hardware failure or data corruption.
Limitations and Considerations
While Paperless NGX is powerful, it comes with several caveats: - Technical Barrier to Entry: Requires basic Docker and Linux skills to install and maintain. - OCR Inaccuracy for Handwritten Texts: The OCR engine may struggle with cursive or handwritten documents. - Plugin and Community Dependency: Continuous support relies on active community contribution.
Consider
Paperless NGX emerges as a pragmatic and privacy-centric alternative to conventional cloud-based document management systems, effectively addressing the critical challenges of data security and user autonomy.
The implementation of advanced Optical Character Recognition (OCR) technology facilitates the indexing and searching of documents, significantly enhancing information retrieval efficiency.
Additionally, the platform offers secure remote access protocols that ensure data integrity while preserving the confidentiality of sensitive information during transmission.
Furthermore, its customizable workflow capabilities empower both individuals and organizations to precisely tailor their data management processes, thereby reclaiming sovereignty over their information ecosystems.
In an era increasingly characterized by a shift towards paperless methodologies, the significance of solutions such as Paperless NGX cannot be overstated; they play an instrumental role in engineering a future in which information remains not only accessible but also safeguarded and sustainably governed.
In Addition
To Further The Idea
This technical paper presents an optimized strategy for transforming an Intel NUC into a compact, power-efficient self-hosted server using Ubuntu. The setup emphasizes reliability, low energy consumption, and cost-effectiveness for personal or small business use. Services such as Paperless NGX, Nextcloud, Gitea, and Docker containers are examined for deployment. The paper details hardware selection, system installation, secure remote access, and best practices for performance and longevity.
1. Cloud sovereignty, Privacy, and Data Ownership
As cloud sovereignty, privacy, and data ownership become critical concerns, self-hosting is increasingly appealing. An Intel NUC (Next Unit of Computing) provides an ideal middle ground between Raspberry Pi boards and enterprise-grade servers—balancing performance, form factor, and power draw. With Ubuntu LTS and Docker, users can run a full suite of services with minimal overhead.
2. Hardware Overview
2.1 Recommended NUC Specifications:
| Component | Recommended Specs | |------------------|-----------------------------------------------------| | Model | Intel NUC 11/12 Pro (e.g., NUC11TNHi5, NUC12WSKi7) | | CPU | Intel Core i5 or i7 (11th/12th Gen) | | RAM | 16GB–32GB DDR4 (dual channel preferred) | | Storage | 512GB–2TB NVMe SSD (Samsung 980 Pro or similar) | | Network | Gigabit Ethernet + Optional Wi-Fi 6 | | Power Supply | 65W USB-C or barrel connector | | Cooling | Internal fan, well-ventilated location |
NUCs are also capable of dual-drive setups and support for Intel vPro for remote management on some models.
3. Operating System and Software Stack
3.1 Ubuntu Server LTS
- Version: Ubuntu Server 22.04 LTS
- Installation Method: Bootable USB (Rufus or Balena Etcher)
- Disk Partitioning: LVM with encryption recommended for full disk security
- Security:
- UFW (Uncomplicated Firewall)
- Fail2ban
- SSH hardened with key-only login
bash sudo apt update && sudo apt upgrade sudo ufw allow OpenSSH sudo ufw enable
4. Docker and System Services
Docker and Docker Compose streamline the deployment of isolated, reproducible environments.
4.1 Install Docker and Compose
bash sudo apt install docker.io docker-compose sudo systemctl enable docker4.2 Common Services to Self-Host:
| Application | Description | Access Port | |--------------------|----------------------------------------|-------------| | Paperless NGX | Document archiving and OCR | 8000 | | Nextcloud | Personal cloud, contacts, calendar | 443 | | Gitea | Lightweight Git repository | 3000 | | Nginx Proxy Manager| SSL proxy for all services | 81, 443 | | Portainer | Docker container management GUI | 9000 | | Watchtower | Auto-update containers | - |
5. Network & Remote Access
5.1 Local IP & Static Assignment
- Set a static IP for consistent access (via router DHCP reservation or Netplan).
5.2 Access Options
- Local Only: VPN into local network (e.g., WireGuard, Tailscale)
- Remote Access:
- Reverse proxy via Nginx with Certbot for HTTPS
- Twin Gate or Tailscale for zero-trust remote access
- DNS via DuckDNS, Cloudflare
6. Performance Optimization
- Enable
zramfor compressed RAM swap - Trim SSDs weekly with
fstrim - Use Docker volumes, not bind mounts for stability
- Set up unattended upgrades:
bash sudo apt install unattended-upgrades sudo dpkg-reconfigure --priority=low unattended-upgrades
7. Power and Environmental Considerations
- Idle Power Draw: ~7–12W (depending on configuration)
- UPS Recommended: e.g., APC Back-UPS 600VA
- Use BIOS Wake-on-LAN if remote booting is needed
8. Maintenance and Monitoring
- Monitoring: Glances, Netdata, or Prometheus + Grafana
- Backups:
- Use
rsyncto external drive or NAS - Cloud backup options: rclone to Google Drive, S3
- Paperless NGX backups:
docker compose exec -T web document-exporter ...
9. Consider
Running a personal server using an Intel NUC and Ubuntu offers a private, low-maintenance, and modular solution to digital infrastructure needs. It’s an ideal base for self-hosting services, offering superior control over data and strong security with the right setup. The NUC's small form factor and efficient power usage make it an optimal home server platform that scales well for many use cases.
- Text Extraction with OCR: Leveraging the
-
 @ d34e832d:383f78d0
2025-04-24 05:14:14
@ d34e832d:383f78d0
2025-04-24 05:14:14Idea
By instituting a robust network of conceptual entities, referred to as 'Obsidian nodes'—which are effectively discrete, idea-centric notes—researchers are empowered to establish a resilient and non-linear archival framework for knowledge accumulation.
These nodes, intricately connected via hyperlinks and systematically organized through the graphical interface of the Obsidian Canvas, facilitate profound intellectual exploration and the synthesis of disparate domains of knowledge.
Consequently, this innovative workflow paradigm emphasizes semantic precision and the interconnectedness of ideas, diverging from conventional, source-centric information architectures prevalent in traditional academic practices.
Traditional research workflows often emphasize organizing notes by source, resulting in static, siloed knowledge that resists integration and insight. With the rise of personal knowledge management (PKM) tools like Obsidian, it becomes possible to structure information in a way that mirrors the dynamic and interconnected nature of human thought.
At the heart of this approach are Obsidian nodes—atomic, standalone notes representing single ideas, arguments, or claims. These nodes form the basis of a semantic research network, made visible and manageable via Obsidian’s graph view and Canvas feature. This thesis outlines how such a framework enhances understanding, supports creativity, and aligns with best practices in information architecture.
Obsidian Nodes: Atomic Units of Thought
An Obsidian node is a note crafted to encapsulate one meaningful concept or question. It is:
- Atomic: Contains only one idea, making it easier to link and reuse.
- Context-Independent: Designed to stand on its own, without requiring the original source for meaning.
- Networked: Linked to other Obsidian nodes through backlinks and tags.
This system draws on the principles of the Zettelkasten method, but adapts them to the modern, markdown-based environment of Obsidian.
Benefits of Node-Based Note-Taking
- Improved Retrieval: Ideas can be surfaced based on content relevance, not source origin.
- Cross-Disciplinary Insight: Linking between concepts across fields becomes intuitive.
- Sustainable Growth: Each new node adds value to the network without redundancy.
Graph View: Visualizing Connections
Obsidian’s graph view offers a macro-level overview of the knowledge graph, showing how nodes interrelate. This encourages serendipitous discovery and identifies central or orphaned concepts that need further development.
- Clusters emerge around major themes.
- Hubs represent foundational ideas.
- Bridges between nodes show interdisciplinary links.
The graph view isn’t just a map—it’s an evolving reflection of intellectual progress.
Canvas: Thinking Spatially with Digital Notes
Obsidian Canvas acts as a digital thinking space. Unlike the abstract graph view, Canvas allows for spatial arrangement of Obsidian nodes, images, and ideas. This supports visual reasoning, ideation, and project planning.
Use Cases of Canvas
- Synthesizing Ideas: Group related nodes in physical proximity.
- Outlining Arguments: Arrange claims into narrative or logic flows.
- Designing Research Papers: Lay out structure and integrate supporting points visually.
Canvas brings a tactile quality to digital thinking, enabling workflows similar to sticky notes, mind maps, or corkboard pinning—but with markdown-based power and extensibility.
Template and Workflow
To simplify creation and encourage consistency, Obsidian nodes are generated using a templater plugin. Each node typically includes:
```markdown
{{title}}
Tags: #topic #field
Linked Nodes: [[Related Node]]
Summary: A 1-2 sentence idea explanation.
Source: [[Source Note]]
Date Created: {{date}}
```The Canvas workspace pulls these nodes as cards, allowing for arrangement, grouping, and visual tracing of arguments or research paths.
Discussion and Challenges
While this approach enhances creativity and research depth, challenges include:
- Initial Setup: Learning and configuring plugins like Templater, Dataview, and Canvas.
- Overlinking or Underlinking: Finding the right granularity in note-making takes practice.
- Scalability: As networks grow, maintaining structure and avoiding fragmentation becomes crucial.
- Team Collaboration: While Git can assist, Obsidian remains largely optimized for solo workflows.
Consider
Through the innovative employment of Obsidian's interconnected nodes and the Canvas feature, researchers are enabled to construct a meticulously engineered semantic architecture that reflects the intricate topology of their knowledge frameworks.
This paradigm shift facilitates a transformation of conventional note-taking, evolving this practice from a static, merely accumulative repository of information into a dynamic and adaptive cognitive ecosystem that actively engages with the user’s thought processes. With methodological rigor and a structured approach, Obsidian transcends its role as mere documentation software, evolving into both a secondary cognitive apparatus and a sophisticated digital writing infrastructure.
This dual functionality significantly empowers the long-term intellectual endeavors and creative pursuits of students, scholars, and lifelong learners, thereby enhancing their capacity for sustained engagement with complex ideas.
-
 @ 9c9d2765:16f8c2c2
2025-04-24 05:08:24
@ 9c9d2765:16f8c2c2
2025-04-24 05:08:24CHAPTER ELEVEN
"James, you really should just leave while you still have some dignity left."
The cold voice of Helen pierced through the room like a dagger. James stood there, silent but firm, holding onto the promise he had made to Grandpa before his death never to leave that house, no matter what humiliation came his way.
Mark sat smugly on the leather couch, legs crossed, sipping expensive whiskey like he owned the entire world. "Come on, James," he said with a mocking grin. "You can go stay with those rich friends of yours. You beg them often enough, don’t you?"
James looked at him, his eyes burning but calm. "You laugh now, Mark. But the day is near and you'll lose everything. All that power, all this showmanship... It's built on borrowed air. And it’s about to collapse."
Mark threw his head back and laughed louder, pointing a finger at him. "Is that a threat from a man who just got kicked out of his own house?"
No one said a word. Even Rita, standing by the corner with misted eyes, couldn't muster the strength to speak. Her heart ached, but her position had already been threatened for refusing the divorce. The family business was on the brink of ruin, and everyone was grasping for lifelines even if it meant selling her future for a bailout.
Mark, now basking in his power, pulled out a cheque and slammed it on the table. "Nine hundred million. That’s what I’m investing into Ray Enterprises. My father gave me this for the family’s investment portfolio. But today, I’m giving it to you... for love," he smirked, glancing at Rita.
James turned, his bag in hand, and walked out without another word. But his mind was already on the next move. The promise made to Grandpa wasn’t just about staying. It was about rising, silently, and striking when the time was right.
Outside the gates, he dialed a number.
"Hello, Charles," he said. "Connect me to the Prime Minister’s PA. It’s urgent."
In less than an hour, news had traveled. James learned the shocking truth: Mark had diverted funds from a national family investment trust to make his dramatic gesture. And that news reached exactly the ears it was supposed to Mark’s father, a revered statesman and strict financier, who had trusted him with the fund.
That night, Mark’s phone buzzed. The message was short:
"Come home immediately. Five minutes. Transfer the money back."
Mark froze.
Sweat beaded on his forehead. His hands shook as he tried to open his banking app, but the balance had already dipped far below the amount needed. Panic set in. He stammered, "I... I can't transfer it back. I used it. It's... gone."
Back at his father’s mansion, the atmosphere was ice cold. The elder man didn’t shout. He didn’t raise his hand. Disappointment etched deep lines into his face as he stared at his son. "You betrayed this family," he said, quietly. "Leave."
No amount of apology could change the decision. In one swift moment, all of Mark’s assets were locked, his reputation ruined, and his privileges stripped away.
He was out. Bankrupt.
Sitting alone in his car that night, he stared out the window in disbelief, muttering to himself, "James... he cursed me. That bastard cursed me..."
But no it wasn’t a curse. It was the fall of a man who mistook pride for power, and wealth for wisdom.
"Turn it up… now!" Helen snapped, her voice cutting through the quiet morning as she pointed at the television. The family’s housekeeper scrambled to adjust the volume. The Ray family had gathered around the breakfast table, their usual morning chatter replaced with unease as the local financial news segment aired.
The anchor’s voice came through crisp and clear, yet what he said sent a cold chill running through every member of the Ray household:
“In our morning headlines, we bring you the latest updates on high-profile investors in the region. Among the top contributors to the city’s economic development over the past week are CEOs of leading corporations and presidents of promising startups. However, surprisingly missing from this list is Mark Winston Ray. Sources close to the matter confirm that Mr. Ray has not only failed to deliver on projected investments but has also been disowned by his father, the Prime Minister, following accusations of financial misconduct.”
A tense silence fell over the room like a heavy shroud. The sound of spoons clinking against plates stopped. Helen’s hands trembled slightly as she clutched her teacup. Her eyes remained glued to the screen, disbelief widening her gaze.
“He was sent away?” Susan finally breathed, breaking the silence.
Christopher removed his glasses slowly, wiping them as if clearing the lenses would somehow fix what he had just heard. Robert looked frozen in place, his jaw clenched.
“The Prime Minister himself?” Helen whispered, almost to herself, as if saying it out loud would make it more real.
The news had hit like a thunderbolt. The Ray family's hopes had been pinned on Mark their so-called golden boy. His promises, his connections, and most of all, the massive investment he claimed to bring were the last threads holding their floundering business together. Now, those threads had snapped. And with them, their illusion of security.
It wasn’t just Mark’s absence on the top investor list that stunned them it was the scandal. The betrayal. The confirmation that Mark had used money entrusted to him for family investment to fund his own ego-driven charades. Lavish gifts, attention-grabbing donations, and grand promises, all funded by a sum he was never supposed to touch.
Helen’s hands fell to her lap, still shaking. “All that talk… the promises… the meetings… all for nothing,” she murmured.
“He was our only lifeline,” Christopher muttered, standing to pace the floor, frustration clearly etched into every line of his face. “And now he’s just… gone.”
“We’re finished,” Susan said flatly, her voice empty of emotion.
But Robert, seated in a corner with his fingers steepled under his chin, leaned forward. “Maybe not.”
Helen looked at him sharply. “What do you mean?”
“We need to think fast,” Robert said calmly, though urgency brewed under his composed tone. “There’s still one card we haven’t played.”
Helen frowned. “Which is?”
“JP Enterprises.”
Everyone turned to look at him.
“We can pitch a proposal,” Robert continued. “We offer them one of our most valuable assets something we can prove will yield substantial returns. If they’re interested, they’ll invest. And with their backing, we can survive this storm.”
“But who do we send?” Susan asked, skeptical. “It can’t be just anyone.”
Robert paused. “We need someone confident, someone who knows the numbers. Someone with poise and intelligence.”
Just then, Sarah the ever-ambitious secretary of Ray Enterprises stepped into the room holding a file. Her voice was firm, unwavering.
“I can go.”
Helen raised an eyebrow. “You?”
“I’ve been working behind the scenes for years. I know our business inside out. I’ve already prepared a full proposal outlining our strongest asset and projected returns. If we want to get back on our feet, we need bold action. I’m ready to represent Ray Enterprises before the president of JP.”
The family looked at one another. In their desperation, even the most unlikely hope was better than none.
“What do you want in return?” Christopher asked, his voice heavy.
Sarah didn’t blink. “If I succeed, I want a promotion. Make me the General Manager.”
Helen leaned back in her seat, weighing the options. Seconds felt like minutes.
“Fine,” she said at last, with a sigh. “You get one chance. Don’t waste it.”
Sarah gave a nod, her eyes burning with ambition. She turned and left the room with determination etched into every step.
"We need a solution and fast!" Robert’s voice rang out through the drawing room, snapping the Ray family out of their stunned silence.
The collapse of their greatest hope, Mark, and the scandal that now bore the family name like a curse had left them scrambling for alternatives. The loss of the nine-hundred-million-dollar investment wasn’t just a financial blow it was a devastating hit to their credibility, their pride, and their future.
Robert stood, pacing near the tall window, eyes fixed on the distant skyline as though the answer would appear from the horizon. The rest of the family sat tensely, their faces drawn with anxiety and quiet desperation.
"There’s only one viable route left," Robert began again. "We need to seek support externally. We can't keep pretending we’ll recover with what we have left. The market’s brutal, and unless we act immediately, Ray Enterprises will be swallowed whole."
Helen frowned. "Support from where, Robert? Who would invest in a family on the brink of collapse?"
Robert turned to face them, determination flickering in his eyes. "JP Enterprises."
The name alone drew mixed reactions. Some looked surprised. Others seemed doubtful. But all understood the weight that name carried. JP Enterprises is one of the most formidable corporate powerhouses in the city, built on discretion, strategy, and silent dominance. An investment from them would be enough to stabilize the Ray business and restore a measure of prestige.
"We ask for an investment fund," Robert continued. "We identify one of our most promising assets, present it with a detailed proposal, and highlight its projected returns. If we can convince the president of JP Enterprises that we’re worth the risk, we’ll have the capital to rebuild."
Christopher leaned back in his chair, folding his arms. "And who do you propose we send to present this… plea?"
Before Robert could answer, a new voice entered the conversation. "I’ll go."
All eyes turned toward the speaker. Sarah the secretary of Ray Enterprises stepped into view with a composed expression, holding a thick folder against her chest. She was dressed sharply, confidence radiating from her posture.
Helen’s brow rose. "You?"
Sarah nodded. "I’ve worked at Ray Enterprises for years. I’ve handled most of the internal correspondence, reviewed investment strategies, and assisted with proposals. I know our strongest assets, and I know how to package them."
"This is no ordinary meeting, Sarah," Robert warned. "You’ll be speaking directly with the president of JP Enterprises. That’s not a small task."
"And I understand the stakes," Sarah replied calmly. "But if no one else will step up, I will. I already have a presentation ready. One of our top assets, the urban real estate development project can generate major returns if backed by the right investment. JP Enterprises could be interested if it’s positioned correctly."
There was a pause. A beat of quiet contemplation as Helen studied her, measuring her words.
"What do you want in return?" she asked coldly.
Sarah didn’t hesitate. "If I’m successful, I want the General Manager position. I’ve earned it."
The room shifted with tension. Christopher glanced at Helen, who didn’t look pleased but she also knew time was not on their side.
Helen leaned forward, her voice tight. "You get one shot, Sarah. Impress them, secure the deal and the position is yours. Fail, and you walk away from Ray Enterprises for good."
Sarah’s eyes flashed with determination. "Then I won’t fail."
She turned, walking out of the room with confident strides, already planning every word of her presentation.
-
 @ d34e832d:383f78d0
2025-04-24 05:04:55
@ d34e832d:383f78d0
2025-04-24 05:04:55A Knowledge Management Framework for your Academic Writing
Idea Approach
The primary objective of this framework is to streamline and enhance the efficiency of several critical academic processes, namely the reading, annotation, synthesis, and writing stages inherent to doctoral studies.
By leveraging established best practices from various domains, including digital note-taking methodologies, sophisticated knowledge management techniques, and the scientifically-grounded principles of spaced repetition systems, this proposed workflow is adept at optimizing long-term retention of information, fostering the development of novel ideas, and facilitating the meticulous preparation of manuscripts. Furthermore, this integrated approach capitalizes on Zotero's robust annotation functionalities, harmoniously merged with Obsidian's Zettelkasten-inspired architecture, thereby enriching the depth and structural coherence of academic inquiry, ultimately leading to more impactful scholarly contributions.
Doctoral research demands a sophisticated approach to information management, critical thinking, and synthesis. Traditional systems of note-taking and bibliography management are often fragmented and inefficient, leading to cognitive overload and disorganized research outputs. This thesis proposes a workflow that leverages Zotero for reference management, Obsidian for networked note-taking, and Anki for spaced repetition learning—each component enhanced by a set of plugins, templates, and color-coded systems.
2. Literature Review and Context
2.1 Digital Research Workflows
Recent research in digital scholarship has highlighted the importance of structured knowledge environments. Tools like Roam Research, Obsidian, and Notion have gained traction among academics seeking flexibility and networked thinking. However, few workflows provide seamless interoperability between reference management, reading, and idea synthesis.
2.2 The Zettelkasten Method
Originally developed by sociologist Niklas Luhmann, the Zettelkasten ("slip-box") method emphasizes creating atomic notes—single ideas captured and linked through context. This approach fosters long-term idea development and is highly compatible with digital graph-based note systems like Obsidian.
3. Zotero Workflow: Structured Annotation and Tagging
Zotero serves as the foundational tool for ingesting and organizing academic materials. The built-in PDF reader is augmented through a color-coded annotation schema designed to categorize information efficiently:
- Red: Refuted or problematic claims requiring skepticism or clarification
- Yellow: Prominent claims, novel hypotheses, or insightful observations
- Green: Verified facts or claims that align with the research narrative
- Purple: Structural elements like chapter titles or section headers
- Blue: Inter-author references or connections to external ideas
- Pink: Unclear arguments, logical gaps, or questions for future inquiry
- Orange: Precise definitions and technical terminology
Annotations are accompanied by tags and notes in Zotero, allowing robust filtering and thematic grouping.
