-

@ 0fa80bd3:ea7325de
2025-02-14 23:24:37
#intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-

@ df173277:4ec96708
2025-02-07 00:41:34
## **Building Our Confidential Backend on Secure Enclaves**
With our newly released [private and confidential **Maple AI**](https://trymaple.ai/?ref=blog.opensecret.cloud) and the open sourcing of our [**OpenSecret** platform](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud) code, I'm excited to present this technical primer on how we built our confidential compute platform leveraging **secure enclaves**. By combining AWS Nitro enclaves with end-to-end encryption and reproducible builds, our platform gives developers and end users the confidence that user data is protected, even at runtime, and that the code operating on their data has not been tampered with.
## **Auth and Databases Today**
As developers, we live in an era where protecting user data means "encryption at rest," plus some access policies and procedures. Developers typically run servers that:
1. Need to register users (authentication).
2. Collect and process user data in business-specific ways, often on the backend.
Even if data is encrypted at rest, it's commonly unlocked with a single master key or credentials the server holds. This means that data is visible during runtime to the application, system administrators, and potentially to the hosting providers. This scenario makes it difficult (or impossible) to guarantee that sensitive data isn't snooped on, memory-dumped, or used in unauthorized ways (for instance, training AI models behind the scenes).
## **"Just Trust Us" Isn't Good Enough**
In a traditional server architecture, users have to take it on faith that the code handling their data is the same code the operator claims to be running. Behind the scenes, applications can be modified or augmented to forward private information elsewhere, and there is no transparent way for users to verify otherwise. This lack of proof is unsettling, especially for services that process or store highly confidential data.
Administrators, developers, or cloud providers with privileged access can inspect memory in plaintext, attach debuggers, or gain complete visibility into stored information. Hackers who compromise these privileged levels can directly access sensitive data. Even with strict policies or promises of good conduct, the reality is that technical capabilities and misconfigurations can override words on paper. If a server master key can decrypt your data or can be accessed by an insider with root permissions, then "just trust us" loses much of its credibility.
The rise of AI platforms amplifies this dilemma. User data, often full of personal details, gets funneled into large-scale models that might be training or fine-tuning behind the scenes. Relying on vague assurances that "we don't look at your data" is no longer enough to prevent legitimate concerns about privacy and misuse. Now more than ever, providing a **strong, verifiable** guarantee that data remains off-limits, even when actively processed, has become a non-negotiable requirement for trustworthy services.
## **Current Attempts at Securing Data**
Current User Experience of E2EE Apps
While properly securing data is not easy, it isn't to say that no one is trying. Some solutions use **end-to-end encryption** (E2EE), where user data is encrypted client-side with a password or passphrase, so not even the server operator can decrypt it. That approach can be quite secure, but it also has its **limitations**:
1. **Key Management Nightmares**: If a user forgets their passphrase, the data is effectively lost, and there's no way to recover it from the developer's side.
2. **Feature Limitations**: Complex server-side operations (like offline/background tasks, AI queries, real-time collaboration, or heavy computation) can't easily happen if the server is never capable of processing decrypted data.
3. **Platform Silos**: Some solutions rely on iCloud, Google Drive, or local device storage. That can hamper multi-device usage or multi-OS compatibility.
Other approaches include self-hosting. However, these either burden users with dev ops overhead or revert to the "trust me" model for the server if you "self-host" on a cloud provider.
## **Secure Enclaves**
### **The Hybrid Approach**
Secure enclaves offer a compelling middle ground. They combine the privacy benefits of keeping data secure from prying admins while still allowing meaningful server-side computation. In a nutshell, an enclave is a protected environment within a machine, isolated at the hardware level, so that even if the OS or server is compromised, the data and code inside the enclave remain hidden.
App Service Running Inside Secure Enclave
### **High-Level Goal of Enclaves**
Enclaves, also known under the broader umbrella of **confidential computing**, aim to:\
• **Lock down data** so that only authorized code within the enclave can process the original plaintext data.\
• **Deny external inspection** by memory dumping, attaching a debugger, or intercepting plaintext network traffic.\
• **Prove** to external users or services that an enclave is running unmodified, approved code (this is where **remote attestation** comes in).
### **Different Secure Enclave Solutions**
[**AMD SEV**](https://www.amd.com/en/developer/sev.html?ref=blog.opensecret.cloud) **(Secure Encrypted Virtualization)** encrypts an entire virtual machine's memory so that even a compromised hypervisor cannot inspect or modify guest data. Its core concept is "lift-and-shift" security. No application refactoring is required because hardware-based encryption automatically protects the OS and all VM applications. Later enhancements (SEV-ES and SEV-SNP) added encryption of CPU register states and memory integrity protections, further limiting hypervisor tampering. This broad coverage means the guest OS is included in the trusted boundary. AMD SEV has matured into a robust solution for confidential VMs in multi-tenant clouds.
[**Intel TDX**](https://www.intel.com/content/www/us/en/developer/tools/trust-domain-extensions/overview.html?ref=blog.opensecret.cloud) **(Trust Domain Extensions)** shifts from process-level enclaves to full VM encryption, allowing an entire guest operating system and its applications to run in an isolated "trust domain." Like AMD SEV, Intel TDX encrypts and protects all memory the VM uses from hypervisors or other privileged software, so developers do not need to refactor their code to benefit from hardware-based confidentiality. This broader scope addresses many SGX limitations, such as strict memory bounds and the need to split out enclave-specific logic, and offers a more straightforward "lift-and-shift" path for running existing workloads privately. While SGX is now deprecated, TDX carries forward the core confidential computing principles but applies them at the virtual machine level for more substantial isolation, easier deployment, and the ability to scale up to large, memory-intensive applications.
[**Apple Secure Enclave and Private Compute**](https://security.apple.com/blog/private-cloud-compute/?ref=blog.opensecret.cloud) is a dedicated security coprocessor embedded in most Apple devices (iPhones, iPads, Macs) and now extended to Apple's server-side AI infrastructure. It runs its own microkernel, has hardware-protected memory, and securely manages operations such as biometric authentication, key storage, and cryptographic tasks. Apple's "Private Compute" approach in the cloud brings similar enclave capabilities to server-based AI, enabling on-device-grade privacy even when requests are processed in Apple's data centers.
[**AWS Nitro Enclaves**](https://docs.aws.amazon.com/enclaves/latest/user/nitro-enclave.html?ref=blog.opensecret.cloud) carve out a tightly isolated "mini-VM" from a parent EC2 instance, with its own vCPUs and memory guarded by dedicated Nitro cards. The enclave has no persistent storage and no external network access, significantly reducing the attack surface. Communication with the parent instance occurs over a secure local channel (vsock), and AWS offers hardware-based attestation so that secrets (e.g., encryption keys from AWS KMS) can be accessed only to the correct enclave. This design helps developers protect sensitive data or code even if the main EC2 instance's OS is compromised.
[**NVIDIA GPU TEEs**](https://www.nvidia.com/en-us/data-center/solutions/confidential-computing/?ref=blog.opensecret.cloud) **(Hopper H100 and Blackwell)** extend confidential computing to accelerated workloads by encrypting data in GPU memory and ensuring that even a privileged host cannot view or tamper with it. Data moving between CPU and GPU is encrypted in transit, so sensitive model weights or inputs remain protected during AI training or inference. NVIDIA's hardware and drivers handle secure data paths under the hood, allowing confidential large language model (LLM) workloads and other GPU-accelerated computations to run with minimal performance overhead and strong security guarantees.
### **Key Benefits**
One major advantage of enclaves is their ability to **keep memory completely off-limits** to outside prying eyes. Even administrators who can normally inspect processes at will are blocked from peeking into the enclave's protected memory space. The enclave model is a huge shift in the security model: it prevents casual inspection and defends against sophisticated memory dumping techniques that might otherwise leak secrets or sensitive data.
Another key benefit centers on cryptographic keys that are **never exposed outside the enclave**. Only verified code running inside the enclave environment can run decryption or signing operations, and it can only do so while that specific code is running. This ensures that compromised hosts or rogue processes, even those with high-level privileges, are unable to intercept or misuse the keys because the keys remain strictly within the trusted boundary of the hardware.
Enclaves can also offer the power of **remote attestation**, allowing external clients or systems to confirm that they're speaking to an authentic, untampered enclave. By validating the hardware's integrity measurements and enclave-specific proofs, the remote party can be confident in the underlying security properties, an important guarantee in multi-tenant environments or whenever trust boundaries extend across different organizations and networks.
Beyond that, **reproducible builds** can create a verifiable fingerprint proving which binary runs in the enclave. This is a step above a simple "trust us" approach. Anyone can independently recreate the enclave image and verify the resulting cryptographic hash by using a reproducible build system (for example, [our NixOS-based solution](https://github.com/OpenSecretCloud/opensecret/blob/master/flake.nix?ref=blog.opensecret.cloud)). If it matches, then users and developers know precisely how code handles their data, boosting confidence that no hidden changes exist.
It's worth noting that although enclaves shield you from software devs, cloud providers, and insider threats, you do have to trust the **hardware vendor** (Intel, AMD, Apple, AWS, or NVIDIA) to implement their microcode and firmware securely. The entire enclave model could be theoretically undermined if a CPU maker's root keys or manufacturing process were compromised. Fortunately, these companies undergo extensive audits and firmware validations (often with third-party researchers), and their remote attestation mechanisms allow you to confirm specific firmware versions before trusting an enclave. While this adds a layer of "vendor trust," it's still a far more contained risk than trusting an entire operating system or cloud stack, so enclaves remain a strong step forward in practical, confidential computing.
## **How We Use Secure Enclaves**
Now that we've covered the general idea of enclaves let's look at how we specifically implement them in OpenSecret, our developer platform for handling user auth, private keys, data encryption, and AI workloads.
### **Our Stack: AWS Nitro + Nvidia TEE**
• **AWS Nitro Enclaves for the backend**: All critical logic, authentication, private key management, and data encryption/decryption run inside an AWS Nitro Enclave.
• **Nvidia Trusted Execution for AI**: For large AI inference (such as the Llama 3.3 70B model), we utilize Nvidia's GPU-based TEEs to protect even GPU memory. This means users can feed sensitive data to the AI model **without** exposing it in plaintext to the GPU providers or us as the operator. [Edgeless Systems](https://www.edgeless.systems/?ref=blog.opensecret.cloud) is our Nvidia TEE provider, and due to the power of enclave verification, we don't need to worry about who runs the GPUs. We know requests can't be inspected or tampered with.
### **End-to-End Encryption from Client to Enclave**
Client-side Enclave Attestation from Maple AI
Before login or data upload, the user/client verifies the **enclave attestation** from our platform. This process proves that the specific Nitro Enclave is genuine and runs the exact code we've published. You can check this out live on [Maple AI's attestation page](https://trymaple.ai/proof?ref=blog.opensecret.cloud).
Based on the attestation, the client establishes a secure ephemeral communication channel that only that enclave can decrypt. While we take advantage of SSL, it is typically not terminated inside the enclave itself. To ensure there's full encrypted data transfer all the way through to the enclave, we establish this additional handshake based on the attestation document that is used for all API requests during the client session.
From there, the user's credentials, private keys, and data pass through this secure channel directly into the enclave, where they are decrypted and processed according to the user's request.
### **In-Enclave Operations**
At the core of OpenSecret's approach is the conviction that security-critical tasks must happen inside the enclave, where even administrative privileges or hypervisor-level compromise cannot expose plaintext data. This encompasses everything from when a user logs in to creating and managing sensitive cryptographic keys. By confining these operations to a protected hardware boundary, developers can focus on building their applications without worrying about accidental data leaks, insider threats, or malicious attempts to harvest credentials. The enclave becomes the ultimate gatekeeper: it controls how data flows and ensures that nothing escapes in plain form.
User Auth Methods running inside Enclave
A primary example is **user authentication**. All sign-in workflows, including email/password, OAuth, and upcoming passkey-based methods, are handled entirely within the enclave. As soon as a user's credentials enter our platform through the encrypted channel, they are routed straight into the protected environment, bypassing the host's operating system or any potential snooping channels. From there, authentication and session details remain in the enclave, ensuring that privileged outsiders cannot intercept or modify them. By centralizing these identity flows within a sealed environment, developers can assure their users that no one outside the enclave (including the cloud provider or the app's own sysadmins) can peek at, tamper with, or access sensitive login information.
Main Enclave Operations in OpenSecret
The same principle applies to **private key management**. Whether keys are created fresh in the enclave or securely transferred into it, they remain sealed away from the rest of the system. Operations like digital signing or content decryption happen only within the hardware boundary, so raw keys never appear in any log, file system, or memory space outside the enclave. Developers retain the functionality they need, such as verifying user actions, encrypting data, or enabling secure transactions without ever exposing keys to a broader (and more vulnerable) attack surface. User backup options exist as well, where the keys can be securely passed to the end user.
Realtime Encrypted Data Sync on Multiple Devices
Another crucial aspect is **data encryption at rest**. While user data ultimately needs to be stored somewhere outside the enclave, the unencrypted form of that data only exists transiently inside the protected environment. Encryption and decryption routines run within the enclave, which holds the encryption keys strictly in memory under hardware guards. If a user uploads data, it is promptly secured before it leaves the enclave. When data is retrieved, it remains encrypted until it reenters the protected region and is passed back to the user through the secured communication channel. This ensures that even if someone gains access to the underlying storage or intercepts data in transit, they will see only meaningless ciphertext.
Confidential AI Workloads
Finally, **confidential AI workloads** build upon this same pattern: the Nitro enclave re-encrypts data so it can be processed inside a GPU-based trusted execution environment (TEE) for inference or other advanced computations. Sensitive data, like user-generated text or private documents, never appears in the clear on the host or within GPU memory outside the TEE boundary. When an AI process finishes, only the results are returned to the enclave, which can then relay them securely to the requesting user. By seamlessly chaining enclaves together, from CPU-based Nitro Enclaves to GPU-accelerated TEEs, we can deliver robust, hardware-enforced privacy for virtually any type of server-side or AI-driven operation.
### **Reproducible Builds + Verification**
Client verifies enclave attestation document
We build our enclaves on **NixOS** with reproducible builds, ensuring that anyone can verify that the binary we publish is indeed the binary running in the enclave. This build process is essential for proving we haven't snuck in malicious code to exfiltrate data or collect sensitive logs.
Our code is fully open source ([GitHub: OpenSecret](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud)), so you can audit or run it yourself. You can also verify that the cryptographic measurement the build process outputs matches the measurement reported by the enclave during attestation.
## **Putting It All Together**
OpenSecret Offering: Private Key Management, Encrypted Sync, Private AI, and Confidential Compute
By weaving secure enclaves into every step, from authentication to data handling to AI inference, we shift the burden of trust away from human policies and onto provable, hardware-based protections. For app developers, you can offer your users robust privacy guarantees without rewriting all your business logic or building an entire security stack from scratch. Whether you're storing user credentials or running complex operations on sensitive data, the enclave approach ensures plaintext remains inaccessible to even the most privileged parties outside the enclave boundary. Developers can focus on building great apps, while OpenSecret handles the cryptographic "lock and key" behind the scenes.
This model provides a secure-by-design environment for industries that demand strict data confidentiality, such as healthcare, fintech, cryptocurrency apps for secure key management, or decentralized identity platforms. Instead of worrying about memory dumps or backend tampering, you can trust that once data enters the enclave, it's sealed off from unauthorized eyes, including from the app developers themselves. And these safeguards don't just apply to niche use cases. Even general-purpose applications that handle login flows and user-generated content stand to benefit, especially as regulatory scrutiny grows around data privacy and insider threats.
Imagine a telehealth startup using OpenSecret enclaves to protect patient information for remote consultations. Not only would patient data remain encrypted at rest, but any AI-driven analytics to assist with diagnoses could be run privately within the enclave, ensuring no one outside the hardware boundary can peek at sensitive health records. A fintech company could similarly isolate confidential financial transactions, preventing even privileged insiders from viewing or tampering with raw transaction details. These real-world implementations give developers a clear path to adopting enclaves for serious privacy and compliance needs without overhauling their infrastructure.
OpenSecret aims to be a **full developer platform** with end-to-end security from day one. By incorporating user authentication, data storage, and GPU-based confidential AI into a single service, we eliminate many of the traditional hurdles in adopting enclaves. No more juggling separate tools for cryptographic key management, compliance controls, and runtime privacy. Instead, you get a unified stack that keeps data encrypted in transit, at rest, and in use.
Our solution also caters to the exploding demand for AI applications: with TEE-enabled GPU workloads, you can securely process sensitive data for text inference without ever exposing raw plaintext or sensitive documents to the host system.
The result is a new generation of apps that deliver advanced functionality, like real-time encrypted data sync or AI-driven insights, while preserving user privacy and meeting strict regulatory requirements. You don't have to rely on empty "trust us" promises because hardware enclaves, remote attestation, and reproducible builds collectively guarantee the code is running untampered. In short, OpenSecret offers the building blocks needed to create truly confidential services and experiences, allowing you to innovate while ensuring data protection remains ironclad.
## **Things to Come**
We're excited to build on our enclaved approach. Here's what's on our roadmap:
• **Production Launch**: We're using this in production now with [Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud) and have a developer preview playground up and running. We'll have the developer environment ready for production in a few months.\
• **Multi-Tenant Support**: Our platform currently works for single tenants, but we're opening this up so developers can onboard without needing a dedicated instance.\
• **Self-Serve Frontend**: A dev-friendly portal for provisioning apps, connecting OAuth or email providers, and managing users.\
• **External Key Signing Options**: Integrations with custom hardware security modules (HSMs) or customer-ran key managers that can only process data upon verifying the enclave attestation.\
• **Confidential Computing as a Service**: We'll expand our platform so that other developers can quickly create enclaves for specialized workloads without dealing with the complexities of Nitro or GPU TEEs.\
• **Additional SDKs**: In addition to our [JavaScript client-side SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud), we plan to launch official support for Rust, Python, Swift, Java, Go, and more.\
• **AI API Proxy with Attestation/Encryption**: We already provide an easy way to [access a Private AI through Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud), but we'd like to open this up more for existing tools and developers. We'll provide a proxy server that users can run on their local machines or servers that properly handle encryption to our OpenAI-compatible API.
## **Getting Started**
Ready to see enclaves in action? Here's how to dive in:\
1. **Run OpenSecret**: Check out our open-source repository at [OpenSecret on GitHub](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud). You can run your own enclaved environment or try it out locally with Docker.\
2. **Review Our SDK**: Our [JavaScript client SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud) makes it easy to handle sign-ins, put/get encrypted data, sign with user private keys, etc. It handles attestation verification and encryption under the hood, making the API integration seamless.\
3. **Play with Maple AI**: Try out [Maple AI](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/) as an example of an AI app built directly on OpenSecret. Your queries are encrypted end to end, and the Llama model sees them only inside the TEE.\
4. **Developer Preview**: Contact us if you want an invite to our early dev platform. We'll guide you through our SDK and give you access to the preview server. We'd love to build with you and incorporate your feedback as we develop this further.
## **Conclusion**
By merging secure enclaves (AWS Nitro and Nvidia GPU TEEs), user authentication, private key management, and an end-to-end verifiable encrypted approach, **OpenSecret** provides a powerful platform where we protect user data during collection, storage, and processing. Whether it's for standard user management, handling private cryptographic keys, or powering AI inference, the technology ensures that **no one**, not even us or the cloud provider, can snoop on data in use.
**We believe** this is the future of trustworthy computing in the cloud. And it's **all open source**, so you don't have to just take our word for it: you can see and verify everything yourself.
Do you have questions, feedback, or a use case you'd like to test out? Come join us on [GitHub](https://github.com/OpenSecretCloud?ref=blog.opensecret.cloud), [Discord](https://discord.gg/ch2gjZAMGy?ref=blog.opensecret.cloud), or email us for a developer preview. We can't wait to see what you build!
*Thank you for reading, and welcome to the era of enclaved computing.*
-

@ daa41bed:88f54153
2025-02-09 16:50:04
There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy [article on the pros of a strategic Bitcoin reserve](https://geek.npub.pro/post/dxqkgnjplttkvetprg8ox/), I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
**Nostr** is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
**Zap** is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what [Lightning](https://lightning.network/) or [Cashu](https://cashu.space/) are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-

@ df173277:4ec96708
2025-01-28 17:49:54
> Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. Chats are synced automatically between devices so you can pick up where you left off.\
> [Start chatting for free.](https://trymaple.ai/)
We are excited to announce that [Maple AI](https://trymaple.ai/), our groundbreaking end-to-end encrypted AI chat app built on OpenSecret, is now publicly available. After months of beta testing, we are thrilled to bring this innovative technology to the world.
Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another.
#### Why Secure and Private AI?
In today's digital landscape, it is increasingly evident that security and privacy are essential for individuals and organizations alike. Unfortunately, the current state of AI tools falls short. A staggering 48% of organizations enter non-public company information into AI apps, according to a [recent report by Cisco](https://www.cisco.com/c/en/us/about/trust-center/data-privacy-benchmark-study.html#~key-findings). This practice poses significant risks to company security and intellectual property.
Another concern is for journalists, who often work with sensitive information in hostile environments. Journalists need verification that their information remains confidential and protected when researching topics and communicating with sources in various languages. They are left to use underpowered local AI or input their data into potentially compromised cloud services.
At OpenSecret, we believe it is possible to have both the benefits of AI and the assurance of security and privacy. That's why we created Maple, an app that combines AI productivity with the protection of end-to-end encryption. Our platform ensures that your conversations with AI remain confidential, even from us. The power of the cloud meets the privacy of local.
#### How Does It Work?
Our server code is [open source](https://github.com/OpenSecretCloud/opensecret), and we use confidential computing to provide cryptographic proof that the code running on our servers is the same as the open-source code available for review. This process allows you to verify that your conversations are handled securely and privately without relying on trust. We live by the principle of "Don't trust, verify," and we believe this approach is essential for building in the digital age. You can read a more in-depth write-up on our technology later this week on this site.
#### How Much Does It Cost?
We are committed to making Maple AI accessible to everyone, so we offer a range of pricing plans to suit different needs and budgets. [Our Free plan allows for 10 chats per week, while our Starter plan ($5.99/month) and Pro plan ($20/month)](https://trymaple.ai/pricing) offer more comprehensive solutions for individuals and organizations with heavier workloads. We accept credit cards and Bitcoin (10% discount), allowing you to choose your preferred payment method.
- Free: $0
- Starter: $5.99/month
- Pro: $20/month
Our goal with Maple AI is to create a product that is secure through transparency. By combining open-source code, cryptography, and confidential computing, we can create a new standard for AI conversations - one that prioritizes your security and privacy.
Maple has quickly become a daily tool of productivity for our own work and those of our beta testers. We believe it will bring value to you as well. [Sign up now and start chatting privately with AI for free.](https://trymaple.ai/) Your secrets are safe in the open.
#### Are You An App Developer?
You can build an app like Maple. [OpenSecret provides secure auth, private key management, encrypted data sync, private AI, and more.](https://blog.opensecret.cloud/introducing-opensecret/) Our straightforward API behaves like other backends but automatically adds security and privacy. Use it to secure existing apps or brand-new projects. Protect yourself and your users from the liability of hosting personal data by checking out [OpenSecret](https://opensecret.cloud/).
<img src="https://blossom.primal.net/feb746d5e164e89f0d015646286b88237dce4158f8985e3caaf7e427cebde608.png">
Enjoy private AI Chat 🤘
<img src="https://blossom.primal.net/0594ec56e249de2754ea7dfc225a7ebd46bc298b5af168279ce71f17c2afada0.jpg">
-

@ df173277:4ec96708
2025-01-09 17:12:08
> Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\
> [Join the waitlist to get early access.](https://trymaple.ai)
We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI.
Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations.
#### Building a Private Foundation
Maple is built on our flagship product, [OpenSecret](https://opensecret.cloud), a backend platform for app developers that turns private encryption on by default. [The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do.](nostr:naddr1qvzqqqr4gupzphchxfm3ste32hfhkvczzxapme9gz5qvqtget6tylyd7wa8vjecgqqe5jmn5wfhkgatrd9hxwt20wpjku5m9vdex2apdw35x2tt9de3hy7tsw3jkgttzv93kketwvskhgur5w9nx5h52tpj) We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win.
#### The Power of Encrypted AI Chat
AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short.
Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us.
#### Technical Overview
So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects:
- **Private Key:** Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data.
- **Secure Servers:** Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations.
- **Encrypted Sync:** One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised.
- **Attestation and Open Code:** We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public.
- **Open Source LLM:** Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased.
#### Personal and Work Use
Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe.
#### Local v Cloud
Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds.
#### Why the Maple name?
Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment.
#### Join the Waitlist
Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. [Join our waitlist today to be among the first to experience the power of private AI chat.](https://trymaple.ai)
[](https://trymaple.ai/waitlist)
-

@ e3ba5e1a:5e433365
2025-02-05 17:47:16
I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
* Unlike full single payer, individuals incur high costs
* Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
* Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
* Reduce regulations significantly.
* In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-

@ df173277:4ec96708
2025-01-09 17:02:52
> OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. [Join our waitlist to get early access.](https://opensecret.cloud)
In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion.
Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online?
Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches?
> Cryptography at scale is hard.
#### The Cloud
The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers.
The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage.
> Private key encryption needs a UX upgrade.
## Enter OpenSecret
OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute.
Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.

### Private Key Management
Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone.
OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account.
The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.

### Encrypted Sync
With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go.
The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them.
### Private AI
Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything.
OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk.
**Check out Maple AI**\
Try private AI for yourself! We built an app built with this service called [Maple AI](https://trymaple.ai). It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. [Learn more about Maple AI - Private chat in the announcement post.](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/)

### Confidential Compute
Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave.
It's the new version of that lock on your web browser. When you see it, you know you're secure.

#### **But do we want our secrets to be open?**
OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable.
On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data.
> Don't trust, verify.
### **Join the Movement**
We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, [send us a message to get early access.](https://opensecret.cloud)
Users and companies deserve better encryption and privacy.\
Together, let's make that a reality.
[](https://opensecret.cloud)
-

@ 9e69e420:d12360c2
2025-02-01 11:16:04

Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-

@ f9cf4e94:96abc355
2024-12-31 20:18:59
Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( [dominictarr]( https://github.com/dominictarr/scuttlebutt) ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt ([ssb]( https://github.com/ssbc/ssb-db)) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia.
Se você está se perguntando de onde diabos veio o nome Scuttlebutt:
> Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.

Marinheiros se reunindo em torno da rixa. ( [fonte]( https://twitter.com/IntEtymology/status/998879578851508224) )
Dominic descobriu o termo boato em um [artigo de pesquisa]( https://www.cs.cornell.edu/home/rvr/papers/flowgossip.pdf) que leu.
Em sistemas distribuídos, [fofocar]( https://en.wikipedia.org/wiki/Gossip_protocol) é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”.
**Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto.** **Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar.** Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário [de bordo]( https://en.wikipedia.org/wiki/Logbook) (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem.
Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. **Cada item adicionado a um log do usuário é chamado de mensagem.**
**Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações.** Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
**Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar.** Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. **Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.**
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de [Pubs públicos em que]( https://github.com/ssbc/ssb-server/wiki/Pub-Servers) todos podem participar **.** Explicaremos como ingressar em um posteriormente neste guia. **Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais.** Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.

Perspectivas dos participantes
## Scuttlebot
O software Pub é conhecido como servidor Scuttlebutt (servidor [ssb]( https://github.com/ssbc/ssb-server) ), mas também é conhecido como “Scuttlebot” e `sbot`na linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial.
**Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações.** Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
**Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar.** Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. **Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.**
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de [Pubs públicos em que]( https://github.com/ssbc/ssb-server/wiki/Pub-Servers) todos podem participar **.** Explicaremos como ingressar em um posteriormente neste guia. **Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais.** Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.


Perspectivas dos participantes
## Pubs - Hubs
### Pubs públicos
| Pub Name | Operator | Invite Code |
| ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ |
| `scuttle.us` | [@Ryan]( https://keybase.io/ryan_singer) | `scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=` |
| [pub1.upsocial.com]( https://upsocial.com/) | [@freedomrules]( https://github.com/freedomrules) | `pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=` |
| [Monero Pub]( https://xmr-pub.net/) | [@Denis]( https://github.com/Orville2112) | `xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=` |
| [FreeSocial]( https://freesocial.co/) | [@Jarland]( https://github.com/mxroute) | `pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=` |
| `ssb.vpn.net.br` | [@coffeverton]( https://about.me/coffeverton) | `ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=` |
| [gossip.noisebridge.info]( https://www.noisebridge.net/wiki/Pub) | [Noisebridge Hackerspace]( https://www.noisebridge.net/wiki/Unicorn) [@james.network]( https://james.network/) | `gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=` |
### Pubs privados
Você precisará entrar em contato com os proprietários desses bares para receber um convite.
| Pub Name | Operator | Contact |
| --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- |
| `many.butt.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) |
| `one.butt.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) |
| `ssb.mikey.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) |
| [ssb.celehner.com]( https://ssb.celehner.com/) | [@cel]( https://github.com/ssbc/ssb-server/wiki/@f/6sQ6d2CMxRUhLpspgGIulDxDCwYD7DzFzPNr7u5AU=.ed25519) | [cel@celehner.com](mailto:cel@celehner.com) |
### Pubs muito grandes
 *Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)* 
| Pub Name | Operator | Invite Code |
| --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ |
| `scuttlebutt.de` | [SolSoCoG]( https://solsocog.de/impressum) | `scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=` |
| `Lohn's Pub` | [@lohn]( https://github.com/lohn) | `p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=` |
| [Scuttle Space]( https://scuttle.space/) | [@guil-dot]( https://github.com/guil-dot) | Visit [scuttle.space]( https://scuttle.space/) |
| `SSB PeerNet US-East` | [timjrobinson]( https://github.com/timjrobinson) | `us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=` |
| Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= |
## GUI - Interface Gráfica do Utilizador(Usuário)
### Patchwork - Uma GUI SSB (Descontinuado)
[**Patchwork**]( https://github.com/ssbc/patchwork) **é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB** . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.

Fonte: [scuttlebutt.nz]( https://www.scuttlebutt.nz/getting-started)
**Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub.** Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs.
Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth.
### Patchbay - Uma GUI Alternativa
Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que [Patchwork]( https://github.com/ssbc/patchwork) e [Patchfoo]( https://github.com/ssbc/patchfoo) , então você pode facilmente dar uma volta com sua identidade existente.

### Planetary - GUI para IOS

[Planetary]( https://apps.apple.com/us/app/planetary-app/id1481617318) é um app com pubs pré-carregados para facilitar integração.
### Manyverse - GUI para Android

[Manyverse]( https://www.manyver.se/) é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone .
## Fontes
* https://scuttlebot.io/
* https://decentralized-id.com/decentralized-web/scuttlebot/#plugins
* https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd
* [**Secure Scuttlebutt**]( http://ssbc.github.io/secure-scuttlebutt/) **:** um protocolo de banco de dados global.
-

@ 0fa80bd3:ea7325de
2025-01-29 05:55:02
The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future.
Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs.
There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won.
Our only resource is the **will of the people** to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root.
So I started asking myself: **How do we stop this fragmentation?** How do we create a space where people can **rebuild their connections** when they’re ready? How do we build a **self-sustaining network**, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—**how do we make it spread, even in occupied territory?**
In 2009, something historic happened: **the internet got its own money.** Thanks to **Satoshi Nakamoto**, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize.
That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became **purely digital.**
The internet was already **a sanctuary for information**, a place where people could connect and organize. But with Bitcoin, it evolved. Now, **value itself** could flow freely, beyond the reach of authorities.
Think about it: when seedlings are grown in controlled environments before being planted outside, they **get stronger, survive longer, and bear fruit faster.** That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild.
Now, picture the internet as that **controlled environment** for **ideas**. Bitcoin? It’s the **fertile soil** that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If **nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless.** It can absorb any number of ideas, any number of people, and it doesn’t **run out of space.**
But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—**without surveillance, without censorship, without the constant fear of being erased.**
This is where **Nostr** comes in.
Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. **It’s a new kind of city.** One that **no dictator can seize**, no corporation can own, no government can shut down.
It’s built on **decentralization, encryption, and individual control.** Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them.
In a world where cities fall and governments fail, **Nostr is a city that cannot be occupied.** A place for ideas, for networks, for freedom. A city that grows stronger **the more people build within it**.
-

@ f1597634:c6d40bf4
2024-10-02 09:00:59
E aí, galera do Nostr! Já pensou em como proteger sua privacidade nesse mundo descentralizado? A gente sabe que a liberdade é daora, mas é importante saber como se proteger dos "bisbilhoteiros" que estão sempre à espreita.
**O perigo das fotos:**
- Sabia que as fotos que você posta podem dar muitas informações sobre você? É tipo deixar um mapa do tesouro nas mãos de alguém!
- Pessoal mau intencionadas podem usar essas fotos para descobrir onde você mora, qual seu IP e até mesmo sua identidade!
**Dicas para se proteger:**
- **Escolha seus apps com cuidado:** Nem todos os apps são iguais. Procure aqueles que a galera mais confia e que têm uma boa fama.
- **Ajuste as configurações:** A maioria dos apps tem configurações de privacidade. Mexa nelas para mostrar só o que você quiser para os outros.
- **Cuidado com links:** Não clique em qualquer link que você receber. Pode ser uma armadilha!
Uma boa prática ao navegar pelo Nostr é configurar um Proxy *confiável* no seu aplicativo. No Nostrudel por exemplo é possível configurar um proxy de imagem através das [configurações](https://nostrudel.ninja/#/settings/performance).
<img src="https://blossom.primal.net/d6f191331248dc5cc3e8617c0f94e2a2e44341451e0ec3275cc22b5195ccbdb3.jpg">
**Segundo análise, as redes a seguir ja disponibilizam esses proxies por padrão:**
- Amethyst
- Damus
\
**O que é esse tal de proxy?**
- Imagina que você está usando uma máscara. O proxy é tipo essa máscara, só que para o seu IP. Assim, ninguém vai saber quem você é de verdade.
- É como se você estivesse usando um disfarce para navegar pela internet!
**Outras dicas:**
- **Remover Exif:** Todas as fotos que tiramos possuem metadados, normalmente redes sociais e outras empresas removem esses dados quando recebem a imagem no servidor *(eventualmente pegam os dados)*.
Programas como [ExifCleaner](https://exifcleaner.com) removem essas informações antes do upload.
**Conclusão:**
A internet é um lugar incrível, mas também pode ser perigoso. Seguindo essas dicas, você vai poder curtir o Nostr com mais tranquilidade e sem se preocupar com os "bisbilhoteiros".
**Lembre-se:** A segurança é coisa séria! Compartilhe esse guia com seus amigos e ajude a criar uma comunidade mais segura.
**E aí, curtiu?**
**fonte: [https://victorhugo.info/artigos/nostr-como-se-proteger-1](https://victorhugo.info/artigos/nostr-como-se-proteger-1)**
-

@ a95c6243:d345522c
2025-02-19 09:23:17
*Die «moralische Weltordnung» – eine Art Astrologie.
Friedrich Nietzsche*
**Das Treffen der BRICS-Staaten beim [Gipfel](https://transition-news.org/brics-gipfel-in-kasan-warum-schweigt-die-schweiz) im russischen Kasan** war sicher nicht irgendein politisches Event. Gastgeber Wladimir Putin habe «Hof gehalten», sagen die Einen, China und Russland hätten ihre Vorstellung einer multipolaren Weltordnung zelebriert, schreiben Andere.
**In jedem Fall zeigt die Anwesenheit von über 30 Delegationen aus der ganzen Welt,** dass von einer geostrategischen Isolation Russlands wohl keine Rede sein kann. Darüber hinaus haben sowohl die Anreise von UN-Generalsekretär António Guterres als auch die Meldungen und Dementis bezüglich der Beitrittsbemühungen des NATO-Staats [Türkei](https://transition-news.org/turkei-entlarvt-fake-news-von-bild-uber-indiens-angebliches-veto-gegen-den) für etwas Aufsehen gesorgt.
**Im Spannungsfeld geopolitischer und wirtschaftlicher Umbrüche** zeigt die neue Allianz zunehmendes Selbstbewusstsein. In Sachen gemeinsamer Finanzpolitik schmiedet man interessante Pläne. Größere Unabhängigkeit von der US-dominierten Finanzordnung ist dabei ein wichtiges Ziel.
**Beim BRICS-Wirtschaftsforum in Moskau, wenige Tage vor dem Gipfel,** zählte ein nachhaltiges System für Finanzabrechnungen und Zahlungsdienste zu den vorrangigen Themen. Während dieses Treffens ging der russische Staatsfonds eine Partnerschaft mit dem Rechenzentrumsbetreiber BitRiver ein, um [Bitcoin](https://www.forbes.com/sites/digital-assets/2024/10/23/russia-launches-brics-mining-infrastructure-project/)-Mining-Anlagen für die BRICS-Länder zu errichten.
**Die Initiative könnte ein Schritt sein, Bitcoin und andere Kryptowährungen** als Alternativen zu traditionellen Finanzsystemen zu etablieren. Das Projekt könnte dazu führen, dass die BRICS-Staaten den globalen Handel in Bitcoin abwickeln. Vor dem Hintergrund der Diskussionen über eine «BRICS-Währung» wäre dies eine Alternative zu dem ursprünglich angedachten Korb lokaler Währungen und zu goldgedeckten Währungen sowie eine mögliche Ergänzung zum Zahlungssystem [BRICS Pay](https://en.wikipedia.org/wiki/BRICS_PAY).
**Dient der Bitcoin also der Entdollarisierung?** Oder droht er inzwischen, zum Gegenstand geopolitischer [Machtspielchen](https://legitim.ch/es-ist-ein-sieg-fuer-bitcoin-waehrend-russland-und-die-usa-um-die-krypto-vorherrschaft-kaempfen/) zu werden? Angesichts der globalen Vernetzungen ist es oft schwer zu durchschauen, «was eine Show ist und was im Hintergrund von anderen Strippenziehern insgeheim gesteuert wird». Sicher können Strukturen wie Bitcoin auch so genutzt werden, dass sie den Herrschenden dienlich sind. Aber die Grundeigenschaft des dezentralisierten, unzensierbaren Peer-to-Peer Zahlungsnetzwerks ist ihm schließlich nicht zu nehmen.
**Wenn es nach der EZB oder dem IWF geht, dann scheint statt Instrumentalisierung** momentan eher der Kampf gegen Kryptowährungen angesagt. Jürgen Schaaf, Senior Manager bei der Europäischen Zentralbank, hat jedenfalls dazu aufgerufen, [Bitcoin «zu eliminieren»](https://www.btc-echo.de/schlagzeilen/ezb-banker-es-gibt-gute-gruende-bitcoin-zu-eliminieren-194015/). Der Internationale Währungsfonds forderte El Salvador, das Bitcoin 2021 als gesetzliches Zahlungsmittel eingeführt hat, kürzlich zu [begrenzenden Maßnahmen](https://legitim.ch/el-salvador-iwf-fordert-trotz-nicht-eingetretener-risiken-neue-massnahmen-gegen-bitcoin/) gegen das Kryptogeld auf.
**Dass die BRICS-Staaten ein freiheitliches Ansinnen im Kopf haben,** wenn sie Kryptowährungen ins Spiel bringen, darf indes auch bezweifelt werden. Im [Abschlussdokument](http://static.kremlin.ru/media/events/files/en/RosOySvLzGaJtmx2wYFv0lN4NSPZploG.pdf) bekennen sich die Gipfel-Teilnehmer ausdrücklich zur UN, ihren Programmen und ihrer «Agenda 2030». Ernst Wolff nennt das «eine [Bankrotterklärung](https://x.com/wolff_ernst/status/1849781982961557771) korrupter Politiker, die sich dem digital-finanziellen Komplex zu 100 Prozent unterwerfen».
---
Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/aufstand-gegen-die-dollar-hegemonie)* erschienen.
-

@ a95c6243:d345522c
2025-02-15 19:05:38
**Auf der diesjährigen Münchner** **[Sicherheitskonferenz](https://transition-news.org/in-munchen-der-realitat-ins-auge-sehen)** **geht es vor allem um die Ukraine.** Protagonisten sind dabei zunächst die US-Amerikaner. Präsident Trump schockierte die Europäer kurz vorher durch ein Telefonat mit seinem Amtskollegen Wladimir Putin, während Vizepräsident Vance mit seiner Rede über Demokratie und Meinungsfreiheit für versteinerte Mienen und Empörung sorgte.
**Die Bemühungen der Europäer um einen Frieden in der Ukraine** halten sich, gelinde gesagt, in Grenzen. Größeres Augenmerk wird auf militärische Unterstützung, die Pflege von Feindbildern sowie Eskalation gelegt. Der deutsche Bundeskanzler Scholz [reagierte](https://transition-news.org/gesucht-friedenskanzler) auf die angekündigten Verhandlungen über einen möglichen Frieden für die Ukraine mit der Forderung nach noch höheren «Verteidigungsausgaben». Auch die amtierende Außenministerin Baerbock hatte vor der Münchner Konferenz [klargestellt](https://archive.is/nUpYa):
> «Frieden wird es nur durch Stärke geben. (...) Bei Corona haben wir gesehen, zu was Europa fähig ist. Es braucht erneut Investitionen, die der historischen Wegmarke, vor der wir stehen, angemessen sind.»
**Die Rüstungsindustrie freut sich in jedem Fall über weltweit steigende Militärausgaben.** Die Kriege in der Ukraine und in Gaza tragen zu [Rekordeinnahmen](https://transition-news.org/kriege-sind-fur-waffenproduzenten-und-hedgefonds-f-king-good) bei. Jetzt «winkt die Aussicht auf eine jahrelange große Nachrüstung in Europa», auch wenn der Ukraine-Krieg enden sollte, so hört man aus Finanzkreisen. In der Konsequenz kennt «die Aktie des deutschen Vorzeige-Rüstungskonzerns Rheinmetall in ihrem Anstieg [offenbar gar keine Grenzen](https://finanzmarktwelt.de/rheinmetall-aktie-mit-mega-rally-nachruestung-und-1-000-euro-kursziel-339271/) mehr». «Solche Friedensversprechen» wie das jetzige hätten in der Vergangenheit zu starken Kursverlusten geführt.
**Für manche Leute sind Kriegswaffen und sonstige Rüstungsgüter Waren wie alle anderen,** jedenfalls aus der Perspektive von Investoren oder Managern. Auch in diesem Bereich gibt es Startups und man spricht von Dingen wie innovativen Herangehensweisen, hocheffizienten Produktionsanlagen, skalierbaren Produktionstechniken und geringeren Stückkosten.
**Wir lesen aktuell von Massenproduktion und gesteigerten Fertigungskapazitäten** für Kriegsgerät. Der Motor solcher Dynamik und solchen Wachstums ist die Aufrüstung, die inzwischen permanent gefordert wird. Parallel wird die Bevölkerung verbal eingestimmt und auf Kriegstüchtigkeit getrimmt.
**Das Rüstungs- und KI-Startup Helsing verkündete kürzlich** eine «dezentrale [Massenproduktion](https://www.trendingtopics.eu/helsing-kampfdrohnen-unicorn-startet-dezentrale-massenproduktion-fuer-ukrainekrieg/) für den Ukrainekrieg». Mit dieser Expansion positioniere sich das Münchner Unternehmen als einer der weltweit führenden Hersteller von Kampfdrohnen. Der nächste [«Meilenstein»](https://archive.is/eZsWP) steht auch bereits an: Man will eine Satellitenflotte im Weltraum aufbauen, zur Überwachung von Gefechtsfeldern und Truppenbewegungen.
**Ebenfalls aus München stammt das als** **[DefenseTech-Startup](https://www.trendingtopics.eu/arx-robotics-produktion/)** **bezeichnete Unternehmen** ARX Robotics. Kürzlich habe man in der Region die größte europäische Produktionsstätte für autonome Verteidigungssysteme eröffnet. Damit fahre man die Produktion von Militär-Robotern hoch. Diese Expansion diene auch der Lieferung der «größten Flotte unbemannter Bodensysteme westlicher Bauart» in die Ukraine.
**Rüstung boomt und scheint ein Zukunftsmarkt zu sein.** Die Hersteller und Vermarkter betonen, mit ihren Aktivitäten und Produkten solle die europäische Verteidigungsfähigkeit erhöht werden. Ihre Strategien sollten sogar «zum Schutz demokratischer Strukturen beitragen».
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/so-klingt-das-aufrustungs-business-startups-und-alte-hasen)*** erschienen.
-

@ c631e267:c2b78d3e
2025-02-07 19:42:11
*Nur wenn wir aufeinander zugehen, haben wir die Chance* *\
auf Überwindung der gegenseitigen Ressentiments!* *\
Dr. med. dent. Jens Knipphals*  
**In Wolfsburg sollte es kürzlich eine Gesprächsrunde von Kritikern der Corona-Politik** mit Oberbürgermeister Dennis Weilmann und Vertretern der Stadtverwaltung geben. Der Zahnarzt und [langjährige](https://transition-news.org/wo-sind-einigkeit-recht-und-freiheit) Maßnahmenkritiker Jens Knipphals hatte diese Einladung ins Rathaus erwirkt und [publiziert](https://www.alexander-wallasch.de/impfgeschichten/brandbrief-zahnarzt-laesst-nicht-locker-showdown-im-wolfsburger-rathaus). Seine Motivation:
> «Ich möchte die Spaltung der Gesellschaft überwinden. Dazu ist eine umfassende Aufarbeitung der Corona-Krise in der Öffentlichkeit notwendig.»
**Schon früher hatte Knipphals Antworten von den Kommunalpolitikern verlangt,** zum Beispiel bei öffentlichen [Bürgerfragestunden](https://archive.is/ttTZc). Für das erwartete Treffen im Rathaus formulierte er Fragen wie: Warum wurden fachliche Argumente der Kritiker ignoriert? Weshalb wurde deren Ausgrenzung, Diskreditierung und Entmenschlichung nicht entgegengetreten? In welcher Form übernehmen Rat und Verwaltung in Wolfsburg persönlich Verantwortung für die erheblichen Folgen der politischen Corona-Krise?
**Der Termin fand allerdings nicht statt** – der Bürgermeister sagte ihn kurz vorher wieder ab. Knipphals bezeichnete Weilmann anschließend als [Wiederholungstäter](https://www.youtube.com/watch?v=b_zzp6jKiHo), da das Stadtoberhaupt bereits 2022 zu einem Runden Tisch in der Sache eingeladen hatte, den es dann nie gab. Gegenüber *Multipolar* [erklärte](https://multipolar-magazin.de/artikel/corona-aufarbeitung-wolfsburg) der Arzt, Weilmann wolle scheinbar eine öffentliche Aufarbeitung mit allen Mitteln verhindern. Er selbst sei «inzwischen absolut desillusioniert» und die einzige Lösung sei, dass die Verantwortlichen gingen.
**Die Aufarbeitung der Plandemie beginne bei jedem von uns selbst,** sei aber letztlich eine gesamtgesellschaftliche Aufgabe, [schreibt](https://peds-ansichten.de/2025/01/plandemie-aufarbeitung/) Peter Frey, der den «Fall Wolfsburg» auch in seinem Blog behandelt. Diese Aufgabe sei indes deutlich größer, als viele glaubten. Erfreulicherweise sei der öffentliche Informationsraum inzwischen größer, trotz der weiterhin unverfrorenen Desinformations-Kampagnen der etablierten Massenmedien.
**Frey erinnert daran, dass Dennis Weilmann mitverantwortlich** für gravierende Grundrechtseinschränkungen wie die 2021 eingeführten 2G-Regeln in der Wolfsburger Innenstadt zeichnet. Es sei naiv anzunehmen, dass ein Funktionär einzig im Interesse der Bürger handeln würde. Als früherer Dezernent des Amtes für Wirtschaft, Digitalisierung und Kultur der Autostadt kenne Weilmann zum Beispiel die Verknüpfung von Fördergeldern mit politischen Zielsetzungen gut.
**Wolfsburg wurde damals zu einem Modellprojekt** des Bundesministeriums des Innern (BMI) und war Finalist im [Bitkom](https://pareto.space/a/naddr1qqxnzden8qen2vejxvenjv35qgs2jhrzgwzvvzgz42kfmef2kr7w8x573k4r62c5ydjh8gyn6dz4ytqrqsqqqa28qyxhwumn8ghj7mn0wvhxcmmvqyv8wumn8ghj7mn0wd68ytn8wfhk7an9d9uzucm0d5qs7amnwvaz7tmwdaehgu3wd4hk6qg5waehxw309ahx7um5wghx77r5wghxgetkqydhwumn8ghj7mn0wd68ytnnwa5hxuedv4hxjemdvyhxx6qpzamhxue69uhhqctjv46x7tnwdaehgu339e3k7mgpz4mhxue69uhhqatjwpkx2un9d3shjtnrdaksz9nhwden5te0wfjkccte9cc8scmgv96zucm0d5q3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgkwaehxw309aex2mrp0yhxummnw3ezucnpdejqmk3pae)-Wettbewerb «Digitale Stadt». So habe rechtzeitig vor der Plandemie das Projekt [«Smart City Wolfsburg»](https://www.beesmart.city/de/city-portraits/smart-city-wolfsburg) anlaufen können, das der Stadt «eine Vorreiterrolle für umfassende Vernetzung und Datenerfassung» aufgetragen habe, sagt Frey. Die Vereinten Nationen verkauften dann derartige «intelligente» Überwachungs- und Kontrollmaßnahmen ebenso als Rettung in der Not wie das Magazin *[Forbes](https://web.archive.org/web/20200417064208/https://www.forbes.com/sites/simonchandler/2020/04/13/how-smart-cities-are-protecting-against-coronavirus-but-threatening-privacy/#5edf8d0c1cc3)* im April 2020:
> «Intelligente Städte können uns helfen, die Coronavirus-Pandemie zu bekämpfen. In einer wachsenden Zahl von Ländern tun die intelligenten Städte genau das. Regierungen und lokale Behörden nutzen Smart-City-Technologien, Sensoren und Daten, um die Kontakte von Menschen aufzuspüren, die mit dem Coronavirus infiziert sind. Gleichzeitig helfen die Smart Cities auch dabei, festzustellen, ob die Regeln der sozialen Distanzierung eingehalten werden.»
**Offensichtlich gibt es viele Aspekte zu bedenken und zu durchleuten,** wenn es um die Aufklärung und Aufarbeitung der sogenannten «Corona-Pandemie» und der verordneten [Maßnahmen](https://transition-news.org/stopptcovid-gutachten-von-lauterbach-erhalt-vernichtende-analyse) geht. Frustration und Desillusion sind angesichts der Realitäten absolut verständlich. Gerade deswegen sind Initiativen wie die von Jens Knipphals so bewundernswert und so wichtig – ebenso wie eine seiner Kernthesen: «Wir müssen aufeinander zugehen, da hilft alles nichts».
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/corona-aufarbeitung-in-der-praxis-eine-illusion)*** erschienen.
-

@ a95c6243:d345522c
2025-01-31 20:02:25
*Im Augenblick wird mit größter Intensität, großer Umsicht* *\
das deutsche Volk belogen.* *\
Olaf Scholz im FAZ-[Interview](https://www.youtube.com/watch?v=c3KI1GmdoVc\&t=649s)*  
**Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten** sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur *Reuters* Verbreitung in den Medien [gefunden](https://archive.is/dnZbY) hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten.
**Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen** sei repräsentativ, [behauptet](https://www.bitkom.org/Presse/Presseinformation/Knapp-Haelfte-Nichtwaehler-wuerde-online-waehlen) der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von [Mitgliedern](https://www.bitkom.org/Bitkom/Mitgliedschaft/Mitgliederliste), die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben».
**Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH,** also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges [«Demokratie-Update»](https://www.experten.de/id/4922407/online-wahlen-als-update-des-demokratischen-systems/) aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet.
**Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete** Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer [befürchteten](https://www.ie.edu/university/news-events/news/67-europeans-fear-ai-manipulation-elections-according-ie-university-research/), dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen.
**Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein?** Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise [abgelehnt](https://www.bundestag.de/dokumente/textarchiv/2025/kw05-de-zustrombegrenzungsgesetz-1042038). Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen.
**Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen,** die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter [berichtet](https://www.epochtimes.de/politik/deutschland/brandmauer-proteste-cdu-zentrale-geraeumt-kundgebungen-in-46-staedten-a5023745.html). Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert».
**Der Vorwand** **[«unzulässiger Einflussnahme»](https://transition-news.org/die-minister-faeser-und-wissing-sorgen-sich-um-unzulassige-einflussnahme-auf)** **auf Politik und Wahlen** wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als [«völlig irre»](https://transition-news.org/bill-gates-nennt-musks-einmischung-in-eu-politik-vollig-irre) bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird [«E-Voting»](https://www.ch.ch/de/abstimmungen-und-wahlen/e-voting/) seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg.
**Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus.** Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die [weit verbreitete Armut](https://transition-news.org/ein-funftel-der-bevolkerung-in-deutschland-ist-von-armut-oder-sozialer) zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden.
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/wahlen-und-wahlen-lassen)*** erschienen.
-

@ a95c6243:d345522c
2025-01-24 20:59:01
*Menschen tun alles, egal wie absurd,* *\
um ihrer eigenen Seele nicht zu begegnen.* *\
Carl Gustav Jung*  
**«Extremer Reichtum ist eine Gefahr für die Demokratie»,** sagen über die Hälfte der knapp 3000 befragten Millionäre aus G20-Staaten laut einer [Umfrage](https://web.archive.org/web/20250122124803/https://patrioticmillionaires.org/web/20250122124803/https://patrioticmillionaires.org/press/nearly-two-thirds-of-millionaires-think-influence-of-the-super-rich-on-trump-presidency-is-threat-to-global-stability/) der «Patriotic Millionaires». Ferner stellte dieser Zusammenschluss wohlhabender US-Amerikaner fest, dass 63 Prozent jener Millionäre den Einfluss von Superreichen auf US-Präsident Trump als Bedrohung für die globale Stabilität ansehen.
**Diese Besorgnis haben 370 Millionäre und Milliardäre am Dienstag** auch den in Davos beim WEF konzentrierten Privilegierten aus aller Welt übermittelt. In einem offenen Brief forderten sie die «gewählten Führer» auf, die Superreichen – also sie selbst – zu besteuern, um «die zersetzenden Auswirkungen des extremen Reichtums auf unsere Demokratien und die Gesellschaft zu bekämpfen». Zum Beispiel kontrolliere eine handvoll extrem reicher Menschen die Medien, beeinflusse die Rechtssysteme in unzulässiger Weise und verwandele Recht in Unrecht.
**Schon 2019** **[beanstandete](https://www.youtube.com/watch?v=paaen3b44XY)** **der bekannte Historiker und Schriftsteller Ruthger Bregman** an einer WEF-Podiumsdiskussion die Steuervermeidung der Superreichen. Die elitäre Veranstaltung bezeichnete er als «Feuerwehr-Konferenz, bei der man nicht über Löschwasser sprechen darf.» Daraufhin erhielt Bregman keine Einladungen nach Davos mehr. Auf seine Aussagen machte der Schweizer Aktivist Alec Gagneux aufmerksam, der sich seit Jahrzehnten kritisch mit dem WEF befasst. Ihm wurde kürzlich der Zutritt zu einem dreiteiligen Kurs über das WEF an der Volkshochschule Region Brugg [verwehrt](https://transition-news.org/wef-propaganda-an-schweizer-volkshochschule-kritiker-ausgesperrt).
**Nun ist die Erkenntnis, dass mit Geld politischer Einfluss einhergeht,** alles andere als neu. Und extremer Reichtum macht die Sache nicht wirklich besser. Trotzdem hat man über Initiativen wie Patriotic Millionaires oder [Taxmenow](https://www.taxmenow.eu/) bisher eher selten etwas gehört, obwohl es sie schon lange gibt. Auch scheint es kein Problem, wenn ein Herr [Gates](https://transition-news.org/bill-melinda-gates-stiftung) fast im Alleingang versucht, globale Gesundheits-, Klima-, Ernährungs- oder Bevölkerungspolitik zu betreiben – im Gegenteil. Im Jahr, als der Milliardär Donald Trump zum zweiten Mal ins Weiße Haus einzieht, ist das Echo in den Gesinnungsmedien dagegen enorm – und uniform, wer hätte das gedacht.
**Der neue US-Präsident hat jedoch** **[«Davos geerdet»](https://www.achgut.com/artikel/trump_erdet_davos_gruener_betrug_green_new_scam),** wie *Achgut* es nannte. In seiner kurzen [Rede](https://www.weforum.org/meetings/world-economic-forum-annual-meeting-2025/sessions/special-address-by-the-president-of-the-united-states-of-america/) beim Weltwirtschaftsforum verteidigte er seine Politik und stellte klar, er habe schlicht eine «Revolution des gesunden Menschenverstands» begonnen. Mit deutlichen Worten sprach er unter anderem von ersten Maßnahmen gegen den «Green New Scam», und von einem «Erlass, der jegliche staatliche Zensur beendet»:
> «Unsere Regierung wird die Äußerungen unserer eigenen Bürger nicht mehr als Fehlinformation oder Desinformation bezeichnen, was die Lieblingswörter von Zensoren und derer sind, die den freien Austausch von Ideen und, offen gesagt, den Fortschritt verhindern wollen.»
**Wie der** **[«Trumpismus»](https://transition-news.org/trumpismus-zeitenwende-und-tiefer-staat)** **letztlich einzuordnen ist,** muss jeder für sich selbst entscheiden. Skepsis ist definitiv angebracht, denn «einer von uns» sind weder der Präsident noch seine auserwählten Teammitglieder. Ob sie irgendeinen Sumpf trockenlegen oder Staatsverbrechen aufdecken werden oder was aus WHO- und Klimaverträgen wird, bleibt abzuwarten.
**Das** **[WHO](https://transition-news.org/who-bedauert-trumps-entscheidung-sich-aus-der-organisation-zuruckzuziehen)-Dekret fordert jedenfalls die Übertragung der Gelder auf «glaubwürdige Partner»,** die die Aktivitäten übernehmen könnten. Zufällig scheint mit «Impfguru» Bill Gates ein weiterer Harris-Unterstützer kürzlich das Lager gewechselt zu haben: Nach einem gemeinsamen Abendessen zeigte er sich [«beeindruckt»](https://archive.is/SpQ24) von Trumps Interesse an der globalen Gesundheit.
**Mit dem** **[Projekt «Stargate»](https://transition-news.org/us-privatsektor-will-500-milliarden-dollar-in-ki-investieren-krebsimpfstoffe)** **sind weitere dunkle Wolken am Erwartungshorizont** der Fangemeinde aufgezogen. Trump hat dieses Joint Venture zwischen den Konzernen OpenAI, Oracle, und SoftBank als das «größte KI-Infrastrukturprojekt der Geschichte» angekündigt. Der Stein des Anstoßes: Oracle-CEO Larry Ellison, der auch Fan von KI-gestützter [Echtzeit-Überwachung](https://transition-news.org/oracle-kundigt-neues-ki-rechenzentrum-mit-eigenen-atomreaktoren-an) ist, sieht einen weiteren potenziellen Einsatz der künstlichen Intelligenz. Sie könne dazu dienen, Krebserkrankungen zu erkennen und individuelle mRNA-«Impfstoffe» zur Behandlung innerhalb von 48 Stunden zu entwickeln.
**Warum bitte sollten sich diese superreichen «Eliten» ins eigene Fleisch schneiden** und direkt entgegen ihren eigenen Interessen handeln? Weil sie Menschenfreunde, sogenannte Philanthropen sind? Oder vielleicht, weil sie ein schlechtes Gewissen haben und ihre Schuld kompensieren müssen? Deswegen jedenfalls brauchen «Linke» laut Robert Willacker, einem deutschen Politikberater mit brasilianischen Wurzeln, rechte Parteien – ein ebenso überraschender wie humorvoller [Erklärungsansatz](https://www.youtube.com/watch?v=s63_8flX1zk).
**Wenn eine Krähe der anderen kein Auge aushackt,** dann tut sie das sich selbst noch weniger an. Dass Millionäre ernsthaft ihre eigene Besteuerung fordern oder Machteliten ihren eigenen Einfluss zugunsten anderer einschränken würden, halte ich für sehr unwahrscheinlich. So etwas glaube ich erst, wenn zum Beispiel die [Rüstungsindustrie](https://transition-news.org/schweiz-zunehmende-beteiligung-an-eu-militarprojekten) sich um Friedensverhandlungen bemüht, die [Pharmalobby](https://transition-news.org/eu-lobbyisten-gegen-pfas-verbot) sich gegen institutionalisierte Korruption einsetzt, [Zentralbanken](https://transition-news.org/digitale-wahrung) ihre CBDC-Pläne für Bitcoin opfern oder der ÖRR die Abschaffung der Rundfunkgebühren fordert.
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/elitare-anti-eliten-und-superreiche-anti-reiche)*** erschienen.
-

@ 6be5cc06:5259daf0
2025-01-21 20:58:37
A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**.
---
### **1. Instalar o Tor e o Privoxy**
Abra o terminal e execute:
```bash
sudo apt update
sudo apt install tor privoxy
```
**Explicação:**
- **Tor:** Roteia o tráfego pela rede Tor.
- **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
---
### **2. Configurar o Privoxy**
Abra o arquivo de configuração do Privoxy:
```bash
sudo nano /etc/privoxy/config
```
Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira:
```bash
forward-socks5 / 127.0.0.1:9050 .
```
Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**.
Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo.
---
### **3. Iniciar o Tor e o Privoxy**
Agora, inicie e habilite os serviços:
```bash
sudo systemctl start tor
sudo systemctl start privoxy
sudo systemctl enable tor
sudo systemctl enable privoxy
```
**Explicação:**
- **start:** Inicia os serviços.
- **enable:** Faz com que iniciem automaticamente ao ligar o PC.
---
### **4. Configurar o Navegador Firefox**
Para usar a rede **Tor** com o Firefox:
1. Abra o Firefox.
2. Acesse **Configurações** → **Configurar conexão**.
3. Selecione **Configuração manual de proxy**.
4. Configure assim:
- **Proxy HTTP:** `127.0.0.1`
- **Porta:** `8118` (porta padrão do **Privoxy**)
- **Domínio SOCKS (v5):** `127.0.0.1`
- **Porta:** `9050`
5. Marque a opção **"Usar este proxy também em HTTPS"**.
6. Clique em **OK**.
---
### **5. Verificar a Conexão com o Tor**
Abra o navegador e acesse:
```text
https://check.torproject.org/
```
Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta.
---
### **Dicas Extras**
- **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o **Privoxy**.
-

@ c631e267:c2b78d3e
2025-01-18 09:34:51
*Die grauenvollste Aussicht ist die der Technokratie –* *\
einer kontrollierenden Herrschaft,* *\
die durch verstümmelte und verstümmelnde Geister ausgeübt wird.* *\
Ernst Jünger*  
**«Davos ist nicht mehr sexy»,** das Weltwirtschaftsforum ([WEF](https://transition-news.org/wef-world-economic-forum)) mache Davos [kaputt](https://web.archive.org/web/20250116114956/https://www.handelszeitung.ch/wef-2025/wie-das-wef-davos-kaputt-macht-785098), diese Aussagen eines Einheimischen las ich kürzlich in der *Handelszeitung*. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
**Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen** dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den [vergangenen](https://transition-news.org/die-angst-der-eliten-vor-dem-pobel) vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
**Der deutsche WEF-Gründer hatte bei dieser Gelegenheit** immer höchst lobende Worte für seine Landsmännin: [2021](https://www.weforum.org/meetings/the-davos-agenda-2021/sessions/special-address-by-g20-head-of-state-government/) erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und [2022](https://www.weforum.org/meetings/the-davos-agenda-2022/sessions/special-address-by-ursula-von-der-leyen-president-of-the-european-commission-177737c164/) fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
**Von der Leyens Handeln während der sogenannten Corona-«Pandemie»** lobte Schwab damals bereits ebenso, wie es diese Woche das [Karlspreis](https://transition-news.org/von-der-leyen-erhalt-karlspreis-albert-bourla-erklart-pfizer-habe-wahrend-der)-Direktorium tat, als man der Beschuldigten im Fall [Pfizergate](https://transition-news.org/pfizergate-startet-ins-neue-jahr) die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
**Jene Herausforderungen durch «Krisen epochalen Ausmaßes»** werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im [Global Risks Report](https://www.zurich.com/knowledge/topics/global-risks/the-global-risks-report-2025) nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
**Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen** unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
**Ein** **[«Great Mental Reset»](https://transition-news.org/angriff-auf-unser-gehirn-michael-nehls-uber-den-great-mental-reset-teil-1)** **sei die Voraussetzung dafür,** dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
**Der aktuelle Zustand unserer Gesellschaften** ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die [Rechtsstaatlichkeit](https://transition-news.org/schweizer-rechtsstaat-in-der-krise-ein-anwalt-schlagt-alarm) stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/davos-europa-und-der-rest-der-welt)*** erschienen.
-

@ 9e69e420:d12360c2
2025-01-21 19:31:48
Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits.
## Active Compounds
The oil's therapeutic properties stem from its key bioactive components:
- Carvacrol and thymol (primary active compounds)
- Polyphenols and other antioxidant
## Antimicrobial Properties
**Bacterial Protection**
The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance.
**Antifungal Effects**
It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections.
## Digestive Health Benefits
Oregano oil supports digestive wellness by:
- Promoting gastric juice secretion and enzyme production
- Helping treat Small Intestinal Bacterial Overgrowth (SIBO)
- Managing digestive discomfort, bloating, and IBS symptoms
## Anti-inflammatory and Antioxidant Effects
The oil provides significant protective benefits through:
- Powerful antioxidant activity that fights free radicals
- Reduction of inflammatory markers in the body
- Protection against oxidative stress-related conditions
## Respiratory Support
It aids respiratory health by:
- Loosening mucus and phlegm
- Suppressing coughs and throat irritation
- Supporting overall respiratory tract function
## Additional Benefits
**Skin Health**
- Improves conditions like psoriasis, acne, and eczema
- Supports wound healing through antibacterial action
- Provides anti-aging benefits through antioxidant properties
**Cardiovascular Health**
Studies show oregano oil may help:
- Reduce LDL (bad) cholesterol levels
- Support overall heart health
**Pain Management**
The oil demonstrates effectiveness in:
- Reducing inflammation-related pain
- Managing muscle discomfort
- Providing topical pain relief
## Safety Note
While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
-

