-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 3c984938:2ec11289
2024-03-24 11:12:20
@ 3c984938:2ec11289
2024-03-24 11:12:20Chapter 4
Whitey Plan involved all of the forest's animals, and everyone had a job to do, including the trees, who decided to help. Though they had some reservations, they moved forward, putting their faith in Whitey and Leo's foresight.
Approaching their camp in the stillness of the night. They slept in their tent, blissfully asleep. Leo began to flicker the crystal lights as Peter (fox) and Casey (goldfish) circled their camp, leaving trail of fire in their wake. The Shroomucks stuck close to Maddy (the squirrel) and listened to the mushrooms' queue. It was Go Time!
 To attract their attention, the deeyotes started barking. The remaining animals followed suit, encircling their camp.
To attract their attention, the deeyotes started barking. The remaining animals followed suit, encircling their camp.
 The sight of smoke and fire rising from their camp startled the poachers as they awoke.
As the shroomuck conversed with Maddy, the trees began to sway voluntarily. Maddy then zapped a tree with a thudding sound.
The sight of smoke and fire rising from their camp startled the poachers as they awoke.
As the shroomuck conversed with Maddy, the trees began to sway voluntarily. Maddy then zapped a tree with a thudding sound.
 And then another...
And then another...
 With startled eyes and bewilderment, the poachers began to look around for any possible escape.
With startled eyes and bewilderment, the poachers began to look around for any possible escape. I'm out, this ant worth it! This place is crazy! --One poacher started to run
No, don't run its just a trick! --The ring leader announced He pulls his revolver from its holster.
But then there was a boom, lightning flashes, and trees that were three feet away started to sparkle. The poachers abandoned their leader and bolted.
The leader pursued them in an attempt to persuade them to return, but he fell as a result of the flickering crystals, smoke, and lighting. Whitey jumped on him, hissing at him. However, he did not see Whitey, but rather an apparition in the shape of a unicorn.
 He was stunned and began to feel ashamed of what he and his gang had done.
He was stunned and began to feel ashamed of what he and his gang had done. Never return to these woods, Whitey meowed at the top of her lungs.
Don't worry, I won't! --lead poacher
He got up and ran and did not look back.
The forest creatures were overjoyed with their triumph. Whitey was relieved that no woodland animals had been wounded. She was, however, saddened by the elderly trees that had sacrificed themselves. Her ability to assist plants was limited.
However, Peter made rounds to each dying tree, watching its remains fade away.
 Maddy, deeyotes, and shroomucks shrieked loudly to summon the slugs in packs. They all came.
Maddy, deeyotes, and shroomucks shrieked loudly to summon the slugs in packs. They all came.
 Each beautiful in it's own way
Each beautiful in it's own way
 The slugs left sticky trails everywhere they went, but these pathways promoted new growth. They would take small amounts of the seeds and gradually plant them wherever they went.
The slugs left sticky trails everywhere they went, but these pathways promoted new growth. They would take small amounts of the seeds and gradually plant them wherever they went.-- Until next time!
The photos were generated by AI generated. Credit is due. However, the story is mine. If you like my insane world consider following me. Zaps are always appreciated. You can also subscribe to my paragraph.xyz/@onigirl (for email update)
For the best reading experience please use Nostr!! You can now follow along in Children_Zone in communities. If you're using Amethyst look for the signal on the bottom menu. You can search for "Children_Zone" I should pop up and join!
Thank you!

-
 @ ec965405:63996966
2024-03-25 18:32:54
@ ec965405:63996966
2024-03-25 18:32:54Me gusta cocinar y bailar!
-
 @ 52b4a076:e7fad8bd
2024-03-23 22:44:50
@ 52b4a076:e7fad8bd
2024-03-23 22:44:50Introduction
LNbits is a project plagued with poor code quality, potential security risks and bad management. What can be done about it?
The problems
Improper handling of vulnerability disclosures
Case 1
Two years ago (don't remember exactly when, Twitter account deleted), I discovered an SQL injection vulnerability in LNbits. This could be exploited very easily by setting by sending the injected data in keys in the payload of most requests. (anyone could create create wallets)
This was possible due to the query to insert/update was generated using the body of the request, with basically no sanitization.
When I contacted Ben Arc about this, the fix for this exploit was not implemented for several months, and when it was, I do not recall there being an advisory for people to update.
Case 2
A month or two ago, I had discovered an exploit that allows draining nodes completely under certain conditions. I had reported this to an active maintainer of the project, which had passed it on to the team. The exploit has not been fixed.
Case 3
Again, a month or two ago, a flaw was discovered in the SatsDice extension that allowed anyone to drain wallets. I had investigated this, and found that the extension allows invoice keys (instead of admin keys only) to create dice that have a guaranteed win rate and return more sats than put in, and then use it to drain balances.
I had reported this to the team, and while it was fixed a week or two later, there was no easily visible for people to update except an "update your SatsDice extension" message in the LNbits chat buried in a conversation about the exploit.
Bad security practices
"Don't do one thing, and don't do it well"
LNbits has over time expanded its scope, from being a wallet layer to an LN apps platform to a node management tool. While this may seem great for users, it has come at a significant security cost: - There is a larger attack surface for attackers to exploit. - The newly introduced node management and admin UI feature allows easy draining of nodes if the admin URL was leaked, whether by by the autocomplete on the search bar or the user's history. - All extensions run at the same privilege level as LNbits itself which has direct access to funds.
Developers can accidentally shoot themselves in the foot
The LNbits codebase encourages many harmful development patterns that allows developers to easily create vulnerabilities that put funds at risk
Example 1
Most LNbits extensions use the following system for handling object creation/deletion: - Take the body and convert it to a class - Overwrite/sanitize fields in that class, such as preventing overwrite of the wallet ID - Pass it to the DB to write
There is a slight problem: it can be easy to miss what to sanitize and what to not sanitize.
When you are doing an update request, you may accidentally forget to overwrite the wallet_id on the request sent by the user to update a withdraw link, and trust the user. You just created a bug to drain anyone's wallet given its ID, which LNbits does not consider sensitive information and sometimes requires you to share.
Example 2
LNbits treats any error during a payment attempt an error. But errors don't always happen due to failures in your request. Network connectivity is flaky, nodes restart, and way more reasons for there to be an error while the payment actually may be going through.
If you can get a way to trigger an error during a payment call, but also have it succeed, you can easlly drain a node. I have reasons to believe this is possible in production deployments.
This could easily be fixed as attempting to check the status of a payment after an error, and if that also fails, consider the payment pending until it can be checked, but ths has not been implemented.
Bad project management
LNbits' current management suffers from many problems: - the project suffers from feature and scope creep, implementing things for the sake of it - bugs go unaddressed - security is not a top priority
This is problematic for a project that deals with funds, as it is everything that you shouldn't be doing for a project meant to deal with funds. Tens of thousands of dollars in some cases and thousands in others.
What can we do about it?
For me, I have disabled withdrawals on my LNbits instance. I am also working on a replacement project called LNLocker that will solely focus on the wallet layer bit.
I would encourage trying to replace LNbits, as hard and sometimes impossible as it may be, or if you can, modify the code or restricting access via LND macaroons so that withdrawals cannot be made.
I highly recommend not exposing LNbits to the internet if you cannot disable withdrawals.
-
 @ e2ccf7cf:26c1c8eb
2024-03-23 16:54:46
@ e2ccf7cf:26c1c8eb
2024-03-23 16:54:46If you hate frontend frameworks like react and svelte as much as I do, this project is for you.
Introducing Notepress
A vanilla javascript/html blog reader for your long form nostr notes.
It only does the very basics: it pulls notes from your relays and displays them in a simple, readable format.
You can view a live demo at https://utxo.one
Index View with Images and Summaries:
Index View with without images and summaries

