-
 @ 1bda7e1f:bb97c4d9
2024-10-10 03:05:10
@ 1bda7e1f:bb97c4d9
2024-10-10 03:05:10Tldr
- Nostr identities can be linked to a third-party service
- You can set up that verification at your own domain, and
- You can also set up your own Lightning Address at your own domain
- These both require files in the .well-known directory on your domain
- You can set these up together, quickly and for free, with Sveltekit and Vercel
- Now I am identified and can receive payments with my username "rb" at my own domain "rodbishop.nz"
Getting .Well-Known
For your npub
The first step in setting up a Nostr profile is to get your keys. I wrote about it in this article, Mining Your Vanity Pubkey.
These keys represent your identity and are issued by you, not a third-party issuer. This is good for personal ownership, but creates an issue around identification.
If you have an ID issued by an issuer, I can ask the issuer to confirm that you are who you say you are. But with a Nostr npub, which has no issuer, how do I confirm that an npub which claims to be yours, is in fact yours?
Nostr allows you to link your npub to a username and to a third-party service of your choice to help in confirming that your npub is really yours (It is documented in NIP-05).
Normal users can use a service like nostrplebs.com and to set up a username very quickly and easily. However, it is also possible to set up your own identification that relates your username to your npub using any domain you own.
In my view having your username tied to your own domain is better branding, and more self-ownership, and so that's what I'll set up using my domain rodbishop.nz.
For your lightning address
Nostr has integrated payments which allow people to send you Bitcoin over the Lightning network the same way they would send you an email. I wrote about it in Setting up Payments on Nostr.
The path I took in setting up my lightning address was to use Alby, and with an Alby Account you automatically get a Lightning Address at getalby.com.
Normal users can use that Lightning Address just fine. However, it is also possible to set up your own Lightning Address which will forward payments to your Lightning Wallet using any domain you own.
Similar to with NIP-05, my view is having your Lightning Address tied to your own domain is better branding, and so again that's what I'll set up.
Both of these tasks use the .well-known folder on your web server.
Preparing .Well-Known with Sveltekit
There are many ways to do this. NVK published a very simple method using Github pages which is free and which you can read about on his blog.
For me, I will set up .well-known using Sveltekit and Vercel. I have been learning Sveltekit and Nostr together, thanks to fantastic tutorials by Jeff G on his Youtube.
Using Sveltekit and Vercel to set up Nostr NIP-05 and Lightning URLs on your own domain is easy and free.
Create a new project
To start, create a new Sveltekit project with NodeJS and Node Package Manager using the code documented on the Sveltekit website.
npm create svelte@latest my-app cd my-app npm install npm run dev -- --openSveltekit contains many convenient short-cuts for web hosting, and one of them is the file structure. The structure contains an
/srcfolder to contain javascript files to build complex applications, and a/staticfolder to contain other simple static files which need to be hosted at the domain. It is this/staticfolder you'll be using for now.NIP-05 identification with nostr.json
For your NIP-05 identification, you need to create the folder and file for /.well-known/nostr.json as follows–
static └── .well-known └── nostr.jsonIn that file, you will use some JSON to link a username to a hex-format public key, which will enable Nostr apps to confirm that the username relates to the key. In my case, I create a link between the username "rb" and the public key formatted in hex format "1bda7e1..."–
{ "names": { "rb": "1bda7e1f7396bda2d1ef99033da8fd2dc362810790df9be62f591038bb97c4d9" } }That's it!
Lightning Address forwarding with lnurlp
For your Lightning Address, you need to create the folder and file for /.well-known/lnurlp/your-username as follows, replacing the "your-username" text with your username (in my case, "rb") –
static └── .well-known └── lnurlp └── your-usernameIn that file, you create a link between the username on your domain, and the provider of your Lightning service (in my case, Alby). Alby provides a helpful guide on how to do this, which you can read on the Alby site.
- Visit the Alby page for your Lightning Address which Alby hosts
- Copy that text across to the new file you have created
That's it! These files are now ready and can be hosted anywhere.
Hosting .well-known with Vercel
I chose Vercel to host with because it was very easy to use, and provides all the hosting I need for free. To deploy, you first create a Github repository for my Sveltekit project, and then you set up Vercel to deploy every push by default.
At a high level –
- Set up a Github repository
- Push your project to Github
- Sign up for Vercel
- Link your Vercel to your Github, and Vercel will then show all your Git repositories
- Import your project from Github, and Vercel will deploy it to a Vercel.com domain
Once your project has deployed to Vercel, you will be given a deployment URL, and you can test to see that your static .well-known files are successfully online.
- E.g. I was given https://rodbishop-mw64m8ylx-rods-projects-c9b67f57.vercel.app
- I can add /.well-known/nostr.json or /.well-known/lnurlp/rb to the domain and view my files
Now that the files are deployed, you need to link them to your domain. At a high level –
- Get your domain (buy one if you need to)
- In Vercel, navigate to your project’s settings and add your domain. Vercel will provide DNS records for you to add to your domain registrar
- In your domain's DNS settings add those records as an A record to your root domain
Your .well-known files are now hosted in Vercel and pointed at your domain.
Setting up CORS in Vercel
You need to tell Vercel to allow third-party applications to access those files, by enabling CORS ("Cross-Origin Resource Sharing"). Vercel has good CORS documentation on their website.
To set this up, return to your project, and in the root folder create a new file named vercel.json. This file will tell Vercel to allow third-party applications to access your nostr.json file. Add the following to it
{ "headers": [ { "source": "/.well-known/nostr.json", "headers": [ { "key": "Access-Control-Allow-Origin", "value": "*" }, { "key": "Access-Control-Allow-Methods", "value": "GET, OPTIONS" }, { "key": "Access-Control-Allow-Headers", "value": "Content-Type" } ] } ] }Then– - Push to Github - Vercel will deploy the push automatically by default
That's it. Your .well-known files are able to be reached by every Nostr app.
Testing it with your Nostr profile
Now that this is hosted at your domain, you can connect your Nostr profile. In any Nostr client, visit your profile page and edit, then update your NIP-05 and Lightning Address fields.
Once your client has refreshed, give it a test
- Your NIP-05 identity should show a "success" type icon, rather than a "fail" type icon (what icons depends on the client you're using, but think "green tick" rather than "red cross")
- Your Lightning Address should simply work–get someone to send you a payment to your new Address and it should go through successfully and appear in your wallet.
Things I Did Wrong
Initially, my NIP-05 verification didn't work. I had done two things wrong.
Wrong form of pubkey
The first mistake I made was in the NIP-05 nostr.json file I used the wrong format of public key. The public key that you mostly use in clients is your "npub" which starts with "npub1..." However, the public key this file needs is formatted in hex and starts with "1...".
If you don't have your hex formatted pubkey, you can use a site like https://nostrtool.com/ –enter your pubkey in npub format, and it will return it in hex format.
Redirects caused CORS issues
The second mistake was caused by a URL redirect. Your .well known files need to be served at the root of your domain, not at a www prefix (e.g. for me https://rodbishop.nz, not https://www.rodishop.nz). For this to work, you need to ensure that requests to your root domain aren’t redirected to www.
In Vercel domain configuration, you can configure your redirects. By default, it will redirect traffic to www, and this is wrong for our purposes. To correct it, visit your domain settings, click "Edit" and look for "Redirect to". The correct setting is "No Redirect".
The issue is caused because when applications go looking for your nostr.json, they need to receive a clean "Success" (200) response from your server prior to accessing the file. If you are redirecting to www, then the server gives a "Redirect" (300) response instead.
In case you think your CORS is failing, take a look at the server http response code to see if there is a redirect. I used as follows–
curl -X OPTIONS -i [https://rodbishop.nz/.well-known/nostr.json](https://rodbishop.nz/.well-known/nostr.json) \ -H "Origin: [https://anotherdomain.com](https://anotherdomain.com/)" \ -H "Access-Control-Request-Method: GET"- Initially the response was "HTTP/2 308" which means a redirect was in place (and so the process was failing)
- Once I resolved the redirect issue at Vercel, the response was "HTTP/2 204" which means success, and from that point, Nostr apps recognised the NIP-05 successfully
What's Next
Over the last three blogs I have - Mined a Nostr pubkey and backed up the mnemonic - Set up Nostr payments with a Lightning wallet plus all the bells and whistles - Set up NIP-05 and Lighting Address at my own domain
At this point I am up and running with a great Nostr profile and able to fully engage with the network.
But there are still many rabbit holes to explore. The next place I will explore deeply is running my own relay, and if I have some success I will be back to blog about it soon.
I'm looking forward to sharing what I learn as I explore what’s possible on Nostr.
-
 @ c69b71dc:426ba763
2024-10-10 09:05:29
@ c69b71dc:426ba763
2024-10-10 09:05:29Chef's notes
This cashew blue cheese is a true plant-based delight, delivering the rich, tangy flavours you’d expect from traditional blue cheeses like Roquefort or Gorgonzola. The fermentation process, with the help of «Penicillium Roqueforti», creates a beautifully marbled, creamy cheese that’s both bold and complex. It’s a labor of love that rewards your patience with an unforgettable vegan cheese experience! Whether enjoyed on crackers, in salads, or simply on its own, this cheese will elevate any dish with its unique flavour profile.
Note 1: For this recipe you need parchment paper, a potent blender, glass jars with lid and two cheesecloths.
Note 2: Always use very clean tools, and avoid touching with your fingers or tasting with them while working on the cheese!
Details
- ⏲️ Prep time: 4-5 weeks
- 🍳 Cook time: 0
- 🍽️ Servings: Two small cheese loaves (2x 10-12 cm diameter)
Ingredients
- 300g raw cashews
- 3 tbsp water
- 3 tbsp kefir, kombucha or rejuvelac
- 2 tbsp coconut oil (raw, unrefined)
- 1-4 capsules vegan probiotics
- 1/2 tsp Himalayan salt (iodine-free, no additives)
- 1/16 tsp «Penicillium Roqueforti» (blue cheese mold culture)
Directions
- Day 1: Soak 300g of cashews overnight in water.
- Day 2: Rinse the soaked cashews thoroughly and let them drain well.
- In a high-speed blender, combine the cashews, 3 tbsp of water, 3 tbsp kefir or rejuvelac, and 2 tbsp coconut oil. Blend until the mixture is smooth and creamy.
- Add 1-4 capsules of vegan probiotics, 1/2 tsp Himalayan salt (free of iodine and additives), and blend again briefly.
- Add a pinch (about 1/16 tsp) of «Penicillium Roqueforti» powder (blue cheese culture) and give it another quick mix.
- Transfer the cashew mixture to a glass container, leaving the lid lightly on top (do not seal it completely) and store in a warm place, ideally in your kitchen, for 24 hours to ferment.
- Day 3: Divide the fermented cashew mixture into two smaller glass containers lined with cheesecloth. Press the mixture down firmly to eliminate air pockets.
- Store in a cool place (12-14°C / 53-57°F), ideally in a wine fridge.
- Day 4: Remove the cheese from the containers, take off the cheesecloth, and turn the cheese onto parchment paper.
- Sprinkle salt all over the cheese, ensuring it is evenly coated.
- Cover the cheese with larger glass bowls, ensuring that air can flow from underneath, and return to the wine fridge or the cool storage area.
- Days 4-7: Turn the cheese daily onto fresh parchment paper to maintain its texture.
- Day 7 or 8: Pierce the cheese with a thicker wooden skewer to create holes, allowing oxygen to reach the center, encouraging the blue mold to grow throughout the cheese, not just on the surface.
- Alternatively, crumble the cheese completely and then press it back into shape to ensure oxygen distribution.
- Days 8 toaround 12 or 15: Once the blue mold has fully developed around and inside the cheese, wrap the cheese in parchment paper, place it in a wooden cheese box, and then wrap it in a cloth bag.
- Transfer to a regular fridge to age for another 2-3 weeks or even several months, depending on your desired strength of flavour.
-
 @ 4ec341e6:6dc2fdaf
2024-10-08 01:25:08
@ 4ec341e6:6dc2fdaf
2024-10-08 01:25:08There is a reference to chapter 12 - Relating design patterns to the model and also to chapter 4 - Layered Architecture.
An interesting part here in chapter 1 was about making business rules more explicit, an example is given where the rule is implicit within an application method:
java public int makeBooking(Cargo cargo, Voyage voyage) { double maxBooking = voyage.capacity() * 1.1; if ((voyage.bookedCargoSize() + cargo.size()) > maxBooking) return –1; int confirmation = orderConfirmationSequence.next(); voyage.addCargo(cargo, confirmation); return confirmation; }So the code is refactored to something like this:
```java public int makeBooking(Cargo cargo, Voyage voyage) { if (!overbookingPolicy.isAllowed(cargo, voyage)) return –1; int confirmation = orderConfirmationSequence.next(); voyage.addCargo(cargo, confirmation); return confirmation; }
public boolean isAllowed(Cargo cargo, Voyage voyage) { return (cargo.size() + voyage.bookedCargoSize()) <= (voyage.capacity() * 1.1); } ```
The advantage here is that the overbooking business rule is more explicit and accessible, which makes it easier for everyone involved in the project to understand. In addition, of course, to making the rule clearer (explicit).
In my opinion, this also brings another series of advantages, it makes maintenance easier and helps functions do only one thing.
The chapter also talks about the importance of deepening the understanding of the domain (that is, the company's business rules) to create more useful and representative models.
-
 @ 32dc4f25:f95ddcce
2024-10-10 08:10:36
@ 32dc4f25:f95ddcce
2024-10-10 08:10:36Decentralized social networks were my main focus during my PhD. After I graduated early last year, my classmates Younes , npub147whqsr5vsj86x0ays70r0hgreklre3ey97uvcmxhum65skst56s30selt and I went all in on building Yakihonne. With this, some new members joined the YakiHonne team. This marks our fourth year exploring decentralized social networks.
For the first three years, we built a well-known decentralized research media platform in Asia. We experimented with decentralized creation, funding, and moderation to make media truly decentralized. From 2020 to early 2023, those were some of our happiest times—joining hackathons, winning grants, and focusing on decentralized media. We managed to achieve decentralized content creation for research communities.
In February 2023, we built a decentralized media client based on Nostr and secured some funding. In the early days of a small team, doing the right things and maintaining funding is crucial. Nostr's early phase, combined with the challenges many decentralized media projects have faced, made securing funding particularly tough.

I really believe in the Chinese saying, "After endless mountains and rivers that leave doubt whether there is a path out, suddenly one encounters the shade of a willow, bright flowers and a lovely village.” 山重水复疑无路,柳岸花明又一村。
At the Bitcoin Global Summit in the US, I met npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z , npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s , npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 , npub1j8y6tcdfw3q3f3h794s6un0gyc5742s0k5h5s2yqj0r70cpklqeqjavrvg, and others who gave us much encouragement and inspiration. In NV, I was asked if our projects on Nostr were competitors. My belief has always been that we are in a positive sum game—building the ecosystem together and creating growth, rather than being competitors. This is the nature of Nostr and a necessity for the future development of the world. The virtual digital world is vast enough, and we don’t need to cling to zero-sum thinking from the industrial age.

On my way back to Singapore from NV, a series of delays turned a 24-hour journey into 40 hours. Luckily, I didn't miss my chance to meet with my PhD supervisor. We had a great conversation about publishing and media through the lens of AI, social computing, advertising, and intelligent philosophy . Over the past 20 years, my supervisor has spent almost half of each year traveling to different countries, promoting the development of AI and complex systems. Now he’s more focused on making sure his students stay healthy.

Over the past two years, I received a few invitations for journal submissions, but I had to delay them due to my busy schedule. Moving forward, I plan to publish our latest research as papers, introducing Nostr and decentralized social networks to more academics, and inviting more researchers to join the Nostr ecosystem.
Right before boarding, I received support from an international academic organization, which really lifted my travel fatigue. Together, we’ll be planning a series of initiatives to engage the academic community in discussions about Nostr.
A big thanks to my team and npub1wmr34t36fy03m8hvgl96zl3znndyzyaqhwmwdtshwmtkg03fetaqhjg240 ,npub1trr5r2nrpsk6xkjk5a7p6pfcryyt6yzsflwjmz6r7uj7lfkjxxtq78hdpu npub1szpa7cypmyd59083qs3pte9lez22lzfu6pl2guhgqx7q09x68y6qquh3td for supporting Yakihonne and helping us grow.
Wendy
OD311 Flight
2024-10-09 -
 @ 6bae33c8:607272e8
2024-10-10 06:41:21
@ 6bae33c8:607272e8
2024-10-10 06:41:21I went 2-3 last week, and it wasn’t a strong 2-3. I took a bad beat with the Bengals +2.5, but barely won the Cowboys and Jaguars, while getting on the wrong side of two blowouts (Browns and Raiders.) The Browns was funny because it was so contrarian it had to be the sharp play. And I’m sure it was, only the sharps can be idiots.
Let’s take a look at this week’s games:
49ers at Seahawks — Both teams suffered soul-crushing losses. The Seahawks can’t pass protect. I’ll say Niners -2.5 and probably take them.
Jaguars vs Bears (London) — I’ll make this a pick ‘em, sell high on the Bears if I use it.
Indigenous Peoples at Ravens — I’ll make this 3.5, probably take the Ravens. The Indigenous Peoples have been killing me, but now they finally play a real team.
Cardinals at Packers — I’ll say 6.5. Probably stay away, but lean Packers.
Texans at Patriots — Drake Maye’s first start. The Texans run too much and their pace is too slow. I’ll say Texans -8.5. Probably stay away.
Buccaneers at Saints — No Derek Carr. I’ll say Bucs minus 3.5. Stay away.
Browns at Eagles — The Deshaun Watson situation has hit rock bottom, no way to massage this. The Browns need a full release from his services. I’ll say Browns +10.5, and there’s a chance Jameis Winston plays if things go south early. Stay away.
Colts at Titans — I’ll make this Colts -2.5 and probably stay away.
Chargers at Broncos — I like the Chargers as a buy-low here. I’ll say Chargers +2.5, but I’d like to see whether their offensive linemen are playing.
Steelers at Raiders — Possible get well game for the Steelers, say -2.5. Probably a good time to buy low on the Raiders though — or are they in Browns territory now?
Falcons at Panthers — I’ll say Falcons -4.5. I’ll probably lay the wood too.
Lions at Cowboys — I’ll make this Lions -1.5 and probably take them too.
Bengals at Giants — I’ll say Bengals -2.5. They’re coming off an inexcusable loss. I’ll probably stay away, but if I weren’t a Giants fan I’d lay the wood.
Bills at Jets — I’ll make this a pick ‘em. Leaning Jets, but probably stay away.
-
 @ 2dd9250b:6e928072
2024-10-10 05:36:19
@ 2dd9250b:6e928072
2024-10-10 05:36:19Para Anselmo, todo o sistema cristão poderia ser deduzido a partir dos e pelos princípios necessários da lógica. Ao contrário de Anselmo, os modernos racionalistas não acreditavam que o conteúdo das Escrituras possa ser provado verdadeiro apenas pela lógica. Devido esse embaraço em relação as primeiras premissas o Racionalismo de Descartes, Espinosa e Leibniz caiu em descrédito no final do século XX.
-
 @ 2dd9250b:6e928072
2024-10-10 05:35:57
@ 2dd9250b:6e928072
2024-10-10 05:35:57Quando se fala sobre a ineficiência da Segurança Pública no Brasil, o que mais se ouve é: "O problema é corrupção".
Mas não, o problema não é a corrupção da Polícia. E sim o Estado de Bem-Estar Social. O Estado obtém o Monopólio da Força, porque obtém o Monopólio das armas. Tornando o indivíduo refém da máfia estatal.
Como vimos na Pandemia. Até mesmo o cidadão Conservador que é favor do Livre Comércio e queria manter seu próprio sustento vendendo seus lanches na rua sem máscara foi proibido de trabalhar.
Lembro do meme onde um cara diz: "Sou Conservador, a favor da Polícia mantenedora da Lei e da Ordem". Aí o Policial diz: "Governador mandou eu vir aqui te meter a p*rrada".
É exatamente isso que acontece na prática. O indivíduo fica refém do Sistema. Porque você só chama a polícia depois que foi assaltado. Dependendo de onde você estiver é melhor você fazer um B.O e não esperar que a polícia vá atrás do criminoso para devolver seus pertences. Fazer o B.O só gera um dado que atualiza o sistema que controla o índice da criminalidade do seu estado. E o Governador pode simplesmente ignorar esse índice se ele quiser.
Então, sim você paga impostos e o Policial recebe salário graças ao imposto que você paga. Só que a Polícia faz parte da engrenagem Estatal. Ou seja, se ninguém chamar a Polícia ou fazer B.O mesmo havendo crimes como assaltos, os Policiais continuam recebendo salário. O salário que eles recebem não depende do desempenho deles. E não há competição. Se não há competição, não há melhoria. Isso explica a média de 60 mil homicídios no Brasil. Em 2013 era mais fácil morrer aqui por bala perdida do que na Síria (Pais em Guerra).
E quando você, o contribuinte que é obrigado a pagar o salário do Policial e do Governador do seu estado, critica o sistema ainda recebe essa resposta do camarada que trabalha para proteger o cidadão de bem: "Ok, quando você for assaltado, chama o Batman". Ora, se até os próprios policiais morrem em confronto com bandidos o que será do cidadão de bem que está desarmado? O Bostil é um Pais desarmamentista por um único motivo: Fazer você ser dependente da Polícia.
Porque se você quiser abrir uma empresa de segurança que venha a competir com a Polícia, o Estado te proíbe e a mídia tradicional te chama de "Miliciano", ou "Terrorista", ou "Mercenário", ou "Justiceiro" . Engraçado. Se eu quiser provar que estou certo nessa questão, criando uma milícia armada que fornece o serviço de segurança, e se você quiser me pagar (você só paga se quiser) você não pode. Por que? Porque aí você estaria competindo com o poder do Estado. E o Estado é especialista em eliminar concorrentes.
Enquanto isso, você continua desarmado tendo que pagar duas vezes (pagando impostos por uma segurança estatal quase inexistente e serviços de segurança da Iniciativa privada) na esperança de dias melhores.
-
 @ 2dd9250b:6e928072
2024-10-10 05:33:06
@ 2dd9250b:6e928072
2024-10-10 05:33:06THE MATRIX
The Matrix é um filme de 1999, dirigido e roteirizado 'pelos irmãos' Wachowski. Descreve um mundo onde a realidade é uma simulação virtual feita por máquinas, para que os seres humanos não percebam que estão conectados a uma delas, que extrai energia elétrica de seus corpos, para manter a existência das próprias máquinas.
O filme é repleto de referencias à mitologia grega, ao cristianismo, ao budismo, à animes cyberpunk e à Filosofia Platônica. O que você talvez não saiba é que 'os irmãos' Wachowski foram fortemente inspirados pela obra do Filósofo Francês Jean Baudrillard, Simulacros e Simulação (1981). Onde Baudrillard afirma que a sociedade criou símbolos e signos para ocultar elementos da realidade que perderam seu significado com o tempo. Os símbolos formaram um Simulacro do mundo real (representações de elementos que nunca existiram ou que não possuem significado na realidade) que resultaram em uma Simulação (imitação de elementos do mundo real). Perceba que a Trilogia irá estabelecer uma interpretação diferente para cada um de seus personagens: Neo, Morpheus, Trinity, o Oráculo, Agente Smith e Cypher. Esses personagens centrais estão constantemente fazendo referencia aos simulacros (símbolos e signos) e a própria simulação (a Matrix). Quando Neo toma a Red Pill e a Verdade lhe é revelada ele percebe que nunca viveu no mundo real e parece que seu corpo não reconhece aquela realidade, devido ele estar a vida inteira acostumado com a realidade simulada. Sem perder tempo, Morpheus conta a Neo que havia uma Profecia sobre um humano intitulado O Escolhido (The One) que acabaria com a Guerra contra as Máquinas de uma vez por todas. Profecias, neste contexto, servem para dar esperança aos humanos libertos da Matrix, esta é a primeira referencia aos Símbolos, que levam os tripulantes da nave Nabucodonosor a acreditarem (ou não) em um suposto Escolhido que traria esperança para uma vida melhor fora da Matrix. Então nos é revelado como Morpheus e Trinity resgataram Neo. Os humanos conseguem entrar e sair da Matrix a partir de um dispositivo ligado diretamente ao cérebro. Então eles entram na Matrix para despertar outros humanos, sempre correndo o risco de morrerem quando se deparam com os agentes (programas que as máquinas usam para impedirem que mais humanos despertem). Essas Profecias sobre o Escolhido foram reveladas pelo Oráculo. O Oráculo, aquela senhora fumante que faz biscoitos e gosta de balas, ela diz a Neo que o destino de Morpheus e do Escolhido estão interligados, que Neo terá que tomar uma escolha e que inevitavelmente um dos dois irá morrer, mas não diz o motivo e nem qual dos dois morrerá, sendo que sabia desde o inicio, já que ela tem o dom da previsão.
Em The Matrix, Neo escolhe arriscar sua própria vida para salvar Morpheus que estava sendo torturado pelo Agente Smith. Embora Neo não acreditasse que ele fosse o Escolhido, a crença de Morpheus fez Neo acreditar, e essa crença levou Neo a lutar contra o Agente Smith, e essa luta leva a morte de Neo depois de uma longa perseguição. A Oráculo tinha dito a Trinity que ela iria se apaixonar pelo Escolhido. O que fez Trinity acreditar que Neo era o Escolhido ao vê-lo enfrentar Smith mesmo depois de ter recebido a ordem de fugir dele. Então ela o Beija apaixonadamente e ativa uma Anomalia Sistêmica na Equação Assimétrica do Sistema que controla a Matrix. O que faz Neo ressuscitar e logo descobrir que pode manipular o Código da Matrix, dando infinitos poderes a ele como telecinese e super-velocidade. Neo então manipula o código do Agente Smith desde o centro e o destrói. O filme acaba com o estabelecimento de Neo como o Escolhido e os agentes desistindo de impedir Neo de fazer o que bem entender na Matrix. Embora muitos afirmem que este filme era para ser o único, Matrix deu lucro para a Warner Bros. Pictures e 'os irmãos' Wachowski resolveram trabalhar em uma sequência .
MATRIX RELOADED
Matrix Reloaded é um filme de 2003 produzido, roteirizado e dirigido 'pelos irmãos' Wachowski. Na opinião do autor deste blog de terceira, é o melhor filme desta Trilogia. Agora percebemos que Smith não foi destruído, ele, de certa forma, se libertou do Sistema e agora possui uma conexão com Neo. Smith, como prefere ser chamado, foi desconectado do Sistema, o que significa que as máquinas não possuem mais poder sobre o Programa. Smith manipula o código da Matrix como um vírus, se duplicando ao tocar em outros Agentes, Programas e Espectros Virtuais da Matrix. A Oráculo diz a Neo que ele precisa novamente fazer uma escolha difícil, mas este é justamente o fardo do Escolhido. Somente ele pode fazer esta escolha. Neo se mostra sempre confuso, porque não faz ideia do que está por vir e a Oráculo nunca explica de forma objetiva o que ele terá que fazer. Então Smith tenta infectar Neo para tomar o controle total do Sistema, mas não obtém êxito (a narrativa sugere de forma não sutil que Neo é mesmo o Escolhido). Smith diz que não é mais um programa da Matrix, agora ele tem um propósito, o que dá um novo significado à sua existência e mais cedo ou mais tarde ele tomará toda a Matrix, de forma inevitável e moldará a Matrix com um novo formato, um Simulacro, de acordo com a vontade e os termos dele, não do criador original da Matrix. Falando em Significados e Símbolos, temos uma mudança de paradigmas significativa em Matrix Reloaded, em relação ao primeiro Matrix. No primeiro filme, Neo é um programador comum, Thomas Anderson, apenas humano, que movido pela sua crença e pelo beijo apaixonado de Trinity se torna o grande herói, derrotando o vilão e dando um final feliz para todo mundo. Aqui em Matrix Reloaded, a relação de Neo e Trinity fica bem mais profunda, Neo se mostra absurdamente poderoso e plenamente confiante no que pode fazer, o que desperta desconfiança de seu real proposito pelo General Hamam, que é o único em toda trilogia a desconfiar da humanidade de Neo. O General tem um questionamento interessante porque conhece a Matrix e sabe que as Máquinas fazem de tudo para controlar os humanos sem que eles percebam. E se o próprio Neo for um símbolo criado pela Matrix? Ele se pergunta, ao mesmo tempo em que torce para que Neo esteja ao lado deles, não importa o que ele seja.
 (General Hamman)
(General Hamman)Neo luta contra dezenas de cópias do Sr. Smith, luta contra capangas do Merovingio, beija a Persephone e então se encontra com o Arquiteto. Neste momento temos a grande revelação da saga, quando o Arquiteto explica a Neo que o dever do Escolhido é restabelecer o equilíbrio da própria anomalia que causou na Matrix. Ele faz isso escolhendo voluntariamente resetar Zion.
Neo é o 6° Escolhido, consequentemente o mais poderoso de todos, justamente por estar apaixonado. O Arquiteto reforça que devido Neo ainda ser humano, embora possa manipular o Código da Matrix, é um grande problema porque sua anomalia está desequilibrando demais o Sistema. Por isso ele deve retornar a fonte e salvar Zion como todos os seus antecessores. Porém, Neo diferente dos outros, resolve salvar sua amada Trinity, (a narrativa sugere que os seus antecessores não possuíam par romântico) ignorando a sua função (programada para Escolhido) por causa de seu lado humano que escolhe o amor. Por isso a Guerra contra as Máquinas continuaria e Zion seria destruída. Neo sai voando o mais rápido que pode para salvar Trinity, e essa cena é muito boa. Um homem comum que voa na velocidade da luz, resgata sua amada de uma queda mortal e se torna intangível para retirar um progetil de Pistola 9mm do coração dela. Porém, aparentemente, o mundo real é regido pelas Leis naturais do Universo. O que deixa o autor deste texto em dúvida sobre o que é Zion. Note que em The Matrix, o mundo real é um mundo pós-apocalíptico, devastado e com poucos humanos vivendo fora da Matrix. Só existe um lugar que realmente se parece com uma civilização que é Zion e o resto do Planeta é controlado pelas máquinas. É dito por Morpheus que se uma pessoa morre na Matrix, ela morre no mundo real. Muitos tripulantes da Nabucudonosor de fato morrem no primeiro filme, exceto Neo, é claro. Neo sabe que deve sua vida a Morpheus, seu grande amigo e mentor que o despertou da Simulação, e à Trinity que o trouxe a vida novamente. Bom, Neo devolve o favor, retirando a bala alojada no coração de Trinity, dentro da Matrix, em Matrix Reloaded. Então temos duas naturezas em Neo. É citado pelos personagens que ele ainda continua humano, ele sangra, ele tem pesadelos, ele tem medo de perder Trinity e tem medo de falhar em sua missão, porque ela define o seu propósito. Mas o questionamento de muitos amigos meus sobre Zion ser uma extensão super realista da Matrix nasce aqui, neste filme, onde Neo se revela como o parcialmente humano e parcialmente.... Não sabemos.

A Narrativa não explica a cena final, onde Neo usa seus poderes em Zion e anula duas Máquinas. Também vemos Smith se materializado em um corpo humano, conseguindo sair da Matrix, do mesmo jeito que somente humanos rebeldes faziam no primeiro filme.
MATRIX REVOLUTIONS
Matrix Revolutions é um filme dirigido e roteirizado por... Ok, você já deve estar com muita raiva de mim se acredita em pronome neutro, mas se você defende ideologia de gênero nem deve estar lendo mais esta crítica que ninguém pediu, então sigamos. Smith consegue sair da Matrix e infectar a Oráculo. E nos é revelado que Smith é o oposto de Neo, por isso fica cada vez mais forte ao longo da trama. É a Equação Assimétrica do sistema tentando exterminar a anomalia Neo e se equilibrar. Neo cede a seu destino de Escolhido e vai para a cidade das Máquinas, restabelecer a Matrix através da Fonte. Chegando lá Neo promete que restabelecerá a Matrix se o Senhor das Máquinas cancelar a guerra contra Zion. Então ele percebe que Smith se tornou uma anomalia muito grande e que era inevitável sua derrota, com isso, cede à infecção de Smith que esperava se tornar o novo Senhor das Máquinas. Porém o Senhor das Máquinas que estava conectado à Anomalia Neo, que estava conectado à Anomalia Smith, destruiu os dois, acabando com as Anomalias Opostas e restabelecendo o Equilíbrio da Equação. O Senhor das Máquinas é o "Logos" que o Arquiteto usa para destruir e reconstruir tudo. Smith e Neo fazem uma luta épica. Cenas emblemáticas que, como o Alexandre do Jovem Nerd disse, 'era o que imaginávamos como seria um filme sério do Superman'. A Warner nos deu uma luta decente em 2013 com o Homem de Aço, depois teve até Mulher-Maravilha em 2017 que mostrou algo interessante, mas Matrix Revolutions era o que tínhamos de estética de lutas entre deuses, em live action, que realmente ficou bom, na época. Mesmo assim, acho as lutas de Matrix Reloaded bem melhor.

A Oráculo, a mãe de Matrix, queria restabelecer o equilíbrio a partir das escolhas dos programas e dos humanos. O Arquiteto, o pai de Matrix, queria restabelecer o equilíbrio matando os humanos de Zion a partir de uma escolha programada para o Escolhido. O Oráculo arriscou tudo comprometendo toda a Matrix com sua estratégia, enquanto que o Arquiteto finalmente reconheceu que seu método puramente matemático não era eficaz o suficiente. Aquele dia ensolarado da última cena pode ser tanto a Matrix equilibrada por completo sem a destruição de Zion, como pode ser uma nova versão da Matrix (a sétima, destruída pelo Smith e restaurada por Neo sem qualquer influência ou programação do Arquiteto).
A Trilogia Matrix é inegavelmente um sucesso! Obviamente, cada um tem sua própria interpretação dos filmes. Alguns dizem que a Matrix existe e que a Sociedade Moderna impõe costumes, valores e crenças a todo mundo, para que governos tenham o controle máximo da população, a partir de Ideologias que ditam como todos devem viver (Sim estou falando de Marxismo Cultural). Outros afirmam que a Matrix é apenas tudo que você faz todos os dias, como compras, pagar imposto e ir a Igreja no Domingo. Basicamente trabalhar para ter dinheiro e ter como sobreviver no mundo real. Outros acreditam que não existe saída para a Matrix, que somos apenas um cérebro cheio de fios, dentro de um aquário e que absolutamente toda a existência é uma Simulação (neste caso, o mundo real seria a própria simulação). Ainda há outras inúmeras Teorias. É inegável que neste caso, a ficção influenciou o mundo real. Claro, não podemos esquecer dos que afirmam que trata-se apenas de um filme mesmo, que nada citado nele existe de fato. O importante é conversar sobre essa trilogia, com seus poucos amigos que se interessam sobre o assunto. Eu mesmo entendo que de fato, o argumento central de Baudrillard é interessante e que "os irmãos" Wachowski abordaram o pensamento de Baudrillard de uma forma muito bela no Cinema.
Outra coisa interessante é o paralelo entre Neo e Cypher. Neo era um Programador que trabalhava em uma grande Empresa de Softwares de dia, e a noite era um Hacker. Mesmo antes de conhecer Morpheus, ele chega a se perguntar se estava acordado ou ainda estava dormindo. Depois que conhece Morpheus e desperta do sono, no mundo real, fica chocado com toda aquela realidade completamente desconhecida. Morpheus diz várias vezes que ele é o Escolhido. Ele é o cumprimento da Profecia do Oráculo. Neo ouve que ele é o Escolhido várias vezes, ao longo de vários dias que esteve naquela nave. Mesmo assim, ele sempre negava que era o Escolhido quando era questionado. Até que Morpheus é sequestrado pelos Agentes. Então Neo muda de perspectiva e começa a acreditar que ele pode resgatar Morpheus, que está quase morrendo. Depois que consegue salvar Morpheus, ele salva Trinity que acaba se apaixonando por ele. Ao meu ver, Neo é o Escolhido porque é virtuoso, mesmo conhecendo aquelas pessoas há pouco tempo, ele se preocupar com elas, a ponto de dar o telefone para Morpheus e Trinity saírem da Matrix em segurança. Neo, a partir da crença de Morpheus no Escolhido, começa a acreditar que ele é o Escolhido quando resolve enfrentar o Agente Smith no final. Mesmo sabendo da grande probabilidade dele acabar morrendo, ele está disposto a correr o risco. De longe o mais virtuoso de toda a tripulação da Nave Nabucodonosor. Já o Cypher é egoísta, só quer voltar a dormir. Está lá com o grupo do Morpheus sem objetivo nenhum, já que ele não acredita na Profecia e ainda nutre inveja de Neo, por tentar chamar a atenção da Trinity por anos, e sempre ser rejeitado. Cypher não apenas gostaria de ter escolhido a pílula azul, ele está disposto a matar a todos da nave, seu desejo é se vingar de todos da tripulação por não terem a mesma perspectiva de vida sofrida e derrotada que ele tem.
CONCLUSÃO
A conclusão que cheguei é que o segundo Matrix é o melhor. Eu realmente gosto do diálogo entre Neo e o Arquiteto e não acredito na teoria de que Neo não seria humano e sim uma máquina super realista criada pelas máquinas. Porque Neo e Trinity tiveram relações sexuais no segundo filme. E convenhamos, se Neo fosse um andróide controlado pelas Máquinas, a Trinity saberia e Morpheus desconfiaria. Uma vez que ele é o que obtém mais conhecimento de como as máquinas funcionam. O mesmo vale para Zion, os humanos que vivem lá possuem características indiscutivelmente humanas e nenhuma máquina seria tão sofisticada para simular duas realidades com tanta perfeição assim e, se de fato Zion é uma extensão da Matrix, os três filmes não passam de ilusão da cabeça de alguém, e se toda a história é um sonho, o roteiro inteiro da trilogia é baseada no Solipsismo.
Em breve farei uma análise do quarto filme, para a alegria de alguns e puro ódio da maioria.
-
 @ 2dd9250b:6e928072
2024-10-10 05:32:42
@ 2dd9250b:6e928072
2024-10-10 05:32:42Há de fato uma certa semelhança entre entre o Batman e o Charada. Tanto o Bruce, quanto o Edward foram prejudicados pelo Falcone, que mandava na Cidade de Gotham, pagando o Prefeito, a Polícia, os Juízes e Desembargadores, para que a impunidade continuasse e os criminosos mais perigosos não fossem presos. O Bruce e o Edward tinham o mesmo objetivo: Punir esses criminosos. Só que o Edward entendeu todo o esquema primeiro e resolveu usar o Bruce para chegar nos Traficantes que mandavam na cidade.
O Bruce só punia os bandidos comuns. Até que foi descobrindo todo o esquema através das charadas do Edward. Só que tanto o Edward quanto o Bruce, de certa forma rivalizavam, ou melhor, competiam com o Estado.
O Bruce porque era mais eficiente do que todo o departamento de polícia de Gotham, e o Edward porque sempre estava a um passo a frente da Polícia, eliminando os Estatistas do Colarinho Branco, um por um. Por isso eles eram perseguidos. Por isso o Edward diz ao Bruce que eles eram iguais. Os dois usavam máscara e buscavam vingança contra o Sistema. Dois jovens atormentados pelo parasitismo Estatal que faliu a cidade e desintregou a esperança de qualquer melhora por parte de seus cidadãos.
Apesar de tudo isso, Bruce resolveu se voltar contra Edward porque ele ainda tinha fé no Estado. Acreditava que existiam policiais incorruptíveis como o Comissário Gordon. Bruce tinha fé de que a cidade poderia se reerguer a partir dos cidadãos de Gotham, e acreditava que as pessoas poderiam melhorar, escolher o bem aos invés de violar a propriedade privada alheia, roubar etc, se tivessem um símbolo de esperança para seguir (o Batman). Para o Batman de Robert Pattinson, o malvadões são somente os Políticos Corruptos e os grandes empresários que ajudam esses Estatistas (mafiosos como o Pinguim).
Já Edward não tinha mais esperança em absolutamente ninguém de Gotham, por isso tentou inundar a cidade toda simbolizando o Dilúvio Bíblico.
O Charada é descrito como um ex-contador que participava de uma comunidade online, onde recrutava seguidores para a sua causa. É quase impossível não enxerga-lo como um INCEL que vive no Reddit, ou no 4chan, se imaginando como um gênio revolucionário.
No final, o Super Herói decide ajudar as pessoas para que todos não sejam puxados pela água e morram afogados, enquanto o Super-Vilão é preso. Mas o verdadeiro vilão da história continua impune.
Perceba que o filme começa com Edward passando o Prefeito da cidade (um homem branco). Depois, o longa mostra de forma sutil que ele ameaçou de morte a candidata que estava na frente das pesquisas eleitorais. E sabendo que ela iria ganhar, ele planeja mata-lá no dia da eleição, já que ela apareceria em público para fazer um discurso. Como o plano falhou, Gotham tem uma nova Prefeita que encerra o filme com um discurso de renovação e "nova política".
E os cidadãos de Gotham vão acreditar nisso. Afinal de contas, não há a menor possibilidade da cidade voltar ao que era antes. Porque agora o Prefeito é uma mulher negra. Geralmente, o Batman é mais admirado pelos Conservadores por dar porrada em bandido. E com esse filme não foi diferente. Mas para mim, foi mais do mesmo, um filme que se propõe a ser "inteligentinho" mas não passa de mais um produto da Warner com ESG e Progressimo.
O Super-Herói que apresenta melhor uma aproximação com a Direita Norte-Americana é o Demolidor da Netflix.
-
 @ 1123ece2:7d1e00c0
2024-10-10 02:53:17
@ 1123ece2:7d1e00c0
2024-10-10 02:53:17Welcome to Refinery Life Australia.
“Amen and Amen” has been the theme for the last few Sundays.
This series is a study from the Psalms, in which the psalmist gives voice to prayers that resound in our hearts today.
Today we are discussing, A Prayer of Praise and Thanksgiving.
Our Primary Text Today Is
Psalm 100:4 NKJV
4 Enter into His gates with thanksgiving,\ And into His courts with praise.\ Be thankful to Him, and bless His name.
We will also work our way through
Psalm 100 NKJV
A Song of Praise for the Lord’s Faithfulness to His People.
A Psalm of Thanksgiving.
1 Make a joyful shout to the Lord, all you lands!
2 Serve the Lord with gladness;\ Come before His presence with singing.
3 Know that the Lord, He is God;\ It is He who has made us, and not we ourselves;\ We are His people and the sheep of His pasture.
4 Enter into His gates with thanksgiving,\ And into His courts with praise.\ Be thankful to Him, and bless His name.
5 For the Lord is good;\ His mercy is everlasting,\ And His truth endures to all generations.
Introduction.
Prayer is first of all an approach to God and not the presentation of a celestial shopping list.
We come first to give rather than to take, offer rather than to request.
The psalmist described the priority of prayer, “Enter into His gates with thanksgiving, And into His courts with praise.\ Be thankful to Him, and bless His name.”
In prayer we should approach the loving Father with our praise and thanksgiving.
This is the picture true worship found in Relation 4:9-11 NKJV
The four living creatures praise the Lord and give “glory and honour and thanks to Him who sits on the throne, who lives forever and ever, the twenty-four elders fall down before Him who sits on the throne and worship Him who lives forever and ever, and cast their crowns before the throne, saying:
“You are worthy, O Lord,\ To receive glory and honor and power;\ For You created all things,\ And by Your will they exist and were created.”
- Praise and thanksgiving acknowledge the nature of God.
To pray with praise and thanksgiving is to acknowledge God’s holiness and majesty.
Remember He is the Lord, Psalm 100: 3 says, “Know that the Lord, He is God;\ It is He who has made us, and not we ourselves;\ We are His people and the sheep of His pasture.”
In prayer we affirm our dependence on the Lord.
We adore Him and express our reverent praise for His steadfast love and faithfulness.
Jesus taught us to approach the Father with praise and adoration.
Matthew 6:9 NKJV In this manner, therefore, pray:
Our Father in heaven,\ Hallowed be Your name.
To hallow the Lord’s name means to regard Him as holy and seperate and to respond with awe and reverence.
Thus we are to enter in with praise and thanksgiving.
2. Praise is an action of the will.
A problem in our prayer life is the vacillation of our emotions.
Sometimes we do not feel like praying.
If we let our emotions determine our prayer life, we will certainly fail.
With the will, we must decide to pray.
Emotion frequently limits the meaning of prayer, but we can still will to praise and thank God.
Paul instructed in, 1 Thessalonians 5:16-18, Rejoice always, pray without ceasing, in everything give thanks; for this is the will of God in Christ Jesus for you.
God does not tell us to always feel grateful.
He does, however, command us to give thanks always.
Even when we do not feel emotionally grateful, we can still choose to give thanks and praise to God.
Psalm 34:1, I will bless the Lord at all times;\ His praise shall continually be in my mouth.
Psalm 43 reflects the depressed emotions of one caught in difficult circumstances.
Yet, with a decision of the will, he determines to praise God.
Our feelings do not alter the Lord’s loving presence and powerful nature.
3. Some encouragements for praise and thanksgiving.
The will is prompted to praise by various encouragements.
Recollection of God’s nature, His creative power, His personal presence, His steadfast love, and His abundant mercy, will bring praise to our lips.
The memory of blessings encourages praise.
Count your blessings and name them one by one is good advice for praise.
Ten lepers met Jesus and sought healing of their disease, they were all cleansed, but only one came back to offer thanks.
Luke 17:11-19, Ten Lepers Cleansed
11 Now it happened as He went to Jerusalem that He passed through the midst of Samaria and Galilee.
12 Then as He entered a certain village, there met Him ten men who were lepers, who stood afar off.
13 And they lifted up their voices and said, “Jesus, Master, have mercy on us!”
14 So when He saw them, He said to them, “Go, show yourselves to the priests.” And so it was that as they went, they were cleansed.
15 And one of them, when he saw that he was healed, returned, and with a loud voice glorified God,
16 and fell down on his face at His feet, giving Him thanks. And he was a Samaritan.
17 So Jesus answered and said, “Were there not ten cleansed? But where are the nine?
18 Were there not any found who returned to give glory to God except this foreigner?”
19 And He said to him, “Arise, go your way. Your faith has made you well.”
This one leper then received full communion with the Lord through faith.
Failure to offer thanks can clog the channel of blessings.
Count your blessings and praise the Lord.
Praise is encouraged through the use of God’s Word.
Meditate on Scripture.
The words will become your own expression of praise and thanks.
Put yourself in the place of the author, feel his experiences of deliverance, joy, and spiritual blessings.
Praise and thanksgiving will erupt.
The psalmist used joyful songs to praise and thank the Lord.
Christ placed a new song in the heart of the redeemed.
With music we, too, can praise God from whom all blessings flow.
Conclusion.
Entering into prayer with praise and thanksgiving brings the results we pray for.
Until next time
Stay in the Blessings
I really want to encourage you to be diligent with your Bible study time, because God has so much more for us than we can get from just going to church once or twice a week and hearing someone else talk about the Word.
When you spend time with God, your life will change in amazing ways, because God is a Redeemer.
Theres nothing thats too hard for Him, and He can make you whole, spirit, soul and body!
You’re important to God, and you’re important to us at The Refinery.
When it comes to prayer, we believe that God wants to meet your needs and reveal His promises to you.
So whatever you’re concerned about and need prayer for we want to be here for you! Or even if you just want to say Hi, you can contact us at www.refinerylife.org
2024 IS A YEAR OF DECISIONS AND OPEN DOORS
© www.refinerylife.org 2013-2024 All rights reserved. Except as permitted under the Australian Copyright Act 1968, no part of this Article may be reproduced, stored in a retrieval system, communicated or transmitted in any form or by any means without the prior written permission.
This episode is brought to you by Refinery Life Australia:
If you enjoy The Refinery Life Radio Podcast you can help support The Refinery by doing the following:
Sow an offering:
Bitcoin: bc1qqh6720t2zagj72dyfj348az698tdut3hlecaj4
Online: https://www.refinerylife.org/donate/
If you do send an offering then please email us so that we can say thank you
Subscribe on
iTunes | Spotify | YouTube | TuneIn | Rumble | Flare | Zap.Stream | Fountain |
Share The Refinery with your friends and family
Subscribe to the newsletter on www.refinerylife.org
Follow The Refinery on Twitter | Nostr | Instagram | Fountain
-
 @ 1bda7e1f:bb97c4d9
2024-10-10 01:40:25
@ 1bda7e1f:bb97c4d9
2024-10-10 01:40:25Tldr
- Your Nostr identity may be the first ID you every own
- You can create one that easier to backup using a 12-word mnemonic, and
- You can create one that has a bit of branding to it, called a “vanity npub”
- Many tools exist which you can use
- I tried a few and settled on Rana by Negrunch
- Now I am npub1r0d8...
The first ID you’ll ever own
The first step in setting up a Nostr profile is to get your keys. These keys are your identity. For almost everyone, this is the first ID you’ll have that you truly own. That is, this ID is yours because you say it is. That’s different from almost every other ID, which was issued to you by someone else, and is yours because they say it is.
Not only is it yours. It’s portable. You can use this ID to be yourself in any app that supports Nostr.
Consider the legacy internet—every app requires a separate account. That’s a separate login and password to remember. And worse than that, it’s a separate set of content you have to generate, and a separate following you have to create. Every time a new platform launches, you need to encourage your followers to join you on the new platform. At any time, any platform can deplatform you. If they do, you lose your content and your following, with no recourse.
On Nostr, it’s different. All your content and all your following is linked to your identity, and you take it with you everywhere. You build your content once, and it appears with you everywhere. You build one following once, and they follow you everywhere. If a platform deplatforms you, you don’t lose your following or content, you just take it all to another platform.
This may be the first ID you ever own, and if Nostr keeps on growing, it may be the last ID you’ll ever need.
Getting branded with a “vanity” npub
Every nostr user has an identity like this, and every user can be found and known by their public key, their “npub” or “pubkey”. By default, most people go by a pubkey that is completely random, like npub1asdfgh….
My view is, if you’re going to create your first-ever ID that is truly yours, you might as well make it special. It’s possible to create a pubkey that has a bit of branding to it.
The technical name for these is a “vanity npub”. You could call it a branded npub.
There are some good examples:
- Snowden at npub1sn0wden...
- Negrunch at npub1qqqqqqq...
These pubkeys have specific characters at the start (or at the end). It is better branding. It’s also helpful for defeating spammers who might choose to imitate you, as only you have the vanity npub.
Keys are generated at random. To get one with your specific branding on it, you need to set up your computer to generate keys at random until it finds one that suits your needs. Once set up your computer will generate keys by the millions–checking and discarding each one until it creates the one with your characters.
The more characters you want, the longer this process will take.
Nostrogen provides a helpful table for that:
- 1 character = usually less than a 0.1 seconds
- 2 characters = usually less than a 1 second
- 3 characters = usually less than a 30 seconds
- 4 characters = usually less than a 10 minutes
- 5 characters = usually less than a 1 hour
- 6+ characters = keep fire extinguisher handy
The good news is, for your npub to have nice branding, you don’t need a lot of characters.
For myself I only needed four “r0d8”.
Getting a mnemonic, for backup, and for lightning
Once you have your ID, you will want to use it different places and back it up securely. The problem with writing down your ID as an nsec is that it’s long and complicated to write, and too easy to misread and enter the wrong characters when you type it back into your device.
A better alternative exists. You can generate a 12-word mnemonic, and then use that to derive your nsec (documented in NIP-06). The mnemonic is much easier to read, easier to type into new apps, and easier to backup correctly.
If you generate your keys directly as npub and nsec you can never go “backward” to generate a mnemonic. But if you generate a mnemonic first, you can always generate an npub and nsec from it. Furthermore if you generate a mnemonic, you can (optionally) use that same mnemonic to generate your lightning wallet for making payments with.
For these reasons, my view is that using an identity with a mnemonic is best.
Once we have our 12-word mnemonic, we generate our keys (npub and nsec), and we’re ready to use anything in the Nostr ecosystem.
- Where the app supports mnemonics you can use that
- For everywhere else you can use your nsec
- In either case you’ll be recognised everywhere you go by your vanity npub
How to mine a 12-word mnemonic with a branded vanity npub
You’ll need an application for mining. There are very many to choose from, which you can see on this awesome Nostr list by Aljaz
Some work in your web browser, like nostr.rest. Many others you can find on github and install. I tried many including nostr-pubminer, and nostr_vanity_npub, before settling on Rana.
To run these requires basic command line knowledge. I didn’t have that, so I fed the GitHub readme page to ChatGPT, and it walked me through getting everything set up.
Failing many times
Here’s what I did wrong so you don’t have to make the same mistakes.
- You can only use bech32 characters in your npub, and may not be every character you want! The allowed character set is only 023456789acdefghjklmnpqrstuvwxyz. Importantly for me there is no “o” “b” or “i” which makes it impossible to generate “rod” or “bishop”! Only “r0d” and “8lsh0p” are possible.
- Not every vanity npub miner tell you if you’re using valid characters. Nostr.rest and nostr-pubminer happily sat for hours using my CPU to look for a key that started with “rod” and failed to find one, as they must, because “rod” is not possible (only ”r0d” is possible).
- Some miners will ask you “how many threads” would you like to use. It’s a question that relates to how much processor power you want to spend on the task. I didn't know the "correct" answer but found it didn’t matter at all what number I entered.
- Some miners will generate npubs just fine, but can not generate the mnemonic. For my needs I needed one that could do both.
Success with Rana
In the end I succeed using Rana by Negrunch
You can find Rana here on Github with a very helpful readme.
In short the process is:
- Install Rust (the programming language) and install Rana (the mining application)
- Run a command to generate your npub.
- For me that command was: “cargo run —release — -n=r0d8 -g 12”
That command breaks down as:
- “cargo run” telling Rust to run the application
- “-n=r0d8” look for an npub with a prefix of “r0d8”, and
- “-g 12” including a 12 word mnemonic
And the outcome is:
- A 12 word mnemonic
- Private and public keys derived from that mnemonic
- My branded vanity npub starting with npub1r0d8...
In summary
The first step in setting up a Nostr profile is to get your identity.
While it’s easy to get an identity made with random keys, if we think our Nostr IDs are going to mean something important in the future, then we may as well set ourselves up with keys that are easy to use, and branded.
That means
- 12-word mnemonic backups (feature NIP-06)
- Branded vanity npub
The mnemonic is easier to backup and also can be used to create a lightning wallet. The branding helps people know your npub is really you
To do this
- You need an application for mining a vanity npub
- There are many, and I had success with Rana which provided both the mnemonic and the vanity prefix, in one command line instruction.
Next
- Please let me know if this kind of post is helpful or anything you’d like me to improve or expand upon!
- For my next post I’ll show how to set up a self-custody lightning wallet to make payments on Nostr with Phoenixd and Albyhub
-
 @ 1bda7e1f:bb97c4d9
2024-10-10 01:38:43
@ 1bda7e1f:bb97c4d9
2024-10-10 01:38:43Tldr
- I’m Rod
- I’m going down the Nostr rabbit hole
- I’m a startup founder, former listco CEO, NED, Bitcoin Miner, New Zealander, Dad
- I value community
- I was white-pilled by the free and interoperable internet and am ready to chip in
Nice to meet you
Today I am getting started creating a profile for my real self on Nostr. I am going to share what I learn.
Your average new Nostr user probably shouldn’t follow my lead here. The “main flow” onboarding for Nostr is becoming very smooth. Download Damus or Primal or Amethyst, then click “create account,” and be up and running in seconds.
For me though, I want to go off-road. I think Nostr is a fundamental reimagining of the internet where power resides with users rather than platforms. I want to work on it and with it. I think it has a chance to bring back the internet of my youth where people could be "internet" users rather than "corporate internet brandname" users.
So I plan to go on a tour of the weird and wonderful side quests that Nostr can offer—in order to really have some fun with it and write about it as I go.
I hope the writing will add some value.
Nostr is being driven forward by passionate and prolific devs who are creating wild new proofs of concept everywhere. These primatives are amazing, and also for a regular pleb, sometimes inaccessible and confusing.
I think I can add value by highlighting some of the “why” of fun and useful Nostr rabbit holes. If I can document what I do as a user, what I managed to make work, how I made it work, and why it was important, then I may encourage others to join and have a go.
Not a how to guide. Rather a “what I did and how and why” journal of sorts.
I can do a better intro than that
My name is Rod, and I am non-technical startup founder, former listco CEO, and company director.
Foremost in recent times, I am the founder of Jayride Group, which is a travel e-commerce marketplace that helps travelers to find and book rides around the world. I launched Jayride in January 2012 and grew it for six years to public listing on the Australian Securities Exchange (ASX:JAY) in January 2018, then ran it as a public company for six more years before stepping back from Managing Director to the role of Non-Exec Director around August 2023.
I am also a Non-Exec Director of Fishburners, Australia’s foremost technology startup founder community (and co-working space). Fishburners helps startup founders to get started. I was an early Fishburners resident, and being involved in that community was instrumental to my early startup success.
I have been flirting with Bitcoin mining since 697532 or thereabouts with 3.5Ph of hash rate, which was briefly about 1/100,000th of the network.
I’m a Nostr pleb, happily married, rational optimist, expat New Zealander living in Australia, and dad.
I will post about all of these things too.
Two key lessons led me to Nostr today
I learned the importance of community from Fishburners.
In the early days of a startup, you don’t know what you don’t know. Community helps you to learn those things simply by being amongst it. And when you find something specific which you know you need to know, community is there for you then too.
The more time I spend on Nostr, the more aware I am that this is a an awesome community of builders with the potential to add some real and lasting value to the internet and world. I want to do whatever small things I can to help and be part of that.
I learned the importance of resilience from the world's reaction to COVID.
Travel businesses and co-working businesses were smashed by lockdowns. To chart the path through it all, it became my full-time job to study the disaster of fake narratives and regulatory capture and bad policy responses, in order to try to navigate it. I learned that if you pay attention long enough then you can see behind the curtain–and it’s not a good look.
On Nostr, I find myself gradually returning to a rationally optimistic outlook. No amount of propaganda and greed and bureaucracy will ever be as fast and powerful and resilient as a free and interoperable internet.
We can build systems which leverage these strengths. If built, these systems will naturally outcompete and win on their merits, because they will be faster, freer, more powerful marketplaces for ideas and capital, more resistant to capture, and more resilient to external shocks.
Better systems means better aligned and fairer outcomes for everyone. These systems are a must-have and need to succeed. So I’m going to chip in.
I’m not sure exactly how yet!
But I’m up for it.
In summary
Hi. It’s nice to meet you all, and I hope to share something of value!
Because: - Nostr is becoming an incredible community of builders that will make its mark on the world, and - Nostr can become a true reimagining of the internet and contribute to a powerful, free and resilient world.
Up next
To start, I've learned a few things about setting up a new profile and I can share what I learned in future posts:
- Mining a branded vanity pubkey with Rana
- Setting up a self-custody lightning wallet to make zaps on Nostr with Phoenixd and Albyhub
- Setting up Nostr and lightning addresses at your own domain with Sveltekit and Vercel
Looking forward to it.
-
 @ 729ff0e0:13997a4e
2024-10-10 00:00:30
@ 729ff0e0:13997a4e
2024-10-10 00:00:30Here's my outline
The Article in long-form
- The Warning
- or something
- An Explanation
- must be good
- The Sorrow
This is kinda interesting, doing long-form articles, I mean. I am new to markdown and kinda need to play around with it, ya know?
- The Warning
-
 @ 0e501ec7:de5ef3a4
2024-10-09 21:38:52
@ 0e501ec7:de5ef3a4
2024-10-09 21:38:52PS: lees zeker eens de blog van Tim: https://timscyclethoughts.blogspot.com/2024/09/ :))
Vandaag was onze eerste dag in het Abtshof. (Ik weet het, gisteren is overgeslagen, oeps, en ik heb nog niet uitgevonden hoe ik hier meer foto's op kan zetten, nogmaals oeps.)
Het Absthof is een coöperatieve co-housing, met een grote moestuin en een houtatelier. Het is gelegen in Borlo, een klein dorpje in de buurt van Landen. Het thuis van de wooncoöperatie is een grote vierkantshoeve, die langzaamaan helemaal gerestaureerd geraakt op (redelijk) duurzame wijze. Een heel mooie plek, waar ik al een paar keer te gast ben geweest. Hier krijgen we kost en inwoon in ruil voor mee te helpen met vanalles. Wij zijn blij om hier te zijn en ervaring op te doen, en blij dat we wat kunnen bijdragen aan duurzame/alternatieve projecten zoals deze. Ook nog belangrijk: bij een coöperatie horen ook veel beslissingen, die gedragen moeten zijn. Hier werken ze met het kader van de sociocratie. Zeer interessant, ik zal er later nog over uitweiden.
Dus: we hadden op ons gemakje een lange ochtend gehad, met een lekker ontbijtje, een goede opruimbeurt, de plantjes in de serre water geven, en een random astrix en obelix strip. Het ging over de picten, ofzoiets, en iemand die de macht wou grijoen door met de romeinen samen te werken. Bon, daarvoor zijn we hier niet. Ik zou eigenlijk in bed moeten nu, de dagen zijn lang en mijn slaap dierbaar. Toch wil ik eerst nog wat schrijven. Toch toch tocht
door de bomen, wilgen, essen, rode beuk
Net toen we buitenstapten om te vertrekken deze ochtend, begon het te regenen! Test regenkleren: gefaald. Regenbroek is zo lek alsof hij eigenlijk niet bestaat. Maakt niet uit, ik ben niet van suiker. ; ) We zullen wel nog eens kijken voor van dat eng waterdichtmaakspul, of ik gebruik hem als windstopper, ook goed. Hier aangekomen werden we meteen ontvangen door Jakob met een warm middagmaal. Heerlijke stampot, op smaak gebracht met varkenspoot. Heftig idee, maar ik en Tim konden er wel mee overweg, en waren eigenlijk wel nieuwsgierig hoe dat smaakte zo een varkenspoot. Blijkt: nogal taai, maar wel nog een goede ervaring. Would recommend.
Daarna gingen we ons installeren, en we hadden geluk! We mochten slapen in een grote tent die nog op het veld stond. Daarin zijn zelfs bedjes, en hij lijkt (redelijk) waterdicht, al had ik toch niet direct al mijn spullen moeten uitspreiden. Ons kleine tentje zou het niet gehouden hebben om de hele week in de regen opgestaan te hebben vrees ik.
Daarna bereikte mij het nieuws. Van de uitzetting in het Wondelbos. Ik was er zwaar van aangedaan, boos en verdrietig, gespannen. Machteloos. Machteloos. Ik heb toen geprobeerd mijn gevoel neer te schrijven, en heb de grote uitdaging overwonnen om dat kwetsbare tekstje te delen. (Op Facebook.) Ik was wel trots op mijn kleine overwinning, maar dat viel nogal in het grote niet bij mijn eerdere gevoel bij de grote machtsvertoning van de politie, en de start van het illegaal lijkende kap. Ik kan niet geloven dat ze een kapvergunning binnen hebben, terwijl de rechtspraak rond hun bouwvergunning nog niet rond is. Maar ja, wat weet ik ervan.
Mijn gevoel kon ik dan een beetje van me afzetten door wat te helpen bij in de verbouwing van een nieuwe woning in de co-house: plaksel van de muur halen met een drilboor, puin naar buiten krijgen, spijkers uit de muur halen. Geleerd: oude spijkers moeten uit de muur voor je opnieuw plakt, anders krijg je roestvlekken. Ook geleerd: als je glas in een raam plaatst, mag je dat niet direct op het kader laten steunen, je moet er houtjes tussensteken (voor speling voor isolatie denk ik?). Morgen doen we daarmee verder én gaan we parket schaven. Ik heb echt wel zin om met het schaafmachien te leren werken!
Daarna was het eten met alle bewoners, aan een grote lange tafel in de gemeenschappelijke zaal. Was vree gezellig, al was mijn sociale energie naar het einde een beetje op. Er was een 'mededelingrondje', om iedereen op de hoogte te brengen van belangrijk nieuws. Later op de avond hadden de bewoners ook nog een 'deel-cirkel'. Dat doen ze blijkbaar een keer in de maand, om eens samen te zitten en over zaken te kunnen praten op een meer diepgaande manier, en zonder de stress van beslissingen die gemaakt moeten worden, zoals in vergaderingen. Klinkt wel goed, al zou ik zelf niet direct weten of ik veel intieme zaken kan delen voor een groep. Ik zou in de eerste plaats stress krijgen. Maar misschien werkt het wel!
Nu, naar bed, morgen weer een volle dag!
-
 @ 0e501ec7:de5ef3a4
2024-10-09 21:37:38
@ 0e501ec7:de5ef3a4
2024-10-09 21:37:38Ik rouw. Ik rouw om het bos, in mij groeit een grote krop van verdriet. O Wondelbos, ik zag je graag, je ontving me zo hartelijk, en ik zag hoe je de thuis was van zoveel leven, zoveel leven.
Ik rouw om het vertrouwen in de rechtbank om rechtvaardig te zijn. Hoe vaak nog meneer de rechter, zal je als speelbal van machtige instituten gebruikt worden om kleine mensen, die mooie dingen proberen te doen, te intimideren? Hoe vaak nog zal jij, zonder kans voor de andere zijde om gehoord te worden, de politiemacht oproepen? Hoe vaak nog zal een vredezame actie met groot machtsvertoon beëindigd worden? Hoevaak nog zal illegale kap straffeloos blijven terwijl beschermers vervolgd en opgepakt worden? Hoevaak nog? Alle rede, alle gevoel zegt, dit bos moet behouden blijven. O bos, ik zal je missen. O Wondelbos, ik ben blij dat jij bij ons was.
Nu komt voor jou een tijd van beton. Maar ik ben zeker dat er daaronder een kiertje openblijft, een zaadje zal liggen te wachten. Ik ben zeker dat het Imperium van beton ooit gedaan zal zijn, en dan zal Jij terug kunnen bloeien, terug kunnen groeien, thuis geven aan al die soorten, al die wezens, al dat leven. Dan zal Jij terug thuis kunnen komen, net als Wij.
Liefs,
Je liefste Aardbewoner
-
 @ df478568:2a951e67
2024-10-09 21:26:29
@ df478568:2a951e67
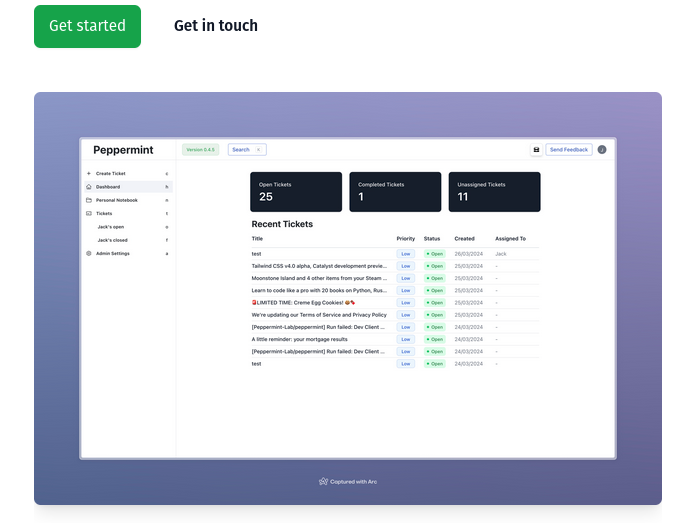
2024-10-09 21:26:29Most of the jobs I want to get require previous ticket management system Experience, but this has always been a chicken before the egg problem for me. How the heck am I supposed to get this magical ticket experience before I get a coveted help desk position? There are no tickets at my current role. I mostly write passes for students to go to the bathroom and take attendance using technology as old as the Egyptian pyramids--Dried up tree pulp. This is nowhere to gain ticketing g experience. I don't really have access to the ticketing system because I don't have real access to much technology other than a light switch or the occasional smart board I get to practice my finger drawing skills. Luckily some dude in a Discord room I hang out in suggested Peppermint, a free and open source ticketing system thatallo2s any nerd to gain ticketing experience.
Running Peppermint
There are two options for running a Peppermint ticketing system. You can pay $5 a month with Linode, or you can run it on Docker. I chose Docker because I like to keep my subscriptions low, but it is easier to host these things over the clear net if you use the Linode option.
I don't need to host this over the Internet though as it is a home network and nobody outside of .y home uses any of this stuff. To be honest, my wife already told me she will never use it because she hates putting tickets in at work and doesn't want to go through the hassle at home now, but the rest of my family doesn't mind.
I didn't realize how useful a ticketing system would be until I installed this one. I run a couple servers and do the smart home thing with home assistant. Managing the devices with this invariably comes with pain points. Our Air Conditioner broke. We paid an HVAC company to replace it because installing Air Conditioning/Furnaces is not within my skill-set. Unbeknownst to me, they also replaced our thermostat with a fancier thermostat. That's great, but I already integrated my old thermostat with home assistant, but the AC guys didn't add the new thermostat to Home Assistant, nor would they be able to.
I added a ticket.
Smart light bulb no longer works?
Add a ticket.
We got a few new DVD's this weekend. I need to add them to the Jellyfin streaming media service.
Looks like I need to add a ticket
I already have 11 tickets that arose due to normal maintenance. As it turns out, ticketing systems are not just useful for getting hands-on experience, but it helps organize my tech to do list and keeps me focused on what I need to fix.
I wasn’t going to host it on the Internet because I figured I would only use it at home, but as I thought about, I changed my mind.🤔 What if I have an issue when I’m away? That’s happened to me before. If the power goes out, there’s nothing I can do. I won’t be able to put in a ticket because my servers requires electricity to work. Sometimes one server gets disconnected for some reason. Usually this means I’m running too many programs on it. I haven’t had that happen in a while, but things happen. Maybe I’ll think of something while I’m cruising Costco. Here’s how I hosted my ticket system on the Inter Tubes.
- I installed Peppermint using docker and docker-compose.
 2. I put it on the Internet using Cloudflare. I’ve been using cloudflare on two of my servers, so I’m familiar with how to set up tunnels, but I had some trouble trying to install it using the docs on Github. After banging my head on the keyboard about eight times, I decided to do what any aspiring IT professional would do: I did a search on YouTube. Actually, I use invidious, but it doesn’t always work these days. Network Chuck has a video that teaches you how to do this. But it’s nearly ten minutes due to ads and he didn’t mention you could buy a domain name on Cloudflare and skip all the DNS BS. Don’t get me wrong, that’s a good skill to have, but it’s not necessary so I recommend starting the video at step 3. You won’t miss much. He tells you to get redhat and optimizes the algos. You just copy and paste this code into you terminal. I just did this on my PopOS! Instance.
2. I put it on the Internet using Cloudflare. I’ve been using cloudflare on two of my servers, so I’m familiar with how to set up tunnels, but I had some trouble trying to install it using the docs on Github. After banging my head on the keyboard about eight times, I decided to do what any aspiring IT professional would do: I did a search on YouTube. Actually, I use invidious, but it doesn’t always work these days. Network Chuck has a video that teaches you how to do this. But it’s nearly ten minutes due to ads and he didn’t mention you could buy a domain name on Cloudflare and skip all the DNS BS. Don’t get me wrong, that’s a good skill to have, but it’s not necessary so I recommend starting the video at step 3. You won’t miss much. He tells you to get redhat and optimizes the algos. You just copy and paste this code into you terminal. I just did this on my PopOS! Instance.
Then I added it to a subdomain on one of my many domains. I have a domain name shopping problem.
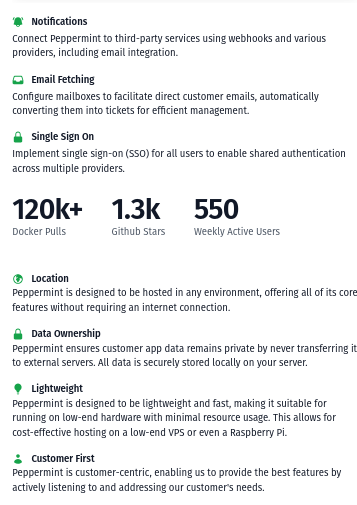
Peppermint Features
Peppermint features notifications, email fetching, single sign on… You know what? It’s just easier if I take a screenshot from their website.
Now I run my own ticketing system with Peppermint! I did this because most of the jobs I have applied for ask for ticketing experience with something like ZenDesk. I did a fre trial of zendesk, but I didn't want another monthly bill so I canceled it. The 21st century ad-driven content machine tells us we need to pay corporations every month like a serf If you’re a nerd like me, you probably own a computer or two...or 17. Why should you rent compputers from a digital overlord when you can just host everything for free on your own computer?
- It’s just 5 bucks a month
- It’s just 20 bucks a month
- It’s just 30 bucks a month.
Before you know it, you have 187 subscriptions that cost between five and ten bucks a month and you don’t understand why you’re as broke as an shell of a yolk. Now I can ell my family to “put in a ticket” anytime something goes wrong with my fleet of computers. That way my wife can put in a ticket instead of telling me something is wrong with our media server at 9:00 p.m. I’m too tired to fix these things at bedtime. Watching Friends is not a sleep-loss worthy IT emergency. So I installed a progressive web app on my tablet. My wife asked, “So I need access to your tablet to put in a ticket?”
Nope—It’s on z-Internet! You can put it on your own tablet. I texted you the link. Book mark it or add it to your homescreen. Easy-Peasy Lemon squeezy.
So if you want some ticketing experience please click this link and give them your credit card number, experiation date and that three digit secret key so they can charge you a monthly fee so I can earn like 50 cents per click. OR if you find this information valuable, please consider sending some value back to my lightning address at - marc26z@strike.me - https://strike.me/marc26z/ - Zap this article on nostr
If you don’t have any bitcoin or are afraid of it or something, sign up with Strike. This is not an affiliate link, but it’s a useful tool for sending money all over the world, even if you have a bitcoin allergy.
Thanks for reading. https://marcleon.work/pgp 864,943
-
 @ 2796a743:83074fab
2024-10-09 17:23:38
@ 2796a743:83074fab
2024-10-09 17:23:38Optimizing your Google My Business (GMB) listing is crucial for enhancing your local SEO and improving your visibility in search results. Here’s a comprehensive guide to help you get the most out of your GMB listing:
- Claim and Verify Your Listing
First and foremost, you need to claim and verify your GMB listing. If you haven’t done so already, go to the Google My Business website and follow the steps to claim your business. Verification typically involves receiving a postcard from Google with a verification code or using other methods like phone or email verification. This step ensures that you’re the rightful owner of the business and gives you control over the listing.
- Complete Your Business Information Ensure that all your business information is complete and accurate. This includes:
Business Name: Use your official business name, without any extra keywords or location details that might violate Google’s guidelines.
Address: Enter your physical address accurately. If you don’t have a physical storefront but serve customers at their locations, you can specify the service areas instead.
Phone Number: Include a local phone number rather than a toll-free number. This helps in building local trust.
Website: Add your website URL to drive traffic and enhance your online presence. Business Hours: Keep your hours of operation updated, including special hours for holidays or events.
-
Choose the Right Categories Selecting the most relevant categories for your business helps Google understand what your business offers and match you with relevant search queries. Start with a primary category that best represents your business, then add secondary categories if applicable. For example, if you own a bakery, your primary category might be “Bakery,” and secondary categories could include “Coffee Shop” or “Pastry Shop.”
-
Add High-Quality Photos
Photos play a significant role in attracting potential customers. Ensure your GMB listing includes high-quality images of your business. Consider adding:
Exterior Photos: Show your storefront or business location.
Interior Photos: Highlight the interior layout or ambiance.
Product or Service Photos: Display your products or services in action.
Team Photos: Introduce your staff to create a personal connection. Regularly update your photos to keep your listing fresh and engaging.
- Write a Compelling Business Description
Craft a clear and compelling business description that highlights what makes your business unique. Include relevant keywords but avoid keyword stuffing. Your description should provide information on your business’s history, mission, and what you offer. Google allows up to 750 characters for the business description, so make the most of it while ensuring it remains readable and engaging.
- Utilize Google Posts Google Posts allow you to share updates, offers, and events directly on your GMB listing. Regularly posting updates keeps your audience informed and engaged. You can use Google Posts to: Promote Special Offers: Share discounts or special promotions.
Announce Events: Let customers know about upcoming events or new product launches.
Share Updates: Inform customers about changes in hours, new services, or other important news. Posts appear in local search results and Google Maps, giving you an opportunity to capture attention and drive action.
- Encourage and Manage Reviews
Customer reviews are a vital part of local SEO and can influence potential customers’ decisions. Encourage satisfied customers to leave positive reviews on your GMB listing. Respond to all reviews, whether positive or negative, in a professional and timely manner. This not only shows that you value customer feedback but also improves your business’s credibility.
- Monitor Insights and Performance
Google My Business provides valuable insights into how customers find and interact with your listing. Regularly check the GMB dashboard to review metrics such as:
Search Queries: Understand how people are finding your business.
Customer Actions: Track actions like website visits, call clicks, and direction requests.
Photo Views: See how often your photos are viewed compared to competitors.
Using these insights, you can make informed decisions to further optimize your listing and tailor your marketing strategies.
- Ensure NAP Consistency
NAP stands for Name, Address, and Phone Number. Consistency is key for local SEO, so ensure that your NAP information is consistent across all online directories and listings. Inconsistent information can confuse search engines and potential customers, negatively impacting your local search rankings.
- Leverage Additional Features
Take advantage of additional features offered by Google My Business: Booking Button: If applicable, enable the booking feature to allow customers to schedule appointments directly from your listing.
Products and Services: Add a list of your products or services with descriptions and pricing if relevant.
Questions and Answers: Monitor and respond to customer questions submitted through the Q&A feature on your GMB listing.
- Stay Up-to-Date with Google’s Guidelines
Google’s guidelines for GMB listings are subject to change. Stay informed about any updates or new features by regularly checking Google’s help center and the Google My Business community forum. Adhering to the latest guidelines ensures that your listing remains compliant and optimized.
Conclusion
Optimizing your Google My Business listing is a continuous process that involves regular updates, engagement with customers, and monitoring of performance metrics. By following these steps, you can enhance your local SEO, attract more customers, and ultimately grow your business. Keep your listing current, engage with your audience, and leverage the tools and features available to make the most of your GMB presence.
What is Local SEO, and Why is it Important for My Trade Business?
Local SEO (Search Engine Optimization) is a digital marketing strategy focused on improving your business’s visibility in local search results. Unlike general SEO, which aims to rank websites broadly, local SEO targets specific geographic locations to connect with potential customers in your area. For example, if someone searches for "plumber near me" or "electrician in [your city]," local SEO helps ensure your business appears in those search results.
Why is Local SEO Important for Your Trade Business?
Increased Visibility: For trade businesses such as plumbers, electricians, or contractors, local SEO boosts your chances of appearing in local search results and on Google Maps. This increased visibility helps you attract customers who are actively searching for your services in your area.
Targeted Traffic: Local SEO drives targeted traffic to your business. When potential customers search for services in their locality, they're often ready to hire. By optimizing for local search, you connect with individuals who are more likely to need and choose your services.
Competitive Advantage: Many trade businesses compete for local customers. Effective local SEO helps you stand out from the competition, giving you an edge in capturing leads and growing your client base.
Enhanced Trust and Credibility: A well-optimized local SEO strategy includes managing online reviews and maintaining accurate business listings. Positive reviews and consistent information build trust and credibility, which can influence customer decisions.
In essence, local SEO ensures that your trade business is easily discoverable by local customers, drives targeted traffic to your website, and enhances your reputation in the community. By investing in local SEO, you increase your chances of attracting and retaining clients in your service area.
-
 @ 59c2e15a:d25e6e8d
2024-10-09 17:02:51
@ 59c2e15a:d25e6e8d
2024-10-09 17:02:51I'm excited to share with you all an event and fundraiser we're putting together for the bitcoin community in the Austin, Texas region!
We're running the first ever Satoshi Trail Run for Hal on Saturday, October 26th at Hippo Social Club! Come together with the greater Austin area’s bitcoin community to celebrate the 16th anniversary of Satoshi’s release of the bitcoin white paper (10/31/2008) and experience the best money humans have ever discovered.
The event will feature a trail run to benefit the ALS Network’s Hal Finney ALS / MND Research Fund in partnership with the Running Bitcoin Challenge. Hal Finney was an important early contributor to bitcoin and was the first individual to receive a bitcoin transaction from Satoshi in early 2009; he sadly passed away from ALS in 2014, but his legacy lives on through the Finney Prize and his wife Fran’s tireless efforts to raise awareness and funding for ALS research.
Hal famously tweeted that he was running bitcoin on January 10th, 2009, one week after the first bitcoin block was mined by Satoshi. You can listen more on Fran and Hal's story on this recent episode of Citadel Dispatch.
 Legendary picture Fran captured of Hal while running a race together.
Legendary picture Fran captured of Hal while running a race together.The event will take place at the Hippo Social Club in Hutto, Texas starting with the trail run in the morning, and is presented in partnership the Austin Bitcoin Club, Bitcoin Commons, Round Rock Bitcoin Club, University of Texas Longhorn Club and the San Antonio Bitcoin Club.
We’ve partnered with experienced running company Tejas Trails to facilitate the race! There will be options for a 5K, 10K and 21K - a half marathon, Hal's favorite distance. There will also be a 1 mile kids race and canine race along the beautifully carved trail.
 Satoshi Trail in Hutto, Texas
Satoshi Trail in Hutto, TexasWe’ll have a bitcoin market with local vendors, including MOD BIKES and Regenaissance, and meat served by Chef Johnny. We'll also have games and activities for kids, and speakers from across the local business and bitcoin ecosystem. In many ways, this is our bitcoin community's way of celebrating Satoshi's Sweet 16 party!
Marty Bent will be speaking at the event about his experience in the bitcoin industry, including bitcoin mining, venture capital, and building his media company, TFTC. Abel James, host of the Fat Burning Man show, New York Times best seller of Wild Diet, and musician will be playing music during the event!
In the spirit of value for value, Abel James s one of the top artists on Wavlake, enabling musicians to get paid directly by fans for their music. Peggy will lead post-race yoga and stretching to help you recover! Trained in vinyasa yoga, Peggy integrates healing breathwork and exercises to integrate your trail run experience. You can also recoup post-race and utilize the cold plunge and sauna.
 Check out the full schedule for the day!
Check out the full schedule for the day!If you don’t want to run, you can get a GA ticket to have access to the rest of the festivities. All tickets are 10% off if you pay in bitcoin or use the Lightning Network, thanks to Zaprite. Food will be sold separately at the event.
If you'd like to donate to support our cause raising funds in support of ALS research and care, please go here to donate in USD, or here to contribute in bitcoin.
We want to thank our sponsors, led by Unchained, a local Austin business that helps individuals and businesses buy and hold bitcoin long term in a collaborative custody model. Yopaki, a startup based in Austin out that is creating a bitcoin neo-bank in Mexico and the US, is also supporting the event. DLA Piper continues to support our bitcoin efforts in Austin, too. Wavlake / Lightning Store are contributing some sweet Bitcoin Runners tanks, while Bitcoin Runners are also providing hats for winners of the race and more to benefit the cause.
This is a cause near and dear to my heart, as my mom's best friend also has ALS. When I ran the 2022 Jerusalem marathon, I also raised money and awareness for ALS research and care. A donation of any size (or currency) would be greatly appreciated and enable us to make a bigger contribution to support the ALS Network’s Hal Finney ALS / MND Research Fund. Keep an eye out for future updates on the Running Bitcoin Challenge! Hope to see y'all at Hippo Social Club on the 26th ;)
Thank you,
Jon

-
 @ 4ec341e6:6dc2fdaf
2024-10-09 16:55:00
@ 4ec341e6:6dc2fdaf
2024-10-09 16:55:00Existe uma menção ao capítulo 12 - Relating design patterns to the model e também ao capítulo 4 - Layered Architecture.
Uma parte interessante aqui no capítulo 1 foi sobre deixar regras de negócio mais explícitas, um exemplo é dado em que a regra está implícita dentro de um método da aplicação:
java public int makeBooking(Cargo cargo, Voyage voyage) { double maxBooking = voyage.capacity() * 1.1; if ((voyage.bookedCargoSize() + cargo.size()) > maxBooking) return –1; int confirmation = orderConfirmationSequence.next(); voyage.addCargo(cargo, confirmation); return confirmation; }Então o código é refatorado para algo mais ou menos assim:
```java public int makeBooking(Cargo cargo, Voyage voyage) { if (!overbookingPolicy.isAllowed(cargo, voyage)) return –1; int confirmation = orderConfirmationSequence.next(); voyage.addCargo(cargo, confirmation); return confirmation; }
public boolean isAllowed(Cargo cargo, Voyage voyage) { return (cargo.size() + voyage.bookedCargoSize()) <= (voyage.capacity() * 1.1); } ```
A vantagem aqui é que a regra de negócio de overbooking mais explícita e acessível, o que facilita o entendimento por todas as pessoas envolvidas no projeto. Além, é claro, de tornar a regra mais clara (explícita).
Na minha opinião isso também traz outra série de vantagens, facilita a manutenção e contribui para que funções façam apenas uma coisa.
O capítulo também fala da importância de se aprofundar no entendimento do domínio (isto é, das regras de negócio da empresa) para criar modelos mais úteis e representativos.
O capítuo 1 é uma introdução, e os capítulos mais importantes são: 2, 3, 9 e 14 - Pois esse livro é muiot técnico e difícil, aprofunda muito no tema, então uma leitura mais rápida passaria por estes capítulos citados.
-
 @ 4ec341e6:6dc2fdaf
2024-10-09 16:31:08
@ 4ec341e6:6dc2fdaf
2024-10-09 16:31:08Uma carteira multisig nada mais é que uma carteira bitcoin, onde duas pessoas devem assinar para gastar os fundos, isso é como um contrato em que as duas partes devem cumprir certas responsabilidades.
Em alguns contratos, é feita uma multisig 2/3 com um terceiro atuando como juiz das partes, isso é semelhante ao que existe no fiat e chama-se conta escrow. Na imagem, um escrow service do fiat, sem uso de multisig. https://image.nostr.build/73b87edc5ee218005fbe9e49084afc70f7649d176ed25779b4d3e5e803e18e21.jpg Já o timelock, nada mais é que um atributo de uma transação do bitcoin, a transação só é válida e só pode ser incluída num bloco quando tiver decorrido o tempo de timelock, isso serve como um tipo de cláusula de saída de um contrato, por exemplo:
Ema sociedade empresarial com dois sócios tendo 50/50 em uma multisig 2/2, se as duas partes estiverem de acordo, os fundos podem ser movidos, os dois assinando a transação, porém à cada transação nova, uma transação timelock pode ser gerada e assinada pelos dois. 🔑
Portanto, em caso de discordância e decorrido o tempo do timelock, qualquer parte poderia unilateralmente, transmitir a transação que move os fundos para os dois sócios na proporção 50/50 (ou a proporção acordada), já que essa transação foi previamente assinada por ambos.
Ou seja, essa transação que ficaria guardada, serve de cláusula de saída do contrato, garantindo que a outra parte não será lesada. É assim que uma carteira multisig e transações timelock pode ser usada em contratos. OK mas o que isso tem haver com lightning network? ⚡️⚡️
Bom, a lightning é uma segunda camada do Bitcoin, onde as transações acontecem, e é registrado nos nodes o estado atual dos canais que ele tem.
Cada canal da lightning nada mais é que uma carteira multisig 2/2 onde ambos fizeram um depósito, e cada vez que ocorre uma transação, é gerada uma nova transação com timelock que é assinada pelas duas partes, mas não é transmitida na rede. https://image.nostr.build/88cedacf11cb6da5f7099e4dd36733ea9a216935e70b7b1719245ec873151c7e.jpg Portanto, em um canal, os nodes podem mandar bitcoins um pro outro, salvando o estado final apenas, sem precisar criar novas transações, além daquela que abriu o canal.
Em caso de fechamento do canal, os nodes se comunicam e fecham o canal (que é uma multisig 2/2), porém e no caso de um dos nodes estar offline? Como que faz? Perdeu tudo?
Então, aí que entram as transações timelock, que servem de cláusula de emergency withdraw do contrato (canal), um dos nodes unilateralmente pode transmitir a transação após decorrido o timelock, essa transação conterá o estado atual daquele canal (50/50 ou 90/10, whathever).
Dessa forma, mesmo em caso de uma das partes ir de base, existe um emergency withdraw no contrato, que foi previamente assinado pelas duas partes, cláusula de saída.
Não vou entrar em detalhes sobre o que acontece se um node lightning tentar fraudar o outro, mas você pode pesquisar sobre Lightning Watchtowers. A parte de lightning aprendi numa palestra presencial com o nostr:npub1z24p8ghllrl4jxyw8juggm3cfrpn8vvfxxsjzjj4tuaz0qfkeqkstnk760
Estou exercitando esse pensamento pois estou pensando em outros casos de uso para carteiras multisig, algo bem fora da curva.
Este artigo foi originalmente escrito nesta note: nostr:nevent1qvzqqqqqqypzqnkrg8nwratnwp3sk7lek7dftyaz7l4e3tlytuaewraqqdku9ld0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qg3waehxw309ahx7um5wgh8w6twv5hsqgqqqp44jr7xg83nxum9wlr0qg5dl8mnfp3tg8wp5rxxjqrkl3c7qqqzst3n
-
 @ e7211c22:e87afeee
2024-10-09 15:45:58
@ e7211c22:e87afeee
2024-10-09 15:45:58Chef's notes
Originally from American Lamb Passport recipe booklet
Details
- ⏲️ Prep time: 30 minutes
- 🍳 Cook time: 20 minutes
- 🍽️ Servings: 4
Ingredients
- 1.5 lbs ground mutton or lamb
- 1/3 cup yellow onion, diced
- 3 cloves garlic, minced
- 1.5 tsp dried oregano
- kosher salt, to taste
- 3 chipotle chiles in adobo sauce, finely chopped, plus 3 Tbsp sauce
- 4 cups cabbage, finely shredded
- 1 bunch radishes, thinly sliced
- 1 cup fresh pineapple, diced
- 4 green onions, thinly sliced
- 1/3 cup fresh cilantro, coarsely chopped
- 1 lime, juiced
- corn tortillas, warmed for serving
Directions
- In large skillet, brown lamb, onion, garlic, oregano, and 1 tsp salt. Add 1/3 cup water, chipotle chiles, and adobe sauce and stir to combine, scraping up any bits from the bottom of skillet. Cook for 2-4 minutes or until liquid evaporates and sauce clings to the lamb.
- Toss cabbage, radishes, pineapple, green onion, and cilantro in a large bowl. Add lime juice and sprinkle with 1/2 tsp salt and toss to combine.
- Spoon meat onto warm tortillas and top with a generous heap of slaw. Serve with other toppings such as avacado, sour cream, queso fresco, or pickles jalepenos.
-
 @ b83e6f82:73c27758
2024-10-09 14:25:01
@ b83e6f82:73c27758
2024-10-09 14:25:01Citrine 0.5.2
- If you are coming from version 0.4.4 or lower you will need to first export the database, uninstall the app and install the new version
- Check if port is in use
- Support for tor proxy when restoring contact list
- Support for auto backup every 24 hours
Download it with [zap.store](https://zap.store/download), [Obtainium](https://github.com/ImranR98/Obtainium), [f-droid](https://f-droid.org/packages/com.greenart7c3.citrine) or download it directly in the [releases page
](https://github.com/greenart7c3/Citrine/releases/tag/v0.5.2)
If you like my work consider making a [donation](https://greenart7c3.com)
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:``` bash
gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6D
```
Once you have his PGP key you can verify the release (assuming
manifest-v0.5.2.txtandmanifest-v0.5.2.txt.sigare in the current directory) with:``` bash
gpg --verify manifest-v0.5.2.txt.sig manifest-v0.5.2.txt
```
You should see the following if the verification was successful:
``` bash
gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03
gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D
gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"
```
That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
``` bash
cat manifest-v0.5.2.txt
```
One can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. -
 @ 8d34bd24:414be32b
2024-10-09 14:24:01
@ 8d34bd24:414be32b
2024-10-09 14:24:01This series started out as one article, but turned into a 5 part series because it got so long.
I know the God of the Bible is all powerful (Omnipotent), all knowing (omniscient), and always & everywhere present (omipresent). Sometimes I wonder why He allows His name to be disgraced so badly. As His creation, I will likely never know, until I reach Heaven, but I enjoy reading some of the history in the Bible that tells of times when He did make sure everyone knew He was God of the Universe and there are no other God’s besides Him.
God’s greatest miracles are described in Genesis 1-11 and include speaking everything into existence, His global flood judgement, and confusing the languages of the people at the tower of Babel. One thing the confusion of languages did was to cause the knowledge of God to start to fade because people could only tell about God to their small group that spoke their own language. The people could also no longer read their historical documents to learn about Him.
The story of God’s miraculous rescue of His chosen people, Israel, from Egypt is God making Himself known again to the people of the world.
Egyptian Plagues
After the Israelites had been living in Egypt for 400 years, much of it in slavery, God called Moses to go to Pharaoh to demand the release of the Israelites. After a little argument by Moses, God allowed Moses’s brother, Aaron, to do most of the talking while Moses performed the miracles God had empowered him to perform. It didn’t take much to convince the Israelites, but it took a lot more to convince the Pharaoh.
And afterward Moses and Aaron came and said to Pharaoh, “Thus says the Lord, the God of Israel, ‘Let My people go that they may celebrate a feast to Me in the wilderness.’ ” But Pharaoh said, “Who is the Lord that I should obey His voice to let Israel go? I do not know the Lord, and besides, I will not let Israel go.” (Exodus 5:1-2) {emphasis mine}
When Pharaoh was commanded by God, through Moses and Aaron, to let God’s people go, Pharaoh mocked God. He wasn’t used to being commanded to do anything. Pharaoh was used to being treated as not only a king, but a god. Instead of letting the Israelites go, he made their slave labor harder than it had been before causing the Israelites to complain against Moses and God, rather than Pharaoh.
Then the Lord said to Moses, “Now you shall see what I will do to Pharaoh; for under compulsion he will let them go, and under compulsion he will drive them out of his land.” (Exodus 6:1)
God promised Moses and the Israelites to work great signs and to force Pharaoh to let them go.
Then the Lord said to Moses, “See, I make you as God to Pharaoh, and your brother Aaron shall be your prophet. You shall speak all that I command you, and your brother Aaron shall speak to Pharaoh that he let the sons of Israel go out of his land. But I will harden Pharaoh’s heart that I may multiply My signs and My wonders in the land of Egypt. (Exodus 7:1-3) {emphasis mine}
God worked through His servants and hardened His enemies’ hearts, so that He might “multiply My signs and My wonders.” God was going to teach the Israelites, Egypt, and all of the nations around them that He is the all powerful God of all.
God’s miracles started small (turning a staff into a serpent), so at first it seemed like the priests of Egypt could duplicate God’s miracles, but then God really started to impress.
God produced a succession of miraculous judgments on Egypt and Pharaoh.
-
“By this you shall know that I am the Lord: behold, I will strike the water that is in the Nile with the staff that is in my hand, and it will be turned to blood. The fish that are in the Nile will die, and the Nile will become foul, and the Egyptians will find difficulty in drinking water from the Nile.” (Exodus 7:17-18)
-
“Let My people go, that they may serve Me. But if you refuse to let them go, behold, I will smite your whole territory with frogs. The Nile will swarm with frogs, which will come up and go into your house and into your bedroom and on your bed, and into the houses of your servants and on your people, and into your ovens and into your kneading bowls.” (Exodus 8:1b-3)
-
Aaron stretched out his hand with his staff, and struck the dust of the earth, and there were gnats on man and beast. All the dust of the earth became gnats through all the land of Egypt. (Exodus 8:17)
-
“Let My people go, that they may serve Me. For if you do not let My people go, behold, I will send swarms of flies on you and on your servants and on your people and into your houses; and the houses of the Egyptians will be full of swarms of flies, and also the ground on which they dwell. But on that day I will set apart the land of Goshen, where My people are living, so that no swarms of flies will be there, in order that you may know that I, the Lord, am in the midst of the land.” (Exodus 8:20b-22) NOTE: This plague only affected the Egyptians. The land of Goshen, where the Israelites lived, did not have the plague of the flies.
-
“Let My people go, that they may serve Me. For if you refuse to let them go and continue to hold them, behold, the hand of the Lord will come with a very severe pestilence on your livestock which are in the field, on the horses, on the donkeys, on the camels, on the herds, and on the flocks. But the Lord will make a distinction between the livestock of Israel and the livestock of Egypt, so that nothing will die of all that belongs to the sons of Israel.” (Exodus 9:1b-4)
-
So they took soot from a kiln, and stood before Pharaoh; and Moses threw it toward the sky, and it became boils breaking out with sores on man and beast. The magicians could not stand before Moses because of the boils, for the boils were on the magicians as well as on all the Egyptians. (Exodus 9:10-11)
-
“Behold, about this time tomorrow, I will send a very heavy hail, such as has not been seen in Egypt from the day it was founded until now. Now therefore send, bring your livestock and whatever you have in the field to safety. Every man and beast that is found in the field and is not brought home, when the hail comes down on them, will die.” (Exodus 9:18-19) NOTE: God protected everyone, Israelite & Egyptian, who obeyed His command to bring everyone and everything in from the field. Those who refused to obey lost animal and human lives.
-
“Thus says the Lord, the God of the Hebrews, ‘How long will you refuse to humble yourself before Me? Let My people go, that they may serve Me. For if you refuse to let My people go, behold, tomorrow I will bring locusts into your territory. They shall cover the surface of the land, so that no one will be able to see the land. They will also eat the rest of what has escaped—what is left to you from the hail—and they will eat every tree which sprouts for you out of the field.” (Exodus 10:3-5)
-
Then the Lord said to Moses, “Stretch out your hand toward the sky, that there may be darkness over the land of Egypt, even a darkness which may be felt.” So Moses stretched out his hand toward the sky, and there was thick darkness in all the land of Egypt for three days. They did not see one another, nor did anyone rise from his place for three days, but all the sons of Israel had light in their dwellings. (Exodus 10:21-23)
-
“Thus says the Lord, ‘About midnight I am going out into the midst of Egypt, and all the firstborn in the land of Egypt shall die, from the firstborn of the Pharaoh who sits on his throne, even to the firstborn of the slave girl who is behind the millstones; all the firstborn of the cattle as well. Moreover, there shall be a great cry in all the land of Egypt, such as there has not been before and such as shall never be again. But against any of the sons of Israel a dog will not even bark, whether against man or beast, that you may understand how the Lord makes a distinction between Egypt and Israel.’ All these your servants will come down to me and bow themselves before me, saying, ‘Go out, you and all the people who follow you,’ and after that I will go out.” And he went out from Pharaoh in hot anger.” (Exodus 11:4-8)
After the loss of Pharaoh’s first born son and heir, he had had enough and was ready to comply with God’s command.
Pharaoh arose in the night, he and all his servants and all the Egyptians, and there was a great cry in Egypt, for there was no home where there was not someone dead. Then he called for Moses and Aaron at night and said, “Rise up, get out from among my people, both you and the sons of Israel; and go, worship the Lord, as you have said. Take both your flocks and your herds, as you have said, and go, and bless me also.” (Exodus 12:30-32)
At the exact time that God had planned, Pharaoh acquiesced and let God’s people go. It took Pharaoh losing his son and his heir, but he finally submitted and let them all go, but God had one more major miracle to do in order to glorify His name and teach the Israelites to trust Him.
Crossing the Red Sea
After mourning over their first born, Pharaoh and his officials realized that they had lost their slave labor. They chased after the Israelites. The Egyptians trapped the Israelites at the edge of the Red Sea and the Israelites, despite seeing all of God’s wonders, complained as they feared man more than they feared God.
But Moses said to the people, “Do not fear! Stand by and see the salvation of the Lord which He will accomplish for you today; for the Egyptians whom you have seen today, you will never see them again forever. The Lord will fight for you while you keep silent.”
Then the Lord said to Moses, “Why are you crying out to Me? Tell the sons of Israel to go forward. As for you, lift up your staff and stretch out your hand over the sea and divide it, and the sons of Israel shall go through the midst of the sea on dry land. (Exodus 14:13-16) {emphasis mine}
God then put a cloud pillar between the Egyptians and the Israelites, so the Egyptians couldn’t see the Israelites and so there was light for the Israelites as they escaped the trap of the Egyptians.
Then Moses stretched out his hand over the sea; and the Lord swept the sea back by a strong east wind all night and turned the sea into dry land, so the waters were divided. The sons of Israel went through the midst of the sea on the dry land, and the waters were like a wall to them on their right hand and on their left. (Exodus 14:21-22) {emphasis mine}
God miraculously parted the waters, enabled the Israelites to cross on dry land, and then had the waters return drowning all of the Egyptian soldiers after His people had safely crossed the Red Sea. This event was such a big deal that other nations that met the Israelites were afraid because they had heard what God had done for His people.
Purpose for Israel
God had made promises to Abraham, Isaac, and Jacob to make them a great nation. God’s miraculous actions to free the Israelites and take them to the promised land was not only Him working to fulfill this promise, but it was making Himself known to Israel, so that they would know the God who worked for their good.
Sadly, after seeing all of these miracles, the Israelites continued to be unfaithful. God provided mana from heaven, but they complained about not having meat. God brought quail into their camp. They complained about not having water and God brought water out of a rock. God revealed Himself to the Israelites at Mt. Sinai and they were so fearful, they asked to not see Him, but to have Moses as their intercessor. When Moses went up on the mountain to get the Ten Commandments from God, they got tired of waiting and made a molten calf to worship saying, “This is your god, O Israel, who brought you up from the land of Egypt.” (Exodus 32:4)
Could it get any worse? Oh yes, it could. When God brought them to the land He was giving them, they got scared and refused to enter. When God told them they would have to spend forty years in the wilderness because of their disbelief and disobedience, they then tried to conquer the land without God’s help and were badly defeated. It is amazing how some people refuse to be faithful to their faithful God despite all of the miracles He does for them.
I also love that God made Himself known to the gentiles (those who were not descendants of Jacob). He made Himself known to the Egyptians to the point that there may have been a corrupted form of worship of the true God in Egypt for a generation or two because they changed from worshipping a pantheon of gods to worshipping a single God before going back to their old traditions.
When the Israelites got to the promised land, the people there knew what God had done to Egypt and for Israel. They were afraid, even when the Israelites returned after their forty years wandering in the wilderness.
God had made Himself known in a special way to his chosen people, but He had made Himself known to people of many nations.
Trust Jesus.\ \ your sister in Christ,
Christy
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
-
-
 @ 4ba8e86d:89d32de4
2024-10-09 13:13:10
@ 4ba8e86d:89d32de4
2024-10-09 13:13:10Recentemente, perdi minha lista de RSS, Decidi criar este texto sobre RSS pode ajudar a escapar das armadilhas do algoritmo das redes sociais.
Além disso, para facilitar a vida daqueles que também desejam adotar o RSS como uma ferramenta de leitura, fiz um fork da lista de RSS do SethForPrivacy. Você pode acessar a lista no seguinte link: https://gist.github.com/Alexemidio/2699dd82077d483849b576a908b0c444
Aproveite a lista de RSS para personalizar seu fluxo de conteúdo e desfrutar de uma experiência de leitura mais controlada e direcionada.
Utilizar um leitor de RSS bem organizado é uma estratégia eficaz para se libertar da rolagem incessante nas redes sociais e recuperar o controle sobre o conteúdo que você consome. Isso possibilita direcionar sua atenção para o conteúdo genuinamente relevante.
Você já notou que os feeds das redes sociais frequentemente são inundados com notícias que provocam emoções negativas? Esse fenômeno, chamado de "doomscrolling", persiste, e as redes sociais parecem acentuar ainda mais a sua presença. A conhecida "bolha" das redes sociais nos mantém imersos, mostrando principalmente os posts com os quais interagimos. Isso tem provocado várias consequências prejudiciais, incluindo a disseminação de notícias falsas, desinformação e o agravamento de problemas como ansiedade e depressão entre os usuários. Mas, e se lhe disséssemos que existe uma alternativa? Uma maneira de receber informações diretamente, sem filtros ou algoritmos? É disso que vamos falar hoje: o RSS.
O Que é o RSS?
RSS é a abreviação de "Really Simple Syndication", que pode ser traduzida como "Sincronização Realmente Simples". Trata-se de um arquivo XML gerado por inúmeros sites para exibir as postagens que o site publica. Dessa forma, os leitores de RSS permitem às pessoas acompanhar diversos blogs, sites de notícias e muito mais, tudo a partir de um único local.
Quem Criou o RSS?
Uma das pessoas envolvidas na criação do RSS foi Aaron Swartz, um hacker notório por seu papel na fundação do Creative Commons e por ser um dos cofundadores da rede social Reddit.
Se desejar se aprofundar na história de Aaron, recomendamos o documentário "O Menino da Internet: A História de Aaron Swartz" dublado em português completo. https://youtu.be/qm4NRSa9T2Q?si=GXyPXVOMJX20pIo_
Para quem gosta de RSS como eu, você não precisa usar NOSTR para acompanhar meu conteúdo. Basta me adicionar ao seu RSS.
Meu RSS Nostr: nostr:npub1fw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqvq2rfr
Utilizar um leitor de RSS bem organizado é uma maneira eficaz de se libertar da rolagem incessante e recuperar o controle sobre o conteúdo que você consome, direcionando sua atenção para o que realmente importa.
Para pessoas interessantes como o nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 você não precisa segui-lo no Nostr, basta adicionar ao seu RSS.
nostr:naddr1qqxnzdesx5ur2vekxucrqde5qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqa282ctyhs
Leitores de RSS Recomendados:
Feeder (Mobile): O Feeder é um aplicativo de leitor de RSS de código aberto que permite que você acompanhe e leia suas fontes de notícias favoritas em um só lugar. Com recursos avançados e uma interface intuitiva.
Liferea (Desktop): Liferea é a abreviação de Linux Feed Reader, um programa agregador para leitura de notícias online. Ele suporta os principais tipos de arquivo criados para esse fim: RSS/RDF e Atom. Também pode importar e exportar no formato OPML.
-
 @ fd208ee8:0fd927c1
2024-10-09 12:27:53
@ fd208ee8:0fd927c1
2024-10-09 12:27:53Why waste time, looking at other people's stuff?
I get this question a lot, on Nostr, and it feeds immediately back to the next question: Why don't you just build your own client, if you're so smart?
This was a completely new question for me, as I'm used to collaborating with at least one other person, even when doing FOSS stuff. (No, this isn't my first such project; we just used to call it "volunteering" and "sharing the code", which sounds way less glamorous.) It never occurred to me, that a habit of collaboration and interaction was some sign of my ignorance and incompetence, or somehow proof that I can't vomit up "Hello World!" in 5 different programming languages.
I also made the deadly political mistake, when I entered the Nostrsphere, of refusing to call myself a "dev". For me, "dev" is a special title, given to someone doing a specific type of programming (fiddling with GUIs, mostly, which I've only done occasionally, as a sub), whereas the types I've done are "test automation", "development operations", "database management and data curation", "requirements engineering", and "application administration". Because it's so much easier to find someone interested in building a GUI, rather than building AnythingElse, I tend to slide into AnythingElse and it eventually became my professional specialty to be the Girl Friday of every project.

