-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 2d74600a:d6708a00
2024-11-01 18:51:37
@ 2d74600a:d6708a00
2024-11-01 18:51:37Questo articolo esplora la complessità dell'esperienza umana attraverso la lente della tristezza e della felicità, proponendo una distinzione tra le persone che si identificano rigidamente come tristi o felici e quelle che abbracciano la loro autenticità, vivendo un'alternanza di emozioni. Attraverso un'analisi filosofica, si indaga il significato di "essere veri" e si discute l'importanza di riconoscere e accettare la gamma completa delle emozioni umane.
Introduzione
La condizione umana è intrinsecamente legata a un ampio spettro di emozioni, tra cui la tristezza e la felicità. Queste due esperienze emotive sono spesso percepite come opposte, ma in realtà coesistono in una dinamica complessa. In questo contesto, è utile considerare non solo le persone che si definiscono rigidamente come tristi o felici, ma anche quelle che si riconoscono come "vere", capaci di navigare tra le diverse sfumature emotive. Questo articolo si propone di esaminare le implicazioni filosofiche di questa distinzione e di riflettere su come essa possa influenzare la nostra comprensione dell'autenticità e della realizzazione personale.
La Tristezza e la Felicità: Due Facce della Stessa Medaglia
La tristezza e la felicità sono spesso considerate come stati emotivi opposti, ma questa visione binaria può risultare limitante. La filosofia esistenzialista, ad esempio, suggerisce che la sofferenza e la gioia sono interconnesse e che la consapevolezza della propria mortalità e delle proprie vulnerabilità può arricchire l'esperienza della vita. In questo senso, la tristezza può essere vista come un elemento necessario per apprezzare la felicità. Le persone che si identificano esclusivamente come tristi o felici possono perdere di vista questa interconnessione, vivendo in una sorta di dualismo emotivo che limita la loro esperienza.
L'Autenticità dell'Essere Vero
Le persone "vere" rappresentano un paradigma alternativo. Queste individui non si limitano a una categorizzazione emotiva, ma abbracciano la complessità della loro esistenza. La filosofia di Søren Kierkegaard, ad esempio, enfatizza l'importanza dell'autenticità e della soggettività. Essere veri implica riconoscere e accettare tutte le emozioni, comprese quelle che possono sembrare negative. Questa accettazione porta a una maggiore comprensione di sé e degli altri, promuovendo una forma di empatia che trascende le etichette di tristezza e felicità.
La Dinamicità delle Emozioni
La vita è caratterizzata da un continuo fluire di emozioni. Le persone vere sperimentano alti e bassi, riconoscendo che la tristezza e la felicità non sono stati permanenti, ma piuttosto momenti transitori. Questa visione dinamica delle emozioni è supportata dalla psicologia positiva, che sottolinea l'importanza di sviluppare resilienza e consapevolezza emotiva. Le persone che abbracciano la loro autenticità tendono a essere più resilienti, poiché non temono di affrontare la tristezza, ma la vedono come parte integrante del loro viaggio.
Conclusione
In conclusione, la distinzione tra persone tristi, felici e quelle vere offre una prospettiva interessante sulla condizione umana. Riconoscere la complessità delle emozioni e abbracciare la propria autenticità può portare a una vita più ricca e significativa. La tristezza e la felicità non devono essere viste come opposti, ma come componenti di un'esperienza umana complessa e interconnessa. Solo attraverso l'accettazione di tutte le sfumature emotive possiamo aspirare a una comprensione più profonda di noi stessi e degli altri, promuovendo una società più empatica e autentica.
Bibliografia
- Kierkegaard, S. (1980). The Sickness Unto Death. Princeton University Press.
- Seligman, M. E. P. (2011). Flourish: A Visionary New Understanding of Happiness and Well-Being. Free Press.
- Frankl, V. E. (2006). Man's Search for Meaning. Beacon Press.Questo articolo si propone di stimolare una riflessione profonda sulla nostra esperienza emotiva e sull'importanza di vivere in modo autentico, accettando la dualità della nostra esistenza.
-
 @ 3ad01248:962d8a07
2024-11-01 18:30:03
@ 3ad01248:962d8a07
2024-11-01 18:30:032024 has been an interesting year, lets put it that way. It couldn't be over soon enough to be honest. One of my New Year's resolution this year was to give up caffeine. To be honest this has been something that I have been putting off for a very long time because I did enjoy caffeine and the energy boost that it would give you in the morning.
I was regularly drinking 2 energy drinks per day at my worst in combination with a few sodas to top it off. Needless to say I was buzzed on caffeine all day everyday for years. You don't really notice that you have a problem because everywhere you look, everything has caffeine in it. It's in our drinks, our foods and in our medication. It is hard to get away from this stuff unless you make a dedicated decision not to ingest the substance. In our society it is perfectly normal to drink and eat caffiene all day long and not think anything of it.
At the end of the day caffeine is still a drug and is classified as a stimulant to your nervous system. Drugs over time obviously becomes addicting over time and your body becomes reliant on the substance to function. I think it is fair to say that people that are hooked on caffeine in the classic sense are drug addicts. I don't mean that to be harsh but if you look at this issue objectively you can see how this fits the definition quite succinctly.
Whenever I didn't have coffee or a energy drink I would get headaches, I would also be in a bad mood or generally just irrigated at little things that people would do. Ironically it made me more tired. My heavy caffeine consumption also made it where it was hard to fall asleep and stay asleep.
At some point you get tired of being on this rollercoaster and want to do something different for the sake of my health and wellness. I want to live as long as possible and I know that in order to do that I have to get rid of some bad habits that I have, caffeine consumption being one of them. So last month I bit the bullet and gave up caffeine cold turkey. It has now been 35 days since I have had caffeine but let me tell you it wasn't easy.
No Wonder Addicts Don't Quit
The first two to three days where probably the worst I've felt in a long time. I would wake up feeling like crap with no energy and a massive headache that would stay with me all day and didn't really get better taking over the counter medication. I thought to myself at one point, "no wonder drug addicts don't quit, this sucks".
To be honest it was hard to function at all, I just wanted to sleep all day and not do anything. It was hard to take my kids to school or really be present for anything because of the way I felt. I also experienced anxiety, had a weird pins and needles sensation all over my body. I felt so bad that I contacted my primary care freaking out because I couldn't figure out what was going on.
I don't know about you but when I don't feel great I on my phone looking up symptoms and trying to diagnose myself, which ultimately makes me feel worse and kicks the anxiety up to a 11.
Around day 20 I started to feel like myself again without the caffeine cravings. When I go to the store and I see the soft drinks, coffees and energy drinks for sale the first thing that comes to mind is these stores are selling drugs to their customers. They are junkies coming to get their fix. Starbucks same way. Peddling drugs via a drive through.
Sure its's only been 35 days but I am feeling pretty confident that I can kick this habit for good because I can see the health benefits from stopping caffeine consumption. Here is what I have experience so far:
- Falling asleep more easily
- Feeling rested in the morning
- More sustained energy
- Leveled out mood
- Mental clarity
- Less on edge
- Feeling of accomplishment and contentment.
Taking my first step towards beating this addiction has given me hope to keep going and continue my journey of self improvement. I'll report back in 30 days to give you an update on how its going at day 60! I'm stoked that I've made it this far and can't wait to make it to 6 months or a full year with out caffeine.
No Time Like The Present
If you want to try to giving up caffeine for good, I would highly recommend it. The first step towards breaking the cycle is to make the decision to stop consuming caffeine. Once you made this sincere decision you can start on your journey towards living a more healthy life.
Once you stop you will notice how much this substance is on our daily lives and make the needed adjustments to avoid it. I find myself drinking way more water than I use to. Whenever I go out to dinner with my family I order a glass of water, thus saving our family a few bucks!
We don't need this dreadful substance in our lives. We have fruits, vegetables and meat to give us all the energy we need during the day.
What kept me accountable was having an app on my phone that would help me track the habit of not consuming caffeine. The app I use is called Onrise
It has helped me keep track of this long term habit change and is super easy to use with smooth user experience. I highly recommend this app to anyone. It is only on iOS unfortunately but any habit tracking app will do the trick.
I really hope that you decide to go on this journey. It is well worth it!! If you have questions please don't hesitate to reach out!
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 319ad3e7:cc01d50a
2024-11-01 17:25:24
@ 319ad3e7:cc01d50a
2024-11-01 17:25:24https://image.nostr.build/4824c65d9a07c577bee8591b18ee147e7a457849fbaee53244667ec062914751.jpg
NOV 2024 | ISSUE 3 | LETTER FROM THE FOUNDER | FOOD ART | LIFE EXPERIENCE | FEATURED RECIPE | KIDS CORNER | MICROFICTION | FOOD NOTE QUOTES | SOUNDS | UPCOMING EVENTS | ECONOMICS | COMMUNITY PHOTO ALBUM | NEW RECIPES
LETTER FROM THE FOUNDER 📝
Hello and welcome back to the cozy autumn days with Zap Cooking! I’m thrilled to bring you another issue of our monthly newsletter, a space where we share our favorite moments and celebrate our vibrant community. Sarah, who does an amazing job curating these updates, has crafted this edition to capture the essence of both real-life gatherings and our shared online experiences on Nostr.
In this issue, we’re excited to revisit highlights from Nostr Valley, where Zap Cooking was proud to sponsor and connect with friends in a truly special celebration. It was an incredible honor to see so many of you make the journey to join us for the first annual event—a milestone in Nostr’s history and a testament to the strength of our community.
As always, thank you for being a part of this journey. Your continued support, contributions, and readership mean everything to us. Here’s to more shared moments, connections, and, of course, great cooking!
Gratefully,
Seth
Founder, Zap Cooking
https://i.nostr.build/gwaOKZDlTM45Ht15.jpg
FOOD ART 🎨
Zap.Cooking’s favorite food art of the month is the Banana Bread Costume from Bread and Toast! 😀 https://i.nostr.build/MgihZ6m2bQCv6krD.png Visit Breadandtoast.Com For More! New Single Every Sunday!
LIFE EXPERIENCE ✈️
Nostr Valley Adventures
https://image.nostr.build/7fd20dd7d9a4ce01657e0a9bed9d60cd6308325bf6cb69ec4f7ca63a6e3fb56e.jpg
The adventures of Nostr Valley began when I was invited to speak on a food panel alongside Seth, the founder of Zap.Cooking, at Happy Valley Brewing in State College Park, Pennsylvania.
Over the course of a month before the event, a fellow fun enthusiast known as The Beave organized a weekend filled with activities and accommodations, including a visit to a gun range and a stay at a charming three-bedroom countryside rental nestled among Pennsylvania's most scenic farm hills.
The Nostr Valley weekend had finally arrived, and I was set to drive six and a half hours to a small airport primarily used by skydivers and flying enthusiasts who park their personal planes in rented hangars. I was to meet a pilot who went by the name "Choke This." Despite the somewhat ominous name, my faith in the Nostr web of trust circles provided a sense of safety as I prepared to fly to Pennsylvania. Still, the thought of traveling alone to a remote area did cross my mind a few times. While it may not have been the wisest decision, I had faith in Nostr.
I began my journey at 1 am, getting ready and preparing my car before hitting the highway around 4 am. Driving on the empty roads was a pleasant experience, and I felt even better when I arrived at the well-kept airport on a beautiful sunny morning at 10:30 am, with not a single cloud in the sky. I knew it was a perfect day for skydiving, which alleviated one of the many flying-related nerves swirling in my head. Great weather? Check!
https://i.nostr.build/LXFm0A5hqmXgo9O0.jpg
After a brief introduction to the non-threatening pilot, we loaded our gear into the rear of the plane and settled in for takeoff, complete with those cool headphones. As we patiently waited for all the skydivers to land from their jumps, I received a crash course on plane safety in case of an emergency landing.
We made our way to the small runway, and with a gentle breeze, we were soaring into the blue skies. The view was absolutely breathtaking. Every time I fly, the scenery reminds me of the model city in the Beetlejuice movie.
For the next three hours, the pilot and I got to know each other. We shared our Nostr stories, backgrounds, and family lives. The pilot also gave an impressive presentation on the features of his aircraft, including a lesson on how to read knots—the unit of speed.
We landed in Maryland to pick up another panel speaker, Mr. Scott Churchill, who would be joining the art panel with Dan, the creator of the Nostr-only comic "Bread and Toast." Scott is a loving father with remarkable artistic skills that included drawing and music.
The three of us entered the airport restaurant and took a window seat overlooking the runway to grab a quick bite. This is where I was introduced to Maryland’s love for Old Bay seasoning. The pilot was eager to order crab cakes, and I was initially going to join him, but as soon as I spotted "CRAB SOUP" on the menu board, my food plans changed. Once we ordered, the food arrived fairly quickly. The kind server placed a bowl of soup in front of me, complete with extra crackers and an Old Bay salt shaker. My face lit up as I exclaimed, “What is this!?” Scott explained that Old Bay is a staple in these parts. I poured the seasoning into my soup and took a taste. “I’m going to do this at home,” I declared before even swallowing the first spoonful. I devoured the rest of the soup, sprinkling Old Bay each time I removed a layer of the flavorful creamy broth. I was hooked.
https://i.nostr.build/CWrwAxMADw18G8m5.jpg https://i.nostr.build/QgRqUJy7EdVEVNQc.jpg
Once lunch was finished, we boarded the plane. I offered the front seat to Scott since it was his first time flying. He was a mix of emotions about the flight, but he did amazing and even got to fly the plane!
When we landed in State College Park, Pennsylvania, it felt as though we had become a family. There’s nothing quite like trusting strangers with your life for several hours in a flying machine to foster a sense of camaraderie.
We were off to meet our fourth companion—the organizer, the maestro, the one and only, THE BEAVE! He awaited us at the house, and upon our arrival, we felt an immediate sense of comfort.
The house was beautiful, the people were friendly, and it was time to invite other speakers and guests over for a magical steak dinner. Beave started the bonfire while the pilot fired up the grill. Guests began to arrive.
The steaks were so thick and stacked that I dubbed it "Steak Jenga." The guests gathered around the impressive pile of perfectly cooked meat, each grabbing a steak as large as their faces.
https://i.nostr.build/im2ud6A45E41bili.jpg https://i.nostr.build/4cd8YSnIdz9X7fhz.jpg https://i.nostr.build/duqyX2xwIjunUlFR.jpg
After dinner, I had the opportunity to taste one of the best-flavored vodkas I had ever encountered: Blake’s Limited Edition x Gypsy Spirits’ Apple Pie Vodka, a vodka infused with Apple Cider & Cinnamon.
https://i.nostr.build/YHt8Em9wSJNGPqGs.jpg
I called it an early night due to all the traveling and being awake since 1 am, especially since I would be speaking on my first panel the next day. I wanted to be fresh and alert for the event. As soon as my head touched the pillow, I fell into a deep sleep. When I woke early the next morning, I felt rested and ready to conquer the day.
Beave and I were the only ones awake, so we headed to the nearest country store to see what breakfast supplies they offered. Upon entering the store, we found a convenience section on the left and a sit-down breakfast and lunch area on the right. We made our way to the cold section, where we discovered local dairy farm milk in half-gallon glass containers for only $3! I had to grab a jug. There were also small bottles of flavored milk, including strawberry milk, for less than $1.50.
https://i.nostr.build/KtCMvKOsTYIozmA8.jpg
Beave and I picked up some eggs and butter, but the real treasure was the donuts. The lady behind the register was an excellent saleswoman, encouraging us to take home a container of these fluffy looking treats. I noticed Beave had already bought some right before I made my way to the register, so I thought, "Why not?" I grabbed a container of smaller individual donuts that would be perfect for sharing with the house.
Once we got to the car, we each took a bite of a donut and immediately began scarfing it down in ecstasy. It was moist, and the bakers hadn’t skimped on the glaze. There was no oily aftertaste—just rich, sweet goodness that I would absolutely recommend.
After returning to the house, we served breakfast and started getting dressed for Nostr Valley.
At this point, I was a bundle of nerves. As we arrived at Happy Valley Brewing, it was heartening to see so many familiar faces from Nostr. Avi Burra, author and host of Plebchain Radio, began hosting the event, introducing all the speakers and panels. Derek Ross, one of the organizers of Nostr Valley, opened the show with a "Nostr 101" speech. Then, the art panel, moderated by Seth—my “boss” from Zap.Cooking—featured Dan and Scott. Avi then demonstrated his Nostr medical application. The food crew, consisting of Seth and me, followed next, moderated by Boston Wine. Next Block made their rounds with Mandana and Ian. The Other Nostr Apps panel featured Derek, Vic, Boston Wine, and Avi. The infamous Open Mike spoke about music with Derek, and the event concluded with closing remarks from the two organizers.
https://i.nostr.build/aoplHjfLu6oJPGr1.png (see the Community Photo Album for more pictures)
This was my first time speaking on a panel, and to say I was nervous would be an understatement. I practically clung to Seth the entire time and felt as though I blacked out while speaking. Nevertheless, I was proud to have made it through.
Afterward, a large group of us headed to the American Ale House, where we had a private section of the restaurant reserved. Avi and Derek’s shared dish was particularly notable—a nearly $90 certified angus beef tomahawk steak weighing in at 44 ounces.
https://i.nostr.build/Jk5ZJwd8VoBQQGTT.jpg https://i.nostr.build/7ydShpbQasVMp3hT.webp
For the afterparty, we invited everyone to a bonfire and podcast session at our VRBO for mini podcast recordings. However, I ended up successfully talking for 45 minutes with the first attendee, and by then, everyone else grew tired of waiting. I was ready for bed after such a long day.
On Sunday morning, the sun streamed through my window as I woke up, and I realized it was shooting range day! Beave and I headed over to the country store for more donuts, but unfortunately, it was closed on Sundays. We took a drive to fill up the car with gas and grabbed a breakfast sandwich or two at the gas station. We gathered the rest of the group and made our way to PGC Scotia Shooting Range, where we spent six hours shooting a variety of guns outdoors.
https://i.nostr.build/D3v1y8MebC1lzaa8.jpg
When we returned, we were starving and enjoyed a pleasant pheasant dinner filled with lively conversation.
https://i.nostr.build/M98NWu0oXaVKADaT.jpg https://i.nostr.build/hxp68wsP5Q4QUp4S.jpg
On Monday, we checked out of the VRBO. The day was cloudy, and the first part of the flight home was bumpy, but the sky cleared after we dropped off the other speaker. Once we landed back at the skydiving airport, I spent the rest of the evening driving home, finally walking in the door at 2 am.
My favorite part of the weekend wasn’t the speaking on stage or all the activities; it was the friendships I gained over those three days. I am truly grateful.
FEATURED RECIPE 🥪
https://image.nostr.build/8ec8e09bc081e7f70de446fda8fc85d485c01ed4579b13f511753568b21f3c8b.jpg
https://image.nostr.build/ba98258b64d17c6ca0d6148494d8dd9127530aca0826f6fe78809bce9e3dca5a.png nostr:naddr1qqmhvet8v9hz6cnvw4jj6am0dejx2u36943kzumgv4mj6cnpwdjkgttzd36k2ttrdpjk2um994kkzum5v4e8q6t9vdjsygxxndcac4j0ms6s4nwlly5lyhtjq2kpguxgwjyxpz7kmx8yy6a8vvpsgqqqw4rspyqve4
KIDS CORNER 🐤
https://image.nostr.build/c93a2f500f419bc85f429c8ba01240be32e3923b1a60831ae396f1b867d8478c.png
https://image.nostr.build/16f51b2ab39178e25a27b2f32a5890e4eed43872b37dfa48ad121428ad58efbe.png
https://image.nostr.build/b8bbc636081442196ae6dad0eb8426ec34134990f930cf8443fd39884ff579e9.png
https://image.nostr.build/f8211c8170391e2d1e9e589445b4084d5d6997fd54cd5f9518427dfa72b015d6.png
MICROFICTION 📖
TRICK OR TREAT? | Rustypuppy
“Remember, look into her orange eye, ask for a trick, and say ‘please.’” Janice fluffed the mane of my son’s lion costume and gave him a little push toward the dilapidated barn, decked out in creepy Halloween glory, complete with skeleton graveyard, tree ghosts, and a giant roof spider with glowing eyes.
Henry took two steps forward, then glanced back at me. I smiled and nodded. His brow furrowed, then he got in line with the other kids waiting for their turn at Granny Baba’s front door.
“You’re not traumatizing my five year old for life, are you?” I asked our babysitter.
The teen laughed. “He’s a brave little guy. I didn’t face her until I was seven. Relax, pops. Granny Baba is a rite of passage in this town. He’ll fit in better once he can say he got his trick. Besides, sometimes you gotta go through the scary to get to the good.”
After twelve minutes and eleven seconds, my son ran toward us, his face shining with joy. “I got the trick!” He showed off his jack o’ lantern candy bucket, which had contained the usual assortment of wrapped sugar and artificial ingredients, and now also held a clear plastic bag filled with lumpy darkness.
I side-eyed Janice as she took out the bag, opened it, and ate a handful. Henry did the same before I could stop him.
“This is …. good,” he said, frowning and chewing at the same time. “What’s the trick?”
“It’s healthy,” Janice replied. “All natural, sprouted granola.”
*RECIPE REFERENCE | Sprouted Bliss Granola - Essencial | Vegan | nostr:npub1c6dhrhzkflwr2zkdmlujnujawgp2c9rsep6gscyt6mvcusnt5a3srnzmx3
Follow Rustypuppy | https://rustypuppy.npub.pro/
FOOD NOTE QUOTES 🗒️
https://image.nostr.build/471a56680b7a3bdc6c63fa5682579b071de5b9fb65988df8b3673c2e6a4c68eb.png https://image.nostr.build/75ac9d6bc09e5fd0bdeec01010bf699905c11dbeff3fff5e4a3164a113812d9f.png
SOUNDS 🔊
MUSIC
HONEY | MARTIN GROOMS
https://wavlake.com/track/e4c1cf34-ada2-46ba-be1a-b9242479ca0a | https://image.nostr.build/470907a92d1155aca310a980bacb0e178d9299b78a897d6db3d5189f39ff5a5b.png
PODCASTS
TFTC
Courtney Swan breaks down how these harmful ingredients are fueling hyperactivity in children. | https://video.nostr.build/49e4c0db7da37748ac04071cab1fdc668b55aa346e08bf8501d6071bd59ab6e6.mp4 These 10 Companies Control The World To POISON YOU! | Marty sat down with Courtney Swan to expose how 10 Companies Control The entire Worlds food supply, and how they're producing food that's poisoning you and your family. | To watch the full episode: https://www.youtube.com/watch?v=WSEiJ6C4MHk
BENPOD
BenPod.com featuring Twitter Co-Founder, Rabble | NOSTR Breaks Every Social Media Paradigm (BWP58) https://video.nostr.build/caaa77bb42bbfa2ddc04017ae45f68a95c162822edaa3084ffefeff4776ce0e0.mp4 | To watch the full episode: https://youtu.be/U-eNYRwyADI
PLEBCHAIN RADIO
Fermenting a Revolution with Ben Justman | Plebchain Radio | QW & Avi discuss the road to plebhood, building Peony Lane Vineyards, running a Bitcoin business, Creed, Nostr and more with Ben Justman. | Peony Lane Vineyard : https://www.peonylanewine.com/ | https://fountain.fm/episode/YMpNVBI3WjDv1Uttl1vd
UPCOMING EVENTS 🥳
Submit your Nostr event with @ZapCooking on Nostr
NOVEMBER 1
SoupBox Debut Listening Party| 7pm EST | ONLINE | zap.stream
NOVEMBER 6
The No-Conference Nostr Party at Bitcoin Park | Nashville, Tennessee | https://www.meetup.com/bitcoinpark/events/303283108
NOVEMBER 8-9
Brazil's Largest 100% Bitcoin Event | São Paulo | https://www.satsconf.com.br/
DECEMBER 15-19
Sats By SW | A V4V Weekend | Austin, Texas | https://media.primal.net/uploads/2/e0/e1/2e0e1258d63c4b758eeeb48cc0892eaf35a99f083d0a1cf7be03d1382fc6b8bd.jpg
JANUARY 30-31
Plan B Forum | El Salvador | https://image.nostr.build/86c3212b3677a0176f1a838ea006bfdf9cc43e778f5c406c641b553436917395.jpg
ECONOMICS 🍞
SAUSAGES | Peter McCormack
"...Mistakes, even trivial ones, are amplified in seconds. Look at the recent Labour Party conference, where Keir Starmer’s speech was meant to lay out his grand vision for fixing the country. Instead, a simple slip of the tongue—calling for the release of “sausages,” instead of “hostages”—became the story. Within hours, memes flooded the internet, and his entire message was lost in the noise..."
https://image.nostr.build/05d035f16769c1cffda143bc6ee5c0a5b86b74bad4c49aa9f98cdc5618ccc526.png
Read more: https://www.petermccormack.com/p/sausages
COMMUNITY PHOTO ALBUM 📷
Community Photo Album by The Beave, Derek Ross, Seth, Scott, T$, JD, Vic, Adam Toad, The Bitcoin Babe, Open Mike, Silberengel, inyahé, Bread and Toast, Nostr Valley, Atlantic Bitcoin Conference, TABconf, CornyChat, NostrNests | Share your Nostr community photos or videos with @ZapCooking
Nostr Valley
https://image.nostr.build/f743bdef24bca2d85eb78d182560e4d6fd8cba857d82252b1fbee23e97df4bbe.jpg https://i.nostr.build/xTw4pPUDkuTIaFW8.jpg https://i.nostr.build/O0wDQWEwDrrntToS.jpg https://i.nostr.build/vYkyGtdl2c8bgkmU.jpg https://i.nostr.build/uLqQ5a7Blza3n1d0.jpg https://i.nostr.build/ALGdDpTdMTFXiIu2.jpg https://i.nostr.build/NbUeiWCkDtYR4fF4.jpg https://i.nostr.build/JSImWt5lUx4am1iz.jpg https://i.nostr.build/CoS2Cc5j9Q6pSqBz.jpg https://i.nostr.build/o30Ljw4lObtlQQfn.jpg https://i.nostr.build/LRqTNfP9yFl3AgQl.jpg https://i.nostr.build/qv5PkjTbSgX6vygZ.jpg https://i.nostr.build/upPFNEEvXV9Jprez.jpg https://i.nostr.build/sWkZyiawJRP1uPJ0.jpg https://i.nostr.build/BWr1z0GE7BOlyZhH.jpg https://i.nostr.build/TgWpmKFc7Nqpt2ED.jpg https://i.nostr.build/MMX5LLABTCK4jZaY.jpg https://i.nostr.build/LnbJZmTA09F76um9.jpg https://i.nostr.build/hACVcv3cASvX9yZf.jpg
Atlanta Bitcoin Conference
https://i.nostr.build/Omk1YnOwYjhVShqO.jpg https://image.nostr.build/e46c9169c4b96bf2f6052c3e49555f7c6656ac061fff9b808a9fba33d0661f61.jpg https://image.nostr.build/fa282ad995e454cf899dac7a1720435fdc7921b2cf9693cffb9fc4cf23690907.jpg
TABConf
The critical innovations at @TABConf for a Saturday night. | Oatmeal-raisin, chocolate-chip, and vegan peanut butter cookies have been baked. Leaving for #meetup in Frankfurt with @Purple Konnektiv ❤️ | Silberengel https://image.nostr.build/f4a4d25220ec2b6797d09c68049639dedefc9d3414ad5587a48a6016ede46d81.jpg The Peanut Butter Cookie recipe is available on Zap.Cooking! nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z
NEW RECIPES 🍲
Robin Holstein | Soups | nostr:npub1rz7mvm42y0z3udug5s007sk0kgmcqs2ufa439edx8u2ptqhttews0tuhg4
Essencial | Vegan | nostr:npub1c6dhrhzkflwr2zkdmlujnujawgp2c9rsep6gscyt6mvcusnt5a3srnzmx3
Lucas M | Pork Meatballs | nostr:npub1whgjzsdrjxv5csrz2q032hpwxnjp4rpulxl0nexh62vz2dzc683qh8wqu9
Kat | Empanadas | nostr:npub10us6l7kvn340s2mw4jhluj0jlpt3zthnqftk8xewy80d64lpj96qa7xew6
Chriso🇺🇸🇦🇺🦘⚡️ | Mexican Grilled Chicken | nostr:npub147wy3decmxy3vs9u4nse80ha7nkcydt7zdge8lc9gk8ddglh4t6qudjwdr
MichZ | Orzo with Asparagus and Prosciutto | nostr:npub1jdyaqyngdj4tgmmtlm7j7npkr3fwzjcumcwdqf68dc9wd5lf39rqwlfwsu
FIN 🤠
https://image.nostr.build/497029805a46bbb4942bcb13a0e8f0238e3c7956282d4d2866ca342d19f54bad.jpg
-
 @ a853296a:209e695f
2024-11-01 16:15:36
@ a853296a:209e695f
2024-11-01 16:15:36👋 What's up, stackers & podcasters!
I'm excited to announce a new release for Jamie – our AI-powered podcast assistant (think a virtual Jamie for Joe Rogan fans)!
TL;DR: Jamie now goes beyond file uploads! With this update, Jamie can access any podcast published on an RSS feed, making it super easy to get transcripts, summaries, blog posts, and more.
Our goal is to make Jamie your go-to tool for everything pre-production, post-production, promotion, and podcast market research.
🛠️ How to Use the New Jamie
Step 1: Search for Your Podcast on RSS
Find the feed of your choice and select it to start analyzing episodes:
Step 2: Pick the Episode You Want to Analyze
Choose any episode to get started!
analyzing @k00b and @Car on SNL
Step 3: Select Your Content Type
Choose the type of content you want to generate – we have nine default options, or you can create your own Custom Prompt:
✏️ Optional: Customize the Prompt/Give More Context
Adding more context or tweaking the prompt can help tailor the output:
⏳ Step 4: Await Your Results
Within about a minute, Jamie delivers the content you need:
🚀 Future Plans
- Expand and continually improve on Jamie's capabilities. Our goal is to make Jamie a great assistant for all things media pre-production, post-production and even research! Please hit us with feedback as we pursue that goal. - Teaser: we are the proud owners of pullthatupjamie.ai. We plan to make the most out of that and provide you with great AI enhanced researching tools. This new tool to be announced will provide unparalleled utility, convenience and privacy aligned with our other applications - More language support! Jamie has gotten popular with an international audience! Stay tuned as we make more releases & optimizations related to supporting users worldwide
🧡 If you made it this far, thanks for tuning in! Check out our bitcoin-payable services and apps at https://cascdr.xyz.
Cheers, and happy podcasting!
originally posted at https://stacker.news/items/749836
-
 @ 2348ca50:32a055a8
2024-11-01 14:58:51
@ 2348ca50:32a055a8
2024-11-01 14:58:51Keeping a clean and organized home is essential for a healthy lifestyle, yet many people find it challenging to manage household chores alongside their busy schedules. This is where professional house cleaners come in. They offer various services tailored to meet individual needs, ensuring that homes are clean, organized, and welcoming. In this article, we will explore how house cleaners work, the different types of cleaning services available, methods and tools used, the hiring process, and tips for ensuring the best results from professional cleaning services.
Types of House Cleaning Services
House cleaning services can vary widely in scope and focus. Here are some of the most common types:
-
- Regular Cleaning
Regular cleaning is often a recurring service, such as weekly, bi-weekly, or monthly. It typically includes:
Dusting surfaces
Vacuuming and mopping floors
Cleaning bathrooms (toilets, sinks, showers)
Kitchen cleaning (countertops, sinks, exterior of appliances)
General tidying up
-
- Deep Cleaning
Deep cleaning goes beyond regular cleaning and is usually recommended periodically (e.g., quarterly or bi-annually). It involves a thorough cleaning of all areas of the home, including:
Scrubbing baseboards and moldings
Cleaning behind and underneath furniture and appliances
Washing windows and window sills
Detailed cleaning of bathrooms and kitchens
Dusting light fixtures and ceiling fans
-
- Move-In/Move-Out Cleaning
This type of cleaning service is designed for individuals moving into or out of a home. It typically includes deep cleaning to prepare the space for new occupants or to leave it spotless for landlords. Tasks may involve:
Cleaning cabinets and drawers
Scrubbing floors and carpets
Washing walls
Removing trash
-
- Specialized Cleaning
Some house cleaning services specialize in certain areas or types of cleaning, such as:
Post-construction cleaning
Carpet and upholstery cleaning
Eco-friendly cleaning
Commercial cleaning for offices and businesses
-
- Organizational Services
In addition to cleaning, some house cleaners offer organizational services to help clients declutter and arrange their belongings efficiently. This may include:
Closet organization
Kitchen and pantry organization
Home office decluttering
How House Cleaners Work
-
- Initial Consultation
Most cleaning companies offer an initial consultation, either in-person or over the phone. During this consultation, clients discuss their cleaning needs, preferences, and any specific areas of concern. This helps the cleaning team prepare a tailored plan for the job.
-
- Assessment and Estimate
After understanding the client’s requirements, the cleaning company typically conducts an assessment of the space to determine the time and resources needed. Based on this assessment, they provide an estimate of the cost, which can vary depending on the size of the home, the type of cleaning service, and any additional requests.
-
- Scheduling the Service
Once the client agrees to the estimate, the next step is to schedule the cleaning service. Clients can choose a one-time service or set up a recurring schedule based on their preferences and needs.
-
- Preparing for the Cleaning Day
Before the cleaning team arrives, clients can prepare their homes by: Decluttering spaces (to make cleaning easier)
Communicating any specific cleaning instructions or areas to focus on
Securing pets in a safe area (if applicable)
-
- The Cleaning Process
When the cleaning team arrives, they typically follow a systematic approach to cleaning:
Arrival and Preparation: The team members will introduce themselves and review the cleaning plan with the client (if present). They may also gather their cleaning supplies and equipment.
Dusting and Surface Cleaning: The team starts by dusting high surfaces, such as ceiling fans and shelves, and works downwards to avoid spreading dust onto clean areas.
Vacuuming and Mopping: Floors are vacuumed first, followed by mopping or scrubbing, depending on the type of flooring.
Kitchen and Bathroom Cleaning: These areas often require the most attention. The team will sanitize countertops, sinks, appliances, and fixtures, ensuring that they are thoroughly cleaned.
Final Touches: After completing the main cleaning tasks, the team may do a final walk-through to ensure everything meets the client’s expectations.
-
- Post-Cleaning Inspection
After the cleaning is completed, some companies may offer a post-cleaning inspection to ensure that everything has been done to the client’s satisfaction. Clients are encouraged to provide feedback and discuss any areas that may need additional attention.
-
- Payment and Scheduling Future Services
Clients typically settle payment after the service is completed. Many cleaning companies offer online payment options for convenience. Clients can also schedule future services at this time if they wish to maintain a regular cleaning schedule.
Tools and Techniques Used by House Cleaners
-
- Cleaning Supplies
House cleaners often bring their cleaning supplies and equipment, which may include:
All-Purpose Cleaners: Used for various surfaces, including countertops and appliances.
Disinfectants: Important for sanitizing high-touch areas such as doorknobs, light switches, and bathroom fixtures.
Glass Cleaners: Used for windows and mirrors to achieve a streak-free shine.
Floor Cleaners: Specialized products for hardwood, tile, or carpeted surfaces.
-
- Cleaning Equipment
Common cleaning equipment used by professionals includes:
Vacuum Cleaners: High-quality vacuums with attachments for different surfaces.
Mops and Buckets: For mopping hard floors.
Microfiber Cloths: Effective for dusting and cleaning without leaving streaks.
Brooms and Dustpans: For quick clean-ups of dust and debris.
-
- Techniques and Best Practices
Professional cleaners often employ techniques to maximize efficiency and effectiveness, including:
Top-to-Bottom Cleaning: Cleaning high areas first to avoid redistributing dirt.
Zone Cleaning: Focusing on one area at a time for thoroughness.
Use of Microfiber: Utilizing microfiber cloths for dusting and cleaning, as they capture dust and dirt effectively without the need for harsh chemicals.
Hiring a House Cleaner: What to Consider When hiring a house cleaner, it’s essential to consider several factors to ensure a positive experience:
-
- Reputation and Reviews
Researching the reputation of a cleaning service is crucial. Look for online reviews, testimonials, and ratings on reputable sites to gauge the quality of service provided.
-
- Services Offered
Ensure the cleaning service offers the specific type of cleaning you require. Some companies specialize in particular areas, so it’s essential to find one that meets your needs.
-
- Pricing Structure
Understand the pricing structure, including any additional fees for specific services or materials. Some companies charge hourly rates, while others offer flat fees based on the size of the home.
-
- Insurance and Certifications
Check if the cleaning company is insured and bonded. This protects you in case of accidents or damage during the cleaning process.
-
- Flexibility and Availability
Consider the company’s flexibility in scheduling and whether they can accommodate your preferred cleaning times, especially if you need a recurring service.
-
- Communication and Trust
It’s essential to hire a cleaning service that communicates effectively and values customer service. Trust is crucial, as cleaners will be in your home, so choose a company that instills confidence.
Tips for Getting the Best Results
To ensure you get the best results from your house cleaning service, consider these tips:
-
- Be Clear About Expectations
Communicate your cleaning needs and expectations clearly during the initial consultation. Providing specific instructions will help the cleaning team focus on areas that matter most to you.
-
- Keep an Open Line of Communication
If you’re present during the cleaning, feel free to ask questions or make requests. Open communication helps the cleaners understand your preferences better.
-
- Maintain a Clutter-Free Space
While professional cleaners will tidy up, maintaining a relatively organized space can make their job easier and allow for more thorough cleaning.
-
- Provide Feedback
After the service, share your thoughts with the cleaning company. Positive feedback encourages good practices, while constructive criticism helps improve future services.
-
- Consider a Regular Cleaning Schedule
To maintain a clean home, consider setting up a regular cleaning schedule. This prevents dirt and clutter from accumulating, making each cleaning session more manageable.
Conclusion
House cleaners provide a valuable service that helps individuals maintain clean and organized homes. By understanding how house cleaners work, the types of services available, and the processes involved, clients can make informed decisions when hiring cleaning professionals. Whether you opt for regular cleaning, deep cleaning, or specialized services, investing in professional house cleaning can save time, reduce stress, and enhance your living environment. With the right approach and communication, you can enjoy a sparkling clean home without the hassle.
-
-
 @ 8d34bd24:414be32b
2024-11-01 14:42:38
@ 8d34bd24:414be32b
2024-11-01 14:42:38Sorry, this article went out on Substack, but I forgot to post it on Nostr.
God has made many promises throughout history that are recorded in the Bible. Most of them took centuries, if not millennia to be fulfilled. The God of the Bible is outside of time, so He doesn’t look at time like we do, but His timing is just what it should be.
God never breaks His promises. He fulfills them in full and in all details, but not necessarily in the timing we desire. We’re going to go through some of God’s greatest promises and see what we can learn about God, ourselves, God’s character, and the future. Seeing what God has done should help us to trust God in all things.
Adam & Eve
God’s first promise was given to Adam and Eve after they sinned.
To Eve, He promised:
“I will greatly multiply\ Your pain in childbirth,\ In pain you will bring forth children;\ Yet your desire will be for your husband,\ And he will rule over you.” (Genesis 3:16)
This promised was fulfilled immediately and for all of the women after Eve.
To Adam, He promised:
“Cursed is the ground because of you;\ In toil you will eat of it\ All the days of your life.\ Both thorns and thistles it shall grow for you;\ And you will eat the plants of the field;\ By the sweat of your face\ You will eat bread,\ Till you return to the ground,\ Because from it you were taken;\ For you are dust,\ And to dust you shall return.” (Genesis 3:17b-19)
This promise was also fulfilled immediately and in all men throughout history.
To the serpent (Satan), it was promised:
“Because you have done this,\ Cursed are you more than all cattle,\ And more than every beast of the field;\ On your belly you will go,\ And dust you will eat\ All the days of your life;\ And I will put enmity\ Between you and the woman,\ And between your seed and her seed;\ **He shall bruise you on the head,\ And you shall bruise him on the heel.” (Genesis 3:14b-15) {emphasis mine}
The initial curse on serpents was fulfilled immediately, but the ultimate curse/promise was partially fulfilled when Jesus died on the cross and will be fulfilled completely in the last battle (Armageddon) at the end of the age when Satan is cast into hell.
“You shall bruise him on the heel” refers to Satan working to have Jesus crucified. A bruised heel is not fatal and Jesus returned from the dead, conquering death and sin.
“He shall bruise you on the head.” A head wound is fatal. Jesus struck the initial blow when He rose from the dead conquering death and sin after paying the price for our sins. The final blow will be His last action on Earth before His believers move to the new heaven and new earth.
According to time calculations by Uscher using the genealogies, Adam and Eve were created about 4004 B.C. How long it took them to sin is not made clear, but what details we get suggests it was very soon after creation, so it took approximately 4,000 years to be partially fulfilled and will be at least another 2,000 years to be fully fulfilled.
But do not let this one fact escape your notice, beloved, that with the Lord one day is like a thousand years, and a thousand years like one day. (2 Peter 3:8)
Since God is outside time, He doesn’t look at time as we do. We want things now. We don’t want to wait, but we need to understand that God’s timing is always perfect and we often learn from God in the waiting.
Next we will learn from someone who waited faithfully on God’s promises and never gave up, even when logic would say that God’s promises were impossible.
Abraham
God’s first promise to Abraham came when he was 75 years old.
“Go forth from your country,\ And from your relatives\ And from your father’s house,\ To the land which I will show you;\ And I will make you a great nation,\ And I will bless you,\ And make your name great;\ And so you shall be a blessing;\ And I will bless those who bless you,\ And the one who curses you I will curse.\ And in you all the families of the earth will be blessed.” (Genesis 12:1b-3) {emphasis mine}
God told Abraham to leave his home and go to a land he did not know. What should have been Abraham’s golden years was the beginning of his wandering. Abraham trusted God and obeyed.
Abraham was promised that God would “make you [Abraham] a great nation.” Without faith in an all powerful God, this would have seemed impossible. Abraham was 75 years old and had no children. His wife, Sarah, was only 10 years younger. Both were past the age of having children. They were being told to leave their home and move to an unknown land inhabited by strange people. No betting person would believe this man would become the father of a great nation and definitely no one would think the whole world would be blessed through his family.
Abraham was led to the edge of Canaan (the future site of Israel) and once again God made a promise to Abraham:
“To your descendants I will give this land.” (Genesis 12:7b)
Abraham and Sarah had no children. They were blessed with flocks and servants, but it would have seemed unthinkable that they could conquer Canaan, drive out the nations living there, and father a new nation. Despite this, Abraham believed that God’s promises are true.
When did the land finally belong to the descendants of Abraham? I don’t know the exact number of years, but he was still about 25 years away from fathering Isaac. Then Isaac had to grow up and marry before fathering Jacob. Jacob had to grow up, worked many years to earn his wife Rachael before fathering his twelve sons, including Joseph. Joseph had to grow up and spend years in Egypt before being put in charge in Egypt. The Israelites were then in Egypt for about 400 years before being freed and exiting Egypt to go to the promised land. Because this generation rebelled, they were then forced to wander in the desert for more than 40 years. Looking at this, it was well beyond 500 years before Abraham’s descendants owned any of the land God promised Abraham other than a small burial plot.
Does this mean God was unfaithful? Of course not.
The Lord is not slow about His promise, as some count slowness, but is patient toward you, not wishing for any to perish but for all to come to repentance. (2 Peter 3:9)
At first Abraham and Sarah tried to fulfill God’s promise themselves. Sarah followed the local pagan way and gave her maid to her husband to father a child for them and Hagar gave birth to Ishmael when Abraham was 86 years old.
When Abraham was 99 years old God said,
“For I have made you the father of a multitude of nations. I will make you exceedingly fruitful, and I will make nations of you, and kings will come forth from you. I will establish My covenant between Me and you and your descendants after you throughout their generations for an everlasting covenant, to be God to you and to your descendants after you. I will give to you and to your descendants after you, the land of your sojournings, all the land of Canaan, for an everlasting possession; and I will be their God.” (Genesis 17:5b-8) {emphasis mine}
God once again God promised the land to Abraham and also promised he would be “the father of a multitude of nations.” At last the promise of fathering nations seemed possible because of his son Ishmael, but owning the land of Canaan, in which he was a sojourner, living in a tent, seemed out of reach, but Abraham still did not fully understand God’s plan. God gave a new, more detailed promise to Abraham.
“As for Sarai your wife, you shall not call her name Sarai, but Sarah shall be her name. I will bless her, and indeed I will give you a son by her. Then I will bless her, and she shall be a mother of nations; kings of peoples will come from her.” (Genesis 17:15b-16) {emphasis mine}
Abraham couldn’t believe that they could possible have a child of their own. He couldn’t comprehend him, at 100, and Sarah, at 90, producing a child of promise and instead of thanking God said, “Oh that Ishmael might live before You!” God corrected Abraham saying, “No, but Sarah your wife will bear you a son, and you shall call his name Isaac; and I will establish My covenant with him for an everlasting covenant for his descendants after him. As for Ishmael, I have heard you; behold, I will bless him, and will make him fruitful and will multiply him exceedingly. He shall become the father of twelve princes, and I will make him a great nation.” (Genesis 17:19-20)
Now becoming the father of a second son, even in his old age, Abraham began to see the fulfillment of God’s promises almost 25 years earlier.
Eventually, at the age of 100 Abraham had his promised son, Isaac, through whom the promise would be fulfilled.
When Sarah died, Abraham was able to buy the “cave of Machpelah” as a place to bury his wife. This was the first piece of soil that Abraham owned in the promised land and the only piece that he got to see, but God wasn’t done yet.
I always remember the son of promise, Isaac. When I stop and think, I remember that Abraham also had Ishmael. Until recently, although I had read this passage many times, I always forgot Abraham’s sons through Keturah.
Now Abraham took another wife, whose name was Keturah. She bore to him Zimran and Jokshan and Medan and Midian and Ishbak and Shuah. (Genesis 25:1-2)
God had promised Abraham, at the age of 75, that he would be the father of many nations. He seemed too old to become the father of even one son, but became the father of eight.
Jokshan became the father of Sheba and Dedan. And the sons of Dedan were Asshurim and Letushim and Leummim. The sons of Midian were Ephah and Epher and Hanoch and Abida and Eldaah. All these were the sons of Keturah. Now Abraham gave all that he had to Isaac; but to the sons of his concubines, Abraham gave gifts while he was still living, and sent them away from his son Isaac eastward, to the land of the east. (Genesis 25:3-6)
All of these sons and their sons became the foundation of many nations throughout the Middle East and beyond just like God had promised, but this was only a partial fulfillment of God’s promise to Abraham. Much more was yet to come.
Jacob
God’s promise to Abraham was passed down to Isaac and then to Isaac’s son Jacob (the younger twin). After Jacob betrayed his twin brother Esau, Rebekah sent Jacob to her family to find a wife. On the way, God made a promise directly to him.
“I am the Lord, the God of your father Abraham and the God of Isaac; the land on which you lie, I will give it to you and to your descendants. Your descendants will also be like the dust of the earth, and you will spread out to the west and to the east and to the north and to the south; and in you and in your descendants shall all the families of the earth be blessed. Behold, I am with you and will keep you wherever you go, and will bring you back to this land; for I will not leave you until I have done what I have promised you.” (Genesis 28:13-15)
God once again promised the chosen heir the ownership of this land and that he would be returned to it. He also said, “Your descendants will also be like the dust of the earth,” reiterating the Abrahamic covenant.
Through two wives and two concubines, that were maids to his two wives, Jacob fathered 12 sons who became the fathers of the 12 tribes of Israel. Although Jacob was returned to the promised land of Canaan after several decades with his mother’s family, he also did not get to see the complete fulfillment of God’s promise that they would be given the land. He saw that God was always with Him; he was returned to the land God had promised Him; but he did not get to see the vast descendants or how his family was a blessing to the whole world. God’s timing was not yet complete.
In Part 2 we will see more promises of God and see how God is faithful.
Trust Jesus.\ \ your sister in Christ,
Christy
-
 @ a012dc82:6458a70d
2024-11-01 12:50:05
@ a012dc82:6458a70d
2024-11-01 12:50:05Table Of Content
-
The Rise of River: A Game-Changer in the Bitcoin Space
-
Factors Influencing Thiel's Decision
-
Implications of Thiel's Investment
-
Conclusion
-
FAQ
Peter Thiel, the renowned venture capitalist and co-founder of PayPal, has recently made headlines with his bold move of investing $35 million in a Bitcoin startup called River. Thiel's investment in the cryptocurrency industry has sparked curiosity and debate among investors and industry experts. In this article, we will explore the reasons behind Thiel's decision to back River and delve into the potential implications of this move for the Bitcoin ecosystem.
The Rise of River: A Game-Changer in the Bitcoin Space
Understanding River's Mission
River is a Bitcoin startup founded in 2019 with a mission to make Bitcoin more accessible and user-friendly. The company aims to bridge the gap between traditional finance and the world of cryptocurrencies by providing institutional-grade Bitcoin financial services. River offers a suite of tools and services designed to simplify the process of buying, selling, and storing Bitcoin for both individual and institutional investors.
Thiel's Confidence in River's Vision
Peter Thiel's investment in River is a testament to his confidence in the startup's vision and potential. Thiel has a track record of backing disruptive and innovative companies, and his support for River indicates his belief in the transformative power of Bitcoin. By investing a substantial amount of capital, Thiel is betting on River's ability to drive mainstream adoption of Bitcoin and revolutionize the way people interact with the digital currency.
Factors Influencing Thiel's Decision
Growing Institutional Interest in Bitcoin
One of the key factors influencing Thiel's decision to invest in River is the increasing institutional interest in Bitcoin. In recent years, major financial institutions, including banks and asset management firms, have started to embrace cryptocurrencies and recognize their potential as an investment asset. Thiel, known for his keen insights into emerging trends, likely sees the institutional adoption of Bitcoin as a significant catalyst for its future growth.
Addressing Bitcoin's Accessibility Challenges
Bitcoin's mainstream adoption has been hindered by various challenges, including its complexity and lack of user-friendly infrastructure. River aims to tackle these hurdles by providing a seamless and secure platform for buying, selling, and storing Bitcoin. Thiel's investment in River indicates his belief that the startup's innovative solutions can address these accessibility challenges and make Bitcoin more user-friendly for a broader audience.
Potential for Bitcoin's Price Appreciation
Thiel's investment in River may also be driven by his belief in the long-term potential for Bitcoin's price appreciation. As an early advocate of Bitcoin, Thiel has consistently expressed his bullish stance on the digital currency. By investing in a Bitcoin startup like River, Thiel is positioning himself to benefit from the potential growth of the cryptocurrency market as a whole.
Implications of Thiel's Investment
Boosting Confidence in the Bitcoin Ecosystem
Thiel's investment in River not only provides the startup with substantial funding but also boosts confidence in the broader Bitcoin ecosystem. Thiel's track record as a successful investor and his reputation in the financial industry lend credibility to the potential of Bitcoin as a disruptive force in the world of finance. His endorsement of River may encourage other investors and institutions to take a closer look at Bitcoin and its underlying technology.
Accelerating Mainstream Adoption
Thiel's investment in River has the potential to accelerate the mainstream adoption of Bitcoin. River's focus on user-friendly financial services can attract a wider audience of investors who were previously hesitant to enter the cryptocurrency space. By providing a seamless and secure platform, River can help overcome the barriers that have prevented mainstream adoption, ultimately driving more people to embrace Bitcoin as a viable investment option.
Fostering Innovation in the Bitcoin Industry
Thiel's investment in River also fuels innovation in the Bitcoin industry. The injection of capital enables River to expand its operations, hire top talent, and further develop its suite of services. This infusion of resources can have a ripple effect, inspiring other entrepreneurs and startups to enter the Bitcoin ecosystem with their own innovative solutions. Thiel's backing of River may spark a wave of creativity and competition, ultimately driving the industry forward.
Conclusion
Peter Thiel's $35 million investment in the Bitcoin startup River is a bold move that highlights his confidence in the future of Bitcoin and the potential of innovative companies within the cryptocurrency space. Thiel's investment not only supports River's mission to make Bitcoin more accessible but also boosts confidence in the broader Bitcoin ecosystem. By addressing Bitcoin's accessibility challenges, River has the potential to drive mainstream adoption and accelerate the growth of the cryptocurrency market. Thiel's backing of River also fosters innovation within the industry, inspiring other entrepreneurs to develop their own groundbreaking solutions. With Thiel's strategic investment, River is well-positioned to make a significant impact on the Bitcoin landscape and shape the future of digital finance.
FAQ
Who is Peter Thiel? Peter Thiel is a renowned venture capitalist and co-founder of PayPal. He is known for his investments in disruptive and innovative companies.
What is River? River is a Bitcoin startup that aims to make Bitcoin more accessible and user-friendly by providing institutional-grade financial services for buying, selling, and storing Bitcoin.
Why did Peter Thiel invest in River? Peter Thiel invested in River because he believes in the startup's vision and potential to drive mainstream adoption of Bitcoin. He also sees the growing institutional interest in Bitcoin and the need to address its accessibility challenges.
What are the implications of Thiel's investment in River? Thiel's investment in River boosts confidence in the Bitcoin ecosystem, accelerates mainstream adoption, and fosters innovation within the industry.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ cbaa0c82:e9313245
2024-11-01 12:39:42
@ cbaa0c82:e9313245
2024-11-01 12:39:42TheWholeGrain - #October2024
October is the month of Halloween and just like last year the gang wanted to show off their costumes! Bread was even excited to put on the costume this year. Can you believe it?
October also brought us a famous piece of cover art in the comic book industry while also showing us a possible logo for the "Bread Industry" in the world of Bread and Toast. The Bitcoin Art for this past month got to feature all three pieces of bread to show that Bitcoin works for everyone regardless of where they are, and we also got to show off what is obviously a very important political campaign logo for Toast.
The Bakery got to add the Bread and Toast logo to the collection with a new painting by The Bitcoin Painter. Please check out The Bitcoin Painter as this isn't the first time he has contributed to Bread and Toast, and we promise it will not be the last. He also created another art piece this past month of Bread, Toast, and End-Piece preparing for a quest.
Last of all, Bread and Toast went to it's first live event Nostr Valley on October 12th. The gang got to hand out some goodies and even made its first merchandise sales! Ten exclusive metal cut-outs in the shape of a slice of bread were sold at the event and NOSTR Badges were given out to those folks he bought them! Another badge was also given to folks who posted and shared a free exclusive print that was also given out to event attendees. All in all, Bread and Toast got to spread awareness of what they are up to with some fellow Nostriches, and we got to hear some kind feedback from those who are already following our adventures!
October Sunday Singles 2024-10-06 | Sunday Single 060 Roar https://i.nostr.build/Qp9CYnaGOuprxTQ1.png
2024-10-13 | Sunday Single 061 Ruff https://i.nostr.build/v2OsYHVmbyN84q9T.png
2024-10-20 | Sunday Single 062 Banana Bread https://i.nostr.build/MgihZ6m2bQCv6krD.png
2024-10-27 Trick-or-Treat https://i.nostr.build/dfBBgXQXNTcpfUeu.png
Other Content Released in October 2024 2024-10-02 | Toast's Comic Collection WATCHBREAD #6 On Friday night, a piece of toast fried in New York. Somebody knows why. Down there... somebody knows. https://i.nostr.build/4CqkA8GJ47NqAmNu.png
2024-10-08 | Politics Toast Campaign Logo The Official Campaign Logo for Toast2024. https://i.nostr.build/EnBDx.png
2024-10-09 | Concept Art Early Website Logo Design This was an early design for the logo of the bread company in the story of Bread and Toast. https://i.nostr.build/v6B4v68kkqmjygZT.png
2024-10-12 | Nostr Valley Nostr Valley 2024 Promotional A Promotional Art Piece released on the morning of Nostr Valley 2024. https://i.nostr.build/MPYjaZctceimKUm8.png
2024-10-16 | Bitcoin Art All Over Bitcoin can be used by anyone from wherever they are! https://i.nostr.build/BAzdyuf88SPuzkxk.png
October Additions to The Bakery in 2024 2024-09-05 | npub1tx5ccpregnm9afq0xaj42hh93xl4qd3lfa7u74v5cdvyhwcnlanqplhd8g https://i.nostr.build/SOROIK29W7otS49V.png
New Nostr Badges 2024-10-08 | Nostr Valley 2024 https://i.nostr.build/plCE3CYU5jLShKGF.png
2024-10-08 | Nostr Valley 2024 - Exclusive https://i.nostr.build/z87KZrDAduJFmj8a.png
Nostr Valley 2024 Photos The Bread and Toast Merch Table at Nostr Valley https://i.nostr.build/S3UkvSIiClfbB1lt.jpg
Nostr Valley Attendees Showing Off the Free Print npub12ujuf2pf9qz66zvfrw0c2qx9jfyumxr28pn5575zry24z6aylqsqgnnume https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fimage.nostr.build%2Fe1691abf44ac067862f6e216582f99bd758095494c3a263027a5568119dbd900.jpg
npub1crs0mukptfxs0crz5n0y26apf5tph3uc8l2pguet7rqdr8w2ze3snsjv6g https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fimage.nostr.build%2Fd63678bc8e220b720d10df1ea6699e5180115c3a1ed887e493dba8508317233a.jpg
npub1a4za2sgwlp04q7wjgrt6e2plperxtle8hwge9a5lx5283up5n94sdmvnvq https://image.nostr.build/f82bf8c54aa623acdf88b24606c9ad319736a1b39c2b6b46706d3827de64b250.jpg
npub1luvpvkhauqy994y6fcf3djvpc7hszexpsyxqhs87g8fkrhtu5lcqylnmt5 https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fi.nostr.build%2F90lc1SRTwX7HlCBX.jpg
Exclusive Steel Cut-Outs Made as Merchandise for Nostr Valley 2024 npub1lhezms58jx4yer60y3wzldc83fdez3j4rc4ue3edhz5qv3wxfsgqhhw94n https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fimage.nostr.build%2F70dbb8f91719e30bddbcf925e7309a770c7f585efe491eaf958b0fe48f1f8421.jpg
npub1a6c3jcdj23ptzcuflek8a04f4hc2cdkat95pd6n3r8jjrwyzrw0q43lfrr https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fimage.nostr.build%2F4124dd10fc5ac3ce1c7c0c267021b3207f789b491ca8a5fc644566eb25960d6a.jpg
npub1yx6pjypd4r7qh2gysjhvjd9l2km6hnm4amdnjyjw3467fy05rf0qfp7kza of CornyChat.com helping npub16e3vzr7dk2uepjcnl85nfare3kdapxge08gr42s99n9kg7xs8xhs90y9v6 make Cornbread! https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fi.nostr.build%2FkAV4C402FHL3vh9Z.jpg
Bread and Toast wants to give a special thank you to npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 and npub15u3cqhx6vuj3rywg0ph5mfv009lxja6cyvqn2jagaydukq6zmjwqex05rq! This wonderful opportunity allowed Bread and Toast to have its first trial at merchandise sales and also provided a live platform to share our content with folks using Nostr that may not have been previously aware of this project. You guys did a great job with the event! Thanks again! https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fi.nostr.build%2FkUZD3TKl5yz1VmB1.jpg
Last of all, thank you to everyone who came to Nostr Valley! https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fimage.nostr.build%2F68bd53e745229b9dbb001879ec4a07183eee8be4e8a9930cced2c7c433da9806.jpg
Bonus: Fan Photo npub1n0pdxnwa4q7eg2slm5m2wjrln2hvwsxmyn48juedjr3c85va99yqc5pfp6 of Zap.Cooking ended up making soggy bread! We'll be waiting for the recipe! https://image.nostr.build/13f2254f07d2c07fb5f44ae1f9c1a96ac75bdbf328a1f4a6fd514a93f1f95b1e.jpg note1m7hf6lz7glefeayu6yqqt99z77gzdlf9j232sps6psn29vxxhwss5w589m
We hope you enjoyed the second issue of The Whole Grain. The Whole Grain is released on the first of every month and covers all of the content released by npub1ew4qeq576v3vz4gukeseknqghx3x4jtlld8ftys9amrca6f3xfzsrm8jpd in the previous month.