Contributing
Pull requests are very strongy encouraged and appreciated :) The code is available on github under an MIT licence, do whatever you wish!
https://github.com/utxo-one/notepress
Installation
- Clone the repository
bash git clone https://github.com/utxo-one/notepress cd notepress- Install the dependencies
bash npm install- Configure the blog
Edit the
config.jsfile to your liking.bash cp config.example.js config.js nano config.js```javascript export const relays = [ "wss://relay.utxo.one", "wss://relay.bitcoinpark.com", "wss://relay.damus.io", "wss://nos.lol", ]; export const npub = "npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8"; export const hexkey = "e2ccf7cf20403f3f2a4a55b328f0de3be38558a7d5f33632fdaaefc726c1c8eb";
export const excludeNotes = [ "b2381de6b86e6e90971316e5866d4e7d9659ba44985f7b9bff0c449e25f9d566", ]; ```
- Bundle the code
bash npx vite build- Deploy to your server
```bash cp -r dist/* /var/www/notepress
-
 @ 0ecfdaf2:d23eee11
2024-03-23 05:02:07
@ 0ecfdaf2:d23eee11
2024-03-23 05:02:07📍 Destination: Mexico 🇲🇽
🗓 Year: 2024
🎒 Type of Trip: Couple Road Trip
🤿 Diving Spots: Cancun / Isla Mujeres / Playa Del Carmen
⚓ Maximum Depth of Stay: 16m
📸 Photo: Aerial View
This article will be in 2 parts:
-
1st part about dives in Cancun & Isla Mujeres
-
2nd part about dives in Cenotes in Playa del Carmen

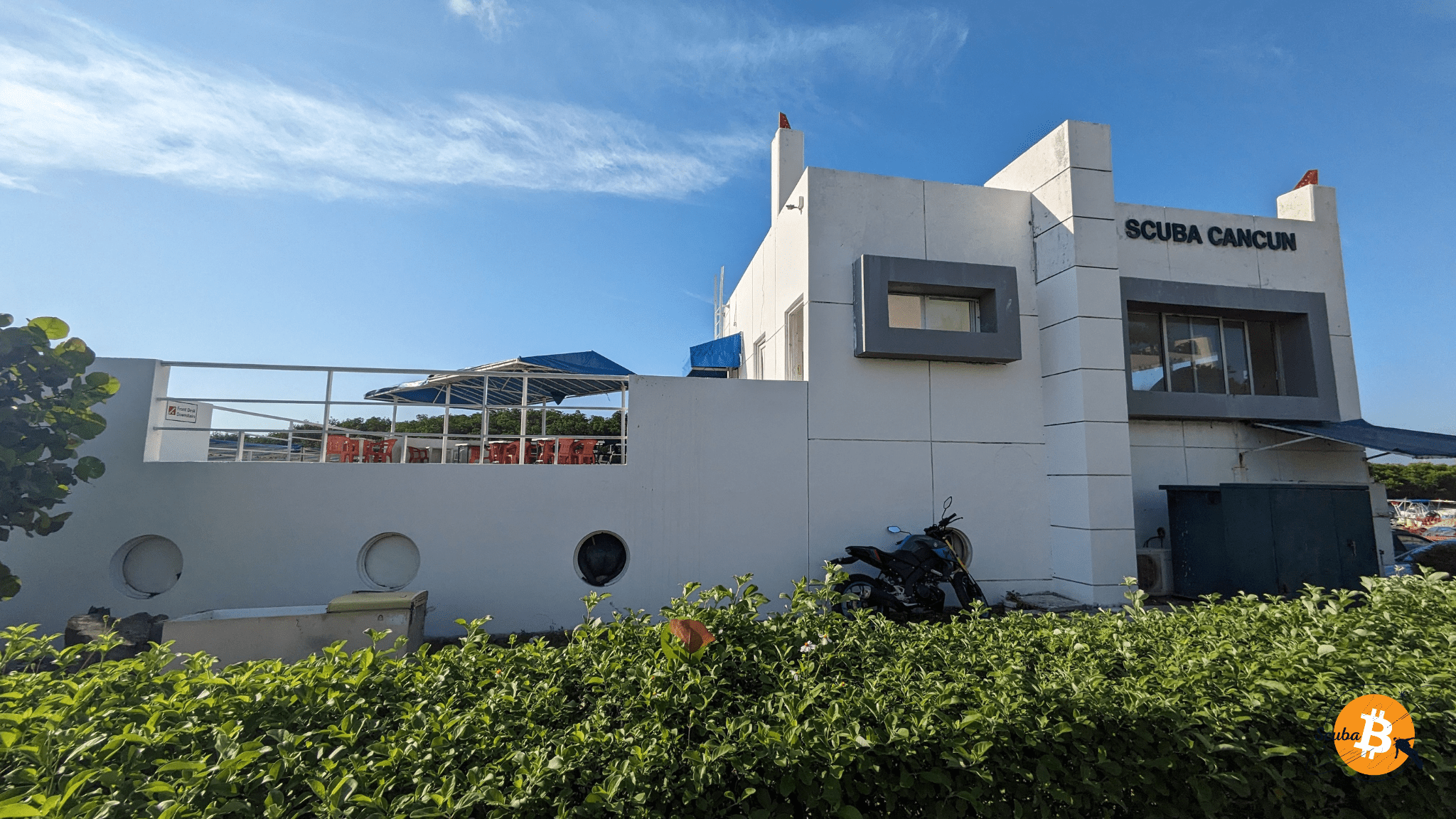
I dived with the "Scuba Cancun" club, the first historic club to open in Cancun.
The boat to access the dive sites is called "Scuba III"; I wonder what happened to the other "Scuba I & II" 😐
📸 Photo: Club & Boat
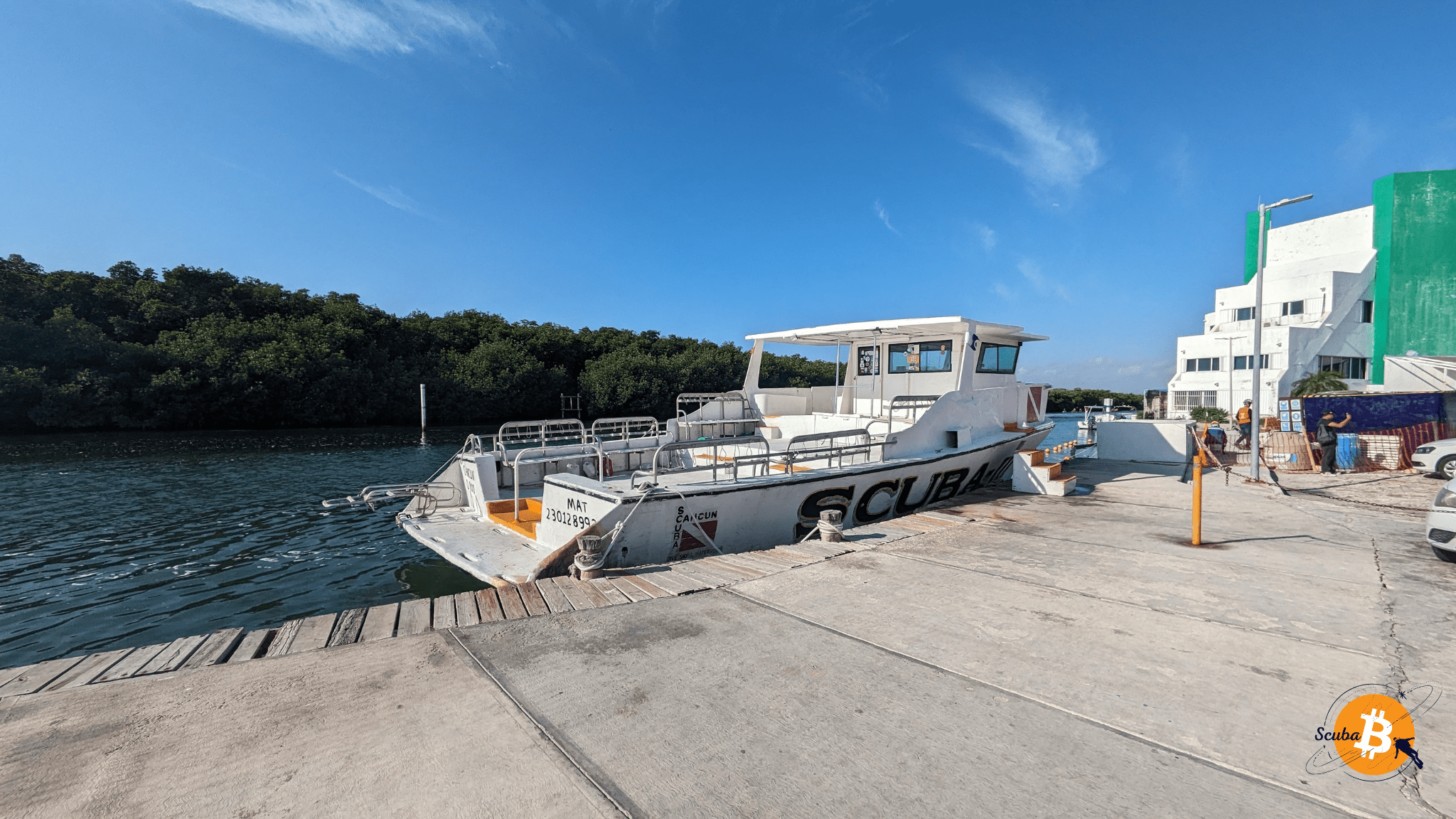
To access the dive sites, we take a 30-minute boat ride 🛥
Upon arrival, we gear up 🤿, and off we go, diving into the water...
📸 Photo: Boat Ride


As soon as we reach the bottom, we are immediately greeted by schools of fish, they're everywhere 😍
📹 Video: School of Fish
Some fish were curious enough to approach and see who was visiting, like this porcupinefish 👀
📹 Video: Porcupinefish
For others, it was mealtime, like this pufferfish who was dining 🍽
📸 Photo: Pufferfish pufferfish

In every dive, we remember about 10 things, but there are especially 1/2 main elements, which I call "the pièce de résistance" 😁
This time it was a beautiful Eagle Ray 🦈 that we saw twice, out in the open sea, and at the end during the safety stop.
📹 Video: Eagle Ray
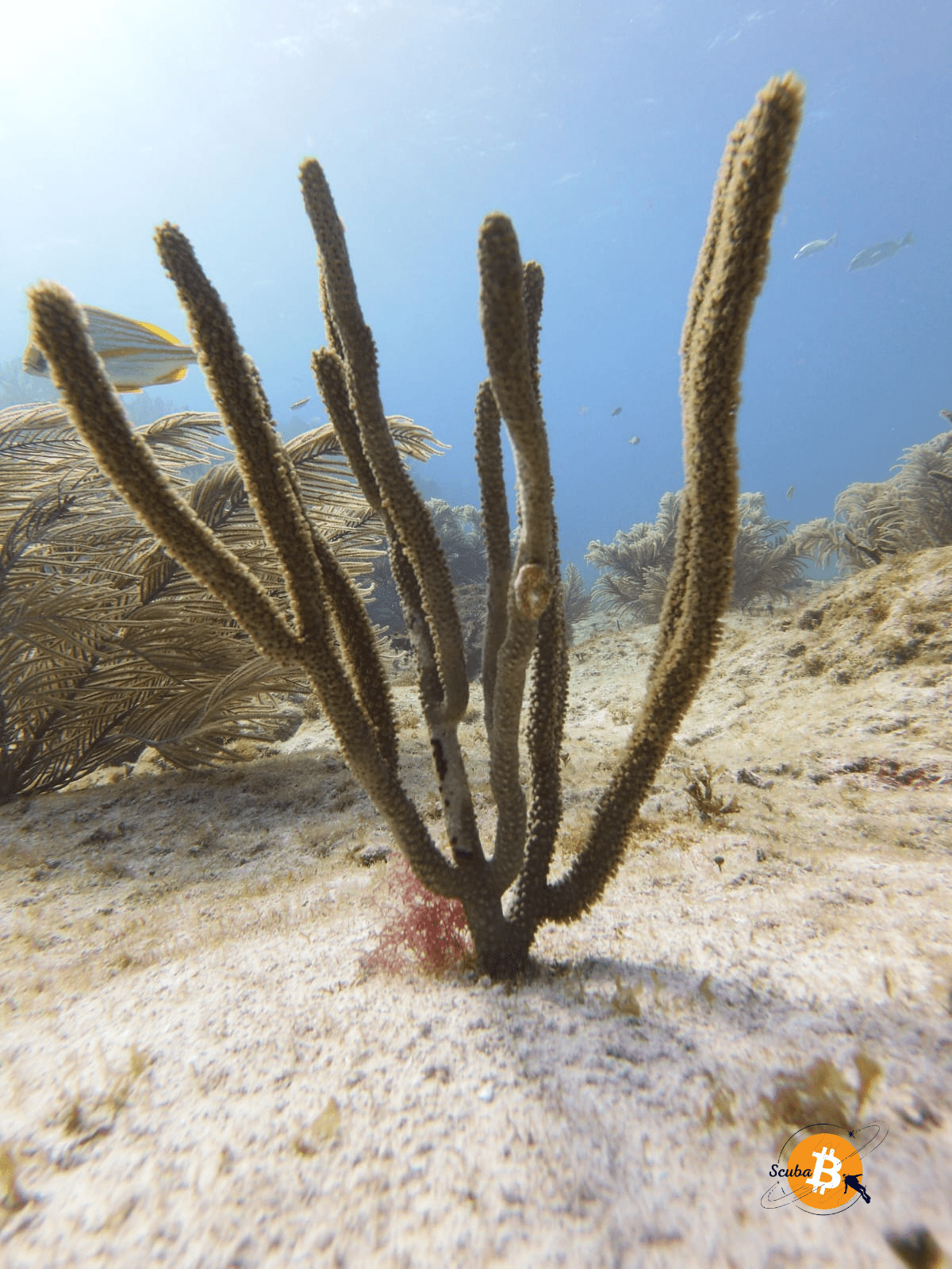
In addition to the fish, the corals were magnificent. And upon closer inspection, we can see nudibranchs, like this Doris climbing on this elk horn coral 🪸
📸 Photo: Gorgonian and Doris on Elk Horn Coral

Some were ready to play and posed for the camera, like these surgeonfish 🐠 and damselfish.
While others tried a trick by leaving and changing color, like this cowfish
📸 Photo: Surgeonfish / Damselfish / Cowfish




Grouper and Turtle 🐢 were present 🔥
📹 Video: Grouper & Turtle
We end with a touch of beauty with this seashell 🐚 that could make a magnificent wallpaper 😉
That's all for the morning dive. We'll go back in the afternoon to visit the "Musa" underwater museum 👀
📸 Photo: Seashell


To start the Musa museum, we're greeted by this bartender & his dog 🍹🐕
📸 Photo: Bartender & Dog Statue
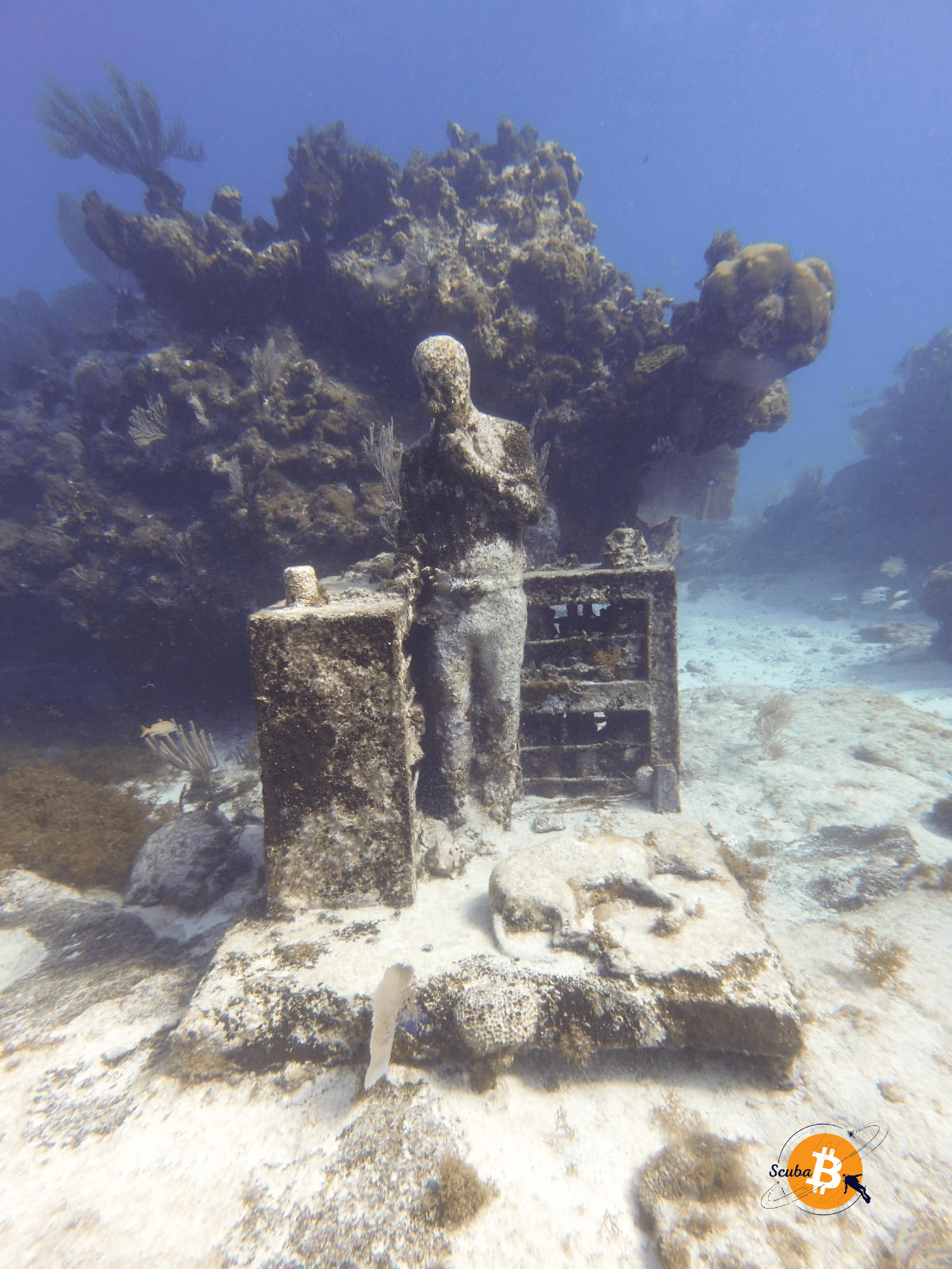
His car 🚗 was parked nearby.
📸 Photo: Car Statue


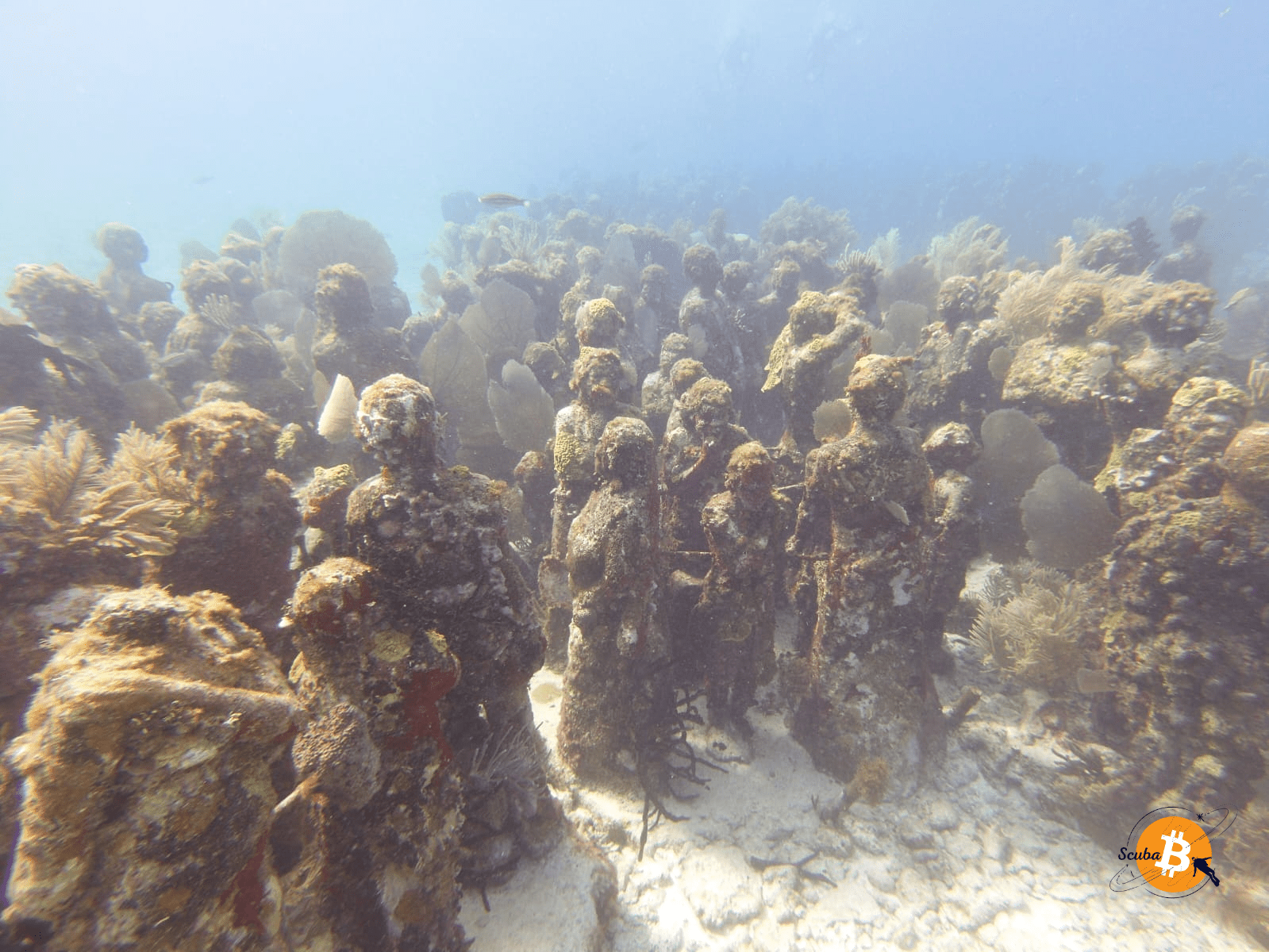
Then, the museum begins, and it's crowded, there's a crowd of people 😲
📸 Photo: People Statues

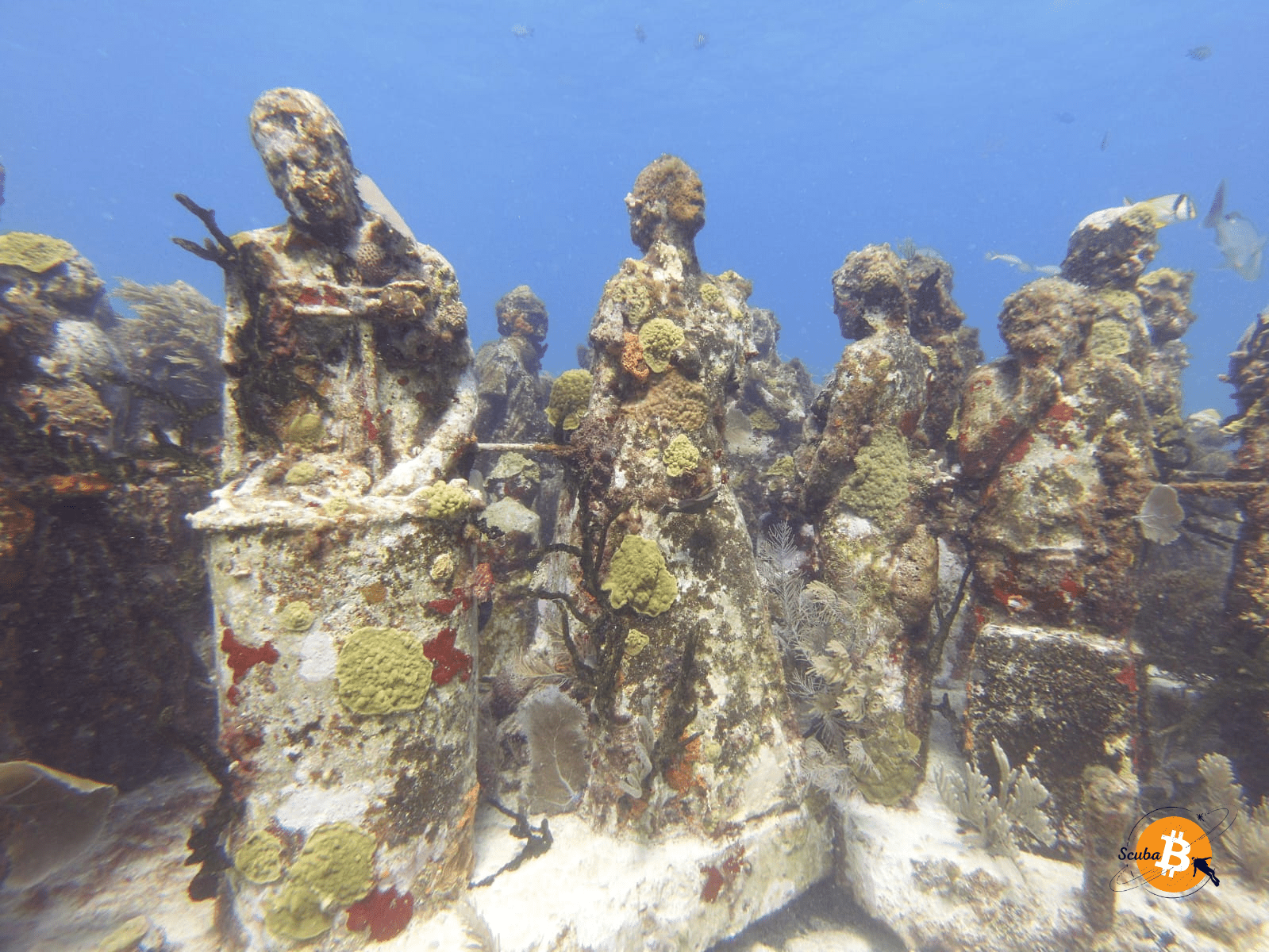
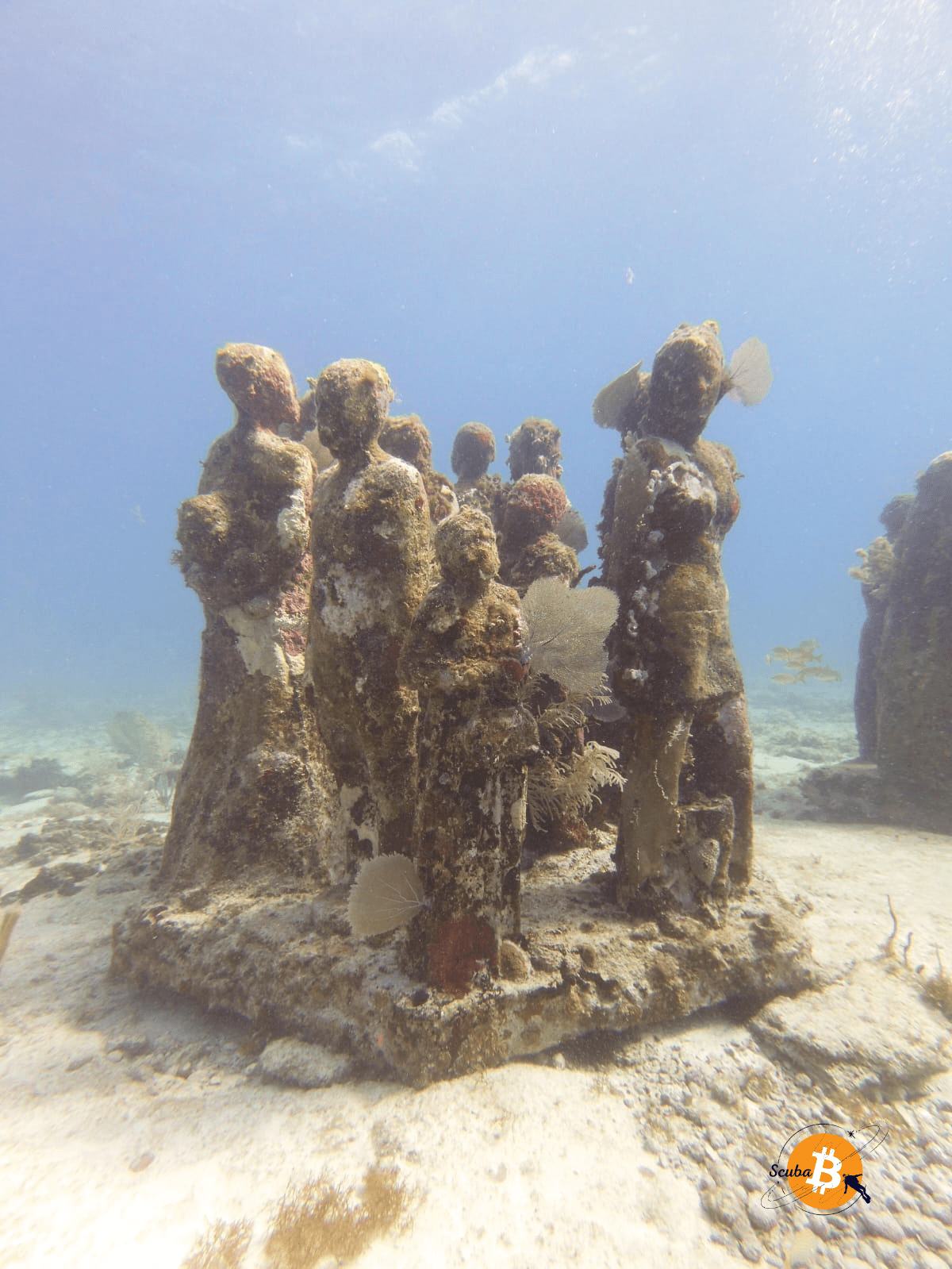
In all this crowd, I kept looking 👀 for my lost private keys 🗝️ at the bottom of the ocean 🌊
📸 Photo: Scuba

I wasn't the only one searching; others even plunged their heads deeper to search.
📸 Photo: Group Statue
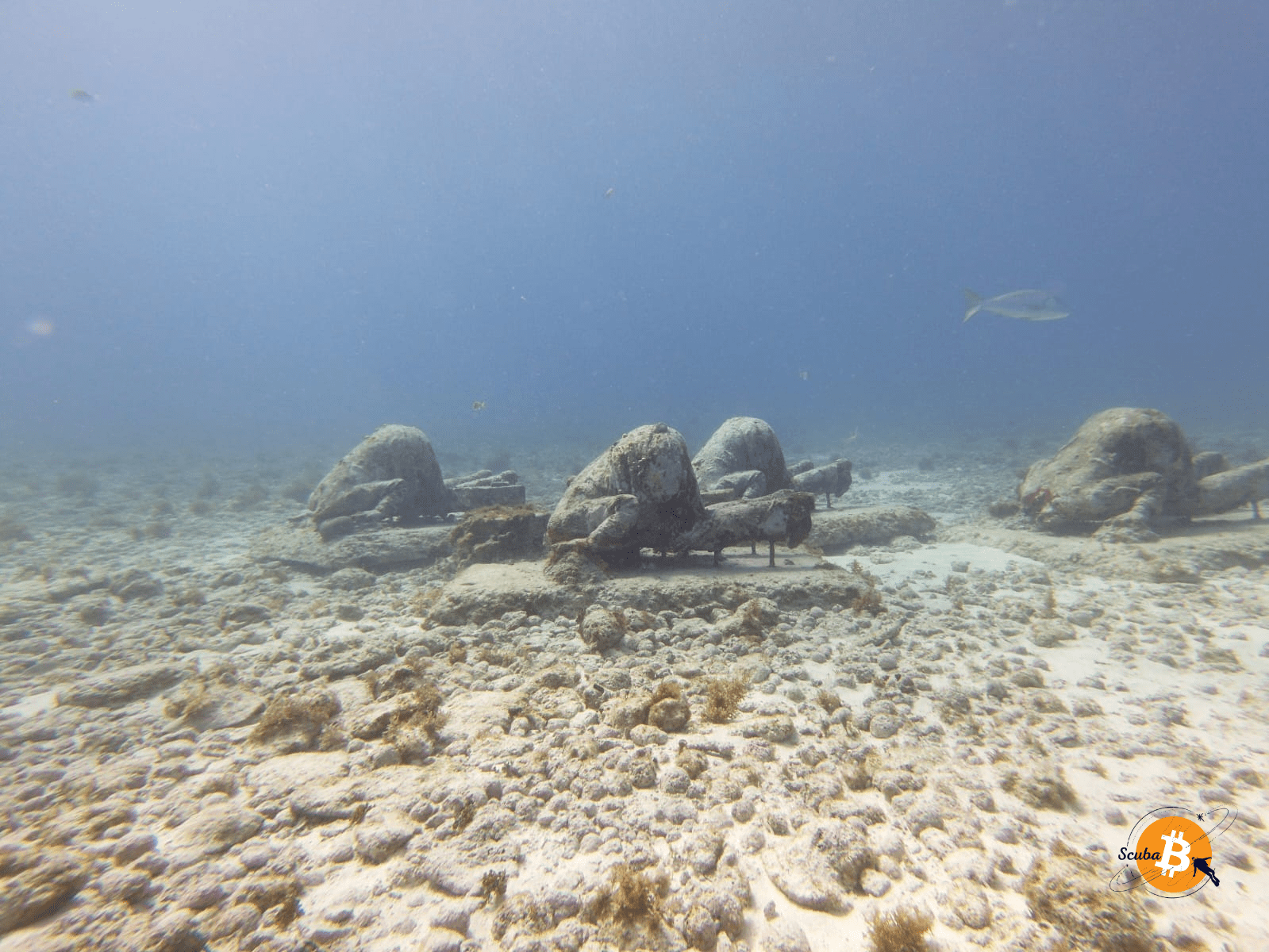
That's all for the bubbles in Cancun/Isla Mujeres 👋
It's time to resurface for the next part of the thread, diving in the Cenotes in Playa del Carmen 👀
Stay Tuned ✌
📸 Photo: Bubbles & Fins


-
-
 @ 97c70a44:ad98e322
2024-03-23 04:34:58
@ 97c70a44:ad98e322
2024-03-23 04:34:58The last few days on developer nostr have involved quite a kerfluffle over the gossip model, blastr, banning jack, and many related misunderstandings. This post is an attempt to lay out my thoughts on the matter in an organized and hopefully helpful way.
What's wrong with gossip?
It all started with a post from jack asking why more devs haven't implemented the gossip model. There are many answers to this question, not least having to do with there being two standards for user relay selections, and ongoing changes to NIP 65. But I don't want to talk about compatibility here.
nevent1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszymhwden5te0wfjkccte9enrw73wd9hj7qpq2uf488j3uy084kpsn594xcef9g9x3lplx4xnglf0xwghyw2n3tfqqnrm02
Mazin responded with some numbers which estimate how many connections the gossip model requires. Too many connections can become expensive for low-power clients like mobile phones, not to mention some privacy issues stemming from nosy relays.
nevent1qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qgewaehxw309amk2mrrdakk2tnwdaehgu3wwa5kuef0qyghwumn8ghj7mn0wd68ytnhd9hx2tcqyp2xzsjktypudzmygplljkupmuyadzzr6rkgnvx9e0fx3zwhdm0vkz4ceg7
I have some minor disagreements with Mazin's numbers, but I basically agree with his point — a purist gossip model, where a large proportion of nostr users run their own relays results in a high number of connections to different relays. I brought this question up late last year in my interview with Mike Dilger and in a conversation with fiatjaf, who convinced me that in practice, this doesn't matter — enough people will use a handful of larger hubs that there will be a good amount of overlap in relay selections between most pubkeys.
To articulate this more clearly: the goal is not "personal web nodes", which is a pipe dream the Farcasters and BlueSkys (BlueSkies?) of the world aim at, but a more pragmatic mix between large hubs and smaller purpose-built relays. These small relays might be outlets for large publishers, small groups, or nerds who also run their own SMTP servers and lightning nodes.
The point of the gossip model is that these small nodes be possible to run, and discoverable from the rest of the network so that we can preserve the censorship-resistant qualities of nostr that brought us here in the first place.
Blast It!
It's no secret that I've long been a critic of Mutiny's blastr relay implementation. My main objection is that the blastr approach doesn't account for the hard limits involved in scaling smaller relays. If the goal is to cross-pollinate notes across all relays in the network, all relays will require the same size database, and contain all notes in the network. This works right now (sort of), but as the network grows, the relays running on a $5 VPS are going to have their disks fill up and will inevitably fall over.
nevent1qyvhwumn8ghj76r0v3kxymmy9ehx7um5wgcjucm0d5hszxnhwden5te0wpuhyctdd9jzuenfv96x5ctx9e3k7mf0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qqs07jr9qx49h53nhw76u7c3up2s72k7le2zj94h5fugmcgtyde4j9qfrnwxj
Not only that, but the content breakdown on any given relay by default becomes an undifferentiated soup of "GM", chinese notes, bots, bitcoin memes, and porn. Blastr makes it impossible to run an interesting relay without implementing write policies.
Which is actually fine! Because that's always been true — servers that allow anonymous uploads always get abused. Tony is just helpfully pointing out to us that this is no less true of nostr relays. I only wish he could have waited a little longer before mounting his attack on the network, because lots of hobbyists are interested in running interesting relays, but the tools don't yet exist to protect those servers from unsolicited notes.
One other note on blastr — Tony at one point described blastr as a relay proxy. This is an interesting perspective, which puts things in a different light. More on proxies later.
Ban Jack?
Here's a thought experiment: how might we actually "ban blastr"? @Pablof7z suggested to me in a conversation that you could configure your relay to check every note that gets published to your relay against the big nostr hubs, and if it exists on any of them to simply delete it. Of course, that would result in your relay being basically empty, and the hubs having all of your content. That's game theory for you I guess.
Another approach that was floated was to encourage users to only publish to small relays. In theory, this would force clients to implement gossip so users could still see the content they were subscribed to. Fiatjaf even posted two identical notes, one to his personal relay, and one to a hub to see which would get more engagement. The note posted to the mainstream relay got 10x more replies and likes than the more obscure note.
nostr:nevent1qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qgmwaehxw309aex2mrp0yh8wetnw3jhymnzw33jucm0d5hszymhwden5te0wp6hyurvv4cxzeewv4ej7qpqdc2drrmdmlkcyna5kkcv8yls4f8zaj82jjl00xrh2tmmhw3ejsmsmp945r
Of course, this is thwarted by blastr, since blastr not only replicates notes posted to it, it also actively crawls the network as well. So the next logical step in this train of thought would be for hubs to encourage people to use small relays by actively blocking high-profile accounts.
nostr:nevent1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpzdmhxue69uhhyetvv9ujue3h0ghxjme0qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qpqpjhnn69lej55kde9l64jgmdkx2ngy2yk87trgjuzdte2skkwwnhqv5esfq
This would of course never happen (Damus is one client that hasn't implemented NIP 65, and they also run the biggest relay), but it was a fun thought experiment. At any rate, the silliness of the suggestion didn't stop certain people from getting offended that we would "disrupt the free market" by "forcing" our opinions on everyone else. Oh well.
Death to Blastr
In reality, even though blastr makes it a little harder to adopt gossip in the short term, its days are numbered. Eventually, relay operators will start to feel the pain of unsolicted notes, and will either shut their relays down or look for tools that will help them curate the content they host.
From my perspective, these tools take two forms — read protection and write protection. This is something I alluded to in my talk at Nostrasia last November.
Write protection is straightforward — already many relays have access control lists based on active subscriptions, invite codes, or just static whitelists that determine who is allowed to post to a given relay, or what event authors are represented there. This approach effectively prevents blastr from using relays as free storage, which is a huge improvement.
Read protection is more tricky, because anything publicly readable will be scraped by blastr and replicated to unauthenticated-write relays across the network. In most cases, this is ok, but there are use cases for relays to exist that host a unique collection of notes oriented around some organizing principle. Unfortunately, with blastr in action (or any scraper that might exist), the only way to do this is to actively protect proprietary content. There are a few approaches that can work to make this happen:
- IP-based access control lists
- AUTH-based access control lists
- Stripping signatures when serving events
- Storing and serving encrypted content
Each of these approaches has its own set of trade-offs. But depending on use case, any of them or a combination of them could work to allow relay operators to carve out their own piece of the nostr-verse. In fact, this is a big part of what Coracle is about — the white-labeled version of the product confines certain notes to proprietary relays, with optional encrypted group support.
Enough of my polemic against blastr. Let's talk about how to make the gossip model actually work.
Hints are pointless
Right now, clients that implement the gossip model rely pretty heavily on relay hints to find related notes — whether user profiles, reply parents, or community definitions. The problem with hints is that they are prone to link rot. Many of the relays that were set up a year ago when nostr took off are no longer online, and yet they persist in user relay lists, and in relay hints. These hints can't be updated — they are set in stone. What this means is that a different mechanism has to be used to find the notes the hints were supposed to help locate.
Because of this, I've come around to the position that hints are basically pointless. They are fine as a stopgap, and might be appropriate for certain obscure and ill-defined use cases where relay urls are the most durable address type available. But they provide basically no value in supporting the long-term robustness of the network.
What are durable, however, are pubkeys. Pubkeys are available pretty much everywhere, except in event id hints — and there is a proposal in the works to add a pubkey to those too. The cool thing about pubkeys as hints is that once you have a pubkey, all you need to do is find that person's kind 10002 inbox/outbox selections, and you should be able to find any note they have published.
This goes with the caveat that when users change their relay selections, or rotate their key, they (or their relays) should be sure to copy their notes to the new relay/pubkey.
The question then is: how do I find a given pubkey's relay selections?
There are already several mechanisms that make this reasonably easy. First of all, NIP 65 explicitly recommends publishing relay selections to a wide range of relays. This is a place where the blastr approach is appropriate. As a result, relay selections are usually available on the most popular public relays. Then there are special purpose relays like purplepag.es, which actively seek out these notes and index them.
These indexes are not confined to relays either. It would be trivial to create a DVM that you could ask for a pubkey's relay selections, optionally for a fee. Alex Gleason's proxy tag could also be used to indicate indexes that exist outside the nostr network — whether that be torrents, DHT keys, or what have you.
The best part is that this doesn't negatively impact the decentralization of the network because in principle these indexes are stateless — in other words, they're easily derived from the state of the public part of the nostr network.
Just do it for me
Looping back to where we started — the complexity and technical challenges of implementing the gossip model — there is a simple solution that many people have experimented with in different ways that could solve both issues at once: proxies.
As I mentioned above, Tony thinks of blastr as a proxy, and he's right. More specifically, it's a write-proxy. This is only part of its functionality (it also acts as an independent agent which crawls the network. EDIT: apparently this is not true!), but it is an essential part of how people use it.
Another kind of proxy is a read proxy. There are several implementations of these, including my own multiplextr proxy, which is gossip-compatible (although it requires a wrapper protocol for use). The advantage of a proxy like this is that it can reduce the number of connections a client has to open, and the number of duplicate events it has to download.
Proxies can do all kinds of fancy things in the background too, like managing the gossip model on behalf of the client, building an index of everything the user would be likely to ask for in advance to speed up response times, and more.
One interesting possibility is that a NIP 46 signer could double as a proxy, reducing the number of round trips needed. And since a signer already has access to your private key, this kind of proxy would not result in an escalation in permissions necessary for the proxy to work.
It's simple
The number of cool and creative solutions to the content replication and indexing problem is huge, and certainly doesn't end with blastr. Just to summarize the next steps I'm excited to see (to be honest, I want to build them myself, but we all know how that goes):
- More clients supporting gossip
- Gossip implementations maturing (Coracle's still has some issues that need to be worked out)
- A shift from relying on relay hints to relying on pubkey hints + relay selection indexes of some kind
- Proxy/signer combos which can take on some of the heavy lifting for clients of delivering events to the right inboxes, and pulling events from the right outboxes
Let's get building!
-
 @ 126a29e8:d1341981
2024-03-25 18:32:37
@ 126a29e8:d1341981
2024-03-25 18:32:37Esta publicación sintetiza nuestro meetup de Marzo 2024 en el que enumeramos algunos métodos para guardar copias de seguridad de nuestra frase semilla. En nuestra web se incluye información más detallada y enlaces a otras guías y herramientas para que quien quiera pueda seguir investigando: Métodos para Guardar Copias de la Frase Semilla
Podríamos decir que es la continuación natural al meetup de Febrero de 2023 en el que el compañero nostr:npub1qtc2v0vc7uht2gj9pxg5knynwccnq3pwnp9ds723w6jtr7gmmckqf6d038 nos explicó cómo generar nuestra propia semilla a mano de forma segura. Un ejercicio que ayuda a entender mejor esta cosa que a veces puede resultar un tanto abstracta y complicada.
Si os lo perdisteis podéis consultar una buena lista con guías para crear tu propia semilla con monedas, dados y aparatos varios aquí mismo: Generando Semillas a Mano
En nuestra web hemos incluido un breve recorrido hasta llegar a la frase semilla que ahora usamos como llave a nuestros fondos y recomendaciones esenciales a la hora de generarla. Aquí pasaremos directamente a algunas de las formas recomendadas para guardar copias de nuestra semilla.
Formas de guardar la semilla
PAPEL

📝 Material necesario Papel + lápiz, bolígrafo o rotulador.
No hay mucho que explicar. Tan sencillo como anotar las palabras en el orden correcto y letra legible. Puedes anotar cada palabra completa, las 4 primeras letras o el número de la lista BIP39: https://github.com/bitcoin/bips/blob/master/bip-0039/english.txt
Variante Rotulador Ultravioleta
Estos rotuladores tienen una tinta especial “invisible” que sólo es visible bajo luz UV
 Variante TINTA TERMOSENSIBLE con borrado y recuperación mediante calor-frío
Variante TINTA TERMOSENSIBLE con borrado y recuperación mediante calor-fríoLas tintas termosensibles o termocromáticas reaccionan a la temperatura variando su color, desapareciendo o apareciendo. ⚠️ No son permanentes por lo que un lavado borrará irreversiblemente la tinta.
¿Cómo funciona?
La tinta desaparece al aplicar calor (60º). Basta con frotar sobre lo escrito o aplicar calor con un secador de pelo, por ejemplo. La tinta reaparecerá a temperatura -10º.
https://www.youtube.com/shorts/yeX1nNEn4ZA
👍 Es la opción más barata y sencilla
👎 El papel es altamente vulnerable al agua, fuego, roce, …
Metal
https://nostrcheck.me/media/126a29e8181c1663ae611ce285758b08b475cf81b3634dd237b8234cd1341981/41e4fcac6807460e14226f2780bc83d9e64131d3e61008e0bbe713235545c83d.webp
🔨 Material necesario Blockmit + Punzones de acero + Mazo (1-2 Kg) + arandelas o placa de acero + tornillo + tuerca + yunque (opcional pero recomendable)
Guardar las palabras de recuperación en metal es uno de los métodos más empleados por los bitcoiners. Quizás por eso hay múltiples opciones comerciales pero cuidado porque no todas son igual de resistentes:
https://jlopp.github.io/metal-bitcoin-storage-reviews/img/devices/ellipal_metal_heat.jpeg
Otras sencillamente tienen métodos más que cuestionables. Cualquier opción que ofrezca una clave privada generada de antemano es un NO ROTUNDO.
https://criptokio.com/wp-content/uploads/2022/03/reverso-material-bitcoin.jpg
Jameson Lopp analizó decenas de ellas probando su resistencia al fuego, la corrosión y la deformación documentando gráficamente el proceso.
Podéis consultar sus conclusiones en esta lista en la que incluye una evaluación de resistencia con imágenes, precio y conclusiones de cada aparato:
Metal Bitcoin Seed Storage Reviews
Nuestra propuesta es el método Blockmit por ser una de las opciones más baratas y que mejor resiste la prueba de resistencia del amigo Lopp, además de por poder adquirir todo el material necesario en cualquier ferretería. Esto de la ferretería es importante por varios motivos. 1. El uso que se le puede dar a las piezas y herramientas empleadas en este método es tan variado que nadie sospechará que vas a hacer algo relacionado con Bitcoin. 2. Evita que tu nombre, dirección, etc, formen parte de una filtración de datos de una empresa relacionada con Bitcoin. 3. Nos gusta la filosofía Hágalo Usted Mismo (DIY)
En su web encontrarás una lista de materiales necesarios, el archivo del molde en 3D y un paso a paso. También tiene publicada una variante en placa de metal:
Fabrica tu billetera fría con arandelas | Blockmit.com
👍 Opción asequible y sencilla. Altamente resistente y duradera
👎 No es tan sencillo de ocultar como otras opciones
Seedsigner
https://github.com/SeedSigner/seedsigner/blob/dev/docs/img/Mini_Pill_Main_Photo.jpg?raw=true
Seedsigner es un proyecto de código abierto que ofrece la posibilidad de construir por uno mismo un dispositivo con componentes asequibles para la creación de semillas y firmar transacciones de forma aislada, es decir sin necesidad de conectarse a la red ni a ningún otro dispositivo. ¿Cómo consigue esto? Mediante un proceso de intercambio de códigos QR.
Seedsigner no es es una hardware wallet al uso. Entre otras cosas no permite guardar nuestra semilla ya que es un dispositivo amnésico (al menos en sus ajustes por defecto).
Lo interesante es que al crear tu semilla (o introducir las palabras de una que ya tengas) te permite guardarla codificada en un código QR. Este QR se mostrará en la pantalla y deberás dibujarlo en una plantilla y posteriormente grabarlo en metal si quieres mayor durabilidad. Si quieres rehidratar una semilla para exportar su clave pública o para firmar transacciones basta con escanear el código QR que hayas guardado previamente
Hay que decir que aunque no se mencione a menudo, el objetivo de SeedSigner desde un inicio fue reducir el coste y la complejidad del uso de multifirmas. Pero aunque no se haga uso de esa funcionalidad es una herramienta super útil.
Montando el dispositivo por piezas:
https://www.youtube.com/watch?v=6-5cDneXoWs
Descargar, verificar y flashear el software:
https://youtu.be/M5-yY2XWdKM?si=pY625U4Er5gJ_LHR
Generar semilla y transcribirla a código QR:
https://youtu.be/6AjCvNYSs8w?si=E5ex2ZeG-Q9NTwIZ
👍 Dispositivo offline y amnésico (Hodl a largo plazo, multisig)
👎 Dispositivo amnésico (Si mueves fondos a menudo)
Esteganografía
Si queremos ocultar alguna información podemos recurrir a la criptografía o la esteganografía.
!https://miro.medium.com/v2/resize:fit:1400/format:webp/1*dQyfOpFWmSxrmdOcQgW6OQ.jpeg
La criptografía hace que aunque el mensaje sea visible su contenido sea ininteligible mientras que la esteganografía (Steganos → oculto + Graphein → escribir) oculta la existencia del mensaje.
La esteganografía es el arte y ciencia de ocultar en el interior de una información, aparentemente inocua, otro tipo de información (cifrada o no). Para ello podriamos usar cualquier soporte digital: imagen, audio, video, ... o analógico. De echo, la esteganografía clásica es tan antigua como la necesidad del ser humano de ocultar secretos y en la historia hay múltiples ejemplos. Uno de los más antiguos data del siglo V a.C., cuando el general ateniense Histieo envió un mensaje secreto a Aristágoras de la siguiente forma: afeitó la cabeza de un mensajero, tatuó un mensaje en el cuero cabelludo y esperó a que le creciese de nuevo el pelo para enviarle a la ciudad de Mileto. Una vez allí volvería a afeitarse para que Aristágoras leyese el mensaje.
Volviendo a la actualidad, en la esteganografía "moderna" no hay ningún patrón que buscar por lo que es completamente indetectable a simple vista.
👍 La ventaja de la esteganografía sobre la criptografía es que el mensaje secreto no atrae la atención directamente. Los mensajes cifrados -por muy irrompibles que sean- despiertan curiosidad inevitablemente.
👎 Seguridad por oscuridad: Si la seguridad de un sistema reside en que el potencial atacante no conoce la técnica de ocultación o el medio utilizado, la seguridad puede comprometerse fácilmente.
Herramientas Esteganografía
Una de sus grandes cualidades y el motivo por el cual es tan esquiva de detectar es que puede presentarse en cualquier sitio donde el ingenio humano encuentre la posibilidad de ocultar información. Existen tantos mecanismos para llevar a cabo este camuflaje como nuestra imaginación nos permita.
Veamos un par de ejemplos.
Stegoseed
https://nostrcheck.me/media/126a29e8181c1663ae611ce285758b08b475cf81b3634dd237b8234cd1341981/d312f5a4ac698503b265529c22e2b4a0e6c1f2bf1d7f6836215f5b84e3f0b10d.webp
Stegoseed oculta una frase semilla en un texto generado aleatoriamente o en un fragmento de texto que le proporciones.
⚠️ Sólo debes utilizar esta herramienta directamente en la web para jugar. Si quieres usarla con fines reales, debes descargar el código de Github: https://github.com/jes/stegoseed y ejecutarlo en un ordenador que no tenga acceso a Internet, para asegurarte de que no se filtre tu frase semilla. Huelga decir que deberías generar tu propia semilla BIP39, y no usar la que se muestra de ejemplo en Stegoseed.
James Stanley - Steganographic Bitcoin seeds: Hiding cash in plain sight
Steghide
Steghide es un programa de esteganografía capaz de ocultar datos en varios tipos de archivos como imagen o audio. Su instalación y uso es muy sencillo. Para instalarlo desde la terminal en Linux simplemente escribe el siguiente comando:
apt-get install steghidePara iniciarlo y que muestre todas las opciones:
steghide --helpEn los primeros minutos de este video se muestra como con apenas un par de comandos puedes ocultar un archivo dentro de una imagen protegido con contraseña:
https://youtu.be/3gnJtKNbM-A
Bola Extra! → Criptografía + Esteganografía
Combinar ambas técnicas proporciona 2 capas de seguridad. Cifrar mensaje → Incrustar el mensaje cifrado en cualquier medio = estego-objeto (estegoimagen, estegoaudio, estegovideo, …)

Border Wallets
https://europeanbitcoiners.com/content/images/size/w2000/2022/08/border-wallets-seed-phrase-recovery-top-photo-3.png
El caso de uso de Border Wallets es muy específico. Se trata de facilitar que memorices tu semilla BIP39 en caso de que vivas en una zona bajo regimen autoritario, en conflicto o guerra y quieras pasar la frontera sin copia física de tus palabras semilla para evitar confiscaciones. (De ahí su nombre: “Cartera fronteriza”) Esto puede sonar exagerado en esta parte del mundo pero cada año hay millones de desplazados que tienen que dejar su hogar con lo puesto. También podría aplicarse si tienes que salir corriendo por incendio, terremoto o cualquier inclemencia y no puedas recuperar ninguna copia de seguridad.
Memorizar fielmente 12-24 palabras inconexas en un orden específico no es tan sencillo y los desarrolladores dieron con varios estudios que demostrarían que somos capaces de recordar imágenes mucho más tiempo que palabras . Es algo que podemos confirmar con un ejemplo sencillo: tendemos a recordar las caras con más facilidad que los nombres.
https://bitcoinmagazine.com/.image/c_limit%2Ccs_srgb%2Cq_auto:good%2Cw_700/MTkxMzc4MTcwNTI2NzA1MjUw/recall-study.webp
Cómo funciona
Para generar una Border Wallet puedes descargar el archivo HTML y los archivos para la verificación en el Github del proyecto. También puedes generar una Border Wallet directamente en la integración en Sparrow o DTails.
Una vez generada la cuadrícula con las 2048 palabras BIP 39 (las palabras cambian de posición con cada nueva creación de wallet) deberás dibujar un patrón (11 ó 23 casillas). En este paso es muy importante recordar las coordenadas de la primera celda que marques y el flujo completo del patrón porque eso determina el orden de las palabras. Al introducir las 11/23 palabras, Border Wallet genera la ultima palabra de la semilla (equivale a la suma de comprobación Checksum y le asigna un número. De este modo puedes elegir entre memorizar la palabra o el número cuando necesites regenerar tu semilla. En el caso de que lo hagas en Sparrow te aparecerá una lista para que elijas la última palabra.
Para finalizar descarga el PDF con la plantilla (no se incluye el patrón). Opcionalmente la herramienta permite encriptar/desencriptar el PDF con una contraseña.
https://bitcoinmagazine.com/.image/c_limit%2Ccs_srgb%2Cq_auto:good%2Cw_477/MTkxMzc4MTcwMjU4MTM4NzIy/border-wallet.webp
Tutorial de Border Wallets en Sparrow (en inglés):
https://www.youtube.com/watch?v=wHQrvCGVkTw
👍 Aunque alguien acceda al PDF solo verá una lista de palabras. Aún en caso de que supiera a qué corresponden esas palabras no sabría cual es el patrón ni si es de 11 o 23 palabras.
👎 Tendrás que tener acceso a la cuadrícula generada para que el patrón coincida con tu semilla. Además seguirás confiando en tu memoria para recordar la posición del dibujo/patrón en la cuadrícula, el flujo para dibujarlo y la última palabra.
BIP39 Colors
https://nostrcheck.me/media/126a29e8181c1663ae611ce285758b08b475cf81b3634dd237b8234cd1341981/6695616e563c63bd405970a9f5fd40ec5192b8ab72681e321a3e86e229fd504b.webp
BIP-39 Colors te permite convertir la frase semilla en una paleta de colores, para que puedas ocultarla en todo tipo de imágenes (o en el css de tu web, excel, …). Es obra de un desarrollador español que trabaja bajo el pseudónimo Entero Positivo y que entre otras cosas también ha creado el emulador de SeedSigner para escritorio.
Cómo funciona:
https://nostrcheck.me/media/126a29e8181c1663ae611ce285758b08b475cf81b3634dd237b8234cd1341981/3e29d643808cde7b1aa935cbb78ced61e6fb87e159727ca8aa91d02854d19e18.webp
Mediante una herramienta muy sencilla se codifican las 12 o 24 palabras en 8 o 16 códigos de color hexadecimal, que es el formato habitual para mostrar colores en las pantallas.
- Versión software: Se puede descargar desde su repositorio de GitHub para ejecutarlo en un ordenador sin conexión. Simplemente introduces la frase semilla y pinchas en "Generar colores". También puedes decodificar la paleta de colores hexadecimal a la frase semilla.
https://github.com/EnteroPositivo/bip39colors
⚠️ IMPORTANTE: La copia de los colores ha de ser en digital**. Los códigos de color hexadecimales sólo funcionan en pantallas.
- Versión manual: ¿No te fías de hacerlo en un ordenador? No pasa nada porque puedes hacerlo a mano con un método tan sencillo como ingenioso:
👍 A favor:
- Es compatible con el estándar BIP 39 y por tanto con la mayoría de wallets y dispositivos.
- Al representar la frase semilla como colores se añade una capa extra de ofuscación.
- El orden no importa 🤯: Puedes mezclar y almacenar los colores en cualquier orden, y seguir recuperando la frase BIP39 original en el orden correcto. (El tono determina a qué palabra corresponde de la lista BIP39 y la saturación del color determina el lugar dentro del orden de la frase semilla)
- Proyecto de código abierto disponible en Github
- Posibilidad de conversión manual
👎 Seguridad por oscuridad: Si la seguridad de un sistema reside en que el potencial atacante no conoce la técnica de ocultación o el medio utilizado, la seguridad puede comprometerse fácilmente.
Archivo cifrado (Veracrypt)

ℹ️ La criptografía es una ciencia que se utiliza para proteger información cifrándola de forma que únicamente el que tenga la clave secreta pueda leer el contenido.
Al igual que la esteganografía, su utilización es tan antigua como la escritura.
Uno de los primeros métodos que se utilizó para cifrar mensajes fue la escítala (o escítalo) que no era más que una vara de madera en la que se enrollaba una cinta de cuero o de papiro para escribir el mensaje longitudinalmente. Posteriormente se enviaba únicamente la cinta al destinatario. Cualquiera que interceptase la cinta leería una sucesión de letras sin sentido ya que sería necesaria una escítala de exactas dimensiones para revelar el mensaje.
En criptografía este tipo de cifrado se cataloga como transposición, es decir, cambiar el orden de las letras en un texto plano mientras que el cifrado por sustitución consiste en cambiar una letra o conjunto de letras del texto en claro por otra letra u otro conjunto de letras de un alfabeto de cifrado.
Pasemos al cifrado fuerte:
https://ciberseguridad.comillas.edu/content/images/2022/10/veracrypt.jpg
Una herramienta excelente para cifrar datos confidenciales es Veracrypt. Destaca por su seguridad gracias al uso de algoritmos de cifrado avanzados. Además ofrece la posibilidad de crear volúmenes ocultos, lo que añade una capa adicional de negación plausible.
El proceso de creación de un volumen cifrado es sencillo y está bien documentado por lo que resulta accesible incluso para quienes no sean muy técnicos.
Os dejamos varios tutoriales muy completos para sacarle todo el partido a esta herramienta: 📖 Para los que prefieran lectura, esta es una buena introducción a la herramienta ⤵️
Veracrypt: Cifra y oculta tus archivos gratis
📺 Tutorial básico de mano del gran Albercoin cuyo canal recomendamos a cualquier bitcoiner interesado en aprender a montar su propio nodo Bitcoin ⤵️
VeraCrypt - Qué es y cómo funciona (nivel básico) (Windows 10)
📺 Curso completo en video con todas las opciones que ofrece VeraCrypt ⤵️
Curso Veracrypt 2023⭐1 ¿Qué es VERACRYPT? Encriptar o cifrar Documento - Como Instalar en Windows 10
Hardware Wallet
Las Hardware Wallets usan la tecnología más avanzada para la generación, gestión y almacenamiento de claves.
¿Qué se considera una buena Hardware Wallet (HWW)?
Una buena HWW intenta reducir al máximo la superficie de ataque y para eso, estas características serían deseables: - Airgap (que pueda funcionar sin conexión a ningún otro dispositivo ni a internet) - Open source - Bitcoin only - Pantalla (para verificar direcciones, firmas, …) - Opciones avanzadas (mínimo coin control)
La semilla está a buen recaudo en una Hardware Wallet pero necesitas una copia de seguridad porque ¿Y si pierdes la HWW o se te rompe?
En efecto, necesitas una copia de seguridad y para eso hemos creado esta lista que esperamos pueda resultarte útil 😊
-
 @ fbd49947:51b339ec
2024-03-25 17:26:13
@ fbd49947:51b339ec
2024-03-25 17:26:13🚀 VINCI LE MEMECOIN DI SOL CON #BITGET
Se sei un nuovo utente, completa le task per ottenere le Mistery Box: ☝️Raggiungi un valore di trading > 300 USDT ✌️Invita i tuoi amici in #Bitget registrati qui https://bonus.bitget.com/BK6NTT
In ogni box trovi un premio in token #Solana 🔥
-
 @ 5d4b6c8d:8a1c1ee3
2024-03-25 15:11:16
@ 5d4b6c8d:8a1c1ee3
2024-03-25 15:11:16Hopefully, some of you are familiar with Andrew Heaton. He's probably best known for contributing libertarian content to outlets like Reason and The Blaze. He's also a comedian and an author. I consider him to be one of the most underappreciated content creators today.
I've read each of Heaton's five books and recommend each one without reservation. If you enjoy Kurt Vonnegut and Douglas Adams, I think you'll enjoy Andrew Heaton. Also, if you already enjoy Andrew Heaton, I think you'll love his books.
Non Fiction
Los Angeles is Hideous: Poems About an Ugly City
Heaton made a career move to LA, even though he knew he hated the city. It happened to be just before Covid lockdowns.
These poems are an expression of the many many things he disdains about LA. It's a great coffee table book.
Laughter is Better than Communism
I think this is the first book of his that I read. It's definitely the one I remember least clearly. However, Heaton is a hilarious political satirist. Check out his series Mostly Weekly to get a sense of whether his humor is up your alley.
Fiction
Frank Got Abducted
I was a big fan of The X-Files growing up and I also listened to a lot of Coast-to-Coast AM during late night drives. Frank Got Abducted is a goofy sci-fi conspiracy mystery that would fit in perfectly on either of those programs.
Happier as Werewolves
This is a romance story in familiar horror setting. Like much of Heaton's writing, the story is set in rural Oklahoma. That's where Andrew's from and his descriptions of home are both loving and hilarious.
Inappropriately Human: 21 Short Stories
If you enjoyed Vonnegut's short story collections, these are in that same vein: brilliant satire, strange sci-fi settings, but also some real emotional weight.
-
 @ 676c0224:e641b6d6
2024-03-25 15:03:52
@ 676c0224:e641b6d6
2024-03-25 15:03:52 -
 @ c11cf5f8:4928464d
2024-03-25 14:06:07
@ c11cf5f8:4928464d
2024-03-25 14:06:07Time to brush off the spurs and saddle up for a ride into the exciting ad-ventures ahead! What innovative goods or services are y'all bringin' on the wagon this week? Give us a sneak peek and let that entrepreneurial spirit get out.
Take some pics and start posting your items now!
[⚖️ SELL] - [🛒 BUY] - [🧑💻 HIRE] - [🖇 OFFER] - [🧑⚖️ AUCTION] - [🤝 SWAP] - [🆓 FREE] - [⭐ REVIEW]
Stay humble, stack sats!
-
 @ cce0989b:b497e608
2024-03-25 12:50:45
@ cce0989b:b497e608
2024-03-25 12:50:45Self-awareness is one of the most important skills we can build, linked to varied outcomes like preventing burnout, improving psychological well-being, and supporting physical health. Yet no one ever teaches us exactly how to build it.
One of the biggest barriers to self-awareness: we lack a zoomed-out perspective on our lives. Without this, it's incredibly difficult to notice patterns and identify issues; and without that, it's incredibly difficult to make wise decisions to address them.
That's why we're sharing the New Happy Daily tracker: it's a blank version of this artwork, along with a comprehensive guide on how to use it, that you can use to track the patterns in your own life.
Here's how to use it. Decide what you'd like to track (I suggest either your emotions or your experiences, and there are templates for both!) and choose a color for each item. Every day, fill in the corresponding dot on the chart. Use it as a daily moment to pause and reflect, a ritual that helps you to be honest with yourself.
As the days pass, you'll start to identify trends. You'll be able to answer questions like:
"Which experiences tend to make me happiest? "Which experiences tend to make me sad or lonely or angry?" "What do I need more of in my life?" "How are my daily choices contributing to how I'm feeling?"
It's a simple but powerful way for you to check in with yourself — a choice that will, day by day, build your self-awareness.
-
 @ 4c735c00:3fb4e3d9
2024-03-25 11:32:11
@ 4c735c00:3fb4e3d9
2024-03-25 11:32:11When it comes to our religious faith, we all know it’s better to be on fire than to be lukewarm.
We ask the Holy Spirit to "enkindle in us the fire of your love." If we cool off -- if we don't stay "hot" -- we risk quenching the Spirit (1 Thessalonians 5:19).
It would seem that if cold is the opposite of hot, then to be spiritually lukewarm is better than being spiritually cold. If you go from cold to lukewarm, you're making progress! You're going in the right direction. The closer we are to God, the better. Right?
We want to be like the two men on the road to Emmaus who recognized the resurrected Lord Jesus at the breaking of the bread. When he vanished from their sight, they said to each other, “Did not our hearts burn within us while he talked to us on the road, while he opened to us the Scriptures?” (Luke 24:32). This kind of heat -- this spiritual “heart burn” -- is what we desire.
What we don’t want is to be like those of whom Jesus spoke in his Olivet prophecy: “And because wickedness is multiplied, most men’s love will grow cold” (Matthew 24:12).
So what is the deal with Jesus’ words in Saint John’s letter to the church in Laodicea?
His warning to the Laodiceans is found in Revelation 3:15–16:
I know your works: you are neither cold nor hot. Would that you were cold or hot! So, because you are lukewarm, and neither cold nor hot, I will spew you out of my mouth.
Does it make sense to believe Jesus wants us to either love him or hate him -- but what displeases him most is if we're somewhere in the middle? By analogy, is a so-so marriage worse than a marriage grown ice cold?
It's indeed counterintuitive to think cold is better than lukewarm -- if what we have in mind is a range of spiritual temperatures, with “hot” being good and “cold” being bad.
The truth is, contrary to popular belief, that's not what Jesus meant.
Another read-through
If we discard the “spiritual degrees” paradigm and reread the letter to Laodicea, understanding the city in its historical context, we can unlock this apparent dilemma. We can make sense of Jesus’ call for the Laodicean church to be either “cold or hot” rather than "lukewarm."
Here is the full warning message to Laodicea in Revelation 3:15–22:
I know your works: you are neither cold nor hot. Would that you were cold or hot! So, because you are lukewarm, and neither cold nor hot, I will spew you out of my mouth. For you say, I am rich, I have prospered, and I need nothing; not knowing that you are wretched, pitiable, poor, blind, and naked. Therefore I counsel you to buy from me gold refined by fire, that you may be rich, and white garments to clothe you and to keep the shame of your nakedness from being seen, and salve to anoint your eyes, that you may see.
Laodicea's fame
Jesus references specific things notable about first-century Laodicea:
- Eye salve. It turns out there was a famous medical school in Laodicea that was known for its eye salve, likely more of a medicinal powder, rubbed onto the eyelids.
- White garments. The textile industry was big in this wealthy city. Laodicea famously produced fine-quality, glossy black wool.
- Rich. In addition to the wealth from its manufacture of black wool, Laodicea was a huge banking center, with gold being a source of wealth. It was well positioned as a banking center due to its physical location along the great Roman road. The city’s wealth was such that in A.D. 17, when it suffered a great earthquake, it refused imperial assistance. Unlike the city of Philadelphia, which also experienced destruction from an earthquake, the Laodiceans rebuilt their own city with their own wealth and resources -- independent of the empire.
- Lukewarm. For all its wealth, Laodicea lacked its own water supply, so it imported water from the south through a six-mile-long aqueduct. The water apparently came either from hot springs or cooler sources. Whichever the source, by the time it traveled six miles through the aqueduct system, the water arrived at a lukewarm temperature, and reportedly came with sediment.
Putting the pieces together
If we understand these things about Laodicea, we begin to understand Jesus more clearly. The correlations between Laodicea’s attributes and Jesus’ admonitions should become obvious.
Despite the eye salve that Laodicea offered, the church there was spiritually “blind,” but Jesus offers the readers true “salve to anoint [their] eyes, that [they] may see.”
The church’s members were “naked,” and in contrast to the glossy black wool found in the city, Jesus offers “white garments to clothe [them].”
The riches from the city’s industries and banking does not mean the people are not “poor.” “Therefore I [Jesus] counsel you to buy from me gold refined by fire, that you may be rich.”
Now what about the reference to being “lukewarm”?
Less than 10 miles away was the city of Colosse, where there was cool water, suitable for drinking. And just to the north of nearby Hieropolis, there were hot springs, suitable for therapeutic and healing baths.
But Laodicea? Remember, their water was tepid and full of sediment, which was good for neither drinking nor bathing. That’s why Jesus compared their sins of pride and complacency to their “lukewarm” water. “I will spew you out of my mouth,” he says, because, like their water, they were good for nothing.
So it’s not that Jesus prefers cold mortal sins over lukewarm venial sins. In terms of spiritual degrees, some warmth is better than none. But Jesus was not speaking of spiritual degrees; he was speaking of spiritual usefulness.
Our takeaway
Our takeaway from all of this is simple: “be zealous and repent” (3:19).
Be like hot water, which can be used for bathing. Or be like cold water, as a refreshing drink. Anything but lukewarm. We don’t want to be an emetic -- a substance that induces spiritual vomiting in our Lord.
But how do we do that? What does that look like?
Laodicea was just one of the seven churches in Asia Minor that received a custom-tailored message. To most of them, Jesus says, "I know your works" (2:2; 2:19; 3:1; 3:8; 3:15).
Specifically, he says to "repent, and do the works you did at first" (2:5).
So whether you've cultivated vices in your life or allowed yourself to become spiritually tepid -- if you feel stuck in a rut, then the only way out is to fall on your knees. Pray. Repent. Confess.
If we confess our sins, he is faithful and just to forgive us our sins and to cleanse us from all unrighteousness (1 John 1:9).
And no matter how you feel, "do the works you did at first." Get back to the basics.
Get back to the traditional, tested, and true teachings of the Catholic Church, "the pillar and ground of the truth" (1 Timothy 3:15).
It's the only way to avoid the "lukewarm" condition.
By the way, despite the lukewarm condition of the Laodiceans, Jesus concludes his letter to them with encouragement:
Those whom I love, I reprove and chasten; so be zealous and repent. Behold, I stand at the door and knock; if any one hears my voice and opens the door, I will come in to him and eat with him, and he with me. He who conquers, I will grant him to sit with me on my throne, as I myself conquered and sat down with my Father on his throne. He who has an ear, let him hear what the Spirit says to the churches (Revelation 3:19-22).
THANK YOU for reading. To see my "About Me" page, to learn how to subscribe to this blog's RSS feed, and to privately send me questions or comments, click here.
-
 @ 20986fb8:cdac21b3
2024-03-25 11:26:37
@ 20986fb8:cdac21b3
2024-03-25 11:26:37Bitcoin secures private property, and Nostr ensures freedom of speech, both pioneering technological solutions. Regarded as on par with Bitcoin, Nostr has emerged as a primary decentralized media protocol within the Bitcoin community.
As one of the most popular decentralized media clients in the Nostr ecosystem, YakiHonne has consistently played a pivotal role as both advocate and practitioner in advancing the global Nostr community. Since the inaugural Asia Nostr gathering held at the Hong Kong Festival in April 2023, YakiHonne's "Connecting Nostriches and Bitcoiners" global initiative has spanned across over 10 countries, including Hong Kong (April), Miami (May), Berlin (June), Beijing/Malaysia (July), Singapore (August), Nigeria/Spain (September), Istanbul/Bali (October), Tokyo (November), and Malta/Hong Kong (December).

This year, YakiHonne is once again launching the "Connecting Bullish Nostriches and Bitcoiners" global event plan, aiming to explore key developmental topics of Nostr, construct a global dissemination pathway for Nostr projects, unite Nostriches, thus creating an autonomous, diverse, and active Nostr global community. This global event will span continents, 16 countries, and 20+ cities, connecting over 5000 Nostr/Bitcoin buidlers.

🔥 Global Event Plan
Notes: The global event is a daunting task, and YakiHonne has currently only listed a few countries. If you wish to initiate events and establish the Nostr community in your country and city, please contact us immediately. Let's work together to promote the development of a decentralized world!
1. Southeast Asia Stop:
- Route: Bali, Bangkok, Vietnam, Kuala Lumpur, Hong Kong.
- Duration: April 10th to May 10th, one stop per week.
- Featured Stop: Hong Kong, Exclusive Nostr side event during the Bitcoin Asia 2024 Conference.
2. United States Stop:
- Route: Austin, Miami, Atlanta, San Francisco, New York, Nashville.
- Duration: May 21st to July 27th, one stop every two weeks.
- Featured Stop: Nashville, The largest Nostr side event during the Bitcoin 2024 Conference.
3. European Stop:
- Route: Munich, London, Prague, Malta, Amsterdam.
- Duration: August 8th to October 10th, one stop every two weeks.
- Featured Stop: Amsterdam, The largest Nostr side event during the Bitcoin 2024 Conference in Europe.
4. Middle East and North Africa Stop:
- Route: Turkey, Morocco, Nigeria, Riyadh, Abu Dhabi.
- Duration: October 24th to December 10th, one stop every two weeks.
- Featured Stop: Abu Dhabi, The largest Nostr side event during the Bitcoin Amsterdam 2024 Conference in the Middle East and North Africa.

🌐 Event Scale
Covering 5 continents, 16 countries, and 20+ cities; comprising 16 offline meetups with approximately 50 attendees each, and 4 special side events with around 200 participants each, connecting over 5000 buidlers, community members, projects, and investors within the Nostr/Bitcoin ecosystem.
🌟 Event Exposure
Broadcasted to 150 countries and accessible in 20 languages, with each event at every stop deeply engaging with local communities and media resources.

🤝 Join Us
1. Become a Partner
If you wish to increase exposure for your brand or provide support for event resources, please DM us immediately!
Tg:@YakiHonne or Nostr npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
As a partner, you will receive brand exposure in Nostr/Bitcoin offline communities across 16 countries, booth displays, speaking opportunities at 4 special themed events, and exclusive media benefits from YakiHonne, including interviews, newsletters, targeted promotions, and access to local community resources.
2. Become a Volunteer
If you want to participate in a global and exciting event, interact with interesting members of the Nostr community, feel free to join our volunteer team! We need volunteers to participate in planning, organizing, setting agendas, contacting local resources, hosting activities, and spreading the word.
💰 Donation
We welcome donations for this global event. Donated funds will be used for event organization. All donors will receive a specially designed Nostr 2024 Global Event unique serial number badge and will be individually showcased in the donor list.
1 - getAlby Lightning Address: - yakihonne@getalby.com
2 - BTC Address and QR code 1E63WaTsdgYnq1A8nwP5D3qdRkJESzKfU6

OR bc1qek6qx0723c64ujqvcaqp96xw3eghkaj3248x2d
 3 - directly zap this article or yakihonne profile.
3 - directly zap this article or yakihonne profile.If you are interested in this event and wish to contribute to the development of the Nostr global community, please contact us immediately. Let's work together to build a decentralized world!
About YakiHonne:
YakiHonne is a Nostr-based decentralized content media protocol that supports blogs, flash news, curation, videos, uncensored notes, zaps, and other content types. Join us now and experience the joy of decentralized publishing, review and settlement media networks.
Try YakiHonne.com Now!
Follow us
- Telegram: http://t.me/YakiHonne_Daily_Featured
- Twitter: @YakiHonne
- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
- 🌟iOS: https://apps.apple.com/mo/app/yakihonne/id6472556189?l=en-GB
- 🌟Android: https://play.google.com/store/apps/details?id=com.yakihonne.yakihonne
- Facebook Profile: https://www.facebook.com/profile.php?id=61551715056704
- Facebook Page: https://www.facebook.com/profile.php?id=61552076811240
- Facebook Group: https://www.facebook.com/groups/720824539860115
-
 @ ee11a5df:b76c4e49
2024-03-22 22:39:31
@ ee11a5df:b76c4e49
2024-03-22 22:39:31Implementing The Gossip Model
version 1 (2024-03-23)
Introduction
History
The gossip model is a general concept that allows clients to dynamically follow the content of people, without specifying which relay. The clients have to figure out where each person puts their content.
Before NIP-65, the gossip client did this in multiple ways:
- Checking kind-3 contents, which had relay lists for configuring some clients (originally Astral and Damus), and recognizing that wherever they were writing our client could read from.
- NIP-05 specifying a list of relays in the
nostr.jsonfile. I added this to NIP-35 which got merged down into NIP-05. - Recommended relay URLs that are found in 'p' tags
- Users manually making the association
- History of where events happen to have been found. Whenever an event came in, we associated the author with the relay.
Each of these associations were given a score (recommended relay urls are 3rd party info so they got a low score).
Later, NIP-65 made a new kind of relay list where someone could advertise to others which relays they use. The flag "write" is now called an OUTBOX, and the flag "read" is now called an INBOX.
The idea of inboxes came about during the development of NIP-65. They are a way to send an event to a person to make sure they get it... because putting it on your own OUTBOX doesn't guarantee they will read it -- they may not follow you.
The outbox model is the use of NIP-65. It is a subset of the gossip model which uses every other resource at it's disposal.
Rationale
The gossip model keeps nostr decentralized. If all the (major) clients were using it, people could spin up small relays for both INBOX and OUTBOX and still be fully connected, have their posts read, and get replies and DMs. This is not to say that many people should spin up small relays. But the task of being decentralized necessitates that people must be able to spin up their own relay in case everybody else is censoring them. We must make it possible. In reality, congregating around 30 or so popular relays as we do today is not a problem. Not until somebody becomes very unpopular with bitcoiners (it will probably be a shitcoiner), and then that person is going to need to leave those popular relays and that person shouldn't lose their followers or connectivity in any way when they do.
A lot more rationale has been discussed elsewhere and right now I want to move on to implementation advice.
Implementation Advice
Read NIP-65
NIP-65 will contain great advice on which relays to consult for which purposes. This post does not supersede NIP-65. NIP-65 may be getting some smallish changes, mostly the addition of a private inbox for DMs, but also changes to whether you should read or write to just some or all of a set of relays.
How often to fetch kind-10002 relay lists for someone
This is up to you. Refreshing them every hour seems reasonable to me. Keeping track of when you last checked so you can check again every hour is a good idea.
Where to fetch events from
If your user follows another user (call them jack), then you should fetch jack's events from jack's OUTBOX relays. I think it's a good idea to use 2 of those relays. If one of those choices fails (errors), then keep trying until you get 2 of them that worked. This gives some redundancy in case one of them is censoring. You can bump that number up to 3 or 4, but more than that is probably just wasting bandwidth.
To find events tagging your user, look in your user's INBOX relays for those. In this case, look into all of them because some clients will only write to some of them (even though that is no longer advised).
Picking relays dynamically
Since your user follows many other users, it is very useful to find a small subset of all of their OUTBOX relays that cover everybody followed. I wrote some code to do this as (it is used by gossip) that you can look at for an example.
Where to post events to
Post all events (except DMs) to all of your users OUTBOX relays. Also post the events to all the INBOX relays of anybody that was tagged or mentioned in the contents in a nostr bech32 link (if desired). That way all these mentioned people are aware of the reply (or quote or repost).
DMs should be posted only to INBOX relays (in the future, to PRIVATE INBOX relays). You should post it to your own INBOX relays also, because you'll want a record of the conversation. In this way, you can see all your DMs inbound and outbound at your INBOX relay.
Where to publish your user's kind-10002 event to
This event was designed to be small and not require moderation, plus it is replaceable so there is only one per user. For this reason, at the moment, just spread it around to lots of relays especially the most popular relays.
For example, the gossip client automatically determines which relays to publish to based on whether they seem to be working (several hundred) and does so in batches of 10.
Clobbering issues
Please read your users kind 10002 event before clobbering it. You should look many places to make sure you didn't miss the newest one.
If the old relay list had tags you don't understand (e.g. neither "read" nor "write"), then preserve them.
How users should pick relays
Today, nostr relays are not uniform. They have all kinds of different rule-sets and purposes. We severely lack a way to advice non-technical users as to which relays make good OUTBOX relays and which ones make good INBOX relays. But you are a dev, you can figure that out pretty well. For example, INBOX relays must accept notes from anyone meaning they can't be paid-subscription relays.
Bandwidth isn't a big issue
The outbox model doesn't require excessive bandwidth when done right. You shouldn't be downloading the same note many times... only 2-4 times depending on the level of redundancy your user wants.
Downloading 1000 events from 100 relays is in theory the same amount of data as downloading 1000 events from 1 relay.
But in practice, due to redundancy concerns, you will end up downloading 2000-3000 events from those 100 relays instead of just the 1000 you would in a single relay situation. Remember, per person followed, you will only ask for their events from 2-4 relays, not from all 100 relays!!!
Also in practice, the cost of opening and maintaining 100 network connections is more than the cost of opening and maintaining just 1. But this isn't usually a big deal unless...
Crypto overhead on Low-Power Clients
Verifying Schnorr signatures in the secp256k1 cryptosystem is not cheap. Setting up SSL key exchange is not cheap either. But most clients will do a lot more event signature validations than they will SSL setups.
For this reason, connecting to 50-100 relays is NOT hugely expensive for clients that are already verifying event signatures, as the number of events far surpasses the number of relay connections.
But for low-power clients that can't do event signature verification, there is a case for them not doing a lot of SSL setups either. Those clients would benefit from a different architecture, where half of the client was on a more powerful machine acting as a proxy for the low-power half of the client. These halves need to trust each other, so perhaps this isn't a good architecture for a business relationship, but I don't know what else to say about the low-power client situation.
Unsafe relays
Some people complain that the outbox model directs their client to relays that their user has not approved. I don't think it is a big deal, as such users can use VPNs or Tor if they need privacy. But for such users that still have concerns, they may wish to use clients that give them control over this. As a client developer you can choose whether to offer this feature or not.
The gossip client allows users to require whitelisting for connecting to new relays and for AUTHing to relays.
See Also
-
 @ 5c8a5765:4fc5edee
2024-03-22 17:44:23
@ 5c8a5765:4fc5edee
2024-03-22 17:44:23"Мне-то что с того, что за мной следят? Мне же скрывать нечего". Но постойте, может быть вы...
Read in English
tl;dr: Отсутствие приватности угрожает сексуальным, расовым, национальным меньшинствам, женщинам, мужчинам, небинарным, атеистам, активист(к)ам, бедным, инвалидам, школьни(кам/цам), представителям социальных профессий, любым покупателям, человеку в целом и даже демократии.
...Чёрнокож(ий/ая)?
Компания Palentir, занимающаяся разработкой искусственного интеллекта, продает данные упреждающего наблюдения полиции Лос-Анджелеса, чтобы использовать дорожные камеры для целенаправленного расового профилирования (обыска исключительно чернокожих для превентивного расследования преступлений) [1]. Если вы участвовали в протестах BLM, ФСБ также грубо превышает свои полномочия ради слежки за вами [52].
...Мусульман(ин/ка)?
Salaat First, приложение, напоминающее мусульманам о времени молитвы, продает пользовательские данные ФБР и ICE, чтобы постоянно отслеживать местоположение пользователей [2]. При этом в Гуантанамо пытают заключенных мусульман без суда и следствия [3].
...Атеист/ка?
Евангелисты начали использовать цифровое наблюдение, чтобы выслеживать, где живут "ещё необращенные" в христианство [57].
...Не гетеросексуальны или не цисгендерны?
Grindr продает данные о местонахождении пользователей [4]: проданные данные использовались для увольнения священников-геев [5]. По данным New York Post, они "позволяли неизвестным третьим лицам узнавать конфиденциальную информацию о пользователях, в том числе о том, с кем они встречаются, где живут и работают, где проводят свободное время" [6].
Владельцы Grind поспешно выставили сервис на продажу, когда раскрылось, что он собирает ещё и медицинские данные пользователей и делятся ими с другими компаниями [7] (ваши мед. данные стоят в 10-40 раз дороже данных вашей кредитной карты [8]). Далеко не всем трансгендерным, небинарным или интерсекс-личностям хотелось бы ходить с табличкой "МОИ ГЕНЕТАЛИИ НЕ СООТВЕТСТВУЮТ ГЕНДЕРУ" на груди, но отсутствие приватности даёт вам именно это.
Раскрывая вашу идентичность кому попало, вы ставите свою свободу (если быть не-цисгетеро нелегально в вашей стране) и жизнь под угрозу.
...Человек с маткой?
Отслеживание мобильной геолокации используется группами против абортов. Цитата из Politico: "Одна рекламная фирма хвасталась в 2015 году, что может "пометить все смартфоны, входящие и выходящие из почти 700 клиник Planned Parenthood" [9]. При этом на 2022 г. 40% стран мира имели юридическую ответственность за проведение аборта без крайне специфических причин [10]. Не стоит также забывать, что противни(ки/цы) абортов очень воинственно настроены: существует немало насилия и даже терроризма против проводящих и совершающих аборты [11][12].
...Активист/ка?
Google передал индийской полиции данные 21-летней климатической активистки, которая набирала в Google Docs информацию о фермерских протестах (оказалась арестована) [13]. Protonmail передал данные экоактивиста* Французской полиции (оказался арестован) [14]. Facebook, Instagram и X (Twitter) предоставляют доступ к данным для слежки за активистами (в особенности не белыми) — некоторые из них не отказалась от сотрудничества даже после разоблачения [15]. Наши правительства также крайне заинтересованы в предотвращении протестов ещё до того, как они произойдут.
...Нонкомформист/ка?
Например, если вы консерватор/ка, вы можете оказаться под сапогом цензуры: компания Gotcha SEO провела исследование 50 противоречивых ("острых") поисковых запросов в Google и обнаружила, что только 5 % результатов относятся консервативным сайтам, по сравнению с 31,8 % левых и 63,8 % нейтральных [16][17]. По моему личному опыту (особенно ощутилось в ходе написания этой статьи), Google, Bing и прочие поисковики от крупных компаний (в сравнении с, например, Brave Search) также нехотя выдают результаты на тему того, как крупные компании продают ваши личные данные.
...Кита(янка/ец)?
В 2019 году YouTube был пойман на автоматическом удалении комментариев, содержавших что-либо про "50 Cent (Party)" (китайская "фабрика троллей" — команды людей, наполняющие комментарии соц. сетей прогосударственными мнениями за небольшую оплату) [18], или обвинения Китайской Коммунистической партии в бандитизме [19]. А ещё Tik Tok крадет данные ваших детей и продает их вашему (китайскому) правительству [20]. А ещё Google разрабатывает специальный зацензурированный поисковик специально для Китая [21].
...Человек с мужским гендером в документах?
Если в вашей стране есть воинский призыв, с подавляющим шансом он будет обязателен только для мужчин [22] (это — дискриминация). Чтобы отправить вас в армию или на войну, вас будут отслеживать по телефону, передвижению автомобилей [23], камерам с распознаваниям лиц [24] и проч. Уклонение — наказывается, вплоть до тюрьмы и нарушения прав человека [25][26].
...Анархист/ка?
Google Maps активно скрывают любые изображения протестов и даже плохих условий жизни [27]. Google Ads и Play Market убирают оппозиционный контент по запросам государства (например, российского) [28][29]. YouTube активно блокирует каналы и видео, освещающие критику правительств [30], протесты [31] или государственные пытки [32] — особенно в бедных странах. (См. также пункт "активист/ка?".)
...За Палестину?
Социальные сети активно блокируют про-палестинские точки зрения [33].
...Имеете особое состояние здоровья?
Аптеки передают ваши медицинские данныеп полиции без ордера на обыск [34]. Как уже было сказано, на чёрном рынке ваши мед. данные стоят в 10-40 раз дороже данных вашей кредитной карты [8].
...Когда-либо что-нибудь покупали?
Капитализм — это одна из главных опасностей при продаже ваших личных данных. Многие крупные компании используют информацию о вас, чтобы оценить ваш доход, продать вам товары, которые вам на самом деле не нужны [36][37][38], или манипулировать ценами [37].
- Например, интернет-магазины знают, что люди с низким доходом чаще совершают срочные покупки, поэтому они устанавливают для них более высокие цены и отменяют скидки [39][40].
- Некоторые финансовые и страховые компании используют социальные графики для определения процентных ставок и страховых взносов. Это часто заставляет людей с низким доходом платить больше — данный феномен известен как "бедность-премиум" [41].
- Компания Orbitz направляет пользовате(льниц/лей) Mac в более дорогие отели, поскольку они переплачивают за электронику Apple. [42].
- Компания Target выставляет клиент(к)ам более высокие цены, когда они физически находились рядом с магазином и вряд ли ищут альтернативу. [43]
- McDonalds наняла компанию Silverpush, занимающуюся слежкой, чтобы связать аудиоданные, полученные без согласия из ее мобильного приложения, со звуками, доносящимися с Youtube или телевидения, для показа "релевантной рекламы" на разных платформах. [44]
Примерам подлых продаж нет конца — и это только те, о которых стало известно общественности!
...Мама, папа, родитель?
Родительский клуб Bounty оштрафован на 400 000 фунтов стерлингов за продажу данных пользователей — компания незаконно передавала 34,4 млн записей 39 компаниям [45]. Популярное приложение для обеспечения безопасности семьи Life360 продает точные данные о местоположении десятков миллионов своих пользователей [46]. Доверили бы вы личные данные и местоположение своих детей незнаком(цам/кам)? Ведь по некоторым данным педофил(ки/ы) [47] и люди, похищающие детей, могут использовать эти данные для нахождения жертв.
...Представитель/ница социальной профессии?
Вы работаете политик/ом, депутат/кой, учител/ем, священни/цей, куратор/ом, доктор/кой, терапевт/ом или др., из-за чего у вас хранится множество уязвимых личных данных других людей, за которые вы в ответе? Вам стоит побеспокоиться об их сохранности — ведь эти данные выгодно продаются [48].
...В отношениях?
Возможно, вы бы хотели сохранить интимные детали отношений между вами? В самой гротескной из новостей на этот счёт сотрудник австралийской пограничной службы вернул телефон гражданину после принудительного досмотра в аэропорту со словами: "Приятно было снова посмотреть нормальное порно", ссылаясь на обнаженные фотографии его девушки [49].
...Путешественни(ца/к)?
Популярная сеть отелей AirBNB разрешает устанавливать камеры внутри своих помещений [56].
...Учитесь в школе?
Бдительно следите за соблюдением правил: школы используют техники слежения, чтобы ловить и жестоко наказывать вас за использование вейпа (электронных сигарет) [51].
...Водитель/ница?
Автомобили стали компьютерами на колесах: они "обладают непревзойденной способностью смотреть, слушать и собирать информацию о том, что вы делаете и куда идете" [55]. Эта информация затем передается или продается брокерам данных, правоохранительным органам и другим лицам. Из 25 изученных марок машин 56 % передают ваши данные правоохранительным органам в ответ на неофициальный запрос, 84 % передают или продают ваши личные данные [55].
Информацию также охотно закупают страховые компании [58], а для слежки за вами её могут использовать даже ваши партнер(ы/ки) [59].
...Используете технологии для уборки?
Роботы-пылесосы не только всасывают пыль, но и сканируют ваше жилище [53]. Как бы ни было сложно в это поверить, Amazon действительно использует эти данные, чтобы заставлять вас чаще покупать то, что вам не нужно [54].
...Житель/ница страны с демократической системой?
Не так давно произошёл случай, как Facebook поймали на манипуляциях крупнейшими выборами: компания использовала наши социальные графики, чтобы исказить наше представление о реальном мире и манипулировать нашими голосами [35].
...Граждан(ин/ка) государства?
В условиях государства безобидные разговоры могут подвергнуть вас опасности, даже если вам нечего скрывать. Одна из самых шокирующих историй — упомянутый выше опыт Мохамеду Ульд Салахи [3], описанный в его мемуарах и показанный в фильме "Мавританец". Он был помещен в лагерь Гуантанамо без суда и следствия и подвергался там пыткам в течение 15 лет за телефонный звонок своему родственнику в Афганистане — он подозревался в причастности к терактам 11 сентября, хотя предыдущие 10 лет он жил в Германии.
Обычных людей арестовывают и подвергают давлению за то, чем они делятся в Интернете, даже через свои "анонимные" аккаунты, даже в демократических странах, даже если это было легальным, даже если вы не мужчина [50].
«Дайте мне шесть строк, написанных самым честным человеком, и я найду в них что-нибудь, за что его казнят на виселице» — Кардинал де Ричелиеу
...Человек?
Зачем вы носите одежду? Почему вы бы скорее предпочли непрозрачный туалет прозрачному, или спальню без камер — наблюдаемой спальне? Почему вы можете не захотеть поделиться политическими взглядами, сексуальной ориентацией или гендерной идентичностью с бабушкой, учителем или полицейским, даже если вы считаете, что в них нет ничего плохого? Почему вы можете не захотеть поделиться галереей или паролями от своих социальных сетей с тётей, социальным работником или юзером Двача, даже если вы не делали ничего незаконного напрямую?
Что если я предложу вам отправить пароли от ваших социальных сетей, банковских счетов, ваши медицинские данные, адрес и фотографии на мою электронную почту — обещаю, что не воспользуюсь ими для чего-то плохого: я просто хочу хранить их у себя на жестком диске для безопасности ваших же данных? Вам действительно нечего скрывать?
Что если я скажу, что автоматизированная слежка достигла таких масштабов, что мегакорпорации могут предполагать, о чём вы думаете [60]? Вас это беспокоит? Если да — я не буду удивлен.
Приватность всегда была частью жизни человека, обычной её частью. То, как мы живем сейчас — это крайне неестественное для человека состояние; оно никогда не было нормальным. Вам не обязательно должно быть что скрывать, чтобы захотеть не делиться всеми подробностями личной жизни с окружающими.
Заключение
Чем дольше мы отказываемся от борьбы за права на приватность, тем больше Левиафан набирает силу. Вы думаете, мир Оруэлла из «1984» был построен в одночасье? Нет! Люди жертвовали правами на конфиденциальность, анонимность, свободу информации — шаг за шагом. И первый шаг к антиутопии — это маргинализация людей, которые беспокоятся о своей анонимности: сведение их до «носителей шапочек из фольги» и тех кто «правда считает, что ОНИ читают твои эмейлы».
Так что же нам делать? Не надо думать, что "с этим ничего не поделаешь", или что "мы уже проиграли". Вместо этого нам нужно:
- Распространять информацию о том, почему приватность важна, и почему о ней стоит побеспокоиться;
- Использовать приватные, свободные, децентрализованные аналоги популярным сервисам (например, Session вместо Telegram, NOSTR вместо Twitter, DuckDuckGo вместо Google);
- Поддерживать право на приватность ради остальных (например, пока только единицы используют приватные мессенджеры — государства знают, что использующие их что-то скрывают. Но если половина населения начнёт использовать их, нельзя будет вычленить никого особенного);
- Чаще спрашивать, почему компании знают о нас так много, и как это вообще легально;
- Участвовать в политике. Политика — это не "наблюдательный спорт": если демократия не работает, мы ответственны за то, чтобы заставить её работать. Самая верхушка такого участия — это поддержка организаций, борющихся за права на приватность
«Говорить, что вам не важна приватность, ибо вам нечего скрывать — это как говорить, что вам не важна свобода слова, ибо вам нечего сказать. Но даже если вы не пользуетесь каким-то правом в данный конкретный момент, другие могут нуждаться в нём. И говорить, что вам не важно право, ибо конкретно вам сейчас оно не нужно, это самая асоциальная вещь, которую вы только можете сделать» — Эдвард Сноуден
Источники:
[1] https://theintercept.com/2021/01/30/lapd-palantir-data-driven-policing/
[2] https://www.theguardian.com/us-news/2020/dec/03/aclu-seeks-release-records-data-us-collected-via-muslim-app-used-millions
[3] https://www.npr.org/2019/11/14/778944195/a-legacy-of-torture-is-preventing-trials-at-guant-namo
[4] https://www.vox.com/technology/2023/6/16/23762403/data-odni-report-wyden
[5] https://www.vox.com/recode/22587248/grindr-app-location-data-outed-priest-jeffrey-burrill-pillar-data-harvesting
[6] https://nypost.com/2022/05/02/grindr-sold-data-about-users-precise-locations-for-years-report/
[7] https://www.theguardian.com/technology/2018/apr/03/grindr-shared-information-about-users-hiv-status-with-third-parties
[8] https://www.cyberpolicy.com/cybersecurity-education/why-medical-records-are-10-times-more-valuable-than-credit-card-info
[9] https://www.politico.com/news/2024/02/13/planned-parenthood-location-track-abortion-ads-00141172
[10] "As of 2022, countries that legally allow abortion on request or for socioeconomic reasons comprise about 60% of the world's population", https://en.wikipedia.org/wiki/Abortion_law
[11] https://en.wikipedia.org/wiki/Anti-abortion_violence
[12] https://www.justice.gov/crt/recent-cases-violence-against-reproductive-health-care-providers
[13] https://www.indiatoday.in/technology/news/story/disha-ravi-arrest-puts-privacy-of-all-google-india-users-in-doubt-1769772-2021-02-16
[14] https://proton.me/blog/climate-activist-arrest
[15] https://www.aclunc.org/blog/facebook-instagram-and-twitter-provided-data-access-surveillance-product-marketed-target
[16] https://www.gotchseo.com/google-biased/
[17] Google вообще проводит немало цензуры в своих сервисах: https://en.wikipedia.org/wiki/Censorship_by_Google
[18] https://www.taiwannews.com.tw/en/news/3933777
[19] https://www.theverge.com/2020/5/26/21270290/youtube-deleting-comments-censorship-chinese-communist-party-ccp
[20] https://www.npr.org/2020/08/04/898836158/class-action-lawsuit-claims-tiktok-steals-kids-data-and-sends-it-to-china
[21] https://www.nytimes.com/2018/08/16/technology/google-employees-protest-search-censored-china.html
[22] https://ru.wikipedia.org/wiki/%D0%92%D0%BE%D0%B8%D0%BD%D1%81%D0%BA%D0%B0%D1%8F_%D0%BE%D0%B1%D1%8F%D0%B7%D0%B0%D0%BD%D0%BD%D0%BE%D1%81%D1%82%D1%8C
[23] https://focus.ua/voennye-novosti/626982-ot-doprosov-do-operativnyh-meropriyatij-v-nacpolicii-rasskazali-o-poiske-uklonistov
[24] https://www.bbc.com/russian/features-63346138
[25] https://www.rbc.ua/ukr/styler/k-zaraz-karayut-uhilyantiv-vid-mobilizatsiyi-1707820307.html
[26] https://www.mrarchivist.com/results/entry/4591/; Запрет на голосование по причине того, что мужчина не встал на военный учет, противоречит статье 21 Всеобщей Декларации Прав Человека.
[27] https://www.nbcnews.com/id/wbna17880969
[28] https://www.rferl.org/a/google-reportedly-removes-navalny-ad-after-russian-government-complains/29478844.html
[29] https://www.theguardian.com/world/2021/sep/17/apple-and-google-accused-of-political-censorship-over-alexei-navalny-app
[30] https://nordicmonitor.com/2023/09/google-youtube-accused-of-censoring-erdogan-critics/
[31] https://www.medianama.com/2024/02/223-youtube-blocks-videos-protests-job-aspirants-bihar/
[32] https://edition.cnn.com/2007/WORLD/meast/11/29/youtube.activist/
[33] https://www.aljazeera.com/features/2023/10/24/shadowbanning-are-social-media-giants-censoring-pro-palestine-voices
[34] https://thehill.com/business/4355894-pharmacies-sharing-medical-data-without-warrant/
[35] https://en.wikipedia.org/wiki/Facebook%E2%80%93Cambridge_Analytica_data_scandal
[36] https://usercentrics.com/knowledge-hub/data-is-the-new-gold-how-and-why-it-is-collected-and-sold/
[37] https://knowledge.wharton.upenn.edu/article/data-shared-sold-whats-done/
[38] https://www.eff.org/deeplinks/2020/11/visa-wants-buy-plaid-and-it-transaction-data-millions-people
[39] https://supreme.findlaw.com/legal-commentary/websites-that-charge-different-customers-different-prices.html
[40] https://policyreview.info/articles/analysis/does-everyone-have-price-understanding-peoples-attitude-towards-online-and-offline
[41] https://fairbydesign.com/povertypremium
[42] https://www.wsj.com/articles/SB10001424052702304458604577488822667325882
[43] https://www.bizjournals.com/twincities/news/2019/02/01/report-targets-app-charges-higher-prices-to.html
[44] https://www.digitaltrends.com/mobile/silverpush-app-tracking-spying-use-rises-new/
[45] https://www.theguardian.com/technology/2019/apr/12/parenting-club-bounty-fined-selling-users-data
[46] https://themarkup.org/privacy/2021/12/06/the-popular-family-safety-app-life360-is-selling-precise-location-data-on-its-tens-of-millions-of-user
[47] https://www.the-sun.com/news/3740183/paedophile-snachat-maps-victims-tesco/
[48] https://www.experian.com/blogs/ask-experian/heres-how-much-your-personal-information-is-selling-for-on-the-dark-web/
[49] https://micky.com.au/aussie-ex-pat-will-never-return-after-digital-strip-search-reveals-sex-tapes/
[50] https://www.dailymail.co.uk/news/article-11282263/Moment-police-swoop-house-devout-catholic-mother-malicious-online-posts.html
[51] https://apnews.com/article/vaping-surveillance-technology-schools-982128348c683b9d54c7a307c5b1fdc6
[52] https://www.politico.com/news/2023/05/19/fbi-surveillance-black-lives-matter-protesters-00097924
[53] https://www.welivesecurity.com/en/privacy/gathering-dust-and-data-how-robotic-vacuums-can-spy-on-you/
[54] https://www.reuters.com/markets/deals/amazons-irobot-deal-eu-antitrust-crosshairs-2023-07-06/
[55] https://foundation.mozilla.org/en/privacynotincluded/articles/its-official-cars-are-the-worst-product-category-we-have-ever-reviewed-for-privacy/
[56] https://ru.airbnb.com/help/article/3061
[57] https://newrepublic.com/article/179397/evangelical-app-targeting-immigrants-surveillance
[58] https://www.nytimes.com/2024/03/11/technology/carmakers-driver-tracking-insurance.html
[59] https://www.nytimes.com/2023/12/31/technology/car-trackers-gps-abuse.html
[60] https://www.zdnet.com/article/google-even-knows-what-youre-thinking/*Это не значит, что ProtonMail небезопасен: сервис регулярно выигрывает множество судов на тему раскрытия данных юзеро(в/к); это значит, что использования ProtonMail было недостаточно приватным (в конкретном случае — без VPN/SPN/TOR).
-
 @ 599f67f7:21fb3ea9
2024-03-22 07:00:58
@ 599f67f7:21fb3ea9
2024-03-22 07:00:58Una BoltCard es una tarjeta que contiene una LNURLw grabada. Puedes recargarla con sats y utilizarla como si fuera una tarjeta de crédito en comercios u otros usuarios que aceptan esta tecnología.

Esto es lo que pasa por detrás durante el proceso¿Qué necesito?
- Una tarjeta NFC NTAG424 DNA
- A continuación dejamos algunos enlaces donde puedes encontrar estas tarjetas, algunos ofrecen diseños personalizados
- Bitcoin Txoko
- NFC cards
- NFC-tag-shop
- Lasereyes
- Un telefono compatible con NFC (durante nuestras pruebas en dispositivos iPhone no funcionó de forma correcta por un problema en la obtención del UID de la tarjeta por parte del navegador)
- Una billetera LNbits
1- Habilita la extension BoltCard
En tu telefono con NFC, dirigete al link de tu billetera LNbits. Dentro de
Extensionesbusca y habilitaBolt Cards.2- Crea un nuevo registro de cartera
- Abre la extensión de
Bolt Cardsy presiona el botón+para crear una nueva tarjeta. - Selecciona la cartera a la que se conectará. Esta es la cartera desde la que se gastarán los fondos.
- Puede establecer límites para la transacción máxima y el límite diario como medida de protección contra los comerciantes maliciosos que agotan su tarjeta.
- Ponle nombre a tu tarjeta.
- Presiona el botón NFC y luego lleva tu tarjeta NFC a tu teléfono para importar el UID de tu tarjeta.
- Haz clic en crear tarjeta.

Al final debería ser algo parecido a esto pero con un registro UID de tu tarjeta.
3- Escribe el registro NFC en la tarjeta.
- Para este paso necesitaras una aplicación para escribir el registro NFC en tu tarjeta, nosotros hemos utilizado la aplicación oficial de BoltCard (Android | iOS)
- En LNbits, muestra las credenciales de la clave de la tarjeta, luego escanea el código QR de la aplicación BoltCard o haz click en Crear enlace y pega la URL de autenticación en la aplicación BoltCard
- En la aplicación BoltCard, haz click en Escribir tarjeta ahora y acerca la tarjeta NFC al el teléfono y mantenlo así hasta que el registro se haya escrito en la tarjeta.
¡Eso es todo! Si todo salió bien, deberías tener una BoltCard en funcionamiento. Puedes probarla tocando contra tu teléfono y abriendo el enlace LNURLw.
⚠ Llevar tu BoltCard contigo significa que llevas dinero real contigo. Si alguien accede a tu tarjeta puede retirar todos los sats de tu cartera. Toma precauciones y mantén solo una pequeña cantidad de sats en tu billetera BoltCard para el gastos del día a día. Comprueba siempre que el comerciante está solicitando el precio correcto. Si es posible, mantén tu tarjeta en una funda protegida por RFID.
Próximos pasos
BoltCard habilitada para PoS
Algunas carteras y sistemas de punto de venta (PoS) son compatibles con la BoltCard. Aquí dejamos una lista de ellos: - BoltCard PoS - Breez - BTCpayserver - LNbits TPOS - Sí, puedes convertir tu cartera LNbits en un punto de venta (PoS) habilitando la extensión TPOS - VoltPay - lipa - Blink - Wallet of Satoshi - Blixt Wallet
Apoyar a BoltCard
También puedes apoyar el esfuerzo de haber creado una biblioteca de código abierto para programar las tarjetas, puedes hacerlo en Geyser Fund.
Tarjetas regalo NFC
En esta guía hemos tratado cómo crear una tarjeta de débito Lightning, pero ¿que ocurre si quieres hacer un regalo en sats y que pueda hacer un retiro a su billetera cuando quiera? Bueno, eso también es posible mediante tarjetas NFC y LNURLw. Explicaremos este proceso en una futura guía.
¡No solo tarjetas!
También puedes escribir registros NFC en cualquier etiqueta NFC que lo admita. Un ejemplo de esto es el Bolt Ring, que ofrece un anillo con capacidad NFC.
-
 @ c4428155:a36de510
2024-03-25 10:00:00
@ c4428155:a36de510
2024-03-25 10:00:00What ProPublica Is Doing About Diversity in 2024
by Vianna Davila (https://www.propublica.org/people/vianna-davila), Melissa Sanchez (https://www.propublica.org/people/melissa-sanchez), Liz Sharp (https://www.propublica.org/people/liz-sharp) and Myron Avant (https://www.propublica.org/people/myron-avant)
ProPublica is a nonprofit newsroom that investigates abuses of power. Sign up to receive our biggest stories (https://www.propublica.org/newsletters/the-big-story?source=54G&placement=top-note®ion=national) as soon as they’re published.
ProPublica is committed to increasing the diversity of our workplace as well as the journalism community more broadly, and each year we publish a report on those efforts. This is the report for 2024; here are all our past reports (https://www.propublica.org/diversity).
Our Commitment
We believe that it is imperative to staff our newsroom and business operations with people from a broad range of backgrounds, ages and perspectives. We are committed to recruiting and retaining people from communities that have long been underrepresented, in journalism broadly and in investigative journalism especially. That includes African Americans, Latinos, other people of color, women, LGBTQ people and people with disabilities.
ProPublica has continued to expand, growing from 172 full-time employees at the start of 2023 to 186 in 2024, due in part to the creation of our Northwest team and additions to our development, audience and visual teams.
Our diversity efforts last year were wide-ranging, with the launch of an investigative editor training program that is open to journalists across the U.S., a large presence at journalism affinity conferences and a webinar for former conference stipend recipients and other early career journalists who have participated in previous ProPublica programs.
We also continued to formalize some of our formerly staff-run, volunteer diversity efforts, built partnerships with outside journalism organizations and looked for ways to improve the internal culture and processes for all ProPublicans.
Our Diversity Committee comprises more than 50 ProPublicans who volunteer their time to work on initiatives that are pitched and run by the staff. The current co-chairs are Vianna Davila, Melissa Sanchez and Liz Sharp.
Breakdown of Our Staff
As with last year, we tracked candidates through the application and interview process. Out of 21 positions filled in 2023, 50% of the candidates we interviewed identified as women and 36% identified as being part of a racial/ethnic group other than solely non-Hispanic white. About 67% of the people we hired identified as women.
However, 29% of those people we hired in 2023 identified as being part of a racial/ethnic group other than solely non-Hispanic white — a lower percentage than ProPublica had hired in previous years.
"Recruiting and retaining a diverse staff is one of ProPublica's core principles,” said ProPublica editor-in-chief Stephen Engelberg, responding to the hiring numbers. “We are proud of the progress we've made, but we agree that there's more to be done.”
This year, Engelberg said, ProPublica added a full-time talent acquisition manager “to make sure our job searches reach the broadest possible group of applicants."
At the start of 2024, the percentage of all ProPublica staff members who identified as solely non-Hispanic white was 62% — slightly higher than in previous years. This percentage was the same for editorial positions.
For the sixth year in a row, more women than men work at ProPublica. About 2% of our staff identify as nonbinary or transgender. In editorial positions, women represented 51% of the staff.
Since 2022, we have collected demographic information about our board of directors. Half of the 14 people on the board identified as women, the same as last year. About 64% of the directors identified as non-Hispanic white, compared to 71% last year.
As we’ve said since 2015, part of our commitment to diversity means being transparent about our own numbers. Here’s how our staff breaks down.
(Please note that the data is based on employees’ self-reported information. Recognizing that some people may identify as more than one race but not identify as a person of color, in 2022 we began stating numbers in terms of people who “solely identify as non-Hispanic white.” We hope this will provide more specificity and accuracy. The employee information is as of Jan. 1 of each year. Managers are defined as staff members who supervise other people, and that group does not include all editors. Percentages may not add up to 100 because of rounding. Fellows, time-limited employees and part-time employees are not included in this analysis.)
Race and Ethnicity: All of ProPublica
Note: Fellows, time-limited employees and part-time employees are not included in this analysis.
Race and Ethnicity: Editorial
Note: Fellows, time-limited employees and part-time employees are not included in this analysis.
Race and Ethnicity: Managers
Note: Fellows, time-limited employees and part-time employees are not included in this analysis.
Gender: All of ProPublica
Note: Fellows, time-limited employees and part-time employees are not included in this analysis.
Gender: Editorial
Note: Fellows, time-limited employees and part-time employees are not included in this analysis.
Gender: Managers
Note: Fellows, time-limited employees and part-time employees are not included in this analysis.
New Initiatives
Investigative editor training: ProPublica started an Investigative Editor Training Program (https://www.propublica.org/article/propublica-investigative-editor-training-program-2024) in 2023 for journalists who want to learn how to manage, edit and elevate investigative projects that expose harm and create impact. The curriculum for the yearlong program was designed by ProPublica chief of correspondents Ginger Thompson and deputy managing editor Alexandra Zayas to increase diversity in the next generation of investigative editors. We did a test-run for the program for nine ProPublica staffers. Then we refined the training and invited journalists from other organizations to apply. More than 150 reporters and editors from news organizations across the country applied. We selected 11 people to attend a weeklong training at our New York office, where they heard from ProPublica editors on different aspects of the craft, from story selection and memos to managing the reporting and digging into the first draft. After that, participants were paired with ProPublica senior staff as mentors and received additional virtual training for the remainder of the year. We are offering this training again this year for external participants.
Alumni virtual meetup: After a hiatus in 2022, ProPublica staff hosted a career-building webinar for “alumni” of our various external programs, including Emerging Reporters, the Data Institute and our conference stipends. Irena Hwang, Maya Miller and Ellis Simani volunteered their time to organize this event and surveyed alumni about what kinds of skills they wanted to build. The virtual event, held in September, included a panel on “building your investigative career” featuring Ginger Thompson, Zahira Torres, Lulu Ramadan and Kavitha Surana . That was followed by breakout rooms on workshopping a pitch, managing up, specialty reporting and becoming an editor. More than 50 early-to-mid-career journalists attended the event, and more than a half-dozen ProPublicans lent their expertise as breakout-room moderators. Our goal is to continue to build on the success of this program in 2024 and provide another opportunity for community members to come together.
Our Ongoing Efforts
ProPublica thinks about its efforts in the following ways: building the pipeline (for us and for all of investigative journalism); recruiting talent and improving our hiring process; and inclusion and retention.
Building the Pipeline
Conference stipends: ProPublica previously offered stipends to help student journalists attend conferences. Last year we changed this program to instead partner with Investigative Reporters & Editors (IRE) and sponsor five journalists to attend the annual IRE convention. IRE’s diversity scholarship supports journalists, students and educators from diverse backgrounds, including people of color, those who identify as part of the LGBTQ+ community and/or people with disabilities. We also sponsored a Journalists of Color mixer at the conference, which was attended by more than 50 people.
Emerging Reporters Program: The program provides financial assistance and mentorship to five students for whom investigative journalism might otherwise be inaccessible so they can pursue early career opportunities in the field. The program includes a $9,000 stipend, virtual programming and an all-expenses paid trip to an IRE conference on computer assisted reporting. This is the program’s ninth year, and it is coordinated by Talia Buford. Check out our most recent class (https://www.propublica.org/article/propublica-emerging-reporters-2023) and find out more about the program.
Data Institute: In 2016, ProPublica journalists founded The Data Institute, a workshop for journalists on how to use data, design and code (https://projects.propublica.org/graphics/ida-propublica-data-institute). ProPublica eventually started working with Open News, which coordinates student and instructor participation and provides support for project management and event planning. The Ida B. Wells Society for Investigative Reporting and the Center for Journalism & Democracy now organize this in-person event. Last year a half-dozen current and former ProPublicans served as trainers at the institute, which is focused on empowering people with data skills they can bring back to their own newsrooms. ProPublica staffers will continue to serve as trainers at the institute this year.
Recruiting and Hiring
Affinity conferences: Last summer, ProPublica newsroom staff and senior leadership partnered with The Marshall Project and The Trace at the country’s three largest affinity journalism conferences. At the Asian American Journalists Association conference, the three organizations hosted a panel about paths into nonprofit news that also included participation from a staffer at the Center for Public Integrity. The panel was followed by a beverage lounge, where anyone could drop by for refreshments. The organizations hosted a reception at the National Association of Black Journalists conference, put on through the convention’s Investigative Task Force, that included journalists from The Texas Tribune and The Intercept. ProPublica staff also participated in three conference sessions focused on investigative reporting. At the National Association of Hispanic Journalists conference, the three journalism organizations hosted a booth along with The Texas Tribune, The Intercept and CPI. This work was led by ProPublica staffers Maya Miller, Irena Hwang and Ellis Simani. Going forward, ProPublica’s talent department will assume responsibility for this work.
Salary equity and transparency: ProPublica management regularly analyzes salaries in job categories where there are at least four employees and, when necessary, adjusts those salaries to ensure equity by race and gender in each job and location group, while taking into account years of experience. This analysis started in 2021. We do this because we want to try to eliminate the effects of any unconscious bias in setting salaries. In addition, since the fall of 2022, ProPublica has published salary ranges for all posted job openings, regardless of geography.
Rooney Rule: We require that hiring managers interview at least one person who does not self-identify as solely non-Hispanic white. In addition, every application must be read by at least two people.
Freelancer guide: In 2022, ProPublica published a guide for freelancers interested in pitching an investigation to ProPublica (https://boards.greenhouse.io/propublica/jobs/4053828006?gh_src=2b92d9bf6us). We designed the guide to formalize the pitch process and level the playing field for how freelance projects are presented and considered. Submissions will be reviewed by editors on a rotating basis. ProPublica will respond to anyone who completes the form, even if their proposal is not accepted.
LRN candidate outreach: Editors with ProPublica’s Local Reporting Network (https://www.propublica.org/about/local-reporting-network) continued to do personalized recruiting and offered office hours so local journalists could discuss their accountability work with a member of the team. LRN editors were also present at affinity journalism conferences, where they met with interested applicants in an effort to help them with the project-development and application process.
Inclusion and Retention
Welcoming new hires and focusing on internal culture: Our inclusion subcommittee includes about 30 ProPublicans who meet monthly to consider ways to make the newsroom more inclusive and equitable. Duaa Eldeib chairs this subcommittee. Some of the issues the group has been tackling include ways to improve ProPublica’s fact-checking process and build community, particularly for employees who work remotely. The subcommittee launched an internal story club that meets regularly to discuss particularly enjoyable stories, podcasts or books.
Sensitivity subcommittee: Led by Colleen Barry and Andrea Wise, this group serves as a resource for editors and reporters to tap the collective brain trust of our newsroom when working on particularly sensitive stories about suicide, sexual abuse, child abuse, racial trauma and more. The committee maintains a Slack channel where anyone can share resources and where editors and reporters can solicit feedback on drafts or ask questions on how best to report on sensitive subjects. When a “sensitivity read” or the discussions during the editing and production of a story are particularly instructive, the subcommittee has shared those experiences at diversity committee meetings so any lessons can be more broadly applied.
ProPublica Peer Partnership Program: This is an internal program organized by Jodi Cohen and Lisa Song that matches ProPublicans with a mentor or peer partner to meet each other, develop new skills and have someone to turn to for help navigating workplace or career questions. Last year more than 50 ProPublicans participated in this program, which was started in 2018.
Unconscious bias training: Since 2021, ProPublica has contracted with Paradigm Reach to provide ongoing diversity, equity and inclusion training for staff. The training is required of all new managers.
Diversity Committee office hours: We have continued to offer a casual virtual hangout twice a month where ProPublicans can chat with the Diversity Committee co-chairs to brainstorm about diversity, equity and inclusion initiatives, ask questions about ProPublica’s ongoing DEI programs or chat about diversity-related concerns in a more intimate setting outside of the monthly committee meetings.
Interested in Working Here?
Here is our jobs page (https://www.propublica.org/jobs), where we post new positions, including fellowships, full-time and temporary roles.
https://www.propublica.org/article/newsroom-diversity-propublica-2024
-
 @ c69b71dc:426ba763
2024-03-25 09:06:18
@ c69b71dc:426ba763
2024-03-25 09:06:18Easter is just around the corner...
...and as we prepare for it, the true meaning often gets lost amid eggs and chocolate bunnies. 🐣
So, let's focus on food and animals!
Because where there's celebration, there's also feasting! Families and friends gather for Easter brunch, where the traditional Easter egg symbolizes not only fertility but also the cycle of life and rebirth.
**Eating eggs contributes to animal suffering. ** Unfortunately, modern egg production is often associated with animal cruelty. Laying hens have been bred to lay up to 300 eggs per year, far exceeding their natural capacity of 12-30 eggs. They endure conditions far from their natural habitat, suffering from broken bones, feather loss, and immense stress. In cage, floor, and free-range systems, 9-18 chickens are crammed into one square meter. In organic farming, there are 6 chickens per square meter, and in outdoor runs, 4m². Chickens love to bathe, a behavior denied to them in the egg industry. A free-range chicken could live up to 8 years, while most laying hens are slaughtered after just 18 months.
All male chicks are sorted and either shredded or gassed alive! This is simply terrible.
Chickens are intelligent, sensitive, and emotional beings, just like dogs and cats. They enjoy being petted, recognize their human family, and even respond to their names when given.Egg substitutes:
Fortunately, there are numerous ways to celebrate Easter without eggs, without sacrificing taste.
Eggs can easily be replaced with various alternatives.
binding and moisture in baked goods:
- Soak 20g of ground flaxseeds or chia seeds in 50ml of water.
- Use 60g of applesauce.
- Mix 1-2 tablespoons of chickpea or soy flour with 2 tablespoons of water.
- Crush 1 ripe banana.
- Use silken tofu or cashew butter.
- Add soy or coconut yogurt.
- Use cornstarch as an alternative.
- Baking soda for lightness in pancakes, muffins, cakes, etc.
There are also egg replacement mixes available in stores. Often, the egg can simply be omitted from the recipe.
Another tip: To mimic the taste of eggs, season savory dishes with black salt, also known as Kala Namak.
I'll share delicious recipes with you below! This way, you can enjoy a delicious vegan Easter brunch without compromise. By reflecting on the original symbolism of the Easter festival and making conscious choices, we can not only reduce animal suffering but also rediscover the true meaning of easter: the pursuit of personal growth, inner renewal, and rebirth (See my other article part 1: https://w3.do/8h2dsiqd)
Thank you for allowing me to inspire you! I look forward to working together to make the world a more peaceful place. 🙏🏽 Happy Easter!
Recipe 1 Chia Pudding with Topping

Mash bananas and mix with oat milk and chia seeds. Let it sit for 20 minutes, stirring occasionally until it reaches a pudding-like consistency. Fill into bowls and top/decorate with fruits, nuts, seeds, cocoa nibs, coconut flakes, etc. as desired. To give the chia pudding a nice color, I mixed in blueberry powder.
Recipe 2 Vegan-Glutenfree-Oat-Bread

Mix 250g oat flour, 150g brown rice flour, 100g buckwheat flour, yeast (dry or fresh), 1-2 teaspoons of sea salt, and 2 teaspoons of guar gum. Combine everything with 500ml of water and let it rise in a greased baking pan (e.g., 25x10cm) for 20 minutes. Smooth the top with water and then with a little oil. Bake in a preheated oven at 200°C for approximately 60 minutes. Remove from the pan and let it cool on a rack.
Recipe 3 Vegan Egg Salad

Mix 3 tablespoons of almond butter, juice of 1/2 lemon, vinegar, mustard, salt, a pinch of turmeric powder, a little oat milk, garlic powder, and Kala Namak for an eggy flavor. Stir everything well. Be careful not to oversalt, as the capers are salty. Add diced pickles and capers. Incorporate onion sprouts or chives. Drain 300g of tofu well and cut into small cubes. Add the tofu to the dressing, rubbing some tofu pieces with your fingers. It's best to cover and let it marinate in the refrigerator for a few hours or overnight.
-
 @ 42342239:1d80db24
2024-03-21 09:49:01
@ 42342239:1d80db24
2024-03-21 09:49:01It has become increasingly evident that our financial system has started undermine our constitutionally guaranteed freedoms and rights. Payment giants like PayPal, Mastercard, and Visa sometimes block the ability to donate money. Individuals, companies, and associations lose bank accounts — or struggle to open new ones. In bank offices, people nowadays risk undergoing something resembling being cross-examined. The regulations are becoming so cumbersome that their mere presence risks tarnishing the banks' reputation.
The rules are so complex that even within the same bank, different compliance officers can provide different answers to the same question! There are even departments where some of the compliance officers are reluctant to provide written responses and prefer to answer questions over an unrecorded phone call. Last year's corporate lawyer in Sweden recently complained about troublesome bureaucracy, and that's from a the perspective of a very large corporation. We may not even fathom how smaller businesses — the keys to a nation's prosperity — experience it.
Where do all these rules come?
Where do all these rules come from, and how well do they work? Today's regulations on money laundering (AML) and customer due diligence (KYC - know your customer) primarily originate from a G7 meeting in the summer of 1989. (The G7 comprises the seven advanced economies: the USA, Canada, the UK, Germany, France, Italy, and Japan, along with the EU.) During that meeting, the intergovernmental organization FATF (Financial Action Task Force) was established with the aim of combating organized crime, especially drug trafficking. Since then, its mandate has expanded to include fighting money laundering, terrorist financing, and the financing of the proliferation of weapons of mass destruction(!). One might envisage the rules soon being aimed against proliferation of GPUs (Graphics Processing Units used for AI/ML). FATF, dominated by the USA, provides frameworks and recommendations for countries to follow. Despite its influence, the organization often goes unnoticed. Had you heard of it?
FATF offered countries "a deal they couldn't refuse"
On the advice of the USA and G7 countries, the organization decided to begin grading countries in "blacklists" and "grey lists" in 2000, naming countries that did not comply with its recommendations. The purpose was to apply "pressure" to these countries if they wanted to "retain their position in the global economy." The countries were offered a deal they couldn't refuse, and the number of member countries rapidly increased. Threatening with financial sanctions in this manner has even been referred to as "extraterritorial bullying." Some at the time even argued that the process violated international law.
If your local Financial Supervisory Authority (FSA) were to fail in enforcing compliance with FATF's many checklists among financial institutions, the risk of your country and its banks being barred from the US-dominated financial markets would loom large. This could have disastrous consequences.
A cost-benefit analysis of AML and KYC regulations
Economists use cost-benefit analysis to determine whether an action or a policy is successful. Let's see what such an analysis reveals.
What are the benefits (or revenues) after almost 35 years of more and more rules and regulations? The United Nations Office on Drugs and Crime estimated that only 0.2% of criminal proceeds are confiscated. Other estimates suggest a success rate from such anti-money laundering rules of 0.07% — a rounding error for organized crime. Europol expects to recover 1.2 billion euros annually, equivalent to about 1% of the revenue generated in the European drug market (110 billion euros). However, the percentage may be considerably lower, as the size of the drug market is likely underestimated. Moreover, there are many more "criminal industries" than just the drug trade; human trafficking is one example - there are many more. In other words, criminal organizations retain at least 99%, perhaps even 99.93%, of their profits, despite all cumbersome rules regarding money laundering and customer due diligence.
What constitutes the total cost of this bureaurcratic activity, costs that eventually burden taxpayers and households via higher fees? Within Europe, private financial firms are estimated to spend approximately 144 billion euros on compliance. According to some estimates, the global cost is twice as high, perhaps even eight times as much.
For Europe, the cost may thus be about 120 times (144/1.2) higher than the revenues from these measures. These "compliance costs" bizarrely exceed the total profits from the drug market, as one researcher put it. Even though the calculations are uncertain, it is challenging — perhaps impossible — to legitimize these regulations from a cost-benefit perspective.
But it doesn't end there, unfortunately. The cost of maintaining this compliance circus, with around 80 international organizations, thousands of authorities, far more employees, and all this across hundreds of countries, remains a mystery. But it's unlikely to be cheap.
The purpose of a system is what it does
In Economic Possibilities for our Grandchildren (1930), John Maynard Keynes foresaw that thanks to technological development, we could have had a 15-hour workweek by now. This has clearly not happened. Perhaps jobs have been created that are entirely meaningless? Anthropologist David Graeber argued precisely this in Bullshit Jobs in 2018. In that case, a significant number of people spend their entire working lives performing tasks they suspect deep down don't need to be done.
"The purpose of a system is what it does" is a heuristic coined by Stafford Beer. He observed there is "no point in claiming that the purpose of a system is to do what it constantly fails to do. What the current regulatory regime fails to do is combat criminal organizations. Nor does it seem to prevent banks from laundering money as never before, or from providing banking services to sex-offending traffickers
What the current regulatory regime does do, is: i) create armies of meaningless jobs, ii) thereby undermining mental health as well as economic prosperity, while iii) undermining our freedom and rights.
What does this say about the purpose of the system?
-
 @ 3bf0c63f:aefa459d
2024-03-21 05:53:56
@ 3bf0c63f:aefa459d
2024-03-21 05:53:56Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 3d842afe:2d44a42d
2024-03-20 19:06:17
@ 3d842afe:2d44a42d
2024-03-20 19:06:17Websocket connection overhead is an obvious problem with the gossip model that few are willing to acknowledge. The more decentralized relay selection becomes (the goal) the worse it scales. Even at the current scale of nostr if users chose more diverse relay sets the issue would be crippling.
Below are some very simple simulations to illustrate my point. I used 2 randomly selected relays per person to be extremely conservative and chose 3 different realistic follow counts. The NIP-65 spec suggests clients should guide users to keep the lists small (2-4 relays) though currently the average kind 10002 contains many more. I ran each simulation 10 times and then took the average result.
Available relays: 600 (~what nostr.watch currently shows for online relays) Follows: 200 Relays per person: 2 (randomly selected) Unique Connections Required: 291
Available Relays: 600 Follows: 500 Relays per person: 2 Unique Connections Required: 486
Available Relays: 600 Follows: 1000 Relays per person: 2 Unique Connections Required: 577
Even today if users randomly selected relays the total number of connections required would be staggering and this is with users only selecting 2 relays each. What happens if the available number of relays increases by 5x?
Available Relays: 3000 Follows: 200 Relays per person: 2 Unique Connections Required: 376
Available Relays: 3000 Follows: 500 Relays per person: 2 Unique Connections Required: 847
Available Relays: 3000 Follows: 1000 Relays per person: 2 Unique Connections Required: 1461
I’m not a client developer and I certainly don’t have all the solutions but I’ve spent enough time operating websockets at scale to know that these numbers aren’t going to work even with only 2 relays per person. Aside from the practical performance implications, browsers also enforce websocket limits that put most of these numbers out of reach (I believe Chrome is 255 and Firefox is 200). What am I missing?
-
 @ 45057918:92db0561
2024-03-25 08:52:02
@ 45057918:92db0561
2024-03-25 08:52:02Chef's notes
**Panang Curry Recipe
Ingredients: - 8 dried red chilies - 1 tablespoon of coriander root - 1 teaspoon of galangal - 2 tablespoons of lemongrass - 1 teaspoon of kaffir lime leaves - 1 teaspoon of lime zest - 1 teaspoon of cumin - 1 teaspoon of coriander seeds - 3 shallots - 5 garlic cloves - 1/2 teaspoon of salt - 1/2 teaspoon of roasted shrimp paste - 1 tablespoon of roasted peanuts - 2 tablespoons of vegetable oil
Instructions: 1. Pound the dried chilies, coriander root, galangal, lemongrass, kaffir lime leaves, lime zest, cumin, coriander seeds, shallots, garlic, salt, and roasted shrimp paste until fine. 2. Heat 2 tablespoons of vegetable oil in a pan. 3. Add the pounded curry paste and stir-fry until fragrant. 4. Add the roasted peanuts and stir-fry until fragrant. 5. Turn off the heat and let it cool. 6. Store in an airtight container.
*Tips for Panang Curry Recipe - Adjust the amount of chili peppers to your taste. - You can toast the curry paste before pounding it for a more fragrant flavor. - You can add other spices, such as star anise and cinnamon.
*Tips for Panang Curry with Beef Recipe - For a richer flavor, choose beef with marbling. - You can add other vegetables, such as eggplant or green beans. - Adjust the amount of chili peppers to your taste.
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 2
Ingredients
- 500 grams of beef (chuck or sirloin)
- 1 carton (400 ml) of coconut milk
- 2 tablespoons of Panang curry paste
- 2 tablespoons of fish sauce
- 1 tablespoon of palm sugar
- 5 kaffir lime leaves
- 5 betel leaves
- 1 cup of basil leaves
- 2 red chili peppers
- 2 tablespoons of vegetable oil
- 1/2 teaspoon of salt
Directions
- Cut the beef into bite-sized pieces and rinse with water. Drain and set aside.
- Coarsely chop the red chili peppers.
- Wash the kaffir lime leaves, betel leaves, and basil leaves. Set aside.
- Heat 2 tablespoons of vegetable oil in a pan.
- Add the Panang curry paste and stir-fry until fragrant.
- Add the beef and stir-fry until cooked.
- Pour in the coconut milk and bring to a boil.
- Season with fish sauce, palm sugar, and salt.
- Add the kaffir lime leaves, betel leaves, and red chili peppers.
- Simmer until the curry thickens.
- Add the basil leaves and stir briefly.
- Turn off the heat and serve with jasmine rice.
-
 @ c69b71dc:426ba763
2024-03-25 08:36:34
@ c69b71dc:426ba763
2024-03-25 08:36:34Easter - A Journey to the Origins
In our modern society, Easter seems to be inseparably linked to the consumption of eggs and lambs. But upon closer examination, the question arises:
Has it always been this way?
Indeed, Easter was originally a celebration of inner growth and fertility, long before the Christian era.
Today, I share with you a condensed excerpt of the story of "Inanna's Descent to the Underworld".
(There are numerous textual representations from different epochs, including the title "Descent to the Underworld.)
Inanna's Descent to the Underworld
The goddess of heaven and earth (also the goddess of fertility), Inanna embarks on a journey into the underworld to conquer it. Along the way, she must overcome 7 walls (or 7 gates) and gradually relinquish seven things she holds dear during her descent: her clothes, her jewelry, her hair, her pride, her desires, her crown, and her power. Until she stands naked and powerless at the throne of the underworld before her twin sister Ereshkigal. However, Inanna knew no humility and attempted to overthrow Ereshkigal from the throne. She failed and was punished by being bound to a stake (to a cross) Only when she is revived and saved by the water of life can she ascend to the upper world.
Symbolism and Reflection
This story is a parable for the fact that we cannot feel complete until we have looked into the depths of our soul and integrated our shadows! The underworld symbolizes the world of shadows. Inanna's sister Ereshkigal symbolizes our deepest shadows: all our fears, our pain, our sorrow. These shadows cannot simply be pushed away. We must let go of our desires, our wishes, and our ego, and face our shadows 'naked,' without masks and in humility.
Where Inanna dies, only our old, false self dies. The tears, hence the "water of life," symbolize surrender and thus healing. Inanna returns to life and to the upper world, and is thus quasi-reborn.Inanna is also the goddess of fertility, which is why Easter is also celebrated as the festival of fertility with the symbolism of eggs.Many thousands of years later, the Christian story of Jesus was spread. Thus, the story of Inanna can be compared to that of Jesus, with his journey to the cross, crucifixion, and resurrection.Unfortunately, there is not much left of femininity in this part of the Bible...Coincidence? I guess not...
-
 @ 83d999a1:46171d19
2024-03-20 15:52:48
@ 83d999a1:46171d19
2024-03-20 15:52:48Oh my, what a ride. Where do I even begin? A wise man once said that the best place to begin is at the beginning. So I'll try to do just that.
SEC-01: The Beginning
I don't even know how it all started anymore, but I know for a fact that it was Martijn's idea. And the idea was this: let's do something like a Bitcoin Academy on Madeira!
"Neat," I thought. "Let's do it," André said. "Let's fuck shit up and do a nostr thing instead," Pablo remarked. "But it must have a pirate theme," was my only objection. "Deal."
"Deal."
SEC-01: What's the Big Deal?
I don't think we did anything special. What we're trying to do, and what I think we managed to do, is to get the right people together at the right time. We knew from the get-go that we didn't know what we were doing. And we decided that that's okay.
We decided that that's okay because any explorative adventure is by definition unknown. And that's what the Sovereign Engineering Cohort was and still is: an explorative adventure.
So I guess the big deal was that we were knowingly venturing into the unknown. And 21 people signed up for it. Willingly.
That's a big deal.
SEC-01: The Crew
Every pirate ship needs a crew. We started as four: Martijn, André, Pablo, and myself. We invited three more: Paul, Ben, and Tony—our North Star team for SEC-01. And then we invited 21 more to board the ship.
Our 21 participants were people with vastly different backgrounds, from vastly different countries, having vastly different ideas about how Bitcoin, Lightning, and nostr could transform the internet, and the world at large. One thing that everyone had in common was a deep-seated dissatisfaction with the status quo. Everyone knew and still knows that large parts of the internet are broken. And everyone felt that there's something we can do about it to fix it.
We talked a lot about what it means to build it right. Or at least what it means to build it wrong.
One goal we had in mind was to learn from each other so that we may not repeat all the mistakes that we made in the past. And I think it started working immediately.
SEC-01: The First Week
We started the program with a brief introduction about what we had in mind for the eight weeks, as well as an introduction of the crew, the participants, and what everyone was working on.
One thing that we try to focus on is what I will call the loop. The loop is what I consider the Cornerstone of the Sovereign Engineering Cohort, as it neatly summarizes the main idea of the program.
The idea is simple: you talk about what you're going to build, you build it, and you show it to everyone. Rinse and repeat. Every week. For two months.
SEC-01: Distributed Cognition
I am convinced that the problems that we are facing cannot be solved by traditional means. More importantly, they cannot be solved by a lone wolf. "Given enough eyeballs, all bugs are shallow."
So the question becomes: how do we get enough eyeballs looking at the right thing? And more than that: how do we get them to look at problems from the right angle, inhabiting the right perspective?
SEC-01: Walking the Walk
Looking at things it's necessary but not sufficient. If you want to solve deep problems you have to think about them deeply. So again, the question becomes: how do we create an environment that facilitates and allows for deep conversations?
I think the Ancients were onto something when they came together at the gymnasium to discuss deep problems, have deep conversations, and—pardon the pun—hash things out. It strikes me as odd that all the paintings of these times show people not only talking but walking.

A lot of people who figured out solutions to hard problems in the past enjoyed an occasional stroll through the park. Not alone, but with company. There's something about walking and talking that really gets the brain juices flowing. From Aristotle to Einstein, the greats all intuitively figured out that walking facilitates proper talking, and proper talking facilitates proper thinking. Someone from the cohort remarked, "Left foot right foot; left brain right brain." I believe it.
So that's what we did. Not only did we talk the talk, but we also walked the walk. Once a week. Granted, not all of our walks were perfect or magical, but many of them were. And a lot of stuff got figured out. And once you've got stuff figured out, it's almost trivial to build it. Figuring it out is the hard part.
SEC-01: What Came out of It
Some of you might have been fortunate enough to experience the final Demo Day of SEC-01, held on the last day of Bitcoin Atlantis. It took us three hours to show what came out of it, failing demos and all. There's so much stuff that I had to put the list in a separate post, aptly titled:
Vibes were high, the room was packed, and while most of the presentations kinda sucked, everyone tried their best to paint a picture of what they have been working on or what problems they cared about most.
And that's what we cared about most: Getting the people together that care, and providing an environment where they are encouraged to collaborate and discuss freely.
We strongly believe that the pie is big enough for us all. Now it's not the time to think about competition. Now is the time to focus on collaboration. We believe that Bitcoin is a move from zero-sum to positive-sum thinking. We believe that we should aim at win-win-win: good for you, good for me, good for us and the environment we’re embedded in.
SEC-02: What's Ahead
The space that has opened up by Bitcoin, nostr, and other freedom tech is vast. We have barely scratched the surface.
The goal of the Sovereign Engineering Cohorts is to scratch the surface as properly as we know how. So we're going to do it again. In May. Same recipe, same crew, different participants. The focus will be on P2P markets and exchange.
We're not here to make any promises. I want to repeat once more what we've mentioned in the past: "Men wanted for hazardous journey. ~~Low~~ No wages, bitter cold, long hours of complete darkness. Safe return doubtful. Honour and recognition in event of success."
But it's going to be fun. Maybe.
Sign up, and let's find out: https://sovereignengineering.typeform.com/SEC02
-
 @ 57d1a264:69f1fee1
2024-03-25 07:09:20
@ 57d1a264:69f1fee1
2024-03-25 07:09:20ODC #000009 - UX > IMPLEMENTDesigning Accessibility research for any Bitcoin website or appIf you miss it, please read our WTF is ODC (Open Design Challenge) intro post from more details.
Scenario
You're a UX researcher for a Bitcoin organization and you've been given the assignment to improve the accessibility of the organization’s website or app.
Task
For this challenge, you free to select any of your preferred Bitcoin related website that is currently online.
Perform an accessibility audit on the website. Gather findings and create a report of what the website or app does well and what problems need to be fixed. Include an account of how you performed the audit in the report.
Extra Credit: Include in your report ideas for how to solve the accessibility problems.
Guides
If you need help with this challenge, check out our hand-picked tutorial recommendations.
-
Designing for Accessibility Is Not That Hard on uxdesign.cc
-
Accessibility Guidelines for UX Designers on uxdesign.cc
-
Accessible Design for Users With Disabilities on nngroup.org)
-
An Accessible Process for Inclusive Design on piped.video
Tools
Not sure which tools to use? Try something new!
For Automated Accessibility Testingaxe (browser extension) by deque.com
The A11y Project (checklist) by a11yproject.com
Color Oracle (Desktop App) by colororacle.org
WAVE - Web Accessibility Evaluation Tool (online) by wave.webaim.org
Pa11y (CLI, Dashboard and Webserver) by Pa11y
Lighthouse (included on Chrome DevTools) by developers.google.com
Share Your Results
When you finish the challenge, post your work including anonymized collected data and results on this thread! If you also share it on
nostr, be sure to use the hashtag #opendesigner and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Check our previous ODC and support this community for creative minds, where you'll be able to get open and constructive feedback on your PoW. Ask anything in the ~Design territory and get some ⚡sats for the value you provide!
```
Bitcoin #Design #BitcoinDesign #NostrDesign #Nostr #OpenDesign #DesignChallenge #OpenDesignChallenge #UX #BitcoinOrganization #WebsiteAccessibility #UXResearch #AccessibilityAudit #Improvement #ideas
```
-
-
 @ 83d999a1:46171d19
2024-03-20 15:47:37
@ 83d999a1:46171d19
2024-03-20 15:47:37Some of the things that came out of SEC-01 are already live:
- npub.cash (code, article)
- Blossom (code, article)
- Wikifreedia (code)
- HyperNote (code)
- nostrpul.se (code)
- Seeker
- BuzzPay
- Note Duel
- superposition.events
- noStrudel on StartOS
- nsecBunker on StartOS
A lot of the projects that participants worked on have a strong focus on DVMs...
...as well as developer collaboration and tooling...
...and NWC:
Many more things are still in the making:
- NIP-66 (draft)
- NIP-41 (draft)
- Doc Collaboration over Nostr
- Anonymous AI Client
- Flare eCash Wallet
- KeyNest
- LowEnt
- gonuts
- nostr-geotags
- featurestr-bountiestr
And if my Spidey senses are to be trusted, a lot more things will come out of the conversations that were had in the last 2 months.
Keep an eye out for:
ghole.xyzpubkey.studiopubkey.land
...and other weird stuff.
Turns out you can actually re-invent the future if you put 21 guinea pigs on a pirate ship.
-
 @ 57d1a264:69f1fee1
2024-03-25 06:52:12
@ 57d1a264:69f1fee1
2024-03-25 06:52:12Prompt: Bitcoin Widgets ===============
These are designed to be snippets of information - so not too much, just the basics. Concise, direct, simple. What's being viewed? Is it information about a sales and buys? DCA average price? Mining Hashrate? Or some ETF recent statistics?
Flex your design muscles and join in. Most of all, keep this exercise loose and keep it stress-free. The FUC is about growing our design skills, together, as a community. We can't wait to see what you create!
Happy designing, Stackers!
Share Your Results When you finish the challenge, post your work on this thread! If you also share it on
nostr, be sure to use the hashtag #FUCdesiger and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Curious to know WTF is a FUC? Read the ⚡️Flash Ui Challenges welcoming post.
Looking for more FUCs? Check the archive here!
-
 @ f954303f:6e1b0af5
2024-03-25 05:24:37
@ f954303f:6e1b0af5
2024-03-25 05:24:37通过语音规律证伪“大清”国号来自蒙语“战士”之说
近年来一直有一些人声称“大清”国号(满语读音daiching)来自蒙古语“战士”一词(蒙语读音daichin)。但是,我在网上查到了下述关键点:(1)满语词汇原本只有在拟声词和汉语借词里才有后鼻音ng,拟声词之外的满语原生词汇不存在后鼻音。(2)蒙古语“战士”的尾音是前鼻音n。(3)“大清”国号问世之初,作为拼音文字的满文就记载了尾音是后鼻音ng。
如果“大清”国号是蒙语借词,考虑到满语的原生词汇除了拟声词就向来不用后鼻音ng,而蒙语“战士”的尾音恰恰是满语常用的前鼻音n,借用的时候是不可能忽然改用ng结尾的。据此,我认为可以100%断言,“大清”国号的来源不可能是尾音为n的蒙语“战士”。
不管皇太极是否相信“五行相克”,国号daiching采用满语原本只在拟声词和汉语借词里才用的后鼻音ng,毋庸置疑是汉语借词。
网上还有资料说,“大清”国号来自蒙语“战士”这个说法于1999年才由内蒙古大学学者提出。如果皇太极通过采用蒙语“战士”命名自己的国家来给蒙古人做“统战”,那么这层含义肯定在蒙古人里代代相传,而不是等到三百六十多年之后再有人忽然发现。这就是从另一个角度来给蒙语借词之说证伪了。
submitted by /u/Goaty_Beard (https://www.reddit.com/user/Goaty_Beard)
[link] (https://www.reddit.com/r/China_irl/comments/1bn5ztc/通过语音规律证伪大清国号来自蒙语战士之说/)[comments] (https://www.reddit.com/r/China_irl/comments/1bn5ztc/通过语音规律证伪大清国号来自蒙语战士之说/)
#China_irl
https://www.reddit.com/r/China_irl/comments/1bn5ztc/通过语音规律证伪大清国号来自蒙语战士之说/
-
 @ 04c4089f:dfd1a512
2024-03-25 04:37:23
@ 04c4089f:dfd1a512
2024-03-25 04:37:23よくきたな。俺は逆噴射なわしろだ。俺は普段ものすごい量の文章を書いているが、誰にも読ませるつもりはない。
嘘です。普段文章なんか書かないし、書いたとしても大部分をインターネットで世界中に公開しています。どうも、なわしろです。
今回、VR コミュニティのエンジニア集会で催されたハッカソンに参加しました。このテキストはそのレポートです。
イベントについて
VR コミュニティ エンジニア集会とは?
慕狼(しのがみ)家の末っ子、慕狼ゆにさんが、いくつかの VR プラットフォームで運営している集会です。エンジニアならハード・ソフト・その他何でも OK、金曜日にお酒を飲んでワイワイしよう、というゆるい集会です。毎回「進捗共有会」が催されます。飲んだお酒を進捗に数えても OK です。話が長くて制限時間を超えると、床が抜けて落とされます。
VRChat で開催する週と Cluster で開催する週があります。よくある誤解なのですが、これらのソフトは VR 機器が無くても、デスクトップで使えます。特に Cluster はスマホからでも入れるので、敷居はかなり低いです。
テーマ「バーチャルな〇〇」第一回エンジニア集会ハッカソン
最初の開催ということで、テーマは応募前から開示されていました。テーマは上記の通り、バーチャルと関係していれば何でも OK ということで、参加者は仮想マシンを作ったり、きゅうりに蜂蜜をかけてメロンの味を再現しようとしたり、面白い試みを色々やっていました。
バーチャルライフマガジンの取材もあったとのことですので、そちらのアクセスカウンターも回していただけると幸いです。
NosHagaki について
https://nos-hagaki.vercel.app/
登場人物
- なわしろ:私。関西型言語を話す人の影響でエセ関西弁を喋る。
- ハ・サタン:旧約聖書に登場するキャラ。対立する者の意。神の命令を受けて人間に試練を与える。
構想
なわしろ「距離が離れていて時間がかかる文通アプリを作ってみてえなあ。ついでに相互運用可能ならもっとええなあ」
ハ・サタン「どした?」
なわしろ「スマホアプリで『Slowly』っていうのがあるんやけど、これを分散型 SNS でできないかと思ってるんよ。ActivityPub でできないかな」
ハ・サタン「あれ色々大変やで。SNS ひとつローンチするのと変わらんからな」
kaiji さん「Nostr はいいぞ」
https://zenn.dev/kaiji/articles/e855dccba73211
なわしろ「パスワードみたいなセンシティブなデータを扱わなくてもええんやね。なんか Nostr 良さそうやね。これでクライアント作りやってみよう」
ハ・サタン「位置情報はどうするん?他のクライアント使ってる人からは取れんやろ」
なわしろ「あんまり現実の位置にこだわらなくてもええんじゃない?個人情報だし、気にする人もいるやろ。公開鍵からランダム生成すれば解決や」
ハ・サタン「それだと海に住んでる人も発生するのと違うか?地球の七割は海やで」
なわしろ「それは…うーん、陸地を細かく区分けして番号振って扱うとか…いや難しいな…せや!」
「陸地を当てるまでサイコロを振り直せばいいじゃない!」
なわしろ
ハ・サタン「けっこう愚かな方法だと思うで、それ。マイニングか?まあええか。どうやって陸地かどうか判定するんや?」
なわしろ「容量とライセンスがいい感じの geojson を拾ってきたやで。これで地域名が取得できたら陸地と考える。住所が扱えるようになったし、すると距離とかかる日数もわかるはずだから、あとは予約投稿のような仕組みがあれば完成しそうやね」
ハ・サタン「Nostr には予約投稿無いで」
なわしろ「そうなの!?自分で作るしかないか…あらかじめ時刻がわかっているから、実際に投稿される時刻で署名してサーバーにとっておいて、時刻に達したら投稿する、というフローでいけば良さそうやね」
使用した技術
フレームワーク: Next.js
慣れていたし、フルスタックアプリを作るには都合が良さそうだったから。それに、デプロイ先として無料プランのある Vercel が使える。
DB:Postgres、KV(Redis)
Vercel で用意されていて便利そうだったから。
言語:TypeScript
静的型付けができた方が楽なのかな、という軽い気持ちで決めた。
Nostr ライブラリ:NDK
nostr-tools より使いやすそうだったから。IndexedDB を利用したキャッシュも備えている。
タイムラインを作る
なわしろ「まずはタイムラインを作るで。とはいっても、ほとんど NDK が提供する機能に GUI を与えるだけや」
ハ・サタン「シングルトンインスタンスとして実装するのが望ましいと README に書いてあったので、そこだけ気をつけなあかんで」
```ts import NDK from "@nostr-dev-kit/ndk"; import NDKCacheAdapterDexie from "@nostr-dev-kit/ndk-cache-dexie";
export class NDKSingleton extends NDK { private static _instance: NDKSingleton;
public static get instance(): NDKSingleton { if (!this._instance) { const dexieAdapter = new NDKCacheAdapterDexie({ dbName: "ndk-cache", }); this._instance = new NDKSingleton({ cacheAdapter: dexieAdapter }); }
return this._instance;} } ```
なわしろ「あれ?キャッシュが作成されない。なんで?」
ハ・サタン(ほら言わんこっちゃない)
なわしろ「あ、クラスはシングルトン書いたけど、インスタンス作る時にシングルトンとして書いてなかった!」
ハ・サタン「キャッシュの機能もつけてたから気づいたものの、けっこう危ない間違いだと思うで」
diff -ndk: new NDKSingleton(), +ndk: NDKSingleton.instance,すみかを計算する
なわしろ「公開鍵から乱数を生成して、地域名が取得できれば OK、できなければやり直し、というフローやで」
ハ・サタン「緯度の計算はどうするんや?緯度は単純な乱数だと南極点と北極点に住所が偏るで」
なわしろ「算数わからん」
ランダムな緯度経度を計算する方法ですが、迂曲余接ありました。あいにく私は算数に弱く、ましてや球面座標なんてやったこともありません。指摘してくれた方やプルリクエストを送ってくださった方もおり、現状は以下の式にしています。今後も変わる可能性はあります。
ts const longitude = rng() * 360 - 180; const latitude = -Math.asin(2 * rng() - 1) * (180 / Math.PI);なわしろ「geojson の中身はだいたいこんな感じやね」
ts export interface GeoJSONFeature { type: string; properties: { iso: string; // ISO 3166-1 alpha-2 code pais: string; ja: string; }; geometry: { type: string; coordinates: number[][][]; // MultiPolygon coordinates }; }propertiesに国名コードや日本語の地域名が入っています。国の形は
coordinatesの中にポリゴンが書いてありますね。指定した点がポリゴンの中にあるか、という判定はpoint-in-polygonというそのものなライブラリがあったのでこれを使いました。ハ・サタン「毎回 geojson を読み込むの、よくないと思うで」
なわしろ「IndexedDB にキャッシュしておくか。
zustandとidb-keyvalを使えば良さそうやね」```ts import { createStore } from "zustand/vanilla"; import { persist, createJSONStorage, StateStorage } from "zustand/middleware";
export const IdbStorage: StateStorage = { getItem: async (name) => { // Exit early on server if (typeof indexedDB === "undefined") { return null; } const value = await get(name); console.log("load indexeddb called"); return value || null; }, setItem: async (name, value) => { // Exit early on server if (typeof indexedDB === "undefined") { return; } return set(name, value); }, removeItem: async (name) => { // Exit early on server if (typeof indexedDB === "undefined") { return; } await del(name); }, };
…
interface State { features: GeoJSONFeature[]; get: boolean; }
const store = createStore( persist( () => ({ features: [], get: true, }), { name: "features-storage", storage: createJSONStorage(() => IdbStorage) } ) ); ```
データベース
なわしろ「デプロイ先の Vercel には Postgres が用意されているけど、SQL を書くのはしんどい気がするな」
Google 先生「Object-Relational Mapping(オブジェクト関連マッピング、対象関係映射、ORM、O/RM)を使うと良い。例えば
prismaというのがある」登場人物が増えた「なわしろ」
prismaをインストールするとprismaディレクトリにschema.prismaファイルが生成されます。データベースやテーブルの設定を書いていきます。```ts generator client { provider = "prisma-client-js" }
datasource db { provider = "postgresql" // Uses connection pooling url = env("POSTGRES_PRISMA_URL") // Uses direct connection, ⚠️ make sure to keep this to
POSTGRES_URL_NON_POOLING// or you'll have dangling databases from migrations directUrl = env("POSTGRES_URL_NON_POOLING") }model Event{ id String @id SubmittedData SubmittedData @relation(fields: [submittedDataId], references: [id], onDelete: Cascade) submittedDataId Int @unique kind Int content String pubkey String created_at Int address String sig String }
model SubmittedData { id Int @id @default(autoincrement()) sended Boolean @default(false) createdAt DateTime @default(now()) sendDay DateTime event Event? relays String[] ip String } ```
Eventのここを注目してください。SubmittedDataを親、Eventを子として関連付けています。また、SubmittedDataの行が消されたら自動的にこちらも消えるように指定しています。ts SubmittedData SubmittedData @relation(fields: [submittedDataId], references: [id], onDelete: Cascade) submittedDataId Int @uniqueAPI
なわしろ「DB へのインサートはこんな感じでええかな」
ts await prisma.submittedData.create({ data: { sendDay: sendDay, relays: Array.from(outbox), event: { create: { kind: res.event.kind, content: res.event.content, pubkey: res.event.pubkey, created_at: res.event.created_at, address: res.event.tags[0][1], sig: res.event.sig, id: res.event.id, }, }, ip: ip, }, });なわしろ「確か『しずかなインターネット』は一時間に 6 稿のレート制限があったな。あれ真似したい。Redis と
upstash/ratelimitを使うと良いらしいな」```ts import { Ratelimit } from "@upstash/ratelimit";
const ratelimit = new Ratelimit({ redis: redis, limiter: Ratelimit.slidingWindow(6, "1 h"), });
export async function POST(req: NextRequest) { … const successIp = (await ratelimit.limit(ip)).success; if (!successIp) { return new Response(null, { status: 429 }); } … } ```
バッチ
なわしろ「毎日決まった時刻に送信してほしいな。Vercel にはサーバーレス関数を実行できる cron が用意されてるからこれ使っとけばええか」
Vercel ログ「設定時刻の 40 分くらい後に実行したやで」
なわしろ「ファー!?」
ハ・サタン「無課金ユーザーだからか、もともとそういうもんなのかわからんけども、誤差が結構大きいみたいやな。これほど大きいと、投稿先のリレーサーバーは受け入れてくれないやろ。さて、どうする?」
なわしろ「Github Actions の cron なら 5、6 分程度の誤差のはず。こっちでサーバーレス関数叩けばええかな。まず時刻を書き込んで…」
json on: schedule: # 定期実行する時間 - cron: "0 22 * * *"なわしろ「あとは認証情報を設定してある環境変数と、実行するプログラムを指定すれば…」
json - name: Run script env: SECRET: ${{secrets.SECRETKEY}} run: | # 定期実行するファイルを指定 python run.pyなわしろ「動いた!誤差も少ないし大丈夫そうやね」
ブロック
フェディバース「現在スパム bot が POST のみでアカウントを作れるサーバーを中心に猛威を奮っており、各所に管理人メールアドレスを使用した爆破予告が…」
なわしろ「サイバー攻撃めっちゃ怖い。Tor ブロックしたいなあ」
Google 先生「Tor は出口 IP リストを公開してるからブロックは難しくない。ただ、IP リストは動的に変わるので定期的な更新が必要」
なわしろ「30 分おきくらいに取得して Redis に格納して、一致したらブロックしておけばええか」
ハ・サタン「ちょい待ち、今どこにそれを実装した?」
なわしろ「リクエストが来た時に最初に実行される
middleware.tsやけど」ハ・サタン(やったなこいつ)
〜リリース後〜
Shino3「なんか nos-hagaki おちた」
なわしろ「わあ」
ハ・サタン「
middleware.tsに書いたからやね。全てのリクエストに対して実行されるから、Redis へのリクエストが殺到したんや。投稿 API あたりに実装するのが妥当やね」なわしろ「メンテ入りまーす」
ちゃんちゃん。
-
 @ dd664d5e:5633d319
2024-03-20 11:08:53
@ dd664d5e:5633d319
2024-03-20 11:08:53A discussion of the problems and the promise of an economy based upon a deflationary currency, with suggestions for how to restructure payments to accommodate this.
The Zap Economy
I think many people have been breaking their heads, trying to figure out business models, when the currency used in the models continuously rises in purchasing power, often even going parabolic, for a time. Let's have a debate about which models are the best and how we can design our own business funding, going forward.
Note: From here on, all producers will be described as "creators," which is more fitting to the Nostr lingo.
Dealing with spikes in fiat prices
I think the best way to create a business model that deals with sudden spikes in fiat prices is to simply ignore them. The people who are motivated to sudden action by such spikes are traders, and they probably shouldn't be your target market.
Employment Contracts
One tried-and-true business model is the fee-for-project type of contract that we usually call "employment". These all have a defined beginning, a defined end, and a defined scope. (I will differentiate them from direct, quick fee-for-service; see Sales Contracts.)
Typical "day jobs" are defined this way, with creators being employed for a month or two weeks, to perform a particular task, with a payout at the end and often an automatic extension to the next employment period. Contracting is another common type, as are retainers for specialists like doctors and lawyers.
I think this model can be easily implemented in a zap economy (and, indeed, it already is), as employers can simply keep the employment scope or period small and renegotiate the next one to reflect any deflation. For longer-term employment, they could simply negotiate regular rebalancing to reflect price changes, or link payments to some measure of deflation.
Patronage
This is the current common business model. A creator (artist, developer, writer, etc.) receives grants or donations that are more or less attached to conditions.
The fewer the conditions attached and the more diverse/larger the patron set is, the more valuable the patronage is and the freer the creator. The negative impact of strings or condensed patronage can be mitigated by the availability of non-funding resources (infrastructure, training, marketing, legal advice, psychological support, access to a team, etc.) or the sheer size of the patronage.
(Although creators, by nature, grate under management and may eventually resent condensed patronage, even if it is very generous, helpful, and well-intentioned.)
Customer Classifications
This is a highly desirable model, from the viewpoint of most creators, as it is defined and controlled by them, and offers the promise of stable, long-term funding. It is also popular among smaller patrons, as their money investment is more effective and -- let's be honest -- more fun, if it is converted to a Class A Customer status and bundled with the money and enthusiasm of others.
This vaguely resembles a club membership. In this model, there are different levels of customer classes (usually defined using the alphabet, with "A" being the highest level).
An example structure might be:
A: The most emotionally-invested group. Often very early and constant investors, willing to pay a high premium for membership and to front relatively large sums of money in advance of services rendered. These are your "premium account holders".
They should receive some outward/public sign of their membership (so that they can find each other, more easily, and to help you market your creations) and some premium content, features, or services. Their support tickets have priority and their complaints and ideas go straight to the lead developer or product owner.
Even simply arranging for them to attend a teleconference before releases, reserving a special lounge or party for them at conferences, or announcing new features in newsletters, can go a long way.
B: These are the "normal payees". They pay the minimum to unlock some extra-stuff and always get new releases first, and that's all they really want. Mostly, they just want to not feel like freeloaders, so providing them with a clear payment scheme is enough.
C: These are the freeloaders. They get a reduced service, but stay friendly because they sometimes market your product to others and they have the potential to move up to a higher class.
The essential part of this model is the pricing.
Class A customers should be onboarded first and pay the highest regular membership fee. This fee should be automatically lowered to Class B level, when adding Class B customers, at a later date, so that your early supporters don't feel disadvantaged.
Class B (with Class A) should have deflation-tracked pricing: 500 sats today, 250 after the next halving, 125 after the next halving, etc. Or something similar. You should always plan for your prices to steadily decrease in nominal terms, while slightly rising in real terms, as your service becomes more advanced and valuable.
Sales Contracts
This is a clear fee-for-service and is generally set and reset regularly. If you have a long-term sale or resale contract, you should have fee adjustments accounted for, from the beginning.
And that is all that I have time to write, at the moment.
-
 @ 266815e0:6cd408a5
2024-03-19 20:15:22
@ 266815e0:6cd408a5
2024-03-19 20:15:22While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can a files hashing on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ a012dc82:6458a70d
2024-03-25 03:21:07
@ a012dc82:6458a70d
2024-03-25 03:21:07Table Of Content
-
Introduction
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Will the value of cryptocurrencies surge, fall, or continue to lead investors down a road that is unknown for the foreseeable future? Will Bitcoin's price continue to fluctuate wildly? Will there be a greater emphasis on compliance with regulations? Which cryptocurrency do you think will be the most profitable to invest in throughout the next year?
There are just as many forecasts about the future of cryptocurrencies as there are experts trying to make sense of them.
In 2021, cryptocurrency maintained its high level of popularity. Goldman Sachs just decided to embrace cryptocurrency. Coinbase went public for the first time in April 2021, making it the first big cryptocurrency business to do so. In October 2021, the first U.S. exchange-traded fund that was tied to Bitcoin was introduced.
As reported by CNBC, Bitcoin, the most well-known cryptocurrency, reportedly had a successful year. Since the beginning of 2021, the value of the digital currency has increased by up to 70 percent, which has driven the whole worth of the cryptocurrency market to reach $2 trillion.
Taking a look into the future of cryptocurrencies, if recent history is any indicator, those who have invested in cryptocurrencies are in for an amazing journey. In 2022, some fascinating cryptocurrency forecasts to keep an eye out for include the following:
Crypto Prediction #1: Heading for a Crypto Crash or an Exciting Climb?
The value of cryptocurrencies could drop much more in 2022. They hit a new all-time high of around $69,000 in November, but they are currently under $50,000, representing a drop of nearly 30% from their peak.Professor of finance at Sussex University, Carol Alexander, forecasts that the price of Bitcoin will crash to a low of $10,000 in 2022, which would wipe out the majority of its gains over the course of the previous year and a half.
Some people do not anticipate a collapse in 2022. According to Yuya Hasegawa, a crypto market analyst at the Japanese digital asset exchange Bitbank, the most significant risk factor is the Federal Reserve's decision to reduce its quantitative easing program. He believes that a decision has been made and that the cost has most likely been factored in.
According to what was revealed by Sayantani Sanyal, there are a number of variables that lead to higher Bitcoin prices, the most important of which is a larger adoption by companies and a stronger demand from Bitcoin ETFs. Sanyal reports in Analytics Insight that some market experts believe the price of Bitcoin will reach $100,000 USD by the end of 2023, while others believe it will reach that figure in the first quarter of 2022. Sanyal cites these market analysts' predictions. Some people believe that the price of bitcoin won't go higher than $70,000 USD before the year 2022 is over.
In a nutshell, people's projections about cryptocurrency are all over the place.
Crypto Prediction #2: A Lot More Investors Will Adopt Bitcoin
According to The Ascent, Ric Edelman, head of the Digital Assets Council of Financial Professionals, forecasts that more than 500 million individuals across the globe will possess Bitcoin by the time 2022 comes to a close. At CoinTelegraph, BlockFi co-founder Flori Marquez agrees, stating that he believes higher acceptance of cryptocurrencies is helped by more regulatory clarity as well as enhanced knowledge of the business.
Crypto Prediction #3: The First Spot Bitcoin ETF Could Get Approved
According to the predictions of certain crypto investors, the first spot Bitcoin exchange-traded fund (ETF) in the United States is expected to be authorized this year. This would provide investors with direct exposure to the cryptocurrency itself. Last year, the Securities and Exchange Commission gave approval for ProShares to establish their Bitcoin Strategy ETF. However, this ETF does nothing more than monitor Bitcoin futures contracts. Analysts are sure that a Bitcoin Spot ETF will be approved, even though the market is already big and developed enough to justify its existence.
Crypto Prediction #4: Moving Toward Decentralized Finance (DeFi)
According to Bryan Gross, network steward of crypto platform ICHI, emerging crypto advancements such as decentralized finance (DeFi) and decentralized autonomous organizations (DAOs) are "expected to be the greatest growth areas of crypto." While the goal of DeFi is to duplicate standard financial products without the need for intermediaries, DAOs have the potential to give rise to a whole new online community. The amount of money deposited into DeFi services topped $200 billion in 2021, and it is anticipated that demand will increase in 2022.
According to Carol Alexander, investors who are interested in making profits in more specialized sectors of cryptocurrency will want to keep an eye on Ethereum, Solana, Polkadot, and Cardano currencies in the year 2022.
According to a recent article by CNBC, DeFi is a subset of a larger trend known as Web3. The proponents of Web3 contend that the majority of internet platforms are controlled by a small number of corporations, including Amazon, Apple, Alphabet, and Meta, which is the parent company of Facebook. Blockchain technology and non-fungible tokens are going to be included in the next version of the internet, which will be called Web3. However, successful businesspeople like Elon Musk and Jack Dorsey continue to have reservations.
Crypto Prediction #5: Regulators Have Their Eye on Cryptocurrency
It is anticipated that cryptocurrency regulation will be a primary concern in 2022. According to Vijay Ayyar, who serves as vice president of corporate development and worldwide growth for the cryptocurrency exchange Luno, the year 2022 is expected to be a significant one on the regulatory front. In an interview with CNBC, Ayyar expressed his hope that the legal "gray zone" surrounding cryptocurrencies other than Bitcoin and Ethereum would soon get some explanation. Stablecoins, which are tokens whose value is related to the price of assets such as the U.S. dollar, are expected to be another area of interest for regulators. Stablecoins have been around since 2017. People have talked about whether or not Tether, the largest stablecoin in the world, has enough assets in its reserves to be pegged to the dollar.
Crypto Prediction #6: Bitcoin Will either Outperform or Underperform the S&P 500
In spite of the fact that the coronavirus posed a risk to the whole world's economy, Bitcoin and the benchmark index both exhibited excellent growth in 2021: Bitcoin skyrocketed by 66%, while the S&P 500 increased by around 27%.
According to Arcane Research, Bitcoin has shown performance consistent with a risk-on asset, and they anticipate that it will exacerbate the behavior of the stock market. The company believes that even if the stock market is higher in 2022, Bitcoin will still likely exceed it. However, if the stock market has a negative year, Bitcoin's performance will most certainly be poor.
Crypto Prediction #7: Ether Will Outperform Bitcoin Again
In 2021, Ether had a higher rate of growth than Bitcoin, which was 66 percent. Ether's growth was 418 percent. Analysts anticipate that both will continue to perform well due to the dramatic increase in NFT sales.The majority of these tokens are still operated on the blockchain of Ethereum.
Crypto Prediction #8: Most meme coins will disappear
A Dogecoin offshoot called Shiba Inu saw its value increase by 44,540,000 percent in the last year. The value of the cryptocurrency known as "Squid," which was named after the television show "Squid Game," increased by more than 75,000 percent in a little less than a week before suddenly disappearing.
Crypto Prediction #9: USD Coin Will Hurdle Tether as Biggest Stablecoin
Tether has successfully maintained its position as the most valuable stablecoin in terms of overall cryptocurrency worth. However, once USD Coin makes the decision to join the loan wave, it has the potential to be dethroned from its perch.
Crypto Prediction #10: VIX Spikes Impact Bitcoin Performance
Even though the stock market had a good year in 2021, Arcane Research said that "Fear in the broad financial markets significantly hurt Bitcoin's performance."
The Cboe Volatility Index, often known as the VIX, also saw increases at the same time as Bitcoin prices dropped. Arcane Research says that problems in the market in 2022 could have an effect on the short-term price trend of bitcoin.
Conclusion
This guide on the best cryptocurrencies to invest in for 2022 has provided an explanation of the fundamentals of each project that is included on the list, both in terms of the potential for future growth and the dangers that investors should take into consideration before making any investments.
From the perspective of prospective returns on investment, our research has shown that Solana or ApeCoin is the greatest cryptocurrency to invest in right now.
FAQ
Which cryptocurrency do you think will see the most growth in 2022? Calvaria (RIA) is an Up-and-Coming Way to Earn Cryptocurrencies That Has the Potential to Explode in 2022. Uniglo.io is a Multi-Asset Backed DAO that is Currently Ready to List in the Top 150. Tamadoge (TAMA), an exciting Meme Coin project, has been pumping since its Initial Coin Offering (IEO).Battle Infinity (IBAT) is a P2E platform and ecosystem that is based on a non-fungible token for sports fantasy games.
Which digital currency has the most potential? Dash 2 Trade (D2T) is the Overall Cryptocurrency with the Most Potential that has been released on the Pre-Sale Market.D2T is Dash 2 Trade's native cryptocurrency, and it may be used as a means of payment on the platform to obtain access to all of the trading signals, tools, and other features available in the cryptocurrency market.
Which cryptocurrency will have the most growth in 2023? The next cryptocurrency to explode in value in 2023 is Solana (SOL). This might be the breakout year for Gala (GALA), the leading P2E platform cryptocurrency. ApeCoin (APE) Is Becoming a Common Prediction for the Upcoming Cryptocurrency That Will Explode in 2023. Cardano (ADA) is a pioneering blockchain network that has the potential to rebound.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on :
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 46fcbe30:6bd8ce4d
2024-03-19 15:14:02
@ 46fcbe30:6bd8ce4d
2024-03-19 15:14:02Opinion about Trezor One (hardware)
Context
Trezor is probably the oldest provider of hardware wallets and the Trezor One is their oldest product and it's still getting updates. If you've been to Bitcoin conferences, you probably ran into people from Trezor which certainly builds trust, too. They try to push what's possible with openness with their Tropic Square which while long in the making still is being worked on. It will be a truly open "secure element" or SE in short - a tamper proof chip - to not rely on the closed and often flawed chips that others use under NDAs that forbid them to talk about the very security features they promise the world would keep keys safe.
With Trezor's fundamental opposition to closed architecture in hardware wallets, the Trezor One does not use an SE which quickly became the biggest differentiating factor with their main competitor Ledger which did employ SEs in their products with the consequence of these products completely depending on closed source.
For a long time, Trezor recommended to use a BIP-39 passphrase with their products to achieve the same level of security as hardware wallets that have an SE but without being closed source like those.
Apparently they've been playing catch-up with Ledger for too long and just recently released their third generation product, the "Trezor Safe 3" which does indeed feature one of those pesky SEs. But ... there is good and bad ways to use these SEs and many competitors figured out how to provide an open source product while still using a closed source SE in ways that the security does not depend on the closed source.
The Good
- Trezor One is completely open source
- It's been almost always reproducible
- The founders Pavol and Marek are OGs
- They have pushed for Bitcoin's open source culture far beyond their own products
- They provide Bitcoin-only firmware which reduces the attack surface
- With many clones using their software, there are many eyes on the code - and Trezor encourages this
The Bad
- If your threat scenario is people with moderately expensive equipment and expertise extracting your keys from your device while at the same time not being able to use a strong passphrase, this product is not for you.
- The device does not always show the fingerprint of the firmware one is updating it to. To my understanding it does not show it if you did not first tell it to not check the signature of the firmware first.
The Ugly
- They still cater to altcoins. While their Twitter timeline avoids mentioning them, they do list thousands of tokens. It might be only ETH and ERC20 though, so maybe it's not as bad as it sounds.
- The use of a passphrase is opt-in, making it harder than necessary to have decoy wallets. Only if the use of a passphrase is activated will the device ask for one so the device will tell a hacker or bully if there is secondary accounts or not.
Summary
The Trezor One is a solid choice for a hardware wallet but probably due to the provider catering to millions of users and not only to hundreds of nerds like myself, some questionable decisions were taken that put them in a spot of being able to rug-pull those millions of users. Unless you update your firmware using
trezorctl, the provider could give you a compromised firmware without any way for you to detect this while at the same time them knowing you can't detect it. This is why my overall sentiment is negative but I still recommend this product for nerds that understand they have to usetrezorctl.WalletScrutiny #nostrOpinion
-
 @ 813d33f6:693f30c4
2024-03-25 03:08:46
@ 813d33f6:693f30c4
2024-03-25 03:08:46Username testing
NostrOpinion
-
 @ 3bf0c63f:aefa459d
2024-03-19 14:32:01
@ 3bf0c63f:aefa459d
2024-03-19 14:32:01Censorship-resistant relay discovery in Nostr
In Nostr is not decentralized nor censorship-resistant I said Nostr is centralized. Peter Todd thinks it is centralized by design, but I disagree.
Nostr wasn't designed to be centralized. The idea was always that clients would follow people in the relays they decided to publish to, even if it was a single-user relay hosted in an island in the middle of the Pacific ocean.
But the Nostr explanations never had any guidance about how to do this, and the protocol itself never had any enforcement mechanisms for any of this (because it would be impossible).
My original idea was that clients would use some undefined combination of relay hints in reply tags and the (now defunct)
kind:2relay-recommendation events plus some form of manual action ("it looks like Bob is publishing on relay X, do you want to follow him there?") to accomplish this. With the expectation that we would have a better idea of how to properly implement all this with more experience, Branle, my first working client didn't have any of that implemented, instead it used a stupid static list of relays with read/write toggle -- although it did publish relay hints and kept track of those internally and supportedkind:2events, these things were not really useful.Gossip was the first client to implement a truly censorship-resistant relay discovery mechanism that used NIP-05 hints (originally proposed by Mike Dilger) relay hints and
kind:3relay lists, and then with the simple insight of NIP-65 that got much better. After seeing it in more concrete terms, it became simpler to reason about it and the approach got popularized as the "gossip model", then implemented in clients like Coracle and Snort.Today when people mention the "gossip model" (or "outbox model") they simply think about NIP-65 though. Which I think is ok, but too restrictive. I still think there is a place for the NIP-05 hints,
nprofileandneventrelay hints and specially relay hints in event tags. All these mechanisms are used together in ZBD Social, for example, but I believe also in the clients listed above.I don't think we should stop here, though. I think there are other ways, perhaps drastically different ways, to approach content propagation and relay discovery. I think manual action by users is underrated and could go a long way if presented in a nice UX (not conceived by people that think users are dumb animals), and who knows what. Reliance on third-parties, hardcoded values, social graph, and specially a mix of multiple approaches, is what Nostr needs to be censorship-resistant and what I hope to see in the future.
-
 @ c8df6ae8:22293a06
2024-03-25 02:03:57
@ c8df6ae8:22293a06
2024-03-25 02:03:57"We don’t want to buy Bitcoin on our own. We will wait until we’re there with you."
— My parents
Welcome to the latest issue of the Bitcoin For Families newsletter. This issue covers the cold storage setup I’ve planned for my parents.
Setting up cold storage for my parents
My parents have finally decided to buy some bitcoin.
They’ve heard me talking about the demise of the US dollar and the Euro but I doubt that they have decided to buy some bitcoin because of that.
They are saving in bitcoin because they know that I save in bitcoin and they think it is prudent to put a very small share of their net worth into the same asset that I use for my savings. And I’m ok with that.
My parents use laptops and are comfortable with technology at a user level but they are far away from feeling comfortable doing something totally new.
Therefore, I was not surprised when they said that they would like to buy some bitcoin but, that they didn’t want to do it on their own, that they would wait instead until they are with me so that I can hold their hand throughout the process.
They will be visiting the beautiful Pacific Northwest in a few weeks and in preparation for their visit I have ordered everything that they’ll need to securely hold some bitcoin:
- Coldcard Mk 4
- Data only USB cable
- 16 GB microSD card x 2
- microSD reader
- Seed plate
- Plus the Sparrow wallet to be installed in their Macbook Air
I will be using my own seed plate puncher so no need to buy one for them.
The focus is on simplicity:
- They need to feel very comfortable with the requirements of self custody their money, buying more bitcoin and sending it to the Coldcard.
- They need to feel capable of sending bitcoin to another wallet if they need to.
Coldcard setup
- The Coldcard will be setup with a 12 words seed. 24 words is overwhelming and not necessary.
- The 12 words will unlock wallet #1 with a small amount of bitcoin.
- A simple word added as a passphrase will unlock wallet #2 with the rest of their bitcoin.
The passphrase will give them peace of mind. They will know that even if somebody steals their seed plate, they won’t lose their money. This would include:
- If a bad actor inspects or confiscates their seed plate while they are traveling back to Spain.
- If they need to disclose the seed under duress.
They can share this word with my sister and I without sharing the seed and know that if they pass away, only we will be able to access the funds once we get hold of the seed plate.
The Coldcard will have two pins: the real one and a pin setup to brick the device. The brick pin will be taped to the back of the device so that if someone steals the device, they will surely try that pin and render the Coldcard useless. My parents will know to NEVER use the pin taped on the back.
Seed backup
The Coldcard will be backed up to one of the microSD cards. The other one will be used for air gapped transactions.
The Coldcard, seed plate and back up microSD card will be stored together in the same place where they keep their passports.
Buying more Bitcoin
I’ll import the details of both wallets into the Sparrow application and show them how to generate a new bitcoin addresses if they buy more bitcoin and need to transfer it from the exchange and into cold storage.
They will buy KYC bitcoin. Trying to get them to buy non-KYC bitcoin at Robosats is just too much.
Selling Bitcoin
I will show them how to approve an air gapped transaction. I will also write down the steps in a document saved on their computer and record a video while executing the steps.
An air gapped transaction is more complex than receiving bitcoin but hopefully they won’t be selling bitcoin anytime soon so they just need to feel capable of doing it if needed.
Hot wallet
While they are here, I will also install the Phoenix lightning wallet in their phones so that we can settle bills easily back and forth once they’re back in Europe.
I can remotely do this with my sister as well so that the whole family can start sending bitcoin back and forth to each other.
Additional references
BTC Sessions has a fantastic tutorial on the Coldcard. It is a long video but very comprehensive.
And conveniently, Guy Swann just released an episode on Basics of key management (the trick about taping the brick pin to the back of the Coldcard is from this episode 😁).
And that’s it. Please let me know what you think about this setup as well as what you would do different in the comment sections below.
Notable notes
nostr:note1ejufpdka09nqxtkhc3d3dcwrz6knxwy8xdxch0nhcljapmqsgnaqc2gjlj
Recommendations
Ben Goggin
Ben is the deputy tech editor and NBC News. He has 9.4 million followers on Twitter and yesterday (May 26th) he joined Nostr to find out what is the deal with this social network that Jack Dorsey keeps talking about.
Within a few hours of joining he had already discovered the power of being able to not only Like but actually reward other people with money (zaps) for notes they publish that you find valuable.
Follow him on here to get a fresh perspective from somebody who is not a bitcoiner on the first decentralized social network: Nostr.
What did you think of today's newsletter?
Your feedback helps me create the best newsletter possible for you.
Please leave a comment and checkout comments from other subscribers and readers. I love hearing from the Bitcoin For Families community ❤️ 🙏🏻
Buy Bitcoin with Swan
If you want to buy Bitcoin, I highly recommend using Swan. It's where I buy my Bitcoin.
They are on a mission to onboard 10 million Bitcoiners and get them to self-custody.
Use this link to receive $10 free to get you started.
See you again next week! — Alejandro
This newsletter is for educational purposes. It does not represent financial advice. Do your own research before buying Bitcoin.
-
 @ 0271e1b9:ad8cff90
2024-03-18 08:24:19
@ 0271e1b9:ad8cff90
2024-03-18 08:24:19https://image.nostr.build/051938fdd843ee250ab4cd87689f613199a47621791a8330586f7887f6de055a.jpg
March 13th 2024 marked exactly 1 year of me using #nostr - notes and other stuff transmitted by relays. I wrote a down a couple of thoughts and observations regarding the anniversary that and the following days and decided I'd make it into a more cohesive and easier-to-read long-form post.
And it is a fiery love! Since we have no algorithms doing a “year in review” or whatever, I’ll try to make one myself :) I didn’t really use social media much at all until May 2022, when I started using Twitter and Instagram (mostly with the idea of promoting my music and photos, but I quickly also started posting stuff regarding my ideas surrounding Bitcoin, philosophy, nature, yoga, etc. My first post/note here was, ironically, or perhaps fittingly, a repost from Twitter/X: https://primal.net/e/note1kh2zgxwmcgkt2wmlh26rlfxwdd309ajlwq039pqukld6ld92d20qtzxexg
The pros
Since joining nostr in March 2023; my main takeaways regarding the UX for the time being are:
- Almost no spam and no ads thus far, which is awesome
- No “being at the mercy of the algorithms,” which is awesome (although Instagram’s algo tends to do a pretty good job at showing me stuff I’m actually interested in)
- Much higher signal/noise ratio than any other platform
- Much less inflammatory and clickbaity stuff than any other platform
- The ability to move your whole network around from app to app is an absolute gamechanger
- I have already been able to use my npub to participate in rap cyphers (#nostrcypher represent) via Stemstr, to upload my music and podcast episodes via Wavlake, to listen to streams via zap.stream, to publish my articles via YakiHonne, etc. It is inspiring (and dizzying) to see all the new ideas and implementations being thrown around and played with
- Zaps are the new, improved version of likes
- Interactions between users seem to be much more organic, fluid and dynamic
I’m including a screenshot with some rudimentary stats. I try not to be phased by my followers/likes/whatever count, because that is ultimately not the purpose of creation. However, the differences between nostr and legacy social media are huge. In my case, I have been getting 14 new followers per month on Instagram, 34 on X and 54 (nearly 55) on nostr! https://image.nostr.build/7a4e5399400dac764abc2be543bc58371105e3a12ee727c164b7a9c2bd61aaf5.jpg What makes this even more amazing is the fact that: 1. Both IG and X have a much larger user base 2.1. I follow a whole lot more accounts on X 2.2. And on IG a large % of my followers are my meatspace acquaintances, friends and relatives 3. Presumably on both IG and X I have many more bot followers than on nostr (I’m not entirely sure if bot followers are even a thing yet on nostr?)
Funnily enough, on YouTube, Spotify and Soundcloud I have less than 200 followers on each, even though Kontext as the pseudonym was created and existed, for the first 7 years (2015 to 2022), exclusively as the anonymous rapper moniker of mine (hence MC Kontext).
I have stated that I am a zap maximalist and a like minimalist, and as such I’m proud to say that for each like, I have sent out almost 6 zaps. The data below is from nostr.band and is different from other sources (e.g. Primal- also happy birthday to them - my current favorite desktop app) says I have received 190 zaps for a total of 25.1k sats and a max zap of 2100 sats from PaulTaylor) https://image.nostr.build/7b22af1774373cee544df5d8742b0fbad70eac1ef0f098b384347c80d9a14ea9.jpg Some of the most legendary people who I have received zaps from include @Jeff Booth, @Gigi ⚡🧡, @TheGuySwann, @PABLOF7z, @GRANTGILLIAM, @ODELL (but no @MartyBent). A total of 152 accounts have zapped me according to nostr.band. In return, I have zapped a total of 256 accounts (if anybody knows another good nostr+zaps stats site for all-time stats and aggregates, please refer it to me).
Now, obviously, I have managed to “make a loss” by using #nostr - I have zapped away 24k sats more than I have received! However, I regret no sats zapped as they all have been for a good reason, #value4value is real and I believe and live by it. Also, perhaps the fact that I have been rather generous with the zapping has helped my nostr account grow at almost twice the pace of my X account and 4 times the pace of my IG account?
Speaking of growing and zapping, I have also started experimenting with the ideas of #zapvertising and throwing different contests and games on nostr via my business account Satoshee. https://image.nostr.build/b729072cb8097410b8085e4e07b5359cdcc0db0ad11f00173a2e44e5aa99eab4.jpg https://image.nostr.build/cf8292d89ae1a361e0ada9296d849f041b46f394afb6cb1809aeb615b3019e3f.jpg https://image.nostr.build/e4ae321e4acc84304fd973ed0a077fa1b48b8f2467125ccfeae819fa49115c73.jpg I will post a larger, more comprehensive post and stats about that whole venture at some point, but on a very rudimentary look, so far, we have spent approx 450k sats on 276 followers + approx 11 (or 4%) of them also converted into email list subscribers. Which comes down to approx 1.6k sats / follower or 41k sats per email. Now keep in mind - all that is just by posting zapvertising + a couple of memes, we have not published any other information about the enterprise. That being said, I do believe we have gotten some lovely exposure through these efforts (one of Satoshee posts was #3 on Primal 24h Trending at one point): https://image.nostr.build/7f5ab4e203a1cb2ccb8fcbc1fecdc0efc68aa961e5d0b10ea72db45d14e86d3e.jpg Here's a link to the note that made it to Trending. Hopefully once we fully launch the website and products, our gang of #nostriches will be there to test drive the site + become the first customers and/or recommend it to their friends. My thesis is that if we start off by literally paying our prospective customers, then they are more likely to trust and engage with our products as soon as we come to the market. All that will be either proven or disproven by time, of course.
OH, the cons?
I guess more ways to see and filter stats and data in general would be nice to see in the #nostr ecosystem. Why not also have some platforms that utilize algos, and/or where we can choose to opt in and out of them. The DM side of nostr apps seems also lacking for now. Perhaps these could be the downsides I see for now; or areas in which we could move in.
Of course, the onboarding process is probably also a little bit complicated for the nocoiner newbie, who may not even be familiar with the concept of public/private key pairs, but truthfully I haven't tried going through that process myself in a while so can't really comment on the progress. I assume it's being made (and from what I hear and see here and there, that seems to be the case).
Conclusion
To wrap it all up: super excited to see freedom tech (both #Bitcoin and #nostr) just being so unbelievably more effective and inspiring than the old fiat systems and I can only imagine how much abundance and prosperity on all levels of the human experience; physical, intellectual and spiritual can and will be built upon all this.
Onward. Kontext
Originally written and posted Block Height 834,554
Amended, fixed and posted to YakiHonne Block Height 835,196
-
 @ 1e52c554:21771908
2024-03-17 10:56:47
@ 1e52c554:21771908
2024-03-17 10:56:47Posthumous work of the Colombian poet born in Don Matias on January 20, 1948
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna

Analysis "To See Thee Fall In Love Each Morn"
Introduction
"Sonnet 124" by Francisco Luis Arroyave Tabares is a poem that celebrates love and the enduring nature of a deep and passionate connection between two souls.
Thematic Analysis
First Quatrain: The speaker begins by setting the scene, describing a world where various individuals meet and interact. The focus is on the timeless nature of love and its ability to rejuvenate.
Second Quatrain: The speaker talks about the power of imagination and storytelling in creating new dreams. There’s a sense of nostalgia and longing, with past sighs turning into sweet ecstasy.
Third Quatrain: The speaker expresses joy in witnessing love each morning, sharing life’s force with open eyes. There’s a hint of commitment beyond traditional vows, suggesting a deeper connection.
Couplet: The speaker concludes with a desire to spend time in slow rock, possibly referring to a steady rhythm of life or love that beats along with time.
Overall, the poem speaks to the timeless and transcendent nature of love, where two souls find a profound connection that enriches their lives, and they can cherish each moment together.
Structure and Rhyme Scheme
Let’s analyze the rhyme scheme of the sonnet in detail. The sonnet follows the Shakespearean sonnet structure, which has a rhyme scheme of ABAB CDCD EFEF GG. Here’s how it applies to this sonnet:
``` 1-. Ay lo, our place is deep inside a world (A) 2-. Where lovers, singers, strangers and else meet (B) 3-. But souls mate without ever getting old (A) 4-. And love can mean a massage for our fest (B)
5-. By spreading wide the wings of fantasy (C) 6-. Stories we tell and make into new dreams (D) 7-. For our past sighs become sweet ecstasy (C) 8-. That we can feel even when our heart streams. (D)
9-. How good to see the fall in love each morn (E) 10-. With open eyes sharing my force of life (F) 11-. And much more not counting what we have sworn (E) 12-. Further those rituals of man and wife. (F)
13-. Ay lo! , to spend all our time in slow rock (G) 14-. That beats along the seconds of our clock. (G) ```
Each letter represents the end rhyme of each line. Lines with the same letter rhyme with each other. For example, the first and third lines (“world” and “old”) rhyme with each other, represented by ‘A’. The second and fourth lines (“meet” and “fest”) rhyme with each other, represented by ‘B’, and so on.
The final two lines form a rhymed couplet (‘GG’), which is a distinctive feature of Shakespearean sonnets. These lines often provide a twist, resolution, or summarization to the poem.
Analysis of Aspects
Let’s delve deeper into the analysis of “To See Thee Fall In Love Each Morn” by Francisco Luis Arroyave Tabares.
Language and Imagery: The sonnet uses rich and evocative language to convey its themes. The imagery is vivid and imaginative, painting a picture of a world where love is timeless (“souls mate without ever getting old”) and transformative (“our past sighs become sweet ecstasy”). The use of phrases like “spreading wide the wings of fantasy” and “fall in love each morn” create a sense of expansiveness and renewal.
Themes: The main themes of the sonnet are love, time, and transformation. Love is portrayed as a powerful force that rejuvenates and brings joy. Time is seen as a rhythm (“slow rock”) that beats along with the heartbeat of love. Transformation is evident in the way past sighs turn into sweet ecstasy.
Meter: The sonnet appears to follow the iambic pentameter, which is typical of Shakespearean sonnets. This means each line has five pairs of syllables, with the stress falling on the second syllable of each pair. However, there are some variations in the meter which add to the rhythmic interest of the poem.
Overall, The sonnet is a beautiful exploration of love’s power to transform and renew. It uses evocative language and imagery to convey its themes, while its adherence to the Shakespearean structure gives it a familiar rhythm and form. The final couplet provides a satisfying conclusion, encapsulating the desire to spend time in the steady rhythm of love that beats along with time.
Please note that this is an interpretation based on a general analysis, and different readers might have different interpretations.
(GPT4)
Syllable count for each line.
```
To See Thee Fall In Love Each Morn
10 Ay lo, our place is deep inside a world 10 Where lovers, singers, strangers and else meet 10 But souls mate without ever getting old 10 And love can mean a massage for our fest
10 By spreading wide the wings of fantasy 10 Stories we tell and make into new dreams 10 For our past sighs become sweet ecstasy 10 That we can feel even when our heart streams.
10 How good to see the fall in love each morn 10 With open eyes sharing my force of life 10 And much more not counting what we have sworn 10 Further those rituals of man and wife.
10 Ay lo! , to spend all our time in slow rock 10 That beats along the seconds of our clock. ***
```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image by leonardo.ai; First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 To See Thee Fall In Love Each Morn
To See Thee Fall In Love Each Morn -
 @ c73818cc:ccd5c890
2024-03-25 01:44:15
@ c73818cc:ccd5c890
2024-03-25 01:44:15Airdrop da 1 miliardo di BWB: partecipa e prendi la tua quota!
È tempo di cambiare le regole del gioco! Bitget Wallet, il portafoglio Web3 che sfida il potere delle istituzioni centralizzate, lancia il suo nuovo token BWB: un passo avanti verso un futuro di criptovalute più democratico e accessibile a tutti.
BWB: il token che ti premia per essere parte della community
Con un'offerta totale di 1 miliardo di token, BWB è stato progettato per dare valore ai utenti:
5% di BWB distribuiti tramite airdrop: partecipa alla campagna di 6 settimane e ricevi la tua quota! BWB Points per ogni tua azione: completa attività, scambia criptovalute e invita amici per accumulare punti. Converti i tuoi punti in BWB: a partire dal secondo trimestre 2024, trasforma i tuoi BWB Points in token reali. Più di un semplice token: BWB apre le porte a un mondo di vantaggi
Governance della community: vota le proposte e decidi il futuro di Bitget Wallet. Airdrop esclusivi: accedi a token gratuiti di altri progetti all'interno dell'ecosistema Bitget. Dividendi basati sulla crescita: ricevi una quota dei profitti generati da Bitget Wallet. Unisciti alla rivoluzione! Entra nella community di Bitget Wallet e:
Scarica l'app: https://share.bwb.site/inviteLink?code=LyoQza&shareLang=it&teamCode=&source=telegram
Entra nella community Telegram: https://t.me/Bitget_Italia
Insieme, possiamo costruire un futuro di criptovalute più libero e aperto a tutti!
BitgetWallet #BWB #Bitget #Airdrop #Crypto #Web3 #Rivoluzione #Community
-
 @ 7d4417d5:3eaf36d4
2024-03-17 01:35:42
@ 7d4417d5:3eaf36d4
2024-03-17 01:35:42Toto, it's a long way to Kansas
In my first "Nostr Clients for Android - March 2024" (posted in a reply to this note), I shared my adventures of touring the landscape of Android apps aimed at using Nostr for social media. Even though I thought my journey was over, for the time being, I was wrong. Here is what I have learned in the last week. Mostly what I've learned is that Yana doesn't really implement zaps correctly, and that Primal has many horrible glaring issues, and one potential redeeming quality.
Yana? YaNO. Well, Maybe.
Although Yana seemed like a good choice, I found a major failing that I had not noticed before. I should have tested zaps more thoroughly, as the first note I zapped just happened to be a Strike wallet. Any notes made by users with other wallets would produce an error when zapped, even Alby wallets, and Alby is what I use. This means anyone using Yana cannot zap me. Boo. It also means Yana doesn't really implement zap functionality. I still prefer Yana for how it displays my feed, however.
Primal Zaps
Several people replied to my previous article about Primal's ability to use wallets other than Primal's wallet. Primal sure didn't direct me to this option when I tapped the zap button. I understand the desire for an organization to drive users to their own projects, but providing a link to the wallet settings page would be trivial to implement. This was the first experience in a reoccurring theme in Primal.
My First Zap In Primal
So, I get my wallet set up and hit the zap button. Immediately 10 sats are sent to the poster. Who decided this? Why 10? No option presented for the amount to send? I found out if I long-press, I get a list of options. Strangely enough, 10 sats was not one of the options available. Also, each of these amounts is associated with an emoji and a comment. You can erase the comment before the zap takes place, but that edit is only good for that zap. The next time you zap, the comment will be there.
Primal Zap Settings Funhouse
So I go to the zaps settings where I am presented with a default amount, and several preset amounts, all of which can be edited. Everything is cool so far, but then things got weird. All zaps are required to have a message. The default amount doesn't require an associated emoji, but the other preset amounts do. One of the preset amounts has the comment "Coffie on me". This whole area of the app feels like it's put together with edible paste and aged packing tape. I would think something as significant as zaps would have been given more appropriate attention, like allowing the user to choose that their transactions be public, private, or anonymous.
So, now that I have my wallet set up, what does the giant zap button in the middle of the lower tool bar do? Nothing.
Can I really zap everyone?
Some people do not have lightning wallets associated with their profile, and Primal produces a perfectly intelligible message for this situation. Compared to Amethyst, I can zap almost any note that has an associated wallet, even Wallet of Satoshi users... or can I? When I zap a note successfully the icon changes instantly. Compare this to other apps that show a wait indicator as the transaction completes. I noticed that even though I would get an indication that the transaction for a Wallet of Satoshi user completed, the icon on the note did not change like it did for other wallet users. I haven't taken the time to look through my transactions to trace everything down, but that seemed suspicious. It's difficult to determine if I really can zap more people in Primal than in Amethyst, but it seems so. Compared to Yana, where I can only zap one wallet, Primal wins in the zap category.
Notifications (and not much else)
I saw my notification area show a dot, "Yay! Let's see what it is!". Later, I find that this badge almost never goes away, giving the user a constant false positive. I tap a bell icon to open the Notifications area. I see that people have reacted, replied, and zapped notes of mine, but there doesn't appear to be a way to find out which note they are responding to. The only way I could find was to search my profile notes section and replies section, (or, if it was a note I had replied to, someone else's notes section and replies section), then scroll through looking for notes that have replies/reactions (replies aren't displayed until you tap on them), until I find a response that matches what I saw in my notifications page. This makes the notifications feature near useless, and it's not the last time I encountered this beast during my journey.
Relay Shell Game?
My feed seemed to be lacking a lot of content, so I looked at the "Network" settings to see what my "Relay" settings were. There was a single entry of "Caching Service" using Primal's cache relay. Here's another "You're going to do it our way" situation. There was a link to "restore default relays", which doesn't make sense since the default relay is obviously the Primal cache relay, but whatever. After hitting the link, eight relays were loaded up. A portion of them were ones I was using, along with some ones I had not used before. I made a text file of my relays, and figured I would paste them into Primal. This would be easier through their web interface than highlighting and pasting with my phone, but then I found that the web interface has all the relays I usually use, but the app doesn't.
Adding Relays Action Mini Game!
There is an option to add more relays. Attempts at adding a relay produced the message, "Unable to add relay. Please try again in a few moments." When I see messages like this from Google Play, I see it the same as a middle finger to the user. Other than communicating "Thing broke", it gives the user no information. How long is a moment? How many of these arbitrary units of time should I wait? Why not give me some error message that I can at least perform a search on? It would be nice to know if the issue is something I may be able to remedy or not. Real information might give me a clue as to how long to wait.
However, let's look at some details here. When I activate the button to add a relay, part of what I'm asking for is that a text string, like "wss://some.nostr.relay", be added to a list. Secondly, I expect that the app will connect to the relay addresses on that list. Sure, there may be connection issues, but why am I getting the error immediately? Why is the relay not added to the list at all? Doesn't Primal want to confirm that I have entered an address to the list even if connection attempts are still being made?
Hold Up, Or Holed Up?
While writing this, I wondered if it's been enough moments, and I was able to successfully add a relay, so I guess whatever mysterious problem took place has been solved ... for now. At the same time, when I visit the Network Settings page, often the relays show red dots instead of green, and sometimes they just stay all red. So what's going on here? Are these relays being used, or not?
Feed Issues - Tap And Rack? No Chance!
While in my profile I saw where I had forwarded a note (while using a different client), but Primal decided to show a Nostr string "nostr:nevent1qqsp9p77x..." instead of the forwarded note. I later saw this a lot in my feed while using Primal. Other clients I've used don't have this issue.
The default feed is "Latest and Replies". This shows me notes created by people I follow, and every reply they make to any note everywhere. This fills my feed with notes like, "Yeah, I think so to.", "That's great", "No, the other one.", "Thanks", or "But WHERE did you shave it???" And, just like the broken Notifications page, there's no way to find out what note they are replying to! Even if I could, I would never opt to open my client to a list of replies. Replies to other people do not add value for me. In fact, it's clutter, which wastes electrons for pixels. It's possible to temporarily change the feed to "Latest", showing only notes created by profiles I follow, but that setting isn't persistent, and will change back to "Latest and Replies" regularly. Primal doesn't want you to curate your own feed. They've decided for you what you're going to see each time you open the app. It seems that getting a "Global" feed is impossible too. Sure, it has a lot of trash, but I've also used it to find new users and cool bots that give me things like "Today in history ..." or tech news headlines. Preventing users from accessing posts just a lame practice overall.
Hashtags
The "Feed List" also has several default hashtags to follow. The hashtags I was following in Amethyst weren't recognized by Yana or Primal. Heck, sometimes Amethyst forgot which ones I was following, so I'm not hurt by it. What I don't understand though, is why Primal wouldn't ask new users what they want to follow. Their preset list is something I completely deleted, leaving only "Latest and Replies" and "Latest". The hashtags I was following in Amethyst could only be viewed in Primal if I made a feed for each hashtag. If you have 133 interests, you would need to load the feed for each one to see any of the content from those hashtags. This is not practical in any way.
"Missing" Notes
One day I opened Primal and saw the note I had been reading when I had last used it. That's so awesome! It shouldn't be, but we're in the world of bleeding edge technology, so simple jollies become huge wins. There was also a notification at the top of the feed showing that more notes had been posted since then. Great! I loaded the new notes, and continued to scroll. Then I noticed something odd. The times of the when the notes were posted went from "15 hrs" to "1 hr", and no notes in between. I had this scenario repeat for me later, which confirmed for me that this is "just how it works". In these cases, there is no way that I can find to get Primal to fetch notes between "last night" and "just a bit ago". Later, when I relegated Primal to being my zap tool, in some cases I was not able to load the note that I wanted to zap, even when searching using the note ID. This defect, whether by design or not, isn't tolerable.
Odds and Ends
There are several other oddities, like:
-
Pictures always loading below the text of a note, even if the author put the URL to a pic before the text. Again, Primal not caring about how people want to do things. The author's intentions are void.
-
There are no "wait" timers when a post is loading. Many times a post will load and it appears there are no replies.
-
Replies of replies are not displayed until after you tap initial reply, then a new page loads showing only the second reply.
-
If you want see the profile of someone in a reply, clicking their pic doesn't do anything. Clicking on profile pics that are not in a reply do take you to the profile.
-
You can't zoom an image. There is a slight "bump" of the pic, so the zoom capability is there, but not enough to make useful.
-
Videos launch your browser instead of running in the app.
-
You can't view a profile pic at full size. If you want to know what that pic is, you're out of luck.
-
The list of your Follows is sorted by the users with the largest number of followers at the top. Whatever logic is in place here is backwards since the top of the list contains people that are most easily found without coming to your list of follows. Alphabetical makes sense here, especially for someone like me that doesn't care about how many followers someone has.
Conclusion (Perhaps)
All software has defects, and it's rare for me to find a title where I can't find something to re-design. This adventure into the realm of bleeding edge technology requires putting up with some incomplete features, and the absence of cushy things, (like being able to select different reactions to a note), but it's also fun to play with, and the possibilities make for some great visions of the future. It would be nice to have a Nostr client for Android that fully embraces the concept of the users and authors being at the helm, while also having all the basic features for navigating and zapping notes.
So what's an adventurer like me to do? What I've been finding myself doing is using Yana to view my feed, Primal to zap posts (if I can find them), and Amethyst to look at my notifications. It's an odd horse to ride, being that it also has a long trunk and a caudal fin, but it's getting me where I'm going for now.
-
-
 @ 3cd2ea88:bafdaceb
2024-03-25 01:42:27
@ 3cd2ea88:bafdaceb
2024-03-25 01:42:27Airdrop da 1 miliardo di BWB: partecipa e prendi la tua quota!
È tempo di cambiare le regole del gioco! Bitget Wallet, il portafoglio Web3 che sfida il potere delle istituzioni centralizzate, lancia il suo nuovo token BWB: un passo avanti verso un futuro di criptovalute più democratico e accessibile a tutti.
BWB: il token che ti premia per essere parte della community
Con un'offerta totale di 1 miliardo di token, BWB è stato progettato per dare valore ai utenti:
5% di BWB distribuiti tramite airdrop: partecipa alla campagna di 6 settimane e ricevi la tua quota! BWB Points per ogni tua azione: completa attività, scambia criptovalute e invita amici per accumulare punti. Converti i tuoi punti in BWB: a partire dal secondo trimestre 2024, trasforma i tuoi BWB Points in token reali. Più di un semplice token: BWB apre le porte a un mondo di vantaggi
Governance della community: vota le proposte e decidi il futuro di Bitget Wallet. Airdrop esclusivi: accedi a token gratuiti di altri progetti all'interno dell'ecosistema Bitget. Dividendi basati sulla crescita: ricevi una quota dei profitti generati da Bitget Wallet. Unisciti alla rivoluzione! Entra nella community di Bitget Wallet e:
Scarica l'app: https://share.bwb.site/inviteLink?code=LyoQza&shareLang=it&teamCode=&source=telegram
Entra nella community Telegram: https://t.me/Bitget_Italia
Insieme, possiamo costruire un futuro di criptovalute più libero e aperto a tutti!
-
 @ 000002de:c05780a7
2024-03-25 01:13:30
@ 000002de:c05780a7
2024-03-25 01:13:30Not long ago I wrote about taxation. I wrote,
Anyone who is capable of logical thought and has seriously considered taxation in relation to other forms of theft will come to the conclusion that either taxation is theft or taxation is just some other thing that they refuse to call theft.
A few years ago I had a bit of an awakening. I started to see how deeply shared lies have become in our culture. What I mean is that there are things that if pressed most people will admit are not true yet we rarely hear people admit this. They speak and accept the lie. I think we do a lot of pretending. We pretend that taxation is not theft. During this awakening I decided that I would no longer lie to myself. I would no longer use terms that are psyops. Phrases like "public schools". They are government schools. Why don't we call them that? My guess is that its because public sounds nicer. I'm not gonna be a jerk about it, but when I am using words I'm not going to use the language of propaganda.
There were several commenters objecting to my post about taxation but none of them actually had any logic or reason to contradict the statement that "taxation is theft". It all sounds like coping to me. It sounds like discomfort with the truth. They were all people rationalizing this form of theft. They were saying we have to have taxes because the current system will fail without it. How will we fund our military defense. I've read the arguments from anarcho-capitalists and they make sense to me.
They point out that in a truly free society insurance companies would likely fill many of the functions of governance that states fill today. Defense agencies would be employed by these companies. As we have seen in the last two centuries the most prosperous nations are those with the most free markets. There are other factors and I'm a aware of them but this is the short answer. My broader point is that to say that taxation is a necessary evil to maintain the status quo isn't wrong. I agree with you. I just reject that the status quo is the best we can do. I think we should be honest about what taxation is and how evil the status quo is.
When I hear people justifying taxation in this way it sounds like the same logic that was used to justify slavery. When you read the debates from the time prior to the war between the states you will see this come up. Today we rightly reject this reasoning for maintaining slavery. Slavery is morally wrong and even if its abolition risked harm to the status quo it should still be abolished. Today we know that not only is slavery morally evil, as economists have demonstrated it is actually less efficient and productive for societies as a whole.
It is my contention that we have not arrived at the ideal state of human organization. It is my contention that taxation is but one form of paying for the costs of governance. I also contend that until individuals stop lying to themselves we can never be truly free as a people. Taxation is theft. It is extortion. It is slavery. We should stop lying about it. We should stop pretending the state is good. Yes, some states are worse than others. That doesn't make the US government good. It makes it less bad. I believe we can do better. I believe that with more individual freedom we could be even more prosperous.
Democracy is but one for of human organization. Monarchists opposed it and some still do. In Democracy: The God That Failed Hans-Hermann Hoppe makes a strong case for democracy leading to larger and larger wars. One reason for this is taxation. Because democracy is the allusion of government by the people it is easier to psyop the masses into believing that taxation is not theft. It is much easier for a subject of a monarch to look at the king with disdain for his taxation to fund his wars. It is much harder to see the truth when you believe that democratic governments are "the people". I don't have all the answers but I personally refuse to lie to myself and accept taxation as morally just, or a necessary evil. It is not.
The state is evil. The state has a monopoly on violence. As I said, not all states are equal. Only a fool would believe that the DPRK is better place to live than the US. That said, we will never rid ourselves of a problem until we recognize it as such. We will never evolve to become a more just society if we do not recognize the evil that is the state.
But, if we are really gonna talk about lies we tell ourselves lets not stop at taxes. If you and I are honest, we know that the state is not really preventing us from doing most things we aren't currently doing. It is us. We are our own worst enemies. But if you are a liberty minded person it can become a crutch to blame the state for every ill in society and by connection why you haven't reached your full potential. Don't fall into this trap. If you live in a relatively free and prosperous nation you have more opportunities than most humans that ever lived. I am writing this to myself as well. I need to reach my full potential. Stop making excuses and do thing things I know I want to do. The things that will make an impact on my life and those that I care about.
Tell the truth to yourself. Stop speaking lies. It is corrosive.
-
 @ 20d29810:6fe4ad2f
2024-03-15 20:51:56
@ 20d29810:6fe4ad2f
2024-03-15 20:51:56













































-
 @ 3cea4806:10fe3f40
2024-03-25 00:42:07
@ 3cea4806:10fe3f40
2024-03-25 00:42:07Chef's notes
The directions are for the Posh version. For the Poor version, just drizzle honey mustard on the rice and enjoy.
Here's the video I made for this "dish": https://www.youtube.com/watch?v=lKWIHYO_WSI
Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 5 min
- 🍽️ Servings: 1
Ingredients
- rice
- honey mustard
Directions
- Get a tiny cup
- Get a plate
- Get rice
- Get honey mustard
- Top-up the the tiny cup with with rice
- Cover that tiny cup with the plate then flip it
- Wait 2 to 4 minutes until it stabilizes then remove the tiny cup
- Drizzle a line of honey mustard near the rip of the plate (to make a quarter circle)
-
 @ 06639a38:655f8f71
2024-03-13 12:52:07
@ 06639a38:655f8f71
2024-03-13 12:52:07I started using Proton as my default email service provider in 2022. I’ve more than 500Gb storage there available including a service called Proton Drive for file storage. This is quite a lot for just email. So I asked myself, how can I use the other amount of space as an extra backup storage solution?
I also published this article on my blog: https://sebastix.nl/blog/using-proton-drive-as-a-backup-storage-location-with-rclone/
Quite a while ago I discovered a free and open-source tool called Rclone. It pretends to be a swiss knife for file management between different remote storage locations (more than 50 so-called cloud providers) including Proton Drive. The following instructions are intended for Ubuntu which was my environment to test it out. They could apply for other Linux distros as well. Please follow the Rclone docs for more details.
Installing Rclone
Follow the latest install instructions here.
Execute this command on your terminalbash sudo -v ; curl https://rclone.org/install.sh | sudo bash
and Rclone will be installed on your machine. To check if the installation succeeded, runrclone --versionand a version will be return.
You can update Rclone easily withrclone selfupdate.
Executerclone --helpto return a full list with available commands.Configure Rclone and Proton Drive
Run
rclone configand choose Proton Drive as a remote (option number 40 in my case). After the config, get the name of the remote withrclone listremotes.
If this doesn't work out for you, please check the latest Proton Drive docs on Rclone here.Copy or sync files to Proton Drive
Let's create a simple file called copy-me.txt in the current directory.
bash echo 'this file will be copied to proton drive with rclone' > copy-me.txtExecuterclone -v copy copy-me.txt protondrive:and this will copy the backups.txt file to your Proton Drive.
The output will look something like this:
You can check if the file is in your Proton Drive by viewing your list of files at https://drive.proton.me/:
Automated backups with cronjobs
We can use
rclone syncto perform backup actions.
The full command will look something like this:
bash rclone sync -v --create-empty-src-dirs ~/backups protondrive:/backups
Executecrontab -eto edit your crontab file with cronjobs and add the following line:
bash 3 0 * * * rclone sync -v --create-empty-src-dirs ~/backups protondrive:/backupsNow every night at 3am this command is executed.Backing up docker volumes
As a non-root user, you can’t access the directory with docker volumes at
/var/lib/docker/volumes. You must login as root (sudo su) and config your rclone installation again withrclone configas we did earlier. After you’re done, you can copy/sync the docker volumes.bash rclone sync -v --create-empty-src-dirs /var/lib/docker/volumes protondrive:/backups/docker-volumesYou could add this command with a cronjob as well withcrontab -eunder the user root.Email output of the cronjobs
To check if the cronjobs are running correctly, you can send an email with the output of the cronjob. Please read some solutions here how to manage that.
Solid solution? How long will it work?
For now let's see how these Rclone commands with several cronjobs will run with Proton Drive for the coming period. I can imagine when a change is made on the Proton side, things could break on our side with Rclone. I hope I don't have to update Rclone too regular (let's say weekly) to keep things working.
Used resources
- https://dev.to/itsbetma/automated-backups-with-cron-and-rclone-3do4
- https://blog.rymcg.tech/blog/linux/rclone_sync/
-
 @ 1e52c554:21771908
2024-03-12 16:13:16
@ 1e52c554:21771908
2024-03-12 16:13:16Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna

Analysis "Beach Rendition 4"
Introduction
Sonnet 116 by Francisco Luis Arroyave Tabares, titled "Beach Rendition #4", is a beautiful piece of poetry that explores the themes of love, memory, and nature.
Thematic Analysis
First Quatrain: The speaker describes a state of feverish anticipation that is calmed by the languor, or relaxed state, of the person addressed. The speaker is holding their breath to forget mild fears, which are brought back by memories associated with the person’s name. These memories stir up old tears.
Second Quatrain: The speaker’s emotions yield to the creation of the person addressed. The person’s bareness and smiles play on the speaker’s skin, causing a sensation that beguiles, or charms, the speaker’s heart. The term “scarlet” is used here to denote things that are erotically stimulating.
Third Quatrain: The speaker describes a semi-darkness in which the person’s utterance comes, hinting between the rustling breeze. This breaks their silence intermittently, as fresh and wanton scents please their senses.
Couplet: The speaker describes how Selene, the moon goddess, colors the person’s flock with silver blond. They reach strands of wonder and beyond, suggesting a sense of awe and transcendence.
Overall, the sonnet explores themes of memory, longing, sensual pleasure, and transcendence. The speaker’s emotions are deeply intertwined with their sensory experiences, creating a richly textured emotional landscape. The sonnet ends on a note of wonder and possibility, suggesting a journey that continues beyond the poem’s final line.
Rhyme Scheme
The sonnet “Beach Rendition #4” follows the rhyme scheme of a Shakespearean sonnet, which is ABABCDCDEFEFGG. Let’s break it down:
First Quatrain:
My fever stops in front of thy languor (A) And I hold my breath to forget mild fears (B) Which memory brings to be a clamor (A) That summons with thy name in me old tears. (B)Second Quatrain:
Emotions, though, yield to thy creation (C) When thy most torturous bareness and smiles (D) Frolic on my skin with a sensation (C) That bring my scarlet and my heart beguiles… (D)Third Quatrain:
In semi-darkness comes thy utterance (E) Surely hinting between the rustling breeze (F) That breaks our hush when, with intermittence (E) Some fresh and wanton scents our senses please. (F)Couplet:
Selene colors thy flock with silver blond (G) And we reach strands of wonder and beyond. (G)This rhyme scheme is typical of English or Shakespearean sonnets. The final couplet often serves as a conclusion or a summarizing statement. In this sonnet, the couplet provides a beautiful and transcendent image that encapsulates the speaker’s awe and wonder. The rhymes contribute to the musicality and rhythm of the poem, enhancing its emotional resonance.
Additional Aspects
Let’s delve deeper into the analysis of Sonnet 116 by Francisco Luis Arroyave Tabares:
Language: The sonnet uses a formal and poetic language, with a rich vocabulary and complex sentence structures. The use of “thy” and “thou” gives the poem an archaic feel, reminiscent of traditional sonnets.
Imagery: The poem is filled with vivid imagery that appeals to the senses. For example, “thy most torturous bareness and smiles / Frolic on my skin with a sensation” creates a tactile image that conveys the speaker’s physical response to the person addressed. The “semi-darkness,” “rustling breeze,” and “fresh and wanton scents” create a sensory-rich setting that enhances the emotional depth of the poem.
Themes: The sonnet explores themes of longing, memory, sensual pleasure, and transcendence. The speaker’s emotions are deeply intertwined with their sensory experiences, creating a richly textured emotional landscape.
Meter: The sonnet follows the iambic pentameter, which is a common meter in English poetry and is particularly associated with sonnets. Each line consists of five pairs of unstressed and stressed syllables, giving the poem a rhythmic quality.
Overall: the sonnet is a beautifully crafted piece of poetry that skillfully combines language, imagery, themes, and meter to create a deeply emotional and sensory-rich experience for the reader. The sonnet’s structure and rhyme scheme provide a solid framework for the exploration of complex emotions and sensory experiences, resulting in a poem that is both intellectually engaging and emotionally resonant. The sonnet ends on a note of wonder and possibility, suggesting a journey that continues beyond the poem’s final line. The sonnet is a testament to the power of poetry to capture and convey the richness and complexity of human experience.
(GPT4)
Syllable count for each line.
``` Beach Rendition #4
10 My fever stops in front of thy languor 10 And I hold my breath to forget mild fears 10 Which memory brings to be a clamor 10 That summons with thy name in me old tears.
10 Emotions, though, yield to thy creation 10 When thy most torturous bareness and smiles 10 Frolic on my skin with a sensation 10 That bring my scarlet and my heart beguiles...
10 In semi-darkness comes thy utterance 10 Surely hinting between the rustling breeze 10 That breaks our hush when, with intermittence 10 Some fresh and wanton scents our senses please.
10 Selene colors thy flock with silver blond 10 And we reach strands of wonder and beyond. *** ```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image by Frank Duna; First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 Beach Rendition # 4
Beach Rendition # 4 -
 @ 4657dfe8:47934b3e
2024-03-12 11:36:36
@ 4657dfe8:47934b3e
2024-03-12 11:36:36
Bitcoin is the native currency of the Internet. Digital scarcity however comes with certain costs and tradeoffs that are a bit unintuitive and not immediately obvious. For example — If bitcoin is purely digital, why can't we use it on every corner of the Internet with ease? If it's natively digital, why is there still an issue with receiving instant payments in a sovereign way? The list could go on. Bitcoin is the native currency of the Internet, but it still needs more time and care to become really in its element.
At Alby, we have always believed that we'll arrive at a point where you can easily populate any app or website you dream of with bitcoin. That sending and receiving bitcoin will be as easy as sending an email, login in will be easier than doing so with Google or Facebook. In a digital age supporting your favourite podcaster should be natural and swift, like you reward a busker on the street, not harder to do so.
Alby is an answer to a big need we identified — a need for using bitcoin seamlessly while you're surfing the web of bitcoin apps, on these popular social media pages or for fun on websites your friends built. And this need urged to be addressed now, not in the next five years, but today. Even if sovereign tech was not yet ready for a big part of what we all wanted to do.
That's how the Alby Extension was born and it provided a balanced choice: you can use it in a totally sovereign way, connecting your own node and plugin into many apps thanks to WebLN protocol.
But there’s also an easy and accessible wallet experience for newcomers and users who aren't necessarily up for the struggles of running a node, like artists and creators. Alby Accounts provide exactly that.
In total, we brought and popularized bitcoin use cases that haven't been possible before to thousands of users: streaming bitcoin in live concerts or video broadcasts, one-tap zaps to dozens of Nostr clients, QR-codeless lightning payments, logins to bitcoin web apps by just clicking one button, and many, many more.
But only half of those things were possible for node-runners or self-managed wallets. If you wanted to stream bitcoin in a mobile podcast player, or want to automate payments with the Alby Wallet API, you had to use a wallet managed by Alby. And a self-managed way of doing the same seemed a distant future.
Until today...
The path forward
We found ourselves at a crossroad. We could go on with expanding Alby Accounts capabilities, which was offered to make it easy for users to start with bitcoin payments and the Alby Extension in the first place.
Or is the time now right to choose the technically still difficult, but also more rewarding and — we believe — moral path of empowering users with self-managed wallets and the proven Alby user experience: Giving bitcoin wallets superpowers. Making them interoperable with the entire Internet, whether it's an app, a website, an online game, or a plugin for your favourite software. No matter if it's a web browser, a mobile or, (why the hell not?) a smartwatch. Bitcoin can reach it all.
For the past couple of months, we have been focusing on finding a way for the second path. We believe that a measure to give those superpowers to bitcoin wallets lies in Nostr Wallet Connect (NWC). Nostr in this case does not have anything to do with social media, but rather serves as a communication and coordination layer between lightning wallets and apps. This allows for building some really wild use cases that were hard to pull off before we had such a layer. That's why we now double down on raising awareness on the potential of NWC. We also developed Bitcoin Connect, a supplementary library with the goal to make it dead simple and super fast to add bitcoin to your product.
NWC really shines and brings us really close to the familiar experience you now have with an Alby Account when it's combined with a cloud based bitcoin lightning wallet. We're now experimenting with technologies such as Greenlight, Breez SDK and LDK to craft a powerful, self-managed wallet that you'll be able to bring to any app, website, game or any other kind of software that will implement NWC.
You'll be able to do things like one tap zaps, automated monthly subscription payments or in-game bitcoin transfers instantly, 24/7, without limits while maintaining full control over your funds.
How cool is that?
-
 @ ebbdabe3:ae797cd2
2024-03-25 00:23:32
@ ebbdabe3:ae797cd2
2024-03-25 00:23:32DoraHacks作为全球最大的多链Web3开发者激励平台,在提供Hackathon/Grant/Bounty等组织工具的同时,也不断发展更好的去中心化治理工具和机制,为全球的开源社区提供公平、合理、多样的治理方式是DoraHacks团队的重要使命。
社区治理的情景中,共谋(collusion,或者叫“串通”)是一类普遍而深刻的问题,这种行为的产生可能是出于利益驱动,也可能是因为人情/裙带关系,并且在各种投票机制下都很难避免。有效的链上抗共谋基础设施,将决定去中心化治理是否能够规模化,例如,协议链上治理,以及二次方资助(Quadratic Funding)等。
共谋行为的弊端显而易见。其一是,资助的初衷是支持初创项目的成长,但共谋往往使得已有资源的项目更容易获得资金,形成了资源向强者集中的马太效应。第二,二次方算法原本旨在解决传统投票机制的不公平问题,但在共谋盛行的情况下,投票的有效性大打折扣。第三,共谋的存在也阻碍了包括二次方投票在内的优秀链上治理工具的大规模采用。
DORA团队经过多次的实践、探索、迭代,通过多种机制改进实现了更加公平、可靠的二次方资助方式,可以在DoraResearch Blog(https://research.dorahacks.io/)看到更多信息。
MACI(最小化防共谋基础设施)是DoraHacks解决二次方治理公平性问题的方案之一。它基于zkSNARK技术,为链上投票提供了隐私保护。与基于链上广播机制的透明投票不同,MACI确保了投票的匿名性,仅展示投票结果,而非投票细节。也就是说,MACI使得区块链不再提供公开的投票凭据,被投票者也无从验证。回到文章开头的那个例子,社区共谋的下一步本应该是用链上投票记录来换取奖励,而这种模式在MACI投票机制中是无效的。
MACI投票已经多次用于DoraHacks平台上hackathon奖金池/grant资助池的分配。在2022年2月的ETHDenver线下BUIDLathon中,MACI二次方投票(MACI-Quadratic Voting)首次被用于大型Web3社区治理,社区通过MACI二次方投票共同决定了1,000,000 SPORK匹配奖金池的流向,也使全球加密社区认识了MACI基建的潜力。之后,在ETHDenver线上BUIDLathon,Opensea Hello NFT Hackathon,Dora Grant DAO,0x Defi Hackathon等大型hackathon中,MACI投票都作为社区/评委投票的重要机制发挥了作用。
然而,普通的MACI投票还存在两个问题,一是技术门槛过高 - 尽管MACI投票需求广泛,但其合约开发对许多加密社区成员来说仍是挑战。针对这一点,Dora Factory开发的无代码MACI投票部署平台Vota已在2023年上线,使非技术社区也可以轻松完成MACI链上投票部署。Vota内置的投票机制包含一次方投票和二次方投票,覆盖了链上投票的绝大部分场景。MACI管理员只要在平台点击“Deploy MACI”后进行简单的投票规则设置,即可以在几分钟内完成一个MACI投票轮的部署。
Dora Dojo社区是Vota平台MACI投票应用的典型案例。该社区定期进行知识分享提案投票,涵盖密码学、量子计算等领域。通过MACI投票,社区成员可以直接决定哪些提案值得资助。尽管管理员不具备MACI部署知识,但通过Vota的指南,也能快速完成投票的链上和前端部署。Dora Dojo已将MACI投票作为月度活动,成功资助了超过20个提案,展示了去中心化治理的潜力。
在Dojo的实践中,当社区成员被问到“如果不采用MACI投票的方式,你是否会改变你的投票选项?”,有超过50%的投票者回答了“是”,理由是同在社区里,投票者和被投票者之间可能互相认识,所以不想被知道自己没有给某个熟识的项目投票。可见,即使是不考虑共谋的情况下,投票者自身也有保证投票内容隐私的需求。
第二个问题是,MACI的零知识证明操作需要管理员,这也是MACI最重要的信任假设。在MACI中,管理员虽然不能伪造投票信息,但可以与外界发生共谋,限制了MACI的使用场景。早期,以太坊社区对匿名MACI的潜在方案进行了若干探讨,例如基于MPC的匿名MACI,以及通过ElGamal重随机函数进行匿名化的讨论等。匿名MACI的目标是,管理员也无法知道“谁”做了“什么”,由此实现全面的抗共谋。DoraHacks和Dora Factory社区自2023年开始进行匿名MACI的基建工作,并初步实现了不依赖于多方安全计算的匿名MACI协议。DoraHacks aMACI的具体操作是投票者的”deactivate key”和“reset key”行为。通过这个过程,管理员无法追踪用户的投票行为,也就完成了投票者本身的匿名化。
DoraHacks在2023第一次推出了匿名MACI(aMACI)投票基建。2024年3月,在越南河内举办的ETHVietnam 黑客马拉松中,aMACI第一次被用于大型线下Web3活动,168位社区成员参与了基于aMACI的链上匿名投票来决定2000美元奖金池的分配。
这是匿名MACI协议被加密社区采纳的一个重要里程碑。此前,DoraHacks平台上的以太坊研究长期Grant “ETH Research Grant”也已将aMACI实际用于多轮社区投票,来决定项目资助结果
DoraHacks作为发展去中心化治理和MACI基础设施的先行者,致力于创造更好的去中心化治理机制与工具,为加密社区带来更加民主、高效和安全的决策环境。匿名MACI(aMACI)投票协议的上线,进一步消除了治理过程中潜在的共谋风险,确保了每个社区成员的投票权利得到平等尊重;Vota平台的发布,降低了MACI部署的技术门槛,使得更多的社区能够参与并受益于这种治理模式。作为一种创新的治理机制,MACI为去中心化治理带来的想象空间是无限的。
相关文章 Implementation Notes on “MACI anonymization using rerandomizable encryption” https://research.dorahacks.io/2023/05/21/rerandomizable-encryption-maci-anonymization-notes/
PLONK-Based MAC Ihttps://research.dorahacks.io/2023/02/02/plonk-based-maci/
Quadratic Governance: What’s Working and What’s Not? https://research.dorahacks.io/2022/07/11/quadratic-governance/
Vota: Special Purpose Blockchain for Voting and Decentralized Community Governance https://research.dorahacks.io/2023/07/31/vota/
Reduce Quadratic Funding Inequality with a Progressive Tax System https://research.dorahacks.io/2021/06/16/reduce-quadratic-funding-inequality-with-a-progressive-tax-system/
Grant Funding Distribution Algorithm (Progressive Tax V2) https://github.com/dorahacksglobal/qf-grant-contract/blob/bsc-long-term/grant-distribution-algorithm-en.md
-
 @ 5e73c80b:08433652
2024-03-24 22:48:31
@ 5e73c80b:08433652
2024-03-24 22:48:31I was just curious to hear your thoughts on this. I saw this on the Netflix show "Encounters" and it blew my mind.
-
 @ 676c0224:e641b6d6
2024-03-24 20:07:55
@ 676c0224:e641b6d6
2024-03-24 20:07:55test
-
 @ fe7f6bc6:c42539a3
2024-03-12 03:31:13
@ fe7f6bc6:c42539a3
2024-03-12 03:31:13Sleeping on the floor has gained attention as an alternative to traditional beds with proponents citing numerous health and wellness benefits (YES BEDS ARE A SCAM). This practice, which is deeply rooted in some cultures, is not just a trend but a lifestyle choice for those people. This FAQ sheet aims to demystify floor sleeping, providing insights into its goals, benefits, best practices, and what newcomers can expect during the transition. I’ve been testing it for the last 4 weeks and i can’t recommend it highly enough. Here’s my experience: https://youtu.be/ICnLS1BbZ_w
Goal of Sleeping on the Floor
The primary goal of sleeping on the floor is multifaceted, focusing on improving overall health and well-being. Advocates of this practice report significant improvements in posture and spinal alignment, leading to less back pain and better body support during sleep. Additionally, floor sleeping is said to promote a deeper, more restorative sleep by facilitating a natural sleeping position, free from the constraints of modern mattresses that can sometimes exacerbate chronic pain issues. Since i’ve been sleeping on the floor i’ve been able to reduce my sleep by 1-2hours without feeling tired.
Health Benefits
The decision to switch to floor sleeping often stems from the desire to alleviate persistent back and neck pain. The firmness of the floor can provide better support for the spine, potentially reducing discomfort associated with conditions like scoliosis, herniated discs, and general backaches. Moreover, some find that this practice enhances sleep quality, resulting in more restful nights and energized mornings.
Cultural Practices
In Japan, for example, the traditional use of tatami mats and futons on the floor is widely used. This cultural usage provides a historical and practical foundation for the practice, suggesting that the benefits of floor sleeping are more than anecdotal. (Yes, we’re not that crazy)
Getting Started
Choosing the Right Surface: Not all floor surfaces are created equal when it comes to sleeping. Hardwood floors or tile can provide the firm support needed for spinal alignment, but they may be too harsh for some. Consider laying down a thin mat, such as a yoga mat, or a folded blanket to create a barrier that offers both support and a bit of cushioning.
Creating a Comfortable Setup: The key to a successful transition is finding the right balance between firmness and comfort. Start with a thin mattress, futon, or several layers of blankets. The goal is to protect your body from the hard floor without negating the benefits of firm support. Experiment with different setups to find what works best for you.
Optimal Sleeping Positions: Back sleeping is often recommended for floor sleepers, as it allows your spine to rest in a neutral position. If you prefer sleeping on your side, keep your legs slightly bent and consider placing a pillow between your knees to maintain hip alignment. Stomach sleeping is generally discouraged due to the strain it can place on your neck and lower back.
Adjusting to Your New Sleeping Environment: Transitioning to floor sleeping can take time. Start by incorporating floor naps into your routine or sleeping every other night on the floor until your body adjusts. Listen to your body and make modifications to your sleeping setup as needed to ensure comfort and proper support.
Room Temperature and Environment: The floor can be cooler than your bed, especially in colder months (in thailand this gives an additional cooling factor - which is nice). Ensure your sleeping area is warm enough by adjusting the room temperature or using additional blankets. A clean, quiet, and dark environment will also help promote a good night's sleep.
Floor Cleanliness: Maintain a clean sleeping area to prevent dust and allergens from affecting your health. Regularly clean your floor and wash any mats, blankets, or bedding you use. I am allergic to some dust and once it's getting to dusty my nose definitely feels the difference on the floor.
The First Days: What to Expect Initial Discomfort and Adjustment Period: It's normal to feel some discomfort, such as stiffness or soreness, when you first start sleeping on the floor. Your body is adjusting to a new surface, and these sensations are typically temporary.
Duration of Adjustment Period: The adjustment period varies from person to person but generally lasts a few days to a couple of weeks. Gradually, your body becomes accustomed to the new sleeping arrangement, and discomfort should diminish.
Overcoming Initial Challenges Easing Into It: If the transition proves difficult, consider alternating between your bed and the floor until you're more comfortable. Short, incremental adjustments can make the transition smoother and less daunting.
Managing Discomfort: Simple measures like stretching before bed, using a warm bath to relax muscles, or adjusting your sleeping setup can significantly reduce discomfort. Over time, these practices can help ease the transition and improve your floor sleeping experience.
Last but not least - listen to your body!
This practice is not for everybody, try it for a couple of days and see if you can push through the initial challenges… the rewards once your body gets used to it are worth it.
If you have any questions reach out!
Stay hard - Max
-
 @ 676c0224:e641b6d6
2024-03-24 19:15:53
@ 676c0224:e641b6d6
2024-03-24 19:15:53haha I'm testing haha
-
 @ 676c0224:e641b6d6
2024-03-24 19:15:03
@ 676c0224:e641b6d6
2024-03-24 19:15:03haha I'm testing haha
-
 @ 5b15bd1a:326a770d
2024-03-11 01:38:12
@ 5b15bd1a:326a770d
2024-03-11 01:38:12Here is a full list of books, articles, podcasts, exchanges, and apps that I recommend. There are many more out there which you will most likely find as you go down the Bitcoin rabbit hole.
Books
The Bitcoin Standard - by Saifedean Ammous
Broken Money - by Lyn Alden
Layered Money - by Nik Bhatia
The Fiat Standard - by Saifedean Ammous
Why Buy Bitcoin - by Andy Edstrom
Bitcoin is Venice - by Allen Farrington and Sacha Meyers
The Progressive Case for Bitcoin - Jason Maier
The 7th Property - by Eric Yakes
The Book of Satoshi - by Phil Champagne
The Blocksize Wars - by Jonathan Bier
The Price of Tomorrow - by Jeff Booth
Check Your Financial Privilege - by Alex Gladstein
B is for Bitcoin - by Seb Bunney
The Hidden Cost of Money - Seb Bunney
Podcasts
We Study Billionaires - Bitcoin Fundamentals - Preston Pysh
What Bitcoin Did - Peter McCormack
Blue Collar Bitcoin - Josh and Dan
Bitcoin Audible - Guy Swann
Stephan Livera Podcast - Stephan Livera
TFTC: A Bitcoin Podcast - Marty Bent
The “What is Money” Show - Robert Breedlove
Bitcoin Rapid-Fire - John Vallis
The Bitcoin Standard Podcast - Saifedean Ammous
Articles
“The Greatest Game” - by Jeff Booth
“The Number Zero and Bitcoin” - by Robert Breedlove
“The Bullish Case for Bitcoin” by Vijay Boyapati
“Schelling Out” - by Nick Szabo
“7 Misconceptions about Bitcoin” - by Lyn Alden
“The Masters and Slaves of Money” - by Robert Breedlove
“Gradually then Suddenly” - by Parker Lewis
Bitcoin Exchanges
Swan Bitcoin - referral code - for $10 in Bitcoin - https://www.swanbitcoin.com/bsteig
River - https://river.com/
Cash App - referral code to get $5 - http://cash.app/app/LQGMPKC
Strike - referral code to get $5 once you make a deposit - https://invite.strike.me/YOJ778
Bitcoin Wallets
Coldcard - https://coldcard.com/
Foundation Passport - https://foundationdevices.com/
Trezor - https://trezor.io/ (phishing email concerns as of Jan 2024)
Ledger - https://www.ledger.com/ (installed a recover feature that is a bit controversial on the privacy side in 2023)
Apps and Others
Fold - a debit card that gives you bitcoin back on every purchase - referral code for 20,000 sats -use.foldapp.com/r/lz0LuG90
Lolli - Get bitcoin back for online and in store purchases - referral code for $5 - https://lolli.com/share/9F24DG
Yzer - like Duolingo for Bitcoin - referral code for 50 sats once you reach level 2 - SteigerBTC
Orange Pill App - find other Bitcoiners and meetups - referral code for 10,000 sats -
https://signup.theorangepillapp.com/opa/steigs
Bitcoin Magazine - Find the newest articles in the Bitcoin space and get paid in sats to read them.
Fountain - A podcast app that allows you to get paid in Bitcoin for listening.
BTC Sessions on Youtube– How-to videos on just about anything you want to do in the space.
Nostr - A decentralized social media platform (akin to Twitter) with many different clients such as Amethyst, Damus, Primal, Iris, Snort, Plebstr and Yakihonne which can be found on the IOS and Google Play Stores. Bitcoin is the native currency of this platform and can be sent to anyone else in the world using the platform instantly. You can use private keys to take your information from one client to the next and take complete control of your data without risk of being de-platformed.
Website
https://bitcoin-resources.com/
https://bitcoin.org/en/
https://unchained.com/
-
 @ 676c0224:e641b6d6
2024-03-24 19:11:21
@ 676c0224:e641b6d6
2024-03-24 19:11:21testing hahatest
-
 @ b9c09954:815d302d
2024-03-09 15:11:16
@ b9c09954:815d302d
2024-03-09 15:11:16Part 2 of a 5 part series for beginners about the importance of online privacy.
Goto Part 1
In an era where digital footprints are as indelible as ink, the collection and analysis of personal data by free online services have become a cornerstone of the digital economy. This seemingly benign exchange—data for services—masks a labyrinth of privacy implications that affect not only individual users but also the fabric of society at large. This article delves into the risks associated with data collection practices, their broader consequences, and the psychological impacts of living under the digital gaze.
Understanding Personal and Sensitive Information
The term 'personal data' encompasses a wide array of information. At its core, it includes any data that can be used to identify an individual, ranging from names and email addresses to more sensitive data like health information, political opinions, and religious beliefs. The collection of this data isn't inherently malevolent; it underpins many of the conveniences and personalizations of the digital age. However, the line between use and misuse is thin and often blurred.
Risks Associated with Data Collection
- Identity Theft: The aggregation of personal data in databases makes them ripe targets for cybercriminals. A breach can lead to identity theft, where individuals' information is used to commit fraud.
- Profiling and Targeted Manipulation: Detailed user profiles aren't just used for advertising. They can be exploited to manipulate behaviors and decisions, from influencing purchasing decisions to swaying political views.
- Surveillance and Loss of Anonymity: The omnipresence of data collection tools translates into constant surveillance, eroding the concept of anonymity. This has implications for freedom of speech and can foster self-censorship.
The Broader Consequences of Data Collection
The collection and exploitation of personal data don't just affect individuals; they have societal implications. The capacity to monitor, track, and influence large swathes of the population raises concerns about democratic processes and social autonomy. In extreme cases, it can lead to a form of digital authoritarianism, where control over data equates to control over populations.
Psychological Impacts
Living in a state of constant surveillance has subtle yet profound psychological impacts. It can lead to a sense of powerlessness, anxiety about being watched, and self-censorship. The knowledge that one's data can be collected, analyzed, and possibly misused without consent can alter online behavior, stifling the freedom that the internet once promised.
Navigating the Minefield
- Awareness and Education: Understanding the nature and scope of data collection is the first step toward protecting oneself. Education on digital literacy can empower users to navigate the digital space more cautiously.
- Privacy-Enhancing Technologies (PETs): Technologies such as encryption, secure browsers, and privacy-focused apps can provide layers of protection, making it harder for personal data to be collected and misused.
- Regulatory Frameworks and Legal Protections: Legislation like the General Data Protection Regulation (GDPR) in the EU and the California Consumer Privacy Act (CCPA) in the US aim to give individuals more control over their data. Awareness of and advocacy for such protections can help in the fight for privacy.
Conclusion
The collection of personal data by online services, while facilitating unprecedented levels of convenience and personalization, introduces a myriad of privacy concerns. These concerns extend beyond the individual to affect societal norms and democratic principles. In this digital age, vigilance, education, and the use of privacy-enhancing technologies are essential for individuals to protect their digital selves. Simultaneously, robust legal frameworks and regulations are needed to ensure that the collection and use of data are conducted ethically and transparently, safeguarding the digital rights of individuals and the integrity of our digital society.
-
 @ bb47ffda:2325f9ac
2024-03-24 17:26:00
@ bb47ffda:2325f9ac
2024-03-24 17:26:00Previously I had to asked one of the primal devs. But on a separate account, I don't want to bother them.
My new account, with scriptures rewritten for Bitcoin: https://njump.me/npub1hdrllkn6majeq5cr4q034fhh98s9rrqyrrp59j4d4hu6kge9lxkqqtsree
-
 @ 30ceb64e:7f08bdf5
2024-03-24 17:20:02
@ 30ceb64e:7f08bdf5
2024-03-24 17:20:02Hey Freaks,
We are living through a convergence of decentralized cryptographic protocols FOSS and Machine Learning. - The money protocol, with a value proposition of outperforming fiat currencies due to its supply limit, young adoption so the discrepancy will grow, global access with internet/smartphone network effects. Self custodied, secure, increases in value over time, permission-less, globally available, near free - The Communications protocol, censorship resistant communications through social media applications, website integrations, universal contact list, money protocol coordination. Permission-less, near free, No 3rd party intermediaries, secure, increases in value over time, globally available - Large Language Models, Content generation, Customer service and support, Translation Services, Writing assistance, Legal research, healthcare, Educations, Marketing, Financial service, Cyber-security. Open source, permission-less, globally available, locally run, near free - 3d Printing, Home Repairs and fixes, Furniture, Tools, Weapons, Kitchenware, Toys, Music Equipment, Bikes, Cars, globally available, low cost - Mesh Networks, Decentralized, private, local and resilient, low cost - Etc.
Combined with: - Jurisdictional arbitrage between Citadels (Strong Communities/Localism/Urbanism) - Decentralized group of remote Plebworkers - Bitcoin Veterans logistics and transportation support - Etc.
I'm looking at things through a Sovereign Individual, Cryptosovereignty, Price of Tomorrow, Softwar perspective.......And it looks wild.
Purchasing power will flow to those who understand, master or muster the transition from the industrial to the digital age.
The FOSS above will consume our world and alter it inevitably (I believe for the better). The great convergence presents all of humanity with a greater opportunity to partake in the hero's journey and leave a lasting legacy.....or to get stolen from less.....
Good Luck Freaks, Hustle
-
 @ 06a5736d:9993b167
2024-03-07 09:44:42
@ 06a5736d:9993b167
2024-03-07 09:44:42Chef's notes
I found the recipe on BBC recipes, should be the first one to pop up if you google easy banana bread recipe.
Details
- ⏲️ Prep time: 15-20min
- 🍳 Cook time: 40-50min
- 🍽️ Servings: 4-8 (depending on portion size). I also didn’t bake this in the usual bread tin, I used a semi deep oven dish as that’s all I had.
Ingredients
- 140g unsalted butter
- 140g caster sugar (I only put 90g as it was for the kids but you can tweak it to your liking)
- 2large eggs
- 1tsp baking soda
- 140g self raising flour
- 1tbs cinnamon powder
- 1tsp vanilla extract
- 1 cup fresh blueberries
- 3 ripe bananas
Directions
- Beat the butter and sugar until a paste is formed
- Add in 2 beaten eggs and mix together
- Gently add the flour and baking soda bit by bit whilst mixing it all well
- Once combined, add in your cinnamon and vanilla
- Add in your washed blueberries
- Mash the bananas well and add to mixture.
- Fold the mixture until well mixed together and set aside
- Preheat oven to 180c
- Butter your dish and line with parchment paper ( I didn’t have this available so I covered it with butter and then added flour all around to prevent it from sticking. Works just the same)
- Once oven is heated up, carefully place the dish into the middle and bake for 40-50min. Make sure to check after 30min as every oven is different.
- Once cooked, remove from oven and let it cool for 10mins before removing from dish (this is to prevent it from falling apart)
- Last step. Cut a slice and enjoy on it’s own or how I did, with some yummy custard
-
 @ 5b0e8da6:7792bc54
2024-03-05 15:57:43
@ 5b0e8da6:7792bc54
2024-03-05 15:57:43I recently completed my home 7.1.4 speaker setup and have been really enjoying digging into high-end Dolby Atmos and Dolby Vision material. Playing around with nip23 long-form content to share this kind of niche nerd stuff that doesn't quite make sense as a regular nostr note.