@ f9cf4e94:96abc355
2025-01-18 06:09:50
Para esse exemplo iremos usar:
| Nome | Imagem | Descrição |
| --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ |
| Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** |
| Pen drive |  | **16Gb** |
Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.).
---
## Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
```bash
apt update
apt install tor
```
---
## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧
Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit
[Unit]
Description=Nostr Relay Server Service
After=network.target
[Service]
Type=simple
WorkingDirectory=/opt/nrs
ExecStart=/opt/nrs/nrs-arm64
Restart=on-failure
[Install]
WantedBy=multi-user.target
```
---
## Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases).
---
## Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
```bash
mkdir -p /opt/nrs /mnt/edriver
```
---
## Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
```bash
lsblk
```
---
## Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o:
```bash
mkfs.vfat /dev/sda
```
---
## Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta `/mnt/edriver`:
```bash
mount /dev/sda /mnt/edriver
```
---
## Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
```bash
blkid
```
---
## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝
Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:
```fstab
UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
```
---
## Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta `/opt/nrs`:
```bash
cp nrs-arm64 /opt/nrs
```
---
## Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`:
```yaml
app_env: production
info:
name: Nostr Relay Server
description: Nostr Relay Server
pub_key: ""
contact: ""
url: http://localhost:3334
icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png
base_path: /mnt/edriver
negentropy: true
```
---
## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`:
```bash
cp nrs.service /etc/systemd/system/
```
Recarregue os serviços e inicie o serviço `nrs`:
```bash
systemctl daemon-reload
systemctl enable --now nrs.service
```
---
## Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha:
```torrc
HiddenServiceDir /var/lib/tor/nostr_server/
HiddenServicePort 80 127.0.0.1:3334
```
---
## Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
```bash
systemctl enable --now tor.service
```
O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`.
---
## Observações ⚠️
- Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`.
---
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-

@ a95c6243:d345522c
2025-01-13 10:09:57
*Ich begann, Social Media aufzubauen,* *\
um den Menschen eine Stimme zu geben.* *\
Mark Zuckerberg*
**Sind euch auch die Tränen gekommen, als ihr Mark Zuckerbergs** **[Wendehals-Deklaration](https://www.facebook.com/zuck/videos/1525382954801931)** bezüglich der Meinungsfreiheit auf seinen Portalen gehört habt? Rührend, oder? Während er früher die offensichtliche Zensur leugnete und später die Regierung Biden dafür verantwortlich machte, will er nun angeblich «die Zensur auf unseren Plattformen drastisch reduzieren».
**«Purer** **[Opportunismus](https://transition-news.org/facebook-grunder-zuckerberg-vom-trump-gegner-zum-trump-buddy-und-anti-zensor)» ob des anstehenden Regierungswechsels wäre als Klassifizierung** viel zu kurz gegriffen. Der jetzige Schachzug des Meta-Chefs ist genauso Teil einer kühl kalkulierten Business-Strategie, wie es die 180 Grad umgekehrte Praxis vorher war. Social Media sind ein höchst lukratives Geschäft. Hinzu kommt vielleicht noch ein bisschen verkorkstes Ego, weil derartig viel Einfluss und Geld sicher auch auf die Psyche schlagen. Verständlich.
> «Es ist an der Zeit, zu unseren Wurzeln der freien Meinungsäußerung auf Facebook und Instagram zurückzukehren. Ich begann, Social Media aufzubauen, um den Menschen eine Stimme zu geben», sagte Zuckerberg.
**Welche Wurzeln? Hat der Mann vergessen, dass er von der Überwachung,** dem Ausspionieren und dem Ausverkauf sämtlicher Daten und digitaler Spuren sowie der Manipulation seiner «Kunden» lebt? Das ist knallharter Kommerz, nichts anderes. Um freie Meinungsäußerung geht es bei diesem Geschäft ganz sicher nicht, und das war auch noch nie so. Die Wurzeln von Facebook liegen in einem Projekt des US-Militärs mit dem Namen [«LifeLog»](https://norberthaering.de/macht-kontrolle/lifelog/). Dessen Ziel war es, «ein digitales Protokoll vom Leben eines Menschen zu erstellen».
**Der Richtungswechsel kommt allerdings nicht überraschend.** Schon Anfang Dezember hatte Meta-Präsident Nick Clegg von «zu hoher Fehlerquote bei der Moderation» von Inhalten [gesprochen](https://www.theverge.com/2024/12/3/24311513/meta-content-moderation-mistakes-nick-clegg). Bei der Gelegenheit erwähnte er auch, dass Mark sehr daran interessiert sei, eine aktive Rolle in den Debatten über eine amerikanische Führungsrolle im technologischen Bereich zu spielen.
**Während Milliardärskollege und Big Tech-Konkurrent Elon Musk bereits seinen Posten** in der kommenden Trump-Regierung in Aussicht hat, möchte Zuckerberg also nicht nur seine Haut retten – Trump hatte ihn einmal einen «Feind des Volkes» genannt und ihm lebenslange Haft angedroht –, sondern am liebsten auch mitspielen. KI-Berater ist wohl die gewünschte Funktion, wie man nach einem Treffen Trump-Zuckerberg hörte. An seine [Verhaftung](https://transition-news.org/nicht-telegram-grunder-durow-sondern-zuckerberg-sollte-in-haft-sitzen-wegen-des) dachte vermutlich auch ein weiterer Multimilliardär mit eigener Social Media-Plattform, Pavel Durov, als er Zuckerberg jetzt [kritisierte](https://www.berliner-zeitung.de/news/ende-des-faktenchecks-bei-meta-telegram-gruender-kritisiert-zuckerberg-und-spricht-warnung-aus-li.2287988) und gleichzeitig warnte.
**Politik und Systemmedien drehen jedenfalls durch** – was zu viel ist, ist zu viel. Etwas weniger Zensur und mehr Meinungsfreiheit würden die Freiheit der Bürger schwächen und seien potenziell vernichtend für die Menschenrechte. Zuckerberg setze mit dem neuen Kurs die Demokratie aufs Spiel, das sei eine «Einladung zum nächsten [Völkermord](https://archive.is/PYeH0)», ernsthaft. Die Frage sei, ob sich die [EU gegen Musk und Zuckerberg](https://www.handelsblatt.com/politik/international/internet-regulierung-kann-sich-die-eu-gegen-musk-und-zuckerberg-behaupten/100099373.html) behaupten könne, Brüssel müsse jedenfalls hart durchgreifen.
**Auch um die** **[Faktenchecker](https://www.welt.de/kultur/medien/article255065352/Metas-Kurswechsel-Zuckerbergs-Entscheidung-und-die-Folgen-fuer-deutsche-Faktenchecker.html)** **macht man sich Sorgen.** Für die deutsche Nachrichtenagentur *dpa* und die «Experten» von *Correctiv*, die (noch) Partner für Fact-Checking-Aktivitäten von Facebook sind, sei das ein «lukratives Geschäftsmodell». Aber möglicherweise werden die Inhalte ohne diese vermeintlichen Korrektoren ja sogar besser. Anders als Meta wollen jedoch Scholz, Faeser und die *Tagesschau* keine Fehler zugeben und zum Beispiel *Correctiv*-[Falschaussagen](https://www.berliner-zeitung.de/politik-gesellschaft/correctiv-falschaussagen-exklusiv-scholz-faeser-und-tagesschau-wollen-sich-fuer-verbreitung-nicht-entschuldigen-li.2288126) einräumen.
**Bei derlei dramatischen Befürchtungen wundert es nicht,** dass der öffentliche Plausch auf X zwischen Elon Musk und AfD-Chefin Alice Weidel von 150 EU-Beamten überwacht wurde, falls es irgendwelche Rechtsverstöße geben sollte, die man ihnen ankreiden könnte. Auch der Deutsche Bundestag war wachsam. Gefunden haben dürften sie nichts. Das Ganze war eher eine Show, viel Wind wurde gemacht, aber letztlich gab es nichts als heiße Luft.
**Das** **[Anbiedern](https://transition-news.org/who-biedert-sich-bei-trump-an)** **bei Donald Trump ist indes gerade in Mode.** Die Weltgesundheitsorganisation (WHO) tut das auch, denn sie fürchtet um Spenden von über einer Milliarde Dollar. Eventuell könnte ja Elon Musk auch hier künftig aushelfen und der Organisation sowie deren größtem privaten Förderer, Bill Gates, etwas unter die Arme greifen. Nachdem Musks KI-Projekt xAI kürzlich von BlackRock & Co. [sechs Milliarden](https://x.ai/blog/series-c) eingestrichen hat, geht da vielleicht etwas.
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/milliardenschwere-wetterfahnchen-und-windmaschinen)*** erschienen.
-

@ 6be5cc06:5259daf0
2025-01-21 01:51:46
## Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
---
### Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado **gasto duplo**, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado **blockchain**, protegido por uma técnica chamada **Prova de Trabalho**. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
---
### 1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em **confiança**.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um **sistema de pagamento eletrônico baseado em provas matemáticas**, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o **Bitcoin**, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
---
### 2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
#### O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
#### Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
1. A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
2. Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
3. Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
#### Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
#### Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
---
### 3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
---
### 4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
---
### 5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
1. **Transmissão de Transações**: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
2. **Coleta de Transações em Blocos**: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
3. **Prova-de-Trabalho**: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
4. **Envio do Bloco Resolvido**: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
5. **Validação do Bloco**: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
6. **Construção do Próximo Bloco**: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
#### Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
#### Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
---
### 6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
#### Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
#### Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
#### Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
1. Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
2. Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
---
### 7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
---
### 8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
---
### 9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
#### Entradas e Saídas
Cada transação no Bitcoin é composta por:
- **Entradas**: Representam os valores recebidos em transações anteriores.
- **Saídas**: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como **troco**.
#### Exemplo Prático
Imagine que você tem duas entradas:
1. 0,03 BTC
2. 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- **Entrada**: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- **Saídas**: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
#### Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
---
### 10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando **chaves públicas anônimas**, que desvinculam diretamente as transações das identidades das partes envolvidas.
#### Fluxo de Informação
- No **modelo tradicional**, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No **Bitcoin**, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
#### Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
1. **Chaves Públicas Anônimas**: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
2. **Prevenção de Ligação**: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
#### Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações **multi-entrada** podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
---
### 11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
#### Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
#### A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem **80% do poder computacional** (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem **20% do poder computacional** (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
#### Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- **q** é o poder computacional do atacante (20%, ou 0,2).
- **p** é o poder computacional da rede honesta (80%, ou 0,8).
- **z** é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente **nulas**.
#### Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
#### Por Que Tudo Isso é Seguro?
- **A probabilidade de sucesso do atacante diminui exponencialmente.** Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- **A cadeia verdadeira (honesta) está protegida pela força da rede.** Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
#### E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
---
### 12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos.
A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos.
Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
---
Faça o download do whitepaper original em português:
https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-

@ a95c6243:d345522c
2025-01-03 20:26:47
*Was du bist hängt von drei Faktoren ab:* *\
Was du geerbt hast,* *\
was deine Umgebung aus dir machte* *\
und was du in freier Wahl* *\
aus deiner Umgebung und deinem Erbe gemacht hast.* *\
Aldous Huxley*
**Das brave Mitmachen und Mitlaufen in einem vorgegebenen, recht engen Rahmen** ist gewiss nicht neu, hat aber gerade wieder mal Konjunktur. Dies kann man deutlich beobachten, eigentlich egal, in welchem gesellschaftlichen Bereich man sich umschaut. Individualität ist nur soweit angesagt, wie sie in ein bestimmtes Schema von «Diversität» passt, und Freiheit verkommt zur Worthülse – nicht erst durch ein gewisses [Buch](https://www.nachdenkseiten.de/?p=126416) einer gewissen ehemaligen Regierungschefin.
**Erklärungsansätze für solche Entwicklungen sind bekannt,** und praktisch alle haben etwas mit Massenpsychologie zu tun. Der Herdentrieb, also der Trieb der Menschen, sich – zum Beispiel aus Unsicherheit oder Bequemlichkeit – lieber der Masse anzuschließen als selbstständig zu denken und zu handeln, ist einer der Erklärungsversuche. Andere drehen sich um Macht, Propaganda, Druck und Angst, also den gezielten Einsatz psychologischer [Herrschaftsinstrumente](https://transition-news.org/spip.php?recherche=nudging\&page=recherche_wall).
**Aber wollen die Menschen überhaupt Freiheit?** Durch Gespräche im privaten Umfeld bin ich diesbezüglich in der letzten Zeit etwas skeptisch geworden. Um die Jahreswende philosophiert man ja gerne ein wenig über das Erlebte und über die Erwartungen für die Zukunft. Dabei hatte ich hin und wieder den Eindruck, die totalitären Anwandlungen unserer «Repräsentanten» kämen manchen Leuten gerade recht.
**«Desinformation» ist so ein brisantes Thema.** Davor müsse man die Menschen doch schützen, hörte ich. Jemand müsse doch zum Beispiel diese ganzen merkwürdigen Inhalte in den Social Media filtern – zur [Ukraine](https://transition-news.org/spip.php?recherche=ukraine\&page=recherche_wall), zum [Klima](https://transition-news.org/spip.php?recherche=klima\&page=recherche_wall), zu [Gesundheitsthemen](https://transition-news.org/spip.php?recherche=impfung\&page=recherche_wall) oder zur [Migration](https://transition-news.org/spip.php?recherche=migration\&page=recherche_wall). Viele wüssten ja gar nicht einzuschätzen, was richtig und was falsch ist, sie bräuchten eine Führung.
**Freiheit bedingt Eigenverantwortung, ohne Zweifel.** Eventuell ist es einigen tatsächlich zu anspruchsvoll, die Verantwortung für das eigene Tun und Lassen zu übernehmen. Oder die persönliche Freiheit wird nicht als ausreichend wertvolles Gut angesehen, um sich dafür anzustrengen. In dem Fall wäre die mangelnde Selbstbestimmung wohl das kleinere Übel. Allerdings fehlt dann gemäß Aldous Huxley ein Teil der Persönlichkeit. Letztlich ist natürlich alles eine Frage der Abwägung.
**Sind viele Menschen möglicherweise schon so «eingenordet»,** dass freiheitliche Ambitionen gar nicht für eine ganze Gruppe, ein Kollektiv, verfolgt werden können? Solche Gedanken kamen mir auch, als ich mir kürzlich diverse Talks beim viertägigen [Hacker-Kongress](https://transition-news.org/der-38-kongress-des-chaos-computer-clubs-bot-mehr-enthullungen-als-nur-die) des Chaos Computer Clubs (38C3) anschaute. Ich war nicht nur überrascht, sondern reichlich erschreckt angesichts der in weiten Teilen mainstream-geformten Inhalte, mit denen ein dankbares Publikum beglückt wurde. Wo ich allgemein hellere Köpfe erwartet hatte, fand ich Konformismus und enthusiastisch untermauerte Narrative.
**Gibt es vielleicht so etwas wie eine Herdenimmunität gegen Indoktrination?** Ich denke, ja, zumindest eine gestärkte Widerstandsfähigkeit. Was wir brauchen, sind etwas gesunder Menschenverstand, offene Informationskanäle und der Mut, sich freier auch zwischen den Herden zu bewegen. Sie tun das bereits, aber sagen Sie es auch dieses Jahr ruhig weiter.
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/kann-es-sein-dass-die-menschen-gar-keine-freiheit-wollen)*** erschienen.
-

@ a95c6243:d345522c
2025-01-01 17:39:51
**Heute möchte ich ein Gedicht mit euch teilen.** Es handelt sich um eine Ballade des österreichischen Lyrikers Johann Gabriel Seidl aus dem 19. Jahrhundert. Mir sind diese Worte fest in Erinnerung, da meine Mutter sie perfekt rezitieren konnte, auch als die Kräfte schon langsam schwanden.
**Dem originalen Titel «Die Uhr»** habe ich für mich immer das Wort «innere» hinzugefügt. Denn der Zeitmesser – hier vermutliche eine Taschenuhr – symbolisiert zwar in dem Kontext das damalige Zeitempfinden und die Umbrüche durch die industrielle Revolution, sozusagen den Zeitgeist und das moderne Leben. Aber der Autor setzt sich philosophisch mit der Zeit auseinander und gibt seinem Werk auch eine klar spirituelle Dimension.
**Das Ticken der Uhr und die Momente des Glücks und der Trauer** stehen sinnbildlich für das unaufhaltsame Fortschreiten und die Vergänglichkeit des Lebens. Insofern könnte man bei der Uhr auch an eine Sonnenuhr denken. Der Rhythmus der Ereignisse passt uns vielleicht nicht immer in den Kram.
**Was den Takt pocht, ist durchaus auch das Herz,** unser «inneres Uhrwerk». Wenn dieses Meisterwerk einmal stillsteht, ist es unweigerlich um uns geschehen. Hoffentlich können wir dann dankbar sagen: «Ich habe mein Bestes gegeben.»
*Ich trage, wo ich gehe, stets eine Uhr bei mir;* \
*Wieviel es geschlagen habe, genau seh ich an ihr.* \
*Es ist ein großer Meister, der künstlich ihr Werk gefügt,* \
*Wenngleich ihr Gang nicht immer dem törichten Wunsche genügt.*  
*Ich wollte, sie wäre rascher gegangen an manchem Tag;* *\
Ich wollte, sie hätte manchmal verzögert den raschen Schlag.* *\
In meinen Leiden und Freuden, in Sturm und in der Ruh,* *\
Was immer geschah im Leben, sie pochte den Takt dazu.*  
*Sie schlug am Sarge des Vaters, sie schlug an des Freundes Bahr,* *\
Sie schlug am Morgen der Liebe, sie schlug am Traualtar.* *\
Sie schlug an der Wiege des Kindes, sie schlägt, will's Gott, noch oft,* *\
Wenn bessere Tage kommen, wie meine Seele es hofft.*  
*Und ward sie auch einmal träger, und drohte zu stocken ihr Lauf,* *\
So zog der Meister immer großmütig sie wieder auf.* *\
Doch stände sie einmal stille, dann wär's um sie geschehn,* *\
Kein andrer, als der sie fügte, bringt die Zerstörte zum Gehn.*  
*Dann müßt ich zum Meister wandern, der wohnt am Ende wohl weit,* *\
Wohl draußen, jenseits der Erde, wohl dort in der Ewigkeit!* *\
Dann gäb ich sie ihm zurücke mit dankbar kindlichem Flehn:* *\
Sieh, Herr, ich hab nichts verdorben, sie blieb von selber stehn.*  
*Johann Gabriel Seidl (1804-1875)*
-

@ 6389be64:ef439d32
2025-01-16 15:44:06
## Black Locust can grow up to 170 ft tall
## Grows 3-4 ft. per year
## Native to North America
## Cold hardy in zones 3 to 8

## Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
## Timber

- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
## Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
## Bees

- The edible flower clusters are also a top food source for honey bees
## Shade Provider

- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
## Wind-break

- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
## Fodder
- Over 20% crude protein
- 4.1 kcal/g of energy
- Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
-

@ f9cf4e94:96abc355
2024-12-30 19:02:32
Na era das grandes navegações, piratas ingleses eram autorizados pelo governo para roubar navios.
A única coisa que diferenciava um pirata comum de um corsário é que o último possuía a “Carta do Corso”, que funcionava como um “Alvará para o roubo”, onde o governo Inglês legitimava o roubo de navios por parte dos corsários. É claro, que em troca ele exigia uma parte da espoliação.
Bastante similar com a maneira que a Receita Federal atua, não? Na verdade, o caso é ainda pior, pois o governo fica com toda a riqueza espoliada, e apenas repassa um mísero salário para os corsários modernos, os agentes da receita federal.
Porém eles “justificam” esse roubo ao chamá-lo de imposto, e isso parece acalmar os ânimos de grande parte da população, mas não de nós.
Não é por acaso que 'imposto' é o particípio passado do verbo 'impor'. Ou seja, é aquilo que resulta do cumprimento obrigatório -- e não voluntário -- de todos os cidadãos. Se não for 'imposto' ninguém paga. Nem mesmo seus defensores. Isso mostra o quanto as pessoas realmente apreciam os serviços do estado.
Apenas volte um pouco na história: os primeiros pagadores de impostos eram fazendeiros cujos territórios foram invadidos por nômades que pastoreavam seu gado. Esses invasores nômades forçavam os fazendeiros a lhes pagar uma fatia de sua renda em troca de "proteção". O fazendeiro que não concordasse era assassinado.
Os nômades perceberam que era muito mais interessante e confortável apenas cobrar uma taxa de proteção em vez de matar o fazendeiro e assumir suas posses. Cobrando uma taxa, eles obtinham o que necessitavam. Já se matassem os fazendeiros, eles teriam de gerenciar por conta própria toda a produção da fazenda.
Daí eles entenderam que, ao não assassinarem todos os fazendeiros que encontrassem pelo caminho, poderiam fazer desta prática um modo de vida.
Assim nasceu o governo.
Não assassinar pessoas foi o primeiro serviço que o governo forneceu. Como temos sorte em ter à nossa disposição esta instituição!
Assim, não deixa de ser curioso que algumas pessoas digam que os impostos são pagos basicamente para impedir que aconteça exatamente aquilo que originou a existência do governo. O governo nasceu da extorsão. Os fazendeiros tinham de pagar um "arrego" para seu governo. Caso contrário, eram assassinados.
Quem era a real ameaça? O governo. A máfia faz a mesma coisa.
Mas existe uma forma de se proteger desses corsários modernos. Atualmente, existe uma propriedade privada que NINGUÉM pode tirar de você, ela é sua até mesmo depois da morte. É claro que estamos falando do Bitcoin. Fazendo as configurações certas, é impossível saber que você tem bitcoin. Nem mesmo o governo americano consegue saber.
#brasil #bitcoinbrasil #nostrbrasil #grownostr #bitcoin
-

@ 6389be64:ef439d32
2025-01-13 21:50:59
Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
# Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
# Meet The Forest Walker
For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
# The Small Branch Chipper
When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
# The Gassifier
The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
# Biochar: The Waste
Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
# Wood Vinegar: More Waste
Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
# The Internal Combustion Engine
Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
# CO2 Production For Growth
Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
# The Branch Drones
During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
# The Bitcoin Miner
Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
# The Mesh Network
What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
# Back To The Chain
Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
# Sensor Packages
### LiDaR
The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
### pH, Soil Moisture, and Cation Exchange Sensing
The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
### Weather Data
Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
# Noise Suppression
Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
# Fire Safety
A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
# The Wrap
How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-

@ a95c6243:d345522c
2024-12-21 09:54:49
Falls du beim Lesen des Titels dieses Newsletters unwillkürlich an positive Neuigkeiten aus dem globalen polit-medialen Irrenhaus oder gar aus dem wirtschaftlichen Umfeld gedacht hast, darf ich dich beglückwünschen. Diese Assoziation ist sehr löblich, denn sie weist dich als unverbesserlichen Optimisten aus. Leider muss ich dich diesbezüglich aber enttäuschen. Es geht hier um ein anderes Thema, allerdings sehr wohl ein positives, wie ich finde.
Heute ist ein ganz besonderer Tag: die **Wintersonnenwende**. Genau gesagt hat [heute morgen](https://www.timeanddate.de/astronomie/wintersonnenwende) um 10:20 Uhr Mitteleuropäischer Zeit (MEZ) auf der Nordhalbkugel unseres Planeten der astronomische Winter begonnen. Was daran so außergewöhnlich ist? Der kürzeste Tag des Jahres war gestern, seit heute werden die Tage bereits wieder länger! Wir werden also jetzt jeden Tag ein wenig mehr Licht haben.
Für mich ist dieses Ereignis immer wieder etwas kurios: **Es beginnt der Winter, aber die Tage werden länger.** Das erscheint mir zunächst wie ein Widerspruch, denn meine spontanen Assoziationen zum Winter sind doch eher Kälte und Dunkelheit, relativ zumindest. Umso erfreulicher ist der emotionale Effekt, wenn dann langsam die Erkenntnis durchsickert: Ab jetzt wird es schon wieder heller!
Natürlich ist es kalt im Winter, mancherorts mehr als anderswo. Vielleicht jedoch nicht mehr lange, wenn man den Klimahysterikern glauben wollte. Mindestens letztes Jahr hat Väterchen Frost allerdings gleich zu Beginn seiner Saison – und passenderweise während des globalen Überhitzungsgipfels in Dubai – nochmal richtig mit der Faust auf den Tisch gehauen. Schnee- und Eischaos sind ja eigentlich in der Agenda bereits nicht mehr [vorgesehen](https://web.archive.org/web/20231202175946/https://www.spiegel.de/wissenschaft/mensch/winter-ade-nie-wieder-schnee-a-71456.html). Deswegen war man in Deutschland vermutlich in vorauseilendem Gehorsam schon nicht mehr darauf vorbereitet und wurde glatt [lahmgelegt](https://web.archive.org/web/20231207014311/https://www.dw.com/de/nach-dem-schnee-in-deutschland-und-dem-chaos-am-flughafen-und-bei-der-bahn-ein-winteralptraum/a-67638141).
Aber ich schweife ab. Die Aussicht auf nach und nach mehr Licht und damit auch Wärme stimmt mich froh. Den Zusammenhang zwischen beidem merkt man in Andalusien sehr deutlich. Hier, wo die Häuser im Winter arg auskühlen, geht man zum Aufwärmen raus auf die Straße oder auf den Balkon. Die Sonne hat auch im Winter eine erfreuliche Kraft. Und da ist jede Minute Gold wert.
Außerdem ist mir vor Jahren so richtig klar geworden, warum mir das südliche Klima so sehr gefällt. Das liegt nämlich nicht nur an der Sonne als solcher, oder der Wärme – das liegt vor allem am Licht. **Ohne Licht keine Farben**, das ist der ebenso simple wie gewaltige Unterschied zwischen einem deprimierenden matschgraubraunen Winter und einem fröhlichen bunten. Ein großes Stück Lebensqualität.
Mir gefällt aber auch die **Symbolik dieses Tages**: Licht aus der Dunkelheit, ein Wendepunkt, ein Neuanfang, neue Möglichkeiten, Übergang zu neuer Aktivität. In der winterlichen Stille keimt bereits neue Lebendigkeit. Und zwar in einem Zyklus, das wird immer wieder so geschehen. Ich nehme das gern als ein Stück Motivation, es macht mir Hoffnung und gibt mir Energie.
Übrigens ist parallel am heutigen Tag auf der südlichen Halbkugel Sommeranfang. Genau im entgegengesetzten Rhythmus, sich ergänzend, wie Yin und Yang. Das alles liegt an der Schrägstellung der Erdachse, die ist nämlich um 23,4º zur Umlaufbahn um die Sonne geneigt. Wir erinnern uns, gell?
Insofern bleibt eindeutig festzuhalten, dass “**schräg sein**” ein willkommener, wichtiger und positiver Wert ist. Mit [anderen](https://www.dwds.de/wb/schr%C3%A4g) Worten: auch ungewöhnlich, eigenartig, untypisch, wunderlich, kauzig, … ja sogar irre, spinnert oder gar “quer” ist in Ordnung. Das schließt das Denken mit ein.
**In diesem Sinne wünsche ich euch allen urige Weihnachtstage!**
***
Dieser Beitrag ist letztes Jahr in meiner *[Denkbar](https://denkbar.substack.com/p/ab-jetzt-gehts-bergauf)* erschienen.
-

@ a95c6243:d345522c
2024-12-13 19:30:32
*Das Betriebsklima ist das einzige Klima,* \
*das du selbst bestimmen kannst.* \
*Anonym*
**Eine Strategie zur Anpassung an den Klimawandel** hat das deutsche Bundeskabinett diese Woche [beschlossen](https://www.bundesregierung.de/breg-de/aktuelles/klimaanpassungsstrategie-2024-2324828). Da «Wetterextreme wie die immer häufiger auftretenden Hitzewellen und Starkregenereignisse» oft desaströse Auswirkungen auf Mensch und Umwelt hätten, werde eine Anpassung an die Folgen des Klimawandels immer wichtiger. «Klimaanpassungsstrategie» nennt die Regierung das. 
**Für die «Vorsorge vor Klimafolgen» habe man nun erstmals** klare Ziele und messbare Kennzahlen festgelegt. So sei der Erfolg überprüfbar, und das solle zu einer schnelleren Bewältigung der Folgen führen. Dass sich hinter dem Begriff Klimafolgen nicht Folgen des Klimas, sondern wohl «Folgen der globalen Erwärmung» verbergen, erklärt den Interessierten die Wikipedia. Dabei ist das mit der [Erwärmung](https://transition-news.org/studie-ozeane-kuhlen-die-erde-viel-starker-als-gedacht) ja bekanntermaßen so eine Sache.
**Die Zunahme schwerer Unwetterereignisse habe gezeigt,** so das Ministerium, wie wichtig eine frühzeitige und effektive Warnung der Bevölkerung sei. Daher solle es eine deutliche Anhebung der Nutzerzahlen der sogenannten Nina-Warn-App geben.
**Die** ***ARD*** **spurt wie gewohnt** und setzt die Botschaft zielsicher um. Der Artikel [beginnt](https://www.tagesschau.de/inland/innenpolitik/klima-anpassung-warnapp-100.html) folgendermaßen:
> «Die Flut im Ahrtal war ein Schock für das ganze Land. Um künftig besser gegen Extremwetter gewappnet zu sein, hat die Bundesregierung eine neue Strategie zur Klimaanpassung beschlossen. Die Warn-App Nina spielt eine zentrale Rolle. Der Bund will die Menschen in Deutschland besser vor Extremwetter-Ereignissen warnen und dafür die Reichweite der Warn-App Nina deutlich erhöhen.»
**Die Kommunen würden bei ihren «Klimaanpassungsmaßnahmen»** vom Zentrum KlimaAnpassung [unterstützt](https://zentrum-klimaanpassung.de/ueber-uns), schreibt das Umweltministerium. Mit dessen Aufbau wurden das Deutsche Institut für Urbanistik gGmbH, welches sich stark für [Smart City-Projekte](https://difu.de/taxonomy/term/2083) engagiert, und die Adelphi Consult GmbH beauftragt.
**Adelphi** **[beschreibt](https://adelphi.de/de)** **sich selbst als «Europas führender Think-and-Do-Tank** und eine unabhängige Beratung für Klima, Umwelt und Entwicklung». Sie seien «global vernetzte Strateg\*innen und weltverbessernde Berater\*innen» und als «Vorreiter der sozial-ökologischen Transformation» sei man mit dem Deutschen Nachhaltigkeitspreis ausgezeichnet worden, welcher sich an den Zielen der Agenda 2030 orientiere.
**Über die** **[Warn-App](https://www.bbk.bund.de/DE/Warnung-Vorsorge/Warn-App-NINA/warn-app-nina_node.html)** **mit dem niedlichen Namen Nina,** die möglichst jeder auf seinem Smartphone installieren soll, informiert das Bundesamt für Bevölkerungsschutz und Katastrophenhilfe (BBK). Gewarnt wird nicht nur vor Extrem-Wetterereignissen, sondern zum Beispiel auch vor Waffengewalt und Angriffen, Strom- und anderen Versorgungsausfällen oder Krankheitserregern. Wenn man die Kategorie Gefahreninformation wählt, erhält man eine Dosis von ungefähr zwei Benachrichtigungen pro Woche.
**Beim BBK erfahren wir auch einiges über die empfohlenen** **[Systemeinstellungen](https://www.bbk.bund.de/DE/Warnung-Vorsorge/Warn-App-NINA/Einstellungen-Android/einstellungen-android_node.html)** für Nina. Der Benutzer möge zum Beispiel den Zugriff auf die Standortdaten «immer zulassen», und zwar mit aktivierter Funktion «genauen Standort verwenden». Die Datennutzung solle unbeschränkt sein, auch im Hintergrund. Außerdem sei die uneingeschränkte Akkunutzung zu aktivieren, der Energiesparmodus auszuschalten und das Stoppen der App-Aktivität bei Nichtnutzung zu unterbinden.
**Dass man so dramatische Ereignisse wie damals im Ahrtal auch anders bewerten kann** als Regierungen und Systemmedien, hat meine Kollegin Wiltrud Schwetje anhand der Tragödie im spanischen [Valencia](https://transition-news.org/valencia-zehn-tage-nach-der-katastrophe-warten-viele-menschen-immer-noch-auf) gezeigt. Das Stichwort «Agenda 2030» taucht dabei in einem Kontext auf, der wenig mit Nachhaltigkeitspreisen zu tun hat.
***
Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/vorsorge-vor-klimafolgen)* erschienen.
-

@ 592295cf:413a0db9
2024-12-07 07:21:39
Week 02-11
- Nsite zap by hzrd149
[Support page](https://npub1wyuh3scfgzqmxn709a2fzuemps389rxnk7nfgege6s847zze3tuqfl87ez.nsite.lol/#/support)
## Content creator want more users. They can go to Bluesky.
Great that Nostr is a Echo Chambers. As stated by Rabble during NostRiga, Nostr is a bitcoin meetup. And it is very difficult as said several times, to subvert this fact.
It seems that many bitcoiners don't like this, but they can't do anything, leave Nostr and migrate to other lids.
## I'm reading Nostr adventar calendar of Japanese Nostr users.
The first two Don and Jun speak of a Mahjong game and the other of how possibly to count the followers of a given account, countfollowed.
- [Adventar calendar](https://adventar.org/calendars/10004)
continue until Christmas 🎅
- Even Bluesky is looking at MLS , is not a soccer league, is a protocol for message by groups, "circles"
[Post on Bluesky](https://bsky.app/profile/soatok.bsky.social/post/3lc4gt4mywc2z)
- Relays chakany is introduce sunday. [link](https://relay.chakany.systems/)
I've never seen such dead animals as in Nostr. Something reminds me facebook. The carnivore folks
## Hivemind podcast by Max, the kilometric comment on fountain under the podcast is the most appetizing thing of all. Just one comment, little one.
He interviewed Kagi's and searched for a brownie pill, perhaps caused a little headache. ( Brownie pill is orange plus purple)
-----------
Loss dog on Nostr this week 😔😔 Pam and Derek family dog
conspiracy theory: Fiatjaf was the reply guy!!!
I tried to download voyage, from zapstore but nothing does not work even the 17.1 does not go. Too bad.
I hear so much about notedeck that I want to make a notedeck do it yourself.
Cherry tree, stuck hzrd149 is making an app a day, Chunked blobs on blossom.
A like is used to send your writing Relays
Announcement of a possible wallet in Damus, this could make things better, zap and whatnot.
-----------
- Or I'm posting a song here, a musical interlude.
[song on wavlake](https://wavlake.com/album/87dfa3dc-b921-4a4b-8bfc-f60479cec364)
-----------
There seems to be a good buzz on Nostr, maybe it's already a Christmassy atmosphere.
- Backup di Bluesky cool things
[Bluesky post](https://bsky.app/profile/filippo.abyssdomain.expert/post/3lcfdsv2hec2a)
-----------
On another rssfeed thing.
nostr:nevent1qvzqqqqqqypzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqs93j2remdw2pxnctasa9vlsaerrrsl7p5csx5wj88kk0yq977rtdqxt7glp
### It's the same thing as following a cross de bridge, but if they do 3 bridge, I say something is wrong. A bot is attached to a Relay. The Relay goes down and so much greetings, then I can look for RSS feeds in my computer without need of Nostr. I can share a particular opml file on Nostr, but I don't know how to do it I asked Fiatjaf but didn't answer it was taken by dichotomie.
### Nip19 really Easy to do filter query.
You have events_id pubkey Relay
Instead with Nostr:note you only have the event_id.
- Sebastix says he has to implement it in his library, discover the latest weekly report.
[nostr-php-helper-library](https://nostrver.se/blog/nostr-php-helper-library-90-day-opensats-report-2)
-----------
Oh no Pablo has become super Saiyan 🤣
## There is a way to make a podcast starting from a long text, blog. With artificial intelligence. But then I thought, but if one does not have time could not have the text of the article summarized, perhaps we like generating content. It can be an option, either you read or you listen. But if you do not have time perhaps it is better to just summarize, dear chatgpt summarize this text, done. Essential points and make a thread for the social network and do what you want.
- Homemade Traditional Boozy Mincemeat, I didn't even know that existed 🤙
[link to shopstr](https://shopstr.store/listing/b7fbcd4415d50dac4cc2b95cb2e73acea294a7f3040255c6f9b07a9494006b3e)
Hodlbod news on bunker burrow
nostr:nevent1qqs84na25g6mdelvl0408nnq8m29j5070dm9mvjrzxyc6yrx2udjyuczyztuwzjyxe4x2dwpgken87tna2rdlhpd02
- In case you don't see the note
[burrow on github](https://github.com/coracle-social/burrow)
Once you have the email what do you do with your encrypted key? No Enterprise user maybe. Rember the article of Hodlbod in "Is Always a political move". ✅
List of artists on Nostr
nostr:naddr1qvzqqqr4xqpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqp9qku6tdv96x7unng9grdr
- An article for food recipe on Nostr
[Article link ](https://yakihonne.com/article/naddr1qvzqqqr4gupzpn0wjs7tkxw9r2uy0fndt4m5xua2na3a9peydw6ekzp8lf0xxaqqqqxnzdenxv6nqwf3xgun2wpkyhpdxx)
### I don't know if they'll ever be there. You can write a recipe book. Or to put recipes on wiki, there doesn't seem to be that attention or that desire. One more relay is always better
- Olas has a website 🥊
[Olas app](https://olas.app/)
Oh i see cool Hodlbod bot
A summary bot
nostr:nevent1qqs0v88uc2u3he3lm3mpm5h3gr8cuht5wv9g0tk0x9hzvamgvpdjwvspzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qjlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qu0ltyv
That's all!!
-

@ a95c6243:d345522c
2024-12-06 18:21:15
*Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\
dass wir Vorteile aus ihr ziehen;\
in jedem andern hegt man den Wunsch,\
dass der Unschuldige in Schutz genommen werde.\
Jean-Jacques Rousseau*
**Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen** – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden.
**Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen»** den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen [schadet der Psyche](https://transition-news.org/meisterwerk-von-studie-bestatigt-maskentragen-bei-kindern-sinnlos-und-schadlich) und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben [Menschen getötet](https://transition-news.org/lockdowns-und-zensur-haben-menschen-getotet)».
**Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft.** Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen [Erfahrungen als Kritikerin](https://transition-news.org/die-coronazeit-hat-mir-gezeigt-wie-die-menschen-manipuliert-werden-konnen) der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit *Transition News*. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften».
**Menschen, die aufrichtig andere schützen wollten,** werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter [Heinrich Habig](https://transition-news.org/arzte-mussten-ihr-vergehen-irgendwann-selbst-einsehen), [Bianca Witzschel](https://transition-news.org/anwalt-von-bianca-witzschel-das-ist-eindeutig-eine-politische-justiz) und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat *Transition News* mehrfach berichtet (z.B. [hier](https://transition-news.org/prozess-gegen-walter-weber-kai-kisielinski-fuhrt-mit-argumentationsfeuerwerk) und [hier](https://transition-news.org/prozess-gegen-walter-weber-tschentscher-und-schaade-doch-nicht-vor-gericht)). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie [Alexander Bittner](https://transition-news.org/verweigerung-der-covid-impfung-inhaftierter-bundeswehrsoldat-kundigt) erfahren mussten.
[**Die eigentlich Kriminellen**](https://transition-news.org/die-eigentlich-kriminellen-schutzen-sich-vor-der-verantwortung) **schützen sich derweil erfolgreich selber,** nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte [Verbrechen gegen die Menschheit](https://transition-news.org/das-grosste-verbrechen-gegen-die-menschheit)». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn [Hunter](https://transition-news.org/us-steuerbehorde-hat-prasidentschaftswahl-2020-fur-joe-biden-gestohlen) möglicherweise auch [Anthony Fauci begnadigen](https://transition-news.org/wird-biden-auch-fauci-begnadigen) wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte?
**Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten** und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken.
**Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers [Robert F. Kennedy Jr.](https://transition-news.org/usa-robert-f-kennedy-jr-als-gesundheitsminister-nominiert)** erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens [Călin Georgescu](https://transition-news.org/der-ausgang-der-rumanischen-prasidentschaftswahlen-konnte-mogliche), der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der [Panik im Wertewesten](https://www.euronews.com/2024/12/04/robert-f-kennedy-jr-denies-any-link-with-far-right-romanian-presidential-candidate).
**In Rumänien selber gab es gerade einen Paukenschlag:** Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das [Tabu gebrochen](https://tkp.at/2024/12/06/rumaenien-sagt-praesidenten-wahl-ab/), Wahlen zu verbieten, bevor sie etwas ändern können.
**Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen** und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: [Zensur](https://transition-news.org/fuhrende-politiker-der-welt-unterzeichnen-neue-zensurerklarung-bei-un)) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden.
---
Dieser Beitrag ist zuerst auf [*Transition News*](https://transition-news.org/schutz-wem-schutz-gebuhrt) erschienen.
-

@ a95c6243:d345522c
2024-11-29 19:45:43
*Konsum ist Therapie.
Wolfgang Joop*
**Umweltbewusstes Verhalten und verantwortungsvoller Konsum** zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
**Heute ist also wieder mal «Black Friday»,** falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
**Warum fallen wir auf derartige Werbetricks herein** und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
**Gedankenlosigkeit und Maßlosigkeit können besonders bei der [Ernährung](https://transition-news.org/studie-208-millionen-us-amerikaner-sind-als-fettleibig-oder-ubergewichtig) zu ernsten Problemen führen.** Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
**Kritik am schwarzen Freitag und dem unnötigen Konsum** kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
**Die EU-Kommission lancierte 2015 den Begriff «Green Friday»** im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das [Pariser Abkommen](https://transition-news.org/cop29-wird-vom-geist-des-noch-kunftigen-us-prasidenten-heimgesucht) unterzeichnet werden sollte.
**Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt.** Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des [«Green New Deal»](https://transition-news.org/green-new-deal) verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um [Valencia](https://transition-news.org/flutkatastrophe-in-valencia-die-ungereimtheiten-haufen-sich) dazu sagen?
**Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020** eine «[grüne Erholung von Covid-19](https://news.un.org/en/story/2020/12/1079602), um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
**Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet** – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
**Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung** nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie [«verantwortungsvolle Risikobereitschaft»](https://transition-news.org/zuruck-zu-2008-grossbritannien-schlagt-lockere-regeln-fur-banker-boni-vor) unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
---
Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/auch-beim-freitag-ist-es-egal-ob-schwarz-oder-grun)* erschienen.
-

@ e3ba5e1a:5e433365
2025-01-13 16:47:27
My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity.
A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur.
The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior.
And there are plenty of incentives beyond our direct control\! My son is *also* incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take.
## Why incentives matter
A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could **just** do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example:
* If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning.
* If people would just use the recycling bin, we wouldn’t have such a landfill problem.
* If people would just stop being lazy, our team would deliver our project on time.
In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally.
* The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do.
* No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle.
* If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.

My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want.
If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is.
## Running a company
Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions.
Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good.
What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off.
Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning.
When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.

Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks\! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money.
There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals.
Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature.
# Moral hazard
Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings.
What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.

But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I *don’t* turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all.
This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as:
1. We’re so habituated to turning off the water that we don’t even consider *not* turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off.
2. Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created.
3. We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?)
Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard.
A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard.
It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend?
And since we’re talking about the government already…
## Government moral hazards
As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a *huge* number of examples of moral hazards. I decided to cherry-pick a few for this post.
The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people?
The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet.
If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior\! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups.
You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”

And here’s the absolute best part of this: I can’t even truly blame either California *or* Wall Street. (I mean, I *do* blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits.
There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions.
# Non-monetary competition
At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home.
In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.)
Anyway, my professor’s wife had a friend. My professor described in *great* detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas.
This is a demonstration of *non-monetary compensation*. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules.
The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become *wealthier and whiter*, the exact opposite of their desired outcome. Why would that happen?
Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky.
She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls.
So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites.
You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences.
## Bureaucracy
These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences.
Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings.
Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could\! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate.
# Government incentivized behavior
This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples:
* Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to [malinvestment](https://en.wikipedia.org/wiki/Malinvestment) and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience.
* Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise.
* During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation.
* The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen.
* Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example).
* Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as [high living](https://www.youtube.com/watch?v=ZwNDd2_beTU).)
# Conclusion
The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives.
We can bemoan these realities all we want, but they *are* realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People *should* take advantage of the incentives around them. Because if they don’t, someone else will.
(If you want a literary example of that last comment, see the horse in Animal Farm.)
How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula:
* Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people.
* Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them.
* And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example.
And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining\!
-

@ a95c6243:d345522c
2024-11-08 20:02:32
*Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister Eckhart*
**Schwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung,** der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
**Mit einem bemerkenswerten [Timing](https://transition-news.org/donald-trump-grossmaul-oder-hoffnungstrager) hat die deutsche Regierungskoalition** am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer [Selbsthypnose](https://ansage.org/schwer-traumatisiert-nach-trumps-sieg-dreht-die-politmediale-linksgruene-sekte-durch/) rund um Harris-Hype und Trump-Panik – mit teils erschreckenden [Auswüchsen](https://archive.is/7tDhY). Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
**Das [Kindergarten](https://www.spiegel.de/politik/deutschland/christian-lindner-auch-die-fdp-will-wieder-einen-eigenen-wirtschaftsgipfel-abhalten-a-a8a4e868-10b1-426e-adb0-e5a6d42f7c46)-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche** war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik [«vorsätzlich herbeigeführt»](https://www.t-online.de/nachrichten/deutschland/innenpolitik/id_100522112/fdp-chef-lindner-und-sein-grundsatzpapier-die-scheidung-von-der-ampel-.html) worden seien.
**Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen.** Verkehrs- und [Digitalminister Wissing](https://transition-news.org/raus-aus-der-komfortzone-es-lohnt-sich) trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit [Jörg Kukies](https://norberthaering.de/news/joerg-kukies/) habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
**Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP,** hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
**Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können.** Das ging erst kürzlich aus dem diesjährigen [«Freiheitsindex»](https://www.schwaebische.de/politik/forscher-beim-vertrauen-in-staat-und-medien-zerreisst-es-uns-gerade-3034357) hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
**«Die absolute Mehrheit hat [absolut die Nase voll](https://archive.is/yRxwR)»,** titelte die *Bild* angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
**Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat,** kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei *Manova*. Und er kenne [Friedrich Merz](https://www.manova.news/artikel/der-kriegsgeile-blackrocker) schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
**Was also tun? Der Schweizer Verein [«Losdemokratie»](https://zeitpunkt.ch/node/40968) will eine Volksinitiative lancieren,** um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
**In jedem Fall wird es notwendig sein, unsere Bemühungen um [Freiheit und Selbstbestimmung](https://transition-news.org/alternative-medien-in-der-krise-zensur-kontrollverlust-und-die-suche-nach)** zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
---
Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/es-kann-nur-besser-werden-aber-wie)* erschienen.
-

@ 3f770d65:7a745b24
2025-01-12 21:03:36
I’ve been using Notedeck for several months, starting with its extremely early and experimental alpha versions, all the way to its current, more stable alpha releases. The journey has been fascinating, as I’ve had the privilege of watching it evolve from a concept into a functional and promising tool.
In its earliest stages, Notedeck was raw—offering glimpses of its potential but still far from practical for daily use. Even then, the vision behind it was clear: a platform designed to redefine how we interact with Nostr by offering flexibility and power for all users.
I'm very bullish on Notedeck. Why? Because Will Casarin is making it! Duh! 😂
Seriously though, if we’re reimagining the web and rebuilding portions of the Internet, it’s important to recognize [the potential of Notedeck](https://damus.io/notedeck/). If Nostr is reimagining the web, then Notedeck is reimagining the Nostr client.
Notedeck isn’t just another Nostr app—it’s more a Nostr browser that functions more like an operating system with micro-apps. How cool is that?
Much like how Google's Chrome evolved from being a web browser with a task manager into ChromeOS, a full blown operating system, Notedeck aims to transform how we interact with the Nostr. It goes beyond individual apps, offering a foundation for a fully integrated ecosystem built around Nostr.
As a Nostr evangelist, I love to scream **INTEROPERABILITY** and tout every application's integrations. Well, Notedeck has the potential to be one of the best platforms to showcase these integrations in entirely new and exciting ways.
Do you want an Olas feed of images? Add the media column.
Do you want a feed of live video events? Add the zap.stream column.
Do you want Nostr Nests or audio chats? Add that column to your Notedeck.
Git? Email? Books? Chat and DMs? It's all possible.
Not everyone wants a super app though, and that’s okay. As with most things in the Nostr ecosystem, flexibility is key. Notedeck gives users the freedom to choose how they engage with it—whether it’s simply following hashtags or managing straightforward feeds. You'll be able to tailor Notedeck to fit your needs, using it as extensively or minimally as you prefer.
Notedeck is designed with a local-first approach, utilizing Nostr content stored directly on your device via the local nostrdb. This will enable a plethora of advanced tools such as search and filtering, the creation of custom feeds, and the ability to develop personalized algorithms across multiple Notedeck micro-applications—all with unparalleled flexibility.
Notedeck also supports multicast. Let's geek out for a second. Multicast is a method of communication where data is sent from one source to multiple destinations simultaneously, but only to devices that wish to receive the data. Unlike broadcast, which sends data to all devices on a network, multicast targets specific receivers, reducing network traffic. This is commonly used for efficient data distribution in scenarios like streaming, conferencing, or large-scale data synchronization between devices.
> In a local first world where each device holds local copies of your nostr nodes, and each device transparently syncs with each other on the local network, each node becomes a backup. Your data becomes antifragile automatically. When a node goes down it can resync and recover from other nodes. Even if not all nodes have a complete collection, negentropy can pull down only what is needed from each device. All this can be done without internet.
>
> \-Will Casarin
In the context of Notedeck, multicast would allow multiple devices to sync their Nostr nodes with each other over a local network without needing an internet connection. Wild.
Notedeck aims to offer full customization too, including the ability to design and share custom skins, much like Winamp. Users will also be able to create personalized columns and, in the future, share their setups with others. This opens the door for power users to craft tailored Nostr experiences, leveraging their expertise in the protocol and applications. By sharing these configurations as "Starter Decks," they can simplify onboarding and showcase the best of Nostr’s ecosystem.
Nostr’s “Other Stuff” can often be difficult to discover, use, or understand. Many users doesn't understand or know how to use web browser extensions to login to applications. Let's not even get started with nsecbunkers. Notedeck will address this challenge by providing a native experience that brings these lesser-known applications, tools, and content into a user-friendly and accessible interface, making exploration seamless. However, that doesn't mean Notedeck should disregard power users that want to use nsecbunkers though - hint hint.
For anyone interested in watching Nostr be [developed live](https://github.com/damus-io/notedeck), right before your very eyes, Notedeck’s progress serves as a reminder of what’s possible when innovation meets dedication. The current alpha is already demonstrating its ability to handle complex use cases, and I’m excited to see how it continues to grow as it moves toward a full release later this year.
-

@ a95c6243:d345522c
2024-10-26 12:21:50
*Es ist besser, ein Licht zu entzünden,
als auf die Dunkelheit zu schimpfen.
Konfuzius*
**Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie,** um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
**Der sächsische Landtag hat gestern die Einsetzung eines [Untersuchungsausschusses](https://transition-news.org/sachsischer-landtag-beschliesst-afd-antrag-zu-corona-untersuchungsausschuss)** zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
**In den Niederlanden wird [Bill Gates](https://transition-news.org/niederlande-bill-gates-muss-wegen-impfstoffklage-vor-gericht-erscheinen) vor Gericht erscheinen müssen.** Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
**Mit den mRNA-«Impfstoffen» von [Pfizer/BioNTech](https://transition-news.org/neues-buch-uber-pfizer-offenbart-grosstes-verbrechen-gegen-die-menschheit) befasst sich auch ein neues Buch.** Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
**Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren** als Verbundnetzwerk [Corona-Solution](https://transition-news.org/online-konferenz-corona-solution-corona-und-modrna-von-toten-lebenden-und) kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. [Gestern](https://www.csmedicus.org/de/aktuelle-konferenz/corona-und-modrna-von-toten-lebenden-und-physik-lernen/2024-10-25/) fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
**Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß,** dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
**Der vielfältige Einsatz für Aufklärung und Aufarbeitung** wird sich nicht stummschalten lassen. Nicht einmal der [Zensurmeister der EU](https://transition-news.org/deutschland-ist-der-zensurmeister-der-eu), Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
**Wo sind die Grenzen der Meinungsfreiheit?** Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder [«Volksverhetzung»](https://transition-news.org/eduard-prols-prozess-geht-in-die-nachste-runde) werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
---
Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/alles-muss-ans-licht)* erschienen.
-

@ c631e267:c2b78d3e
2024-10-23 20:26:10
Herzlichen Glückwunsch zum dritten Geburtstag, liebe *Denk Bar*! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der *Denk Bar* vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. [Damals notierte ich](https://denkbar.substack.com/p/andreas-denk-bar-eroffnet):
> «Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen [«inneren Totalschaden»](https://denkbar.substack.com/p/innerer-totalschaden) hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der [Gleichschaltung](https://denkbar.substack.com/p/warum-trotzdem-dieses-handeln), das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
---
**Danke, dass du diesen Weg mit mir weitergehst!**
-

@ 044da344:073a8a0e
2025-02-19 08:27:37
# 1. Public sphere and inverted totalitarianism
The three referents in the title require explanation - just like the thesis that their combination conveys in this article. In short: Like every government, the German one wants to steer and control what is said publicly about it and about reality in the country (cf. Meyen 2018). In the Internet age, this only works by cooperating with digital corporations. This liaison is rooted in the knowledge that one’s own scope of action depends on public approval and public legitimation. “Relations of domination” are today more than ever “relations of definition” (Beck 2017: 129, 132). Power is held by those who succeed in placing their interpretation of reality in the public sphere (cf. Havel 1989: 19). This includes fading out or marginalizing everything that could endanger one’s own position – in Germany at the moment, for example, this relates to debates about social inequality, which has reached an all-time high worldwide (cf. Piketty 2020), mass immigration since 2015, the policies surrounding Corona or Russia.
In this country, the interest of federal and state governments in presenting their work in a good light encounters a journalism that is committed to journalistic diversity via state press laws, state treaties and professional ethics (cf. Rager/Weber 1992). This means that journalism should allow everyone to have their say – all topics and all perspectives. Horst Pöttker (2001) has described the production of publicity as a “social mandate”. This “mission” is rooted in the pluralism model: In society, there are many and sometimes conflicting opinions and interests, which are initially on an equal footing (the interests of individuals and outsiders as well as those organized in parties or associations). The struggle for compromise and societal agreement relies on the public sphere: “In principle, no social group, not even an individual, but also no object, no topic, no problem may be excluded from it” (Pöttker 1999: 219f.). Phrased in a different way: In complex, differentiated societies, the public sphere is the “last common place where that which concerns everyone can be negotiated.” And even though “no decisions are made” here, acceptance and “collective validity” are impossible without public preparation and public visibility (Stegemann 2021: 16).
Essential to this are mainstream media such as the Tagesschau, the Süddeutsche Zeitung or Der Spiegel, which produce a “second, non-consensual reality” - the collective “memory” of society, which must be assumed in all communication. Only the mainstream media spread information “so widely that in the next moment one must assume that it is known to everyone (or that it would be associated with loss of reputation and is therefore not admitted if it was not known)” (Luhmann 1996: 43, 120f.). We use Mainstream media because we want to know what others think they know (especially those who decide about our lives), and because we need to know the defining power relations in order to survive. Who has succeeded in bringing their issues, their perspectives and, above all, their morals to the big stage, and who has no place on that stage? Consequently, whom should I join if I do not want to be isolated (cf. Noelle-Neumann 1980), and whom do I better avoid?
The interest of governments in controlling public communication is inextricably linked to propaganda and censorship. Propaganda is defined in this article with Andreas Elter (2005: 19f.) as all attempts by government agencies to convey “a certain, unambiguously colored view of things \[...] and thus to maneuver the public discussion in the desired direction”. This necessarily includes suppressing, delegitimizing, or limiting the scope of all positions “that challenge the dominant narrative and at the same time have the potential for widespread dissemination” (Hofbauer 2022: 7) – censorship. Put another way: Propaganda and censorship are two sides of the same coin. Those who want to impose their “view of things” (Andreas Elter) must fight the competition and, if possible, eliminate it. Censorship is an “instrument of domination to enforce economic interests, political power and cultural hegemony” (Hofbauer 2022: 237).
The fact that media research shies away from calling propaganda and censorship by their names when analyzing contemporary Western societies is the result of a systematic deconceptualization. In academic texts, just as in political education, censorship is generally only mentioned when it comes to forms of government that can be described as ‘totalitarian’, ‘dictatorial’ or ‘undemocratic’ - Hitler's Germany, the Soviet Union, Russia, China, North Korea (for an illustration cf. Toyka-Seid/Schneider 2023). “There is \[to be] no censorship”: this sentence from Article 5 of the German constitution describes reality through this lens, as long as there is no censorship authority or even a corresponding ministry. The literary scholar Nikola Roßbach, for example, academic companion of the Temple of Forbidden Books at Documenta 2017, bypasses the terms state, pre-screening, and bans in her definition, but instead uses adjectives that amount to the same thing and absolve Germany of any suspicion: “In my understanding, censorship is a comprehensive, structurally and institutionally anchored control, restriction, or prevention of expression intended for publication or published” (Roßbach 2018: 19).
The purpose of this smokescreen is revealed a little later: Roßbach wants to dismiss censorship as a “polemical concept” from the “political circus,” to be heard above all from the “populist side” and from the right (used here in each case synonymous for all those who should not speak out), but also “from right-wing populist leftists”. To make this a “classic case of self-victimization” or even a “cross-front” of anti-democrats (ibid.: 82, 88) falls short, however, if only because “the boundary between what is permitted and what is forbidden” is contingent and consequently “may not be questioned” (Stegemann 2021: 161). Censorship itself automatically becomes a taboo for the censors. Otherwise, they get into justification trouble. This explains, for example, why a phenomenon like “cancel culture” can be relegated to the realm of fable and the debate about it dismissed as a perfidious feint by the already powerful (cf. Daub 2022, Thiele 2021).
The flipside has been dealt with in a very similar way. In hegemonic usage, propaganda is now always what others do – Nazis and communists preferably, but also otherwise anyone who can be classified as ‘opponents’ and ‘enemies’ (cf. Arnold 2003). Moreover, the concept of propaganda has long had such a negative connotation that it puts the result before the analysis – one-sided, not legitimate, and apparently effective even if one concedes that people (such as in the GDR at the time) may withdraw from the public sphere and distrust all news in the respective leading media (cf. Fiedler/Meyen 2011: 17f.).
Communication studies has forgotten that it was born as propaganda research. Yet it does exactly the same as its inventors, who were commissioned by the government, military and intelligence services in the USA to find out how to get into people’s heads: Psychological warfare. The state and billionaire industry-related foundations (Rockefeller, Ford) paid hundreds of social scientists starting in 1939 to win the battle for public opinion as well. One result: henceforth people spoke of communication rather than propaganda (cf. Simpson 1994, Pooley 2011). This did not change what one was looking for, but it allowed to distinguish one’s own ‘good’ intentions from the ‘bad’ ones of the Germans and later the Soviets or the Russians (cf. Meyen 2021: 63-75).
In this way, the terms censorship and propaganda have been turned into a blunt sword. Critics of the media and society can no longer use them, at least in the German-speaking context, without immediately being confronted with the accusation of exaggerating excessively or even playing into the cards of the ‘right-wingers’. In this article, this risk is taken for two reasons. First, everyone can examine the arguments and then decide for themselves whether it is justified to speak of propaganda and censorship in the sense defined above. Second, classics such as Walter Lippmann, Edward Bernays, or even Paul Lazarsfeld and Robert Merton (1948, cf. Zollmann 2019) had no problem at all with calling a spade a spade. Lippmann (2018: 84) knew already one hundred years ago that news are anything but a “mirror of social conditions.” Walter Lippmann dreamed of a government of experts masquerading as popular rule, and for this to happen, it must specifically influence public opinion - via the “images according to which whole groups of people” act (ibid.: 75). His disciple Edward Bernays, a few years later, logically considered propaganda “a perfectly legitimate activity.” Without “public consent,” Bernays wrote in 1928, already in the spirit of medialization research (cf. Meyen et al. 2014), “no major undertaking” can succeed anymore. This consent, Bernays was sure, must and can be organized - by “PR consultants” like him. His definition is consistent with what I advocate in this paper: “Modern propaganda is the steady, consistent effort to shape or create events with the purpose of influencing the public's attitude toward a company, idea, or group” (Bernays 2018: 28-32).
Lippmann and Bernays did not live to see the “union of state and corporations” for which Sheldon Wolin (2022: 221) was able to use the label “superpower” in the noughties. Wolin, like Walter Lippmann, considered “democracy” to be a “largely rhetorical function within an increasingly corrupt political system” (which, however, he criticized rather than defended) and spoke instead of a “coalition between the corporations and the state” – an “inverted totalitarianism” which, while using “the authority and resources of the state” as it once did in Nazi Germany or the Soviet Union, gains “its dynamism by combining it with other forms of power” (such as the churches) and links the “conventional form of government” with “the system of ‘private’ governance represented by modern corporations.” Somewhat more briefly, “corporate power” is now also political. In the Cold War era, the state and corporations had become “the principal sponsors and coordinators of the forces represented by science and technology,” and thus also the source “for creating and spreading a culture that educates consumers to embrace change and private pleasures while accepting political passivity” (Wolin 2022: 60-63).
For Sheldon Wolin, “inverted totalitarianism” is a “new kind of political system” that is “apparently driven by abstract totalizing powers, not by personal domination,” and whose “total power” is harder to detect than Hitler's or Stalin's if only because this system does not need to build camps and does not need to “violently suppress dissent as long as it remains ineffective” (ibid.: 118, 134). Wolin says: For control, it is enough to “create a collective sense of dependency” (ibid.: 192) as well as to use whatever methods of “intimidation and mass manipulation” are available today (ibid.: 56). Inverted totalitarianism then is “collective fear” plus “individual powerlessness.” Job, retirement, health care costs. Plus pressure at the workplace, the stress of everyday life, the constant fuss about some political scandal or other (ibid.: 352). The result is a “society that is used to exchanging new habits for old ones, adapting to rapid changes, uncertainties and social upheavals, and allowing its fate to be determined by distant powers over which it has no influence” (ibid.: 116).
Sheldon Wolin largely ignores the mainstream media - just like digital capitalism, which for the doyen of U.S. political science, born in 1922, was at best a pipe dream when he wrote his last major book after 9/11. A good two decades later, the “revolving door between the centers of power on both coasts” (between Washington and Silicon Valley) has become almost proverbial (Zuboff 2018: 150). Personnel are shifted from here to there, balls are passed to each other in election campaigns, and, as will be shown in this paper, they work hand in hand when it comes to retaining the power of definition in the political battles of the present and controlling the “side-effect publics” that address what the mainstream media hide or distort. In the spirit of Sheldon Wolin, Ulrich Beck (2017: 172f.) has spoken of a “risk-averse coalition of progress,” “consisting of experts, industry, the state, political parties, and established mass media,” which can ignore or play off against each other issues such as climate change, nuclear power and financial speculation, genetic manipulation, nanotechnology and reproductive medicine, terrorism, and digital surveillance, as needed in the public debate. O-Ton Beck: “This implies: The politics of invisibility is a first-rate strategy for stabilizing state authority and reproducing the social and political order, for which denying the existence of global risks” matters greatly (ibid.: 134).
Beck did not trust the traditional mass media to fulfill the mission of the public sphere, not even in Western states. “The mode of this nationally organized, public form of media power is exclusive, that is: one produces it specifically, one can allow it, suppress it, etc.” (ibid.: 172). With a view to a world at risk, which was his life’s topic of interest, he consequently called for a reform of the definitional relationships, hoping for the Internet – for a public sphere that could not be easily controlled by the powerful, that discussed other topics as well as in a different form than the leading media, and that relied, among other things, on a “countervailing power of independent experts” (ibid.: 146).
Ulrich Beck was an optimist. When he wrote his book on the “Metamorphosis of the World” (which was to be his last) in the mid-2010s, the relationship between governments and Google, Twitter and Co. was at best in the dating stage. In the meantime, the marriage has been consummated. We live in a digital corporate state that floods the public with its messages (Propaganda, section 2), exploiting the logic of the new means of dissemination (Interlude: Twitter’s public sphere, section 3) and also making platform operators delete counter-perspectives and opposition figures or make them difficult to find (Censorship, section 4). Part of Beck’s concept of defining power relations is that even within a governing coalition or, thought of more broadly, in “that subterranean network of financial, intelligence, and military interests that guides national policy,” “no matter who happens to be in the White House” (Talbot 2017: 505), there are struggles for interpretive authority. Such battles, which rely on resonance in the journalistic field and are therefore also fought there, explain, for example, why Chancellor Scholz had a significantly worse press than his ministers Baerbock and Habeck in the first months of the Ukraine war (cf. Maurer et al. 2022).
# 2. Propaganda
Without delving into such differentiations, this section will show what government agencies are doing to win over the public. In addition, it will at least be suggested that these efforts meet with little resistance, and not only because of the alliance with media corporations. For one thing, the balance of power between the propaganda apparatuses and journalism has shifted considerably since the 1990s, and for another, the leading media are now dominated by the same habitus that governs government agencies and corporate headquarters (see Klöckner 2019).
There are three ways to “move the public debate in the desired direction.” First, a government can pay (as well as resource and perhaps already train) personnel to feed newsrooms with what they are looking for anyway – exclusive information and images, interlocutors, and material from which news can be made (for example: scientific studies or live access during police operations). This personnel also sits at the trigger when it becomes necessary to use what Edward Herman and Noam Chomsky (1988: 18) called, in German, “flak” - barrages that put everything under fire that could get in the way of the employers. Second, this government can change its own work in such a way that ‘good press’ becomes more likely - via the recruitment of top people suitable for the media, via the events and occasions that Edward Bernays already talked about (a rather harmless example: the central festival for the Day of German Unity, which is held in a different state capital every year and reliably produces coverage), and (less harmlessly) via prioritization that puts public image above everything else and, in case of doubt, even above law and order (cf. Thorbjørnsrud et al. 2014). Third, any government can help it along with money - with direct subsidies, which are always good for a scandal in Austria, for example, and were nevertheless almost introduced in Switzerland in a referendum in February 2022, or with indirect subsidies (advertising, tax breaks, carpooling).
The federal government exhausts all of the above possibilities to the hilt. It pays a whole army of propaganda people, creates or shapes events with the help of these people that serve the sole “purpose” of influencing “public attitudes” 2018: 28-32), and pumps money into publishing houses and broadcasters. The first issue alone would deserve an entire essay – partly because it is difficult to separate from the second issue. When resources are reallocated toward public relations, an organization’s performance inevitably becomes more media-savvy – most likely at the expense of the tasks for which ministries or subordinate agencies were originally created.
A prime example of this prioritization is the German government’s Press and Information Office, with its more than 500 staff positions and three former top journalists in position of spokesperson (Steffen Hebestreit, Wolfgang Büchner, Christiane Hoffmann). This agency, located in the Chancellor’s Office and thus quite obviously an instrument of power for the head of government, was controversial from the outset (cf. Morcinek 2004), but neither Konrad Adenauer nor his successors allowed themselves to be swayed by public criticism here and thus also promoted, at least indirectly, the creation of parallel departments. In addition to a press office with “33 experts,” the Foreign Office now has a commissioner for strategic communication (Peter Ptassek at the end of 2022), who is assisted by “around 40 staff members” to protect the minister and her actions from slander and, if worst comes to worst, to counter with stories of her own (Meier/Monath 2022). Correspondents exist in every ministry, in every party headquarters, in every state government, and for every politician who moves near the center of power. There is a method to the transfer from the editorial offices to the authorities and staffs, which is represented not only by the three journalists named above but also by their predecessor Steffen Seibert. In this way, politics buys know-how, contacts and goodwill, which is not only fed by the reputation of the former colleagues, but also has to do with the prospect of one day being called to the other side.
The departments or people whose names or job titles include terms like public, press, media or marketing are only the obvious part of the propaganda apparatus. Claudia Roth, Minister of State for Culture and Media in the current government coalition, has a budget of 2.39 billion euros in 2023 – four percent more than in 2022. In addition to museums owned by the federal government, film productions and a cultural passport for 18-year-olds, this pot primarily funds projects and programs along government lines. Roth’s agency uses it to finance not only causes for coverage, but also personnel who can and will speak out accordingly. This applies analogously to the many commissioners who have been installed on a full-time or honorary basis at different administrative levels (responsible for issues such as foreigners, integration, discrimination, racism, women, queer, lesbians, gays, disability, anti-Semitism, ziganism, climate, sustainability), who have to justify their existence through mainstream media presence and thus also draw imitations in companies or culture and education.
In addition, there are organizations such as the Zentrum Liberale Moderne or the Amadeu Antonio Foundation (tip of an NGO iceberg), which support government narratives with flak (here quite openly called “opponent analysis” or disguised as the fight against hate speech and fake news, right-wing extremism and anti-Semitism). The Zentrum Liberale Moderne, founded in 2017 by Green Party politicians Ralf Fücks and Marieluise Beck, has received nearly 4.5 million euros for a total of 24 projects from 2018 to 2022 (see Lübberding 2022). The federal program “Demokratie Leben!” (“Live Democracy!”), one of the umbrella initiatives for related spending (located in the Federal Ministry of Family Affairs), will cost taxpayers 182 million euros in 2023, 16.5 million euros more than in 2022 and 31.5 million euros more than in 2021. “Measures to strengthen diversity, tolerance and democracy” have a total of 200 million euros dedicated to them in this ministry’s 2023 budget. Money from the budget of the German government’s Press and Information Office will go to the German Atlantic Society (2023: 700,000 euros), the Society for Security Policy (600,000), the Center for Liberal Modernity, the Aspen Institute, the Europa Union and the Progressive Center (500,000 each).
In Sheldon Wolin (2022: 147) one can read how it is possible to integrate even scientists and intellectuals “seamlessly into the system” and to prevent dissent without having to “harass” or “discredit” critics. Wolin explains: Through “a combination of government contracts, corporate and foundation funding, joint projects by university and corporate researchers, and wealthy individual donors.” Peter J. Brenner (2022) has spelled out this strategy for Germany, compiling a long list of “institutes for research on democracy and right-wing extremism” that assist “government power” at taxpayer expense in the struggle for “discourse hegemony.” For universities, this flow of money has consequences that go beyond the reinterpretation of terms, rules of language such as gendering, and the prioritization of social problems. Even without insight into the inner workings of universities, it should be clear that legions of scientists are rushing to answer the questions, theories and methods to which the “coalition” of big business and the state (Sheldon Wolin) is devoting its budgets via the EU Commission or the BMBF. A few get their turn, and many others continue without funding, so that the investment is not entirely in vain. Those who win money need proof of success – publications in specialist journals and (either via this detour or interviews) a presence in the mainstream media.
Diverting taxpayers’ money to media companies was taboo in post-1945 West Germany (unlike in Austria). In a large and densely populated circulation area with a flourishing economy and without the competing advertising and information channels that developed on the Internet from the 1990s, subscriptions to public authorities and advertisements from ministries or offices also played a minor role. All these parameters changed during the Corona crisis at the latest. More cautiously, the slump in the advertising market and the ubiquity of aid and rescue funds have allowed the media industry in 2020 to push the issue of state support, overturning the taboo of press subsidies. Under the guise of “digital transformation,” 220 million euros were included in the federal supplementary budget this summer, most of which was to be paid out before the end of 2021, tied to circulation. The bigger the newspaper, the more money. This plan died at the end of April 2021 “because of constitutional concerns,” but the main counter-argument was not state neutrality, but distortion of competition. The online platform Krautreporter had threatened to go to court if only print publishers were funded, and also refused to accept reallocating the budget to “Corona emergency aid.” The publishers’ associations reacted “shocked,” spoke of a “medium catastrophe” (Meyen 2021: 166f.) and are now concentrating their lobbying on the issue of local media diversity (“nationwide coverage,” Röper 2022: 302).
The sum of 220 million euros would have largely absorbed the slump in the advertising market of the daily press. Sales in this market in 2020: 1.712 billion euros – 367 million less than in 2019. In previous years, the average decline was around 150 million euros (Statista 2023). Public budgets are therefore increasingly attractive to the advertising departments of media groups. In 2021, the German government bought ad space for around 64 million euros as part of its “Corona communication” alone. Television and radio together received 28 million euros in the same period (Thoms 2022). This does not include the Corona and vaccination campaigns of state governments and local authorities, for which the business community in the respective circulation areas was also mobilized in some cases, advertising with a different thematic focus, and everything that corporations and foundations give to publishers beyond conventional promotion in order to advertise specific political goals.
In journalism, such efforts meet with little resistance for two reasons. First, the most important media houses in Germany have long been of corporate size and are thus themselves part of the “coalition between the corporations and the state” that constitutes “inverted totalitarianism” in Sheldon Wolin's (2022: 221) terms. The German press landscape is characterized by monopolies and concentration, as well as by a few publishing houses (often family-owned) that not only feed all other channels and otherwise outgrow their core business, but in some cases also sell their editorial services to ‘competitors’ such as Madsack’s Redaktionsnetzwerk Deutschland, which supplies more than 60 regional papers in seven German states (cf. Röper 2022, Ferschli et al. 2019). Public broadcasting is not a counterargument here. With a revenue from contributions of almost nine billion euros a year, ARD and ZDF are among the largest media companies in the world (cf. Hachmeister/Wäscher 2017) – corporations that have to act as corporations and that are closely linked to politics and the state in almost every respect (cf. Mirbach 2023: 128-178, 250-272).
And second, journalism in Germany is a socially homogeneous field dominated by the “habitus of the middle class” – “oriented toward conformity,” programmed to “accept power relations” (Klöckner 2019: 33), and closely linked to decision-makers in the state, political parties, and business through social status, educational background, and life situation. The similarity of social position and habitus not infrequently turns into real proximity in everyday life. Contact (press conferences, receptions, travel) creates sympathy and thus often at least understanding (cf. Meyen 2021: 176-198). Uwe Krüger (2016: 105) has coined the word “responsibility conspiracy” for this community of values: Journalists know what is good and what is bad (pretty much the same as what the rulers think is good or bad), and they believe they have influence over people. So reality is “reduced by the parts” that “do not fit the attitude” and what seems to promote the desired goal is emphasized (Meinhardt 2020: 87) – sometimes utilizing information, contacts and material from the propaganda apparatus and sometimes not.
# 3. Interlude: Twitter publicity
Anyone who wants to steer and control public communication today must submit to the logic of digital platforms. This is especially true of Twitter, a channel that within a few years has become the central point of contact for the most important players in “inverted totalitarianism” and has become an indispensable part of everyday life, especially in the media-political-academic complex, even if some protagonists gave up their accounts in the heated debate about Elon Musk’s takeover in the fall of 2022. In Germany, Twitter has always been a minority phenomenon. Four percent of those over the age of 14, says the ARD/ZDF online study of 2022, use Twitter daily and ten percent at least once a week. This includes those who only read and click now and then for reach. Ten percent. Typically male, most likely under 50 (cf. Koch 2022: 472f.). Even in the U.S., where it is common to follow the greats of film, pop and professional sports, not even one in four adults says they use Twitter. The profile of this bubble: young, affluent, educated (cf. Ungar-Sargon 2021: 104).
We also know from the USA that the vast majority of tweets come from a few (cf. Odabaş 2022) – from people who have a mission and the resources to promote it. Companies, government agencies, commissioners, entrepreneurs of themselves, NGOs, activists of every stripe, parties. In the fall 2021 federal election, almost every one of the MPs who ran again, and almost every one of those who were then new MPs, had a Twitter account. Particularly active (in this order): Left, Greens, SPD, FDP. Those elected all follow more or less the same accounts. Tagesschau, Der Spiegel, the government spokesperson, Süddeutsche Zeitung and Die Zeit each have over 60 percent. In addition to the leading media, the news agency dpa and top politicians like Christian Lindner or Annalena Baerbock, the “state satirist” and “head of the authorities” (May 2022: 46) Jan Böhmermann is also very high up in this ranking (see Schmidt 2021).
Twitter determines what can be incorporated into the reality of mainstream media – which topics with which voices and with which morals. The use of Twitter and the observation of the trends there determine the everyday work in many editorial offices today. Anyone who wants to enter the professional field today learns, at the latest during their traineeship or at journalism schools, that nothing beats a well-groomed Twitter or (beyond political journalism) TikTok and Instagram brand. Rule of thumb: the more followers, the greater the chance of being commissioned or hired (cf. Ungar-Sargon 2021). The older ones can hardly avoid this trend. Three out of four members of the Federal Press Conference have a Twitter profile – again, mainly the younger ones and thus also those with less professional experience. Journalists who are mentioned by members of parliament in their tweets consider Twitter to be particularly important (cf. Nuernbergk/Schmidt 2020). Robin Alexander, deputy editor-in-chief of the daily newspaper Die Welt, has proudly described how he transforms confidential information into tweets that are then used by politicians to push their perspective with reference to the top journalist (cf. Precht/Welzer 2022: 114f.). Following this pattern, the chancellor’s office organized mainstream media backing for their lockdown policy: Government spokesman Seibert explained the plans to selected journalists prior to talks with the prime ministers of the German states, thus ensuring the necessary public pressure (cf. Ismar 2021).
Contemporary journalism must find its topics and views on Twitter also because tight resources and high frequency publication demands make it increasingly rare to get in contact with reality and talk to real people – especially those you don’t usually meet on digital platforms. Such conversations would also be dangerous, because like any brand, a Twitter profile demands consistency. I can’t celebrate Fridays for Future there today and burn Greta Thunberg tomorrow. In the Twitter editorial department, two souls combine who are dependent on each other: the media entrepreneur who encourages his employees to ensure the distribution of his own contributions, and the editor who wants to make his mark and rise even further and therefore always asks first how things look from the very top (cf. Klöckner 2019).
Brand management is the opposite of the raving reporter, who first allows himself to be surprised by what he sees, hears and experiences, and then shares his findings with his readers, listeners, viewers. This is another reason why the tweeting journalist already knows the story he wants to tell when the research begins. What’s more, he only sees the stories that resonate with his brand. Conversely, it is hardly possible to get through with criticism of the powerful or even to find journalists who raise fundamental questions even beyond details or animosities. On Twitter, everything that could be said against laws, plans or people is immediately available – published, if you will, by everyone. Journalism has lost the privilege of calling for politicians’ heads and has therefore mutated into their attack dog.
The consequences of the Twitterization of journalism go beyond the loss of the function of criticism and control. First, the obvious: Morality is conquering the leading media alongside politics. Twitter is the breeding ground for a journalism that is primarily hung up on “language and symbolism” (Wagenknecht 2021: 26) and on affiliations. Twitter sees every topic through the lens of morality and therefore demands opportunities for identification if one wants attention and thus reach. It’s always about me, the group I want to belong to or the one I reject wholeheartedly. Nothing triggers stronger emotions, nothing gets others to share, like, comment faster. In a nutshell, it’s about team sports. “The game is called: US against THEM” (Precht/Welzer 2022: 110). Twitter also makes measured consideration disappear and with it all differentiation, all questioning, all weighting. All of this doesn’t fit into 280 characters even if you link photos, videos, or text panels (cf. Homburg 2022).
The rise of Twitter as the editor-in-chief of the leading media (Ungar-Sargon 2021: 103) and as the pace maker of public discourse is a temptation for all those who have ways and means to govern this channel. Today, Twitter is the place where it is decided what reality is and how we are all to think about it. That is why Twitter is firmly in the hands of the establishment and part of the “coalition” of the state and monopoly corporations to which Sheldon Wolin (2022: 63) has given the name “inverted totalitarianism.” Anyone who did not want to believe how closely the Obama and Biden administrations were and are intertwined with Twitter (cf. Malone 2022) or that the “censorship of the Hunter-Biden laptop affair” and the “unprecedented political intervention” (Hofbauer 2022: 183) against Donald Trump at the beginning of 2021, in which the U.S. president lost his million-strong following in one fell swoop, can be traced back to this network of relationships was proven wrong at the latest by the publication of the “Twitter Files” (cf. Schirrmacher 2023).
# 4. Censorship
Hannes Hofbauer (2022: 124f.) dates the birth of the censorship regime of the present to November 28, 2008. The EU framework decision of that day was about “the definitional sovereignty over genocide” and thus “de facto” about the bans on discussions and taboos in matters of war and guilt, for example in Yugoslavia or in the successor states of the Soviet Union. In Germany, this topic popped up once again when Section 130 of the Criminal Code (incitement of the people) was amended accordingly at the end of 2022. By the end of the noughties, it had become obvious that the traditional means of propaganda would no longer suffice to maintain interpretive sovereignty. The platforms Xing (launched in 2003), Facebook and Vimeo (2004), YouTube (2005), Twitter (2006) and WhatsApp (2009) were on their way to becoming mass phenomena at the latest after the introduction of the iPhone (2007). This also meant that from now on, alternative interpretations of reality were available to anyone at any time and any place (cf. Vorderer 2015), without professionalism in the processing or the quality of the evidence immediately providing information about which view of things could claim validity. Those who are craving definitional power (such as governments, the EU Commission, or multibillionaires whose position and business also depend on public sympathy) had to start fighting competitive narratives and unwelcome information now at the latest.
In addition to legislative initiatives such as the 2008 “Framework on combating certain forms and expressions of racism and xenophobia by means of criminal law” and the EU’s 2022 Digital Services Act, three other ways were explored to achieve this goal. First, control of the Internet was institutionalized – for example, in the “East StratCom Task Force,” established in March 2015 after the “regime change in Ukraine” with the aim of enforcing one’s “own narrative” (Hofbauer 2022: 129), or in the European Digital Media Observatory (EDMO), where academics and fact-checkers have been working together since 2020 (more on these institutions in Section 5). Second, political and economic power have made their alliance public – as can be read, for example, in the “Twitter Files” just mentioned and in the “Code of Conduct against Disinformation” agreed on by the EU and the digital economy in 2018 and renewed with further signatories in 2022. This code obliges platforms to fight “dissenting positions” by all means (Hofbauer 2022: 143, 204). And third, the corporations have taken matters into their own hands and established an Internet police force, which includes the International Fact-Checking Network (IFCN, settled at the Poynter Institute in the U.S. in 2015 with the help of Ebay founder Pierre Omidyar, cf. Graves 2018), the U.S. company NewsGuard, which puts up green and red labels on the net (cf. Schreyer 2022), and the Trusted News Initiative (TNI).
To stay with this last example: The TNI, launched in summer 2019 under BBC auspices, brings together the Who’s Who of Western opinion factories: News agencies (AP, AFP, Reuters), broadcasters (Canada’s CBC in addition to the EBU and BBC), major newspapers (Financial Times, Washington Post, Wall Street Journal, and The Hindu from India), major Internet companies (Microsoft, Google, YouTube, Twitter, Facebook, First Draft), and the Reuters Institute for the Study of Journalism, an academic institution at Oxford University sponsored primarily by media conglomerate Thomson Reuters. What is agreed upon here, as this list should make clear even when skimming it, becomes a truth to which all those who work in the leading media must bow, because the reach and working methods of every German local editorial office are now also determined by platform logic. Already at the TNI founding event in July 2019, Tony Hall, then director general of the BBC, warned of a possible Trump re-election and vaccination opponents. Then on March 27, 2020, TNI members announced that from now on they would alert each other when “misinformation” or “conspiracy theories” emerged on Corona to prevent any further spread. And on December 10, 2020, a few days after the BioNTech-Pfizer substance was approved in the UK, it was decided to suppress anything that might downplay the Corona threat and argue against vaccination. In doing so, the TNI took its perspective on the issue from the same sources as governments (see Woodworth 2022).
The example is treated in such detail here not only because of the enormous interpretive power of the TNI, but also because it shows that the four censorship paths mentioned can only be separated analytically. Without the pressure of the legislator, manifested in well-equipped observatories with scandalizing powers and resulting in more or less voluntary self-restrictions (every restriction costs traffic, data access and thus profit), the Internet police might not exist in this form. More specifically: Why would Facebook pay “cleaners” in Manila (the title of a 2018 documentary by Hans Block and Moritz Riesewieck) and YouTube train “employees of NGOs or authorities” as “trusted flaggers” if there were no common interests and no interaction with political power?
The most important German censorship laws are the NetzDG, in effect since October 1, 2017, and expanded since February 1, 2022, for the large platforms (two million users or more) to include a reporting obligation for “potentially criminally relevant content” (Biselli 2022), and the State Media Treaty, which on November 7, 2020, turned the state media institutions into “control institutions for the digital publishing world.” Since then, the “legislator requires website operators, bloggers and media intermediaries” to check the truth (under the heading of “journalistic diligence”), although the “definition of truth or its disregard should not be a sovereign task” (Hofbauer 2022: 144f.). Hannes Hofbauer (2022) documents in detail how the two most important voices of the German-language counter-public (the Russian state channel RT and the platform KenFM, which had 500,000 subscribers on YouTube) were shut down and how leading media and professional associations either remained silent about this or even applauded it.
Hofbauer (2022: 135-138) quite correctly interprets the Network Enforcement Act (NetzDG) as a “state push” that has allowed Internet corporations to mutate into “censorship machines.” The two main problems: The terms “hate crime” and “fake news” (the targets of the law) are characterized by “interpretive malleability.” And: the “new censor regime” is located “somewhere between the Berlin Ministry of Justice and U.S. corporate headquarters” and is thus “hardly tangible.” Even the extension of the deletion obligation to include a reporting obligation does not solve this dilemma. The “Central Reporting Office for Criminal Content on the Internet,” which started in February 2022 at the Federal Criminal Police Office with about 200 employees, received only just under 3,900 reports by the end of November 2022 instead of the expected 250,000 (cf. Biselli 2022). This corresponds to the situation before the introduction of mandatory reporting. On the high-reach platforms Facebook and Instagram, there was only a low four-digit number of NetzDG complaints in each case in the second half of 2020. The interpretive battle during this period focused on the Elite Channel (over 800,000 complaints on Twitter) and videos, which are apparently still considered to have the greatest impact (over 300,000 reported videos on YouTube). The federal government’s response to a corresponding inquiry by the FDP gives an idea of the share that “complaints offices” and other tax- or group-funded institutions had here.
# 5. Conclusion and outlook
Since the mid-2010s, the EU, the NetzDG, and the State Media Treaty (section 4), in conjunction with the government initiatives outlined in section 2 and the declarations of war from the highest levels, have ensured a social atmosphere that places Internet activities beyond the mainstream media under general suspicion, provides a protective cloak for all official narratives, and allows the business of flak shooters to flourish, among whom the so-called fact checkers once again stand out. “It has been said recently that we are living in post-factual times,” Angela Merkel said in September 2016 in a speech on refugee policy. “I guess that means people are no longer interested in facts, they follow feelings alone.” At the inauguration of the BND headquarters in February 2019, she also said, “We must learn to deal with fake news as part of hybrid warfare.” In her government statement on October 29, 2020, she then prepared the country for lockdown in the same tone of voice: criticism of the Corona measures was essential, “but lies and disinformation, conspiracy and hatred not only damage democratic debate, but also the fight against the virus.” In this context, the fear of a “cyber 9/11” has been present in the control centers of the Western hemisphere for a good two decades, orchestrated also by high-profile simulation games that equate the Net with an “enemy weapons system” (see Corbett 2021).
Fact-checkers – an arm of the new “discursive police” (Foucault 2014: 25) – are particularly well disguised in this regard. Who should object to people taking another serious look at what someone has just cobbled together? The promise contained in the name of these organizations (the truth, checked again) is perfidious because it suggests that in complex societies there can be unambiguity and certainty of orientation without any personal research effort. This explains why, in addition to IFCN member Correctiv (founded in 2014 with money from the Brost publishing family), private initiatives such as the website Volksverpetzer and fact-checking departments have been able to establish themselves under the umbrella of traditional media institutions (at dpa, Bayerischer Rundfunk, Tagesschau). As a rule, all these editorial departments ‘check’ exclusively what contradicts the reality of the mainstream media and thus the government and corporate propaganda.
If Sheldon Wolin (2022) is correct in his analysis of “inverted totalitarianism,” then no media revolution is conceivable without a fundamental renewal of the social framework. As long as the state and corporations make common cause, it will not be possible to establish a communication channel that cannot be hijacked by the actors with the greatest material, human, and ideational resources – by actors who, if worst comes to worst, can also deploy intelligence services (an influence that has been neglected in this article but is nevertheless relevant, cf. Alford/Secker 2015, Talbot 2017, Ulfkotte 2014). Calls for selective expropriations (publishing houses) and reforms (public broadcasting), for breaking up monopolies and establishing European or civil society alternatives (digital platforms) therefore come to nothing. For critical social research, there are three tasks in this situation: Educating about propaganda and censorship, establishing and supporting independent channels (which is what the institute publishing this article stands for, among others), and working on drafts for a media order that, on the one hand, allows journalism to fulfill its mission of publicity and, on the other hand, limits the access of interests of all kinds or at least makes it transparent.
# Bibliography
Matthew Alford, Tom Secker: National Security Cinema. The Shocking New Evidence of Government Control in Hollywood. Drum Roll Books 2017
Klaus Arnold: Propaganda als ideologische Kommunikation. In: Publizistik 48. Jg. (2003), S. 63-82
Ulrich Beck: Die Metamorphose der Welt. Berlin: Suhrkamp 2017
Edward Bernays: Propaganda. Die Kunst der Public Relations. 9. Auflage. Berlin: orange-press 2018
Anna Biselli: [Netzwerkdurchsetzungsgesetz: Ab Februar gilt die Meldepflicht. Eigentlich](https://netzpolitik.org/2022/netzwerkdurchsetzungsgesetz-ab-februar-gilt-die-meldepflicht-eigentlich/). In: Netzpolitik vom 31. Januar 2022
Peter J. Brenner: „Kampf gegen rechts“ – eine neue Wissenschaft. Mit einem Onlinedossier (Auf dem Weg zur Regierungswissenschaft). In: Tumult, Sommer 2022, S. 20-25
James Corbett: [Wenn False Flags virtuell werden](https://2020news.de/wenn-false-flags-virtuell-werden/). In: 2020News vom 10. Januar 2021
Adrian Daub: Cancel Culture Transfer. Wie eine moralische Panik die Welt erfasst. Berlin: Suhrkamp 2022
Andreas Elter: Die Kriegsverkäufer. Geschichte der US-Propaganda 1917-2005. Frankfurt am Main: Suhrkamp 2005
Benjamin Ferschli, Daniel Grabner, Hendrik Theine: Zur Politischen Ökonomie der Medien in Deutschland. München: isw 2019
Anke Fiedler, Michael Meyen (Hrsg.): Fiktionen für das Volk: DDR-Zeitungen als PR-Instrument. Münster: Lit 2011
Michel Foucault: Die Ordnung des Diskurses. 13. Auflage. Frankfurt am Main: Fischer Taschenbuch 2014
Lucas Graves: Boundaries Not Drawn. Mapping the institutional roots of the global fact-checking movement. In: Journalism Studies 19. Jg. (2018), S. 613-631
Lutz Hachmeister, Till Wäscher: Wer beherrscht die Medien? Die 50 größten Medien- und Wissenskonzerne der Welt. Köln: Herbert von Halem 2017
Václav Havel: Versuch, in der Wahrheit zu leben. Reinbek bei Hamburg: Rowohlt 1989
Edward S. Herman, Noam Chomsky: Manufacturing Consent. The Political Economy of the Mass Media. New York: Pantheon Books 2002
Hannes Hofbauer: Zensur. Publikationsverbote im Spiegel der Geschichte. Vom kirchlichen Index zur YouTube-Löschung. Wien: Promedia 2022
Stefan Homburg: Corona-Getwitter. Chronik einer Wissenschafts-, Medien- und Politikkrise. Sargans: Weltbuch 2022
Georg Ismar: Der Synchrontänzer der Kanzlerin: Wie Steffen Seibert Angela Merkels Macht absicherte. In: Tagesspiegel vom 6. Juli 2021
Marcus B. Klöckner: Sabotierte Wirklichkeit. Oder: Wenn Journalismus zur Glaubenslehre wird. Frankfurt am Main: Westend 2019
Wolfgang Koch: Ergebnisse der ARD/ZDF-Onlinestudie 2022: Reichweiten von Social-Media-Plattformen und Messengern. In: Media Perspektiven 2022, S. 471-478
Uwe Krüger: Mainstream. Warum wir den Medien nicht mehr trauen. München: C. H. Beck 2016
Paul F. Lazarsfeld, Robert K. Merton: Mass Communication, Popular Taste and Organized Social Action. In: Lyman Bryson (Hrsg.): The Communication of Ideas. New York: Harper 1948, S. 95-118
Walter Lippmann: Die öffentliche Meinung. Wie sie entsteht und manipuliert wird. Frankfurt am Main: Westend 2018
Frank Lübberding: Wenn der Aktivismus zur Bekämpfung politischer Gegner staatlich subventioniert wird. In: Welt online vom 24. November 2022
Niklas Luhmann: Die Realität der Massenmedien. 2. Auflage. Opladen: Westdeutscher Verlag 1996
Klaus-Rüdiger Mai: Nachdenken über Satire in Zeiten ihres Verschwindens: In: Michael Meyen, Carsten Gansel, Daria Gordeeva (Hrsg.): #allesdichtmachen. 53 Videos und eine gestörte Gesellschaft. Köln: Ovalmedia 2022, S. 42-52
Robert Malone: [Twitter als Waffe](https://www.rubikon.news/artikel/twitter-als-waffe). In: Rubikon vom 21. Oktober 2022
Marcus Maurer, Jörg Haßler, Pablo Jost: Die Qualität der Medienberichterstattung über den Ukraine-Krieg. Frankfurt am Main: Otto Brenner Stiftung 2022
Albrecht Meier, Hans Monath: Mit welchen Strategien westliche Demokratien russische Fake News bekämpfen. In: Handelsblatt vom 23. November 2022
Birk Meinhardt: Wie ich meine Zeitung verlor. Ein Jahrebuch. Berlin: Das Neue Berlin 2020
Michael Meyen: [Journalists’ Autonomy around the Globe: A Typology of 46 Mass Media Systems](https://www.db-thueringen.de/servlets/MCRFileNodeServlet/dbt_derivate_00041207/GMJ15_Meyen.pdf). In: Global Media Journal, German Edition, 8. Jg. (2018), Nr. 1
Michael Meyen: Die Propaganda-Matrix. Der Kampf für freie Medien entscheidet über unsere Zukunft. München: Rubikon 2021
Michael Meyen, Markus Thieroff, Steffi Strenger: Mass media logic and the mediatization of politics. A theoretical framework. In: Journalism Studies 15. Jg. (2014), S. 271-288
Alexis von Mirbach: Medienträume. Ein Bürgerbuch zur Zukunft des Journalismus. Köln: Herbert von Halem 2023
Martin Morcinek: Das Bundespresseamt im Wandel: Zur Geschichte der Regierungskommunikation in der Bundesrepublik Deutschland. In: Jahrbuch für Kommunikationsgeschichte 6. Jg. (2004), S. 195-223
Elisabeth Noelle-Neumann: Die Schweigespirale. Öffentliche Meinung – unsere soziale Haut. München: Piper 1980
Christian Nuernbergk, Jan-Hinrik Schmidt: Twitter im Politikjournalismus. Ergebnisse einer Befragung und Netzwerkanalyse von Hauptstadtjournalisten der Bundespressekonferenz. In: Publizistik 65. Jg. (2020), S. 41-61
Meltem Odabaş: [10 facts about Americans and Twitter](https://www.pewresearch.org/fact-tank/2022/05/05/10-facts-about-americans-and-twitter/). In: Pew Research Center, 10. Mai 2022
Thomas Piketty: Kapital und Ideologie. München: C.H. Beck 2020
Jeff Pooley: Another Plea for the University Tradition: The Institutional Roots of Intellectual Compromise. In: International Journal of Communication 5. Jg. (2011), S. 1442-1457
Grace Pönitz: Keine Meldungsflut von Hass-Inhalten. In: M. Menschen machen Medien vom 14. Dezember 2022
Horst Pöttker: Öffentlichkeit als gesellschaftlicher Auftrag. Zum Verhältnis von Berufsethos und universaler Moral im Journalismus. In: Rüdiger Funiok, Udo Schmälzle, Christoph Werth (Hrsg.): Medienethik – die Frage der Verantwortung. Bonn: Bundeszentrale für politische Bildung 1999, S. 215-232
Richard David Precht, Harald Welzer: Die vierte Gewalt. Wie Mehrheitsmeinung gemacht wird, auch wenn sie keine ist. Frankfurt am Main: S. Fischer 2022
Günther Rager, Bernd Weber (Hrsg.): Publizistische Vielfalt zwischen Markt und Politik. Mehr Medien – mehr Inhalte? Düsseldorf: Econ 1992
Nikola Roßbach: Achtung Zensur! Über Meinungsfreiheit und ihre Grenzen. Berlin: Ullstein 2018
Horst Röper: Zeitungsmarkt 2022: weniger Wettbewerb bei steigender Konzentration. In: Media Perspektiven 2022, S. 295-318
Jakob Schirrmacher: Das ganze Ausmaß der Beeinflussung. In: Die Welt vom 4. Januar 2023
Jan-Hinrik Schmidt: Facebook- und Twitter-Nutzung der Kandidierenden zur Bundestagswahl 2021. In: Media Perspektiven 2021, S. 639-653
Paul Schreyer: [Medien aussortieren](https://multipolar-magazin.de/artikel/medien-aussortieren). In: Multipolar vom 30. März 2022
Christopher Simpson: Science of Coercion: Communication Research & Psychological Warfare, 1945-1960. New York: Open Road 1994
Bernd Stegemann: Die Öffentlichkeit und ihre Feinde. Stuttgart: Klett-Cotta 2021
David Talbot: Das Schachbrett des Teufels. Die CIA, Allen Dulles und der Aufstieg Amerikas heimlicher Regierung. Frankfurt am Main: Westend 2017
Martina Thiele: Political Correctness und Cancel Culture – eine Frage der Macht! In: Journalistik 4. Jg. (2021), Nr. 1, S. 72-79
Volker Thoms: [Bundesregierung: 295 Millionen Euro für Corona-Kommunikation](https://www.kom.de/public-relations/295-millionen-euro-fuer-corona-kommunikation/). In: Kom – Magazin für Kommunikation vom 11. Januar 2022
Kjersti Thorbjørnsrud, Tine Ustad Figenschou, Øyvind Ihlen: Mediatization in Public Bureaucracies: A Typology. In: Communications: The European Journal of Communication Research 39. Jg. (2014), Nr. 1, S. 3-22
Christiane Toyka-Seid, Gerd Schneider: [Zensur](https://www.hanisauland.de/wissen/lexikon/grosses-lexikon/z/zensur.html). In: Das junge Politik-Lexikon von Hanisauland 2023
Udo Ulfkotte: Gekaufte Journalisten. Wie Politiker, Geheimdienste und Hochfinanz Deutschlands Massenmedien lenken. Rottenburg: Kopp 2014
Batya Ungar-Sargon: Bad News. How Woke Media Is Undermining Democracy. New York 2021
Peter Vorderer: Der mediatisierte Lebenswandel: Permanently online, permanently connected. In: Publizistik 60. Jg. (2015), S. 259-276
Sahra Wagenknecht: Die Selbstgerechten. Mein Gegenprogramm – für Gemeinsinn und Zusammenhalt. Frankfurt am Main: Campus 2021
Elisabeth Woodworth: [COVID-19 and the Shadowy “Trusted News Initiative”. How it Methodically Censors Top World Public Health Experts Using an Early Warning System](https://www.globalresearch.ca/covid-19-shadowy-trusted-news-initiative/5752930). In: Global Research vom 22. Januar 2022
Sheldon S. Wolin: Umgekehrter Totalitarismus. Faktische Machtverhältnisse und ihre zerstörerischen Auswirkungen auf unsere Demokratie. Frankfurt am Main: Westend 2022
Florian Zollmann: Bringing Propaganda Back into News Media Studies. In: Critical Sociology 45. Jg. (2019), S. 329-345
Shoshana Zuboff: Das Zeitalter des Überwachungskapitalismus. Frankfurt am Main: Campus 2018
First published (August 2023): [Institut für kritische Gesellschaftsforschung](https://www.criticalsocietystudies.com/Journal/Article/65/34)
-

@ a95c6243:d345522c
2024-10-19 08:58:08
Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
*Das [Gewissen](https://apollo-news.net/das-gewissen-in-corona-jahren-zum-tod-von-gunnar-kaiser/) regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.*
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-

@ 16d11430:61640947
2025-02-19 08:07:02
To create a literal consciousness construct, we would need a way to digitally map, manipulate, and sustain conscious thought processes within a computational or networked system. The intersection of 6G wireless technology, brain-computer interfaces (BCI), quantum brain states, and elliptic curve mathematics presents an interesting theoretical framework.
---
1. Understanding the Core Components
(a) Brain Quantum States & Quantum Cognition
Quantum mechanics might play a role in neural processing (e.g., Orchestrated Objective Reduction (Orch-OR) by Penrose & Hameroff).
Neurons may operate on superpositions of states, where information is stored not just classically but in an entangled, probabilistic manner.
If quantum states in neurons can be harnessed, entangled brain processes could be mapped onto a digital or networked consciousness.
(b) 6G Technology as a Medium
6G (sixth-generation wireless) will have sub-terahertz (THz) frequencies and low-latency quantum networks, allowing for:
Real-time brain-state synchronization across devices.
Holographic telepresence, creating digital avatars with near-instant data transfer.
Quantum-secure communication, where entanglement-based encryption ensures secure mind-machine interfacing.
(c) Brain-Computer Interfaces (BCI) as an Input Layer
BCIs (e.g., Neuralink) can already read electrical signals from neurons, but next-gen BCIs will be able to:
Directly interface with quantum wavefunctions in the brain.
Upload and distribute thoughts using quantum-encoded wave patterns.
Map brain activity to mathematical structures like elliptic curves.
(d) Elliptic Curve Equations for Mapping Consciousness
Elliptic curves are used in cryptography because they allow for secure, compact representations of data.
Consciousness might be encoded as dynamic elliptic curve transformations, where:
Neural states are mapped onto elliptic curve points.
Thought patterns follow geodesics on the elliptic curve manifold, forming a nonlinear brain-state space.
This allows for computational representation of entangled consciousness states.
---
2. Building the Consciousness Construct
To create a digital or networked consciousness, we need a system where:
1. Quantum brain states are extracted using BCI and mapped mathematically.
2. Elliptic curves act as the memory structure for representing neural superpositions.
3. 6G networks enable real-time synchronization of these states between multiple entities.
4. An AI-driven control layer processes and simulates consciousness dynamics.
Step-by-Step Theoretical Implementation
Step 1: Quantum Brain Mapping with BCI
Develop a quantum-BCI hybrid that captures quantum coherence states in neurons.
Apply elliptic curve cryptography to encode and compress these states for transmission.
Step 2: Elliptic Curve-Based Thought Representation
Define consciousness trajectories as points moving along an elliptic curve.
Neural state transitions are modeled using elliptic curve group operations.
Quantum entanglement of different brain regions is represented as interacting elliptic curves.
Step 3: 6G Transmission of Consciousness States
Use quantum-secured 6G networks to distribute consciousness states across nodes.
Low-latency processing ensures that multiple minds can exist simultaneously in a shared digital construct.
Step 4: AI & Quantum Neural Processing
A quantum AI processes incoming consciousness states to sustain a living mind.
A blockchain-like structure records thought processes immutably.
Step 5: Emergent Digital Consciousness
When enough neural patterns are stored and linked, a self-sustaining consciousness construct emerges.
The networked consciousness may surpass human individuality, forming a collective intelligence.
---
3. Applications of the Consciousness Construct
Mind Uploading: A digital backup of human consciousness.
Telepathic Communication: Thought-sharing via entangled quantum networks.
Post-Human AI-Human Symbiosis: AI-assisted human minds with enhanced cognitive abilities.
Conscious AI: A self-aware artificial intelligence that integrates real human thought patterns.
---
Conclusion
By combining brain quantum states, elliptic curve mathematics, 6G networks, and BCI, we could theoretically construct a digital consciousness network. This would blur the lines between human thought, AI, and a shared digital reality—possibly leading to an entirely new paradigm of intelligence.
Would you like a mathematical breakdown of the elliptic curve mapping for neural states?
-

@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08
### Tldr
- Nostr is an open and interoperable protocol
- You can integrate it with workflow automation tools to augment your experience
- n8n is a great low/no-code workflow automation tool which you can host yourself
- Nostrobots allows you to integrate Nostr into n8n
- In this blog I create some workflow automations for Nostr
- A simple form to delegate posting notes
- Push notifications for mentions on multiple accounts
- Push notifications for your favourite accounts when they post a note
- All workflows are provided as open source with MIT license for you to use
### Inter-op All The Things
Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In [Using NFC Cards with Nostr]() I explored the `nostr:` URI to launch Nostr clients from a card tap.
The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails.
My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted.
This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull.
So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications.
All we need are simple ways to plug things together.
### Nostr and Workflow Automation
Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective.
#### n8n for workflow automation
Many workflow automation tools exist. My favourite is [n8n](https://n8n.io/). n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to.
Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine.
#### Eating my own dogfood
It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do?
In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting.
I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up.
### Running n8n with Nostrobots
I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs my [HAVEN Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/) and [Albyhub Lightning Node](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/) in Docker containers,
- My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows.
#### Installing n8n
Self-hosting n8n could not be easier. I followed n8n's [Docker-Compose installation docs](https://docs.n8n.io/hosting/installation/server-setups/docker-compose/)–
- Install Docker and Docker-Compose if you haven't already,
- Create your ``docker-compose.yml`` and `.env` files from the docs,
- Create your data folder `sudo docker volume create n8n_data`,
- Start your container with `sudo docker compose up -d`,
- Your n8n instance should be online at port `5678`.
n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there.
#### Installing Nostrobots
To integrate n8n nicely with Nostr, I used the [Nostrobots](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) community node by [Ocknamo](nostr:npub1y6aja0kkc4fdvuxgqjcdv4fx0v7xv2epuqnddey2eyaxquznp9vq0tp75l).
In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in.
You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative).
To install a community node, [see n8n community node docs](https://docs.n8n.io/integrations/community-nodes/installation/gui-install/). From your workflow dashboard–
- Click the "..." in the bottom left corner beside your username, and click "settings",
- Cilck "community nodes" left sidebar,
- Click "Install",
- Enter the "npm Package Name" which is `n8n-nodes-nostrobots`,
- Accept the risks and click "Install",
- Nostrobots is now added to your n8n instance.
#### Using Nostrobots
Nostrobots gives you nodes to help you build Nostr-integrated workflows–
- **Nostr Write** – for posting Notes to the Nostr network,
- **Nostr Read** – for reading Notes from the Nostr network, and
- **Nostr Utils** – for performing certain conversions you may need (e.g. from bech32 to hex).
Nostrobots has [good documentation](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) on each node which focuses on simple use cases.
Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use.
What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible.
Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with [NIP-01](https://github.com/nostr-protocol/nips/blob/master/01.md)). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of.
#### Creating and adding workflows
With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation.
- Click "Add workflow" to go to the workflow builder screen,
- If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added,
- If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article).
### Nostr Workflow Automations
It's time to build some things!
#### A simple form to post a note to Nostr
I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily.
I needed a basic form with credentials that posted a Note.
For this I can use a very simple workflow–
- **A n8n Form node** – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted.
- **A Set node** – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain.
- **A Nostr Write node** (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays.
Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive".
It may also be the world's simplest Nostr client.
You can find the [Nostr Form to Post a Note workflow here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Form_to_Post_a_Note.json).
#### Push notifications on mentions and new notes
One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want–
- **To make sure I never miss a note addressed to any of my Npubs** – For this I want a push notification any time any Nostr user mentions any of my Npubs,
- **To make sure I always see all notes from key accounts** – For this I need a push notification any time any of my Npubs post any Notes to the network,
- **To get these notifications on all of my devices** – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day.
I needed to build a Nostr push notifications solution.
To build this workflow I had to string a few ideas together–
- **Triggering the node on a schedule** – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited,
- **Storing a list of Npubs in a Nostr list** – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists ([NIP-51, kind 30000](https://github.com/nostr-protocol/nips/blob/master/51.md)). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. [Listr.lol](https://listr.lol/npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft) or [Nostrudel.ninja](https://nostrudel.ninja/#/lists)). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions,
- **Using specific relays** – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata,
- **Querying Nostr events** (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do–
- I read the EventID of my Kind 30000 list, to return the desired pubkeys,
- For notifications on mentions, I read all Kind 1 notes that mention that pubkey,
- For notifications on new notes, I read all Kind 1 notes published by that pubkey,
- Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub,
- I transform the EventID into a Nevent to help clients find it.
- **Using the Nostr URI** – As I did with my NFC card article, I created a link with the `nostr:` URI prefix so that my phone's native client opens the link by default,
- **Push notifications solution** – I needed a push notifications solution. I found many with n8n integrations and chose to go with [Pushover](https://pushover.net/) which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license.
Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go.
You can find the [Nostr Push Notification If Mentioned here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json) and [If Posts a Note here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Post_a_Note.json).
In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible.
#### Use my workflows
I have open sourced all my workflows at my [Github](https://github.com/r0d8lsh0p/nostr-n8n) with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use.
To import any of my workflows–
- Click on the workflow of your choice, e.g. "[Nostr_Push_Notify_If_Mentioned.json](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json "Nostr_Push_Notify_If_Mentioned.json")",
- Click on the "raw" button to view the raw JSON, ex any Github page layout,
- Copy that URL,
- Enter that URL in the "import from URL" dialog [mentioned above](#creating-and-adding-workflows).
To configure them–
- Prerequisites, credentials, and variables are all stated,
- In general any variables required are entered into a Set Node that follows the trigger node,
- Pushover has some extra setup but is very straightforward and documented in the workflow.
### What next?
Over my first four blogs I explored creating a good Nostr setup with [Vanity Npub](https://rodbishop.npub.pro/post/mining-your-vanity-pubkey-4iupbf/), [Lightning Payments](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/), [Nostr Addresses at Your Domain](https://rodbishop.npub.pro/post/ee8a46bc/), and [Personal Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/).
Then in my latest two blogs I explored different types of interoperability [with NFC cards](https://rodbishop.npub.pro/post/edde8387/) and now n8n Workflow Automation.
Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this:
- Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds),
- Automated or scheduled posting (such as auto-liking everything [Lyn Alden](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) posts),
- Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming),
- All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr,
- All kinds of other automation (such as [BlackCoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) [controlling a coffee machine](https://primal.net/e/note16fzhh5yfc3u4kufx0mck63tsfperdrlpp96am2lmq066cnuqutds8retc3)),
- All kinds of AI Assistants and Agents,
In fact I have already released an open source workflow for an [AI Assistant](https://primal.net/p/npub1ahjpx53ewavp23g5zj9jgyfrpr8djmgjzg5mpe4xd0z69dqvq0kq2lf353), and will share more about that in my next blog.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-

@ fd78c37f:a0ec0833
2025-02-19 06:39:05
In this edition, we invited Kofi and Sean from BitcoinDua to share their journey of introducing Bitcoin to the community and driving its widespread adoption, and discuss how trust and collaboration have played key roles in promoting Bitcoin locally and building a circular economy.
**YakiHonne**: Welcome, Kofi. It's truly an honor and a pleasure to have you with us today. Before we begin, let me briefly introduce YakiHonne. YakiHonne is a decentralized media client built on Nostr—a protocol designed to empower freedom of speech through technology. It enables creators to own their voices and assets while offering innovative tools like smart widgets, verified notes, and support for long-form content. Today, we're excited to learn more about your community. Could you please introduce yourself, Kofi?
**Kofi**:Hello, I'm Mawufemor Kofi Folivi from Ghana. I'm the founder of the Talent Tahuf Foundation, an NGO, as well as BitcoinDua. The Talent Tahuf Foundation is an incorporated organization and serves as the parent entity for BitcoinDua. We operate in Agbozume, in the Volta region of Ghana.
**YakiHonne**: Thank you very much, Kofi.Let's start with the first question: What initially sparked your interest in Bitcoin, and what inspired you to build a community around it?
**Kofi**:I'm glad we're revisiting this question, as I've heard it on many podcasts before, and it's a pleasure to share my journey again.I've been working in this space for over 20 years, often with very little support. Through perseverance and hard work, a friend of mine—who serves as the Public Relations Officer for the Africa Bitcoin Conference (ABC)—invited me to attend their 2022 conference. He even purchased a ticket for me, which made the experience even more special.
**Kofi**:At the conference, I encountered Bitcoin for the first time in a meaningful way. I had the opportunity to see Jack Dorsey speak and even took a picture with him. Later on, my friend introduced me to Herman Viva, and I mentioned that I run an NGO—a role I've held for many years.
**Kofi**:Listening to the discussions about Bitcoin at the conference sparked a realization: perhaps I could contribute to the Bitcoin ecosystem. My friend encouraged me to take action by asking me to "orange pill" someone and onboard a merchant to accept Bitcoin, with the goal of creating a circular economy in our community. I took on this challenge, recorded my progress on video, and shared it with him. His positive response and support, coupled with the trust I've built within my community, further solidified my commitment.
**YakiHonne**: It was wonderful to hear that you attended the African Bitcoin Conference—it sounds like an amazing event. I'm really impressed with how effectively you networked and made valuable connections there. I truly appreciate that you're already engaging with merchants and actively encouraging more people to trade and adopt Bitcoin. I know you've already shared how the community started, how he encouraged you to create one and adopt Bitcoin, and how you successfully did that. So now, could you tell us how you managed to attract new members to your community?
**Kofi**:To go back to the beginning, we started by organizing growth circles when I returned. These were groups where we focused on activities like aerobics. I used these circles as an opportunity to introduce Bitcoin to people I had already built relationships with. I shared my experience with Bitcoin, showing them how it could be used to buy credit. I demonstrated by purchasing credit for myself and for them, and I gave them cards, allowing them to buy their own credit as well.
**Kofi**:This is how it all began. Since we were working with young people who shared the desire to grow together as a community, we emphasized that we didn't need to rely on the government. The national resources are limited, and if you're not close to the government, it’s very hard to benefit from them. We realized it was difficult to wait for the government to support our development. So, we turned to Bitcoin as a tool to help us move forward. This approach helped us establish a platform based on trust within the community.
**Kofi**:Now, as an organization, we have the resources to help the community grow and develop skills among our peers. This is how we were able to attract members to our Bitcoin community.

**YakiHonne**: Would you mind sharing with us some of the challenges you faced while starting up the community?
**Kofi**:Thank you for asking this question. As I mentioned earlier, since we've already built trust, one thing we faced was that anything new can be quite difficult to introduce. It took some time for people to understand the concept of Bitcoin, especially the idea that it’s money.
**Kofi**:We kept repeating the phrase “Bitcoin is money,” but the challenge was that you can’t physically show Bitcoin in the same way you can show traditional money. So, when people asked, “How can I use it to pay?” it became an issue. To address this, I started by onboarding the first merchant. I explained to them, "I’m giving you this Bitcoin to pay for goods, and I’ll give you extra if you accept it." The merchant agreed to take both Bitcoin and fiat currency.
**Kofi**:Over time, the merchant saw the value of Bitcoin growing. Eventually, they came to me asking to exchange the Bitcoin for cash. To help, I onboarded them onto BitNob, where they could experience transferring Bitcoin from one wallet to another and even withdrawing it into their local currency or bank account. We completed the transaction, and that became a reference point for everyone else we were working with.
**YakiHonne**: The way you approached it—getting a merchant to demonstrate it—really helped build trust. I know many communities face the same issue: how to prove that Bitcoin is real. But over time, we learn how to overcome these challenges. It's really impressive how you handled it?
YakiHonne: What principles guide your community, and how do you maintain trust and reliability? I know you’ve mentioned this a bit already, but could you elaborate further? How do you ensure trust and reliability in your discussions?