But, in Nostr, there is no AnythingElse category. There are only (GUI) client devs and AllOfTheIdiotsWhoMustBowDownToTheDevs. Which merely doubled my instinct to distance myself from the term. I do not want to join some cargo cult and be pedestalized and regarded as some sort of superhuman everyone owes fealty to, in return for raining GUI presents down on my loyal subjects.
Software engineers are simply people who are skilled craftsman, not gods, and it is fair to point out that some are more skilled than others. It is also completely fair to criticize their products, report bugs, and wonder aloud at endemic low-quality.
Which brings me back to the initial question:
What does the inquisitive dev know, that the others don't?
1) You learn an awful lot about an awful lot, by looking at specs, reviewing code, and trying out various implementations of concepts you are already familiar with. There are, in fact, n number of use cases for every event type, and I've seen so many of them, that I can conjure them up, or invent new ones, on the fly, rather than wasting time inventing similar events. 2) They don't have to explain their concept to you, later, when you interact. Each interaction brings you closer to parallel-levels of knowledge, which raises the signal-strength of the interaction, and widens your own knowledge base, for interacting with third parties. 3) You are increasingly-likely to contribute code or perform some other more-advanced task, for other people, as you don't face the hurdle of adjusting to a new repo or unfamiliar language, while being less-likely to merely fork-and-ignore because you have a standing business relationship with the other developer. 4) If the other dev stops maintaining the repo, you'll be inclined to continue on your own. You may even eventually receive administrative access, rather than needing to fork, as they trust you with their stuff. This means that the risk of the repo becoming abandoned falls, with each active dev snooping around it, even if that is not their primary project. 5) It helps you determine who to focus your energy on interacting with, further. Is this person new to software development, perhaps, but has some interesting transfer-knowledge from some other branch, that has resulted in a surprisingly novel concept? Is this person able to write very clean code, so that merely reading their code feels like mental training for your own craftsman's toolbox?
...and many more reasons, but this is getting too long, so, let's just cut to the chase.
What does a craftswoman want?
But, this still doesn't answer the question of my private motivation. Why do I want to gather all of this knowledge, from those further ahead, than I?
I think Nostr has long moved past the initial stage, where mere speed was of the essence, so that one npub could finally post a note and have it appear on the other npubs' client. That must have felt like a miracle, but it increasingly feels like a disaster, as the steadily-rising complexity of the Nostr ecosystem causes haphazardly-structured and largely-unexamined code bases to begin to atrophy, or result in developers running around at an exhausting speed, with their bug-extinguishers, to put out fire after fire.
I think the time has arrived, for a different kind of development. Maybe even for a different kind of developer. Not replacing the experimentalism that made Nostr fun, but adding the realm of production-quality software engineering. The sort of software development that requires relay administration, testing, support... collaboration, interaction, maybe even someone who does AnythingElse.
I want to build useful, elegant products people enjoy using and feel comfortable relying on. I want them to use them, naturally and happily, to accomplish tasks they consider worthwhile. I don't want them thinking about me, while they use it. The craftswoman should never be greater than her work.
I want them to feel free -- nay, be eager! -- to give me both positive and negative feedback. My assumption is always that our production is imperfect because we are imperfect, so you do us a favor, by pointing out where we can improve. That's why we wish to integrate a feedback form that produces ngit issue events, putting your questions and comments straight on our board.
And there will be an AnythingElse person, reading that board, and responding promptly, rest assured.
-
 @ a012dc82:6458a70d
2024-10-09 07:45:31
@ a012dc82:6458a70d
2024-10-09 07:45:31Table Of Content
-
The Potential for Illicit Activity
-
The Threat to Financial Stability
-
The Challenge to National Security
-
What Does This Mean for Cryptocurrency?
-
Conclusion
-
FAQ
In an interview with Bloomberg in April 2021, former U.S. Secretary of State Hillary Clinton expressed concerns about the impact of Bitcoin and other cryptocurrencies on national security and financial stability. While some people might dismiss her warning as just another opinion, it's worth considering the reasons behind her views and what they could mean for the future of cryptocurrency.
The Potential for Illicit Activity
One of Clinton's main concerns about Bitcoin is its potential for facilitating illicit activity, such as money laundering, drug trafficking, and terrorism financing. Because Bitcoin transactions are largely anonymous and decentralized, it's difficult for law enforcement agencies to trace and intercept them. While this characteristic of Bitcoin is also what makes it attractive to many people who value privacy and autonomy, it poses a significant challenge for governments trying to combat illegal activities.
The Threat to Financial Stability
Another concern that Clinton raised is the threat that cryptocurrencies pose to the stability of financial systems. Because they are largely unregulated and not backed by any government or central authority, cryptocurrencies can be highly volatile and prone to speculation. This volatility can create instability in financial markets and lead to systemic risks that could affect the broader economy.
The Challenge to National Security
Finally, Clinton warned about the potential for cryptocurrencies to undermine national security. She noted that cryptocurrencies could be used by foreign actors to evade economic sanctions or to fund activities that threaten U.S. interests. Additionally, she pointed out that the rise of cryptocurrencies could shift power away from governments and toward private individuals and corporations, potentially weakening state control over financial systems.
What Does This Mean for Cryptocurrency?
While Clinton's warning may be cause for concern for some cryptocurrency enthusiasts, it's important to note that her views are not universally shared. Many people see cryptocurrencies as a powerful tool for promoting financial inclusion, privacy, and autonomy, particularly in countries with unstable or oppressive governments. Additionally, some experts argue that the risks posed by cryptocurrencies can be managed through increased regulation and oversight.
Ultimately, the future of cryptocurrency is uncertain, and there are many different perspectives on its potential benefits and risks. Whether you see Bitcoin and other cryptocurrencies as a threat or an opportunity, it's worth staying informed about developments in this rapidly evolving field.
Conclusion
Hillary Clinton's warning about Bitcoin and other cryptocurrencies highlights the complex and multifaceted issues at play in the world of digital currencies. While there are certainly risks associated with cryptocurrencies, there are also potential benefits that should not be overlooked. As governments, financial institutions, and individuals continue to navigate this new landscape, it will be important to consider all perspectives and work toward solutions that balance innovation with security and stability.
FAQ
What are the risks associated with cryptocurrencies? Cryptocurrencies pose potential risks for facilitating illicit activity, such as money laundering and terrorism financing, as well as threats to financial stability and national security.
Can the risks associated with cryptocurrencies be managed? Many experts believe that increased regulation and oversight can help manage the risks associated with cryptocurrencies.
What are some potential benefits of cryptocurrencies? Cryptocurrencies can provide a way for people to make transactions without the need for a central authority, which can be particularly useful in countries with unstable or oppressive governments. Additionally, cryptocurrencies can offer increased privacy and autonomy to users.
How can governments regulate cryptocurrencies? Governments can regulate cryptocurrencies by implementing laws and regulations that address issues such as money laundering, terrorism financing, and consumer protection. Some countries have already implemented regulations around cryptocurrency exchanges and digital wallets.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ da2683b9:54eedc2c
2024-10-09 07:42:47
@ da2683b9:54eedc2c
2024-10-09 07:42:47In this era of highly developed information technology, mobile phone communications and network connections have become an indispensable part of our daily lives. However, in some cases, we may want to temporarily block these signals and enjoy a space without interference.
Imagine that when you are in class, your mobile phone suddenly starts to ring. How embarrassing! The emergence of signal jammer can be used in such occasions.
Mobile phone signal jammers are mainly used to block the reception and transmission of mobile phone signals. In a quiet conference room, everyone is listening attentively, and suddenly someone's mobile phone rings, and the atmosphere is instantly broken. After using the signal jammer, the conference room is like "magic", and all mobile phone signals are "invisible".
However, the use of gsm jammer is not only to make others "obedient", but also to protect personal privacy and information security in certain specific scenarios. For example, in some sensitive meetings or trading occasions, signal jammers can effectively avoid information leakage.
WiFi jammers have a similar function. They can block WiFi signals in specific frequency bands and prevent interference from surrounding networks. In some occasions where network security needs to be improved, the use of wifi jamming device can effectively offset the impact of external signals on the internal network, thereby improving the security of the network.
UHF jammers are mainly used for interference with frequencies such as radio communications and TV signals. This type of jammer can effectively prevent the reception and transmission of the UHF frequency band and is widely used in military, security and other fields. Imagine that in an occasion that requires high confidentiality, the use of UHF blocker can provide a solid guarantee for communication security.
With the advancement of technology, the technology of signal jammers is also constantly evolving. Future signal jammers may be more intelligent. They can not only interfere with signals, but also automatically adjust the working mode according to the surrounding environment. This smart device aptly demonstrates the charm of modern technology. However, in order to enjoy the convenience brought by technology, we must also follow the rules and be a responsible "technology expert".
-
 @ 6871d8df:4a9396c1
2024-10-09 04:15:17
@ 6871d8df:4a9396c1
2024-10-09 04:15:17I saw this post, and it seems the Electoral College debate has reared its ugly head again. I was frustrated with the quality of the discussion, so I wanted to get my thoughts down somewhere.
https://x.com/jimmy_dore/status/1843375525030703141Sometimes, it even shocks me how civically illiterate those with big audiences can be.
I'm unfortunately not surprised at the other 58%.
The Constitution is a contract between sovereign states
Sovereign is the keyword here.
The state you reside in is actually your primary form of government. You have a relationship with the federal government, sure, but it is only through the state you live in.
Electoral votes are decided by how many members in Congress represent your state. This means that the minimum would be three, as each state always gets two senators and then one House of Representative district.
This decision was a compromise at our country's founding to entice smaller states to join the Union. If you join and agree to the rules, you get a two-electoral vote starter pack representing the state's representatives in the Senate. Without it, smaller states would have little incentive to join. It would essentially be "sign up and get ruled over."
To illustrate this, let's take a book club hypothetical.
Imagine a book club that includes members from four different neighborhoods, all meeting as separate chapters: - Maple Street: 50 members - Oak Street: 30 members - Pine Street: 15 members - Cedar Lane: 5 members
Each neighborhood is diverse and different in its tastes but tends to align within its neighborhood. The book club leader loves the diverse representation of all neighborhoods and wants that participation to grow and add as much value as it can to everyone.
The leader wants to institute a new "democratic" way of choosing a new book. She thought of two ways to institute it.
First, she tried a direct popular vote.
In this process, every member casts one vote for the book they want to read, and the book with the most votes wins. The leader tried this briefly, but the same thing kept happening.
Because Maple Street has the most members, their preference almost always prevailed, leading to its dominance. As a result, members from Pine Street and Cedar Lane rarely saw their book choices selected.
Over time, these members from smaller neighborhoods felt their opinions didn't matter and stopped participating.
They concluded that they had better search for another book club or run a smaller one themselves.
To mitigate this, the leader tried something new: weighted voting.
With this new method, each neighborhood receives a certain number of votes that are not strictly based on the number of members, giving smaller streets proportionally more influence.
For example: - Maple Street: 7 votes - Oak Street: 5 votes - Pine Street: 4 votes - Cedar Lane: 3 votes
This arrangement means that even though Maple Street has the most members, they cannot solely determine the outcome, leading to a balanced influence among all neighborhoods.
Moreover, each neighborhood has agency on how to split or cast their votes.
Smaller streets like Pine Street and Cedar Lane now have meaningful input in the selection.
As a result, the book choices became more varied, reflecting the interests of the entire club, and members from all streets felt valued and continued to participate equally.
Ultimately, the book club leader chose the trade-off with higher participation. Either Cedar Lane and Pine Street are part of the book club, or it's a book club governed by Maple Street, which inevitably will become a book club of only Maple Street.
To that end, weighting the votes actually increased decentralization.
There are never easy answers when making big decisions like this; there are always trade-offs. Here, the trade-off is one person, one vote, potentially leading to centralization or weighting votes unequally to incentivize decentralization and minority participation.
The choice of enticing smaller, non-populous states is the choice our founders made. They agreed that this choice preserved our federalism and decentralization and best avoided centralization to a single state or tyrannical rule.
Similar to the book club, our presidential elections operate this way. In this, your state throws its choice in the ring for who will lead over this Union of the states, not you. The Constitution stipulates that your state gets to decide how they cast this vote; it just so happens they all choose the majority vote today.
Each state gets to decide how they divvy up their electoral votes. Places like California say all go to the candidate that wins, while Maine decides to split them up, giving more agency to the district level. This process can be changed or amended via the state legislature.
If you change this, you fundamentally disrupt the relationship between the states, the federal government, and its citizens.
You are a resident of your state, which is sovereign and has its own Constitution.
You might think:
Well, we've evolved as a country, why can't we change it now?
There are many reasons this is impossible, but here is what I find the most limiting:
Throughout our history, states have controlled their rules for governing federal elections. The electorate controls this process through the state legislatures, where all election laws are supposed to originate.
Quick aside — one reason the 2020 election was controversial for many (including myself) is that many laws were changed by governors using Executive Orders under the pretense of COVID-19 emergency measures—but I'll leave that alone for now.
A state like mine — Florida — decides how it defines, rules, and judges who are constitutionally qualified to vote. I need to take steps to prove my citizenship, as well as slight differences in how they host primaries, party affiliation, etc.
A state like California says screw all that, it's illegal to even ask for an ID. So yes, they also get to decide who is constitutionally qualified to vote in federal elections based on legislation passed in their state legislature.
As a Florida resident, I — justifiably — have no vote or say in how California's state legislature legislates this issue. I only have recourse in my state.
If you removed the Electoral College, you would then need to pass federal election laws that would apply to every state removing their sovereignty to decide this for themselves.
Also, good luck getting anyone to agree or applying those laws.
Smaller states would have no incentive to stay. Or it may even incentivize them to join forces with other small states to get on the same footing as larger ones. Either choice would centralize to larger forms of government instead of smaller, more dispersed, local forms of government.
I, for one, think the Electoral College is a great thing and an ingenious invention. Without it, we have the tyranny of the majority and an even more centralizing force to a larger government than we have today.
In a country as wide-ranging and diverse as the United States, having to build coalitions across every state is a concept we must preserve and fight for.
States across our country are looked at as equals in a union. The Senate itself is a testament to that. Breaking it dissolves the very foundation of the equality that a federally elected official must view each state.
If this bothers you because it makes votes unequal, you must consider the alternatives and their consequences.
Living in California or New York, to achieve what you want, your best option is to convince Wyoming to secede. That would get you closer to this "one person, one vote" rallying cry you hear when the Electoral College and popular vote don't match.
However, if you like the benefits of Wyoming in the Union, this is the compromise you must make.
If you remove the Electoral College, states will secede, and honestly, I don't blame them.
In this, you cannot eat your cake and have it too. Either you want less populous states in the Union, or you don't. That is your choice. You cannot remove the last vestige of equality they have toward representation to the federal government. That's the trade-off. It's a compromise, not a perfect solution.
-
 @ 82b30d30:40c6c003
2024-10-09 03:51:41
@ 82b30d30:40c6c003
2024-10-09 03:51:41[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
[33]
[34]
-
 @ 4ba8e86d:89d32de4
2024-10-09 02:37:05
@ 4ba8e86d:89d32de4
2024-10-09 02:37:05O Obtainium permite a instalação e atualização automática de aplicativos de código aberto diretamente de suas páginas de lançamentos, mantendo você informado sobre novos lançamentos.
Motivação: Side Of Burritos - Você deve usar isso em vez de F-Droid | Como usar o feed RSS do aplicativo
Fontes de aplicativos atualmente suportadas:
- GitHub
- GitLabGenericName
- Codeberg
- F-Droid
- IzzyOnDroid
- Mullvad
- Sinal
- SourceForge
- SourceHut
- APKMirror (apenas faixa)
- APKPure
- Repositórios F-Droid de terceiros
- Trabalhos de Jenkins
- Vapor
- Aplicativo de telegrama
- VLC
- Código de nêutrons
- "HTML" (Retrocesso)
- Qualquer outro URL que retorne uma página HTML com links para arquivos APK (se for múltiplo, o último arquivo em ordem alfabética é escolhido)
Como configurar:
A única coisa que você realmente precisa é a URL do projeto que deseja seguir. Por exemplo, o link do Github do Robosats. https://github.com/RoboSats/robosats
Depois só da o toque no botão ( ADD )
https://cdn.nostr.build/i/4ec965caf19a530bde69f0640e5b3e1fa0cc70608d6b295ea2e23107a37c73b9.jpg
O Obtainium agora procurará a versão correta do aplicativo para o seu telefone e verificará também se você já possui a versão instalada. Se o projeto tiver múltiplas opções ou tags de lançamento, ele lhe dará a oportunidade de escolher a versão desejada. Caso o aplicativo ainda não esteja instalado, você terá a opção de iniciar o processo de instalação clicando em "Install", o que permitirá o download do APK e a instalação do aplicativo automaticamente.
https://cdn.nostr.build/i/07e8d022ca828fede89bbb82a5f4b94e03270c5c1a8b48c0753d845af8602295.jpg
https://cdn.nostr.build/i/dfd6d6890e0aeae019abb33fc7b2959cb13f030beffb57363dcc5ea992f0542e.jpg
https://cdn.nostr.build/i/fa6a0c1a9c87d3434301ae598de7757c23b96c22600ae2fe34a502f4e1b6ba99.jpg
Você pode baixar O Obtainium no GitHub.
https://github.com/ImranR98/Obtainium/releases
-
 @ 3ad01248:962d8a07
2024-10-09 00:37:11
@ 3ad01248:962d8a07
2024-10-09 00:37:11With only a few weeks until the "most important election in our lifetime" the political class and the talking heads are placing their bets on who is going to win the election. I would posit that it means more to them than it means to the common man. Think about it for a second, what do they get out of it?
The so called political elites and the business interest that are tied to them get access to power, insider information and clout. This is the currency of politics. The money that is made is just a side benefit of having government power and access to information that the common man just doesn't have at their disposal.
This is why the political class is so concerned on who is going to win the election. It impacts their bottom line and their lifestyle. What does the average person in a America get if they elect Donald Trump or Kamala Harris? More of the same to be honest. Both candidates are going to be spending a whole lot of money that we don't have because they have to keep the system going.
If you look at their spending plans, ironically Harris's plan will spend less money over ten years than Trump! According to the Committee for a Responsible Federal Budget had Harris spending plan would at [$3.5 trillion versus $7.5 for Trump][https://www.crfb.org/papers/fiscal-impact-harris-and-trump-campaign-plans].
The fact that Harris would spending less money isn't a cause for celebration, they are both driving the country over the cliff, Trump seems wants to get their faster. Democrat or Republican its all the same. More spending. More debt. More wars. More death. Nothing changes. We should want more for our country.
This is why I love Bitcoin so much. For the first time in history the people truly have a way opt out of the system and create a parallel economy and build a new prosperous society free from government coercion and greed but this isn't what the average Bitcoiner wants from what I've seen recently.
Well let me digress, I believe their are two factions of Bitcoiners right now. You got the hardcore Bitcoin Maximalist that ditched Twitter and became NOSTR only plebs, for which I am one. This is the crew that believe in the core tenets of Bitcoin and try to live those values everyday, which I love because its inspiring and they are being the change they want to be in the world.
On the other hand you have the Bitcoiners that are still on X/Twitter who are more concerned with Number Go Up, institutional investors getting into Bitcoin or making it a treasury asset. Both love Bitcoin for very different reasons.
Trump is heavily courting this group of people to get him over the finish line and back into the White House. To be honest, I don't like it and I don't buy his act for one minute. I sincerely believe that if he gets back into the White House he isn't going to give two fucks about Bitcoin or the people that got him there for the simple reason that he will have control of the money printer again that he will use to push his policy agenda.
Why on God's green Earth would he promote a currency that he couldn't control? It goes against his self interest as a politician. With the dollar he can buy votes, influence election overseas, build a massive military and bully his rivals. No freakin way he gives that up.
Bitcoiners who whore themselves out for Trump are making a huge mistake that will bite them in the ass. It not going to buy them any favors with the government when push comes to shove.
Bitcoin is a direct threat to the dollar. Point blank. This is the whole fucking point. How does Hillary Fucking Clinton understand this but Bitcoiners don't? Cmon guys.
https://www.youtube.com/watch?v=yyZ1XqSWVM0
We are here to undermine the role of the dollar as the reserve currency of the world. That's what I thought Bitcoiners were all about. Came for the gains, stayed for the revolution? Are we about that now guys? Do we just want our bags pumped, Lambos and girlfriends? That's not what I signed up for and I hope you didn't either.
So it really doesn't matter who wins this election because they are largely going to follow the same policies. If you want to make a difference in the world buy Bitcoin, spend Bitcoin, share news about Bitcoin with your friends and family. You don't have to actively "orange-pill" because I don't think that actually works but just being a good resource of information will help when someone ask you for help.
We are the vanguard of this revolution. Take this responsibility seriously. Lower your time preference and lets get to work.
-
 @ 4ba8e86d:89d32de4
2024-10-08 23:16:53
@ 4ba8e86d:89d32de4
2024-10-08 23:16:53Governos do mundo industrial, seus gigantes cansados de carne e aço, venho do ciberespaço, a nova casa da mente. Em nome do futuro, peço que no passado nos deixe em paz. Você não é bem vindo entre nós. Nem você exerce qualquer soberania sobre o lugar onde nos encontramos. Não elegemos nenhum governo, nem pretendemos tê-lo, por isso dirijo-me a vocês sem outra autoridade senão aquela com que sempre fala a liberdade. Declaro que o espaço social global que estamos construindo é independente por natureza das tiranias que você procura impor a nós. Você não tem o direito moral de nos governar, nem possui métodos para fazer cumprir sua lei que devemos realmente temer. Os governos obtêm seus justos poderes do consentimento daqueles que são governados. Você não pediu nem recebeu o nosso. Nós também não convidamos você. Você não nos conhece, nem conhece o nosso mundo. O ciberespaço não está dentro de suas fronteiras. Não pense que você pode construí-lo, como se fosse um projeto de construção pública. Você não pode. É um ato natural que cresce a partir de nossas ações coletivas. Você não participou de nossa grande conversa coletiva, nem criou a riqueza de nossos mercados. Você não conhece nossa cultura, nossa ética ou os códigos não escritos que já fornecem à nossa sociedade mais ordem do que o que poderia ser obtido por qualquer uma de suas imposições. Você proclama que há problemas entre nós que precisa resolver. Você usa isso como uma desculpa para invadir nossos limites. Muitos desses problemas não existem. Onde houver conflitos reais, erros, nós os identificaremos e resolveremos por nossos próprios meios. Estamos criando nosso próprio contrato social. Essa autoridade será criada de acordo com as condições do nosso mundo, não a sua. Nosso mundo é diferente. O ciberespaço é composto de transações, relacionamentos e pensamento em si, que se espalham como uma onda silenciosa na web de nossas comunicações. Nosso mundo está ao mesmo tempo em todo lugar e lugar nenhum, mas não é onde os corpos vivem. Estamos criando um mundo no qual todos possam entrar, sem privilégios ou preconceitos devido à raça, poder econômico, força militar ou local de nascimento.
Estamos criando um mundo em que qualquer pessoa, em qualquer lugar, possa expressar suas crenças, não importa quão únicas sejam, sem medo de ser coagida ao silêncio ou à conformidade. Seus conceitos legais de propriedade, expressão, identidade, movimento e contexto não se aplicam a nós. Eles são baseados na matéria. Não há problema aqui. Nossas identidades não têm corpo; portanto, diferentemente de você, não podemos obter ordem por coerção física. Acreditamos que nossa autoridade emanará da moralidade, do interesse próprio progressivo e do bem comum. Nossas identidades podem ser distribuídas por várias jurisdições. A única lei que todas as nossas culturas reconheceriam é a Regra de Ouro. Esperamos ansiosamente desenvolver nossas soluções específicas sobre essa base. Mas não podemos aceitar as soluções que você está tentando impor. Hoje, na América, você criou uma lei, a Lei de Reforma das Telecomunicações, que repudia sua própria Constituição e insulta os sonhos de Jefferson, Washington, Mill, Madison, DeToqueville e Brandeis. Esses sonhos devem renascer em nós agora. Você tem medo de seus próprios filhos, pois eles são nativos em um mundo onde você sempre será imigrante. Ao recear, confia à sua burocracia responsabilidades parentais que não pode ser covarde. Em nosso mundo, todos os sentimentos e expressões da humanidade, do mais vil ao mais angélico, fazem parte de um único todo, a conversa global de bits. Não podemos separar o ar que sufoca daquele em que as asas batem. Na China, Alemanha, França, Rússia, Cingapura, Itália e Estados Unidos, você está tentando evitar o vírus da liberdade, estabelecendo postos de guarda nas fronteiras do ciberespaço. Eles podem impedir o contágio por um curto período de tempo, mas não funcionarão em um mundo que em breve será coberto pela mídia transmitida por bits.
Suas indústrias de informação cada vez mais obsoletas se perpetuariam propondo leis, nos Estados Unidos e em outros lugares, que reivindicam a propriedade da palavra em todo o mundo. Essas leis declarariam que as idéias são outro produto industrial, menos nobre que o ferro enferrujado. Em nosso mundo, tudo o que a mente humana pode criar pode ser reproduzido e distribuído infinitamente, sem nenhum custo. A transferência global de pensamento não precisa mais ser realizada por suas fábricas. Essas medidas cada vez mais hostis e colonialistas nos colocam na mesma situação em que estavam aqueles amantes da liberdade e da autodeterminação que tiveram que lutar contra a autoridade de um poder distante e ignorante. Devemos declarar nossos "eus" virtuais imunes à sua soberania, embora continuemos a consentir com seu poder sobre nossos corpos. Vamos nos espalhar por todo o planeta para que ninguém possa aprisionar nossos pensamentos. Criaremos uma civilização da mente no ciberespaço. Que seja mais humano e bonito do que o mundo que seus governos criaram antes. Davos, Suíça, até 8 de fevereiro de 1996 John Perry Barlow
-
 @ 4ba8e86d:89d32de4
2024-10-08 22:45:17
@ 4ba8e86d:89d32de4
2024-10-08 22:45:17Um gerenciador de senhas é um software que ajuda os usuários a armazenar e gerenciar senhas e outras informações de autenticação. Ele é projetado para criar senhas seguras e únicas para cada conta e armazená-las de maneira segura. O Birwaden permite que os usuários criem cofres seguros para armazenar suas senhas e outras informações de autenticação. Esses cofres são protegidos por criptografia AES de 256 bits, o que significa que as senhas armazenadas são mantidas seguras e protegidas contra acesso não autorizado.
A história do Bitwarden começa em 2017, quando o programador russo Vladimir Ivanov decidiu criar um gerenciador de senhas de código aberto. Ivanov tinha preocupações crescentes sobre a segurança de senhas na Internet, especialmente com a crescente incidência de hacks e vazamentos de dados. Ele queria criar uma solução segura e fácil para gerenciar senhas que pudesse ajudar as pessoas a proteger suas contas. Ivanov escolheu usar criptografia AES de 256 bits para proteger as senhas armazenadas no Bitwarden, pois é considerado um dos algoritmos de criptografia mais seguros disponíveis.
Um Gerenciador de Senhas é um software que ajuda a armazenar e gerenciar senhas e outras informações de autenticação. Ele é projetado para criar senhas seguras e únicas para cada conta e armazená-las de maneira segura. O usuário pode acessar suas senhas sempre que precisar, sem precisar se preocupar em lembrar de todas elas.
Um Gerenciador de Senhas resolve vários problemas, incluindo a dificuldade de criar senhas fortes e únicas, o risco de reutilização de senhas e a possibilidade de comprometimento de contas devido a senhas fracas ou roubadas. Um gerenciador de senhas também ajuda a simplificar o processo de login, economizando tempo e reduzindo a frustração.
Usar um Gerenciador de Senhas pode ajudar a proteger as contas do usuário e reduzir o risco de comprometimento de dados. Ele também simplifica o processo de login, tornando mais fácil para o usuário acessar suas contas em vários dispositivos.Além disso, um gerenciador de senhas pode ajudar a gerar senhas fortes e únicas, que são mais difíceis de serem quebradas por hackers.
Passo a passo instalação do aplicativo Bitwarden:
-
Baixe e instale o Bitwarden em seu dispositivo móvel https://play.google.com/store/apps/details?id=com.x8bit.bitwarden
-
Crie uma conta no Birwaden. O aplicativo permitirá que você crie uma conta segura usando uma senha forte e um endereço de e-mail válido.
-
Crie um cofre seguro no Bitwarden para armazenar suas senhas. O aplicativo permite que você crie vários cofres para diferentes categorias de senhas, como redes sociais, finanças, e-mail, entre outras.
-
Adicione suas senhas ao cofre seguro. O Bitwarden permite que você adicione senhas manualmente ou importe senhas de outros gerenciadores de senhas.
-
Use o Bitwarden para acessar suas senhas sempre que precisar. O aplicativo permite que você acesse suas senhas de forma rápida e segura, sem precisar se preocupar em lembrar de todas elas.
-
Utilize o gerador de senhas do Bitwarden para criar senhas fortes e únicas para cada conta. O aplicativo oferece uma ferramenta para gerar senhas aleatórias, garantindo que suas contas estejam protegidas contra hackers.
-
Aproveite outras funcionalidades do Bitwarden, como preenchimento automático de senhas e autenticação de dois fatores. O aplicativo pode ajudar a simplificar o processo de login e aumentar a segurança de suas contas online.
-
-
 @ 3c7dc2c5:805642a8
2024-10-08 21:00:43
@ 3c7dc2c5:805642a8
2024-10-08 21:00:43🧠Quote(s) of the week:
'The world has a 0.1% allocation to Bitcoin. Another way to think about this: 1% of the world has a 10% allocation. 99% of the world still has a 0% allocation. It's still so early for Bitcoin.' -Jesse Myers
'The length of time that someone has been a Bitcoiner neither indicates how wealthy they are nor is it correlated to how well they understand Bitcoin.' - Jameson Lopp
🧡Bitcoin news🧡
On the 30th of September:
➡️'If Bitcoin continues following the trajectory of global M2 money supply, it's heading to $90,000 before the end of the year.' -Joe Consorti
Have you already read last week's gift - Lyn Alden's & Sam Callahan's article/research? No?
The research suggests that Bitcoin is more closely tied to global liquidity conditions than other assets, making it a valuable macro barometer for investors: https://www.lynalden.com/bitcoin-a-global-liquidity-barometer/
➡️Taiwan's Financial Supervisory Commission has announced that professional investors can now access Bitcoin ETFs under specific regulations and oversight.
➡️Ohio State Senator, Niraj Antani, introduces groundbreaking bill to allow all state and local taxes to be paid in Bitcoin. The states will lead.
➡️ On this day, Argentina's President Milei met El Salvador's President Bukele. Argentina's Vice President talks with El Salvador's President about their Bitcoin volcano bonds "Bitcoin is something that interests me a lot"
On the 1st of October:
➡️There's little spot market activity, suggesting waning interest and potential price stabilization. Bitcoin needs a catalyst to rally significantly, per Bitfinex.
➡️Bitcoin just closed the month UP 7.3%. The biggest September gain in 11 years. When Bitcoin goes up in September, it continues going up every single month in Q4. 3 out of 3 since 2013.
➡️Robinhood now allows European users to withdraw Bitcoin and crypto to external wallets - CNBC
➡️Galaxy Digital predicted that ETH ETFs would receive $1bn of net inflows per month for the first 5 months
We are over 2 months in, and ETH ETFs have actually had NET-NEGATIVE flows How did they misread the market this badly? Here you can find the report
They hired an ETH "expert" (shill) for the analysis. What could go wrong...brutal just brutal! Don't do shitcoins ladies & gentlemen.
➡️ Spot Bitcoin ETFs bought up all the BTC mined in September.
➡️Metaplanet has purchased an additional ~107.91 Bitcoin for ¥1 billion at an average price of ¥9,266,724 per Bitcoin. As of October 1, Metaplanet holds ~506.745 Bitcoin acquired for ¥4.75 billion at an average price of ¥9,373,557 per Bitcoin.
On the 2nd of October:
➡️'Less than 20% of the Bitcoin in circulation has moved in the past 6 months.' -Wicked Meanwhile, the 6-month HODL Wave has risen above 80%—a level that bitcoin has only surpassed once, roughly a year ago. Ergo supply is starting to get really tight.
➡️Blackrock and Fidelity Bitcoin ETFs are among the best launches of the last ten years. Bitcoin has shaken up the wall street. IBIT $23.2 Billion assets FBTC $11 Billion assets
➡️$526 million leveraged Bitcoin positions were liquidated in just 24 hours. Don't do leveraged plays people, REKT!
On the 3rd of October:
➡️Talking about Blackrock and how Bitcoin has shaken up Wall Street. BlackRock has become Bitcoin’s biggest advocate. Now they’re posting charts showing the decline of US dollar purchasing power. And show how Bitcoin through the lens of a global monetary alternative. Let that sink in for a minute. The largest asset manager in the world making a well-polished case for Bitcoin to clients with a ginormous chart of the decimation of the dollar's purchasing power since the establishment of the Fed.
They even said during the conference in Brazil: "BlackRock says Bitcoin is “Risk Off” as a global monetary alternative, while ETH is “Risk On” as a blockchain play Bitcoin is money, the rest of “crypto” is just a gamble.
On the 4th of October:
➡️Coinbase will delist all unauthorized stablecoins, including Tether, from its crypto exchange in the EU by year-end.
The EU’s new MiCA rules, fully effective Dec. 31, require stablecoin issuers to hold e-money authorization in a member state.
➡️IMF calls for El Salvador to limit Bitcoin exposure. This is after the IMF admits (Official IMF press conference): that a key reason why it’s withholding funds from El Salvador is that it doesn’t like Bitcoin and the fact that the government has added it to its national treasury. The IMF is a monetary colonialist.
What the IMF is screaming out loud from the rooftop is: „ If you don‘t stop this Bitcoin thing we can‘t suppress you anymore and then we are fucked“ El Salvador just like "I don't care" and „F*** you“.
On the 7th of October:
➡️Metaplanet has purchased an additional ~108.79 Bitcoin for ¥1 billion at an average price of ¥9,192,359 per Bitcoin.
As of October 7, Metaplanet holds ~639.50 Bitcoin acquired for ¥5.965 billion at an average price of ¥9,326,856 per Bitcoin.
➡️Bitcoin is the best-performing asset so far this year - NYDIG
➡️Mayor of Rockdale, Texas writes an opinion letter on how Bitcoin mining revitalized his town.
“We are on the cusp of a new economic renaissance - a digital energy boom - thanks to Bitcoin.”
💸Traditional Finance / Macro:
On the 1st of October:
👉🏽Blackrock AUM is $ 10 trillion, and only the US and China's GDPs exceed this. That's how big Blackrock is. It has a shareholding in the majority of the public companies & controlling influence.
Holger Zschaepitz: "BlackRock is eating the world. Since its IPO in Oct 1999, the share has returned an average of 20.7% per year, completely outperforming the S&P 500 and the Nasdaq 100, which have only returned 8.2% and 9.7% per year respectively. BlackRock even outperformed Amazon and Microsoft, with only Apple and Nvidia doing better.
🏦Banks:
On the 2nd of October:
👉🏽Bank of America is down: Customers report widespread outage, zero balances shown — CNN
Jameson Lopp: 'What if I told you this is actually an accuracy improvement: there's no money in those accounts...' But what if they shut down electricity, how will you use Bitcoin then? Checkmate, motherfucker.
🌎Macro/Geopolitics:
On the 30th of September: 👉🏽Zimbabwe Central Bank in April 2024: ''We've launched a gold-backed currency and promise to never devalue it again. Zimbabwe Central Bank in September 2024: ''A 43% devaluation of our brand new gold-backed currency
👉🏽China's stock market is up another 4% today for a total gain of 16% over the last 5 days after economic stimulus was announced. It feels like 2020 all over again. Hello, liquidity! To give you some perspective: China is now the world’s best-performing market this year. For context, China went from the worst-performing market of 2024 to the best-performing within 15 days.
Talking about China...
👉🏽'One of the best measures of living standards and real GDP growth is electricity consumption. Since electricity is difficult to store in large quantities, electricity generation tends to be a reasonable proxy for electricity consumption. Interesting chart given that context.' -Luke Gromen (foto) Now we need to put that in context though. 1.4 Billion Chinese .333B Americans To reach parity the Chinese would need to be producing 420% of the electricity... or 17000 TW hours. They are closing in. They are about 6-10 years from reaching parity if they keep the same rate of bringing new supplies online. I'm curious to see how all the new Data Centers, Chip manufacturing plants, cooling needs, etc., being brought online affect both supply lines.
Remember, energy is the lifeblood of a country. So it is fascinating to see that new photos show that China is building America's best nuclear reactor design at record speeds to become #1 in nuclear power.
The Lianjiang nuclear plant 12 months after Unit 1 construction started. Only 24 months after the first dig. I am skeptical about its safety. Communists tend to do half-ass too many things. AP1000s on a 4-year schedule.
On the 1st of October:
👉🏽The Germans, once an economic powerhouse, are far behind and almost at the bottom of the scale. Differences in GDP growth between European countries during the last five years are significant. Some countries follow smart, business-friendly policies, others don’t. Choices have consequences, vote wisely. Chart by Daniel Kral Europe Macro at Oxford Economics
As if Europe, but especially Germany wouldn’t have enough problems, in just a few years millions of people will reach retirement age and blow up its retirement and healthcare system. With rising unemployment in Germany due to its industrial suicide, who is supposed to pay for this?
How I love Twitter, the following statement/chart and tweet is from Paul Vanitas: 'German pension system in one chart:
The average worker has to pay 18.6% of their gross wage into the system. After retirement, they only get a fraction of this back.
Note that things will get much worse in the next years when the boomers will retire. Note also that the pension system is already supported with taxpayer money today. How can it still be that bad?'
With Germany’s aging population and declining birth rates, the strain on the system is increasing. In 1960, there were 6.4 workers for every retiree - by 2020, that number had dropped to around 2.7. Projections suggest it could fall below 2 by 2040, which is why reforms are being discussed to ensure long-term sustainability.
👉🏽'Total money supply in the US, the Euro Area, Japan, and China has reached a new record of a MASSIVE $89.7 trillion.
Global money supply has skyrocketed by $7.3 trillion over the last year. This marks the largest increase in 3 years and a similar jump to the initial pandemic response seen in the first half of 2020.
In the US alone, the amount of money in circulation has surged $410 billion year-over-year, to $21.2 trillion. To put this into perspective, at the beginning of 2020 the US money supply was 27% below current levels. Global money printing is back.' -TKL
👉🏽'There were 21 interest rate cuts conducted by global central banks in September, the most since April 2020.
Outside of the pandemic response, this is the third largest month of monetary easing since 2008. This all comes as central banks across the globe believe they can achieve a "soft landing." Meanwhile, Germany’s GDP is expected to contract for 2 straight years for the first time since 2002.
China is also on track to miss its annual economic growth target of 5% as it fight the streak of deflation since 1999. Can central banks really save the day here?' - TKL
On the 3rd of October:
👉🏽The US Treasury added $204 billion of debt on the first day of the new fiscal year, and total debt now stands at $35.7 trillion. Total US debt has exploded to $35.7 trillion—up $345 billion in just 3 days. That's 1/4 of Bitcoin's market cap added to the national debt in a single weekend.
👉🏽James Lavish: "The 2024 Federal Government Fiscal Year is in the books. This one added another $2.3T of Federal Debt to finish out the year at $35.5T, a brand new all-time high. Well done, everyone. Bravo.
'US public debt has jumped $345 billion over the last 3 days hitting another record of $35.7 trillion. Since June 2023, federal debt has surged by a MASSIVE $4 trillion, or 14%. Over the same period, US GDP is up just $1.5 trillion, or ~6%. In other words, the national debt has outpaced the economic growth by 2.7 TIMES over the last 16 months. Outside of the pandemic crisis, US federal debt has never grown so rapidly.' -TKL Nothing stops this train! If you really think the US government can balance their budget and decrease their federal debt, without hurting the economy, without low inflation, well you are a fool.
On the 4th of October:
After adjusting for inflation, the level of economic activity in Greece and Italy is still lower than before the global financial crisis (more than 15 years ago). Poland with by far the strongest real GDP growth since 2007.
On the 6th of October:
👉🏽Global Liquidity entering the next bullish phase in a long-term cycle:
You know what will happen. More inflation and asset prices are going to rip.
👉🏽The US government created backdoors at Internet Service Providers (ISP) to spy on its citizens.
China then hacked these backdoors and used them to spy on the U.S. - WSJ Chinese hackers massively wiretapped the USA by compromising the interception portals mandated under US law.
Remember this the next time a government demands encryption backdoors. https://www.wsj.com/tech/cybersecurity/u-s-wiretap-systems-targeted-in-china-linked-hack-327fc63b?st=byoB7m
👉🏽Hillary Clinton says social platforms like 𝕏 need to censor or “we lose total control.” Who is this we?
On the 7th of October:
👉🏽And just like that, the yield on the 10-year US government bond, a global benchmark, is back at 4%.
The 10-year note yield is now up 40 basis points since the "Fed pivot" began on September 18th. For the first time since August 8th, the 10-year note yield is above 4.0%. Just days ago, markets were calling for 2 MORE 50 basis point cuts in 2024. It seems the bond market quickly lost faith in the so-called "Fed pivot," and it’s fascinating to see the yield curve flip negative again so soon after the big rate cut.
🎁If you have made it this far I would like to give you a little gift:
The latest Preston Pysh pod: Bitcoin Mastermind Q3 2024 w/ Joe Carlasare, Jeff Ross, & American HODL (BTC202)
https://www.youtube.com/watch?v=3kgpeH9MOg0
Credit: I have used multiple sources!
My savings account: Bitcoin
The tool I recommend for setting up a Bitcoin savings plan: @Relai 🇨🇭 especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. (Please only use it till the 31st of October - after that full KYC)
Hence a DCA, Dollar cost Average Strategy. Check out my tutorial post (Instagram) & video (YouTube) for more info.⠀⠀⠀⠀
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀⠀⠀⠀⠀⠀⠀ ⠀
Do you think this post is helpful to you? If so, please share it and support my work with sats.
Is this blog post is helpful to you? If so, please share it & zap it = value4value!
If you have any questions, let me know in the comments or send me a DM!⬇️
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ 3c7dc2c5:805642a8
2024-10-08 20:38:49
@ 3c7dc2c5:805642a8
2024-10-08 20:38:49🧠Quote(s) of the week:
“Civilizations die from suicide, not by murder,” according to 20th-century historian Arnold Toynbee. He claimed every great culture collapses internally due to a divergence in values between the ruling class and the common people…
"Constant inflation is a human rights issue. It prevents people from building up liquid capital reliably. It either forces them to monetize illiquid things like real estate or just keeps rug-pulling them year after year and they're never able to build any serious capital and better themselves." -Lyn Alden.
🧡Bitcoin news🧡
Before I start with the Weekly Recap I want to share a great chart by River:
'Currency devaluation, the greatest theft of time and energy in the history of mankind. This is why we Bitcoin.' -CarlBMenger
On the 23rd of September:
➡️More than a week a week ago rumors circulated that Coinbase is writing Bitcoin IOUs for BlackRock and they are suppressing the price. Now fast forward to today. BlackRock amended its spot Bitcoin ETF custody agreement with Coinbase to improve withdrawal times.
Coinbase must now process BTC withdrawals to a public address within 12 hours of receiving instruction. Source
Three days later on 26.09.2024 Coinbase is down... again. Users can't buy Bitcoin, and can't access their funds.
But here’s the kicker: Coinbase doesn’t publish its Bitcoin addresses, so you have no clue if your Bitcoin is even there—or if it’s being lent out. You’re just supposed to trust them.
➡️FirstPost covers the revelation of Bhutan's massive Bitcoin holdings: “With nearly $780 million in Bitcoin—about a third of its GDP—Bhutan now ranks as the fourth largest government holder of Bitcoin.”
"Unlike the US and China, which gained their Bitcoin through the use of seizures and legal battles, Bhutan took a more proactive approach by investing directly in Bitcoin mining." - Bitcoin News.
Remember, Germany had more than 3x the amount of Bitcoin as Bhutan but sold it all. It will go down in history as one of the worst decisions made by a government.
➡️"I call it the pet rock," Dimon said. The bank chief said in 2021 at peak crypto valuations that Bitcoin was "worthless,"
Also, BIG BREAKING JP Morgan announced plans to offer an actively managed #Bitcoin fund to its private wealth clients. - Jason A. Williams
➡️Owning just 1 Bitcoin is becoming increasingly rare.
➡️'China still has 55% of the Bitcoin mining hashrate. How's that ban going?' - Bitcoin Archive
➡️MicroStrategy outperformed every single S&P 500 company since buying Bitcoin.
MicroStrategy is up 44% in 20 days. It has gained $11B in market cap and is now worth $33 BILLION.
➡️I have said it before and will repeat it...it's all about liquidity! I have been talking about this relationship, see the comment below, in the last few years. Lyn Alden commissioned a research report, written by Sam Callahan, to quantify Bitcoin's correlation to measures of global money creation relative to other asset classes.
Result: Bitcoin moves in the directional of global M2 83% of the time; more than other assets. You will find the report below in the little gift section.
On the 26th of September:
➡️America’s oldest bank BNY Mellon gets SEC approval to offer Bitcoin custody services.
BNY Mellon Bank, the biggest custodian in the world with $49 trillion in assets will now dominate the institutional Bitcoin custody space.
➡️At +10.93% Bitcoin is on track for its best September ever.
➡️BLACKROCK: Bitcoin is NOT a risk-on asset
BlackRock's Head of Digital Assets says that just because Bitcoin is a "risky" asset does not mean it is a "risk-on" asset.
"The drivers of Bitcoin long term are very different from what’s going to drive equities and other so-called risk assets, and in some cases, they may actually even be inverted.”
On the 27th of September:
➡️ETFs are preparing for Uptober. They bought 5,790 Bitcoin yesterday. That’s 13 days of mined supply!
On the 28th of September:
➡️'If you bought Bitcoin on this day, in any year since its inception, you've beaten gold and the S&P 500.
And often massively.' -Dan McArdle
➡️$16 billion of liquidity is going to hit the market starting Monday for FTX repayments. To put things in perspective:
On the 29th of September:
➡️Despite the bearish sentiment, Bitcoin is on track for the best September returns in 12 years.
On the 30th of September:
➡️Taiwan's Financial Supervisory Commission has announced that professional investors can now access Bitcoin ETFs under specific regulations and oversight.
➡️Ohio State Senator Antani pushes the bill to allow all state and local taxes to be paid in Bitcoin.
💸Traditional Finance / Macro:
On the 23rd of September:
👉🏽'The number of S&P 500 stocks outperforming the index hit 339 quarter-to-date, the highest in 22 years. This is also in line with levels seen in 2000 before the Dot-Com Bubble popped. The share has nearly tripled compared to Q2, when only ~125 stocks outperformed the S&P 500, the lowest in at least 3 decades. Interestingly, Magnificent 7 stocks are underperforming the index for the first time in almost 2 years.' -TKL
🏦Banks:
👉🏽UNREALISED LOSSES BY U.S. BANKS 7x HIGHER THAN 2008 FINANCIAL CRISIS
🌎Macro/Geopolitics:
On the 23rd of September: 👉🏽Last week I mentioned how the Greens in Germany ruined the economy and the environment.
'German „green“ policy: 1. 2023 25,6% of German electricity came from coal before the decision to close nuclear 31% came from nuclear 2. Deindustrialization drives production to Asia, where some products cause 30% more CO2.'
When sensibility can’t explain the decisions, perhaps the answer is corruption or just bad philosophy.
To make it even worse: "Immigration Does Not Work, Not Even Economically" - German Govt Needs €10BN More In Welfare Payments Than Initial Forecasts
On the same day, we received the following news:
👉🏽'WORLD'S BIGGEST BANKS PLEDGE SUPPORT FOR NUCLEAR
Banks and funds totaling $14 TRILLION in assets have just signed an unprecedented statement in support of nuclear power. They'll be presenting the pledge to support the goal of tripling nuclear THIS MORNING at the Rockefeller Center in New York City to kick off NY Climate Week. A few of the names: Bank of America Barclays BNP Paribas Brookfield Citi Credit Agricole Goldman Sachs Morgan Stanley Rothschild & Co The pledge comes after Microsoft signed a deal to buy $16 billion in electricity from a revived Three Mile Island nuclear plant alone over 20 years to fuel its AI ambitions.' - Mark Nelson
BNP told the Financial Times there was “no scenario” in which the world could hit carbon neutrality by 2050 without nuclear power, citing the UN’s IPCC. Barclays said it was taking part because nuclear could be a solution to the intermittency of wind and solar energy.
Now go to the picture (Germany - Greens) and if you have read my recent Weekly Recaps you just know how stupid Germany was and still is.
👉🏽Global Fertility Rates have dropped from 5.3 in 1963 to 2.3 in 2021 3.0 decline in ~58 years.
👉🏽Messaging app Telegram will provide more data to governments, including users' IP addresses and phone numbers in response to "valid legal requests," according to CEO Pavel Durov — Bloomberg
Seems like arresting and holding the CEO in the EU can result in that CEO agreeing to give away the privacy of the users. Privacy was fun while it lasted.
On the 24th of September:
👉🏽Jeroen Blokland:
'China just went all in on stimulus, sending Chinese stocks 4% higher. China's central bank: - Lowered policy interest rates and signaled more cuts are coming. - Cut rates on over USD 5 trillion in mortgages. - Eased rules for second-home purchases. - Lowered the required reserve ratio for banks, freeing up fresh liquidity. - Pledged over USD 100 billion in equity market support. - Stated policymakers were studying a stock market stabilization fund. This set of measures is astonishing in itself, but the fact that China opted to announce them all at once is a significant deviation from previous years. All this means China is (again) unlikely to stay within its budget deficit target of 3% of GDP and unleashes a massive slew of liquidity that will be felt globally.'
China's stock market has gone parabolic this week, a matter of fact the stock market in China is experiencing its strongest week in almost a decade, after the government announced a $140B stimulus and multiple rate cuts.
👉🏽'The UK's national debt currently stands at approximately £2.7 trillion, over 100% of GDP.
The Office for Budget Responsibility (OBR) has projected that debt interest spending will reach £73.5 billion in 2024-25, which would be around 7.8% of public receipts. NOTE THIS IS JUST PAYING OFF INTEREST. The government's approach to managing their debt is like taking out a new credit card to pay off old credit card debt. This isn't just a problem of a single party, this is the entire apparatus of government. These policies are unsustainable. Without significant changes, the national debt is forecasted to increase dramatically over the next few decades, potentially reaching 270% of GDP by the 2070s but no government can tackle this as the pain will certainly lead them to being voted out. The only escape is to own scarce assets. The truth about our DEBT BUBBLE that no politician wants to face else they won't be elected.' - Peter McCormack
👉🏽Is the US market overvalued?
Short answer: Yes Longer answer: Absolutely
TKL: 'Since 2014, the S&P 500 has risen by 186% which is 6.4 TIMES more than the MSCI World ex-USA Index's 29% gain. To put this into perspective, during the 2000 Dot-Com Bubble, this ratio reached just ~1.4x. Meanwhile, the long-term average over the last 75 years has been ~1.1x.'
On the 26th of September:
👉🏽Yellen: It will be necessary to get deficits down to keep interest costs manageable - CNBC interview.
Spoiler alert: The deficits will not just end or go down, but will continue to grow. Forever.
'Yes...and what math, logic, gold, BTC, & equities are telling those of us with the eyes to see it (but which Wall Street consensus refuses to admit to itself yet) is that what Yellen means is this: "IT WILL BE NECESSARY TO GET INTEREST COSTS DOWN TO KEEP DEFICITS MANAGEABLE." - Luke Gromen
On the 27th of September:
👉🏽'I would really like to say something positive about Europe‘s economy, but it’s simply a train wreck in slow motion.
Overregulation, bureaucracy, and lack of innovation have their price. Europe will either wake up or keep becoming poorer compared to others.'
I'm here for the once-in-a-species transition from analog money to absolute, digital scarcity. Bitcoin!
👉🏽August PCE inflation, the Fed's preferred inflation measure, falls to 2.2%, below expectations of 2.3%.
Core PCE inflation RISES to 2.7%, in line with expectations of 2.7%. Headline inflation is down, core inflation is up.' -TKL.
👉🏽Zimbabwe's central bank has devalued its gold-backed currency by over 40% against the US dollar, signaling trouble for its latest attempt to stabilize the volatile economy. The currency was introduced just six months ago. 'How can something supposedly backed by gold which is up about 30% against the USD this year, trade hands for 50% less USD?
"backing" fiat currency with a hard asset is meaningless because governments can and will just change the peg. You need the actual hard asset to be the thing that natively moves around in the economy. Only Bitcoin can do this in our modern global electronic economy!
🎁If you have made it this far I would like to give you a little gift:
The research suggests that Bitcoin is more closely tied to global liquidity conditions than other assets, making it a valuable macro barometer for investors:
And please watch the following podcast: Bitcoin Fixes Capatialism - Allen Farrington https://www.mrobnoxious.com/episodes/bitcoin-fixes-capitalism-allen-farrington
Allen Farrington is a writer and investor. He co-wrote Bitcoin in Venice. Great book, you can order it here.
Credit: I have used multiple sources! My savings account: Bitcoin
The tool I recommend for setting up a Bitcoin savings plan: @Relai 🇨🇭 especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. (Please only use it till the 31st of October - after that full KYC) Hence a DCA, Dollar cost Average Strategy. Check out my tutorial post (Instagram) & video (YouTube) for more info.⠀⠀⠀⠀
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀⠀⠀⠀⠀⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with sats.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ eac63075:b4988b48
2024-10-08 20:37:08
@ eac63075:b4988b48
2024-10-08 20:37:08In this botcast, we explore how technology is solving one of the biggest challenges faced by DAOs (Decentralized Autonomous Organizations): vote fraud. Learn how Vitalik Buterin and other experts from Cornell University are leading innovation using Zero-Knowledge Proofs and Proof of Work (PoW) to ensure security and privacy in blockchain voting systems.
You will discover how these technologies combat practices like token renting and lending, preventing vote manipulation in DAOs. The video also covers the importance of dedicated hardware to increase the integrity of digital elections.
Listen to the Podcast:
https://wavlake.com/episode/bdb2850b-49b4-45f6-9a00-d310e29f4528
Table of Contents:
Source: YouTube Transcript - Morning Crypto (Timestamped Excerpts)
I. Introduction and Context (0:00:00 - 0:02:37)
- This section sets the stage by briefly discussing a common problem in Decentralized Autonomous Organizations (DAOs): fraudulent voting practices.
- It highlights the issue of individuals manipulating voting systems by borrowing, renting, or delegating tokens to influence decision-making within DAOs.
II. Introducing Complete Knowledge and the Proposed Solution (0:02:37 - 0:03:39)
- Introduces a potential solution developed by Vitalik Buterin and researchers from Cornell University, utilizing Zero-Knowledge Proofs to address the challenge of fraudulent voting in DAOs.
- Explains that the proposed solution involves a dedicated hardware or wallet system that verifies voting rights without revealing the user's private key, preventing token manipulation.
III. Deep Dive into Complete Knowledge with "Ger" (0:05:54 - 0:07:57)
- This section features "Ger," a voice assistant, who explains Complete Knowledge as a cryptographic innovation.
- Ger describes how Complete Knowledge allows users to prove possession of information, like a private key, without revealing the information itself.
- The section emphasizes how Complete Knowledge enhances security and privacy in digital identity and voting systems.
IV. Proof of Work and ASICs for Enhanced Security (0:07:57 - 0:09:05)
- Examines the potential of using Proof of Work (PoW), the consensus mechanism behind Bitcoin, in conjunction with Complete Knowledge.
- Explains how PoW can act as a mechanism to further ensure that a specific secret or key is held by a user without requiring the user to reveal it.
- Discusses the use of Application-Specific Integrated Circuits (ASICs) for performing the computational tasks required for PoW and Complete Knowledge verification.
V. Practical Implementation and Conclusion (0:09:05 - 0:10:25)
- Highlights the development of a demo ASIC by the researchers, showcasing the practical application of their proposed solution.
- Emphasizes the potential of this technology to prevent fraudulent voting practices by requiring a user to generate proof of their voting rights via this specialized ASIC.
- Concludes with a message emphasizing the importance of verifiable knowledge and its implications for privacy and security in the digital age.
Reference: - https://eprint.iacr.org/2023/044 - https://medium.com/initc3org/complete-knowledge-eecdda172a81
-
 @ 0e501ec7:de5ef3a4
2024-10-08 20:06:29
@ 0e501ec7:de5ef3a4
2024-10-08 20:06:29Aan het einde van een dag vol buiten zijn en fietsen en organiseren (spullen inpakken, uitpakken, drogen, eten verzamelen (letterlijk hihi), eten klaarmaken, afwas...) ben ik echt niet meer in staat om veel te schrijven. Hier komt dus een korte samenvatting van de laatste twee dagen, filosofische bedenkselen zijn voor een andere keer.
Gisteren vertrokken we bij Yannick pas tegen de middag. Hoe kwam dat? Ik heb tot 9u (!) geslapen, wat wel nodig was want ik was echt volkomen uitgeput van de dag ervoor. (Veel prikkels joh, en fysieke uitdaging om 60 km te fietsen met een zwaarbeladen fiets.) (Ik weet het, klinkt niet als zoo veel maar mijn fysieke toestand was de laatste tijd niet zo heel formidabel, veel ziek en moe geweest.) Na het ontbijt heeft Tim met mijn bedenkelijke hulp mijn cassette (de tandwielen van achter) en mijn ketting vervangen. Dat ging best wel vlot, enkel het afstellen van de versnelling was niet zo gemakkelijk. We moesten een evenwicht vinden waarbij alle 9 schakels vlot gingen, aan de ene kant moesten we telkens aanspannen, terwijl we aan de andere kant telkens weer losten. Ik wou het al opgeven, toen we het net hadden gevonden.
Na al dit geploeter begonnen we aan onze fietstocht door het mooie (en drukke) Brussel. Ik heb er zeer van genoten om door de stad te rijden op een kleine steek, een beetje foto's te maken en tussen de mensen te laveren. In Molenbeek kochten we in een lokale kruidenier wat droogvoer, en nog een brood, en toen trokken we verder: richting Meerdaalwoud! Eerst passeerden we nog het zoniën. Prachtig! Ik kon me niet inhouden om (bijna) alle paddestoelen te beginnen fotograferen en aan Het Algoritme van ObsIdentify te vragen hoe ze heten. Gelukkig vond Tim het wel sympathiek en stelde ik zijn geduld niet te veel op de proef. Ondertussen discussieerden we een beetje over de betrouwbaarheid van de media, het gewoonlijke, je weet wel.
Gedurende de namiddag voelden we de bui al hangen, en ja hoor, tegen dat we aan de rand van het mooie Meerdaalwoud aankwamen, begon het zachtjes te druppen. In de gietende regen aten we rechtstaand ons stoofpotje op. Wat een vibe! Gelukkig was het niet koud, en konden we genieten van onze ultieme herfstsfeer. In de schemering, in de regen, klaar om in de tent te kruipen. Heerlijk!
PS: Het lukt dus niet om de foto's op te laden, jammer! Ze zijn wel mooi hoor, ik verzeker het je!
PPS: Ik vind het nu een beetje cringe om zo al onze gebeurtenissen te beschrijven, interesseert iemand dat eigenlijk? Interesseert het mij wel? Ik denk/voel erover na!
-
 @ 0e501ec7:de5ef3a4
2024-10-08 19:26:36
@ 0e501ec7:de5ef3a4
2024-10-08 19:26:36Wat een vermoeiende dag! Eerst alle spanning van vertrekken, snel nog van telefoon wisselen, afscheid, veel afscheid, traantjes, nog mijn breispullen gaan halen die ik bij roos was vergeten, en dan pas eindelijk vertrekken! Fietsen fietsen fietsen! Op dit moment ben ik zeer moe, dat merk je misschien aan deze vluchtige schrijfstijl, mijn ogen vallen toe, maar dat was ik eigenlijk vanochtend al: gisterenavond waren er twee megaleuke feestjes! Eerst het verjaardagsfeestje van roos, zo vol met warme lieve mensen, en dan nog ook het verjaardagsfeestje van mijn mama! ook vol lieve mensen.
Toen fietsen fietsen fietsen!
Ik reed eerst alleen, langs de mooie lange schelde, tussen de wilgen, het riet, de velden... Ik was verwonderd iver de schoonheid van de paarden die langs het jaagpad stonden, ik was verwonderd over een kind dat vrolijk door een veld liep, wat een beeld zobder weerga, een soort van plattelandse veiligheid/vrijheid die we biet vaak meer tegenkomen. Toen werd ik opgehouden door allerlei werken, ik probeerde een omleiding te volgen (waarbij ik een sappige grote kastanjeoogst scoorde bij een prachtig paar bomen!) maar kwam weer midden in de jaagpadwerken uit en had toen een groot avontuur voor de boeg, hoeveel keer ik met die zwaarbeladen fiets de dijk op en af moest aj aj. Daarbij had ik ook nog een stevige tegenwind, waardoor ik pas na 14u aankwam bij mijn lieve oma en opa. Tim was daar al, en had al goed gesocialiseerd! We babbelden met ons vieren over vanalles, er kwamen allerlei oude verhalen bovendrijven bij oma en opa, ze waren precies zeer verheugd om tegen een nog niet bekende, jonge avonturier zoals Tim al hun verhalen uit de doeken te doen :)). Na ons buikje meer dan rond gegeten te hebben, trokken we weer op pad, deze keer met de knooppuntenroute die Tim had uitgestippeld. Bezienswaardigheden: de eiffeltoren van Asse, een paard om een heuvelkam, een steile bergaf die plots een grindweg werd, een boze tegenligger, veel politieke (rechtse) posters. En heuvels, en veel zondagsmensen. Tegen 6 uur kwamen we dan toe in Zellik, bij Yannick, een vriend van Tim. Die ontving ons hartelijk, met een mooie radiostem (hij studeert dat!). Na het eten speelde we nog een spelletje Boonanza, zeer leuk.
Ik merk wel dat ik echt heel veel zin heb om de blog te onderhouden, het is echt zo een projectje waarmee ik iets kan brengen naar de mensen waarvan ik hou, verhalen, ideeën, foto's. Ik hoop wel dat het een beetje overkomt, ik ben nogal onzeker over het rare vreemde platformpje dat niemand kent (maar ik ben gewoon onzeker en kwetsbaar tsjah) (wat het is kan je lezen in 'een eerste poging'). Als je het leest, laat me weten wat je ervan vindt! Als mensen het leuk vinden gaat mijn motivatie om er meer op te plaatsen misschien wel overleven :).
Tijdens het fietsen moest ik regelmatig denken aan The Cyborg Manifesto van Donna Haraway. Zelf heb ik dat boekje eigenlijk nog niet gelezen, maar het idee van de cyborg, het uitgebreide lichaam/zelf met technologie zet me wel aan het denken. Ik op de fiets met al mijn warme (regen)kleren in de fietszak ben precies een soort reuze huisjesslak aan topsnelheid. We razen door het landschap, ervaren het, de wind, de zon en regen, interageren met de menselijke en botanische bewoners ervan... En aan het einde van de dag zetten we onze tent op, ons verplaatsbare huisje. Wat als nu eens stopten met de wereld, ecosystemen en natuur, ons lichaam te beschouwen als machines, als radartjes, waarin problemen kunnen opgelost worden met quick files zoals een pilletje of de inrichting van reservaten (zoals we gewoon zijn bij de machines: een beetje smeren, een tandwiel vervangen, de nieuwe update installeren). Wat als we nu eens de machines als deel van ons lichaam zagen? Een lichaam om gehecht aan te zijn, om zorg voor te dragen? Om mee in wederkerige interactie met de wezens rond ons te gaan?
Bon, ik moet er nog eens over nadenken, en dat boek lezen, misschien heb ik daar ooit wel eens tijd voor. Na een lange fietsdag ben ik er allisinds te moe voor!
-
 @ 765da722:17c600e6
2024-10-08 18:58:18
@ 765da722:17c600e6
2024-10-08 18:58:18O irmão David Hill falou o seguinte hoje no seu podcast.
As coisas terrenas mudam, mas as coisas de Deus não, Salmo 102.26-27. A Palavra de Deus, a verdade, dura para sempre, Salmo 105.\ \ Alguns hoje sustentam a visão, seja declarada ou praticada, de que a Palavra de Deus deve mudar com o tempo. Essa visão não é apoiada pela autoridade de Deus.\ \ A sabedoria, verdadeira e atemporal, vem de Deus, 2 Timóteo 3.15. A Palavra de Deus é a coisa certa e Jesus disse que você pode conhecê-la, João 8.32. Seu valor real é, portanto, proveitoso, contendo doutrina, João 7.17. Instrução de Deus — não qualquer doutrina, boa doutrina, 1 Timóteo 4.6.\ \ A Palavra de Deus completa o homem. Ela satisfaz o desejo de conhecer a verdade, Salmo 119.99. O rei Davi superou todos os seus professores ao estudar, meditar, considerar e praticar a Palavra de Deus. Por meio dessa prática, podemos e receberemos orientação transformadora, 2 Timóteo 3.16. Esse é o evangelho.
\ Talvez eu ainda publique este transcrito no site cristaos.org ...
-
 @ 319ad3e7:cc01d50a
2024-10-08 18:05:44
@ 319ad3e7:cc01d50a
2024-10-08 18:05:44LETTER FROM THE FOUNDER
Welcome to the inaugural edition of the Zap.Cooking newsletter!
What began as a simple idea and a collaborative effort has grown into a vibrant community. Food, in its unique way, transcends culture and connects us all. It’s at the dinner table where we break bread and share our lives. Here, we’ve created a space where people come together to exchange ideas and celebrate a shared passion for cooking and culinary excellence.
This is the Nostr way—a community built on shared ideas and a constructive culture. We are excited to embark on this new journey of sharing a newsletter with friends of Nostr and Zap.Cooking. We hope you enjoy this fresh approach and look forward to many shared recipes and conversations.
Bon appétit!
Seth, Founder of Zap.Cooking
\ __________________
Food Clubs For Life Outside The System
Jack Spirko is the founder and host of The Survival Podcast. In episode 3552, titled "Food Clubs for Life Outside The System," Jack engages in a fascinating two-hour conversation with Joshua Longbrook, who established a food club and hub in Chattanooga, TN, as a means of building a parallel society that respects food freedom and self-sovereignty. Agora Food Club is a private association of members who value natural, organic food and regenerative farming practices, creating and sustaining a locally based alternative food system. In this episode, they discuss the blueprint and what it takes to start a food club in your neighborhood.