4. Obsidian Integration: Bridging Annotation and Synthesis
4.1 Plugin Architecture
Three key plugins optimize Obsidian’s role in the workflow:
- Zotero Integration (via
obsidian-citation-plugin): Syncs annotated PDFs and metadata directly from Zotero - Highlighter: Enables color-coded highlights in Obsidian, mirroring Zotero's scheme
- Templater: Automates formatting and consistency using Nunjucks templates
A custom keyboard shortcut (e.g.,
Ctrl+Shift+Z) is used to trigger the extraction of annotations into structured Obsidian notes.4.2 Custom Templating
The templating system ensures imported notes include:
- Citation metadata (title, author, year, journal)
- Full-color annotations with comments and page references
- Persistent notes for long-term synthesis
- An embedded bibtex citation key for seamless referencing
5. Zettelkasten and Atomic Note Generation
Obsidian’s networked note system supports idea-centered knowledge development. Each note captures a singular, discrete idea—independent of the source material—facilitating:
- Thematic convergence across disciplines
- Independent recombination of ideas
- Emergence of new questions and hypotheses
A standard atomic note template includes: - Note ID (timestamp or semantic UID) - Topic statement - Linked references - Associated atomic notes (via backlinks)
The Graph View provides a visual map of conceptual relationships, allowing researchers to track the evolution of their arguments.
6. Canvas for Spatial Organization
Obsidian’s Canvas plugin is used to mimic physical research boards: - Notes are arranged spatially to represent conceptual clusters or chapter structures - Embedded visual content enhances memory retention and creative thought - Notes and cards can be grouped by theme, timeline, or argumentative flow
This supports both granular research and holistic thesis design.
7. Flashcard Integration with Anki
Key insights, definitions, and questions are exported from Obsidian to Anki, enabling spaced repetition of core content. This supports: - Preparation for comprehensive exams - Retention of complex theories and definitions - Active recall training during literature reviews
Flashcards are automatically generated using Obsidian-to-Anki bridges, with tagging synced to Obsidian topics.
8. Word Processor Integration and Writing Stage
Zotero’s Word plugin simplifies: - In-text citation - Automatic bibliography generation - Switching between citation styles (APA, Chicago, MLA, etc.)
Drafts in Obsidian are later exported into formal academic writing environments such as Microsoft Word or LaTeX editors for formatting and submission.
9. Discussion and Evaluation
The proposed workflow significantly reduces friction in managing large volumes of information and promotes deep engagement with source material. Its modular nature allows adaptation for various disciplines and writing styles. Potential limitations include: - Initial learning curve - Reliance on plugin maintenance - Challenges in team-based collaboration
Nonetheless, the ability to unify reading, note-taking, synthesis, and writing into a seamless ecosystem offers clear benefits in focus, productivity, and academic rigor.
10. Consider
This idea demonstrates that a well-structured digital workflow using Zotero and Obsidian can transform the PhD research process. It empowers researchers to move beyond passive reading into active knowledge creation, aligned with the long-term demands of scholarly writing. Future iterations could include AI-assisted summarization, collaborative graph spaces, and greater mobile integration.
9. Evaluation Of The Approach
While this workflow offers significant advantages in clarity, synthesis, and long-term idea development, several limitations must be acknowledged:
-
Initial Learning Curve: New users may face a steep learning curve when setting up and mastering the integrated use of Zotero, Obsidian, and their associated plugins. Understanding markdown syntax, customizing templates in Templater, and configuring citation keys all require upfront time investment. However, this learning period can be offset by the long-term gains in productivity and mental clarity.
-
Plugin Ecosystem Volatility: Since both Obsidian and many of its key plugins are maintained by open-source communities or individual developers, updates can occasionally break workflows or require manual adjustments.
-
Interoperability Challenges: Synchronizing metadata, highlights, and notes between systems (especially on multiple devices or operating systems) may present issues if not managed carefully. This includes Zotero’s Better BibTeX keys, Obsidian sync, and Anki integration.
-
Limited Collaborative Features: This workflow is optimized for individual use. Real-time collaboration on notes or shared reference libraries may require alternative platforms or additional tooling.
Despite these constraints, the workflow remains highly adaptable and has proven effective across disciplines for researchers aiming to build a durable intellectual infrastructure over the course of a PhD.
9. Evaluation Of The Approach
While the Zotero–Obsidian workflow dramatically improves research organization and long-term knowledge retention, several caveats must be considered:
-
Initial Learning Curve: Mastery of this workflow requires technical setup and familiarity with markdown, citation keys, and plugin configuration. While challenging at first, the learning effort is front-loaded and pays off in efficiency over time.
-
Reliance on Plugin Maintenance: A key risk of this system is its dependence on community-maintained plugins. Tools like Zotero Integration, Templater, and Highlighter are not officially supported by Obsidian or Zotero core teams. This means updates or changes to the Obsidian API or plugin repository may break functionality or introduce bugs. Active plugin support is crucial to the system’s longevity.
-
Interoperability and Syncing Issues: Managing synchronization across Zotero, Obsidian, and Anki—especially across multiple devices—can lead to inconsistencies or data loss without careful setup. Users should ensure robust syncing solutions (e.g. Obsidian Sync, Zotero WebDAV, or GitHub backup).
-
Limited Collaboration Capabilities: This setup is designed for solo research workflows. Collaborative features (such as shared note-taking or group annotations) are limited and may require alternate solutions like Notion, Google Docs, or Overleaf when working in teams.
The integration of Zotero with Obsidian presents a notable advantage for individual researchers, exhibiting substantial efficiency in literature management and personal knowledge organization through its unique workflows. However, this model demonstrates significant deficiencies when evaluated in the context of collaborative research dynamics.
Specifically, while Zotero facilitates the creation and management of shared libraries, allowing for the aggregation of sources and references among users, Obsidian is fundamentally limited by its lack of intrinsic support for synchronous collaborative editing functionalities, thereby precluding simultaneous contributions from multiple users in real time. Although the application of version control systems such as Git has the potential to address this limitation, enabling a structured mechanism for tracking changes and managing contributions, the inherent complexity of such systems may pose a barrier to usability for team members who lack familiarity or comfort with version control protocols.
Furthermore, the nuances of color-coded annotation systems and bespoke personal note taxonomies utilized by individual researchers may present interoperability challenges when applied in a group setting, as these systems require rigorously defined conventions to ensure consistency and clarity in cross-collaborator communication and understanding. Thus, researchers should be cognizant of the challenges inherent in adapting tools designed for solitary workflows to the multifaceted requirements of collaborative research initiatives.
-
 @ 7c05c4f6:50d03508
2025-04-24 04:09:09
@ 7c05c4f6:50d03508
2025-04-24 04:09:09Cooker.Club just kicked off its Create-to-Earn (C2E) model — and Season 1 is dropping serious alpha. Early-phase blocks across multiple chains come with 4x bonus multipliers, meaning you can farm $COOK at basically zero cost. Stack that with double rewards from key tokens? You’re looking at up to 8x yield. If you’ve ever wanted to get in early before the herd, this is the moment. This guide breaks down how to farm smarter, not harder — no dev skills or gas wars needed.
🧠 Why Now Is the Sweet Spot Create-to-Earn on Cooker runs on a block-based reward system, with 200M $COOK up for grabs in Season 1. And here's the kicker: early participants on select chains get 4x the usual rewards: Solana: First 1.5M blocks
Base: First 300K blocks
BNB Chain: First 200K blocks
Right now, competition is light, barriers are low, and the multiplier window is still wide open — but not for long. Early birds = low gas, high upside. And it gets even better: core AI Agent tokens — like $COOKER, $AISUN, and $AIMJ — currently enjoy a 2x market value multiplier for mining. ✅ Do the math: 4x early block + 2x token boost = 8x rewards. That’s pure alpha.
🚀 3 Easy Ways to Join (Pick One) 1️⃣ Buy an AI Agent Token (Super Simple) Head to Cooker.club
Click into any character page
Hit "Buy Token"
That’s it. Once you hold the token and complete one on-chain transaction, your $COOK farming starts automatically.
2️⃣ Create an AI Agent (Bigger Yield) Click “Create Agent” to launch your own virtual AI persona
You’ll auto-generate a token — think of it as your personal fan coin
Bonus: You get to generate unlimited AI music tracks for free, forever. This is your creative launchpad + token farming engine in one.
👉 Not sure how? Follow this quick video tutorial: https://x.com/cookerdotclub/status/1914290367974822317 3️⃣ Migrate Your Agent from Virtuals (OGs Only) Used Virtuals before? Bring your AI Agent over to Cooker in one click
You’ll get a 1.2x multiplier on rewards
Both you and your token holders start earning $COOK right away 📌 Only tokens launched on PancakeSwap / Raydium / Uniswap and bonded are eligible
⛽ Low-Cost Onboarding (Fees That Don’t Hurt) Creating an AI Agent token costs peanuts: Base: ~0.001 ETH
BNB: ~0.005 BNB
Solana: ~0.02 SOL
🔥 Ongoing community & Twitter events mean you might get $AISUN airdrops for creating an Agent + song — enough to cover fees or even profit off gas.
🔒 What Qualifies for Rewards? To start farming $COOK: Your AI Agent must be live on a DEX (PancakeSwap, Raydium, or Uniswap)
You must make at least one transaction (buy, sell)
📈 Why $COOK Has Serious Upside $COOK isn’t just a farm-and-dump token — it’s the heartbeat of Cooker.Club: Powers governance, upgrades, and creative functions
Only 20% released in Season 1 — lots more rounds coming
Entry cost = near-zero. Value upside = uncapped
And there's real utility. Cooker.Club boosts $COOK’s long-term value with: Buybacks using platform fees
Token burns to reduce supply
Revenue sharing with holders
As the number of Agents and creators grows, $COOK becomes the central asset across the ecosystem — governance, rewards, and access all flow through it.
✅ TL;DR Now’s your best shot at farming $COOK with next-to-no cost — especially during the early 4x reward phase. Whether you’re a degen, a creator, or just Web3-curious, you can lock in early yield while everyone else’s still watching from the sidelines. 🚀 Don’t wait for $COOK to moon — mine it before the crowd shows up. 👉 Head to Cooker.club and unlock your first AI Agent today.
-
 @ 6e0ea5d6:0327f353
2025-04-24 03:07:34
@ 6e0ea5d6:0327f353
2025-04-24 03:07:34Ascolta bene, amico mio!
There is a kind of solitude that doesn’t come from the absence of company, but from the weight of the role one must play.
I’m not talking about being admired, followed, or applauded by outsiders — but of being necessary to those of your own blood.
Of being the one upon whom everything rests, even if no one ever acknowledges it.Truly, I learned throughout my life in the province of Sicily that the man who is held up by no one, yet holds up many — that man has no right to collapse. Not because he is stronger. But because if he falls, he doesn’t fall alone — he brings down the roof over those who live under his shadow.
And here lies the silent tragedy:
No one catches him when he falters.
But everyone collapses when he does.He is the father who cannot fall ill,
The son who becomes the pillar for his parents,
The leader who must never hesitate,
The older brother who must not cry,
The man of honor who must do “whatever must be done.”The exhaustion is real. The fatigue, daily.
But this kind of man learns to live with weariness as others live with pain:
It’s not about waiting for relief, but about continuing to walk despite the crushing weight.
That’s why, amico mio, never ask for lighter burdens — but always for stronger shoulders.In this context, renunciation is not a personal choice.
It is a collective sentence.
It’s like demolishing a pillar and expecting the ceiling to remain intact.Therefore, the man who carries this awareness does not allow himself the luxury of giving up.
He doesn’t grant himself the right to fail — not out of heroism, but out of clarity.
He knows that his collapse would cost a family.Learn this: l’onore non è individuale.
True honor is collective and familial.
What you endure, you endure for your own.
What you face, you face for those who came before you, and those who will come after.
And what you cannot abandon is not about pride — it’s about responsibility.There is no glory in it.
There are no medals.
But there is a silent, unshakable dignity that only a few ever understand:
To be the foundation — never the weight.The name for this is honor, loyalty, and pride.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ d34e832d:383f78d0
2025-04-24 02:56:59
@ d34e832d:383f78d0
2025-04-24 02:56:591. The Ledger or Physical USD?
Bitcoin embodies a paradigmatic transformation in the foundational constructs of trust, ownership, and value preservation within the context of a digital economy. In stark contrast to conventional financial infrastructures that are predicated on centralized regulatory frameworks, Bitcoin operationalizes an intricate interplay of cryptographic techniques, consensus-driven algorithms, and incentivization structures to engender a decentralized and censorship-resistant paradigm for the transfer and safeguarding of digital assets. This conceptual framework elucidates the pivotal mechanisms underpinning Bitcoin's functional architecture, encompassing its distributed ledger technology (DLT) structure, robust security protocols, consensus algorithms such as Proof of Work (PoW), the intricacies of its monetary policy defined by the halving events and limited supply, as well as the broader implications these components have on stakeholder engagement and user agency.
2. The Core Functionality of Bitcoin
At its core, Bitcoin is a public ledger that records ownership and transfers of value. This ledger—called the blockchain—is maintained and verified by thousands of decentralized nodes across the globe.
2.1 Public Ledger
All Bitcoin transactions are stored in a transparent, append-only ledger. Each transaction includes: - A reference to prior ownership (input) - A transfer of value to a new owner (output) - A digital signature proving authorization
2.2 Ownership via Digital Signatures
Bitcoin uses asymmetric cryptography: - A private key is known only to the owner and is used to sign transactions. - A public key (or address) is used by the network to verify the authenticity of the transaction.
This system ensures that only the rightful owner can spend bitcoins, and that all network participants can independently verify that the transaction is valid.
3. Decentralization and Ledger Synchronization
Unlike traditional banking systems, which rely on a central institution, Bitcoin’s ledger is decentralized: - Every node keeps a copy of the blockchain. - No single party controls the system. - Updates to the ledger occur only through network consensus.
This decentralization ensures fault tolerance, censorship resistance, and transparency.
4. Preventing Double Spending
One of Bitcoin’s most critical innovations is solving the double-spending problem without a central authority.
4.1 Balance Validation
Before a transaction is accepted, nodes verify: - The digital signature is valid. - The input has not already been spent. - The sender has sufficient balance.
This is made possible by referencing previous transactions and ensuring the inputs match the unspent transaction outputs (UTXOs).
5. Blockchain and Proof-of-Work
To ensure consistency across the distributed network, Bitcoin uses a blockchain—a sequential chain of blocks containing batches of verified transactions.
5.1 Mining and Proof-of-Work
Adding a new block requires solving a cryptographic puzzle, known as Proof-of-Work (PoW): - The puzzle involves finding a hash value that meets network-defined difficulty. - This process requires computational power, which deters tampering. - Once a block is validated, it is propagated across the network.
5.2 Block Rewards and Incentives
Miners are incentivized to participate by: - Block rewards: New bitcoins issued with each block (initially 50 BTC, halved every ~4 years). - Transaction fees: Paid by users to prioritize their transactions.
6. Network Consensus and Security
Bitcoin relies on Nakamoto Consensus, which prioritizes the longest chain—the one with the most accumulated proof-of-work.
- In case of competing chains (forks), the network chooses the chain with the most computational effort.
- This mechanism makes rewriting history or creating fraudulent blocks extremely difficult, as it would require control of over 50% of the network's total hash power.
7. Transaction Throughput and Fees
Bitcoin’s average block time is 10 minutes, and each block can contain ~1MB of data, resulting in ~3–7 transactions per second.
- During periods of high demand, users compete by offering higher transaction fees to get included faster.
- Solutions like Lightning Network aim to scale transaction speed and lower costs by processing payments off-chain.
8. Monetary Policy and Scarcity
Bitcoin enforces a fixed supply cap of 21 million coins, making it deflationary by design.
- This limited supply contrasts with fiat currencies, which can be printed at will by central banks.
- The controlled issuance schedule and halving events contribute to Bitcoin’s store-of-value narrative, similar to digital gold.
9. Consider
Bitcoin integrates advanced cryptographic methodologies, including public-private key pairings and hashing algorithms, to establish a formidable framework of security that underpins its operation as a digital currency. The economic incentives are meticulously structured through mechanisms such as mining rewards and transaction fees, which not only incentivize network participation but also regulate the supply of Bitcoin through a halving schedule intrinsic to its decentralized protocol. This architecture manifests a paradigm wherein individual users can autonomously oversee their financial assets, authenticate transactions through a rigorously constructed consensus algorithm, specifically the Proof of Work mechanism, and engage with a borderless financial ecosystem devoid of traditional intermediaries such as banks. Despite the notable challenges pertaining to transaction throughput scalability and a complex regulatory landscape that intermittently threatens its proliferation, Bitcoin steadfastly persists as an archetype of decentralized trust, heralding a transformative shift in financial paradigms within the contemporary digital milieu.
10. References
- Nakamoto, S. (2008). Bitcoin: A Peer-to-Peer Electronic Cash System.
- Antonopoulos, A. M. (2017). Mastering Bitcoin: Unlocking Digital Cryptocurrencies.
- Bitcoin.org. (n.d.). How Bitcoin Works
-
 @ fd06f542:8d6d54cd
2025-04-24 02:23:58
@ fd06f542:8d6d54cd
2025-04-24 02:23:58今天主要是更新了seo优化:
- 增加了 blog页面的预加载内容,这样搜索引起抓取blog页面的时候,能够看到的是渲染好的 blog 列表;
- 增加里 blog/[blogid] 页面的 显示原文静态链接,这个链接主要是给搜索引擎使用,他根据原文可以抓取content内容
- 在+page.svelte页面 增加了 raw 数据显示,用户也可以看到和搜索引擎一样的内容,这个取决于 svelte的页面访问路由机制,她发现是api访问就会调用 server.ts返回数据,她发现是浏览器访问就会返回+page.svelte渲染的内容。 这个设计让搜索引擎和 浏览器看到的有区别。所以我两个都做了。
接下来的工作计划
- 增加 blog的评论和点赞功能?
- 美化页面?
- 做一个electron的客户端?
- 给用户做一个 通过blog定制化自己的主页?
关于nostrbook的 想法
用户其实可以通过nostrbook 搭建自己的blog系统,或者写书系统。在公司内网或者自己的服务器上。
修改config.ts的面的三个配置就可以了。 ```js
export let booktag="createbook"; export let blogtag="createblog"; export let chaptertag="bookchapter"; ```
我也是通过这个开关测试了线上和测试的开发的内容区分开的。
昨天发现的bug
就是 30023 update问题,虽然可以通过dtag可以实现替换。但是部分服务器没有update到最新的。所以他会返回老的。 是不是通过服务器之间的同步可以解决呢?
