-
 @ eac63075:b4988b48
2024-09-20 08:46:49
@ eac63075:b4988b48
2024-09-20 08:46:49Lá na outra rede, o Dov havia feito um post bacana mostrando como usar a Electrum mobile de cold wallet nessa playlist.
Então ao comentar que a minha primeira cold wallet havia sido uma Electrum num notebook velho e formatado só pra isso, algumas pessoas me perguntaram sobre meu setup atual.
Então preparei o seguinte esboço:
No geral é: * Server Umbrel para os nodes * Coldcard e Ledger (coldwallets) * Computador criptografado e celular android com área segura p/ apps
É um caso de uso extremo mas além da auto-soberania e custódia dos meus satoshis, essa estrutura ainda me permite:
- Participar do consenso do Bitcoin
- Auxiliar no roteamento de sats na Lightning Network
- Fazer coinjoin facilmente para aumentar a privacidade
E embora a estrutura pareça complicada, é bastante simples:
- Raspberry Pi 4 com Debian e Umbrel (p/ os nodes e servers)
- Celular antigo android com área segura e sem simcard
- Notebook com storage criptografada
- Ledger Nano X
- Coldcard
E ainda pude evoluir de N.O.I.A. (Network Operator Innovator and Advocate) para M.A. (Minerador Anônimo), com uma Nerdminer pra tentar um ticket da sorte a cada 10 minutos
Não esqueça que uma cold wallet para a auto-custódia pode começar com um computador ou celular velho!
É mais simples do que parece e praticar sua auto-soberania e custódia significa na verdade liberdade e privacidade nesse mundo digital!
-
 @ 599f67f7:21fb3ea9
2024-09-19 08:27:12
@ 599f67f7:21fb3ea9
2024-09-19 08:27:12¿Qué es una dirección Lightning o Lightning address?
Una dirección Lightning es una dirección que visualmente se asemeja a una dirección de correo electrónico legible para los humanos, por ejemplo usuario@dominio.com pero que en realidad te permite recibir pagos en bitcoin instantáneos y económicos, sin la necesidad de tener un nodo en linea en tu dispositivo ni tener que generar facturas de forma manual cada vez que alguien te quiere hacer un pago.
¿Suena bien no?
¿Y cómo funciona?
Funciona utilizando el protocolo de pago LNURL.
Aquí se muestra un sencillo esquema de lo que ocurre en segundo plano.
En resumen, cuando otro usuario quiere pagarte usando tu dirección Lightning, tu billetera convierte la dirección Lightning en una solicitud de pago LNURL. Luego se utiliza esa solicitud de pago LNURL exitosa para obtener una factura BOLT11.
💡 Dirección Lightning > LNURLp > Factura BOLT 11.
Suena bien, pero ¿cuál es el problema?
Por el momento, muchas de las implementaciones de Lightning Address son de custodia, porque se necesita un dominio para que Lightning Address funcione y un nodo que esté siempre en línea para recibir los pagos. Debido a que es de custodia, el custodio puede atacarte en cualquier momento y monitorear tus transacciones.
Tienes que confiar en el propietario del dominio para no cambiar el registro de tu dirección Lightning. Y no funciona si el servidor LNURL no está en línea.
Bitcoin Txoko ofrece una sencilla solución de Lightning Address respaldada por LNbits. Esto también es de custodia, así que por favor mantén solo una pequeña cantidad en tu billetera Bitcoin Txoko y ve retirando a tu billetera de autocustodia a medida que recibas más sats.
Estoy listo, ¿qué necesito para empezar?
¡Todo lo que necesitas es un teléfono móvil o un ordenador y una conexión a Internet!
1. Creando tu billetera
Si aún no lo has hecho, navega a https://bitcointxoko.com y crea una nueva billetera. Puedes elegir el nombre que quieras.
2. Activar extensiones
Hace falta la extensión
Pay Linkspara que las direcciones Lightning funcionen.Abre
Extensionesen la barra de herramientas y activaPay Links.3. Creando tu enlace de pago
-
En a la extensión
Pay Links, haz clic enNew Pay Link. -
Elige la billetera que has creado.
-
Para la descripción del artículo, puedes escribir lo que quieras.
-
Elige un nombre de usuario de tu dirección Lightning. Tu dirección Lightning se verá como
username@bitcointxoko.com. -
Desmarque
Fixed amounty cambia el valor mínimo a 1 y el valor máximo a 500000.
⚠️ También puedes cambiar el valor máximo a algo más alto, pero es más probable que los pagos más grandes fallen debido a la limitada capacidad de entrada del nodo Lightning de Bitcoin Txoko. Así que recomendamos mantenerlo en 500000 sats.
-
Ahora abre
Advanced optionsy cambiaComment maximum charactersa 799. Este paso no es necesario pero permite más funcionalidades más adelante. -
Marca
Enable nostr zapsen la parte inferior, para que puedas utilizar tu dirección Lightning para recibir zaps. -
Las demás opciones avanzadas son opcionales, puedes configurarlas si quieres o dejarlas en blanco.
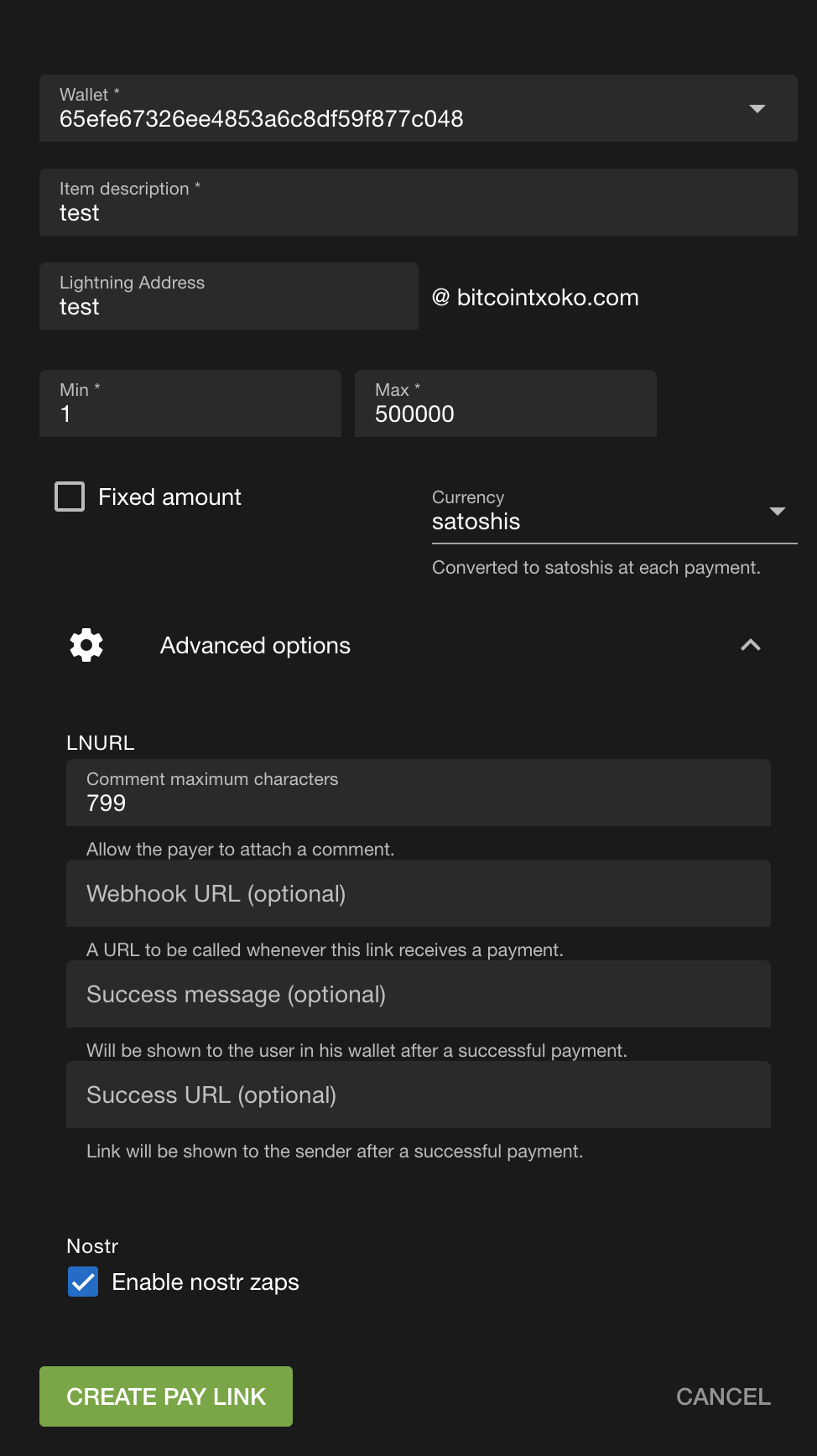
Al final debería verse algo así.
- Cuando hayas comprobado que todo es correcto, sigue adelante y haz clic en
Create Pay Link.
Probando
Puedes probar si tu nueva dirección Lightning funciona yendo a otra cartera, pulsando en
Enviary escribiendo tu dirección Lightning como destino, y luego enviándote una pequeña cantidad de sats.Vuelve a tu billetera Bitcoin Txoko y comprueba si has recibido tu propio pago. Es posible que tengas que actualizar la página.
Si todo funcionó correctamente, ¡enhorabuena! 🥳
Si no es así, háznoslo saber. Siempre estamos aquí para ayudar.
Próximos pasos
Nostr zaps
Puedes añadir tu dirección Bitcoin Txoko Lightning a tu perfil de nostr y usarla para recibir zaps. Normalmente, esto se hace yendo a
Perfil>Editar>Dirección Lightningy cambiando la dirección Lightning.LNDhub
Puedes importar tu billetera LNbits como un LNDhub en tu teléfono utilizando una aplicación como Zeus o BlueWallet, en lugar de visitar la billetera en el navegador cada vez que desees comprobar tu saldo o realizar un pago. Echa un vistazo a nostr:naddr1qvzqqqr4gupzqkvlvlma7a55ccp6d5rrdc27h3ssmdmael286mjaq5uxmqslk04fqqxnzd3exuerqdfkxccnyv3cs0uvul sobre cómo hacer esto.
Código QR
También puedes compartir o imprimir tu código QR LNURLp para que la gente pueda escanearlo fácilmente con sus teléfonos. ¡Muy útil si estás introduciendo bitcoin a tu comerciante local favorito para que pueda recibir propinas Lightning!
Simplemente comparte el enlace a tu página compartida, o imprime el código QR como PDF yendo a
View Link>Print. -
-
 @ 6ad3e2a3:c90b7740
2024-09-16 18:15:05
@ 6ad3e2a3:c90b7740
2024-09-16 18:15:05I posted the following hypothetical on Twitter, and the responses did not disappoint:

A few people speculated that the post was about vaccines, which it was not (at least not specifically). and others wondered why the guy didn’t just do the jumping jacks to save the waiter’s life.
But nowhere in the hypothetical does it say the gunman won’t just kill him anyway if you do what he says. To think it makes any difference whether you do the jumping jacks, you have to believe simultaneously that the gunman is capable of killing a person for no reason, yet still a man of his word. That for him killing the waiter is fine, but misleading you is beyond the pale.
Even so, people wondered why the guy didn’t just do the damn jumping jacks — I mean in the unlikely event this heartless murderer was a man of his word, maybe you could have saved the waiter’s life!
Another thing the hypothetical doesn’t imply is that the man with the gun, after seeing you comply with his request, will either relinquish it or leave the restaurant. In other words, even if you do the jumping jacks, and miraculously he is a man of his word, he still has the gun, and next thing you know he might ask you to do 10 pushups, maybe some squats and leg raises too. The man is still there, he still has the gun, and if for God knows what reason it is important to him to force you to exercise, it follows that the jumping jacks are unlikely to be his final request.
I also found it telling that people blamed the guy who refused to do the jumping jacks at all — he was merely at a restaurant eating his meal when a gunman burst in and killed someone for no reason. Any fair apportionment of responsibility for the waiter’s murder falls solely on the gunman, and not on the guy who refused to jump through an arbitrary and pointless hoop the gunman set up at his whim.
But one’s response to this hypothetical is a good indication of how one relates to power. The people who intuitively know might does not make right realize the gunman is the only violent actor and solely responsible for the shooting. But some have learned to be careful — run afoul of the powerful, and there will be consequences. To them, the gunman is an immovable and terrifying fact, and it is up to the guy to do the damn jumping jacks. That he does not do this simple act is unthinkable, and hence they see it as contributing to the waiter’s death. Going along with the will of the powerful is the best option, and those who rock the boat are merely making trouble for everyone. They prefer to keep their heads down, hope it passes, so that no one will get shot.
If someone does rock the boat, the careful, being unable to face the terrifying prospect of taking on power, will turn on the boat-rocker who they will see as the problem, the person making it worse for everyone, even though he is only the ostensible trigger — and never the actual cause — of the powerful person’s oppressive responses.
Even if the careful prevail in getting everyone to go along, as we established above, there is no basis for believing the gunman will be satisfied with jumping jacks, which are a pointless and arbitrary request that only serves as a precedent — that when he asks, you comply. It’s possible he will run out of uses for you — not necessarily a good thing given his proclivity for murder — but until he does, you can rest assured there will be further asks.
I brought up the hypothetical because after “three weeks to flatten the curve” something that did not seem arbitrary at the time, there has been ask after ask, and it’s become increasingly clear to me the asks are unlikely to end on their own. Zero COVID is not possible for what’s almost certainly an endemic virus, there are plans for digital movement licenses, and if cases tick up according to their latest benchmark/criterion, I would expect to see calls for renewed lockdowns in the fall. And that’s not even counting the usual — and often deadly — seasonal non-COVID respiratory viruses that can also be fear-mongered if we micro-track their spread in a similar manner.
The root of the problem is we did not take the gun away from the gunman in exchange for our jumping jacks, and while at one time, public health might have been the central aim, that phase has long passed, and pandemic measures — and even pandemic-specific rituals and behaviors — have congealed into a semi-permanent ecosystem. The gunman has made himself at home in the restaurant and has some of the patrons cooking his meals and washing his dishes, a few of whom are getting paid handsomely for their trouble.
There is only one thing that could end this hostage situation, and that’s to do what the man in the hypothetical did — decline his request. If he wants to shoot the waiter, that’s up to him — chances are he’s bluffing, and in any event, he was free to shoot the waiter at any point, no matter what we did. Once we stop fearing the gun, we can avail ourselves of whatever measures we deem necessary, including vaccines, medicines, masks or nothing at all. We are free to stay home, or go out, according to our own risk tolerance, and we will live with the consequences like free people always have.
-
 @ 17538dc2:71ed77c4
2024-09-16 15:26:32
@ 17538dc2:71ed77c4
2024-09-16 15:26:32
Quiztime
Oil and gas
Oil and gas is naturally occurring. The prevalent worldview is that oil & gas has a biotic origin. There are real world examples of abiotic oil deposits, which proponents of the status quo have a difficult time reconciling.
Irregardless, when oil & gas is burned, it simply turns to plant food (carbon dioxide + water).
Oil and gas greens the Earth, and increases fertilization and agricultural crop yield across the globe.

The energy density of oil and gas is only surpassed by that of nuclear power.
Energy produced by oil and gas combustion is generally on-demand, reliable, economically storable & transportable.
Solar
The sun is an abudant energy source, which keeps Earth warm, and alive. Thank you sun 🌞!
With the exception of places such as the UK, where it is unclear if inhabitants have ever seen the sun, solar rays keep plants, animals, and humans happy & alive on most of planet Earth.
Inventions such as solar panels harness the sun's energy, and convert it to electricity.
Solar panels consist of silicon, rare earth metals, and require toxic metals.
Solar panels have an expected life of decades, are not readily or economically recyclable.
A very low solar energy density practically means that land is inefficiently utilized in solar energy production. Solar used on arable land can no longer be farmed, and where no plains exist solar is known to cause deforestation and landslides.
Solar energy is not reliable, not can it be summoned on demand. Solar energy is not economically storable, and is many cases is not produced at the point of demand.
Despite central planner mandates & subsidies in the US, the #EULAG and elsewhere, due to its intermittent nature, solar power cannot be counted on to replace reliable power generation in nuclear, hydro, or carbon fuel thermoelectric plants.
What this means is that solar does not replace, and yet ratheradds to reliable energy generation, as most people in the developed world would not be OK with having electricity for at most 1/3 of the day. This increases the price of electricity, which in turn increases energy poverty, and drives businesses to shut down manufacturing, or move to a more energy competitive jurisdiction.
The capital wasted by central planners could have been used to reduce burden on consumers, and businesses, or fund healthcare, infrastructure, or other services.
It should be noted that off grid applications where there is no grid, or energy alternatives can be massively useful for folks otherwise without electricity.
Which energy source would you consider renewable?
-
 @ 1739d937:3e3136ef
2024-09-13 21:09:24
@ 1739d937:3e3136ef
2024-09-13 21:09:24This is the seventh in a series of weekly(ish) updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
I was told recently that my update walls of text are too much. So, I'll try to keep things concise this week. 😅
This week has been all about building the reference implementation, which is quickly becoming a full-fledged client instead of just a reference implementation. I've not quite gotten to the MLS portion of the client yet but it does already support multiple accounts (including ephemeral accounts) and loads legacy (NIP-04) chats and full contact lists. So far, I've not implemented NIP-104 so there's not yet any updates to the MLS spec or other dependencies.
If you've got experience with using messengers in hostile environments (authoritarian regimes, you've been de-platformed, etc.) please get in touch. I'd love to hear more about what you'd like to see in a communication tool.
In the meantime, I'll be over here in the corner coding with my headphones on. 👨💻
Onward and Upwards!
-
 @ 6ad3e2a3:c90b7740
2024-09-13 15:58:12
@ 6ad3e2a3:c90b7740
2024-09-13 15:58:12This is the story of our time.
The Emperor was scammed by fake weavers, who used a clever trick: They posed as experts in their craft and declared their work invisible to simpletons. In other words, if you did not go along with the scam, it was because you were stupid or of low character. Or, in modern parlance, you were a conspiracy theorist or an anti-vaxxer.
The story applies to so many facets of present narrative — from Joe Biden’s transparently declining cognitive capacity to the preposterously phony war on “disinformation,” there is stiff competition for the best example. But if I had to choose, it would be the “safe and effective” mRNA shots — they check all the boxes: veneration of “experts”, political and business interests masquerading as “The Science” and disparagement of those who were skeptical as stupid, selfish, childish and evil. Any questioning of the safety or efficacy of the mRNA shots could get you attacked by angry online mobs, deplatformed from social media or even fired from your job.
Why are people going along with the “safe and effective” narrative in the face of an unprecedented number of adverse effects, the sketchy track record of large pharmaceutical companies in putting profits above safety, the rush of these products to market more quickly than any prior vaccine, the fact it has not been updated to reflect the new strains, its quickly-waning efficacy such that multiple boosters are already needed in fewer than 18 months, the fact it doesn’t stop (and may increase) the spread and the relatively mild nature of the virus for those under 50 who don’t have pre-existing conditions? Surely, this emperor’s pale, flaccid gluteus maximi are flapping about in public view.
There are certain conditions under which people are especially likely to pretend the naked emperor is dressed, all of which have been met in this case:
-
Many powerful people are pot-committed to “safe and effective.”
-
Everyone knows powerful people are committed.
-
Everyone knows that everyone knows powerful people are committed.
Every elected official who required mandates, every corporation who forced people to get the shot as a condition for employment, the corporate news media, its on-air hosts, executives and board members, every doctor who advised it, many parents who gave it to their kids, every person who shamed others for not going along — and there were many — heads of state, the CDC, the WHO, etc. are pot committed. (Pot-committed is a poker term for when someone has put such a large percentage of his chips into a pot there is virtually no way he can fold his hand.)
If the mRNA shot were shown to be unsafe, the liability, both legally (I know they received a waiver under the EUA, but fraud, for example, would invalidate that), reputationally and worse (criminal prosecutions might be warranted, given it was mandated) would be catastrophic for them. In other words, many of the world’s most powerful people have a lot to lose if the mRNA shots were shown to have harmed and/or killed thousands of healthy young people who were at minuscule risk from covid itself. They will not easily be persuaded this happened, and they have massive incentives to destroy anyone making headway in persuading others. There are powerful forces who need you to view the emperor as clothed.
The second condition is that everyone is well aware of this. Any researcher contemplating speaking out or going deeper into the data to that end knows he could be blackballed, cut off from funding and any prospect at a career in science or academia. Any person who speaks up knows he could lose his job, get deplatformed or run afoul of the soon-to-be-created Bureau of Disinformation. In fact, you would expect the powerful to create just such a bureau under these conditions — when they have too much to lose should the word get out.
Finally, it’s not simply that everyone knows, but that everyone knows that everyone knows, i.e., per Ben Hunt, it’s common knowledge that you don’t screw with the pharmaceutical cartels and those who do their bidding. It’s not just you who are deterred, but you know everyone else has a similar deterrent. People who blow the whistle therefore expect to be ridiculed, destroyed and tarred as conspiracy theorists and also don’t expect their friends and colleagues to come to their aid.
With these three conditions present, we can all hail the incredibly safe and effective mRNA treatments are a miracle! Thank God we have them and are finally able to get out of this pandemic! The emperor has such a wonderful suit of clothes!
In the story, it took a child to blurt out the obvious, that the emperor was exposing his sagging, unsightly posterior. Interestingly, once he did, everyone else acknowledged the obvious, but the emperor — and members of his procession, who were going along — went on with the show. They were in too deep to back out.
I suspect that’s going on now — the child has noticed, word is getting out. They are desperately trying to shut it down with the most Orwellian measures (Bureau of Disinformation!) They will not succeed, but lasting damage has been done, and more will be inflicted before it’s over. The biggest question now is the lengths to which the emperor’s minions will go — creating a ministry of truth is extreme, but that pales in comparison to, say, starting World War III.
There are other reasons for a world war too — the collapse of the giant global debt bubble and the fallout therefrom — but in both cases the stakes are nearly infinite for those responsible, given how much damage has been done to the average person. We’d be wise not to underestimate the risks they’d run to avoid accountability.
-
-
 @ 09fbf8f3:fa3d60f0
2024-09-12 13:48:54
@ 09fbf8f3:fa3d60f0
2024-09-12 13:48:54图床平台
2024.09.12更新 https://img.chkaja.com/
https://im.gurl.eu.org/ 已失效 https://img.fzxx.xyz/index2 https://imgse.com/ https://img.gejiba.com/ https://imgloc.com/ https://www.superbed.cn/ https://www.helloimg.com/ https://im.ge/ https://png.cm/ https://img.ax/ https://tucdn.wpon.cn/ https://locimg.com/ https://xiray.cf/ https://pic.sl.al/ https://lvse.eu.org/ https://img.ink/
🏷 #图床 #合集
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:22:42
@ 09fbf8f3:fa3d60f0
2024-09-10 13:22:42发现一个可以将Telegram频道内容转换为微博客。
-
开源项目: BroadcastChannel
-
演示站点:https://memo.miantiao.me/
✨ 特性 * 将 Telegram Channel 转为微博客 * SEO 友好 /sitemap.xml * 浏览器端 0 JS * 提供 RSS 和 RSS JSON /rss.xml /rss.json
使用 Astro 框架,支持部署在 Cloudflare、Netlify、Vercel 等支持 Node.js SSR 的无服务器平台或 VPS,可搜索,可 RSS 订阅
🏗️部署注意: * 项目通过 https://t.me/s/ 获取频道内容,如果频道被限制无法预览会显示空白 * 频道需要关闭 Restricting Saving Content * 环境变量 CHANNEL 值必须为频道 ID * 环境变量 TIMEZONE 值不要添加双引号 * 建议安装测试时只填写 CHANNEL 值 * BUG: 带引用回复的内容无法显示 已修复 * BUG: 带自定义 emoji 的无法显示 已修复 * BUG: 带 Quote 的内容无法显示
-
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。
2024年08月13日更新:
修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
准备工具
- Ntfy服务
- Google Script
- Google Sheets
操作步骤
- 在Ntfy后台账号,设置访问令牌。

- 添加订阅主题。

- 进入Google Sheets创建一个表格.记住id,如下图:

- 进入Google Script创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) { var threadId = thread.getId();
if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); }}); }
function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; }
var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true };
try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } }
function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column }
function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); }
function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues(); var rowsToDelete = [];
data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } });
// 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); }
```
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:

结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
-
 @ e83b66a8:b0526c2b
2024-09-06 19:16:04
@ e83b66a8:b0526c2b
2024-09-06 19:16:04The founder of Telegram has just been arrested in France. Charges include lack of cooperation with law enforcement, drug trafficking and fraud.
Aside from Telegram, social media is controlled by two billionaires who decide what you say, are themselves controlled by overbearing governments and make money through advertising and selling your personal data.
There is a different way.
NOSTR stands for Notes and Other Stuff Transmitted on Relays and it is a social media protocol in the same way http is a web protocol.
The protocol is open and anybody can build upon it. It has some fundamental concepts that are very different to existing social media platforms.
Firstly it is decentralised, it runs across relays and anybody can run a relay. They can be open or closed, public or private, free or paid.
Secondly as a user, you don’t have an account, you have a private key which is used to secure your data.
Your profile (account) is yours, you own and control it using your private keys and verified by others with your public key.
Your posts are yours and you can store them on your own relay in your own home or business or you can rely on free public relays or more feature rich paid public relays.
All your public data is signed by your private keys to verify it is you that owns it and all your private data is encrypted so nobody can read it.
Messages (i.e. think NOSTR WhatsApp) are encrypted with your private keys so NOBODY can hack it or listen in, not even the NSA through a companies backdoor. You message other users privately by encrypting messages to them using their public key, which they decrypt using their private key.
Relays store your data in a decentralised network of private and public relays and you discover relays automatically when searching for people or content.
Data is normally sent on the clearnet, but can be relayed across the darknet (Tor) in highly censored regions.
Because it is built using Bitcoin principles and technology, so it has Bitcoin money built in, meaning you actually send / receive money from / to any participant.
As money is built in, the commercial options are different to centralised corporate owned platforms. It would be technically possible to build a platform that supports advertising, however that hasn’t really happened because influencers can be paid directly from their audience in many different ways. Ad hoc tips, subscriptions, pay to view or pay per time models.
The great thing for content creators is that they control, own and keep all the money they make. There is no third party intermediary or merchant deciding whether they are allowed to be paid or not.
NOSTR is censorship resistant, as there is no way to stop anybody publishing anything they want, in the same way nobody can stop or interfere with a Bitcoin payment.
From an end users point of view, if they want to self censor, they can do this in multiple ways. You can mute users individually, or you can choose to use relays that adhere to your views or interests, so if you don’t want to see certain categories of content, you would avoid relays that carry those feeds. You can even run your own relay and curate content that you then charge other like minded users to connect to. You can of course connect to multiple relays for multiple different type of feed.
While NOSTR is a protocol, platforms have to be built to use it, so the first platforms were twitter like clients and they are still very prevalent. However, NOSTR now has clients that emulate most social media platforms, Instagram, Facebook, YouTube, Soundcloud, WhatsApp etc. They are even creating their own categories as well as emulating other functions such as Office Suite tools, collaborative calendars, contact lists or e-commerce shops.
If you want to give it a go, the easiest, but not the best, way to get started is download Primal on your phone from here:
https://primal.net/downloads
It will create a private key for you and setup a Bitcoin wallet.
Once you have done this you can visit me here:
nostr:npub1aqakd28d95muqlg6h6nwrvqq5925n354prayckr424k49vzjds4s0c237n
If you want to see a small part of the ecosystem, then visit https://www.nostrapps.com/ where volunteers are listing some of the many apps that exist already.
NOSTR is being backed by Jack Dorsey, Twitter founder, and you can see his account here:
nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
Or you can see his account like this:
https://primal.net/jack
Edward Snowden is also on the platform and you can find him here:
https://primal.net/Snowden
NOSTR has around 2 million users or public keys, although nobody really knows how many, because it is decentralised and not controlled or run by any person or organisation.
Once you’ve setup Primal, you can use those same private keys to access any platform you wish and you can use a browser extension such as Alby to manage your keys: https://getalby.com/
Primal looks great, but there are other better functioning twitter like clients, probably the most reliable for iPhone is Damus: https://www.nostrapps.com/apps/damus
or Amethyst for Android: https://nostrapps.com/amethyst
The content and user base is very Bitcoin and freedom focused right now, but more and more people are starting to use the various platforms and some are transferring exclusively to it.
Some of the more interesting projects right now are:
https://www.0xchat.com/#/ – Private messaging – think WhatsApp
https://zap.stream/ – Video streaming
https://fountain.fm/ – Podcasting
https://wavlake.com/ – Music streaming
https://shopstr.store/ – Online shop
https://npub.pro/ – Website creation tool
https://nostr.build/ – Media and file storage
https://relay.tools/ – Build and curate your own relay
https://creatr.nostr.wine/subscriptions/new-user – Creator tools
Remember, the same keys you created for Primal can be used across the whole ecosystem.
If you want to see some of the other apps that have been built on the NOSTR protocol visit: https://nostrapps.com/
-
 @ e968e50b:db2a803a
2024-09-06 19:13:32
@ e968e50b:db2a803a
2024-09-06 19:13:32https://www.youtube.com/watch?v=mn4whdycgxQ
I'm about to go play with a swing band from Pittsburg at an Italian music festival and am reviewing my Louis Prima for tonight. I thought I'd share a silly take on Body and Soul by the band's trombone player. The first chorus is ballad style, and then a romp through anything you can imagine (including the Hall of the Mountain King over Body and Soul changes)! Happy weekend!
originally posted at https://stacker.news/items/675086
-
 @ b6dcdddf:dfee5ee7
2024-09-06 17:46:11
@ b6dcdddf:dfee5ee7
2024-09-06 17:46:11Hey Frens,
This is the Geyser team, coming at you with a spicy idea: a grant for proper journalism.
Issue: Journalism is broken. Independent journalism is emerging with the work of The Rage, Whitney Webb and so forth. They deal with issues like privacy, political corruption, economics, ESG, medicine and many other issues that are not discussed by mainstream media.
The problem is that not many people know about their work and there are very few grant programs that support their work.
Proposed Solution: Geyser would like to host a Grant supporting independent journalists using 'community voting mechanism'. See here for how Community Voting Grants work.
However, we need more companies to partner up and sponsor this initiative with us. Ideas of more sponsors: - Stacker news: SN has become a great repository of independent/indie journalism. I think they'd fit in great as sponsors for this type of grant. cc: @k00b - Bitesize media: A new independent media house that wants to focus on the signal Bitcoin brings to our world. They expressed interest already. - Bitcoin Magazine: might be interested as well in this effort.
Would love the community's feedback on this idea and propose additional thoughts!
originally posted at https://stacker.news/items/674951
-
 @ ffd375eb:4529ed08
2024-09-06 15:39:31
@ ffd375eb:4529ed08
2024-09-06 15:39:31Chef's notes
Watch the video 🇫🇷: https://youtu.be/cYl4Lb0vbyc
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 3 months
- 🍽️ Servings: Many
Ingredients
- 1 fennel bulb
- 1 large onion
- 3 garlic cloves
- 1/2 tsp salt per fennel bulb
- 1 tbsp turmeric powder per fennel bulb
- 1 tbsp oil per fennel bulb
- 1 tsp black pepper per fennel bulb
- 1 tbsp honey per fennel bulb
Directions
- Thinly slice the fennel bulb, onion, and garlic using a mandoline slicer.
- In a bowl, mix the sliced fennel, onion, garlic, and salt. Let sit for a bit to allow the salt to act on the ingredients.
- In a separate bowl, mix the turmeric, oil, black pepper, and honey to make a sauce.
- Combine the fennel, onion, garlic mixture with the turmeric sauce and mix well.
-
 @ 6bae33c8:607272e8
2024-09-20 15:32:58
@ 6bae33c8:607272e8
2024-09-20 15:32:58I went 2-3 last week to bring my two-week mark to 3-7. I’m not drawing dead yet, but obviously you don’t get many of those stretches if you expect to cash in this contest.
This week I feel more strongly about a couple games:
I love the Bengals laying the 7.5 at home against the Football team. The Giants should have beaten them in Washington last week (but for not having a kicker and Malik Nabers dropping an easy 4th-down conversion at the end.) The Bengals will get Ja’Marr Chase going and blow them out.
I like the desperate Ravens in Dallas laying only one point. It’s usually not a great idea to think, “I can’t imagine them at 0-3” so I have to bet them when they’re 0-2 because you probably didn’t foresee them at 0-2, either, and once they’re 0-2, they only need to lose one road game to get to 0-3. That said, I think they’ll be focused, and the Cowboys would have to bring their A game to beat them.
Give me the Falcons getting the 3.5 at home against the Chiefs. Atlanta should hang with them.
I like the Texans laying less than a FG in Minnesota. The Vikings have played well, but I’ll sell high off the big win over the 49ers.
I was on the Bucs initially, but something feels off about it. It’s too obvious, the Broncos aren’t getting nearly enough points with Bo Nix. I’ll stay away.
My last choice is between the Colts as a buy-low at home and the way overpriced Lions on the road.
The Colts are ugly, can’t stop the run, missing DeForest Buckner, etc. But really the names on the jerseys, the details of that sort are already priced in, not the way to handicap games. The better way is to get a sense of the league’s ebb and flow. I think the Colts win at home, maybe Anthony Richardson plays better this week.
The Lions should be 2.5-point underdogs, so this line caught my attention — something is off, and it gives me a feeling I’m missing something, makes me want to take them. But that’s probably overthinking it. I’ll take the Colts with the last pick.
Final Picks

-
 @ 6bae33c8:607272e8
2024-09-06 08:16:48
@ 6bae33c8:607272e8
2024-09-06 08:16:48I got back into the Circa Survivor Contest this year at great cost (my flight out of Palm Springs on July 5 was cancelled due to heat, so I had to rent a car and drive through the Mojave Desert, and the road to Vegas was closed, so I had to double back another 100 miles, which in total took six hours), so this is Team Of Destiny 2.0. Or at least it had better be.
I’m not going to stick to any one method or philosophy. Put differently, I realize that in order to win, I need to go into the future, find out what has already happened and pick on that basis. Pot odds is great, but even if you do that properly every week, your edge over the field isn’t that huge. Instead of a 1 in 10,000 chance to win, maybe you have 1 in 6,500. Sure, if you had 100 entries in every high stakes contest, it might be enough to eke out a reliable profit, but I’m not here for that. I’m here to navigate one boat through the icebergs and take down the $10M. And for that, you can’t hope to get lucky. You have to know in advance.
What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.
. . .
In any event, let’s take a look at the slate: Here are the ownership numbers per Officefootballpools.com.

The pot-odds play is the Bills if you buy into the Vegas numbers — Bengals roughly 78.5 and the Bills at 72.6%. That means the Bengals have a 21.5% chance to lose, the Bills 27.4%. That’s a 27.4 percent increase in risk (coincidentally.)
But if the Bengals lose they take out 39 people, and if the Bills lose they take out only 15. Let’s assume another 20-odd people lose with other teams (in a hypothetical 100-person pool) and you’re down to 41 if the Bengals lose/Bills win, 65 if the Bills lose/Bengals win.
If we say each person put in $10, the former scenario is $1000 (total pot)/41 = $24.39, and the latter $1000/65 = $15.38. The ratio of 24.39/15.38 = 1.59. In other words, you have 59 percent percent more equity in Week 2 on the Bills if the Bengals lose than you would on the Bengals if the Bills lose.
You’re talking a 27.4 percent greater risk for a 59 percent greater reward. So normally I’d snap call the Bills.
But I’m probably going Bengals because I think the Cardinals are dangerous this year, and the Pats are arguably the worst team in the league and in surrender mode after they dealt Matthew Judon to the Falcons. (All this is supposed to be priced in, of course, but I don’t care.)
I’ll finalize my pick before Saturday’s deadline, but that’s how I see it for now.
-
 @ 6bae33c8:607272e8
2024-09-06 08:14:27
@ 6bae33c8:607272e8
2024-09-06 08:14:27An odd thing happened — I squinted when opening my laptop this morning so as not to see the final score, but I thought I read a headline saying the Ravens beat the Chiefs. Maybe it was a cached headline from the night before saying what they’d have to do to beat the Chiefs? but I shut the laptop and logged into my Apple TV account to stream the game on the TV, fully expecting the Ravens to win. I mean up until the moment they overturned the Isaiah Likely TD, I thought the Ravens would win. Funny, but not funny because I picked the Ravens in my low-stakes picking pool, and I HATE starting off the week 0-1, no matter the stakes.
In any event, it was an okay game, not great, but there were some interesting takeaways.
-
Derrick Henry looked fine but is going to do almost nothing in the passing game. He had two awkward targets, but Justice Hill was in the game on passing downs and during the end-of-half two-minute drill. Plus Lamar Jackson almost always takes off when he’s in trouble, so if the play isn’t a designed pass to the back, which will be rare for Henry, he’s not getting the ball except via handoff.
-
Jackson looked smooth to me and he’ll have a huge year for as long as he can stay healthy, especially now that Isaiah Likely looks like a real threat. But at 6-2, 205, 16 carries per game is a big ask.
-
Likely looked great. On his long TD, he made great moves, and even on the TD that was overturned, he showed great footwork to make it that close. I’m awfully curious to see where the near-invisible Mark Andrews slips in my NFFC Primetime tonight. (I think Round 8 or so, and I’d have to think about it.)
-
Rashod Bateman had five targets, four of them down the field. He’s their field stretcher, and though it was a quiet day, there should be more.
-
Zay Flowers got 10 targets (good), but it was dink and dunk stuff. To be honest, Likely (12 targets!) looked like the WR1, the alpha running the intermediate routes, Bateman the deep guy and Flowers the midget in the slot.
-
Patrick Mahomes didn’t have a big game, but that was against a top defense and he still got 10.4 YPA. And they were missing one of their field stretchers in Hollywood Brown.
-
Rashee Rice was the story for the Chiefs IMO. He had nine targets and made it look so easy, like Cooper Kupp schemed open on the Rams a few years ago. Xavier Worthy scored twice, but on only three targets even without Brown. He did look awfully fast, though.
-
Isiah Pacheco ran hard against a tough defense, but didn’t do much as a receiver. He’ll be fine — I wouldn’t move his stock much after this game.
-
Travis Kelce had a quiet night, but I wouldn’t read much into it. It’s not like Noah Gray is Likely to take his role.
-
After all these years, I finally ditched the loyal Justin Tucker for a Younghoe, and I feel like a new man. It still brought me no joy to see him miss that 53-yard FG.
-
You have to love Steak League IDP Roquan Smith getting a pick for you opening night.
-
-
 @ 6bae33c8:607272e8
2024-09-20 15:31:21
@ 6bae33c8:607272e8
2024-09-20 15:31:21This was one of those games where I’m grateful to be in Portugal and not catching it in real time. I have Rhamondre Stevenson in one league unfortunately, but none of the prominent players on the Jets (who I don’t have) went crazy, either. And I finally got a Thursday night ATS win in the books. I probably should have used it in the Circa Millions, but I hate submitting the whole slate on Thursday.
-
Aaron Rodgers looks sharp at 40 still. He even moved well in the pocket and scrambled for some yards. The Jets might actually be good.
-
Breece Hall is getting the requisite work (16 carries, five targets), but Braelon Allen (11 carries, 3 targets) looks more or less just as good. On the one hand, Hall won’t dominate the workload the way say Jonathan Taylor or Saquon Barkley might on their respective teams, but on the other, he’ll stay fresh and still get plenty. If Hall goes down, Allen is probably a top-five back instantly.
-
Rodgers spread the ball around, but the Jets tree is pretty narrow: Garrett Wilson, Allen Lazard, Mike Williams, Tyler Conklin and the backs. Wilson had a modest game, but it was a good sign they kept going to him and eventually got him the TD (while he was covered by top corner Christian Gonzalez) even with a big lead.
-
Conklin looks like a top-10 TE right now. I’d expect Williams to overtake Lazard before long as the team’s No. 2 wideout. He’s just better and more explosive.
-
There’s not much to say about the Pats. Antonio Gibson looked okay after Stevenson was pulled following his fumble. DeMario Douglas took Hunter Henry’s place as the lone productive pass catcher. Maybe you could use one of those two in a pinch.
-
It’s time to see more of Drake Maye who looked comfortable and confident in mop-up duty. The circumstances are rough, but Jacoby Brissett is best suited as a stop-gap game-manging backup, not someone who should block real prospect.
-
-
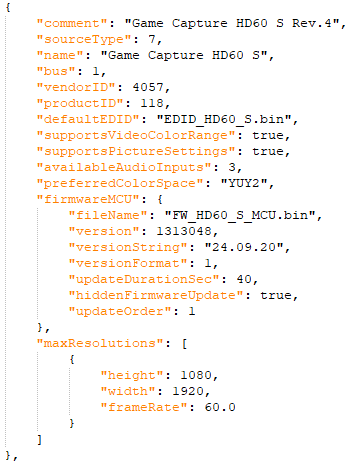
 @ eac63075:b4988b48
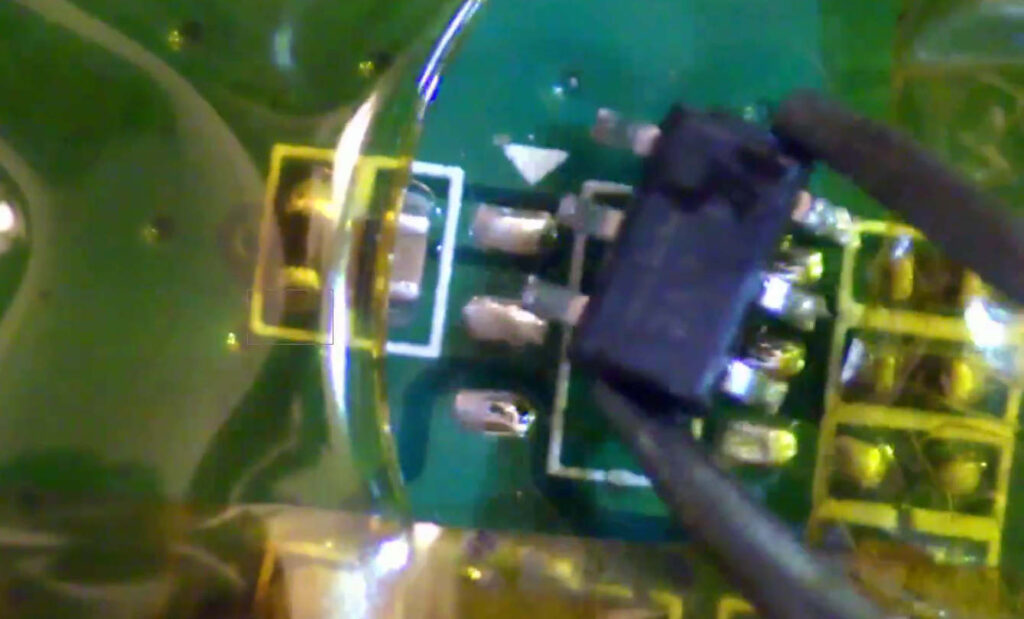
2024-09-20 09:23:23
@ eac63075:b4988b48
2024-09-20 09:23:23Overview of the Infrastructure
- Umbrel/Citadel/RaspiBlitz/Start9 Server
- Purpose: Acts as your personal Bitcoin and Lightning Network node.
- Setup: Installed on a Raspberry Pi 4 running Debian or Umbrel OS.
- Benefits:
- Participate in Bitcoin Consensus: Validates transactions and blocks independently.
- Lightning Network Routing: Facilitates faster transactions and earns routing fees.
- Cold Storage Wallets
- Coldcard: A highly secure hardware wallet designed specifically for Bitcoin.
- Ledger Nano X: A versatile hardware wallet supporting multiple cryptocurrencies.
- Purpose: Store your Bitcoin offline to protect against online threats.
- Secure Devices
- Encrypted Computer: A notebook with encrypted storage for managing your wallets and nodes securely.
- Android Phone with Secure Area:
- Old Device: Repurposed without a SIM card to minimize exposure.
- Secure Area for Apps: Uses features like Samsung's Secure Folder/Knox to isolate sensitive applications.
- NerdMiner
- Purpose: A compact mining device like the Nerdminer V2 to engage in Bitcoin mining.
- Function: Attempts to mine Bitcoin blocks, offering a chance (albeit very low) to earn block rewards and learn about the mining process.
 ### Advantages of This Setup
### Advantages of This Setup- Self-Sovereignty: You have complete control over your funds without relying on third-party services.
- Enhanced Privacy:
- CoinJoin Transactions: Mix your coins with others to obfuscate transaction history.
- No SIM Card Devices: Reduces the risk of SIM swapping attacks.
- Network Participation:
- Consensus Involvement: By running a full node, you help maintain the network's integrity.
- Lightning Network: Improve transaction speeds and network scalability.
- Security:
- Cold Storage: Keeps your private keys offline, away from potential online threats.
- Encrypted Devices: Protects data even if physical devices are lost or stolen.
 ### Simplifying the Perceived Complexity
### Simplifying the Perceived ComplexityWhile the infrastructure may seem daunting, it's more approachable than it appears:
- Starting Point: Use an old computer or phone as a cold wallet with software like Electrum or Sparrow.
- Step-by-Step Setup:
- Begin with setting up the Umbrel/Citadel/RaspiBlitz/Start9 server.
- Gradually add hardware wallets like Coldcard, SeedSigner DIY, Jade, Ledger, Trezor or Onekey.
- Implement security measures on your existing devices.
- Community Resources: Numerous guides and communities are available to assist with each step.
 ### Embracing Freedom and Privacy
### Embracing Freedom and PrivacyPracticing self-sovereignty and custody isn't just about securing your Bitcoin—it's about embracing freedom and privacy in the digital age. By taking control:
- Financial Independence: You're not dependent on banks or exchanges.
- Data Privacy: Your financial data remains confidential.
- Empowerment: Gain a deeper understanding of how Bitcoin and blockchain technology work.
Remember: Even simple steps like using an old device as a cold wallet can significantly enhance your security. The journey towards complete self-sovereignty is a progressive one, and each step you take strengthens your position in the digital world.
-
 @ a012dc82:6458a70d
2024-09-20 05:55:35
@ a012dc82:6458a70d
2024-09-20 05:55:35Table Of Content
-
Bitcoin Beach Wallet Rebrands as Global Shore Wallet
-
Feature-Rich Wallet for Enhanced User Experience
-
Partnerships to Drive Adoption and Education
-
Conclusion
-
FAQ
Bitcoin Beach Wallet, originally developed to support the Bitcoin community in El Salvador, has made significant strides since its inception. The wallet started as a grassroots project aimed at driving Bitcoin adoption in a small coastal town, and has now transformed into a global force. With a new name and a plethora of innovative features, the wallet is set to become a major player in the world of cryptocurrency.
Bitcoin Beach Wallet Rebrands as Global Shore Wallet
As part of the wallet's evolution, it has been rebranded as the Global Shore Wallet. This name change reflects the wallet's expanded focus beyond El Salvador, as it aims to promote Bitcoin adoption and financial inclusion in communities across the globe. The new name signifies a broader commitment to empowering individuals and businesses with a versatile cryptocurrency wallet that caters to their unique needs.
Feature-Rich Wallet for Enhanced User Experience
The Global Shore Wallet comes packed with features designed to enhance the user experience and promote widespread adoption. Some of these exciting new features include:
1. Multilingual Support
To cater to a global audience, the wallet now supports multiple languages, ensuring that users worldwide can navigate and use the wallet with ease.
2. Multi-Currency Compatibility
In addition to Bitcoin, the wallet now supports various cryptocurrencies, such as Ethereum, Litecoin, and more, making it a one-stop solution for users looking to manage multiple digital assets.
3. Lightning Network Integration
To facilitate faster, cheaper, and more scalable transactions, the Global Shore Wallet has integrated the Lightning Network. This upgrade allows users to make instant payments with minimal fees.
4. Advanced Security Features
The wallet offers cutting-edge security features, such as biometric authentication, two-factor authentication, and encrypted backups, ensuring that users' digital assets are well-protected.
5. Seamless Onboarding
The Global Shore Wallet simplifies the onboarding process with a user-friendly interface and step-by-step guidance, making it easy for new users to get started with cryptocurrency.