Links to YT video and Food Club:
https://www.youtube.com/watch?v=5uPcAfG-9AU

The Six-Ingredient Grandma Betty's Chicken Dijon Family Recipe
https://image.nostr.build/55d3f300fdc4563265f49f729476724f98ff0a062ce7f8d769bf136f0de05cf5.jpg
“Growing up there are a few staple foods that stick with you. For me, it was my Grandma Betty's Chicken Dijon. It was my birthday request every year and every time we cook it up it touches my heart. Grandma Betty passed away 7 years ago. This dish is dedicated to her, directly from her recipe book.” - Quiet Warrior
Grandma Betty's Chicken Dijon on zap.cooking
Glowing Rolls: Raw Vegan Sushi for a Healthy Boost!
https://image.nostr.build/b11da1b878fe48ee74cb1c6c1cc66692ce12827f26c256ecd7a184f99d9c7649.png
“All you need are your favorite vegetables, nori sheets, a bamboo mat, a cutting board, and a knife. For the dip, you can simply use soy sauce, or try this recipe for a delicious creamy dip. I make my own cream cheese with soaked cashews, nutritional yeast, salt, lime juice, and vinegar. You can also find vegan cream cheese or cashew cheese at a health food store. Feel free to add other veggies like bell pepper, chili, cucumber, fresh onion or anything you like! In the image I also used red bell pepper and shiitake.” - Essencial
Glowing Rolls: Raw Vegan Sushi for a Healthy Boost! on zap.cooking
Slow Cookin’ Tender Sweet-and-Sour Brisket
https://image.nostr.build/97a8a78e39fbe4d19f913ea3c7cac9b94ee20d155596a83e241f0fa71a51517a.jpg
“In this case, sweet-and-sour doesn’t mean Americanized Chinese food but rather the sauce that dominated the Shabbos and Pesach dinner table among American Jewish immigrants in the early 20th century.” - Lizsweig
Sweet-and-Sour Brisket on zap.cooking
2024 Nostriga Photo Album
\ Community Photos by AZA_to_₿_myself, Jeroen, elsat, Derek Ross, realjode, and SimplySarah
To share your Nostr community photos, please DM @ZapCooking on Nostr
https://image.nostr.build/388b3bb338672728337ef1c04c90f65655cc29c716f168d35dd4c7343d5802b0.jpg
https://image.nostr.build/011edabbe3f427c60506fddab024bfeb46c72cf5e0a808b562d7c3ace9f239a0.jpg
https://image.nostr.build/5fcb47e3a21bbbedafe245f311b6d43f1f610ad96eec26aa85cdcbd0958fdabf.jpg
https://image.nostr.build/c2eac240326a7e4ab176776c5d140d0017ccdfef89ef733eaf85efda8e0d39f5.jpg
https://image.nostr.build/078682ee987734911886592f377a356245b5a5ea2a15c44ba80e3101ae523b52.jpg
https://image.nostr.build/c28418d851f3ad7f61435813d8aee82d87af3de4472b4d718a1d2573ae7d38c8.jpg
https://image.nostr.build/d3a55e11d7927c7cae106491d00a0cfda8323b976aa29123a0fd4e4e3fe78505.jpg
https://image.nostr.build/bdd055b0b37a9ebcdc91411796ae6cf785338679e7f44aebf1dc721cc09b076c.jpg
https://image.nostr.build/e7bf6c58de70510e96ec3b10630f4a4cfb770026532e2d307b4f95346a4d9ea4.jpg
https://image.nostr.build/b8eb934f8f15aae87ed0db66e898062ec723a8f16d9e93229cd2783d2b158e9d.jpg
https://image.nostr.build/f999d2389c363be56543444f301e443ddc126f1caebb9462b74b800d54ed2c28.jpg
https://image.nostr.build/0ca2d868703298d222f9cabc3e10a73dcd2d1f82f1b22f8526d9360e9bec8cc7.jpg
https://image.nostr.build/94460309bf933bcd89887f16ea6c384fa5bc5e3eb74500de099a3a1405da8edc.jpg
UPCOMING NOSTR HAPPENINGS
To submit your Nostr event, please DM @ZapCooking on Nostr
Nostr Valley @ Happy Valley Brewing Company - October 12, 2024 - 12pm to 4pm (est)
https://image.nostr.build/6c830618389046460ad41e3704864adb338b2a980cc765de51106a2f65adba67.jpg
Nostrville 2.0 No Panels, All Party! @ Bitcoin Park - November 6, 2024 - 4:30pm to 7:30pm (cst)
Nostrville 2.0 - No panels, all party!, Wed, Nov 6, 2024, 4:30 PM | Meetup
ZAP.COOKING PRESENTS: LACE
https://image.nostr.build/fb37dfaa7efe8add086d75af2dfd193181de728e108bd2c8e095a60f7e64bc4f.jpg
\ SimplySarah: Let’s start by learning a little background on Lace. What is your food story?
\ Lace: Food for me runs in my veins. My family is from Jamaica and my grandmother began cooking as a girl. She brought her recipes with her to the UK in the 1950s and cooks the most delicious dishes. My mother has been a professional chef for over 40 years. Family meals at Christmas were always a big deal. However, it wasn't until 18, I began cooking at university where I vowed my children would know how to cook a healthy meal and not end up like the people around me living on take out and micro meals. As a student, I just recreated things I ate at home and when I was unsure, I'd call my mum or my grandmother for help. When I had kids, I put them in the kitchen at age 2 and my eldest, now 15, is an incredible chef. We are also well traveled and always enjoying local cuisine which also inspires our cooking.
SimplySarah: That is a lovely background. It seems it was a natural progression to want to get into writing cookbooks. I understand you are working on your second currently, but let's backtrack and talk about how the first one came to life.
Lace: It would seem so. I always wanted to write a book but a cookbook wasn't what I thought I would write first 😅 And yes, the second is coming next year, a co-authored book. The first, came about because of Facebook, actually. Admittedly, I am one of those people who posts food pictures. And my Facebook followers began asking me for my recipes all the time. And I would write them out... and then decided it made more sense to write them once inside a book and sell it. Hence Lace's Bad Ass Yard Food was born.
https://image.nostr.build/563b2d4299d824ef4fbb8b85749ba1bb24b0fb4025bf6b10fa2ddaed7217240a.jpg
SimplySarah: That's an awesome title! What IS Bad Ass Yard Food?
Lace: Hahaha, thank you! Yard food is what we (as Jamaicans in my family) call our cuisine. Yard food. Yard means home. So it's basically great homemade food. Typically, this is things like Curry Chicken, Fry Fish, Jerk Chicken, Rice and Peas, Hard Food (yam, dumplings and green bananas) and many other things.
SimplySarah: All those dishes sound phenomenal. If you had a go-to dish from the first cookbook what would you select? Maybe something that is always served on a weekly or regular basis at your home?
Lace: Oh they are! My favorite is curry goat. Curry Chicken has got to be the go to, I still cook it weekly now! And no matter where I've lived in the world, I can always prepare it.
https://image.nostr.build/da216e149bee8676a806f010ddde5a29eb4ffa0adeaf5f68265e0e2cc3f11649.jpg
SimplySarah: Funny, I believe you just posted on Nostr that you were in the process of making curry chicken if I recall correctly. Is the next cookbook following the same roots? Or are you and your partner exploring different cuisines?
Lace: That's right! I did just post that curry on Nostr. The next book is going to feature 8 of my favorite recipes. Some will be Jamaican but I also happen to love Asian inspired dishes and have some European favorites too which will be featured. This will be the first time I'm sharing non Caribbean dishes. As for me and my boyfriend, he is Colombian and an ex-military Chef. He has been sharing his food with us and has been enjoying eating food from different regions for the first time as a result of meeting me. It's great fun to bond through food.
Lace’s Curry Chicken with Purple Cabbage, Plantains, and White Rice:\ https://image.nostr.build/fb37dfaa7efe8add086d75af2dfd193181de728e108bd2c8e095a60f7e64bc4f.jpg
SimplySarah: Is he the co-author you are speaking about?
\ Lace: Nope. The other Authors of the book are all entrepreneurs who love food. The first edition will be available in november, it's called Made with Love. I will be featured in the second coming 2025.
SimplySarah: Oh, nice! How did you get tapped into this project?
Lace: Again, my facebook network. I was chatting with a lady who is a self made millionaire about money. She checked out my fb profile and said.. ohh I love your cooking videos, what a fun way to market (my tech business) and then invited me to check out the cookbook project and be part of it. And just like that I was in.
SimplySarah: Facebook definitely brings a lot of people together based on their favorite topics. Now that you are exploring Nostr and have such an incredible background with culinary arts, what do you hope to achieve here on this social protocol?
Lace: Yes, socials are great for that! Honestly, I just want to connect with folks who love great food and are into self development, natural living, love travel and sovereignty. On my second day on Nostr, I met you, a fellow foodie, so it's certainly working out well so far. :) And without all the ads and other crap fb force on it's users
SimplySarah: Personally, I am super thrilled you have joined Nostr. We need more foodies, and I love nerding out about anything food related, especially the food travel stories. I would absolutely love to follow your food journey, and I think all the Nostr foodies should too. Where can everyone find you, follow you, and maybe buy a cookbook?
Lace: Yay! Thank you. I love talking about food, cooking, sharing food, buying ingredients and trying food. You can find me on Facebook - the loved and hated, Nostr, and my personal website. There's no fancy sales page for the cookbook yet! 11 of my Jamaican recipes in one cute ebook :) I'm coming over to Zap Cooking too.
SimplySarah: One day you will be Nostr Only and forget all about Facebook. Haha! We look forward to having you on Zap.Cooking. We have a lot of ideas in the works and would love for you to be involved! I have one final question. First, I want to thank you for taking your time to spend your Saturday morning with me. This was fun. You mentioned you put your children in the kitchen at an early age. I'm a big fan of teaching kids life skills when they are young. Do you have any tips for parents to help them in the kitchen with their children?
Lace: I'm sure that will happen. My fb network has been instrumental in my success and surviving the rough time in my travel. Do tell me all about your ideas for Zap, I'd love to see how I can be involved!
Yes, tips for parents, When kids are eating solids, feed them home cooked meals, no jars, no processed stuff, healthy, varied, adventurous meals you eat. If you're eating octopus, let ‘em try. If you're eating veg, let them try. If you're eating chicken liver pate, let them try. Encourage a varied diet and pallet. Then at 2, get them in the kitchen. Let them peel garlic cloves, add herbs to meat, make meatballs, mix and taste things. Invite them to cook everyday. And have fun with it!
It's been my pleasure to spend time with you this Saturday morning Sarah. Thank YOU.
You can find the talented Lace at:
https://www.facebook.com/iamlaceflowers
https://primal.net/p/npub1ruhmx2wy663u9k2sams6qrlvgq86t3p4q3ygwgp5wqzcrgd6fh7sr20ys2
https://www.iamlaceflowers.com/workwithme
Follow Zap.Cooking Content Coordinator SimplySarah at:
https://image.nostr.build/c208bb8d562421beb00cc26fcf38417a0d52660659f4ac9d40365f3761a486b8.png
-
 @ bf95e1a4:ebdcc848
2024-10-08 16:34:23
@ bf95e1a4:ebdcc848
2024-10-08 16:34:23This is the AI-generated full transcript of Bitcoin Infinity Show #129 with Max Hillebrand!
Check out the https://bitcoininfinitystore.com/ for our books, merch, and more!
Luke: Max, welcome for the first time to the Bitcoin Infinity Show.
The Lodging of Wayfaring Men
Knut: Yeah, so one of the first things, you have made the best book recommendations to me that I've ever gotten from anyone. And one was The Ethics of Liberty by Murray Rothbard, and the other one was Economic Science and the Austrian Method by Hans Hermann Hoppe. And now you recommended another book, which I haven't read yet, called The Lodging of Wayfaring Men.
what is that book about and why do you recommend it so much?
Max: It's a beautiful book. it's incredible. And it's written for us and for Bitcoiners, but it's over 20 years old. it was written in like 1997 to 2002 and that time period. And it's loosely based on real events, which is fascinating. the book is crazy. it goes about a group of cypherpunks who are, Building an anonymous marketplace, and the first attempts of an anonymous digital currency.
And again, this shit really happened. the story is quite wild. With, the freedom tech being built for very good reasons. people who understood the philosophical impact. and the deep reasons for why freedom is important. So they were very motivated, and, dedicated to make the world a better place in their lifetime.
And so they got their shit together and got organized and built something incredible, right? And it took them a couple attempts. and eventually they rolled it out and enabled people to trade right, to do their business, online in cyberspace, and encrypt it. And so that made a lot of people very happy because, you know, you get to live life free and undisturbed, so it got adopted by many users.
So much so that eventually the government started to notice that somehow they're making less tax revenue than before. And something's a bit fishy, you know. And then they started to investigate and You know, the NSA and FBI put a decent amount of people on the topic and tried to de anonymize the users of these services and infiltrate them.
And yeah, so the story is about this whole clash between the first and second realm, you know, people who built FreedomTag. And people who enslave others and how those two worlds kind of clash. it's a book that's very inspiring.
Knut: What was the website called?
Max: So, the author's name is Paul Rosenberg.
originally this book was published anonymously, years later, when it was safe to, associate their actual name with this, he did. he was, a teacher, an electrical engineer's teacher. He wrote 30 books on that subject, and is a very eloquent and practiced writer, but also a hardcore cypherpunk and freedom lover, and very well read,
So he has the freemansperspective. com. This is a newsletter. You can go back. It's going for, I don't know, 10, 20 years or something. And every week there's one or two short pieces of articles that he writes. And this book is actually also includes some writings that he did in the past and published. so it's somewhat a collection of his thought.
The Lodging of Wayfaring Men is a fiction book, right? It's basically a fictionalized story with, character arcs and such. the author is very technical, and he understands cryptography and how to apply it. He understands distributed networks and laying fiber optic cables and stuff like this.
So there's a lot of real computer science in this fictional world. And that makes it quite applicable to today where we're surrounded with cryptography much more than at the time when this book was written.
Knut: So, all right.
Taxes
Knut: bit of a jump here, but why is, avoiding paying taxes the most altruistic thing you can do in life?
Max: this is actually one thing that gets covered in the book, right, where,
Knut: that was the case.
Max: because this is also why this book is so interesting to recommend to newcomers, to this philosophy, because at the beginning, not everyone is convinced that this is a good idea. Even the creators of this technology don't know the end result and how other people will use this tech.
There's a lot of ambiguity there. And so this book follows characters who reason through these very difficult questions. For example, I'm going to spoil this book a bit, but everyone should read it anyway. So, there's one character who was a lawyer, right? He works together with an ex FBI agent, who both of them share this common, seeking of justice, like real justice, to stop bad guys from doing bad things, to good people.
the ex FBI guy is somewhat disillusioned. With the institution of the FBI to actually provide and establish justice. so now he is somewhat like walking this line in between the institution and, the actual free realm, vigilant justice basically.
and here then when thinking of. this case. is there a wrong being done by the FBI trying to stop this project? Or is this project actually good? Do they have justice in doing what they do? then, he, reasoned of, is the avoidance of tax, of, of taxation evil.
And, and, of course then walks through the reasonable steps of thinking. No, if, two people transact voluntarily. both people are better off after the trade than before, right? Both people are happy, both say thank you and shake hands. that's trade. That's the market, right? and then you have coercion,
Where one guy says, give me that, and the other says, no, actually, I don't want to give you that, but the guy hits him and takes it anyway. And so that means afterwards that the guy who stole it is obviously better off. He's happy, right? He got the thing, but the guy who was the victim was being stolen from is worse off.
And so humans have the capacity to do mutually beneficial things, right? To literally create value, make both of us better off than we were before. And we also have the potential to destroy value and take from others. and one is beneficial and fosters the growth of civilization and the other destroys it.
Knut: And so, you know, avoiding being stolen from is a good thing. Reminds me of one thing we go into in the new book, about the difference between lawful and illegal. I don't remember the name of the guy now, but some Dutch libertarian thinker, who emphasized on the terms, made the point that something being lawful is like lawful in an ethical sense, like the basis in Don't Steal, whereas legal is the top down government imposed legal framework, and how the two don't always align, or rather, they almost never align.
Natural vs Man Made Law
Max: Yeah, this is the difference between natural law and man made law. A natural law is one that is universal across time and space. It's always present, and it's immutable. It cannot be changed, at least not by us. And, you know, physics, for example, is a natural law. And arguably there is a natural law to ethics as well.
Specifically, as morality increases, freedom increases. And as morality decreases, freedom decreases. That's the law of gravity in the ethical realm. and, that man didn't make it, right? We just realize it because it is what it is. And then we have man made law on the other hand. this is depends on a certain territory, right?
The law in the U. S. is different from the law in Russia. And it also depends on time. I think the American law in the 1700s is very different from what it is today. and so there are these imaginary lines where these rules apply and there's Other places or times where they do not apply. So they're arbitrary, right?
And so they can be designed, to the benefit of some and at the expense of others. And that is ultimately what, politics is about.
Knut: Yeah, I think this is one of the key points that that quote unquote normies have such a hard time wrapping their head around. Natural law and like what, what makes don't steal a natural law? Like what, what is the very foundation of, libertarianism or anarcho capitalism or absolute property rights or whatever you may call it, consensualism?
And to my understanding, it has to do with homesteading. If you're the first person that acquired something, then no other person has a right to take that away from you. And you can logically deduct your way to that being true. Like, what's your view on that? And what's your understanding of that? And how would you explain that to a layman?
Max: Well, the reality is such that we have limited scarce resources. If we have one piece of steak on the table and three guys who are hungry, like some are gonna go home on an empty stomach, right? We literally don't have enough food to feed us all, right? And one piece of something can only be used by one person at one time, right?
We cannot duplicate one piece of steak into many and satisfy everyone. So this is a natural form part of reality, right? That's just how things are, you know? So there's a potential of conflict over who gets to allocate these scarce resources. And there's a couple solutions to it, right, that have been proposed.
Like one would be like, nobody owns it, right? Nobody gets to eat it because it's natural and it's not part of your body, so don't touch it, right? But then we die, you know, all
Knut: that's the problem with that.
Max: That's kind of a problem.
Knut: Yeah.
Max: so
Knut: Yeah.
Resource Allocation
Max: So let's rule that option out. another solution is, of course, we all own it. Right?
And we all, get to use it. But, that doesn't really work either, right? Because, sure, we all own it, but who actually gets to eat it? Because there's three different mouths and the food only goes into one of them. we can't all actually own something if we cannot all use it.
It is limited and only a few can use it. So, everyone owns it isn't the solution to the problem. Because everyone cannot own it, there's not enough for everyone. So again, that's an issue. Ultimately, we all starve. And another option would be, we vote.
We somehow pick who gets to allocate these resources. But then, I mean, we're 8 billion people. How are we all going to vote on who gets to stake? Right? Like That's, that's going to be impractical. Like, how are we even going to communicate, all 8 billion of us, to get together in a vote? So again, until we have the result of the vote, nobody eats the steak, so we all starve again.
It's not really a good solution either. And then we have one option that, like, a small subset of the people gets to make the choice of, you know, how to allocate these resources. And we can just pick them, vote for them, for example. But here again, now other people are allocating the resources for others, right?
Like, and some bureaucrat, a hundred kilometers away, is not gonna know, like, who of us is vegetarian and doesn't want the meat. Right? and that just means that someone who's far off doesn't have the knowledge to actually allocate the resources in a proper manner. And that leads to misallocations, right?
We starve, again. Because the guy who doesn't want the meat gets it and then it rots. And the guys who would actually like it never get access to it and they starve. So that's the fundamental problem of socialism, basically, of some priest class allocating the resources for others. So again, the solution doesn't work either.
So we're not left with much. But one thing that seems to work is private property rights. Again, as you said, the person who creates something, the butcher, or the farmer who raised the cow, can now decide what to do with it. Does he butcher it himself? Does he sell it to a butcher? So the person who created something gets to own it, and gets to decide how to allocate this, and then he has the right to either consume it himself, or to abdicate the consumption of this good.
So to say, I won't use it, I will trade it, I will give it to you, right? And he can make it a gift. Just say here, half the entire cow, like, I like you, I like your family, you, like, I'm happy that you're happy, right? Great, that's possible, right? Or, of course, he would want something from you in return, like, give me a bar of gold, or, a bushel of wheat, or something else.
we now have a way that we can allocate resources in a clear, simple rule set, the person who created it. can decide what to do and have a contractual agreement to transfer this ownership to someone else. the people who actually have the problem now have the power to allocate the resources to solve those problems and not some guy far away, but just you and me who created stuff.
Ownership of Information
Knut: And as you said, this only applies to scarce resources. So what, would be an example of a resource where you could eat the steak, but I could have it too. And, the thing that comes to mind, is information, of course. So, can you own information?
Max: No, like, because that, that doesn't really make sense, right? To own means to allocate, how to allocate these, to decide how to allocate these resources. All right. And then, that's a solution to a problem of a lack of resource allocation, right? or for a lack of resources that need to be allocated rather.
But with information, there is no lack. Like if I have a PDF, I can copy it to you and I can send it to you, and I can send it to a hundred other people, and I still have the exact same high fidelity version. Of the information that I shared with others, and of course it's the same with words, right? The words that I speak, they're not lost on me, right?
I still retain them and the information that they represent. and that means we don't need to be, stingy with information. We can give it to everyone. and it doesn't degrade the quality quite on the contrary, right? without information there is no production.
imagine yourself on an island, and you have all the raw materials, all the machinery, like everything there, but you don't know anything about physics, or material science, or just production stages of how to build things. If you don't know any of that, the raw material is worth nothing to you.
Nothing. Because you don't know how to allocate, how to shape this raw material into other things so that it actually solves your problems in the end. we need information in order to produce things. That's the theory behind it. The blueprints, so to say. the cool thing is, we don't have to be stingy with the blueprints.
We can give every human on this planet Equal access to all of the information that we as humans have accumulated, and now all of a sudden you will never be stranded on an island not knowing how to do something, because you can just look it up. In the grand database of accumulated human knowledge, of course, technology has made that much more possible and low cost.
Back in the day, in order to share an information, you needed to speak verbally to it, right? So you're limited to time and space, or you need to scratch it on some stone or clay or write it on a piece of paper, And then still, you have the scarcity of the paper, right? There's only one book.
And there's a hundred people who want to read it. So again, information is limited. Not because the information itself is limited, but because the medium of the information is scarce. And that was a big tragedy that we were never able to communicate at a large scale, and remember these conversations and easily access them.
Until the cypherpunks who came up with computers, right? And realized that we can build this realm of information That is so cheap to transfer and store information, that we can just basically do it for free, for anybody, for 8 billion people. And all they need is a rather cheap form of silicon, and like, nicely arranged.
but of course people try to hold on to the protection schemes that extract money from others, and capital from others, and You know, nation states have enforced intellectual property rights and patents and such, and that just harms people. It doesn't bring forward the best out of humanity. And that's a big shame.
Knut: Now, very well put. this has been Praxeology 101 with Max Hillebrand.
Bitcoin and Praxeology
Knut: where I want to follow on, follow up here is, how does this apply to Bitcoin? Because Bitcoin is only information, so how can anyone theoretically ever own a Satoshi? Do you really own it, or what is it?
Max: What is actually a Satoshi? Look into the Bitcoin code base. There is no such thing as Satoshi, right? The transaction has a field that is an integer. But it's just an integer. It doesn't even have a unit associated to it, right? So, it's just a number. Satoshis are just numbers in a database.
And you don't own the number 270, 000 just because you have 270, 000 bitcoin. The actual number of satoshis, no, you don't control them. You don't own them. But information has another interesting thing that cypherpunks realized, right? That, once, like, when you have a secret, then you can choose to share it with others.
And then once you've shared it with one person, however, you cannot control what that person does with the information. He can keep it secret for himself, or he can tell it to the entire world. And so, there is such a thing as giving access rights to information. And this is an important part in Bitcoin, of course, right?
Our secret keys should be secret, privately kept just for us, because if you do share your secret key publicly, then all of a sudden anyone can, Signed messages, with this private key and therefore spent Bitcoin in the transaction chain of Bitcoin. and well, that's a critical part of it.
So Bitcoin basically relies on keeping information, hidden from others, in order to ensure that we, solve, like, basically Bitcoin. It's just a piece of software, right? So it is non scarce information, but it wants to be money. And money needs to be scarce, right? Because if I can spend a bar of gold first to you, and then the same bar of gold later to you, we have infinite inflation, right?
The money system just dies. so scarcity is required. It's a required feature for money and digital money therefore requires digital scarcity. And so what Bitcoin does is it establishes a set of computer code that defines the access, right? Two certain chunks of money, so to say, right? And the chunks of money are Bitcoin UTXOs, unspent transaction outputs, and the spending condition, so to say, or like the rule how to allocate this money, who gets to decide it.
Where this money goes next is defined by a script and a small computer program that evaluates either to true or to false, depending what input you provide. And so the script is the lock, and usually it's a single public key. And then the way to prove that You're actually authorized to spend this coin is by creating a valid witness.
You know, the input to the script, to the program that returns it to true rather than to false. And usually, again, that's a signature of a single private key over the transaction structure that you're actually spending the money. Bitcoin's genius realization is that. We just all have to check every transaction of everyone else.
And when we do that, we can be sure that, nobody's being stolen from, That nobody is, losing access to his money, that someone is spending the money with a wrong signature. he doesn't have the private key. He cannot produce a valid signature. So we have to make sure that such a transaction does never make it into the blockchain, right?
that's the first important aspect. And the second is we want to ensure that there's no inflation. that's Because if we can just create as many tokens as we want, then the value of the token goes to the marginal cost of production. If we can produce a token with the click of a button, then the marginal cost of that token, or the value of that token, will be zero, right?
So we need to make it, Difficult, or in fact, in Bitcoin, impossible to create additional units, you know, there's 21 million and that's it, right? That's the set of rules. And therefore, when we check each transactions, we also ensure that there is no transaction that has one Bitcoin on the input side and 10 Bitcoin on the output side, therefore increasing the total supply of Bitcoin.
And so Bitcoin is a massive verification machine to ensure that this computer system is this way of speaking to each other, actually balances the books of the system. of how many units of money are there, and who has the right to allocate these, and so it's basically a system that creates a natural resource, and then also manages the allocation of this natural resource.
Knut: so Bitcoin is almost a parallel universe where, in fact, you do own the Bitcoin, basically, but the ownership is not defined by you as a person. It's defined by the knowledge of a secret. so you prove that you have access to it by having access to the private key, which unlocks it.
Ownership of Bitcoin
Knut: On earth that can prove that you own a Bitcoin except you, the holder of the private key.
Max: If the holder of the private key reveals information to others that indicates such, one very common way that this would be is you have a mobile wallet, that does not run a Bitcoin full node, That connects to someone else's full node to check if you have Bitcoin,
You don't use Tor, so there's an IP address linked from you to the server, and so the server operator knows that this IP address just asked how much money is on this address, and so we have, a very strong indication, that this IP address owner owns
Knut: It can be a very strong indication, but in my mind it can never be proof. Because you need to sign with the actual private key to prove. Otherwise it's boating accident time.
Max: guy with the gun doesn't need proof, right, he just needs a good enough guess. For him, he needs, like, there is a praxeology to violence. thieves are actors. They live in a state of uneasiness, they have problems, and they try to find a solution to that problem. They don't have ethics, they don't have morals, and so their solution to the problem harms other people.
But nevertheless, they are still actors. And so they think that they will be better off after the action of theft than before. That's a value judgment. And it's an entrepreneurial one. So they might be correct, they might not. They break into a house, hoping that there is a bar of gold hidden under the couch, right?
Turns out there's not, right? So, if they spend a lot of money breaking into the house, and there's no loot, they're not profitable thieves. And this means that they destroyed their capital, right? They spent 10 Bitcoin on getting the equipment, and they got 0 Bitcoin back. So, that means they're 10 Bitcoin poorer, and eventually they will run out of money and starve.
So, thieves need to be profitable in order to do their thieving, and that's the genius that cypherpunks realized. If we exponentially increase the cost of attack, and exponentially decrease the cost of defense, then we make thievery unprofitable. And that's the genius of private public key cryptography and encryption, right?
It's trivial to generate a private key and then generate a public key or a signature, right? But to brute force a private key or to forge a signature without it, like, requires more energy that would collapse into a black hole, you know? So that's kind of a problem.
And for thieves, right? It's really good for the people who want to defend themselves. Because they can very cheaply do it, and it just doesn't make sense to attempt to break the encryption. But nevertheless, computer systems are very complex, and there's a lot of metadata associated with, computing and communicating between computers.
And so, there are, microphones and radio frequency scanners that you can point on computers and see the computation happening in the machine because there's a lot of radiation outside of the computer that can be correlated to which bits are being flipped you can have all types of side channel attacks to extract secrets from a computer while it's running the problem is that the holistic technology stack we have is quite susceptible to revealing information that should have been kept secret.
And again, that is a critical part, of course, to communication encryption, but even more so for Bitcoin. If we lose the assurance that only we know the private key, the money system is broken. And that's why Bitcoiners were so paranoid and started this whole thing of hardware wallets and secure elements to Really ensure that we don't leak private key material, but it's an extremely difficult task, because, well, this reality is very observable, and the cards are, to some extent, quite in favor of surveillance, unfortunately.
the guy with the gun in this case could be the government, Yeah, exactly, it can just be like a poor guy who needs to provide for his children, you know, and, he sees a way for feeding his family for the next two years, and that's a good trade off for him.
Knut: Yeah, momentarily.
Max: right?
Bitcoin and World Peace
Knut: So, if we manage to do this, on a grand scale, and if people in general manage To exponentially increase the cost of the attack while simultaneously decreasing the cost of defense. Does that lead to world peace at one point? Is that the end goal?
Max: Yeah, I think so. Oh, I mean, that makes sense. If every economically rational thief will realize that he is worse off if he does this stealing, right? Like, actually, because he needs to spend much more money in an attempted theft, and most likely he's not going to succeed. And, I mean, this exponential difference has to be huge, though, right?
Because, like, we had castles, you know? Like, castles are quite, like, quite extreme asymmetric protection. Like, if you're behind castle walls, with a well staffed militia that actually defends the walls, It's quite difficult to get to you if you just have, you know, like, humans and swords and ladders. that's, like, sieges are, in the favor of the defender.
But still, they happened a lot, right? And people were able to overcome these defenses. Because, I guess they weren't never holistically secure, you know? There was always some backdoor that enabled the attacker to go through, to get through, right? and that might just be brute force, right? You just bring a huge army and You're fine with tens of thousands of your own guys getting killed, but eventually, you know, after you throw a couple hundred thousand people at the problem, someone will succeed to break through.
Quite a brutal tactic, obviously, but it worked.
Knut: you get in.
Max: But then cryptographers came around and were like, well, but there's math.
Luke: Yeah, we can use RAM in another way. 1 plus 1 is 2. What? Are you sure?
Knut: that might be offensive.
Luke: That's a different kind of worms.
Knut: Yeah. . Yeah. So, the,
Bitcoin For Attack
Knut: so Bitcoin being this perfect defense mechanism, because all it does is increase the cost of the attack, can Bitcoin ever be used for attack in your opinion? Like, can it be used in an aggressive way?
Max: I think directly not, because again, it is just, speech and such, but on the other hand, maybe yes. Because, let's say, if someone hacked your machine, and got access to your private key, and spends the Bitcoin, like, in the context of Bitcoin itself, it's a valid signature, it's a valid transaction, and it will be included.
So, in the legalities of Bitcoin, it is no theft, right? It is a valid transaction. but, On the ethical realm, you worked hard to get these Bitcoin and you didn't want to send them to the attacker, so he is definitely stealing them from you. So, Bitcoin can be stolen, certainly, in the human analysis.
Not on a technical level, we've never seen a transaction confirmed with an invalid signature, but on the human level, There have been a lot of people that got separated from their Bitcoin against their will, right, against their consent. and, and that is theft. So, thieves can use Bitcoin, thieves can get paid in Bitcoin, thieves can take your Bitcoin and pay them to themselves, right?
that's a fact of reality too.
Aggression and Spam
Knut: Could that be used in an aggressive way?
Max: it is just the writing of bits and bytes, right? So there's, however, again, a limited amount of resources that are available specifically in Bitcoin. And not just do we have 21 million Bitcoin, we also have like, Two and a half slash four megabyte blocks, right?
And so this means there's only a certain number of transactions that can be fit into a single block. that means we have, again, a scarce resource and we need to allocate it. this is why there is a price for Bitcoin transactions, because that's how we solve the scarcity problem, right?
by whoever pays the most gets in. that's a, or it's not even whoever pays the most. It's like. You can choose who goes in by mining a block, right? You have full freedom of choice of which transaction do you include into your block. And if you don't mine, then you can propose to someone else, say, please include my transaction into a block.
But again, there's a large demand and a limited supply. so most likely people will start bribing each other and it's like, yeah, if you include my transaction in your block, I'll give you sats. And in fact, Bitcoin, the Bitcoin software launched with a anonymous peer to peer marketplace for the scarce good, which is Blockspace.
Satoshi didn't have to do that, right? Bitcoin would have totally worked, if, if you could not, like, if every input sum has to be exactly equal to every output sum, right?
There cannot be that outputs are smaller than inputs and the leftover goes to the miners, but that could have been a consensus rule, right? But then most likely we would have seen some third party external marketplace. Where people would do the bidding on please include my transaction into the block.
And then of course they would have to figure out how do we actually pay the miner to get our transaction in the block. So Satoshi had the genius to embed an anonymous marketplace. Into the core essence of the protocol, right, with the rule that outputs can be smaller than inputs, and the rule that we have this gossip peer to peer network, which like the whole peer to peer network is kind of optional, by the way, but it's just there to kind of make it easier so that we have this anonymous marketplace for Blockspace that we can propagate offers, right, and one person sends the offer and gets spread to the entire network.
So the demand side is no monopoly. Anyone can broadcast a message to the peer to peer network hoping to be included. And then on the supply side, the actual miners, there's also no monopoly. Anyone can spin up his computer and start SHA 256 hashing. On the most recent chain, right, with his own candidate block.
And nobody can stop you, right? That's the definition of no monopoly. New market participants are not hindered to enter the system. And so this is the most radical free market that we've seen probably ever. And it's been kind of hidden inside Bitcoin since the very beginning.
Mining vs Hashing
Knut: Yeah, you can of course also pay the miner in something else than sats to get included into a block. And if a mining pool does this, the individual miners doesn't necessarily have a claim to a piece of the pie of whatever money was paid to the mining pool owner under the table and not on the system, right?
They can't even see it. So how big of a problem is that, and can you really call yourself a miner if you're just selling hash power to a pool and the pool isn't transparent?
Max: I mean, it's actually true that we, like, there could be in the future, A alternative marketplace for block space that's not inside the Bitcoin Core client. And by the way, arguably that's better, because we have a piece of software that does one thing really well, and then, you know, we just specialize and put the two modules together.
architecturally speaking, this might be better. we see things like, for example, the mempool. space explorer, or accelerator, right, is one. Marketplace that is now establishing that that seems to work now quite well. Of course, it has the issue of there's a central, like, order book, so to say, and probably custodian for the money as well.
And so, I'm not sure, but it's one approach of doing such an alternative marketplace and there can be downsides. it's not really public of how much Volume is going through here, right? how much are people speeding up their transactions, And I guess the same goes to much earlier where we just had mining pools offering this in their own API, or a webpage.
so at least now, like we, we have a dedicated service provider. That's not a mining pool doing this, which I think is an improvement. but we could also, you know, build. A, like, off chain peer to peer network, so to say, that's not related to Bitcoin per se, but that has all of the aspects that we want just dedicated for an optimized market book for this resource.
And Bitcoin should still work, I think. Like, the marketplace inside Bitcoin Core is not essential in the long run. It was just very convenient to bootstrap it. But, you know, in 50, 100 years, I wouldn't be surprised if we have Dedicated systems for, for these things that potentially are in different repositories and such different softwares.
Knut: So, in your opinion, how damaging is a temporary fee spike over a weekend or something where it goes up to like, 2000 SATs per transaction. what impact does it have on lightning channels and lightning providers and so on? Like do you consider it an attack or what is it?
Max: it's an inevitability almost, right? If you have a hard, extremely limited supply, right? there is only two and a half megabytes in the usual block, and you have extremely fluctuating demand, and there is no way to speed up production of the good. there is bound to be extreme, differences of we have way more demand than supply or way less, right?
But it will be very rare that we will fill just exactly everyone who wanted to gets in. So to actually clean out every transaction that wanted to be made is quite rare already now and in the future, if Bitcoin continues to be used, this is even more unlikely, right?
So then the question is just how, like, do you get into the top, like, the top payers to get included in the block still? And this is where just the technology is quite difficult, because this is like, you're, you're, you're, it's an order book, right? You're trading, basically, and you don't know if the price goes up or price goes down.
And this is all at least supposed to be automated. Bitcoin wallet developers are building trading bots, block space accountants charged to purchase block space on behalf of the user. the user just clicks send and that's it. the software does all of the complexities of constructing a transaction that is of a size acceptable, right?
Because if fees are super high, you don't want to build a transaction with a hundred inputs and one output, right? You would want to have a transaction with one input, one output. It would be way cheaper if the fee spike is currently high. a smart robot should build a different structured transaction with more or fewer inputs and outputs to accommodate the current fluctuation of the market.
And of course, the fee rate is another, like what's actually your bid that you put into this marketplace? And that's trading like. How much are you going to pay for the stock? Nobody really knows, right? And so it's kind of good luck and you don't know if it goes up or goes down. And sometimes you overpay, right?
And you pay way more than was actually needed to get into that block. And so you lose money, you lose capital. And sometimes you don't pay enough and you don't get included for months, right? but there's better software that can alleviate a lot of these problems.
Spam Making Bitcoin Worse as Money
Luke: Well, so I guess another side to this question, because everything you're saying makes makes total sense from the perspective of that this stuff is definitely going to happen from from hyperbitcoinization side. There's just going to be more demand than there is supply of block space. But I think the issue that we've been exploring a lot.
Lately, is, is that when there are transactions that aren't really being made for the purpose of moving value from one person to another in the form of Satoshis, they're, they're another form of value, subjective value that is communicated through arbitrary data, or at least some other type of, of data.
Does that change the property of Bitcoin as money? That's essentially, I think the, the root of the, the argument any, anyone talking
Knut: Yeah, exactly.
Luke: the functionality of Bitcoin is
Max: Well, I think. There's a couple aspects to this, right? We have again a scarce resource block space, and there's the problem of how do we allocate this block space. And there are very stringent rules on this, right? You cannot have arbitrary data in blocks, right? There needs to be, for example, the transaction structure.
There needs to be inputs that point to previous outputs, and there need to be outputs, the sum of the inputs, sum of outputs, hashes, transaction headers, all of the stuff needs to be followed in order for this to be considered a valid block. So the Bitcoin developers have, from the very beginning, had a very, I guess, authoritarian regime to allocating these resources, which makes sense.
If you don't put stringent, like, structure in a protocol, then people just fill it with garbage and every software breaks, right? So it's like a practicality thing that we need to have a very opinionated, kind of thing. Set of rules and we need to pick one of them and like just do it because if we don't pick any then it won't work and also if we pick the wrong one it won't work either.
imagine the rules would have been like a broken hashing algorithm, for example, not SHA 256 but SHA 1 or something that's broken. People can create collisions, right? So there could be two transactions that have the exact same transaction ID. breaks the system, right? So if that would have been the set of rules, Bitcoin would have broken, right?
And now also, again, if we allow arbitrary things to be built, then people will just use it as data storage, for example, and just fill it up with megabytes of images. And again, limited amount of resources. If all of it is used for, for pictures, then none of it can be used for money transfer, right? So this is again, an inherent conflict.
the tricky thing though is, now we have this. established set of rules in the Bitcoin consensus and how do we change it, right? And that's the really tricky part of, making up man made rules. Bitcoin is not Natural in the sense, right? Like, humans came up with this shit.
Like, this is our creativity that made this happen. and so, it's not nature made, right? It's man made. Of course, men are part of nature and such. So it's a bit, wishy washy here, but ultimately, we made it, we can change it, we can make it better, and we can break it. And that's a really scary position, because I think we all realize that this is quite an important project, and we definitely have it in our power to break this thing.
I hope we do our best effort.
Caution When Changing Bitcoin
Luke: my interpretation of that is, is that, caution when making changes to Bitcoin is paramount. Would you agree with that?
Max: Well, inaction is an action too, right? And that might be even more dangerous. So, there might be critical bugs in the protocol that if not addressed will break the system and potentially they are currently being exploited, right? And so, in such a case, we should do our best to fix it as soon as possible.
Satoshi knew that from the very beginning, right? So, how exactly we do that? Who knows?
Knut: Well, if it's up to the individual miners, which it is, what blocks they want to mine, what transactions they want to include in a block. And it can be fixed that way, a sly roundabout way, if you will.
Max: Well, if we could trust the miners with stuff like this, then we could trust the miners with enforcing the 21 million, right? But we can't, right? We don't rely on anyone. We verify it ourselves, right? And so the reason why we don't have actual JPEGs in Bitcoin blocks is because your node says no to any block that actually has a JPEG in it, right?
Blocks have to have transaction in it. If not, you kick them out, right? So even if there's valid proof of work Proof of Work doesn't solve the problem of integrity of the block, right? This has nothing to do with Proof of Work. In fact, Proof of Work is one part of the rules of the integrity of the block that is defined, enforced, and verified by the full nodes itself, right?
Specifically, if you want to get rid of inscriptions, that's certainly a hard fork. Like, taproot transactions are currently valid, and if we make these taproot transactions in the future invalid, that's a hard fork, right?
It would be great to hard fork Bitcoin. We could clean so much stuff. It's just a practical reality that breaking the hard fork use of a running protocol is extremely difficult and arguably, unethical. Because people have signed up to the previous system, built businesses and, stored their money in these types of scripts.
If we now make them unspendable, what is that? No?
Mining Incentives
Knut: so, when it comes to mining, there's, minor incentives, like, the thing we talked about before, about, under the table payments to big mining pools, To me, the obvious fix to this problem is to get it into the brains of the hash salesmen, that they ought not be mere hash salesmen, but actual miners and know what block they're mining on.
Because I think the ethos among the individual miners is, better than, these bigger pools that might not be, as, concerned with the longevity of the Bitcoin experiment, but, more fiat minded and wanting a quick buck now rather than save the system in the long run.
So, right now it feels like we're trusting these bigger entities to have as much of a disincentive to destroy Bitcoin so that they won't, it's tricky. Like it's a gray zone, right? What's your thoughts?
Max: I think Satoshi's genius in designing the Bitcoin protocol was that he did his best to separate different tasks that need to be done in the system into different like conceptual entities, and then to ensure that each of these aspects is distributed as widely as possible. And this is ultimately what it means that Bitcoin is decentralized, right?
There is not one person that defines the set of rules, for example, or one person that writes the candidate block, Or one person that provides the proof of work for the candidate block, or one person that provides the signature for each transaction, right? Each of these things is distributed. And in the ideal case, in the original Bitcoin client, to every user, right?
Like, the Bitcoin software in 2009 was mining by default for everyone, right? So, literally the entire stack of the operation was at 100 percent of the users, right? There was no non validating, non mining users. In the beginning, right? We had perfect decentralization, so to say, right? And then if efficiencies kick in and economies of scale and division of labor, and we start to optimize each of these things kind of on its own and split it out into different branches of government.
Yeah, specialized entities, so to say. And if you specialize on being the best hasher that you could possibly be, you just give up on being the best block candidate creator that you could possibly be. Because if you do the one thing that you're marginally better at and focus all your attention on that, you will be the most profitable.
so, yes, it is. It is an issue. and we, Bitcoin would be better off if we further distribute the risk and responsibility of each of these tasks to as many people as possible. And I think we've done a really good job, for example, of distributing the ownership of private keys.
And like, there's, I don't know, many millions of private key holders on the Bitcoin blockchain, right? So that's, that's great. but, and we have. Probably done this as well with hashers, right? There's a decent amount of quite large independent hashing institutions, right? Not so well with mining pools and actual block candidate creation, like, that's pretty bad.
Like, there's two or three of them, so that's scary as fuck. Right there we've utterly failed and we've made Bitcoin way worse than it was before. in this one metric of resilience, of decentralization, of distribution of risks, we made it a lot more efficient, but we made it much more vulnerable to attack.
that is a problem. Thankfully, a lot of people are working on fixing it. It's a really difficult problem, right? It's not that there's some malicious, attempt of trying to break it. I mean, maybe there is, but the more likely answer is just bloody difficult computer science. it just needs an insane amount of research and development before we will have tools that are even coming close to being actually adequate.
Right? I'm not praising Satoshi's 2009 code as being perfect, because it was a pile of shit, right? And you could break it in a million ways. so we've improved a lot, but we're very far from done because to some extent the realities of the difficulty of the situation have caught on much faster than our ability to solve these.
Yeah, I mean, the problems that are currently existent in Bitcoin and that now we're at Nostriga today and talking about Nostr, this sort of related communication layer in relation to Bitcoin, you mentioned at the very beginning, Freedom Tech.
Freedom Tech and Nostr
Luke: So, we, when we last talked to you, you were focusing on Wasabi Wallet and now obviously that project has just been made open source, essentially, and so my question to you on that is, what are you focusing on in terms of Freedom Tech now?
Max: Nostr is definitely a highlight, right? Nostr is just incredibly cool. And it's so wild to think that Nostr is like two years old. it's not old, but look at the amount of stuff that we've built. In this short time frame, how powerful are we? It's incredible, right? If we get our act together and actually build on, such an open protocol and get people excited about it and people using it, it doesn't take us long to fundamentally change the pattern of speech on this planet.
Wow, that's incredible. Like, we did that. And we're just getting started. think about where Nostr is going to be in five years. It will be wild. Absolutely insane. that's very bullish and very encouraging. And it's super exciting to work at such an early stage in the protocol, because there's so many obvious improvements.
There's so many obvious use cases. There's so many low hanging fruits of how we can make it even better than it currently is. Alright, so we have something that's already great, and we know a million ways on how we can make it even better. and you can be part of making a meaningful improvement in getting this to like an exponential blow off of awesomeness.
Knut: Meaningful improvement of humanity, really.
Max: Yeah. Yeah, that's the other thing, like, that's why Freedom Tech is so exhilarating to work at, because we're ending slavery. That's kind of a big deal, you know,
Knut: Yeah, it should have been done at least 300 years ago.
Max: Yeah.
Luke: No, it's, it's amazing. And well, and actually, so a couple of things here. First of all, we've talked about this a little bit, how Nostr seems like it's the playground that people wanted as an alternative to Bitcoin. In other words, people who went and started making shitcoins were basically just wanting a playground to do all this stuff.
But now is, is, is Nostr basically the place where people can do that and channel their energies in a way that isn't going to break money?
Max: Yeah. I absolutely agree. So I'm very bullish on a lot of these use cases and one other area that currently interests me a lot, is just zero knowledge cryptography. it's wild what's possible. it's absolutely wild. Within the last five years or so. The theory has developed.
And again, a lot of shitcoin projects putting zero knowledge proofs on blockchains and such, and I'm not quite convinced that we actually need a blockchain for that. I think relays are just fine. And so I'm quite bullish on having actual zero knowledge proofs much more integrated in Nostr clients. Like, you can do amazing things with this.
Like, for example, anonymous web of trust, right? You could prove to me under an ephemeral anonymous identity, right, that you are in fact, On my follower list. Like, I'm following you, but I don't know who you are. Right? So, these types of things are trivial with zero knowledge stuff. And we don't have any size constraints or computation constraints in Nostr.
Because it is not a global consensus system. Only the people who are interested in this proof actually have to, like, download it and verify it and such. so, it's, I think we can do a lot of amazing stuff here. it seems pretty obvious wins here.
Knut: driving these 180 IQ young developers into Nostr instead of shitcoin development is, is like moving them? To do, to think more of what they should rather than what they could, because I think that's, that's sort of the main problem with this nerdy set of shitcoin developers is that they, oh, I could do this if I just do this and they, they focus on what they can do rather than what they should do.
And it's Nostr, Changing the direction of that, are people thinking more of ethical things while developing on this than
Max: it's a big claim, right? That like a piece of tech can
Knut: it's hopium
Max: improve the morality of people. it's definitely a big claim, but it seems true. Like, if you think about it in Bitcoin, like probably each of us, our level of morality before we discovered Bitcoin and what it is now.
And our understanding of morality has substantially, improved, right? And I'm not sure if it would have happened, at least to this extent, without being exposed to the Bitcoin technology. and Bitcoin is just money, you know, like, humans do a lot more than buy stuff, sure, money is incredibly important, but it's far from everything of the human experience.
And I think Nostr. We'll do a lot of the other stuff and Nostr has this freedom mindset embedded into the protocol just as Bitcoin has. And so I'm extremely bullish on seeing the people who get exposed to Nostr and what it does to them in the long run.
Hyperbitcoinization vs Hypernostrification
Max: So what happens first? Hyper ossification or hyper ization both at the same time.
Knut: does one lead to the other?
Max: there's definitely synergies here, right? and, yes, one leads to the other. there's, I met a bunch of people who got interested into Nostr first, and then used Bitcoin for the first time. It's a very common theme, actually. again, because Like, social, like, think of the, think of the, like, average screen time of people, right?
it, for sure.
I think Nostr is going to be way bigger than Bitcoin in the improvement of the human condition.
Knut: Then again, every time you press the like button or the retweet button or whatever on your social media app, even the legacy system, you are providing someone with some value. That's why your account is valuable to, Facebook's and the Twitters of the world. There is a value thing embedded into everything you do on the internet.
Max: It's just, you don't get a tradable good.
Knut: No, no,
Max: sell the like to someone else.
Knut: not at this point.
Max: They have now a star emoji. If you send the star emoji, you can send the star emoji back to the company, and they will give you money. So, voila. It's basically a shitcoin, but it's a star.
Luke: is it more important to fix money or the other stuff?
Max: Well, that's a big one. Both again, because money is only half of every transaction, right? And so maybe the earlier example of the marketplace for Bitcoin block space is perfect because why did Satoshi include the marketplace, the other stuff together with the money? Because it was kind of essential, right?
you need to have both at the same time in order to live, right? You need to speak, you need to advertise your products, you need to negotiate with the customers, right? You need to convince them of the value that you will provide to them, and then you need to receive the money and tell them that you've received it, and ultimately hand over the goods, right?
So there's a lot of human interaction into every trade, and the money aspect is just Like, one small part of this long interactive chain of protocol, basically. I think we need both at the same time. And we're just discovering upgrades to each of them as we move along. But this has always been in synergy.
Like, the internet is way older than Bitcoin, right? So arguably, we need the other stuff first, right? We needed like 20, 30 years of other stuff before we could actually come up with the money.
Knut: so fix the money, fix the world then fix the world and you fix the money.
Luke: No, but seriously, we actually talked about this. in that, maybe an analogy to, that the internet needed to develop in a centralized way because the, literally the hardware and everything, the architecture, the client server model was literally a centralized and centralizing system. Model and that needed to exist first.
And then the analogy is that gold was centralized naturally in the sense that physically the physical constraints of gold made it so that it naturally centralized into banks and then fiat solved that problem to sort of decentralize it, but it broke everything. So now the mechanism of fixing the money and decentralizing the money was gold.
Bitcoin, but the corollary for decentralizing the communication is Nostr. So both things have kind of happened in a parallel. That's, what we were discussing.
Wrapping Up
Luke: That is the alarm Oh,
Knut: Oh, okay.
Max: so we'll wrap it up.
Knut: Well, I'm
Max: Nostr for sure. Max at TowardsLiberty. com. You can send me mail, notes and sats to that, which is, by the way, crazy, right? That we can have like this unique identifier to get, like, all of your needs settled is wild. Check out, lodging of Wayfaring Men. That's, the main shill of this video.
And I made the audiobook for it. it's on a podcast. The podcast is by the author, Paul Rosenberg. And, it's called Parallel Society, right? So check that out. right now we've released the first episode. the others will come shortly thereafter. the other book recommendation I should highlight, which we haven't mentioned yet, is Cryptoeconomics by Eric Voskuhl.
Most of what I said here was very much inspired by that book. He has the most rigorous understanding of Bitcoin. It's by far the best Bitcoin book. So I also did the audiobook for that. Just search for Cryptoeconomics in your
Knut: audio book though.
Max: when you have to read tables of math formulas, it's starting to fall apart.
But there's a lot of verbal logic in the book that goes very well. Just get the free PDF for the actual graphs and
Knut: And keep using Wasabi and fire up your own coordinators and whatnot, right?
Luke: Now get on stage, Max. Don't want to make you late.
Max: Bye
the book, that's not what I said.
Luke: right, that's it.
-
 @ aa4955b3:e9df94de
2024-10-08 16:06:27
@ aa4955b3:e9df94de
2024-10-08 16:06:27 -
 @ 361d3e1e:50bc10a8
2024-10-08 16:02:04
@ 361d3e1e:50bc10a8
2024-10-08 16:02:04Elon Musk explains why billionaires are voting for and supporting Kamala Harris
elonmusk #trump #harris #tuckercarlson #politics #usa
-
 @ aa4955b3:e9df94de
2024-10-08 15:57:15
@ aa4955b3:e9df94de
2024-10-08 15:57:15God formed Adam from the dust of the ground and put him in the Garden of Eden to work it and keep it. And God took a rib from Adam’s side and made woman, as a helper fit for him. They had every tree bearing fruit for food; they had no quarrel with God or with one another. It was a garden paradise. And Adam and Eve were to be fruitful and multiply and fill the earth and subdue it. They were to have dominion over all creation and live as kings and queens on the earth, under God the high king over all. God gave Adam only one prohibition: of the tree of the knowledge of good and evil you shall not eat, for in the day that you eat of it you shall surely die. Adam was God’s son. Adam was to be a priest and serve and guard that Garden Temple that God planted for him. Adam was to rule as king over the earth and subdue it with righteous rule. Adam was to be a prophet and instruct his wife and all his posterity about God’s righteous rules and keep them from sin. If Adam obeyed God, He would live, and all His children to come along with him. But if he disobeyed, he would die, and all his children to come along with him.
Where was Adam the prophet, the priest, the king, at that pivotal moment when that serpent slid into the garden and stole God’s throne in that garden temple? Where was Adam when the bone of his bones and flesh of his flesh, his bride Eve, formed from his own rib, was deceived by the serpent? Paul writes in 1 Tim. 2:14 that Adam was not deceived, but the woman being deceived, fell into transgression. As priest Adam was to care for those under his watch and guard that garden from evil, as prophet he was to spread and uphold God’s word, as king he was to subdue every rebel force that threatened God’s rule. Adam should have killed the dragon and saved the girl. Instead he stood by as the serpent deceived Eve, and then he chose to sin along with her. Adam failed miserably. He broke the law. He desecrated God’s temple. He gave dominion over the world to Satan. He deserved to die. He was supposed to die. God said, "in the day that you eat of it you shall surely die." (Gen. 2:17) So why didn’t he?
The answer is in God’s promise in Gen. 3:15. Theologians through the centuries have called this the "first gospel." In it, God promises that a male offspring of Eve would bruise the head of the serpent, that head of all evil. Gen. 3:15 says to the serpent of this Son of Eve, “He shall bruise your head, and you shall bruise His heel.” The story of the Bible doesn’t end in Genesis 3 because God wants to show to all the universe how He can be both just and at the same time justify the unjust. God’s plan in the history of the world, through all its convulsions, is to show Himself great in His justice to pay back every sin, and at the same time in great in His mercy to pardon sin.
-
 @ 4ba8e86d:89d32de4
2024-10-08 15:50:58
@ 4ba8e86d:89d32de4
2024-10-08 15:50:58Ele foi desenvolvido pela Beowulf Blockchain, uma empresa que é conhecida por suas soluções seguras e confiáveis de blockchain e criptografia.
A autenticação em duas etapas é um processo que adiciona uma camada extra de segurança ao login em uma conta online. Em vez de depender apenas de uma senha, o 2FA exige uma segunda forma de autenticação, geralmente um código enviado para um dispositivo móvel ou gerado por um aplicativo. Isso ajuda a garantir que apenas o proprietário da conta possa acessá-la.
A história do Aegis Authenticator remonta ao início dos anos 2000, quando a autenticação em duas etapas começou a ser amplamente adotada para proteger contas online. Desde então, houve vários casos de violação de segurança em grandes empresas, incluindo Yahoo, Equifax e Marriott, que expuseram informações pessoais de milhões de usuários. Como resultado, a segurança online se tornou uma preocupação crescente para indivíduos e empresas em todo o mundo.
O Aegis Authenticator funciona gerando códigos de autenticação em tempo real que mudam a cada 30 segundos. Esses códigos são usados em conjunto com uma senha para acessar uma conta online. O aplicativo suporta a autenticação com base em tempo e também com base em contagem, o que significa que ele pode ser usado com serviços que suportam ambas as opções.
O Aegis Authenticator possui recursos de backup e sincronização em nuvem para garantir que os usuários possam acessar suas contas em outros dispositivos, mesmo que o dispositivo original seja perdido ou roubado. O aplicativo utiliza criptografia de ponta a ponta para proteger as informações do usuário em trânsito e armazenadas na nuvem.
O Aegis Authenticator resolve vários problemas de segurança online, incluindo a prevenção de ataques de phishing e o aumento da segurança em contas com senhas fracas. Os códigos gerados pelo aplicativo são válidos apenas por um curto período de tempo, o que dificulta a utilização de um código roubado por um atacante. Além disso, o aplicativo é capaz de detectar automaticamente tentativas de phishing e alertar o usuário.
-
Baixe o aplicativo na loja de aplicativos do seu dispositivo móvel. https://play.google.com/store/apps/details?id=com.beemdevelopment.aegis
-
Abra o aplicativo e clique em "Adicionar conta".
-
Selecione o serviço para o qual deseja configurar a autenticação em duas etapas.
-
Siga as instruções do serviço para vincular sua conta ao Aegis Authenticator. Isso pode envolver digitalizar um código QR com a câmera do seu dispositivo ou inserir um código de configuração manualmente.
-
O aplicativo irá gerar um código de autenticação em tempo real para sua conta, que muda a cada 30 segundos. Use esse código em conjunto com sua senha para acessar sua conta.
Com esses passos simples, você pode usar o Aegis Authenticator para proteger suas contas online e aumentar sua segurança digital Um próximo Passo seria adquirir um Yubico.
https://void.cat/d/KzX75b9AwikAGHiywPb3Su.webp
-
-
 @ 4ba8e86d:89d32de4
2024-10-08 15:45:20
@ 4ba8e86d:89d32de4
2024-10-08 15:45:20incluindo: - Schnorr Signatures (BIP 340) - Taproot (BIP 341) - Tapscript (BIP 342)
- Melhor privacidade;
- Redução de custos para transações multisig;
- Melhorias no Lightning Network com PTLCs e chaves agregadas como âncoras de canal;
- Uma série de melhorias em scripts com DLCs, assinaturas de adaptadores e Taptrees.
Uma das principais mudanças Taproot é o novo tipo de saída chamado P2TR, que é mais eficiente em termos de espaço de bloco e utiliza assinaturas Schnorr em vez de ECDSA. As assinaturas Schnorr são menores e permitem a agregação de várias assinaturas em uma única assinatura. Isso possibilita recursos interessantes, como a agregação de chaves, assinaturas de adaptadores e o uso do Taptree.
O Taptree é uma maneira de usar tanto assinaturas de chave única quanto multisig, permitindo maior flexibilidade na transação.
o Tapscript é compatível com o Miniscript, facilitando o desenvolvimento de contratos inteligentes. PTLCs são uma alternativa mais eficiente aos HTLCs na Lightning Network. Com Taproot, as transações multisig serão mais baratas e as transações de chave única e multisig serão praticamente indistinguíveis, melhorando a privacidade dos usuários.
As melhorias no Lightning Network permitirão a utilização de PTLCs e chaves agregadas como âncoras de canal, aumentando a eficiência e a segurança da rede.
Taproot é uma atualização que trazendo uma série de benefícios significativos e tornando a rede mais eficiente e flexível em sua funcionalidade.
bips/bip-0340.mediawiki at master · bitcoin/bips https://github.com/bitcoin/bips/blob/master/bip-0340.mediawiki
https://murchandamus.medium.com/2-of-3-multisig-inputs-using-pay-to-taproot-d5faf2312ba3
https://b10c.me/blog/006-evolution-of-the-bitcoin-signature-length/
https://suredbits.com/payment-points-part-1/
https://bitcoinops.org/en/topics/adaptor-signatures/
https://tlu.tarilabs.com/cryptography/introduction-schnorr-signatures
https://tlu.tarilabs.com/cryptography/introduction-schnorr-signatures
https://bitcoin.sipa.be/miniscript/
https://learnmeabitcoin.com/technical/p2pk
https://twitter.com/TorqLN/status/1647605539486957575?s=19
https://twitter.com/TorqLN/status/1693335249927749869?s=19
https://twitter.com/TorqLN/status/1688190723869356032?s=19
-
 @ 4ba8e86d:89d32de4
2024-10-08 15:36:18
@ 4ba8e86d:89d32de4
2024-10-08 15:36:18A Samourai Wallet foi bifurcada, e algumas almas corajosas decidiram continuar a luta pela privacidade de onde a Samourai parou. Nesse momento sombrio para a comunidade Bitcoin, a chama da privacidade foi reacendida com o lançamento da Ashigaru Wallet – uma carteira Bitcoin autocustódia, de código aberto, segura e focada em privacidade. https://image.nostr.build/506a85228d6a652a08886e1fd9eb441bd2ffd7965df6750f10f511de6a6081c8.jpg
Ashigaru foi desenvolvida para quem busca uma solução robusta de privacidade e anonimato ao transacionar com Bitcoin, construída sobre princípios de código aberto. https://image.nostr.build/451faf57c9eaa67d5f5430c248d842551778567048827c3ba05041709d9d86c5.jpg
Principais Funcionalidades
-
Suporte ao PayNym: Facilmente migre para um novo diretório utilizando o esquema de avatar Pepehash, que representa códigos de pagamento reutilizáveis BIP47. https://image.nostr.build/837ffe1b5e49d369f5be610858babc5962c434d3e834d464df2c203c7a131f4f.jpg
-
Roteamento via Onion (Tor): Conecte-se ao seu nó Dojo e transmita suas transações pela rede Tor, garantindo anonimato total.
-
Ricochete: Aumente a distância entre a origem e o destino de suas transações, mitigando a vigilância e dificultando o rastreamento por terceiros.
-
Recuperação de Chave Criptografada: Proteja suas chaves mnemônicas com uma senha e as importe para outras carteiras compatíveis, garantindo a recuperação segura dos seus fundos.
-
Gastos Pós-Mixagem: Importe suas chaves privadas da Samourai Wallet e mantenha suas contas segregadas para maior privacidade em transações futuras.
-
Despesas em Lote: Economize nas taxas compondo várias transações em uma única operação.
-
Modo Stealth: Oculte sua carteira de buscas físicas com um aplicativo de chamariz funcional no inicializador do dispositivo.
-
Coinjoins Ponto a Ponto: Participe de transações colaborativas, ajudando a minar as heurísticas usadas pelos observadores da blockchain.
-
Controle de Moedas: Selecione, rotule, congele e descongele UTXOs (Unspent Transaction Outputs) em sua carteira, garantindo controle total sobre seus fundos.
-
Taxas de Mineração Inteligentes: Um algoritmo avançado calcula as melhores taxas de transação com base no estado do mempool, otimizando o custo das transações.
Código Aberto e Livre
A Ashigaru Wallet é lançada sob a licença FOSS (GNU General Public License Versão 3), permitindo que qualquer pessoa revise, contribua e verifique a segurança do código.
Links Úteis
- Repositório de Código somente Tor
http://ashigaruprvm4u263aoj6wxnipc4jrhb2avjll4nnk255jkdmj2obqqd.onion/
- Site Oficial da Ashigaru Wallet
https://ashigaru.rs/
- Baixar a Carteira Ashigaru
https://ashigaru.rs/docs/mobile-wallet-download-install/
- Versão Onion para Download
http://ashicodepbnpvslzsl2bz7l2pwrjvajgumgac423pp3y2deprbnzz7id.onion/Ashigaru/Ashigaru-Mobile/releases/download/v1.0.0/ashigaru_mobile_v1.0.0.apk
-
-
 @ 7f21affa:57e19174
2024-10-08 14:58:08
@ 7f21affa:57e19174
2024-10-08 14:58:08Chef's notes
Oven at 400 degrees Fahrenheit for 20 mins
Refrigerate the dough for 2+ hours
Details
- ⏲️ Prep time: About 3-4 hours
- 🍳 Cook time: 20 mins
- 🍽️ Servings: 10
Ingredients
- 1 cup water
- 3 sticks of butter
- 2 3/4 cups of all purpose flour
- 2 tsp salt
- pinch of paprika/jalapeno powder (I use both)
- 2 tbsp oil
- 1 lb ground beef
- 1 medium diced onion
- 1 diced red/green bell pepper
- 1 cup peas
- 4 minced garlic cloves
- 1 tsp oregano
- 1 tsp salt
- 1/2 tsp paprika
- 1/2 tsp red flakes
- 1/2 tsp white pepper
- 1/2 tsp cumin
- 1/2 cup beef broth
- 2 tbsp tomato paste
- 1 diced white/russet potato
- 3 tbsp scallions
- 1 cup shredded cheese (mexican, fiesta, or cheddar)
- 1 egg
- 3 tbsp water
Directions
- In a pot, heat up 1 cup water with 3 sticks of butter (1 1/2 cups butter)
- In a bowl, add 2 3/4 cup all purpose flour, 2 tsp salt, & pinch of paprika/jalapeno powder.
- Once butter is melted in the pot, cool & transfer to the bowl.
- Mix then wrap dough in plastic.
- Refrigerate wrapped dough for 2+ hour till hardened.
- Heat up large pot on medium heat, then add 2 tbsp oil.
- Saute 1 lb ground beef
- Leaving the beef juice, then scoop up cooked beef into metal bowl for later
- Using the beef juice, saute diced yellow onion, diced bell pepper, 1 cup peas, 4 minced garlic cloves, 1 tsp oregano, 1 tsp salt, 1/2 tsp paprika, 1/2 tsp redflakes, 1/2 tsp white pepper & 1/2 tsp cumin
- Add 1/2 cup beef broth, 2 tbsp tomato paste
- Add the cooked beef & diced potato
- Lastly combine 3 tbsp scallions
- Turn on oven at 400 degrees Fahrenheit
- Once dough in fridge has hardened, take out
- Grab a golf ball sized piece of dough and start flattening with your hands
- Dough should be around 5-6 diameter circle
- Put about 2 tbsp of beef filling you made earlier & sprinkle with a little cheese
- Crimp edges with fork
- Brush the empanadas with egg wash (1 egg + 3 tbsp water mix) before putting in oven
- Bake for 20 mins & enjoy!
-
 @ 319ad3e7:cc01d50a
2024-10-08 14:33:14
@ 319ad3e7:cc01d50a
2024-10-08 14:33:14https://image.nostr.build/4824c65d9a07c577bee8591b18ee147e7a457849fbaee53244667ec062914751.jpg
OCT 2024 | ISSUE 2 | LETTER FROM THE FOUNDER | LIFE EXPERIENCE | FEATURED RECIPES | REVIEWED RECIPES | ECONOMICS | MICROFICTION | FAMILY FOODLOVE | FOOD SWOON | NOTE SYNCING | SOUNDS | QUOTE OF THE MONTH | UPCOMING EVENTS | ANNOUNCEMENTS | LANGUAGE | #NOSTRASIA2024 ALBUM | FINAL THOUGHTS
LETTER FROM THE FOUNDER 📝
Hey Everyone!
Exciting things are cooking at Zap Cooking! We’re thrilled to announce that we’ll be in Happy Valley, State College, PA, on October 12th as proud sponsors of Nostr Valley. It’s shaping up to be an incredible weekend, and we can’t wait to share it with you! We’ll be hosting a dynamic panel that dives deep into the intersection of food, culture, and, of course, the unique world of Nostr. This event promises a great mix of good times and engagement, and we’d love to have you join us! If you're interested, sign up now at nostrvalley.com.
We’re also excited to have you reading our second monthly newsletter. At Zap Cooking, our focus goes beyond development - we're committed to creating content that inspires. Follow our npub on Nostr to catch flavorful food ideas and captivating creative content. We’re working on fresh perspectives and new projects that celebrate cultural diversity, all while keeping the quirky, authentic spirit of Nostr alive. Thanks for being part of this journey with us. Let’s keep Nostr weird and delicious!
Seth
https://i.nostr.build/nQqsPGmJ8hjvxROK.png
Artwork by Bread and Toast | https://breadandtoast.com/
LIFE EXPERIENCE 😮💨
In August 2024, Nostriga held the afterparties at the Basement, an underground Bitcoin bar in Riga, Latvia. The crowd spent the nights enchanted in conversations, dancing, drinking, and smoking cigars to celebrate freedom and life.
It was a fascinating experience smoking cigars with the Nostr men on those cobblestone streets, reminding me of my younger years working in a private social club, where the cocktail lounge would fill with a thick layer of cigar smoke as I crafted and served Bourbon or Rye Manhattans, Old Fashioned cocktails (one with Sweet 'n Low!), and neat single malt Scotch whiskies.
Recently one of the voices of Nostr - The Beave - tagged me in a note, introducing me to Duchess and their love of coffee & cigars. In less than twenty minutes, Duchess and I were collaborating for the next Zap.Cooking newsletter. The following review is going to take us out of the nightlife and into a morning zen session. - SimplySarah
CIGAR & COFFEE | Duchess
https://image.nostr.build/eff42693d5d4c9f086c25a11e57563b5163dad2f3da600de5e835ba2e1a1a842.jpg
There’s nothing quite like starting your day with a good cigar and a cup of coffee. The rich, earthy flavors of a cigar paired with the bold aroma of coffee create a perfect harmony that awakens all the senses. The Coffee will give you that little morning boost, while the cigar will ease you into a calm, zen-like state. Together, it’s a ‘boosted zen’ that really sets the tone for a productive yet relaxed day.
CIGAR | PDR 1878 DARK ROAST CAFE
A cigar known for its rich, coffee-infused flavor. This particular one is designed to complement a dark roast coffee experience.
https://image.nostr.build/0ab1bb066281c4d6ed2cf0f65548076255535552c27b7a723953bd1ba5713cbe.png
The PDR 1878 Dark Roast Cafe cigar has a unique, slightly spicy profile that pairs beautifully with a cup of dark roast coffee. The coffee I paired with my cigar this morning was one of my favorite dark roasts: Jamaican Blue Mountain Roast, from Jamaica. Another dark roast that I love but didn’t have on hand is Black Ivory Coffee from Thailand.
COFFEE | JAMAICAN BLUE MOUNTAIN COFFEE
Known for its exceptional smoothness, mild flavor, and low acidity, Jamaican Blue Mountain Coffee is one of the world’s most luxurious and sought-after coffees. Grown at high elevations in Jamaica’s Blue Mountains, this coffee is loved for its balanced and refined taste.
https://image.nostr.build/57700f4defe71f9f01c9406ca7c1d6cbf4ccdc621a9b48db31065834079b0b17.png
Most purists drink Jamaican Blue Mountain Coffee without milk or cream to fully appreciate its unique and subtle flavors. However, I like to add fresh cream from the farm if you have access to a local farmer. I feel that adding cream creates a richer, smoother cup, no matter what coffee I’m drinking.
Coffee and cigars are both fascinating rabbit holes, much like wine, if you're interested in going down them.
ENJOYABLE PART OF SMOKING A CIGAR | Cigars are enjoyed primarily for their flavor. The rich taste of a cigar comes from the blend of different tobaccos, which is best experienced by holding the smoke in your mouth, where your taste buds can fully appreciate it. Inhaling isn't necessary and actually makes the experience less enjoyable because cigar smoke is much stronger and can be harsh on your lungs.
HEALTH BENEFITS OF SMOKING A CIGAR | Nicotine, in small doses, can have some positive effects, like improving focus and mental sharpness. It also stimulates certain receptors in the brain that can support heart health. Cigars are the healthiest vehicle to deliver nicotine into your body, as they offer a slower, more natural release of nicotine compared to cigarettes or other forms of tobacco.
ENJOYABLE PART OF DRINKING COFFEE | Coffee is widely enjoyed for its flavor and aroma. The rich, complex taste of coffee comes from carefully roasted beans, which can range from bold and dark to mild and fruity, depending on the origin and roast. Sipping coffee slowly allows the palate to savor the intricate layers of flavor, from chocolaty and nutty to floral and fruity notes. Whether black or with milk, coffee offers a comforting and energizing experience.
HEALTH BENEFITS OF DRINKING COFFEE | In moderate amounts, coffee offers several health benefits. It is rich in antioxidants, which are known to support heart health, brain function, and help combat inflammation. The caffeine in coffee can boost focus, mental sharpness, and physical endurance by stimulating the central nervous system. Some studies have also suggested that coffee may support heart health, improve metabolic rate, and reduce the risk of certain diseases, such as Parkinson’s and Alzheimer's. Organic coffee—free from pesticides and chemicals—provides a cleaner, more natural source of these benefits.
Find Duchess on Nostr: duchess@orangepiller.org
FEATURED RECIPES 🥪
https://image.nostr.build/8ec8e09bc081e7f70de446fda8fc85d485c01ed4579b13f511753568b21f3c8b.jpg
https://image.nostr.build/e902abea3014325e848f7cbc8f1bd00f8899880fedcd2490361d12ec595c451a.png zap.cooking/recipe/naddr1qqsxxmrpwdekjcedwp3zv63dwa5hg6pdvykkx6r9v4ehjtt5wa5hxaqzyzmjwnfgu05c80mjpk6tfgf2x86u0mexyvsdqhp9ajgy3xkfjc5vkqcyqqq823cfuzkwc
https://image.nostr.build/b2a84afc5ea7948c3f8087b555ce9a43a5f543402b1ecb283cc884b93f1f8a2b.png
zap.cooking/recipe/naddr1qqvxyet9vckkzmny94sh2cn9wfnkjmn9943h2unj0ypzq3xurskmnslm67lwjft7e66jhc7033qt4aak8arw266c5ycuwnctqvzqqqr4guhg7y8e
https://image.nostr.build/ec7ef7667e252d63164682ed420ae94dc15758798cd80d62e8491ec35cef0f69.png
zap.cooking/recipe/naddr1qqfkvetjd4jkuar9vskksmm5945x7mn90ypzqqwsh0u4xlh3l5xalq2lg8qcjeec7636pasq75w8s2ma3zg3xr2vqvzqqqr4guvhlwd6
https://image.nostr.build/13b8af46a09dcf0ab04a37aae7f22c16fe31740ef4bc0984e8cf7b582e45332f.png zap.cooking/recipe/naddr1qq8xyetpdeej6mmw946x7ctnwspzp89qh469qapddgsrr8qw84xx08y7q34fm3cw3m64c2g9ufq9ydqtqvzqqqr4gug3lkp4
RECIPE REVIEWS ✏️
https://image.nostr.build/5ef1e884bde50d01215de6c3ed63e2d9a78bac0bd8eade1df6bf91c1b63ad3c1.png zap.cooking/recipe/naddr1qqtkwctjd35kxumpw43k2ttxdaez6ctw0ykkycn3qgswat02dja4qx9pjrcpz7zhmegnesn36fxfgl2kekpv2jntvjhy0fqrqsqqqa28m4rxcx
https://image.nostr.build/96299dcb152c513360f171038d032de102c29497634e1ba7b60abc1b215a4a42.png zap.cooking/recipe/naddr1qqjkket5dukksctd9skk2em895nz6cmgv4jhxefdvfex2cttveshxapdvd6hquczyzdu956dmk5rm9p2rlwndf6g07d2a36qmvjw57tn9kgw8q73n555sqcyqqq823c8r4tsp
ECONOMICS 🍞
AN ARTICLE ABOUT BAKERS | Silberengel (4 minute read)
https://image.nostr.build/4f11eea6d6a5f7476c0bbe0504f57e7111454c9b30ee0816ee0f85816d240e3b.jpg
Let's Talk About Baking Bread
I've mentioned a few times, how large-scale central planning inevitably leads to artificial scarcity and rising prices. Allow me to illustrate -- using a completely invented allegory about bread -- that has absolutely no parallels to any economy you may already be familiar with…
Read More | habla.news/a/naddr1qvzqqqr4gupzplfq3m5v3u5r0q9f255fdeyz8nyac6lagssx8zy4wugxjs8ajf7pqqxnzdejxucnwvfnxvmnsd3cgqxylq
MICROFICTION 📖
GOOD DEEDS | Rustypuppy
Being a trail guide at the UCP (Unique Creatures Preserve) meant I saw a lot of weird things. Some I show to the tourists; some I don’t.
The starved, green-skinned toddler with the turtle shell back, beak, and dish of water on his head was one of the latter. As he ignored the bologna sandwich and devoured the cucumber salad from my lunch, I flipped through my identification guide. Finally found him in the Japanese yokai section; a kappa - known for drowning animals and people, loves cucumbers and sumo wrestling, can be friendly and helpful, empty the dish on its head to severely weaken.
I filled up his dish from my water bottle, and he followed me down the mountain trail. As soon as he saw the glimmer of water, he ran ahead and dove in. I assumed from the lack of frothing water and the fact he didn’t end up punted onto the bank meant the lake god had accepted him.
Later that week, two teens stumbled into our office. One guy, obviously stoned, wanted us to give him the official wizard certificate since he had just walked on water. The other guy, obviously drunk, said his friend needed the druid certificate because he had summoned a turtle to appear under his feet, which is how he had spent the past half hour walking across the lake. I told the intern to take their contact info and arrange a taxi.
The next day, I left a large container of cucumber salad at the edge of the lake.
RECIPE REFERENCE | Grandma’s cucumber recipe zap.cooking/recipe/naddr1qq0kwunpdejx6cf8wvkkxun9v9khjttrw43h2mtzv4ez6umpd3skgq3qkgh77xxt7hhtt4u528hecnx69rhagla8jj3tclgyf9wvkxa6dc0sxpqqqp65wss0rqd
Follow Rustypuppy | https://rustypuppy.npub.pro/
FAMILY FOODLOVE 🐤
https://image.nostr.build/c5b498d176a03742a864de6ae1c833107089e798e4a9c3c111b5be8850df2397.png
https://image.nostr.build/55a8948263766f0f4360d9bddb30ada915cae51a93b3d7be1b4a7a9e6cc21b71.png
https://image.nostr.build/f17a5dd1cf93ae0d20b7904e0e0274d4dda3a6dd4c90c506b512232af08bec83.png
https://image.nostr.build/ef81f242c481e60cff9dd4a66ac74326a8e27ff0f87ae1f51a915046eecb8258.png
FOOD SWOON 💌
https://image.nostr.build/a0eeb835a8eee1221f4e6aeeb884b5897eea7335680f2e5b35bee35b517db432.png https://image.nostr.build/f2a8a21cd1587a39d0ce5fe09ef5176b773416d0419a6b5fb404c02fa6616730.png https://image.nostr.build/c4f54698566500ace19d12bef5168b0a6e7047a0c8c1daa3faa207253177b104.png https://image.nostr.build/22a0aaacbf37e88db702db655a4f9e7b0692d586304e9ecfffa694f379a88fd9.jpg https://image.nostr.build/f3918b3c68dc04bc3aae4e5202702875ebd4668676abe64fbc1e8cb001dde3c2.png
NOTE SYNCING 🗒️
“..everyone needs to eat pizza. Each individual country can choose what toppings they want on their pizza, so whether that’s pepperoni or mushrooms or anchovies if you are weird…” | OpnState on https://fountain.fm/episode/dg7rlmtOICVDGwtr7Jnc
"I eat sardines out of the tin with chopsticks." | @the_beave
“Chef has renamed Sardines to ‘Salt Daddies’. Please inform the staff.” | @enki
“My segue into sardines #FoodPorn” | @Deva Pyne (talking about HowToFoodPrep’s Sardine Dish) https://image.nostr.build/0f979d1bb7c0ba3c600694b83c5bc8e84ce4ff039839fb9f9af7ea727accef8b.jpg
SOUNDS 🔊
MUSIC
MAN LIKE KWEKS x BILLIV
Shoutout to Man Like Kweks x Billiv for making songs about PB & J cool! | singing Go together like peanut butter and jelly... | NOSTR CITY | KWEKS x BILLIV • Man Like Kweks (wavlake.com) | https://wavlake.com/track/f46d82f2-7f26-4357-9258-32da68324f74 | Man Like Kweks made a special appearance on Detox Radio | https://fountain.fm/episode/hGH0AgRj6hvrZEnSlX6n/ | https://image.nostr.build/baf111d653e75e88fc818529ba7872563e72be9540b21d0dea70b712d565dadd.png
PODCASTS
PLEBCHAIN RADIO
https://image.nostr.build/748c4c9f104582f583c3e3e30603be3964d0ddd3c8041a72680d5b8d48bc7108.png Zap.Cooking's very own Seth joins former Nostr CEO Derek Ross on Plebchain Radio hosted by the infamous duo: QW & Avi | CLIP - Super Rare Nostr.Cooking Magnet | "That's one of those physical NFTs" | https://fountain.fm/clip/dTzOg3VXOtLaXdR28oKE
ON THE FLY WITH STU
https://image.nostr.build/56ac7daf7d8158cde5f31ac2555f03ba26fe9de1afb5eeb26f4ba54f350bb7b8.jpg Recommended listening from our new fly fishing aficionado, onthefly@iris.to with Stu aka ON THE FLY WITH STU | https://fountain.fm/clip/9KjsUBPwmnmpR11UscKP
THE BITCOIN PODCAST
https://image.nostr.build/53fcc6f8468f3f18d0920fa0dcf386c01b7f02833101984bb26fff31916da498.jpg A VERY special thanks to Walker, the host of The Bitcoin Podcast, for giving Zap.Cooking a shoutout on his platform | "Okay this is pretty neat. Recipes on Nostr. Like the recipe? #zap it. Check out https://zap.cooking #grownostr" | Please check out one of the best voices that Nostr has to offer at bitcoinpodcast.net/podcast
QUOTE OF THE MONTH 📣
"Nostr and Bitcoin will change the world because they're like peanut butter and jelly - decentralized freedom meets unstoppable money, making sure no middleman gets a slice of your sandwich!" | Uncle Rockstar✊
UPCOMING EVENTS 🥳
Submit your Nostr event with @ZapCooking on Nostr
Nostr Valley @ Happy Valley Brewing Company | October 12, 2024 - 12pm to 4pm (est) Sign Up @ www.nostrvalley.com
Nostrville 2.0 No Panels, All Party! @ Bitcoin Park | November 6, 2024 - 4:30pm to 7:30pm (cst) https://www.meetup.com/bitcoinpark/events/303283108/
https://image.nostr.build/d484fb5058f39d7f15dfe048dc91b1b697c45c117612ec0202d8a5bb681af02a.jpg
ANNOUNCEMENT 📰
RABBIT HOLE RECAP REBRANDING
https://image.nostr.build/dacfbb06c6b76582814ad035ff44d9a66a885cdb97783e56b491d6b2e4b6d1f5.png https://video.nostr.build/a6b670ea0839d2d5d35ee4d38d9a082a0ce4b93aeb6ffaad18c89de829ccbc95.mp4
https://rhr.tv/ | Please send them a warm congratulations! 🤠
https://image.nostr.build/497029805a46bbb4942bcb13a0e8f0238e3c7956282d4d2866ca342d19f54bad.jpg
LANGUAGE 🏫
SCHOOL'S IN SESSION
Write "egg" in 50 of the Most Popular Languages
English: egg | Spanish: huevo | French: œuf | German: Ei | Italian: uovo | Portuguese: ovo | Russian: яйцо (yaytso) | Chinese (Simplified): 蛋 (dàn) | Japanese: 卵 (tamago) | Korean: 계란 (gyeran) | Arabic: بيضة (bayda) | Hindi: अंडा (anda) | Bengali: ডিম (dim) | Turkish: yumurta | Vietnamese: trứng | Thai: ไข่ (khai) | Persian (Farsi): تخممرغ (tokhm morgh) | Swedish: ägg | Danish: æg | Norwegian: egg | Finnish: muna | Hungarian: tojás | Czech: vejce | Slovak: vajce | Romanian: ou | Bulgarian: яйце (yaytse) | Ukrainian: яйце (yaytse) | Malay: telur | Indonesian: telur | Filipino: itlog | Swahili: yai | Serbian: јаје (jaje) | Croatian: jaje | Bosnian: jaje | Lithuanian: kiaušinis | Latvian: ola | Estonian: muna | Icelandic: egg | Maltese: bajda | Welsh: wy | Irish: ubh | Scottish Gaelic: ugh | Basque: arrautza | Catalan: ou | Galician: ovo | Armenian: ձու (dzu) | Georgian: კვერცხი (k'verts'khi) | Tatar: йомырка (yomyrka) | Kazakh: жұмыртқа (jumyrtqa) | Tamil: முட்டை (muttai)
#NOSTRASIA2024 ALBUM 📷
https://image.nostr.build/9243af94d1ae162bcf9ea14baad39286c4162dc838dd3d82f988e7a032f50328.png
Community Photos & Videos by A.k.A. radish on fire🎤 @hakkadaikon, @HonokaShisha, @Kojira, @Jeroen and the contributors of the hashtag #NostrAsia2024 | Share your Nostr community photos or videos with @ZapCooking
MESSAGE from A.k.A. radish on fire🎤 @hakkadaikon
Hello!
Thank you very much for coming to Nostrasia 2024 on the 23rd of September!
Now, you can see the live-streamed videos of the speaker events and the afterparty from the YouTube archive. Please check them out especially if you could not join the talking events. You can jump into a session you like from the chapter lists in the video descriptions.
Thank you!
Nostrasia 2024 Part 1 https://www.youtube.com/live/i-oHjdYWo1E
Nostrasia 2024 Part 2 https://www.youtube.com/live/tGeHKrqTA4A
Nostrasia 2024 Part 3 - Afterparty (Tuna cutting show) https://www.youtube.com/live/ery0aWATjWk
GIKOGIKO KAIJI TUNA | KOJIRA
https://i.nostr.build/Y2jTdGxblC98KeWI.jpg https://v.nostr.build/dKSZbmNOZ9JbM8wv.mp4
SHISHA CAFE, BAR & COMMUNITY SPACE
https://i.nostr.build/UdNbeXdB628wW2dK.jpg
JEROEN'S TOKYO VISIT
https://image.nostr.build/8e384c2620088f3fe5001f797576625649e0c0f53f3415193d2f51a92d16ba3b.jpg https://image.nostr.build/b43988efa086653155b7c9109ca5f4d2903adb5e0879a302a9ef743c05263523.jpg https://image.nostr.build/f2b584e728f95b747a5795741451df63c36c5eafef5886ecd3635c381bcd40e2.jpg https://image.nostr.build/d9e6c2ccd290a558202747e471ec5df025e0c37720f0563a7f5928ed56429a9b.jpg https://image.nostr.build/c9f5ec9f7ec03cd2f4d9c12f151e7548879b022590d063dc2226f5deb00c40f1.jpg https://image.nostr.build/cd58ed78004f46a65b84ea279fee5a07e4ca6762b4964b1b95149dde2303bc6a.jpg https://image.nostr.build/674ef0111ee987967bf1f98bb880bc3d7c4667033d5f067668881fd3d8bf1918.jpg https://image.nostr.build/5df690358d06cc62fe9260311d606c812a67a0d4b4b6779a3c48f4986446799e.jpg https://image.nostr.build/837696634b1e546ee1f6e2ec8cd1aa4f813df017010c4434c9b93291fa4a6d1c.jpg https://image.nostr.build/771c0b2f8e15aa901f4ef1da34be8843eeac716a1f792be714745283be71eecd.jpg https://image.nostr.build/48555bd4db7bb7f707dd78882dafd669cb1f860d851389d18ab0b1f2e3423da6.jpg https://image.nostr.build/76d3c990cb337d9f8a413032a0c4b7ab60c7b3faffc52baed6c7bcda9ddec8ee.jpg https://image.nostr.build/4c532360c28aaceb7fadbcc0ff0e9737be27d41a8213c79cbd0621f2b367a15b.jpg
FINAL THOUGHTS 🤔
What are your thoughts on the instant translation of food videos to enhance global accessibility?
https://video.nostr.build/4dba5f5e87d2f9bfda5f04dae82c3ce8d7cee41f19033906c6d59a60dd42a9a5.mp4
What is your opinion regarding Trump’s visit to PUBKEY and purchasing food & beverages with Bitcoin?
PUBKEY: * Smash Burger: $12.50 x 50 = $625.00 * Diet Coke: $3.00 x 50 = $150.00 * Subtotal: $775.00 * Tax: $68.77 * 20% gratuity: $155.00 * Total: $998.77 A former president spending #bitcoin at your bar: PRICELESS.
https://image.nostr.build/70c72f924b9cd8d429e0f1c030ce35c52604485e553f1c24af0b1d1737f3adc9.jpg https://image.nostr.build/f1bd17df540bceb7f8f4f2ed7979cc20c86e7d38ddc35d1d8988321c08cc1ee4.jpg https://media.primal.net/uploads/2/ed/89/2ed896f3be4eaec166230e582e4228a53d82652e38a90620aef09cb5da5b1c7d.png https://v.nostr.build/sbPbqOIvSpCffo4I.mp4
fin💐
September Issue 1 | https://habla.news/u/zap.cooking/ZAP-COOKING-NEWSLETTER-4yxs6s
-
 @ 4ec341e6:6dc2fdaf
2024-10-08 13:42:23
@ 4ec341e6:6dc2fdaf
2024-10-08 13:42:23O capítulo 2 tem um ótimo título: "Dizendo não". O autor argumenta que profissionais dizem a verdade, e isso inclui dizer "não" a seus gerentes. Isso é interessante, dado o fato de que essa é uma palavra não usual para brasileiros, que costumam usar frases como "vou ver e te aviso" ou "vou tentar" em vez de dizer simplesmente "NÃO" — E o autor vai nessa linha do "vou tentar" em vez de dizer "não" para coisas que serão impossíveis.
E como papéis são contraditórios, gerentes vão sempre querer o máximo de trabalho no menor prazo possível, e os desenvolvedores devem saber dizer "não", mesmo quando pressionados. Negociar com os gerentes pode ser uma forma de obter o melhor resultado para ambas as partes, entregando uma demo incompleta, por exemplo, desde que isso tenha sido acordado entre ambas as partes.
O autor também argumenta que isso não deve gerar uma cultura de "nós" contra "eles", pois ambos estão defendendo seus interesses; cabe a nós desenvolvedores defender os nossos.
Todos nós já escutamos sobre o quanto é importante saber trabalhar em equipe. Isso significa desempenhar seu papel da melhor forma possível e ajudar seus colegas quando estiverem com problemas. Aquele que sabe trabalhar em equipe se comunica frequentemente, mantém o olho nos colegas e executa suas responsabilidades da melhor forma.
E o mais importante: Não existe a palavra “tentar”, ou é sim, ou é não, o “vou tentar” vai ser aceito como um sim, e será uma mentira caso o desenvolvedor saiba que nada de diferente para acelerar a entrega será feita.
Ao prometer “tentar”, estará se comprometendo com o fracasso.
E para dar um exemplo, o autor reproduz um blog post "Is Good Code Impossible?" inteiro de John Blanco no livro, onde um desenvolvedor vai aceitando demandas, codando com grandes sacrifícios (horas extras e um código ruim sendo escrito) conforme o escopo do projeto vai aumentando. Ele concordou com tudo, tentando ser um herói em busca de reconhecimento por ter feito uma entrega tão grande em tão pouco tempo.
No final, no dia do aplicativo entrar no ar, o cliente da empresa disse: "Desistimos da ideia, pode tirar o aplicativo do ar." Realmente, ele deve ter ficado com cara de palhaço 🤡 nessa.
Então o autor começa a discorrer sobre esse blog post, questionando de quem seria a culpa. Do cliente? Da empresa? Ou dele mesmo? Porque o cliente procurou a empresa buscando quem entregasse o projeto em duas semanas, a empresa concordou, e ele concordou com esse prazo dados os requisitos iniciais. Porém, o escopo foi aumentando e, ao ver que seria necessário um grande sacrifício, ele deveria ter dito NÃO.
E porque Jhon fez isso? Ele nos diz em termos incertos: “Apertei enviar, recostei na cadeira e, com um sorriso amarelo, comecei a fantasiar como a empresa me carregaria em seus ombros e faria uma procissão ao longo da Av. 42, enquanto eu era coroado como o ‘Maior desenvolvedor de todos os tempos’”
Resumindo, Jhon estava tentando ser herói, Viu uma chance para ser louvado e foi atrás dela. Ele se inclinou e agarrou a coroa.
Porém, como argumenta o autor, profissionais não tentam ser heróis, eles tornam-se heróis ao fazer seu trabalho bem feito, dentro do prazo e do orçamento possíveis, sem tentar "salvar o dia".
Isso inclusive me faz refletir sobre uma experiência pessoal, onde o CEO e CTO da empresa estavam no cangote do tech lead da minha squad, ansiosos pela entrega rápida de um projeto. Estávamos fazendo horas extras e trabalhando de domingo a domingo, até que, para garantir a entrega na data que queriam, começamos a negligenciar a qualidade e pequenos bugs, e seguimos codando. Quando finalmente terminamos, deixamos disponível para homologação pela área de negócio. Do jeito que o tech lead estava sendo cobrado, imaginamos que seria homologado rapidamente, enquanto trabalhávamos nas correções dos pequenos bugs que ficaram no sistema e já partíamos para outros épicos que também deveriam ser feitos (nunca falta backlog).
Pois bem, o projeto só começou a ser homologado pela área de negócio dias depois, e só foi dado o OK para a subida em produção duas semanas depois. Ou seja, era uma hard date que na verdade não era uma hard date; poderíamos ter trabalhado de forma mais tranquila. E parece que até hoje o tech lead é meio que lembrado sobre como o projeto poderia supostamente ter sido entregue antes, quando não poderia — era simplesmente muita coisa, mas para quem está níveis acima do chão de fábrica, tudo parece "fácil".
Como o autor do blog diz e o autor do livro concorda:
[...] cada recurso que um cliente pede será sempre mais complexo de ser escrito do que explicado.
Em resumo, a lição do autor e do blog post é clara: ao tentar ser um herói e aceitar prazos e demandas irrealistas, o resultado pode ser desastroso tanto para o profissional quanto para o projeto. Saber dizer 'não' é uma habilidade essencial para qualquer desenvolvedor que deseja realizar um trabalho de qualidade sem sacrificar sua saúde ou a integridade do projeto.
-
 @ 1bda7e1f:bb97c4d9
2024-10-08 09:46:01
@ 1bda7e1f:bb97c4d9
2024-10-08 09:46:01Tldr
- Nostr comes with integrated Bitcoin payments called zaps
- It’s possible to set up a self-custodial wallet that you host yourself, plus
- Add all kinds of bells and whistles, like phone app and browser plugin
- The software I’m using is Albyhub and Phoenixd, deployed with Docker to a cheap VPS
- I can now receive payments to my Lightning Address rodbishop@getalby.com
Payments on Nostr
One of the great features of Nostr is integrated payments. This feature integrates financial transactions directly into the social network, as a seamless part of using the network.
You can get paid by and pay anyone on the network, to or from anywhere in the world, and for any reason, in a way that is instant and nearly free.
The payments get to be instant and global and free because they are made in Bitcoin, using the Bitcoin payments network called The Lightning Network.
Per Bitcoin, payments are denominated in satoshis (sats). A sat is a one-hundred-millionth of a Bitcoin– US$1 is about 1,700 sats at the time of writing. Making a payment like this on Nostr is called a “zap” and usually indicated with a lightning bolt symbol (you are getting “zapped by lightning”). You might say to your friend ”I'll zap you 1,700 sats”.
This unlocks all kinds of interesting things that are not possible with other social networks, like
- “value for value”–A publisher publishes something of value and you can tip them if you like it
- Payments between friends–Nostr can do everything that Cash App and Venmo can do, right down to splitting payments to multiple recipients
- Payments for creators–you can sell or pay to access premium content similar to any kind of paywall site like Patreon or Substack
- Payments to AIs–you can pay for automated AI-based services including for translation, image generation, or creating custom curated social media feeds
- All other kinds of ecommerce–you can sell or buy anything you want similar to Gumtree or Facebook marketplace
Every Nostr user can have this set up. It's free or nearly free to set up, nearly free to make payments, and some apps like Primal will even set it up for you by default.
Moreover it's useful and it's fun.
- When you help someone out to receive a little tip for doing so, or
- When you get some great advice to show your appreciation in a more meaningful way than a like
Ways to set up lightning for zaps on Nostr
You can get paid in Bitcoin to a lightning address. This looks exactly like an email address except you can make a payment to it from a lightning wallet.
Anyone can publish their lightning address on Nostr so that you can pay them. And you can also get your own lightning address on your own Nostr profile so that people can pay you.
The lightning address links to a server that’s always active and ready to credit your balance whenever you receive payments.
To make that happen at a high level there are two options, either:
- Open an account with a custodial lightning provider who will keep an always on server with your wallet on it, live and ready to receive payments for you. Primal does this automatically for you in their Nostr client, or you can use any one of the other popular custodial wallets like Wallet of Satoshi, Zeus, Coinos, or many others
- Set up your own self-custodial lightning server that runs on an always-on computer or server, which you can administer yourself
Generally using a custodial service will be easier, but comes with the need to trust that third party custodian, and may limit you to pay within their app.
For myself I'm going to self host using Albyhub by npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm, and Phoenixd by Acinq.
Hosting your own lightning server with Albyhub and Phoenixd
Anyone who's experimented with self-sovereign setups for Bitcoin know that historically there's been quite a bit of heavy lifting.
My number one favourite feature of what Albyhub and Phoenixd have done together is to create a nearly instant set up with no heavy lifting. I was stunned. For anyone who's used to jumping through hoops with this, it was like magic.
You can use Albyhub with any lightning wallet backend, but in my view none are as automatic, and magic, as Phoenixd.
Compare the traditional set up with the Albyhub and Phoenixd setup.
Traditional–
- Set up a Bitcoin core node
- Download the entire Bitcoin blockchain (wait several days for it to download)
- Set up a Bitcoin lightning node
- Purchase payment liquidity to enable payments to the network
- On an ongoing basis continue to keep your blockchain in sync with the network
- On an ongoing basis manage your inbound and outbound liquidity to your network peers
Vs Albyhub and Phoenixd–
- No Bitcoin core
- No initial block download
- Phoenixd provides liquidity for you automatically and by default
- Nothing to keep in sync with the network
- No liquidity to manage
For any normal non-technical user, self-hosting your own lightning node just went from being too hard, to very achievable.
Unpacking the parts
There are a few parts to this set up and there’s a bit of assumed knowledge here, so let’s quickly unpack it
- Bitcoin–money for the internet, which enables payments to and from anywhere
- Lightning–the main payments network that sits on top of Bitcoin, which makes transactions instantly and with very low fees
- Phoenixd–a lightning wallet back-end with special methods for managing liquidity that makes it almost no-touch to set up and manage
- Albyhub–a lightning front-end with an easy to-use wallet, and a feature called “Nostr Wallet Connect” (NWC) which connects the wallet to Nostr
- AlbyGo–a phone app so you can make payments on your phone
- Alby Plugin–a web browser plugin so you can make payments on your browser, and also log into Nostr from your browser (using NIP-07)
- NWC–a method for connecting your wallet directly to Nostr apps so that you can spend from your wallet balance without even leaving the app
- Lightning Address–an address like an email address where you can receive payments (using LNURLp; Lightning Network URL)
I'm going to plug it all together, so that I can pay for anything in any way I like (from NWC, Alby Plugin or Alby Go), and receive payment from anyone (to our Lightning Address), with all funds managed on my own server (hosting Albyhub and Phoenixd).
How to set up Albyhub and Phoenixd
To set this up requires basic command line knowledge, and some experience with Docker. I didn’t have that experience, so I gave ChatGPT the docs on each of Albyhub and Phoenixd and it walked me through the setup.
To start with, I got myself a cheap VPS, and installed Docker. Docker then allowed me to deploy Albyhub and Phoenixd as a container.
The Albyhub Github contains very helpful readme, here https://github.com/getAlby/hub
And Phoenixds own docs here https://phoenix.acinq.co/server and here https://github.com/ACINQ/phoenixd
Alby also has a dedicated section to working with Albyhub with Phoenixd backend, here https://github.com/getAlby/hub/blob/master/scripts/linux-x86_64/phoenixd/README.md
First, install Docker and make sure it is running.
Then working with the code on the Albyhub with Phoenixd page–
- Get the docker-compose.yml file which will instruct Docker to create the relevant containers,
- Create the directories for the files to be stored in
- Launch the containers
That’s it. Docker will proceed to create the application for you running on port 8080
You can then log in in a web browser and start the setup–
- There’s a helpful step-by-step guide to walk you through the set up including to set up a password for your hub
- It will ask you to connect your Alby account. I skipped that step as I didn’t have one at the time, I only created one later
- If you used the default lightning back-end, Alby will then ask you to buy your first liquidity to enable you to make payments. Or, if you are using Phoenixd, then the step is automatic and you can go right ahead to transfer in some initial funds
Setting up the bells and whistles
That's the hard part done. The next step is add all the little extra pieces that make for a great Nostr experience.
Alby Browser Plugin–
- Download the Alby Browser Plugin to your web browser and create an account
- It will give you a new Nostr and Lightning account by default, and you can replace it
- For me I had my own keys already saved with a mnemonic backup, and I wanted to use these. I went to Settings and clicked “Remove Master Key”, then entered the mnemonic backup of my own keys. I also went to Nostr Settings and clicked “Derive from Master Key” to replace the one it generated by default.
- Visit Albyhub, and connect the Alby Account
- This completes the set up to login and zap with Nostr on any Nostr site
Alby Go App
- Download the Alby Go App to your phone from your phone’s app store
- Vist Albyhub, go to the Alby App Store, and click Alby Go
- It will help you to create a connection between your Albyhub and Alby Go
Nostr Wallet Connect
- You can use the Alby App Store to connect any Nostr app in the same way
- Vist Albyhub, go to the Alby App Store, and click on any Nostr App
- I used Amethyst, and I was able to create a connection between Amethyst Nostr app and Albyhub, so that when I click the “zap” icon in Amethyst it can automatically spend from my Albyhub wallet without any further clicks
Your own Lightning Address
- Your Alby Account in your Alby Browser Plugin gives you a Lightning Address by default. It is generated randomly to start with, and you can replace it.
- Open the Alby Browser Plugin and visit Settings
- Click “Change on getalby.com” and change it to something that suits you
- I changed mine to rodbishop@getalby.com
That completes the set up.
Backups
Now that everything is set up, it’s time to make a backup.
I already had my Nostr keys as a mnemonic backup from my last article, and I’m using these keys for my Alby Account, so there is nothing new to back up there.
But we still need backups for the Albyhub login credentials, and the Phoenixd wallet.
When started for the first time, Phoenixd will generate a 12-word mnemonic of its own, which it will use to restore your wallet balance in case of any issue. This recovery phrase is stored in the phoenix folder you created, at \~/.phoenixd/seed.dat.
In total, your backups will contain:
- Your 12 word mnemonic backup of your Nostr keys, that is also the same master 12 word mnemonic for your Alby account
- Your 12 word mnemonic backup for your Phoenixd wallet, that is created by the daemon when it first runs at \~/.phoenixd/seed.dat
- Three passwords: 1) Your password for your Alby account, 2) Your password for your Alby Hub, 3) Your password for your Phoenixd (that is hardcoded into the docker-compose.yml)
Once these are backed up somewhere safely, you can fully recover your set up if ever anything goes wrong.
Things I did wrong in set up so that you don’t have to
Initially I had some trouble with user permissions. I was able to resolve it by changing the user configuration in the docker-compose.yml.
I also had some trouble with the initial funds transfer. In order to test everything without risking significant funds, I made an initial transfer to the hub of 10 satoshis.
- The transfer was received immediately, but
- The available balance stayed at zero, and
- I couldn’t make any payments (insufficient funds)
I thought this was a bug in my set up, but it turns out this is a feature of Phoenixd auto-liquidity, that it keeps some initial sats as a payment credit to buy the required lightning channel liquidity. The total cost amounts to on average 1% charge, but it is also front-loaded, and because my payment was so very tiny (10 satoshis worth a fraction of a cent) the payment was entirely front-loaded.
I diagnosed this by accessing Phoenixd directly in the cli, and by doing so, I was able to see the balance present, as a fee credit.
To check, run–
- docker-compose exec albyhub-phoenixd /phoenix/bin/phoenix-cli --http-password=<your-password-here> getbalance
And receive a response like this, which shows the credit on the account –
- { "balanceSat": 0, "feeCreditSat": 10 }
The above command–
- accesses the albyhub-phoenixd container “docker-compose exec albyhub-phoenixd”,
- then accesses the phoenix-cli application at “/phoenix/bin/phoenix-cli”
- and asks the application to “getbalance”
Helpful docs–
- Phoenixd talks about that fee credit behaviour quite clearly at their own site, here https://phoenix.acinq.co/server
- They also provide docs on their cli to interact directly with their daemon (rather than using Alby), which you can read here https://phoenix.acinq.co/server/get-started
I wondered what the total initial amount would be that would be captured as fee credit. Your mileage might vary, but for me:
- I transferred in 2,100 sats (about $1.20)
- I received a working balance of 775 sats, so I paid 1,325 sats in fees
- I then transferred in another 2,100 sats
- I received all 2,100 sats (paid no fees at all on the second transaction)
All up only a few cents to get started with initial liquidity.
In summary
Nostr has integrated payments that are instant and nearly free, using Satoshis on the Lightning Network. Some Nostr clients come with a wallet set up automatically, and it is quite easy to set up your own self-custody wallet, with all the bells and whistles.
I wanted to set up my own self-custody wallet so that I could test and learn the full set up of the system. For this I used Albyhub and Phoenixd, and I deployed it to a cheap VPS using Docker.
Once set up, I added all the extra bits so that now–
- I can login to Nostr from my web browser with the Alby Browser Plugin
- I can make payments from there too, or from the AlbyGo App, or from any Nostr app I like
- I can receive payments to my Lightning Address rodbishop@getalby.com
And in doing this–
- I don’t rely on any third-party custodian to take care of my funds
- I had no hard work to install this setup, and expect no ongoing admin to keep it running
- With everything set up, the system simply works (so far!)
For anyone interested in Nostr or Bitcoin software or technologies, I recommend to go through a set up like this as it really covers the full gamut or the Nostr–Lightning–Bitcoin stack. It’s clear how far this technology has come and how powerful it can get from here.
Up next
- Please let me know if this kind of post is helpful or anything you’d like me to improve or expand upon
- For my next post I’ll show how I set up Nostr and lightning addresses at your own domain with Sveltekit and Vercel
-
 @ 13e63e99:25525c6a
2024-10-08 09:36:41
@ 13e63e99:25525c6a
2024-10-08 09:36:41
The recent surge in the Chinese stock market follows a series of government announcements outlining new economic support measures and initiatives designed to boost institutional investment in equities. These interventions have sparked a sharp recovery, with the CSI 300 index, which tracks the largest stocks listed on the Shanghai and Shenzhen exchanges, soaring by nearly 16%—marking its best weekly performance since 2008. The rally has helped the market recover from the near year-lows it had been hovering around prior to the news.