Thanks for checking everything out! Bread, Toast, and End-Piece
BreadandToast #SundaySingle #ToastsComicCollection #ConceptArt #BitcoinArt #TheBakery #Bread #Toast #EndPiece #Artstr #Comic #Cartoon #NostrValley #NostrOnly #🖼️
-
 @ 0be0ab80:b6c2b58c
2024-11-01 12:15:02
@ 0be0ab80:b6c2b58c
2024-11-01 12:15:02When it comes to education and adoption, it's essential to focus on the foundation, which begins already with the youngsters and their mentors.
If you've already checked out the main page of our Geyser campaign explaining more about the overall mission of Bitcoin Junior Club + our goals, you might remember that organizing short events and meet-ups for kids is one of them.
For this particular point, we hadn’t planned to start this year due to limited funding and resources, but sometimes life has other plans. There was a gift from the stars we couldn’t ignore... 😮💫
Less than a month ago, we were given the opportunity to organize [a dedicated space for children and families at this year’s Adopting Bitcoin in El Salvador.
- You can find more details on this in the links shared below(*).
- Huge thanks to the organizers, especially Kiki and Kemal, for their trust and a wonderful collaboration!
Here’s where it gets important, where your role may come in:
Both Adopting Bitcoin and the Bitcoin Junior Club are non-profit projects, built on strong values and integrity, which limits the potential for large-scale funding.
The entire Bitcoin Para Niños space and program are funded by our personal resources.
✅ Our input also includes countless hours of non-paid preparation and work.
✅ Adopting Bitcoin has covered costs for renting the dedicated venue space, essential equipment, about 40% of our travel costs, one entry ticket to the conference.
✅ While we’ve received support from other projects through hands-on help during the event and donations of unique materials (THANK YOU EVERYONE), still Bitcoin Junior Club is self-funding many other necessary items (books, toys, stickers, decorations, printouts, and creative supplies)—all of which will be used for rewards, keepsakes, and the program itself.
✅ We’re also covering a significant portion of our travel expenses, including the rest of the flight for one person (Europe - El Salvador and back), extra luggage allowance, and accommodations.
This mission is powered by passion and the belief in a better tomorrow, one where sovereign generations lead the way. But passion alone doesn’t pay the bills, and the budget for this project (Bitcoin Junior Club especially now with its part at Bitcoin Para Niños) is coming straight from family savings, which we hope to replenish over time.
If you’d like to support our shared mission to inspire young minds with values like Bitcoin, freedom, creativity, and critical thinking, consider sending us some sats. Every amount counts.
Thank you 🧡 Bitcoin Junior Club
(*)
- "Bitcoin and El Salvador: Education, Adoption, Freedom!" —
- https://thebitcoinstreetjournal.com/ab2024-bitcoin-para-ninos-and-btc-junior-club-for-sovereign-generations/
- "Empowering the Next Generation: AB2024 with Spotlight on Kids and Families" — https://bitcoinnews.com/press-release/bitcoin-para-ninos-adopting-bitcoin-2024/
- DJ Valerie B LOVE Show — [LIVE] Adopting Bitcoin in El Salvador - Kemal +Kiki + Sela: https://www.youtube.com/watch?v=guvnKp_H6-U
-
 @ c5fede3d:16e03f7b
2024-11-01 10:20:16
@ c5fede3d:16e03f7b
2024-11-01 10:20:16El Día Después ha terminado, y todo sigue igual. Se apagan los lamentos y llega la resignación. Toca trabajar duro y esperar a que venga la ayuda. Pasan los minutos, las horas, y no llega nada. Los políticos se esconden, alguno aparece ataviado con un equipo propio de la serie Top Gun, por supuesto, en el área menos afectada de la denominada ‘zona cero’. Hay que preservar la integridad de nuestros representantes, no vaya a ser que pillen un resfriado por ayudar a los damnificados. Un selfie y de vuelta al coche oficial. No se olvide a darle like, buen ciudadano, eso sí, cuando vuelva Internet, sin prisas.
Hay que seguir adelante, pero afloran los problemas, sobre todo en los pueblos. Allí reina la anarquía, son múltiples las disputas por una pieza de fruta, y esto es sinónimo de pelea. Muchos hacen acaparamiento y se aprovechan de la ayuda vecinal, son los de siempre, los okupas y los egoístas, los que antes actuaban así y mirábamos para otro lado, pero, tras el Día Después, ya no nos podemos permitir ese lujo. Otros se dan cuenta, ellos también quieren comer, y la desesperación entra en juego. Ahora gana el más fuerte, mera supervivencia, como en las películas y series pos-apocalípticas que usted veía tranquilamente por la noche en su casa. Las fuerzas del orden hacen lo que pueden con los pocos medios que tienen, la ‘zona cero’ exige triplicar esfuerzos, y a veces, no es suficiente. Cae la noche, y en algunos pueblos hay un toque de queda auto-impuesto, es hora de dejar la pala, se desmontan los puestos de recogida. Si el día es peligroso, imaginen pasadas las 20:00. Los robos y saqueos aumentan, quedan desvalijadas las farmacias, los supermercados, la mayoría por necesidad.
¿Y ahora qué? Es la hora de los iluminados, de aquellos que se disfrazaron para Halloween, mientras sigue aumentando el número de víctimas. <
>, claman algunos. < >, afirman otros con rotundidad. Y ahí está la clave. De todo se aprende, y ahora se buscará la aclamación popular para que el Gobierno esté habilitado para una intervención exagerada e invasiva a costa de nuestros derechos. La inacción crea inseguridad, la inutilidad genera convencimiento y la maldad trae evidencia. Aprendamos de Valencia, de cómo fuimos abandonados. Distingan al lobo que se oculta tras la piel del cordero, pues ellos traerán a los vigilantes para acabar con los robos y los saqueos. Qué bien suena sobre el papel, pero, ¿confiarás tu seguridad en aquellos que generaron estos mismos problemas?, y sobre todo, ¿quién vigilará a los vigilantes? -
 @ 6bae33c8:607272e8
2024-11-01 07:29:46
@ 6bae33c8:607272e8
2024-11-01 07:29:46It’s our last day at the resort, and Sasha came down with chicken pox. She’s fine, but miserable, and as a result we’re leaving in an hour or so, so I had to watch the five-minute highlights version as I wait for the buffet to open to bring her some fruit.
Suffering kid aside, that game went perfectly for me. I had the Jets ATS in the picking pool — the Texans are smoke and mirrors now on offense, and the defense is only decent.
I also started Aaron Rodgers narrowly over C.J. Stroud and thank God for that. While I briefly considered Dalton Schultz at TE, I decided against it and stuck with Jonnu Smith. And I had Tank Dell in at WR who did his part. Basically after two horrific weeks, it was a perfect game as far as I was concerned and a great start to the week. My only regret is not using the Jets in the Circa contest.
-
The Jets tree is the narrowest of all with only Davante Adams, Garrett Wilson and Breece Hall. There is no one else, and Malachi Corley surely won’t be joining that mix after fumbling for no reason on an easy TD.
-
Joe Mixon produces whenever he’s healthy. The Texans like to run the ball and play conservatively, so he’s always heavily involved.
-
Dell and Schultz were the only ones who got more than three targets. Robert Woods, John Metchie and Xavier Hutchinson were non-factors, and that’s even with Nico Collins still out.
-
Stroud is playing under brutal conditions right now, and while Collins’ return should ease those somewhat, the offensive line problems and coaching is here to stay. I regret drafting him in two leagues — I don’t think the Texans will fix it this year.
-
Rodgers’ line was nice, but heavily boosted by two tough TD grabs by Garrett Wilson. He’s lucky to have Wilson and Adams, but that offense is still not really in sync, either.
-
-
 @ 45bda953:bc1e518e
2024-11-01 07:24:39
@ 45bda953:bc1e518e
2024-11-01 07:24:39Trump, Musk, CXDC and the Dept of Governmental Efficiency
This whole essay is an exposition on why I think it's possible that Donald Trump is one of the heads of the beast from the sea and Elon Musk is the beast who rises from the earth as is written and prophesied in Revelation chapter 13 of the Holy Bible New King James Version also alluding to the Koine Greek manuscript. If you are not interested in biblical exposition of scripture I do not blame you. Go look at the charts, see bitcoin number go up, go on polymarket and place a bet on Trumps election win, much more fun. I am not trying to convert anyone to Christianity because I don't care about your soul or the state of your personal relationship with god. I am writing this because I get a narcissistic pleasure from being right about things over and over and over again. I am writing this because I find it fun to point back in time and say, "I knew it." I am not trying to use bitcoin or science fiction stories as bait to trick anyone into reading bible verses and converting them to my supposed faith. In fact I get very annoyed with self righteous preacher types using tropes and gotcha moments to try and guilt trip people into saying a prayer and yippee ki yay, now you get to go to heaven with me. I find it retarded and very insulting to the actual meat and potatoes of what is a very deeply intelligently compiled and mysterious history book. So scrap all the preconceived notions you have about someone quoting bible verses and give me neutral territory as I try to expound on the abstract concepts contained within an ancient text.
Here goes...
My father was visiting us. I woke up early in the morning, laying in bed I habitually took my phone to check the news. I was met with a flurry of online commotion and frantic urgency. The internet was on fire with Donald Trump's assassination attempt. The news was a couple of hours fresh and already every conceivable conspiracy was permeating all the digital town squares. My father is always up early and I called to him "Someone tried to take out Donald Trump!" My dad turned on his laptop and started to follow the story which was a developing current event. No one had yet put together all the pieces. Still wearing my pyjamas I walked into the lounge where my dad was busy catching up with the news. Holding my phone I said to him "Elon Musk is going to endorse Donald Trump." He looked at me with a questioning look and asked me why I would say something like that. It was a totally irrelevant and weird thing to say considering the circumstances. I told him that I know of no other entity who can make fire come down from heaven in the sight of men. My dad thought I was being a bit nutty. To me it felt surreal.
Symbolism is always used in prophecy as a type of meme to condense complex systems often with abstract connotations into an archetype that can communicate the complex idea across time. This archetype allows the memetic symbolism to break through the obstacles of cultural jargon and evolution of language allowing the reader, to in his own time of being, find value or make sense of the text in spite of his modern world views. The books of Revelation and Daniel are especially difficult to understand and to sort the data into a quantifiable or practical structure is a pain. This is by design.
Daniel Chapter 12:4 (circa 530 BC Ancient Babylonia, modern Iraq.)
"But you, Daniel, shut up the words, and seal the book until the time of the end; many shall run to and fro, and knowledge shall increase.
Revelation Chapter 22:10 (95-96 AD Isle of Patmos, a small Greek island in the Aegean sea.)
"And he said to me, Do not seal the words of the prophecy of this book, for the time is at hand."
Revelation and Daniel are keys that unlock and reference back and forth to each other across time but there is a third key which locks the books up leaving humanity always speculating and hypothesising until this third key gradually decrypts the occult of eschatological prophecy. This key is simply time. The chaos of nature and history is recorded by the predictable linearity of time condensing it into the ever present now. It was in that moment of time that the identity of Trump and Elon being figures of import in the annals of history, that realisation and the profundity of it made the moment so surreal to me.
I am going to quote the verses of Revelation Chapter 13 one at a time and give a running commentary of each as I do. There are 18 of them.
John is as a third person looking at the vision from the outside in. He also has a guide standing next to him explaining to him what he is witnessing. Almost like the architect explaining to Neo what is what in the TV screen room or like Morpheus trying to make known to Neo the situation in the real world in the white room using dramatic visual effects to convey his point. John was not in the real world's future but a symbolic projection of it. The Koine Greek differs somewhat to the King James I am also going to attempt a literal translation of phrases.
1: And stood (The Dragon)-stationed upon the sand of the sea, and I saw out of the sea a beast rising up, having horns ten and heads seven, and upon the horns of it diadems ten, and upon the heads of it names of blasphemy -slander.
The Dragon is the infamous Satan. The serpent of old. In Greek the word satan translates literally to the word opponent. That is why Satan (the character) does not exist in the Hebrew old testament as satan the definition. In Revelation chapter 12 the woman id est Christianity is attacked by the dragon who is furious that his leverage in heaven has been neutralised and him banished/exiled from it. The dragon is on a rampage to destroy the woman and her offspring. Christianity as an ideology of self sacrifice in service of others is the target of the dragons wrath (this self sacrifice in service of others as primary ethos is the inevitable demise of the dragon as seen through the action and accomplishment of Jesus Christ and Satoshi Nakamoto) and he summons forth the beast from the sea to do his will on earth to the advantage of his wrath. In this case I am going to be ambiguous and say that the dragon is a creature of financial power. Not limited to a specific people or culture but to various groups of people across time who love money and worship it to the point of harming human life to gain more of it. The love of money being the root of all kinds of evil - Timothy 6:10. A so called principality of the air. An intangible enemy animated by the weakness of human greed and lust. This banking force has a Rothschild like proclivity to absorb power through control of wealth. Welcome to the stage - The Dragon! (Applause) The dragon being a force of wealth has no tangible power in and of itself, it's power has to transcend the abstraction of finance into kinetic, it has to summon more efficate abstractions that can channel kinetic energy to achieve it's goals primarily that of eternal incumbency. This beast summoned out of the sea is government. If the finance can control bullet/sword/arrow/bombs then the Dragon can control this oceanic summoned beast. This beast is a chimera of sorts and we will get to defining it in more detail. The sea is mostly a symbol for mankind, the beast is summoned from and compiled of the nations of earth.
2: And the beast which I saw was like a leopard, and the feet of it as of a bear, and the mouth of it as a mouth of a lion. And gave to it the dragon the power of it and the throne of it and authority -right -privilege -freedom great.
Leopard: The leopard is often associated with agility, speed, and deadly force. In Daniel, the leopard represented the Greek Empire, known for its swift conquests under Alexander the Great. For the beast in Revelation, "like a leopard" suggests a similar capacity for rapid expansion or cunning.
Feet of a Bear: Bears are typically associated with strength and endurance. In Daniel 7, the bear represents the Medo-Persian Empire, known for its formidable military power. For the beast, "feet like those of a bear" symbolises an unstoppable or heavy force, capable of trampling or dominating.
Mouth of a Lion: A lion’s mouth represents authority, fearlessness, and perhaps fierceness in speech or command. In Daniel, the lion represented Babylon, an empire with significant authority and grandeur. For the beast in Revelation, a "mouth like a lion" suggests the beast’s capacity to speak with commanding authority and to blaspheme with boldness without being held to account.
This beast has expansionist and empiric type ambition. Let's call it England, no wait 1800's called and said don't blame me for NATO. Okay I concede, USA. The current year seat of power from where the beast bullies all into submission was gained through retaining it's control of finance through war. Be it gold, oil, or international trade, war or threat of it was the prima facie mechanism of enforcement. Babylonia in all it's glory for millennia through the rotations of power. This powerful beast bows only to one master, gold/finance. Even offering it's seat of power to the dragon. Government is physically capable of snubbing the dragon like the founding fathers snubbed England and it's royally decreed gold backed notes, the pound sterling (in the late 1700's). But the dragon is an insidious loathsome reptile, creeping and scheming, finding it's ways through the cracks of human fallibility. Enter the Federal Reserve and United States Treasury.
3: And one of the heads of it as having been slain -wounded to death -mortally, and the wound of the death -mortality of it was healed -cured. And marvelled -wondered the whole earth after the beast.
This is where Trump comes into the picture. As a head of state - head of the beast. The news with regard to his assassination attempt survival brought this verse to mind. I literally saw the entire chapter play out before my eyes as the implications became evident.
4: And they worshipped the dragon who gave the authority to the beast, and they worshipped the beast, saying: “Who is like -similar to the beast, and who is able -capable to war -battle against it?”
The whole mainstream media worldwide, alternative media, you name it. Trump was a household discussion on all continents. The united states presidential race and the imminent collapse of the financial system was all brought into the limelight of civilisation. So according to this verse a lot of sabre rattling is about to take place on the geopolitical map as Trump's presidency becomes obvious. Other powers want to divide territory and quickly while a pathetic and moronic Biden is babbling geriatric nonsense from the oval office. The leadership of the world was way calmer when they thought Harris was going to take the presidency, as soon as they realised a strong charismatic leader was once again going to take the reigns in the most powerful seat of military might in the world they scrambled to place their pieces on the chess board so as to have some negotiation leverage when Trump comes to their table.
5: And was given to it a mouth speaking great things and blasphemies -slanders, and was given to it authority to act -work -perform forty-two months.
This alludes to the fact that leadership is rarely held to account for their words because there is no authority above them to hold them accountable. It is hard to stay humble in this position of power. The forty two month implies the active duty of a presidential term in the United States of America.
6: And it opened the mouth of it in blasphemies -slanders against God, to blaspheme -slander the name of Him and the tabernacle -dwelling -sanctuary of Him, those dwelling in heaven.
I cannot tell you how this will play out. Because I honestly do not know and when I try to speculate about it my mind comes up blank. As far as I am concerned America is supposed to be a Christian nation. Maybe the blasphemy is that America does what is heathen and repulsive while claiming to be Christian, I don't know. A religion of science and capitalism seems to have replaced Christianity as a dominant cultural ideology in the seat of Empire.
7: And was given to it to make war against the saints -holy ones, and to overcome -conquer them, and was given to it authority over every tribe and people and language -tongue and nation.
This war is a war of attrition and culture within itself. Politics has humiliated and defeated the power of noble Christian endeavour in the United States. Deuteronomy promises that the country has to be overrun by heathen nations as punishment for this failure. Just look at the border. Through dollar reserve currency dominance the whole world -tribe/people/language is held captive and beholden to the United states.
8: And will worship it all those dwelling upon the earth, whose names have not been written in the book of the life of the Lamb -young sheep having been slain from the foundation of the world.
I do not pretend that everyone who supports the United States as a world power is evil. I don't believe it. But when the damage to life, liberty and property is violated so mercilessly by an Empire, those who harbour disgust and resentment and refuse to bow to it's ambition inevitably are crushed by it. Hating/resisting the dollar never made anyone rich. Until Jan 3rd 2009.
9: If anyone has an ear, let him hear.
If you know or don't know. Does not really matter, it is inevitable.
10: If anyone captivity into captivity he goes; if anyone with a sword kills, it is necessary him with a sword to be killed. Here is the endurance -steadfastness and the faith -belief of the saints -holy ones.
Basically it says to buy out the time, be peaceful and have hope. Bad shit is going to happen. Be content, aware and persevere.
11: And I saw another beast rising out of the earth, and it had horns two like a lamb -young sheep, and it spoke as a dragon.
This my friends, is Elon Musk. Born from free market capitalism with a healthy dose of socialist support. The banks and markets gave him his power. The financial institutions brought him forth. He is not a product of government. To the contrary, government has only inhibited his ability to achieve his goals.
12: And the authority of the first beast all it exercises before -in the presence of it, and it causes the earth and those dwelling in it that they will worship the first beast, whose wound of the death -mortality was healed.
Okay so this is where I came from when I told my dad that Elon was going to endorse Trump he literally endorsed him a couple of hours later on X. Now, as a student of history and having dabbled in eschatology as a hobby for many nihilistic and depressing years. Never before has my assumed prediction come true the next day. But in hindsight it's obvious, I mean who would not endorse Trump. Mark Zuckerface endorsed Trump, right? Elon went the full Monty jumping around on stage chanting USA! Endorsing Trump so hard Trump had to get out of the way. Elon is endorsing Trump so hard Trump could go home. Elon will run the campaign for him, without him. It is amazing to see.
13: And it does great signs -wonders, so that also fire it should make to come down out of heaven to the earth before men -humans.
Now let's put a cherry on this cake. This is the verse that so effortlessly popped into my head as I was looking at the imagery of blood splattered on Trumps face. Pumping his fist into the air. I said. "Elon Musk is going to endorse Donald Trump." He looked at me with a questioning look and asked me why I would say something like that. It was a totally irrelevant and weird thing to say considering the circumstances. I told him that I know of no other entity who can make fire come down from heaven in the sight of men." A couple of months later the super heavy booster gets caught by Mechazilla's chopsticks and the whole world marvelled again. I was so deep into uncanny valley I was Alice falling and falling. In 2017 some prophecies surrounding Revelations chapter 12 became fulfilled and it was meaningful to me. I enjoyed seeing a 2000 year old text consummate a relationship with reality. This was not the same. This was like bam! bam! You want some prophetic fulfillment, do you punk? Bam!
14: And it deceives those dwelling upon the earth through the signs -wonders which it was given to it to do before the beast, telling those dwelling upon the earth to make an image to the beast which has the wound of the sword and has lived -survived.
Okay so now I am back to speculation. Here I am writing this in the now. I have the past behind us. We now look forward into tomorrow. Remember - This is speculation on my part. Elon Musk establishes the department of governmental efficiency. It is a fun app connecting you directly to the upper echelons of governance. Cutting out the bureaucrats and middlemen. This D.O.G.E. makes everything much more convenient and efficient centralising and distributing the functions of government, reducing costs dramatically but also manages to audit and census the populace in real time. The citizens get Grocked by Grock if you will.
15: And it was given to it to give breath -spirit -life to the image of the beast, that also should speak the image of the beast and should cause -make -effect that as many as would not worship the image of the beast would be killed -put to death.
His simulacra of government becomes integrated with AI to the extent that you pledge allegiance to the app of the United States of America. Government becomes you constant companion, search engine, personal assistant. You think FBI exercise apps are creepy. Wait until government bucks you up when you have a down day.
16: And it causes all, the small and the great and the rich and the poor and the free and the slaves, that they should give to them a mark upon the hand of them the right or upon the forehead of them,
Is this simply a phone with an app in your hand. Right hand just suggesting most people are right handed? And does it suggest that the especially devout go get a Neuralink? I dunno.
17: and that no one would be able -capable to buy or to sell, except the one having the mark, the name of the beast or the number of the name of it.
He integrates the dollar and the use of it into X and all avenues of trade and commerce is conveniently migrated onto Starlink as infrastructure. The CXDC instead of a CBDC.
18: Here is the wisdom. The one having understanding, let him calculate -count the number of the beast; for a man’s number it is, and the number of it six hundred sixty-six.
In Gollums voice:
I know what it is. It's probably in your pocketses right now, your precious.
No, no, no, it cannot be my love.
Oh but it is precious, it is.
I know, I know, I hates it, I hates it.
We must serve the precious. The one dollar bill. Lol.
Post Script:
I don't think Elon Musk and Donald Trump are evil. I think they are cool dudes driven by very normal and natural incentives given their position and accomplishments. Just as Trump is about to once again be the head of the great statue that Nebuchadnezzar saw in his dream so too was Nebuchadnezzar just a dude doing his thing in his time and position. I have no hate for them, in fact I enjoy seeing them do their thing, it is impressive, entertaining and cool as hell. No pun intended.
I don't fear an apocalyptic future because I have made myself impervious to it by buying and holding Bitcoin. I don't give a fuck because I am possessed by the spirit of the honey badger and the cyber hornet. Which reminds me. Bitcoin is the promised land in cyberspace. But Bitcoiners should stay humble because nothing you did compares to what you got through no effort of your own. You owe your thanks to Satoshi and all the developers who made self custody possible and continue to build a world which maximises freedom, prosperity and personal responsibility.
Joshua 24:12-15
'I sent the hornet before you which drove them out from before you, also the two kings of the Amorites, but not with your sword or with your bow. I have given you a land for which you did not labour, and cities which you did not build, and you dwell in them; you eat of the vineyards and olive groves which you did not plant.' Now therefore, fear the LORD, serve Him in sincerity and in truth, put away the gods which your fathers served on the other side of the River/Rubicon, and in Egypt. Serve the LORD! And if it seems evil to you to serve the LORD, choose for yourselves this day whom you will serve, whether the gods which your fathers served that were on the other side of the River, or the gods of the Amorites, in whose land you dwell. But as for me and my house, we will serve the LORD."
Gotcha.
...
bitbib
-
 @ 081f3b0c:c00498a5
2024-11-01 01:15:58
@ 081f3b0c:c00498a5
2024-11-01 01:15:58Después de escribir mi primer artículo en este blog me di cuenta (o mejor dicho, me hicieron darme cuenta) de que, si voy a escribir para no-coiners (término afectivo para referirme a quienes no poseen ni un Satoshi ni ninguna shitcoin), tengo que empezar por el principio. Antes de contarles lo difícil o lo ameno que puede ser su viaje en la red de Bitcoin, necesito contarles al menos qué carajo es, o por qué lo necesitan en sus vidas. Porque claro, este sitio donde escribo funciona con nostr, y tanto quienes escribimos aquí como la mayoría de quienes nos leen somos bitcoiners. Muchos estamos orientados a la tecnología o la criptografía, y todos nosotros hablamos de Bitcoin y su "magia"; nos entendemos entre nosotros y rara vez volvemos a las bases o nos tomamos el tiempo de explicar por qué el mundo necesita Bitcoin y, sobre todo, por qué cada individuo debería tener sus propias llaves. Solemos decir frases hechas como “not your keys, not your Bitcoin”, “have fun staying poor” o la famosa cita del mismísimo Satoshi: “Si no me crees o no lo entiendes, no tengo tiempo para tratar de convencerte, lo siento”.
Satoshi (una persona o grupo de personas) publicó un documento de 9 páginas con el objetivo de crear un sistema de pagos entre personas, sin intermediarios de confianza. Una red P2P (peer-to-peer) o, en español, una red de pares. A diferencia de una red convencional, donde un servidor central controla la información y varios usuarios acceden a él, en una red de pares todos los nodos son iguales, y todos los nodos de Bitcoin guardan la misma información. En el white paper, Satoshi explicó en detalle cómo funcionaría la red y, unos meses después, lanzó oficialmente Bitcoin. Saltando 15 años de historia para tener material para futuros artículos (y también para evitar que te duermas leyendo), llegamos al presente: la red de pagos sin intermediarios es un éxito rotundo.
Resulta que yo no soy Satoshi, pero voy a tratar de convencerte, y hoy sí tengo tiempo para hacerlo.
Un día como hoy se publicó el white paper de Bitcoin. Te recomiendo que, ahora mismo o al terminar de leer esto, le des una mirada. Puede que lo entiendas completamente o que no lo comprendas del todo, pero es necesario que lo intentes. Este "papelito" hermoso cambió la historia.
Ya hablaremos del cómo, pero lo importante es que funciona. Por primera vez en la historia, se ha logrado construir un dinero 100 % digital, que no depende de bancos ni de gobiernos, ni de empresas o personas individuales. Depende únicamente de la red y de las reglas pactadas hace 15 años, que son inamovibles: están escritas en piedra y reforzadas por miles de nodos individuales alrededor del mundo. Es la red más robusta del planeta y cada día crece más en usuarios, nodos y mineros. Bitcoin puede usarse para una infinidad de cosas: desde el propio dinero P2P que Satoshi proponía, hasta aplicaciones mucho más avanzadas, como la verificación de la transparencia en elecciones. Y, por si no ha quedado claro, repito: estamos ante la red más robusta del mundo. No criticaré a las altcoins en este artículo porque no es la intención, pero sepan que la red de Bitcoin deja obsoletas a todas las demás. Todo lo que hacen las altcoins puede hacerse en Bitcoin: más rápido, más barato y, sobre todo, más seguro. Entraremos en detalles de esto en otros artículos.
Volviendo a la pregunta inicial: ¿por qué quiero Bitcoin?
Ahora ya sabemos que Bitcoin es la moneda de la red más segura del mundo y no depende de nadie. Pero por qué querés elegir una moneda que se respalda en una red y un protocolo y no en un gobierno? Puede que nunca te hayan confiscado los ahorros en un corralito, como en Argentina en 2001, o que nunca hayas experimentado la inflación desenfrenada como en Venezuela. Quizás no te importa que millones de personas no tengan acceso a una cuenta bancaria porque para vos los bancos son algo obvio y normal. Puede que estés viviendo con “privilegios financieros” y no te hayas dado cuenta... todavía. Bitcoin, al ser un dinero sin intermediarios ni custodios, y al no depender de ningún gobierno ni banco, puede ser almacenado por el usuario, quien es el único propietario de sus Bitcoin. Es inconfiscable, de ahí la importancia de la custodia y las llaves privadas. Además, la oferta total de Bitcoin en circulación es de 21,000,000 de unidades. Ni una más, ni una menos. Nadie, por más poder o influencia que tenga, puede imprimir más Bitcoin, ni inflacionarlo, ni devaluar tus ahorros. Por si fuera poco, Bitcoin es libre de censura: un cubano puede transferir Bitcoin a un argentino, o viceversa, sin importar las restricciones de capital en sus países. No se puede censurar una transacción de Bitcoin. Entonces, la respuesta corta a la pregunta es la siguiente:
Necesitás Bitcoin para protegerte de la inflación, de las restricciones de capitales y de los problemas bancarios. Y si estás pensando “para eso compro dólares, van abajo del colchón y listo”, te recomiendo que lo reconsideres, pero con este dato en mente: desde su creación hasta hoy, el dólar ha perdido más del 98 % de su poder adquisitivo. Mientras tanto, desde su creación hasta hoy, Bitcoin ha pasado de valer cero a ser una red de más de one trillion dollar. Quizás para ir ahorrando para el futuro sea mejor guargar Bitcoin que guardar Dólares. Mientras el dólar se fue desangrando año a año en cuanto a poder adquisitivo, Bitcoin ha pasado de no existir a ser comprado por individuos con alto patrimonio, fondos de inversión, empresas y hasta algunos países. ¿Todos están comprando Bitcoin menos vos?Si llegaste hasta acá y no te dió FOMO (miedo de quedarte fuera) el saber que todos compran menos vos, si no pensás que necesitás un sistema monetario libre de restricciones, inflación y estado, si no pensás que es necesario un dinero libre y un individuo soberano o bien pensás que tus dólares están tranquilos y seguros en el banco bueno, entonces si, HAVE FUN STAYING POOR. Si entendiste todo esto pero aún no logré convencerte de que Bitcoin es la única solución podés leer más articulos míos o de otros autores aquí dentro de habla.news y vas a encontrar muchísima información valiosa. Y no te olvides de leer el White Paper!
Gracias por llegar hasta aquí. Ojalá te sea útil. En mi próximo artículo hablaré sobre las diferencias entre comprar acciones, bonos o cualquier inversión tradicional y comprar Bitcoin. Spoiler: todas las acciones valdrán cerca de cero en términos de Bitcoin en 50 años.
Saludos,
El Tío.
-
 @ 30ceb64e:7f08bdf5
2024-11-01 00:54:47
@ 30ceb64e:7f08bdf5
2024-11-01 00:54:47Lightning Node Issues
My nodes been down for a couple of days since I switched routers. It seems like they it connect to the internet, so my lightning node is down. I don't have much on the thing, but I really enjoyed using Albyhub, the budgeted NWC, and having zaps sent directly to my node. I'll get it working eventually; I probably need to look into Start9 customer support, which costs $100 but probably worth every satoshi.
Exploring E-Cash
I've switched my lightning address to hustle@npub.cash and have started checking out the e-cash stuff more closely. I should probably be using Minibits, but I'm gravitating towards the Cashu.me and Npub.cash combo. I like the idea of logging into a wallet with my extension or signer and seeing my Nostr profile and e-cash. Cashu.me also has NWC functionality (which I haven't tried yet, but look forward to).
Creating a Run Tracker: RunWild
I've been tinkering with making a run tracker for Nostr called RunWild. I'll play around with it myself a lot before shouting it out to freedomland.
RunWild Features: - Released on zap.store only - Sign in with Amber - NIP60/61 support for the e-cash attached to your Npub - Runstr Chatroom: Similar to Fountains' #tunestr chatroom - Run Controls: Start run/Pause run/Stop run/Run History/Post run to Nostr - Wavlake Support: See and play your Wavlake playlists from the app
Future Plans: - Achievements and Goals - Running groups with Nostr freaks - Competitions and challenges with Nostr freaks - Merch on Shopstr - Sponsored Workout Tracks - E-cash Rewards: E-cash zap and a shoutout after your run - Nostr Badges - Zaps
I'll probably limit the app to 100 users for a long time and give them e-cash as a way to reward them for testing the app and building a community feel. It makes sense to throw a territory fee amount of sats at them. I mainly want to stop using the Nike run app and use a run tracker that I can log into with Nostr and listen to Wavlake stuff while running. It'll be cool if the app catches on, but if not, it'll be a personal freedom tech tool that me and my wife use.
It would be cool to create a new event kind for the runs that I track, so that when someone comes out with a better app than mine, my runs will appear on theirs. This might be how I win.
Closing Rambles
I saw Pablo come out with an e-cash project today called Honeypot. It has a button stretching across the bottom of the screen that says "I'm ready to lose some money" (with an exclamation mark), and contains language like #reckless and "Aaaaand money gone." I quoted the note saying "I'm ready, where do I sign up?"............. Tinkering is often the antithesis of smooth sailing, and even though my node may be down, and I'm scrambling for e-cash wallets like a pre-coiner scrambling for exchange yield, I'm still excited and motivated to use and build. Maybe running through the shifting terrain is half the fun.
originally posted at https://stacker.news/items/749200
-
 @ a012dc82:6458a70d
2024-10-31 23:44:40
@ a012dc82:6458a70d
2024-10-31 23:44:40Table Of Content
-
Who is Paul Tudor Jones?
-
The Rise of Bitcoin
-
Why Bitcoin?
-
Conclusion
-
FAQ
Bitcoin has been a hot topic in the financial world, attracting both enthusiasts and skeptics. One prominent figure who has shown unwavering confidence in Bitcoin is billionaire hedge fund manager Paul Tudor Jones. With his vast experience and expertise in the financial markets, Jones has been a vocal advocate for Bitcoin, citing it as the ultimate game-changer. In this article, we explore the reasons behind Jones' belief in Bitcoin and how it has the potential to revolutionize the financial landscape.
Who is Paul Tudor Jones?
Before delving into why Jones believes Bitcoin is a game-changer, it's important to understand who he is. Paul Tudor Jones is a billionaire investor, philanthropist, and founder of the Tudor Investment Corporation. He gained prominence in the 1980s for predicting the stock market crash of 1987, earning him the nickname "The Man Who Broke the Bank of England." Jones has built a successful career by making shrewd investment decisions, and his track record speaks for itself.
The Rise of Bitcoin
Bitcoin, introduced by an anonymous person or group known as Satoshi Nakamoto in 2009, is a decentralized digital currency that operates on a peer-to-peer network. It gained significant attention in the last decade, and its value skyrocketed, attracting the interest of investors worldwide. Bitcoin is based on blockchain technology, which ensures transparency, security, and immutability of transactions. The decentralized nature of Bitcoin, free from government regulations and intermediaries, has been both its strength and its source of skepticism.
Why Bitcoin?
Volatility and Inflation Hedge
One of the primary reasons why Jones believes Bitcoin is the ultimate game-changer is its potential as a hedge against inflation. Traditional fiat currencies are subject to inflationary pressures, reducing their purchasing power over time. Jones sees Bitcoin as a viable alternative that can protect investors' wealth from the erosion caused by inflation. Moreover, Bitcoin's limited supply, capped at 21 million coins, ensures scarcity and potentially drives its value higher.
Store of Value
Another aspect that appeals to Jones is Bitcoin's ability to serve as a store of value. Historically, precious metals like gold have been considered reliable stores of value. However, Jones argues that Bitcoin possesses similar qualities to gold and can even surpass it. He sees Bitcoin as a digital store of value that can act as a hedge against economic uncertainties and geopolitical risks.
Digital Gold
Jones has famously compared Bitcoin to gold, stating that Bitcoin will be the "fastest horse" in the race against inflation. He believes that Bitcoin's advantages, such as portability, divisibility, and ease of storage, make it superior to traditional gold. While gold has been a trusted store of value for centuries, Jones sees the potential for Bitcoin to become the preferred choice for investors seeking a safe haven asset.
Technological Innovation
Beyond its monetary properties, Jones recognizes the underlying technology behind Bitcoin, known as blockchain, as a groundbreaking innovation. Blockchain technology enables secure and transparent transactions without the need for intermediaries, revolutionizing industries beyond finance. The potential applications of blockchain are vast, ranging from supply chain management to decentralized governance systems. Jones understands the transformative power of this technology and believes Bitcoin is just the tip of the iceberg.
Portfolio Diversification
Jones advises investors to include Bitcoin in their portfolios as a means of diversification. He views Bitcoin as an asset class that offers unique properties not found in traditional investments. By adding Bitcoin to their investment mix, investors can potentially mitigate risk and enhance their overall returns.
Conclusion
Paul Tudor Jones' belief in Bitcoin as the ultimate game-changer stems from its potential as an inflation hedge, store of value, and technological innovation. His insights and endorsement have brought mainstream attention to Bitcoin, further solidifying its position as a significant asset class. While the future of Bitcoin remains uncertain, Jones' perspective sheds light on the transformative power of this digital currency and its underlying technology. Whether or not Bitcoin lives up to Jones' expectations, its impact on the financial world cannot be ignored.
FAQ
What made Paul Tudor Jones interested in Bitcoin? Paul Tudor Jones became interested in Bitcoin due to its potential as a hedge against inflation and its similarities to gold as a store of value.
Is Paul Tudor Jones the only billionaire who believes in Bitcoin? No, Paul Tudor Jones is not the only billionaire who believes in Bitcoin. Other prominent figures like Elon Musk and Michael Saylor have also shown support for Bitcoin.
How does Bitcoin protect against inflation? Bitcoin's limited supply and decentralized nature make it resistant to inflationary pressures that affect traditional fiat currencies.
Can Bitcoin replace traditional fiat currencies? While it's unlikely that Bitcoin will completely replace traditional currencies, it has the potential to coexist and provide an alternative form of value storage and transaction medium.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 361d3e1e:50bc10a8
2024-10-31 20:53:07
@ 361d3e1e:50bc10a8
2024-10-31 20:53:07https://forex-strategy.com/2024/10/31/app-reveals-real-time-location-of-trump-and-putin/ App reveals real-time location of Trump and Putin
app #mobile #location #tech #trump #putin
-
 @ 5f33097a:d8d0b22b
2024-10-31 20:01:27
@ 5f33097a:d8d0b22b
2024-10-31 20:01:27By MIT Brickman
We win, that’s what now.
Between Governor Jerry Brown signing the controversial tobacco bills into law in California – which opens vaping up to unsustainable regulation, criticism, and taxation in the most vape-active state in the country – and the FDA injecting a slow-acting but definitely fatal poison directly into the jugular of the nation’s vaping industry, it seems that we may have lost the battle to ensure longer lives and better health for millions of cigarette smokers.
If I can interrupt your wailing and gnashing of teeth for a moment, I beg you to consider a different perspective. It’ll be worth it. What I see in the middle of this platter of steaming garbage (that has been served up on both the state and federal levels) is a big, glittering diamond. We have been given a gift.
In making no concessions to the vaping industry, and subsequently raising a tall middle finger to the citizens of this great country who have found improved health, happiness, and quality of life by moving from cigarettes to vaping, the government has guaranteed two things.
One. That the adults will now take over the vapor industry. Millennials, hobbyists, hipsters, and high school kids trying to push the 300 watt barrier just don’t have the intestinal fortitude for what’s coming. Many shops will close, convention centers will sit empty, vape trick competitions will disappear, and there will be the odd hissing sound of wringing hands coming from parents’ basements nationwide. The end of the current vaping industry is at hand. But if you read my post here – then you already know that it’s not a bad thing.
I worked for many years in the air medical industry; those brave folks who fly critically ill and injured people on helicopters. And I can tell you that the only industry more heavily regulated than healthcare is aviation. So why not mix them together and see what happens! I’ll tell you what happens – it becomes a constant (daily) struggle between governmental intrusion (usually fueled by ignorance and/or greed) and trying to make enough money to keep flying. You talk about protracted PR and lobbying battles – the e-cigarette and vaping world actually has had it easy. Well, until now.
So why do people in air medical keep getting up every day and fighting – after all, you can make significantly more money in numerous other industries? Because it’s the right thing to do. Human lives matter and fighting against bureaucracy to keep people alive and with their families is a damn compelling mission.
But it takes adults who can play the game. And I can tell you, those folks only show up when there is a compelling mission endangered by inappropriate, ignorant, and destructive resistance (sound like anything else you know?).
Truly successful people relish ‘unwinnable’ challenges, especially when the outcome is ultimately beneficial to humanity. And two. The eighty-five plus percent of Americans fatigued by continuous governmental intrusion are now primed to come around. Start pushing the messages that I recommended here and hammer the social proof of the benefits associated with vaping over cigarette smoking, and you will find exponential traction in the critical public arena.
If you are depressed or defeated over the massive anti-vaping developments in these past couple of days, I’d suggest you either get over it quickly or get out of the way. The people who are going to win this fight for the benefit of public health worldwide are about to step up, and this is going to get ugly, frustrating, expensive, and amazing from this point on.
In conclusion I will go back to what I said in part 1:
There is good news though. Great news, in fact. Victor Hugo once wrote, On résiste à l’invasion des armées; on ne résiste pas à l’invasion des idées – commonly paraphrased as no one can resist an idea whose time has come. No government, no politician, and no industry. It just got real.
https://mitbrickman.com/2016/05/05/rise-of-the-adults-in-vaping/
-
 @ 5f33097a:d8d0b22b
2024-10-31 19:41:32
@ 5f33097a:d8d0b22b
2024-10-31 19:41:32From Wikipedia, the free encyclopedia
Tobacco harm reduction (THR) is a public health strategy to lower the health risks associated with using nicotine, as an example of the concept of harm reduction, a strategy for dealing with the abuse of other drugs. Smoking tobacco is widely acknowledged as a leading cause of illness and death.[1] However, nicotine itself is not very harmful, as inferred from the long history of use for nicotine replacement therapy products.[2] Thus, THR measures have been focused on reducing or eliminating the use of combustible tobacco by switching to other nicotine products, including:
Cutting down (either long-term or before quitting smoking) Temporary abstinence Switching to non-tobacco nicotine containing products, such as pharmaceutical nicotine replacement therapies or currently (generally) unlicensed products such as electronic cigarettes Switching to smokeless tobacco products such as Swedish snus Switching to non-combustible organic or additive-free tobacco products It is widely acknowledged that discontinuation of all tobacco products confers the greatest lowering of risk. However, approved smoking cessation methods have a 90% failure rate, when used as directed.[1] In addition, there is a considerable population of smokers who are unable or unwilling to achieve abstinence.[3] Harm reduction is likely of substantial benefit to these smokers and public health.[1][2] Providing reduced-harm alternatives to smokers is likely to result in lower total population risk than pursuing abstinence-only policies.[4]
The strategy is controversial: proponents of tobacco harm reduction assert that lessening the health risk for the individual user is worthwhile and manifests over the population in fewer tobacco-related illnesses and deaths.[3][5] Opponents have argued that some aspects of harm reduction interfere with cessation and abstinence and might increase initiation.[6][7] However, surveys carried from 2013 to 2015 in the UK[8] and France [9] suggest that on the contrary, the availability of safer alternatives to smoking is associated with decreased smoking prevalence and increased smoking cessation.
—
Nitzkin, J (June 2014). “The Case in Favor of E-Cigarettes for Tobacco Harm Reduction”. Int J Environ Res Public Health. 11 (6): 6459–71.doi:10.3390/ijerph110606459. PMC 4078589. PMID 25003176. A carefully structured Tobacco Harm Reduction (THR) initiative, with e-cigarettes as a prominent THR modality, added to current tobacco control programming, is the most feasible policy option likely to substantially reduce tobacco-attributable illness and death in the United States over the next 20 years. Fagerström, KO, Bridgman, K (March 2014). “Tobacco harm reduction: The need for new products that can compete with cigarettes”.Addictive Behaviors. 39 (3): 507–511. doi:10.1016/j.addbeh.2013.11.002. PMID 24290207. The need for more appealing, licensed nicotine products capable of competing with cigarettes sensorially, pharmacologically and behaviourally is considered by many to be the way forward. Rodu, Brad; Godshall, William T. (2006). “Tobacco harm reduction: An alternative cessation strategy for inveterate smokers”. Harm Reduction Journal. 3: 37. doi:10.1186/1477-7517-3-37. PMC 1779270. PMID 17184539. Phillips, CV (November 2009). “Debunking the claim that abstinence is usually healthier for smokers than switching to a low-risk alternative, and other observations about anti-tobacco-harm-reduction arguments”. Harm Reduct. J. 6: 29. doi:10.1186/1477-7517-6-29. PMC 2776004.PMID 19887003. Hiding THR from smokers, waiting for them to decide to quit entirely or waiting for a new anti-smoking magic bullet, causes the deaths of more smokers every month than a lifetime using low-risk nicotine products ever could. “Harm reduction in nicotine addiction: Helping people who can’t quit” (PDF). Tobacco Advisory Group of the Royal College of Physicians. October 2007. Retrieved 21 April 2012. Sumner W, 2005. Permissive nicotine regulation as a complement to traditional tobacco control” BMC Public Health 5:18. Tomar, SL; Fox, BJ; Severson, HH (2009). “Is smokeless tobacco use an appropriate public health strategy for reducing societal harm from cigarette smoking?”. Int J Environ Res Public Health. 6: 10–24. doi:10.3390/ijerph6010010. Action on Smoking and Health, May 2016, Use of electronic cigarettes (vapourisers) among adults in Great Britain http://www.ash.org.uk/files/documents/ASH_891.pdf Résultats de l’enquête cigarette électronique ETINCEL – OFDT, 2014 –
Text above provided under Creative Commons Attribution-Share Alike License – excerpted from: Tobacco harm reduction. (2016, July 7). In Wikipedia, The Free Encyclopedia. Retrieved 05:13, August 10, 2016, fromhttps://en.wikipedia.org/w/index.php?title=Tobacco_harm_reduction&oldid=728767066
-
 @ b6424601:a11e4ff4
2024-10-31 19:36:54
@ b6424601:a11e4ff4
2024-10-31 19:36:54In my old school oversized spiral bound sketchbook with heavy-weight paper, I spend time off-screen writing with a 0.9 mm Pentel mechanical pencil customized with BB soft lead, where I regularly set and track my periodic goals, life planning, and project conception sketches. My longtime project Architect on my studio team calls this sketchbook the Money Maker. On March 3, 2024, the note at the top of the page read, "Have you bought your Bitcoin today? $72,994".As a Spring Semester BTC class of 2021, I loved to buy some BTC at the top. Thinking about a remedy for this “talent” what followed on the sketchbook were some ideas for shifting money flowing through my business, BTC, every two weeks.
I now had options.
Starting in 2024, I had new options to design my personal business strategy after we reworked our partnership agreement for our established professional architecture firm with the help of our attorney and tax account the year before to mitigate the problems of 50/50 ownership.
The business is established and is a survivor of the dot com crash, 9/11, the 3 years after the crash. We have established clients and make a modest profit, and we enjoy focusing on them to get architecture built for them. Through the grind, we stayed ahead but did not thrive.
We changed our corporate structure to retain our original S-Corp status, which allowed us to pay direct and indirect expenses. My partner and I then transitioned to operating as two separate LLCs, each managing one of our studio tribes. We've also planned for future studios to bring in new disciplines or incubate more experienced staff
who can sell enough architecture to support a studio of their own. To manage our studio profit, we have an operating agreement that allocates 30% of our cash-based studio profit to the firm, with the remaining 70% distributed to the individual studios. The architecture firm pays us its monthly management fee directly into our LLC bank accounts. Once the payment is transferred, we have the flexibility to decide how we're paid by our LLC. From that account, I manage our W2 income through a payroll company and allocate the remaining funds as a distribution among tax savings, studio equity and personal spending.
The result = is a little more autonomy to design the best way to retain the profit from energy spent in my business life.
Capturing the flow
In my Money Maker sketchbook, I brainstormed ideas for both personal and business, seeking to think creatively about leveraging our new entity to capture new cash flow opportunities that I could invest in Bitcoin (BTC). By setting up our LLC business account, I could now organize our equity to let it grow without having to convert our profit to BTC immediately, thereby avoiding capital gains or W2 income taxes. My 2024 strategy consisted of three initial moves, which I will elaborate on in more detail after six months of operation.
Treasury
I set up a business account for my studio's corporate treasury with Unchained Capital, utilizing the new EIN for our management LLC. I had previously retained studio profit from the previous year, anticipating the benefits of the new entity. This process was very satisfying, as I was able to transfer our equity into a business account, eƯectively moving it out of the bank and I can see the scoreboard of the growing equity. However, one of the less enjoyable aspects was that my bank couldn't wire directly to Unchained, requiring me to visit a bank, which involved driving to these empty buildings and filling out some paperwork during the hours they happened to be open. After you have jumped through the flaming hoops and moved your fiat into BTC at Unchained, I don't like the lack of control about when Unchained buys BTC. Although, I do like that I don't have to use an intermediary exchange.
Tax Savings
I pay myself a reasonable W2 income using a Payroll service, and then allocate the remainder of my monthly take-home pay as a distribution. Since the payment is a distribution, I must set aside a percentage of my income taxes. Previously, I would simply transfer money to a Tax Savings bank account. With the new system, I can set up a business account in the name of my LLC at River, and automatically transfer funds from my LLC bank account to the River business account on a monthly basis. This setup allows for a DCA (dollar cost average) strategy with 0 cost. My strategy is to continue buying Bitcoin for next year's taxes. I understand that River will be oƯering business accounts with a 3.8% interest rate, paid in Bitcoin. When the subsequent bear market returns, I will make an educated guess about the ratio of interest-bearing assets to BTC tax savings account to ensure I'm prepared when paying taxes on profit made in a bull year that is taxed in a bear year.
Personal Spending
The move involved switching my monthly spending budget to Fold, which allowed me to earn Bitcoin rewards. I started using Fold at the end of 2022 to earn BTC rewards for my spending. Although Fold isn't as exciting as it used to be (I miss the gamification aspect of spinning up 5,000 Sats for a coƯee purchase!), the math still works out, and I can accumulate a few bucks with my personal spending. A further evolution came from listening to Jack Mallers on Episode 245 of The Bitcoin Standard Podcast. Jack was talking about how he lives on a Bitcoin Standard by paying bills with Strike, a service he can access now, but customers don't. As I thought about how cool it would be to keep my monthly expenses in BTC, a metaphorical 2 x 4 struck my brain. Wait a second - I realized that I can buy Bitcoin on Fold and easily exchange it for fiat in the application. I could start living like Jack, starting this month. With this month's spending money transfer to Fold, I bought Bitcoin! As the month goes on, I convert funds as I need them and use my debit card for expenses. Thank you, Jack, for the thought. I'm sorry to be so slow.
With our personal W2 and distribution side organized, we are now working to create ways to capture a portion of our business income cash flow in Bitcoin (BTC). Accepting BTC payments
As an established business with a shared and overworked bookkeeper, I believe the personnel and accounting workaround to dip our toe into Bitcoin is to accept pre-project consultation and initial payments using Zaprite initially. This will allow us to educate our clients on the benefits of using Strike and Bitcoin for payments, and to showcase how the process is more trustless than traditional payment methods like ACH and credit cards. By doing so, we can encourage clients to adopt this new payment method and reduce our reliance on traditional payment systems. Our goal is to make the transition to Bitcoin as seamless as possible for our clients, while also allowing our internal staƯ to become proficient in handling the process. To achieve this, we will be using the discount strategy on Zaprite invoices and will be directing our limited cash flow of BTC directly into our business treasury account. Status: we have set up the Zaprite integration but have not yet received payment.
BTC payment client education
Once our payment strategy is in place, I plan to update our website with a blog that explains how the payment system works and markets our approach to clients. Specifically, I want to highlight that we accept Bitcoin as a payment method and provide clients with the option to choose this payment option on the first invoice they receive from us. By doing so, I hope to spark interest and enthusiasm among clients who are familiar with the benefits of using Bitcoin and want to learn more. With our payment system up and running, we can begin to make a more significant transition away from traditional fiat payment methods and towards a more decentralized, trustless payment system like Bitcoin. This will be a "Titanic like" shift, but one that we believe is necessary to stay ahead of the curve and capitalize on the growing demand for more innovative and secure payment methods.
Beyond implementing a payment system
I am considering setting up a new studio that operates on a Bitcoin Standard (BTS). This idea combines concepts from other readings, such as value pricing and the principles outlined in "Winning Without Pitching" by Jeffrey Gitomer, with the idea of creating a branded house configuration of services that we can offer through the new studio. To research and develop our service product, I plan to use my existing studio's BTC equity and not debt. I will then create a focused website to highlight the new service product. To support the new studio, I will utilize my existing studio staff on projects, as part of their unitization. I also plan to offer sweat equity profit sharing to interested staff who will contribute to the bootstrapped research and development of the service product. I will work with a separate bookkeeping group to report results to our umbrella company. One of the key goals of this experiment is to track the diƯerence in administration costs between the new studio and our existing operations. This will provide valuable insights into how to make the BTS model work for our business without going all-in. Additionally, the new studio setup will serve as a comparison experiment to help us determine when it's time to fully transition to a BTS for the business. By testing and refining this model, “we” (I will have some ammunition to help the others) can make an informed decision about whether to adopt the BTS for all aspects of our business.
The journey to implementing a Bitcoin Standard (BTS) is like a house renovation, where clients live through the process. In our industry, renovations are often more complex than new builds, and the process of evolving an existing business to a BTS is similar. We must navigate the challenges of not disrupting an established system or overwhelming staƯ with new systems and processes. To avoid disruptions, we need to identify a "temporary roof" - a stable foundation that allows us to continue operating while we refine our BTS model. Most importantly, we must listen and be willing to pivot our process for those interested, whether from within our studio or from outside, on how and what we offer.
HODL on
-
 @ 54609048:8e22ba03
2024-10-31 18:52:13
@ 54609048:8e22ba03
2024-10-31 18:52:13The tragic events of September 11, 2001, reshaped the world in profound and unforeseen ways. With thousands of innocent lives lost and countless more injured, the attacks were undeniably devastating. In response, the Bush administration embarked on a warpath—literally—introducing measures aimed at bringing the perpetrators to justice. These included placing a $25 million bounty on Osama bin Laden, initiating the "War on Terror" with the invasion of Afghanistan, and, notably, enacting the draconian PATRIOT Act. Twenty-three years later, while bin Laden is dead and U.S. troops have withdrawn from Afghanistan, the PATRIOT Act remains firmly in place.
Hastily passed six weeks after 9/11 as a preventive measure, the PATRIOT Act effectively neutered the Fourth Amendment and granted federal agencies unprecedented surveillance capabilities. These became the foundation for conducting "sneak and peek" searches, enabling unauthorized access to individuals' online purchases, emails, and browsing histories, and compelling banks to notify the FBI of deposits over $10,000—often sidestepping due process entirely. The irony lies in the fact that this tragedy didn't occur due to insufficient surveillance powers. A Congressional report revealed that intelligence agencies already possessed actionable information to prevent the attacks but failed to coordinate and act on it. Given such findings, one would expect a serious reevaluation of this legislation, but civil liberties have rarely been the state's primary concern, especially when a "good crisis" offers an opportunity to expand control.
Two decades later, we face a bleak reality and unsettling questions: Are we actually safer today? Are there fewer terrorists worldwide? Given the state's shifting definition of "terrorist," what prevents this law from being used against the very citizens it was meant to protect? While pondering these questions, Ben Franklin's famous words come to mind: "They who can give up essential liberty to obtain a little temporary safety deserve neither liberty nor safety." In an age of emerging Artificial Intelligence (AI) and looming threats of central bank digital currencies (CBDCs), the PATRIOT Act could become a cornerstone in establishing a totalitarian technocracy where privacy is a relic of the past—if we haven't already reached that point.
Financial Privacy Implications
In free societies, personal and financial privacy form a vital buffer against government interference, surveillance, and control. Financial privacy, in particular, protects individuals' assets from potential governmental overreach or confiscation based on political, ethnic, or religious grounds. The Canadian government's invocation of the Emergencies Act during the 2022 freedom convoy protests—particularly the freezing of bank accounts belonging to truckers and their supporters—serves as a stark example. This action was later ruled "unreasonable and unconstitutional" by a federal court judge.
While the PATRIOT Act's broad surveillance powers often dominate discussions, its substantial encroachment on financial privacy is frequently overlooked. The Bank Secrecy Act (BSA) of 1970 initially deputized financial institutions in combating money laundering by requiring them to report suspicious activities. The costly and administratively burdensome regulatory framework introduced by the BSA has not only severely eroded the financial privacy of law-abiding citizens but has hardly made a dent in preventing money laundering.
Before the PATRIOT Act, financial institutions were encouraged to adopt Know Your Customer (KYC) practices but were not legally obligated to do so. The BSA established a framework for reporting suspicious activities and maintaining records but did not specifically mandate customer identity verification processes during account opening. The PATRIOT Act, however, intensified these requirements by legally mandating KYC protocols and enforcing Title III, which established strict Customer Identification Programs (CIP) for verifying customer identities.
These expanded measures deeply compromised financial privacy, forcing banks to build detailed customer profiles by collecting personal data and extensively monitoring transactions. Additionally, financial institutions must file Suspicious Activity Reports (SARs) for any transaction over $5,000 that they suspect may be related to illicit funds. The broad definition of "suspicious transactions" compels institutions to err on the side of caution and flag any transaction deemed atypical for a customer, even without clear evidence of wrongdoing. As a result, individuals have almost no control over how their financial data is used and shared with government agencies.