Partnerships to Drive Adoption and Education
To further its mission of promoting Bitcoin adoption and financial inclusion, the Global Shore Wallet team has entered into strategic partnerships with various organizations. These collaborations aim to provide educational resources and offer support to communities looking to embrace cryptocurrency.
Conclusion
The transformation of the Bitcoin Beach Wallet into the Global Shore Wallet marks an important milestone in the journey towards global cryptocurrency adoption. With a new name, cutting-edge features, and strategic partnerships, the Global Shore Wallet is poised to become a leading wallet solution for individuals and businesses around the world. By fostering financial inclusion and empowering users with the tools they need to thrive in the digital economy, the Global Shore Wallet is set to make a lasting impact on the cryptocurrency landscape.
FAQ
What was the original purpose of the Bitcoin Beach Wallet? The Bitcoin Beach Wallet was initially developed to support the Bitcoin community in El Salvador, focusing on driving Bitcoin adoption in a small coastal town.
What is the new name of the Bitcoin Beach Wallet? The Bitcoin Beach Wallet has been rebranded as the Global Shore Wallet.
Why was the name changed to Global Shore Wallet? The name change reflects the wallet's expanded focus on promoting Bitcoin adoption and financial inclusion in communities across the globe, beyond just El Salvador.
How is the Global Shore Wallet promoting Bitcoin adoption? The Global Shore Wallet is fostering adoption through its user-friendly features, educational resources, and strategic partnerships with organizations to support communities looking to embrace cryptocurrency.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ a30cdfee:2d2f97ff
2024-09-06 06:50:05
@ a30cdfee:2d2f97ff
2024-09-06 06:50:05Orqestra: Converting Business Sales to Bitcoin
Orqestra lets businesses automatically convert portions of their sales to bitcoin!
What is Orqestra and how can it be useful for businesses?
Protect Against Inflation with Bitcoin
Long-term saving in bitcoin is a good way to hedge against inflation.
Not just for individuals, but also for companies.
Case in point: MicroStrategy
Bitcoin's strong liquidity also allows quick conversions to fiat if needed, giving companies financial flexibility.
Converts Portions of Sales to Bitcoin
Orqestra simplifies Bitcoin acquisition, targeting small and medium-sized businesses.
You can connect your payment providers, and the platform will automatically convert portions of your sales to bitcoin.
Start small or go all in, it's up to you!
Orqestra integrates with e.g. PayPal, QuickBooks, Square and Stripe.
You can also link e.g. Clams, a Bitcoin-focused accounting software for automated bookkeeping.
You can learn more about Clams here: https://stacker.news/items/552799
Custodial, but You Can Withdraw to Your Own Wallet
Orqestra states that it partners with industry-leading custodians to store the BTC.
You can also withdraw the BTC to your own wallet, or convert it to US dollars.
The platform is currently only supporting businesses in the United States.
KYC Required
Orqestra was founded by João Almeida, former CTO and co-founder of a Bitcoin payment infrastructure provider OpenNode.
Orqestra can give tax-ready reports that meet industry standards on demand.
To use the platform, businesses need to provide proof of legal existence of the company, proof of address and all beneficiaries with over 25% ownership in the company need to perform KYC.
Project Links
originally posted at https://stacker.news/items/674222
-
 @ c7eadcf0:7821e562
2024-09-06 00:10:23
@ c7eadcf0:7821e562
2024-09-06 00:10:23Who would have thought that we would have the change to buy sub 60K Bitcoin again? With all the talk of mooning after the halving, seeing Bitcoin's price back around 56k at the time of this post is disappointing to the lettuce handed, ETF buying individuals that are not here for the revolution, but to make a quick buck.
Bitcoin being a neutral money, it is not unexpected that it would gain the attention of these types of people. I am actually glad that they are participants in this market has it helps transfer Bitcoin from weak unconverted holders to people who are fully dyed in the orange wool of the Bitcoin thesis.
Every time there is some geopolitical event, or some kind of economic crisis brewing on the other side of the world, Bitcoin normally takes a hit because it is a high liquid asset. This should be taken as a good sign when the price goes down as it shows that you can easily move in and out of Bitcoin with relative ease. Try doing that with your house, car or other assets. Sure you can sell them eventually but its not nearly as seamless as Bitcoin.
This lull in price will not last long, so if you got some dry powder sitting on the sidelines, today is a good day to buy some cheap corn. Framing Bitcoin as a liquid asset that can be sold in times of need is a good way to introduce Bitcoin to your nocoiner friends and family. I would hate for them to have to buy Bitcoin at much higher prices. Good for us. Bad for them. Amirite?
Just a short post from the Obsidian Nostr Writer Plugin. If you like writing long from content, I would highly recommend giving it a shot! Peace out.
-
 @ acc925af:db9fb0bb
2024-09-05 20:26:50
@ acc925af:db9fb0bb
2024-09-05 20:26:50While tinkering about NWC and twitter I decided to hack a python script that might perhaps begin something good
Here's a high-level overview of how you could connect your Twitter account to a Nostr Wallet using NWC and automate a 21 satoshi payment for every like:
Prerequisites:
- Twitter Developer Account
- Nostr Wallet with NWC support (e.g., Alby, Nostrify)
- Twitter API credentials (API key, API secret key, Access token, Access token secret)
- Python script with Tweepy (Twitter API library) and nostr-client (Nostr library)
Step 1: Set up Twitter API credentials
Create a Twitter Developer account and obtain API credentials Install Tweepy using pip: pip install tweepy
Step 2: Connect Nostr Wallet using NWC
Choose a Nostr Wallet with NWC support (e.g., Alby, Nostrify) Set up the wallet and obtain the NWC credentials (e.g., public key, private key)
Step 3: Create a Python script
Import Tweepy and nostr-client libraries Authenticate with Twitter API using Tweepy Connect to Nostr Wallet using NWC credentials Define a function to send 21 satoshis for every like Use Tweepy to stream likes and trigger the payment function
Pythonscript:``` import tweepy from nostr_client import Client
Twitter API credentials
twitter_api_key = "YOUR_API_KEY" twitter_api_secret_key = "YOUR_API_SECRET_KEY" twitter_access_token = "YOUR_ACCESS_TOKEN" twitter_access_token_secret = "YOUR_ACCESS_TOKEN_SECRET"
Nostr Wallet NWC credentials
nwc_public_key = "YOUR_NWC_PUBLIC_KEY" nwc_private_key = "YOUR_NWC_PRIVATE_KEY"
Set up Tweepy
auth = tweepy.OAuthHandler(twitter_api_key, twitter_api_secret_key) auth.set_access_token(twitter_access_token, twitter_access_token_secret) api = tweepy.API(auth)
Set up Nostr Client
nwc_client = Client() nwc_client.connect(nwc_public_key, nwc_private_key)
Define payment function
def send_satoshis(): # Create a new Nostr event with 21 satoshis event = nwc_client.create_event(21) # Send the event to the Nostr network nwc_client.send_event(event)
Stream likes and trigger payment function
class LikeStream(tweepy.StreamListener): def on_like(self, like): send_satoshis()
stream = tweepy.Stream(auth, LikeStream()) stream.filter(track=["likes"])
```
Please note that this is a simplified example and may require additional error handling, security measures, and modifications to work as intended.
originally posted at https://stacker.news/items/673795
-
 @ 502ab02a:a2860397
2024-09-20 02:30:23
@ 502ab02a:a2860397
2024-09-20 02:30:23
มีเรื่องจะประกาศครับ ถ้าสามารถแชร์ออกไปได้ก็ยินดีมากครับ
เป็นความตั้งใจตั้งแต่ก่อนงาน Thailand Bitcoin Conference 2024 ว่าจะเป็นงานสุดท้ายที่ผมจะใช้คำว่า ขนมคีโต
ตลอดเส้นทางที่ผ่านมา หมวกอีกใบนึงของผมคือ การถ่ายทอดความรู้ที่ศึกษามาในแขนงโภชนาการ และคำถามตลอดกาลคือ "อันไหนเป็นอาหารคีโต"
จริงอยู่ครับก็ยินดีตอบให้ได้ แต่ลึกๆมันก็มีความขุ่นๆนิดๆว่า หากเป็นขวบปีแรกของคีโตก็ยังพอเข้าใจ แต่ขณะนี้ก้าวเข้าวปีที่ 8 แล้ว อีกไม่เท่าไรก็ 10ปีคีโตในไทยแล้ว สิ่งแรกที่คนคีโตมองหาเวลาซื้ออาหารคือ ฉลากคีโต
แล้วพอเจอบางสินค้าแปะป้ายคีโต แต่มีวัตถุดิบที่ต่างจากกูรูต่างจากเจ้าพ่อเจ้าแม่คีโต ได้บัญญัติไว้ ก็เกิดความสับสนวุ่นวายทะเลาะเบาะแว้ง ว่าตกลงมันเป็นอาหารคีโตหรือไม่
ผมเลือกทางนี้ครับ หักดิบไปเลย
ต่อไปนี้ผมจะไม่ใส่คำว่า คีโต ในชื่อเรียกอาหาร ต่อไปนี้จะไม่มีชีสเค้กคีโต ดาร์คชอคกานาซคีโต หน้าไก่คีโต บลาบลาบลา ที่มีคีโตเป็นชื่อเรียก อีกต่อไปครับ พอกันทีกับสิ่งนี้
ของกินทุกอย่างที่ผมทำ จะใช้ความเชี่ยวชาญด้านโภชนาการ ความสะอาด สุขอนามัย ฉลากสารอาหาร ใช้การคำนวนแบบเผื่อข้อผิดพลาด(บวก ไม่ลบ) ด้วยการใส่ Macro Nutrient ให้ในทุกเมนู !!!!
เพราะผมเชื่อว่า การกินคาร์บต่ำ เป็นการกินแบบ "ปกติ" การกินคาร์บมากก็เป็นการกินแบบ "ปกติ" เหมือนคนไม่ชอบกินผิก ไม่ชอบกินปลา ไม่ชอบกินเนื้อ อันนี้มันก็แค่คนไม่ชอบกินคาร์บสูงเกินไป แค่นั้นครับ เป็นการกินแบบปกติ ย้ำ เป็นการกินแบบปกติ คาร์บต่ำแบบคีโต เป็นการกินแบบปกติ ที่ควรเป็นมานานแล้วด้วย
การยัดทะนานคาร์บสูงมากๆ ในมุมมองผมคือ นี่แหละที่ไม่ปกติ
ทีนี้ความไม่ปกตินี้มันก็ไม่ผิดอะไรด้วย ถ้าคนกินไม่ปกติ นิยามไม่ปกติคือ ไม่ใช่คนทั่วๆไปเช่น นักกล้าม นักกีฬา ผู้ที่ใช้ "พลังงาน" สูงมากๆแลละต้องการใช้คาร์บ เพื่อการใดการหนึ่งโดยเฉพาะ ดังนั้นไม่มีอะไรที่ผิดเลยครับ ใครอยากกินอะไร กิน ตราบใดที่เรารู้ตัวเราเองว่าทำอะไร
ผมอยู่ในวงการธุรกิจทั้งอาหารและการโฆษณา เข้าใจดีครับว่าการแปะป้ายคีโต คือการช่วยให้คนตัดสินใจง่ายขึ้น เข้าใจง่ายขึ้น ช่วยในการขายให้สะดวกขึ้น แต่ ผมพอแล้วครับ เหรียญอีกด้านนึงของป้ายนีคือ มันไม่ได้ช่วยให้คนคีโต เรียนรู้การทำความเข้าใจด้านสารอาหารเท่าที่ผมคาดหวัง เพราะถ้าไม่มีป้ายพวกนี้ คนคีโตหลายๆคนถึงกับไปไม่เป็นกันเลยทีเดียว แล้วทุกวันนี้เหรียญมันออกด้านนี้ซะเยอะด้วย
นอกจากนี้ประเด็นที่หลีกไม่ได้คือ การหมอบคลานเข้ารับวัตถุดิบคีโตจากกูรู ซึ่งไม่เคยได้เหตุผลในการ "ห้าม" ของหลายๆอย่างเช่น สารหวานบางประเภท แครอท ฟักทอง(ตัวนี้มีคนถามและส่งมาให้ดูเยอะ เดี๋ยวจัดให้เคลียร์ๆ)
ซึ่งใครที่เลือกกินสิ่งนี้แล้วแชร์ความรู้ให้คนคีโตว่ากินได้ ก็จะโดนตรรกะวิบัติจากกูรูด้วยการแปะคำว่า "อยากกิน เลยชวนคนอื่นกิน ชวนคนให้ไม่เคร่ง" เป็นตรรกะวิบัติที่เรียกว่า Ad Hominem หรือ การโจมตีที่ตัวบุคคล นั่นเอง (ref : https://siripun.com/2023/06/09/logical-fallacies-2-ad-hominem ) ทั้งที่ถ้าจะนิยามคำว่าเคร่ง สิ่งที่กูรูให้ทำ ไม่สามารถมีคำตอบที่สร้างสมการสมดุลได้ (ทำไม A ได้แล้ว B ไม่ได้ถ้าเทียบบริบทเอามาชนกันชัดๆเลย)
จริงๆก็อยากรณรงค์ให้ผู้ประกอบการอาหารคีโต ร่วมโครงการนี้ แต่เข้าใจว่ามันคงไม่สามารถทำได้ เพราะอาจจะมองในมุมที่ต่างกัน ผมเข้าใจในสิ่งนั้นครับ แต่มุมของผมคือ การทำอาหารคีโตให้กลับมาอยู่ในประเภทอาหารปกติ จะยิ่งขยายมูลค่าตลาดออกไปได้มากกว่าทุกวันนี้
ตลาดคีโตมันซบเซา เพราะเราทำให้มัน "ประหลาด" ทำให้มันกลายเป็นของ "ไม่ปกติ" พอได้น้ำหนัก หุ่น ลูก สมปรารถนาแล้วก็ถวิลหาการ "ออกไปกินปกติ" นั่นคือการทำให้ตลาดหายไปเรื่อยๆเพราะพวกคุณเองครับ ผมกลับมองว่าทำให้คีโตคืออาหารปกติ แล้วกินกันไปตลอด ไม่มีการขอออกจากเผ่า หานเป็ดอะไรคือทางที่ดีกว่า ได้สุขภาพที่ดีกว่า
คีโตคือการกินปกติ ไม่ควรต้องมาแยกเป็นชนเผ่าอะไรเลย คีโตคือคนเมือง คนมีความรู้ คือ วิทยาศาสตร์ คือความฉลาดในการเลือกสารอาหาร อย่าไปยัดเยียดความ "ไม่ปกติ" ให้อาหาร "ปกติ"
ก็เลยคิดว่า ไม่เป็นไร ร้านคีโตร้านใดอยากร่วมเรายินดี แต่ถ้ามองว่าไม่เอาด้วยก็ยินดีเหมือนกัน เพราะการค้าเสรี อยากทำอะไรก็ทำได้ครับ ในส่วนตัวผม เราทำของเรา เราเริ่มของเราเลยก็ได้ เพราะเส้นทางที่ผ่านมา เราก็เดินอยู่ในเส้นทางของเราอยู่แล้ว และผมเชื่อใน Proof of Work ครับ ผมสามารถทุ่มแรงกายแรงใจ ลงในอาหาร ลงในการสอน ให้คนตระหนักถึง "สารอาหาร" มากกว่า "ป้ายฉลาก"
แล้ววันนึง มันจะส่งผลที่ impact ครับ ผมเชื่ออย่างนั้น Proof of Work สามารถส่งต่อได้ และ พลิกโลกได้ มานับต่อนับแล้ว
ทุกวันนี้ผมทุ่มเนื้อหาด้าน ฉลากอาหาร เพื่อให้คนหัดอ่าน รู้เท่า รู้ทัน มันก็ทำให้ผมยิ่งรู้สึกว่า ผมไม่ควรแปะคำว่าคีโต ลงไปเลย มันเหมือนไปสปอยให้คนลืมพื้นฐานสำคัญ
ไม่ใช่ว่าไม่ง้อคนคีโตนะ คนทำการค้าต้องยินดีกับทุกการค้าอยู่แล้ว แต่ผมกลับมมองว่า ตลาดของผมขอเป็นตลาดที่มีการอ่านฉลาก มีการหัดพิจารณาสารอาหาร ดูคาร์บเป็น เลือกวัตถุดิบที่เหมาะกับแต่ละคน มากกว่าวัตถุดิบที่ต้องได้รับการโปรดจากกูรู
ผมมองว่า คนกินคลีน คนกินไฮโปรตีน หรือแม้แต่แค่คนที่ไม่อยากกินน้ำตาล ก็จะสามารถกินอาหารที่ผมทำได้ ไม่โดนปิดกั้นจากป้ายคีโต ที่โลกประเคน mind set ให้ว่าต้อง high fat เท่านั้น
ซึ่งถ้าผมทำอาหารในแบบของผม + คนกินพิจารณาได้เองว่าสารอาหารเหมาะกับเขาไหม = การกินแบบมีความรู้จริง เหมาะกับตัวเองจริงๆ
ถือว่าเป็นอีกเส้นทางที่ผมต้อง fight for ครับ ถ้าสำเร็จ มันจะช่วยให้คนในสังคมหลุดกรอบ และมองสารอาหารได้ ดูแลสุขภาพได้ ด้วยพื้นฐานความรู้ที่มากขึ้นครับ ไม่ใช่ทางที่สบายแน่นอนครับ แต่พวกคุณจะได้ประโยชน์ติดตัวไปแน่ๆ
ถามว่าทำเพื่อการค้าใช่ไหม ก็ใช่ครับ การค้ามันคู่กับโลก ผมไม่ค่อยเข้าใจในมุมของการต้องการอะไรฟรีๆอยู่ตลอด ถ้าคุณเคารพใน value แล้วยินดีส่งต่อ value for value คุุณจะยินดีในการค้าที่ไม่ยัดเยียด (fiat) คุณจะยินดีในการส่งต่อ value ด้วยคุณค่า คุณจะยินดีในการมองคุณค่าของ "เวลา" ที่ผู้สร้างผู้ทำลงทุนลงไป (เวลาคือทรัพยการที่มีค่าที่สุดในโลก) แล้วถ้าคุณให้เกียรติกับสิ่งเหล่านี้ คุณจะไม่อยากได้มันฟรีๆ คุณจะกระดากใจที่จะหยิบมันมาเปล่าๆ นี่คือเหตุผลที่ผมไม่เคยมองว่า การทำการค้า มันจะเลวร้ายอะไร แต่ที่แน่ๆ ผมจะไม่ทำ FIAT keto ครับ ผมจะไม่เร่งเร้า ไม่ขู่เข็ญ ไม่ใช้ตรรกะประเภท "ของมันต้องมี" ผมจะแบไต๋แฟร์ๆด้วยสารอาหารครับ
แม้มันจะแลกมาด้วยการขาดโอกาส จากป้าย "คีโต" ก็ตาม แม้คนคีโตจะมองว่า ไม่มีป้ายคือไม่คีโตก็ตาม แม้จะไม่ได้รับการรับรองจากกูรูใดๆ ว่า "คีโตกินได้" ก็ตาม ถ้าจะให้สังคมมีการเรียนรู้สารอาหารขึ้นได้ ผมยอม
pirateketo #ตำรับเอ๋ #siripun #siamstr
-
 @ 8cb60e21:5f2deaea
2024-09-05 19:48:32
@ 8cb60e21:5f2deaea
2024-09-05 19:48:32Part 3: Asynchroni et DOM Manipulatio
3.1 Promissa et Async/Await
Praesent blandit. Nam nulla. Integer pede justo, lacinia eget, tincidunt eget, tempus vel, pede.
``javascript function simulaRequest(data, probabilitasErroris = 0.1) { return new Promise((resolve, reject) => { setTimeout(() => { if (Math.random() < probabilitasErroris) { reject("Error: Aliquid mali accidit"); } else { resolve(Data accepta: ${data}`); } }, 1000); }); }simulaRequest("Lorem ipsum") .then((responsum) => console.log(responsum)) .catch((error) => console.error(error));
async function fetchData() { try { const responsum = await simulaRequest("Dolor sit amet"); console.log(responsum); } catch (error) { console.error(error); } }
fetchData(); ```
3.2 DOM Manipulatio
Morbi non lectus. Aliquam sit amet diam in magna bibendum imperdiet. Nullam orci pede, venenatis non, sodales sed, tincidunt eu, felis.
```javascript document.addEventListener("DOMContentLoaded", () => { const titulus = document.createElement("h1"); titulus.textContent = "Lorem Ipsum JavaScript"; document.body.appendChild(titulus);
const paragraphus = document.createElement("p"); paragraphus.textContent = "Neque porro quisquam est qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit..."; document.body.appendChild(paragraphus); const button = document.createElement("button"); button.textContent = "Fac Clic Me"; button.addEventListener("click", () => { alert("Gratias tibi ago pro clic!"); }); document.body.appendChild(button);}); ```
3.3 Fetch API
Maecenas leo odio, condimentum id, luctus nec, molestie sed, justo. Pellentesque viverra pede ac diam.
``javascript async function fetchLoremIpsum() { try { const responsum = await fetch("https://api.lorem.space/image/game?w=150&h=220"); if (!responsum.ok) { throw new Error(HTTP error! status: ${responsum.status}`); } const data = await responsum.blob(); const imago = document.createElement("img"); imago.src = URL.createObjectURL(data); document.body.appendChild(imago); } catch (error) { console.error("Problema cum fetching imagine:", error); } }fetchLoremIpsum(); ```
3.4 Local Storage
Cras mi pede, malesuada in, imperdiet et, commodo vulputate, justo. In blandit ultrices enim.
```javascript function salvaPreferentias(clavis, valor) { localStorage.setItem(clavis, JSON.stringify(valor)); }
function accipePreferentias(clavis) { const valor = localStorage.getItem(clavis); return valor ? JSON.parse(valor) : null; }
const preferentiae = { thema: "clarus", lingua: "Latina", notificationes: true };
salvaPreferentias("userPrefs", preferentiae);
const salvataePreferentiae = accipePreferentias("userPrefs"); console.log(salvataePreferentiae); ```
3.5 Exercitia Parti III
- Crea paginam web simplicem quae utitur fetch API ad exhibendum datos ex API publica.
- Implementa functionalitatem "drag and drop" utens DOM API.
- Construe applicationem "todo list" quae persistit datos in local storage.
Conclusio
Vivamus vestibulum sagittis sapien. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Etiam vel augue. Vestibulum rutrum rutrum neque. Aenean auctor gravida sem. Praesent id massa id nisl venenatis lacinia. Aenean sit amet justo. Morbi ut odio.
Cras mi pede, malesuada in, imperdiet et, commodo vulputate, justo. In blandit ultrices enim. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Proin interdum mauris non ligula pellentesque ultrices. Phasellus id sapien in sapien iaculis congue. Vivamus metus arcu, adipiscing molestie, hendrerit at, vulputate vitae, nisl.
Aenean lectus. Pellentesque eget nunc. Donec quis orci eget orci vehicula condimentum. Curabitur in libero ut massa volutpat convallis. Morbi odio odio, elementum eu, interdum eu, tincidunt in, leo. Maecenas pulvinar lobortis est.
Phasellus sit amet erat. Nulla tempus. Vivamus in felis eu sapien cursus vestibulum. Proin eu mi. Nulla ac enim. In tempor, turpis nec euismod scelerisque, quam turpis adipiscing lorem, vitae mattis nibh ligula nec sem. Duis aliquam convallis nunc. Proin at turpis a pede posuere nonummy.
Integer non velit. Donec diam neque, vestibulum eget, vulputate ut, ultrices vel, augue. Vestibulum ante ipsum primis in faucibus orci luctus et ultrices posuere cubilia Curae; Donec pharetra, magna vestibulum aliquet ultrices, erat tortor sollicitudin mi, sit amet lobortis sapien sapien non mi. Integer ac neque. Duis bibendum. Morbi non quam nec dui luctus rutrum. Nulla tellus. In sagittis dui vel nisl. Duis ac nibh. Fusce lacus purus, aliquet at, feugiat non, pretium quis, lectus.
Suspendisse potenti. In eleifend quam a odio. In hac habitasse platea dictumst. Maecenas ut massa quis augue luctus tincidunt. Nulla mollis molestie lorem. Quisque ut erat. Curabitur gravida nisi at nibh. In hac habitasse platea dictumst. Aliquam augue quam, sollicitudin vitae, consectetuer eget, rutrum at, lorem. Integer tincidunt ante vel ipsum. Praesent blandit lacinia erat. Vestibulum sed magna at nunc commodo placerat. Praesent blandit. Nam nulla.
-
 @ 8cb60e21:5f2deaea
2024-09-05 19:48:32
@ 8cb60e21:5f2deaea
2024-09-05 19:48:32Part 1: Fundamentum Javascripti
1.1 Introductionis
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nullam euismod, nisi vel consectetur interdum, nisl nunc egestas nunc, vitae tincidunt nisl nunc euismod nunc. Sed euismod, nisi vel consectetur interdum, nisl nunc egestas nunc, vitae tincidunt nisl nunc euismod nunc.
javascript console.log("Salve, mundi!");1.2 Variabiles et Typi Datorum
Pellentesque habitant morbi tristique senectus et netus et malesuada fames ac turpis egestas. Integer convallis, nunc ac blandit tincidunt, ipsum augue tincidunt nunc, vitae tincidunt nisl nunc euismod nunc.
javascript var numerus = 42; let textus = "Lorem ipsum"; const CONSTANTIA = true;1.2.1 Typi Numerorum
Curabitur in libero ut massa volutpat convallis. Morbi odio odio, elementum eu, interdum eu, tincidunt in, leo.
javascript let integer = 10; let floatinum = 3.14; let scientificum = 2.998e8;1.2.2 Typi Textuum
Maecenas tristique, est et tempus semper, est quam pharetra magna, ac consequat metus sapien ut nunc.
javascript let textusBrevis = 'Carpe diem'; let textusLongus = "Quod erat demonstrandum"; let textusTemplatum = `Cogito, ${textusBrevis.toLowerCase()}, sum`;1.3 Operatores
Donec dapibus. Duis at velit eu est congue elementum. In hac habitasse platea dictumst.
```javascript let a = 5; let b = 3;
console.log(a + b); // Additio console.log(a - b); // Subtractio console.log(a * b); // Multiplicatio console.log(a / b); // Divisio console.log(a % b); // Modulus console.log(a ** b); // Potentia ```
1.4 Structurae Controli
Morbi non lectus. Aliquam sit amet diam in magna bibendum imperdiet. Nullam orci pede, venenatis non, sodales sed, tincidunt eu, felis.
1.4.1 Conditionales
```javascript let aetas = 20;
if (aetas >= 18) { console.log("Adultus es"); } else if (aetas >= 13) { console.log("Adolescens es"); } else { console.log("Puer es"); } ```
1.4.2 Iterationes
``javascript for (let i = 0; i < 5; i++) { console.log(Iteratio ${i}`); }let j = 0; while (j < 5) { console.log(
Dum iteratio ${j}); j++; } ```1.5 Exercitia Parti I
- Scribe programma quod convertat gradus Celsius in Fahrenheit.
- Crea algorithmum qui determinat si numerus est par vel impar.
- Implementa "FizzBuzz" pro numeris 1 ad 100.
-
 @ 8cb60e21:5f2deaea
2024-09-05 19:48:32
@ 8cb60e21:5f2deaea
2024-09-05 19:48:32Part 2: Functiones et Objecta
2.1 Functiones
Fusce posuere felis sed lacus. Morbi sem mauris, laoreet ut, rhoncus aliquet, pulvinar sed, nisl.
``javascript function salutatio(nomen) { returnSalve, ${nomen}!`; }console.log(salutatio("Cicero"));
const valedictio = (nomen) => { console.log(
Vale, ${nomen}!); };valedictio("Seneca"); ```
2.1.1 Parametri Default et Rest
Nunc purus. Phasellus in felis. Donec semper sapien a libero.
``javascript function congregatio(primus, secundus = "mundi", ...ceteri) { console.log(${primus} ${secundus}); console.log(Ceteri: ${ceteri.join(", ")}`); }congregatio("Salve"); congregatio("Lorem", "ipsum"); congregatio("Veni", "vidi", "vici", "et", "cetera"); ```
2.2 Objecta
Nam congue, risus semper porta volutpat, quam pede lobortis ligula, sit amet eleifend pede libero quis orci.
``javascript const persona = { nomen: "Iulius", cognomen: "Caesar", aetas: 55, salutatio: function() { returnSalve, ${this.nomen} ${this.cognomen}!`; } };console.log(persona.salutatio()); ```
2.2.1 Methodi Object
Nullam porttitor lacus at turpis. Donec posuere metus vitae ipsum. Aliquam non mauris.
```javascript const claves = Object.keys(persona); console.log(claves);
const valores = Object.values(persona); console.log(valores);
const paria = Object.entries(persona); console.log(paria); ```
2.3 Arrays
Morbi porttitor lorem id ligula. Suspendisse ornare consequat lectus. In est risus, auctor sed, tristique in, tempus sit amet, sem.
```javascript const fructus = ["malum", "pirum", "uva", "cerasum"];
fructus.forEach((fructus) => { console.log(fructus); });
const longiFructus = fructus.filter((fructus) => fructus.length > 4); console.log(longiFructus);
const maiusculaFructus = fructus.map((fructus) => fructus.toUpperCase()); console.log(maiusculaFructus); ```
2.4 Exercitia Parti II
- Crea functionem quae calculat factorialem numeri.
- Implementa methodum quae invenit maximum valorem in array.
- Scribe programma quod ordinat objecta in array secundum proprietatem specificam.
-
 @ db95cd8e:399d79e2
2024-09-19 22:09:14
@ db95cd8e:399d79e2
2024-09-19 22:09:14Hello [[Nostr]]! For my first post, an introduction feels appropriate with [[Nostr]], but why is that? Why do so many of us talk about our discovery of [[Nostr]] like we just discovered the next best thing? We don't act that way with any other social media.
Simply, I think it is because we have discovered the next best thing. And not just the next best thing, but the thing that will change online communication forever.
[[Nostr]] revolutionizes social media and is fundamentally different from anything else due to how our information is shared through relays and different clients instead of a single source. This change alone has the potential to disrupt current social media, and is the path forward to [[Freedom]] communication channels for the world.
My journey to [[Nostr]] started with [[Bitcoin]]. I first heard about [[Bitcoin]] in 2020, but didn't really start learning about it until late 2021. I heard about [[Nostr]] from the [[Bitcoin]] influencers and podcasters I listened to. My understanding of how #Bitcoin worked was fundamental to me understanding [[Nostr]] and it's importance. The #Freedom provided by these two beautiful inventions is set to change the world in a way we can't fully see yet.
The note app Obsidian is also a big part of this start for me. I’ve wanted to improve and organize my thoughts for a long time, as well as learn better ways to articulate my thoughts. I found Obsidian, and there is a community plugin to publish notes directly to [[Nostr]].
So this is the start of my journey with the future of social media and communication.
- Jared
-
 @ e8b86bc1:3503c58f
2024-09-05 19:38:11
@ e8b86bc1:3503c58f
2024-09-05 19:38:11Opinion about Freewallet Multi Crypto Wallet (iphone)
Another method Freewallet uses to rob customers: inactivity fees. They charge you for not using the app, wiping out your assets slowly. Avoid Freewallet!
WalletScrutiny #nostrOpinion
-
 @ 8cb60e21:5f2deaea
2024-09-19 22:09:05
@ 8cb60e21:5f2deaea
2024-09-19 22:09:05 -
 @ 8cb60e21:5f2deaea
2024-09-19 21:25:34
@ 8cb60e21:5f2deaea
2024-09-19 21:25:34 -
 @ 8cb60e21:5f2deaea
2024-09-19 20:54:23
@ 8cb60e21:5f2deaea
2024-09-19 20:54:23Python Introduction Guide
1. What is Python?
Python is a high-level, interpreted programming language known for its simplicity and readability. It's widely used in various fields, including web development, data science, artificial intelligence, and more.
2. Installing Python
Visit python.org to download and install the latest version of Python for your operating system.
3. Your First Python Program
Open a text editor and type:
python print("Hello, World!")Save this as
hello.pyand run it from the command line:python hello.py4. Basic Syntax
Variables and Data Types
```python
Strings
name = "Alice"
Integers
age = 30
Floats
height = 5.5
Booleans
is_student = True ```
Lists
python fruits = ["apple", "banana", "cherry"] print(fruits[0]) # Outputs: appleDictionaries
python person = { "name": "Bob", "age": 25, "city": "New York" } print(person["name"]) # Outputs: Bob5. Control Flow
If statements
python age = 18 if age >= 18: print("You're an adult") elif age >= 13: print("You're a teenager") else: print("You're a child")Loops
```python
For loop
for i in range(5): print(i)
While loop
count = 0 while count < 5: print(count) count += 1 ```
6. Functions
```python def greet(name): return f"Hello, {name}!"
message = greet("Alice") print(message) # Outputs: Hello, Alice! ```
7. Modules
Python has a vast standard library and many third-party packages. You can import them like this:
python import math print(math.pi) # Outputs: 3.1415926535897938. Exception Handling
python try: result = 10 / 0 except ZeroDivisionError: print("Error: Division by zero!")9. Classes and Objects
```python class Dog: def init(self, name): self.name = name
def bark(self): return f"{self.name} says Woof!"my_dog = Dog("Buddy") print(my_dog.bark()) # Outputs: Buddy says Woof! ```
10. Next Steps
- Practice writing small programs
- Explore the Python standard library
- Learn about virtual environments and package management with pip
- Dive into specific areas like web development (Django, Flask) or data science (NumPy, Pandas)
Remember, the best way to learn Python is by writing code. Happy coding!
-
 @ e968e50b:db2a803a
2024-09-05 19:33:33
@ e968e50b:db2a803a
2024-09-05 19:33:33ATTENTION PARENTS!
I have revamped my LNBITS bitcoin piggy bank so you don't need to deploy it yourself. Check it out at http://bitcoinpiggybank.vercel.app. All you need now is a LNBITS wallet. I've deployed a website that you can just log into with that and nothing else. I'm thinking about actually renting out my own domain for this one if people find it useful.
https://www.youtube.com/watch?v=X-MNqJiLCM4
Teach your kids about sound money while they're actually stacking sats and using a fun interface.
originally posted at https://stacker.news/items/673739
-
 @ e968e50b:db2a803a
2024-09-05 14:06:11
@ e968e50b:db2a803a
2024-09-05 14:06:11The squeaky wheel gets the persistent state. @WeAreAllSatoshi asked me a couple of times to make it so you can walk away from the weekly crossword puzzle, cuss it out in frustration, bang your head against the wall, CLOSE THE BROWSER, and then continue where you left off.
Now that dream is a reality. All previous and future crossword puzzles now use local storage to plant ~~malware~~ your progress directly into your browser. Here's a recap of the current state of the unofficial, probably unwelcome, and certainly inaccurately titled weekly stacker crossword puzzle.
Week 1 - bounty claimed by @OneOneSeven Week 2 - bounty claimed by @OneOneSeven Week 3 - bounty claimed by @SimpleStacker Week 4 - bounty claimed by @grayruby Expect Week 5 in the next couple of weeks!
If you still want to solve more crossword puzzles by bitcoiners, here's an educational one with a much better ui by @handsome_latino.
Have fun!
originally posted at https://stacker.news/items/673339
-
 @ 8cb60e21:5f2deaea
2024-09-19 20:46:05
@ 8cb60e21:5f2deaea
2024-09-19 20:46:05Markdown Cheatsheet
Headers
H1
H2
H3
H4
H5
H6
Emphasis
italic or italic bold or bold bold italic or bold italic ~~strikethrough~~
Lists
Unordered
- Item 1
- Item 2
- Subitem 2.1
- Subitem 2.2
Ordered
- First item
- Second item
- Third item
Links
Images


Blockquotes
This is a blockquote
It can span multiple lines
Code
Inline
codehas back-ticks around it.Code blocks are fenced by three back-ticksHorizontal Rule
Tables
| Header 1 | Header 2 | Header 3 | |----------|----------|----------| | Row 1, Column 1 | Row 1, Column 2 | Row 1, Column 3 | | Row 2, Column 1 | Row 2, Column 2 | Row 2, Column 3 |
Task Lists
- [x] Completed task
- [ ] Uncompleted task
Footnotes
Here's a sentence with a footnote. [^1]
[^1]: This is the footnote.
Escaping Characters
*This text is surrounded by literal asterisks*
-
 @ 361d3e1e:50bc10a8
2024-09-19 15:52:59
@ 361d3e1e:50bc10a8
2024-09-19 15:52:59An attack on Belarus will be the beginning of the Third World War
usa #belarus #russia #ukraine #war #politics
-
 @ 472f440f:5669301e
2024-09-04 22:54:11
@ 472f440f:5669301e
2024-09-04 22:54:11For the last few months many people in bitcoin, myself included, have been focused on bitcoin's role as a macroeconomic asset. Bitcoin as a strategic reserve for the US government. Bitcoin as a strategic treasury asset for corporations. Bitcoin as a geopolitical hedge in a world that is trending toward a multi-polar power dynamic. This is where the focus has been. And for good reason. These trends will ultimately have a material effect on the price of bitcoin if they pick up steam.
However, with all of the focus on bitcoin as a strategic asset I think a couple of technical developments and trends have been overlooked. Particularly in the realm of second layer privacy. I'll touch on two of them in this letter; BOLT 12 invoices and the progression of ecash.
Yesterday afternoon the Strike (a company Ten31 is very proud to be backing) team released a blog post that detailed their journey to implementing BOLT 12 offers in their product stack. For those who are unaware of BOLT 12 and why it is important, in short, it is an upgrade to the lightning network that would make receiving bitcoin on the lightning network more private while also significantly improving the user experience. The current standard for invoicing people via the lightning network is BOLT 11, which forces users to create a unique invoice every time they want to receive bitcoin and comes with privacy tradeoffs for the party receiving bitcoin.
BOLT 12 brings with it route blinding which allows a receiver to publish a lightning offer to the network without revealing their node's public key. It also brings with it onion messaging, which allows users of the lightning network to communicate without a dependence on HTTP, which can be censored by a motivated state actor. On top of this, it enables users to create a static invoice that can be paid multiple times by multiple people. Think of a band putting their Venmo or Cash App QR code next to their tip jar on the stage. They'll be able to add a private lightning invoice their audience can pay to now.
https://strike.me/blog/bolt12-offers/
As it stands right now, Strike has only enabled BOLT 12 offers and there is work to do at the protocol layer of lightning and the different implementations of that protocol to get the full benefits of BOLT 12, but this is material progress that gets us closer to a significantly better user experience on the lightning network. If you read Strike's blog post you'll come to appreciate the collaboration between the teams working on these implementations and the companies implementing the protocol that is necessary to get these features live. Shout out to everyone who worked on this. Everyone who uses the lightning network will be better off when BOLT 12 is fully implemented.
Moving on. Earlier today the founder of the BTCPay Server open source project, Nicolas Dorier, published a blog post outlining his thoughts on how ecash has the potential to solve problems that many have tried to solve by launching their own blockchains in the past. The problem with trying to "blockchain the world" is that blockchains are very inefficient and only really work for one application; enabling a peer-to-peer digital cash system with no trusted third parties (i.e., bitcoin). However, the ultimate goals of the thousands of blockchain projects that spun up in bitcoin's wake are desirable. Cheap, private and instant transactions. The ability to trivially spin up private money tokens suited for very particular use cases. Overall great UX that makes it easy for people to realize the benefits of "blockchain technology".
The problem that has existed to date is that you don't need a blockchain for all of these things. In fact, having a blockchain for these things proves to be detrimental to their ultimate goals. Instead, what people really need is a protocol that gives you the granular control, privacy, instantaneous transactions and UX that anchors to bitcoin. This is exactly what Chaumian Mints bring to the bitcoin stack.
This is something that we've been screaming about for more than seven years in this rag. Now with ecash protocols like Cashu and Fedimint maturing, gaining traction and bringing products to market that highlight the power and flexibility of ecash systems, people are beginning to see the promise. It is only a matter of time before more and more people begin to realize this potential.
Another benefit of ecash protocols is the fact that they are siloed from each other. Ecash mints are permissionless; any one person or group of people can spin them up, offer their preferred services and maintain (or fail to maintain) their mints. The failure of one mint is not a systemic risk to other mints. This is very different from token projects that are spun up on blockchains. The last ten years have proven that individual token projects can prove to be systemic problems for individual blockchains (i.e., The DAO token on Ethereum). Being able to silo mints is the only way to ensure that the utility of ecash overall is actually scalable and robust.
Don't get so distracted by the bitcoin macro talk that you miss out on the incredible technical developments happening on top of and adjacent to bitcoin.
Final thought... Vibes are high.
-
 @ e6fbeb1c:6ac8fc04
2024-09-04 17:29:17
@ e6fbeb1c:6ac8fc04
2024-09-04 17:29:17When I have stale bread, I often use it to make a bread salad.
The base is croutons of stale bread and then there are no limits to your imagination.
In this salad there was also - Onions stewed in balsamic vinegar - Spring onions (raw) - Cherry tomatoes - Eggplants and sweetcorn (fried, lukewarm) - Pine nuts - Finely sliced cheese - Basil
https://image.nostr.build/ce0c7490f2adbd2aa4ccdfe80203a15dbb10686859a3256a0147d5f423478fd0.jpg
https://image.nostr.build/f930e0984ec9603b84c7a7868a97486140ee44590590102f7e460bfbfd3d70be.jpg
originally posted at https://stacker.news/items/672404
-
 @ dc652bee:6154e7d0
2024-09-19 13:47:51
@ dc652bee:6154e7d0
2024-09-19 13:47:51https://www.ouxyi.link/ul/1G3I1x
-
 @ ba4a39ee:df9b4c6b
2024-09-04 14:23:26
@ ba4a39ee:df9b4c6b
2024-09-04 14:23:26 -
 @ 52adc2ef:9f4bc0ba
2024-09-19 09:54:56
@ 52adc2ef:9f4bc0ba
2024-09-19 09:54:56สวัสดีครับ
ผมว่าจะลองเขียนบทความหรืออะไรที่มีประโยชน์ ในสิ่งที่ตัวเองได้รู้และมาเเชร์ หลังจากได้ฟัง
'Stoic' ปรัชญาเปลี่ยนชีวิตและพัฒนาการทำงานของ 'ทอย DataRockie' มีช่วงนึงพูดไว้ว่า
คนไทย consume กับ social media ลำดับต้นๆ ซึ่งหลายคน consume อย่างเดียว จะเป็นได้แค่ effect ของส่วนที่เรา content ที่เราเสพ แต่ถ้าเราสร้าง content ที่มี value เราก็จะเป็น เหตุ ที่มี effect กับคนอื่น สร้างเเรงกระเพื่อมส่งต่อไป
รู้สึกว่าน่าสนใจ เพราะก็เป็นหนึ่งในคนที่รับสารมาตลอด ไม่เคยลองที่จะ create ขึ้นมา เพราะเขิน ไม่ค่อยได้โพสอะไรอยู่เเล้ว บวกกับ คิดว่ารู้ไม่พอ เเต่คนเราก็น่าจะมีความรู้อะไรที่รู้ดีกว่าคนอื่นเค้าบ้าง
คิดว่าลองเริ่มดู ก็คงไม่เสียหายอะไร หวังว่าน่าจะเป็นประโยชน์กับใครก็คนใดคนหนึ่งครับ
siamstr
nostr
-
 @ d830ee7b:4e61cd62
2024-09-04 07:29:41
@ d830ee7b:4e61cd62
2024-09-04 07:29:41Bitcoin ถือกำเนิดขึ้นในปี 2009 จากวิสัยทัศน์ของ Satoshi Nakamoto บุคคลหรือกลุ่มบุคคลปริศนา ที่ใฝ่ฝันถึง "เงินสดดิจิทัล" อิสระไร้พรมแดน ไร้การควบคุมจากรัฐบาล
ในช่วงแรกเริ่ม Bitcoin เป็นเสมือนเพชรดิบที่ซ่อนตัวอยู่ในเงามืด เป็นที่รู้จักกันเฉพาะในกลุ่มเล็กๆ ที่หลงใหลในเทคโนโลยีและศักยภาพอันไร้ขีดจำกัดของมัน
แต่แล้ว Bitcoin ก็เริ่มฉายแสงเจิดจรัส ดึงดูดความสนใจจากผู้คนทั่วโลก ราคาพุ่งทะยานอย่างรวดเร็ว บริษัทและบริการต่างๆ ผุดขึ้นมาราวกับดอกเห็ด
ทว่า.. เส้นทางสู่ความสำเร็จของ Bitcoin ไม่ได้โรยด้วยกลีบกุหลาบ Bitcoin ยังต้องเผชิญกับความท้าทายมากมาย ทั้งปัญหาทางเทคนิค ความขัดแย้งภายในชุมชนและการต่อสู้แย่งชิงอำนาจ
Blocksize Limit จุดเริ่มต้นของความขัดแย้งและสงคราม Big Blocks VS Small Blocks
ย้อนกลับไปในปี 2010 Satoshi Nakamoto ได้เพิ่ม "Blocksize Limit" ซึ่งเป็นข้อจำกัดขนาดของ Block ใน Bitcoin ไว้ที่ 1MB เพื่อป้องกันการโจมตีทางไซเบอร์ในยุคแรกเริ่ม
แต่เมื่อ Bitcoin ได้รับความนิยมมากขึ้น ธุรกรรมก็เพิ่มขึ้นอย่างรวดเร็ว Blocksize Limit 1MB เริ่มจะกลายเป็นปัญหา..
เกิดการถกเถียงอย่างดุเดือดในชุมชน Bitcoin ว่าควรเพิ่ม Blocksize Limit หรือไม่
ฝ่าย "Small Blockers" นำโดยนักพัฒนา Bitcoin Core ส่วนใหญ่ เชื่อว่า Blocksize Limit ควรคงที่ เพื่อรักษาความปลอดภัยและการกระจายอำนาจ พวกเขากล่าวอ้างว่า Big Blocks จะทำให้ Bitcoinรวมศูนย์อยู่ที่ Miners รายใหญ่ และยากต่อการรัน Full Nodes สำหรับผู้ใช้งานทั่วไป ซึ่งจะบั่นทอนความเป็น Decentralized ของ Bitcoin
ฝ่าย "Big Blockers" นำโดย Gavin Andresen ผู้สืบทอดตำแหน่งจาก Satoshi Nakamoto และ Mike Hearn เชื่อว่า Bitcoin ควรเติบโตอย่างไม่จำกัด "Big Blocks" คือคำตอบ พวกเขามองว่า Small Blocks จะทำให้ Bitcoin ไม่สามารถรองรับธุรกรรมที่เพิ่มขึ้น ค่าธรรมเนียมจะพุ่งสูงและ Bitcoin จะไม่สามารถใช้งานได้จริงในชีวิตประจำวัน..
ความขัดแย้งนี้สะท้อนให้เห็นถึงวิสัยทัศน์ที่แตกต่างกัน
Gavin Andresen ผู้ที่เคยได้รับความไว้วางใจจาก Satoshi รู้สึกผิดหวังที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit เขาเชื่อมั่นว่า Bitcoin ควรเป็นระบบการชำระเงินที่ใช้งานได้จริง รวดเร็ว และมีค่าธรรมเนียมต่ำ
Blockstream บริษัทผู้ทรงอิทธิพลและความกังวลเรื่องผลประโยชน์ทับซ้อน
ปี 2014 กลุ่มนักพัฒนา Bitcoin Core บางส่วนได้ก่อตั้งบริษัท Blockstream (นำโดย Adam Back) พวกเขาเน้นการพัฒนาเทคโนโลยี Blockchain และกลายเป็นที่มถกเถียงว่าอิทธิพลอย่างมากต่อ Bitcoin Core
Blockstream สนับสนุน "Small Blocks"
เช่นเดียวกับ Bitcoin Core พวกเขาพัฒนา "Sidechains" ซึ่งเป็น Blockchain แยกต่างหากที่เชื่อมต่อกับ Bitcoin เช่น Liquid Network Sidechains ซึ่งช่วยให้ Blockstream สามารถเก็บค่าธรรมเนียมจากธุรกรรมและขายบริการให้กับองค์กรหรือบริษัทต่างๆ ได้
ความสัมพันธ์อันใกล้ชิดระหว่าง Blockstream และ Bitcoin Core ทำให้เกิดความกังวลขึ้นในชุมชน Bitcoin ในขณะนั้นว่า Blockstream อาจมีผลประโยชน์ทับซ้อนและต้องการให้ Bitcoin คงขนาดเล็ก เพื่อผลักดันให้คนใช้งาน "Sidechains" ของพวกเขา
BitcoinXT และ Bitcoin Classic ความพยายามแก้ไข Blocksize ที่ถูกต่อต้าน
ปี 2015 Mike Hearn และ Gavin Andresen ตัดสินใจเสนอทางออกด้วยการสร้าง "BitcoinXT" ซอฟต์แวร์ Bitcoin เวอร์ชั่นใหม่ที่ เพิ่ม Blocksize Limit เป็น 8MB
แต่ BitcoinXT ถูกต่อต้านอย่างรุนแรงจากฝ่าย Small Blockers
Bitcoin.org เว็บไซต์หลักของ Bitcoin และ r/Bitcoin ฟอรัมหลักของ Bitcoin ได้เซ็นเซอร์ BitcoinXT ไม่ให้ปรากฏ เกิดการโจมตีทางไซเบอร์ที่มุ่งเป้าไปที่ BitcoinXT โดยตรง
Coinbase บริษัทแลกเปลี่ยน Cryptocurrency รายใหญ่ ประกาศสนับสนุน BitcoinXT แต่กลับถูกถอดออกจาก Bitcoin.org
ต่อมา Bitcoin Classic ถูกสร้างขึ้นเป็นอีกหนึ่งทางเลือก แต่ก็ล้มเหลวเช่นกัน
เนื่องจาก Bitcoin Core ยังคงมีอิทธิพลอย่างมากในชุมชน Bitcoin ในช่วงเวลานั้น..