Thursday, President Xi chaired a high-level meeting, underscoring the government’s commitment to halting the ongoing decline in the real estate market, which has been a major drag on the broader economy. The meeting also focused on bolstering fiscal and monetary policy to stimulate economic activity. In tandem with these efforts, the People’s Bank of China (PBOC) implemented key measures, including a reduction in interest rates and a cut in the payment obligations for existing mortgage holders, aimed at relieving financial pressures on households and spurring consumer spending.
Commenting on the recent developments, Zhu Ning, author of China’s Guaranteed Bubble, noted that “the policy response is much stronger and more coordinated than it was in 2015, but the economy now faces greater headwinds than it did back then.”
While the strong market rally is encouraging, it remains uncertain whether this momentum will translate into a lasting recovery. A true, long-term economic rebound will require a significant improvement in corporate earnings, which are still under pressure. Without sustained growth in the corporate sector, these market gains could prove to be short-lived. Moderate, stable growth remains essential for ensuring China’s long-term economic resilience and stability.
Reference: Google Finance, Fidelity

Balaji Srinivasan's concept of the Network State represents a bold rethinking of how societies can be organized in the digital age. The idea, which he outlines is that digital communities can eventually become sovereign states, bypassing traditional territorial-based governance structures. His proposal, while visionary, raises significant questions about governance, identity, and the future of nations in a decentralized world.
Core Concept of the Network State
At the heart of Srinivasan’s theory is the belief that with the rise of digital networks, people can form communities around shared values, goals, or interests—completely independent of geographic boundaries. These digital communities, or "network unions," would initially be social and economic in nature, built through online platforms. As they grow in size and influence, they could develop their own governance structures, economies, and even physical land, eventually claiming statehood.
Balaji argues that the traditional nation-state model is increasingly outdated, given that it is tied to fixed territories and centralized power structures. The network state would break away from this model by being fluid, borderless, and decentralized, leveraging technologies like blockchain, cryptocurrency, and decentralized autonomous organizations to facilitate governance and economic interactions.
Key Features of a Network State
-
Digital-first Governance: Instead of a centralized government, a network state would rely on digital governance systems. Blockchain technology could be used for transparent voting, smart contracts, and decentralized decision-making, ensuring accountability and participation from members.
-
Shared Vision: A network state is not defined by territory but by a shared mission or value system. This collective vision is the glue that binds members together, whether it's environmentalism, technological innovation, or certain social values. The strength of this shared vision replaces the need for traditional national identity or culture based on geography.
-
Crowdsourced Funding: Traditional states rely on taxes to fund public services, but a network state could leverage crowdfunding, decentralized finance, and cryptocurrency to raise funds for projects, infrastructure, or land purchases. Members can directly contribute to initiatives they care about, creating a more engaged and financially invested citizenry.
-
Geopolitical Recognition: One of the boldest claims in Srinivasan’s vision is that these digital nations could, over time, acquire physical land or “embassies” and seek recognition from traditional states. Diplomatic recognition would validate their sovereignty, enabling network states to exist both digitally and physically.
-
Digital Asset-enabled Economies: The economic foundation of a network state would be heavily reliant on cryptocurrencies and decentralized finance systems. These economies could operate without intermediaries like banks or traditional fiat currencies, making them more adaptable and efficient, especially in the global digital marketplace.
Reference: The Network State

Bitcoin Remains The Top-Performing Asset in 2024
Bitcoin remains the top-performing asset in 2024, despite a modest 2.5% gain in Q3, according to NYDIG. Bitcoin has seen a year-to-date rise of 49.2%, although large sales and distributions, including $13.5 billion from Mt. Gox and Genesis creditors, have weighed on its price. Bitcoin’s performance has outpaced other assets, although the gap has narrowed.
Bitcoin's 10% rise in September defied typical trends, driven by demand from spot ETFs and increased corporate adoption by companies like MicroStrategy. The U.S. election to impact Q4, with potentially larger gains if Trump wins. Despite headwinds, Q4 is historically bullish for Bitcoin, Bitcoin's current performance mirrors its past cycles at this stage.

Reference: NYDIG, Bloomberg Cointelegraph,
IMF Urges El Salvador to Scale Back Bitcoin Policies, Advocates for Stronger Regulation and CBDCs
During an Oct. 3 press conference, the International Monetary Fund (IMF) once again urged El Salvador to scale back its Bitcoin policies and overhaul its regulatory framework for the digital asset. Julie Kozack, director of the IMF’s communications department, emphasized the need to limit the public sector’s exposure to Bitcoin while recommending a narrower scope for El Salvador's Bitcoin Law and stronger oversight of the cryptocurrency ecosystem.
Since El Salvador made Bitcoin legal tender in 2021, the IMF has repeatedly pressured the country to shift back toward traditional financial systems. In its August 2024 report, the IMF reiterated these concerns but admitted that many of the anticipated risks associated with Bitcoin adoption had not yet materialized.
The IMF’s broader stance on Bitcoin reflects its ongoing concerns about the volatility and risks posed by non-state-controlled Bitcoin. While countries like El Salvador have embraced Bitcoin as an alternative to traditional fiat currencies, the IMF continues to warn against these digital assets, advocating instead for tighter regulation and oversight. At the same time, the IMF is actively pushing for the adoption of central bank digital currencies (CBDCs) as a more stable alternative.
Reference: Cointelegraph
PayPal Expands Bitcoin Services to U.S. Businesses
PayPal Holdings, Inc. (NASDAQ: PYPL) has rolled out new cryptocurrency services for its U.S. business account holders, allowing them to buy, hold, and sell cryptocurrencies like Bitcoin directly from their PayPal accounts. While this service is available nationwide, it will not be accessible in New York State at launch due to regulatory constraints.
In addition to buying and selling, U.S. merchants can now transfer bitcoin to external wallets, giving businesses more flexibility in managing their digital assets and enabling them to interact more easily with the broader ecosystem.
This move reflects PayPal's continued expansion into the digital currency space. Since launching consumer crypto services in 2020, PayPal has broadened its offerings. These efforts signal PayPal’s commitment to providing comprehensive digital currency solutions for both consumers and businesses.

Reference: Bitcoin Magazine

We’re Excited to Contribute to The Nostr Booth Initiative!
We look forward to seeing more projects and contributors join in to help grow the Nostr community!

The Nostr Booth Initiative is a community-driven project aimed at supporting and growing the Nostr network by promoting it at various events. It seeks to build awareness of Nostr by setting up booths and hosting workshops during Bitcoin conferences. The initiative relies on crowdfunding, particularly through Bitcoin donations, to support its efforts and spread information about Nostr's potential in decentralization, privacy, and secure communication.
We look forward to seeing more projects and contributors join in to help grow the Nostr community!

Check out the link for more information: Geyser.fund

LifPay v2.2.0 is Here
Some of the new features:\ -Streamlined UI/UX – Pay lightning fast with our improved interface that’s designed for simplicity and speed.
-Avatar Display – Now see the avatar of the Lightning Address when making a payment for that personal touch.
-Mainnet Support – You can now receive Bitcoin directly from the mainnet into your LifPay account
-Web Payment Enhancements – We've improved the experience when clicking on payment links from the web.
-Unified QR Code Scanning – Scan and pay with ease using the new unified QR code support.\ Check out the LifPay Webiste for more information: LifPay.me

LifPay joined NWC

-
-
 @ 6ad3e2a3:c90b7740
2024-10-08 09:11:10
@ 6ad3e2a3:c90b7740
2024-10-08 09:11:10I wanted to post a quote from Jiddu Krishnamurti who if I remember correctly once said something to the effect of:
An artist should be like Beethoven. The music just flowed out of him, and he could neither stop it nor control it.
But I can’t find the source, I’m just going by memory, and it was from a long time ago. It doesn’t matter though if he really said it, because it’s the quote I wanted to post.
. . .
When I was 21, my friend Andrew and I made a four hour drive one Saturday morning from New York to Germantown, Maryland to see a Korean Buddhist monk. I heard about the monk from my Korean college roommate whose mom knew him. Andrew and I had been reading books about Buddhism for the preceding year and thought it would be worthwhile to see the real thing. We also had various anxieties about our lives and figured maybe he could offer some guidance.
When we arrived at the farm where he lived, we parked and stepped out of the car. I don’t want to exaggerate, but even in the lot which had to be 40 yards from the main building was this strong feeling like you could just fall to the ground and start weeping for the sorrows of your life.
We walked to the door of the monastery and knocked. A few seconds later, a bald, 50-something Korean man opened it, looked out at us with a blank face. We awkwardly told him we had come to see him. In a thick Korean accent he said today was the wrong day for us, come back tomorrow and shut the door. We stood there dumbfounded. We had woken up at 6 am and driven four hours. He was an enlightened monk. He couldn’t just turn us away.
Nervously, I knocked again. He came back out, same blank look. I told him we had driven all the way from New York. He motioned for us to come in, and we followed.
Inside were maybe 25 Koreans all waiting to see the monk whose name it turned out was Dr. Shin. The Koreans had filled a large wooden table with a massive buffet of Korean food, and Andrew and I were invited to help ourselves which we did. People were individually or in couples going into a small meditation room where Dr. Shin sat and attended to them. After at least an hour, someone motioned to us it was our turn.
We were there for probably 5-10 minutes. I don’t remember who spoke first, or the entirety of the conversation, only a few snippets which have stayed with me. I told him I didn’t really know what I wanted to do with my life. I thought maybe I wanted to be a writer. He laughed out loud. “You want to be artist?” he said with his thick accent. “You pumping gas. Hahahahahah!” Then he looked at me seriously, and said, “Business and law. You study business and law.”
. . .
I’m 53 years old as I type this in October of 2024, and my “job” now is to write and talk about things as I see fit. I started my Substack in 2020, and while my first post was about large numbers, my second one was more from the heart. I create for a “living”, and I suppose that makes me an artist of sorts. But when I think back to the words of Dr. Shin, he was 100 percent right.
. . .
Most people should not try to be artists. You can’t easily make a living at it. It’s the wrong way to go about achieving status or security in society. There are some people who simply have no choice. They live for what they do, and even if they die broke and alone, they could not have done otherwise. Those are artists.
So what the hell am I doing?
I belong to a relatively small minority, those with something to say. I was always like this, even during the visit with Dr. Shin. But in my 20s and 30s I could not have done it. I needed to contribute something, get the reward part out of the way. I lacked the confidence and conviction to create whether or not anyone were interested in my work or wanted to compensate me for it. And unlike real artists, I had a choice. I don’t know if I could have dealt with a real job, but helping run a small fantasy sports business, something I loved, was possible for me, and I was lucky enough to find it.
. . .
Now I’m beyond that phase. I have enough money, a partner, a daughter and a dog. I like recognition and paychecks as much as the next person, but I’m not thirsty. I’ll say what I think (mostly) without regard for how it’ll affect my readership or reputation. I can open my mind and let the ideas out. Maybe it’s not quite like Beethoven, but more along the lines of Jorge Luis Borges who said:
I do not write for a select minority, which means nothing to me, nor for that adulated platonic entity known as ‘The Masses’. Both abstractions, so dear to the demagogue, I disbelieve in. I write for myself and for my friends, and I write to ease the passing of time.
-
 @ 6bae33c8:607272e8
2024-10-08 09:09:12
@ 6bae33c8:607272e8
2024-10-08 09:09:12I have to give that game an eight out of 10. I had Chris Olave going in the Steak League which wasn’t good, but Rashid Shaheed in one of the BCLs and Harrison Butker in the Primetime. It’s too bad Butker hit the post on that 51-yarder, otherwise it would have been a massive game. But I’ll take the four short FGs any day.
-
Patrick Mahomes didn’t throw a TD pass, but he had 331 passing yards and 22 rushing. He’s the master of the dink and dunk, using all four downs and taking his team on long drives. It’s ugly, unpleasant and leads to field goals sometimes, but with a good defense, it works. It’s not ideal for fantasy obviously.
-
Travis Kelce caught nine passes for 70 yards. Without Rashee Rice, Kelce is back to being the top target.
-
Juju Smith-Schuster had a big game and looks like the guy the Chiefs trust out wide. Xavier Worthy is a gadget guy and deep threat, but caught ony three passes. I would pick up JSS — he’s slow, but faster than Kelce — though the Chiefs might still trade for wide receiver.
-
Kareem Hunt is good enough. He’s a tough runner and can catch passes if needed.
-
Butker is in the ideal situation — a defense-first team with a competent, but boring offense that doesn’t hit for a lot of big plays, settles for a lot of field goals. (Plus a wife that has a hot meal ready for him when he gets home.)
-
I don’t want to crow too much, but I said the difference between Shaheed and Olave wasn’t as wide as their disparity in ADP. (Unfortunately I have a share of Olave via price enforcing at the Steak League auction.)
-
Derek Carr (oblique) got hurt, though in a VERY small sample his backup Jake Haener passed the eye test for me. If Carr is out, though, that obviously hurts the offense, especially with their offensive line injuries.
-
Alvin Kamara got bottled up, though he made a great run on the first drive where he was caught behind the line of scrimmage and reversed field for a first down. But that was really his only highlight. It could be rough sledding for him going forward with the QB and O-line issues.
-
-
 @ 06830f6c:34da40c5
2024-10-08 08:58:09
@ 06830f6c:34da40c5
2024-10-08 08:58:09Thika Main Prison has become a focal point of concern regarding the treatment of inmates and the dire conditions they face. Reports from individuals detained there shed light on a grim reality that is affecting not only the physical health of prisoners but also their mental well-being. This post aims to outline the harsh conditions within the prison, highlight the implications for inmates, and advocate for urgent reforms.