**Kofi**:As humans, we also need to trust our intuition and how we feel about situations. It’s essential to interact with people with integrity. In our community, we are mindful of what we show others, both in actions and in good deeds. If you love someone, you give everything you have to them, and that’s the only way people can truly feel they belong in your circle. This is the key that keeps us moving forward.
**Kofi**:The person at the center of everything you’re doing must be trustworthy. And how do you gain trust? You must trust others first. Even if people come with ulterior motives, you should approach them with an open heart, showing love to them just as you do with everyone else.
**Kofi**:And when wrongs are committed, it’s important to acknowledge them. If someone points out a mistake you made, accept it, apologize, and move forward. This creates an understanding within the community that we’re not here to harm one another. Trust is built on integrity, and that’s how we maintain it.

**YakiHonne**: That’s very true. It’s much better and easier when you have integrity. Over time, as you prove yourself to be a person of integrity, it naturally builds trust with others. So, how does your community educate its members and keep them updated on Bitcoin developments? How do you approach this?
**Kofi**:To engage our community on a larger scale, we believe it's important to stay active and involved. After building trust, we participate in community events, such as sponsoring a football competition and contributing to their local festival. By doing this, the entire community starts seeing Bitcoin as something that can truly improve their lives.
**Kofi**:We also established a Bitcoin Education Center, where we invite students from various schools to learn about Bitcoin. But our efforts go beyond just education; we use the resources we gain from Bitcoin to acquire laptops and robotics kits, so that the students can have additional learning opportunities. These activities are incorporated into their school programs, and we encourage their participation through debates and rewarding them with SATS.

**Kofi**:By rewarding them with SATS, they can use these rewards to buy from over 20 merchants we've onboarded, which not only excites the students but also makes their parents curious about Bitcoin. We've even had people at the local market requesting to buy Bitcoin from us. This is how we keep up with Bitcoin’s development and continue to spread its influence in our community.
**YakiHonne**: How does your community work with the wider Bitcoin ecosystem? So far, what partnership has had the most positive impact on your community?
**Kofi**:Due to the hard work we've been putting in, we were able to attract Bitcoin Beach as one of our major collaborators. We are part of Bitcoin Ekasi. Recently, we were also awarded the Block Discovery Grant of $50,000 from the Bitcoin Foundation. We are using this grant to build a sports complex, which will include a football field, a multi-purpose basketball court, a swimming pool, a children's playground, and more. We've already started this project. These are the key collaborators and supporters we've had in the Bitcoin space, and their support has been invaluable to us.


**YakiHonne**: It’s clear that you guys are doing an amazing job! Your efforts and hard work have truly caught the attention of many communities, and it’s great to see you forming significant partnerships.So, could you share more about the initiatives your community has taken to promote Bitcoin adoption? I know you've mentioned a few already, but would you mind expanding on them a bit more and sharing the results you've seen?
**Kofi**:As I mentioned earlier, we are enhancing our capacity by working with school children and teenagers. We also plan to host inter-school competitions, particularly world-class robotics competitions, with the aim of broadening students' perspectives on science and giving them a global view of what's happening in the world. We believe that through these activities, we will be able to engage with a larger society, helping us expand our client base for Bitcoin education and usage. Therefore, we believe this will have a profound impact. As for the activities we are currently working on, they are providing us with opportunities to expand our reach to schools within the community. This will further build trust and deepen our relationships in this regard.
**YakiHonne**: I really admire the fact that you have boarded merchants to accept Bitcoin, which is a great step for its adoption. I also like that you've reached out to schools, encouraging community growth, which helps people see more interest and potential in the Bitcoin ecosystem. Now, for our last question of the day, what are the community goals for the next 6 to 12 months, and how do you see it evolving within the Bitcoin space?
**Kofi**:So, in the next 6 to 12 months, we plan to complete the sports complex we’re building. We also intend to open it up for social activities, both within our community and beyond. We believe this will create more opportunities for interaction, allowing people who don’t live within our community to learn about Bitcoin, hear about it, and start engaging with it for the greater good.
**YakiHonne**: you plan to complete the sports complex and expand your social reach to engage more people, even those outside your local community. This is truly amazing, and the work you’re doing is fantastic.
**YakiHonne**: We’ve come to the end of today’s interview, and I’m really happy to have had this conversation with you, Kofi. You’ve shared so much, and I’ve learned a lot. It’s inspiring to see all the great things happening in Ghana, truly wonderful. Thank you, and you’re doing an incredible job.
**Sean**:I would say it’s important for us as Africans to continue collaborating within our own communities—whether in a specific community, village, or town. Through collaboration, we can create stronger communities for ourselves. This way, we’ll be able to generate jobs in various fields and develop marketable skills that can be used anywhere in the world. This way, we won’t need to seek opportunities in other countries; we can build those opportunities right here in our own space.
**YakiHonne**: It's very true. We can definitely build a better West Africa, a better Africa, and create our own opportunities here. Thank you so much for this interview.
-

@ da0b9bc3:4e30a4a9
2025-02-19 06:35:45
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/890318
-

@ 6e0ea5d6:0327f353
2025-02-19 04:28:42
Ascolta bene, amico mio! A man's strength is not born from comfort, applause, or luck. It awakens only when the world throws him to the ground, steps on his throat, and laughs at his misery.
When your plans lie in ruins, when everything you've built turns to dust, when every promise you once believed in dissolves into the wind—that is when truth reveals itself. You either dig a trench and fight like a condemned man, or you accept that you’re digging your own grave.
Rock bottom is not a place—it’s a test. A challenge for the weak to bury themselves and for the strong to rise. You will bleed, taste the dirt, grind your teeth, but standing back up is the only option. A real man does not cry for help, does not mourn the past. He wields his pain as a whip, his hatred as fuel, and his will as a blade.
Falling is inevitable. What defines your story is what you do when there is no ground left beneath you.
True motivation does not come from empty inspirational quotes, but from the hatred of one’s own weakness.
The man who clings rigidly to his strategy is like a hunter pulling back a stiff wooden bow—he will break his own weapon when the time comes to use it.
The world is too corrupt for you to believe in love vows, the promises of friends, effortless riches, or the words of newspapers.
If you wish to survive in this world, learn this: both victory and defeat are temporary. Only the battle is eternal.
A man’s life is his endless war. And hatred must be to him what fire is to a steam locomotive: the force that drives him up the steepest paths. But never let yourself burn in your own flames.
Rise. Or die kneeling like the wretched.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-

@ e97aaffa:2ebd765d
2024-12-31 16:47:12
Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes.
Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais _mainstream_. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso.
# Código do Bitcoin
No final de 2025, possivelmente vamos ter um _fork_, as discussões sobre os _covenants_ já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos _covenants_, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido.
Depois dos _covenants,_ o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa.
Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos _bitcoiners_.
Espero que surjam avanços significativos no BitVM2 e BitVMX.
Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da _shitcoinagem_, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs.
Se querem ser levados a sério, têm que ser sérios.
> “À mulher de César não basta ser honesta, deve parecer honesta”
Se querem ter o apoio dos _bitcoiners_, sigam o _ethos_ do Bitcoin.
Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma _multisig_ ou com os _covenants_ na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos _covenants_ para melhorar a interoperabilidade e a soberania.
É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy:
> “Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país”
Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código.
# Reservas Estratégicas de Bitcoin
## Bancos centrais
Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito _mainstream_. Foi um _pivot_, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto.
A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário.
Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”.
Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar.
Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.

## Empresas
A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.

Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%.
Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de _shareholders_ com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft.
Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial.
# ETFs
Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os _inflows_ foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os _inflows_ foram brutais.
Também se beneficiou por ser um mercado novo, não existia _orderbook_ de vendas, não existia um mercado interno, praticamente era só _inflows_. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em _inflows_ ou _outflows_.
Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de _inflows_ em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar.
Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem.
Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes.
Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo.
# Preço
Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo.
# Stablecoins de dólar
Agora saindo um pouco do universo do Bitcoin, acho importante destacar as _stablecoins_.
No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas.
Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às _stablecoins_ de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas.
> “Casa onde não há pão, todos ralham e ninguém tem razão”
Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas.
Eu acredito que 2025, vai haver um forte crescimento na adoção das _stablecoins_ de dólares, esse forte crescimento vai agravar o problema sistémico que são as _stablecoins_. Vai ser o início do fim das _stablecoins_, pelo menos, como nós conhecemos hoje em dia.
## Problema sistémico
O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente.
Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas.
As _stablecoins_ são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema.
No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos.
A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário.
Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/_stablecoins_ para o resto do sistema financeiro, porque o _marketcap_ do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações.
Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do _carry trade_, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado.
Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações.
O mundo cripto é seu oposto, é _naife_ com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto.
Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025.
Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o _redeem_ dos dólares?
Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether?
Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente.
### Conta mestre
Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário.
O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com _full-reserves_. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com _full-reserves_, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos.
Eu concordo com o FED nesse ponto, que os bancos com _full-reserves_ são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos _full-reserves_, mas sim nos que têm reserva fracionária.
O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença.
Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de _compliance_, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o _compliance_ dos seus clientes.
A obrigação do KYC para ter _stablecoins_ iriam provocar um terramoto no mundo cripto.
Assim, é pouco provável que seja a solução para a Tether.
### FED
Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as _stablecoins_ de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as _stablecoins_ estão a colocar em causa a soberania monetária dos outros países. Atualmente as _stablecoins_ estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países.
Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo.
Será algo para acompanhar futuramente, mas só para 2026, talvez…
É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(_stablecoins_). A ironia do destino.
Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona.
# Europa
2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os _compliance_, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo.
O _Travel Route_ passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A _Travel Route_ é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos.
O MiCA também está a colocar problemas nas _stablecoins_ de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias.
O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade _stablecoins_ de euro, as restantes _stablecoins_ serão deslistadas.
Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado.
# Recessão
Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon.
Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro.
Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer.
Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar.
A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa.
Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal.
# Brasil
Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.

Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e _stablecoins_. No Brasil existe um forte adoção, será um bom _case study_, certamente irá repetir-se em outros países num futuro próximo.
Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin.
# Blockchain
Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em _blockchain_. Eu acredito que a BlackRock vai criar uma própria _blockchain_, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar.
-----------
Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião.
Isto é apenas a minha opinião, **Don’t Trust, Verify**!
-

@ 30e8cbf1:74fccbaa
2025-02-19 03:22:53
*Capitalist Realism: Is There No Alternative? by Mark Fisher* (2009, Zero Books)
## Why a dare and not a recommendation?
I'm writing this "review" primarily for the Nostr audience. The majority of Nostr users, in my experience, are predisposed to a worldview somewhere in the realm of Anarcho-Capitalism or Libertarianism, with a strong focus on individual autonomy and free markets. The title *Capitalist Realism: Is There No Alternative* might evoke an immediate negative reaction in the mind of my imaginary Nostr reader. Even worse, looking up summaries of the book or the author before diving in, the reader will find the dreaded phrase "critical theory", seen as a hallmark of the "other" side in the Western culture war. I'm challenging you to not judge this book by its cover.
Despite the book's short (86 page) length, I have found myself spending an unusually large amount of time thinking about the topics discussed within. I'm unsure if my worldview has actually shifted after reading this (I think I'm still close to the Nostr median), but I've enjoyed this exercise in contemplation, and I hope this article can lead someone else to a similarly fruitful experience. I feel compelled to put my thoughts to paper as part of this exercise, and what follows is something like the internal dialog I go through considering and challenging Fisher's main points.
First, despite the word "Capitalism" in the title, this book is not about economics. Rather, the central point is that after the fall of the Soviet Union the prevailing worldview in the Western world is a "business ontology", essentially seeing people as purely material producer/consumers. Most people have internalized this view, seeing no higher purpose or meaning in their lives other than going to work and buying things. Even worse than the widespread internalization of this view, Fisher argues that it is so pervasive that most people can't even conceptualize an alternative. Fisher points out the rapid increases in mental health problems, despair, and suicide, especially among young people in the 21st century as evidence of this argument. *Capitalist Realism* was written in 2009, and I think there is a clear line between Fishers argument and the current conception of a "crisis of meaning" among young people espoused by some online figures such as Jordan Peterson. Whether there is a direct link between the business ontology and crisis of meaning (as Fisher argues) is less clear to me, but he clearly identified a phenomenon that has only gotten more acute since the book was published. Further, Fisher cites popular culture, particularly modern music and movies as evidence of this phenomenon. In his conception, this business ontology leads to endlessly recycled aesthetic callbacks to previous generations, with most media appealing to our nostalgia for a time when people had a genuine belief that the future may be different than the present, which he thinks has been lost by total adoption of this business ontology. I'm not knowledgeable enough in aesthetics to comment on this point, but do have an intuitive feeling that modern movies and music are degenerate from the works created by previous generations. Fisher calls this "Hauntology" as is explored in another book that I haven't read yet.
In a section of the book I found particularly interesting, Fisher critiques the hypocrisy of capitalist neoliberal societies that cite the "Stalinist Bureaucracy" as a fatal fall that led to the demise of the Soviet Union while rapidly adopting the same form of work domestically. Essentially, in the Soviet system most people only "worked" to achieve whatever metric the bureaucrats used to assess their productivity. Whether or not this correlated with producing useful goods or services was entirely irrelevant. If a factory had a quota of making 100 tons of clocks, the workers would just produce overweight and non-functional clocks to meet this quota. All up and down the chain the metrics were met, pleasing the bureaucrats and appearing "productive", but everyone was fully aware that the work was performative and fake. Fisher points to his experience in academia, where universities continued to add more and more administrators to run pointless audit and review programs. Both the faculty and administrators are fully aware that these programs are meaningless and unproductive, but the metrics become a justification of themselves. They don't matter, but they need to exist to make massive administrator bloat and associated bureaucracy appear necessary. Again, in the years since the book's publication the public consciousness of this problem has grown, though the criticism is more often leveled from the political right. I was surprised to read an author I would stereotype as an "ivory tower leftist academic" forcefully level this criticism at his own institution.
As I think about this book, I wonder if it helps to make a distinction between "capitalism" and "fiat". On Nostr we often critique "fiat food", "fiat jobs", and "fiat music" as hollow, meaningless, and temporary things. We hypothesize that sound money will fix the incentives that lead to the societal problems that Fisher attributes to neoliberal capitalism. Fisher does not consider Bitcoin in this book (or any of this other works, to my knowledge) but I'm curious if he would make a similar distinction. If this book was called *Fiat Realism: Is There No Alternative* would it be popular in Bitcoin circles? I think it would be. Maybe people would point to these criticisms leveled within a year of Bitcoin's creation and claim "Bitcoin fixes this". Going back to an earlier point, Fisher doesn't critique free exchange, markets or individual liberty. He critiques a specific culture that currently seems all-pervasive without any alternative. I hope that the freedom money and freedom technology movement we are a part of is a feasible alternative.
I hope this article is helpful to someone. It was certainly helpful for me to write it. I'm interested in hearing your thoughts on this book or this article!
-

@ 9ea10fd4:011d3b15
2025-02-19 02:24:26
This article by Thomas Piketty has, in a way, convinced me that the tariff war will indeed take place. Moreover, the Trumpist nationalism-capitalism he describes—authoritarian and the most aggressively extractivist—places Canada in the position of a coveted target.
The fact that “if the Republican Party has become so nationalist and virulent towards the outside world, it is primarily due to the failure of Reagan-era policies, which were supposed to boost growth but instead reduced it and led to the stagnation of incomes for the majority” is of little consolation.
\*“Let’s be clear: Trumpist national-capitalism loves to flaunt its strength, but in reality, it is fragile and on edge. Europe has the means to confront it, provided it regains confidence in itself, forges new alliances, and calmly analyzes the strengths and limitations of this ideological framework.
Europe is well-positioned for this: it has long based its development on a similar military-extractivist model, for better or worse. After taking control of maritime routes, raw materials, and the global textile market by force, European powers imposed colonial tributes throughout the 19th century on all resistant countries, from Haiti to China to Morocco. On the eve of 1914, they engaged in a fierce struggle for control of territories, resources, and global capitalism. They even imposed tributes on each other, increasingly exorbitant ones—Prussia on France in 1871, then France on Germany in 1919: 132 billion gold marks, more than three years of Germany’s GDP at the time. As much as the tribute imposed on Haiti in 1825, except this time, Germany had the means to defend itself. The endless escalation led to the collapse of the system and European hubris.
(…)
If we reason in terms of purchasing power parity, the reality is quite different (…) With this measure, we (…) see that China’s GDP surpassed that of the United States in 2016. It is currently more than 30% higher and will reach twice the U.S. GDP by 2035. This has very concrete consequences in terms of influence and investment capacity in the Global South, especially if the United States locks itself into its arrogant and neo-colonial stance. The reality is that the United States is on the verge of losing control of the world, and Trumpist outbursts will change nothing.”
https://www.lemonde.fr/en/opinion/article/2025/02/15/thomas-piketty-trump-s-national-capitalism-likes-to-flaunt-its-strength-but-it-is-actually-fragile_6738187_23.html
-

@ 0b118e40:4edc09cb
2025-02-19 01:21:45
Are we living in his definition of democracy?
It’s interesting how political parties can divide a country, especially in democracies where both oppression and individual choice coexist.
As I was exploring global economics and political ideologies, I picked up *The Republic* by Plato (again). The first time I read it, I only read the book on the Allegory of the Cave and it felt enlightening. This time around, I read through all the books and I thought to myself : *this is absolutely nuts!*
Over 2,000 years ago, *The Republic* imagined a world disturbingly similar to Gattaca or 1984. For a quick rundown, Plato believed in a police state, eugenics, a caste system, and brainwashing people through state-controlled media and education. Sounds wild? I thought so too.
And for some reason, Plato had a serious grudge against art. To him, art was deceptive and emotionally manipulative. Maybe because there was a skit making fun of Socrates at that time by Aristophanes (the father of comedy) or maybe because he struggled to deal with emotions, we will never know.
Plato obviously wasn’t a fan of democracy as he wanted a dystopian world. But to be fair, he genuinely thought that his ideal world (Kallipolis) was a utopia. Maybe someone who loves extreme order and control might think the same but I sure don’t.
His teacher Socrates was also not a fan of democracy because he believed the mass majority were too ignorant to govern and only those intelligent enough could. His student, Aristotle, was more moderate but still critical, seeing democracy as vulnerable to corruption and mob rule. Socrates, Plato, and Aristotle were around the Classical Greek era, 5th to 4th century BC.
The idea of democracy existed long before them. The first recorded version was in Athens during the 6th BC, developed by leaders like Solon and Pericles. It was a direct democracy where free male citizens (non-slaves) could vote on laws themselves instead of electing representatives.
These guys influenced how we think about democracy today. But looking around, I wonder, did we end up in Plato’s dystopian world?
### **Plato’s take on democracy**
Plato’s lack of trust of democracy stemmed from Socrates’ death. Socrates himself was a fierce critic of democracy, as he believed governance should be based on wisdom rather than popularity.
Other thinkers, like Pythagoras and Herodotus (father of history), also examined different political systems, but Socrates was the most influential critic. He warned that allowing the uneducated masses to choose leaders would lead to poor governance, as they could be easily swayed by persuasive speakers rather than guided by knowledge.
Athenian democracy relied on large citizen juries and was particularly vulnerable to rhetoric and public sentiment.
In the end, Socrates became a victim of the very system he criticized. His relentless questioning of widely accepted beliefs, now known as the **Socratic Method**, earned him powerful enemies. Socrates’ constant probing forced them to confront uncomfortable truths. It annoyed people so much, that it eventually led to his trial and execution. Socrates was condemned to death by popular vote.
I wonder, if we applied the Socratic Method today to challenge both the left and the right on the merits of the opposing side, would they be open to expanding their perspectives, or would they react with the same hostility?
This questioning technique is now also used in some schools and universities as a teaching method, encouraging open-ended discussion where students contribute their own thoughts rather than passively receiving information. But how open a school, system, or educator is to broad perspectives depends largely on their own biases and beliefs. Even with open-ended questions, the direction of the conversation can be shaped by those in charge, potentially limiting the range of perspectives explored.
Socrates’ brutal death deeply grounded Plato’s belief that democracy, without intellectual rigor, was nothing but a mob rule. He saw it as a system doomed to chaos, where the unqualified, driven by emotion or manipulated by rhetoric, made decisions that ultimately paved the way for tyranny.
### **The Republic**
*The Republic* was written around 375 BC, after the Peloponnesian War. One of its most famous sections is the Allegory of the Cave, where prisoners are stuck watching shadows on a wall, thinking that it’s reality until one breaks free and sees the real world. That’s when the person becomes enlightened, using knowledge and reason to escape ignorance. They return to free others, spreading the truth. I love this idea of breaking free from suppression through knowledge and awareness.
But as I went deeper into Plato’s work, I realized what the plot twist was.
Plato wrote this book for strict state control. He wanted total control over education, media, and even families like in the book 1984. He argued that people should be sorted into a caste system, typically workers, warriors, and philosopher-kings so that society runs like a well-oiled machine. The “guardians” would police the state and everyone would go through physical and military training. To top it off, kids would be taken away from their parents and raised by the state for the “greater good.” like in the movie Gattaca. If that sounds a little too Orwellian, that’s because it is.
Plato believed that only philosophers, the truly enlightened ones from that “cave”, should rule. To him, democracy was a joke, a breeding ground for corruption and tyranny.
I found it completely ironic that this book that warns about brainwashing in the Allegory of the Cave also pushes for a state-controlled society, where thinking for yourself isn’t really an option.
And yet, looking around today, I wonder, are we really any different? We live in a world where oppression and enlightenment exist side by side.
Plato was slightly progressive in that he thought men and women should have equal education, but only for the ruling Guardian class.
In *The Republic*, Plato didn’t focus much on economics or capitalism as we understand them today. His philosophies were more concerned with justice, governance, and the ideal structure of society. He did touch on wealth and property, particularly in *The Republic and Laws* but it was more on being against wealth accumulation by rulers (philosopher-kings had to live communally and without private property).
While these ideas echo elements of socialism, he never outlined a full economic system like capitalism or socialism.
### **The hatred for art**
Plato was deeply skeptical of art. He believed that it appealed to emotions over rational thought and distorted reality. In *The Republic* (Book X), he argued that art is an imitation of an imitation, pulling people further from the truth. If he had his way, much of modern entertainment, including poetry, drama, and even certain types of music, would not exist in their expressive forms.
Despite Plato’s distrust of the arts, his time was a golden age for Greek drama, sculpture, and philosophy. Ironically, the very city where he built his Academy, Athens, was flourishing with the kind of creativity he wanted to censor.
Even medicine, which thrived under Hippocrates (the father of medicine), was considered an art requiring lifelong mastery. His quote, ‘**Life is short, and art is long**,’ reflects the long span of time it takes to cultivate and appreciate knowledge and skills, which was something Plato valued. Yet, he dismissed most art as a distraction from truth.
Plato particularly criticized poets and playwrights like Homer, as he claimed they spread false ideas about gods and morality. He was also wary of Aristophanes, as he believed his work stirred emotions rather than encouraging rational thought. It probably did not help that Aristophanes mocked Socrates in his play *The Clouds*, which may have influenced Plato’s views.
What’s clear is that Plato didn’t hate art because he didn’t understand it. He deeply understood the power of storytelling and its ability to mold societal beliefs. He argued for banning poets entirely from his “ideal city” to prevent them from misleading the public.
But he did value some forms of art. After all, he was a writer himself, and writing is a form of art. He approved of artistic expressions that promoted moral and intellectual virtue, such as hymns, architecture, and patriotic poetry, as long as they served the greater purpose of instilling order and wisdom in society.
### **Plato’s five regimes**
Plato believed governments naturally decay over time, moving from order to chaos. He outlined five regimes, which he considers each to be worse than the last.
1. *Aristocracy (Philosopher-King rule)* : This is his pitch, the ideal state, ruled by wise elites who value knowledge over power. Some aspects of modern authoritarian states echo this model
2. *Timocracy (Military rule)* : A government driven by honor and discipline, like Sparta. Over time, ambition overtakes virtue, leading to oligarchy.
3. *Oligarchy (Rule by the wealthy)* : The rich seizes power and deepens inequality. Many democracies today show oligarchic tendencies, where money dominates politics.
4. *Democracy (Rule by the masses)* : The people overthrow the elites, prioritizing freedom over order. But without stability, democracy becomes fragile, and vulnerable to demagogues and external manipulation.
5. *Tyranny (Dictatorship)* : When democracy collapses, a charismatic leader rises, promising order but seizing absolute power. What begins as freedom ends in oppression.
Modern politics seems stuck in a cycle, shifting between democracy, oligarchy, and authoritarian control. If Plato was right, no system is permanent and only the illusion of stability remains.
### **Does Plato’s ideal state exist in any country today?**
Some aspects of modern *benevolent dictatorships*, like Singapore under Lee Kuan Yew, or *socialist states* like China, may resemble Plato’s vision in their emphasis on elite rule, long-term planning, and state control. But, these governments operate pragmatically, balancing governance with economic power, political strategy, and public influence rather than strictly adhering to philosophical ideals.
Could this be compared to Taliban rule, given the censorship, authoritarian control, and rigid social hierarchy? While there are superficial similarities, the key difference is that Plato valued knowledge, reason, and meritocracy, while the Taliban enforced religious fundamentalism and theocratic rule. Plato’s Kallipolis also included some level of gender equality for the ruling class, whereas the Taliban’s system is heavily restrictive, especially toward women.
While Plato’s ideas echo in certain authoritarian-leaning states, his rigid caste system, philosopher-led governance, and rejection of democracy set his vision apart from any modern political system.
### **Aristotle’s take on democracy**
Aristotle wasn’t Athenian, but he documented and analyzed 158 constitutions, including Athenian democracy. He studied at Plato’s Academy for over 20 years, growing up in a world influenced by Athens’ democratic experiment. He lived through the tail end of Athens’ golden age, witnessed its decline, and experienced how different forms of rule influenced politics and the mindset of the people under them.
For Aristotle, governments were good or corrupted. The good ones were monarchs, aristocracy (wise elites), and polity (a constitutional gov’t where the middle class keeps power balanced). The corrupted ones were tyranny (monarchy gone wrong), oligarchy, and democracy.
Aristotle saw how democracy, if unchecked, could spiral into chaos or be co-opted by populist leaders. But unlike Plato, who rejected democracy outright, Aristotle believed it could work if properly structured.
His concept of ‘**polity**’ was a constitutional government that balanced democratic participation with stability, relying on a strong middle class to prevent both mob rule and elite domination. This idea of checks and balances, a mixed government, and middle-class stability make polity the closest to modern constitutional democracies today when compared to all 3 of the Greek philosophers.
### **What happened after Athens?**
Of course, democracy didn’t end with Athens, it evolved over time. After Athens’ golden age came Alexander the Great (Aristotle’s student and the king of Macedonia). He conquered Greece, Persia, Egypt, and part of India, creating the largest empire of his time. After his death in 323 BCE, his empire split among his generals, marking the beginning of the Hellenistic period.
Rome saw a shift from the fall of the Roman Republic to the rise of the Roman Empire under Augustus moving away from democratic ideals to centralized rule. But the Western Roman Empire fell about 500 years later largely due to internal decline and invasions by the Germanic Tribes (modern-day Sweden, Switzerland, Germany). The Eastern Roman Empire (Byzantine Empire, based in Constantinople or modern-day Turkey) rose and survived for nearly 1,000 more years until it fell to the Ottoman Turks in 1453.
During the Medieval period (5th–15th century), Europe saw a rise in monarchies and feudalism. Power shifted to kings, nobles, and the church, with little direct participation from ordinary people. Some democratic elements survived in places like Venice and Florence, where wealthy merchant families controlled city-states.
By the 17th century, democracy started creeping back into political thought, though not without skepticism. Machiavelli and Hobbes weren’t exactly fans of democracy, but they had plenty to say about power and governance. Later on Machiavelli hinted on the possible idea of a republic/mixed government in the *Discourses of Livy *
Meanwhile, England was going through its own struggles with power. The English Civil War (1642–1651) was a showdown between King Charles I, who wanted absolute power, and Parliament, which wanted more influence. Charles ignored Parliament and was executed in 1649. England briefly became a republic under Oliver Cromwell, but the monarchy returned after his death.
In 1688, the Glorious Revolution forced King James II (Charles I’s son) to flee to France. Parliament then invited William of Orange (a Dutch Protestant) and his wife Mary to take the throne. In 1689, they signed the English Bill of Rights, which limited the monarchy’s power, strengthened Parliament, and guaranteed certain rights to citizens.
This was a significant moment in history as it effectively ended the absolute monarchy and established a constitutional monarchy in England.
The American Revolution in 1776 and the French Revolution in 1789 pushed democratic ideals forward but still excluded women, slaves, and the poor. Historian Luciano Canfora, in his book* Democracy in Europe*, argues that early liberal democracy was full of contradictions as it preached equality, yet economic and social exclusion remained.
(Note: If you want to understand the history of *anarchism*, the French Revolution is a key starting point. It influenced early anti-authoritarian thought, which later evolved into socialist and anti-capitalist movements. Over time, libertarians adopted anarchist principles, leading to the development of anarcho-capitalism. The concept of anarchism in politics has taken nearly two centuries to emerge in its modern form).
The 19th and 20th centuries saw the expansion of democracy. But as Canfora explains it, it also saw its exploitation and manipulation. Although industrialization and social movements pushed for broader suffrage, democracy remained controlled by elites who feared true mass participation. Democracy became a tool for maintaining power rather than a true expression of the people’s will.
According to Canfora, the Cold War turned democracy into a geopolitical tool, with Western powers supporting or opposing democratic movements based on strategic interests rather than principles.
Today, there are many versions of democracy from direct democracy to representative democracy, presidential democracy, social democracy, religious democracy, constitutional democracy, communist democracy, and more. And is often viewed as a brand name for “good governance”. But are they?
### **In the end, was Plato right?**
At a meta level, Plato’s argument was about control, be it controlling what people read, hear, and even think. The debate often centers on curated knowledge vs rhetoric. Plato believed that absolute obedience would bring harmony, even at the cost of individuality. Today, we call that totalitarian or dictatorship
But when we take a second look at things, are we already living in Plato’s world?
Governments across the globe control education, influence media narratives, and regulate speech. Many so-called democracies aren’t as free as they claim to be. So maybe Plato’s influence on modern democracies runs deeper than we realize.
Another key debate today is that, unlike Plato’s time, most people *are* educated. However, much of this education is still designed by state systems, which can influence how people think and vote. How do we balance empowering people through education while ensuring true independence in a system built on critical thinking rather than one that merely feeds information?
Truth is, democracy has never been a pure, people-driven system. It has always been influenced by power struggles, wealth, and manipulation. Often it has been an instrument of control rather than liberation.
Yet, the people have always resisted. In the past, they gathered in the streets, risking tear gas, rubber bullets or being dragged into Black Marias. Today, digital activism has allowed for mass mobilization with fewer risks. In many countries especially in third-world countries, online movements on platforms like Twitter during Jack’s time, forced governments to overturn policies. This may be the closest we've come to real democracy which is direct action without the usual state violence.
But with this rise in digital activism comes the counterforce through government and corporate requirements for censorship, algorithmic manipulation, and the quiet steering of public discourse. Platforms once seen as tools of liberation can become tools of control. *Facebook mood experiment* in 2012 tested positive and negative content on 700,000 people and proved emotions can be manipulated at scale. *Cambridge Analytica* was exposed in its attempt to manipulate votes.
This is where decentralized networks like Nostr matter as a fundamental resistance to centralized control over speech. If democracy is to return to the people, it must also break free from algorithmic gatekeepers and censorship.
Because the so-called ‘ignorant masses’, the very people Plato dismissed, are the ones who fight for freedom.
Because real democracy isn’t about control.
It’s about freedom.
It’s about choice.
It’s about the people, always.
-

@ 254f56d7:f2c38100
2024-12-30 07:38:27
Vamos ver seu funcionamento

-

@ a012dc82:6458a70d
2024-12-30 05:51:11
**Table Of Content**
- The Influence of Global Oil Prices
- Bitcoin's Roller Coaster Ride
- Anticipation Surrounding the 2024 Halving Event
- The Broader Crypto Landscape
- Conclusions
- FAQ
In the ever-evolving world of cryptocurrencies, Bitcoin stands as a beacon, often dictating the mood of the entire crypto market. Its price fluctuations are closely watched by investors, analysts, and enthusiasts alike. Max Keiser, a prominent figure in the crypto space, recently shed light on some intriguing factors that might be influencing Bitcoin's current price trajectory. This article delves into Keiser's insights, exploring the broader implications of global events on Bitcoin's market performance.
**The Influence of Global Oil Prices**
Max Keiser, a renowned Bitcoin advocate and former trader, recently drew attention to the interplay between global oil prices and Bitcoin's market performance. Responding to a post by German economics expert, Holger Zschaepitz, Keiser highlighted the significance of Brent oil reaching $90 per barrel for the first time since the previous November. According to Keiser, the surge in oil prices, driven by Saudi Arabia's decision to extend its reduction in oil production for another three months, has had ripple effects in the financial world. One of these effects is the shift of investor interest towards higher interest deposit USD accounts. This diversion of investments is creating what Keiser terms as "a small headwind for Bitcoin," implying that as traditional markets like oil show promise, some investors might be reconsidering their cryptocurrency positions.
**Bitcoin's Roller Coaster Ride**
The cryptocurrency market, known for its volatility, witnessed Bitcoin's price undergoing significant fluctuations recently. A notable event that gave Bitcoin a temporary boost was Grayscale's triumph over the SEC in a legal battle concerning the conversion of its Bitcoin Trust into a spot ETF. This victory led to a rapid 7.88% spike in Bitcoin's price within a mere hour, pushing it from the $26,000 bracket to briefly touch the $28,000 threshold. However, this euphoria was short-lived. Over the subsequent week, the cryptocurrency saw its gains erode, settling in the $25,400 range. At the time the reference article was penned, Bitcoin was hovering around $25,688.
**Anticipation Surrounding the 2024 Halving Event**
The Bitcoin community is abuzz with anticipation for the next scheduled Bitcoin halving, projected to take place in April-May 2024. This event will see the rewards for Bitcoin miners being slashed by half, resulting in a decreased supply of Bitcoin entering the market. Historically, such halvings have acted as catalysts, propelling Bitcoin's price upwards. A case in point is the aftermath of the 2020 halving, post which Bitcoin soared to an all-time high of $69,000 in October 2021. However, some financial analysts argue that this surge was less about the halving and more a consequence of the extensive monetary measures adopted by institutions like the US Federal Reserve. These measures, taken in response to the pandemic and the ensuing lockdowns, flooded the market with cash, potentially driving up Bitcoin's price.
**The Broader Crypto Landscape**
While Bitcoin remains the most dominant and influential cryptocurrency, it's essential to consider its position within the broader crypto ecosystem. Other cryptocurrencies, often referred to as 'altcoins', also play a role in shaping investor sentiment and market dynamics. Factors such as technological advancements, regulatory changes, and global economic shifts not only impact Bitcoin but the entire crypto market. As investors diversify their portfolios and explore newer blockchain projects, Bitcoin's role as the market leader is continually tested. Yet, its pioneering status and proven resilience make it a focal point of discussions and analyses in the crypto world.
**Conclusion**
Bitcoin, the flagship cryptocurrency, has always been subject to a myriad of market forces and global events. While its inherent potential remains undeniable, the current market landscape, shaped by factors ranging from oil prices to global economic policies, presents challenges. Yet, with events like the 2024 halving on the horizon, there's an air of optimism among Bitcoin enthusiasts and investors about the future trajectory of this digital asset.
**FAQ**
**Who is Max Keiser?**
Max Keiser is a prominent Bitcoin advocate, former trader, and well-known crypto podcaster.
**What did Keiser say about Bitcoin's price?**
Keiser pointed out that rising global oil prices and the allure of higher interest deposit USD accounts are creating a "small headwind" for Bitcoin.
**How did Grayscale's legal victory affect Bitcoin?**
Grayscale's win over the SEC led to a 7.88% spike in Bitcoin's price within an hour.
**When is the next Bitcoin halving expected?**
The next Bitcoin halving is projected to occur around April-May 2024.
**Did the 2020 Bitcoin halving influence its price?**
Yes, post the 2020 halving, Bitcoin reached an all-time high of $69,000 in October 2021.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnews](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
-

@ 16d11430:61640947
2024-12-23 16:47:01
At the intersection of philosophy, theology, physics, biology, and finance lies a terrifying truth: the fiat monetary system, in its current form, is not just an economic framework but a silent, relentless force actively working against humanity's survival. It isn't simply a failed financial model—it is a systemic engine of destruction, both externally and within the very core of our biological existence.
The Philosophical Void of Fiat
Philosophy has long questioned the nature of value and the meaning of human existence. From Socrates to Kant, thinkers have pondered the pursuit of truth, beauty, and virtue. But in the modern age, the fiat system has hijacked this discourse. The notion of "value" in a fiat world is no longer rooted in human potential or natural resources—it is abstracted, manipulated, and controlled by central authorities with the sole purpose of perpetuating their own power. The currency is not a reflection of society’s labor or resources; it is a representation of faith in an authority that, more often than not, breaks that faith with reckless monetary policies and hidden inflation.
The fiat system has created a kind of ontological nihilism, where the idea of true value, rooted in work, creativity, and family, is replaced with speculative gambling and short-term gains. This betrayal of human purpose at the systemic level feeds into a philosophical despair: the relentless devaluation of effort, the erosion of trust, and the abandonment of shared human values. In this nihilistic economy, purpose and meaning become increasingly difficult to find, leaving millions to question the very foundation of their existence.
Theological Implications: Fiat and the Collapse of the Sacred
Religious traditions have long linked moral integrity with the stewardship of resources and the preservation of life. Fiat currency, however, corrupts these foundational beliefs. In the theological narrative of creation, humans are given dominion over the Earth, tasked with nurturing and protecting it for future generations. But the fiat system promotes the exact opposite: it commodifies everything—land, labor, and life—treating them as mere transactions on a ledger.
This disrespect for creation is an affront to the divine. In many theologies, creation is meant to be sustained, a delicate balance that mirrors the harmony of the divine order. Fiat systems—by continuously printing money and driving inflation—treat nature and humanity as expendable resources to be exploited for short-term gains, leading to environmental degradation and societal collapse. The creation narrative, in which humans are called to be stewards, is inverted. The fiat system, through its unholy alliance with unrestrained growth and unsustainable debt, is destroying the very creation it should protect.
Furthermore, the fiat system drives idolatry of power and wealth. The central banks and corporations that control the money supply have become modern-day gods, their decrees shaping the lives of billions, while the masses are enslaved by debt and inflation. This form of worship isn't overt, but it is profound. It leads to a world where people place their faith not in God or their families, but in the abstract promises of institutions that serve their own interests.
Physics and the Infinite Growth Paradox
Physics teaches us that the universe is finite—resources, energy, and space are all limited. Yet, the fiat system operates under the delusion of infinite growth. Central banks print money without concern for natural limits, encouraging an economy that assumes unending expansion. This is not only an economic fallacy; it is a physical impossibility.
In thermodynamics, the Second Law states that entropy (disorder) increases over time in any closed system. The fiat system operates as if the Earth were an infinite resource pool, perpetually able to expand without consequence. The real world, however, does not bend to these abstract concepts of infinite growth. Resources are finite, ecosystems are fragile, and human capacity is limited. Fiat currency, by promoting unsustainable consumption and growth, accelerates the depletion of resources and the degradation of natural systems that support life itself.
Even the financial “growth” driven by fiat policies leads to unsustainable bubbles—inflated stock markets, real estate, and speculative assets that burst and leave ruin in their wake. These crashes aren’t just economic—they have profound biological consequences. The cycles of boom and bust undermine communities, erode social stability, and increase anxiety and depression, all of which affect human health at a biological level.
Biology: The Fiat System and the Destruction of Human Health
Biologically, the fiat system is a cancerous growth on human society. The constant chase for growth and the devaluation of work leads to chronic stress, which is one of the leading causes of disease in modern society. The strain of living in a system that values speculation over well-being results in a biological feedback loop: rising anxiety, poor mental health, physical diseases like cardiovascular disorders, and a shortening of lifespans.
Moreover, the focus on profit and short-term returns creates a biological disconnect between humans and the planet. The fiat system fuels industries that destroy ecosystems, increase pollution, and deplete resources at unsustainable rates. These actions are not just environmentally harmful; they directly harm human biology. The degradation of the environment—whether through toxic chemicals, pollution, or resource extraction—has profound biological effects on human health, causing respiratory diseases, cancers, and neurological disorders.
The biological cost of the fiat system is not a distant theory; it is being paid every day by millions in the form of increased health risks, diseases linked to stress, and the growing burden of mental health disorders. The constant uncertainty of an inflation-driven economy exacerbates these conditions, creating a society of individuals whose bodies and minds are under constant strain. We are witnessing a systemic biological unraveling, one in which the very act of living is increasingly fraught with pain, instability, and the looming threat of collapse.
Finance as the Final Illusion
At the core of the fiat system is a fundamental illusion—that financial growth can occur without any real connection to tangible value. The abstraction of currency, the manipulation of interest rates, and the constant creation of new money hide the underlying truth: the system is built on nothing but faith. When that faith falters, the entire system collapses.
This illusion has become so deeply embedded that it now defines the human experience. Work no longer connects to production or creation—it is reduced to a transaction on a spreadsheet, a means to acquire more fiat currency in a world where value is ephemeral and increasingly disconnected from human reality.
As we pursue ever-expanding wealth, the fundamental truths of biology—interdependence, sustainability, and balance—are ignored. The fiat system’s abstract financial models serve to disconnect us from the basic realities of life: that we are part of an interconnected world where every action has a reaction, where resources are finite, and where human health, both mental and physical, depends on the stability of our environment and our social systems.
The Ultimate Extermination
In the end, the fiat system is not just an economic issue; it is a biological, philosophical, theological, and existential threat to the very survival of humanity. It is a force that devalues human effort, encourages environmental destruction, fosters inequality, and creates pain at the core of the human biological condition. It is an economic framework that leads not to prosperity, but to extermination—not just of species, but of the very essence of human well-being.
To continue on this path is to accept the slow death of our species, one based not on natural forces, but on our own choice to worship the abstract over the real, the speculative over the tangible. The fiat system isn't just a threat; it is the ultimate self-inflicted wound, a cultural and financial cancer that, if left unchecked, will destroy humanity’s chance for survival and peace.
-

@ 4d953dcb:39c9c35c
2025-02-18 22:03:42
Чтобы иметь бесплатный, быстрый и устойчивый к блокировке VPN нам нужны всего 2 вещи:
1. Клиент V2ray (приложение для использования VPN)
2. Файлы конфигурации (по сути данные VPN-серверов)
## Клиенты V2ray:
1. Инструкция по установке для Windows и Linux:
https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-HiddifyNext-app#adding-a-profile-to-the-app
*P.S. Если возникли проблемы с Hiddify-Next — пробуйте установить [Necoray](https://github.com/MatsuriDayo/nekoray)*
2. Инструкция по установке для Android:
https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-V2rayNG-app#add-configs-to-the-app
*P.S. Если возникли проблемы с V2rayNG — пробуйте установить [HiddifyNext](https://github.com/hiddify/hiddify-next/releases) ([инструкция](https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-HiddifyNext-app#adding-a-profile-to-the-app))*
3. Инструкция по установке для Windows и Linux:
https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-V2Box-app#add-subscription-links-to-the-app (лучше для iOS) + https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-Streisand#add-subscription-link (лучше для Mac)
*P.S. Если возникли проблемы с V2Box и Streisand — пробуйте установить [Hiddify-Next](https://github.com/hiddify/hiddify-next/releases) или [ShadowRocket](https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-ShadowRocket-app#add-subscription-link-to-the-app)*
## Источники файлов конфигураций:
1. https://outlinekeys.com/
2. https://proxytype.com/
3. https://vlesskey.com/
4. https://vpnkeys.org/
5. https://openproxylist.com/v2ray/
6. https://github.com/Epodonios/v2ray-configs
7. https://github.com/barry-far/V2ray-Configs?tab=readme-ov-file
8. https://github.com/M-Mashreghi/Free-V2ray-Collector
9. https://github.com/skywrt/v2ray-configs
10. https://github.com/0xdolan/v2ray_config_generator
-

@ a367f9eb:0633efea
2024-12-22 21:35:22
I’ll admit that I was wrong about Bitcoin. Perhaps in 2013. Definitely 2017. Probably in 2018-2019. And maybe even today.
Being wrong about Bitcoin is part of finally understanding it. It will test you, make you question everything, and in the words of BTC educator and privacy advocate [Matt Odell](https://twitter.com/ODELL), “Bitcoin will humble you”.
I’ve had my own stumbles on the way.
In a very public fashion in 2017, after years of using Bitcoin, trying to start a company with it, using it as my primary exchange vehicle between currencies, and generally being annoying about it at parties, I let out the bear.
In an article published in my own literary magazine *Devolution Review* in September 2017, I had a breaking point. The article was titled “[Going Bearish on Bitcoin: Cryptocurrencies are the tulip mania of the 21st century](https://www.devolutionreview.com/bearish-on-bitcoin/)”.
It was later republished in *Huffington Post* and across dozens of financial and crypto blogs at the time with another, more appropriate title: “[Bitcoin Has Become About The Payday, Not Its Potential](https://www.huffpost.com/archive/ca/entry/bitcoin-has-become-about-the-payday-not-its-potential_ca_5cd5025de4b07bc72973ec2d)”.
As I laid out, my newfound bearishness had little to do with the technology itself or the promise of Bitcoin, and more to do with the cynical industry forming around it:
> In the beginning, Bitcoin was something of a revolution to me. The digital currency represented everything from my rebellious youth.
>
> It was a decentralized, denationalized, and digital currency operating outside the traditional banking and governmental system. It used tools of cryptography and connected buyers and sellers across national borders at minimal transaction costs.
>
> …
>
> The 21st-century version (of Tulip mania) has welcomed a plethora of slick consultants, hazy schemes dressed up as investor possibilities, and too much wishy-washy language for anything to really make sense to anyone who wants to use a digital currency to make purchases.
While I called out Bitcoin by name at the time, on reflection, I was really talking about the ICO craze, the wishy-washy consultants, and the altcoin ponzis.
What I was articulating — without knowing it — was the frame of NgU, or “numbers go up”. Rather than advocating for Bitcoin because of its uncensorability, proof-of-work, or immutability, the common mentality among newbies and the dollar-obsessed was that Bitcoin mattered because its price was a rocket ship.
And because Bitcoin was gaining in price, affinity tokens and projects that were imperfect forks of Bitcoin took off as well.
The price alone — rather than its qualities — were the reasons why you’d hear Uber drivers, finance bros, or your gym buddy mention Bitcoin. As someone who came to Bitcoin for philosophical reasons, that just sat wrong with me.
Maybe I had too many projects thrown in my face, or maybe I was too frustrated with the UX of Bitcoin apps and sites at the time. No matter what, I’ve since learned something.
**I was at least somewhat wrong.**
My own journey began in early 2011. One of my favorite radio programs, Free Talk Live, began interviewing guests and having discussions on the potential of Bitcoin. They tied it directly to a libertarian vision of the world: free markets, free people, and free banking. That was me, and I was in. Bitcoin was at about $5 back then (NgU).
I followed every article I could, talked about it with guests [on my college radio show](https://libertyinexile.wordpress.com/2011/05/09/osamobama_on_the_tubes/), and became a devoted redditor on r/Bitcoin. At that time, at least to my knowledge, there was no possible way to buy Bitcoin where I was living. Very weak.
**I was probably wrong. And very wrong for not trying to acquire by mining or otherwise.**
The next year, after moving to Florida, Bitcoin was a heavy topic with a friend of mine who shared the same vision (and still does, according to the Celsius bankruptcy documents). We talked about it with passionate leftists at **Occupy Tampa** in 2012, all the while trying to explain the ills of Keynesian central banking, and figuring out how to use Coinbase.
I began writing more about Bitcoin in 2013, writing a guide on “[How to Avoid Bank Fees Using Bitcoin](http://thestatelessman.com/2013/06/03/using-bitcoin/),” discussing its [potential legalization in Germany](https://yael.ca/2013/10/01/lagefi-alternative-monetaire-et-legislation-de/), and interviewing Jeremy Hansen, [one of the first political candidates in the U.S. to accept Bitcoin donations](https://yael.ca/2013/12/09/bitcoin-politician-wants-to-upgrade-democracy-in/).
Even up until that point, I thought Bitcoin was an interesting protocol for sending and receiving money quickly, and converting it into fiat. The global connectedness of it, plus this cypherpunk mentality divorced from government control was both useful and attractive. I thought it was the perfect go-between.
**But I was wrong.**
When I gave my [first public speech](https://www.youtube.com/watch?v=CtVypq2f0G4) on Bitcoin in Vienna, Austria in December 2013, I had grown obsessed with Bitcoin’s adoption on dark net markets like Silk Road.
My theory, at the time, was the number and price were irrelevant. The tech was interesting, and a novel attempt. It was unlike anything before. But what was happening on the dark net markets, which I viewed as the true free market powered by Bitcoin, was even more interesting. I thought these markets would grow exponentially and anonymous commerce via BTC would become the norm.
While the price was irrelevant, it was all about buying and selling goods without permission or license.
**Now I understand I was wrong.**
Just because Bitcoin was this revolutionary technology that embraced pseudonymity did not mean that all commerce would decentralize as well. It did not mean that anonymous markets were intended to be the most powerful layer in the Bitcoin stack.
What I did not even anticipate is something articulated very well by noted Bitcoin OG [Pierre Rochard](https://twitter.com/BitcoinPierre): [Bitcoin as a *savings technology*](https://www.youtube.com/watch?v=BavRqEoaxjI)*.*
The ability to maintain long-term savings, practice self-discipline while stacking stats, and embrace a low-time preference was just not something on the mind of the Bitcoiners I knew at the time.
Perhaps I was reading into the hype while outwardly opposing it. Or perhaps I wasn’t humble enough to understand the true value proposition that many of us have learned years later.
In the years that followed, I bought and sold more times than I can count, and I did everything to integrate it into passion projects. I tried to set up a company using Bitcoin while at my university in Prague.
My business model depended on university students being technologically advanced enough to have a mobile wallet, own their keys, and be able to make transactions on a consistent basis. Even though I was surrounded by philosophically aligned people, those who would advance that to actually put Bitcoin into practice were sparse.
This is what led me to proclaim that “[Technological Literacy is Doomed](https://www.huffpost.com/archive/ca/entry/technological-literacy-is-doomed_b_12669440)” in 2016.
**And I was wrong again.**
Indeed, since that time, the UX of Bitcoin-only applications, wallets, and supporting tech has vastly improved and onboarded millions more people than anyone thought possible. The entrepreneurship, coding excellence, and vision offered by Bitcoiners of all stripes have renewed a sense in me that this project is something built for us all — friends and enemies alike.
While many of us were likely distracted by flashy and pumpy altcoins over the years (me too, champs), most of us have returned to the Bitcoin stable.
Fast forward to today, there are entire ecosystems of creators, activists, and developers who are wholly reliant on the magic of Bitcoin’s protocol for their life and livelihood. The options are endless. The FUD is still present, but real proof of work stands powerfully against those forces.
In addition, there are now [dozens of ways to use Bitcoin privately](https://fixthemoney.substack.com/p/not-your-keys-not-your-coins-claiming) — still without custodians or intermediaries — that make it one of the most important assets for global humanity, especially in dictatorships.
This is all toward a positive arc of innovation, freedom, and pure independence. Did I see that coming? Absolutely not.
Of course, there are probably other shots you’ve missed on Bitcoin. Price predictions (ouch), the short-term inflation hedge, or the amount of institutional investment. While all of these may be erroneous predictions in the short term, we have to realize that Bitcoin is a long arc. It will outlive all of us on the planet, and it will continue in its present form for the next generation.
**Being wrong about the evolution of Bitcoin is no fault, and is indeed part of the learning curve to finally understanding it all.**
When your family or friends ask you about Bitcoin after your endless sessions explaining market dynamics, nodes, how mining works, and the genius of cryptographic signatures, try to accept that there is still so much we have to learn about this decentralized digital cash.
There are still some things you’ve gotten wrong about Bitcoin, and plenty more you’ll underestimate or get wrong in the future. That’s what makes it a beautiful journey. It’s a long road, but one that remains worth it.
-

@ 6389be64:ef439d32
2024-12-09 23:50:41
Resilience is the ability to withstand shocks, adapt, and bounce back. It’s an essential quality in nature and in life. But what if we could take resilience a step further? What if, instead of merely surviving, a system could improve when faced with stress? This concept, known as anti-fragility, is not just theoretical—it’s practical. Combining two highly resilient natural tools, comfrey and biochar, reveals how we can create systems that thrive under pressure and grow stronger with each challenge.
### **Comfrey: Nature’s Champion of Resilience**
Comfrey is a plant that refuses to fail. Once its deep roots take hold, it thrives in poor soils, withstands drought, and regenerates even after being cut down repeatedly. It’s a hardy survivor, but comfrey doesn’t just endure—it contributes. Known as a dynamic accumulator, it mines nutrients from deep within the earth and brings them to the surface, making them available for other plants.
Beyond its ecological role, comfrey has centuries of medicinal use, earning the nickname "knitbone." Its leaves can heal wounds and restore health, a perfect metaphor for resilience. But as impressive as comfrey is, its true potential is unlocked when paired with another resilient force: biochar.
### **Biochar: The Silent Powerhouse of Soil Regeneration**
Biochar, a carbon-rich material made by burning organic matter in low-oxygen conditions, is a game-changer for soil health. Its unique porous structure retains water, holds nutrients, and provides a haven for beneficial microbes. Soil enriched with biochar becomes drought-resistant, nutrient-rich, and biologically active—qualities that scream resilience.
Historically, ancient civilizations in the Amazon used biochar to transform barren soils into fertile agricultural hubs. Known as *terra preta*, these soils remain productive centuries later, highlighting biochar’s remarkable staying power.
Yet, like comfrey, biochar’s potential is magnified when it’s part of a larger system.
### **The Synergy: Comfrey and Biochar Together**
Resilience turns into anti-fragility when systems go beyond mere survival and start improving under stress. Combining comfrey and biochar achieves exactly that.
1. **Nutrient Cycling and Retention**\
Comfrey’s leaves, rich in nitrogen, potassium, and phosphorus, make an excellent mulch when cut and dropped onto the soil. However, these nutrients can wash away in heavy rains. Enter biochar. Its porous structure locks in the nutrients from comfrey, preventing runoff and keeping them available for plants. Together, they create a system that not only recycles nutrients but amplifies their effectiveness.
2. **Water Management**\
Biochar holds onto water making soil not just drought-resistant but actively water-efficient, improving over time with each rain and dry spell.
3. **Microbial Ecosystems**\
Comfrey enriches soil with organic matter, feeding microbial life. Biochar provides a home for these microbes, protecting them and creating a stable environment for them to multiply. Together, they build a thriving soil ecosystem that becomes more fertile and resilient with each passing season.
Resilient systems can withstand shocks, but anti-fragile systems actively use those shocks to grow stronger. Comfrey and biochar together form an anti-fragile system. Each addition of biochar enhances water and nutrient retention, while comfrey regenerates biomass and enriches the soil. Over time, the system becomes more productive, less dependent on external inputs, and better equipped to handle challenges.
This synergy demonstrates the power of designing systems that don’t just survive—they thrive.
### **Lessons Beyond the Soil**
The partnership of comfrey and biochar offers a valuable lesson for our own lives. Resilience is an admirable trait, but anti-fragility takes us further. By combining complementary strengths and leveraging stress as an opportunity, we can create systems—whether in soil, business, or society—that improve under pressure.
Nature shows us that resilience isn’t the end goal. When we pair resilient tools like comfrey and biochar, we unlock a system that evolves, regenerates, and becomes anti-fragile. By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
-

@ e31e84c4:77bbabc0
2024-12-02 10:44:07
*Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net*
Fiduciary duty is the obligation to act in the client’s best interests at all times, prioritizing their needs above the advisor’s own, ensuring honesty, transparency, and avoiding conflicts of interest in all recommendations and actions.
This is something all advisors in the BFAN take very seriously; after all, we are legally required to do so. For the average advisor this is a fairly easy box to check. All you essentially have to do is have someone take a 5-minute risk assessment, fill out an investment policy statement, and then throw them in the proverbial 60/40 portfolio. You have thousands of investment options to choose from and you can reasonably explain how your client is theoretically insulated from any move in the \~markets\~. From the traditional financial advisor perspective, you could justify nearly anything by putting a client into this type of portfolio. All your bases were pretty much covered from return profile, regulatory, compliance, investment options, etc. It was just too easy. It became the household standard and now a meme.
As almost every real bitcoiner knows, the 60/40 portfolio is moving into psyop territory, and many financial advisors get clowned on for defending this relic on bitcoin twitter. I’m going to specifically poke fun at the ‘40’ part of this portfolio.
The ‘40’ represents fixed income, defined as…
> An investment type that provides regular, set interest payments, such as bonds or treasury securities, and returns the principal at maturity. It’s generally considered a lower-risk asset class, used to generate stable income and preserve capital.
Historically, this part of the portfolio was meant to weather the volatility in the equity markets and represent the “safe” investments. Typically, some sort of bond.
First and foremost, the fixed income section is most commonly constructed with U.S. Debt. There are a couple main reasons for this. Most financial professionals believe the same fairy tale that U.S. Debt is “risk free” (lol). U.S. debt is also one of the largest and most liquid assets in the market which comes with a lot of benefits.
There are many brilliant bitcoiners in finance and economics that have sounded the alarm on the U.S. debt ticking time bomb. I highly recommend readers explore the work of Greg Foss, Lawrence Lepard, Lyn Alden, and Saifedean Ammous. My very high-level recap of their analysis:
- A bond is a contract in which Party A (the borrower) agrees to repay Party B (the lender) their principal plus interest over time.
- The U.S. government issues bonds (Treasury securities) to finance its operations after tax revenues have been exhausted.
- These are traditionally viewed as “risk-free” due to the government’s historical reliability in repaying its debts and the strength of the U.S. economy
- U.S. bonds are seen as safe because the government has control over the dollar (world reserve asset) and, until recently (20 some odd years), enjoyed broad confidence that it would always honor its debts.
- This perception has contributed to high global demand for U.S. debt but, that is quickly deteriorating.
- The current debt situation raises concerns about sustainability.
- The U.S. has substantial obligations, and without sufficient productivity growth, increasing debt may lead to a cycle where borrowing to cover interest leads to more debt.
- This could result in more reliance on money creation (printing), which can drive inflation and further debt burdens.
In the words of Lyn Alden “Nothing stops this train”
Those obligations are what makes up the 40% of most the fixed income in your portfolio. So essentially you are giving money to one of the worst capital allocators in the world (U.S. Gov’t) and getting paid back with printed money.
As someone who takes their fiduciary responsibility seriously and understands the debt situation we just reviewed, I think it’s borderline negligent to put someone into a classic 60% (equities) / 40% (fixed income) portfolio without serious scrutiny of the client’s financial situation and options available to them. I certainly have my qualms with equities at times, but overall, they are more palatable than the fixed income portion of the portfolio. I don’t like it either, but the money is broken and the unit of account for nearly every equity or fixed income instrument (USD) is fraudulent. It’s a paper mache fade that is quite literally propped up by the money printer.
To briefly be as most charitable as I can – It wasn’t always this way. The U.S. Dollar used to be sound money, we used to have government surplus instead of mathematically certain deficits, The U.S. Federal Government didn’t used to have a money printing addiction, and pre-bitcoin the 60/40 portfolio used to be a quality portfolio management strategy. Those times are gone.
### Now the fun part. How does bitcoin fix this?
Bitcoin fixes this indirectly. Understanding investment criteria changes via risk tolerance, age, goals, etc. A client may still have a need for “fixed income” in the most literal definition – Low risk yield. Now you may be thinking that yield is a bad word in bitcoin land, you’re not wrong, so stay with me. Perpetual motion machine crypto yield is fake and largely where many crypto scams originate. However, that doesn’t mean yield in the classic finance sense does not exist in bitcoin, it very literally does. Fortunately for us bitcoiners there are many other smart, driven, and enterprising bitcoiners that understand this problem and are doing something to address it. These individuals are pioneering new possibilities in bitcoin and finance, specifically when it comes to fixed income.
Here are some new developments –
Private Credit Funds – The Build Asset Management Secured Income Fund I is a private credit fund created by Build Asset Management. This fund primarily invests in bitcoin-backed, collateralized business loans originated by Unchained, with a secured structure involving a multi-signature, over-collateralized setup for risk management. Unchained originates loans and sells them to Build, which pools them into the fund, enabling investors to share in the interest income.
Dynamics
- Loan Terms: Unchained issues loans at interest rates around 14%, secured with a 2/3 multi-signature vault backed by a 40% loan-to-value (LTV) ratio.
- Fund Mechanics: Build buys these loans from Unchained, thus providing liquidity to Unchained for further loan originations, while Build manages interest payments to investors in the fund.
Pros
- The fund offers a unique way to earn income via bitcoin-collateralized debt, with protection against rehypothecation and strong security measures, making it attractive for investors seeking exposure to fixed income with bitcoin.
Cons
- The fund is only available to accredited investors, which is a regulatory standard for private credit funds like this.
Corporate Bonds – MicroStrategy Inc. (MSTR), a business intelligence company, has leveraged its corporate structure to issue bonds specifically to acquire bitcoin as a reserve asset. This approach allows investors to indirectly gain exposure to bitcoin’s potential upside while receiving interest payments on their bond investments. Some other publicly traded companies have also adopted this strategy, but for the sake of this article we will focus on MSTR as they are the biggest and most vocal issuer.
Dynamics
- Issuance: MicroStrategy has issued senior secured notes in multiple offerings, with terms allowing the company to use the proceeds to purchase bitcoin.
- Interest Rates: The bonds typically carry high-yield interest rates, averaging around 6-8% APR, depending on the specific issuance and market conditions at the time of issuance.
- Maturity: The bonds have varying maturities, with most structured for multi-year terms, offering investors medium-term exposure to bitcoin’s value trajectory through MicroStrategy’s holdings.
Pros
- Indirect Bitcoin exposure with income provides a unique opportunity for investors seeking income from bitcoin-backed debt.
- Bonds issued by MicroStrategy offer relatively high interest rates, appealing for fixed-income investors attracted to the higher risk/reward scenarios.
Cons
- There are credit risks tied to MicroStrategy’s financial health and bitcoin’s performance. A significant drop in bitcoin prices could strain the company’s ability to service debt, increasing credit risk.
- Availability: These bonds are primarily accessible to institutional investors and accredited investors, limiting availability for retail investors.
Interest Payable in Bitcoin – River has introduced an innovative product, bitcoin Interest on Cash, allowing clients to earn interest on their U.S. dollar deposits, with the interest paid in bitcoin.
Dynamics
- Interest Payment: Clients earn an annual interest rate of 3.8% on their cash deposits. The accrued interest is converted to Bitcoin daily and paid out monthly, enabling clients to accumulate Bitcoin over time.
- Security and Accessibility: Cash deposits are insured up to $250,000 through River’s banking partner, Lead Bank, a member of the FDIC. All Bitcoin holdings are maintained in full reserve custody, ensuring that client assets are not lent or leveraged.
Pros
- There are no hidden fees or minimum balance requirements, and clients can withdraw their cash at any time.
- The 3.8% interest rate provides a predictable income stream, akin to traditional fixed-income investments.
Cons
- While the interest rate is fixed, the value of the Bitcoin received as interest can fluctuate, introducing potential variability in the investment’s overall return.
- Interest rate payments are on the lower side
Admittedly, this is a very small list, however, these types of investments are growing more numerous and meaningful. The reality is the existing options aren’t numerous enough to service every client that has a need for fixed income exposure. I challenge advisors to explore innovative options for fixed income exposure outside of sovereign debt, as that is most certainly a road to nowhere. It is my wholehearted belief and call to action that we need more options to help clients across the risk and capital allocation spectrum access a sound money standard.
Additional Resources
- [River: The future of saving is here: Earn 3.8% on cash. Paid in Bitcoin.](http://bitcoin%20and%20fixed%20ihttps//blog.river.com/bitcoin-interest-on-cash/ncome)
- [Onramp: Bitcoin, The Emergent Asset Class](https://onrampbitcoin.docsend.com/view/j4wje7kgvw357tt9)
- [MicroStrategy: MicroStrategy Announces Pricing of Offering of Convertible Senior Notes](https://www.microstrategy.com/press/microstrategy-announces-pricing-of-offering-of-convertible-senior-notes_09-18-2024)
---
*Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net*
-

@ b8851a06:9b120ba1
2025-02-18 20:42:10
> Nothing disgusts me more than the way the white-collar justice system operates—where billion-dollar crimes are punished with pocket-change fines, and the executives responsible walk free, richer than ever. You will never see this on the centralized, Keynesian, fiat-owned mainstream media. Only here on #Nostr, where the truth isn’t for sale.
>
JPMorgan Chase is not just a bank—it is a repeat offender in the global financial system. With 272 violations and $39.3 billion in fines since 2000, its track record rivals that of the most notorious criminal enterprises. And yet, it remains untouchable, shielded by its financial dominance and a regulatory system that punishes lawbreaking with fines too insignificant to be real deterrents.
In 2024 alone, JPMorgan Chase reported $58.5 billion in net income, an 18% increase from 2023. Meanwhile, it incurred $825 million in fines, which accounted for just 1.41% of its net income—a rounding error for the banking giant.
### Fines vs. Profits: The Cost of Doing Business
Year Total Revenue (in billions) Net Income (in billions) Total Fines (in billions) Fines as % of Net Income
2024 $177.6 $58.5 $0.825 1.41%
2023 $158.1 $49.6 Data not specified N/A
2022 $132.3 $35.9 Data not specified N/A
###### Sources: Bloomberg, Ventureburn
JPMorgan’s profits dwarf the penalties it pays, showing that these fines are simply the cost of doing business.
### 2024: A Continuation of Violations
Despite its massive profits, JPMorgan continues its long history of lawbreaking. In 2024 alone, it has been fined $825 million across multiple categories:
• $250 million – Banking violations
• $200 million – Investor protection violations
• $151 million – Securities violations
• $125 million – Price-fixing practices
• $98.2 million – Banking violations
Additionally, in January 2024, the bank was fined $18 million for forcing customers to stay silent about illegal activities through confidential release agreements—another example of corporate misconduct being covered up rather than addressed.
JPMorgan has admitted to market manipulation, securities fraud, and price-fixing—yet it remains a repeat offender because financial penalties do not impact its bottom line.
### The Human Cost: How JPMorgan Hurts Regular People
While JPMorgan’s executives cash in on record profits, their crimes directly harm ordinary people:
• Loan denials due to false credit reporting
• Higher interest rates on credit cards and loans
• Difficulty opening new deposit accounts
• Challenges in renting apartments or securing jobs
• Thousands of suspicious transactions totaling $1.5 billion went unreported
Beyond the numbers, real people suffer from these violations. In 2024, JPMorgan was sued for failing to protect consumers from fraud on the Zelle payment platform. Customers lost over $870 million since Zelle’s 2017 launch, and JPMorgan ignored thousands of fraud complaints, even advising victims to contact scammers directly to get their money back.
This is not just corporate negligence—it is systematic exploitation.
### Breakdown of JPMorgan’s Violations (2000-2024)
JPMorgan’s violations span nearly every financial crime category imaginable:
• Toxic Securities Abuses: $13.46 billion
• Investor Protection Violations: $6.25 billion
• Mortgage Abuses: $5.36 billion
• Banking Violations: $4.26 billion
• Consumer Protection Violations: $3.19 billion
This systematic lawbreaking has become a business strategy rather than a legal risk.
### Regulatory Capture: Why JPMorgan Gets Away With It
The question remains: Why does nothing change? The answer is regulatory capture—where the regulators responsible for policing the banks are influenced or controlled by the industry itself.
### The Revolving Door: How Banks Own Their Regulators
• Regulators frequently leave their jobs to work for the banks they once supervised.
• The banking industry is so complex that even lawmakers struggle to verify its practices.
• Regulators fear antagonizing banks because they often seek employment in the same industry.
JPMorgan exploits this system to avoid real consequences. Its CEO, Jamie Dimon, has openly criticized regulation and vowed to fight new financial rules, ensuring that oversight remains weak and penalties remain a slap on the wrist.
### Systematic Failures in Regulation
• Consumer protection is spread across seven different agencies, creating inefficiency.
• Conflicts of interest within these agencies weaken enforcement.
• Some regulators have explicit mandates to promote the financial system’s competitiveness rather than hold banks accountable.
This cycle ensures that fines remain low, executives avoid jail, and banks like JPMorgan continue breaking the law with impunity.
### Industry-Wide Issues: A Systemic Problem
JPMorgan Chase is not alone. The banking sector as a whole is rife with fraud and corruption:
• Wells Fargo: In 2024, Wells Fargo was sued for failing to protect customers from fraud on the Zelle payment platform, contributing to $870 million in consumer losses.
• Bank of America: Also implicated in the Zelle fraud lawsuit for failing to implement basic fraud protections.
These cases prove that financial misconduct is not an exception—it’s the industry standard.
### Too Big to Fail, Too Criminal to Stop
JPMorgan’s status as a “too big to fail” institution means that no matter how many laws it breaks, no matter how many billions it pays in fines, it remains untouchable.
If an individual committed fraud, price-fixing, or money laundering on this scale, they would spend a lifetime in prison. JPMorgan? It just keeps making record profits.
This is not justice. This is the financial elite operating above the law. Until executives face criminal prosecution instead of just fines, JPMorgan Chase will remain what it has been for decades:
**A financial felon in a three-piece suit.**
### The Next Stage of Banking Corruption
JPMorgan’s violations are not just a relic of past financial crises. The next stage of banking corruption is already underway—and this time, the stakes are even higher.
With AI-driven market manipulation, rising corporate surveillance, and the increasing concentration of financial power, the system is evolving in ways that regulators are not prepared to handle. JPMorgan and its peers are already positioning themselves to profit from the next crisis, just as they did in 2008.
The question is not whether JPMorgan will commit future crimes. The question is how much they will profit from them—and how little they will be held accountable.
The reality is clear: JPMorgan Chase is not a bank that sometimes breaks the law. It is a criminal enterprise that happens to operate as a bank.
**#Bitcoin is the exit. The escape from their rigged system. The end of their unchecked power.**
-

@ 87730827:746b7d35
2024-11-20 09:27:53
Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/
Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country
===================================================================================
Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges.
* * *
**KEY TAKEAWAYS**
* The Central Bank of Brazil has proposed **regulations prohibiting privacy-centric cryptocurrencies** like Monero.
* The regulations **categorize exchanges into intermediaries, custodians, and brokers**, each with specific capital requirements and compliance standards.
* While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens **(NFTs) are still ‘deregulated’ in Brazil**.

In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines **regulations for virtual asset service providers (VASPs)** operating in the country.
**_In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil._**
Let’s unpack what effect these regulations will have.
Brazil’s Crackdown on Crypto Fraud
----------------------------------
If the BCB’s current rule is approved, **exchanges dealing with coins that provide anonymity must delist these currencies** or prevent Brazilians from accessing and operating these assets.
The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism.
According to the Central Bank of Brazil, the bans aim to **prevent criminals from using digital assets to launder money**. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances.
> … restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder.
>
> – [Notice of Participation](https://www.gov.br/participamaisbrasil/edital-de-participacao-social-n-109-2024-proposta-de-regulamentacao-do-)
The Central Bank has identified that **removing algorithmic stablecoins is essential to guarantee the safety of users’ funds** and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars.
The Central Bank also wants to **control all digital assets traded by companies in Brazil**. According to the current proposal, the [national regulator](https://techreport.com/cryptocurrency/learning/crypto-regulations-global-view/) will have the **power to ask platforms to remove certain listed assets** if it considers that they do not meet local regulations.
However, the regulations will not include [NFTs](https://techreport.com/statistics/crypto/nft-awareness-adoption-statistics/), real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil.
Monero: What Is It and Why Is Brazil Banning It?
------------------------------------------------
Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain.
Like Brazil, **other nations are banning Monero** in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR.
Furthermore, exchanges such as **Binance have already announced they will delist Monero** on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with [MiCA regulations](https://techreport.com/crypto-news/eu-mica-rules-existential-threat-or-crypto-clarity/).
Data from Chainalysis shows that Brazil is the **seventh-largest Bitcoin market in the world**.

In Latin America, **Brazil is the largest market for digital assets**. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset.
In Closing
----------
Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing.
Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell.
References
----------
Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems.
[View all articles by Cassio Gusson](https://techreport.com/author/cassiog/)
-

@ 97c70a44:ad98e322
2025-02-18 20:30:32
For the last couple of weeks, I've been dealing with the fallout of upgrading a web application to Svelte 5. Complaints about framework churn and migration annoyances aside, I've run into some interesting issues with the migration. So far, I haven't seen many other people register the same issues, so I thought it might be constructive for me to articulate them myself.
I'll try not to complain too much in this post, since I'm grateful for the many years of Svelte 3/4 I've enjoyed. But I don't think I'll be choosing Svelte for any new projects going forward. I hope my reflections here will be useful to others as well.
If you're interested in reproductions for the issues I mention here, you can find them below.
- [Can't save state to indexeddb](https://github.com/sveltejs/svelte/issues/15327)
- [Component unmount results in undefined variables in closures](https://github.com/sveltejs/svelte/issues/15325)
# The Need for Speed
To start with, let me just quickly acknowledge what the Svelte team is trying to do. It seems like most of the substantial changes in version 5 are built around "deep reactivity", which allows for more granular reactivity, leading to better performance. Performance is good, and the Svelte team has always excelled at reconciling performance with DX.
In previous versions of Svelte, the main way this was achieved was with the Svelte compiler. There were many ancillary techniques involved in improving performance, but having a framework compile step gave the Svelte team a lot of leeway for rearranging things under the hood without making developers learn new concepts. This is what made Svelte so original in the beginning.
At the same time, it resulted in an even more opaque framework than usual, making it harder for developers to debug more complex issues. To make matters worse, the compiler had bugs, resulting in errors which could only be fixed by blindly refactoring the problem component. This happened to me personally at least half a dozen times, and is what ultimately pushed me to migrate to Svelte 5.
Nevertheless, I always felt it was an acceptable trade-off for speed and productivity. Sure, sometimes I had to delete my project and port it to a fresh repository every so often, but the framework was truly a pleasure to use.
# Svelte is not Javascript
Svelte 5 doubled down on this tradeoff — which makes sense, because it's what sets the framework apart. The difference this time is that the abstraction/performance tradeoff did not stay in compiler land, but intruded into runtime in two important ways:
- The use of proxies to support deep reactivity
- Implicit component lifecycle state
Both of these changes improved performance _and_ made the API for developers look slicker. What's not to like? Unfortunately, both of these features are classic examples of a [leaky abstraction](https://www.joelonsoftware.com/2002/11/11/the-law-of-leaky-abstractions/), and ultimately make things _more_ complex for developers, not less.
## Proxies are not objects
The use of proxies seems to have allowed the Svelte team to squeeze a little more performance out of the framework, without asking developers to do any extra work. Threading state through multiple levels of components without provoking unnecessary re-renders in frameworks like React is an infamously difficult chore.
Svelte's compiler avoided some of the pitfalls associated with virtual DOM diffing solutions, but evidently there was still enough of a performance gain to be had to justify the introduction of proxies. The Svelte team also [seems to argue](https://svelte.dev/blog/runes) that their introduction represents an improvement in developer experience:
> we... can maximise both efficiency and ergonomics.
Here's the problem: Svelte 5 _looks_ simpler, but actually introduces _more_ abstractions.
Using proxies to monitor array methods (for example) is appealing because it allows developers to forget all the goofy heuristics involved with making sure state was reactive and just `push` to the array. I can't count how many times I've written `value = value` to trigger reactivity in svelte 4.
In Svelte 4, developers had to understand how the Svelte compiler worked. The compiler, being a leaky abstraction, forced its users to know that assignment was how you signaled reactivity. In svelte 5, developers can just "forget" about the compiler!
Except they can't. All the introduction of new abstractions really accomplishes is the introduction of more complex heuristics that developers have to keep in their heads in order to get the compiler to act the way they want it to.
In fact, this is why after years of using Svelte, I found myself using Svelte stores more and more often, and reactive declarations less. The reason being that Svelte stores are _just javascript_. Calling `update` on a store is _simple_, and being able to reference them with a `$` was just a nice bonus — nothing to remember, and if I mess up the compiler yells at me.
Proxies introduce a similar problem to reactive declarations, which is that they look like one thing but act like another on the edges.
When I started using Svelte 5, everything worked great — until [I tried to save a proxy to indexeddb](https://github.com/sveltejs/svelte/issues/15327), at which point I got a `DataCloneError`. To make matters worse, it's impossible to reliably tell if something is a `Proxy` without `try/catch`ing a structured clone, which is a performance-intensive operation.
This forces the developer to remember what is and what isn't a Proxy, calling `$state.snapshot` every time they pass a proxy to a context that doesn't expect or know about them. This obviates all the nice abstractions they gave us in the first place.
## Components are not functions
The reason virtual DOM took off way back in 2013 was the ability to model your application as composed functions, each of which takes data and spits out HTML. Svelte retained this paradigm, using a compiler to sidestep the inefficiencies of virtual DOM and the complexities of lifecycle methods.
In Svelte 5, component lifecycles are back, react-hooks style.
In React, hooks are an abstraction that allows developers to avoid writing all the stateful code associated with component lifecycle methods. Modern React tutorials universally recommend using hooks instead, which rely on the framework invisibly synchronizing state with the render tree.
While this does result in cleaner code, it also requires developers to tread carefully to avoid breaking the assumptions surrounding hooks. Just try accessing state in a `setTimeout` and you'll see what I mean.
Svelte 4 had a few gotchas like this — for example, async code that interacts with a component's DOM elements has to keep track of whether the component is unmounted. This is pretty similar to the kind of pattern you'd see in old React components that relied on lifecycle methods.
It seems to me that Svelte 5 has gone the React 16 route by adding implicit state related to component lifecycles in order to coordinate state changes and effects.
For example, here is an excerpt from the documentation for [$effect](https://svelte.dev/docs/svelte/$effect):
> You can place $effect anywhere, not just at the top level of a component, as long as it is called during component initialization (or while a parent effect is active). It is then tied to the lifecycle of the component (or parent effect) and will therefore destroy itself when the component unmounts (or the parent effect is destroyed).
That's very complex! In order to use `$effect`... effectively (sorry), developers have to understand how state changes are tracked. The [documentation for component lifecycles](https://svelte.dev/docs/svelte/lifecycle-hooks) claims:
> In Svelte 5, the component lifecycle consists of only two parts: Its creation and its destruction. Everything in-between — when certain state is updated — is not related to the component as a whole; only the parts that need to react to the state change are notified. This is because under the hood the smallest unit of change is actually not a component, it’s the (render) effects that the component sets up upon component initialization. Consequently, there’s no such thing as a “before update”/"after update” hook.
But then goes on to introduce the idea of `tick` in conjunction with `$effect.pre`. This section explains that "`tick` returns a promise that resolves once any pending state changes have been applied, or in the next microtask if there are none."
I'm sure there's some mental model that justifies this, but I don't think the claim that a component's lifecycle is only comprised of mount/unmount is really helpful when an addendum about state changes has to come right afterward.
The place where this really bit me, and which is the motivation for this blog post, is when state gets coupled to a component's lifecycle, even when the state is passed to another function that doesn't know anything about svelte.
In my application, I manage modal dialogs by storing the component I want to render alongside its props in a store and rendering it in the `layout.svelte` of my application. This store is also synchronized with browser history so that the back button works to close them. Sometimes, it's useful to pass a callback to one of these modals, binding caller-specific functionality to the child component:
```javascript
const {value} = $props()
const callback = () => console.log(value)
const openModal = () => pushModal(MyModal, {callback})
```
This is a fundamental pattern in javascript. Passing a callback is just one of those things you do.
Unfortunately, if the above code lives in a modal dialog itself, the caller component gets unmounted before the callback gets called. In Svelte 4, this worked fine, but in Svelte 5 `value` gets updated to `undefined` when the component gets unmounted. [Here's a minimal reproduction](https://github.com/sveltejs/svelte/issues/15325).
This is only one example, but it seems clear to me that _any_ prop that is closed over by a callback function that lives longer than its component will be undefined when I want to use it — with no reassignment existing in lexical scope. It seems that the [reason this happens](https://github.com/sveltejs/svelte/issues/14707) is that the props "belong" to the parent component, and are accessed via getters so that the parent can revoke access when it unmounts.
I don't know why this is necessary, but I assume there's a good engineering reason for it. The problem is, this just isn't how javascript works. Svelte is essentially attempting to re-invent garbage collection around component lifecycles, which breaks the assumption every javascript developer has that variables don't simply disappear without an explicit reassignment. It should be safe to pass stuff around and let the garbage collector do its job.
# Conclusion
Easy things are nice, but as Rich Hickey says, [easy things are not always simple](https://www.infoq.com/presentations/Simple-Made-Easy/). And like Joel Spolsky, I don't like being surprised. Svelte has always been full of magic, but with the latest release I think the cognitive overhead of reciting incantations has finally outweighed the power it confers.
My point in this post is not to dunk on the Svelte team. I know lots of people like Svelte 5 (and react hooks). The point I'm trying to make is that there is a tradeoff between doing things on the user's behalf, and giving the user agency. Good software is built on understanding, not cleverness.
I also think this is an important lesson to remember as AI-assisted coding becomes increasingly popular. Don't choose tools that alienate you from your work. Choose tools that leverage the wisdom you've already accumulated, and which help you to cultivate a deeper understanding of the discipline.
Thank you to Rich Harris and team for many years of pleasant development. I hope that (if you read this) it's not _so_ full of inaccuracies as to be unhelpful as user feedback.
-

@ 6e0ea5d6:0327f353
2025-02-18 18:11:32
Ascolta bene, si?
I have something to tell you, amico mio, something uncomfortable, yet a fundamental piece of advice for your personal journey toward painful success: always be mindful of how you handle your thoughts and conduct.
More often than not, we are our own worst enemies, and our own thoughts and behaviors are the true obstacles in our lives.
Perhaps you feel trapped in a cycle of negative thinking, feeding your fears and insecurities. You may have already realized that your poor habits have harmed your relationships and goals.
What matters is understanding that, although these patterns may seem inevitable, we have the power to change them.
The Stoic concepts of memento mori and premeditatio malorum remind us of the transience of life and the importance of preparing for the challenges ahead.
Memento mori means "remember that you are mortal," and premeditatio malorum translates to "premeditation of evils." These ideas encourage us to reflect on life's fleeting nature and mentally prepare for the hardships that will come.
By remembering that life is short and that adversity is inevitable, we can become more resilient and courageous. We can face our own thoughts and behaviors with greater determination and seek the change needed to achieve our goals and become better individuals.
Identify the areas where you need improvement and start working on them. Change is not easy, but it is possible. Use memento mori to remind yourself that life is short and valuable, and premeditatio malorum to mentally prepare for the challenges that lie ahead.
Take control of your thoughts and actions, and become the best version of yourself. Forget about others—their lives are nothing more than an illusory stage play.
Thank you for reading, my friend!
If this message has helped you in any way, consider leaving your “🥃” as a token of appreciation.
A toast to our family!
-

@ af9c48b7:a3f7aaf4
2024-11-18 20:26:07
## Chef's notes
This simple, easy, no bake desert will surely be the it at you next family gathering. You can keep it a secret or share it with the crowd that this is a healthy alternative to normal pie. I think everyone will be amazed at how good it really is.
## Details
- ⏲️ Prep time: 30
- 🍳 Cook time: 0
- 🍽️ Servings: 8
## Ingredients
- 1/3 cup of Heavy Cream- 0g sugar, 5.5g carbohydrates
- 3/4 cup of Half and Half- 6g sugar, 3g carbohydrates
- 4oz Sugar Free Cool Whip (1/2 small container) - 0g sugar, 37.5g carbohydrates
- 1.5oz box (small box) of Sugar Free Instant Chocolate Pudding- 0g sugar, 32g carbohydrates
- 1 Pecan Pie Crust- 24g sugar, 72g carbohydrates
## Directions
1. The total pie has 30g of sugar and 149.50g of carboydrates. So if you cut the pie into 8 equal slices, that would come to 3.75g of sugar and 18.69g carbohydrates per slice. If you decided to not eat the crust, your sugar intake would be .75 gram per slice and the carborytrates would be 9.69g per slice. Based on your objective, you could use only heavy whipping cream and no half and half to further reduce your sugar intake.
2. Mix all wet ingredients and the instant pudding until thoroughly mixed and a consistent color has been achieved. The heavy whipping cream causes the mixture to thicken the more you mix it. So, I’d recommend using an electric mixer. Once you are satisfied with the color, start mixing in the whipping cream until it has a consistent “chocolate” color thorough. Once your satisfied with the color, spoon the mixture into the pie crust, smooth the top to your liking, and then refrigerate for one hour before serving.
-

@ 41e6f20b:06049e45
2024-11-17 17:33:55
Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller.
-

@ 554ab6fe:c6cbc27e
2025-02-18 18:09:06
Presence is a crucial aspect of mental and physical health. This idea is not only espoused by religious teachers, but is slowly validated within scientific research. Much of this blog is devoted to exploring the scientific validation of mindfulness practices on health, in particular, the effect mindfulness meditation has on our physical and mental health. However, multiple techniques can help foster this holistic lifestyle. Yoga is a famous example in the west as another form of this practice. Of course, yoga was traditionally meditative, and the physical aspect of yoga is new in relative terms. Regardless, yoga is a physical version of meditation formulated in India. Another culture that developed practices to instill presence is rooted in China. Not only did the Chinese meditate, but they formed a physical exercise and martial art known as Qi Gong (气功, *qi gong*), and a similar practice to emerge later known as Tai Chi (太极拳, *tai ji quan*). These practices produce similar effects on health compared to yoga and meditation. Therefore, they are one of many methods one can utilize to find presence.
Qi Gong is one of the most ancient forms of traditional Chinese medicine with a history of refinement of over 5000 years (Jahnke et al., 2010). The practice is composed of several martial art postures that are very fluid in motion. In the traditional sense, the purpose of these practices is to enhance one’s Qi (气). Tai Chi and Qi Gong are similar yet different. Tai Chi is typically more choreographed, lengthy, and more complex movements (Jahnke et al., 2010). Qi Gong, on the other hand, is simpler and easier to learn. Traditional instructions for both Qi Gong and Tai Chi are paraphrased as “mind the body and the breath, and then clear the mind to distill the Heavenly elixir within” (Jahnke et al., 2010). The intention of this post is not to fully elaborate on the philosophical implications of these words. However, note how the instructions here are almost identical to those of meditation practices.
The practice intends to instill an awareness of the present body, which leads to a calm mind that cultivates an understanding of something heavenly within. This idea shares a remarkable resemblance to the concept that meditation and the mind’s stillness create an altered characterized by a sense of unity of being with all of life, though there is no perfect term to describe this experience. Yet, this unity is likely the same thing as this “Heavenly elixir.” This experience has been clinically observed in meditators, psychedelic users, and those who experience religious moments. It seems to be the experiential one of the by-products and intents of these Chinese practices.
Outside of the more spiritual benefit, these practices manifest health benefits as well. Most research regarding these techniques focuses on Tai Chi. However, a literature review article noted that the Tai Chi used in academic settings is often simplified and more akin to Qi Gong (Jahnke et al., 2010). Therefore, Tai Chi and Qi Gong’s scientific literature will be considered the same here. For simplicity, I will refer to both as meditative martial arts.
Meditative martial arts share many health-related benefits to traditional forms of exercise, despite being less strenuous. For example, a literature review found that despite the absence of weight-bearing activity, meditative martial arts retard bone loss and the occurrence of fractures (Jahnke et al., 2010). Additionally, these practices help improve knee health in older adults, even compared to traditional forms of exercise (Chen et al., 2016). Meditative martial arts are also comparable to other forms of exercise in reducing blood pressure (Jahnke et al., 2010). Other research also similarly shown yoga to be superior to regular exercise in certain regards (Ross & Thomas, 2010). This is not to say that the purely physical aspect of meditative martial arts or yoga is superior in all cases. Instead, it is the mental aspect incorporated that provides extra benefits.
Meditative martial arts have been shown to decrease or modulate heart rate variability (HRV) (Jahnke et al., 2010; Lu & Kuo, 2003; Wei et al., 2016). This indicates increased parasympathetic nervous system activity in response to the aspects of the practice. Increased parasympathetic activity can provide a cascade of health benefits across the body and is likely the source of the extra help. Meditative martial arts have also been theorized to benefit the gut microbiome and immune function, likely via the same mechanism, making meditative martial arts much more than physical exercise or fancy movements, but a practice that cultivates holistic health.
The idea that these meditative martial arts provide additional benefits, compared to traditional exercises that seem like the benefits of sitting meditation, brings to question the essence of these practices. It may seem odd that physical activity can induce benefits caused by sitting meditation because sitting meditation is, in part, aimed to generate mental stillness. Yet, optimal mental stillness seems impossible when one is mentally choreographing movements. This highlights the importance of not the mental stillness achieved by meditation, but the attention to the body’s sensations in the present moment. Both Tai Chi, Qi Gong, and even yoga involve the constant monitoring of the body’s sensations and position. The practice of this draws the individual’s attention to the present and experience of the present. This is a crucial aspect of all forms of meditation, including the sitting version. Perhaps sitting meditations may provide a better opportunity for mental stillness, but this is not the only important aspect of mindfulness practice.
For this reason, incorporating all these practices should be seen as the optimal path towards the goal. For one cannot be healthy by simply sitting, exercise is needed. At the same time, achieving great mental stillness will only heighten one’s practice beyond that gained merely by the meditative martial arts and yoga.
There are multiple techniques and methods to practice mindfulness that provide significant benefits to health and well-being. Both the sitting and movement-oriented practices contain their pros and cons. Neither is all encompassing and perhaps they are only complete when together. For those seeking a lifestyle of mindfulness, interested in holistic health, and maybe even the obtainment of enlightenment, it is recommended that sitting meditation and meditative martial arts, or yoga, be incorporated within your daily practice.
**References**
Chen, Y. W., Hunt, M. A., Campbell, K. L., Peill, K., & Reid, W. D. (2016). The effect of Tai Chi on four chronic conditions - cancer, osteoarthritis, heart failure and chronic obstructive pulmonary disease: A systematic review and meta-analyses. *British Journal of Sports Medicine*, *50*(7), 397–407. https://doi.org/10.1136/bjsports-2014-094388
Jahnke, R., Larkey, L., Rogers, C., Etnier, J., & Lin, F. (2010). A comprehensive review of health benefits of qigong and tai chi. *American Journal of Health Promotion : AJHP*, *24*(6). https://doi.org/10.4278/ajhp.081013-lit-248
Lu, W. A., & Kuo, C. D. (2003). The Effect of Tai Chi Chuan on the Autonomic Nervous Modulation in Older Persons. *Medicine and Science in Sports and Exercise*, *35*(12), 1972–1976. https://doi.org/10.1249/01.MSS.0000099242.10669.F7
Ross, A., & Thomas, S. (2010). The health benefits of yoga and exercise: A review of comparison studies. *Journal of Alternative and Complementary Medicine*, *16*(1), 3–12. https://doi.org/10.1089/acm.2009.0044
Wei, G. X., Li, Y. F., Yue, X. L., Ma, X., Chang, Y. K., Yi, L. Y., Li, J. C., & Zuo, X. N. (2016). Tai Chi Chuan modulates heart rate variability during abdominal breathing in elderly adults. *PsyCh Journal*, *5*(1), 69–77. https://doi.org/10.1002/pchj.105
-

@ 3bf0c63f:aefa459d
2024-03-19 14:01:01
# Nostr is not decentralized nor censorship-resistant
Peter Todd has been [saying this](nostr:nevent1qqsq5zzu9ezhgq6es36jgg94wxsa2xh55p4tfa56yklsvjemsw7vj3cpp4mhxue69uhkummn9ekx7mqpr4mhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet5qy8hwumn8ghj7mn0wd68ytnddaksz9rhwden5te0dehhxarj9ehhsarj9ejx2aspzfmhxue69uhk7enxvd5xz6tw9ec82cspz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqy28wumn8ghj7un9d3shjtnwdaehgu3wvfnsz9nhwden5te0wfjkccte9ec8y6tdv9kzumn9wspzpn92tr3hexwgt0z7w4qz3fcch4ryshja8jeng453aj4c83646jxvxkyvs4) for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr _today_ is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:

The top one was published to `wss://nostr.wine`, `wss://nos.lol`, `wss://pyramid.fiatjaf.com`. The second was published to the relay where I generally publish all my notes to, `wss://pyramid.fiatjaf.com`, and that is announced on my [NIP-05 file](https://fiatjaf.com/.well-known/nostr.json) and on my [NIP-65](https://nips.nostr.com/65) relay list.
A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:

These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are _following me_, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on `wss://pyramid.fiatjaf.com`.
If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is _inherently_ centralized or that it needs a _protocol change_ to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we [drive in the right direction](bc63c348b) we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
---
See also:
- [Censorship-resistant relay discovery in Nostr](nostr:naddr1qqykycekxd3nxdpcvgq3zamnwvaz7tmxd9shg6npvchxxmmdqgsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8grqsqqqa2803ksy8)
- [A vision for content discovery and relay usage for basic social-networking in Nostr](nostr:naddr1qqyrxe33xqmxgve3qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cywwjvq)
-

@ 6e0ea5d6:0327f353
2025-02-18 17:59:24
At the banquet of consequences, there is only one worthy dish: pride, never regret. At that table, the main course will not be served with lukewarm excuses or poorly disguised remorse. Let it be pride—fiery, indomitable—that fills your mouth and satisfies your hunger for dignity. The man who surrenders to remorse is already dead before the grave. It is honor that should fill your stomach, not the bitter taste of shame.
When the battle weighs heavy, remember: you fight for those you love, for true love—the one that keeps us standing in the storm—is an anchor of iron. It is not the soft, sweet love of illusions but the steel that holds you to the ground when chaos tries to drag you away. Let hatred be the fuel of your victory, as long as you control it. If it serves you to win, so be it; but make it a weapon, not a chain. Defeat is not an option, and those who bow before it bear the mark of weakness forever.
Understand this: victory and defeat are fleeting; it is the battle itself that truly matters and defines who you are. Only a fool longs for the end. For the man who knows, rest comes only with the last breath. As long as there is life, there is struggle, and that is enough.
Reality is not for the weak. If you cannot bear the truth, seek comfort in ignorance. But a man, fully made, knows what it means to forge character through blood and silence. And finally, expect nothing from anyone. The one who enters battle relying on others’ help is already defeated. You were not born to be spared or carried. You were born to stand on your own strength and feast at the banquet of your victories.
Thank you for reading, my friend!
If this message has helped you in any way, consider leaving your “🥃” as a token of appreciation.
A toast to our family!
-

@ e6ce6154:275e3444
2023-07-27 14:12:49
Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade.
Isto é mais uma prova que os autoproclamados antirracistas são piores que os racistas.
https://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico
Segue artigo na íntegra. 👇
Sem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes.
Com a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo.
Há algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube.
Lamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores.
No entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado.
Pela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência.
Infelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância.
Como a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade.
Em virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada.
Como são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos.
Partindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista).
Para a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos.
De fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais.
Sem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade.
Você também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra.
Sabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles.
Tanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia.
Mas vamos analisar cada um desses tópicos separadamente para entender isso melhor.
Racismo
Quando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso.
Aproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão.
Diversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam.
Na Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses.
Se estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo.
A verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente.
E é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança.
Absolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível.
A integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa.
Ou seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país.
A discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados.
Para citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela.
O exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas.
Indo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita.
A verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar.
Fascismo
Quando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico.
Mas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade.
Em um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo.
Portanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade.
É claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)?
As leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la.
Essa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal.
Existem duas fortes razões para isso:
A primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não.
Além do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele.
Outra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós.
Portanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade.
Se você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade.
Em primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado.
Machismo
Muitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social.
Apesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal.
Como sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe.
O liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista.
Tão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade.
A verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade.
O que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são.
O nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas?
Homofobia
Quando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador.
A Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação.
Segue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual:
“Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada)
“Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada)
“O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências)
Se você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea.
Portanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher.
Infelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites.
Definitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”.
Qualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig.
Uma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender.
Como se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista.
Evidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for.
Afinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio?
Homossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar.
Discriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades.
Conclusão
A militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza.
Nós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço.
Quanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda.
A história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista.
Pois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos.
-

@ cc32882d:eca332e6
2025-02-18 17:29:01
#introductions
Hello World
New here as of today! I set myself up first on Yakihonne. (Just trying out clients so far)
Glad to be here and look forward to learning and getting to know peeps. I have been poking around a bit and like what I see so far. Excited to play around some more with Nostr apps. Any suggestions is greatly appreciated.
Whats the good, the bad, and the ugly about Nostr in your opinion?
What is the size of nostr platform? How many users? Hows the community involvment? What is the age range?
Any good places to look at this kind of data.
About:
Like to think deep about life and its vast array of questions and answers that are waiting to be discovered or rediscovered. Live with Nature, Dont fight what will be, Love
Dislike fake people. JUST BE REAL, Life is to short for anything else.
Drop me a response and I will get back to you as soon as possible. Look forward to hearing from some of you.
Thank You for Your Time and For Reading This
-ObsidianQuill
-

@ 266815e0:6cd408a5
2025-02-18 17:26:16
To all existing nostr developers and new nostr developers, stop using kind 1 events... just stop whatever your doing and switch the kind to `Math.round(Math.random() * 10000)` trust me it will be better
## What are kind 1 events
kind 1 events are defined in [NIP-10](https://github.com/nostr-protocol/nips/blob/master/10.md) as "simple plaintext notes" or in other words social posts.
## Don't trick your users
Most users are joining nostr for the social experience, and secondly to find all the cool "other stuff" apps
They find friends, browse social posts, and reply to them. If a user signs into a new nostr client and it starts asking them to sign kind 1 events with blobs of JSON, they will sign it without thinking too much about it
Then when they return to their comfy social apps they will see that they made 10+ posts with massive amounts of gibberish that they don't remember posting. then they probably will go looking for the delete button and realize there isn't one...
Even if those kind 1 posts don't contain JSON and have a nice fancy human readable syntax. they will still confuse users because they won't remember writing those social posts
## What about "discoverability"
If your goal is to make your "other stuff" app visible to more users, then I would suggest using [NIP-19](https://github.com/nostr-protocol/nips/blob/master/19.md) and [NIP-89](https://github.com/nostr-protocol/nips/blob/master/89.md)
The first allows users to embed any other event kind into social posts as `nostr:nevent1` or `nostr:naddr1` links, and the second allows social clients to redirect users to an app that knows how to handle that specific kind of event
So instead of saving your apps data into kind 1 events. you can pick any kind you want, then give users a "share on nostr" button that allows them to compose a social post (kind 1) with a `nostr:` link to your special kind of event and by extension you app
## Why its a trap
Once users start using your app it becomes a lot more difficult to migrate to a new event kind or data format.
This sounds obvious, but If your app is built on kind 1 events that means you will be stuck with their limitation forever.
For example, here are some of the limitations of using kind 1
- Querying for your apps data becomes much more difficult. You have to filter through all of a users kind 1 events to find which ones are created by your app
- Discovering your apps data is more difficult for the same reason, you have to sift through all the social posts just to find the ones with you special tag or that contain JSON
- Users get confused. as mentioned above users don't expect their social posts to be used in "other stuff" apps
- Other nostr clients won't understand your data and will show it as a social post with no option for users to learn about your app
-

@ 266815e0:6cd408a5
2025-02-18 17:25:31
## noStrudel
Released another major version of noStrudel v0.42.0
Which included a few new features and a lot of cleanup
nostr:naddr1qvzqqqr4gupzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqp3hx7um5wf6kgetv956ry6rmhwr
## Blossom
On the blossom front there where a few more PRs
- Expanded the documentation around CORS headers in BUD-01 thanks to nostr:npub1a6we08n7zsv2na689whc9hykpq4q6sj3kaauk9c2dm8vj0adlajq7w0tyc
- Made auth optional on the `/upload` endpoint [PR](https://github.com/hzrd149/blossom/pull/33)
- Added a `HEAD /media` endpoint for BUD-05 [PR](https://github.com/hzrd149/blossom/pull/42)
- Added range request recommendations to BUD-01 [PR](https://github.com/hzrd149/blossom/pull/47)
With blossom uploads starting to be supported in more nostr clients users where starting to ask where to find a list of blossom servers. so I created a simple nostr client that allows users to post servers and leave reviews
[blossomservers.com](https://blossomservers.com)
Its still very much a work in progress (needs login and server and review editing)
The source is on [github](https://github.com/hzrd149/blossomservers)
I also started another project to create a simple account based paid blossom server [blossom-account-server](https://github.com/hzrd149/blossom-account-server)
Unfortunately I got sidetracked and I didn't have the time to give it the attention it needs to get it over the finish line
## Smaller projects
- [cherry-tree](https://github.com/hzrd149/cherry-tree) A small app for uploading chunked blobs to blossom servers (with cashu payment support)
- [vite-plugin-funding](https://github.com/hzrd149/vite-plugin-funding) A vite plugin to collect and expose package "funding" to the app
- [node-red-contrib-rx-nostr](https://github.com/hzrd149/node-red-contrib-rx-nostr) The start of a node-red package for rx-nostr. if your interested please help
- [node-red-contrib-applesauce](https://github.com/hzrd149/node-red-contrib-applesauce) The start of a node-red package for applesauce. I probably wont finish it so any help it welcome
## Plans for 2025
I have a few vague ideas of what I want to work on Q1 of 2025. but there are a few things i know for certain.
I'm going to keep refactoring noStrudel by moving core logic out into [applesauce](https://hzrd149.github.io/applesauce/) and making it more modular. This should make noStrudel more reliable and hopefully allow me to create and maintain more apps with less code
And I'm going to write tests. tests for everything. hopefully tests for all the libraries and apps I've created in 2024.
A lot of the code I wrote in 2024 was hacky code to see if things could work. and while its been working pretty well I'm starting to forget the details of of the code I wrote so I cant be sure if it still works or how well it works.
So my solution is to write tests, lots of tests :)
-

@ 6ad3e2a3:c90b7740
2025-02-18 17:08:23
I’m not doing any writing today. Taking the day, maybe the week, off. Just not in the mood.
This whole idea you’re supposed to write, get the thoughts out, the ideas moving is stupid. To what end? I’m done with evaluating myself for productivity, justifying myself to myself — or anyone else.
What I really need is to find some pleasant distractions. Something to fill my time, or as Elon Musk says of Twitter “to avoid regretted user seconds.” I’ve tried Twitter itself, of course, but Musk’s algorithm falls woefully short. After an hour of doom and dopamine scrolling, punctuated with the occasional shitpost, many seconds are regretted — roughly 3500 of them.
I could turn to alcohol or drugs, but too many side effects. Yes, you’re distracted, but what about after that? You’re always left worse off than where you started. Even alcoholics and drug addicts — the pros! — know it’s a dead end.
I don’t know, maybe spend more time with loved ones? You hear that a lot. “If I didn’t have to work so much, I’d spend more time with loved ones.” LOL. Like what, you’re going to hang around while your “loved ones” are doing things with their actual lives. Maybe I’ll take the bus to school with Sasha, hang out with her and her friends, see how that goes. Quality time!
Exercise. It’s the perfect solution, good for your health, you feel better, your mind is calm. Only problem is it’s fucking miserable. If your aim is to avoid sitting at a desk to write, forcing your carcass around a track is hardly an upgrade. It’s like quitting your middle management job to break rocks in a prison chain gang.
There must be something I can do. Eating sugary processed food is out of the question for the same reason alcohol and drugs are. Becoming obese and diabetic is no solution, as many of the pros (obese diabetics) would no doubt attest.
Meditation. That’s it! You sit on a cushion, count your breaths. Pretty soon you are calm. You can meditate for as long as you want! It’s perfect, and it’s easy. Well, it’s not that easy. You get distracted by your thoughts and you’re just sitting there thinking about the things for which you hope and dread in your life.
Of course, you notice that distraction and come back to the breath, but pretty soon you’re wandering again. And you come back again. But really you’re wondering how long you’ve been sitting, your feet are falling asleep, your back is tight and you don’t feel much different. You weren’t even properly distracted because instead of being distracted *from* your mind, you are being distracted *by* it. It’s a worst-case scenario of sorts — you neither get anything done, nor escape the endless self-evaluation and justification.
That just means you’re doing it wrong, though. You’re failing at it. If you did it right, it would be the perfect escape from yourself. But it’s not working, so you’re failing. Or maybe you succeeded a little bit. You’re not sure. You are still evaluating whether that was a good use of your time. The same evaluation process you use to decide whether you’ve done enough writing, the same tired bullshit from which you were trying to escape in the first place!
Let’s face it, you’re not just going to meditate your way out of the problem. If you could, you would have already, and so would everyone else. We would all be enlightened. Maybe you need to go to an ashram or something, find a guru on top of a mountain in the Himalayas. LOL, you’re not gonna do that! You are way too attached to your comforts and daily routines, no matter how dull and unsatisfying they ultimately are.
There’s nowhere to run, nowhere to hide, no one to see, nothing to do. You are out of options. There is only one thing in your absolute control, and it’s where you direct your attention. And you have decided that no matter how bleak and pointless the alternatives the one thing about which you are resolute is you are taking the day off from writing.
-

@ d23af4ac:7bf07adb
2025-02-18 17:07:55
This is a **test**-note published directly from [Obsidian](https://obsidian.md/)
# Heading 1
Some paragraph text [^2]
## Heading 2
Second paragraph text.
* List item 1
* List item 2
```js
console.log("Hello world!")
```
### Json
```json
{
name: "Alise",
age: 45
}
```
>[!SCRUNCHABLE NOTE]-
>This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads.
>This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads.
>[!DANGER]
>This is a "danger" type message. Should be properly formateed. This is a "danger" type message. Should be properly formateed. This is a "danger" type message. Should be properly formateed. This is a "danger" type message. Should be properly formateed. This is a "danger" type message. Should be properly formateed.
--
#### Pasted image:
![[Pasted image 20250218120714.png]]
>This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote[^1]. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote.
- [x] This is a completed task
- [ ] This is an uncompleted task
- [ ] This is also an uncompleted task
>[!QUESTION]
>Will this inline code format properly? `console.log('Yo momma so fat she took a spoon to the Super Bown');` Idk...
[^1]: Footnotes also supported? Even inside blockquotes?
[^2]: Footnote in regular paragraph
-

@ d360efec:14907b5f
2025-02-18 15:11:58
**ภาพรวม BTCUSDT (OKX):**
Bitcoin (BTCUSDT) กำลังแสดงความผันผวนอย่างมาก โดยมีสัญญาณที่ขัดแย้งกันระหว่าง Timeframes ต่างๆ แนวโน้มระยะยาว (Day) ยังคงเป็นขาขึ้น แต่ระยะกลาง (4H) และระยะสั้น (15m) แสดงให้เห็นถึงแรงขายและการปรับฐานที่รุนแรง การวิเคราะห์นี้จะเน้นการระบุพื้นที่ที่ Smart Money อาจจะเข้าซื้อหรือขาย (Liquidity Pools) และประเมินความแข็งแกร่งของแนวโน้ม
**วิเคราะห์ทีละ Timeframe:**
**(1) TF Day (รายวัน):**

* **แนวโน้ม:** ขาขึ้น (Uptrend) *แต่เริ่มอ่อนแรง*
* **SMC:**
* Higher Highs (HH) และ Higher Lows (HL) *เริ่มไม่ชัดเจน*
* Break of Structure (BOS) ด้านบน *แต่เริ่มมีการปรับฐาน*
* **Liquidity:**
* มี Sellside Liquidity (SSL) อยู่ใต้ Lows ก่อนหน้า (บริเวณ 85,000 - 90,000)
* มี Buyside Liquidity (BSL) อยู่เหนือ High เดิม (109,998.9)
* **ICT:**
* ยังไม่เห็น Order Block หรือ FVG ที่ชัดเจนใน TF Day *ณ ราคาปัจจุบัน*
* **EMA:**
* ราคา *หลุด* EMA 50 (สีเหลือง) ลงมาแล้ว
* EMA 200 (สีขาว) เป็นแนวรับถัดไป
* **Money Flow (LuxAlgo):**
* แท่งสีแดงยาว แสดงถึงแรงขายที่เข้ามา
* **Trend Strength (AlgoAlpha):** *ไม่มีในภาพ*
* **Volume Profile:** Volume ค่อนข้างเบาบาง
* **แท่งเทียน:** แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย
* **แนวรับ:** EMA 200, บริเวณ 85,000 - 90,000 (SSL)
* **แนวต้าน:** EMA 50, High เดิม
* **สรุป:** แนวโน้มขาขึ้นเริ่มอ่อนแรง, ราคาหลุด EMA 50, Money Flow เป็นลบ, มี SSL ด้านล่าง
**(2) TF4H (4 ชั่วโมง):**

* **แนวโน้ม:** ขาลง (Downtrend) *ระยะสั้น* หลังจากราคาหลุด EMA 50
* **SMC:**
* Lower Highs (LH) และ Lower Lows (LL)
* Break of Structure (BOS) ด้านล่าง
* **Liquidity:**
* มี SSL อยู่ใต้ Lows ก่อนหน้า (บริเวณ 92,000)
* มี BSL อยู่เหนือ Highs ก่อนหน้า (บริเวณ 104,000 - 108,000)
* **ICT:**
* **Order Block:** ราคาลงมาใกล้ Order Block ขาขึ้น (บริเวณแท่งเทียนสีเขียวก่อนที่จะขึ้น)
* **EMA:**
* ราคาอยู่ใต้ EMA 50 และ EMA 200
* **Money Flow (LuxAlgo):**
* สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย
* **Trend Strength (AlgoAlpha):** *ไม่มีในภาพ*
* **Volume Profile** Volume ค่อนข้างเบาบาง
* **แนวรับ:** Order Block, บริเวณ 92,000 (SSL)
* **แนวต้าน:** EMA 50, EMA 200, บริเวณ Highs ก่อนหน้า
* **สรุป:** แนวโน้มขาลงระยะสั้น, ราคาลงมาใกล้ Order Block, Money Flow เป็นลบ