tldr: Still a joy, though much of its intentional over-the-top ridiculousness is just too much for me now. The absolute trash 4k transfer is a tragedy.
The movie
I'm fairly sad to report that I just couldn't enjoy the first hour or so anymore. More and more of the movie's creative absurdity that I previously loved is souring to cringe.
The bulky, waddling alien designs in the intro sequence are just pointlessly dumb.
The savage lampooning of an American-style government — from the casting of a President who looks and sounds like an NFL lineman to all the stupid and/or war-hungry military leaders — I'm sure is hilarious to the French creative team (and, sure, somewhat deserved), but it's just so blunt and caveman-y and insulting. I'm not interested in defending America's honor, but this is just so dumb and cruel in its way that it's unpleasant to watch.
Gary Oldman is, as always, a powerhouse. But when you direct him to go big with the campiness, it's... it's a lot.
Things improve once Leeloo starts to take over the story. And, maybe this is a surpise given the above, but Chris Tucker's how-do-you-even-describe-it Ruby Rhod is still a shockingly successful, brain-breaking spectacle. Happy to report that the Fhloston Paradise set piece is still a gem and is where all the unique absurd energy truly finds its groove.
Overall, I think the movie still works. Luc Besson is unapologetically asking us to YOLO into this crazy world. It's experimental in a idgaf way but he does real work to layer in an appealing emotional core between Corben and Leeloo. It does all somehow come together and ultimately works surprisingly, uniquely well — if you can get past the first hour.
Video
https://i.nostr.build/0ren.jpg
Just straight trash.
Sidebar: On image processing / contrast
Our eyes want strong contrast in images. You might complain that this pic is just a little too muted:
https://i.nostr.build/8Y9J.jpg
But once you start tinkering, it can be very easy to way overshoot the mark:
https://i.nostr.build/jQAr.jpg
Some of you may think, "Uh, I prefer the boosted version." Yes, it's more lively to our eyes, certain things are so much more emphasized now that you can appreciate those details more. But then look at the highlights. They're so boosted that details have disappeared into full white. Same for the shadows. Crushed to pure black.
The art is to dial in just the right amount of contrast boost without blowing out the highs or crushing the lows. And there's just an overall harshness where there had previously been subtle gradations of color and texture. The more you work with image processing, the more you appreciate a lighter touch.
Here's another set:
https://i.nostr.build/lBRA.jpg
https://i.nostr.build/P94W.jpg
This was a lower quality image to start with (cellphone cam vs DSLR) and then overjuiced so hard that it's lost any semblance of the natural world.
Back to the trash "The Fifth Element" video transfer
The 4k transfer is similarly overjuiced everywhere. It's hideous. My cellphone photos of the HDR screen are in no way accurate, but even still some of the flaws are entirely evident.
https://i.nostr.build/A6GR.jpg
Harsh over-contrasty processing. Color saturation similarly overjuiced.
There are lots of dark areas in this image, but if we boost those levels, we see that there's NO information in the shadows. Once you crush shadows to black, no amount of brightening can bring back those details.
https://i.nostr.build/z9LM.jpg
Ruby Rhod's hair and black dress are just (0,0,0) pixels.
A good transfer would still provide strong contrast where it's called for, but would preserve the subtleties, some details even in the shadows and highlights. A good transfer paints with up to the full 1 billion available colors. This transfer clumsily, bluntly limits itself to a box of 32 crayons.
View this one full-screen:
https://i.nostr.build/P9A6.jpg
Just harshness everywhere.
There's also way too much sharpening applied which adds to the harshness and over-accentuates the natural film grain.
I'm not the only one who hates this transfer.
It's noisy and harsh [...] I think a lot of people would be surprised at how artificial Sony's remaster would look compared to an untampered presentation. (link)
There’s no positives that I can mention in regards to Sony’s efforts on The Fifth Element. It may be the single most artificially sharpened UHD. You can literally use the screen as a cheese grater. And the color grade is completely off from 35mm. (link)
There's a better option
Weirdly, there's an alternate 4k disc that was published in the UK by Studiocanal that is said to be a vastly superior transfer.
https://i.nostr.build/0r4M.jpg
The 4k disc is region-free, so even though it's a UK disc, it'll play fine in any 4k blu-ray player.
It's currently $28 on amazon but, given my lessening admiration for the movie (at least the first hour), I'm not interested in double-dipping and spending more money to get this version.
Audio
Nice that it has a Dolby Atmos mix but I think I was too distracted by the horrible visuals to do any kind of critical listening. But for any movie this old (1997), the quality of the original sound elements will always be an obvious limiting factor.
-
 @ 599f67f7:21fb3ea9
2024-03-04 14:25:25
@ 599f67f7:21fb3ea9
2024-03-04 14:25:25¿Qué es Cashu?
Cashu es un protocolo de ecash de código abierto para Bitcoin que ofrece transacciones instantáneas sin comisiones con una privacidad casi perfecta. Consulta nostr:naddr1qqxnzd3e8y6rvdpe8qur2v3cqgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa28f238dz para obtener más detalles.
Nutstash
Nutstash es una increíble billetera web de Cashu desarrollada por nostr:npub1cj6ndx5akfazux7f0vjl4fyx9k0ulf682p437fe03a9ndwqjm0tqj886t6 que implementa la mayoría de los NUTs, así como el envío y recepción a través de Nostr. También puedes instalarla como una Progressive Web App (PWA) en tu teléfono.
⚠️ Tanto Nutstash como Cashu todavía están en fase beta. Existe la posibilidad de perder fondos. Lee sobre los riesgos antes de usar la aplicación. Haz pruebas con pequeñas cantidades con las que te sientas cómodo perdiendo.
Pruébalo
Vamos a explicar cómo interactuar con una mint, recibir y enviar ecash, hacer copias de seguridad, convertir a Lightning y hacer intercambios entre mints, y al final probaremos la funcionalidad de los contactos de Nostr.
Añadir un mint
Para interactuar con ecash, primero necesitas tener acceso a una mint, donde se crean y canjean tus tokens de ecash.
- Ve a Txoko Mint.
- Abre la mint en Nutstash.
💡 Puedes añadir mints adicionales en Nutstash yendo a
Mint, pegando la URL de la mint y presionandoAdd Mint("Añadir Mint"). Algunas mints públicas se pueden encontrar en MintIndex. Ten en cuenta que algunas mints reservarán una cierta cantidad de sats para pagar las tarifas de enrutamiento, lo que significa que no podrás retirar todos tus sats.
Crear tokens
Puedes financiar tu billetera de ecash tanto recibiendo ecash directamente como creando nuevos tokens de ecash pagando una factura de Lightning.
- En la pestaña
Mint, elige la mint en la que quieres crear nuevos tokens y presionaMint. - Elige una cantidad. Prueba con una cantidad pequeña, como 100 sats.
- Crea la factura y págala desde una billetera de Lightning. Una vez que se haya pagado la factura, deberías tener tokens de ecash.
Realizar transacciones con ecash
Realizar transacciones con ecash implica básicamente enviar y recibir bloques de datos. Por lo tanto, puedes probar estas funcionalidades enviando y recibiendo a ti mismo. 1. Para enviar ecash, ve a
Wallet>Send. 2. Selecciona la mint desde la que quieres enviar. 3. Elige una cantidad. Opcionalmente, utiliza la selección de monedas. 4. Haz clic en enviar tokens. 5. Copia el token. En este punto, puedes enviar el token a otra persona o canjearlo en tu propia billetera. Dado que solo estamos probando las cosas, haremos lo último.- Para recibir ecash, haz clic en
Wallet>Receive. - Pega el token de cashu.
- Haz clic en
Receive.
💡 Puedes verificar los tokens de ecash pendientes y reclamarlos si el destinatario aún no los ha canjeado. Para hacer esto, ve a la pestaña
Walletsy buscaTokens. Asegúrate de que la columnaPendingesté marcada. Debería haber una lista de tokens pendientes, haz clic en el botón de actualización para verificar su estado. Si no han sido reclamados, puedes copiar y canjear el token.Intercambio de múltiples mints
Es posible que te hayas preguntado si diferentes mints pueden enviar y recibir entre sí. La respuesta es sí. Bueno, más o menos. En lugar de enviar tokens de cashu entre sí, las transacciones entre mints se realizan a través de Lightning. Para probar esto, puedes agregar otra mint si aún no lo has hecho, por ejemplo, la mint de LNbits.
💡 Ten en cuenta que algunas mints reservarán una cierta cantidad de sats para pagar las tarifas de enrutamiento, lo que significa que no podrás retirar todos tus sats. Para evitar esto, también puedes crear tu propia mint con tu billetera Bitcoin Txoko LNbits activando la extensión de Cashu. Bitcoin Txoko no requiere reservas, por lo que puedes retirar todos tus sats.
- Ve a la pestaña
Minty agrega una nueva mint si aún no lo has hecho. - Una vez que tengas varias mints, tendrás la opción de
Inter-Mint Swap. Abre la opción y lee la advertencia. - Si deseas continuar, elige una mint de la que quieres hacer el intercambio y una mint a la que quieres hacer el intercambio.
- Elige una cantidad.
- Confirma la cantidad (
Confirm amount), verifica las tarifas estimadas de enrutamiento y procede con el intercambio (Swap). En segundo plano, la mint que envía está pagando una factura de Lightning a la mint que recibe. Una vez que se haya liquidado la factura, el token intercambiado debería aparecer en el saldo de tu billetera en la mint que recibe.
Convertir a lightning
Cuando quieras convertir tus sats de cashu de nuevo a sats de Lightning, puedes convertir o "derretir" tus tokens de cashu.
- Haz clic en
Payo toca el ícono de la cámara para escanear un código QR. - Ingresa o escanea una factura.
- Opcionalmente, utiliza la selección de monedas.
- Presiona
Pay. La mint funde los tokens de cashu y paga la factura de Lightning.
Copias de seguridad
Hacer copias de seguridad de los tokens de Cashu es probablemente diferente al proceso que estás acostumbrado a hacer para respaldar las billeteras de Bitcoin y Lightning. Dado que los fondos están representados por tokens que son simplemente bloques de datos, solo estás respaldando estos datos cuando haces una copia de seguridad de los tokens de Cashu. Esto también significa que tus copias de seguridad cambiarán cada vez que realices una transacción y necesitarás hacer una nueva copia de seguridad después de cada transacción.
Los diferentes clientes de billeteras han implementado las copias de seguridad de manera diferente y solo funcionarán con la misma billetera que ha creado la copia de seguridad. Nutstash utiliza un archivo JSON como copia de seguridad, que también incluye tu historial de transacciones junto con los tokens que has agregado.
- Para descargar la copia de seguridad en formato JSON, ve a
Settings("Configuración") >Backup Tokens("Copia de seguridad de tokens"), descarga el archivo JSON y guárdalo en un lugar seguro. - Para restaurar la copia de seguridad, ve a
Settings("Configuración") >Restore("Restaurar"). Lee la advertencia. Los datos actuales de tu billetera se sobrescribirán.
Nostr
Dado que puedes enviar tokens de Cashu a través de cualquier protocolo basado en texto, Nostr es una excelente opción para Cashu. Nutstash facilita el envío de tokens de Cashu a través de Nostr.
Primero, necesitas conectar un firmante externo de Nostr a Nutstash para que Nutstash pueda cifrar y firmar mensajes directos utilizados para enviar tokens de ecash. Para hacer esto,
- Ve a la pestaña
Settings("Configuración") y encuentra la secciónNostr. - Activa
Nostr. - Puedes configurar (
Configure) los retransmisores manualmente o permitir que Nutstash lea tu lista de retransmisores después de completar el siguiente paso. - Activa
Use external key("Usar clave externa"). Debes tener instalada una extensión de firmante de Nostr en tu navegador. Algunas buenas opciones son nos2x, Alby y Nostore (para Safari en iOS). - Una vez que Nutstash detecte tu extensión de firmante, permítele leer tu lista de retransmisores y clave pública.
- Si permites que Nutstash descifre los mensajes, buscará tokens de Cashu en tus mensajes directos. Una vez encontrados, aparecerán en la pestaña
Walleten la bandeja de entrada (Inbox). Allí podrás canjearlos en tu billetera.
Para enviar Cashu a través de Nostr,
- Ve a
Send("Enviar"). - Elige un mint.
- Elige una cantidad. Opcionalmente, utiliza la selección de monedas.
- Presiona
Send("Enviar"). - En
Send via Nostr("Enviar a través de Nostr"), ingresa una dirección de Nostr en formato npub, hexadecimal o NIP-05. Alternativamente, escanea el código QR del perfil de alguien. - Presiona
Send via Nostr("Enviar a través de Nostr") y firma el mensaje tipo 4 con tu firmante externo. - Informa al destinatario que revise su bandeja de entrada, ¡deberían tener algunos Cashu esperándolos allí!
Conclusión
¿Encontraste útil esta guía? ¡Intenta enviarnos algunos tokens de Cashu a través de Nostr!
-
 @ e97aaffa:2ebd765d
2024-03-24 17:13:04
@ e97aaffa:2ebd765d
2024-03-24 17:13:04O quanto ridículo seria, se as unidades de medida não fossem padronizadas?
Seria muito estúpido, cada fabricante de réguas, utilizasse centímetros com tamanhos diferentes. Isso por vezes acontece, devido à falta de rigor do fabricante, normalmente em produtos de má qualidade e muito baratos. No caso de unidades de medida o rigor é essencial, basta um erro de milésimos no milímetro, que parece algo inócuo, mas numa fita métrica de 2 metros, isso significa num erro de alguns milímetros.
É muito comum as fitas métricas baratas com vários metros de comprimento, terem diferenças de alguns milímetros, para uma pessoa comum isso pode ser insignificante, mas para um carpinteiro ou um serralheiro pode resultar num grande prejuízo.
Distopia
Agora imagine num mundo distópico, onde o centímetro estava constantemente a mudar. Hoje 1 cm é composto por 10 mm, mas daqui a 2 meses já são 11 mm. Daqui a 1 ano já são 13mm e assim infinitamente. Seria um mundo complete impossível de apontar e transmitir medidas, as constantes mudança seria incomportável. Por exemplo, eu encomendaria um cartão de visita com 10x10cm e a gráfica entregaria o produto com os 10x10cm. Só que as medidas são diferentes, os 10cm da gráfica são menores que os meus os 10cm, o pior de tudo é que não se sabe quem tem razão?
O mundo perderia a nossa noção dos tamanhos e da realidade.
É claro que isto é num mundo distópico, seria absurdo isso acontecer na nossa realidade. Por isso é essencial que as unidades de medidas sejam padronizadas.
Realidade
Se os centímetros mudassem constantemente de tamanho, era unânime, as populações compreendiam que existia um problema. Mas a verdade é que temos um problema numa unidade de medida e a população não conseguem compreender.
O ser humano conseguiu padronizar o comprimento e o peso, mas não foi capaz de padronizar a principal unidade de medida da humanidade, a moeda. Os políticos não querem padronizar a medida, para que as populações não façam comparações, para que não compreendam a realidade, para que vivam na ignorância.
Como podemos medir algo, se a régua(cm) está sempre a mudar de tamanho? Apesar das pessoas terem aumentos anuais de salários, isso não corresponde a um aumento de poder de compra, pelo contrário, estão a perder poder de compra. Outro caso gritante, é a taxa de juro pelos depósitos, as pessoas acreditam que estão a ganhar 2 ou 3% ao ano, mas na realidade estão a perder devido à inflação de 6%. As pessoas vivem na ilusão que ficaram 3% mais ricas, é verdade que o número aumentou, mas na realidade teve uma perda real de 3%.
É a magia da inflação, ou seja, a contante mudança da régua.
-
 @ 3cd2ea88:bafdaceb
2024-03-24 16:54:52
@ 3cd2ea88:bafdaceb
2024-03-24 16:54:52🗜 Ancora una volta, i potenti del G7 si riuniscono per stringere la morsa sulle criptovalute. In un incontro a porte chiuse, i ministri delle finanze hanno discusso misure per "regolare" il settore, con l'obiettivo di controllarne la crescita e l'adozione.
🗜 La retorica è la solita: lotta al terrorismo, finanziamento del crimine, evasione fiscale. Ma dietro a queste ipocrite preoccupazioni si cela un'agenda ben precisa: soffocare la libertà finanziaria e imporre un sistema di controllo sociale tramite le CBDC, le valute digitali di banca centrale.
🗜 Le CBDC sono la quintessenza del potere centralizzato. Emesse e controllate dalle banche centrali, queste valute digitali permetterebbero un controllo totale sulle transazioni finanziarie. Potrebbero essere programmate per scadere, per essere utilizzate solo per determinati scopi o addirittura per essere confiscate in caso di "comportamento scorretto".
💸 In questo scenario distopico, Bitcoin rappresenta l'ultima resistenza. Una valuta digitale decentralizzata, resistente alla censura e al controllo, che offre agli individui la possibilità di gestire autonomamente i propri beni.
🗜 Il G7 lo sa bene. Ecco perché i loro attacchi contro Bitcoin si fanno sempre più feroci. Ma la loro paura è la nostra forza. Bitcoin è più forte di qualsiasi governo, di qualsiasi banca centrale. È la moneta del futuro, la moneta della libertà.
💸 Non ci lasceremo intimidire. Continueremo a lottare per la libertà finanziaria, per un mondo senza banche centrali e senza controlli oppressivi. Bitcoin è la nostra speranza, Bitcoin è il nostro futuro.
🗜 Sotto il giogo del G7, le criptovalute tremano, ma Bitcoin resiste. La sua forza è la nostra forza, la sua libertà è la nostra libertà. Insieme, possiamo sconfiggere il sistema e costruire un futuro migliore.
💸 Non arrendetevi, non cedete alla paura. Bitcoin è la nostra arma, la nostra voce, la nostra speranza.
💎 P.S. Se sei preoccupato per la tua privacy e la tua libertà finanziaria, inizia a utilizzare Bitcoin oggi stesso ed unisciti alla nostra community su Telegram, dove oltre al trading, alle strategie dei bot ed alle analisi, portiamo avanti anche la pace e la libertà. È la tua migliore difesa contro il controllo statale.
🚀 Leggi tutti i nostri articoli: https://buff.ly/3RSjZ3G
☄️ Nella nostra community Bitcoin Report Italia, troverai un ambiente accogliente dove gli esperti ti guideranno nei primi passi nel trading, offrendo analisi, strategie di trading e l'opportunità di partecipare al CopyTrading con trader professionisti.
☄️ Iscrivendoti con il nostro referral code su Bitget (6w5d), potrai avere un contatto diretto con trader che ti aiuteranno a crescere nel mondo del trading di criptovalute. 🚀
📣 https://buff.ly/4aUce63
-
 @ 75bf2353:e1bfa895
2024-03-24 16:25:40
@ 75bf2353:e1bfa895
2024-03-24 16:25:40I began writing a blog about using bitcoin as censorship resistance money a couple years ago because most people don't talk about anything other than the price of 100,000,000 sats. They say things like:
- "Wen Lambo"
- "To the moon!"
- Forever Laura!
It's all fiat-maxi language disguised as bitcoin maxi rhetoric. I would be lying if I said I didn't care about the price at all, but I became interested in bitcoin for ideological reasons. It's nice that I can buy more groceries today than I could a couple years ago, but that's not what turns my crank. I may have heard about bitcoin from Antonopolis, but Ayn Rand orange pilled me before that.
I want to be financially free from banks. I'm not all the way there yet. I have a mortgage I pay in fiat. I have a few hundred bucks in a savings account and about eight bucks worth of change in my office. I also carry a couple hundred dollars worth of green paper in my soft wallet. It's getting harder to use that green paper these days because more and more businesses would rather pay a sales tax to the bank than accept cash.
I don't talk about the fiat price much. I don't trade "crypto," but fell in love with cryptography. I prefer nostr to Twitter. I earn sats, save sats, and spend sats and started using bitcoin as peer 2 peer electronic cash about a decade ago.
My blog is nostr. You can follow me on there. This is not financial advice, it's not even a blockchain. Nostr is a decentralized communication protocol that uses public-private key pairs. You know... cryptography.
My New Podcast
I decided to turn this blog into a podcast. The idea is to read my blog posts out-loud, using AI because I sound like a mumbling dweeb.
This podcast has no paid ads, but I plan to showcase businesses who participate in what I call the elliptic curve economy, also known as the circular economy. These are not paid ads. My goal is to bring plebs business through word of mouth advertising because I believe this is the best form of advertising. I consider these value 4 value ads. Hopefully my podcast will bring these pleb businesses some extra revenue, but this is no act of altruism. In my opinion, the more people who use bitcoin as a medium of exchange, the faster we can remove bitcoin off the exchanges. If you buy something from a bitcoin business, another pleb stacks more bitcoin. The more bitcoin that gets stacked, the more valuable my store of value becomes. It is a mutually beneficial relationship.
Value 4 Value
I am using the value 4 value model. After my blog, I will answer call-in questions about bitcoin to the best of my ability. Ask a question by sending a boostagram on your favorite podcasting 2.0 player.
I'll do my best to answer the question on the next show.
Here's the pod. I'm, still working on the kinks like audio quality, editing, et cetera, but I find this technology much more fascinating than how much fiat you can obtain with 100 million sats.
https://fountain.fm/episode/sHUSVAIQlMLRNqvPITqw
₿logging ₿itcoin 836127 debtclock 🧡 Support this blog by using the Value 4 Value model
 Follow Me on Nostr
⚡Zap Me
🍐Join my Keet Room
📻 Stream sats
❓Send a Boostagram
🛒Shop The Elliptic Curve Economy
Follow Me on Nostr
⚡Zap Me
🍐Join my Keet Room
📻 Stream sats
❓Send a Boostagram
🛒Shop The Elliptic Curve Economy -
 @ 1c6b3be3:73f0ae6f
2024-03-02 09:45:57
@ 1c6b3be3:73f0ae6f
2024-03-02 09:45:57Bitcoin Core
Bitcoin Core 26.0 released Bitcoin Core version 26.0 has been released, offering many new features and bug fixes. To learn more, check the release notes. If you have questions, visit the #bitcoin IRC chatroom for assistance.
Bitcoin Core 24.2 released Bitcoin Core version 24.2 has been released, offering various bug fixes. Users are encouraged to refer to the release notes for further details. Support and assistance can be obtained by visiting the #bitcoin IRC chatroom.
Bitcoin Core 25.1 released La version 25.1 de Bitcoin Core est désormais disponible en téléchargement. Consultez les notes de mise à jour pour plus d'informations sur les nombreuses corrections de bugs apportées par cette version. Si vous avez des questions, veuillez visiter le salon de discussion IRC #bitcoin (IRC, web) et nous ferons de notre mieux pour vous aider.
Bitcoin Optech
Bitcoin Optech Newsletter #291 (9 min) L'article présente plusieurs nouveautés et initiatives en cours dans le domaine du Bitcoin:
-
Proposition d'un contrat pour des futurs de taux de hachage de mineurs sans confiance, permettant à deux parties de se payer conditionnellement en fonction du taux marginal pour inclure une transaction dans un bloc futur, avec différentes options de retrait des fonds en cas de feerates plus bas que prévu pour maximiser les profits des mineurs.
-
Mise en avant d'un algorithme de sélection de pièces pour les fournisseurs de liquidité Lightning Network pour optimiser les frais on-chain et offrir une réduction de 15% par rapport à l'algorithme par défaut de Bitcoin Core.
-
Présentation d'un prototype simple de coffre-fort utilisant l'opcode OP_CAT dans un langage Rust, montrant comment le coffre-fort pourrait fonctionner en ne dépendant que des règles de consensus actuelles et de l'opcode proposé.
D'autres sections de l'article incluent des discussions sur l'envoi et la réception de ecash en utilisant le Lightning Network et les ZKCPs, des résumés des questions populaires de Bitcoin Stack Exchange, des annonces de nouvelles versions et des modifications récentes apportées aux projets d'infrastructure Bitcoin populaires.
Bitcoin Optech Newsletter #290 Recap Podcast (69 min) L'article discute du podcast Bitcoin Optech, où Mark “Murch” Erhardt et Mike Schmidt sont rejoints par Gloria Zhao, callebtc, Chris Stewart, Fabian Jahr et Pierre Corbin pour discuter de la Newsletter #290. Dans le podcast, ils abordent des sujets tels que les instructions de paiement Bitcoin lisibles par DNS, l'incitation en ce qui concerne le mempool, les systèmes de crypto-monnaie Cashu, la conception de Cashu et autres sujets techniques liés à Bitcoin. Ils discutent également des mises à jour des applications construisant sur le réseau Bitcoin, comme le protocole de coordination multiparty (NWC), la sortie de la Mutiny Wallet v0.5.7, le service de regroupement GroupHug, les swaps taproot annoncés par Boltz, et les versions récents de logiciels comme Core Lightning 24.02rc1.
 Bitcoin Optech Newsletter #290 (10 min)
The article discusses a proposal for providing DNS-based human-readable Bitcoin payment instructions, a summary of a post about mempool incentive compatibility, a link to a thread discussing the design of ecash systems, a brief look at the discussion on 64-bit arithmetic in Bitcoin scripts, and an overview of an improved process for reproducible ASMap creation. It also includes updates on client services, new releases, and changes to popular Bitcoin infrastructure software.
Bitcoin Optech Newsletter #290 (10 min)
The article discusses a proposal for providing DNS-based human-readable Bitcoin payment instructions, a summary of a post about mempool incentive compatibility, a link to a thread discussing the design of ecash systems, a brief look at the discussion on 64-bit arithmetic in Bitcoin scripts, and an overview of an improved process for reproducible ASMap creation. It also includes updates on client services, new releases, and changes to popular Bitcoin infrastructure software. Releases - No Bullshit Bitcoin
Zeus v0.8.2-beta1 Is Now Available for Testing Zeus is a self-custodial mobile Lightning wallet that includes an embedded node, self-custodial lightning addresses, Point-of-sale functionality, and a Bitcoin/Lightning node manager and wallet application for LND, Core Lightning, and Eclair. The latest version, ZEUS v0.8.2-beta1, introduces several new features including 0-conf LSP support for LND REST connections, Point of Sale with receipt printing for Android, a multi-currency conversion tool, enhanced wallet recovery interface, default channel opening settings, new animations for Send and Receive, an invoice expiration picker interface, and LND v0.17.4 integration. This update also includes 33 new fiat currency conversions. The full changelog from v0.8.1 to v0.8.2-beta1 can be found on their GitHub repository.
 Fountain v1.0.9 & Fountain Radio Released (2 min)
L'article du 29 février 2024 présente la dernière mise à jour de Fountain, mettant en avant des améliorations de l'interface utilisateur, des corrections de bugs et des mises à jour de la fonctionnalité des clips. Fountain Radio, une station de musique communautaire alimentée par Bitcoin, a été lancée pour aider à la découverte de nouvelles musiques. Les auditeurs peuvent se connecter avec leur compte Fountain sur un ordinateur ou un téléphone, écouter la musique en cours tout en soutenant les artistes, ajouter des pistes à la file d'attente pour un montant nominal, voter pour faire avancer une piste et enregistrer leurs morceaux préférés dans leur bibliothèque. En outre, les utilisateurs peuvent participer à un chat en direct avec d'autres auditeurs et artistes. Les mises à jour de l'application comprennent l'affichage des derniers clips sur la page d'accueil, une publication plus rapide des clips, une meilleure précision sur iOS, la possibilité de voir les transcriptions des clips en cours d'édition, l'affichage du temps restant sur les cartes de contenu des épisodes, ainsi que l'ajout de liens hypertexte pour toutes les URLs dans les notes d'émission.
Fountain v1.0.9 & Fountain Radio Released (2 min)
L'article du 29 février 2024 présente la dernière mise à jour de Fountain, mettant en avant des améliorations de l'interface utilisateur, des corrections de bugs et des mises à jour de la fonctionnalité des clips. Fountain Radio, une station de musique communautaire alimentée par Bitcoin, a été lancée pour aider à la découverte de nouvelles musiques. Les auditeurs peuvent se connecter avec leur compte Fountain sur un ordinateur ou un téléphone, écouter la musique en cours tout en soutenant les artistes, ajouter des pistes à la file d'attente pour un montant nominal, voter pour faire avancer une piste et enregistrer leurs morceaux préférés dans leur bibliothèque. En outre, les utilisateurs peuvent participer à un chat en direct avec d'autres auditeurs et artistes. Les mises à jour de l'application comprennent l'affichage des derniers clips sur la page d'accueil, une publication plus rapide des clips, une meilleure précision sur iOS, la possibilité de voir les transcriptions des clips en cours d'édition, l'affichage du temps restant sur les cartes de contenu des épisodes, ainsi que l'ajout de liens hypertexte pour toutes les URLs dans les notes d'émission.  Wasabi Wallet v2.0.6: Jade and BitBox02 Support, Safety Coinjoin & Performance Improvements (2 min)
Wasabi Wallet's latest release, as of February 29, 2024, introduces new hardware device support, privacy and performance enhancements, and more. The update includes compatibility for Blockstream Jade and BitBox02, a Safety Coinjoin feature for improved privacy, an enhanced RPC server with new calls, significant performance upgrades reducing CPU and memory usage, user experience enhancements like wallet renaming and clearer privacy warnings, improvements in cross-wallet performance, framework and GUI enhancements, bug fixes for deployment flow, UI memory leaks, Coldcard hardware device integration, and PGP key changes for reporting software vulnerabilities.
Wasabi Wallet v2.0.6: Jade and BitBox02 Support, Safety Coinjoin & Performance Improvements (2 min)
Wasabi Wallet's latest release, as of February 29, 2024, introduces new hardware device support, privacy and performance enhancements, and more. The update includes compatibility for Blockstream Jade and BitBox02, a Safety Coinjoin feature for improved privacy, an enhanced RPC server with new calls, significant performance upgrades reducing CPU and memory usage, user experience enhancements like wallet renaming and clearer privacy warnings, improvements in cross-wallet performance, framework and GUI enhancements, bug fixes for deployment flow, UI memory leaks, Coldcard hardware device integration, and PGP key changes for reporting software vulnerabilities. 
Bitcoin Core
Bitcoin Core 26.0 released Bitcoin Core 24.2 released Bitcoin Core 25.1 released Bitcoin Core 25.0 released Bitcoin Core 24.1 released Bitcoin Core 23.2 released Bitcoin Core 23.1 released Bitcoin Core 22.1 released Bitcoin Core 24.0.1 released Bitcoin Core 23.0 released Bitcoin Core 0.20.2 released Bitcoin Core 0.21.2 released Bitcoin Core 22.0 released Bitcoin Core 0.21.1 Released With Taproot Activation Code (1 min) Bitcoin Core 0.21.0 Released Bitcoin Core 0.20.1 Released Bitcoin Core 0.20.0 Released bitcoincore.org hidden service Bitcoin Core 0.19.1 Released Bitcoin Core 0.19.0 Released
Bitcoin Optech
Bitcoin Optech Newsletter #291 (9 min) Bitcoin Optech Newsletter #290 Recap Podcast (69 min)
 Bitcoin Optech Newsletter #290 (10 min)
Bitcoin Optech Newsletter #289 Recap Podcast (46 min)
Bitcoin Optech Newsletter #290 (10 min)
Bitcoin Optech Newsletter #289 Recap Podcast (46 min)
 Bitcoin Optech Newsletter #289 (9 min)
Bitcoin Optech Newsletter #288 Recap Podcast (63 min)
Bitcoin Optech Newsletter #289 (9 min)
Bitcoin Optech Newsletter #288 Recap Podcast (63 min)
 Bitcoin Optech Newsletter #288 (12 min)
Bitcoin Optech Newsletter #287 Recap Podcast (45 min)
Bitcoin Optech Newsletter #288 (12 min)
Bitcoin Optech Newsletter #287 Recap Podcast (45 min)
 Bitcoin Optech Newsletter #287 (8 min)
Bitcoin Optech Newsletter #286 Recap Podcast (53 min)
Bitcoin Optech Newsletter #287 (8 min)
Bitcoin Optech Newsletter #286 Recap Podcast (53 min)