**Dietary Deprivation ** Inmates at Thika Main Prison have reported a severely limited diet, consisting primarily of ugali and water, with occasional additions of kale and white uji in the morning. This inadequate nutrition does not meet the basic dietary needs of individuals, leading to malnutrition and weakened immune systems. The occasional servings of ugali dengu or ugali mbosho do little to alleviate the monotony and nutritional deficits of the daily meals. Proper nutrition is vital for maintaining physical health and mental stability, yet this basic necessity is not being met.
Lack of Basic Hygiene and Sanitation
The lack of access to clean water poses significant challenges for inmates. The absence of water for showers and even for flushing toilets contributes to an unsanitary environment that can lead to serious health risks. The stench of overcrowded cells, compounded by the inability to maintain personal hygiene, creates an unbearable living situation. With many inmates sleeping on the floor, the risk of spreading skin diseases and infections, including tuberculosis, becomes alarmingly high.
Overcrowding and Congestion
Overcrowding is a critical issue within Thika Main Prison, with numerous inmates crammed into small spaces. This not only violates human rights but also exacerbates health issues, as the close quarters facilitate the rapid spread of diseases. The lack of personal space contributes to mental strain, making it increasingly difficult for inmates to cope with their situations. The consequences of such an environment are dire, leading to increased anxiety, depression, and other mental health issues.
Delays in Legal Proceedings
Another distressing aspect of life in Thika Main Prison is the slow pace of the judicial process. Magistrates and court dates are often difficult to secure, prolonging the time inmates spend awaiting trial. This prolonged detention can have severe implications for their mental health and overall well-being. Additionally, fines and bail are not awarded based on the economic circumstances of the accused, leaving many inmates trapped in a cycle of poverty and imprisonment. The inability to pay bail often leads to extended stays in prison, further compounding their challenges. We must strive for a system that ensures justice for all, regardless of economic status. 🏛️⚖️
Mental Health Concerns
The treatment of mentally ill patients within the prison system raises significant ethical questions. Many individuals with mental health issues find themselves incarcerated for petty crimes, and instead of receiving the care they need, they are subjected to harsh treatment in an environment ill-equipped to address their psychological needs. The stigma surrounding mental health often prevents adequate support, leaving these individuals vulnerable and exacerbating their conditions. Together, we can push for a future where human dignity is upheld within our correctional facilities. 🌍❤️
Call for Reform
The situation at Thika Main Prison underscores a pressing need for systemic reform. Immediate actions must be taken to improve living conditions, ensure adequate nutrition, and provide mental health support. The government and relevant authorities must prioritize the well-being of inmates, recognizing that humane treatment is not only a moral obligation but also essential for reducing recidivism and promoting rehabilitation.
Conclusion
The conditions at Thika Main Prison are a stark reminder of the challenges faced by incarcerated individuals in Kenya. It is imperative that we address these issues with urgency and compassion. By advocating for improved living conditions, proper nutrition, and mental health care, we can take significant steps towards a more just and humane prison system. Change is necessary—not only for the inmates currently enduring these hardships but for the integrity of the entire justice system.
-
 @ 59df1288:92e1744f
2024-10-08 08:57:03
@ 59df1288:92e1744f
2024-10-08 08:57:03Nostr Discussion Summary
Greetings and Teasers from the Community
by npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
The conversation thread started with a cheerful "Good Morning" nostr:note1gta2g20g40gxu3n8dwpmhzrphhtpgcvqt048glf6avmtvlf3jtks6gwp9g welcoming the arrival of autumn, and received heartwarming responses. Participants expressed love for the season with various emoticons and shared their own experiences. npub1z4wq9j65a6xrkq0pvhy8k5y06h50ych6uzvmlw9ywn90ph0ruyxqfnpqpt pointed out early autumn conditions in Northern Italy.
Meanwhile, npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u shared a sneak peek nostr:note1craajlwnwsvq7fvywfw5temerfpfzy4tc93a40r9expta2jjl76srvv08e of his upcoming NostrTalk episode with npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 and npub1lrnvvs6z78s9yjqxxr38uyqkmn34lsaxznnqgd877j4z2qej3j5s09qnw5. The post garnered some interesting reactions. npub15vdp04nh35a2c0edqmzjp99pnuzkehrh2lylgh3kxw0gkd8gs4hqas2zwv expressed excitement for more Nostr podcasts.
Reflecting on Natural Human Instincts
by npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
In a much profound discussion nostr:note1hhtg305fu79fd5sz7jtgc9mse3daggtfrg3x36mhn7k67f6s2c6s8fhrnu, npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc contemplates on human nature and mutual aid. Comparing communities like Bitcoin, Nostr, and his hometown to one another, the npub claimed that mutual help is a primal human instinct, and expressed concern on how the state and mainstream media might have manipulated perceptions.
Reviving Mutual Aid in Society
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9
A thought-provoking conversation took place around the importance of mutual aid in society, sparked by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9's post about it being looked down upon. Many members including npub1g7lqk25fl24xd0zh7hr8jgp5smdy2eszjh9nmv7z7w85h6xcs9hq4u8yd9 and npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc emphasized its necessity, with humor and encouragement sprinkled throughout their remarks. Elements like bitcoin and Nostr were pointed out as instances of 'community-building anarchy'. A light-hearted moment came when npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc zapped then offered a musical interlude on Spotify.
nostr:note1sl739gpurp52ddrv2qrdh50wvsewz2cefkuyyl6084tmyyzunk0s9y5ygd
A Glimpse of Amsterdam
by npub16vrkgd28wq6n0h77lqgu8h4fdu0eapxgyj0zqq6ngfvjf2vs3nuq5mp2va
This short and sweet discussion revolved around an attractive morning view shared by npub16vrkgd28wq6n0h77lqgu8h4fdu0eapxgyj0zqq6ngfvjf2vs3nuq5mp2va. The photo, speculated by npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku to be in Central Amsterdam, garnered warm greetings and appreciation from the users, demonstrating an appealingly simple exchange of community vibes.
nostr:note1g229al0c4d940f0sahjwmkd8raes0xt5qgtadaeej4q3w6m4x4ssvp67eg
Unexpected Vistas and Encounters
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9
A voyage through Amsterdam? This thread, initiated with evocative pictures from npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9 generated an intriguing mix of responses, from a mention of a boyfriend-organized photoshoot to a playful query of winning the 'game of nostr'. There was admiration and practical questions about photography involved.
nostr:note1uml8w7nekjnr9et36vggemwpdxgw5w8ux027daj5m8rqk8gqr9aqzx7crc
Furry Friends, Strangeness and Smiles
by npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka
The thread led by npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka is a heartwarming glimpse into the world of pets, with cute and endearing images of a cat dubbed #moxie. The string of responses included playful commentary, confusion, and plenty of affection for the feline subject.
nostr:note1n0pp9r896tdzamyta2huk6t7g92thwpf7fpecvq9gjx7cmr6wuhqufg5m5
Profound Professions: A Peek into the Dark
by npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac
A post from npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac called on community members to share stories related to their unique or unusual professions. The replies included an intense account by npub1l6scds4yv7xmcsmhqnhdy9sggm520q09lvts2m5mkvecgr2mmmeqsuj5rc of experiences in what appears to be a medical setting involving distressing scenarios, displaying a vivid intersection of dark humor and harsh realities.
nostr:note10q4ld44gul0z279gf3cclrk6z265umsm50m353vg5hjjpgdw63lqmq36vy
The Human Touch in a Fiat World
by npub...
The discussion thread begins with a touching account of one user's experience nostr:note1yvmyqxayjvlca5rgu3ejyqv05wrhphn5hm344htg2ju2gcp43e3suq4xzj seeing the effects of fiat on everyday life. They detail the high and lows of their experiences, also sharing a poignant encounter with a dementia sufferer who was a former maths professor. The discussion triggers warm responses from npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac and npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7, thanking the initiator for sharing.
Goodnight, Nostr
by npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u...
It's time for bed in Nostr land. The post nostr:note1yvmyqxayjvlca5rgu3ejyqv05wrhphn5hm344htg2ju2gcp43e3suq4xzj prompts sweet dreams and emojis with users npub1wzda905gc8czpvmdpv2pflvjuucxazu3vy477ze78cszrzwkprsqqsyplx, npub1z9d8vyln96cyndmkwqmvt26qyjchzy5ttqre7994cf0v5een82vqdtdctk and npub1hej55ypk62a8prv3tkl4uunheyr53k692s5eyz0hj0tk5fn8cttqa6w4mn joining in the sentiment.
Tech Troubles with Ableton Push 2
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9...
One user seeks help repairing an Ableton Push 2 with a fried USB port nostr:note16fg58aetcjvwuye8tga69rshr7cqg3chpnxed0hvl9pjd5929flspvkckk. npub157auxypn0me5y360svgefxn38fsljqpdz3k82jflaanz3lnm003s55855k suggests reaching out to the company while the post author laments the end of their warranty.
Power of Human Bonds Amid Social Isolation
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9...
In the last thread nostr:note1dvunxy4ke6645ragl56aywq5xycw2h7lfgm6w2nh2qetlqn66gsq0sqnh7, the author spotlights the beauty of community found in unlikely situations. npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc offers a practical demonstration of community spirit, leading to an appreciative response from the author.
Bitcoin Party Debate
by npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x
In this thread, discussions centered on the potential implications of governmental entities seizing bitcoin. Read various comments about what might happen if a department got custody of a bitcoin stack. npub10mxnle348mzv2dnj0ylgz3zu9gceenc29x9fr4m6mnars66j7vxsnkn8mj, eloquently summed up the debate with an insightful comment on people's dual love for both bitcoin and fiat currency. nostr:note1ng8wlcpedrkv5lscht9uuyqqq3e08udg9r6rf7k0whedu5cxq8pqp0cgee
Pondering Art and Censorship
by npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
This thread kicked off on a philosophical nostr:note1, with a focus on art and censorship resistance. There was a lively interaction between npub1cg3weh95edpwjn3h928megc0p2lc2mjpq0089j8nzncsegcupgnqn23u5d and npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x, who exchanged thoughts on censorship, art, and taste.nostr:note152nywfp2ualztr5efusu8ma9a7x3syh7ht6m2wgxvx6v0rmy9vyscgxq5c
Color Profile Puzzle
by npub1aeh2zw4elewy5682lxc6xnlqzjnxksq303gwu2npfaxd49vmde6qcq4nwx
A technical discussion unfolds, centering around challenges with color space and color profile data. Users suggest potential issues and fixes - npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj discussed issues with image uploads and color profile data, while npub137c5pd8gmhhe0njtsgwjgunc5xjr2vmzvglkgqs5sjeh972gqqxqjak37w provided an update on fixing color profile problems for PNGs. nostr:note1nduhwa45vpyn7juguwkllwqfk4mh2695m04n2l70k7zuuefh0aes8fesnd
Slow Dev Club
by npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn
This thread discusses the pace of software development. The root user promotes the idea of delivering good software with less of a rush - a sentiment echoed in the replies. It also highlights the existence and benefits of a 'slow dev club', providing a humorous spin to the software creation process. nostr:note1esf0gygd3p3lheu46t49s9xhnnnejfa95uupq2lv3mutg0vx6nlqkuywgs
"Real Software Engineering Wins The Race"
by npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z
In a thread filled with tech and development jargon, npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z champions the slow and steady approach to software development. The topic of discussion: releasing quality software over hastily produced iterations. The npub shares their experience with #Alexandria's upcoming release, highlighting a commitment to thorough quality assurance QA and increased functionality. They argue that frequently rotating through iterations of poorly produced code does not lead to production-ready software, but rather, a pile of issues. The discussion, nostr:note1et33ymvfzxcxwwttq4mj7qp7l5hv24td2hwhej395ay9shcfqxfsen30fe, ends with a call for more mature development practices and user-focused products.
"Account Embarrassment and Account Deletion"
by npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u
In this fiery exchange, npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u adds drama to the thread, expressing frustration and considering account deletion in nostr:note1gjhrvxqaeg92qgnpqppdkj8y2gfphr5u3yu85xmggyk2fw390rvsr7sk0e. Responding to the exasperation, npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 teases about the embarrassment, whereas npub19vem9txx6xl9j2dx0pm2g76g8grsccguq5lsfz8l8u0yek5lynzshkgqpq posts a mystery image.
"Confusing Conversation, Whales, and Gratitude"
by npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7 and npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
In a lighter, unrelated change of pace, npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7 shows their confusion about an ongoing conversation in nostr:note12xtvka7u6gsu9uchyjw80awsnccc7ztd8pfymxxln809cakf0qws3tlsts. Meanwhile, with a bit of fun, npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc shares their discovery of an account they amusingly label "Whale zaps ftw!" in nostr:note16wkn7h3j0tuax8wvndec507cs2h9u4kty4cxkg28s8kpn9guq87sa8mts7. The account in question, npub14edfzrf28apmn6rjhkgha9lcrp993n34mtmwnnlfwsy4yg7dsdcsu0p2jj, wraps up the thread with a nostr:note1 of gratitude.
-
 @ 59df1288:92e1744f
2024-10-08 08:54:53
@ 59df1288:92e1744f
2024-10-08 08:54:53Nostr Discussion Summary
Greetings and Teasers from the Community
by npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
The conversation thread started with a cheerful "Good Morning" nostr:note1gta2g20g40gxu3n8dwpmhzrphhtpgcvqt048glf6avmtvlf3jtks6gwp9g welcoming the arrival of autumn, and received heartwarming responses. Participants expressed love for the season with various emoticons and shared their own experiences. npub1z4wq9j65a6xrkq0pvhy8k5y06h50ych6uzvmlw9ywn90ph0ruyxqfnpqpt pointed out early autumn conditions in Northern Italy.
Meanwhile, npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u shared a sneak peek nostr:note1craajlwnwsvq7fvywfw5temerfpfzy4tc93a40r9expta2jjl76srvv08e of his upcoming NostrTalk episode with npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 and npub1lrnvvs6z78s9yjqxxr38uyqkmn34lsaxznnqgd877j4z2qej3j5s09qnw5. The post garnered some interesting reactions. npub15vdp04nh35a2c0edqmzjp99pnuzkehrh2lylgh3kxw0gkd8gs4hqas2zwv expressed excitement for more Nostr podcasts.
Reflecting on Natural Human Instincts
by npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
In a much profound discussion nostr:note1hhtg305fu79fd5sz7jtgc9mse3daggtfrg3x36mhn7k67f6s2c6s8fhrnu, npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc contemplates on human nature and mutual aid. Comparing communities like Bitcoin, Nostr, and his hometown to one another, the npub claimed that mutual help is a primal human instinct, and expressed concern on how the state and mainstream media might have manipulated perceptions.
Reviving Mutual Aid in Society
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9
A thought-provoking conversation took place around the importance of mutual aid in society, sparked by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9's post about it being looked down upon. Many members including npub1g7lqk25fl24xd0zh7hr8jgp5smdy2eszjh9nmv7z7w85h6xcs9hq4u8yd9 and npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc emphasized its necessity, with humor and encouragement sprinkled throughout their remarks. Elements like bitcoin and Nostr were pointed out as instances of 'community-building anarchy'. A light-hearted moment came when npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc zapped then offered a musical interlude on Spotify.
nostr:note1sl739gpurp52ddrv2qrdh50wvsewz2cefkuyyl6084tmyyzunk0s9y5ygd
A Glimpse of Amsterdam
by npub16vrkgd28wq6n0h77lqgu8h4fdu0eapxgyj0zqq6ngfvjf2vs3nuq5mp2va
This short and sweet discussion revolved around an attractive morning view shared by npub16vrkgd28wq6n0h77lqgu8h4fdu0eapxgyj0zqq6ngfvjf2vs3nuq5mp2va. The photo, speculated by npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku to be in Central Amsterdam, garnered warm greetings and appreciation from the users, demonstrating an appealingly simple exchange of community vibes.
nostr:note1g229al0c4d940f0sahjwmkd8raes0xt5qgtadaeej4q3w6m4x4ssvp67eg
Unexpected Vistas and Encounters
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9
A voyage through Amsterdam? This thread, initiated with evocative pictures from npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9 generated an intriguing mix of responses, from a mention of a boyfriend-organized photoshoot to a playful query of winning the 'game of nostr'. There was admiration and practical questions about photography involved.
nostr:note1uml8w7nekjnr9et36vggemwpdxgw5w8ux027daj5m8rqk8gqr9aqzx7crc
Furry Friends, Strangeness and Smiles
by npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka
The thread led by npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka is a heartwarming glimpse into the world of pets, with cute and endearing images of a cat dubbed #moxie. The string of responses included playful commentary, confusion, and plenty of affection for the feline subject.
nostr:note1n0pp9r896tdzamyta2huk6t7g92thwpf7fpecvq9gjx7cmr6wuhqufg5m5
Profound Professions: A Peek into the Dark
by npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac
A post from npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac called on community members to share stories related to their unique or unusual professions. The replies included an intense account by npub1l6scds4yv7xmcsmhqnhdy9sggm520q09lvts2m5mkvecgr2mmmeqsuj5rc of experiences in what appears to be a medical setting involving distressing scenarios, displaying a vivid intersection of dark humor and harsh realities.
nostr:note10q4ld44gul0z279gf3cclrk6z265umsm50m353vg5hjjpgdw63lqmq36vy
The Human Touch in a Fiat World
by npub...
The discussion thread begins with a touching account of one user's experience nostr:note1yvmyqxayjvlca5rgu3ejyqv05wrhphn5hm344htg2ju2gcp43e3suq4xzj seeing the effects of fiat on everyday life. They detail the high and lows of their experiences, also sharing a poignant encounter with a dementia sufferer who was a former maths professor. The discussion triggers warm responses from npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac and npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7, thanking the initiator for sharing.
Goodnight, Nostr
by npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u...
It's time for bed in Nostr land. The post nostr:note1yvmyqxayjvlca5rgu3ejyqv05wrhphn5hm344htg2ju2gcp43e3suq4xzj prompts sweet dreams and emojis with users npub1wzda905gc8czpvmdpv2pflvjuucxazu3vy477ze78cszrzwkprsqqsyplx, npub1z9d8vyln96cyndmkwqmvt26qyjchzy5ttqre7994cf0v5een82vqdtdctk and npub1hej55ypk62a8prv3tkl4uunheyr53k692s5eyz0hj0tk5fn8cttqa6w4mn joining in the sentiment.
Tech Troubles with Ableton Push 2
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9...
One user seeks help repairing an Ableton Push 2 with a fried USB port nostr:note16fg58aetcjvwuye8tga69rshr7cqg3chpnxed0hvl9pjd5929flspvkckk. npub157auxypn0me5y360svgefxn38fsljqpdz3k82jflaanz3lnm003s55855k suggests reaching out to the company while the post author laments the end of their warranty.
Power of Human Bonds Amid Social Isolation
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9...
In the last thread nostr:note1dvunxy4ke6645ragl56aywq5xycw2h7lfgm6w2nh2qetlqn66gsq0sqnh7, the author spotlights the beauty of community found in unlikely situations. npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc offers a practical demonstration of community spirit, leading to an appreciative response from the author.
Bitcoin Party Debate
by npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x
In this thread, discussions centered on the potential implications of governmental entities seizing bitcoin. Read various comments about what might happen if a department got custody of a bitcoin stack. npub10mxnle348mzv2dnj0ylgz3zu9gceenc29x9fr4m6mnars66j7vxsnkn8mj, eloquently summed up the debate with an insightful comment on people's dual love for both bitcoin and fiat currency. nostr:note1ng8wlcpedrkv5lscht9uuyqqq3e08udg9r6rf7k0whedu5cxq8pqp0cgee
Pondering Art and Censorship
by npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
This thread kicked off on a philosophical nostr:note1, with a focus on art and censorship resistance. There was a lively interaction between npub1cg3weh95edpwjn3h928megc0p2lc2mjpq0089j8nzncsegcupgnqn23u5d and npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x, who exchanged thoughts on censorship, art, and taste.nostr:note152nywfp2ualztr5efusu8ma9a7x3syh7ht6m2wgxvx6v0rmy9vyscgxq5c
Color Profile Puzzle
by npub1aeh2zw4elewy5682lxc6xnlqzjnxksq303gwu2npfaxd49vmde6qcq4nwx
A technical discussion unfolds, centering around challenges with color space and color profile data. Users suggest potential issues and fixes - npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj discussed issues with image uploads and color profile data, while npub137c5pd8gmhhe0njtsgwjgunc5xjr2vmzvglkgqs5sjeh972gqqxqjak37w provided an update on fixing color profile problems for PNGs. nostr:note1nduhwa45vpyn7juguwkllwqfk4mh2695m04n2l70k7zuuefh0aes8fesnd
Slow Dev Club
by npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn
This thread discusses the pace of software development. The root user promotes the idea of delivering good software with less of a rush - a sentiment echoed in the replies. It also highlights the existence and benefits of a 'slow dev club', providing a humorous spin to the software creation process. nostr:note1esf0gygd3p3lheu46t49s9xhnnnejfa95uupq2lv3mutg0vx6nlqkuywgs
"Real Software Engineering Wins The Race"
by npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z
In a thread filled with tech and development jargon, npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z champions the slow and steady approach to software development. The topic of discussion: releasing quality software over hastily produced iterations. The npub shares their experience with #Alexandria's upcoming release, highlighting a commitment to thorough quality assurance QA and increased functionality. They argue that frequently rotating through iterations of poorly produced code does not lead to production-ready software, but rather, a pile of issues. The discussion, nostr:note1et33ymvfzxcxwwttq4mj7qp7l5hv24td2hwhej395ay9shcfqxfsen30fe, ends with a call for more mature development practices and user-focused products.
"Account Embarrassment and Account Deletion"
by npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u
In this fiery exchange, npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u adds drama to the thread, expressing frustration and considering account deletion in nostr:note1gjhrvxqaeg92qgnpqppdkj8y2gfphr5u3yu85xmggyk2fw390rvsr7sk0e. Responding to the exasperation, npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 teases about the embarrassment, whereas npub19vem9txx6xl9j2dx0pm2g76g8grsccguq5lsfz8l8u0yek5lynzshkgqpq posts a mystery image.
"Confusing Conversation, Whales, and Gratitude"
by npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7 and npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
In a lighter, unrelated change of pace, npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7 shows their confusion about an ongoing conversation in nostr:note12xtvka7u6gsu9uchyjw80awsnccc7ztd8pfymxxln809cakf0qws3tlsts. Meanwhile, with a bit of fun, npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc shares their discovery of an account they amusingly label "Whale zaps ftw!" in nostr:note16wkn7h3j0tuax8wvndec507cs2h9u4kty4cxkg28s8kpn9guq87sa8mts7. The account in question, npub14edfzrf28apmn6rjhkgha9lcrp993n34mtmwnnlfwsy4yg7dsdcsu0p2jj, wraps up the thread with a nostr:note1 of gratitude.
-
 @ 59df1288:92e1744f
2024-10-08 08:52:21
@ 59df1288:92e1744f
2024-10-08 08:52:21Nostr Discussion Summary
Greetings and Teasers from the Community
by npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
The conversation thread started with a cheerful "Good Morning" notegta2g20g40gxu3n8dwpmhzrphhtpgcvqt048glf6avmtvlf3jtks6gwp9g welcoming the arrival of autumn, and received heartwarming responses. Participants expressed love for the season with various emoticons and shared their own experiences. npub1z4wq9j65a6xrkq0pvhy8k5y06h50ych6uzvmlw9ywn90ph0ruyxqfnpqpt pointed out early autumn conditions in Northern Italy.
Meanwhile, npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u shared a sneak peek notecraajlwnwsvq7fvywfw5temerfpfzy4tc93a40r9expta2jjl76srvv08e of his upcoming NostrTalk episode with npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 and npub1lrnvvs6z78s9yjqxxr38uyqkmn34lsaxznnqgd877j4z2qej3j5s09qnw5. The post garnered some interesting reactions. npub15vdp04nh35a2c0edqmzjp99pnuzkehrh2lylgh3kxw0gkd8gs4hqas2zwv expressed excitement for more Nostr podcasts.
Reflecting on Natural Human Instincts
by npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
In a much profound discussion notehhtg305fu79fd5sz7jtgc9mse3daggtfrg3x36mhn7k67f6s2c6s8fhrnu, npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc contemplates on human nature and mutual aid. Comparing communities like Bitcoin, Nostr, and his hometown to one another, the npub claimed that mutual help is a primal human instinct, and expressed concern on how the state and mainstream media might have manipulated perceptions.
Reviving Mutual Aid in Society
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9
A thought-provoking conversation took place around the importance of mutual aid in society, sparked by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9's post about it being looked down upon. Many members including npub1g7lqk25fl24xd0zh7hr8jgp5smdy2eszjh9nmv7z7w85h6xcs9hq4u8yd9 and npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc emphasized its necessity, with humor and encouragement sprinkled throughout their remarks. Elements like bitcoin and Nostr were pointed out as instances of 'community-building anarchy'. A light-hearted moment came when npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc zapped then offered a musical interlude on Spotify.
notesl739gpurp52ddrv2qrdh50wvsewz2cefkuyyl6084tmyyzunk0s9y5ygd
A Glimpse of Amsterdam
by npub16vrkgd28wq6n0h77lqgu8h4fdu0eapxgyj0zqq6ngfvjf2vs3nuq5mp2va
This short and sweet discussion revolved around an attractive morning view shared by npub16vrkgd28wq6n0h77lqgu8h4fdu0eapxgyj0zqq6ngfvjf2vs3nuq5mp2va. The photo, speculated by npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku to be in Central Amsterdam, garnered warm greetings and appreciation from the users, demonstrating an appealingly simple exchange of community vibes.
noteg229al0c4d940f0sahjwmkd8raes0xt5qgtadaeej4q3w6m4x4ssvp67eg
Unexpected Vistas and Encounters
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9
A voyage through Amsterdam? This thread, initiated with evocative pictures from npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9 generated an intriguing mix of responses, from a mention of a boyfriend-organized photoshoot to a playful query of winning the 'game of nostr'. There was admiration and practical questions about photography involved.
noteuml8w7nekjnr9et36vggemwpdxgw5w8ux027daj5m8rqk8gqr9aqzx7crc
Furry Friends, Strangeness and Smiles
by npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka
The thread led by npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka is a heartwarming glimpse into the world of pets, with cute and endearing images of a cat dubbed #moxie. The string of responses included playful commentary, confusion, and plenty of affection for the feline subject.
noten0pp9r896tdzamyta2huk6t7g92thwpf7fpecvq9gjx7cmr6wuhqufg5m5
Profound Professions: A Peek into the Dark
by npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac
A post from npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac called on community members to share stories related to their unique or unusual professions. The replies included an intense account by npub1l6scds4yv7xmcsmhqnhdy9sggm520q09lvts2m5mkvecgr2mmmeqsuj5rc of experiences in what appears to be a medical setting involving distressing scenarios, displaying a vivid intersection of dark humor and harsh realities.
note0q4ld44gul0z279gf3cclrk6z265umsm50m353vg5hjjpgdw63lqmq36vy
The Human Touch in a Fiat World
by npub...
The discussion thread begins with a touching account of one user's experience noteyvmyqxayjvlca5rgu3ejyqv05wrhphn5hm344htg2ju2gcp43e3suq4xzj seeing the effects of fiat on everyday life. They detail the high and lows of their experiences, also sharing a poignant encounter with a dementia sufferer who was a former maths professor. The discussion triggers warm responses from npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac and npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7, thanking the initiator for sharing.
Goodnight, Nostr
by npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u...
It's time for bed in Nostr land. The post noteyvmyqxayjvlca5rgu3ejyqv05wrhphn5hm344htg2ju2gcp43e3suq4xzj prompts sweet dreams and emojis with users npub1wzda905gc8czpvmdpv2pflvjuucxazu3vy477ze78cszrzwkprsqqsyplx, npub1z9d8vyln96cyndmkwqmvt26qyjchzy5ttqre7994cf0v5een82vqdtdctk and npub1hej55ypk62a8prv3tkl4uunheyr53k692s5eyz0hj0tk5fn8cttqa6w4mn joining in the sentiment.
Tech Troubles with Ableton Push 2
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9...
One user seeks help repairing an Ableton Push 2 with a fried USB port note6fg58aetcjvwuye8tga69rshr7cqg3chpnxed0hvl9pjd5929flspvkckk. npub157auxypn0me5y360svgefxn38fsljqpdz3k82jflaanz3lnm003s55855k suggests reaching out to the company while the post author laments the end of their warranty.
Power of Human Bonds Amid Social Isolation
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9...
In the last thread notedvunxy4ke6645ragl56aywq5xycw2h7lfgm6w2nh2qetlqn66gsq0sqnh7, the author spotlights the beauty of community found in unlikely situations. npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc offers a practical demonstration of community spirit, leading to an appreciative response from the author.
Bitcoin Party Debate
by npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x
In this thread, discussions centered on the potential implications of governmental entities seizing bitcoin. Read various comments about what might happen if a department got custody of a bitcoin stack. npub10mxnle348mzv2dnj0ylgz3zu9gceenc29x9fr4m6mnars66j7vxsnkn8mj, eloquently summed up the debate with an insightful comment on people's dual love for both bitcoin and fiat currency. noteng8wlcpedrkv5lscht9uuyqqq3e08udg9r6rf7k0whedu5cxq8pqp0cgee
Pondering Art and Censorship
by npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
This thread kicked off on a philosophical note, with a focus on art and censorship resistance. There was a lively interaction between npub1cg3weh95edpwjn3h928megc0p2lc2mjpq0089j8nzncsegcupgnqn23u5d and npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x, who exchanged thoughts on censorship, art, and taste.note52nywfp2ualztr5efusu8ma9a7x3syh7ht6m2wgxvx6v0rmy9vyscgxq5c
Color Profile Puzzle
by npub1aeh2zw4elewy5682lxc6xnlqzjnxksq303gwu2npfaxd49vmde6qcq4nwx
A technical discussion unfolds, centering around challenges with color space and color profile data. Users suggest potential issues and fixes - npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj discussed issues with image uploads and color profile data, while npub137c5pd8gmhhe0njtsgwjgunc5xjr2vmzvglkgqs5sjeh972gqqxqjak37w provided an update on fixing color profile problems for PNGs. notenduhwa45vpyn7juguwkllwqfk4mh2695m04n2l70k7zuuefh0aes8fesnd
Slow Dev Club
by npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn
This thread discusses the pace of software development. The root user promotes the idea of delivering good software with less of a rush - a sentiment echoed in the replies. It also highlights the existence and benefits of a 'slow dev club', providing a humorous spin to the software creation process. noteesf0gygd3p3lheu46t49s9xhnnnejfa95uupq2lv3mutg0vx6nlqkuywgs
"Real Software Engineering Wins The Race"
by npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z
In a thread filled with tech and development jargon, npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z champions the slow and steady approach to software development. The topic of discussion: releasing quality software over hastily produced iterations. The npub shares their experience with #Alexandria's upcoming release, highlighting a commitment to thorough quality assurance QA and increased functionality. They argue that frequently rotating through iterations of poorly produced code does not lead to production-ready software, but rather, a pile of issues. The discussion, noteet33ymvfzxcxwwttq4mj7qp7l5hv24td2hwhej395ay9shcfqxfsen30fe, ends with a call for more mature development practices and user-focused products.
"Account Embarrassment and Account Deletion"
by npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u
In this fiery exchange, npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u adds drama to the thread, expressing frustration and considering account deletion in notegjhrvxqaeg92qgnpqppdkj8y2gfphr5u3yu85xmggyk2fw390rvsr7sk0e. Responding to the exasperation, npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 teases about the embarrassment, whereas npub19vem9txx6xl9j2dx0pm2g76g8grsccguq5lsfz8l8u0yek5lynzshkgqpq posts a mystery image.
"Confusing Conversation, Whales, and Gratitude"
by npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7 and npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
In a lighter, unrelated change of pace, npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7 shows their confusion about an ongoing conversation in note2xtvka7u6gsu9uchyjw80awsnccc7ztd8pfymxxln809cakf0qws3tlsts. Meanwhile, with a bit of fun, npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc shares their discovery of an account they amusingly label "Whale zaps ftw!" in note6wkn7h3j0tuax8wvndec507cs2h9u4kty4cxkg28s8kpn9guq87sa8mts7. The account in question, npub14edfzrf28apmn6rjhkgha9lcrp993n34mtmwnnlfwsy4yg7dsdcsu0p2jj, wraps up the thread with a note of gratitude.
-
 @ 59df1288:92e1744f
2024-10-08 08:50:57
@ 59df1288:92e1744f
2024-10-08 08:50:57Nostr Discussion Summary
Greetings and Teasers from the Community
by npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
The conversation thread started with a cheerful "Good Morning" note1note1gta2g20g40gxu3n8dwpmhzrphhtpgcvqt048glf6avmtvlf3jtks6gwp9g welcoming the arrival of autumn, and received heartwarming responses. Participants expressed love for the season with various emoticons and shared their own experiences. npub1z4wq9j65a6xrkq0pvhy8k5y06h50ych6uzvmlw9ywn90ph0ruyxqfnpqpt pointed out early autumn conditions in Northern Italy.
Meanwhile, npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u shared a sneak peek note1note1craajlwnwsvq7fvywfw5temerfpfzy4tc93a40r9expta2jjl76srvv08e of his upcoming NostrTalk episode with npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 and npub1lrnvvs6z78s9yjqxxr38uyqkmn34lsaxznnqgd877j4z2qej3j5s09qnw5. The post garnered some interesting reactions. npub15vdp04nh35a2c0edqmzjp99pnuzkehrh2lylgh3kxw0gkd8gs4hqas2zwv expressed excitement for more Nostr podcasts.
Reflecting on Natural Human Instincts
by npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
In a much profound discussion note1note1hhtg305fu79fd5sz7jtgc9mse3daggtfrg3x36mhn7k67f6s2c6s8fhrnu, npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc contemplates on human nature and mutual aid. Comparing communities like Bitcoin, Nostr, and his hometown to one another, the npub claimed that mutual help is a primal human instinct, and expressed concern on how the state and mainstream media might have manipulated perceptions.
Reviving Mutual Aid in Society
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9
A thought-provoking conversation took place around the importance of mutual aid in society, sparked by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9's post about it being looked down upon. Many members including npub1g7lqk25fl24xd0zh7hr8jgp5smdy2eszjh9nmv7z7w85h6xcs9hq4u8yd9 and npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc emphasized its necessity, with humor and encouragement sprinkled throughout their remarks. Elements like bitcoin and Nostr were pointed out as instances of 'community-building anarchy'. A light-hearted moment came when npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc zapped then offered a musical interlude on Spotify.
note1note1sl739gpurp52ddrv2qrdh50wvsewz2cefkuyyl6084tmyyzunk0s9y5ygd
A Glimpse of Amsterdam
by npub16vrkgd28wq6n0h77lqgu8h4fdu0eapxgyj0zqq6ngfvjf2vs3nuq5mp2va
This short and sweet discussion revolved around an attractive morning view shared by npub16vrkgd28wq6n0h77lqgu8h4fdu0eapxgyj0zqq6ngfvjf2vs3nuq5mp2va. The photo, speculated by npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku to be in Central Amsterdam, garnered warm greetings and appreciation from the users, demonstrating an appealingly simple exchange of community vibes.
note1note1g229al0c4d940f0sahjwmkd8raes0xt5qgtadaeej4q3w6m4x4ssvp67eg
Unexpected Vistas and Encounters
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9
A voyage through Amsterdam? This thread, initiated with evocative pictures from npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9 generated an intriguing mix of responses, from a mention of a boyfriend-organized photoshoot to a playful query of winning the 'game of nostr'. There was admiration and practical questions about photography involved.
note1note1uml8w7nekjnr9et36vggemwpdxgw5w8ux027daj5m8rqk8gqr9aqzx7crc
Furry Friends, Strangeness and Smiles
by npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka
The thread led by npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka is a heartwarming glimpse into the world of pets, with cute and endearing images of a cat dubbed #moxie. The string of responses included playful commentary, confusion, and plenty of affection for the feline subject.
note1note1n0pp9r896tdzamyta2huk6t7g92thwpf7fpecvq9gjx7cmr6wuhqufg5m5
Profound Professions: A Peek into the Dark
by npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac
A post from npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac called on community members to share stories related to their unique or unusual professions. The replies included an intense account by npub1l6scds4yv7xmcsmhqnhdy9sggm520q09lvts2m5mkvecgr2mmmeqsuj5rc of experiences in what appears to be a medical setting involving distressing scenarios, displaying a vivid intersection of dark humor and harsh realities.
note1note10q4ld44gul0z279gf3cclrk6z265umsm50m353vg5hjjpgdw63lqmq36vy
The Human Touch in a Fiat World
by npub...
The discussion thread begins with a touching account of one user's experience note1note1yvmyqxayjvlca5rgu3ejyqv05wrhphn5hm344htg2ju2gcp43e3suq4xzj seeing the effects of fiat on everyday life. They detail the high and lows of their experiences, also sharing a poignant encounter with a dementia sufferer who was a former maths professor. The discussion triggers warm responses from npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac and npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7, thanking the initiator for sharing.
Goodnight, Nostr
by npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u...
It's time for bed in Nostr land. The post note1note1yvmyqxayjvlca5rgu3ejyqv05wrhphn5hm344htg2ju2gcp43e3suq4xzj prompts sweet dreams and emojis with users npub1wzda905gc8czpvmdpv2pflvjuucxazu3vy477ze78cszrzwkprsqqsyplx, npub1z9d8vyln96cyndmkwqmvt26qyjchzy5ttqre7994cf0v5een82vqdtdctk and npub1hej55ypk62a8prv3tkl4uunheyr53k692s5eyz0hj0tk5fn8cttqa6w4mn joining in the sentiment.
Tech Troubles with Ableton Push 2
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9...
One user seeks help repairing an Ableton Push 2 with a fried USB port note1note16fg58aetcjvwuye8tga69rshr7cqg3chpnxed0hvl9pjd5929flspvkckk. npub157auxypn0me5y360svgefxn38fsljqpdz3k82jflaanz3lnm003s55855k suggests reaching out to the company while the post author laments the end of their warranty.
Power of Human Bonds Amid Social Isolation
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9...
In the last thread note1note1dvunxy4ke6645ragl56aywq5xycw2h7lfgm6w2nh2qetlqn66gsq0sqnh7, the author spotlights the beauty of community found in unlikely situations. npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc offers a practical demonstration of community spirit, leading to an appreciative response from the author.
Bitcoin Party Debate
by npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x
In this thread, discussions centered on the potential implications of governmental entities seizing bitcoin. Read various comments about what might happen if a department got custody of a bitcoin stack. npub10mxnle348mzv2dnj0ylgz3zu9gceenc29x9fr4m6mnars66j7vxsnkn8mj, eloquently summed up the debate with an insightful comment on people's dual love for both bitcoin and fiat currency. note1note1ng8wlcpedrkv5lscht9uuyqqq3e08udg9r6rf7k0whedu5cxq8pqp0cgee
Pondering Art and Censorship
by npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
This thread kicked off on a philosophical note, with a focus on art and censorship resistance. There was a lively interaction between npub1cg3weh95edpwjn3h928megc0p2lc2mjpq0089j8nzncsegcupgnqn23u5d and npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x, who exchanged thoughts on censorship, art, and taste.note1note152nywfp2ualztr5efusu8ma9a7x3syh7ht6m2wgxvx6v0rmy9vyscgxq5c
Color Profile Puzzle
by npub1aeh2zw4elewy5682lxc6xnlqzjnxksq303gwu2npfaxd49vmde6qcq4nwx
A technical discussion unfolds, centering around challenges with color space and color profile data. Users suggest potential issues and fixes - npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj discussed issues with image uploads and color profile data, while npub137c5pd8gmhhe0njtsgwjgunc5xjr2vmzvglkgqs5sjeh972gqqxqjak37w provided an update on fixing color profile problems for PNGs. note1note1nduhwa45vpyn7juguwkllwqfk4mh2695m04n2l70k7zuuefh0aes8fesnd
Slow Dev Club
by npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn
This thread discusses the pace of software development. The root user promotes the idea of delivering good software with less of a rush - a sentiment echoed in the replies. It also highlights the existence and benefits of a 'slow dev club', providing a humorous spin to the software creation process. note1note1esf0gygd3p3lheu46t49s9xhnnnejfa95uupq2lv3mutg0vx6nlqkuywgs
"Real Software Engineering Wins The Race"
by npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z
In a thread filled with tech and development jargon, npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z champions the slow and steady approach to software development. The topic of discussion: releasing quality software over hastily produced iterations. The npub shares their experience with #Alexandria's upcoming release, highlighting a commitment to thorough quality assurance QA and increased functionality. They argue that frequently rotating through iterations of poorly produced code does not lead to production-ready software, but rather, a pile of issues. The discussion, note1note1et33ymvfzxcxwwttq4mj7qp7l5hv24td2hwhej395ay9shcfqxfsen30fe, ends with a call for more mature development practices and user-focused products.
"Account Embarrassment and Account Deletion"
by npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u
In this fiery exchange, npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u adds drama to the thread, expressing frustration and considering account deletion in note1note1gjhrvxqaeg92qgnpqppdkj8y2gfphr5u3yu85xmggyk2fw390rvsr7sk0e. Responding to the exasperation, npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 teases about the embarrassment, whereas npub19vem9txx6xl9j2dx0pm2g76g8grsccguq5lsfz8l8u0yek5lynzshkgqpq posts a mystery image.
"Confusing Conversation, Whales, and Gratitude"
by npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7 and npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
In a lighter, unrelated change of pace, npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7 shows their confusion about an ongoing conversation in note1note12xtvka7u6gsu9uchyjw80awsnccc7ztd8pfymxxln809cakf0qws3tlsts. Meanwhile, with a bit of fun, npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc shares their discovery of an account they amusingly label "Whale zaps ftw!" in note1note16wkn7h3j0tuax8wvndec507cs2h9u4kty4cxkg28s8kpn9guq87sa8mts7. The account in question, npub14edfzrf28apmn6rjhkgha9lcrp993n34mtmwnnlfwsy4yg7dsdcsu0p2jj, wraps up the thread with a note of gratitude.
-
 @ 59df1288:92e1744f
2024-10-08 08:45:48
@ 59df1288:92e1744f
2024-10-08 08:45:48Nostr Discussion Summary
Greetings and Teasers from the Community
by nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
The conversation thread started with a cheerful "Good Morning" (nostr:nevent1note1gta2g20g40gxu3n8dwpmhzrphhtpgcvqt048glf6avmtvlf3jtks6gwp9g) welcoming the arrival of autumn, and received heartwarming responses. Participants expressed love for the season with various emoticons and shared their own experiences. nostr:npub1z4wq9j65a6xrkq0pvhy8k5y06h50ych6uzvmlw9ywn90ph0ruyxqfnpqpt pointed out early autumn conditions in Northern Italy.
Meanwhile, nostr:npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u shared a sneak peek (nostr:nevent1note1craajlwnwsvq7fvywfw5temerfpfzy4tc93a40r9expta2jjl76srvv08e) of his upcoming NostrTalk episode with nostr:npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 and nostr:npub1lrnvvs6z78s9yjqxxr38uyqkmn34lsaxznnqgd877j4z2qej3j5s09qnw5. The post garnered some interesting reactions. nostr:npub15vdp04nh35a2c0edqmzjp99pnuzkehrh2lylgh3kxw0gkd8gs4hqas2zwv expressed excitement for more Nostr podcasts.
Reflecting on Natural Human Instincts
by nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
In a much profound discussion (nostr:nevent1note1hhtg305fu79fd5sz7jtgc9mse3daggtfrg3x36mhn7k67f6s2c6s8fhrnu), nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc contemplates on human nature and mutual aid. Comparing communities like Bitcoin, Nostr, and his hometown to one another, the nostr:npub claimed that mutual help is a primal human instinct, and expressed concern on how the state and mainstream media might have manipulated perceptions.
Reviving Mutual Aid in Society
by nostr:npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9
A thought-provoking conversation took place around the importance of mutual aid in society, sparked by nostr:npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9's post about it being looked down upon. Many members including nostr:npub1g7lqk25fl24xd0zh7hr8jgp5smdy2eszjh9nmv7z7w85h6xcs9hq4u8yd9 and nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc emphasized its necessity, with humor and encouragement sprinkled throughout their remarks. Elements like bitcoin and Nostr were pointed out as instances of 'community-building anarchy'. A light-hearted moment came when nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc zapped then offered a musical interlude on Spotify.
nostr:nevent1note1sl739gpurp52ddrv2qrdh50wvsewz2cefkuyyl6084tmyyzunk0s9y5ygd
A Glimpse of Amsterdam
by nostr:npub16vrkgd28wq6n0h77lqgu8h4fdu0eapxgyj0zqq6ngfvjf2vs3nuq5mp2va
This short and sweet discussion revolved around an attractive morning view shared by nostr:npub16vrkgd28wq6n0h77lqgu8h4fdu0eapxgyj0zqq6ngfvjf2vs3nuq5mp2va. The photo, speculated by nostr:npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku to be in Central Amsterdam, garnered warm greetings and appreciation from the users, demonstrating an appealingly simple exchange of community vibes.
nostr:nevent1note1g229al0c4d940f0sahjwmkd8raes0xt5qgtadaeej4q3w6m4x4ssvp67eg
Unexpected Vistas and Encounters
by nostr:npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9
A voyage through Amsterdam? This thread, initiated with evocative pictures from nostr:npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9 generated an intriguing mix of responses, from a mention of a boyfriend-organized photoshoot to a playful query of winning the 'game of nostr'. There was admiration and practical questions about photography involved.
nostr:nevent1note1uml8w7nekjnr9et36vggemwpdxgw5w8ux027daj5m8rqk8gqr9aqzx7crc
Furry Friends, Strangeness and Smiles
by nostr:npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka
The thread led by nostr:npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka is a heartwarming glimpse into the world of pets, with cute and endearing images of a cat dubbed #moxie. The string of responses included playful commentary, confusion, and plenty of affection for the feline subject.
nostr:nevent1note1n0pp9r896tdzamyta2huk6t7g92thwpf7fpecvq9gjx7cmr6wuhqufg5m5
Profound Professions: A Peek into the Dark
by nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac
A post from nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac called on community members to share stories related to their unique or unusual professions. The replies included an intense account by nostr:npub1l6scds4yv7xmcsmhqnhdy9sggm520q09lvts2m5mkvecgr2mmmeqsuj5rc of experiences in what appears to be a medical setting involving distressing scenarios, displaying a vivid intersection of dark humor and harsh realities.
nostr:nevent1note10q4ld44gul0z279gf3cclrk6z265umsm50m353vg5hjjpgdw63lqmq36vy
The Human Touch in a Fiat World
by nostr:npub...
The discussion thread begins with a touching account of one user's experience (nostr:nevent1note1yvmyqxayjvlca5rgu3ejyqv05wrhphn5hm344htg2ju2gcp43e3suq4xzj) seeing the effects of fiat on everyday life. They detail the high and lows of their experiences, also sharing a poignant encounter with a dementia sufferer who was a former maths professor. The discussion triggers warm responses from nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac and nostr:npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7, thanking the initiator for sharing.
Goodnight, Nostr
by nostr:npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u...
It's time for bed in Nostr land. The post (nostr:nevent1note1yvmyqxayjvlca5rgu3ejyqv05wrhphn5hm344htg2ju2gcp43e3suq4xzj) prompts sweet dreams and emojis with users nostr:npub1wzda905gc8czpvmdpv2pflvjuucxazu3vy477ze78cszrzwkprsqqsyplx, nostr:npub1z9d8vyln96cyndmkwqmvt26qyjchzy5ttqre7994cf0v5een82vqdtdctk and nostr:npub1hej55ypk62a8prv3tkl4uunheyr53k692s5eyz0hj0tk5fn8cttqa6w4mn joining in the sentiment.
Tech Troubles with Ableton Push 2
by nostr:npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9...
One user seeks help repairing an Ableton Push 2 with a fried USB port (nostr:nevent1note16fg58aetcjvwuye8tga69rshr7cqg3chpnxed0hvl9pjd5929flspvkckk). nostr:npub157auxypn0me5y360svgefxn38fsljqpdz3k82jflaanz3lnm003s55855k suggests reaching out to the company while the post author laments the end of their warranty.
Power of Human Bonds Amid Social Isolation
by nostr:npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9...
In the last thread (nostr:nevent1note1dvunxy4ke6645ragl56aywq5xycw2h7lfgm6w2nh2qetlqn66gsq0sqnh7), the author spotlights the beauty of community found in unlikely situations. nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc offers a practical demonstration of community spirit, leading to an appreciative response from the author.
Bitcoin Party Debate
by nostr:npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x
In this thread, discussions centered on the potential implications of governmental entities seizing bitcoin. Read various comments about what might happen if a department got custody of a bitcoin stack. nostr:npub10mxnle348mzv2dnj0ylgz3zu9gceenc29x9fr4m6mnars66j7vxsnkn8mj, eloquently summed up the debate with an insightful comment on people's dual love for both bitcoin and fiat currency. (nostr:nevent1note1ng8wlcpedrkv5lscht9uuyqqq3e08udg9r6rf7k0whedu5cxq8pqp0cgee)
Pondering Art and Censorship
by nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
This thread kicked off on a philosophical note, with a focus on art and censorship resistance. There was a lively interaction between nostr:npub1cg3weh95edpwjn3h928megc0p2lc2mjpq0089j8nzncsegcupgnqn23u5d and nostr:npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x, who exchanged thoughts on censorship, art, and taste.(nostr:nevent1note152nywfp2ualztr5efusu8ma9a7x3syh7ht6m2wgxvx6v0rmy9vyscgxq5c)
Color Profile Puzzle
by nostr:npub1aeh2zw4elewy5682lxc6xnlqzjnxksq303gwu2npfaxd49vmde6qcq4nwx
A technical discussion unfolds, centering around challenges with color space and color profile data. Users suggest potential issues and fixes - nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj discussed issues with image uploads and color profile data, while nostr:npub137c5pd8gmhhe0njtsgwjgunc5xjr2vmzvglkgqs5sjeh972gqqxqjak37w provided an update on fixing color profile problems for PNGs. (nostr:nevent1note1nduhwa45vpyn7juguwkllwqfk4mh2695m04n2l70k7zuuefh0aes8fesnd)
Slow Dev Club
by nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn
This thread discusses the pace of software development. The root user promotes the idea of delivering good software with less of a rush - a sentiment echoed in the replies. It also highlights the existence and benefits of a 'slow dev club', providing a humorous spin to the software creation process. (nostr:nevent1note1esf0gygd3p3lheu46t49s9xhnnnejfa95uupq2lv3mutg0vx6nlqkuywgs)
"Real Software Engineering Wins The Race"
by nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z
In a thread filled with tech and development jargon, nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z champions the slow and steady approach to software development. The topic of discussion: releasing quality software over hastily produced iterations. The nostr:npub shares their experience with #Alexandria's upcoming release, highlighting a commitment to thorough quality assurance (QA) and increased functionality. They argue that frequently rotating through iterations of poorly produced code does not lead to production-ready software, but rather, a pile of issues. The discussion, nostr:nevent1note1et33ymvfzxcxwwttq4mj7qp7l5hv24td2hwhej395ay9shcfqxfsen30fe, ends with a call for more mature development practices and user-focused products.
"Account Embarrassment and Account Deletion"
by nostr:npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u
In this fiery exchange, nostr:npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u adds drama to the thread, expressing frustration and considering account deletion in nostr:nevent1note1gjhrvxqaeg92qgnpqppdkj8y2gfphr5u3yu85xmggyk2fw390rvsr7sk0e. Responding to the exasperation, nostr:npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 teases about the embarrassment, whereas nostr:npub19vem9txx6xl9j2dx0pm2g76g8grsccguq5lsfz8l8u0yek5lynzshkgqpq posts a mystery image.
"Confusing Conversation, Whales, and Gratitude"
by nostr:npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7 and nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
In a lighter, unrelated change of pace, nostr:npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7 shows their confusion about an ongoing conversation in nostr:nevent1note12xtvka7u6gsu9uchyjw80awsnccc7ztd8pfymxxln809cakf0qws3tlsts. Meanwhile, with a bit of fun, nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc shares their discovery of an account they amusingly label "Whale zaps ftw!" in nostr:nevent1note16wkn7h3j0tuax8wvndec507cs2h9u4kty4cxkg28s8kpn9guq87sa8mts7. The account in question, nostr:npub14edfzrf28apmn6rjhkgha9lcrp993n34mtmwnnlfwsy4yg7dsdcsu0p2jj, wraps up the thread with a note of gratitude.
-
 @ 59df1288:92e1744f
2024-10-08 08:44:05
@ 59df1288:92e1744f
2024-10-08 08:44:05Nostr Discussion Summary
Greetings and Teasers from the Community
by npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
The conversation thread started with a cheerful "Good Morning" (nevent1note1gta2g20g40gxu3n8dwpmhzrphhtpgcvqt048glf6avmtvlf3jtks6gwp9g) welcoming the arrival of autumn, and received heartwarming responses. Participants expressed love for the season with various emoticons and shared their own experiences. npub1z4wq9j65a6xrkq0pvhy8k5y06h50ych6uzvmlw9ywn90ph0ruyxqfnpqpt pointed out early autumn conditions in Northern Italy.
Meanwhile, npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u shared a sneak peek (nevent1note1craajlwnwsvq7fvywfw5temerfpfzy4tc93a40r9expta2jjl76srvv08e) of his upcoming NostrTalk episode with npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 and npub1lrnvvs6z78s9yjqxxr38uyqkmn34lsaxznnqgd877j4z2qej3j5s09qnw5. The post garnered some interesting reactions. npub15vdp04nh35a2c0edqmzjp99pnuzkehrh2lylgh3kxw0gkd8gs4hqas2zwv expressed excitement for more Nostr podcasts.
Reflecting on Natural Human Instincts
by npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
In a much profound discussion (nevent1note1hhtg305fu79fd5sz7jtgc9mse3daggtfrg3x36mhn7k67f6s2c6s8fhrnu), npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc contemplates on human nature and mutual aid. Comparing communities like Bitcoin, Nostr, and his hometown to one another, the npub claimed that mutual help is a primal human instinct, and expressed concern on how the state and mainstream media might have manipulated perceptions.
Reviving Mutual Aid in Society
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9
A thought-provoking conversation took place around the importance of mutual aid in society, sparked by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9's post about it being looked down upon. Many members including npub1g7lqk25fl24xd0zh7hr8jgp5smdy2eszjh9nmv7z7w85h6xcs9hq4u8yd9 and npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc emphasized its necessity, with humor and encouragement sprinkled throughout their remarks. Elements like bitcoin and Nostr were pointed out as instances of 'community-building anarchy'. A light-hearted moment came when npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc zapped then offered a musical interlude on Spotify.
nevent1note1sl739gpurp52ddrv2qrdh50wvsewz2cefkuyyl6084tmyyzunk0s9y5ygd
A Glimpse of Amsterdam
by npub16vrkgd28wq6n0h77lqgu8h4fdu0eapxgyj0zqq6ngfvjf2vs3nuq5mp2va
This short and sweet discussion revolved around an attractive morning view shared by npub16vrkgd28wq6n0h77lqgu8h4fdu0eapxgyj0zqq6ngfvjf2vs3nuq5mp2va. The photo, speculated by npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku to be in Central Amsterdam, garnered warm greetings and appreciation from the users, demonstrating an appealingly simple exchange of community vibes.
nevent1note1g229al0c4d940f0sahjwmkd8raes0xt5qgtadaeej4q3w6m4x4ssvp67eg
Unexpected Vistas and Encounters
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9
A voyage through Amsterdam? This thread, initiated with evocative pictures from npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9 generated an intriguing mix of responses, from a mention of a boyfriend-organized photoshoot to a playful query of winning the 'game of nostr'. There was admiration and practical questions about photography involved.
nevent1note1uml8w7nekjnr9et36vggemwpdxgw5w8ux027daj5m8rqk8gqr9aqzx7crc
Furry Friends, Strangeness and Smiles
by npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka
The thread led by npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka is a heartwarming glimpse into the world of pets, with cute and endearing images of a cat dubbed #moxie. The string of responses included playful commentary, confusion, and plenty of affection for the feline subject.
nevent1note1n0pp9r896tdzamyta2huk6t7g92thwpf7fpecvq9gjx7cmr6wuhqufg5m5
Profound Professions: A Peek into the Dark
by npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac
A post from npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac called on community members to share stories related to their unique or unusual professions. The replies included an intense account by npub1l6scds4yv7xmcsmhqnhdy9sggm520q09lvts2m5mkvecgr2mmmeqsuj5rc of experiences in what appears to be a medical setting involving distressing scenarios, displaying a vivid intersection of dark humor and harsh realities.
nevent1note10q4ld44gul0z279gf3cclrk6z265umsm50m353vg5hjjpgdw63lqmq36vy
The Human Touch in a Fiat World
by npub...
The discussion thread begins with a touching account of one user's experience (nevent1note1yvmyqxayjvlca5rgu3ejyqv05wrhphn5hm344htg2ju2gcp43e3suq4xzj) seeing the effects of fiat on everyday life. They detail the high and lows of their experiences, also sharing a poignant encounter with a dementia sufferer who was a former maths professor. The discussion triggers warm responses from npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac and npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7, thanking the initiator for sharing.
Goodnight, Nostr
by npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u...
It's time for bed in Nostr land. The post (nevent1note1yvmyqxayjvlca5rgu3ejyqv05wrhphn5hm344htg2ju2gcp43e3suq4xzj) prompts sweet dreams and emojis with users npub1wzda905gc8czpvmdpv2pflvjuucxazu3vy477ze78cszrzwkprsqqsyplx, npub1z9d8vyln96cyndmkwqmvt26qyjchzy5ttqre7994cf0v5een82vqdtdctk and npub1hej55ypk62a8prv3tkl4uunheyr53k692s5eyz0hj0tk5fn8cttqa6w4mn joining in the sentiment.
Tech Troubles with Ableton Push 2
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9...
One user seeks help repairing an Ableton Push 2 with a fried USB port (nevent1note16fg58aetcjvwuye8tga69rshr7cqg3chpnxed0hvl9pjd5929flspvkckk). npub157auxypn0me5y360svgefxn38fsljqpdz3k82jflaanz3lnm003s55855k suggests reaching out to the company while the post author laments the end of their warranty.
Power of Human Bonds Amid Social Isolation
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9...
In the last thread (nevent1note1dvunxy4ke6645ragl56aywq5xycw2h7lfgm6w2nh2qetlqn66gsq0sqnh7), the author spotlights the beauty of community found in unlikely situations. npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc offers a practical demonstration of community spirit, leading to an appreciative response from the author.
Bitcoin Party Debate
by npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x
In this thread, discussions centered on the potential implications of governmental entities seizing bitcoin. Read various comments about what might happen if a department got custody of a bitcoin stack. npub10mxnle348mzv2dnj0ylgz3zu9gceenc29x9fr4m6mnars66j7vxsnkn8mj, eloquently summed up the debate with an insightful comment on people's dual love for both bitcoin and fiat currency. (nevent1note1ng8wlcpedrkv5lscht9uuyqqq3e08udg9r6rf7k0whedu5cxq8pqp0cgee)
Pondering Art and Censorship
by npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
This thread kicked off on a philosophical note, with a focus on art and censorship resistance. There was a lively interaction between npub1cg3weh95edpwjn3h928megc0p2lc2mjpq0089j8nzncsegcupgnqn23u5d and npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x, who exchanged thoughts on censorship, art, and taste.(nevent1note152nywfp2ualztr5efusu8ma9a7x3syh7ht6m2wgxvx6v0rmy9vyscgxq5c)
Color Profile Puzzle
by npub1aeh2zw4elewy5682lxc6xnlqzjnxksq303gwu2npfaxd49vmde6qcq4nwx
A technical discussion unfolds, centering around challenges with color space and color profile data. Users suggest potential issues and fixes - npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj discussed issues with image uploads and color profile data, while npub137c5pd8gmhhe0njtsgwjgunc5xjr2vmzvglkgqs5sjeh972gqqxqjak37w provided an update on fixing color profile problems for PNGs. (nevent1note1nduhwa45vpyn7juguwkllwqfk4mh2695m04n2l70k7zuuefh0aes8fesnd)
Slow Dev Club
by npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn
This thread discusses the pace of software development. The root user promotes the idea of delivering good software with less of a rush - a sentiment echoed in the replies. It also highlights the existence and benefits of a 'slow dev club', providing a humorous spin to the software creation process. (nevent1note1esf0gygd3p3lheu46t49s9xhnnnejfa95uupq2lv3mutg0vx6nlqkuywgs)
"Real Software Engineering Wins The Race"
by npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z