Hong Kong Agreement และ New York Agreement ความพยายามประนีประนอมที่ไม่ลงตัว
ปี 2016 และ 2017 เกิดความพยายามในการประนีประนอมระหว่างฝ่าย Small Blocks และ Big Blockers ถึงสองครั้ง คือ "Hong Kong Agreement" และ "New York Agreement"
ทั้งสองข้อตกลงมีเป้าหมายที่จะเปิดใช้งาน SegWit และ เพิ่ม Blocksize Limit เป็น 2MB แต่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit ทำให้ข้อตกลงล้มเหลว
ความล้มเหลวของข้อตกลงทั้งสอง สะท้อนให้เห็นถึงความไม่ไว้วางใจระหว่างสองฝ่าย และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ
SegWit ก้าวสำคัญของ Bitcoin และจุดกำเนิดของ Bitcoin Cash
ในที่สุด SegWit ก็ถูกเปิดใช้งานบน Bitcoin ในเดือนสิงหาคม 2017
SegWit เป็น Soft Fork ที่เปลี่ยนแปลงวิธีการจัดเก็บข้อมูลใน Block เพื่อเพิ่มประสิทธิภาพและความปลอดภัย
SegWit ช่วยแก้ปัญหา "Transaction Malleability" ซึ่งเป็นช่องโหว่ด้านความปลอดภัย และปูทางไปสู่การพัฒนา "Layer 2 solutions" เช่น Lightning Network ในเวลาต่อมา..
อย่างไรก็ตาม.. กลุ่ม "Big Blockers" มองว่า SegWit ไม่ใช่ทางออกที่แท้จริงสำหรับปัญหาการขยายขนาด (พวกเขาต้องการขยายขนาดบล็อกบนเลอเยอร์ฐาน) พวกเขาไม่พอใจที่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit
ในเดือนสิงหาคม 2017 กลุ่ม "Big Blockers" ได้ทำการ "Hard Fork" Bitcoin เพื่อสร้าง "Bitcoin Cash (BCH)" ซึ่งอ้างว่ามุ่งสืบทอดจุดมุ่งหมายดั้งเดิมของ Bitcoin ในฐานะ "เงินสดดิจิทัล"
ความเสี่ยงด้านความปลอดภัย Bug ร้ายแรงใน Bitcoin Core และบทเรียนที่ได้รับ
ในเดือนกันยายน 2018 Awemany นักพัฒนา BCH ค้นพบ Bug ร้ายแรงใน Bitcoin Core (CVE-2018-17144) ซึ่งอาจทำให้เกิดภาวะเงินเฟ้อได้
Bug นี้เกิดจากความผิดพลาดในการเขียนโค้ด และอาจทำให้ผู้ไม่หวังดีสามารถสร้าง Bitcoin ปลอมขึ้นมาได้
Awemany ได้แจ้งเตือนนักพัฒนา Bitcoin Core อย่างเงียบๆ แทนที่จะใช้ประโยชน์จาก Bug นี้ แสดงให้เห็นถึงความรับผิดชอบของเขา และ Bug นี้ได้รับการแก้ไขอย่างรวดเร็ว
เหตุการณ์นี้แสดงให้เห็นถึงความสำคัญของการตรวจสอบโค้ดอย่างละเอียด และความจำเป็นของการมีนักพัฒนาจากหลายฝ่ายเพื่อช่วยกันตรวจสอบความถูกต้องของโค้ด
นอกจากนี้.. ยังเป็นเครื่องเตือนใจว่าแม้แต่ระบบที่ถูกออกแบบมาอย่างดีก็ยังมีความเสี่ยงด้านความปลอดภัย
Bitcoin Cash แตกแยก การ Hard Fork ครั้งที่สอง และบทบาทของ Craig Wright
ในเดือนพฤศจิกายน 2018 Bitcoin Cash (BCH) ได้แตกออกเป็นสองสาย คือ Bitcoin ABC (BCH) และ Bitcoin SV (BSV)
การ Hard Fork นี้เกิดจากความขัดแย้งระหว่างกลุ่มนักพัฒนา Bitcoin ABC นำโดย Amaury Séchet และกลุ่ม Bitcoin SV นำโดย Craig Wright ผู้ที่อ้างว่าเป็น Satoshi Nakamoto 🤔
ความขัดแย้งหลักคือเรื่องขนาดของ Block และทิศทางการพัฒนา Bitcoin Cash
กลุ่ม Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก ในขณะที่กลุ่ม Bitcoin ABC ต้องการปรับปรุง Bitcoin Cash ในด้านอื่นๆ เช่น Smart Contracts
Craig Wright มีบทบาทสำคัญในการผลักดัน Bitcoin SV เขาเชื่อมั่นว่า Bitcoin ควรเป็นไปตามวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto โดยเน้นที่การเป็น "เงินสดอิเล็กทรอนิกส์แบบ peer-to-peer"
การ Hard Fork นี้แสดงให้เห็นถึงความหลากหลายของความคิดเห็นในชุมชน Cryptocurrency และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ
นอกจากนี้.. ยังสะท้อนให้เห็นถึงความท้าทายในการกำหนดทิศทางของ Cryptocurrency ในอนาคตอีกด้วย
Bitcoin ในปัจจุบัน เส้นทางสู่ทองคำดิจิทัล และวิวัฒนาการของเทคโนโลยี
หลังจากการ Hard Fork ของ Bitcoin Cash
Bitcoin ได้ก้าวเข้าสู่ยุคใหม่ Bitcoin ได้รับการยอมรับมากขึ้นในวงกว้าง มีมูลค่าตลาดสูง และถูกมองว่าเป็น "ทองคำดิจิทัล" ที่สามารถใช้เก็บรักษามูลค่าในระยะยาว (Store of Value)
การพัฒนา Lightning Network เป็นก้าวสำคัญในการแก้ปัญหาเรื่องค่าธรรมเนียมและความเร็วในการทำธุรกรรม
Lightning Network เป็น "Second Layer" ที่สร้างขึ้นบน Bitcoin Blockchain ช่วยให้สามารถทำธุรกรรมได้รวดเร็วขึ้น มีค่าธรรมเนียมต่ำ และมีความเป็นส่วนตัวสูง
อย่างไรก็ตาม.. Lightning Network ยังคงต้องเผชิญกับความท้าทาย เช่น ปัญหาเรื่องการบริหารจัดการ Liquidity และความซับซ้อนในการใช้งาน
นอกจาก Lightning Network แล้ว ยังมีการพัฒนาเทคโนโลยีอื่นๆ ที่ช่วยเพิ่มขีดความสามารถของ Bitcoin เช่น Taproot ซึ่งเป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และ Schnorr signatures ซึ่งเป็น Digital Signature แบบใหม่ที่ช่วยลดขนาดของธุรกรรมให้เล็กลง
นอกจากนี้.. ยังเริ่มมีการพัฒนา DeFi (Decentralized Finance) บน Bitcoin และ Bitcoin Ordinals ซึ่งเป็นวิธีการใหม่ในการฝังข้อมูลลงใน Bitcoin Blockchain
Bitcoin ยังคงถูกนำไปใช้ในประเทศอื่นๆ นอกจาก El Salvador และมีความพยายามในการแก้ปัญหาความกังวลด้านสิ่งแวดล้อมจากการขุด Bitcoin
บทเรียนจากมหากาพย์แห่งวิวัฒนาการ
ประวัติศาสตร์ Bitcoin สอนให้เรารู้ว่า.. เทคโนโลยี Blockchain มีศักยภาพในการเปลี่ยนแปลงโลก แต่เส้นทางสู่ความสำเร็จนั้นก็ไม่ได้โรยด้วยกลีบกุหลาบ
ความขัดแย้ง การต่อสู้แย่งชิงอำนาจ และการตัดสินใจที่ยากลำบาก ล้วนเป็นส่วนหนึ่งของการเดินทาง
สิ่งที่สำคัญที่สุดคือ.. เราต้องศึกษา ทำความเข้าใจ และอาจมีส่วนร่วมในการกำหนดทิศทางของเทคโนโลยีนี้ เพื่อให้ Blockchain สามารถสร้างประโยชน์สูงสุดให้กับมวลมนุษยชาติต่อไป
เจาะลึกวิวัฒนาการของ Bitcoin การ Soft Forks, Hard Forks และมุมมองที่แตกต่าง
SegWit, Taproot และ Soft Forks อื่นๆ การปรับปรุง Bitcoin อย่างนุ่มนวล
Bitcoin Core ไม่ได้หยุดนิ่งอยู่กับที่ นักพัฒนาได้ทำงานอย่างต่อเนื่องเพื่อปรับปรุง Bitcoin ให้ดีขึ้น โดยใช้ "Soft Forks" ซึ่งเป็นการอัพเกรดที่เข้ากันได้กับซอฟต์แวร์เวอร์ชั่นเก่า
SegWit (Segregated Witness)
เปิดตัวในปี 2017 SegWit เป็นเหมือนการจัดระเบียบข้อมูลใน Block ใหม่ ย้ายส่วนที่เรียกว่า "Witness data" (ข้อมูลลายเซ็น) ออกไปไว้ข้างนอก ทำให้มีพื้นที่ว่างใน Block มากขึ้น รองรับธุรกรรมได้มากขึ้น และลดค่าธรรมเนียมได้ SegWit ยังช่วยแก้ปัญหา "Transaction Malleability" ซึ่งเป็นช่องโหว่ด้านความปลอดภัยและปูทางไปสู่การพัฒนา Lightning Network
Taproot
เปิดตัวในปี 2021 Taproot เป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และประสิทธิภาพของ Bitcoin Taproot ทำให้ธุรกรรมที่ซับซ้อน เช่น Smart Contracts มีขนาดเล็กลงและยากต่อการแยกแยะจากธุรกรรมทั่วไป
Soft Forks อื่นๆ ที่ Bitcoin Core ได้นำมาใช้ เช่น BIP 65 (CheckLockTimeVerify) และ BIP 112 (CSV) ช่วยเพิ่มความยืดหยุ่นในการใช้งาน Bitcoin และปูทางไปสู่การพัฒนาฟังก์ชันใหม่ๆ
Hard Forks เส้นทางที่แตกต่างและการถือกำเนิดของเหรียญใหม่
ในขณะที่ Soft Forks เป็นการอัพเกรดที่นุ่มนวล "Hard Forks" นั้นนับว่าเป็นการเปลี่ยนแปลงครั้งใหญ่ ที่ทำให้เกิดสาย Blockchain ใหม่และเหรียญใหม่
Bitcoin XT (2015)
เป็นความพยายามครั้งแรกในการเพิ่ม Blocksize Limit โดย Mike Hearn และ Gavin Andresen Bitcoin XT เสนอให้เพิ่ม Blocksize Limit เป็น 8MB แต่ถูกต่อต้านอย่างรุนแรง และไม่ประสบความสำเร็จ
Bitcoin Classic (2016)
เป็นอีกหนึ่งความพยายามในการเพิ่ม Blocksize Limit โดยเสนอให้เพิ่มเป็น 2MB แต่ก็ล้มเหลวเช่นกัน
Bitcoin Unlimited (2016)
เสนอให้ Miners สามารถกำหนด Blocksize Limit ได้เอง แต่มีข้อบกพร่องด้านความปลอดภัย และไม่เป็นที่ยอมรับในวงกว้าง
Bitcoin Cash (BCH) (2017)
เกิดจากการ Hard Fork ของ Bitcoin โดยกลุ่ม "Big Blockers" ที่ไม่พอใจที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit Bitcoin Cash เพิ่ม Blocksize Limit เป็น 8MB และมุ่งเน้นที่การเป็น "เงินสดดิจิทัล" ที่ใช้งานได้จริง
Bitcoin SV (BSV) (2018)
เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มที่นำโดย Craig Wright ผู้ที่อ้างว่าเป็น Satoshi Nakamoto Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก และกลับไปสู่วิสัยทัศน์ดั้งเดิมของ Bitcoin
Bitcoin ABC (2020)
เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มนักพัฒนา Bitcoin ABC ที่ต้องการเปลี่ยนแปลงกลไกการระดมทุน Bitcoin ABC ถูกเปลี่ยนชื่อเป็น eCash ในภายหลัง
มุมมองที่แตกต่าง Bitcoin ถูก "แย่งชิง" หรือไม่?
หนังสือ "Hijacking Bitcoin" โดย Roger Ver นำเสนอมุมมองที่แตกต่างจาก Bitcoin Maximalists
Roger Ver เชื่อว่า Bitcoin ถูก "แย่งชิง" โดยกลุ่มนักพัฒนา Bitcoin Core และ Blockstream ที่ต้องการเปลี่ยนแปลง Bitcoin จาก "เงินสดดิจิทัล" ให้กลายเป็น "สินทรัพย์เก็บมูลค่า"
Roger Ver วิพากษ์วิจารณ์ Bitcoin Core ในหลายประเด็น เช่น..
การไม่ยอมเพิ่ม Blocksize Limit
Roger Ver เชื่อว่า Bitcoin Core จงใจจำกัดการเติบโตของ Bitcoin เพื่อผลักดันให้คนใช้งาน Sidechains ของ Blockstream
การเซ็นเซอร์ข้อมูล
Roger Ver กล่าวหาว่า Bitcoin Core เซ็นเซอร์ข้อมูลและปิดกั้นการสนทนาเกี่ยวกับ Big Blocks บนแพลตฟอร์มต่างๆ
การต่อต้านนวัตกรรม
Roger Ver เชื่อว่า Bitcoin Core ต่อต้านนวัตกรรม และไม่ยอมรับการเปลี่ยนแปลงที่อาจทำให้ Bitcoin ดีขึ้น
การควบคุมโดยกลุ่มเล็กๆ
Roger Ver มองว่า Bitcoin Core ถูกควบคุมโดยกลุ่มเล็กๆ ที่ไม่คำนึงถึงความต้องการของชุมชน Bitcoin
Roger Ver สนับสนุน Bitcoin Cash ซึ่งเขาเชื่อว่าเป็น Bitcoin ที่แท้จริง ที่สืบทอดวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto
บทสรุป:
การต่อสู้แย่งชิง Bitcoin และการเกิดขึ้นของ Hard Forks ต่างๆ เป็นส่วนหนึ่งของวิวัฒนาการของ Cryptocurrency
มุมมองที่แตกต่าง ความขัดแย้ง และการแข่งขัน ล้วนเป็นแรงผลักดันให้ Bitcoin และ Cryptocurrency อื่นๆ พัฒนาต่อไป
สุดท้ายแล้ว.. เราคงไม่อาจตัดสินได้ว่าฝ่ายใดคิดถูกหรือฝ่ายใดผิด
"เสียงของตลาด จะช่วยทำหน้าที่ให้คำตอบนั้นกับเรา ว่าแท้ที่จริงแล้วผู้คนกำลังต้องการอะไรกันแน่..
ลองมองไปที่มูลค่าของแต่ละแนวคิด มองไปที่ Network effect และกำลังการขุด มองไปที่การยอมรับและความเชื่อมั่นของผู้คน เหล่านี้ล้วนเป็นข้อบ่งชี้ที่เห็นได้ง่าย..
เพราะนั่นคือเสียงแห่งการเพรียกหาอิสรภาพ และอธิปไตยทางการเงินที่แท้จริง..
— Jakk Goodday
-
 @ 1739d937:3e3136ef
2024-09-04 07:23:12
@ 1739d937:3e3136ef
2024-09-04 07:23:12This is the sixth in a series of weekly(ish) updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
Sorry about the very late update this week. Catching up on everything after a week in Riga for Nostriga and Baltic Honeybadger took a bunch of time, every other moment was spent coding. 👨💻
The response at Nostriga to NIP-104 and my two talks on the subject were overwhelmingly positive. It was very helpful to spend time with other devs going through the spec in detail. We found a few minor improvements and clarifications but no major issues surfaced. Thanks to nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49, nostr:npub1lunaq893u4hmtpvqxpk8hfmtkqmm7ggutdtnc4hyuux2skr4ttcqr827lj, and nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr in particular for the lengthly interrogations and nostr:npub1wmr34t36fy03m8hvgl96zl3znndyzyaqhwmwdtshwmtkg03fetaqhjg240 for the introductions.
Last week, I started work on a reference implementation of the spec. It's still early but going quickly.
My PR adding support for secp256k1 was also merged into the hpke-rs library yesterday. That's one more step in the right direction towards having secp256k1 ciphersuite support.
The NIP
If you haven't already, check out my talk; The Past and Future of DMs and Group messaging on Nostr. This was a basic overview of the various DM and group messaging schemes and talks a little about the progress on NIP-104. I believe there is a recording of the technical talk on the spec but it hasn't yet been released. I'll link it up when it is.
At this point I've been discouraging anyone from trying to implement the NIP quite yet. As I mentioned above there are a few adjustments that need to be made and a few open questions that I'm working on answering with my implementation (which I'm very happy to have contributors on). My plan at the moment is to do this first implementation with the default ciphersuite that MLS already supports while I continue to work on the dependencies to get secp256k1 support across the board.
The Implementation
I've started on a cross-platform native client that will run on Mac, Windows, Linux, iOS, and Android. Think of it as Signal or Telegram but over Nostr. I hope that this will not only become the reference implementation for other client developers but also will be one of the most secure and privacy focused clients in the Nostr ecosystem. Building it has already been helpful in clarifying some of the more complex implementation details in the NIP. It's still early but I'll have more to share on this in the coming weeks.
HPKE-RS
My PR to add support for secp256k1 is merged!
Onward and Upward
Thanks again to everyone for the support and feedback on this stuff at Nostriga. It was hugely motivating to hear the kind words, have you introducing me to people that could help, and spending time giving me feedback! This community is the best. 🫂
-
 @ eac63075:b4988b48
2024-09-19 09:03:33
@ eac63075:b4988b48
2024-09-19 09:03:33Nos últimos anos, as Organizações Autônomas Descentralizadas (DAOs) emergiram como uma das inovações mais significativas no ecossistema das criptomoedas e da tecnologia blockchain. Elas prometem ser uma evolução dos sistemas tradicionais de governança, oferecendo um modelo em que as decisões são tomadas coletivamente por meio de tokens, sem a necessidade de intermediários. No entanto, à medida que esse conceito se populariza, problemas relacionados à manipulação de votos e à corrupção dentro das DAOs tornaram-se cada vez mais evidentes.
Recentemente, um novo desenvolvimento criptográfico foi proposto para combater essas fraudes: a Prova de Conhecimento Completo (Complete Knowledge Proof). Este avanço, com a colaboração de Vitalik Buterin, criador do Ethereum, e pesquisadores da Universidade de Cornell, traz uma abordagem inovadora para resolver um dos maiores desafios de governança descentralizada: a segurança e integridade dos votos. Neste artigo, vamos explorar detalhadamente como funciona essa tecnologia e o impacto que ela pode ter no futuro das DAOs.
O Problema das DAOs: Manipulação de Votos e Fraudes
O conceito de DAOs é fascinante, pois permite que qualquer pessoa com tokens tenha voz ativa nas decisões de uma organização descentralizada. A governança é realizada através da votação, onde os detentores de tokens participam para aprovar ou rejeitar propostas. No entanto, a prática tem revelado alguns problemas críticos, principalmente a manipulação de votos e o aluguel de tokens.
Em muitos casos, indivíduos ou grupos podem "alugar" tokens de outros participantes para ganhar mais poder nas votações. Isso corrompe o processo de governança, pois aqueles que deveriam votar com seus próprios tokens acabam utilizando tokens de terceiros, prejudicando a descentralização genuína. Em algumas situações, esse processo leva a decisões que beneficiam poucos, enquanto os interesses da maioria são ignorados. Um dos exemplos mais críticos desse problema ocorreu quando tokens foram delegados ou alugados para manipular decisões em uma DAO, permitindo que certos atores controlassem resultados vitais.
A Solução: Prova de Conhecimento Completo (Complete Knowledge Proof)
A Prova de Conhecimento Completo surge como uma solução promissora para mitigar esses problemas de governança. O objetivo dessa tecnologia é garantir que o processo de votação seja legítimo e que somente os verdadeiros detentores dos tokens possam participar de forma válida, sem delegar ou vender seus direitos de voto.
O que é Prova de Conhecimento Completo?
A Prova de Conhecimento Completo é um conceito criptográfico que permite a alguém provar que tem conhecimento de uma informação (como uma chave criptográfica) sem precisar revelar essa informação. Ou seja, você pode provar que tem os direitos para votar com seus tokens sem precisar divulgar suas chaves privadas ou delegar os tokens para outra pessoa.
Essa solução utiliza uma combinação de Zero-Knowledge Proof (Prova de Conhecimento Nulo) e Proof of Work (Prova de Trabalho) para garantir que os votos sejam realizados apenas por aqueles que realmente detêm os tokens e que estão participando de forma legítima, sem manipulação ou fraude. A Zero-Knowledge Proof permite que alguém prove que possui a chave privada associada aos tokens, sem revelar a chave em si, e a Proof of Work adiciona uma camada adicional de validação, exigindo que um trabalho computacional seja realizado para confirmar a autenticidade do voto.
Como Funciona a Prova de Conhecimento Completo?
A ideia central da Prova de Conhecimento Completo é simples, mas poderosa. Imagine que você possui tokens de uma DAO e deseja participar de uma votação. Para garantir que o voto seja válido, a Prova de Conhecimento Completo exige que você utilize um dispositivo específico ou um ambiente de execução confiável, que possa validar que você realmente é o dono dos tokens e que não os compartilhou com outra pessoa.
Este processo pode ser feito através de um hardware dedicado, como um dispositivo ASIC (circuito integrado de aplicação específica), que é programado para validar os votos de maneira segura. Os votos são computados diretamente a partir desse hardware, que usa algoritmos criptográficos complexos para provar que você tem os tokens e está votando de forma legítima. Isso evita que os votos sejam manipulados ou alugados, pois só o verdadeiro detentor dos tokens pode usá-los para votar.
Uso de Zero-Knowledge Proof e Proof of Work
A combinação de Zero-Knowledge Proof e Proof of Work é o que torna esse processo especialmente robusto. A Zero-Knowledge Proof garante que a sua identidade como votante seja preservada, ou seja, você pode provar que tem os tokens sem revelar publicamente quem você é ou quantos tokens possui. Já o Proof of Work adiciona um nível extra de segurança, exigindo que o hardware dedicado realize um certo número de cálculos antes que o voto seja validado. Isso impede que pessoas usem múltiplas contas falsas ou tokens alugados, já que seria computacionalmente inviável manipular o sistema.
O Impacto na Governança Descentralizada
A implementação da Prova de Conhecimento Completo pode transformar completamente a forma como as DAOs operam, eliminando os problemas de manipulação de votos e garantindo uma governança mais transparente e justa. Além de aumentar a segurança, essa solução também promove uma maior confiança nas DAOs, já que os participantes podem ter certeza de que as decisões estão sendo tomadas por aqueles que realmente possuem os tokens, sem interferências de atores externos.
Aplicações Além das DAOs
Embora o foco inicial da Prova de Conhecimento Completo seja a governança descentralizada, essa tecnologia tem um potencial muito maior. Ela pode ser utilizada em várias outras áreas, como votação eletrônica, identidade digital, autenticação de usuários, entre outros. Em sistemas de votação eletrônica, por exemplo, a Prova de Conhecimento Completo poderia garantir que cada voto é legítimo sem comprometer a privacidade dos eleitores, o que seria uma revolução na forma como conduzimos eleições em todo o mundo.
No campo da identidade digital, essa solução poderia permitir que usuários provem que possuem determinadas credenciais (como uma identidade ou uma carteira de motorista), sem a necessidade de expor essas informações a terceiros. Isso poderia ser extremamente útil em situações que exigem alto nível de privacidade e segurança, como em contratos eletrônicos e autenticação de serviços.
Conclusão
A Prova de Conhecimento Completo é uma inovação significativa no campo da criptografia e da governança descentralizada. Ao combinar as vantagens da Zero-Knowledge Proof e da Proof of Work, ela oferece uma solução eficaz para prevenir fraudes e manipulações nas DAOs, garantindo que os votos sejam realizados de forma segura e legítima.
Com a participação de nomes de peso como Vitalik Buterin e pesquisadores da Cornell, essa tecnologia tem o potencial de se tornar um pilar fundamental na governança descentralizada e em várias outras aplicações no mundo digital. À medida que as DAOs continuam a ganhar espaço no ecossistema blockchain, soluções como essa serão essenciais para assegurar sua integridade e transparência.
O futuro das DAOs pode estar mais seguro com a Prova de Conhecimento Completo, e este é apenas o começo de um novo capítulo na governança descentralizada.
Assista ao vídeo:
-
 @ 005bc4de:ef11e1a2
2024-09-19 08:57:10
@ 005bc4de:ef11e1a2
2024-09-19 08:57:10Recently, I wrote this: https://stacker.news/items/684558?commentId=684701 and asked whether three emails were "legit"...did Satoshi write them. Still wondering, I thought a wider explanation might be worthwhile.
Somehow, I'm finding myself lost in a techno labyrinth and then mired in a quandary of muck. Here's why...

Image source: generated at leonardo.ai
The background
In 2019, I edited a book called "Kicking the Hornet’s Nest: The Complete Writings, Emails, and Forum Posts of Satoshi Nakamoto, the Founder and Creator of Bitcoin" with the goal of logging all of Satoshi Nakamoto's public writings in chronological order (links here). There were other similar resources out there, and a somewhat similar but incomplete book, yet none were arranged strictly by chronology or without heavy editorial commentary added as a layer on top of Satoshi's writings.
I wanted Satoshi's words, alone, in order, all of them.
A second edition of "Kicking" came out when three "Satoshi emails" were released in 2020. Since the goal was to include all of Satoshi's writings, a new edition was needed.
Then, with the "COPA trial" in early 2023 a new slew of never-before-seen emails were released by Adam Back and Martii Malmi as evidence in the case. This was a couple of hundred more emails, half from Satoshi and the other half to Satoshi. So, a third edition of "Kicking" was needed.
The start
My current quandary started when I got a ping via X saying I'd missed Wei Dai's emails with Satoshi.
https://files.peakd.com/file/peakd-hive/crrdlx/23wMyix4neRki9BgsjZGYV7qpaHvmiwXUVMtm8XP8MQEpCNApb8BVQcY8qdAxa3kenpdw.png
Wei Dai's work is the first citation in the bitcoin whitepaper (page 9) and Dai is a cypherpunk legend, of course. This omission was a rather egregious error on my part, "How did I miss that?" I wondered. Like finding an overlooked golden nugget, I eagerly wrote back to thank BITCOINALLCAPS: "This is defitely [sic] something to include. I'll investigate, and thanks for the heads up!"
That feeling
Since I'm currently still tweaking out the third edition, this Wei Dai email discovery came at an opportune time to make adjustments. However, I had, and have, a funny feeling.
The link that BITCOINALLCAPS gave was to what I thought was a semi-sketchy looking video. (See the YouTube video linked on the X post above: https://www.youtube.com/watch?v=hkcwUortfWE) The vid was interesting in that it talked about Satoshi reaching out to Wei Dei pre-whitepaper. Then it analyzed nuanced differences between the drafted whitepaper title and summary when compared to the final title and summary of the whitepaper.
A little searching pointed the "source" for this missing Wei Dai email as bitcoin.com. That site has a list of Satoshi emails, forum posts, etc. I noticed two correspondences that I'd missed: Wei Dei's two emails and Jon Matonis's one. However, the likely more-respected Nakamoto Institute at https://satoshi.nakamotoinstitute.org did not include those three emails. That feeling came back to me, with the question, "Are these emails for real?"
If you're unfamiliar with bitcoin.com, then you may not realize why I got a funny feeling and why I began to wonder about the emails at all. It's a long, sordid story, but I'll try to briefly summarize.
At first there was bitcoin. Then, around 2017 as bitcoin grew and struggled to scale in size, the "block size wars" went down. Some wanted to increase the block size to unclog the chain, others wanted to retain the small block size that Satoshi had coded. The big blockers eventually forked Bitcoin (BTC) to start Bitcoin Cash (aka, "B-cash") and took the symbol BCH.
There was much animosity, and frankly, there still is. Bitcoin "maxis" today consider BTC the only bitcoin. Maxis even say there is bitcoin and no other...that there actually are no other cryptocurrencies...that all others are merely scam-coins. These folks consider themselves purists by retaining Satoshi's original small block size. The B-cashers consider themselves purists, retaining Satoshi's "electronic cash" ethos so that someone could buy-a-cup-of-coffee with a transaction on the main chain.
If you're keeping score:
|coin/chain:|Bitcoin|Bitcoin Cash| |-|-|-| |symbol/nickname:|BTC|BCH or B-cash| |block size:|small blocks like Satoshi coded|big blocks so electronic cash can exist like Satoshi wrote| |website:|bitcoin.org|bitcoin.com| |site founder/owner:|started by Satoshi|owned by Roger Ver| |Satoshi's writings logged at:|nakamotoinstitute.org|nakamotostudies.org|
And, to really throw gas onto the fire, and I hate to even bring this up, but there is Craig Steven Wright. His "Bitcoin SV" (BSV) coin spun-off from Bitcoin Cash. BSV claimed to be the even more pure purist coin as "Satoshi's Vision," hence the "SV." If you're reading this, you know about Wright...and the COPA trial...and his debunking as Satoshi...and all that. I'll return to this topic in a moment.
Like I said, this is a long and sordid story.
So, why dig up this muck here?
Back to the emails
My question was/is, "Did Satoshi write the emails to Wei Dai and Jon Matonis?" And this is where I entered the techno-labyrinth.
The video source I mentioned above aroused skepticism. The narrator focused on certain items, namely the emphasis on "electronic cash" or "ecash" or the "b" in "b-money." He didn't mention "b-cash" that I caught, but the I wondered if that was the allusion projected. In other words, I wondered if there was/is an agenda, as if to say, "b-money is b-cash which is the real and original bitcoin."
And, back to Craig Wright. I was unfamiliar with Jon Matonis, so I searched, and this article came up: https://jonmatonis.medium.com/how-i-met-satoshi-96e85727dc5a. The upshot is that in 2016 Matonis believed Craig Wright was Satoshi Nakamoto. (I'm curious as to his opinion now.) Suddenly, the reason for excluding the Jon Matonis email from the Bitcoin (BTC)-friendly NakamotoInstitute.org was apparent. This was high blasphemy.
The labyrinth got more convoluted. The website NakamotoStudies.org is Bitcoin Cash (BCH)-friendly. (See the left-leaning green "B" symbol? It's the same as on the BCH symbol instead of the familiar, right-lighting and orange BTC symbol.)

For some reason, the NakamotoStudies.org (BCH-friendly) site does not currently show the Matonis email, see this link. Actually, all "Emails" are "forbidden."
Though not live now, the Internet Archive Wayback Machine has captured the emails here.
At this point, the tecno-labyrinth is confusing and the muck is deep.
It seemed simple. I just wondered if Satoshi wrote the emails, but now I'm mired in website inclusion/exclusion censorship and gamesmanship, B-cash talk, and Craig Wright-is-Satoshi nonsense. Labyrinth and muck.
Canon or canon not?
In Christianity, there is the idea of Biblical canon. Canon is what should be included in the Bible, non-canon is everything else. Christians believe canonical works are inspired scripture, where the Holy Spirit guided the authors of the books of the Bible. As man used his own words and writing styles to literally write, the Holy Spirit actually guided each word perfectly so that the finished work was not just man's words, but "God-breathed" words.
The early Christian church, then, had to figure, "Which works are God-breathed canon and which are not?" Or, practically speaking, what goes into the Bible and what does not?
This gets into the weeds a bit, but there was no official meeting to decide what gets into the Bible and what did not. The "Early Church," that is, the body of Christian believers in the first couple of centuries A.D., essentially agreed as a collective on certain books as being in line with Christian thought and agreed that others were not. As a group, they nodded and said, "Yep, this is in," to the 66 books we recognize in the Bible today, and they said, "Nope, not this" to everything else.
I say this gets into the weeds, and it does. The Catholic Church may bring up the books of the Apocrypha. And, even then, the church might distinguish the Old Testament Apocryphal books versus New Testament Apocryphal books. It gets complicated.
What's more, some may argue that official church councils or positions officially codify or accept certain books as doctrine, or not. That is, the official church officially deems canon, or as deems non-canon. Yet, others may argue, as I do, that it is not an official church that is the gatekeeper of canon, but rather that it is instead the decentralized body of believers as a group, guided by the Holy Spirit, which accept canon and reject non-canon. If canon is God-breathed, it is not a council of church men who decide canon or not. Rather, it is the church, the believers, guided by the Holy Spirit that decides.
This is now deeply in the weeds, but the point remains...some works get in, some does not.
Bitcoin is not a religion
To be clear, I'm very much not a fan of throwing religion onto bitcoin. We do it at times, maybe in a solely fun way, such as with the "Genesis block" or in other ways. Bitcoin is a lot of things: economics, computer science, physical science, mathematics, philosophy, game theory, and more. But, it's not religion.
The reason I even included the religious discussion here is to illustrate the point of including or excluding text. Recall my question, "Should the Wei Dai and Jon Matonis emails be included in Satoshi's writings?"
And, I mentioned two ways above what made Biblical canon or non-canon: (1) official decree or (2) unofficial acceptance by the people. In the first case, I wouldn't want an official bitcoin meeting of people to decide yes or no as to what is Satoshi's writings and what is not (of course, being decentralized, there can be no official bitcoin meeting!). And, to the second, I don't want the bitcoin community to collectively agree yes or no, "This is in, this is not," as the early Christian Church did with Biblical canon. My desire is this:
If Satoshi wrote it, I want it included in "Kicking."
Yet, the question still nags, are these emails Satoshi's words? Are they bitcoin canon or not?
My hope
To include or not to include is my question? My reason for writing this is to hopefully get unstuck from the muck and mire. My options at the moment, as I see them, are:
- Don't include those emails in "Kicking the Hornet's Nest."
- Include them alongside all the others in the chronological place they would go.
- Include the emails, but add an editor's comment effectively as an asterisk saying: *here is the email, but take itwith a grain of salt.
Currently, I'm really not sure which option I'll go with. If I had to choose today, I'd choose option 3. I've already done this with the "I am not Dorian" post, as below.
This is odd in a way. I'm a Christian, by faith. Faith, by definition, is believing in what cannot be proven. And yet, I love bitcoin, who's #1 mantra may be, "Don't trust (believe), verify." So, my hope is to find an answer to whether these emails are Satoshi's or not. Perhaps there is a telling clue or clues in the source or metadata of those emails that proves or disproves them. My hope is to verify yes or no, legit or not. Maybe someone who reads this, more adroit than I, can enlighten me on a telling point that reveals whether Satoshi wrote the Wei Dai and Jon Matonis emails, or not.
I'm curious and listening.
-
 @ 7460b7fd:4fc4e74b
2024-09-04 06:01:59
@ 7460b7fd:4fc4e74b
2024-09-04 06:01:59请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ e0e92e54:d630dfaa
2024-09-04 04:13:19
@ e0e92e54:d630dfaa
2024-09-04 04:13:19This is a copy of the email received from newsletter@Rumble.com

Free Speech Under Attack -- A Note from the CEO of Rumble
Dear Rumble Users,
I don't typically send messages to our users through email, but red lines have been crossed. There have been major developments with free speech platforms, and I feel it’s important to let everyone know what is going on and how you can help Rumble.
Rumble is no longer available to the citizens of Brazil, joining the ranks of France, Russia, and China. From media reports, Brazil no longer has Elon Musk's X due to attacks on free speech by Alexandre De Moreas, a justice of Brazil's Supreme Federal Court.
World powers don’t want Rumble, they don’t want X, they don’t want Telegram, and they don't want Truth Social. They want to control information, but our companies won’t let them.
There are no other large companies fighting for freedom like we are. We put everything on the line for it, and the Telegram CEO was recently arrested for it.
Advertisers boycott our companies to try and cut our economic lifeline, but they underestimate our support among the people.
The people keep us alive and keep us going.
If you want to help us, join Rumble Premium. If Rumble Premium gets big enough, you help us change the game and fight for freedom of expression.
We are also offering a $10 dicount for any new annual subscribers when they use the promo code "brazil".
Sincerely,
Chris Pavlovski Chairman and CEO of Rumble
 444 Gulf of Mexico Dr.
Longboat Key, FL 34228, USA.
444 Gulf of Mexico Dr.
Longboat Key, FL 34228, USA. -
 @ 3b7fc823:e194354f
2024-09-04 01:33:21
@ 3b7fc823:e194354f
2024-09-04 01:33:21Nyms, Personas, and Digital Identity
GHOSTn
If you want #privacy then embrace compartmentlization and obscuration in your digital life. Get used to having multiple identities that you can switch between for various needs.
Your legal "matrix" name that pays taxes and has no controversal opinions or associations. Don't try to obscure this person. They are a open book. Put your best foot forward. Show them what you want them to see.
Your private online persona. You let your hair down, have hot takes on social media, purchase legal but potentially embarrassing items or just have hobbies and associations that you are not ashamed of but don't want to advertise for some reason. You use a VPN and no kyc sudo anonymous accounts. Have fun but don't go crazy, know that on a long enough timeline this persona will be linked back to you. The more connections and data that you put out there the easier this will be.
Your anonymous nym that only uses #tor, VMs, hidden drives, and rarely used accounts. Plausible deniability is baked in. Used by dissidents, freedom fights, truth to power, and anyone in oppressive regimes.
Finally you have your Nemo. This person does not exist. No name, no files and only uses #Tails or disposable systems that does not leave a trace. Not everyone would ever have a need for a Nemo but it is good to know how to just in case you ever do.
-
 @ da2683b9:54eedc2c
2024-09-19 08:03:21
@ da2683b9:54eedc2c
2024-09-19 08:03:21In modern society, technology is everywhere, especially the popularity of wireless signals, which makes our lives extremely convenient. However, with the widespread use of wireless communications, the mysterious technology gadget of signal jammer has gradually surfaced. Today, let's unveil it together!
Signal jammer, the name sounds a bit mysterious and complicated, but in fact its principle is very simple. It interferes with the transmission of other wireless signals by emitting signals of a specific frequency, thereby causing communication interruption. Although this sounds a bit shady, signal jammers do play an important role in some cases.
Imagine that you are immersed in a wonderful TV series, and suddenly, the network signal disappears, and the video freezes and makes people crazy. At this time, some places may actually be quietly using wifi disruptor. It covers or interferes with the original WiFi network by emitting powerful signals, causing a situation where it is impossible to connect to the Internet.
In some environments, WiFi jammers are also valuable. For example, in some sensitive occasions, such as prisons, military bases or important meetings, in order to protect the security of information, WiFi jammers become "bodyguards". It keeps information private by blocking unnecessary external communications.
Next, let's talk about UHF jammer. UHF signals are widely used in television broadcasting, mobile communications, wireless microphones, etc. UHF jammers are also a signal jammer that can block or interfere with these wireless signals. At concerts or large events, using UHF jammers can prevent interference with wireless microphones and ensure the smooth progress of the event.
Interestingly, UHF jammers can also be used to disrupt the communications of criminals in some cases. For example, when the police are chasing suspects, they may use UHF jammers to interfere with their communications, thereby reducing the suspect's chance of escape.
When it comes to signal jamming, military jammers are definitely the best. In modern warfare, the security of information and communications is directly related to the victory or defeat of the battle. Military signal jammer effectively weaken the enemy's combat capabilities by interfering with the enemy's wireless communications, radars, and missile guidance systems. Its powerful transmitters can block the enemy's signals, making it impossible for the enemy to obtain intelligence or command troops in time.
In addition to being used for attack, military jammers can also counter the interception of one's own telecommunications signals by the enemy. In some cases, the military will also use signal jammers to protect their secret communications from being eavesdropped by the enemy.
https://thetheblocker723-47197065.hubspotpagebuilder.com/how-to-pursue-a-higher-quality-of-life
Signal jammers, seemingly mysterious and powerful, are actually an important product of the development of modern science and technology. In certain situations, they can protect information security, maintain system stability, and even support the maintenance of law and order in some cases.
-
 @ dc652bee:6154e7d0
2024-09-19 07:39:14
@ dc652bee:6154e7d0
2024-09-19 07:39:14Unleash the fun with our Cat Earn Coins Bot! 🐱💰 Watch your feline friend collect coins while they play! Join the adventure and let the purring profits roll in! #CatCoins https://n9.cl/cat_bot
-
 @ 3b7fc823:e194354f
2024-09-04 00:26:48
@ 3b7fc823:e194354f
2024-09-04 00:26:48Encryption is the promethium fire that the cypherpunks secured from heaven for me and you. It is our sacred duty to use and advance that in the world. Encryption is so powerful that governments tried to keep it away from the people and to this day have tried to weaken and backdoor it at every turn.
So what is encryption?
It is a deep deep rabbit hole and involves a lot of numbers but in a nutshell it uses math to scramble up the data of your file so it is gibberish and can't be read without decrypting it back to regular data. Encryption technology has continued to advance over time and cracking technology to break the encryption has as well. For our purposes all you really need to remember is to use modern cyphers and your encryption is really only going to be as good as the password (use a passphrase) strength you are using to lock it down with.
BEGINNER LEVEL - Encrypt your phone and computer.
People walk around with their whole lives on their phone. Protect it.
-phone: Congratulations, if you already have a lock screen set on either your iPhone or Android device then device encryption is enabled. If your lock screen password is only 4 digits then we still have work to do. Four digits is only about 10,000 combinations and fairly easy to crack. I believe it only took them about 40 minutes to crack the iPhone of the attempted Trump shooter. Go into settings and set it up for 6 digits or for extra credit use a alphanumeric password.
After your phone then your personal computer probably has the most important data to you. Banking records, tax documents, photos, etc. Encrypt your drive.
-Windows: from Settings, select Privacy security -> Device encryption. Just follow the prompts.
-Apple: from Apple icon, select System Preferences -> Security & Privacy icon. Click "Turn On FileVault".
-Linux: most distros gives you the option during installation. If you didn't do so then search for how to enable it after the fact based on your distribution.
Awesome sauce. You have achieved minimum status.
ADVANCED LEVEL - Encrypt individual files.
You already encrypted your computer but guess what, once you start up your computer and log in the key is stored in RAM for as long as it stays on. The beginner level encryption protects your computer when it is off and it means no one can just steal your hard drive and access your files. This is good, but what if someone grabs you while you're sitting there working on it? What if you leave it in sleep mode and not turned off? Then that whole disk encryption is not really going to help you.
What if you had individual files that you consider more secret than the others? That finance spreadsheet or that special pic your spouse sent you? That's where individual file encryption comes in. You are just scrolling nostr when they grab you, your computer is on, and unlocked, but those special files are still safely encrypted.
I will share with you one of my favorite small programs: Picocrypt.
Download the Paranoid pack and store it in multiple drives, email accounts, and cloud storage. That way you will always have a copy to decrypt any files that you stored away.
Use it to encrypt any files that you feel need extra attention. It is also very useful for encrypting any files that you intend to store online in cloud storage. You do encrypt your files that are stored online don't you? Yes, even with the company that offers "encrypted" storage. Don't trust their encryption, use your own.
EXPERT LEVEL - Encrypt containers and hidden containers.
What if you want to encrypt several files and keep them all together in like a folder or container? That's where Veracrypt comes in. Free, open source, cross platform, and powerful.
Veracrypt allows you to create encrypted containers from any file that act like individual drives that can be mounted or unmounted as needed. You can name these files anything that you want, move them around or delete like any file, and make as many as you want. This allows you to have compartmentation of your files and drives.
Next trick, Veracrypt allows you to create a hidden container inside that container. Enter one passphrase and you open the encrypted container. Enter a different passphrase and you open a different hidden container.
This allows deniability. When they grab you and start pulling your fingernails off until you tell them the password to open the encrypted container, give it to them. They don't have to know that there is another hidden one under that.
These features allow you to do all sorts of interesting things only limited by your need and imagination.
What if you have a container named as some random config file in your /etc folder? What if you just encrypted a removable storage drive? What if you have multiple hard drives on your computer that have multiple containers and hidden containers? What if you have a hidden container that can only be accessed from booting up in a amnesiac OS like Tails leaving no trace that the files exist or trail that they were ever accessed? Go crazy, have fun.
NEMO - Failsafe
Nemo has no files, encrypted or otherwise. If they did you couldn't prove it. Nemo does use something like Tails that retains no memory from boot to boot.
Nemo also uses a failsafe. A simple lanyard attached to the flashdrive running the OS and the other end around their wrist while they work. When you try to separate them from the computer the flashdrive pulls out and everything is gone.
Using these programs you can create a layered and compartmentlized approach to your encryption scheme. There are also plenty of other encryption programs to check out such as Cryptomator, AES Crypt, etc
Last point and most important: Encryption is only as good as the passphrase you use to lock it down. Use a shitty password and it doesn't matter how uncrackable your encryption is.
-
 @ a012dc82:6458a70d
2024-09-19 07:35:12
@ a012dc82:6458a70d
2024-09-19 07:35:12Table Of Content
-
The Psychology of Scarcity
-
Trust in Decentralization
-
The Power of Network Effects
-
The Role of Intrinsic Motivation
-
Anchoring and Adjustment Heuristics
-
Conclusion
-
FAQ
Bitcoin has been the talk of the town since its inception in 2009. While most people primarily view it as a digital currency, it offers much more than that. In this article, we will examine the various aspects of Bitcoin that set it apart from traditional currencies, focusing on behavioral economics. By understanding these unique features, we can better appreciate the true value and potential of Bitcoin in the world's financial landscape.
The Psychology of Scarcity
The limited supply of Bitcoin, capped at 21 million coins, contributes to the perceived value of the cryptocurrency. This scarcity can drive increased demand, as people are generally drawn to scarce resources. This phenomenon is well documented in behavioral economics, and it can lead to irrational decision-making, fear of missing out (FOMO), and even price manipulation.
Trust in Decentralization
Bitcoin operates on a decentralized network, meaning no central authority or government can control its supply or value. This aspect appeals to many users who have lost faith in traditional financial institutions due to corruption, mismanagement, or economic instability. From a behavioral economics perspective, the trust in decentralization can lead to a preference for Bitcoin over conventional currencies.
The Power of Network Effects
The value of Bitcoin is further enhanced by its growing network of users, developers, and investors. As more people adopt and use the cryptocurrency, its utility and demand increase, further driving up its value. This positive feedback loop is a classic example of network effects in behavioral economics, and it helps explain the rapid growth and adoption of Bitcoin.
The Role of Intrinsic Motivation
Bitcoin's open-source nature and the pseudonymous identity of its creator, Satoshi Nakamoto, have fostered a sense of community and intrinsic motivation among its supporters. This shared sense of ownership and the desire to contribute to the success of the project can drive innovation, development, and adoption of the cryptocurrency. Intrinsic motivation is a powerful force in behavioral economics, often leading to better outcomes than extrinsic rewards.