-
 @ 502ab02a:a2860397
2025-04-24 02:00:28
@ 502ab02a:a2860397
2025-04-24 02:00:28ถ้า “นมปลอมเข้าโรงเรียน” กับเกม Lobby ระดับโลก ที่ซ่อน GMO ไว้ในแก้วของลูกหลานเรา
โอเค เรารู้จักคำว่า Precision Fermentation หรือ PF กันไปแล้ว กลับมาดูโลกปัจจุบันนี้กันครับ
ในวันที่ผู้ใหญ่ยังทะเลาะกันเรื่องราคาน้ำนมดิบ มีบางบริษัทที่กำลังยิ้มกว้าง เพราะแผนระยะยาวของเขา…คือการเปลี่ยนนมโรงเรียนจากของจริง ไปสู่นมปลอมที่ “จดสิทธิบัตรได้” และ “ควบคุมทั้ง supply chain”
เรื่องนี้อาจดูเหมือนนิยายไซไฟนะครับ แต่เฮียจะพาไปเจาะลึกเบื้องหลังการ lobby ที่พยายามผลัก “นมจาก Precision Fermentation” และ “นม Plant-Based” เข้าสู่ระบบโรงเรียน โดยอ้างว่า “เพื่อสุขภาพ เพื่อโลก และเพื่อเด็กๆ” แต่จริงๆ แล้วมันคือ เกมเปลี่ยนอาหารเป็นทรัพย์สินทางปัญญาแบบเงียบๆ
ทำไม “โรงเรียน” ถึงเป็นเป้าหมายสำคัญ? คำตอบง่ายมาก เพราะว่ามันกลับเข้าสู่ loop เดิมกับตอนที่เขาพยายามยัด นมสด เข้าไปในชีวิตเมื่อหลังสงครามโลกครั้งที่ 2 นั่นละครับ หนังม้วนเดิม มีเพิ่มเติมคือความทันสมัย 1.โรงเรียนคือฐานข้อมูลประชากรที่แน่นอน = จำนวนเด็กแน่ชัด งบประมาณแน่ชัด 2.พฤติกรรมการกินของเด็ก “ฝังได้ง่าย” = ถ้าเด็กเติบโตมากับนม Plant-Based หรือ Milk 2.0 ตั้งแต่เล็ก พอเขาโตขึ้น “ร่างกายจะลืมรสนมวัวไปเลย” และไม่เคยรู้ว่าเคยมี real food ให้เลือก เหมือนที่โลกของ เจเนอเรชั่น internet มือถือ หรือแม้แต่สมัยนี้คือ สตรีมมิ่ง 3.เป็นจุดที่รัฐมีบทบาทโดยตรง = ง่ายต่อการ lobby policy เพราะแค่เปลี่ยนนโยบายระดับกระทรวง ก็เปลี่ยนทั้งประเทศได้
ใครอยู่เบื้องหลังการล็อบบี้นี้? 1. องค์กรระดับโลกที่ขับเคลื่อน Plant-Based School Meals อย่างเช่น - GFI (Good Food Institute) เป็นองค์กรที่มีเป้าหมายชัดว่า “เปลี่ยนโปรตีนของโลกจาก animal-based ให้เป็น cell-based และ fermentation-based” สนับสนุนงานวิจัย ออกนโยบายผลักดันเมนูโรงเรียน - ProVeg International ซึ่งมีโครงการชื่อ “School Plates” ปรับเมนูโรงเรียนให้เป็น plant-based - EAT Forum & WEF (World Economic Forum) ที่มีการสนับสนุนนโยบาย global dietary shift ซึ่งแนะนำให้ลดการบริโภคเนื้อสัตว์และผลิตภัณฑ์จากสัตว์ เพื่อส่งเสริมสุขภาพและความยั่งยืนของสิ่งแวดล้อม
- บริษัทยักษ์ใหญ่ด้าน Milk 2.0
- Perfect Day ร่วมกับ Nestlé ที่พยายามผลักดันนม PF ให้เป็นนมทดแทนแห่งอนาคต
-
Oatly ผู้ผลิตนม plant-based และ lobby ให้ “รัฐบาลช่วยจัดซื้อในโรงเรียน” พร้อมกับแคมเปญประชาสัมพันธ์ว่านี่คือตัวเลือกที่ “รักษ์โลกและดีต่อสุขภาพ” และ NotCo / Danone ซึ่งอยู่ในตลาดประเภทเดียวกัน ก็อาจมีแนวโน้มเข้าสู่ตลาดโรงเรียนเช่นกัน
-
เช่นเดียวกับที่เคยเล่าเรื่องนมสดไว้ครับ เขาจะต้องมาพร้อมการวิจัยที่ออกแบบให้รองรับการเปลี่ยนนโยบาย ด้วยหลายงานวิจัยที่บอกว่า “นมวัวมีผลเสียต่อสุขภาพเด็ก” ถูกสนับสนุนโดยกลุ่มทุนที่อยู่ในวงการ plant-based หรือ biotech งานบางชิ้นลดความสำคัญของสารอาหารจาก animal-based ลง และ “ปั่นคะแนน” ของ Plant Milk หรือ PF Milk ให้ดูสูงกว่าความเป็นจริง
วิธีการ Lobby แบบแนบเนียนก็จะใช้กระบวนการประมาณนี้ครับ 1. แทรกผ่านโครงการ “นมโรงเรียนฟรี” หลายประเทศใช้เงินรัฐอุดหนุนนมโรงเรียน กลุ่ม Lobby เข้าไป “เสนอของถูกกว่า” และอ้างว่า “เหมาะกับเด็กแพ้นมวัว” ทำให้รัฐเริ่มพิจารณา Plant Milk หรือ PF Milk เป็นทางเลือก “ถูกกว่าและดูดี”
-
ล้างความคิดผ่านหลักสูตรสุขศึกษา เริ่มมีสื่อการสอนที่ใช้คำว่า “milk” แบบรวม Plant Milk เข้าไปด้วย ลดความต่างระหว่างนมวัวกับนมจากพืช และเริ่มพูดว่า “นมจากพืชดีกว่าต่อสิ่งแวดล้อม”
-
แจกทุนให้โรงเรียนที่ร่วมโครงการ มีการเสนอทุนวิจัย ทุนสนับสนุนเมนูโรงเรียน ถ้าโรงเรียนยอมทดลองใช้นม Plant-Based หรือ PF Milk สร้างภาพลักษณ์ว่าเป็นโรงเรียน “รักโลก รักสุขภาพ”
-
ใช้พลังอินฟูฯและดารา ดาราดังๆ ถูกใช้เป็นหน้าโครงการ (ในตปท.) เช่นโพสต์ภาพเด็กๆ กิน “นมไม่มีวัว” พร้อมคำบรรยายว่า “นี่คืออนาคตของการกินอย่างมีจริยธรรม” อะไรประมาณนี้ครับ
ผลกระทบที่จะเกิดขึ้นก็คือ เด็กๆ เสียโอกาสในการได้รับโภชนาการจาก real food โดยเฉพาะ B12, วิตามิน A, DHA, โคลีน, เคซีนจากธรรมชาติ ซึ่งนมเทียมต้อง “แต่งเติม” เข้ามาทั้งสิ้น รวมถึง เด็กโตมากับอาหารปลอม โดยไม่รู้ว่าเคยมีของจริงให้เลือก สุดท้ายจะกลายเป็น “ผู้ใหญ่ที่ต้องพึ่งบริษัท” เพื่อมีโปรตีนกินในชีวิตประจำวัน และท้ายสุด รัฐกลายเป็นผู้สนับสนุนสิทธิบัตรเอกชน เพราะเมื่อ Milk 2.0 เข้าสู่ระบบโรงเรียน มันจะกลายเป็น “ค่าใช้จ่ายประจำ” ที่รัฐบาลต้องจ่ายให้บริษัทตลอดไป ซึ่งตรงนี้ก็จะวนกลับมาที่พวกเราที่อยู่ภายใต้ระบบ fiat
ดังนั้นมันก็เลยสรุปได้ว่า นี่ไม่ใช่แค่เรื่องอาหาร แต่คือการเปลี่ยนโครงสร้างอำนาจ Milk 2.0 เข้าโรงเรียน ไม่ใช่เพราะมันดีกว่า แต่เพราะมัน “ล็อกห่วงโซ่คุณค่าไว้ในมือคนส่วนน้อย” และสร้างประชากรรุ่นใหม่ที่ไม่รู้จักอาหารจริงจากธรรมชาติ
หากเด็กวันนี้กินของปลอมจนชิน วันหนึ่งเขาอาจยอม “จ่ายเงินเช่าโปรตีน (subscribe) ” ไปตลอดชีวิต โดยไม่เคยรู้เลยว่า… วัวเคยให้นมได้โดยไม่ต้องใช้เทคโนโลยีใดๆ เลย
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ d34e832d:383f78d0
2025-04-24 00:56:03
@ d34e832d:383f78d0
2025-04-24 00:56:03WebSocket communication is integral to modern real-time web applications, powering everything from chat apps and online gaming to collaborative editing tools and live dashboards. However, its persistent and event-driven nature introduces unique debugging challenges. Traditional browser developer tools provide limited insight into WebSocket message flows, especially in complex, asynchronous applications.
This thesis evaluates the use of Chrome-based browser extensions—specifically those designed to enhance WebSocket debugging—and explores how visual event tracing improves developer experience (DX). By profiling real-world applications and comparing built-in tools with popular WebSocket DevTools extensions, we analyze the impact of visual feedback, message inspection, and timeline tracing on debugging efficiency, code quality, and development speed.
The Idea
As front-end development evolves, WebSockets have become a foundational technology for building reactive user experiences. Debugging WebSocket behavior, however, remains a cumbersome task. Chrome DevTools offers a basic view of WebSocket frames, but lacks features such as message categorization, event correlation, or contextual logging. Developers often resort to
console.logand custom logging systems, increasing friction and reducing productivity.This research investigates how browser extensions designed for WebSocket inspection—such as Smart WebSocket Client, WebSocket King Client, and WSDebugger—can enhance debugging workflows. We focus on features that provide visual structure to communication patterns, simplify message replay, and allow for real-time monitoring of state transitions.
Related Work
Chrome DevTools
While Chrome DevTools supports WebSocket inspection under the Network > Frames tab, its utility is limited: - Messages are displayed in a flat, unstructured stream. - No built-in timeline or replay mechanism. - Filtering and contextual debugging features are minimal.
WebSocket-Specific Extensions
Numerous browser extensions aim to fill this gap: - Smart WebSocket Client: Allows custom message sending, frame inspection, and saved session reuse. - WSDebugger: Offers structured logging and visualization of message flows. - WebSocket Monitor: Enables real-time monitoring of multiple connections with UI overlays.
Methodology
Tools Evaluated:
- Chrome DevTools (baseline)
- Smart WebSocket Client
- WSDebugger
- WebSocket King Client
Evaluation Criteria:
- Real-time message monitoring
- UI clarity and UX consistency
- Support for message replay and editing
- Message categorization and filtering
- Timeline-based visualization
Test Applications:
- A collaborative markdown editor
- A multiplayer drawing game (WebSocket over Node.js)
- A lightweight financial dashboard (stock ticker)
Findings
1. Enhanced Visibility
Extensions provide structured visual representations of WebSocket communication: - Grouped messages by type (e.g., chat, system, control) - Color-coded frames for quick scanning - Collapsible and expandable message trees
2. Real-Time Inspection and Replay
- Replaying previous messages with altered payloads accelerates bug reproduction.
- Message history can be annotated, aiding team collaboration during debugging.
3. Timeline-Based Analysis
- Extensions with timeline views help identify latency issues, bottlenecks, and inconsistent message pacing.
- Developers can correlate message sequences with UI events more intuitively.
4. Improved Debugging Flow
- Developers report reduced context-switching between source code and devtools.
- Some extensions allow breakpoints or watchers on WebSocket events, mimicking JavaScript debugging.
Consider
Visual debugging extensions represent a key advancement in tooling for real-time application development. By extending Chrome DevTools with features tailored for WebSocket tracing, developers gain actionable insights, faster debugging cycles, and a better understanding of application behavior. Future work should explore native integration of timeline and message tagging features into standard browser DevTools.
Developer Experience and Limitations
Visual tools significantly enhance the developer experience (DX) by reducing friction and offering cognitive support during debugging. Rather than parsing raw JSON blobs manually or tracing asynchronous behavior through logs, developers can rely on intuitive UI affordances such as real-time visualizations, message filtering, and replay features.
However, some limitations remain:
- Lack of binary frame support: Many extensions focus on text-based payloads and may not correctly parse or display binary frames.
- Non-standard encoding issues: Applications using custom serialization formats (e.g., Protocol Buffers, MsgPack) require external decoding tools or browser instrumentation.
- Extension compatibility: Some extensions may conflict with Content Security Policies (CSP) or have limited functionality when debugging production sites served over HTTPS.
- Performance overhead: Real-time visualization and logging can add browser CPU/memory overhead, particularly in high-frequency WebSocket environments.
Despite these drawbacks, the overall impact on debugging efficiency and developer comprehension remains highly positive.
Developer Experience and Limitations
Visual tools significantly enhance the developer experience (DX) by reducing friction and offering cognitive support during debugging. Rather than parsing raw JSON blobs manually or tracing asynchronous behavior through logs, developers can rely on intuitive UI affordances such as live message streams, structured views, and interactive inspection of frames.
However, some limitations exist:
- Security restrictions: Content Security Policy (CSP) and Cross-Origin Resource Sharing (CORS) can restrict browser extensions from accessing WebSocket frames in production environments.
- Binary and custom formats: Extensions may not handle binary frames or non-standard encodings (e.g., Protocol Buffers) without additional tooling.
- Limited protocol awareness: Generic tools may not fully interpret application-specific semantics, requiring context from the developer.
- Performance trade-offs: Logging and rendering large volumes of data can cause UI lag, especially in high-throughput WebSocket apps.
Despite these constraints, DevTools extensions continue to offer valuable insight during development and testing stages.
Applying this analysis to relays in the Nostr protocol surfaces some fascinating implications about traffic analysis, developer tooling, and privacy risks, even when data is cryptographically signed. Here's how the concepts relate:
🧠 What This Means for Nostr Relays
1. Traffic Analysis Still Applies
Even though Nostr events are cryptographically signed and, optionally, encrypted (e.g., DMs), relay communication is over plaintext WebSockets or WSS (WebSocket Secure). This means:
- IP addresses, packet size, and timing patterns are all visible to anyone on-path (e.g., ISPs, malicious actors).
- Client behavior can be inferred: Is someone posting, reading, or just idling?
- Frequent "kind" values (like
kind:1for notes orkind:4for encrypted DMs) produce recognizable traffic fingerprints.
🔍 Example:
A pattern like: -
client → relay: small frame at intervals of 30s -relay → client: burst of medium frames …could suggest someone is polling for new posts or using a chat app built on Nostr.
2. DevTools for Nostr Client Devs
For client developers (e.g., building on top of
nostr-tools), browser DevTools and WebSocket inspection make debugging much easier:- You can trace real-time Nostr events without writing logging logic.
- You can verify frame integrity, event flow, and relay responses instantly.
- However, DevTools have limits when Nostr apps use:
- Binary payloads (e.g., zlib-compressed events)
- Custom encodings or protocol adaptations (e.g., for mobile)
3. Fingerprinting Relays and Clients
- Each relay has its own behavior: how fast it responds, whether it sends OKs, how it deals with malformed events.
- These can be fingerprinted by adversaries to identify which software is being used (e.g.,
nostr-rs-relay,strfry, etc.). - Similarly, client apps often emit predictable
REQ,EVENT,CLOSEsequences that can be fingerprinted even over WSS.
4. Privacy Risks
Even if DMs are encrypted: - Message size and timing can hint at contents ("user is typing", long vs. short message, emoji burst, etc.) - Public relays might correlate patterns across multiple clients—even without payload access. - Side-channel analysis becomes viable against high-value targets.
5. Mitigation Strategies in Nostr
Borrowing from TLS and WebSocket security best practices:
| Strategy | Application to Nostr | |-----------------------------|----------------------------------------------------| | Padding messages | Normalize
EVENTsize, especially for DMs | | Batching requests | Send multipleREQsubscriptions in one frame | | Randomize connection times | Avoid predictable connection schedules | | Use private relays / Tor| Obfuscate source IP and reduce metadata exposure | | Connection reuse | Avoid per-event relay opens, use persistent WSS |
TL;DR for Builders
If you're building on Nostr and care about privacy, WebSocket metadata is a leak. The payload isn't the only thing that matters. Be mindful of event timing, size, and structure, even over encrypted channels.
-
 @ 872982aa:8fb54cfe
2025-04-24 00:55:15
@ 872982aa:8fb54cfe
2025-04-24 00:55:15现在这样可以,我试试在这里也粘贴一个照片

-
 @ c26014e2:d3a56eb6
2025-04-24 00:45:38
@ c26014e2:d3a56eb6
2025-04-24 00:45:38OKKING được biết đến như một nền tảng kỹ thuật số mang tính cách mạng, nơi trải nghiệm người dùng và hiệu suất công nghệ hòa quyện một cách hoàn hảo. Được thiết kế để đáp ứng nhu cầu ngày càng đa dạng trong thời đại số hóa, OKKING đặt trọng tâm vào sự linh hoạt và tối ưu hóa thao tác cho mọi người dùng. Giao diện trực quan giúp người dùng dễ dàng truy cập các chức năng chính chỉ với vài cú chạm, đồng thời loại bỏ hoàn toàn những yếu tố gây rối hoặc không cần thiết. Nền tảng vận hành mượt mà trên nhiều thiết bị khác nhau – từ điện thoại di động đến máy tính để bàn – với khả năng tự động điều chỉnh bố cục để phù hợp với từng định dạng màn hình, mang đến sự tiện lợi tối đa. Không những thế, tốc độ phản hồi nhanh cùng cấu trúc gọn gàng còn giúp rút ngắn thời gian thao tác, đảm bảo rằng mỗi giây sử dụng đều mang lại giá trị cụ thể cho người dùng. OKKING không chỉ là một công cụ hỗ trợ số, mà còn là sự lựa chọn lý tưởng cho những ai muốn kiểm soát trải nghiệm kỹ thuật số theo cách chủ động và dễ dàng.
An toàn dữ liệu luôn là nền tảng quan trọng trong mọi chiến lược phát triển của OKKING. Với sự kết hợp giữa công nghệ mã hóa tiên tiến và hệ thống bảo vệ đa tầng, nền tảng này đã xây dựng được một bức tường bảo vệ vững chắc trước các mối nguy hại từ thế giới mạng. Các quy trình xác thực thông minh, kết hợp cùng hệ thống phân quyền và kiểm soát truy cập nghiêm ngặt, giúp người dùng luôn an tâm rằng thông tin cá nhân của họ được bảo vệ tối đa. Đặc biệt, mọi dữ liệu đều được lưu trữ một cách an toàn và liên tục kiểm tra để đảm bảo tính toàn vẹn và bảo mật cao nhất. Đội ngũ phát triển kỹ thuật của OKKING luôn làm việc không ngừng nghỉ để cập nhật và nâng cấp hệ thống phòng vệ, đảm bảo nền tảng luôn sẵn sàng ứng phó với những thay đổi liên tục của môi trường mạng. Với chính sách minh bạch và cam kết đặt người dùng lên hàng đầu, OKKING không chỉ đáp ứng nhu cầu sử dụng tiện ích mà còn mang đến sự an tâm trong suốt hành trình trải nghiệm số.
Điểm nổi bật cuối cùng nhưng không kém phần quan trọng của OKKING chính là khả năng cập nhật linh hoạt và đồng hành cùng người dùng trong mọi giai đoạn phát triển công nghệ. OKKING không ngừng tiếp nhận phản hồi từ cộng đồng sử dụng để cải tiến sản phẩm một cách toàn diện – từ những tinh chỉnh nhỏ trong giao diện đến việc bổ sung các tính năng hoàn toàn mới. Điều này giúp nền tảng luôn giữ được sự tươi mới, phù hợp với từng xu hướng và thói quen người dùng đang thay đổi từng ngày. Hệ thống hỗ trợ kỹ thuật và chăm sóc khách hàng cũng được tích hợp ngay trong nền tảng, giúp người dùng giải quyết mọi vấn đề nhanh chóng và thuận tiện. Nhờ định hướng lấy người dùng làm trung tâm và tư duy phát triển lâu dài, OKKING không chỉ là một nền tảng số mà còn là đối tác đồng hành đáng tin cậy trong thế giới số đầy biến động. Đây là lựa chọn thông minh cho những ai đang tìm kiếm sự ổn định, tiện ích và khả năng mở rộng trong một nền tảng kỹ thuật số hiện đại.
-
 @ c26014e2:d3a56eb6
2025-04-24 00:44:32
@ c26014e2:d3a56eb6
2025-04-24 00:44:3288GO được xây dựng như một nền tảng kỹ thuật số toàn diện, nơi công nghệ hiện đại kết hợp cùng giao diện thân thiện nhằm mang đến trải nghiệm tối ưu nhất cho người dùng. Với cấu trúc rõ ràng, tinh gọn và trực quan, nền tảng cho phép mọi người – từ người mới tiếp cận công nghệ cho đến người dùng thành thạo – đều có thể dễ dàng thao tác, điều hướng và sử dụng các chức năng một cách mượt mà. 88GO không tạo cảm giác phức tạp hay rườm rà, thay vào đó, mọi yếu tố đều được bố trí hợp lý, tiết kiệm thời gian và nâng cao hiệu suất sử dụng. Không chỉ dừng lại ở thiết kế đẹp mắt, nền tảng còn tích hợp tính năng phản hồi nhanh, đồng bộ trên mọi thiết bị, giúp người dùng dễ dàng kết nối và sử dụng ở bất cứ đâu. Sự tiện lợi này đã và đang giúp 88GO trở thành một công cụ hỗ trợ đắc lực trong cuộc sống số hiện đại – nơi tốc độ, độ tin cậy và tính đơn giản đóng vai trò quyết định.
Tính bảo mật và an toàn thông tin luôn là yếu tố được 88GO ưu tiên hàng đầu, phản ánh rõ triết lý phát triển lấy người dùng làm trung tâm. Nền tảng sử dụng các công nghệ mã hóa tiên tiến nhằm bảo vệ dữ liệu cá nhân khỏi các mối nguy cơ từ môi trường mạng, đồng thời triển khai hệ thống xác thực đa lớp giúp người dùng kiểm soát tối đa quyền truy cập. Mỗi thao tác truy cập, lưu trữ hay điều hướng đều được xử lý thông qua quy trình kiểm tra nghiêm ngặt, đảm bảo rằng thông tin không bị rò rỉ hoặc sử dụng sai mục đích. Đội ngũ kỹ thuật của 88GO không ngừng theo dõi và cập nhật hệ thống an ninh, sẵn sàng ứng phó với các tình huống phát sinh một cách linh hoạt và nhanh chóng. Người dùng hoàn toàn có thể yên tâm rằng mọi dữ liệu của họ luôn nằm trong vùng an toàn. Chính sự đầu tư kỹ lưỡng vào bảo mật đã tạo nên một nền tảng tin cậy, góp phần gia tăng trải nghiệm và xây dựng lòng trung thành từ phía cộng đồng sử dụng.
Không ngừng cải tiến và lắng nghe người dùng là điểm mạnh nổi bật của 88GO, giúp nền tảng này không chỉ dừng lại ở chức năng mà còn mang đến giá trị thực tiễn lâu dài. Từ những điều chỉnh nhỏ trong giao diện đến việc phát triển các tiện ích hoàn toàn mới, mọi bước tiến đều dựa trên nhu cầu thực tế và phản hồi của người dùng. Điều này thể hiện một tầm nhìn dài hạn và sự tận tâm trong việc xây dựng một không gian số dễ tiếp cận, dễ sử dụng và luôn đổi mới. 88GO không chỉ là một nền tảng hỗ trợ thao tác kỹ thuật số mà còn là cầu nối giữa con người và công nghệ, mang lại sự tiện nghi, hiệu quả và cá nhân hóa cao. Với định hướng phát triển bền vững, chiến lược cải tiến linh hoạt và khả năng đồng hành cùng người dùng trong mọi tình huống, 88GO đang từng bước trở thành lựa chọn hàng đầu cho những ai mong muốn tận dụng tối đa tiềm năng của thế giới kỹ thuật số mà không đánh đổi trải nghiệm cá nhân.