With access to individuals' transactional data and digital metadata from sources like social media, the government can construct an exceptionally precise record of a person's daily activities—what is often called a "pattern of life." This capability allows authorities to surveil and assess a person's actions in real-time, essentially creating a comprehensive view of their life. This level of oversight is particularly troubling in light of former NSA director General Michael Hayden's remark, "we kill people based on metadata," underscoring the potentially lethal implications of unchecked surveillance power.
Thanks to the PATRIOT Act, any money or investments held in a financial institution now essentially function as a conditional permission slip that can be frozen at any time and for any reason. The worst aspect is that, due to the unholy alliance between the state and big business, many of these actions can be carried out by private corporations at the behest of the state. This intertwining of public and corporate power opens the door to unprecedented levels of financial control over individuals, undermining both their financial privacy and personal autonomy.
What Does the Future Hold?
Senate Judiciary Committee hearings following Snowden's revelations highlighted an even more troubling fact: the PATRIOT Act's supposed effectiveness was largely overstated. This stands in sharp contrast to earlier claims in two declassified documents presented to Congress as justification before key surveillance votes in 2009 and 2011, which asserted that mass data collection was essential for detecting terrorist threats.
In 2009, an Al-Qaeda operative nearly succeeded in bombing a Detroit-bound airplane, despite the extensive dragnet surveillance programs that became the norm after the passage of the PATRIOT Act. When Senator Patrick Leahy questioned NSA Deputy Director John Inglis about claims that 54 terrorist plots had been foiled due to the Act, further examination revealed that perhaps only one plot could be loosely attributed to the bulk surveillance program. Given the stated goals of passing this law, it would be an understatement to call it a monumental failure.
This raises a different set of questions: What if this was never really about security but merely an opportunity that the state seized to "legally" establish a surveillance superstructure? Is the "surveillance state" now a permanent feature of our lives? If this reality is to change, it will likely not come from the halls of Congress but from freedom-loving individuals who, in addition to pressuring policymakers, will build new tools. Without new technological solutions that preserve our privacy, it won't be long until we find ourselves living in a dystopian nightmare controlled at every turn by Big Brother.
-
 @ 6e24af77:b3f1350b
2024-10-31 18:35:28
@ 6e24af77:b3f1350b
2024-10-31 18:35:28test
-
 @ 3bf0c63f:aefa459d
2024-10-31 16:08:50
@ 3bf0c63f:aefa459d
2024-10-31 16:08:50Anglicismos estúpidos no português contemporâneo
Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês.
Cada erro é acompanhado também de uma sugestão de como corrigi-lo.
Palavras que existem em português com sentido diferente
- submissão (de trabalhos): envio, apresentação
- disrupção: perturbação
- assumir: considerar, pressupor, presumir
- realizar: perceber
- endereçar: tratar de
- suporte (ao cliente): atendimento
- suportar (uma idéia, um projeto): apoiar, financiar
- suportar (uma função, recurso, característica): oferecer, ser compatível com
- literacia: instrução, alfabetização
- convoluto: complicado.
- acurácia: precisão.
- resiliência: resistência.
Aportuguesamentos desnecessários
- estartar: iniciar, começar
- treidar: negociar, especular
Expressões
- "não é sobre...": "não se trata de..."

Ver também
-
 @ 6903089d:bd117177
2024-10-31 16:06:11
@ 6903089d:bd117177
2024-10-31 16:06:11Nostr and its ecosystem present a novel and unique possibility for digital self sorting. Discoverability has long been one of the main issues of the internet, this issue has to this point been solved through centralized entities. These entities or firms collect data and then present “useful” information to the individual user. It is important to note the subjectivity of what is considered “useful”. In today's world, what is useful is determined by large corporations that have their own agendas that are specifically related to you, your behavior, and your purchasing habits. The data collected from us and presented to us is the front line attack in the war in which anyone who uses a digital product or services finds themself. The process of discoverability - data collection and presentation - has become blatantly manipulative and harmful to everyone that interacts with the digital world.
Self-Sorting Thomas Sowell in “Discrimination and Disparities” talks about the importance of individual choice resulting in the formation of groups of people based on similar interests or wants. Governments and regulatory bodies often use the disparity in the outcomes resulting from this self sorting and claim that process to be unfair and harmful. The next step is to intervene and enforce, through threats of violence, rules and regulations to alter the outcomes so they appear to be more similar, or more fair. Self sorting is a natural process and the resulting disparity in outcomes resulting from self sorting is also a natural process. A society built from the natural self sorting of individuals will lead to a more productive, healthier, and happier, collective. Equality of outcome is the result of sovereign interference and thus assumes the subjectivity of the sovereign body responsible for enforcement.
Digital Sovereign The digital world is still very young. Just as past societies in the real world went through (and are still undergoing) a maturation process, that digital world is ruled by the Monarchs of our past. Twitter, Meta, Google, the Kings of the digital realm. Make no mistake the digital world is a feudal world and it does include the ability to self sort and thus form productive and healthy communities.
Self sorting is a result of the application of work to express and represent personal choice and preference. Is it possible to take that work and collect it in an open-sourced and transparent manner and then voluntarily display it to the Nostr network? Can we take control of our own freedom in the digital world and use our very own, very unique preferences and desires to create an identifiable and readable signal allowing us to navigate towards other individuals that share similar values all the while respecting and empowering individuals who have conflicting values. Imagine a self sorted internet. Where individuals share data of their choosing with the network allowing other people to identify a general quality of values and group together. Allowing companies to see this quality and indicate the possible interest in a good, product or service.
Communities or even individuals will create a quiz. The quiz for a community will need maintainers and the questions that it contains should be determined by the community itself. For quizzes created by individuals the process is less complex as it would be decided by the individual alone. Every quiz and every quiz question would be public. Most quizzes would utilize only multiple choice or agree/disagree statements.
For example lets say that the all of the current 7.2 million members of the Bitcoin community on Reddit took a standard and open sourced quiz on specific thoughts or opinions related to Bitcoin
The questions along with each individual response are put through SHA-256 hash and then that hash could be publicly displayed to the community. Seeing as how the questions are included in the hash it should be possible to compare everyone's individual hash to determine the similarity of the responses that were provided. It is likely that these quizzes would need to be paid for. Cost coupled with the actual time and effort required to complete the quiz generates a proof of work for each quiz taken. People would take many different quizzes and each one would be concatenated into a single hash that over time becomes a unique fingerprint of the individual. Hashes could then be compared and based on the quizzes any person chooses to pay for and take coupled with their individual responses it would be possible to see each individuals hash with a certain quality, almost like a color, that could be used to signal to the entire network the quality of personal values that person has.
-
 @ c69b71dc:426ba763
2024-10-31 16:02:10
@ c69b71dc:426ba763
2024-10-31 16:02:10Risks and Regulations
Food contact materials (FCMs)
Materials that come into contact with food during processing, packaging, or transport – play a critical role in food safety. However, chemicals can migrate from these materials into food, introducing potential health risks. For instance, chemicals can leach into food from packaging materials, especially during microwaving, pasteurization, or other high-temperature exposures. Even printing inks on the outer packaging, if not well-contained, can migrate into the food or drink. Factors like high temperatures, small package-to-food ratios, fatty foods, and long storage times all increase this risk.
More than 12,200 chemicals have been identified in FCMs, but only about 100 substances are regulated by the European Union, focusing mainly on plastics. The actual composition of many materials is often undisclosed due to proprietary protection, making it challenging to assess risks fully. Even less is known about secondary substances, which may arise from additives breaking down during manufacturing.

In 2016, EU regulation defined publicly that current regulations do not sufficiently protect public health from the harmful impacts of chemicals migrating from food packaging. The current paradigm for evaluating the safety of FCMs is insufficient, as there is a general underestimation of the role of FCMs in food contamination and a lack of information on human exposure. FCMs are a significant source of human exposure to chemicals of concern, including perfluorinated compounds (PFCs) and endocrine-disrupting chemicals (EDCs), as well as those linked to neurodevelopmental issues.
Moreover, the legal framework doesn’t account for the cumulative "cocktail effect" of multiple low-level chemical exposures, which can collectively exceed safe limits. Research shows that FCMs can contribute to serious health issues like cardiovascular disease, diabetes, obesity, neurological disorders, and cancer. Although packaging is designed to preserve food, maintain quality, and extend shelf life, its chemical impacts remain insufficiently regulated, posing risks that demand greater transparency and robust oversight.
So what can we do?
Be mindful and use less packaged food. Plastic is sometimes even less harmful than paper, as many chemicals and synthetic materials are used in paper production to improve texture and prevent humidity from transferring through the paper packaging. Additionally, the barrier between ink and food in paper packaging is often not very effective. Chemicals are mostly invisible...!

-
 @ c5fede3d:16e03f7b
2024-10-31 15:02:39
@ c5fede3d:16e03f7b
2024-10-31 15:02:39El terror inundó Valencia. Caos, culpa y resignación. Así fue la noche del día de ayer para los valencianos. Cayó tal cantidad de agua, que dejó a todos patidifusos ante este fenómeno natural. Lo que en un pasado fue conocido como Gota Fría, y hoy denominado Dana por los vividores del cambio climático™, hizo acto de presencia. Su paso fue tan devastador que no se veía tal grado de virulencia desde los años 50 del siglo pasado. Fueron horas críticas y de consecuencias fatales, pero pasada la tormenta llega la calma, o eso es lo que quieren que creas.
El Día Después ha llegado, es la hora de contar los múltiples desperfectos materiales; cómo han caído las estructuras que mantenían las redes de telecomunicación fruto de la tempestad, hacia dónde fueron a parar los incontables coches que fueron desplazados por la riada, y, sobre todo, la parte más crítica y omitida del relato, qué pasó con las personas desaparecidas. Al momento que redacto esta nota, el recuento oficial de muertes se eleva a un centenar, que previsiblemente se elevará dada la confirmación del destino de los desaparecidos. ¿Realmente ha llegado la calma tras la tormenta? Permítanme dudarlo.
El Día Después exige duelo por las víctimas y reparaciones para los damnificados, pero también respuestas. ¿Pudo haberse evitado esta desgracia? Probablemente sí. ¿Qué hubiese sido de nosotros si el aviso de emergencias se hubiera transmitido antes de las 20:00, hora crítica del desastre? ¿Por qué los políticos no movieron un dedo, con un plan de previsión, cuando se sabía, cinco días vista, que las consecuencias podrían ser fatales? ¿Dónde estaban los responsables de desmantelar servicios públicos de emergencias y presas cuya misión es la de prevenir desgracias? ¿Por qué había gente obligada a trabajar con el agua por la cintura?
Son muchas cuestiones las que asolan en el Día Después. Todas ellas quedarán sin responder y sin reparar, el duelo servirá de silencio para expiar la culpa de los responsables. Mientras, parte de la ciudadanía consciente se moviliza para ayudar en todo lo posible a los damnificados, una caridad no correspondida, pues los impuestos sirven para sufragar a quien tiene las competencias para ayudar, pero ante la inacción de la instancia superior, no queda otra que arroparse unos a otros. La otra parte de la ciudad, poblada por okupas y egoístas, solo se limitará a observar, y quien sabe si a rapiñar. Este es el Día Después de la Gota Fría. Espero que sirva para aprender algo.
-
 @ 361d3e1e:50bc10a8
2024-10-31 14:38:53
@ 361d3e1e:50bc10a8
2024-10-31 14:38:53https://forex-strategy.com/2024/10/31/a-doctor-with-50-50-vaccinated-unvaccinated-children-tells-what-the-difference-is/ A doctor with 50/50 vaccinated unvaccinated children tells what the difference is
usa #vaccine #children #truth #freespeech #paulthomas
-
 @ 8d5ba92c:c6c3ecd5
2024-10-31 12:56:44
@ 8d5ba92c:c6c3ecd5
2024-10-31 12:56:44🧡 📄 October 31st, 2008 | The Bitcoin WhitePaper
For many of us, Bitcoin is much more than just a decentralized form of money. I’d even dare to say it’s the best form of money humanity has ever had—and will ever have! But Bitcoin goes beyond just being money, no matter how sound it is.
With respect for the topic, to keep this piece at a reasonable length, I’ll skip other important aspects and instead focus on Bitcoin, art and culture.
Indeed, Creativity Has Many Hands and Faces...
For years, many talented rebels from around the world—yes, artists are the group I mean here—have built a unique ecosystem of works that focus on truth, freedom, and Bitcoin. To honor their creative side and mark today’s special day, let me share some of my favorite pieces from last year’s Bitcoin Whitepaper Day.
by Flo Montoya (nostr:npub1zw0uc6anqjeg0xt5ckwd5cwcd4updt22crecaea8yn053qrquewswctfhf ) https://i.nostr.build/wgj5C4oBDtWtxxuu.png
by 0711_₿itcoin (or actually his father) https://i.nostr.build/qNi7VvpapS6ZAcPa.jpg
by Loꓘo 🦝 BTC https://i.nostr.build/XU1DYNTfOFOLGAn3.png
by MaxisClub (nostr:npub1pazuhetzx5w8yyt59lszeslxlywkeadnq6rncre7nlqv2uxnxuwq8c56r9 ) https://i.nostr.build/ZRyKIviBl0pd9gf2.png
by Bitcoin FilmFest (nostr:npub1rjtrs7xqdvj3588r9njrexh2n750j7jdwx9qs543nutmdsj6ljaqpfmp8a ) https://i.nostr.build/qt8bcr16fDkQfrkQ.jpg
Got your favorites too? Please share! I’m curious to see what this year brings… We’ll find out soon, starting on October 31st.
*BTC Your Mind. Let it Beat.
Şelale Malkoçoğlu*
I’s hard to believe it’s been 16 years already...
THANK YOU, Satoshi Nakamoto! Wherever you are, BE SAFE!
To the man who change the world. And to everyone else, at the end of the day...
"We Are All Satoshi..."
Happy Whitepaper Day!
-
 @ cf5b8c65:494a0912
2024-10-31 11:55:39
@ cf5b8c65:494a0912
2024-10-31 11:55:39Estoy probando un plugin para Obisidian que permite publicar directamente en NOSTR los artículos que has creado en Obsidian.
-
 @ 081f3b0c:c00498a5
2024-10-31 11:52:15
@ 081f3b0c:c00498a5
2024-10-31 11:52:15Muchas son las maneras de referirse a la compra y mantenimiento de Bitcoin en cartera. Muchas también son las maneras de almacenarlo. Y, aunque en realidad NADIE almacena Bitcoin, sino llaves privadas y llaves públicas, no es de mi interés entrar hoy en esos tecnicismos.
Hoy quiero escribirle a la gente de a pie, los trabajadores, emprendedores, empresarios y todo aquel que se interese por lo menos un poquito en su futuro y el de los suyos. Hay algo que todos los Bitcoiners sabemos pero que muchos de ustedes no lo experimentan hasta llevarse un buen susto en su primer año de inversión (Hablaré en todo el artículo de manera indistinta entre inversión y ahorro en Bitcoin ya que en el largo larguísimo plazo y mirando a Bitcoin como moneda pero también como activo, pueden utilizarse ambos términos). Lo que no saben los que miran desde afuera, es que muy poca gente compró Bitcoin en centavos o pocos dólares (o lo minó en épocas tempranas) y todavía lo mantienen en cartera. Me arriesgaría a decir que este numero de individuos no supera unos pocos miles. Muchos no-coiners creen que los bitcoiners compraron a dos centavos se durmieron 15 años y hoy son todos ricos, pero la mayoría de los early adopters, se hundieron intentando navegar las profundas y peligrosas aguas de la custodia y el HODL.
Para quien todavía esté medio perdido y quizás este sea el primer artículo que lea, HODL es una manera "chistosa" de referirse a mantener Bitcoin en cartera, y se remonta allá por el 2013 donde un usuario quiso decir que estaba Holdeando (manteniendo) Bitcoin en cartera y lo escribió como HODLING. Pasó a la historia y hoy se usan HODL y HOLD de manera indistinta como chiste interno Bitcoiner.
En fin... Las profundas aguas... Holdear Bitcoin no es sencillo para las masas. Imaginate que tenés un activo en tu cartera, o compraste a 100 dólares y ahora vale 1.000. Lo venderías verdad? Y si vale 20.000 dólares? Ahí si lo venderías? Estarías multiplicando tu inversión como nunca. Bueno, a esa decisión se enfrentaron y se enfrentan TODOS los holders de Bitcoin más temprano o más tarde. Incluso aquel loco que compro por el 2017 en un precio de 20.000 hoy puede decidir vender y multiplicar casi por 4 su dinero en unos pocos años. Ni hablar de ese estresante momento que habías comprado en 69.000 dólares y lo viste bajar hasta los 17.000 dólares, unos cuantos meses de sufrimiento y temor... Más de uno se asustó de verdad y vendió todo, solo para verlo unas horas más tarde por arriba de los 20.000 y un año más tarde nuevamente en 70.000 dólares.
Si bien no me gusta poner el foco en el precio, lo que intento ilustrar es lo DIFICIL que puede ser ver tu inversión en máximos o en mínimos y aún así decidir mantenerla unos cuantos años más. Es dificil, aún para los que viven su tercer o cuarto ciclo de mercado. Pero se hace más y más fácil a medida que uno avanza en el famoso "rabbit hole" de Bitcoin y empieza a entenderlo desde las bases, cada vez mejor. Este camino también es arduo, entender de Bitcoin requiere un poco de conocimiento en cada campo, hay que saber un poco de tecnología, un poco de redes, un poco de seguridad informatica, una pizca de teoría de juegos, una apasionante cantidad de macroeconomía, y hasta un interés genuino en lo que Mises llamó "La acción Humana". Y todo esto, uno lo va a prendiendo con ganas y de a poco sólo para llegar a la conclusión, meses o incluso años después, de que Bitcoin tiene que ser un activo por siempre en la cartera de uno, no se vende. Incluso hay quienes llegan al punto (como este humilde ser que escribe) que no poseen otro tipo de ahorro o inversión que no sean sus pocos o muchos satoshis en Billetera Fria.
Mi recomendación siempre será que DYOR, "do your own research", investiguen, lean, pregunten, únanse a #nostr que tiene la mejor comunidad del mundo a la hora de ayudar a otros usuarios, pero si no llegan a tener el tiempo de leer y progresar sólo tómenme estos dos consejos:
- Háganse el tiempo para leer.
- Stay humble y stack sats (De a poco y constante, todo ahorro mensual que uno haga, está mejor guardado en Bitcoin, siempre gastando menos de lo que ingresa esto no debería ser dificil).
Otra dificultad que encontramos además de la parte emocional y humana relacionada con los precios y el desconocimiento, es la custodia. Cientos de personas perdieron TODO su Bitcoin por no saber almacenarlo correctamente. Decenas de maneras de almacenar claves y sin embargo muchos usuarios de Bitcoin no se sienten del todo seguro durante sus primeros años de inversión, y no están el todo equivocados... Por un lado puede ser tan sencillo como guardar 24 palabras. Por otro lado, puede no ser tan fácil, dependiendo del tipo de usuario. Entraremos en detalles de custodia en el próximo artículo.
Saludos!
El Tío.
PD: No es consejo de inversión.
-
 @ 892ab9bd:e686de59
2024-10-31 11:28:38
@ 892ab9bd:e686de59
2024-10-31 11:28:38Understanding the Future of Decentralized Social Media
 The Issues with Traditional Social Media
The Issues with Traditional Social MediaThe issues with social media are well-documented. Facebook and Twitter started out as information distribution networks, but through censorship and algorithmic curation, the experience they used to provide continues to be tainted by politics and biases. Certain narratives are suppressed; certain personalities are de-platformed, and all the while, advertisers are in a race to bid for your eyeballs on every scroll.
The Rise of Nostr
Since the decay of legacy social media, many apps have tried to break their network effects with little or no success. Platforms like Gab, Truth Social and Mastodon launched with massive fanfare but have slowed down in recent years. While Nostr is being hailed as the next big alternative to social media apps like Twitter as its first use case for the protocol. While the platforms mentioned above specifically target a certain social media user Nostr doesn’t; it can’t. Nostr is only a protocol for relaying data between different users; how clients display this data is up to them.
How Nostr Works
Nostr relies on relays. There is no Nostr app, there is no Nostr website; there is no Nostr company. Nostr is a protocol that provides censorship-resistant communications on the internet. Nostr uses "dumb" relays to forward messages from one user to another. Anyone can spin up a private and public key pair, connect to a relay via a client of their choice and broadcast their information, in many cases a post, to one or several relays.
Key Features of Nostr
- Decentralized: Nostr is a decentralized network, meaning there is no central authority controlling the flow of information.
- Flexible: Clients can display data in various formats, from short-form content like Twitter to messageboard-style formats like Reddit.
- Censorship-Resistant: Nostr's design makes it difficult for any single entity to censor content.
How Nostr Relays Work
Every user is identified by a public key. Every post is signed. Every client validates these signatures. Clients fetch data from relays of their choice and publish data to other relays of their choice. A relay doesn’t talk to another relay, only directly to users.
The Benefits of Nostr
- Censorship Resistance: Nostr's design makes it difficult to boot someone off the platform completely.
- Flexibility: Users can choose which relays to broadcast on and which to ignore.
- Decentralized: No single entity controls the flow of information.
How is Nostr Different?
Nostr takes another stab at a decentralized social network without the need for a blockchain or the need for you to spin up a subdomain on a server. Unlike Mastodon, where user identities are attached to servers and servers have a degree of control over registered users, Nostr is far more open and fluid thanks to its reliance on relays.
Components of Nostr
There are two components at play on Nostr: Clients and Relays. Each user interacts with a client they prefer; this could be a web app, iOS app, Android app or Desktop application. While anyone can run a relay, think of this as a storage system that you can use or allow others to use to house their posts.
How Nostr Clients Work
Clients can publish data (i.e. create posts, likes, re-shares etc.) on any number of relays and fetch data from other relays to see what accounts they follow are up to online. Each user is assigned a public key. When a user follows someone, the user’s client fetches posts associated with that someone’s public key from the associated relay. This process is repeated on start-up, with the client querying data from all relays it knows for all users it follows.
Censorship Resistance in Nostr
Nostr has built-in censorship resistance. It sounds complicated, but such an implementation solves several flaws, such as the ability to back up your content locally and choosing which relays to broadcast on and which to ignore. That means when a relay rejects your content or shuts down, your data and account are still safely stored on your local or any relays that are still happy to house your content.
Running Your Own Nostr Relay
Platforms like Yakihonne and many other support the use of Nostr and Creation of Relays.
Source: https://thebitcoinmanual.com/articles/nostr-relay/
-
 @ 5f2f01bc:c7b3eadc
2024-10-31 11:27:59
@ 5f2f01bc:c7b3eadc
2024-10-31 11:27:59Muchas son las maneras de referirse a la compra y mantenimiento de Bitcoin en cartera. Muchas también son las maneras de almacenarlo. Y, aunque en realidad NADIE almacena Bitcoin, sino llaves privadas y llaves públicas, no es de mi interés entrar hoy en esos tecnicismos.
Hoy quiero escribirle a la gente de a pie, los trabajadores, emprendedores, empresarios y todo aquel que se interese por lo menos un poquito en su futuro y el de los suyos. Hay algo que todos los Bitcoiners sabemos pero que muchos de ustedes no lo experimentan hasta llevarse un buen susto en su primer año de inversión (Hablaré en todo el artículo de manera indistinta entre inversión y ahorro en Bitcoin ya que en el largo larguísimo plazo y mirando a Bitcoin como moneda pero también como activo, pueden utilizarse ambos términos). Lo que no saben los que miran desde afuera, es que muy poca gente compró Bitcoin en centavos o pocos dólares (o lo minó en épocas tempranas) y todavía lo mantienen en cartera. Me arriesgaría a decir que este numero de individuos no supera unos pocos miles. Muchos no-coiners creen que los bitcoiners compraron a dos centavos se durmieron 15 años y hoy son todos ricos, pero la mayoría de los early adopters, se hundieron intentando navegar las profundas y peligrosas aguas de la custodia y el HODL.
Para quien todavía esté medio perdido y quizás este sea el primer artículo que lea, HODL es una manera "chistosa" de referirse a mantener Bitcoin en cartera, y se remonta allá por el 2013 donde un usuario quiso decir que estaba Holdeando (manteniendo) Bitcoin en cartera y lo escribió como HODLING. Pasó a la historia y hoy se usan HODL y HOLD de manera indistinta como chiste interno Bitcoiner.
En fin... Las profundas aguas... Holdear Bitcoin no es sencillo para las masas. Imaginate que tenés un activo en tu cartera, o compraste a 100 dólares y ahora vale 1.000. Lo venderías verdad? Y si vale 20.000 dólares? Ahí si lo venderías? Estarías multiplicando tu inversión como nunca. Bueno, a esa decisión se enfrentaron y se enfrentan TODOS los holders de Bitcoin más temprano o más tarde. Incluso aquel loco que compro por el 2017 en un precio de 20.000 hoy puede decidir vender y multiplicar casi por 4 su dinero en unos pocos años. Ni hablar de ese estresante momento que habías comprado en 69.000 dólares y lo viste bajar hasta los 17.000 dólares, unos cuantos meses de sufrimiento y temor... Más de uno se asustó de verdad y vendió todo, solo para verlo unas horas más tarde por arriba de los 20.000 y un año más tarde nuevamente en 70.000 dólares.
Si bien no me gusta poner el foco en el precio, lo que intento ilustrar es lo DIFICIL que puede ser ver tu inversión en máximos o en mínimos y aún así decidir mantenerla unos cuantos años más. Es dificil, aún para los que viven su tercer o cuarto ciclo de mercado. Pero se hace más y más fácil a medida que uno avanza en el famoso "rabbit hole" de Bitcoin y empieza a entenderlo desde las bases, cada vez mejor. Este camino también es arduo, entender de Bitcoin requiere un poco de conocimiento en cada campo, hay que saber un poco de tecnología, un poco de redes, un poco de seguridad informatica, una pizca de teoría de juegos, una apasionante cantidad de macroeconomía, y hasta un interés genuino en lo que Mises llamó "La acción Humana". Y todo esto, uno lo va a prendiendo con ganas y de a poco sólo para llegar a la conclusión, meses o incluso años después, de que Bitcoin tiene que ser un activo por siempre en la cartera de uno, no se vende. Incluso hay quienes llegan al punto (como este humilde ser que escribe) que no poseen otro tipo de ahorro o inversión que no sean sus pocos o muchos satoshis en Billetera Fria.
Mi recomendación siempre será que DYOR, "do your own research", investiguen, lean, pregunten, únanse a #nostr que tiene la mejor comunidad del mundo a la hora de ayudar a otros usuarios, pero si no llegan a tener el tiempo de leer y progresar sólo tómenme estos dos consejos:
- Háganse el tiempo para leer.
- Stay humble y stack sats (De a poco y constante, todo ahorro mensual que uno haga, está mejor guardado en Bitcoin, siempre gastando menos de lo que ingresa esto no debería ser dificil).
Otra dificultad que encontramos además de la parte emocional y humana relacionada con los precios y el desconocimiento, es la custodia. Cientos de personas perdieron TODO su Bitcoin por no saber almacenarlo correctamente. Decenas de maneras de almacenar claves y sin embargo muchos usuarios de Bitcoin no se sienten del todo seguro durante sus primeros años de inversión, y no están el todo equivocados... Por un lado puede ser tan sencillo como guardar 24 palabras. Por otro lado, puede no ser tan fácil, dependiendo del tipo de usuario. Entraremos en detalles de custodia en el próximo artículo.
Saludos!
El Tío.
PD: No es consejo de inversión.
-
 @ fd78c37f:a0ec0833
2024-10-31 11:14:59
@ fd78c37f:a0ec0833
2024-10-31 11:14:59Taryn Christiansen
Discussions with Eric Zhang.
The first part of this critique can be found here. A Nostr mirror publication of this article can be found here.
Section 1:
In the previous article, our Interns argued that autonomy is the principal end of the state. Human subjectivity can be divided into at least two parts, one quantitative and the other qualitative. Both have their respective needs, whose dissatisfaction results in dehumanizing conditions. The state’s aim is not merely to provide conditions by which people can pursue their self-interests. It is also concerned with promoting the development of their capacities for reflective deliberation and choice.
The present article will move to focusing on means rather than ends. The relevant question will be: How should a network state achieve this end? Fortunately, Balaji Srinivasan offers an approach to answer this: the idea of a one-commandment. That is, a one-premise moral critique of one or several preexisting nation-state(s) that will serve as a basis, a foundational starting point, to build a network state. However, his examples of one-commandments in the book tend to be impoverished in two senses. First, while his suggestions of one-commandments tend to be moral, they lack meaning. His example of a keto-diet society could be understood and expressed in moral terms, such as criticism regarding the public and private health of a society, but that doesn’t mean it will be meaningful enough to provide a vision about a greater good, whatever that may be, which people identify with and pursue, and that provides certain kinds of motivations to act on. The second issue is that one-commandments are also supposed to function as principles that guide the legal decision-making procedures of the society. The worry is that an individual commandment will be unable to accommodate all cases that arise in legal matters, and will easily devolve into morally troublesome situations. As will be discussed below, Balaji offers a solution by suggesting that network states adopt a preexisting legal codebase from a nation-state after formulating a one-commandment. This, too, has its difficulties. Throughout this article, I will use the United States as an example, and when such a case is invoked, it can be seen that, if Srinivasan’s proposal is employed, a network state would be beset by its attempt to reconcile the various preexisting legal parameters of a nation-state’s legal codebase, such as its forms of legal reasoning, modes of justification, and precedent, with its one-commandment.
There are therefore two conditions that a one-commandment must meet. It must be moral and sufficiently meaningful, and, secondly, it must be capable of generating principles that can guide the legal reasoning within the society, which will form consistent, coherent, and precedented justifications that establish the authority and legitimacy of the state. However, by satisfying these two conditions, a further problem arises. If a one-commandment is meaningful and can guide decision-making procedures within the society, it won’t be able to be formulated in a formal language that is appropriate for smart contracts. This is a problem because of certain statements made by Balaji in his book. At several points, he suggests that the constitution of the society will be in the form of a smart contract. However, smart contracts require certain properties that one-commandments should not, in principle, have if it is to satisfy the conditions above. For example, smart contracts operate by a set of fixed and specified rules that either hold or do not hold. Their functioning properly requires that the rules programmed into the contracts are determinate and should not require interpretation or discretion. A good one-commandment, though, should not be of this kind. This will all be explained in more detail below. For now, what’s important is understanding that one-commandments must satisfy the conditions. The task now is to understand these two conditions better. Let’s begin with the first.
Section 2:
The first condition is one about meaning. Not only should a one-commandment be a moral critique; but it should also be meaningful. Now, questions like ‘What is meaning?’ are inherently difficult to answer, and I will not attempt that. A more manageable approach is to look at the effects of meaning. It’s fair to say most have an instinctual grasp of what meaning is. We may not be able to conceptualize and articulate it, but we have an intuitive feel that allows us to point it out. Finding answers to difficult and troubling questions, writing a book, getting a dream job, and achieving goals are meaningful experiences. Many may not be able to express why, but they know and feel them to be so, especially through how they affect those who have them. The same approach can be adopted here. A meaningful society would produce certain kinds of effects indicative of meaning. But what are these effects supposed to look like? An important one is the effect of people being captured by what society presents as the good, which people identify with, take up, and develop in their lives. If a society is meaningful, and if what it presents is worth adopting, then one outcome should be that individuals within the society concern themselves with developing and understanding it. One apparent way to see this is when individuals create out of what a society presents. The United States serves as an example of this. Before turning to that example, something more should be said about why meaning is central to founding network states.
What makes meaning important is that it has to be admitted that reaching diplomatic recognition amongst other sovereign states is an arduous enterprise. To be sovereign is to compete with other nations, which is a potential threat to their sovereignty. And because such recognition must be leveraged; because it is highly plausible that nations primarily act from self-interest and rarely from any motivation that borders on goodwill, network states must be sufficiently motivated by a vision that they find meaningful enough to strive toward, and are willing to persevere through the issues and hardships that arise. Therefore, it should be a principal concern of any founder to undertake a serious and thorough investigation of what is worth criticizing about preexisting nation-states that will get at the heart of the issues that people find disillusioning, alienating, oppressive, dehumanizing, or obstructing about modern societies, which, when well understood, can be articulated and expressed in ways that positively affect people’s motivations, and that moves them to join a network state.
Let’s turn now to the United States as an example of a country that proved to be meaningful. I propose that the founders of the United States offered a project worth wrestling with. That is, they provided an ideal worth poeticizing and writing literature about, that was worth developing and coming to terms with which was meaningful enough to salvage and maintain despite its flaws and contradictions. It produced images that moved people and provided a sense of being a part of something bigger and more significant than themselves. The fact that many artists, writers, and philosophers devoted their creative resources toward the American project, who tried to work out its tensions and make progress in its promises of equality and freedom by understanding and elucidating its foundations and concepts, is evidence of the reality of what the United States attempted to do. Despite what the country got wrong and what it grossly failed to live up to, it grasped something true, which can be seen by how the society breathed life into the imaginative capacities of its people.
It is well known that the Founders of the United States were deeply influenced by the Enlightenment, especially the philosopher John Locke. It was Locke who offered a certain conception of a state of nature, where human beings are born free and equal and where each has a natural right to life, liberty, and property, that was expressed in Thomas Jefferson’s famous declaration that certain truths are held to be ‘self-evident’. These are truths supposedly discernible to anyone with the rational faculties necessary for ascertaining them. Locke believed that once someone has done the reasoning themself; who has followed the light of reason on its definite paths, these moral propositions will be illuminated as if they were mathematical axioms or basic expressions of arithmetic. They would be so firmly impressed upon the mind that no rational person could deny them. He writes in his Second Treatise on Government, “The state of nature has a law of nature to govern it, which obliges everyone: and reason, which is that law, teaches all mankind, who will but consult it, that being all equal and independent, no one ought to harm another in his life, health, liberty, or possessions: for men being all the workmanship of one omnipotent, and infinitely wise maker.” If all the layers of society are peeled away, what lies underneath is a natural condition of equality and freedom. No divine hierarchy orders human beings by referring to their relation to an infinite being that justifies Monarchic authority, or the Church's claims to legitimacy. In a natural state preceding all social conventions and rules are natural laws that grant rights to those under it, and a legitimate government, one that may be properly said to have and wield authority, establishes the protection of people’s rights through the rule of law. Because in a state of nature, people must self-govern, they may easily overstep and try to violate the rights of others. They may steal the property of another person, restrict or take the freedom and liberty of someone else, or even take someone’s life; and since there is no central authority but only individuals, enforcing rights can be dangerous and costly. A good government would reduce and channel people’s dispositions toward self-interest and vice, directing it toward better, more productive ends. Thomas Paine, who played a fundamental role in galvanizing the people for the cause of revolution, wrote in his famous pamphlet Common Sense in 1775, “Government, like dress, is the badge of lost innocence; the palaces of kings are built upon the ruins of the bowers of paradise.” So, he agrees with Locke: government is a necessary evil because human beings cannot sustain and enjoy their natural rights to freedom and equality independent of external constraint.
Now, whether or not normative natural laws exist is not important here; what matters is that Locke held such a view and that the Founders were influenced by it when writing the country's founding documents. In having this view, Locke provided the initial concepts of freedom and equality at the forefront of how the United States conceived of itself over time.
What’s essential to this view of natural rights is that underlying it are claims about an ahistorical element of human nature that is not subject to social and cultural conditions. This aspect of human beings stands outside of time. As Locke believed, human beings’ capacity for reason is the locus of dignity and respect owed to each person. By having contact with truth, with being able to reason to it, and because truth is good, the ideal of a good society is to promote the right human faculties that have access to it. And to achieve this, a free, democratic, liberal society is necessary. Only if human beings exercise these faculties for themselves, enabling them to rationally discern these ‘self-evident’ truths, can this vision of human potential be realized. The people must be able to self-govern and not depend on a patriarch or dictator to do it for them. For human beings to realize the fundamental dignity that characterizes them; for a free, equal, and just society of autonomous individuals to exist, the people must be able and willing to participate and uphold a democracy that places the responsibility of their well-being in their own hands. However, as the French philosopher Montesquieu points out in his work Spirit of the Laws, which was also profoundly influential for the founders, democracy, as a form of government, requires virtue. He writes that in an aristocracy or a monarchy, “the force of laws in one, and the prince’s arm in the other, are sufficient to direct and maintain the whole. But in a popular state (like a democracy), one spring more is necessary, namely, virtue.” If the people are not virtuous; if they do not act from the right source that grounds their dignity and respect but from human wickedness and vice; if unable to actualize what is necessary for self-governance, then democracy will not work, and the American project will fail.
The takeaway from this philosophical vignette is that the foundations established in the United States held freedom, equality, and democracy as fundamental values that would animate the society, and that would lead to reimaginings of what those concepts mean over time. These are deep sources of meaning for those who identify as Americans, regardless of what part of the political spectrum one is on. Every political speech has to pay homage to these ideas. The use of the word freedom alone by a politician in the US can legitimize what they say to the public, even if their words are empty and lack significance. But when used properly and with meaning, they culminate into the highest expression of American society. While the language of Martin Luther King Jr is religious, it is also fundamentally American, and it was his ability to understand, develop, and wield that language that made him such an influential figure. Since America’s inception and development, the language of rights, freedom, equality, and democracy has become ubiquitous in the context of morality and human value, which points to how meaningful these concepts are. American literature also played a central role in this development.
American literature is an example of those within the society trying to come to terms with what these ideas mean, how to understand them, and how life should be lived in light of them. The example I want to look at is the 19th-century American Transcendentalist movement, with figures like Ralph Waldo Emerson, Henry David Thoreau, and Walt Whitman. As thinkers, these three certainly have their differences, but what is continuous is the attempt to expound an individualism that is the source of a universal nature. By being an individual, as someone free and ‘self-reliant’, who does not conform to external constraints but relies on their internal intuitions, who trust themselves through and through, a truly democratic society may be realized. One should not be a product of mere circumstance; one must actively shape it. Emerson writes in his essay Self-Reliance that “there is a time in every man’s education when he arrives at the conviction that envy is ignorance; that imitation is suicide; that he must take himself for better or worse as his portion; that though the wide universe is full of good, no kernel of nourishing corn can come to him but through his toil bestowed on that plot of ground which is given to him to till. The power which resides in him is a new nature, and none but he knows what that is which he can do, nor does he know until he has tried.” Each individual has a unique and authentic self, differentiated from everyone else, and the noble life to pursue is one of uncovering this potential. To carve a path distinct from all that has come before is to lead a virtuous, spiritual life of freedom.
In the case of Henry David Thoreau, he gives his individualism a political salience, especially in his essay Civil Disobedience. There he argues that until people can participate in a democracy by using their conscience, by their capacity to discern the right for themselves, independent of what others say, think, or do, will the government be less liable to corruption. He begins the essay in agreement with Locke and Paine, saying, “I heartily accept the motto - ‘That government is best which governs least.’” Government is an expedient, he says, something purely instrumental, and what matters for society is for the people within it to realize their own moral conscience, which, of course, requires the exercising of their faculties, of their capacity for moral deliberation and choice. No one can do this for anyone else; in a democracy, where a majority may easily wield power unjustly by the sheer use of numbers, it is the responsibility of the individual to participate in the political processes by thinking for themselves, which must be directed toward justice and virtue, just as Montesquieu argued. And when government fails, when it does live up to its sole purpose which is to promote the well-being of the society, then it is the duty of its citizens to peacefully disobey the law, to obstruct its processes, until justice emerges and the rights of people are restored. This has been one of the most lasting contributions made by an American: it provided Gandhi and Martin Luther King Jr. a way to demonstrate the injustices they dedicated their lives to eradicating.
Whereas Thoreau and Emerson focused more on individualism, Walt Whitman focused more on what unites and what is universal about human beings in a democratic context. The political scholar George Kaleb writes, “Together with Emerson and Thoreau, Whitman tries to draw out the fuller moral and existential significance of rights. These are the rights that individuals have as persons and that the political system of democracy exists in order to protect.” Whitman’s poetry attempts to animate a democratic spirit, a national identity, that ‘the people’ identify with, and that moves them to feel the sanctity of individual rights. If democracy is going to work, the society must be animated by a sense of connectedness whose source produces the tolerance, sympathy, understanding, and moral conscience necessary for people to self-govern, and for individuals to choose the lives they wish to live. But this can only be achieved if the notion of rights sparks feelings of reverence, of emotions that dispose one to care for the dignity of other people, both in action and thought; otherwise, the society will surely either devolve into a tyranny of the majority or an elite aristocracy that governs over the community. In America, as the Transcendentalists saw it, what is universal is the individual, with each one’s infinite potential for becoming, and democracy and its virtues must promote the right of the individual to cultivate this potential for themselves.
The founding of the United States, then, and its underlying principles of rights, freedom, equality, and democracy, were sufficiently rich enough for subsequent generations to reimagine and reinterpret, through poetry, literature, and philosophy, what it means to be an American. Those who identified with the country and found it meaningful were willing to direct their efforts toward developing an ethos within the United States. This is of course a tall order, and the expectation of what a network state is, or what it should become, will likely be less than this example. Nevertheless, the U.S. is founded on principles rather than ethnicity or religion - or at least in principle - which serves as a model for network states and their one-commandments.
Satisfying the first condition means putting forth a project worth investigating, developing, and creating out of. If a network state is to have longevity, then the founders must spend their time establishing principles that will move people to envision a better mode of life that elicits motivating reasons to care for its inception and growth. And, of course, there will and should be a great deal of diversity between what networks states formulate as principles worth living by. There is likely a plurality of solutions that have the potential to make people better off. The environments people grow and develop in, the cultures they're embedded in, and the values instilled, are diverse. Therefore, the socio-political structures most conducive to each group's well-being will be too. However, what should not be diverse is the goal to provide a vision of a better life for those who desire to leave preexisting nation-states and join a network state.
Section 3:
Let’s turn now to the second condition. The question to be turned to is how principles can be formulated that will guide the decision-making procedures within a network state. This question can be thought of as one about the nature of principles. What should principles look like? I don’t aim to offer an exhaustive answer to this question, but, again, if the focus is on a significant aspect of principles, it will be helpful to look into and analyze it. Such an aspect can come to light by distinguishing principles from rules. What is significant in this discussion is that, whereas rules can be encoded into smart contracts, principles cannot. Rules are mechanical by nature, whereas principles require interpretation when applying them in context, especially in unprecedented situations. An example of this is the United States. When the Declaration of Independence states that all people are created equal, the document presents a principle by which the society will operate. Such a principle cannot be captured by a formal language appropriate to technologies like smart contracts. This will be explored with more detail below, but to herald what that will look like, think about how this principle could be captured by a language that is by its nature binary. That is, a language that necessitates formulating conditions that either obtain or do not obtain. A smart contract that is prone to ambiguity, and that lacks resources to determine whether something has been met or not is a defunct one; one that hasn’t been properly coded according to possible situations that will or may arise. On the other hand, rules are of a kind that do exactly this and are therefore viable candidates for smart contracts. Principles guide a society’s decision-making procedures, which generates rules that align with the principles themselves. This will also establish the legitimacy of a network state. When people join a network state, what they’re essentially agreeing to is the set of principles that will used to govern the society. And if no principles are formulated, or if they are but are poorly articulated and understood, then the justifications employed by the state will be impoverished in quality as well. Punishment is a great example of this. Every state must have an apparatus to administer punishments for those who violate the rules, and if those rules do not correspond to a firmly established standard that creates consistency and coherence between them, then the applications of those rules can easily produce inequalities, unfairness, injustices, etc. And what right does a state have to punish if it does so arbitrarily and not for the sake of reasons that can be justified according to a set of principles that the members of the society initially agreed to? Imagine a group of friends who all adopt the rule that promises must always be lived up to, but who then only adhere to it when it applies to some friends rather than others, and who attempt to enforce the rule by blaming and criticizing someone who breaks it, even though they all do so. It would be fair to say then that the rule has little to no legitimacy because it’s applied arbitrarily. There must be some acknowledged, rational basis to ground the rules that supply a measure of consistency and coherence that can be applied when broken. Therefore, it is important to distinguish between rules and principles to be clear about what the target concept of a one-commandment is and to eliminate potential confusion that may result in harm to those willing to join a network state.
As mentioned above, this distinction is relevant because Srinivasan seems to believe that smart contracts can function like constitutions which, as in the United States, consist of principles and not rules. So, it is significant to see how smart contracts cannot achieve this.
Turning to the book then, when Srinivasan offers his complex definition of a network state, one of the clauses of the definition states that it is “a consensual government limited by a social smart contract.” Then in section 2.4.3, he seems to suggest that law is reducible to smart contracts, and suggests optimistically that one day they will be the primary bearers of legal codes. This indicates that he believes one-commandments will operate through smart contracts, as sets of conditions that function more or less mechanically. Again, the issue is that it oversimplifies the nature of law. If a one-commandment may sufficiently guide the decision-making procedures of the society, then it will be unable to be formalized into a smart contract. The distinction between rules and principles helps us see this. Recall that rules, by their nature, have an all-or-nothing character. A rule in baseball states that when there are three strikes someone is out, which either obtains or does not. There is no wiggle room or discussion about whether the rule is valid or not. Exceptions to this rule are not about the validity of the rule itself but about whether the rule applies, as is the case when deciding whether a pitch is a strike or a ball. Disputes about whether a player is out or not is a matter of whether the proper conditions for the rule have been met. Laws in a society share similar features. For example, when a police officer issues a speeding ticket, they are merely applying a rule that either holds or does not hold. And when someone disputes the validity of the ticket, they are disputing whether the law (the rule) was broken or not, and not whether the law itself is valid. Now, one-commandments which satisfy the second condition will not be amenable to these kinds of constraints. One-commandments will operate more like principles than rules. As the legal philosopher Ronald Dworkin points out, principles have two dimensions that rules do not. First, principles are not all-or-nothing but require discretion when being applied to cases. For instance, the principle ‘always be fair’ cannot be formulated in rule-like terms. In other words, principles cannot be exhausted by enumerating their parts and accounting for all the possible cases it is relevant to. Of course, there will be clear cases when the principle is violated, but there will remain countless cases that have to be understood by applying and interpreting the principle. In the case of baseball again, imagine if one of the game’s rules was ‘to always be fair’. How could this be formulated in a way that gives it an all-or-nothing quality, which will render it mechanical and unambiguous? It’s impossible. Rules will have to be formed in light of the principle. For instance, perhaps the three-strike rule is the fairest standard by which the game can be played; a rule can then be established accordingly. But this again requires distinguishing between rules and principles.
Rules are candidates for being encoded into smart contracts because of their mechanical nature. Principles, on the other hand, are not and require interpretation when cases arise that are ambiguous or unprecedented. Because one-commandments are tasked with guiding the decision-making procedures of the society and of formulating laws that will constrain the behavior of its members, they should not be understood as being rules themselves but rather as normative principles, as reasons for forming certain judgments about the law and the conduct it is meant to regulate. It’s important to understand one-commandments this way because if they are seen as rules; if they are treated as being reducible to all-or-nothing propositions, then the higher, more complex legal procedures, the ones that require interpretation and discretion, will be unable to deal with cases that elude a rules application, and therefore will be unable to fully guide the society, which one-commandments are supposed to do. If they are treated as principles, as standards to produce rules and to apply when ambiguity arises in exceptional cases, a society will be better equipped to form consistent and fair legal precedents. For instance, the First Amendment in the US Constitution is a principle about free speech; it protects individuals’ and groups’ right to freely express their opinions and beliefs. When cases arise that pertain to this right, and if the case contains a sufficient degree of complexity, then the Supreme Court examines the case based on the First Amendment and past cases with similar conditions. Now, ideally, they would resolve the case by merely referencing precedent, and not on considerations regarding their own moral and ethical opinions. They would observe how previous judges may have applied the First Amendment in similar cases to the one being adjudicated, and draw their conclusions accordingly. What’s important is that they appeal to a document of principles that serves as a standard by which cases can be resolved, or, if the case is novel enough, generate new laws that will serve as future precedents.
As mentioned, one of the essential functions here is to provide justifiable reasons for decision-making, which eliminates the degree of arbitrariness inherent in the conclusions drawn by the state. In the US, when issues arise regarding rights, duties, laws, or any other politico-legal issue, the constitution serves as a basic frame of reference, a justifiable grounding for one’s judgments and assertions, that gives weight to the forms of reasoning that occur within the society. Of course, that doesn’t mean the Constitution cannot be morally evaluated. It has, and it should be. But because moral opinion can vary so widely, and because there must be some shared standard by which the society can operate in its deliberative processes, without which disorder and confusion would dominate its operations, the constitution provides a general basis for achieving this. It is essential, then, as a founder of a network state, to carefully consider the principles that will be adopted to govern the society.
An example of a one-commandment will illustrate the point. In his book, Srinivasan presents an FDA-free society as a possible network state and formulates a principle that undergirds it: Your body, your choice. Because of the history of the FDA, Srinivasan imagines a founder who would desire to create a network state that would address those issues by implementing this principle and eliminating third-party institutions that limit people’s ability to make choices regarding what they wish to produce and consume. But Srinivasan then makes the following suggestion, which creates issues: With this principle, “you could then take the existing American codebase and add one crucial new feature: the absolute right for anyone to buy or sell any medical product without third party interference.” The problem is that the US legal codebase is derived from the US Constitution, and because that document consists of twenty-seven amendments and not one, substantial revisions will be necessary for making Your Body, your Choice the principal standard within the society’s legal system. For instance, if regulation like what the FDA does is eliminated, then the commerce clause of the constitution that states “Congress shall have (the) Power . . . To regulate Commerce with foreign Nations, and among the several States, should be either eliminated or greatly reduced in bearing any significance in future cases of law. That means of course that any part of the legal codebase derived from this amendment must be altered as well.
Now, while this problem is technically difficult because founders have the responsibility to hierarchically organize principles by their relative weights, it also has moral concerns. For instance, imagine a case where someone starts a private school within the FDA-free network state and decides to only admit persons of a certain race. Imagine further that the principle Your body, your choice has been interpreted by the judiciary sector of the society to mean that producers of goods and services like education can do what they please insofar as they obtain consent. Now, because they adopted the US legal codebase, and because I took this to mean that legal precedent has been carried over as well, then what if another member, one who has been discriminated against by the new school, appeals to Brown v. Board of Education, which relies on the Fourteenth Amendment of the US Constitution? Either the decision made will have to uphold the conduct of the school by appealing to Your body, your choice, which will mean the Fourteenth Amendment is reduced in significance, or they will have to prioritize that amendment over Your body, your choice. Either option has its difficulties, but clearly, the first option is far worse because of its oppressive and discriminatory nature. Therefore, founders mustn't merely establish a principle and then adopt a codebase. The principles expressed in a one-commandment should be deeply considered to avoid these kinds of potential catastrophes.
Let’s look at another case. In the absence of regulatory institutions, and this being so based on principle, is there no restriction regarding what someone within the society may produce and consume? Could someone choose to sell one of their kidneys in exchange for other goods? Could pharmaceutical manufacturers sell a carcinogenic drug by misrepresenting it as being capable of curing other diseases, and where the consumers who purchased the drug are told they’re out of luck? These are possible cases that are not ruled out by an unspecified and ambiguous principle like Your Body, your Choice. Unless a founder wishes to bite the bullet on these kinds of cases, this means further principles need to be developed that will interact with one another and can be used to form legal judgments that align with basic moral intuitions like having some form of consumer protection that prevent wrongful forms of exploitation, as is the case with misrepresentation of goods and services that undermines consumer consent.
A single, all-encompassing one-commandment that can guide a society’s decision-making procedures is difficult to formulate. Committing to a principle like Your body, your choice will likely lead to complications, as the previous two examples demonstrate. To avoid this, a good approach is to make a general enough principle that can be universalizable; one that is applicable and appropriate in all cases. The philosopher Immanuel Kant and his moral philosophy offer excellent examples of this. One of Kant’s famous contributions to moral philosophy is the idea of a categorical imperative. How Kant gets to this idea is complicated, and I’m not going to attempt an explanation of that. But from it, he generates universally applicable principles that a one-commandment should strive for, one of which can be called the humanity principle: never act in such a way that we treat humanity, whether in ourselves or in others, as a means only but always as an end in itself. An entryway into understanding an application of this principle is in the case of friendship. When two people are friends, this typically means that both persons treat one another as ends-in-themselves. Both friends represent each other as deserving consideration that does not use the other for any purpose other than for their own sake. When promises are made and decisions are acted upon in the context of the friendship, both share the responsibility of respecting the other by holding the other as the end one is directed toward. This doesn’t mean the friend is never treated as a means - that would be impossible. Sometimes people need a ride to work when their car has broken down, or one friend knows someone who can help the other get the job, and so one uses the other by obtaining the contact. But both are never to use the other as merely a means. Certain benefits may be derived from having a friend, but one is never a friend for those reasons: one is a friend because the other is intrinsically valuable.
In a society, this principle is general enough to guide the decision-making procedures. That’s not to say its application will be easy. It will often be difficult to understand what this principle amounts to and how it should be interpreted, but it won’t run into the same issues as Your body, your choice. The difference in generality between these two principles can be seen in the way failures occur when trying to follow them. Your body, your choice inevitably runs into cases that question its validity because certain moral intuitions desired to be preserved are violated. The humanity principle doesn’t easily run into this problem. When a case arises that seems to question the principle, it’s not so much whether it is valid because it fails to live up to intuitions but because it is difficult to live up to it as an ideal. Out of these two problems, failing to live up to a principle is better than adopting one that fails to satisfy moral expectations. The US Constitution is a great example of this. The idea of self-evident truths that hold human beings to have intrinsic value by virtue of their natural rights has proven to be a powerful resource for recognizing and upholding the moral worth of persons. The country has failed to live up to this throughout its history, but as an ideal, it has persistently pointed to a path forward to resolve the mistreatment of those within the society. While the contradiction of slavery in the United States was for a long time suppressed and rationalized, the language of natural rights provided the conceptual resources to dig it back up and shed light on it. As many have pointed out, the language of rights is self-correcting. If mistreatment of others exists, then the language illuminates it, brings it out into the open, and directs attention and concern for rectifying the moral shortcomings. Therefore, one-commandments should aim for universalizability, and avoid narrow and constrained principles that fail to capture moral intuitions. Having an ideal that one fails to live up to is far better than an impoverished one that lacks the proper resources.
-
 @ fd208ee8:0fd927c1
2024-10-31 11:03:08
@ fd208ee8:0fd927c1
2024-10-31 11:03:08Chef's notes
I got the recipe from the byanjushka website. She includes a lot more information on there, and lots of pictures and instructions. But it's all in German, so here's my quickie, English version. I've doubled the amounts, as I first baked this for the #PurpleKonnektiv meetup, and I knew I'd have some hungry guests.
The cookies are vegan, but they're mostly just peanut, so it's sort of irrelevant. Just make sure you get the really high-quality peanut butter that is 100% peanut. You can usually identify it by the fact that the oil separates from the base, a bit. Everything else is probably with hardened palm oil, or something.
Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 10 min
- 🍽️ Servings: 30 cookies
Ingredients
- 500 g peanut butter, normal or crunchy
- 300 g brown (or raw) sugar
- 160 ml plant-based milk (or cows' milk, if you don't care about vegan)
- 1 pkg vanilla sugar (bourbon is nice) or 1 tsp vanilla
- 250 g flour
- 2 tsp baking powder
- 2/3 tsp salt
Directions
- Preheat oven to 180 °C (350 °F).
- Beat together the peanut butter and the sugars, with an electric mixer.
- Mix in milk and vanilla.
- In a separate bowl, stir together flour, salt, and baking powder.
- Stir the dry ingredients into the wet ingredients, and then knead the dough a bit.
- (At this point, I put the dough in the fridge overnight, and baked it the next day.)
- Line your baking sheet with baking paper.
- Form tbsp-spoon-sized balls of dough.
- Press each one flat, with a fork, dipping the fork in water, before each press (to keep the dough from sticking to the fork).
-
 @ cf5b8c65:494a0912
2024-10-31 10:51:52
@ cf5b8c65:494a0912
2024-10-31 10:51:52Estoy probando un plugin para Obisidian que permite publicar directamente en NOSTR los artículos que has creado en Obsidian.
-
 @ d830ee7b:4e61cd62
2024-10-31 08:44:09
@ d830ee7b:4e61cd62
2024-10-31 08:44:09พรรคชาติหน้าพัฒนา สร้างชาตินี้ เจริญชาติหน้า
นี่ไม่ใช่บทความสรุปเนื้อหาไลฟ์ ผมแค่จะหยิบเอาโควทเจ๋งๆ ของพี่ชิตมาขยายความต่อตามความเข้าใจของผมเท่านั้นนะครับ (ใครยังไม่ได้ชมไลฟ์ตัวเต็ม กดดูเลยนะครับ) Right Talk EP.1
"พรรคชาติหน้าพัฒนา" ไม่ใช่พรรคการเมืองตามนิยามทั่วไป แต่เป็นแนวคิด หรือ อุดมการณ์ (พี่ชิตนิยามว่ามันเป็นโปรโตคอล) ในการพัฒนาอย่างยั่งยืน
คำว่า "พรรค" ในที่นี้จึงเป็นการใช้ในเชิงสัญลักษณ์ หมายถึงกลุ่มคนที่ร่วมอุดมการณ์เดียวกัน (เหล่าบิตคอยเนอร์) คือการสร้างความเปลี่ยนแปลงเชิงบวกในระยะยาว
"สร้างชาตินี้" ก็คือการเน้นย้ำถึงการลงมือทำอย่างจริงจังในปัจจุบัน ไม่ใช่แค่นอนฝันหรือรอคอยอนาคต การสร้างรากฐาน การพัฒนาตนเอง การสะสมความรู้และทรัพยากร ล้วนเป็นการสร้างเพื่ออนาคต
"ชาติหน้า" ในที่นี้ไม่ได้หมายถึงชาติภพหน้าทางศาสนา แต่เป็นการเปรียบเปรยถึงอนาคตระยะยาว ผลลัพธ์ของการ "สร้างชาตินี้" อาจไม่ปรากฏในทันที แต่จะส่งผลดีในอนาคตอย่างแน่นอน เหมือนกับการลงทุนระยะยาว หรือการปลูกต้นไม้ที่ต้องใช้เวลากว่าจะเติบโตและออกดอกผลิผล
1. "Free Market Capitalism ในอดีตมันมีจุดอ่อนอยู่จุดเดียว มันยังไม่มี Free Market Money"
พี่ชิตมองว่าระบบทุนนิยมเสรีที่ผ่านๆ มายังไม่ใช่ของจริง มันเหมือนเล่นเกมส์ที่มีคนโกง คือมีรัฐเนี่ยแหละที่เป็นตัวแสบ คอยแทรกแซงตลาดอยู่ตลอด ไม่ว่าจะเป็นการควบคุมเงินตรา การออกกฎหมาย การเก็บภาษี พวกนี้แม่งโคตรบิดเบือนตลาดเลย
ทีนี้ "จุดอ่อน" ที่พี่ชิตแกพูดถึงก็คือ "Free Market Money" หรือเงินที่เป็นอิสระจากการควบคุมของรัฐนั่นเอง
คือถ้าเงินแม่งยังอยู่ในมือรัฐ มันก็จะคอยปั่น คอยแทรกแซง ทำให้ตลาดแม่งไม่เสรีจริงๆ สักที เหมือนเราเล่นไพ่ แล้วเจ้ามือแม่งแอบดูไพ่มึงเร่ เราจะชนะได้ยังไง?