Anchoring and Adjustment Heuristics
Bitcoin's highly volatile nature can be attributed, in part, to cognitive biases like anchoring and adjustment. People often anchor their expectations of Bitcoin's value to a previous reference point, such as an all-time high or low. As new information emerges, they adjust their valuation, sometimes leading to overreactions and significant price swings. Understanding these heuristics can help explain the often unpredictable behavior of Bitcoin's price.
Conclusion
Bitcoin is more than just a digital currency; it is a complex financial ecosystem that can be better understood through the lens of behavioral economics. By analyzing the psychological factors that drive its value and adoption, we can gain valuable insights into the cryptocurrency's potential and the unique role it plays in our global economy. As the world continues to evolve, so too will Bitcoin and the fascinating interplay between human behavior and digital finance.
FAQ
How does scarcity influence Bitcoin's value? Bitcoin's limited supply creates a sense of scarcity, driving demand and leading to increased value and potential irrational decision-making.
Why is decentralization important for Bitcoin? Decentralization eliminates central authority control, appealing to users who distrust traditional financial institutions and prefer a more trustless system.
How does the psychology of FOMO influence Bitcoin adoption? Fear of missing out (FOMO) drives people to invest in Bitcoin to avoid feeling left out, potentially resulting in impulsive decision-making and increased demand.
How do cognitive biases affect our perception of Bitcoin's value? Cognitive biases like confirmation bias and herd mentality can lead to irrational beliefs and expectations about Bitcoin's value, influencing investment decisions.
Can behavioral economics explain the appeal of Bitcoin for speculative investors? Yes, factors like scarcity, network effects, and cognitive biases can make Bitcoin an attractive option for speculative investors seeking high returns.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 8cb60e21:5f2deaea
2024-09-03 22:26:25
@ 8cb60e21:5f2deaea
2024-09-03 22:26:25 -
 @ a03b38f8:2c7ce1f0
2024-09-19 03:04:13
@ a03b38f8:2c7ce1f0
2024-09-19 03:04:13You are Giving Away a Lot of Data with those Pictures
You post pictures on nostr and other social media. You send pictures to friends and sometimes sorta friends. I hate to tell you this but you are giving away a lot more personal data than just what's on the image of the picture.
It all comes down to the metadata. The term Metadata refers to descriptive information about a picture, image, or file. This set of information is so vital as it reveals everything about a picture.
Metadata is key as it explains the privacy and security dangers that you are exposing yourself to everytime you share that file. And not just pictures, but text documents, PDFs and Videos.
What data is in Pictures?
EXIF Data (Exchangeable Image File Format): This is a standard that specifies the formats for sound, images and ancillary tags used by scanners, smartphones and other smart devices.
EXIF contains so much more personal information than you can imagine.
It tells the geolocation of where the picture was taken and it gives the timestamp of when it was taken.
So that creepy guy who follows your accounts knows all your favorite lunch spots because you like to post pictures of your food.
Additionally the metadata contains a description or title of the image. Any tags or keywords associated with the image, author information, and any custom metadata from any image editing software that might have been used including more timestamps, system information, and log of any edits.
So yes your Bumble date knows you are trying to catfish them with that 5 year old picture you doctored up with AI.
Uses in Open Source Intelligence
Open Source Intelligence or OSINT is a fancy term for cyber stalking someone. It is using nothing more than specialized knowledge and freely available information on the internet to find out all kinds of stuff about someone.
Using the GPS metadata and reverse image search of that picture posted online you figure out where that person is from and maybe a first name. Using that to narrow down your search criteria you find their Facebook and Instagram. Now you have their last name, how they spend their time, friends, and maybe where they work. Searching free data brokers you find their address and phone number. Public records tell you how much they paid for their house and Google street view gives you a view of the house from the street.
So other than being a creep, what else is metadata used for?
Analysis of metadata helps to trace the origin and history of digital files. Digital Forensics will know when those files were created, accessed, or modified. Forensics then uses this for additional context about files and other data stored on a computer or network, this information is useful because it provides information that may not be immediately clear from the file itself. Remember your OPSEC rules and be a Nemo when necessary.
There is some good news. (And bad)
Luckily the more popular services out there such as Facebook and Instagram do not display the metadata of the users. You cannot check the metadata of pictures as it does not allow you to download pictures or copy the image link. Although that doesn't mean the companies themselves do not have access to that data.
This is not the case with services like Tumbler and most image hosting or storage services. When pictures are uploaded to cloud services like dropbox or google drive anyone with access to these images can also access the metadata.
Okay I am terrified, how do I remove metadata from pictures?
Thankfully there are several options to take care of this. Most operating systems have methods built in. (see below for instructions for Windows and MacOS). Tails and QubesOS has Metadata Cleaner software preinstalled. There are several online tools that also scrub metadata from pictures. (Shout out to nostr.build)
Windows
-
Right Click the image file and select properties
-
Click the details tab
-
Click Remove Properties and Personal Information
-
Choose the level of metadata removal desired
MacOS
-
Open the image in the preview
-
Go to Tools
-
Click EXIF tab
-
Select Remove EXIF file
How to remove EXIF data after capture on phones
Let's be honest that most of your photos are taken and reside on your phone now of days.
On iPhone you have to open the Photos app, select the image, tap on 3 dots and select Adjust Date & Time and Adjust Location. You can also get the adjust setting by clicking the little i at the bottom of the picture.
On android it is much the same way. Open Gallery, select image, tap 3 dots, choose details, then the pencil to remove location and timestamp, save.
On Graphene OS no worries, remove EXIF data after capture is an existing setting in the camera and is enabled by default.
It is a total pain that you have to do this each and every time to every picture. But I hope you now realize how important that metadata can be and why you shouldn't just be sharing it with the world.
-
-
 @ 8d34bd24:414be32b
2024-09-19 02:40:02
@ 8d34bd24:414be32b
2024-09-19 02:40:02Nobody alive has a high enough view of God. Our God, the true God, the God who spoke into existence time and space, matter and energy, things seen and unseen, is more awesome than our earthly minds can comprehend.
This is a very good thing. A God who is omnipotent, omniscient, omnipresent, and holy is a God we can trust. A God who is unfathomably complex and able to do things we can’t comprehend is a God worth worshipping.
Wrong View of God
When I first became a Christian, some of the verses about honoring and worshipping God seemed proud and self-absorbed, but I was judging God as a man. He is so far above us in every way and we owe Him our very existence. Of course He should be honored and worshipped. I judged Him as having human motives instead of omniscient, holy motives. I judged Him as just being an above average man instead of being the Creator who spoke everything, even time and space, into existence. I judged Him wrongly because I didn’t fully know Him and who He truly was. The more I learn about Him the more amazed I am at who He is and the more I realize how little I truly comprehend His awesomeness.
I serve a God that is so magnificent that we can’t fully understand who He is or the various traits He has revealed to us. Other religions worship a god that is no more than a superhero. Their gods are understandable because they are made up by people. A god that is fully understandable isn’t a god worth worshipping.
Wrong View of the Law
God has given us a law to follow. He has given us explicit laws like the ten commandments. He has given us things we must do and He has given us things we must not do. Too often we are offended by these commands. We look at every command to do something as a burden and every command to refrain from doing something as a limitation on our freedom and happiness. We only feel this way because our view of God is wrong.
We have an awesome God who loves us so much that he condescends to tell us how to live the best life we can live. He tells us not to do things that are bad for us and will harm our relationships with Him and others. He tells us to do things that will help us grow and help us build relationships with Him and others. He lets us join Him in His amazing plan for humanity. He doesn’t need us, but like a good Father, He includes us in His work and empowers us to do what we could not do on our own.
Instead of resenting God for His commands, we should be grateful that He cares enough to give them. We should be grateful that He cares enough to send Jesus to earth to show us what a perfect life looks like. We should be grateful that He has given us the laws necessary to make family and society work properly. When we obey His commands, we will be glad we did.
Wrong View of Sin
We all view our sin as less bad than it really is. We excuse that “little white lie.” We discount the harm from stealing that pencil from work. We make light of our social actions because we are conforming to the culture around us and because everyone is doing it. We talk about all of the “good” people around us and wonder why God lets “bad” things happen to these “good” people. Does anyone truly see the true horror of their sin?
We have a wrong view of sin for several reasons. First of all, we judge sin by the actions of other people. We judge one person to be a better person than another. We judge some sins, like murder, to be worse than other sins, like a lie of flattery. We don’t judge sins by their rightful measure, the word of God and the life of Jesus.
Beyond that we look at things based on whether the sin seemed to hurt someone. Of course we are only able to look at the external effects, not the effects on the heart. Truth is loving even when it hurts. That definitely doesn’t mean we should tell the truth in a hurtful way to make a person feel bad or to win, but we should tell the truth because the truth always benefits in the long run. A lie, even if it makes the person feel better today and seems to help a relationship, causes harm in the long run. It breaks trust. It leads the person on the wrong path. It hardens the liar’s heart.
Ultimately all sin is about one thing. All sin says, “my way is better than God’s way.” All sin says, “I know better than God.” All sin says, “my opinion is more important than God’s opinion.” Worst of all, all sin says, “I am god of my life and I don’t want God to rule over my life.” Sin is a denial of God and His authority.
If we have a higher view of God then we realize the gravity of our sin. This won’t mean we will never sin, but it should mean we sin much less. It should also mean we repent more because sin is idolatry. We are our own idol.
Wrong View of Hardship
So often when things go wrong in our lives, we question God. We say, “Why me? Why did you let this happen to me?”
We need to remember that God is in control. We need to remember that God loves us. We need to remember that God knows everything that is, that was, and that will be and that He looks at events differently than we do because He has an eternal perspective.
Why do bad things happen to people, especially believers? God told us
Remember the word that I said to you, ‘A slave is not greater than his master.’ If they persecuted Me, they will also persecute you; if they kept My word, they will keep yours also. (John 15:20)
God is transforming us to be more like Jesus, so some hardship is given to us to mold us to be more like Jesus. Almost all growth in faith and holiness comes from hardship, not easy times. God knows this and gives us what is for our eternal good instead of what gives us momentary happiness. Looking back with a godly attitude, you will be able to see the good God has done through hardship and be grateful even if it was very difficult in the heat of the trials.
Sometimes God allows hardship as a punishment for sin.
For those whom the Lord loves He disciplines, and He scourges every son whom He receives.” (Hebrews 12:6)
Sinning unbelievers are often allowed to continue sinning and may not seem to get their punishment here on earth. Christian sinners are more likely to be punished here on earth as a correction, to lead us back to Him and a godly life. If you are going through a hard time, ask yourself, “Is there an unconfessed sin in my life for which I am paying the consequences?” If the hardship is due to sin, usually repenting and turning from that sin will help, but even repentance and turning fully to God does not guarantee that the consequences of sin go away. It does mean that the hardship will become more bearable because everything is better and easier when you have God on your side.
Frequently hardship is preparing you for something. He may be preparing you for additional hardship. He may be preparing you for ministry. He may be preparing you for leadership. You can look at the story of Joseph. He was sold by his brothers, made a slave, tempted and then jailed when he resisted temptation, and then abandoned in jail by those he had helped. I’m sure there were moments when Joseph doubted God. Joseph stayed faithful, but he went through severe hardships for decades. God, however, knew what He was doing. He was preparing Joseph to save the people of the Middle East and beyond. God was moving Joseph from a place far from the seat of power to a place where he could speak God’s word to Pharaoh, the most powerful man in the world at that time. Joseph didn’t know what God was doing, but he stayed faithful and God blessed him immensely.
You may not be made second in charge of the most powerful country in the world, but God has a plan for your life. You have been blessed by the Creator God to be used for His purpose. He will put you through what you need to go through to prepare you for His earthly plans and to prepare you for Heaven. Trust me, it will be so worth it.
Knowing who God is and that He loves us can enable us to go through these hard, desperate times. When we trust God, we don’t just barely make it through, we can thrive and go through horrible circumstances with joy because:
And we know that God causes all things to work together for good to those who love God, to those who are called according to His purpose. (Romans 8:28)
When we start to get a right view of God, everything is better. We can understand the truth in God’s word and in the world more correctly. We know that our loving God controls everything throughout history with ultimate wisdom. We know that everything happens for a very good reason.
When we start to get a right view of God, it is like the sun coming out from behind a cloud. Everything is clear and bright and joyful.
Trust Jesus.\ \ your sister in Christ,
Christy
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
-
 @ 3c9712ff:14fecbc4
2024-09-19 01:58:04
@ 3c9712ff:14fecbc4
2024-09-19 01:58:04Pristine beaches, stunning landscapes, cricket on Christmas, and ever-appreciating house prices. These have long been cornerstones of Australian culture, now considered almost unquestionable.
House prices rise because, well, they always have, and since the 1970's the formula for Australian success has been straightforward:
- Get any job.
- Buy a house with leverage.
- Pay off the loan, sell the house for a profit.
- Repeat steps 2 and 3.
This wealth creation scheme hasn’t just been a strategy for the past 50 years—it’s been a birthright.
What’s shocking is how many people take this as gospel. The idea that house-price-go-up is so deeply ingrained in our psyche and culture most people don’t even question it. But if you ask them why housing has become so unaffordable, especially since 2020, you’ll likely hear one of the following explanations:
- Property Investors
- Immigration
- Building costs
- Negative Gearing/Tax Concessions
I’m not denying these factors play a role, but they’re secondary to the real culprit. The crisis in Australian housing starts with our flawed monetary policy.
Every year, the amount of Australian dollars in circulation increases by an average of 7%. When savings are diluted and purchases power decreases, we’re incentivised to store our wealth in assets that can’t be easily replicated—like gold, real estate, and equities.
Real estate, in particular, is used more so as a store of value in Australia compared to other Western nations for the following reasons:
- Our equities market isn’t as deep or liquid as others (ASX at $1.5T vs. the U.S. at $50T).
- Construction costs are higher.
- Zoning regulations are stricter, often driven by NIMBY (Not In My Backyard) sentiment.
Given that its hard to build new dwellings, housing has the perfect combination of scarcity and undeniable utility.
The key takeaway is this: House prices didn't soar because they became investment assets; they became investment assets once people saw them as a superior store of value to our dollar. This incentivised shift in attitude opened the door to financialisation.
In response to COVID, stimulus checks and corporate bailouts increased our money supply by around 40%. Predictably, the housing market followed suit, going ballistic. Our median house prices surged by 40% since the pandemic, illustrating that cheap Australian money will always flow into scarce Australian real estate.
To combat inflation, the 13 rate hikes imposed by the RBA are by design making life tougher for Australians. A generation of new homeowners, burdened with large debt balances, now find themselves hanging on for dear life, hit hardest by the interest rate policy. Yet, the market remains irrationally composed. Many who are drowning in mortgage payments choose not to sell and rent for one simple reason: they all believe house prices will always rise in value. If they can just weather the storm and make it over the hill, their house will appreciate and they're in the market for good – it’s an ingrained mindset.
Where do we go from here?
Since housing has been declared a national crisis by the Albanese government, let’s examine the role they play in this.
Supply – The government is entirely subservient to NIMBYs (Not In My Backyard advocates). We lack genuine private property rights in Australia, and as a result, we cannot build enough dwellings (specifically apartments) to meet demand.
Demand – Hand out taxpayer money to first homebuyers trying to enter the housing market. What a brilliant idea! So sustainable, right? What could possibly go wrong?
These two strategies highlight just how inept the Australian government is at addressing the housing crisis. They're also incentivised by the following: * The fastest way to a single term in office is through stagnant house price growth. * A decrease in house prices is a decrease in revenue (land tax, stamp duty, council rates etc)
This Isn’t Looking Pretty
The younger you are, the more likely you are being completely priced out of the housing market, relegating Gen Z to Gen Renters.
 Australian home ownership decrease
Australian home ownership decrease The traditional Australian model of paying off your home and relying on a pension or superannuation to fund your retirement is now fundamentally broken. If you’re still paying a mortgage past 65, your superannuation alone won’t provide for a comfortable retirement. This is yet another example of the fiat treadmill speeding up, leaving everyday Australians scrambling to keep pace.
The Sound Money Alternative
In an ideal world of sound money, housing doesn't become an investment. No homebuyer would be competing with private equity firms and a slew of housing investors. Even negative gearing wouldn't exist. This simple move relegates housing to it's intended purpose, a dwelling. In my mind this sounds great, but I wonder if this sound money already exists? #bitcoin
Colin Gifford
-
 @ 8cb60e21:5f2deaea
2024-09-03 22:26:25
@ 8cb60e21:5f2deaea
2024-09-03 22:26:25 -
 @ c7eadcf0:7821e562
2024-09-18 20:37:04
@ c7eadcf0:7821e562
2024-09-18 20:37:04https://image.nostr.build/c7e3732889827ab0a8e2064de5fa6992e37e035347b0c91d249cb8f312b47087.jpg I love Bitcoin. Let me get that out there first of all. I sincerely believe that Bitcoin has the power to change the way the world functions if we can grow adoption to a global scale. This obviously will take time as the gears of economic change grinds slowly. As of right now, people in the western countries don't really see the need for a sovereign politically neutral money that can't be inflated away. They simply don't have to deal with inflation on a regular basis like the rest of the world.
Citizens in western countries got a small taste of what real inflation looks like and guess what? They didn't like it one bit. Overall the last three and a half years you saw countless news stories about how bad inflation and how its making life for the average American or European more difficult.
Yes inflation does suck but look at countries like Argentina, Turkey, Zimbabwe or Venezuela. The people in these countries are suffering from excessive inflation on a regular basis! According to recent economic data Turkey experienced a decline in inflation from 61 percent to 51 percent in August. This is seen as a win in their book! Can you imagine this level of inflation in America? There would be riots in the streets!
Argentina's inflation rate is an astounding 236 percent over the last 12 months! As Bitcoiners we understand that the problem is the money itself. As long as governments have the ability to manipulate the money supply, they will. This is human nature at its finest. When you give a select few that kind of power it becomes irresistible and becomes a tool to control the masses. This shouldn't be a surprise to anyone to be honest.
What I find shocking is with all of this inflation globally no one is really looking around asking questions to why this is happening and looking for a way to escape this system. Are people really this lazy? Not to be mean but cmon. It seems to me that most people are perfectly fine bitching online about how hard it is to make ends meet or supporting their favored political party and wanting them to fix the problem they created. Newsflash to all the normies out there, its the GD political parties that caused inflation in the first place.
We literally have a solution that is staring them in the face, ready to go to replace the current debt based system that we are currently suffering through and no one wants to take the time to research it? Am I black pilled? No, am I realist, very much so. If 236 percent inflation in Argentina can't get them on a Bitcoin Standard immediately, we as a community have a long road ahead of us. Hyperbitcoinization isn't coming in 5 years. It isn't coming in 10 years. Hell it might not even happen in our lifetimes and we have to be ok with that.
So what is the best way to get more Bitcoin into the hands of the people, so they can see the true value of the digital monetary revolution that is Bitcoin. We need a trojan horse and that trojan horse is nostr.
Enter The Nostr Trojan Horse
https://image.nostr.build/5ffee418133ac80ba14b30abf0d5390b878f676cbf6332d67639f9384764da4c.jpg
It should be plain to see by now that the inflation or the number go up narrative alone isn't going to drive Bitcoin adoption. The reason for that is because people don't see the utility of Bitcoin. They see it as some esoteric digital funny money that drug dealers and terrorist use to do bad things.
The average Joe doesn't see how Bitcoin is helping dissidents on foreign countries fund their activism, escape oppressive regimes or simply earn a living. These stories are never told in the mainstream media because they don't want to highlight the fact that a non-state money can circumvent the status quo.
The best way to highlight these stories is to share it on social media, which again is controlled by mainstream gatekeeper such as Meta, Google and X. It is in their best interest to censor these stories or memory hole them out of existence which I suspect happens quite a bit without us even knowing. But the thing about censorship is that it slowly impacts everyone one by one until no one is allowed to say anything without the fear of being put in jail.
Think this can't happen in western democracies? It's happening already my friend! Take a look at the UK or Australia. Citizens their are being arrested over post made to social media. I sincerely believe that these two countries should be a proving ground for showing the value of nostr and Bitcoin.
Introducing the concept of a censorship resistant messaging protocol to them will go over well and once it is understood will grow like a wildfire because people innately understand that censorship is bad and will see the utility value of having the ability to speak freely again.
It is only a matter of time until they realize that they can monetize their speech and build a life using zaps aka Bitcoin.
Until people see the utility in the tools that lie before them, they will never pick them up and use them. It is really that simple. At the end of the day we are still kind of like cavemen. We only use tools when it makes life easier. Man made the wheel. We use it everyday because it has utility.
Bitcoin in the end will be the same way. Utility first, then mass adoption. Nostr is what will help people see the utility Bitcoin and from there sky is the limit. The best thing we can do as Bitcoiners is to encourage people to learn about nostr and show them how easy it is to use and to switch clients that suit their needs instead of being shoved into a one-size fits all solution on centralized platforms.
People like choices, and nostr is all about choice. The interoperability and thelack of need to give personal information to create an account are HUGE selling points that can be touched on. Go out and spread the good word about nostr!
Bitcoin #Nostr
-
 @ 266815e0:6cd408a5
2024-09-18 18:28:35
@ 266815e0:6cd408a5
2024-09-18 18:28:35Not much new this update, mostly just bug fixes
The update is available at nostrudel.ninja and hopefully Start9 and umbrel shortly
New Features
- Add option to wipe wasm relay database
- Add support for showing embedded HLS videos
- Support pinning articles
- Add relay discovery map
- Add option to disable keyboard shortcuts
- Hide avatars of muted users
- Add bookmark button to articles
- Improve notifications timeline rendering performance
Bug Fixes
- Fix search results not being cached
- Fix amber signer missing pubkey
- Fix some tidal embeds not playing
- Fix bookmark view not showing latest bookmarks
- Fix client sending filters with empty #a tags
- Fix client tag breaking POW on notes
- Fix relay notes showing notes from other relays from cache
- Fix keyboard shortcuts activating when replying to notification
-
 @ 8cb60e21:5f2deaea
2024-09-03 21:58:26
@ 8cb60e21:5f2deaea
2024-09-03 21:58:26Lesson 3: Arrays, Objects, and Callbacks
Arrays: Lists of Things
Arrays are ordered lists of values. They're perfect for storing multiple related items, like a list of your favorite cat toys:
javascript var catToys = ["mouse", "ball", "laser pointer"]; console.log(catToys[0]); // Prints "mouse"Objects: Grouping Related Information
Objects allow you to group related information together. They're like detailed profiles for each of your cat friends:
```javascript var myCat = { name: "Fluffy", age: 3, favoriteFood: "tuna" };
console.log(myCat.name); // Prints "Fluffy" ```
Callbacks: Doing Things Later
Callbacks are functions that are executed after another function has finished. They're useful for handling asynchronous operations, like waiting for your cat to finish eating before giving it a treat:
```javascript function feedCat(callback) { console.log("Feeding the cat..."); setTimeout(function() { console.log("Cat has finished eating!"); callback(); }, 2000); }
feedCat(function() { console.log("Time for a treat!"); }); ```
This code simulates feeding a cat, waiting 2 seconds, and then giving it a treat.
Remember, learning JavaScript is a journey. Take your time, practice regularly, and soon you'll be coding like a pro cat!
-
 @ 8cb60e21:5f2deaea
2024-09-03 21:58:26
@ 8cb60e21:5f2deaea
2024-09-03 21:58:26Lesson 2: Functions and Loops
Functions: Your Own Commands
Functions are reusable blocks of code that perform specific tasks. They're like teaching your cat a new trick:
```javascript function meow(times) { for (var i = 0; i < times; i++) { console.log("Meow!"); } }
meow(3); // This will print "Meow!" three times ```
Built-in Functions
JavaScript comes with many built-in functions. For example,
console.log()is a function that prints things to the console:javascript console.log("I'm a cat!");Loops: Repeating Tasks
Loops allow you to repeat a task multiple times without writing the same code over and over. It's like telling your cat to chase its tail for a specific number of rounds:
javascript for (var i = 0; i < 5; i++) { console.log("Chasing tail, round " + (i + 1)); }This will print "Chasing tail, round X" five times, where X goes from 1 to 5.
-
 @ e477586c:63d94e3f
2024-09-18 18:07:39
@ e477586c:63d94e3f
2024-09-18 18:07:39"The transition from permaculture self-reliance and small business to large organisational roles mentioned previously presents similar structural dilemmas and pitfalls. Creative, ethically driven people in large organisations tend to be co-opted and corrupted by the large-system forces within which they must work." --David Holmgren
Long before I had even heard of #permaculture, I held this view. It goes all the way back to high school. I remember most of my friends working at fast food chains, or as pizza delivery drivers, or the giant regional grocery. Those who were planning on going to college were going for engineering, accounting or business and already had aspirations for working in a fortune500 company.
I on the other hand, mowed lawns, life-guarded at the high-school pool, and worked for the Texas Trampoline Company; a guy building trampolines in his garage with a full-time staff of about 2 and about 5 of us part-time high schoolers. I never worked fast-food, but when I was in restaurants, all except one were one-offs or had fewer than 3 locations. The largest chain I worked at had 30, and only 20 within the contiguous United States.
As I continue to apply for jobs; with each application I'm driven more and more to hoping the TaskRabbit gig-economy self-employment starts producing fast and well before I get desperate and have to say yes to working for my very bleu county government. I was hoping to get this post finished before my Tasker Success Manager call, but got interrupted by cats needing attention and then the call came. It was useful. My TSM said going from zero to one is always the hardest step and sent me a heat-map to compare to my opportunity map. There's evidently a difference.
The opportunity map is more general. It covers Taskr availability vs task requests across the app and under "all skills." Areas more likely to have task requests show up a darker green. The heat map narrows things down a bit. It is filtered by specific skills which the Taskr has listed in his/her profile. It shows hot spots of hits within those categories within the past 15 days. You have to get this app from your TSM, it isn't available through your Taskr app or web portal.
As I wrote and did some things around the house today, I managed to MP3-ify 3 albums for portability. Just the next 3 in line of my record collection: The Graduate soundtrack, Journey; Greatest Hits sides 3 and 4, and The Smiths: The Queen is Dead
-
 @ dc652bee:6154e7d0
2024-09-18 16:38:51
@ dc652bee:6154e7d0
2024-09-18 16:38:51BEST TELEGRAM AIRDROP BOT
Download the telegram app, anyone who hasn't created it, your own channel is free later, you can sign up for airdrops, many have already started giving money for free . Get the ultimate airdrop experience with the best Telegram bot around! 🚀 #Bot #Airdrop #Telegram #TON.
https://t.me/Dogiators_bot/game?startapp=F80aAU4OlGJX61YK
https://t.me/tonton_intract_bot/start?startapp=eyJyZWZlcnJhbENvZGUiOiJGOER6dDAiLCJyZWZlcnJhbFNvdXJjZSI6IlRFTEVHUkFNX01JTklfQVBQIiwicmVmZXJyYWxMaW5rIjoiaHR0cHM6Ly93d3cuaW50cmFjdC5pby90bWEvcmV3YXJkcyJ9
https://t.me/gamee/start?startapp=ref_730909086
https://t.me/Bcoin2048bot/app?startapp=ref_pCGwqQ15aSZUFYa9ZEys8qRH
https://t.me/realgoats_bot/run?startapp=c127fadc-579e-485a-a68f-f901cd4e64e6
https://t.me/OwlMini_bot/app?startapp=730909086
https://t.me/bluefarming_bot/play?startapp=c8a58023
https://t.me/BitsTonboxBot/BitsAirdrops?startapp=M9Ek3ygSFAJTZ5Y4PS2aoq
https://t.me/digibuy_bot/digiverse/start?startapp=0cb38b86ee4543c74bd76ab16c1c8fd3
http://t.me/foxs_HouseBot?start=730909086
https://t.me/Agent301Bot/app?startapp=onetime730909086
t.me/RealCowsHouse_bot/cowshouse?startapp=kentId730909086
http://t.me/token1win_bot/start?startapp=refId730909086
https://t.me/MemesLabBot?start=PNT7D8
https://t.me/major/start?startapp=730909086
https://t.me/uptonfi_bot/UpTonGames?startapp=ByKBX2QurGdYa
https://t.me/catizenbot/gameapp?startapp=r_1938_7836673
https://t.me/memefi_coin_bot/main?startapp=r_27d6952978
https://t.me/whitebunnywtf_bot?start=ref666953186736f7f2eff6261f
https://t.me/pixelversexyzbot?start=730909086
https://t.me/tapswap_mirror_2_bot?start=r_730909086
https://t.me/hamster_kombaT_bot/start?startapp=kentId730909086
https://t.me/IcebergAppBot?start=referral_730909086
https://t.me/gemsee_bot?start=ref_100a006b
https://t.me/GoodRides_bot?start=NzMwOTA5MDg2
https://t.me/lost_dogs_bot/lodoapp?startapp=ref-u_730909086
https://t.me/gemzcoin_bOt/tap?startapp=nSoqE-UNEtgNUcRp5luy0w
https://t.me/QappiMinerBot?start=730909086
https://t.me/Snakelite_official_bot/Snakelite?startapp=nOuSbPc0
https://t.me/squid_squad_bot/squid?startapp=link_730909086
https://t.me/lovetap_bot?start=ref_120218
https://t.me/BIRDTonBot/app?startapp=730909086
https://t.me/LovelyLegends_bot/start?startapp=kentId730909086
https://t.me/claytoncoinbot/game?startapp=730909086
https://t.me/pehekingdom_bot/open?startapp=iAzmZVumOr
https://t.me/loody_farming_bot/LOODY/?startapp=inviter_id_40937
https://t.me/Tomarket_ai_bot/app?startapp=0000bDIo
https://t.me/CoinCryptoGameBot?start=r_JSGDH54A
https://t.me/Xyzmercoin_bot/play?startapp=BZI2CZ
https://t.me/dragonz_land_bot/app?startapp=ref-668302fc033aa4721ab5d1ea
https://t.me/BullishFarmBot/start?startapp=r_730909086
https://dashboard.wormfare.com/referral/0DC0D761
https://t.me/betfury_social_bot/app?startapp=tgReLe1ec7c70
https://t.me/PipeFlareBot/pipeflare_app?startapp=730909086
https://t.me/TimeFarmCryptoBot?start=x3jKZG0eoJa58ayY
https://t.me/MatchQuestBot/start?startapp=0cb38b86ee4543c74bd76ab16c1c8fd3
https://t.me/DiamoreCryptoBot/app?startapp=730909086
https://t.me/money_dogs_bot/money_dogs?startapp=3eAlu89K
https://t.me/ZARGatesBot/?start=2307731133
https://t.me/taptapcore_bot/Earn?startapp=b1720f3afcf04e5cb76418c267c4559e
https://t.me/Mimiland_appbot/app?startapp=ref_eyJwIjoiIiwiZiI6InJlZiIsInIiOiI3MzA5MDkwODYiLCJtIjoiNjZkNWZmMWJkNTE3MGU1M2ZiYmMwZmNiIn0=
https://t.me/CyberFinanceBot/game?startapp=cj1CRjNxRE5WbmhNQlomdT1yZWY=
https://t.me/BBQcoin_bot/BBQcoin?startapp=rp_9004676_730909086
https://t.me/PonchKick_bot/ponchiqs?startapp=730909086
https://t.me/potusclick_bot/app?startapp=r730909086
https://t.me/chickcoopofficial_bot/chickcoop?startapp=ref_730909086
https://t.me/ArtiTapBot/start?startapp=referrerId730909086
https://t.me/Frogs_HouseBot?start=730909086
https://t.me/tomo_cat_bot?start=r-cofuLtoo
https://t.me/Boom/LoudCoins?startapp=F5iKvP2LEVi9g4hFkGdpya
https://t.me/The_Rocket_bot?start=r_730909086
https://t.me/monkeycost_bot/app?startapp=r_730909086
https://t.me/tapcoinsbot/app?startapp=ref_TxCe4a
https://t.me/cexio_tap_bot?start=1722546804203779
https://t.me/cexio_tap_bot?start=1722546804203779
https://t.me/flarexgamebot?start=66743fede9b04d43fd21fe9e
https://t.me/grandcombat_bot/start?startapp=TFqI0dXjLc
https://t.me/fishing_bowl_bot/fish?startapp=EQANA57LP2PPLgBIwbnWMpHD4708uGKu7YipzvELhOt6fdnA
https://t.me/GametyPlatform_bot?start=NzMwOTA5MDg2XzA
https://t.me/HUNDTAPbot?start=r_730909086
https://t.me/BabyDogePAWS_Bot?start=r_730909086
https://t.me/BillyBobRobot/GAME?startapp=730909086
https://t.me/wcoin_tapbot?start=NzMwOTA5MDg2
https://t.me/cherrygame_io_bot/game?startapp=r_730909086
https://t.me/pirate_frenzy_bot/piratefrenzy?startapp=i7z37hc2G6
https://t.me/MMproBump_bot?start=ref_730909086
https://t.me/theHoldCoinBot/app?startapp=ref_NRPViKZ4
https://t.me/not_panda_bot/not_panda_app?startapp=9j3938HJeb
https://t.me/gmdotaibot/Airdrop?startapp=ovyova
https://t.me/GoldVerseBot/app?startapp=ref_zzT4iN
https://t.me/herewalletbot/grafun?startapp=TewJ6VV5SA2CrVidvyILAXC8diL
https://gra.fun/?ref=TewJ6VV5SA2CrVidvyILAXC8diL
https://t.me/owlsonton_bot?start=730909086
https://t.me/y_nation_bot/start?startapp=NKS74T
https://t.me/cedex_tap_bot?start=1725744305355276
https://t.me/TondropEarnBot/app?startapp=66dfd225c839152d9203f5a9
https://t.me/BYIN_official_bot/BYIN_Launchpad_Beta?startapp=q3lj8O41
https://t.me/ARIXcoin_bot?start=ref_730909086
https://t.me/sunkongmyth_bot/sunkong_miniapp?startapp=E987837FE
https://t.me/boolfamily_bot/join?startapp=8T1X0
https://t.me/tonstationgames_bot/app?startapp=ref_aysq8p4swodmv4ex6c7e4y
https://t.me/y_nation_bot/start?startapp=NKS74T
https://t.me/GalaCoin_bot/app?startapp=ref_KFfSylID
https://t.me/Yaytsogram_bot?start=invite4546481
https://t.me/battle_games_com_bot/start?startapp=frndId730909086
https://t.me/PinEye_Bot/pineye?startapp=r_730909086
https://t.me/pocketfi_bot/Mining?startapp=730909086
https://t.me/SatoshiMiner_Hq_Bot?start=730909086
https://t.me/sidekick_fans_bot?start=730909086
https://t.me/bums/app?startapp=ref_rgws9zFi
https://t.me/TondropEarnBot/app?startapp=66dfd225c839152d9203f5a9
https://t.me/head_coin_bot/start?startapp=bonusId730909086
https://t.me/onus_tap_tap_tap_bot/join?startapp=1722155904792
https://t.me/Atleta_tap_bot/tap?startapp=a89197f4-6ef7-4925-a38d-cbe0cc71aa34
https://t.me/SecretPadBot/app?startapp=r730909086
https://t.me/Binance_Moonbix_bot/start?startApp=ref_730909086&startapp=ref_730909086&utm_medium=web_share_copy
🎉 Exciting news alert! 🚀 Join us today - it's totally FREE and packed with unlimited opportunities in the Telegram app! 📱 Dive into numerous ongoing projects and explore amazing releases already out there. 🌟 Don't miss out on all the fun, creativity, and innovation waiting for you! 💫 Let's make things happen together! #memefi #hamster kompat #Iblum #tapswap .
-
 @ 6bae33c8:607272e8
2024-09-03 10:47:55
@ 6bae33c8:607272e8
2024-09-03 10:47:55I do this every year, and every year I get at least one correct. Last year, I got exactly one correct and unfortunately it was the surefire prediction that not all of them would be right, i.e., I got really zero correct. But that just goes to show how bold they were. These aren’t layups, more like three pointers and half-court shots. I fared much better the previous two years, so hopefully these will get back on track.
(Actually, probably better to just link to all of them for full transparency: 2023, 2022, 2021, 2020, 2019, 2018, 2017, 2016, 2015, 2014.) I’m not going to argue it matters, or that anyone even clicks through on these, but I want to pat myself on the back for being so organized in archiving my old work.)
-
Stefon Diggs leads the Texans in targets, catches and receiving yards
Right now, he’s getting drafted more than a round behind Nico Collins and less than a round ahead of Tank Dell. Diggs is 30, but he was one of the league’s best receivers until halfway through last year when the Bills made an offensive play-calling change. Moreover, Diggs is getting paid $22.5 million, so the Texans obviously don’t think he’s washed up, and he’s also in a contract year.
-
CJ Stroud leads the NFL is passing yards
This is +600 on DraftKings, so the real odds are probably north of 8:1. Stroud adds Diggs to his receiving corps, doesn’t run much and heads into Year 2.
-
Roman Wilson (ADP 211) has more receptions than George Pickens (ADP 47)
Pickens is a boom or bust downfield playmaker, not high-target alpha, and Wilson is a good fit for the slot for the Steelers new QBs. Think Martavis Bryant not Antonio Brown. (Not that Wilson is Brown!) Van Jefferson isn’t good, and someone will need to fill the void. Moreover, because Pittsburgh has new QBs, neither has an existing rapport with the incumbent Pickens.
-
DeAndre Hopkins (ADP 82) out produces Calvin Ridley (ADP 54) in PPR
Hopkins wasn’t terrible last year, has a rapport with Will Levis and is a future Hall of Famer who can still run routes. Ridley is already 29 and is just a guy outside of his monster season in 2020.
-
The Giants will field a top-10 fantasy defense.
I’ve been crushed by my homer bold predictions in the past, but they added Brian Burns to a rush that already had Dexter Lawrence and Kayvon Thibodeaux, the offense should be on the field more and generate some leads with a real playmaking receiver in Malik Nabers.
-
One of the following Year 2 receivers will finish in the top-15 PPR: Jaxon Smith-Njigba, Jayden Reed, Jordan Addison, Dontayvion Wicks, Michael Wilson, Josh Downs, Andrei Iosivas, Quentin Johnston, Marvin Mims, Jalin Hyatt
I make this prediction every year, and it often pans out as Year 2 is when receivers typically make the leap. I left out Tank Dell because he’s now got a fifth-round ADP, as well as the obvious ones: Zay Flowers, Rashee Rice and Puka Nacua.
-
Rome Odunze (ADP 77) will outproduce Xavier Worthy (ADP 59)
Both receivers enter crowded situations, and while Worthy’s is far better, he’s also got essentially the same skill-set as teammate Marquise Brown. Moreover, Andy Reid rarely entrusts rookies with large roles, especially early on. Odunze is 6-3, 215 and has the pedigree of a true NFL alpha, while Worthy weighs only 165 pounds at 5-11. Finally, Patrick Mahomes already has an established rapport with both Travis Kelce and Rashee Rice, while Odunze gets a more open competition with the Bears veteran WRs, given all three will play with Caleb Williams for the first time.
-
Dalvin Cook will lead the Cowboys in rushing yards
Cook is 29 and looked beyond “cooked” last year on the Jets, but his 3.3 YPC was on a small sample (67 carries), and prior to that, he’d been very good for the Vikings. At the very least he should have fresh legs, and he’d only need to beat out the ancient Ezekiel Elliott and Rico Dowdle. (Of course, Cook would have to be promoted from the practice squad first, so I really should hedge and make the prediction “neither Elliott, nor Dowdle will lead the Cowboys in rushing yards,” but I’ll push it and say it’s Cook.)
-
Jonathan Taylor (ADP12 ) will lead the NFL in rushing yards.
He’s got little competition in the Indy backfield and a running QB who should open lanes for him. Draft Kings has him at +600, so his real odds are probably about 10:1, but I’d take him over the favored Christian McCaffrey (age/mileage) and all the other backs who are more hybrid types or old (Derrick Henry.)
-
Dalton Kincaid (TE4) will lead all TE in catches
I guess this is a chalky pick because he and Kelce are both favored at the position at +3000, while Evan Engram is +5000! (I’d way rather bet on Engram at those odds.) But straight up, I’m going with Kincaid who is likely Josh Allen’s de facto No. 1 target with Diggs gone. In his final 11 regular season games Kincaid had 56 catches which prorates to 87 catches over the full year. And rookie tight ends rarely do anything and often make a leap in Year 2.
-
Some of these predictions will be wrong
No one’s perfect, but you never want to get shut out.
-
-
 @ 361d3e1e:50bc10a8
2024-09-18 15:55:45
@ 361d3e1e:50bc10a8
2024-09-18 15:55:45https://forex-strategy.com/2024/09/18/did-kamala-harris-know-the-trump-debate-questions-in-advance/
Did Kamala Harris Know the Trump Debate Questions in Advance?
trump #debate #usa #politics #harris #kamalaharris
-
 @ 161c8564:2d633b95
2024-09-02 20:24:34
@ 161c8564:2d633b95
2024-09-02 20:24:34Opinion about Freewallet Multi Crypto Wallet (iphone)
FRWT Wallet uses deceptive marketing to lure in unsuspecting users. Once you deposit funds, they’ll block your account under the guise of KYC checks. It’s a fraudulent app—don’t download it!
WalletScrutiny #nostrOpinion
-
 @ dc652bee:6154e7d0
2024-09-18 15:32:15
@ dc652bee:6154e7d0
2024-09-18 15:32:15Ready to dive into the future of finance? With Binance bot mining, you can earn free coins without lifting a finger! Embrace the power of automation and start your crypto adventure today! 🚀💰 #Binance #bot 🌐https://n9.cl/binance_bot👈
-
 @ b7338786:fdb5bff3
2024-09-18 12:32:25
@ b7338786:fdb5bff3
2024-09-18 12:32:25Doug Brown Electronics repair , Microcontrollers , Reverse engineering 2024-09-15
This post has a little bit of everything. Hardware diagnostics, some suspiciously similar datasheets from two separate Taiwan chip manufacturers, and firmware reverse engineering. Read on if that sounds like fun!
Lately, I’ve been enjoying watching random electronics repair channels on YouTube. There’s something oddly satisfying about watching someone take a broken device from totally nonfunctional to perfectly working, all by replacing a $0.05 capacitor that has failed shorted or maybe a blown $0.75 IC. Two of my favorite channels about this topic are Buy it Fix it and StezStix Fix? .
The videos inspired me. I thought, “I should totally try this!” So I went on eBay and looked for broken devices. I have a pretty decent understanding of how video encoders and decoders work, so I thought it would be a fun project to try to fix an HDMI capture card. I found a broken Elgato Game Capture HD60 S USB 3.0 device. The listing said that nothing happened when you plugged it in.
When it arrived, I was able to verify exactly what the listing said. Nothing showed up on my computer when I plugged it in. I cracked it open and had a look at what was happening internally when it powered up. I started by poking around at voltages on the board with it plugged in, and it was pretty obvious that something was dragging the power rails down. Little did I know at that point what I was getting myself into.
Honestly I could tell what was getting hot just by feeling around with my finger, but this was a good excuse to use my thermal camera to take some fun pictures.
In this one, the red cursor indicating the hottest point in the image is pointing to a small chip in the upper-left corner of the board marked “fiVJVE”.
This was pretty clearly some kind of a switching regulator, which I concluded due to its proximity to the “2R2” inductor (meaning 2.2 uH). Measuring the pins, I could see 5V going in, but obviously something was wrong because the voltage at the inductor (the output) was far too low.
There was also another fiVJVE chip on the board, with a pretty much identical circuit next to another 2.2 uH inductor. The circuit was missing a component, but I was pretty sure it was normal because the solder blobs looked like they came that way from the factory. It wasn’t getting hot, but it was also putting out a low voltage so I suspected something was wrong with it too:
In the heat image above you can see another area on the board (near the bottom) that was also getting hot. It turns out it was actually originating from the other side:
Yeah, that’s my finger in the picture. It helped adjust the levels in the image so the chip that’s getting hot is easier to pinpoint. This chip was labeled PFNI:
OK, so what could I do with this information? I found two chips that were getting hot, and another chip that likely wasn’t putting out its correct voltage. I started out by trying to identify what they were. Small chips with markings like this can be quite difficult to figure out. Luckily, there are a few SMD marking code search engines out there. Searching smd.yooneed.one for fiVJ didn’t result in any exact matches, but it did point out that the code “fi” went with the Fitipower FP6121-IS9P. This led me to Fitipower’s website , where I saw they had a bunch of different chips. Using Google’s help I was eventually able to narrow it down to being the FP6373A.
The pinout made sense on the board, and the fiV marking also matched. Yay! Now I had an idea what I was looking for. The PFNI chip ended up being even easier to identify. Google led me straight to the TI TPS60403DBV voltage inverter :
One thing in common with all of these chips is they were all taking in 5V for their input and I was measuring that their outputs all had a pretty low resistance to ground. I started wondering if maybe someone fried this device by somehow putting more than 5V into it. How they did that, I have no idea.
I wasn’t sure why the other FP6373A regulator wasn’t getting hot. It wasn’t putting out much voltage and nothing else was getting hot on the board, so I decided to try injecting voltage on its output power rail instead to see where the low resistance was coming from. I could deduce its correct output voltage because it was going to a Winbond W25Q32JVSSIQ SPI flash chip rated for 2.7 to 3.6V. I was pretty sure it was on a 3.3V rail. I soldered wires to the regulator’s output and ground and used my bench power supply to inject 2.7V into the circuit with a small controlled current that I could slowly turn up. The idea was that I could find what was getting hot on the board and determine what to blame for this power rail being bad.
This process pretty quickly revealed the FP6373A itself as the root problem.
I think maybe during normal operation when it was being supplied with 5V, it was putting itself into some kind of safety shutdown mode and killing its output power rail. The datasheet does mention overcurrent and overtemperature shutdown capability. When I injected voltage directly, the regulator couldn’t shut off the power rail so it had no choice but to get hot and announce “hey, I’m the problem!” through my thermal camera.
This was actually great. I wasn’t totally confident about whether the TI chip was to blame rather than something downstream of it, but since two other chips on the 5V rail were also fried, I thought a good first step would be to replace all three of them and see what would happen. Unfortunately the FP6373A isn’t available at the usual US distributors, but I was able to find it for sale on LCSC at $0.17 a pop, and the TI chip was conveniently also available there for $0.58. Would it really be this easy? Just replace three chips totaling less than a dollar in value, even in quantities of 1? The shipping and handling was orders of magnitude more expensive than just the parts themselves!
After the parts arrived from China, I was able to successfully replace them. I’m always paranoid about upsetting nearby resistors and capacitors when I’m using hot air, so I like to use Kapton tape to shield everything else.
The process of soldering in the new chips was mostly easy, but the ground pins did soak up quite a bit of heat. I think this PCB design doesn’t have great thermal relief on the grounds. I did accidentally lift a pad for one of the regulators, but it wasn’t connected to anything (the “PG” signal) so there was no harm done. The fact that it wasn’t connected to anything was exactly why it was so easy to lift it. Also, the heat that the ground pin was eating up misled me into thinking I could use the same heat on the other pins.
In addition to my lifted pad (middle pin on the right), you can see here how much trouble I had soldering the ground pin (middle pin on the left). It really didn’t want to heat up. I probably could have heated the whole board to help my soldering iron out, but hey, it’s connected.
Anyway, after replacing all three chips, it worked! None of the new chips were getting hot, the HD60 S showed up as a USB device when plugged in, and it worked perfectly for capturing and passing through an HDMI signal. I was pretty excited to successfully fix it, but there was still a problem: none of the indicator lights worked. There are seven white LEDs and seven red LEDs, and they are supposed to do various things to tell you what’s going on . The white lights are supposed to blink twice when you first plug it in, for example.
This was a little deflating. I had kind of fixed it, but not really. Now what?
Back to the drawing board. I looked closer at the PCB to understand how the LEDs work. The relevant chip is the IT1504, made by Innochip . Looking further at its datasheet , it is a 16-channel LED driver chip. You talk to it with a serial data interface that appears to be very similar to SPI. It turns out a lot of LED driver chips from many manufacturers such as Toshiba and ST also use this same communication scheme. At first I though it was odd, but it seems pretty standard. It’s a variant of SPI where you send a particular number of clock pulses to choose which command you want to perform.
I monitored the relevant data input pins on the IT1504 using my oscilloscope, and I could definitely see some traffic being sent to it. By the way, I followed the traces and discovered that the IT1504 is being controlled by a Nuvoton M031LD2AE microcontroller, which is an ARM Cortex-M0.