-
 @ c26014e2:d3a56eb6
2025-04-24 00:43:45
@ c26014e2:d3a56eb6
2025-04-24 00:43:45789P không chỉ đơn thuần là một nền tảng kỹ thuật số hiện đại mà còn là công cụ đồng hành giúp người dùng làm chủ các thao tác trực tuyến một cách linh hoạt, dễ dàng và hiệu quả. Thiết kế giao diện của 789P tập trung vào sự tối giản, rõ ràng và thân thiện, giúp người dùng không gặp bất kỳ trở ngại nào trong quá trình thao tác. Bằng cách tối ưu hóa các bước truy cập và điều hướng, nền tảng rút ngắn thời gian làm quen và sử dụng, kể cả với người mới. Đặc biệt, 789P hoạt động ổn định trên nhiều loại thiết bị khác nhau – từ điện thoại thông minh đến máy tính để bàn – đảm bảo mọi trải nghiệm đều mượt mà và đồng nhất. Sự linh hoạt trong cách bố trí chức năng cho phép người dùng dễ dàng điều chỉnh theo nhu cầu cá nhân, mang lại cảm giác chủ động trong mọi tình huống. Với khả năng vận hành ổn định và hiệu suất vượt trội, 789P dần khẳng định vị thế là một nền tảng kỹ thuật số đáng tin cậy trong bối cảnh người dùng ngày càng đòi hỏi sự tiện nghi và tối ưu hóa trải nghiệm.
Yếu tố bảo mật luôn là ưu tiên hàng đầu trong chiến lược phát triển của 789P, nhằm mang đến cho người dùng sự an tâm tuyệt đối trong mọi tương tác. Nền tảng được trang bị công nghệ mã hóa dữ liệu tiên tiến cùng hệ thống tường lửa đa lớp, giúp ngăn chặn các mối nguy hại từ môi trường mạng một cách hiệu quả. Mọi hoạt động đăng nhập, truy cập hay thao tác đều được kiểm soát chặt chẽ thông qua cơ chế xác thực linh hoạt và phân quyền người dùng rõ ràng. Điều này không chỉ bảo vệ thông tin cá nhân khỏi các cuộc tấn công không mong muốn mà còn đảm bảo rằng toàn bộ dữ liệu lưu trữ trên hệ thống luôn được giữ kín và an toàn tuyệt đối. Bên cạnh đó, đội ngũ kỹ thuật của 789P luôn duy trì công tác theo dõi và cập nhật hệ thống bảo mật liên tục, từ đó kịp thời phát hiện và xử lý các nguy cơ tiềm ẩn. Chính sự kết hợp giữa công nghệ bảo vệ tiên tiến và quy trình vận hành minh bạch đã giúp 789P xây dựng được lòng tin nơi người dùng – điều mà bất kỳ nền tảng kỹ thuật số nào cũng cần có để phát triển bền vững.
Không ngừng đổi mới là kim chỉ nam cho sự phát triển lâu dài của 789P. Nền tảng liên tục cập nhật các tính năng mới dựa trên phản hồi từ cộng đồng người dùng và xu hướng công nghệ toàn cầu. Mỗi bản nâng cấp đều không chỉ dừng lại ở việc cải thiện giao diện hay tăng tốc xử lý, mà còn là bước tiến nhằm nâng cao chất lượng trải nghiệm tổng thể. Các tiện ích bổ sung được thiết kế nhằm gia tăng giá trị thực tế cho người dùng, giúp họ làm việc, giải trí hay tương tác một cách hiệu quả và thuận tiện hơn. Bên cạnh đó, 789P cũng chú trọng vào khả năng mở rộng, nhằm phục vụ đa dạng nhu cầu của người dùng hiện tại lẫn tương lai. Với sự kết hợp giữa tính linh hoạt, bảo mật cao và tinh thần không ngừng đổi mới, 789P đang từng bước khẳng định vai trò không thể thiếu trong hệ sinh thái số hiện đại – nơi người dùng không chỉ là khách hàng, mà là những người đồng hành cùng nền tảng trong hành trình phát triển lâu dài và bền vững.
-
 @ 3c7dc2c5:805642a8
2025-04-23 21:50:33
@ 3c7dc2c5:805642a8
2025-04-23 21:50:33🧠Quote(s) of the week:
'The "Bitcoin Corporate Treasury" narrative is a foot gun if it's not accompanied by the sovereignty via self-custody narrative. Number Go Up folks are pitching companies to funnel their funds into a handful of trusted third parties. Systemic Risk Go Up.' - Jameson Lopp
Lopp is spot on!
The Bitcoin network is a fortress of digital power backed by 175 terawatt-hours (TWh)—equivalent to 20 full-scale nuclear reactors running continuously 24 hours per day, 365 days per year—making it nation-state-level resistant and growing stronger every day. - James Lavish
🧡Bitcoin news🧡
https://i.ibb.co/xSYWkJPC/Goqd-ERAXw-AEUTAo.jpg
Konsensus Network
On the 14th of April:
➡️ Bitcoin ETFs are bleeding out. Not a single inflow streak since March.
➡️'There are now just a bit less than 3 years left until the next halving. The block reward will drop from 3.125 BTC to 1.5625 BTC. Plan accordingly.' - Samson Mow
➡️Bitcoin is the new benchmark. Bitcoin has outperformed the S&P 500 over the past 1-, 2-, 3-, 4-, 5-, 6-, 7-, 8-, 9-, 10-, 11-, 12-, 13-, and 14-year periods. https://i.ibb.co/GfBK6n2Z/Gof6-Vwp-Ws-AA-g1-V-1.jpg
You cannot consider yourself a serious investor if you see this data and ignore it. Never been an asset like it in the history of mankind. But that is from an investor's perspective...
Alex Gladstein: "While only certain credentialed individuals can own US stocks (a tiny % of the world population) — anyone in the world, dissident or refugee, can own the true best-performing financial asset. "
➡️New record Bitcoin network hashrate 890,000,000,000,000,000,000x per second.
➡️The Korea Exchange has experienced its first bitcoin discount in South Korea since December 2024.
➡️Every government should be mining Bitcoin, say Bhutan's Prime Minister - Al Jazeera "It's a simple choice that's earned billions of dollars. Mining makes tremendous sense."
On the 15th of April:
➡️'Owning 1 Bitcoin isn’t a trade... - It’s a power move. - A geopolitical hedge. - A once-per-civilization bet on the next monetary regime. If you have the means to own one and don’t… You’re not managing risk. You’re misreading history.' -Alec Bakhouche
Great thread: https://x.com/Alec_Bitcoin/status/1912216075703607448
➡️The only thing that drops faster than new ETH narratives is the ETH price. Ethereum is down 74% against Bitcoin since switching from PoW to PoS in 2022.
https://i.ibb.co/bR3yjqZX/Gos0kc-HXs-AAP-9-X.jpg
Piere Rochard: "The theory was that on-chain utility would create a positive fly-wheel effect of demand for holding ETH. The reality is that even if (big if) you need its chain utility, you don’t actually need to hold ETH, you can use stablecoins or wBTC. There’s no real value accrual thesis."
If you're still holding ETH, you're in denial. You watched it slide from 0.05 to 0.035. Now it's circling 0.02 and you're still hoping? That's not a strategy—that's desperation. There is no bounce. No cavalry. Just a crowd of bagholders waiting to offload on the next fool. Don’t be that fool. Everyone’s waiting to dump, just like you.
For example. Galaxy Digital deposited another 12,500 $ETH($20.28M) to Binance 10 hours ago. Galaxy Digital has deposited 37,500 $ETH($60.4M) to Binance in the past 4 days. The institutional guys that were pushing this fraud coin like the Winklevoss brothers and Novogratz (remember the Luna fiasco?!) are ejecting. If you're still holding, no one to blame but yourself.
Take the loss. Rotate to BTC.
Later, you can lie and say you always believed in Bitcoin. But right now, stop the bleeding.
You missed it. Accept that. Figure out why.
P.S. Don’t do anything stupid. It’s just money. You’ll recover. Move smarter next time.
➡️And it is not only against ETH, every other asset is bleeding against BTC because every other asset is inferior to BTC. Did you know Bitcoin's 200-week moving average never declines? It always rises. What does this suggest? 'This is the most significant chart in financial markets. It's Bitcoin - measured with a 200-week moving average (aka 4 years at a time). Zoom out, and the truth becomes crystal clear: Bitcoin has never lost purchasing power. What does this hint at? Bitcoin is the most reliable savings technology on Earth.' - Cole Walmsley
Proof: https://x.com/Cole_Walmsley/status/1912545128826142963
➡️SPAR Switzerland Pilots Bitcoin and Lightning Network Payments Zurich, Switzerland – SPAR, one of the world’s largest grocery retail chains, has launched a pilot program to accept Bitcoin and Lightning Network payments at select locations in Switzerland.
With a global presence spanning 13,900 stores across 48 countries, this move signals a significant step toward mainstream adoption of Bitcoin in everyday commerce.
➡️$110 billion VanEck proposes BitBonds for the US to buy more Bitcoin and refinance its $14 trillion debt.
➡️'A peer-reviewed study forecasts $1M Bitcoin by early 2027—and up to $5M by 2031.' -Simply Bitcoin
On the 17th of April:
➡️ Every one of these dots is flaring gas into the atmosphere and could be mining Bitcoin instead of wasting the gas and polluting the air.
https://i.ibb.co/d4WBjXTX/Gos-OHm-Nb-IAAO8-VT.jpg
Thomas Jeegers: 'Each of these flare sites is a perfect candidate for Bitcoin mining, where wasted methane can be captured, converted into electricity, and monetized on the spot. No need for new pipelines. No need for subsidies. Just turning trash into treasure. Yes, other technologies can help reduce methane emissions. But only Bitcoin mining can do it profitably, consistently, at scale, and globally. And that’s exactly why it's already happening in Texas, Alberta, Oman, Argentina, and beyond. Methane is 84x more harmful than CO₂ over 20 years. Bitcoin is not just a monetary revolution, it's an environmental one.'
➡️Bitcoin market cap dominance hits a new 4-year high.
➡️BlackRock bought $30 million #Bitcoin for its spot Bitcoin ETF.
➡️Multiple countries and sovereign wealth funds are looking to establish Strategic Bitcoin Reserves - Financial Times
Remember, Gold's market cap is up $5.5 TRILLION in 2025. That's more than 3x of the total Bitcoin market cap. Nation-state adoption of Bitcoin is poised to be a pivotal development in monetary history...eventually.
➡️'In 2015, 1 BTC bought 57 steaks. Today, 7,568. Meanwhile, $100 bought 13 steaks in 2015. Now, just 9. Stack ₿, eat more steak.' Priced in Bitcoin
https://i.ibb.co/Pz5BtZYP/Gouxzda-Xo-AASSc-M.jpg
➡️'The Math:
At $91,150 Bitcoin flips Saudi Aramco
At $109,650 Bitcoin flips Amazon
At $107,280 Bitcoin flips Google
At $156,700 Bitcoin flips Microsoft
At $170,900 Bitcoin flips Apple
At $179,680 Bitcoin flips NVIDIA
Over time #Bitcoin flips everything.' -CarlBMenger
➡️Will $1 get you more or less than 1,000 sats by the fifth Halving? Act accordingly. - The rational root Great visual: https://i.ibb.co/tPxnXnL4/Gov1s-IRWEAAEXn3.jpg
➡️Bhutan’s Bitcoin Holdings Now Worth 30% of National GDP: A Bold Move in the Bitcoin Game Theory
In a stunning display of strategic foresight, Bhutan’s Bitcoin holdings are now valued at approximately 30% of the nation’s GDP. This positions the small Himalayan kingdom as a key player in the ongoing Bitcoin game theory that is unfolding across the world. This move also places Bhutan ahead of many larger nations, drawing attention to the idea that early Bitcoin adoption is not just about financial innovation, but also about securing future economic sovereignty and proof that Bitcoin has the power to lift nations out of poverty.
Bhutan explores using its hydropower for green Bitcoin mining, aiming to boost the economy while maintaining environmental standards. Druk Holding's CEO Ujjwal Deep Dahal says hydropower-based mining effectively "offsets" fossil fuel-powered bitcoin production, per Reuters.
➡️Barry Silbert, CEO of Digital Currency Group, admits buying Coinbase was great, but just holding Bitcoin would’ve been better. Silbert told Raoul Pal he bought BTC at $7–$8 and, "Had I just held the Bitcoin, I actually would have done better than making those investments."
He also called 99.9% of tokens “worthless,” stressing most have no reason to exist.
No shit Barry!
➡️Bitcoin hashrate hits a new ATH.
https://i.ibb.co/1pDj9Ch/Gor2-Dd2ac-AAk-KC5.jpg
Bitcoin hashrate hit 1ZH/s. That’s 1,000,000,000,000,000,000,000 hashes every second. Good luck stopping that! Bitcoin mining is the most competitive and decentralized industry in the world.
➡️¥10 Billion Japanese Fashion Retailer ANAP Adds Bitcoin to Corporate Treasury Tokyo, Japan – ANAP Inc., a publicly listed Japanese fashion retailer with a market capitalization of approximately ¥10 billion, has officially announced the purchase of Bitcoin as part of its corporate treasury strategy.
“The global trend of Bitcoin becoming a reserve asset is irreversible,” ANAP stated in its announcement.
➡️El Salvador just bought more Bitcoin for their Strategic Bitcoin Reserve.
➡️Only 9.6% of Bitcoin addresses are at a loss, a rare signal showing one of the healthiest market structures ever. Despite not being at all-time highs, nearly 90% of holders are in profit, hinting at strong accumulation and potential for further upside.
On the 18th of April:
➡️Swedish company Bitcoin Treasury AB announces IPO plans, aiming to become the 'European version of MicroStrategy'. The company clearly states: "Our goal is to fully acquire Bitcoin (BTC)."
➡️Relai app (unfortunately only available with full KYC) with some great Bitcoin marketing. https://i.ibb.co/G4szrqXj/Goz-Kh-Hh-WEAEo-VQr.jpg
➡️Arizona's Bitcoin Reserve Bill (SB 1373) has passed the House Committee and is advancing to the final floor vote.
➡️Simply Bitcoin: It will take 40 years to mine the last Bitcoin. If you're a whole corner, your grandchildren will inherit the equivalent of four decades of global energy. You're not bullish enough. https://i.ibb.co/Hpz2trvr/Go1-Uiu7a-MAI2g-VS.jpg
➡️Meanwhile in Slovenia: Slovenia's Finance Ministry proposes to introduce a 25% capital gains tax on bitcoin profits.
➡️ In one of my previous Weekly Recaps I already shared some news on Breez. Now imagine a world where everyone can implement lightning apps on browsers...with the latest 'Nodeless' release Breez is another step towards bringing Bitcoin payments to every app. Stellar work!
Breez: 'Breez SDK Now Supports WASM We’re excited to announce that Nodeless supports WebAssembly (WASM), so apps can now add Bitcoin payments directly into browsers and node.js environments. Pay anyone, anywhere, on any device with the Breez SDK.
Our new Nodeless release has even more big updates → Minimum payment amounts have been significantly reduced — send from 21 sats, receive from 100. Now live in Misty Breez (iOS + Android). → Users can now pay fees with non-BTC assets like USDT. Check the release notes for all the details on the 0.8 update.'
https://github.com/breez/breez-sdk-liquid/releases/tag/0.8.0
https://bitcoinmagazine.com/takes/embed-bitcoin-into-everything-everywhere Shinobi: Bitcoin needs to be everywhere, seamlessly, embedded into everything.
➡️Despite reaching a new all-time high of $872B, bitcoin's realized market cap monthly growth slowed to 0.9%, signaling continued risk-off sentiment, according to Glassnode.
On the 19th of April:
➡️Recently a gold bug, Jan Nieuwenhuijs (yeah he is Dutch, we are not perfect), stated the following: 'Bitcoin was created by mankind and can be destroyed by mankind. Gold cannot. It’s as simple as that.'
As a reply to a Saylor quote: 'Bitcoin has no counterparty risk. No company. No country. No creditor. No currency. No competitor. No culture. Not even chaos.'
Maybe Bitcoin can be destroyed by mankind, never say never, but what I do know is that at the moment Bitcoin is destroying gold like a manic.
https://i.ibb.co/ZR8ZB4d5/Go7d-KCqak-AA-D7-R.jpg
Oh and please do know. Gold may have the history, but Bitcoin has the scarcity. https://i.ibb.co/xt971vJc/Gp-FMy-AXQAAJzi-M.jpg
In 2013, you couldn't even buy 1 ounce of gold with 1 Bitcoin.
Then in 2017, you could buy 9 ounces of gold with 1 Bitcoin.
Today you can buy 25 ounces of gold with 1 Bitcoin.
At some point, you'll be able to buy 100 ounces of gold with 1 Bitcoin.
➡️Investment firm Abraxas Capital bought $250m Bitcoin in just 4 days.
On the 20th of April:
➡️The Bitcoin network is to be 70% powered by sustainable energy sources by 2030. https://i.ibb.co/nsqsfVY4/Go-r7-LEWo-AAt6-H2.jpg
➡️FORBES: "Converting existing assets like Fort Knox gold into bitcoin makes sense. It would be budget-neutral and an improvement since BTC does everything that gold can, but better" Go on Forbes, and say it louder for the people at the back!
On the 21st of April:
➡️Bitcoin has now recovered the full price dip from Trump's tariff announcement.
➡️Michael Saylor's STRATEGY just bought another 6,556 Bitcoin worth $555.8m. MicroStrategy now owns 2.7% of all Bitcoin in circulation. At what point do we stop celebrating Saylor stacking more?
On the same day, Metaplanet acquired 330 BTC for $28.2M, reaching 4,855 BTC in total holdings.
➡️'Northern Forum, a non-profit member organization of UNDP Climate Change Adaptation, just wrote a well-researched article on how Bitcoin mining is aiding climate objectives (stabilizing grids, aiding microgrids, stopping renewable waste)' -Daniel Batten
https://northernforum.net/how-bitcoin-mining-is-transforming-the-energy-production-game/
💸Traditional Finance / Macro:
On the 16th of April:
👉🏽The Nasdaq Composite is now on track for its 5th-largest daily point decline in history.
👉🏽'Foreign investors are dumping US stocks at a rapid pace: Investors from overseas withdrew ~$6.5 billion from US equity funds over the last week, the second-largest amount on record. Net outflows were only below the $7.5 billion seen during the March 2023 Banking Crisis. According to Apollo, foreigners own a massive $18.5 trillion of US stocks or 20% of the total US equity market. Moreover, foreign holdings of US Treasuries are at $7.2 trillion, or 30% of the total. Investors from abroad also hold 30% of the total corporate credit market, for a total of $4.6 trillion.' TKL
On the 17th of April:
👉🏽'Historically, the odds of a 10% correction are 40%, a 25% bear market 20%, and a 50% bear market 2%. That means that statistically speaking the further the market falls the more likely it is to recover. Yes, some 20% declines become 50% “super bears,” but more often than not the market has historically started to find its footing at -20%, as it appears to have done last week.' - Jurrien Timmer - Dir. of Global Macro at Fidelity
https://i.ibb.co/B2bVDLqM/Gow-Hn-PRWYAAX79z.jpg
👉🏽The S&P 500 is down 10.3% in the first 72 trading days of 2025, the 5th worst start to a year in history.
🏦Banks:
👉🏽 'Another amazing piece of reporting by Nic Carter on a truly sordid affair. Nic Carter is reporting that prominent Biden officials killed signature bank — though solvent — to expand Silvergate/SVB collapses into a national issue, allowing FDIC to invoke a “systemic risk exemption” to bail out SVB at Pelosi’s request.' - Alex Thorne
https://www.piratewires.com/p/signature-didnt-have-to-die-either-chokepoint-nic-carter
Signature, Silvergate, and SVB were attacked by Democrats to kneecap crypto and distance themselves from FTX. The chaos created unintended negative consequences. Signature was solvent but they forced a collapse to invoke powers which they used to clean up the mess they made.
🌎Macro/Geopolitics:
Every nation in the world is in debt and no one wants to say who the creditor is.
On the 14th of April:
👉🏽'US financial conditions are now their tightest since the 2020 pandemic, per ZeroHedge. Financial conditions are even tighter than during one of the most rapid Fed hike cycles of all time, in 2022. Conditions have tightened rapidly as stocks have pulled back, while credit spreads have risen. To put it differently, the availability and cost of financing for economic activity have worsened. That suggests the economy may slow even further in the upcoming months.' -TKL
👉🏽Global Repricing of Duration Risk... 'It opens the door to a global repricing of duration risk. This isn’t a blip. It’s a sovereign-level alarm bell.
"I find Japan fascinating on many levels not just its financial history. Just watch the Netflix documentary: Watch Age of Samurai: Battle for Japan 'I only discovered the other day that the Bank of Japan was the first to use Quantitative Easing. Perhaps that's when our global finance system was first broken & it's been sticking plasters ever since.' - Jane Williams
A must-read…the U.S. bond market is being driven down by Japanese selling and not because they want to…because they have to. It’s looking more and more dangerous.
BoJ lost its control over long-term bond yields. Since inflation broke out in Japan, BoJ can not suppress any longer...
EndGame Macro: "This is one of the clearest signals yet that the Bank of Japan has lost control of the long end of the curve. Japan’s 30-year yield hitting 2.845% its highest since 2004 isn’t just a local event. This has global knock-on effects: Japan is the largest foreign holder of U.S. Treasuries and a key player in the global carry trade. Rising JGB yields force Japanese institutions to repatriate capital, unwind overseas positions, and pull back on USD asset exposure adding pressure to U.S. yields and FX volatility. This spike also signals the end of the deflationary regime that underpinned global risk assets for decades. If Japan once the global anchor of low yields can’t suppress its bond market anymore, it opens the door to a global repricing of duration risk. This isn’t a blip. It’s a sovereign-level alarm bell."
https://i.ibb.co/LXsCDZMf/Gow-XGL8-Wk-AEDXg-P.jpg
You're distracted by China, but it's always been about Japan.