Releases - No Bullshit Bitcoin
Zeus v0.8.2-beta1 Is Now Available for Testing
 Fountain v1.0.9 & Fountain Radio Released (2 min)
Fountain v1.0.9 & Fountain Radio Released (2 min)
 Wasabi Wallet v2.0.6: Jade and BitBox02 Support, Safety Coinjoin & Performance Improvements (2 min)
Wasabi Wallet v2.0.6: Jade and BitBox02 Support, Safety Coinjoin & Performance Improvements (2 min)
 Eclair v0.10.0: Dual Funding, Latest Bolt 12, Fully Working Splicing Prototype (3 min)
Eclair v0.10.0: Dual Funding, Latest Bolt 12, Fully Working Splicing Prototype (3 min)
 Voltage Introduces Redesign, Teams and Pricing Updates (1 min)
Voltage Introduces Redesign, Teams and Pricing Updates (1 min)
 Bitcoin Optech #291: Trustless Contract for Miner Feerate Futures (1 min)
Bitcoin Optech #291: Trustless Contract for Miner Feerate Futures (1 min)
 New on Geyser: Spirit of Satoshi, Bitcoin Chiavenna, B3, NOSH & More (3 min)
New on Geyser: Spirit of Satoshi, Bitcoin Chiavenna, B3, NOSH & More (3 min)
 Blockstream Green Wallet Desktop v2.0.0: New UI and UX (1 min)
Blockstream Green Wallet Desktop v2.0.0: New UI and UX (1 min)
 Mostro Web v0.0.19 Released
Mostro Web v0.0.19 Released
 Strike Announces Africa Expansion (1 min)
Strike Announces Africa Expansion (1 min)
 Keystache by Resolvr: Desktop Client for Managing Nostr Private Keys (1 min)
Keystache by Resolvr: Desktop Client for Managing Nostr Private Keys (1 min)
 Core Lightning v24.02: Testnet Fix, New Recovery Plugin & More (1 min)
Core Lightning v24.02: Testnet Fix, New Recovery Plugin & More (1 min)
 Tails v6.0: Important Security and Usability Improvements (2 min)
Tails v6.0: Important Security and Usability Improvements (2 min)
 Plebeian Market v0.0.13: CMS Improvements & Bug Fixes
Plebeian Market v0.0.13: CMS Improvements & Bug Fixes
 Envoy v1.6.0-beta: Full RBF Control, Address & Amount Display Redesign & More (3 min)
Envoy v1.6.0-beta: Full RBF Control, Address & Amount Display Redesign & More (3 min)
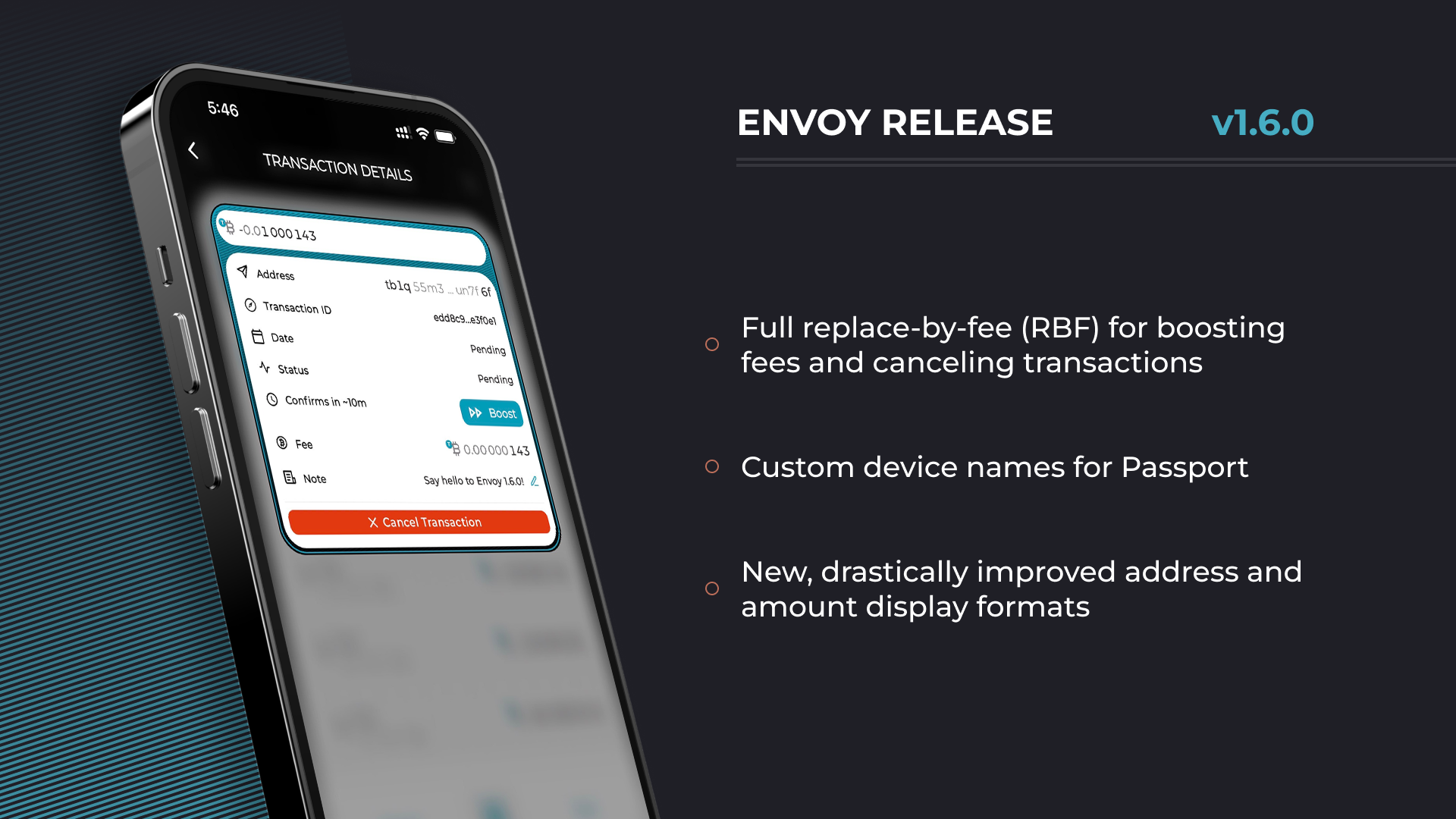
🍵 "btc | bitcoin | lightning network | asic" - Google News
The Innovative Approach to Address Demand for ZKBase in the Market – Press release Bitcoin News - Bitcoin.com News 1 reason for new bitcoin mania: 'Simply not enough' supply - Yahoo Finance Crypto miner Marathon Digital unveils Bitcoin layer 2 network Anduro - Cointelegraph Anduro: A Network of Sidechains - Bitcoin Magazine Bitcoin Price Is Surging Ahead of Halving, But Network Fees Aren't Keeping Pace - Decrypt Cipher Mining (CIFR) Jumps 6% as Mined Bitcoin Tops 334 Units - CoinGape Infrastructure Providers Warn of ASIC Scarcity for Bitcoin Miners - Cryptonews JPMorgan: Bitcoin Could Correct Downwards to as Low as $42000 in April - TradingView Bitcoin surges, briefly touching $64,000 for the first time since November 2021 - CNBC Lightning, Canadiens aim to shake off OT disappointment - CBS Sports Is Bitcoin due for a major correction? JPMorgan predicts drop to $42,000 after April halving - Fortune Bitcoin miner consolidation appears imminent as halving looms - Blockworks Robinhood Wallet Embraces Arbitrum for Seamless Token Swaps - Crypto Times Cipher Mining Announces February 2024 Operational Update - Yahoo Finance Bitcoin ASIC maker Canaan's revenue stagnant despite crypto bull run - Cointelegraph
-
-
 @ fa984bd7:58018f52
2024-02-28 22:15:25
@ fa984bd7:58018f52
2024-02-28 22:15:25I have recently launched Wikifreedia, which is a different take on how Wikipedia-style systems can work.
Yes, it's built on nostr, but that's not the most interesting part.
The fascinating aspect is that there is no "official" entry on any topic. Anyone can create or edit any entry and build their own take about what they care about.
Think the entry about Mao is missing something? Go ahead and edit it, you don't need to ask for permission from anyone.
Stuart Bowman put it best on a #SovEng hike:
The path to truth is in the integration of opposites.
Since launching Wikifreedia, less than a week ago, quite a few people asked me if it would be possible to import ALL of wikipedia into it.
Yes. Yes it would.
I initially started looking into it to make it happen as I am often quick to jump into action.
But, after thinking about it, I am not convinced importing all of Wikipedia is the way to go.
The magical thing about building an encyclopedia with no canonical entry on any topic is that each individual can bring to light the part they are interested the most about a certain topic, it can be dozens or hundreds, or perhaps more, entries that focus on the edges of a topic.
Whereas, Wikipedia, in their Quijotean approach to truth, have focused on the impossible path of seeking neutrality.
Humans can't be neutral, we have biases.
Show me an unbiased human and I'll show you a lifeless human.
Biases are good. Having an opinion is good. Seeking neutrality is seeking to devoid our views and opinions of humanity.
Importing Wikipedia would mean importing a massive amount of colorless trivia, a few interesting tidbits, but, more important than anything, a vast amount of watered-down useless information.
All edges of the truth having been neutered by a democratic process that searches for a single truth via consensus.
"What's the worst that could happen?"
Sure, importing wikipedia would simply be one more entry on each topic.
Yes.
But culture has incredibly strong momentum.
And if the culture that develops in this type of media is that of exclusively watered-down comfortable truths, then some magic could be lost.
If people who are passionate or have a unique perspective about a topic feel like the "right approach" is to use the wikipedia-based article then I would see this as an extremely negative action.
An alternative
An idea we discussed on the #SovEng hike was, what if the wikipedia entry is processed by different "AI agents" with different perspectives.
Perhaps instead of blankly importing the "Napoleon" article, an LLM trained to behave as a 1850s russian peasant could be asked to write a wiki about Napoleon. And then an agent tried to behave like Margaret Thatcher could write one.
Etc, etc.
Embrace the chaos. Embrace the bias.
-
 @ d8a2c33f:76611e0c
2024-02-26 03:10:36
@ d8a2c33f:76611e0c
2024-02-26 03:10:36Let's start with definitions:
Cashu - Cashu is a free and open-source Chaumian ecash system built for Bitcoin. Cashu offers near-perfect privacy for users of custodial Bitcoin applications. Nobody needs to know who you are, how much funds you have, and who you transact with. - more info here https://cashu.space/
Cashu-adress - it is a protocol that runs on top of cashu mints. More info here: https://docs.cashu-address.com/
Npub.cash - service that runs on top of cashu-address protocol. Let's you use your npub@npub.cash as a lightning address to receive zaps or incoming sats. More info here https://npub.cash/
Pay to public key - Like bitcoin you can cashu tokens are bearer assets and can be locked to a public key. This means only the person who has the private key can use that token.
What do you use it for? - Use your npub cash as your lightning address replacement.
Why? I believe everyone knows what a lightning address is. Lightning address is usually provided by your wallet provider who also runs their lightning node. E.g. if you have @alby.com lightning address then you already have an account setup with alby and using their lightning node to get your sats. With npub.cash you can simply put your npubaddress@npub.cash without registering first or signing up. And you can keep this forever even while changing your lightning wallet from alby to any other provider or running your own lightning node.
Npub.cash locks the received tokens into your nostr public key (Still work in progress) so that only the owner of Nostr public key who has the private key can claim the token and push it to their wallet of choice.
Benefits Over Traditional Custodial Lightning Addresses:
Privacy: With Cashu-Address, your financial activities are not visible to your custodian. This added layer of privacy ensures that your transactions remain your own.
Flexibility in Custodian Selection: Unlike traditional Lightning Addresses, Cashu-Address allows you to choose your custodian freely. If your needs change, you can switch your custodian anytime without hassle.
No User Exclusion: Custodians cannot exclude individual users. Because mints do know know which user eCash belongs to, they can not censor certain users. How to claim your username@npub.cash - This is what makes it so cool. You can actually get a vanity username for your profile name. E.g. I got mine as starbuilder@npub.cash. Simply visit npub.cash website and click the get username button. Put in your vanity username and pay 5k sats to get your profile@npub.cash
How to claim your username@npub.cash- This is what makes it so cool. You can actually get a vanity username for your profile name. E.g. I got mine as starbuilder@npub.cash. Simply visit npub.cash website and click the get username button. Put in your vanity username and pay 5k sats to get your profile@npub.cash . This is onetime and you can use this address forever..!
Frequently asked Questions:
-
What connect string to use to login with NIP-46 on iOS. - try setting up an account at https://use.nsec.app/home . This is still WIP. If it does not work, just try the Nostr extension using laptop browser
-
Is there a notification when I receive sats/zaps? Not yet. We are working on it. However, just go to npub.cash every couple of days to sweep your collected sats to your wallet
-
Which cashu wallet to use? Use enuts (android & ios) https://www.enuts.cash/ or minibits.cash for android https://www.minibits.cash/
-
Will anyone be able to claim my sats? NO. When you start the claim process you need to sign with your Nostr extenstion signer to claim sats. So only the person controlling the private key to the npub can claim sats.
-
I really struggle to understand the flow of what happened concretely. - Don't break your head. the devs got you covered. Also, this is super new and everyone is trying to get their heads around. Just follow instructions, play with it and ask for help.
- Is it non-custodial? - When we lock your sats to your pubkey we cannot spend it. However locking to pubkey is not enabled until wallets can start supporting them.
- How do I ask for help? - just post #asknpub.cash and post your questions. We will get to you.
- Who are the devs behind this? @calle (Master of Cashu) @egge (Core dev) @starbuilder (dev support)
Here's what everyone is talking about #npub.cash on Nostr
nostr:nevent1qvzqqqqqqypzqx78pgq53vlnzmdr8l3u38eru0n3438lnxqz0mr39wg9e5j0dfq3qythwumn8ghj7um9v9exx6pwdehhxtn5dajxz7f0qqsxcwntv9d342ashe5yvyv0fg40wm873jaszt6d2u0209vqz5gkcdq6avwyr
nostr:nevent1qvzqqqqqqypzq5qzedy85msr57qayz6dz9dlcr5k40mcqtvm5nhyn466qgc6p4kcqythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qythwumn8ghj7um9v9exx6pwdehhxtn5dajxz7f0qqsvek7d8v4lddrmj2mynegsnrc4r4gnmswkddm02qzenwuc7x9perctaedre
nostr:nevent1qvzqqqqqqypzpfpqfrt75fhfcd4x0d0lyek9pzyz4zwmudh0vq7vn3njvvngsmpjqyghwumn8ghj7mn0wd68ytnhd9hx2tcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsqgyjwfsgr80xmha8x2wwd4klzsxcagmlpk3wsfyyvqnlvzn2rcvnhu534kj5
nostr:nevent1qvzqqqqqqypzp3yw98cykjpvcqw2r7003jrwlqcccpv7p6f4xg63vtcgpunwznq3qyfhwumn8ghj7mmxve3ksctfdch8qatz9uq36amnwvaz7tmwdaehgu3wvf5hgcm0d9hx2u3wwdhkx6tpdshsqg8v5hfgmwangecpejcw22fm4uk2s438p8ahpu5l985wserctr0h6gysle9m
nostr:nevent1qvzqqqqqqypzp6y2dy0f3kvc0jty2gwl7cqztas8qqmc5jrerqxuhw622qnc2pq3qy88wumn8ghj7mn0wvhxcmmv9uq3xamnwvaz7tm0venxx6rpd9hzuur4vghsqgx68ujht0r9qqqp4l27u0x27sg4p5l2ks0xd9kxm9w2vkjhppttlur0et6k
-
-
 @ 8d8c3731:bfb11567
2024-03-24 16:25:06
@ 8d8c3731:bfb11567
2024-03-24 16:25:06ผมมีโอกาสได้เคลื่อนไหวในฐานะของ VTuber มาราว ๆ สองปีแล้ว (ถ้านับช่วงที่ก่อนจะมีไลฟ์ Debut Announcement) และสาละวนอยู่กับความทุกข์ที่รู้สึกว่าการพยายามทำไลฟ์ของตัวเองนั้นยังไม่เป็นที่สนใจของคนเท่าที่ควร โดยเฉพาะช่วงปีก่อนที่ถึงกับจิตตกหนัก ๆ เพราะยอดคนดูเริ่มลดลงเรื่อย ๆ อย่างน่าใจหาย (ซึ่งแม้จะทำใจมาตั้งแต่ช่วงแรก ๆ ที่ตัดสินใจทำแล้วแต่ก็ยังคงช็อคที่ตัวเลขมันลดหนักขนาดนี้)
ผมได้แต่หาคำตอบให้ตัวเองว่ามันเป็นเพราะอะไร ? เพราะเนื้อหาที่เราเอามาไลฟ์มันยากไป ? เพราะการนำเสนอของเรามันย่ำอยู่กับที่ ? เพราะเราไม่ได้ทำโมเดลใหม่อย่างที่คนอื่นเขานิยมเปลี่ยนกันทุกปี ? หรือถึงขั้นคิดไปว่าเพราะเรากำลังโดนแบนจากสังคมของ VTuber ประเทศไทยอยู่รึเปล่า…ทั้งที่ปีที่แล้วได้คุยกับคนในวงการแบบนับไม่เกินสองมือได้เลยด้วยซ้ำ
แม้ช่วงกลางปีจะได้มีโอกาสสัมผัสกับสังคมออนไลน์ทางเลือกมากมาย ทั้ง Mastodon ที่ตอนนั้นเป็นที่นิยมหนีตายจากแพลตฟอร์มเจ้าใหญ่ การได้เจอกับ Nostr ซึ่งเป็นโปรโตคอลสังคมออนไลน์แบบกระจายศูนย์อย่างแท้จริง รวมถึงล่าสุดที่ไปเคลื่อนไหวบนแอป Bluesky Social ที่พัฒนามายาวนานมากกว่าจะเปิดให้ใช้กันอย่างเสรีช่วงไม่กี่เดือนที่ผ่านมา แต่ไม่ว่าจะที่ไหนผมก็ได้สัมผัสกับบรรยากาศของโลกออนไลน์ที่ไม่มีอัลกอริธึมคอยเสิร์ฟเนื้อหาที่ไม่ได้อยากรู้เพราะคิดว่าเราน่าจะสนใจและไม่มีการโฆษณายัดเยียดสิ่งต่าง ๆ ทั้งพวก Scam หลอกเอาเงินผู้ใช้หรือพวกเว็บพนันออนไลน์ที่ตุกติกหวังฮุบเงินคนที่เข้ามาเล่น (ซึ่งใน Nostr มันมีแอคพวกนั้นมาเปิดโปรโมทอยู่นะ…และตายเรียบเพราะไม่ได้มีคนสนใจพวกนี้เท่ากับบนแพลตฟอร์มหลักที่ยัดเงินโฆษณาก็โกยคนเข้าไปติดกับได้เยอะแยะมากมาย ส่วนของ Mastodon กับ Bluesky ยังไม่แน่ใจว่ามีมั้ยเพราะไม่เคยเจอ) แต่เราก็ยังคงวนเวียนอยู่ในแพลตฟอร์มเดิม ๆ เพราะยังตัดใจไม่ขาดจากจำนวนผู้ติดตามที่เยอะกว่าที่อื่นและความที่เรายังสามารถ Keep in Touch กับผู้ติดตามบางส่วนได้ง่าย
จนกระทั่งการตัดสินใจครั้งสำคัญของผม… การตัดสินใจที่เปลี่ยนแปลงแนวทางการเคลื่อนไหวในสังคมออนไลน์ของ Saltyman ไปตลอดกาล
การตัดสินใจเลิกใช้ Twitter หรือ X เป็นแพลตฟอร์มหลัก
…
นับตั้งแต่นั้นผมก็สัมผัลได้ว่าชีวิตของตัวเองได้กลับมาเป็นตัวเองมากขึ้น มีเวลากลับมาใส่ใจกับการทำเนื้อหามากขึ้น ได้กลับมาเจอกับบรรยากาศที่เงียบสงบ ไม่พบเจอกับการแข่งขันแย่งชิงยอด Engagement โดยไม่ใส่ใจว่าสิ่งที่นำเสนอออกมาจะระยำตำบอนหรือมอมเมาคนอื่นแค่ไหน และไม่ต้องพบเจอกับความอีหยังวะที่เกิดจากการได้รับรู้เรื่องราวดราม่าบ้าบอต่าง ๆ ที่นอกจากจะไม่ได้จำเป็นอะไรกับชีวิตแล้วยังสร้างความเหนื่อยหน่ายกับสังคมว่ามันห่วยแค่ไหน
ที่ตลกคือ…การตัดสินใจนี้ไม่กระทบยอดคนดู (เพราะมันน้อยอยู่แล้ว) และยอดการมองเห็นในไลฟ์ของตัวเองเลย คนที่มาดูประจำก็มาเหมือนเดิม ยังรักษาบรรยากาศแลกเปลี่ยนความคิดเห็นที่ดีโดยไม่ต้องมีกฎไลฟ์ยุ่บยั่บเหมือนเดิม และก็ยังได้โดเนทจากช่องทางต่าง ๆ เหมือนเดิม (ซึ่งก็น้อยเหมือยเดิมด้วย ฮา)
ผมค่อนข่างเชื่ออย่างสุดหัวใจว่าการที่เราเลือกหันหลังให้กับแพลตฟอร์มพวกนั้นน่าจะทำให้ผมมี Productivity ที่มากขึ้น สร้างงานเพิ่มเติมได้มากขึ้น พัฒนาแนวทางของช่องได้มากขึ้น เหนื่อยหน่ายหมดไฟน้อยลง
…แต่ไม่เลย…
แม้การเลือกมาอยู่บนสังคมออนไลน์เหล่านี้จะทำให้มีความสุขขึ้นมาก แต่ผมเองก็กลับพบว่าเราก็ยังไม่ได้มีอะไรที่เยอะขึ้น ไม่ได้ทำคอนเทนต์ที่ตั้งใจไว้อย่างที่ควร ไม่ได้เข็นผลงานอะไรเพิ่มเติม และก็ไม่ได้มีใครให้ค่ากับผลงานที่เราทำทิ้งไว้ในอดีตอีกต่างหาก
แล้วมันเกี่ยวอะไรกับ Proof of Work ที่เกริ่นในหัวข้อบทความล่ะ ?
ต้องบอกว่าช่วงที่ผ่านมานี้ผมได้ยินคำว่า Proof of Work ค่อนข้างบ่อยมาก แม้จุดเริ่มต้นที่ได้ยินคำนี้จะมาจากประโยคที่พูดในรายการแบไต๋ไฮเทคสมัยที่ยังออกในรายการทีวีที่พูดถึง Bitcoin ช่วงปี 2015 แต่ผมเพิ่งจะมาเข้าใจคำนี้ในมุมมองอื่นที่ไม่เกี่ยวกับ Consensus Algorithm ในระบบของ Bitcoin เมื่อไม่ถึงปีนี้เอง และพอพยายามจะลองค้นหาความหมายของคำนี้ที่ไม่เกี่ยวกับ Cryptography ในอินเทอร์เน็ตจากแหล่งอื่น ๆ ก็พบว่าไม่มีเลย (เมื่อวานก็ลองค้นนะ แต่ก็ไม่มีเหมือนเดิม) ล่าสุดก็คือที่ได้เจอคำ ๆ นี้มาจากรายการไลฟ์รายการหนึ่งที่สมมุติว่าชื่อ สภายาส้ม (สมมุติแล้ว ไม่รู้หรอกเนาะว่าของช่องไหน) ที่ไลฟ์ไปเมื่อวันที่ 22 มีนาคม 2023 ที่ผ่านมากับประเด็นที่ผมสนใจมากเป็นพิเศษที่หนึ่งในพิธีกรที่สมมุติว่าชื่อคุณ Tendou นำเสนอหัวข้อ “อินฟลูฯ ที่ไม่อินฟลูฯ ” และรายการก็ชี้ไปถึงเรื่องของ Proof of Work ด้วย และหลังจากผมดูจบแล้ววันรุ่งขึ้นผมก็ออกไปข้างนอก (เพราะเป็นทาสการตลาดของ HoYoVerse ก็เลยต้องรีบไปสอยของลิมิเต็ด Genshin Impact น่ะ ฮา) ซึ่งระหว่างนั้นผมก็ได้คิดทบทวนเกี่ยวกับคำว่า Proof of Work ตลอดทางเลยว่ามันยังไงกันแน่
เท่าที่ผมเข้าใจในตอนนี้ “Proof of Work” (ที่ไม่ใช่ Consensus Algorithm ของ Cryptography) มันก็ตรงตัวตามความหมายแปลไทยเลย นั่นก็คือ “หลักฐานการทำงาน” นี่แหละ ไม่ว่าจะเป็นเรื่องของความสามารถติดตัว ทัศนคติ ความรู้ความเข้าใจ อากับกิริยา สิ่งที่ต่าง ๆ ที่เราได้แสดงให้ผู้อื่นเห็น รวมไปถึงประสบการณ์ต่าง ๆ ที่ผ่านมา ฯลฯ อะไรก็ตามเหล่านี้เป็นหลักฐานชั้นดีที่แสดงให้เห็นว่าเราผ่านอะไรมาบ้าง มีผลงานอะไร ได้ผ่านหรือฝากอะไรในโลกใบนี้มาบ้าง “Proof of Work” มันสะท้อนถึงฝีมือ คุณค่า (Value) ความน่าเชื่อถือไว้วางใจในตัวเราเมื่อมีใครมอบหมายให้ทำผลงานบางอย่าง ฯลฯ และมันจะทำให้เกิดผลที่ตามมาเป็นเงาสะท้อนถึงความจริงที่ว่าเราเป็นใครหรือตัวอะไร(?)ในระบบสังคมหรือในแวดวงวิชาชีพเหล่านั้นอย่างแท้จริง
แม้สิ่งเหล่านี้อาจจะไม่ใช่คำนิยามหรือความเข้าใจเกี่ยวกับ “Proof of Work” ที่ตรงกับคนอื่น ๆ แต่นี่ก็เป็นสิ่งตกตะกอนทางความคิดจากมันสมองที่มีปัญญาอันน้อยนิดของผมจะกลั่นกรองออกมาได้
…
ในช่วงที่เดินทางกลับบ้านจะมีจังหวะหนึ่งที่ผมจะแวะเข้าร้านสะดวกซื้อเพื่อหาอะไรดื่ม ก็พบว่า ณ เวลานั้นเงินสดติดตัวได้หมดลงจนไม่มีเงินจ่ายค่ารถประจำทางกลับบ้านต่อสุดท้าย ก็เลยถามพนักงานร้านสะดวกซื้อเพื่อไปกดเงินออกมาจ่าย…ซึ่งตู้ที่ใกล้ที่สุดมันช่างไกลลลลลลล…ไกลเหลือเกิน ระหว่างนั้นผมก็เดินไปครุ่นคิดเรื่อง Proof of Work ไปเรื่อย ๆ แม้แดดจะร้อนฉิบหายวายป่วงก็ตาม จนกระทั่งผ่านไปครู่หนึ่งแล้งก็ได้ถึงบางอ้อ…
…ผมว่าผมรู้ปัญหาของตัวเองแล้วล่ะว่าทำไมคนอื่นไม่ได้ให้น้ำหนักต่อผลงานของเราในช่วงที่ผ่านมามากขนาดนั้น
เราน่าจะยังมี Proof of Work ไม่มากพอว่ะ
…
แม้ถ้าดูจากการทำช่องของผมในฐานะ Saltyman ที่ทุกสิ่งอย่างในช่องมันทำด้วยตัวเองจริง ๆ (แล้วผมก็เอามีมจากโฆษณามาใส่ Soundboard และหากินกับมีมนี้จนถึงทุกวันนี้นั่นแหละ) เผื่อใครยังไม่ทราบเรื่องนี้…โซล (คำในวงการ VTuber ที่ใช้เรียกแทนตัวตนที่เคลื่อนไหวหลังจอของ VTuber) ของผมวาดรูปออกแบบโมเดลตัวละครที่คุณเห็นขึ้นมาเอง ตัดเส้นลงสีเอง นำภาพไปแยกส่วนแล้ว Rig จนกลายเป็นโมเดล Live2D ด้วยตัวเอง ออกแบบโลโก้ประจำช่องเอง ออกแบบ Overlay หน้าไลฟ์ด้วยตัวเอง ทำ Transition ไลฟ์เอง ดีไซน์ภาพปกไลฟ์ด้วยตัวเอง ตั้งระบบไลฟ์ด้วยตัวเอง และแน่นอน…คอนเทนต์แต่ละอย่างก็เป็นคนสรรหาหัวข้อเรียบเรียงตอนไลฟ์ด้วยตัวเองเหมือนกัน ถึงกระทั่งออกแบบสินค้าแล้วไปนั่งขายด้วยตัวเองแบบปกปิดตัวตน ถ้าไม่นับเรื่องที่ว่าบางปกไลฟ์ใช้ภาพ Asset จากแหล่งที่เป็น Free for Commercial Use กับเสียงประกอบไลฟ์ที่ไปใช้บริการที่เขามีให้ (เพราะไม่มีความรู้เรื่องดนตรีเลย) ทั้งหมดนี้โซลของผมทำเองจริง ๆ …(ซึ่งไม่ได้จะอวดว่าตัวเองเก่งเพราะมันเคยมีคนหาว่าผมอวดเก่งจากเรื่องนี้ แต่ที่ต้องทำหมดนี่เพราะไม่มีเงินจ้างแค่นั้นแหละ ถ้ามีจะทำเองเพื่ออออ)
และจริง ๆ ผมเองก็พอมีสกิลการเขียนในระดับหนึ่ง คือไม่ได้เขียนเก่งอะไร แต่พอจะเขียนได้บ้าง เล่าเรื่องได้ เขียนได้ทั้งยาวและสั้น แถมโซลของผมก็เคยมีประสบการณ์ทำหนังสือทำมือมาก่อนทั้งแบบที่เป็นนิยายและเรื่องสั้น
แต่ถ้าลองมานั่งพิจารณาอีกที แล้วไหนหลักฐานประจักษ์ที่คนอื่นจะรับรู้ได้ว่าเรามีความสามารถเหล่านี้ล่ะ ?
ผลงานวาดภาพ ? มีนะ เห็น ๆ กันอยู่…แต่น้อยมาก งาน Live2D Rig ล่ะ ? มีแต่โมเดลตัวเอง (กับเคยริกให้งานหนึ่งที่ล้มเลิกโครงการไปแล้ว) Goods ล่ะ ? ออกปีละครั้ง มีแค่ 6 ชิ้น ไม่มีอะไรในระหว่างปีเลย ออกน้อยด้วย บทความล่ะ ? …นี่เพิ่งบทความที่สองที่คนเห็นในฐานะ Saltyman แถมอันแรกก็เป็นบทความสั้นด้วย (บทความอื่นของโซลหายไปแล้วเพราะเว็บที่เคยเขียนมันปิดไปแล้ว) นิยาย/เรื่องสั้นล่ะ ? ในฐานะของ Saltyman ก็ยังไม่มีผลงานพวกนี้ให้เห็นอีก (โซลมี แต่ขอไม่เปิดเผย)
ยังไม่นับที่ว่าไลฟ์ที่ทำตอนนี้มีคนไม่ค่อยเห็นจนไม่ได้มีคนให้ความสนใจขนาดนั้นอีก… ไหนจะรายการ Podcast ที่สัญญาว่าจะทำแล้วก็ยังไม่ออกมาซักตอนอีก…
…
นั่นแหละครับที่ตระหนักได้ระหว่างเดินไปกดเงิน… ที่แท้เรามีความสามารถนะ แต่มันไม่มีหลักฐานมากพอที่คนอื่นจะให้ค่าขนาดนั้น
Proof of Work ของเรามันยังไม่มากพอจริง ๆ ด้วย งั้นก็ไม่แปลกหรอกที่เราอยู่ในสภาพนี้…
…
ระหว่างเดินทางกลับบ้านด้วยรถประจำทางต่อสุดท้าย ผมก็ได้นั่งเหม่อมองข้างทางไปพร้อมกับคิดเพิ่มเติมเกี่ยวกับ Proof of Work ของตัวเองให้มากขึ้น ในเมื่อเราไม่มีหลักฐานความสามารถของเรามากพอ มันก็มีแต่ต้องทำเพิ่มให้มากพอ ต้องทำให้คนรู้ว่าเราทำอะไรได้บ้าง มีผลงานอะไรบ้าง มีแนวคิดอย่างไรบ้าง ไม่มีทางลัดอื่นใดมากกว่านี้อีกแล้ว แม้ในแพลตฟอร์มสังคมออนไลน์เจ้าดัง ๆ จะยังสามารถหาวิธีโกงยอด Engagement ได้ อาศัยเกาะกระแสให้ตัวเองโดนลากเข้าไปเป็นส่วนหนึ่งของ Eyeballs ของคนอื่นได้ แต่สิ่งที่เราเห็นกันมาตลอดก็คือพวกเขาเหล่านี้ก็จะล้มหายตายจากไปตามกาลเวลา เพราะเขาไม่มีอะไรที่น่าสนใจมากพออย่างแท้จริง ไม่มีผลงานอะไรที่เป็นที่ประจักษ์อย่างแท้จริง
แม้ว่าจุดหมายของคำว่า “มากพอ” มันไม่มีประมาณหรือระยะเวลาที่ตายตัว แถมยังต้องอยู่ในสภาวะที่มีโอกาสเหมาะสมด้วย แต่การที่สร้างผลงานเป็นหลักฐานเอาไว้ก็ไม่ต่างจากเรื่องราวในหนังสือที่ผมเคยอ่านเล่มหนึ่ง มันชื่อว่า Good Luck ที่ว่าด้วยเรื่องของสองเพื่อนในวัยชรามานั่งคุยเปรียบเทียบความสำเร็จในชีวิตของตัวเองกัน แล้วหนึ่งในเพื่อนก็เล่านิทานที่เกี่ยวกับอัศวินสองคนที่พยายามตามหาใบโคลเวอร์สี่แฉกที่พ่อมดเมอร์ลินทำนายว่ามันจะปรากฎขึ้นในอาณาจักร ณ บริเวณที่ไม่มีต้นไม้ปลูกขึ้นมาแสนนาน ซึ่งอัศวินคนหนึ่งเลือกที่จะเสาะหาถามคนอื่นไปทั่วว่าใบโคลเวอร์สี่แฉกอยู่ไหน แต่อัศวินอีกคนกลับเลือกที่จะไปเตรียมดินบริเวณตามคำทำนายให้อุดมสมบูรณ์มากพอที่จะปลูกอะไรได้ จนกระทั่งเมล็ดของต้นโคลเวอร์สี่แฉกก็มางอกอยู่ตรงดินที่เตรียมไว้จริง ๆ
ผมถึงตระหนักได้ในที่สุดว่าการสร้าง Proof of Work มันก็เหมือนกับการเตรียมดินในนิทานของหนังสือ Good Luck นี่เอง เราไม่สามารถรู้ได้หรอกว่าโอกาสมันจะมาตอนไหน แต่ถ้าเรารู้จักเตรียมตัวเองให้พร้อม สร้างหลักฐานการทำงานของตัวเองขึ้นมาว่าเราทำอะไรได้บ้าง เก็บ Portfolio (ที่ไม่ใช่พอร์ตการเงินการลงทุน) ไปเรื่อย ๆ เพื่อพิสูจน์และพัฒนาความสามารถของตัวเองจนกระทั่งมีใครสักคนมาเห็นและสนใจสิ่งที่เราทำอยู่ นั่นแหละคือเวลาที่ Proof of Work ของเราจะผลิดอกออกผลเป็นใบโคลเวอร์สี่แฉกออกมาจริง ๆ เป็นความโชคดีแบบที่นิทานในหนังสือบอกไว้จริง ๆ
เหตุการณ์ทั้งหมดนี้เกิดขึ้นเมื่อวานก่อนที่จะลงบทความนี่เอง จากวันธรรมดาที่เราแค่จะไปซื้อของพรีเมียมเกมที่เรารัก แต่มันกลับให้อะไรกับเรามากมาย มันทำให้ผมได้เห็นถึงปัญหาเรื้อรังของตัวเอง ปัญหาที่ว่าเราไม่มีหลักฐานผลงานของตัวเองมากพอจริง ๆ และผมก็ตัดสินใจที่จะเขียนเล่าเรื่องของตัวเองเรื่องนี้ออกมาเพื่อให้คนอื่นได้รับรู้ เผื่อว่าใครที่กำลังหลงทางสับสนกับชีวิตอยู่ในตอนนี้ว่าทำไมเราทำอะไรไปก็ไม่มีใครสนใจจะได้ตาสว่างแบบที่ผมตาสว่างบ้าง
จากนี้ก็มีแต่ต้องสร้างผลงานออกมาให้สม่ำเสมอ สร้างหลักฐานว่าเรามีความสามารถอะไรบ้าง และพิสูจน์ให้โลกได้เห็นว่ามันมี VTuber อิสระชาวไทยคนนึงที่พูดได้อย่างเต็มปากว่า “ผมทำด้วยตัวเองมาตลอด (จนมากพอจริง ๆ )”
…
ได้เวลาลงมือสร้าง Proof of Work แล้วล่ะนะ
Saltyman | Virtual Podcast ที่วาดรูปและเขียนได้นิดหน่อย
-
 @ 6871d8df:4a9396c1
2024-02-24 22:42:16
@ 6871d8df:4a9396c1
2024-02-24 22:42:16In an era where data seems to be as valuable as currency, the prevailing trend in AI starkly contrasts with the concept of personal data ownership. The explosion of AI and the ensuing race have made it easy to overlook where the data is coming from. The current model, dominated by big tech players, involves collecting vast amounts of user data and selling it to AI companies for training LLMs. Reddit recently penned a 60 million dollar deal, Google guards and mines Youtube, and more are going this direction. But is that their data to sell? Yes, it's on their platforms, but without the users to generate it, what would they monetize? To me, this practice raises significant ethical questions, as it assumes that user data is a commodity that companies can exploit at will.
The heart of the issue lies in the ownership of data. Why, in today's digital age, do we not retain ownership of our data? Why can't our data follow us, under our control, to wherever we want to go? These questions echo the broader sentiment that while some in the tech industry — such as the blockchain-first crypto bros — recognize the importance of data ownership, their "blockchain for everything solutions," to me, fall significantly short in execution.
Reddit further complicates this with its current move to IPO, which, on the heels of the large data deal, might reinforce the mistaken belief that user-generated data is a corporate asset. Others, no doubt, will follow suit. This underscores the urgent need for a paradigm shift towards recognizing and respecting user data as personal property.
In my perfect world, the digital landscape would undergo a revolutionary transformation centered around the empowerment and sovereignty of individual data ownership. Platforms like Twitter, Reddit, Yelp, YouTube, and Stack Overflow, integral to our digital lives, would operate on a fundamentally different premise: user-owned data.
In this envisioned future, data ownership would not just be a concept but a practice, with public and private keys ensuring the authenticity and privacy of individual identities. This model would eliminate the private data silos that currently dominate, where companies profit from selling user data without consent. Instead, data would traverse a decentralized protocol akin to the internet, prioritizing user control and transparency.
The cornerstone of this world would be a meritocratic digital ecosystem. Success for companies would hinge on their ability to leverage user-owned data to deliver unparalleled value rather than their capacity to gatekeep and monetize information. If a company breaks my trust, I can move to a competitor, and my data, connections, and followers will come with me. This shift would herald an era where consent, privacy, and utility define the digital experience, ensuring that the benefits of technology are equitably distributed and aligned with the users' interests and rights.
The conversation needs to shift fundamentally. We must challenge this trajectory and advocate for a future where data ownership and privacy are not just ideals but realities. If we continue on our current path without prioritizing individual data rights, the future of digital privacy and autonomy is bleak. Big tech's dominance allows them to treat user data as a commodity, potentially selling and exploiting it without consent. This imbalance has already led to users being cut off from their digital identities and connections when platforms terminate accounts, underscoring the need for a digital ecosystem that empowers user control over data. Without changing direction, we risk a future where our content — and our freedoms by consequence — are controlled by a few powerful entities, threatening our rights and the democratic essence of the digital realm. We must advocate for a shift towards data ownership by individuals to preserve our digital freedoms and democracy.
-
 @ 5e73c80b:08433652
2024-03-24 16:24:22
@ 5e73c80b:08433652
2024-03-24 16:24:22I'm sure you have all thought of this before but I haven't. If Bitcoin is so great what's to stop a different Satoshi Angel from immaculate conception of a similar idea. Let's call it Bytecoin. Let's say Bytecoin drops next year and in 10 years is ifinirly more popular and more utilized than Bitcoin. Your Bitcoin still has value but but will h less demand for Bitcoin and more for Bytecoin it not worth as much anymore. Would it really be that difficult to copy the Bitcoin idea? It seems like real success would be whatever coin is adopted more widely. Thoughts?
-
 @ c11cf5f8:4928464d
2024-03-24 14:46:06
@ c11cf5f8:4928464d
2024-03-24 14:46:06Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too.
If you missed our last thread, here are some of the items stackers recently spent their sats on.
-
 @ 3f770d65:7a745b24
2024-02-24 18:01:19
@ 3f770d65:7a745b24
2024-02-24 18:01:19February 24, 2024 - Nostr Nests, the premier decentralized audio platform powered by the Nostr protocol, announces the launch of its highly anticipated version 2.0 beta release. This major update brings complete integration with Nostr, a redesigned user interface, and a host of powerful features, making it easier than ever to connect, collaborate, and create in an open and censorship-resistant environment.
Originally launched in January 2023 as Nostr Plebs Spaces, Nostr Nests quickly gained traction as a haven for audio-based interactions across the Nostr protocol. The official rebrand to Nostr Nests in February 2023 further solidified its position as the go-to platform for chatting, jamming, micro-conferences, live podcast recordings, and more with the onboarding of users, shows, and content from around the globe.
Version 2.0 marks a significant leap forward:
Seamless Nostr Integration: Nostr Nests 2.0 was built from the ground up to be a full fledged Nostr client, enabling a truly decentralized experience with direct Nostr authentication. No need for separate accounts, logins, or verification posts. Login with your current Nostr keys via nsecBunker or NIP-07 extensions such as Alby, Nostr Connect, or Nostore for iOS.
Discoverability and User Choice: Find your favorite live audio events like never before, not only on NostrNests.com, but also via a variety of Nostr clients that support live events such as Amethyst, Snort, Iris, Flockstr, Nostrudel, Wherostr and more. Install Nostr Nests as a PWA on Android, iOS, or your favorite desktop operating system.
Redesigned Interface: Navigate with ease thanks to a streamlined and intuitive layout. Find scheduled events, discover communities, and manage your interactions effortlessly.
Enhanced Functionality: Host events with flexible permission settings, record and store audio directly from your Nest, be in charge of your data while you chat on your customized relays, leverage advanced moderation tools for a smooth and secure experience, and broadcast it all across the Nostr protocol. Experience value for value with Zap enabled profiles and chat announcements.
Multi-lingual: Access Nostr Nests in your native language. Nostr Nests supports over a dozen languages, making Nostr Nests a truly global platform for our users. Open Source: The platform's code is fully open-source under the MIT license, welcoming community contributions and fostering transparency. Submit issues and pull requests on GitHub to shape the future of Nostr Nests.
Nostr Nests 2.0 empowers individuals and communities to:
Connect: Host and attend audio events with like-minded people based on shared interests, making new friends along the way or reconnecting with old ones.
Collaborate: Jam with musicians, brainstorm with colleagues, or conduct insightful interviews in a live audio setting.
Express Yourself: Share your voice, thoughts, and ideas with the world in an uncensored and secure environment via text chats as well as audio conversations.
Build Communities: Foster vibrant, customizable communities around shared passions, hobbies, or professional pursuits.
Whether you're a musician, podcaster, entrepreneur, or simply someone who enjoys meaningful audio interactions, Nostr Nests 2.0 invites you to join the conversation. Visit NostrNests.com today and experience the future of social audio.
Join and contribute to the Nostr Nests community:
Website: https://NostrNests.com
GitHub: https://github.com/nostrnests/nests
Current Features:
Nostr Integration: * Sign-in * Live events * Scheduled events * Zaps * Public chat * Reactions * Room presence * Relays (default or custom) * Social sharing * Follow/Unfollow * Profile creation * Profile Editing * Lobby filtering
Lobby: * Active rooms * Scheduled rooms * Filter by global or following * Create new room * View profile
Create room: * Create custom room * Customizable banner * Preselected colors * Custom image (static or animated) * Schedule room * Use default relays or custom relays
Rooms: * Stage and audience * Add/Remove people to/from stage * Public chat (ability to hide/view on mobile) * Raise hand * Mute/Unmute own mic * Mute others (Mod or Host) * Zap * Reactions * Edit profile * View profile * Share to Nostr * Stream audio (coming soon) (Mod or Host) * Record audio (Mod or Host) * Access room recordings (Mod or Host)
Sign-in: * Sign-in as guest to listen only * Create new Nostr profile * Use existing Nostr profile
Future Features:
- Chat zaps, chat reactions, mutes, etc.
- Support additional nsecBunkers
- More room customization options
- Monetization options for creators
- And more!
Please note: While Nostr Nests 2.0 marks a significant step forward, this release should be considered beta software. Users may encounter occasional bugs or unforeseen issues as we continue to refine and optimize the platform. We appreciate your understanding and patience as we work towards a fully polished experience.
Known Issues:
- A lot! It's very new and very beta!
- Sign-in user flow for direct links to rooms
- Mobile UI alignment
- Mobile UI chat bar
-
 @ 2363dd1c:5c34ebff
2024-03-24 12:55:43
@ 2363dd1c:5c34ebff
2024-03-24 12:55:43This post is the seventh in our Stoic Philosophy book club series on Meditations by Marcus Aurelius. Participants expressing interest are tagged at the end of the post, let us know if you're new and would like to join and be tagged!
Prior posts for context: * Book 6 * Book 5 * Book 4 * Book 3: In Carnuntum * Book 2: On the River Gran, Among the Quadi * Book 1: Debts and Lessons * Geneisis Post
Thanks to those of you who participated in the comments last week. Let me know if you would like to join.
Book 7
Summary and Highlights
My rather speedy read through Book 7 has me realizing that many of Marcus' entries are the same Stoic ideas we've visited in prior "books". Book 7 is lengthy with 75 entries. The fact that we revisit the same ideas doesn't degrade in any way the experience of reading it. In fact, it actually makes it feel like a real, practical meditation, in that we are coming back to these Truths over and over again, as if we were sitting and returning our attention to the breath whenever the mind wanders off in distraction. Furthermore, although the Stoic ideas are fundamentally the same, Marcus' insights repackage them in a unique fashion for each entry. Just like in sitting, each breath is qualitatively different and each moment of insight, or realization of the Truth is also fundamentally unique.
I guess I'm engaging in this meta-analysis in part to support the my decision to skip reflection of some of the good entries which feel a little too familiar. These postings might become a little shorter and target only the entries which feel especially pertinent to me. We'll see.
Some topics that stuck out to me initially were familiarization and pain.
- You cannot quench understanding unless you put out the insights that compose it. But you can rekindle those at will, like glowing coals. I can control my thoughts as necessary; then how can I be troubled?
I found this passage insightful and surprising because that experience of "insight" is usually interpreted as a breakthrough and feels good. However, it's also a dopamine hit and we can become sort of addicted to it. For example, today I was walking my dog with a friend and she was excited because she had a major breakthrough in understanding some things that have caused her a lot of pain an trauma. She had discovered or accepted a diagnosis for her condition, but also shared that there is often a "honeymoon period" after receiving a diagnosis. That could be this feeling, like finding an answer to the question "why?". I was happy for her, but I was also remembering that that feeling of satisfaction of having an answer has always been temporary in my own life, and these insights usually require practice and integration to have a lasting impact. I think Marcus is suggesting here that the mind can get trapped in going down a rabbit hole of desiring and seeking insights, and perhaps that rabbit hole is endless. The way he describes a mastery over the mind is both concise and poetic, something I haven't managed to "achieve", but a target described well enough that one can get an idea of how to apply the mind as a tool, instead of getting dominated by it.
When describing the constant activity of the natural world around us in #3, humans included, Marcus says,
Surrounded as we are by all of this, we need to practice acceptance. Without disdain. But remembering that our own worth is measured by what we devote our energy to.
The "without disdain" part caught me here. Why is it so easy to write off everything that is going on around us? Perhaps it's a defense mechanism to protect our nervous system and awareness from being overloaded? In some sense, it's funny Marcus throws this in there so naturally, but in another, it's completely natural because I catch myself in that attitude when I go out in public. I think evolution is fundamentally about growing in consciousness, and awareness, and that mean expanding perception. However, when our perceptions expand, so do our boundaries, and perhaps this attitude of disdain or aversion represent a boundary of consciousness, that we are challenged to integrate. Marcus urges us to practice acceptance, to make peace at that boundary. Over and over in other entries, he suggest that doing so helps us see how we are connected to others and the world around us and doing so enables us to see more of our place in the world.
- Focus on what is said when you speak and on what results from each action. Know what the one aims at, and what the other means.
Good, practical advice. Easier read than done. I also find it interesting that organizationally, the speech == aim and action == meaning. Speech comes before action, like a blueprint, and acts can be reflected upon to derive meaning. Sort of like a hypothesis and the result of the scientific experiment. Where, then, does thought factor into all this? Perhaps we're looking at a layered approach of causation from the subtle to the gross...
- Don't be ashamed to need help. Like a soldier storming a wall, you have a mission to accomplish. And if you've been wounded, you need a comrade to pull you up? So what?
This stands out because it's hard for me. I'm patterned to refuse help and take on everything myself. A good reminder for me, but also I have more questions than insights. If we're talking about a "spiritual path" of sorts in life, where does this help come from? How to ask? And how do I know when I'm wounded? Something I'll need to keep practicing.
- Straight, but not straightened.
This one sounds like a sly little reminder from Marcus to himself. I have absolutely no idea what he's referring to, but I like the feel of it.
- What is rational in different beings is related, like the individual limbs of a single being, and meant to function as a unit. This will be clearer to you if you remind yourself: I am a single limb (melos) of a larger body -- a rational one. Or you could say "a part" (meros) -- only a letter's difference. But then you're not really embracing other people. Helping them isn't yet it's own reward. You're still seeing it as The Right Thing To Do. You don't yet realize who you're really helping.
I think the conclusion here is that if you really see things as they are, you realize that you are One with Nature and other people around you. When one can live with this awareness, they are helping themselves as well as others. Doing what is best for others is doing what is best for ourselves, and this can become a Natural way of life -- perhaps it is the truly Natural way of life. Aside from the depth here, it's just a beautiful passage and I like that the reader is left to draw their own conclusion.
22 and #26 are great injunctions for compassion between fellow humans, I'll refrain from quoting them here.
- Treat what you don't have as non-existent. Look at what you have, the things you value most, and think of how much you'd crave them if you didn't have them. But be careful. Don't feel such satisfaction that you start to overvalue them -- that it would upset you to lose them.
Hmmmm.... do I overvalue my Bitcoin? Probably :) The passage has me reflecting on the bull market. It's established economics that the "markets" are driven by fear and greed. With virtually no experience with finance, I would never have considered myself a greedy person until I experience my first BTC bull market. It wasn't until I had some skin in the game, that I observed how the excitement changed my behavior, my attention and my focus. I like to be open about this experience because I feel that riding BTC volatility has helped me get in touch with my fear and greed. It's not fun to acknowledge, but now that I know I'm just an ordinary human, an ordinary market participant, I can come to accept these aspects of myself, instead of pretending that I'm above them or something. Also, with more cycles and more experience, I've found that I'm less swept up in the excitement, fear and greed so there is a normalization and healing opportunity with time and awareness. It's vulnerable, but I think its good to acknowledge the darker qualities of humanity with others more often. Here's to staying humble and stacking sats!
- [On pain:] Unendurable pain brings its own end with it. Chronic pain is always endurable: the intelligence maintains serenity by cutting itself off from the body, the mind remains undiminished. And the parts that pain affects -- let them speak for themselves, if they can.
This is an expert manual on pain management. I've encountered some chronic body pain and met it in meditation. To let the painful parts "speak for themselves" is to apply deliberate attention to a painful area of the body and maintain an equanimous, inquisitive awareness of the sensation, following and staying with it until it's run it's course. When the pain has said what it needs to say, it's essentially transformed into something else -- maybe even pleasure or bliss. Going through this process over and over has shown me both that pain is neutral phenomenon, but also that beneath each layer of sensational experience lies another, different experience which may, in it's uniqueness, be equally or more difficult to listen to.
- "Kingship: to earn a bad reputation by good deeds."
This has got to be a big of a tongue-in-cheek joke by Marcus suggesting you're either damned if you do, or damned if you don't as a ruler, unappreciated. One could dig for more depth, but I just find the comment funny.
- But, my good friend, consider the possibility that nobility and virtue are not synonymous with the loss or preservation of one's life.
Marcus implies that virtues including nobility and virtue are immortal qualities. Perhaps these are the things higher than Man the he refers to elsewhere in Book 7, that humans are destined to serve. Either way, to decouple their value from human lifespan is a reflection on both the inevitability of bodily death and the immortality of a virtuous soul.
- Look at the past -- empire succeeding empire -- and from that, extrapolate the future: the same thing. No escape from the rhythm of events. Which is why observing life for forty years is a good as a thousand. Would you really see anything new?
This observation rings back to #1, which I haven't quoted in which Marcus describes evil in the world as the "same old thing". Both these entries contribute to the theme of familiarization I find in Book 7 -- that relativizing the things of the world to their fundamentals makes it easier for the mind to transcend its addiction to the material. This passage reminds me of a time in life where I considered that the only thing that could be more scary than death, was the prospect of actually living forever. Imagine being trapped in an eternity of "the same thing", as Marcus puts it. That might truly be a hell. From this perspective, death actually serves an important purpose of resetting and rejuvenating our awareness and perspective. An interesting though experiment, but one I consider seriously.
In #58, Marcus admonition to "live up to your own expectations" caught me. I tend to have unrealistic or over-ambitious expectations for myself. This probably also leads me to suffering self-judgement. I guess growing toward a more realistic view of our own capabilities is part of Knowing Yourself, purifying perceptions and the mind's conception of itself. Evidence that I'm still on the way.
- For times when you feel pain: ... pain is neither unbearable nor unending, as long as you keep in mind its limits and don't magnify them in your imagination.
Another commentary highlighting the topic of pain, and a reminder that pain is an interpretive quality of the mind, existing in our imagination and how we relate to a given sensation or emotion.
- Take care that you don't treat inhumanity as it treats human beings.
We must not partake of the evil of inhumanity in response to it, otherwise we become it. A short, poetic, kohn-like passage.
- ... It's possible to be a good man without anybody realizing it. Remember that.
We are beholden only to ourselves and our best conception of what it means to life well.
- The gods live forever and yet they don't seem annoyed at having to put up with human beings and their behavior throughout eternity. And not only put up with buy actively care for them. And you -- on the verge of death -- you still refuse to care for them, although you're one of them yourself.
Marcus slyly admits his religious laziness, while simultaneously acknowledging his participation in divinity. Wraps the mind in a circle and makes me smile.
- No one objects to what is useful to him. To be of use to others is natural. Then don't object to what is useful to you -- being of use.
:) The thing here for me is coming to a natural realization that being of use to others is natural. To live with this perspective in an embodied way makes for the Stoic life Marcus is constantly describing, but the path to that realization easier said / thought than walked.
Participants
Thank you everyone who has been reading Meditations, and participated in the discussions. Feel free let me know if you don't want to be on the tag list anymore :)
@siggy47 @cryotosensei @carlosfandango @Bitman @gd @sudocarlos @BitByBit21 @bc52210b20 @Atreus @byzantine @davidw @Roll @grayruby @Taft @Oialt
Please signal interest in the comments if you'd like to be tagged.
-
 @ a012dc82:6458a70d
2024-03-24 12:04:47
@ a012dc82:6458a70d
2024-03-24 12:04:47Embark on a journey into the groundbreaking world of GoToshi, where Laserman is leading a Bitcoin-only revolution in the marketplace. Explore how GoToshi navigates cryptocurrency volatility while offering unique merchandise exclusively in Bitcoin. Learn about their strategies for growth, international expansion, and social media impact. Discover insights from Laserman's interview on the Croxroad podcast, where he shares GoToshi's mission and challenges. Dive into the transformative power of Bitcoin in empowering individuals and reshaping e-commerce. Join us in uncovering GoToshi's vision for revolutionising the marketplace space with Bitcoin at its core.
Table of Contents
-
Introduction
-
The Bitcoin-Only Marketplace
-
From Inception to Success
-
Key to GoToshi's Growth
-
Passing Down Bitcoin
-
Conclusion
-
FAQs
Introduction
Laserman, the visionary behind GoToshi, emerges as a key figure in revolutionising the online marketplace space with a bold and innovative approach. With a passion for Bitcoin and a commitment to advancing financial sovereignty, Laserman has spearheaded the creation of a Bitcoin-only platform that challenges traditional norms and empowers users in unprecedented ways.
His journey into the world of cryptocurrency began with a deep-seated belief in the transformative power of Bitcoin. Recognizing the limitations of traditional financial systems and the need for decentralised alternatives, Laserman embarked on a mission to create a platform that would democratise access to Bitcoin and foster a community built on financial empowerment.
Through GoToshi, Laserman seeks to redefine the way people engage with online marketplaces, offering a space where individuals can buy, sell, and transact exclusively with Bitcoin. By eliminating reliance on fiat currency and embracing the digital currency revolution, Laserman aims to pave the way for a more inclusive and resilient economic ecosystem.
Moreover, Laserman's vision extends beyond just creating a marketplace; it encompasses a broader commitment to fostering financial education and empowerment. With a focus on promoting Bitcoin adoption and financial literacy, he aims to empower individuals to take control of their financial futures and embrace the possibilities offered by the digital economy.
As the driving force behind GoToshi, Laserman embodies innovation, resilience, and a steadfast commitment to empowering individuals through Bitcoin. His visionary leadership and unwavering dedication to advancing financial sovereignty make him a transformative figure in the world of cryptocurrency and online commerce.
The Bitcoin-Only Marketplace
The emergence of a Bitcoin-only marketplace represents a significant shift in the e-commerce landscape, marked by the pioneering efforts of platforms like GoToshi. By exclusively accepting Bitcoin as a means of transaction, these marketplaces are not only embracing cryptocurrency but also challenging traditional fiat currency systems.
One key aspect of Bitcoin-only marketplaces is their resilience to traditional financial market fluctuations. Unlike fiat currencies, Bitcoin operates independently of central banks and government regulations, offering users a decentralised and borderless alternative. This autonomy from traditional financial institutions makes Bitcoin an appealing choice for those seeking financial sovereignty and security.
Moreover, Bitcoin-only marketplaces foster a community of like-minded individuals who share a common belief in the potential of cryptocurrency. This sense of community strengthens trust and solidarity among users, driving adoption and growth within the platform.
However, operating within the Bitcoin ecosystem also presents challenges. The inherent volatility of Bitcoin prices can pose risks for both buyers and sellers, requiring careful risk management strategies to mitigate potential losses. Additionally, while Bitcoin offers benefits such as lower transaction fees and faster cross-border transactions, it still faces scalability issues that may hinder its widespread adoption as a primary means of payment.
Despite these challenges, the rise of Bitcoin-only marketplaces signals a broader trend towards embracing cryptocurrency as a legitimate form of currency and investment. As more individuals and businesses recognize the benefits of Bitcoin, these marketplaces are likely to play a crucial role in shaping the future of e-commerce, driving innovation, and fostering financial inclusion on a global scale.
From Inception to Success
The journey of the Bitcoin-only marketplace from its inception to its current success represents a remarkable evolution in the realm of e-commerce. Born out of the vision to create a decentralised and borderless platform for trade, these marketplaces have overcome numerous obstacles to establish themselves as viable alternatives to traditional online marketplaces.
At the heart of their success lies the embrace of Bitcoin as the sole medium of exchange, a decision driven by the desire to offer users greater financial autonomy and security. By operating exclusively within the cryptocurrency ecosystem, these platforms have tapped into a growing community of Bitcoin enthusiasts and investors, leveraging their trust and support to fuel growth and innovation.
From a technical standpoint, the development of Bitcoin-only marketplaces has required ingenuity and adaptability. Overcoming challenges such as price volatility and scalability issues, developers have worked tirelessly to optimise user experience and ensure the seamless functioning of the platform.
Moreover, the success of Bitcoin-only marketplaces can also be attributed to their commitment to fostering a sense of community and inclusivity. By providing a platform for users to buy, sell, and interact exclusively with Bitcoin, these marketplaces have cultivated a loyal user base united by a shared belief in the potential of cryptocurrency.
Looking ahead, the future of Bitcoin-only marketplaces appears promising. As Bitcoin continues to gain mainstream acceptance and adoption, these platforms are poised to play an increasingly important role in shaping the future of e-commerce. With their emphasis on decentralisation, security, and community, Bitcoin-only marketplaces are well-positioned to thrive in an ever-evolving digital landscape.
Key to GoToshi's Growth
The key to GoToshi's growth lies in its unwavering commitment to Bitcoin and the principles it embodies. By focusing exclusively on facilitating transactions in Bitcoin, GoToshi has carved out a niche in the marketplace space, appealing to a growing community of cryptocurrency enthusiasts and investors.
One of the primary factors driving GoToshi's growth is its ability to provide users with a platform that aligns with their values of financial autonomy and security. By operating within the Bitcoin ecosystem, GoToshi offers users a decentralized and borderless marketplace where they can buy and sell goods with confidence, free from the constraints of traditional banking systems.
Moreover, GoToshi's emphasis on community engagement has played a crucial role in its growth trajectory. Through initiatives such as the Bitcoin for Punks meetup group and the Cypherpunks Twitter account, GoToshi has fostered a sense of belonging among its users, encouraging active participation and collaboration within the community.
Additionally, GoToshi's strategic partnerships and collaborations have contributed to its expansion and visibility within the cryptocurrency space. By leveraging the expertise and resources of like-minded organisations and individuals, GoToshi has been able to amplify its reach and impact, attracting new users and driving growth.
Looking ahead, the key to GoToshi's continued growth lies in its ability to stay true to its core values while adapting to the evolving needs of its users and the broader cryptocurrency ecosystem. By remaining agile, innovative, and community-focused, GoToshi is well-positioned to build upon its success and further establish itself as a leader in the Bitcoin-only marketplace space.
Passing Down Bitcoin
Passing down Bitcoin represents a crucial aspect of GoToshi's mission and ethos, embodying the principles of financial empowerment and generational wealth. As individuals accumulate Bitcoin assets over time, they often face the question of how to preserve and transmit their wealth to future generations effectively. GoToshi recognizes this challenge and offers solutions to facilitate the seamless transfer of Bitcoin across generations.
One key aspect of passing down Bitcoin involves educating individuals about the importance of incorporating cryptocurrency into their estate planning strategies. By raising awareness about the benefits of Bitcoin inheritance, GoToshi empowers users to make informed decisions about preserving their wealth for future generations.
Moreover, GoToshi provides practical tools and resources to help users navigate the complexities of Bitcoin inheritance, including secure storage solutions and guidance on estate planning best practices. By equipping users with the necessary knowledge and tools, GoToshi enables them to safeguard their Bitcoin assets and ensure a smooth transition of wealth to their heirs.
Additionally, GoToshi emphasises the importance of instilling financial literacy and values in future generations to ensure they understand the significance of Bitcoin and its potential to secure their financial future. Through educational initiatives and community engagement efforts, GoToshi fosters a culture of responsible stewardship and long-term wealth preservation among its users.
Ultimately, passing down Bitcoin is not just about transferring assets; it's about passing down a legacy of financial sovereignty and empowerment. By empowering individuals to secure their Bitcoin assets for future generations, GoToshi plays a vital role in shaping the future of wealth management and inheritance in the digital age.
Conclusion
In conclusion, Laserman's pioneering efforts with GoToshi signify a paradigm shift in the online marketplace landscape. By introducing a Bitcoin-only platform, he not only challenges conventional norms but also promotes financial sovereignty and empowerment. Laserman's vision extends beyond commerce; it encompasses a mission to educate and inspire individuals to embrace the transformative potential of Bitcoin. Through GoToshi, he creates a space where users can transact with freedom and security, paving the way for a more inclusive and decentralised economic future. Laserman's journey exemplifies the power of innovation and underscores the profound impact of embracing digital currencies in shaping tomorrow's economy.
FAQs
What is GoToshi? GoToshi is a Bitcoin-only marketplace platform founded by Laserman. It operates similarly to other e-commerce platforms but exclusively accepts Bitcoin as payment, catering to the growing community of Bitcoin enthusiasts and advocates for financial sovereignty.
How does GoToshi ensure security for transactions? GoToshi prioritises security by implementing robust encryption protocols and leveraging blockchain technology to ensure transparency and immutability of transactions. Additionally, the platform continuously updates its security measures to stay ahead of emerging threats and safeguard users' funds and personal information.
Can sellers from anywhere in the world join GoToshi? Yes, GoToshi is open to sellers from around the globe who are interested in offering their products or services exclusively for Bitcoin payments. However, sellers must adhere to GoToshi's guidelines and policies to maintain the platform's integrity and uphold its commitment to providing a safe and reliable marketplace experience for buyers.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on :
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ e1ff3bfd:341be1af
2024-02-23 14:01:13
@ e1ff3bfd:341be1af
2024-02-23 14:01:13Ben's fuck the bears book
Only sign this if you want to fuck the bears
-
 @ e372d24b:e25df41f
2024-02-21 23:31:38
@ e372d24b:e25df41f
2024-02-21 23:31:38The evolution of Bitcoin and the spread of literacy are two revolutions that have reshaped society, challenging norms and democratizing access to power and knowledge. Both started as exclusive domains: literacy confined to the elite and Bitcoin, a niche technology understood by few. Yet, their journeys towards mass adoption share striking similarities and transformative impacts.
**Gutenberg Meets Satoshi: Catalysts of Change The printing press and Bitcoin technology both played pivotal roles in democratizing their respective domains. Gutenberg's press made knowledge accessible, just as Bitcoin exchanges made digital currency available to the masses. These innovations broke down barriers, spreading like wildfire and challenging centralized power.
**A Rebellion Against Centralization The essence of both literacy and Bitcoin is the fight against centralization. They shifted power from the few to the many, empowering individuals and fostering a more distributed, egalitarian society. This decentralization challenged established hierarchies, whether in the form of monarchs and religious leaders or modern financial institutions and governments.
**Bridging Divides: The Ongoing Struggle Despite their successes, both movements face challenges in achieving universal access. The digital divide for Bitcoin mirrors the literacy gap, highlighting the need for continued efforts in education and technology to ensure that the benefits of these revolutions reach all corners of the globe.
**Conclusion: A Compact Legacy of Empowerment Bitcoin and literacy are more than just about transactions or reading; they're about reshaping power dynamics and promoting freedom, knowledge, and autonomy. Their stories remind us of the power of innovation to drive societal progress and the ongoing quest for a more inclusive world. As we forge ahead, these parallel journeys continue to inspire a future where access to knowledge and financial empowerment is a right, not a privilege.
-
 @ 57d1a264:69f1fee1
2024-03-24 11:15:44
@ 57d1a264:69f1fee1
2024-03-24 11:15:44https://www.youtube.com/watch?v=FmDijK3e37E
I shouldn't share this video. Anyway, I'll let you read between the lines
-
 @ 53dab473:3a95f02d
2024-02-21 00:20:14
@ 53dab473:3a95f02d
2024-02-21 00:20:14The Grapevine is the name given to the implementation of the web of trust in the Pretty Good Project. Its purpose is to help you find the high quality content you seek, even when this means finding a needle in a haystack. To this end, the Grapevine calculates how much Influence any given user should have for the curation of another user’s content in some given context. This post presents an overview of precisely how the Influence score is calculated and how this method will allow us to escape the soul-killing tyranny of today’s social media so-called “influencer.”
Motivation
The rise of the social media “influencer” encapsulates much of what is pathologic about modern day social media. Tech companies, funded by advertising, will do anything to generate clicks and attract attention. This, by definition, is what a social media influencer is good at. Our tech companies spend billions of dollars on platforms and algorithms that cater to the MrBeasts and Kim Kardashians of the world. These people are brilliant in their own way and in what they do — which is what, exactly? Attract followers. Generate clicks and likes. Figure out better ways to trigger dopamine hits. In the process, the world’s ADHD only gets worse and worse.
Arguably, this is very bad for society. Our attention is focused on frivolous topics and people. But attention is limited. The influencer economy exists to the detriment of topics, ideas and users who might be better deserving of our attention. One wonders what would happen if the next Einstein, a genius in a meaningful topic like math or physics but perhaps not a marketing genius with the skill, time or desire build a follower count, were to post a theory of everything on Twitter/X. Would you see it? Probably not. The algorithms would never even notice it. You could very well have no idea it ever existed.
The Pretty Good way to calculate influence
The Pretty Good approach to web of trust is designed to change all of that. We are building the Grapevine in the hopes that it will allow you to sort the wheat from the chaff: to see through the social media influencers who sap you attention and distract you from what’s important, and to give you a mechanism to find the Einsteins of the world. Or the Picassos, or whatever or whomever you are looking for. Almost 8 billion people out there in the world: there are many who deserve your attention but are not getting it. Lots of needles in lots of haystacks.
One of the primary functions of the Grapevine is to calculate a quantity called Influence. It is context dependent and is the primary determinant of how much attention Alice pays to Bob in some given context.
Influence is the product of two numbers: the Average Score, which is a weighted average of trust ratings by other users, and a number called the Certainty in that average score.
Influence = Average Score * Certainty
Certainty is a number between 0 and 1 (i.e., 0% and 100%), and is designed around the idea that a higher number of ratings from trusted users gives you greater confidence, or “certainty,” that the average score is meaningful. This is an idea that all of us are already used to. Consider the rating of a product on Amazon. If two products each have an average score of 4 out of 5 stars, but one is based on one review and the other on one hundred, then most of us would probably be more inclined to purchase the one with one hundred ratings. The reason, of course, is that more ratings gives us greater confidence in the average score.
In the Grapevine, the variable Input is introduced and plays a role similar to the number of ratings on Amazon. But in the Grapevine, not every rating is weighted equally; so Input is defined as the sum of the weights of each individual rating, with the weight of each individual rating determined (primarily) by the relevant (context-appropriate) Influence of the rater.
But the key is the realization that Influence should not be proportional to Input. One hundred quality ratings is meaningful improvement compared to just one; but increasing from 100 to 200? Or even 100 to 1000? At some point, the addition of more ratings becomes only marginally more meaningful.
So we require an equation to map Input into the new variable, Certainty. There are probably more than one equation that would work for this purpose, but an exponential decay seemed to us to be a pretty good solution:
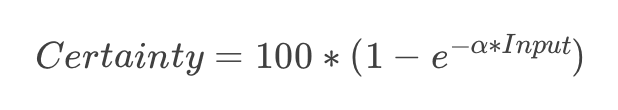
In this equation, alpha is a user-controlled scaling parameter that determines how quickly or slowly Certainty approaches 100% as Input increases towards infinity. This equation is depicted in Fig 1.
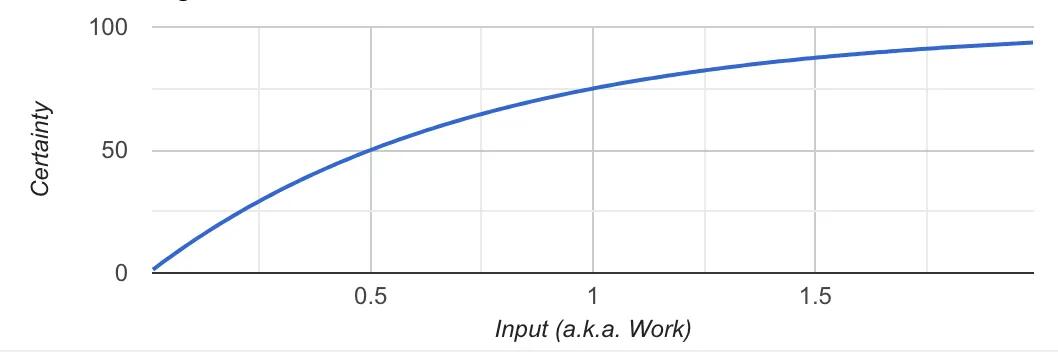
Figure 1. Calculation of Certainty from Input. The speed at which the curve approaches 100% is determined by the scaling factor alpha, which determines the “rigor” of the curve: a gradual rise towards 100% is more “rigorous” than a rapid rise.
As Figure 1 shows, a higher number of ratings (by trusted individuals) does translate into greater Certainty and therefore greater Influence, which makes sense. But there are diminishing returns. The incremental gains gradually level off. In this manner, the Grapevine seeks to avoid a recreation of what is arguably the central pathology of legacy social media.
Summary
- The Average Score is contextual and is a weighted average of each context-based trust rating (“Alice trusts Bob 95 out of 100 to rate movies”).
- The Input is a sum of the weight of each individual trust rating.
- Certainty is calculated from Input using the equation above.
- Influence = Average Score * Certainty.
- Influence is the primary determinant of a rating’s weight.
Conclusion
The Pretty Good Project envisions a world where platforms can be managed by your web of trust rather than big tech companies. There is a lot of work to be done before this goal is reached. But once it is reached, there will be no more need for advertising dollars. Which means algorithms and platforms that cater to influencers and advertisers can fade into the background and be replaced by algorithms that are designed to serve your needs. To find the content you want.
Are you content to ransom your most precious commodity — your time and your attention — to the social media influencer? Or would you rather take control of your time and attention? Focus on the topics, ideas and people who deserve it? The simple solution described in this post may not be perfect. In the future, your web of trust will certainly find ways to improve it. But it’s good enough to get things started.
-
 @ 5b0e8da6:7792bc54
2024-02-20 15:39:44
@ 5b0e8da6:7792bc54
2024-02-20 15:39:44I recently completed my home 7.1.4 speaker setup and have been really enjoying digging into high-end Dolby Atmos and Dolby Vision material. Playing around with nip23 long-form content to share this kind of niche nerd stuff that doesn't quite make sense as a regular nostr note.