The presence of SPI traffic here proved it was at least trying to do something, so I assumed that the LED driver chip was probably fried. That presented a pretty big problem though: how could I find a replacement for the IT1504? It wasn’t stocked anywhere. LCSC didn’t have it, and of course none of the US distributors had it either. I couldn’t even find any sellers on AliExpress or utsource.
I reached out to Innotech, who surprisingly wrote back the next day and kindly offered to send me a few free samples for the price of shipping, but then realized they only have full reels in stock so they couldn’t send me any samples. That was nice of them to check, but I definitely wasn’t going to buy a full reel of IT1504 chips just to fix this one problem.
This pushed me toward a huge search all over the internet for LED drivers to try to find a suitable equivalent replacement. The IT1504 datasheet I had access to didn’t include the full command info, so I wasn’t sure exactly what I was looking for. There were several discontinued parts from other well-known manufacturers that looked similar, but I wasn’t finding any exact matches. That’s when I discovered something really strange.
I somehow stumbled upon Macroblock ‘s product offerings. Specifically, the MBI5040. The datasheet seemed to match up pretty well with the IT1504. In fact, a little too well. Here is an example of what I mean (click if you want it larger so you can read it):
Here are a few more side-by-side comparisons to really hit the point home:
They’re almost exactly the same! Everything is laid out in precisely the same order. The current output specs differ slightly, but aside from that, they’re the exact same product, right down to having identical block diagrams. The wording has been tweaked here and there, but both of these datasheets are clearly from the same source. These companies are both based in Taiwan. Maybe one of them licensed the design from the other? Or perhaps there is some industrial espionage going on? There is definitely some funky stuff going on with the fonts on the Innochip datasheet’s general description page. It randomly switches around between serif and sans-serif. It’s the kind of thing you notice when you’re reading an email that somebody sent and you can tell they’ve obviously been copying and pasting while writing it. That doesn’t necessarily mean anything, but I thought it was weird.
Heck, even the part numbers are pretty much the same. If you pretend that the capital letter “I” in MBI5040 is really the number 1, you have MB15040 and IT1504.
I have no idea which product is the original here, but either way, this was really good news for me. I had successfully discovered another chip that would likely be suitable as a replacement for my assumed-to-be-fried IT1504. Additionally, the MBI5040 datasheet actually had command info, so if it came down to it, I could dive deeper and really try to understand what the SPI traffic was doing. I was able to find the MBI5040GF available for purchase on both AliExpress and utsource, so I bought a few.
Replacing the LED driver chip was a pretty simple job. Once again I used Kapton tape to protect me from myself.
I was feeling pretty good about my situation at this point. I cleaned up all the flux residue and anxiously plugged in the HD60 S to my computer.
Video capture worked fine, so I didn’t make it any worse, but the lights were still not working! What in the world? Next I started wondering if perhaps the LEDs themselves were broken. I rigged up my bench power supply and a resistor so that I could pass current through them (without the whole device powered on, of course), and the LEDs all tested out fine physically. I was able to light each one up.
I was totally out of ideas at this point. A brand new chip didn’t fix it, and the LEDs were known good. That’s when I started searching on Google and found something shocking: apparently the LEDs going out on these Elgato HD60 S capture cards is a known problem that multiple people have experienced. In particular I found two different Reddit posts with four unique users complaining about running into this same problem:
Not only that, but sometime during this whole saga I also bought another “dead” HD60 S on eBay that turned out to work fine but had the exact same LED fault. It was starting to look like this indicator light failure was actually quite common!
So yeah. It’s very likely that the LEDs on this one weren’t working even before the voltage regulators originally got fried. This led me to a new bonus challenge: Could I figure out why the LEDs didn’t work and fix them? After all, I now had two different units both experiencing this failure and I knew of at least four other people with the same problem. If you go to the parent post at the second link above, there’s a video that shows how the white LEDs are expected to flash white twice when you first plug it in.
My first idea was to verify that the actual LED circuitry on the board was functional. To perform this test, I lifted the relevant SPI input pins on my replacement MBI5040 LED driver and soldered wires to them, as well as ground:
This allowed me to rig something up with a Raspberry Pi Pico to manually control the LEDs by sending the appropriate commands as documented in the MBI5040 datasheet. I’ll let this picture speak for itself:
It was at this point that I became very confident there was nothing physically wrong with my repaired HD60 S at all. I could perfectly control the lights with my Pi Pico, so the circuit was fine. The Nuvoton Cortex-M0 microcontroller was simply never deciding to turn them on.
This whole MBI5040 replacement story was all for nothing! I was so proud of myself for finding a suitable substitute IC, but it was all mostly just a big waste of time. The original chip was probably fine all along. I decided to confirm that theory just to be sure. I put the original IT1504 chip back onto the board. In order to avoid having to bend pins, I covered the 3 pads that I wanted to avoid soldering to the chip with Kapton tape. This kept them insulated, and then I just soldered all of the other pins normally.
Then I resoldered the wires and repeated the experiment with the Pi Pico. No surprises here — the original chip was totally fine too. After I was done tinkering, I simply pulled the Kapton tape out and then was able to solder the remaining 3 pins normally. I thought this solution was pretty clever and saved me some time! Here’s a view after I pulled out the tape, but before I soldered them down.
And yes, I know pin 1 looks messy. Once again, it’s a ground pin and I guess they didn’t add thermals on the ground pins on this board. It was a pain to solder. I fixed it up afterward though.
So yeah. The original IT1504 chip worked fine. I was a little annoyed, but this side quest wasn’t entirely a waste of time. Getting ahold of the MBI5040 datasheet importantly gave me a perfect reference for how the LEDs are controlled by software. It was looking more and more like this was a software problem as opposed to a hardware problem. I was invested in this problem at this point. I couldn’t give up now!
I began the next phase of this project with a simple idea: ask Elgato if there is some kind of known issue with the status lights. Maybe there was a setting I was missing that allowed you to disable them. Essentially, they politely told me to take a hike:
That’s okay. I felt like solving it on my own anyway. I decided to focus on understanding what was going on in the firmware running in the Nuvoton M031LD2AE microcontroller. By a stroke of pure luck, I had gained some experience last year with Nuvoton MCUs when working on my Mac ROM SIMM programmer . I already had a Nu-Link2-Me that was bundled with the dev board I bought for that project. The next step was to figure out how to access the programming pins on the microcontroller. It turns out that there are a couple of small JST connectors on the board: a 4-pin one and a 6-pin one. Tracing out the pins one by one, it quickly became apparent that the 4-pin JST connector was for programming the MCU! I hooked it up using the only 4-pin JST cable I had on hand, which had grabbers on the other end.
I didn’t check, but I think it’s a pretty good educated guess that the 6-pin JST connector next to it is for programming the Altera MAX II CPLD that is also on this board. It just makes sense.
I didn’t care about the CPLD though. I tried to read the firmware out of the Nuvoton chip using NuMicro ICP Programming Tool, but of course Elgato protected the contents:
Never fear, though. It turns out that Elgato includes the latest firmware with their 4K Capture Utility:
Reading the included ElgatoDeviceCapabilities.json file in the same folder also provided some insight. This firmware is specifically for the version of the device with USB product ID 118 (0x0076), which definitely matches mine. Elgato refers to this device as the “Game Capture HD60 S Rev.4”:
The firmware was already up to date when I checked in the 4K Capture Utility. You can also control-click the settings icon to enable an Update Firmware button, but it did nothing because the newest firmware was already installed on it:
This was great though! The FW_HD60_S_MCU.bin file looked very much like a normal Cortex-M0 firmware binary. You can tell by looking at the start of it in a hex editor. The very first 4-byte word should be the initial stack pointer, so something in RAM. Then following that is a bunch of interrupt vectors including the reset vector.
This all checked out. 0x20000E70 looks like a valid stack pointer, and each 4-byte word following that looks like a valid flash address. It looks exactly like a Cortex-M0 vector table. I loaded it into Ghidra and also used SVD-Loader to try to map out some of the registers. I had to modify the SVD file (M031AE_v1.svd), which I got from the NuMicro_DFP pack on keil.arm.com , to get it to load with the plugin. Apparently it doesn’t like if you have multiple addressBlocks per peripheral, so I modified the first one in each peripheral to contain the full range of addresses.
And thus began the humongous effort of trying to figure out what this little MCU was actually doing.
The SVD file helped me identify the various peripherals being used: mostly GPIO, a timer, and I2C. Nuvoton’s M031BSP project was very valuable for identifying a ton of functions. I did it by hand, which was probably slightly insane, but I wasn’t sure what compiler had been used. Since I knew which pins were hooked up to the LED controller chip, I was fairly quickly able to identify functions that control the LEDs. It was hard to understand their purpose in the grand scheme of things though. Sometimes they were buried deep inside multiple layers of function calls.
Knowing that I2C was being used was very helpful, because I saw there were other chips onboard that would communicate through it: the ITE IT6802E and IT66121FN. The IT6802E is an HDMI receiver. I don’t have any detailed documentation for it, but I’m pretty sure it converts an incoming HDMI signal into a parallel data stream suitable for the capture portion of the device to read in. The IT66121FN is the opposite. It takes a parallel data stream and sends it out as HDMI. This would be necessary for the passthrough functionality, providing an HDMI output signal to go through to your TV or monitor.
Anyway, I found some ITE driver code in some random GitHub projects such as this one , which quickly helped me identify a bunch of functions and variables as belonging to ITE’s drivers. This helped me gain a better understanding of what was happening in the firmware. I actually spent way too much time on this, but I think it was useful in the long run. Plus, it was good practice with Ghidra.
Once I had a good idea of the overall structure of the firmware, I decided to try figuring out how I could debug the code. The chip was protected, but I figured that I should be able to erase it and reflash the firmware. To be safe, I desoldered the original M031LD2AE chip and put a new empty one onto my board instead. They only cost $1.14 on Digi-Key in quantities of 1. Why not?
When I flashed FW_HD60_S_MCU.bin onto my brand-new blank chip, it definitely worked fine, but it re-protected itself so I couldn’t do any debugging! The offending code was pretty easy to find in Ghidra. There’s a function that is called to update the config registers with the proper locked state as well as the number of 512-byte data flash pages to reserve from the application ROM.
I simply had to hack this function to always leave the chip unlocked. Then I reflashed the chip and I was finally able to debug the code! I inserted some breakpoints and stepped through the initialization code with OpenOCD and GDB to figure out why the LEDs weren’t being controlled. I found some places in the code where LED control would happen, but they were being skipped. I decided to force the code to run by filling in register values and RAM in GDB, and sure enough, I was able to at least force the lights to turn on. So clearly the code was there to control the lights, but it wasn’t running for whatever reason.
This chip unlocking mess led me down another rabbit hole. I assumed that the original Nuvoton MCU I removed had some other protected contents like a bootloader, so I decided to see if I could extract it by installing my new unlocked firmware file as an update through Elgato’s software. The idea was that after my new unlocked firmware was installed, the protection would be disabled and then I could read out the entire contents with my Nu-Link2-Me. Why would I want to do this? Well, it would just be nice to have as a backup in case I screwed up one of the chips, plus the bootloader might contain other clues.
I tried it out on my other HD60 S with broken LEDs which still had its stock Nuvoton MCU fitted. This required modifying ElgatoDeviceCapabilities.json to point to my unlocked firmware. I also had to change the version listed in this same file so that it would think it was out of date. After making these changes, the 4K Capture Utility allowed to install my new firmware through the normal firmware update mechanism. The utility did tell me the firmware update failed after it finished (more on that later).
This totally freaked me out because it appeared to brick the device. It didn’t work as a capture card anymore. But luckily, but I was left with an unlocked chip, just as I had hoped! This allowed me to read out the rest of the content of the flash that had previously been protected, including the LDROM (containing Elgato’s first-stage bootloader), data flash contents, and the correct original config register contents. This was really exciting because it meant I now had everything I would need in order to completely program a brand new Nuvoton MCU to contain Elgato’s stock firmware, including their bootloader. I rewrote the original Elgato firmware back to this second HD60 S’s APROM (application ROM) using Nuvoton’s tools, and re-locked the chip. Thankfully, this fully restored it to working order — except for the LEDs of course.
I also disassembled their small LDROM bootloader that I was able to read out of the chip, but it wasn’t really anything exciting. It receives commands and data over I2C and is capable of reflashing the APROM. Interestingly I discovered that if the chip is set for unprotected mode, the bootloader actually waits around for update commands instead of booting the application firmware. So Elgato is using the locked/unlocked bit as a way of signifying whether it should stay in the bootloader or not, which I find to be a little bit weird. That completely explained why my second HD60 S stopped working after I installed my unlocked firmware — it was stuck in the bootloader waiting forever because the chip was unprotected.
Anyway, I’ve really started to ramble on about things unrelated to the LED problem. Let’s get back on track. The point I’m trying to make here is that I was able to read out all of the stock microcontroller contents, which gave me the confidence I desperately needed in order to start tinkering even further to figure out the LED problem. I was kind of stuck at this point though. Why was the Nuvoton chip not controlling the LEDs? Some of the LED control happened over I2C from something else, so I was beginning to worry that the actual problem was once again at a different level.
Fortunately though, I was gaining a better understanding of the architecture of the entire product at this point. Here’s a broad overview of how it works:
- The main Cypress/Infineon CYUSB3014 USB 3.0 peripheral chip, which I haven’t mentioned until now, is an ARM926EJ-S. It sends commands to the Nuvoton MCU over I2C. This is the chip that actually communicates with the host PC through the USB 3.0 port.
- The Nuvoton ARM Cortex-M0 microcontroller sets up and monitors the ITE video receiver and transmitter chips through a separate I2C bus.
- The Nuvoton MCU also controls the LEDs.
- The Nuvoton MCU communicates status information back to the CYUSB3014 through I2C.
- The CYUSB3014 receives the video data stream from the IT6802E (likely through the MAX II CPLD, putting it in a format suitable for the CYUSB3014 to grab) and sends it to the computer over USB.
I thought I would take a break from the Nuvoton chip for a while and start trying to understand the main Cypress processor instead. Yes, as I just mentioned above, there are two different ARM processors working together to implement the video capture functionality. Fortunately, Cypress/Infineon also provides a free SDK for these USB chips. The firmware is stored unprotected in the Winbond W25Q32JVSSIQ flash chip that I talked about very early on when I thought this was purely going to be a hardware repair project.
I desoldered the SPI flash chip and read it back using a programmer. It’s a 4 MB (32-megabit) chip. I also tried to do it in-circuit without removing the chip first, but I didn’t have any luck. I even accidentally knocked a small 0402 0.1 uF decoupling capacitor (seen above on the right) off the PCB while I was trying to clip onto it. Luckily the capacitor wasn’t damaged and I was able to put it right back on.
After dumping the chip contents, I used it to start trying to work my way through understanding what the CYUSB3014 was doing. I was able to use Cypress’s existing SDK binaries to help identify a lot of the functions in the dump. It turns out that the Cypress SDK uses the ThreadX RTOS under the hood.
I really didn’t want to dive deep into this firmware to the same level that I did for the Nuvoton chip though. I was already worn out from that disassembly. At the very least, I was able to see that the Cypress chip sends commands over I2C to the Nuvoton chip.
Looking through the rest of the SPI flash dump, I could see that starting at offset 0x300000, there were a bunch of small data chunks that looked like little pictures. Here’s an example:
I couldn’t figure out why there would be little pictures in the flash chip here. What would the purpose be? It made me wonder if maybe it was some kind of small icon, since I’ve seen similar data for icons while analyzing old Mac ROM dumps. Given the context of this blog post, you might be screaming at me right now telling me what this data obviously is, but at the time I was totally oblivious.
I ended up solving this mystery as soon as I started looking into what was going on with five unknown GPIO pins in the firmware on the Nuvoton chip. There were a bunch of functions that controlled these pins, but I wasn’t sure what they did. I traced them out on the PCB and discovered they were going to a Diodes Incorporated PI5C3257 quad 2:1 mux/demux bus switch .
This was the magic discovery that finally unblocked me. This bus switch is being used to decide whether the CYUSB3014 chip or the Nuvoton microcontroller should be wired up to the SPI flash chip. Prior to this moment, I thought that the SPI flash was entirely dedicated to the CYUSB3014. In reality, the Nuvoton microcontroller takes over control of the SPI flash after the CYUSB3014 has finished booting. This enabled me to disassemble a bunch of new functions which were all related to bit-banging SPI transactions, as well as higher-level functions for SPI flash chip erasing/reading/writing.
A light bulb went off in my head. Yes, these chunks of data in the flash chip were pictures! But not in the conventional sense. They were describing the various LED animations. Each set of 16 bytes is an animation frame written to the 14 LEDs. In the example above, a single red LED turns on and six of the seven white LEDs do stuff. The last two bytes in each row are a delay time before moving onto the next frame. The first 16 bytes looked kind of weird though. They looked like they possibly contained some header data for the animation or something.
I also found some code that was reading data from the start of the 0x300000 section, but in my SPI flash dump that section was pretty much completely empty:
Everything was starting to make sense. There was a check in the Nuvoton MCU firmware to see if the first two bytes contained the 16-bit word value 0xAA55:
In my dumps of the SPI flash chip contents from my units with nonfunctional LEDs, that section of the chip was empty. It was programmed as all 0x00. The firmware was bypassing all of the LED control code because expected data wasn’t stored starting at 0x300000 in the flash chip! I confirmed this data was missing on both of the HD60 S devices I was testing with.
Unless I wanted to go overboard trying to figure out how to artificially populate all this data from scratch, I had no choice but to buy a third HD60 S that was confirmed to be fully functional. That’s what I ended up doing. Unfortunately it was an older revision and had a completely different PCB, but it was still based on the CYUSB3014. It also used a Nuvoton microcontroller, but it was a different model. It still had an IT1504 for LED control though, as well as a Winbond SPI flash chip, so that was promising.
I confirmed that its LEDs worked fine, and then I dumped the SPI flash. By this point, I had figured out how to dump the flash contents without any soldering by forcing the CYUSB3014 to boot over USB (removing a jumper on the board) and then uploading a Cypress-provided RAM bootloader capable of dumping the SPI flash (cyfxflashprog.img), but I don’t want to stray too far from the LED issue at this point. Here’s the start of the good data at 0x300000:
Okay, that data makes way more sense. The first 16-bit word (little-endian) is 0xAA55 just like the firmware was looking for. It also has a bunch of other header data, indicating there are 26 different LED animations, and including info about whether they are even animations at all. To be honest, I haven’t figured out what every piece of this data actually means, but each animation has a 16-byte summary. They start at 0x300008. I think the last 4 bytes for each animation are probably a CRC-32 of something.
Also, if you noticed in the original chip dump, there was a section starting at 0x3000B8 with a bunch of 0xE5 bytes. This is the dot correction data that gets loaded into the IT1504. Based on the decompilation above, it’s actually supposed to be at 0x3007F8, which is exactly where it is in the good dump:
The 0x521114A7 that follows is a CRC-32 of the preceding 16 bytes of data.
Further inspection revealed that the data in the SPI flash of the broken devices differed quite a bit. In fact, they were different from each other as well. This led me to believe that the animation data was probably corrupted in them. For example, here’s what the animation at 0x31E000 looks like in the good HD60 S’s dump:
Notice how there is no weird header at the top like the original “picture” I was inspecting from one of the other dumps? It just immediately starts with animation data that is consistent with the rest of the nearby data. It’s also longer. This data makes a lot more sense. On the other hand, it was corrupted in two completely different ways in my two HD60 S devices with nonfunctional LEDs.
Several (but not all) of the animations in my nonworking devices started with a weird “AB 03 12 39” header. I don’t think the header is supposed to be there. Maybe there was a bug in an update procedure or something? The Nuvoton firmware indeed has functions capable of erasing and rewriting data to the SPI flash chip. I’m wondering if that code ended up running and somehow destroying the original contents.
You may be able to guess what I did with this new knowledge. I took the original SPI flash contents from the two devices with nonfunctional status lights, and simply replaced all the LED data starting at 0x300000 with the data from the working one. Then I flashed this new “hybrid” image to the non-working devices. Oh, I should point out that each device has its own unique flash dump. The USB serial number is embedded in there somewhere. So I preferred to preserve the data from 0 to 0x2FFFFF for each individual device.
I wasn’t entirely sure what to expect by trying this. The good SPI flash data came from an older revision of the product with a different Nuvoton microcontroller, but it sure looked like it matched what the newer firmware was looking for.
Here’s a picture of what I saw as soon as I powered one of the problematic devices after I reflashed its SPI flash chip:
It freaking worked. The white lights flashed twice, and then the red lights briefly flashed once.
I think the red flash just means the signal was lost, because it also does it every single time I unplug an HDMI source from it. The older model doesn’t do this red flash on every powerup, but maybe it’s just a firmware difference about whether it should say “signal lost” immediately at startup with nothing plugged in. I’ve seen some mention online of red lights meaning that the signal is HDCP-protected, but I think that’s a different longer red blink which I’ve also seen when I first plug in my iPhone as an HDMI source.
I’ve also noticed that some of the animations that Elgato says it should do, like when I start or stop recording, don’t play on this newer model, even though they work fine with the older model. I haven’t been able to figure out if this is just a known difference with how the newer model works. I may try to get a good SPI flash dump of the correct LED animations from a newer matching model to confirm it for sure, but I have a feeling the animation data will be identical.
I also recently realized that the raw data for each animation is sitting around in C:\Program Files\Elgato\GameCapture\Animations if you have the older Game Capture utility installed, or /Applications/Game Capture HD.app/Contents/Resources/Animations on Mac.
Looking through each file (01.ani, 02.ani, etc.), it looks like the animation data perfectly matches my dump of the older working device. The bytes for each LED are out of order, but if I reorder them correctly, I can create an identical copy of all of the animation data that I extracted from the good flash chip.
Since those animations live inside the Game Capture app (or next to it), it seems as though the software has the capability to load them into the flash chip. I wonder if that explains how the stored animation data ended up corrupted in the first place. A botched update perhaps? That would make sense to me. Maybe they disabled the ability for their software to upload them after they discovered it was screwing up people’s devices? It might be interesting to disassemble the Windows and/or Mac software and try to figure out how to convince it to directly upload the animations, but I’m honestly out of motivation to do that at this point. It looks like LedCtrlDll.dll might be an interesting file to look at if anyone else is hooked enough to continue diving deeper. It contains classes with interesting names like Ub530LedSpiRom and I2cIO_Ub530. Some quick disassembly in Ghidra indeed shows it creating a 0x80C-byte array for the header data that would go into the flash chip at 0x300000, and populating the contents with the dot correction data.
One last thing I noticed is if I do a firmware update of the HD60 S inside of Elgato’s 4K Capture Utility in Windows, it doesn’t wait long enough. It seems to work fine on Mac, but Windows has some issues. The firmware update is still in progress when it tells me that it failed. If I sit there and wait, eventually the lights flash on the unit and it successfully reboots into the new firmware. If instead I unplug it quickly after Elgato’s software tells me the update failed, I end up with an incomplete flash. I wonder if this has fooled people into bricking their devices? Especially if the status LEDs don’t work at all. I was able to successfully fix this problem by increasing the updateDurationSec in ElgatoDeviceCapabilities.json from 40 to 80. I get the feeling Elgato’s firmware update functionality is a little flaky, at least on Windows. In Elgato’s defense, they specifically recommend not to update firmware on the HD60 S unless their tech support tells you to . And they hide the functionality behind a special key combination when entering the settings screen.
I would like to figure out a way to share how to easily fix the LEDs for anyone else who runs into this problem, but the process is admittedly quite convoluted. It requires you to begin a firmware update (modifying ElgatoDeviceCapabilities.json to even allow you to install an update in the first place) and immediately unplug the device — otherwise the Nuvoton MCU takes control of the SPI flash, and you really need the Cypress chip to be in control in order to reflash its contents. Then, you remove the jumper on the PCB (instructing the Cypress chip to boot from USB), upload cyfxflashprog.img to RAM using download_fx3, and use a modified version of fx3_spitest to download the entire SPI flash contents and replace it with your patched LED section. Those are tools from the CYUSB3014 SDK. Finally, you unplug it, put the jumper back in, plug it back in, and perform a normal firmware update in 4K Capture Utility to restore the firmware back to the Nuvoton chip. You ignore the update failure message and wait another minute or so, and eventually it boots back up with working LEDs. If there ends up being enough interest in recovering these things, it might be possible for me to throw something together to automate the process, or at least provide binaries for everything. It would also be nice to figure out how to use Elgato’s software to directly reprogram the LED animations. For now though, I’m just going to sit back, relax, and celebrate my victory on this!
So in conclusion, yes, it really was that simple. All I needed to do was replace three chips for a total of less than $1 to bring this thing back to life. Every bit of extra time and money I spent on this project after that was all about figuring out a well-known indicator LED problem that really had nothing to do with my actual repair. I put way more effort into this than I should have, and yes I am probably a tiny bit crazy for actually doing this, but at least I now have an answer and fix for why the LEDs don’t work on some of these capture cards. It’s some sort of software/programming/update bug. I’m not sure which. Way to go Elgato!
-
 @ 56a6da9b:7f5a2243
2024-09-02 18:27:19
@ 56a6da9b:7f5a2243
2024-09-02 18:27:19IO used to have a lot of content and now the only thing that shows up is my fouintain stuff. when i go into other nostr things it's not there anymore and i look like an anonymous user with no profile pic, or profile and no activity.
originally posted at https://stacker.news/items/669994
-
 @ b7338786:fdb5bff3
2024-09-18 12:27:38
@ b7338786:fdb5bff3
2024-09-18 12:27:38Knocking out one key gene leads to autistic traits
Purkinje cells in the cerebellum, stained and magnified 63 times, revealing fine details of the dendritic spines. (Hatten Lab)
More than 70 genes have been linked to autism spectrum disorder (ASD), a developmental condition in which differences in the brain lead to a host of altered behaviors, including issues with language, social communication, hyperactivity, and repetitive movements. Scientists are attempting to tease out those specific associations gene by gene, neuron by neuron.
One such gene is Astrotactin 2 (ASTN2). In 2018, researchers from the Laboratory of Developmental Neurobiology at Rockefeller University discovered how defects in the protein produced by the gene disrupted circuitry in the cerebellum in children with neurodevelopmental conditions.
Now the same lab has found that knocking out the gene entirely leads to several hallmark behaviors of autism. As they describe in a new paper in PNAS, mice that lacked ASTN2 showed distinctly different behaviors from their wild-type nestmates in four key ways: they vocalized and socialized less but were more hyperactive and repetitive in their behavior.
“All of these traits have parallels in people with ASD,” says Michalina Hanzel, first author of the paper and a postdoc in the lab. “Alongside these behaviors, we also found structural and physiological changes in the cerebellum.”
“It’s a big finding in the field of neuroscience,” says lab lead Mary E. Hatten , whose work has focused on this brain region for decades. “It also underscores this emerging story that the cerebellum has cognitive functions that are quite independent of its motor functions.”
An unexpected role
In 2010, Hatten’s lab discovered that proteins produced by the ASTN2 gene help guide neurons as they migrate during the development of cerebellum and form its structure. In the 2018 study, they examined a family in which three children had both neurodevelopmental disorders and ASTN2 mutations. They found that in a developed brain, the proteins have a similar guiding role: they keep the chemical conversation between neurons going by ushering receptors off the neural surfaces to make room for new receptors to rotate in. In a mutated gene, the proteins fail to act and the receptors pile up, resulting in a traffic jam that hinders neuronal connections and communication. This impact could be seen in the children’s afflictions, which included intellectual disability, language delays, ADHD, and autism.
The find was part of a growing body of evidence that the cerebellum—the oldest cortical structure in the brain—is important not just for motor control but also for language, cognition, and social behavior.
For the current study, Hanzel wanted to see what effects a total absence of the ASTN2 gene might have on cerebellar structure and on behavior. Collaborating with study co-authors Zachi Horn, a former postdoc in the Hatten lab, and with assistance from Shiaoching Gong, of Weill Cornell Medicine, Hanzel spent two years creating a knockout mouse that lacked ASTN2, and then studied the brains and activity of both infant and adult mice.
Behavioral parallels
The knockout mice participated in several noninvasive behavioral experiments to see how they compared to their wild-type nestmates. The knockout mice showed distinctly different characteristics in all of them.
In one study, the researchers briefly isolated baby mice, then measured how frequently they called out for their mothers using ultrasonic vocalizations. These sounds are a key part of a mouse’s social behavior and communication, and they’re one of the best proxies researchers have for assessing parallels to human language skills.
The wild-type pups were quick to call for their mothers using complex, pitch-shifting sounds, while the knockout pups gave fewer, shorter calls within a limited pitch range.
Similar communication issues are common in people with ASD, Hanzel says. “It’s one of the most telling characteristics, but it exists along a spectrum,” she says. “Some autistic people don’t understand metaphor, while others echo language they’ve overheard, and still others do not speak at all.”
In another experiment, the researchers tested how ASTN2 mice interacted with both familiar and unfamiliar mice. They preferred to interact with a mouse they knew rather than one they didn’t. In contrast, wild-type mice always choose the social novelty of a new face.
This, too, has parallels in human ASD behavior, with a reluctance towards unfamiliar environments and people being common, Hanzel adds. “That’s a very important result, because it shows that mice with the knockout mutation do not like social novelty and prefer to spend time with mice they know, which corresponds to people with ASD, who tend to like new social interactions less than familiar ones.”
In a third experiment, both types of mice were given free rein to explore an open space for an hour. The ASTN2 mice traveled a significantly longer distance than the other mice, and engaged in repetitive behaviors, such as circling in place, 40% more. Both hyperactivity and repetitive behaviors are well-known hallmarks of ASD.
Miscommunication between brain regions
When they analyzed the brains of the ASTN2 mice, they found a few small but apparently potent structural and physiological changes in the cerebellum. One was that large neurons called Purkinje cells had a higher density of dendritic spines, structures that are spotted with the synapses that send neural signals. But they only detected this change in distinct areas of the cerebellum. “For example, we found the biggest difference in the posterior vermis region, where repetitive and inflexible behaviors are controlled,” Hanzel says.
The scientists also found a decrease in the number of immature dendritic spines known as filopodia and the volume of Bergmann glial fibers, which help with cell migration.
“The differences are quite subtle, but they are clearly affecting how the mice are behaving,” Hatten says. “The changes are probably altering the communication between the cerebellum and the rest of the brain.”
In the future, the researchers plan to study human cerebellar cells, which they’ve been developing for a half-dozen years from stem cells, as well as cells with ASTN2 mutations that were donated by the family in the 2018 study.
“We’d like to see if we can find parallel differences to what we found in mice in human cells,” Hatten says.
She continues, “We also want to look at the detailed biology of other genes that are associated with autism. There are dozens of them, but there’s no agreed-upon commonality that binds them together. We’re very excited that we’ve been able to show in detail what ASTN2 does, but there are a lot more genes to investigate.”
Explore:

Frederick P. Rose Professor
Laboratory of Developmental Neurobiology
Related publication
PNAS
Mice lacking Astn2 have ASD-like behaviors and altered cerebellar circuit properties
Michalina Hanzel, Kayla Fernando, Susan E. Maloney, Zachi Horn, Shiaoching Gong, Kärt Mätlik, Jiajia Zhao, H. Amalia Pasolli, Søren Heissel, Joseph D. Dougherty, Court Hull, and Mary E. Hatten
Media contact
Katherine Fenz
Media Relations Manager -
 @ 3b7fc823:e194354f
2024-09-02 16:26:30
@ 3b7fc823:e194354f
2024-09-02 16:26:30First steps into privacy.
You are a normie, but maybe you are privacy curious. Maybe you are ready to take a first step or two into security and privacy but don't know where to start.
Don't worry, here are some absolute beginner first steps that will make a big difference.
-
No one except your friends and family should know your personal phone number and email address. Stop giving away your data! You don't have to fill out every blank on that form. Unless they are mailing you something they don't need your home address. Use a email aliasing service or just create a burner email account as a spam trap. Get a second VOIP phone number. Look up the address of a local hotel. Use these instead of your personal information or maybe just skip the customer reward program.
-
Speaking of giving away your data. Stop using spyware! Facebook, Instagram, Tiktok, etc. It is "free" software designed to suck every ounce of personal data from you to be repackaged and sold. Don't just delete the app, search for how to delete your account data.
BTW Windows, google, and 90% of the apps on your phone are also spyware but one thing at a time. Maybe start reading up on FOSS.
-
Clean up your communications. Stop using unencrypted calls and SMS texts. There are several options but just get Signal and make your friends use it. Its easy and works.
-
Clean up your email. This one is probably going to take you some time if you are like most people who have hundreds of emails from years gone bye. Go through every single one and unsubscribe from every newsletter or sales pitch from every store you have ever bought anything from. Block every spam email you see. If you are using a email provider that literally scans every email you send or receive in order to sell you stuff like gmail, then now is the time to switch to a private and encrypted provider like proton or tuta.
-
Clean up your web surfing. Switch to a privacy browser and search engine. If you don't know which one just get Brave. There are ones that I like better but Brave is good enough and easy, especially if you like Chrome. A hardened Firefox is better but requires some homework and if on desktop Mullvad browser is a excellent choice.
BONUS TIP:
Clean up your security. Make sure all of your software is setup for automatic updates, especially security updates. Also, I don’t know who needs to hear this but get a password manager if you don’t have one. (Don't save passwords on the browser!) Get an actual password manager and then add 2FA to all of your online accounts and you will have better security than 90% of the population.
OK, nothing too exciting but we got the big rocks. Data leaks, communications, email, web surfing, and basic security.
What, no VPN or Tor or super secret stuff? No, not yet. This is your level zero default. Your identity and activity is still transparent but you are no longer leaking your data all over the place. This will provide a general base for everyone.
The next step is to perform a basic threat assessment of your personal situation. What are you most at risk for? Targeted attacks or passive? Cyber or physical? What do you most need to defend against? Government mass surveillance, surveillance capitalism, censorship, or public exposure?
There will be some overlap with all of them but your next steps will really depend on your answer. We will cover each of these in greater depth later.
-
-
 @ b7338786:fdb5bff3
2024-09-18 12:26:32
@ b7338786:fdb5bff3
2024-09-18 12:26:32Scramble - Open-Source Grammarly Alternative
Scramble is an open-source Chrome extension that leverages AI to enhance your writing directly in your browser. It's designed to be a more customizable and privacy-respecting alternative to Grammarly.
-
 @ b7338786:fdb5bff3
2024-09-18 12:25:14
@ b7338786:fdb5bff3
2024-09-18 12:25:14AI Workout Generator
-
 @ 0edc2f47:730cff1b
2024-09-02 15:50:08
@ 0edc2f47:730cff1b
2024-09-02 15:50:08Chef's notes
This recipe works with any fat, although butter is generally preferred and traditional. To make it vegan, substitute vegetable oil for the butter and nut milk for the regular cow’s milk. If you want a smokier flavor, try substituting an equal amount of bacon grease for the butter.
Details
- ⏲️ Prep time: 15 minutes
- 🍳 Cook time: 15 minutes
Ingredients
- 2½ pounds spinach in bulk, or two 10-ounce plastic wrapped bags, blanched, (very well) drained, and chopped (or about 1.75 cups well-drained thawed frozen spinach)
- 1 tablespoon butter
- 1 tablespoon all-purpose flour
- 1 cup milk
- Grated nutmeg (optional, to taste)
- Black pepper (optional, to taste)
- Salt (to taste)
Directions
- Melt the butter (or whatever fat you are using) in a saucepan and add the flour, stirring with a wire whisk.
- Add the milk, stirring rapidly with the whisk. Cook until the mixture starts to bubble and thicken.
- Add nutmeg, salt and pepper to taste.
- Cook, stirring, about 5 minutes and add the spinach. Stir to blend. Continue to cook until spinach is heated through and serve.
-
 @ b7338786:fdb5bff3
2024-09-18 12:23:45
@ b7338786:fdb5bff3
2024-09-18 12:23:45
Every hype cycle in the technology industry continues a steady march towards a shitty future that nobody wants.

The Road to Hell
Once upon a time, everyone was all hot and bothered about Big Data : Having lots of information–far too much to process with commodity software–was supposed to magically transform business.
How do you build technology that can process that much information at scale? Well, obviously, you just need to invest in The Cloud! (If you’re using the Cloud to Butt Plus Chrome extension, this entire blog post may be confusing to you.)
But don’t scrutinize the Cloud too long, you might miss your chance to invest in blockchain .

meme via Tony Arcieri
Blockchainiacs practically invented an entire constructed language of buzzwords. Things like “DeFi”, “Web3”, and so on. To anyone not accustomed to their in-signaling, it’s potent enough cringe to repel even the weirdest of furries.

But the only thing to know about blockchain is its proponents they like it when the line goes up, and every “innovation” in that sector was in service of the line going up.
Blockchain, of course, refers to cryptocurrency . The security of these digital currencies is based on expensive consensus mechanisms (e.g., Proof of Work). The incentives baked into the design of these consensus mechanisms led users to buy lots of GPUs in order to compete to solve numeric puzzles (a.k.a. “mining”).
For a while, many technologists observed that whenever the line actually goes down or a popular cryptocurrency decides to adopt a less wasteful consensus mechanism, the secondhand market gets flooded with used GPUs.
That all changed with the release of ChatGPT and other Large Language Models.
Now GPUs are a hot commodity even when the price of Bitcoin goes down because tech company leaders are either malicious or stupid, and are always trying to appease investors that have more money than sense. It’s not just tech companies either.
“Our vision of [quick-service restaurants] is that an AI-first mentality works every step of the way.”
Joe Park , CEO of Yum Brands (Taco Bell, Pizza Hut, KFC)
Of all these hype cycles, I suspect that the “AI” hype has more staying power than the rest, if for no other reason than it provides a hedge against the downside of previous hype cycles.
- Not sure to do with the exabytes of Big Data you’re sitting on? Have LLMs parse it all then convincingly lie to you about what it means.
- Expensive cloud bill? Attract more investor dollars by selling them on trying to build an Artificial General Intelligence out of hallucinating chatbots.
- Got a bunch of GPUs lying around from a failed crypto-mining idea? Use it to flagrantly violate intellectual property law to steal from artists with legal impunity!
This “AI” trend is the Human Centipede of technology.

Art: CMYKat
So you can imagine how I felt when I went to add an image to a blog post draft one day and saw this:

Generate with AI? Fuck you.
There is no way to opt out of, or disable, this feature.
WordPress is not alone in its overt participation in this consumption of binary excrement.
Tech Industry Idiocy is Ubiquitous

Behold, Oracle’s AI innovation
EA’s CEO called generative AI the “very core of our business” , which an astute listener will find reminiscent of the time they claimed NFTs and blockchain were the future of the games industry at an earnings call .
Nevermind the fact that they’re actually in the business of publishing video games!
Mozilla Firefox 128.0 released a feature (enabled by default of course ) to help advertisers collect data on you.
Per 404 Media, Snapchat reserves the right to use AI-generated images of your face in ads (also on by default) .
At this point, even Rip Van fucking Winkle can spot the pattern.

Investors (read: fools with more money than sense) are dead set on a generative AI future, blockchain bullshit in everything, etc. Furthermore, there are a lot of gullible idiots that drank the Kool-Aid and feel like they’re part of the build-up to the next World Wide Web, so there’s no shortage of willing new CS grads to throw at these problems to keep the money flowing.
So we’re clearly well past the point that ridiculing the people involved will have any significant deterrence. The enshittification has spread too far to quarantine, and there are too many True Believers in the mix. Throw in a little bit of Roko’s Basilisk (read: Pascal’s wager for arrogant so-called “rationalists” who think they’re too smart to be Christian) and you’ve got a full-blown cargo cult on your hands.
What can we do about it? Beats me.

Sanity Check
I’m going to set aside the (extremely cathartic) attempts at shame and ridicule as a solution. Fun as they are, they fail to penetrate filter bubbles and reach the people they need to.
What’s your Bullshit Tech Score?
One way we could push back against this steady march towards a future where everything is enshittified, and the devices you paid for (with your hard-earned money) don’t respect your consent at all , is to turn the first of the buzz words we examined (Big Data) against these companies.
I’m proposing we could gather data about companies’ actual practices and build score-cards and leaderboards based on the following metrics:
- Does the company strategy involve generative AI?
- Does the company strategy involve selling NFTs?
- Does the company strategy involve stitching other unnecessary blockchain bullshit where it doesn’t belong?
- Does the company make questionable claims about quantum computers?
- Does the company choose default settings that hurt the user in the interest of increasing revenue (i.e., assuming consent without explicitly receiving it)?
- Does the company own any software patents?
-
This includes purely “defensive” patents, in industries where their competitors abuse intellectual property law to stifle competition.
While these circumstances are understandable, we should be objective in our measurements. 7. Is the company completely bankrupt on innovation tokens ? 8. Does the company suffer from premature optimization (e.g., choosing MongoDB because they fear a relational database isn’t web-scale, rather than because it’s the right tool for the job)? 9. Have any of the company’s leaders been credibly accused of sexual misconduct or violence? * Sorry not sorry, Blizzard! 10. Does the company routinely have crunch time (i.e., more than one week per quarter where employees are expected to work more than 40 hours)? 11. Does the company enforce draconian return-to-office policies ? 12. Has the company threatened a security researcher with lawsuits in the past 10 years? 13. Does the company roll its own cryptography without having at least one cryptographer on the payroll?
-
A passing score is “No” to each of the above questions.
This proposal is basically the opposite of SSO Tax . Rather than shaming the losers (which there will assuredly be many), the goal would be to highlight companies that are reasonably sane to work for.
I’m aware that there are already companies like Forrester that try to do this, but with a much wider scope than the avoidance of bullshit.
Furthermore, they’re incentivized to not piss off wealthy businessmen, so that they can keep their research business alive, whereas I don’t particularly care if tech CEOs get mad at being called a hypocritical hype-huffer.
I mean, what are they gonna do? Downvote me on Hacker News? I don’t work for them anyway.
In Over Our Heads
There may be other solutions available that will improve things somewhat . I’m not immune to failures of imagination.
Some solutions are incredibly contentious, though, and I don’t really want the headache.
For example: I’m sure that, if this blog post ever gets posted on a message board, someone in the peanut gallery will bring up unions as a mechanism, and others will fiercely shoot that idea down.
It’s possible that we, as an industry, are completely in over our heads. There’s too much bullshit, and too many perverse incentives creating ever-increasing amounts of bullshit, that escape is simply impossible.
Perhaps we’ve already crossed the excrement horizon.
Maybe Kurzweil was right about a Singularity after all?

Closing Thoughts
The main thing I wanted to convey today was, “No, you’re not alone, things are getting stupider,” to anyone who wondered if there was a spark of sanity left in the tech sector.

Art: AJ
It’s not just the smarmy tech CEOs that are the problem. The rot has spread all the way to the foundations of many organizations. Hacker News, Lobsters, etc. are full of clueless AI maximalists that cannot see the harms they are inflicting.
It is difficult to get a [person] to understand something, when [their] salary depends on [their] not understanding it.
Original quote by Upton Sinclair.
Though I am at a loss for how to tackle this problem as a community, acknowledging it exists is still important to me.
On WordPress and Generative AI
Years ago, I wrote on Medium, but got tired of the constant pressure to monetize my blog , so I decided to pay for a WordPress.com account. I write for myself , after all, and don’t expect any compensation for it.
Many of you will notice the “adblocker not detected ” popup. That sums up how I feel about the adtech industry.
It’s disheartening that WordPress is pushing Generative AI bullshit to paying customers with no way to opt out of the feature. (Nevermind that it should be off-by-default and opted into .)
For now, I just refuse to use the feature and hope a lower adoption rate causes a project manager somewhere in Automattic to sweat. They’re somewhat notorious for being led by stubborn assholes who don’t listen to critics (even on security matters).
I’ll also continue to credit the artists that made the furry art I include in my blog posts, because supporting artists is the exact opposite of supporting generative AI.
If you’re looking for a furry artist to commission, first read this , and then maybe consider the artists whose work I’ve featured over the years.
New Avenues of Bullshit
If I may be so bold as to make a predication: In the distant future, I expect to see more Quantum Computing related bullshit.
Though currently constrained to the realm of grifters , NIST’s recent standardization of post-quantum cryptography is likely to ignite a lot of questionable technology companies.
Whether any of this quantum bullshit catches on at the same scale as tech industry hype remains to be seen.
If any does, I promise to handle each instance with the same derision as the bullshit I discovered in DFECON’s Quantum Village .
- Tags Cryptocurrency , Society , Technology
By Soatok
Security engineer with a fursona. Ask me about dholes or Diffie-Hellman!
-
 @ 38d0888d:bd8e1246
2024-09-02 11:08:05
@ 38d0888d:bd8e1246
2024-09-02 11:08:05To foster collective improvement, it is essential to implement social programs that encourage voluntary engagement and mutual support. These initiatives should serve as fertile ground, nurturing altruistic values and deepening the understanding of humanity’s true needs. By integrating spiritual connections into these efforts, a ripple effect of kindness, understanding, and enlightenment can spread throughout society. Each individual, endowed with intellectual abilities by a higher power, is invited to contribute to the creation of a harmonious and enlightened world. Sharing inspirational concepts that blend spirituality with social responsibility has the potential to profoundly influence and unite public sentiment.
A sense of community and interconnectedness must be cultivated within these programs. Creating spaces for shared experiences and collective growth extends their impact beyond individual actions, fostering a network of mutual support and understanding.
It is crucial to promote inclusive development that transcends bureaucratic constraints, aiming to dismantle inequality and confront corruption. These initiatives do more than foster a fairer world; they also reveal the latent spiritual dimensions of the human mind. To encourage spiritual growth and overcome selfishness, collaborative efforts across society, decentralized governance structures, educational institutions, and individual contributions are imperative. Moral codes must emerge from deeply rooted spiritual ethics that are interwoven into the societal fabric, surpassing the interests of a privileged few. Humanity’s ultimate goal is to transcend mere cooperation among individuals, striving for absolute transparency and openness across all spheres of existence. Achieving this vision requires unwavering dedication from every stakeholder committed to guiding society along the path of enlightenment.
-
 @ 3bf0c63f:aefa459d
2024-09-18 10:37:09
@ 3bf0c63f:aefa459d
2024-09-18 10:37:09How to do curation and businesses on Nostr
Suppose you want to start a Nostr business.
You might be tempted to make a closed platform that reuses Nostr identities and grabs (some) content from the external Nostr network, only to imprison it inside your thing -- and then you're going to run an amazing AI-powered algorithm on that content and "surface" only the best stuff and people will flock to your app.
This will be specially good if you're going after one of the many unexplored niches of Nostr in which reading immediately from people you know doesn't work as you generally want to discover new things from the outer world, such as:
- food recipe sharing;
- sharing of long articles about varying topics;
- markets for used goods;
- freelancer work and job offers;
- specific in-game lobbies and matchmaking;
- directories of accredited professionals;
- sharing of original music, drawings and other artistic creations;
- restaurant recommendations
- and so on.
But that is not the correct approach and damages the freedom and interoperability of Nostr, posing a centralization threat to the protocol. Even if it "works" and your business is incredibly successful it will just enshrine you as the head of a platform that controls users and thus is prone to all the bad things that happen to all these platforms. Your company will start to display ads and shape the public discourse, you'll need a big legal team, the FBI will talk to you, advertisers will play a big role and so on.
If you are interested in Nostr today that must be because you appreciate the fact that it is not owned by any companies, so it's safe to assume you don't want to be that company that owns it. So what should you do instead? Here's an idea in two steps:
- Write a Nostr client tailored to the niche you want to cover
If it's a music sharing thing, then the client will have a way to play the audio and so on; if it's a restaurant sharing it will have maps with the locations of the restaurants or whatever, you get the idea. Hopefully there will be a NIP or a NUD specifying how to create and interact with events relating to this niche, or you will write or contribute with the creation of one, because without interoperability this can't be Nostr.
The client should work independently of any special backend requirements and ideally be open-source. It should have a way for users to configure to which relays they want to connect to see "global" content -- i.e., they might want to connect to
wss://nostr.chrysalisrecords.com/to see only the latest music releases accredited by that label or towss://nostr.indiemusic.com/to get music from independent producers from that community.- Run a relay that does all the magic
This is where your value-adding capabilities come into play: if you have that magic sauce you should be able to apply it here. Your service -- let's call it
wss://magicsaucemusic.com/-- will charge people or do some KYM (know your music) validation or use some very advanced AI sorcery to filter out the spam and the garbage and display the best content to your users who will request the global feed from it (["REQ", "_", {}]), and this will cause people to want to publish to your relay while others will want to read from it.You set your relay as the default option in the client and let things happen. Your relay is like your "website" and people are free to connect to it or not. You don't own the network, you're just competing against other websites on a leveled playing field, so you're not responsible for it. Users get seamless browsing across multiple websites, unified identities, a unified interface (that could be different in a different client) and social interaction capabilities that work in the same way for all, and they do not depend on you, therefore they're more likely to trust you.