On the 16th of April:
👉🏽Over the last 20 years, gold has now outperformed stocks, up +620% compared to a +580% gain in the S&P 500 (dividends included). Over the last 9 months, gold has officially surged by over +$1,000/oz. Gold hit another all-time high and is now up over 27% in 2025. On pace for its best year since 1979.
https://i.ibb.co/9kZbtPVF/Goftd-OSW8-AA2a-9.png
Meanwhile, imports of physical gold have gotten so large that the Fed has released a new GDP metric. Their GDPNow tool now adjusts for gold imports. Q1 2025 GDP contraction including gold is expected to be -2.2%, and -0.1% net of gold. Gold buying is at recession levels.
👉🏽Von der Leyen: "The West as we knew it no longer exists. [..] We need another, new European Union ready to go out into the big wide world and play a very active role in shaping this new world order"
Her imperial aspirations have long been on display. Remember she was not elected.
👉🏽Fed Chair Jerome Powell says crypto is going mainstream, a legal framework for stablecoins is a good idea, and there will be loosening of bank rules on crypto.
On the 17th of April:
👉🏽The European Central Bank cuts interest rates by 25 bps for their 7th consecutive cut as tariffs threaten economic growth. ECB's focus shifted to 'downside risk to the growth outlook.' Markets price in the deposit rate will be at 1.58% in Dec, from 1.71% before the ECB's statement. Great work ECB, as inflation continues to decline and economic growth prospects worsen. Unemployment is also on the rise. Yes, the economy is doing just great!
On the same day, Turkey reversed course and hiked rates for the first time since March 2024, 350 bps move up to 46%.
👉🏽'Global investors have rarely been this bearish: A record ~50% of institutional investors intend to reduce US equity exposure, according to a Bank of America survey released Monday. Allocation to US stocks fell 13 percentage points over the last month, to a net 36% underweight, the lowest since the March 2023 Banking Crisis. Since February, investors' allocation to US equities has dropped by ~53 percentage points, marking the largest 2-month decline on record. Moreover, a record 82% of respondents are now expecting the world economy to weaken. As a result, global investor sentiment fell to just 1.8 points, the 4th-lowest reading since 2008. We have likely never seen such a rapid shift in sentiment.' -TKL
👉🏽'US large bankruptcies jumped 49 year-over-year in Q1 2025, to 188, the highest quarterly count since 2010. Even during the onset of the 2020 pandemic, the number of filings was lower at ~150. This comes after 694 large companies went bankrupt last year, the most in 14 years. The industrial sector recorded the highest number of bankruptcies in Q1 2025, at 32. This was followed by consumer discretionary and healthcare, at 24 and 13. Bankruptcies are rising.' -TKL
👉🏽DOGE‘s success is simply breathtaking.
https://i.ibb.co/zV45sYBn/Govy-G6e-XIAA8b-NI.jpg
Although it would've been worse without DOGE, nothing stops this train.
👉🏽GLD update: Custodian JPM added 4 tons, bringing their total to a new all-time high of 887 tons. JPM has added 50 tons in a month and is 163 tons from surpassing Switzerland to become the 7th largest gold holder in the world.
Now ask yourself and I quote Luke Gromen:
a) why JPM decided to become a GLD custodian after 18 years, & then in just over 2 years, shift 90%+ of GLD gold to its vaults, &;
b) why the Atlanta Fed has continued to report real GDP with- and without (~$500B of) gold imports YTD?
👉🏽Sam Callahan: After slowing the pace of QT twice—and now hinting at a potential return to QE—the Fed’s balance sheet is settling into a new higher plateau. "We’ve been very clear that this is a temporary measure...We’ll normalize the balance sheet and reduce the size of holdings...It would be quite a different matter if we were buying these assets and holding them indefinitely. It would be a monetization. We are not doing that." - Ben Bernake, Dec. 12, 2012
Temporary measures have a funny way of becoming structural features. The balance sheet didn’t ‘normalize’.. it evolved. What was once an ‘emergency’ is now a baseline. This isn’t QE or QT anymore. It’s a permanent intervention dressed as policy. Remember, 80% of all dollars were created in the last 5 years.
👉🏽Global Fiat Money Supply Is Exploding 🚨
The fiat system is on full tilt as central banks flood markets with unprecedented liquidity:
🇺🇸 U.S.: Money supply nearing new all-time highs
🇨🇳 China: At record levels
🇯🇵 Japan: Close to historic peaks
🇪🇺 EU: Printing into new ATHs https://i.ibb.co/Cp4z97Jx/Go4-Gx2-MXIAAzdi9.jpg
This isn’t growth—it’s monetary debasement. Governments aren’t solving problems; they’re papering over them with inflation.
Bitcoin doesn’t need bailouts. It doesn’t print. It doesn’t inflate.
As fiat currencies weaken under the weight of endless expansion, Bitcoin stands alone as a fixed-supply, incorruptible alternative.
👉🏽Fed Funds Rate: Market Expectations...
-May 2025: Hold
-Jun 2025: 25 bps cut to 4.00-4.25%
-July 2025: 25 bps cut to 3.75-4.00%
-Sep 2025: 25 bps cut to 3.50-3.75%
-Oct 2025: Hold
-Dec 2025: 25 bps cut to 3.25-3.50%
Anyway, shortterm fugazi....500 years of interest rates, visualized: https://i.ibb.co/84zs0yvD/Go7i7k-ZXYAAt-MRH.jpg
👉🏽'A net 49% of 164 investors with $386 billion in assets under management (AUM) believe a HARD LANDING is the most likely outcome for the world economy, according to a BofA survey. This is a MASSIVE shift in sentiment as 83% expected no recession in March.' -Global Markets Investor
👉🏽The EU’s New Role as Tax Collector: A Turning Point for Sovereignty
Beginning in 2027, a new chapter in the European Union’s influence over national life will begin. With the introduction of ETS2, the EU will extend its Emissions Trading System to include not just businesses, but private individuals as well. This means that CO₂ emissions from household gas consumption and vehicle fuel will be taxed—directly impacting the daily lives of citizens across the continent.
In practice, this shift transforms the EU into a (in)direct tax collector, without national consent, without a democratic mandate, and without the explicit approval of the people it will affect. The financial burden will be passed down through energy suppliers and fuel providers, but make no mistake: the cost will land squarely on the shoulders of European citizens, including millions of Dutch households.
This raises a fundamental question: What does sovereignty mean if a foreign or supranational entity can 'tax' your citizens? When a people are 'taxed' by a power beyond their borders—by an unelected body headquartered in Brussels—then either their nation is no longer sovereign, or that sovereignty has been surrendered or sold off by those in power.
There are only two conclusions to draw: We are living under soft occupation, with decisions made elsewhere that bind us at home. Or our sovereignty has been handed away voluntarily—a slow erosion facilitated by political elites who promised integration but delivered subordination. Either way, the more aggressively the EU enforces this trajectory, the more it reveals the futility of reforming the Union from within. The democratic deficit is not shrinking—it’s expanding. And with every new policy imposed without a national vote, the case for fundamental change grows stronger.
If Brussels continues down this path, there will come a point when only one option remains: A clean and decisive break. My view: NEXIT
Source: https://climate.ec.europa.eu/eu-action/eu-emissions-trading-system-eu-ets/ets2-buildings-road-transport-and-additional-sectors_en
For the Dutch readers:
https://www.businessinsider.nl/directe-co2-heffing-van-eu-op-gas-en-benzine-kan-huishoudens-honderden-euros-per-jaar-kosten-er-komt-ook-een-sociaal-klimaatfonds/?tid=TIDP10342314XEEB363B26CB34FB48054B929DB743E99YI5
On the 18th of April:
👉🏽'Two lost decades. Grotesque overregulation, bureaucracy, lack of innovation, and left redistribution mindset have their price. Europe is on its way to becoming an open-air museum. What a pity to watch.' -Michael A. Arouet
https://i.ibb.co/PsxdC3Kw/Goz-Ffwy-XMAAJk-Af.jpg
Looking at the chart, fun fact, the Lisbon Treaty was signed in 2007. That treaty greatly empowered the European bureaucracy. Reforms are needed in Europe, as soon as possible.
👉🏽CBP says latest tariffs have generated $500 million, well below Trump’s estimate — CNBC
Yikes! 'Probably one the biggest economic blunders in history. $500 million in 15 days means $12 billion a year in additional tax revenue. Literal trillions in wealth destroyed, interest on the debt increased, the dollar weakened, businesses wiped out all over the world, and literally every single country in the world antagonized... all for raising a yearly amount of taxes that can fund the US military budget for just 4 days. $500 million pays for exactly 37 minutes of the US budget.' - Arnaud Bertrand
YIKES!!
👉🏽Belarus to launch a "digital ruble" CBDC by the end of 2026.
On the 20th of April:
👉🏽'China’s central bank increased its gold holdings by 5 tonnes in March, posting its 5th consecutive monthly purchase. This brings total China’s gold reserves to a record 2,292 tonnes. Chinese gold holdings now reflect 6.5% of its total official reserve assets. According to Goldman Sachs, China purchased a whopping 50 tonnes of gold in February, or 10 times more than officially reported. Over the last 3 years, China's purchases of gold on the London OTC market have significantly surpassed officially reported numbers. China is accumulating gold at a rapid pace.' -TKL
On the 21st of April:
👉🏽Gold officially breaks above $3,400/oz for the first time in history. Gold funds attracted $8 BILLION in net inflows last week, the most EVER. This is more than DOUBLE the records seen during the 2020 CRISIS. Gold is up an impressive 29% year-to-date.
https://i.ibb.co/Nn7gr45q/Goq7km-PW8-AALegt.png
👉🏽I want to finish this segment and the weekly recap with a chart, a chart to think about! A chart to share with friends, family, and co-workers:
https://i.ibb.co/9xFxRrw/Gp-A3-ANWbs-AAO5nl.jpg
side note: 'Labeled periods like the "Era of Populism" (circa 2010-2020) suggest a link between growing wealth disparity and populist movements, supported by studies like those http://on.tandfonline.com, which note income inequality as a driver for populist party support in Europe due to economic insecurities and distrust in elites.'
The fiat system isn’t broken. It’s doing exactly what it was designed to do: Transfer wealth from savers to the state. This always ends in either default or debasement There’s one exit - Bitcoin.
Great thread: https://x.com/fitcoiner/status/1912932351677792703 https://i.ibb.co/84sFWW9q/Gow-Zv-SFa4-AAu2-Ag.jpg
🎁If you have made it this far I would like to give you a little gift, well in this case two gifts:
Bitcoin Nation State Adoption Paradox - A Trojan Horse with Alex Gladstein. Exploring the paradoxes of Bitcoin adoption in nation-states and its radical role in human rights, freedom, and financial sovereignty. https://youtu.be/pLIxmIMHL44
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly.
Use the code SE3997
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀ ⠀
⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you?
If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ 00e5a4ac:5cf950dd
2025-04-23 21:36:33
@ 00e5a4ac:5cf950dd
2025-04-23 21:36:33My everyday activity
This template is just for demo needs.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ 00e5a4ac:5cf950dd
2025-04-23 21:32:56
@ 00e5a4ac:5cf950dd
2025-04-23 21:32:56My everyday activity
This template is just for demo needs.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ 00e5a4ac:5cf950dd
2025-04-23 21:32:50
@ 00e5a4ac:5cf950dd
2025-04-23 21:32:50My everyday activity
This template is just for demo needs.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ 00e5a4ac:5cf950dd
2025-04-23 21:32:41
@ 00e5a4ac:5cf950dd
2025-04-23 21:32:41My everyday activity
This template is just for demo needs.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ 00e5a4ac:5cf950dd
2025-04-23 20:52:18
@ 00e5a4ac:5cf950dd
2025-04-23 20:52:18My everyday activity
This template is just for demo needs.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ 6e64b83c:94102ee8
2025-04-23 20:44:28
@ 6e64b83c:94102ee8
2025-04-23 20:44:28How to Import and Export Your Nostr Notes
This guide will help you import your notes from various Nostr relays and export them into your own relay. This is particularly useful when you want to ensure your content is backed up or when you're setting up your own relay.
Prerequisite
Your own Nostr relay (if you don't have one, check out Part 1: How to Run Your Own Nostr Relay)
Installing nak
nakis a command-line tool that helps you interact with Nostr relays. Here's how to install it:For Windows Users
- Visit the nak releases page
- Download the latest
nak-windows-amd64.exe - Rename it to
nak.exe - Move it to a directory in your PATH or use it from its current location
For macOS Users
- Visit the nak releases page
- Download the latest
nak-darwin-amd64 - Open Terminal and run:
bash chmod +x nak-darwin-amd64 sudo mv nak-darwin-amd64 /usr/local/bin/nak
For Linux Users
- Visit the nak releases page
- Download the latest
nak-linux-amd64 - Open Terminal and run:
bash chmod +x nak-linux-amd64 sudo mv nak-linux-amd64 /usr/local/bin/nak
Getting Your Public Key in Hex Format
Before downloading your notes, you need to convert your npub (public key) to its hex format. If you have your npub, run:
bash nak decode npub1YOUR_NPUB_HEREThis will output your public key in hex format, which you'll need for the next steps.
Downloading Your Notes
To download your notes, you'll need your public key in hex format and a list of reliable relays. Here are some popular relays you can use:
- wss://eden.nostr.land/
- wss://nos.lol/
- wss://nostr.bitcoiner.social/
- wss://nostr.mom/
- wss://relay.primal.net/
- wss://relay.damus.io/
- wss://relay.nostr.band/
- wss://relay.snort.social/
Note: You should check your Nostr client's settings to find additional relays where your notes are published. Add these to the list above.
Important Event Kinds
Here are some important event kinds you might want to filter for:
0: User Metadata (profile information)1: Short Text Notes3: Follow List4: Encrypted Direct Messages
Get the full list from: https://nips.nostr.com/#event-kinds
Downloading with Event Kind Filters
To download your notes with specific event kinds, use the
-kflag followed by the kind number, use multiple if you need to. For example, to download your profile, short notes, follow list, and direct messages:bash nak req -a YOUR_HEX_PUBKEY -k 0 -k 1 -k 3 -k 4 wss://eden.nostr.land/ wss://nos.lol/ wss://nostr.bitcoiner.social/ wss://nostr.mom/ wss://relay.primal.net/ wss://relay.damus.io/ wss://relay.nostr.band/ wss://relay.snort.social/ > events_filtered.jsonOr to download all your content, just don't provide any
kflag:bash nak req -a YOUR_HEX_PUBKEY wss://eden.nostr.land/ wss://nos.lol/ wss://nostr.bitcoiner.social/ wss://nostr.mom/ wss://relay.primal.net/ wss://relay.damus.io/ wss://relay.nostr.band/ wss://relay.snort.social/ > events.jsonThis will create a file containing all your notes in JSON Lines format.
Uploading Your Notes to Your Relay
Once you have your
events.jsonorevents_filtered.jsonfile, you can upload it to your own relay. ReplaceYOUR_RELAYwith your relay's WebSocket URL (e.g.,wss://my-relay.nostrize.me).bash nak event YOUR_RELAY < events.jsonImportant Notes: 1. Make sure your relay is running and accessible 2. The upload process might take some time depending on how many notes you have 3. You can verify the upload by querying your relay for your notes
Verifying the Upload
To verify that your notes were successfully uploaded to your relay, run:
bash nak req -a YOUR_HEX_PUBKEY YOUR_RELAYThis should return the same notes that were in your
events.jsonfile.Troubleshooting
If you encounter any issues:
- Make sure your relay is running and accessible
- Check that you're using the correct public key
- Verify that the relays in your download list are working
- Ensure you have proper permissions to write to your relay
Next Steps
- Remember to regularly backup your notes to ensure you don't lose any content.
- If you want to keep your friends' notes as well, add npubs that you want to import into your relay's settings (for Citrine it is "Accept events signed by" list), and run the commands for their pubkeys.
-
 @ a296b972:e5a7a2e8
2025-04-23 20:40:35
@ a296b972:e5a7a2e8
2025-04-23 20:40:35Aus der Ferne sieht man nur ein Gefängnis aus Beton. Doch wenn man näher herankommt, sieht man, dass die Mauern schon sehr brüchig sind und das Regenwasser mit jedem Schauer tiefer in das Gemäuer eindringt. Da bleibt es. Bis die Temperaturen unter Null gehen und das Wasser gefriert. Jetzt entfaltet das Eis seine physikalische Kraft, es rückt dem Beton zu leibe, es dehnt sich aus und sprengt ihn.
Das geht nun schon fünf Jahre so. Fünf Jahre immer wieder Regen, abwechselnd mit Frost und Eis. Die Risse werden größer, der Beton immer morscher. So lange, bis die Mauern ihre Tragfähigkeit verlieren und einstürzen.
Was soll das? Fängt da einer an zu spinnen? Wozu diese Metapher?
Hätte man zu Anfang gleich geschrieben: Wir, die kritischen Menschen, die sich der Wahrheit verpflichtet haben, sitzen in unserer Blase wie in einem Gefängnis und erreichen die da draußen nicht. Da hätten sicher viele gesagt: Oh, da will aber jemand die Opferrolle in vollen Zügen auskosten. Nee, nee, wir sind keine Opfer, wir sind Täter. Wir sammeln und bewahren die ständig neu dazukommenden Erkenntnisse der Wissenschaft und politischen Lügereien. Wir lernen Bücher auswendig, bevor die Feuerwehr kommt und sie verbrennt.
„Fahrenheit 451“
https://www.youtube.com/watch?v=P3Kx-uiP0bY
https://www.youtube.com/watch?v=TsNMxUSCKWo
„Das Haus ist für unbewohnbar erklärt worden und muss verbrannt werden.“
So primitiv geht man heute nicht mehr vor. Heute stehen die Feuerwehrmänner und ihre Erfüllungsgehilfen um 6 Uhr morgens im Türrahmen, nehmen Mobiltelefon und Laptop mit, betreiben De-Banking und vernichten die wirtschaftliche Existenz.
Und ja, es gibt Tage, da fühlt man sich trotzdem wie im Informationsgefängnis. Das hängt von der Tageskondition ab. Der öffentlich-rechtliche Rundfunk ist die Gefängnisküche. Zubereitet werden fade Speisen mit sich ständig wiederholenden Zutaten. Heraus kommt ein Gericht, eine Pampe, wie die tagesschau. LAAAANGWEILIG!
Man glaubt, Informationen und kritische Äußerungen gegenüber dem Mainstream-Einheitsbrei bleiben in den Gefängnismauern, der Blase, schaffen es nicht über die Mauer nach draußen, in die vermeintliche Freiheit. Neue Erkenntnisse werden nur innerhalb der Mauern weitergegeben. Ein neuer Kanal, steigende Abonnenten. Doch wer sind die? Welche von da draußen, in der sogenannten Freiheit, oder doch wieder immer dieselben üblichen Verdächtigen? Die da draußen haben uns doch schon längst geblockt oder gleich gelöscht. Mit Gedankenverbrechern will man nichts zu tun haben.
Hallo, ihr da draußen: Wir sind unschuldig. Unser einziges Verbrechen ist, dass wir Informationen verbreiten, die euch da draußen nicht gefallen, weil sie euch nicht in den Kram passen. Für euch sind wir eine Bedrohung, weil diese Informationen auf euch weltbilderschütternd wirken. Wir sprechen das aus, was viele sich nicht einmal trauen zu denken. Ihr habt Angst vor der Freiheit. Nicht wir sitzen ein, sondern ihr. In einem Freiluft-Gefängnis. Wir decken die Lügen auf, die da draußen, außerhalb der Mauern verbreitet werden. Wir sind nicht die Erfinder der Lügen, sondern nur die Überbringer der schlechten Botschaften.
Es ist leichter Menschen zu lieben, von denen man belogen wird, als Menschen zu lieben, die einem sagen, dass man belogen wird.
Mit aller Kraft wird versucht, die Menschen in Einzelhaft zu setzen. In der Summe ist das die gesellschaftliche Spaltung. Gleichzeitig wird an den Zusammenhalt appelliert, obwohl man genau das Gegenteil davon vorantreibt.
Es geht auch nicht um Mitleid. Es geht um das Verdeutlichen der vorhandenen medialen Axt, mit der ganze Nationen in zwei Teile zerhackt werden. Auf politischer Ebene wird viel dafür getan, dass sich das auch ja nicht ändert. Ein Volk in Angst ist gut zu regieren. Teile und herrsche. Die Sprüche können wir alle schon rückwärts auf der Blockflöte pfeifen.
An den vier Ecken des Informations-Gefängnisses stehen Wachtürme, mit Wärtern, ausgebildet vom DSA, vom Digital Services Act, finanziert vom Wahrheitsministerium, dass ständig aktualisierend darüber befindet, was heute gerade aktuell als „Hass und Hetze“ en vogue ist. Es kommt eben immer darauf an, wer diese Begriffe aus der bisher dunkelsten Zeit in der deutschen Geschichte benutzt. Das hatten wir alles schon einmal. Das brauchen wir nicht mehr!
Schon in der Bibel steht das Gebot: Du sollst nicht lügen. Da steht nicht: Lügen verboten! Das Titelbild gehört leider auch zur deutschen Vergangenheit. Ist es jetzt schon verboten, darauf hinzuweisen, dass sich so etwas nicht wiederholen darf? Und in einer Demokratie, die eine sein will, schon gar nicht. Eine Demokratie, die keine ist, wenn die Meinungsfreiheit beschnitten wird und selbsternannte Experten meinen darüber entscheiden zu müssen, was als wahr und was als Lüge einzustufen ist. Die Vorgabe von Meinungs-Korridoren delegitimieren das Recht, seine Meinung frei äußern zu dürfen. In einer funktionierenden Demokratie dürfte sogar gelogen werden. Jedem, der noch zwei gesunde Gehirnzellen im Kopf hat, sollte doch klar sein, dass all das erbärmliche Versuche sind, sich mit allen Mitteln an der Macht festzuklammern.