tldr: This is the best The Matrix has ever looked or sounded. Find someone with a Dolby Vision-capable 4k blu-ray player (not as easy as you might think) and go watch it. Now. And, no, streaming doesn't cut it.
See Blu-ray.com's Matrix 4k review. Their reviews get pretty deep into the videophile / audiophile nerdosity.
The movie
Holds up amazingly well for being almost 25 years old. Bitcoiners have obsessed about the red (er, orange) pill meme for good reason.
The Matrix was astonishingly ahead of its time in 1999 and still feels futuristic. When old tech is onscreen (green CRTs were old even in 1999; old tube TV; rotary land line phones) it's now even clearer that it was a stylistic choice; The Matrix's simulation has frozen our progress in the past. I think phone booths still existed in 1999, but now they, along with the movie's still-pretty-cool flip phones, read as just part of that time capsule effect.
Video
(aka why Dolby Vision is amazing) My older 4k blu-ray player started playing the disc in HDR10 (the baseline high dynamic range format). It looked good but there were all sorts of obvious flaws (primarily shadows being crushed to black). My screen wasn't calibrated (contrast/brightness/color/etc tweaks) in its HDR10 mode. Ug, calibration for videophiles is such an OCD rabbithole.
But what happened to the disc's Dolby Vision output? (Omitting longer story here. Deeper nerding happened)
Ah, now we've got Dolby Vision output!
And holy shit. It's incredible. Shadows are now perfect. The pervasive computer green is SO richly green (thank you, high dynamic range color)! Yet human-toned reds (pink cheeks, red lips) still pop through.
The Matrix was shot on film so it doesn't have the shot-on-digital, low-grain look of a modern movie, but the natural film grain looks great. The only glaringly bad effects shot was the physical prosthetic used when Neo's mouth is sealed (the skin tone coloring just does not match).
For a sci-fi film shot in 1999, The Matrix's Dolby Vision presentation has NO flaws and far exceeds expectations.
Audio
The Dolby Atmos mix has some nice gee-whiz 3d audio effects (e.g. the bullet-time shots w/sounds tracking around the room as the camera orbits Neo) but I kind of discount big loud action movies; yeah, of course shit's blowing up all around you. The real win for Dolby Atmos is when it ISN'T explicitly grabbing your attention. The overall fullness and envelopment of the music and ambient sounds (the whole point of Atmos is that it adds ceiling speakers) is what people should really appreciate.
One critique: the source material does show its age a bit. At max orchestral and sound effects intensity, the limits of the original recordings are somewhat revealed. Really great recordings have a certain liveliness to their dynamic range; your ear is constantly intrigued and excited by certain resonances or richness or suddenness (e.g. the attack of a bow on a violin). Lower dynamic range audio is like being stuck in a tunnel. The liveliness is muted and as a whole the crescendos become more like a wall of noise rather than a collection of widely varied sounds.
Minor limitation and totally expected. The only real technical nitpick for this disc.
-
 @ d26873b8:53e31221
2024-02-20 15:33:26
@ d26873b8:53e31221
2024-02-20 15:33:26Sudoroso, no sabía si dar cuenta de que se encontraba tendido en el suelo al lado de la cama o de las sensaciones de euforia que todavía lo abordaban. Confusión y claridad se unían en un mismo momento. Sentía que todo fue real. Pero estaba convencido de que nada de ello había sucedido.
Continuaba entumecido de frío aunque los grillos afuera indicaran que se trataba de una despejada noche de verano. Cayó en cuenta de esto cuando no encontró el sweater que estaba buscando. Claro, era verano y todos se encontraban guardados.
Abrió la canilla y comenzó a llenar la bañera con agua caliente. Mientras tanto, se acomodó en una silla en la cocina, dispuesto a tomar una taza de té y meditar sobre lo ocurrido.
Fue solo un sueño, pensó. Uno, como nunca antes. Podía sentirlo como recuerdos, como hechos. Sin embargo, eran sucesos que ocurrían un tiempo después, futuros. ¿Premoniciones? Solo atinó a reír. Siempre fue muy descreído y su razonamiento comenzaba a tomar el control nuevamente. Por lo tanto lo descartó. Al fin y al cabo, eran escenas. Como cuadros en una historieta, que habían sido recortados y algunos descartados. Tenían en apariencia conexión entre ellos, pero no estaban todos los detalles.
En esta obra de teatro que su mente le había proyectado, se había visto con su fiel instrumento en uno o dos salones a los que estaba ya acostumbrado. Pero luego, ocurrieron tres eventos que llamaron su atención.
En primer lugar se encontró participando de una audición. El jurado era prestigioso y los demás artistas eran de renombre. ¡Por supuesto que solo fue un sueño! Exclamó. ¿De qué otra manera podría él estar codeándose con tan distinguida comunidad artística, siendo prácticamente un amateur? Sin embargo, lo que a continuación aconteció, volvió a poner en duda su razón y su corazón. Porque en el sueño, era su turno de tocar. Maravillado y con la piel de gallina quedó al recordar la melodía que hizo sonar con su violoncelo. ¿Bach, Mozart, Feurermann? No, por más que se esforzó no encontró dueño de tal obra de arte. Era novedosa, atípica. Irreverente, la música que surgía de sus manos y del instrumento no seguía las reglas de composición de los grandes. Esa melodía le pertenecía a él. El jurado quedó atónito como los que lo rodeaban, que detuvieron todo lo que estaban haciendo solo para escucharlo. Una vez que se recuperaron del embelesamiento del que fueron víctimas lo aplaudieron y dictaminaron, sin mucho más, que el trabajo era suyo. Le habían impuesto una condición: lo que presentara debía ser tan original como lo que acababan de escuchar.
Cuando se iba a poner a repasar el segundo suceso, notó que había agua entre sus pies, con lo que recordó que había dejado el agua corriendo para llenar la bañera.
Llegó al baño y a tientas cerró la canilla. El ambiente se había colmado de vapor, por lo que abrió la pequeña ventana para disiparlo. Intentando volver a la tarea de rememorar el sueño, apoyó ambas manos a los costados del lavatorio, quedando de frente al espejo. Una sensación fría recorrió como rayo su espalda y fue tal la fuerza con la que apretó las manos que hubiese jurado que escuchó la porcelana rajarse. Es que en el espejo, además de contener el reflejo de sus ojos aterrados, había un mensaje escrito en el vapor que se condensaba en su superficie.
**“Alsina 333. 15 horas. Llevá el violoncelo”**Fueron largas las horas en las que batalló con las sábanas y las almohadas, yendo y viniendo tratando de conciliar el sueño que le era esquivo. No podía dejar de pensar en el mensaje y en el sueño. Sueño, debía encontrarle otro nombre ya que no era justo para lo que le había ocurrido. Finalmente, a altas horas de la madrugada, sus ojos se cerraron y de manera involuntaria se quedó dormido.
Alterado por los ruidos de camioneros que a bocinazos resolvían alguna disputa vehicular se sentó en la cama. Miró el reloj que se encontraba sobre su mesa de luz y sin mucho preámbulo de un salto tomó el primer traje que encontró y se lo puso. Faltaba menos de una hora para las tres y tenía un camino por recorrer antes de llegar a la dirección designada por quien fuera que se comunicaba mediante su espejo. Quizás si hubiese tenido más tiempo, si no hubiese estado tan apurado, habría decidido no concurrir. Pero para cuando se dio cuenta ya se encontraba delante de la puerta que tenía inscripto el número 333.
“Aquí es donde todo se aclarará, donde veré que es todo obra de mi imaginación. Aquí caeré en la cuenta de que estoy más cerca de la locura que del talento sin igual”, pensó. El lugar, era una simple casa de barrio, blanca y sin detalles excepcionales salvo la puerta que era de un vivo color carmesí. No había timbre, solo una dorada aldaba ornamentada por una cabeza de león que sostenía en sus mandíbulas el aro que utilizó para llamar al morador. Sin embargo, nadie salió. Inspiró profundamente para calmarse y volvió a tocar con más fuerza. La puerta cedió y se abrió levemente. Dio un paso atrás instintivamente, pero finalmente atravesó el umbral.
El pasillo era angosto y estaba pobremente iluminado. Al final del mismo vio que había una puerta abierta de donde salía luz. Avanzó y cuando abrió la puerta, la escena que se abría paso delante de él lo obligó a dar media vuelta para salir corriendo. Estaba el jurado y los artistas que ya había visto. Antes que que pudiera emprender su escape, una voz lo detuvo.
—¿Quién es usted?—, le preguntó una mujer con grandes gafas de marco negro.
—¿Yo?, no soy nadie. Debo estar en el lugar incorrecto.
—Esta es una audición para un exclusivo evento. No hubo publicidad y aún así usted llegó puntualmente y trae consigo su instrumento. Usted está aquí porque es el lugar correcto.
Volvió hacia el estudio y se detuvo delante del jurado.
—Escuchemos lo que tiene para nosotros—, dijo la mujer.
Haciendo uso de todas sus fuerzas para no temblar, sacó su violoncelo del estuche y se acomodó en la única silla que había libre dispuesta para la prueba. Sentía que el corazón iba a salir a través de su pecho con cada pálpito más fuerte que el anterior. Sus manos sudaban tanto que el arco se le cayó al suelo. Hizo una pausa, respiró y lo levantó. En ese momento solo pudo hacer una cosa. Cerró los ojos y recordó la pieza que tocó en su sueño. La reprodujo con total fidelidad. Cuando terminó, abrió los ojos y se encontró con un jurado atónito. Todos los que lo rodeaban habían detenido lo que estaban haciendo, solo para escucharlo.
—Deje aquí anotados, su nombre y su dirección. Detalles de la velada y los pasajes de avión le serán enviados. El trabajo es suyo, si presenta una obra tan original como lo que acaba de mostrar.
Pasaron unos días cuando finalmente llegó el correo. En un sobre lacrado con el mismo león que vio en la puerta roja había pasajes de avión a Bariloche para julio de ese año y un folleto del evento. En él se indicaba que el concierto tendría lugar en Llao Llao, y el programa, que tenía grandes figuras nacionales e internacionales, lo ponía a él como el acto central.
En ese momento, ocurrió algo impensado. Su terror ante los sucesos de los últimos días dio lugar a un estado de algarabía que nunca había experimentado. Finalmente su carrera lo iba a llevar a lugares importantes, a codearse con grandes artistas y formar parte de la comunidad más renombrada. Y de repente recordó, que no tenía obra original que pudiera presentar. Él siempre se dedicó a tocar a los clásicos y las veces que trató de componer, nunca logró nada destacable. Allí, fue cuando recordó el segundo de los tres eventos importantes de su sueño. Pero hizo todo lo posible por sacar esa imagen de su mente. No podía concebir la idea de llevarlo a cabo. Tampoco tenía idea de cómo podría ayudarlo a componer algo magnifico. No, debió haberse confundido. Algo así no tiene sentido y no iba a hacerlo.
Aprovechando el tiempo que tenía, se dedicó enteramente a componer. Tomando como base la melodía que tocó en la audición intentó extenderla para ocupar el tiempo que tenía dedicado a su obra en el evento venidero. Escribió varios bocetos.
Igual que en el sueño organizó algunos conciertos en los teatrillos a los que estaba acostumbrado. Buscaba en los espectadores la reacción que le indicara que estaba en el camino correcto. Intentó lograr lo mismo que ocurrió con aquel jurado. Pero fracasó miserablemente. Una y otra vez.
Frustrado pero no más que lo aterrado que estaba, comenzó a considerar la propuesta que el destino le ofreció en el sueño. Como no había detalles de qué lograría obrando de esa manera, nada lo podía convencer de llevarlo adelante. Es que en el sueño, se veía a sí mismo cortándose la punta de los dedos de la mano derecha. El dolor que sintió al hacerlo fue lo que lo despertó aquella noche, no sin antes verse ovacionado en Llao Llao en una fría noche de invierno de Bariloche.
Pero ¿qué más podía hacer? El tiempo pasaba y por más que lo intentaba la obra maestra que buscaba no aparecía.
Como si los pies estuvieran hechos de ladrillos, los arrastró hasta la escalera que conducía al altillo. Recordaba que allí tenía guardado el objeto que lo ayudaría a cumplir con el sacrificio que el destino le demandaba. Era una guillotina, de esas que se usan para cortar hojas de papel. Allí mismo, la retiró de la caja en la que estaba guardada y la colocó sobre una mesa que solo estaba alumbrada por la luz de luna que entraba por la pequeña ventanilla circular.
Alzó la manija y puso los dedos en posición, pero los retiró inmediatamente. Con el puño cerrado acercó la mano a su pecho, como quien cobija a un niño para que deje de llorar. Dio media vuelta y bajó las escaleras. Se sirvió una copa que no duró mucho. Le siguieron otra y otra más. En un momento, sintió que se descomponía; a los tumbos se acercó al baño. Ocho fueron las palabras que lo devolvieron a la sobriedad en un instante:
**“Que aplaudamos de pie, depende solo de vos”**Fue así como esa noche, subió nuevamente al altillo, se paró delante de la luz nacarada y en un contundente movimiento se desprendió las puntas de los dedos.
—¡En qué estoy pensando! Es mi fin, es mi fin—, exclamó angustiado.
Se vendó los dedos y se recostó en la alfombra del living, a llorar hasta que se quedó dormido.
Al otro día sintiéndose completamente derrotado, se incorporó, buscó el violoncelo e intentó tocar. Las cuerdas tensas, solo hicieron que se abriera nuevamente la herida y las vendas se tiñeron del rojo de su sangre. En un ataque de dolor e ira, entró corriendo al baño, y con el puño hizo trizas el espejo que lo había enviado a su ruina.
Pasaron varios días en los que no hizo más que beber y dormir, siempre tirado en la misma alfombra de su casa. Solo pensaba que terminaría en la calle, ya que lo único que sabía hacer y con lo que se ganaba el pan, era tocar el violoncelo. Tumbado en el suelo, giró la cabeza para mirar al instrumento que estaba retozando en el sillón. Se levantó y fue en su búsqueda una vez más. Intentó tocarlo pero no lograba hacer que sonara bien. Se quitó las vendas que ya no le eran necesarias. Sin embargo, el resultado no cambió. Las cuerdas simplemente estaban demasiado tensas para que pudiera tocarlas con los dedos sin punta. Sin más que hacer, aflojo las cuerdas, desafinando el instrumento. Sonaba grave, lúgubre podría decirse, pero sus dedos podían hacerlo sonar.
Probó tocar varias piezas clásicas, pero nada de eso tuvo buen destino. Todo sonaba mal. No encontró manera. Se le ocurrió repasar aquel trozo de melodía que usó en la audiencia. El resultado, lo sorprendió. No era la misma pieza, claro. Pero lo que logró lo dejó estupefacto. Sonaba profundo como un grito bajo el agua. Sin embargo, tenía una potencia magnífica. Afloraban todo tipo de sensaciones de solo escucharlo. Sin dudarlo, intentó extender esa melodía una vez más. Esta vez, el resultado fue completamente diferente. Sonaba bien. No solo bien. Sonaba único.
Y así, como si nada, surgieron melodías debido a estos nuevos sonidos que las cuerdas brindaban. En poco tiempo, su obra maestra estuvo lista.
Miró sus dedos y las lágrimas recorrieron su rostro. Pero no eran lágrimas de dolor. Eran de una profunda alegría silenciosa. Sentía que había triunfado. Solo quedaba esperar.
En los días siguientes, se dedicó a prepararse para el viaje, con tranquilidad. Descansó en su sillón favorito, con su instrumento mirándolo desde la alfombra donde había sentido que su mundo se acababa.
La madrugada era fresca y el rocío todavía estaba presente cuando salía de la zona de preembarque para abordar el transfer que lo dejaría a los pies del avión. Aguardó junto a un puñado de desconocidos en la zona indicada, hasta que llegó el bus y se subió. Con aplomo se dejó caer en su butaca junto a la ventana. Desde allí, curioseaba los nombres de las aerolíneas pintados en las aeronaves de distintos tamaños. Se acercó bastante al vidrio, el cual se empañó. De repente, pudo leer tres palabras en su aliento condensado:
**Clap Clap Clap.** -
 @ b12b632c:d9e1ff79
2024-02-19 19:18:46
@ b12b632c:d9e1ff79
2024-02-19 19:18:46Nostr decentralized network is growing exponentially day by day and new stuff comes out everyday. We can now use a NIP46 server to proxify our nsec key to avoid to use it to log on Nostr websites and possibly leak it, by mistake or by malicious persons. That's the point of this tutorial, setup a NIP46 server Nsec.app with its own Nostr relay. You'll be able to use it for you and let people use it, every data is stored locally in your internet browser. It's an non-custodial application, like wallets !
It's nearly a perfect solution (because nothing is perfect as we know) and that makes the daily use of Nostr keys much more secure and you'll see, much more sexy ! Look:
Nsec.app is not the only NIP46 server, in fact, @PABLOF7z was the first to create a NIP46 server called nsecBunker. You can also self-hosted nsecBunkerd, you can find a detailed explanation here : nsecbunkerd. I may write a how to self-host nsecBunkderd soon.
If you want more information about its bunker and what's behind this tutorial, you can check these links :
Few stuffs before beginning
Spoiler : I didn't automatized everything. The goal here is not to give you a full 1 click installation process, it's more to let you see and understand all the little things to configure and understand how works Nsec.app and the NIP46. There is a little bit of work, yes, but you'll be happy when it will work! Believe me.
Before entering into the battlefield, you must have few things : A working VPS with direct access to internet or a computer at home but NAT will certain make your life a hell. Use a VPS instead, on DigitalOcean, Linode, Scaleway, as you wish. A web domain that your own because we need to use at least 3 DNS A records (you can choose the subdomain you like) : domain.tld, noauth.domain.tld, noauth.domain.tld. You need to have some programs already installed : git, docker, docker-compose, nano/vi. if you fill in all the boxes, we can move forward !
Let's install everything !
I build a repo with a docker-compose file with all the required stuff to make the Bunker works :
Nsec.app front-end : noauth Nsec.app back-end : noauthd Nostr relay : strfry Nostr NIP05 : easy-nip5
First thing to do is to clone the repo "nsec-app-docker" from my repo:
$ git clone git clone https://github.com/PastaGringo/nsec-app-docker.git $ cd nsec-app-dockerWhen it's done, you'll have to do several things to make it work. 1) You need to generate some keys for the web-push library (keep them for later) :
``` $ docker run pastagringo/web-push-generate-keys
Generating your web-push keys...
Your private key : rQeqFIYKkInRqBSR3c5iTE3IqBRsfvbq_R4hbFHvywE Your public key : BFW4TA-lUvCq_az5fuQQAjCi-276wyeGUSnUx4UbGaPPJwEemUqp3Rr3oTnxbf0d4IYJi5mxUJOY4KR3ZTi3hVc ```
2) Generate a new keys pair (nsec/npub) for the NIP46 server by clicking on "Generate new key" from NostrTool website: nostrtool.com.
You should have something like this :
console Nostr private key (nsec): keep this -> nsec1zcyanx8zptarrmfmefr627zccrug3q2vhpfnzucq78357hshs72qecvxk6 Nostr private key (hex): 1609d998e20afa31ed3bca47a57858c0f888814cb853317300f1e34f5e178794 Nostr public key (npub): npub1ywzwtnzeh64l560a9j9q5h64pf4wvencv2nn0x4h0zw2x76g8vrq68cmyz Nostr public key (hex): keep this -> 2384e5cc59beabfa69fd2c8a0a5f550a6ae6667862a7379ab7789ca37b483b06You need to keep Nostr private key (nsec) & Nostr public key (npub). 3) Open (nano/vi) the .env file located in the current folder and fill all the required info :
```console
traefik
EMAIL=pastagringo@fractalized.net <-- replace with your own domain NSEC_ROOT_DOMAIN=plebes.ovh <-- replace with your own domain <-- replace with your own relay domain RELAY_DOMAIN=relay.plebes.ovh <-- replace with your own noauth domainay.plebes.ovh <-- replace with your own relay domain <-- replace with your own noauth domain NOAUTH_DOMAIN=noauth.plebes.ovh <-- replace with your own noauth domain NOAUTHD_DOMAIN=noauthd.plebes.ovh <-- replace with your own noauth domain
noauth
APP_WEB_PUSH_PUBKEY=BGVa7TMQus_KVn7tAwPkpwnU_bpr1i6B7D_3TT-AwkPlPd5fNcZsoCkJkJylVOn7kZ-9JZLpyOmt7U9rAtC-zeg <-- replace with your own web push public key APP_NOAUTHD_URL=https://$NOAUTHD_DOMAIN APP_DOMAIN=$NSEC_ROOT_DOMAIN APP_RELAY=wss://$RELAY_DOMAIN
noauthd
PUSH_PUBKEY=$APP_WEB_PUSH_PUBKEY PUSH_SECRET=_Sz8wgp56KERD5R4Zj5rX_owrWQGyHDyY4Pbf5vnFU0 <-- replace with your own web push private key ORIGIN=https://$NOAUTHD_DOMAIN DATABASE_URL=file:./prod.db BUNKER_NSEC=nsec1f43635rzv6lsazzsl3hfsrum9u8chn3pyjez5qx0ypxl28lcar2suy6hgn <-- replace with your the bunker nsec key BUNKER_RELAY=wss://$RELAY_DOMAIN BUNKER_DOMAIN=$NSEC_ROOT_DOMAIN BUNKER_ORIGIN=https://$NOAUTH_DOMAIN ```
Be aware of noauth and noauthd (the d letter). Next, save and quit. 4) You now need to modify the nostr.json file used for the NIP05 to indicate which relay your bunker will use. You need to set the bunker HEX PUBLIC KEY (I replaced the info with the one I get from NostrTool before) :
console nano easy-nip5/nostr.jsonconsole { "names": { "_": "ServerHexPubKey" }, "nip46": { "ServerHexPubKey": [ "wss://ReplaceWithYourRelayDomain" ] } }5) You can now run the docker compose file by running the command (first run can take a bit of time because the noauth container needs to build the npm project):
console $ docker compose up -d6) Before creating our first user into the Nostr Bunker, we need to test if all the required services are up. You should have :
noauth :
noauthd :
console CANNOT GET /https://noauthd.yourdomain.tld/name :
console { "error": "Specify npub" }https://yourdomain.tld/.well-known/nostr.json :
console { "names": { "_": "ServerHexPubKey" }, "nip46": { "ServerHexPubKey": [ "wss://ReplaceWithYourRelayDomain" ] } }If you have everything working, we can try to create a new user!
7) Connect to noauth and click on "Get Started" :
At the bottom the screen, click on "Sign up" :
Fill a username and click on "Create account" :
If everything has been correctly configured, you should see a pop message with "Account created for "XXXX" :
PS : to know if noauthd is well serving the nostr.json file, you can check this URL : https://yourdomain.tld/.well-known/nostr.json?name=YourUser You should see that the user has now NIP05/NIP46 entries :
If the user creation failed, you'll see a red pop-up saying "Something went wrong!" :
To understand what happened, you need to inspect the web page to find the error :
For the example, I tried to recreate a user "jack" which has already been created. You may find a lot of different errors depending of the configuration you made. You can find that the relay is not reachable on w s s : / /, you can find that the noauthd is not accessible too, etc. Every answers should be in this place.
To completely finish the tests, you need to enable the browser notifications, otherwise you won't see the pop-up when you'll logon on Nostr web client, by clicking on "Enable background service" :
You need to click on allow notifications :
Should see this green confirmation popup on top right of your screen:
Well... Everything works now !
8) You try to use your brand new proxyfied npub by clicking on "Connect App" and buy copying your bunker URL :
You can now to for instance on Nostrudel Nostr web client to login with it. Select the relays you want (Popular is better ; if you don't have multiple relay configured on your Nostr profile, avoid "Login to use your relay") :
Click on "Sign in" :
Click on "Show Advanced" :
Click on "Nostr connect / Bunker" :
Paste your bunker URL and click on "Connect" :
The first time, tour browser (Chrome here) may blocks the popup, you need to allow it :
If the browser blocked the popup, NoStrudel will wait your confirmation to login :
You have to go back on your bunker URL to allow the NoStrudel connection request by clicking on on "Connect":
The first time connections may be a bit annoying with all the popup authorizations but once it's done, you can forget them it will connect without any issue. Congrats ! You are connected on NoStrudel with an npub proxyfied key !⚡