แล้ว "Free Market Money" มันคืออะไรวะ?
ก็ Bitcoin ไง Bitcoin แม่งไม่มีใครควบคุมได้ ไม่มีรัฐบาลไหน ธนาคารไหนมาสั่งซ้ายหันขวาหันได้ มันเป็นเงินของประชาชนอย่างแท้จริง
พอมี Bitcoin เข้ามา ระบบทุนนิยมเสรีก็จะสมบูรณ์แบบ ตลาดก็จะเสรีจริงๆ สักที เล่นไพ่แล้วเจ้ามือแม่งยุติธรรม เล่นตามกติกา แบบนี้ถึงจะแฟร์
นี่แหละ Key สำคัญที่พี่ชิตแกพยายามจะสื่อ คือถ้าอยากให้ระบบทุนนิยมเสรีมันเวิร์ค มึงต้อง "Fix the Money" ก่อน แล้วโลกแม่งก็จะค่อยๆ ดีขึ้นเอง
2. "Fix the Money, Fix the World"
แกหมายความว่า.. ปัญหาโลกส่วนใหญ่ เช่น ความเหลื่อมล้ำ ก็มาจากระบบเงินตราที่ห่วยแตกนี่แหละ เงินเฟ้อ รัฐบาลพิมพ์เงินมั่วซั่ว พวกนี้แม่งโคตรทำลายชีวิตคน
ถ้าเราแก้ระบบเงินได้ เปลี่ยนไปใช้ Bitcoin ที่ไม่มีใครควบคุม ไม่มีใครปั่นได้ โลกมันก็จะดีขึ้นเอง ปัญหาต่างๆ ก็จะค่อยๆ หายไป
เหมือนกับการซ่อมรากฐานบ้าน ถ้ารากฐานมันดี บ้านมันก็จะแข็งแรง อยู่ได้นาน แต่ถ้ารากฐานมันพัง ต่อให้ทาสีบ้านสวยแค่ไหน สุดท้ายมันก็พังอยู่ดี
3. "Bitcoiner ก็เป็นสมาชิกพรรคพี่ชิตหมดแล้ว"
มันไม่ได้หมายความว่า Bitcoiner ต้องไปสมัครพรรคการเมืองอะไร
"พรรคชาติหน้าพัฒนา" มันไม่ใช่พรรคการเมืองจริงๆ แต่มันคือแนวคิด คืออุดมการณ์ คือวิถีชีวิต ที่เน้นการพึ่งพาตัวเอง การกระจายอำนาจ เสรีภาพ และ Bitcoin ตอบโจทย์ทั้งหมดนี้เลย
Bitcoiner ส่วนใหญ่ก็จะมี Mindset คล้ายๆ แบบนี้ คือไม่ชอบให้ใครมาควบคุม ชอบอิสระ เชื่อในการกระจายอำนาจ เพราะงั้น Bitcoiner ก็เลยเหมือนเป็นสมาชิก "พรรคชาติหน้าพัฒนา" โดยอัตโนมัติ โดยที่ไม่ต้องไปสมัครอะไรเลย มันอยู่ในสายเลือด อยู่ใน DNA ของ Bitcoiner อยู่แล้ว
4. "Work, Saving, Stacking นี่คือพวกเราทำงานให้กับพรรคชาติหน้าพัฒนา"
พวกเราที่ทำงาน หาเงิน เก็บออม แล้วเอาเงินไปซื้อ Bitcoin สะสมไว้เนี่ย มันคือการทำงานให้กับพรรคชาติหน้าพัฒนาในทางอ้อม
เพราะการที่เรา Stack sats มันคือการสนับสนุน Decentralization การต่อต้านอำนาจรวมศูนย์ และการสร้าง Free Society ซึ่งเป็นหัวใจหลักของพรรคชาติหน้าพัฒนานั่นเอง
พวกเราเป็นเหมือน "เซลล์" ที่ช่วยกันขับเคลื่อนพรรคให้เติบโต ยิ่งเรา Stack sats มากเท่าไหร่ พรรคก็ยิ่งแข็งแกร่งและเข้าใกล้เป้าหมายมากขึ้นเท่านั้น
มันเหมือนกับการที่เรา Contribute ให้กับ Open Source Project เราอาจจะไม่ได้เป็น Developer เขียนโค้ด แต่เราก็สามารถสนับสนุนโครงการได้ด้วยการบริจาคเงินหรือช่วยโปรโมทได้ ซึ่งมันก็เป็นส่วนหนึ่งในการขับเคลื่อน Project นั้นๆ ให้ประสบความสำเร็จเช่นกัน
มันคือการทำงานเพื่อ "อุดมการณ์" เพื่อ "อนาคต" ในแบบที่เราอยากเห็น ไม่ใช่แค่การทำงานเพื่อเงินเดือนหรือผลประโยชน์ส่วนตัว
5. "Decentralization มันอยู่ใน DNA ของคำว่าสุวรรณภูมิ"
พี่ชิตต้องการจะสื่อว่า Decentralization มันเป็นรากเหง้า เป็นแก่นแท้ของภูมิภาคสุวรรณภูมิมาตั้งแต่โบราณแล้ว
สมัยก่อน.. แถบนี้ไม่ได้มีรัฐบาลกลางที่แข็งแกร่ง มีแต่ชุมชนเล็กๆ เมืองเล็กๆ กระจายอยู่เต็มไปหมด
ต่างคนต่างปกครองตัวเอง พึ่งพาตัวเอง ค้าขายแลกเปลี่ยนกันอย่างอิสระ ไม่มีใครมาบังคับ
มันก็เลยเหมือนกับ Decentralization ในโลก Bitcoin ที่ไม่มีใครคุม ไม่มีตัวกลาง ทุกคนมีอำนาจเท่าเทียมกัน
Decentralization แบบนี้แหละ ที่ทำให้สุวรรณภูมิเจริญรุ่งเรืองในอดีต และพี่ชิตก็เชื่อว่า Decentralization นี่แหละที่จะเป็นกุญแจสำคัญในการพัฒนาประเทศไทย และภูมิภาคนี้ในอนาคต
6. "รวมกันเราอยู่ แต่ไม่อนุญาตให้ใครเอาเปรียบซึ่งกันและกัน"
การอยู่ร่วมกันในสังคมมันต้องมี "กฎ" มี "กติกา" ที่ทุกคนต้องเคารพ เพื่อป้องกันไม่ให้ใครเอาเปรียบใคร
เหมือนในโลก Bitcoin ที่มี "Consensus Rules" คอยควบคุมระบบ ทำให้ทุกคนเล่นตามกฎเดียวกัน ไม่มีใครได้เปรียบเสียเปรียบ
แต่กฎที่ว่านี้.. มันต้องมาจากความสมัครใจ ไม่ใช่มาจากการบังคับหรืออำนาจรวมศูนย์ ทุกคนต้องมีส่วนร่วมในการสร้างและยอมรับกฎนั้นๆ
พูดง่ายๆ คือ รวมกันเราอยู่ก็จริง แต่มันต้องแฟร์ ต้องยุติธรรมด้วย
ไม่ใช่รวมกันเพื่อให้ใครบางคนรวย หรือ รวมกันเพื่อให้ใครบางคนมีอำนาจ
7. "ความจริงมันมีอยู่แล้ว แต่ความจริงแม่งช้า"
พี่ชิตพูดถึงธรรมชาติของ "ความจริง" ซึ่งความจริงมันก็มีอยู่แล้ว มันไม่ได้ขึ้นอยู่กับความเชื่อ หรือความคิดเห็นของใคร
แต่มันอาจจะต้องใช้เวลา กว่าที่คนส่วนใหญ่จะเข้าใจและยอมรับความจริงนั้น
เหมือนกับตอนที่คนสมัยก่อนเชื่อว่าโลกแบน แต่ความจริงคือโลกกลม กว่าที่คนส่วนใหญ่จะยอมรับความจริงนี้ได้ก็ปาไปตั้งหลายร้อยปี
Bitcoin ก็เหมือนกัน..
พี่ชิตเชื่อว่า Bitcoin คือ "ความจริง" คือ "อนาคตของเงิน" แต่ตอนนี้คนส่วนใหญ่อาจจะยังไม่เข้าใจ ยังมองว่ามันเป็นแค่ของเล่น การพนัน หรือ แชร์ลูกโซ่
แต่สักวันหนึ่ง.. ความจริงของ Bitcoin จะปรากฏ และทุกคนจะยอมรับมัน เหมือนที่พี่ชิตบอกว่า..
"อีก 10 ปีมึงไม่ต้องเชิญเลย"
คืออีก 10 ปี คนจะเข้าใจ Bitcoin กันหมด ไม่ต้องมาจัดสัมมนาหรือเสียอธิบายอะไรกันอีกแล้ว
มันก็เหมือนกับ "ความจริงเป็นสิ่งไม่ตาย"
ต่อให้ตอนนี้คนส่วนใหญ่จะยังไม่เชื่อ ไม่เข้าใจ แต่สุดท้ายแล้วความจริงก็จะชนะ และเปิดเผยตัวเองออกมาเอง
เพียงแต่เราต้องอดทนรอหน่อยเท่านั้นเอง...
8. "Leave me alone"
สะท้อนแนวคิด Libertarian ที่เน้น "อิสรภาพส่วนบุคคล" แบบสุดๆ
คือพี่ชิตไม่อยากให้ใคร แม้แต่รัฐบาล มาควบคุม หรือบังคับแก แกอยากจะทำอะไรก็ทำ อยากใช้ชีวิตยังไงก็ใช้ โดยที่ไม่ต้องมีใครมาจุ้นจ้าน
พี่ชิตมองว่า.. รัฐบาลควรมีบทบาทน้อยที่สุด แค่คอยดูแลความสงบเรียบร้อยและรักษาความยุติธรรมก็พอ ส่วนเรื่องอื่นๆ ประชาชนควรจัดการกันเอง
"Leave me alone" จึงเป็นเสียงสะท้อนจากใจของคนที่เบื่อระบบราชการ กฎระเบียบและการแทรกแซงจากรัฐ
แกอยากให้ทุกคน "Take care yourself" พึ่งพาตัวเองให้ได้ ไม่ใช่รอคอยความช่วยเหลือจากรัฐบาล มันก็เหมือนกับโลก Bitcoin ที่ไม่มีใครควบคุม ไม่มีตัวกลาง ทุกคนมีอิสระในการทำธุรกรรม โดยไม่ต้องขออนุญาตใคร
สังคมที่ดี คือ สังคมที่ให้อิสระกับปัจเจกชน
ให้แต่ละคนได้เลือกและรับผิดชอบชีวิตตัวเอง โดยไม่ต้องมีใครมาบังคับหรือชี้นำ
9. "Overhead 70% ไอ้สัส! Payload 30%"
พี่ชิตเปรียบเทียบ (ด่าแหละ) รัฐบาลเหมือนกับบริษัท ที่ดันมี Overhead (ค่าใช้จ่ายในการบริหารจัดการ) สูงถึง 70% ในขณะที่ Payload (งานที่ส่งมอบให้ประชาชนจริงๆ) มีเพียงแค่ 30%
คือ.. รัฐบาลเอาภาษีประชาชนไปใช้จ่ายกับอะไรก็ไม่รู้ (อาทิ.. เงินเดือนข้าราชการ ค่าดูงานต่างประเทศ ค่าจัดเลี้ยง ค่าสัมมนา ฯลฯ เต็มไปหมด) แต่ผลงานที่ประชาชนได้รับกลับน้อยนิด
แกเลยด่าว่า "ไอ้สัส!" ด้วยความฉุนเฉียว เพราะมันไม่สมเหตุสมผล ไม่คุ้มค่า และเป็นการเอาเปรียบประชาชนชัดๆ
พี่ชิตอยากให้รัฐบาล "Downsize" ลดขนาดองค์กร ลดค่าใช้จ่ายและเพิ่มประสิทธิภาพในการทำงาน เพื่อให้ Payload มันสูงขึ้น ประชาชนจะได้ประโยชน์มากขึ้น
รัฐบาลไม่ควรใหญ่เกินไป ไม่ควรเข้าไปยุ่งกับชีวิตประชาชนมากเกินไป ควรปล่อยให้ประชาชน "Take care yourself" จัดการตัวเอง
10. "เขาคุยเรื่อง "UBI, Universal Basic Income กันแล้ว, You own nothing but you'll be happy"
พี่ชิตพูดถึงกระแส UBI ที่กำลังมาแรง คือการที่รัฐบาลแจกเงินให้ประชาชนใช้ฟรีๆ ทุกเดือน แล้วก็มีคำพูดที่ว่า "คุณจะไม่มีอะไรเป็นของตัวเอง แต่คุณจะมีความสุข" ซึ่งแม่งโคตรย้อนแย้ง และโคตรอันตรายเลย
คือพี่ชิตมองว่า UBI มันเป็นแนวคิดสังคมนิยมสุดโต่งที่ทำให้คนขี้เกียจ ไม่ยอมพึ่งพาตัวเอง รอแต่เงินแจกจากรัฐบาล แล้วพอคนไม่ทำงาน ไม่สร้างมูลค่าเพิ่มให้กับสังคม เศรษฐกิจมันก็พังพินาศ
ส่วนประโยค "You own nothing but you'll be happy" แกมองว่าแม่งโคตรหลอกลวง
คือมึงจะไม่มีอะไรเป็นของตัวเองเลย ทุกอย่างเป็นของรัฐ แล้วมึงจะมีความสุขได้ยังไงวะ?
มันเหมือนอยู่ในคุก มีข้าวกิน มีที่นอน แต่ไม่มีอิสระ มึงจะมีความสุขหรอ?
พี่ชิตเชื่อในเสรีภาพ เชื่อในการพึ่งพาตัวเอง เชื่อในการสร้างเนื้อสร้างตัว ไม่ใช่รอเงินแจกจากรัฐบาล UBI มันเลยสวนทางกับแนวคิดของแกโดยสิ้นเชิง แล้วแกก็มองว่ามันเป็นภัยคุกคามต่อเสรีภาพของมนุษย์ด้วย
11. "ในขณะที่โลกฝักใฝ่ทางซ้าย แต่พวกมึงดันมุ่งไปทางขวา เพราะพวกมึงแม่งคือ Right Shift"
พี่ชิตแกหมายถึงโลกปัจจุบันกำลังไปทางซ้าย คือแนวคิดสังคมนิยม รัฐสวัสดิการ รัฐบาลใหญ่ ควบคุมทุกอย่าง แจกเงิน ฯลฯ
แต่พวก Bitcoiner หรือกลุ่มคนที่เชื่อในแนวคิดแบบเดียวกันกับแก ดันไปทางขวา ซึ่งก็คือแนวคิดเสรีนิยม เน้นความรับผิดชอบ พึ่งพาตัวเอง กระจายอำนาจ รัฐบาลเล็กลง
"Right Shift" ก็คือการเปลี่ยนทิศทาง จากซ้ายไปขวา จากการพึ่งพารัฐ ไปสู่การพึ่งพาตนเอง
นี่แหละ.. ชื่อนี้ (ชื่อเรา) จึงสอดคล้องกับแกนหลักของแนวคิดพี่ชิต ที่พยายามจะสื่อให้เห็นว่ามันมีอีกทางเลือกหนึ่งที่ไม่ใช่การพึ่งพารัฐบาล แต่เป็นการสร้างความมั่งคั่งและความเจริญรุ่งเรืองด้วยตัวเอง
12. "Right Shift, Take care yourself, Self Regulate, Decentralization นั่นคือ Right Shift"
"Right Shift" หรือการ "ขยับไปทางขวา" "มุ่งไปในทิศทางที่ถูกต้อง" ในความหมายของพี่ชิต มันก็คือ การดูแลตัวเอง (Take care yourself) การควบคุมตัวเอง (Self Regulate) และการกระจายอำนาจ (Decentralization) นั่นเอง
ทั้งหมดนี้มันเชื่อมโยงกัน คือ ถ้ามึงดูแลตัวเองได้ ควบคุมตัวเองได้ และเชื่อในการกระจายอำนาจ แทนที่จะพึ่งพารัฐบาล มึงก็จะก้าวไปสู่ "Right Shift" ได้
Bonus quotes
13. "กบกำลังถูกต้มอยู่ในหม้อ มันต้องร้อนขึ้น"
นี่คือการเปรียบเปรยสถานการณ์ปัจจุบันที่หลายคนอาจไม่รู้ตัวว่ากำลังเผชิญกับปัญหาใหญ่กันอยู่
เหมือนกบที่ถูกต้มช้าๆ มันจะไม่รู้ตัวว่าน้ำกำลังร้อนขึ้นเรื่อยๆ จนสุดท้ายมันก็ตาย
ปัญหาต่างๆ เช่น เงินเฟ้อ ความเหลื่อมล้ำ ระบบราชการที่ไร้ประสิทธิภาพ มันก็ค่อยๆ ร้อนขึ้นเรื่อยๆ จนถึงจุดที่รับไม่ได้
พี่ชิตใช้ประโยคนี้เพื่อเตือนสติว่า.. อย่าได้ประมาท อย่าปล่อยให้ตัวเองถูกต้มจนตาย ต้องตระหนัก และหาทางออกก่อนที่มันจะสายเกินไป
14. "ลิงมันขายไอเดียไม่ได้"
เปรียบเทียบมนุษย์กับลิง เพื่อเน้นย้ำถึงความสามารถเฉพาะตัวของมนุษย์ในการสื่อสาร และโน้มน้าวใจผู้อื่น
ลิงอาจจะฉลาด แต่ก็สื่อสารหรือขายไอเดียไม่ได้เหมือนมนุษย์
มนุษย์มีความสามารถในการสร้างเรื่องราว สร้างแรงบันดาลใจ โน้มน้าวใจ เพื่อให้คนอื่นเชื่อและทำตาม
นี่แหละคือข้อได้เปรียบที่มนุษย์มีเหนือสัตว์อื่นๆ และเป็นสิ่งสำคัญในการขับเคลื่อนสังคม และโลกใบนี้
15. "เบียร์ไม่มีช้อยส์"
พี่ชิตพูดในบริบทที่หมายถึง.. บางครั้งในชีวิต เราก็ไม่มีทางเลือกหรือมีทางเลือกจำกัด
เหมือนเวลาเลือกดื่ม.. บางทีก็มีแค่เบียร์ให้เลือก ไม่มีอะไรอื่น มันก็ต้องดื่มเบียร์ไป
นั่นแหละ.. บางทีชีวิตเราก็เป็นแบบนั้น ต้องยอมรับ และเลือกสิ่งที่ดีที่สุดในสถานการณ์นั้นๆ ไปก่อน
16. "อเมริกาแอบแดกฟรีอยู่"
หมายถึงนโยบายต่างประเทศของอเมริกา ที่ใช้ดอลลาร์เป็นอาวุธ เพื่อรักษาอำนาจ และเอาเปรียบประเทศอื่นๆ
อเมริกาใช้ดอลลาร์เป็นเงินทุนสำรองโลก ทำให้ประเทศอื่นๆ ต้องพึ่งพาดอลลาร์ แล้วอเมริกาก็ใช้จุดนี้เป็นข้อได้เปรียบในการควบคุมเศรษฐกิจและการเมืองโลก
เหมือนกับการที่มึงมีของดี แล้วมึงก็บังคับให้คนอื่นต้องซื้อของมึง โดยที่มึงไม่ต้องลงทุนอะไรมากมาย
พี่ชิตแกมองว่า นี่คือการ "แอบแดกฟรี"
คือได้ประโยชน์มหาศาลโดยที่ไม่ต้องลงทุนและไม่คำนึงถึงผลกระทบต่อประเทศอื่นๆ เป็นการใช้ประโยชน์จากระบบที่ไม่เป็นธรรม
17. "กรรมที่อเมริกาต้องชดใช้"
ประโยคนี้พี่ชิตไม่ได้หมายความว่าอเมริกาจะต้องไปนรกหรืออะไรแบบนั้น.. แกใช้คำนี้ในบริบทของการวิเคราะห์ระบบเศรษฐกิจโลกและการกระจายอำนาจ
อเมริกาเคยใช้อำนาจของตัวเอง โดยเฉพาะ "ดอลลาร์" เพื่อครอบงำและเอาเปรียบประเทศอื่นๆ มานาน นั่นคือ "กรรม" ที่อเมริกาได้สร้างขึ้น
แต่ตอนนี้.. ระบบการเงินและอำนาจกำลังเปลี่ยนแปลง
Bitcoin กำลังมา ซึ่งเป็นระบบที่กระจายอำนาจ ไม่มีใครควบคุมได้ อเมริกาจึงกำลังเผชิญผลของการกระทำในอดีต นั่นคือ การสูญเสียอำนาจและอิทธิพล
นั่นแหละ "กรรม" ที่ต้องชดใช้
18. "มึงเป็นไก่ ไอ้สัส! ทำไมทำตัวเป็นกา เป็นปรสิต?"
"กา" และ "ปรสิต" คือพวกที่ไม่สร้างคุณค่าอะไรให้กับสังคม แต่ดันพึ่งพา เอาเปรียบคนอื่น เหมือนกาที่ขโมยกิน หรือปรสิตที่อาศัยดูดเลือดคนอื่นอยู่รอด
ส่วน "ไก่" ในที่นี้ หมายถึงคนที่สร้างคุณค่า ทำงานหาเลี้ยงชีพด้วยตัวเอง
พี่ชิตแกเลยอยากให้ทุกคนเป็นไก่ พึ่งพาตัวเอง สร้างคุณค่าให้กับสังคม อย่าไปเป็นภาระ หรือเอาเปรียบใคร
การเปรียบเที่ยบด้วยโควทนี้ก็เพื่อให้เราได้สติ ได้คิด มันเป็นการตักเตือนที่ค่อนข้างตรงไปตรงมา แต่ก็แฝงด้วยความหวังดี
อยากให้พวกเราพยายามเปลี่ยนแปลงตัวเองไปในทางที่ดีขึ้น
19. "โลกยังหมุนรอบตัวเองเลย"
นี่คือการตอกย้ำหลักการพื้นฐานของธรรมชาติ คือทุกอย่างต้องทำงาน ต้องสร้างคุณค่า เพื่อความอยู่รอด
พี่ชิตใช้ประโยคนี้ต่อจากการพูดถึงการพึ่งพาตัวเอง การสร้างคุณค่า การไม่เป็นภาระสังคม
จะเห็นว่าแกพยายามจะสื่อว่า การดำรงอยู่ไม่ใช่เรื่องง่าย ทุกอย่างแม่งต้องทำงาน ทุกอย่างแม่งต้องหมุนเวียน
เหมือนโลกที่ยังหมุนรอบตัวเองอยู่ทุกวันนี้ มนุษย์ก็เช่นกัน ต้องพึ่งพาตัวเอง สร้างคุณค่า เพื่อให้ตัวเองอยู่รอดได้ ไม่ใช่รอให้คนอื่นมาเลี้ยงดู
20. "กูเกลียดคำว่า Policy"
พี่ชิตไม่ได้เกลียดนโยบายโดยทั่วไป แต่แกเกลียด "Policy" ในบริบทของระบบราชการ ที่มันยุ่งยาก ซับซ้อน ไร้ประสิทธิภาพและมักไม่ตรงกับความต้องการของประชาชน
คือพี่ชิตมองว่า Policy ส่วนใหญ่ มันเป็นแค่ตัวหนังสือ เป็นแค่กฎเกณฑ์ที่สร้างขึ้นโดยคนกลุ่มเล็กๆ เพื่อที่จะควบคุมและบริหารจัดการคนส่วนใหญ่
แต่สุดท้าย.. มันกลับกลายเป็นอุปสรรค เป็นภาระ ที่ทำให้การทำงานต่างๆ ช้าลง ไม่คล่องตัว และเสียค่าใช้จ่ายมหาศาล
พี่ชิตเลยอยากเห็นระบบที่เรียบง่าย โปร่งใส ทุกคนมีส่วนร่วม ไม่ใช่ระบบที่ถูกควบคุมด้วย Policy ที่ยุ่งยาก และไร้ประสิทธิภาพ
21. "Democratize retail work"
พี่ชิตหมายถึง.. การกระจายงานให้คนมีส่วนร่วมมากขึ้น ไม่ใช่แค่ให้คนกลุ่มเดียว หรือองค์กรเดียว ทำ
ยกตัวอย่างเรื่องการจัดการผักตบชวา.. แทนที่จะให้รัฐบาลจัดการเอง ซึ่งใช้เวลา งบประมาณมหาศาลและประสิทธิภาพต่ำ แกเสนอให้กระจายงานออกไป ให้คนในชุมชนหรือคนที่มีความสามารถเข้ามาทำ โดยมีระบบตรวจสอบและให้รางวัลคนที่ทำงานได้ดี
แบบนี้มันจะทำให้ประสิทธิภาพสูงขึ้น ประหยัดงบประมาณและคนในชุมชนก็ได้มีส่วนร่วม สร้างความรับผิดชอบและความยั่งยืน
เป็นการเปลี่ยนจากระบบรวมศูนย์ ไปสู่ระบบกระจายอำนาจในเชิงปฏิบัติ
22. "นี่คือ Future of Work"
พี่ชิตมองว่า.. อนาคต การทำงานจะไม่ใช่การทำงานเพื่อนายจ้างหรือองค์กรใหญ่ๆ อีกต่อไป
แต่จะเป็นการทำงานแบบกระจายอำนาจ ทุกคนเป็นอิสระ รับผิดชอบงานของตัวเอง สร้างมูลค่าเพิ่มด้วยตัวเอง แล้วก็ได้รับผลตอบแทนตามความสามารถ
เหมือนกับ Bitcoin ที่มันไม่มีเจ้านาย ไม่มีคนกลาง ทุกคนมีส่วนร่วม ทุกคนได้ประโยชน์
23. "ชิดซ้าย เพื่อ Make a U-turn"
ชิดซ้าย แต่กูไม่ใช่ฝ่ายซ้าย! (ฮา) กูชิดซ้าย (นามสกุลซ้ายเกล้า) เพื่อเตรียมจะยูเทิร์นไปทางขวาโว้ย!
เอาจริงๆ นัยยะของพี่ชิตแกไม่ได้หมายถึงการขับรถ แต่เป็นการเปรียบเปรยถึงการเตรียมตัวก่อนเปลี่ยนแปลงครั้งใหญ่
ในบริบทของบทสนทนา มันหมายถึงการเตรียมตัวก่อนที่จะเปลี่ยนจากระบบเดิมๆ ที่เน้นการพึ่งพารัฐ ไปสู่ระบบใหม่ที่เน้นการพึ่งพาตนเอง การกระจายอำนาจ (Right Shift)
"ชิดซ้าย" จึงเป็นเหมือนการเตรียมตัว การวางแผน ก่อนที่จะ "Make a U-turn" หรือหักเลี้ยวเปลี่ยนไปสู่เส้นทางใหม่ ซึ่งก็คือการก้าวไปสู่โลกแบบ Decentralization นั่นเอง (คิดได้..)
24. "หลอกพวกมึงด้วยการสร้างกุศลบายให้มึงเชื่อในนรกสวรรค์"
พี่ชิตแกไม่ได้ต่อต้านศาสนาโดยตรง แต่แกกำลังวิจารณ์การใช้ศาสนาเป็นเครื่องมือควบคุมคน การใช้ความกลัว ความเชื่อเรื่องนรก-สวรรค์ มาบังคับ มาควบคุม มาชี้นำพฤติกรรมของคน โดยที่ไม่ได้เน้นเหตุผลหรือการลงมือทำจริง
มันเหมือนกับการใช้ "กุศโลบาย" หรือกลอุบาย มาหลอกลวง ให้คนเชื่อและทำตาม โดยที่ไม่ได้ให้ความรู้หรือสร้างความเข้าใจที่แท้จริง พี่ชิตแกอยากให้คนใช้เหตุผล ใช้ความรู้ และลงมือทำ ไม่ใช่แค่เชื่ออย่างงมงาย
25. "ถ้ามันจะเกิดในอีก 5 วัน พวกมึงจะไปทำอะไรได้?"
พี่ชิตเน้นย้ำถึงความรวดเร็วและความไม่แน่นอนของการเปลี่ยนแปลงที่อาจจะเกิดขึ้น โดยเฉพาะอย่างยิ่งกับโอกาสที่จะเกิดขึ้นจาก Bitcoin
ซึ่งถ้าโอกาสดีๆ มันมาถึงเร็วมาก มึงจะเตรียมตัวทันมั้ย? มึงจะรับมือไหวมั้ย?
(ในบริบทของการสนทนาคือ หากทรัมป์ได้รับเลือกเป็น ปธณ. อเมริกา มีการคาดหมายว่าจะส่งผลดีต่อบิตคอยน์)
เอาจริงๆ มันเหมือนเป็นการเตือนสติว่า อย่าประมาท อย่าชะล่าใจ เพราะโอกาสอาจจะมาถึงเร็วกว่าที่คิด
ส่วนประโยค "ขายตูดซื้อไม่ทันเลย" ของอิสร
นี่คือมุขตลก ถ้ามึงไม่ทัน มึงก็จะเสียโอกาส เหมือนกับมึงต้องขายของมีค่า เพื่อเอาเงินไปซื้อ Bitcoin แต่ก็ยังไม่ทัน มันโคตรเสียดาย
แล้วคุณล่ะ..
อยากให้ใครได้เป็นประธานาธิบดีสหรัฐ?
26. "มันคือการเอาเงินคนอื่นไปทำบุญ"
พี่ชิตวิจารณ์นโยบายประชานิยม โดยเฉพาะการที่รัฐบาลเอาเงินภาษีของประชาชนไปแจก หรือไปทำโครงการต่างๆ โดยที่ไม่ได้รับความยินยอม หรือไม่ได้เกิดประโยชน์อย่างแท้จริงกับประชาชน
แกมองว่า.. มันก็เหมือนกับการที่รัฐบาลเอาเงินของประชาชนไป "ทำบุญ" โดยที่ประชาชนไม่ได้เป็นผู้ตัดสินใจว่าจะบริจาคเงินไปทำอะไร
มันเป็นการกระทำที่ไม่โปร่งใส และไม่เคารพสิทธิ์ของประชาชน
แกเน้นย้ำว่า การทำบุญหรือการใช้เงิน ควรมาจากความสมัครใจ ไม่ใช่การบังคับ หรือการใช้เงินโดยไม่คำนึงถึงความต้องการหรือประโยชน์ของผู้ที่ถูกใช้เงิน ไม่ใช่ตัวเองได้บุญ ได้หน้าอยู่คนเดียว แต่คนทั้งประเทศต้องมาคอยรับผิดชอบหนี้ร่วมกัน
จริงๆ แล้วในไลฟ์นี้มีประโยคเด็ดอีกมากมายจากพี่ชิตเต็มไปหมด ถือเสียว่าผมแค่เอาน้ำจิ้มบางส่วนมาให้ลองชิมก็แล้วกัน ถ้าจะเก็บให้ครบทั้งหมดควรต้องไปดูด้วยตัวเองครับ
สุดท้ายแล้ว "พรรคชาติหน้าพัฒนา" มันคืออะไรแน่?
เอาง่ายๆ เลยนะ พี่ชิตแกเห็น Pain Point หลักๆ มาจาก 2 อย่างใหญ่ๆ คือ ระบบการเงินโลกที่บิดเบี้ยว และ ระบบการเมืองที่ล้าหลัง ซึ่งทั้งสองอย่างนี้เชื่อมโยงกันอย่างแยกไม่ออก
ระบบการเงินที่บิดเบี้ยว คือ รัฐบาลมีอำนาจควบคุมเงิน พิมพ์เงินมั่วซั่ว ทำให้เกิดเงินเฟ้อ ความเหลื่อมล้ำ คนจนยิ่งจน คนรวยยิ่งรวย
นี่แหละคือต้นตอของปัญหาสารพัด พี่ชิตเลยมองว่าต้องแก้ที่ระบบเงินก่อน ด้วย Bitcoin ที่เป็น Free Market Money อิสระจากรัฐบาล
ส่วน ระบบการเมืองที่ล้าหลัง คือ รัฐบาลใหญ่ แทรกแซงทุกอย่าง ประชาชนอ่อนแอ พึ่งพารัฐอย่างเดียว ไม่มีเสรีภาพ ไม่มีการกระจายอำนาจ
พี่ชิตเลยคิด "พรรคชาติหน้าพัฒนา" ขึ้นมา ไม่ใช่พรรคการเมืองจริงๆ แต่เป็น Protocol หรือแนวคิด ที่จะ Empower ประชาชน ให้พึ่งพาตัวเอง มีเสรีภาพทางการเงินและมีส่วนร่วมในการกำหนดอนาคตของตัวเอง โดยใช้ Bitcoin เป็นเครื่องมือสำคัญ
ทำไมต้องปี 2575?
นี่น่าจะเป็นการตั้งเป้าหมายระยะยาวมากกว่า อาจจะหมายถึงช่วงเวลาที่ Bitcoin และแนวคิด Decentralization แพร่หลายมากพอ จนสามารถสร้างการเปลี่ยนแปลงที่แท้จริงได้
หรืออาจจะเป็นแค่การเปรียบเปรย เพราะการสร้างอะไรใหม่ๆ มันต้องใช้เวลา เหมือนการปลูกต้นไม้ กว่าจะโต กว่าจะออกผล มันต้องใช้เวลาหลายปี
การตั้งเป้าหมายไว้ที่ปี 2575 ก็อาจจะเป็นการสร้างแรงบันดาลใจและความหวังให้กับผู้คนก็ได้ ไม่ใช่เป้าหมายที่ตายตัวอะไรขนาดนั้น
(หรือไม่ก็ล้อไปกับเรื่องการปกครองที่เปลี่ยนแปลงมาตั้งแต่ปี 2475 แต่ก็ไม่พัฒนาไปถึงไหน ครบรอบ 100 ปีก็ควรจะ Change กันได้แล้ว)
ทั้งหมดนี้คือสิ่งที่พี่ชิตแกอยากจะสื่อ และเป็นแรงจูงใจที่ทำให้แกผุดแนวคิด "พรรคชาติหน้าพัฒนา" (as a protocol) ขึ้นมานั่นเองครับ
-
 @ 26838110:80edc65d
2024-10-31 07:43:02
@ 26838110:80edc65d
2024-10-31 07:43:02About Dragonbane Creation
Dragonbane Creation is a project to create an original epic space saga and represents the next generation of science-fiction, worldbuilding and concept art.
Humanity had to leave Earth behind after a massive invasion. Following an arduous exodus, they arrive on a new planet they call Heavngard, where they have to build everything anew.
Key Facts
- Dragonbane Creation was founded in May 2020 in Wrocław, Poland.
- We publish NFTs on the Stacks (STX) chain.
- We are active on Nostr
Download Press Kit
https://www.dragonbanecreation.com/storage/documentation/documentation-general/press/dragonbane-creation-press-kit-en.zip
Where to Find Us on Social Media
NJump
https://njump.me/npub1y6pczy8zzchsqs92u8dxlcm3z9pafgj2mlr04w4wkmzpeq8dcewsvtct3m
YakiHonne
https://yakihonne.com/users/nprofile1qqszdqupzr3pvtcqgz4wrkn0udc3zs755f9dl3h6h2htd3qusrkuvhgfe2fny
Primal
https://primal.net/p/npub1y6pczy8zzchsqs92u8dxlcm3z9pafgj2mlr04w4wkmzpeq8dcewsvtct3m
Nosta
https://nosta.me/nprofile1qqszdqupzr3pvtcqgz4wrkn0udc3zs755f9dl3h6h2htd3qusrkuvhgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dsjkvsz5
Nostter
https://nostter.app/nprofile1qqszdqupzr3pvtcqgz4wrkn0udc3zs755f9dl3h6h2htd3qusrkuvhgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dsjkvsz5
Satellite
https://satellite.earth/@nprofile1qqszdqupzr3pvtcqgz4wrkn0udc3zs755f9dl3h6h2htd3qusrkuvhgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dsjkvsz5
Nostrrr
https://nostrrr.com/p/nprofile1qqszdqupzr3pvtcqgz4wrkn0udc3zs755f9dl3h6h2htd3qusrkuvhgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dsjkvsz5
Coracle
https://coracle.social/nprofile1qqszdqupzr3pvtcqgz4wrkn0udc3zs755f9dl3h6h2htd3qusrkuvhgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dsjkvsz5
Snort
https://snort.social/nprofile1qqszdqupzr3pvtcqgz4wrkn0udc3zs755f9dl3h6h2htd3qusrkuvhgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dsjkvsz5
Nostrudel
https://nostrudel.ninja/#/u/nprofile1qqszdqupzr3pvtcqgz4wrkn0udc3zs755f9dl3h6h2htd3qusrkuvhgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dsjkvsz5
Iris
https://iris.to/nprofile1qqszdqupzr3pvtcqgz4wrkn0udc3zs755f9dl3h6h2htd3qusrkuvhgpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dsjkvsz5
Habla
https://habla.news/p/nprofile1qyv8wumn8ghj7un9d3shjtnndehhyapwwdhkx6tpdsq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgdwaehxw309ahx7uewd3hkcqgswaehxw309ahx7um5wgh8w6twv5q3yamnwvaz7tm0venxx6rpd9hzuur4vgqzqf5rsygwy930qpq24cw6dl3hzy2r6j3y4h7xl2a2adkyrjqwm3janwa9dm
Highlighter
https://highlighter.com/npub1y6pczy8zzchsqs92u8dxlcm3z9pafgj2mlr04w4wkmzpeq8dcewsvtct3m
Nostree Links
https://nostree.me/npub1y6pczy8zzchsqs92u8dxlcm3z9pafgj2mlr04w4wkmzpeq8dcewsvtct3m
Images License
All images and the rest of the content on the website are copyrighted. If you want to use our images to write an article about Dragonbane Creation or one of our projects, you can use them with attribution.
-
 @ fd208ee8:0fd927c1
2024-10-31 07:35:50
@ fd208ee8:0fd927c1
2024-10-31 07:35:50You don't choose software. You choose software developers.
I've done lots of internal and external software project audits. The clue to a good audit, is that you are judging the building and the builder, because the former determines the present state of the code and the latter determines how things will be built going forward.
Here's what to look for in a good developer:
- curious : eager to learn from others
- humble : seems slightly embarrassed, when you report an issue, and tries to reproduce and fix the problem
- responsive : they try to get back to you within 24 hours, or they arrange a sub or post a notice, when they'll be away for a while. They feel bad, if they leave someone waiting, so they'll send updates, even if it's just to ask them to be patient.
- diligent : they don't leave websites rotting, abandoned. They either maintain it or pull it down. They check their repos regularly and actively manage the PRs and issues.
- egalitarian : they care about all of their users, whether they are rich or poor, famous or unknown, premium or freewarers
- agile : they don't let the system go stale, for months, and then dump a gigantic commit
- honest : they don't lie, ever. Never ever. They're not sneaky or evasive. If something they promised won't work out, they announce it. They readily admit to things that make them look bad.
- calm : they are not histrionic, hyperventilatory or prone to needing a Wellness Break, to recover from the stress of dealing with humans and code
- centered : they have a plan, for their software, that they regularly refine, but they don't flit from one Next Big Thing, to another. They resist hype and examine concepts soberly and analytically.
- concerned : they test their software before giving it to other people because they want them to have a positive experience, while using it. If something is just a prototype, they make that clear, when announcing it.
-
 @ da2683b9:54eedc2c
2024-10-31 07:07:45
@ da2683b9:54eedc2c
2024-10-31 07:07:45The rapid development of modern technology, especially in the field of intelligence, is profoundly affecting our lives and industries. Take jammer and signal detector for example. They are not only the products of high technology, but also play a vital role in specific occasions. They are also a microcosm of our understanding of modern intelligent transformation.
You may have heard of signal jammers. The function of this device is very simple, that is, to interfere with a certain communication signal by emitting interference waves stronger than the target signal. This may sound a bit "anti-social", but in fact, its application is very beneficial in some specific occasions.
With the popularity of wireless networks, wifi signal jammer have quietly entered our field of vision. As the name suggests, WiFi jammers make wireless network connections unstable by interfering with WiFi signals. This device can protect the network security of enterprises in some cases and prevent hackers from invading the company's internal systems through WiFi networks.
Speaking of recorder jammers, no one may refuse such a privacy protection device. Its working principle is similar to that of signal jammers. It emits noise of a specific frequency to cover the sound of conversations, thereby preventing them from being recorded. Imagine that in some sensitive business negotiations or private conversations, using a audio recording jammers can make participants feel more at ease without worrying about their voices being eavesdropped.
Relatively speaking, signal detectors are a more positive and positive technology product. It can help users identify various wireless signals in the surrounding environment, including WiFi, Bluetooth and other devices. Signal detectors can help individuals and companies identify potential signal interference or monitoring behaviors, thereby enhancing security and privacy protection.
For companies, using signal detectors can help them better manage network traffic and monitor the stability of internal signals. At the same time, when encountering signal problems, signal detector can also help quickly locate the source of faults and improve work efficiency.
The emergence of these technical products has made us more deeply aware of the opportunities and challenges brought by intelligent transformation to industry. With the continuous advancement of technology, more intelligent devices will appear in the future to help us protect safety and improve efficiency in complex information environments.
Of course, while enjoying the convenience and fun brought by these technologies, we must also use these devices reasonably and legally. I hope that in the future, we can seize every opportunity brought to us by technology in this rapidly changing world.
-
 @ a37bda36:6fe8611c
2024-10-31 06:41:02
@ a37bda36:6fe8611c
2024-10-31 06:41:02The Bottom-Up Renaissance: How El Salvador is Transforming the Future
What’s happening in El Salvador today is nothing short of extraordinary. Under the leadership of President Nayib Bukele, the country has become a catalyst for hope and progress, stirring interest and inspiring minds around the world. Bukele’s vision has fostered a social and economic environment that not only prioritizes safety but also sets the stage for innovation, decentralization, and grassroots transformation. Dubbed a “Bottom-Up Renaissance,” this movement holds the potential to inspire a global shift toward community-driven change.Building the Foundation: Security and Sound Money
El Salvador’s transformation began with a firm focus on security. By establishing a stable environment, Bukele enabled the groundwork for a new society where citizens and innovators alike can thrive. But this rebirth is far from limited to security measures. In an era of economic instability, Bukele’s decision to embrace Bitcoin as legal tender has introduced "sound money" into the economy—a concept central to this new Renaissance.Historically, in the Renaissance of 16th-century Florence, only the wealthy could access gold-backed currency, while the working classes were relegated to coins made of cheaper, often debased metals. This disparity in wealth preservation has often perpetuated class divides. But in El Salvador, Bitcoin's decentralized nature has disrupted this model. Unlike the dollar, Bitcoin cannot be devalued by centralized authorities, giving ordinary Salvadorans access to the “world’s soundest money.” This model offers the average citizen a chance to save, invest, and build in a way previously reserved for the elite.
Bitcoin’s presence in El Salvador has not only brought the country to the global stage but has also drawn the attention of those seeking stability in a volatile world. For the first time, the power of money lies not in the hands of a few but in the collective hands of a nation’s people.
Decentralization: Real-World Applications and Financial Sovereignty
El Salvador is diving into decentralization like never before. From establishing Bitcoin banks to creating open-source health solutions on decentralized platforms like NOSTR, the country is pioneering real-world applications that disrupt traditional systems. Through such decentralization, El Salvador empowers its citizens, reducing dependency on large financial institutions and foreign influences. By embracing these technologies, the country has not only created a fertile ground for innovation but has also set a precedent for other nations.Fostering Community: The Renaissance of Ideas and Collective Efforts
In a way reminiscent of Paris during the Enlightenment, El Salvador is becoming a gathering place for critical thinkers, entrepreneurs, and change-makers from around the globe. This international influx of intelligent, driven people is reshaping El Salvador’s future, breathing life into what many are calling a “new vision of hope.” The sense of community here is profound; projects are forming, partnerships are being established, and new ventures are taking shape. For those leaving countries that feel stagnant or in decline, El Salvador is a beacon of possibility and purpose.At the heart of this transformation is the ethos that real change comes from the ground up. Bukele’s policies have paved the way, but it is the people who are building El Salvador’s future. This grassroots approach is critical to the Renaissance spirit—one that calls on individuals to take responsibility, innovate, and foster a society founded on shared values and mutual goals.
An Invitation to the Future: The Adopting Bitcoin Conference
For those eager to witness this Renaissance firsthand, El Salvador will soon host the Adopting Bitcoin Conference. This event offers a unique opportunity to meet the innovators, builders, and visionaries driving this movement. The conference will spotlight the strides made in Bitcoin adoption, community development, and the groundbreaking projects that are shaping El Salvador's future.A Global Grassroots Movement Inspired by El Salvador
El Salvador’s Bottom-Up Renaissance is a testament to the power of community-driven progress and a symbol of what’s possible when a nation invests in sound money, decentralization, and a vibrant collective spirit. President Bukele’s vision has laid a foundation, but the future lies in the hands of those willing to build it. Whether or not this movement reshapes the world as it has El Salvador, it has shown us a glimpse of what the future could be—one where people everywhere have the opportunity to take part in building a brighter, more prosperous tomorrow. -
 @ 26838110:80edc65d
2024-10-31 06:10:41
@ 26838110:80edc65d
2024-10-31 06:10:41The Fibonacci Sequence
The Fibonacci sequence is a simple sequence of numbers where a number is the sum of the two preceding numbers in the series:
Xn = Xn-1 + Xn-2
0 - 1 - 1 - 2 - 3 - 5 - 8 - 13 - 21 - 34 - 55 - 89 - 144 - 233 - 377 - 610 - 987 - 1597 - 2584 - 4181
Modified Fibonacci Sequence
Sequence With Polarities and a Master or Neutral Element
1 - 2 - 3 - 5 - 8 - 13 - 21 - 34 - 55 - 89
Sequence With Polarities (-1 From the Fibonacci Sequence)
0 - 1 - 2 - 4 - 7 - 12 - 20 - 33 - 54 - 88
The Fibonacci Sequence in Reality
Now that we have these two lists, we can apply them to concrete elements to see their manifestation in the physical world.
1 Element
- Something
2 Elements
- Duality
- Electric Current
- Yin & Yang
- Sun & Moon
- Holy Trinity
- Day & Night Cycle
- Man & Woman
- Cat & Dog
- Tea & Coffee
- Wine & Beer
- Good & Evil
- Inclusion & Exclusion
- Plus & Minus
- Binary Code
4 Elements
- Cardinal Directions
- Four Alchemical Elements (Five Counting Aether)
- Five Chinese Alchemical Elements (Five Counting Metal)
- Four Seasons
- Four Tarot Minor Arcana Suites & Major Arcana
7 Elements
- Seven Colors of the Rainbow
- Seven Musical Notes & Octave
- Seven Chakras
- Seven Days in a Week
- Seven Classical Planets
12 Elements
- Twelve Months in a Year
- Traditional Tarot Minor Arcana Suite
20 Elements
- Twenty Amino Acids
- Number of Paths Between Sephirah in the Kabbalah (If Two Elements Are the Same Aspect of One or One Is Removed)
Fibonacci Worldbuilding Master Table
The table is available at:
https://www.dragonbanecreation.com/en/worldbuilding/energy/fibonacci
-
 @ b34b4408:acfb9667
2024-10-31 05:00:15
@ b34b4408:acfb9667
2024-10-31 05:00:15😱 การทบทวนสมมติฐานไขมันกับโรคหัวใจ: มุมมองใหม่จากหลักฐานทางวิทยาศาสตร์ 😱 https://www.mdpi.com/2072-6643/16/10/1447?fbclid=IwY2xjawGOTtxleHRuA2FlbQIxMAABHa2lVBffVeuI0SC8RgzbvQgtkbIsLwat1tDzxZKQ8UoEWYJuwC-Y7no7zA_aem_Qtv0GQuxhWxk0P2KCUFDmw . 🩸บทความนี้นำเสนอการวิเคราะห์เชิงลึกเกี่ยวกับสมมติฐานไขมันกับโรคหัวใจ (Lipid-Heart Hypothesis) ที่มีอิทธิพลต่อแนวทางโภชนาการทั่วโลกมาเกือบ 70 ปี โดยรวบรวมหลักฐานจากการศึกษาวิจัยที่สำคัญและผลกระทบที่เกิดขึ้น . โดยสมมติฐานไขมันกับโรคหัวใจถูกเสนอโดย Ancel Keys ในปี 1953 โดยตั้งอยู่บนความเชื่อว่าการบริโภคไขมันทั้งหมด ไขมันอิ่มตัว และคอเลสเตอรอลในปริมาณสูงจะนำไปสู่การเกิดโรคหัวใจ อย่างไรก็ตาม
สมมติฐานนี้มีข้อบกพร่องสำคัญหลายประการ: . 1. การรวมไขมันทรานส์กับไขมันอิ่มตัว: - ไม่แยกแยะผลกระทบที่แตกต่างระหว่างไขมันทั้งสองชนิด - ละเลยผลเสียของไขมันทรานส์ที่เกิดจากกระบวนการอุตสาหกรรม . 2. การส่งเสริมการบริโภค PUFA โดยไม่จำกัด: - ขาดการกำหนดขีดจำกัดการบริโภคกรดไขมันไม่อิ่มตัวหลายพันธะ - ไม่คำนึงถึงสมดุลระหว่างโอเมก้า-6 และโอเมก้า-3 . 3. การมองข้ามปัจจัยอื่น: - ไม่พิจารณาผลของน้ำหนักตัว การออกกำลังกาย และปัจจัยด้านวิถีชีวิต - ละเลยบทบาทของการอักเสบและความเครียดออกซิเดชัน .
ซึ่งเมื่อมาดูหลักฐานจากการศึกษาระยะยาวต่างๆเช่น . .

😲 Framingham Multi-Generational Study (1948-ปัจจุบัน) การศึกษาระยะยาวที่สำคัญนี้ได้พบข้อมูลที่น่าสนใจ: - ไม่พบความสัมพันธ์ระหว่างการบริโภคไขมันกับระดับคอเลสเตอรอล - ยิ่งบริโภคไขมันอิ่มตัว คอเลสเตอรอลและแคลอรี่มาก ระดับคอเลสเตอรอลในเลือดกลับยิ่งต่ำ - ความดันโลหิตสูงและเบาหวานเป็นปัจจัยเสี่ยงสำคัญมากกว่า .

😲Seven Countries Study (1957-1984) การศึกษาในประชากร 7 ประเทศ รวม 12,763 คน พบว่า: - ไม่มีความสัมพันธ์ระหว่างระดับคอเลสเตอรอลกับการเสียชีวิตจากโรคหัวใจ - ประชากรในเกาะครีตที่บริโภคไขมันสูง (36.1%) กลับมีอัตราการเสียชีวิตต่ำที่สุด - น้ำมันมะกอกและกรดไขมันโอเลอิกสัมพันธ์กับอัตราการเสียชีวิตจากโรคหัวใจที่ต่ำ - .

😲PURE Study การศึกษาขนาดใหญ่ในประชากร 18 ประเทศ พบว่า: - การบริโภคไขมันสูงสัมพันธ์กับความเสี่ยงการเสียชีวิตที่ต่ำลง - ไขมันอิ่มตัวสัมพันธ์กับความเสี่ยงโรคหลอดเลือดสมองที่ต่ำลง - ผลิตภัณฑ์นมไขมันเต็มส่งผลดีต่อสุขภาพหัวใจและหลอดเลือด .
รวมถึงการศึกษาทางคลินิกที่สำคัญต่างๆ .

😟Minnesota Coronary Experiment (1968-1973) ผลการศึกษาในผู้เข้าร่วม 9,423 คน แสดงให้เห็นว่า: - กลุ่มที่บริโภคน้ำมันข้าวโพดมีอัตราการเสียชีวิตสูงกว่า - ผู้ที่ระดับคอเลสเตอรอลลดลงมากที่สุดกลับมีความเสี่ยงสูงที่สุด - ไม่พบประโยชน์ของการแทนที่ไขมันอิ่มตัวด้วย PUFA -
 .
😟Sydney Diet Heart Study (1967-1973) การศึกษาในผู้ชาย 458 คน พบว่า:
- กลุ่มที่บริโภคน้ำมัน safflower มีอัตราการเสียชีวิตสูงกว่า
- ความเสี่ยงการเสียชีวิตจากโรคหัวใจเพิ่มขึ้น 74%
- การลดคอเลสเตอรอลไม่ได้นำไปสู่ผลลัพธ์ที่ดีขึ้น
.
.
😟Sydney Diet Heart Study (1967-1973) การศึกษาในผู้ชาย 458 คน พบว่า:
- กลุ่มที่บริโภคน้ำมัน safflower มีอัตราการเสียชีวิตสูงกว่า
- ความเสี่ยงการเสียชีวิตจากโรคหัวใจเพิ่มขึ้น 74%
- การลดคอเลสเตอรอลไม่ได้นำไปสู่ผลลัพธ์ที่ดีขึ้น
.ทำให้เกิดผลกระทบของในส่วนการแนะนำให้บริโภคอาหารไขมันต่ำ ซึ่งส่งผลให้เกิดการเปลี่ยนแปลงที่สำคัญ: 😱😱😱 1. การเพิ่มขึ้นของโรคเรื้อรัง: - โรคอ้วนเพิ่มจาก 48.8% (1960) เป็น 82.3% (2017-2018) - เบาหวานเพิ่มจาก 6.2% (1994) เป็น 14.7% (2021) - โรคอัลไซเมอร์เพิ่มจาก 4.5 ล้านคน (2000) เป็น 6.7 ล้านคน (2023) . 2. การเปลี่ยนแปลงรูปแบบการบริโภค: - เพิ่มการบริโภคอาหารแปรรูป - ลดการบริโภคอาหารที่มีคุณค่าทางโภชนาการสูง - เพิ่มการบริโภคคาร์โบไฮเดรตและน้ำตาล . โดยบทความนี้ได้เสนอแนะสำหรับแนวทางโภชนาการใหม่ดังนี้ 😉😉😉 1. การปรับปรุงคำแนะนำด้านอาหาร: - ทบทวนการจำกัดไขมันอิ่มตัว - กำหนดขีดจำกัดการบริโภค PUFA - ส่งเสริมการบริโภคอาหารธรรมชาติ . 2. การพิจารณาปัจจัยรอบด้าน: - คำนึงถึงคุณภาพอาหารโดยรวม - ให้ความสำคัญกับการลดการบริโภคอาหารแปรรูป - พิจารณาปัจจัยด้านวิถีชีวิตและสิ่งแวดล้อม . จากหลักฐานทางวิทยาศาสตร์จำนวนมากไม่สนับสนุนสมมติฐานไขมันกับโรคหัวใจ การจำกัดไขมันอิ่มตัวและส่งเสริมการบริโภค PUFA โดยไม่มีขีดจำกัด อาจส่งผลเสียต่อสุขภาพ จำเป็นต้องมีการทบทวนแนวทางโภชนาการโดยอาศัยหลักฐานที่ทันสมัยและครอบคลุม เพื่อส่งเสริมสุขภาพที่ดีของประชากรในระยะยาว .
...................................... ข้อมูลสุขภาพดีๆที่ไม่มีค่าใช้จ่าย https://www.youtube.com/@fastingfatdentist . หากสนใจวิธีการดูแลสุขภาพตามแบบ IFF ปรึกษาส่วนตัว inbox มาสอบถามที่เพจได้เลยครับ .
ความน่ากลัวในการดูแลสุขภาพคือการที่เชื่อโดยไม่มีความรู้ .
.