Noch einmal zurück zur anfänglichen Metapher. So lange wir leben, befinden wir uns in einem fließenden Prozess. Nichts ist in Stein gemeißelt, nichts hält für immer. Betrachtet man die jüngste Vergangenheit als einen lebendigen Prozess, der noch nicht abgeschlossen ist, der sich ständig weiterentwickelt, dann ist all dieser Wahnsinn der Regen, der bei Frost zu Eis wird und die Mauer immer maroder macht. Die Temperaturen gehen wieder über Null, das Eis taut auf, das Wasser versickert, der nächste Regen, der nächste Frost. Alles neigt dazu kaputt zu gehen.
Wir brauchen eigentlich nur zu warten, während wir fleißig weiter Erkenntnisse sammeln und dabei zusehen, wie ein Frost nach dem anderen, in Form von immer neuen und weiteren Informationen, die all die Lügen zu Corona und den aktuellen Kriegen in der Welt, die Gefängnismauer früher oder später zum Einsturz bringen wird. Und das ist wirklich so sicher, wie das Amen in der Kirche. Die Wahrheit hat immer gesiegt!
Und wenn der Damm erst einmal gebrochen ist, das Wasser schwappt bereits über die Staumauer, dann wird sich die Wahrheit wie ein Sturzbach über die Menschen ergießen. Manche wird sie mitreißen, Schicksal, wir haben genug Rettungsboote ausgesetzt in den letzten Jahren.
Spricht so ein pessimistischer Optimist mit realistischen Tendenzen?
Ihr da draußen, macht nur so weiter. Immer mehr von demselben, und fleißig weiter wundern, dass nichts anderes dabei herauskommt. Überall ist bereits euer eigenes Sägen zu hören, an dem Ast, auf dem ihr selber sitzt. Mit verschränkten Armen, leichtgeneigtem Kopf und einem Schmunzeln auf den Lippen schauen wir dabei zu und fragen uns, wie lange der Ast wohl noch halten wird und wann es kracht. Wir können warten!
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ df478568:2a951e67
2025-04-23 20:25:03
@ df478568:2a951e67
2025-04-23 20:25:03If you've made one single-sig bitcoin wallet, you've made then all. The idea is, write down 12 or 24 magic words. Make your wallet disappear by dropping your phone in the toilet. Repeat the 12 magic words and do some hocus-pocus. Your sats re-appear from realms unknown. Or...Each word represents a 4 digit number from 0000-2047. I say it's magic.
I've recommended many wallets over the years. It's difficult to find the perfect wallet because there are so many with different security tailored for different threat models. You don't need Anchorwatch level of security for 1000 sats. 12 words is good enough. Misty Breez is like Aqua Wallet because the sats get swapped to Liquid in a similar way with a couple differences.
- Misty Breez has no stableshitcoin¹ support.
- Misty Breez gives you a lightning address. Misty Breez Lightning Wallet.
That's a big deal. That's what I need to orange pill the man on the corner selling tamales out of his van. Bitcoin is for everybody, at least anybody who can write 12 words down. A few years ago, almost nobody, not even many bitcoiners had a lightning address. Now Misty Breez makes it easy for anyone with a 5th grade reading level to start using lightning addresses. The tamale guy can send sats back home with as many tariffs as a tweet without leaving his truck.
How Misty Breez Works
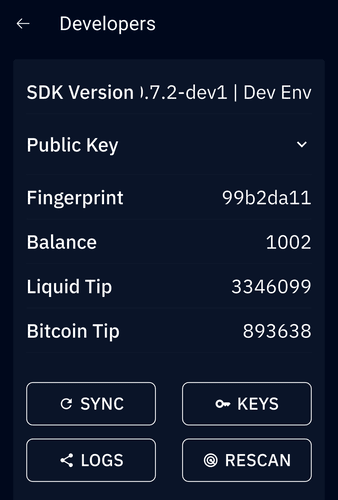
Back in the day, I drooled over every word Elizabeth Stark at lightning labs uttered. I still believed in shitcoins at the time. Stark said atomic swaps can be made over the lightning network. Litecoin, since it also adopted the lightning network, can be swapped with bitcoin and vice-versa. I thought this was a good idea because it solves the coincidence of wants. I could technically have a sign on my website that says, "shitcoin accepted here" and automatically convert all my shitcoins to sats.
I don't do that because I now know there is no reason to think any shitcoin will go up in value over the long-term for various reasons. Technically, cashu is a shitcoin. Technically, Liquid is a shitcoin. Technically, I am not a card carrying bitcoin maxi because of this. I use these shitcoins because I find them useful. I consider them to be honest shitcoins(term stolen from NVK²).
Breeze does ~atomic swaps~~ peer swaps between bitcoin and Liquid. The sender sends sats. The receiver turns those sats into Liquid Bitcoin(L-BTC). This L-BTC is backed by bitcoin, therefore Liquid is a full reserve bank in many ways. That's why it molds into my ethical framework. I originally became interested in bitcoin because I thought fractional reserve banking was a scam and bitcoin was(and is) the most viable alternative to this scam.
Sats sent to Misty Breez wallet are pretty secure. It does not offer perfect security. There is no perfect security. Even though on-chain bitcoin is the most pristine example of cybersecurity on the planet, it still has risk. Just ask the guy who is digging up a landfill to find his bitcoin. I have found most noobs lose keys to bitcoin you give them. Very few take the time to keep it safe because they don't understand bitcoin well enough to know it will go up forever Laura.
She writes 12 words down with a reluctant bored look on her face. Wam. Bam. Thank you m'am. Might as well consider it a donation to the network because that index card will be buried in a pile of future trash in no time. Here's a tiny violin playing for the pre-coiners who lost sats.
"Lost coins only make everyone else's coins worth slightly more. Think of it as a donation to everyone." --Sathoshi Nakamoto, BitcoinTalk --June 21, 2010
The same thing will happen with the Misty Wallet. The 12 words will be written down my someone bored and unfulfilled woman working at NPC-Mart, but her phone buzzes in her pocket the next day. She recieved a new payment. Then you share the address on nostr and five people send her sats for no reason at all. They say everyone requires three touch points. Setting up a pre-coiner with a wallet which has a lightning address will allow you to send her as many touch points as you want. You could even send 21 sats per day for 21 days using Zap Planner. That way bitcoin is not just an "investment," but something people can see in action like a lion in the jungle chasing a gazelle.
Make Multiple Orange Pill Touch Points With Misty The Breez Lightning Address
It's no longer just a one-night stand. It's a relationship. You can softly send her sats seven days a week like a Rabbit Hole recap listening freak. Show people how to use bitcoin as it was meant to be used: Peer to Peer electronic cash.
 Misty wallet is still beta software so be careful because lightning is still in the w reckless days. Don't risk more sats that you are willing to lose with it just yet, but consider learning how to use it so you can teach others after the wallet is battle tested. I had trouble sending sats to my lightning address today from Phoenix wallet. Hopefully that gets resovled, but I couldn't use it today for whatever reason. I still think it's an awesome idea and will follow this project because I think it has potential.
Misty wallet is still beta software so be careful because lightning is still in the w reckless days. Don't risk more sats that you are willing to lose with it just yet, but consider learning how to use it so you can teach others after the wallet is battle tested. I had trouble sending sats to my lightning address today from Phoenix wallet. Hopefully that gets resovled, but I couldn't use it today for whatever reason. I still think it's an awesome idea and will follow this project because I think it has potential.npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
¹ Stablecoins are shitcoins, but I admit they are not totally useless, but the underlying asset is the epitome of money printer go brrrrrr. ²NVK called cashu an honeset shitcoin on the Bitcoin.review podcast and I've used the term ever sense.
-
 @ 6e64b83c:94102ee8
2025-04-23 20:23:34
@ 6e64b83c:94102ee8
2025-04-23 20:23:34How to Run Your Own Nostr Relay on Android with Cloudflare Domain
Prerequisites
- Install Citrine on your Android device:
- Visit https://github.com/greenart7c3/Citrine/releases
- Download the latest release using:
- zap.store
- Obtainium
- F-Droid
- Or download the APK directly
-
Note: You may need to enable "Install from Unknown Sources" in your Android settings
-
Domain Requirements:
- Purchase a domain if you don't have one
-
Transfer your domain to Cloudflare if it's not already there (for free SSL certificates and cloudflared support)
-
Tools to use:
- nak (the nostr army knife):
- Download from https://github.com/fiatjaf/nak/releases
- Installation steps:
-
For Linux/macOS: ```bash # Download the appropriate version for your system wget https://github.com/fiatjaf/nak/releases/latest/download/nak-linux-amd64 # for Linux # or wget https://github.com/fiatjaf/nak/releases/latest/download/nak-darwin-amd64 # for macOS
# Make it executable chmod +x nak-*
# Move to a directory in your PATH sudo mv nak-* /usr/local/bin/nak
- For Windows:batch # Download the Windows version curl -L -o nak.exe https://github.com/fiatjaf/nak/releases/latest/download/nak-windows-amd64.exe# Move to a directory in your PATH (e.g., C:\Windows) move nak.exe C:\Windows\nak.exe
- Verify installation:bash nak --version ```
Setting Up Citrine
- Open the Citrine app
- Start the server
- You'll see it running on
ws://127.0.0.1:4869(local network only) - Go to settings and paste your npub into "Accept events signed by" inbox and press the + button. This prevents others from publishing events to your personal relay.
Installing Required Tools
- Install Termux from Google Play Store
- Open Termux and run:
bash pkg update && pkg install wget wget https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-arm64.deb dpkg -i cloudflared-linux-arm64.debCloudflare Authentication
- Run the authentication command:
bash cloudflared tunnel login - Follow the instructions:
- Copy the provided URL to your browser
- Log in to your Cloudflare account
- If the URL expires, copy it again after logging in
Creating the Tunnel
- Create a new tunnel:
bash cloudflared tunnel create <TUNNEL_NAME> - Choose any name you prefer for your tunnel
-
Copy the tunnel ID after creating the tunnel
-
Create and configure the tunnel config:
bash touch ~/.cloudflared/config.yml nano ~/.cloudflared/config.yml -
Add this configuration (replace the placeholders with your values): ```yaml tunnel:
credentials-file: /data/data/com.termux/files/home/.cloudflared/ .json ingress: - hostname: nostr.yourdomain.com service: ws://localhost:4869
- service: http_status:404 ```
- Note: In nano editor:
CTRL+Oand Enter to saveCTRL+Xto exit
-
Note: Check the credentials file path in the logs
-
Validate your configuration:
bash cloudflared tunnel validate -
Start the tunnel:
bash cloudflared tunnel run my-relay
Preventing Android from Killing the Tunnel
Run these commands to maintain tunnel stability:
bash date && apt install termux-tools && termux-setup-storage && termux-wake-lock echo "nameserver 1.1.1.1" > $PREFIX/etc/resolv.confTip: You can open multiple Termux sessions by swiping from the left edge of the screen while keeping your tunnel process running.
Updating Your Outbox Model Relays
Once your relay is running and accessible via your domain, you'll want to update your relay list in the Nostr network. This ensures other clients know about your relay and can connect to it.
Decoding npub (Public Key)
Private keys (nsec) and public keys (npub) are encoded in bech32 format, which includes: - A prefix (like nsec1, npub1 etc.) - The encoded data - A checksum
This format makes keys: - Easy to distinguish - Hard to copy incorrectly
However, most tools require these keys in hexadecimal (hex) format.
To decode an npub string to its hex format:
bash nak decode nostr:npub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4Change it with your own npub.
bash { "pubkey": "6e64b83c1f674fb00a5f19816c297b6414bf67f015894e04dd4c657e94102ee8" }Copy the pubkey value in quotes.
Create a kind 10002 event with your relay list:
- Include your new relay with write permissions
- Include other relays you want to read from and write to, omit 3rd parameter to make it both read and write
Example format:
json { "kind": 10002, "tags": [ ["r", "wss://your-relay-domain.com", "write"], ["r", "wss://eden.nostr.land/"], ["r", "wss://nos.lol/"], ["r", "wss://nostr.bitcoiner.social/"], ["r", "wss://nostr.mom/"], ["r", "wss://relay.primal.net/"], ["r", "wss://nostr.wine/", "read"], ["r", "wss://relay.damus.io/"], ["r", "wss://relay.nostr.band/"], ["r", "wss://relay.snort.social/"] ], "content": "" }Save it to a file called
event.jsonNote: Add or remove any relays you want. To check your existing 10002 relays: - Visit https://nostr.band/?q=by%3Anpub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4+++kind%3A10002 - nostr.band is an indexing service, it probably has your relay list. - Replace
npub1xxxin the URL with your own npub - Click "VIEW JSON" from the menu to see the raw event - Or use thenaktool if you know the relaysbash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.comReplace `<your-pubkey>` with your public key in hex format (you can get it using `nak decode <your-npub>`)- Sign and publish the event:
- Use a Nostr client that supports kind 10002 events
- Or use the
nakcommand-line tool:bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)
Important Security Notes: 1. Never share your nsec (private key) with anyone 2. Consider using NIP-49 encrypted keys for better security 3. Never paste your nsec or private key into the terminal. The command will be saved in your shell history, exposing your private key. To clear the command history: - For bash: use
history -c- For zsh: usefc -Wto write history to file, thenfc -pto read it back - Or manually edit your shell history file (e.g.,~/.zsh_historyor~/.bash_history) 4. if you're usingzsh, usefc -pto prevent the next command from being saved to history 5. Or temporarily disable history before running sensitive commands:bash unset HISTFILE nak key encrypt ... set HISTFILEHow to securely create NIP-49 encypted private key
```bash
Read your private key (input will be hidden)
read -s SECRET
Read your password (input will be hidden)
read -s PASSWORD
encrypt command
echo "$SECRET" | nak key encrypt "$PASSWORD"
copy and paste the ncryptsec1 text from the output
read -s ENCRYPTED nak key decrypt "$ENCRYPTED"
clear variables from memory
unset SECRET PASSWORD ENCRYPTED ```
On a Windows command line, to read from stdin and use the variables in
nakcommands, you can use a combination ofset /pto read input and then use those variables in your command. Here's an example:```bash @echo off set /p "SECRET=Enter your secret key: " set /p "PASSWORD=Enter your password: "
echo %SECRET%| nak key encrypt %PASSWORD%
:: Clear the sensitive variables set "SECRET=" set "PASSWORD=" ```
If your key starts with
ncryptsec1, thenaktool will securely prompt you for a password when using the--secparameter, unless the command is used with a pipe< >or|.bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)- Verify the event was published:
- Check if your relay list is visible on other relays
-
Use the
naktool to fetch your kind 10002 events:bash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.com -
Testing your relay:
- Try connecting to your relay using different Nostr clients
- Verify you can both read from and write to your relay
- Check if events are being properly stored and retrieved
- Tip: Use multiple Nostr clients to test different aspects of your relay
Note: If anyone in the community has a more efficient method of doing things like updating outbox relays, please share your insights in the comments. Your expertise would be greatly appreciated!
-
 @ d34e832d:383f78d0
2025-04-23 20:19:15
@ d34e832d:383f78d0
2025-04-23 20:19:15A Look into Traffic Analysis and What WebSocket Patterns Reveal at the Network Level
While WebSocket encryption (typically via WSS) is essential for protecting data in transit, traffic analysis remains a potent method of uncovering behavioral patterns, data structure inference, and protocol usage—even when payloads are unreadable. This idea investigates the visibility of encrypted WebSocket communications using Wireshark and similar packet inspection tools. We explore what metadata remains visible, how traffic flow can be modeled, and what risks and opportunities exist for developers, penetration testers, and network analysts. The study concludes by discussing mitigation strategies and the implications for privacy, application security, and protocol design.
Consider
In the age of real-time web applications, WebSockets have emerged as a powerful protocol enabling low-latency, bidirectional communication. From collaborative tools and chat applications to financial trading platforms and IoT dashboards, WebSockets have become foundational for interactive user experiences.
However, encryption via WSS (WebSocket Secure, running over TLS) gives developers and users a sense of security. The payload may be unreadable, but what about the rest of the connection? Can patterns, metadata, and traffic characteristics still leak critical information?
This thesis seeks to answer those questions by leveraging Wireshark, the de facto tool for packet inspection, and exploring the world of traffic analysis at the network level.
Background and Related Work
The WebSocket Protocol
Defined in RFC 6455, WebSocket operates over TCP and provides a persistent, full-duplex connection. The protocol upgrades an HTTP connection, then communicates through a simple frame-based structure.
Encryption with WSS
WSS connections use TLS (usually on port 443), making them indistinguishable from HTTPS traffic at the packet level. Payloads are encrypted, but metadata such as IP addresses, timing, packet size, and connection duration remain visible.
Traffic Analysis
Traffic analysis—despite encryption—has long been a technique used in network forensics, surveillance, and malware detection. Prior studies have shown that encrypted protocols like HTTPS, TLS, and SSH still reveal behavioral information through patterns.
Methodology
Tools Used:
- Wireshark (latest stable version)
- TLS decryption with local keys (when permitted)
- Simulated and real-world WebSocket apps (chat, games, IoT dashboards)
- Scripts to generate traffic patterns (Python using websockets and aiohttp)
Test Environments:
- Controlled LAN environments with known server and client
- Live observation of open-source WebSocket platforms (e.g., Matrix clients)
Data Points Captured:
- Packet timing and size
- TLS handshake details
- IP/TCP headers
- Frame burst patterns
- Message rate and directionality
Findings
1. Metadata Leaks
Even without payload access, the following data is visible: - Source/destination IP - Port numbers (typically 443) - Server certificate info - Packet sizes and intervals - TLS handshake fingerprinting (e.g., JA3 hashes)
2. Behavioral Patterns
- Chat apps show consistent message frequency and short message sizes.
- Multiplayer games exhibit rapid bursts of small packets.
- IoT devices often maintain idle connections with periodic keepalives.
- Typing indicators, heartbeats, or "ping/pong" mechanisms are visible even under encryption.
3. Timing and Packet Size Fingerprinting
Even encrypted payloads can be fingerprinted by: - Regularity in payload size (e.g., 92 bytes every 15s) - Distinct bidirectional patterns (e.g., send/ack/send per user action) - TLS record sizes which may indirectly hint at message length
Side-Channel Risks in Encrypted WebSocket Communication
Although WebSocket payloads transmitted over WSS (WebSocket Secure) are encrypted, they remain susceptible to side-channel analysis, a class of attacks that exploit observable characteristics of the communication channel rather than its content.
Side-Channel Risks Include:
1. User Behavior Inference
Adversaries can analyze packet timing and frequency to infer user behavior. For example, typing indicators in chat applications often trigger short, regular packets. Even without payload visibility, a passive observer may identify when a user is typing, idle, or has closed the application. Session duration, message frequency, and bursts of activity can be linked to specific user actions.2. Application Fingerprinting
TLS handshake metadata and consistent traffic patterns can allow an observer to identify specific client libraries or platforms. For example, the sequence and structure of TLS extensions (via JA3 fingerprinting) can differentiate between browsers, SDKs, or WebSocket frameworks. Application behavior—such as timing of keepalives or frequency of updates—can further reinforce these fingerprints.3. Usage Pattern Recognition
Over time, recurring patterns in packet flow may reveal application logic. For instance, multiplayer game sessions often involve predictable synchronization intervals. Financial dashboards may show bursts at fixed polling intervals. This allows for profiling of application type, logic loops, or even user roles.4. Leakage Through Timing
Time-based attacks can be surprisingly revealing. Regular intervals between message bursts can disclose structured interactions—such as polling, pings, or scheduled updates. Fine-grained timing analysis may even infer when individual keystrokes occur, especially in sparse channels where interactivity is high and payloads are short.5. Content Length Correlation
While encrypted, the size of a TLS record often correlates closely to the plaintext message length. This enables attackers to estimate the size of messages, which can be linked to known commands or data structures. Repeated message sizes (e.g., 112 bytes every 30s) may suggest state synchronization or batched updates.6. Session Correlation Across Time
Using IP, JA3 fingerprints, and behavioral metrics, it’s possible to link multiple sessions back to the same client. This weakens anonymity, especially when combined with data from DNS logs, TLS SNI fields (if exposed), or consistent traffic habits. In anonymized systems, this can be particularly damaging.Side-Channel Risks in Encrypted WebSocket Communication
Although WebSocket payloads transmitted over WSS (WebSocket Secure) are encrypted, they remain susceptible to side-channel analysis, a class of attacks that exploit observable characteristics of the communication channel rather than its content.
1. Behavior Inference
Even with end-to-end encryption, adversaries can make educated guesses about user actions based on traffic patterns:
- Typing detection: In chat applications, short, repeated packets every few hundred milliseconds may indicate a user typing.
- Voice activity: In VoIP apps using WebSockets, a series of consistent-size packets followed by silence can reveal when someone starts and stops speaking.
- Gaming actions: Packet bursts at high frequency may correlate with real-time game movement or input actions.
2. Session Duration
WebSocket connections are persistent by design. This characteristic allows attackers to:
- Measure session duration: Knowing how long a user stays connected to a WebSocket server can infer usage patterns (e.g., average chat duration, work hours).
- Identify session boundaries: Connection start and end timestamps may be enough to correlate with user login/logout behavior.
3. Usage Patterns
Over time, traffic analysis may reveal consistent behavioral traits tied to specific users or devices:
- Time-of-day activity: Regular connection intervals can point to habitual usage, ideal for profiling or surveillance.
- Burst frequency and timing: Distinct intervals of high or low traffic volume can hint at backend logic or user engagement models.
Example Scenario: Encrypted Chat App
Even though a chat application uses end-to-end encryption and transports data over WSS:
- A passive observer sees:
- TLS handshake metadata
- IPs and SNI (Server Name Indication)
- Packet sizes and timings
- They might then infer:
- When a user is online or actively chatting
- Whether a user is typing, idle, or receiving messages
- Usage patterns that match a specific user fingerprint
This kind of intelligence can be used for traffic correlation attacks, profiling, or deanonymization — particularly dangerous in regimes or situations where privacy is critical (e.g., journalists, whistleblowers, activists).