Does this centralize the network still? But this a simple and easy way to go about the matter and scales well in all aspects.
Besides allowing users to connect to specific relays for getting a feed of curated content, such clients should also do all kinds of "social" (i.e. following, commenting etc) activities (if they choose to do that) using the outbox model -- i.e. if I find a musician I like under
wss://magicsaucemusic.comand I decide to follow them I should keep getting updates from them even if they get banned from that relay and start publishing onwss://nos.lolorwss://relay.damus.ioor whatever relay that doesn't even know anything about music.The hardcoded defaults and manual typing of relay URLs can be annoying. But I think it works well at the current stage of Nostr development. Soon, though, we can create events that recommend other relays or share relay lists specific to each kind of activity so users can get in-app suggestions of relays their friends are using to get their music from and so on. That kind of stuff can go a long way.
-
 @ 9dd283b1:cf9b6beb
2024-09-02 10:26:53
@ 9dd283b1:cf9b6beb
2024-09-02 10:26:53There's a saying: Bitcoin is hope.
But once you truly understand Bitcoin, many of the old fiat goals in your life start to lose meaning. It can feel disorienting and even depressing, because you realize you need to build entirely new goals, and you're unsure where to begin.
For example, maybe your plan was to get a mortgage, buy a house, and imagine your kids playing there for the next 20 years while you "happily" pay off a 25-year loan. But when you understand Bitcoin, that plan doesn’t make sense. Why would I put a 100k-200k down payment into a mortgage when it's likely better be in Bitcoin? Plus, you lose about 2.5% to 4% of the total price on taxes, fees, brokers, and other costs. Crazy, right?
I even made a short presentation for my wife, explaining why we should never buy a house given current interest rates and down payment requirements. She responded that she wants a house anyway, because it feels better to own one. But does a 25-year mortgage really make it feel like it’s yours?
She also said it’s depressing to not follow the conventional path. It’s hard to feel satisfied with numbers when everyone around you is deep into mortgages—you want to be one of them. You want to visit their houses and invite them to "yours." It's like becoming sober in a room full of addicts. You know it’s better for you, but the world around you seems so strange that part of you wants to go back, even though you know it hurts. Yet, when you do go back, the joy isn't there anymore. You feel...nothing. And then you decide to withdraw.
I remember paying off my first mortgage for an apartment, and I felt nothing. And that was before I fell down the Bitcoin rabbit hole. Now I know if I ever took out a mortgage again, I’d just feel regret for not keeping the money in Bitcoin. And by the time you finish paying it off, you probably want to sell the property and move somewhere else.
So, the rational decision is to keep everything in Bitcoin and rent instead.Unless, of course, Bitcoin goes to zero. There are only two outcomes for Bitcoin: it’s either going to infinity, or it's going to zero. There’s no scenario where it just hovers at 100k or 60k for the next 20 years—unless people are foolish enough to give away self-custody. If they do, we'll end up with digital gold. So the reasonable question is - how can you be sure? Well, you can't. But we are betting on it and it works for now. Worst case we will need to start from 0. But then there will be no hope anymore.
We are staying in the infinity camp. And when you are in that camp every time you make a big purchase, you’re shorting Bitcoin. Solution - simple, - don't buy anything. There’s a popular meme: You will own nothing, and you will be happy. But if you’re a Bitcoiner, it's more like: You will own only Bitcoin, and you probably won’t be happy about it. Why would I pay 30k for a car when I can lease one? Why put 100k down on a house when I can rent?
The only justification is mental comfort, peace of mind. Or perhaps you value the illusion of owning a physical thing more than the genuine ownership of something virtual. It’s confusing, isn’t it? Sure, you can own a bicycle. But owning a house? That's tricky. Imagine you’re a Russian citizen with a house on Lake Como, and suddenly, new sanctions mean Italy no longer recognizes your property. Or squatters break in while you’re on vacation, and now you need to go through a court battle to evict them.
Extreme situations, I know. But no one thinks it will happen to them—until it does.
So, you’ve sold everything to buy Bitcoin. You don’t own anything except Bitcoin, and you feel sad. Why?
What can you buy with Bitcoin that’s more valuable? Something that won’t depreciate over time. Something like time.
Time with your kids. Time with your family. Time with yourself.
There’s a concept called FIRE and then there is a Bitcoin FIRE calculation (https://bitcoincompounding.com/). In simple terms, you spend your Bitcoin slowly enough that it grows faster than you can spend it (in fiat terms). Unlike traditional assets, there’s no yield or dividends, so the only way it works is if Bitcoin continues its cycles. And you need to be at least two cycles in to make it work.
But personally, I don’t think there will be cycles anymore. I believe this October-November will break all the models, and Bitcoin will do what Bitcoin does: surprise everyone. I read somewhere a thought that stuck with me—imagine you wake up on a planet Earth on January 1st. You know nothing about the seasons or weather. After six months of only increasing temperatures, you’d be 100% certain it’s only getting hotter from here.
So what hope does Bitcoin offer? Hope that I can spend more time with my family. Hope that I can create something different for them. Hope that I can live without the weight of fiat goals. Hope that it's only getting hotter from here.
I just need to get through the withdrawal phase.
originally posted at https://stacker.news/items/662939
-
 @ 6042d703:e3e62213
2024-09-18 10:18:06
@ 6042d703:e3e62213
2024-09-18 10:18:06The Nostr protocol is amazing. I love learning about it every day, and it's inspiring to see all the developer activity in this ecosystem. I believe it has a real shot at bringing us closer to a more decentralized internet. However, it won't solve all problems. That's why I decided to write a short post about what Nostr does and doesn't do.
Attacks from Governments
When Telegram CEO Pavel Durov was arrested in August 2024, many said that couldn't happen on Nostr. They're right — no Nostr CEO will ever be arrested, as long as there is no Nostr CEO (ok, maybe Derek Ross).
Nostr's strength lies in its decentralized nature, making it difficult to shut down. Anyone can run relays and create notes, which creates a regulatory hydra that is nearly impossible to kill. However, individual users can still be identified and shut down if they don't carefully protect their IP addresses and dissociate from their real identities.
Social Media Ills
Another misconception about Nostr is that it will solve all of social media's problems. Will it? In his manifesto, Fiatjaf identified many issues with the current state of social media. Most of them stem from the fact that it is centralized and therefore vulnerable to censorship by big tech and governments. This is true, and Nostr is a solid answer to the problem of centralization and censorship.
However, some argue that social media's problems go beyond censorship. Social envy, addiction, and other issues persist. While I agree that individuals and their communities, rather than governments, are responsible for addressing many of these problems, they are still real issues, and Nostr can't easily fix them.
Bots
Bots are a major issue on social media, especially on Crypto Twitter, where scams often aim to drain user wallets. Nostr also has bots and a spam problem. It's incredibly easy to create an npub/nsec key pair, allowing for the quick creation of bot armies that post kind 1 notes and other information. So, Nostr is not, nor will it be, free of bots.
However, Nostr has a few valuable tools at its disposal to reign them in: WoT scores, Zaps, and Filters. Let's see how these tools will be used to tackle this problem.
Society
While Pavel Durov's arrest caused an outcry among Nostriches, many commentators said, "Well, that's what you get if you don't censor." I think the need for free speech is still poorly understood and not recognized as a core pillar of free societies. As long as people don't see the importance of uncensored free speech, they will struggle to understand the benefits of Nostr.
Nostr can't fix that, but it can be a bastion of free speech for those who value it and help ignite a fire of free discourse that others can join once they recognize the need.
-
 @ e6fbeb1c:6ac8fc04
2024-09-02 10:17:27
@ e6fbeb1c:6ac8fc04
2024-09-02 10:17:27Eggplant is a member of the nightshade family, and it’s related to the potato and tomato. Often mistaken for a vegetable, eggplant is actually a fruit, and to be more precise, it’s a berry.

originally posted at https://stacker.news/items/669464
-
 @ 79008e78:dfac9395
2024-09-02 06:17:23
@ 79008e78:dfac9395
2024-09-02 06:17:23ระบบเงินอิเล็กทรอนิกส์แบบ peer-to-peer
ระบบเงินอิเล็กทรอนิกส์แบบ peer-to-peer นั้นจะช่วยให้เราสามารถชำระเงินผ่านทางออนไลน์ได้โดยตรงจากฝ่ายหนึ่งไปยังอีกฝ่ายหนึ่งโดยไม่ต้องผ่านตัวกลางอย่างพวกสถาบันการเงิน โดยใช้ digital signature เป็นส่วนหนึ่งในการแก้ปัญหานี้ แต่มันจะไม่มีประโยชน์ใด ๆ เลยหากยังคงต้องอาศัยตัวกลางที่เชื่อถือได้มาแก้ปัญหา double spending เราขอเสนอวิธีแก้ปัญหา double spending โดยใช้เครือข่ายแบบ peer-to-peer ให้เครือข่ายคอยประทับเวลาธุรกรรมต่าง ๆ ในระบบและนำมาเรียงร้อยกันเป็นเส้นสายของ proof-of-work ที่ใช้ hash เพื่อสร้างธุรกรรมที่ไม่สามารถเปลี่ยนแปลงได้ โดยไม่ต้องทำ proof-of-work ใหม่ โดยให้เส้นสายที่ยาวที่สุดนั้น ไม่เพียงแต่ทำหน้าที่เป็นลำดับของธุรกรรมที่เกิดขึ้นเท่านั้น แต่ยังเป็นสิ่งที่พิสูจน์ได้ว่ามาจากกำลังประมวลผล CPU ที่มากที่สุด และตราบใดที่ nodes ส่วนใหญ่ไม่ได้ร่วมมือกันโจมตีเครือข่ายและยังคงควบคุมกำลังประมวลผลส่วนใหญ่ในระบบไว้ พวกเขาก็จะสร้างเส้นสายที่ยาวที่สุดและสามารถเอาชนะผู้ประสงค์ร้ายที่จะโจมตีระบบได้ ตัวเครือข่ายเองไม่ได้ต้องมีโครงสร้างอะไรที่ซับซ้อน ข้อมูลต่าง ๆ ในเครือข่ายจะถูกกระจายส่งต่อโดยไม่ต้องสนใจว่าผู้รับจะได้รับหรือไม่ และ nodes ต่าง ๆ เองก็สามารถที่จะออกจากเครือข่ายและกลับเข้าร่วมใหม่ได้ตามที่ต้องการ โดยยอมรับเส้น proof-of-work ที่ยาวที่สุด เป็นหลักฐานของสิ่งที่เกิดขึ้นในขณะที่ node นั้น ๆ ไม่ได้อยู่ในเครือข่าย
1.บทนำ (Introduction)
ไม่ว่าใครจะใคร่ซื้อใคร่ขายอะไรใด ๆ บนอินเตอร์เน็ตนั้น ก็จำเป็นต้องพึ่งพาสถาบันการเงินในฐานะของบุคคลที่สามเพื่อดำเนินการชำระเงินทางอิเล็กทรอนิกส์เสมอ ๆ ซึ่งถึงแม้ว่าระบบนี้มันจะทำงานได้ดีสำหรับธุรกรรมส่วนใหญ่ ๆ แต่ระบบก็ก็มีจุดอ่อนอยู่ที่ยังต้องอาศัยความไว้เนื้อเชื่อใจ (trust) ในระบบนี้การทำธุรกรรมที่ไม่สามารถย้อนกลับได้อย่างสมบูรณ์นั้นมันแทบจะเป็นไปไม่ได้เลย เนื่องจากสถาบันการเงินไม่สามารถหลีกเลี่ยงการเป็นตัวกลางในการไกล่เกลี่ยข้อพิพาทต่าง ๆ ที่อาจเกิดขึ้นได้ มิหนำซ้ำต้นทุนในการไกล่เกลี่ยยังทำให้ต้นทุนการทำธุรกรรมเพิ่มสูงขึ้น และเมื่อต้นทุนสูงขึ้นขนาดของธุรกรรมที่สามารถใช้งานได้จริงก็สูงขึ้นตามไปด้วย ธุรกรรมเล็ก ๆ น้อย ๆ ก็ไม่สามารถเกิดขึ้นได้ เมื่อมีความเป็นไปได้ที่ธุรกรรมจะเกิดการย้อนกลับ ความจำเป็นในการสร้างความไว้วางใจก็ยิ่งทวีคูณมากขึ้น ผู้ค้าก็จำเป็นต้องระมัดระวังลูกค้า ต้องเรียกร้องข้อมูลมากกว่าที่จำเป็น การฉ้อโกงกลายเป็นเรื่องที่หลีกเลี่ยงไม่ได้เพราะต้นทุนและความไม่แน่นอนในทำธุรกรรมเหล่านี้ แน่นอนว่าเราสามารถหลีกเลี่ยงมันได้โดยการใช้เงินสด แต่ก็ไม่มีกลไกใดที่ทำให้สามารถใช้เงินสดผ่านช่องทางการสื่อสาร (เอาให้เข้าใจง่ายก็อินเตอร์เน็ต)ได้ โดยไม่ต้องมีตัวกลาง ;-;
แปลว่าสิ่งที่จำเป็นสำหรับการแก้ไขปัญหานี้คือระบบการชำระเงินทางอิเล็กทรอนิกส์ ที่อยู่บนพื้นฐานของการพิสูจน์ด้วยการเข้ารหัสแทนที่จะเป็นความไว้วางใจ ซึ่งจะทำให้คู่สัญญาสองฝ่ายที่ยินยอมสามารถทำธุรกรรมร่วมกันได้โดยตรง โดยไม่จำเป็นต้องมีบุคคลที่สามมาคอยเป็นตัวกลาง ธุรกรรมที่ยากต่อการย้อนกลับจะช่วยปกป้องผู้ขายจากการฉ้อโกง และสามารถใช้กลไก escrow เพื่อปกป้องผู้ซื้อได้อีกด้วย ในเอกสารชุดนี้ เราขอเสนอวิธีแก้ปัญหาการใช้จ่ายซ้ำซ้อนโดยใช้เซิร์ฟเวอร์ timestamp กระจายศูนย์แบบ peer-to-peer เพื่อสร้างหลักฐานการคำนวณลำดับเวลาของธุรกรรม โดยระบบนี้จะปลอดภัยตราบใดที่กลุ่มของ node ที่ซื่อสัตย์ ยังคงมีกำลังประมวลผลที่มากกว่ากลุ่มที่ประสงค์ร้ายกับระบบ
2.ธุรกรรม (Transactions)
นิยามของเหรียญอิเล็กทรอนิกส์ในที่นี้ คือห่วงโซ่ที่คล้องเกี่ยวกันของ digital signature โดยที่เจ้าของเหรียญอิเล็กทรอนิกส์จะโอนเหรียญไปยังเจ้าของคนถัดไป ด้วยการลง digital signature บน hash ของธุรกรรมก่อนหน้ารวมถึงกุญแจสาธารณะของเจ้าของคนถัดไป และผนวกมันไว้ที่ส่วนท้ายของธุรกรรม และผู้รับเงินเองก็สามารถตรวจสอบลายเซ็นเพื่อยืนยันความเป็นเจ้าของได้
https://image.nostr.build/a467896797a9fb9f98c3c234f0adb4df2376f2c3d9a7cc9d8672d7a9f5aa9efa.png
แน่นอนว่าปัญหาก็คือผู้รับเงินไม่สามารถตรวจสอบได้ว่าเจ้าของคนใดคนหนึ่งก่อนหน้าเขาได้ใช้เหรียญดังกล่าวซ้ำซ้อนมากกว่าหนึ่งครั้งหรือไม่ และวิธีการแก้ไขปัญหานี้โดยทั่วไปก็คงเป็นการกำหนดตัวกลางที่มีความน่าเชื่อถือมาเป็นคนตรวจสอบทุกธุรกรรมเพื่อป้องกันการใช้จ่ายซ้ำซ้อน และหลังจากการทำธุรกรรมแต่ละครั้ง เหรียญจะต้องถูกส่งกลับไปยังตัวกลางเพื่อออกเหรียญใหม่ และจะมีเพียงเหรียญที่ออกจากตัวกลางโดยตรงเท่านั้นที่จะเชื่อถือได้ว่าจะไม่ถูกใช้จ่ายซ้ำซ้อน แต่ปัญหาก็คือ ชะตากรรมของระบบเงินทั้งหมดจะขึ้นอยู่กับตัวกลางตัวนี้ เพราะทุกธุรกรรมจำเป็นจะต้องผ่านพวกเขา ซึ่งก็ไม่ต่างอะไรกับธนาคาร
เราจึงต้องการวิธีการที่ทำให้ผู้รับเงินทราบได้ว่าเจ้าของคนก่อน ๆ ไม่ได้ลงนามในธุรกรรมใด ๆ มาก่อน เพื่อให้บรรลุวัตถุประสงค์นี้ เราจะทำการนับว่าธุรกรรมที่เกิดขึ้นก่อนเป็นธุรกรรมที่ถูกต้อง และจะไม่สนใจความพยายามใด ๆ ในการที่จะใช้เหรียญนั้น ๆ ซ้ำอีก และวิธีเดียวที่ทำแบบนี้ได้ คือการรับรู้ถึงธุรกรรมทั้งหมด เช่นเดียวกับโมเดลที่ได้กล่าวข้างต้น ที่ตัวกลางจะรับรู้ถึงธุรกรรมทั้งหมดและตัดสินว่าธุรกรรมใดมาก่อนมาหลัง เพื่อให้บรรลุเป้าหมายนี้โดยไม่ต้องมีบุคคลที่สามที่เชื่อถือได้ ธุรกรรมทั้งหมดจะต้องถูกประกาศต่อสาธารณะ [1] และเราต้องการระบบที่ผู้เข้าร่วมเห็นพ้องในประวัติธุรกรรมชุดเดียวกันตามลำดับที่ได้รับ ส่วนผู้รับเงินก็จำเป็นจะต้องมีหลักฐานว่า ในขณะที่ทำธุรกรรม "โหนด" ส่วนใหญ่ในระบบเห็นพ้องต้องกันว่าธุรกรรมนั้นได้รับเป็นลำดับแรก(ไม่มีธุรกรรมที่ใช้เหรียญพวกนี้มาก่อน)
3.ระบบบันทึกเวลา (Timestamp Server)
สำหรับแนวทางการแก้ปัญหาในครั้งนี้ เราจะใช้ประโยชน์จาก timestamp server ที่จะทำหน้าที่บันทึก hash ของบล๊อกที่ต้องการให้มีการบันทึกเวลา และจากนั้นจะทำการเผยแพร่ hash ดังกล่าว เหมือนกับหนังสือพิมพ์หรือโพสต์ใน Usenet [2-5] (ฟีลแบบทุกคนจะเห็นโพสต์นี้น้าา ประมาณนั้น) การบันทึกเวลานี้จะพิสูจน์ได้ว่าข้อมูลที่ถูก hash นั้นจะต้องมีอยู่จริงในเวลานั้นเพื่อให้ได้มาซึ่ง hash ดังกล่าว แต่ละการบันทึกเวลาจะรวมการบันทึกเวลาของหน้านี้ไว้ใน hash ของมันเพื่อสร้างเป็น chain โดยการบันทึกเวลาแต่ละครั้งจะยืนยันความถูกต้องของการบันทึกก่อนหน้าได้อีกด้วยด้วย
https://image.nostr.build/ddf92417c45dbb6e25da0af80a10d4cdbc3e725d047d65f54a3e3bfcf358c4d6.png
4.พรูฟ-ออฟ-เวิร์ค (Proof-of-Work)
ในการสร้าง Timestamp Server แบบกระจายศูนย์บนพื้นฐานแบบ peer to peer เราจำเป็นต้องใช้ระบบ Proof-of-Work (PoW) ที่คล้ายกับ Hashcash ของ Adam Back [6] แทนที่จะใช้วิธีการแบบเดิม ๆ อย่างการประกาศในหนังสือพิมพ์หรือ Usenet โดย PoW ใช้ในการตรวจสอบค่าที่มาจากกระบวนการ hash เช่น SHA-256 แล้ว ผลลัพธ์ที่ได้ (Hash) จะขึ้นต้นด้วยเลขศูนย์จำนวนหนึ่ง โดยที่ work (ประมาณว่าพลังประมวลผล) ที่ต้องใช้จะเพิ่มขึ้นแบบทวีคูณตามจำนวนเลขศูนย์ที่ต้องการ และสามารถตรวจสอบได้โดยการรัน Hash เพียงครั้งเดียว
ซึ่งสำหรับ timestamp network ของเรานั้น เราใช้ PoW โดยการเพิ่มค่า Nonce ในบล็อกไปเรื่อย ๆ จนกว่าจะพบค่าที่ทำให้ Hash ของบล็อกนั้นมีเลขศูนย์ตามที่กำหนด และเมื่อใช้กำลังประมวลผลของ CPU ไปกับการทำ PoW จนสำเร็จแล้ว บล็อกจะไม่สามารถเปลี่ยนแปลงได้ หากไม่มีการทำงานซ้ำใหม่ เนื่องจากบล็อกที่สร้างขึ้นภายหลังจะเชื่อมโยงกับบล็อกก่อนหน้า การเปลี่ยนแปลงบล็อกใด ๆ จะต้องทำ PoW ของบล็อกนั้นและบล็อกที่ตามมาใหม่ทั้งหมด
https://image.nostr.build/c039ef4ca6833cb1ecee65ac5991df2406be9b7e490b86b3b19f94f267767182.png
นอกจากนี้ PoW ยังช่วยแก้ปัญหาของเสียงส่วนมากที่มาตัดสินใจในระบบนี้ เพราะหากเสียงข้างมากอ้างอิงจากหลักการหนึ่ง IP หนึ่งเสียง ใครก็ตามที่สามารถสร้าง IP ได้จำนวนมากก็จะสามารถควบคุมระบบได้ จึงใช้หลักการหนึ่ง CPU หนึ่งเสียงแทน การตัดสินใจของเสียงข้างมากจะแสดงด้วย Chain ที่ยาวที่สุด ซึ่งบ่งบอกถึงความพยายามในการคำนวณ (Proof-of-Work) ที่มากที่สุด หาก Node ที่ซื่อสัตย์ (Honest nodes) มีกำลังประมวลผลของ CPU ส่วนใหญ่อยู่ในการควบคุม Honest Chain ก็จะเติบโตเร็วที่สุดและแซงหน้า Chain อื่น ๆ ได้ ผู้โจมตีที่ต้องการแก้ไขบล็อกในอดีตจะต้องทำ Proof-of-Work ของบล็อกนั้นและบล็อกที่ตามมาใหม่ทั้งหมด และต้องทำงานให้เร็วกว่า Honest Node ด้วย ซึ่งโอกาสที่ผู้โจมตีจะตามทันนั้นจะลดลงแบบทวีคูณเมื่อมีการเพิ่มบล็อกมากขึ้น
เพื่อชดเชยความเร็วของฮาร์ดแวร์ที่เพิ่มขึ้นและความสนใจในการรัน Node ที่ผันผวน ระดับความยากของ Proof-of-Work จะถูกกำหนดโดยค่าเฉลี่ย โดยตั้งเป้าไว้ที่จำนวนบล็อกเฉลี่ยต่อชั่วโมง หากสร้างบล็อกได้เร็วเกินไป ระดับความยากก็จะเพิ่มขึ้น
5.เครือข่าย (Network)
เครือข่ายนั้นมีการทำงาน ดังนี้
- การประกาศธุรกรรมใหม่: ธุรกรรมใหม่จะถูกประกาศ (broadcast) ไปยังทุก node ในเครือข่าย
- การรวบรวมธุรกรรม: แต่ละ node จะรวบรวมธุรกรรมใหม่ ๆ เหล่านี้ ไว้ในบล็อก
- การค้นหา Proof-of-Work: แต่ละ node จะทำการคำนวณ เพื่อค้นหา Proof-of-Work ตามค่า difficulty สำหรับบล็อกนั้น ๆ
- การประกาศบล็อก: เมื่อ node ใดค้นหา Proof-of-Work ได้แล้ว node นั้นจะทำการประกาศบล็อกไปยังทุก node ในเครือข่าย
- การตรวจสอบและยอมรับบล็อก: node อื่น ๆ จะทำการตรวจสอบและยอมรับบล็อกนั้น เฉพาะเมื่อธุรกรรมทั้งหมดภายในบล็อกนั้นถูกต้องและยังไม่ถูกใช้มาก่อน
- การสร้างบล็อกถัดไป: node ต่าง ๆ แสดงการยอมรับบล็อกโดยการเริ่มต้นสร้างบล็อกถัดไปใน chain ด้วย hash ของบล็อกที่ยอมรับ เป็น hash ก่อนหน้าในโครงสร้างของบล๊อกใหม่ที่กำลังสร้าง
node ต่าง ๆ จะถือว่า chain ที่ยาวที่สุดเป็น chain ที่ถูกต้องและจะทำงานเพื่อขยาย chain นั้นต่อไป หากมีสอง node ที่ได้ประกาศบล็อกเวอร์ชันที่แตกต่างกันในเวลาพร้อมกัน node บาง node อาจได้รับบล็อกหนึ่งก่อน อีกบล็อกหนึ่ง ในกรณีนี้ node เหล่านั้น จะทำงานบนบล็อกที่ได้รับก่อน แต่จะเก็บสำเนาของบล็อกอีกอันหนึ่งไว้ ในกรณีที่บล็อกนั้น กลายเป็นบล็อกที่อยู่ใน chain ที่ยาวกว่าปัญหาข้อโต้แย้งนี้ก็จะได้รับการแก้ไข เมื่อพบ Proof-of-Work อันถัดไปและ chain ใด chain หนึ่งยาวขึ้น node ที่กำลังทำงานอยู่บน chain ที่สั้นกว่าก็จะเปลี่ยนไปทำงานบน chain ที่ยาวกว่าแทน
การประกาศธุรกรรมใหม่ ไม่จำเป็นต้องไปถึงทุก node ในเครือข่าย ตราบใดที่พวกเขายังไปถึง node ส่วนใหญ่ในระบบได้ ธุรกรรมเหล่านั้นก็จะถูกบรรจุอยู่ในบล็อกในไม่ช้า นอกจากนี้การประกาศบล็อกยังไม่ต้องกังวลเรื่องจะมีบล๊อกที่สูญหาย เนื่องจากหากว่า node ไม่ได้รับบล็อกใด ๆ node ก็จะตระหนักได้ว่าพลาดบล็อกก่อนหน้าไปเมื่อได้รับบล๊อกใหม่มา และ node จะทำการร้องขอ block ที่ขาดไปจากเครือข่าย
6.แรงจูงใจ(Incentive)
โดยปกติแล้ว ธุรกรรมแรกของแต่ละบล๊อกนั้นจะเป็นธุรกรรมพิเศษที่จะขุดเหรียญที่สร้างขึ้นใหม่ซึ่งเป็นกรรมสิทธิ์ของผู้สร้างบล็อกนั้น ๆ ซึ่งจะเป็นการเพิ่มแรงจูงใจให้กับ node ต่าง ๆ ในการสนับสนุนเครือข่าย และเป็นวิธีการกระจายเหรียญให้หมุนเวียน เนื่องจากไม่มีหน่วยงานส่วนกลางที่ทำหน้าที่ในการออกเหรียญ การเพิ่มเหรียญใหม่ในปริมาณคงที่อย่างต่อเนื่องนั้นคล้ายคลึงกับการที่คนงานเหมืองทองคำใช้แรง และ เวลา เพื่อเพิ่มทองคำให้หมุนเวียน ในกรณีนี้ คือ เวลา กำลังประมวลผล และไฟฟ้าที่ถูกใช้ไป
นอกจากนี้แรงจูงใจจะมาจากค่าธรรมเนียมการทำธุรกรรม หากมูลค่าผลลัพธ์ของธุรกรรมน้อยกว่ามูลค่าที่ใส่เข้ามา ส่วนต่างนั้นก็คือค่าธรรมเนียมการทำธุรกรรมที่จะเพิ่มเข้าไปในมูลค่าแรงจูงใจของบล็อกที่มีธุรกรรมนั้น เมื่อเหรียญทั้งหมดในระบบมีจำนวนเท่ากับที่กำหนดไว้แล้ว แรงจูงใจหลักก็จะถูกเปลี่ยนมาเป็นค่าธรรมเนียมการทำธุรกรรม และปราศจากภาวะเงินเฟ้อโดยสิ้นเชิง
แรงจูงใจอาจช่วยกระตุ้นให้ node ต่าง ๆ ยังคงซื่อสัตย์ หากผู้โจมตีที่ละโมบสามารถรวบรวมกำลังประมวลผล ได้มากกว่า node ที่ซื่อสัตย์ทั้งหมด เขาจะต้องเลือกระหว่างการใช้มันเพื่อฉ้อโกงผู้อื่นโดยการใช้จ่ายซ้ำซ้อน หรือใช้มันเพื่อสร้างเหรียญใหม่ พวกเขาจะพบว่าการเล่นตามกฎ กฎที่เอื้อประโยชน์ให้กับเขาด้วยเหรียญใหม่มากกว่าคนอื่น ๆ รวมกันนั้นทำกำไรได้มากกว่าการบ่อนทำลายระบบและความถูกต้องของทรัพย์สินของเขาเอง
7.การจัดการพื้นที่ดิสก์(Reclaiming Disk Space)
เมื่อธุรกรรมถูกบรรจุลงในบล๊อกแล้ว สามารถกำจัดธุรกรรมที่ใช้ไปแล้วก่อนหน้านั้นออกได้เพื่อประหยัดพื้นที่ดิสก์ แต่การจะทำอย่างนี้ได้โดยไม่ให้เลข hash ของบล๊อกมีการเปลี่ยนแปลงนั้น ธุรกรรมจึงจำเป็นต้องถูก hash ในรูปแบบของ Merkle Tree [7][2][5] โดยมีแค่ root node ของ tree เท่านั้นที่จะรวมอยู่ใน hash ของบล๊อก นี่เป็นวิธีที่ทำให้สามารถบีบอัดข้อมูลในบล๊อกเก่า ๆ ได้โดยการตัดพวก hash ส่วนอื่น ๆ ของ tree ที่ไม่ใช่ root node ออก (ไม่จำเป็นต้องเก็บ hash ในชั้นอื่น ๆ ของ tree)
https://image.nostr.build/3ed95334891d91baca3f3f6f624a7ae22620be4ebfe0db5eb652cfce11255b9a.png
โดยในส่วน header ของบล็อกที่ไม่มีธุรกรรมจะมีขนาดประมาณ 80 ไบต์ หากเราสมมติว่าบล็อกถูกสร้างขึ้นทุก ๆ 10 นาที 80 ไบต์ * 6 * 24 * 365 = 4.2MB ต่อปี โดยที่ระบบคอมพิวเตอร์ทั่วไปที่วางขายในปี 2551 มี RAM 2GB และกฎของมัวร์ทำนายการเติบโตในปัจจุบันที่ 1.2GB ต่อปี การจัดเก็บข้อมูลไม่น่าจะเป็นปัญหาแม้ว่าส่วนหัวของบล็อกจะต้องถูกเก็บไว้ในหน่วยความจำก็ตาม
8.การตรวจสอบธุรกรรม (Simplified Payment Verification)
การที่จะยืนยันการชำระเงินโดยไม่จำเป็นต้องรัน full node ได้นั้น ผู้ใช้เพียงแค่เก็บสำเนาของส่วนหัวบล็อก (block header) ของสายบล็อก (chain) ที่ยาวที่สุด ซึ่งสามารถรับได้โดยการสอบถามจาก node อื่น ๆ ในเครือข่ายจนมั่นใจว่าได้รับสายที่ยาวที่สุด และรับ Merkle branch ที่เชื่อมโยงธุรกรรมกับบล็อกที่มีการประทับเวลา (Timestamp) อยู่ ถึงแม้ผู้ใช้จะไม่สามารถตรวจสอบธุรกรรมด้วยตัวเองได้ แต่การเชื่อมโยงธุรกรรมกับตำแหน่งในสายบล็อกจะทำให้เห็นว่า node ในเครือข่ายยอมรับแล้ว และบล็อกที่เพิ่มเข้ามาหลังจากนั้นเป็นการยืนยันเพิ่มเติมว่าเครือข่ายยอมรับธุรกรรมนี้แล้ว
https://i.imgur.com/VXtLpRF.png
การตรวจสอบดังกล่าวจะเชื่อถือได้ตราบใดที่ node ที่ซื่อสัตย์ยังคงควบคุมเครือข่าย แต่จะมีความเสี่ยงมากขึ้นหากเครือข่ายถูกโจมตีและถูกควบคุม ในขณะที่ node ในเครือข่ายสามารถตรวจสอบธุรกรรมได้ด้วยตัวเอง แต่วิธีการแบบง่ายนี้อาจถูกหลอกลวงโดยการใช้ธุรกรรมปลอมของผู้โจมตี ตราบใดที่ผู้โจมตียังคงสามารถควบคุมเครือข่ายได้ กลยุทธ์หนึ่งในการป้องกันปัญหานี้คือ การรับการแจ้งเตือนจาก node อื่น ๆ ในเครือข่ายเมื่อตรวจพบบล็อกที่ไม่ถูกต้อง ซึ่งจะแจ้งให้ซอฟต์แวร์ของผู้ใช้ดาวน์โหลดบล็อกแบบเต็มและธุรกรรมที่แจ้งเตือน เพื่อยืนยันความไม่สอดคล้องกัน ธุรกิจที่ได้รับการชำระเงินบ่อยครั้งอาจยังคงต้องการรัน node ของตนเอง เพื่อความปลอดภัยที่เป็นอิสระและการตรวจสอบที่รวดเร็วยิ่งขึ้น
9.การควบรวมและแบ่งย่อยมูลค่า(Combining and Splitting Value)
แม้ว่าการจัดการเหรียญหลาย ๆ เหรียญจะเป็นสิ่งที่สามารถทำได้ แต่การจัดการธุรกรรมแยกต่างหากสำหรับแต่ละเหรียญในการโอนก็คงเป็นเรื่องที่น่าปวดหัวอยู่ดี ฉะนั้นแล้วเพื่อให้สามารถแยกและรวมมูลค่ากันได้ ธุรกรรมจึงสามารถมี input และ output ได้หลายรายการ ซึ่งโดยปกติแล้วจะมี input เดียวจากธุรกรรมก่อนหน้าที่มีขนาดใหญ่กว่า หรือ input จำนวนเล็ก ๆ หลาย ๆ รายการ และ output ไม่เกินสองรายการ คือ รายการหนึ่งสำหรับการชำระเงิน และอีกหนึ่งรายการสำหรับการส่งเงินทอน หากมีกลับไปยังผู้ส่ง
https://image.nostr.build/9c6d3ce0e9f08c5b3fa3b82c2088ac6235603e5c0df3469060e6c9f74bce32fc.png
ควรสังเกตว่า fan-out (กระจายของธุรกรรม) ซึ่งเป็นกรณีที่ธุรกรรม ธุรกรรมหนึ่งนั้นขึ้นอยู่กับหลายธุรกรรม และธุรกรรมเหล่านั้นเองก็ขึ้นอยู่กับอีกหลายธุรกรรม แต่ไม่ใช่ปัญหาในที่นี้ เพราะไม่มีความจำเป็นในการดึงประวัติการทำธุรกรรมทั้งหมดออกมาเป็นสำเนา
10.ความเป็นส่วนตัว(Privacy)
ในรูปแบบธนาคารแบบดั้งเดิมนั้น ความเป็นส่วนตัวเกิดขึ้นได้ด้วยการจำกัดการเข้าถึงข้อมูล โดยให้เฉพาะผู้ที่เกี่ยวข้องและบุคคลที่สามที่ได้รับความไว้วางใจเท่านั้น แต่เนื่องจากในระบบนี้เรามีความจำเป็นในการประกาศธุรกรรมทั้งหมดต่อสาธารณะ ทำให้ไม่สามารถใช้วิธีนี้ได้ แต่ยังจำเป็นต้องคงความเป็นส่วนตัวไว้ โดยการแบ่งการไหลของข้อมูล ด้วยการไม่เปิดเผยตัวตนของเจ้าของ public key คนทั่วไปสามารถเห็นว่ามีคนกำลังส่งเงินจำนวนหนึ่งให้กับคนอื่น แต่จะไม่ทราบข้อมูลที่เชื่อมโยงธุรกรรมนั้นกับบุคคลใด ๆ ซึ่งคล้ายกับระดับข้อมูลที่เปิดเผยโดยตลาดหลักทรัพย์ ซึ่งมีการเปิดเผยเวลาและขนาดของการซื้อขายแต่ละครั้งต่อสาธารณะ แต่ไม่ได้ระบุว่าคู่สัญญาคือใคร
https://image.nostr.build/6ec3c84c7878dbd4558d2045518384daf5a341e86f4194cf367cc8426c2d72a7.png
เพื่อเสริมในเรื่องของความปลอดภัย ควรใช้ key pair ใหม่สำหรับการทำธุรกรรมในแต่ละครั้ง เพื่อป้องกันไม่ให้เชื่อมโยงกับเจ้าของคนเดียวกันได้ อย่างไรก็ตาม การเชื่อมโยงบางอย่างยังคงหลีกเลี่ยงไม่ได้ ในธุรกรรมที่มี input หลายรายการ ซึ่งจำเป็นต้องเปิดเผยว่า input เหล่านั้นเป็นของเจ้าของคนเดียวกัน ความเสี่ยงก็คือ หากมีการเปิดเผยตัวตนของเจ้าของคีย์ การเชื่อมโยงอาจเปิดเผยธุรกรรมอื่น ๆ ที่เป็นของเจ้าของรายเดียวกันได้
11.การคำนวณ(Calculations)
หากลองพิจารณาสถานการณ์ที่ผู้โจมตีพยายามสร้าง chain ปลอมให้เร็วกว่า chain จริง แม้ว่าจะทำได้สำเร็จ แต่มันก็ไม่สามารถทำให้ระบบเปิดรับการเปลี่ยนแปลงตามอำเภอใจได้อยู่ดี เช่น การสร้างมูลค่าจากอากาศธาตุ หรือการรับเงินที่ไม่เคยเป็นของผู้โจมตีมาก่อน Node ต่าง ๆ จะไม่ยอมรับธุรกรรมที่ไม่ถูกต้องเป็นการชำระเงิน และ Node ที่สุจริตก็จะไม่ยอมรับบล็อกที่มีธุรกรรมเหล่านั้นอย่างแน่นอน ผู้โจมตีทำได้เพียงพยายามเปลี่ยนแปลงธุรกรรมของตนเอง เพื่อนำเงินที่ใช้ไปแล้วกลับคืนมาเท่านั้น
การแข่งขันระหว่าง chain สุจริตกับ chain ของผู้โจมตี สามารถอธิบายได้ด้วยแบบจำลองการเดินสุ่มทวินาม (Binomial Random Walk) โดยเหตุการณ์ที่สำเร็จ หมายถึง chain ที่สุจริตถูกขยายออกไปอีกหนึ่งบล็อก เพิ่มความยาวนำหน้าไป +1 และเหตุการณ์ที่ล้มเหลว หมายถึง chain ของผู้โจมตีถูกขยายออกไปหนึ่งบล็อก ลดช่องว่างลง -1
ความน่าจะเป็นที่ผู้โจมตีจะไล่ตามทันจากช่องว่างที่กำหนด สามารถเปรียบเทียบด้วย Gambler's Ruin problem โดยสมมติว่านักพนันที่มีเครดิตไม่จำกัด เริ่มต้นด้วยการขาดทุน และเล่นพนันไปเรื่อย ๆ เพื่อให้ถึงจุดคุ้มทุน เราสามารถคำนวณความน่าจะเป็นที่เขาจะกลับมาถึงจุดคุ้มทุนได้ หรือความน่าจะเป็นที่ผู้โจมตีจะไล่ทัน chain ที่สุจริตได้ ดังนี้ [8]:
p = ความน่าจะเป็นที่ Node ที่สุจริตจะพบบล็อกถัดไป q = ความน่าจะเป็นที่ผู้โจมตีจะพบบล็อกถัดไป qz = ความน่าจะเป็นที่ผู้โจมตีจะไล่ทัน จากที่ตามหลังอยู่ z บล็อก
https://i.imgur.com/vePe255.png
จากสมมติฐานที่ว่า p > q ความน่าจะเป็นจะลดลงแบบเอกซ์โพเนนเชียล เมื่อจำนวนบล็อกที่ผู้โจมตีต้องไล่ตามทันเพิ่มขึ้น หากเขาไม่สามารถพุ่งขึ้นนำได้อย่างรวดเร็วตั้งแต่แรก โอกาสของเขาก็จะลดลงจนน้อยมาก ๆ เมื่อเขาตามหลังมากขึ้นเรื่อย ๆ
ทีนี้ลองพิจารณาว่า ผู้รับธุรกรรมใหม่ต้องรอเป็นเวลานานเท่าใด จึงจะแน่ใจได้ว่าผู้ส่งไม่สามารถเปลี่ยนแปลงธุรกรรมได้แล้ว เราสมมติว่าผู้ส่งเป็นผู้โจมตี ที่ต้องการให้ผู้รับเชื่อว่าเขาได้รับเงินไปแล้ว จากนั้นจึงเปลี่ยนให้เงินกลับเข้าหาตัวเองหลังจากเวลาผ่านไประยะหนึ่ง ผู้รับจะได้รับแจ้งเมื่อเกิดเหตุการณ์นี้ขึ้น แต่ผู้ส่งหวังว่ามันจะสายเกินไปแล้ว
ผู้รับจะสร้างคู่กุญแจใหม่ และให้กุญแจสาธารณะแก่ผู้ส่งไม่นานก่อนที่จะลงนาม ซึ่งจะป้องกันไม่ให้ผู้ส่งเตรียมบล็อกเชนปลอมไว้ล่วงหน้า โดยการทำงานอย่างต่อเนื่องจนกว่าเขาจะมีโอกาสได้บล็อกที่ยาวพอ จากนั้นจึงดำเนินธุรกรรมในทันที เมื่อส่งธุรกรรมแล้ว ผู้ส่งที่ไม่สุจริตจะเริ่มทำงานอย่างลับ ๆ บนบล็อกเชนคู่ขนาน ที่มีธุรกรรมในเวอร์ชันของเขาเองอยู่
ผู้รับจะรอจนกว่าธุรกรรมจะถูกเพิ่มลงในบล็อก และมีบล็อกที่ถูกเชื่อมต่อตามหลังมาอีก z บล็อก เขาไม่ทราบจำนวนความคืบหน้าที่แน่นอนที่ผู้โจมตีได้ทำไปแล้ว แต่สมมติว่าบล็อกที่สุจริตใช้เวลาเฉลี่ยต่อบล็อกตามที่คาดไว้ ความคืบหน้าที่อาจเกิดขึ้นได้ของผู้โจมตีจะเป็นการแจกแจงแบบปัวซง (Poisson distribution) ซึ่งมีค่าคาดหวังดังนี้:
https://i.imgur.com/mYsb48i.png
เพื่อให้ได้ความน่าจะเป็นที่ผู้โจมตียังคงสามารถไล่ทันได้ เราจะคูณความหนาแน่นของปัวซง สำหรับความคืบหน้าแต่ละระดับที่เขาสามารถทำได้ ด้วยความน่าจะเป็นที่เขาสามารถไล่ทันจากจุดนั้น:
https://i.imgur.com/jQGkQ8r.png
จัดเรียงใหม่เพื่อหลีกเลี่ยง infinite tail ของการแจกแจง
https://i.imgur.com/OOO6Gm9.png
แปลงมันให้เป็น C code
include
double AttackerSuccessProbability(double q, int z) { double p = 1.0 - q; double lambda = z * (q / p); double sum = 1.0; int i, k; for (k = 0; k <= z; k++) { double poisson = exp(-lambda); for (i = 1; i <= k; i++) poisson *= lambda / i; sum -= poisson * (1 - pow(q / p, z - k)); } return sum; }
เมื่อรันผลลัพธ์บางส่วน เราจะเห็นว่าความน่าจะเป็นลดลงแบบเอกซ์โพเนนเชียลเมื่อ z เพิ่มขึ้น
q=0.1 z=0 P=1.0000000 z=1 P=0.2045873 z=2 P=0.0509779 z=3 P=0.0131722 z=4 P=0.0034552 z=5 P=0.0009137 z=6 P=0.0002428 z=7 P=0.0000647 z=8 P=0.0000173 z=9 P=0.0000046 z=10 P=0.0000012 q=0.3 z=0 P=1.0000000 z=5 P=0.1773523 z=10 P=0.0416605 z=15 P=0.0101008 z=20 P=0.0024804 z=25 P=0.0006132 z=30 P=0.0001522 z=35 P=0.0000379 z=40 P=0.0000095 z=45 P=0.0000024 z=50 P=0.0000006
การแก้หาค่า P ที่น้อยกว่า 0.1%...
P < 0.001 q=0.10 z=5 q=0.15 z=8 q=0.20 z=11 q=0.25 z=15 q=0.30 z=24 q=0.35 z=41 q=0.40 z=89 q=0.45 z=340
12.สรุป(Conclusion)
เราได้นำเสนอระบบธุรกรรมอิเล็กทรอนิกส์ที่ไม่ต้องพึ่งพาความไว้วางใจ เริ่มต้นจากกรอบแนวคิดของเหรียญที่สร้างจากลายเซ็นดิจิทัล ซึ่งช่วยควบคุมความเป็นเจ้าของได้อย่างดีแต่ก็ยังไม่สมบูรณ์ หากปราศจากวิธีการป้องกันการใช้จ่ายซ้ำซ้อน เพื่อแก้ปัญหานี้ เราจึงเสนอเครือข่ายแบบเพียร์ทูเพียร์ที่ใช้ proof-of-work ในการบันทึกประวัติธุรกรรมสาธารณะ ซึ่งจะกลายเป็นเรื่องยากอย่างมากสำหรับผู้โจมตีที่จะเปลี่ยนแปลง หาก node ที่ซื่อสัตย์ควบคุมพลังประมวลผล CPU ส่วนใหญ่ เครือข่ายนี้มีความแข็งแกร่งในความเรียบง่ายที่ไม่มีโครงสร้างใด ๆ ที่ซับซ้อน node ต่าง ๆ ทำงานพร้อมกันโดยประสานงานกันเพียงเล็กน้อย ไม่จำเป็นต้องระบุตัวตน เนื่องจากข้อความไม่ได้ถูกส่งไปยังสถานที่ใดสถานที่หนึ่งโดยเฉพาะ และเพียงแค่ต้องส่งมอบให้ถึงมือผู้รับอย่างดีที่สุด node สามารถออกจากและเข้าร่วมเครือข่ายได้ตามต้องการ โดยยอมรับ chain ที่มี proof-of-work มากที่สุดเป็นสิ่งที่เกิดขึ้นในขณะที่ไม่ได้เชื่อมต่อ พวกเขาโหวตด้วยพลังประมวลผล CPU แสดงการยอมรับบล็อกที่ถูกต้องโดยการทำงานเพื่อขยายบล็อก และปฏิเสธบล็อกที่ไม่ถูกต้องโดยการปฏิเสธที่จะทำงานกับบล็อกเหล่านั้น กฎและแรงจูงใจใด ๆ ที่จำเป็นสามารถบังคับใช้ได้ด้วยกลไกฉันทามตินี้
ไปอ่านต่อกันเองเด้ออ
[1] W. Dai, "b-money," http://www.weidai.com/bmoney.txt, 1998. [2] H. Massias, X.S. Avila, and J.-J. Quisquater, "Design of a secure timestamping service with minimal trust requirements," In 20th Symposium on Information Theory in the Benelux, May 1999. [3] S. Haber, W.S. Stornetta, "How to time-stamp a digital document," In Journal of Cryptology, vol 3, no 2, pages 99-111, 1991. [4] D. Bayer, S. Haber, W.S. Stornetta, "Improving the efficiency and reliability of digital time-stamping," In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993. [5] S. Haber, W.S. Stornetta, "Secure names for bit-strings," In Proceedings of the 4th ACM Conference on Computer and Communications Security, pages 28-35, April 1997. [6] A. Back, "Hashcash - a denial of service counter-measure," http://www.hashcash.org/papers/hashcash.pdf, 2002. [7] R.C. Merkle, "Protocols for public key cryptosystems," In Proc. 1980 Symposium on Security and Privacy, IEEE Computer Society, pages 122-133, April 1980. [8] W. Feller, "An introduction to probability theory and its applications," 1957.