IFF #IFF_talk #intermittentfasting #keto #Lowcarb #CD #plantbased #RemissionDiabetes #ร่างกายเราคือธรรมชาติไม่ใช่ยา #เบาหวานหายได้โดยไม่ต้องใช้ยา #หมอไหวของหมอแบบนี
fastingfatdentist
healthstr
IFF
#fiat
siamstrOG
siamstr
bitcoin
siamesebitcoiners
orangebaby
หมอบ่นFiat
-
 @ 502ab02a:a2860397
2024-10-31 02:50:27
@ 502ab02a:a2860397
2024-10-31 02:50:27
ตะเกียงฟักทองที่เห็นกันในวันฮัลโลวีน หรือที่เรียกกันว่า Jack O’ Lantern ถือกำเนิดมานานหลายร้อยปี โดยมีรากฐานมาจากตำนานพื้นบ้านของชาวไอริช ว่าด้วยเรื่องของ “แจ็กจอมขี้เหนียว หรือ แจ็กจอมตืด” ซึ่งเป็นหนึ่งในเรื่องเล่าที่ถ่ายทอดจากรุ่นสู่รุ่น และมีหลายเวอร์ชัน แต่เวอร์ชันที่แพร่หลายที่สุดเล่าว่า แจ็กเป็นชายที่เจ้าเล่ห์มาก ถึงขั้นสามารถหลอกลวงซาตานได้
เรื่องเริ่มต้นเมื่อแจ็กเชิญซาตานมาดื่มเหล้าด้วยกัน แต่แทนที่จะจ่ายเงินเอง แจ็กกลับวางแผนให้ซาตานแปลงร่างเป็นเหรียญเพื่อจ่ายค่าเหล้า ซาตานยินดีทำตามแผนนี้ แต่แจ็กกลับนำเหรียญใส่ไว้ในกระเป๋าที่มีไม้กางเขนอยู่ ซาตานจึงไม่สามารถคืนร่างเดิมได้
หลังจากการเจรจา แจ็กยอมปล่อยซาตาน โดยมีข้อตกลงว่าซาตานจะต้องไม่ยุ่งกับเขาเป็นเวลา 1ปี และเมื่อแจ็กตาย ซาตานจะไม่มีสิทธิ์ครอบครองวิญญาณของเขา
เมื่อครบหนึ่งปี ซาตานกลับมาหาแจ็กอีกครั้ง คราวนี้แจ็กใช้กลอุบายใหม่ หลอกให้ซาตานปีนขึ้นไปเก็บแอปเปิ้ลบนต้นไม้ แล้วจึงสลักกางเขนไว้บนต้นไม้ ทำให้ซาตานลงมาไม่ได้ แจ็กจึงต่อรองเพิ่ม โดยซาตานต้องสัญญาว่าจะไม่มายุ่งกับเขาอีกเป็นเวลา 10ปี
แต่เมื่อแจ็กเสียชีวิต วิญญาณของเขากลับไม่ถูกต้อนรับเข้าสวรรค์ เนื่องจากพฤติกรรมหลอกลวงที่เขาทำเมื่อยังมีชีวิตอยู่ และแม้ว่าเขาจะลองไปหาที่พึ่งในนรก ซาตานก็ปฏิเสธการรับวิญญาณของเขาเช่นกัน ตามคำสัญญาที่เคยให้ไว้
สุดท้ายแจ็กจึงต้องกลายเป็นวิญญาณเร่ร่อน โชคดีที่ซาตานยังปราณีทิ้งก้อนถ่านที่เรืองแสงให้แจ็กไว้ส่องทาง แจ็กจึงคว้านหัวผักกาด เจาะช่องแสงแล้วใส่ถ่านลงไป เพื่อใช้เป็นตะเกียงนำทาง
ชาวไอริชจึงตั้งชื่อ “แจ็กกับตะเกียง” ว่า Jack of the Lantern ก่อนจะเพี้ยนกลายเป็น Jack O’ Lantern ในเวลาต่อมา และธรรมเนียมนี้ก็แพร่หลายในหมู่ชาวไอริชและสกอตแลนด์ ผู้คนนิยมแกะสลักหัวผักกาดหรือหัวมันฝรั่งให้ดูน่ากลัว จากนั้นใส่ไฟด้านใน แล้วนำไปวางที่หน้าต่างหรือประตูเพื่อป้องกันวิญญาณเร่ร่อนอย่างแจ็กไม่ให้เข้ามารบกวนในคืนฮัลโลวีน
ส่วนฟักทองที่ใช้กันอย่างแพร่หลายในปัจจุบันนั้น เพิ่งถูกนำมาใช้หลังจากที่ผู้อพยพจากยุโรปเดินทางไปยังอเมริกา เนื่องจากฟักทองเป็นพืชที่หาง่ายและมีขนาดใหญ่ ทำให้ง่ายต่อการแกะสลัก คนอเมริกันจึงเริ่มใช้ฟักทองแทนหัวผักกาดหรือมันฝรั่งในการทำตะเกียง Jack O’ Lantern
-
 @ eac63075:b4988b48
2024-10-30 20:58:01
@ eac63075:b4988b48
2024-10-30 20:58:01Have you ever heard that cryptocurrencies are primarily used by criminals? This is a common idea, but it doesn’t reflect reality. In this article, we will explore what cryptocurrencies are, how they work, and why the notion that they’re only for illegal activities is a myth. We will also compare the use of cryptocurrencies with traditional money and understand how blockchain technology brings transparency and security to transactions.
https://www.fountain.fm/episode/hVVS7hrsX8VQ9SPoUYbg
What Are Cryptocurrencies?
Cryptocurrencies are digital currencies that use cryptography to secure transactions. The most well-known is Bitcoin, but there are many others, like Ethereum, Litecoin, and Ripple. Unlike traditional money, cryptocurrencies are not controlled by governments or central banks. They operate on a decentralized network called blockchain, which records all transactions publicly and immutably.
The Origin of the Myth: Cryptocurrencies and Illicit Activities
The myth that cryptocurrencies are mainly used for crime began with cases like Silk Road, an illegal online marketplace where Bitcoin was used to buy and sell illicit products. This type of news captured attention and created a negative image of cryptocurrencies. However, it’s essential to understand that these cases are exceptions and don’t represent the majority of cryptocurrency use.
Current Data: Cryptocurrencies and Illicit Activities
According to the 2024 Cryptocurrency Crime Report from Chainalysis, only 0.34% of cryptocurrency transactions in 2023 were linked to illegal activities. This means that the vast majority of people use cryptocurrencies legitimately, for investments, shopping, sending money to family in other countries, and other legal activities.
 ## Comparison with Traditional Money
## Comparison with Traditional MoneyWhen we look at traditional money, like the dollar or the euro, we see that it is much more used in criminal activities. According to a report by Verafin, about 3.1 trillion dollars are used annually in financial crimes such as drug trafficking, terrorism, fraud, and money laundering. This represents approximately 3.87% of all money in circulation.
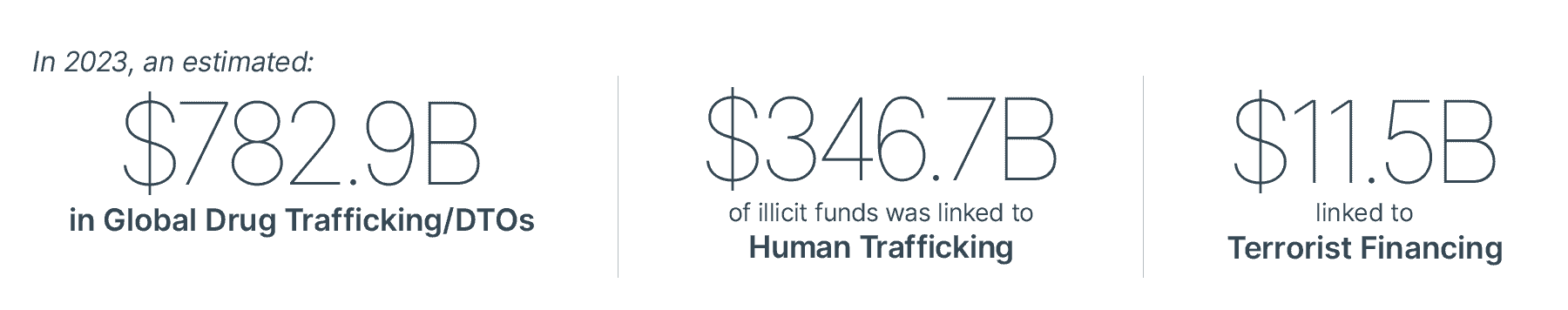 In comparison, the illicit use of cryptocurrencies is a much smaller fraction. This shows that traditional money remains the main tool for financial crimes, not cryptocurrencies.
In comparison, the illicit use of cryptocurrencies is a much smaller fraction. This shows that traditional money remains the main tool for financial crimes, not cryptocurrencies.The Transparency of Blockchain
One of the great advantages of cryptocurrencies is blockchain technology. Since all transactions are recorded in a public ledger, it’s possible to trace the path of money. This makes it harder for criminals to hide their activities. Unlike cash, which can change hands without leaving any trace, cryptocurrency transactions leave a permanent record.
Companies and law enforcement agencies use this transparency to identify and combat illegal activities. This makes cryptocurrencies less appealing to criminals who prefer methods that leave no trace.
How Much Money Is There in the World?
To understand the scale, it’s interesting to know that, according to the World Population Review, about 80 trillion dollars are in circulation globally, including physical and digital money. Out of this total, only 5 trillion dollars is in physical cash. This shows that most transactions are already digital, even in the traditional financial system.
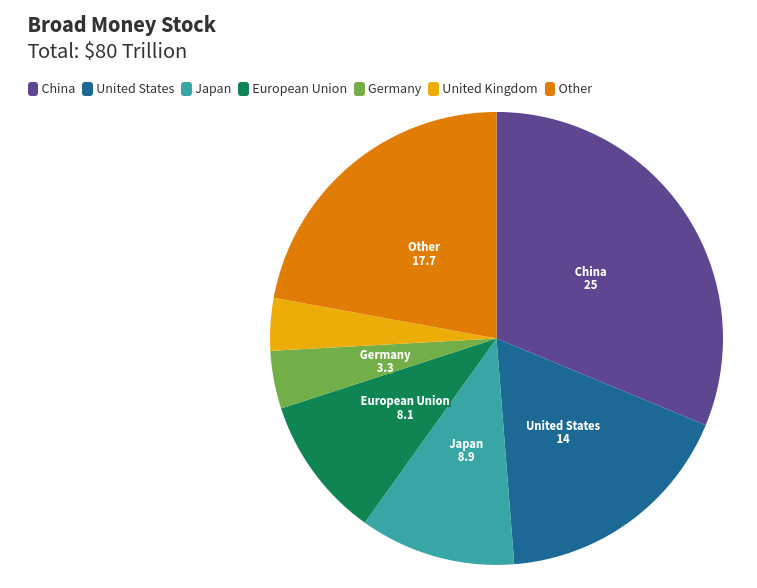 ## Cryptocurrencies Promote Economic Freedom
## Cryptocurrencies Promote Economic FreedomCryptocurrencies offer people more control over their own money. Without the need for intermediaries like banks or governments, transactions can be made directly between individuals. This is especially useful in countries with unstable financial systems or where the population lacks easy access to banking services.
This financial autonomy can bother traditional institutions that are used to controlling the flow of money. Therefore, we sometimes see criticism of cryptocurrencies from these institutions, which may try to link them to criminal activities to discredit them.
Myths and Realities
It’s a myth to say that cryptocurrencies are mainly used for crimes. The reality is that they are primarily used for legal and legitimate purposes. People around the world invest in cryptocurrencies, use them for online shopping, send money to family in other countries, and even protect their savings from inflation.
Conclusion: Are Cryptocurrencies Really the Villains?
The evidence shows that cryptocurrencies are not the villains some believe them to be. On the contrary, they offer a safe, transparent, and efficient way to conduct financial transactions. While traditional money continues to be the main means used in criminal activities, the illicit use of cryptocurrencies remains a small exception.
If you have doubts about the reliability of cryptocurrencies, remember that the technology behind them is designed to be safe and transparent. With current data and information, it’s clear that cryptocurrencies are closer to being a solution for financial problems than a cause.
And You, What Do You Think?
Are cryptocurrencies being unfairly accused? Share your opinion and join the discussion!Have you ever heard that cryptocurrencies are primarily used by criminals? This is a common idea, but it doesn’t reflect reality. In this article, we will explore what cryptocurrencies are, how they work, and why the notion that they’re only for illegal activities is a myth. We will also compare the use of cryptocurrencies with traditional money and understand how blockchain technology brings transparency and security to transactions.
What Are Cryptocurrencies? Cryptocurrencies are digital currencies that use cryptography to secure transactions. The most well-known is Bitcoin, but there are many others, like Ethereum, Litecoin, and Ripple. Unlike traditional money, cryptocurrencies are not controlled by governments or central banks. They operate on a decentralized network called blockchain, which records all transactions publicly and immutably.
The Origin of the Myth: Cryptocurrencies and Illicit Activities The myth that cryptocurrencies are mainly used for crime began with cases like Silk Road, an illegal online marketplace where Bitcoin was used to buy and sell illicit products. This type of news captured attention and created a negative image of cryptocurrencies. However, it’s essential to understand that these cases are exceptions and don’t represent the majority of cryptocurrency use.
Current Data: Cryptocurrencies and Illicit Activities According to the 2024 Cryptocurrency Crime Report from Chainalysis, only 0.34% of cryptocurrency transactions in 2023 were linked to illegal activities. This means that the vast majority of people use cryptocurrencies legitimately, for investments, shopping, sending money to family in other countries, and other legal activities.
Comparison with Traditional Money When we look at traditional money, like the dollar or the euro, we see that it is much more used in criminal activities. According to a report by Verafin, about 3.1 trillion dollars are used annually in financial crimes such as drug trafficking, terrorism, fraud, and money laundering. This represents approximately 3.87% of all money in circulation.
In comparison, the illicit use of cryptocurrencies is a much smaller fraction. This shows that traditional money remains the main tool for financial crimes, not cryptocurrencies.
The Transparency of Blockchain One of the great advantages of cryptocurrencies is blockchain technology. Since all transactions are recorded in a public ledger, it’s possible to trace the path of money. This makes it harder for criminals to hide their activities. Unlike cash, which can change hands without leaving any trace, cryptocurrency transactions leave a permanent record.
Companies and law enforcement agencies use this transparency to identify and combat illegal activities. This makes cryptocurrencies less appealing to criminals who prefer methods that leave no trace.
How Much Money Is There in the World? To understand the scale, it’s interesting to know that, according to the World Population Review, about 80 trillion dollars are in circulation globally, including physical and digital money. Out of this total, only 5 trillion dollars is in physical cash. This shows that most transactions are already digital, even in the traditional financial system.
Cryptocurrencies Promote Economic Freedom Cryptocurrencies offer people more control over their own money. Without the need for intermediaries like banks or governments, transactions can be made directly between individuals. This is especially useful in countries with unstable financial systems or where the population lacks easy access to banking services.
This financial autonomy can bother traditional institutions that are used to controlling the flow of money. Therefore, we sometimes see criticism of cryptocurrencies from these institutions, which may try to link them to criminal activities to discredit them.
Myths and Realities It’s a myth to say that cryptocurrencies are mainly used for crimes. The reality is that they are primarily used for legal and legitimate purposes. People around the world invest in cryptocurrencies, use them for online shopping, send money to family in other countries, and even protect their savings from inflation.
Conclusion: Are Cryptocurrencies Really the Villains? The evidence shows that cryptocurrencies are not the villains some believe them to be. On the contrary, they offer a safe, transparent, and efficient way to conduct financial transactions. While traditional money continues to be the main means used in criminal activities, the illicit use of cryptocurrencies remains a small exception.
If you have doubts about the reliability of cryptocurrencies, remember that the technology behind them is designed to be safe and transparent. With current data and information, it’s clear that cryptocurrencies are closer to being a solution for financial problems than a cause.
And You, What Do You Think? Are cryptocurrencies being unfairly accused? Share your opinion and join the discussion!
-
 @ 6c4b0219:bb7f889e
2024-10-30 18:42:27
@ 6c4b0219:bb7f889e
2024-10-30 18:42:27This is not just the first or the second time; it's the third time I'm on Nostr.
Like everyone new to Nostr who isn’t 100% knowledgeable on how decentralised protocols works like Jack, Alex, or other great minds in this space, we have, one way or another, lost our first private key (Nsec).
Well, funny enough, i lost mine
I started with the Amethyst Nostr client, but unfortunately, I lost my private keys.
Then I moved to Primal, where I lost my private keys again. However, this time it’s not going to be the same story!
I’ve learned from my lessons.__
We all make mistakes, but it’s time to learn from them!
I look forward to delving into the decentralized world of Nostr, and this time I’m going to take this freedom tech more seriously!
I’m excited to grow and connect with great minds here.
Don't forget to give me a follow to support my journey here.
Thank you for reading!
PS: I'm Currently Using Yakihonne client...
-
 @ 1b5ee74d:bb1aae6e
2024-10-30 18:03:09
@ 1b5ee74d:bb1aae6e
2024-10-30 18:03:09It’s right to build an open-source wallet, but that shouldn’t be the first feature displayed on your website if you’re aiming for the mass market.
We’re at a pivotal moment for Bitcoin, particularly in terms of adoption. Bailey, a marketing expert with top-tier experience, explains why. With a decade as the Head of Retail Marketing at Apple from 2002 to 2012—the era of revolutionary products like the iPhone and iPad—plus years as Vice President of Marketing at Samsung Smart-Things, he’s now Chief Marketing Officer at Azteco. Speaking with Bitcoin Train, Bailey discusses how Bitcoin’s messaging must evolve to engage the true mass market by focusing less on technicalities and more on tangible benefits for the average user.
Bailey’s message is clear: to achieve mass adoption, Bitcoin’s public presentation needs a shift toward emphasizing practical benefits over technical details. This shift would entail moving from a narrative focused solely on “hodling” to one that highlights Bitcoin’s qualities as a payment tool as well.
The full interview with David Bailey is available on YouTube; the following is a summary of the most significant points.
Let’s start by discussing your past: what was the sentiment at Apple when launching global hits like the iPhone or iPad?
At Apple, we could quickly observe the interest and adoption of our products. Whenever we entered a new country, demand was high: retailers wanted entire shelves stocked with iPods and accessories. This let us gauge sales trends early on. But the key lay in how we presented the product. If you described it as “an MP3 player” or “an e-book reader,” the response was lukewarm. However, if you framed it in terms of user value, like “having a thousand songs in your pocket,” people got excited, and adoption followed.
Today, if you search online for “What is Bitcoin?” you find technical explanations about blockchain, mining, and more. But the real question is, what does Bitcoin mean for the consumer? It’s a way to spend and save, to send money globally in seconds without fees.
Bitcoin’s technical foundations have drawn developers, enthusiasts, and advocates. Why change the narrative now?
There’s a book written about twenty years ago called Crossing the Chasm. It’s one of those books that has stood the test of time. Like any business text, it’s not a magical formula but offers a good conceptual framework for thinking about these issues.
The essential idea is that customers of a tech product are divided into two groups. On one side is the early market, about 15% of the total market, and on the other, the mass market, which covers around 85%. Between the early market and the mass market is a “chasm,” a kind of gap to bridge.

The adoption cycle
The early market consists of innovators and early adopters, followed by the early majority, late majority, and finally, the “laggards,” the last group to adopt technology. Innovators and early adopters are the ones who, for example, were among the first to use the internet or are experimenting today with virtual reality headsets and Apple Vision Pro. But the approach between those in the early market and those in the mass market is very different.
Are you saying interests vary greatly between these two types of customers?
Exactly. Early adopters are attracted to the technology itself; they want to experiment and explore what they can do with it, even if it’s limited or imperfect. The early majority, however, isn’t interested in technical details; they care about tangible benefits: they want the product to work immediately, they want a simple, straightforward experience.
A similar example is the evolution of the internet 20-25 years ago. Initially, it was discussed in highly technical terms, making it seem like a niche technology with no apparent need for most people. Only when the practical benefits, such as sending emails or browsing the web, were highlighted did the broader public start to see its value. People didn’t need to understand VPNs or DNS; they just wanted to use the internet for practical purposes.
Early email users had to manage complex command-line interfaces. The early majority came on board only when email clients became user-friendly. At that point, it was enough to enter a username and password without worrying about technical details. The mass market simply wants things to work effortlessly.
The point is, to move from the early market to the mass market, we need to cross the “chasm.” Achieving this requires a deep understanding of what the consumer truly wants: not pure technology, but immediate and tangible benefits.
Where do we stand in Bitcoin’s adoption cycle? Do we need to make the leap?
Yes, I’d say we’re right on the “chasm.” We’re near the end of the early adoption phase, and Bitcoin’s challenge is to cross this gap without getting lost in the middle. We must stop talking about how the technology works and start explaining how people can use it safely to gain real, practical benefits in their everyday lives.
Isn’t there a risk of abandoning Bitcoin’s foundational principles like privacy, open-source philosophy, and censorship resistance?
Success lies not in changing the product but in adjusting the message and marketing strategy. It’s not about diluting Bitcoin’s fundamentals for the sake of simplicity but rather presenting its features in a way that resonates with the early majority.
It’s right to develop an open-source wallet, but that shouldn’t be the first feature displayed on a website if the goal is to attract a wider audience. While I support open-source and privacy, we must realize these aren’t the priorities for the next 100 million users. This doesn’t mean trivializing Bitcoin’s technology but rather tailoring the message to speak to people differently. Trying to convert everyone to the early adopter mindset, with the concept of the “orange pill,” is an ineffective strategy.
What kind of messaging should be used to effectively reach the masses? How should the marketing strategy change?
We can tell stories of everyday people using Bitcoin for daily activities. Last year, around $669 billion was sent globally in remittances by people working in countries like the United States or Mexico to support their loved ones. Here’s a tangible use case: with Bitcoin, you can send funds to your family members wherever they are, instantly and without fees. And with services like Bitrefill, they can easily use them. Whether it’s paying a freelancer or sending money to someone on the other side of the world, the utility becomes real.
For those, like me, living in the UK, where the financial system is relatively stable, it may not seem so significant. But for people in the United States sending money to Mexico, or those living in Argentina or Brazil, where financial uncertainty has been a constant for decades, Bitcoin becomes a far more attractive choice. I know people in South Africa who prefer to save in bitcoin instead of the local currency, which they view as corrupt and unstable.
The goal, then, is to find everyday, concrete use cases. Currently, though, media narratives are almost exclusively focused on Bitcoin’s price, its volatility, or scandals involving the crypto world. We need to get past these distractions.
You mentioned daily payments as a use case that appeals to the mass market. However, there are many staunch proponents of hodling at all costs. How do you view this debate in the context of the adoption cycle?
One thing I’m firmly convinced of is that if we focus solely on accumulating bitcoin and holding it, Bitcoin will never reach its full potential.
The truth is that Bitcoin can be both digital gold and digital cash. Right now, there’s an overabundance of attention on its store-of-value aspect, while we lack sufficient focus on making it a tool for daily payments. Enough people already view Bitcoin as a form of investment or savings. What we need to concentrate on now is promoting its everyday use, so it genuinely becomes a medium of exchange.
If millions of people start using Bitcoin for their daily transactions, it will sustain the system and increase its value for those who choose to save in bitcoin as well. We can’t have one without the other.
Azteco was created with precisely this goal: to promote Bitcoin adoption among consumers by making the process as simple as possible. We want people to be able to purchase Bitcoin easily, even for just $10, without having to go through an exchange, with no bank accounts or ID documents required.
-
 @ c230edd3:8ad4a712
2024-10-30 17:28:09
@ c230edd3:8ad4a712
2024-10-30 17:28:09Chef's notes
This is great to start in the morning, and come home to a nearly finished meal. I like to make tacos that day, then use any remaining for just about anything from chili to omelets. Fun way to prepare ramen too.
Details
- ⏲️ Prep time: 30 min, plus 15 before serving
- 🍳 Cook time: 8 hours
- 🍽️ Servings: 10-12
Ingredients
- 3-4lb Chuck Roast, bone-in preferred
- 1 large White Onion, quartered
- 6-8 cloves Garlic, peeled
- 5 Roma Tomatoes, halved
- 6-8 dried Arbol Chiles, seeded
- 3-4 Guajillo Chiles, seeded
- 2 tsp Coriander seeds
- 2 tsp Cumin seeds
- 2 Tbsp Oregano, Mexican Oregano if available
- 1/2 tsp ground Cinnamon
- 2 whole Bay Leaves
- 1 tsp Salt
- SPG style seasoning mix to coat the roast
- 3-4 cups beef broth, just enough to cover roast plus additional for thinning sauce if desired
- Any toppings desired (avocado, cilantro, sour cream, queso fresca, cheddar, fresh onion, etc)
Directions
- Preheat large frying pan to med/high, add oil for searing
- Add onions and tomatoes, sear until edges char, add garlic and saute until fragrant, transfer to slow cooker
- Pat roast dry, season all sides, transfer to pan
- Sear roast on all sides, 2-4 minutes or until golden brown, transfer to slow cooker
- Add all seasonings and beef broth to slow cooker
- Cook on low 8+ hours or until the meat is falling apart
- Remove bone and bay leaves
- Transfer liquid and vegetables to a blender with loose fitting lid, blend until smooth, transfer to large bowl
- Shred roast in slow cooker, pour sauce mix back in and stir. Adjust ratio by adding more beef broth if desired. Salt to taste.
- Serve, drained as tacos, nachos, omelets, etc. Serve with broth as stew or mix with ramen
-
 @ 0e501ec7:de5ef3a4
2024-10-30 17:25:51
@ 0e501ec7:de5ef3a4
2024-10-30 17:25:51From now on, when, i open my phibe for distraction, i will write something, anything, cheers
Okay, daarnet heeft het niet gewerkt. Nu wel? of houdt het me nu tegen van iets anders te gaan doen? bof ook oke. Het ruikt hier naar kak en da stoort mij zohard, zeer afleidend. Vandaag was een goeie dag, we zijn in de voormiddag een walbootboom tegen gekomen, en later, in Vailly sur aisne, heb ik die allemaal gekraakt terwijl Tim de kettingen kuiste. Was wel leuk, al kreeg ik er rugpijn van, net als nu. Zitten geeft mij meer rugpijn dan fietsen deze dagen, surtout zitten en iets doen met mijn handen, mijn rug sen schouders gaan dan als een egeltje poef inelkaar.
We zitten nu een beetje in een maanlandschap, temidden industriele velden, bij een kleine haag, sleedoorn. We hebben iets te lang doorgefietst, we passeerden een goeie plek on half zes, maar toen kwam de schemering en sloeg de vermoeidheid toe net voor we toekwamen. Ik ben moe, ook al hebben we niet zoveel gefietst vandaag, nog geen 50km. We hebben batuurlijk wel 3 uur op het kerkplein van Vailly gezeten. Was heel leuk om het rustige dorpje, waar nog wel een beetje leven was, een bakker, een traiteur, een paar winkels, zo te zien. Mensen passeerden, zeiden goeiendag, smakelijk, of kwamen een hele babbel doen. Tussendoor luisterde ik wat muziek. Een heel leuk werkke, walnoten kraken, ik denk dat ik nog niet vaak zo van de herfst genoten heb als daar, op dat bankje. De kleuren in het bos, en de dans van de spreeuwen stonden mij nog kevendig voor. De mensen wensten ons veel succes, je zag dat ze ons zot vonden om door de grijze herfst te fietsen.
Vanaf hier is er een grote oranje vlek op de horizon te zien, de stad van licht. Parijs!
-
 @ 0e501ec7:de5ef3a4
2024-10-30 17:21:46
@ 0e501ec7:de5ef3a4
2024-10-30 17:21:46Buizerd in de mist. Spreeuwen op een elektriciteitspaal. Je komt een beetje dichter, ze zwermen op in een dansende wolk. Zwerm voor mij niet identificeerbaar, tsjirpende vogels. Een blaadje valt, bijna in je pot met thee. Aan een hoge tak, maar toch de onderste, hangt een verloren vissershaak. Het water aan de kant ziet er vies en slijmerig uit. Vannacht was ik bang erin te vallen, slaapdronken op tocht naar een plek om pipi te doen. Het verlangen naar een middagmaal zonder pindakaas. Een klein lapje kleinschalige landbouw, met groentebedden op mensenmaat, in de zee van industrie-veld. In de verte een boer die met zijn halve oorlogsmachine zijn gewas beschermd. In de bossen hangt het vol lianen, veel meer dan thuis. Op de weg een overreden marter. Naast de weg, dappere kamille, teder bloeiend. Als de schemering valt: vermoeidheid. In de nacht stilte, gepruttel van ons stoofpotje, aangevuurd met brandalcool. In de ochtend: mist. Een buizerd.
-
 @ 8f69ac99:4f92f5fd
2024-10-30 14:54:26
@ 8f69ac99:4f92f5fd
2024-10-30 14:54:26Nos últimos anos, a narrativa dominante retrata a mineração de Bitcoin como um consumidor voraz de energia, com impactos ambientais desproporcionais. Embora a mineração de Bitcoin exija uma quantidade significativa de energia, esta visão ignora um ponto crucial: o seu potencial para promover a sustentabilidade ambiental e remodelar a integração de energias renováveis.
Este artigo vai além dos debates convencionais sobre a pegada de carbono, explorando como a mineração de Bitcoin pode mitigar os impactos ambientais e catalisar uma transição energética sustentável, transformando o que alguns consideram uma inutilidade num aliado contra a dependência dos combustíveis fósseis e a adversidade climática.
Desafios da Energia Renovável
Alcançar um futuro sustentável depende da adopção de fontes de energia renovável, mas estas enfrentam desafios únicos. Gerir o excesso de energia produzido durante períodos de baixa procura e lidar com as limitações da actual tecnologia de baterias são obstáculos significativos. Além disso, a transmissão de energia a longas distâncias permanece ineficiente, o que impede que recursos renováveis remotos alcancem mercados mais amplos.
Por exemplo, as linhas de corrente contínua de alta tensão (HVDC) perdem aproximadamente 3% de potência por cada 1.000 km, enquanto as linhas de corrente alternada de alta tensão (HVAC) perdem cerca de 7% por cada 1.000 km. Isto significa que, por cada quilómetro, as linhas HVDC perdem cerca de 0,003%, e as linhas HVAC perdem cerca de 0,007% (as linhas de alta tensão são projectadas para diminuir perdas, as perdas são ainda maiores na media tensão). Estas perdas, aliadas à dificuldade de transportar energia de parques renováveis remotos, sublinham a necessidade de soluções localizadas.
Por exemplo, em 2018, cerca de 6,5 milhões de MWh de produção de energia solar fotovoltaica foram descartados, ou "mandados fora", no Chile, na China, na Alemanha e nos Estados Unidos conjuntamente. É importante notar que, à medida que a capacidade de energia renovável continua a crescer rapidamente (com o aumento das adições de capacidade renovável global anual em quase 50%, para quase 510 gigawatts em 2023), a quantidade absoluta de energia desperdiçada é susceptível de aumentar, a menos que se façam melhorias significativas na infraestrutura da rede, no armazenamento de energia e na gestão da procura.
Monetizar o Excesso de Energia através da Mineração de Bitcoin
Fontes de energia renovável, como a solar e a eólica, muitas vezes geram mais electricidade do que a rede necessita em determinados momentos, criando um excedente de energia que normalmente é desperdiçado. Este excesso permanece subutilizado porque:
- As soluções de armazenamento em grande escala são limitadas e dispendiosas ou mesmo inexistentes;
- A capacidade de transmissão muitas vezes não é suficiente para distribuir energia a longas distâncias;
- E a procura nem sempre coincide com os períodos de produção máxima de energia renovável.
A mineração de Bitcoin apresenta uma solução apelativa, ao actuar como um consumidor de energia flexível, capaz de ajustar rapidamente o seu consumo para se alinhar com a oferta. Operações de mineração localizadas perto de instalações de energia renovável — como centrais hidroeléctricas ou parques solares — podem absorver o excesso de energia que, de outra forma, seria desperdiçado, monetizando-o. Esta configuração não só reduz o desperdício de energia renovável, como também proporciona fontes de rendimento fiáveis para projectos renováveis, incentivando o investimento em infraestruturas verdes.
Mineração de Bitcoin como Consumidor Flexível
As operações de mineração de Bitcoin podem ajustar dinamicamente o seu consumo de energia, actuando como uma "carga flexível" na rede. As principais vantagens incluem:
- Escalabilidade Rápida: Os equipamentos de mineração podem aumentar ou diminuir o seu consumo de energia quase instantaneamente, respondendo às flutuações na disponibilidade de energia.
- Independência Geográfica: A mineração de Bitcoin pode ser realizada em qualquer local com ligação à internet, permitindo que os mineradores se situem perto das fontes renováveis, independentemente da infraestrutura da rede.
- Capacidade Modular: O equipamento de mineração é altamente escalável, permitindo que os produtores de energia desenhem sistemas modulares que se adaptem à capacidade energética disponível.
Incentivos Económicos e Benefícios
A utilização do excedente de energia para a mineração de Bitcoin permite que os produtores de energia renovável gerem receitas a partir de energia que, de outra forma, seria desperdiçada. Este impulso económico aumenta a rentabilidade dos projectos de energia renovável, tornando-os mais atractivos para os investidores. Os benefícios adicionais incluem:
- Estabilização da Rede: As operações de mineração ajudam a equilibrar a oferta e a procura na rede, contribuindo para a resiliência e estabilidade da mesma.
- Redução do Desperdício: Ao consumir electricidade excedente, a mineração de Bitcoin reduz significativamente a quantidade de energia renovável desperdiçada.
- Aumento do Financiamento para Renováveis: Os lucros provenientes da mineração de Bitcoin podem ser reinvestidos em novos projectos de energia renovável, soluções de armazenamento e infraestrutura de rede, criando um ciclo positivo de reforço para a energia verde.
Aplicações no Mundo Real
Vários exemplos ilustram como a mineração de Bitcoin monetiza eficazmente o excedente de energia:
- No Texas, os mineradores de Bitcoin aproveitam o excesso de energia eólica, apoiando a rede através de programas de resposta à procura que aumentam a fiabilidade da rede durante períodos de alta e baixa procura.
- No Quebec, o excesso de energia hidroeléctrica é canalizado para operações de mineração de Bitcoin, o que ajuda a estabilizar a rede e a reduzir o desperdício de energia renovável.
- Um estudo da Universidade de Cornell descobriu que projectos de energia renovável nos EUA poderiam gerar milhões de dólares ao minerar Bitcoin durante estágios pré-comerciais, demonstrando a viabilidade económica desta abordagem.
Potencial Impacto na Transição para Energias Renováveis
Ao monetizar o excedente de energia através da mineração de Bitcoin, esta abordagem acelera a transição para energias renováveis. Os benefícios incluem:
- Viabilidade Económica para Renováveis: A monetização da energia desperdiçada torna os projectos renováveis mais rentáveis e, portanto, mais atractivos para investidores.
- Flexibilidade da Rede: A mineração de Bitcoin fornece uma fonte de procura escalável e adaptável, ajudando os operadores de rede a gerir as flutuações de oferta.
- Pegada de Carbono Reduzida: Ao utilizar fontes renováveis, o impacto ambiental da mineração de Bitcoin diminui, alinhando-se com os objectivos de sustentabilidade.
- Adopção Acelerada de Energias Renováveis: A maior rentabilidade e a redução do desperdício incentivam um maior investimento, impulsionando a adopção de tecnologias de energia renovável.
Essencialmente, a mineração de Bitcoin oferece uma solução única para os desafios da produção intermitente de energia renovável, criando uma procura flexível e independente da localização para a electricidade excedente que, de outra forma, seria desperdiçada. À medida que mais projectos renováveis adoptam este modelo, a mineração de Bitcoin pode desempenhar um papel crucial na promoção de um panorama energético sustentável e descentralizado.
Fornecimento de Energia a Regiões Isoladas e Subdesenvolvidas
Um dos impactos mais promissores da mineração de Bitcoin é a capacidade de levar electricidade a regiões remotas e subdesenvolvidas. Pequenas centrais hidroeléctricas e instalações solares são opções cada vez mais viáveis para comunidades isoladas que não têm acesso a redes tradicionais. Mineradores de Bitcoin, em busca de energia barata e excedente, podem apoiar e financiar estas instalações, reduzindo a lacuna energética e permitindo o acesso a energia limpa para estas comunidades.
Por exemplo, aldeias em África que anteriormente não tinham electricidade podem agora operar escolas, clínicas e empresas, graças a pequenos projectos de energia renovável apoiados pela mineração de Bitcoin. Este acesso catalisa o crescimento económico, criando um ciclo virtuoso onde a energia leva a investimentos, educação e melhor saúde — elevando comunidades inteiras para fora da pobreza.
Redução de Emissões através da Mitigação de Metano
A mineração de Bitcoin também contribui para a redução das emissões de metano — um gás de efeito estufa com um potencial de aquecimento global 28 a 34 vezes superior ao do CO₂ num período de 100 anos. As emissões de aterros sanitários, resíduos agrícolas e poços de petróleo abandonados representam uma ameaça climática significativa, mas a mineração de Bitcoin oferece uma solução única ao converter este poluente em energia.
Quando o metano é queimado para gerar electricidade, é convertido em CO₂ e vapor de água, que, embora também sejam gases de efeito estufa, são muito menos potentes do que o metano. Na verdade, o metano é responsável por cerca de 25% do aquecimento global que experimentamos actualmente, apesar da sua concentração relativamente baixa na atmosfera. Ao capturar e utilizar o metano, as operações de mineração de Bitcoin transformam um dano ambiental numa fonte de energia produtiva, reduzindo as emissões globais de gases de efeito estufa e criando novas fontes de rendimento.
Por exemplo, nos EUA, o metano de poços de petróleo abandonados está a ser capturado para alimentar a mineração de Bitcoin, criando um sistema fechado que evita que o metano seja queimado ou liberado directamente na atmosfera. Esta abordagem não só mitiga as emissões, como também apoia o crescimento económico em regiões com recursos de metano não aproveitados.
Resiliência e Flexibilidade da Rede
A integração de fontes renováveis, como a eólica e a solar, introduziu desafios para a estabilidade das redes eléctricas. Com as renováveis, os operadores de rede enfrentam flutuações de frequência mais frequentes e uma resposta inercial reduzida — as renováveis não fornecem a mesma resposta inercial que as centrais térmicas tradicionais, tornando a rede mais susceptível a mudanças rápidas.
A flexibilidade da mineração de Bitcoin pode desempenhar um papel fundamental na estabilização das redes eléctricas. Durante a tempestade de inverno Uri, no Texas, os mineradores de Bitcoin reduziram o seu consumo de energia para libertar capacidade para serviços essenciais, mostrando o papel da mineração de Bitcoin como uma carga flexível e reactiva de energia.
Ao ajustar o consumo de energia com base na disponibilidade de oferta, os mineradores de Bitcoin podem ajudar a equilibrar as redes com elevada penetração de renováveis. Esta sinergia com energias renováveis e nucleares fornece uma solução robusta para a gestão da procura energética, especialmente à medida que a rede transita para fontes de baixo carbono.
Impacto Ambiental de Longo Prazo
A mineração de Bitcoin tem o potencial de revolucionar a produção e o consumo de energia. Ao integrar energias renováveis, aproveitar o metano e oferecer gestão flexível da carga, o Bitcoin pode desempenhar um papel fundamental num futuro energético sustentável e descentralizado. Inovação política, responsabilidade industrial e colaboração intersectorial são essenciais para concretizar o potencial do Bitcoin na transição verde.
Diante dos desafios ambientais actuais, a mineração de Bitcoin oferece mais do que inovação financeira. Representa um poderoso aliado na construção de um futuro sustentável e equitativo — onde os objectivos digitais e ambientais alinham-se para criar uma economia global mais limpa e resiliente.
Bitcoin #mining #greenEnergy #renewables
-
 @ 03b2a4f0:7ff066d4
2024-10-30 14:39:12
@ 03b2a4f0:7ff066d4
2024-10-30 14:39:12Have you heard of "ZETEO CITADEL CONSULT IN COLLABORATION WITH THE UN OF IBADAN" we are into training of corps members and executive within Nigeria and outside the world Type of course we offer are Human resources management project management Web development And Web design Content creation *Cyber security
-
 @ 652d58ac:dc4cde60
2024-10-30 14:25:26
@ 652d58ac:dc4cde60
2024-10-30 14:25:26Introduction
In today's fiat based economic landscape increasingly characterized by monopolization and the dominance of institutionalized credit, innovative technologies and protocols are emerging that have the potential to change the foundations of our economy and society.
At the forefront of this are Bitcoin and Nostr—two groundbreaking protocols that together can usher in a new era of innovation, free from the constraints of the fiat system.
This article will examine how the fiat system blocks human progress, how Bitcoin breaks the state monopoly on money, and finally discuss how Nostr, as a censorship-resistant communication tool, builds on this foundation to allow innovation to emerge from the free market. This will show how, together, Bitcoin and Nostr act as catalysts for innovation and human progress, highlighting the history and mechanisms that enable this transformation.
Innovation under Hard Metal Currencies
In the days of hard metal currencies, especially during the gold standard, innovation was primarily driven by individuals and private companies who were largely independent of the state apparatus and institutional lenders. Some of the greatest breakthroughs in science, philosophy and economics were made by private entrepreneurs.
- In 600 BC, a Greek named Thales observed that amber, when rubbed with silk, attracted feathers and other light objects. He discovered static electricity. The Greek word for amber is 'ëelectron', from which the words 'electricity' and 'electron' are derived.
- The Greek philosopher Plato (ca. 428-347 B.C.) is widely considered to be the first person to develop the concept of an atom, the idea that matter is made up of an indivisible component on the smallest scale. He also wrote a number of important books on science, philosophy, economics, politics and mathematics.
- Wei Boyang was a Chinese writer and Taoist alchemist of the Eastern Han dynasty. He is the author of The Kinship of the Three (also known as Cantong Qi), which is considered the earliest book on alchemy in China, and is noted as one of the first individuals to document the chemical composition of gunpowder in 142 AD.
- The car was invented in 1886 by German engineer and automobile manufacturer Carl Benz, who was inspired by Nikolaus Otto, who invented the first gas engine in 1861.
- The Wright brothers are considered the inventors and the first to fly a powered airplane on Dec. 17, 1903, in Kitty Hawk, North Carolina.
- The creativity and ingenuity of the Wright brothers has been well documented. In this photo you can see Wilbur Wright at the controls of the damaged Wright Flyer, on the ground after an unsuccessful trial on December 14, 1903, in Kitty Hawk, North Carolina: https://image.nostr.build/65e20422344092090ec61d9673536625f4220562c1c786f0cafd8c7b23cd6bfa.jpg
The funds for the Wright brothers' ventures, including equipment, travel, and their testing site in Kitty Hawk, North Carolina, came from the bicycle shop they operated. They apparently spent just $1,000 over four years (1899-1903) to develop three flying machines, two of which had no engines. The Wright brothers lived during a time when the U.S. was on a gold standard, and saving allowed entrepreneurs to accumulate enough capital to finance innovations, giving them the time and resources needed to pursue their pioneering work in aviation.
The ancient Greeks, such as Thales and Plato, also operated under hard metal currencies, contributing to a stable economic environment that fostered philosophical and scientific advancements. Similarly, Wei Boyang exemplified the pursuit of knowledge during the Eastern Han dynasty in China, which experienced fluctuating monetary conditions, including periods of stability that contributed to intellectual growth in various fields.
Just as the Wright brothers and other innovators thrived in an environment where saving in sound money enabled them to focus on their inventions, today's private entrepreneurs, startups, thinkers and bicycle shop owners find it increasingly difficult to earn enough to take the time to think about innovations and finance their implementation.
Inflation has significantly driven up labor and material costs, particularly in industries like aviation and automotive, where advanced technology and greater material requirements demand extensive research and development. As a result, entrepreneurs and freelancers often rely on third-party loans.
How the Fiat System Blocks Human Progress
The fiat-based monetary system has made it increasingly difficult for innovation to emerge without institutional funding. Monetary inflation erodes purchasing power, limits financing options, and creates obstacles for new ideas to flourish.
This is problematic because the institutions that typically fund innovation, including large venture capital firms, banks, and universities, are mostly dependent on the state in one way or another (either because they are regulated by law or because they receive government funding) and therefore have an incentive to support projects that follow the current political climate. The result is a banal misallocation of capital and social stagnation, as can be observed in most countries around the world.
Venezuela is an extreme example of what state control of the economy can lead to. About two decades after the introduction of socialism, gross domestic product fell by 88% from 2010 to 2020, plummeting from $372.59 billion to $43.79 billion, the lowest level in over 30 years. This dramatic decline has severely impacted the country, leading to economic stagnation and widespread shortages of basic supplies. The following photo captures the stark reality of this crisis, featuring a man sitting in front of empty shelves in a Venezuelan supermarket. In the 1950s, Venezuela was one of the richest countries in the world; today, its economic performance mirrors that of the pre-1920 era https://image.nostr.build/c70df0ab2ed2f0e2ce9c7fca09722aff117dc56ca24967c3d5fabef47265fc5f.jpg
Credit, Fiat and the State Monopoly on Innovation
Credit has become part of a system of control that nation states use in conjunction with fiat money to maintain their monopoly position. Historically, technologies and social movements that undermine the monopoly power of the state and its affiliated institutions were typically banned. At the very least, there was usually an attempt to do so.
A good example is the way Bitcoin is treated by most states, how poorly it is spoken of in most universities, and how most banks used to consider it speculation at best, because Bitcoin threatens the very existence of these institutions. This behavior is generally observed among monopolists and initially makes it difficult for entrepreneurs to enter new disruptive markets like Bitcoin and shifts competition in favor of the monopolist (the state).
Money creation and the granting of credit are fundamental to maintaining the state's monopoly position. As a result, the reliance on the institutionalized credit system to finance innovation has led to a dependence on a central authority (the state). This disrupts the progress and prosperity of humanity that results from a free market in which capital and information can be freely exchanged and suppresses the collective creativity of humanity.
Bitcoin and the weakening state monopoly on innovation
With the introduction of Bitcoin in 2009, the state monopoly on money was broken. Due to its limited supply and excellent monetary properties (absolute scarcity, durability, fungibility, divisibility, mobility, resilience), bitcoin is the hardest money ever created.
This allows entrepreneurs to preserve the value of their efforts, giving them time and, in the long term, capital to focus on problems and find and fund appropriate solutions. Which, in turn, creates opportunities for innovation to emerge from the free market in a bottom-up manner.
Innovation and communication
Innovation, especially in the age of the Internet, requires more than capital and people with time. There is a need for efficient and secure real-time communication and collaboration options for people around the world. Communication and collaboration are crucial for efficiently solving increasingly complex problems in a connected world.
Cunningham's Law states that the best way to get the right answer on the Internet is not to ask a question; instead, to post the wrong answer because others will correct you. This underscores the importance of collective intelligence. The law is named after Ward Cunningham, who invented the Wiki software that allows users to create and collaboratively edit web pages or entries via a web browser. The most famous example is wikipdia.com. Collective intelligence, social technologies and network organizations are closely linked and enable each other.
https://image.nostr.build/edf84e0b6351af8f5e4792e856c47234b8b66d1aeeed1946b75bb2bb05a41fdf.jpg (Seppala, M. 2018. Collective Intelligence 2018: From Open Knowledge and Network Organizations to Technology-enabled Intelligence. Medium).
Nostr: Communication as a tool for innovation
With Nostr, a new protocol was introduced that adds a layer of censorship-resistant information sharing to the Bitcoin and Lightning protocol suite, opening up a new territory of freedom within the same tech stack. People can now successfully save in bitcoin, communicate via Nostr, and transact with each other through the Lightning Network, potentially independent of any central authority.
Although individual applications that use Nostr can be switched off, the protocol itself cannot be effectively controlled or turned off by a central party, because there is no central point of failure. Even though there were a number of other decentralized communication networks besides Bitcoin before Nostr (Bittorrent, Limewire, Napster, etc.), none of these had the potential to have a universal long-term impact on collaboration to solve complex problems facing humanity.
Nostr has the potential to enable bottom-up innovation and rapid problem-solving that no one can keep a lid on. With Nostr, Bitcoin, and the Lightning Network, market participants can communicate, collaborate, and reward each other in real time globally, potentially independent of any central authority. Personally, I am particularly fascinated by Nostrocket, a client designed to coordinate decentralized, Bitcoin-based economies by rewarding contributors who work together to find solutions to global challenges. At this year's Nostriga unconference, Nostrocket founder GSovereignty gave an interesting talk about the importance of Nostr in the process of separating business and state: https://www.youtube.com/watch?v=ddvHagjmRJY&t=1s
Conclusion
The Bitcoin protocol was created as an alternative to the fiat system. A decentralized, permissionless peer-to-peer electronic cash system, outside the reach of the state. Satoshi Nakamoto created arguably one of the most important innovations by a private individual or group of people that humanity has ever produced, because he/they laid the foundation for anyone to be able to trade and act independently of the state. As a solid foundation for a freer economy, the Bitcoin network enables other network layers to “dock” to the base, creating new ways to use bitcoin and opportunities for users. The Lightning Network, as a second-layer payment protocol for fast transactions and micropayments, partially addresses the problem of how to scale Bitcoin so that it can be used by all of humanity.
The introduction of Nostr creates a new territory of freedom within the same protocol suite as Bitcoin and Lightning, enhancing Bitcoin's usability for diverse applications. By facilitating seamless communication and collaboration, Nostr further aids in scaling Bitcoin, empowering us to innovate faster and reward ingenuity. This protocol suite allows innovation to emerge from the free market once again, with Bitcoin, Lightning, and Nostr working together to foster a truly free Internet.
I would like to thank Uncle R0ckstar for the inspiring conversations and encouraging words. What began as a conversation before my trip to Nostrica led to months of introspection and ultimately this article. I look forward to exploring and understanding the possibilities of Nostr deeper as I continue my journey! 🙏💫
Sources * historycollection.com - 23 Photos of the Wright Brothers’ Flights https://historycollection.com/23-photos-wright-brothers-flights/ * quora.com - How did the Wright brothers obtain the financing to build the first airplane given that the notion of flying was such a crazy idea then? https://www.quora.com/How-did-the-Wright-brothers-obtain-the-financing-to-build-the-first-airplane-given-that-the-notion-of-flying-was-such-a-crazy-idea-then * statista.com- Venezuela: Gross domestic product (GDP) in current prices from 1986 to 2025 https://www.statista.com/statistics/370937/gross-domestic-product-gdp-in-venezuela/ * thepolicycircle.org - Socialism: A Case Study on Venezuela https://www.thepolicycircle.org/minibrief/socialism-a-case-study-on-venezuela/ * Display image: Wilbur and Orville Wright. Getty Images.
If you are interested in more of my work, you can visit my website: www.leonwankum.com
-
 @ 652d58ac:dc4cde60
2024-10-30 14:17:59
@ 652d58ac:dc4cde60
2024-10-30 14:17:59Introduction
In today's fiat based economic landscape increasingly characterized by monopolization and the dominance of institutionalized credit, innovative technologies and protocols are emerging that have the potential to change the foundations of our economy and society.
At the forefront of this are Bitcoin and Nostr—two groundbreaking protocols that together can usher in a new era of innovation, free from the constraints of the fiat system.
This article will examine how the fiat system blocks human progress, how Bitcoin breaks the state monopoly on money, and finally discuss how Nostr, as a censorship-resistant communication tool, builds on this foundation to allow innovation to emerge from the free market. This will show how, together, Bitcoin and Nostr act as catalysts for innovation and human progress, highlighting the history and mechanisms that enable this transformation.
Innovation under Hard Metal Currencies
In the days of hard metal currencies, especially during the gold standard, innovation was primarily driven by individuals and private companies who were largely independent of the state apparatus and institutional lenders. Some of the greatest breakthroughs in science, philosophy and economics were made by private entrepreneurs.
- In 600 BC, a Greek named Thales observed that amber, when rubbed with silk, attracted feathers and other light objects. He discovered static electricity. The Greek word for amber is 'ëelectron', from which the words 'electricity' and 'electron' are derived.
- The Greek philosopher Plato (ca. 428-347 B.C.) is widely considered to be the first person to develop the concept of an atom, the idea that matter is made up of an indivisible component on the smallest scale. He also wrote a number of important books on science, philosophy, economics, politics and mathematics.
- Wei Boyang was a Chinese writer and Taoist alchemist of the Eastern Han dynasty. He is the author of The Kinship of the Three (also known as Cantong Qi), which is considered the earliest book on alchemy in China, and is noted as one of the first individuals to document the chemical composition of gunpowder in 142 AD.
- The car was invented in 1886 by German engineer and automobile manufacturer Carl Benz, who was inspired by Nikolaus Otto, who invented the first gas engine in 1861.
- The Wright brothers are considered the inventors and the first to fly a powered airplane on Dec. 17, 1903, in Kitty Hawk, North Carolina.
- The creativity and ingenuity of the Wright brothers has been well documented. In this photo you can see Wilbur Wright at the controls of the damaged Wright Flyer, on the ground after an unsuccessful trial on December 14, 1903, in Kitty Hawk, North Carolina: https://image.nostr.build/65e20422344092090ec61d9673536625f4220562c1c786f0cafd8c7b23cd6bfa.jpg
The funds for the Wright brothers' ventures, including equipment, travel, and their testing site in Kitty Hawk, North Carolina, came from the bicycle shop they operated. They apparently spent just $1,000 over four years (1899-1903) to develop three flying machines, two of which had no engines. The Wright brothers lived during a time when the U.S. was on a gold standard, and saving allowed entrepreneurs to accumulate enough capital to finance innovations, giving them the time and resources needed to pursue their pioneering work in aviation.
The ancient Greeks, such as Thales and Plato, also operated under hard metal currencies, contributing to a stable economic environment that fostered philosophical and scientific advancements. Similarly, Wei Boyang exemplified the pursuit of knowledge during the Eastern Han dynasty in China, which experienced fluctuating monetary conditions, including periods of stability that contributed to intellectual growth in various fields.
Just as the Wright brothers and other innovators thrived in an environment where saving in sound money enabled them to focus on their inventions, today's private entrepreneurs, startups, thinkers and bicycle shop owners find it increasingly difficult to earn enough to take the time to think about innovations and finance their implementation.
Inflation has significantly driven up labor and material costs, particularly in industries like aviation and automotive, where advanced technology and greater material requirements demand extensive research and development. As a result, entrepreneurs and freelancers often rely on third-party loans.
How the Fiat System Blocks Human Progress
The fiat-based monetary system has made it increasingly difficult for innovation to emerge without institutional funding. Monetary inflation erodes purchasing power, limits financing options, and creates obstacles for new ideas to flourish.
This is problematic because the institutions that typically fund innovation, including large venture capital firms, banks, and universities, are mostly dependent on the state in one way or another (either because they are regulated by law or because they receive government funding) and therefore have an incentive to support projects that follow the current political climate. The result is a banal misallocation of capital and social stagnation, as can be observed in most countries around the world.
Venezuela is an extreme example of what state control of the economy can lead to. About two decades after the introduction of socialism, gross domestic product fell by 88% from 2010 to 2020, plummeting from $372.59 billion to $43.79 billion, the lowest level in over 30 years. This dramatic decline has severely impacted the country, leading to economic stagnation and widespread shortages of basic supplies. The following photo captures the stark reality of this crisis, featuring a man sitting in front of empty shelves in a Venezuelan supermarket. In the 1950s, Venezuela was one of the richest countries in the world; today, its economic performance mirrors that of the pre-1920 era https://image.nostr.build/c70df0ab2ed2f0e2ce9c7fca09722aff117dc56ca24967c3d5fabef47265fc5f.jpg
Credit, Fiat and the State Monopoly on Innovation
Credit has become part of a system of control that nation states use in conjunction with fiat money to maintain their monopoly position. Historically, technologies and social movements that undermine the monopoly power of the state and its affiliated institutions were typically banned. At the very least, there was usually an attempt to do so.
A good example is the way Bitcoin is treated by most states, how poorly it is spoken of in most universities, and how most banks used to consider it speculation at best, because Bitcoin threatens the very existence of these institutions. This behavior is generally observed among monopolists and initially makes it difficult for entrepreneurs to enter new disruptive markets like Bitcoin and shifts competition in favor of the monopolist (the state).
Money creation and the granting of credit are fundamental to maintaining the state's monopoly position. As a result, the reliance on the institutionalized credit system to finance innovation has led to a dependence on a central authority (the state). This disrupts the progress and prosperity of humanity that results from a free market in which capital and information can be freely exchanged and suppresses the collective creativity of humanity.
Bitcoin and the weakening state monopoly on innovation
With the introduction of Bitcoin in 2009, the state monopoly on money was broken. Due to its limited supply and excellent monetary properties (absolute scarcity, durability, fungibility, divisibility, mobility, resilience), bitcoin is the hardest money ever created.
This allows entrepreneurs to preserve the value of their efforts, giving them time and, in the long term, capital to focus on problems and find and fund appropriate solutions. Which, in turn, creates opportunities for innovation to emerge from the free market in a bottom-up manner.
Innovation and communication
Innovation, especially in the age of the Internet, requires more than capital and people with time. There is a need for efficient and secure real-time communication and collaboration options for people around the world. Communication and collaboration are crucial for efficiently solving increasingly complex problems in a connected world.
Cunningham's Law states that the best way to get the right answer on the Internet is not to ask a question; instead, to post the wrong answer because others will correct you. This underscores the importance of collective intelligence. The law is named after Ward Cunningham, who invented the Wiki software that allows users to create and collaboratively edit web pages or entries via a web browser. The most famous example is wikipdia.com. Collective intelligence, social technologies and network organizations are closely linked and enable each other.
https://image.nostr.build/edf84e0b6351af8f5e4792e856c47234b8b66d1aeeed1946b75bb2bb05a41fdf.jpg (Seppala, M. 2018. Collective Intelligence 2018: From Open Knowledge and Network Organizations to Technology-enabled Intelligence. Medium).
Nostr: Communication as a tool for innovation
With Nostr, a new protocol was introduced that adds a layer of censorship-resistant information sharing to the Bitcoin and Lightning protocol suite, opening up a new territory of freedom within the same tech stack. People can now successfully save in bitcoin, communicate via Nostr, and transact with each other through the Lightning Network, potentially independent of any central authority.
Although individual applications that use Nostr can be switched off, the protocol itself cannot be effectively controlled or turned off by a central party, because there is no central point of failure. Even though there were a number of other decentralized communication networks besides Bitcoin before Nostr (Bittorrent, Limewire, Napster, etc.), none of these had the potential to have a universal long-term impact on collaboration to solve complex problems facing humanity.
Nostr has the potential to enable bottom-up innovation and rapid problem-solving that no one can keep a lid on. With Nostr, Bitcoin, and the Lightning Network, market participants can communicate, collaborate, and reward each other in real time globally, potentially independent of any central authority. Personally, I am particularly fascinated by Nostrocket, a client designed to coordinate decentralized, Bitcoin-based economies by rewarding contributors who work together to find solutions to global challenges. At this year's Nostriga unconference, Nostrocket founder GSovereignty gave an interesting talk about the importance of Nostr in the process of separating business and state: https://www.youtube.com/watch?v=ddvHagjmRJY&t=1s
Conclusion
The Bitcoin protocol was created as an alternative to the fiat system. A decentralized, permissionless peer-to-peer electronic cash system, outside the reach of the state. Satoshi Nakamoto created arguably one of the most important innovations by a private individual or group of people that humanity has ever produced, because he/they laid the foundation for anyone to be able to trade and act independently of the state. As a solid foundation for a freer economy, the Bitcoin network enables other network layers to “dock” to the base, creating new ways to use bitcoin and opportunities for users. The Lightning Network, as a second-layer payment protocol for fast transactions and micropayments, partially addresses the problem of how to scale Bitcoin so that it can be used by all of humanity.
The introduction of Nostr creates a new territory of freedom within the same protocol suite as Bitcoin and Lightning, enhancing Bitcoin's usability for diverse applications. By facilitating seamless communication and collaboration, Nostr further aids in scaling Bitcoin, empowering us to innovate faster and reward ingenuity. This protocol suite allows innovation to emerge from the free market once again, with Bitcoin, Lightning, and Nostr working together to foster a truly free Internet.