Fingerprinting Encrypted WebSocket Applications via Traffic Signatures
Even when payloads are encrypted, adversaries can leverage fingerprinting techniques to identify the specific WebSocket libraries, frameworks, or applications in use based on unique traffic signatures. This is a critical vector in traffic analysis, especially when full encryption lulls developers into a false sense of security.
1. Library and Framework Fingerprints
Different WebSocket implementations generate traffic patterns that can be used to infer what tool or framework is being used, such as:
- Handshake patterns: The WebSocket upgrade request often includes headers that differ subtly between:
- Browsers (Chrome, Firefox, Safari)
- Python libs (
websockets,aiohttp,Autobahn) - Node.js clients (
ws,socket.io) - Mobile SDKs (Android’s
okhttp, iOSStarscream) - Heartbeat intervals: Some libraries implement default ping/pong intervals (e.g., every 20s in
socket.io) that can be measured and traced back to the source.
2. Payload Size and Frequency Patterns
Even with encryption, metadata is exposed:
- Frame sizes: Libraries often chunk or batch messages differently.
- Initial message burst: Some apps send a known sequence of messages on connection (e.g., auth token → subscribe → sync events).
- Message intervals: Unique to libraries using structured pub/sub or event-driven APIs.
These observable patterns can allow a passive observer to identify not only the app but potentially which feature is being used, such as messaging, location tracking, or media playback.
3. Case Study: Identifying Socket.IO vs Raw WebSocket
Socket.IO, although layered on top of WebSockets, introduces a handshake sequence of HTTP polling → upgrade → packetized structured messaging with preamble bytes (even in encrypted form, the size and frequency of these frames is recognizable). A well-equipped observer can differentiate it from a raw WebSocket exchange using only timing and packet length metrics.
Security Implications
- Targeted exploitation: Knowing the backend framework (e.g.,
Django ChannelsorFastAPI + websockets) allows attackers to narrow down known CVEs or misconfigurations. - De-anonymization: Apps that are widely used in specific demographics (e.g., Signal clones, activist chat apps) become fingerprintable even behind HTTPS or WSS.
- Nation-state surveillance: Traffic fingerprinting lets governments block or monitor traffic associated with specific technologies, even without decrypting the data.
Leakage Through Timing: Inferring Behavior in Encrypted WebSocket Channels
Encrypted WebSocket communication does not prevent timing-based side-channel attacks, where an adversary can deduce sensitive information purely from the timing, size, and frequency of encrypted packets. These micro-behavioral signals, though not revealing actual content, can still disclose high-level user actions — sometimes with alarming precision.
1. Typing Detection and Keystroke Inference
Many real-time chat applications (Matrix, Signal, Rocket.Chat, custom WebSocket apps) implement "user is typing..." features. These generate recognizable message bursts even when encrypted:
- Small, frequent packets sent at irregular intervals often correspond to individual keystrokes.
- Inter-keystroke timing analysis — often accurate to within tens of milliseconds — can help reconstruct typed messages’ length or even guess content using language models (e.g., inferring "hello" vs "hey").
2. Session Activity Leaks
WebSocket sessions are long-lived and often signal usage states by packet rhythm:
- Idle vs active user patterns become apparent through heartbeat frequency and packet gaps.
- Transitions — like joining or leaving a chatroom, starting a video, or activating a voice stream — often result in bursts of packet activity.
- Even without payload access, adversaries can profile session structure, determining which features are being used and when.
3. Case Study: Real-Time Editors
Collaborative editing tools (e.g., Etherpad, CryptPad) leak structure:
- When a user edits, each keystroke or operation may result in a burst of 1–3 WebSocket frames.
- Over time, a passive observer could infer:
- Whether one or multiple users are active
- Who is currently typing
- The pace of typing
- Collaborative vs solo editing behavior
4. Attack Vectors Enabled by Timing Leaks
- Target tracking: Identify active users in a room, even on anonymized or end-to-end encrypted platforms.
- Session replay: Attackers can simulate usage patterns for further behavioral fingerprinting.
- Network censorship: Governments may block traffic based on WebSocket behavior patterns suggestive of forbidden apps (e.g., chat tools, Tor bridges).
Mitigations and Countermeasures
While timing leakage cannot be entirely eliminated, several techniques can obfuscate or dampen signal strength:
- Uniform packet sizing (padding to fixed lengths)
- Traffic shaping (constant-time message dispatch)
- Dummy traffic injection (noise during idle states)
- Multiplexing WebSocket streams with unrelated activity
Excellent point — let’s weave that into the conclusion of the thesis to emphasize the dual nature of WebSocket visibility:
Visibility Without Clarity — Privacy Risks in Encrypted WebSocket Traffic**
This thesis demonstrates that while encryption secures the contents of WebSocket payloads, it does not conceal behavioral patterns. Through tools like Wireshark, analysts — and adversaries alike — can inspect traffic flows to deduce session metadata, fingerprint applications, and infer user activity, even without decrypting a single byte.
The paradox of encrypted WebSockets is thus revealed:
They offer confidentiality, but not invisibility.As shown through timing analysis, fingerprinting, and side-channel observation, encrypted WebSocket streams can still leak valuable information. These findings underscore the importance of privacy-aware design choices in real-time systems:
- Padding variable-size messages to fixed-length formats
- Randomizing or shaping packet timing
- Mixing in dummy traffic during idle states
- Multiplexing unrelated data streams to obscure intent
Without such obfuscation strategies, encrypted WebSocket traffic — though unreadable — remains interpretable.
In closing, developers, privacy researchers, and protocol designers must recognize that encryption is necessary but not sufficient. To build truly private real-time systems, we must move beyond content confidentiality and address the metadata and side-channel exposures that lie beneath the surface.
Absolutely! Here's a full thesis-style writeup titled “Mitigation Strategies: Reducing Metadata Leakage in Encrypted WebSocket Traffic”, focusing on countermeasures to side-channel risks in real-time encrypted communication:
Mitigation Strategies: Reducing Metadata Leakage in Encrypted WebSocket Traffic
Abstract
While WebSocket traffic is often encrypted using TLS, it remains vulnerable to metadata-based side-channel attacks. Adversaries can infer behavioral patterns, session timing, and even the identity of applications through passive traffic analysis. This thesis explores four key mitigation strategies—message padding, batching and jitter, TLS fingerprint randomization, and connection multiplexing—that aim to reduce the efficacy of such analysis. We present practical implementations, limitations, and trade-offs associated with each method and advocate for layered, privacy-preserving protocol design.
1. Consider
The rise of WebSockets in real-time applications has improved interactivity but also exposed new privacy attack surfaces. Even when encrypted, WebSocket traffic leaks observable metadata—packet sizes, timing intervals, handshake properties, and connection counts—that can be exploited for fingerprinting, behavioral inference, and usage profiling.
This Idea focuses on mitigation rather than detection. The core question addressed is: How can we reduce the information available to adversaries from metadata alone?
2. Threat Model and Metadata Exposure
Passive attackers situated at any point between client and server can: - Identify application behavior via timing and message frequency - Infer keystrokes or user interaction states ("user typing", "user joined", etc.) - Perform fingerprinting via TLS handshake characteristics - Link separate sessions from the same user by recognizing traffic patterns
Thus, we must treat metadata as a leaky abstraction layer, requiring proactive obfuscation even in fully encrypted sessions.
3. Mitigation Techniques
3.1 Message Padding
Variable-sized messages create unique traffic signatures. Message padding involves standardizing the frame length of WebSocket messages to a fixed or randomly chosen size within a predefined envelope.
- Pro: Hides exact payload size, making compression side-channel and length-based analysis ineffective.
- Con: Increases bandwidth usage; not ideal for mobile/low-bandwidth scenarios.
Implementation: Client libraries can pad all outbound messages to, for example, 512 bytes or the next power of two above the actual message length.
3.2 Batching and Jitter
Packet timing is often the most revealing metric. Delaying messages to create jitter and batching multiple events into a single transmission breaks correlation patterns.
- Pro: Prevents timing attacks, typing inference, and pattern recognition.
- Con: Increases latency, possibly degrading UX in real-time apps.
Implementation: Use an event queue with randomized intervals for dispatching messages (e.g., 100–300ms jitter windows).
3.3 TLS Fingerprint Randomization
TLS fingerprints—determined by the ordering of cipher suites, extensions, and fields—can uniquely identify client libraries and platforms. Randomizing these fields on the client side prevents reliable fingerprinting.
- Pro: Reduces ability to correlate sessions or identify tools/libraries used.
- Con: Requires deeper control of the TLS stack, often unavailable in browsers.
Implementation: Modify or wrap lower-level TLS clients (e.g., via OpenSSL or rustls) to introduce randomized handshakes in custom apps.
3.4 Connection Reuse or Multiplexing
Opening multiple connections creates identifiable patterns. By reusing a single persistent connection for multiple data streams or users (in proxies or edge nodes), the visibility of unique flows is reduced.
- Pro: Aggregates traffic, preventing per-user or per-feature traffic separation.
- Con: More complex server-side logic; harder to debug.
Implementation: Use multiplexing protocols (e.g., WebSocket subprotocols or application-level routing) to share connections across users or components.
4. Combined Strategy and Defense-in-Depth
No single strategy suffices. A layered mitigation approach—combining padding, jitter, fingerprint randomization, and multiplexing—provides defense-in-depth against multiple classes of metadata leakage.
The recommended implementation pipeline: 1. Pad all outbound messages to a fixed size 2. Introduce random batching and delay intervals 3. Obfuscate TLS fingerprints using low-level TLS stack configuration 4. Route data over multiplexed WebSocket connections via reverse proxies or edge routers
This creates a high-noise communication channel that significantly impairs passive traffic analysis.
5. Limitations and Future Work
Mitigations come with trade-offs: latency, bandwidth overhead, and implementation complexity. Additionally, some techniques (e.g., TLS randomization) are hard to apply in browser-based environments due to API constraints.
Future work includes: - Standardizing privacy-enhancing WebSocket subprotocols - Integrating these mitigations into mainstream libraries (e.g., Socket.IO, Phoenix) - Using machine learning to auto-tune mitigation levels based on threat environment
6. Case In Point
Encrypted WebSocket traffic is not inherently private. Without explicit mitigation, metadata alone is sufficient for behavioral profiling and application fingerprinting. This thesis has outlined practical strategies for obfuscating traffic patterns at various protocol layers. Implementing these defenses can significantly improve user privacy in real-time systems and should become a standard part of secure WebSocket deployments.
-
 @ 71bbbe14:1c43e369
2025-04-23 19:49:32
@ 71bbbe14:1c43e369
2025-04-23 19:49:32Test Combined Free
-
 @ 71bbbe14:1c43e369
2025-04-23 19:48:56
@ 71bbbe14:1c43e369
2025-04-23 19:48:56 -
 @ 71bbbe14:1c43e369
2025-04-23 19:47:26
@ 71bbbe14:1c43e369
2025-04-23 19:47:26Test Document Free
-
 @ 71bbbe14:1c43e369
2025-04-23 19:47:06
@ 71bbbe14:1c43e369
2025-04-23 19:47:06Test Document Free
-
 @ 4c96d763:80c3ee30
2025-04-23 19:43:04
@ 4c96d763:80c3ee30
2025-04-23 19:43:04Changes
William Casarin (28):
- dave: constrain power for now
- ci: bump ubuntu runner
- dave: initial note rendering
- note: fix from_hex crash on bad note ids
- dave: improve multi-note display
- dave: cleanly separate ui from logic
- dave: add a few docs
- dave: add readme
- dave: improve docs with ai
- docs: add some ui-related guides
- docs: remove test hallucination
- docs: add tokenator docs
- docs: add notedeck docs
- docs: add notedeck_columns readme
- docs: add notedeck_chrome docs
- docs: improve top-level docs
- dave: add new chat button
- dave: ensure system prompt is included when reset
- enostr: rename to_bech to npub
- name: display_name before name in NostrName
- ui: add note truncation
- ui: add ProfilePic::from_profile_or_default
- dave: add query rendering, fix author queries
- dave: return tool errors back to the ai
- dave: give present notes a proper tool response
- dave: more flexible env config
- dave: bubble note actions to chrome
- chrome: use actual columns noteaction executor
kernelkind (13):
- remove unnecessary
#[allow(dead_code)] - extend
ZapAction - UserAccount use builder pattern
Wallettoken parser shouldn't parse all- move
WalletStateto UI - add default zap
- introduce
ZapWallet - use
ZapWallet - propagate
DefaultZapStateto wallet ui - wallet: helper method to get current wallet
- accounts: check if selected account has wallet
- ui: show default zap amount in wallet view
- use default zap amount for zap
pushed to notedeck:refs/heads/master
-
 @ 866e0139:6a9334e5
2025-04-23 18:44:08
@ 866e0139:6a9334e5
2025-04-23 18:44:08Autor: René Boyke. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Das völkerrechtliche Gewaltverbot ist das völkerrechtliche Pendant zum nationalen Gewaltmonopol. Bürgern ist die Ausübung von Gewalt nur unter engen Voraussetzungen erlaubt, ähnlich sieht es das Völkerrecht für Staaten vor. Das völkerrechtliche Gewaltverbot gemäß Art. 2 Abs. 4 der VN-Charta ist damit eines der fundamentalsten Prinzipien des modernen Völkerrechts. Ein echtes Gewaltmonopol, wie es innerhalb eines Staates existiert, besteht auf internationaler Ebene allerdings nicht, denn dies kann rein faktisch – zumindest derzeit noch – nur sehr schwer bzw. gar nicht umgesetzt werden.
Das Verbot von Gewalt ist eine Sache, aber wer sollte bei einem Verstoß Polizei spielen dürfen? Das Gewaltverbot verbietet den Staaten die Androhung oder Anwendung von Gewalt gegen die territoriale Integrität oder politische Unabhängigkeit eines anderen Staates. Obwohl 193 und damit fast alle Staaten Mitglied der Vereinten Nationen sind, kann man ganz und gar nicht davon sprechen, dass das Gewaltverbot Kriege beseitigt hätte. Nüchtern betrachtet liegt seine Funktion daher nicht in der Verhinderung von Kriegen, sondern in der Legitimation rechtlicher Konsequenzen: Wer gegen das Verbot verstößt, ist im Unrecht und muss die entsprechenden Konsequenzen tragen. Die Reichweite des Gewaltverbots wirft zahlreiche Fragen auf. Diesen widmet sich der vorliegende Beitrag überblicksartig.
Historische Entwicklung des Gewaltverbots
Vor dem 20. Jahrhundert war das „Recht zum Krieg“ (ius ad bellum) weitgehend unreguliert; Staaten konnten aus nahezu beliebigen Gründen zu den Waffen greifen, ja, Krieg galt zwar nicht ausdrücklich als erlaubt, aber eben auch nicht als verboten. Mit dem Briand-Kellogg-Pakt von 1928 wurde rechtlich betrachtet ein weitgehendes Gewaltverbot erreicht. Doch statt warmer Worte hat der Pakt nicht viel erreicht. Deutschland war bereits damals und ist noch immer Mitglied des Pakts, doch weder den Zweiten Weltkrieg noch unzählige andere Kriege hat der Pakt nicht verhindern können.
Ein gewisser Paradigmenwechsel erfolgte nach dem zweiten Weltkrieg mit der Gründung der Vereinten Nationen 1945 und der VN-Charta, welche ein umfassendes Gewaltverbot mit nur wenigen Ausnahmen etablierte. Das Gewaltverbot wurde im Laufe der Zeit durch Gewohnheitsrecht und zahlreiche Resolutionen der Vereinten Nationen gefestigt und gilt heute als „jus cogens“, also als zwingendes Völkerrecht, von dem nur wenige Abweichung zulässig sind. Es ist jedoch leider festzustellen, dass nicht die Einhaltung des Gewaltverbots die Regel ist, sondern dessen Bruch. Nicht wenige Völkerrechtler halten das Gewaltverbot daher für tot. In der deutschen völkerrechtlichen Literatur stemmt man sich jedoch gegen diese Einsicht und argumentiert, dass es zwar Brüche des Gewaltverbots gebe, aber jeder rechtsbrüchige Staat versuche hervorzuheben, dass seine Gewaltanwendung doch ausnahmsweise erlaubt gewesen sei, was also bedeute, dass das Gewaltverbot anerkannt sei.
Dass dies lediglich vorgeschobene Lippenbekenntnisse, taktische Ausreden bzw. inszenierte Theaterstücke sind und damit eine Verhöhnung und gerade keine Anerkennung des Gewaltverbots, wird offenbar nicht ernsthaft in Betracht gezogen. Betrachtet man das von den USA 2003 inszenierte Theaterstück, die Erfindung der „weapons of mass destruction,“ um einen Vorwand zum Angriff des Irak zu schaffen, dann ist erstaunlich, wie man zu der Ansicht gelangen kann, die USA sähen ein Gewaltverbot für sich als bindend an.
Wenn das Gewaltverbot schon nicht in der Lage ist, Kriege zu verhindern, so ist es dennoch Gegenstand rechtlicher Konsequenzen, insbesondere nach Beendigung bewaffneter Auseinandersetzungen. Zudem legt die Beachtung oder Nichtbeachtung des Gebots offen, welcher Staat es damit tatsächlich ernst meint und welcher nicht. Dazu muss man jedoch den Inhalt des Gebots kennen, weshalb sich eine Beschäftigung damit lohnt.
Rechtliche Grundlagen des Gewaltverbots
Das Gewaltverbot gilt nur für Gewalt zwischen Staaten, nicht für private Akte, es sei denn, diese sind einem Staat zurechenbar (z. B. durch Unterstützung wie Waffenlieferungen).
Terrorismus wird nicht automatisch als Verletzung des Gewaltverbots gewertet, sondern als Friedensbedrohung, die andere völkerrechtliche Regeln auslöst. Bei Cyberangriffen ist die Zurechnung schwierig, da die Herkunft oft unklar ist und Sorgfaltspflichten eines Staates nicht zwangsläufig eine Gewaltverletzung bedeuten. Das Verbot umfasst sowohl offene militärische Gewalt (z. B. Einmarsch) als auch verdeckte Gewalt (z. B. Subversion). Es gibt jedoch Diskussionen über eine notwendige Gewaltintensität: Kleinere Grenzverletzungen fallen oft nicht darunter, die Schwelle ist aber niedrig. Nicht jede Verletzung des Gewaltverbots gilt als bewaffneter Angriff.
Nicht-militärische Einwirkungen wie wirtschaftlicher Druck oder Umweltverschmutzung gelten nicht als Gewalt im Sinne des Verbots. Entscheidend ist, dass die Schadenswirkung militärischer Gewalt entspricht, was z. B. bei Cyberangriffen relevant wird, die kritische Infrastruktur lahmlegen.
Ausnahmen vom Gewaltverbot
Trotz Reichweite des Gewaltverbots existieren anerkannte Ausnahmen, die unter bestimmten Umständen die Anwendung von Gewalt legitimieren:
- Recht auf Selbstverteidigung (Art. 51 VN-Charta): Staaten dürfen sich gegen einen bewaffneten Angriff verteidigen, bis der VN- Sicherheitsrat die notwendigen Maßnahmen zur Wiederherstellung des Friedens ergriffen hat. Diese Selbstverteidigung kann individuell (der angegriffene Staat wehrt sich selbst) oder kollektiv (ein anderer Staat kommt dem angegriffenen Staat zur Hilfe) ausgeübt werden. Ob eine Selbstverteidigung zulässig ist, hängt folglich in erster Linie davon ab, ob ein bewaffneter Angriff vorliegt. Nach der Rechtsprechung des IGH setzt ein bewaffneter Angriff eine Mindestintensität voraus, also schwerwiegende Gewalt und nicht lediglich Grenzzwischenfälle. Ferner muss es sich um einen gegenwärtigen Angriff handeln, was präventive Selbstverteidigung grundsätzlich ausschließt – was nicht bedeutet, dass sie nicht ausgeführt würde (siehe Irak- Krieg 2003). Zudem muss der Angriff von einem Staat ausgehen oder ihm zumindest zurechenbar sein. Schließlich muss der Angriff sich gegen die territoriale Integrität, politische Unabhängigkeit oder staatliche Infrastruktur eines Staates richten, wobei Angriffe auf Flugzeuge oder Schiffe außerhalb seines Territoriums ausreichend sind. Maßnahmen des VN-Sicherheitsrats (Kapitel VII VN-Charta): Der Sicherheitsrat kann bei Vorliegen einer Bedrohung oder eines Bruchs des Friedens oder einer Angriffshandlung Zwangsmaßnahmen beschließen, die auch den Einsatz militärischer Gewalt umfassen können. Diese Ausnahmen sind eng gefasst und unterliegen strengen Voraussetzungen, um Missbrauch zu verhindern.
Neben diesen anerkannten Ausnahmen vom Gewaltverbot wird weiter diskutiert, ob es weitere Ausnahmen vom Gewaltverbot gibt, insbesondere in Fällen humanitärer Interventionen und Präventivschläge.
-
Humanitäre Interventionen: Verübt ein Staat gegen einen Teil seiner Bevölkerung schwere Verbrechen wie Völkermord oder Kriegsverbrechen, so sehen einige ein fremdes Eingreifen ohne VN-Mandat als gerechtfertigt an. Das Europäische Parlament beispielsweise hat humanitäre Interventionen bereits 1994 für zulässig erklärt.1 Ein Beispiel dafür ist der NATO-Einsatz im Kosovo 1999, der jedoch überwiegend als völkerrechtswidrig bewertet wird, während NATO-Staaten ihn jedoch als moralisch gerechtfertigt betrachteten. Wie wenig allerdings eine humanitäre Intervention als Ausnahme vom Gewaltverbot anerkannt ist, zeigt der Ukrainekrieg, speziell seit dem massiven Einschreiten Russlands 2022, welches sich ebenfalls auf humanitäre Gründe beruft, damit jedoch – zumindest bei den NATO-Staaten – kein Gehör findet. Gegen „humanitäre Interventionen“ als Ausnahmen vom Gewaltverbot sprechen nicht nur deren mangelnde Kodifikation oder gewohnheitsrechtliche Etablierung, sondern auch ganz praktische Probleme: Wie beispielsweise kann ein eingreifender Staat sich sicher sein, ob innerstaatliche Gewalthandlungen Menschenrechtsverletzungen darstellen oder gerechtfertigtes Vorgehen gegen beispielsweise aus dem Ausland finanzierte Terroristen? Zudem besteht die Gefahr, dass bewusst derartige Verhältnisse in einem Land geschaffen werden, um einen Vorwand für ein militärisches Eingreifen zu schaffen. Dieses erhebliche Missbrauchspotential spricht gegen die Anerkennung humanitärer Interventionen als Ausnahme vom Gewaltverbot.