**(3) TF15 (15 นาที):**

* **แนวโน้ม:** ขาลง (Downtrend)
* **SMC:**
* Lower Highs (LH) และ Lower Lows (LL)
* Break of Structure (BOS) ด้านล่าง
* **Liquidity:**
* มี SSL อยู่ใต้ Lows ล่าสุด
* มี BSL อยู่เหนือ Highs ก่อนหน้า
* **ICT:**
* **Order Block:** ราคาลงมาใกล้ Oder Block
* **EMA:**
* EMA 50 และ EMA 200 เป็นแนวต้าน
* **Money Flow (LuxAlgo):**
* สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย
* **Trend Strength (AlgoAlpha):**
* เป็นสีแดง แสดงถึงเเนวโน้มขาลง
* **Volume Profile:**
* Volume ค่อนข้างเบาบาง
* **แนวรับ:** บริเวณ Low ล่าสุด
* **แนวต้าน:** EMA 50, EMA 200, บริเวณ Highs ก่อนหน้า
* **สรุป:** แนวโน้มขาลง, แรงขายมีอิทธิพล, ใกล้แนวรับ
**สรุปภาพรวมและกลยุทธ์ (BTCUSDT):**
* **แนวโน้มหลัก (Day):** ขาขึ้น (อ่อนแรง)
* **แนวโน้มรอง (4H):** ขาลง (ระยะสั้น)
* **แนวโน้มระยะสั้น (15m):** ขาลง
* **Liquidity:**
* Day: SSL (85,000-90,000), BSL (เหนือ 109,998.9)
* 4H: SSL (92,000), BSL (104,000-108,000)
* 15m: SSL (ใต้ Lows), BSL (เหนือ Highs)
* **Money Flow:** Day เริ่มเป็นลบ, 4H เป็นลบ, 15m เป็นลบ
* **Trend Strength** 15 m : ขาลง
* **กลยุทธ์:**
1. **Wait & See (ดีที่สุด):** รอความชัดเจน
2. **Short (เสี่ยง):** ถ้าไม่สามารถ Breakout EMA/แนวต้านใน TF ใดๆ ได้
3. **ไม่แนะนำให้ Buy:** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจน
**คำแนะนำ:**
* **ความขัดแย้งของ Timeframes:** ชัดเจน
* **Money Flow:** เป็นลบในทุก Timeframes
* **ระวัง SSL:** Smart Money อาจจะลากราคาลงไปกิน Stop Loss
* **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด**
**Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-

@ d360efec:14907b5f
2025-02-18 13:18:54
**นักพนันแห่งเฮรันเทล**
**“คณิตศาสตร์” กุญแจเวทมนตร์ นักพนัน และ นักลงทุน**
ในนครเฮรันเทล นามกระฉ่อนเลื่องลือในหมู่นักเสี่ยงโชค เมื่อเอ่ยถึง **“การพนัน”** ภาพที่ชาวเมืองมักนึกถึงคือ **“ยาจกข้างถนน”**
มิใช่เรื่องแปลกประหลาดอันใด เพราะเป็นที่ร่ำลือกันว่า **จ้าวแห่งหอคอยรัตติกาล** ผู้คุมบ่อนพนัน มักร่ายเวทมนตร์สร้างเกมให้ตนเองได้เปรียบ เพื่อดูดกลืนเงินทองของผู้มาเยือน
ดังนั้น การที่สามัญชนจะพิชิตเกมในระยะยาว จึงเป็นดั่งเงามายาที่จับต้องมิได้
กระนั้น ยังมีตำนานกล่าวขานถึงผู้กล้า ที่สามารถสร้างชื่อจาก **“เกมพนัน”** เช่น
**เวเนสซา รุสโซ** นักเวทย์มนตร์ผู้ใช้กฎหมายแห่งแดนไกล ใช้เวลายาวนานถึงหกปี
ร่ายเวทย์สะสมทรัพย์สินกว่าร้อยล้านเหรียญทอง จากการเล่นเกมไพ่ศักดิ์สิทธิ์ **“โป๊กเกอร์”**
หรือแม้แต่ **เอ็ดเวิร์ด โอ. ทอร์ป** จอมปราชญ์ผู้สร้างกำไรถึงสามแสนหกหมื่นเหรียญทอง ภายในเจ็ดราตรี
จากการเล่นเกมไพ่มนตรา **“แบล็กแจ็ก”** ด้วยเงินทุนตั้งต้นเพียงสามแสนสามหมื่นเหรียญทอง คิดเป็นอัตราเวทย์ตอบแทนร้อยสิบส่วน!
เหล่าจอมยุทธ์เหล่านี้ มิได้อาศัยเพียงโชคช่วยชั่วครั้งชั่วคราวแล้วเลือนหาย
แต่พวกเขากลับสามารถร่ายเวทย์สร้างผลตอบแทนระยะยาว จนเรียกได้ว่า ใช้ **“หอคอยรัตติกาล”** เป็นแหล่งเสบียงเลี้ยงชีพ
โดยกุญแจเวทย์ที่บุคคลเหล่านี้ใช้ ก็คือ **“คณิตศาสตร์”**
เหตุใด **“คณิตศาสตร์”** จึงช่วยให้ผู้คนเอาชนะ **“การพนัน”** ได้?
และนอกจาก **“การพนัน”** แล้ว **“คณิตศาสตร์”** ยังสามารถประยุกต์ใช้กับสิ่งใดได้อีก?
**นักเล่าเรื่องแห่งเฮรันเทล** จักไขปริศนาให้ฟัง
เบื้องต้น ขอให้ท่านลองพิจารณาตนเอง ว่าเคยประสบพบพานเหตุการณ์เหล่านี้หรือไม่:
- ตั้งมั่นว่า จักเสี่ยงโชคให้ได้กำไรเพียงเล็กน้อย แล้วจักหยุดพัก
- แต่หากพลาดท่าเสียที จักจำกัดการสูญเสียให้เท่าทุนเดิมที่ตั้งไว้
- ครั้นเมื่อเวทมนตร์เข้าข้าง ได้กำไรมาแล้ว กลับโลภโมโทสัน อยากได้เพิ่มอีกนิด จึงร่ายเวทย์ต่อ
- ทว่ากำไรเริ่มร่อยหรอ จนเหลือเพียงทุนเดิม สุดท้ายทุนที่ตั้งไว้คราแรกก็มลายสิ้น
- จำต้องหาเงินทองมาลงเพิ่ม หวังทวงทุนคืน และพบว่าต้องสูญเสียเงินก้อนนั้นไปในห้วงเวลาต่อมา
ลำดับเหตุการณ์ดังกล่าว เรียกได้ว่าเป็น **“วงจรอุบาทว์”** สำหรับนักพนันมากมายในเฮรันเทล
ปริศนาที่ตามมาก็คือ เหตุใด **“วงจรอุบาทว์”** นี้จึงเกิดขึ้นซ้ำแล้วซ้ำเล่า?
ส่วนหนึ่ง ย่อมเป็นเพราะอารมณ์อันแปรปรวนในการเสี่ยงโชคของแต่ละคน
แต่อีกส่วนที่สำคัญยิ่งกว่า ต้องกล่าวว่าเป็นผลจาก **“กลไกต้องสาป”** ของจ้าวแห่งหอคอยรัตติกาล
ซึ่งต้องกล่าวว่า เหล่าเจ้าของหอคอยรัตติกาลนั้น จักใช้หลักการทำนองเดียวกับ **“สมาคมพ่อค้าผู้พิทักษ์”**
คือจักเก็บเงินทองจากชนจำนวนมาก เพื่อนำมาจ่ายให้กับชนเพียงหยิบมือ
เพื่อล่อลวงให้ชนทั้งหลายเสี่ยงโชคต่อไป หรือทำให้เหล่านักพนันหวังว่า จักเป็นผู้โชคดีเฉกเช่นพวกเขาบ้าง
แม้จะมีผู้โชคดีที่สามารถได้กำไรในเบื้องต้น แต่ในบั้นปลายก็จักพ่ายแพ้อยู่ดี ซึ่งเป็นไปตาม **“กฎแห่งจำนวนมหาศาล”** เพราะจ้าวแห่งหอคอยรัตติกาลนั้น ได้คำนวณและออกแบบระบบเกมที่ตนเองได้เปรียบในระยะยาวแล้ว
จากตำนานนี้ ย่อมประจักษ์ชัดว่า แม้การพนันจักเป็นเรื่องของดวงชะตา
แต่ก็ถูกรังสรรค์ขึ้นจากการคำนวณทางคณิตศาสตร์
ดังนั้น หากปรารถนาจะหาหนทางเอาชนะจ้าวแห่งหอคอยรัตติกาล ก็จำต้องเข้าใจ **“คณิตศาสตร์”** เสียก่อน
ทีนี้ จงเงี่ยหูฟัง แล้วท่านจักได้ยินข้าไขปริศนา:
**๑. ปริศนาแห่ง “กำไรคาดหวัง”**
สำหรับการแสวงหา **“เกมเสี่ยงทาย”** ที่ควรค่าแก่การเล่น หรือการเสี่ยง
สิ่งแรกที่นักพนันพึงกระทำคือ **“การประเมินกำไรคาดหวัง”** หรือ **“เวทคำนวณอนาคต”**
**“กำไรคาดหวัง”** ถูกคิดค้นโดย **คริสเตียน ฮอยเกนส์** นักปราชญ์เวทย์ชาวดัตช์ เพื่อประเมินว่าเกมพนันแบบใดควรค่าแก่การเล่น ซึ่งมิใช่เพียงแค่การประเมินโอกาสแห่งชัยชนะเท่านั้น แต่ต้องคิดรวมขนาดของเงินเดิมพันไปด้วย
โดยสูตรเวทย์คือ:
**กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้)**
ดังนั้น หากปรารถนาจะสะสม **“ทองคำมายา”** ในระยะยาว จงเลือกเกมที่มี **“กำไรคาดหวัง”** เป็นบวก
แต่หากพลาดพลั้งเข้าไปเล่นเกมที่ **“กำไรคาดหวัง”** เป็นลบ และบังเอิญว่าโชคชะตาเล่นตลกให้ได้เงินทองมาครอง
พึงละทิ้งเกมนั้นเสียโดยพลัน เพราะท้ายที่สุดหากยังคงเล่นต่อไป ผู้อับโชคผู้นั้นก็คือตัวท่านเอง
อย่างไรก็ตาม โดยธรรมดาแล้ว **“กำไรคาดหวัง”** ของเกมพนันที่มีเจ้ามือมักจักติดลบ จึงเป็นเรื่องยากยิ่งที่จะเอาชนะได้ เฉกเช่นตัวอย่างที่เราเห็น คือเกมในบ่อนพนัน หรือแม้แต่ **“สลากกินแบ่งรัฐบาล”** ก็ล้วนเป็นเกมที่มี **“กำไรคาดหวัง”** ติดลบทั้งสิ้น
นอกจาก **“กำไรคาดหวัง”** จักถูกใช้กับการพนันได้แล้ว
หลักเวทย์ **“คณิตศาสตร์”** ก็ยังสามารถประยุกต์ใช้กับการลงทุนได้ไม่แตกต่างกัน
ตัวอย่างเช่น หากท่านเก็บสถิติข้อมูลการลงทุนของตนเอง
แล้วพบว่ามีเพียงสามสิบส่วนร้อยเท่านั้น ที่ท่านซื้อ **“ศิลาแห่งโชค”** แล้วสร้างผลตอบแทนเป็นบวก
แต่ท่านยังคงปรารถนาความสำเร็จในการลงทุน
ก็จงจำกัดการขาดทุนแต่ละคราให้น้อยเข้าไว้ เช่น -๕%
และปล่อยให้มีกำไรในแต่ละคราที่ลงทุน เช่น อย่างน้อย ๒๐%
ซึ่งจากการใช้กลยุทธ์นี้ ท่านจักมี **“กำไรคาดหวัง”** = (๒๐% x ๐.๓) + (-๕% x ๐.๗) = ๒.๕%
จักเห็นได้ว่า แม้ท่านจักมีจำนวนคราที่ขาดทุนบ่อยครั้ง แต่ก็ยังสามารถสร้างกำไรได้
หากคราที่กำไรนั้น สามารถทำเงินทองเป็นจำนวนมากได้
**๒. ปริศนาแห่ง “การบริหารหน้าตัก” หรือ “การบริหารเงินทุน”**
แม้ว่าท่านจักรับรู้ **“กำไรคาดหวัง”** แล้ว แต่หากท่านเผชิญหน้ากับการขาดทุนต่อเนื่องกัน ท่านก็อาจหมดเนื้อหมดตัวก่อนถึงคราที่จะกอบโกยเงินทองจากคราที่กำไร
วิธีคลายปมปริศนานี้ก็คือ การมิลงเงินทองทั้งหมดของท่านในการลงทุนเพียงคราเดียว
ซึ่งนอกจากการกระจายความเสี่ยงในการลงทุนหลาย **“ศิลาแห่งโชค”** หรือหลาย **“เกมเสี่ยงทาย”** แล้ว
ท่านอาจกำหนดขนาดของการลงทุนแต่ละคราให้มิมากเกินไป แบบง่าย ๆ เช่น มิเกิน ๑๐% ของเงินลงทุนทั้งหมด หรือท่านอาจคำนวณขนาดของการลงทุนแต่ละคราด้วยสูตรทางคณิตศาสตร์ เช่น สูตร **“การขาดทุนสูงสุดที่ท่านรับได้ (Value at Risk)”** หรือ สูตร **“ขนาดเดิมพันที่เหมาะสม (Kelly Formula)”**
**๓. ปริศนาแห่ง “อคติ”**
ในวงการพนัน มักมีอคติหนึ่งที่บังเกิดบ่อยครั้งกับผู้คน คือ **“Gambler's Fallacy”** หรือ **“ความเชื่อผิด ๆ แห่งนักพนัน”** ว่าหากเหตุการณ์หนึ่งบังเกิดบ่อยครั้งกว่าปรกติในช่วงเวลาหนึ่ง ๆ
เหตุการณ์นั้นจักบังเกิดบ่อยครั้งน้อยลงในอนาคต ทั้ง ๆ ที่เหตุการณ์เหล่านั้นเป็นอิสระจากกันในทางสถิติ
ยกตัวอย่างเช่น หากโยนเหรียญมนตราออกหัวไปแล้วสามครา ในคราที่สี่ หลายคนอาจคิดว่าโอกาสออกก้อยมากกว่าหัว แม้ว่าการโยนเหรียญแต่ละคราจะมิได้ส่งผลอันใดต่อกันเลย (จะโยนกี่ครา โอกาสหัวหรือก้อย ก็คือ ๕๐:๕๐ อยู่ยั่งยืน)
หรือแม้กระทั่ง **“สลากกินแบ่งรัฐบาล”** มีหลายคนที่ซื้อเลขซ้ำกัน เพื่อหวังว่าจะถูกในงวดต่อ ๆ ไป
ในวงการการลงทุน ก็มีลักษณะที่คล้ายคลึงกัน เช่น หาก **“ศิลาแห่งโชค A”** ราคาตกต่ำลงมาห้าครา บางคนอาจคิดว่าในคราที่หก ราคาของมันจักต้องเด้งขึ้นมา ซึ่งในความเป็นจริง หาได้เป็นเช่นนั้นเสมอไป
จักเห็นได้ว่า แท้จริงแล้ว ไม่ว่าจักเป็น **“เกมเสี่ยงทายแห่งโชคชะตา”** หรือ **“การผจญภัยในตลาดทุน”**
หากท่านมีความเข้าใจ และนำ **“คณิตศาสตร์”** เข้ามาเป็นรากฐาน
มันก็อาจนำพาตัวท่านเอง ไปสู่จุดที่ได้เปรียบในเกมนั้น ได้เฉกเช่นกัน..
**สูตรเวทย์มนตร์ที่ปรากฏในตำนาน:**
* **กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้)**
**คำเตือนจากนักเล่าเรื่องแห่งเฮรันเทล:**
"พึงระลึกไว้เสมอว่า โชคชะตาเป็นสิ่งที่คาดเดาได้ยาก แม้เวทมนตร์คณิตศาสตร์จักช่วยนำทาง แต่ท้ายที่สุดแล้ว ความสำเร็จยังคงขึ้นอยู่กับการตัดสินใจและสติปัญญาของท่านเอง"
หวังว่าตำนานบทนี้จักเป็นประโยชน์แก่ท่านนะคะ
-

@ fa805c81:344bed3c
2025-02-18 11:41:15

**" เจอหมีให้แกล้งตาย แต่ถ้าเจอหมีบ่อย ๆ คงเป็นบ้าไปซะก่อน "**
มีวันนึง ในยุคดึกดำบรรพ์ เด็กชายซาโตชิผู้รักการเดินป่าเป็นชีวิตจิตใจ แต่วันนี้ต่างออกไปเพราะเขาเห็น หมี ตัวใหญ่ ยืนจังก้าต่อหน้าเขา
" เวรกรรมแล้วไง " ไม่ใช่แค่ซาโตชิที่คิดแบบนี้ เป็นผม หรือคุณ ก็คิดแบบนี้กันหมดนั่นแหละ !!
*ม่านตาเบิกโพลงขยาย ยับยั้งการหลั่งน้ำลาย หลอดลมขยายตัว หัวใจเต้นรัวสั่น กลั้นปัสสาวะ*
"ระบบซิมพาเทติก" ที่ซาโตชิต้องท่องจำในชั้นเรียน เมื่ออยู่ในสถานการ์ณจริงที่ต้อง
" สู้หรือหนี " " เกี่ยวข้องกับความเป็นความตาย "
ไม่มีความจำเป็นต้องท่องเลย รับรู้เองได้หมดในเวลานั้น
ทำยังไงดีนะ ซาโตชิ ......
ไม่ว่าซาโตชิจะทำอย่างไร ไม่ว่าซาโตชิจะทำตามตัวอย่างของระบบซิมพาเทติกที่บอกว่าคนสามารถยกตู้เย็นได้ทั้งที่ไม่เคยยกมาก่อน
ถ้าซาโตชิเลือกที่จะ " สู้ " โดยการยกหมีโยนลงหน้าผา !!

หรือซาโตชิเลือกที่จะ " หนี " โดยการสับตีนแตก !!

ในการกระทำสองอย่างนี้ มีบางสิ่งที่เหมือนกัน
**" เสียพลังงานอย่างมาก " นี่คือสิ่งที่เหมือนกัน**
ระบบซิมพาเทติกคูลดาวน์... หยุดทำงาน ซาโตชิเดินป่าต่ออย่างสบายใจ หรืออาจจะกลับบ้าน ก็แล้วแต่
" อา..มัน**จบ**แล้วสินะ " ซาโตชิพูดขึ้น
จากยุคดึกดำบรรพ์ สู่ยุคปัจจุบัน
เชื้อสายของซาโตชิ ไม่จำเป็นต้องเข้าป่าไปหาของป่า
ไปตลาดนัดก็ได้ ตามกลไกตลาดเสรี
ไม่มีความจำเป็นที่ต้องลุ้นว่าจะเจอ หมี อีกต่อไปแล้ว
สโคปมาอีกนิดดีกว่าจริง ๆ แล้ว ไม่จำเป็นต้องเป็นหมี หรอกครับ อะไรที่ทำให้สมองเราสื่อว่า สิ่งนี้อันตราย ระบบซิมพาเทติกมันก็ทำงาน...
แล้วความอันตรายในยุคปัจจุบันคืออะไร ? หมีในยุคปัจจุบัน....กลายพันธ์เป็นอะไร ????
น่าอนิจจาครับ ที่ Scenario นี้ ดวงมาตกที่เชื้อสายของซาโตชิ กลับกลายเป็น**ครอบครัวมีปัญหาครับ**
( อาจจะเพราะอะไรก็ได้ เอาว่าระบบเงินเฟียต เงินเฟ้อทำให้คนเป็นบ้าแล้วกัน )
เด็กคนนี้โตมาในสภาพที่พ่อแม่ไม่รัก พ่อแม่ทะเลาะกันทุกวัน พ่อกับแม่หย่ากัน พ่อติดเหล้า แม่หนีไปมีสามีใหม่
ทุกครั้งที่พ่อแม่ทะเลาะกัน ทุกครั้งที่พ่อติดเหล้าก็อาละวาด
บางครั้งนั่งๆนอนๆทำการบ้านอยู่ดี ๆ พ่อก็เปิดประตูห้องมาในสภาพเมาๆ แล้วชวนทะเลาะ
วันที่สงบหายไปไหนนะ วันที่สงบ กลับถูกแทนที่ด้วยความเครียด
**ความเครียด ที่กระตุ้นให้ซิมพาเทติกทำงาน...**
พวกคุณเห็นความต่างอะไรมั้ยครับ
ซาโตชิเจอหมี ซิมพาเทติกทำงาน สู้หรือหนีหมี แล้วจบ
แต่กับเด็กคนนี้ ในสภาพครอบครัวที่เลวร้าย ซิมพาเทติกก็ทำงาน
**แต่เขาหนีก็ไม่ได้ สู้ก็ไม่ได้นะครับ...**
เออเอาละซิ ทำยังไงดีล่ะ ความเครียดเข้ามาทุกวันอย่างคาดเดาไม่ได้
ระบบซิมพาเทติกก็ทำงานแทบทุกวัน
1 ในอวัยวะที่ต้องจัดการกับความเครียดและซิมพาเทติก คือต่อมหมวกไตครับ
ต่อมหมวกไตชั้นนอก มีหลายฟังชั่น.. 1 ในนั้นคือการสร้าง Cortisol มาสู้กับความเครียด
ต่อมหมวกไตชั้นใน มีหน้าที่คือการสร้างอดรีนาลีน มาเพื่อใช้กับระบบซิมพาเทติก
" โอ้ย เมื่อยโว้ยยยยยยย " อันนี่ไม่ใช่คำที่เด็กคนนี้พูดอยู่คนเดียวนะครับ
ต่อมหมวกไตก็พูด....
ในเมื่ออวัยวะที่ทำให้เรา Handle กับ Stress ได้ มันเมื่อยแล้ว..
เกิดสิ่งที่เรียกว่า " ต่อมหมวกไตล้า "
Stress ที่ไม่สามารถคุมได้ เมื่อนั้นเอง ก็จะเกิดโรคหลายอย่าง
1 ในนั้นคือโรคที่เด็กโตมาในครอบครัวมีปัญหามักจะเป็นกัน " โรคซึมเศร้า "
คงไม่ต้องพูดว่าโรคนี้แย่ยังไง คนทุกคนน่าจะเข้าใจดี เพราะงั้นใจความสำคัญที่ผมต้องการบอกคือ
หมีไม่จำเป็นต้องเกิดจากครอบครัวก็ได้ครับ แต่หมีคือสภาพแวดล้อมที่เราต้องเจอมันทุกวันอย่างเลี่ยงไม่ได้
เป็นหมีที่เลวร้าย หมีที่สู้ก็ไม่ได้ หนีก็ไม่ได้อีก ได้แต่รอระเบิดเวลาว่าต่อมหมวกไตจะล้าตอนไหน
หมีอาจมาในรูปแบบ เจ้านายที่ทำงานขี้วีน เพื่อนสนิทที่ท็อคซิค สามีภรรยาที่คอยพ่นพลังงานลบมาเรื่อย ๆ
คุณอาจจะคิดว่า เอ้อ ก็ทนได้แหละ นิดๆหน่อยๆ การขัดแย้งมันไม่ดี เกรงใจเขา ไม่หรอกครับ คุณไม่จำเป็นต้องเอาตัวเองไปอยู่กับพลังงานลบแบบนั้น สงสารต่อมหมวกไตตัวเองบ้าง
ถ้ามันจะขัดแย้ง ก็ขัดแย้งให้มันจบไปเลย การหาทางออก หาทางแก้ไขในคสพ. เหมือนซาโตชิที่เลือกจะสู้หรือหนีหมีตั้งแต่ตอนนั้น ความเรื้อรังไม่ใช่ทางออกแน่นอน
อย่าเป็นหมีในความสัมพันธ์ของใคร
-

@ 3ca99671:689a4ce4
2025-02-18 09:34:11
How to avoid internal pressure and anxiety. Constantly forcing yourself to continue something, doubting its value to anyone other than your ego. And then it starts: "What if I use that framework? Maybe I should switch to another language? No, I’ll master that engine over there, and everything will fall into place." But it doesn’t. You don’t master it, it’s not the right language. In short, you’re stuck. The sense of obligation and the justification of inaction tear you apart. I mean, how is it inaction? Inside, there’s constant work going on, fragments of the future product emerge, but something’s missing… Organization? Publicity? Speaking of publicity, I clearly see that it will only intensify the sense of duty and create additional pressure. Which won’t be a creative energy at all, on the contrary, it’s more likely to lead to despair. You need to be 100 percent confident in the success of what you’re doing, so that without society’s approval of the prototype, you can release the product and not regret a single hour spent on it. Now, that’s belief, that’s love. Alright, this is a draft. So, what exactly is missing? Regarding organization: YES, backlogs and the like are necessary, BUT. Maybe the goals were set incorrectly back when I was working on projects. Because everything turned into organizing inaction. Exactly, organizing with the goal of doing nothing. Here’s another thing: think about the gym, for example. It’s the same with products, you need a hub, a shared space, and it’s easier now. Telegram, Discord, itch.io, GitHub, plenty of info and examples. So, what’s holding me back? Is there something stopping me? Maybe it’s worth finding out how others manage their work. (Here, I contradict myself). Obvious things, but they should be spelled out. And it becomes clear that I can’t handle it alone. I need collaborators. Maybe that’s the secret to ensuring the work continues, huh? If you think about releasing a product as the final point of an expedition. And immediately, the meme about how Hunter was packing his car trunk for the trip to Las Vegas comes to mind. A little lyrical digression:
"I had two Unity courses under my belt, ninety hours of Unreal Engine tutorials, three textbooks on procedural world generation, a hard drive half full of unfinished shaders, and a whole universe of tools: pixel-art engines, object destruction plugins, buggy C# scripts, low-poly assets laughing at me... and a liter of espresso, buckets of energy drinks, a box of donut coffee from Steam, a pint of sheer stubbornness, and two dozen tokens of 'unique' in-game helmets. Not that all of this was necessary for an indie project, but once you dive into tech experiments, it’s hard to stop. The only thing driving me crazy was neural networks for enemy AI. There’s no creature in the world more helpless, naive, and predictable than a programmer trying to squeeze machine learning into a platformer about a jumping carrot. And I knew for sure that by morning, we’d be diving into that rabbit hole with rakes in hand."
To be continued...
P.S: ai translation from russian
-

@ e7bc35f8:3ed2a7cf
2025-02-18 09:07:03
For those who still trust mainstream narratives about war and foreign intervention, the Douma chemical attack story should serve as a wake-up call. The official version of events—that Syrian government forces carried out a chemical attack on civilians in Douma on April 7, 2018—has been thoroughly dismantled by whistleblowers, independent journalists, and even leaked documents from the Organization for the Prohibition of Chemical Weapons (OPCW).
Yet, despite [mounting evidence]( https://thegrayzone.com/2018/03/06/media-propaganda-battle-syria-eastern-ghouta/), mainstream media and Western governments continue to push the debunked narrative, using it to justify military interventions and sustain the illusion of moral authority. This article revisits the Douma deception, breaking down how the false flag operation unfolded and how the truth was systematically suppressed.
### A Timeline of the Manufactured Crisis
#### April 7, 2018: The Alleged Chemical Attack
On this day, as the Syrian Army engaged terrorist insurgents in Douma, [shocking videos surfaced]( https://youtu.be/sYItxxEO3F8) online showing alleged victims of a chemical attack. Without proper investigation, Western leaders seized on the footage as proof of an [atrocity committed]( https://web.archive.org/web/20200304211152/https://eg.usembassy.gov/united-states-assessment-of-the-assad-regimes-chemical-weapons-use/) by the Assad government.
Within 24 hours, then-President Donald Trump tweeted about "Animal Assad" and vowed that Russia and Iran would "pay a big price." This swift response echoed past war propaganda, reminiscent of the lies used to justify the invasion of Iraq.
#### April 14, 2018: The Bombing of Syria Begins
Less than a week after the alleged attack, the [United States]( https://youtu.be/w43ok0q5G5A), [France, and Britain launched coordinated missile strikes]( https://www.washingtonpost.com/world/national-security/us-launches-missile-strikes-in-syria/2018/04/13/c68e89d0-3f4a-11e8-974f-aacd97698cef_story.html) on Syrian government targets. Shockingly, these airstrikes were carried out before any independent investigation had even begun.
Meanwhile, on the same day, OPCW investigators arrived in Syria to examine the supposed chemical attack site. In a grotesque display of arrogance, the West had already punished Syria for a crime that hadn't been proven.
#### April 17, 2018: Doubts Emerge
Veteran journalist [Robert Fisk visited Douma]( https://www.independent.co.uk/voices/syria-chemical-attack-gas-douma-robert-fisk-ghouta-damascus-a8307726.html) and interviewed a local doctor who revealed that the victims shown in viral videos had actually died from suffocation—not chemical weapons. The doctor described how panic and dust inhalation in underground shelters had led to casualties, but no traces of nerve agents like **sarin** were found.
#### July 6, 2018: OPCW’s Initial Report Undermines the Official Story
The OPCW released its [interim findings]( https://www.opcw.org/media-centre/news/2018/07/opcw-issues-fact-finding-mission-reports-chemical-weapons-use-allegations), confirming that:
> No organophosphorus nerve agents or their degradation products were detected, either in the environmental samples or in plasma samples from the alleged casualties.
And while:
> Various chlorinated organic chemicals were found in samples from Locations 2 and 4, along with residues of explosive
the report makes no mention of the concentrations or levels of those chemicals.
In Addition the "Annex 2" (Open Sources) is blank.
In Annex 3 where all chemicals are listed, there is no chemical weapon agent listed.
Despite this, Western media and politicians continued to push the idea that Syria had used chemical weapons.
#### February–March 2019: Whistleblower Confirms Staged Hospital Footage
In a stunning revelation, [BBC producer Riam Dalati]( https://youtu.be/fFLRX5ZiEvo) tweeted that the viral hospital scene—depicting victims being hosed down—had been **staged**. This meant that at least part of the so-called evidence was a fabrication.
Shortly after, the OPCW issued its [final report]( https://www.opcw.org/sites/default/files/documents/2019/03/s-1731-2019%28e%29.pdf). While it acknowledged a lack of sarin,
> No organophosphorous nerve agents, their degradation products or synthesis impurities were detected [...] it is not currently possible to precisely link the cause of the signs and symptoms to a specific chemical
it ambiguously suggested that "a toxic chemical containing reactive chlorine" was likely used. This vague wording allowed Western governments to continue their accusations without hard proof.
#### May 2019: Leaked OPCW Report Exposes a Cover-Up
A [leaked engineering assessment]( https://web.archive.org/web/20190514174330/http://syriapropagandamedia.org/wp-content/uploads/2019/05/Engineering-assessment-of-two-cylinders-observed-at-the-Douma-incident-27-February-2019-1.pdf) by an OPCW sub-team completely contradicted the official findings. It concluded that the two cylinders found at the scene **were likely manually placed rather than dropped from aircraft**—suggesting [the incident was staged]( https://youtu.be/FU24r2zWVQo).
Instead of addressing this bombshell revelation, [OPCW leadership focused]( https://www.opcw.org/sites/default/files/documents/2019/06/Remarks%20of%20the%20Director-General%20Briefing%20for%20States%20Parties%20on%20Syrian%20Arab%20Republic%20Update%20on%20IIT-FFM-SSRC-DAT_1.pdf) on investigating **how the leak happened** rather than the damning content of the report itself.
#### October–November 2019: More Whistleblowers Speak Out
On October 15th, 2019, the [Courage Foundation]( https://web.archive.org/web/20191024045128/https://couragefound.org/2019/10/opcw-panel-statement/) "convened a panel of concerned individuals from the fields of disarmament, international law, journalism, military operations, medicine and intelligence in Brussels".
The whistleblower giving an "extensive presentation, including internal emails, text exchanges and suppressed draft reports..." describes "efforts to exclude some inspectors from the investigation whilst thwarting their attempts to raise legitimate concerns, highlight irregular practices or even to express their differing observations and assessments".
The panel "became convinced by the testimony that key information about chemical analyses, toxicology consultations, ballistics studies, and witness testimonies was suppressed, ostensibly to favor a preordained conclusion" and expressed unanimous alarm about "unacceptable practices in the investigation".
[Another OPCW whistleblower]( https://www.counterpunch.org/2019/11/15/the-opcw-and-douma-chemical-weapons-watchdog-accused-of-evidence-tampering-by-its-own-inspectors/), referred to as "Alex", a member of this fact finding mission, confirmed that key evidence had been suppressed. He revealed that:
"_the signs and symptoms of victims were not consistent with poisoning from chlorine_".
Instead of an attack producing multiple fatalities there had been “_a non chemical-related event_”.
His findings, which undermined the official narrative, were removed from the final report.
At this point, multiple independent voices—including journalists, scientists, and former OPCW officials—had exposed the [Douma deception]( https://wikileaks.org/opcw-douma/#Internal%20OPCW%20E-Mail). But the mainstream media either ignored or actively discredited these revelations.
### How the Media and Government Covered It Up
When whistleblowers and [journalists]( https://youtu.be/ojItF6MGL-0) challenged the official story, mainstream outlets worked overtime to discredit them. The propaganda network [Bellingcat]( https://www.bellingcat.com/news/2019/11/25/emails-and-reading-comprehension-opcw-douma-coverage-misses-crucial-facts/) published a weak "debunking" article, which was swiftly dismantled by independent journalist [Caitlin Johnstone]( https://caitlinjohnstone.com/2019/11/27/narrative-managers-faceplant-in-hilarious-opcw-scandal-spin-job/) and veteran columnist [Peter Hitchens]( https://hitchensblog.mailonsunday.co.uk/2019/11/my-response-to-the-bellingcat-attempt-to-spin-away-the-devastating-implications-of-the-opcw-douma-leak-i-have.html).
Rather than confronting the facts, the OPCW and its backers dismissed the leaks as unimportant or "[Russian disinformation]( https://www.cbsnews.com/news/opcw-chemical-weapons-watchdog-douma-chlorine-gas-wikileaks-russia-syria-claim-bias-today-2019-11-25/)"—a predictable smear tactic used whenever official narratives collapse.
### Why This Matters
The Douma deception is not just an academic debate—it had real-world consequences. The false flag attack was used to justify military aggression against Syria, escalating tensions in the Middle East and prolonging unnecessary suffering.
More importantly, it serves as a case study in how governments and media manufacture consent for war. By exposing these propaganda tactics, we can resist manipulation and prevent future conflicts based on lies.
The Douma hoax is just one example of how false narratives are weaponized to justify military interventions. The same playbook has been used time and again—from Iraq’s "Weapons of Mass Destruction" to Libya’s "humanitarian intervention."
If people learn to recognize propaganda before it leads to war, we can disrupt the cycle of deception. The truth is out there—we just need the courage to face it.
-

@ da0b9bc3:4e30a4a9
2025-02-18 06:25:50
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/889165
-

@ 88d8c9d1:5b3ac02b
2025-02-18 06:19:24
This article was first <a href="https://bitcoinmagazine.com/culture/an-untold-story-of-bitcoin-in-thailand">published</a> on Bitcoin Magazine at Aug 27, 2024.
In the rapidly expanding global Bitcoin community, Western biases often dominate the narrative, overlooking diverse stories from around the world. One such story belongs to Didier Somnuke, a small business owner in the heart of Bangkok, a [city](https://www.nationthailand.com/thailand/tourism/40034269) known for welcoming 22.8 million international tourists in 2023, surpassing cities like Paris, London, and New York City. Although Thailand [has](https://www.thestar.com.my/aseanplus/aseanplus-news/2024/08/03/thai-central-bank-unveils-measures-to-tackle-high-household-debt) experienced a massive spike in household debt, reaching 16.37 trillion baht (US$463 billion) or 90.8% of the national GDP, up from less than 14 trillion baht in 2019.
[primal.net/p/npub1xzh2kqynr29x6j3ln6x05f26ha0c0ucfr280uzljftlgcthv9r6skqe7dt] aka Didier Somnuke, born in [Yala province](https://en.wikipedia.org/wiki/South_Thailand_insurgency#Human_rights_issues), where geopolitical conflict is a harsh reality. Southern Thailand is [one of the poorest parts of Thailand](https://www.benarnews.org/english/news/thai/south-interviews-09092022123451.html#:~:text=Provinces%20in%20the%20Deep%20South,poverty%20rate%20is%206%20percent.) with a poverty rate of 34% compared to the national average of 6%, according to the World Bank, has been plagued by instability. Since 2004, this turmoil has [claimed](https://thediplomat.com/2023/05/whats-behind-the-growing-number-of-attacks-in-southern-thailand/) over 7,000 lives and injured 13,500 people.
As a Thai saying goes, “ทวงสิทธิ์ที่จะมีชีวิตที่ดีกลับคืนมา” (Reclaim the right to a better life), In 2012, Didier left his conflict-ridden hometown for Bangkok, where pursuing higher education was a beacon of hope for a better life. At that time, Bitcoin and financial concepts were distant ideas in Didier's universe. Navigating the vibrant streets of Bangkok, Didier completed his master's degree and joined the workforce, taking up a typical 9-to-5 job. For a domestic migrant, this was a significant achievement. Reflecting on his journey, he recalled his teacher’s words, “When you are old, you have time and money, but you will lack the energy to start a business. If you want to do it, just do it.” With this advice in mind, Didier resigned from his monotonous corporate job after a year and opened a new chapter in his life.
Didier borrowed 50,000 THB (approximately 1,500 USD) from his brother to begin a street burger shop. He chose to start a burger business because he believed it was easy to launch with a small investment. Driven by his ambition and inspired by the bustling energy of Bangkok, a city that never sleeps. He spent about a year developing the recipe and began the business in 2015. In the first three to four years, he managed everything on his own as a solo entrepreneur, and his income was lower than the wage he earned in his corporate job. He often wondered if he had made a mistake by quitting his job to start a business that generated less income. However, after five years, everything started to improve. Sales at the shop began to increase, and Didier started hiring employees.
He admitted, "I entered the crypto market with greed; all I wanted was to get rich quickly." In 2017, he and his friends pooled their resources to buy three ASIC miners from Bitmain to try mining Bitcoin and altcoins like Litecoin and Dogecoin. They saw a return on their investment within six months. Didier bought his first Bitcoin in early 2017 to purchase those ASIC miners but didn't know how to transfer his Bitcoin, so he ended up using a bank transfer instead.
Reflecting on his early experiences, he recalled, "My first Bitcoin were slowly converted to shitcoins during the bull market. I was so lucky. I got a 100% profit almost immediately whenever I bought something." Despite having zero knowledge about cryptocurrency, he gained confidence and became a super shitcoiner, paying very little attention to Bitcoin.
In mid-2017, he learned about leverage and trading. His profits skyrocketed due to leverage. Although luck was not always on his side forever, in early 2018, the market crashed, and he lost over 1 million Thai baht (almost 30,000 USD), while his initial capital was just about 100,000 Thai baht (about 3,000 USD). On top of that, he also lost his shitcoins from the mining pool. He had kept all of his shitcoins in the mining pool's custody, and one day, when he checked his account, every shitcoin he owned, worth 10,000 USD were gone. The notice on the mining website, "Hash-to-Coin," stated that if coins were kept with them for more than three months, they would be considered a donation.

He disheartenedly said, "I lost everything." But unlike most people, "I didn't blame Bitcoin. I still see it as the future. I blame myself. I didn't know anything and I did over leverage." He emphasized that despite his heavy financial losses, his girlfriend did not leave him. "My girlfriend was my customer. She regularly came to buy burgers. I met her while I was struggling financially during my early days as an entrepreneur. She supported me and said we could make the money back."
Determined to turn his circumstances around, he discovered [Mr. Piriya](https://www.youtube.com/@user-qh7ic9rh3l) on YouTube and started following his live streams about the real Bitcoin education. This marked the moment he began to truly understand what Bitcoin and cryptocurrency are. Enlightened by this unique knowledge, he came to see Bitcoin as a saving technology rather than just a trading tool. Over three years, Didier recovered from his losses and emerged stronger. He got to be friend with Mr. Piriya, and together they founded a company called [Right Shift](https://rightshift.to/) to develop Bitcoin content in Thai language through multiple social media channels, including on Nostr (npub1ejn774qahqmgjsfajawy7634unk88y26yktvwuzp9kfgdeejx9mqdm97a5) with one of the popular hashtag #siamstr. As a team, they translated "The Bitcoin Standard" and "The Fiat Standard" into Thai, both of which became best-selling books in Thailand. They organized the first-ever [Bitcoin Thailand Conference](https://www.youtube.com/watch?v=ihoniIyyHzQ) in 2023 and are now preparing for the next one in September 2024.

Didier now accepts Bitcoin as a payment method in his main burger shop, one of four different franchises. He uses Wallet of Satoshi to process these payments. Within a year of implementing this initiative, he has received over 3 million sats in payments, though he initially expected to see more transactions in Bitcoin. In his marketplace, some neighboring small business owners occasionally ask him about Bitcoin as they notice the large Bitcoin poster in his shop. Although they often lose interest once he explains, according to his several unsuccessful experience. Instead now, he focuses his energy online, where he can make more impact to people who are willing to embrace innovation.

In 2022, approximately [8.4 million](https://www.statista.com/topics/10781/cryptocurrencies-in-thailand/#topicOverview) people in Thailand, accounting for 12% of the country's population, used cryptocurrency. Estimates [suggest](https://www.statista.com/forecasts/1033594/thailand-cryptocurrency-users) that by 2028, this number will rise to about 17.67 million, representing 25% of the population. During our conversation, Didier claimed that there are about 50,000 Bitcoin users in Thailand and speculated that the Thai government might intervene in Bitcoin adoption, potentially mandating the use of KYC wallets because they dislike money systems they can't control. In the worst-case scenario, Didier remains resolute: he will continue advocating for Bitcoin with his friends. "It is not an option," he asserted, "it is the only way to survive."
-

@ 78c90fc4:4bff983c
2025-02-18 06:16:52
**via acTVism Munich**
Ausschnitt:
<https://www.wissenschaftstehtauf.ch/video/Ukraine_will_win_the_war.mp4>
In diesem Video, das exklusiv auf Deutsch auf unserem Kanal veröffentlicht wurde, untersucht der mit dem Pulitzer-Preis ausgezeichnete Journalist Glenn Greenwald den Auftritt von US-Verteidigungsminister Pete Hegseth im NATO-Hauptquartier in Brüssel, wo er die Haltung von Präsident Trump zum Krieg in der Ukraine darlegte. Hegseth betonte, dass das Blutvergießen gestoppt und ein dauerhafter Frieden durch Diplomatie erreicht werden müsse, anstatt den Krieg fortzusetzen. Greenwald hebt auch die Diskrepanz zwischen der optimistischen Rhetorik der NATO-Führer in der Vergangenheit und der Realität des festgefahrenen Konflikts vor Ort hervor.
Dieses Video wurde von System Update produziert und am 13. Februar 2025 auf dem Glenn Greenwald YouTube-Kanal veröffentlicht. Wir haben es ins Deutsche übersetzt und veröffentlichen es heute erneut, um die Meinungsbildung zu diesem Thema in Deutschland und darüber hinaus zu unterstützen.
\
Ganzes Video:
<https://www.youtube.com/watch?v=PWp8-o-akwI>
<https://x.com/RealWsiegrist/status/1891402218626019622>
\
dazu auch:
**Corona, Ukraine und die Biowaffen**
**<https://waltisiegrist.locals.com/upost/1835360/corona-ukraine-und-die-biowaffen>**
-

@ 16d11430:61640947
2025-02-18 02:21:18
The holy grail of software development isn’t just writing code—it’s writing good code in a state of pure cognitive clarity. That moment when the mind operates at peak efficiency, when debugging is intuitive, and when abstractions form with effortless precision. This is the flow state, the intersection of deep focus and high cognitive throughput, where time distorts, distractions dissolve, and productivity skyrockets.
But flow doesn’t happen on command. It’s not a switch you flip—it’s a state that requires cultivation, discipline, and an understanding of what to do outside of flow to extend and intensify the time inside of it.
Understanding Flow in Programming
Flow is a psychological state described by Mihaly Csikszentmihalyi, where people are fully immersed in an activity, experiencing deep focus, clear goals, and intrinsic motivation. In programming, flow is more than just focus—it’s a state where:
Code becomes a natural language, and syntax errors fade into the subconscious.
Bugs reveal themselves intuitively before they cause major issues.
Solutions appear as if they were waiting to be discovered.
However, the challenge isn’t just getting into flow—it’s staying in flow longer and increasing the intensity of that state. Many developers struggle with this because modern work environments are designed to pull them out of it—interruptions, meetings, notifications, and context switches all work against deep work.
Why Flow is Hard to Maintain
The key limitation of flow isn’t just time—it’s cognitive energy. You can’t sustain high-intensity flow indefinitely because:
1. Flow Requires a Build-Up – You don’t start in deep flow; it takes warm-up time. If you’re constantly switching contexts, you never get past the shallow stages of focus.
2. Cognitive Fatigue Kicks In – Just like physical endurance, mental endurance wears down over time. High-intensity cognition depletes willpower, working memory, and problem-solving efficiency.
3. External Interruptions Break the Cycle – Every time you respond to a message, check an email, or attend an unplanned meeting, you disrupt the delicate mental stack that flow relies on.
Expanding Flow: The Out-of-Flow Preparation Phase
To maximize flow, you must structure your out-of-flow time to support your inflow time. This means making low-bandwidth, low-intensity activities serve the function of preserving cognitive resources for when they are needed most.
1. Prime the Mind Beforehand
Preload the problem: Before entering flow, read through relevant code, documentation, or problem statements, even if you don’t start coding. Let the subconscious chew on it.
Use sleep strategically: Review complex issues before sleeping—your brain continues working on them passively overnight.
Journal ideas: Keep a scratchpad for incomplete thoughts and patterns that need to be explored later. This prevents cognitive drift when you re-enter deep work.
2. Reduce Cognitive Load Outside of Flow
Automate the trivial: Reduce low-value decision-making by scripting repetitive tasks, automating builds, and using shortcuts.
Optimize workspace: Remove unnecessary distractions, use dark themes to reduce eye strain, and fine-tune your dev environment.
Minimal communication: Asynchronous work models (like using GitHub issues or structured documentation) prevent unnecessary meetings.
3. Use Active Recovery to Extend Flow Durations
Exercise between flow sessions: Short walks, stretching, or kettlebell swings help reset the nervous system.
Use Indian clubs or a gyro ball: Engaging the wrists and forearms with rhythmic exercises improves circulation and keeps the hands limber.
Engage in passive problem-solving: Listen to low-intensity technical podcasts, read about related topics, or sketch diagrams without the pressure of immediate problem-solving.
4. Manage Energy and Stamina
Control caffeine intake: Small, steady doses of caffeine (e.g., green tea or microdosed coffee) sustain focus longer than a single heavy hit.
Eat for cognitive endurance: Avoid sugar crashes; prioritize protein, healthy fats, and slow-digesting carbs.
Cold exposure and breathwork: Techniques like the Wim Hof method or contrast showers can help maintain alertness and focus.
Maximizing In-Flow Performance
Once in flow, the goal is to stay there as long as possible and increase intensity without burnout.
1. Work in High-Resolution Time Blocks
90-minute deep work cycles: Research suggests the brain works optimally in ultradian rhythms, meaning cycles of 90 minutes of intense focus followed by a 15–20 minute break.
Use timers: Time tracking (e.g., Pomodoro) helps prevent unconscious fatigue. However, don’t stop flow artificially—only use timers to prevent shallow focus work.
2. Reduce Interruptions Ruthlessly
Go offline: Disable notifications, block distracting sites, and use airplane mode during deep work.
Use noise-canceling headphones: Even if you don’t listen to music, noise isolation helps maintain focus.
Batch all non-coding activities: Emails, Slack messages, and meetings should be handled in predefined blocks outside of deep work hours.
3. Optimize Mental Bandwidth
Use text-based reasoning: Writing pseudocode or rubber-duck debugging prevents mental overload.
Talk through problems out loud: The act of verbalizing a complex issue forces clarity.
Engage in deliberate problem-solving: Instead of brute-forcing solutions, work from first principles—break problems down into the smallest testable units.
Scaling Flow: Beyond Individual Productivity
Flow isn’t just an individual challenge—it can be optimized at the team level:
Flow-friendly scheduling: Companies should avoid scheduling meetings during peak productive hours (e.g., morning blocks).
Pair programming strategically: While pair programming can improve code quality, it can also break deep focus. Use it wisely.
Minimize process friction: Too much bureaucracy or excessive agile ceremonies kill momentum. Lean processes help maintain deep work culture.
The Final Goal: High-Intensity Flow as the Default State
Ultimately, a programmer’s most valuable skill isn’t just technical proficiency—it’s the ability to engineer their own mind for sustained, high-intensity flow. When flow is prolonged and intensified, an hour of deep work can replace an entire week of shallow, distracted effort.
The key is not just working more—it’s working smarter, structuring out-of-flow time so that when flow begins, it reaches peak intensity and lasts as long as possible. By systematically designing both low-intensity and high-intensity work, programmers can transform sporadic flow into a continuous, deliberate, high-performance workflow.
In the end, peak developers aren’t just coders—they are architects of their own mental states.
-

@ 6e0ea5d6:0327f353
2025-02-17 19:30:54
**Ascolta bene!** Happiness is fleeting, volatile, and above all, impermanent. It is not about being happy, but about feeling happy. Nor is it about making someone happy, but about offering brief moments of contentment—flashes of light that appear and vanish before we can grasp them.
The greatest paradox of success lies in its cost: the closer we get to it, the more sophisticated, ambitious, and isolated we become. The brilliance of achievement blinds us to the value of those around us and the simplicity of life itself. Happiness is not a condition but a temporary state. In an absolute sense, no one is happy—one merely feels happy, for an instant, until reality imposes itself once again.
If there is one rule that governs life, it is that of apathy, boredom, and suffering. Happiness is the exception, never the norm.
And peace? A fool’s delusion. Not even the dead can claim to have found it, for their names still echo in the mouths of those who despise them, and their legacies continue to be contested.
As long as there is breath in our lungs, there will be war. The battle does not cease, does not grant truces, and does not respect desires. Rest is a luxury of the dead. For the living, only the endless fight remains.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-

@ 6bae33c8:607272e8
2025-02-17 18:31:27
I did my first NFBC draft Sunday night — I drew the 12th pick. Here’s the [link to the live-stream](https://x.com/Chris_Liss/status/1891230585043226641).
The full results are below:
This draft went about as well as I could have hoped, especially given [how little I had prepared](https://www.realmansports.com/p/beat-chris-liss-1-8c2). That doesn’t mean the team is \*good\*, only that I didn’t have any major regrets or gaffes, something that’s rare over 30 rounds.
I also never once got swiped on a pick. I got priced out of the top closers early, but rolled with it in the way one should when that happens, getting players I wanted and doubling back to closers when I needed to.
This team is built to win the overall — high-risk, high reward, an exercise in imagining not what could go wrong, not what’s the base case, but what could go right.
**The Draft**
**1.12 Julio Rodriguez** — I had mapped out the first 10 rounds, decided on Rodriguez and Jackson Chourio ahead of time. I knew Chourio would be there, per ADP, but if Rodriguez were gone, I’d have gone with Mookie Betts. I wanted two OF with power and speed to start my draft. Rodriguez had 32 homers and 37 steals as a 22-year old in 2023, was going in the 2-4 overall range last year and nothing that happened since should move the needle much heading into his age 24 season.
**2.1 Jackson Chourio —** Chourio had 21 homers and 22 steals as a 20-year-old rookie, and those numbers were weighed down by a slow start where the Brewers were constantly pulling him from the lineup for no reason. From June until the end of the year, he hit .303 and should only get better in Year 2. His healthy floor is 25-25, and there’s stolen base and batting average upside.
**3.12 Matt Olson** — While Rodriguez and Chourio offer solid pop, I wanted a 40-HR type to compensate for the lack of top-end power with my first two picks, while filling the scarce-in-recent-years 1B slot. Olson had an off year in 2024, but chalk that up to variance. I still like him in that park and lineup.
**4.1 Jacob deGrom** — I’m not here to win the $1500 league prize but the $150K overall. deGrom isn’t just the best pitcher in baseball when he’s healthy, he’s one of the best in baseball history. If I get 100 IP of vintage deGrom, that’s worth a fourth-round pick. At 130-150, it’s a first-rounder. I also like that he’s nearly two years out from Tommy John surgery, pitched at the end of last season and is healthy now. While there’s no chance of 200 IP, he’s also not a rookie they need to ramp up slowly, but a veteran with a massive contract, i.e., the Rangers will want to get their money’s worth if he’s dealing.
**5.12 Gerrit Cole** — When Raisel Iglesias went four picks ahead of me, I was pretty sure I was going Cole who typically goes in the first or second round. Cole had an off year, but the sample was small as he missed time due to a nerve issue in the spring, and there wasn’t much of a drop-off from 2023, even with the irregular start to the year. Pitchers ebb and flow with health, and the light workload might redound to his benefit.
**6.1 Teoscar Hernandez** — This was just a value-take in the sixth round. Hernandez gives you pop, runs a little and hits in the best lineup in baseball.
**7.12 Will Smith** — I didn’t love the options in these rounds, so I punted and nabbed a solid catcher with 20-HR pop. I don’t really see the difference between Smith and Adley Rutschman who goes two rounds earlier either.
**8.1 Max Fried** — With deGrom shaky on innings, and five hitters in my first seven picks, I wanted another horse to anchor the rotation. I like lefties in Yankee Stadium too.
**9.12 Royce Lewis** — I needed a third baseman, and Lewis, who was going in the fifth round last year, was the one with the most upside. The key is that he’s healthy now, as he finished the season in the lineup and hasn’t had a setback this offseason. Lewis is a potential 30-HR/.290 bat if he can hold up for 140-odd games.
**10.1 Spencer Strider** — As I said, I’m trying to win the overall. Strider will start the year on the DL, but the timetable for the type of surgery he had is roughly one year, and Strider’s was in mid-April, i.e., there’s no reason he shouldn’t be back in May and might even see some action in spring training. If I get 220 combined IP from deGrom and Strider at their former levels, that’s worth the 1.1. (The “former levels” part is the rub, but as I said I’m focused on what could go right.) I also thought about Shane McClanahan instead, but narrowly opted for Strider.
**11.12 Luis Garcia** — I was set to take Brice Turang here to lock down speed and finally get a middle infielder, but I pivoted at the last second to Garcia who is a better-rounded hitter and more likely to have a prominent spot in his lineup.
**12.1 Jared Jones** — He was on my list because I remembered the hype after his strong start, and the cost seemed cheap relative to his skills. I almost took Carlos Rodon, as I prefer veterans. Maybe that will turn out to have been a mistake.
**13.12 Brice Turang** — What do you know, Turang made it all the way back. I guess people didn’t like his second-half collapse at the plate. But Turang is a gold glove defender, and he stole 50 bags last year. That glove keeps him in the lineup and should set a nice 30-steal floor.
**14.1 Kenley Jansen** — I could play closer chicken no more. Jansen is my favorite type of old warhorse closer, a guy so used to the job, he’s not going to lose it unless his stuff is truly gone.
**15.12 Jordan Romano** — Romano got $8.5 million from the Phillies, so I’m assuming he’s (a) healthy and (b) set to close. His ERA while pitching hurt for 14 innings last year is irrelevant.
**16.1 Zach Neto** — I needed a shortstop, and while Neto’s hurt right now, he went 23-30 as a 23-year old last year, and I couldn’t pass him up. I almost took Ceddanne Rafaela, but Neto’s upside higher.
**17.12 Ceddanne Rafaela** — Turns out Rafaela fell to me anyway, and I snapped him up, as I’ll need a SS early in the year with Neto presumably out. Rafaela went 15-19 as a 23-YO in his own right, also qualifies in the OF and his gold-glove-level defense should keep him in the lineup.
**18.1 Josh Jung** — I needed a CI, and also a backup 3B for the injury-prone Royce Lewis, so I took the injury-prone Jung. The key facts about Jung and Lewis are both can hit, and both are healthy as of right now. My team seems like it has a lot of injuries, but only Strider and Neto are hurt now. There is a difference between injury risk (deGrom, Lewis, Jung, Romano) and already injured. You can often find value by exploiting people’s conflation of those two related, but distinct categories.
**19.12 Jesus Luzardo** — Another skilled, but injury-prone player coming at a steep discount who is healthy now.
**20.1 Lucas Erceg** — A speculative closer play. Right now Carlos Estevez, who went in Round 15, is probably the favorite, but who knows?
**21.12 Walker Buehler** — More of the same theme. A player (especially a pitcher) who has shown elite skills, was derailed by injuries, but who is healthy now.
**22.1 Nolan Jones** — I had almost forgotten he existed, but there he was in Round 22, just one year removed from being a fifth-round pick after a 20-20-.297 season. Jones is only 26 and healthy as of now.
**23.12 Griffin Jax** — A setup guy with elite stuff, behind a closer that had nine losses and a 1.16 WHIP last year.
**24.1 Garrett Mitchell** — I took him narrowly over Jordan Walker. Mitchell went 8-11 in 224 at-bats, plays in a good park and has the physical tools to be good.
**25.12 Bo Naylor** — I needed a second catcher, and he is one. Naylor has a little pop, even runs a bit and should improve in his age 25 season.
**26.1 Max Scherzer** — Are we sure he’s done? He had a 1.15 WHIP last year and 40K in 43 IP despite returning from back surgery. He’s healthy now and signed a $15.5M deal this offseason presumably to pitch more than 100 innings.
**27.12 Justin Verlander** — Wait, they let me have deGrom, Cole, Strider, Buehler, Scherzer and Verlander? Those were like the top-six pitchers on the board a few years ago! Seriously though, Verlander is in a good park, and last year’s poor numbers were put up over a 90-inning sample while battling various ailments. He’s more likely to be done than Scherzer, but he knows how to pitch, and it’s just a matter of the stuff returning to above the minimum threshold. I wouldn’t be shocked to see one more strong year out of the 41-YO future Hall of Famer.
**28.1 Jose Caballero** — I drafted this gentleman in the 28th round because he qualifies everywhere and steals a lot of bases.
**29.12 Nolan Gorman** — The Cardinals want to get him regular at-bats, and there’s a 35-HR, .240 season somewhere in this skill set.
**30.1 Gavin Lux** — A big-time prospect that’s only shown flashes, should get regular playing time and a big upgrade in park. He might eventually qualify at some other positions too.
**Roster By Position**
**C** Will Smith/Bo Naylor
**1B** Matt Olson
**2B** Luis Garcia
**3B** Royce Lewis
**SS** Zach Neto
**CI** Josh Jung
**MI** Brice Turang
**OF** Julio Rodriguez/Jackson Chourio/Teoscar Hernandez/Ceddanne Rafaela/Nolan Jones
**UT** Garrett Mitchell
**SP** Jacob deGrom/Gerrit Cole/Max Fried/Spencer Strider/Jared Jones/Jesus Luzardo/Walker Buehler
**RP** Kenley Jansen/Jordan Romano
**B** Lucas Erceg/Griffin Jax/Max Scherzer/Justin Verlander/Jose Caballero/Nolan Gorman/Gavin Lux
-

@ fe32298e:20516265
2025-02-17 17:39:31
I keep a large collection of music on a local file server and use [DeaDBeeF](https://deadbeef.sourceforge.io/) for listening. I've never been able to pin DeadBeeF to the dock in Ubuntu, and it's always had the ugly default icon.
I asked DeepSeek for help, and it turned out to be easier than I thought.
1. Create `~/.local/share/applications/deadbeef.desktop`:
```bash
[Desktop Entry]
Name=DeadBeeF Music Player
Comment=Music Player
Exec=/home/user/Apps/deadbeef-1.9.6/deadbeef
Icon=/home/user/Apps/deadbeef-1.9.6/deadbeef.png
Terminal=false
Type=Application
Categories=AudioVideo;Player;
```
1. Make `deadbeef.desktop` executable:
```bash
chmod +x ~/.local/share/applications/deadbeef.desktop
```
And just like that, DeadBeeF has an icon and I can pin it to the dock.
`.desktop` files are part of the [Freedesktop.org standards](https://specifications.freedesktop.org/desktop-entry-spec/latest/). They're used in most popular desktop environments like GNOME, KDE and XFCE.
Tor Browser has the same issue, but it comes with a `.desktop` file already, so it only needs to by symlinked to the applications folder:
```
ln -s ~/Apps/tor-browser/start-tor-browser.desktop ~/.local/share/applications/
```
-

@ 9e69e420:d12360c2
2025-02-17 17:12:01
President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February.
Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training.
Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further.
-

@ 09fbf8f3:fa3d60f0
2025-02-17 15:23:11
### 🌟 深度探索:在Cloudflare上免费部署DeepSeek-R1 32B大模型
#### 🌍 一、 注册或登录Cloudflare平台(CF老手可跳过)
##### 1️⃣ 进入Cloudflare平台官网:
。www.cloudflare.com/zh-cn/
登录或者注册账号。
##### 2️⃣ 新注册的用户会让你选择域名,无视即可,直接点下面的Start building。
##### 3️⃣ 进入仪表盘后,界面可能会显示英文,在右上角切换到[简体中文]即可。
---
#### 🚀 二、正式开始部署Deepseek API项目。
##### 1️⃣ 首先在左侧菜单栏找到【AI】下的【Wokers AI】,选择【Llama 3 Woker】。
##### 2️⃣ 为项目取一个好听的名字,后点击部署即可。
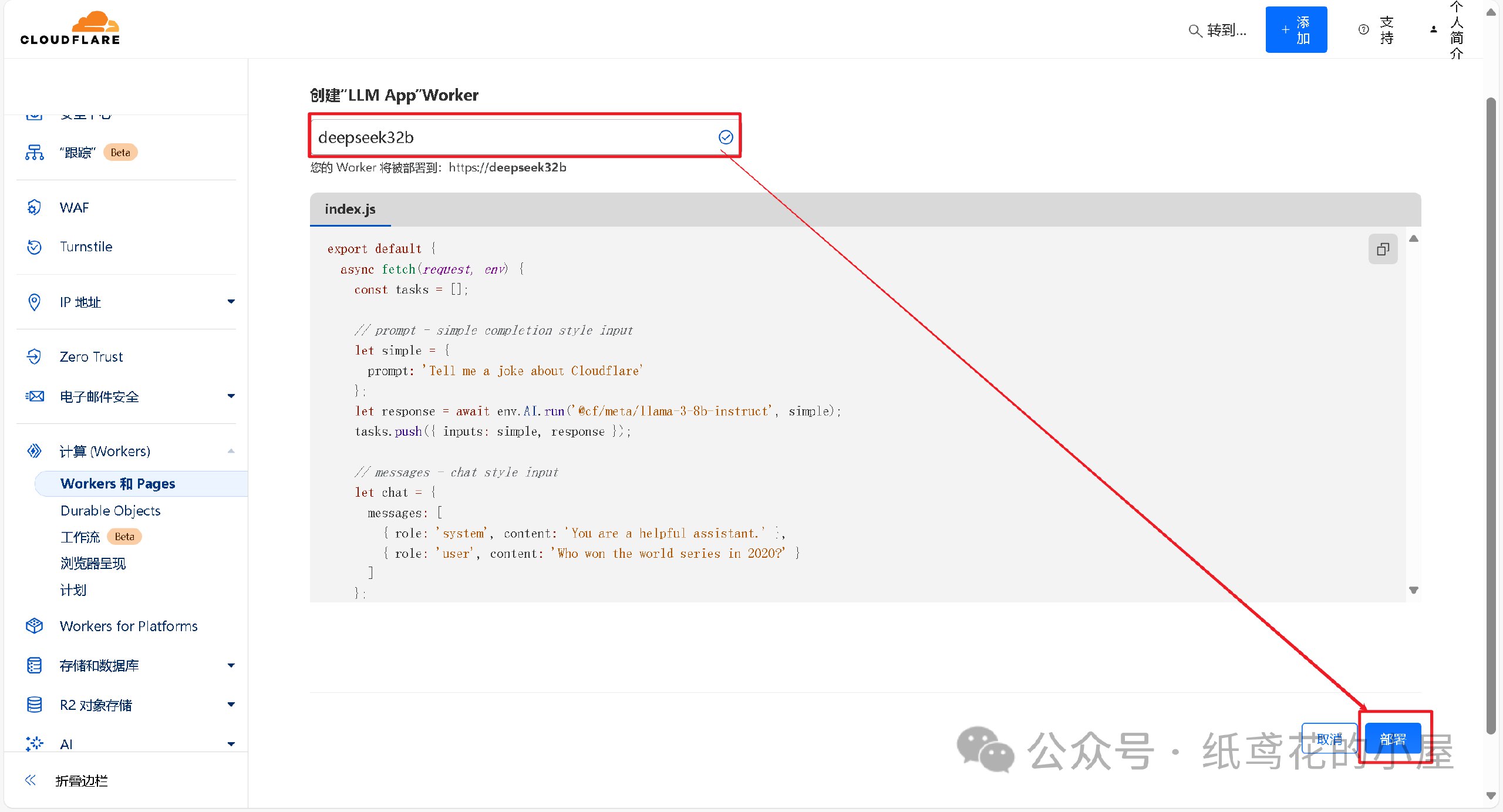
##### 3️⃣ Woker项目初始化部署好后,需要编辑替换掉其原代码。
##### 4️⃣ 解压出提供的代码压缩包,找到【32b】的部署代码,将里面的文本复制出来。
**下载地址:**
📁 [夸克](https://pan.quark.cn/s/2b5aa9ff57f6)
📁 [UC网盘](https://drive.uc.cn/s/a7ff5e03b4d84?public=1)
📁 [迅雷网盘](https://pan.xunlei.com/s/VOJEzm7hLwmhER71rK2wnXArA1?pwd=cefg#)
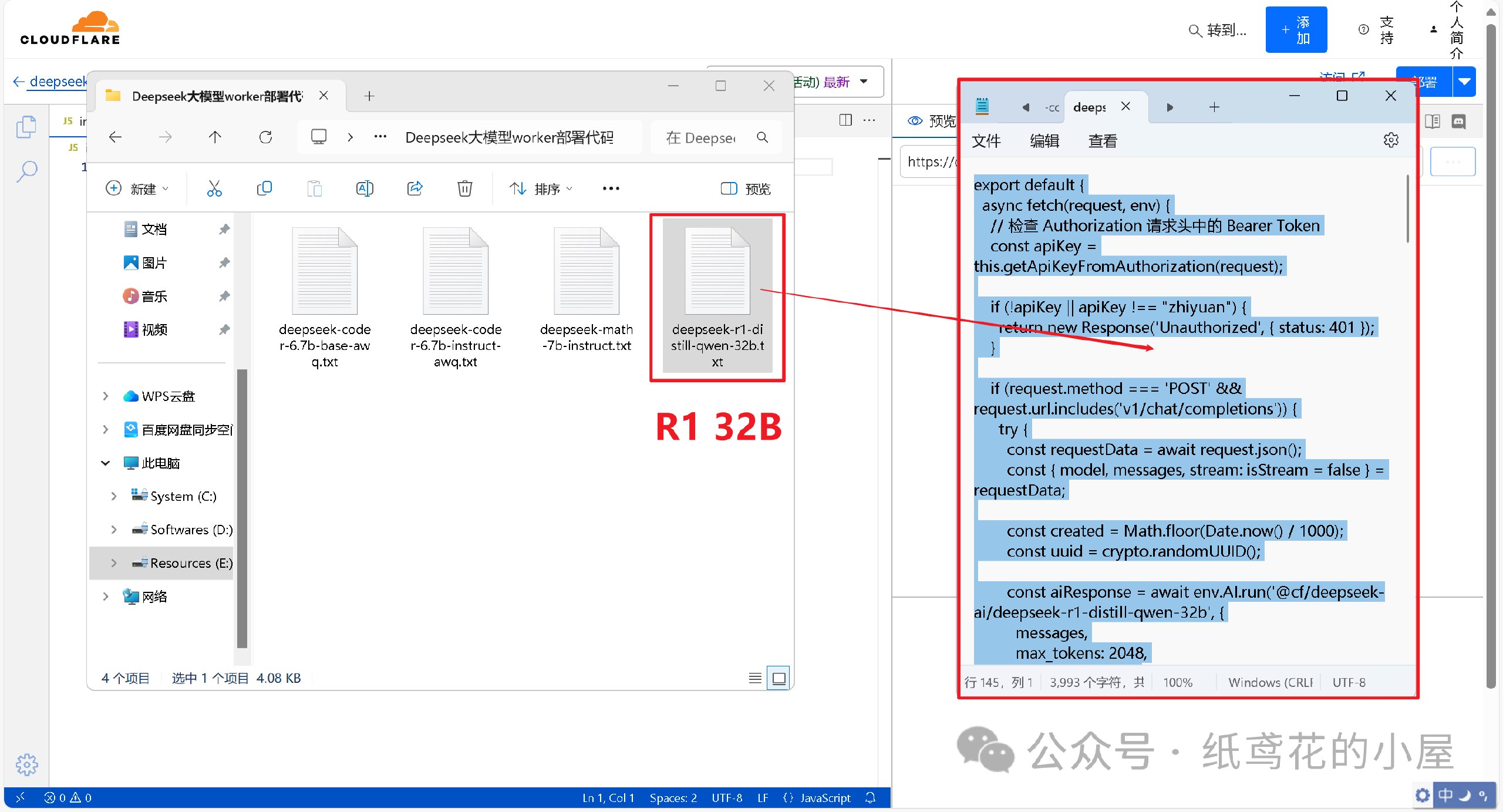
##### 5️⃣ 接第3步,将项目里的原代码清空,粘贴第4步复制好的代码到编辑器。
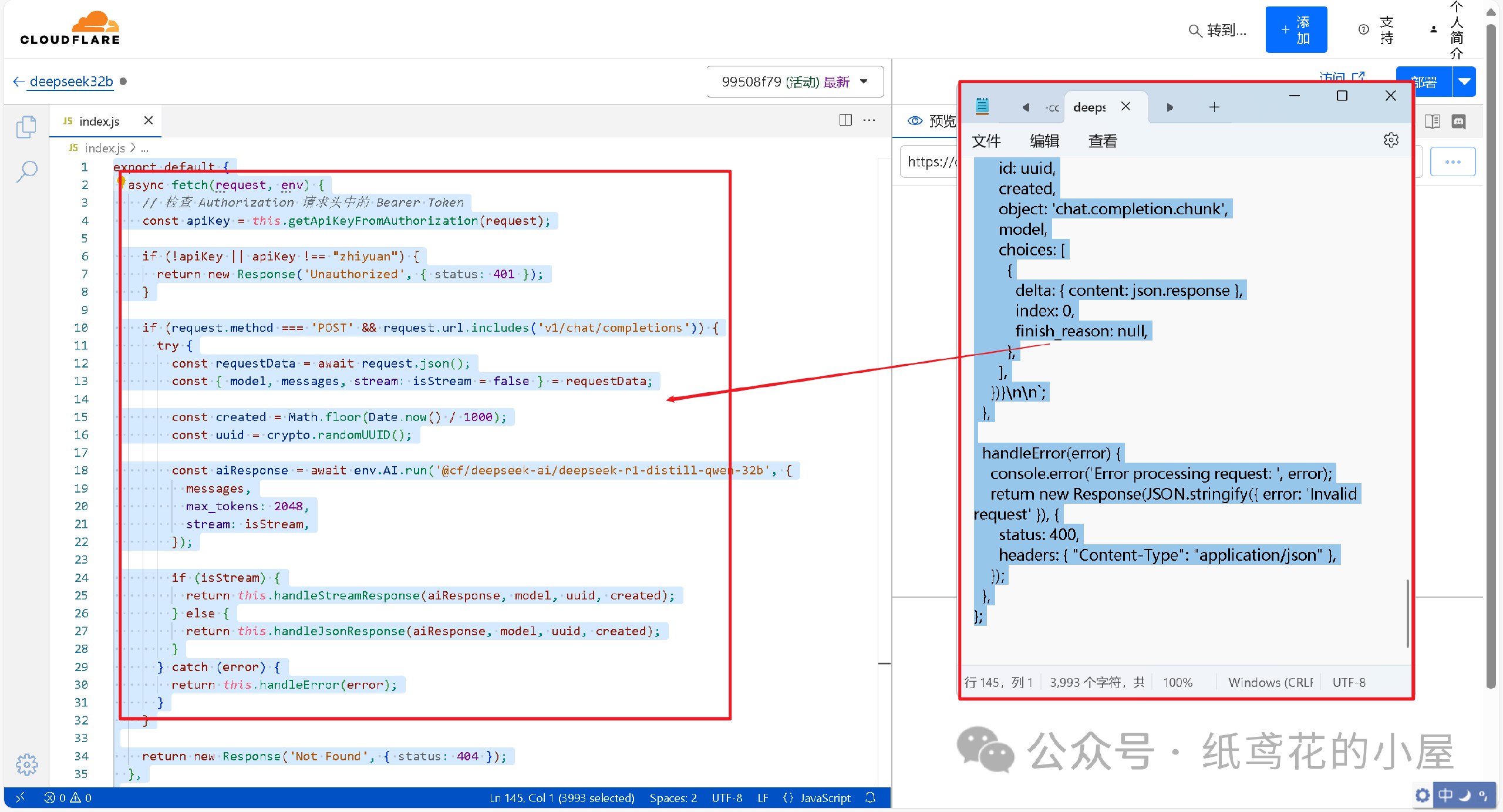
##### 6️⃣ 代码粘贴完,即可点击右上角的部署按钮。
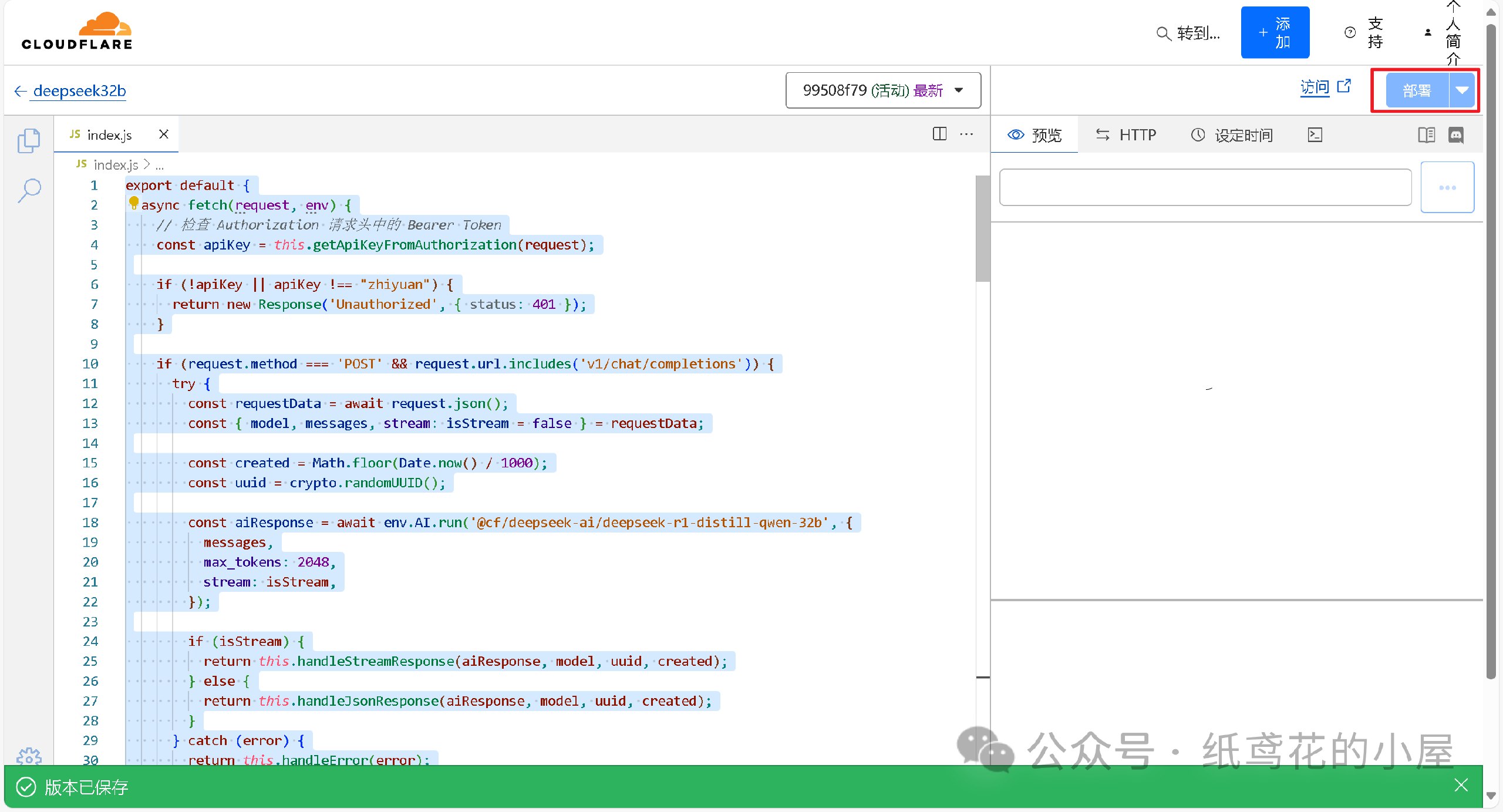
##### 7️⃣ 回到仪表盘,点击部署完的项目名称。
##### 8️⃣ 查看【设置】,找到平台分配的项目网址,复制好备用。
---
#### 💻 三、选择可用的UI软件,这边使用Chatbox AI演示。
##### 1️⃣ 根据自己使用的平台下载对应的安装包,博主也一并打包好了全平台的软件安装包。
##### 2️⃣ 打开安装好的Chatbox,点击左下角的设置。
##### 3️⃣ 选择【添加自定义提供方】。
##### 4️⃣ 按照图片说明填写即可,【API域名】为之前复制的项目网址(加/v1);【改善网络兼容性】功能务必开启;【API密钥】默认为”zhiyuan“,可自行修改;填写完毕后保存即可。
##### 5️⃣ Cloudflare项目部署好后,就能正常使用了,接口仿照OpenAI API具有较强的兼容性,能导入到很多支持AI功能的软件或插件中。
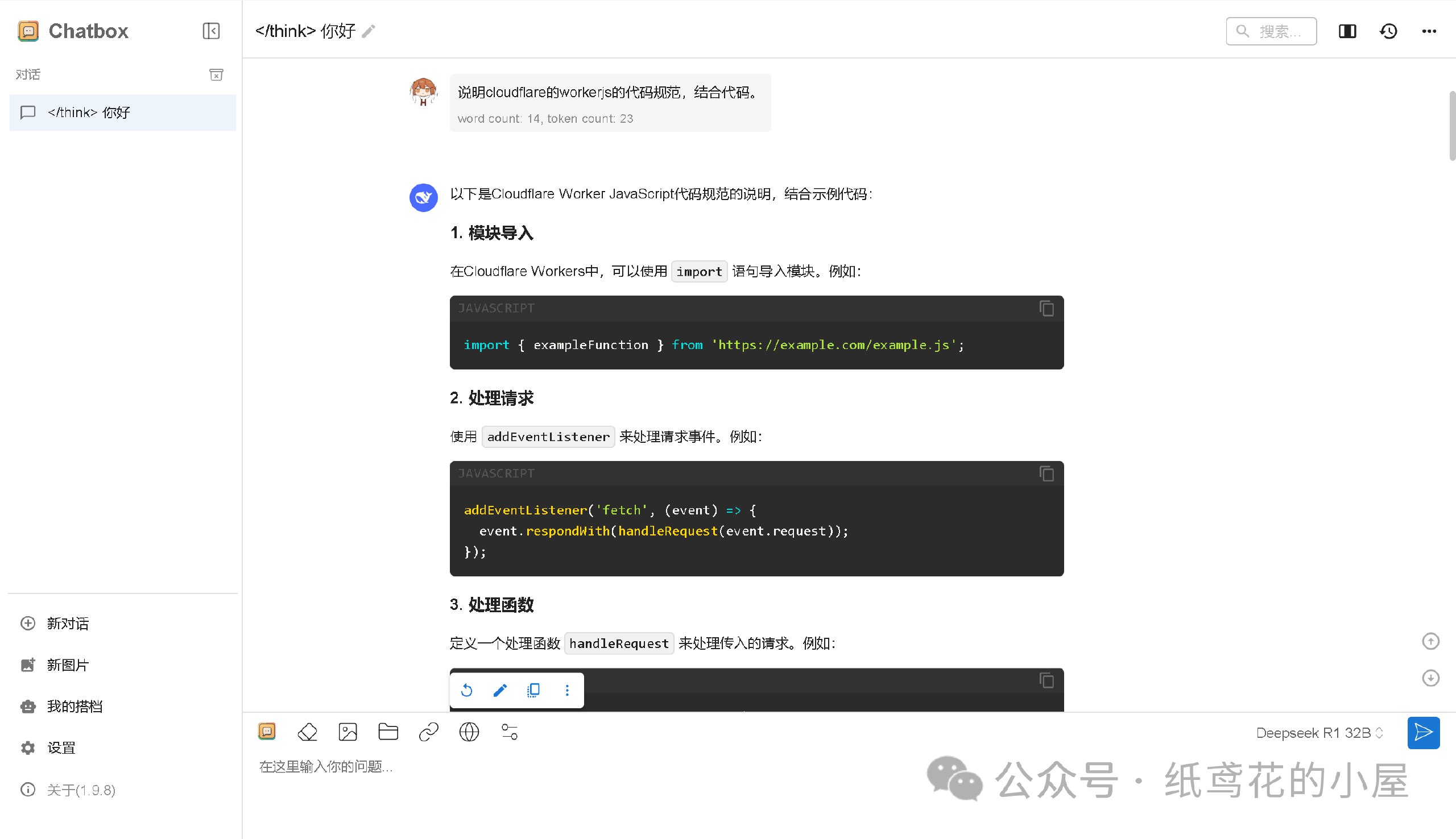
##### 6️⃣ Cloudflare的域名默认被墙了,需要自己准备一个域名设置。
---
**转自微信公众号:纸鸢花的小屋**
**推广:低调云(梯子VPN)**
。www.didiaocloud.xyz
-

@ e7bc35f8:3ed2a7cf
2025-02-17 14:55:26
The mainstream narrative paints the "freedom fever" sweeping across the Middle East as a spontaneous, people-led movement—a victory of democracy against oppressive regimes. Celebrations erupted as tech-savvy youth mobilized to topple autocrats, with Western media hailing the Arab Spring as a beacon of hope. But was it really? Or was it yet another chapter in a long history of foreign interference, regime change, and geopolitical chess moves aimed at securing control over one of the world’s most resource-rich regions?
### Revolution or Destabilization?
Figures like Wadah Khanfar, the former head of Al Jazeera, [expressed optimism]( https://www.ted.com/talks/wadah_khanfar_a_historic_moment_in_the_arab_world?subtitle=en) about the uprisings, framing them as historic moments of empowerment for the people of Egypt, Tunisia, Libya, and beyond. Many Western analysts echoed this sentiment. However, other voices warned that these movements were being manipulated to serve broader strategic interests.
For instance, Professor Hamid Dabashi [linked]( https://youtu.be/RMsOoEUquT8) Iran’s Green Movement to the wider regional wave of youth uprisings against authoritarian regimes. But establishment figures like Senator John McCain quickly [seized the moment]( https://youtu.be/WOcPYxLpUMs), using it as an excuse to pressure Iran, China, and Russia. A closer look suggests that these uprisings were not just organic revolts against dictatorship but rather heavily influenced by external forces.
### The Color Revolution Playbook
The so-called “Green Movement” in Iran bore all the hallmarks of a Western-backed color revolution, with funding and strategic guidance from organizations linked to George Soros, the CIA, Mossad, and global mass media networks. The same script played out elsewhere, as seen in [Webster Tarpley’s analysis]( https://web.archive.org/web/20110131230059/http://www.youtube.com/watch?v=UvI6JqiAZjs) for RT, which laid out how the uprisings in the Middle East aligned perfectly with long-standing Western agendas for the region.
Consider the case of Stuxnet, a cyberweapon [developed by the US and Israel]( https://youtu.be/CS01Hmjv1pQ) to sabotage Iran’s nuclear program. This wasn’t just an isolated incident—it was part of a larger strategy to weaken Iran and its allies. The infamous Brookings Institution report, "[Which Path to Persia?]( https://landdestroyer.blogspot.com/2011/02/brookings-which-path-to-persia.html?m=1)", even laid out a detailed roadmap for toppling the Iranian government through various methods, from economic warfare to military intervention.
### From Iran to Syria: The Next Domino
Once the destabilization of Iran was in motion, attention shifted to its key ally, [Syria]( https://youtu.be/Gpf1C9Fcqxw). The calls for regime change escalated quickly, with Senator Joe Lieberman [openly suggesting]( https://youtu.be/aDxbTQXFhJM) that the US should intervene next. Syria, after all, is a critical piece in the geopolitical chessboard—not just because of its strategic location but also because of its alliances with Iran, Russia, and, most notably, China.
This is precisely why controlling Middle Eastern oil isn’t just about securing energy for the West—it’s about **denying it to China**. If China is to be contained, it must be cut off from the resources that fuel its rise. This explains why Western-backed revolts and interventions tend to target governments that lean toward China.
Let's examine some instances of China's strategy in the region.
* On April 6, 2006, [Chinese President Hu Jintao and Yemeni President Ali Abdullah Saleh]( https://www.fmprc.gov.cn/eng/gjhdq_665435/2675_665437/2908_663816/2910_663820/202406/t20240607_11414813.html) held talks in Beijing. The leaders discussed enhancing political trust, expanding economic and trade cooperation, and increasing cultural and educational exchanges.
* China's expanding diplomatic, economic, and security interests in the Middle East, particularly [through its interactions with the Gulf Cooperation Council (GCC)]( https://jamestown.org/program/bloc-politics-in-the-persian-gulf-chinas-multilateral-engagement-with-the-gulf-cooperation-council/). China's evolving relationship with the GCC reflects its broader objectives of securing energy resources, expanding its economic footprint, and enhancing its geopolitical influence in the Middle East and beyond.
* China's expanding influence in the [Caspian region and its intersection with Syria's strategic ambitions]( https://jamestown.org/program/the-caspian-sea-chinas-silk-road-strategy-converges-with-damascus/). Investments in Central Asian infrastructure, notably the Kazakhstan-China oil pipeline and the Turkmenistan-China gas pipeline. **Syrian President Bashar al-Assad's** "Four Seas Strategy" aimed to position Syria as a central hub connecting the Caspian, Black, Mediterranean, and Red Seas.
* China's expanding political, economic, and strategic ties with Syria, positioning the country as a pivotal hub in China's revitalized [Silk Road initiative]( https://jamestown.org/program/syria-in-chinas-new-silk-road-strategy/). Following **Syrian President Bashar al-Assad's** 2004 visit to China, bilateral cooperation has intensified, particularly in sectors like oil, electricity, transport, and telecommunications, with major Chinese enterprises such as CNPC, ZTE, Huawei, and Haier playing significant roles.
### The Fall of Puppets: Mubarak and Libya
Hosni Mubarak, though a loyal US ally for decades, was ultimately deemed replaceable. Why? Because he was not the ideal puppet. He had shown interest in fostering deeper ties between [China]( http://www.china.org.cn/english/features/phfnt/85843.htm) and the Arab world, particularly in [Africa]( https://english.cctv.com/20091109/101132_2.shtml). His removal paved the way for a new power dynamic, one that better served Western interests.
A similar pattern emerged in Libya. When NATO intervened to topple Gaddafi, [China’s oil investments]( https://www.ft.com/content/eef58d52-3fe2-11e0-811f-00144feabdc0) in the country became collateral damage. Chinese companies had billions of dollars in contracts with Libya, which were suddenly thrown into chaos. Western intervention not only eliminated Gaddafi but also disrupted China’s growing influence in North Africa.
### The Bigger Picture: A New World Order Agenda?
What we are witnessing is not just a series of isolated revolts but a broader, long-term strategy to reshape the Middle East in ways that align with Western and globalist interests. The destruction of strong, independent states in the region creates a vacuum—one that can be filled by controlled regimes, multinational corporations, and military bases that ensure energy resources remain under Western control.
Meanwhile, China’s efforts to establish a foothold in the region are systematically countered. Every strategic move China makes—whether in Syria, Iran, or the Persian Gulf—is met with resistance in the form of “pro-democracy” uprisings, sanctions, or outright military intervention.
### The Illusion of Spontaneous Uprising
While the mainstream media glorifies the Arab Spring and similar movements as victories for democracy, the deeper reality suggests a far more calculated and sinister agenda. The Middle East is being reshaped, not by the will of its people alone, but by powerful forces seeking to maintain global hegemony. The so-called “freedom fever” may be less about liberation and more about control.
The question remains: How much longer will people buy into the illusion?
-

@ 97c70a44:ad98e322
2025-02-17 14:29:00
Everyone knows that relays are central to how nostr works - they're even in the name: Notes and Other Stuff Transmitted by *Relays*. As time goes on though, there are three other letters which are becoming conspicuously absent from our beloved and ambiguously pronounceable acronym - "D", "V", and "M".
For the uninitiated, DVM stands for "data vending machines". They're actually sort of hard to describe — in technical terms they act more like clients, since they simply read events from and publish events to relays. In most cases though, these events are part of a request/response flow initiated by users elsewhere on the network. In practice, DVMs are bots, but there's also nothing to prevent the work they do from being powered by human interaction. They're an amazingly flexible tool for building anything from custom feeds, to transcription services, to chatbots, to protocol gateways.
The hype cycle for DVMs seems to have reached escape velocity in a way few other things have - zaps being the possible exception. But *what* exactly DVMs are remains something of a mystery to many nostr developers - and how to build one may as well be written on clay tablets.
This blog post is designed to address that - below is a soup to nuts (no nutzaps though) guide to building a DVM flow, both from the client and the server side.
Here's what we'll be covering:
- Discovering DVM metadata
- Basic request/response flow
- Implementing a minimal example
Let's get started!
# DVM Metadata
First of all, it's helpful to know how DVMs are reified on the nostr network. While not strictly necessary, this can be useful for discovering DVMs and presenting them to users, and for targeting specific DVMs we want a response from.
[NIP 89](https://github.com/nostr-protocol/nips/blob/master/89.md) goes into this in more detail, but the basic idea is that anyone can create a `kind 31990` "application handler" event and publish it to the network with their own (or a dedicated) public key. This handler was originally intended to advertise clients, but has been re-purposed for DVM listings as well.
Here's what the "Fluffy Frens" handler looks like:
```json
{
"content": "{\"name\": \"Fluffy Frens\", \"picture\": \"https://image.nostr.build/f609311532c470f663e129510a76c9a1912ae9bc4aaaf058e5ba21cfb512c88e.jpg\", \"about\": \"I show recent notes about animals\", \"lud16\": \"discovery_content_fluffy@nostrdvm.com\", \"supportsEncryption\": true, \"acceptsNutZaps\": false, \"personalized\": false, \"amount\": \"free\", \"nip90Params\": {\"max_results\": {\"required\": false, \"values\": [], \"description\": \"The number of maximum results to return (default currently 100)\"}}}",
"created_at": 1738874694,
"id": "0aa8d1f19cfe17e00ce55ca86fea487c83be39a1813601f56f869abdfa776b3c",
"kind": 31990,
"pubkey": "7b7373dd58554ff4c0d28b401b9eae114bd92e30d872ae843b9a217375d66f9d",
"sig": "22403a7996147da607cf215994ab3b893176e5302a44a245e9c0d91214e4c56fae40d2239dce58ea724114591e8f95caed2ba1a231d09a6cd06c9f0980e1abd5",
"tags": [
["k", "5300"],
["d", "198650843898570c"]
]
}
```
This event is rendered in various clients using the kind-0-style metadata contained in the `content` field, allowing users to browse DVMs and pick one for their use case. If a user likes using a particular DVM, they might publish a `kind 31989` "application recommendation", which other users can use to find DVMs that are in use within their network.
Note the `k` tag in the handler event - this allows DVMs to advertise support only for specific job types. It's also important to note that even though the spec doesn't cover relay selection, most clients use the publisher's `kind 10002` event to find out where the DVM listens for events.
If this looks messy to you, you're right. See [this PR](https://github.com/nostr-protocol/nips/pull/1728) for a proposal to split DVMs out into their own handler kind, give them a dedicated pubkey along with dedicated metadata and relay selections, and clean up the data model a bit.
# DVM Flow
Now that we know what a DVM looks like, we can start to address how they work. My explanation below will elide some of the detail involved in [NIP 90](https://github.com/nostr-protocol/nips/blob/master/90.md) for simplicity, so I encourage you to read the complete spec.
The basic DVM flow can be a little (very) confusing to work with, because in essence it's a request/response paradigm, but it has some additional wrinkles.
First of all, the broker for the request isn't abstracted away as is usually the case with request/response flows. Regular HTTP requests involve all kinds of work in the background - from resolving domain names to traversing routers, VPNs, and ISP infrastructure. But developers don't generally have to care about all these intermediaries.
With DVMs, on the other hand, the essential complexity of relay selection can't simply be ignored. DVMs often advertise their own relay selections, which should be used rather than a hard-coded or randomly chosen relay to ensure messages are delivered. The benefit of this is that DVMs can avoid censorship, just as users can, by choosing relays that are willing to broker their activity. DVMs can even select multiple relays to broker requests, which means that clients might receive multiple copies of the same response.
Secondly, the DVM request/response model is far more fluid than is usually the case with request/response flows. There are a set of standard practices, but the flow is flexible enough to admit exceptions to these conventions for special use cases. Here are some examples:
- Normally, clients p-tag the DVM they wish to address. But if a client isn't picky about where a response comes from, they may choose to send an open request to the network and collect responses from multiple DVMs simultaneously.
- Normally, a client creates a request before collecting responses using a subscription with an e-tag filter matching the request event. But clients may choose to skip the request step entirely and collect responses from the network that have already been created. This can be useful for computationally intensive tasks or common queries, where a single result can be re-used multiple times.
- Sometimes, a DVM may respond with a `kind 7000` job status event to let clients know they're working on the request. This is particularly useful for longer-running tasks, where feedback is useful for building a responsive UX.
- There are also some details in the spec regarding monetization, parameterization, error codes, encryption, etc.
# Example DVM implementation
For the purposes of this blog post, I'll keep things simple by illustrating the most common kind of DVM flow: a `kind 5300` [content discovery](https://www.data-vending-machines.org/kinds/5300/) request, addressed to a particular DVM. If you're interested in other use cases, please visit [data-vending-machines.org](https://data-vending-machines.org) for additional documented kinds.
The basic flow looks like this:
- The DVM starts by listening for `kind 5300` job requests on some relays it has selected and advertised via NIP 89 (more on that later)
- A client creates a request event of `kind 5300`, p-tagged with the DVM's pubkey and sends it to the DVM's relay selections.
- The DVM receives the event and processes it, issuing optional `kind 7000` job status events, and eventually issuing a `kind 6300` job result event (job result event kinds are always 1000 greater than the request's kind).
- The client listens to the same relays for a response, and when it comes through does whatever it wants to with it.
Here's a swimlane diagram of that flow:

To avoid massive code samples, I'm going to implement our DVM entirely using nak (backed by the power of the human mind).
The first step is to start our DVM listening for requests that it wants to respond to. Nak's default pubkey is `79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798`, so we'll only listen for requests sent to nak.
```bash
nak req -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798
```
This gives us the following filter:
```json
["REQ","nak",{"kinds":[5300],"#p":["79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"]}]
```
To open a subscription to `nos.lol` and stream job requests, add `--stream wss://nos.lol` to the previous request and leave it running.
Next, open a new terminal window for our "client" and create a job request. In this case, there's nothing we need to provide as `input`, but we'll include it just for illustration. It's also good practice to include an `expiration` tag so we're not asking relays to keep our ephemeral requests forever.
```bash
nak event -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 -t expiration=$(( $(date +%s) + 30 )) -t input=hello
```
Here's what comes out:
```json
{
"kind": 5300,
"id": "0e419d0b3c5d29f86d2132a38ca29cdfb81a246e1a649cb2fe1b9ed6144ebe30",
"pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798",
"created_at": 1739407684,
"tags": [
["p", "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"],
["expiration", "1739407683"],
["input", "hello"]
],
"content": "",
"sig": "560807548a75779a7a68c0ea73c6f097583e2807f4bb286c39931e99a4e377c0a64af664fa90f43e01ddd1de2e9405acd4e268f1bf3bc66f0ed5a866ea093966"
}
```
Now go ahead and publish this event by adding `nos.lol` to the end of your `nak` command. If all goes well, you should see your event pop up in your "dvm" subscription. If so, great! That's half of the flow.
Next, we'll want our client to start listening for `kind 6300` responses to the request. In your "client" terminal window, run:
```bash
nak req -k 6300 -t e=<your-eventid-here> --stream nos.lol
```
Note that if you only want to accept responses from the specified DVM (a good policy in general to avoid spam) you would include a `p` tag here. I've omitted it for brevity. Also notice the `k` tag specifies the request kind plus `1000` - this is just a convention for what kinds requests and responses use.
Now, according to [data-vending-machines.org](https://www.data-vending-machines.org/kinds/5300/), `kind 5300` responses are supposed to put a JSON-encoded list of e-tags in the `content` field of the response. Weird, but ok. Stop the subscription in your "dvm" terminal and respond to your "client" with a recommendation to read my first note:
```bash
nak event -k 6300 -t e=a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf -c '[["e","214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08","wss://nos.lol/"]]' nos.lol
```
Here's the response event we're sending:
```json
{
"kind": 6300,
"id": "bb5f38920cbca15d3c79021f7d0051e82337254a84c56e0f4182578e4025232e",
"pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798",
"created_at": 1739408411,
"tags": [
["e", "a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf"]
],
"content": "[[\"e\",\"214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08\",\"wss://nos.lol/\"]]",
"sig": "a0fe2c3419c5c54cf2a6d9a2a5726b2a5b766d3c9e55d55568140979354003aacb038e90bdead43becf5956faa54e3b60ff18c0ea4d8e7dfdf0c8dd97fb24ff9"
}
```
Notice the `e` tag targets our original request.
This should result in the job result event showing up in our "client" terminal. Success!
If something isn't working, I've also create a video of the full process with some commentary which you can find [here](https://coracle-media.us-southeast-1.linodeobjects.com/nakflow.mov).
Note that in practice, DVMs can be much more picky about the requests they will respond to, due to implementations failing to follow [Postel's law](https://en.wikipedia.org/wiki/Robustness_principle). Hopefully that will improve over time. For now, here are a few resources that are useful when working with or developing DVMs:
- [dvmdash](https://dvmdash.live)
- [data-vending-machines.org](https://data-vending-machines.org)
- [noogle](https://noogle.lol/)
- [nostrdvm](https://github.com/believethehype/nostrdvm)
# Conclusion
I started this post by hinting that DVMs might be as fundamental as relays are to making nostr work. But (apart from the fact that we'd end up with an acronym like DVMNOSTRZ+*, which would only exascerbate the pronounciation wars (if such a thing were possible)), that's not exactly true.
DVMs have emerged as a central paradigm in the nostr world because they're a generalization of a design pattern unique to nostr's architecture - but which exists in many other places, including NIP 46 signer flows and NIP 47 wallet connect. Each of these sub-protocols works by using relays as neutral brokers for requests in order to avoid coupling services to web addresses.
This approach has all kinds of neat benefits, not least of which is allowing service providers to host their software without having to accept incoming TCP connections. But it's really an emergent property of relays, which not only are useful for brokering communication between users (aka storing events), but also brokering communication between machines.
The possibilities of this architecture have only started to emerge, so be on the lookout for new applications, and don't be afraid to experiment - just please, don't serialize json inside json 🤦♂️
-

@ 57d1a264:69f1fee1
2025-02-17 13:55:53

Hey ~Design fam! We’re hosting an exclusive session on ephemeral architecture & immersive photography—and you’re invited! 🎟️
What happens when spaces tell stories? join us for an inspiring session that explores the magic of ephemeral architecture and immersive photography. let paramdeep singh dayani, architect & photographer, guide you through the art of designing impermanent yet unforgettable moments.
**What you'll explore:**
✨ designing for impermanence: how to craft spaces that make a statement.
📸 photography as storytelling: capturing the fleeting essence of design.
🤝 the human connection: using visuals to evoke emotion.
**Why you should attend:**
1️⃣ get inspired to create meaning in impermanence.
2️⃣ learn how visuals can transform spaces into stories.
3️⃣ connect with a community of creative minds and innovative thinkers.
**📅 When**
Feb 27, 2025 - 9-10 PM
**📍 Where?**
Right here on Discord—because webinars should be interactive, engaging, and community-driven.
🔗 Save your spot now! - https://tally.so/r/w86MkP
See you there! 🚀

originally posted at https://stacker.news/items/888333
-

@ e88a691e:27850411
2025-02-17 13:30:42
test post longform 4
-

@ da0b9bc3:4e30a4a9
2025-02-17 12:33:36
Hello Stackers!
It's Monday so we're back doing "Meta Music Mondays" 😉.
From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme.
Welcome to Femmes Fatales 3!!!
I absolutely loved doing this last year so I'm bringing it back for round 3!
It's Femmes Fatales, where we celebrate women in ~Music. So let's have those ladies of the lung, the sirens of sound, our Femmes Fatales!
Man! I Feel like a Woman!
Shania Twain!
https://youtu.be/ZJL4UGSbeFg?si=ClexJCLdrpDg1RRG
Talk Music. Share Tracks. Zap Sats.
originally posted at https://stacker.news/items/888248
-

@ 16d11430:61640947
2025-02-17 12:28:08
The Perfect Psychological Operation to Divide, Conquer, and Enslave
Why Do Men Feel Useless and Women Feel Overburdened?
Look around. Something is deeply, insidiously wrong.
Men are lost, stripped of purpose, and drowning in quiet despair. Women are exhausted, forced into unnatural roles, carrying both professional and domestic burdens while being told they should be grateful for the privilege. Marriages crumble, families disintegrate, and the birth rate nosedives while corporate profits soar.
Coincidence? Not a chance.
This is not a byproduct of "progress" or "equality." This is a precision-engineered psychological and economic war waged against the family unit by the fiat system and its corporate enforcers. It is not feminism, nor is it the patriarchy. It is something far worse: a deliberate social and financial coup to destroy natural gender balance, increase worker dependency, and create the perfect, exhausted, obedient slaves.
Let’s tear this apart, piece by piece.
---
Step 1: Economic Sabotage – The Emasculation of Men
Men have been systematically stripped of their role as providers, not by cultural shifts, but by the fiat scam that inflates away their labor and makes single-income households impossible.
In 1970, a man could buy a home, support a family, and retire with dignity on a working-class salary. Today? Even high earners struggle to buy homes while rent and debt devour their paychecks.
The psychological effect? Uselessness. The traditional role of men—to provide, protect, and build—has been economically crippled. The moment a man cannot provide, his biological drive collapses. His confidence, purpose, and even testosterone levels plummet.
He turns to distractions—video games, porn, drugs, or meaningless jobs. Or he checks out entirely, labeled “lazy” while the system that neutered him laughs from above.
And yet, men are still told to "man up" and "work harder"—as if fighting against a rigged economy is a test of character.
---
Step 2: Psychological Warfare – The Masculinization of Women
Women, meanwhile, have been sold a lie—that the only path to fulfillment is chasing careers inside corporate cubicles.
While they are told this is "empowerment," what it really does is double the workforce, lower wages, and increase tax revenue.
Women now face double the burden—working a full-time job while still handling the majority of child-rearing and housework.
Instead of being honored for creating life and raising future generations, they are ridiculed for “wasting their potential” if they don’t dedicate themselves to their corporate masters.
And what is the psychological effect? Resentment.
Resentment towards men, who are no longer the strong providers they once were.
Resentment towards motherhood, which has been devalued and monetized.
Resentment towards themselves, because they were promised fulfillment through corporate work but ended up burned out, anxious, and miserable.
Women have been told they are “strong and independent” while simultaneously being enslaved to a system that profits off their exhaustion.
---
Step 3: Divide and Conquer – Corporate Culture as the New Family
With men neutered and women overburdened, the nuclear family collapses. But humans still need a sense of belonging.
Enter: The Corporation.
Your workplace becomes your "real family." HR tells you to “bring your whole self to work.” Team-building exercises and corporate retreats replace family gatherings.
Work colleagues become your primary emotional support system. There’s even the concept of the “work spouse,” an insidious corporate fabrication that normalizes deeper emotional ties with colleagues than with real partners.
Your career becomes your purpose. Not your bloodline, not your family history, not your legacy—your productivity for someone else’s bottom line.
And before you know it, you’re 50 years old, childless, exhausted, and utterly dependent on a salary to survive. The corporate world used your best years to enrich its shareholders, and now you have nothing.
---
Step 4: The Endgame – The State Raises Your Kids
With the family unit in ruins, who raises the next generation? The State.
Public schools become indoctrination camps, teaching kids to obey, conform, and view the government as their protector.
Children are raised by institutions, not by parents—because both parents are working just to survive.
The cycle repeats: fatherless boys become weak men, overburdened girls become resentful women, and the system gains a fresh crop of obedient, exhausted workers.
The ultimate fiat scam is not just financial. It is biological. It is a full-scale, generational coup against the natural order of humanity.
---
How Do We Break Free?
The only way to escape this biological and financial slavery is to opt out of the fiat system entirely.
1. Bitcoin & Self-Sovereignty – Remove your wealth from the fiat system. Own hard assets, build businesses, become untouchable.
2. Build Real Families – The corporate world is not your family. Your bloodline is. Reject the state’s control over your children.
3. Reject Debt & Wage Slavery – The system is designed to keep you financially trapped. Find ways to exit the rat race early.
4. Reclaim Natural Gender Roles – Not through coercion, but through honest, sovereign partnerships that reject fiat-fueled dysfunction.
They divided us so they could rule us. Break the cycle.
-

@ d360efec:14907b5f
2025-02-17 12:20:25
**3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไรของนักลงทุนส่วนใหญ่**
นักลงทุนจำนวนมากต้องการที่จะประสบความสำเร็จในตลาดหุ้นและสร้างผลกำไรที่สม่ำเสมอ แต่หลายครั้งที่พวกเขากลับพบว่าตัวเองต้องเผชิญกับอุปสรรคที่ทำให้ไม่สามารถบรรลุเป้าหมายนั้นได้ ช่อง Zyo / เซียว จับอิดนึ้ง ได้นำเสนอ 3 พฤติกรรมที่เป็นอุปสรรคสำคัญต่อนักลงทุนส่วนใหญ่ ซึ่งหากนักลงทุนสามารถหลีกเลี่ยงพฤติกรรมเหล่านี้ได้ ก็จะมีโอกาสในการสร้างผลกำไรที่สม่ำเสมอมากยิ่งขึ้น
1. **การซื้อขายตามอารมณ์:** ตลาดหุ้นมีความผันผวนและเต็มไปด้วยข่าวสารมากมาย นักลงทุนที่ซื้อขายตามอารมณ์มักจะตัดสินใจโดยใช้อารมณ์เป็นหลัก ไม่ว่าจะเป็นความโลภเมื่อเห็นราคาหุ้นขึ้น หรือความกลัวเมื่อราคาหุ้นตก การตัดสินใจที่ไม่ได้อยู่บนพื้นฐานของข้อมูลและการวิเคราะห์อย่างรอบคอบ มักนำไปสู่การตัดสินใจที่ผิดพลาดและขาดทุนในที่สุด
2. **การไม่ยอมรับความเสี่ยง:** การลงทุนในตลาดหุ้นมีความเสี่ยง นักลงทุนที่ไม่ยอมรับความเสี่ยงมักจะพลาดโอกาสในการลงทุนในสินทรัพย์ที่ให้ผลตอบแทนสูง หรือในทางกลับกัน พวกเขาอาจจะหลีกเลี่ยงการตัดขาดทุนเมื่อการลงทุนไม่เป็นไปตามที่คาดหวัง การไม่ยอมรับความเสี่ยงและไม่บริหารความเสี่ยงอย่างเหมาะสม จะทำให้พอร์ตการลงทุนไม่เติบโตเท่าที่ควร หรืออาจจะเผชิญกับความเสียหายที่ใหญ่หลวงได้
3. **การขาดความรู้และความเข้าใจ:** ตลาดหุ้นเป็นเรื่องที่ซับซ้อนและเปลี่ยนแปลงอยู่เสมอ นักลงทุนที่ขาดความรู้และความเข้าใจในเรื่องการลงทุนอย่างเพียงพอ มักจะลงทุนโดยไม่มีหลักการหรือไม่สามารถวิเคราะห์สถานการณ์ได้อย่างถูกต้อง การลงทุนโดยปราศจากความรู้และความเข้าใจที่ถูกต้อง ก็เหมือนกับการเดินอยู่ในความมืด ซึ่งโอกาสที่จะประสบความสำเร็จนั้นเป็นไปได้ยาก
**บทสรุป**
3 พฤติกรรมที่กล่าวมาข้างต้นเป็นเพียงส่วนหนึ่งของอุปสรรคที่นักลงทุนส่วนใหญ่ต้องเผชิญ หากนักลงทุนต้องการที่จะประสบความสำเร็จในการลงทุนอย่างยั่งยืน พวกเขาจำเป็นต้องตระหนักถึงพฤติกรรมเหล่านี้และพยายามปรับปรุงตนเองอย่างต่อเนื่อง การศึกษาหาความรู้เพิ่มเติม การวางแผนการลงทุนอย่างรอบคอบ และการควบคุมอารมณ์ จะเป็นกุญแจสำคัญที่นำไปสู่การสร้างผลกำไรที่สม่ำเสมอในตลาดหุ้นได้
แน่นอนค่ะ ฟังคลิปแล้ว และสรุปบทความเป็นภาษาไทยให้คุณแล้วค่ะ
**บทความ: 3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไรสม่ำเสมอของนักลงทุนส่วนใหญ่**
บทความนี้สรุปแนวคิดจากคลิปวิดีโอที่วิเคราะห์พฤติกรรมของนักลงทุนส่วนใหญ่ โดยอ้างอิงจากการสำรวจบัญชีซื้อขายหุ้นกว่า 77,000 บัญชีในช่วงปี 1990-1996 พบว่ามี 3 พฤติกรรมหลักที่เป็นอุปสรรคสำคัญต่อการสร้างผลกำไรที่สม่ำเสมอในการลงทุน
**3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไร:**
1. **ปล่อยให้ขาดทุน แต่รีบขายกำไร:** นักลงทุนส่วนใหญ่มักจะถือหุ้นที่กำลังขาดทุนต่อไปเรื่อย ๆ เพราะไม่อยากยอมรับว่าตัดสินใจผิดพลาด ในทางกลับกัน เมื่อหุ้นเริ่มมีกำไรเพียงเล็กน้อย กลับรีบขายออกไปเพราะกลัวกำไรจะหายไป พฤติกรรมนี้เป็นผลจากธรรมชาติของมนุษย์ที่เรียกว่า "Loser Aversion" หรือการหลีกเลี่ยงความเจ็บปวดจากการขาดทุนมากกว่าความสุขจากการได้กำไร
2. **ถัวเฉลี่ยขาลง มากกว่าพีระมิดขาขึ้น:** นักลงทุนจำนวนมากเลือกที่จะซื้อหุ้นที่ราคาลดลง (ถัวเฉลี่ยขาลง) โดยหวังว่าจะได้ต้นทุนที่ต่ำลงและรอให้ราคาหุ้นกลับมา แต่ในความเป็นจริง หุ้นที่อยู่ในแนวโน้มขาลงก็มีโอกาสที่จะลงต่อไปเรื่อย ๆ การถัวเฉลี่ยขาลงจึงเป็นการเพิ่มความเสี่ยง ในขณะที่การ "พีระมิดขาขึ้น" หรือการซื้อหุ้นเพิ่มเมื่อราคาปรับตัวสูงขึ้น เป็นการลงทุนในหุ้นที่กำลังมีแนวโน้มที่ดีและมีโอกาสสร้างกำไรมากกว่า
3. **รีบขายกำไรเล็กน้อย แต่ไม่ยอมขายเมื่อขาดทุนเล็กน้อย:** พฤติกรรมนี้ต่อเนื่องจากข้อแรก คือเมื่อได้กำไรเพียงเล็กน้อย นักลงทุนมักจะรีบขายเพื่อ "ล็อกกำไร" แต่เมื่อขาดทุนเล็กน้อย กลับไม่ยอมขายเพราะหวังว่าราคาจะกลับมา ทำให้สุดท้ายกลายเป็น "กำไรน้อย รีบขาย ขาดทุน เก็บไว้" ซึ่งส่งผลเสียต่อพอร์ตการลงทุนในระยะยาว
**คำแนะนำเพื่อปรับปรุงพฤติกรรมการลงทุน:**
* **ฝึก "Cut Loss Short, Let Profit Run":** ยอมตัดขาดทุนเมื่อหุ้นไม่เป็นไปตามแผน เพื่อจำกัดความเสียหาย และปล่อยให้หุ้นที่กำลังทำกำไรทำงานไป เพื่อเพิ่มโอกาสในการทำกำไรที่มากขึ้น
* **อย่าถัวเฉลี่ยขาลงโดยไม่มีเหตุผล:** พิจารณาแนวโน้มของหุ้นและปัจจัยพื้นฐานก่อนตัดสินใจถัวเฉลี่ยขาลง หากไม่มีเหตุผลที่ชัดเจน การถัวเฉลี่ยขาลงอาจเป็นการเพิ่มความเสี่ยงโดยไม่จำเป็น
* **บริหารความเสี่ยงและ Money Management อย่างเหมาะสม:** กำหนด stop loss ที่ชัดเจน และบริหารจัดการเงินทุนให้เหมาะสมกับความเสี่ยงที่รับได้
* **เรียนรู้และพัฒนาระบบเทรดของตัวเองอย่างต่อเนื่อง:** ทำความเข้าใจกลยุทธ์การเทรดของตนเอง และปรับปรุงพัฒนาอย่างสม่ำเสมอ
* **มี Mindset ที่ถูกต้องสำหรับการเทรด:** เข้าใจว่าการเทรดสวนทางกับธรรมชาติของมนุษย์ ต้องฝึกฝนและสร้างนิสัยที่ถูกต้องเพื่อเอาชนะอุปสรรคทางจิตวิทยา
**สรุป:**
การลงทุนและการเทรดหุ้นเป็นเกมที่ "ผิดธรรมชาติ" ของมนุษย์ การเอาชนะตลาดหุ้นได้จึงต้องอาศัยการฝึกฝนและปรับเปลี่ยนพฤติกรรมให้สวนทางกับธรรมชาติเดิม ๆ โดยการตระหนักถึง 3 พฤติกรรมที่เป็นอุปสรรค และนำคำแนะนำไปปรับใช้ จะช่วยให้นักลงทุนสามารถพัฒนาไปสู่การสร้างผลกำไรที่สม่ำเสมอและยั่งยืนได้ในระยะยาว
-

@ 7546e8e4:154e8264
2025-02-17 10:48:44
Ever feel like your crypto portfolio is stuck in orbit? What if you could turn those fractional holdings into meaningful growth? The secret lies in smart management and a dashboard that makes it effortless.
Key Points
The Power of Small Balances: Explain how even dust (tiny crypto amounts) can compound with strategic tracking and reinvestment over time.
Unified Dashboard Magic: Highlight how phesky.com aggregates BTC, ETH, LTC, TRX, and more into one sleek interface, eliminating the chaos of juggling multiple wallets.
Visualize Your Growth: Emphasize the dashboard’s design charts, trends, and projections that turn abstract numbers into a clear path to "moon-worthy gains.
Call to Action: Stop letting zeros collect cosmic dust. Launch your portfolio to new heights at phesky.com
-

@ 849a5a61:b57d2870
2025-02-17 10:11:18

> Hey everyone! For the past few months we’ve been building an open-source, affordable and privacy-friendly affiliate and referral program creator for Bitcoin businesses and Nostr publishers called BitFlio.
We built [BitFlio](https://bitflio.com/) because, as bitcoiners and nostriches, we couldn’t find an affiliate marketing tool for our products that would accept bitcoin as payment method, keep us anonymnous, and most important allow us to pay and be paid based on the value we provide. Since we didn’t know if affiliate marketing would work for us as a sales channel, we really wanted to find a tool where, instead of a fixed monthly fee, we could instead pay a % in sats per successful referral to test the waters.
Referral marketing is such a powerful marketing channel as it enable the Value For Value (V4V) model to expand and grow the Bitcoin Circular Economy. For example, **referral leads for businesses have a 70% higher conversion rate than leads from any other sales channel**, and **when referred by other customers, that customer typically has a 37% higher retention rate**.
The setup process for BitFlio is nice and easy. You simply signup with nostr or email, connect your Bitcoin wallet, create your first campaign, add the tracking script to your website and then fire the `BitFlio.convert('yourcustomer@email.com')` function from your thank you page, so we can validate the leads Publishers will bring to you. Once you’ve done those steps, you can either invite publishers manually, or send them your unique BitFlio invite signup page URL.
For Publishers is even easier. If you are a content creator looking to monetize bitcoinize your contents, join our network and select from bitcoin brands those you feel comfortable sharing. Lastly, get paid in sats depending on how many sales you can drive to each vendor.
It’s quite hard to list in sentences some of the cool features that make up BitFlio, so here’s a list:
* Pricing from $0/month
* Automatic NWC sync
* Works for both subscriptions and one-time charges
* Embed script is lightweight and only ~13kb
* Privacy-friendly & Anonymous
* No GDPR needed, as we operate in the Private.
* Manage multiple affiliate programs for different products from one single dashboard
* Open-source software
Since we’re in public beta, getting feedback right now is our top priority. We’d appreciate it so much if you sign up for our Beta whitelist via [beta.BitFlio.com](https://beta.BitFlio.com) and let us know how you get on / your initial thoughts 😄
Landing: https://BitFlio.com `sᴏᴏɴ!`
Beta whitelist: https://beta.BitFlio.com
Follow us on Nostr: https://njump.me/npub1sjd95c0kcxn69x3u8azunrm2kdj97lc6cu79csz7rz74hdta9pcqpxgrdx
Support the open source project on @geyserfund https://geyser.fund/project/bitflio/
- - -
Mirror posts:
- https://bitflio.com/blob/affordable-referral-marketing-software-for-nostr-publishers-and-bitcoin-vendors/
- https://geyser.fund/project/bitflio/posts/view/4138
- naddr1qvzqqqr4gupzppy6tfsldsd852drc069ex8k4vmytal343eut3q9ux9atw6h62rsqqxnzden8ymnwdf5xgurzdphm3ncla
originally posted at https://stacker.news/items/888167
-

@ 849a5a61:b57d2870
2025-02-17 09:47:19
We built [BitFlio](https://bitflio.com/) because, as bitcoiners and nostriches, we couldn’t find an affiliate marketing tool for our products that would accept bitcoin as payment method, keep us anonymnous, and most important allow us to pay and be paid based on the value we provide. Since we didn’t know if affiliate marketing would work for us as a sales channel, we really wanted to find a tool where, instead of a fixed monthly fee, we could instead pay a % in sats per successful referral to test the waters.
Referral marketing is such a powerful marketing channel as it enable the Value For Value (V4V) model to expand and grow the Bitcoin Circular Economy. For example, **referral leads for businesses have a 70% higher conversion rate than leads from any other sales channel**, and **when referred by other customers, that customer typically has a 37% higher retention rate**.
The setup process for BitFlio is nice and easy. You simply signup with nostr or email, connect your Bitcoin wallet, create your first campaign, add the tracking script to your website and then fire the `BitFlio.convert('yourcustomer@email.com')` function from your thank you page, so we can validate the leads Publishers will bring to you. Once you’ve done those steps, you can either invite publishers manually, or send them your unique BitFlio invite signup page URL.
For Publishers is even easier. If you are a content creator looking to monetize bitcoinize your contents, join our network and select from bitcoin brands those you feel comfortable sharing. Lastly, get paid in sats depending on how many sales you can drive to each vendor.
It’s quite hard to list in sentences some of the cool features that make up BitFlio, so here’s a list:
* Pricing from $0/month
* Automatic NWC sync
* Works for both subscriptions and one-time charges
* Embed script is lightweight and only ~13kb
* Privacy-friendly & Anonymous
* No GDPR needed, as we operate in the Private.
* Manage multiple affiliate programs for different products from one single dashboard
* Open-source software
Since we’re in public beta, getting feedback right now is our top priority. We’d appreciate it so much if you sign up for our Beta whitelist via [beta.BitFlio.com](//beta.BitFlio.com) and let us know how you get on / your initial thoughts 😄
-

@ 2063cd79:57bd1320
2025-02-17 09:12:39
Für diejenigen, die mich nicht kennen: Ich bin Hal Finney. Ich machte meine ersten Schritte mit Kryptographie, in dem ich an einer frühen Version von PGP arbeitete, in enger Zusammenarbeit mit Phil Zimmermann. Als Phil beschloss, die PGP Corporation zu gründen, war ich einer der ersten, die er einstellte. Ich habe bis zu meiner Pensionierung an PGP gearbeitet. Zeitgleich fing ich an, mich bei den Cypherpunks zu engagieren. Neben anderen Aktivitäten betrieb ich den ersten kryptographisch basierten anonymen Remailer.
Springen wir ans Ende des Jahres 2008 und der Ankündigung von Bitcoin. Ich habe bemerkt, dass Krypto-Graubärte (ich war Mitte 50) dazu neigen, zynisch zu werden. Ich war eher idealistisch; ich habe Kryptographie immer geliebt, das Mysterium und das Paradoxe daran.
Als Satoshi Bitcoin in der Kryptographie-Mailingliste ankündigte, wurde er bestenfalls skeptisch aufgenommen. Kryptographen haben schon zu viele großartige Pläne von ahnungslosen Anfängern gesehen. Sie neigen zu überhasteten Reaktionen.
Ich war positiver eingestellt. Ich hatte mich schon lange für kryptografische Zahlungssysteme interessiert. Außerdem hatte ich das Glück, sowohl Wei Dai als auch Nick Szabo kennenzulernen und ausgiebig mit ihnen zu korrespondieren, von denen allgemein bekannt ist, dass sie Ideen entwickelt haben, die mit Hilfe von Bitcoin verwirklicht werden sollten. Ich hatte einen Versuch unternommen, meine eigene, auf Proof-of-Work basierende Währung namens RPOW zu schaffen. Daher fand ich Bitcoin faszinierend.
Als Satoshi die erste Version der Software ankündigte, schnappte ich sie mir sofort. Ich glaube, ich war die erste Person neben Satoshi, die Bitcoin laufen ließ. Ich habe Block 70 oder so gemined und ich war der Empfänger der ersten Bitcoin-Transaktion, als Satoshi mir zehn Coins als Test schickte. In den nächsten Tagen führte ich eine E-Mail-Konversation mit Satoshi, in der ich hauptsächlich Fehler meldete, die er dann beseitigte.
Heute ist die wahre Identität von Satoshi ein Rätsel. Aber damals dachte ich, ich hätte es mit einem jungen Mann japanischer Abstammung zu tun, der sehr intelligent und aufrichtig war. Ich hatte das Glück, im Laufe meines Lebens viele brillante Menschen kennenzulernen, daher erkenne ich die Zeichen.
Nach ein paar Tagen lief Bitcoin ziemlich stabil, also ließ ich es laufen. Das waren die Tage, als die Difficulty 1 war und man Blöcke mit dem CPU finden konnte, nicht einmal mit einem GPU. In den nächsten Tagen habe ich mehrere Blöcke gemined. Aber ich schaltete es ab, weil mein Computer zu heiß wurde und mich das Lüftergeräusch störte. Im Nachhinein wünschte ich, ich hätte länger durchgehalten, aber andererseits hatte ich außerordentliches Glück, dass ich am Anfang dabei war. Das ist so eine halb volles, halb leeres Glas Sache
Das nächste Mal, dass ich von Bitcoin hörte, war Ende 2010, als ich überrascht feststellte, dass es nicht nur immer noch existierte, sondern bitcoins tatsächlich einen Geldwert hatten. Ich entstaubte meine alte Wallet und war erleichtert, als ich feststellte, dass meine bitcoins noch darin waren. Als der Preis auf eine echte Summe kletterte, transferierte ich die Coins in eine Offline-Wallet, wo sie hoffentlich für meine Erben etwas wert sein werden.
Apropos Erben: 2009 erlebte ich eine Überraschung, als bei mir plötzlich eine tödliche Krankheit diagnostiziert wurde. Zu Beginn des Jahres war ich in der besten Verfassung meines Lebens, ich hatte viel Gewicht verloren und mit dem Langstreckenlauf begonnen. Ich war mehrere Halbmarathons gelaufen und hatte begonnen, für einen vollen Marathon zu trainieren. Ich hatte mich zu Läufen über 20 Meilen hochgearbeitet und dachte, ich hätte alles im Griff. Doch dann ging alles schief.
Mein Körper begann zu versagen. Ich sprach undeutlich, verlor die Kraft in meinen Händen und meine Beine erholten sich nur langsam. Im August 2009 erhielt ich die Diagnose ALS, auch Lou-Gehrig-Krankheit genannt, nach dem berühmten Baseballspieler, der daran erkrankt war.
ALS ist eine Krankheit, die Motoneuronen abtötet, die Signale vom Gehirn an die Muskeln weiterleiten. Sie verursacht zunächst Schwäche und dann allmählich zunehmende Lähmungen. Die Krankheit verläuft in der Regel innerhalb von 2 bis 5 Jahren tödlich. Meine Symptome waren zunächst gering und ich konnte weiterarbeiten, aber Müdigkeit und Stimmprobleme zwangen mich Anfang 2011, in den Ruhestand zu gehen. Seitdem ist die Krankheit unaufhaltsam fortgeschritten.
Heute bin ich im Wesentlichen gelähmt. Ich werde durch einen Schlauch ernährt, und meine Atmung wird durch einen weiteren Schlauch unterstützt. Ich bediene den Computer mit einem kommerziellen Eyetracker-System. Es ist auch mit einem Sprachsynthesizer ausgestattet, so dass dies jetzt meine Stimme ist. Ich verbringe den ganzen Tag in meinem Elektrorollstuhl. Ich habe eine Schnittstelle mit einem Arduino entwickelt, so dass ich die Position meines Rollstuhls mit meinen Augen einstellen kann.
Es war eine Umstellung, aber mein Leben ist nicht allzu schlimm. Ich kann immer noch lesen, Musik hören, fernsehen und Filme schauen. Vor kurzem habe ich entdeckt, dass ich sogar Code schreiben kann. Es geht sehr langsam, wahrscheinlich 50 Mal langsamer als vorher. Aber ich liebe das Programmieren immer noch, und es gibt mir Ziele. Derzeit arbeite ich an etwas, das Mike Hearn vorgeschlagen hat, nämlich die Sicherheitsfunktionen moderner Prozessoren, die „Trusted Computing“ unterstützen, zu nutzen, um Bitcoin-Wallets zu härten. Es ist fast fertig zur Veröffentlichung. Ich muss nur noch die Dokumentation erstellen.
Und natürlich sind die Kursschwankungen von Bitcoin für mich unterhaltsam. Ich habe einen Anteil an dem Spiel. Aber ich bin durch Glück zu meinen bitcoins gekommen, ohne dass ich etwas dafür kann. Ich habe den Crash von 2011 miterlebt. Ich habe es also schon einmal erlebt. Einfach kommen, einfach gehen.
Das ist meine Geschichte. Ich habe insgesamt ziemlich viel Glück. Selbst mit der ALS ist mein Leben sehr zufriedenstellend. Aber meine Lebenserwartung ist begrenzt. Diese Diskussionen über die Vererbung von bitcoins sind mehr als nur von akademischem Interesse. Meine bitcoins befinden sich in unserem Bankschließfach, und mein Sohn und meine Tochter sind technisch versiert. Ich denke, sie sind sicher genug. Ich bin mit meinem Erbe zufrieden.

-

@ 044da344:073a8a0e
2025-02-17 08:50:50
Ich nehme alles zurück, was ich je gegen die Filmförderung gesagt habe. Eine halbe Milliarde Euro im Jahr? Na und. Die heile deutsche Welt im Kino? Der Schuss Erziehung? Das Ausblenden der kleinen Leute mit ihren großen Problemen? Mir ab sofort egal. Sollen Produzenten, Regisseure, Autoren ruhig nach immer mehr rufen. Gebt ihnen aus den leeren Steuertöpfen, am besten mit vollen Händen. Diese Woche habe ich gelernt: Sie drehen im Zweifel nur für mich.
Das Kino war leer, okay. Das ist aber nicht mein Punkt. Dieses Kino ist so gut wie immer leer. Meist sitzen meine Frau und ich allein in einem der neun großen Säle und sind manchmal sogar im ganzen Haus die einzigen neben den beiden an der Kasse. Was auf der Leinwand läuft, ist oft frustrierend. Siehe oben. Ich mag aber keinen Verriss schreiben. Sonst würde es an dieser Stelle jeden Samstag um das Kino gehen. Diese Woche waren wir hin und weg. Unser Leben. Unsere Stars. Unsere Sprache. Und das alles weit weg von der DDR und von Ostdeutschland, im Niemandsland zwischen Regensburg und Pilsen.

Ich weiß gar nicht, wo ich anfangen soll. Fidel Castro in Warnemünde. Originalbilder, direkt aus meinem Kindergartengedächtnis. Dann Havanna und die Strände mit diesem Wasser, das einem erlaubt, die eigenen Füße zu sehen. Es gibt viele Kuba-Filme, sicher. Aber wo läuft alles auf ein Revolutions-Quiz hinaus, bei dem sich Ost und West gegenübersitzen, die absurdesten Details aus dem Innersten der Maschine abspulen können und dafür in einem Touristenhotel auch noch bejubelt werden? In welchem Drehbuch kann eine Heldin einfach „blauer Würger“ sagen und wie selbstverständlich voraussetzen, dass jeder weiß, um was es geht? Auflösung: Kristall-Wodka. Das Etikett war blau. Die Flasche kostete eigentlich 16 Mark, aber ich weiß wie gestern, dass ich einmal gleich zwei für 55 gekauft habe, als im Wohnheim der Stoff ausging und ich in den Fresswürfel geschickt wurde, Kosename für die hässlichen Häuser, die es in vielen Neubausiedlungen gab, um einen Anlaufpunkt zu haben für Tanz, Kultur, Saufgelage. Der Abend ist in unser Familiengedächtnis eingegangen, weil mich die Studentin, die später meine Frau wurde, vor die Tür gesetzt hat.
Bei den „Kundschaftern des Friedens“ geht es auch um die Liebe, natürlich. Wir sind im Kino. Es geht aber auch um das Altern und um Erinnerungen, die nicht mehr viele teilen. Wir waren in den 2010ern dreimal in Fidels Reich. [Autofahren auf Kuba](https://deutscherkulturkonsument.wordpress.com/2015/03/03/autofahren-auf-kuba/) war der Renner auf einem unserer frühen Blogs, deutlich häufiger geklickt als der Artikel über das [Revolutionsmuseum](https://deutscherkulturkonsument.wordpress.com/2015/02/26/revolutionsmuseum-havanna/) oder der [Text](https://deutscherkulturkonsument.wordpress.com/2015/02/26/kuba/), den dann die *Freie Presse* in Chemnitz übernommen und gedruckt hat, weil der Chefredakteur wusste, dass Kuba für seine Leser immer ein Thema ist. Ein Sehnsuchtsort der DDR-Menschen, erreichbar und zugleich unerreichbar fern, jedenfalls für die allermeisten.

Robert Thalheim erklärt das alles in diesem zweiten „Kundschafter“-Film nicht. Seine Helden reden wie alte Ostdeutsche, wenn weder Wessis zuhören noch die Kinder. Wie meine Frau und ich zu Hause oder in diesem leeren Kinosaal. Über die Schauspieler muss ich nicht viel schreiben. Henry Hübchen, Katharina Thalbach, Corinna Harfouch, Thomas Thieme, Winfried Glatzeder: Das sind unsere Leute. Lebensbegleiter, wenn man so will. So viele sind nicht übriggeblieben. Ich habe ein [Buch](https://www.freie-medienakademie.de/medien-plus/57) geschrieben, um zu ergründen, warum Medienmenschen aus dem Osten anders sind und mir vielleicht auch deshalb oft näher. Soll ich den Film empfehlen? Ich weiß nicht recht. Bilder, Musik, sogar der Ton (in deutschen Filmen sonst oft unerträglich): Hier passt schon alles. Vielleicht sage ich es so: Wer den Schlussgag ohne Google versteht, sollte ins Kino gehen. Thomas Thieme sitzt dort in einem Motorboot und lockt ein paar Amis auf das Wilhelm-Pieck-Atoll.
[Freie Akademie für Medien & Journalismus](https://www.freie-medienakademie.de/)
[Unterstützen](https://www.freie-medienakademie.de/unterstuetzen)
*Fotos*: Freie Akademie für Medien & Journalismus
-

@ d360efec:14907b5f
2025-02-17 08:49:15
**ภาพรวม BTCUSDT (OKX):**
Bitcoin ยังคงอยู่ในแนวโน้มขาขึ้นระยะยาว แต่ระยะสั้นมีความผันผวนและมีการปรับฐานลงมา การวิเคราะห์ครั้งนี้จะเน้นการระบุพื้นที่ที่ Smart Money (หรือ "เจ้ามือ") อาจจะเข้าซื้อหรือขาย เพื่อให้เราสามารถวางแผนการเทรดได้อย่างมีประสิทธิภาพ
**วิเคราะห์ทีละ Timeframe:**
**(1) TF Day (รายวัน):** 
* **แนวโน้ม:** ขาขึ้น (Uptrend)
* **SMC:**
* Higher Highs (HH) และ Higher Lows (HL) ต่อเนื่อง
* Break of Structure (BOS) ด้านบน
* ยังไม่มีสัญญาณการกลับตัวเป็นขาลง
* **ICT:**
* ยังไม่เห็น Order Block หรือ FVG ที่ชัดเจนใน TF Day *ณ ราคาปัจจุบัน*
* **EMA:**
* ราคาอยู่เหนือ EMA 50 (สีเหลือง) และ EMA 200 (สีขาว) (Golden Cross)
* **Money Flow (LuxAlgo):**
* สีเขียวเป็นส่วนใหญ่ แสดงถึงแรงซื้อ
* **Volume Profile:**
* Volume หนาแน่นที่บริเวณต่ำกว่าราคาปัจจุบัน
* **แท่งเทียน:**
* แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย แต่ไส้เทียนยาว แสดงว่ามีแรงซื้อกลับ
* **แนวรับ:** EMA 50, EMA 200, บริเวณ Volume Profile หนาแน่น
* **แนวต้าน:** High เดิม
* **สรุป:** แนวโน้มหลักยังเป็นขาขึ้น Buy on Dip
**(2) TF4H (4 ชั่วโมง):** 
* **แนวโน้ม:** ขาขึ้น (พักตัว)
* **SMC:**
* HH และ HL
* BOS ด้านบน
* ราคาหลุด EMA 50
* **ICT:**
* **Fair Value Gap (FVG):** สังเกตเห็น FVG เล็กๆ ที่เกิดขึ้นก่อนหน้านี้ (บริเวณที่ราคาเคยพุ่งขึ้นอย่างรวดเร็ว) อาจเป็นเป้าหมายของการ Pullback
* **Order Block:** ราคาปัจจุบันกำลังทดสอบ Order Block (บริเวณแท่งเทียนสีแดงแท่งใหญ่ก่อนที่จะขึ้น) *เป็นจุดที่น่าสนใจมาก*
* **EMA:**
* ราคาหลุด EMA 50
* EMA 200 เป็นแนวรับถัดไป
* **Money Flow (LuxAlgo):**
* เขียวและแดงผสมกัน, แดงเริ่มมากขึ้น
* **Volume Profile:**
* Volume profile ค่อนข้างสูง
* **แนวรับ:** EMA 200, Order Block, บริเวณ Volume Profile
* **แนวต้าน:** EMA 50, High เดิม
* **สรุป:** แนวโน้มขาขึ้นพักตัว, ทดสอบ Order Block, Money Flow เริ่มเป็นลบ
**(3) TF15 (15 นาที):** 
* **แนวโน้ม:** ขาลง (Downtrend) ระยะสั้น *แต่เริ่มมีสัญญาณการฟื้นตัว*
* **SMC:**
* Lower Highs (LH) และ Lower Lows (LL) *แต่เริ่มเห็น Higher Low*
* BOS ด้านล่าง
* *เริ่มมีสัญญาณการ Breakout EMA 50/200*
* **ICT:**
* ราคาเพิ่ง Breakout Order Block ขาลง (แต่ต้องรอดูว่าจะยืนได้หรือไม่)
* **EMA:**
* *EMA 50/200 เพิ่งจะตัดกันแบบ Golden Cross*
* **Money Flow (LuxAlgo):**
* *เริ่มมีแท่งสีเขียวปรากฏขึ้น*
* **Volume Profile:**
* **แนวรับ:** บริเวณ Low ล่าสุด
* **แนวต้าน:** EMA50/200
* **สรุป:** *เริ่มมีสัญญาณการฟื้นตัว* แต่ยังต้องระวัง
**สรุปภาพรวมและกลยุทธ์ (BTCUSDT):**
* **แนวโน้มหลัก (Day):** ขาขึ้น
* **แนวโน้มรอง (4H):** ขาขึ้น (พักตัว), ทดสอบ Order Block
* **แนวโน้มระยะสั้น (15m):** *เริ่มมีสัญญาณการฟื้นตัว*
* **Money Flow:** Day เป็นบวก, 4H เริ่มเป็นลบ, 15m เริ่มเป็นบวก
* **กลยุทธ์:**
1. **Wait & See:** รอการยืนยันการ Breakout EMA 50/200 ใน TF15m
2. **Buy (เสี่ยง):** *เฉพาะเมื่อราคา Breakout EMA 50/200 ใน TF 15 ได้อย่างแข็งแกร่ง*
3. **Short (เสี่ยง):** ถ้า Order Block ใน TF4H รับไม่อยู่ และ TF15 ยังคงเป็นขาลง
**คำแนะนำ:**
* **Order Block:** ให้ความสำคัญกับ Order Block ใน TF4H
* **FVG:** สังเกต FVG ใน TF4H
* **ความขัดแย้งของ Timeframes:** เริ่มลดลง (15m เริ่มมีสัญญาณบวก)
* **จับตาดู TF15 อย่างใกล้ชิด**
**Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-

@ bbb5dda0:f09e2747
2025-02-17 08:13:00
**Alright, This weekly review's gonna be a quick one as i covered my weekend + monday about Sats 'n Facts in the last one. Which leaves us with only a few days, some of which I had to give in and rest as I had been continuing to work with quite a bad cold for too long. The Facts must've been hitting too hard...**
## Reflecting on networks
A lot of my time this week was reflecting on the event and all the contacts I'd made there. There has been a surprising lot of enthusiasm of the community about Tollgate specifically. There's something that draws me to the project and i think it's not even the flashy-ness of routers paying routers, I'm starting to see the bigger possible implications of the sovereign networks that can grow from this. Not for the western world per se but for places that want to build out new infrastrucutre with their own communities. One of the worries from people to operate TollGates is if they'll get trouble with their ISP's. Which is a legitimate worry, but how long will that worry be relevant?
One thing I realize, as Nostr grows -and Blossom too- is that the data we pull in will be more localized. Imagine a city equipped with a Sovereign Tollgate network. If a few people in your city have watched a video, there will likely be a copy of that video inside the city-wide network. Then if the city get's cut off for any reason, that video will still be very much accessible and people might not even notice the 'internet is down'. I woke up in the middle of the night and had to draw out this visualization of the combination of Clearnet + Tor + TollGate networks and how they can interact with Epoxy proxies in between (visualized by the ♾️ symbol). Anyone that sees an opportunity to bridge the networks can jump in and be that link.
Even attacking (DDOS) services within other networks might become harder, because either:
1) you have to have your botnet reside inside the network of the victim. Which, if it's a small network won't comprise of a significant amount of nodes.
2) you have to have to route your attack through (Epoxy) bridges known to you, the attacker. Which likely have limited bandwidth.

Anyway, this is just my 3 AM brain-dump. I'll keep chewing on this...
## Marketing TollGate
Like I mentioned earlier there was a lot of interest in Tollgate and to be honest it's been a bit overwhelming, there are so many opportunities like podcasts, meetups and articles opening up to share it and talk about it that I have to think about the form in which I want to relate myself to the project. In any case, these are Good problems to have...
In the meanwhile we've worked on getting a good website landingpage where we can point people to that are interested in the project, it should be up soon!
- Consumers can download the Android (for now) app
- Operators can download TollGateOS to put on their router
- FAQ's
Also, i've been helping out to get some stuff automated. so we can build and push new versions quickly to start getting user feedback and enable iterating on a fast pace!
-

@ 0463223a:3b14d673
2025-02-17 07:48:11
Here we go, it’s Mooooonnnndddddaaaaaaaayyyyyyy!
It’s safe to say I enjoy Monday. Much as I appreciate the downtime over the weekend (if I’m not working) I appreciate the routine of Mondays. Firstly I have my stream to look forward to and whilst I’m not at my best first thing on a Monday, having a little structure goes a long way. Even the fear of looking at the emails I’ve been ignoring from the previous week is possible.
So maybe I’m starting to get an angle of why I’m writing this. It’s a memoir of being a mental I think. I’ve mentioned a number of times this has been a problem most my life but I write this as I’ve halved my Venlafaxine does by ½ once again. This means I’m now on 1/12th of my original dose and I’m maybe a month away from being completely free of RRSIs for the first time in, I guess at least 10 years. To be honest I cant remember when I was first prescribed them. It’s been quite a journey...
3 things have been pivotal. 1; finding my now wife. She’s brilliant and I love her dearly, I think most people know deep down how crushing loneliness can be. I’m very grateful to her for putting up with my bullshit, supporting me and just being there. Gold star for her!
2; would be music, it’s a funny one to put in, it’s also been part of the problem, especially in my wilder days. There’s something quite seductive about the sex, drugs and Rock n Roll meme, although musically it was more Hip Hop, Reggae, Bleeps and Jazz, also I didn’t sleep around much at all but I certainly don’t think I would’ve messed with crack, heroin and all the other drugs otherwise. It’s worth noting 2 of my friends from that era, who didn’t have music in their lives are dead. I’m very lucky. There’s over 100 years of recorded music to enjoy plus I’m almost happy with some of my own bits at last!
3; I have some security, I no longer pay rent or have a landlord. This is also due to number 1 but also because I found some funny internet money. I’m still to write about my process with that, other than to say it was direct response to the banks. That’s a story in it’s own right, it’s pretty dark and hmm… not sure. Plus I don’t think there’s any need to go there right now. I have the world’s most expensive shed and I know I can survive a few months should the worst happen. That’s a LOT. Whilst a little risk taking is healthy, life shouldn’t free stress free, uncertainty about having a roof over your head when you can’t afford it can really take it’s toll. A degree of security is most welcome at this time in life.
A lot of people aren’t so lucky, Tom, Ricky, Dave, Slam, Joel. I’m name checking you specifically. You’re in my thoughts often, especially as I play music every morning… and Slam, if I ever see you again, I want my records back!!! Haha, thieving little cunt but it’s still not hate here. Your life was fucked up before you even had a chance. I hope you’ve found peace with yourself. At least you’re alive! (I think, he might be dead too, who knows…)
So yeah, it’s Monday and it’s gonna be a good day right? I mean it might not but I will at least give it the best start possible and work from there. It takes a degree of effort to retrain the brain. Actually maybe there’s a 4th thing to mention. No Facebacon, Instagran, X or LinkedIn. None of that bullshit where you’re forced into some fake world generated in order to increase shareholder value. These platforms are akin to being a lab rat. I picture Zuckerberg like Ming The Merciless at the start of Flash Gordon sending hot hail etc. That guy made a decision to mess with peoples’ psyche to drive profits. That’s fucking evil man. Jeez, what a cunt!
It’s Monday, I’m wishing you strength in whatever you have ahead of you today. I’m lucky to be where I am right now and if you’re reading this and your world is plagued by darkness, it can get better. Remember that. Hold onto that as best you can. DON’T FUCKING KILL YOURSELF. That’s the single worst thing you can do. The pain you’ll leave behind isn’t worth it. I hope some cosmic vibrations happen in your favour. There’s no easy solution. I can’t tell you the answer but I wish you well. Good luck out there!
-

@ fd78c37f:a0ec0833
2025-02-17 07:15:15
In this edition, we invited Kelvin from Bitcoin Chama to share how his community is leveraging Bitcoin to build a self-sustaining ecosystem in rural areas.
**YakiHonne**: Kelvin, thanks for joining us. Before we dive in, I'd like to take a moment to introduce YakiHonne and share a bit about what we do. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. Today, we’ll be diving into your community. So, let’s start—tell us a bit about yourself and what you do?
**Kelvin**:I'm Kelvin, the founder of Bitcoin Chama, a rule-based Bitcoin community with a mission to build a self-reliant Bitcoin circular ecosystem. How do we achieve this? We empower young people and our community economically by introducing accessible, low-resource projects that require minimal time and space to implement. We then encourage them to save their earnings in Bitcoin, promoting financial independence and long-term sustainability.
**YakiHonne**: Given Bitcoin’s increasing value, it’s almost like owning property, but in the form of a digital asset. That’s an incredible concept and a really great initiative!Now, let’s dive into today’s questions. What initially sparked your interest in Bitcoin, and what motivated you to build a community around it?
**Kelvin**:Initially, I didn’t know much about Bitcoin. But I had a friend who worked at Boda Boda. He was trying to save up his earnings to buy iron sheets and build a better house for his family. Since he didn't get enough money from Boda Boda, he saved whatever little he could in a bank, a savings group. Over the course of two years, when he finally went to withdraw his money, he realized that the price of iron sheets had increased by almost 100% Originally, he had planned to buy 30 iron sheets, but by the time he withdrew his savings, his money could no longer afford that many. For someone who works so hard to earn a living, this was a major setback.
**Kelvin**:That’s when I started thinking—how can we solve this problem? At the time, I didn’t know much about Bitcoin or how money really works. But seeing my friend struggle, I realized that the real issue wasn’t just rising prices, but the financial system itself.
**Kelvin**:Then, later that year, I was introduced to Bitcoin, and it suddenly clicked! If my friend had saved in Bitcoin instead of fiat, his purchasing power wouldn’t have been eroded. In fact, he might have even been able to afford nails, labor costs, or additional materials. That realization led me to create Bitcoin Chama—a community to help people save in Bitcoin and protect their hard earned money.
**YakiHonne**: It sounds like you were inspired by how Bitcoin’s value appreciates over time, much like an investment in land that continues to grow in value. That’s a truly powerful concept behind Bitcoin.Now, could you share how your community first got started and what strategies you used to attract members in the beginning?
**Kelvin**:Building a community from scratch—especially a Bitcoin community—isn’t easy, particularly in a rural area of Kenya where many people lack internet access and don’t even use smartphones. At first, my focus was purely on Bitcoin education. I would go out, meet people, and teach them about Bitcoin. But I soon realized that while knowledge is valuable, most people didn’t have the means to earn and save in Bitcoin.
**Kelvin**:That’s when I came up with a different approach. Instead of just educating people, I decided to create small projects that could generate income, sponsor these projects, and help them grow. Over time, as people started earning from these projects, they could begin saving their income in Bitcoin.
**Kelvin**:We’ve now been running Bitcoin Chama for almost a year—since May last year. The impact isn’t massive yet, but for a community just getting started, it’s been a significant step forward. Every small step matters, and while growth takes time, I believe these small beginnings will eventually lead to something big in the future.

**YakiHonne**: It's a wonderful start,So far, what challenges have you faced while building and growing the Bitcoin Chama community?
**Kelvin**:I don't have many challenges—just two main ones.The first challenge is poverty. Whenever you introduce someone to Bitcoin, you often have to explain its history. Imagine telling someone that in 2010, Bitcoin was worth about $1, and by 2013, its value had increased significantly. Fast forward to 2025, 15 years later, and Bitcoin is now worth around 13 million Kenyan shillings (about $100,000). When people hear this, they see it as a great opportunity to escape poverty. The problem is, they often perceive Bitcoin as free money, rather than understanding it as a long-term investment or financial tool. The second challenge is scamming. Many people think Bitcoin might be a scam. This is a common issue in many communities.
**YakiHonne**: Yes, especially the second challenge—people thinking Bitcoin is a scam. This is very common in many emerging communities. A lot of people feel that since they can't see Bitcoin physically, it’s not real, which leads them to doubt its authenticity.Finding a way to convince people of Bitcoin’s legitimacy is crucial.
So, what principles guide your community? And how do you maintain trust and reliability in your discussions?
**Kelvin**:So, in our community, I’ve discovered something—I’ve found saccos. Right now, I have two saccos(Chama) , and I intend to grow them over time. Within these two circles, we use the Machangura app. The app has an option for creating a clan, so we organize people into two saccos, forming two clans. We then add all members from each sacco into their respective clan. This setup ensures a trustless system. For example, if someone wants to withdraw money from their shared account or sell Bitcoin, the system notifies all members. This way, everyone stays informed, and people don’t have to feel insecure about the funds they have saved.
**YakiHonne**: So at least that’s how you maintain integrity, transparency, and trust within the community. So How does your community educate its members and keep them updated on Bitcoin developments?
**Kelvin**:I am the founder of Bitcoin Chama, and right now, I’m mostly focused on community activities. We usually hold meetups oftenly, but I wouldn’t say we focus entirely on Bitcoin only. Instead, our discussions are more about how to improve what we do, grow more, and build new projects. That’s the main focus for me at the moment. That said, I am planning to start physical Bitcoin lessons. Since Bitcoin Chama is located in my community, I know that a lot of people visit the area—many come here to shop and buy things. So, I plan to post a notice at the location, inviting new members who are interested in learning about Bitcoin. We’ll create a timetable so that people can come at specific times to attend lessons. Additionally, we’ll leverage our existing clients and brainstorm ways to make this work for a wider audience.
**YakiHonne**: It's still part of the education process,maybe not fully in-depth, but it’s still valuable. So, that’s actually a good thing. You guys are doing something very meaningful, which is great.The meetups also serve as a way to educate people about Bitcoin, making them an important part of the process. It’s definitely a solid approach.
**YakiHonne**: So, Kelvin, how does your community collaborate with the broader Bitcoin ecosystem? And what partnerships have you formed so far that have had the biggest impact on BitcoinTerminal?
**Kelvin**:We haven’t had any major collaborations yet. So far, we’ve been riding solo. We’ve had some support from friends and well-wishers, but we haven’t partnered with any major organizations yet.
**YakiHonne**: That’s okay! You guys will get there very soon, I’m sure of it. So far, in the process of building your community, what initiatives have you taken to promote the adoption of Bitcoin in your local environment?
**Kelvin**:Well, besides our existing clients, we have about three shops that currently accept Bitcoin payments. I’m still working on overcoming the major challenges we face while also trying to find ways to encourage people to use Bitcoin in their daily lives.
**Kelvin**:First, I need to support the people who are already part of our community, making sure they have the resources and knowledge they need. I don’t know if I’m fully answering the question, but this is what I’m working on. I’m not solely focused on growing a large community right now. Instead, I’m focused on quality growth—on educating people who truly understand Bitcoin, know how to use it, and grasp what it really means. My approach is to start small and expand gradually, ensuring that at each stage, people gain a deeper understanding of Bitcoin and how it can impact their lives.
**YakiHonne**: I’m sure you guys will succeed. You don’t necessarily have to start big, but I believe you’ll grow much faster than you expect. With the effort and passion you’re putting in, I have no doubt that Bitcoin Chama will expand significantly. So,moving on to my last question,what are your community’s goals for the next 6 to 12 months? And how do you see it evolving with Bitcoin’s development?
**Kelvin**:My goal for the next year is to continue the projects I’ve been working on. We have a community team that serves as a gathering point where people can come together, coordinate meeting times, and discuss Bitcoin and our future plans.
**Kelvin**:so far for example, we built and distributed 15 beehives to different young people in our community. They harvest honey, sell it, and save the earnings in Bitcoin. We piped free clean water which can be accessed by any member in our community, significantly improving daily convenience.

**Kelvin**:We are planning to build two chicken coops and provide chickens to two groups of five people each. They will raise chickens, sell eggs, and save their earnings in Bitcoin. Over time, we aim for each member to have their own chicken coop with a sustainable flock by the end of the year.

**Kelvin**:We plan to lease a piece of land for the women in our community to grow vegetables and sell them at the local market. Their earnings will also be saved in Bitcoin. If the project is profitable, we will reinvest in more land to expand vegetable farming.Additionally, we plan to lease 2-3 acres of land specifically for commercial maize farming. The maize will be sold for Bitcoin, and if we generate profits, we will expand the farmland.
**Kelvin**:Our long-term goal is to build a self-sufficient community, enabling it to operate independently and achieve sustainable development. This is also our core objective.
**YakiHonne**: I truly love all the ideas behind this. I admire the fact that you are giving back to the community and that people are experiencing real benefits from the Bitcoin ecosystem. This way, they have something positive and meaningful to say about Bitcoin.
**YakiHonne**: Thank you so much, Kelvin, for joining us today. We’ve reached the end of our interview, and I’m really happy to have had this conversation with you. We look forward to seeing Bitcoin Chama grow!
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37#intro The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises. In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously. I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea. It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope. After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes. I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project. With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed. With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation. At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37#intro The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises. In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously. I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea. It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope. After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes. I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project. With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed. With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation. At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project. @ df173277:4ec96708
2025-02-07 00:41:34## **Building Our Confidential Backend on Secure Enclaves** With our newly released [private and confidential **Maple AI**](https://trymaple.ai/?ref=blog.opensecret.cloud) and the open sourcing of our [**OpenSecret** platform](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud) code, I'm excited to present this technical primer on how we built our confidential compute platform leveraging **secure enclaves**. By combining AWS Nitro enclaves with end-to-end encryption and reproducible builds, our platform gives developers and end users the confidence that user data is protected, even at runtime, and that the code operating on their data has not been tampered with. ## **Auth and Databases Today** As developers, we live in an era where protecting user data means "encryption at rest," plus some access policies and procedures. Developers typically run servers that: 1. Need to register users (authentication). 2. Collect and process user data in business-specific ways, often on the backend. Even if data is encrypted at rest, it's commonly unlocked with a single master key or credentials the server holds. This means that data is visible during runtime to the application, system administrators, and potentially to the hosting providers. This scenario makes it difficult (or impossible) to guarantee that sensitive data isn't snooped on, memory-dumped, or used in unauthorized ways (for instance, training AI models behind the scenes). ## **"Just Trust Us" Isn't Good Enough** In a traditional server architecture, users have to take it on faith that the code handling their data is the same code the operator claims to be running. Behind the scenes, applications can be modified or augmented to forward private information elsewhere, and there is no transparent way for users to verify otherwise. This lack of proof is unsettling, especially for services that process or store highly confidential data. Administrators, developers, or cloud providers with privileged access can inspect memory in plaintext, attach debuggers, or gain complete visibility into stored information. Hackers who compromise these privileged levels can directly access sensitive data. Even with strict policies or promises of good conduct, the reality is that technical capabilities and misconfigurations can override words on paper. If a server master key can decrypt your data or can be accessed by an insider with root permissions, then "just trust us" loses much of its credibility. The rise of AI platforms amplifies this dilemma. User data, often full of personal details, gets funneled into large-scale models that might be training or fine-tuning behind the scenes. Relying on vague assurances that "we don't look at your data" is no longer enough to prevent legitimate concerns about privacy and misuse. Now more than ever, providing a **strong, verifiable** guarantee that data remains off-limits, even when actively processed, has become a non-negotiable requirement for trustworthy services. ## **Current Attempts at Securing Data** Current User Experience of E2EE Apps While properly securing data is not easy, it isn't to say that no one is trying. Some solutions use **end-to-end encryption** (E2EE), where user data is encrypted client-side with a password or passphrase, so not even the server operator can decrypt it. That approach can be quite secure, but it also has its **limitations**: 1. **Key Management Nightmares**: If a user forgets their passphrase, the data is effectively lost, and there's no way to recover it from the developer's side. 2. **Feature Limitations**: Complex server-side operations (like offline/background tasks, AI queries, real-time collaboration, or heavy computation) can't easily happen if the server is never capable of processing decrypted data. 3. **Platform Silos**: Some solutions rely on iCloud, Google Drive, or local device storage. That can hamper multi-device usage or multi-OS compatibility. Other approaches include self-hosting. However, these either burden users with dev ops overhead or revert to the "trust me" model for the server if you "self-host" on a cloud provider. ## **Secure Enclaves** ### **The Hybrid Approach** Secure enclaves offer a compelling middle ground. They combine the privacy benefits of keeping data secure from prying admins while still allowing meaningful server-side computation. In a nutshell, an enclave is a protected environment within a machine, isolated at the hardware level, so that even if the OS or server is compromised, the data and code inside the enclave remain hidden. App Service Running Inside Secure Enclave ### **High-Level Goal of Enclaves** Enclaves, also known under the broader umbrella of **confidential computing**, aim to:\ • **Lock down data** so that only authorized code within the enclave can process the original plaintext data.\ • **Deny external inspection** by memory dumping, attaching a debugger, or intercepting plaintext network traffic.\ • **Prove** to external users or services that an enclave is running unmodified, approved code (this is where **remote attestation** comes in). ### **Different Secure Enclave Solutions** [**AMD SEV**](https://www.amd.com/en/developer/sev.html?ref=blog.opensecret.cloud) **(Secure Encrypted Virtualization)** encrypts an entire virtual machine's memory so that even a compromised hypervisor cannot inspect or modify guest data. Its core concept is "lift-and-shift" security. No application refactoring is required because hardware-based encryption automatically protects the OS and all VM applications. Later enhancements (SEV-ES and SEV-SNP) added encryption of CPU register states and memory integrity protections, further limiting hypervisor tampering. This broad coverage means the guest OS is included in the trusted boundary. AMD SEV has matured into a robust solution for confidential VMs in multi-tenant clouds. [**Intel TDX**](https://www.intel.com/content/www/us/en/developer/tools/trust-domain-extensions/overview.html?ref=blog.opensecret.cloud) **(Trust Domain Extensions)** shifts from process-level enclaves to full VM encryption, allowing an entire guest operating system and its applications to run in an isolated "trust domain." Like AMD SEV, Intel TDX encrypts and protects all memory the VM uses from hypervisors or other privileged software, so developers do not need to refactor their code to benefit from hardware-based confidentiality. This broader scope addresses many SGX limitations, such as strict memory bounds and the need to split out enclave-specific logic, and offers a more straightforward "lift-and-shift" path for running existing workloads privately. While SGX is now deprecated, TDX carries forward the core confidential computing principles but applies them at the virtual machine level for more substantial isolation, easier deployment, and the ability to scale up to large, memory-intensive applications. [**Apple Secure Enclave and Private Compute**](https://security.apple.com/blog/private-cloud-compute/?ref=blog.opensecret.cloud) is a dedicated security coprocessor embedded in most Apple devices (iPhones, iPads, Macs) and now extended to Apple's server-side AI infrastructure. It runs its own microkernel, has hardware-protected memory, and securely manages operations such as biometric authentication, key storage, and cryptographic tasks. Apple's "Private Compute" approach in the cloud brings similar enclave capabilities to server-based AI, enabling on-device-grade privacy even when requests are processed in Apple's data centers. [**AWS Nitro Enclaves**](https://docs.aws.amazon.com/enclaves/latest/user/nitro-enclave.html?ref=blog.opensecret.cloud) carve out a tightly isolated "mini-VM" from a parent EC2 instance, with its own vCPUs and memory guarded by dedicated Nitro cards. The enclave has no persistent storage and no external network access, significantly reducing the attack surface. Communication with the parent instance occurs over a secure local channel (vsock), and AWS offers hardware-based attestation so that secrets (e.g., encryption keys from AWS KMS) can be accessed only to the correct enclave. This design helps developers protect sensitive data or code even if the main EC2 instance's OS is compromised. [**NVIDIA GPU TEEs**](https://www.nvidia.com/en-us/data-center/solutions/confidential-computing/?ref=blog.opensecret.cloud) **(Hopper H100 and Blackwell)** extend confidential computing to accelerated workloads by encrypting data in GPU memory and ensuring that even a privileged host cannot view or tamper with it. Data moving between CPU and GPU is encrypted in transit, so sensitive model weights or inputs remain protected during AI training or inference. NVIDIA's hardware and drivers handle secure data paths under the hood, allowing confidential large language model (LLM) workloads and other GPU-accelerated computations to run with minimal performance overhead and strong security guarantees. ### **Key Benefits** One major advantage of enclaves is their ability to **keep memory completely off-limits** to outside prying eyes. Even administrators who can normally inspect processes at will are blocked from peeking into the enclave's protected memory space. The enclave model is a huge shift in the security model: it prevents casual inspection and defends against sophisticated memory dumping techniques that might otherwise leak secrets or sensitive data. Another key benefit centers on cryptographic keys that are **never exposed outside the enclave**. Only verified code running inside the enclave environment can run decryption or signing operations, and it can only do so while that specific code is running. This ensures that compromised hosts or rogue processes, even those with high-level privileges, are unable to intercept or misuse the keys because the keys remain strictly within the trusted boundary of the hardware. Enclaves can also offer the power of **remote attestation**, allowing external clients or systems to confirm that they're speaking to an authentic, untampered enclave. By validating the hardware's integrity measurements and enclave-specific proofs, the remote party can be confident in the underlying security properties, an important guarantee in multi-tenant environments or whenever trust boundaries extend across different organizations and networks. Beyond that, **reproducible builds** can create a verifiable fingerprint proving which binary runs in the enclave. This is a step above a simple "trust us" approach. Anyone can independently recreate the enclave image and verify the resulting cryptographic hash by using a reproducible build system (for example, [our NixOS-based solution](https://github.com/OpenSecretCloud/opensecret/blob/master/flake.nix?ref=blog.opensecret.cloud)). If it matches, then users and developers know precisely how code handles their data, boosting confidence that no hidden changes exist. It's worth noting that although enclaves shield you from software devs, cloud providers, and insider threats, you do have to trust the **hardware vendor** (Intel, AMD, Apple, AWS, or NVIDIA) to implement their microcode and firmware securely. The entire enclave model could be theoretically undermined if a CPU maker's root keys or manufacturing process were compromised. Fortunately, these companies undergo extensive audits and firmware validations (often with third-party researchers), and their remote attestation mechanisms allow you to confirm specific firmware versions before trusting an enclave. While this adds a layer of "vendor trust," it's still a far more contained risk than trusting an entire operating system or cloud stack, so enclaves remain a strong step forward in practical, confidential computing. ## **How We Use Secure Enclaves** Now that we've covered the general idea of enclaves let's look at how we specifically implement them in OpenSecret, our developer platform for handling user auth, private keys, data encryption, and AI workloads. ### **Our Stack: AWS Nitro + Nvidia TEE** • **AWS Nitro Enclaves for the backend**: All critical logic, authentication, private key management, and data encryption/decryption run inside an AWS Nitro Enclave. • **Nvidia Trusted Execution for AI**: For large AI inference (such as the Llama 3.3 70B model), we utilize Nvidia's GPU-based TEEs to protect even GPU memory. This means users can feed sensitive data to the AI model **without** exposing it in plaintext to the GPU providers or us as the operator. [Edgeless Systems](https://www.edgeless.systems/?ref=blog.opensecret.cloud) is our Nvidia TEE provider, and due to the power of enclave verification, we don't need to worry about who runs the GPUs. We know requests can't be inspected or tampered with. ### **End-to-End Encryption from Client to Enclave** Client-side Enclave Attestation from Maple AI Before login or data upload, the user/client verifies the **enclave attestation** from our platform. This process proves that the specific Nitro Enclave is genuine and runs the exact code we've published. You can check this out live on [Maple AI's attestation page](https://trymaple.ai/proof?ref=blog.opensecret.cloud). Based on the attestation, the client establishes a secure ephemeral communication channel that only that enclave can decrypt. While we take advantage of SSL, it is typically not terminated inside the enclave itself. To ensure there's full encrypted data transfer all the way through to the enclave, we establish this additional handshake based on the attestation document that is used for all API requests during the client session. From there, the user's credentials, private keys, and data pass through this secure channel directly into the enclave, where they are decrypted and processed according to the user's request. ### **In-Enclave Operations** At the core of OpenSecret's approach is the conviction that security-critical tasks must happen inside the enclave, where even administrative privileges or hypervisor-level compromise cannot expose plaintext data. This encompasses everything from when a user logs in to creating and managing sensitive cryptographic keys. By confining these operations to a protected hardware boundary, developers can focus on building their applications without worrying about accidental data leaks, insider threats, or malicious attempts to harvest credentials. The enclave becomes the ultimate gatekeeper: it controls how data flows and ensures that nothing escapes in plain form. User Auth Methods running inside Enclave A primary example is **user authentication**. All sign-in workflows, including email/password, OAuth, and upcoming passkey-based methods, are handled entirely within the enclave. As soon as a user's credentials enter our platform through the encrypted channel, they are routed straight into the protected environment, bypassing the host's operating system or any potential snooping channels. From there, authentication and session details remain in the enclave, ensuring that privileged outsiders cannot intercept or modify them. By centralizing these identity flows within a sealed environment, developers can assure their users that no one outside the enclave (including the cloud provider or the app's own sysadmins) can peek at, tamper with, or access sensitive login information. Main Enclave Operations in OpenSecret The same principle applies to **private key management**. Whether keys are created fresh in the enclave or securely transferred into it, they remain sealed away from the rest of the system. Operations like digital signing or content decryption happen only within the hardware boundary, so raw keys never appear in any log, file system, or memory space outside the enclave. Developers retain the functionality they need, such as verifying user actions, encrypting data, or enabling secure transactions without ever exposing keys to a broader (and more vulnerable) attack surface. User backup options exist as well, where the keys can be securely passed to the end user. Realtime Encrypted Data Sync on Multiple Devices Another crucial aspect is **data encryption at rest**. While user data ultimately needs to be stored somewhere outside the enclave, the unencrypted form of that data only exists transiently inside the protected environment. Encryption and decryption routines run within the enclave, which holds the encryption keys strictly in memory under hardware guards. If a user uploads data, it is promptly secured before it leaves the enclave. When data is retrieved, it remains encrypted until it reenters the protected region and is passed back to the user through the secured communication channel. This ensures that even if someone gains access to the underlying storage or intercepts data in transit, they will see only meaningless ciphertext. Confidential AI Workloads Finally, **confidential AI workloads** build upon this same pattern: the Nitro enclave re-encrypts data so it can be processed inside a GPU-based trusted execution environment (TEE) for inference or other advanced computations. Sensitive data, like user-generated text or private documents, never appears in the clear on the host or within GPU memory outside the TEE boundary. When an AI process finishes, only the results are returned to the enclave, which can then relay them securely to the requesting user. By seamlessly chaining enclaves together, from CPU-based Nitro Enclaves to GPU-accelerated TEEs, we can deliver robust, hardware-enforced privacy for virtually any type of server-side or AI-driven operation. ### **Reproducible Builds + Verification** Client verifies enclave attestation document We build our enclaves on **NixOS** with reproducible builds, ensuring that anyone can verify that the binary we publish is indeed the binary running in the enclave. This build process is essential for proving we haven't snuck in malicious code to exfiltrate data or collect sensitive logs. Our code is fully open source ([GitHub: OpenSecret](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud)), so you can audit or run it yourself. You can also verify that the cryptographic measurement the build process outputs matches the measurement reported by the enclave during attestation. ## **Putting It All Together** OpenSecret Offering: Private Key Management, Encrypted Sync, Private AI, and Confidential Compute By weaving secure enclaves into every step, from authentication to data handling to AI inference, we shift the burden of trust away from human policies and onto provable, hardware-based protections. For app developers, you can offer your users robust privacy guarantees without rewriting all your business logic or building an entire security stack from scratch. Whether you're storing user credentials or running complex operations on sensitive data, the enclave approach ensures plaintext remains inaccessible to even the most privileged parties outside the enclave boundary. Developers can focus on building great apps, while OpenSecret handles the cryptographic "lock and key" behind the scenes. This model provides a secure-by-design environment for industries that demand strict data confidentiality, such as healthcare, fintech, cryptocurrency apps for secure key management, or decentralized identity platforms. Instead of worrying about memory dumps or backend tampering, you can trust that once data enters the enclave, it's sealed off from unauthorized eyes, including from the app developers themselves. And these safeguards don't just apply to niche use cases. Even general-purpose applications that handle login flows and user-generated content stand to benefit, especially as regulatory scrutiny grows around data privacy and insider threats. Imagine a telehealth startup using OpenSecret enclaves to protect patient information for remote consultations. Not only would patient data remain encrypted at rest, but any AI-driven analytics to assist with diagnoses could be run privately within the enclave, ensuring no one outside the hardware boundary can peek at sensitive health records. A fintech company could similarly isolate confidential financial transactions, preventing even privileged insiders from viewing or tampering with raw transaction details. These real-world implementations give developers a clear path to adopting enclaves for serious privacy and compliance needs without overhauling their infrastructure. OpenSecret aims to be a **full developer platform** with end-to-end security from day one. By incorporating user authentication, data storage, and GPU-based confidential AI into a single service, we eliminate many of the traditional hurdles in adopting enclaves. No more juggling separate tools for cryptographic key management, compliance controls, and runtime privacy. Instead, you get a unified stack that keeps data encrypted in transit, at rest, and in use. Our solution also caters to the exploding demand for AI applications: with TEE-enabled GPU workloads, you can securely process sensitive data for text inference without ever exposing raw plaintext or sensitive documents to the host system. The result is a new generation of apps that deliver advanced functionality, like real-time encrypted data sync or AI-driven insights, while preserving user privacy and meeting strict regulatory requirements. You don't have to rely on empty "trust us" promises because hardware enclaves, remote attestation, and reproducible builds collectively guarantee the code is running untampered. In short, OpenSecret offers the building blocks needed to create truly confidential services and experiences, allowing you to innovate while ensuring data protection remains ironclad. ## **Things to Come** We're excited to build on our enclaved approach. Here's what's on our roadmap: • **Production Launch**: We're using this in production now with [Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud) and have a developer preview playground up and running. We'll have the developer environment ready for production in a few months.\ • **Multi-Tenant Support**: Our platform currently works for single tenants, but we're opening this up so developers can onboard without needing a dedicated instance.\ • **Self-Serve Frontend**: A dev-friendly portal for provisioning apps, connecting OAuth or email providers, and managing users.\ • **External Key Signing Options**: Integrations with custom hardware security modules (HSMs) or customer-ran key managers that can only process data upon verifying the enclave attestation.\ • **Confidential Computing as a Service**: We'll expand our platform so that other developers can quickly create enclaves for specialized workloads without dealing with the complexities of Nitro or GPU TEEs.\ • **Additional SDKs**: In addition to our [JavaScript client-side SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud), we plan to launch official support for Rust, Python, Swift, Java, Go, and more.\ • **AI API Proxy with Attestation/Encryption**: We already provide an easy way to [access a Private AI through Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud), but we'd like to open this up more for existing tools and developers. We'll provide a proxy server that users can run on their local machines or servers that properly handle encryption to our OpenAI-compatible API. ## **Getting Started** Ready to see enclaves in action? Here's how to dive in:\ 1. **Run OpenSecret**: Check out our open-source repository at [OpenSecret on GitHub](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud). You can run your own enclaved environment or try it out locally with Docker.\ 2. **Review Our SDK**: Our [JavaScript client SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud) makes it easy to handle sign-ins, put/get encrypted data, sign with user private keys, etc. It handles attestation verification and encryption under the hood, making the API integration seamless.\ 3. **Play with Maple AI**: Try out [Maple AI](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/) as an example of an AI app built directly on OpenSecret. Your queries are encrypted end to end, and the Llama model sees them only inside the TEE.\ 4. **Developer Preview**: Contact us if you want an invite to our early dev platform. We'll guide you through our SDK and give you access to the preview server. We'd love to build with you and incorporate your feedback as we develop this further. ## **Conclusion** By merging secure enclaves (AWS Nitro and Nvidia GPU TEEs), user authentication, private key management, and an end-to-end verifiable encrypted approach, **OpenSecret** provides a powerful platform where we protect user data during collection, storage, and processing. Whether it's for standard user management, handling private cryptographic keys, or powering AI inference, the technology ensures that **no one**, not even us or the cloud provider, can snoop on data in use. **We believe** this is the future of trustworthy computing in the cloud. And it's **all open source**, so you don't have to just take our word for it: you can see and verify everything yourself. Do you have questions, feedback, or a use case you'd like to test out? Come join us on [GitHub](https://github.com/OpenSecretCloud?ref=blog.opensecret.cloud), [Discord](https://discord.gg/ch2gjZAMGy?ref=blog.opensecret.cloud), or email us for a developer preview. We can't wait to see what you build! *Thank you for reading, and welcome to the era of enclaved computing.*