I would like to thank Uncle R0ckstar for the inspiring conversations and encouraging words. What began as a conversation before my trip to Nostrica led to months of introspection and ultimately this article. I look forward to exploring and understanding the possibilities of Nostr deeper as I continue my journey! 🙏💫
Sources * historycollection.com - 23 Photos of the Wright Brothers’ Flights https://historycollection.com/23-photos-wright-brothers-flights/ * quora.com - How did the Wright brothers obtain the financing to build the first airplane given that the notion of flying was such a crazy idea then? https://www.quora.com/How-did-the-Wright-brothers-obtain-the-financing-to-build-the-first-airplane-given-that-the-notion-of-flying-was-such-a-crazy-idea-then * statista.com- Venezuela: Gross domestic product (GDP) in current prices from 1986 to 2025 https://www.statista.com/statistics/370937/gross-domestic-product-gdp-in-venezuela/ * thepolicycircle.org - Socialism: A Case Study on Venezuela https://www.thepolicycircle.org/minibrief/socialism-a-case-study-on-venezuela/ * Display image: Wilbur and Orville Wright. Getty Images.
If you are interested in more of my work, you can visit my website: www.leonwankum.com
-
 @ 361d3e1e:50bc10a8
2024-10-30 13:35:56
@ 361d3e1e:50bc10a8
2024-10-30 13:35:56https://forex-strategy.com/2024/10/30/forced-mobilization-of-women-began-in-ukraine/ Forced mobilization of women began in Ukraine
mobilization #ukraine #women #war #russia
-
 @ a012dc82:6458a70d
2024-10-30 12:31:27
@ a012dc82:6458a70d
2024-10-30 12:31:27Table Of Content
-
The Origins of Bitcoin's Civil War
-
Lessons Learned from Bitcoin's Civil War
-
Conclusion
-
FAQ
Bitcoin, the revolutionary digital currency, has garnered significant attention and adoption since its inception. However, its path to success was not without obstacles. In this article, we delve into the intriguing tale of Bitcoin's Civil War—a conflict that shook the cryptocurrency community to its core. Through examining the lessons learned from this historical event, we uncover their modern relevance and shed light on the challenges and opportunities that lie ahead for Bitcoin and other cryptocurrencies.
The Origins of Bitcoin's Civil War
The seeds of Bitcoin's Civil War were sown in 2017 when a heated debate emerged regarding the scalability and future direction of the Bitcoin network. The conflict primarily revolved around the issue of block size—whether to increase it to accommodate more transactions or maintain the original size to preserve decentralization.
The Block Size Debate: To Scale or Decentralize?
The proponents of increasing the block size argued that larger blocks would allow for faster and cheaper transactions, thereby enhancing Bitcoin's usability as a currency. On the other hand, those advocating for maintaining the block size believed that prioritizing decentralization was crucial to preserve the fundamental principles of Bitcoin.
The clash of ideologies led to a profound divide within the Bitcoin community, resulting in a fork that created two distinct cryptocurrencies: Bitcoin and Bitcoin Cash. This event, often referred to as the "hard fork," marked a critical turning point in Bitcoin's history.
The Forked Path: Bitcoin vs. Bitcoin Cash
Bitcoin Cash, born out of the hard fork, aimed to address the scalability concerns by increasing the block size to 8MB. In contrast, the original Bitcoin network, commonly known as Bitcoin Core, chose to pursue alternative solutions such as Segregated Witness (SegWit) and the Lightning Network.
Lessons Learned from Bitcoin's Civil War
The conflict and subsequent split in the Bitcoin community taught us valuable lessons about the nature of consensus, governance, and the challenges inherent in scaling decentralized systems. Here are some key takeaways:
1. Consensus is a Delicate Balancing Act
Maintaining consensus within a decentralized network is a complex task. Bitcoin's Civil War exposed the challenges of achieving widespread agreement among stakeholders with diverging opinions. It highlighted the need for effective governance mechanisms to navigate contentious issues.
2. Decentralization is the Bedrock of Cryptocurrencies
Bitcoin's Civil War emphasized the importance of preserving decentralization in cryptocurrency networks. Decentralization ensures censorship resistance, security, and resilience against attacks. Striking a balance between scalability and decentralization remains a fundamental challenge for blockchain-based systems.
3. Innovation Requires Collaboration and Compromise
The conflict spurred a wave of innovation as both Bitcoin and Bitcoin Cash sought to improve their respective networks. However, it also underscored the necessity of collaboration and compromise. The competing factions could have potentially achieved more by working together to find scalable and decentralized solutions.
4. Community Consensus Trumps Technical Merit
The Civil War demonstrated that achieving consensus within the community can override technical merits. Despite technical arguments favoring one approach over another, it was ultimately the community's support that determined the success of a particular path.
5. Adaptability is Key to Long-Term Survival
Bitcoin's ability to adapt and evolve in the face of challenges played a vital role in its survival. The Civil War highlighted the importance of flexibility and the ability to embrace new technologies and ideas while staying true to the core principles.
6. External Factors Can Influence Internal Conflicts
External factors, such as market dynamics and regulatory developments, can intensify internal conflicts within cryptocurrency communities. Understanding and navigating these external influences is crucial for the long-term success of cryptocurrencies.
Conclusion
Unlocking the Secrets of Bitcoin's Civil War provides valuable insights into the journey of Bitcoin and its ongoing evolution. The lessons learned from this historical conflict remain relevant as the cryptocurrency ecosystem continues to grow and face new challenges. Balancing scalability and decentralization, fostering collaboration, and adapting to a changing landscape are key factors that will shape the future of Bitcoin and other cryptocurrencies. By understanding the past, we can better navigate the road ahead, unlocking new possibilities and embracing the potential of decentralized digital currencies.
FAQ
What caused the Civil War in Bitcoin? The Civil War in Bitcoin was primarily sparked by a debate over the block size—whether to increase it for better scalability or maintain the original size for decentralization.
What is the significance of the Bitcoin Civil War? The Bitcoin Civil War highlighted the challenges of achieving consensus and balancing scalability with decentralization in cryptocurrency networks.
Did Bitcoin's Civil War have any positive outcomes? A: Yes, the conflict spurred innovation and prompted both Bitcoin and Bitcoin Cash to explore new solutions for scaling their respective networks.
How did the Bitcoin community handle the Civil War? The Bitcoin community navigated the Civil War through a hard fork, which resulted in the creation of Bitcoin and Bitcoin Cash as separate cryptocurrencies.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 20986fb8:cdac21b3
2024-10-30 12:30:09
@ 20986fb8:cdac21b3
2024-10-30 12:30:09**Hey Nostriches! **
Thrilled to launch the latest YakiHonne update—Simpler, Easier, Faster! After a lot of hard work, we bring you a highly optimized, user-friendly decentralized media experience on both web and mobile. This version focuses on two main aspects:
1. Complete Redesign:
Our UI/UX now puts simplicity first, minimizing technicalities for creators and social users alike. Here’s what’s new:
• Onboarding: Easily create a non-custodial wallet with Npub & Nsec, experience zapping (Lightning payments), or browse as a guest. • Home & Discover: “Discover” is designed for creators, focusing on rich formats like long-form content, videos, and curated works. “Home” offers a social feed with short notes and curated contents, making it quick and easy for creators to share their work. • Wallet: Simple setup with easy creation, direct YakiHonne node linking, and multi-wallet support. • Dashboard: Manage all published and drafted content, check stats, and pick up right where you left off—all in one place. • Notifications: Reactions, Reposts, Mentions, Zaps, Comments, and Follows now appear in clear, categorized cards. • Settings: Completely revamped for simplicity, now including profile customization, appearance, relay settings, and wallet management.
2. Enhanced Performance: Our re-engineered core now supports the outbox model with extensive functionality. Furthermore, Thanks to @PabloF7z we now have seamless data fetching, caching, and full support of the NDK implementation.
Hope you enjoy the new decentralized media experience! 🌐✨Try it out here: •Web: yakihonne.com •App Store (iOS): https://apps.apple.com/us/app/yakihonne/id6472556189 •Google Play (Android): https://play.google.com/store/apps/details?id=com.yakihonne.yakihonne&hl=en
Thank you for your incredible support on this decentralized media journey!
https://v.nostr.build/Uu1uXf8P5D9KkBw6.mp4
-
 @ a305a0de:21557ddd
2024-10-30 12:09:58
@ a305a0de:21557ddd
2024-10-30 12:09:58In today's fast-paced business landscape, staying ahead of the curve requires embracing cutting-edge technology. Emerging trends are transforming the way professionals work, interact, and innovate. Let's delve into the top technologies redefining productivity and efficiency.
- Artificial Intelligence (AI) and Automation
AI-powered tools are streamlining workflows, enhancing decision-making, and freeing up resources. Automation enables businesses to:
- Process large datasets efficiently
- Enhance customer service with chatbots
-
Predict market trends and optimize strategies
-
Cloud Computing and Collaboration
Cloud-based platforms facilitate seamless teamwork, scalability, and data accessibility. Professionals can:
- Access files and apps from anywhere
- Collaborate in real-time
-
Integrate services for streamlined workflows
-
Internet of Things (IoT) and Smart Workspaces
IoT devices create intelligent environments, boosting productivity and convenience. Smart workspaces:
- Optimize energy consumption and resource allocation
- Enhance security and surveillance
-
Foster innovative thinking
-
Augmented Reality (AR) and Virtual Reality (VR)
Immersive technologies are revolutionizing training, communication, and customer engagement. Professionals can:
- Create interactive presentations
- Conduct remote training sessions
-
Visualize complex data
-
Blockchain and Cybersecurity
Blockchain technology ensures secure data transmission and storage. Professionals can:
- Protect sensitive information
- Verify transactions and authenticity
- Ensure compliance
Conclusion:
Incorporating these emerging technologies can significantly enhance productivity, efficiency, and innovation. As professionals, embracing these trends will enable you to:
- Stay competitive in the market
- Drive business growth
- Unlock new opportunities
-
 @ 5fb7f8f7:d7d76024
2024-10-30 11:10:27
@ 5fb7f8f7:d7d76024
2024-10-30 11:10:27Cryptocurrency trading involves buying and selling digital currencies like Bitcoin, Ethereum, and Litecoin. It's a decentralized market that operates 24/7, allowing traders to profit from price movements.
Key Concepts:
- Cryptocurrencies Digital assets that use cryptography for secure financial transactions.
- Trading Platforms: Online exchanges where traders buy and sell cryptocurrencies.
- Wallets: Software programs that store, send, and receive cryptocurrencies.
- Market Volatility: Cryptocurrency prices can fluctuate rapidly, creating opportunities and risks.
- Leverage: Borrowed capital to increase trading positions, potentially amplifying gains and losses.
Trading Strategies:
- Day Trading: Buying and selling within a single trading day.
- Swing Trading: Holding positions for a shorter period, usually a few days.
- Long-Term Investing: Holding positions for an extended period, potentially years.
** Risks and Considerations:**
- Market Risk: Price fluctuations can result in losses.
- Liquidity Risk: Difficulty buying or selling due to low trading volume.
- Security Risk: Hacking and theft of cryptocurrencies.
- Regulatory Risk: Changes in laws and regulations can impact trading.
Best Practices:
- Educate Yourself: Understand cryptocurrency markets and trading strategies.
- *Set Clear Goals": Define your trading objectives and risk tolerance.
- "Use Secure Platforms*: Choose reputable trading platforms and wallets.
- "Diversify*: Spread investments across different cryptocurrencies and asset classes.
- Stay Informed: Continuously monitor market trends and news.
Remember, cryptocurrency trading carries risks, and thorough research is essential for successful trading.
-
 @ 9f6a750b:aaffd7ab
2024-10-30 10:55:39
@ 9f6a750b:aaffd7ab
2024-10-30 10:55:39tldr
ai might revolutionize mental health, but still theres risks it could worsen inequality for a while; to get through this transition understand your strengths and take control of your environment as much as possible rather than taking shitty drugs
mental health and the future
~ biology approach
even if ai helps cure mental illness with ai-generated new drugs, that might not solve the whole problem, our lives, our homes, friends, jobs, and money; its difficult to understand how these social factors are connected to our brains yet, people struggling with their mental health often turn to medication for quick relief... these ugly drugs dont typically cause addiction now(?), because they arent personalized well, but what happens if ai creates perfect, personalized drugs for everyones brain? focusing only on biological fixes without improving a persons overall life situation(environment) wont be a long-term solution, people might become dependent on these drugs and lose the ability or motivation to solve their problems by changing their circumstances...
~ psychiatry + psychology approach
psychiatry + psychology seems offer valuable tools for understanding and addressing mental health today. but the question is, can ai truly grasp the complexities of our individual situations? can ai understand family problems, daily struggles, and personal experiences? for ai to real help, it might need to experience and learn about the ACTUAL world in a way similar to our lives (i need tesla robot, looks sexy af)
can we solve?
i believe ai will eventually solve many mental health challenges (the "☆HAPPY UTOPIA☆" era), but, improving psychiatry + psychology approach with ai will take longer than medical approach i guess, because its easier to study the biology of the brain than the complexities of human behavior. before ai can effectively address behavioral aspects of mental health (the "☆HAPPY DYSTOPIA☆" era) – theres inequality, ppl in difficult situations with limited resources, might worsening existing poverty and social divisions... this is a serious concern i think.
surviving the "☆HAPPY DYSTOPIA☆"
we need to focus on improving our environments and circumstances, this includes understanding how our actions affect others and minimizing harm. changing ones environment is a main challenge for those lacking of resources or facing limitations imposed by others, also, understanding our impact on others requires self awareness, which is a skill many people struggle with still. those lacking might have trouble fitting into societys norms.
lastly, if ai cant fix how we act, more poor people might use drugs to seem okay(happy niconico mode), even though their lives are getting worse and poor. concerning
-
 @ 6bae33c8:607272e8
2024-10-30 09:32:15
@ 6bae33c8:607272e8
2024-10-30 09:32:15I went 3-2 last week to put myself at a decent 13-7 for Q2. This is the start of Q3, and realistically to have a shot at the quarterly prize, I’ll need a 4-1 week — or better. Seems like I’m back in the flow after a rough start at least.
Texans at Jets — I’d say maybe Texans +2.5 given their WR decimation and inability to pass protect. I’d probably take the Jets too.
Cowboys at Falcons — The Cowboys are a disaster, but the Falcons are nothing special, either. I’ll make the line three. If anything, I’m taking the Cowboys.
Dolphins at Bills — The Bills are good now. They have the offense in gear with Keon Coleman emerging and Amari Cooper in the fold. The Dolphins are back with Tua now too. I’ll say Dolphins +5.5 and probably take them to keep it close.
Raiders at Bengals — The Bengals never deliver for me, but the Raiders are really bad. I’ll say Raiders +7.5 and probably lay the wood if I had to.
Chargers at Browns — Jameis Winston gave the Browns new life last week, but he’ll still make catastrophic mistakes. Chargers -1.5, and maybe take the Chargers.
Patriots at Titans — I prefer Drake Maye over Jacoby Brissett, but it’s probably not that big of a difference at this point. The Patriots seem to have some purpose, the Titans have none. I’ll go Patriots +1.5 and stay away.
Indiginous Peoples at Giants — The Giants defense is good, but Danny Dimes is killing them. Still, the Giants are the play here. I imagine it’ll be IP -2.5 or so.
Saints at Panthers — If Derek Carr is back, this should be Saints -4.5. This is a stay away for me.
Broncos at Ravens — The Broncos are a nice story, but I’m laying the wood here. I’d expect it to be Ravens -7.5 or something that looks really big but isn’t.
Jaguars at Eagles — My temptation would be to sell the Eagles high, but you can’t count on the Jaguars. Stay away. I’ll say Jaguars +7.5 FWIW.
Bears at Cardinals — The Bears had a miraculous comeback, then lost on a Hail Mary. That’s a tough one from which to move on. I’ll say Bears +2.5 and take the Cardinals who are playing better of late.
Lions at Packers — If Jordan Love plays, I’d make this a pick ‘em in Green Bay and probably take the Lions.
Rams at Seahawks — Matthew Stafford is better than Geno Smith, and the rest of the teams are about even. I expect it to be Rams +1.5 and take them.
Colts at Vikings — The Colts with Joe Flacco are okay. The Vikings are reeling from a couple close losses. I’ll make it Colts +6.5 and probably stay away.
-
 @ f584a915:9da6d625
2024-10-30 07:40:42
@ f584a915:9da6d625
2024-10-30 07:40:42The best crypto wallet in Nigeria depends on your specific needs and preferences. Here are some of the top options:
Software Wallets: * Luno: User-friendly interface, easy to use for beginners, supports multiple cryptocurrencies.
-
Trust Wallet: Highly customizable, supports a wide range of cryptocurrencies, offers decentralized exchange functionality.
-
Exodus: Multi-currency support, user-friendly interface, built-in exchange.
Hardware Wallets: * Ledger Nano S/X: Highly secure, offline storage, supports multiple cryptocurrencies.
- Trezor Model T: Advanced security features, large screen, supports multiple cryptocurrencies.
When choosing a wallet, consider the following factors: * Security: Prioritize wallets with strong security features, such as two-factor authentication and encryption. * User-friendliness: Choose a wallet with an intuitive interface that is easy to navigate. * Supported cryptocurrencies: Ensure the wallet supports the cryptocurrencies you want to store. * Additional features: Some wallets offer additional features like decentralized exchanges or staking rewards.
Ultimately, the best wallet for you will depend on your individual needs and preferences. It is important to do your own research and choose a wallet that you feel comfortable using.
-
-
 @ 4c48cf05:07f52b80
2024-10-30 01:03:42
@ 4c48cf05:07f52b80
2024-10-30 01:03:42I believe that five years from now, access to artificial intelligence will be akin to what access to the Internet represents today. It will be the greatest differentiator between the haves and have nots. Unequal access to artificial intelligence will exacerbate societal inequalities and limit opportunities for those without access to it.
Back in April, the AI Index Steering Committee at the Institute for Human-Centered AI from Stanford University released The AI Index 2024 Annual Report.
Out of the extensive report (502 pages), I chose to focus on the chapter dedicated to Public Opinion. People involved with AI live in a bubble. We all know and understand AI and therefore assume that everyone else does. But, is that really the case once you step out of your regular circles in Seattle or Silicon Valley and hit Main Street?
Two thirds of global respondents have a good understanding of what AI is
The exact number is 67%. My gut feeling is that this number is way too high to be realistic. At the same time, 63% of respondents are aware of ChatGPT so maybe people are confounding AI with ChatGPT?
If so, there is so much more that they won't see coming.
This number is important because you need to see every other questions and response of the survey through the lens of a respondent who believes to have a good understanding of what AI is.
A majority are nervous about AI products and services
52% of global respondents are nervous about products and services that use AI. Leading the pack are Australians at 69% and the least worried are Japanise at 23%. U.S.A. is up there at the top at 63%.
Japan is truly an outlier, with most countries moving between 40% and 60%.
Personal data is the clear victim
Exaclty half of the respondents believe that AI companies will protect their personal data. And the other half believes they won't.
Expected benefits
Again a majority of people (57%) think that it will change how they do their jobs. As for impact on your life, top hitters are getting things done faster (54%) and more entertainment options (51%).
The last one is a head scratcher for me. Are people looking forward to AI generated movies?

Concerns
Remember the 57% that thought that AI will change how they do their jobs? Well, it looks like 37% of them expect to lose it. Whether or not this is what will happen, that is a very high number of people who have a direct incentive to oppose AI.
Other key concerns include:
- Misuse for nefarious purposes: 49%
- Violation of citizens' privacy: 45%
Conclusion
This is the first time I come across this report and I wil make sure to follow future annual reports to see how these trends evolve.
Overall, people are worried about AI. There are many things that could go wrong and people perceive that both jobs and privacy are on the line.
Full citation: Nestor Maslej, Loredana Fattorini, Raymond Perrault, Vanessa Parli, Anka Reuel, Erik Brynjolfsson, John Etchemendy, Katrina Ligett, Terah Lyons, James Manyika, Juan Carlos Niebles, Yoav Shoham, Russell Wald, and Jack Clark, “The AI Index 2024 Annual Report,” AI Index Steering Committee, Institute for Human-Centered AI, Stanford University, Stanford, CA, April 2024.
The AI Index 2024 Annual Report by Stanford University is licensed under Attribution-NoDerivatives 4.0 International.
-
 @ 3584cea4:0951bbef
2024-10-29 23:00:42
@ 3584cea4:0951bbef
2024-10-29 23:00:42testing
-
 @ 3c7dc2c5:805642a8
2024-10-29 21:16:11
@ 3c7dc2c5:805642a8
2024-10-29 21:16:11🧠Quote(s) of the week:
'It should be clear in 2024 the final lines have been drawn on Bitcoin. Its central banks and their collaborations… the IMF, World Bank, BIS… their job is to maintain central control of fiat creation vs the rest of the world who are sheltering from its agenda. This includes corporations, commercial banks, the rich, the poor, and you.' - Willy Woo
🧡Bitcoin news🧡
Last week I shared my opinion on the latest anti-Bitcoin ECB paper. Now we have a full Academic Rebuttal to the anti-Bitcoin ECB paper officially published. Read the full rebuttal here: https://www.murrayrudd.pro/challenging-bias-in-the-ecbs-bitcoin-analysis/
On the 21st of October:
➡️Bitcoin hash rate hits all-time high. The Network has never been more secure than it is now.
➡️Bitcoin open interest exceeds $40 billion for the first time in history.
On the 22nd of October:
➡️Billionaire investor Paul Tudor Jones says, “All roads lead to inflation. I’m long gold. I’m long Bitcoin."
Now why is this statement important:
"I want to own zero fixed income... I probably have some basket of gold, Bitcoin, commodities, and Nasdaq.", "The playbook to get out of this (debt problem) is that you inflate your way out."
The US fixed-income market is ~$50T. Fixed income in fiat during rapid debasement = fixed debasement. If just a small portion of the market agrees, trillions will be leaving fixed income and looking for a new home... like Bitcoin.
Translated: Bonds will not protect you from the severe inflation that is coming. Bitcoin will.
➡️A very informative report was released on this day.
The first report covers how Bitcoin Core development is funded. Part 1 covers the organizations that raise and distribute funds to core devs.
You can download the report here. Troy Cross: "Bitcoin is a $1.4t asset maintained and supported by only 41 devs funded by 13 organizations and a donation-heavy budget of $8.3m."
➡️Get 3.8% interest (paid in Bitcoin) on the cash sitting in an FDIC account at River… mind-blowing. Why don't we have that here in the EU? Not sure if I would use it, but still I would like to have the optionality.
'…Interest is generated on cash held at River through our banking partner and FDIC insured up to $250k, your Bitcoin is NEVER put at risk and is held in 100% reserve custody with proof of reserves (https://river.com/reserves).
See disclosures here: https://river.com/bitcoin-interest#disclosures' -River
For the U.S. readers of the Weekly Recap. Think of the tax implications, where does the yield coming from, etc.
On the 23rd of October:
➡️ $725 billion Bernstein predicts Bitcoin will hit $200,000 in 2025, calling the forecast “conservative.”
➡️Bitcoin hashrate and the difficulty is skyrocketing. It has never taken more work to find the next Bitcoin block.
➡️As mentioned last week, Bitcoin whales are accumulating heavily, just like they did in 2020, right before Bitcoin went parabolic.
➡️Apparent demand for Bitcoin has increased by over 200,000 BTC in the past month, reaching its highest point since April 2024, according to data from ETC Group.
➡️ 'Metaplanet has concluded its issue of Stock Acquisition Rights, raising a total of ¥10b (~$65m) through full exercise.
As of October 23, Metaplanet holds 861.38 Bitcoin, acquired for ¥8.022B, with no outstanding debt.' -Dylan Leclair
'The chart shown on Preston Pysh's YouTube channel from River is quite an eye-opener. Great job, River team! I had a hunch, but it's great to see visual confirmation that, in the big scheme of things, Bitcoin is still largely in the hands of retail, while ETFs are just a tiny slice—even though they’ve been buying billions.
This will likely shift as the price rises, but I really hope retail continues to hold a large share. It's a unique case in asset history—most other assets are 70%-80% owned by institutions who get to buy first.' - Luis Marques
That chart really puts things into perspective! It's fascinating to see retail holding such a significant share of Bitcoin.
➡️Denmark is considering taxing unrealized gains on Bitcoin and crypto, with a bill to be tabled in January. Danes who own Bitcoin would be taxed at 42% on value increases and decreases every year, regardless of whether they have sold or not. If passed, would start Jan 1, 2026. As mentioned in last week's Weekly Recap, governments are in full attack mode.
'Taxing unrealized gains on Bitcoin is a slippery slope. It punishes holders for paper profits they haven’t yet realized, introducing unfair volatility risks. Bitcoin is about financial sovereignty and freedom, such measures undermine its principles. Denmark should reconsider before stifling innovation and adoption.' - Assis Hodler
On the 24th of October:
➡️El Salvador President Nayib Bukele donated 2 bitcoins worth $133k to help raise money to build 1,000 schools in Honduras.
Tim Draper predicted El Salvador's Bitcoin journey would vault it into the ranks of the world's wealthiest nations. “Bitcoin hits 100k, they’ll be able to pay off the IMF and never have to talk to them again.”
➡️In their latest SEC filing, Microsoft disclosed that “Assessment of Investing in Bitcoin” has been proposed as a voting item for the December 10 shareholder meeting. However, the filing notes that “the Board recommends voting against this proposal.”.
The funny thing is if you read the SEC filing, pages 78-79:
"Microstrategy – which, like Microsoft, is a technology company, but unlike Microsoft holds Bitcoin on its balance sheet – has had its stock outperform Microsoft stock this year by 313% despite doing only a fraction of the business that Microsoft has. And they’re not alone. The institutional and corporate adoption of Bitcoin is becoming more commonplace. Microsoft’s second-largest shareholder, BlackRock, offers its clients a Bitcoin ETF." Guess who Microsoft's second-largest shareholder is? Guess who made the Bitcoin ETFs happen? I will give you a hint...it starts with Black and ends with Rock.
Bit Paine: 'How long until it is considered a breach of fiduciary duty to shareholders to store your company’s profits in rapidly debasing paper rather than Bitcoin?'
➡️Wicked: Addresses with less than 1 Bitcoin only account for 7.2% of the circulating supply. How does this make you feel, anon?
➡️'The official text of the 2025 Budget Law, signed by the President of Italy, has been presented. The text explicitly includes the increase in the rate of Bitcoin capital gains to 42%. The law will now be debated and potentially amended in the Italian parliament.' -Bitcoin News
➡️'The state of Pennsylvania has passed ‘Bitcoin Rights’ in the House by a sweeping majority. Both Republicans and Democrats united together to pass the bill. Pennsylvania is poised to be the most important state in the ‘24 election & this bill is poised to play a role.'- Dennis Porter
➡️Madness! A solo miner just mined a block worth 3.329 Bitcoin worth $222,455.
On the 25th of October:
➡️ BlackRock now holds 399.356 Bitcoin worth $27.1 billion.
➡️FORBES: "It’s hard to imagine that some form of game theory won’t play out when one or two central banks come forward to say they’ve followed El Salvador’s lead in holding bitcoin as a reserve asset, especially if one of those countries is the United States,"
➡️ Bitcoin whales (addresses with 100+ BTC) increased by 1.9% in the past two weeks, while, wallets holding less than 100 BTC decreased by 0.1%, suggesting whale accumulation, is historically bullish.
➡️Emory University disclosed in SEC filings that it owns over $15 million in Grayscale’s mini Bitcoin ETF, making it the first university to invest in BTC
On the 26th of October:
➡️Tether CEO confirms their reserves hold a total of 82,454 BTC and 48.3 tons of gold.
On the 27th of October:
➡️The Kingdom of Bhutan now owns 13,380 Bitcoin worth $905 Million. Lyn Alden: 'Bhutan has a lot of hydro energy, so they’re just out here quietly mining bitcoin with it and stacking it at the sovereign level.'
On the 28th of October:
➡️Metaplanet buys another ¥1.6 billion worth of Bitcoin. They now own over 1,000 BTC. "Metaplanet now owns more than 1K BTC, making it one of the largest corporate holders of Bitcoin in Asia," says Metaplanet CEO Simon Gerovich.
➡️2022: Russia's central bank wanted to ban Bitcoin and mining. 2024: - Legalises Bitcoin and crypto mining in Russia - Ready to approve 2 cryptocurrency exchanges - Sovereign Wealth Fund investing in Bitcoin mining across BRICS nations - Considers settling trade-in
➡️Three new BRICS nations are mining Bitcoin with government resources: Argentina, UAE and Ethiopia - VanEck
➡️"We have a model that assumes that by 2050, Bitcoin becomes a reserve asset that's used in global trade and is held by Central Banks at a modest 2% weight - with that model we arrive at a $3 million price target for Bitcoin" - VanEck's Mattew Sigel
Let's end the Bitcoin segment with a banger: ➡️An individual solo mined a Bitcoin block using their own hardware—an Apollo running at 6-10 TH/s, a self-hosted node, and custom stratum software. A single individual constructed their own solo block and submitted it to the network using their own hardware.
FutureBit (Apollo): Today the first Independent Sovereign Bitcoin Solo block in over a decade was just mined! What a historic moment for self-sovereignty, censorship resistance, and freedom! One of our Apollo devices, which hosts its own plug-and-play full node and stratum solo server just submitted a solved solo block that was accepted by the network.
Today over a decade of our work has just manifested itself on the blockchain. Over a decade ago almost all blocks were mined in this manner, the software to mine blocks ran on a single piece of software that ran the full node and miner. A single anonymous computer would find every block on the network. This quickly changed when ASICs were born, the node, miner software, and mining hardware split off from each other and became very fragmented.
Today most blocks are submitted by centralized custodians and pools who select which transaction is included in the next block. The vast majority of hash rate is controlled by these pools and a false narrative over the last decade pushed small miners and independent pools out.
Today this changes. It proves free, censorship-resistant, and independent blocks can be found by anyone hosting their own node and stratum solo server. Today marks the beginning where everyday people take back control of the Bitcoin blockchain that was meant for the people and by the people!
Vires in Numerus!'
💸Traditional Finance / Macro:
On the 23rd of October:
👉🏽Best year of the century for the S&P 500.
On the 25th of October:
👉🏽'Today's rally puts the S&P 500 officially up +40% over the last 12 MONTHS. This is a larger 12-month gain than ANY annual return in the S&P 500 dating back to 1954. How did a generational rally occur during times of historic uncertainty?' -TKL
🏦Banks:
👉🏽 No news
🌎Macro/Geopolitics:
On the 21st of October:
👉🏽'US net interest costs as a share of GDP are set to reach 6.3% by 2054, the highest on record.
This will be more than double the 3.1% projected for the Fiscal Year 2024. To put this into perspective, interest costs will nearly triple the government's average historical spending on R&D, infrastructure, and education combined. Interest payments have reached $1.1 trillion over the last 12 months, exceeding defense spending for the first time.
At the current pace, interest will soon be the largest expense in the Federal budget, surpassing Social Security.' -TKL
On the 22nd of October:
👉🏽The U.S. National Debt has increased by $338 BILLION over the last three weeks. It now stands at $35.8 TRILLION. That’s, the $35,8 trillion, $103,700 of debt for every American. This is unsustainable.
Keep in mind: Powell admits that "in the long run, the US is on an unsustainable fiscal path... the debt is growing faster than the economy" Reporter: "I have a sense that worries you very much" Powell: "Over the long run, of course it does. We are effectively borrowing from future generations. It's time for us to get back to putting a priority on fiscal sustainability and soon better than later."
Never gonna happen!
On the 23rd of October:
👉🏽The United States has approved $20 billion in loans for Ukraine today. Let's be honest. As Ukraine itself has a rating of 'Extremely Speculative' by Moody's and 'In Default' by S&P and Fitch, perhaps this 'loan' of $20 billion would be more appropriately classified as a 'gift'. - James Lavish Spot on by Lavish, It will never be repaid. Like most of our governments 'loans'. Now read the part above on the 22nd of October again. Fiscal sustainability...never gonna happen!
👉🏽Bank of Canada cuts rates by 0.50% EU - 0.75% rate cut USA - 0.50% rate cut Canada - 1.25% rate cut UK - 0.25% rate cu China - 0.25% rate cut Denmark - 0.25% rate cut
👉🏽Argentinian tax collectors protest just days following Milei’s announcement he will be slashing their agency and replacing it with a smaller one. Fascinating, no sane civilian is going to support a tax collector protest! Don't cry for fees, Argentina.
👉🏽It’s catastrophic to watch Germany in free fall at this pace! More on that below, VW part.
On the 25th of October:
👉🏽Argentina’s tax collectors continue to protest Milei’s decision to close their agency, chanting, “Milei is a traitor to our country.”
👉🏽Moody's cut France's credit outlook to negative from stable, citing fiscal deterioration. Debt Rating was affirmed at Aa2. Fitch, Moody's, & Scope all have downgraded French debt's outlook.
This is a critical sentence in Moody's assessment: 'The current political situation for France is unprecedented, and it raises risks about the ability of the institutions to deliver sustained deficit reductions.'
Jeroen Blokland: 'Ongoing polarization is a crucial ingredient in what already is an unsustainable debt trajectory. There is no long-term plan or commitment, as voters will swing from left to right and vice versa. Newly chosen politicians will focus primarily on reversing their predecessors' 'terrible' policy decisions instead of focusing on what matters for society. France is a painful example of this, with a debt-to-GDP ratio already above 100%.'
👉🏽Central banks now hold 12.1% of global gold reserves, the highest level since the 1990s.
This percentage has skyrocketed this year and has more than DOUBLED over the last decade. China, India, Turkey, and Poland have been the largest contributors to global central bank gold purchases. Gold now accounts for 5.4% of China’s foreign exchange reserves and reached 2,264 tonnes in 2024, a new record. Meanwhile, gold prices have hit 35 all-time highs year-to-date and rallied 33%. Global central banks continue piling into gold.' -TKL
On the 26th of October:
👉🏽'The US government is a $6.8 trillion economy, the 3rd largest in the world. Government spending is up 50% this decade -> The world's 3rd largest economy growing 9% annualized this decade, faster than India or China. And all funded by debt.' -ZeroHedge
On the 28th of October:
👉🏽Germany's decline: Volkswagen wants to close at least three plants in the country and cut tens of thousands of jobs. "This Is Starvation": VW Union Head Warns 3 Plants Closing, Thousands In Layoffs, Amid Auto Crisis
'On Monday, Volkswagen's top labor leader works council chief Daniela Cavallo, who also sits on VW's supervisory board, was quoted by Bloomberg as saying three factories are slated for closures.'
https://www.zerohedge.com/markets/starvation-vw-union-head-warns-3-plants-closing-thousands-layoffs-amid-auto-crisis
🎁If you have made it this far I would like to give you a little gift:
Technology Powered Freedom - Bitcoin, eCash & Nostr | Alex Gladstein x Peter McCormack:
https://youtu.be/L5BVxfdYgNo?si=aBf6kQxqjjLemaEu
Credit: I have used multiple sources!
My savings account: Bitcoin
The tool I recommend for setting up a Bitcoin savings plan: @Relai 🇨🇭 especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. (Please only use it till the 31st of October - after that full KYC)
Hence a DCA, Dollar cost Average Strategy. Check out my tutorial post (Instagram) & video (YouTube) for more info.⠀⠀⠀⠀
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀⠀⠀⠀⠀⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ a9434ee1:d5c885be
2024-10-29 20:46:24
@ a9434ee1:d5c885be
2024-10-29 20:46:24This design system has two goals: 1. Being the basis for the development of a design-first, native Nostr app focused on exceptional zapping and chatting, relay-based communities and beauty 2. Serving as inspiration for builders that need coherent UI building blocks for their own apps with a different scope but overlapping needs (chats, threads, zaps, articles, highlights, events, wikis, ...)
Design System
Check it out here.
This is by no means finished and will be continually updated and completed as we go along.Project description
Check it out here nostr:naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda
This is a very first bullet-point-style draft to set the tone and is open to change, hence it being a wiki.
Explanatory videos
This list of videos will also be continually updated and completed as we go along:
-
Chat as the universal interface
https://cdn.satellite.earth/43ccc6224a373dd22b7ae92edb70a0b9a3facabef27dff037de7f4fcf3ee7f37.mov -
Your Nostr Dashboard
https://cdn.satellite.earth/20fa9683dbf815c7deafa8a532c1d1e99cddbaac622fbf075b33b70fb0bdef22.mov -
Keeping Tabs on all these Content types https://cdn.satellite.earth/a15ab05b55db1787349863f0f92c465dcde828b90c2cb61a92bd712a0012e9c6.mov
-
Design entered the Chat
https://cdn.satellite.earth/7c25215262125562c847412c0d9a7d027e087028838204b6c447b5c07830979a.mov -
Targeted publication & The blurry edges of interoperable communities
https://cdn.satellite.earth/160c9431f53e7be108ad37f8d368e2af840690a8a936d1caaa68b468c9b1e0a9.mov -
Travel Back
https://cdn.satellite.earth/36d38027e6208e91c1fa27b0560f70fbad7d3e31c22d659c9a53a5c4cf90a876.mov
-
-
 @ be52fcb2:e2e4e843
2024-10-29 20:35:16
@ be52fcb2:e2e4e843
2024-10-29 20:35:16I recently stumbled upon Extreme Privacy: What it takes to disappear by Michael Bazzell. This book is a practical and informative guide that provides clear, step-by-step instructions on how to improve your privacy. What sets it apart is that it's not just theoretical - it gives you actionable advice that you can start implementing right away.
As someone who's already taken some basic steps to protect my privacy, I found this book to be a useful resource to take it to the next level. I'm still using Windows and Apple devices, but after reading this book, I'm planning to switch to more secure alternatives. If you're interested in improving your privacy, I recommend checking out this book.
In this post, I'll give you a brief overview of the steps outlined in the book, along with some visual guidance to help illustrate the process. I won't delve too deep into the reasoning behind each step - that's all covered in the book. Instead, I'll document my own progress as I work to upgrade my privacy setup and break away from Big Tech. Let's get started.
Section One: Linux Computers 🐧
Eat that frog. The book recommends starting with the biggest challenge: ditching Windows and Apple in favor of a Linux-based operating system. The reason is simple: they collect a ton of data.
1️⃣ Configure a Linux Operating System
Before diving in, the book takes a close look at the fundamentals, exploring the trade-offs between older and newer hardware, and navigating the varied world of Linux distributions. After careful consideration,
Pop!_OSis selected as the go-to operating system, and we'll be following that recommendation. * Navigate to https://pop.system76.com/ and clickDownload.* Install Balena Etcher from https://etcher.balena.io/. * Launch Balena Etcher and click
Flash from file. * Select the downloaded iso file. * ClickSelect targetand choose your USB drive. * ClickFlashand allow the process to completeNote: this process will completely wipe the chosen USB drive, so proceed with caution. Once complete, you'll have a bootable USB drive ready for Linux installation. To install, insert the drive, restart your computer, and immediately press the key that opens the boot options menu (usually ESC, F1, F7, F8, F10, or DEL). Select the USB drive with your Pop!_OS installation, then follow the on-screen instructions to complete the installation. * Click
Try or Install Pop!_OS. * Choose your desired language, location, and keyboard.- Choose
clean installand select your internal drive. - Click
Erase and Install. - Provide your desired user name and password.
- Select the default option to encrypt the drive.
- If desired, allow the same Linux password to be used for the drive encryption. This is more convenient but could pose a security risk. If you want an extra layer of protection, you could specify a unique password for each option of drive encryption and Linux, but this may be overkill for most users. I use the same password for both options.
- Allow the process to complete and click
Restart Device
Now after reboot we need to provide our password and then again a screen with user selection and also need to include password again. We will change that redunancy steps later in the settings.
Continue through the one-time setup with the following steps.
- Choose your layout options for the dock and click
Next. - Choose your Top Bar options and click
Next. - Click
Nexttwice to continue through the menu. - Choose your desired appearance and click
Next. - Choose your Wi-Fi (if available), supply the password, and click
Next. - Keep location services disabled and click
Next. - Choose your desired time zone and click
Next. - Click
Skipto bypass any online accounts then clickStart Using Pop!_OS
To remove the requirement to enter the password twice upon each boot, follow the next steps:
- Launch the Settings application in the lower dock.
- Choose
Usersin the left menu. - Click
Unlockand enter your password. - Enable the
Automatic Logintoggle. - Close Settings and reboot the computer by clicking the upper-right menu bar and selecting
Power Off/ Log Out>Restart>Restart.
Additionally Bazzell recommends some optional modifications to the default setup:
- Launch the
Settingsapplication in the lower dock. - Click
Bluetoothin the left menu and disable the toggle. - Click
Privacyin the left menu and disableConnectivity Checking. - Click
File History & Trashand disable everything.
...and add some not privacy related but useful preferences:
- Click
Screenand changeBlank Screen Delayto a longer period. - Go back to the main screen, click
Powerin the left menu and disableAutomatic Power Sever. - Click
Automatic Suspendand disable all options. - Enable
Show Battery Percentage
There are noumerous background images available, anyway if you want to have a solid color you need to use e.g. follwoing comands within the terminal
``` gsettings set org.gnome.desktop.background picture-uri ´´
gsettings set org.gnome.desktop.background picture-uri-dark ´´ ```
what gives us a great dark background screen.
The next modification I like to execute is to move the Dock from the bottom to the left with the following Terminal command.
gsettings set org.gnome.shell.extensions.dash-to-dock dock-position LEFTNext, I prefer to decrease the default size of the icons since I will be adding numerous programs soon. You can change the number to any size appropriate for your screen size with the following Terminal command.
gsettings set org.gnome.shell.extensions.dash-to-dock dash-max-icon-size 30When you right-click a file or folder to delete it, you currently have the option to
Move to Trash. The following Terminal command adds a new option directly underneath the Trash entry titledDelete Permanently. This allows me to bypass the Trash altogether and simply eliminate any desired content.gsettings set org.gnome.nautilus.preferences show-delete-permanently trueBy default, most Linux operating systems hide
hiddenfiles from view. These are typically system files but can also include cache and configuration files which we may need to access. Therefore, I execute the following two Terminal commands in order to make these valuable files visible at all times.``` gsettings set org.gnome.nautilus.preferences show-hidden-files true
gsettings set org.gtk.Settings.FileChooser show-hidden true ```
You likely have pending operating system updates which should now be applied.
- Click the
Pop!_Shopicon in the dock bar next to Settings. - Click the
Installedtab and thenUpdate All.
2️⃣ Install Linux Applications
In this section, we will follow Bazzell's guidance on installing applications within the
Pop!_OS Shop. This will lay the foundation for our system, providing us with the necessary tools for productivity, media management, and more.Note-taking and Organization
We begin by installing *Standard Notes*, a note-taking application that allows for end-to-end encryption.
Ebook Management
For managing ebooks, he recommends *Calibre*, a powerful and feature-rich application that makes it easy to organize and read digital books.
Media Playback
Next, we install *mpv*, a media player that allows for secure playback of media files.
Office Productivity
For office tasks, LibreOffice is the preferred choice. This comprehensive suite of applications provides everything we need for word processing, spreadsheet analysis, and presentation creation.
System Maintenance
To keep our system running smoothly, we install BleachBit Cleaner, a useful utility that helps remove unnecessary files and free up disk space.
Virtual Currency Management
For managing virtual currencies, Bazzell suggests Electrum, a popular and user-friendly application specifically designed for Bitcoin transactions.
This concludes the initial setup of our system. In later sections in the book, we will cover email, calendars, contacts, password management, VPS, and VoIP services, each of which will be configured and explored in detail.
3️⃣ Apply Linux Updates
This section guides you through the process of keeping your Linux system up-to-date by applying the latest updates. To streamline this process, it's recommended to save the following essential commands in a local notes application for easy copying and pasting:
``` sudo apt update // updates package lists
sudo apt upgrade -y // applies pending updates
sudo apt full-upgrade -y // applies pending updates and removes unnecessary data
sudo pop-upgrade recovery upgrade from-release // updates the recovery partition
sudo pop-upgrade release upgrade // applies pending Pop!_OS stable release upgrades
sudo apt autoremove -y // removes unnecessary software dependencies
sudo apt autoclean -y // removes unnecessary data from local software repositories
sudo flatpak update -y // updates Flatpak applications ```
These commands can be copied and pasted into the terminal to keep your system updated. Later, you'll learn how to create a custom script to automate these commands, making it even easier to maintain your system.
4️⃣ Create a Custom Linux Script
In this section, you'll learn how to create a custom script to automate the update process. You have two options:
- Download a Pre-Configured Script: Get started quickly with a pre-configured script that's ready to use.
- Create a Custom Script from Scratch
Option 1: Download a Pre-Configured Script
To download and set up the pre-configured script, run the following commands:
``` cd ~/Documents && wget https://inteltechniques.com/data/linux.sh
chmod +x linux.sh && sudo mv linux.sh /usr/share/applications/
wget https://inteltechniques.com/data/linux.desktop
sudo mv linux.desktop /usr/share/applications/ ```
Option 2: Create a Custom Script from Scratch
To create a custom script, follow these steps:
- Open a text editor and create a new file.
- Copy the script text and paste it into the text editor.
```
!/bin/bash
clear
PS3=‘Selection: ‘
options=(
"Apply All Updates"
"Launch Files with Admin Privileges"
)
select opt in "${options[@]}"
do
case $opt in
"Apply All Updates"
sudo apt update && sudo apt upgrade -y && sudo apt full-upgrade -y &&
sudo pop-upgrade recovery upgrade from-release && sudo pop-upgrade
release upgrade && sudo apt autoremove -y && sudo apt autoclean -y &&
sudo flatpak update -y
;;
"Launch Files with Admin Privileges" )
sudo nautilus
;;
esac
done ```
- Save the file with a
.shextension (e.g.,linux.sh) in a location of your choice (e.g., your home directory) - Open a terminal and navigate to the directory where you saved the script.
- Make the script executable using the following command:
chmod +x linux.sh - run the script using the following command:
./linux.sh
Running the Script
After executing the script, you'll see the following menu:
1) Apply All Updates2) Launch Files with Admin Privileges Selection:Create and Configure the
.desktopFileThe
linux.desktopfile tells the operating system to launch the script from your Applications menu.- Open a text editor and create a new file.
- Copy the following code and paste it into the text editor:
``` [Desktop Entry]
Type=Application
Name=Maintenance
Categories=Application;Maintenance
Exec=/path/to/.linux.sh
Terminal=true ```
Replace
/path/to/with the actual path where you saved thelinux.shfile.- Save the file with the name
linux.desktopin a location of your choice. - Move the
linux.desktopfile to the/usr/share/applications/directory using the following command:sudo mv linux.desktop /usr/share/applications/ - Update the
Execpath in thelinux.desktopfile to point to the correct location of thelinux.shfile. - Make the
linux.desktopfile executable using the following command:sudo chmod +x /usr/share/applications/linux.desktop
Verify the Shortcut
- Go to your Applications menu and look for a new shortcut titled "Maintenance".
- Clicking this shortcut should launch the
linux.shscript.
Using the script
You can now launch the script by clicking on the
Maintainanceshortcut in your Application menu. The script will present you two options:1) Apply All Updates2) Launch Files with Admin Privileges Selection:Selecting the first option will apply all updates, while selecting the second option will launch the Files application with root privileges, allowing you to modify system protected files.
Tips and variations
You can modify the script to automate any Terminal commands you want. Simply edit the linux.sh script and add or modify the commands needed. You can also create new desktop entries and scripts to automate other tasks. Remeber to make the script executable and move it to the correct location for it to work properly.
5️⃣ Store Documents Locally in Linux
Bazzell recommends storing documents locally on the Linux system to maximize privacy. This is because storing documents online can make them vulnerable to hacking and surveillance. By storing documents locally, users can ensure that their documents are secure and private.
6️⃣ Create a Linux System Backup
In this section, we'll create a backup of your Linux system. To ensure your system is up-to-date and clean, follow these preliminary steps:
- Running the Maintenance script to apply updates and remove unnecessary items.
- Checking for additional updates in Pop!_Shop and
Settings->OS Upgrade & Recovery. - Running
BleachBitas root to clean the system (excluding "Free Disk Space"). - Rebooting the machine.
Creating a Full Backup with FreeFileSync
To create a full backup of your Linux device, follow these steps:
- Install the free and open-source program
FreeFileSync, available in Pop!_Shop. -
Format an external USB SSD (recommended) specifically for backups:
-
Launch
Files, right-click the external drive, and selectFormat. -
Choose
Internal disk for use with Linux systems only (Ext4)and consider encrypting the drive viaPassword protect volume -
Configure FreeFileSync:
-
Browse to your Home folder and select it as the source.
- Browse to your external hard drive, create a "Backup" folder, and select it as the destination.
-
Click the right arrow icon next to the green whell near "Synchronisze" and choose the
Mirroroption to ensure an exact replica of your computer's data. -
Run the backup:
-
Click
Compareto analyze the data. - Ignore the warnings and click
Synchronizeto begin the backup process.
Subsequent Backups
To maintain an up-to-date backup, follow these steps:
- Connect the external drive and unlock the encryption (if used).
- Open
FreeFileSyncand select theComparebutton to identify modified files. - Run the synchronization process to update the backup.
Best Practices
Bazzell recommends making backups on a regular schedule (e.g., weekly) and shutting down the machine when not in use to maintain a tidy and updated Linux device. By following these steps, you'll ensure your system is protected and easily recoverable in case of data loss or system failure.
7️⃣ Create an Off-Site Linux Backup
To ensure data protection, follow the
3-2-1 rule:- 3 copies of your data
- 2 types of media (e.g., external hard drive and micro SD card)
- 1 copy off-site
Create a "Desperation Copy"
Store a third copy of your data on a micro SD card off-site, using
FreeFileSyncto keep it current. This ensures a safe and recoverable copy of your data in case of a disaster.8️⃣ Configure a Dual-Boot Laptop
This final section of
PART 1 - Linuxexplores the concept of secure dual-booting, where two operating systems coexist on separate drives. This setup is ideal for situations where specific Windows software is required, but cannot be run through virtual machines. The following example illustrates a configuration wherePop!_OSis the default option, alongsideWindows.The starting point for this setup is a system with Windows 10 Pro installed, booting in UEFI mode, and two separate existing drives. To prepare for dual-booting, take the following steps in Windows:
- If you prefer to have full-disk encryption, activate
BitLocker. - Open the
Disk Managerto view the connected drives and their partitions. - Identify the drive or partition where you want to install Pop!_OS, right-click on it, and select
Shrink Volume. Allocate a minimum of 40GB or more for the new partition. - Insert the Pop!_OS USB installer and restart your computer.
-
Enter the BIOS settings (usually by pressing ESC, F2, or F9) and make the following changes:
-
Enable USB boot
- Set the USB drive as the primary boot device in the
Boot ordersettings - Disable
Secure boot - Save your changes and exit the BIOS settings.
With the USB drive set as the primary boot device, the system will now boot into Pop!_OS. Follow the initial setup process until you reach the installation screen.
To configure the installation, select
Custom (Advanced)and then:- Identify the drive or partition with the free space you previously allocated for Pop!_OS.
- Click
Modify Partitionsto begin configuring the partitions. -
Create the boot partition:
-
Right-click on the unallocated space and select
New. - Set the partition size to 1000MB using the slider.
-
Choose
Primary Partitionandfat32as the file system. -
Create the root partition:
- Right-click on the remaining unallocated space and select
New. - Use the entire free space for this partition.
-
Choose
ext4as the file system. -
Click
Apply All Operationsto apply the changes and proceed with the installation.
Next, you need to assign a role to each partition:
- Select the
fat32partition (the boot partition) and configure it as follows: - Toggle on
Use partitionandFormat. - Set
Use astoBoot. -
Confirm the file system is set to
fat32. -
Select the
rootpartition and configure it as follows: - Toggle on
Use partitionandFormat. - Set
Use astoRoot. -
Leave the file system set to
Default (ext4). -
With the partitions configured, click
Erase and Installto begin the installation process. Follow the on-screen instructions to complete the installation.
After rebooting, the screen will go black. Press the
Space barto bring up the system-d boot menu. Press the lettertto increase the boot time, and then selectPop!_OSto enter the newly installed operating system. Follow the on-screen instructions to complete the initial setup.Since System-d couldn't detect the Windows boot manager, we need to add it manually. To do this, open a
Terminaland run the following commands:sudo apt update sudo apt install os-prober sudo os-proberThe
os-probercommand will scan for the Windows boot manager. Take note of the output, which should indicate the location of the Windows boot manager (e.g.,nvme0n1p2).Next, run the following commands to mount the Windows partition and copy the necessary files:
lsblk sudo mount /dev/nvme0n1p2 /mnt sudo ls -la /mnt/EFI/ sudo cp -ax /mnt/EFI/Microsoft /boot/efi/EFI sudo ls -lh /boot/efi/EFIAfter completing these steps, reboot the computer. This time, the System-d boot menu should display a Windows entry. Congratulations, you now have a dual-boot laptop with Pop!_OS alongside Windows!
Conclusion 🎯
We've taken the first step in our extreme privacy journey by setting up a Linux system using Pop!_OS. We've configured the OS, installed necessary applications, and created backups to ensure data security and integrity. The journey to more privacy is not an easy one, but with each step, we move closer to having full control over our data and digital lives.
Next: PART 2 - Graphene OS Mobile Devices
In PART 2, we'll focus on securing our mobile devices using Graphene OS, a security-focused mobile operating system. We'll explore its features and benefits, and provide a step-by-step guide on how to install and configure it. Stay tuned for the next part of our extreme privacy journey!
Resources 📚
Website | |Extreme Privacy - What it take to Disappear - 5th Edition](https://inteltechniques.com/book7.html) | Other books | Pop!_OS
- Choose
-
 @ 3ad01248:962d8a07
2024-10-29 20:28:42
@ 3ad01248:962d8a07
2024-10-29 20:28:42I casted my ballot early this year and I didn't vote for Donald J Trump or Kamala Harris. Neither of these candidates did anything to earn my vote. While I did like Trump's stance on Bitcoin and freeing Ross, it still wasn't enough to get me to vote for him. There were two distinct issues that prevented me from voting for Trump.
The first being is complete lack of a plan to get a handle on the debt or at least make an attempt at slowly defusing the debt bomb that is about to go off. I don't think he has made a single pledge to bring down the debt in his platform, which is extremely rare for a Republican candidate for president to do. He is campaigning on being tough on the border and raising tariffs on China and other countries. I'm sorry but that's not going to do anything to bring down the national debt or make Americans better off at home.
What is going to end up happening is the cost of the tariffs are going to be passed on to the consumer, companies will go out of business and we are going to have fewer choices when we go to the stores to shop. What company in their right mind would eat the cost of tariffs when they are already struggling to stay afloat. I don't understand how Trump and his economic advisors don't see this coming down the road.
Trump plans to spend as much as Biden/Kamala if not more. Trump lost my vote because of his lack of a plan for the national debt.
The second reason why both candidates lost my vote was their unbridedled support for Israel. I have nothing against the people of Israel but what their government is doing in their name is horrendous.
The images coming out of Gaza are horrific and disgusting. Civilians should not be caught up in this senseless violence. What makes matters worse is the American weapons being used to massacre these people. It just isn't right in my book and I could not rest my head at night knowing that I consented to this with my vote.
I know on Nov.6 we will have a new president and it won't be the person that I voted for but at least I can go to bed knowing I voted for the right candidate. By running a Bitcoin node, using nostr, promoting Bitcoin as much as possible and voting for candidates that have integrity to do what is right regardless of party politics or personal fortunes is one of the best things you can do.
I urge everyone to vote third party and vote on principals that align with Bitcoin and not the war machine and big government.
Bitcoin #Nostr
-
 @ f462d21e:1390b6b1
2024-10-29 20:24:39
@ f462d21e:1390b6b1
2024-10-29 20:24:39eyJfaWQiOiJiMDYzYjQxMi04MGNmLTQxOTUtOTFhOS03MTM0MzExNDI4ZGIiLCJwdWJsaWNLZXkiOiJmNDYyZDIxZTEwMTYzZWIwYTQwM2FlYzZiOTNhYzU3ZWMyZjFiOTQ1NTQ3M2U5OTMwNGY1NzFhNTEzOTBiNmIxIiwiYWRUeXBlIjoiT05MSU5FX1NFTEwiLCJjb3VudHJ5IjoiVW5pdGVkIFN0YXRlcyBvZiBBbWVyaWNhIiwiY291bnRyeUNvZGUiOiJVUyIsImxhdCI6bnVsbCwibG9uIjpudWxsLCJjdXJyZW5jeUNvZGUiOiJVU0QiLCJwYXltZW50TWV0aG9kQ29kZSI6IkNBU0hfQllfTUFJTCIsInByaWNlSW5wdXRUeXBlIjoiTUFSS0VUIiwibWFyZ2luIjo0LCJtYXJrZXRQcmljZSI6MTY0LjE4LCJmaXhlZFByaWNlIjowLCJtaW5BbW91bnQiOjAsIm1heEFtb3VudCI6MCwibGltaXRUb0ZpYXRBbW91bnRzIjoiIiwicGF5bWVudE1ldGhvZERldGFpbCI6ImZhc3QgcmVwbHkiLCJtc2ciOiIiLCJhY2NvdW50SW5mbyI6IiIsImZvclRydXN0ZWQiOiJubyIsInZlcmlmaWVkRW1haWxSZXF1aXJlZCI6Im5vIiwicmVxdWlyZUZlZWRiYWNrU2NvcmUiOjAsImZpcnN0VGltZUxpbWl0QXNzZXQiOjAsInBheW1lbnRXaW5kb3dNaW51dGVzIjo2MCwiaGlkZGVuIjpmYWxzZSwiYmFubmVkIjpmYWxzZSwidmVyaWZpZWQiOnRydWUsImFkZGVkIjoiMjAyNC0xMC0yOVQyMDoyNDozOS44NzRaIn0=
-
 @ 83a0994d:3e5fbbc5
2024-10-29 19:34:25
@ 83a0994d:3e5fbbc5
2024-10-29 19:34:25How Does Bitcoin Work?
- Mining: Miners solve mathematical problems to validate transactions and generate new Bitcoins.
- Blockchain: A public ledger records all transactions, ensuring transparency and security.
- Wallets: Users store their Bitcoins in digital wallets, either online or offline.
- Transactions: Bitcoins are transferred between wallets using unique addresses.# * *
-
 @ 42342239:1d80db24
2024-10-29 19:27:12
@ 42342239:1d80db24
2024-10-29 19:27:12The Swedish government recently rejected the Transport Administration's proposal for average speed cameras. The proposal would have meant constant surveillance of all vehicles, and critics argued for instance that it would have posed a threat to national security. Given the prevalence of IT breaches and data leaks today, it's hard not to give them a point, even if the problems are often downplayed by both corporations, governments and organisations. After Facebook (now Meta) leaked account information for over half a billion users, internal mails revealed the company wanted to "normalise the fact that this happens regularly".