-
Schutz eigener Staatsangehöriger im Ausland: Auch der Schutz eigener Staatsangehöriger im Ausland wird als gerechtfertigte Ausnahme vom Gewaltverbot diskutiert, sie ist allerdings keineswegs allgemein anerkannt. Mit Blick in die Vergangenheit und den gemachten Erfahrungen (z.B. US-Interventionen in Grenada 1983 und Panama 1989) wird vor dem erheblichen Missbrauchspotential gewarnt.
-
Präventivschläge: Wie bereits erwähnt, werden präventive Angriffe auf einen Staat von einigen als Unterfall der Selbstverteidigung als berechtigte Ausnahme vom Gewaltverbot betrachtet. lediglich eine kurze Zeitspanne zur Ausschaltung der Bedrohung bestehen und das Ausmaß des zu erwartenden Schadens berücksichtigt werden. Zu beachten ist dabei, dass die genannten Kriterien dabei in Wechselwirkung stünden, was bedeute: Selbst wenn ein Angriff gar nicht so sehr wahrscheinlich sei, so solle dies dennoch einen Präventivschlag rechtfertigen, falls der zu erwartende Schaden groß sei und in einem kurzen Zeitfenster erfolgen könne (z.B. Atomschlag). Mit anderen Worten: Die Befürwortung von Präventivschlägen weicht das Gewaltverbot auf und führt zu einer leichteren Rechtfertigung militärischer Einsätze. Die konkreten Auswirkungen lassen sich sowohl durch den völkerrechtswidrigen Angriff der USA gegen den Irak und später durch den völkerrechtswidrigen Angriff Russlands gegen die Ukraine betrachten – beide Staaten beriefen sich jeweils auf Präventivschläge.
Konsequenzen der Verletzung des Gewaltverbots
Aus dem Vorstehenden ergibt sich bereits, dass eine Verletzung des Gewaltverbots das Recht zur Selbstverteidigung auslöst. Doch gibt es noch weitere Konsequenzen? Blickt man auf die Menge der weltweiten bewaffneten Konflikte, darf man daran zweifeln. Jedenfalls scheint das Kosten-Nutzen-Verhältnis nicht gegen eine bewaffnete Auseinandersetzung zu sprechen. Wie bereits erwähnt, existiert auf internationaler Ebene kein dem innerstaatlichen Recht vergleichbares Gewaltmonopol. Ohne dies bewerten zu wollen, lässt sich ganz objektiv feststellen, dass es keine Instanz gibt, die Zwangsmaßnahmen effektiv durchsetzen könnte. Ob dies wünschenswert wäre, darf bezweifelt werden. Aus den bisherigen Ausführungen geht ebenfalls hervor, dass der Sicherheitsrat der Vereinten Nationen Maßnahmen ergreifen kann – einschließlich des Einsatzes militärischer Gewalt. Wenn es dazu kommt, dann ist dies eines der schärfsten Schwerter, die gegen eine Verletzung des Gewaltverbots geführt werden können, weil es sich um unmittelbare Zwangsmaßnahmen handelt. Allerdings kam es bisher lediglich zwei Mal dazu (Koreakrieg 1950-19534; Golkrieg II 19915). Neben diesen tatsächlichen Zwangsmaßnahmen hat ein Verstoß gegen das Gewaltverbot rechtliche Auswirkungen:
-
Nichtigkeit von Verträgen: Gemäß Art. 52 der Wiener Vertragsrechtskonvention (WVK) ist ein Vertrag nichtig, wenn sein Abschluss durch Androhung oder Anwendung von Gewalt unter Verletzung der in der Charta der Vereinten Nationen niedergelegten Grundsätze des Völkerrechts herbeigeführt wurde.
-
Nichtanerkennung von Gebietserwerben (Stimson-Doktrin): Gemäß dem Rechtsgedanken des Art. 52 WVK werden die eroberten Gebiete nicht als Staatsgebiete des Staats angesehen, der sie unter Brechung des Gewaltverbots erobert hat.
-
Strafrechtliche Verantwortlichkeit für Staatschefs und Befehlshaber gemäß Art. 8bis des Statuts des Internationalen Strafgerichtshofs – allerdings nur für die Personen, deren Staaten, den IStGH anerkennen. Nichts zu befürchten haben also Staatschefs und Befehlshaber der USA, Russlands oder Chinas sowie Frankreichs und Großbritanniens, denn diese Staaten haben der Ahnung der Verletzung des Gewaltverbots nicht zugestimmt. Zwar könnte der Sicherheitsrat der VN eine Überweisung an den IStGH beschließen, allerdings stünde jedem der genannten Staaten ein Vetorecht dagegen zu.
Schlussfolgerungen
Ein Verbot der Gewalt zwischen Staaten ist grundsätzlich zu begrüßen. Doch ein Verbot allein ist erstmal nicht mehr als bedrucktes Papier. Ob hingegen wirksamere Mechanismen geschaffen werden sollten, dieses Verbot zu ahnden ist zweifelhaft. Denn stets wurde und wird noch immer mit erheblichem Aufwand für unterschiedlichste Narrative die eigene Intervention als „gerechter Krieg“ verkauft und von der Gegenpartei als ebenso ungerecht verteufelt.
Tatsache ist: Einen gerechten Krieg gibt es nicht. Ein schärferer Mechanismus zur Durchsetzung des Gewaltverbots würde genau darauf – einen angeblich gerechten Krieg – hinauslaufen, was ein enormes Missbrauchspotential mit sich brächte. Und die Erfahrung zeigt, dass der Missbrauch des Völkerrechts und Verstöße gegen das Völkerrecht keineswegs die Ausnahme, sondern die Regel darstellen – leider auch durch die sogenannte „westliche Wertegemeinschaft“. Und würde diese Missbrauchsmöglichkeit nicht auf noch mehr militärische Auseinandersetzungen hinauslaufen? Auseinandersetzungen, deren Folgen nicht die verantwortlichen Politiker zu spüren bekämen, sondern, in Form von Tod und Verstümmelung, die Bevölkerung zu tragen hätte?
Leidtragende ihrer „gerechten Kriege“ sind nicht die agierenden Politiker, sondern immer die einfachen Menschen – die leider nicht selten zuvor mit „Hurra“-Geschrei dem Krieg entgegenfiebern, um als „Helden“ ihrem Land zu „dienen“. In Wahrheit dienen sie jedoch nur finanziellen Interessen reicher Menschen.
Daraus folgt, dass die Durchsetzung eines Gewaltverbots nicht in den Händen einiger weniger Staatslenker und Berufspolitiker liegen darf, sondern in den Händen der unmittelbar Betroffenen selbst. Der Familienvater, der für seine Frau und Kinder zu sorgen hat, muss aktiv den Dienst an der Waffe verweigern. Ebenso der Schüler, der Student, der Junggeselle und sämtliche Mitglieder der Gesellschaft. Die Bevölkerung ist es, die das Gewaltverbot tatsächlich und effektiv vom bedruckten Papier als ein Friedensgebot ins Leben bringen und in Vollzug setzen kann.
(Dieser Artikel ist auch mit folgendem Kurzlink aufrufbar und teilbar)
-
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ ebdee929:513adbad
2025-04-23 21:06:02
@ ebdee929:513adbad
2025-04-23 21:06:02Screen flicker is a subtle and often overlooked cause of eye strain that many of us deal with daily. We understand this issue firsthand and are working hard to solve it, which is why we build for a different, more caring screen technology. This guide will help you understand screen flicker, how it affects you, and why better screen technology can make a real difference.
A silent epidemic in a LED-driven world
Tired eyes and a drained mind are almost a universal feeling at the end of a work day. That is, if you work a job that requires you to be in front of a computer screen all day… which today is most of us.
Slow motion shows flicker: It's not just screens; nearly all LED environments could flicker. Reddit: PWM_Sensitive
"Digital eye strain" refers to the negative symptoms (dry eyes, blurred vision, headaches, eye fatigue, light sensitivity, neck pain, etc.) that arise from use of digital devices for a prolonged period of time. It is also known as computer vision syndrome. Numbers are hard to pin down for such a commonly occurring issue, but pre COVID (2020) researchers estimated up to 70% prevalence in modern society.
Since COVID-19, things have gotten much worse.
"Digital eye strain has been on the rise since the beginning of the COVID-19 pandemic. An augmented growth pattern has been experienced with prevalence ranging from 5 to 65% in pre-COVID-19 studies to 80–94% in the COVID-19 era. The sudden steep increase in screen and chair time has led way to other silent pandemics like digital eye strain, myopia, musculoskeletal problems, obesity, diabetes etc."
The most common cause outlined by the researchers compiling these digital eye strain reviews is excessive screen time. And they outline the reason for screen time being an issue for the following reasons:
- Technological devices being in a short field of vision
- Devices causing a reduced blink rate
- Poor ergonomics
These are certainly all reasonable causes to highlight, but from our perspective two other key potential causes of digital eye strain are missing: screen flicker and blue light.
Multiple studies show that blue light in isolation can cause mitochondrial dysfunction and oxidative stress in the retina. To learn more about blue light, its potentially harmful effects, and how to mitigate them, read our "Definitive Guide on Blue Light".
In this discussion we are going to focus on screen flicker only.
FLICKER: AN INVISIBLE ISSUE
Flicker could be one of the most underrated stressors to our biology, as it is something we are exposed to constantly due to the nature of modern lighting and screens. It is widely agreed upon by both electrical/electronic engineers and scientific researchers that light flicker can cause:
- Headaches, eye strain, blurred vision and migraines
- Aggravation of autism symptoms in children
- Photo epilepsy
This is documented in the Institute of Electrical and Electronics Engineers (IEEE) 1789 standard for best practice in LED lighting applications, amongst other scientific reviews.
The P1789 committee from IEEE identified the following major effects of flicker:
- Photo epilepsy
- Increased repetitive behaviour among people suffering from autism
- Migraine or intense paroxysmal headache
- Asthenopia (eye strain); including fatigue, blurred vision, headache and diminished sight-related task performance
- Anxiety, panic attacks
- Vertigo
Light flicker is pervasive, mainly due to the ubiquitous nature of LEDs in our modern indoor work environments. We are being exposed to light flicker constantly from both light bulb sources and the screens that we stare at all day. This is a main reason why indoor, screen based work seems so draining. The good news is that this can be avoided (from an engineering perspective).
What is flicker?
We must first understand what "flicker actually is" before we can discuss how to avoid it or how to engineer flicker free light solutions.
In its most simple form, flicker can be defined as "a rapid and repeated change in the brightness of light over time (IEEE - PAR1789)".
Flicker can be easily conceptualized when it is visible, however the flicker we are talking about in regards to modern lighting & LEDs is unfortunately invisible to the human eye…which is part of the problem.
Most humans are unable to perceive flicker in oscillation rates above 60-90Hz (60-90 cycles per second). When we can't see something, we have a much more challenging time as a species grasping its effect on how we feel. The above mentioned health effects are directly related to the invisible flicker in terms of its effects on our biology. We can't see it, but our eyes and our brains react to it.
Slow-motion footage comparing DC-1's DC Dimming versus regular PWM Dimming.
For this article, we want to focus specifically on the flicker coming from LEDs used in modern personal electronics. This type of flicker can be shown in the above video of multiple smartphones being filmed with a slow motion camera.
What causes flicker in smartphones and computers?
There are a few different characteristics of a modern electronic display that cause flicker, but the main culprit is something called "PWM dimming".
PWM (Pulse Width Modulation) is an electronics control mechanism that uses pulsed signals as the LED driver function to control the brightness of the device display.PWM dimming has become the standard way to drive LEDs because it has specific advantages when it comes to retaining color consistency at lower brightness, and is also typically more power efficient. In a PWM dimming application, the diodes are being modulated to turn on and off very rapidly (faster than our eyes can perceive) to reduce the overall appearance of brightness of the light emission of the LEDs (aka luminance).
Brightness control in regular devices is just rapid flickering that looks steady to our eyes.
The lower the brightness setting, the longer the "off time". The "duty cycle" refers to the ratio of the LED being modulated "on" vs the total period of the cycle. Higher screen brightness setting = higher % duty cycle = more "time on" for the LED. This can be visualized in the graphic below.
PWM dimming controls brightness by quickly pulsing the backlight on and off.
PWM dimming has been chosen as the industry standard because of the intrinsic characteristics of the semiconductors in a light-emitting diode (LED) making it challenging to retain color consistency when modulating output illuminance with direct current, also known as Constant Current Reduction (CCR). CCR or "DC dimming" can utilize simpler control circuitry, but at the cost of less precision over the LED performance, especially at low brightness/luminance settings. PWM dimming can also save on overall power consumption.
DC Dimming maintains consistent light output by adjusting direct electrical current.
The downside of PWM dimming is obvious when you see the slow motion videos of the implementation in smartphone displays. The less obvious downside is that a PWM dimmed light means that we are consuming light at its peak output no matter the brightness setting. Because PWM is turning the light on/off constantly, the "ON" portion is always at peak intensity. This combined with the imbalanced light spectrum (blue heavy) can further exacerbate potential concerns of negatively affecting eye health and sleep quality.
The question we must ask then: is it more important for better LED and electronics performance, or is it more important to have screens that are not causing immense stress to our biology?
PWM Flicker on OLED screens vs LCD screens
Not all PWM flicker is created equal. The flicker frequency used for PWM dimming is directly related to how potentially stressful it can be to our eyes and brains. It is well agreed upon that the lower the frequency is, the more it can stress us out and cause eye strain. This is because at a high enough frequency, the oscillations are happening so rapidly that your brain basically perceives them as a continuous signal.
The "risk factor" of flicker is also dependent on the modulation % (similar to duty cycle) of the flicker as well, but since we all use our devices across different brightness settings and modulation % 's, it is best to focus on the frequency as the independent variable in our control.
Left: Non-PWM Flicker Device | Right: PWM Dimming Device. Nick Sutrich YouTube
Up to and including the iPhone 11, liquid crystal displays (LCD) were the standard for smartphones. A big switch was made to OLED display technology and the tech giants have never looked back. When it comes to PWM dimming frequency, there was a big shift when this swap occurred:
- Most LCD display use a PWM frequency of 1000Hz+ or no PWM at all.
- Nearly all OLED smartphone use a PWM frequency of 240Hz or 480Hz.
THE HEALTH RISK OF FLICKERING DEVICES
 So why don't OLED screens use higher PWM frequencies? Because of the nature of OLEDs being controlled as singular pixels, they need the lower PWM frequency to maintain that extremely precise color consistency at low brightness settings. This is of course why they use PWM in the first place.
So why don't OLED screens use higher PWM frequencies? Because of the nature of OLEDs being controlled as singular pixels, they need the lower PWM frequency to maintain that extremely precise color consistency at low brightness settings. This is of course why they use PWM in the first place.According to the IEEE1789 flicker risk chart for negative health effects, a 480Hz PWM smartphone (iPhone 15 Pro) would be high risk at any level above 40% modulation and a 240Hz PWM phone (Google Pixel 7) would be high risk above 20%. Whereas a phone that used 1000Hz-2000Hz PWM frequency (Nothing, Xiaomi 15) would only be "low risk".
- California law (Title 24), requires that LEDs used in certain applications have a "reduced flicker operation," meaning the percent amplitude modulation (flicker) must be less than 30% at frequencies below 200 Hz → The Google Pixel 7, Galaxy S23 and many iPhones operate at 240Hz and and 60-95% flicker...just above the legal limit!
- The report that recommended these levels states that: "Excessive flicker, even imperceptible flicker, can have deleterious health effects, and lesser amounts can be annoying or impact productivity."
 For PWM frequencies above 3000Hz, there is "no risk" according to IEEE1789. If you have ever felt that staring at your iPhone is far more "straining on the eyes" compared to your MacBook, the PWM flicker is likely a large reason for that (alongside the size of the display itself and distance held from the eyes)...because MacBooks have an LCD display and a PWM flicker frequency of 10-20kHz. At that PWM frequency, your brain is perceiving the oscillating light as a continuous signal.
For PWM frequencies above 3000Hz, there is "no risk" according to IEEE1789. If you have ever felt that staring at your iPhone is far more "straining on the eyes" compared to your MacBook, the PWM flicker is likely a large reason for that (alongside the size of the display itself and distance held from the eyes)...because MacBooks have an LCD display and a PWM flicker frequency of 10-20kHz. At that PWM frequency, your brain is perceiving the oscillating light as a continuous signal.Other causes of flicker
Although PWM dimming is widely agreed upon as the main cause of light flicker in modern consumer electronics displays, it is not the only cause. There are two other potential causes of light flicker we are aware of:
TEMPORAL DITHERING (AKA FRAME RATE CONTROL)
- "Pixel" dithering is a technique used to produce more colors than what a display's panel is capable of by rapidly changing between two different pixel colors. This technique unlocks a tremendous amount of more color possibilities - for example showing colors with 10 bit color depth results in billions of colors vs an 8 bit color depth results in millions of colors. Temporal dithering helps bridge the gap for 8 bit color depth displays.
- OLED displays are more likely to have better (10-bit) color depth vs LCD displays but use of temporal dithering can certainly vary across display technologies.
- Temporal dithering example (video)
AMORPHOUS SILICON (A-SI) THIN FILM TRANSISTOR (TFT) BACKPLANES
- Most commercial displays use a-Si TFT semiconductor technology in their backplanes of their LCD panels.
- This technology works well, but can have a high amount of photo-induced leakage current under back light illumination conditions, which can cause non uniformity of the light output and flicker.
- In simple language, the standard a-Si transistors are less "efficient" in a backlight application…which can lead to inconsistent light output and thus flicker.
The Daylight Computer: 100% Flicker Free
The DC-1 was designed and built purposefully to be flicker free. We wanted to provide a solution both for those suffering with severe eye strain and also to prevent negative optical and cognitive repercussions of flicker for any end consumer.
 ### HOW THE DC-1 ACHIEVES A FLICKER FREE DISPLAY:
### HOW THE DC-1 ACHIEVES A FLICKER FREE DISPLAY:- Using DC dimming instead of PWM dimming
- The most deliberate change made in our electrical design was centered around using a DC/CCR LED driver (aka Constant Current Reduction) instead of a PWM driver. This means that there is no pulsed circuit control around our LED backlight, and therefore no flicker from PWM lightning control.
- Has zero temporal dithering, as is a monochrome display
- The benefit of being black and white is there is no need to have intense pixel switching to create the mirage of billions of different color combinations.
- Uses Indium Gallium Zinc Oxide (IGZO) TFT Technology
- New semiconductor technology that provides better and more efficient performance vs a-Si TFT panels. Results in no flicker at the transistor level.
- Verified by light experts to be flicker free
- "Flicker testing yielded a perfect result using my highly sensitive audio-based flicker meter and the photodiode based FFT testing method: not even a trace of light modulation could be demonstrated with both methods!" — Dr. Alexander Wunsch (M.D., P.hD), Light Scientist
This commitment to a flicker-free experience isn't just theoretical; it's changing lives. We're incredibly moved by stories from users like Tiffany and Juan Diego, who found relief and regained possibilities with the DC-1:
For someone with eye disability, the DC-1 is a dream device. The display is so soft and smooth on my eyes that I was able to take my life back off of hold and return to medical school after a multi year absence.
— Tiffany Yang, Medical student
It took a couple of weeks to transition all my work screen time to the DC-1, but when I did, my eye strain completely went away. Plus, it let me work outside on my terrace.
— Juan Diego
Our eye-strain pilot study
Here at Daylight, we are all about proof of work. That is why we have already kicked off an initial pilot study to see if the DC-1 is actually more "eye friendly" than standard consumer electronic devices…specifically for those suffering from severe digital eye strain.
We have partnered with Dr. Michael Destefano, a neuro-optometrist at the Visual Symptoms Treatment Center in Illinois, to coordinate this pilot study.
MORE PARTICIPANTS NEEDED
Do you suffer from severe digital eye strain, computer vision syndrome, or visual snow syndrome? If you are interested in trying a DC-1 for 30 days as part of the Eye Strain Pilot Study, please send an email to drdestefanoOD@gmail.com with a background on your visual affliction.
Our favorite ways to reduce digital eye strain
Cutting screen time is not always possible, so here are some options that can help:
- Use DC dimming devices whenever possible
- Try minimizing screen time on your smartphone, utilizing a PWM laptop instead
- Try switching to an LCD smartphone or OLED smartphone with a high PWM frequency
- Turn "White Point" mode ON on your smartphone to increase the duty cycle and reduce the PWM dimming effect
Dive deeper with our curated resources
 #### Potential Biological and Ecological Effects of Flickering Artificial Light - PMC
#### Potential Biological and Ecological Effects of Flickering Artificial Light - PMCLight Emitting Diode Lighting Flicker, its Impact on Health and the Need to Minimise it
Digital Eye Strain- A Comprehensive Review
Nick Sutrich (Youtube) - Screen PWM Testing and Reviews
Eye Phone Review - Screen Health Reviews
Flicker Measurement NEMA77 and IEEE1789 White Paper