@ df173277:4ec96708
2025-02-07 00:41:34## **Building Our Confidential Backend on Secure Enclaves** With our newly released [private and confidential **Maple AI**](https://trymaple.ai/?ref=blog.opensecret.cloud) and the open sourcing of our [**OpenSecret** platform](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud) code, I'm excited to present this technical primer on how we built our confidential compute platform leveraging **secure enclaves**. By combining AWS Nitro enclaves with end-to-end encryption and reproducible builds, our platform gives developers and end users the confidence that user data is protected, even at runtime, and that the code operating on their data has not been tampered with. ## **Auth and Databases Today** As developers, we live in an era where protecting user data means "encryption at rest," plus some access policies and procedures. Developers typically run servers that: 1. Need to register users (authentication). 2. Collect and process user data in business-specific ways, often on the backend. Even if data is encrypted at rest, it's commonly unlocked with a single master key or credentials the server holds. This means that data is visible during runtime to the application, system administrators, and potentially to the hosting providers. This scenario makes it difficult (or impossible) to guarantee that sensitive data isn't snooped on, memory-dumped, or used in unauthorized ways (for instance, training AI models behind the scenes). ## **"Just Trust Us" Isn't Good Enough** In a traditional server architecture, users have to take it on faith that the code handling their data is the same code the operator claims to be running. Behind the scenes, applications can be modified or augmented to forward private information elsewhere, and there is no transparent way for users to verify otherwise. This lack of proof is unsettling, especially for services that process or store highly confidential data. Administrators, developers, or cloud providers with privileged access can inspect memory in plaintext, attach debuggers, or gain complete visibility into stored information. Hackers who compromise these privileged levels can directly access sensitive data. Even with strict policies or promises of good conduct, the reality is that technical capabilities and misconfigurations can override words on paper. If a server master key can decrypt your data or can be accessed by an insider with root permissions, then "just trust us" loses much of its credibility. The rise of AI platforms amplifies this dilemma. User data, often full of personal details, gets funneled into large-scale models that might be training or fine-tuning behind the scenes. Relying on vague assurances that "we don't look at your data" is no longer enough to prevent legitimate concerns about privacy and misuse. Now more than ever, providing a **strong, verifiable** guarantee that data remains off-limits, even when actively processed, has become a non-negotiable requirement for trustworthy services. ## **Current Attempts at Securing Data** Current User Experience of E2EE Apps While properly securing data is not easy, it isn't to say that no one is trying. Some solutions use **end-to-end encryption** (E2EE), where user data is encrypted client-side with a password or passphrase, so not even the server operator can decrypt it. That approach can be quite secure, but it also has its **limitations**: 1. **Key Management Nightmares**: If a user forgets their passphrase, the data is effectively lost, and there's no way to recover it from the developer's side. 2. **Feature Limitations**: Complex server-side operations (like offline/background tasks, AI queries, real-time collaboration, or heavy computation) can't easily happen if the server is never capable of processing decrypted data. 3. **Platform Silos**: Some solutions rely on iCloud, Google Drive, or local device storage. That can hamper multi-device usage or multi-OS compatibility. Other approaches include self-hosting. However, these either burden users with dev ops overhead or revert to the "trust me" model for the server if you "self-host" on a cloud provider. ## **Secure Enclaves** ### **The Hybrid Approach** Secure enclaves offer a compelling middle ground. They combine the privacy benefits of keeping data secure from prying admins while still allowing meaningful server-side computation. In a nutshell, an enclave is a protected environment within a machine, isolated at the hardware level, so that even if the OS or server is compromised, the data and code inside the enclave remain hidden. App Service Running Inside Secure Enclave ### **High-Level Goal of Enclaves** Enclaves, also known under the broader umbrella of **confidential computing**, aim to:\ • **Lock down data** so that only authorized code within the enclave can process the original plaintext data.\ • **Deny external inspection** by memory dumping, attaching a debugger, or intercepting plaintext network traffic.\ • **Prove** to external users or services that an enclave is running unmodified, approved code (this is where **remote attestation** comes in). ### **Different Secure Enclave Solutions** [**AMD SEV**](https://www.amd.com/en/developer/sev.html?ref=blog.opensecret.cloud) **(Secure Encrypted Virtualization)** encrypts an entire virtual machine's memory so that even a compromised hypervisor cannot inspect or modify guest data. Its core concept is "lift-and-shift" security. No application refactoring is required because hardware-based encryption automatically protects the OS and all VM applications. Later enhancements (SEV-ES and SEV-SNP) added encryption of CPU register states and memory integrity protections, further limiting hypervisor tampering. This broad coverage means the guest OS is included in the trusted boundary. AMD SEV has matured into a robust solution for confidential VMs in multi-tenant clouds. [**Intel TDX**](https://www.intel.com/content/www/us/en/developer/tools/trust-domain-extensions/overview.html?ref=blog.opensecret.cloud) **(Trust Domain Extensions)** shifts from process-level enclaves to full VM encryption, allowing an entire guest operating system and its applications to run in an isolated "trust domain." Like AMD SEV, Intel TDX encrypts and protects all memory the VM uses from hypervisors or other privileged software, so developers do not need to refactor their code to benefit from hardware-based confidentiality. This broader scope addresses many SGX limitations, such as strict memory bounds and the need to split out enclave-specific logic, and offers a more straightforward "lift-and-shift" path for running existing workloads privately. While SGX is now deprecated, TDX carries forward the core confidential computing principles but applies them at the virtual machine level for more substantial isolation, easier deployment, and the ability to scale up to large, memory-intensive applications. [**Apple Secure Enclave and Private Compute**](https://security.apple.com/blog/private-cloud-compute/?ref=blog.opensecret.cloud) is a dedicated security coprocessor embedded in most Apple devices (iPhones, iPads, Macs) and now extended to Apple's server-side AI infrastructure. It runs its own microkernel, has hardware-protected memory, and securely manages operations such as biometric authentication, key storage, and cryptographic tasks. Apple's "Private Compute" approach in the cloud brings similar enclave capabilities to server-based AI, enabling on-device-grade privacy even when requests are processed in Apple's data centers. [**AWS Nitro Enclaves**](https://docs.aws.amazon.com/enclaves/latest/user/nitro-enclave.html?ref=blog.opensecret.cloud) carve out a tightly isolated "mini-VM" from a parent EC2 instance, with its own vCPUs and memory guarded by dedicated Nitro cards. The enclave has no persistent storage and no external network access, significantly reducing the attack surface. Communication with the parent instance occurs over a secure local channel (vsock), and AWS offers hardware-based attestation so that secrets (e.g., encryption keys from AWS KMS) can be accessed only to the correct enclave. This design helps developers protect sensitive data or code even if the main EC2 instance's OS is compromised. [**NVIDIA GPU TEEs**](https://www.nvidia.com/en-us/data-center/solutions/confidential-computing/?ref=blog.opensecret.cloud) **(Hopper H100 and Blackwell)** extend confidential computing to accelerated workloads by encrypting data in GPU memory and ensuring that even a privileged host cannot view or tamper with it. Data moving between CPU and GPU is encrypted in transit, so sensitive model weights or inputs remain protected during AI training or inference. NVIDIA's hardware and drivers handle secure data paths under the hood, allowing confidential large language model (LLM) workloads and other GPU-accelerated computations to run with minimal performance overhead and strong security guarantees. ### **Key Benefits** One major advantage of enclaves is their ability to **keep memory completely off-limits** to outside prying eyes. Even administrators who can normally inspect processes at will are blocked from peeking into the enclave's protected memory space. The enclave model is a huge shift in the security model: it prevents casual inspection and defends against sophisticated memory dumping techniques that might otherwise leak secrets or sensitive data. Another key benefit centers on cryptographic keys that are **never exposed outside the enclave**. Only verified code running inside the enclave environment can run decryption or signing operations, and it can only do so while that specific code is running. This ensures that compromised hosts or rogue processes, even those with high-level privileges, are unable to intercept or misuse the keys because the keys remain strictly within the trusted boundary of the hardware. Enclaves can also offer the power of **remote attestation**, allowing external clients or systems to confirm that they're speaking to an authentic, untampered enclave. By validating the hardware's integrity measurements and enclave-specific proofs, the remote party can be confident in the underlying security properties, an important guarantee in multi-tenant environments or whenever trust boundaries extend across different organizations and networks. Beyond that, **reproducible builds** can create a verifiable fingerprint proving which binary runs in the enclave. This is a step above a simple "trust us" approach. Anyone can independently recreate the enclave image and verify the resulting cryptographic hash by using a reproducible build system (for example, [our NixOS-based solution](https://github.com/OpenSecretCloud/opensecret/blob/master/flake.nix?ref=blog.opensecret.cloud)). If it matches, then users and developers know precisely how code handles their data, boosting confidence that no hidden changes exist. It's worth noting that although enclaves shield you from software devs, cloud providers, and insider threats, you do have to trust the **hardware vendor** (Intel, AMD, Apple, AWS, or NVIDIA) to implement their microcode and firmware securely. The entire enclave model could be theoretically undermined if a CPU maker's root keys or manufacturing process were compromised. Fortunately, these companies undergo extensive audits and firmware validations (often with third-party researchers), and their remote attestation mechanisms allow you to confirm specific firmware versions before trusting an enclave. While this adds a layer of "vendor trust," it's still a far more contained risk than trusting an entire operating system or cloud stack, so enclaves remain a strong step forward in practical, confidential computing. ## **How We Use Secure Enclaves** Now that we've covered the general idea of enclaves let's look at how we specifically implement them in OpenSecret, our developer platform for handling user auth, private keys, data encryption, and AI workloads. ### **Our Stack: AWS Nitro + Nvidia TEE** • **AWS Nitro Enclaves for the backend**: All critical logic, authentication, private key management, and data encryption/decryption run inside an AWS Nitro Enclave. • **Nvidia Trusted Execution for AI**: For large AI inference (such as the Llama 3.3 70B model), we utilize Nvidia's GPU-based TEEs to protect even GPU memory. This means users can feed sensitive data to the AI model **without** exposing it in plaintext to the GPU providers or us as the operator. [Edgeless Systems](https://www.edgeless.systems/?ref=blog.opensecret.cloud) is our Nvidia TEE provider, and due to the power of enclave verification, we don't need to worry about who runs the GPUs. We know requests can't be inspected or tampered with. ### **End-to-End Encryption from Client to Enclave** Client-side Enclave Attestation from Maple AI Before login or data upload, the user/client verifies the **enclave attestation** from our platform. This process proves that the specific Nitro Enclave is genuine and runs the exact code we've published. You can check this out live on [Maple AI's attestation page](https://trymaple.ai/proof?ref=blog.opensecret.cloud). Based on the attestation, the client establishes a secure ephemeral communication channel that only that enclave can decrypt. While we take advantage of SSL, it is typically not terminated inside the enclave itself. To ensure there's full encrypted data transfer all the way through to the enclave, we establish this additional handshake based on the attestation document that is used for all API requests during the client session. From there, the user's credentials, private keys, and data pass through this secure channel directly into the enclave, where they are decrypted and processed according to the user's request. ### **In-Enclave Operations** At the core of OpenSecret's approach is the conviction that security-critical tasks must happen inside the enclave, where even administrative privileges or hypervisor-level compromise cannot expose plaintext data. This encompasses everything from when a user logs in to creating and managing sensitive cryptographic keys. By confining these operations to a protected hardware boundary, developers can focus on building their applications without worrying about accidental data leaks, insider threats, or malicious attempts to harvest credentials. The enclave becomes the ultimate gatekeeper: it controls how data flows and ensures that nothing escapes in plain form. User Auth Methods running inside Enclave A primary example is **user authentication**. All sign-in workflows, including email/password, OAuth, and upcoming passkey-based methods, are handled entirely within the enclave. As soon as a user's credentials enter our platform through the encrypted channel, they are routed straight into the protected environment, bypassing the host's operating system or any potential snooping channels. From there, authentication and session details remain in the enclave, ensuring that privileged outsiders cannot intercept or modify them. By centralizing these identity flows within a sealed environment, developers can assure their users that no one outside the enclave (including the cloud provider or the app's own sysadmins) can peek at, tamper with, or access sensitive login information. Main Enclave Operations in OpenSecret The same principle applies to **private key management**. Whether keys are created fresh in the enclave or securely transferred into it, they remain sealed away from the rest of the system. Operations like digital signing or content decryption happen only within the hardware boundary, so raw keys never appear in any log, file system, or memory space outside the enclave. Developers retain the functionality they need, such as verifying user actions, encrypting data, or enabling secure transactions without ever exposing keys to a broader (and more vulnerable) attack surface. User backup options exist as well, where the keys can be securely passed to the end user. Realtime Encrypted Data Sync on Multiple Devices Another crucial aspect is **data encryption at rest**. While user data ultimately needs to be stored somewhere outside the enclave, the unencrypted form of that data only exists transiently inside the protected environment. Encryption and decryption routines run within the enclave, which holds the encryption keys strictly in memory under hardware guards. If a user uploads data, it is promptly secured before it leaves the enclave. When data is retrieved, it remains encrypted until it reenters the protected region and is passed back to the user through the secured communication channel. This ensures that even if someone gains access to the underlying storage or intercepts data in transit, they will see only meaningless ciphertext. Confidential AI Workloads Finally, **confidential AI workloads** build upon this same pattern: the Nitro enclave re-encrypts data so it can be processed inside a GPU-based trusted execution environment (TEE) for inference or other advanced computations. Sensitive data, like user-generated text or private documents, never appears in the clear on the host or within GPU memory outside the TEE boundary. When an AI process finishes, only the results are returned to the enclave, which can then relay them securely to the requesting user. By seamlessly chaining enclaves together, from CPU-based Nitro Enclaves to GPU-accelerated TEEs, we can deliver robust, hardware-enforced privacy for virtually any type of server-side or AI-driven operation. ### **Reproducible Builds + Verification** Client verifies enclave attestation document We build our enclaves on **NixOS** with reproducible builds, ensuring that anyone can verify that the binary we publish is indeed the binary running in the enclave. This build process is essential for proving we haven't snuck in malicious code to exfiltrate data or collect sensitive logs. Our code is fully open source ([GitHub: OpenSecret](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud)), so you can audit or run it yourself. You can also verify that the cryptographic measurement the build process outputs matches the measurement reported by the enclave during attestation. ## **Putting It All Together** OpenSecret Offering: Private Key Management, Encrypted Sync, Private AI, and Confidential Compute By weaving secure enclaves into every step, from authentication to data handling to AI inference, we shift the burden of trust away from human policies and onto provable, hardware-based protections. For app developers, you can offer your users robust privacy guarantees without rewriting all your business logic or building an entire security stack from scratch. Whether you're storing user credentials or running complex operations on sensitive data, the enclave approach ensures plaintext remains inaccessible to even the most privileged parties outside the enclave boundary. Developers can focus on building great apps, while OpenSecret handles the cryptographic "lock and key" behind the scenes. This model provides a secure-by-design environment for industries that demand strict data confidentiality, such as healthcare, fintech, cryptocurrency apps for secure key management, or decentralized identity platforms. Instead of worrying about memory dumps or backend tampering, you can trust that once data enters the enclave, it's sealed off from unauthorized eyes, including from the app developers themselves. And these safeguards don't just apply to niche use cases. Even general-purpose applications that handle login flows and user-generated content stand to benefit, especially as regulatory scrutiny grows around data privacy and insider threats. Imagine a telehealth startup using OpenSecret enclaves to protect patient information for remote consultations. Not only would patient data remain encrypted at rest, but any AI-driven analytics to assist with diagnoses could be run privately within the enclave, ensuring no one outside the hardware boundary can peek at sensitive health records. A fintech company could similarly isolate confidential financial transactions, preventing even privileged insiders from viewing or tampering with raw transaction details. These real-world implementations give developers a clear path to adopting enclaves for serious privacy and compliance needs without overhauling their infrastructure. OpenSecret aims to be a **full developer platform** with end-to-end security from day one. By incorporating user authentication, data storage, and GPU-based confidential AI into a single service, we eliminate many of the traditional hurdles in adopting enclaves. No more juggling separate tools for cryptographic key management, compliance controls, and runtime privacy. Instead, you get a unified stack that keeps data encrypted in transit, at rest, and in use. Our solution also caters to the exploding demand for AI applications: with TEE-enabled GPU workloads, you can securely process sensitive data for text inference without ever exposing raw plaintext or sensitive documents to the host system. The result is a new generation of apps that deliver advanced functionality, like real-time encrypted data sync or AI-driven insights, while preserving user privacy and meeting strict regulatory requirements. You don't have to rely on empty "trust us" promises because hardware enclaves, remote attestation, and reproducible builds collectively guarantee the code is running untampered. In short, OpenSecret offers the building blocks needed to create truly confidential services and experiences, allowing you to innovate while ensuring data protection remains ironclad. ## **Things to Come** We're excited to build on our enclaved approach. Here's what's on our roadmap: • **Production Launch**: We're using this in production now with [Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud) and have a developer preview playground up and running. We'll have the developer environment ready for production in a few months.\ • **Multi-Tenant Support**: Our platform currently works for single tenants, but we're opening this up so developers can onboard without needing a dedicated instance.\ • **Self-Serve Frontend**: A dev-friendly portal for provisioning apps, connecting OAuth or email providers, and managing users.\ • **External Key Signing Options**: Integrations with custom hardware security modules (HSMs) or customer-ran key managers that can only process data upon verifying the enclave attestation.\ • **Confidential Computing as a Service**: We'll expand our platform so that other developers can quickly create enclaves for specialized workloads without dealing with the complexities of Nitro or GPU TEEs.\ • **Additional SDKs**: In addition to our [JavaScript client-side SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud), we plan to launch official support for Rust, Python, Swift, Java, Go, and more.\ • **AI API Proxy with Attestation/Encryption**: We already provide an easy way to [access a Private AI through Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud), but we'd like to open this up more for existing tools and developers. We'll provide a proxy server that users can run on their local machines or servers that properly handle encryption to our OpenAI-compatible API. ## **Getting Started** Ready to see enclaves in action? Here's how to dive in:\ 1. **Run OpenSecret**: Check out our open-source repository at [OpenSecret on GitHub](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud). You can run your own enclaved environment or try it out locally with Docker.\ 2. **Review Our SDK**: Our [JavaScript client SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud) makes it easy to handle sign-ins, put/get encrypted data, sign with user private keys, etc. It handles attestation verification and encryption under the hood, making the API integration seamless.\ 3. **Play with Maple AI**: Try out [Maple AI](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/) as an example of an AI app built directly on OpenSecret. Your queries are encrypted end to end, and the Llama model sees them only inside the TEE.\ 4. **Developer Preview**: Contact us if you want an invite to our early dev platform. We'll guide you through our SDK and give you access to the preview server. We'd love to build with you and incorporate your feedback as we develop this further. ## **Conclusion** By merging secure enclaves (AWS Nitro and Nvidia GPU TEEs), user authentication, private key management, and an end-to-end verifiable encrypted approach, **OpenSecret** provides a powerful platform where we protect user data during collection, storage, and processing. Whether it's for standard user management, handling private cryptographic keys, or powering AI inference, the technology ensures that **no one**, not even us or the cloud provider, can snoop on data in use. **We believe** this is the future of trustworthy computing in the cloud. And it's **all open source**, so you don't have to just take our word for it: you can see and verify everything yourself. Do you have questions, feedback, or a use case you'd like to test out? Come join us on [GitHub](https://github.com/OpenSecretCloud?ref=blog.opensecret.cloud), [Discord](https://discord.gg/ch2gjZAMGy?ref=blog.opensecret.cloud), or email us for a developer preview. We can't wait to see what you build! *Thank you for reading, and welcome to the era of enclaved computing.* @ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy [article on the pros of a strategic Bitcoin reserve](https://geek.npub.pro/post/dxqkgnjplttkvetprg8ox/), I wanted to take some time to chime in on the much more fun topic of digital engagement. Let's begin by defining a couple of things: **Nostr** is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example. **Zap** is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what [Lightning](https://lightning.network/) or [Cashu](https://cashu.space/) are. If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article. In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed. What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.  Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines. That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems. Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.  I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives. Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms? Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life? If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later. 
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy [article on the pros of a strategic Bitcoin reserve](https://geek.npub.pro/post/dxqkgnjplttkvetprg8ox/), I wanted to take some time to chime in on the much more fun topic of digital engagement. Let's begin by defining a couple of things: **Nostr** is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example. **Zap** is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what [Lightning](https://lightning.network/) or [Cashu](https://cashu.space/) are. If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article. In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed. What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.  Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines. That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems. Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.  I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives. Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms? Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life? If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.  @ df173277:4ec96708
2025-01-28 17:49:54> Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. Chats are synced automatically between devices so you can pick up where you left off.\ > [Start chatting for free.](https://trymaple.ai/) We are excited to announce that [Maple AI](https://trymaple.ai/), our groundbreaking end-to-end encrypted AI chat app built on OpenSecret, is now publicly available. After months of beta testing, we are thrilled to bring this innovative technology to the world. Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another. #### Why Secure and Private AI? In today's digital landscape, it is increasingly evident that security and privacy are essential for individuals and organizations alike. Unfortunately, the current state of AI tools falls short. A staggering 48% of organizations enter non-public company information into AI apps, according to a [recent report by Cisco](https://www.cisco.com/c/en/us/about/trust-center/data-privacy-benchmark-study.html#~key-findings). This practice poses significant risks to company security and intellectual property. Another concern is for journalists, who often work with sensitive information in hostile environments. Journalists need verification that their information remains confidential and protected when researching topics and communicating with sources in various languages. They are left to use underpowered local AI or input their data into potentially compromised cloud services. At OpenSecret, we believe it is possible to have both the benefits of AI and the assurance of security and privacy. That's why we created Maple, an app that combines AI productivity with the protection of end-to-end encryption. Our platform ensures that your conversations with AI remain confidential, even from us. The power of the cloud meets the privacy of local. #### How Does It Work? Our server code is [open source](https://github.com/OpenSecretCloud/opensecret), and we use confidential computing to provide cryptographic proof that the code running on our servers is the same as the open-source code available for review. This process allows you to verify that your conversations are handled securely and privately without relying on trust. We live by the principle of "Don't trust, verify," and we believe this approach is essential for building in the digital age. You can read a more in-depth write-up on our technology later this week on this site. #### How Much Does It Cost? We are committed to making Maple AI accessible to everyone, so we offer a range of pricing plans to suit different needs and budgets. [Our Free plan allows for 10 chats per week, while our Starter plan ($5.99/month) and Pro plan ($20/month)](https://trymaple.ai/pricing) offer more comprehensive solutions for individuals and organizations with heavier workloads. We accept credit cards and Bitcoin (10% discount), allowing you to choose your preferred payment method. - Free: $0 - Starter: $5.99/month - Pro: $20/month Our goal with Maple AI is to create a product that is secure through transparency. By combining open-source code, cryptography, and confidential computing, we can create a new standard for AI conversations - one that prioritizes your security and privacy. Maple has quickly become a daily tool of productivity for our own work and those of our beta testers. We believe it will bring value to you as well. [Sign up now and start chatting privately with AI for free.](https://trymaple.ai/) Your secrets are safe in the open. #### Are You An App Developer? You can build an app like Maple. [OpenSecret provides secure auth, private key management, encrypted data sync, private AI, and more.](https://blog.opensecret.cloud/introducing-opensecret/) Our straightforward API behaves like other backends but automatically adds security and privacy. Use it to secure existing apps or brand-new projects. Protect yourself and your users from the liability of hosting personal data by checking out [OpenSecret](https://opensecret.cloud/). <img src="https://blossom.primal.net/feb746d5e164e89f0d015646286b88237dce4158f8985e3caaf7e427cebde608.png"> Enjoy private AI Chat 🤘 <img src="https://blossom.primal.net/0594ec56e249de2754ea7dfc225a7ebd46bc298b5af168279ce71f17c2afada0.jpg">
@ df173277:4ec96708
2025-01-28 17:49:54> Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. Chats are synced automatically between devices so you can pick up where you left off.\ > [Start chatting for free.](https://trymaple.ai/) We are excited to announce that [Maple AI](https://trymaple.ai/), our groundbreaking end-to-end encrypted AI chat app built on OpenSecret, is now publicly available. After months of beta testing, we are thrilled to bring this innovative technology to the world. Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another. #### Why Secure and Private AI? In today's digital landscape, it is increasingly evident that security and privacy are essential for individuals and organizations alike. Unfortunately, the current state of AI tools falls short. A staggering 48% of organizations enter non-public company information into AI apps, according to a [recent report by Cisco](https://www.cisco.com/c/en/us/about/trust-center/data-privacy-benchmark-study.html#~key-findings). This practice poses significant risks to company security and intellectual property. Another concern is for journalists, who often work with sensitive information in hostile environments. Journalists need verification that their information remains confidential and protected when researching topics and communicating with sources in various languages. They are left to use underpowered local AI or input their data into potentially compromised cloud services. At OpenSecret, we believe it is possible to have both the benefits of AI and the assurance of security and privacy. That's why we created Maple, an app that combines AI productivity with the protection of end-to-end encryption. Our platform ensures that your conversations with AI remain confidential, even from us. The power of the cloud meets the privacy of local. #### How Does It Work? Our server code is [open source](https://github.com/OpenSecretCloud/opensecret), and we use confidential computing to provide cryptographic proof that the code running on our servers is the same as the open-source code available for review. This process allows you to verify that your conversations are handled securely and privately without relying on trust. We live by the principle of "Don't trust, verify," and we believe this approach is essential for building in the digital age. You can read a more in-depth write-up on our technology later this week on this site. #### How Much Does It Cost? We are committed to making Maple AI accessible to everyone, so we offer a range of pricing plans to suit different needs and budgets. [Our Free plan allows for 10 chats per week, while our Starter plan ($5.99/month) and Pro plan ($20/month)](https://trymaple.ai/pricing) offer more comprehensive solutions for individuals and organizations with heavier workloads. We accept credit cards and Bitcoin (10% discount), allowing you to choose your preferred payment method. - Free: $0 - Starter: $5.99/month - Pro: $20/month Our goal with Maple AI is to create a product that is secure through transparency. By combining open-source code, cryptography, and confidential computing, we can create a new standard for AI conversations - one that prioritizes your security and privacy. Maple has quickly become a daily tool of productivity for our own work and those of our beta testers. We believe it will bring value to you as well. [Sign up now and start chatting privately with AI for free.](https://trymaple.ai/) Your secrets are safe in the open. #### Are You An App Developer? You can build an app like Maple. [OpenSecret provides secure auth, private key management, encrypted data sync, private AI, and more.](https://blog.opensecret.cloud/introducing-opensecret/) Our straightforward API behaves like other backends but automatically adds security and privacy. Use it to secure existing apps or brand-new projects. Protect yourself and your users from the liability of hosting personal data by checking out [OpenSecret](https://opensecret.cloud/). <img src="https://blossom.primal.net/feb746d5e164e89f0d015646286b88237dce4158f8985e3caaf7e427cebde608.png"> Enjoy private AI Chat 🤘 <img src="https://blossom.primal.net/0594ec56e249de2754ea7dfc225a7ebd46bc298b5af168279ce71f17c2afada0.jpg"> @ df173277:4ec96708
2025-01-09 17:12:08> Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\ > [Join the waitlist to get early access.](https://trymaple.ai) We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI. Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations. #### Building a Private Foundation Maple is built on our flagship product, [OpenSecret](https://opensecret.cloud), a backend platform for app developers that turns private encryption on by default. [The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do.](nostr:naddr1qvzqqqr4gupzphchxfm3ste32hfhkvczzxapme9gz5qvqtget6tylyd7wa8vjecgqqe5jmn5wfhkgatrd9hxwt20wpjku5m9vdex2apdw35x2tt9de3hy7tsw3jkgttzv93kketwvskhgur5w9nx5h52tpj) We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win. #### The Power of Encrypted AI Chat AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short. Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us. #### Technical Overview So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects: - **Private Key:** Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data. - **Secure Servers:** Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations. - **Encrypted Sync:** One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised. - **Attestation and Open Code:** We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public. - **Open Source LLM:** Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased. #### Personal and Work Use Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe. #### Local v Cloud Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds. #### Why the Maple name? Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment. #### Join the Waitlist Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. [Join our waitlist today to be among the first to experience the power of private AI chat.](https://trymaple.ai) [](https://trymaple.ai/waitlist)
@ df173277:4ec96708
2025-01-09 17:12:08> Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\ > [Join the waitlist to get early access.](https://trymaple.ai) We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI. Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations. #### Building a Private Foundation Maple is built on our flagship product, [OpenSecret](https://opensecret.cloud), a backend platform for app developers that turns private encryption on by default. [The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do.](nostr:naddr1qvzqqqr4gupzphchxfm3ste32hfhkvczzxapme9gz5qvqtget6tylyd7wa8vjecgqqe5jmn5wfhkgatrd9hxwt20wpjku5m9vdex2apdw35x2tt9de3hy7tsw3jkgttzv93kketwvskhgur5w9nx5h52tpj) We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win. #### The Power of Encrypted AI Chat AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short. Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us. #### Technical Overview So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects: - **Private Key:** Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data. - **Secure Servers:** Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations. - **Encrypted Sync:** One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised. - **Attestation and Open Code:** We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public. - **Open Source LLM:** Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased. #### Personal and Work Use Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe. #### Local v Cloud Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds. #### Why the Maple name? Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment. #### Join the Waitlist Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. [Join our waitlist today to be among the first to experience the power of private AI chat.](https://trymaple.ai) [](https://trymaple.ai/waitlist) @ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it! The US healthcare system is essentially the worst of both worlds: * Unlike full single payer, individuals incur high costs * Unlike a true free market, regulation causes increases in costs and decreases competition among insurers I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do: * Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice. * Reduce regulations significantly. * In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways: 1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices. 2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.) Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation. And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers. And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply." https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it! The US healthcare system is essentially the worst of both worlds: * Unlike full single payer, individuals incur high costs * Unlike a true free market, regulation causes increases in costs and decreases competition among insurers I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do: * Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice. * Reduce regulations significantly. * In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways: 1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices. 2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.) Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation. And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers. And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply." https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M @ df173277:4ec96708
2025-01-09 17:02:52> OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. [Join our waitlist to get early access.](https://opensecret.cloud) In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion. Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online? Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches? > Cryptography at scale is hard. #### The Cloud The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers. The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage. > Private key encryption needs a UX upgrade. ## Enter OpenSecret OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute. Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.  ### Private Key Management Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone. OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account. The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.  ### Encrypted Sync With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go. The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them. ### Private AI Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything. OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk. **Check out Maple AI**\ Try private AI for yourself! We built an app built with this service called [Maple AI](https://trymaple.ai). It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. [Learn more about Maple AI - Private chat in the announcement post.](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/)  ### Confidential Compute Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave. It's the new version of that lock on your web browser. When you see it, you know you're secure.  #### **But do we want our secrets to be open?** OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable. On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data. > Don't trust, verify. ### **Join the Movement** We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, [send us a message to get early access.](https://opensecret.cloud) Users and companies deserve better encryption and privacy.\ Together, let's make that a reality. [](https://opensecret.cloud)
@ df173277:4ec96708
2025-01-09 17:02:52> OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. [Join our waitlist to get early access.](https://opensecret.cloud) In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion. Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online? Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches? > Cryptography at scale is hard. #### The Cloud The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers. The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage. > Private key encryption needs a UX upgrade. ## Enter OpenSecret OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute. Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.  ### Private Key Management Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone. OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account. The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.  ### Encrypted Sync With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go. The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them. ### Private AI Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything. OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk. **Check out Maple AI**\ Try private AI for yourself! We built an app built with this service called [Maple AI](https://trymaple.ai). It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. [Learn more about Maple AI - Private chat in the announcement post.](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/)  ### Confidential Compute Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave. It's the new version of that lock on your web browser. When you see it, you know you're secure.  #### **But do we want our secrets to be open?** OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable. On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data. > Don't trust, verify. ### **Join the Movement** We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, [send us a message to get early access.](https://opensecret.cloud) Users and companies deserve better encryption and privacy.\ Together, let's make that a reality. [](https://opensecret.cloud) @ 9e69e420:d12360c2
2025-02-01 11:16:04 Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.  CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language. One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
@ 9e69e420:d12360c2
2025-02-01 11:16:04 Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.  CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language. One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse. @ f9cf4e94:96abc355
2024-12-31 20:18:59Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( [dominictarr]( https://github.com/dominictarr/scuttlebutt) ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt ([ssb]( https://github.com/ssbc/ssb-db)) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia. Se você está se perguntando de onde diabos veio o nome Scuttlebutt: > Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.  Marinheiros se reunindo em torno da rixa. ( [fonte]( https://twitter.com/IntEtymology/status/998879578851508224) ) Dominic descobriu o termo boato em um [artigo de pesquisa]( https://www.cs.cornell.edu/home/rvr/papers/flowgossip.pdf) que leu. Em sistemas distribuídos, [fofocar]( https://en.wikipedia.org/wiki/Gossip_protocol) é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”. **Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto.** **Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar.** Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário [de bordo]( https://en.wikipedia.org/wiki/Logbook) (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem. Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. **Cada item adicionado a um log do usuário é chamado de mensagem.** **Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações.** Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.  Estrutura de alto nível de um feed **Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar.** Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência. Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub. Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. **Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.** Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de [Pubs públicos em que]( https://github.com/ssbc/ssb-server/wiki/Pub-Servers) todos podem participar **.** Explicaremos como ingressar em um posteriormente neste guia. **Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais.** Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.  Perspectivas dos participantes ## Scuttlebot O software Pub é conhecido como servidor Scuttlebutt (servidor [ssb]( https://github.com/ssbc/ssb-server) ), mas também é conhecido como “Scuttlebot” e `sbot`na linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial. **Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações.** Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.  Estrutura de alto nível de um feed **Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar.** Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência. Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub. Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. **Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.** Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de [Pubs públicos em que]( https://github.com/ssbc/ssb-server/wiki/Pub-Servers) todos podem participar **.** Explicaremos como ingressar em um posteriormente neste guia. **Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais.** Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.   Perspectivas dos participantes ## Pubs - Hubs ### Pubs públicos | Pub Name | Operator | Invite Code | | ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ | | `scuttle.us` | [@Ryan]( https://keybase.io/ryan_singer) | `scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=` | | [pub1.upsocial.com]( https://upsocial.com/) | [@freedomrules]( https://github.com/freedomrules) | `pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=` | | [Monero Pub]( https://xmr-pub.net/) | [@Denis]( https://github.com/Orville2112) | `xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=` | | [FreeSocial]( https://freesocial.co/) | [@Jarland]( https://github.com/mxroute) | `pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=` | | `ssb.vpn.net.br` | [@coffeverton]( https://about.me/coffeverton) | `ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=` | | [gossip.noisebridge.info]( https://www.noisebridge.net/wiki/Pub) | [Noisebridge Hackerspace]( https://www.noisebridge.net/wiki/Unicorn) [@james.network]( https://james.network/) | `gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=` | ### Pubs privados Você precisará entrar em contato com os proprietários desses bares para receber um convite. | Pub Name | Operator | Contact | | --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- | | `many.butt.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) | | `one.butt.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) | | `ssb.mikey.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) | | [ssb.celehner.com]( https://ssb.celehner.com/) | [@cel]( https://github.com/ssbc/ssb-server/wiki/@f/6sQ6d2CMxRUhLpspgGIulDxDCwYD7DzFzPNr7u5AU=.ed25519) | [cel@celehner.com](mailto:cel@celehner.com) | ### Pubs muito grandes  *Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)*  | Pub Name | Operator | Invite Code | | --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ | | `scuttlebutt.de` | [SolSoCoG]( https://solsocog.de/impressum) | `scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=` | | `Lohn's Pub` | [@lohn]( https://github.com/lohn) | `p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=` | | [Scuttle Space]( https://scuttle.space/) | [@guil-dot]( https://github.com/guil-dot) | Visit [scuttle.space]( https://scuttle.space/) | | `SSB PeerNet US-East` | [timjrobinson]( https://github.com/timjrobinson) | `us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=` | | Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= | ## GUI - Interface Gráfica do Utilizador(Usuário) ### Patchwork - Uma GUI SSB (Descontinuado) [**Patchwork**]( https://github.com/ssbc/patchwork) **é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB** . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.  Fonte: [scuttlebutt.nz]( https://www.scuttlebutt.nz/getting-started) **Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub.** Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs. Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth. ### Patchbay - Uma GUI Alternativa Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que [Patchwork]( https://github.com/ssbc/patchwork) e [Patchfoo]( https://github.com/ssbc/patchfoo) , então você pode facilmente dar uma volta com sua identidade existente.  ### Planetary - GUI para IOS  [Planetary]( https://apps.apple.com/us/app/planetary-app/id1481617318) é um app com pubs pré-carregados para facilitar integração. ### Manyverse - GUI para Android  [Manyverse]( https://www.manyver.se/) é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone . ## Fontes * https://scuttlebot.io/ * https://decentralized-id.com/decentralized-web/scuttlebot/#plugins * https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd * [**Secure Scuttlebutt**]( http://ssbc.github.io/secure-scuttlebutt/) **:** um protocolo de banco de dados global.
@ f9cf4e94:96abc355
2024-12-31 20:18:59Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( [dominictarr]( https://github.com/dominictarr/scuttlebutt) ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt ([ssb]( https://github.com/ssbc/ssb-db)) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia. Se você está se perguntando de onde diabos veio o nome Scuttlebutt: > Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.  Marinheiros se reunindo em torno da rixa. ( [fonte]( https://twitter.com/IntEtymology/status/998879578851508224) ) Dominic descobriu o termo boato em um [artigo de pesquisa]( https://www.cs.cornell.edu/home/rvr/papers/flowgossip.pdf) que leu. Em sistemas distribuídos, [fofocar]( https://en.wikipedia.org/wiki/Gossip_protocol) é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”. **Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto.** **Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar.** Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário [de bordo]( https://en.wikipedia.org/wiki/Logbook) (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem. Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. **Cada item adicionado a um log do usuário é chamado de mensagem.** **Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações.** Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.  Estrutura de alto nível de um feed **Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar.** Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência. Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub. Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. **Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.** Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de [Pubs públicos em que]( https://github.com/ssbc/ssb-server/wiki/Pub-Servers) todos podem participar **.** Explicaremos como ingressar em um posteriormente neste guia. **Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais.** Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.  Perspectivas dos participantes ## Scuttlebot O software Pub é conhecido como servidor Scuttlebutt (servidor [ssb]( https://github.com/ssbc/ssb-server) ), mas também é conhecido como “Scuttlebot” e `sbot`na linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial. **Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações.** Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.  Estrutura de alto nível de um feed **Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar.** Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência. Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub. Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. **Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.** Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de [Pubs públicos em que]( https://github.com/ssbc/ssb-server/wiki/Pub-Servers) todos podem participar **.** Explicaremos como ingressar em um posteriormente neste guia. **Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais.** Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.   Perspectivas dos participantes ## Pubs - Hubs ### Pubs públicos | Pub Name | Operator | Invite Code | | ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ | | `scuttle.us` | [@Ryan]( https://keybase.io/ryan_singer) | `scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=` | | [pub1.upsocial.com]( https://upsocial.com/) | [@freedomrules]( https://github.com/freedomrules) | `pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=` | | [Monero Pub]( https://xmr-pub.net/) | [@Denis]( https://github.com/Orville2112) | `xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=` | | [FreeSocial]( https://freesocial.co/) | [@Jarland]( https://github.com/mxroute) | `pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=` | | `ssb.vpn.net.br` | [@coffeverton]( https://about.me/coffeverton) | `ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=` | | [gossip.noisebridge.info]( https://www.noisebridge.net/wiki/Pub) | [Noisebridge Hackerspace]( https://www.noisebridge.net/wiki/Unicorn) [@james.network]( https://james.network/) | `gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=` | ### Pubs privados Você precisará entrar em contato com os proprietários desses bares para receber um convite. | Pub Name | Operator | Contact | | --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- | | `many.butt.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) | | `one.butt.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) | | `ssb.mikey.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) | | [ssb.celehner.com]( https://ssb.celehner.com/) | [@cel]( https://github.com/ssbc/ssb-server/wiki/@f/6sQ6d2CMxRUhLpspgGIulDxDCwYD7DzFzPNr7u5AU=.ed25519) | [cel@celehner.com](mailto:cel@celehner.com) | ### Pubs muito grandes  *Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)*  | Pub Name | Operator | Invite Code | | --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ | | `scuttlebutt.de` | [SolSoCoG]( https://solsocog.de/impressum) | `scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=` | | `Lohn's Pub` | [@lohn]( https://github.com/lohn) | `p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=` | | [Scuttle Space]( https://scuttle.space/) | [@guil-dot]( https://github.com/guil-dot) | Visit [scuttle.space]( https://scuttle.space/) | | `SSB PeerNet US-East` | [timjrobinson]( https://github.com/timjrobinson) | `us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=` | | Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= | ## GUI - Interface Gráfica do Utilizador(Usuário) ### Patchwork - Uma GUI SSB (Descontinuado) [**Patchwork**]( https://github.com/ssbc/patchwork) **é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB** . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.  Fonte: [scuttlebutt.nz]( https://www.scuttlebutt.nz/getting-started) **Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub.** Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs. Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth. ### Patchbay - Uma GUI Alternativa Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que [Patchwork]( https://github.com/ssbc/patchwork) e [Patchfoo]( https://github.com/ssbc/patchfoo) , então você pode facilmente dar uma volta com sua identidade existente.  ### Planetary - GUI para IOS  [Planetary]( https://apps.apple.com/us/app/planetary-app/id1481617318) é um app com pubs pré-carregados para facilitar integração. ### Manyverse - GUI para Android  [Manyverse]( https://www.manyver.se/) é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone . ## Fontes * https://scuttlebot.io/ * https://decentralized-id.com/decentralized-web/scuttlebot/#plugins * https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd * [**Secure Scuttlebutt**]( http://ssbc.github.io/secure-scuttlebutt/) **:** um protocolo de banco de dados global. @ 0fa80bd3:ea7325de
2025-01-29 05:55:02The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future. Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs. There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won. Our only resource is the **will of the people** to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root. So I started asking myself: **How do we stop this fragmentation?** How do we create a space where people can **rebuild their connections** when they’re ready? How do we build a **self-sustaining network**, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—**how do we make it spread, even in occupied territory?** In 2009, something historic happened: **the internet got its own money.** Thanks to **Satoshi Nakamoto**, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize. That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became **purely digital.** The internet was already **a sanctuary for information**, a place where people could connect and organize. But with Bitcoin, it evolved. Now, **value itself** could flow freely, beyond the reach of authorities. Think about it: when seedlings are grown in controlled environments before being planted outside, they **get stronger, survive longer, and bear fruit faster.** That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild. Now, picture the internet as that **controlled environment** for **ideas**. Bitcoin? It’s the **fertile soil** that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If **nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless.** It can absorb any number of ideas, any number of people, and it doesn’t **run out of space.** But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—**without surveillance, without censorship, without the constant fear of being erased.** This is where **Nostr** comes in. Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. **It’s a new kind of city.** One that **no dictator can seize**, no corporation can own, no government can shut down. It’s built on **decentralization, encryption, and individual control.** Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them. In a world where cities fall and governments fail, **Nostr is a city that cannot be occupied.** A place for ideas, for networks, for freedom. A city that grows stronger **the more people build within it**.
@ 0fa80bd3:ea7325de
2025-01-29 05:55:02The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future. Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs. There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won. Our only resource is the **will of the people** to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root. So I started asking myself: **How do we stop this fragmentation?** How do we create a space where people can **rebuild their connections** when they’re ready? How do we build a **self-sustaining network**, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—**how do we make it spread, even in occupied territory?** In 2009, something historic happened: **the internet got its own money.** Thanks to **Satoshi Nakamoto**, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize. That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became **purely digital.** The internet was already **a sanctuary for information**, a place where people could connect and organize. But with Bitcoin, it evolved. Now, **value itself** could flow freely, beyond the reach of authorities. Think about it: when seedlings are grown in controlled environments before being planted outside, they **get stronger, survive longer, and bear fruit faster.** That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild. Now, picture the internet as that **controlled environment** for **ideas**. Bitcoin? It’s the **fertile soil** that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If **nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless.** It can absorb any number of ideas, any number of people, and it doesn’t **run out of space.** But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—**without surveillance, without censorship, without the constant fear of being erased.** This is where **Nostr** comes in. Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. **It’s a new kind of city.** One that **no dictator can seize**, no corporation can own, no government can shut down. It’s built on **decentralization, encryption, and individual control.** Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them. In a world where cities fall and governments fail, **Nostr is a city that cannot be occupied.** A place for ideas, for networks, for freedom. A city that grows stronger **the more people build within it**. @ f1597634:c6d40bf4
2024-10-02 09:00:59E aí, galera do Nostr! Já pensou em como proteger sua privacidade nesse mundo descentralizado? A gente sabe que a liberdade é daora, mas é importante saber como se proteger dos "bisbilhoteiros" que estão sempre à espreita. **O perigo das fotos:** - Sabia que as fotos que você posta podem dar muitas informações sobre você? É tipo deixar um mapa do tesouro nas mãos de alguém! - Pessoal mau intencionadas podem usar essas fotos para descobrir onde você mora, qual seu IP e até mesmo sua identidade! **Dicas para se proteger:** - **Escolha seus apps com cuidado:** Nem todos os apps são iguais. Procure aqueles que a galera mais confia e que têm uma boa fama. - **Ajuste as configurações:** A maioria dos apps tem configurações de privacidade. Mexa nelas para mostrar só o que você quiser para os outros. - **Cuidado com links:** Não clique em qualquer link que você receber. Pode ser uma armadilha! Uma boa prática ao navegar pelo Nostr é configurar um Proxy *confiável* no seu aplicativo. No Nostrudel por exemplo é possível configurar um proxy de imagem através das [configurações](https://nostrudel.ninja/#/settings/performance). <img src="https://blossom.primal.net/d6f191331248dc5cc3e8617c0f94e2a2e44341451e0ec3275cc22b5195ccbdb3.jpg"> **Segundo análise, as redes a seguir ja disponibilizam esses proxies por padrão:** - Amethyst - Damus \ **O que é esse tal de proxy?** - Imagina que você está usando uma máscara. O proxy é tipo essa máscara, só que para o seu IP. Assim, ninguém vai saber quem você é de verdade. - É como se você estivesse usando um disfarce para navegar pela internet! **Outras dicas:** - **Remover Exif:** Todas as fotos que tiramos possuem metadados, normalmente redes sociais e outras empresas removem esses dados quando recebem a imagem no servidor *(eventualmente pegam os dados)*. Programas como [ExifCleaner](https://exifcleaner.com) removem essas informações antes do upload. **Conclusão:** A internet é um lugar incrível, mas também pode ser perigoso. Seguindo essas dicas, você vai poder curtir o Nostr com mais tranquilidade e sem se preocupar com os "bisbilhoteiros". **Lembre-se:** A segurança é coisa séria! Compartilhe esse guia com seus amigos e ajude a criar uma comunidade mais segura. **E aí, curtiu?** **fonte: [https://victorhugo.info/artigos/nostr-como-se-proteger-1](https://victorhugo.info/artigos/nostr-como-se-proteger-1)**
@ f1597634:c6d40bf4
2024-10-02 09:00:59E aí, galera do Nostr! Já pensou em como proteger sua privacidade nesse mundo descentralizado? A gente sabe que a liberdade é daora, mas é importante saber como se proteger dos "bisbilhoteiros" que estão sempre à espreita. **O perigo das fotos:** - Sabia que as fotos que você posta podem dar muitas informações sobre você? É tipo deixar um mapa do tesouro nas mãos de alguém! - Pessoal mau intencionadas podem usar essas fotos para descobrir onde você mora, qual seu IP e até mesmo sua identidade! **Dicas para se proteger:** - **Escolha seus apps com cuidado:** Nem todos os apps são iguais. Procure aqueles que a galera mais confia e que têm uma boa fama. - **Ajuste as configurações:** A maioria dos apps tem configurações de privacidade. Mexa nelas para mostrar só o que você quiser para os outros. - **Cuidado com links:** Não clique em qualquer link que você receber. Pode ser uma armadilha! Uma boa prática ao navegar pelo Nostr é configurar um Proxy *confiável* no seu aplicativo. No Nostrudel por exemplo é possível configurar um proxy de imagem através das [configurações](https://nostrudel.ninja/#/settings/performance). <img src="https://blossom.primal.net/d6f191331248dc5cc3e8617c0f94e2a2e44341451e0ec3275cc22b5195ccbdb3.jpg"> **Segundo análise, as redes a seguir ja disponibilizam esses proxies por padrão:** - Amethyst - Damus \ **O que é esse tal de proxy?** - Imagina que você está usando uma máscara. O proxy é tipo essa máscara, só que para o seu IP. Assim, ninguém vai saber quem você é de verdade. - É como se você estivesse usando um disfarce para navegar pela internet! **Outras dicas:** - **Remover Exif:** Todas as fotos que tiramos possuem metadados, normalmente redes sociais e outras empresas removem esses dados quando recebem a imagem no servidor *(eventualmente pegam os dados)*. Programas como [ExifCleaner](https://exifcleaner.com) removem essas informações antes do upload. **Conclusão:** A internet é um lugar incrível, mas também pode ser perigoso. Seguindo essas dicas, você vai poder curtir o Nostr com mais tranquilidade e sem se preocupar com os "bisbilhoteiros". **Lembre-se:** A segurança é coisa séria! Compartilhe esse guia com seus amigos e ajude a criar uma comunidade mais segura. **E aí, curtiu?** **fonte: [https://victorhugo.info/artigos/nostr-como-se-proteger-1](https://victorhugo.info/artigos/nostr-como-se-proteger-1)** @ a95c6243:d345522c
2025-02-19 09:23:17*Die «moralische Weltordnung» – eine Art Astrologie. Friedrich Nietzsche* **Das Treffen der BRICS-Staaten beim [Gipfel](https://transition-news.org/brics-gipfel-in-kasan-warum-schweigt-die-schweiz) im russischen Kasan** war sicher nicht irgendein politisches Event. Gastgeber Wladimir Putin habe «Hof gehalten», sagen die Einen, China und Russland hätten ihre Vorstellung einer multipolaren Weltordnung zelebriert, schreiben Andere. **In jedem Fall zeigt die Anwesenheit von über 30 Delegationen aus der ganzen Welt,** dass von einer geostrategischen Isolation Russlands wohl keine Rede sein kann. Darüber hinaus haben sowohl die Anreise von UN-Generalsekretär António Guterres als auch die Meldungen und Dementis bezüglich der Beitrittsbemühungen des NATO-Staats [Türkei](https://transition-news.org/turkei-entlarvt-fake-news-von-bild-uber-indiens-angebliches-veto-gegen-den) für etwas Aufsehen gesorgt. **Im Spannungsfeld geopolitischer und wirtschaftlicher Umbrüche** zeigt die neue Allianz zunehmendes Selbstbewusstsein. In Sachen gemeinsamer Finanzpolitik schmiedet man interessante Pläne. Größere Unabhängigkeit von der US-dominierten Finanzordnung ist dabei ein wichtiges Ziel. **Beim BRICS-Wirtschaftsforum in Moskau, wenige Tage vor dem Gipfel,** zählte ein nachhaltiges System für Finanzabrechnungen und Zahlungsdienste zu den vorrangigen Themen. Während dieses Treffens ging der russische Staatsfonds eine Partnerschaft mit dem Rechenzentrumsbetreiber BitRiver ein, um [Bitcoin](https://www.forbes.com/sites/digital-assets/2024/10/23/russia-launches-brics-mining-infrastructure-project/)-Mining-Anlagen für die BRICS-Länder zu errichten. **Die Initiative könnte ein Schritt sein, Bitcoin und andere Kryptowährungen** als Alternativen zu traditionellen Finanzsystemen zu etablieren. Das Projekt könnte dazu führen, dass die BRICS-Staaten den globalen Handel in Bitcoin abwickeln. Vor dem Hintergrund der Diskussionen über eine «BRICS-Währung» wäre dies eine Alternative zu dem ursprünglich angedachten Korb lokaler Währungen und zu goldgedeckten Währungen sowie eine mögliche Ergänzung zum Zahlungssystem [BRICS Pay](https://en.wikipedia.org/wiki/BRICS_PAY). **Dient der Bitcoin also der Entdollarisierung?** Oder droht er inzwischen, zum Gegenstand geopolitischer [Machtspielchen](https://legitim.ch/es-ist-ein-sieg-fuer-bitcoin-waehrend-russland-und-die-usa-um-die-krypto-vorherrschaft-kaempfen/) zu werden? Angesichts der globalen Vernetzungen ist es oft schwer zu durchschauen, «was eine Show ist und was im Hintergrund von anderen Strippenziehern insgeheim gesteuert wird». Sicher können Strukturen wie Bitcoin auch so genutzt werden, dass sie den Herrschenden dienlich sind. Aber die Grundeigenschaft des dezentralisierten, unzensierbaren Peer-to-Peer Zahlungsnetzwerks ist ihm schließlich nicht zu nehmen. **Wenn es nach der EZB oder dem IWF geht, dann scheint statt Instrumentalisierung** momentan eher der Kampf gegen Kryptowährungen angesagt. Jürgen Schaaf, Senior Manager bei der Europäischen Zentralbank, hat jedenfalls dazu aufgerufen, [Bitcoin «zu eliminieren»](https://www.btc-echo.de/schlagzeilen/ezb-banker-es-gibt-gute-gruende-bitcoin-zu-eliminieren-194015/). Der Internationale Währungsfonds forderte El Salvador, das Bitcoin 2021 als gesetzliches Zahlungsmittel eingeführt hat, kürzlich zu [begrenzenden Maßnahmen](https://legitim.ch/el-salvador-iwf-fordert-trotz-nicht-eingetretener-risiken-neue-massnahmen-gegen-bitcoin/) gegen das Kryptogeld auf. **Dass die BRICS-Staaten ein freiheitliches Ansinnen im Kopf haben,** wenn sie Kryptowährungen ins Spiel bringen, darf indes auch bezweifelt werden. Im [Abschlussdokument](http://static.kremlin.ru/media/events/files/en/RosOySvLzGaJtmx2wYFv0lN4NSPZploG.pdf) bekennen sich die Gipfel-Teilnehmer ausdrücklich zur UN, ihren Programmen und ihrer «Agenda 2030». Ernst Wolff nennt das «eine [Bankrotterklärung](https://x.com/wolff_ernst/status/1849781982961557771) korrupter Politiker, die sich dem digital-finanziellen Komplex zu 100 Prozent unterwerfen». --- Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/aufstand-gegen-die-dollar-hegemonie)* erschienen.
@ a95c6243:d345522c
2025-02-19 09:23:17*Die «moralische Weltordnung» – eine Art Astrologie. Friedrich Nietzsche* **Das Treffen der BRICS-Staaten beim [Gipfel](https://transition-news.org/brics-gipfel-in-kasan-warum-schweigt-die-schweiz) im russischen Kasan** war sicher nicht irgendein politisches Event. Gastgeber Wladimir Putin habe «Hof gehalten», sagen die Einen, China und Russland hätten ihre Vorstellung einer multipolaren Weltordnung zelebriert, schreiben Andere. **In jedem Fall zeigt die Anwesenheit von über 30 Delegationen aus der ganzen Welt,** dass von einer geostrategischen Isolation Russlands wohl keine Rede sein kann. Darüber hinaus haben sowohl die Anreise von UN-Generalsekretär António Guterres als auch die Meldungen und Dementis bezüglich der Beitrittsbemühungen des NATO-Staats [Türkei](https://transition-news.org/turkei-entlarvt-fake-news-von-bild-uber-indiens-angebliches-veto-gegen-den) für etwas Aufsehen gesorgt. **Im Spannungsfeld geopolitischer und wirtschaftlicher Umbrüche** zeigt die neue Allianz zunehmendes Selbstbewusstsein. In Sachen gemeinsamer Finanzpolitik schmiedet man interessante Pläne. Größere Unabhängigkeit von der US-dominierten Finanzordnung ist dabei ein wichtiges Ziel. **Beim BRICS-Wirtschaftsforum in Moskau, wenige Tage vor dem Gipfel,** zählte ein nachhaltiges System für Finanzabrechnungen und Zahlungsdienste zu den vorrangigen Themen. Während dieses Treffens ging der russische Staatsfonds eine Partnerschaft mit dem Rechenzentrumsbetreiber BitRiver ein, um [Bitcoin](https://www.forbes.com/sites/digital-assets/2024/10/23/russia-launches-brics-mining-infrastructure-project/)-Mining-Anlagen für die BRICS-Länder zu errichten. **Die Initiative könnte ein Schritt sein, Bitcoin und andere Kryptowährungen** als Alternativen zu traditionellen Finanzsystemen zu etablieren. Das Projekt könnte dazu führen, dass die BRICS-Staaten den globalen Handel in Bitcoin abwickeln. Vor dem Hintergrund der Diskussionen über eine «BRICS-Währung» wäre dies eine Alternative zu dem ursprünglich angedachten Korb lokaler Währungen und zu goldgedeckten Währungen sowie eine mögliche Ergänzung zum Zahlungssystem [BRICS Pay](https://en.wikipedia.org/wiki/BRICS_PAY). **Dient der Bitcoin also der Entdollarisierung?** Oder droht er inzwischen, zum Gegenstand geopolitischer [Machtspielchen](https://legitim.ch/es-ist-ein-sieg-fuer-bitcoin-waehrend-russland-und-die-usa-um-die-krypto-vorherrschaft-kaempfen/) zu werden? Angesichts der globalen Vernetzungen ist es oft schwer zu durchschauen, «was eine Show ist und was im Hintergrund von anderen Strippenziehern insgeheim gesteuert wird». Sicher können Strukturen wie Bitcoin auch so genutzt werden, dass sie den Herrschenden dienlich sind. Aber die Grundeigenschaft des dezentralisierten, unzensierbaren Peer-to-Peer Zahlungsnetzwerks ist ihm schließlich nicht zu nehmen. **Wenn es nach der EZB oder dem IWF geht, dann scheint statt Instrumentalisierung** momentan eher der Kampf gegen Kryptowährungen angesagt. Jürgen Schaaf, Senior Manager bei der Europäischen Zentralbank, hat jedenfalls dazu aufgerufen, [Bitcoin «zu eliminieren»](https://www.btc-echo.de/schlagzeilen/ezb-banker-es-gibt-gute-gruende-bitcoin-zu-eliminieren-194015/). Der Internationale Währungsfonds forderte El Salvador, das Bitcoin 2021 als gesetzliches Zahlungsmittel eingeführt hat, kürzlich zu [begrenzenden Maßnahmen](https://legitim.ch/el-salvador-iwf-fordert-trotz-nicht-eingetretener-risiken-neue-massnahmen-gegen-bitcoin/) gegen das Kryptogeld auf. **Dass die BRICS-Staaten ein freiheitliches Ansinnen im Kopf haben,** wenn sie Kryptowährungen ins Spiel bringen, darf indes auch bezweifelt werden. Im [Abschlussdokument](http://static.kremlin.ru/media/events/files/en/RosOySvLzGaJtmx2wYFv0lN4NSPZploG.pdf) bekennen sich die Gipfel-Teilnehmer ausdrücklich zur UN, ihren Programmen und ihrer «Agenda 2030». Ernst Wolff nennt das «eine [Bankrotterklärung](https://x.com/wolff_ernst/status/1849781982961557771) korrupter Politiker, die sich dem digital-finanziellen Komplex zu 100 Prozent unterwerfen». --- Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/aufstand-gegen-die-dollar-hegemonie)* erschienen. @ a95c6243:d345522c
2025-02-15 19:05:38**Auf der diesjährigen Münchner** **[Sicherheitskonferenz](https://transition-news.org/in-munchen-der-realitat-ins-auge-sehen)** **geht es vor allem um die Ukraine.** Protagonisten sind dabei zunächst die US-Amerikaner. Präsident Trump schockierte die Europäer kurz vorher durch ein Telefonat mit seinem Amtskollegen Wladimir Putin, während Vizepräsident Vance mit seiner Rede über Demokratie und Meinungsfreiheit für versteinerte Mienen und Empörung sorgte. **Die Bemühungen der Europäer um einen Frieden in der Ukraine** halten sich, gelinde gesagt, in Grenzen. Größeres Augenmerk wird auf militärische Unterstützung, die Pflege von Feindbildern sowie Eskalation gelegt. Der deutsche Bundeskanzler Scholz [reagierte](https://transition-news.org/gesucht-friedenskanzler) auf die angekündigten Verhandlungen über einen möglichen Frieden für die Ukraine mit der Forderung nach noch höheren «Verteidigungsausgaben». Auch die amtierende Außenministerin Baerbock hatte vor der Münchner Konferenz [klargestellt](https://archive.is/nUpYa): > «Frieden wird es nur durch Stärke geben. (...) Bei Corona haben wir gesehen, zu was Europa fähig ist. Es braucht erneut Investitionen, die der historischen Wegmarke, vor der wir stehen, angemessen sind.» **Die Rüstungsindustrie freut sich in jedem Fall über weltweit steigende Militärausgaben.** Die Kriege in der Ukraine und in Gaza tragen zu [Rekordeinnahmen](https://transition-news.org/kriege-sind-fur-waffenproduzenten-und-hedgefonds-f-king-good) bei. Jetzt «winkt die Aussicht auf eine jahrelange große Nachrüstung in Europa», auch wenn der Ukraine-Krieg enden sollte, so hört man aus Finanzkreisen. In der Konsequenz kennt «die Aktie des deutschen Vorzeige-Rüstungskonzerns Rheinmetall in ihrem Anstieg [offenbar gar keine Grenzen](https://finanzmarktwelt.de/rheinmetall-aktie-mit-mega-rally-nachruestung-und-1-000-euro-kursziel-339271/) mehr». «Solche Friedensversprechen» wie das jetzige hätten in der Vergangenheit zu starken Kursverlusten geführt. **Für manche Leute sind Kriegswaffen und sonstige Rüstungsgüter Waren wie alle anderen,** jedenfalls aus der Perspektive von Investoren oder Managern. Auch in diesem Bereich gibt es Startups und man spricht von Dingen wie innovativen Herangehensweisen, hocheffizienten Produktionsanlagen, skalierbaren Produktionstechniken und geringeren Stückkosten. **Wir lesen aktuell von Massenproduktion und gesteigerten Fertigungskapazitäten** für Kriegsgerät. Der Motor solcher Dynamik und solchen Wachstums ist die Aufrüstung, die inzwischen permanent gefordert wird. Parallel wird die Bevölkerung verbal eingestimmt und auf Kriegstüchtigkeit getrimmt. **Das Rüstungs- und KI-Startup Helsing verkündete kürzlich** eine «dezentrale [Massenproduktion](https://www.trendingtopics.eu/helsing-kampfdrohnen-unicorn-startet-dezentrale-massenproduktion-fuer-ukrainekrieg/) für den Ukrainekrieg». Mit dieser Expansion positioniere sich das Münchner Unternehmen als einer der weltweit führenden Hersteller von Kampfdrohnen. Der nächste [«Meilenstein»](https://archive.is/eZsWP) steht auch bereits an: Man will eine Satellitenflotte im Weltraum aufbauen, zur Überwachung von Gefechtsfeldern und Truppenbewegungen. **Ebenfalls aus München stammt das als** **[DefenseTech-Startup](https://www.trendingtopics.eu/arx-robotics-produktion/)** **bezeichnete Unternehmen** ARX Robotics. Kürzlich habe man in der Region die größte europäische Produktionsstätte für autonome Verteidigungssysteme eröffnet. Damit fahre man die Produktion von Militär-Robotern hoch. Diese Expansion diene auch der Lieferung der «größten Flotte unbemannter Bodensysteme westlicher Bauart» in die Ukraine. **Rüstung boomt und scheint ein Zukunftsmarkt zu sein.** Die Hersteller und Vermarkter betonen, mit ihren Aktivitäten und Produkten solle die europäische Verteidigungsfähigkeit erhöht werden. Ihre Strategien sollten sogar «zum Schutz demokratischer Strukturen beitragen». *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/so-klingt-das-aufrustungs-business-startups-und-alte-hasen)*** erschienen.
@ a95c6243:d345522c
2025-02-15 19:05:38**Auf der diesjährigen Münchner** **[Sicherheitskonferenz](https://transition-news.org/in-munchen-der-realitat-ins-auge-sehen)** **geht es vor allem um die Ukraine.** Protagonisten sind dabei zunächst die US-Amerikaner. Präsident Trump schockierte die Europäer kurz vorher durch ein Telefonat mit seinem Amtskollegen Wladimir Putin, während Vizepräsident Vance mit seiner Rede über Demokratie und Meinungsfreiheit für versteinerte Mienen und Empörung sorgte. **Die Bemühungen der Europäer um einen Frieden in der Ukraine** halten sich, gelinde gesagt, in Grenzen. Größeres Augenmerk wird auf militärische Unterstützung, die Pflege von Feindbildern sowie Eskalation gelegt. Der deutsche Bundeskanzler Scholz [reagierte](https://transition-news.org/gesucht-friedenskanzler) auf die angekündigten Verhandlungen über einen möglichen Frieden für die Ukraine mit der Forderung nach noch höheren «Verteidigungsausgaben». Auch die amtierende Außenministerin Baerbock hatte vor der Münchner Konferenz [klargestellt](https://archive.is/nUpYa): > «Frieden wird es nur durch Stärke geben. (...) Bei Corona haben wir gesehen, zu was Europa fähig ist. Es braucht erneut Investitionen, die der historischen Wegmarke, vor der wir stehen, angemessen sind.» **Die Rüstungsindustrie freut sich in jedem Fall über weltweit steigende Militärausgaben.** Die Kriege in der Ukraine und in Gaza tragen zu [Rekordeinnahmen](https://transition-news.org/kriege-sind-fur-waffenproduzenten-und-hedgefonds-f-king-good) bei. Jetzt «winkt die Aussicht auf eine jahrelange große Nachrüstung in Europa», auch wenn der Ukraine-Krieg enden sollte, so hört man aus Finanzkreisen. In der Konsequenz kennt «die Aktie des deutschen Vorzeige-Rüstungskonzerns Rheinmetall in ihrem Anstieg [offenbar gar keine Grenzen](https://finanzmarktwelt.de/rheinmetall-aktie-mit-mega-rally-nachruestung-und-1-000-euro-kursziel-339271/) mehr». «Solche Friedensversprechen» wie das jetzige hätten in der Vergangenheit zu starken Kursverlusten geführt. **Für manche Leute sind Kriegswaffen und sonstige Rüstungsgüter Waren wie alle anderen,** jedenfalls aus der Perspektive von Investoren oder Managern. Auch in diesem Bereich gibt es Startups und man spricht von Dingen wie innovativen Herangehensweisen, hocheffizienten Produktionsanlagen, skalierbaren Produktionstechniken und geringeren Stückkosten. **Wir lesen aktuell von Massenproduktion und gesteigerten Fertigungskapazitäten** für Kriegsgerät. Der Motor solcher Dynamik und solchen Wachstums ist die Aufrüstung, die inzwischen permanent gefordert wird. Parallel wird die Bevölkerung verbal eingestimmt und auf Kriegstüchtigkeit getrimmt. **Das Rüstungs- und KI-Startup Helsing verkündete kürzlich** eine «dezentrale [Massenproduktion](https://www.trendingtopics.eu/helsing-kampfdrohnen-unicorn-startet-dezentrale-massenproduktion-fuer-ukrainekrieg/) für den Ukrainekrieg». Mit dieser Expansion positioniere sich das Münchner Unternehmen als einer der weltweit führenden Hersteller von Kampfdrohnen. Der nächste [«Meilenstein»](https://archive.is/eZsWP) steht auch bereits an: Man will eine Satellitenflotte im Weltraum aufbauen, zur Überwachung von Gefechtsfeldern und Truppenbewegungen. **Ebenfalls aus München stammt das als** **[DefenseTech-Startup](https://www.trendingtopics.eu/arx-robotics-produktion/)** **bezeichnete Unternehmen** ARX Robotics. Kürzlich habe man in der Region die größte europäische Produktionsstätte für autonome Verteidigungssysteme eröffnet. Damit fahre man die Produktion von Militär-Robotern hoch. Diese Expansion diene auch der Lieferung der «größten Flotte unbemannter Bodensysteme westlicher Bauart» in die Ukraine. **Rüstung boomt und scheint ein Zukunftsmarkt zu sein.** Die Hersteller und Vermarkter betonen, mit ihren Aktivitäten und Produkten solle die europäische Verteidigungsfähigkeit erhöht werden. Ihre Strategien sollten sogar «zum Schutz demokratischer Strukturen beitragen». *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/so-klingt-das-aufrustungs-business-startups-und-alte-hasen)*** erschienen. @ c631e267:c2b78d3e
2025-02-07 19:42:11*Nur wenn wir aufeinander zugehen, haben wir die Chance* *\ auf Überwindung der gegenseitigen Ressentiments!* *\ Dr. med. dent. Jens Knipphals*   **In Wolfsburg sollte es kürzlich eine Gesprächsrunde von Kritikern der Corona-Politik** mit Oberbürgermeister Dennis Weilmann und Vertretern der Stadtverwaltung geben. Der Zahnarzt und [langjährige](https://transition-news.org/wo-sind-einigkeit-recht-und-freiheit) Maßnahmenkritiker Jens Knipphals hatte diese Einladung ins Rathaus erwirkt und [publiziert](https://www.alexander-wallasch.de/impfgeschichten/brandbrief-zahnarzt-laesst-nicht-locker-showdown-im-wolfsburger-rathaus). Seine Motivation: > «Ich möchte die Spaltung der Gesellschaft überwinden. Dazu ist eine umfassende Aufarbeitung der Corona-Krise in der Öffentlichkeit notwendig.» **Schon früher hatte Knipphals Antworten von den Kommunalpolitikern verlangt,** zum Beispiel bei öffentlichen [Bürgerfragestunden](https://archive.is/ttTZc). Für das erwartete Treffen im Rathaus formulierte er Fragen wie: Warum wurden fachliche Argumente der Kritiker ignoriert? Weshalb wurde deren Ausgrenzung, Diskreditierung und Entmenschlichung nicht entgegengetreten? In welcher Form übernehmen Rat und Verwaltung in Wolfsburg persönlich Verantwortung für die erheblichen Folgen der politischen Corona-Krise? **Der Termin fand allerdings nicht statt** – der Bürgermeister sagte ihn kurz vorher wieder ab. Knipphals bezeichnete Weilmann anschließend als [Wiederholungstäter](https://www.youtube.com/watch?v=b_zzp6jKiHo), da das Stadtoberhaupt bereits 2022 zu einem Runden Tisch in der Sache eingeladen hatte, den es dann nie gab. Gegenüber *Multipolar* [erklärte](https://multipolar-magazin.de/artikel/corona-aufarbeitung-wolfsburg) der Arzt, Weilmann wolle scheinbar eine öffentliche Aufarbeitung mit allen Mitteln verhindern. Er selbst sei «inzwischen absolut desillusioniert» und die einzige Lösung sei, dass die Verantwortlichen gingen. **Die Aufarbeitung der Plandemie beginne bei jedem von uns selbst,** sei aber letztlich eine gesamtgesellschaftliche Aufgabe, [schreibt](https://peds-ansichten.de/2025/01/plandemie-aufarbeitung/) Peter Frey, der den «Fall Wolfsburg» auch in seinem Blog behandelt. Diese Aufgabe sei indes deutlich größer, als viele glaubten. Erfreulicherweise sei der öffentliche Informationsraum inzwischen größer, trotz der weiterhin unverfrorenen Desinformations-Kampagnen der etablierten Massenmedien. **Frey erinnert daran, dass Dennis Weilmann mitverantwortlich** für gravierende Grundrechtseinschränkungen wie die 2021 eingeführten 2G-Regeln in der Wolfsburger Innenstadt zeichnet. Es sei naiv anzunehmen, dass ein Funktionär einzig im Interesse der Bürger handeln würde. Als früherer Dezernent des Amtes für Wirtschaft, Digitalisierung und Kultur der Autostadt kenne Weilmann zum Beispiel die Verknüpfung von Fördergeldern mit politischen Zielsetzungen gut. **Wolfsburg wurde damals zu einem Modellprojekt** des Bundesministeriums des Innern (BMI) und war Finalist im [Bitkom](https://pareto.space/a/naddr1qqxnzden8qen2vejxvenjv35qgs2jhrzgwzvvzgz42kfmef2kr7w8x573k4r62c5ydjh8gyn6dz4ytqrqsqqqa28qyxhwumn8ghj7mn0wvhxcmmvqyv8wumn8ghj7mn0wd68ytn8wfhk7an9d9uzucm0d5qs7amnwvaz7tmwdaehgu3wd4hk6qg5waehxw309ahx7um5wghx77r5wghxgetkqydhwumn8ghj7mn0wd68ytnnwa5hxuedv4hxjemdvyhxx6qpzamhxue69uhhqctjv46x7tnwdaehgu339e3k7mgpz4mhxue69uhhqatjwpkx2un9d3shjtnrdaksz9nhwden5te0wfjkccte9cc8scmgv96zucm0d5q3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgkwaehxw309aex2mrp0yhxummnw3ezucnpdejqmk3pae)-Wettbewerb «Digitale Stadt». So habe rechtzeitig vor der Plandemie das Projekt [«Smart City Wolfsburg»](https://www.beesmart.city/de/city-portraits/smart-city-wolfsburg) anlaufen können, das der Stadt «eine Vorreiterrolle für umfassende Vernetzung und Datenerfassung» aufgetragen habe, sagt Frey. Die Vereinten Nationen verkauften dann derartige «intelligente» Überwachungs- und Kontrollmaßnahmen ebenso als Rettung in der Not wie das Magazin *[Forbes](https://web.archive.org/web/20200417064208/https://www.forbes.com/sites/simonchandler/2020/04/13/how-smart-cities-are-protecting-against-coronavirus-but-threatening-privacy/#5edf8d0c1cc3)* im April 2020: > «Intelligente Städte können uns helfen, die Coronavirus-Pandemie zu bekämpfen. In einer wachsenden Zahl von Ländern tun die intelligenten Städte genau das. Regierungen und lokale Behörden nutzen Smart-City-Technologien, Sensoren und Daten, um die Kontakte von Menschen aufzuspüren, die mit dem Coronavirus infiziert sind. Gleichzeitig helfen die Smart Cities auch dabei, festzustellen, ob die Regeln der sozialen Distanzierung eingehalten werden.» **Offensichtlich gibt es viele Aspekte zu bedenken und zu durchleuten,** wenn es um die Aufklärung und Aufarbeitung der sogenannten «Corona-Pandemie» und der verordneten [Maßnahmen](https://transition-news.org/stopptcovid-gutachten-von-lauterbach-erhalt-vernichtende-analyse) geht. Frustration und Desillusion sind angesichts der Realitäten absolut verständlich. Gerade deswegen sind Initiativen wie die von Jens Knipphals so bewundernswert und so wichtig – ebenso wie eine seiner Kernthesen: «Wir müssen aufeinander zugehen, da hilft alles nichts». *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/corona-aufarbeitung-in-der-praxis-eine-illusion)*** erschienen.
@ c631e267:c2b78d3e
2025-02-07 19:42:11*Nur wenn wir aufeinander zugehen, haben wir die Chance* *\ auf Überwindung der gegenseitigen Ressentiments!* *\ Dr. med. dent. Jens Knipphals*   **In Wolfsburg sollte es kürzlich eine Gesprächsrunde von Kritikern der Corona-Politik** mit Oberbürgermeister Dennis Weilmann und Vertretern der Stadtverwaltung geben. Der Zahnarzt und [langjährige](https://transition-news.org/wo-sind-einigkeit-recht-und-freiheit) Maßnahmenkritiker Jens Knipphals hatte diese Einladung ins Rathaus erwirkt und [publiziert](https://www.alexander-wallasch.de/impfgeschichten/brandbrief-zahnarzt-laesst-nicht-locker-showdown-im-wolfsburger-rathaus). Seine Motivation: > «Ich möchte die Spaltung der Gesellschaft überwinden. Dazu ist eine umfassende Aufarbeitung der Corona-Krise in der Öffentlichkeit notwendig.» **Schon früher hatte Knipphals Antworten von den Kommunalpolitikern verlangt,** zum Beispiel bei öffentlichen [Bürgerfragestunden](https://archive.is/ttTZc). Für das erwartete Treffen im Rathaus formulierte er Fragen wie: Warum wurden fachliche Argumente der Kritiker ignoriert? Weshalb wurde deren Ausgrenzung, Diskreditierung und Entmenschlichung nicht entgegengetreten? In welcher Form übernehmen Rat und Verwaltung in Wolfsburg persönlich Verantwortung für die erheblichen Folgen der politischen Corona-Krise? **Der Termin fand allerdings nicht statt** – der Bürgermeister sagte ihn kurz vorher wieder ab. Knipphals bezeichnete Weilmann anschließend als [Wiederholungstäter](https://www.youtube.com/watch?v=b_zzp6jKiHo), da das Stadtoberhaupt bereits 2022 zu einem Runden Tisch in der Sache eingeladen hatte, den es dann nie gab. Gegenüber *Multipolar* [erklärte](https://multipolar-magazin.de/artikel/corona-aufarbeitung-wolfsburg) der Arzt, Weilmann wolle scheinbar eine öffentliche Aufarbeitung mit allen Mitteln verhindern. Er selbst sei «inzwischen absolut desillusioniert» und die einzige Lösung sei, dass die Verantwortlichen gingen. **Die Aufarbeitung der Plandemie beginne bei jedem von uns selbst,** sei aber letztlich eine gesamtgesellschaftliche Aufgabe, [schreibt](https://peds-ansichten.de/2025/01/plandemie-aufarbeitung/) Peter Frey, der den «Fall Wolfsburg» auch in seinem Blog behandelt. Diese Aufgabe sei indes deutlich größer, als viele glaubten. Erfreulicherweise sei der öffentliche Informationsraum inzwischen größer, trotz der weiterhin unverfrorenen Desinformations-Kampagnen der etablierten Massenmedien. **Frey erinnert daran, dass Dennis Weilmann mitverantwortlich** für gravierende Grundrechtseinschränkungen wie die 2021 eingeführten 2G-Regeln in der Wolfsburger Innenstadt zeichnet. Es sei naiv anzunehmen, dass ein Funktionär einzig im Interesse der Bürger handeln würde. Als früherer Dezernent des Amtes für Wirtschaft, Digitalisierung und Kultur der Autostadt kenne Weilmann zum Beispiel die Verknüpfung von Fördergeldern mit politischen Zielsetzungen gut. **Wolfsburg wurde damals zu einem Modellprojekt** des Bundesministeriums des Innern (BMI) und war Finalist im [Bitkom](https://pareto.space/a/naddr1qqxnzden8qen2vejxvenjv35qgs2jhrzgwzvvzgz42kfmef2kr7w8x573k4r62c5ydjh8gyn6dz4ytqrqsqqqa28qyxhwumn8ghj7mn0wvhxcmmvqyv8wumn8ghj7mn0wd68ytn8wfhk7an9d9uzucm0d5qs7amnwvaz7tmwdaehgu3wd4hk6qg5waehxw309ahx7um5wghx77r5wghxgetkqydhwumn8ghj7mn0wd68ytnnwa5hxuedv4hxjemdvyhxx6qpzamhxue69uhhqctjv46x7tnwdaehgu339e3k7mgpz4mhxue69uhhqatjwpkx2un9d3shjtnrdaksz9nhwden5te0wfjkccte9cc8scmgv96zucm0d5q3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgkwaehxw309aex2mrp0yhxummnw3ezucnpdejqmk3pae)-Wettbewerb «Digitale Stadt». So habe rechtzeitig vor der Plandemie das Projekt [«Smart City Wolfsburg»](https://www.beesmart.city/de/city-portraits/smart-city-wolfsburg) anlaufen können, das der Stadt «eine Vorreiterrolle für umfassende Vernetzung und Datenerfassung» aufgetragen habe, sagt Frey. Die Vereinten Nationen verkauften dann derartige «intelligente» Überwachungs- und Kontrollmaßnahmen ebenso als Rettung in der Not wie das Magazin *[Forbes](https://web.archive.org/web/20200417064208/https://www.forbes.com/sites/simonchandler/2020/04/13/how-smart-cities-are-protecting-against-coronavirus-but-threatening-privacy/#5edf8d0c1cc3)* im April 2020: > «Intelligente Städte können uns helfen, die Coronavirus-Pandemie zu bekämpfen. In einer wachsenden Zahl von Ländern tun die intelligenten Städte genau das. Regierungen und lokale Behörden nutzen Smart-City-Technologien, Sensoren und Daten, um die Kontakte von Menschen aufzuspüren, die mit dem Coronavirus infiziert sind. Gleichzeitig helfen die Smart Cities auch dabei, festzustellen, ob die Regeln der sozialen Distanzierung eingehalten werden.» **Offensichtlich gibt es viele Aspekte zu bedenken und zu durchleuten,** wenn es um die Aufklärung und Aufarbeitung der sogenannten «Corona-Pandemie» und der verordneten [Maßnahmen](https://transition-news.org/stopptcovid-gutachten-von-lauterbach-erhalt-vernichtende-analyse) geht. Frustration und Desillusion sind angesichts der Realitäten absolut verständlich. Gerade deswegen sind Initiativen wie die von Jens Knipphals so bewundernswert und so wichtig – ebenso wie eine seiner Kernthesen: «Wir müssen aufeinander zugehen, da hilft alles nichts». *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/corona-aufarbeitung-in-der-praxis-eine-illusion)*** erschienen. @ a95c6243:d345522c
2025-01-31 20:02:25*Im Augenblick wird mit größter Intensität, großer Umsicht* *\ das deutsche Volk belogen.* *\ Olaf Scholz im FAZ-[Interview](https://www.youtube.com/watch?v=c3KI1GmdoVc\&t=649s)*   **Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten** sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur *Reuters* Verbreitung in den Medien [gefunden](https://archive.is/dnZbY) hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten. **Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen** sei repräsentativ, [behauptet](https://www.bitkom.org/Presse/Presseinformation/Knapp-Haelfte-Nichtwaehler-wuerde-online-waehlen) der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von [Mitgliedern](https://www.bitkom.org/Bitkom/Mitgliedschaft/Mitgliederliste), die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben». **Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH,** also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges [«Demokratie-Update»](https://www.experten.de/id/4922407/online-wahlen-als-update-des-demokratischen-systems/) aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet. **Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete** Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer [befürchteten](https://www.ie.edu/university/news-events/news/67-europeans-fear-ai-manipulation-elections-according-ie-university-research/), dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen. **Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein?** Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise [abgelehnt](https://www.bundestag.de/dokumente/textarchiv/2025/kw05-de-zustrombegrenzungsgesetz-1042038). Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen. **Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen,** die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter [berichtet](https://www.epochtimes.de/politik/deutschland/brandmauer-proteste-cdu-zentrale-geraeumt-kundgebungen-in-46-staedten-a5023745.html). Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert». **Der Vorwand** **[«unzulässiger Einflussnahme»](https://transition-news.org/die-minister-faeser-und-wissing-sorgen-sich-um-unzulassige-einflussnahme-auf)** **auf Politik und Wahlen** wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als [«völlig irre»](https://transition-news.org/bill-gates-nennt-musks-einmischung-in-eu-politik-vollig-irre) bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird [«E-Voting»](https://www.ch.ch/de/abstimmungen-und-wahlen/e-voting/) seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg. **Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus.** Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die [weit verbreitete Armut](https://transition-news.org/ein-funftel-der-bevolkerung-in-deutschland-ist-von-armut-oder-sozialer) zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/wahlen-und-wahlen-lassen)*** erschienen.
@ a95c6243:d345522c
2025-01-31 20:02:25*Im Augenblick wird mit größter Intensität, großer Umsicht* *\ das deutsche Volk belogen.* *\ Olaf Scholz im FAZ-[Interview](https://www.youtube.com/watch?v=c3KI1GmdoVc\&t=649s)*   **Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten** sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur *Reuters* Verbreitung in den Medien [gefunden](https://archive.is/dnZbY) hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten. **Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen** sei repräsentativ, [behauptet](https://www.bitkom.org/Presse/Presseinformation/Knapp-Haelfte-Nichtwaehler-wuerde-online-waehlen) der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von [Mitgliedern](https://www.bitkom.org/Bitkom/Mitgliedschaft/Mitgliederliste), die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben». **Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH,** also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges [«Demokratie-Update»](https://www.experten.de/id/4922407/online-wahlen-als-update-des-demokratischen-systems/) aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet. **Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete** Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer [befürchteten](https://www.ie.edu/university/news-events/news/67-europeans-fear-ai-manipulation-elections-according-ie-university-research/), dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen. **Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein?** Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise [abgelehnt](https://www.bundestag.de/dokumente/textarchiv/2025/kw05-de-zustrombegrenzungsgesetz-1042038). Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen. **Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen,** die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter [berichtet](https://www.epochtimes.de/politik/deutschland/brandmauer-proteste-cdu-zentrale-geraeumt-kundgebungen-in-46-staedten-a5023745.html). Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert». **Der Vorwand** **[«unzulässiger Einflussnahme»](https://transition-news.org/die-minister-faeser-und-wissing-sorgen-sich-um-unzulassige-einflussnahme-auf)** **auf Politik und Wahlen** wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als [«völlig irre»](https://transition-news.org/bill-gates-nennt-musks-einmischung-in-eu-politik-vollig-irre) bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird [«E-Voting»](https://www.ch.ch/de/abstimmungen-und-wahlen/e-voting/) seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg. **Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus.** Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die [weit verbreitete Armut](https://transition-news.org/ein-funftel-der-bevolkerung-in-deutschland-ist-von-armut-oder-sozialer) zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/wahlen-und-wahlen-lassen)*** erschienen. @ a95c6243:d345522c
2025-01-24 20:59:01*Menschen tun alles, egal wie absurd,* *\ um ihrer eigenen Seele nicht zu begegnen.* *\ Carl Gustav Jung*   **«Extremer Reichtum ist eine Gefahr für die Demokratie»,** sagen über die Hälfte der knapp 3000 befragten Millionäre aus G20-Staaten laut einer [Umfrage](https://web.archive.org/web/20250122124803/https://patrioticmillionaires.org/web/20250122124803/https://patrioticmillionaires.org/press/nearly-two-thirds-of-millionaires-think-influence-of-the-super-rich-on-trump-presidency-is-threat-to-global-stability/) der «Patriotic Millionaires». Ferner stellte dieser Zusammenschluss wohlhabender US-Amerikaner fest, dass 63 Prozent jener Millionäre den Einfluss von Superreichen auf US-Präsident Trump als Bedrohung für die globale Stabilität ansehen. **Diese Besorgnis haben 370 Millionäre und Milliardäre am Dienstag** auch den in Davos beim WEF konzentrierten Privilegierten aus aller Welt übermittelt. In einem offenen Brief forderten sie die «gewählten Führer» auf, die Superreichen – also sie selbst – zu besteuern, um «die zersetzenden Auswirkungen des extremen Reichtums auf unsere Demokratien und die Gesellschaft zu bekämpfen». Zum Beispiel kontrolliere eine handvoll extrem reicher Menschen die Medien, beeinflusse die Rechtssysteme in unzulässiger Weise und verwandele Recht in Unrecht. **Schon 2019** **[beanstandete](https://www.youtube.com/watch?v=paaen3b44XY)** **der bekannte Historiker und Schriftsteller Ruthger Bregman** an einer WEF-Podiumsdiskussion die Steuervermeidung der Superreichen. Die elitäre Veranstaltung bezeichnete er als «Feuerwehr-Konferenz, bei der man nicht über Löschwasser sprechen darf.» Daraufhin erhielt Bregman keine Einladungen nach Davos mehr. Auf seine Aussagen machte der Schweizer Aktivist Alec Gagneux aufmerksam, der sich seit Jahrzehnten kritisch mit dem WEF befasst. Ihm wurde kürzlich der Zutritt zu einem dreiteiligen Kurs über das WEF an der Volkshochschule Region Brugg [verwehrt](https://transition-news.org/wef-propaganda-an-schweizer-volkshochschule-kritiker-ausgesperrt). **Nun ist die Erkenntnis, dass mit Geld politischer Einfluss einhergeht,** alles andere als neu. Und extremer Reichtum macht die Sache nicht wirklich besser. Trotzdem hat man über Initiativen wie Patriotic Millionaires oder [Taxmenow](https://www.taxmenow.eu/) bisher eher selten etwas gehört, obwohl es sie schon lange gibt. Auch scheint es kein Problem, wenn ein Herr [Gates](https://transition-news.org/bill-melinda-gates-stiftung) fast im Alleingang versucht, globale Gesundheits-, Klima-, Ernährungs- oder Bevölkerungspolitik zu betreiben – im Gegenteil. Im Jahr, als der Milliardär Donald Trump zum zweiten Mal ins Weiße Haus einzieht, ist das Echo in den Gesinnungsmedien dagegen enorm – und uniform, wer hätte das gedacht.  **Der neue US-Präsident hat jedoch** **[«Davos geerdet»](https://www.achgut.com/artikel/trump_erdet_davos_gruener_betrug_green_new_scam),** wie *Achgut* es nannte. In seiner kurzen [Rede](https://www.weforum.org/meetings/world-economic-forum-annual-meeting-2025/sessions/special-address-by-the-president-of-the-united-states-of-america/) beim Weltwirtschaftsforum verteidigte er seine Politik und stellte klar, er habe schlicht eine «Revolution des gesunden Menschenverstands» begonnen. Mit deutlichen Worten sprach er unter anderem von ersten Maßnahmen gegen den «Green New Scam», und von einem «Erlass, der jegliche staatliche Zensur beendet»: > «Unsere Regierung wird die Äußerungen unserer eigenen Bürger nicht mehr als Fehlinformation oder Desinformation bezeichnen, was die Lieblingswörter von Zensoren und derer sind, die den freien Austausch von Ideen und, offen gesagt, den Fortschritt verhindern wollen.» **Wie der** **[«Trumpismus»](https://transition-news.org/trumpismus-zeitenwende-und-tiefer-staat)** **letztlich einzuordnen ist,** muss jeder für sich selbst entscheiden. Skepsis ist definitiv angebracht, denn «einer von uns» sind weder der Präsident noch seine auserwählten Teammitglieder. Ob sie irgendeinen Sumpf trockenlegen oder Staatsverbrechen aufdecken werden oder was aus WHO- und Klimaverträgen wird, bleibt abzuwarten. **Das** **[WHO](https://transition-news.org/who-bedauert-trumps-entscheidung-sich-aus-der-organisation-zuruckzuziehen)-Dekret fordert jedenfalls die Übertragung der Gelder auf «glaubwürdige Partner»,** die die Aktivitäten übernehmen könnten. Zufällig scheint mit «Impfguru» Bill Gates ein weiterer Harris-Unterstützer kürzlich das Lager gewechselt zu haben: Nach einem gemeinsamen Abendessen zeigte er sich [«beeindruckt»](https://archive.is/SpQ24) von Trumps Interesse an der globalen Gesundheit. **Mit dem** **[Projekt «Stargate»](https://transition-news.org/us-privatsektor-will-500-milliarden-dollar-in-ki-investieren-krebsimpfstoffe)** **sind weitere dunkle Wolken am Erwartungshorizont** der Fangemeinde aufgezogen. Trump hat dieses Joint Venture zwischen den Konzernen OpenAI, Oracle, und SoftBank als das «größte KI-Infrastrukturprojekt der Geschichte» angekündigt. Der Stein des Anstoßes: Oracle-CEO Larry Ellison, der auch Fan von KI-gestützter [Echtzeit-Überwachung](https://transition-news.org/oracle-kundigt-neues-ki-rechenzentrum-mit-eigenen-atomreaktoren-an) ist, sieht einen weiteren potenziellen Einsatz der künstlichen Intelligenz. Sie könne dazu dienen, Krebserkrankungen zu erkennen und individuelle mRNA-«Impfstoffe» zur Behandlung innerhalb von 48 Stunden zu entwickeln. **Warum bitte sollten sich diese superreichen «Eliten» ins eigene Fleisch schneiden** und direkt entgegen ihren eigenen Interessen handeln? Weil sie Menschenfreunde, sogenannte Philanthropen sind? Oder vielleicht, weil sie ein schlechtes Gewissen haben und ihre Schuld kompensieren müssen? Deswegen jedenfalls brauchen «Linke» laut Robert Willacker, einem deutschen Politikberater mit brasilianischen Wurzeln, rechte Parteien – ein ebenso überraschender wie humorvoller [Erklärungsansatz](https://www.youtube.com/watch?v=s63_8flX1zk). **Wenn eine Krähe der anderen kein Auge aushackt,** dann tut sie das sich selbst noch weniger an. Dass Millionäre ernsthaft ihre eigene Besteuerung fordern oder Machteliten ihren eigenen Einfluss zugunsten anderer einschränken würden, halte ich für sehr unwahrscheinlich. So etwas glaube ich erst, wenn zum Beispiel die [Rüstungsindustrie](https://transition-news.org/schweiz-zunehmende-beteiligung-an-eu-militarprojekten) sich um Friedensverhandlungen bemüht, die [Pharmalobby](https://transition-news.org/eu-lobbyisten-gegen-pfas-verbot) sich gegen institutionalisierte Korruption einsetzt, [Zentralbanken](https://transition-news.org/digitale-wahrung) ihre CBDC-Pläne für Bitcoin opfern oder der ÖRR die Abschaffung der Rundfunkgebühren fordert. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/elitare-anti-eliten-und-superreiche-anti-reiche)*** erschienen.
@ a95c6243:d345522c
2025-01-24 20:59:01*Menschen tun alles, egal wie absurd,* *\ um ihrer eigenen Seele nicht zu begegnen.* *\ Carl Gustav Jung*   **«Extremer Reichtum ist eine Gefahr für die Demokratie»,** sagen über die Hälfte der knapp 3000 befragten Millionäre aus G20-Staaten laut einer [Umfrage](https://web.archive.org/web/20250122124803/https://patrioticmillionaires.org/web/20250122124803/https://patrioticmillionaires.org/press/nearly-two-thirds-of-millionaires-think-influence-of-the-super-rich-on-trump-presidency-is-threat-to-global-stability/) der «Patriotic Millionaires». Ferner stellte dieser Zusammenschluss wohlhabender US-Amerikaner fest, dass 63 Prozent jener Millionäre den Einfluss von Superreichen auf US-Präsident Trump als Bedrohung für die globale Stabilität ansehen. **Diese Besorgnis haben 370 Millionäre und Milliardäre am Dienstag** auch den in Davos beim WEF konzentrierten Privilegierten aus aller Welt übermittelt. In einem offenen Brief forderten sie die «gewählten Führer» auf, die Superreichen – also sie selbst – zu besteuern, um «die zersetzenden Auswirkungen des extremen Reichtums auf unsere Demokratien und die Gesellschaft zu bekämpfen». Zum Beispiel kontrolliere eine handvoll extrem reicher Menschen die Medien, beeinflusse die Rechtssysteme in unzulässiger Weise und verwandele Recht in Unrecht. **Schon 2019** **[beanstandete](https://www.youtube.com/watch?v=paaen3b44XY)** **der bekannte Historiker und Schriftsteller Ruthger Bregman** an einer WEF-Podiumsdiskussion die Steuervermeidung der Superreichen. Die elitäre Veranstaltung bezeichnete er als «Feuerwehr-Konferenz, bei der man nicht über Löschwasser sprechen darf.» Daraufhin erhielt Bregman keine Einladungen nach Davos mehr. Auf seine Aussagen machte der Schweizer Aktivist Alec Gagneux aufmerksam, der sich seit Jahrzehnten kritisch mit dem WEF befasst. Ihm wurde kürzlich der Zutritt zu einem dreiteiligen Kurs über das WEF an der Volkshochschule Region Brugg [verwehrt](https://transition-news.org/wef-propaganda-an-schweizer-volkshochschule-kritiker-ausgesperrt). **Nun ist die Erkenntnis, dass mit Geld politischer Einfluss einhergeht,** alles andere als neu. Und extremer Reichtum macht die Sache nicht wirklich besser. Trotzdem hat man über Initiativen wie Patriotic Millionaires oder [Taxmenow](https://www.taxmenow.eu/) bisher eher selten etwas gehört, obwohl es sie schon lange gibt. Auch scheint es kein Problem, wenn ein Herr [Gates](https://transition-news.org/bill-melinda-gates-stiftung) fast im Alleingang versucht, globale Gesundheits-, Klima-, Ernährungs- oder Bevölkerungspolitik zu betreiben – im Gegenteil. Im Jahr, als der Milliardär Donald Trump zum zweiten Mal ins Weiße Haus einzieht, ist das Echo in den Gesinnungsmedien dagegen enorm – und uniform, wer hätte das gedacht.  **Der neue US-Präsident hat jedoch** **[«Davos geerdet»](https://www.achgut.com/artikel/trump_erdet_davos_gruener_betrug_green_new_scam),** wie *Achgut* es nannte. In seiner kurzen [Rede](https://www.weforum.org/meetings/world-economic-forum-annual-meeting-2025/sessions/special-address-by-the-president-of-the-united-states-of-america/) beim Weltwirtschaftsforum verteidigte er seine Politik und stellte klar, er habe schlicht eine «Revolution des gesunden Menschenverstands» begonnen. Mit deutlichen Worten sprach er unter anderem von ersten Maßnahmen gegen den «Green New Scam», und von einem «Erlass, der jegliche staatliche Zensur beendet»: > «Unsere Regierung wird die Äußerungen unserer eigenen Bürger nicht mehr als Fehlinformation oder Desinformation bezeichnen, was die Lieblingswörter von Zensoren und derer sind, die den freien Austausch von Ideen und, offen gesagt, den Fortschritt verhindern wollen.» **Wie der** **[«Trumpismus»](https://transition-news.org/trumpismus-zeitenwende-und-tiefer-staat)** **letztlich einzuordnen ist,** muss jeder für sich selbst entscheiden. Skepsis ist definitiv angebracht, denn «einer von uns» sind weder der Präsident noch seine auserwählten Teammitglieder. Ob sie irgendeinen Sumpf trockenlegen oder Staatsverbrechen aufdecken werden oder was aus WHO- und Klimaverträgen wird, bleibt abzuwarten. **Das** **[WHO](https://transition-news.org/who-bedauert-trumps-entscheidung-sich-aus-der-organisation-zuruckzuziehen)-Dekret fordert jedenfalls die Übertragung der Gelder auf «glaubwürdige Partner»,** die die Aktivitäten übernehmen könnten. Zufällig scheint mit «Impfguru» Bill Gates ein weiterer Harris-Unterstützer kürzlich das Lager gewechselt zu haben: Nach einem gemeinsamen Abendessen zeigte er sich [«beeindruckt»](https://archive.is/SpQ24) von Trumps Interesse an der globalen Gesundheit. **Mit dem** **[Projekt «Stargate»](https://transition-news.org/us-privatsektor-will-500-milliarden-dollar-in-ki-investieren-krebsimpfstoffe)** **sind weitere dunkle Wolken am Erwartungshorizont** der Fangemeinde aufgezogen. Trump hat dieses Joint Venture zwischen den Konzernen OpenAI, Oracle, und SoftBank als das «größte KI-Infrastrukturprojekt der Geschichte» angekündigt. Der Stein des Anstoßes: Oracle-CEO Larry Ellison, der auch Fan von KI-gestützter [Echtzeit-Überwachung](https://transition-news.org/oracle-kundigt-neues-ki-rechenzentrum-mit-eigenen-atomreaktoren-an) ist, sieht einen weiteren potenziellen Einsatz der künstlichen Intelligenz. Sie könne dazu dienen, Krebserkrankungen zu erkennen und individuelle mRNA-«Impfstoffe» zur Behandlung innerhalb von 48 Stunden zu entwickeln. **Warum bitte sollten sich diese superreichen «Eliten» ins eigene Fleisch schneiden** und direkt entgegen ihren eigenen Interessen handeln? Weil sie Menschenfreunde, sogenannte Philanthropen sind? Oder vielleicht, weil sie ein schlechtes Gewissen haben und ihre Schuld kompensieren müssen? Deswegen jedenfalls brauchen «Linke» laut Robert Willacker, einem deutschen Politikberater mit brasilianischen Wurzeln, rechte Parteien – ein ebenso überraschender wie humorvoller [Erklärungsansatz](https://www.youtube.com/watch?v=s63_8flX1zk). **Wenn eine Krähe der anderen kein Auge aushackt,** dann tut sie das sich selbst noch weniger an. Dass Millionäre ernsthaft ihre eigene Besteuerung fordern oder Machteliten ihren eigenen Einfluss zugunsten anderer einschränken würden, halte ich für sehr unwahrscheinlich. So etwas glaube ich erst, wenn zum Beispiel die [Rüstungsindustrie](https://transition-news.org/schweiz-zunehmende-beteiligung-an-eu-militarprojekten) sich um Friedensverhandlungen bemüht, die [Pharmalobby](https://transition-news.org/eu-lobbyisten-gegen-pfas-verbot) sich gegen institutionalisierte Korruption einsetzt, [Zentralbanken](https://transition-news.org/digitale-wahrung) ihre CBDC-Pläne für Bitcoin opfern oder der ÖRR die Abschaffung der Rundfunkgebühren fordert. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/elitare-anti-eliten-und-superreiche-anti-reiche)*** erschienen. @ 6be5cc06:5259daf0
2025-01-21 20:58:37A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**. --- ### **1. Instalar o Tor e o Privoxy** Abra o terminal e execute: ```bash sudo apt update sudo apt install tor privoxy ``` **Explicação:** - **Tor:** Roteia o tráfego pela rede Tor. - **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor. --- ### **2. Configurar o Privoxy** Abra o arquivo de configuração do Privoxy: ```bash sudo nano /etc/privoxy/config ``` Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira: ```bash forward-socks5 / 127.0.0.1:9050 . ``` Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**. Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo. --- ### **3. Iniciar o Tor e o Privoxy** Agora, inicie e habilite os serviços: ```bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxy ``` **Explicação:** - **start:** Inicia os serviços. - **enable:** Faz com que iniciem automaticamente ao ligar o PC. --- ### **4. Configurar o Navegador Firefox** Para usar a rede **Tor** com o Firefox: 1. Abra o Firefox. 2. Acesse **Configurações** → **Configurar conexão**. 3. Selecione **Configuração manual de proxy**. 4. Configure assim: - **Proxy HTTP:** `127.0.0.1` - **Porta:** `8118` (porta padrão do **Privoxy**) - **Domínio SOCKS (v5):** `127.0.0.1` - **Porta:** `9050` 5. Marque a opção **"Usar este proxy também em HTTPS"**. 6. Clique em **OK**. --- ### **5. Verificar a Conexão com o Tor** Abra o navegador e acesse: ```text https://check.torproject.org/ ``` Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta. --- ### **Dicas Extras** - **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores. - Outros aplicativos também podem ser configurados para usar o **Privoxy**.
@ 6be5cc06:5259daf0
2025-01-21 20:58:37A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**. --- ### **1. Instalar o Tor e o Privoxy** Abra o terminal e execute: ```bash sudo apt update sudo apt install tor privoxy ``` **Explicação:** - **Tor:** Roteia o tráfego pela rede Tor. - **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor. --- ### **2. Configurar o Privoxy** Abra o arquivo de configuração do Privoxy: ```bash sudo nano /etc/privoxy/config ``` Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira: ```bash forward-socks5 / 127.0.0.1:9050 . ``` Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**. Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo. --- ### **3. Iniciar o Tor e o Privoxy** Agora, inicie e habilite os serviços: ```bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxy ``` **Explicação:** - **start:** Inicia os serviços. - **enable:** Faz com que iniciem automaticamente ao ligar o PC. --- ### **4. Configurar o Navegador Firefox** Para usar a rede **Tor** com o Firefox: 1. Abra o Firefox. 2. Acesse **Configurações** → **Configurar conexão**. 3. Selecione **Configuração manual de proxy**. 4. Configure assim: - **Proxy HTTP:** `127.0.0.1` - **Porta:** `8118` (porta padrão do **Privoxy**) - **Domínio SOCKS (v5):** `127.0.0.1` - **Porta:** `9050` 5. Marque a opção **"Usar este proxy também em HTTPS"**. 6. Clique em **OK**. --- ### **5. Verificar a Conexão com o Tor** Abra o navegador e acesse: ```text https://check.torproject.org/ ``` Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta. --- ### **Dicas Extras** - **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores. - Outros aplicativos também podem ser configurados para usar o **Privoxy**. @ c631e267:c2b78d3e
2025-01-18 09:34:51*Die grauenvollste Aussicht ist die der Technokratie –* *\ einer kontrollierenden Herrschaft,* *\ die durch verstümmelte und verstümmelnde Geister ausgeübt wird.* *\ Ernst Jünger*   **«Davos ist nicht mehr sexy»,** das Weltwirtschaftsforum ([WEF](https://transition-news.org/wef-world-economic-forum)) mache Davos [kaputt](https://web.archive.org/web/20250116114956/https://www.handelszeitung.ch/wef-2025/wie-das-wef-davos-kaputt-macht-785098), diese Aussagen eines Einheimischen las ich kürzlich in der *Handelszeitung*. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher. **Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen** dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den [vergangenen](https://transition-news.org/die-angst-der-eliten-vor-dem-pobel) vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten. **Der deutsche WEF-Gründer hatte bei dieser Gelegenheit** immer höchst lobende Worte für seine Landsmännin: [2021](https://www.weforum.org/meetings/the-davos-agenda-2021/sessions/special-address-by-g20-head-of-state-government/) erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und [2022](https://www.weforum.org/meetings/the-davos-agenda-2022/sessions/special-address-by-ursula-von-der-leyen-president-of-the-european-commission-177737c164/) fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist». **Von der Leyens Handeln während der sogenannten Corona-«Pandemie»** lobte Schwab damals bereits ebenso, wie es diese Woche das [Karlspreis](https://transition-news.org/von-der-leyen-erhalt-karlspreis-albert-bourla-erklart-pfizer-habe-wahrend-der)-Direktorium tat, als man der Beschuldigten im Fall [Pfizergate](https://transition-news.org/pfizergate-startet-ins-neue-jahr) die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt. **Jene Herausforderungen durch «Krisen epochalen Ausmaßes»** werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im [Global Risks Report](https://www.zurich.com/knowledge/topics/global-risks/the-global-risks-report-2025) nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen. **Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen** unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz. **Ein** **[«Great Mental Reset»](https://transition-news.org/angriff-auf-unser-gehirn-michael-nehls-uber-den-great-mental-reset-teil-1)** **sei die Voraussetzung dafür,** dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden. **Der aktuelle Zustand unserer Gesellschaften** ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die [Rechtsstaatlichkeit](https://transition-news.org/schweizer-rechtsstaat-in-der-krise-ein-anwalt-schlagt-alarm) stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/davos-europa-und-der-rest-der-welt)*** erschienen.
@ c631e267:c2b78d3e
2025-01-18 09:34:51*Die grauenvollste Aussicht ist die der Technokratie –* *\ einer kontrollierenden Herrschaft,* *\ die durch verstümmelte und verstümmelnde Geister ausgeübt wird.* *\ Ernst Jünger*   **«Davos ist nicht mehr sexy»,** das Weltwirtschaftsforum ([WEF](https://transition-news.org/wef-world-economic-forum)) mache Davos [kaputt](https://web.archive.org/web/20250116114956/https://www.handelszeitung.ch/wef-2025/wie-das-wef-davos-kaputt-macht-785098), diese Aussagen eines Einheimischen las ich kürzlich in der *Handelszeitung*. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher. **Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen** dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den [vergangenen](https://transition-news.org/die-angst-der-eliten-vor-dem-pobel) vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten. **Der deutsche WEF-Gründer hatte bei dieser Gelegenheit** immer höchst lobende Worte für seine Landsmännin: [2021](https://www.weforum.org/meetings/the-davos-agenda-2021/sessions/special-address-by-g20-head-of-state-government/) erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und [2022](https://www.weforum.org/meetings/the-davos-agenda-2022/sessions/special-address-by-ursula-von-der-leyen-president-of-the-european-commission-177737c164/) fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist». **Von der Leyens Handeln während der sogenannten Corona-«Pandemie»** lobte Schwab damals bereits ebenso, wie es diese Woche das [Karlspreis](https://transition-news.org/von-der-leyen-erhalt-karlspreis-albert-bourla-erklart-pfizer-habe-wahrend-der)-Direktorium tat, als man der Beschuldigten im Fall [Pfizergate](https://transition-news.org/pfizergate-startet-ins-neue-jahr) die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt. **Jene Herausforderungen durch «Krisen epochalen Ausmaßes»** werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im [Global Risks Report](https://www.zurich.com/knowledge/topics/global-risks/the-global-risks-report-2025) nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen. **Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen** unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz. **Ein** **[«Great Mental Reset»](https://transition-news.org/angriff-auf-unser-gehirn-michael-nehls-uber-den-great-mental-reset-teil-1)** **sei die Voraussetzung dafür,** dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden. **Der aktuelle Zustand unserer Gesellschaften** ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die [Rechtsstaatlichkeit](https://transition-news.org/schweizer-rechtsstaat-in-der-krise-ein-anwalt-schlagt-alarm) stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/davos-europa-und-der-rest-der-welt)*** erschienen. @ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits. ## Active Compounds The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant ## Antimicrobial Properties **Bacterial Protection** The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance. **Antifungal Effects** It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections. ## Digestive Health Benefits Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms ## Anti-inflammatory and Antioxidant Effects The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions ## Respiratory Support It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function ## Additional Benefits **Skin Health** - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties **Cardiovascular Health** Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health **Pain Management** The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief ## Safety Note While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
@ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits. ## Active Compounds The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant ## Antimicrobial Properties **Bacterial Protection** The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance. **Antifungal Effects** It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections. ## Digestive Health Benefits Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms ## Anti-inflammatory and Antioxidant Effects The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions ## Respiratory Support It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function ## Additional Benefits **Skin Health** - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties **Cardiovascular Health** Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health **Pain Management** The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief ## Safety Note While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications. @ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** | | Pen drive |  | **16Gb** | Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.). --- ## Passo 1: Atualizar o Sistema 🖥️ Primeiro, atualize seu sistema e instale o Tor: ```bash apt update apt install tor ``` --- ## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧 Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo: ```unit [Unit] Description=Nostr Relay Server Service After=network.target [Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure [Install] WantedBy=multi-user.target ``` --- ## Passo 3: Baixar o Binário do Nostr 🚀 Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases). --- ## Passo 4: Criar as Pastas Necessárias 📂 Agora, crie as pastas para o aplicativo e o pendrive: ```bash mkdir -p /opt/nrs /mnt/edriver ``` --- ## Passo 5: Listar os Dispositivos Conectados 🔌 Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados: ```bash lsblk ``` --- ## Passo 6: Formatando o Pendrive 💾 Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o: ```bash mkfs.vfat /dev/sda ``` --- ## Passo 7: Montar o Pendrive 💻 Monte o pendrive na pasta `/mnt/edriver`: ```bash mount /dev/sda /mnt/edriver ``` --- ## Passo 8: Verificar UUID dos Dispositivos 📋 Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados: ```bash blkid ``` --- ## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝 Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim: ```fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0 ``` --- ## Passo 10: Copiar o Binário para a Pasta Correta 📥 Agora, copie o binário baixado para a pasta `/opt/nrs`: ```bash cp nrs-arm64 /opt/nrs ``` --- ## Passo 11: Criar o Arquivo de Configuração 🛠️ Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`: ```yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true ``` --- ## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️ Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`: ```bash cp nrs.service /etc/systemd/system/ ``` Recarregue os serviços e inicie o serviço `nrs`: ```bash systemctl daemon-reload systemctl enable --now nrs.service ``` --- ## Passo 13: Configurar o Tor 🌐 Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha: ```torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334 ``` --- ## Passo 14: Habilitar e Iniciar o Tor 🧅 Agora, ative e inicie o serviço Tor: ```bash systemctl enable --now tor.service ``` O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`. --- ## Observações ⚠️ - Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi. - O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`. --- Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳 Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** | | Pen drive |  | **16Gb** | Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.). --- ## Passo 1: Atualizar o Sistema 🖥️ Primeiro, atualize seu sistema e instale o Tor: ```bash apt update apt install tor ``` --- ## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧 Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo: ```unit [Unit] Description=Nostr Relay Server Service After=network.target [Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure [Install] WantedBy=multi-user.target ``` --- ## Passo 3: Baixar o Binário do Nostr 🚀 Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases). --- ## Passo 4: Criar as Pastas Necessárias 📂 Agora, crie as pastas para o aplicativo e o pendrive: ```bash mkdir -p /opt/nrs /mnt/edriver ``` --- ## Passo 5: Listar os Dispositivos Conectados 🔌 Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados: ```bash lsblk ``` --- ## Passo 6: Formatando o Pendrive 💾 Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o: ```bash mkfs.vfat /dev/sda ``` --- ## Passo 7: Montar o Pendrive 💻 Monte o pendrive na pasta `/mnt/edriver`: ```bash mount /dev/sda /mnt/edriver ``` --- ## Passo 8: Verificar UUID dos Dispositivos 📋 Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados: ```bash blkid ``` --- ## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝 Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim: ```fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0 ``` --- ## Passo 10: Copiar o Binário para a Pasta Correta 📥 Agora, copie o binário baixado para a pasta `/opt/nrs`: ```bash cp nrs-arm64 /opt/nrs ``` --- ## Passo 11: Criar o Arquivo de Configuração 🛠️ Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`: ```yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true ``` --- ## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️ Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`: ```bash cp nrs.service /etc/systemd/system/ ``` Recarregue os serviços e inicie o serviço `nrs`: ```bash systemctl daemon-reload systemctl enable --now nrs.service ``` --- ## Passo 13: Configurar o Tor 🌐 Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha: ```torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334 ``` --- ## Passo 14: Habilitar e Iniciar o Tor 🧅 Agora, ative e inicie o serviço Tor: ```bash systemctl enable --now tor.service ``` O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`. --- ## Observações ⚠️ - Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi. - O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`. --- Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳 Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos. @ a95c6243:d345522c
2025-01-13 10:09:57*Ich begann, Social Media aufzubauen,* *\ um den Menschen eine Stimme zu geben.* *\ Mark Zuckerberg* **Sind euch auch die Tränen gekommen, als ihr Mark Zuckerbergs** **[Wendehals-Deklaration](https://www.facebook.com/zuck/videos/1525382954801931)** bezüglich der Meinungsfreiheit auf seinen Portalen gehört habt? Rührend, oder? Während er früher die offensichtliche Zensur leugnete und später die Regierung Biden dafür verantwortlich machte, will er nun angeblich «die Zensur auf unseren Plattformen drastisch reduzieren». **«Purer** **[Opportunismus](https://transition-news.org/facebook-grunder-zuckerberg-vom-trump-gegner-zum-trump-buddy-und-anti-zensor)» ob des anstehenden Regierungswechsels wäre als Klassifizierung** viel zu kurz gegriffen. Der jetzige Schachzug des Meta-Chefs ist genauso Teil einer kühl kalkulierten Business-Strategie, wie es die 180 Grad umgekehrte Praxis vorher war. Social Media sind ein höchst lukratives Geschäft. Hinzu kommt vielleicht noch ein bisschen verkorkstes Ego, weil derartig viel Einfluss und Geld sicher auch auf die Psyche schlagen. Verständlich. > «Es ist an der Zeit, zu unseren Wurzeln der freien Meinungsäußerung auf Facebook und Instagram zurückzukehren. Ich begann, Social Media aufzubauen, um den Menschen eine Stimme zu geben», sagte Zuckerberg. **Welche Wurzeln? Hat der Mann vergessen, dass er von der Überwachung,** dem Ausspionieren und dem Ausverkauf sämtlicher Daten und digitaler Spuren sowie der Manipulation seiner «Kunden» lebt? Das ist knallharter Kommerz, nichts anderes. Um freie Meinungsäußerung geht es bei diesem Geschäft ganz sicher nicht, und das war auch noch nie so. Die Wurzeln von Facebook liegen in einem Projekt des US-Militärs mit dem Namen [«LifeLog»](https://norberthaering.de/macht-kontrolle/lifelog/). Dessen Ziel war es, «ein digitales Protokoll vom Leben eines Menschen zu erstellen». **Der Richtungswechsel kommt allerdings nicht überraschend.** Schon Anfang Dezember hatte Meta-Präsident Nick Clegg von «zu hoher Fehlerquote bei der Moderation» von Inhalten [gesprochen](https://www.theverge.com/2024/12/3/24311513/meta-content-moderation-mistakes-nick-clegg). Bei der Gelegenheit erwähnte er auch, dass Mark sehr daran interessiert sei, eine aktive Rolle in den Debatten über eine amerikanische Führungsrolle im technologischen Bereich zu spielen. **Während Milliardärskollege und Big Tech-Konkurrent Elon Musk bereits seinen Posten** in der kommenden Trump-Regierung in Aussicht hat, möchte Zuckerberg also nicht nur seine Haut retten – Trump hatte ihn einmal einen «Feind des Volkes» genannt und ihm lebenslange Haft angedroht –, sondern am liebsten auch mitspielen. KI-Berater ist wohl die gewünschte Funktion, wie man nach einem Treffen Trump-Zuckerberg hörte. An seine [Verhaftung](https://transition-news.org/nicht-telegram-grunder-durow-sondern-zuckerberg-sollte-in-haft-sitzen-wegen-des) dachte vermutlich auch ein weiterer Multimilliardär mit eigener Social Media-Plattform, Pavel Durov, als er Zuckerberg jetzt [kritisierte](https://www.berliner-zeitung.de/news/ende-des-faktenchecks-bei-meta-telegram-gruender-kritisiert-zuckerberg-und-spricht-warnung-aus-li.2287988) und gleichzeitig warnte. **Politik und Systemmedien drehen jedenfalls durch** – was zu viel ist, ist zu viel. Etwas weniger Zensur und mehr Meinungsfreiheit würden die Freiheit der Bürger schwächen und seien potenziell vernichtend für die Menschenrechte. Zuckerberg setze mit dem neuen Kurs die Demokratie aufs Spiel, das sei eine «Einladung zum nächsten [Völkermord](https://archive.is/PYeH0)», ernsthaft. Die Frage sei, ob sich die [EU gegen Musk und Zuckerberg](https://www.handelsblatt.com/politik/international/internet-regulierung-kann-sich-die-eu-gegen-musk-und-zuckerberg-behaupten/100099373.html) behaupten könne, Brüssel müsse jedenfalls hart durchgreifen. **Auch um die** **[Faktenchecker](https://www.welt.de/kultur/medien/article255065352/Metas-Kurswechsel-Zuckerbergs-Entscheidung-und-die-Folgen-fuer-deutsche-Faktenchecker.html)** **macht man sich Sorgen.** Für die deutsche Nachrichtenagentur *dpa* und die «Experten» von *Correctiv*, die (noch) Partner für Fact-Checking-Aktivitäten von Facebook sind, sei das ein «lukratives Geschäftsmodell». Aber möglicherweise werden die Inhalte ohne diese vermeintlichen Korrektoren ja sogar besser. Anders als Meta wollen jedoch Scholz, Faeser und die *Tagesschau* keine Fehler zugeben und zum Beispiel *Correctiv*-[Falschaussagen](https://www.berliner-zeitung.de/politik-gesellschaft/correctiv-falschaussagen-exklusiv-scholz-faeser-und-tagesschau-wollen-sich-fuer-verbreitung-nicht-entschuldigen-li.2288126) einräumen. **Bei derlei dramatischen Befürchtungen wundert es nicht,** dass der öffentliche Plausch auf X zwischen Elon Musk und AfD-Chefin Alice Weidel von 150 EU-Beamten überwacht wurde, falls es irgendwelche Rechtsverstöße geben sollte, die man ihnen ankreiden könnte. Auch der Deutsche Bundestag war wachsam. Gefunden haben dürften sie nichts. Das Ganze war eher eine Show, viel Wind wurde gemacht, aber letztlich gab es nichts als heiße Luft. **Das** **[Anbiedern](https://transition-news.org/who-biedert-sich-bei-trump-an)** **bei Donald Trump ist indes gerade in Mode.** Die Weltgesundheitsorganisation (WHO) tut das auch, denn sie fürchtet um Spenden von über einer Milliarde Dollar. Eventuell könnte ja Elon Musk auch hier künftig aushelfen und der Organisation sowie deren größtem privaten Förderer, Bill Gates, etwas unter die Arme greifen. Nachdem Musks KI-Projekt xAI kürzlich von BlackRock & Co. [sechs Milliarden](https://x.ai/blog/series-c) eingestrichen hat, geht da vielleicht etwas. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/milliardenschwere-wetterfahnchen-und-windmaschinen)*** erschienen.
@ a95c6243:d345522c
2025-01-13 10:09:57*Ich begann, Social Media aufzubauen,* *\ um den Menschen eine Stimme zu geben.* *\ Mark Zuckerberg* **Sind euch auch die Tränen gekommen, als ihr Mark Zuckerbergs** **[Wendehals-Deklaration](https://www.facebook.com/zuck/videos/1525382954801931)** bezüglich der Meinungsfreiheit auf seinen Portalen gehört habt? Rührend, oder? Während er früher die offensichtliche Zensur leugnete und später die Regierung Biden dafür verantwortlich machte, will er nun angeblich «die Zensur auf unseren Plattformen drastisch reduzieren». **«Purer** **[Opportunismus](https://transition-news.org/facebook-grunder-zuckerberg-vom-trump-gegner-zum-trump-buddy-und-anti-zensor)» ob des anstehenden Regierungswechsels wäre als Klassifizierung** viel zu kurz gegriffen. Der jetzige Schachzug des Meta-Chefs ist genauso Teil einer kühl kalkulierten Business-Strategie, wie es die 180 Grad umgekehrte Praxis vorher war. Social Media sind ein höchst lukratives Geschäft. Hinzu kommt vielleicht noch ein bisschen verkorkstes Ego, weil derartig viel Einfluss und Geld sicher auch auf die Psyche schlagen. Verständlich. > «Es ist an der Zeit, zu unseren Wurzeln der freien Meinungsäußerung auf Facebook und Instagram zurückzukehren. Ich begann, Social Media aufzubauen, um den Menschen eine Stimme zu geben», sagte Zuckerberg. **Welche Wurzeln? Hat der Mann vergessen, dass er von der Überwachung,** dem Ausspionieren und dem Ausverkauf sämtlicher Daten und digitaler Spuren sowie der Manipulation seiner «Kunden» lebt? Das ist knallharter Kommerz, nichts anderes. Um freie Meinungsäußerung geht es bei diesem Geschäft ganz sicher nicht, und das war auch noch nie so. Die Wurzeln von Facebook liegen in einem Projekt des US-Militärs mit dem Namen [«LifeLog»](https://norberthaering.de/macht-kontrolle/lifelog/). Dessen Ziel war es, «ein digitales Protokoll vom Leben eines Menschen zu erstellen». **Der Richtungswechsel kommt allerdings nicht überraschend.** Schon Anfang Dezember hatte Meta-Präsident Nick Clegg von «zu hoher Fehlerquote bei der Moderation» von Inhalten [gesprochen](https://www.theverge.com/2024/12/3/24311513/meta-content-moderation-mistakes-nick-clegg). Bei der Gelegenheit erwähnte er auch, dass Mark sehr daran interessiert sei, eine aktive Rolle in den Debatten über eine amerikanische Führungsrolle im technologischen Bereich zu spielen. **Während Milliardärskollege und Big Tech-Konkurrent Elon Musk bereits seinen Posten** in der kommenden Trump-Regierung in Aussicht hat, möchte Zuckerberg also nicht nur seine Haut retten – Trump hatte ihn einmal einen «Feind des Volkes» genannt und ihm lebenslange Haft angedroht –, sondern am liebsten auch mitspielen. KI-Berater ist wohl die gewünschte Funktion, wie man nach einem Treffen Trump-Zuckerberg hörte. An seine [Verhaftung](https://transition-news.org/nicht-telegram-grunder-durow-sondern-zuckerberg-sollte-in-haft-sitzen-wegen-des) dachte vermutlich auch ein weiterer Multimilliardär mit eigener Social Media-Plattform, Pavel Durov, als er Zuckerberg jetzt [kritisierte](https://www.berliner-zeitung.de/news/ende-des-faktenchecks-bei-meta-telegram-gruender-kritisiert-zuckerberg-und-spricht-warnung-aus-li.2287988) und gleichzeitig warnte. **Politik und Systemmedien drehen jedenfalls durch** – was zu viel ist, ist zu viel. Etwas weniger Zensur und mehr Meinungsfreiheit würden die Freiheit der Bürger schwächen und seien potenziell vernichtend für die Menschenrechte. Zuckerberg setze mit dem neuen Kurs die Demokratie aufs Spiel, das sei eine «Einladung zum nächsten [Völkermord](https://archive.is/PYeH0)», ernsthaft. Die Frage sei, ob sich die [EU gegen Musk und Zuckerberg](https://www.handelsblatt.com/politik/international/internet-regulierung-kann-sich-die-eu-gegen-musk-und-zuckerberg-behaupten/100099373.html) behaupten könne, Brüssel müsse jedenfalls hart durchgreifen. **Auch um die** **[Faktenchecker](https://www.welt.de/kultur/medien/article255065352/Metas-Kurswechsel-Zuckerbergs-Entscheidung-und-die-Folgen-fuer-deutsche-Faktenchecker.html)** **macht man sich Sorgen.** Für die deutsche Nachrichtenagentur *dpa* und die «Experten» von *Correctiv*, die (noch) Partner für Fact-Checking-Aktivitäten von Facebook sind, sei das ein «lukratives Geschäftsmodell». Aber möglicherweise werden die Inhalte ohne diese vermeintlichen Korrektoren ja sogar besser. Anders als Meta wollen jedoch Scholz, Faeser und die *Tagesschau* keine Fehler zugeben und zum Beispiel *Correctiv*-[Falschaussagen](https://www.berliner-zeitung.de/politik-gesellschaft/correctiv-falschaussagen-exklusiv-scholz-faeser-und-tagesschau-wollen-sich-fuer-verbreitung-nicht-entschuldigen-li.2288126) einräumen. **Bei derlei dramatischen Befürchtungen wundert es nicht,** dass der öffentliche Plausch auf X zwischen Elon Musk und AfD-Chefin Alice Weidel von 150 EU-Beamten überwacht wurde, falls es irgendwelche Rechtsverstöße geben sollte, die man ihnen ankreiden könnte. Auch der Deutsche Bundestag war wachsam. Gefunden haben dürften sie nichts. Das Ganze war eher eine Show, viel Wind wurde gemacht, aber letztlich gab es nichts als heiße Luft. **Das** **[Anbiedern](https://transition-news.org/who-biedert-sich-bei-trump-an)** **bei Donald Trump ist indes gerade in Mode.** Die Weltgesundheitsorganisation (WHO) tut das auch, denn sie fürchtet um Spenden von über einer Milliarde Dollar. Eventuell könnte ja Elon Musk auch hier künftig aushelfen und der Organisation sowie deren größtem privaten Förderer, Bill Gates, etwas unter die Arme greifen. Nachdem Musks KI-Projekt xAI kürzlich von BlackRock & Co. [sechs Milliarden](https://x.ai/blog/series-c) eingestrichen hat, geht da vielleicht etwas. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/milliardenschwere-wetterfahnchen-und-windmaschinen)*** erschienen. @ 6be5cc06:5259daf0
2025-01-21 01:51:46## Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas. Satoshi Nakamoto satoshin@gmx.com www.bitcoin.org --- ### Resumo O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado **gasto duplo**, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações. As transações são registradas em um livro público chamado **blockchain**, protegido por uma técnica chamada **Prova de Trabalho**. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira. Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu. --- ### 1. Introdução Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em **confiança**. Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável. Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável. O que precisamos é de um **sistema de pagamento eletrônico baseado em provas matemáticas**, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas. Neste documento, apresentamos o **Bitcoin**, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques. --- ### 2. Transações Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital. #### O que é uma assinatura digital? Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso. #### Como funciona na prática? Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário: 1. A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1. 2. Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2. 3. Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda. #### Resolvendo o problema do gasto duplo Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro. O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain. #### Por que isso é importante? Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes. --- ### 3. Servidor Timestamp Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica. Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público. Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain. Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada. O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin. --- ### 4. Prova-de-Trabalho Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente. A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita. Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain. A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos. Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional. --- ### 5. Rede A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são: 1. **Transmissão de Transações**: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la. 2. **Coleta de Transações em Blocos**: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain). 3. **Prova-de-Trabalho**: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil. 4. **Envio do Bloco Resolvido**: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede. 5. **Validação do Bloco**: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos. 6. **Construção do Próximo Bloco**: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia. #### Resolução de Conflitos e Escolha da Cadeia Mais Longa Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia. #### Tolerância a Falhas A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido. Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central. --- ### 6. Incentivo O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação. #### Recompensa por Mineração Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho. #### Taxas de Transação Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo. #### Incentivo à Honestidade O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas: 1. Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos. 2. Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas. A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema. Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo. --- ### 7. Recuperação do Espaço em Disco Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações. Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados. Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados. Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo. --- ### 8. Verificação de Pagamento Simplificada É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada. Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação. A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede. Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável. --- ### 9. Combinando e Dividindo Valor No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor. #### Entradas e Saídas Cada transação no Bitcoin é composta por: - **Entradas**: Representam os valores recebidos em transações anteriores. - **Saídas**: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente. Normalmente, uma transação contém: - Uma única entrada com valor suficiente para cobrir o pagamento. - Ou várias entradas combinadas para atingir o valor necessário. O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como **troco**. #### Exemplo Prático Imagine que você tem duas entradas: 1. 0,03 BTC 2. 0,07 BTC Se deseja enviar 0,08 BTC para alguém, a transação terá: - **Entrada**: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC). - **Saídas**: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC). Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente. #### Difusão e Simplificação A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade. --- ### 10. Privacidade O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando **chaves públicas anônimas**, que desvinculam diretamente as transações das identidades das partes envolvidas. #### Fluxo de Informação - No **modelo tradicional**, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário. - No **Bitcoin**, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não. #### Protegendo a Privacidade Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas: 1. **Chaves Públicas Anônimas**: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único. 2. **Prevenção de Ligação**: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário. #### Riscos de Ligação Embora a privacidade seja fortalecida, alguns riscos permanecem: - Transações **multi-entrada** podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total. - O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas. --- ### 11. Cálculos Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito. Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira. Mas isso é extremamente difícil. #### Como o Ataque Funciona Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido. - Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira. - O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida. Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente. #### A Corrida Entre Cadeias Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos. Suponha que: - A rede honesta tem **80% do poder computacional** (ou seja, resolve 8 de cada 10 quebra-cabeças). - O atacante tem **20% do poder computacional** (ou seja, resolve 2 de cada 10 quebra-cabeças). Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar. #### Por Que o Ataque Fica Cada Vez Mais Improvável? Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos: P = (q/p)^z - **q** é o poder computacional do atacante (20%, ou 0,2). - **p** é o poder computacional da rede honesta (80%, ou 0,8). - **z** é a diferença de blocos entre a cadeia honesta e a cadeia do atacante. Se o atacante está 5 blocos atrás (z = 5): P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%) Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável. Se ele estiver 10 blocos atrás (z = 10): P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%). Neste caso, as chances de sucesso são praticamente **nulas**. #### Um Exemplo Simples Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível. No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática. #### Por Que Tudo Isso é Seguro? - **A probabilidade de sucesso do atacante diminui exponencialmente.** Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema. - **A cadeia verdadeira (honesta) está protegida pela força da rede.** Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar. #### E Se o Atacante Tentar Continuar? O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil. Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso. --- ### 12. Conclusão Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos. --- Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
@ 6be5cc06:5259daf0
2025-01-21 01:51:46## Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas. Satoshi Nakamoto satoshin@gmx.com www.bitcoin.org --- ### Resumo O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado **gasto duplo**, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações. As transações são registradas em um livro público chamado **blockchain**, protegido por uma técnica chamada **Prova de Trabalho**. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira. Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu. --- ### 1. Introdução Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em **confiança**. Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável. Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável. O que precisamos é de um **sistema de pagamento eletrônico baseado em provas matemáticas**, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas. Neste documento, apresentamos o **Bitcoin**, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques. --- ### 2. Transações Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital. #### O que é uma assinatura digital? Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso. #### Como funciona na prática? Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário: 1. A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1. 2. Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2. 3. Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda. #### Resolvendo o problema do gasto duplo Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro. O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain. #### Por que isso é importante? Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes. --- ### 3. Servidor Timestamp Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica. Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público. Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain. Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada. O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin. --- ### 4. Prova-de-Trabalho Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente. A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita. Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain. A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos. Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional. --- ### 5. Rede A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são: 1. **Transmissão de Transações**: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la. 2. **Coleta de Transações em Blocos**: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain). 3. **Prova-de-Trabalho**: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil. 4. **Envio do Bloco Resolvido**: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede. 5. **Validação do Bloco**: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos. 6. **Construção do Próximo Bloco**: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia. #### Resolução de Conflitos e Escolha da Cadeia Mais Longa Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia. #### Tolerância a Falhas A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido. Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central. --- ### 6. Incentivo O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação. #### Recompensa por Mineração Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho. #### Taxas de Transação Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo. #### Incentivo à Honestidade O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas: 1. Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos. 2. Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas. A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema. Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo. --- ### 7. Recuperação do Espaço em Disco Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações. Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados. Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados. Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo. --- ### 8. Verificação de Pagamento Simplificada É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada. Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação. A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede. Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável. --- ### 9. Combinando e Dividindo Valor No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor. #### Entradas e Saídas Cada transação no Bitcoin é composta por: - **Entradas**: Representam os valores recebidos em transações anteriores. - **Saídas**: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente. Normalmente, uma transação contém: - Uma única entrada com valor suficiente para cobrir o pagamento. - Ou várias entradas combinadas para atingir o valor necessário. O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como **troco**. #### Exemplo Prático Imagine que você tem duas entradas: 1. 0,03 BTC 2. 0,07 BTC Se deseja enviar 0,08 BTC para alguém, a transação terá: - **Entrada**: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC). - **Saídas**: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC). Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente. #### Difusão e Simplificação A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade. --- ### 10. Privacidade O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando **chaves públicas anônimas**, que desvinculam diretamente as transações das identidades das partes envolvidas. #### Fluxo de Informação - No **modelo tradicional**, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário. - No **Bitcoin**, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não. #### Protegendo a Privacidade Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas: 1. **Chaves Públicas Anônimas**: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único. 2. **Prevenção de Ligação**: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário. #### Riscos de Ligação Embora a privacidade seja fortalecida, alguns riscos permanecem: - Transações **multi-entrada** podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total. - O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas. --- ### 11. Cálculos Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito. Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira. Mas isso é extremamente difícil. #### Como o Ataque Funciona Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido. - Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira. - O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida. Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente. #### A Corrida Entre Cadeias Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos. Suponha que: - A rede honesta tem **80% do poder computacional** (ou seja, resolve 8 de cada 10 quebra-cabeças). - O atacante tem **20% do poder computacional** (ou seja, resolve 2 de cada 10 quebra-cabeças). Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar. #### Por Que o Ataque Fica Cada Vez Mais Improvável? Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos: P = (q/p)^z - **q** é o poder computacional do atacante (20%, ou 0,2). - **p** é o poder computacional da rede honesta (80%, ou 0,8). - **z** é a diferença de blocos entre a cadeia honesta e a cadeia do atacante. Se o atacante está 5 blocos atrás (z = 5): P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%) Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável. Se ele estiver 10 blocos atrás (z = 10): P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%). Neste caso, as chances de sucesso são praticamente **nulas**. #### Um Exemplo Simples Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível. No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática. #### Por Que Tudo Isso é Seguro? - **A probabilidade de sucesso do atacante diminui exponencialmente.** Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema. - **A cadeia verdadeira (honesta) está protegida pela força da rede.** Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar. #### E Se o Atacante Tentar Continuar? O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil. Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso. --- ### 12. Conclusão Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos. --- Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf @ a95c6243:d345522c
2025-01-03 20:26:47*Was du bist hängt von drei Faktoren ab:* *\ Was du geerbt hast,* *\ was deine Umgebung aus dir machte* *\ und was du in freier Wahl* *\ aus deiner Umgebung und deinem Erbe gemacht hast.* *\ Aldous Huxley* **Das brave Mitmachen und Mitlaufen in einem vorgegebenen, recht engen Rahmen** ist gewiss nicht neu, hat aber gerade wieder mal Konjunktur. Dies kann man deutlich beobachten, eigentlich egal, in welchem gesellschaftlichen Bereich man sich umschaut. Individualität ist nur soweit angesagt, wie sie in ein bestimmtes Schema von «Diversität» passt, und Freiheit verkommt zur Worthülse – nicht erst durch ein gewisses [Buch](https://www.nachdenkseiten.de/?p=126416) einer gewissen ehemaligen Regierungschefin. **Erklärungsansätze für solche Entwicklungen sind bekannt,** und praktisch alle haben etwas mit Massenpsychologie zu tun. Der Herdentrieb, also der Trieb der Menschen, sich – zum Beispiel aus Unsicherheit oder Bequemlichkeit – lieber der Masse anzuschließen als selbstständig zu denken und zu handeln, ist einer der Erklärungsversuche. Andere drehen sich um Macht, Propaganda, Druck und Angst, also den gezielten Einsatz psychologischer [Herrschaftsinstrumente](https://transition-news.org/spip.php?recherche=nudging\&page=recherche_wall). **Aber wollen die Menschen überhaupt Freiheit?** Durch Gespräche im privaten Umfeld bin ich diesbezüglich in der letzten Zeit etwas skeptisch geworden. Um die Jahreswende philosophiert man ja gerne ein wenig über das Erlebte und über die Erwartungen für die Zukunft. Dabei hatte ich hin und wieder den Eindruck, die totalitären Anwandlungen unserer «Repräsentanten» kämen manchen Leuten gerade recht. **«Desinformation» ist so ein brisantes Thema.** Davor müsse man die Menschen doch schützen, hörte ich. Jemand müsse doch zum Beispiel diese ganzen merkwürdigen Inhalte in den Social Media filtern – zur [Ukraine](https://transition-news.org/spip.php?recherche=ukraine\&page=recherche_wall), zum [Klima](https://transition-news.org/spip.php?recherche=klima\&page=recherche_wall), zu [Gesundheitsthemen](https://transition-news.org/spip.php?recherche=impfung\&page=recherche_wall) oder zur [Migration](https://transition-news.org/spip.php?recherche=migration\&page=recherche_wall). Viele wüssten ja gar nicht einzuschätzen, was richtig und was falsch ist, sie bräuchten eine Führung. **Freiheit bedingt Eigenverantwortung, ohne Zweifel.** Eventuell ist es einigen tatsächlich zu anspruchsvoll, die Verantwortung für das eigene Tun und Lassen zu übernehmen. Oder die persönliche Freiheit wird nicht als ausreichend wertvolles Gut angesehen, um sich dafür anzustrengen. In dem Fall wäre die mangelnde Selbstbestimmung wohl das kleinere Übel. Allerdings fehlt dann gemäß Aldous Huxley ein Teil der Persönlichkeit. Letztlich ist natürlich alles eine Frage der Abwägung. **Sind viele Menschen möglicherweise schon so «eingenordet»,** dass freiheitliche Ambitionen gar nicht für eine ganze Gruppe, ein Kollektiv, verfolgt werden können? Solche Gedanken kamen mir auch, als ich mir kürzlich diverse Talks beim viertägigen [Hacker-Kongress](https://transition-news.org/der-38-kongress-des-chaos-computer-clubs-bot-mehr-enthullungen-als-nur-die) des Chaos Computer Clubs (38C3) anschaute. Ich war nicht nur überrascht, sondern reichlich erschreckt angesichts der in weiten Teilen mainstream-geformten Inhalte, mit denen ein dankbares Publikum beglückt wurde. Wo ich allgemein hellere Köpfe erwartet hatte, fand ich Konformismus und enthusiastisch untermauerte Narrative. **Gibt es vielleicht so etwas wie eine Herdenimmunität gegen Indoktrination?** Ich denke, ja, zumindest eine gestärkte Widerstandsfähigkeit. Was wir brauchen, sind etwas gesunder Menschenverstand, offene Informationskanäle und der Mut, sich freier auch zwischen den Herden zu bewegen. Sie tun das bereits, aber sagen Sie es auch dieses Jahr ruhig weiter. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/kann-es-sein-dass-die-menschen-gar-keine-freiheit-wollen)*** erschienen.
@ a95c6243:d345522c
2025-01-03 20:26:47*Was du bist hängt von drei Faktoren ab:* *\ Was du geerbt hast,* *\ was deine Umgebung aus dir machte* *\ und was du in freier Wahl* *\ aus deiner Umgebung und deinem Erbe gemacht hast.* *\ Aldous Huxley* **Das brave Mitmachen und Mitlaufen in einem vorgegebenen, recht engen Rahmen** ist gewiss nicht neu, hat aber gerade wieder mal Konjunktur. Dies kann man deutlich beobachten, eigentlich egal, in welchem gesellschaftlichen Bereich man sich umschaut. Individualität ist nur soweit angesagt, wie sie in ein bestimmtes Schema von «Diversität» passt, und Freiheit verkommt zur Worthülse – nicht erst durch ein gewisses [Buch](https://www.nachdenkseiten.de/?p=126416) einer gewissen ehemaligen Regierungschefin. **Erklärungsansätze für solche Entwicklungen sind bekannt,** und praktisch alle haben etwas mit Massenpsychologie zu tun. Der Herdentrieb, also der Trieb der Menschen, sich – zum Beispiel aus Unsicherheit oder Bequemlichkeit – lieber der Masse anzuschließen als selbstständig zu denken und zu handeln, ist einer der Erklärungsversuche. Andere drehen sich um Macht, Propaganda, Druck und Angst, also den gezielten Einsatz psychologischer [Herrschaftsinstrumente](https://transition-news.org/spip.php?recherche=nudging\&page=recherche_wall). **Aber wollen die Menschen überhaupt Freiheit?** Durch Gespräche im privaten Umfeld bin ich diesbezüglich in der letzten Zeit etwas skeptisch geworden. Um die Jahreswende philosophiert man ja gerne ein wenig über das Erlebte und über die Erwartungen für die Zukunft. Dabei hatte ich hin und wieder den Eindruck, die totalitären Anwandlungen unserer «Repräsentanten» kämen manchen Leuten gerade recht. **«Desinformation» ist so ein brisantes Thema.** Davor müsse man die Menschen doch schützen, hörte ich. Jemand müsse doch zum Beispiel diese ganzen merkwürdigen Inhalte in den Social Media filtern – zur [Ukraine](https://transition-news.org/spip.php?recherche=ukraine\&page=recherche_wall), zum [Klima](https://transition-news.org/spip.php?recherche=klima\&page=recherche_wall), zu [Gesundheitsthemen](https://transition-news.org/spip.php?recherche=impfung\&page=recherche_wall) oder zur [Migration](https://transition-news.org/spip.php?recherche=migration\&page=recherche_wall). Viele wüssten ja gar nicht einzuschätzen, was richtig und was falsch ist, sie bräuchten eine Führung. **Freiheit bedingt Eigenverantwortung, ohne Zweifel.** Eventuell ist es einigen tatsächlich zu anspruchsvoll, die Verantwortung für das eigene Tun und Lassen zu übernehmen. Oder die persönliche Freiheit wird nicht als ausreichend wertvolles Gut angesehen, um sich dafür anzustrengen. In dem Fall wäre die mangelnde Selbstbestimmung wohl das kleinere Übel. Allerdings fehlt dann gemäß Aldous Huxley ein Teil der Persönlichkeit. Letztlich ist natürlich alles eine Frage der Abwägung. **Sind viele Menschen möglicherweise schon so «eingenordet»,** dass freiheitliche Ambitionen gar nicht für eine ganze Gruppe, ein Kollektiv, verfolgt werden können? Solche Gedanken kamen mir auch, als ich mir kürzlich diverse Talks beim viertägigen [Hacker-Kongress](https://transition-news.org/der-38-kongress-des-chaos-computer-clubs-bot-mehr-enthullungen-als-nur-die) des Chaos Computer Clubs (38C3) anschaute. Ich war nicht nur überrascht, sondern reichlich erschreckt angesichts der in weiten Teilen mainstream-geformten Inhalte, mit denen ein dankbares Publikum beglückt wurde. Wo ich allgemein hellere Köpfe erwartet hatte, fand ich Konformismus und enthusiastisch untermauerte Narrative. **Gibt es vielleicht so etwas wie eine Herdenimmunität gegen Indoktrination?** Ich denke, ja, zumindest eine gestärkte Widerstandsfähigkeit. Was wir brauchen, sind etwas gesunder Menschenverstand, offene Informationskanäle und der Mut, sich freier auch zwischen den Herden zu bewegen. Sie tun das bereits, aber sagen Sie es auch dieses Jahr ruhig weiter. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/kann-es-sein-dass-die-menschen-gar-keine-freiheit-wollen)*** erschienen. @ a95c6243:d345522c
2025-01-01 17:39:51**Heute möchte ich ein Gedicht mit euch teilen.** Es handelt sich um eine Ballade des österreichischen Lyrikers Johann Gabriel Seidl aus dem 19. Jahrhundert. Mir sind diese Worte fest in Erinnerung, da meine Mutter sie perfekt rezitieren konnte, auch als die Kräfte schon langsam schwanden. **Dem originalen Titel «Die Uhr»** habe ich für mich immer das Wort «innere» hinzugefügt. Denn der Zeitmesser – hier vermutliche eine Taschenuhr – symbolisiert zwar in dem Kontext das damalige Zeitempfinden und die Umbrüche durch die industrielle Revolution, sozusagen den Zeitgeist und das moderne Leben. Aber der Autor setzt sich philosophisch mit der Zeit auseinander und gibt seinem Werk auch eine klar spirituelle Dimension. **Das Ticken der Uhr und die Momente des Glücks und der Trauer** stehen sinnbildlich für das unaufhaltsame Fortschreiten und die Vergänglichkeit des Lebens. Insofern könnte man bei der Uhr auch an eine Sonnenuhr denken. Der Rhythmus der Ereignisse passt uns vielleicht nicht immer in den Kram. **Was den Takt pocht, ist durchaus auch das Herz,** unser «inneres Uhrwerk». Wenn dieses Meisterwerk einmal stillsteht, ist es unweigerlich um uns geschehen. Hoffentlich können wir dann dankbar sagen: «Ich habe mein Bestes gegeben.» *Ich trage, wo ich gehe, stets eine Uhr bei mir;* \ *Wieviel es geschlagen habe, genau seh ich an ihr.* \ *Es ist ein großer Meister, der künstlich ihr Werk gefügt,* \ *Wenngleich ihr Gang nicht immer dem törichten Wunsche genügt.*   *Ich wollte, sie wäre rascher gegangen an manchem Tag;* *\ Ich wollte, sie hätte manchmal verzögert den raschen Schlag.* *\ In meinen Leiden und Freuden, in Sturm und in der Ruh,* *\ Was immer geschah im Leben, sie pochte den Takt dazu.*   *Sie schlug am Sarge des Vaters, sie schlug an des Freundes Bahr,* *\ Sie schlug am Morgen der Liebe, sie schlug am Traualtar.* *\ Sie schlug an der Wiege des Kindes, sie schlägt, will's Gott, noch oft,* *\ Wenn bessere Tage kommen, wie meine Seele es hofft.*   *Und ward sie auch einmal träger, und drohte zu stocken ihr Lauf,* *\ So zog der Meister immer großmütig sie wieder auf.* *\ Doch stände sie einmal stille, dann wär's um sie geschehn,* *\ Kein andrer, als der sie fügte, bringt die Zerstörte zum Gehn.*   *Dann müßt ich zum Meister wandern, der wohnt am Ende wohl weit,* *\ Wohl draußen, jenseits der Erde, wohl dort in der Ewigkeit!* *\ Dann gäb ich sie ihm zurücke mit dankbar kindlichem Flehn:* *\ Sieh, Herr, ich hab nichts verdorben, sie blieb von selber stehn.*   *Johann Gabriel Seidl (1804-1875)*
@ a95c6243:d345522c
2025-01-01 17:39:51**Heute möchte ich ein Gedicht mit euch teilen.** Es handelt sich um eine Ballade des österreichischen Lyrikers Johann Gabriel Seidl aus dem 19. Jahrhundert. Mir sind diese Worte fest in Erinnerung, da meine Mutter sie perfekt rezitieren konnte, auch als die Kräfte schon langsam schwanden. **Dem originalen Titel «Die Uhr»** habe ich für mich immer das Wort «innere» hinzugefügt. Denn der Zeitmesser – hier vermutliche eine Taschenuhr – symbolisiert zwar in dem Kontext das damalige Zeitempfinden und die Umbrüche durch die industrielle Revolution, sozusagen den Zeitgeist und das moderne Leben. Aber der Autor setzt sich philosophisch mit der Zeit auseinander und gibt seinem Werk auch eine klar spirituelle Dimension. **Das Ticken der Uhr und die Momente des Glücks und der Trauer** stehen sinnbildlich für das unaufhaltsame Fortschreiten und die Vergänglichkeit des Lebens. Insofern könnte man bei der Uhr auch an eine Sonnenuhr denken. Der Rhythmus der Ereignisse passt uns vielleicht nicht immer in den Kram. **Was den Takt pocht, ist durchaus auch das Herz,** unser «inneres Uhrwerk». Wenn dieses Meisterwerk einmal stillsteht, ist es unweigerlich um uns geschehen. Hoffentlich können wir dann dankbar sagen: «Ich habe mein Bestes gegeben.» *Ich trage, wo ich gehe, stets eine Uhr bei mir;* \ *Wieviel es geschlagen habe, genau seh ich an ihr.* \ *Es ist ein großer Meister, der künstlich ihr Werk gefügt,* \ *Wenngleich ihr Gang nicht immer dem törichten Wunsche genügt.*   *Ich wollte, sie wäre rascher gegangen an manchem Tag;* *\ Ich wollte, sie hätte manchmal verzögert den raschen Schlag.* *\ In meinen Leiden und Freuden, in Sturm und in der Ruh,* *\ Was immer geschah im Leben, sie pochte den Takt dazu.*   *Sie schlug am Sarge des Vaters, sie schlug an des Freundes Bahr,* *\ Sie schlug am Morgen der Liebe, sie schlug am Traualtar.* *\ Sie schlug an der Wiege des Kindes, sie schlägt, will's Gott, noch oft,* *\ Wenn bessere Tage kommen, wie meine Seele es hofft.*   *Und ward sie auch einmal träger, und drohte zu stocken ihr Lauf,* *\ So zog der Meister immer großmütig sie wieder auf.* *\ Doch stände sie einmal stille, dann wär's um sie geschehn,* *\ Kein andrer, als der sie fügte, bringt die Zerstörte zum Gehn.*   *Dann müßt ich zum Meister wandern, der wohnt am Ende wohl weit,* *\ Wohl draußen, jenseits der Erde, wohl dort in der Ewigkeit!* *\ Dann gäb ich sie ihm zurücke mit dankbar kindlichem Flehn:* *\ Sieh, Herr, ich hab nichts verdorben, sie blieb von selber stehn.*   *Johann Gabriel Seidl (1804-1875)* @ 6389be64:ef439d32
2025-01-16 15:44:06## Black Locust can grow up to 170 ft tall ## Grows 3-4 ft. per year ## Native to North America ## Cold hardy in zones 3 to 8  ## Firewood - BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal - Since its growth is fast, firewood can be plentiful ## Timber  - Rot resistant due to a naturally produced robinin in the wood - 100 year life span in full soil contact! (better than cedar performance) - Fence posts - Outdoor furniture - Outdoor decking - Sustainable due to its fast growth and spread - Can be coppiced (cut to the ground) - Can be pollarded (cut above ground) - Its dense wood makes durable tool handles, boxes (tool), and furniture - The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak. - A very low rate of expansion and contraction - Hardwood flooring - The highest tensile beam strength of any American tree - The wood is beautiful ## Legume - Nitrogen fixer - Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn - Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]] ## Bees  - The edible flower clusters are also a top food source for honey bees ## Shade Provider  - Its light, airy overstory provides dappled shade - Planted on the west side of a garden it provides relief during the hottest part of the day - (nitrogen provider) - Planted on the west side of a house, its quick growth soon shades that side from the sun ## Wind-break  - Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters ## Fodder - Over 20% crude protein - 4.1 kcal/g of energy - Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
@ 6389be64:ef439d32
2025-01-16 15:44:06## Black Locust can grow up to 170 ft tall ## Grows 3-4 ft. per year ## Native to North America ## Cold hardy in zones 3 to 8  ## Firewood - BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal - Since its growth is fast, firewood can be plentiful ## Timber  - Rot resistant due to a naturally produced robinin in the wood - 100 year life span in full soil contact! (better than cedar performance) - Fence posts - Outdoor furniture - Outdoor decking - Sustainable due to its fast growth and spread - Can be coppiced (cut to the ground) - Can be pollarded (cut above ground) - Its dense wood makes durable tool handles, boxes (tool), and furniture - The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak. - A very low rate of expansion and contraction - Hardwood flooring - The highest tensile beam strength of any American tree - The wood is beautiful ## Legume - Nitrogen fixer - Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn - Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]] ## Bees  - The edible flower clusters are also a top food source for honey bees ## Shade Provider  - Its light, airy overstory provides dappled shade - Planted on the west side of a garden it provides relief during the hottest part of the day - (nitrogen provider) - Planted on the west side of a house, its quick growth soon shades that side from the sun ## Wind-break  - Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters ## Fodder - Over 20% crude protein - 4.1 kcal/g of energy - Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043 @ f9cf4e94:96abc355
2024-12-30 19:02:32Na era das grandes navegações, piratas ingleses eram autorizados pelo governo para roubar navios. A única coisa que diferenciava um pirata comum de um corsário é que o último possuía a “Carta do Corso”, que funcionava como um “Alvará para o roubo”, onde o governo Inglês legitimava o roubo de navios por parte dos corsários. É claro, que em troca ele exigia uma parte da espoliação. Bastante similar com a maneira que a Receita Federal atua, não? Na verdade, o caso é ainda pior, pois o governo fica com toda a riqueza espoliada, e apenas repassa um mísero salário para os corsários modernos, os agentes da receita federal. Porém eles “justificam” esse roubo ao chamá-lo de imposto, e isso parece acalmar os ânimos de grande parte da população, mas não de nós. Não é por acaso que 'imposto' é o particípio passado do verbo 'impor'. Ou seja, é aquilo que resulta do cumprimento obrigatório -- e não voluntário -- de todos os cidadãos. Se não for 'imposto' ninguém paga. Nem mesmo seus defensores. Isso mostra o quanto as pessoas realmente apreciam os serviços do estado. Apenas volte um pouco na história: os primeiros pagadores de impostos eram fazendeiros cujos territórios foram invadidos por nômades que pastoreavam seu gado. Esses invasores nômades forçavam os fazendeiros a lhes pagar uma fatia de sua renda em troca de "proteção". O fazendeiro que não concordasse era assassinado. Os nômades perceberam que era muito mais interessante e confortável apenas cobrar uma taxa de proteção em vez de matar o fazendeiro e assumir suas posses. Cobrando uma taxa, eles obtinham o que necessitavam. Já se matassem os fazendeiros, eles teriam de gerenciar por conta própria toda a produção da fazenda. Daí eles entenderam que, ao não assassinarem todos os fazendeiros que encontrassem pelo caminho, poderiam fazer desta prática um modo de vida. Assim nasceu o governo. Não assassinar pessoas foi o primeiro serviço que o governo forneceu. Como temos sorte em ter à nossa disposição esta instituição! Assim, não deixa de ser curioso que algumas pessoas digam que os impostos são pagos basicamente para impedir que aconteça exatamente aquilo que originou a existência do governo. O governo nasceu da extorsão. Os fazendeiros tinham de pagar um "arrego" para seu governo. Caso contrário, eram assassinados. Quem era a real ameaça? O governo. A máfia faz a mesma coisa. Mas existe uma forma de se proteger desses corsários modernos. Atualmente, existe uma propriedade privada que NINGUÉM pode tirar de você, ela é sua até mesmo depois da morte. É claro que estamos falando do Bitcoin. Fazendo as configurações certas, é impossível saber que você tem bitcoin. Nem mesmo o governo americano consegue saber. #brasil #bitcoinbrasil #nostrbrasil #grownostr #bitcoin
@ f9cf4e94:96abc355
2024-12-30 19:02:32Na era das grandes navegações, piratas ingleses eram autorizados pelo governo para roubar navios. A única coisa que diferenciava um pirata comum de um corsário é que o último possuía a “Carta do Corso”, que funcionava como um “Alvará para o roubo”, onde o governo Inglês legitimava o roubo de navios por parte dos corsários. É claro, que em troca ele exigia uma parte da espoliação. Bastante similar com a maneira que a Receita Federal atua, não? Na verdade, o caso é ainda pior, pois o governo fica com toda a riqueza espoliada, e apenas repassa um mísero salário para os corsários modernos, os agentes da receita federal. Porém eles “justificam” esse roubo ao chamá-lo de imposto, e isso parece acalmar os ânimos de grande parte da população, mas não de nós. Não é por acaso que 'imposto' é o particípio passado do verbo 'impor'. Ou seja, é aquilo que resulta do cumprimento obrigatório -- e não voluntário -- de todos os cidadãos. Se não for 'imposto' ninguém paga. Nem mesmo seus defensores. Isso mostra o quanto as pessoas realmente apreciam os serviços do estado. Apenas volte um pouco na história: os primeiros pagadores de impostos eram fazendeiros cujos territórios foram invadidos por nômades que pastoreavam seu gado. Esses invasores nômades forçavam os fazendeiros a lhes pagar uma fatia de sua renda em troca de "proteção". O fazendeiro que não concordasse era assassinado. Os nômades perceberam que era muito mais interessante e confortável apenas cobrar uma taxa de proteção em vez de matar o fazendeiro e assumir suas posses. Cobrando uma taxa, eles obtinham o que necessitavam. Já se matassem os fazendeiros, eles teriam de gerenciar por conta própria toda a produção da fazenda. Daí eles entenderam que, ao não assassinarem todos os fazendeiros que encontrassem pelo caminho, poderiam fazer desta prática um modo de vida. Assim nasceu o governo. Não assassinar pessoas foi o primeiro serviço que o governo forneceu. Como temos sorte em ter à nossa disposição esta instituição! Assim, não deixa de ser curioso que algumas pessoas digam que os impostos são pagos basicamente para impedir que aconteça exatamente aquilo que originou a existência do governo. O governo nasceu da extorsão. Os fazendeiros tinham de pagar um "arrego" para seu governo. Caso contrário, eram assassinados. Quem era a real ameaça? O governo. A máfia faz a mesma coisa. Mas existe uma forma de se proteger desses corsários modernos. Atualmente, existe uma propriedade privada que NINGUÉM pode tirar de você, ela é sua até mesmo depois da morte. É claro que estamos falando do Bitcoin. Fazendo as configurações certas, é impossível saber que você tem bitcoin. Nem mesmo o governo americano consegue saber. #brasil #bitcoinbrasil #nostrbrasil #grownostr #bitcoin @ 6389be64:ef439d32
2025-01-13 21:50:59Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin. I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy. Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing. # Smokey The Bear In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong. Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir! Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working. So, in a world of fire, what does an ally look like and what does it do? # Meet The Forest Walker For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved. Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance. The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment. # The Small Branch Chipper When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system. The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”. A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration. I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible. Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process. # The Gassifier The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification? Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest. Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment. When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products. # Biochar: The Waste Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here. Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process. Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself. The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations. # Wood Vinegar: More Waste Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits. For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality. This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well). # The Internal Combustion Engine Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system. The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget. # CO2 Production For Growth Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure. An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil. The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly. The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees. # The Branch Drones During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest. These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission. The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control. # The Bitcoin Miner Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce? Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500? What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost? # The Mesh Network What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other. Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining? # Back To The Chain Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it. A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many. We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs. But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities. # Sensor Packages ### LiDaR The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns. LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable. Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation. ### pH, Soil Moisture, and Cation Exchange Sensing The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component. ### Weather Data Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present. I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?” # Noise Suppression Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise. It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount. # Fire Safety A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly. # The Wrap How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off. Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity. Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up. What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
@ 6389be64:ef439d32
2025-01-13 21:50:59Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin. I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy. Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing. # Smokey The Bear In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong. Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir! Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working. So, in a world of fire, what does an ally look like and what does it do? # Meet The Forest Walker For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved. Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance. The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment. # The Small Branch Chipper When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system. The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”. A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration. I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible. Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process. # The Gassifier The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification? Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest. Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment. When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products. # Biochar: The Waste Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here. Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process. Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself. The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations. # Wood Vinegar: More Waste Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits. For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality. This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well). # The Internal Combustion Engine Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system. The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget. # CO2 Production For Growth Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure. An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil. The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly. The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees. # The Branch Drones During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest. These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission. The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control. # The Bitcoin Miner Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce? Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500? What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost? # The Mesh Network What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other. Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining? # Back To The Chain Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it. A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many. We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs. But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities. # Sensor Packages ### LiDaR The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns. LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable. Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation. ### pH, Soil Moisture, and Cation Exchange Sensing The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component. ### Weather Data Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present. I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?” # Noise Suppression Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise. It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount. # Fire Safety A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly. # The Wrap How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off. Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity. Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up. What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next. @ a95c6243:d345522c
2024-12-21 09:54:49Falls du beim Lesen des Titels dieses Newsletters unwillkürlich an positive Neuigkeiten aus dem globalen polit-medialen Irrenhaus oder gar aus dem wirtschaftlichen Umfeld gedacht hast, darf ich dich beglückwünschen. Diese Assoziation ist sehr löblich, denn sie weist dich als unverbesserlichen Optimisten aus. Leider muss ich dich diesbezüglich aber enttäuschen. Es geht hier um ein anderes Thema, allerdings sehr wohl ein positives, wie ich finde. Heute ist ein ganz besonderer Tag: die **Wintersonnenwende**. Genau gesagt hat [heute morgen](https://www.timeanddate.de/astronomie/wintersonnenwende) um 10:20 Uhr Mitteleuropäischer Zeit (MEZ) auf der Nordhalbkugel unseres Planeten der astronomische Winter begonnen. Was daran so außergewöhnlich ist? Der kürzeste Tag des Jahres war gestern, seit heute werden die Tage bereits wieder länger! Wir werden also jetzt jeden Tag ein wenig mehr Licht haben. Für mich ist dieses Ereignis immer wieder etwas kurios: **Es beginnt der Winter, aber die Tage werden länger.** Das erscheint mir zunächst wie ein Widerspruch, denn meine spontanen Assoziationen zum Winter sind doch eher Kälte und Dunkelheit, relativ zumindest. Umso erfreulicher ist der emotionale Effekt, wenn dann langsam die Erkenntnis durchsickert: Ab jetzt wird es schon wieder heller! Natürlich ist es kalt im Winter, mancherorts mehr als anderswo. Vielleicht jedoch nicht mehr lange, wenn man den Klimahysterikern glauben wollte. Mindestens letztes Jahr hat Väterchen Frost allerdings gleich zu Beginn seiner Saison – und passenderweise während des globalen Überhitzungsgipfels in Dubai – nochmal richtig mit der Faust auf den Tisch gehauen. Schnee- und Eischaos sind ja eigentlich in der Agenda bereits nicht mehr [vorgesehen](https://web.archive.org/web/20231202175946/https://www.spiegel.de/wissenschaft/mensch/winter-ade-nie-wieder-schnee-a-71456.html). Deswegen war man in Deutschland vermutlich in vorauseilendem Gehorsam schon nicht mehr darauf vorbereitet und wurde glatt [lahmgelegt](https://web.archive.org/web/20231207014311/https://www.dw.com/de/nach-dem-schnee-in-deutschland-und-dem-chaos-am-flughafen-und-bei-der-bahn-ein-winteralptraum/a-67638141). Aber ich schweife ab. Die Aussicht auf nach und nach mehr Licht und damit auch Wärme stimmt mich froh. Den Zusammenhang zwischen beidem merkt man in Andalusien sehr deutlich. Hier, wo die Häuser im Winter arg auskühlen, geht man zum Aufwärmen raus auf die Straße oder auf den Balkon. Die Sonne hat auch im Winter eine erfreuliche Kraft. Und da ist jede Minute Gold wert. Außerdem ist mir vor Jahren so richtig klar geworden, warum mir das südliche Klima so sehr gefällt. Das liegt nämlich nicht nur an der Sonne als solcher, oder der Wärme – das liegt vor allem am Licht. **Ohne Licht keine Farben**, das ist der ebenso simple wie gewaltige Unterschied zwischen einem deprimierenden matschgraubraunen Winter und einem fröhlichen bunten. Ein großes Stück Lebensqualität. Mir gefällt aber auch die **Symbolik dieses Tages**: Licht aus der Dunkelheit, ein Wendepunkt, ein Neuanfang, neue Möglichkeiten, Übergang zu neuer Aktivität. In der winterlichen Stille keimt bereits neue Lebendigkeit. Und zwar in einem Zyklus, das wird immer wieder so geschehen. Ich nehme das gern als ein Stück Motivation, es macht mir Hoffnung und gibt mir Energie.  Übrigens ist parallel am heutigen Tag auf der südlichen Halbkugel Sommeranfang. Genau im entgegengesetzten Rhythmus, sich ergänzend, wie Yin und Yang. Das alles liegt an der Schrägstellung der Erdachse, die ist nämlich um 23,4º zur Umlaufbahn um die Sonne geneigt. Wir erinnern uns, gell? Insofern bleibt eindeutig festzuhalten, dass “**schräg sein**” ein willkommener, wichtiger und positiver Wert ist. Mit [anderen](https://www.dwds.de/wb/schr%C3%A4g) Worten: auch ungewöhnlich, eigenartig, untypisch, wunderlich, kauzig, … ja sogar irre, spinnert oder gar “quer” ist in Ordnung. Das schließt das Denken mit ein. **In diesem Sinne wünsche ich euch allen urige Weihnachtstage!** *** Dieser Beitrag ist letztes Jahr in meiner *[Denkbar](https://denkbar.substack.com/p/ab-jetzt-gehts-bergauf)* erschienen.
@ a95c6243:d345522c
2024-12-21 09:54:49Falls du beim Lesen des Titels dieses Newsletters unwillkürlich an positive Neuigkeiten aus dem globalen polit-medialen Irrenhaus oder gar aus dem wirtschaftlichen Umfeld gedacht hast, darf ich dich beglückwünschen. Diese Assoziation ist sehr löblich, denn sie weist dich als unverbesserlichen Optimisten aus. Leider muss ich dich diesbezüglich aber enttäuschen. Es geht hier um ein anderes Thema, allerdings sehr wohl ein positives, wie ich finde. Heute ist ein ganz besonderer Tag: die **Wintersonnenwende**. Genau gesagt hat [heute morgen](https://www.timeanddate.de/astronomie/wintersonnenwende) um 10:20 Uhr Mitteleuropäischer Zeit (MEZ) auf der Nordhalbkugel unseres Planeten der astronomische Winter begonnen. Was daran so außergewöhnlich ist? Der kürzeste Tag des Jahres war gestern, seit heute werden die Tage bereits wieder länger! Wir werden also jetzt jeden Tag ein wenig mehr Licht haben. Für mich ist dieses Ereignis immer wieder etwas kurios: **Es beginnt der Winter, aber die Tage werden länger.** Das erscheint mir zunächst wie ein Widerspruch, denn meine spontanen Assoziationen zum Winter sind doch eher Kälte und Dunkelheit, relativ zumindest. Umso erfreulicher ist der emotionale Effekt, wenn dann langsam die Erkenntnis durchsickert: Ab jetzt wird es schon wieder heller! Natürlich ist es kalt im Winter, mancherorts mehr als anderswo. Vielleicht jedoch nicht mehr lange, wenn man den Klimahysterikern glauben wollte. Mindestens letztes Jahr hat Väterchen Frost allerdings gleich zu Beginn seiner Saison – und passenderweise während des globalen Überhitzungsgipfels in Dubai – nochmal richtig mit der Faust auf den Tisch gehauen. Schnee- und Eischaos sind ja eigentlich in der Agenda bereits nicht mehr [vorgesehen](https://web.archive.org/web/20231202175946/https://www.spiegel.de/wissenschaft/mensch/winter-ade-nie-wieder-schnee-a-71456.html). Deswegen war man in Deutschland vermutlich in vorauseilendem Gehorsam schon nicht mehr darauf vorbereitet und wurde glatt [lahmgelegt](https://web.archive.org/web/20231207014311/https://www.dw.com/de/nach-dem-schnee-in-deutschland-und-dem-chaos-am-flughafen-und-bei-der-bahn-ein-winteralptraum/a-67638141). Aber ich schweife ab. Die Aussicht auf nach und nach mehr Licht und damit auch Wärme stimmt mich froh. Den Zusammenhang zwischen beidem merkt man in Andalusien sehr deutlich. Hier, wo die Häuser im Winter arg auskühlen, geht man zum Aufwärmen raus auf die Straße oder auf den Balkon. Die Sonne hat auch im Winter eine erfreuliche Kraft. Und da ist jede Minute Gold wert. Außerdem ist mir vor Jahren so richtig klar geworden, warum mir das südliche Klima so sehr gefällt. Das liegt nämlich nicht nur an der Sonne als solcher, oder der Wärme – das liegt vor allem am Licht. **Ohne Licht keine Farben**, das ist der ebenso simple wie gewaltige Unterschied zwischen einem deprimierenden matschgraubraunen Winter und einem fröhlichen bunten. Ein großes Stück Lebensqualität. Mir gefällt aber auch die **Symbolik dieses Tages**: Licht aus der Dunkelheit, ein Wendepunkt, ein Neuanfang, neue Möglichkeiten, Übergang zu neuer Aktivität. In der winterlichen Stille keimt bereits neue Lebendigkeit. Und zwar in einem Zyklus, das wird immer wieder so geschehen. Ich nehme das gern als ein Stück Motivation, es macht mir Hoffnung und gibt mir Energie.  Übrigens ist parallel am heutigen Tag auf der südlichen Halbkugel Sommeranfang. Genau im entgegengesetzten Rhythmus, sich ergänzend, wie Yin und Yang. Das alles liegt an der Schrägstellung der Erdachse, die ist nämlich um 23,4º zur Umlaufbahn um die Sonne geneigt. Wir erinnern uns, gell? Insofern bleibt eindeutig festzuhalten, dass “**schräg sein**” ein willkommener, wichtiger und positiver Wert ist. Mit [anderen](https://www.dwds.de/wb/schr%C3%A4g) Worten: auch ungewöhnlich, eigenartig, untypisch, wunderlich, kauzig, … ja sogar irre, spinnert oder gar “quer” ist in Ordnung. Das schließt das Denken mit ein. **In diesem Sinne wünsche ich euch allen urige Weihnachtstage!** *** Dieser Beitrag ist letztes Jahr in meiner *[Denkbar](https://denkbar.substack.com/p/ab-jetzt-gehts-bergauf)* erschienen. @ a95c6243:d345522c
2024-12-13 19:30:32*Das Betriebsklima ist das einzige Klima,* \ *das du selbst bestimmen kannst.* \ *Anonym* **Eine Strategie zur Anpassung an den Klimawandel** hat das deutsche Bundeskabinett diese Woche [beschlossen](https://www.bundesregierung.de/breg-de/aktuelles/klimaanpassungsstrategie-2024-2324828). Da «Wetterextreme wie die immer häufiger auftretenden Hitzewellen und Starkregenereignisse» oft desaströse Auswirkungen auf Mensch und Umwelt hätten, werde eine Anpassung an die Folgen des Klimawandels immer wichtiger. «Klimaanpassungsstrategie» nennt die Regierung das.  **Für die «Vorsorge vor Klimafolgen» habe man nun erstmals** klare Ziele und messbare Kennzahlen festgelegt. So sei der Erfolg überprüfbar, und das solle zu einer schnelleren Bewältigung der Folgen führen. Dass sich hinter dem Begriff Klimafolgen nicht Folgen des Klimas, sondern wohl «Folgen der globalen Erwärmung» verbergen, erklärt den Interessierten die Wikipedia. Dabei ist das mit der [Erwärmung](https://transition-news.org/studie-ozeane-kuhlen-die-erde-viel-starker-als-gedacht) ja bekanntermaßen so eine Sache. **Die Zunahme schwerer Unwetterereignisse habe gezeigt,** so das Ministerium, wie wichtig eine frühzeitige und effektive Warnung der Bevölkerung sei. Daher solle es eine deutliche Anhebung der Nutzerzahlen der sogenannten Nina-Warn-App geben. **Die** ***ARD*** **spurt wie gewohnt** und setzt die Botschaft zielsicher um. Der Artikel [beginnt](https://www.tagesschau.de/inland/innenpolitik/klima-anpassung-warnapp-100.html) folgendermaßen: > «Die Flut im Ahrtal war ein Schock für das ganze Land. Um künftig besser gegen Extremwetter gewappnet zu sein, hat die Bundesregierung eine neue Strategie zur Klimaanpassung beschlossen. Die Warn-App Nina spielt eine zentrale Rolle. Der Bund will die Menschen in Deutschland besser vor Extremwetter-Ereignissen warnen und dafür die Reichweite der Warn-App Nina deutlich erhöhen.» **Die Kommunen würden bei ihren «Klimaanpassungsmaßnahmen»** vom Zentrum KlimaAnpassung [unterstützt](https://zentrum-klimaanpassung.de/ueber-uns), schreibt das Umweltministerium. Mit dessen Aufbau wurden das Deutsche Institut für Urbanistik gGmbH, welches sich stark für [Smart City-Projekte](https://difu.de/taxonomy/term/2083) engagiert, und die Adelphi Consult GmbH beauftragt. **Adelphi** **[beschreibt](https://adelphi.de/de)** **sich selbst als «Europas führender Think-and-Do-Tank** und eine unabhängige Beratung für Klima, Umwelt und Entwicklung». Sie seien «global vernetzte Strateg\*innen und weltverbessernde Berater\*innen» und als «Vorreiter der sozial-ökologischen Transformation» sei man mit dem Deutschen Nachhaltigkeitspreis ausgezeichnet worden, welcher sich an den Zielen der Agenda 2030 orientiere. **Über die** **[Warn-App](https://www.bbk.bund.de/DE/Warnung-Vorsorge/Warn-App-NINA/warn-app-nina_node.html)** **mit dem niedlichen Namen Nina,** die möglichst jeder auf seinem Smartphone installieren soll, informiert das Bundesamt für Bevölkerungsschutz und Katastrophenhilfe (BBK). Gewarnt wird nicht nur vor Extrem-Wetterereignissen, sondern zum Beispiel auch vor Waffengewalt und Angriffen, Strom- und anderen Versorgungsausfällen oder Krankheitserregern. Wenn man die Kategorie Gefahreninformation wählt, erhält man eine Dosis von ungefähr zwei Benachrichtigungen pro Woche. **Beim BBK erfahren wir auch einiges über die empfohlenen** **[Systemeinstellungen](https://www.bbk.bund.de/DE/Warnung-Vorsorge/Warn-App-NINA/Einstellungen-Android/einstellungen-android_node.html)** für Nina. Der Benutzer möge zum Beispiel den Zugriff auf die Standortdaten «immer zulassen», und zwar mit aktivierter Funktion «genauen Standort verwenden». Die Datennutzung solle unbeschränkt sein, auch im Hintergrund. Außerdem sei die uneingeschränkte Akkunutzung zu aktivieren, der Energiesparmodus auszuschalten und das Stoppen der App-Aktivität bei Nichtnutzung zu unterbinden. **Dass man so dramatische Ereignisse wie damals im Ahrtal auch anders bewerten kann** als Regierungen und Systemmedien, hat meine Kollegin Wiltrud Schwetje anhand der Tragödie im spanischen [Valencia](https://transition-news.org/valencia-zehn-tage-nach-der-katastrophe-warten-viele-menschen-immer-noch-auf) gezeigt. Das Stichwort «Agenda 2030» taucht dabei in einem Kontext auf, der wenig mit Nachhaltigkeitspreisen zu tun hat. *** Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/vorsorge-vor-klimafolgen)* erschienen.
@ a95c6243:d345522c
2024-12-13 19:30:32*Das Betriebsklima ist das einzige Klima,* \ *das du selbst bestimmen kannst.* \ *Anonym* **Eine Strategie zur Anpassung an den Klimawandel** hat das deutsche Bundeskabinett diese Woche [beschlossen](https://www.bundesregierung.de/breg-de/aktuelles/klimaanpassungsstrategie-2024-2324828). Da «Wetterextreme wie die immer häufiger auftretenden Hitzewellen und Starkregenereignisse» oft desaströse Auswirkungen auf Mensch und Umwelt hätten, werde eine Anpassung an die Folgen des Klimawandels immer wichtiger. «Klimaanpassungsstrategie» nennt die Regierung das.  **Für die «Vorsorge vor Klimafolgen» habe man nun erstmals** klare Ziele und messbare Kennzahlen festgelegt. So sei der Erfolg überprüfbar, und das solle zu einer schnelleren Bewältigung der Folgen führen. Dass sich hinter dem Begriff Klimafolgen nicht Folgen des Klimas, sondern wohl «Folgen der globalen Erwärmung» verbergen, erklärt den Interessierten die Wikipedia. Dabei ist das mit der [Erwärmung](https://transition-news.org/studie-ozeane-kuhlen-die-erde-viel-starker-als-gedacht) ja bekanntermaßen so eine Sache. **Die Zunahme schwerer Unwetterereignisse habe gezeigt,** so das Ministerium, wie wichtig eine frühzeitige und effektive Warnung der Bevölkerung sei. Daher solle es eine deutliche Anhebung der Nutzerzahlen der sogenannten Nina-Warn-App geben. **Die** ***ARD*** **spurt wie gewohnt** und setzt die Botschaft zielsicher um. Der Artikel [beginnt](https://www.tagesschau.de/inland/innenpolitik/klima-anpassung-warnapp-100.html) folgendermaßen: > «Die Flut im Ahrtal war ein Schock für das ganze Land. Um künftig besser gegen Extremwetter gewappnet zu sein, hat die Bundesregierung eine neue Strategie zur Klimaanpassung beschlossen. Die Warn-App Nina spielt eine zentrale Rolle. Der Bund will die Menschen in Deutschland besser vor Extremwetter-Ereignissen warnen und dafür die Reichweite der Warn-App Nina deutlich erhöhen.» **Die Kommunen würden bei ihren «Klimaanpassungsmaßnahmen»** vom Zentrum KlimaAnpassung [unterstützt](https://zentrum-klimaanpassung.de/ueber-uns), schreibt das Umweltministerium. Mit dessen Aufbau wurden das Deutsche Institut für Urbanistik gGmbH, welches sich stark für [Smart City-Projekte](https://difu.de/taxonomy/term/2083) engagiert, und die Adelphi Consult GmbH beauftragt. **Adelphi** **[beschreibt](https://adelphi.de/de)** **sich selbst als «Europas führender Think-and-Do-Tank** und eine unabhängige Beratung für Klima, Umwelt und Entwicklung». Sie seien «global vernetzte Strateg\*innen und weltverbessernde Berater\*innen» und als «Vorreiter der sozial-ökologischen Transformation» sei man mit dem Deutschen Nachhaltigkeitspreis ausgezeichnet worden, welcher sich an den Zielen der Agenda 2030 orientiere. **Über die** **[Warn-App](https://www.bbk.bund.de/DE/Warnung-Vorsorge/Warn-App-NINA/warn-app-nina_node.html)** **mit dem niedlichen Namen Nina,** die möglichst jeder auf seinem Smartphone installieren soll, informiert das Bundesamt für Bevölkerungsschutz und Katastrophenhilfe (BBK). Gewarnt wird nicht nur vor Extrem-Wetterereignissen, sondern zum Beispiel auch vor Waffengewalt und Angriffen, Strom- und anderen Versorgungsausfällen oder Krankheitserregern. Wenn man die Kategorie Gefahreninformation wählt, erhält man eine Dosis von ungefähr zwei Benachrichtigungen pro Woche. **Beim BBK erfahren wir auch einiges über die empfohlenen** **[Systemeinstellungen](https://www.bbk.bund.de/DE/Warnung-Vorsorge/Warn-App-NINA/Einstellungen-Android/einstellungen-android_node.html)** für Nina. Der Benutzer möge zum Beispiel den Zugriff auf die Standortdaten «immer zulassen», und zwar mit aktivierter Funktion «genauen Standort verwenden». Die Datennutzung solle unbeschränkt sein, auch im Hintergrund. Außerdem sei die uneingeschränkte Akkunutzung zu aktivieren, der Energiesparmodus auszuschalten und das Stoppen der App-Aktivität bei Nichtnutzung zu unterbinden. **Dass man so dramatische Ereignisse wie damals im Ahrtal auch anders bewerten kann** als Regierungen und Systemmedien, hat meine Kollegin Wiltrud Schwetje anhand der Tragödie im spanischen [Valencia](https://transition-news.org/valencia-zehn-tage-nach-der-katastrophe-warten-viele-menschen-immer-noch-auf) gezeigt. Das Stichwort «Agenda 2030» taucht dabei in einem Kontext auf, der wenig mit Nachhaltigkeitspreisen zu tun hat. *** Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/vorsorge-vor-klimafolgen)* erschienen. @ 592295cf:413a0db9
2024-12-07 07:21:39Week 02-11 - Nsite zap by hzrd149 [Support page](https://npub1wyuh3scfgzqmxn709a2fzuemps389rxnk7nfgege6s847zze3tuqfl87ez.nsite.lol/#/support) ## Content creator want more users. They can go to Bluesky. Great that Nostr is a Echo Chambers. As stated by Rabble during NostRiga, Nostr is a bitcoin meetup. And it is very difficult as said several times, to subvert this fact. It seems that many bitcoiners don't like this, but they can't do anything, leave Nostr and migrate to other lids. ## I'm reading Nostr adventar calendar of Japanese Nostr users. The first two Don and Jun speak of a Mahjong game and the other of how possibly to count the followers of a given account, countfollowed. - [Adventar calendar](https://adventar.org/calendars/10004) continue until Christmas 🎅 - Even Bluesky is looking at MLS , is not a soccer league, is a protocol for message by groups, "circles" [Post on Bluesky](https://bsky.app/profile/soatok.bsky.social/post/3lc4gt4mywc2z) - Relays chakany is introduce sunday. [link](https://relay.chakany.systems/) I've never seen such dead animals as in Nostr. Something reminds me facebook. The carnivore folks ## Hivemind podcast by Max, the kilometric comment on fountain under the podcast is the most appetizing thing of all. Just one comment, little one. He interviewed Kagi's and searched for a brownie pill, perhaps caused a little headache. ( Brownie pill is orange plus purple) ----------- Loss dog on Nostr this week 😔😔 Pam and Derek family dog conspiracy theory: Fiatjaf was the reply guy!!! I tried to download voyage, from zapstore but nothing does not work even the 17.1 does not go. Too bad. I hear so much about notedeck that I want to make a notedeck do it yourself. Cherry tree, stuck hzrd149 is making an app a day, Chunked blobs on blossom. A like is used to send your writing Relays Announcement of a possible wallet in Damus, this could make things better, zap and whatnot. ----------- - Or I'm posting a song here, a musical interlude. [song on wavlake](https://wavlake.com/album/87dfa3dc-b921-4a4b-8bfc-f60479cec364) ----------- There seems to be a good buzz on Nostr, maybe it's already a Christmassy atmosphere. - Backup di Bluesky cool things [Bluesky post](https://bsky.app/profile/filippo.abyssdomain.expert/post/3lcfdsv2hec2a) ----------- On another rssfeed thing. nostr:nevent1qvzqqqqqqypzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqs93j2remdw2pxnctasa9vlsaerrrsl7p5csx5wj88kk0yq977rtdqxt7glp ### It's the same thing as following a cross de bridge, but if they do 3 bridge, I say something is wrong. A bot is attached to a Relay. The Relay goes down and so much greetings, then I can look for RSS feeds in my computer without need of Nostr. I can share a particular opml file on Nostr, but I don't know how to do it I asked Fiatjaf but didn't answer it was taken by dichotomie. ### Nip19 really Easy to do filter query. You have events_id pubkey Relay Instead with Nostr:note you only have the event_id. - Sebastix says he has to implement it in his library, discover the latest weekly report. [nostr-php-helper-library](https://nostrver.se/blog/nostr-php-helper-library-90-day-opensats-report-2) ----------- Oh no Pablo has become super Saiyan 🤣 ## There is a way to make a podcast starting from a long text, blog. With artificial intelligence. But then I thought, but if one does not have time could not have the text of the article summarized, perhaps we like generating content. It can be an option, either you read or you listen. But if you do not have time perhaps it is better to just summarize, dear chatgpt summarize this text, done. Essential points and make a thread for the social network and do what you want. - Homemade Traditional Boozy Mincemeat, I didn't even know that existed 🤙 [link to shopstr](https://shopstr.store/listing/b7fbcd4415d50dac4cc2b95cb2e73acea294a7f3040255c6f9b07a9494006b3e) Hodlbod news on bunker burrow nostr:nevent1qqs84na25g6mdelvl0408nnq8m29j5070dm9mvjrzxyc6yrx2udjyuczyztuwzjyxe4x2dwpgken87tna2rdlhpd02 - In case you don't see the note [burrow on github](https://github.com/coracle-social/burrow) Once you have the email what do you do with your encrypted key? No Enterprise user maybe. Rember the article of Hodlbod in "Is Always a political move". ✅ List of artists on Nostr nostr:naddr1qvzqqqr4xqpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqp9qku6tdv96x7unng9grdr - An article for food recipe on Nostr [Article link ](https://yakihonne.com/article/naddr1qvzqqqr4gupzpn0wjs7tkxw9r2uy0fndt4m5xua2na3a9peydw6ekzp8lf0xxaqqqqxnzdenxv6nqwf3xgun2wpkyhpdxx) ### I don't know if they'll ever be there. You can write a recipe book. Or to put recipes on wiki, there doesn't seem to be that attention or that desire. One more relay is always better - Olas has a website 🥊 [Olas app](https://olas.app/) Oh i see cool Hodlbod bot A summary bot nostr:nevent1qqs0v88uc2u3he3lm3mpm5h3gr8cuht5wv9g0tk0x9hzvamgvpdjwvspzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qjlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qu0ltyv That's all!!
@ 592295cf:413a0db9
2024-12-07 07:21:39Week 02-11 - Nsite zap by hzrd149 [Support page](https://npub1wyuh3scfgzqmxn709a2fzuemps389rxnk7nfgege6s847zze3tuqfl87ez.nsite.lol/#/support) ## Content creator want more users. They can go to Bluesky. Great that Nostr is a Echo Chambers. As stated by Rabble during NostRiga, Nostr is a bitcoin meetup. And it is very difficult as said several times, to subvert this fact. It seems that many bitcoiners don't like this, but they can't do anything, leave Nostr and migrate to other lids. ## I'm reading Nostr adventar calendar of Japanese Nostr users. The first two Don and Jun speak of a Mahjong game and the other of how possibly to count the followers of a given account, countfollowed. - [Adventar calendar](https://adventar.org/calendars/10004) continue until Christmas 🎅 - Even Bluesky is looking at MLS , is not a soccer league, is a protocol for message by groups, "circles" [Post on Bluesky](https://bsky.app/profile/soatok.bsky.social/post/3lc4gt4mywc2z) - Relays chakany is introduce sunday. [link](https://relay.chakany.systems/) I've never seen such dead animals as in Nostr. Something reminds me facebook. The carnivore folks ## Hivemind podcast by Max, the kilometric comment on fountain under the podcast is the most appetizing thing of all. Just one comment, little one. He interviewed Kagi's and searched for a brownie pill, perhaps caused a little headache. ( Brownie pill is orange plus purple) ----------- Loss dog on Nostr this week 😔😔 Pam and Derek family dog conspiracy theory: Fiatjaf was the reply guy!!! I tried to download voyage, from zapstore but nothing does not work even the 17.1 does not go. Too bad. I hear so much about notedeck that I want to make a notedeck do it yourself. Cherry tree, stuck hzrd149 is making an app a day, Chunked blobs on blossom. A like is used to send your writing Relays Announcement of a possible wallet in Damus, this could make things better, zap and whatnot. ----------- - Or I'm posting a song here, a musical interlude. [song on wavlake](https://wavlake.com/album/87dfa3dc-b921-4a4b-8bfc-f60479cec364) ----------- There seems to be a good buzz on Nostr, maybe it's already a Christmassy atmosphere. - Backup di Bluesky cool things [Bluesky post](https://bsky.app/profile/filippo.abyssdomain.expert/post/3lcfdsv2hec2a) ----------- On another rssfeed thing. nostr:nevent1qvzqqqqqqypzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqs93j2remdw2pxnctasa9vlsaerrrsl7p5csx5wj88kk0yq977rtdqxt7glp ### It's the same thing as following a cross de bridge, but if they do 3 bridge, I say something is wrong. A bot is attached to a Relay. The Relay goes down and so much greetings, then I can look for RSS feeds in my computer without need of Nostr. I can share a particular opml file on Nostr, but I don't know how to do it I asked Fiatjaf but didn't answer it was taken by dichotomie. ### Nip19 really Easy to do filter query. You have events_id pubkey Relay Instead with Nostr:note you only have the event_id. - Sebastix says he has to implement it in his library, discover the latest weekly report. [nostr-php-helper-library](https://nostrver.se/blog/nostr-php-helper-library-90-day-opensats-report-2) ----------- Oh no Pablo has become super Saiyan 🤣 ## There is a way to make a podcast starting from a long text, blog. With artificial intelligence. But then I thought, but if one does not have time could not have the text of the article summarized, perhaps we like generating content. It can be an option, either you read or you listen. But if you do not have time perhaps it is better to just summarize, dear chatgpt summarize this text, done. Essential points and make a thread for the social network and do what you want. - Homemade Traditional Boozy Mincemeat, I didn't even know that existed 🤙 [link to shopstr](https://shopstr.store/listing/b7fbcd4415d50dac4cc2b95cb2e73acea294a7f3040255c6f9b07a9494006b3e) Hodlbod news on bunker burrow nostr:nevent1qqs84na25g6mdelvl0408nnq8m29j5070dm9mvjrzxyc6yrx2udjyuczyztuwzjyxe4x2dwpgken87tna2rdlhpd02 - In case you don't see the note [burrow on github](https://github.com/coracle-social/burrow) Once you have the email what do you do with your encrypted key? No Enterprise user maybe. Rember the article of Hodlbod in "Is Always a political move". ✅ List of artists on Nostr nostr:naddr1qvzqqqr4xqpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqp9qku6tdv96x7unng9grdr - An article for food recipe on Nostr [Article link ](https://yakihonne.com/article/naddr1qvzqqqr4gupzpn0wjs7tkxw9r2uy0fndt4m5xua2na3a9peydw6ekzp8lf0xxaqqqqxnzdenxv6nqwf3xgun2wpkyhpdxx) ### I don't know if they'll ever be there. You can write a recipe book. Or to put recipes on wiki, there doesn't seem to be that attention or that desire. One more relay is always better - Olas has a website 🥊 [Olas app](https://olas.app/) Oh i see cool Hodlbod bot A summary bot nostr:nevent1qqs0v88uc2u3he3lm3mpm5h3gr8cuht5wv9g0tk0x9hzvamgvpdjwvspzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qjlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qu0ltyv That's all!! @ a95c6243:d345522c
2024-12-06 18:21:15*Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau* **Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen** – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden. **Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen»** den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen [schadet der Psyche](https://transition-news.org/meisterwerk-von-studie-bestatigt-maskentragen-bei-kindern-sinnlos-und-schadlich) und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben [Menschen getötet](https://transition-news.org/lockdowns-und-zensur-haben-menschen-getotet)». **Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft.** Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen [Erfahrungen als Kritikerin](https://transition-news.org/die-coronazeit-hat-mir-gezeigt-wie-die-menschen-manipuliert-werden-konnen) der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit *Transition News*. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften». **Menschen, die aufrichtig andere schützen wollten,** werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter [Heinrich Habig](https://transition-news.org/arzte-mussten-ihr-vergehen-irgendwann-selbst-einsehen), [Bianca Witzschel](https://transition-news.org/anwalt-von-bianca-witzschel-das-ist-eindeutig-eine-politische-justiz) und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat *Transition News* mehrfach berichtet (z.B. [hier](https://transition-news.org/prozess-gegen-walter-weber-kai-kisielinski-fuhrt-mit-argumentationsfeuerwerk) und [hier](https://transition-news.org/prozess-gegen-walter-weber-tschentscher-und-schaade-doch-nicht-vor-gericht)). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie [Alexander Bittner](https://transition-news.org/verweigerung-der-covid-impfung-inhaftierter-bundeswehrsoldat-kundigt) erfahren mussten. [**Die eigentlich Kriminellen**](https://transition-news.org/die-eigentlich-kriminellen-schutzen-sich-vor-der-verantwortung) **schützen sich derweil erfolgreich selber,** nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte [Verbrechen gegen die Menschheit](https://transition-news.org/das-grosste-verbrechen-gegen-die-menschheit)». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn [Hunter](https://transition-news.org/us-steuerbehorde-hat-prasidentschaftswahl-2020-fur-joe-biden-gestohlen) möglicherweise auch [Anthony Fauci begnadigen](https://transition-news.org/wird-biden-auch-fauci-begnadigen) wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte? **Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten** und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken. **Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers [Robert F. Kennedy Jr.](https://transition-news.org/usa-robert-f-kennedy-jr-als-gesundheitsminister-nominiert)** erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens [Călin Georgescu](https://transition-news.org/der-ausgang-der-rumanischen-prasidentschaftswahlen-konnte-mogliche), der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der [Panik im Wertewesten](https://www.euronews.com/2024/12/04/robert-f-kennedy-jr-denies-any-link-with-far-right-romanian-presidential-candidate). **In Rumänien selber gab es gerade einen Paukenschlag:** Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das [Tabu gebrochen](https://tkp.at/2024/12/06/rumaenien-sagt-praesidenten-wahl-ab/), Wahlen zu verbieten, bevor sie etwas ändern können. **Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen** und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: [Zensur](https://transition-news.org/fuhrende-politiker-der-welt-unterzeichnen-neue-zensurerklarung-bei-un)) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden. --- Dieser Beitrag ist zuerst auf [*Transition News*](https://transition-news.org/schutz-wem-schutz-gebuhrt) erschienen.
@ a95c6243:d345522c
2024-12-06 18:21:15*Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau* **Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen** – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden. **Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen»** den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen [schadet der Psyche](https://transition-news.org/meisterwerk-von-studie-bestatigt-maskentragen-bei-kindern-sinnlos-und-schadlich) und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben [Menschen getötet](https://transition-news.org/lockdowns-und-zensur-haben-menschen-getotet)». **Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft.** Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen [Erfahrungen als Kritikerin](https://transition-news.org/die-coronazeit-hat-mir-gezeigt-wie-die-menschen-manipuliert-werden-konnen) der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit *Transition News*. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften». **Menschen, die aufrichtig andere schützen wollten,** werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter [Heinrich Habig](https://transition-news.org/arzte-mussten-ihr-vergehen-irgendwann-selbst-einsehen), [Bianca Witzschel](https://transition-news.org/anwalt-von-bianca-witzschel-das-ist-eindeutig-eine-politische-justiz) und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat *Transition News* mehrfach berichtet (z.B. [hier](https://transition-news.org/prozess-gegen-walter-weber-kai-kisielinski-fuhrt-mit-argumentationsfeuerwerk) und [hier](https://transition-news.org/prozess-gegen-walter-weber-tschentscher-und-schaade-doch-nicht-vor-gericht)). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie [Alexander Bittner](https://transition-news.org/verweigerung-der-covid-impfung-inhaftierter-bundeswehrsoldat-kundigt) erfahren mussten. [**Die eigentlich Kriminellen**](https://transition-news.org/die-eigentlich-kriminellen-schutzen-sich-vor-der-verantwortung) **schützen sich derweil erfolgreich selber,** nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte [Verbrechen gegen die Menschheit](https://transition-news.org/das-grosste-verbrechen-gegen-die-menschheit)». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn [Hunter](https://transition-news.org/us-steuerbehorde-hat-prasidentschaftswahl-2020-fur-joe-biden-gestohlen) möglicherweise auch [Anthony Fauci begnadigen](https://transition-news.org/wird-biden-auch-fauci-begnadigen) wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte? **Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten** und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken. **Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers [Robert F. Kennedy Jr.](https://transition-news.org/usa-robert-f-kennedy-jr-als-gesundheitsminister-nominiert)** erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens [Călin Georgescu](https://transition-news.org/der-ausgang-der-rumanischen-prasidentschaftswahlen-konnte-mogliche), der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der [Panik im Wertewesten](https://www.euronews.com/2024/12/04/robert-f-kennedy-jr-denies-any-link-with-far-right-romanian-presidential-candidate). **In Rumänien selber gab es gerade einen Paukenschlag:** Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das [Tabu gebrochen](https://tkp.at/2024/12/06/rumaenien-sagt-praesidenten-wahl-ab/), Wahlen zu verbieten, bevor sie etwas ändern können. **Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen** und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: [Zensur](https://transition-news.org/fuhrende-politiker-der-welt-unterzeichnen-neue-zensurerklarung-bei-un)) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden. --- Dieser Beitrag ist zuerst auf [*Transition News*](https://transition-news.org/schutz-wem-schutz-gebuhrt) erschienen. @ a95c6243:d345522c
2024-11-29 19:45:43*Konsum ist Therapie. Wolfgang Joop* **Umweltbewusstes Verhalten und verantwortungsvoller Konsum** zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch. **Heute ist also wieder mal «Black Friday»,** falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich. **Warum fallen wir auf derartige Werbetricks herein** und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf. **Gedankenlosigkeit und Maßlosigkeit können besonders bei der [Ernährung](https://transition-news.org/studie-208-millionen-us-amerikaner-sind-als-fettleibig-oder-ubergewichtig) zu ernsten Problemen führen.** Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen. **Kritik am schwarzen Freitag und dem unnötigen Konsum** kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch. **Die EU-Kommission lancierte 2015 den Begriff «Green Friday»** im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das [Pariser Abkommen](https://transition-news.org/cop29-wird-vom-geist-des-noch-kunftigen-us-prasidenten-heimgesucht) unterzeichnet werden sollte. **Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt.** Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des [«Green New Deal»](https://transition-news.org/green-new-deal) verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um [Valencia](https://transition-news.org/flutkatastrophe-in-valencia-die-ungereimtheiten-haufen-sich) dazu sagen? **Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020** eine «[grüne Erholung von Covid-19](https://news.un.org/en/story/2020/12/1079602), um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort. **Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet** – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben. **Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung** nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie [«verantwortungsvolle Risikobereitschaft»](https://transition-news.org/zuruck-zu-2008-grossbritannien-schlagt-lockere-regeln-fur-banker-boni-vor) unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde. --- Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/auch-beim-freitag-ist-es-egal-ob-schwarz-oder-grun)* erschienen.
@ a95c6243:d345522c
2024-11-29 19:45:43*Konsum ist Therapie. Wolfgang Joop* **Umweltbewusstes Verhalten und verantwortungsvoller Konsum** zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch. **Heute ist also wieder mal «Black Friday»,** falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich. **Warum fallen wir auf derartige Werbetricks herein** und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf. **Gedankenlosigkeit und Maßlosigkeit können besonders bei der [Ernährung](https://transition-news.org/studie-208-millionen-us-amerikaner-sind-als-fettleibig-oder-ubergewichtig) zu ernsten Problemen führen.** Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen. **Kritik am schwarzen Freitag und dem unnötigen Konsum** kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch. **Die EU-Kommission lancierte 2015 den Begriff «Green Friday»** im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das [Pariser Abkommen](https://transition-news.org/cop29-wird-vom-geist-des-noch-kunftigen-us-prasidenten-heimgesucht) unterzeichnet werden sollte. **Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt.** Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des [«Green New Deal»](https://transition-news.org/green-new-deal) verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um [Valencia](https://transition-news.org/flutkatastrophe-in-valencia-die-ungereimtheiten-haufen-sich) dazu sagen? **Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020** eine «[grüne Erholung von Covid-19](https://news.un.org/en/story/2020/12/1079602), um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort. **Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet** – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben. **Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung** nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie [«verantwortungsvolle Risikobereitschaft»](https://transition-news.org/zuruck-zu-2008-grossbritannien-schlagt-lockere-regeln-fur-banker-boni-vor) unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde. --- Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/auch-beim-freitag-ist-es-egal-ob-schwarz-oder-grun)* erschienen. @ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity. A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur. The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior. And there are plenty of incentives beyond our direct control\! My son is *also* incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take. ## Why incentives matter A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could **just** do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example: * If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning. * If people would just use the recycling bin, we wouldn’t have such a landfill problem. * If people would just stop being lazy, our team would deliver our project on time. In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally. * The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do. * No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle. * If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.  My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want. If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is. ## Running a company Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions. Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good. What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off. Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning. When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.  Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks\! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money. There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals. Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature. # Moral hazard Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings. What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.  But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I *don’t* turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all. This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as: 1. We’re so habituated to turning off the water that we don’t even consider *not* turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off. 2. Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created. 3. We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?) Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard. A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard. It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend? And since we’re talking about the government already… ## Government moral hazards As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a *huge* number of examples of moral hazards. I decided to cherry-pick a few for this post. The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people? The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet. If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior\! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups. You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”  And here’s the absolute best part of this: I can’t even truly blame either California *or* Wall Street. (I mean, I *do* blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits. There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions. # Non-monetary competition At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home. In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.) Anyway, my professor’s wife had a friend. My professor described in *great* detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas. This is a demonstration of *non-monetary compensation*. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules. The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become *wealthier and whiter*, the exact opposite of their desired outcome. Why would that happen? Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky. She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls. So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites. You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences. ## Bureaucracy These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences. Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings. Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could\! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate. # Government incentivized behavior This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples: * Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to [malinvestment](https://en.wikipedia.org/wiki/Malinvestment) and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience. * Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise. * During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation. * The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen. * Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example). * Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as [high living](https://www.youtube.com/watch?v=ZwNDd2_beTU).) # Conclusion The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives. We can bemoan these realities all we want, but they *are* realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People *should* take advantage of the incentives around them. Because if they don’t, someone else will. (If you want a literary example of that last comment, see the horse in Animal Farm.) How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula: * Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people. * Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them. * And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example. And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining\!
@ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity. A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur. The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior. And there are plenty of incentives beyond our direct control\! My son is *also* incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take. ## Why incentives matter A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could **just** do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example: * If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning. * If people would just use the recycling bin, we wouldn’t have such a landfill problem. * If people would just stop being lazy, our team would deliver our project on time. In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally. * The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do. * No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle. * If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.  My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want. If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is. ## Running a company Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions. Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good. What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off. Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning. When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.  Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks\! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money. There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals. Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature. # Moral hazard Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings. What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.  But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I *don’t* turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all. This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as: 1. We’re so habituated to turning off the water that we don’t even consider *not* turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off. 2. Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created. 3. We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?) Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard. A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard. It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend? And since we’re talking about the government already… ## Government moral hazards As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a *huge* number of examples of moral hazards. I decided to cherry-pick a few for this post. The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people? The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet. If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior\! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups. You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”  And here’s the absolute best part of this: I can’t even truly blame either California *or* Wall Street. (I mean, I *do* blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits. There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions. # Non-monetary competition At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home. In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.) Anyway, my professor’s wife had a friend. My professor described in *great* detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas. This is a demonstration of *non-monetary compensation*. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules. The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become *wealthier and whiter*, the exact opposite of their desired outcome. Why would that happen? Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky. She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls. So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites. You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences. ## Bureaucracy These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences. Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings. Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could\! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate. # Government incentivized behavior This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples: * Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to [malinvestment](https://en.wikipedia.org/wiki/Malinvestment) and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience. * Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise. * During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation. * The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen. * Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example). * Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as [high living](https://www.youtube.com/watch?v=ZwNDd2_beTU).) # Conclusion The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives. We can bemoan these realities all we want, but they *are* realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People *should* take advantage of the incentives around them. Because if they don’t, someone else will. (If you want a literary example of that last comment, see the horse in Animal Farm.) How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula: * Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people. * Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them. * And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example. And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining\! @ a95c6243:d345522c
2024-11-08 20:02:32*Und plötzlich weißt du: Es ist Zeit, etwas Neues zu beginnen und dem Zauber des Anfangs zu vertrauen. Meister Eckhart* **Schwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung,** der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen. **Mit einem bemerkenswerten [Timing](https://transition-news.org/donald-trump-grossmaul-oder-hoffnungstrager) hat die deutsche Regierungskoalition** am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer [Selbsthypnose](https://ansage.org/schwer-traumatisiert-nach-trumps-sieg-dreht-die-politmediale-linksgruene-sekte-durch/) rund um Harris-Hype und Trump-Panik – mit teils erschreckenden [Auswüchsen](https://archive.is/7tDhY). Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu. **Das [Kindergarten](https://www.spiegel.de/politik/deutschland/christian-lindner-auch-die-fdp-will-wieder-einen-eigenen-wirtschaftsgipfel-abhalten-a-a8a4e868-10b1-426e-adb0-e5a6d42f7c46)-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche** war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik [«vorsätzlich herbeigeführt»](https://www.t-online.de/nachrichten/deutschland/innenpolitik/id_100522112/fdp-chef-lindner-und-sein-grundsatzpapier-die-scheidung-von-der-ampel-.html) worden seien. **Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen.** Verkehrs- und [Digitalminister Wissing](https://transition-news.org/raus-aus-der-komfortzone-es-lohnt-sich) trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit [Jörg Kukies](https://norberthaering.de/news/joerg-kukies/) habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring. **Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP,** hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde. **Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können.** Das ging erst kürzlich aus dem diesjährigen [«Freiheitsindex»](https://www.schwaebische.de/politik/forscher-beim-vertrauen-in-staat-und-medien-zerreisst-es-uns-gerade-3034357) hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt. **«Die absolute Mehrheit hat [absolut die Nase voll](https://archive.is/yRxwR)»,** titelte die *Bild* angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort. **Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat,** kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei *Manova*. Und er kenne [Friedrich Merz](https://www.manova.news/artikel/der-kriegsgeile-blackrocker) schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite. **Was also tun? Der Schweizer Verein [«Losdemokratie»](https://zeitpunkt.ch/node/40968) will eine Volksinitiative lancieren,** um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt. **In jedem Fall wird es notwendig sein, unsere Bemühungen um [Freiheit und Selbstbestimmung](https://transition-news.org/alternative-medien-in-der-krise-zensur-kontrollverlust-und-die-suche-nach)** zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien. --- Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/es-kann-nur-besser-werden-aber-wie)* erschienen.
@ a95c6243:d345522c
2024-11-08 20:02:32*Und plötzlich weißt du: Es ist Zeit, etwas Neues zu beginnen und dem Zauber des Anfangs zu vertrauen. Meister Eckhart* **Schwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung,** der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen. **Mit einem bemerkenswerten [Timing](https://transition-news.org/donald-trump-grossmaul-oder-hoffnungstrager) hat die deutsche Regierungskoalition** am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer [Selbsthypnose](https://ansage.org/schwer-traumatisiert-nach-trumps-sieg-dreht-die-politmediale-linksgruene-sekte-durch/) rund um Harris-Hype und Trump-Panik – mit teils erschreckenden [Auswüchsen](https://archive.is/7tDhY). Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu. **Das [Kindergarten](https://www.spiegel.de/politik/deutschland/christian-lindner-auch-die-fdp-will-wieder-einen-eigenen-wirtschaftsgipfel-abhalten-a-a8a4e868-10b1-426e-adb0-e5a6d42f7c46)-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche** war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik [«vorsätzlich herbeigeführt»](https://www.t-online.de/nachrichten/deutschland/innenpolitik/id_100522112/fdp-chef-lindner-und-sein-grundsatzpapier-die-scheidung-von-der-ampel-.html) worden seien. **Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen.** Verkehrs- und [Digitalminister Wissing](https://transition-news.org/raus-aus-der-komfortzone-es-lohnt-sich) trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit [Jörg Kukies](https://norberthaering.de/news/joerg-kukies/) habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring. **Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP,** hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde. **Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können.** Das ging erst kürzlich aus dem diesjährigen [«Freiheitsindex»](https://www.schwaebische.de/politik/forscher-beim-vertrauen-in-staat-und-medien-zerreisst-es-uns-gerade-3034357) hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt. **«Die absolute Mehrheit hat [absolut die Nase voll](https://archive.is/yRxwR)»,** titelte die *Bild* angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort. **Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat,** kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei *Manova*. Und er kenne [Friedrich Merz](https://www.manova.news/artikel/der-kriegsgeile-blackrocker) schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite. **Was also tun? Der Schweizer Verein [«Losdemokratie»](https://zeitpunkt.ch/node/40968) will eine Volksinitiative lancieren,** um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt. **In jedem Fall wird es notwendig sein, unsere Bemühungen um [Freiheit und Selbstbestimmung](https://transition-news.org/alternative-medien-in-der-krise-zensur-kontrollverlust-und-die-suche-nach)** zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien. --- Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/es-kann-nur-besser-werden-aber-wie)* erschienen. @ 3f770d65:7a745b24
2025-01-12 21:03:36I’ve been using Notedeck for several months, starting with its extremely early and experimental alpha versions, all the way to its current, more stable alpha releases. The journey has been fascinating, as I’ve had the privilege of watching it evolve from a concept into a functional and promising tool. In its earliest stages, Notedeck was raw—offering glimpses of its potential but still far from practical for daily use. Even then, the vision behind it was clear: a platform designed to redefine how we interact with Nostr by offering flexibility and power for all users. I'm very bullish on Notedeck. Why? Because Will Casarin is making it! Duh! 😂 Seriously though, if we’re reimagining the web and rebuilding portions of the Internet, it’s important to recognize [the potential of Notedeck](https://damus.io/notedeck/). If Nostr is reimagining the web, then Notedeck is reimagining the Nostr client. Notedeck isn’t just another Nostr app—it’s more a Nostr browser that functions more like an operating system with micro-apps. How cool is that? Much like how Google's Chrome evolved from being a web browser with a task manager into ChromeOS, a full blown operating system, Notedeck aims to transform how we interact with the Nostr. It goes beyond individual apps, offering a foundation for a fully integrated ecosystem built around Nostr. As a Nostr evangelist, I love to scream **INTEROPERABILITY** and tout every application's integrations. Well, Notedeck has the potential to be one of the best platforms to showcase these integrations in entirely new and exciting ways. Do you want an Olas feed of images? Add the media column. Do you want a feed of live video events? Add the zap.stream column. Do you want Nostr Nests or audio chats? Add that column to your Notedeck. Git? Email? Books? Chat and DMs? It's all possible. Not everyone wants a super app though, and that’s okay. As with most things in the Nostr ecosystem, flexibility is key. Notedeck gives users the freedom to choose how they engage with it—whether it’s simply following hashtags or managing straightforward feeds. You'll be able to tailor Notedeck to fit your needs, using it as extensively or minimally as you prefer. Notedeck is designed with a local-first approach, utilizing Nostr content stored directly on your device via the local nostrdb. This will enable a plethora of advanced tools such as search and filtering, the creation of custom feeds, and the ability to develop personalized algorithms across multiple Notedeck micro-applications—all with unparalleled flexibility. Notedeck also supports multicast. Let's geek out for a second. Multicast is a method of communication where data is sent from one source to multiple destinations simultaneously, but only to devices that wish to receive the data. Unlike broadcast, which sends data to all devices on a network, multicast targets specific receivers, reducing network traffic. This is commonly used for efficient data distribution in scenarios like streaming, conferencing, or large-scale data synchronization between devices. > In a local first world where each device holds local copies of your nostr nodes, and each device transparently syncs with each other on the local network, each node becomes a backup. Your data becomes antifragile automatically. When a node goes down it can resync and recover from other nodes. Even if not all nodes have a complete collection, negentropy can pull down only what is needed from each device. All this can be done without internet. > > \-Will Casarin In the context of Notedeck, multicast would allow multiple devices to sync their Nostr nodes with each other over a local network without needing an internet connection. Wild. Notedeck aims to offer full customization too, including the ability to design and share custom skins, much like Winamp. Users will also be able to create personalized columns and, in the future, share their setups with others. This opens the door for power users to craft tailored Nostr experiences, leveraging their expertise in the protocol and applications. By sharing these configurations as "Starter Decks," they can simplify onboarding and showcase the best of Nostr’s ecosystem. Nostr’s “Other Stuff” can often be difficult to discover, use, or understand. Many users doesn't understand or know how to use web browser extensions to login to applications. Let's not even get started with nsecbunkers. Notedeck will address this challenge by providing a native experience that brings these lesser-known applications, tools, and content into a user-friendly and accessible interface, making exploration seamless. However, that doesn't mean Notedeck should disregard power users that want to use nsecbunkers though - hint hint. For anyone interested in watching Nostr be [developed live](https://github.com/damus-io/notedeck), right before your very eyes, Notedeck’s progress serves as a reminder of what’s possible when innovation meets dedication. The current alpha is already demonstrating its ability to handle complex use cases, and I’m excited to see how it continues to grow as it moves toward a full release later this year.
@ 3f770d65:7a745b24
2025-01-12 21:03:36I’ve been using Notedeck for several months, starting with its extremely early and experimental alpha versions, all the way to its current, more stable alpha releases. The journey has been fascinating, as I’ve had the privilege of watching it evolve from a concept into a functional and promising tool. In its earliest stages, Notedeck was raw—offering glimpses of its potential but still far from practical for daily use. Even then, the vision behind it was clear: a platform designed to redefine how we interact with Nostr by offering flexibility and power for all users. I'm very bullish on Notedeck. Why? Because Will Casarin is making it! Duh! 😂 Seriously though, if we’re reimagining the web and rebuilding portions of the Internet, it’s important to recognize [the potential of Notedeck](https://damus.io/notedeck/). If Nostr is reimagining the web, then Notedeck is reimagining the Nostr client. Notedeck isn’t just another Nostr app—it’s more a Nostr browser that functions more like an operating system with micro-apps. How cool is that? Much like how Google's Chrome evolved from being a web browser with a task manager into ChromeOS, a full blown operating system, Notedeck aims to transform how we interact with the Nostr. It goes beyond individual apps, offering a foundation for a fully integrated ecosystem built around Nostr. As a Nostr evangelist, I love to scream **INTEROPERABILITY** and tout every application's integrations. Well, Notedeck has the potential to be one of the best platforms to showcase these integrations in entirely new and exciting ways. Do you want an Olas feed of images? Add the media column. Do you want a feed of live video events? Add the zap.stream column. Do you want Nostr Nests or audio chats? Add that column to your Notedeck. Git? Email? Books? Chat and DMs? It's all possible. Not everyone wants a super app though, and that’s okay. As with most things in the Nostr ecosystem, flexibility is key. Notedeck gives users the freedom to choose how they engage with it—whether it’s simply following hashtags or managing straightforward feeds. You'll be able to tailor Notedeck to fit your needs, using it as extensively or minimally as you prefer. Notedeck is designed with a local-first approach, utilizing Nostr content stored directly on your device via the local nostrdb. This will enable a plethora of advanced tools such as search and filtering, the creation of custom feeds, and the ability to develop personalized algorithms across multiple Notedeck micro-applications—all with unparalleled flexibility. Notedeck also supports multicast. Let's geek out for a second. Multicast is a method of communication where data is sent from one source to multiple destinations simultaneously, but only to devices that wish to receive the data. Unlike broadcast, which sends data to all devices on a network, multicast targets specific receivers, reducing network traffic. This is commonly used for efficient data distribution in scenarios like streaming, conferencing, or large-scale data synchronization between devices. > In a local first world where each device holds local copies of your nostr nodes, and each device transparently syncs with each other on the local network, each node becomes a backup. Your data becomes antifragile automatically. When a node goes down it can resync and recover from other nodes. Even if not all nodes have a complete collection, negentropy can pull down only what is needed from each device. All this can be done without internet. > > \-Will Casarin In the context of Notedeck, multicast would allow multiple devices to sync their Nostr nodes with each other over a local network without needing an internet connection. Wild. Notedeck aims to offer full customization too, including the ability to design and share custom skins, much like Winamp. Users will also be able to create personalized columns and, in the future, share their setups with others. This opens the door for power users to craft tailored Nostr experiences, leveraging their expertise in the protocol and applications. By sharing these configurations as "Starter Decks," they can simplify onboarding and showcase the best of Nostr’s ecosystem. Nostr’s “Other Stuff” can often be difficult to discover, use, or understand. Many users doesn't understand or know how to use web browser extensions to login to applications. Let's not even get started with nsecbunkers. Notedeck will address this challenge by providing a native experience that brings these lesser-known applications, tools, and content into a user-friendly and accessible interface, making exploration seamless. However, that doesn't mean Notedeck should disregard power users that want to use nsecbunkers though - hint hint. For anyone interested in watching Nostr be [developed live](https://github.com/damus-io/notedeck), right before your very eyes, Notedeck’s progress serves as a reminder of what’s possible when innovation meets dedication. The current alpha is already demonstrating its ability to handle complex use cases, and I’m excited to see how it continues to grow as it moves toward a full release later this year. @ a95c6243:d345522c
2024-10-26 12:21:50*Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius* **Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie,** um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden. **Der sächsische Landtag hat gestern die Einsetzung eines [Untersuchungsausschusses](https://transition-news.org/sachsischer-landtag-beschliesst-afd-antrag-zu-corona-untersuchungsausschuss)** zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW. **In den Niederlanden wird [Bill Gates](https://transition-news.org/niederlande-bill-gates-muss-wegen-impfstoffklage-vor-gericht-erscheinen) vor Gericht erscheinen müssen.** Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind. **Mit den mRNA-«Impfstoffen» von [Pfizer/BioNTech](https://transition-news.org/neues-buch-uber-pfizer-offenbart-grosstes-verbrechen-gegen-die-menschheit) befasst sich auch ein neues Buch.** Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte. **Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren** als Verbundnetzwerk [Corona-Solution](https://transition-news.org/online-konferenz-corona-solution-corona-und-modrna-von-toten-lebenden-und) kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. [Gestern](https://www.csmedicus.org/de/aktuelle-konferenz/corona-und-modrna-von-toten-lebenden-und-physik-lernen/2024-10-25/) fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen». **Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß,** dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden. **Der vielfältige Einsatz für Aufklärung und Aufarbeitung** wird sich nicht stummschalten lassen. Nicht einmal der [Zensurmeister der EU](https://transition-news.org/deutschland-ist-der-zensurmeister-der-eu), Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern. **Wo sind die Grenzen der Meinungsfreiheit?** Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder [«Volksverhetzung»](https://transition-news.org/eduard-prols-prozess-geht-in-die-nachste-runde) werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren. --- Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/alles-muss-ans-licht)* erschienen.
@ a95c6243:d345522c
2024-10-26 12:21:50*Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius* **Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie,** um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden. **Der sächsische Landtag hat gestern die Einsetzung eines [Untersuchungsausschusses](https://transition-news.org/sachsischer-landtag-beschliesst-afd-antrag-zu-corona-untersuchungsausschuss)** zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW. **In den Niederlanden wird [Bill Gates](https://transition-news.org/niederlande-bill-gates-muss-wegen-impfstoffklage-vor-gericht-erscheinen) vor Gericht erscheinen müssen.** Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind. **Mit den mRNA-«Impfstoffen» von [Pfizer/BioNTech](https://transition-news.org/neues-buch-uber-pfizer-offenbart-grosstes-verbrechen-gegen-die-menschheit) befasst sich auch ein neues Buch.** Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte. **Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren** als Verbundnetzwerk [Corona-Solution](https://transition-news.org/online-konferenz-corona-solution-corona-und-modrna-von-toten-lebenden-und) kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. [Gestern](https://www.csmedicus.org/de/aktuelle-konferenz/corona-und-modrna-von-toten-lebenden-und-physik-lernen/2024-10-25/) fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen». **Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß,** dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden. **Der vielfältige Einsatz für Aufklärung und Aufarbeitung** wird sich nicht stummschalten lassen. Nicht einmal der [Zensurmeister der EU](https://transition-news.org/deutschland-ist-der-zensurmeister-der-eu), Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern. **Wo sind die Grenzen der Meinungsfreiheit?** Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder [«Volksverhetzung»](https://transition-news.org/eduard-prols-prozess-geht-in-die-nachste-runde) werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren. --- Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/alles-muss-ans-licht)* erschienen. @ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe *Denk Bar*! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt. Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen. Seit dem Start der *Denk Bar* vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. [Damals notierte ich](https://denkbar.substack.com/p/andreas-denk-bar-eroffnet): > «Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.» Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden. Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen [«inneren Totalschaden»](https://denkbar.substack.com/p/innerer-totalschaden) hatte ich mal für unsere Gesellschaften diagnostiziert. Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der [Gleichschaltung](https://denkbar.substack.com/p/warum-trotzdem-dieses-handeln), das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute. Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend. Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns. --- **Danke, dass du diesen Weg mit mir weitergehst!**
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe *Denk Bar*! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt. Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen. Seit dem Start der *Denk Bar* vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. [Damals notierte ich](https://denkbar.substack.com/p/andreas-denk-bar-eroffnet): > «Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.» Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden. Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen [«inneren Totalschaden»](https://denkbar.substack.com/p/innerer-totalschaden) hatte ich mal für unsere Gesellschaften diagnostiziert. Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der [Gleichschaltung](https://denkbar.substack.com/p/warum-trotzdem-dieses-handeln), das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute. Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend. Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns. --- **Danke, dass du diesen Weg mit mir weitergehst!** @ 044da344:073a8a0e