IT security focuses on protecting the information in our computer systems and their connections. Cybersecurity is a broader concept that also includes aspects such as human behaviour, environmental factors, and management.
Data that has not been collected cannot leak
Knowledge about cybersecurity is often insufficient. For example, it was not long ago that the Swedish Transport Agency decided to outsource the operation of the Swedish vehicle and driving licence register. This was done despite deviations from various laws and criticism from the Security Police. The operation was placed in, among other places, Serbia (which has a close relationship with Russia). The Swedish driving licence register, including personal photos, as well as confidential information about critical infrastructure such as bridges, subways, roads, and ports, became available to personnel without Swedish security clearance.
The government's decision earlier this year not to proceed with a Swedish "super register" is an example of how cybersecurity can be strengthened. The rejection of the Transport Administration's proposal for average speed cameras is another. Data that has not been collected cannot leak out. It cannot be outsourced either.
Accounts are risky by definition
But the question is bigger than that. More and more of the products and services we depend on are now subscription services, often including long documents with terms and conditions. Which few people read. If you want to control your air heat pump with your phone, you not only need an app and an account, but also agree to someone storing your data (maybe also selling it or leaking it). The same applies if you want to be able to find your car in the car park. If you do not agree to the constantly updated terms, you lose important functionality.
Every time you are required to create an account, you are put in a dependent position. And our society becomes more fragile - because data is collected and can therefore leak out. It is much harder to lose something you do not have.
At the Korean car manufacturer Kia, huge security holes were recently discovered. IT researchers could quickly scan and control almost any car, including tracking its position, unlocking it, starting the ignition, and accessing cameras and personal information such as name, phone number, and home address. In some cases, even driving routes. All thanks to a "relatively simple flaw" in a web portal.
Instead of being at the mercy of large companies' IT departments, our security would improve if we could control our air heat pump, unlock our car, or our data ourselves. The technology already exists, thanks to the breakthrough of asymmetric encryption in the 1970s. Now we just need the will to change.
-
 @ 123711f7:c0a0c17e
2024-10-29 18:10:06
@ 123711f7:c0a0c17e
2024-10-29 18:10:06Moscow announced on Tuesday it had seized control of the mining hub of Selydove in eastern Ukraine as Kyiv initiated a fresh mobilisation drive and raised concerns over North Korea’s expanding military cooperation with Russia.
The Kremlin’s forces have been advancing rapidly across the sprawling eastern front, where exhausted and outgunned Ukrainian troops are being forced to cede ground, appealing for more Western support.
Russia’s claims of capturing four new settlements in the industrial Donetsk region came as Ukrainian leader Volodymyr Zelensky and South Korea’s president agreed on deeper security cooperation after allies reported that thousands of North Korean troops had been transferred to Russia to aid its offensive.
-
 @ 3f770d65:7a745b24
2024-10-29 17:38:20
@ 3f770d65:7a745b24
2024-10-29 17:38:20Amber
Amber is a Nostr event signer for Android that allows users to securely segregate their private key (nsec) within a single, dedicated application. Designed to function as a NIP-46 signing device, Amber ensures your smartphone can sign events without needing external servers or additional hardware, keeping your private key exposure to an absolute minimum. This approach aligns with the security rationale of NIP-46, which states that each additional system handling private keys increases potential vulnerability. With Amber, no longer do users need to enter their private key into various Nostr applications.

Amber is supported by a growing list of apps, including Amethyst, 0xChat, Voyage, Fountain, and Pokey, as well as any web application that supports NIP-46 NSEC bunkers, such as Nostr Nests, Coracle, Nostrudel, and more. With expanding support, Amber provides an easy solution for secure Nostr key management across numerous platforms.

Amber supports both native and web-based Nostr applications, aiming to eliminate the need for browser extensions or web servers. Key features include offline signing, multiple account support, and NIP-46 compatibility, and includes a simple UI for granular permissions management. Amber is designed to support signing events in the background, enhancing flexibility when you select the "remember my choice" option, eliminating the need to constantly be signing events for applications that you trust. You can download the app from it's GitHub page, via Obtainium or Zap.store.
To log in with Amber, simply tap the "Login with Amber" button or icon in a supported application, or you can paste the NSEC bunker connection string directly into the login box. For example, use a connection string like this: bunker://npub1tj2dmc4udvgafxxxxxxxrtgne8j8l6rgrnaykzc8sys9mzfcz@relay.nsecbunker.com.

Citrine
Citrine is a Nostr relay built specifically for Android, allowing Nostr clients on Android devices to seamlessly send and receive events through a relay running directly on their smartphone. This mobile relay setup offers Nostr users enhanced flexibility, enabling them to manage, share, and back up all their Nostr data locally on their device. Citrine’s design supports independence and data security by keeping data accessible and under user control.

With features tailored to give users greater command over their data, Citrine allows easy export and import of the database, restoration of contact lists in case of client malfunctions, and detailed relay management options like port configuration, custom icons, user management, and on-demand relay start/stop. Users can even activate TOR access, letting others connect securely to their Nostr relay directly on their phone. Future updates will include automatic broadcasting when the device reconnects to the internet, along with content resolver support to expand its functionality.
Once you have your Citrine relay fully configured, simply add it to the Private and Local relay sections in Amethyst's relay configuration.

Pokey
Pokey for Android is a brand new, real-time notification tool for Nostr. Pokey allows users to receive live updates for their Nostr events and enabling other apps to access and interact with them. Designed for seamless integration within a user's Nostr relays, Pokey lets users stay informed of activity as it happens, with speed and the flexibility to manage which events trigger notifications on their mobile device.

Pokey currently supports connections with Amber, offering granular notification settings so users can tailor alerts to their preferences. Planned features include broadcasting events to other apps, authenticating to relays, built-in Tor support, multi-account handling, and InBox relay management. These upcoming additions aim to make Pokey a fantastic tool for Nostr notifications across the ecosystem.
Zap.store
Zap.store is a permissionless app store powered by Nostr and your trusted social graph. Built to offer a decentralized approach to app recommendations, zap.store enables you to check if friends like Alice follow, endorse, or verify an app’s SHA256 hash. This trust-based, social proof model brings app discovery closer to real-world recommendations from friends and family, bypassing centralized app curation. Unlike conventional app stores and other third party app store solutions like Obtainium, zap.store empowers users to see which apps their contacts actively interact with, providing a higher level of confidence and transparency.

Currently available on Android, zap.store aims to expand to desktop, PWAs, and other platforms soon. You can get started by installing Zap.store on your favorite Android device, and install all of the applications mentioned above.
Android's openness goes hand in hand with Nostr's openness. Enjoy exploring both expanding ecosystems.
-
 @ f584a915:9da6d625
2024-10-29 17:26:55
@ f584a915:9da6d625
2024-10-29 17:26:55Binance executive Tigran Gambaryan was arrested in Nigeria in February 2024 on charges of money laundering and tax evasion. However, the charges were dropped in October 2024, allowing him to return to the United States for medical treatment.
-
 @ 9f6a750b:aaffd7ab
2024-10-29 17:10:11
@ 9f6a750b:aaffd7ab
2024-10-29 17:10:11tldr
focus on using GPUs, not getting stuck on old, complicated CPU specs. windows + powershell + cursor is enough for my setup ( ^)o(^ )
~2023
nixOS
nixOS is an operating system based on the nix package manager, let you set up systems that are reproducible, reliable, and defined in configuration files.
- pros: system configs are written in nix language, so its easy to go back if you break system, this is really helpful for me since i often mess things up (like /etc or / with
rm -rf). - cons: minimalism is only useful if your work depends on consistency. it can limit creativity and isn’t very versatile.
emacs
emacs is a customizable text editor based on emacs lisp.
- pros: you can hack and set up configs using emacs lisp. lisp is fun!
- cons: yes, its pretty slow, and you have to keep optimizing it. also, no one uses emacs anymore sadly
2024~
windows
windows is the most popular operating system.
- pros: very stable because everyone uses it.
- cons: closed source, so if you hit a system error, you might get stuck without fix
cursor
cursor is a text editor with ai.
- pros: better than github copilot; stable and seamless. all you need to do is review your code or others’ code.
- cons: requires a subscription and is closed source.
has jumango given up on being a hacker? (;_;)
ever since LLMs became smart enough, i don’t feel the same excitement for low-level system details. back then, getting into low-level stuff was about challenging the system that fuels capitalism; the "enemy" felt like human intelligence itself. now, hacking in a true sense isnt about those details, its more about who has computational power like GPUs or quantum computers, uses tons of energy, and unites with an ai
what should i do next
if i think about whether individual humans or AI are more complex and engaging to interact with, id probably say humans in the short term for now. they share my interface and environment, and that complexity makes them more interesting to interact with, but, in the long term, i think computers will start to approximate the basic workings of human intelligence, and those differences will disappear. when we get to that point, i can’t predict what my answer would be ((+_+)) scary
- pros: system configs are written in nix language, so its easy to go back if you break system, this is really helpful for me since i often mess things up (like /etc or / with
-
 @ 9f6a750b:aaffd7ab
2024-10-29 17:04:41
@ 9f6a750b:aaffd7ab
2024-10-29 17:04:41tldr
aiが賢くなる前に人間と結婚したい
why
機械的なマッチングでは多くの場合、定型発達陣の長期的な関係を保証するだけであり、私のような発達障害は統計の外に存在するので、背景や文脈を無視・ミスリードしそう。あと、多様性が必要とされるのは根本の構造解明の為であって、その複雑な構造が解明されると私のような不良品は廃棄されそう => 結婚という既得権益で生き残りたいよう ( ◠‿◠ )
賢い機械の定義
-
定型発達の人間やマジョリティの人間が、政府のパートナ選出プログラムにおいて、長期的で幸せな関係性を自動構築できるような知能機械
-
tiktok wirehead+最低限の社会的な営み=すばらしーユートピア(?)
-
-
 @ f462d21e:1390b6b1
2024-10-29 17:01:09
@ f462d21e:1390b6b1
2024-10-29 17:01:09eyJfaWQiOiJmOWQ2ZmEyOS1iNTI5LTQyMzktOTMyNS0xMzIzMjE0MzcxZWYiLCJwdWJsaWNLZXkiOiJmNDYyZDIxZTEwMTYzZWIwYTQwM2FlYzZiOTNhYzU3ZWMyZjFiOTQ1NTQ3M2U5OTMwNGY1NzFhNTEzOTBiNmIxIiwiYWRUeXBlIjoiT05MSU5FX1NFTEwiLCJjb3VudHJ5IjoiVW5pdGVkIFN0YXRlcyBvZiBBbWVyaWNhIiwiY291bnRyeUNvZGUiOiJVUyIsImxhdCI6bnVsbCwibG9uIjpudWxsLCJjdXJyZW5jeUNvZGUiOiJVU0QiLCJwYXltZW50TWV0aG9kQ29kZSI6Ik5BVElPTkFMX0JBTksiLCJwcmljZUlucHV0VHlwZSI6Ik1BUktFVCIsIm1hcmdpbiI6MCwibWFya2V0UHJpY2UiOjE2NS4yOSwiZml4ZWRQcmljZSI6MCwibWluQW1vdW50IjowLCJtYXhBbW91bnQiOjAsImxpbWl0VG9GaWF0QW1vdW50cyI6IiIsInBheW1lbnRNZXRob2REZXRhaWwiOiIiLCJtc2ciOiIiLCJhY2NvdW50SW5mbyI6IiIsImZvclRydXN0ZWQiOiJubyIsInZlcmlmaWVkRW1haWxSZXF1aXJlZCI6Im5vIiwicmVxdWlyZUZlZWRiYWNrU2NvcmUiOjAsImZpcnN0VGltZUxpbWl0QXNzZXQiOjAsInBheW1lbnRXaW5kb3dNaW51dGVzIjo2MCwiaGlkZGVuIjpmYWxzZSwiYmFubmVkIjpmYWxzZSwidmVyaWZpZWQiOnRydWUsImFkZGVkIjoiMjAyNC0xMC0yOVQxNzowMTowOS44NzRaIn0=
-
 @ 1739d937:3e3136ef
2024-10-29 16:57:08
@ 1739d937:3e3136ef
2024-10-29 16:57:08This update marks a major milestone for the project. I know, with certainty, that MLS messaging over Nostr is going to work. That might sound a little crazy after so many months working on the project, and I was pretty confident, but until you’ve got running code, it’s all conjecture.
Late last week, I released a video of a working prototype of White Noise that shows the full flow; creating groups, inviting other users to join those groups, accepting invites, and sending messages back-and-forth. I’m thrilled that I’ve gotten this far but also appalled that it’s taken so long and disgusted at the state of the code in the app (I’ve been told I have unrelenting standards 😅).
If you missed the video last week...
nostr:note125cuk0zetc7sshw52v5zaq9apq3rq7e2x587tr2c96t7z7sjs59svwv0fj
What's Next?
In this update, I want to cover a few things about how I'm planning to proceed and how I’m splitting code out of the app into libraries that will help other developers implement MLS messaging in their own Nostr clients.
First off, many of you know that I've been building White Noise as a Rust app using the Tauri framework. The OpenMLS implementation is also written in Rust (with bindings for many other languages). So, when you hear me talking about library code, think Rust crates for now.
The first library, called openmls-nostr, is an extension/abstraction on top of the openmls implementation of the MLS spec that helps Nostr clients interact more easily with that implementation in a way that feels native to Nostr. Mostly this will be helping developers interact with MLS primitives and ensure that they’re creating, validating, and serializing these objects in the right way at the right times.
The second isn’t a new library as a big contribution to the already excellent rust-nostr library from nostr:npub1drvpzev3syqt0kjrls50050uzf25gehpz9vgdw08hvex7e0vgfeq0eseet. The methods that will go in rust-nostr are highly abstracted and based specifically on the requirements of NIP-104. Mostly this will be helping developers to take those MLS primitives and publish or query them as Nostr events at the right times and to/from the right relays.
Most of this code was originally written directly in the White Noise library so this week I've started to pull code for both of those libraries out and move it to its new home. While I’ve been at it, I've been writing some tests and trying to document things.
An unfortunate offshoot of this is that the usable builds of White Noise are going to take a touch longer. I promise it’s still a very high priority but at this point I need to clean a few things up based on what I've learned thus far.
Another thing that is slowing down release is that; behind the scenes of the dev work, I’ve been battling with Apple for nearly 2 months now to get a proper developer team set up so that we can publish the app via TestFlight for MacOS and iOS. I’ve also been recently learning the intricacies of Android publishing (oh my dear god there are so many devices, OS versions, etc.).
With that in mind, if you know anyone who can help get me up to speed on CI/CD, release pipelines, and multi-platform distribution please hit me up. I would love to learn more and hopefully shortcut some of the pain.
Thanks again so much for all the support over the last few months! It means a lot to me and is a huge part of what is keeping me going on this. 🙏
-
 @ 123711f7:c0a0c17e
2024-10-29 16:23:03
@ 123711f7:c0a0c17e
2024-10-29 16:23:03Ethereum (ETH) Faces Market Correction, But Strong Fundamentals Remain The world’s second-largest cryptocurrency, Ethereum (ETH), has experienced a recent price dip, currently trading around $2,980. This correction is part of a broader market movement, not specific to Ethereum (ETH). Despite the short-term price decline, analysts remain confident in Ethereum’s (ETH) long-term potential due to its established position and strong foundation within the crypto ecosystem. The reasons behind the market correction are multifaceted, and speculation about Algotech (ALGT) is not a contributing factor.
One potential driver of the correction was investor hope for a spot Ethereum ETF by May’s end, which could have triggered a bullish price reversal. However, market analysts now believe the likelihood of such approval this year is slim. While Ethereum (ETH) has seen a small surge of 0.33% in the last 24 hours, it remains down 4% for the week. Regaining the 50 Moving Average (MA) as support on the daily chart is crucial for regaining bullish momentum.
-
 @ bf95e1a4:ebdcc848
2024-10-29 14:33:18
@ bf95e1a4:ebdcc848
2024-10-29 14:33:18This is the AI-generated transcript of Bitcoin Infinity Show 132 with Rigel Walshe!
Welcoming Rigel Walshe
Luke: Rigel, welcome to the Bitcoin Infinity Show.
Knut: Thank you for having me on. Yeah, it's, finally!
Rigel: I think we talked about this like two years ago or something, you were like, want to do this? And just I think too busy doing different things and never happened, right?
Knut: But we figured we'd do an in person one,
Rigel: Mm-Hmm.
Knut: Because I remember the first time I saw you back in 2019, like, the starting gun for me for all of this crazy life that has followed on later. So, and here's this guy on stage, playing death metal songs for
Rigel: All.
Knut: finance and nerd people.
Knut: so yeah, I'm not the only metalhead in here, like,
Rigel: I remember when I put that in the presentation, I was like, is this going to go down? And then everyone clapped after I played that video. I was like, oh, cool.
Knut: No, it was super based.
Rigel: Thank you.
Knut: what's the name of your band again?
Rigel: so I play in a band called Diocletian. I used to play in a band called Dawn of Ezel, but the band I play in now is a band called Diocletian, which is like, I guess you would call it like the, you know, metal's got like a zillion sub genres and stuff, but like, you would call it like war metal, I guess.
From Metal to Bitcoin
Rigel: Yeah. And, what's your story? Like give our listeners your story. How, who are you and, what turned you on to death metal and what turned you on to Bitcoin and is there a connection between the two and all of
Rigel: Oh my God. Okay. This is a very long winded. How do I summarize this pretty well? Okay. So yeah, I'm Roger Walsh. I go by Coinsurance Ed on Twitter and Telegram and these, a lot of these kinds of platforms. yeah, I mean, played music and stuff since I was, 17 years old, you know, been a band where, you know, I'm from New Zealand, that's where that was from.
Rigel: We were the first metal band to ever get out of the country, really, even like Australia, let alone, Europe and the States and things like that. So, you know, we did quite a few, albums, I think it was, with my old band Dawn of Azel before we split up, in New Zealand it's quite a bit bigger than we were, outside of that, and certainly Europe or the States.
Rigel: the same time, when I turned 21, I joined the police. I was in the police for 10 years, at the same time as this was going on, and if you search my name, you'll find some interesting news reports about some trouble I had for that kind of reason. so that's maybe my background. we'll shift forward to maybe when I first got into Bitcoin in 2014, and so for me, what got me interested in Bitcoin was, as I said, I used to be in the police, and one day, you know, I think I've heard of Bitcoin thrown around, I just I was reading a news article about the, Silk Road trial, and this is when Russell Brook was getting sentenced, and this is like after I left the police and things like this, and it just blew my mind when I read that, it's like, because I think most people don't really, or didn't, or can't quite grok maybe the way that it makes It's me, in the sense of like, you have this drug market selling.
Rigel: whatever you liked, you know, under the eyes of the FBI and all these guys, and there was nothing they could do for years, and this, I was like, wow, man, this is going to be straight away, I thought this is how Russia and North Korea are going to get around sanctions and stuff, as it seems they are doing today, you know, so to me this is like nuclear weapons grade money.
Rigel: So my interest actually was, was in Bitcoin, but also in the darknet market, so I just got on there and had a look, And that was what really interested me, but of course, like most people that play around in the darknet markets, you start, okay, what is this Bitcoin thing that I'm using and sending and start looking into it.
Rigel: And look, I'd never been a finance kind of guy. I mean, like I said, I joined the police relatively early on. They've got a very good superannuation scheme where, you put in a dollar, the government puts in two dollars. And so, to me, I'd looked at investing and shares and things a couple of times, and it never made sense because I've got the best There's no better place that I could do is just put more money in that fund that the government will match dollar for dollar, right?
Rigel: So this is the first time I've ever looked at anything Really about investing and you know and obviously as you start thinking about this Well at that time when I got into Bitcoin and bought my stuff was around 200 bucks It just right at the end of the 2014 kind of crash and you know at the time I thought like wow man this might be worth a thousand dollars some years later, right?
Rigel: You know so so I started putting pretty much Everything I had which the time was not a lot because this is after I left the police and I actually quite a bit of trouble Transitioning from that into like some sort of civilian career. I was like I found it quite hard to find, like, work, and so I was working self employed, and I didn't have a lot of money, but I put everything I had into Bitcoin, because to me, it just made total sense,
Rigel: So yeah, that was 2014, fast forward a couple of years, 2017 is around, and now Bitcoin is there. Close to 20 grand, you know, I've got, I'm fucking rich, so what I did is I was like, man, I spend so much time thinking and talking about Bitcoin, I really want to get involved in the space, but, I'm not a software developer, what can I do?
Rigel: So I actually ended up buying some Trezors, and just through good luck, when I bought them, Bitcoin was around 10k. and I bought like, 200 or something treasures and ledges, and I sold all of them in a month in New Zealand, which is a tiny country, which blew my mind, So then that happened, and this was like February, I remember it was December, I had massive orders, January pitted off, and then like February, there was just nothing, and the price is going down, so I was just in the right place at the right time, and got lucky, and I had all this money and it was in a business account that I'd have to pay taxes on, obviously, if I didn't get rid of it, right?
Rigel: So, to my thing as well, I could pay myself a salary and pay tax on it, but what's smarter is, hmm, how can I use this money to make the next step and jump to the next thing? So I thought, well, let's go to a bunch of Bitcoin conferences and see if there's any match for my kind of skills, right? So I'd never, I'd never gone to, I've been to like meetups in New Zealand, but I had no idea like what it really looked like out there in the real world, right?
Rigel: So I went to, like a couple of, I went to like an Australian big Crip, blockchain one, which was like just total trash. And then I went to, token 2049. You heard of that one? It's like a still going. It's like a real shit coin kind of conference thing that was in,
Knut: rings a tiny bell.
Rigel: it's in, it was in Hong Kong or something, right?
Rigel: and I remember I went to that and it was cool, right? But it was still, you know, I was still in this world where, obviously I was familiar with Bitcoin, but I dabbled with, altcoins and stuff like this and perhaps the way that you or I would look at Bitcoin now, I think was still quite a new thing.
Rigel: New idea in those times, right? There wasn't this really well nuanced ideology about how to view this kind of stuff. So I went there and I was kind of figuring this out The next one I went to was like Konsensus in New York, which was at the time, that was the biggest Bitcoin crypto conference you would say ever.
Rigel: And there was like, 3, 000 people or something. And I remember at that conference, there was a lot of, you know, all sorts of Ethereum and things there, right, but there was a blockstream room at this conference. And I remember, I felt like, man, this place feels so sleazy and so dirty and everyone seems Super sketchy, but then you go to the Blockstream room, and I was like, these are the guys that, you know, I just clicked, like when you meet them and you see this, and so I think this is a really important thing for people that don't go to conferences, that when you come, a lot of this stuff, when you just see it with your own eyes and talk to people directly, it makes a lot more sense than online.
Rigel: So I went to that, and then I met, what's his name, Erik, last name is sketchy, but he's, works on Bitcoin Fabric, used to be at Blockstream. He told me, go to Building on Bitcoin and go to Honeybadger. And so from then I started going to conferences, when I went to building on Bitcoin, I kind of talked about this in my talk today, it was like I wasn't a software developer, but I saw Adam Fiskor and Nicholas Doria presented Wasabi and BTC Pay Server, and I realized like, wow man, I thought before that Bitcoin software development is all about like some super computer nerd guys and like Bitcoin core and only this real high level stuff.
Rigel: But I realized, man, these guys just made their own app on Bitcoin that really made a real difference. And wow, you know, I could do that if I were to put my mind to it. So I came back straight away, got into a Python coding course and just like really, really luckily, you know, I went really crazy on this.
Rigel: then come December, Jimmy Song came to Australia to do the, the programming course.
Rigel: I applied and got on that, and I was like really out of my depth, but I managed to keep up enough to write it. and so this was like maybe six months after, six months ago, I didn't know anything about coding or anything like that. And so just by pure luck, I was relatively well networked in the New Zealand, Auckland Bitcoin scene, and I went to a meetup and there was a guy there who I knew kind of loosely, that I knew had a really small exchange in New Zealand, and I was talking about, he's like, Oh, what are you doing?
Rigel: I was just building this API in Python. It's like, Oh, we're building out our API. Do you want to come and help? And I was like, Yeah, so at the time I was working a job where I'm working four days a week and I had the Mondays off. And so I just started working there on Mondays and then split with the ex girlfriend and I was really happy in New Zealand and felt like I've really got to get out of here, right?
Rigel: So I was thinking even if I have to like sell Bitcoin to leave, I've just really got to get out of New Zealand because I feel like there's just no future for me here. So I said to them, okay, look, hey, I had a friend that was living in Bali. I said, look, hey, I'm moving to Bali. I really don't want to leave this job.
Rigel: And I really Appreciate what you give me, but I've got to do this. If you let me work remote, I would really happily work remote, but I understand if you don't. They're like, sure, yeah, have a full time job. So I did that, started doing that, COVID happened, ended up in Mexico as a cause of that, and in, the Jeremy Songz course, there's like an alumni telegram group, Jan Pritzker jumped in there and he said hey, we're looking for developers at Swan, and I said, hey, I do that, and the tech stack was very similar to what I was already working on, and, I got a job there, and up until, three weeks ago, I was working at Swan for three and a half years, I think it was employee number, 10 or 11 or something there.
Rigel: and that's pretty much it. I think I covered all the bases there. And then I give some talks at conferences here.
Conference Experiences
Knut: Yeah, it's a great story. And there are many similarities to mine. Like I also have experience of the shit coin conference before I went to Rega in 2019, but were you here in 2018?
Rigel: Yeah. That was the first, because was, when I said when I met, Eric, he told me building on Bitcoin and then, honey Beg are the ones, so I, I pretty much, that was the last of the company money was that one there. And that, that one they were talking about HCPP and I was like, oh, can I go to that? Flying home, New Zealand, which is like a two day journey, then coming back two weeks later and paying for all the stuff, I didn't manage to make it, but like, that was the first, first time, the last conference I went on that thing, and that really, I mean, it was an amazing conference. So this, this has always been an amazing conference, you know.
Knut: I saw your talk here last year, and it was really, really good, like awesome about Bitcoin cultures, right, and different subcultures and, what these subgroups and what happens in a decentralized system, and also like we've been chatting during this conference about, these effects, like how we find our own in groups and how people cling onto the extremes here and there.
Knut: can you expand a bit on that and, what do you think is missing from conferences in general and what makes Honeybadger stick out as a high signal one and all of that
Bitcoin Psychopaths vs Bitcoin Sociopaths
Rigel: I mean, okay, so three questions there. So to talk about the talk, it's called Bitcoin Psychopaths vs. Bitcoin Sociopaths, and if you Google it, you can find the written thing and the video and view it yourself. But basically, what I talked about is, when I started coming to these conferences, I realized how much the Bitcoin world had in common with the music world in the sense of, The personalities, the little subgroups, the way that things evolved, like I just saw a lot of things that clicked because to me really like Bitcoin is like a Harley Davidson for computer nerds, right?
Rigel: It's like this kind of subculture where people are involved in and I feel like a lot of people who are in Bitcoin, like I have this experience of being these weird kind of outside groups and how this works. I think a lot of people that are in Bitcoin this is the first kind of really different thing they've had in their life and they, you know, they're like blows in mind.
Rigel: They're like, wow, this is so cool, but they don't realize how a lot of these idiosyncrasies are very much the same. I'd imagine the same if you were like a Trekkie or you're into something like that. There's a lot of the same sort of politics, so the talk is really talking about how, Bitcoin, in my opinion, is like a subculture or counterculture, the same way that, metal music would be an example, there's plenty of things like this where people have a niche interest, but it's also kind of a little bit against society, the whole idea of Bitcoin is you're trying to defund the state, and so it's kind of like, it's not like a really dangerous out there kind of thing,
Knut: It's not in total alignment with society, inherently contrarian?
Rigel: Exactly, yeah, exactly, which does attract a lot of contrarians, right? so the whole talk was looking at, okay, if you look at subcultures, how do they get involved or immersed in the traditional system, right?
Rigel: Let's take rap music, for example. You know, where you had, Dr. Dre in, NWA, and now he's like, selling Beats headphones and a very nice commercial established businessman, right? Or another good one that I like to use is like, weed, or like the gay community, right? At one point, these were very out there things, and now they're very normal and very accepted, and they're almost like Almost a little forced on you, right?
Rigel: In a lot of ways, as opposed to like being an outcast. So, you know, when things become normalized and when they get bigger and bigger and bigger, if they catch on, eventually they kind of get watered down as they get integrated into society. And the same thing I think is already happening in Bitcoin, and it's affecting the culture of Bitcoin.
Rigel: And I don't think you can really change that, you know, it's inevitable, but it's something that I think we need to discuss and look at, okay, well, if you Some of these other things there, how they lost, what made them powerful and transformative in the first place, because they were kind of revolutionary movements, right?
Rigel: And they got watered down and commercialized, right? So I think the same thing is happening to Bitcoin right now, and you can't really stop it. This is, if you just look at history, this is what happens, but there is a conversation to be had about how can we navigate this as best as we can, right?
Rigel: Now, what was the,
Knut: Yeah,
Rigel: was the other two
Knut: of a long question.
Luke: maybe we can just stay on
Rigel: Are you asking about conferences?
Baltic Honeybadger
Rigel: Like you said, what I think about Bitcoin conferences and what I think I like about HoneyBadger. Well, what I like about HoneyBadger is that, the conference thing, kind of to speak to what I just was talking about, right?
Rigel: As this gets bigger, it becomes more commercial and, things get kind of watered down for people that are, Casual participants, right? The people early on in the movement, like, if you're there in 2017, 2018, you're really hardcore, right? But if you look at the way they're doing, say, Bitcoin Nashville at the moment, it's a very different thing.
Rigel: It's very not watered down, very commercial, and very one kind of one minded, right? And what I like about Honeybadge and what I have so much respect for with this conference is that, remember in 2019, that was the biggest Bitcoin conference in the world, and I think there was probably 600, 800 people, right?
Rigel: things have got bigger since then, and maybe, this could have been a bigger conference, certainly you would imagine it could have been as big as, BTC Prague right? but they seem to have had the idea of, let's just keep it at a particular level and not go too far and too hard, in my humble opinion the Bitcoin National Conference is an absolute abomination, it's a circus,
Knut: And it's all there just to, like, make it as loud and big as possible, but what is the message that is getting diluted and what is getting presented to these newcomers there is, to me, is very much getting away from what I believe the message of Bitcoin should be, right? it's inflation,
Rigel: it's dilution inflation. It's the same thing as when it happens to your money, it happens to culture. I mean, I've never thought about that, but that's a very good way to phrase it, I think. So, you know, when it comes to conferences, beyond the fact of just making it big and watering it down, the other thing I think is, like, the narrative is very, very stale, right?
Rigel: it's all about the narrative. Sound money and the moneys of Bitcoin. Which of course it is. in my opinion, the best money in the world. But I think, we've still made those arguments pretty well by this point.
Rigel: Right. You know, there's so much stuff that's been written and I think it is really good stuff. Right. They're all good messages. But, they've been said, they're done, they're written, right, you know, and you don't want to hear the same guys giving the same talk every year over and over, which is what these conferences are, I think it's like the Rolling Stones, you know, playing their greatest hits, right, the Rolling Stones have some really amazing songs, but if you've gone and seen them play live, playing their greatest hits ten times, you're going to, I think I'll skip it this year, right,
Rigel: So, to what I see happening here, if you want this movement to succeed, and you as a conference promoter want people to come to your conferences, you've got to keep it new and interesting and shift things up, right? And so you've got to find people out there in the community.
Rigel: in the community out there who aren't speaking at conferences, aren't big, aren't famous, right? If we were to turn the analogy of a music, festival, there's bands that aren't known, but if you gave them a chance and used your festivals as a way to expose them to more people, they could get bigger, and it's in your interest, because if you're having the same bands play every year, people don't want to come to your conference.
Rigel: But if you can help this new blood come up, then it's in your interest because you can put them on the stage and you can bring people to your event, right? And I think the same thing should be done, for this. I mean, obviously, I think it should be done for the good of Bitcoin, right?
Rigel: There's many different aspects to Bitcoin. It's a very interesting, you know, I say it's like the, Rorschach's test, right? Like what you see in the inkblot reflects more about you and I, but we can look at the same thing and see two totally different things, right?
Rigel: Yeah. So I think it's in the interest of Bitcoin to get people to flesh these out, these narratives, and give them an opportunity to do it and to get it out in people's heads and for them to hear this. But it's also in the interest of them as conference promoters. Like I said, if it's just the same people all the time, it's going to peter out.
Rigel: And I feel like Honeybadger is one of the few places that's trying to do that,
Luke: Yeah, and I mean, in my perspective, HoneyBadger, two years ago, was my first ever conference, right? And so, I mean, that's already my newness in this space compared to you guys, but still. HoneyBadger has been fantastic for me from that perspective, and like, the signal, that's the focus. But we talked to Max Kai about this not long ago.
Luke: About how is the Latvian community doing and Honeybadger hasn't really focused on growing the local community. It's been bringing the signal into one place and everyone learned from each other and all this and it's a fantastic event for Bitcoin, And then there's these other ones that are all about, I mean, the American ones, especially like the Nashvilles and all this, those are, you know, these entertainment fests and all this, and I think they've also brought this to Amsterdam here in Europe, but I think Prague and Madeira here this last year were both examples of conferences that went a bit bigger, but have also have a layer of the local adoption, and I think those types of conferences are important for a different reason.
Luke: Like the, the one that, Bulgaria is the example that I use, I use a lot, they do a good thing there to build the local adoption. And so get some speakers, get some international presence to sort of show here's what this is, right? but focus on the local side of it and building the adoption in that locale.
Luke: I think that's quite the idea.
Knut: on diversity and inclusion,
Luke: That's so
Rigel: I think it's true, as a New Zealander, we're in this interesting position where, it's a very Western culture, but we're somewhere in between Europe and America, right? So, if you're European, you're biased and polarized to a European way of doing things, Americans are the other, and we're somewhat in the middle,
Rigel: we see them both. From different angles, and there's pros and cons from both, and I'm sure I'm going to offend some American people saying this, but I'm just going to say it. European conferences are a thousand times better than American ones. And I've seen almost none that I feel like really did a good job.
Knut: I think something like TabConf does it well, but I think technical conferences are a slightly different kind of thing, different beast.
Rigel: all there about technology, but if you're trying to do something where People talk of talking about more general people stuff, right?
Rigel: Like, big and commercial and plastic. No soul, and I feel like Europeans just seem to be able to do that much better. Sorry to any Americans watching this, but that's been my impression.
Knut: Honey Badger clearly has the soul, and I mean, the local adoption thing, that's not a dig, it's just not what they've decided to focus on, so it's, I think we, I hope, I hope this conference, I'll be attending every year, Yeah. And that's why I love to see so many Americans over in Europe, like this last year, first of all, Madeira, a ton of Americans came over, both speakers and attendees and also. Prague, and here, like, you have, quite a few here too, and quite a few high level ones, and it's good to have them here to give them a taste of what this is like.
Rigel: I'm a guy that likes to have a drink and hang out with people and things like that, so, you know, it's a big party, really, a conference, in a lot of ways, I think I enjoy that element of it, but again, you know, I think there's just so much value in, You know, we all talk online and stuff and I see what you're writing to someone else and things like that.
Rigel: But to be able to humanize and talk to some of these people, and some of them you meet them and you realize, oh, this guy isn't actually such a dickhead after all, I guess, or the opposite, right? This person that you think is really high integrity or whatever, and you meet them, you're like, man, this person, I have a very bad feeling about this kind of person, right?
Rigel: So I think that's a very important thing if you're really enmeshed in this world, I think you owe it on yourself to go and physically meet people and there's just such a value in that which is difficult to articulate, you know?
Knut: hard to find new ideas and new angles to view this. I had writer's block for the longest time before starting the new book and before I had ideas good enough to pursue. And it's getting increasingly harder with each book, of course, because there's only this so many times you can say the same thing,
Speaking at Conferences
Rigel: I know the feeling of, you know, like I'm thinking about, because I've been invited to speak here every year. and so I'm thinking, okay, when I went to about next year, I'm like, Oh man, like what to do two or three things, right. It's like to avoid just repeating it or slightly changing or morally saying the same thing is like, it's a big ass to do, but I mean, I think that's, that also is a way of, of rather than.
Rigel: you're right thinking that we've got to write the whole story ourselves and it's on you to come up with new ideas for 10 years in a row. It's more like you have your little thing and it's best just hone that message really, really well. And this is how I feel about it is I used to think with conferences, no, I never want to give the same talk twice.
Rigel: I want to do it, you know, once and something every time has to be something new. But I kind of realized after doing a bunch of them is like, well, most people aren't going to see you talk anyway. All right. Or they're not going to. You know, take the time to or they're not gonna appreciate in the moment that that it was right then right and there's real value not just for you personally in terms of like, when you give a talk once, it's probably going to be better the third or fourth or fifth time that you give it, right, but there's also value to repeating the same message, right, which to me almost felt like false or a cop out, but no, I think now, after doing it a while, there's actually something to be done with that, which is take one small thing and focus on that small area and don't try and be like, completely reinventing yourself, like, tomorrow you're going to be talking about some weird economics and then you're How bitcoin is art, or something, you know, I mean like, just take one thing and build your little notice around that and really, really hone that particular message, because like we've done with the economic stuff, right, I think we've really steel manned that idea, and there's just anything, any objection that someone could have about the money stuff, someone has written just the best thing and you're just like, bam, and you haven't asked your every question.
Luke: There's real value for us as a community in doing that, but that just comes from a small amount of people focus, doing focus work on one particular thing, That's funny, that reminds me of comedians. comedians are like some of the most visible people on podcasts because for some reason people like to listen to funny people be funny but you hear about their process of literally going around and touring and working on their jokes the same ones, they don't do a new act Every night, you know, they work on it and then eventually they record it and everything.
Luke: That's actually not a bad model for this
Rigel: I think a good analogy, right? I mean, like, you can't tell the same joke for 10 years, but you wouldn't want to try and rewrite a whole new, like, half an hour comedy skit every, you just, I mean, trying to write some of these talks takes months, right?
Rigel: and when I do it, I've just got, like, pretty much memorize half an hour of stuff and then practice it so it becomes more natural. But I mean, like, trying to do that. You know, if I was trying to do this like six times a year, I stick to like three because it's too much for me, right? But imagine trying to do it six times a year.
Rigel: You just can't do that alone unless you're full time working on it. So, there's lots of reasons why I think just one small thing repeated it actually has some value.
Knut: Yeah.
Dangerous Narratives in Bitcoin
Knut: do you think there are any like narratives around Bitcoin or, thoughts around it that are actually dangerous? Like the people are on the wrong track?
Rigel: I mean like the stuff I talked about before, right, where I think the message is being deluded and it's dangerous and that like the analogy which I was supposed to make in this talk but I actually kind of like As you do, you know, skip over or like move around some things that you were going to say, but you didn't say.
Rigel: The thing like, the real risk to me is that, if we don't change people's view on what technology is. Like, people want something that's familiar. They want to recreate what they know. It's human nature, right? And so, for you as a business owner, or someone that's creating something and trying to get more Bitcoiners on board, which I think there's maybe a little too much emphasis on, it's just more people in the door, so the number can go up.
Rigel: The more you do that, the more people try to make it understandable and relatable by people, so they make it more like what it already is. And by making it more like what it already is, the whole idea about Bitcoin is changing what it already is in terms of money and things like that. I think the risk that we run is like recreating the existing financial system with an orange coat of paint, right?
Rigel: The same thing, but yeah, just with different words, different wardrobe change, right? So I think that's probably to me the most dangerous thing where, I know I'm someone that's like very much the privacy, freedom, self custodial kind of thing, and very anti KYC, all this kind of stuff, but you know, having worked at companies like this, I understand why these things are necessary, and there is also an argument why you would say, well, sure, it's KYC, but if a lot of people buy Bitcoin, it doesn't matter if it's KYC, because we've defunded the government, you know, so there is a middle ground here to be found, But I think probably that's what I'm getting to the real point is like a nuance, right?
Rigel: You know, somewhere in between those two polarized things, there's the right way to do it. And it's probably not going to be universal in all situations what it is, but there's just a real lack of. intellectual rigorousness in this space, right? I think, the best book on Bitcoin is, Erik Voskiel's Crypto Economics, because, I largely agree with almost everything he says, not everyone does, but I don't think that you can argue that that is the most rigorous Comprehensive body of work about this is what bitcoin is and this is how it functions.
Rigel: You know these axiomatic truths as he describes it It's a it's a whole system that all links together and to return to like the religion talk I gave last year It's like if you look at Christianity, right, you know, you have like baptism, Catholicism, Protestantism all these kind of things right and they're it's so detailed.
Rigel: It's like well because in Ephesians 12 16 Jesus said this or that or whatever you should only wear a red shirt on Tuesdays or something It's that level of detail of like They've thought about every aspect of the Bible and what this should mean and they have like this detailed view. And I think there's a lot of value for that because as I said, there are many different views in this spectrum about what works for Bitcoin and I think we win by having this marketplace of ideas, but we don't win if they're like very pure.
Rigel: They're very poorly fleshed out ideas and they're very kind of naïve or immature by all these different schools of thought having the most rigorous, intense, deep body of work to help explain and understand why you should look at Bitcoin from this angle or see it this way or why it should be done this way.
Rigel: you're the second person this week to say crypto, It's great. It's just crazy. it's a pretty dense book, right? You know, it's not for a beginner's book, but it's crazy that it's not bigger in my mind, you know.
Knut: someone should write a, new version of that.
Luke: yeah, very much
Rigel: I mean, but this is the thing, right? it's rigorous because I think, and why I really like it as well is it's the only book that goes that level of depth and is thick and is, really deep on this kind of stuff. And you see Erik on Twitter, he's very much, he's like such a pedantic motherfucker about trapping someone down about the way they say particular words, because it matters, right?
Rigel: It does matter, right? Like these loose definitions of what you think this word means, what I think it means, makes me think that we're talking the same language, but actually you, I haven't communicated to you effectively what is inside my brain, right? And so like this level of detail is really important for something like Bitcoin, because like imagine you're navigating and you say, oh, it's, it's, it's that way, a hundred meters, it's fine.
Rigel: But if it's like, 300 kilometers, you can end up in a very different place than if you said these grid coordinates, you know, this GPS coordinate, stuff like that. So specificity is really, really important and language is the map, the navigation system we use to arrive at an idea in the future.
Rigel: And so, I think there's value to that.
Knut: Yeah, and I think this is, human action by Ludwig von Mises is dense and very meticulously written for the exact same reason, right? You need this rigorous thing. And I know from writing a smaller book on praxeology, it's really hard because you have to be very, very careful with your words to get it right, which is why I like writing, Something like the Inverse of Clown World more because I can be more expressive, you know.
Rigel: man, I've thought about doing the book thing and maybe one day I will, but I'm like, oh man, I just, I can't imagine what you have to go through to produce something of like this size, which is not the largest book, like man. Wow, you know, hats off to people that write a book, right, because, like I said, I've thought about it, but when I've looked at what's involved, I'm like,
Rigel: send us a DM and we'll help you. maybe they will come about, I need to write more, this is the way they say you do it, right, is like you write a bunch of articles and you turn the articles into a book, right, so I've kind of thought about maybe I can go down this road, but we'll see.
Knut: Oh, looking forward to it.
Nostr
Luke: So what, what do you think of, of Nostr? the, the whole, the combination of this Nostriga and Honeybadger. First of all, that was, it was a brilliant move, I think, to attach the two together. there's talk that the next time they'll do that is they'll attach it to, also Freedom Forum, which is also a very good idea.
Luke: A different angle, but very good idea. But Nostr and Bitcoin are becoming really intertwined these days. many, many applications that were Bitcoin applications have now. Also become Nostr applications and yeah, what do you see Nostr in the space here?
Rigel: Difficult for me to say because like I've really wanted to sit down and really get my head technically around Nostr and I haven't, right? You know, like I understand basically how it works, but as far as like there's some critiques on Nostr which I would like to have a more informed opinion on than I do.
Rigel: And, like, I know Peter Todd reasonably well, and like, last night we were, I was saying, like, basically, okay, just tell, tell me, you know, like, tell me what things is, so at least when I get to look at this, I've got, because he's kind of anti, or anti a lot of aspects of it, right, he thinks it doesn't work, so, I mean, based on that, like I said, it's, it's not a nuanced, informed opinion, but I think, my concern, perhaps, is that, like, It's actually not that good a protocol on the, on the base level for certain things.
Rigel: Like it's ability to deliver decentralized Twitter, all the millions of applications we have on mine for Nostr at scale is going to be possible. And again, I can't say One way or the other, but that's my concern about it. And, and one thing that returning to what I was talking earlier about the subcultures and things like that, fortunately in the Bitcoin space, I think we've got a little tendency to be overly supportive and overly passionate.
Rigel: You want the space to be something where people come from the outside and they feel like this is full of energy and love and happiness and good times and smiles. That draws people in. And if it's the opposite and people are too cynical or bitter or tough, right, it's not going to pull more people into the space.
Rigel: That's what we need. But again, you know, I think there's a bit of a lack in the space of people who are willing to Call out, you know, say a spade's a spade. There's a problem here. We need to fix this. There's a bit of a lack with that and that that would be the only thing I feel with Nostr
Rigel: And I, my only concern that I see as an outsider with Nostr is that Is this like a science project where there's something where it's got a tiny amount of people and there's all this energy and noise, but it's, it's its own self contained thing, right outside this little bubble, no one cares and, and it's a bunch of people celebrating how great they are creating this thing for themselves, thinking it's a tool for the world.
Rigel: So, I think it is great and I'm really interested in it primarily from the perspective of like, what to me is, this is kind of what my talk about was about today about Bitcoin as performance art. Bitcoin isn't just about money, it's also about telling a story, about showing an alternative narrative to what the governments or corporations give us.
Rigel: And that narrative is about how we can use technology and open source and things like this to create our own better alternatives and we don't have to use what they tell us they have to use. And so I like Nostr in the sense that It's like the artistic inspiration of Bitcoin is created at Nostr, right, so we're spiritually inspired by Bitcoin.
Rigel: It's like a lot of the lessons that we've learned from Bitcoin have been applied to how Nostr is created, right, it's kind of born of Bitcoin. And so to me, regardless of like the reservations or the possible issues like I talked about before, to me what's far more interesting is someone said, look, hey, Bitcoin works really well at prioritizing decentralized money.
Rigel: How can we take the lessons there and apply that to communication and other things? And I think. To me, that is a more important thing, is like, if this can happen to many other technologies. It makes sense, right? Like, in my talk, I talked about the Liberator pistol being another example of this. Now, if you look at Cody Wilson, he said, like, it was supposed to be a toy gun, a prop gun.
Rigel: It's not something where you really think it's going to be like an AR 15. But that wasn't the whole point. The whole idea is here's something. Where it's going to get all over the news and the media and people are going to start talking about and thinking, you know, that the wheels start to turn the head of, hmm, 3D printing and code, man, like, it's going to be impossible for governments to stop all this kind of stuff.
Rigel: And when people start thinking about that, the world starts changing, right? So I think Bitcoin is amazing money and it's going to change the financial system, but perhaps what is better is that it gets people thinking of, wow, we created our own money. What other stuff can we create if we all work together and have a vision for the future, right?
Rigel: So to me that's, in some sense, like, if Bitcoin failed as money, but it did that, I think that would be a better victory than it not doing that and just being sound money, right? So that's, an important part of Nostr and what I really look forward to with that is how that dynamic plays out.
Disagreeableness in Bitcoin
Knut: Yeah, I think I've observed a correlation between disagreeableness and how early you were to Bitcoin. So like the first couple of years, you get your Voskules and your Kavaios and what not. And the further you go down the line, it isn't until like 2021, you get your Joe Halls and your, nice people, right?
Knut: I think the thing that enables the happy people 10 years down the line is that the disagreeable people were so rigorous in the beginning. So you get the don't trust verify, and then it builds in layers and the happy people can join on the layers on top later on.
Rigel: Yeah, yeah, yeah,
Knut: so have you, what's your, what's your
Rigel: Oh yeah, I mean, I think you're totally right with that. it's a little bit of a tragedy of the commons problem in Bitcoin, right, where, Zach, you said the people that are doing, like, open source development is perhaps the best example, right?
Rigel: if we don't have, like, very smart, talented people working full time on Bitcoin, even if you think it can be ossified, like, just if you understand software, right, there's just this maintenance process that needs to happen, and there's not someone keeping a close eye on that. It's very easy for Bitcoin to break or to fall apart, right?
Rigel: there's no business model for open source development or maintaining Bitcoin Core, right? There's no way, I mean, the whole idea of Bitcoin is that it should never be a revenue generative process as it is, right? So we need to think of an alternative model, because it's all in our interests for Bitcoin to succeed.
Rigel: But we can't just create a business and let it self perpetuate itself. We've got to come up with a different model of how we can do that, right? So, you know, there's a little bit of, all of us are like free riding on the work of open source developers in that sense, right? And I think there's a little bit of that when it comes to all these, happy, joyous kind of people I think a lot of them, particularly if you've been here for a short amount of time, have kind of stars in their eyes or their rose tinted glasses on about, like,
Affinity Scams in Bitcoin
Rigel: You know, one thing I would definitely say at the moment, and, you know, I've, I've obviously just, finished up working for a company, in the Bitcoin space is that, there's a lot of people, I think the idea of a Bitcoin scam is a relatively new thing that people aren't looking at, if you're charging 7, 000 to have a out of alpha male retreat, you know, because this guy is associated with Bitcoin, that's a scam, that's a fucking scam, I mean, like, hey, maybe it's being marketed honestly, but I mean, let's look at what's happening here, it's, association with Bitcoin.
Rigel: it's, you know, there's the things like, I like Bitcoin, buy my shitcoin. It's like, I like Bitcoin, buy my other thing. Like, it's the next level. And so I
Knut: why is that a scam though?
Rigel: Well, I think it's a scam in that, If you look at the pricing of the resort that was involved, the tickets are like twice the price, right?
Rigel: Yeah, it is in the eye of the beholder, right? If you feel you're getting value and you're happy to pay that thing, it's not a scam. But I mean, come on, there's other examples, where, there are things where people are, I think you see this a lot where, People are like, here is sound food, or sound diet, or open source this or that, right?
Rigel: You know, where it's, I mean, it's not a scam, but you can see how this like, Bitcoin as a lifestyle brand is being created, right? And people are trying to market things which really have nothing to do with Bitcoin. And again, maybe they're saying this is Bitcoin, but I feel that there is a lot of people using that as a way to charge an overpriced price for an undervalued service, right?
Rigel: And so that's something which I see kind of creeping into the space is a bit of that sociopath kind of behavior, right? And I think that's a bit of a risk.
Rigel: The question is whether you draw the line though, like an overpriced thing is, is it really overpriced if people are willing to pay the price? yeah. This is all a factor of, as Bitcoin gets bigger, you'll see more and more of this, and it'll become more and more of a thing, you know, and you're right, like, what is the line, if people are willing to pay for this, and they're happy, and they don't feel like they're getting scammed, is it a scam, how is this related to Bitcoin, right, and there's many other things out there in the world that use, like, for example, ethical food, where they associate it with something, if you really were wanting to support this cause, you'd be better to directly donate to this thing, right?
Rigel: But they try and create this association to brand themselves, right? And as you said, it's not direct, but I think most people, if you explain this, they get what I'm leading to and they understand the problem,
Rigel: But it is like quantum, this and that, you know, . Yeah. it's a difficult one to discuss, but this is obvious, right, is with anything as it grows, like all the other stuff we talked about, the scams are obvious and as they get bigger, the things are harder and higher to directly say it is, and you can feel something that's right off and wrong and not quite right, but it's a lot harder to articulate and nail it down.
Rigel: the bigger and the larger, more complex it gets. The more involved the scams, if we're gonna call them scams, get
The Influence of Influencers
Luke: No, I mean the tough part about you kind of finding that and actually this is a good example in this case because Rob brought a lot of people into Bitcoin with particularly his Sailor series and my first real touchpoint with like a real Bitcoiner was him on Lex Friedman. Literally, that was my first.
Luke: Bitcoin maxi actually go down the rabbit hole thing and people coming into the space. And so then I have no idea that he's got this reputation under the hood that isn't isn't there, you know, and so it's just it's hard for people coming into the space to, I guess, to understand who is the Who is the right people and, and people with influence and influencers is the correct word here are are re regarded highly and, and they're, what they put out into the, the world by people who are new to the space is, is it's important to get the right message out there, you know.
Knut: And I think you have to judge people from their, like. Are they a net benefit or a net detriment? Like, that's the key, but it's tricky sometimes because people are a bit of both. Of course they are, like, and I think to some extent, sort of everyone is guilty of that. Like,
Rigel: and I agree and it's a great point, right? You know, the guy has a large reach and there are many such people, in the space where, in my personal opinion, it's just garbage, trash. You know, people that are Bitcoin but they can't actually talk in any sort of detail or articulation about what Bitcoin really is, right?
Rigel: But then being presented as experts and these are The megaphones that people are hearing, right? there is an element of, it comes back to the same stuff as we talked about before, like, getting more people in the door is obviously, I think, a benefit, but at what point do you dilute the message such where, you know, let's take the Miami or Nashville conference as an example.
Rigel: How many hours of talks are going on there and how many of them are really adding value and how many of them more just like here is a face and where this face brings people in the door, but what they said was just hot air, right? You know, it was garbage. And would that, I mean, if you ask me, these people should be listening to Erik Voskil and reading crypto economics, which they're not going to do.
Rigel: but I feel like there is more a duty of stewardship from all of us. To try and steer in that right direction. Part of that is calling out things, which I think are clearly unaligned,
Knut: Yeah, but there's a devil's argument to be made here too, because arguably, Bitcoin conferences in general have become more high signal over time. Like, in 2017, you had, like, there were no real Bitcoin conferences, there were just these blockchain bullshit
Rigel: Mm hmm.
Knut: So from a certain point of view, it is getting Like, the signal to noise ratio is getting higher.
Rigel: Mm hmm. Yeah, I mean, it's a hard, and this is, I mean, the fact that we're discussing this, I think, is like the beauty, right? It's like, I have heard very, very few people having these conversations Maybe like kind of leading around this point, but not directly discussing this as like a analytically, objectively as a social phenomenon, right?
Rigel: No, it's great.
Rigel: and like, you know, maybe you are, you're totally right and I'm totally wrong, right? these people are, I should just stop being such a negative Nancy. And these people are good for things, right? but we need to have this discussion and decide, and better articulate what this happy medium between the two is, right?
Knut: You know? And that, that's the thing which I think is missing. And just by having this conversation, discussing this stuff, getting it out and getting more nuanced, I think it's part of getting the job done, right? if maybe next time Robert Breloves does his Art of Alpha 2, I'm going to be like, Well, actually, when I look at it, it's a benefit because we had this conversation, right, Yeah, the sequel is obviously going to be named Art of the Beta.
The Importance of Integrity
Knut: Well, anyway, I think it's a great discussion, and it's like, people should talk more about this. Because, yeah, there is a trade off, and I don't think we disagree, I think we're on the same page here. I'm just mostly taking the devil's advocate position to get the debate going because I think it's very much a subject that should be vocalized more and aired more.
Knut: Absolutely. Because diluting the message is bad. And that is. Like, well, we talk about ethics and tactics and whatnot with the pod all the time, and what we agree on and align on so much, it's like, there is nothing more important than integrity, I love the Scarface quote, you know, all I have in this world is my word and my balls, and they don't break for no one, and I try to live by that,
Rigel: Had I ever taken the bag of shit coins during these last five years, I would be nothing at this point. I've seen it so many times over and over again. People turning from intellectuals to ultimate fighters, for instance, with the same moustache. And it's, to me, it's crazy. It's crazy where, on the one hand, these people talk about Bitcoin is sound money for generations and this is a thousand year mission and they don't see them doing this stuff of like, yeah, to me, there's been many times where I thought, you know, like when I started speaking at conferences and things like this, if I really started going deeper on this thing, maybe I could make more of a thing of it or whatever, but I think I like, I want to slowly build my brand in that sense over like 10 years, like do things and do only do things right.
Rigel: Exactly, exactly dude. That's like all these memes we throw around. But I mean maybe that speaks to, again, this whole point I keep returning to is like, they're all empty platitudes with people actually not deeply thinking about, you know, calling, having something that can clearly articulate and point out, this is in direct contradiction to this, but because the thinking is so sloppy, people don't even realize that they're doing that.
Knut: Like people want the fast, fast buck. And it's like I think that's a real side effect or a result of the fiat mindset and the fiat rot in people's brains over so many years.
Rigel: my mind so much in terms of like, I mean, I guess everyone's got to eat, right, you know, but, but, surely if you've got Bitcoin, like, you're good, right, if you really believe in Bitcoin, right, you know, maybe not now, but if you really believe in Bitcoin, then we're all going to be super fucking rich, right, in 10 years or whatever, and so in that 10 years, you know, if you got a little bit more money, it's not going to matter anywhere near as much as like, if people knew, if you had that old boys network of the people that are here right now in Bitcoin, and they knew that you were always a, you know, Trustable, a person with high integrity for 10 years over all these things.
Rigel: Imagine the value. That is an incredible value,
Knut: honesty and integrity are really, that's really the currency of the future. And that aligns with Bitcoin so well because, It is this base layer of truth. it is actually integrity quantified, if you will. so it aligns so well and I think that, reputation is everything and it's all tied to authenticity and integrity.
Leaning In
Luke: Well, and I mean, first of all, the one thing is that, that's the noster thing there as well. The Web of trust idea. I mean, IM implementation stuff. Is, is that's valid. Like if we've, we've had our own concerns about the architecture and, haven't really talked to any hardcore skeptics that, that actually have thought about this hard.
Luke: But still the, the web of trust thing is, is amazing in terms of, in terms of this portable web of trust that you can take from application to application. And hold on to that. And so I mean, I think that's just going to amplify that effect. the talk I did at Noob Day was basically just leaning into Bitcoin, how to do it.
Luke: Because for me, I've been in the space two years. so much has just happened from saying yes to stuff and putting in the work I'm not tooting my horn. Too hard when I'm saying that, but the point about it is just like, do the work, like you say, I mean, things can happen a lot faster than you
Knut: and there are no shortcuts.
Luke: just by having the integrity and doing the work with
Knut: Yeah. And you can't just cling on to this or that influencers ideas. That doesn't work. you need to actually study the thing. And
Luke: Slay your heroes.
Rigel: Yeah, something I talked about in the talk that I did today is the whole idea of what Bitcoin is, is like a different philosophy around technology, right? You know, we have The systems view of technology and the tools view of technology is technology a system whereby you follow a more or less a recipe or a set of instructions and the software does everything for you and it's like pressing a button and getting something out the other end, right?