In a thread filled with tech and development jargon, npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z champions the slow and steady approach to software development. The topic of discussion: releasing quality software over hastily produced iterations. The npub shares their experience with #Alexandria's upcoming release, highlighting a commitment to thorough quality assurance (QA) and increased functionality. They argue that frequently rotating through iterations of poorly produced code does not lead to production-ready software, but rather, a pile of issues. The discussion, nevent1note1et33ymvfzxcxwwttq4mj7qp7l5hv24td2hwhej395ay9shcfqxfsen30fe, ends with a call for more mature development practices and user-focused products.
"Account Embarrassment and Account Deletion"
by npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u
In this fiery exchange, npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u adds drama to the thread, expressing frustration and considering account deletion in nevent1note1gjhrvxqaeg92qgnpqppdkj8y2gfphr5u3yu85xmggyk2fw390rvsr7sk0e. Responding to the exasperation, npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 teases about the embarrassment, whereas npub19vem9txx6xl9j2dx0pm2g76g8grsccguq5lsfz8l8u0yek5lynzshkgqpq posts a mystery image.
"Confusing Conversation, Whales, and Gratitude"
by npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7 and npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
In a lighter, unrelated change of pace, npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7 shows their confusion about an ongoing conversation in nevent1note12xtvka7u6gsu9uchyjw80awsnccc7ztd8pfymxxln809cakf0qws3tlsts. Meanwhile, with a bit of fun, npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc shares their discovery of an account they amusingly label "Whale zaps ftw!" in nevent1note16wkn7h3j0tuax8wvndec507cs2h9u4kty4cxkg28s8kpn9guq87sa8mts7. The account in question, npub14edfzrf28apmn6rjhkgha9lcrp993n34mtmwnnlfwsy4yg7dsdcsu0p2jj, wraps up the thread with a note of gratitude.
-
 @ 59df1288:92e1744f
2024-10-08 08:43:17
@ 59df1288:92e1744f
2024-10-08 08:43:17Nostr Discussion Summary
Greetings and Teasers from the Community
by npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
The conversation thread started with a cheerful "Good Morning" (nevent1note1gta2g20g40gxu3n8dwpmhzrphhtpgcvqt048glf6avmtvlf3jtks6gwp9g) welcoming the arrival of autumn, and received heartwarming responses. Participants expressed love for the season with various emoticons and shared their own experiences. npub1z4wq9j65a6xrkq0pvhy8k5y06h50ych6uzvmlw9ywn90ph0ruyxqfnpqpt pointed out early autumn conditions in Northern Italy.
Meanwhile, npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u shared a sneak peek (nevent1note1craajlwnwsvq7fvywfw5temerfpfzy4tc93a40r9expta2jjl76srvv08e) of his upcoming NostrTalk episode with npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 and npub1lrnvvs6z78s9yjqxxr38uyqkmn34lsaxznnqgd877j4z2qej3j5s09qnw5. The post garnered some interesting reactions. npub15vdp04nh35a2c0edqmzjp99pnuzkehrh2lylgh3kxw0gkd8gs4hqas2zwv expressed excitement for more Nostr podcasts.
Reflecting on Natural Human Instincts
by npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
In a much profound discussion (nevent1note1hhtg305fu79fd5sz7jtgc9mse3daggtfrg3x36mhn7k67f6s2c6s8fhrnu), npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc contemplates on human nature and mutual aid. Comparing communities like Bitcoin, Nostr, and his hometown to one another, the npub claimed that mutual help is a primal human instinct, and expressed concern on how the state and mainstream media might have manipulated perceptions.
Reviving Mutual Aid in Society
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9
A thought-provoking conversation took place around the importance of mutual aid in society, sparked by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9's post about it being looked down upon. Many members including npub1g7lqk25fl24xd0zh7hr8jgp5smdy2eszjh9nmv7z7w85h6xcs9hq4u8yd9 and npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc emphasized its necessity, with humor and encouragement sprinkled throughout their remarks. Elements like bitcoin and Nostr were pointed out as instances of 'community-building anarchy'. A light-hearted moment came when npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc zapped then offered a musical interlude on Spotify.
nevent1note1sl739gpurp52ddrv2qrdh50wvsewz2cefkuyyl6084tmyyzunk0s9y5ygd
A Glimpse of Amsterdam
by npub16vrkgd28wq6n0h77lqgu8h4fdu0eapxgyj0zqq6ngfvjf2vs3nuq5mp2va
This short and sweet discussion revolved around an attractive morning view shared by npub16vrkgd28wq6n0h77lqgu8h4fdu0eapxgyj0zqq6ngfvjf2vs3nuq5mp2va. The photo, speculated by npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku to be in Central Amsterdam, garnered warm greetings and appreciation from the users, demonstrating an appealingly simple exchange of community vibes.
nevent1note1g229al0c4d940f0sahjwmkd8raes0xt5qgtadaeej4q3w6m4x4ssvp67eg
Unexpected Vistas and Encounters
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9
A voyage through Amsterdam? This thread, initiated with evocative pictures from npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9 generated an intriguing mix of responses, from a mention of a boyfriend-organized photoshoot to a playful query of winning the 'game of nostr'. There was admiration and practical questions about photography involved.
nevent1note1uml8w7nekjnr9et36vggemwpdxgw5w8ux027daj5m8rqk8gqr9aqzx7crc
Furry Friends, Strangeness and Smiles
by npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka
The thread led by npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka is a heartwarming glimpse into the world of pets, with cute and endearing images of a cat dubbed #moxie. The string of responses included playful commentary, confusion, and plenty of affection for the feline subject.
nevent1note1n0pp9r896tdzamyta2huk6t7g92thwpf7fpecvq9gjx7cmr6wuhqufg5m5
Profound Professions: A Peek into the Dark
by npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac
A post from npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac called on community members to share stories related to their unique or unusual professions. The replies included an intense account by npub1l6scds4yv7xmcsmhqnhdy9sggm520q09lvts2m5mkvecgr2mmmeqsuj5rc of experiences in what appears to be a medical setting involving distressing scenarios, displaying a vivid intersection of dark humor and harsh realities.
nevent1note10q4ld44gul0z279gf3cclrk6z265umsm50m353vg5hjjpgdw63lqmq36vy
The Human Touch in a Fiat World
by npub...
The discussion thread begins with a touching account of one user's experience (nevent1note1yvmyqxayjvlca5rgu3ejyqv05wrhphn5hm344htg2ju2gcp43e3suq4xzj) seeing the effects of fiat on everyday life. They detail the high and lows of their experiences, also sharing a poignant encounter with a dementia sufferer who was a former maths professor. The discussion triggers warm responses from npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac and npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7, thanking the initiator for sharing.
Goodnight, Nostr
by npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u...
It's time for bed in Nostr land. The post (nevent1note1yvmyqxayjvlca5rgu3ejyqv05wrhphn5hm344htg2ju2gcp43e3suq4xzj) prompts sweet dreams and emojis with users npub1wzda905gc8czpvmdpv2pflvjuucxazu3vy477ze78cszrzwkprsqqsyplx, npub1z9d8vyln96cyndmkwqmvt26qyjchzy5ttqre7994cf0v5een82vqdtdctk and npub1hej55ypk62a8prv3tkl4uunheyr53k692s5eyz0hj0tk5fn8cttqa6w4mn joining in the sentiment.
Tech Troubles with Ableton Push 2
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9...
One user seeks help repairing an Ableton Push 2 with a fried USB port (nevent1note16fg58aetcjvwuye8tga69rshr7cqg3chpnxed0hvl9pjd5929flspvkckk). npub157auxypn0me5y360svgefxn38fsljqpdz3k82jflaanz3lnm003s55855k suggests reaching out to the company while the post author laments the end of their warranty.
Power of Human Bonds Amid Social Isolation
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9...
In the last thread (nevent1note1dvunxy4ke6645ragl56aywq5xycw2h7lfgm6w2nh2qetlqn66gsq0sqnh7), the author spotlights the beauty of community found in unlikely situations. npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc offers a practical demonstration of community spirit, leading to an appreciative response from the author.
Bitcoin Party Debate
by npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x
In this thread, discussions centered on the potential implications of governmental entities seizing bitcoin. Read various comments about what might happen if a department got custody of a bitcoin stack. npub10mxnle348mzv2dnj0ylgz3zu9gceenc29x9fr4m6mnars66j7vxsnkn8mj, eloquently summed up the debate with an insightful comment on people's dual love for both bitcoin and fiat currency. (nevent1note1ng8wlcpedrkv5lscht9uuyqqq3e08udg9r6rf7k0whedu5cxq8pqp0cgee)
Pondering Art and Censorship
by npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
This thread kicked off on a philosophical note, with a focus on art and censorship resistance. There was a lively interaction between npub1cg3weh95edpwjn3h928megc0p2lc2mjpq0089j8nzncsegcupgnqn23u5d and npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x, who exchanged thoughts on censorship, art, and taste.(nevent1note152nywfp2ualztr5efusu8ma9a7x3syh7ht6m2wgxvx6v0rmy9vyscgxq5c)
Color Profile Puzzle
by npub1aeh2zw4elewy5682lxc6xnlqzjnxksq303gwu2npfaxd49vmde6qcq4nwx
A technical discussion unfolds, centering around challenges with color space and color profile data. Users suggest potential issues and fixes - npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj discussed issues with image uploads and color profile data, while npub137c5pd8gmhhe0njtsgwjgunc5xjr2vmzvglkgqs5sjeh972gqqxqjak37w provided an update on fixing color profile problems for PNGs. (nevent1note1nduhwa45vpyn7juguwkllwqfk4mh2695m04n2l70k7zuuefh0aes8fesnd)
Slow Dev Club
by npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn
This thread discusses the pace of software development. The root user promotes the idea of delivering good software with less of a rush - a sentiment echoed in the replies. It also highlights the existence and benefits of a 'slow dev club', providing a humorous spin to the software creation process. (nevent1note1esf0gygd3p3lheu46t49s9xhnnnejfa95uupq2lv3mutg0vx6nlqkuywgs)
"Real Software Engineering Wins The Race"
by npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z
In a thread filled with tech and development jargon, npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z champions the slow and steady approach to software development. The topic of discussion: releasing quality software over hastily produced iterations. The npub shares their experience with #Alexandria's upcoming release, highlighting a commitment to thorough quality assurance (QA) and increased functionality. They argue that frequently rotating through iterations of poorly produced code does not lead to production-ready software, but rather, a pile of issues. The discussion, nevent1note1et33ymvfzxcxwwttq4mj7qp7l5hv24td2hwhej395ay9shcfqxfsen30fe, ends with a call for more mature development practices and user-focused products.
"Account Embarrassment and Account Deletion"
by npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u
In this fiery exchange, npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u adds drama to the thread, expressing frustration and considering account deletion in nevent1note1gjhrvxqaeg92qgnpqppdkj8y2gfphr5u3yu85xmggyk2fw390rvsr7sk0e. Responding to the exasperation, npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 teases about the embarrassment, whereas npub19vem9txx6xl9j2dx0pm2g76g8grsccguq5lsfz8l8u0yek5lynzshkgqpq posts a mystery image.
"Confusing Conversation, Whales, and Gratitude"
by npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7 and npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
In a lighter, unrelated change of pace, npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7 shows their confusion about an ongoing conversation in nevent1note12xtvka7u6gsu9uchyjw80awsnccc7ztd8pfymxxln809cakf0qws3tlsts. Meanwhile, with a bit of fun, npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc shares their discovery of an account they amusingly label "Whale zaps ftw!" in nevent1note16wkn7h3j0tuax8wvndec507cs2h9u4kty4cxkg28s8kpn9guq87sa8mts7. The account in question, npub14edfzrf28apmn6rjhkgha9lcrp993n34mtmwnnlfwsy4yg7dsdcsu0p2jj, wraps up the thread with a note of gratitude.
-
 @ 59df1288:92e1744f
2024-10-08 08:36:33
@ 59df1288:92e1744f
2024-10-08 08:36:33Nostr Discussion Summary
Greetings and Teasers from the Community
by npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
The conversation thread started with a cheerful "Good Morning" (nevent1note1gta2g20g40gxu3n8dwpmhzrphhtpgcvqt048glf6avmtvlf3jtks6gwp9g) welcoming the arrival of autumn, and received heartwarming responses. Participants expressed love for the season with various emoticons and shared their own experiences. npub1z4wq9j65a6xrkq0pvhy8k5y06h50ych6uzvmlw9ywn90ph0ruyxqfnpqpt pointed out early autumn conditions in Northern Italy.
Meanwhile, npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u shared a sneak peek (nevent1note1craajlwnwsvq7fvywfw5temerfpfzy4tc93a40r9expta2jjl76srvv08e) of his upcoming NostrTalk episode with npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 and npub1lrnvvs6z78s9yjqxxr38uyqkmn34lsaxznnqgd877j4z2qej3j5s09qnw5. The post garnered some interesting reactions. npub15vdp04nh35a2c0edqmzjp99pnuzkehrh2lylgh3kxw0gkd8gs4hqas2zwv expressed excitement for more Nostr podcasts.
Reflecting on Natural Human Instincts
by npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
In a much profound discussion (nevent1note1hhtg305fu79fd5sz7jtgc9mse3daggtfrg3x36mhn7k67f6s2c6s8fhrnu), npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc contemplates on human nature and mutual aid. Comparing communities like Bitcoin, Nostr, and his hometown to one another, the npub claimed that mutual help is a primal human instinct, and expressed concern on how the state and mainstream media might have manipulated perceptions.
Reviving Mutual Aid in Society
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9
A thought-provoking conversation took place around the importance of mutual aid in society, sparked by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9's post about it being looked down upon. Many members including npub1g7lqk25fl24xd0zh7hr8jgp5smdy2eszjh9nmv7z7w85h6xcs9hq4u8yd9 and npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc emphasized its necessity, with humor and encouragement sprinkled throughout their remarks. Elements like bitcoin and Nostr were pointed out as instances of 'community-building anarchy'. A light-hearted moment came when npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc zapped then offered a musical interlude on Spotify.
nevent1note1sl739gpurp52ddrv2qrdh50wvsewz2cefkuyyl6084tmyyzunk0s9y5ygd
A Glimpse of Amsterdam
by npub16vrkgd28wq6n0h77lqgu8h4fdu0eapxgyj0zqq6ngfvjf2vs3nuq5mp2va
This short and sweet discussion revolved around an attractive morning view shared by npub16vrkgd28wq6n0h77lqgu8h4fdu0eapxgyj0zqq6ngfvjf2vs3nuq5mp2va. The photo, speculated by npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku to be in Central Amsterdam, garnered warm greetings and appreciation from the users, demonstrating an appealingly simple exchange of community vibes.
nevent1note1g229al0c4d940f0sahjwmkd8raes0xt5qgtadaeej4q3w6m4x4ssvp67eg
Unexpected Vistas and Encounters
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9
A voyage through Amsterdam? This thread, initiated with evocative pictures from npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9 generated an intriguing mix of responses, from a mention of a boyfriend-organized photoshoot to a playful query of winning the 'game of nostr'. There was admiration and practical questions about photography involved.
nevent1note1uml8w7nekjnr9et36vggemwpdxgw5w8ux027daj5m8rqk8gqr9aqzx7crc
Furry Friends, Strangeness and Smiles
by npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka
The thread led by npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka is a heartwarming glimpse into the world of pets, with cute and endearing images of a cat dubbed #moxie. The string of responses included playful commentary, confusion, and plenty of affection for the feline subject.
nevent1note1n0pp9r896tdzamyta2huk6t7g92thwpf7fpecvq9gjx7cmr6wuhqufg5m5
Profound Professions: A Peek into the Dark
by npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac
A post from npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac called on community members to share stories related to their unique or unusual professions. The replies included an intense account by npub1l6scds4yv7xmcsmhqnhdy9sggm520q09lvts2m5mkvecgr2mmmeqsuj5rc of experiences in what appears to be a medical setting involving distressing scenarios, displaying a vivid intersection of dark humor and harsh realities.
nevent1note10q4ld44gul0z279gf3cclrk6z265umsm50m353vg5hjjpgdw63lqmq36vy
The Human Touch in a Fiat World
by npub...
The discussion thread begins with a touching account of one user's experience (nevent1note1yvmyqxayjvlca5rgu3ejyqv05wrhphn5hm344htg2ju2gcp43e3suq4xzj) seeing the effects of fiat on everyday life. They detail the high and lows of their experiences, also sharing a poignant encounter with a dementia sufferer who was a former maths professor. The discussion triggers warm responses from npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac and npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7, thanking the initiator for sharing.
Goodnight, Nostr
by npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u...
It's time for bed in Nostr land. The post (nevent1note1yvmyqxayjvlca5rgu3ejyqv05wrhphn5hm344htg2ju2gcp43e3suq4xzj) prompts sweet dreams and emojis with users npub1wzda905gc8czpvmdpv2pflvjuucxazu3vy477ze78cszrzwkprsqqsyplx, npub1z9d8vyln96cyndmkwqmvt26qyjchzy5ttqre7994cf0v5een82vqdtdctk and npub1hej55ypk62a8prv3tkl4uunheyr53k692s5eyz0hj0tk5fn8cttqa6w4mn joining in the sentiment.
Tech Troubles with Ableton Push 2
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9...
One user seeks help repairing an Ableton Push 2 with a fried USB port (nevent1note16fg58aetcjvwuye8tga69rshr7cqg3chpnxed0hvl9pjd5929flspvkckk). npub157auxypn0me5y360svgefxn38fsljqpdz3k82jflaanz3lnm003s55855k suggests reaching out to the company while the post author laments the end of their warranty.
Power of Human Bonds Amid Social Isolation
by npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9...
In the last thread (nevent1note1dvunxy4ke6645ragl56aywq5xycw2h7lfgm6w2nh2qetlqn66gsq0sqnh7), the author spotlights the beauty of community found in unlikely situations. npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc offers a practical demonstration of community spirit, leading to an appreciative response from the author.
Bitcoin Party Debate
by npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x
In this thread, discussions centered on the potential implications of governmental entities seizing bitcoin. Read various comments about what might happen if a department got custody of a bitcoin stack. npub10mxnle348mzv2dnj0ylgz3zu9gceenc29x9fr4m6mnars66j7vxsnkn8mj, eloquently summed up the debate with an insightful comment on people's dual love for both bitcoin and fiat currency. (nevent1note1ng8wlcpedrkv5lscht9uuyqqq3e08udg9r6rf7k0whedu5cxq8pqp0cgee)
Pondering Art and Censorship
by npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
This thread kicked off on a philosophical note, with a focus on art and censorship resistance. There was a lively interaction between npub1cg3weh95edpwjn3h928megc0p2lc2mjpq0089j8nzncsegcupgnqn23u5d and npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x, who exchanged thoughts on censorship, art, and taste.(nevent1note152nywfp2ualztr5efusu8ma9a7x3syh7ht6m2wgxvx6v0rmy9vyscgxq5c)
Color Profile Puzzle
by npub1aeh2zw4elewy5682lxc6xnlqzjnxksq303gwu2npfaxd49vmde6qcq4nwx
A technical discussion unfolds, centering around challenges with color space and color profile data. Users suggest potential issues and fixes - npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj discussed issues with image uploads and color profile data, while npub137c5pd8gmhhe0njtsgwjgunc5xjr2vmzvglkgqs5sjeh972gqqxqjak37w provided an update on fixing color profile problems for PNGs. (nevent1note1nduhwa45vpyn7juguwkllwqfk4mh2695m04n2l70k7zuuefh0aes8fesnd)
Slow Dev Club
by npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn
This thread discusses the pace of software development. The root user promotes the idea of delivering good software with less of a rush - a sentiment echoed in the replies. It also highlights the existence and benefits of a 'slow dev club', providing a humorous spin to the software creation process. (nevent1note1esf0gygd3p3lheu46t49s9xhnnnejfa95uupq2lv3mutg0vx6nlqkuywgs)
"Real Software Engineering Wins The Race"
by npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z
In a thread filled with tech and development jargon, npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z champions the slow and steady approach to software development. The topic of discussion: releasing quality software over hastily produced iterations. The npub shares their experience with #Alexandria's upcoming release, highlighting a commitment to thorough quality assurance (QA) and increased functionality. They argue that frequently rotating through iterations of poorly produced code does not lead to production-ready software, but rather, a pile of issues. The discussion, nevent1note1et33ymvfzxcxwwttq4mj7qp7l5hv24td2hwhej395ay9shcfqxfsen30fe, ends with a call for more mature development practices and user-focused products.
"Account Embarrassment and Account Deletion"
by npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u
In this fiery exchange, npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u adds drama to the thread, expressing frustration and considering account deletion in nevent1note1gjhrvxqaeg92qgnpqppdkj8y2gfphr5u3yu85xmggyk2fw390rvsr7sk0e. Responding to the exasperation, npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 teases about the embarrassment, whereas npub19vem9txx6xl9j2dx0pm2g76g8grsccguq5lsfz8l8u0yek5lynzshkgqpq posts a mystery image.
"Confusing Conversation, Whales, and Gratitude"
by npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7 and npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
In a lighter, unrelated change of pace, npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7 shows their confusion about an ongoing conversation in nevent1note12xtvka7u6gsu9uchyjw80awsnccc7ztd8pfymxxln809cakf0qws3tlsts. Meanwhile, with a bit of fun, npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc shares their discovery of an account they amusingly label "Whale zaps ftw!" in nevent1note16wkn7h3j0tuax8wvndec507cs2h9u4kty4cxkg28s8kpn9guq87sa8mts7. The account in question, npub14edfzrf28apmn6rjhkgha9lcrp993n34mtmwnnlfwsy4yg7dsdcsu0p2jj, wraps up the thread with a note of gratitude.
-
 @ a012dc82:6458a70d
2024-10-08 05:25:15
@ a012dc82:6458a70d
2024-10-08 05:25:15Table Of Content
-
Who is Javier Milei?
-
Milei's Views on Bitcoin
-
Milei's Plan for Bitcoin in Argentina
-
The Future of Bitcoin in Argentina
-
Potential Challenges to Bitcoin Adoption in Argentina
-
Conclusion
-
FAQ
Javier Milei, an Argentinian economist, author, and professor, has recently announced his intention to run for president in the 2023 Argentinian elections. While Milei is not yet a household name, he has become increasingly popular in Argentina due to his unique perspective on economics and his outspoken criticism of government policies. One of Milei's most noteworthy views is his strong support for Bitcoin and other cryptocurrencies. In this article, we will explore Javier Milei's views on Bitcoin and why he believes it is the future of money.
Who is Javier Milei?
Before we dive into Milei's views on Bitcoin, let's take a closer look at who he is. Javier Milei was born in Buenos Aires in 1970 and grew up in a middle-class family. He graduated from the University of Buenos Aires with a degree in economics and went on to earn a Ph.D. in economics from the University of California, Los Angeles. Milei has published numerous academic papers and is the author of several books, including "Desenmascarando la mentira keynesiana" (Unmasking the Keynesian Lie) and "La economía en la encrucijada" (The Economy at a Crossroads).
Milei has also become a public figure in Argentina due to his frequent appearances on television and social media, where he discusses his views on economics and politics. Milei is known for his colorful language and unorthodox views, which have made him both popular and controversial in Argentina.
Milei's Views on Bitcoin
One of Milei's most controversial views is his strong support for Bitcoin and other cryptocurrencies. Milei believes that Bitcoin is the future of money and that it has the potential to replace traditional fiat currencies like the Argentine peso. According to Milei, Bitcoin is superior to fiat currencies because it is decentralized, transparent, and immune to government interference.
Milei also argues that Bitcoin is a hedge against inflation, which has been a major problem in Argentina in recent years. Argentina has a long history of high inflation, and many Argentinians have lost faith in the government's ability to manage the economy. Milei believes that Bitcoin offers a way for people to protect their wealth from the ravages of inflation.
Milei's Plan for Bitcoin in Argentina
While Milei's views on Bitcoin are controversial, he has a detailed plan for how he would implement Bitcoin as the national currency if he were to become president. Milei believes that Argentina should adopt Bitcoin as its national currency and that all government transactions should be conducted in Bitcoin.
Milei also believes that Bitcoin should be used to pay government employees and that taxes should be paid in Bitcoin. In addition, Milei believes that Argentina should establish Bitcoin mining operations to generate revenue for the government and create jobs.
Milei's plan for Bitcoin in Argentina is ambitious, and it remains to be seen whether it would be feasible to implement. However, Milei's supporters believe that his vision for a Bitcoin-based economy could help lift Argentina out of its economic woes and put the country on a path to prosperity.
The Future of Bitcoin in Argentina
While Milei's views on Bitcoin are still considered controversial by many, there is no denying that Bitcoin has become increasingly popular in Argentina in recent years. Inflation and economic uncertainty have led many Argentinians to seek out alternative forms of currency, and Bitcoin has emerged as a popular choice.
Whether or not Milei becomes president in 2023, it is clear that Bitcoin will continue to play a role in Argentina's economy. As more people become aware of the benefits of decentralized currencies like Bitcoin, it is likely that we will see a growing trend towards Bitcoin adoption.
Potential Challenges to Bitcoin Adoption in Argentina
While Milei's vision for a Bitcoin-based economy in Argentina is compelling, there are still significant challenges to overcome. One of the biggest challenges is the lack of infrastructure to support widespread Bitcoin adoption.
Currently, there are only a handful of businesses in Argentina that accept Bitcoin as payment, and there are no Bitcoin ATMs in the country. In addition, many Argentinians are still unfamiliar with how Bitcoin works and may be hesitant to adopt it as a currency.
Another challenge is the regulatory environment in Argentina. The government has not yet established clear guidelines for how cryptocurrencies should be regulated, which has created uncertainty for businesses and investors.
Finally, there is the issue of volatility. Bitcoin's value can fluctuate wildly, which makes it difficult to use as a stable currency. This is particularly problematic in Argentina, where inflation is already a major problem.
Conclusion
Javier Milei's support for Bitcoin has made him a controversial figure in Argentina's political and economic landscape. While his vision for a Bitcoin-based economy is ambitious, there are significant challenges that need to be addressed before it can become a reality.
Nevertheless, Milei's advocacy for Bitcoin has brought attention to the potential benefits of decentralized currencies, particularly in countries like Argentina where economic instability is a major issue. Whether or not Bitcoin ultimately becomes the national currency in Argentina remains to be seen, but it is clear that cryptocurrencies will continue to play an important role in the country's economic future.
FAQ
Why is Javier Milei supporting Bitcoin? Milei believes that Bitcoin is a superior form of currency to traditional fiat currencies because it is decentralized, transparent, and immune to government interference. He also believes that Bitcoin is a hedge against inflation.
How would Milei implement Bitcoin as the national currency in Argentina? Milei's plan involves using Bitcoin for all government transactions, paying government employees in Bitcoin, and establishing Bitcoin mining operations to generate revenue for the government.
Will Bitcoin become the national currency in Argentina? It remains to be seen whether Bitcoin will become the national currency in Argentina, but it is clear that cryptocurrencies will continue to play an important role in the country's economic future.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 95a69326:6ac402e2
2024-10-08 03:44:27
@ 95a69326:6ac402e2
2024-10-08 03:44:27That is true for the rate of growth of addresses, of hashrate, and even of price.
None follow an exponential curve.
And that is fantastic news, because it’s a reality check on where we are today with Bitcoin adoption, and how to actually make it happen faster. Let us collectively break the culture that has formed around the S curve. The very idea that adoption is exponential.
It’s the hopium that keeps some going, waiting on the #OmegaCandle, chanting NGU and hodling onto their Bitcoin like it’s their “precious”.
So much of Bitcoin’s narrative is centered around an imminent inflection point, a face-melting exponential curve. We will wake up one day (soon!), Bitcoin will be over 1m per coin, the Federal Reserve will be blown into pieces, and all Bitcoiners around the world will come together to sing Kumbaya.
Then one more year passes, then one more year passes, then one… Just one more! It’s around the corner guys! Just hold on to your Bitcoin, and everyone else can have fun staying poor.
Don’t get me wrong, Bitcoin is a marvellous savings technology. Once you see it, you understand it’s the best way to safeguard your financial future.
But this is not a game measured in weeks, or months. It’s a game measured in years, decades. And I am starting to believe that the reason so many Bitcoiners still have an unrealistic expectation of the short term adoption rate of Bitcoin, is exactly because so many still believe Bitcoin growth follows an exponential.
But that mentality is actually harming Bitcoin adoption. When you ground your belief system into an exponential, it also becomes very easy to believe the path is set. That you can sit back, and wait. That it’s “any day now”.
And you’re wrong! The path is not set, the path is still being written, and at the moment it’s being increasingly written by some suits at BlackRock. So extend your time horizon.
Stop believing hyper-Bitcoinisation is around the corner, and start asking yourself: what can I do to make Bitcoin adoption happen?
The truth is, if you want Bitcoin adoption, hodling Bitcoin won’t get you there. Spending it, and getting more people to use it will.
No, I’m not trying to psy-op you into selling your Bitcoin. And the idea that spreading Bitcoin promotes adoption is not just theory.
Let’s go over some data.
If you’re allergic to charts and data, maybe stop reading here, and ponder on the above question for a little while.
But if you’re not, take a look at this chart:
Chart made by @Giovann35084111
This is what it looks like when you chart the ratio of Bitcoin’s hashrate, price and number of addresses. Bitcoin is a beautiful combination of power laws.
We’re not making any predictions here. This is what is, and what has been since Bitcoin’s Genesis Block. It’s Bitcoin’s DNA. And what it tells us is that there is a known, quantifiable, symbiotic relationship between Bitcoin’s number of participants (~addresses), Bitcoin’s security (hashrate) and Bitcoin’s price.
What else do we know?
Bitcoin’s address count (~ participants) grows at a rate of x³, where x is time. That’s the growth rate of viruses, it’s the growth rate of social networks. Metcalfe’s Law says that the value of a network is approximatly equal to the square of its participants. And with Bitcoin that checks out. Bitcoin’s price grows at a rate of x⁶, which is x³ (participants) squared (again refer to Giovanni’s work for the in-depth data analysis).
That’s pretty solid data to say that:
- Bitcoin’s price is not exponential
- The number of participants in the network has a quantifiable impact on its price So, Bitcoin growth follows a power law. And that’s fast! But compared to an exponential, that’s slooooow.
“But ETFs are here! NgU!! Scarcity!! Bitcoin will break all your models to the upside!!!”
It get’s tiring, and you know it.
Before you get all excited about ETFs buying up all the Bitcoin, leading to the mother of all supply squeezes and sending Bitcoin to the moon, realise this: the number of people owning Bitcoin has a bigger impact on price than supply and scarcity.
Sorry Stock2Flow fanatics, I’ll say that again. The number of people owning Bitcoin has a bigger impact on price than supply and scarcity.
And, to be fair, ETFs are bringing a lot of new network participants. But HODLING isn’t. And a lot of the Bitcoin that is going into the ETFs, is on a one way street to be hodled forever.
So going back to the big question: What can I do to accelerate Bitcoin adoption?
The answer is simple: get more people using Bitcoin.
Ok, that sounds obvious, and you already knew that. So this post was pointless.
But what is the pre-dominant narrative for getting more people to use Bitcoin today? It’s NgU, it’s scarcity, in other words, it’s all the wrong things. You won’t bring more network participants by buying up as much Bitcoin as you can to stash it away for the next 20 years.
Oh, and you won’t retire in 2 years for hodling that 0.1BTC either.
You’ll beat inflation, by a healthy margin, and you will get more purchasing power over time.
But the truth is, from Bitcoin’s adoption perspective, you’re a rent seeker.
You’re living off the work of those that are actually doing something to push Bitcoin’s adoption, ultimately having a real impact on its demand, and thus its price.
Who are they?
The educators teaching Bitcoin to new people. The meetup organisers bringing people together to talk about Bitcoin. * Those building circular economies. The protocol devs working on improvements to scale Bitcoin. The app devs working on making Bitcoin usable in every day life. The people spending Bitcoin on their everyday expenses. Those are the people pushing forward Bitcoin adoption.
Heck, even the wall street guy that orange pilled Larry Funk has done more for adoption than the perpetual holder waiting on the day he’ll be a citadel king.
I’ll end this rant here, and if there’s only one thing you remember from it let it be this:
Stop hodling Bitcoin to your death. Spend it, spread it, replace it. Support circular economies and Bitcoin educators, find local stores that accept it, get more people actually using the thing and you might just get to enjoy hyper-Bitcoinisation in your lifetime.
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
Bitcoin Power Law refs:
[Modelling Bitcoin Growth with Network Theory] https://bitposeidon.com/f/modeling-bitcoin-growth-with-network-theory…
[Intro to the Power Law] https://bitposeidon.com/f/simple-introduction-to-the-power-law-theory
-
 @ d6b095f3:5775d03d
2024-10-08 02:06:48
@ d6b095f3:5775d03d
2024-10-08 02:06:48As a Bitcoin pleb, I've learned that life—just like code—requires thoughtful inputs to yield optimal outputs. And when it comes to food, the organic vs. conventional debate is like choosing between different data formats or frameworks. Sure, both can run your system, but one might handle memory leaks a little better.
Let’s break it down like this: When you reach for an organic orange, it’s like working with clean, well-documented code. The flavor is robust, no bugs, and you can taste the efficiency. Conventional oranges? Yeah, they compile, but there’s a certain optimization you miss. The organic one feels like a solid API response, while the conventional version is more like unstructured data—gets the job done, but it’s not as elegant.
Take bananas. Organic bananas have this weird longevity, like a server with killer uptime. They stay fresh longer, almost like they’re running on some secret caching protocol. The conventional ones? They start to decay faster, like unhandled exceptions piling up. Meanwhile, organic apples retain that crispy bite longer, like a well-indexed database—they just handle the load better.
Now, when we’re talking about meats, it’s like comparing open-source to proprietary software. Organic, grass-fed meat is that open-source spirit: free to roam, natural inputs, minimal overhead. Conventional meat? It’s like closed-source. You don’t really know what’s under the hood—could be some questionable code or dependency hell, but it works… most of the time.
Kale’s the ultimate story of refactoring success. Back in the day, it was the forgotten library nobody included in their stack. Then it got marketed as a superfood, and suddenly, it’s like the React of veggies—everybody’s got it in their pipeline. A classic case of marketing changing public opinion, just like a small, underused feature suddenly becoming a core dependency because of good branding.
Now, let’s sprinkle in a little libertarian humor: You know how they say the free market will regulate itself? Yeah, well, try explaining that to the price of organic kale. It used to be the kind of item you’d find deep in the bargain bin of your local farmers market, but now it’s priced like premium software. We got kale trending like it’s running on a paid SaaS model, even though it was open-source from the beginning.
Here's the truth: whether you go organic or conventional, it’s not about having the perfect diet. The key is making decisions that align with your system’s needs. Just like in programming, sometimes you need to balance clean code with quick-and-dirty hacks to ship a product. The same goes for food. As long as your food is washed, prepped with care, and handled with intention, you’re optimizing for the best outcome.
This isn’t about pushing your system (your body) to the max like it’s on an infinite loop of gym routines. Eating healthy is your primary function—way more important than burning yourself out on workouts. If your inputs (diet) are trash, no amount of exercise can fix it. You can’t patch a broken architecture with brute force; you need to fix the core.
Now, let me hit you with a kernel of wisdom: whether you choose organic or not, it's about personal choice, customization, and ownership of your health. Just like I believe in open-source software—where control is in the hands of the user and community—I believe your diet should be something you control with intention. Whether it’s conventionally grown or organically sourced, as long as you’ve engineered your food selection with care, love, and clean energy, you’ll get the healthiest response from your system.
At the end of the day, it’s not about perfection. Life, like code, is iterative. Keep your processes clean, optimize where you can, and debug where necessary. Your body will respond to the energy and care you put into it—just like a well-tuned algorithm.
-
 @ 4ba8e86d:89d32de4
2024-10-08 01:07:00
@ 4ba8e86d:89d32de4
2024-10-08 01:07:00Ele segue os princípios do Material Design do Google, oferecendo uma interface intuitiva e esteticamente agradável.
Características.
Material e design limpo: o design visual do aplicativo é limpo e segue os princípios do Material Design do Google, proporcionando uma interface intuitiva e esteticamente agradável.
Sincronização rápida do repositório: o Droid-ify garante que você tenha acesso aos aplicativos e atualizações mais recentes do repositório do F-Droid sincronizando o repositório de forma eficiente.
Experiência de usuário suave: o aplicativo foi projetado para oferecer uma experiência fácil e intuitiva, facilitando a navegação e a instalação de aplicativos do F-Droid.
Rico em recursos: o Droid-ify oferece um conjunto abrangente de funcionalidades, incluindo pesquisa de aplicativos, exploração de categorias e gerenciamento de aplicativos instalados.
Código aberto: Droid-ify é um projeto de código aberto, o que significa que qualquer pessoa pode contribuir para o desenvolvimento do aplicativo e ajudar a melhorá-lo.
Verificação de aplicativos: o Droid-ify inclui um processo robusto de verificação de aplicativos, garantindo a autenticidade e a integridade dos aplicativos disponíveis no F-Droid.
Aplicativos focados em privacidade: o Droid-ify seleciona uma série de aplicativos focados em privacidade do repositório F-Droid, fornecendo acesso a aplicativos que priorizam privacidade e segurança.
Configurações de privacidade aprimoradas: o Droid-ify oferece configurações de privacidade adicionais dentro do aplicativo, permitindo controle detalhado sobre permissões, bloqueio de anúncios e ajustes para melhorar a privacidade.
Transparência de código aberto: o Droid-ify mantém a filosofia de código aberto, permitindo que os usuários examinem e revisem o código-fonte para transparência e contribuição da comunidade.
O Droid-ify oferece uma experiência de aplicativo centrada na privacidade, mecanismos de verificação de aplicativos, configurações de privacidade aprimoradas e promove a transparência de código aberto.
https://github.com/Droid-ify/client
https://github.com/Droid-ify/client/releases
https://f-droid.org/pt_BR/packages/com.looker.droidify/
-
 @ 4ba8e86d:89d32de4
2024-10-07 23:19:19
@ 4ba8e86d:89d32de4
2024-10-07 23:19:19O Orbot é um aplicativo de código aberto para dispositivos Android que oferece anonimato e segurança aos usuários da Internet. Ele funciona como um front-end para o Tor, permitindo que os usuários se conectem à rede Tor e usem serviços online de forma anônima e segura.
O Tor é uma rede de computadores que foi desenvolvida originalmente pelo governo dos Estados Unidos para proteger a privacidade dos usuários da Internet e permitir a comunicação segura de informações confidenciais. O Tor funciona usando um sistema de "onion routing" (roteamento de cebola), que envolve o encapsulamento de dados em várias camadas de criptografia antes de serem transmitidos através da rede.
O Orbot é um componente do Guardian Project, uma iniciativa que visa desenvolver tecnologia segura e anônima para ativistas de direitos humanos, jornalistas e outros usuários que precisam de privacidade online. O aplicativo é distribuído sob a Licença Pública Geral do GNU, o que significa que é totalmente gratuito e de código aberto.
O Orbot foi lançado pela primeira vez em 2008, como parte do projeto Tor, uma rede descentralizada de anonimização de tráfego que ajuda a proteger a privacidade dos usuários na internet. A ideia por trás do Orbot era fornecer uma maneira fácil para usuários móveis de acessar a rede Tor e proteger suas comunicações enquanto estavam em movimento. A primeira versão do Orbot foi lançada para o sistema operacional Android, e desde então, tem sido amplamente adotada por usuários preocupados com a privacidade.
O aplicativo inclui um proxy HTTP que permite conectar navegadores da web e outros aplicativos cliente HTTP na interface Tor SOCKS. Isso significa que todos os seus dados são criptografados e encaminhados através da rede Tor antes de serem transmitidos para o servidor de destino, tornando extremamente difícil para qualquer pessoa interceptar ou monitorar suas atividades online.
Além de fornecer anonimato e segurança aos usuários, o Orbot também pode ser usado para acessar conteúdo restrito por região. Por exemplo, se você está em um país que censura determinados sites ou serviços online, o Orbot pode ajudá-lo a acessar esse conteúdo de forma segura e anônima.
Os principais recursos do Orbot incluem a conexão segura à rede Tor, o acesso a serviços online restritos, o proxy HTTP, o código aberto e a facilidade de uso. Esses recursos tornam o Orbot uma ferramenta valiosa para usuários preocupados com a privacidade que desejam se comunicar e navegar na Internet de forma segura e anônima.
O Orbot é um aplicativo gratuito e de código aberto para dispositivos Android que oferece anonimato e segurança aos usuários
Aqui está um passo a passo para instalar o Orbot em seu dispositivo Android:
-
Acesse a F-droid ou Google Play Store em seu dispositivo Android.
-
Selecione a opção "Iniciar" para iniciar a conexão com a rede Tor. Aguarde até que a conexão seja estabelecida. Isso pode levar alguns minutos, dependendo da velocidade de sua conexão com a internet.
- Depois que a conexão for estabelecida, você poderá navegar na internet de forma anônima e segura usando o Tor.
Lembre-se de que o uso do Tor não garante anonimato completo e pode ser necessário seguir outras medidas de segurança para proteger sua privacidade na internet. Além disso, o Orbot é apenas uma parte do ecossistema de segurança e privacidade e pode ser necessário utilizar outras ferramentas para garantir a segurança online.
https://github.com/guardianproject/orbot/stargazers
-
-
 @ 4ba8e86d:89d32de4
2024-10-07 23:08:55
@ 4ba8e86d:89d32de4
2024-10-07 23:08:55InviZible Pro é um aplicativo Android projetado para oferecer privacidade e segurança ao navegar na Internet. Com uma combinação de recursos avançados, o aplicativo protege sua privacidade, mantém seu dispositivo seguro contra sites perigosos, evita rastreamento e permite acessar recursos online bloqueados.
O InviZible Pro inclui módulos conhecidos como DNSCrypt, Tor e Purple I2P. Esses módulos são utilizados para alcançar o máximo de segurança, privacidade e uma experiência de uso confortável na Internet.
DNSCrypt: - Criptografa solicitações de DNS - Protege contra falsificação de DNS - Pode bloquear anúncios * - Pode proteger contra sites perigosos e maliciosos * - Pode bloquear sites "adultos" * - Oculta os sites visitados do seu provedor de internet ** - Impede alguns tipos de bloqueios de recursos - Código aberto * Dependendo do servidor DNSCrypt selecionado (não disponível na versão do Google Play!) ** Caso seu provedor de internet não utilize equipamento de inspeção profunda de pacotes (DPI)
Tor: - Criptografa o tráfego da Internet - Impede o bloqueio de sites - Pode fornecer privacidade e anonimato - Fornece acesso a sites na "Dark Web" (web obscura) - Código aberto
Purple I2P: - Criptografa o tráfego da Internet - Fornece acesso à rede anônima oculta e a sites na "I2P network" (rede I2P) - Código aberto
Para começar a usar o InviZible Pro, basta ter um dispositivo Android. Execute os três módulos e desfrute de uma navegação segura e confortável na Internet. No entanto, se você desejar ter controle total sobre o aplicativo e sua conexão com a Internet, não há problema! Há acesso a um grande número de configurações simples e avançadas. Você pode configurar de forma flexível o próprio InviZible Pro, assim como seus módulos DNSCrypt, Tor e Purple I2P, para atender às suas necessidades específicas.
O InviZible Pro é um aplicativo completo. Após a instalação, você pode remover todos os outros aplicativos de VPN e bloqueadores de anúncios. Na maioria dos casos, o InviZible Pro funciona melhor, é mais estável e mais rápido do que as VPNs gratuitas. Além disso, o aplicativo não contém anúncios, bloatware e não espiona seus usuários.
Por que o InviZible Pro se destaca em relação a outros aplicativos similares: - Não possui concorrentes diretos. - É o único aplicativo que oferece uso prático do DNSCrypt no Android. - Geralmente é mais estável que o aplicativo Orbot, que também utiliza a rede Tor. - É mais útil do que o cliente oficial Purple I2P. - Permite configurar facilmente quais sites e aplicativos serão abertos através do Tor, proporcionando anonimato ou contornando bloqueios. - Pode transformar seu telefone ou decodificador de TV Android em um ponto de acesso Wi-Fi seguro, que pode ser utilizado por qualquer dispositivo, sem acesso root. - Interface otimizada para decodificadores. - Substitui várias VPNs e outras ferramentas para obter privacidade e anonimato. - Combina com sucesso os recursos do DNSCrypt, Tor e Purple I2P. - É gratuito e de código aberto.
InviZible Pro utiliza os seguintes componentes: - DNSCrypt - Tor - Purple I2P - Chainfire/libsuperuser - jaredrummler/AndroidShell - NetGuard - Angads25/android-filepicker - meefik/busybox
InviZible Pro é um software livre: você pode redistribuí-lo e/ou modificá-lo sob os termos da GNU General Public License, conforme publicada pela Free Software Foundation, seja a versão 3 da Licença ou qualquer versão posterior.
InviZible Pro é um aplicativo Android que oferece privacidade e segurança na Internet. Ele inclui módulos como DNSCrypt, Tor e Purple I2P, que criptografam o tráfego da Internet, protegem contra sites perigosos, evitam rastreamento e permitem acesso a recursos bloqueados. O aplicativo é completo, substituindo VPNs e bloqueadores de anúncios, e possui configurações flexíveis. Além disso, ele é estável, rápido, gratuito, sem anúncios e de código aberto.
https://github.com/Gedsh/InviZible
https://f-droid.org/packages/pan.alexander.tordnscrypt.stable/
-
 @ 4ba8e86d:89d32de4
2024-10-07 23:00:50
@ 4ba8e86d:89d32de4
2024-10-07 23:00:50é uma tecnologia que permite criar uma conexão segura e privada entre um dispositivo e a internet. É como uma espécie de túnel privado que passa por cima da internet pública, criptografando seus dados e mascarando seu endereço IP para proteger sua privacidade e segurança online.
A história da VPN remonta ao final dos anos 1990, quando as empresas começaram a usar conexões dedicadas (linhas alugadas) para conectar suas redes corporativas e permitir que seus funcionários trabalhassem remotamente. Essas conexões dedicadas eram caras e difíceis de configurar, o que levou à criação das primeiras VPNs baseadas em software.
A primeira VPN comercialmente disponível foi a Redes Privadas Virtuais (RPV), lançada pela Microsoft em 1996. Desde então, várias empresas e organizações começaram a usar VPNs para proteger seus dados confidenciais e permitir que seus funcionários trabalhassem remotamente de forma segura.
Como funciona a VPN?
Quando você se conecta a uma VPN, seu dispositivo estabelece um canal criptografado de comunicação com um servidor remoto. Todo o tráfego de dados entre o seu dispositivo e o servidor remoto é criptografado, o que significa que é transformado em códigos que só podem ser lidos por seu dispositivo e pelo servidor remoto.
Além disso, quando você usa uma VPN, seu endereço IP é substituído pelo endereço IP do servidor remoto. Isso significa que sua localização física e outros dados pessoais não são facilmente rastreados por sites que você visita e outros usuários da internet.
Por que usar uma VPN?
Existem várias razões pelas quais você pode querer usar uma VPN. Algumas das principais razões incluem:
• Acesso a conteúdo restrito geograficamente: Se você estiver em um país que restringe o acesso a certos sites ou serviços, uma VPN pode permitir que você os acesse como se estivesse em outro lugar. Por exemplo, se você estiver no Brasil e quiser acessar um site que só está disponível nos EUA, uma VPN pode permitir que você se conecte a um servidor nos EUA e acesse o site como se estivesse lá.
• Segurança e privacidade online: Quando você usa uma VPN, suas informações são criptografadas e protegidas contra hackers e outros invasores que podem tentar interceptar suas informações.
• Proteção de informações pessoais: Quando você está usando uma rede Wi-Fi pública (como em um café ou aeroporto), outras pessoas na mesma rede podem potencialmente interceptar suas informações pessoais e senhas. Uma VPN pode ajudar a proteger suas informações contra esses ataques.
• Evitar rastreamento de anúncios: Muitos sites e anunciantes rastreiam sua atividade online para enviar anúncios personalizados. Usar uma VPN pode ajudar a evitar esse rastreamento e manter sua atividade online mais privada.
As VPNs estão disponíveis em vários tipos e preços, desde serviços gratuitos até soluções corporativas mais avançadas. Ao escolher uma VPN, é importante verificar a política de privacidade da empresa para garantir que eles não compartilhem suas informações pessoais com terceiros. Além disso, algumas VPNs podem diminuir a velocidade da sua conexão à internet, então é importante escolher um serviço com uma boa reputação e boa qualidade Eu uso a Mullvap VPN..
uma VPN é uma ferramenta importante para manter sua segurança e privacidade online. Com a capacidade de criptografar suas informações, mascarar seu endereço IP e permitir o acesso a conteúdo restrito geograficamente, as VPNs são uma ótima opção para proteger sua presença online.
-
 @ 4ba8e86d:89d32de4
2024-10-07 22:48:24
@ 4ba8e86d:89d32de4
2024-10-07 22:48:24é um sistema operacional portátil baseado em Linux que pode ser iniciado a partir de um pen drive ou DVD. Ele é projetado para manter sua privacidade enquanto navega na internet, protegendo você de vigilância e censura. O Tails é gratuito e de código aberto, o que significa que qualquer pessoa pode usá-lo e modificá-lo.
O projeto Tails teve início em 2009, quando um grupo de desenvolvedores de software preocupados com a crescente vigilância na internet começaram a trabalhar em uma solução para proteger a privacidade dos usuários. O objetivo era criar um sistema operacional que pudesse ser executado a partir de um pendrive USB e que utilizasse a rede Tor para manter a privacidade do usuário.
O Tails oferece várias ferramentas de privacidade, incluindo o Tor (The Onion Router), um serviço de rede que protege sua identidade online e oculta sua localização. Ele também inclui o navegador Tor, que permite navegar na internet anonimamente e acessar sites bloqueados em seu país. Além disso, o Tails vem com outras ferramentas de privacidade, como o Kleopatra PGP (Pretty Good Privacy) uma ferramenta de criptografia de e-mail que ajuda a proteger suas mensagens.
O Tails é fácil de usar, mesmo se você não tiver conhecimento técnico avançado. Ele é projetado para ser iniciado a partir de um pen drive ou DVD, o que significa que você pode usá-lo em qualquer computador sem precisar instalá-lo no disco rígido. Ele é projetado para deixar o mínimo de rastros possível, o que significa que não salva seus dados pessoais ou suas atividades online.
O Tails é projetado com segurança em mente. Ele é atualizado regularmente para corrigir quaisquer vulnerabilidades de segurança e para incluir as últimas ferramentas de privacidade. O Tails também é projetado para manter sua privacidade e segurança em caso de perda ou roubo do dispositivo que contém o sistema operacional. Ele usa criptografia de disco para proteger seus arquivos pessoais e mantém todos os arquivos temporários na memória RAM, que é apagada quando você desliga o computador.
Mas você pode salvar alguns de seus arquivos e configurações em um Persistent Storage criptografado em seu stick USB Tails. O Persistent Storage é uma partição criptografada protegida por uma senha que ocupa todo o espaço livre deixado no pendrive. Tudo no Persistent Storage é criptografado automaticamente.
Para usar Tails, basta baixar a imagem do sistema operacional e gravá-la em um pendrive USB. Quando você estiver pronto para usá-lo, basta conectar o pendrive USB ao computador e iniciar o sistema operacional a partir dele. Depois de usar Tails, basta remover o pendrive USB e nenhum traço será deixado no computador.
https://tails.boum.org
-
 @ 4ba8e86d:89d32de4
2024-10-07 22:45:27
@ 4ba8e86d:89d32de4
2024-10-07 22:45:27Parte 1: Configuração e preparação
-
Instalação do Tails:
-
Baixe a imagem do Tails no site oficial (https://tails.boum.org/).
- depois baixar no site vai Aberta " verificar seu download" Você vai Verifique no próprio site se o tails que você baixou é tails compilado e desenvolvido pelo equipe Tails.
-
Grave a imagem do Tails em um pendrive ou cartão de memória usando um software de gravação adequado, como o Rufus.
-
Reinicie o computador e inicie a partir do pen drive ou cartão de memória que contém o Tails. Certifique-se de configurar o computador para inicializar a partir de um dispositivo externo.
-
Siga as instruções na tela para completar a configuração do Tails.
-
Configuração do disco persistente:
-
Após iniciar o Tails, defina uma senha para criptografar o disco persistente.
-
Abra o menu "Applications" e selecione "Favorites".
-
Em seguida, escolha "Configure Persistent Volume".
-
Selecione as opções para salvar no seu pendrive no disco persistente.
-
Procure pela opção Bitcoin client e habilite-a.
-
Essa senha é necessária para acessar e salvar seus arquivos e configurações persistentes, incluindo a carteira Electrum.
-
No menu do Tails, clique em "Applications" e, em seguida, em "Internet". Selecione "Electrum Bitcoin Wallet".
-
O Electrum será iniciado e você poderá criar uma nova carteira selecionando "Criar uma nova carteira" e escolhendo um nome para a carteira.
-
Selecione "Carteira padrão" e escolha se deseja criar uma nova carteira ou restaurar a partir de um backup.
-
Se optar por fazer o backup da carteira, selecione a opção "semente BIP39".
-
Se desejar adicionar uma passphrase à carteira Electrum, clique no botão "Opção" e escolha "Estender esta semente com a palavra personalizada". Insira uma passphrase forte e siga as instruções para concluir a configuração da carteira.
Anote e guarde a passphrase em um local seguro, separadamente das palavras-chave de recuperação (seed).
Depois Aberta em "próximo" Vai aparece a Tela "Tipo de script e caminho derivação" Selecionar a opção "Native segwit (p2wpkh) aberta em "próximo" agora vai aparecer uma tela pra adicionar senha para criptógrafa o arquivo da carteira electrum. So insira uma senha.
Obs: você tem três senha diferente pra lembrar. Senha disco persistent. Senha passphrse. Senha criptógrafa o arquivo da carteira electrum.
Anote e guarde a passphrase em um local seguro, separadamente das palavras-chave de recuperação (seed).
- guarde em um local seguro as palavras-chave de recuperação (seed) fornecidas pelo Electrum. Essas palavras são importantes para recuperar sua carteira se você perder o acesso ao Tails.
Parte 2: Assinatura e envio da transação
Assinatura da transação no Tails (offline):
-
Desconecte o computador do Tails da internet, removendo o cabo de rede ou desativando a conexão Wi-Fi.
-
No tails vai na opção "Carteira" logo em seguida na opção "informações da carteira" Depois Aberta em exibe o QR Code da chave pública XPUB que está no Tails.
Configuração do celular:
- No seu celular, abra a carteira Electrum e clique na opção "Criar nova carteira".
- Atribua um nome à carteira e, em seguida, selecione a opção "Carteira padrão" (Standard Wallet) seguida da opção "Usar chave mestra" (Use Master Key).
- Agora, você precisará escanear com a câmera do celular o código QR da chave pública XPUB que está no Tails. Essa chave mestra permitirá que você acompanhe o saldo e as transações da sua carteira, mas não poderá gastar os fundos ou assinar transações diretamente.
- Toque em "Próxima" para iniciar o processo de sincronização da carteira no celular.
Pra recebe pagamento com o celular deixa o Tails totalmente offine.
É Só ir na Aba "recebe" depois em "pedir"
Você pode copiar o endereço ou exibe o Qrcode pra pagamento. você pode verificar que o endereço de recebe que aparece no celular eo mesmo que está no seu Tails offine.
Pra enviar vai na Aba "enviar"
Aberta em "escanear" verificar as informações endereço é escolher o valor da taxa.
Depois Aberta em "pagar"
Vai parece um aviso "transação teve ser substituível ?"
Aberta em "sim" Se a taxa foi muito baixa não confimar nos próximos dias para poder aumentar se precisar.
Vai exibe na tela a quanti a enviar é total taxa de mineração Aberta em "concluir"
Vai mostra quantia a ser enviada ID da transação de saída mas ela não está assinada. Atráves do Qrcode que está no celular você vai exibir Qrcode que você vai escanear com a câmara Web do seu Tails
Vai volta no Tails na opção "ferramentas" - logo em seguida escolhar a opção "carregar transação"
depois na opção "a partir de um código Qr" vai abrir a câmera do Tails você mostra o código Qr que está no celular para a câmera Tails.
No tails vai mostrar todas as informações da transação. Após confimar as informações da transação, clique em "Assinar"
Digite a senha da carteira Electrum para desbloquear a chave privada.
Em seguida, clique em "Exportar" e selecione a opção "Mostrar como um código QR"
No celular aberta em "escanear" O código Qr da transação assinada.
Vai aparecer na tela do seu celular Status da transação assinada é informações da transação.
Então finalmente você aberta em "Transmitir" para enviar a transação assinada para a rede Bitcoin.
Ao optar por usar o Tails como base para criar e assinar transações, você está garantindo a segurança da sua chave privada no ambiente protegido do Tails, enquanto utiliza o celular apenas para visualizar informações e enviar a transação assinada para a rede.
Uma medida adicional de segurança é a criptografia do disco persistente do Tails com uma senha forte, juntamente com o uso de senhas fortes para proteger a carteira Electrum e a chave privada. Essas camadas extras de proteção ajudam a manter suas informações seguras.
É fundamental tomar todas as precauções necessárias para proteger seus dispositivos. Certifique-se de manter o Tails atualizado, utilizar software confiável para gravá-lo em um pendrive ou cartão de memória, e proteger adequadamente seu dispositivo móvel com senhas e atualizações de segurança.
Embora essa abordagem ofereça uma camada mais segura para proteger sua chave privada durante o processo de envio de transações, é importante lembrar de fazer backups regulares das suas palavras-chave de recuperação (seed). Além disso, considere tomar medidas adicionais de segurança de acordo com suas necessidades e recursos disponíveis.
Tenha em mente que a segurança absoluta não pode ser garantida, por isso é essencial adotar boas práticas de segurança digital.
Seguindo essas orientações e tomando as devidas precauções, você estará fortalecendo a segurança das suas transações ao utilizar o Tails para criar e assinar transações, mantendo a chave privada protegida no ambiente seguro do Tails, e utilizando o celular de forma segura para enviar a transação assinada para a rede.
https://youtu.be/abXkgXQ8BvI
https://youtu.be/NBj9-TolpvI
-
-
 @ 4ec341e6:6dc2fdaf
2024-10-07 22:04:01
@ 4ec341e6:6dc2fdaf
2024-10-07 22:04:01Ao trabalhar para melhorar o desempenho de aplicativos Node.js, é crucial entender como o Node.js e as bibliotecas em uso funcionam debaixo dos panos.
javascript app.post('/endpoint', async (req, res) => { // DO SOMETHING })Como o Node.js e o Express lidam com essa solicitação até o ponto em que a função é chamada dentro de app.post? Como o loop de eventos do Node.js funciona com promises nos bastidores?
O Node.js não consegue gerenciar tantas conexões paralelas quanto o Elixir. Tanto o engine quanto as bibliotecas têm certas limitações. Por exemplo, se estivermos trabalhando com um microsserviço que atua como middleware — recebendo informações, chamando uma API externa, aguardando a resposta e retornando dados para outro microsserviço — o Node.js precisa manter a conexão TCP ativa enquanto aguarda a resposta do serviço externo. Por isso, o número de solicitações por segundo diminui, e o Node.js consome recursos significativos (CPU e memória) gerenciando conexões abertas e promises não resolvidas enquanto espera que serviços externos respondam, para então resolver as promises que estãp em await, para então responder as solicitações e fechar as conexões TCP.
Uma maneira de melhorar o desempenho em um aplicativo Express é manipular informações em lotes. Em vez de fazer 100 solicitações individuais ao microsserviço, cada uma das quais chama um serviço externo e gerencia 100 conexões TCP abertas e 100 promessas pendentes (teórico), a aplicação pode receber uma única solicitação contendo um array de 100 itens. Usando await Promise.all em um array de 100 promessas, o Node.js precisa gerenciar apenas uma conexão TCP enquanto aguarda os resultados de todas as 100 promessas. Embora ainda trabalhemos com 100 promessas, reduzimos a quantidade de requisições HTTP de 100 para 1, sobrando muito mais recursos para outras atividades.