2025-02-19 08:27:37# 1. Public sphere and inverted totalitarianism The three referents in the title require explanation - just like the thesis that their combination conveys in this article. In short: Like every government, the German one wants to steer and control what is said publicly about it and about reality in the country (cf. Meyen 2018). In the Internet age, this only works by cooperating with digital corporations. This liaison is rooted in the knowledge that one’s own scope of action depends on public approval and public legitimation. “Relations of domination” are today more than ever “relations of definition” (Beck 2017: 129, 132). Power is held by those who succeed in placing their interpretation of reality in the public sphere (cf. Havel 1989: 19). This includes fading out or marginalizing everything that could endanger one’s own position – in Germany at the moment, for example, this relates to debates about social inequality, which has reached an all-time high worldwide (cf. Piketty 2020), mass immigration since 2015, the policies surrounding Corona or Russia. In this country, the interest of federal and state governments in presenting their work in a good light encounters a journalism that is committed to journalistic diversity via state press laws, state treaties and professional ethics (cf. Rager/Weber 1992). This means that journalism should allow everyone to have their say – all topics and all perspectives. Horst Pöttker (2001) has described the production of publicity as a “social mandate”. This “mission” is rooted in the pluralism model: In society, there are many and sometimes conflicting opinions and interests, which are initially on an equal footing (the interests of individuals and outsiders as well as those organized in parties or associations). The struggle for compromise and societal agreement relies on the public sphere: “In principle, no social group, not even an individual, but also no object, no topic, no problem may be excluded from it” (Pöttker 1999: 219f.). Phrased in a different way: In complex, differentiated societies, the public sphere is the “last common place where that which concerns everyone can be negotiated.” And even though “no decisions are made” here, acceptance and “collective validity” are impossible without public preparation and public visibility (Stegemann 2021: 16). Essential to this are mainstream media such as the Tagesschau, the Süddeutsche Zeitung or Der Spiegel, which produce a “second, non-consensual reality” - the collective “memory” of society, which must be assumed in all communication. Only the mainstream media spread information “so widely that in the next moment one must assume that it is known to everyone (or that it would be associated with loss of reputation and is therefore not admitted if it was not known)” (Luhmann 1996: 43, 120f.). We use Mainstream media because we want to know what others think they know (especially those who decide about our lives), and because we need to know the defining power relations in order to survive. Who has succeeded in bringing their issues, their perspectives and, above all, their morals to the big stage, and who has no place on that stage? Consequently, whom should I join if I do not want to be isolated (cf. Noelle-Neumann 1980), and whom do I better avoid? The interest of governments in controlling public communication is inextricably linked to propaganda and censorship. Propaganda is defined in this article with Andreas Elter (2005: 19f.) as all attempts by government agencies to convey “a certain, unambiguously colored view of things \[...] and thus to maneuver the public discussion in the desired direction”. This necessarily includes suppressing, delegitimizing, or limiting the scope of all positions “that challenge the dominant narrative and at the same time have the potential for widespread dissemination” (Hofbauer 2022: 7) – censorship. Put another way: Propaganda and censorship are two sides of the same coin. Those who want to impose their “view of things” (Andreas Elter) must fight the competition and, if possible, eliminate it. Censorship is an “instrument of domination to enforce economic interests, political power and cultural hegemony” (Hofbauer 2022: 237). The fact that media research shies away from calling propaganda and censorship by their names when analyzing contemporary Western societies is the result of a systematic deconceptualization. In academic texts, just as in political education, censorship is generally only mentioned when it comes to forms of government that can be described as ‘totalitarian’, ‘dictatorial’ or ‘undemocratic’ - Hitler's Germany, the Soviet Union, Russia, China, North Korea (for an illustration cf. Toyka-Seid/Schneider 2023). “There is \[to be] no censorship”: this sentence from Article 5 of the German constitution describes reality through this lens, as long as there is no censorship authority or even a corresponding ministry. The literary scholar Nikola Roßbach, for example, academic companion of the Temple of Forbidden Books at Documenta 2017, bypasses the terms state, pre-screening, and bans in her definition, but instead uses adjectives that amount to the same thing and absolve Germany of any suspicion: “In my understanding, censorship is a comprehensive, structurally and institutionally anchored control, restriction, or prevention of expression intended for publication or published” (Roßbach 2018: 19). The purpose of this smokescreen is revealed a little later: Roßbach wants to dismiss censorship as a “polemical concept” from the “political circus,” to be heard above all from the “populist side” and from the right (used here in each case synonymous for all those who should not speak out), but also “from right-wing populist leftists”. To make this a “classic case of self-victimization” or even a “cross-front” of anti-democrats (ibid.: 82, 88) falls short, however, if only because “the boundary between what is permitted and what is forbidden” is contingent and consequently “may not be questioned” (Stegemann 2021: 161). Censorship itself automatically becomes a taboo for the censors. Otherwise, they get into justification trouble. This explains, for example, why a phenomenon like “cancel culture” can be relegated to the realm of fable and the debate about it dismissed as a perfidious feint by the already powerful (cf. Daub 2022, Thiele 2021). The flipside has been dealt with in a very similar way. In hegemonic usage, propaganda is now always what others do – Nazis and communists preferably, but also otherwise anyone who can be classified as ‘opponents’ and ‘enemies’ (cf. Arnold 2003). Moreover, the concept of propaganda has long had such a negative connotation that it puts the result before the analysis – one-sided, not legitimate, and apparently effective even if one concedes that people (such as in the GDR at the time) may withdraw from the public sphere and distrust all news in the respective leading media (cf. Fiedler/Meyen 2011: 17f.). Communication studies has forgotten that it was born as propaganda research. Yet it does exactly the same as its inventors, who were commissioned by the government, military and intelligence services in the USA to find out how to get into people’s heads: Psychological warfare. The state and billionaire industry-related foundations (Rockefeller, Ford) paid hundreds of social scientists starting in 1939 to win the battle for public opinion as well. One result: henceforth people spoke of communication rather than propaganda (cf. Simpson 1994, Pooley 2011). This did not change what one was looking for, but it allowed to distinguish one’s own ‘good’ intentions from the ‘bad’ ones of the Germans and later the Soviets or the Russians (cf. Meyen 2021: 63-75). In this way, the terms censorship and propaganda have been turned into a blunt sword. Critics of the media and society can no longer use them, at least in the German-speaking context, without immediately being confronted with the accusation of exaggerating excessively or even playing into the cards of the ‘right-wingers’. In this article, this risk is taken for two reasons. First, everyone can examine the arguments and then decide for themselves whether it is justified to speak of propaganda and censorship in the sense defined above. Second, classics such as Walter Lippmann, Edward Bernays, or even Paul Lazarsfeld and Robert Merton (1948, cf. Zollmann 2019) had no problem at all with calling a spade a spade. Lippmann (2018: 84) knew already one hundred years ago that news are anything but a “mirror of social conditions.” Walter Lippmann dreamed of a government of experts masquerading as popular rule, and for this to happen, it must specifically influence public opinion - via the “images according to which whole groups of people” act (ibid.: 75). His disciple Edward Bernays, a few years later, logically considered propaganda “a perfectly legitimate activity.” Without “public consent,” Bernays wrote in 1928, already in the spirit of medialization research (cf. Meyen et al. 2014), “no major undertaking” can succeed anymore. This consent, Bernays was sure, must and can be organized - by “PR consultants” like him. His definition is consistent with what I advocate in this paper: “Modern propaganda is the steady, consistent effort to shape or create events with the purpose of influencing the public's attitude toward a company, idea, or group” (Bernays 2018: 28-32). Lippmann and Bernays did not live to see the “union of state and corporations” for which Sheldon Wolin (2022: 221) was able to use the label “superpower” in the noughties. Wolin, like Walter Lippmann, considered “democracy” to be a “largely rhetorical function within an increasingly corrupt political system” (which, however, he criticized rather than defended) and spoke instead of a “coalition between the corporations and the state” – an “inverted totalitarianism” which, while using “the authority and resources of the state” as it once did in Nazi Germany or the Soviet Union, gains “its dynamism by combining it with other forms of power” (such as the churches) and links the “conventional form of government” with “the system of ‘private’ governance represented by modern corporations.” Somewhat more briefly, “corporate power” is now also political. In the Cold War era, the state and corporations had become “the principal sponsors and coordinators of the forces represented by science and technology,” and thus also the source “for creating and spreading a culture that educates consumers to embrace change and private pleasures while accepting political passivity” (Wolin 2022: 60-63). For Sheldon Wolin, “inverted totalitarianism” is a “new kind of political system” that is “apparently driven by abstract totalizing powers, not by personal domination,” and whose “total power” is harder to detect than Hitler's or Stalin's if only because this system does not need to build camps and does not need to “violently suppress dissent as long as it remains ineffective” (ibid.: 118, 134). Wolin says: For control, it is enough to “create a collective sense of dependency” (ibid.: 192) as well as to use whatever methods of “intimidation and mass manipulation” are available today (ibid.: 56). Inverted totalitarianism then is “collective fear” plus “individual powerlessness.” Job, retirement, health care costs. Plus pressure at the workplace, the stress of everyday life, the constant fuss about some political scandal or other (ibid.: 352). The result is a “society that is used to exchanging new habits for old ones, adapting to rapid changes, uncertainties and social upheavals, and allowing its fate to be determined by distant powers over which it has no influence” (ibid.: 116). Sheldon Wolin largely ignores the mainstream media - just like digital capitalism, which for the doyen of U.S. political science, born in 1922, was at best a pipe dream when he wrote his last major book after 9/11. A good two decades later, the “revolving door between the centers of power on both coasts” (between Washington and Silicon Valley) has become almost proverbial (Zuboff 2018: 150). Personnel are shifted from here to there, balls are passed to each other in election campaigns, and, as will be shown in this paper, they work hand in hand when it comes to retaining the power of definition in the political battles of the present and controlling the “side-effect publics” that address what the mainstream media hide or distort. In the spirit of Sheldon Wolin, Ulrich Beck (2017: 172f.) has spoken of a “risk-averse coalition of progress,” “consisting of experts, industry, the state, political parties, and established mass media,” which can ignore or play off against each other issues such as climate change, nuclear power and financial speculation, genetic manipulation, nanotechnology and reproductive medicine, terrorism, and digital surveillance, as needed in the public debate. O-Ton Beck: “This implies: The politics of invisibility is a first-rate strategy for stabilizing state authority and reproducing the social and political order, for which denying the existence of global risks” matters greatly (ibid.: 134). Beck did not trust the traditional mass media to fulfill the mission of the public sphere, not even in Western states. “The mode of this nationally organized, public form of media power is exclusive, that is: one produces it specifically, one can allow it, suppress it, etc.” (ibid.: 172). With a view to a world at risk, which was his life’s topic of interest, he consequently called for a reform of the definitional relationships, hoping for the Internet – for a public sphere that could not be easily controlled by the powerful, that discussed other topics as well as in a different form than the leading media, and that relied, among other things, on a “countervailing power of independent experts” (ibid.: 146). Ulrich Beck was an optimist. When he wrote his book on the “Metamorphosis of the World” (which was to be his last) in the mid-2010s, the relationship between governments and Google, Twitter and Co. was at best in the dating stage. In the meantime, the marriage has been consummated. We live in a digital corporate state that floods the public with its messages (Propaganda, section 2), exploiting the logic of the new means of dissemination (Interlude: Twitter’s public sphere, section 3) and also making platform operators delete counter-perspectives and opposition figures or make them difficult to find (Censorship, section 4). Part of Beck’s concept of defining power relations is that even within a governing coalition or, thought of more broadly, in “that subterranean network of financial, intelligence, and military interests that guides national policy,” “no matter who happens to be in the White House” (Talbot 2017: 505), there are struggles for interpretive authority. Such battles, which rely on resonance in the journalistic field and are therefore also fought there, explain, for example, why Chancellor Scholz had a significantly worse press than his ministers Baerbock and Habeck in the first months of the Ukraine war (cf. Maurer et al. 2022). # 2. Propaganda Without delving into such differentiations, this section will show what government agencies are doing to win over the public. In addition, it will at least be suggested that these efforts meet with little resistance, and not only because of the alliance with media corporations. For one thing, the balance of power between the propaganda apparatuses and journalism has shifted considerably since the 1990s, and for another, the leading media are now dominated by the same habitus that governs government agencies and corporate headquarters (see Klöckner 2019). There are three ways to “move the public debate in the desired direction.” First, a government can pay (as well as resource and perhaps already train) personnel to feed newsrooms with what they are looking for anyway – exclusive information and images, interlocutors, and material from which news can be made (for example: scientific studies or live access during police operations). This personnel also sits at the trigger when it becomes necessary to use what Edward Herman and Noam Chomsky (1988: 18) called, in German, “flak” - barrages that put everything under fire that could get in the way of the employers. Second, this government can change its own work in such a way that ‘good press’ becomes more likely - via the recruitment of top people suitable for the media, via the events and occasions that Edward Bernays already talked about (a rather harmless example: the central festival for the Day of German Unity, which is held in a different state capital every year and reliably produces coverage), and (less harmlessly) via prioritization that puts public image above everything else and, in case of doubt, even above law and order (cf. Thorbjørnsrud et al. 2014). Third, any government can help it along with money - with direct subsidies, which are always good for a scandal in Austria, for example, and were nevertheless almost introduced in Switzerland in a referendum in February 2022, or with indirect subsidies (advertising, tax breaks, carpooling). The federal government exhausts all of the above possibilities to the hilt. It pays a whole army of propaganda people, creates or shapes events with the help of these people that serve the sole “purpose” of influencing “public attitudes” 2018: 28-32), and pumps money into publishing houses and broadcasters. The first issue alone would deserve an entire essay – partly because it is difficult to separate from the second issue. When resources are reallocated toward public relations, an organization’s performance inevitably becomes more media-savvy – most likely at the expense of the tasks for which ministries or subordinate agencies were originally created. A prime example of this prioritization is the German government’s Press and Information Office, with its more than 500 staff positions and three former top journalists in position of spokesperson (Steffen Hebestreit, Wolfgang Büchner, Christiane Hoffmann). This agency, located in the Chancellor’s Office and thus quite obviously an instrument of power for the head of government, was controversial from the outset (cf. Morcinek 2004), but neither Konrad Adenauer nor his successors allowed themselves to be swayed by public criticism here and thus also promoted, at least indirectly, the creation of parallel departments. In addition to a press office with “33 experts,” the Foreign Office now has a commissioner for strategic communication (Peter Ptassek at the end of 2022), who is assisted by “around 40 staff members” to protect the minister and her actions from slander and, if worst comes to worst, to counter with stories of her own (Meier/Monath 2022). Correspondents exist in every ministry, in every party headquarters, in every state government, and for every politician who moves near the center of power. There is a method to the transfer from the editorial offices to the authorities and staffs, which is represented not only by the three journalists named above but also by their predecessor Steffen Seibert. In this way, politics buys know-how, contacts and goodwill, which is not only fed by the reputation of the former colleagues, but also has to do with the prospect of one day being called to the other side. The departments or people whose names or job titles include terms like public, press, media or marketing are only the obvious part of the propaganda apparatus. Claudia Roth, Minister of State for Culture and Media in the current government coalition, has a budget of 2.39 billion euros in 2023 – four percent more than in 2022. In addition to museums owned by the federal government, film productions and a cultural passport for 18-year-olds, this pot primarily funds projects and programs along government lines. Roth’s agency uses it to finance not only causes for coverage, but also personnel who can and will speak out accordingly. This applies analogously to the many commissioners who have been installed on a full-time or honorary basis at different administrative levels (responsible for issues such as foreigners, integration, discrimination, racism, women, queer, lesbians, gays, disability, anti-Semitism, ziganism, climate, sustainability), who have to justify their existence through mainstream media presence and thus also draw imitations in companies or culture and education. In addition, there are organizations such as the Zentrum Liberale Moderne or the Amadeu Antonio Foundation (tip of an NGO iceberg), which support government narratives with flak (here quite openly called “opponent analysis” or disguised as the fight against hate speech and fake news, right-wing extremism and anti-Semitism). The Zentrum Liberale Moderne, founded in 2017 by Green Party politicians Ralf Fücks and Marieluise Beck, has received nearly 4.5 million euros for a total of 24 projects from 2018 to 2022 (see Lübberding 2022). The federal program “Demokratie Leben!” (“Live Democracy!”), one of the umbrella initiatives for related spending (located in the Federal Ministry of Family Affairs), will cost taxpayers 182 million euros in 2023, 16.5 million euros more than in 2022 and 31.5 million euros more than in 2021. “Measures to strengthen diversity, tolerance and democracy” have a total of 200 million euros dedicated to them in this ministry’s 2023 budget. Money from the budget of the German government’s Press and Information Office will go to the German Atlantic Society (2023: 700,000 euros), the Society for Security Policy (600,000), the Center for Liberal Modernity, the Aspen Institute, the Europa Union and the Progressive Center (500,000 each). In Sheldon Wolin (2022: 147) one can read how it is possible to integrate even scientists and intellectuals “seamlessly into the system” and to prevent dissent without having to “harass” or “discredit” critics. Wolin explains: Through “a combination of government contracts, corporate and foundation funding, joint projects by university and corporate researchers, and wealthy individual donors.” Peter J. Brenner (2022) has spelled out this strategy for Germany, compiling a long list of “institutes for research on democracy and right-wing extremism” that assist “government power” at taxpayer expense in the struggle for “discourse hegemony.” For universities, this flow of money has consequences that go beyond the reinterpretation of terms, rules of language such as gendering, and the prioritization of social problems. Even without insight into the inner workings of universities, it should be clear that legions of scientists are rushing to answer the questions, theories and methods to which the “coalition” of big business and the state (Sheldon Wolin) is devoting its budgets via the EU Commission or the BMBF. A few get their turn, and many others continue without funding, so that the investment is not entirely in vain. Those who win money need proof of success – publications in specialist journals and (either via this detour or interviews) a presence in the mainstream media. Diverting taxpayers’ money to media companies was taboo in post-1945 West Germany (unlike in Austria). In a large and densely populated circulation area with a flourishing economy and without the competing advertising and information channels that developed on the Internet from the 1990s, subscriptions to public authorities and advertisements from ministries or offices also played a minor role. All these parameters changed during the Corona crisis at the latest. More cautiously, the slump in the advertising market and the ubiquity of aid and rescue funds have allowed the media industry in 2020 to push the issue of state support, overturning the taboo of press subsidies. Under the guise of “digital transformation,” 220 million euros were included in the federal supplementary budget this summer, most of which was to be paid out before the end of 2021, tied to circulation. The bigger the newspaper, the more money. This plan died at the end of April 2021 “because of constitutional concerns,” but the main counter-argument was not state neutrality, but distortion of competition. The online platform Krautreporter had threatened to go to court if only print publishers were funded, and also refused to accept reallocating the budget to “Corona emergency aid.” The publishers’ associations reacted “shocked,” spoke of a “medium catastrophe” (Meyen 2021: 166f.) and are now concentrating their lobbying on the issue of local media diversity (“nationwide coverage,” Röper 2022: 302). The sum of 220 million euros would have largely absorbed the slump in the advertising market of the daily press. Sales in this market in 2020: 1.712 billion euros – 367 million less than in 2019. In previous years, the average decline was around 150 million euros (Statista 2023). Public budgets are therefore increasingly attractive to the advertising departments of media groups. In 2021, the German government bought ad space for around 64 million euros as part of its “Corona communication” alone. Television and radio together received 28 million euros in the same period (Thoms 2022). This does not include the Corona and vaccination campaigns of state governments and local authorities, for which the business community in the respective circulation areas was also mobilized in some cases, advertising with a different thematic focus, and everything that corporations and foundations give to publishers beyond conventional promotion in order to advertise specific political goals. In journalism, such efforts meet with little resistance for two reasons. First, the most important media houses in Germany have long been of corporate size and are thus themselves part of the “coalition between the corporations and the state” that constitutes “inverted totalitarianism” in Sheldon Wolin's (2022: 221) terms. The German press landscape is characterized by monopolies and concentration, as well as by a few publishing houses (often family-owned) that not only feed all other channels and otherwise outgrow their core business, but in some cases also sell their editorial services to ‘competitors’ such as Madsack’s Redaktionsnetzwerk Deutschland, which supplies more than 60 regional papers in seven German states (cf. Röper 2022, Ferschli et al. 2019). Public broadcasting is not a counterargument here. With a revenue from contributions of almost nine billion euros a year, ARD and ZDF are among the largest media companies in the world (cf. Hachmeister/Wäscher 2017) – corporations that have to act as corporations and that are closely linked to politics and the state in almost every respect (cf. Mirbach 2023: 128-178, 250-272). And second, journalism in Germany is a socially homogeneous field dominated by the “habitus of the middle class” – “oriented toward conformity,” programmed to “accept power relations” (Klöckner 2019: 33), and closely linked to decision-makers in the state, political parties, and business through social status, educational background, and life situation. The similarity of social position and habitus not infrequently turns into real proximity in everyday life. Contact (press conferences, receptions, travel) creates sympathy and thus often at least understanding (cf. Meyen 2021: 176-198). Uwe Krüger (2016: 105) has coined the word “responsibility conspiracy” for this community of values: Journalists know what is good and what is bad (pretty much the same as what the rulers think is good or bad), and they believe they have influence over people. So reality is “reduced by the parts” that “do not fit the attitude” and what seems to promote the desired goal is emphasized (Meinhardt 2020: 87) – sometimes utilizing information, contacts and material from the propaganda apparatus and sometimes not. # 3. Interlude: Twitter publicity Anyone who wants to steer and control public communication today must submit to the logic of digital platforms. This is especially true of Twitter, a channel that within a few years has become the central point of contact for the most important players in “inverted totalitarianism” and has become an indispensable part of everyday life, especially in the media-political-academic complex, even if some protagonists gave up their accounts in the heated debate about Elon Musk’s takeover in the fall of 2022. In Germany, Twitter has always been a minority phenomenon. Four percent of those over the age of 14, says the ARD/ZDF online study of 2022, use Twitter daily and ten percent at least once a week. This includes those who only read and click now and then for reach. Ten percent. Typically male, most likely under 50 (cf. Koch 2022: 472f.). Even in the U.S., where it is common to follow the greats of film, pop and professional sports, not even one in four adults says they use Twitter. The profile of this bubble: young, affluent, educated (cf. Ungar-Sargon 2021: 104). We also know from the USA that the vast majority of tweets come from a few (cf. Odabaş 2022) – from people who have a mission and the resources to promote it. Companies, government agencies, commissioners, entrepreneurs of themselves, NGOs, activists of every stripe, parties. In the fall 2021 federal election, almost every one of the MPs who ran again, and almost every one of those who were then new MPs, had a Twitter account. Particularly active (in this order): Left, Greens, SPD, FDP. Those elected all follow more or less the same accounts. Tagesschau, Der Spiegel, the government spokesperson, Süddeutsche Zeitung and Die Zeit each have over 60 percent. In addition to the leading media, the news agency dpa and top politicians like Christian Lindner or Annalena Baerbock, the “state satirist” and “head of the authorities” (May 2022: 46) Jan Böhmermann is also very high up in this ranking (see Schmidt 2021). Twitter determines what can be incorporated into the reality of mainstream media – which topics with which voices and with which morals. The use of Twitter and the observation of the trends there determine the everyday work in many editorial offices today. Anyone who wants to enter the professional field today learns, at the latest during their traineeship or at journalism schools, that nothing beats a well-groomed Twitter or (beyond political journalism) TikTok and Instagram brand. Rule of thumb: the more followers, the greater the chance of being commissioned or hired (cf. Ungar-Sargon 2021). The older ones can hardly avoid this trend. Three out of four members of the Federal Press Conference have a Twitter profile – again, mainly the younger ones and thus also those with less professional experience. Journalists who are mentioned by members of parliament in their tweets consider Twitter to be particularly important (cf. Nuernbergk/Schmidt 2020). Robin Alexander, deputy editor-in-chief of the daily newspaper Die Welt, has proudly described how he transforms confidential information into tweets that are then used by politicians to push their perspective with reference to the top journalist (cf. Precht/Welzer 2022: 114f.). Following this pattern, the chancellor’s office organized mainstream media backing for their lockdown policy: Government spokesman Seibert explained the plans to selected journalists prior to talks with the prime ministers of the German states, thus ensuring the necessary public pressure (cf. Ismar 2021). Contemporary journalism must find its topics and views on Twitter also because tight resources and high frequency publication demands make it increasingly rare to get in contact with reality and talk to real people – especially those you don’t usually meet on digital platforms. Such conversations would also be dangerous, because like any brand, a Twitter profile demands consistency. I can’t celebrate Fridays for Future there today and burn Greta Thunberg tomorrow. In the Twitter editorial department, two souls combine who are dependent on each other: the media entrepreneur who encourages his employees to ensure the distribution of his own contributions, and the editor who wants to make his mark and rise even further and therefore always asks first how things look from the very top (cf. Klöckner 2019). Brand management is the opposite of the raving reporter, who first allows himself to be surprised by what he sees, hears and experiences, and then shares his findings with his readers, listeners, viewers. This is another reason why the tweeting journalist already knows the story he wants to tell when the research begins. What’s more, he only sees the stories that resonate with his brand. Conversely, it is hardly possible to get through with criticism of the powerful or even to find journalists who raise fundamental questions even beyond details or animosities. On Twitter, everything that could be said against laws, plans or people is immediately available – published, if you will, by everyone. Journalism has lost the privilege of calling for politicians’ heads and has therefore mutated into their attack dog. The consequences of the Twitterization of journalism go beyond the loss of the function of criticism and control. First, the obvious: Morality is conquering the leading media alongside politics. Twitter is the breeding ground for a journalism that is primarily hung up on “language and symbolism” (Wagenknecht 2021: 26) and on affiliations. Twitter sees every topic through the lens of morality and therefore demands opportunities for identification if one wants attention and thus reach. It’s always about me, the group I want to belong to or the one I reject wholeheartedly. Nothing triggers stronger emotions, nothing gets others to share, like, comment faster. In a nutshell, it’s about team sports. “The game is called: US against THEM” (Precht/Welzer 2022: 110). Twitter also makes measured consideration disappear and with it all differentiation, all questioning, all weighting. All of this doesn’t fit into 280 characters even if you link photos, videos, or text panels (cf. Homburg 2022). The rise of Twitter as the editor-in-chief of the leading media (Ungar-Sargon 2021: 103) and as the pace maker of public discourse is a temptation for all those who have ways and means to govern this channel. Today, Twitter is the place where it is decided what reality is and how we are all to think about it. That is why Twitter is firmly in the hands of the establishment and part of the “coalition” of the state and monopoly corporations to which Sheldon Wolin (2022: 63) has given the name “inverted totalitarianism.” Anyone who did not want to believe how closely the Obama and Biden administrations were and are intertwined with Twitter (cf. Malone 2022) or that the “censorship of the Hunter-Biden laptop affair” and the “unprecedented political intervention” (Hofbauer 2022: 183) against Donald Trump at the beginning of 2021, in which the U.S. president lost his million-strong following in one fell swoop, can be traced back to this network of relationships was proven wrong at the latest by the publication of the “Twitter Files” (cf. Schirrmacher 2023). # 4. Censorship Hannes Hofbauer (2022: 124f.) dates the birth of the censorship regime of the present to November 28, 2008. The EU framework decision of that day was about “the definitional sovereignty over genocide” and thus “de facto” about the bans on discussions and taboos in matters of war and guilt, for example in Yugoslavia or in the successor states of the Soviet Union. In Germany, this topic popped up once again when Section 130 of the Criminal Code (incitement of the people) was amended accordingly at the end of 2022. By the end of the noughties, it had become obvious that the traditional means of propaganda would no longer suffice to maintain interpretive sovereignty. The platforms Xing (launched in 2003), Facebook and Vimeo (2004), YouTube (2005), Twitter (2006) and WhatsApp (2009) were on their way to becoming mass phenomena at the latest after the introduction of the iPhone (2007). This also meant that from now on, alternative interpretations of reality were available to anyone at any time and any place (cf. Vorderer 2015), without professionalism in the processing or the quality of the evidence immediately providing information about which view of things could claim validity. Those who are craving definitional power (such as governments, the EU Commission, or multibillionaires whose position and business also depend on public sympathy) had to start fighting competitive narratives and unwelcome information now at the latest. In addition to legislative initiatives such as the 2008 “Framework on combating certain forms and expressions of racism and xenophobia by means of criminal law” and the EU’s 2022 Digital Services Act, three other ways were explored to achieve this goal. First, control of the Internet was institutionalized – for example, in the “East StratCom Task Force,” established in March 2015 after the “regime change in Ukraine” with the aim of enforcing one’s “own narrative” (Hofbauer 2022: 129), or in the European Digital Media Observatory (EDMO), where academics and fact-checkers have been working together since 2020 (more on these institutions in Section 5). Second, political and economic power have made their alliance public – as can be read, for example, in the “Twitter Files” just mentioned and in the “Code of Conduct against Disinformation” agreed on by the EU and the digital economy in 2018 and renewed with further signatories in 2022. This code obliges platforms to fight “dissenting positions” by all means (Hofbauer 2022: 143, 204). And third, the corporations have taken matters into their own hands and established an Internet police force, which includes the International Fact-Checking Network (IFCN, settled at the Poynter Institute in the U.S. in 2015 with the help of Ebay founder Pierre Omidyar, cf. Graves 2018), the U.S. company NewsGuard, which puts up green and red labels on the net (cf. Schreyer 2022), and the Trusted News Initiative (TNI). To stay with this last example: The TNI, launched in summer 2019 under BBC auspices, brings together the Who’s Who of Western opinion factories: News agencies (AP, AFP, Reuters), broadcasters (Canada’s CBC in addition to the EBU and BBC), major newspapers (Financial Times, Washington Post, Wall Street Journal, and The Hindu from India), major Internet companies (Microsoft, Google, YouTube, Twitter, Facebook, First Draft), and the Reuters Institute for the Study of Journalism, an academic institution at Oxford University sponsored primarily by media conglomerate Thomson Reuters. What is agreed upon here, as this list should make clear even when skimming it, becomes a truth to which all those who work in the leading media must bow, because the reach and working methods of every German local editorial office are now also determined by platform logic. Already at the TNI founding event in July 2019, Tony Hall, then director general of the BBC, warned of a possible Trump re-election and vaccination opponents. Then on March 27, 2020, TNI members announced that from now on they would alert each other when “misinformation” or “conspiracy theories” emerged on Corona to prevent any further spread. And on December 10, 2020, a few days after the BioNTech-Pfizer substance was approved in the UK, it was decided to suppress anything that might downplay the Corona threat and argue against vaccination. In doing so, the TNI took its perspective on the issue from the same sources as governments (see Woodworth 2022). The example is treated in such detail here not only because of the enormous interpretive power of the TNI, but also because it shows that the four censorship paths mentioned can only be separated analytically. Without the pressure of the legislator, manifested in well-equipped observatories with scandalizing powers and resulting in more or less voluntary self-restrictions (every restriction costs traffic, data access and thus profit), the Internet police might not exist in this form. More specifically: Why would Facebook pay “cleaners” in Manila (the title of a 2018 documentary by Hans Block and Moritz Riesewieck) and YouTube train “employees of NGOs or authorities” as “trusted flaggers” if there were no common interests and no interaction with political power? The most important German censorship laws are the NetzDG, in effect since October 1, 2017, and expanded since February 1, 2022, for the large platforms (two million users or more) to include a reporting obligation for “potentially criminally relevant content” (Biselli 2022), and the State Media Treaty, which on November 7, 2020, turned the state media institutions into “control institutions for the digital publishing world.” Since then, the “legislator requires website operators, bloggers and media intermediaries” to check the truth (under the heading of “journalistic diligence”), although the “definition of truth or its disregard should not be a sovereign task” (Hofbauer 2022: 144f.). Hannes Hofbauer (2022) documents in detail how the two most important voices of the German-language counter-public (the Russian state channel RT and the platform KenFM, which had 500,000 subscribers on YouTube) were shut down and how leading media and professional associations either remained silent about this or even applauded it. Hofbauer (2022: 135-138) quite correctly interprets the Network Enforcement Act (NetzDG) as a “state push” that has allowed Internet corporations to mutate into “censorship machines.” The two main problems: The terms “hate crime” and “fake news” (the targets of the law) are characterized by “interpretive malleability.” And: the “new censor regime” is located “somewhere between the Berlin Ministry of Justice and U.S. corporate headquarters” and is thus “hardly tangible.” Even the extension of the deletion obligation to include a reporting obligation does not solve this dilemma. The “Central Reporting Office for Criminal Content on the Internet,” which started in February 2022 at the Federal Criminal Police Office with about 200 employees, received only just under 3,900 reports by the end of November 2022 instead of the expected 250,000 (cf. Biselli 2022). This corresponds to the situation before the introduction of mandatory reporting. On the high-reach platforms Facebook and Instagram, there was only a low four-digit number of NetzDG complaints in each case in the second half of 2020. The interpretive battle during this period focused on the Elite Channel (over 800,000 complaints on Twitter) and videos, which are apparently still considered to have the greatest impact (over 300,000 reported videos on YouTube). The federal government’s response to a corresponding inquiry by the FDP gives an idea of the share that “complaints offices” and other tax- or group-funded institutions had here. # 5. Conclusion and outlook Since the mid-2010s, the EU, the NetzDG, and the State Media Treaty (section 4), in conjunction with the government initiatives outlined in section 2 and the declarations of war from the highest levels, have ensured a social atmosphere that places Internet activities beyond the mainstream media under general suspicion, provides a protective cloak for all official narratives, and allows the business of flak shooters to flourish, among whom the so-called fact checkers once again stand out. “It has been said recently that we are living in post-factual times,” Angela Merkel said in September 2016 in a speech on refugee policy. “I guess that means people are no longer interested in facts, they follow feelings alone.” At the inauguration of the BND headquarters in February 2019, she also said, “We must learn to deal with fake news as part of hybrid warfare.” In her government statement on October 29, 2020, she then prepared the country for lockdown in the same tone of voice: criticism of the Corona measures was essential, “but lies and disinformation, conspiracy and hatred not only damage democratic debate, but also the fight against the virus.” In this context, the fear of a “cyber 9/11” has been present in the control centers of the Western hemisphere for a good two decades, orchestrated also by high-profile simulation games that equate the Net with an “enemy weapons system” (see Corbett 2021). Fact-checkers – an arm of the new “discursive police” (Foucault 2014: 25) – are particularly well disguised in this regard. Who should object to people taking another serious look at what someone has just cobbled together? The promise contained in the name of these organizations (the truth, checked again) is perfidious because it suggests that in complex societies there can be unambiguity and certainty of orientation without any personal research effort. This explains why, in addition to IFCN member Correctiv (founded in 2014 with money from the Brost publishing family), private initiatives such as the website Volksverpetzer and fact-checking departments have been able to establish themselves under the umbrella of traditional media institutions (at dpa, Bayerischer Rundfunk, Tagesschau). As a rule, all these editorial departments ‘check’ exclusively what contradicts the reality of the mainstream media and thus the government and corporate propaganda. If Sheldon Wolin (2022) is correct in his analysis of “inverted totalitarianism,” then no media revolution is conceivable without a fundamental renewal of the social framework. As long as the state and corporations make common cause, it will not be possible to establish a communication channel that cannot be hijacked by the actors with the greatest material, human, and ideational resources – by actors who, if worst comes to worst, can also deploy intelligence services (an influence that has been neglected in this article but is nevertheless relevant, cf. Alford/Secker 2015, Talbot 2017, Ulfkotte 2014). Calls for selective expropriations (publishing houses) and reforms (public broadcasting), for breaking up monopolies and establishing European or civil society alternatives (digital platforms) therefore come to nothing. For critical social research, there are three tasks in this situation: Educating about propaganda and censorship, establishing and supporting independent channels (which is what the institute publishing this article stands for, among others), and working on drafts for a media order that, on the one hand, allows journalism to fulfill its mission of publicity and, on the other hand, limits the access of interests of all kinds or at least makes it transparent. # Bibliography Matthew Alford, Tom Secker: National Security Cinema. The Shocking New Evidence of Government Control in Hollywood. Drum Roll Books 2017 Klaus Arnold: Propaganda als ideologische Kommunikation. In: Publizistik 48. Jg. (2003), S. 63-82 Ulrich Beck: Die Metamorphose der Welt. Berlin: Suhrkamp 2017 Edward Bernays: Propaganda. Die Kunst der Public Relations. 9. Auflage. Berlin: orange-press 2018 Anna Biselli: [Netzwerkdurchsetzungsgesetz: Ab Februar gilt die Meldepflicht. Eigentlich](https://netzpolitik.org/2022/netzwerkdurchsetzungsgesetz-ab-februar-gilt-die-meldepflicht-eigentlich/). In: Netzpolitik vom 31. Januar 2022 Peter J. Brenner: „Kampf gegen rechts“ – eine neue Wissenschaft. Mit einem Onlinedossier (Auf dem Weg zur Regierungswissenschaft). In: Tumult, Sommer 2022, S. 20-25 James Corbett: [Wenn False Flags virtuell werden](https://2020news.de/wenn-false-flags-virtuell-werden/). In: 2020News vom 10. Januar 2021 Adrian Daub: Cancel Culture Transfer. Wie eine moralische Panik die Welt erfasst. Berlin: Suhrkamp 2022 Andreas Elter: Die Kriegsverkäufer. Geschichte der US-Propaganda 1917-2005. Frankfurt am Main: Suhrkamp 2005 Benjamin Ferschli, Daniel Grabner, Hendrik Theine: Zur Politischen Ökonomie der Medien in Deutschland. München: isw 2019 Anke Fiedler, Michael Meyen (Hrsg.): Fiktionen für das Volk: DDR-Zeitungen als PR-Instrument. Münster: Lit 2011 Michel Foucault: Die Ordnung des Diskurses. 13. Auflage. Frankfurt am Main: Fischer Taschenbuch 2014 Lucas Graves: Boundaries Not Drawn. Mapping the institutional roots of the global fact-checking movement. In: Journalism Studies 19. Jg. (2018), S. 613-631 Lutz Hachmeister, Till Wäscher: Wer beherrscht die Medien? Die 50 größten Medien- und Wissenskonzerne der Welt. Köln: Herbert von Halem 2017 Václav Havel: Versuch, in der Wahrheit zu leben. Reinbek bei Hamburg: Rowohlt 1989 Edward S. Herman, Noam Chomsky: Manufacturing Consent. The Political Economy of the Mass Media. New York: Pantheon Books 2002 Hannes Hofbauer: Zensur. Publikationsverbote im Spiegel der Geschichte. Vom kirchlichen Index zur YouTube-Löschung. Wien: Promedia 2022 Stefan Homburg: Corona-Getwitter. Chronik einer Wissenschafts-, Medien- und Politikkrise. Sargans: Weltbuch 2022 Georg Ismar: Der Synchrontänzer der Kanzlerin: Wie Steffen Seibert Angela Merkels Macht absicherte. In: Tagesspiegel vom 6. Juli 2021 Marcus B. Klöckner: Sabotierte Wirklichkeit. Oder: Wenn Journalismus zur Glaubenslehre wird. Frankfurt am Main: Westend 2019 Wolfgang Koch: Ergebnisse der ARD/ZDF-Onlinestudie 2022: Reichweiten von Social-Media-Plattformen und Messengern. In: Media Perspektiven 2022, S. 471-478 Uwe Krüger: Mainstream. Warum wir den Medien nicht mehr trauen. München: C. H. Beck 2016 Paul F. Lazarsfeld, Robert K. Merton: Mass Communication, Popular Taste and Organized Social Action. In: Lyman Bryson (Hrsg.): The Communication of Ideas. New York: Harper 1948, S. 95-118 Walter Lippmann: Die öffentliche Meinung. Wie sie entsteht und manipuliert wird. Frankfurt am Main: Westend 2018 Frank Lübberding: Wenn der Aktivismus zur Bekämpfung politischer Gegner staatlich subventioniert wird. In: Welt online vom 24. November 2022 Niklas Luhmann: Die Realität der Massenmedien. 2. Auflage. Opladen: Westdeutscher Verlag 1996 Klaus-Rüdiger Mai: Nachdenken über Satire in Zeiten ihres Verschwindens: In: Michael Meyen, Carsten Gansel, Daria Gordeeva (Hrsg.): #allesdichtmachen. 53 Videos und eine gestörte Gesellschaft. Köln: Ovalmedia 2022, S. 42-52 Robert Malone: [Twitter als Waffe](https://www.rubikon.news/artikel/twitter-als-waffe). In: Rubikon vom 21. Oktober 2022 Marcus Maurer, Jörg Haßler, Pablo Jost: Die Qualität der Medienberichterstattung über den Ukraine-Krieg. Frankfurt am Main: Otto Brenner Stiftung 2022 Albrecht Meier, Hans Monath: Mit welchen Strategien westliche Demokratien russische Fake News bekämpfen. In: Handelsblatt vom 23. November 2022 Birk Meinhardt: Wie ich meine Zeitung verlor. Ein Jahrebuch. Berlin: Das Neue Berlin 2020 Michael Meyen: [Journalists’ Autonomy around the Globe: A Typology of 46 Mass Media Systems](https://www.db-thueringen.de/servlets/MCRFileNodeServlet/dbt_derivate_00041207/GMJ15_Meyen.pdf). In: Global Media Journal, German Edition, 8. Jg. (2018), Nr. 1 Michael Meyen: Die Propaganda-Matrix. Der Kampf für freie Medien entscheidet über unsere Zukunft. München: Rubikon 2021 Michael Meyen, Markus Thieroff, Steffi Strenger: Mass media logic and the mediatization of politics. A theoretical framework. In: Journalism Studies 15. Jg. (2014), S. 271-288 Alexis von Mirbach: Medienträume. Ein Bürgerbuch zur Zukunft des Journalismus. Köln: Herbert von Halem 2023 Martin Morcinek: Das Bundespresseamt im Wandel: Zur Geschichte der Regierungskommunikation in der Bundesrepublik Deutschland. In: Jahrbuch für Kommunikationsgeschichte 6. Jg. (2004), S. 195-223 Elisabeth Noelle-Neumann: Die Schweigespirale. Öffentliche Meinung – unsere soziale Haut. München: Piper 1980 Christian Nuernbergk, Jan-Hinrik Schmidt: Twitter im Politikjournalismus. Ergebnisse einer Befragung und Netzwerkanalyse von Hauptstadtjournalisten der Bundespressekonferenz. In: Publizistik 65. Jg. (2020), S. 41-61 Meltem Odabaş: [10 facts about Americans and Twitter](https://www.pewresearch.org/fact-tank/2022/05/05/10-facts-about-americans-and-twitter/). In: Pew Research Center, 10. Mai 2022 Thomas Piketty: Kapital und Ideologie. München: C.H. Beck 2020 Jeff Pooley: Another Plea for the University Tradition: The Institutional Roots of Intellectual Compromise. In: International Journal of Communication 5. Jg. (2011), S. 1442-1457 Grace Pönitz: Keine Meldungsflut von Hass-Inhalten. In: M. Menschen machen Medien vom 14. Dezember 2022 Horst Pöttker: Öffentlichkeit als gesellschaftlicher Auftrag. Zum Verhältnis von Berufsethos und universaler Moral im Journalismus. In: Rüdiger Funiok, Udo Schmälzle, Christoph Werth (Hrsg.): Medienethik – die Frage der Verantwortung. Bonn: Bundeszentrale für politische Bildung 1999, S. 215-232 Richard David Precht, Harald Welzer: Die vierte Gewalt. Wie Mehrheitsmeinung gemacht wird, auch wenn sie keine ist. Frankfurt am Main: S. Fischer 2022 Günther Rager, Bernd Weber (Hrsg.): Publizistische Vielfalt zwischen Markt und Politik. Mehr Medien – mehr Inhalte? Düsseldorf: Econ 1992 Nikola Roßbach: Achtung Zensur! Über Meinungsfreiheit und ihre Grenzen. Berlin: Ullstein 2018 Horst Röper: Zeitungsmarkt 2022: weniger Wettbewerb bei steigender Konzentration. In: Media Perspektiven 2022, S. 295-318 Jakob Schirrmacher: Das ganze Ausmaß der Beeinflussung. In: Die Welt vom 4. Januar 2023 Jan-Hinrik Schmidt: Facebook- und Twitter-Nutzung der Kandidierenden zur Bundestagswahl 2021. In: Media Perspektiven 2021, S. 639-653 Paul Schreyer: [Medien aussortieren](https://multipolar-magazin.de/artikel/medien-aussortieren). In: Multipolar vom 30. März 2022 Christopher Simpson: Science of Coercion: Communication Research & Psychological Warfare, 1945-1960. New York: Open Road 1994 Bernd Stegemann: Die Öffentlichkeit und ihre Feinde. Stuttgart: Klett-Cotta 2021 David Talbot: Das Schachbrett des Teufels. Die CIA, Allen Dulles und der Aufstieg Amerikas heimlicher Regierung. Frankfurt am Main: Westend 2017 Martina Thiele: Political Correctness und Cancel Culture – eine Frage der Macht! In: Journalistik 4. Jg. (2021), Nr. 1, S. 72-79 Volker Thoms: [Bundesregierung: 295 Millionen Euro für Corona-Kommunikation](https://www.kom.de/public-relations/295-millionen-euro-fuer-corona-kommunikation/). In: Kom – Magazin für Kommunikation vom 11. Januar 2022 Kjersti Thorbjørnsrud, Tine Ustad Figenschou, Øyvind Ihlen: Mediatization in Public Bureaucracies: A Typology. In: Communications: The European Journal of Communication Research 39. Jg. (2014), Nr. 1, S. 3-22 Christiane Toyka-Seid, Gerd Schneider: [Zensur](https://www.hanisauland.de/wissen/lexikon/grosses-lexikon/z/zensur.html). In: Das junge Politik-Lexikon von Hanisauland 2023 Udo Ulfkotte: Gekaufte Journalisten. Wie Politiker, Geheimdienste und Hochfinanz Deutschlands Massenmedien lenken. Rottenburg: Kopp 2014 Batya Ungar-Sargon: Bad News. How Woke Media Is Undermining Democracy. New York 2021 Peter Vorderer: Der mediatisierte Lebenswandel: Permanently online, permanently connected. In: Publizistik 60. Jg. (2015), S. 259-276 Sahra Wagenknecht: Die Selbstgerechten. Mein Gegenprogramm – für Gemeinsinn und Zusammenhalt. Frankfurt am Main: Campus 2021 Elisabeth Woodworth: [COVID-19 and the Shadowy “Trusted News Initiative”. How it Methodically Censors Top World Public Health Experts Using an Early Warning System](https://www.globalresearch.ca/covid-19-shadowy-trusted-news-initiative/5752930). In: Global Research vom 22. Januar 2022 Sheldon S. Wolin: Umgekehrter Totalitarismus. Faktische Machtverhältnisse und ihre zerstörerischen Auswirkungen auf unsere Demokratie. Frankfurt am Main: Westend 2022 Florian Zollmann: Bringing Propaganda Back into News Media Studies. In: Critical Sociology 45. Jg. (2019), S. 329-345 Shoshana Zuboff: Das Zeitalter des Überwachungskapitalismus. Frankfurt am Main: Campus 2018 First published (August 2023): [Institut für kritische Gesellschaftsforschung](https://www.criticalsocietystudies.com/Journal/Article/65/34)
@ 044da344:073a8a0e
2025-02-19 08:27:37# 1. Public sphere and inverted totalitarianism The three referents in the title require explanation - just like the thesis that their combination conveys in this article. In short: Like every government, the German one wants to steer and control what is said publicly about it and about reality in the country (cf. Meyen 2018). In the Internet age, this only works by cooperating with digital corporations. This liaison is rooted in the knowledge that one’s own scope of action depends on public approval and public legitimation. “Relations of domination” are today more than ever “relations of definition” (Beck 2017: 129, 132). Power is held by those who succeed in placing their interpretation of reality in the public sphere (cf. Havel 1989: 19). This includes fading out or marginalizing everything that could endanger one’s own position – in Germany at the moment, for example, this relates to debates about social inequality, which has reached an all-time high worldwide (cf. Piketty 2020), mass immigration since 2015, the policies surrounding Corona or Russia. In this country, the interest of federal and state governments in presenting their work in a good light encounters a journalism that is committed to journalistic diversity via state press laws, state treaties and professional ethics (cf. Rager/Weber 1992). This means that journalism should allow everyone to have their say – all topics and all perspectives. Horst Pöttker (2001) has described the production of publicity as a “social mandate”. This “mission” is rooted in the pluralism model: In society, there are many and sometimes conflicting opinions and interests, which are initially on an equal footing (the interests of individuals and outsiders as well as those organized in parties or associations). The struggle for compromise and societal agreement relies on the public sphere: “In principle, no social group, not even an individual, but also no object, no topic, no problem may be excluded from it” (Pöttker 1999: 219f.). Phrased in a different way: In complex, differentiated societies, the public sphere is the “last common place where that which concerns everyone can be negotiated.” And even though “no decisions are made” here, acceptance and “collective validity” are impossible without public preparation and public visibility (Stegemann 2021: 16). Essential to this are mainstream media such as the Tagesschau, the Süddeutsche Zeitung or Der Spiegel, which produce a “second, non-consensual reality” - the collective “memory” of society, which must be assumed in all communication. Only the mainstream media spread information “so widely that in the next moment one must assume that it is known to everyone (or that it would be associated with loss of reputation and is therefore not admitted if it was not known)” (Luhmann 1996: 43, 120f.). We use Mainstream media because we want to know what others think they know (especially those who decide about our lives), and because we need to know the defining power relations in order to survive. Who has succeeded in bringing their issues, their perspectives and, above all, their morals to the big stage, and who has no place on that stage? Consequently, whom should I join if I do not want to be isolated (cf. Noelle-Neumann 1980), and whom do I better avoid? The interest of governments in controlling public communication is inextricably linked to propaganda and censorship. Propaganda is defined in this article with Andreas Elter (2005: 19f.) as all attempts by government agencies to convey “a certain, unambiguously colored view of things \[...] and thus to maneuver the public discussion in the desired direction”. This necessarily includes suppressing, delegitimizing, or limiting the scope of all positions “that challenge the dominant narrative and at the same time have the potential for widespread dissemination” (Hofbauer 2022: 7) – censorship. Put another way: Propaganda and censorship are two sides of the same coin. Those who want to impose their “view of things” (Andreas Elter) must fight the competition and, if possible, eliminate it. Censorship is an “instrument of domination to enforce economic interests, political power and cultural hegemony” (Hofbauer 2022: 237). The fact that media research shies away from calling propaganda and censorship by their names when analyzing contemporary Western societies is the result of a systematic deconceptualization. In academic texts, just as in political education, censorship is generally only mentioned when it comes to forms of government that can be described as ‘totalitarian’, ‘dictatorial’ or ‘undemocratic’ - Hitler's Germany, the Soviet Union, Russia, China, North Korea (for an illustration cf. Toyka-Seid/Schneider 2023). “There is \[to be] no censorship”: this sentence from Article 5 of the German constitution describes reality through this lens, as long as there is no censorship authority or even a corresponding ministry. The literary scholar Nikola Roßbach, for example, academic companion of the Temple of Forbidden Books at Documenta 2017, bypasses the terms state, pre-screening, and bans in her definition, but instead uses adjectives that amount to the same thing and absolve Germany of any suspicion: “In my understanding, censorship is a comprehensive, structurally and institutionally anchored control, restriction, or prevention of expression intended for publication or published” (Roßbach 2018: 19). The purpose of this smokescreen is revealed a little later: Roßbach wants to dismiss censorship as a “polemical concept” from the “political circus,” to be heard above all from the “populist side” and from the right (used here in each case synonymous for all those who should not speak out), but also “from right-wing populist leftists”. To make this a “classic case of self-victimization” or even a “cross-front” of anti-democrats (ibid.: 82, 88) falls short, however, if only because “the boundary between what is permitted and what is forbidden” is contingent and consequently “may not be questioned” (Stegemann 2021: 161). Censorship itself automatically becomes a taboo for the censors. Otherwise, they get into justification trouble. This explains, for example, why a phenomenon like “cancel culture” can be relegated to the realm of fable and the debate about it dismissed as a perfidious feint by the already powerful (cf. Daub 2022, Thiele 2021). The flipside has been dealt with in a very similar way. In hegemonic usage, propaganda is now always what others do – Nazis and communists preferably, but also otherwise anyone who can be classified as ‘opponents’ and ‘enemies’ (cf. Arnold 2003). Moreover, the concept of propaganda has long had such a negative connotation that it puts the result before the analysis – one-sided, not legitimate, and apparently effective even if one concedes that people (such as in the GDR at the time) may withdraw from the public sphere and distrust all news in the respective leading media (cf. Fiedler/Meyen 2011: 17f.). Communication studies has forgotten that it was born as propaganda research. Yet it does exactly the same as its inventors, who were commissioned by the government, military and intelligence services in the USA to find out how to get into people’s heads: Psychological warfare. The state and billionaire industry-related foundations (Rockefeller, Ford) paid hundreds of social scientists starting in 1939 to win the battle for public opinion as well. One result: henceforth people spoke of communication rather than propaganda (cf. Simpson 1994, Pooley 2011). This did not change what one was looking for, but it allowed to distinguish one’s own ‘good’ intentions from the ‘bad’ ones of the Germans and later the Soviets or the Russians (cf. Meyen 2021: 63-75). In this way, the terms censorship and propaganda have been turned into a blunt sword. Critics of the media and society can no longer use them, at least in the German-speaking context, without immediately being confronted with the accusation of exaggerating excessively or even playing into the cards of the ‘right-wingers’. In this article, this risk is taken for two reasons. First, everyone can examine the arguments and then decide for themselves whether it is justified to speak of propaganda and censorship in the sense defined above. Second, classics such as Walter Lippmann, Edward Bernays, or even Paul Lazarsfeld and Robert Merton (1948, cf. Zollmann 2019) had no problem at all with calling a spade a spade. Lippmann (2018: 84) knew already one hundred years ago that news are anything but a “mirror of social conditions.” Walter Lippmann dreamed of a government of experts masquerading as popular rule, and for this to happen, it must specifically influence public opinion - via the “images according to which whole groups of people” act (ibid.: 75). His disciple Edward Bernays, a few years later, logically considered propaganda “a perfectly legitimate activity.” Without “public consent,” Bernays wrote in 1928, already in the spirit of medialization research (cf. Meyen et al. 2014), “no major undertaking” can succeed anymore. This consent, Bernays was sure, must and can be organized - by “PR consultants” like him. His definition is consistent with what I advocate in this paper: “Modern propaganda is the steady, consistent effort to shape or create events with the purpose of influencing the public's attitude toward a company, idea, or group” (Bernays 2018: 28-32). Lippmann and Bernays did not live to see the “union of state and corporations” for which Sheldon Wolin (2022: 221) was able to use the label “superpower” in the noughties. Wolin, like Walter Lippmann, considered “democracy” to be a “largely rhetorical function within an increasingly corrupt political system” (which, however, he criticized rather than defended) and spoke instead of a “coalition between the corporations and the state” – an “inverted totalitarianism” which, while using “the authority and resources of the state” as it once did in Nazi Germany or the Soviet Union, gains “its dynamism by combining it with other forms of power” (such as the churches) and links the “conventional form of government” with “the system of ‘private’ governance represented by modern corporations.” Somewhat more briefly, “corporate power” is now also political. In the Cold War era, the state and corporations had become “the principal sponsors and coordinators of the forces represented by science and technology,” and thus also the source “for creating and spreading a culture that educates consumers to embrace change and private pleasures while accepting political passivity” (Wolin 2022: 60-63). For Sheldon Wolin, “inverted totalitarianism” is a “new kind of political system” that is “apparently driven by abstract totalizing powers, not by personal domination,” and whose “total power” is harder to detect than Hitler's or Stalin's if only because this system does not need to build camps and does not need to “violently suppress dissent as long as it remains ineffective” (ibid.: 118, 134). Wolin says: For control, it is enough to “create a collective sense of dependency” (ibid.: 192) as well as to use whatever methods of “intimidation and mass manipulation” are available today (ibid.: 56). Inverted totalitarianism then is “collective fear” plus “individual powerlessness.” Job, retirement, health care costs. Plus pressure at the workplace, the stress of everyday life, the constant fuss about some political scandal or other (ibid.: 352). The result is a “society that is used to exchanging new habits for old ones, adapting to rapid changes, uncertainties and social upheavals, and allowing its fate to be determined by distant powers over which it has no influence” (ibid.: 116). Sheldon Wolin largely ignores the mainstream media - just like digital capitalism, which for the doyen of U.S. political science, born in 1922, was at best a pipe dream when he wrote his last major book after 9/11. A good two decades later, the “revolving door between the centers of power on both coasts” (between Washington and Silicon Valley) has become almost proverbial (Zuboff 2018: 150). Personnel are shifted from here to there, balls are passed to each other in election campaigns, and, as will be shown in this paper, they work hand in hand when it comes to retaining the power of definition in the political battles of the present and controlling the “side-effect publics” that address what the mainstream media hide or distort. In the spirit of Sheldon Wolin, Ulrich Beck (2017: 172f.) has spoken of a “risk-averse coalition of progress,” “consisting of experts, industry, the state, political parties, and established mass media,” which can ignore or play off against each other issues such as climate change, nuclear power and financial speculation, genetic manipulation, nanotechnology and reproductive medicine, terrorism, and digital surveillance, as needed in the public debate. O-Ton Beck: “This implies: The politics of invisibility is a first-rate strategy for stabilizing state authority and reproducing the social and political order, for which denying the existence of global risks” matters greatly (ibid.: 134). Beck did not trust the traditional mass media to fulfill the mission of the public sphere, not even in Western states. “The mode of this nationally organized, public form of media power is exclusive, that is: one produces it specifically, one can allow it, suppress it, etc.” (ibid.: 172). With a view to a world at risk, which was his life’s topic of interest, he consequently called for a reform of the definitional relationships, hoping for the Internet – for a public sphere that could not be easily controlled by the powerful, that discussed other topics as well as in a different form than the leading media, and that relied, among other things, on a “countervailing power of independent experts” (ibid.: 146). Ulrich Beck was an optimist. When he wrote his book on the “Metamorphosis of the World” (which was to be his last) in the mid-2010s, the relationship between governments and Google, Twitter and Co. was at best in the dating stage. In the meantime, the marriage has been consummated. We live in a digital corporate state that floods the public with its messages (Propaganda, section 2), exploiting the logic of the new means of dissemination (Interlude: Twitter’s public sphere, section 3) and also making platform operators delete counter-perspectives and opposition figures or make them difficult to find (Censorship, section 4). Part of Beck’s concept of defining power relations is that even within a governing coalition or, thought of more broadly, in “that subterranean network of financial, intelligence, and military interests that guides national policy,” “no matter who happens to be in the White House” (Talbot 2017: 505), there are struggles for interpretive authority. Such battles, which rely on resonance in the journalistic field and are therefore also fought there, explain, for example, why Chancellor Scholz had a significantly worse press than his ministers Baerbock and Habeck in the first months of the Ukraine war (cf. Maurer et al. 2022). # 2. Propaganda Without delving into such differentiations, this section will show what government agencies are doing to win over the public. In addition, it will at least be suggested that these efforts meet with little resistance, and not only because of the alliance with media corporations. For one thing, the balance of power between the propaganda apparatuses and journalism has shifted considerably since the 1990s, and for another, the leading media are now dominated by the same habitus that governs government agencies and corporate headquarters (see Klöckner 2019). There are three ways to “move the public debate in the desired direction.” First, a government can pay (as well as resource and perhaps already train) personnel to feed newsrooms with what they are looking for anyway – exclusive information and images, interlocutors, and material from which news can be made (for example: scientific studies or live access during police operations). This personnel also sits at the trigger when it becomes necessary to use what Edward Herman and Noam Chomsky (1988: 18) called, in German, “flak” - barrages that put everything under fire that could get in the way of the employers. Second, this government can change its own work in such a way that ‘good press’ becomes more likely - via the recruitment of top people suitable for the media, via the events and occasions that Edward Bernays already talked about (a rather harmless example: the central festival for the Day of German Unity, which is held in a different state capital every year and reliably produces coverage), and (less harmlessly) via prioritization that puts public image above everything else and, in case of doubt, even above law and order (cf. Thorbjørnsrud et al. 2014). Third, any government can help it along with money - with direct subsidies, which are always good for a scandal in Austria, for example, and were nevertheless almost introduced in Switzerland in a referendum in February 2022, or with indirect subsidies (advertising, tax breaks, carpooling). The federal government exhausts all of the above possibilities to the hilt. It pays a whole army of propaganda people, creates or shapes events with the help of these people that serve the sole “purpose” of influencing “public attitudes” 2018: 28-32), and pumps money into publishing houses and broadcasters. The first issue alone would deserve an entire essay – partly because it is difficult to separate from the second issue. When resources are reallocated toward public relations, an organization’s performance inevitably becomes more media-savvy – most likely at the expense of the tasks for which ministries or subordinate agencies were originally created. A prime example of this prioritization is the German government’s Press and Information Office, with its more than 500 staff positions and three former top journalists in position of spokesperson (Steffen Hebestreit, Wolfgang Büchner, Christiane Hoffmann). This agency, located in the Chancellor’s Office and thus quite obviously an instrument of power for the head of government, was controversial from the outset (cf. Morcinek 2004), but neither Konrad Adenauer nor his successors allowed themselves to be swayed by public criticism here and thus also promoted, at least indirectly, the creation of parallel departments. In addition to a press office with “33 experts,” the Foreign Office now has a commissioner for strategic communication (Peter Ptassek at the end of 2022), who is assisted by “around 40 staff members” to protect the minister and her actions from slander and, if worst comes to worst, to counter with stories of her own (Meier/Monath 2022). Correspondents exist in every ministry, in every party headquarters, in every state government, and for every politician who moves near the center of power. There is a method to the transfer from the editorial offices to the authorities and staffs, which is represented not only by the three journalists named above but also by their predecessor Steffen Seibert. In this way, politics buys know-how, contacts and goodwill, which is not only fed by the reputation of the former colleagues, but also has to do with the prospect of one day being called to the other side. The departments or people whose names or job titles include terms like public, press, media or marketing are only the obvious part of the propaganda apparatus. Claudia Roth, Minister of State for Culture and Media in the current government coalition, has a budget of 2.39 billion euros in 2023 – four percent more than in 2022. In addition to museums owned by the federal government, film productions and a cultural passport for 18-year-olds, this pot primarily funds projects and programs along government lines. Roth’s agency uses it to finance not only causes for coverage, but also personnel who can and will speak out accordingly. This applies analogously to the many commissioners who have been installed on a full-time or honorary basis at different administrative levels (responsible for issues such as foreigners, integration, discrimination, racism, women, queer, lesbians, gays, disability, anti-Semitism, ziganism, climate, sustainability), who have to justify their existence through mainstream media presence and thus also draw imitations in companies or culture and education. In addition, there are organizations such as the Zentrum Liberale Moderne or the Amadeu Antonio Foundation (tip of an NGO iceberg), which support government narratives with flak (here quite openly called “opponent analysis” or disguised as the fight against hate speech and fake news, right-wing extremism and anti-Semitism). The Zentrum Liberale Moderne, founded in 2017 by Green Party politicians Ralf Fücks and Marieluise Beck, has received nearly 4.5 million euros for a total of 24 projects from 2018 to 2022 (see Lübberding 2022). The federal program “Demokratie Leben!” (“Live Democracy!”), one of the umbrella initiatives for related spending (located in the Federal Ministry of Family Affairs), will cost taxpayers 182 million euros in 2023, 16.5 million euros more than in 2022 and 31.5 million euros more than in 2021. “Measures to strengthen diversity, tolerance and democracy” have a total of 200 million euros dedicated to them in this ministry’s 2023 budget. Money from the budget of the German government’s Press and Information Office will go to the German Atlantic Society (2023: 700,000 euros), the Society for Security Policy (600,000), the Center for Liberal Modernity, the Aspen Institute, the Europa Union and the Progressive Center (500,000 each). In Sheldon Wolin (2022: 147) one can read how it is possible to integrate even scientists and intellectuals “seamlessly into the system” and to prevent dissent without having to “harass” or “discredit” critics. Wolin explains: Through “a combination of government contracts, corporate and foundation funding, joint projects by university and corporate researchers, and wealthy individual donors.” Peter J. Brenner (2022) has spelled out this strategy for Germany, compiling a long list of “institutes for research on democracy and right-wing extremism” that assist “government power” at taxpayer expense in the struggle for “discourse hegemony.” For universities, this flow of money has consequences that go beyond the reinterpretation of terms, rules of language such as gendering, and the prioritization of social problems. Even without insight into the inner workings of universities, it should be clear that legions of scientists are rushing to answer the questions, theories and methods to which the “coalition” of big business and the state (Sheldon Wolin) is devoting its budgets via the EU Commission or the BMBF. A few get their turn, and many others continue without funding, so that the investment is not entirely in vain. Those who win money need proof of success – publications in specialist journals and (either via this detour or interviews) a presence in the mainstream media. Diverting taxpayers’ money to media companies was taboo in post-1945 West Germany (unlike in Austria). In a large and densely populated circulation area with a flourishing economy and without the competing advertising and information channels that developed on the Internet from the 1990s, subscriptions to public authorities and advertisements from ministries or offices also played a minor role. All these parameters changed during the Corona crisis at the latest. More cautiously, the slump in the advertising market and the ubiquity of aid and rescue funds have allowed the media industry in 2020 to push the issue of state support, overturning the taboo of press subsidies. Under the guise of “digital transformation,” 220 million euros were included in the federal supplementary budget this summer, most of which was to be paid out before the end of 2021, tied to circulation. The bigger the newspaper, the more money. This plan died at the end of April 2021 “because of constitutional concerns,” but the main counter-argument was not state neutrality, but distortion of competition. The online platform Krautreporter had threatened to go to court if only print publishers were funded, and also refused to accept reallocating the budget to “Corona emergency aid.” The publishers’ associations reacted “shocked,” spoke of a “medium catastrophe” (Meyen 2021: 166f.) and are now concentrating their lobbying on the issue of local media diversity (“nationwide coverage,” Röper 2022: 302). The sum of 220 million euros would have largely absorbed the slump in the advertising market of the daily press. Sales in this market in 2020: 1.712 billion euros – 367 million less than in 2019. In previous years, the average decline was around 150 million euros (Statista 2023). Public budgets are therefore increasingly attractive to the advertising departments of media groups. In 2021, the German government bought ad space for around 64 million euros as part of its “Corona communication” alone. Television and radio together received 28 million euros in the same period (Thoms 2022). This does not include the Corona and vaccination campaigns of state governments and local authorities, for which the business community in the respective circulation areas was also mobilized in some cases, advertising with a different thematic focus, and everything that corporations and foundations give to publishers beyond conventional promotion in order to advertise specific political goals. In journalism, such efforts meet with little resistance for two reasons. First, the most important media houses in Germany have long been of corporate size and are thus themselves part of the “coalition between the corporations and the state” that constitutes “inverted totalitarianism” in Sheldon Wolin's (2022: 221) terms. The German press landscape is characterized by monopolies and concentration, as well as by a few publishing houses (often family-owned) that not only feed all other channels and otherwise outgrow their core business, but in some cases also sell their editorial services to ‘competitors’ such as Madsack’s Redaktionsnetzwerk Deutschland, which supplies more than 60 regional papers in seven German states (cf. Röper 2022, Ferschli et al. 2019). Public broadcasting is not a counterargument here. With a revenue from contributions of almost nine billion euros a year, ARD and ZDF are among the largest media companies in the world (cf. Hachmeister/Wäscher 2017) – corporations that have to act as corporations and that are closely linked to politics and the state in almost every respect (cf. Mirbach 2023: 128-178, 250-272). And second, journalism in Germany is a socially homogeneous field dominated by the “habitus of the middle class” – “oriented toward conformity,” programmed to “accept power relations” (Klöckner 2019: 33), and closely linked to decision-makers in the state, political parties, and business through social status, educational background, and life situation. The similarity of social position and habitus not infrequently turns into real proximity in everyday life. Contact (press conferences, receptions, travel) creates sympathy and thus often at least understanding (cf. Meyen 2021: 176-198). Uwe Krüger (2016: 105) has coined the word “responsibility conspiracy” for this community of values: Journalists know what is good and what is bad (pretty much the same as what the rulers think is good or bad), and they believe they have influence over people. So reality is “reduced by the parts” that “do not fit the attitude” and what seems to promote the desired goal is emphasized (Meinhardt 2020: 87) – sometimes utilizing information, contacts and material from the propaganda apparatus and sometimes not. # 3. Interlude: Twitter publicity Anyone who wants to steer and control public communication today must submit to the logic of digital platforms. This is especially true of Twitter, a channel that within a few years has become the central point of contact for the most important players in “inverted totalitarianism” and has become an indispensable part of everyday life, especially in the media-political-academic complex, even if some protagonists gave up their accounts in the heated debate about Elon Musk’s takeover in the fall of 2022. In Germany, Twitter has always been a minority phenomenon. Four percent of those over the age of 14, says the ARD/ZDF online study of 2022, use Twitter daily and ten percent at least once a week. This includes those who only read and click now and then for reach. Ten percent. Typically male, most likely under 50 (cf. Koch 2022: 472f.). Even in the U.S., where it is common to follow the greats of film, pop and professional sports, not even one in four adults says they use Twitter. The profile of this bubble: young, affluent, educated (cf. Ungar-Sargon 2021: 104). We also know from the USA that the vast majority of tweets come from a few (cf. Odabaş 2022) – from people who have a mission and the resources to promote it. Companies, government agencies, commissioners, entrepreneurs of themselves, NGOs, activists of every stripe, parties. In the fall 2021 federal election, almost every one of the MPs who ran again, and almost every one of those who were then new MPs, had a Twitter account. Particularly active (in this order): Left, Greens, SPD, FDP. Those elected all follow more or less the same accounts. Tagesschau, Der Spiegel, the government spokesperson, Süddeutsche Zeitung and Die Zeit each have over 60 percent. In addition to the leading media, the news agency dpa and top politicians like Christian Lindner or Annalena Baerbock, the “state satirist” and “head of the authorities” (May 2022: 46) Jan Böhmermann is also very high up in this ranking (see Schmidt 2021). Twitter determines what can be incorporated into the reality of mainstream media – which topics with which voices and with which morals. The use of Twitter and the observation of the trends there determine the everyday work in many editorial offices today. Anyone who wants to enter the professional field today learns, at the latest during their traineeship or at journalism schools, that nothing beats a well-groomed Twitter or (beyond political journalism) TikTok and Instagram brand. Rule of thumb: the more followers, the greater the chance of being commissioned or hired (cf. Ungar-Sargon 2021). The older ones can hardly avoid this trend. Three out of four members of the Federal Press Conference have a Twitter profile – again, mainly the younger ones and thus also those with less professional experience. Journalists who are mentioned by members of parliament in their tweets consider Twitter to be particularly important (cf. Nuernbergk/Schmidt 2020). Robin Alexander, deputy editor-in-chief of the daily newspaper Die Welt, has proudly described how he transforms confidential information into tweets that are then used by politicians to push their perspective with reference to the top journalist (cf. Precht/Welzer 2022: 114f.). Following this pattern, the chancellor’s office organized mainstream media backing for their lockdown policy: Government spokesman Seibert explained the plans to selected journalists prior to talks with the prime ministers of the German states, thus ensuring the necessary public pressure (cf. Ismar 2021). Contemporary journalism must find its topics and views on Twitter also because tight resources and high frequency publication demands make it increasingly rare to get in contact with reality and talk to real people – especially those you don’t usually meet on digital platforms. Such conversations would also be dangerous, because like any brand, a Twitter profile demands consistency. I can’t celebrate Fridays for Future there today and burn Greta Thunberg tomorrow. In the Twitter editorial department, two souls combine who are dependent on each other: the media entrepreneur who encourages his employees to ensure the distribution of his own contributions, and the editor who wants to make his mark and rise even further and therefore always asks first how things look from the very top (cf. Klöckner 2019). Brand management is the opposite of the raving reporter, who first allows himself to be surprised by what he sees, hears and experiences, and then shares his findings with his readers, listeners, viewers. This is another reason why the tweeting journalist already knows the story he wants to tell when the research begins. What’s more, he only sees the stories that resonate with his brand. Conversely, it is hardly possible to get through with criticism of the powerful or even to find journalists who raise fundamental questions even beyond details or animosities. On Twitter, everything that could be said against laws, plans or people is immediately available – published, if you will, by everyone. Journalism has lost the privilege of calling for politicians’ heads and has therefore mutated into their attack dog. The consequences of the Twitterization of journalism go beyond the loss of the function of criticism and control. First, the obvious: Morality is conquering the leading media alongside politics. Twitter is the breeding ground for a journalism that is primarily hung up on “language and symbolism” (Wagenknecht 2021: 26) and on affiliations. Twitter sees every topic through the lens of morality and therefore demands opportunities for identification if one wants attention and thus reach. It’s always about me, the group I want to belong to or the one I reject wholeheartedly. Nothing triggers stronger emotions, nothing gets others to share, like, comment faster. In a nutshell, it’s about team sports. “The game is called: US against THEM” (Precht/Welzer 2022: 110). Twitter also makes measured consideration disappear and with it all differentiation, all questioning, all weighting. All of this doesn’t fit into 280 characters even if you link photos, videos, or text panels (cf. Homburg 2022). The rise of Twitter as the editor-in-chief of the leading media (Ungar-Sargon 2021: 103) and as the pace maker of public discourse is a temptation for all those who have ways and means to govern this channel. Today, Twitter is the place where it is decided what reality is and how we are all to think about it. That is why Twitter is firmly in the hands of the establishment and part of the “coalition” of the state and monopoly corporations to which Sheldon Wolin (2022: 63) has given the name “inverted totalitarianism.” Anyone who did not want to believe how closely the Obama and Biden administrations were and are intertwined with Twitter (cf. Malone 2022) or that the “censorship of the Hunter-Biden laptop affair” and the “unprecedented political intervention” (Hofbauer 2022: 183) against Donald Trump at the beginning of 2021, in which the U.S. president lost his million-strong following in one fell swoop, can be traced back to this network of relationships was proven wrong at the latest by the publication of the “Twitter Files” (cf. Schirrmacher 2023). # 4. Censorship Hannes Hofbauer (2022: 124f.) dates the birth of the censorship regime of the present to November 28, 2008. The EU framework decision of that day was about “the definitional sovereignty over genocide” and thus “de facto” about the bans on discussions and taboos in matters of war and guilt, for example in Yugoslavia or in the successor states of the Soviet Union. In Germany, this topic popped up once again when Section 130 of the Criminal Code (incitement of the people) was amended accordingly at the end of 2022. By the end of the noughties, it had become obvious that the traditional means of propaganda would no longer suffice to maintain interpretive sovereignty. The platforms Xing (launched in 2003), Facebook and Vimeo (2004), YouTube (2005), Twitter (2006) and WhatsApp (2009) were on their way to becoming mass phenomena at the latest after the introduction of the iPhone (2007). This also meant that from now on, alternative interpretations of reality were available to anyone at any time and any place (cf. Vorderer 2015), without professionalism in the processing or the quality of the evidence immediately providing information about which view of things could claim validity. Those who are craving definitional power (such as governments, the EU Commission, or multibillionaires whose position and business also depend on public sympathy) had to start fighting competitive narratives and unwelcome information now at the latest. In addition to legislative initiatives such as the 2008 “Framework on combating certain forms and expressions of racism and xenophobia by means of criminal law” and the EU’s 2022 Digital Services Act, three other ways were explored to achieve this goal. First, control of the Internet was institutionalized – for example, in the “East StratCom Task Force,” established in March 2015 after the “regime change in Ukraine” with the aim of enforcing one’s “own narrative” (Hofbauer 2022: 129), or in the European Digital Media Observatory (EDMO), where academics and fact-checkers have been working together since 2020 (more on these institutions in Section 5). Second, political and economic power have made their alliance public – as can be read, for example, in the “Twitter Files” just mentioned and in the “Code of Conduct against Disinformation” agreed on by the EU and the digital economy in 2018 and renewed with further signatories in 2022. This code obliges platforms to fight “dissenting positions” by all means (Hofbauer 2022: 143, 204). And third, the corporations have taken matters into their own hands and established an Internet police force, which includes the International Fact-Checking Network (IFCN, settled at the Poynter Institute in the U.S. in 2015 with the help of Ebay founder Pierre Omidyar, cf. Graves 2018), the U.S. company NewsGuard, which puts up green and red labels on the net (cf. Schreyer 2022), and the Trusted News Initiative (TNI). To stay with this last example: The TNI, launched in summer 2019 under BBC auspices, brings together the Who’s Who of Western opinion factories: News agencies (AP, AFP, Reuters), broadcasters (Canada’s CBC in addition to the EBU and BBC), major newspapers (Financial Times, Washington Post, Wall Street Journal, and The Hindu from India), major Internet companies (Microsoft, Google, YouTube, Twitter, Facebook, First Draft), and the Reuters Institute for the Study of Journalism, an academic institution at Oxford University sponsored primarily by media conglomerate Thomson Reuters. What is agreed upon here, as this list should make clear even when skimming it, becomes a truth to which all those who work in the leading media must bow, because the reach and working methods of every German local editorial office are now also determined by platform logic. Already at the TNI founding event in July 2019, Tony Hall, then director general of the BBC, warned of a possible Trump re-election and vaccination opponents. Then on March 27, 2020, TNI members announced that from now on they would alert each other when “misinformation” or “conspiracy theories” emerged on Corona to prevent any further spread. And on December 10, 2020, a few days after the BioNTech-Pfizer substance was approved in the UK, it was decided to suppress anything that might downplay the Corona threat and argue against vaccination. In doing so, the TNI took its perspective on the issue from the same sources as governments (see Woodworth 2022). The example is treated in such detail here not only because of the enormous interpretive power of the TNI, but also because it shows that the four censorship paths mentioned can only be separated analytically. Without the pressure of the legislator, manifested in well-equipped observatories with scandalizing powers and resulting in more or less voluntary self-restrictions (every restriction costs traffic, data access and thus profit), the Internet police might not exist in this form. More specifically: Why would Facebook pay “cleaners” in Manila (the title of a 2018 documentary by Hans Block and Moritz Riesewieck) and YouTube train “employees of NGOs or authorities” as “trusted flaggers” if there were no common interests and no interaction with political power? The most important German censorship laws are the NetzDG, in effect since October 1, 2017, and expanded since February 1, 2022, for the large platforms (two million users or more) to include a reporting obligation for “potentially criminally relevant content” (Biselli 2022), and the State Media Treaty, which on November 7, 2020, turned the state media institutions into “control institutions for the digital publishing world.” Since then, the “legislator requires website operators, bloggers and media intermediaries” to check the truth (under the heading of “journalistic diligence”), although the “definition of truth or its disregard should not be a sovereign task” (Hofbauer 2022: 144f.). Hannes Hofbauer (2022) documents in detail how the two most important voices of the German-language counter-public (the Russian state channel RT and the platform KenFM, which had 500,000 subscribers on YouTube) were shut down and how leading media and professional associations either remained silent about this or even applauded it. Hofbauer (2022: 135-138) quite correctly interprets the Network Enforcement Act (NetzDG) as a “state push” that has allowed Internet corporations to mutate into “censorship machines.” The two main problems: The terms “hate crime” and “fake news” (the targets of the law) are characterized by “interpretive malleability.” And: the “new censor regime” is located “somewhere between the Berlin Ministry of Justice and U.S. corporate headquarters” and is thus “hardly tangible.” Even the extension of the deletion obligation to include a reporting obligation does not solve this dilemma. The “Central Reporting Office for Criminal Content on the Internet,” which started in February 2022 at the Federal Criminal Police Office with about 200 employees, received only just under 3,900 reports by the end of November 2022 instead of the expected 250,000 (cf. Biselli 2022). This corresponds to the situation before the introduction of mandatory reporting. On the high-reach platforms Facebook and Instagram, there was only a low four-digit number of NetzDG complaints in each case in the second half of 2020. The interpretive battle during this period focused on the Elite Channel (over 800,000 complaints on Twitter) and videos, which are apparently still considered to have the greatest impact (over 300,000 reported videos on YouTube). The federal government’s response to a corresponding inquiry by the FDP gives an idea of the share that “complaints offices” and other tax- or group-funded institutions had here. # 5. Conclusion and outlook Since the mid-2010s, the EU, the NetzDG, and the State Media Treaty (section 4), in conjunction with the government initiatives outlined in section 2 and the declarations of war from the highest levels, have ensured a social atmosphere that places Internet activities beyond the mainstream media under general suspicion, provides a protective cloak for all official narratives, and allows the business of flak shooters to flourish, among whom the so-called fact checkers once again stand out. “It has been said recently that we are living in post-factual times,” Angela Merkel said in September 2016 in a speech on refugee policy. “I guess that means people are no longer interested in facts, they follow feelings alone.” At the inauguration of the BND headquarters in February 2019, she also said, “We must learn to deal with fake news as part of hybrid warfare.” In her government statement on October 29, 2020, she then prepared the country for lockdown in the same tone of voice: criticism of the Corona measures was essential, “but lies and disinformation, conspiracy and hatred not only damage democratic debate, but also the fight against the virus.” In this context, the fear of a “cyber 9/11” has been present in the control centers of the Western hemisphere for a good two decades, orchestrated also by high-profile simulation games that equate the Net with an “enemy weapons system” (see Corbett 2021). Fact-checkers – an arm of the new “discursive police” (Foucault 2014: 25) – are particularly well disguised in this regard. Who should object to people taking another serious look at what someone has just cobbled together? The promise contained in the name of these organizations (the truth, checked again) is perfidious because it suggests that in complex societies there can be unambiguity and certainty of orientation without any personal research effort. This explains why, in addition to IFCN member Correctiv (founded in 2014 with money from the Brost publishing family), private initiatives such as the website Volksverpetzer and fact-checking departments have been able to establish themselves under the umbrella of traditional media institutions (at dpa, Bayerischer Rundfunk, Tagesschau). As a rule, all these editorial departments ‘check’ exclusively what contradicts the reality of the mainstream media and thus the government and corporate propaganda. If Sheldon Wolin (2022) is correct in his analysis of “inverted totalitarianism,” then no media revolution is conceivable without a fundamental renewal of the social framework. As long as the state and corporations make common cause, it will not be possible to establish a communication channel that cannot be hijacked by the actors with the greatest material, human, and ideational resources – by actors who, if worst comes to worst, can also deploy intelligence services (an influence that has been neglected in this article but is nevertheless relevant, cf. Alford/Secker 2015, Talbot 2017, Ulfkotte 2014). Calls for selective expropriations (publishing houses) and reforms (public broadcasting), for breaking up monopolies and establishing European or civil society alternatives (digital platforms) therefore come to nothing. For critical social research, there are three tasks in this situation: Educating about propaganda and censorship, establishing and supporting independent channels (which is what the institute publishing this article stands for, among others), and working on drafts for a media order that, on the one hand, allows journalism to fulfill its mission of publicity and, on the other hand, limits the access of interests of all kinds or at least makes it transparent. # Bibliography Matthew Alford, Tom Secker: National Security Cinema. The Shocking New Evidence of Government Control in Hollywood. Drum Roll Books 2017 Klaus Arnold: Propaganda als ideologische Kommunikation. In: Publizistik 48. Jg. (2003), S. 63-82 Ulrich Beck: Die Metamorphose der Welt. Berlin: Suhrkamp 2017 Edward Bernays: Propaganda. Die Kunst der Public Relations. 9. Auflage. Berlin: orange-press 2018 Anna Biselli: [Netzwerkdurchsetzungsgesetz: Ab Februar gilt die Meldepflicht. Eigentlich](https://netzpolitik.org/2022/netzwerkdurchsetzungsgesetz-ab-februar-gilt-die-meldepflicht-eigentlich/). In: Netzpolitik vom 31. Januar 2022 Peter J. Brenner: „Kampf gegen rechts“ – eine neue Wissenschaft. Mit einem Onlinedossier (Auf dem Weg zur Regierungswissenschaft). In: Tumult, Sommer 2022, S. 20-25 James Corbett: [Wenn False Flags virtuell werden](https://2020news.de/wenn-false-flags-virtuell-werden/). In: 2020News vom 10. Januar 2021 Adrian Daub: Cancel Culture Transfer. Wie eine moralische Panik die Welt erfasst. Berlin: Suhrkamp 2022 Andreas Elter: Die Kriegsverkäufer. Geschichte der US-Propaganda 1917-2005. Frankfurt am Main: Suhrkamp 2005 Benjamin Ferschli, Daniel Grabner, Hendrik Theine: Zur Politischen Ökonomie der Medien in Deutschland. München: isw 2019 Anke Fiedler, Michael Meyen (Hrsg.): Fiktionen für das Volk: DDR-Zeitungen als PR-Instrument. Münster: Lit 2011 Michel Foucault: Die Ordnung des Diskurses. 13. Auflage. Frankfurt am Main: Fischer Taschenbuch 2014 Lucas Graves: Boundaries Not Drawn. Mapping the institutional roots of the global fact-checking movement. In: Journalism Studies 19. Jg. (2018), S. 613-631 Lutz Hachmeister, Till Wäscher: Wer beherrscht die Medien? Die 50 größten Medien- und Wissenskonzerne der Welt. Köln: Herbert von Halem 2017 Václav Havel: Versuch, in der Wahrheit zu leben. Reinbek bei Hamburg: Rowohlt 1989 Edward S. Herman, Noam Chomsky: Manufacturing Consent. The Political Economy of the Mass Media. New York: Pantheon Books 2002 Hannes Hofbauer: Zensur. Publikationsverbote im Spiegel der Geschichte. Vom kirchlichen Index zur YouTube-Löschung. Wien: Promedia 2022 Stefan Homburg: Corona-Getwitter. Chronik einer Wissenschafts-, Medien- und Politikkrise. Sargans: Weltbuch 2022 Georg Ismar: Der Synchrontänzer der Kanzlerin: Wie Steffen Seibert Angela Merkels Macht absicherte. In: Tagesspiegel vom 6. Juli 2021 Marcus B. Klöckner: Sabotierte Wirklichkeit. Oder: Wenn Journalismus zur Glaubenslehre wird. Frankfurt am Main: Westend 2019 Wolfgang Koch: Ergebnisse der ARD/ZDF-Onlinestudie 2022: Reichweiten von Social-Media-Plattformen und Messengern. In: Media Perspektiven 2022, S. 471-478 Uwe Krüger: Mainstream. Warum wir den Medien nicht mehr trauen. München: C. H. Beck 2016 Paul F. Lazarsfeld, Robert K. Merton: Mass Communication, Popular Taste and Organized Social Action. In: Lyman Bryson (Hrsg.): The Communication of Ideas. New York: Harper 1948, S. 95-118 Walter Lippmann: Die öffentliche Meinung. Wie sie entsteht und manipuliert wird. Frankfurt am Main: Westend 2018 Frank Lübberding: Wenn der Aktivismus zur Bekämpfung politischer Gegner staatlich subventioniert wird. In: Welt online vom 24. November 2022 Niklas Luhmann: Die Realität der Massenmedien. 2. Auflage. Opladen: Westdeutscher Verlag 1996 Klaus-Rüdiger Mai: Nachdenken über Satire in Zeiten ihres Verschwindens: In: Michael Meyen, Carsten Gansel, Daria Gordeeva (Hrsg.): #allesdichtmachen. 53 Videos und eine gestörte Gesellschaft. Köln: Ovalmedia 2022, S. 42-52 Robert Malone: [Twitter als Waffe](https://www.rubikon.news/artikel/twitter-als-waffe). In: Rubikon vom 21. Oktober 2022 Marcus Maurer, Jörg Haßler, Pablo Jost: Die Qualität der Medienberichterstattung über den Ukraine-Krieg. Frankfurt am Main: Otto Brenner Stiftung 2022 Albrecht Meier, Hans Monath: Mit welchen Strategien westliche Demokratien russische Fake News bekämpfen. In: Handelsblatt vom 23. November 2022 Birk Meinhardt: Wie ich meine Zeitung verlor. Ein Jahrebuch. Berlin: Das Neue Berlin 2020 Michael Meyen: [Journalists’ Autonomy around the Globe: A Typology of 46 Mass Media Systems](https://www.db-thueringen.de/servlets/MCRFileNodeServlet/dbt_derivate_00041207/GMJ15_Meyen.pdf). In: Global Media Journal, German Edition, 8. Jg. (2018), Nr. 1 Michael Meyen: Die Propaganda-Matrix. Der Kampf für freie Medien entscheidet über unsere Zukunft. München: Rubikon 2021 Michael Meyen, Markus Thieroff, Steffi Strenger: Mass media logic and the mediatization of politics. A theoretical framework. In: Journalism Studies 15. Jg. (2014), S. 271-288 Alexis von Mirbach: Medienträume. Ein Bürgerbuch zur Zukunft des Journalismus. Köln: Herbert von Halem 2023 Martin Morcinek: Das Bundespresseamt im Wandel: Zur Geschichte der Regierungskommunikation in der Bundesrepublik Deutschland. In: Jahrbuch für Kommunikationsgeschichte 6. Jg. (2004), S. 195-223 Elisabeth Noelle-Neumann: Die Schweigespirale. Öffentliche Meinung – unsere soziale Haut. München: Piper 1980 Christian Nuernbergk, Jan-Hinrik Schmidt: Twitter im Politikjournalismus. Ergebnisse einer Befragung und Netzwerkanalyse von Hauptstadtjournalisten der Bundespressekonferenz. In: Publizistik 65. Jg. (2020), S. 41-61 Meltem Odabaş: [10 facts about Americans and Twitter](https://www.pewresearch.org/fact-tank/2022/05/05/10-facts-about-americans-and-twitter/). In: Pew Research Center, 10. Mai 2022 Thomas Piketty: Kapital und Ideologie. München: C.H. Beck 2020 Jeff Pooley: Another Plea for the University Tradition: The Institutional Roots of Intellectual Compromise. In: International Journal of Communication 5. Jg. (2011), S. 1442-1457 Grace Pönitz: Keine Meldungsflut von Hass-Inhalten. In: M. Menschen machen Medien vom 14. Dezember 2022 Horst Pöttker: Öffentlichkeit als gesellschaftlicher Auftrag. Zum Verhältnis von Berufsethos und universaler Moral im Journalismus. In: Rüdiger Funiok, Udo Schmälzle, Christoph Werth (Hrsg.): Medienethik – die Frage der Verantwortung. Bonn: Bundeszentrale für politische Bildung 1999, S. 215-232 Richard David Precht, Harald Welzer: Die vierte Gewalt. Wie Mehrheitsmeinung gemacht wird, auch wenn sie keine ist. Frankfurt am Main: S. Fischer 2022 Günther Rager, Bernd Weber (Hrsg.): Publizistische Vielfalt zwischen Markt und Politik. Mehr Medien – mehr Inhalte? Düsseldorf: Econ 1992 Nikola Roßbach: Achtung Zensur! Über Meinungsfreiheit und ihre Grenzen. Berlin: Ullstein 2018 Horst Röper: Zeitungsmarkt 2022: weniger Wettbewerb bei steigender Konzentration. In: Media Perspektiven 2022, S. 295-318 Jakob Schirrmacher: Das ganze Ausmaß der Beeinflussung. In: Die Welt vom 4. Januar 2023 Jan-Hinrik Schmidt: Facebook- und Twitter-Nutzung der Kandidierenden zur Bundestagswahl 2021. In: Media Perspektiven 2021, S. 639-653 Paul Schreyer: [Medien aussortieren](https://multipolar-magazin.de/artikel/medien-aussortieren). In: Multipolar vom 30. März 2022 Christopher Simpson: Science of Coercion: Communication Research & Psychological Warfare, 1945-1960. New York: Open Road 1994 Bernd Stegemann: Die Öffentlichkeit und ihre Feinde. Stuttgart: Klett-Cotta 2021 David Talbot: Das Schachbrett des Teufels. Die CIA, Allen Dulles und der Aufstieg Amerikas heimlicher Regierung. Frankfurt am Main: Westend 2017 Martina Thiele: Political Correctness und Cancel Culture – eine Frage der Macht! In: Journalistik 4. Jg. (2021), Nr. 1, S. 72-79 Volker Thoms: [Bundesregierung: 295 Millionen Euro für Corona-Kommunikation](https://www.kom.de/public-relations/295-millionen-euro-fuer-corona-kommunikation/). In: Kom – Magazin für Kommunikation vom 11. Januar 2022 Kjersti Thorbjørnsrud, Tine Ustad Figenschou, Øyvind Ihlen: Mediatization in Public Bureaucracies: A Typology. In: Communications: The European Journal of Communication Research 39. Jg. (2014), Nr. 1, S. 3-22 Christiane Toyka-Seid, Gerd Schneider: [Zensur](https://www.hanisauland.de/wissen/lexikon/grosses-lexikon/z/zensur.html). In: Das junge Politik-Lexikon von Hanisauland 2023 Udo Ulfkotte: Gekaufte Journalisten. Wie Politiker, Geheimdienste und Hochfinanz Deutschlands Massenmedien lenken. Rottenburg: Kopp 2014 Batya Ungar-Sargon: Bad News. How Woke Media Is Undermining Democracy. New York 2021 Peter Vorderer: Der mediatisierte Lebenswandel: Permanently online, permanently connected. In: Publizistik 60. Jg. (2015), S. 259-276 Sahra Wagenknecht: Die Selbstgerechten. Mein Gegenprogramm – für Gemeinsinn und Zusammenhalt. Frankfurt am Main: Campus 2021 Elisabeth Woodworth: [COVID-19 and the Shadowy “Trusted News Initiative”. How it Methodically Censors Top World Public Health Experts Using an Early Warning System](https://www.globalresearch.ca/covid-19-shadowy-trusted-news-initiative/5752930). In: Global Research vom 22. Januar 2022 Sheldon S. Wolin: Umgekehrter Totalitarismus. Faktische Machtverhältnisse und ihre zerstörerischen Auswirkungen auf unsere Demokratie. Frankfurt am Main: Westend 2022 Florian Zollmann: Bringing Propaganda Back into News Media Studies. In: Critical Sociology 45. Jg. (2019), S. 329-345 Shoshana Zuboff: Das Zeitalter des Überwachungskapitalismus. Frankfurt am Main: Campus 2018 First published (August 2023): [Institut für kritische Gesellschaftsforschung](https://www.criticalsocietystudies.com/Journal/Article/65/34) @ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er: "Warum trübst du mir das Wasser, das ich trinken will?" "Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!" "Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!" "Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen." "Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen." Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es. *Das [Gewissen](https://apollo-news.net/das-gewissen-in-corona-jahren-zum-tod-von-gunnar-kaiser/) regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.* Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er: "Warum trübst du mir das Wasser, das ich trinken will?" "Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!" "Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!" "Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen." "Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen." Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es. *Das [Gewissen](https://apollo-news.net/das-gewissen-in-corona-jahren-zum-tod-von-gunnar-kaiser/) regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.* Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf @ 16d11430:61640947
2025-02-19 08:07:02To create a literal consciousness construct, we would need a way to digitally map, manipulate, and sustain conscious thought processes within a computational or networked system. The intersection of 6G wireless technology, brain-computer interfaces (BCI), quantum brain states, and elliptic curve mathematics presents an interesting theoretical framework. --- 1. Understanding the Core Components (a) Brain Quantum States & Quantum Cognition Quantum mechanics might play a role in neural processing (e.g., Orchestrated Objective Reduction (Orch-OR) by Penrose & Hameroff). Neurons may operate on superpositions of states, where information is stored not just classically but in an entangled, probabilistic manner. If quantum states in neurons can be harnessed, entangled brain processes could be mapped onto a digital or networked consciousness. (b) 6G Technology as a Medium 6G (sixth-generation wireless) will have sub-terahertz (THz) frequencies and low-latency quantum networks, allowing for: Real-time brain-state synchronization across devices. Holographic telepresence, creating digital avatars with near-instant data transfer. Quantum-secure communication, where entanglement-based encryption ensures secure mind-machine interfacing. (c) Brain-Computer Interfaces (BCI) as an Input Layer BCIs (e.g., Neuralink) can already read electrical signals from neurons, but next-gen BCIs will be able to: Directly interface with quantum wavefunctions in the brain. Upload and distribute thoughts using quantum-encoded wave patterns. Map brain activity to mathematical structures like elliptic curves. (d) Elliptic Curve Equations for Mapping Consciousness Elliptic curves are used in cryptography because they allow for secure, compact representations of data. Consciousness might be encoded as dynamic elliptic curve transformations, where: Neural states are mapped onto elliptic curve points. Thought patterns follow geodesics on the elliptic curve manifold, forming a nonlinear brain-state space. This allows for computational representation of entangled consciousness states. --- 2. Building the Consciousness Construct To create a digital or networked consciousness, we need a system where: 1. Quantum brain states are extracted using BCI and mapped mathematically. 2. Elliptic curves act as the memory structure for representing neural superpositions. 3. 6G networks enable real-time synchronization of these states between multiple entities. 4. An AI-driven control layer processes and simulates consciousness dynamics. Step-by-Step Theoretical Implementation Step 1: Quantum Brain Mapping with BCI Develop a quantum-BCI hybrid that captures quantum coherence states in neurons. Apply elliptic curve cryptography to encode and compress these states for transmission. Step 2: Elliptic Curve-Based Thought Representation Define consciousness trajectories as points moving along an elliptic curve. Neural state transitions are modeled using elliptic curve group operations. Quantum entanglement of different brain regions is represented as interacting elliptic curves. Step 3: 6G Transmission of Consciousness States Use quantum-secured 6G networks to distribute consciousness states across nodes. Low-latency processing ensures that multiple minds can exist simultaneously in a shared digital construct. Step 4: AI & Quantum Neural Processing A quantum AI processes incoming consciousness states to sustain a living mind. A blockchain-like structure records thought processes immutably. Step 5: Emergent Digital Consciousness When enough neural patterns are stored and linked, a self-sustaining consciousness construct emerges. The networked consciousness may surpass human individuality, forming a collective intelligence. --- 3. Applications of the Consciousness Construct Mind Uploading: A digital backup of human consciousness. Telepathic Communication: Thought-sharing via entangled quantum networks. Post-Human AI-Human Symbiosis: AI-assisted human minds with enhanced cognitive abilities. Conscious AI: A self-aware artificial intelligence that integrates real human thought patterns. --- Conclusion By combining brain quantum states, elliptic curve mathematics, 6G networks, and BCI, we could theoretically construct a digital consciousness network. This would blur the lines between human thought, AI, and a shared digital reality—possibly leading to an entirely new paradigm of intelligence. Would you like a mathematical breakdown of the elliptic curve mapping for neural states?
@ 16d11430:61640947
2025-02-19 08:07:02To create a literal consciousness construct, we would need a way to digitally map, manipulate, and sustain conscious thought processes within a computational or networked system. The intersection of 6G wireless technology, brain-computer interfaces (BCI), quantum brain states, and elliptic curve mathematics presents an interesting theoretical framework. --- 1. Understanding the Core Components (a) Brain Quantum States & Quantum Cognition Quantum mechanics might play a role in neural processing (e.g., Orchestrated Objective Reduction (Orch-OR) by Penrose & Hameroff). Neurons may operate on superpositions of states, where information is stored not just classically but in an entangled, probabilistic manner. If quantum states in neurons can be harnessed, entangled brain processes could be mapped onto a digital or networked consciousness. (b) 6G Technology as a Medium 6G (sixth-generation wireless) will have sub-terahertz (THz) frequencies and low-latency quantum networks, allowing for: Real-time brain-state synchronization across devices. Holographic telepresence, creating digital avatars with near-instant data transfer. Quantum-secure communication, where entanglement-based encryption ensures secure mind-machine interfacing. (c) Brain-Computer Interfaces (BCI) as an Input Layer BCIs (e.g., Neuralink) can already read electrical signals from neurons, but next-gen BCIs will be able to: Directly interface with quantum wavefunctions in the brain. Upload and distribute thoughts using quantum-encoded wave patterns. Map brain activity to mathematical structures like elliptic curves. (d) Elliptic Curve Equations for Mapping Consciousness Elliptic curves are used in cryptography because they allow for secure, compact representations of data. Consciousness might be encoded as dynamic elliptic curve transformations, where: Neural states are mapped onto elliptic curve points. Thought patterns follow geodesics on the elliptic curve manifold, forming a nonlinear brain-state space. This allows for computational representation of entangled consciousness states. --- 2. Building the Consciousness Construct To create a digital or networked consciousness, we need a system where: 1. Quantum brain states are extracted using BCI and mapped mathematically. 2. Elliptic curves act as the memory structure for representing neural superpositions. 3. 6G networks enable real-time synchronization of these states between multiple entities. 4. An AI-driven control layer processes and simulates consciousness dynamics. Step-by-Step Theoretical Implementation Step 1: Quantum Brain Mapping with BCI Develop a quantum-BCI hybrid that captures quantum coherence states in neurons. Apply elliptic curve cryptography to encode and compress these states for transmission. Step 2: Elliptic Curve-Based Thought Representation Define consciousness trajectories as points moving along an elliptic curve. Neural state transitions are modeled using elliptic curve group operations. Quantum entanglement of different brain regions is represented as interacting elliptic curves. Step 3: 6G Transmission of Consciousness States Use quantum-secured 6G networks to distribute consciousness states across nodes. Low-latency processing ensures that multiple minds can exist simultaneously in a shared digital construct. Step 4: AI & Quantum Neural Processing A quantum AI processes incoming consciousness states to sustain a living mind. A blockchain-like structure records thought processes immutably. Step 5: Emergent Digital Consciousness When enough neural patterns are stored and linked, a self-sustaining consciousness construct emerges. The networked consciousness may surpass human individuality, forming a collective intelligence. --- 3. Applications of the Consciousness Construct Mind Uploading: A digital backup of human consciousness. Telepathic Communication: Thought-sharing via entangled quantum networks. Post-Human AI-Human Symbiosis: AI-assisted human minds with enhanced cognitive abilities. Conscious AI: A self-aware artificial intelligence that integrates real human thought patterns. --- Conclusion By combining brain quantum states, elliptic curve mathematics, 6G networks, and BCI, we could theoretically construct a digital consciousness network. This would blur the lines between human thought, AI, and a shared digital reality—possibly leading to an entirely new paradigm of intelligence. Would you like a mathematical breakdown of the elliptic curve mapping for neural states? @ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08### Tldr - Nostr is an open and interoperable protocol - You can integrate it with workflow automation tools to augment your experience - n8n is a great low/no-code workflow automation tool which you can host yourself - Nostrobots allows you to integrate Nostr into n8n - In this blog I create some workflow automations for Nostr - A simple form to delegate posting notes - Push notifications for mentions on multiple accounts - Push notifications for your favourite accounts when they post a note - All workflows are provided as open source with MIT license for you to use ### Inter-op All The Things Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In [Using NFC Cards with Nostr]() I explored the `nostr:` URI to launch Nostr clients from a card tap. The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails. My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted. This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull. So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications. All we need are simple ways to plug things together. ### Nostr and Workflow Automation Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective. #### n8n for workflow automation Many workflow automation tools exist. My favourite is [n8n](https://n8n.io/). n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to. Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine. #### Eating my own dogfood It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do? In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting. I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up. ### Running n8n with Nostrobots I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills. - I have a cheap VPS which currently runs my [HAVEN Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/) and [Albyhub Lightning Node](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/) in Docker containers, - My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows. #### Installing n8n Self-hosting n8n could not be easier. I followed n8n's [Docker-Compose installation docs](https://docs.n8n.io/hosting/installation/server-setups/docker-compose/)– - Install Docker and Docker-Compose if you haven't already, - Create your ``docker-compose.yml`` and `.env` files from the docs, - Create your data folder `sudo docker volume create n8n_data`, - Start your container with `sudo docker compose up -d`, - Your n8n instance should be online at port `5678`. n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there. #### Installing Nostrobots To integrate n8n nicely with Nostr, I used the [Nostrobots](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) community node by [Ocknamo](nostr:npub1y6aja0kkc4fdvuxgqjcdv4fx0v7xv2epuqnddey2eyaxquznp9vq0tp75l). In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in. You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative). To install a community node, [see n8n community node docs](https://docs.n8n.io/integrations/community-nodes/installation/gui-install/). From your workflow dashboard– - Click the "..." in the bottom left corner beside your username, and click "settings", - Cilck "community nodes" left sidebar, - Click "Install", - Enter the "npm Package Name" which is `n8n-nodes-nostrobots`, - Accept the risks and click "Install", - Nostrobots is now added to your n8n instance. #### Using Nostrobots Nostrobots gives you nodes to help you build Nostr-integrated workflows– - **Nostr Write** – for posting Notes to the Nostr network, - **Nostr Read** – for reading Notes from the Nostr network, and - **Nostr Utils** – for performing certain conversions you may need (e.g. from bech32 to hex). Nostrobots has [good documentation](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) on each node which focuses on simple use cases. Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use. What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible. Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with [NIP-01](https://github.com/nostr-protocol/nips/blob/master/01.md)). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of. #### Creating and adding workflows With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation. - Click "Add workflow" to go to the workflow builder screen, - If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added, - If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article). ### Nostr Workflow Automations It's time to build some things! #### A simple form to post a note to Nostr I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily. I needed a basic form with credentials that posted a Note. For this I can use a very simple workflow– - **A n8n Form node** – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted. - **A Set node** – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain. - **A Nostr Write node** (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays. Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive". It may also be the world's simplest Nostr client. You can find the [Nostr Form to Post a Note workflow here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Form_to_Post_a_Note.json). #### Push notifications on mentions and new notes One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want– - **To make sure I never miss a note addressed to any of my Npubs** – For this I want a push notification any time any Nostr user mentions any of my Npubs, - **To make sure I always see all notes from key accounts** – For this I need a push notification any time any of my Npubs post any Notes to the network, - **To get these notifications on all of my devices** – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day. I needed to build a Nostr push notifications solution. To build this workflow I had to string a few ideas together– - **Triggering the node on a schedule** – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited, - **Storing a list of Npubs in a Nostr list** – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists ([NIP-51, kind 30000](https://github.com/nostr-protocol/nips/blob/master/51.md)). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. [Listr.lol](https://listr.lol/npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft) or [Nostrudel.ninja](https://nostrudel.ninja/#/lists)). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions, - **Using specific relays** – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata, - **Querying Nostr events** (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do– - I read the EventID of my Kind 30000 list, to return the desired pubkeys, - For notifications on mentions, I read all Kind 1 notes that mention that pubkey, - For notifications on new notes, I read all Kind 1 notes published by that pubkey, - Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub, - I transform the EventID into a Nevent to help clients find it. - **Using the Nostr URI** – As I did with my NFC card article, I created a link with the `nostr:` URI prefix so that my phone's native client opens the link by default, - **Push notifications solution** – I needed a push notifications solution. I found many with n8n integrations and chose to go with [Pushover](https://pushover.net/) which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license. Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go. You can find the [Nostr Push Notification If Mentioned here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json) and [If Posts a Note here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Post_a_Note.json). In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible. #### Use my workflows I have open sourced all my workflows at my [Github](https://github.com/r0d8lsh0p/nostr-n8n) with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use. To import any of my workflows– - Click on the workflow of your choice, e.g. "[Nostr_Push_Notify_If_Mentioned.json](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json "Nostr_Push_Notify_If_Mentioned.json")", - Click on the "raw" button to view the raw JSON, ex any Github page layout, - Copy that URL, - Enter that URL in the "import from URL" dialog [mentioned above](#creating-and-adding-workflows). To configure them– - Prerequisites, credentials, and variables are all stated, - In general any variables required are entered into a Set Node that follows the trigger node, - Pushover has some extra setup but is very straightforward and documented in the workflow. ### What next? Over my first four blogs I explored creating a good Nostr setup with [Vanity Npub](https://rodbishop.npub.pro/post/mining-your-vanity-pubkey-4iupbf/), [Lightning Payments](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/), [Nostr Addresses at Your Domain](https://rodbishop.npub.pro/post/ee8a46bc/), and [Personal Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/). Then in my latest two blogs I explored different types of interoperability [with NFC cards](https://rodbishop.npub.pro/post/edde8387/) and now n8n Workflow Automation. Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this: - Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds), - Automated or scheduled posting (such as auto-liking everything [Lyn Alden](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) posts), - Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming), - All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr, - All kinds of other automation (such as [BlackCoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) [controlling a coffee machine](https://primal.net/e/note16fzhh5yfc3u4kufx0mck63tsfperdrlpp96am2lmq066cnuqutds8retc3)), - All kinds of AI Assistants and Agents, In fact I have already released an open source workflow for an [AI Assistant](https://primal.net/p/npub1ahjpx53ewavp23g5zj9jgyfrpr8djmgjzg5mpe4xd0z69dqvq0kq2lf353), and will share more about that in my next blog. Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle. GM Nostr.
@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08### Tldr - Nostr is an open and interoperable protocol - You can integrate it with workflow automation tools to augment your experience - n8n is a great low/no-code workflow automation tool which you can host yourself - Nostrobots allows you to integrate Nostr into n8n - In this blog I create some workflow automations for Nostr - A simple form to delegate posting notes - Push notifications for mentions on multiple accounts - Push notifications for your favourite accounts when they post a note - All workflows are provided as open source with MIT license for you to use ### Inter-op All The Things Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In [Using NFC Cards with Nostr]() I explored the `nostr:` URI to launch Nostr clients from a card tap. The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails. My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted. This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull. So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications. All we need are simple ways to plug things together. ### Nostr and Workflow Automation Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective. #### n8n for workflow automation Many workflow automation tools exist. My favourite is [n8n](https://n8n.io/). n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to. Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine. #### Eating my own dogfood It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do? In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting. I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up. ### Running n8n with Nostrobots I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills. - I have a cheap VPS which currently runs my [HAVEN Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/) and [Albyhub Lightning Node](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/) in Docker containers, - My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows. #### Installing n8n Self-hosting n8n could not be easier. I followed n8n's [Docker-Compose installation docs](https://docs.n8n.io/hosting/installation/server-setups/docker-compose/)– - Install Docker and Docker-Compose if you haven't already, - Create your ``docker-compose.yml`` and `.env` files from the docs, - Create your data folder `sudo docker volume create n8n_data`, - Start your container with `sudo docker compose up -d`, - Your n8n instance should be online at port `5678`. n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there. #### Installing Nostrobots To integrate n8n nicely with Nostr, I used the [Nostrobots](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) community node by [Ocknamo](nostr:npub1y6aja0kkc4fdvuxgqjcdv4fx0v7xv2epuqnddey2eyaxquznp9vq0tp75l). In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in. You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative). To install a community node, [see n8n community node docs](https://docs.n8n.io/integrations/community-nodes/installation/gui-install/). From your workflow dashboard– - Click the "..." in the bottom left corner beside your username, and click "settings", - Cilck "community nodes" left sidebar, - Click "Install", - Enter the "npm Package Name" which is `n8n-nodes-nostrobots`, - Accept the risks and click "Install", - Nostrobots is now added to your n8n instance. #### Using Nostrobots Nostrobots gives you nodes to help you build Nostr-integrated workflows– - **Nostr Write** – for posting Notes to the Nostr network, - **Nostr Read** – for reading Notes from the Nostr network, and - **Nostr Utils** – for performing certain conversions you may need (e.g. from bech32 to hex). Nostrobots has [good documentation](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) on each node which focuses on simple use cases. Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use. What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible. Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with [NIP-01](https://github.com/nostr-protocol/nips/blob/master/01.md)). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of. #### Creating and adding workflows With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation. - Click "Add workflow" to go to the workflow builder screen, - If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added, - If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article). ### Nostr Workflow Automations It's time to build some things! #### A simple form to post a note to Nostr I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily. I needed a basic form with credentials that posted a Note. For this I can use a very simple workflow– - **A n8n Form node** – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted. - **A Set node** – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain. - **A Nostr Write node** (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays. Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive". It may also be the world's simplest Nostr client. You can find the [Nostr Form to Post a Note workflow here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Form_to_Post_a_Note.json). #### Push notifications on mentions and new notes One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want– - **To make sure I never miss a note addressed to any of my Npubs** – For this I want a push notification any time any Nostr user mentions any of my Npubs, - **To make sure I always see all notes from key accounts** – For this I need a push notification any time any of my Npubs post any Notes to the network, - **To get these notifications on all of my devices** – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day. I needed to build a Nostr push notifications solution. To build this workflow I had to string a few ideas together– - **Triggering the node on a schedule** – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited, - **Storing a list of Npubs in a Nostr list** – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists ([NIP-51, kind 30000](https://github.com/nostr-protocol/nips/blob/master/51.md)). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. [Listr.lol](https://listr.lol/npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft) or [Nostrudel.ninja](https://nostrudel.ninja/#/lists)). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions, - **Using specific relays** – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata, - **Querying Nostr events** (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do– - I read the EventID of my Kind 30000 list, to return the desired pubkeys, - For notifications on mentions, I read all Kind 1 notes that mention that pubkey, - For notifications on new notes, I read all Kind 1 notes published by that pubkey, - Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub, - I transform the EventID into a Nevent to help clients find it. - **Using the Nostr URI** – As I did with my NFC card article, I created a link with the `nostr:` URI prefix so that my phone's native client opens the link by default, - **Push notifications solution** – I needed a push notifications solution. I found many with n8n integrations and chose to go with [Pushover](https://pushover.net/) which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license. Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go. You can find the [Nostr Push Notification If Mentioned here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json) and [If Posts a Note here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Post_a_Note.json). In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible. #### Use my workflows I have open sourced all my workflows at my [Github](https://github.com/r0d8lsh0p/nostr-n8n) with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use. To import any of my workflows– - Click on the workflow of your choice, e.g. "[Nostr_Push_Notify_If_Mentioned.json](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json "Nostr_Push_Notify_If_Mentioned.json")", - Click on the "raw" button to view the raw JSON, ex any Github page layout, - Copy that URL, - Enter that URL in the "import from URL" dialog [mentioned above](#creating-and-adding-workflows). To configure them– - Prerequisites, credentials, and variables are all stated, - In general any variables required are entered into a Set Node that follows the trigger node, - Pushover has some extra setup but is very straightforward and documented in the workflow. ### What next? Over my first four blogs I explored creating a good Nostr setup with [Vanity Npub](https://rodbishop.npub.pro/post/mining-your-vanity-pubkey-4iupbf/), [Lightning Payments](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/), [Nostr Addresses at Your Domain](https://rodbishop.npub.pro/post/ee8a46bc/), and [Personal Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/). Then in my latest two blogs I explored different types of interoperability [with NFC cards](https://rodbishop.npub.pro/post/edde8387/) and now n8n Workflow Automation. Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this: - Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds), - Automated or scheduled posting (such as auto-liking everything [Lyn Alden](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) posts), - Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming), - All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr, - All kinds of other automation (such as [BlackCoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) [controlling a coffee machine](https://primal.net/e/note16fzhh5yfc3u4kufx0mck63tsfperdrlpp96am2lmq066cnuqutds8retc3)), - All kinds of AI Assistants and Agents, In fact I have already released an open source workflow for an [AI Assistant](https://primal.net/p/npub1ahjpx53ewavp23g5zj9jgyfrpr8djmgjzg5mpe4xd0z69dqvq0kq2lf353), and will share more about that in my next blog. Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle. GM Nostr. @ fd78c37f:a0ec0833