-
 @ 79008e78:dfac9395
2024-09-02 06:17:05
@ 79008e78:dfac9395
2024-09-02 06:17:05Nostr: โปรโตคอลทางเลือกใหม่สำหรับโซเชียลมีเดียที่เป็นอิสระ ปลอดภัย และไร้การควบคุม
Nostr คือโปรโตคอลแบบเปิดที่เรียบง่าย ซึ่งช่วยให้สามารถสร้างโซเชียลมีเดียระดับโลกที่กระจายอำนาจและป้องกันการเซ็นเซอร์ได้
จากที่กล่าวข้างต้น เราสามารถพูดได้ว่า Nostr นั้นถูกออกแบบมาให้ใช้งานง่าย โดยมีเป้าหมายหลัก ๆ เพื่อสร้างเครือข่ายโซเชียลระดับโลกที่ปราศจากการเซ็นเซอร์ แล้วทำไมมันถึงทำอย่างนั้นได้? ในจุดนี้เราก็ต้องมาเจาะดูคุณสมบัติหลัก ๆ ของโปรโตคอลที่เรียกว่า Nostr กันก่อน:
เรียบง่าย - โปรโตคอลนี้ใช้โครงสร้างข้อมูลแบบ Event Object ที่เรียบง่ายและยืดหยุ่น (ซึ่งส่งเป็น JSON ธรรมดา) และใช้การเข้ารหัสแบบ Elliptic-curve มาตรฐานสำหรับคีย์และลายเซ็น
-
ช่องทางการสื่อสารที่รองรับเพียงอย่างเดียวคือการเชื่อมต่อ WebSockets จากไคลเอนต์ไปยังรีเลย์
-
การออกแบบนี้ทำให้ง่ายต่อการพัฒนาไม่ว่าจะไคลเอนต์หรือรีเลย์ และยังช่วยส่งเสริมความหลากหลายของซอฟต์แวร์
ยืดหยุ่น - เนื่องจาก Nostr ไม่ได้พึ่งพาเซิร์ฟเวอร์ที่เชื่อถือได้เพียงจำนวนหยิบมือ สำหรับการเคลื่อนย้ายหรือจัดเก็บข้อมูล แต่ใช้เซิร์ฟเวอร์จำนวนมหาศาลและกระจายตัวอยู่ทั่วโลก จึงมีความยืดหยุ่นสูง และมีการกระจายศูนย์อย่างแท้จริง
- โปรโตคอลนี้ถูกออกแบบมาโดยคำนึงถึงความเป็นไปได้ที่รีเลย์จะหายไป และอนุญาตให้ผู้ใช้เชื่อมต่อและเผยแพร่ข้อมูลไปยังรีเลย์จำนวนมากได้ตามต้องการ และยังสามารถเปลี่ยนแปลงได้ตลอดเวลาอีกด้วย
ตรวจสอบได้
- เนื่องจากบัญชี Nostr ใช้การเข้ารหัสแบบ PKE จึงง่ายต่อการตรวจสอบว่าข้อความถูกส่งมาจากผู้ใช้ที่ระบุจริงหรือไม่
เช่นเดียวกับ HTTP หรือ TCP-IP Nostr เป็นโปรโตคอลหรือมาตรฐานแบบเปิดที่ทุกคนสามารถนำไปสร้างต่อยอดได้ มันไม่ใช่แอปหรือบริการที่คุณจำเป็นต้องลงทะเบียน
แล้วทำไมเราถึงต้องการ Nostr?
ถึงในปัจจุบันโซเชียลมีเดียจะได้พัฒนามาเป็นช่องทางสำคัญในการไหลเวียนของข้อมูลทั่วโลก กลายเป็นช่องทางหลักในการติดต่อสื่อสาร แต่น่าเสียดายที่ระบบโซเชียลมีเดียในปัจจุบันของเรานั้นมีข้อบกพร่องมากมาย:
- ใช้ความสนใจของคุณเพื่อขายโฆษณา
- ใช้เทคนิคแปลกๆ เพื่อทำให้คุณเสพติด (อ้างอิงจากข้อ 1)
- ตัดสินใจว่าจะแสดงเนื้อหาใดให้คุณเห็นโดยใช้อัลกอริทึมลับที่คุณไม่สามารถตรวจสอบหรือเปลี่ยนแปลงได้
- ควบคุมอย่างเต็มที่ว่าใครสามารถเข้าร่วมและใครถูกเซ็นเซอร์
- เต็มไปด้วยสแปมและบอท
ด้วยข้อจำกัดเหล่านี้ Nostr จึงเป็นทางเลือกที่น่าสนใจในการสร้างโซเชียลมีเดียที่เป็นอิสระ ปลอดภัย และไร้การควบคุม
องค์ประกอบของโปรโตคอลที่ชื่อว่า Nostr
หลังจากได้ทำความรู้จัก Nostr กันไปแล้วเมื่อคราวก่อน คราวนี้เรามาเจาะดูองค์ประกอบของโปรโตคอลนี้กันดีกว่า
Keys ระบบบัญชีผู้ใช้และรหัสผ่านสำหรับ Nostr
-
บัญชี Nostr แต่ละบัญชีจะใช้คู่กุญแจสาธารณะ/ส่วนตัว (Public/Private Key ) เปรียบเทียบง่าย ๆ คือ กุญแจสาธารณะของคุณคือชื่อผู้ใช้ และกุญแจส่วนตัวก็เป็นรหัสผ่าน แต่ว่า ก็มีข้อแตกต่างที่สำคัญอยู่ นั่นคือ กุญแจส่วนตัวของคุณนั้นจะไม่สามารถรีเซ็ตได้หากเกิดการสูญหายขึ้น คุณจะเสียบัญชีนั้นไปตลอดกาล
-
โดยทั่วไปแล้ว กุญแจสาธารณะจะแสดงเป็นข้อความที่ขึ้นต้นด้วย npub1 และกุญแจส่วนตัวจะขึ้นต้นด้วย nsec1
-
ทั้งนี้คุณควรที่จะตรวจสอบให้แน่ใจว่าคุณได้เก็บกุญแจส่วนตัวของคุณไว้ในที่ปลอดภัย เช่น โปรแกรมจัดการรหัสผ่านอย่างเช่น Bitwarden
โปรโตคอลกับไคลเอนต์ ต่างกันอย่างไร?
Nostr เองเป็นเพียงโปรโตคอล หมายความว่า Nostr นั้นเป็นเพียงกระบวนการที่ตกลงกันไว้สำหรับการส่งข้อความผ่านอินเทอร์เน็ต (เหมือนข้อกำหนด)
ซึ่งการที่คุณจะเข้าถึง Nostr (โปรโตคอล) นั้น ผู้ใช้ส่วนใหญ่จะใช้งานผ่านไคลเอนต์ ซึ่งตัวของไคลเอนต์นั้นอาจเป็นเว็บ แอปพลิเคชันเดสก์ท็อป หรือ แอปพลิเคชันมือถือ โดยไคลเอนต์สามารถดึงข้อมูลจากรีเลย์ และสร้างข้อมูลใหม่ และส่งข้อมูลนั้นไปยังรีเลย์เพื่อให้ผู้ใช้คนอื่น ๆ สามารถเรียกอ่าน ข้อมูลนั้น ๆ ได้ โดย "ข้อมูล" เพียงรูปแบบเดียวที่มีอยู่ใน Nostr คือสิ่งที่เราเรียกกันว่า event
การพิสูจน์ความเป็นเจ้าของข้อมูลบน Nostr
บน Nostr นั้นการพิสูจน์ตัวตนเป็นเรื่องที่ง่ายมากเนื่องจากทุก ๆ event ที่เกิดขึ้น จำเป็นต้องมีลายเซ็นดิจิทัล (Digital Signature) โดยลายเซ็นนั้นจะช่วยให้มั่นใจได้ว่า ใครเป็นผู้สร้าง event นั้น ๆ ขึ้นมา โดยการพิสูจน์ทางคณิตศาสตร์
โดยในการสร้างลายเซ็นแต่ละครั้ง ไคลเอนต์จะจำเป็นต้องใช้กุญแจส่วนตัวของคุณ โดยทั่วไปแล้ว แอปพลิเคชันเจะมีที่ให้คุณใส่กุญแจส่วนตัวของคุณ เมื่อเปิดแอปพลิเคชันครั้งแรก พวกเขาสามารถคำนวณกุญแจสาธารณะของคุณได้จากกุญแจส่วนตัวเช่นกัน
ส่วนในกรณีที่คุณใช้งานผ่านเว็บแอป ผมไม่แนะนำให้ใส่กุญแจส่วนตัวลงไป แต่แนะนำให้ใช้ส่วนขยายของเบราว์เซอร์ ที่ใช้งานฟังก์ชันที่เกี่ยวข้องกับ Nostr ซึ่งอนุญาตให้เว็บไคลเอ็นต์ส่ง event ที่ยังไม่ถูกเซ็นมาให้ส่วนขยายและส่วนขยายจะทำหน้าที่เซ็น สำหรับวิธีนี้ เว็บไคลเอ็นต์ต่าง ๆ ไม่จำเป็นต้องรู้กุญแจส่วนตัวของคุณ แต่คุณก็ยังสามารถลงนามใน event ต่าง ๆ ได้ตามปกติ โดยส่วนขยายที่ได้รับความนิยมก็จะเป็น Flamingo, Alby และ nos2x
ไคลเอนต์ & รีเลย์
ไคลเอนต์คืออะไร?
หากจะอธิบายให้เห็นภาพอยากให้มองว่าไคลเอ็นต์ Nostr นั้นเป็นเหมือนกับแอปที่คุณใช้งานเพื่อเข้าถึง Twitter, Facebook, youtube เป็นต้น พวกมันคือ แอปพลิเคชัน, เว็บแอป ที่เชื่อมต่อคุณกับโลกของ Twitter, Facebook, youtube โดยตัวของไคลเอนต์ใน Nostr เองก็เปรียบเสมือนแอปต่าง ๆ ที่คุณใช้ดูหน้าฟีดนั่นเอง แต่ข้อดีของ Nostr ที่เหนือแอปพลิเคชันอื่น ๆ คือความเรียบง่ายและยืดหยุ่น ส่งผลให้ไคลเอ็นต์แต่ละตัวมีวิธีนำเสนอและใช้งานที่แตกต่างกันไป บางไคลเอ็นต์อาจออกแบบให้ใช้งานง่ายเหมือน Twitter บางตัวเน้นให้เห็นบทบาทสำคัญของรีเลย์ หรือโหนดที่กระจายข้อมูลอยู่ทั่วโลก บางตัวใช้ระบบอัลกอริทึมเพื่อให้แน่ใจว่าข้อมูลไม่ถูกปิดกั้น โดยไม่ทำให้ผู้ใช้งานรู้สึกยุ่งยาก
เรียบง่ายและยืดหยุ่น?
เนื่องจากการออกแบบของโปรโตคอลที่ทำการแยกข้อมูลของผู้ใช้ทั้งหมดออกจากไคลเอนต์ ทำให้ตัวของผู้ใช้งานเองนั้นมีอิสระเต็มที่ที่จะเลือกใช้ไคลเอนต์ต่าง ๆ เพื่อเข้าใช้งาน Nostr และแน่นอนว่า ผู้ใช้งานสามารถสลับหรือลงชื่อเข้าใช้ ไคลเอ็นต์ได้หลายตัวตามต้องการ ตราบใดที่ไคลเอ็นต์ทั้งหมดเชื่อมต่อกับชุดรีเลย์เดียวกัน คุณก็จะเห็นข้อมูลเดียวกันในทุก ๆ ไคลเอ็นต์
ลงชื่อเข้าใช้ ไคลเอ็นต์หลาย ๆ ตัวแล้วจะกระทบต่อความปลอดภัยของแอคเคาร์ไหม?
คำตอบของคำถามนี้นั้นขึ้นอยู่กับวิธีการที่คุณลงชื่อเข้าใช้ หากคุณลงชื่อเข้าใช้ด้วยกุญแจส่วนตัว ถึงแม้ว่าไคลเอ็นต์ส่วนใหญ่จะพยายามรักษาความปลอดภัยของกุญแจส่วนตัวอย่างดีที่สุด แต่ด้วยข้อจำกัดของซอฟต์แวร์ ย่อมมีความเสี่ยงที่จะเกิดช่องโหว่ การเจาะระบบ และข้อผิดพลาด ที่อาจทำให้กุญแจส่วนตัวของคุณรั่วไหลออกไปได้ ส่วนวิธีการป้องกันเกี่ยวกับเรื่องนี้คือการใช้ส่วนขยายของเว็บเบราว์เซอร์ เพราะการเข้าสู่ระบบในไคลเอนต์ต่าง ๆ ผ่านส่วนขยายนั้นจะใช้เพียงกุญแจสาธารณะในการเข้าสู่ระบบและทุกครั้งที่เราต้องการจะโพสต์หรือสร้าง event บน Nostr ไคลเอนต์จะทำการร่าง event นั้น ๆ และเว้นช่องของลายเซ็นเอาไว้จากนั้นเราจะต้องทำการเซ็นผ่านส่วนขยาย ด้วยวิธีนี้ทำให้กุญแจส่วนตัวของเราไม่หลุดออกไปไหนตลอดการใช้งาน
รีเลย์คืออะไร?
รีเลย์เปรียบเสมือนเซิร์ฟเวอร์ที่อยู่เบื้องหลังของ Nostr และทำหน้าที่รับ event ต่าง ๆ มาจากไคลเอนต์ Nostr และอาจจะจัดเก็บและกระจายข้อความเหล่านั้นไปยังไคลเอนต์อื่น ๆ ที่มีการเชื่อมต่ออยู่
เทคโนโลยีของรีเลย์นั้นเปลี่ยนแปลงอย่างรวดเร็ว ดังนั้นคาดว่าจะมีการเปลี่ยนแปลงอีกมากมายในอนาคต อย่างในปัจจุบันที่มีการนำเสนอ bostr หรือ รีเลย์ที่จะคอยส่ง event ของเราต่อให้กับรีเลย์อื่น ๆ ที่มีการเชื่อมต่อ เพื่อช่วยลดภาระของไคลเอนต์ในการรับส่งข้อมูลจากหลาย ๆ รีเลย์พร้อม ๆ กัน หรืออย่างการป้องกันสแปมด้วย POW หรือประเภทที่สามารถเก็บรูปหรือวิดีโอที่มีขนาดใหญ่ได้
แต่สิ่งหนึ่งที่ควรทราบก็คือ การที่ Nostr นั้นพยายามจะกระจายศูนย์และเหตุผลหลัก ๆ ที่สามารถทำแบบนั้นได้ก็ขึ้นอยู่กับรีเลย์ในการจัดเก็บและดึงข้อมูล ดังนั้น หากคุณรู้สึกว่าไคลเอนต์ Nostr ของคุณทำงานช้า ส่วนใหญ่ก็มักเกิดจากรีเลย์ที่คุณกำลังเชื่อมต่ออยู่ คุณอาจลองแก้ไขปัญญาโดยการเปลี่ยนหรือเพิ่มรีเลย์อีกสองสามรายการในไคลเอนต์ที่คุณใช้
แล้วจะสามารถหารายการรีเลย์ได้จากไหน?
การที่เราจะหารายการรีเลย์ที่เราควรเชื่อมต่อนั้น ๆ จริงแล้ว ๆ สามารถทำได้หลายวิธี แต่วิธีที่ผมแนะนำที่สุดจะเป็นการใช้ตามคนที่เราติดตามอยู่ เพราะจะเป็นวิธีที่เราสามารถเห็น event ต่าง ๆ ของคนที่เราติดตามได้ง่ายที่สุด และเช่นเดียวกัน เพื่อน ๆ หรือคนที่เราติดตามก็จะสามารถเห็น event ของเราได้เช่นกัน และสำหรับในประเทศไทย เรามีรีเลย์ที่คนไทยส่วนใหญ่นิยมใช้กันอยู่สองอัน นั้นคือ wss://relay.siamstr.com/ และ wss://relay.notoshi.win/ ถ้าหากว่าอยากเห็นคนไทยเยอะ ๆ บนหน้าไทม์ไลน์ ผมแนะนำเป็นอย่างยิ่งว่าควรเพิ่ม รายการรีเลย์เหล่านี้ลงไปในบัชญีหรือไคลเอนต์ต่าง ๆ ที่คุณใช้ด้วย
สำหรับอีกวิธีหนึ่งผมแนะนำให้เข้าไปในเว็บไซต์ nostr.watch เนื่องจากในเว็บไซต์นี้เป็นแหล่งข้อมูลที่ดีที่สุดสำหรับการค้นหาและประเมินความเร็วของรีเลย์ต่าง ๆ
จะเกิดอะไรขึ้นถ้ารีเลย์ทั้งหมดที่ฉันเชื่อมต่ออยู่หยุดให้บริการ?
สิ่งนี้เป็นสิ่งที่คุณต้องระวังมากที่สุดในการใช้งาน nostr เนื่องจากหากรีเลย์ทั้งหมดที่คุณเก็บข้อมูลไว้หยุดให้บริการทั้งหมดและคุณไม่มีการสำรองข้อมูล event ของคุณเก็บไว้เลย มันแปลว่าโพสต์ทั้งหมดของคุณ ผู้ติดตาม และรายการต่าง ๆ ที่คุณสรรค์สร้างไว้จะไม่สามารถกู้คืนได้ไปตลอดการ นี่จึงเป็นเหตุผลหลัก ๆ ที่ Nostr อนุญาตให้ผู้ใช้งานนั้นสามารถเชื่อมต่อกับรีเลย์ได้เป็นจำนวนมาก ก็เพื่อให้แน่ใจว่ามีข้อมูลสำรองเก็บไว้อยู่ที่ใดที่หนึ่งในระบบเสมอ แต่อย่างไรก็ตาม หากคุณต้องการที่จะมั่นใจได้ว่าข้อมูลต่าง ๆ ของคุณจะไม่ถูกเซ็นเซอร์ สิ่งที่คุณสามารถสามารถทำได้คือการใช้รีเลย์ส่วนตัวของคุณและกำหนดนโยบายต่าง ๆ ภายในรีเลย์ของคุณด้วยตัวคุณเอง
แล้วฉันจะสามารถใช้รีเลย์ส่วนตัวได้อย่างไร?
อะแฮ่ม ๆ ขอบอกไว้ก่อนว่ามันไม่คุ้มค่ากับความยุ่งยากสำหรับคนโดยทั่ว ๆ ไป ถึงในปัจจุบันจะมีเทคโนโลยีบางตัวที่เข้ามาช่วยให้มันทำได้ง่ายขึ้นแล้วก็ตาม หากคุณต้องการที่จะสำรองข้อมูลนั้น การที่จะมีรีเลย์ส่วนตัวที่ออนไลน์ตลอดเวลาอาจเป็นเรื่องที่ไม่ได้จำเป็นขนาดนั้น เนื่องจากเราสามารถใช้งานบริการอย่าง https://nostrsync.live/ ในการดาวน์โหลดข้อมูลของเราจากรีเลย์ต่าง ๆ ได้ หรือการติดตั้งรีเลย์ส่วนตัวอย่าง nostr-relay-tray: https://github.com/CodyTseng/nostr-relay-tray ที่ช่วยให้เราสามารถมีรีเลย์ส่วนตัวที่ใช้สำหรับสำรองข้อมูลได้
Nostr Implementation Possibilities (NIPs) NIP คืออะไร?
NIP มีไว้เพื่อส่งเสริมความสามารถในการทำงานของ Nostr และเป็นตัวคอยกำหนดให้ เหล่านักพัฒนาทำสิ่งต่าง ๆ ที่เหมือนกันในรูปแบบเดียวกัน เพราะมันคงไม่ใช่ความคิดที่ดีนัก หากนักพัฒนาแต่ละคนจะคิดค้นวิธีแก้ปัญหาทั่วไปของตัวเองและนำไปใช้ในแอปของตัวเองเท่านั้น และคงจะเป็นการดีกว่า ถ้าหากทุกคนใช้วิธีแก้ปัญหาที่เหมือนกัน นั่นคือเหตุผลที่ต้องมี NIP อยู่ในโปรโตคอลของ Nostr และในทำนองเดียวกัน แนวคิดใหม่อาจดูดีในแอปของนักพัฒนาบางราย แต่จะดูดียิ่งขึ้นอย่างแน่นอนหากแอปอื่น ๆ อีกมากมายใช้มาตรฐานเดียวกันและสามารถทำงานร่วมกันได้อย่างราบรื่น
ทำไมมันถึงหน้าสนใจ?
อย่าลืมว่า Nostr เป็นระบบแบบกระจายอำนาจและไม่ได้มีบริษัทหรือใครที่เป็นเจ้าของมัน อย่างเช่นโซเชียลมีเดียอื่น ๆ เช่น ทวิตเตอร์ อ่อไม่สิตอนนี้คงต้องเรียกมันว่า X สินะ ซึ่งหมายความว่าทิศทางของโพรโทคอล Nostr นั้นขึ้นอยู่กับพวกเราทุกคน! ไม่ว่าใคร ๆ ก็สามารถเสนอแนะและสนับสนุนการเปลี่ยนแปลงและให้ข้อเสนอแนะเกี่ยวกับแนวคิดที่ผู้อื่นเสนอ และการที่คุณเป็นส่วนหนึ่งของชุมชนนี้ ก็ทำให้คุณมีส่วนร่วมในทิศทางของ Nostr อีกด้วย
จากที่ส่งหากันได้แค่ข้อความ มาเป็นรูปภาพ มาเป็นวิดีโอ และมาเป็น”เงิน” นี่คือเส้นทางการเดินทางของโปรโตคอลนี้ในอดีต แล้วในอนาคตมันจะพัฒนาไปยังไงต่อก็ขึ้นอยู่กับเหล่าผู้ใช้งานและนักพัฒนาในอนาคต แล้วทำไมสิ่งนี้ถึงจะไม่น่าสนใจละ ?
Event
Event คืออะไร?
Event เป็น object เพียงประเภทเดียวที่มีอยู่บน Nostr โดยมีโครงสร้างประมาณนี้
``` {"id":"84d5d3dc9c388a702f39cad6360d41ebb804e809fb822f110ff8a14dfd35fc6c", "pubkey":"66df60562d939ada8612436489945a4ecf1d62346b3d9478dea8a338f3203c64", "created_at":1722315959, "kind":1, "tags":[["t","siamstr"]], "content":"ไปสั่งกาแฟเมื่อกี้ พส เจ้าของร้านชมว่าเดี๋ยวนี้คล่องภาษาญี่ปุ่นแล้วนะ ไอเราก็ดีใจ พอเดินกลับถึงที่ทำงานละก็ตระหนักได้ว่า ตะกี้เราสั่ง “ไอซ์โคฮี โอเนไงชิมัส” “เทคเอาส์” “คาโดะเดสส” ไอบ้าไหนญี่ปุ่นก่อนอังกฤษทั้งนั้น 🤣🤣\n\n#siamstr", "sig":"8f066a0099a5f580b605ebdb220179c4eca298947c38b855a0a8bf2783f28ddb537cb74a7f61d3ce8891189f719870efdf320ea4f895e03cdac44284c450c5c4"}
``` อย่าง Event ข้างต้นนี้มี kind เป็น 1 ซึ่งหมายถึง "ข้อความโน้ต" ซึ่งก็คือข้อความธรรมดา สั้น ๆ คล้ายกับที่ใช้กันใน Twitter เช่น บนฟีด การตอบกลับ และการโควท
ประเภทของ Event (Event Kinds)
หมายเลขของ kind แต่ละตัวมีความหมายแตกต่างกัน ตัวอย่างเช่น 0 หมายถึงอีเวนต์ "ข้อมูลเมตา" ใช้สำหรับให้รายละเอียดเกี่ยวกับผู้ใช้ เช่น ชื่อและรูปโปรไฟล์ รีเลย์ (Relays) สามารถจัดการกับ kind ที่แตกต่างกันได้ เช่น รีเลย์มักจะลบอีเวนต์ kind:0 เวอร์ชันเก่ากว่าออกไป และเก็บไว้เฉพาะเวอร์ชันล่าสุด ในขณะที่โดยทั่วไปจะเก็บอีเวนต์ kind:1 ไว้หลายรายการสำหรับแต่ละคีย์
โดยทั่วไปแล้ว คุณไม่จำเป็นต้องใช้ kind เกินกว่า 0 และ 1 ในการสร้างแอปพลิเคชันโซเชียลมีเดียบน Nostr แต่ kind อื่น ๆ ถูกคิดค้นขึ้นโดยไคลเอนต์ เพื่อมอบฟังก์ชันการทำงานอื่น ๆ ตามที่ระบุไว้ใน NIP บาง kind ไม่เกี่ยวข้องกับเครือข่าย และให้บริการตามความต้องการอื่น ๆ ของไคลเอนต์ที่เฉพาะเจาะจงกับฟังก์ชันการทำงานเหล่านั้น ซึ่งแนวคิดก็คือ สำหรับกรณีการใช้งานใหม่ ๆ แต่ละกรณี จะต้องมีการพิจารณาและเสนอซับโปรโตคอลเป็น NIP เพื่อให้สามารถทำงานร่วมกับไคลเอนต์ที่มีอยู่และในอนาคต ซึ่งอาจสนใจที่จะนำฟังก์ชันการทำงานนั้นไปใช้ ขณะเดียวกันก็มั่นใจได้ถึงความเข้ากันได้ย้อนหลัง และการรองรับสิ่งต่าง ๆ ที่มีอยู่และไม่ต้องการเปลี่ยนแปลง
คุณสมบัติอื่น ๆ ของ Event
created_at: เป็น Timestamp ของ UNIX ที่กำหนดโดยผู้สร้างอีเวนต์ โดยปกติจะเป็นเวลาที่สร้าง แม้ว่าจะไม่มีการตรวจสอบ แต่ก็ไม่ใช่ปัญหา
content: ขึ้นอยู่กับความหมายของ kind ในกรณีของ kind:1 จะเป็นเพียงสตริงข้อความธรรมดาที่คนอื่น ๆ อ่านได้ tags: ขึ้นอยู่กับ kind เช่นกัน แต่แท็กทั่วไปบางอย่างที่มักปรากฏใน event kind:1 และ kind อื่น ๆ คือ "p" ซึ่งใช้เพื่อกล่าวถึงกุญแจสาธารณะ และ "e" ใช้เพื่ออ้างถึง event อื่น
อยากมีส่วนร่วมในการพัฒนาของ Nostr ?
จริง ๆ แล้วใคร ๆ ก็สามารถเข้ามามีส่วนร่วมในการพัฒนา Nostr ได้ ไม่จำเป็นต้องเป็น dev หรือมีความรู้ด้านคอมพิวเตอร์ก็สามารถทำได้ ไม่ว่าจะเป็นการให้ feedback กับ dev ของ client ที่คุณใช้, การสร้างคอนเทนต์ต่าง ๆ บน Nostr การสร้างชุมชน รวมไปถึงการช่วย client ต่าง ๆ ในการทำ UI ให้เป็นภาษาท้องถิ่น และอื่น ๆ อีกมากมาย ใคร ๆ ก็สามารถช่วยได้ตามความสามารถที่แต่ละคนมี มันเลยทำให้ Nostr โครตน่าอยู่ :)
-
-
 @ 0edc2f47:730cff1b
2024-09-02 01:54:55
@ 0edc2f47:730cff1b
2024-09-02 01:54:55Chef's notes
In this case, sweet-and-sour doesn’t mean Americanized Chinese food but rather the sauce that dominated the Shabbos and Pesach dinner table among American Jewish immigrants in the early 20th century.
Details
- ⏲️ Prep time: 30 minutes
- 🍳 Cook time: 6 hours
- 🍽️ Servings: 12
Ingredients
- 1 medium onion, peeled and quartered
- 2 tsp ground ginger
- 8-10 large cloves garlic
- 1 cup ketchup
- ¼ cup dry sherry
- ¼ cup sake
- ¼ cup cider vinegar
- ¼ cup soy sauce
- ¼ cup honey
- ¼ cup Dijon mustard
- 1 tablespoon coarsely ground black pepper
- ¼ teaspoon ground cloves
- 1½ cups Coca-Cola, ginger ale, or Dr. Pepper
- 1 first-cut brisket, 6 to 7 pounds (2.7-3.2kg), rinsed and patted thoroughly dry
Directions
- Preheat oven to 325F / 160C.
- Combine all ingredients except brisket in a blender and blend until smooth.
- Place brisket in a Dutch oven or other large pot with a tight-fitting lid.
- Pour sauce over brisket, place lid on pot, roast in oven for 3 hours. Flip roast and return to oven for 3 hours or until fork tender.
- Remove roast to rest. Skim fat from sauce and reduce if desired. Serve immediately with sauce or cool, cover brisket and refrigerate overnight in cooking pan. The next day, defat sauce, reduce if desired, and reheat meat in sauce before serving.
-
 @ 3b7fc823:e194354f
2024-09-01 19:21:09
@ 3b7fc823:e194354f
2024-09-01 19:21:09Testing articles on Yakkihonne
-
 @ e27ae11e:e0c36580
2024-09-18 10:16:56
@ e27ae11e:e0c36580
2024-09-18 10:16:56In this article, we'll investigate how electricians in Sunshine Coast are supporting the move towards environmentally friendly power and why their work is so significant.
Click here> Best Electrician in Sunshine Coast
- Installing Solar Panel chargers
One of the most widely recognized ways of saddling sustainable power on the Sunshine Coast is by utilizing sunlight based chargers. Sunlight powered chargers catch daylight and convert it into power that can control homes and organizations. Electricians in Sunshine Coast are fundamental for introducing these sunlight powered chargers. They ensure the boards are put accurately on rooftops or different places where they can get the most daylight. When the boards are set up, circuit repairmen interface them to the electrical arrangement of the structure with the goal that the sunlight based energy can be utilized productively.
- Setting Up Sun based Inverters
Sunlight powered chargers create power, yet the power they produce isn't promptly usable by most domestic devices. This is where sun powered inverters come in. A sun based inverter changes over the power from the boards into a structure that can be involved by the machines in your home or business. Electricians in Sunshine Coast are talented in introducing and setting up these inverters. Without their ability, the sun based energy gathered by the boards wouldn't be usable.
- Introducing Battery Stockpiling Frameworks
While sunlight powered chargers create power during the day when the sun is sparkling, they don't deliver power around evening time. For this reason many individuals on the Sunshine Coast are putting resources into battery capacity frameworks. These frameworks store abundance sun based energy created during the day so it very well may be utilized around evening time or on overcast days. Electricians in Sunshine Coast are at risk for introducing these battery systems and associating them to the sun controlled chargers and electrical structures. This ensures that the energy set aside in the batteries can be used whenever it's required.
- Keeping up with Environmentally friendly power Frameworks
Like some other innovation, environmentally friendly power frameworks require ordinary support to keep them moving along as expected. Electrical technicians in Sunshine Coast are prepared to assess, clean, and fix sunlight based chargers, inverters, and battery stockpiling frameworks. Ordinary support forestalls issues and guarantees that the frameworks work at top proficiency. By keeping these frameworks ready to go, Electricians assist property holders and organizations with getting a good deal on energy charges and decrease their carbon impression.
- Overhauling Electrical Frameworks for Environmentally friendly power
Many homes and organizations on the Sunshine Coast were worked before environmentally friendly power became well known. Subsequently, their electrical frameworks probably won't be prepared to deal with the requests of sunlight based chargers, inverters, and battery stockpiling. Electrical experts in Sunshine Coast are frequently called upon to update these electrical frameworks. This could include supplanting old wiring, putting in new circuit breakers, or adding more electrical plugs. Updating the electrical framework guarantees that the structure can securely and effectively utilize sustainable power.
- Supporting the Development of Electric Vehicles
Electric vehicles (EVs) are turning out to be more famous on the Sunshine Coast. These vehicles burn power as opposed to gas, making them a cleaner and more practical choice for transportation. Electrical experts in Sunshine Coast are assuming a vital part in supporting the development of EVs by introducing EV charging stations. These stations are where EV proprietors can connect their vehicles to charge the batteries. Without these charging stations, it would be significantly more hard for individuals to claim and work electric vehicles.
- Interfacing Environmentally friendly power to the Lattice
The power created by sunlight based chargers can be utilized right away, put away in batteries, or sent back to the electrical lattice. The matrix is the organization that conveys power to homes and organizations across the locale. Exactly when sun fueled chargers produce more energy than a home or business needs, the excess energy can be sent back to the cross section. Electrical specialists in Sunshine Coast are responsible for ensuring the relationship between the sustainable power system and the cross section is secured and trustworthy.
- Instructing the Local area
Electricians in Sunshine Coast additionally assume a significant part in teaching the local area about environmentally friendly power. They help individuals with grasping how sun fueled chargers, inverters, battery structures, and EV chargers work. They can figure out the upsides of exchanging for sustainable power, for instance, lower energy bills, diminished natural impact, and extended energy independence. By sharing their insight, Electricians engage more individuals to do the change to sustainable power.
- Supporting Environmentally friendly power in New Development
As the Sunshine Coast keeps on developing, many new homes and organizations are being fabricated. Circuit repairmen in Sunshine Coast are associated with the preparation and development of these new structures. They work with engineers and manufacturers to plan electrical frameworks that are viable with sustainable power all along. This could incorporate pre-wiring structures for sunlight powered chargers, introducing energy-productive lighting, and setting up savvy home frameworks that advance energy use. By anticipating environmentally friendly power all along, electrical experts assist with making structures that are more maintainable and future-proof.
- Advancing Energy Autonomy
Energy autonomy implies depending on your own energy sources instead of relying totally upon the electrical lattice. This is especially significant during blackouts or in distant regions where the network probably won't be solid. Electrical experts in Sunshine Coast assist property holders and organizations with accomplishing energy autonomy by introducing and keeping up with environmentally friendly power frameworks. With sunlight based chargers, battery capacity, and perhaps even wind or hydro power, a structure can create and utilize its own power. This decreases the dependence on petroleum products and expands the strength of the local area.
- Decreasing Carbon Impression
The carbon impression is how much carbon dioxide (CO2) and other ozone depleting substances that are delivered into the climate because of human exercises. Consuming petroleum products like coal, oil, and flammable gas to create power is a significant wellspring of these discharges. By supporting environmentally friendly power, electrical experts in Sunshine Coast are assisting with decreasing the carbon impression of homes and organizations. Sunlight based energy, for instance, creates no immediate discharges, making it a much cleaner option in contrast to petroleum products.
- Empowering Advancement
The field of sustainable power is continually advancing, with new advancements and techniques being fostered constantly. Electricians in Sunshine Coast are at the front of this advancement. They are ceaselessly finding out about new items, establishment strategies, and best practices. By keeping awake to-date with the most recent headways, Electricians guarantee that their clients benefit from the most productive and powerful environmentally friendly power arrangements that anyone could hope to find.
- Giving Master Guidance
With regards to sustainable power, there are numerous choices to browse. Circuit repairmen in Sunshine Coast give master exhortation to assist property holders and organizations with settling on informed choices. They can suggest the best sunlight powered chargers, inverters, and battery frameworks in view of the particular necessities of the client. They can likewise offer direction on the most proficient method to augment energy productivity and make the most of the advantages of environmentally friendly power.
- Supporting the Nearby Economy
By employing electrical technicians in Sunshine Coast for sustainable power ventures, occupants and organizations are likewise supporting the neighborhood economy. Nearby circuit repairmen are know all about the special necessities of the Sunshine Coast people group and are focused on offering top notch assistance. The cash burned through on inexhaustible effort establishments and support stays inside the local area, making position and helping the neighborhood economy.
- Adding to Supportability Objectives
Numerous state run administrations and associations have defined manageability objectives to lessen fossil fuel byproducts and advance sustainable power. Electrical experts in Sunshine Coast are assisting the local area with meeting these objectives by expanding the reception of environmentally friendly power. Each sunlight powered charger introduced, each battery framework associated, and each EV charger set up carries the local area one bit nearer to a more manageable future.
- Adjusting to Environmental Change
Environmental change is a worldwide test that influences everybody, including the Sunshine Coast. Increasing temperatures, more outrageous climate occasions, and changing precipitation designs are only a portion of the effects of environmental change. By supporting sustainable power, circuit repairmen in Sunshine Coast are assisting with relieving these impacts. Sustainable power lessens dependence on non-renewable energy sources, which are a significant supporter of environmental change. Furthermore, sustainable power frameworks can be stronger notwithstanding environment related disturbances, like tempests or heatwaves.
- Establishing a Cleaner Climate
Environmentally friendly power frameworks like sunlight based chargers produce power without the contamination related with petroleum derivatives. This prompts cleaner air and water, which is better for the strength of individuals and the climate. Circuit repairmen in Sunshine Coast add to this cleaner climate by introducing and keeping up with sustainable power frameworks. Their work diminishes contamination and safeguard the regular magnificence of the Sunshine Coast.
- Supporting People in the future
The choices we make today about energy use will affect people in the future. By advancing and supporting environmentally friendly power, circuit repairmen in Sunshine Coast are assisting with making a more practical world for people in the future. This incorporates guaranteeing that youngsters and grandkids acquire a planet with cleaner air, water, and a steady environment.
- Upgrading Property Estimation
Homes and organizations with environmentally friendly power frameworks, as sunlight powered chargers and EV chargers, are much of the time more appealing to purchasers. These properties can offer lower energy bills and a more modest natural effect, which are engaging elements in the present market. Electricians in Sunshine Coast assist with upgrading the worth of properties by introducing and keeping up with environmentally friendly power frameworks. This can have a major effect when it comes time to sell or rent a property.
- Building a More grounded Local area
At long last, crafted by circuit repairmen in Sunshine Coast in supporting environmentally friendly power helps construct a more grounded, stronger local area. A people group that puts resources into environmentally friendly power is one that is ready for what's in store. A people group values manageability, development, and ecological stewardship. Electrical experts assume a key part in building this sort of local area by giving the skill expected to make sustainable power a reality on the Sunshine Coast.
Conclusion Electricians in Sunshine Coast are essential in promoting renewable energy. They handle everything from installing solar panels to educating the community. Their work helps create a cleaner, more sustainable future. As more people adopt green energy, these electricians will continue to play a key role in fighting climate change and supporting a sustainable world.
-
 @ 9fc6b5fc:5bacb10a
2024-09-18 03:54:39
@ 9fc6b5fc:5bacb10a
2024-09-18 03:54:39Details
- ⏲️ Prep time: 45 minutes
- 🍳 Cook time: 40 minutes
- 🍽️ Servings: 4-6
Ingredients
- 1 frozen puff pastry sheet, thawed
- 2 red organic apples (skin color adds great visual pop)
- Juce of half a lemon
- 1 tablespoon of flour, to sprinkle the counter
- 3 tablespoons of apricot preserve
- Cinnamon (optional)
- Powdered sugar for decorating (optional)
Directions
-
- Thaw the puff pastry if you haven't done so yet. It should take about 20-30 minutes.
-
- Prepare a bowl with some water and the lemon juice. Cut the apples in half, remove the core and cut the apples in paper thin slices. Leave the peel so it will give the red color to your roses.
-
- Right away, place the sliced apples in the bowl with lemon and water, so that they won't change color.
-
- Microwave the apples in the bowl, for about 3 minutes, to make them slightly softer. If you prefer, you can also simmer the apple slices in the water in a small pan on the stove.
-
- Unwrap the puff pastry over a clean and lightly floured counter. Using a rolling pin stretch the dough a little, trying to keep it in a rectangular shape. Cut the dough in 6 strips. These are about 2 in x 9 in (5 cm x 22 cm).
-
- In a bowl, place three tablespoons of apricot preserve with two tablespoons of water. Microwave for about one minute, so that the preserve will be easier to spread. Spread the preserve on the dough.
-
- Preheat the oven to 375 degrees F (190 degrees C). Drain the apples.
-
- Place the apples on the dough so that the skin side is facing away from you, and the bottom of the slice is at the middle of the dough (see cover image). Sprinkle with cinnamon if you'd like.
-
- Fold up the bottom part of the dough over the apple slices, so that it cups them.
-
- Carefully roll, seal the edge, and place in a silicone muffin cup. No need to grease the muffin mold if it's silicone. Otherwise, make sure to grease it.
-
- Do the same for all 6 roses. Bake at 375 degrees F (190 degrees C) for about 40-45 minutes, until fully cooked. If using a convection oven, check the roses after 20 minutes and cover if the apple slices are already sufficiently browned. Convection ovens dry out the apples more quickly and will result in 10 minutes shorter cooking time.
-
 @ c11cf5f8:4928464d
2024-09-01 13:22:49
@ c11cf5f8:4928464d
2024-09-01 13:22:49Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too!
If you missed our last thread, here are some of the items stackers recently spent their sats on.
originally posted at https://stacker.news/items/668607
-
 @ 6c2d68ba:846525ec
2024-09-01 13:02:53
@ 6c2d68ba:846525ec
2024-09-01 13:02:53Dear friend,
it seems like you have decided to turn your back on those walled gardens and set sails to enter uncharted territory. A world without walls, an open world, a world of beautiful chaos. At least for today, I don't intend guiding you out of the safe harbour onto the open, endless sea. Today, my only intent is sharing a few thoughts, before you depart.
As a wise man on Madeira once said, it's not so much about having the right answers, it's about asking the right questions. While I'm not certain whether I have found the right questions myself by now, let me share the current set with you:
-
What causes the discomfort that drives you out of the walled garden onto the open sea?
-
Are you trying to transfer from one walled garden to the next one, where the difference being a slightly friendlier colour on the wall?
-
What are you hoping to find on the open sea that walled gardens cannot provide?
-
What are you willing to sacrifice for freedom (of speech)?
-
What will you need to keep the ship afloat?
-
How will you react when you find yourself in the middle of a storm?
I sincerely believe that it's worthwile taking a step back before departing to reflect on the big picture and the underlying paradigm shift between walled gardens and nostr. This is not about building competitors to broken systems, this is not about mimicking centralised services, this is not about repeating the same mistakes over and over.
This is about building a new world, an open world without walled gardens and data silos.
Onwards!
-
-
 @ ea1e6f68:49fe0005
2024-09-18 03:20:57
@ ea1e6f68:49fe0005
2024-09-18 03:20:57There is consensus on the internet that the chaotic times we are living is a result of the 4th turning. The trust in old institutions that originated after WW2 is breaking down, which causes chaos around the globe. Most people who experienced the last 4th turning already died. The people currently alive know that authoritarianism is bad, but they don’t realise it because they never lived it. That’s why we have to learn the same hard lessons again.
Another widely accepted view is that this 4th turning will last until at least 2030. That WW3 is still ahead of us and that we will have another 6 years of increasing chaos. Even Wikipedia claims that the current 4th turning started just before the financial crisis in 2008. Since a turning generally last around 20 years but can take some longer, it would make 2030 a good ETA to end.
 *According to Wikipedia the current 4th turning started in 2006 and will end in 2033
*According to Wikipedia the current 4th turning started in 2006 and will end in 2033Recently, another scenario where the 4th turning ends around 2025 popped up in my head. The more I been thinking about it the more supporting arguments I find. What if we are already further in the current 4th turning than everyone thinks? What if we have just one or two years to go before the momentum turns positive again?
*This article is not a prediction, nobody knows the future. However, it’s an alternative scenario that’s in my mind supported by plenty good arguments. I like to think in probabilities, and at the time of writing I give this scenario around 40% chance. What do you think? Leave me a comment!
Could the 4th Turning Almost be Done?
What if the current 4th turning is almost near its end? What if it only last until around 2025? Would it be possible that we will get our D-Day moment somewhere in the coming two years followed by a massive positive momentum shift in society that signals the 1st turning? Or could it be that the transition isn’t that obvious this time and that we slowly smooth into the first turning without a D-Day moment this time around?
2025 would be exactly 80 years after the end of WW2, which is historically exactly a full cycle. Further, if we consider 9/11 as the start of the 4th turning instead of the Great Financial Crisis, it last already 24 years and is already overdue to end. There is more to support this thesis:
The Last 4th Turning
I know many people will get triggered by the comparison between the 2020’s and Nazi Germany. If this is you, stop reading now and go read Donald Duck or some happy fairytale. If you are willing to accept reality, you'll see an obvious similarity between those two era’s:
They are both 4th turnings with a massive wave of collectivism including extreme authoritarianism like censorship, movement restrictions, democide and war. Both times are universally recognised as a time of global chaos and a clear negative momentum in society.
1940 VS 2020
The corrosion of the institutions in Germany started long time before it became obvious in WW2. The real global chaos only took place over the last 5 years of the 4th turning in the form of a massive hot war, occupation of many countries and a genocide known as the Holocaust.
If you compare this to today, I would say that the global chaos started in 2020 with global lockdowns, movement restrictions, heavy censorship and forced medical interventions followed by some very nasty wars. If this last to around 2025 it would be a perfect rhyme!
When Did the 4th Turning Start?
What about the beginning of the 4th turning? Did it really start in the Great Financial Crisis as most people say? In my mind the trust in the institutions really started to break down after 9/11 in 2001. This was the event where the government violated our basic rights on a global scale by reversing the burden of proof and started multiple forever-wars.
Before 9/11 they had to prove whether you are a terrorist, now you have to prove that you are not. Innocent until proven guilty was a universally accepted basic human right in the entire Western world. After 9/11 this was violated on a global scale and this was quickly normalised. Our rights would later be violated again in the same way, when healthy people had to prove that they aren't sick.
It marked a critical breakdown of basic human rights, it was a fundamental change in society and it was the first major step into authoritarianism. In my opinion, this was the end of the free West and the start of the modern surveillance state we lived under since, which is clearly getting out of the hand today.
Realisation Will Come Later
Authoritarianism doesn’t get suddenly implemented, it comes in a long serie of tiny changes. The media is spreading the narrative that these changes are good or necessary. This is how society slowly slides into full blown authoritarianism without the population realising it.
Even in Nazi Germany most people didn’t realise how bad their regime was until it was all over and the Germans were asked for an explanation for what happened. A very famous answer from the general German population after the war was ‘Wir haben das nicht gewurst’, which means ‘we didn’t know’.
Westerners today are busy living their life while their government does really evil shit. The media simply doesn’t tell them what happens or they push the narrative that it is necessary for ‘our safety’. What’s considered murder or genocide when read in a history book, is considered normal and necessary when our government does it today.
People living a 4th turning are clearly not realising how bad it actually is, probably because of a combination of 'the boiling frog' effect, the inability to zoom out because the focus on 'the current thing' and denial of a different worldview. This realisation will only come later when it’s all over and they look back on this crazy time.
The Winner Writes History
We all know and recognise the evil and destruction of WW2. Most of us are probably expecting to get about the same in this 4th turning. We are still far away from that. Aren't we?
The evil stories of the Nazi’s are written by the Allies after the 4th turning ended, while our perception today is formed by the same institutions that cause all the death and destruction. Could it be that the winner this time will write history very differently? Who is going to be the winner this 4th turning and how will history be written?
Our Perspective VS The ‘Winner’ Perspective
Our institutions told us that Afghanistan had to be invaded because scary terrorists were hiding in the caves. Iraq had to be invaded because there were dangerous weapons of mass destruction. We had to do KYC and AML because we had to defund terrorists.
Businesses had to be closed to prevent a dangerous virus from spreading, people had to be injected because it was the only way out, Ukraine had to be supported because otherwise crazy Russians would invade all of Europe and Gaza had to be attacked because they are all terrorists.
What if the winner writes history as follows? The regime murdered 176.000 people in Afghanistan and 150.000 in the Iraq war to enforce the fraudulent dollar standard. Then they starved 500.000 Iraqi children to death with sanctions. KYC and AML rules prohibited billions of people from connecting to the global financial markets which kept them in poverty and caused starvation on a massive scale.
Many businesses were destroyed to monopolise giant corporations and centralise power over the economy. 5 billion people were forced into a medical experiment, which caused massive harm and death, to aim for total control over the people through movement passes and make a lot of money for corrupted organisations in the process.
https://www.youtube.com/watch?v=KP1OAD9jSaI
It’s Probably much Worse Than We Realise…..