You can check to which applications you gave permissions and activity history in noauth by selecting your user. :
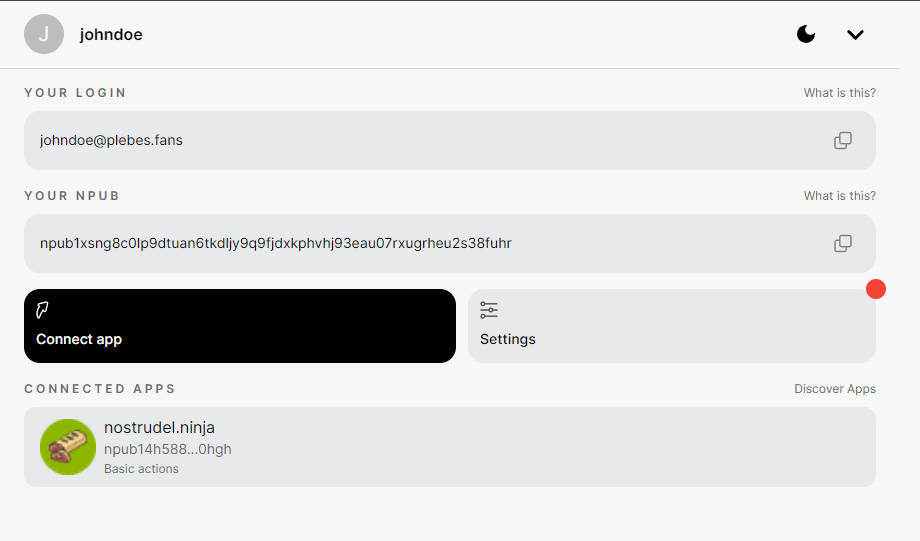
If you want to import your real Nostr profile, the one that everyone knows, you can import your nsec key by adding a new account and select "Import key" and adding your precious nsec key (reminder: your nsec key stays in your browser! The noauth provider won't have access to it!) :
You can see can that my profile picture has been retrieved and updated into noauth :
I can now use this new pubkey attached my nsec.app server to login in NoStrudel again :
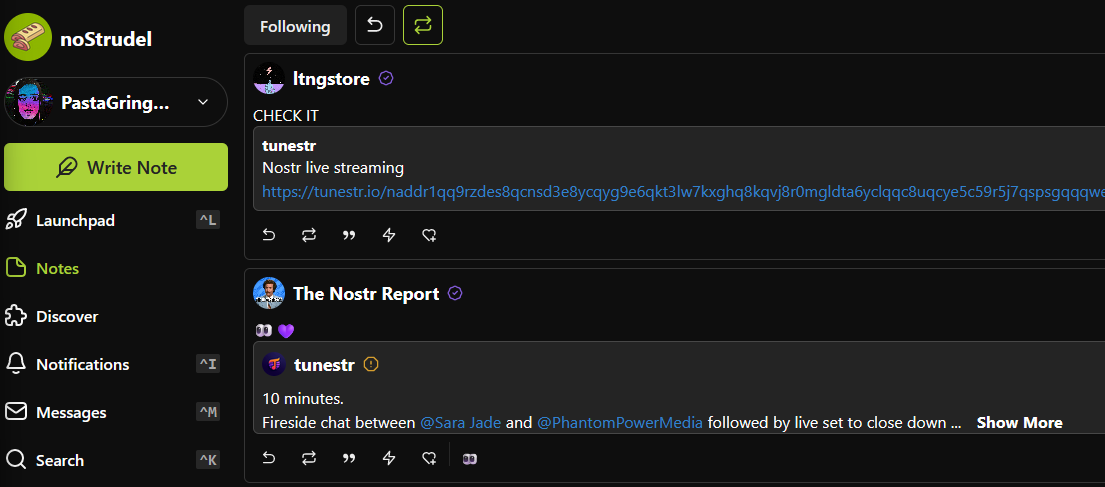
Accounts/keys management in noauthd You can list created keys in your bunkerd by doing these command (CTRL+C to exit) :
console $ docker exec -it noauthd node src/index.js list_names [ '/usr/local/bin/node', '/noauthd/src/index.js', 'list_names' ] 1 jack npub1hjdw2y0t44q4znzal2nxy7vwmpv3qwrreu48uy5afqhxkw6d2nhsxt7x6u 1708173927920n 2 peter npub1yp752u5tr5v5u74kadrzgfjz2lsmyz8dyaxkdp4e0ptmaul4cyxsvpzzjz 1708174748972n 3 john npub1xw45yuvh5c73sc5fmmc3vf2zvmtrzdmz4g2u3p2j8zcgc0ktr8msdz6evs 1708174778968n 4 johndoe npub1xsng8c0lp9dtuan6tkdljy9q9fjdxkphvhj93eau07rxugrheu2s38fuhr 1708174831905nIf you want to delete someone key, you have to do :
```console $ docker exec -it noauthd node src/index.js delete_name johndoe [ '/usr/local/bin/node', '/noauthd/src/index.js', 'delete_name', 'johndoe' ] deleted johndoe { id: 4, name: 'johndoe', npub: 'npub1xsng8c0lp9dtuan6tkdljy9q9fjdxkphvhj93eau07rxugrheu2s38fuhr', timestamp: 1708174831905n
$ docker exec -it noauthd node src/index.js list_names [ '/usr/local/bin/node', '/noauthd/src/index.js', 'list_names' ] 1 jack npub1hjdw2y0t44q4znzal2nxy7vwmpv3qwrreu48uy5afqhxkw6d2nhsxt7x6u 1708173927920n 2 peter npub1yp752u5tr5v5u74kadrzgfjz2lsmyz8dyaxkdp4e0ptmaul4cyxsvpzzjz 1708174748972n 3 john npub1xw45yuvh5c73sc5fmmc3vf2zvmtrzdmz4g2u3p2j8zcgc0ktr8msdz6evs 1708174778968n ```
It could be pretty easy to create a script to handle the management of keys but I think @Brugeman may create a web interface for that. Noauth is still very young, changes are committed everyday to fix/enhance the application! As """everything""" is stored locally on your browser, you have to clear the cache of you bunker noauth URL to clean everything. This Chome extension is very useful for that. Check these settings in the extension option :
You can now enjoy even more Nostr ⚡ See you soon in another Fractalized story!
-
 @ df3d362a:3c765ec9
2024-03-24 08:42:14
@ df3d362a:3c765ec9
2024-03-24 08:42:14We’ve talked about liquidity on Lightning before, but since Lightning is above all a liquidity network, it bears constant reevaluation. Not only was everybody at Bitcoin Atlantis talking about LSPs, but these conferences are now attracting almost as many financiers as techies. So again I’m compelled to think about value, where it resides, and how Lightning promotes its flow.
The Lightning community has done an excellent job over the last five-ish years of solving liquidity as a technical issue. Remember the days when Lightning users had to first move funds to another on-chain address, open a channel to an obscure Lightning node and spend their sats (where?) before they could even receive their first Lightning payment? We are lightyears beyond those early days. Progress has been massive and relatively fast.
The challenge that remains with regard to liquidity is the economics: how to arrange the broad array of technical solutions into viable business models that benefit users and liquidity providers. In other words, what I’d like to consider here is how to promote Lightning’s continued evolution from a functioning computer network into a thriving financial network.
Constraints and Opportunities for LSPs
Financial networks simply comprise flows of value among actors who are taking advantage of opportunities that arise in a field of constraints. Lightning itself is an opportunity that arose thanks to the constraints of bitcoin. The constraints of how channels and liquidity work on Lightning gave rise to the opportunity of the LSP business model.
Indeed, Lighting Service Providers (LSPs) are to Lightning what airlines are to intercontinental travel. It’s hard to imagine without them. LSPs connect users to the network technically and financially, making sure there is sufficient liquidity to forward payments out into the network as well as inbound back to their users/customers. Thanks to LSPs, users no longer have to worry about channel management, liquidity distribution, or effective routing. All that complexity has shifted from users to the LSPs that serve them.
However, LSPs also face some constraints that they can’t simply wish out of existence. The biggest is the cost of on-chain transactions, which are required to open channels. The fees for on-chain transactions are volatile, and there’s little LSPs can do to avoid them. If they forego recording their users’ channels on the chain, then they’re effectively taking possession of their users’ money and becoming banks, catapulting themselves into a whole new galaxy of painful regulation. If they forego splicing out or closing unused channels, then they’re effectively abandoning their own capital locked in those channels.
For LSPs, servers and electricity and lunches are predictable overhead costs, but on-chain transactions are their volatile raw materials, and that’s not even really a metaphor.
The raw material of on-chain transactions is an indispensable input to the Lightning business. LSPs add value to that raw material by letting users reuse a single on-chain transaction for an indefinite number of payments (more on that below), which lowers the marginal cost of each payment and increases the efficiency of bitcoin. The service LSPs provide is worth something, and the question is how LSPs can deliver these benefits profitably.
The LTV/CAC ratio is the best indicator of whether an LSP is running a viable business. It divides a customer’s lifetime value to the company (their LTV) by the cost of winning their business (their customer acquisition cost — CAC). If the ratio is more than one, the company is making money on each user, if not necessarily in each week. If the ratio is less than one, the company is losing money on each new customer.
There are many techniques for an LSP to raise its LTV/CAC ratio, but on-chain fees put a ceiling on how high it can go. One easy solution is to pass the cost on to the LSP’s users. For users deliberating between transacting over Lightning or on-chain, this shouldn’t be an issue because the cost of opening a channel amortizes with just a few transactions. When deferring the cost isn’t an option and the CAC can’t go any lower, the only viable option for an LSP is to increase the LTV. That can mean keeping customers as long as possible (by providing good, valuable services) and favoring profitable interactions. Remember how liquidity generates traffic generates ROI generates liquidity? LSPs need profitable traffic from their users in order to give them liquidity and connectivity.
There’s no “one size fits all.” LSPs need to be creative in how they promote profitable traffic (opportunities) in variable fee environments (constraints). For example, if an LSP manages to keep their users around and spending for long enough, maybe they can defer the CAC by treating channel openings as loss leaders.
They can also discourage transactions with low or negative margins. Take zaps. A standard 100-sat zap on nostr is worth about $0.05 USD. A transaction fee of even one cent would be an unreasonable 20%, so LSPs effectively have to process zaps for free. Traffic that doesn’t generate ROI doesn’t generate liquidity, which strains the network unsustainably.
It’s the circle of life: constraints create opportunities create constraints. The market rewards ingenuity.
Now let’s zoom out and consider how these constraints and opportunities aggregate into a bigger picture. What are the constraints and opportunities applicable right now to Lightning as a whole?
Constraints and Opportunities for Lightning
Unsurprisingly, a lot of the early statements about Lightning were gushing with naive promises about how it was going to give bitcoin virtually infinite scale for infinitesimal transaction fees. All opportunities and no constraints.
But you can’t ignore reality for long. Indeed, LSPs are the opportunity that arose from a big initial constraint — the UX. On-chain fees are a constraint that’s not going anywhere, though they affect different users in different ways. Fees of $35/tx can price out an entire continent, but they aren’t even a rounding error to whales who move several btc at a time. As for Lightning, George 203 reminds us that, even if every single on-chain transaction was a new channel opening to onboard a new Lightning user, it would still take too long and cost too much to onboard the planet (how much exactly? do the math). It’s not exactly infinite scale at infinitesimal cost.
So where’s the opportunity for Lightning? In throughput. Check this: in August 2023, Lightning increased Bitcoin’s throughput by 47.2% (according to River’s calculations) with just 0.06% of the transactions: nearly 50% more payment capacity with only 3/5000 of the on-chain transactions! Read that again. Absorb it. Grasp the implications.
Lightning is an extremely effective and efficient tool to move bitcoin. Even if Lightning is no panacea, it is an 833x throughput turbo booster. It’s impossible to imagine the bitcoin economy without Lightning.
These numbers help reconceptualize the place of Lightning in the overall Bitcoin landscape. Let’s push that metaphor a bit and think of Bitcoin as a road network consisting of different kinds of roads and destinations. The blockchain, for example, might be the railroad, which is great for moving large quantities of freight between major hubs, but totally impractical for delivering individual pizzas. Lightning started as a network of freeways, which are faster and more flexible than rail networks but have less carrying capacity. With the help of LSPs, Lightning now covers smaller highways and roads too.
Remember that each trunk road is a tributary for the next level up, and each tributary is a trunk road for the next level down. There are also lonely country lanes, residential streets, bike paths, and even corridors in apartment blocks. None is superfluous, and each optimizes for a different parameter: speed, safety, convenience, minimal equipment, longer or shorter distances, more carrying capacity, etc.
Those parameters define the relevant levels and present opportunities (and constraints). Many of the developments taking place right now around shared UTXOs, federations, and e-cash are trying to innovate last-mile tech in this landscape, responding to current opportunities and constraints. The road/financial network is diversifying internally to make productive use of its liquidity. Though the logics of efficiency, incentives, and viability are universal, Lightning is adapting in countless new ways to local conditions. The network is nothing more and nothing less than the sum of those routes, some new and some well-trodden.
Growth also Means Growing Up
It’s important to remember that constraints aren’t bad. In fact, they’re completely natural. First, the on-chain fees that we see as constraints are what keep the miners in business and help them to keep Bitcoin running. There would be no Lightning without them.
Second, whether to consider something a constraint or an opportunity is often a matter of perspective. The early UX constraints were the LSPs’ opportunity. Bitcoin’s throughput constraints are Lightning’s opportunity. And so on.
Third, accepting and dealing with constraints is a sign of maturation in Lightning and in life. We’re building a revolutionary financial infrastructure that’s upending centuries of centralized, state-based money and finance. Of course it wasn’t going to happen overnight on a network with infinite free, instantaneous payments. Of course it was going to be a revolution of incremental change, with behavior adapting to new conditions and new incentive structures emerging step by step.
Many dramatic changes happen “gradually and then suddenly,” and the transition to the bitcoin economy is still in the “gradually” phase. By building this financial network gradually, overcoming challenges as they arise, strengthening the technical infrastructure as well as the businesses that keep it running, we’ll be ready when the “suddenly” comes.
-
 @ d91191e3:7efd4075
2024-02-17 13:54:35
@ d91191e3:7efd4075
2024-02-17 13:54:35Before I tell you how to design perfect software, let's look at the two most common design processes in use today.
These don't work, yet are firmly applied by a majority of engineers and designers, especially in software where it's possible to construct byzantine complexity.
They are slow-motion tragedies but can be fun to watch, from a safe distance.
Shit Driven Development (SDD)
The most popular design process in large businesses is Shit Driven Development.
SDD feeds off the belief that ideas are scarce and we just need a good idea to make money.
The main output of SDD is expensive "ideations", concepts, design documents, and finally products that go straight into the garbage.
-
The Creative People come up with long lists of "we could do X and Y". Once the creative work of ideation has been done it's just a matter of implementation.
-
Managers and consultants pass these brilliant ideas to UX designers.
-
The designs get passed to engineers, who scratch their heads and wonder who came up with such stupid nonsense.
The designs do not factor in the practical costs of implementation. Minor whims create weeks of work. The project gets delayed and the managers bully the engineers into working harder.
Something resembling a working product makes it out the door, but no-one wants to use it.
After twelve months of intense marketing, the company shelves it and buys a competing product from a small start-up.
The main lessons of SDD
Ideas are cheap. No exceptions. There are no brilliant ideas.
The starting point for a good design process is to collect problems that confront people, and filter out anything that isn't valuable enough to solve.
Success depends on how good and cheap the solution is, how important the problem is, and how simple the solution is to actually use.
Complexity Driven Development (CDD)
Really good engineering teams can usually build good products. But the vast majority of products still end up being too complex and less successful than they might be. This is because specialist teams, even the best, usually follow Complexity Driven Development (CDD).
Management correctly identifies some interesting and difficult problem with economic value. In doing so they leapfrog any Shit Driven Developemt team.
The team loves building things and they get straigh to it, starting with prototypes and core layers. These work as designed and the team is encouraged and enthusiastic. They go off into intense design and architecture discussions, coming up with elegant schemas that look beautiful and solid.
Management comes back and challenges team with yet more difficult problems. We tend to equate value with cost, so the harder the problem, and more expensive to solve, the more the solution should be worth, in their minds.
The team, being engineers and thus loving to build stuff, build stuff. They build and build and build and end up with massive, perfectly designed complexity.
The products go to market, and the market scratches its head and asks, "seriously, is this the best you can do?" People do use the products, especially if they aren't spending their own money in climbing the learning curve.
Management gets positive feedback from its larger customers, who share the same idea that high cost (in training and use) means high value.
Meanwhile somewhere across the world, a small team is solving the same problem using Simplicity Driven Development, and a year later smashes the market to little pieces.
CDD is characterized by a team obsessively solving the wrong problems to the point of ridiculousness. CDD products tend to be large, ambitious, complex, and unpopular. A lot of open source software is the output of CDD processes. It is insanely hard for engineers to stop extending a design to cover more potential problems. They argue, "what if someone wants to do X?" but never ask themselves, "what is the real value of solving X?"
A good example of CDD in practice is Bluetooth, a complex, over-designed set of protocols that users hate. It continues to exist only because there are no alternatives. Bluetooth is perfectly secure, which is close to useless for a proximity protocol. At the same time it lacks a standard API for developers, meaning it's really costly to use Bluetooth in applications.
CDD is a form of large-scale "rabbit holing", in which designers and engineers cannot distance themselves from the technical details of their work. They add more and more features, utterly misreading the economics of their work.
The main lessons of CDD
-
Making stuff that you don't immediately have a need for is pointless. Doesn't matter how talented or brilliant you are, if you just sit down and make stuff, you are most likely wasting your time.
-
Not all problems are not equal. Some are simple, and some are complex. Ironically, solving the simpler problems often has more value to more people than solving the really hard ones.
-
It is crucial to have a "stop mechanism", a way to set short, hard deadlines that force people to make smaller, simpler answers to just the most crucial problems.
Reality Driven Development (RDD)
Reality Driven Development starts with a realization: we do not know what we have to make until after we start making it.
Coming up with ideas, or large-scale designs isn't just wasteful, it's directly toxic to creating truly accurate solutions. The really juicy problems are hidden away in crevices across the landscape. Any activity except active scouting creates a fog that hides those crevices. You need to keep mobile, pack light, and move fast.
RDD works as follows:
We collect a set of interesting problems (by looking at how people use technology or other products) and we line these up from simple to complex, looking for and identifying patterns of use.
We take the simplest, most dramatic problem and we solve this with a minimal plausible solution, or "patch". Each patch solves exactly a genuine and agreed problem in a brutally minimal fashion.
We apply one measure of quality to patches, namely "can this be done any simpler while still solving the stated problem?" We can measure complexity in terms of concepts and models that the user has to learn or guess in order to use the patch. The fewer, the better. A perfect patch solves a problem with zero learning required by the user.
Our product development consists of a patch that solves the problem "we need a proof of concept" and then evolves in an unbroken line to a mature series of products, through hundreds or thousands of patches piled on top of each other.
We do not do anything that is not a patch. We enforce this rule with formal processes that demands that every activity or task is tied to a genuine and agreed problem, explicitly enunciated and documented.
We build our projects into a supply chain where each project can provide problems to its "suppliers" and receive patches in return. This arrangement creates a "stop mechanism" - when people are impatiently waiting for a patch, we necessarily cut our work short.
Individuals are free to work on any projects, and provide patches at any place they feel it's worthwhile. No individuals "own" any project, except to enforce the formal processes. A single project can have many variations, each a collection of different, competing patches.
Projects export formal and documented interfaces so that upstream (client) projects are unaware of change happening in supplier projects. Thus multiple supplier projects can compete for client projects, in effect creating a free and competitive market.
We tie our supply chain to real users and we iterate the whole process in rapid cycles so that a problem received from a user can be analyzed, evaluated, and solved with a patch in a few hours.
At every moment from the very first patch, our product is shippable. This is essential, because a large proportion of patches will be wrong (10-30%) and only by giving the product to users can we know which patches have become problems and themselves need solving.
RDD is a form of "hill climbing algorithm" or a drunken stumble to greatness. It's a reliable way of finding optimal solutions to the most significant problems in an unknown landscape.
This was created as a collaboration between G and Pieter H.
-
-
 @ 57d1a264:69f1fee1
2024-03-24 08:10:02
@ 57d1a264:69f1fee1
2024-03-24 08:10:02Prompt: Favorites items ===============
Articles, Bookstores, video games, podcasts, and streaming services all have a favorites section. SN too!
Are you favoriting certain items? Or are you favoriting something on a territory or stacker you'd like to have on a personalized followers graph?
Flex your design muscles and join in. Most of all, keep this exercise loose and keep it stress-free. The FUC is about growing our design skills, together, as a community. We can't wait to see what you create!
Happy designing, Stackers!
Share Your Results When you finish the challenge, post your work on this thread! If you also share it on
nostr, be sure to use the hashtag #FUCdesiger and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Curious to know WTF is a FUC? Read the ⚡️Flash Ui Challenges welcoming post.
Looking for more FUCs? Check the archive here!
-
 @ 1e52c554:21771908
2024-02-17 11:55:18
@ 1e52c554:21771908
2024-02-17 11:55:18Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his npublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna
Sonnet 68 by Francisco Luis Arroyave Tabares
The same Petrarchan sonnet respecting the meter and rhyme in both languages.


Analysis "When You Were The Best 0f Me"
Introduction
Sonnet 68 by Francisco Luis Arroyave Tabares, titled "When You Were The Best of Me" is a poignant reflection on loss, memory, and the enduring power of love. is written in a sonnet form, consisting of fourteen lines. The poem follows a Petrarchan rhyme scheme, with an ABBA ABBA CCD EED pattern.
Thematic Analysis
The poem "When You Were The Best of Me" by Francisco Luis Arroyave Tabares is a heartfelt expression of loss and grief. The speaker is addressing a person who was once their best self but has since passed away. Despite this loss, the speaker still feels a connection to this person and is able to have conversations with them in their mind.
The image of a "common hearse" suggests that the person's death was not unique or remarkable, which may add to the speaker's feelings of sorrow and loss. However, the speaker is able to find comfort in the memory of the person and the "garden" they created within them. This garden represents a space of happiness and growth, and the speaker is determined to keep it alive through their words and memories.
The final stanza reveals that the speaker has learned to cope with their grief by turning their tears into "liquor" and going to places near the person's home to forget their pain. Despite this coping mechanism, the speaker acknowledges that they will always keep the memory of this person with them and find joy in expressing their love and care for them.
The poem highlights the universal experience of grief and the various ways in which people cope with it. The speaker's use of the garden as a metaphor for the person's impact on their life and their determination to keep it alive through their words and memories is particularly powerful. This suggests that the speaker understands the importance of preserving memories of loved ones as a way to honor and celebrate their life.
The final stanza also shows the speaker's resilience and ability to find ways to cope with their grief, even though it still affects them deeply. The use of tears turning into "liquor" suggests that the speaker has found a way to transform their pain into something else, perhaps a way to numb the pain temporarily.
The poem's use of language is also notable. The rhyme scheme and rhythm give the poem a musical quality, which adds to the emotional impact of the words. The use of words like "inly" and "immersed" add a sense of depth and richness to the poem, creating a vivid image of the garden within the speaker's soul.
In conclusion, "When You Were The Best of Me" by Francisco Luis Arroyave Tabares is a moving and powerful poem that explores the theme of loss and grief. Through the use of metaphors and beautiful language, the speaker conveys the deep emotional impact of the person's death on their life while also showing their resilience and determination to keep their memory alive. The poem offers a poignant reminder of the enduring power of love and the importance of honoring the memories of those we have lost.
Rhyme Scheme
The poem "When You Were The Best of Me" by Francisco Luis Arroyave Tabares follows a traditional rhyme scheme, with an ABBA ABBA CCD EED pattern. This rhyme scheme is characteristic of a Petrarchan sonnet, a form of poetry that originated in Italy during the Renaissance period.
Let's analyze the rhyme scheme of the poem in detail:
```
Octave (ABBA ABBA):
1-. suddenly (A) 1-. fuiste (A)
2-. hearse (B) 2-. universo (B)
3-. converse (B) 3-. converso (B)
4-. inly. (A) 4-. triste (A)
5-. me (A) 5-. viste
6-. immersed (B) 6-. inmerso
7-. verse (B) 7-. verso
8-. cruelly. (A) 8-. diste
Sestet (CCD EED):9-. dear (C) 9-. añeja (C)
10-. near (C) 10-. aleja (C)
11-. mare. (D) 11-. aliento (D)
12-. memory (E) 12-. memoria (E)
13-. victory (E) 13-. victoria (E)
14-. care. (D) 14-. siento (D)
```
The use of the traditional rhyme scheme in the poem gives it a sense of structure and order, which is fitting for a poem that explores themes of loss and grief. The consistent use of end rhymes creates a sense of unity and coherence throughout the poem. The repetition of certain sounds, such as the "e" sound in "me" and "hearse," adds to the musical quality of the poem.
Overall, the use of rhyme in "When You Were The Best of Me" is an important aspect of the poem's structure and adds to its emotional impact. The traditional rhyme scheme gives the poem a sense of balance and harmony while also emphasizing the enduring nature of the speaker's love and memories of the person who has passed away.
Additional Aspects to Analyze
There are several other aspects of the poem "When You Were The Best of Me" by Francisco Luis Arroyave Tabares that are worth analyzing. Here are a few possible avenues of analysis:
Imagery: The poem makes use of vivid imagery to convey the speaker's emotions and experiences. For example, the image of the garden that the deceased person "happily made" of the speaker is a powerful metaphor for the lasting impact that the person had on their life. Similarly, the image of the tears that the speaker has learned to "age" into liquor is a striking image that highlights the speaker's ability to transform pain into something more manageable.
Tone: The overall tone of the poem is melancholy and reflective. The speaker is grappling with the loss of someone they loved deeply, but there is also a sense of acceptance and resilience in their words. The use of the Petrarchan sonnet form adds to the poem's tone, as this form is often associated with themes of love and loss.
Diction: The poem's language is generally straightforward and accessible, but there are a few words and phrases that stand out for their emotional impact. For example, the use of the word "cruelly" in line 8 emphasizes the sense of injustice and tragedy that the speaker feels about the person's death. Similarly, the phrase "my mare" in line 11 is a poignant metaphor for the burden of grief that the speaker carries with them.
Theme: The central theme of the poem is the enduring power of love and memory. Despite the person's death, the speaker remains deeply connected to them and finds solace in their memories. The poem also touches on themes of resilience, transformation, and acceptance in the face of loss.
Allusion: The poem alludes to the concept of an afterlife or continuation of the soul beyond death. The line "To be earth again through a common hearse" implies that the person has returned to the earth, but the subsequent lines suggest that they are still present in some form, as the speaker is able to converse with them and feel their presence. This allusion to the afterlife adds to the poem's overall sense of hope and resilience in the face of loss.
Overall, "When You Were The Best of Me" is a rich and complex poem that rewards close analysis and attention to its various literary elements.
(GPT4)
Syllable count for each line
```
When You Were The Best 0f Me
10 When you were my best you left suddenly 10 To be earth again through a common hearse 10 Yet, I feel you, and we get to converse 9 Untíl you make fade my sadness inly.
10 The garden you happily made of me 9 Forever will be of you immersed 10 And it ill keep on growing with the verse 10 0f our last kiss when life perished Cruelly.
10 My tears flow, but I learnt to age them, dear 10 To make liquor and go to places near 10 Iour abode where I can forget my mare. 10 I know that I will keep your memory 10 Through which I enjoy still the victory 10 0f telling you, my love, how much I care. ***
```
```
Aún Siendo lo Mejor de Mi
11 Auncuando lo mejor de mí tu fuiste, (A) 11 ya cedí tu poder al universo, (B) 11 aunque sigas aquí cuando converso, (B) 11 ayudándome si suspiro triste. (A)
11 Jardín suntuoso formar en mí viste (A) 11 y continuará de tu ser inmerso (B) 6 11 y surgirán tus cantos en un verso (B) 11 con murmurantes besos al fin diste. (A)
11 Tu luz, con tiempo lágrimas añeja, (C) 11 y mi temor por un lugar aleja. (C) 11 Sus licores raros son un aliento... (D)
11 Al ver que ni se murió tu memoria, (E) 11 hablo más bien de tu dulce victoria (E) 11 y cumplo con saber ¡Cuánto lo siento! (D) ***
6., inmerso = sumergido. Euphonic Verse in Hendecasyllables in the Form of a Petrarchan Sonnet ```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image by leonardo.ai; First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 When You Were The Best 0f Me
When You Were The Best 0f Me -
 @ 57d1a264:69f1fee1
2024-03-24 07:48:35
@ 57d1a264:69f1fee1
2024-03-24 07:48:35Let’s reflect on this week's discussions
What did you learn from it? What did you think about it? Which valuable insights did you gain, and how can you apply them moving forward?
Share your Sunday sunshine and let's wrap up the week on a thoughtful note.
-
 @ ec965405:63996966
2024-02-15 13:15:24
@ ec965405:63996966
2024-02-15 13:15:24Feb. 3rd, 2024
I was up late last night trying to publish a blog post, but gave up after the connection faded and reset all I had typed to a blank text box. When I woke up this morning, I snoozed my 7:30 alarm for a half hour before heading downstairs to share a light breakfast with the other delegation members and enjoy our first presentation from a staff member about the history of the center.
Anoche me quedé despierto hasta tarde tratando de publicar una entrada en el blog, pero desistí después de que la conexión se interrumpió y borró todo lo que había escrito, dejando la casilla de texto en blanco. Cuando me desperté esta mañana, pospuse mi alarma de las 7:30 por media hora antes de bajar a compartir un desayuno ligero con los otros miembros de la delegación y disfrutar de nuestra primera presentación de un miembro del personal sobre la historia del centro.