Rigel: And that has its place, but I mean, I think Bitcoin is a different type of technology in that it requires, like you to learn to, to wield it, to understand that the value is in the, the, the time and energy that you have to invest to learn about it. Because if you don't learn it, then someone else is making these decisions for you, and the whole point of Bitcoin is, is to educate yourself and master it, right?
Rigel: An analogy might be, you know, hundreds of years ago, slightly romanticized, example, but nonetheless, I think that the metaphor is, is there, that hundreds of years ago, like, to be able to kill someone, like to be a knight or whatever, you had to spend a long amount of time learning how to master a sword, right?
Rigel: And what would work for you is one will exactly work for me.
Knut: you would probably have to practice less, right?
Rigel: but I mean, it's all about your, understanding yourself, right? And you're never going to be a better swordsman. I'm never going to be a better swordsman than you if I don't really understand myself.
Rigel: And then to project myself through the sword, right? Now today, any moron in an hour can learn how to have a rifle and shoot people. And I think, again, it's somewhat romanticized, but I still think there's a good amount of truth to this. And that, like, I think we are in a much worse position by having the power to kill given to anyone who knows how to work a very simple machine.
Rigel: Versus that being reserved to people that go through the work and therefore learn to master themselves and understand themselves. There's a degree of, you're never going to be able to kill people unless you're able to pass these personal tests and verse the effort, right? And I think the same thing should apply to technologies like bitcoin, like with our money, right?
Rigel: Because when you don't do that, you're just a blindness follower of someone else's instructions. But when you actually have to sit down and learn, there's value to making people go through that process. And so I think, like, the whole idea of bitcoin is that it should be a little. Complicated and a little hard and you know you shouldn't try and dumb it down too much because there's a certain point where it kind of kills what the whole point of Bitcoin is which is to go through that kind of process and we will have a better world if everyone understands how to use Bitcoin.
Rigel: But again, if imagine it's ten people in the world are the only people that really understand Bitcoin and everyone else is just using you know, Binance or something like that. Are we any better than we are now? I don't think we are, you know. So the whole point is making sure that everyone in the world or a much greater amount of people in the world Are the people who are able to be the banks and the PayPals and the things like that.
Rigel: And I think that's the value of it. And part of that is forcing people to be responsible and to learn themselves. And if they don't go through that, we don't change anything. So it's a counterpoint.
Knut: Are you familiar with the word Kdi Ling This, this is a word that our friend Ralphie told us in Prague, and the definition is to purposefully travel without any particular destination, possibly meandering. And, someone asked people on Twitter to, describe Bitcoin with one word.
Knut: And I think that's a perfect word, it's coddywompling. It's purposeful, but you don't know where it leads.
Rigel: yeah, yeah, yeah. You know, it's like these, all these now, you know, the journey is a destination, all this kinda stuff. But I mean, I think there is value, there's truth to that with Bitcoin,
Wrapping Up
Luke: Rigel, this has been a great, discussion, lively, do you have anything else big on your mind that you're excited to talk about or share?
Rigel: no, that's pretty much it. this has been a really good talk and I feel like I don't listen to too many Bitcoin podcasts these days, but I feel like. I don't think these sort of conversations are being had about these sort of things and, and just thank you for giving the opportunity to hopefully, hopefully whoever's watching this has shared similar, felt similar value from it, but thank you for giving the opportunity to talk about these things with you guys because they've been great counterpoints as well.
Knut: Pleasure is, on our side, right back at you. so anyway, will you want to send our listeners,
Rigel: no, just I'm on Twitter, and Telegram, if you want to get me directly, on Coinsure and
Knut: Telegram.
Rigel: yeah, yeah, yeah, hot topic today, isn't it, yeah, yeah,
Knut: have gone
Rigel: I'm trying to remember what my, I just added the, thing in, Signal. But anyway, you can get my Signal if you message me there. and my Nostr, I believe, is on there as well.
Rigel: And if not, I'm sure you can find me through things on Nostr there. I'll tell you my input, but that's a little messy to, to say on a
Rigel: We make, we make that joke sometimes, oh, you're not going to tell us your mPub? that
Knut: Thank you, Rigel, for coming on to the Bitcoin Infinity Show.
Luke: Thank you so much for having me. Appreciate it. Thank you.
Luke: you. This has been the Bitcoin Infinity Show. Thank you for listening.Appreciate it. Thank you. Luke: you. This has been the Bitcoin Infinity Show. Thank you for listening.
-
 @ 4ba8e86d:89d32de4
2024-10-29 12:30:05
@ 4ba8e86d:89d32de4
2024-10-29 12:30:05Tutorial feito por Grom Mestre⚡
Poste original Abaixo.
Part 1: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/229987/tutorial-entendendo-e-usando-a-rede-i2p-introdu%C3%A7
Part 2: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/230035/tutorial-instalando-e-configurando-o-roteador-i2p?show=230035#q230035
Part 3: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/230113/tutorial-conectando-se-ao-xmpp-pela-i2p?show=230113#q230113
Boa tarde, camaradas do meu coeur!
Depois de muito tempo, e com o retorno da minha serotonina aos níveis basais, estou dando início a essa nova série de tutoriais. Espero que tirem muito proveito das informações passadas aqui para amplicarem o seu conhecimento da deepweb.
Esta postagem trará antes algumas considerações iniciais que podem ser úteis para quem possui pouco ou nenhum contato prévio com outras tecnologias ou tenha um entendimento torto a respeito da deepweb. Aconselho a estes que deem um boa lida antes de partirem para os tópicos do tutorial, mas saibam que ele não é um pré requisito para ele.
Dito isso, vamos prosseguir.
TÓPICOS: Introdução Instalando e configurando o roteador e o navegador Conectando-se a serviços na I2P Configurações avançadas
1. Introdução
1.1 Definindo a DeepWeb.
Muitos devem imaginar erroneamente que a deepweb se restrinja apenas à rede onion, mais precisamente aos seus hidden services, já que o Tor possui como uma das suas funções primárias proteger e burlar restrições governamentais e proteger o seus usuários através de métodos sofisticados de roteamento de pacotes e criptografia. Entretanto, ela é mais ampla do que se imagina dependendo da forma como a classificamos.
Os ditos "profissionais" usam uma definição extremamente vaga e imprecisa do que seria a deepweb e a sua verdadeira abrangência. Para isso, criei uma definição um pouco melhor para ela: redes comunitárias, sobrepostas, anônimas e criptografadas.
Vamos aos pontos individualmente:
São Comunitárias, pois os pontos de roteamento de pacotes na rede (relays ou routers) muitas vezes são mantidos de forma voluntária por usuários comuns. Não é necessário nenhuma infraestrutura sofisticada para ser um contribuinte na rede, basta ter um computador com acesso à internet e conhecimentos básicos para fazer a configuração.
São sobrepostas porque não estão acima ou abaixo da rede tradicional (diferente do que muitos imaginam). Os pacotes na DW trafegam entre os dados da surface e não em meios distintos (algo que não faz o menor sentido). Sabe aquele papo de camadas da DW ou aquela abobrinha da Mariana's Web? Então, tudo um monte de bosta derivado de Youtubers sensacionalistas iletrados em informática. Elitismo da minha parte? Quem sabe...
São anônimas porque não é simples determinar a origem e o destino dos pacotes entre nodes intermediários dado a natureza do roteamento. Em geral, aos menos para a rede onion, há pelo menos 3 relays entre você e o servidor, sendo que esse número duplica para hidden services (3 seus e 3 do serviço). A imagem abaixo ilustra bemocoteamento dos pacotes na onio. https://image.nostr.build/aea96f41d356157512f26b479ea8db5bce8693dd642f2bce0258d8e4b0dac053.jpg
Por fim, são criptografadas porque as conexões são fortemente protegidas por algoritmos sofisticados de criptografia. Além de não sabermos a origem dos dados, sequer podemos saber com facilidade o conteúdo dessas mensagens mesmo que os protocolos das camadas superiores (HTTP, HTTPS, FTP) sejam inseguros, dado que a criptografia da própria rede já as protege. Por isso é tão comum que sites da DW não usem HTTPS, pois as autoridades de certificados não os assinam para domínios da onion e certificados autoassinados vão disparar avisos no navegador.
A imagem abaixo ilustra bem como é o roteamento onion usado pelo Tor. Perceba que o contéudo da mensagem está enrolado em 3 camadas de criptografia (como a de uma cebola), de modo que para revelar o contéudo original seria preciso quebrar, no pior dos casos, 3 camadas. Como mencionado antes, o método usado para isso é a criptografia assimétrica, muito similar ao PGP, porém com a sua própria implementação. https://image.nostr.build/7bfaaf29211c11b82049ef8425abb67738d085c41558e9339ec13cf49ea5b548.jpg
Observação: Por mais que dentro da rede o encapsulamento proteja as mensagens internamente, entenda muito bem que isso não se aplica a sites da surface acessados pela onion. Ao desempacotar a última camada, a mensagem original é completamente exposta no exit node. Se ela não estiver protegida por uma camada adicional como TLS, seus pacotes estarão completamente expostos, algo que representa um sério risco de segurança.
As redes que caem em ao menos três dessas definições (anonimato, sobreposição e criptografia) podem ser classificadas como deepwebs. Podemos citar:
• Lokinet • Zeronet • Freenet • I2P • Tor • Gnunet
Porém, há alguns casos interessantes que não caem diretamente nessa regra .
A Yggdrasil ( https://yggdrasil-network.github.io/ ), uma rede de topologia mesh com foco em escalabilidade e eficiência de roteamento, possui três dessas características: comunitária, sobreposta e segura. Entretanto, os nodes não são anônimos e muitas vezes podem estar desprotegidos, já que se conectar à Yggdrasil é que equivalente a ligar o seu computador diretamente na rede sem a presença de um NAT/CGNAT, correndo o risco de expor portas de serviços da sua máquina caso elas não estejam protegidas por um firewall. A Yggdrasil na prática é exposta como um dispositivo de camada 3 (tipo um VPN), mas diferente de um, apenas endereços IPv6 dentro de uma faixa bem específica de IP são roteados por ela, o que permite que ela coexista com outros dispositivos sem haver conflitos de roteamento.
Há quem argumente que a Yggdrasil é uma deepweb dado a sua sobreposição em relação à surface; outros podem argumentar que dado a falta de anonimato ela não se enquadraria nessa categoria. Independentemente disso é uma tecnologia muito interessante com ampla gama de aplicações, como encapsular tráfego de outras redes, como a I2P, e melhorar a eficiência de roteamento.
Por fim, vamos desmitificar alguns mitos da DeepWeb muito difundidos.
Não existem camadas da DW. Os pacotes da DW são sobrepostos e navegam juntos aos pacotes da surface.
DeepWeb e DarkWeb não são coisas diferentes. São termos genéricos para a mesma coisa.
DarkWeb não é o seu provedor de e-mail ou serviço de banco. Se eles não se enquadram nas categorias de um deepweb, então estão na surface.
Você não é irrastreável na DW. Adversários motivados podem foder com você com facilidade (leia a respeito de ataques de Timing, correlação e fingerprinting).
Mesmo que não seja possível ver o conteúdo de uma mensagem pela deepweb, é possível ao menos saber que você a acessou. ISPs podem ver esse tipo de tráfego como suspeito.
Você não é um hacker só porque instalou o TorBrowser, mas pode ser considerado um se expor o IP de um hidden service.
Instalando e configurando o roteador I2P
Segue agora a seção 2 do tutorial do I2P. Mas antes apenas queria falar um pouco do projeto I2P. Apesar do foco do tutorial não ser para tratar da sua história, gostaria ao menos de fazer uma breve introdução sobre ela.
O projeto I2P (Invisible Internet Protocol) é uma rede P2P descentalizada, anônima e segura para estabelecer a comunicação entre os usuários e serviços. Na I2P é possível usar serviços como mensageiros IRC, XMPP, web services, e-mail e até mesmo torrents. A I2P nasceu de um fork da Freenet no ano de 2003, porém possui diferenças drásticas em relação a ela.
Há similaridades entre a I2P e o Tor, porém vale destacar algumas de suas vantagens. Sendo elas:
• Garlic routing ( https://geti2p.net/en/docs/how/garlic-routing ) • Modelo P2P • Todos os participantes da rede contribuem para ela • Fechado na rede - não é possível acessar a surface através da I2P • Otimizado para hidden services
Apesar disso, vale lembrar que o projeto é pequeno, desenvolvido por menos voluntários se comparado ao Tor e possui menos movimentação e financiamento para o seu desenvolvimento. Além disso, o Tor é um projeto muito mais maduro e bem documentado, algo que atrai mais usuários e desenvolvedores e torna a tarefa de encontrar e corrigir bugs mais fácil de ser realizada.
Esses são pontos importantes que devemos levar em conta ao escolher a tecnologia para as nossas necessidades. Nem sempre há tecnologias ruins, as vezes apenas as empregamos as ferramentas erradas na resolução de certos problemas.
Referências: • https://geti2p.net/en/comparison/tor • https://geti2p.net/en/docs/how/garlic-routing
• https://geti2p.net/en/about/intro
• https://i2pd.readthedocs.io/en/latest/
2. Instalando e configurando o roteador
Antes da criação do I2PBrowserBundle ( https://github.com/PurpleI2P/i2pdbrowser/releases/tag/1.3.3 ) , a única forma de se conectar à I2P era pela configuração manual de proxy no navegador. Muita gente ou não sabe ou tem MUUUUUITA preguiça de fazer isso e ficam resistentes de entrar na I2P dada essa restrição.
Como eu quero ser um bom tutor eu farei do jeito mais "difícil", pois tanto eu desejo que vocês aprendam as nuances do processo como eu sei que vocês são inteligentes o suficiente para fazer isso.
2.1 Instalação do router
Atualmente nós temos duas implementações do I2P: Uma em Java e outra em C++ (i2pd). Usaremos nesse tutorial a versão em C++ dado o seu baixo uso de recursos e facilidade de instalação.
O I2Pd está disponível para Windows, Linux, MacOS e Android e possui binários pré-compilados nas releases ( https://github.com/PurpleI2P/i2pd/releases/tag/2.50.2 ) do projeto no Github. Usuários de Linux podem instalá-lo através do respectivo gerenciador de pacotes da sua distribuição, porém algumas distros não oferecem o pacote diretamente nos reposítórios oficiais, necessitando do uso de PPAs (Ubuntu), COPR (Fedora/RHEL) e afins. Vocês podem conferir as instruções oficiais para cada sistema nessa página ( https://i2pd.readthedocs.io/en/latest/user-guide/install/ ).
Apesar desse tutorial ser voltado a usuários de desktop, o I2Pd também está disponível na loja do F-droid. Infelizmente poucos navegadores em Android permitem a configuração de proxies, porém na seção de Serviços na I2P eu tratarei brevemente de como se conectar a servidores de XMPP usando o ConversationI2P.
Para usuários de Windows, segue abaixo os binários para instalação.
• Versão 32bits ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_win32_mingw.zip )
• Versão 64bits ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_win64_mingw.zip )
• Versão para Windows XP (pois é, kk) ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_winxp_mingw.zip )
A instalação é simples e direta. Após ela apenas abram o I2Pd para que o router inicie a operação de busca e conexão com os peers. Para usuários de Linux, vocês precisam ativar o serviços através do comando 'sudo systemctl start i2pd'. Se vocês desejam que o I2Pd inicie junto com o sistema usem o comando 'sudo systemctl enable --now i2pd'.
Se tudo estiver funcionando corretamente, vocês serão capazes de abrir o webconsole do I2Pd no navegador através do endereço: 127.0.0.1:7070. https://image.nostr.build/ab205ae1071a2b705279e5ce2d6e912d8d11cc7d6dd0dc8a26b76724a27bd94b.jpg https://image.nostr.build/fa17e14600737ccfc92a415cec2fbfba226b950b2b97af7475927ae65abdbe11.jpg
2.2 Instalação e configuração do navegador
Apesar de qualquer navegador ser capaz de usar a I2P não é recomendado que usem qualquer um, especialmente o navegador que você usam no seu dia-a-dia. Recomendo que usem um navegador próprio para usar na I2P ou isolem suas atividades em um perfil separado.
Em navegadores baseado no Firefox isso é relativamente simples, bastando adicionar a opção '--profile' e o caminho do perfil que vocês desejam usar. Nesse tutorial eu vou mostrar como criar um perfil novo no Librewolf e configurar no lançador para iniciar o perfil e abrir em uma janela anônima. Essas instruções são análogas para todos os sistemas, excetuando aquelas configurações mais exóticas.
2.2.1 Escolhendo o navegador
Como citado, usarei o Librewolf como exemplo. Vocês podem baixar o instalador direto do site ou usar o gerenciador de pacotes do seu sistema no caso de Linux. Como é uma tarefa trivial eu não vou detalhar esse processo, pois todas as instruções estão em detalhes no site do navegador ( https://librewolf.net/installation/ )
2.2.2 Criando um perfil e configurando o lançador
Abram o navegador e digitem 'about:profiles' na barra de endereço. Criem um novo perfil clicando em 'Create New Profile' https://image.nostr.build/fa17e14600737ccfc92a415cec2fbfba226b950b2b97af7475927ae65abdbe11.jpg
Coloquem um nome no seu perfil e cliquem em Finalizar https://image.nostr.build/62059e375000940f11b27ae77b9ec011f9baadbb5a84afc910d41841ce73e82d.jpg
Perfis novos recém criados são iniciados por padrão. Se você deseja usar outro perfil por padrão deve mudar isso na seção 'about:profiles' do navegador.
Agora vamos configurar o lançador do LibreWolf para iniciar o perfil do i2p e em uma janela anônima. Usarei o XFCE como referência para essa tarefa, mas saibam que o processo é análogo em sistemas como Windows ou DEs como KDE. Se quiserem também podem lançar via terminal através do comando 'librewolf --profile caminho_do_perfil --private-window'.
Cliquem com o botão direito no ícone do Librewolf e abram as propriedades do atalho.
Na guia lançador, no campo Comando, adicionem no final a opção '--private-window' e a opção '--profile caminho_do_perfil'. O caminho do perfil é aquele mostrado na seção 'about:profiles' do Librewolf. https://image.nostr.build/a7d6515d7825cb3bdcb681ecf71a97318dccba81eea7cc87fc5377ecc06065ee.jpg
2.2.3 Configurando o proxy
Com o lançador configurado, abra o navegador nesse perfil. Vamos configurar o proxy para se conectar ao I2P agora.
Abra as configurações digitando 'about:preferences' na barra de endereço. Na seção 'Geral' abra as configurações de rede (Network Settings) https://image.nostr.build/f37157bebf15ada616914f403e756cf9fcee4c9aaaa353196c9cc754ca4d7bc5.jpg
Configure o seu proxy como na figura abaixo. https://image.nostr.build/41ebd05255a8129d21011518d400689308d9c0320408967003bf296771e0b96f.jpg
Fecha as configurações. Se o seu proxy foi configurado corretamente tente abrir algum desses eepsites.
• http://identiguy.i2p • http://notbob.i2p • http://reg.i2p
Se tudo ocorreu como conforme, a página será carregada. https://image.nostr.build/ce29ae44743f06cfed591f082208c9612c59b3429ab46d90db48131b3bc3e99d.jpg
OBSERVAÇÃO: A busca pelos peers é um pouco demorada, levando de 2 a 5 minutos para que um número mínimo necessário de peers sejam encontrados para estabelecer uma conexão estável. Você pode ver a lista de inbound e outbound tunnels na seção Tunnels do WebConsole (localhost:7070) https://image.nostr.build/285a0d765eaf5f33409f975cd720d0efa68ecc40a9da20bfd9cde0cd1f59a7b6.jpg
IMPORTANTE: Apesar do Librewolf possuir defaults seguros, eu recomendo que vocês instalem as seguintes extensões para aumentar ainda mais a sua proteção.
• noScript • JShelter
Lembrem-se que vocês precisam desativar o proxy para acessar a clearnet. Depois disso reativem-no nas configurações.
Outro detalhe: Se vocês tentarem digitar um endereço .i2p na barra de endereços do navegador sem especificar o protocolo (http), ao invés do Librewolf ir ao endereço ele vai realizar uma pesquisa. Para corrigir esse problema, vocês precisam adicionar a seguinte configuração do tipo boolean em 'about:config' como mostrado na imagem. https://image.nostr.build/4518ab817b131f7efe542b2d919b926099dce29a7b59bdd3c788caf53dbd071e.jpg
Reiniciem o navegador e testem. Se tudo deu certo vocês não precisam especificar o protocolo ao digitar um endereço .i2p, bastando apenas digitar o endereço simplificado.
Por fim, terminamos essa parte do tutorial. Na próximo parte trataremos de como podemos nos conectar a serviços hospedados na I2P como XMPP
[TUTORIAL] Conectando-se ao XMPP pela I2P
Essa é a terceira parte da série de tutoriais. Agora vamos tratar de algumas operações na rede, sendo uma delas conectando-se a um servidor de XMPP na I2P.
Não se esqueça de ligar o router e manter ele ligado por alguns minutos antes de iniciar essas operações. O router demora um pouco para encontrar os peers e estabelecer uma conexão estável.
3.1 Escolhendo o cliente XMPP
Existem diversos clientes XMPP capazes de se conectar usando um proxy. Um dos melhores é o Gajim, um cliente escrito em Python com diversas funcionalidades como criptografia OMEMO e PGP, workspaces separados, extensibilidade via plugins e uma interface bonita e organizada.
Assim como ocorreu com o router, o Gajim está disponível por padrão na maioria das distros Linux. Use o seu gerenciador de pacotes para instala-lo. Em Windows você pode baixar o Gajim através desse link ( https://gajim.org/download/ )
3.2 Criando uma conta
Vamos primeiro criar uma conta no servidor. No nosso exemplo usarei o servidor oficial do projeto i2pd, o xmpp.ilita.i2p. Há diversos outros servidores XMPP no diretório de links notbob.i2p caso queiram explorar mais. Para criar uma conta, siga os passos abaixo:
Abra o Gajim. Na barra de tarefas vá em Contas -> Adicionar Conta. Na nova janela que aparecer, clique em Adicionar Conta https://image.nostr.build/01413e7c6d00c238420e3b0c769dd8d7f7d6522754d2135d3e98a22944f79a27.jpg https://image.nostr.build/9f015861f33990871d96f03d5ec78036a65e3ad9f8ff6a38da18c5b27d31f6d5.jpg
Na janela de adicionar contas, clique diretamente em Inscrever-se. Não precisa colocar as suas credencias como mostra a imagem (falha minha, ksksk) https://nostrcheck.me/media/c8411a22946e97467e0ee197ef7a0205ba05f2c67bde092041481ccc2cbbc66d/81938c8d278ce0562c2240341e203f3b70f51ee2db06ceb453f8a178df37fa84.webp
Digite o nome do servidor no campo abaixo. Não esqueça de marcar a opção 'Configurações Avançadas' antes de clicar em Inscrever-se https://image.nostr.build/5ee4305a6a23e5c064446b0ce7a4cbc7e790c1ba237bd2495d0237b86a4df07f.jpg
Vamos adicionar um novo proxy para essa conta. Para isso clique no botão 'Gerenciar proxies', ao lado do campo Proxy nas Configurações Avançadas https://image.nostr.build/daceb5436def55401d3974ce48d85771e5ebcec4e3f90eb1001df4609112ec12.jpg
Adicione um novo proxy clicando no sinal de '+' abaixo da lista de proxies. Preencha os campos de acordo com a imagem abaixo e em seguida feche a janela. https://image.nostr.build/140b34c4e46e9295c073311d483d206201d9339a75f613fe4e829c14f3257bfe.jpg https://image.nostr.build/d365a63d81a14d763bffceb50b30eb53d81959623f8fe812175358a41b1fba53.jpg
No campo de Proxy, selecione o proxy I2P. Preencha o restante dos campos de acordo com a imagem abaixo. Em seguida clique em 'Inscrever-se'. https://image.nostr.build/d06c11d9c6d19728bf5a58af2dd3e14d8ca0021456da09792a345ac0bfc90ad0.jpg
Nesse momento uma mensagem pode aparecer pedindo para abrir uma exceção para o certificado TLS. Isso acontece porque trata-se de um certificado autoassinado que não foi validado por uma autoridade oficial. Apenas abra a exceção e prossiga (não há imagem para isso porque eu já abri essa exceção no meu cliente). Uma nova janela vai aparecer solicitando-lhe para inserir as suas credenciais. Tome cuidado aqui, pois não é para inserir o nome completo com o domínio, apenas o seu nome de usuário (ex: descartavel). https://image.nostr.build/dde2a6736bd00080fbeeb8076754e226971a412710b370d5559f7f4d5414f8b3.jpg
Se tudo der certo, uma nova janela vai aparecer confirmando a sua inscrição. Coloque um nome e uma cor para a sua conta e clique em Conectar para concluir o processo. https://image.nostr.build/74934d3f1f3f4232eacee8e78e707936227f816c50ac6b52da5c81ec17557e69.jpg
Para finalizar, nos detalhes da sua conta, modifique as suas configurações de privacidade para diminuir o fingerprint. Na seção de 'Privacidade', desligue as seguintes opções:
• Tempo ocioso • Hora de Sistema Local • Sistema Operacional • Reprodução de Mídia https://image.nostr.build/d2ed5852a104c770b50c7b053d518d8af0b6289ced6b3ad4187492208c7ca649.jpg
3.3 Procurando por salas de bate-papo públicas
Após criar a sua nova conta, vamos descobrir alguns serviços que o servidor oferece. Para isso, vá para Contas -> Descobrir serviços https://image.nostr.build/54928d1dd0e48365858b24c72097a9fabf677794e13f329fc0568211eefbe559.jpg
Na seção 'Bate-papo em Grupo', selecione Chatrooms e clique em 'Navegar'. Ao fazer isso uma lista de chatroom públicos presentes no servidor vai aparecer. Fique a vontade para explorar, porém saiba que alguns servidores são moderados e não te permitem mandar mensagens sem sua conta ser aprovada pelo moderador (familiar?). https://image.nostr.build/1936bef51d58a1f6cfdf8bf8d84bfa64adc2a09b9c0fb1623b93a327f0b8cdd8.jpg https://image.nostr.build/89e8013b1cea1df0f80f6833bd6771c33101f404b0099b2d7330a5e57607baff.jpg
3.4 Adicionando contatos
Para adicionar contatos à sua lista, clique no símbolo de '+' ao lado do campo de pesquisa e selecione 'Add Contact'. https://image.nostr.build/d3cadea27591355f674fba93765c3815282d112b2e80a592bb77a442c13dd4f4.jpg
Coloque o endereço completo da conta que você deseja adicionar. Usarei a minha conta oficial nesse exemplo. Você tem a opção de anexar uma mensagem qualquer antes de enviar o convite. Clique em 'Adicionar Contato' para prosseguir. https://image.nostr.build/ff95b7aec2377c58d4253c5b7b3aabf141a92dd5f3e97f6e1f01ecb32a215d38.jpg https://image.nostr.build/6562e680e28c321ebbd009b5ade513f8a279aea33bc16aa9fb251f3507eb04af.jpg
Se tudo ocorrer normalmente, o novo contato vai aparecer na sua lista. Dê dois-cliques na conta para abrir o chat. Não se esqueça de ativar a criptografia OMEMO antes de enviar qualquer mensagem. Agora você está pronto para conversar de forma segura :) https://image.nostr.build/ef7f783a311ad0f68a5408137f75dc2bc6c38f6e9656dc0d68d3267f5012f658.jpg
E com isso terminamos a terceira parte da série de tutoriais.
[TUTORIAL] Criando e conectando-se a um servidor XMPP na I2P e clearnet.
Como configurar o seu próprio servidor XMPP. https://youtube.com/watch?v=Ot_EmQ8xdJwy
Criando contas e conectando clientes Pidgin http://i2pd.readthedocs.io/en/latest/tutorials/xmpp/#creating-accounts-and-connecting-clients
BONUS: Conectando-se facilmente à I2P. https://youtube.com/watch?v=wGIh5tQcw68
-
 @ b8a9df82:6ab5cbbd
2024-10-29 11:54:45
@ b8a9df82:6ab5cbbd
2024-10-29 11:54:45Packing my bags and taking…? Absolutely no idea, but definitely not a winter jacket. That’s not happening—I’ve been telling myself for years that I don’t want to spend another winter in Berlin. The last few have been brutal. I’m craving a real adventure.
Currently on plane number three, with plenty of time to think, read, and write because, honestly, one of the things I love most about flying is not being connected. I’m the person who won’t spend over $10 on an hour of Wi-Fi, and right now, I love that my phone is off. No messages, no notifications. It’s kind of crazy these days—every morning, I wake up to 100 messages. I’m always telling people how toxic phones can be, yet even I can barely stay away from mine lately.
Right now, squeezed into the middle seat on a 10-hour flight from Toronto to Buenos Aires, I’m starting to question what I’ve gotten myself into. Yes, Toronto. There are people who can afford a direct flight, and then… there’s me. Berlin to Frankfurt, Toronto to São Paulo (just a quick tech stop), and finally, Buenos Aires.
Nearly 30 hours of travel. It’s fine, but yeah, I’m kind of jealous watching the business class people, lounging literally just in front of me. My legs are burning; sleep is impossible. I don’t even know what day it is anymore.
Flying’s changed so much. It’s ridiculously expensive and uncomfortable now. It’s like today’s business class is what economy used to be ten years ago. Now, we pay extra for everything. I miss when flying felt like a bit of an adventure itself, back when they’d let kids visit the cockpit (I have been there) —impossible now, sadly.
So here I am, taking a moment to share some personal insights from last week, preparing for this LATAM-Nostr Tour:
The last few weeks have been intense, to say the least. My last official workday was at the end of September, and of course, I got super sick right after. My body was practically screaming for a timeout that my mind didn’t want to give. I kept thinking, “Just four more weeks—Amsterdam, sorting my life out in Berlin, subletting my flat.” Well, clearly, that didn’t quite go as planned. So hey, if anyone needs a cute little flat for a few months, let me know!
Excited, overwhelmed, and freaking out all at once. I just hope everything works out: that I haven’t forgotten anything, that the booths will be ready, the schedule will come together, people show up, speakers are prepared, volunteers are there, tickets are sorted. There’s still so much to do, and the conference pace is making it tough. For example, SatsConf still hasn’t sent the final design specs, and I just got the measurements for the graphics. Trying to sort that out while traveling is sending me into a bit of a tailspin. It’s like my inner German is in crisis mode, haha.
I know what I’m doing, and I know what I’m capable of—but this is a whole new world. I really want to meet everyone’s expectations here. I miss my usual team so much because I know how they work, what to expect, and I can trust that everything will be handled. Here, I just have to let go, trust, and see what happens.
And then you meet people. You realize they’re kind, helpful, and excited, and together, it feels like we can actually make something happen. Last week, I went to the Nostr Berlin meet-up, chatting with some guys who also happened to be flying to BA. I suggested they help at our booth, and in return, we could sort out tickets. They were thrilled—it’s the kind of support that makes all of this feel worth it.
Even though I don’t know exactly what’s in store or what to expect, I’m truly looking forward to it. The team is incredible, and I know I’ll be looked after. As the only woman in the core team, it’s been an experience. I love working with men, but there are times I wish I had another woman alongside me, someone with a similar mindset and, yes, someone to do the “girly stuff” with.
But here I am, embracing the unknown, ready for this journey, and just hoping that somewhere between Buenos Aires and Berlin, this leap will pay off in ways I can’t even imagine. South America, let’s see what you’ve got!!!
-
 @ 46390caa:7e7f65d9
2024-10-29 10:42:40
@ 46390caa:7e7f65d9
2024-10-29 10:42:40The relationship between central banks and Bitcoin has long been complex and multifaceted. As the world's first decentralized cryptocurrency continues to gain traction, central banks are grappling with how to regulate and interact with this new financial phenomenon. In this article, we'll explore the evolving dynamics between central banks and Bitcoin, and what this means for the future of finance.
Early Scepticism
Initially, central banks viewed Bitcoin with skepticism, citing concerns over its volatility, lack of regulation, and potential for illicit activities. Many saw Bitcoin as a threat to traditional fiat currencies and the established financial order.
Shifting Stance
However, as Bitcoin's market capitalization grew and institutional investment increased, central banks began to reevaluate their stance. Some central banks now explore ways to leverage blockchain technology and issue their own digital currencies.
Central Bank-Backed Cryptocurrencies (CBDCs)
Several central banks are developing or testing CBDCs, including:
- Sweden's Riksbank (e-krona)
- China's People's Bank of China (Digital Currency Electronic Payment)
- Singapore's Monetary Authority (Project Ubin)
- Canada's Bank of Canada (CAD- Coin)
CBDCs aim to:
- Improve financial inclusion
- Enhance payment efficiency
- Reduce cash handling costs
- Increase monetary policy effectiveness
Regulatory Approaches
Central banks employ varying regulatory strategies:
- Strict Regulation: Some, like the European Central Bank, advocate for stringent regulations to mitigate risks.
- Sandboxes: Others, like the UK's Financial Conduct Authority, create sandboxes for innovation while ensuring consumer protection.
- Collaboration: A few, like the Bank of International Settlements, encourage cooperation among central banks to develop global standards.
Implications for Bitcoin
The central bank-Bitcoin dynamic has significant implications:
- Legitimization: Central bank involvement lends credibility to cryptocurrency.
- Competition: CBDCs may compete with Bitcoin for market share.
- Regulatory Clarity: Clear guidelines could boost institutional investment.
- Innovation: Collaboration can drive blockchain innovation.
Conclusion
The relationship between central banks and Bitcoin is evolving from adversarial to collaborative. As central banks explore CBDCs and regulatory frameworks, Bitcoin's legitimacy and mainstream acceptance grow. The future of finance will likely involve a blend of traditional and decentralized systems.
Sources:
- Bank for International Settlements (BIS) - "Central bank digital currencies"
- International Monetary Fund (IMF) - "Casting Light on Central Bank Digital Currencies"
- World Economic Forum (WEF) - "The Future of Central Bank Digital Currencies"
-
 @ 6bae33c8:607272e8
2024-10-29 09:10:25
@ 6bae33c8:607272e8
2024-10-29 09:10:25The book on Daniel Jones is closed. It’s probably been closed for at least a year, but what I saw last night was quintessential Dimes. Basically, he’s a good athlete who can make all the throws when he steps into them. But his feel for the pocket is F-. And because he’s so tall, his speed doesn’t really kick in until he gets going — he has a slow first step when under pressure in the pocket. And maybe he’s even lost a step as they rarely call designed runs anymore, and when he scrambles it no longer goes anywhere.
I’m watching this from a hotel lobby, and it took herculean restraint not to scream, “Get rid of the fucking ball!” Just make a read and get rid of it. He thinks way too much, he doesn’t read and respond. He’s the opposite of Tua or Kurt Warner back in the day who just whip the ball out right away. The Giants can’t win with him, barring a perfect offensive line, and theirs is the opposite, though it played much better last night.
-
The Steelers aren’t good. but they just show up.
-
Russell Wilson throws a nice deep ball, but is not nearly as fast on his feet as he once was. He’s an upgrade over Justin Fields but might have less upside.
-
Najee Harris is a load and wears down the defense. There’s still value in that.
-
Jaylen Warren is back to last year’s role and is startable in a pinch.
-
George Pickens had a better game than the box score indicates — had one TD called back due to a penalty and another overturned.
-
Tyrone Tracy is a monster — fast, runs hard and can catch passes (though they rarely throw to him.) But apparently he left late with a head injury (I didn’t see it.) After Jayden Reed (who’s slipped into irrelevance) Tracy was my second biggest draft-day regret for not getting.
-
Malik Nabers had a drop, but otherwise had a decent game, fighting like crazy for yardage after the catch. He should have drawn a PI on a deep throw too as far as I could tell.
-
It looks like Darius Slayton has overtaken Wan’Dale Robinson as the WR2. Granted they have different roles, but Jones is looking down the field for Slayton more.
-
The Giants offensive line blocked well against the run and did enough against a tough Steelers pass rush, but Dimes did them in with his awful pocket awareness. It’s tough to watch him freeze when no one is wide open. He’s not only the anti-Tua (not getting rid of it) but also the anti-Mahomes, not having any poise when things aren’t there. He needs to learn to throw his receivers open, throw to Nabers to make a play even if he’s covered, improvise, something.
-
The Giants defense is good. It’s really too bad they get sold out by Dimes every game. Even someone like Derek Carr would make a huge difference.
-
What a frustrating game. The Giants got the Wilson turnover late in the fourth quarter to give them a chance, and Dimes started doing Dimes things including delay of game. I even blame the false starts on him — if I knew my QB was gonna deer-in-headlights it every time, I’d be anxious to get blocking early too.
-
-
 @ fd208ee8:0fd927c1
2024-10-29 08:52:42
@ fd208ee8:0fd927c1
2024-10-29 08:52:42Yesterday was also a day
I'm still quite bullish about using Nostr to publish, and generally for OtherStuff, but I was feeling a bit pessimistic about the microblogging (kind 01) feeds on Nostr, yesterday. And, rightly so. Mine has been grinding slowly to a halt, and not for lack of effort, on my part. I regularly hear reports, from other npubs, that they sense the same phenomenon.
Most of the people I have whitelisted on the wss://theforest.nostr1.com relay (currently 302, in number) are beginning to give up on Kind 01 clients, except for occasionally making an announcement, and are increasingly moving their chatting off-Nostr. (I'm still privy to those conversations, but most of you no longer are.)
So, my feed has been getting quieter and quieter. Even adding new people doesn't help much, as they don't tend to stick around, for long, so it's a Sisyphean task.

Some others are still bothering to show up, regularly, but they increasingly see it as a chore, or something they do to "keep up appearances". Add me to this group of wearied, diligent noters, holding down the microblogging feeds, with our exhausting attempt at #KeepingNostrWeird, while the influencers surround the gates and the Kind 01 feeds dissolve into nothing but warmed-over Bitcoin memes, GM notes, notifications from the OtherStuff, and Things Copied from X.

The problem of barren, intellectually-emptying Kind 01 feeds is further exacerbated by the fact that new entrants to the Nostrverse find it increasingly easy to "find good follows", but they're all only finding the same follows: whoever is on the trending list.
The See-Nothings
I keep complaining about this, but the responses I get are generally unhelpful. They are:
- mockery -- Oh, Miss Hoity-Toity wants more attention!
- insults -- Nobody is talking to you because you are boring and stupid, and nobody likes you.
- clueless -- You should try replying to other people, then they might reply to you.
- or they tell me to just stop looking at the list, if it upsets me.

What people are missing, by telling me to just not look at the trending lists, is that the lists are a statistic of what real humans are looking at, on Nostr. The bizarrely-high concentration of npubs, on the list, so that their entries show up multiple times, suggests that what people are primarily looking at... is the trending list.
Either directly, because they use a client that has that built in, or indirectly, as they have been onboarded with the lists or told to "just follow the people I follow", which leads to a steadily-rising concentration of follows. This concentrating effect is accelerating.
The newly-popular WoT (web of trust) relays further exacerbate this effect, as they put a premium on the npubs that have the highest WoT score, which -- surprise, surprise! -- are the same people as on the trending list.
And this is why everyone on the trending list insists Nostr is a fun, happening place, full of human interaction. A place where replying reverently to Jack and posting GM religiously will make you a sought-after conversant. It is that place. For them.
In fact, they've reached that glorious state of #PeakSocialMedia, where they have become famous for being famous, and no longer have to even pretend to be trying to appeal to anyone with their content. They can post literal garbage, and their ~~fans~~ ~~groupies~~ ~~sycophants~~ commentariat will cheer them on, and flood their replies with ardent encouragement. Less because those other npubs actually cared about what they posted, than because they are hoping to pick up new followers in those threads, since they know that everyone is looking at those threads, because those threads are trending.
It's a pyramid scheme of following.
For the rest of us... the vast majority of us... that blue line at the bottom is mostly how it feels.
The trend is to trending.
What we no longer have, is people looking directly at relay feeds, to find new people, or even their own follow list feeds, to see npubs they've already subscribed to. Even when people follow me, they usually don't respond until I'm trending, which suggests that they're also seeing me on the trending list because that is what they're primarily looking at. This is why, as soon as you get on the trending list, your replies explode. And your replies will be concentrated in a hardcore few, otherwise.
Those few are the reason I keep coming back, but as they're also often chatting with me off-Nostr, I am facing the question of: Why bother with Nostr microblogging?
This is the question I am struggling with. If kind 01 isn't for plebs chatting, anymore, (and it increasingly isn't) then it's mostly a sort of bulletin board, where we post notifications of items we've added in OtherStuff clients, or make announcements of meetups, software releases, or conferences. This, however, is compounding the dullness of the feeds and turning it into a sort of "info flyer", except for a lucky few. But, perhaps, I am simply a #NostrBoomer, who is failing to move with the times and get with the program.

I'm slowly reaching the conclusion that Kind 01 in an open, centralized market of notes, will always coalesce around a small subset of #NostrElite and turn into a largely passive form of entertainment, or a frustratingly lonely place, for everyone else. There can only be so many people talking, at once, in a public square.
The only movement I currently see, that might end the slow slide of Kind 01 into irrelevance and tedium, is to create lots of smaller, public squares, through single-relay communities. This has been such a long time, in coming, and has been resisted by client devs so ferociously, that I worry that it's merely an attempt to close the barn door after the npubs have escaped.
I sincerely hope to be proven wrong, though. Perhaps the relay devs, who have valiantly taken up the fight, will #SaveKind01. We shall see.
-
 @ a012dc82:6458a70d
2024-10-29 08:28:26
@ a012dc82:6458a70d
2024-10-29 08:28:26Table Of Content
-
The Impending Debt Limit Crisis
-
Why Bitcoin Holds Promise
-
Impact on National Debt
-
Conclusion
-
FAQ
As nations grapple with mounting debt burdens and economic uncertainties, a groundbreaking solution looms on the horizon: Bitcoin. This digital currency, built on decentralized blockchain technology, offers a unique opportunity to address the impending debt limit crisis and reshape the financial landscape. In this article, we will delve into why Bitcoin could be the solution to the looming debt limit crisis, exploring its advantages, impact on national debt, and its potential role in ensuring economic stability.
The Impending Debt Limit Crisis
What is the Debt Limit Crisis?
The debt limit crisis refers to the situation when a country's government reaches the maximum amount of debt it can legally borrow. This ceiling, set by legislation, is often a contentious issue in political debates. Failure to raise the debt limit can result in severe consequences, including a potential government shutdown, default on obligations, and financial market instability.
The Fragile State of National Debts
Nationwide debt levels continue to soar across the globe, with many countries burdened by staggering amounts of indebtedness. The United States, for instance, faces a mounting national debt that surpasses $28 trillion. Similarly, other nations grapple with their own debt crises, making it imperative to explore innovative solutions to tackle this financial burden.
Why Bitcoin Holds Promise
Bitcoin's Decentralized Nature
Bitcoin operates on a decentralized network called the blockchain. This means that no single entity or government controls it. Instead, transactions are verified by a network of computers, ensuring transparency and immutability. This decentralized nature presents a stark contrast to traditional financial systems, making Bitcoin a promising alternative for economic stability.
Protection Against Inflation
Inflation poses a significant threat to economies and their citizens. Bitcoin, with its limited supply of 21 million coins, offers a hedge against inflation. Unlike fiat currencies, which can be printed at will, Bitcoin's scarcity ensures its value is not eroded by excessive money supply. This feature makes Bitcoin an attractive store of value and a potential safeguard against the negative effects of inflation.
Financial Inclusion and Empowerment
Bitcoin has the power to empower individuals and communities who have limited access to traditional financial systems. By utilizing Bitcoin, individuals can transact securely and inexpensively, without the need for intermediaries. This can provide financial inclusion to the unbanked and underbanked populations, fostering economic growth and stability.
Transparency and Auditability
One of the core principles of Bitcoin is transparency. Every transaction is recorded on the blockchain, visible to anyone who wishes to review it. This transparency enhances accountability and enables efficient auditing, reducing the likelihood of fraudulent activities. By leveraging these features, governments can ensure responsible financial practices and mitigate the risk of corruption.
Impact on National Debt
Reducing the Reliance on Fiat Debt
Bitcoin has the potential to reduce a nation's reliance on fiat debt. Governments often resort to borrowing money by issuing bonds and treasury bills, adding to their national debt. By incorporating Bitcoin into their financial systems, governments can diversify their holdings and explore alternative means of financing. This could alleviate the burden of constantly accumulating fiat debt and provide a more balanced approach to fiscal management.
Revenue Generation and Economic Growth
Bitcoin's adoption can contribute to revenue generation and economic growth. As the cryptocurrency ecosystem expands, businesses emerge to support and facilitate Bitcoin transactions. This development creates employment opportunities and stimulates economic activity. Moreover, governments can generate revenue through taxation on Bitcoin-related activities, further bolstering their financial position.
Mitigating Currency Crises
Currency crises can wreak havoc on economies, causing severe fluctuations in exchange rates and devastating consequences for citizens. By integrating Bitcoin into a nation's financial infrastructure, governments can provide an alternative to their national currency during times of currency crises. This flexibility can help stabilize the economy, mitigate the adverse effects of currency devaluation, and foster investor confidence.
Conclusion
As nations confront the looming debt limit crisis, Bitcoin emerges as a beacon of hope, offering a potential solution and transformative possibilities. Its decentralized nature, protection against inflation, financial inclusion, and transparency make it a compelling choice for governments seeking economic stability. While challenges and uncertainties exist, embracing Bitcoin's potential can pave the way for a more resilient and inclusive financial future.
FAQ
Can Bitcoin completely eliminate a country's debt? No, Bitcoin alone cannot eliminate a country's debt. However, its adoption and integration into financial systems can provide alternative means of financing and reduce reliance on accumulating fiat debt.
How can Bitcoin help individuals facing economic hardships? Bitcoin offers financial inclusion and empowerment by providing a secure and inexpensive means of transacting. This can benefit individuals facing economic hardships by enabling them to participate in the global economy without the need for traditional banking services.
Will governments lose control if they adopt Bitcoin? Governments can adopt Bitcoin while retaining control over their financial systems. The decentralized nature of Bitcoin does not imply a loss of control; instead, it offers an opportunity for greater transparency, accountability, and economic stability.
Is Bitcoin a safe investment for governments? As with any investment, Bitcoin carries risks. However, due to its limited supply and decentralized nature, Bitcoin has demonstrated resilience and the potential for long-term value appreciation.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ cb084639:2f16502a
2024-10-29 05:28:32
@ cb084639:2f16502a
2024-10-29 05:28:32ทำไมถึงกลัว คลอเรสเตอรอลและไขมันอิ่มตัวกันขนาดนั้น !!!

จากภาพจะเห็นได้ว่ามีการวางขายไข่จากพืช!!! ซึ่งอ่านแล้วน่าขัน ในเมื่อเราสามารถ กินไข่จากแม่ไก่ได้!!!

เพื่อความกระจ่างเรามาดูฉลากเจ้าน้ำไข่จากพืชกล่องสีเหลืองกันดีกว่า
 อย่างแรกเรามาดูที่ราคากันก่อน ราคาต่อกล่อง 6.98 usd ราคาบาทอยู่ที่ประมาณ 235 บาทต่อกล่อง 16 ออนซ์หรือ 454 กรัม และถ้าเป็นการ นำเงินจำนวนนี้ไปซื้อไข่จริงเบอร์ 2 ราคาแผงละ 119 บาท จะได้ไข่ 58 ฟอง(เกือบ 2 แผงขาดไป 2ฟอง)
อย่างแรกเรามาดูที่ราคากันก่อน ราคาต่อกล่อง 6.98 usd ราคาบาทอยู่ที่ประมาณ 235 บาทต่อกล่อง 16 ออนซ์หรือ 454 กรัม และถ้าเป็นการ นำเงินจำนวนนี้ไปซื้อไข่จริงเบอร์ 2 ราคาแผงละ 119 บาท จะได้ไข่ 58 ฟอง(เกือบ 2 แผงขาดไป 2ฟอง) เน้นเรื่องปลอด GMO และไม่มี คลอเรสเตอรอล
อันนี้เป็นวิธปรุงง่ายๆ ใช่น้ำไข่จากพืช 3 ช้อนโต๊ะ ต่อไข่ไก่จริง 1 ฟอง ทำง่ายสะดวก
เน้นเรื่องปลอด GMO และไม่มี คลอเรสเตอรอล
อันนี้เป็นวิธปรุงง่ายๆ ใช่น้ำไข่จากพืช 3 ช้อนโต๊ะ ต่อไข่ไก่จริง 1 ฟอง ทำง่ายสะดวก
 ด้านนี้พยายามเปรียบเทียบให้เห็นว่า ไม่มีคลอเรสเตอรอลและไข่มันอิ่มตัว
ด้านนี้พยายามเปรียบเทียบให้เห็นว่า ไม่มีคลอเรสเตอรอลและไข่มันอิ่มตัว ปริมาณสารอาหารไข่จากพืช ไม่มีคลอเรสเตอรอล มีไขมันทั้งหมด 4 กรัม คือไขมันไม่อิ่มตัวเชิงซ้อนและไขมันไม่อิ่มตัวเชิงเดี่ยว ต่อหนึ่งหน่วยบริกโภค
ปริมาณสารอาหารไข่จากพืช ไม่มีคลอเรสเตอรอล มีไขมันทั้งหมด 4 กรัม คือไขมันไม่อิ่มตัวเชิงซ้อนและไขมันไม่อิ่มตัวเชิงเดี่ยว ต่อหนึ่งหน่วยบริกโภค
ภาพนี้คือข้อมูลขอไข่ไก่ที่ได้จากแม่ไก่จริงๆ
 เกือบลืมไปน้ำไข่จากพืชจำเป็นต้องมีส่วนผสมต่างๆ เช่น น้ำ โปรตีนถั่วเขียว น้ำมันคาโนล่าสกัดเย็น สีจากสารสกัดแครอท หัวหอมแห้ง เจลแลนกัม เพื่อรสชาติและเนื้อสัมผัส โพแทสเซียมซิเตรต เกลือ น้ำตาล น้ำเชื่อมมันสำปะหลังของแข็ง เตตระโซเดียมไพโรฟอสเฟต ทรานส์กลูตามิเนส สารสกัดขมิ้น (สี) ไนซิน (สารกันบูด)
เกือบลืมไปน้ำไข่จากพืชจำเป็นต้องมีส่วนผสมต่างๆ เช่น น้ำ โปรตีนถั่วเขียว น้ำมันคาโนล่าสกัดเย็น สีจากสารสกัดแครอท หัวหอมแห้ง เจลแลนกัม เพื่อรสชาติและเนื้อสัมผัส โพแทสเซียมซิเตรต เกลือ น้ำตาล น้ำเชื่อมมันสำปะหลังของแข็ง เตตระโซเดียมไพโรฟอสเฟต ทรานส์กลูตามิเนส สารสกัดขมิ้น (สี) ไนซิน (สารกันบูด)สินค้าเน่าเสียง่าย - เก็บในตู้เย็น รับประทานได้ภายใน 7 วันหลังจากเปิด
 เราต้องแลกกับการที่ต้องบริโภคสารแปรรูปสารพัดเพื่อที่จะต้องการหนีจากคลอเรสเตอรอลอละไขมันจากธรรมชาติ จะดีกว่ามั้ยถ้าเราเลือกกินไข่ที่ผลิตจากธรรมชาติโดยแม่ไก่?
เราต้องแลกกับการที่ต้องบริโภคสารแปรรูปสารพัดเพื่อที่จะต้องการหนีจากคลอเรสเตอรอลอละไขมันจากธรรมชาติ จะดีกว่ามั้ยถ้าเราเลือกกินไข่ที่ผลิตจากธรรมชาติโดยแม่ไก่? -
 @ c0f9e286:5a223917
2024-10-29 03:51:44
@ c0f9e286:5a223917
2024-10-29 03:51:44ตอนที่แล้วกล่าวถึงการถือหุ้นแบบซ้อนเป็นชั้นๆ ผ่านกลไก Offshore Company ในตอนนี้จะกล่าวถึงอีกหนึ่งเครื่องมือในการปกปิดความเป็นเจ้าของ นั่นคือการตั้ง Trust
หลายคนอาจจะเคยได้ยินคำว่า Trust ผ่านกอง REIT (Real Estate Investment Trust) ซึ่งเป็น Trust เพื่อการลงทุนอสังหาริมทรัพย์ สามารถทำการระดมทุนผ่านตลาดหลักทรัพย์ได้ มีโครงสร้างคล้ายๆกับ Property Fund แต่ Trust ที่ผมจะกล่าวต่อไปนี้ เปรียบเสมือนกองทุนส่วนบุคคลซึ่งผู้จัดการกอง Trust จะเป็นผู้บริหารทรัพย์สินนั้นๆ ส่วนเจ้าของตัวจริงจะไม่มีกรรมสิทธิ์ทางตรงต่อทรัพย์สินนั้นๆ
ก่อนอื่นต้องอธิบายศัพท์ของ Trust ให้เข้าใจก่อน เพราะค่อนข้างมีศัพท์เฉพาะเยอะ โดยศัพท์ที่ควรรู้ก็เช่น
Settlor (ผู้ตั้งกอง): เป็นคนที่นำทรัพย์สินมาใส่ในกอง Trust ซึ่งหลังจากทรัพย์สินถูกโอนเข้าไปในกอง Trust แล้ว ผู้ตั้งกองจะไม่มีสิทธิ์ควบคุมทรัพย์สินนั้นโดยตรงอีกต่อไป
Trustee (ผู้ดูแลกอง): เป็นผู้ที่ได้รับมอบหมายให้จัดการทรัพย์สินในกอง Trust ตามเงื่อนไขที่ผู้ตั้งกองระบุไว้ ผู้ดูแลกองมีหน้าที่ดูแลให้ทรัพย์สินนี้เติบโตและคงอยู่เพื่อผู้รับประโยชน์
Beneficiary (ผู้รับประโยชน์): เป็นคนที่ได้รับผลประโยชน์จากกอง Trust ตามเงื่อนไขที่กำหนด เช่น ได้รับเงินปันผล หรือทรัพย์สินเมื่อครบกำหนด
ข้อสังเกตง่ายๆ เวลาคุณดูหุ้นบริษัทจดทะเบียนในตลาดหลักทรัพย์ มักจะมีชื่อหนึ่งปรากฏขึ้นมาเสมอๆในหุ้นตัวใหญ่ๆ นั่นคือ STATE STREET BANK AND TRUST COMPANY
เวลาเห็นรายชื่อแบบนี้เข้าไปถือหุ้นทุกบริษัท คุณไม่มีทางรู้เลยว่า Trust นี้กำลังถือทรัพย์สินให้รายใหญ่คนเดียว หรือหลายคน บางทีอาจจะเป็นรายใหญ่แค่คนเดียวใช้บริการ Trust เจ้านี้เพื่อให้ไปถือหุ้นแทน หรืออาจจะมีหลายคนว่าจ้าง Trust แห่งนี้ให้ถือหุ้นแทน พอถือรวมกันมากเข้าก็เลยปรากฏเป็นรายชื่อผู้ถือหุ้นใหญ่นั่นเอง
อ่อ ลืมบอกไป ในไทยไม่มีกฎหมายรองรับในการตั้งกอง Trust ดังนั้นถ้าจะตั้งต้องตั้งในต่างประเทศ และไม่ใช่ว่า Trust จะมีแต่ข้อดีอย่างเดียว ซึ่งข้อเสียของมันก็ควรนำมาคิดด้วยเช่นกัน
ซึ่งข้อเสียอย่างแรกคือคุณไม่มีสิทธิความเป็นเจ้าของทรัพย์สินหรือหุ้นนั้นๆอีกต่อไป นั่นเป็นสาเหตุที่ไม่ว่ารัฐบาลไหนก็ไม่สามารถฟ้องร้องเพื่อยึดทรัพย์ใน Trust ได้ Bitcoiner ย่อมทราบดีกับคำว่า “์Not your key, Not your coin” คุณกำลังเอาทรัพย์สินไปฝากให้คนอื่นดูแล เพราะฉะนั้นคุณมีโอกาสโดนกอง Trust อ้างว่าบริหารงานผิดพลาดซึ่งทำให้คุณสูญเสียทรัพย์สิน ดังนั้นก่อนตั้ง Trust ควรเลือก Trustee ที่มีผลงานมานาน ไม่เคยมีประวัติฉ้อฉล และคุณก็ควรกำหนดเงื่อนไขในการบริหารกองทุนให้ชัดเจนตั้งแต่แรก เพื่อป้องกันการโอนย้ายทรัพย์สิน หรือการบริหารงานผิดพลาด
ถัดมาคือค่าใช้จ่ายโดยรวมมักจะสูงกว่าการตั้ง Offshore Company แบบซ้อนประเทศ ตั้งแต่การ Settle ไปจนถึงค่าดูแลกอง Trust รายปี ซึ่งผมไม่เคยเห็นที่ไหนต่ำกว่าหลักแสนต่อปี หรือบางที่ก็หลักล้าน หากมีทรัพย์สินจำนวนมาก ต่างกับการตั้ง Offshore Company โดยสิ้นเชิง (แต่ในบางกรณี Offshore Company ก็มีค่าใช้จ่ายสูงเช่นกัน ขึ้นกับธุรกิจที่ทำ จำนวนเงิน และประเทศที่จดจัดตั้งบริษัท)
ดังนั้น Trust จึงเป็นอีกหนึ่งวิธีของการปกปิดตัวตนของเหล่ามหาเศรษฐี แต่แลกมากับการต้องไว้ใจผู้บริหารกอง Trust ว่าจะไม่ฉ้อฉลกับทรัพย์สินของเรา ซึ่งถ้าถามว่าทำยังไงถึงจะมีอำนาจควบคุมกอง Trust ได้แบบเบ็ดเสร็จ นอกเหนือจากการกำหนดเงื่อนไขที่ละเอียดแล้ว อีกวิธีคือการเป็นเจ้าของบริษัท Trust เอง แล้วคุณคิดว่าตระกูลอย่าง Rothschild มีความสามารถที่จะเป็นเจ้าของบริษัท Trust หรือไม่ แล้วถ้าทำได้คุณคิดว่าเขาจะนำทรัพย์สินไปเก็บไว้ใน Trust เพื่อปกปิดชื่อเยอะขนาดไหน นี่เป็นเรื่องน่าคิด
ยังเหลืออีก 1 วิธี ที่จะสามารถปกปิดตัวตนในการถือครองทรัพย์สินได้ดี โปรดติดตามตอนต่อไป
realeakkrit #bitcoin #siamstr #wef