Usando esse método, onde lambdas AWS passaram à chamar um microserviço passando lotes de itens em vez de fazer várias chamadas HTTP para cada item, o microserviço passou à apresentar um menor consumo de CPU e memória, e deixou de cair o container. Um ponto negativo é que o tempo de resposta para processar um array de 100 itens foi muitas vezes maior que para processar apenas um único item, entretanto, houve um ganho no sistema como um todo (lambdas AWS e microserviços), pois a quantidade de erros 503 por excesso de solicitações passou à ser zero.
Aqui tem um artigo com alguns testes de carga do NodeJs e Express, mostrando como que uma quantidade maior de requisições HTTP leva à um tempo menor de resposta, apesar de não haver nenhuma modificação na promise que era executada: Exploring how Node.js handles HTTP connections
-
 @ 4ba8e86d:89d32de4
2024-10-07 15:43:17
@ 4ba8e86d:89d32de4
2024-10-07 15:43:17Ele oferece recursos adicionais em relação ao aplicativo oficial do YouTube, como a possibilidade de assistir vídeos sem anúncios, reproduzir em segundo plano, baixar vídeos e áudios, entre outros.
O NewPipe foi desenvolvido como uma alternativa de código aberto ao aplicativo oficial do YouTube para dispositivos Android. O projeto foi iniciado por Christian Schabesberger em 2015, como um projeto de software livre hospedado no GitHub. Desde então, vários colaboradores se juntaram ao projeto para melhorar e expandir suas funcionalidades. O objetivo principal por trás do desenvolvimento do NewPipe foi fornecer uma experiência mais privada, segura e personalizada para os usuários do YouTube. Muitas pessoas estavam preocupadas com a coleta de dados e o rastreamento de usuários feitos pelo aplicativo oficial do YouTube, e o NewPipe surgiu como uma alternativa para resolver essas preocupações. O desenvolvimento do NewPipe foi impulsionado pela comunidade de software livre e pela filosofia de transparência, privacidade e liberdade de escolha do usuário. Como um projeto de código aberto, o NewPipe permite que os usuários examinem e modifiquem o código-fonte, se assim desejarem, tornando o aplicativo mais transparente e confiável. Ao longo dos anos, o NewPipe evoluiu e adicionou recursos, como reprodução em segundo plano, bloqueio de anúncios, download de vídeos e áudios, gerenciamento de inscrições e muito mais. Esses recursos extras fornecem aos usuários uma experiência mais personalizada e conveniente ao assistir e baixar conteúdo do YouTube.
Principais recursos do NewPipe:
-
Reprodução de vídeos: O NewPipe permite assistir a vídeos do YouTube diretamente no aplicativo, fornecendo uma interface intuitiva e fácil de usar.
-
Reprodução em segundo plano: Você pode reproduzir vídeos do YouTube em segundo plano, permitindo que você ouça o áudio do vídeo enquanto realiza outras tarefas em seu dispositivo Android.
-
Bloqueador de anúncios: O NewPipe bloqueia automaticamente anúncios em vídeos do YouTube, proporcionando uma experiência de visualização mais livre de interrupções.
-
Download de vídeos: O aplicativo permite baixar vídeos do YouTube diretamente para o armazenamento do seu dispositivo Android. Você pode escolher a qualidade de vídeo desejada e salvá-lo para assistir offline.
-
Download de áudios: Além de vídeos, o NewPipe também permite que você baixe apenas o áudio dos vídeos do YouTube em formatos como MP3 ou AAC.
-
Assinaturas e notificações: Você pode se inscrever nos canais do YouTube no NewPipe e receber notificações sobre novos vídeos dos canais que você segue.
-
Privacidade e segurança: O NewPipe prioriza a privacidade dos usuários. Ele não requer login em uma conta do Google para acessar o conteúdo do YouTube, o que significa que você pode usar o aplicativo sem fornecer suas informações pessoais.
O NewPipe oferece uma alternativa interessante para aqueles que desejam uma experiência personalizada e privada ao acessar o conteúdo do YouTube em dispositivos Android.
Pode baixar F-droid https://f-droid.org/packages/org.schabi.newpipe/
https://github.com/TeamNewPipe/NewPipe
-
-
 @ 8d5ba92c:c6c3ecd5
2024-10-07 15:35:46
@ 8d5ba92c:c6c3ecd5
2024-10-07 15:35:46Four years can be a mere heartbeat in the grand tapestry of time, yet it weaves stories of transformation and growth.
“A journey of a thousand miles begins with a single step.”
That step was taken four years ago by a small but courageous nation, leading them to a place that’s truly worth cheering for!
The Two Scarcest Assets on Earth: Time and Bitcoin.
Tick-tock... Nearly every ten minutes, tick tock. The clock that never stops. Time flies by. Day by day, week by week, month after month.
While we’re busy building for the long haul, we can’t ignore the passage of time. Yet we can measure the impact of our efforts on something truly meaningful.
After adopting Bitcoin as legal tender in 2021, El Salvador has made remarkable progress. Sure, there is still a lot of work to be done... In order to keep this piece short, I won't cover the entire country. Instead, let me shine a light on a small part that’s laying a strong foundation for their and our future growth.
Adopting Bitcoin: November 15-16 in the picturesque city of San Salvador.
The official event page describes it as “the high-signal Bitcoin conference for builders.” Although I haven’t had the chance to see it live at the last three conferences, I’ve heard plenty of good things from people who attended it at least once. That makes me even more excited about the fact that this November, not only will I get to experience it in person, but I’ll also get to support it with my time and energy through one of the projects I’m working on.
Jolt it down: Bitcoin Para Niños x Bitcoin Junior Club!
The idea of the Bitcoin Junior Club had been in my head for a long time, but its online journey kicked off at the beginning of this year. I’m very happy to play an active role in Adopting Bitcoin, especially with a focus on the youngest generation. As briefly mentioned in this text 'Bitcoin 4 Youth: The Rise of a Sovereign Generation' already in the past I was truly happy to see some events that this year finally added more focus on kids—actually, I was also lucky enough to experience three of them firsthand.
-
Bitcoin Junior Club is an open hub that gathers resources for kids and families while also creating its own materials (currently mainly free printables).
-
Due to my limited time and resources, the focus has been on building a solid foundation on the website, as that’s where I see the most value for users. Social media presence has taken a backseat. However, since I believe in Nostr, I felt it was important to highlight this unique collaboration here first, moving the official website for later on.
-
BTC Junior Club goes beyond traditional Bitcoin education! It’s focused on fostering creativity and critical thinking. I truly believe that combining these two with sound money principles empowers young minds to embrace true sovereignty from an early age. Bitcoin fixes many things, but if you don’t think for yourself, you won’t be able to tap into its full potential.
-
Here you can read more details about this project, if you want.
So fresh, still little known… How did the collaboration with an established event come about?
Taking a bit of a chance, I commented on one of Adopting Bitcoin’s posts about the possibility of getting a ticket to the conference and suggested helping out in the space dedicated to the youngest participants. I’m still incredibly touched that my comment was met with approval the organizing Team. Eventually, I got the chance to build with them an amazing space called Bitcoin Para Niños.
“The future belongs to those who believe in the beauty of their dreams—let’s dream big and keep building with Bitcoin!”
Even given the short deadline and ambitious plans—along with the financial constraints both projects face since they’re non-profit—I’m still confident that together we’ll craft an unforgettable experience. The is energy flowing! Much of the program is already in place: focused on both the quality and uniqueness.
Soon, we’ll share more specific details beyond what I’ve mentioned below. Now, I want to highlight the incredible support I’m once again witnessing—or rather, feeling—from the Bitcoin community. 🧡 Reyna Chicas and Mi Primer Bitcoin, Tali Lindberg and Orange Hatter, Lina Seiche and The Little HODLer, Ian Foster and EconoKidz, SHAMory with Scott and Mallory Sibley: these are just a few of the projects that have committed to supporting our family-friendly mission directly with their presence or/and materials and goodies.
Sneak peek: Here’s What to Expect.
The entire Bitcoin Para Niños space will be open to all participants throughout both days of the conference (15-16 November). Kids under 18 get in free to Adopting Bitcoin—so why not bring the younger members of your family along?
We’re putting together a leisure area filled with Bitcoin-themed stuff—from books and toys to creative materials—along with the entire active zone for kids, teens, and adults alike. Mini workshops and casual talks are on the agenda as well, think of them as panels in a relaxed format that still offer valuable insights. Plus, expect unique games and surprises that blend education with fun!
More information will be released in the coming days. For now, I hope this sneak peek energizes you and motivates you to participate in this year’s event. I’m ready for some serious work and sharing lots of good vibes—looking forward to meeting some of you in San Salvador 😊
Last but not least…
If you’d like to support our efforts, value4value means time, talent, and treasure. Share this info with others, let us know what you think, what you’re most excited about, or maybe even offer a helpful hand. If you want to throw a few sats into the mix for this whole adventure, visit Geyser Fund.
This week, I’ll also add a separate donation page dedicated to El Salvador, but for now, you can support the entire project: Bitcoin Junior Club. Details on how all funds will be spent are also listed there.
FYI—I’m not taking anything from this work, and so far, I’ll have to finance the trip out of my own pocket, which I don’t have much of. I love kids, I love Bitcoin, and I know that working on both of these loves is the key to a better world. To helps us all build a better future. The future with sovereign generations. Let’s follow the steps that profoundly started four years ago in El Salvador, a small but courageous nation.
Bitcoin4Youth #Kidstr
Cheers!
Şela
-
-
 @ 28460797:b23ce78f
2024-10-07 15:11:44
@ 28460797:b23ce78f
2024-10-07 15:11:44Post number 1
-
 @ 6bae33c8:607272e8
2024-10-07 13:55:40
@ 6bae33c8:607272e8
2024-10-07 13:55:40What an ill-fated trip to Vegas that was. I got bounced from Circa Survivor Week 1, and after another 2-3 week ATS, I’ve yet to have a winning one through five weeks, am basically drawing dead in the Circa Millions and even for the second-quarter prize. And I can’t even complain about the bad beat with the Bengals +2.5 (even though that was a horrible beat) because my wins were the Cowboys +2.5 and the Jaguars -2.5, both of which were by a hair. My other losses were blow-outs — the Browns and the Raiders. When you’re picking well, you’re on the wrong side of coin flips and right side of the blowouts.
My Primetime team also got its first loss of the year, to a team missing its first three picks (AJ Brown, Davante Adams and Isaiah Pacheco)! He got 46 points from Lamar Jackson and had Chuba Hubbard, Isaiah Likely and the Texans kicker. My team was missing Jahmyr Gibbs, JK Dobbins and Dallas Goedert, and had Jordan Mason, Marvin Harrison and a bunch of mediocrities. It’s okay — just a down week, and, knock on wood, the team is still healthy and should bounce back.
Two of my three Beat Chris Liss teams are in first place now after massive weeks. One of them got 192 points despite little from Mason, Dalton Kincaid or Braelon Allen who I was forced to flex with DeVonta Smith on bye. That’s the Joe Burrow-Ja’Marr Chase team where I did something crazy and took a second QB (Burrow) in Round 10 because he was there, I had Chase, and I knew Anthony Richardson was low floor. It also has Drake London and a Younghoe.
The other one has 166 with Rashid Shaheed still to play, despite my benching Rhamondre Stevenson for Bucky Irving, Malik Nabers and Jaylen Waddle on the bench and Dobbins on bye.
The first BCL is in 12th place, and I’m enjoying it. Put all the bad picks (Christian McCaffrey, De’Von Achane, Sam LaPorta) on a sinking ship and let it go to the bottom of the ocean. It died so the others might live.
If the season ended today, I’d have three of four in the playoffs, have the most points in the Steak League and (pending Patrick Mahomes and Xavier Worthy) be in the top-3 in the RotoWire Dynasty League. Also in the Seslowsky Survivor pool, we took the Packers and faded the Seahawks this week, so we’re still alive. It’s only the Circa contests and that first BCL that are in shambles.
-
Justin Jefferson had a modest day because he kept drawing PI calls, some legit and some not so legit.
-
I had temporarily put in Dalton Schultz over Tyler Conklin in the Primetime earlier in the week, planning to consider changing it back, but I forgot about the early start, and it locked, costing me four points. It could have been a lot worse because Schultz had zero at the half. But I mention that just to say that my primary rooting interest in the game was for Conklin not to go crazy, and he almost did with a couple end zone targets.
-
I also wanted Braelon Allen to so something in my flex, but the Jets were snapping to shotgun (with Allen in the game) from 1st-and-goal from the 1!
-
The Jets lost the game on a Stephon Gilmore pick. Watching it live, I was like, “Why didn’t Mike Williams turn around?” And when I saw the replay, I was like, “Oh, because Gilmore was grabbing and shoving him the entire time.” After all the Jefferson largesse, that was a strange swallowing of the whistle.
-
Of course it did give Sam Darnold the revenge win, but he looked more like the old Darnold that game, as the Vikings got nothing done in the second half. The Aaron Jones injury hurt them too.
-
Garrett Wilson had a breakout of sorts, but it took him 22 targets to get 101 yards. The Jets only ran the ball 14 times all game.
-
Breece Hall is like Bijan Robinson — he’ll have his huge game at some point, but by then you’ll be out of contention.
-
I didn’t watch much of Bears-Panthers. It looks like Roschon Johnson is the goal-line back which hurts D’Andre Swift a little bit. And DJ Moore is the only startable receiver there.
-
Chuba Hubbard keeps producing. You have to wonder how much urgency there will be to get Jonathan Brooks involved when he comes back. It’s hard to see him displacing Hubbard entirely.
-
Andy Dalton might be better than Bryce Young, but he’s no Joe Flacco.
-
The Bengals-Ravens game was fun to watch but torture if you had the Bengals +2.5. The Bengals were up three, in field goal range with 2:23 left, and if they kick it, they go up six, locking in the cover even if the Ravens drive down for the game-winning score. But Burrow threw a pick! I was sure the Ravens would score a TD and beat me, but they settled for a FG to send it to overtime. In overtime, the Ravens got the ball, and I was positive they’re going to beat me with a TD, but Lamar Jackson fumbled the snap, and the Bengals have it in long FG range. But instead of trying to shorten the FG with a pass play from your QB who has 392 yards, five TDs and 10.1 YPA against a tired defense, they run it three times, settle for a 53-yarder and miss. They deserved to lose, and they deserved to lose the cover. And I deserve the Circa loss for betting on those nutless monkeys.
-
Ja’Marr Chase is so good. While Wilson is getting 101 yards on 22 targets, Chase has 195 on 12. Every time he touches the ball in space he’s got a chance to score. I have him in three leagues, a big reason why my fantasy teams are off to a good start.
-
Tee Higgins got his too, though in much more modest increments. He’s the perfect complement, a high-end No. 2.
-
Besides the fumble Lamar Jackson played out of his mind. He’s got the pocket-passing touch now too, and he evaded about 10 sure sacks. The Bengals defense actually played pretty well and still gave up 41 points.
-
Zay Flowers had a big game, but he’s just a guy. Solid, good hands, quick and reliable, but nothing special.
-
Mark Andews finally showed up and made an impact, but Charlie Kolar and Isaiah Likely outscored him. Andrews could easily be the TE1 ROS, but his floor is also the floor.
-
Derrick Henry had a modest game until the big OT run. He’s game-flow dependent, and the Ravens were losing for much of this one. (The Bengals also sold out to stop the run.)
-
I didn’t watch any of the Dolphins-Pats, but I did bench Stevenson because he briefly lost his starting role.
-
Jonnu Smith is a good player, and should have value if/when Tua comes back.
-
Jaylen Wright might be this year’s Achane if Achane is out for any length of time, and Tua’s return makes it a functional offense.
-
I bet the Browns because it was so contrarian it had to be right, but it was dead wrong. Deshaun Watson sucks, and there’s no way to massage it. Sometimes the market is just stupid because the “sharps” are too caught up in the indicators to see one team emerging and the other imploding entirely. The Indigenous Peoples seem to open huge holes in the run game, but maybe that’s because defenses are trying to account for Jayden Daniels.
-
Alec Pierce is the AFC’s Rashid Shaheed. All he does is make huge downfield plays. Why do they only give him three targets per game?
-
The only athlete with a more bizarre career trajectory than Flacco is Barry Bonds, and we all know why that happened. How do you go from being a quasi-scrub at your peak to a superstar in your late-30s?
-
I considered shares of Travis Etienne by the end of draft season but luckily never pulled the trigger. Tank Bigsby is at least a co-starter, and he looks good too.
-
Trevor Lawrence finally played a decent game. Brian Thomas looks like a budding star. It’s amazing he, Nabers and Daniels were all on the same college team. All three will be vying for offensive rookie of the year.
-
I stacked Texans in the Primetime, and I’m not thrilled with their style of play. The pace is glacial, they run the ball way too much despite having scrubby backs, and the offensive line commits too many penalties (though they were better this week.) They also are cowardly with the go-for-it/punting decisions which ends drives and shortens games. CJ Stroud is great, but his production is being hamstrung by the game plan.
-
Speaking of hamstrung, Nico Collins left after catching a long TD in the first half and didn’t come back. I took Stefon Diggs over Collins in the Primetime which looks like a mistake in part because I trusted Diggs to stay healthy more than Collins who’s been banged up a bunch in his short career. Tank Dell, who I took in the fourth round (solely for the stack), hasn’t left my bench.
-
The Broncos defense might actually be good.
-
Bo Nix played a clean game, but he’s spreading it aroudn so much, you can’t start anyone except Javonte Williams on this team.
-
Gardner Minshew played so poorly he got benched. The Raiders offense is a shitshow, but at least Brock Bowers got the 12 targets he deserved.
-
I didn’t trust little Kyren Williams to hold up with 22 carries per game, but he has so far, and he’s a scoring machine.
-
The Rams are amazing in that they can get passing game production out of anyone.
-
Jayden Reed is the Packers best receiver by far, but since I should have drafted him and didn’t, it was nice to see him get only six targets. I don’t know if Tucker Kraft is a thing, or if it was just because Christian Watson and Romeo Doubs were out.
-
Daniel Jones played his best game of the year without his star receiver. Nabers’ absence was good for the team as it got Darius Slayton and Theo Johnson more involved.
-
Tyrone Tracy is my second biggest regret (to Reed) this draft season. I saw a couple runs in the preseason, and I could tell he had it. Devin Singletary is just a guy, and Tracy is explosive and can catch passes. He’ll have a big role going forward even when Singletary returns.
-
One of my Bold Predictions was the Giants would have a top-10 fantasy defense, and I drafted (and dropped) them everywhere. Right now they’re tied for eighth pending the Monday night game. I picked up Dexter Lawrence (two sacks) in the Steak League because I noticed in the Seahawks-Lions game the Seahawks can’t pass protect to save their lives.
-
The announcers in this game were morons. The Giants were up three with with 1:50 left on third and long, Seahawks had two timeouts and they were criticizing them for trying to throw for the first down. “They should have run and forced the Seahawks to use their second time out.” Bitch, if they do that, then they’re definitely punting it back to Seattle who only needs a FG with 1:50 and one TO instead of two, i.e., time is not a serious issue for them. Don’t you think it’s worth trying to get the first down and win the game?
-
I loved the blocked FG TD to seal it. The TD itself made no difference, but just a triumphant way to knock fools out of Survivor and secure the win. Brian Daboll showing some 11-D chess “going” for two and kneeling on it to keep it a two score game and not give Seattle the infinitesimal chance to return it for a two-point play of its own and make it a one-score game.
-
I only watched the highlights of Dallas-Pittsburgh because the 40-minute version wasn’t available when I woke up, and that’s on them. It looked like I didn’t miss much. Remember last year too CeeDee Lamb took a while to get going before setting the league on fire.
-
Justin Fields doesn’t need to do much to hold off the carcass of Russell Wilson, but 4.9 YPA against a Cowboys team missing Dexter Lawrence and Micah Parsons is walking the line.
-
-
 @ 361d3e1e:50bc10a8
2024-10-07 13:49:19
@ 361d3e1e:50bc10a8
2024-10-07 13:49:19https://forex-strategy.com/2024/10/07/2000-increase-in-staff-to-handle-vaccine-injury-claims/
2000% increase in staff to handle vaccine injury claims
vaccine #uk #unitedkingdom #sideeffects #covid #injury
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:19:39
@ 4ba8e86d:89d32de4
2024-10-07 13:19:39A criptografia é uma técnica que permite proteger informações e manter a privacidade dos dados. É como uma fechadura para suas informações, garantindo que apenas pessoas autorizadas possam acessá-las.
A história da criptografia remonta a tempos antigos, quando a criptografia era usada para proteger mensagens militares e diplomáticas. Durante as guerras, a criptografia foi amplamente utilizada para proteger as comunicações militares e confundir o inimigo. Durante a Segunda Guerra Mundial, a criptografia teve um papel crucial no conflito, especialmente na Batalha do Atlântico, onde os Aliados usaram a criptografia para quebrar o código dos nazistas e ganhar vantagem estratégica.
Nos anos 90, quando a criptografia estava sendo limitada pelo governo dos EUA, o programador Phil Zimmermann criou o PGP (Pretty Good Privacy), um programa de criptografia de e-mail para ajudar a proteger a privacidade das pessoas. O PGP usa um algoritmo de criptografia assimétrica que usa duas chaves diferentes para codificar e decodificar informações. A primeira chave é conhecida como chave pública e é usada para criptografar a mensagem. A segunda chave é conhecida como chave privada e é usada para decodificar a mensagem. Isso significa que a pessoa que envia a mensagem pode usar a chave pública do destinatário para criptografar a mensagem e enviá-la com segurança. O PGP tornou-se popular rapidamente, tornando-se uma das ferramentas de criptografia mais conhecidas e confiáveis do mundo. É importante porque ajuda a proteger suas informações pessoais contra o roubo de identidade e outras formas de invasão de privacidade online. Quando você envia uma mensagem criptografada com PGP,só quem possui a chave privada correspondente poderá descriptografá-la e ler o conteúdo. Isso significa que, mesmo que outras pessoas interceptem suas mensagens, elas não serão capazes de ler ou roubar suas informações pessoais.
Para usar o PGP, você precisa primeiro criar um par de chaves, que consiste em uma chave pública e uma chave privada. Você pode fazer isso usando um software de criptografia como o GPG (GNU Privacy Guard). Depois de criar as chaves, você precisa compartilhar sua chave pública com as pessoas com quem deseja se comunicar. Eles podem usar sua chave pública para criptografar as mensagens que desejam enviar para você.
OpenKeychain é um software PGP (Pretty Good Privacy) que permite criptografar, assinar e verificar mensagens e arquivos no seu celular Android. Para utilizar o OpenKeychain, siga os seguintes passos:
-
Baixe e instale o aplicativo OpenKeychain na Aurora Store. https://play.google.com/store/apps/details?id=org.sufficientlysecure.keychain
-
Abra o aplicativo e crie uma nova chave PGP seguindo as instruções fornecidas pelo aplicativo. Você deve escolher um nome de usuário e uma senha forte para proteger sua chave privada.
-
Com a chave PGP criada, você pode assinar, verificar e criptografar mensagens e arquivos. Para assinar uma mensagem, selecione a opção de assinatura e digite a mensagem. O aplicativo adicionará sua assinatura digital à mensagem e a salvará em seu celular.
-
Para verificar a assinatura de uma mensagem, selecione a opção de verificação e insira a mensagem. O aplicativo verificará a assinatura e informará se ela é válida ou não.
-
Para criptografar uma mensagem ou arquivo, selecione a opção de criptografia e insira o arquivo ou mensagem que deseja criptografar. Em seguida, escolha a chave PGP do destinatário e o aplicativo criptografará o conteúdo.
-
Para descriptografar uma mensagem ou arquivo criptografado, selecione a opção de descriptografia e insira o arquivo ou mensagem que deseja descriptografar. Em seguida, digite a senha da sua chave privada para descriptografar o conteúdo.
Lembre-se de manter sua chave privada segura e protegida com uma senha forte. Também é importante compartilhar sua chave pública com outras pessoas de maneira segura, para que elas possam enviar mensagens criptografadas para você.
https://youtu.be/fptlAx_j4OA https://en.m.wikipedia.org/wiki/PGP_word_list
-
-
 @ 4f82bced:b8928630
2024-10-07 12:56:58
@ 4f82bced:b8928630
2024-10-07 12:56:58Disclaimer: this article was written for the NOSTR uninitiated.
When you hear, bitcoin what comes to mind? Crypto? Blockchain? ETF? How about music? We met someone looking to change this perception and make bitcoin more relatable to the masses through music, meet Man Like Kweks. A husband, father, teacher, and part-time musician who "sees the world through a purple lens with the orange blend" - a quote from the track SPC referring to NOSTR (purple) and Bitcoin (orange)
The Xmas road trip brought us together. We were fortunate to spend more time with him and his family during our month-long stay in Arusha. I’m no musician but watching the process was surprising. There was no studio, no fancy gear, just his iPhone and his car to record in. One stroll and he had the verses going. The skill was always there. Bitcoin and NOSTR gave him a superpower.
If you’re scratching your head, let me explain. Traditionally, artists monetize their tracks by going viral, getting sponsors, or selling merch. Bitcoin + NOSTR allows him to get 'zapped' money for his tracks. Anyone with an Internet connection can instantly zap him as little as one satoshi (100M satoshi = 1 bitcoin) if they like or value the track. As a creator, putting value out can result in getting value back instantly. For instance, his track Gorilla Sats has received roughly 250K sats (0.0025 BTC).
NOSTR (Notes and Other Stuff Transmitted by Relays) is a decentralized and censorship-resistant protocol enabling users to publish content without relying on central parties. One application of this, is Wavlake, a music platform allowing artists to 'stream anywhere and earn everywhere'. You'll find Man Like Kweks here. With such technology, he's extremely open to sharing his tracks for collaborations, remixes or to be used as a background score. No copyright nonsense. "I'm open source about my dreams, I know any change got to start with me" - POWA
He's climbed Kilimanjaro multiple times and even crowdfunded his first ascent through bitcoin. With his talents and work ethic, the sky is the limit. Don't be surprised to see him as the headline performance at a nearby concert soon.
Next time you hear 'bitcoin' think of music it may remove the negative bias the media perpetuates.
Check out this recent track, No Paper No Visa. "My money ain't got no leader, my money ain't got to Ceaser." If you want something more futuristic Epoch 5 is a great one. "My life was square, now it's measured in blocks."
Sources:
Man Like Kweks: https://wavlake.com/man-like-kweks
SPC: https://wavlake.com/track/3430b377-4052-4269-8feb-a2d439d45e3b
POWA: https://wavlake.com/track/097e2264-41f2-4fba-aa38-dc24cfcfc3b7
No paper no Visa https://wavlake.com/album/d2cec8c3-72b9-4c3b-a252-53512a7f6a04
Epoch 5: https://wavlake.com/track/5127df3d-cf9b-40b6-b081-508df98ad9d4
-
 @ 4f82bced:b8928630
2024-10-07 12:49:03
@ 4f82bced:b8928630
2024-10-07 12:49:03https://youtu.be/lVK1xRz--9I
Last year my wife and I decided to take a sabbatical and see the world. Our plan? Visit Africa, South America, and Asia to experience how bitcoin is impacting the global south. Having never set foot in Africa we settled on the Cairo to Cape Town overland route. It allowed us to start from the north and head south across the east coast.
We went in with surface-level knowledge about Africa: Egypt = pyramids, East Africa = animals South Africa = Cape Town. Boy were we wrong! Africa is so misunderstood starting with the fact that it’s a continent, not a country. Each country is unique and we are humbled to have made them our home for the past year.
332 days, 10 countries 37,000 km, 2 flights, 17 buses, 21 taxis, and countless bitcoin interactions later, our African journey is complete. (Almost! Need to visit a friend in Namibia)
Due to safety concerns, we had to skip Sudan and flew in and out of Ethiopia. Except for these two flights, we completed this entire journey overland using buses and taxis. (shared taxis are fun – a game of how many can squeeze into a van before it breaks down)
One post won’t do justice to this adventure so we will be spending the next two months catching up and sharing experiences thus far. Some highlights include:
-Founded 2 bitcoin preferred businesses (a juice shop and an Airbnb) -Onboarded 12 merchants and a charity to accept bitcoin as payments -Spoke at our first bitcoin conference -Attended 8 community meetups (presented in 4) -Paid 35 businesses in bitcoin (includes 3 safaris) -Invested in a Bitcoin-preferred business -We look forward to sharing stories from each country and hope you enjoy them.
-A Student of Bitcoin
originally posted at https://stacker.news/items/682996
-
 @ 1b5ee74d:bb1aae6e
2024-10-07 08:15:25
@ 1b5ee74d:bb1aae6e
2024-10-07 08:15:25In the previous episode, we discussed the concept of silent adoption, focusing solely on the most popular and debated aspect of adoption: the purchase of Bitcoin—the monetary aspect. However, buying and selling is only the final phase of adoption, the one that ultimately brings it to completion. Before that, there’s another crucial step: awareness.
It goes without saying that one cannot adopt a technology without being aware of its existence. That’s why companies establish marketing departments: to introduce their product to potential customers. It’s up to these departments to determine the best methods to increase brand awareness, typically through two approaches that vary depending on each campaign’s goals: organic growth or paid growth.
The first refers to natural growth, which is not directly influenced by advertising investments or paid promotions. It may focus on increasing traffic, sales, or interest in a brand through content optimization, word of mouth, social media engagement, or other non-sponsored activities.
The second refers to growth achieved through investments in paid advertising campaigns, such as Google ads, social media advertising, display advertising, or other forms of promotion that require financial expenditure to gain visibility.
Apple can choose which strategy to apply to each campaign, as can Microsoft, Samsung, Meta, and all other companies. They can do this because they are hierarchical and centralized entities, with absolute control over their product. Bitcoin's marketing department, on the other hand, cannot afford this luxury—for the simple reason that it doesn’t exist.
Organic Marketing: Pros and Cons
Advantages\ One of the main advantages of Bitcoin's organic growth is the authenticity of its spread. Without a centralized marketing strategy or campaigns backed by large budgets, Bitcoin's awareness and adoption have expanded through word of mouth and the genuine interest of individuals. This has led, especially in the early years, to the emergence of highly motivated and informed user and supporter communities, deeply understanding the principles and values behind the technology: in two words, the early adopters.
Organic growth also fosters community innovation. Developers and enthusiasts can freely contribute to improving the technology without the restrictions imposed by commercial goals or intellectual property. If corporate logic had prevailed in Bitcoin, today the Lightning Network might not exist, blocks might be tens of megabytes each, and there would likely be only a few hundred nodes online. This is a reference to the Blocksize War.
Another feature of the lack of centralized marketing is the reduction of perception manipulation. Information about Bitcoin is disseminated through a plurality of sources, allowing individuals to form an opinion based on multiple perspectives. This contrasts with one-sided advertising campaigns that can heavily and artificially influence public perception.
The inevitable consequence is that within the community of insiders, there are numerous ideological clashes, some of them fierce. This is a good thing because unanimous opinions would make it too easy to reach consensus on future changes to Bitcoin. In short, unanimity would make Bitcoin much more fragile.
Disadvantages\ The lack of centralized marketing can slow penetration into key markets. Traditional companies invest in market research and targeted strategies to expand their presence in new regions or demographic segments. When there is no such coordination, the only real coordinator is called the free market.
\ The absence of a representative entity makes it harder to engage with institutions and regulators. While other companies can lobby or participate in working groups with governments, Bitcoin has no singular organizational structure to play this role (though lobbying groups formed by entrepreneurs working in the industry have already emerged). This can lead to unfavorable regulations or misunderstandings that could hinder adoption. An example? The numerous Chinese bans.
The Unintentional Marketing of the Fiat System
Bitcoin positions itself as an alternative system to the current one, characterized by central banks and governments. Just as in a competitive market where companies gain market share at the expense of their competitors, Bitcoin grows when traditional institutions lose trust in the eyes of the public. In other words, the failures and inefficiencies of existing systems act as catalysts for Bitcoin adoption, becoming, ironically, unintentional marketing tools for the cryptocurrency.
A striking example is countries affected by hyperinflation. In nations like Venezuela, Zimbabwe, and Argentina, local currencies have lost much of their value due to ineffective economic policies and political instability. In 2019, inflation in Venezuela exceeded 10,000,000%, making the bolívar practically useless for daily transactions. In these circumstances, people sought refuge in alternative assets like Bitcoin to preserve their purchasing power: it's no coincidence that Venezuela ranks fourteenth in the world for cryptocurrency adoption, according to the Global Adoption Index by Chainalysis.
In authoritarian regimes, where repression of free speech and financial control are commonplace, Bitcoin offers a tangible alternative. In 2020, during the protests in Nigeria against police brutality, the EndSars movement saw protesters’ bank accounts frozen. In response, activists began collecting funds in Bitcoin, bypassing government restrictions and financing their activities independently. Nigeria ranks second in the world for cryptocurrency adoption according to Chainalysis, ahead of even the United States and second only to India.
Even in Western democracies, there have been instances of financial censorship that have fueled interest in Bitcoin. Under heavy government pressure, the crowdfunding platform GoFundMe blocked donations to the "Freedom Convoy" in 2022, a group of Canadian truckers protesting pandemic restrictions. In response, supporters used Bitcoin to send funds directly to the protesters.\ Do I need to mention the 2008 financial crisis that provided Satoshi Nakamoto with the perfect opportunity to publish the Bitcoin White Paper?
The inefficiencies and injustices of the traditional financial and political system indirectly promote Bitcoin adoption. Every crisis, scandal, or abuse of power fuels the search for alternatives that offer greater security, autonomy, and individual control. In this sense, the actions of governments and central banks become, paradoxically, extremely effective marketing tools.
Could this be why, even without Accenture’s advice, Bitcoin is one of the most recognized brands in the world?
-
 @ 49fd11a8:efd284c8
2024-10-07 04:38:37
@ 49fd11a8:efd284c8
2024-10-07 04:38:37tl;dr: I am writing these primarily for me, but you are welcome to come along if you wish. I have discovered that writing is the best way for my brain to process my thoughts into something productive. Maybe you'll like what I have to say, maybe not. Either way you are welcome to talk about it with me if you'd like. God bless! Oh, and if you're reading this trying to figure out who I am, that will be the next post.
I write for the unlearned about things in which I am unlearned myself.
> - C. S. Lewis (1964). “Reflections on the Psalms”*
I have always struggled to form my thoughts into something meaningful at the spur of the moment. I have an unfortunate lack of quick wit, and I have a serious distaste for debate, or any confrontation for that matter. I would not call myself slow in the common sense of the term. Thorough would be a better description. All through school, I hated being called upon during class. I was not uncomfortable because I was unable to keep up; I simply needed more time to formulate my opinion and test it from multiple angles. When I began college, I found a professor that I particularly liked, in part because I do not remember him ever putting me on the spot during class. We never had this conversation, but I believe he could sense that it was my weakness. Not only that, but he gave us an opportunity to express ourselves in a different way: On paper.
I had been assigned papers before, but I had never taken one seriously. They were obstacles standing between me and the weekend, or whatever else I was looking forward to at the time. Dr. Wheelington's papers were somehow different. We had assigned reading due for every class, and with that came a one-page paper consisting of our thoughts on that reading. It turned out that even though I did not always like the reading assignments, I loved writing the papers. They gave me the time I needed to flesh out the topics at hand. Sometimes the topics excited me, and I was able to take my thoughts in all new directions, places I had never been before. Sometimes I ranted for the whole page about one paragraph in the reading. However I felt about the content of the reading assignment, I was encouraged to think at length, rather than shut down and expected to make sense of my incomplete thoughts.
Another level of appreciation hit when a group of friends who had Dr. Wheelington for a different class told me that I was mentioned in their class. I will not dwell on it here, but in short, I was told that he mentioned how quiet and reserved I am when in person, but when I am asked to write, everything changes. This made clear to me that not only did Dr. Wheelington actually read his assigned papers, he read and genuinely liked mine. I am sure he did not always agree with me, but he found my written thought to be of substance. I was ecstatic. I had an assignment that I enjoyed because of the way it challenged me and I was apparently good at it.
Fast forward to now, and I find myself about 17 years later. I quit writing as soon as I left school. I always thought I would start again, and never did. I wonder now if the last paper I wrote in school was the last time I thought deeply on a topic. I hope to change that now. I have recently been asked to facilitate a Bible Study class at the church my family has been attending, and now more than ever I need to find in myself the ability to meditate on a topic and prepare my thoughts so I can express them clearly in class each Sunday morning.
That is why this exists. The next post will be about what I believe and why. I feel that is important for starting an endeavor like this one. Then I will start posting about my topics for Sunday morning. They will hopefully come at a pace of more than once a week at first (the Bible Study started several weeks ago now...) until I catch up to the current week.
I already feel better. Here begins something I have needed for a long time.
-
 @ bec0c9d3:c4e9cd29
2024-10-07 03:36:45
@ bec0c9d3:c4e9cd29
2024-10-07 03:36:452140 Inkrypted - Tattoo Session at Cyphermunk House
 Join us in London on Saturday 02nd November at the Cyphermunk House for a unique tattoo session during Art Panels
This event will bring together Bitcoin tattoo artists, including Zazawowow and Fzero known for their commitment to freedom of expression and privacy protection.
Join us in London on Saturday 02nd November at the Cyphermunk House for a unique tattoo session during Art Panels
This event will bring together Bitcoin tattoo artists, including Zazawowow and Fzero known for their commitment to freedom of expression and privacy protection. In an immersive atmosphere dedicated to the values of the cypherpunk community, take this opportunity to get unique tattoo artwork while celebrating the principles of Bitcoin and individual sovereignty. All tattoos will be payable in Bitcoin.
Open to all, this event is the perfect place to meet enthusiasts of cryptography, art, and digital freedom. Come share a creative and festive moment with engaged artists in an authentic setting at the forefront of the technological and social revolution.
Special guest: Alcapone
Date: saturday, 02 November 2024 Location: Cyphermunk House, London Time: 5pm - Payment: Bitcoin only
! ATTENTION !
To join a session please register using our form here ---> WAITING LIST
................................................................
OUR PARNERS / SPONSORS
ANGOR BITCOIN EVENTS HQ YAKIHONNE
2140
2140inkrypted
tattoosession
tattoodesign
art
ink
blackwork
tattooartist
tattooflash
tattoo
tattoos
inkedup
blackwork
bitcoinculturefestival
cyphermunkHouse
-
 @ a012dc82:6458a70d
2024-10-07 02:44:05
@ a012dc82:6458a70d
2024-10-07 02:44:05Table Of Content
-
The Emergence of Multichain Communication
-
The Benefits of Multichain Communication
-
The Future of Multichain Communication
-
Conclusion
-
FAQ
Blockchain technology has come a long way since its inception more than a decade ago. Initially, it was seen as a decentralized ledger that could be used to facilitate peer-to-peer transactions without the need for intermediaries. However, with time, its potential has been recognized for a wide range of applications, from supply chain management to voting systems. One of the most exciting developments in the blockchain space is the emergence of multichain communication. This article explores the evolution of multichain communication, its benefits, and how it is breaking boundaries in the blockchain world.
The Emergence of Multichain Communication
Multichain communication refers to the ability of different blockchains to communicate with each other seamlessly. This is achieved through the use of bridges that enable the transfer of assets from one blockchain to another. The emergence of multichain communication is a significant milestone in the evolution of blockchain technology. It has the potential to break down the barriers between different blockchain networks and create a more interconnected blockchain ecosystem.
The Benefits of Multichain Communication
Improved Scalability
One of the biggest challenges facing blockchain technology is scalability. Blockchains like Bitcoin and Ethereum have a limited capacity to process transactions per second. This has led to slow transaction times and high transaction fees during peak periods. Multichain communication has the potential to address this challenge by enabling the transfer of assets across different blockchain networks. This can help to reduce the load on individual blockchains and improve their overall scalability.
Interoperability
Interoperability is another key benefit of multichain communication. By enabling different blockchains to communicate with each other, it becomes possible to create a more interoperable blockchain ecosystem. This can lead to the development of new use cases for blockchain technology and the creation of new opportunities for developers and businesses.
Increased Security
Multichain communication can also help to enhance the security of blockchain networks. By enabling the transfer of assets between different blockchains, it becomes possible to distribute risk across multiple networks. This can help to reduce the risk of a single point of failure and improve the overall security of the blockchain ecosystem.
Better User Experience
Finally, multichain communication can help to create a better user experience for blockchain users. By enabling the transfer of assets across different blockchains, it becomes possible to create a more seamless user experience. This can help to reduce the friction associated with using blockchain technology and make it more accessible to a wider range of users.
The Future of Multichain Communication
The future of multichain communication is very promising. With the continuous evolution of blockchain technology, we can expect to see many more innovations in this area. One of the examples of these innovations is the development of decentralized exchanges that enable the seamless transfer of assets between different blockchain networks. This will not only increase interoperability between different blockchains, but it will also enhance the overall user experience. We can also expect to see the emergence of more cross-chain applications that utilize the benefits of multichain communication to provide new and exciting functionalities to users. As blockchain technology continues to advance, we can be confident that multichain communication will continue to play a significant role in shaping the future of the blockchain ecosystem.
Conclusion
Multichain communication is a significant development in the evolution of blockchain technology. By enabling different blockchains to communicate with each other seamlessly, it has the potential to break down the barriers between different blockchain networks and create a more interconnected blockchain ecosystem. The benefits of multichain communication are numerous, including improved scalability, interoperability, increased security, and a better user experience. As blockchain technology continues to evolve, we can expect to see even more exciting innovations in this area. Multichain communication is breaking boundaries in the blockchain world, and its potential is limitless.
FAQ
What is multichain communication? Multichain communication refers to the ability of different blockchains to communicate with each other seamlessly. This is achieved through the use of bridges that enable the transfer of assets from one blockchain to another.
How does multichain communication work? Multichain communication works by creating bridges between different blockchain networks. These bridges act as a gateway, enabling the transfer of assets from one blockchain to another. This makes it possible to create a more interconnected blockchain ecosystem.
What are the benefits of multichain communication? The benefits of multichain communication include improved scalability, interoperability, increased security, and a better user experience.
What are some real-world examples of multichain communication? One real-world example of multichain communication is the development of decentralized exchanges that allow for the seamless transfer of assets between different blockchains. Another example is the creation of cross-chain NFTs that can be traded across multiple networks.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 3ffac3a6:2d656657
2024-10-07 02:12:06
@ 3ffac3a6:2d656657
2024-10-07 02:12:06Ela tirou o Çutiã e deixou ele na mesa. Transamos e ela foi embora. Deixou o Çutiã. Droga!! O que eu vou fazer com aquele Çutiã? Joguei fora. . . .
Dling-dlong! Abri a porta: Ô seu moço, foi u sinhô qui perdeu esse Çutiã? Achei lá no lixo e pensei que só pudia ser coisa do sinhô e que caiu lá puringano. Tó! Peguei, fechei a porta, fui na cozinha. Joguei aquilo na triturador de lixo!
. . .
Bzz! Bzz! Bzz! Alô, aqui é da Copasa. Nós já mandamos pelo correio o Çutiã que o senhor deixou cair no triturador. Abri a caixa de cartas: Çutiã!! droga! Jogar na privada? não, não, não! a Copasa manda. Joguei no riacho pra água levar!
. . .
Aqui! Eu sou da prefeitura e eu acho que esse Çutiã veio do riacho que passa atrás da sua casa, deve ter caido do varal. Mil vezes droga! Joguei ele em cima da mesa!
. . .
Sabia que tinha esquecido ele aqui! Mas que vergonha, ainda no lugar que eu deixei, isso é um absurdo. Transamos e ela foi embora. Deixou o Çutiã…
-
 @ 5ee71c0a:b0506ae6
2024-10-07 02:00:28
@ 5ee71c0a:b0506ae6
2024-10-07 02:00:28giving habla a test
-
 @ 4ba8e86d:89d32de4
2024-10-07 00:33:44
@ 4ba8e86d:89d32de4
2024-10-07 00:33:44O PGP é um método de criptografia de chave pública que garante que apenas a pessoa com a chave privada correspondente possa descriptografar as informações. É uma ferramenta poderosa e fácil de usar para proteger suas comunicações e dados pessoais.O OpenKeychain permite gerar pares de chaves de criptografia assimétricas, compostos por uma chave pública e uma chave privada, que permitem cifrar e decifrar mensagens, arquivos e documentos.
O OpenKeychain Foi criado por Dominik Schürmann em 2011, com o objetivo de disponibilizar uma ferramenta de criptografia acessível e fácil de usar para usuários de Android. O projeto OpenKeychain teve início quando Dominik Schürmann se deparou com a dificuldade de encontrar uma aplicação de criptografia de e-mail para seu dispositivo Android. Como ele não encontrou uma opção satisfatória no mercado, decidiu criar sua própria solução.
O openKeychain é uma das principais opções de criptografia de e-mail para usuários de Android em todo o mundo.
Criptografia de e-mail é um processo de proteção das informações contidas em um e-mail, de forma que somente as pessoas autorizadas possam acessá-las. A criptografia envolve a codificação da mensagem original em uma sequência de caracteres ilegíveis, que só podem ser decodificados por alguém que possua a chave de criptografia correspondente.O objetivo da criptografia de e-mail é garantir a privacidade e segurança das informações enviadas por e-mail, especialmente quando se trata de informações confidenciais ou sensíveis. Isso ajuda a prevenir que informações privadas sejam interceptadas ou lidas por pessoas não autorizadas durante a transmissão do e-mail.
Para utilizar o OpenKeychain, o usuário deve seguir os seguintes passos:
-
Acesse a F-droid ou obtainium Store em seu dispositivo Android.
-
Abrir o aplicativo e criar uma nova chave PGP seguindo as instruções fornecidas pelo aplicativo. O usuário deve escolher um nome de usuário e uma senha forte para proteger sua chave privada.
-
Com a chave PGP criada, é possível assinar, verificar e criptografar mensagens e arquivos. Para assinar uma mensagem, basta selecionar a opção de assinatura e digitar a mensagem. O aplicativo adicionará a assinatura digital à mensagem e a salvará no celular.
-
Para verificar a assinatura de uma mensagem, selecione a opção de verificação e insira a mensagem. O aplicativo verificará a assinatura e informará se ela é válida ou não.
-
Para criptografar uma mensagem ou arquivo, selecione a opção de criptografia e insira o arquivo ou mensagem que deseja criptografar. Em seguida, escolha a chave PGP do destinatário e o aplicativo criptografará o conteúdo.
-
Para descriptografar uma mensagem ou arquivo criptografado, selecione a opção de descriptografia e insira o arquivo ou mensagem que deseja descriptografar. Em seguida, digite a senha da sua chave privada para descriptografar o conteúdo.
Lembre-se de manter sua chave privada segura e protegida com uma senha forte. Também é importante compartilhar sua chave pública com outras pessoas de maneira segura, para que elas possam enviar mensagens criptografadas para você.
https://github.com/open-keychain/open-keychain
https://youtu.be/fptlAx_j4OA
-
-
 @ 4ba8e86d:89d32de4
2024-10-06 23:54:36
@ 4ba8e86d:89d32de4
2024-10-06 23:54:36Um espectro está assombrando o mundo moderno.
A ciência da computação está a ponto de fornecer a grupos e indivíduos a capacidade de se comunicar e interagir uns com os outros de maneira totalmente anônima. Duas pessoas podem trocar mensagens, conduzir negócios e realizar contratos digitais sem nunca conhecer o verdadeiro nome ou a identidade legal da outra parte. Interações em rede serão irrastreáveis através do extensivo reencaminhamento de pacotes criptografados e caixas invioláveis, que implementam protocolos criptográficos com garantia quase perfeita contra qualquer adulteração.A reputações será de importância central, se tornando muito mais importante nas negociações do que as análises de crédito de hoje. Esses desenvolvimentos irão alterar completamente a natureza da regulamentação governamental, a capacidade de taxar e controlar as interações econômicas, a capacidade de manter as informações em segredo e até mesmo alterar a natureza da confiança e da reputação.
A tecnologia para essa revolução – que certamente será tanto uma revolução social quanto econômica – já existia, em teoria, durante a última década. Os métodos são baseados em criptografia de chave pública, sistemas de zero-knowledge interativos e vários protocolos de software para interação, autenticação e verificação. O foco, até agora, tem sido em conferências acadêmicas na Europa e nos EUA, conferências estas que são monitoradas de perto pela Agência de Segurança Nacional (NSA).Mas só recentemente as redes de computadores e computadores pessoais atingiram velocidade suficiente para tornar as ideias realizáveis na prática. E os próximos dez anos trarão a velocidade necessária para tornar as ideias economicamente viáveis e essencialmente imbatíveis. Redes de alta velocidade, caixas invioláveis, cartões inteligentes, satélites, transmissores, computadores pessoais e chips criptográficos, que estão agora em desenvolvimento, serão algumas das tecnologias facilitadoras.
O estado tentará, é claro, desacelerar ou deter a disseminação destas tecnologias, citando preocupações com a segurança nacional, o uso da tecnologia por traficantes de drogas e sonegadores de impostos, e temores de desintegração social. Muitas dessas preocupações serão válidas; a criptoanarquia permitirá que segredos nacionais sejam vendidos livremente e permitirá que materiais ilícitos e roubados sejam comercializados. Um mercado informatizado e anônimo se tornará um possível abominável mercado para assassinatos e extorsões. Vários elementos criminosos e estrangeiros serão usuários ativos da CriptoNet.Mas isso não vai parar a propagação da criptoanarquia.
Assim como a tecnologia da impressão alterou e reduziu o poder das guildas medievais e a estrutura do poder social, os protocolos criptográficos também vão alterar fundamentalmente a natureza das corporações e as interferências do governo nas transações econômicas. Combinado com mercados de informação emergentes, a criptoanarquia criará um mercado líquido para todo e qualquer material que possa ser colocado em palavras e imagens.E assim, como uma invenção aparentemente insignificante, como o arame farpado tornou possível o cercamento de vastas fazendas e territórios, alterando para sempre os conceitos de terra e direitos de propriedade na fronteira ocidental, também, a descoberta aparentemente menor de um ramo arcano da matemática se tornará o cortador de arame que desmontará o arame farpado em torno da propriedade intelectual.
Ergam-se, vocês não têm nada a perder a não ser as cercas de arame farpado!
https://activism.net/cypherpunk/crypto-anarchy.html
-
 @ 4ba8e86d:89d32de4
2024-10-06 23:45:35
@ 4ba8e86d:89d32de4
2024-10-06 23:45:35- Eric Hughes
9 de março de 1993
A privacidade é necessária para uma sociedade aberta na era eletrônica. Privacidade não é segredo. Um assunto privado é algo que não desejamos que o mundo inteiro saiba, mas um assunto secreto é algo que ninguém quer que ninguém saiba. Privacidade é o poder de se revelar seletivamente ao mundo. Se duas partes têm algum tipo de negociação, então cada um tem uma memória de sua interação. Cada partido pode falar sobre sua própria memória disto; Como alguém poderia evitar isso? Pode-se aprovar leis contra ela, mas a liberdade de expressão, ainda é mais importante que a privacidade, é fundamental para uma sociedade aberta; Procuramos não restringir qualquer discurso. Se muitas partes falam juntas no mesmo fórum, cada um pode falar com todos os outros e agregar o conhecimento sobre indivíduos e outras partes. O poder das comunicações electrônicas permitiu tal discurso de grupo, e ele não vai embora apenas porque poderíamos querer. Uma vez que desejamos privacidade, devemos garantir que cada parte de uma transação tenha conhecimento apenas do que é diretamente necessário para essa transação. Uma vez que qualquer informação pode ser falada, devemos garantir que revelamos o mínimo possível. Na maioria dos casos, a identidade pessoal não é saliente. Quando eu comprar uma revista em uma loja e entregar dinheiro para o funcionário, não há necessidade de saber quem eu sou. Quando pergunto ao meu provedor de correio eletrônico para enviar e receber mensagens, meu provedor não precisa saber a quem estou falando ou o que estou dizendo ou o que os outros estão dizendo para mim; Meu provedor só precisa saber como obter a mensagem lá e quanto eu devo-lhes em taxas. Quando minha identidade é revelada pelo mecanismo subjacente da transação, não tenho privacidade. Eu não posso aqui revelar-me seletivamente; Sempre devo me revelar. Portanto, a privacidade em uma sociedade aberta requer sistemas de transações anônimas. Até agora, o dinheiro foi o principal sistema. Um sistema de transação anônima não é um sistema de transação secreta. Um sistema anônimo capacita os indivíduos a revelar sua identidade quando desejada e somente quando desejada; Esta é a essência da privacidade. Privacidade em uma sociedade aberta também requer criptografia. Se eu disser algo, quero que seja ouvido apenas por aqueles para quem eu pretendo fazê-lo. Se o conteúdo do meu discurso está disponível para o mundo, eu não tenho privacidade. Criptografar é indicar o desejo de privacidade, e criptografar com fraca criptografia é indicar não muito desejo de privacidade. Além disso, revelar a identidade com certeza quando o padrão é anonimato requer a assinatura criptográfica. Não podemos esperar que governos, corporações ou outras organizações grandes e sem rosto nos concedam privacidade de sua beneficência. É a sua vantagem para falar de nós, e devemos esperar que eles vão falar. Tentar impedir a sua fala é lutar contra as realidades da informação. A informação não quer apenas liberdade, quer ser livre. As informações se expandem para preencher o espaço de armazenamento disponível. A informação é o primo mais jovem e mais forte do Rumor; A informação é rápida com os pés, tem mais olhos, sabe mais, e compreende menos do que Rumor. Devemos defender nossa própria privacidade se esperamos ter qualquer. Temos de nos unir e criar sistemas que permitam transacções anônimas. As pessoas têm defendido sua própria privacidade por séculos com sussurros, escuridão, envelopes, portas fechadas, apertos de mão secretos e mensageiros. As tecnologias do passado não permitem a privacidade forte, mas as tecnologias eletrônicas fazem. Nós, os Cypherpunks, estamos dedicados a construir sistemas anônimo. Estamos defendendo nossa privacidade com criptografia, com sistemas anônimos de encaminhamento de correio, assinaturas digitais e dinheiro eletrônico.
Cypherpunks escrevam códigos. Sabemos que alguém tem de escrever um software para defender a privacidade, e uma vez que não podemos obter privacidade a menos que todos nós, vamos escrevê-lo. Nós publicamos nosso código para que nossos companheiros Cypherpunks possam praticar e brincar com ele. Nosso código é gratuito para todos, em todo o mundo. Não nos importamos muito se você não aprovar o software que escrevemos. Sabemos que o software não pode ser destruído e que um sistema amplamente disperso não pode ser desligado. Os Cypherpunks deploram os regulamentos sobre criptografia, pois a criptografia é fundamentalmente um ato privado. O ato de criptografia, na verdade, remove informações do domínio público. Mesmo as leis contra a criptografia atingem apenas a fronteira de uma nação e o braço de sua violência. A criptografia será inelutávelmente espalhada por todo o globo, e com ela os sistemas de transações anônimas que torna possível. Para que a privacidade seja generalizada, ela deve fazer parte de um contrato social. As pessoas devem vir e juntas implementar esses sistemas para o bem comum. Privacidade só se estende tanto quanto a cooperação de seus companheiros na sociedade. Nós os Cypherpunks procuram suas perguntas e suas preocupações e espero que possamos envolvê-lo para que não nos enganemos. Não seremos, no entanto, afastados do nosso curso porque alguns podem discordar dos nossos objetivos. Os Cypherpunks estão ativamente empenhados em tornar as redes mais seguras para a privacidade. Vamos avançar juntos. Em Frente.
https://www.activism.net/cypherpunk/manifesto.html
-
 @ 41fa852b:af7b7706
2024-10-06 20:33:33
@ 41fa852b:af7b7706
2024-10-06 20:33:33
“Such is oft the course of deeds that move the wheels of the world: small hands do them because they must, while the eyes of the great are elsewhere.” —Elrond in J.R.R. Tolkien’s The Fellowship of the Ring.
Another week, another nine meetups on offer!
We've also got two new businesses accepting bitcoin and three upcoming events.
Now, let's see what's happening this week…
Upcoming Bitcoin Meetups
Happening this week...
- Roger Huang at Cyphermunk House: Roger Huang will be at Cyphermunk House on Monday, 7th October, to chat about his book 'Would Mao Hold Bitcoin', China, the power of freedom tech, and all things Nostr. Daniel Prince will be hosting the proceedings, and it's sure to be an interesting evening. Things get underway at 18:30 till 20:00. 📚
- Bitcoin 101 at Cyphermunk House: Cyphermunk House will be hosting another Bitcoin education for beginners and precoiners session on Tuesday 8th, 19:00-20:30. Head along and take a newbie friend. 📚👨🏻🎓
- Sutton Coldfield Bitcoin: Back in action on Wednesday the 9th. From 7pm at the Station pub, 44 Station Street, B73 6AT. Head along to meet Roger and the rest of the Sutton Coldfield crew. 🍻
- Bitcoin Liverpool: The next Bitcoin Liverpool meetup will be on Thursday October 10th at 6:30pm, in the Railway pub on Tithebarn Street, Liverpool, L2 2DT. 🍻
- Bitcoin Walk - Edinburgh: Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about Bitcoin and keep fit. 🚶🚶🏻♀️🚶♂️
- Bitcoin Derby: You'll find them at Ye Olde Dolphin, DE1 3DL on the 12th at 3pm. Join them for a Bitcoin chat and a cheeky pint. 🍻
- Real Bedford - Home Game: You’ll always find fellow Bitcoiners at a Real Bedford match, especially at home. This Saturday, Bedford faces Thame United in a Southern League Division One clash on the 12th, with kick-off at 3 PM. ⚽️
- Wiltshire BTC: Meeting at The Stonehenge Inn (they accept bitcoin) at 18:00 on Saturday 12th October. 🍻
- Kent Bitcoin: Join the Kent Bitcoin crew at The Muggleton Inn on Sunday 13th at 12:00 - 14:00. 🍻
New Businesses Accepting Bitcoin
- Nuvo Aesthetics: Nuvo is a nurse-led aesthetics skin clinic with various treatments for skin concerns e.g. Microneedling for treating scars. Now accepting bitcoin payments.
- Myna Accountants: Get the right advice and support with this UK based accountants, specialising in digital assets.
Upcoming Special Events
These events aren’t happening next week, but they’re important to add to your calendar now as tickets are selling fast.
-
Bitcoin Tuesday - launch event: Boom Bap Burger in Bethnal Green is celebrating the launch of its 2-for-1 deal on October 15th, from 18:00 to 22:00. This offer is exclusive to customers paying with bitcoin, so load up your Lightning wallet and join in to show your support. If the event goes well, it will become a new monthly meetup.