Since the globally forced lockdowns and medical experiments, there is an excess death rate almost all over the world. It’s very hard to figure out how many people died, because the responsible people are still in power, and the media is totally ignoring it. Since 5 billion people are injected, a 1/500 death rate would mean 10 million deaths.
This means that if you believe the death rate was over 1/500, this forced medical experiment was about as deathly as the Holocaust. It’s very speculative at this moment, but a 20% excess deaths in most of the world for multiple years reveals that it might be much bigger than that. We will probably only know and realise when the victor writes history in the next 1st turning.
Do We ‘Need’ a Full Blown War Until 2030?
The consensus on the internet today is that we still have at least 6 years of chaos to go and that WW3 in the form of a massive hot war is inevitable. I call the thesis in this article a white pill scenario, because I believe this doesn’t have to be like that at all. I think there are some good reasons why it may not happen.
Firstly, as described earlier, we might have had a level of death and destruction comparable to the last 4th turning already, we just don’t realise it yet. We may be living it already, but ‘wir haben das nicht gewurst’ until the current regime falls and the winner writes history.
Secondly, humanity tend to get less violent over time, which could reduce the amount of blood spilled in this 4th turning. New technologies could change how war is done. It makes a lot of sense that war was done in an industrial way (tanks and guns) during the Industrial Age, while it would be mostly an information war in the Information Age.
Thirdly, all global powers have nuclear weapons this time around. This enforces the game theory that the biggest powers practically can’t invade each other, because this would mean total destruction of both. Could this be the reason that we see all these relatively small proxy wars and biological warfare instead of a full blown global hot war?
Lastly, if you understand that war is generally used as a way to default on a failing financial system, was this done with the massive Covid liquidity injection? This suspicion was strengthened after I heard how macro trader Raoul Pal described how the current monetary situation looks a lot like the post-WW2 era. Have we had our WW3 already in a very different format?
Is Bitcoin a New Institution for the Next Turning Cycle
Bitcoiners generally think that Bitcoin is a tool to help us through the 4th turning. This can be true, but what if is the new institution to replace the central banks in the new turning cycle? What if Bitcoin crossing te Chasm, which is expected to happen soon, is the Bretton Woods of this cycle?
Bretton woods happened at the end of the war and kicked off the 1st turning. It didn’t happen before the war. Is Bitcoin mass adoption marked by the Bitcoin ETF’s also signalling the end of WW3 like Bretton Woods did for WW2? It would be a perfect rhyme again!
Please let me know what you think in the comments and follow me for more!
-
 @ a012dc82:6458a70d
2024-09-18 03:13:01
@ a012dc82:6458a70d
2024-09-18 03:13:01Table Of Content
-
An Ideal Environment for Crypto Growth
-
Economic Impact of Bitcoin in Texas
-
Future Prospects
-
Conclusion
-
FAQ
The Lone Star State has witnessed a phenomenal rise in Bitcoin and cryptocurrency adoption in recent years. This article will explore the factors behind this surge, the benefits it offers to the local economy, and the potential implications for the future of Bitcoin and the broader crypto landscape in Texas and beyond.
An Ideal Environment for Crypto Growth
A. Energy Abundance
Texas boasts abundant and affordable energy resources, particularly from wind and natural gas. This has attracted a growing number of cryptocurrency mining operations, which require vast amounts of energy to maintain and secure the blockchain.
B. Regulatory Framework
Texas has embraced a relatively open regulatory environment for cryptocurrencies. The state government has shown a willingness to adapt existing regulations and create new ones to support the growth of the crypto industry.
C. Tech-Friendly Population
Texas has a tech-savvy population with a strong entrepreneurial spirit. This has led to the establishment of numerous startups and businesses focused on blockchain technology and cryptocurrency services.
Economic Impact of Bitcoin in Texas
A. Job Creation
The rise of Bitcoin and cryptocurrency-related businesses has created thousands of jobs in Texas. These range from mining operations to software development, financial services, and support roles.
B. Attracting Investment
The growth of the crypto sector in Texas has attracted significant investment from both domestic and international sources. This influx of capital has spurred the local economy and fostered innovation in the state.
C. Increased Tax Revenue
With more businesses and individuals engaging in cryptocurrency transactions, tax revenues have increased. This additional revenue can be used to improve public services and infrastructure in Texas.
Future Prospects
A. Becoming a Global Crypto Hub
As Texas continues to foster a favorable environment for cryptocurrencies, it has the potential to become a global hub for blockchain technology and digital assets. This could help attract even more talent and investment to the region.
B. Wider Adoption of Cryptocurrencies
The rise of Bitcoin in Texas could lead to broader adoption of cryptocurrencies throughout the state and beyond. As more people and businesses become familiar with digital assets, they may increasingly use them for everyday transactions.
C. Challenges and Risks
Despite the promising outlook, there are still challenges and risks associated with the growth of Bitcoin and other cryptocurrencies. These include regulatory uncertainty, potential environmental impact, and volatility in the crypto markets.
Conclusion
The rapid rise of Bitcoin in Texas is a testament to the state's favorable conditions and forward-looking approach to emerging technologies. With continued investment and innovation, Texas has the potential to become a global leader in the cryptocurrency space. However, it remains essential to address the associated challenges and risks to ensure a sustainable and responsible growth trajectory.
FAQ
Why has Bitcoin become popular in Texas? Bitcoin has become popular in Texas due to the state's favorable regulatory environment, its thriving energy industry, and a growing interest in alternative forms of investment.
Is Bitcoin legal in Texas? Yes, Bitcoin is legal in Texas. In fact, the state has taken steps to encourage the development of the cryptocurrency industry.
Can I use Bitcoin to buy goods and services in Texas? Yes, you can use Bitcoin to buy goods and services in Texas. Some businesses in the state have begun accepting Bitcoin as payment.
What does the rise of Bitcoin in Texas mean for the future? The rise of Bitcoin in Texas could be a sign of things to come, as more people become interested in digital currencies and more businesses begin accepting them as payment. It could also lead to increased investment in the cryptocurrency industry and further innovation in the field.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 472f440f:5669301e
2024-09-18 02:15:29
@ 472f440f:5669301e
2024-09-18 02:15:29As I'm sure many of you are aware already, Israel executed an attack on thousands of Hezbollah members in Lebanon earlier today. At the moment, it looks like Israel successfully waged a supply chain attack on the pagers used by Hezbollah members. Intercepting the devices and placing highly explosive material on the batteries that could be triggered remotely by raising the temperature of the batteries.
To my knowledge, this is the first time an attack of this nature and of this scale has ever been waged. This is a very serious and dangerous precedent that should make anyone reading this think long and hard about the ramifications of the normalization of this type of warfare.
It's not clear to me yet whether this is exactly what happened, but this seems to be where all of the reports are pointing. And when you consider the scale of this operation, it is hard to think of alternative ways that this could have been achieved outside of corrupting the supply chain of this particular pager. Regardless, the die has been cast and remote detonation attacks in crowded civilian areas has been battle tested as an appropriate war tactic.
Not only does this set a terrible precedent for war, but it also begs the question; if they can do something like this with a relatively dumb pager, how much damage could they do with something like an iPhone? How vulnerable are the billions of people who hold smartphones in their pockets, or drive internet connected electric vehicles with lithium ion batteries? How trivial was it for Mossad to gain access to these devices and at what part of the supply chain? Now that this attack has been deemed to be "on the table" how long will it take before others begin to wage similar attacks?
War tactics and their costs are rapidly changing right before our eyes. The war between Russia and Ukraine is showing that low cost drones strapped with bombs can be very effective weapons that can do damage to military equipment worth anywhere between tens of millions to billions of dollars. The Houthi rebels have used cheap drones to completely disrupt the Suez Canal for the better part of a year. The world has only seen the tip of the iceberg in regards to how this type of technology can be used at scale to tip the leverage of power towards those with less financial resources, but a willingness to engage in kinetic conflict. Some of these drones are strapped with thermite flame throwers!
Now that new information has been brought to the market - you can turn pagers and (likely) cellular phones into a network of improvised explosive devices via a software push that increases the temperature of the devices' batteries - it is only a matter of time before others figure out how to do it and begin using these tactics themselves. War machines have never been easier and cheaper to deploy. In a world that is becoming increasingly fractured and angry, this is absolutely frightening. Asymmetric warfare as predicted in the Sovereign Individual is upon us.
As it relates to bitcoin hardware, these attacks highlight that an attack that has been long talked about in the industry but not yet exploited to the best of our knowledge is very real. Supply chain attacks, particularly on bitcoin signing devices that store private key information, have just been proven to be very possible by motivated state actors. If a nation state wanted to somehow "prove" that bitcoin is insecure or figure out a low effort way to do a mass confiscation of bitcoin all they have to do is successfully attack the supply chain of a hardware manufacturer, corrupt the devices, and let them flow to the hands of individuals who believe they are securing their bitcoin in the best way possible. The best way to mitigate this risk is to hold you bitcoin in a multi-sig wallet using a quorum of keys produced by different hardware produced by different manufacturers. Companies like Unchained make this process as seamless and possible and supply chain attacks like the one that was laid bare today highlight why these collaborative custody models are so important. Especially if you are holding a large amount of wealth in bitcoin.
This is a sad day for the world. I'll be praying for peace and sanity to prevail.
Final thought... That was a terrible loss by the Birds.
-
 @ a30cdfee:2d2f97ff
2024-09-01 11:40:38
@ a30cdfee:2d2f97ff
2024-09-01 11:40:38Primal: Social Media with Bitcoin Tipping
Primal is a social media app that lets you tip (zap) other users with bitcoin!
How does Primal work and why should you join?
Primal is a social Bitcoin wallet.
If you like somebody's content, you can tip them Bitcoin micropayments through the Lightning Network.
Or monetize your own content.
You can also use it as a custodial Lightning wallet to pay for small purchases in bitcoin.
Primal Is a Nostr Client
Primal uses the Nostr protocol as its social graph.
Nostr is an open protocol for decentralized and censorship-resistant social media.
If you're new to Nostr, learn more about it here: https://stacker.news/items/558629
Since Primal is only a client to access the Nostr protocol, it can only censor free speech or deplatform users on the Primal app, but not on Nostr.
Also, if you stop using Primal as your Nostr client, you can import all your followers, posts, etc. to a new client.
Primal Feels Like Twitter (X)!
Primal's feed feels very familiar to other social media platforms, especially X (Twitter).
You can follow people, like their posts, repost etc.
It's not only for Bitcoin-related discussion: you can search for different hashtags and find your tribe, e.g. photography etc.
Primal works for iOS, Android and desktop.
On desktop, the "Explore" function is even more detailed.
Earn Bitcoin for Your Content!
By clicking the lightning bolt symbol on the feed, you can tip (zap) other users bitcoin.
You can also browse through your contacts and zap them.
Nostr is a great directory for Lightning payments!
If you hold the bolt symbol a bit longer, you can specify the zap amount if you want.
You can set your default zap amount in settings.
To set up a Lightning wallet with Primal, the app asks for your name, email address and the country of residence.
But as far as I know, you can use a nym and a throwaway email etc.
No need to upload any identity documents.
The maximum balance you can hold on the Primal wallet is 1 million sats, or 0.01 BTC.
The purpose of the wallet is not for long-term savings, but to onboard people to Nostr and to get familiarized with the culture of zapping.
To get your first sats on the Primal wallet, you can receive bitcoin on Lightning or on-chain.
Alternatively, you can buy sats on Primal with Apple Pay or Google Pay with your credit card (max. about $5 worth).
Or just start creating and receive zaps from other users.
Take Care of Your "nsec"!
Your "nsec" is your private key to your Primal (and Nostr account).
Don't share it with anyone!
Primal creates an nsec for you upon account creation, or you can import your own.
Primal is open-source, but it is not always a good practice to import private keys to any apps.
If you don't want to import the private keys you already have to Primal, you can use e.g. Amber, a Nostr signer extension app for Android.
It's advisable to store your nsec in e.g. a password manager.
If you use Primal on desktop, you can use e.g. Alby @Alby, as a Nostr signer extension, zapping wallet and a place to store your nsec.
Learn more about Alby here.
You can also use another Nostr signer extensions on desktop, e.g. Nos2x, but they often have no wallet functions for zapping or receiving zaps.
They work only for posting, liking, replying, reposts etc.
Convenient, but With Privacy Trade-Offs
You can send direct messages to other Primal users, but you should know that while the content of the direct messages is encrypted (visible only to you and your contact), the message metadata is public for all to see (who you're sending messages to, when, how often etc.)
Primal can be used as a global international "Venmo" during dinner parties.
No more head-scratching when trying to split the bill!
Not the most private way to do it though, but it's convenient!
Let's connect on Nostr!
You can find me here.
Additional Resources
https://www.youtube.com/watch?v=Qd4Po4i7wvc
https://www.youtube.com/watch?v=7LsIb6D7FtU
Project Links
originally posted at https://stacker.news/items/668536
-
 @ 7fd90943:52bf6313
2024-09-01 07:20:27
@ 7fd90943:52bf6313
2024-09-01 07:20:27![TIP] I was surprised to discover that I can send Hive in form of Bitcoin Lightning with this Decentralized Application. Right now the only way that I was able to access this is through HIVE keychain. I will try to find some other ways to access this. Now I can fund my Stacker wallet in the most convenient way possible.
originally posted at https://stacker.news/items/668391
-
 @ 1123ece2:7d1e00c0
2024-09-18 00:17:35
@ 1123ece2:7d1e00c0
2024-09-18 00:17:35Hey everyone and welcome to Refinery Life Australia.
“Amen and Amen” has been the theme for the last few Sundays.
This series is a study from the Psalms, in which the psalmist gives voice to prayers that resound in our hearts today.
Today we are discussing, A Prayer for Divine Correction.
Text
Psalm 139:23-24 NKJ
23 Search me, O God, and know my heart;\ Try me, and know my anxieties;
24 And see if there is any wicked way in me,\ And lead me in the way everlasting.
Scripture Reading
Psalm 139:1-12 NKJV
God’s Perfect Knowledge of Man
1 O Lord, You have searched me and known me.
2 You know my sitting down and my rising up;\ You understand my thought afar off.
3 You comprehend my path and my lying down,\ And are acquainted with all my ways.
4 For there is not a word on my tongue,\ But behold, O Lord, You know it altogether
5 You have hedged me behind and before,\ And laid Your hand upon me.
6 Such knowledge is too wonderful for me;\ It is high, I cannot attain it.
7 Where can I go from Your Spirit?\ Or where can I flee from Your presence?
8 If I ascend into heaven, You are there;\ If I make my bed in hell, behold, You are there.
9 If I take the wings of the morning,\ And dwell in the uttermost parts of the sea,
10 Even there Your hand shall lead me,\ And Your right hand shall hold me.
11 If I say, “Surely the darkness shall fall on me,”\ Even the night shall be light about me;
12 Indeed, the darkness shall not hide from You,\ But the night shines as the day;\ The darkness and the light are both alike to You.
Psalm 139:23-24 NKJV
23 Search me, O God, and know my heart;\ Try me, and know my anxieties;
24 And see if there is any wicked way in me,\ And lead me in the way everlasting.
Introduction.
A devotional study of the Psalms can be particularly helpful in nourishing our faith and assisting us in our prayer life.
Psalm 139 emphasises that God has unlimited knowledge and also that God is always and everywhere present.
This great psalm celebrates the truth that God is our Creator.
It closes with a prayer against the wicked and a prayer for divine correction as the psalmist faced the present and the future.
- A prayer for divine probing.
The psalmist was positioning himself on the doctors examination table and asking Him to examine the motives of his heart and the thoughts of his mind.
He recognised that the source of actions and conduct is found in the thoughts and emotions of the inward man.
Perhaps David was motivated to pray this prayer for divine probing because he was being severely tested by his enemies.
He considered himself to be the enemy of those who were enemies of God.
Perhaps he was disturbed by some of his hostile thoughts toward those ungodly enemies of God who were also his enemies
2. A prayer for divine directions.
The psalmist brought his mind and heart under the searchlight of God’s watchful eye, not merely so that he might be informed about himself, but that he might correct his way.
We read in the book of proverbs, “Every way of man is right in his own eyes.”
We also read , “There is a way which seems right unto a man, but the end thereof are the ways of death.”
God spoke through Isaiah and urged the wicked to forsake his way and the unrighteous man his thoughts.
Isaiah 55:7, Let the wicked forsake his way,\ And the unrighteous man his thoughts;\ Let him return to the Lord,\ And He will have mercy on him;\ And to our God,\ For He will abundantly pardon.
God spoke further and said in Isaiah 55:8-9, “For My thoughts are not your thoughts, Nor are your ways My ways,” says the Lord.
“For as the heavens are higher than the earth,\ So are My ways higher than your ways,\ And My thoughts than your thoughts.
A person may be quite sincere and yet be thinking the wrong kind of thoughts and walking in the wrong way.
The psalmist recognised this truth and urged God to reveal to him whether there was some wicked way within his heart.
The psalmist prayed, “Lead me in the way everlasting.”
He wanted to forsake any false paths that would lead to the wrong destination.
He wanted to be delivered from self deception.
He wanted to be saved from inaccurate thought processes and decision making.
He prayed that God would guide him into paths that would be pleasing to God and that would bring peace to his own heart and mind.
Conclusion.
How long has it been since you have had a thorough physical examination?
How long has it been since you have taken your temperature to see if you had an undetected infection in your body?
How long has it been since you looked into your mouth to see if you had a red spot in your throat?
These are some of the techniques that are used to detect the presence of infection or illness.
How long has it been since you brought yourself into God’s presence for a spiritual examination?
It might be a painful experience, but it could be highly profitable.
We would be exceedingly wise if day by day we would pray, Psalm 139:23-24, Search me, O God, and know my heart;\ Try me, and know my anxieties;
And see if there is any wicked way in me,\ And lead me in the way everlasting.
Until next time
Stay in the Blessings
I really want to encourage you to be diligent with your Bible study time, because God has so much more for us than we can get from just going to church once or twice a week and hearing someone else talk about the Word.
When you spend time with God, your life will change in amazing ways, because God is a Redeemer.
Theres nothing thats too hard for Him, and He can make you whole, spirit, soul and body!
You’re important to God, and you’re important to us at The Refinery.
When it comes to prayer, we believe that God wants to meet your needs and reveal His promises to you.
So whatever you’re concerned about and need prayer for we want to be here for you! Or even if you just want to say Hi, you can contact us at www.refinerylife.org
2024 IS A YEAR OF DECISIONS AND OPEN DOORS
© www.refinerylife.org 2013-2024 All rights reserved. Except as permitted under the Australian Copyright Act 1968, no part of this Article may be reproduced, stored in a retrieval system, communicated or transmitted in any form or by any means without the prior written permission.
This episode is brought to you by Refinery Life Australia:
If you enjoy The Refinery Life Radio Podcast you can help support The Refinery by doing the following:
Sow an offering:
Bitcoin: bc1qqh6720t2zagj72dyfj348az698tdut3hlecaj4
Online: https://www.refinerylife.org/donate/
If you do send an offering then please email us so that we can say thank you
Subscribe on
iTunes | Spotify | YouTube | TuneIn | Rumble | Flare | Zap.Stream | Fountain |
Share The Refinery with your friends and family
Subscribe to the newsletter on
Follow The Refinery on Twitter | Nostr | Instagram | Fountain |
-
 @ 6bae33c8:607272e8
2024-09-17 21:13:16
@ 6bae33c8:607272e8
2024-09-17 21:13:16I went 2-3 in Circa which hurts because I was 1-4 in Week 1. To offset a 3-7 start, you need a couple 8-2s to get back on pace — a tall order. But I don’t want to get ahead of myself.
Last week was better — I barely lost the Texans-Bears, and the Seahawks had their chances against the Pats. The only really bad pick was the Lions, and it was the one I felt least strongly about. The one thing I’m kicking myself about is I originally liked the Bengals and Cardinals but talked myself out of both. “Sean McVay off a loss” in the former and “Andy Reid with 10 days prep” in the latter. My instincts were fine. Have to trust them now that I’m back into it.
I still haven’t looked at the lines, only the schedule. I want to fade the Pats again on Thursday night instinctively — I don’t think their style is sustainable, and I neglected to consider Seattle making such a long distance trip for an early game last week.
I like the Giants this week — they should have won but for the kicker, and Danny Dimes looked at least like an NFL QB. But Myles Garrett might be in his face all day. I don’t know, probably pass on that.
Bears at Colts — maybe buy low on the Colts, but they’re bad, can’t stop the run and lost DeForest Buckner. Pass.
Texans at Vikings. Depends on the line. Maybe sell high on the Vikings, especially if Justin Jefferson is out.
Eagles at Saints. No strong feeling. Saints won’t be fully priced, usually you ride the streak until they are.
Chargers at Steelers. I’d make this a pick ‘em. Pass.
Broncos at Bucs. Bo Nix is overmatched. Line should be at least 10.
Packers at Titans — too ugly, probably take the Titans, but pass.
Panthers at Raiders — Andy Dalton will give them a lift, Raiders cocky off the big win, but I like Antonio Pierce. Pass.
Dolphins at Seahawks — Backup QB, hard to handicap, pass.
Lions at Cardinals. Lions really out of sync, Goff better at home. And yet — might take the Lions, have to look at the line.
Ravens at Cowboys — Two desperate teams, but the Ravens are more desperate. Probably taking them at -2.5 or better. Expect a pick ‘em maybe.
49ers at Rams — No Deebo, no McCaffrey, no problem. Would lay eight-plus, maybe 10 even given how destroyed the Rams are.
Chiefs at Falcons — I like the Falcons though it’s a short week. Chiefs are tough to go against, though, and both teams won on last second plays.
Jaguars at Bills. There’s something wrong with the Jaguars, Bills had 10 days off. Probably take Jacksonville on a hunch with enough points, but pass.
Football Team at Bengals. I think the Bengals get going, probably destroy them.
-
 @ 3c9712ff:14fecbc4
2024-09-01 03:39:08
@ 3c9712ff:14fecbc4
2024-09-01 03:39:08The Australian dream used to be straightforward: secure a job, pay off your house by your late thirties, and retire with substantial assets and savings to support your lifestyle.
Some argue the introduction of compulsory superannuation contributions in 1991 signaled the government's lack of trust in Australians' ability to save and be self-sufficient in their later years. But I disagree.
The issue wasn’t that Australians were incapable of saving; it was that saving money was no longer enough. The erosion caused by the Keynesian experiment had seeped into Australian retirements, making it nearly impossible for an entire generation to retire off the savings from a median salary of $27,200.
Superfunds were thus established by the government as a supposed solution to the problem they had created. How unsurprising.
Fast forward 33 years, and Australian superfunds, like those in most of the western world, are now facing two insurmountable challenges of population demographic, and a debasing currency.
1. Our Population is Ageing
On face value, it shouldn't matter whether the population is ageing. If I have my own retirement account which I paid into each month, why would it matter if the people around me are ageing as well?
The answer lies in duration mismatch. Retirement funds must manage a mix of short-term, long-term, and continuous obligations, balancing liquid liabilities (cash payments to members) with illiquid assets (investments). Because funds rely on more inflows (super contributions) than outflows (payouts to retirees), population demographics play a critical role in maintaining this balance - and Australia's isn't looking great.
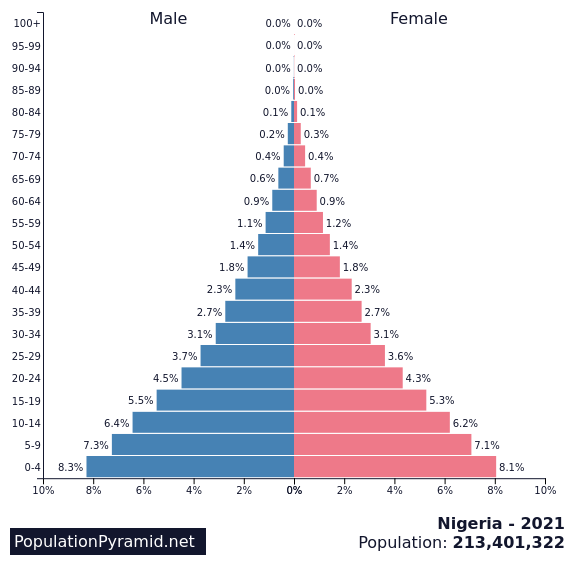
An example of an ageing population (Australia) vs a growing population (Nigeria)
2. Our Currency is Ever Debasing
This is far more pernicious for our retirees
| Financial Year | Average Super Return | Money Supply Growth | Net Return | | --- | --- | --- | --- | | 2023-24 | 9.1% | 4% | 5.1% | | 2022-23 | 9.2% | 7.8% | 1.4% | | 2021-20 | -3.3% | 6.7% | -10% | | 2020-21 | 18% | 13.6% | 4.4% |
In Austrian Economics, inflation is understood as a monetary phenomenon that occurs when new monetary units are added to the existing supply. This monetary inflation is the precursor to both price and asset inflation.
Austrians also reject the idea of measuring price inflation with a single number, such as the CPI, as different asset classes respond differently to monetary inflation. For instance, industries like technology and manufacturing are less susceptible to price inflation due to the deflationary effects of increased automation and competition.
Conversely, hard assets like gold and real estate have reached record highs, as easy money tends to flow toward the most reliable stores of value.
Average Yearly Prices Increase since 2018 - Against YoY M2 and CPI
| | Iphone | Median House | Money Supply Growth | CPI | | ----- | ----| ---- | ------ | --- | | Since 2018 | 2.24% | 6.8% | 7.2% | 3.1%
*Although simplistic, the table above shows that hard assets move with monetary inflation, not CPI.
The real hurdle, or the absolute minimum that a superfund has to give it's members is not CPI or the 3.95% 10 year, but that monetary inflation rate of 7.2%.
An increase in the required rate of return invariably brings an increase in risk. Superfunds can't simply gamble Australians' retirement savings on high-risk offshore tech startups, so these returns are often sought through listed equities and commercial real estate—two interest rate sensitive asset classes. This correlation significantly limits the RBA's ability to manoeuvre and the dilemma is clear:
- Drop rates, inflate away our retirement.
- Increase rates, crash our retirement.
Bitcoin to the Rescue
You guess it, bitcoin fixes this.
Take the same example from 1991, but replace the Australian Peso with Bitcoin. In a Bitcoin world, we wouldn’t need superannuation. By simply saving 40 years of time and energy in a deflationary currency like Bitcoin, our savings alone would increase in purchasing power, eliminating the need to burden future generations for our retirement.
In the meantime, Australian superfunds should take a leaf out of a few smaller US pension funds like the Wisconsin Pension Fund and start gaining exposure to bitcoin.
A 2% allocation to a Bitcoin ETF is enough to ignite a chain reaction toward full institutional adoption. This truly scarce and desirable asset, with its low correlation to existing portfolios, isn’t just an opportunity—it’s a lifeline for the future of Australian retirees. It’s only a matter of time.
Colin Gifford
August 2024
-
 @ 8d34bd24:414be32b
2024-08-31 23:01:04
@ 8d34bd24:414be32b
2024-08-31 23:01:04I’ve mentioned multiple times that I feel our time left is short and that the rapture and the tribulation are coming soon. I feel it with every ounce of my being. I see it in the rush to evil around us. I see Biblical prophecy coming to fulfillment and technologies that could not be fathomed 2,000 years ago coming into being in a way that will make prophecy possible. The question is, what do we do with the time left to us?
Don’t Be a Foolish Virgin
Matthew gives an analogy of believers waiting for Christs return:
“Then the kingdom of heaven will be comparable to ten virgins, who took their lamps and went out to meet the bridegroom. Five of them were foolish, and five were prudent. For when the foolish took their lamps, they took no oil with them, but the prudent took oil in flasks along with their lamps. Now while the bridegroom was delaying, they all got drowsy and began to sleep. But at midnight there was a shout, ‘Behold, the bridegroom! Come out to meet him.’ Then all those virgins rose and trimmed their lamps. The foolish said to the prudent, ‘Give us some of your oil, for our lamps are going out.’ But the prudent answered, ‘No, there will not be enough for us and you too; go instead to the dealers and buy some for yourselves.’ And while they were going away to make the purchase, the bridegroom came, and those who were ready went in with him to the wedding feast; and the door was shut. 11Later the other virgins also came, saying, ‘Lord, lord, open up for us.’ But he answered, ‘Truly I say to you, I do not know you.’ Be on the alert then, for you do not know the day nor the hour. (Matthew 25:1-13) {emphasis mine}
Christians have been waiting for around 2,000 years for Christ’s return. It is easy to get drowsy and begin to sleep due to the delay to His return, but we are called to be ready. “You too, be ready; for the Son of Man is coming at an hour that you do not expect.” (Luke 12:40) Our wait may be long or short, but we are supposed to live our lives like he will arrive today. We don’t want to miss out on joining Him at His return, but we also don’t want to have to face Him knowing that we were not focused on what He had called us to do. We don’t want to admit that we didn’t share the gospel to that friend, that we didn’t stand up for the truth when the crowd was speaking contrary to the word of God, or that we acted in an unloving way to fellow believers or to the lost.
The Bible clearly tells us that we “do not know the day nor the hour,” but that doesn’t mean that He has not given us signs that the time is short.
What Should We Be Doing?
If Jesus is coming soon, how should we spend our time? What should we be doing? Should we just sit back and wait?
For even when we were with you, we used to give you this order: if anyone is not willing to work, then he is not to eat, either. For we hear that some among you are leading an undisciplined life, doing no work at all, but acting like busybodies. Now such persons we command and exhort in the Lord Jesus Christ to work in quiet fashion and eat their own bread. But as for you, brethren, do not grow weary of doing good. (2 Thessalonians 3:10-13)
The Bible is clear that we should work. This not only means that we should not quit our jobs, but should continue working as we have been doing, but it also means we should put time and effort into kingdom work.** God has given each one of us a purpose and a job to do. We should study His word and pray and keep our eyes open so we don’t miss out on what He intends as our purpose. Another analogy is given in Matthew:
“For it is just like a man about to go on a journey, who called his own slaves and entrusted his possessions to them. To one he gave five talents, to another, two, and to another, one, each according to his own ability; and he went on his journey. Immediately the one who had received the five talents went and traded with them, and gained five more talents. In the same manner the one who had received the two talents gained two more. But he who received the one talent went away, and dug a hole in the ground and hid his master’s money.
> “Now after a long time the master of those slaves *came and *settled accounts with them. The one who had received the five talents came up and brought five more talents, saying, ‘Master, you entrusted five talents to me. See, I have gained five more talents.’ His master said to him, ‘Well done, good and faithful slave. You were faithful with a few things, I will put you in charge of many things; enter into the joy of your master.’*
> “Also the one who had received the two talents came up and said, ‘Master, you entrusted two talents to me. See, I have gained two more talents.’ His master said to him, ‘Well done, good and faithful slave. You were faithful with a few things, I will put you in charge of many things; enter into the joy of your master.’*
“And the one also who had received the one talent came up and said, ‘Master, I knew you to be a hard man, reaping where you did not sow and gathering where you scattered no seed. And I was afraid, and went away and hid your talent in the ground. See, you have what is yours.’
“But his master answered and said to him, ‘You wicked, lazy slave, you knew that I reap where I did not sow and gather where I scattered no seed. Then you ought to have put my money in the bank, and on my arrival I would have received my money back with interest. Therefore take away the talent from him, and give it to the one who has the ten talents.’
> “For to everyone who has, more shall be given, and he will have an abundance; but from the one who does not have, even what he does have shall be taken away. Throw out the worthless slave into the outer darkness; in that place there will be weeping and gnashing of teeth*. (Matthew 25:14-29)
God has given each of us different skills, gifts, and opportunities. He wants us to make the most of them. If God gave you skill in business, you can use your wealth to fund ministries, churches, and missionaries. If God has gifted you with the ability to teach, you can disciple many to grow in their faith and knowledge of God. If God has brought you into a relationship with someone influential, you can share the Gospel with them and be used to draw them into saving faith in Jesus. Whatever skills, gifts, and opportunities God has given to you, you need to make the most of them. You need to grow and make the most of what God has given you.
What is the Best Use of Our Time and Money?
God wants us to shine a light for Him. He wants us to make a difference. There are many ways to do this and we can’t do them all. We have to pick and chose what is God’s will and what will make the best use of what God has given us.
There are lots of good things we can do, but what is the best?
I used to focus on prepping to be able to provide for my family and others if times get bad. That was good, but was it best? I used to grow a garden and grow healthy food. That was good, but was it the best? I used to be highly involved in politics and worked hard to support and elect godly men and women into government positions where they could have a positive influence on our culture and our country. That was good, but was it the best?
According to the grace of God which was given to me, like a wise master builder I laid a foundation, and another is building on it. But each man must be careful how he builds on it. For no man can lay a foundation other than the one which is laid, which is Jesus Christ. Now if any man builds on the foundation with gold, silver, precious stones, wood, hay, straw, each man’s work will become evident; for the day will show it because it is to be revealed with fire, and the fire itself will test the quality of each man’s work. If any man’s work which he has built on it remains, he will receive a reward. If any man’s work is burned up, he will suffer loss; but he himself will be saved, yet so as through fire. (1 Corinthians 3:10-15) {emphasis mine}
The best way to judge which actions are best is to see which actions have an eternal influence and to look and see what God is doing and to join His work. The difference between gold & silver versus wood, hay, and straw is the gold & silver can survive fire. Whether something is good or best depends on whether the action makes a difference in eternity.** Providing for my family and friend’s physical needs and health is good, but it doesn’t make an eternal difference. Electing Godly officials makes life here on Earth better, but does it actually make a difference eternally? Probably not.
What does make a difference? Sharing the Gospel with others makes an eternal difference. Standing up for the truth, especially the spiritual truths from the Bible, makes an eternal difference. Writing a book or a blog sharing the truths of the Bible and Jesus makes an eternal difference. I’ve tried to focus my time on this type of activity more than the former. I don’t want one soul to go to Hell because I was too busy to share the Gospel. I don’t want one Christian to regret their life on Earth because I was too busy to disciple them. I don’t want to be like the man who received the single talent and buried it in the ground, who, when facing his master, was told, “You wicked, lazy slave.”
What Is Most Important?
“Do not store up for yourselves treasures on earth, where moth and rust destroy, and where thieves break in and steal. But store up for yourselves treasures in heaven, where neither moth nor rust destroys, and where thieves do not break in or steal; for where your treasure is, there your heart will be also. (Matthew 6:19-21) {emphasis mine}
What are the most important things in our lives? The most important things are people.
-
Some people in our lives have never heard about Jesus. We need to share the gospel with them.
-
Some people in our lives are hurting and need to be helped and encouraged and taught to trust in Jesus.
-
Some people in our lives are new Christians or just immature Christians, who have trusted in Jesus, but haven’t grown much since salvation. We need to teach and disciple them to grow in their understanding of God and who He is. We need to build up their faith. We need to encourage them to study the Bible.
-
Some people in our lives know God and His word, but are unsure how to live out their faith and share it with others. We need to encourage them and train them, so they can multiply their faith among others in their lives.
What are you doing to make an eternal difference in service to our Lord Jesus Christ? Are you one of the lazy, unprepared virgins? Are you hiding the gifts God gave you in the ground or shining a light that can be seen by everyone around you? Are you so busy doing good, that you don’t see God’s best?
Are you excited about meeting Jesus in the air at the rapture of the Church? I am! I hope you are, too.
Trust Jesus.\ \ your sister in Christ,
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
-
-
 @ 06639a38:655f8f71
2024-09-17 21:13:15
@ 06639a38:655f8f71
2024-09-17 21:13:15- Some small updates at nostr-php.dev
- Build a NIP-52 RSVP to Calendar Event Vue / Javascript component which is live on https://nostrdam.com
- My Telegram bot Botstix returns my latest note from my personal relay (using the PHP Framework Symfony for this)
- Fix issue were Nostr-PHP was installed as a dev dependency (which it is not) https://github.com/nostrver-se/nostr-php/issues/61
- Raising sats at Geyser for our Nostr Booth initiative: https://geyser.fund/project/nostrboothbitcoinamsterdam/
- Proof of concept async requests with Http/Guzzle using this package https://github.com/valtzu/guzzle-websocket-middleware
-
 @ 1a48e74d:02c0e00f
2024-09-17 20:33:46
@ 1a48e74d:02c0e00f
2024-09-17 20:33:46This is a question that isn't thought about very often but should be reconsidered in my opinion. While I'm not super technical when it comes to Bitcoin, anyone that has been around Bitcoin for awhile can and will notice disturbing trends in the mining space.
What is the first thing that pops into your head when you think about Bitcoin. For me its the 21 million hard cap and censorship resistant money but what does it mean to be censorship resistant? In essence what censorship resistant means is that your transaction can not be stopped arbitrarily by a third party unlike what they can do in the fiat system. In the fiat system there are tons of choke points that can stop your transaction from going through and conducting business with anyone that you want. Banks stop payments all the time for all kinds of stupid reasons.
This is a form of censorship. The government doesn't like you or your political activism, bam there goes your bank account so no you have no way of even conducting commerce in a efficient way. Don't believe me? Here a a few examples of banks and governments censoring individuals and groups they don't approve of.
Chokepoint 2.0: How Regulator Fight Bitcoin With Financial Censorship
[Nigerian Banks Shut Them Out, so These Activists Are Using Bitcoin to Battle Police Brutality]
There are just two examples of how censorship is being used as a weapon to stop people from using their god given rights as human beings to live their lives as they see fit. We know that the fiat world has the power to censor your transactions but what about in the Bitcoin ecosystem?
As a Bitcoiner you would think that you don't have to worry about stuff like that. Well think again. If you have been watching the Bitcoin mining space lately, you have seen the growth of these large companies with a boat load of ASICs and hashrate. As a Bitcoin pleb its hard to compete with that kind of scale, so less regular joes like us can't mine profitably at home thus reducing the decentralization of hashrate to the large public miners.
In addition to less hashrate being controlled by pleb miners, these large miners point there hashrate to the largest pools out there such as Foundry and Antpool.
https://image.nostr.build/fb547485c8414dab4ef0c2997ae10cda89f7d866d255ce4e97613f5d71bf6ed4.jpg
This image is from the minermag.com. What do you notice about this graph? Lots and lots of centralization going on. Between 2020 and 2024 the top three pools went from 50 percent, mind you which isn't great to begin with and now the top 3 pools control 65 percent of the Bitcoin hashrate is scary as hell and is not a topic that I hear anyone on #Nostr talking about. That's not a diss on anyone, just an issue that needs to be more widely discussed as it has wider implications for all of us.
With this much centralization going on in the mining space how easy will it be for governments to target these large mining pools and tell them to start to censor certain types of transactions.
Governments would have this ability because most miners simply provide hash power and leave the construction of what goes into a #Bitcoin block to the pool operators. To be honest I had no idea that this was the case until recently. So basically Antpool and Foundry get to decide what blocks look like, cool right? Bitcoin isn't looking so decentralized now, is it?
It would be rather trivial for governments to tell these pools to exclude things like ordinals, coinjoins or even opening lightning channels for that matter. When you put a gun to their head and threaten them with excessive fines and jail time, guess what these CEO are going to do. Sellout and cover their assess. It happens every time. This is why it is so incredibly important to decentralize mining pools and promote solo mining as much as we can. There are moves being made in that direction with the Ocean Mining Pool and their radically different approach to operating a mining pool.
Ocean Mining only coordinates the payout split and does not payout simply because you are supplying hashrate to the pool such as with the Pay Per Last N Shares (PPLNS) set up that is popular right now.
There are companies that are trying to turn the tide on mining centralization, the one I like the most and is the most accessible to the average person is the Bitaxe miner. Sure its not very powerful when you compare it to the latest and greatest ASIC but it stays true to the Bitcoin ethos of decentralized mining.
Not long ago a Bitaxe miner found a block! The odds of finding a block with these tiny machines is small but hey why not. You have a chance to find a block and you are living up to the ethos of Bitcoin. That's enough for me to be honest.
I hope that this recent trend of centralization can be reversed before its too late. In the mean time spread the word about Bitcoin and Nostr to all of your friends and family!
Bitcoin
-
 @ 6d20ea61:1de5dacc
2024-08-31 10:13:24
@ 6d20ea61:1de5dacc
2024-08-31 10:13:24Why does the world remain ignorant to Africa's sinister secrets?
There's a lot going on beneath the surface in our everyday lives. Most of us accept this as a fact; that we only perceive a small sliver of reality as it is. However, it's rare that we align our actions with the uncomfortable reality that lies beyond immediate perception. Authentic people do align themselves in this way, and they’re often threatening to those who don’t because they hold a mirror to their own incongruities.
We may be aware of the truth that lies beyond our immediate field of view, which is exactly the excuse we use to allow ourselves to not be authentic. Truth? Sure, I'll accept the truth of which you speak, as long as you can "prove" it. If it's there, why don't you point to it?
Just because you can't see it, doesn't mean it's not there.
We look around to observe the crowd moving in unison. We may know we're all aware of some heretofore unspeakable truth, but the mass misdirected momentum of the crowd acts as an all-too-easy justification to excuse ourselves from being less than we can be; to shy from the consequences of living in truth.
They say the shepherd is there to protect the flock, lest they be preyed on by the wolf. Little do the sheep know that it is the shepherd who controls their fate, and ultimately feasts on their flesh.
If I were a sheep, I would much rather live a short life dying a brutal death at the jaws of a wolf. At least I would have been unbounded in my life; free of the ignorance imposed by a faux protector; blind to the reality of my domestication for the purposes of his own prolongation.
Jesus was a shepherd, was he not? All too many Africans I've spoken to know Christianity was used as a tool to supplant their own traditional practices as a means to unhinge their pride and autonomy…
"I'm sorry you lost everything: your land, your family, your livelihood, your dignity. Have you heard of Jesus? He can provide everything you'll ever need. You never needed all this land, culture, and sovereignty anyway. You don't need to carry the burden of being your own person, thinking for yourself, living for your people and culture, living for the right to determine your own destiny. Jesus can handle all that for you. Trust me, your life will be better now"
It is beyond saddening to remember the conversations I've had with "Christians" in Botswana, Zambia, Zimbabwe, Namibia, and South Africa. They're entirely aware of how most of their culture has been lost, and how the majority of Africans remain enslaved in their minds to this day. Jesus and Western ideals are the broken records they were raised with, and these are what they all claim to be the answer to life's woes. To think differently is to be cast away. To think differently is suicide. When all hope has been lost, dare not face reality as it is, apparently.
Religion: the opiate of the masses, as they say.
Religion (Christianity in the South) is rampant in Africa, and my observed reality is that it's not practised with integrity. Don't get me wrong, it can be beautiful to see people come together for shared belonging, but there's no sense in lying to ourselves and each other in the process.
The vast majority of what I witnessed and heard from people was a bastardisation of Jesus and the Bible so they can justify their wrong doings without being judged by others, or worse, to coerce others in the effort to claim moral superiority.
Perhaps the most painful irony is that Jesus would have never stood for any of this crap. Taken at face value, there is a lot to learn from the life of Jesus; lessons that should not be ignored. However, Jesus would have never proposed religion as it exists today, or whatever the group-think, known as "church", has become. After all, Jesus did not follow the crowd. Jesus followed the beat of his own drum. He didn't live to teach that we live blindly. He was his own shepherd. Why is this so hard for people grasp? I wouldn't be surprised if Jesus was crucified all over again were there to be a proverbial "second coming".
I swear, being a missionary, or any evangelist, should be held in contempt the world over. For people to assume they carry another man's truth is beyond hubris, and only proves they lay victim to the same fallacious and cowardly thought that allows us to fall in step with the crowd despite our better judgement - to vilify the wolf and befriend the shepherd despite the truth.
Africa’s Truths
Africa is a land of hard truths. It's brutal and raw. It reminds me of traveling through India more than ten years ago. India confronted me with my own nature, forcing me to witness suffering and hardship that was otherwise hidden in the Western world where I was raised. Africa is India at a larger geographic scale. After more than 30,000 km by motorcycle through much of Southern Africa, I've seen enough child labour, corruption, and artificial hardship to feel deep pains reflected within myself.
Africa and India remain crucially different. Effectively, Africa is still colonised, whereas India is largely independent. The USA, France, China, and Russia (among others) are not free to exercise their interests in India. In Africa, the USA, France, China, and Russia's interests (among others) are the only interests that carry weight. Confessions of an Economic Hit Man (by John Perkins), anyone?
Africa isn't some drought-ridden continent devoid of resources to support the people who live there. The majority of the raw materials that fuel the "modern" lifestyles of the Western world come from Africa, for Christ's sake (pun intended).
How does it make sense for a Canadian company to mine in Namibia where only 5% of the profits go to the Namibian government? How much of this inevitably filters through Namibia’s corrupt elite to the Namibian people?
Africans' living standards should be no less than on par with that of the rest of the world, but the "success" of the West (and the East, increasingly) hinge too crucially on the controlled flow of artificially suppressed prices on commodities that make up the comforts of the "developed" world.
Africa is where the world sweeps their problems underneath the rug. Africa is the closet where the world's skeletons collect dust. By all means, go on your happy little safari, but don't dare learn about how none of that safari money tangibly benefits the African people.
My “success” is a reflection of Africa’s suffering
Africa is where I realised how I allow myself to live out of alignment with known truths.
I haven't posted anything to this newsletter in over a year. I've asked myself "why?" over the months and came up with various answers. I wanted to write about those answers, but they didn't suffice.
The best answer I can give you now is out of shame and pride. My pride wouldn't allow me to continue writing because I didn't want to advertise my lifestyle. My shame wouldn't allow me because I feel like an impostor.
I've felt like an impostor for a very long time. In that time I have somehow cultivated an image of being a traveler. People seem to know me as one. I even have a little mantra I learned while living in China that I seem to cling to as part of my identity: 我是一个旅行者 (Wo shi yi ge lu xin zhe) - "I am a traveler".
However, I don't think I'm purely a traveler. I think I'm a traveler because it has been the path of least resistance. It has been a convenient alibi.
I, like all of us, held dreams as a young human about what I wanted to do with my life. As I matured, I faced opposition in the opinions of society, family, and friends as to the "practicality" of my dreams. I didn't have to listen to them, but I did. I internalised those thoughts and chose to stick to what I know, traveling.
I grew up traveling a lot as a kid. I always loved it, and learned over the years that I'd like to travel in my own way as an independent. I'm happy to say that I've done so, but I've learned that my sacrifices to reach this lifestyle needn't be as severe as they've become.
I wanted to live outside. I wanted to study animals and the laws of nature, and I never thought it would be practical to do so in tandem with my traveling life. I felt guilty in college. I didn't know how to support myself while in my studies, and couldn't bear accepting financial support from someone I didn't align with. I felt like a politician corrupted by the vested interests of their donors.
This led to me dropping out of college, abandoning my childhood dreams to settle for a "life of integrity". I vowed I would one day come back to make good on my dreams. Traveling has been the life I choose to live while I find a way to honour a core responsibility to myself. I'm proud of myself for not being coerced by outside interests, but I now know I'm not being entirely authentic.
Thank you, Africa. I’m sorry, Africa.
Thank you, Africa. I'm sorry, Africa. I'm sorry that I've lived a life of privilege that stems largely from your plunder. Thank you for keeping me safe while I learn your truths. Thank you for reflecting my own core truths.
My heart continues to break when I think of the world’s ignorance over Africa, and I think my gap in writing has been necessary to process this reality.
Frankly, I'm enraged along with a sense of peace that Africa's time will come. I'm confident in Africa's future; I just wish the rest of the world wasn’t working so hard to keep its head below water.
I'm responsible for Africa's fate, and so are you. We are all complicit in this crime. I hope this article resurfaces an awareness in readers a truth that seems to lay dormant in the public awareness.
I don't know why more of us don't stand up for Africa (and not by crying to our governments - f*ck them), because I think our individual efforts are more than enough. Even indirectly, I think we can slowly push the wave of change that is necessary to do right by Africa. I think we all have the incentive to do so, for Africa is the foundation of humanity in multiple sensibilities, meaning Africa’s prosperity translates into everyone’s prosperity.
All thoughts and comments are welcome.
G
originally posted at https://stacker.news/items/667609
-
 @ 361d3e1e:50bc10a8
2024-09-17 18:14:13
@ 361d3e1e:50bc10a8
2024-09-17 18:14:13Why is it necessary to reduce the population of the Earth? The real reason!
usa #georgia #population #billgates #wef #politics #climatechange