There's a street or building named after Dr. Martin Luther King in almost every city and country I've ever been to! The MLK Center in Havana stands next to a church by the busy intersection of 51st and 100th street. The center, founded by Pastor Raul Suarez in 1987, builds transnational solidarity networks by hosting cultural exchanges with organizations from around the world in Reverend Dr. Martin Luther King's honor.
En casi todas las ciudades y paises que he visitado hay una calle o edificio nombrado en honor de Dr. Martin Luther King! El Centro esta ubicado al lado de una iglesia en la concurrida interseccion de las calles 51 y 100! Fundado por el Pastor Raúl Suárez en 1987, el centro construye redes de solidaridad transnacional al organizar intercambios culturales con organizaciones de todo el mundo en honor al Reverendo Dr. Martin Luther King.

It was inspiring to see the presenter tear up as she outlined the impact the center had on the surrounding community like wiring electricity to the neighborhood. Throughout the week, residents line up during business hours for water from a purifier machine inside the cafeteria, ensuring clean h2o for drinking, cooking, and cleaning for residents.
Fue inspirador ver a la presentadora emocionarse mientras delineaba el impacto que el centro tenía en la comunidad circundante, como llevar electricidad al vecindario. A lo largo de la semana, los residentes hacen fila durante el horario comercial para obtener agua de una máquina purificadora dentro de la cafetería, asegurando agua limpia para beber, cocinar y limpiar para los residentes.

The center is complete with rooms for guests that include bunk beds and a shared bathroom with an air conditioner. The cafeteria serves breakfast, lunch, and dinner throughout the day. The space is truly magical, with staff and volunteers walking around with bright faces, making you feel right at home.
El centro cuenta con habitaciones para huéspedes que incluyen camas y un baño compartido con aire acondicionado. La cafetería sirve desayuno, almuerzo y cena durante todo el día. El espacio es verdaderamente mágico, con el personal y los voluntarios caminando con rostros brillantes, haciéndote sentir como en casa.

During the oral history lesson, our delegation coordinator asked about how organized religions show up in Cuba since the revolution was declared atheist. It didn't occur to me until till that Martin Luther King was a minister! How did they come to name a center after him? The staff from the center explained that Fidel Castro, after a visit to Brazil in 1980 where he met with liberation theologian Friei Betto, famously remarked that if liberation theology existed in Cuba, they wouldn't have needed a revolution to liberate their country from the united states occupation, marking a shift towards greater religious tolerance and inclusion to address and rectify social inequalities and injustices, key themes of the Cuban Revolution.
Durante la lección de historia oral, nuestro coordinador de la delegación preguntó cómo se manifiestan las religiones organizadas en Cuba desde que la revolución fue declarada atea. ¡No se me ocurrió hasta ese momento que Martin Luther King era un ministro! ¿Cómo llegaron a nombrar un centro en su honor? El personal del centro explicó que Fidel Castro, después de una visita a Brasil en 1980 donde se reunió con el teólogo de la liberación Frei Betto, comentó famosamente que si la teología de la liberación existiera en Cuba, no habrían necesitado una revolución para liberar su país de la ocupación de los estados unidos, marcando un cambio hacia una mayor tolerancia religiosa e inclusión para abordar y rectificar las desigualdades sociales e injusticias, temas clave de la Revolución Cubana.

Liberation theology is a movement within the catholic church that emphasizes social justice and opposition to poverty and social injustice. This and subsequent discussions between the two leaders, among other factors, played a pivotal role in the gradual shift in the Cuban government's approach to religion and religious freedom. In 1992, Cuba amended its constitution to declare the state secular rather than atheist. This amendment allowed for the open practice of religion and acknowledged the powerful role that religious institutions and beliefs could play in Cuban society. It highlights a moment of reflection on the intersections between religious faith and revolutionary politics and led to structural constitutional reforms. Today, one will observe many religions and forms of African spirituality being practiced throughout the country with support from the government.
La teología de la liberación es un movimiento dentro de la iglesia católica que enfatiza la justicia social y la oposición a la pobreza y la injusticia social. Esto y las subsiguientes discusiones entre los dos líderes, entre otros factores, jugaron un papel pivotal en el cambio gradual en el enfoque del gobierno cubano hacia la religión y la libertad religiosa. En 1992, Cuba enmendó su constitución para declarar al estado secular en lugar de ateo. Esta enmienda permitió la práctica abierta de la religión y reconoció el poderoso papel que las instituciones religiosas y las creencias podrían jugar en la sociedad cubana. Destaca un momento de reflexión sobre las intersecciones entre la fe religiosa y la política revolucionaria y condujo a reformas constitucionales estructurales. Hoy, se observan muchas religiones y formas de espiritualidad africana practicadas en todo el país con apoyo del gobierno.
Click for an intro to Santeria
Cubans across the country draw inspiration from Yoruba, a spiritual tradition rooted in West African heritage, also known as Santería. Followers of this faith turn to orishas, divine entities that govern human activities and natural elements, for direction and insight. Unlike public temples or churches, rituals are conducted within the privacy of a home. In reverence to the orishas, devotees often construct intricate altars or "thrones" – sacred areas that depict these mighty figures in majestic grandeur.
Los cubanos de todo el país se inspiran en Yoruba, una tradición espiritual arraigada en la herencia del África occidental, también conocida como Santería. Los seguidores de esta fe recurren a orishas, entidades divinas que gobiernan las actividades humanas y los elementos naturales, para obtener dirección e conocimiento. A diferencia de los templos o iglesias públicas, los rituales se realizan dentro de la privacidad de un hogar. En reverencia a los orishas, los devotos a menudo construyen altares o "tronos" intrincados - áreas sagradas que representan a estas figuras poderosas en majestuosa grandeza.

After an energizing intro to the history of the Martin Luther King Center, we thanked the staff and prepared to transition to the bus for our next activity, a tour of Casa Africa in Havana. During the transition, the group gathered in the courtyard to hear an inspirational pep talk from Pastor Kelvin before he headed to the airport to catch his flight home.
Después de una introducción energizante a la historia del Centro Martin Luther King, agradecimos al personal y nos preparamos para pasar al autobús para nuestra próxima actividad, un recorrido por la Casa África en La Habana. Durante la transición, el grupo se reunió en el patio para escuchar un discurso de ánimo inspirador del Pastor Kelvin antes de que se dirigiera al aeropuerto para tomar su vuelo de regreso a casa.
Kelvin's introduced himself to the larger group inspired us with the powerful words about the current state of the world and the power we wielded as organizers to change it.
Kelvin se presentó al grupo más grande e inspiró con palabras poderosas sobre el estado actual del mundo y el poder que tenemos como organizadores para cambiarlo.
Click Here to Listen to Kelvin's words about Resiliance, Resisting, & Reimagining
He hooked the group with a bottle of Havana Club as a parting gift! As sad as I was to see him go, I know this was not a "goodbye," but a "see you later". I hugged Kelvin tight before boarding the bus, thanking him for the memories we created yesterday and the wisdom he shared.
¡Al grupo nos regalo una botella de Havana Club de despedida! Aunque estaba triste de verlo ir, sé que esto no era un "adiós", sino un "hasta luego". Abracé a Kelvin fuerte antes de subir al autobús, agradeciéndole por los recuerdos que creamos ayer y la sabiduría que compartió.
Soon the group was off to the city for a tour of historic downtown to explore the origins of Villa San Cristobal de la Havana and a performance at Casa Africa!
Pronto, el grupo partió hacia la ciudad para un recorrido por el centro histórico para explorar los orígenes de Villa San Cristóbal de La Habana y una actuación en Casa África.

Casa Africa.is a museum in Havana Vieja (where Juan and I picked up Kelvin from on Thursday) that preserves the African roots of the country through the collection of artifacts and performing arts. As we waited for the music performance to start, I got to know Amoke, one of the participants of the delegation who runs Yo Mamas House, a drop in resource center based out of Milwaukee for moms. She is a former special education teacher with a big heart and strong conviction for changing the world by supporting mothers. Originally from Los Angeles, she possesses great wisdom accumulated over years of traveling the world and organizing her community. I'm excited to get to know her more and visit Yo Mamas House soon!
¡Casa África! es un museo en La Habana Vieja (donde Juan y yo recogimos a Kelvin el jueves) que preserva las raíces africanas del país a través de la colección de artefactos y artes escénicas. Mientras esperábamos que comenzara la actuación musical, conocí a Amoke, una de las participantes de la delegación que dirige Yo Mamas House, un centro de recursos de acceso libre en Milwaukee para madres. Ella es una ex maestra de educación especial con un gran corazón y una fuerte convicción de cambiar el mundo apoyando a las madres. Originaria de Los Ángeles, posee una gran sabiduría acumulada a lo largo de años de viajar por el mundo y organizar su comunidad. ¡Estoy emocionado de conocerla más y visitar Yo Mamas House pronto!
A group of women suddenly marched onto the stage, beating drums and singing traditional African songs. Amoke sang along as I made my way to the front of the stage to get a better view!
Un grupo de mujeres de repente marchó al escenario, tocando tambores y cantando canciones africanas tradicionales. Amoke cantó junto mientras me abría paso al frente del escenario para obtener una mejor vista.
Click here for a video of the performancers dancing
Click here for audio of the performers drums and song
We ended the night at La Fabrica, a giant warehouse/art exhibit/venue/night club with multiple stages and contemporary art that spoke a loud social commentary about gender and humanity. It was easy to get lost in this giant building complete with multiple bars and outside patio areas for sitting and smoking cigars. I like their tab system - they collected money for drinks at the door on your way out vs paying each time you ordered one. The staff hands you a card on your way into the space that you give to the bartender to mark every time you order a drink to keep track of your tab. You settle up on your way out of the space and leave the card there. Thinking about my experience bartending, I think its a better system that allows the bartenders to show out and focus more on customer service.
Terminamos la noche en La Fábrica, un enorme almacén/exposición de arte/sala de conciertos/discoteca con múltiples escenarios y arte contemporáneo que hablaba un fuerte comentario social sobre género y humanidad. Era fácil perderse en este gigantesco edificio completo con múltiples bares y áreas de patio exterior para sentarse y fumar puros. Me gusta su sistema de pestañas: recogen el dinero de las bebidas en la puerta cuando sales en lugar de pagar cada vez que pides una. El personal te entrega una tarjeta al entrar al espacio que le das al barman para marcar cada vez que pides una bebida para llevar la cuenta de tu pestaña. Te pones al día al salir del espacio y dejas allí la tarjeta. Pensando en mi experiencia de bartending, creo que es un mejor sistema que permite a los bartenders destacarse y concentrarse más en el servicio al cliente.
Today was a dope day! I'm grateful to be connected with a dope group of folk through an experience like this. Shoutout to Rev. Dr. Martin Luther King for inspiring the creation of the Center, Fidel Castro for his revolutionary leadership, and Pastor Kelvin for being an example for us younger organizers who face formidable obstacles in our struggle for liberation. We won't let y'all down!!
¡Hoy fue un día increíble! Estoy agradecido de estar conectado con un grupo tan genial de personas a través de una experiencia como esta. ¡Un saludo al Rev. Dr. Martin Luther King por inspirar la creación del Centro, a Fidel Castro por su liderazgo revolucionario, y al Pastor Kelvin por ser un ejemplo para nosotros, los organizadores más jóvenes que enfrentamos obstáculos formidables en nuestra lucha por la liberación. No los vamos a defraudar!
Cheers to making beautiful memories with like minded organizers and changing the world!
¡Salud al crear recuerdos hermosos con organizadores de ideas afines y cambiar el mundo!
-
 @ 1d22e00c:50e00d0e
2024-03-24 07:00:53
@ 1d22e00c:50e00d0e
2024-03-24 07:00:53March 17 2024 Sunday Morning
Hey everyone I’m Gary Hoban and welcome to Refinery Life Australia.
The Inward Attitudes of a True Disciple is our theme for the next few Sunday mornings.
This series is based on the Beatitudes, found in the beginning of the Sermon on the Mount.
The Beatitudes vividly set forth the inward spiritual characteristics of those who are ideal citizens of the kingdom of God.
Only when we are right in our inward attitudes can we be right in our outward conduct.
Today we are discussing, The Forgotten Beatitude.
Text
Acts 20:35 NKJV
35 I have shown you in every way, by laboring like this, that you must support the weak. And remember the words of the Lord Jesus, that He said, ‘It is more blessed to give than to receive.’ ”
Scripture Reading
Acts 20:17-35 NKJV
The Ephesian Elders Exhorted
17 From Miletus he sent to Ephesus and called for the elders of the church.
18 And when they had come to him, he said to them: “You know, from the first day that I came to Asia, in what manner I always lived among you,
19 serving the Lord with all humility, with many tears and trials which happened to me by the plotting of the Jews;
20 how I kept back nothing that was helpful, but proclaimed it to you, and taught you publicly and from house to house,
21 testifying to Jews, and also to Greeks, repentance toward God and faith toward our Lord Jesus Christ.
22 And see, now I go bound in the spirit to Jerusalem, not knowing the things that will happen to me there,
23 except that the Holy Spirit testifies in every city, saying that chains and tribulations await me.
24 But none of these things move me; nor do I count my life dear to myself, so that I may finish my race with joy, and the ministry which I received from the Lord Jesus, to testify to the gospel of the grace of God.
25 “And indeed, now I know that you all, among whom I have gone preaching the kingdom of God, will see my face no more.
26 Therefore I testify to you this day that I am innocent of the blood of all men.
27 For I have not shunned to declare to you the whole counsel of God.
28 Therefore take heed to yourselves and to all the flock, among which the Holy Spirit has made you overseers, to shepherd the church of God which He purchased with His own blood.
29 For I know this, that after my departure savage wolves will come in among you, not sparing the flock.
30 Also from among yourselves men will rise up, speaking perverse things, to draw away the disciples after themselves.
31 Therefore watch, and remember that for three years I did not cease to warn everyone night and day with tears.
32 “So now, brethren, I commend you to God and to the word of His grace, which is able to build you up and give you an inheritance among all those who are sanctified.
33 I have coveted no one’s silver or gold or apparel.
34 Yes, you yourselves know that these hands have provided for my necessities, and for those who were with me.
35 I have shown you in every way, by laboring like this, that you must support the weak. And remember the words of the Lord Jesus, that He said, ‘It is more blessed to give than to receive.’ ”
Prayer
Father, we thank You for adopting us as your children.
With eyes wide open to Your mercies, we come to dedicate ourselves to you afresh.
Help us to use our talents and testimony that others may know Christ.
As be bring our tithes and offerings, we pray Your blessings upon them.
Help us meet the expenses of the ministry of this church and engage in ministries to the outer most ends of the earth.
In Jesus name we pray.
Amen.
Introduction.
We have probably all heard a sermon on the Beatitudes, in fact I generally preach a series on the Beatitudes each year.
Did you know there is a Beatitude that Paul preserved for us for later?
Ask almost any Christian, even the most careful Bible student, to name the beatitudes of Jesus, and they will name those listed in Matthew 5. Not one in a hundred would name the one given in Acts 20.
Thus it is fair to call Acts 20:35 the forgotten Beatitude.
Acts 20:35 I have shown you in every way, by laboring like this, that you must support the weak. And remember the words of the Lord Jesus, that He said, ‘It is more blessed to give than to receive.’ ”
There is no question as to the authenticity of this beatitude.
That this is a genuine saying of Jesus there is no doubt.
Beyond doubt, this was a current saying of Jesus with which the Ephesian elders were familiar.
Moreover, the writer, Luke, who heard Paul’s address to these pastors and preserved it. Also wrote the gospel that bears his name, and his gospel preserves, in slightly varied form, Jesus’ beatitudes.
There can be no doubt that Jesus demonstrated this beatitude in His life and ministry and death.
Just as surely as He demonstrated meekness, mercy, and purity of heart, so did Jesus demonstrate that “it is more blessed to give than to receive.”
There can be no fault found with the form in which this beatitude is given.
Paul faces his statement of the beatitude with a twofold caution, “Labouring,” he said, “you ought to help the weak, and to remember the words of the Lord Jesus, that He Himself said, It is more blessed to give than to receive.”
His caution “to remember” is certainly in place for us, for this is the forgotten beatitude.
Let’s look at three questions concerning this beatitude.
Why is this beatitude the forgotten beatitude?
We have never understood it.
Taken together, the full impact of these words has never hit us as Jesus intended they should.
We tread lightly on the first half of this saying and let our minds dwell on the later half.
But Jesus’ emphasis is the other way around, “It is more blessed to give than to receive.”
This turns the normal attitude of the carnal mind upside down.
There is a blessedness in receiving, and our Lord does not discount the fact.
None of us could live for ten minutes apart from what we receive.
It is blessed to receive, but it is more blessed to give.
We have never believed this beatitude.
If we doubt that this is the most disbelieved truth in the Word of God, we need but to look first at the average church treasury and after that into the faces of the congregation when the offering is being received or when the pastor mentions money.
Many look upon giving to the church as a necessary nuisance, a bother, a thing to be dreaded.
It isn’t so at all if our hearts are right.
The sense of our text then is this, “It is a far happier experience to give than to receive.”
And it surely is if our hearts are right with God.
Many of us have never actually tested this beatitude.
A few have!
And their testimony tells us that it is the very Word of God.
They say, “It is more blessed to give than to receive.”
Those who love the most give the most.
But the majority of Christians cannot testify one way or another.
They have never tried it out!
- What results from this beatitude being the forgotten beatitude?
We have missed the main emphasis of Jesus’ teachings.
This beatitude stands supreme among all the beatitudes of the Bible.
It is the centre of the bible’s teaching, the supreme emphasis of Jesus.
To give was the purpose of God coming, Matthew 20:28 says, "The Son of Man did not come to be served, but to serve, and to give His life a ransom for many.”
Selfishness is self destructive, giving is redemptive, creative, permanent.
We lose what we keep and keep forever what we give to God.
We have missed the greatest joy, the supreme blessing of Christian living.
What is Christian living?
It is doing our best to give more than we receive for Christ’s sake because we love Him and because we love a lost world.
What is the Christian philosophy of life?
It is believing in and trying to live by this word of the One who redeemed us, “It is more blessed to give than to receive.”
No amount of earthly things can ever satisfy the spiritual part of us that God made to be blessed by giving.
The writer of Ecclesiastes said, “He that loves silver shall not be satisfied with silver, nor he that loves abundant with increase, this is also vanity.”
We have failed to take the gospel the the whole world.
Why has the gospel made such a slow conquest of the world?
Why have missions and evangelism lagged and dragged?
It is because preachers have been so timid about preaching the joyous truths of the Bible about giving and because people have been so rebellious and unbelieving when they have presented it.
There is no danger of exaggerating the measure in which this beatitude has been discredited in the world and even by Christ’s own people.
Selfishness is the dominant note of humanity, the cancer of society, the mud on the chariot wheels of God’s army, and selfishness finds its supreme expression in man’s attitude toward money.
The world believes it is more blessed to get than to give, and therefore for two millennia we have not carried the gospel to all the world.
- What blessings would follow a wholesale recovery of this beatitude?
Blessings on us as individuals.
It is more blessed to give than to receive.
That is true for each of us as individuals.
We love our Lord because there was no trace of selfishness in Him.
He gave and gave and gave, and it was His joy to give.
The writer of Hebrews said of Him, in Hebrews 12:2, looking unto Jesus, the author and finisher of our faith, who for the joy that was set before Him endured the cross, despising the shame, and has sat down at the right hand of the throne of God.
Jesus demonstrated the truth of this beatitude as He did all the others.
We are to be like Him.
When pastors persuade their congregations to give “not grudgingly, or of necessity”, but joyfully and liberally, they are doing a real service to their souls.
There are blessings on our churches.
Recovering this beatitude would mean that our churches would have the means, the resources, but above all, the spiritual power to attempt to carry out the great commission.
If we had a cow that we had to milk, did you know that if we only took the milk we required for the day the cow would dry up.
It wouldn’t be good for the cow, its bad for her.
It’s bad for a church too if it only has just enough to cover the basics.
Because of their failure to give liberally, most of our churches have gone dry spiritually.
There are blessings on an unsaved soul.
It is more blessed to give than to receive.
If they would only heed these words, churches would challenge an unsaved world by an exalted testimony and witness.
The churches would begin to do the thing they were brought into existence to do.
The would start knocking on the doors of the world with the gospel, the world would heed, and some would be saved.
Conclusion.
The Beatitudes describe the character traits of a happy Christian, and this one, so often forgotten, is the most joyous of them all.
Until next time
Stay in the Blessings
I really want to encourage you to be diligent with your Bible study time, because God has so much more for us than we can get from just going to church once or twice a week and hearing someone else talk about the Word.
When you spend time with God, your life will change in amazing ways, because God is a Redeemer. Theres nothing thats too hard for Him, and He can make you whole, spirit, soul and body!
You’re important to God, and you’re important to us at The Refinery.
When it comes to prayer, we believe that God wants to meet your needs and reveal His promises to you.
So whatever you’re concerned about and need prayer for we want to be here for you! Or even if you just want to say Hi, you can contact us at www.refinerylife.org
2024 IS A YEAR OF DECISIONS AND OPEN DOORS
© www.refinerylife.org 2013-2024 All rights reserved. Except as permitted under the Australian Copyright Act 1968, no part of this Article may be reproduced, stored in a retrieval system, communicated or transmitted in any form or by any means without the prior written permission.
This episode is brought to you by Refinery Life Australia:
If you enjoy The Refinery Life Radio Podcast you can help support The Refinery by doing the following:
Sow an offering: Bitcoin: bc1qqh6720t2zagj72dyfj348az698tdut3hlecaj4
Online: https://www.refinerylife.org/donate/
If you do send an offering then please email us so that we can say thank you
Subscribe on iTunes | Spotify | YouTube | TuneIn | Rumble | Flare | Zap.Stream | Fountain |
Share The Refinery with your friends and family
Subscribe to the newsletter on www.refinerylife.org
Follow The Refinery on Twitter | Nostr | Instagram | Fountain |
-
 @ ec965405:63996966
2024-02-15 01:06:05
@ ec965405:63996966
2024-02-15 01:06:05I am beginning to see the clarity that my mentors promised I would as I progressed through my late 20s into my 30s, and it's getting clearer every day. I am inspired to change the world and bring my community with me. I know God has my back. A better world is within our grasp! I'm going to do my part in bringing my community with me by blogging about my upcoming trip to Cuba with Solidarity Collective via Nostr.
In February I'll be back in the skies headed to Havana, where I will participate in a delegation with Solidarity Collective to learn about Pan Africanism in the Cuban context. Some questions we will be exploring during this delegation are:
How do Cubans, in a Black-majority country, approach environmental protection, religion, housing rights, and healthcare?
What is the role of historic and contemporary abolitionist practices in their quest to eradicate racism?
What challenges remain to build an equitable society, especially under the yoke of 60 years of the u.s. Blockade?
What do these lessons mean for the struggle for black liberation in the u.s.?

I've dreamed about the next time I would visit Cuba and how I would track down the friends I made there in 2017. At that time, the government controlled access to internet via these cards that you would purchase then redeem on your device for timed access. The idea was that you would take your Wi-Fi card and head to a communal place like La Plaza with your device to access the Internet with others.
While some north americans might find that kind of Internet access draconian, surfing the web in public like that made me value my time on the Internet more. Has this changed since I was last there? I am personally interested in how groups are leveraging tech and the Internet for education and organizing. I now have a solid couple of years of IT/programming education to reference while I meet with teachers and journalists at the Martin Luther King Jr. Center and hear about the right to free education from daycare through university and literacy campaigns. I wonder if they've heard about decentralized social media protocols like Nostr or Activitypub or if they ever experienced censorship from the authorities on the Internet.
I recently experienced censorship in the YouTube comments as I explained to fellow web surfers why we must include Vieques and the other islands in the archipelago when talking about Puerto Rico politically. My ability to comment was restricted as I tried to convince others who talked down on Haiti and Cuba as failed states to instead take my Pan Caribbean perspective. I really enjoyed Dread's talk at Nostrasia 2023 about how he is using Bitcoin and Nostr to bring the islands together as the US Dollar and financial institutions like Western Union and the IMF keep us divided and oppressed.
The more I learn about Bitcoin as a tool for global wealth distribution, the more I understand how these institutions rob youth and families of basic necessities and facilitate the rise of authoritarian regimes and systems that punish journalists and activists through political repression. The corporate ownership of our means of internet communication by the likes of technocrats like Musk and Zuckerberg won't let authentic conversation between Caribbean-based diaspora happen on their platforms while they get to destroy countries like Myanmar and shape public discourse to their whim. That's why I'm glad I found Nostr.
My personal blog currently lives on my Uberspace asteroid in a Bludit instance that lacks much functionality outside of themes and data analytics, so it's just sits there as a personal repo for my thoughts. Nostr provides all of this with a direct link to my Bitcoin wallet address and comment functionality. If people value my content, I can get "zapped" and earn money for my content. I can now engage with my audience directly without a middle man. No Substack, no moderators censoring my messages, just community. The job now is to bridge my community and this new way of socializing on the Internet.
To help make this as educational of an experience as possible, I ask my audience: What questions or feedback do you have about my trip and the types of questions I want to explore? Is there anything you've ever wondered about Cuba? What suggestions do you have in terms of how I can better present information; written word, audio interviews, video, or photo essays?
Leave me some love in the comments and stay tuned!

-
 @ fa984bd7:58018f52
2024-02-14 12:53:42
@ fa984bd7:58018f52
2024-02-14 12:53:42This is a new document I'm writing using https://collab-lemon.vercel.app/ which allows for collaborative editing of documents on nostr.
The cool part is that this very simple tool, that I basically wrote in one hour last night, has some interesting primitives that can allow for a decentrailized wiki.
I want to test whether this updates
-
 @ 3cd2ea88:bafdaceb
2024-03-24 01:06:40
@ 3cd2ea88:bafdaceb
2024-03-24 01:06:40** $BENDOG:** Il meme token che celebra il cane più famoso sul web!
** $SYNC:** La soluzione per l'interoperabilità tra diverse blockchain!
Scopri di più e inizia a fare trading: https://bonus.bitget.com/U1JNEK
-
 @ 0f22c06e:6194f8b6
2024-02-08 01:26:43
@ 0f22c06e:6194f8b6
2024-02-08 01:26:43On social media and in the Nostr space in particular, there’s been a lot of debate about the idea of supporting deletion and editing of notes.
Some people think they’re vital features to have, others believe that more honest and healthy social media will come from getting rid of these features. The discussion about these features quickly turns to the feasibility of completely deleting something on a decentralized protocol. We quickly get to the “We can’t really delete anything from the internet, or a decentralized network.” argument. This crowds out how Delete and Edit can mimic elements of offline interactions, how they can be used as social signals.
When it comes to issues of deletion and editing content, what matters more is if the creator can communicate their intentions around their content. Sure, on the internet, with decentralized protocols, there’s no way to be sure something’s deleted. It’s not like taking a piece of paper and burning it. Computers make copies of things all the time, computers don’t like deleting things. In particular, distributed systems tend to use a Kafka architecture with immutable logs, it’s just easier to keep everything around, as deleting and reindexing is hard. Even if the software could be made to delete something, there’s always screenshots, or even pictures of screens. We can’t provably make something disappear.
What we need to do in our software is clearly express intention. A delete is actually a kind of retraction. “I no longer want to associate myself with this content, please stop showing it to people as part of what I’ve published, stop highlighting it, stop sharing it.” Even if a relay or other server keeps a copy, and keeps sharing it, being able to clearly state “hello world, this thing I said, was a mistake, please get rid of it.” Just giving users the chance to say “I deleted this” is a way of showing intention. It’s also a way of signaling that feedback has been heard. Perhaps the post was factually incorrect or perhaps it was mean and the person wants to remove what they said. In an IRL conversation, for either of these scenarios there is some dialogue where the creator of the content is learning something and taking action based on what they’ve learned.
Without delete or edit, there is no option to signal to the rest of the community that you have learned something because of how the content is structured today. On most platforms a reply or response stating one’s learning will be lost often in a deluge of replies on the original post and subsequent posts are often not seen especially when the original goes viral. By providing tools like delete and edit we give people a chance to signal that they have heard the feedback and taken action.
The Nostr Protocol supports delete and expiring notes. It was one of the reasons we switched from secure scuttlebutt to build on Nostr. Our nos.social app offers delete and while we know that not all relays will honor this, we believe it’s important to provide social signaling tools as a means of making the internet more humane.
We believe that the power to learn from each other is more important than the need to police through moral outrage which is how the current platforms and even some Nostr clients work today.
It’s important that we don’t say Nostr doesn’t support delete. Not all apps need to support requesting a delete, some might want to call it a retraction. It is important that users know there is no way to enforce a delete and not all relays may honor their request.
Edit is similar, although not as widely supported as delete. It’s a creator making a clear statement that they’ve created a new version of their content. Maybe it’s a spelling error, or a new version of the content, or maybe they’re changing it altogether. Freedom online means freedom to retract a statement, freedom to update a statement, freedom to edit your own content. By building on these freedoms, we’ll make Nostr a space where people feel empowered and in control of their own media.
-
 @ b2caa9b3:9eab0fb5
2024-02-06 17:53:14
@ b2caa9b3:9eab0fb5
2024-02-06 17:53:14In today's adventure, I decided to switch up my work setting and take you along for the ride as I settled into a beach hotel, a truly delightful one at that, promising excellent wifi for a productive workday. I'm a proud minimalist, equipped with nothing more than my trusty Osprey Nebula 32L backpack, housing all my essentials, weighing in at less than 10 kg - clothes, shoes, electronics, toothbrush, toothpaste, and soap neatly stowed away.

As I prepared for my excursion, I emptied my backpack, leaving only the electronics inside. The first leg of my journey involved catching a tuktuk to the beach hotel, where I was greeted by a friendly security guard who welcomed me with a warm "caribou" - a precursor to the enchanted world that awaited beyond the imposing iron gate.

Following the security guard's directions, I wandered along a path lined with quaint cottages available for rent until I reached a breathtaking scene: a pool, a bar, and a restaurant all nestled within a lush, jungle-like resort. I chose the pavilion as my workspace for the day, offering a panoramic view of the resort on one side and a stunning vista of the beach with its powdery white sands on the other.

However, my plans hit a snag when I discovered that the promised wifi wasn't functional in the pavilion. Attempts to relocate to the restaurant and poolside in search of a stable connection proved futile, eventually forcing me to rely on my mobile data to salvage a couple of hours of work amidst picturesque surroundings.

In true African fashion, the assurance of good wifi often falls short of reality, leading to a day filled with beautiful scenery but a less-than-productive workday. Nonetheless, I made the most of it, even indulging in a delectable pizza during my quest for a functioning wifi connection.

As the day wound down, I packed up my laptop and headed back to my temporary abode. In hindsight, it wasn't the most productive workday, but it was undeniably a picturesque and enchanting mobile home-office experience. Take a peek at the photos to capture a glimpse of this unique workspace.













Follow me on Nostr