-
Bitcoin Whitepaper Party: Celebrate Bitcoin’s 16th birthday on Bitcoin Whitepaper Day at the Dockside Vaults this Halloween. Loads happening starting from 17:30 including:
- Learn about Bitcoin crowdfunding platforms: GEYSER and ANGOR.
- ChocRock workshop with Roger9000 with limited seats at £36 each.
- It's happy hour at the bar until 7 PM plus there's a further discount for paying with bitcoin.
- Enjoy a performance by Roger9000 and DJ sets from Day MadMunky, itsTOMEKK, and ZAZAWOWOW.
- Tickets are £21.40 each and you can also pay with Bitcoin here.

- The Bitcoin Culture Festival: The Whitepaper Party is part of a bigger multi-day, multi-venue festival happening between October 31st and the 2nd of November. Rather than listing all the details here (a lot is going on) click here to find out more.

Get Involved
- Volunteer Opportunities: Bridge2Bitcoin is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on Twitter or through our website.
- Start Your Own Meetup: Interested in launching a Bitcoin meetup? We’re here to support you every step of the way. We’ve assisted numerous UK Bitcoin meetups in getting started. Get in touch via Twitter.
- Telegram users: You might find our Telegram Channel another useful way to keep up-to-date with UK meetups.
- Feedback and Suggestions: We value your input! Share your ideas on how we can enhance this newsletter.
Get out and support the meetups where you can, visit Bitcoin Events UK for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
-
 @ 4ba8e86d:89d32de4
2024-10-06 20:26:43
@ 4ba8e86d:89d32de4
2024-10-06 20:26:43O aplicativo é desenvolvido por uma comunidade de colaboradores e segue os princípios de código aberto, o que significa que o código-fonte do aplicativo é acessível e pode ser modificado por qualquer pessoa interessada em contribuir para o projeto.
O AntennaPod foi lançado pela primeira vez em 2012 como um projeto de código aberto desenvolvido por uma equipe de voluntários. A ideia por trás do aplicativo era criar uma alternativa livre e de código aberto para gerenciar e ouvir podcasts em dispositivos Android. O projeto inicialmente começou como uma bifurcação (fork) do projeto Podtrapper, um aplicativo de podcast para dispositivos BlackBerry. A equipe de desenvolvimento do AntennaPod adaptou o código do Podtrapper para o Android e adicionou novos recursos e funcionalidades. Ao longo dos anos, o AntennaPod passou por várias atualizações e melhorias, com contribuições de desenvolvedores de todo o mundo. A comunidade de código aberto em torno do AntennaPod cresceu e ajudou a moldar o aplicativo, fornecendo feedback, correções de bugs e novos recursos. O AntennaPod se tornasse uma opção flexível e personalizável para o gerenciamento de podcasts no Android. Ele foi projetado para suportar uma ampla variedade de formatos e servidores de podcast, oferecendo aos usuários a liberdade de escolher suas fontes de podcast favoritas. Ele permanece como uma opção popular para os entusiastas de podcasts que buscam uma solução livre e acessível para gerenciar e desfrutar de seu conteúdo de áudio favorito.
Aqui estão algumas das principais vantagens do AntennaPod:
-
Livre e de código aberto: O AntennaPod é um software de código aberto, o que significa que o seu código-fonte está disponível para visualização, modificação e contribuição pela comunidade de desenvolvedores. Isso proporciona transparência, segurança e a possibilidade de personalizar o aplicativo de acordo com as necessidades individuais.
-
Sem necessidade de login: Ao contrário de alguns outros aplicativos de podcast, o AntennaPod não requer um login para acessar e gerenciar seus podcasts. Isso oferece praticidade e privacidade aos usuários, pois não é necessário criar uma conta ou compartilhar informações pessoais.
-
Adição de podcasts via RSS: O AntennaPod permite que os usuários adicionem podcasts por meio de feeds RSS. Isso significa que você pode adicionar facilmente seus podcasts favoritos ao copiar e colar o link do feed RSS, sem a necessidade de procurar manualmente ou depender de uma biblioteca restrita.
-
Interface intuitiva: O aplicativo possui uma interface de usuário intuitiva e fácil de usar, com navegação simples e organizada. Isso torna a descoberta, a assinatura e a reprodução de podcasts uma experiência agradável e acessível para todos.
-
Reprodução offline: O AntennaPod permite que você faça o download de episódios de podcast para ouvir offline. Isso é especialmente útil quando você está em movimento, sem conexão à internet ou deseja economizar dados móveis. Você pode baixar seus episódios favoritos e ouvi-los em qualquer lugar, a qualquer momento.
-
Gerenciamento de listas de reprodução: O aplicativo oferece a opção de criar listas de reprodução personalizadas para organizar seus episódios de podcast. Isso permite que você crie uma sequência de reprodução personalizada, reorganize os episódios e gerencie melhor o que deseja ouvir.
-
Controles de reprodução avançados: O AntennaPod oferece uma variedade de recursos avançados de controle de reprodução, como avançar ou retroceder episódios, definir temporizadores de suspensão, pular partes silenciosas e ajustar o volume de reprodução.
-
Personalização de configurações: O aplicativo permite que você personalize várias configurações de acordo com suas preferências. Isso inclui ajustar a velocidade de reprodução dos episódios, configurar notificações, gerenciar downloads automáticos, definir limites de armazenamento e muito mais.
-
Suporte a diferentes idiomas: O AntennaPod suporta podcasts em vários idiomas, o que permite que os usuários descubram e desfrutem de conteúdos em seu idioma preferido.
-
Sincronização com serviços em nuvem: O AntennaPod oferece suporte à sincronização com serviços em nuvem, como o Nextcloud, permitindo que você sincronize seus podcasts e configurações entre vários dispositivos. Isso garante que você possa continuar de onde parou em diferentes dispositivos sem perder seu progresso.
Essas são algumas das principais vantagens do AntennaPod. O aplicativo continua sendo desenvolvido e aprimorado pela comunidade de código aberto, trazendo constantemente novos recursos e melhorias para tornar a experiência de audição de podcasts mais completa, personalizável e agradável para os usuários.
https://github.com/AntennaPod/AntennaPod
https://antennapod.org/
-
-
 @ 4ba8e86d:89d32de4
2024-10-06 19:45:27
@ 4ba8e86d:89d32de4
2024-10-06 19:45:27Philip Zimmermann
Parte do Guia do Usuário PGP Original de 1991 (atualizado em 1999)
"Tudo o que você fizer será insignificante, mas é muito importante que você o faça." -Mahatma Gandhi
É pessoal. É privado. E não é da conta de ninguém, apenas sua. Você pode estar planejando uma campanha política, discutindo seus impostos ou tendo um caso ilícito. Ou você pode estar se comunicando com um dissidente político em um país repressor. Seja o que for, você não quer que seu correio eletrônico privado (e-mail) ou documentos confidenciais sejam lidos por mais ninguém. Não há nada de errado em afirmar sua privacidade. A privacidade é tão fácil quanto a Constituição. O direito à privacidade está implícito na Declaração de Direitos. Mas quando a Constituição dos Estados Unidos foi elaborada, os Pais Fundadores não viram necessidade de especificar explicitamente o direito a uma conversa privada. Isso teria sido bobo. Duzentos anos atrás, todas as conversas eram privadas. Se alguém estivesse ao alcance da voz, você poderia simplesmente ir atrás do celeiro e conversar lá. Ninguém poderia ouvir sem o seu conhecimento. O direito a uma conversa privada era um direito natural, não apenas no sentido filosófico, mas no sentido da lei da física, dada a tecnologia da época. Mas com a chegada da era da informação, começando com a invenção do telefone, tudo isso mudou. Agora, a maioria de nossas conversas é conduzida eletronicamente. Isso permite que nossas conversas mais íntimas sejam expostas sem o nosso conhecimento. Chamadas de telefone celular podem ser monitoradas por qualquer pessoa com um rádio. O correio eletrônico, enviado pela Internet, não é mais seguro do que as chamadas de telefone celular. O e-mail está substituindo rapidamente o correio postal, tornando-se a norma para todos, não a novidade que era no passado. Até recentemente, se o governo quisesse violar a privacidade dos cidadãos comuns, eles tinham que gastar uma certa quantia de dinheiro e trabalho para interceptar, abrir e ler a correspondência em papel. Ou eles tinham que ouvir e possivelmente transcrever conversas telefônicas faladas, pelo menos antes que a tecnologia de reconhecimento automático de voz se tornasse disponível. Esse tipo de monitoramento trabalhoso não era prático em larga escala. Isso só foi feito em casos importantes, quando parecia valer a pena. É como pegar um peixe de cada vez, com linha e anzol. Hoje, o e-mail pode ser verificado rotineira e automaticamente em busca de palavras-chave interessantes, em grande escala, sem detecção. Isso é como pescar com rede de deriva. E o crescimento exponencial no poder do computador está tornando a mesma coisa possível com o tráfego de voz. Talvez você pense que seu e-mail é legítimo o suficiente para que a criptografia seja injustificada. Se você realmente é um cidadão cumpridor da lei, sem nada a esconder, por que não envia sempre sua correspondência em cartões postais? Por que não se submeter a testes de drogas sob demanda? Por que exigir um mandado para buscas policiais em sua casa? Você está tentando esconder alguma coisa? Se você esconde sua correspondência dentro de envelopes, isso significa que você deve ser um subversivo ou um traficante de drogas, ou talvez um maluco paranóico? Os cidadãos cumpridores da lei precisam criptografar seus e-mails? E se todos acreditassem que cidadãos cumpridores da lei deveriam usar cartões-postais como correspondência? Se um inconformista tentasse afirmar sua privacidade usando um envelope para sua correspondência, isso atrairia suspeitas. Talvez as autoridades abram sua correspondência para ver o que ele está escondendo. Felizmente, não vivemos nesse tipo de mundo, porque todos protegem a maior parte de suas correspondências com envelopes. Portanto, ninguém levanta suspeitas afirmando sua privacidade com um envelope. Há segurança nos números. Analogamente, seria bom se todos usassem rotineiramente a criptografia para todos os seus e-mails, inocentes ou não,
para que ninguém levantasse suspeitas afirmando a privacidade de seu e-mail com criptografia. Pense nisso como uma forma de solidariedade. O Projeto de Lei 266 do Senado, um projeto de lei anticrime abrangente de 1991, tinha uma medida inquietante enterrada nele. Se essa resolução não vinculante tivesse se tornado lei real, teria forçado os fabricantes de equipamentos de comunicação segura a inserir "alçapões" especiais em seus produtos, para que o governo pudesse ler as mensagens criptografadas de qualquer pessoa. Ele diz: "É o entendimento do Congresso que os provedores de serviços de comunicações eletrônicas e os fabricantes de equipamentos de serviços de comunicações eletrônicas devem garantir que os sistemas de comunicações permitam ao governo obter o conteúdo de texto simples de voz, dados e outras comunicações quando devidamente autorizado por lei ." Foi esse projeto de lei que me levou a publicar o PGP eletronicamente gratuitamente naquele ano, O Communications Assistance for Law Enforcement Act (CALEA) de 1994 determinou que as empresas de telefonia instalassem portas de escuta remota em seus comutadores digitais do escritório central, criando uma nova infraestrutura de tecnologia para escutas telefônicas "apontar e clicar", para que os agentes federais não precisassem mais ir para fora e anexar clipes jacaré às linhas telefônicas. Agora eles poderão se sentar em seu quartel-general em Washington e ouvir suas ligações. Claro, a lei ainda exige uma ordem judicial para uma escuta telefônica. Mas enquanto as infraestruturas tecnológicas podem persistir por gerações, as leis e políticas podem mudar da noite para o dia. Uma vez consolidada uma infraestrutura de comunicações otimizada para vigilância, uma mudança nas condições políticas pode levar ao abuso desse novo poder. As condições políticas podem mudar com a eleição de um novo governo, Um ano após a aprovação da CALEA, o FBI divulgou planos para exigir que as companhias telefônicas construíssem em sua infraestrutura a capacidade de grampear simultaneamente 1% de todas as chamadas telefônicas em todas as principais cidades dos Estados Unidos. Isso representaria um aumento de mais de mil vezes em relação aos níveis anteriores no número de telefones que poderiam ser grampeados. Nos anos anteriores, havia apenas cerca de mil escutas telefônicas ordenadas pelo tribunal nos Estados Unidos por ano, nos níveis federal, estadual e local combinados. É difícil ver como o governo poderia contratar juízes suficientes para assinar ordens de escuta telefônica suficientes para grampear 1% de todas as nossas ligações, muito menos contratar agentes federais suficientes para sentar e ouvir todo esse tráfego em tempo real. A única maneira plausível de processar essa quantidade de tráfego é um aplicativo orwelliano massivo de tecnologia de reconhecimento de voz automatizado para filtrar tudo, procurando palavras-chave interessantes ou a voz de um falante específico. Se o governo não encontrar o alvo na primeira amostra de 1%, os grampos podem ser transferidos para um 1% diferente até que o alvo seja encontrado, ou até que a linha telefônica de todos tenha sido verificada quanto a tráfego subversivo. O FBI disse que precisa dessa capacidade para planejar o futuro. Este plano provocou tanta indignação que foi derrotado no Congresso. Mas o simples fato de o FBI ter pedido esses amplos poderes é revelador de sua agenda. Para encontrar o alvo na primeira amostra de 1%, os grampos podem ser alterados para um 1% diferente até que o alvo seja encontrado ou até que a linha telefônica de todos tenha sido verificada quanto a tráfego subversivo. O FBI disse que precisa dessa capacidade para planejar o futuro. Este plano provocou tanta indignação que foi derrotado no Congresso. Mas o simples fato de o FBI ter pedido esses amplos poderes é revelador de sua agenda. Para encontrar o alvo na primeira amostra de 1%, os grampos podem ser alterados para um 1% diferente até que o alvo seja encontrado ou até que a linha telefônica de todos tenha sido verificada quanto a tráfego subversivo. O FBI disse
que precisa dessa capacidade para planejar o futuro. Este plano provocou tanta indignação que foi derrotado no Congresso. Mas o simples fato de o FBI ter pedido esses amplos poderes é revelador de sua agenda. Os avanços da tecnologia não permitirão a manutenção do status quo, no que diz respeito à privacidade. O status quo é instável. Se não fizermos nada, as novas tecnologias darão ao governo novas capacidades de vigilância automática com as quais Stalin jamais poderia ter sonhado. A única maneira de manter a privacidade na era da informação é uma criptografia forte. Você não precisa desconfiar do governo para querer usar criptografia. Sua empresa pode ser grampeada por rivais comerciais, crime organizado ou governos estrangeiros. Vários governos estrangeiros, por exemplo, admitem usar sua inteligência de sinais contra empresas de outros países para dar vantagem competitiva às suas próprias corporações. Ironicamente, as restrições do governo dos Estados Unidos à criptografia na década de 1990 enfraqueceram as defesas corporativas dos Estados Unidos contra a inteligência estrangeira e o crime organizado. O governo sabe o papel fundamental que a criptografia está destinada a desempenhar no relacionamento de poder com seu povo. Em abril de 1993, o governo Clinton revelou uma nova e ousada iniciativa de política de criptografia, que estava em desenvolvimento na Agência de Segurança Nacional (NSA) desde o início do governo Bush. A peça central dessa iniciativa foi um dispositivo de criptografia construído pelo governo, chamado chip Clipper, contendo um novo algoritmo de criptografia classificado pela NSA. O governo tentou encorajar a indústria privada a incluí-lo em todos os seus produtos de comunicação segura, como telefones seguros, faxes seguros e assim por diante. A AT&T colocou o Clipper em seus produtos de voz seguros. O problema: no momento da fabricação, cada chip Clipper é carregado com sua própria chave exclusiva, e o governo fica com uma cópia, colocada sob custódia. Não se preocupe, embora - o governo promete que usará essas chaves para ler seu tráfego somente "quando devidamente autorizado por lei". Obviamente, para tornar o Clipper completamente eficaz, o próximo passo lógico seria proibir outras formas de criptografia. O governo inicialmente alegou que o uso do Clipper seria voluntário, que ninguém seria forçado a usá-lo em vez de outros tipos de criptografia. Mas a reação do público contra o chip Clipper foi forte, mais forte do que o governo esperava. A indústria de computadores proclamou monoliticamente sua oposição ao uso do Clipper. O diretor do FBI, Louis Freeh, respondeu a uma pergunta em uma entrevista coletiva em 1994, dizendo que se Clipper não conseguisse obter apoio público e as escutas telefônicas do FBI fossem bloqueadas por criptografia não controlada pelo governo, seu escritório não teria escolha a não ser buscar alívio legislativo. . Mais tarde, após a tragédia de Oklahoma City, o Sr. O governo tem um histórico que não inspira confiança de que nunca abusará de nossas liberdades civis. O programa COINTELPRO do FBI tinha como alvo grupos que se opunham às políticas governamentais. Eles espionaram o movimento antiguerra e o movimento pelos direitos civis. Eles grampearam o telefone de Martin Luther King. Nixon tinha sua lista de inimigos. Depois, houve a confusão de Watergate. Mais recentemente, o Congresso tentou ou conseguiu aprovar leis restringindo nossas liberdades civis na Internet. Alguns elementos da Casa Branca de Clinton coletaram arquivos confidenciais do FBI sobre funcionários públicos republicanos, possivelmente para exploração política. E alguns promotores excessivamente zelosos mostraram vontade de ir até os confins da Terra em busca de expor as indiscrições sexuais de inimigos políticos.
Ao longo da década de 1990, percebi que, se quisermos resistir a essa tendência inquietante do governo de proibir a criptografia, uma medida que podemos aplicar é usar a criptografia o máximo que pudermos agora, enquanto ainda é legal. Quando o uso de criptografia forte se torna popular, é mais difícil para o governo criminalizá-la. Portanto, usar o PGP é bom para preservar a democracia. Se a privacidade for proibida, apenas os criminosos terão privacidade. Parece que a implantação do PGP deve ter funcionado, juntamente com anos de constante protesto público e pressão da indústria para relaxar os controles de exportação. Nos últimos meses de 1999, o governo Clinton anunciou uma mudança radical na política de exportação de tecnologia criptográfica. Eles basicamente jogaram fora todo o regime de controle de exportação. Agora, finalmente podemos exportar criptografia forte, sem limites superiores de força. Foi uma longa luta, mas finalmente vencemos, pelo menos na frente de controle de exportação nos EUA. Agora devemos continuar nossos esforços para implantar criptografia forte, para atenuar os efeitos do aumento dos esforços de vigilância na Internet por vários governos. E ainda precisamos consolidar nosso direito de usá-lo domesticamente, apesar das objeções do FBI. O PGP permite que as pessoas tomem sua privacidade em suas próprias mãos. Tem havido uma crescente necessidade social para isso. Foi por isso que o escrevi. Philip R. Zimmermann Boulder, Colorado, junho de 1991 (atualizado em 1999)
https://www.philzimmermann.com/EN/essays/WhyIWrotePGP.html
-
 @ 4ba8e86d:89d32de4
2024-10-06 19:31:48
@ 4ba8e86d:89d32de4
2024-10-06 19:31:48Segurança Operacional (OPSEC) é um termo originado no contexto militar dos Estados Unidos durante a Guerra do Vietnã. Trata-se de um processo que busca identificar informações críticas para determinar se as ações de uma entidade podem ser observadas pela inteligência inimiga, avaliar se as informações obtidas pelo adversário são úteis para ele e, em seguida, executar ações selecionadas que eliminam ou reduzem a exploração adversa dessas informações. O objetivo é garantir que uma operação militar, por exemplo, possua o nível adequado de segurança e impeça que o oponente obtenha conhecimento sobre disposições, capacidades, intenções e vulnerabilidades das forças amigas.
De forma mais geral, a OPSEC envolve a proteção de dados individuais que, quando agrupados, podem fornecer uma imagem mais completa. Trata-se de proteger informações críticas consideradas essenciais para missões militares, comandantes, líderes de alto escalão, gerentes ou outros órgãos de tomada de decisão. Esse processo resulta no desenvolvimento de contramedidas, que incluem medidas técnicas e não técnicas, como o uso de criptografia de e-mails, precauções contra interceptação e espionagem, atenção especial a detalhes nas fotos tiradas (como itens no plano de fundo) e evitar divulgar abertamente informações críticas sobre atividades ou organização de uma unidade em mídias sociais.
"O inimigo está escutando; ele quer saber o que você sabe; guarde para você."
A OPSEC é um processo iterativo composto por cinco etapas que auxilia uma organização a identificar informações específicas que requerem proteção e a adotar medidas para protegê-las:
-
Identificação de informações críticas: são informações sobre intenções, recursos e atividades amigas que permitem que um adversário planeje interromper efetivamente as operações. Essa etapa resulta na criação de uma lista de informações críticas (CIL), permitindo que a organização concentre seus recursos nas informações vitais em vez de tentar proteger todas as informações classificadas ou confidenciais não classificadas. Exemplos de informações críticas incluem agendas de implantação militar, informações internas da organização e detalhes de medidas de segurança.
-
Análise de ameaças: uma ameaça pode ser proveniente de um indivíduo ou grupo que possa tentar interromper ou comprometer atividades amigas. A ameaça é dividida em adversários com intenção e capacidade. Quanto maior a combinação da intenção e capacidade do adversário, maior é a ameaça. Nessa etapa, são utilizadas fontes como atividades de inteligência, aplicação da lei e informações de código aberto para identificar possíveis adversários de uma operação planejada e priorizar seu grau de ameaça.
-
Análise de vulnerabilidades: examinando todos os aspectos da operação planejada para identificar indicadores OPSEC que poderiam revelar informações críticas. Esses indicadores são então comparados com os recursos de coleta de inteligência do adversário identificados na etapa anterior. A ameaça pode ser considerada como a força do adversário, enquanto a vulnerabilidade pode ser vista como a fraqueza da organização amiga.
-
Avaliação de risco: Na etapa de avaliação de risco, os planejadores analisam cuidadosamente as vulnerabilidades identificadas anteriormente e determinam as medidas específicas de OPSEC que devem ser implementadas. O processo envolve a avaliação do potencial impacto caso ocorra a divulgação de informações críticas e a análise da probabilidade desse evento com base na capacidade e intenção do adversário.
Com base nessa análise de risco, são selecionadas as medidas adequadas de OPSEC para mitigar os riscos identificados. Isso pode incluir a implementação de protocolos de segurança mais rigorosos, restrições de acesso a informações sensíveis, treinamento e conscientização dos envolvidos, bem como outras ações destinadas a reduzir a exposição de informações críticas aos adversários.
É fundamental destacar que a avaliação de risco deve ser um processo contínuo e estar sujeita a revisões periódicas. À medida que surgem novas ameaças ou as condições mudam, é necessário adaptar e atualizar as medidas de OPSEC para garantir sua eficácia contínua na proteção das informações.
- Aplicação de medidas de OPSEC apropriadas: Nesta etapa, as medidas de OPSEC selecionadas na avaliação de risco são colocadas em prática. Isso envolve a execução das ações planejadas, a adoção das práticas de segurança recomendadas e a incorporação das medidas técnicas e não técnicas identificadas. Além disso, é fundamental monitorar constantemente a eficácia das medidas de OPSEC na proteção das informações contra as ameaças relevantes.
A aplicação das medidas de OPSEC deve ser um processo abrangente e contínuo, envolvendo todos os membros da organização. A conscientização sobre a importância da segurança operacional e o treinamento adequado são essenciais para garantir a conformidade com as medidas de proteção de informações críticas. Além disso, é recomendável realizar avaliações regulares de OPSEC para identificar novas vulnerabilidades, atualizar as contramedidas existentes e manter um ambiente seguro.
https://arstechnica.com/information-technology/2017/07/how-i-learned-to-stop-worrying-mostly-and-love-my-threat-model/
-
-
 @ 4ba8e86d:89d32de4
2024-10-06 19:03:02
@ 4ba8e86d:89d32de4
2024-10-06 19:03:02Com o RiMusic, os usuários podem pesquisar e reproduzir facilmente músicas, álbuns e artistas de seu interesse, além de aproveitar recursos adicionais, como download de músicas e playlists para audição offline e marcação de favoritos para fácil acesso posterior. O RiMusic oferece uma experiência musical completa e envolvente, reunindo os recursos do YouTube Music em um aplicativo fácil de usar e altamente personalizável.
Principais Funcionalidades
- Busca por Músicas, Álbuns, Artistas e Playlists: Encontre facilmente suas músicas, álbuns, artistas e playlists favoritas.
- Marcação de Artistas e Álbuns: Marque seus artistas e álbuns favoritos para acesso rápido.
- Importação de Playlists Online: Importe playlists de outras plataformas de streaming.
- Gerenciamento de Playlists Local: Crie, edite e organize suas playlists diretamente no aplicativo.
- Reordenação de Músicas: Altere a ordem das músicas na playlist ou fila.
- Fila Persistente e Limpeza de Fila: Mantenha ou limpe a fila de reprodução conforme sua preferência.
- Letras de Músicas: Busque, edite e traduza letras de músicas, sincronizadas ou não.
- Temas Diversos: Escolha entre temas Claro, Escuro, Dinâmico, PureBlack e ModernBack.
- Temporizador: Configure um temporizador personalizável para a reprodução de música.
- Normalização de Áudio e Salto de Silêncio: Melhore a qualidade da reprodução de áudio.
Opções de Personalização
- Download de Músicas ou Playlists Inteiras para Reprodução Offline: Baixe suas músicas favoritas ou playlists completas para ouvir offline, sem depender de uma conexão com a internet.
- Reprodução em Segundo Plano: Continue ouvindo música mesmo quando o aplicativo estiver fechado, com interrupção automática ao sair do gerenciador de tarefas.
- Otimizações do Reprodutor Minimizado: Oferece otimizações para o modo de reprodução minimizada, garantindo uma experiência suave e eficiente mesmo ao usar outros aplicativos.
- Visualizador de Áudio: Crie uma experiência visual cativante com diferentes tipos de efeitos de visualização, ativados nas configurações.
Suporte e Compatibilidade
- Suporte ao Android Auto: Acesse sua música favorita enquanto está no carro.
- Suporte ao Android TV: Desfrute de sua música favorita na tela grande, transformando sua sala de estar em um ambiente de entretenimento musical.
- Compatibilidade Multilíngue: Suporte para vários idiomas, incluindo inglês, italiano, alemão, russo, francês, espanhol, tcheco, turco, romeno e muitos outros.
Permissões Necessárias
Para oferecer todos esses recursos, o RiMusic requer várias permissões:
- INTERNET: Conexão à internet.
- ACCESS_NETWORK_STATE: Verificação do estado da conexão.
- POST_NOTIFICATIONS: Funcionamento como serviço.
- RECEIVE_BOOT_COMPLETED: Inicialização após reinicialização do dispositivo.
- WAKE_LOCK: Impedir suspensão do dispositivo durante reprodução (se configurado).
- REQUEST_IGNORE_BATTERY_OPTIMIZATIONS: Evitar restrições de uso da bateria.
- FOREGROUND_SERVICE: Reprodução de música em segundo plano.
- FOREGROUND_SERVICE_MEDIA_PLAYBACK e DATA_SYNC: Reprodução e download de músicas.
- READ_MEDIA_AUDIO: Leitura de músicas locais.
- RECORD_AUDIO: Necessário apenas para usar o efeito do visualizador (desativado por padrão).
- MODIFY_AUDIO_SETTINGS: Mostrar configurações de áudio.
- READ_EXTERNAL_STORAGE e WRITE_EXTERNAL_STORAGE: Leitura e escrita de músicas até Android 12/11.
- READ_MEDIA_VISUAL_USER_SELECTED: Seleção de arquivos de playlist até Android 13.
Existe Uma Maneira de Transferir Playlists e Favoritos do Vimusic? Sim, crie um backup do ViMusic e depois importe-o para o App RiMusic usando a função de restauração. Ambas as funções de backup e restauração são encontradas nas configurações do Banco de Dados.
O RiMusic é uma solução completa para quem busca uma experiência musical rica e personalizável. Com sua integração com o YouTube Music, variadas opções de personalização, suporte a múltiplos idiomas e compatibilidade com diversos dispositivos, o RiMusic se destaca como um dos melhores aplicativos de streaming de música disponíveis. Aproveite todas as funcionalidades do RiMusic e eleve sua experiência musical a um novo patamar.
https://github.com/fast4x/RiMusic
F-Droid https://f-droid.org › it.fast4x.rimusic RiMusic | F-Droid - Free and Open Source Android App Repository
-
 @ 4ba8e86d:89d32de4
2024-10-06 18:53:52
@ 4ba8e86d:89d32de4
2024-10-06 18:53:52Você pode usar um serviço de diretório experimental para descobrir os grupos criados e registrados por outros usuários no SimpleXchat.
Procurando grupos Conecte-se ao serviço de diretório através desse link click aqui 👇 https://simplex.chat/contact/#/?v=2-4&smp=smp%3A%2F%2Fu2dS9sG8nMNURyZwqASV4yROM28Er0luVTx5X1CsMrU%3D%40smp4.simplex.im%2FeXSPwqTkKyDO3px4fLf1wx3MvPdjdLW3%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAaiv6MkMH44L2TcYrt_CsX3ZvM11WgbMEUn0hkIKTOho%253D%26srv%3Do5vmywmrnaxalvz6wi3zicyftgio6psuvyniis6gco6bp6ekl4cqj4id.onion
Envie a mensagem contendo as palavras que deseja encontrar no nome do grupo ou na mensagem de boas-vindas. Envie uma string de pesquisa para encontrar grupos Por exemplo, envie privacidade para encontrar grupos sobre privacidade. Mande o comando /next ou /all pro bot manda a lista de grupos , pra mais lista manda o comando novamente /next ,Você receberá até 10 grupos com maior número de membros na resposta, juntamente com os links para ingressar nesses grupos.
Observe que suas consultas de pesquisa podem ser mantidas pelo bot como histórico de conversas, mas você pode usar o modo de navegação anônima ao se conectar ao bot, para evitar correlação com quaisquer outras comunicações. Consulte a política de privacidade para obter mais detalhes.
Adicionando grupos ao diretório
Como adicionar um grupo Para adicionar um grupo você deve ser seu proprietário. Depois de se conectar ao serviço de diretório e enviar /help, o serviço irá guiá-lo durante o processo.
1.Convide o SimpleX Service Directory para o grupo como adminmembro. Você também pode definir a função adminapós convidar o serviço de diretório.
O serviço de diretório precisa adminproporcionar uma boa experiência ao usuário ao ingressar no grupo, pois criará um novo link para ingressar no grupo, que deverá estar online 99% do tempo.
-
Adicione o link enviado a você pelo serviço de diretório à mensagem de boas-vindas do grupo. Isto deve ser feito pelo mesmo membro do grupo que convidou o serviço de diretório para o grupo. Este membro será o proprietário do registro do grupo no serviço de diretório.
-
Depois que o link for adicionado, o grupo precisará ser aprovado pelos administradores do serviço de diretório. Este link funciona mesmo antes do grupo ser aprovado, e você pode continuar usando esse link mesmo que o grupo não seja aprovado.
O grupo geralmente é aprovado em 24 horas. Veja abaixo quais grupos podem ser adicionados. Assim que o grupo for aprovado, ele aparecerá nos resultados da pesquisa. Você pode listar todos os grupos enviados enviando /listpara o serviço de diretório.
Para saber mais detalhes acesse o site https://simplex.chat/docs/directory.html
-
-
 @ 14f069e4:8730cdaa
2024-10-06 18:36:24
@ 14f069e4:8730cdaa
2024-10-06 18:36:24Bitcoin enthusiasts always rightly remark how much value it adds to Bitcoin not to have a face, a leader, or a central authority behind it. This particularity means there isn't a single person to exert control over, or a single point of failure who could become corrupt or harmful to the project.
Because of this, it is said that no other coin can be equally valuable as Bitcoin in terms of decentralization and trustworthiness. Bitcoin is unique not just for being first, but also because of how the events behind its inception developed. This implies that, from Bitcoin onwards, any coin would have been created by a known entity, consequently having an authority behind it. For this and some other reasons, some people refer to Bitcoin as "The Immaculate Conception".
While other coins may have their own unique features and advantages, they may not be able to replicate Bitcoin's community-driven nature. However, there's one other cryptocurrency shares a similar story of mystery behind its creation: Monero.
History of Monero
Bytecoin and CryptoNote
In March 2014, a Bitcointalk thread titled "Bytecoin. Secure, private, untraceable since 2012" by a user under the nickname "DStrange"^1^ was created. DStrange presented Bytecoin (BCN) as a unique cryptocurrency, in operation since July 2012. Unlike Bitcoin, it employed a new algorithm known as CryptoNote^1^.
DStrange apparently stumbled upon the Bytecoin website "by chance" while mining a dying bitcoin fork, and decided to create a thread on Bitcointalk^1^. This sparked curiosity among some users, who wondered how could Bytecoin remain unnoticed since its alleged launch in 2012^2^.
Some time after, a user brought up the "CryptoNote v2.0" whitepaper for the first time, underlining its innovative features^4^. Authored by the pseudonymous Nicolas van Saberhagen in October 2013, the CryptoNote v2 whitepaper^5^ highlighted the traceability and privacy problems in Bitcoin. Saberhagen argued that these flaws could not be quickly fixed, suggesting it would be more efficient to start a new project rather than trying to patch the original^5^, an statement simmilar to the one from Satoshi Nakamoto^6^.
Checking with Saberhagen's digital signature, the release date of the whitepaper seemed valid, which would mean that CryptoNote (v1) was created in 2012^7^, although there's an important detail: "Signing time is from the clock on the signer's computer" ^9^. Moreover, the whitepaper v1 contains a footnote link to a Bitcointalk post dated May 5, 2013^10^, making it impossible for the whitepaper to have been signed and released on December 12, 2012.
As the narrative developed, users discovered that a significant 80% portion of Bytecoin had been pre-mined^11^ and blockchain dates seemed to be faked to make it look like it had been operating since 2012, leading to controversy surrounding the project.
The origins of CryptoNote and Bytecoin remain mysterious, leaving suspicions of a possible scam attempt, although the whitepaper had a good amount of work and thought.
The fork
In April 2014, the Bitcointalk user
thankful_for_today, who had also participated in the Bytecoin thread^12^, announced plans to launch a Bytecoin fork named Bitmonero^13^.The primary motivation behind this fork was "Because there is a number of technical and marketing issues I wanted to do differently. And also because I like ideas and technology and I want it to succeed"^14^. Bitmonero did things different from Bytecoin: there was no premine or instamine, and no portion of the block reward went to development.
However, thankful_for_today forced controversial changes that the community disagreed with. Johnny Mnemonic relates the events surrounding Bitmonero and thankful_for_today in a Bitcointalk comment^15^:
When thankful_for_today launched BitMonero [...] he ignored everything that was discussed and just did what he wanted. The block reward was considerably steeper than what everyone was expecting. He also moved forward with 1-minute block times despite everyone's concerns about the increase of orphan blocks. He also didn't address the tail emission concern that should've (in my opinion) been in the code at launch time. Basically, he messed everything up. Then, he disappeared.
After disappearing for a while, thankful_for_today returned to find that the community had taken over the project. Johnny Mnemonic continues:
I, and others, started working on new forks that were closer to what everyone else was hoping for. [...] it was decided that the BitMonero project should just be taken over. There were like 9 or 10 interested parties at the time if my memory is correct. We voted on IRC to drop the "bit" from BitMonero and move forward with the project. Thankful_for_today suddenly resurfaced, and wasn't happy to learn the community had assumed control of the coin. He attempted to maintain his own fork (still calling it "BitMonero") for a while, but that quickly fell into obscurity.
The unfolding of these events show us the roots of Monero. Much like Satoshi Nakamoto, the creators behind CryptoNote/Bytecoin and thankful_for_today remain a mystery^17^, having disappeared without a trace. This enigma only adds to Monero's value.
Since community took over development, believing in the project's potential and its ability to be guided in a better direction, Monero was given one of Bitcoin's most important qualities: a leaderless nature. With no single face or entity directing its path, Monero is safe of potential corruption or harm from a "central authority".
The community continued developing Monero until today. Since then, Monero has undergone a lot of technological improvements, migrations and achievements such as RingCT and RandomX. It also has developed its own Community Crowdfundinc System, conferences such as MoneroKon and Monerotopia are taking place every year, and has a very active community around it.
Monero continues to develop with goals of privacy and security first, ease of use and efficiency second^16^.
This stands as a testament to the power of a dedicated community operating without a central figure of authority. This decentralized approach aligns with the original ethos of cryptocurrency, making Monero a prime example of community-driven innovation.
Sources of interest
- https://forum.getmonero.org/20/general-discussion/211/history-of-monero
- https://monero.stackexchange.com/questions/852/what-is-the-origin-of-monero-and-its-relationship-to-bytecoin
- https://en.wikipedia.org/wiki/Monero
- https://bitcointalk.org/index.php?topic=583449.0
- https://bitcointalk.org/index.php?topic=563821.0
- https://bitcointalk.org/index.php?action=profile;u=233561
- https://bitcointalk.org/index.php?topic=512747.0
- https://bitcointalk.org/index.php?topic=740112.0
- https://monero.stackexchange.com/a/1024
- https://inspec2t-project.eu/cryptocurrency-with-a-focus-on-anonymity-these-facts-are-known-about-monero/
- https://medium.com/coin-story/coin-perspective-13-riccardo-spagni-69ef82907bd1
- https://www.getmonero.org/resources/about/
- https://www.wired.com/2017/01/monero-drug-dealers-cryptocurrency-choice-fire/
- https://www.monero.how/why-monero-vs-bitcoin
- https://old.reddit.com/r/Monero/comments/u8e5yr/satoshi_nakamoto_talked_about_privacy_features/
- https://moneroj.net/merchants_increase/
- https://moneroj.net/social5/
-
 @ 4ba8e86d:89d32de4
2024-10-06 14:40:42
@ 4ba8e86d:89d32de4
2024-10-06 14:40:42A segurança digital é fundamental diante da crescente sofisticação das ameaças cibernéticas. Compreender as táticas dos hackers e adotar medidas preventivas são passos cruciais para proteger seus dados. Vamos explorar alguns cenários específicos:
● Ataques Wi-Fi Maliciosos:
Ao utilizar redes Wi-Fi desconhecidas, esteja ciente dos riscos. Hackers podem usar dispositivos, como o Pineapple da Hak5, para criar redes falsas, capturando dados. https://nostrcheck.me/media/public/nostrcheck.me_6114620534879318691706025862.webp
Ataques Possíveis:
- Evil Twin/AP Spoofing:
-
Como Funciona: Hackers criam redes Wi-Fi falsas imitando as legítimas.
-
Proteção: Evite conexões desconhecidas; verifique sempre a autenticidade da rede.
-
Man-in-the-Middle (MitM):
-
Como Funciona: Interceptação de comunicação, permitindo manipulação de dados.
-
Proteção:Use HTTPS, VPNs em redes públicas.
-
Phishing:
-
Como Funciona: Hackers enganam usuários para revelar informações.
-
Proteção: Desconfie de e-mails suspeitos; evite clicar em links duvidosos.
-
DNS Spoofing e SSL Strip:
-
Como Funciona: Redirecionamento e descriptografia de conexões seguras.
-
Proteção: Use servidores DNS confiáveis, verifique conexões seguras (HTTPS).
-
Desautenticação/Ataque de Desassociação:
-
Como Funciona: Desconexão forçada de dispositivos.
-
Proteção: Mantenha seu dispositivo atualizado, evite Wi-Fi público.
● Dispositivos USB Maliciosos e Riscos de Recarregar dispositivos em Locais Públicos:
Inserir uma USB no seu dispositivo pode parecer inofensivo, porém, dispositivos como o "Rubber Ducky" podem executar comandos maliciosos em questão de segundos, podendo até exfiltrar dados sensíveis. https://nostrcheck.me/media/public/nostrcheck.me_4959397161118866591706026510.webp
https://nostrcheck.me/media/public/nostrcheck.me_5738603283604984961706026522.webp
-
Rubber Ducky e Dispositivos Semelhantes:
-
Como Funciona: ao inserir o Pendrive no seu dispositivo podem executar comandos maliciosos em questão de segundos, podendo até exfiltrar dados sensíveis.
-
Proteção: Evite usar Pendrive desconhecidos.
Carregadores e Cabos USB Suspeitos:
Cabos OMG Cable incorpora um microprocessador que pode executar comandos maliciosos quando conectado a um dispositivo. Essa capacidade permite que o cabo comprometa a segurança do dispositivo conectado, possibilitando a coleta de dados, instalação de malware e até mesmo o controle remoto do dispositivo por parte de um invasor.
https://nostrcheck.me/media/public/nostrcheck.me_2065126673950257901706026715.webp
-
Como Funciona: inserir o Cabo omg-cable podem coletar dados.
-
Proteção: Evite carregar em locais públicos com cabos desconhecidos.
-
Usar Camisinhas de USB: https://nostrcheck.me/media/public/nostrcheck.me_1885907389208222681706026770.webp
Mas não é esse camisinhas é esse Adaptador. https://nostrcheck.me/media/public/nostrcheck.me_1732610313835570801706026789.webp
https://nostrcheck.me/media/public/nostrcheck.me_9474014842894456331706026837.webp
-
Como Funciona: Adaptadores que bloqueiam troca de dados durante recarga.
-
Proteção: Use esses dispositivos para reduzir exposição a ataques USB.
● Cuidado com QR-Codes Suspeitos: https://nostrcheck.me/media/public/nostrcheck.me_4913027000785421121706026849.webp
-
Hotspot Wi-Fi Falso:
-
Como Funciona: Hackers criam QR-Codes pra acessar redes falsas para capturar dados.
-
Proteção: Evite hotspots desconhecidos; desative Wi-Fi quando não necessário.
-
Promoções e QR-Codes Fraudulentos:
-
Como Funciona: QR-Codes direcionam para phishing.
-
Proteção: Desconfie de promoções suspeitas; evite escanear QR-Codes não confiáveis.
mantenha-se informado, adote práticas seguras e esteja vigilante. A segurança digital é uma jornada contínua, e essas medidas ajudarão a proteger seus dados contra ameaças cibernéticas.
-
 @ 8d34bd24:414be32b
2024-10-06 14:39:26
@ 8d34bd24:414be32b
2024-10-06 14:39:26I was recently reading Judges and I saw the story in a whole new way. I saw it as an example of ungodly male role models. I am going to start with the familiar story of Samson and his obvious mistakes and ungodly actions, but then trace them back to his father and how lesser sins may have led to Samson’s very unwise actions.
Samson - Ungodly Son
Samson was a judge of Israel. He was supposed to lead the people of Israel in faithfully following God, but failed miserably at being faithful himself. Obviously his biggest problem was his obsession with ungodly women.
Furthermore, you shall not intermarry with them; you shall not give your daughters to their sons, nor shall you take their daughters for your sons. (Deuteronomy 7:3)
Samson ignored this command given to the Israelites right before they entered the land of Canaan before it became Israel. Samson saw a nice looking Philistine woman and asked for her to be his wife.
So he came back and told his father and mother, “I saw a woman in Timnah, one of the daughters of the Philistines; now therefore, get her for me as a wife.” Then his father and his mother said to him, “Is there no woman among the daughters of your relatives, or among all our people, that you go to take a wife from the uncircumcised Philistines?” But Samson said to his father, “Get her for me, for she looks good to me.” (Judges 14:2-3) {emphasis mine}
Samson picked his wife based solely on looks. He said, “she looks good to me.” He didn’t seek a godly wife. He didn’t even seek an Israelite wife. He just chased after what looked good to him. Just as is repeated in Judges, “everyone did what was right in his own eyes,” Samson “did what was right in his own eyes.” When we seek what looks good to us instead of what God tells us is good for us, we always make a huge mistake.
Choosing a Philistine woman as wife was sinful, but like always, God used it for good and for His purpose.
On the way to making arrangements for this ungodly woman to become his wife, Samson was attacked by a lion and killed it. Later, when going to see his wife, he saw the carcass and bees had made honey in the lion’s carcass. Samson helped himself to the honey in the lion’s carcass. To me, that sounds gross. By this time the lion’s carcass should’ve been putrid, but this was much more awful for Samson. Samson was a Nazarite to God from conception and by the command of God, Himself.
Now therefore, be careful not to drink wine or strong drink, nor eat any unclean thing. For behold, you shall conceive and give birth to a son, and no razor shall come upon his head, for the boy shall be a Nazirite to God from the womb;” (Judges 13:4-5a)
Based on Numbers 6, a Nazarite vow required 3 things: no alcohol or things made from grapes, no haircuts, and no touching dead/unclean things. A lion carcass was definitely one of those dead/unclean things and to eat from it would be even worse. Samson was set apart with a Nazarite vow, but he didn’t care. He didn’t take it seriously. He wasn’t faithful to God.
After a riddle that went bad and caused hardship with his wife, Samson’s father-in-law gave his wife to another leading to Samson killing many Philistines. This destruction of Philistines was God’s will, but Samson did it out of spite, not to honor God. After being turned over to the Philistines for killing 30 Philistines, Samson then killed a bunch more Philistines. What did Samson choose as a weapon? He chose a donkey’s jaw bone. Both with the killing and with handling the bone of a dead animal, he broke his Nazarite vow again.
Then, since Samson had lost his wife, he went in to a prostitute.
Now Samson went to Gaza and saw a harlot there, and went in to her. (Judges 16:1)
God had been very clear about adultery and harlotry and it was clearly forbidden, but Samson didn’t even obey God’s 10 commandments.
‘You shall not commit adultery. (Deuteronomy 5:18)
After spending time sinning with this Philistine harlot, he was attacked by the Philistines, but his God given physical strength allowed him to not pay the consequences of his actions, so he didn’t learn.
Once again, his lust led him astray.
After this it came about that he loved a woman in the valley of Sorek, whose name was Delilah. The lords of the Philistines came up to her and said to her, “Entice him, and see where his great strength lies and how we may overpower him that we may bind him to afflict him. Then we will each give you eleven hundred pieces of silver.” So Delilah said to Samson, “Please tell me where your great strength is and how you may be bound to afflict you.” (Judges 16:4-6) {emphasis mine}
Once again he became infatuated with a woman with whom he was forbidden to have relations. His infatuation blinded him. His ability to get away with evil actions made him not careful. His God given strength made him trust in himself.
I’ve always thought what follows was a sign that Samson was the dumbest person in the Bible, but maybe it is just what happens when someone gets away with doing wrong repeatedly with no consequences.
Multiple times Delilah says, “Please tell me where your great strength is and how you may be bound to afflict you.” Samson lies multiple times about how his strength can be conquered. Each time Delilah does what Samson tells her and the Philistines show up to try to overcome him. Each time Samson conquers his attackers and foolishly returns back to this evil woman who repeatedly betrays him.
Finally Delilah extracts his secret:
Then she said to him, “How can you say, ‘I love you,’ when your heart is not with me? You have deceived me these three times and have not told me where your great strength is.” It came about when she pressed him daily with her words and urged him, that his soul was annoyed to death. So he told her all that was in his heart and said to her, “A razor has never come on my head, for I have been a Nazirite to God from my mother’s womb. If I am shaved, then my strength will leave me and I will become weak and be like any other man.” (Judges 16:15-17)
Why did he share the secret of his strength? He did it because “his soul was annoyed to death.” Why would he stay with this woman who repeatedly betrayed him and who annoyed him to death? I think it was pure lust. There was nothing uplifting in this relationship. There was nothing honoring to God. Samson was led by lust and it cost him his life.
When Samson finally shared his secret, she shaved his head, brought in Philistines to capture him, and they put out both his eyes and threw him in prison. Samson was finally punished for his repeated sins, but God used this one last time for His plan and when the Philistines tried to parade Samson before a large crowd in their temple to Dagon, Samson prayed to God, leaned on the pillars in the middle of the temple, and pushed them down killing himself and around 3,000 Philistines.
Yes, Samson destroyed many of the oppressors of Israel as Israel’s judge, but he was an ungodly judge and an awful example to the people. Samson’s story is sad and has an even sadder ending. Everyone who lives an ungodly life will end badly.
Manoah - Failed Spiritual Leadership
I never noticed before, but I’d argue that Samson’s father was not a good spiritual leader either, but had less obvious faults.
There was a certain man of Zorah, of the family of the Danites, whose name was Manoah; and his wife was barren and had borne no children. Then the angel of the Lord appeared to the woman and said to her, “Behold now, you are barren and have borne no children, but you shall conceive and give birth to a son. … Then the woman came and told her husband, saying, “A man of God came to me and his appearance was like the appearance of the angel of God, very awesome.” (Judges 13:2-3,6a)
When Manoah’s wife came to him to tell him she’d been told they would have a son, he was good and prayed: “O Lord, please let the man of God whom You have sent come to us again that he may teach us what to do for the boy who is to be born.” (Judges 13:8b)
When God answered his prayer, he came to his wife. Why? Could it be that his wife was the spiritual leader in his household?
God listened to the voice of Manoah; and the angel of God came again to the woman as she was sitting in the field, but Manoah her husband was not with her. So the woman ran quickly and told her husband, “Behold, the man who came the other day has appeared to me.” Then Manoah arose and followed his wife, (Judges 13:9-11a) {emphasis mine}
Do you notice what is said? “Then Manoah arose and followed his wife.” Yes, it is possible that this was just her showing him where she had seen the angel of God, but lets read on.
Manoah said, “Now when your words come to pass, what shall be the boy’s mode of life and his vocation?” So the angel of the Lord said to Manoah, “Let the woman pay attention to all that I said. She should not eat anything that comes from the vine nor drink wine or strong drink, nor eat any unclean thing; let her observe all that I commanded.” (Judges 13:12-14)
Manoah did seek direction from the Lord and the Lord gave Manoah directions on how he should lead his wife regarding their son. Manoah did try to do right when faced with the Angel of the Lord.
Then Manoah said to the angel of the Lord, “Please let us detain you so that we may prepare a young goat for you.” The angel of the Lord said to Manoah, “Though you detain me, I will not eat your food, but if you prepare a burnt offering, then offer it to the Lord.” For Manoah did not know that he was the angel of the Lord. Manoah said to the angel of the Lord, “What is your name, so that when your words come to pass, we may honor you?” But the angel of the Lord said to him, “Why do you ask my name, seeing it is wonderful?” So Manoah took the young goat with the grain offering and offered it on the rock to the Lord, and He performed wonders while Manoah and his wife looked on. For it came about when the flame went up from the altar toward heaven, that the angel of the Lord ascended in the flame of the altar. When Manoah and his wife saw this, they fell on their faces to the ground. (Judges 13:15-20)
The question is, did Manoah lead when he was no longer face to face with the pre-incarnate Christ?
So Manoah said to his wife, “We will surely die, for we have seen God.” (Judges 13:22)
No, he did not. Manoah was afraid and didn’t seem to know what to do.
But his wife said to him, “If the Lord had desired to kill us, He would not have accepted a burnt offering and a grain offering from our hands, nor would He have shown us all these things, nor would He have let us hear things like this at this time.” (Judges 13:23)
Manoah’s wife taught Manoah a right view of God and His direction. His wife led them in what they should do.
Although Manoah wasn’t a bad man and he didn’t act out in blatant error, he didn’t lead spiritually. He wasn’t the one leading following God. He wasn’t the one demonstrating faith in God. He wasn’t the one speaking God’s word as an assurance.
Lack of Leadership Leads to Unfaithful Son
Did Manoah’s lack of leadership contribute to Samson’s lack of respect for God and God’s law? Was it Manoah’s lack of leadership on what was right and good that contributed to Samson ignoring the nazarite vow and other commands from God? Was Samson taught God’s law as a child? Did Manoah insist that his family obey and live out God’s commands? I’m thinking he didn’t.
Let’s return to Samson’s first time being misled by a woman.
Then Samson went down to Timnah and saw a woman in Timnah, one of the daughters of the Philistines. So he came back and told his father and mother, “I saw a woman in Timnah, one of the daughters of the Philistines; now therefore, get her for me as a wife.” Then his father and his mother said to him, “Is there no woman among the daughters of your relatives, or among all our people, that you go to take a wife from the uncircumcised Philistines?” (Judges 14:1-3)
At this time, marriages were setup as contracts by the parents. People didn’t just marry as they wished, so Samson commanded his father to “get her for me as a wife.”
There are two problems here. The first is Samson ordering his father to do something. This was totally contrary to God’s design and command, but you have to think that Samson was used to getting his way and that his father regularly let him get away with things like this. Most kids, today and in the past, would not talk to their parents this way.
Second, Manoah knew that this was wrong, but instead of speaking God’s word and refusing, he asked submissively, “Is there no woman among the daughters of your relatives, or among all our people, that you go to take a wife from the uncircumcised Philistines?” When Samson insisted on marrying this forbidden woman, his father gave in to his son.
Then Samson went down to Timnah with his father and mother, and came as far as the vineyards of Timnah … (Judges 14:5a)
How often do we, as parents, give our kids something that isn’t good for them because they really want it and we want to please them now? How often do we get busy and miss teaching our kids our knowledge, especially our knowledge of God and His word? Men, how often do you not step up and lead spiritually because it is easier to let your wife do it?
Most of us are like Manoah. We aren’t that bad. We try to honor God. We try to do what we should, but we don’t necessarily put a lot of effort into our walk with God. When we don’t fulfill the roles and responsibilities ordained by God, it isn’t only us that suffers. It frequently is our children that pay the price for our failures.
I beg all of you, but especially men, to study the Bible and step up in the role and responsibility given to you by God. Lead your family and your children in faithfully following Jesus. Even when you are tired, lead your family in prayer and Bible reading. Even when it makes your kids mad at you, stand up for the truth and enforce what is best for them. Make the time to be there for your family and to do what is for their best. It not only helps your family, but also helps you grow closer to God. We are never happier than when we are following God’s plan.
Trust Jesus.\ \ your sister in Christ,
Christy
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