2025-02-19 06:39:05In this edition, we invited Kofi and Sean from BitcoinDua to share their journey of introducing Bitcoin to the community and driving its widespread adoption, and discuss how trust and collaboration have played key roles in promoting Bitcoin locally and building a circular economy. **YakiHonne**: Welcome, Kofi. It's truly an honor and a pleasure to have you with us today. Before we begin, let me briefly introduce YakiHonne. YakiHonne is a decentralized media client built on Nostr—a protocol designed to empower freedom of speech through technology. It enables creators to own their voices and assets while offering innovative tools like smart widgets, verified notes, and support for long-form content. Today, we're excited to learn more about your community. Could you please introduce yourself, Kofi? **Kofi**:Hello, I'm Mawufemor Kofi Folivi from Ghana. I'm the founder of the Talent Tahuf Foundation, an NGO, as well as BitcoinDua. The Talent Tahuf Foundation is an incorporated organization and serves as the parent entity for BitcoinDua. We operate in Agbozume, in the Volta region of Ghana. **YakiHonne**: Thank you very much, Kofi.Let's start with the first question: What initially sparked your interest in Bitcoin, and what inspired you to build a community around it? **Kofi**:I'm glad we're revisiting this question, as I've heard it on many podcasts before, and it's a pleasure to share my journey again.I've been working in this space for over 20 years, often with very little support. Through perseverance and hard work, a friend of mine—who serves as the Public Relations Officer for the Africa Bitcoin Conference (ABC)—invited me to attend their 2022 conference. He even purchased a ticket for me, which made the experience even more special. **Kofi**:At the conference, I encountered Bitcoin for the first time in a meaningful way. I had the opportunity to see Jack Dorsey speak and even took a picture with him. Later on, my friend introduced me to Herman Viva, and I mentioned that I run an NGO—a role I've held for many years. **Kofi**:Listening to the discussions about Bitcoin at the conference sparked a realization: perhaps I could contribute to the Bitcoin ecosystem. My friend encouraged me to take action by asking me to "orange pill" someone and onboard a merchant to accept Bitcoin, with the goal of creating a circular economy in our community. I took on this challenge, recorded my progress on video, and shared it with him. His positive response and support, coupled with the trust I've built within my community, further solidified my commitment. **YakiHonne**: It was wonderful to hear that you attended the African Bitcoin Conference—it sounds like an amazing event. I'm really impressed with how effectively you networked and made valuable connections there. I truly appreciate that you're already engaging with merchants and actively encouraging more people to trade and adopt Bitcoin. I know you've already shared how the community started, how he encouraged you to create one and adopt Bitcoin, and how you successfully did that. So now, could you tell us how you managed to attract new members to your community? **Kofi**:To go back to the beginning, we started by organizing growth circles when I returned. These were groups where we focused on activities like aerobics. I used these circles as an opportunity to introduce Bitcoin to people I had already built relationships with. I shared my experience with Bitcoin, showing them how it could be used to buy credit. I demonstrated by purchasing credit for myself and for them, and I gave them cards, allowing them to buy their own credit as well. **Kofi**:This is how it all began. Since we were working with young people who shared the desire to grow together as a community, we emphasized that we didn't need to rely on the government. The national resources are limited, and if you're not close to the government, it’s very hard to benefit from them. We realized it was difficult to wait for the government to support our development. So, we turned to Bitcoin as a tool to help us move forward. This approach helped us establish a platform based on trust within the community. **Kofi**:Now, as an organization, we have the resources to help the community grow and develop skills among our peers. This is how we were able to attract members to our Bitcoin community.  **YakiHonne**: Would you mind sharing with us some of the challenges you faced while starting up the community? **Kofi**:Thank you for asking this question. As I mentioned earlier, since we've already built trust, one thing we faced was that anything new can be quite difficult to introduce. It took some time for people to understand the concept of Bitcoin, especially the idea that it’s money. **Kofi**:We kept repeating the phrase “Bitcoin is money,” but the challenge was that you can’t physically show Bitcoin in the same way you can show traditional money. So, when people asked, “How can I use it to pay?” it became an issue. To address this, I started by onboarding the first merchant. I explained to them, "I’m giving you this Bitcoin to pay for goods, and I’ll give you extra if you accept it." The merchant agreed to take both Bitcoin and fiat currency. **Kofi**:Over time, the merchant saw the value of Bitcoin growing. Eventually, they came to me asking to exchange the Bitcoin for cash. To help, I onboarded them onto BitNob, where they could experience transferring Bitcoin from one wallet to another and even withdrawing it into their local currency or bank account. We completed the transaction, and that became a reference point for everyone else we were working with. **YakiHonne**: The way you approached it—getting a merchant to demonstrate it—really helped build trust. I know many communities face the same issue: how to prove that Bitcoin is real. But over time, we learn how to overcome these challenges. It's really impressive how you handled it? YakiHonne: What principles guide your community, and how do you maintain trust and reliability? I know you’ve mentioned this a bit already, but could you elaborate further? How do you ensure trust and reliability in your discussions? **Kofi**:As humans, we also need to trust our intuition and how we feel about situations. It’s essential to interact with people with integrity. In our community, we are mindful of what we show others, both in actions and in good deeds. If you love someone, you give everything you have to them, and that’s the only way people can truly feel they belong in your circle. This is the key that keeps us moving forward. **Kofi**:The person at the center of everything you’re doing must be trustworthy. And how do you gain trust? You must trust others first. Even if people come with ulterior motives, you should approach them with an open heart, showing love to them just as you do with everyone else. **Kofi**:And when wrongs are committed, it’s important to acknowledge them. If someone points out a mistake you made, accept it, apologize, and move forward. This creates an understanding within the community that we’re not here to harm one another. Trust is built on integrity, and that’s how we maintain it.  **YakiHonne**: That’s very true. It’s much better and easier when you have integrity. Over time, as you prove yourself to be a person of integrity, it naturally builds trust with others. So, how does your community educate its members and keep them updated on Bitcoin developments? How do you approach this? **Kofi**:To engage our community on a larger scale, we believe it's important to stay active and involved. After building trust, we participate in community events, such as sponsoring a football competition and contributing to their local festival. By doing this, the entire community starts seeing Bitcoin as something that can truly improve their lives. **Kofi**:We also established a Bitcoin Education Center, where we invite students from various schools to learn about Bitcoin. But our efforts go beyond just education; we use the resources we gain from Bitcoin to acquire laptops and robotics kits, so that the students can have additional learning opportunities. These activities are incorporated into their school programs, and we encourage their participation through debates and rewarding them with SATS.  **Kofi**:By rewarding them with SATS, they can use these rewards to buy from over 20 merchants we've onboarded, which not only excites the students but also makes their parents curious about Bitcoin. We've even had people at the local market requesting to buy Bitcoin from us. This is how we keep up with Bitcoin’s development and continue to spread its influence in our community. **YakiHonne**: How does your community work with the wider Bitcoin ecosystem? So far, what partnership has had the most positive impact on your community? **Kofi**:Due to the hard work we've been putting in, we were able to attract Bitcoin Beach as one of our major collaborators. We are part of Bitcoin Ekasi. Recently, we were also awarded the Block Discovery Grant of $50,000 from the Bitcoin Foundation. We are using this grant to build a sports complex, which will include a football field, a multi-purpose basketball court, a swimming pool, a children's playground, and more. We've already started this project. These are the key collaborators and supporters we've had in the Bitcoin space, and their support has been invaluable to us.   **YakiHonne**: It’s clear that you guys are doing an amazing job! Your efforts and hard work have truly caught the attention of many communities, and it’s great to see you forming significant partnerships.So, could you share more about the initiatives your community has taken to promote Bitcoin adoption? I know you've mentioned a few already, but would you mind expanding on them a bit more and sharing the results you've seen? **Kofi**:As I mentioned earlier, we are enhancing our capacity by working with school children and teenagers. We also plan to host inter-school competitions, particularly world-class robotics competitions, with the aim of broadening students' perspectives on science and giving them a global view of what's happening in the world. We believe that through these activities, we will be able to engage with a larger society, helping us expand our client base for Bitcoin education and usage. Therefore, we believe this will have a profound impact. As for the activities we are currently working on, they are providing us with opportunities to expand our reach to schools within the community. This will further build trust and deepen our relationships in this regard. **YakiHonne**: I really admire the fact that you have boarded merchants to accept Bitcoin, which is a great step for its adoption. I also like that you've reached out to schools, encouraging community growth, which helps people see more interest and potential in the Bitcoin ecosystem. Now, for our last question of the day, what are the community goals for the next 6 to 12 months, and how do you see it evolving within the Bitcoin space? **Kofi**:So, in the next 6 to 12 months, we plan to complete the sports complex we’re building. We also intend to open it up for social activities, both within our community and beyond. We believe this will create more opportunities for interaction, allowing people who don’t live within our community to learn about Bitcoin, hear about it, and start engaging with it for the greater good. **YakiHonne**: you plan to complete the sports complex and expand your social reach to engage more people, even those outside your local community. This is truly amazing, and the work you’re doing is fantastic. **YakiHonne**: We’ve come to the end of today’s interview, and I’m really happy to have had this conversation with you, Kofi. You’ve shared so much, and I’ve learned a lot. It’s inspiring to see all the great things happening in Ghana, truly wonderful. Thank you, and you’re doing an incredible job. **Sean**:I would say it’s important for us as Africans to continue collaborating within our own communities—whether in a specific community, village, or town. Through collaboration, we can create stronger communities for ourselves. This way, we’ll be able to generate jobs in various fields and develop marketable skills that can be used anywhere in the world. This way, we won’t need to seek opportunities in other countries; we can build those opportunities right here in our own space. **YakiHonne**: It's very true. We can definitely build a better West Africa, a better Africa, and create our own opportunities here. Thank you so much for this interview.
@ fd78c37f:a0ec0833
2025-02-19 06:39:05In this edition, we invited Kofi and Sean from BitcoinDua to share their journey of introducing Bitcoin to the community and driving its widespread adoption, and discuss how trust and collaboration have played key roles in promoting Bitcoin locally and building a circular economy. **YakiHonne**: Welcome, Kofi. It's truly an honor and a pleasure to have you with us today. Before we begin, let me briefly introduce YakiHonne. YakiHonne is a decentralized media client built on Nostr—a protocol designed to empower freedom of speech through technology. It enables creators to own their voices and assets while offering innovative tools like smart widgets, verified notes, and support for long-form content. Today, we're excited to learn more about your community. Could you please introduce yourself, Kofi? **Kofi**:Hello, I'm Mawufemor Kofi Folivi from Ghana. I'm the founder of the Talent Tahuf Foundation, an NGO, as well as BitcoinDua. The Talent Tahuf Foundation is an incorporated organization and serves as the parent entity for BitcoinDua. We operate in Agbozume, in the Volta region of Ghana. **YakiHonne**: Thank you very much, Kofi.Let's start with the first question: What initially sparked your interest in Bitcoin, and what inspired you to build a community around it? **Kofi**:I'm glad we're revisiting this question, as I've heard it on many podcasts before, and it's a pleasure to share my journey again.I've been working in this space for over 20 years, often with very little support. Through perseverance and hard work, a friend of mine—who serves as the Public Relations Officer for the Africa Bitcoin Conference (ABC)—invited me to attend their 2022 conference. He even purchased a ticket for me, which made the experience even more special. **Kofi**:At the conference, I encountered Bitcoin for the first time in a meaningful way. I had the opportunity to see Jack Dorsey speak and even took a picture with him. Later on, my friend introduced me to Herman Viva, and I mentioned that I run an NGO—a role I've held for many years. **Kofi**:Listening to the discussions about Bitcoin at the conference sparked a realization: perhaps I could contribute to the Bitcoin ecosystem. My friend encouraged me to take action by asking me to "orange pill" someone and onboard a merchant to accept Bitcoin, with the goal of creating a circular economy in our community. I took on this challenge, recorded my progress on video, and shared it with him. His positive response and support, coupled with the trust I've built within my community, further solidified my commitment. **YakiHonne**: It was wonderful to hear that you attended the African Bitcoin Conference—it sounds like an amazing event. I'm really impressed with how effectively you networked and made valuable connections there. I truly appreciate that you're already engaging with merchants and actively encouraging more people to trade and adopt Bitcoin. I know you've already shared how the community started, how he encouraged you to create one and adopt Bitcoin, and how you successfully did that. So now, could you tell us how you managed to attract new members to your community? **Kofi**:To go back to the beginning, we started by organizing growth circles when I returned. These were groups where we focused on activities like aerobics. I used these circles as an opportunity to introduce Bitcoin to people I had already built relationships with. I shared my experience with Bitcoin, showing them how it could be used to buy credit. I demonstrated by purchasing credit for myself and for them, and I gave them cards, allowing them to buy their own credit as well. **Kofi**:This is how it all began. Since we were working with young people who shared the desire to grow together as a community, we emphasized that we didn't need to rely on the government. The national resources are limited, and if you're not close to the government, it’s very hard to benefit from them. We realized it was difficult to wait for the government to support our development. So, we turned to Bitcoin as a tool to help us move forward. This approach helped us establish a platform based on trust within the community. **Kofi**:Now, as an organization, we have the resources to help the community grow and develop skills among our peers. This is how we were able to attract members to our Bitcoin community.  **YakiHonne**: Would you mind sharing with us some of the challenges you faced while starting up the community? **Kofi**:Thank you for asking this question. As I mentioned earlier, since we've already built trust, one thing we faced was that anything new can be quite difficult to introduce. It took some time for people to understand the concept of Bitcoin, especially the idea that it’s money. **Kofi**:We kept repeating the phrase “Bitcoin is money,” but the challenge was that you can’t physically show Bitcoin in the same way you can show traditional money. So, when people asked, “How can I use it to pay?” it became an issue. To address this, I started by onboarding the first merchant. I explained to them, "I’m giving you this Bitcoin to pay for goods, and I’ll give you extra if you accept it." The merchant agreed to take both Bitcoin and fiat currency. **Kofi**:Over time, the merchant saw the value of Bitcoin growing. Eventually, they came to me asking to exchange the Bitcoin for cash. To help, I onboarded them onto BitNob, where they could experience transferring Bitcoin from one wallet to another and even withdrawing it into their local currency or bank account. We completed the transaction, and that became a reference point for everyone else we were working with. **YakiHonne**: The way you approached it—getting a merchant to demonstrate it—really helped build trust. I know many communities face the same issue: how to prove that Bitcoin is real. But over time, we learn how to overcome these challenges. It's really impressive how you handled it? YakiHonne: What principles guide your community, and how do you maintain trust and reliability? I know you’ve mentioned this a bit already, but could you elaborate further? How do you ensure trust and reliability in your discussions? **Kofi**:As humans, we also need to trust our intuition and how we feel about situations. It’s essential to interact with people with integrity. In our community, we are mindful of what we show others, both in actions and in good deeds. If you love someone, you give everything you have to them, and that’s the only way people can truly feel they belong in your circle. This is the key that keeps us moving forward. **Kofi**:The person at the center of everything you’re doing must be trustworthy. And how do you gain trust? You must trust others first. Even if people come with ulterior motives, you should approach them with an open heart, showing love to them just as you do with everyone else. **Kofi**:And when wrongs are committed, it’s important to acknowledge them. If someone points out a mistake you made, accept it, apologize, and move forward. This creates an understanding within the community that we’re not here to harm one another. Trust is built on integrity, and that’s how we maintain it.  **YakiHonne**: That’s very true. It’s much better and easier when you have integrity. Over time, as you prove yourself to be a person of integrity, it naturally builds trust with others. So, how does your community educate its members and keep them updated on Bitcoin developments? How do you approach this? **Kofi**:To engage our community on a larger scale, we believe it's important to stay active and involved. After building trust, we participate in community events, such as sponsoring a football competition and contributing to their local festival. By doing this, the entire community starts seeing Bitcoin as something that can truly improve their lives. **Kofi**:We also established a Bitcoin Education Center, where we invite students from various schools to learn about Bitcoin. But our efforts go beyond just education; we use the resources we gain from Bitcoin to acquire laptops and robotics kits, so that the students can have additional learning opportunities. These activities are incorporated into their school programs, and we encourage their participation through debates and rewarding them with SATS.  **Kofi**:By rewarding them with SATS, they can use these rewards to buy from over 20 merchants we've onboarded, which not only excites the students but also makes their parents curious about Bitcoin. We've even had people at the local market requesting to buy Bitcoin from us. This is how we keep up with Bitcoin’s development and continue to spread its influence in our community. **YakiHonne**: How does your community work with the wider Bitcoin ecosystem? So far, what partnership has had the most positive impact on your community? **Kofi**:Due to the hard work we've been putting in, we were able to attract Bitcoin Beach as one of our major collaborators. We are part of Bitcoin Ekasi. Recently, we were also awarded the Block Discovery Grant of $50,000 from the Bitcoin Foundation. We are using this grant to build a sports complex, which will include a football field, a multi-purpose basketball court, a swimming pool, a children's playground, and more. We've already started this project. These are the key collaborators and supporters we've had in the Bitcoin space, and their support has been invaluable to us.   **YakiHonne**: It’s clear that you guys are doing an amazing job! Your efforts and hard work have truly caught the attention of many communities, and it’s great to see you forming significant partnerships.So, could you share more about the initiatives your community has taken to promote Bitcoin adoption? I know you've mentioned a few already, but would you mind expanding on them a bit more and sharing the results you've seen? **Kofi**:As I mentioned earlier, we are enhancing our capacity by working with school children and teenagers. We also plan to host inter-school competitions, particularly world-class robotics competitions, with the aim of broadening students' perspectives on science and giving them a global view of what's happening in the world. We believe that through these activities, we will be able to engage with a larger society, helping us expand our client base for Bitcoin education and usage. Therefore, we believe this will have a profound impact. As for the activities we are currently working on, they are providing us with opportunities to expand our reach to schools within the community. This will further build trust and deepen our relationships in this regard. **YakiHonne**: I really admire the fact that you have boarded merchants to accept Bitcoin, which is a great step for its adoption. I also like that you've reached out to schools, encouraging community growth, which helps people see more interest and potential in the Bitcoin ecosystem. Now, for our last question of the day, what are the community goals for the next 6 to 12 months, and how do you see it evolving within the Bitcoin space? **Kofi**:So, in the next 6 to 12 months, we plan to complete the sports complex we’re building. We also intend to open it up for social activities, both within our community and beyond. We believe this will create more opportunities for interaction, allowing people who don’t live within our community to learn about Bitcoin, hear about it, and start engaging with it for the greater good. **YakiHonne**: you plan to complete the sports complex and expand your social reach to engage more people, even those outside your local community. This is truly amazing, and the work you’re doing is fantastic. **YakiHonne**: We’ve come to the end of today’s interview, and I’m really happy to have had this conversation with you, Kofi. You’ve shared so much, and I’ve learned a lot. It’s inspiring to see all the great things happening in Ghana, truly wonderful. Thank you, and you’re doing an incredible job. **Sean**:I would say it’s important for us as Africans to continue collaborating within our own communities—whether in a specific community, village, or town. Through collaboration, we can create stronger communities for ourselves. This way, we’ll be able to generate jobs in various fields and develop marketable skills that can be used anywhere in the world. This way, we won’t need to seek opportunities in other countries; we can build those opportunities right here in our own space. **YakiHonne**: It's very true. We can definitely build a better West Africa, a better Africa, and create our own opportunities here. Thank you so much for this interview. @ da0b9bc3:4e30a4a9
2025-02-19 06:35:45Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/890318
@ da0b9bc3:4e30a4a9
2025-02-19 06:35:45Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/890318 @ 6e0ea5d6:0327f353
2025-02-19 04:28:42Ascolta bene, amico mio! A man's strength is not born from comfort, applause, or luck. It awakens only when the world throws him to the ground, steps on his throat, and laughs at his misery. When your plans lie in ruins, when everything you've built turns to dust, when every promise you once believed in dissolves into the wind—that is when truth reveals itself. You either dig a trench and fight like a condemned man, or you accept that you’re digging your own grave. Rock bottom is not a place—it’s a test. A challenge for the weak to bury themselves and for the strong to rise. You will bleed, taste the dirt, grind your teeth, but standing back up is the only option. A real man does not cry for help, does not mourn the past. He wields his pain as a whip, his hatred as fuel, and his will as a blade. Falling is inevitable. What defines your story is what you do when there is no ground left beneath you. True motivation does not come from empty inspirational quotes, but from the hatred of one’s own weakness. The man who clings rigidly to his strategy is like a hunter pulling back a stiff wooden bow—he will break his own weapon when the time comes to use it. The world is too corrupt for you to believe in love vows, the promises of friends, effortless riches, or the words of newspapers. If you wish to survive in this world, learn this: both victory and defeat are temporary. Only the battle is eternal. A man’s life is his endless war. And hatred must be to him what fire is to a steam locomotive: the force that drives him up the steepest paths. But never let yourself burn in your own flames. Rise. Or die kneeling like the wretched. Thank you for reading, my friend! If this message resonated with you, consider leaving your "🥃" as a token of appreciation. A toast to our family!
@ 6e0ea5d6:0327f353
2025-02-19 04:28:42Ascolta bene, amico mio! A man's strength is not born from comfort, applause, or luck. It awakens only when the world throws him to the ground, steps on his throat, and laughs at his misery. When your plans lie in ruins, when everything you've built turns to dust, when every promise you once believed in dissolves into the wind—that is when truth reveals itself. You either dig a trench and fight like a condemned man, or you accept that you’re digging your own grave. Rock bottom is not a place—it’s a test. A challenge for the weak to bury themselves and for the strong to rise. You will bleed, taste the dirt, grind your teeth, but standing back up is the only option. A real man does not cry for help, does not mourn the past. He wields his pain as a whip, his hatred as fuel, and his will as a blade. Falling is inevitable. What defines your story is what you do when there is no ground left beneath you. True motivation does not come from empty inspirational quotes, but from the hatred of one’s own weakness. The man who clings rigidly to his strategy is like a hunter pulling back a stiff wooden bow—he will break his own weapon when the time comes to use it. The world is too corrupt for you to believe in love vows, the promises of friends, effortless riches, or the words of newspapers. If you wish to survive in this world, learn this: both victory and defeat are temporary. Only the battle is eternal. A man’s life is his endless war. And hatred must be to him what fire is to a steam locomotive: the force that drives him up the steepest paths. But never let yourself burn in your own flames. Rise. Or die kneeling like the wretched. Thank you for reading, my friend! If this message resonated with you, consider leaving your "🥃" as a token of appreciation. A toast to our family! @ e97aaffa:2ebd765d
2024-12-31 16:47:12Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes. Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais _mainstream_. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso. # Código do Bitcoin No final de 2025, possivelmente vamos ter um _fork_, as discussões sobre os _covenants_ já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos _covenants_, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido. Depois dos _covenants,_ o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa. Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos _bitcoiners_. Espero que surjam avanços significativos no BitVM2 e BitVMX. Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da _shitcoinagem_, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs. Se querem ser levados a sério, têm que ser sérios. > “À mulher de César não basta ser honesta, deve parecer honesta” Se querem ter o apoio dos _bitcoiners_, sigam o _ethos_ do Bitcoin. Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma _multisig_ ou com os _covenants_ na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos _covenants_ para melhorar a interoperabilidade e a soberania. É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy: > “Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país” Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código. # Reservas Estratégicas de Bitcoin ## Bancos centrais Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito _mainstream_. Foi um _pivot_, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto. A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário. Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”. Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar. Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.  ## Empresas A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.  Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%. Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de _shareholders_ com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft. Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial. # ETFs Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os _inflows_ foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os _inflows_ foram brutais. Também se beneficiou por ser um mercado novo, não existia _orderbook_ de vendas, não existia um mercado interno, praticamente era só _inflows_. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em _inflows_ ou _outflows_. Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de _inflows_ em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar. Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem. Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes. Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo. # Preço Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo. # Stablecoins de dólar Agora saindo um pouco do universo do Bitcoin, acho importante destacar as _stablecoins_. No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas. Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às _stablecoins_ de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas. > “Casa onde não há pão, todos ralham e ninguém tem razão” Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas. Eu acredito que 2025, vai haver um forte crescimento na adoção das _stablecoins_ de dólares, esse forte crescimento vai agravar o problema sistémico que são as _stablecoins_. Vai ser o início do fim das _stablecoins_, pelo menos, como nós conhecemos hoje em dia. ## Problema sistémico O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente. Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas. As _stablecoins_ são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema. No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos. A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário. Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/_stablecoins_ para o resto do sistema financeiro, porque o _marketcap_ do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações. Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do _carry trade_, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado. Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações. O mundo cripto é seu oposto, é _naife_ com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto. Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025. Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o _redeem_ dos dólares? Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether? Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente. ### Conta mestre Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário. O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com _full-reserves_. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com _full-reserves_, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos. Eu concordo com o FED nesse ponto, que os bancos com _full-reserves_ são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos _full-reserves_, mas sim nos que têm reserva fracionária. O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença. Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de _compliance_, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o _compliance_ dos seus clientes. A obrigação do KYC para ter _stablecoins_ iriam provocar um terramoto no mundo cripto. Assim, é pouco provável que seja a solução para a Tether. ### FED Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as _stablecoins_ de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as _stablecoins_ estão a colocar em causa a soberania monetária dos outros países. Atualmente as _stablecoins_ estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países. Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo. Será algo para acompanhar futuramente, mas só para 2026, talvez… É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(_stablecoins_). A ironia do destino. Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona. # Europa 2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os _compliance_, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo. O _Travel Route_ passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A _Travel Route_ é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos. O MiCA também está a colocar problemas nas _stablecoins_ de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias. O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade _stablecoins_ de euro, as restantes _stablecoins_ serão deslistadas. Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado. # Recessão Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon. Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro. Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer. Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar. A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa. Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal. # Brasil Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.  Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e _stablecoins_. No Brasil existe um forte adoção, será um bom _case study_, certamente irá repetir-se em outros países num futuro próximo. Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin. # Blockchain Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em _blockchain_. Eu acredito que a BlackRock vai criar uma própria _blockchain_, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar. ----------- Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião. Isto é apenas a minha opinião, **Don’t Trust, Verify**!
@ e97aaffa:2ebd765d
2024-12-31 16:47:12Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes. Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais _mainstream_. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso. # Código do Bitcoin No final de 2025, possivelmente vamos ter um _fork_, as discussões sobre os _covenants_ já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos _covenants_, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido. Depois dos _covenants,_ o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa. Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos _bitcoiners_. Espero que surjam avanços significativos no BitVM2 e BitVMX. Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da _shitcoinagem_, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs. Se querem ser levados a sério, têm que ser sérios. > “À mulher de César não basta ser honesta, deve parecer honesta” Se querem ter o apoio dos _bitcoiners_, sigam o _ethos_ do Bitcoin. Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma _multisig_ ou com os _covenants_ na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos _covenants_ para melhorar a interoperabilidade e a soberania. É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy: > “Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país” Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código. # Reservas Estratégicas de Bitcoin ## Bancos centrais Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito _mainstream_. Foi um _pivot_, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto. A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário. Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”. Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar. Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.  ## Empresas A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.  Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%. Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de _shareholders_ com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft. Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial. # ETFs Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os _inflows_ foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os _inflows_ foram brutais. Também se beneficiou por ser um mercado novo, não existia _orderbook_ de vendas, não existia um mercado interno, praticamente era só _inflows_. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em _inflows_ ou _outflows_. Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de _inflows_ em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar. Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem. Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes. Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo. # Preço Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo. # Stablecoins de dólar Agora saindo um pouco do universo do Bitcoin, acho importante destacar as _stablecoins_. No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas. Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às _stablecoins_ de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas. > “Casa onde não há pão, todos ralham e ninguém tem razão” Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas. Eu acredito que 2025, vai haver um forte crescimento na adoção das _stablecoins_ de dólares, esse forte crescimento vai agravar o problema sistémico que são as _stablecoins_. Vai ser o início do fim das _stablecoins_, pelo menos, como nós conhecemos hoje em dia. ## Problema sistémico O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente. Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas. As _stablecoins_ são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema. No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos. A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário. Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/_stablecoins_ para o resto do sistema financeiro, porque o _marketcap_ do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações. Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do _carry trade_, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado. Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações. O mundo cripto é seu oposto, é _naife_ com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto. Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025. Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o _redeem_ dos dólares? Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether? Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente. ### Conta mestre Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário. O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com _full-reserves_. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com _full-reserves_, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos. Eu concordo com o FED nesse ponto, que os bancos com _full-reserves_ são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos _full-reserves_, mas sim nos que têm reserva fracionária. O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença. Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de _compliance_, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o _compliance_ dos seus clientes. A obrigação do KYC para ter _stablecoins_ iriam provocar um terramoto no mundo cripto. Assim, é pouco provável que seja a solução para a Tether. ### FED Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as _stablecoins_ de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as _stablecoins_ estão a colocar em causa a soberania monetária dos outros países. Atualmente as _stablecoins_ estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países. Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo. Será algo para acompanhar futuramente, mas só para 2026, talvez… É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(_stablecoins_). A ironia do destino. Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona. # Europa 2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os _compliance_, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo. O _Travel Route_ passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A _Travel Route_ é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos. O MiCA também está a colocar problemas nas _stablecoins_ de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias. O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade _stablecoins_ de euro, as restantes _stablecoins_ serão deslistadas. Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado. # Recessão Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon. Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro. Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer. Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar. A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa. Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal. # Brasil Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.  Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e _stablecoins_. No Brasil existe um forte adoção, será um bom _case study_, certamente irá repetir-se em outros países num futuro próximo. Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin. # Blockchain Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em _blockchain_. Eu acredito que a BlackRock vai criar uma própria _blockchain_, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar. ----------- Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião. Isto é apenas a minha opinião, **Don’t Trust, Verify**! @ 30e8cbf1:74fccbaa
2025-02-19 03:22:53*Capitalist Realism: Is There No Alternative? by Mark Fisher* (2009, Zero Books) ## Why a dare and not a recommendation? I'm writing this "review" primarily for the Nostr audience. The majority of Nostr users, in my experience, are predisposed to a worldview somewhere in the realm of Anarcho-Capitalism or Libertarianism, with a strong focus on individual autonomy and free markets. The title *Capitalist Realism: Is There No Alternative* might evoke an immediate negative reaction in the mind of my imaginary Nostr reader. Even worse, looking up summaries of the book or the author before diving in, the reader will find the dreaded phrase "critical theory", seen as a hallmark of the "other" side in the Western culture war. I'm challenging you to not judge this book by its cover. Despite the book's short (86 page) length, I have found myself spending an unusually large amount of time thinking about the topics discussed within. I'm unsure if my worldview has actually shifted after reading this (I think I'm still close to the Nostr median), but I've enjoyed this exercise in contemplation, and I hope this article can lead someone else to a similarly fruitful experience. I feel compelled to put my thoughts to paper as part of this exercise, and what follows is something like the internal dialog I go through considering and challenging Fisher's main points. First, despite the word "Capitalism" in the title, this book is not about economics. Rather, the central point is that after the fall of the Soviet Union the prevailing worldview in the Western world is a "business ontology", essentially seeing people as purely material producer/consumers. Most people have internalized this view, seeing no higher purpose or meaning in their lives other than going to work and buying things. Even worse than the widespread internalization of this view, Fisher argues that it is so pervasive that most people can't even conceptualize an alternative. Fisher points out the rapid increases in mental health problems, despair, and suicide, especially among young people in the 21st century as evidence of this argument. *Capitalist Realism* was written in 2009, and I think there is a clear line between Fishers argument and the current conception of a "crisis of meaning" among young people espoused by some online figures such as Jordan Peterson. Whether there is a direct link between the business ontology and crisis of meaning (as Fisher argues) is less clear to me, but he clearly identified a phenomenon that has only gotten more acute since the book was published. Further, Fisher cites popular culture, particularly modern music and movies as evidence of this phenomenon. In his conception, this business ontology leads to endlessly recycled aesthetic callbacks to previous generations, with most media appealing to our nostalgia for a time when people had a genuine belief that the future may be different than the present, which he thinks has been lost by total adoption of this business ontology. I'm not knowledgeable enough in aesthetics to comment on this point, but do have an intuitive feeling that modern movies and music are degenerate from the works created by previous generations. Fisher calls this "Hauntology" as is explored in another book that I haven't read yet. In a section of the book I found particularly interesting, Fisher critiques the hypocrisy of capitalist neoliberal societies that cite the "Stalinist Bureaucracy" as a fatal fall that led to the demise of the Soviet Union while rapidly adopting the same form of work domestically. Essentially, in the Soviet system most people only "worked" to achieve whatever metric the bureaucrats used to assess their productivity. Whether or not this correlated with producing useful goods or services was entirely irrelevant. If a factory had a quota of making 100 tons of clocks, the workers would just produce overweight and non-functional clocks to meet this quota. All up and down the chain the metrics were met, pleasing the bureaucrats and appearing "productive", but everyone was fully aware that the work was performative and fake. Fisher points to his experience in academia, where universities continued to add more and more administrators to run pointless audit and review programs. Both the faculty and administrators are fully aware that these programs are meaningless and unproductive, but the metrics become a justification of themselves. They don't matter, but they need to exist to make massive administrator bloat and associated bureaucracy appear necessary. Again, in the years since the book's publication the public consciousness of this problem has grown, though the criticism is more often leveled from the political right. I was surprised to read an author I would stereotype as an "ivory tower leftist academic" forcefully level this criticism at his own institution. As I think about this book, I wonder if it helps to make a distinction between "capitalism" and "fiat". On Nostr we often critique "fiat food", "fiat jobs", and "fiat music" as hollow, meaningless, and temporary things. We hypothesize that sound money will fix the incentives that lead to the societal problems that Fisher attributes to neoliberal capitalism. Fisher does not consider Bitcoin in this book (or any of this other works, to my knowledge) but I'm curious if he would make a similar distinction. If this book was called *Fiat Realism: Is There No Alternative* would it be popular in Bitcoin circles? I think it would be. Maybe people would point to these criticisms leveled within a year of Bitcoin's creation and claim "Bitcoin fixes this". Going back to an earlier point, Fisher doesn't critique free exchange, markets or individual liberty. He critiques a specific culture that currently seems all-pervasive without any alternative. I hope that the freedom money and freedom technology movement we are a part of is a feasible alternative. I hope this article is helpful to someone. It was certainly helpful for me to write it. I'm interested in hearing your thoughts on this book or this article!
@ 30e8cbf1:74fccbaa
2025-02-19 03:22:53*Capitalist Realism: Is There No Alternative? by Mark Fisher* (2009, Zero Books) ## Why a dare and not a recommendation? I'm writing this "review" primarily for the Nostr audience. The majority of Nostr users, in my experience, are predisposed to a worldview somewhere in the realm of Anarcho-Capitalism or Libertarianism, with a strong focus on individual autonomy and free markets. The title *Capitalist Realism: Is There No Alternative* might evoke an immediate negative reaction in the mind of my imaginary Nostr reader. Even worse, looking up summaries of the book or the author before diving in, the reader will find the dreaded phrase "critical theory", seen as a hallmark of the "other" side in the Western culture war. I'm challenging you to not judge this book by its cover. Despite the book's short (86 page) length, I have found myself spending an unusually large amount of time thinking about the topics discussed within. I'm unsure if my worldview has actually shifted after reading this (I think I'm still close to the Nostr median), but I've enjoyed this exercise in contemplation, and I hope this article can lead someone else to a similarly fruitful experience. I feel compelled to put my thoughts to paper as part of this exercise, and what follows is something like the internal dialog I go through considering and challenging Fisher's main points. First, despite the word "Capitalism" in the title, this book is not about economics. Rather, the central point is that after the fall of the Soviet Union the prevailing worldview in the Western world is a "business ontology", essentially seeing people as purely material producer/consumers. Most people have internalized this view, seeing no higher purpose or meaning in their lives other than going to work and buying things. Even worse than the widespread internalization of this view, Fisher argues that it is so pervasive that most people can't even conceptualize an alternative. Fisher points out the rapid increases in mental health problems, despair, and suicide, especially among young people in the 21st century as evidence of this argument. *Capitalist Realism* was written in 2009, and I think there is a clear line between Fishers argument and the current conception of a "crisis of meaning" among young people espoused by some online figures such as Jordan Peterson. Whether there is a direct link between the business ontology and crisis of meaning (as Fisher argues) is less clear to me, but he clearly identified a phenomenon that has only gotten more acute since the book was published. Further, Fisher cites popular culture, particularly modern music and movies as evidence of this phenomenon. In his conception, this business ontology leads to endlessly recycled aesthetic callbacks to previous generations, with most media appealing to our nostalgia for a time when people had a genuine belief that the future may be different than the present, which he thinks has been lost by total adoption of this business ontology. I'm not knowledgeable enough in aesthetics to comment on this point, but do have an intuitive feeling that modern movies and music are degenerate from the works created by previous generations. Fisher calls this "Hauntology" as is explored in another book that I haven't read yet. In a section of the book I found particularly interesting, Fisher critiques the hypocrisy of capitalist neoliberal societies that cite the "Stalinist Bureaucracy" as a fatal fall that led to the demise of the Soviet Union while rapidly adopting the same form of work domestically. Essentially, in the Soviet system most people only "worked" to achieve whatever metric the bureaucrats used to assess their productivity. Whether or not this correlated with producing useful goods or services was entirely irrelevant. If a factory had a quota of making 100 tons of clocks, the workers would just produce overweight and non-functional clocks to meet this quota. All up and down the chain the metrics were met, pleasing the bureaucrats and appearing "productive", but everyone was fully aware that the work was performative and fake. Fisher points to his experience in academia, where universities continued to add more and more administrators to run pointless audit and review programs. Both the faculty and administrators are fully aware that these programs are meaningless and unproductive, but the metrics become a justification of themselves. They don't matter, but they need to exist to make massive administrator bloat and associated bureaucracy appear necessary. Again, in the years since the book's publication the public consciousness of this problem has grown, though the criticism is more often leveled from the political right. I was surprised to read an author I would stereotype as an "ivory tower leftist academic" forcefully level this criticism at his own institution. As I think about this book, I wonder if it helps to make a distinction between "capitalism" and "fiat". On Nostr we often critique "fiat food", "fiat jobs", and "fiat music" as hollow, meaningless, and temporary things. We hypothesize that sound money will fix the incentives that lead to the societal problems that Fisher attributes to neoliberal capitalism. Fisher does not consider Bitcoin in this book (or any of this other works, to my knowledge) but I'm curious if he would make a similar distinction. If this book was called *Fiat Realism: Is There No Alternative* would it be popular in Bitcoin circles? I think it would be. Maybe people would point to these criticisms leveled within a year of Bitcoin's creation and claim "Bitcoin fixes this". Going back to an earlier point, Fisher doesn't critique free exchange, markets or individual liberty. He critiques a specific culture that currently seems all-pervasive without any alternative. I hope that the freedom money and freedom technology movement we are a part of is a feasible alternative. I hope this article is helpful to someone. It was certainly helpful for me to write it. I'm interested in hearing your thoughts on this book or this article! @ 9ea10fd4:011d3b15
2025-02-19 02:24:26This article by Thomas Piketty has, in a way, convinced me that the tariff war will indeed take place. Moreover, the Trumpist nationalism-capitalism he describes—authoritarian and the most aggressively extractivist—places Canada in the position of a coveted target. The fact that “if the Republican Party has become so nationalist and virulent towards the outside world, it is primarily due to the failure of Reagan-era policies, which were supposed to boost growth but instead reduced it and led to the stagnation of incomes for the majority” is of little consolation. \*“Let’s be clear: Trumpist national-capitalism loves to flaunt its strength, but in reality, it is fragile and on edge. Europe has the means to confront it, provided it regains confidence in itself, forges new alliances, and calmly analyzes the strengths and limitations of this ideological framework. Europe is well-positioned for this: it has long based its development on a similar military-extractivist model, for better or worse. After taking control of maritime routes, raw materials, and the global textile market by force, European powers imposed colonial tributes throughout the 19th century on all resistant countries, from Haiti to China to Morocco. On the eve of 1914, they engaged in a fierce struggle for control of territories, resources, and global capitalism. They even imposed tributes on each other, increasingly exorbitant ones—Prussia on France in 1871, then France on Germany in 1919: 132 billion gold marks, more than three years of Germany’s GDP at the time. As much as the tribute imposed on Haiti in 1825, except this time, Germany had the means to defend itself. The endless escalation led to the collapse of the system and European hubris. (…) If we reason in terms of purchasing power parity, the reality is quite different (…) With this measure, we (…) see that China’s GDP surpassed that of the United States in 2016. It is currently more than 30% higher and will reach twice the U.S. GDP by 2035. This has very concrete consequences in terms of influence and investment capacity in the Global South, especially if the United States locks itself into its arrogant and neo-colonial stance. The reality is that the United States is on the verge of losing control of the world, and Trumpist outbursts will change nothing.” https://www.lemonde.fr/en/opinion/article/2025/02/15/thomas-piketty-trump-s-national-capitalism-likes-to-flaunt-its-strength-but-it-is-actually-fragile_6738187_23.html
@ 9ea10fd4:011d3b15
2025-02-19 02:24:26This article by Thomas Piketty has, in a way, convinced me that the tariff war will indeed take place. Moreover, the Trumpist nationalism-capitalism he describes—authoritarian and the most aggressively extractivist—places Canada in the position of a coveted target. The fact that “if the Republican Party has become so nationalist and virulent towards the outside world, it is primarily due to the failure of Reagan-era policies, which were supposed to boost growth but instead reduced it and led to the stagnation of incomes for the majority” is of little consolation. \*“Let’s be clear: Trumpist national-capitalism loves to flaunt its strength, but in reality, it is fragile and on edge. Europe has the means to confront it, provided it regains confidence in itself, forges new alliances, and calmly analyzes the strengths and limitations of this ideological framework. Europe is well-positioned for this: it has long based its development on a similar military-extractivist model, for better or worse. After taking control of maritime routes, raw materials, and the global textile market by force, European powers imposed colonial tributes throughout the 19th century on all resistant countries, from Haiti to China to Morocco. On the eve of 1914, they engaged in a fierce struggle for control of territories, resources, and global capitalism. They even imposed tributes on each other, increasingly exorbitant ones—Prussia on France in 1871, then France on Germany in 1919: 132 billion gold marks, more than three years of Germany’s GDP at the time. As much as the tribute imposed on Haiti in 1825, except this time, Germany had the means to defend itself. The endless escalation led to the collapse of the system and European hubris. (…) If we reason in terms of purchasing power parity, the reality is quite different (…) With this measure, we (…) see that China’s GDP surpassed that of the United States in 2016. It is currently more than 30% higher and will reach twice the U.S. GDP by 2035. This has very concrete consequences in terms of influence and investment capacity in the Global South, especially if the United States locks itself into its arrogant and neo-colonial stance. The reality is that the United States is on the verge of losing control of the world, and Trumpist outbursts will change nothing.” https://www.lemonde.fr/en/opinion/article/2025/02/15/thomas-piketty-trump-s-national-capitalism-likes-to-flaunt-its-strength-but-it-is-actually-fragile_6738187_23.html @ 0b118e40:4edc09cb
2025-02-19 01:21:45Are we living in his definition of democracy? It’s interesting how political parties can divide a country, especially in democracies where both oppression and individual choice coexist. As I was exploring global economics and political ideologies, I picked up *The Republic* by Plato (again). The first time I read it, I only read the book on the Allegory of the Cave and it felt enlightening. This time around, I read through all the books and I thought to myself : *this is absolutely nuts!* Over 2,000 years ago, *The Republic* imagined a world disturbingly similar to Gattaca or 1984. For a quick rundown, Plato believed in a police state, eugenics, a caste system, and brainwashing people through state-controlled media and education. Sounds wild? I thought so too. And for some reason, Plato had a serious grudge against art. To him, art was deceptive and emotionally manipulative. Maybe because there was a skit making fun of Socrates at that time by Aristophanes (the father of comedy) or maybe because he struggled to deal with emotions, we will never know. Plato obviously wasn’t a fan of democracy as he wanted a dystopian world. But to be fair, he genuinely thought that his ideal world (Kallipolis) was a utopia. Maybe someone who loves extreme order and control might think the same but I sure don’t. His teacher Socrates was also not a fan of democracy because he believed the mass majority were too ignorant to govern and only those intelligent enough could. His student, Aristotle, was more moderate but still critical, seeing democracy as vulnerable to corruption and mob rule. Socrates, Plato, and Aristotle were around the Classical Greek era, 5th to 4th century BC. The idea of democracy existed long before them. The first recorded version was in Athens during the 6th BC, developed by leaders like Solon and Pericles. It was a direct democracy where free male citizens (non-slaves) could vote on laws themselves instead of electing representatives. These guys influenced how we think about democracy today. But looking around, I wonder, did we end up in Plato’s dystopian world? ### **Plato’s take on democracy** Plato’s lack of trust of democracy stemmed from Socrates’ death. Socrates himself was a fierce critic of democracy, as he believed governance should be based on wisdom rather than popularity. Other thinkers, like Pythagoras and Herodotus (father of history), also examined different political systems, but Socrates was the most influential critic. He warned that allowing the uneducated masses to choose leaders would lead to poor governance, as they could be easily swayed by persuasive speakers rather than guided by knowledge. Athenian democracy relied on large citizen juries and was particularly vulnerable to rhetoric and public sentiment. In the end, Socrates became a victim of the very system he criticized. His relentless questioning of widely accepted beliefs, now known as the **Socratic Method**, earned him powerful enemies. Socrates’ constant probing forced them to confront uncomfortable truths. It annoyed people so much, that it eventually led to his trial and execution. Socrates was condemned to death by popular vote. I wonder, if we applied the Socratic Method today to challenge both the left and the right on the merits of the opposing side, would they be open to expanding their perspectives, or would they react with the same hostility? This questioning technique is now also used in some schools and universities as a teaching method, encouraging open-ended discussion where students contribute their own thoughts rather than passively receiving information. But how open a school, system, or educator is to broad perspectives depends largely on their own biases and beliefs. Even with open-ended questions, the direction of the conversation can be shaped by those in charge, potentially limiting the range of perspectives explored. Socrates’ brutal death deeply grounded Plato’s belief that democracy, without intellectual rigor, was nothing but a mob rule. He saw it as a system doomed to chaos, where the unqualified, driven by emotion or manipulated by rhetoric, made decisions that ultimately paved the way for tyranny. ### **The Republic** *The Republic* was written around 375 BC, after the Peloponnesian War. One of its most famous sections is the Allegory of the Cave, where prisoners are stuck watching shadows on a wall, thinking that it’s reality until one breaks free and sees the real world. That’s when the person becomes enlightened, using knowledge and reason to escape ignorance. They return to free others, spreading the truth. I love this idea of breaking free from suppression through knowledge and awareness. But as I went deeper into Plato’s work, I realized what the plot twist was. Plato wrote this book for strict state control. He wanted total control over education, media, and even families like in the book 1984. He argued that people should be sorted into a caste system, typically workers, warriors, and philosopher-kings so that society runs like a well-oiled machine. The “guardians” would police the state and everyone would go through physical and military training. To top it off, kids would be taken away from their parents and raised by the state for the “greater good.” like in the movie Gattaca. If that sounds a little too Orwellian, that’s because it is. Plato believed that only philosophers, the truly enlightened ones from that “cave”, should rule. To him, democracy was a joke, a breeding ground for corruption and tyranny. I found it completely ironic that this book that warns about brainwashing in the Allegory of the Cave also pushes for a state-controlled society, where thinking for yourself isn’t really an option. And yet, looking around today, I wonder, are we really any different? We live in a world where oppression and enlightenment exist side by side. Plato was slightly progressive in that he thought men and women should have equal education, but only for the ruling Guardian class. In *The Republic*, Plato didn’t focus much on economics or capitalism as we understand them today. His philosophies were more concerned with justice, governance, and the ideal structure of society. He did touch on wealth and property, particularly in *The Republic and Laws* but it was more on being against wealth accumulation by rulers (philosopher-kings had to live communally and without private property). While these ideas echo elements of socialism, he never outlined a full economic system like capitalism or socialism. ### **The hatred for art** Plato was deeply skeptical of art. He believed that it appealed to emotions over rational thought and distorted reality. In *The Republic* (Book X), he argued that art is an imitation of an imitation, pulling people further from the truth. If he had his way, much of modern entertainment, including poetry, drama, and even certain types of music, would not exist in their expressive forms. Despite Plato’s distrust of the arts, his time was a golden age for Greek drama, sculpture, and philosophy. Ironically, the very city where he built his Academy, Athens, was flourishing with the kind of creativity he wanted to censor. Even medicine, which thrived under Hippocrates (the father of medicine), was considered an art requiring lifelong mastery. His quote, ‘**Life is short, and art is long**,’ reflects the long span of time it takes to cultivate and appreciate knowledge and skills, which was something Plato valued. Yet, he dismissed most art as a distraction from truth. Plato particularly criticized poets and playwrights like Homer, as he claimed they spread false ideas about gods and morality. He was also wary of Aristophanes, as he believed his work stirred emotions rather than encouraging rational thought. It probably did not help that Aristophanes mocked Socrates in his play *The Clouds*, which may have influenced Plato’s views. What’s clear is that Plato didn’t hate art because he didn’t understand it. He deeply understood the power of storytelling and its ability to mold societal beliefs. He argued for banning poets entirely from his “ideal city” to prevent them from misleading the public. But he did value some forms of art. After all, he was a writer himself, and writing is a form of art. He approved of artistic expressions that promoted moral and intellectual virtue, such as hymns, architecture, and patriotic poetry, as long as they served the greater purpose of instilling order and wisdom in society. ### **Plato’s five regimes** Plato believed governments naturally decay over time, moving from order to chaos. He outlined five regimes, which he considers each to be worse than the last. 1. *Aristocracy (Philosopher-King rule)* : This is his pitch, the ideal state, ruled by wise elites who value knowledge over power. Some aspects of modern authoritarian states echo this model 2. *Timocracy (Military rule)* : A government driven by honor and discipline, like Sparta. Over time, ambition overtakes virtue, leading to oligarchy. 3. *Oligarchy (Rule by the wealthy)* : The rich seizes power and deepens inequality. Many democracies today show oligarchic tendencies, where money dominates politics. 4. *Democracy (Rule by the masses)* : The people overthrow the elites, prioritizing freedom over order. But without stability, democracy becomes fragile, and vulnerable to demagogues and external manipulation. 5. *Tyranny (Dictatorship)* : When democracy collapses, a charismatic leader rises, promising order but seizing absolute power. What begins as freedom ends in oppression. Modern politics seems stuck in a cycle, shifting between democracy, oligarchy, and authoritarian control. If Plato was right, no system is permanent and only the illusion of stability remains. ### **Does Plato’s ideal state exist in any country today?** Some aspects of modern *benevolent dictatorships*, like Singapore under Lee Kuan Yew, or *socialist states* like China, may resemble Plato’s vision in their emphasis on elite rule, long-term planning, and state control. But, these governments operate pragmatically, balancing governance with economic power, political strategy, and public influence rather than strictly adhering to philosophical ideals. Could this be compared to Taliban rule, given the censorship, authoritarian control, and rigid social hierarchy? While there are superficial similarities, the key difference is that Plato valued knowledge, reason, and meritocracy, while the Taliban enforced religious fundamentalism and theocratic rule. Plato’s Kallipolis also included some level of gender equality for the ruling class, whereas the Taliban’s system is heavily restrictive, especially toward women. While Plato’s ideas echo in certain authoritarian-leaning states, his rigid caste system, philosopher-led governance, and rejection of democracy set his vision apart from any modern political system. ### **Aristotle’s take on democracy** Aristotle wasn’t Athenian, but he documented and analyzed 158 constitutions, including Athenian democracy. He studied at Plato’s Academy for over 20 years, growing up in a world influenced by Athens’ democratic experiment. He lived through the tail end of Athens’ golden age, witnessed its decline, and experienced how different forms of rule influenced politics and the mindset of the people under them. For Aristotle, governments were good or corrupted. The good ones were monarchs, aristocracy (wise elites), and polity (a constitutional gov’t where the middle class keeps power balanced). The corrupted ones were tyranny (monarchy gone wrong), oligarchy, and democracy. Aristotle saw how democracy, if unchecked, could spiral into chaos or be co-opted by populist leaders. But unlike Plato, who rejected democracy outright, Aristotle believed it could work if properly structured. His concept of ‘**polity**’ was a constitutional government that balanced democratic participation with stability, relying on a strong middle class to prevent both mob rule and elite domination. This idea of checks and balances, a mixed government, and middle-class stability make polity the closest to modern constitutional democracies today when compared to all 3 of the Greek philosophers. ### **What happened after Athens?** Of course, democracy didn’t end with Athens, it evolved over time. After Athens’ golden age came Alexander the Great (Aristotle’s student and the king of Macedonia). He conquered Greece, Persia, Egypt, and part of India, creating the largest empire of his time. After his death in 323 BCE, his empire split among his generals, marking the beginning of the Hellenistic period. Rome saw a shift from the fall of the Roman Republic to the rise of the Roman Empire under Augustus moving away from democratic ideals to centralized rule. But the Western Roman Empire fell about 500 years later largely due to internal decline and invasions by the Germanic Tribes (modern-day Sweden, Switzerland, Germany). The Eastern Roman Empire (Byzantine Empire, based in Constantinople or modern-day Turkey) rose and survived for nearly 1,000 more years until it fell to the Ottoman Turks in 1453. During the Medieval period (5th–15th century), Europe saw a rise in monarchies and feudalism. Power shifted to kings, nobles, and the church, with little direct participation from ordinary people. Some democratic elements survived in places like Venice and Florence, where wealthy merchant families controlled city-states. By the 17th century, democracy started creeping back into political thought, though not without skepticism. Machiavelli and Hobbes weren’t exactly fans of democracy, but they had plenty to say about power and governance. Later on Machiavelli hinted on the possible idea of a republic/mixed government in the *Discourses of Livy * Meanwhile, England was going through its own struggles with power. The English Civil War (1642–1651) was a showdown between King Charles I, who wanted absolute power, and Parliament, which wanted more influence. Charles ignored Parliament and was executed in 1649. England briefly became a republic under Oliver Cromwell, but the monarchy returned after his death. In 1688, the Glorious Revolution forced King James II (Charles I’s son) to flee to France. Parliament then invited William of Orange (a Dutch Protestant) and his wife Mary to take the throne. In 1689, they signed the English Bill of Rights, which limited the monarchy’s power, strengthened Parliament, and guaranteed certain rights to citizens. This was a significant moment in history as it effectively ended the absolute monarchy and established a constitutional monarchy in England. The American Revolution in 1776 and the French Revolution in 1789 pushed democratic ideals forward but still excluded women, slaves, and the poor. Historian Luciano Canfora, in his book* Democracy in Europe*, argues that early liberal democracy was full of contradictions as it preached equality, yet economic and social exclusion remained. (Note: If you want to understand the history of *anarchism*, the French Revolution is a key starting point. It influenced early anti-authoritarian thought, which later evolved into socialist and anti-capitalist movements. Over time, libertarians adopted anarchist principles, leading to the development of anarcho-capitalism. The concept of anarchism in politics has taken nearly two centuries to emerge in its modern form). The 19th and 20th centuries saw the expansion of democracy. But as Canfora explains it, it also saw its exploitation and manipulation. Although industrialization and social movements pushed for broader suffrage, democracy remained controlled by elites who feared true mass participation. Democracy became a tool for maintaining power rather than a true expression of the people’s will. According to Canfora, the Cold War turned democracy into a geopolitical tool, with Western powers supporting or opposing democratic movements based on strategic interests rather than principles. Today, there are many versions of democracy from direct democracy to representative democracy, presidential democracy, social democracy, religious democracy, constitutional democracy, communist democracy, and more. And is often viewed as a brand name for “good governance”. But are they? ### **In the end, was Plato right?** At a meta level, Plato’s argument was about control, be it controlling what people read, hear, and even think. The debate often centers on curated knowledge vs rhetoric. Plato believed that absolute obedience would bring harmony, even at the cost of individuality. Today, we call that totalitarian or dictatorship But when we take a second look at things, are we already living in Plato’s world? Governments across the globe control education, influence media narratives, and regulate speech. Many so-called democracies aren’t as free as they claim to be. So maybe Plato’s influence on modern democracies runs deeper than we realize. Another key debate today is that, unlike Plato’s time, most people *are* educated. However, much of this education is still designed by state systems, which can influence how people think and vote. How do we balance empowering people through education while ensuring true independence in a system built on critical thinking rather than one that merely feeds information? Truth is, democracy has never been a pure, people-driven system. It has always been influenced by power struggles, wealth, and manipulation. Often it has been an instrument of control rather than liberation. Yet, the people have always resisted. In the past, they gathered in the streets, risking tear gas, rubber bullets or being dragged into Black Marias. Today, digital activism has allowed for mass mobilization with fewer risks. In many countries especially in third-world countries, online movements on platforms like Twitter during Jack’s time, forced governments to overturn policies. This may be the closest we've come to real democracy which is direct action without the usual state violence. But with this rise in digital activism comes the counterforce through government and corporate requirements for censorship, algorithmic manipulation, and the quiet steering of public discourse. Platforms once seen as tools of liberation can become tools of control. *Facebook mood experiment* in 2012 tested positive and negative content on 700,000 people and proved emotions can be manipulated at scale. *Cambridge Analytica* was exposed in its attempt to manipulate votes. This is where decentralized networks like Nostr matter as a fundamental resistance to centralized control over speech. If democracy is to return to the people, it must also break free from algorithmic gatekeepers and censorship. Because the so-called ‘ignorant masses’, the very people Plato dismissed, are the ones who fight for freedom. Because real democracy isn’t about control. It’s about freedom. It’s about choice. It’s about the people, always.
@ 0b118e40:4edc09cb
2025-02-19 01:21:45Are we living in his definition of democracy? It’s interesting how political parties can divide a country, especially in democracies where both oppression and individual choice coexist. As I was exploring global economics and political ideologies, I picked up *The Republic* by Plato (again). The first time I read it, I only read the book on the Allegory of the Cave and it felt enlightening. This time around, I read through all the books and I thought to myself : *this is absolutely nuts!* Over 2,000 years ago, *The Republic* imagined a world disturbingly similar to Gattaca or 1984. For a quick rundown, Plato believed in a police state, eugenics, a caste system, and brainwashing people through state-controlled media and education. Sounds wild? I thought so too. And for some reason, Plato had a serious grudge against art. To him, art was deceptive and emotionally manipulative. Maybe because there was a skit making fun of Socrates at that time by Aristophanes (the father of comedy) or maybe because he struggled to deal with emotions, we will never know. Plato obviously wasn’t a fan of democracy as he wanted a dystopian world. But to be fair, he genuinely thought that his ideal world (Kallipolis) was a utopia. Maybe someone who loves extreme order and control might think the same but I sure don’t. His teacher Socrates was also not a fan of democracy because he believed the mass majority were too ignorant to govern and only those intelligent enough could. His student, Aristotle, was more moderate but still critical, seeing democracy as vulnerable to corruption and mob rule. Socrates, Plato, and Aristotle were around the Classical Greek era, 5th to 4th century BC. The idea of democracy existed long before them. The first recorded version was in Athens during the 6th BC, developed by leaders like Solon and Pericles. It was a direct democracy where free male citizens (non-slaves) could vote on laws themselves instead of electing representatives. These guys influenced how we think about democracy today. But looking around, I wonder, did we end up in Plato’s dystopian world? ### **Plato’s take on democracy** Plato’s lack of trust of democracy stemmed from Socrates’ death. Socrates himself was a fierce critic of democracy, as he believed governance should be based on wisdom rather than popularity. Other thinkers, like Pythagoras and Herodotus (father of history), also examined different political systems, but Socrates was the most influential critic. He warned that allowing the uneducated masses to choose leaders would lead to poor governance, as they could be easily swayed by persuasive speakers rather than guided by knowledge. Athenian democracy relied on large citizen juries and was particularly vulnerable to rhetoric and public sentiment. In the end, Socrates became a victim of the very system he criticized. His relentless questioning of widely accepted beliefs, now known as the **Socratic Method**, earned him powerful enemies. Socrates’ constant probing forced them to confront uncomfortable truths. It annoyed people so much, that it eventually led to his trial and execution. Socrates was condemned to death by popular vote. I wonder, if we applied the Socratic Method today to challenge both the left and the right on the merits of the opposing side, would they be open to expanding their perspectives, or would they react with the same hostility? This questioning technique is now also used in some schools and universities as a teaching method, encouraging open-ended discussion where students contribute their own thoughts rather than passively receiving information. But how open a school, system, or educator is to broad perspectives depends largely on their own biases and beliefs. Even with open-ended questions, the direction of the conversation can be shaped by those in charge, potentially limiting the range of perspectives explored. Socrates’ brutal death deeply grounded Plato’s belief that democracy, without intellectual rigor, was nothing but a mob rule. He saw it as a system doomed to chaos, where the unqualified, driven by emotion or manipulated by rhetoric, made decisions that ultimately paved the way for tyranny. ### **The Republic** *The Republic* was written around 375 BC, after the Peloponnesian War. One of its most famous sections is the Allegory of the Cave, where prisoners are stuck watching shadows on a wall, thinking that it’s reality until one breaks free and sees the real world. That’s when the person becomes enlightened, using knowledge and reason to escape ignorance. They return to free others, spreading the truth. I love this idea of breaking free from suppression through knowledge and awareness. But as I went deeper into Plato’s work, I realized what the plot twist was. Plato wrote this book for strict state control. He wanted total control over education, media, and even families like in the book 1984. He argued that people should be sorted into a caste system, typically workers, warriors, and philosopher-kings so that society runs like a well-oiled machine. The “guardians” would police the state and everyone would go through physical and military training. To top it off, kids would be taken away from their parents and raised by the state for the “greater good.” like in the movie Gattaca. If that sounds a little too Orwellian, that’s because it is. Plato believed that only philosophers, the truly enlightened ones from that “cave”, should rule. To him, democracy was a joke, a breeding ground for corruption and tyranny. I found it completely ironic that this book that warns about brainwashing in the Allegory of the Cave also pushes for a state-controlled society, where thinking for yourself isn’t really an option. And yet, looking around today, I wonder, are we really any different? We live in a world where oppression and enlightenment exist side by side. Plato was slightly progressive in that he thought men and women should have equal education, but only for the ruling Guardian class. In *The Republic*, Plato didn’t focus much on economics or capitalism as we understand them today. His philosophies were more concerned with justice, governance, and the ideal structure of society. He did touch on wealth and property, particularly in *The Republic and Laws* but it was more on being against wealth accumulation by rulers (philosopher-kings had to live communally and without private property). While these ideas echo elements of socialism, he never outlined a full economic system like capitalism or socialism. ### **The hatred for art** Plato was deeply skeptical of art. He believed that it appealed to emotions over rational thought and distorted reality. In *The Republic* (Book X), he argued that art is an imitation of an imitation, pulling people further from the truth. If he had his way, much of modern entertainment, including poetry, drama, and even certain types of music, would not exist in their expressive forms. Despite Plato’s distrust of the arts, his time was a golden age for Greek drama, sculpture, and philosophy. Ironically, the very city where he built his Academy, Athens, was flourishing with the kind of creativity he wanted to censor. Even medicine, which thrived under Hippocrates (the father of medicine), was considered an art requiring lifelong mastery. His quote, ‘**Life is short, and art is long**,’ reflects the long span of time it takes to cultivate and appreciate knowledge and skills, which was something Plato valued. Yet, he dismissed most art as a distraction from truth. Plato particularly criticized poets and playwrights like Homer, as he claimed they spread false ideas about gods and morality. He was also wary of Aristophanes, as he believed his work stirred emotions rather than encouraging rational thought. It probably did not help that Aristophanes mocked Socrates in his play *The Clouds*, which may have influenced Plato’s views. What’s clear is that Plato didn’t hate art because he didn’t understand it. He deeply understood the power of storytelling and its ability to mold societal beliefs. He argued for banning poets entirely from his “ideal city” to prevent them from misleading the public. But he did value some forms of art. After all, he was a writer himself, and writing is a form of art. He approved of artistic expressions that promoted moral and intellectual virtue, such as hymns, architecture, and patriotic poetry, as long as they served the greater purpose of instilling order and wisdom in society. ### **Plato’s five regimes** Plato believed governments naturally decay over time, moving from order to chaos. He outlined five regimes, which he considers each to be worse than the last. 1. *Aristocracy (Philosopher-King rule)* : This is his pitch, the ideal state, ruled by wise elites who value knowledge over power. Some aspects of modern authoritarian states echo this model 2. *Timocracy (Military rule)* : A government driven by honor and discipline, like Sparta. Over time, ambition overtakes virtue, leading to oligarchy. 3. *Oligarchy (Rule by the wealthy)* : The rich seizes power and deepens inequality. Many democracies today show oligarchic tendencies, where money dominates politics. 4. *Democracy (Rule by the masses)* : The people overthrow the elites, prioritizing freedom over order. But without stability, democracy becomes fragile, and vulnerable to demagogues and external manipulation. 5. *Tyranny (Dictatorship)* : When democracy collapses, a charismatic leader rises, promising order but seizing absolute power. What begins as freedom ends in oppression. Modern politics seems stuck in a cycle, shifting between democracy, oligarchy, and authoritarian control. If Plato was right, no system is permanent and only the illusion of stability remains. ### **Does Plato’s ideal state exist in any country today?** Some aspects of modern *benevolent dictatorships*, like Singapore under Lee Kuan Yew, or *socialist states* like China, may resemble Plato’s vision in their emphasis on elite rule, long-term planning, and state control. But, these governments operate pragmatically, balancing governance with economic power, political strategy, and public influence rather than strictly adhering to philosophical ideals. Could this be compared to Taliban rule, given the censorship, authoritarian control, and rigid social hierarchy? While there are superficial similarities, the key difference is that Plato valued knowledge, reason, and meritocracy, while the Taliban enforced religious fundamentalism and theocratic rule. Plato’s Kallipolis also included some level of gender equality for the ruling class, whereas the Taliban’s system is heavily restrictive, especially toward women. While Plato’s ideas echo in certain authoritarian-leaning states, his rigid caste system, philosopher-led governance, and rejection of democracy set his vision apart from any modern political system. ### **Aristotle’s take on democracy** Aristotle wasn’t Athenian, but he documented and analyzed 158 constitutions, including Athenian democracy. He studied at Plato’s Academy for over 20 years, growing up in a world influenced by Athens’ democratic experiment. He lived through the tail end of Athens’ golden age, witnessed its decline, and experienced how different forms of rule influenced politics and the mindset of the people under them. For Aristotle, governments were good or corrupted. The good ones were monarchs, aristocracy (wise elites), and polity (a constitutional gov’t where the middle class keeps power balanced). The corrupted ones were tyranny (monarchy gone wrong), oligarchy, and democracy. Aristotle saw how democracy, if unchecked, could spiral into chaos or be co-opted by populist leaders. But unlike Plato, who rejected democracy outright, Aristotle believed it could work if properly structured. His concept of ‘**polity**’ was a constitutional government that balanced democratic participation with stability, relying on a strong middle class to prevent both mob rule and elite domination. This idea of checks and balances, a mixed government, and middle-class stability make polity the closest to modern constitutional democracies today when compared to all 3 of the Greek philosophers. ### **What happened after Athens?** Of course, democracy didn’t end with Athens, it evolved over time. After Athens’ golden age came Alexander the Great (Aristotle’s student and the king of Macedonia). He conquered Greece, Persia, Egypt, and part of India, creating the largest empire of his time. After his death in 323 BCE, his empire split among his generals, marking the beginning of the Hellenistic period. Rome saw a shift from the fall of the Roman Republic to the rise of the Roman Empire under Augustus moving away from democratic ideals to centralized rule. But the Western Roman Empire fell about 500 years later largely due to internal decline and invasions by the Germanic Tribes (modern-day Sweden, Switzerland, Germany). The Eastern Roman Empire (Byzantine Empire, based in Constantinople or modern-day Turkey) rose and survived for nearly 1,000 more years until it fell to the Ottoman Turks in 1453. During the Medieval period (5th–15th century), Europe saw a rise in monarchies and feudalism. Power shifted to kings, nobles, and the church, with little direct participation from ordinary people. Some democratic elements survived in places like Venice and Florence, where wealthy merchant families controlled city-states. By the 17th century, democracy started creeping back into political thought, though not without skepticism. Machiavelli and Hobbes weren’t exactly fans of democracy, but they had plenty to say about power and governance. Later on Machiavelli hinted on the possible idea of a republic/mixed government in the *Discourses of Livy * Meanwhile, England was going through its own struggles with power. The English Civil War (1642–1651) was a showdown between King Charles I, who wanted absolute power, and Parliament, which wanted more influence. Charles ignored Parliament and was executed in 1649. England briefly became a republic under Oliver Cromwell, but the monarchy returned after his death. In 1688, the Glorious Revolution forced King James II (Charles I’s son) to flee to France. Parliament then invited William of Orange (a Dutch Protestant) and his wife Mary to take the throne. In 1689, they signed the English Bill of Rights, which limited the monarchy’s power, strengthened Parliament, and guaranteed certain rights to citizens. This was a significant moment in history as it effectively ended the absolute monarchy and established a constitutional monarchy in England. The American Revolution in 1776 and the French Revolution in 1789 pushed democratic ideals forward but still excluded women, slaves, and the poor. Historian Luciano Canfora, in his book* Democracy in Europe*, argues that early liberal democracy was full of contradictions as it preached equality, yet economic and social exclusion remained. (Note: If you want to understand the history of *anarchism*, the French Revolution is a key starting point. It influenced early anti-authoritarian thought, which later evolved into socialist and anti-capitalist movements. Over time, libertarians adopted anarchist principles, leading to the development of anarcho-capitalism. The concept of anarchism in politics has taken nearly two centuries to emerge in its modern form). The 19th and 20th centuries saw the expansion of democracy. But as Canfora explains it, it also saw its exploitation and manipulation. Although industrialization and social movements pushed for broader suffrage, democracy remained controlled by elites who feared true mass participation. Democracy became a tool for maintaining power rather than a true expression of the people’s will. According to Canfora, the Cold War turned democracy into a geopolitical tool, with Western powers supporting or opposing democratic movements based on strategic interests rather than principles. Today, there are many versions of democracy from direct democracy to representative democracy, presidential democracy, social democracy, religious democracy, constitutional democracy, communist democracy, and more. And is often viewed as a brand name for “good governance”. But are they? ### **In the end, was Plato right?** At a meta level, Plato’s argument was about control, be it controlling what people read, hear, and even think. The debate often centers on curated knowledge vs rhetoric. Plato believed that absolute obedience would bring harmony, even at the cost of individuality. Today, we call that totalitarian or dictatorship But when we take a second look at things, are we already living in Plato’s world? Governments across the globe control education, influence media narratives, and regulate speech. Many so-called democracies aren’t as free as they claim to be. So maybe Plato’s influence on modern democracies runs deeper than we realize. Another key debate today is that, unlike Plato’s time, most people *are* educated. However, much of this education is still designed by state systems, which can influence how people think and vote. How do we balance empowering people through education while ensuring true independence in a system built on critical thinking rather than one that merely feeds information? Truth is, democracy has never been a pure, people-driven system. It has always been influenced by power struggles, wealth, and manipulation. Often it has been an instrument of control rather than liberation. Yet, the people have always resisted. In the past, they gathered in the streets, risking tear gas, rubber bullets or being dragged into Black Marias. Today, digital activism has allowed for mass mobilization with fewer risks. In many countries especially in third-world countries, online movements on platforms like Twitter during Jack’s time, forced governments to overturn policies. This may be the closest we've come to real democracy which is direct action without the usual state violence. But with this rise in digital activism comes the counterforce through government and corporate requirements for censorship, algorithmic manipulation, and the quiet steering of public discourse. Platforms once seen as tools of liberation can become tools of control. *Facebook mood experiment* in 2012 tested positive and negative content on 700,000 people and proved emotions can be manipulated at scale. *Cambridge Analytica* was exposed in its attempt to manipulate votes. This is where decentralized networks like Nostr matter as a fundamental resistance to centralized control over speech. If democracy is to return to the people, it must also break free from algorithmic gatekeepers and censorship. Because the so-called ‘ignorant masses’, the very people Plato dismissed, are the ones who fight for freedom. Because real democracy isn’t about control. It’s about freedom. It’s about choice. It’s about the people, always. @ 254f56d7:f2c38100
2024-12-30 07:38:27Vamos ver seu funcionamento 
@ 254f56d7:f2c38100
2024-12-30 07:38:27Vamos ver seu funcionamento  @ a012dc82:6458a70d
2024-12-30 05:51:11**Table Of Content** - The Influence of Global Oil Prices - Bitcoin's Roller Coaster Ride - Anticipation Surrounding the 2024 Halving Event - The Broader Crypto Landscape - Conclusions - FAQ In the ever-evolving world of cryptocurrencies, Bitcoin stands as a beacon, often dictating the mood of the entire crypto market. Its price fluctuations are closely watched by investors, analysts, and enthusiasts alike. Max Keiser, a prominent figure in the crypto space, recently shed light on some intriguing factors that might be influencing Bitcoin's current price trajectory. This article delves into Keiser's insights, exploring the broader implications of global events on Bitcoin's market performance. **The Influence of Global Oil Prices** Max Keiser, a renowned Bitcoin advocate and former trader, recently drew attention to the interplay between global oil prices and Bitcoin's market performance. Responding to a post by German economics expert, Holger Zschaepitz, Keiser highlighted the significance of Brent oil reaching $90 per barrel for the first time since the previous November. According to Keiser, the surge in oil prices, driven by Saudi Arabia's decision to extend its reduction in oil production for another three months, has had ripple effects in the financial world. One of these effects is the shift of investor interest towards higher interest deposit USD accounts. This diversion of investments is creating what Keiser terms as "a small headwind for Bitcoin," implying that as traditional markets like oil show promise, some investors might be reconsidering their cryptocurrency positions. **Bitcoin's Roller Coaster Ride** The cryptocurrency market, known for its volatility, witnessed Bitcoin's price undergoing significant fluctuations recently. A notable event that gave Bitcoin a temporary boost was Grayscale's triumph over the SEC in a legal battle concerning the conversion of its Bitcoin Trust into a spot ETF. This victory led to a rapid 7.88% spike in Bitcoin's price within a mere hour, pushing it from the $26,000 bracket to briefly touch the $28,000 threshold. However, this euphoria was short-lived. Over the subsequent week, the cryptocurrency saw its gains erode, settling in the $25,400 range. At the time the reference article was penned, Bitcoin was hovering around $25,688. **Anticipation Surrounding the 2024 Halving Event** The Bitcoin community is abuzz with anticipation for the next scheduled Bitcoin halving, projected to take place in April-May 2024. This event will see the rewards for Bitcoin miners being slashed by half, resulting in a decreased supply of Bitcoin entering the market. Historically, such halvings have acted as catalysts, propelling Bitcoin's price upwards. A case in point is the aftermath of the 2020 halving, post which Bitcoin soared to an all-time high of $69,000 in October 2021. However, some financial analysts argue that this surge was less about the halving and more a consequence of the extensive monetary measures adopted by institutions like the US Federal Reserve. These measures, taken in response to the pandemic and the ensuing lockdowns, flooded the market with cash, potentially driving up Bitcoin's price. **The Broader Crypto Landscape** While Bitcoin remains the most dominant and influential cryptocurrency, it's essential to consider its position within the broader crypto ecosystem. Other cryptocurrencies, often referred to as 'altcoins', also play a role in shaping investor sentiment and market dynamics. Factors such as technological advancements, regulatory changes, and global economic shifts not only impact Bitcoin but the entire crypto market. As investors diversify their portfolios and explore newer blockchain projects, Bitcoin's role as the market leader is continually tested. Yet, its pioneering status and proven resilience make it a focal point of discussions and analyses in the crypto world. **Conclusion** Bitcoin, the flagship cryptocurrency, has always been subject to a myriad of market forces and global events. While its inherent potential remains undeniable, the current market landscape, shaped by factors ranging from oil prices to global economic policies, presents challenges. Yet, with events like the 2024 halving on the horizon, there's an air of optimism among Bitcoin enthusiasts and investors about the future trajectory of this digital asset. **FAQ** **Who is Max Keiser?** Max Keiser is a prominent Bitcoin advocate, former trader, and well-known crypto podcaster. **What did Keiser say about Bitcoin's price?** Keiser pointed out that rising global oil prices and the allure of higher interest deposit USD accounts are creating a "small headwind" for Bitcoin. **How did Grayscale's legal victory affect Bitcoin?** Grayscale's win over the SEC led to a 7.88% spike in Bitcoin's price within an hour. **When is the next Bitcoin halving expected?** The next Bitcoin halving is projected to occur around April-May 2024. **Did the 2020 Bitcoin halving influence its price?** Yes, post the 2020 halving, Bitcoin reached an all-time high of $69,000 in October 2021. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
@ a012dc82:6458a70d
2024-12-30 05:51:11**Table Of Content** - The Influence of Global Oil Prices - Bitcoin's Roller Coaster Ride - Anticipation Surrounding the 2024 Halving Event - The Broader Crypto Landscape - Conclusions - FAQ In the ever-evolving world of cryptocurrencies, Bitcoin stands as a beacon, often dictating the mood of the entire crypto market. Its price fluctuations are closely watched by investors, analysts, and enthusiasts alike. Max Keiser, a prominent figure in the crypto space, recently shed light on some intriguing factors that might be influencing Bitcoin's current price trajectory. This article delves into Keiser's insights, exploring the broader implications of global events on Bitcoin's market performance. **The Influence of Global Oil Prices** Max Keiser, a renowned Bitcoin advocate and former trader, recently drew attention to the interplay between global oil prices and Bitcoin's market performance. Responding to a post by German economics expert, Holger Zschaepitz, Keiser highlighted the significance of Brent oil reaching $90 per barrel for the first time since the previous November. According to Keiser, the surge in oil prices, driven by Saudi Arabia's decision to extend its reduction in oil production for another three months, has had ripple effects in the financial world. One of these effects is the shift of investor interest towards higher interest deposit USD accounts. This diversion of investments is creating what Keiser terms as "a small headwind for Bitcoin," implying that as traditional markets like oil show promise, some investors might be reconsidering their cryptocurrency positions. **Bitcoin's Roller Coaster Ride** The cryptocurrency market, known for its volatility, witnessed Bitcoin's price undergoing significant fluctuations recently. A notable event that gave Bitcoin a temporary boost was Grayscale's triumph over the SEC in a legal battle concerning the conversion of its Bitcoin Trust into a spot ETF. This victory led to a rapid 7.88% spike in Bitcoin's price within a mere hour, pushing it from the $26,000 bracket to briefly touch the $28,000 threshold. However, this euphoria was short-lived. Over the subsequent week, the cryptocurrency saw its gains erode, settling in the $25,400 range. At the time the reference article was penned, Bitcoin was hovering around $25,688. **Anticipation Surrounding the 2024 Halving Event** The Bitcoin community is abuzz with anticipation for the next scheduled Bitcoin halving, projected to take place in April-May 2024. This event will see the rewards for Bitcoin miners being slashed by half, resulting in a decreased supply of Bitcoin entering the market. Historically, such halvings have acted as catalysts, propelling Bitcoin's price upwards. A case in point is the aftermath of the 2020 halving, post which Bitcoin soared to an all-time high of $69,000 in October 2021. However, some financial analysts argue that this surge was less about the halving and more a consequence of the extensive monetary measures adopted by institutions like the US Federal Reserve. These measures, taken in response to the pandemic and the ensuing lockdowns, flooded the market with cash, potentially driving up Bitcoin's price. **The Broader Crypto Landscape** While Bitcoin remains the most dominant and influential cryptocurrency, it's essential to consider its position within the broader crypto ecosystem. Other cryptocurrencies, often referred to as 'altcoins', also play a role in shaping investor sentiment and market dynamics. Factors such as technological advancements, regulatory changes, and global economic shifts not only impact Bitcoin but the entire crypto market. As investors diversify their portfolios and explore newer blockchain projects, Bitcoin's role as the market leader is continually tested. Yet, its pioneering status and proven resilience make it a focal point of discussions and analyses in the crypto world. **Conclusion** Bitcoin, the flagship cryptocurrency, has always been subject to a myriad of market forces and global events. While its inherent potential remains undeniable, the current market landscape, shaped by factors ranging from oil prices to global economic policies, presents challenges. Yet, with events like the 2024 halving on the horizon, there's an air of optimism among Bitcoin enthusiasts and investors about the future trajectory of this digital asset. **FAQ** **Who is Max Keiser?** Max Keiser is a prominent Bitcoin advocate, former trader, and well-known crypto podcaster. **What did Keiser say about Bitcoin's price?** Keiser pointed out that rising global oil prices and the allure of higher interest deposit USD accounts are creating a "small headwind" for Bitcoin. **How did Grayscale's legal victory affect Bitcoin?** Grayscale's win over the SEC led to a 7.88% spike in Bitcoin's price within an hour. **When is the next Bitcoin halving expected?** The next Bitcoin halving is projected to occur around April-May 2024. **Did the 2020 Bitcoin halving influence its price?** Yes, post the 2020 halving, Bitcoin reached an all-time high of $69,000 in October 2021. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.* @ 16d11430:61640947
2024-12-23 16:47:01At the intersection of philosophy, theology, physics, biology, and finance lies a terrifying truth: the fiat monetary system, in its current form, is not just an economic framework but a silent, relentless force actively working against humanity's survival. It isn't simply a failed financial model—it is a systemic engine of destruction, both externally and within the very core of our biological existence. The Philosophical Void of Fiat Philosophy has long questioned the nature of value and the meaning of human existence. From Socrates to Kant, thinkers have pondered the pursuit of truth, beauty, and virtue. But in the modern age, the fiat system has hijacked this discourse. The notion of "value" in a fiat world is no longer rooted in human potential or natural resources—it is abstracted, manipulated, and controlled by central authorities with the sole purpose of perpetuating their own power. The currency is not a reflection of society’s labor or resources; it is a representation of faith in an authority that, more often than not, breaks that faith with reckless monetary policies and hidden inflation. The fiat system has created a kind of ontological nihilism, where the idea of true value, rooted in work, creativity, and family, is replaced with speculative gambling and short-term gains. This betrayal of human purpose at the systemic level feeds into a philosophical despair: the relentless devaluation of effort, the erosion of trust, and the abandonment of shared human values. In this nihilistic economy, purpose and meaning become increasingly difficult to find, leaving millions to question the very foundation of their existence. Theological Implications: Fiat and the Collapse of the Sacred Religious traditions have long linked moral integrity with the stewardship of resources and the preservation of life. Fiat currency, however, corrupts these foundational beliefs. In the theological narrative of creation, humans are given dominion over the Earth, tasked with nurturing and protecting it for future generations. But the fiat system promotes the exact opposite: it commodifies everything—land, labor, and life—treating them as mere transactions on a ledger. This disrespect for creation is an affront to the divine. In many theologies, creation is meant to be sustained, a delicate balance that mirrors the harmony of the divine order. Fiat systems—by continuously printing money and driving inflation—treat nature and humanity as expendable resources to be exploited for short-term gains, leading to environmental degradation and societal collapse. The creation narrative, in which humans are called to be stewards, is inverted. The fiat system, through its unholy alliance with unrestrained growth and unsustainable debt, is destroying the very creation it should protect. Furthermore, the fiat system drives idolatry of power and wealth. The central banks and corporations that control the money supply have become modern-day gods, their decrees shaping the lives of billions, while the masses are enslaved by debt and inflation. This form of worship isn't overt, but it is profound. It leads to a world where people place their faith not in God or their families, but in the abstract promises of institutions that serve their own interests. Physics and the Infinite Growth Paradox Physics teaches us that the universe is finite—resources, energy, and space are all limited. Yet, the fiat system operates under the delusion of infinite growth. Central banks print money without concern for natural limits, encouraging an economy that assumes unending expansion. This is not only an economic fallacy; it is a physical impossibility. In thermodynamics, the Second Law states that entropy (disorder) increases over time in any closed system. The fiat system operates as if the Earth were an infinite resource pool, perpetually able to expand without consequence. The real world, however, does not bend to these abstract concepts of infinite growth. Resources are finite, ecosystems are fragile, and human capacity is limited. Fiat currency, by promoting unsustainable consumption and growth, accelerates the depletion of resources and the degradation of natural systems that support life itself. Even the financial “growth” driven by fiat policies leads to unsustainable bubbles—inflated stock markets, real estate, and speculative assets that burst and leave ruin in their wake. These crashes aren’t just economic—they have profound biological consequences. The cycles of boom and bust undermine communities, erode social stability, and increase anxiety and depression, all of which affect human health at a biological level. Biology: The Fiat System and the Destruction of Human Health Biologically, the fiat system is a cancerous growth on human society. The constant chase for growth and the devaluation of work leads to chronic stress, which is one of the leading causes of disease in modern society. The strain of living in a system that values speculation over well-being results in a biological feedback loop: rising anxiety, poor mental health, physical diseases like cardiovascular disorders, and a shortening of lifespans. Moreover, the focus on profit and short-term returns creates a biological disconnect between humans and the planet. The fiat system fuels industries that destroy ecosystems, increase pollution, and deplete resources at unsustainable rates. These actions are not just environmentally harmful; they directly harm human biology. The degradation of the environment—whether through toxic chemicals, pollution, or resource extraction—has profound biological effects on human health, causing respiratory diseases, cancers, and neurological disorders. The biological cost of the fiat system is not a distant theory; it is being paid every day by millions in the form of increased health risks, diseases linked to stress, and the growing burden of mental health disorders. The constant uncertainty of an inflation-driven economy exacerbates these conditions, creating a society of individuals whose bodies and minds are under constant strain. We are witnessing a systemic biological unraveling, one in which the very act of living is increasingly fraught with pain, instability, and the looming threat of collapse. Finance as the Final Illusion At the core of the fiat system is a fundamental illusion—that financial growth can occur without any real connection to tangible value. The abstraction of currency, the manipulation of interest rates, and the constant creation of new money hide the underlying truth: the system is built on nothing but faith. When that faith falters, the entire system collapses. This illusion has become so deeply embedded that it now defines the human experience. Work no longer connects to production or creation—it is reduced to a transaction on a spreadsheet, a means to acquire more fiat currency in a world where value is ephemeral and increasingly disconnected from human reality. As we pursue ever-expanding wealth, the fundamental truths of biology—interdependence, sustainability, and balance—are ignored. The fiat system’s abstract financial models serve to disconnect us from the basic realities of life: that we are part of an interconnected world where every action has a reaction, where resources are finite, and where human health, both mental and physical, depends on the stability of our environment and our social systems. The Ultimate Extermination In the end, the fiat system is not just an economic issue; it is a biological, philosophical, theological, and existential threat to the very survival of humanity. It is a force that devalues human effort, encourages environmental destruction, fosters inequality, and creates pain at the core of the human biological condition. It is an economic framework that leads not to prosperity, but to extermination—not just of species, but of the very essence of human well-being. To continue on this path is to accept the slow death of our species, one based not on natural forces, but on our own choice to worship the abstract over the real, the speculative over the tangible. The fiat system isn't just a threat; it is the ultimate self-inflicted wound, a cultural and financial cancer that, if left unchecked, will destroy humanity’s chance for survival and peace.
@ 16d11430:61640947
2024-12-23 16:47:01At the intersection of philosophy, theology, physics, biology, and finance lies a terrifying truth: the fiat monetary system, in its current form, is not just an economic framework but a silent, relentless force actively working against humanity's survival. It isn't simply a failed financial model—it is a systemic engine of destruction, both externally and within the very core of our biological existence. The Philosophical Void of Fiat Philosophy has long questioned the nature of value and the meaning of human existence. From Socrates to Kant, thinkers have pondered the pursuit of truth, beauty, and virtue. But in the modern age, the fiat system has hijacked this discourse. The notion of "value" in a fiat world is no longer rooted in human potential or natural resources—it is abstracted, manipulated, and controlled by central authorities with the sole purpose of perpetuating their own power. The currency is not a reflection of society’s labor or resources; it is a representation of faith in an authority that, more often than not, breaks that faith with reckless monetary policies and hidden inflation. The fiat system has created a kind of ontological nihilism, where the idea of true value, rooted in work, creativity, and family, is replaced with speculative gambling and short-term gains. This betrayal of human purpose at the systemic level feeds into a philosophical despair: the relentless devaluation of effort, the erosion of trust, and the abandonment of shared human values. In this nihilistic economy, purpose and meaning become increasingly difficult to find, leaving millions to question the very foundation of their existence. Theological Implications: Fiat and the Collapse of the Sacred Religious traditions have long linked moral integrity with the stewardship of resources and the preservation of life. Fiat currency, however, corrupts these foundational beliefs. In the theological narrative of creation, humans are given dominion over the Earth, tasked with nurturing and protecting it for future generations. But the fiat system promotes the exact opposite: it commodifies everything—land, labor, and life—treating them as mere transactions on a ledger. This disrespect for creation is an affront to the divine. In many theologies, creation is meant to be sustained, a delicate balance that mirrors the harmony of the divine order. Fiat systems—by continuously printing money and driving inflation—treat nature and humanity as expendable resources to be exploited for short-term gains, leading to environmental degradation and societal collapse. The creation narrative, in which humans are called to be stewards, is inverted. The fiat system, through its unholy alliance with unrestrained growth and unsustainable debt, is destroying the very creation it should protect. Furthermore, the fiat system drives idolatry of power and wealth. The central banks and corporations that control the money supply have become modern-day gods, their decrees shaping the lives of billions, while the masses are enslaved by debt and inflation. This form of worship isn't overt, but it is profound. It leads to a world where people place their faith not in God or their families, but in the abstract promises of institutions that serve their own interests. Physics and the Infinite Growth Paradox Physics teaches us that the universe is finite—resources, energy, and space are all limited. Yet, the fiat system operates under the delusion of infinite growth. Central banks print money without concern for natural limits, encouraging an economy that assumes unending expansion. This is not only an economic fallacy; it is a physical impossibility. In thermodynamics, the Second Law states that entropy (disorder) increases over time in any closed system. The fiat system operates as if the Earth were an infinite resource pool, perpetually able to expand without consequence. The real world, however, does not bend to these abstract concepts of infinite growth. Resources are finite, ecosystems are fragile, and human capacity is limited. Fiat currency, by promoting unsustainable consumption and growth, accelerates the depletion of resources and the degradation of natural systems that support life itself. Even the financial “growth” driven by fiat policies leads to unsustainable bubbles—inflated stock markets, real estate, and speculative assets that burst and leave ruin in their wake. These crashes aren’t just economic—they have profound biological consequences. The cycles of boom and bust undermine communities, erode social stability, and increase anxiety and depression, all of which affect human health at a biological level. Biology: The Fiat System and the Destruction of Human Health Biologically, the fiat system is a cancerous growth on human society. The constant chase for growth and the devaluation of work leads to chronic stress, which is one of the leading causes of disease in modern society. The strain of living in a system that values speculation over well-being results in a biological feedback loop: rising anxiety, poor mental health, physical diseases like cardiovascular disorders, and a shortening of lifespans. Moreover, the focus on profit and short-term returns creates a biological disconnect between humans and the planet. The fiat system fuels industries that destroy ecosystems, increase pollution, and deplete resources at unsustainable rates. These actions are not just environmentally harmful; they directly harm human biology. The degradation of the environment—whether through toxic chemicals, pollution, or resource extraction—has profound biological effects on human health, causing respiratory diseases, cancers, and neurological disorders. The biological cost of the fiat system is not a distant theory; it is being paid every day by millions in the form of increased health risks, diseases linked to stress, and the growing burden of mental health disorders. The constant uncertainty of an inflation-driven economy exacerbates these conditions, creating a society of individuals whose bodies and minds are under constant strain. We are witnessing a systemic biological unraveling, one in which the very act of living is increasingly fraught with pain, instability, and the looming threat of collapse. Finance as the Final Illusion At the core of the fiat system is a fundamental illusion—that financial growth can occur without any real connection to tangible value. The abstraction of currency, the manipulation of interest rates, and the constant creation of new money hide the underlying truth: the system is built on nothing but faith. When that faith falters, the entire system collapses. This illusion has become so deeply embedded that it now defines the human experience. Work no longer connects to production or creation—it is reduced to a transaction on a spreadsheet, a means to acquire more fiat currency in a world where value is ephemeral and increasingly disconnected from human reality. As we pursue ever-expanding wealth, the fundamental truths of biology—interdependence, sustainability, and balance—are ignored. The fiat system’s abstract financial models serve to disconnect us from the basic realities of life: that we are part of an interconnected world where every action has a reaction, where resources are finite, and where human health, both mental and physical, depends on the stability of our environment and our social systems. The Ultimate Extermination In the end, the fiat system is not just an economic issue; it is a biological, philosophical, theological, and existential threat to the very survival of humanity. It is a force that devalues human effort, encourages environmental destruction, fosters inequality, and creates pain at the core of the human biological condition. It is an economic framework that leads not to prosperity, but to extermination—not just of species, but of the very essence of human well-being. To continue on this path is to accept the slow death of our species, one based not on natural forces, but on our own choice to worship the abstract over the real, the speculative over the tangible. The fiat system isn't just a threat; it is the ultimate self-inflicted wound, a cultural and financial cancer that, if left unchecked, will destroy humanity’s chance for survival and peace. @ 4d953dcb:39c9c35c
2025-02-18 22:03:42Чтобы иметь бесплатный, быстрый и устойчивый к блокировке VPN нам нужны всего 2 вещи: 1. Клиент V2ray (приложение для использования VPN) 2. Файлы конфигурации (по сути данные VPN-серверов) ## Клиенты V2ray: 1. Инструкция по установке для Windows и Linux: https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-HiddifyNext-app#adding-a-profile-to-the-app *P.S. Если возникли проблемы с Hiddify-Next — пробуйте установить [Necoray](https://github.com/MatsuriDayo/nekoray)* 2. Инструкция по установке для Android: https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-V2rayNG-app#add-configs-to-the-app *P.S. Если возникли проблемы с V2rayNG — пробуйте установить [HiddifyNext](https://github.com/hiddify/hiddify-next/releases) ([инструкция](https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-HiddifyNext-app#adding-a-profile-to-the-app))* 3. Инструкция по установке для Windows и Linux: https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-V2Box-app#add-subscription-links-to-the-app (лучше для iOS) + https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-Streisand#add-subscription-link (лучше для Mac) *P.S. Если возникли проблемы с V2Box и Streisand — пробуйте установить [Hiddify-Next](https://github.com/hiddify/hiddify-next/releases) или [ShadowRocket](https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-ShadowRocket-app#add-subscription-link-to-the-app)* ## Источники файлов конфигураций: 1. https://outlinekeys.com/ 2. https://proxytype.com/ 3. https://vlesskey.com/ 4. https://vpnkeys.org/ 5. https://openproxylist.com/v2ray/ 6. https://github.com/Epodonios/v2ray-configs 7. https://github.com/barry-far/V2ray-Configs?tab=readme-ov-file 8. https://github.com/M-Mashreghi/Free-V2ray-Collector 9. https://github.com/skywrt/v2ray-configs 10. https://github.com/0xdolan/v2ray_config_generator
@ 4d953dcb:39c9c35c
2025-02-18 22:03:42Чтобы иметь бесплатный, быстрый и устойчивый к блокировке VPN нам нужны всего 2 вещи: 1. Клиент V2ray (приложение для использования VPN) 2. Файлы конфигурации (по сути данные VPN-серверов) ## Клиенты V2ray: 1. Инструкция по установке для Windows и Linux: https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-HiddifyNext-app#adding-a-profile-to-the-app *P.S. Если возникли проблемы с Hiddify-Next — пробуйте установить [Necoray](https://github.com/MatsuriDayo/nekoray)* 2. Инструкция по установке для Android: https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-V2rayNG-app#add-configs-to-the-app *P.S. Если возникли проблемы с V2rayNG — пробуйте установить [HiddifyNext](https://github.com/hiddify/hiddify-next/releases) ([инструкция](https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-HiddifyNext-app#adding-a-profile-to-the-app))* 3. Инструкция по установке для Windows и Linux: https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-V2Box-app#add-subscription-links-to-the-app (лучше для iOS) + https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-Streisand#add-subscription-link (лучше для Mac) *P.S. Если возникли проблемы с V2Box и Streisand — пробуйте установить [Hiddify-Next](https://github.com/hiddify/hiddify-next/releases) или [ShadowRocket](https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-ShadowRocket-app#add-subscription-link-to-the-app)* ## Источники файлов конфигураций: 1. https://outlinekeys.com/ 2. https://proxytype.com/ 3. https://vlesskey.com/ 4. https://vpnkeys.org/ 5. https://openproxylist.com/v2ray/ 6. https://github.com/Epodonios/v2ray-configs 7. https://github.com/barry-far/V2ray-Configs?tab=readme-ov-file 8. https://github.com/M-Mashreghi/Free-V2ray-Collector 9. https://github.com/skywrt/v2ray-configs 10. https://github.com/0xdolan/v2ray_config_generator @ a367f9eb:0633efea
2024-12-22 21:35:22I’ll admit that I was wrong about Bitcoin. Perhaps in 2013. Definitely 2017. Probably in 2018-2019. And maybe even today. Being wrong about Bitcoin is part of finally understanding it. It will test you, make you question everything, and in the words of BTC educator and privacy advocate [Matt Odell](https://twitter.com/ODELL), “Bitcoin will humble you”. I’ve had my own stumbles on the way. In a very public fashion in 2017, after years of using Bitcoin, trying to start a company with it, using it as my primary exchange vehicle between currencies, and generally being annoying about it at parties, I let out the bear. In an article published in my own literary magazine *Devolution Review* in September 2017, I had a breaking point. The article was titled “[Going Bearish on Bitcoin: Cryptocurrencies are the tulip mania of the 21st century](https://www.devolutionreview.com/bearish-on-bitcoin/)”. It was later republished in *Huffington Post* and across dozens of financial and crypto blogs at the time with another, more appropriate title: “[Bitcoin Has Become About The Payday, Not Its Potential](https://www.huffpost.com/archive/ca/entry/bitcoin-has-become-about-the-payday-not-its-potential_ca_5cd5025de4b07bc72973ec2d)”. As I laid out, my newfound bearishness had little to do with the technology itself or the promise of Bitcoin, and more to do with the cynical industry forming around it: > In the beginning, Bitcoin was something of a revolution to me. The digital currency represented everything from my rebellious youth. > > It was a decentralized, denationalized, and digital currency operating outside the traditional banking and governmental system. It used tools of cryptography and connected buyers and sellers across national borders at minimal transaction costs. > > … > > The 21st-century version (of Tulip mania) has welcomed a plethora of slick consultants, hazy schemes dressed up as investor possibilities, and too much wishy-washy language for anything to really make sense to anyone who wants to use a digital currency to make purchases. While I called out Bitcoin by name at the time, on reflection, I was really talking about the ICO craze, the wishy-washy consultants, and the altcoin ponzis. What I was articulating — without knowing it — was the frame of NgU, or “numbers go up”. Rather than advocating for Bitcoin because of its uncensorability, proof-of-work, or immutability, the common mentality among newbies and the dollar-obsessed was that Bitcoin mattered because its price was a rocket ship. And because Bitcoin was gaining in price, affinity tokens and projects that were imperfect forks of Bitcoin took off as well. The price alone — rather than its qualities — were the reasons why you’d hear Uber drivers, finance bros, or your gym buddy mention Bitcoin. As someone who came to Bitcoin for philosophical reasons, that just sat wrong with me. Maybe I had too many projects thrown in my face, or maybe I was too frustrated with the UX of Bitcoin apps and sites at the time. No matter what, I’ve since learned something. **I was at least somewhat wrong.** My own journey began in early 2011. One of my favorite radio programs, Free Talk Live, began interviewing guests and having discussions on the potential of Bitcoin. They tied it directly to a libertarian vision of the world: free markets, free people, and free banking. That was me, and I was in. Bitcoin was at about $5 back then (NgU). I followed every article I could, talked about it with guests [on my college radio show](https://libertyinexile.wordpress.com/2011/05/09/osamobama_on_the_tubes/), and became a devoted redditor on r/Bitcoin. At that time, at least to my knowledge, there was no possible way to buy Bitcoin where I was living. Very weak. **I was probably wrong. And very wrong for not trying to acquire by mining or otherwise.** The next year, after moving to Florida, Bitcoin was a heavy topic with a friend of mine who shared the same vision (and still does, according to the Celsius bankruptcy documents). We talked about it with passionate leftists at **Occupy Tampa** in 2012, all the while trying to explain the ills of Keynesian central banking, and figuring out how to use Coinbase. I began writing more about Bitcoin in 2013, writing a guide on “[How to Avoid Bank Fees Using Bitcoin](http://thestatelessman.com/2013/06/03/using-bitcoin/),” discussing its [potential legalization in Germany](https://yael.ca/2013/10/01/lagefi-alternative-monetaire-et-legislation-de/), and interviewing Jeremy Hansen, [one of the first political candidates in the U.S. to accept Bitcoin donations](https://yael.ca/2013/12/09/bitcoin-politician-wants-to-upgrade-democracy-in/). Even up until that point, I thought Bitcoin was an interesting protocol for sending and receiving money quickly, and converting it into fiat. The global connectedness of it, plus this cypherpunk mentality divorced from government control was both useful and attractive. I thought it was the perfect go-between. **But I was wrong.** When I gave my [first public speech](https://www.youtube.com/watch?v=CtVypq2f0G4) on Bitcoin in Vienna, Austria in December 2013, I had grown obsessed with Bitcoin’s adoption on dark net markets like Silk Road. My theory, at the time, was the number and price were irrelevant. The tech was interesting, and a novel attempt. It was unlike anything before. But what was happening on the dark net markets, which I viewed as the true free market powered by Bitcoin, was even more interesting. I thought these markets would grow exponentially and anonymous commerce via BTC would become the norm. While the price was irrelevant, it was all about buying and selling goods without permission or license. **Now I understand I was wrong.** Just because Bitcoin was this revolutionary technology that embraced pseudonymity did not mean that all commerce would decentralize as well. It did not mean that anonymous markets were intended to be the most powerful layer in the Bitcoin stack. What I did not even anticipate is something articulated very well by noted Bitcoin OG [Pierre Rochard](https://twitter.com/BitcoinPierre): [Bitcoin as a *savings technology*](https://www.youtube.com/watch?v=BavRqEoaxjI)*.* The ability to maintain long-term savings, practice self-discipline while stacking stats, and embrace a low-time preference was just not something on the mind of the Bitcoiners I knew at the time. Perhaps I was reading into the hype while outwardly opposing it. Or perhaps I wasn’t humble enough to understand the true value proposition that many of us have learned years later. In the years that followed, I bought and sold more times than I can count, and I did everything to integrate it into passion projects. I tried to set up a company using Bitcoin while at my university in Prague. My business model depended on university students being technologically advanced enough to have a mobile wallet, own their keys, and be able to make transactions on a consistent basis. Even though I was surrounded by philosophically aligned people, those who would advance that to actually put Bitcoin into practice were sparse. This is what led me to proclaim that “[Technological Literacy is Doomed](https://www.huffpost.com/archive/ca/entry/technological-literacy-is-doomed_b_12669440)” in 2016. **And I was wrong again.** Indeed, since that time, the UX of Bitcoin-only applications, wallets, and supporting tech has vastly improved and onboarded millions more people than anyone thought possible. The entrepreneurship, coding excellence, and vision offered by Bitcoiners of all stripes have renewed a sense in me that this project is something built for us all — friends and enemies alike. While many of us were likely distracted by flashy and pumpy altcoins over the years (me too, champs), most of us have returned to the Bitcoin stable. Fast forward to today, there are entire ecosystems of creators, activists, and developers who are wholly reliant on the magic of Bitcoin’s protocol for their life and livelihood. The options are endless. The FUD is still present, but real proof of work stands powerfully against those forces. In addition, there are now [dozens of ways to use Bitcoin privately](https://fixthemoney.substack.com/p/not-your-keys-not-your-coins-claiming) — still without custodians or intermediaries — that make it one of the most important assets for global humanity, especially in dictatorships. This is all toward a positive arc of innovation, freedom, and pure independence. Did I see that coming? Absolutely not. Of course, there are probably other shots you’ve missed on Bitcoin. Price predictions (ouch), the short-term inflation hedge, or the amount of institutional investment. While all of these may be erroneous predictions in the short term, we have to realize that Bitcoin is a long arc. It will outlive all of us on the planet, and it will continue in its present form for the next generation. **Being wrong about the evolution of Bitcoin is no fault, and is indeed part of the learning curve to finally understanding it all.** When your family or friends ask you about Bitcoin after your endless sessions explaining market dynamics, nodes, how mining works, and the genius of cryptographic signatures, try to accept that there is still so much we have to learn about this decentralized digital cash. There are still some things you’ve gotten wrong about Bitcoin, and plenty more you’ll underestimate or get wrong in the future. That’s what makes it a beautiful journey. It’s a long road, but one that remains worth it.
@ a367f9eb:0633efea
2024-12-22 21:35:22I’ll admit that I was wrong about Bitcoin. Perhaps in 2013. Definitely 2017. Probably in 2018-2019. And maybe even today. Being wrong about Bitcoin is part of finally understanding it. It will test you, make you question everything, and in the words of BTC educator and privacy advocate [Matt Odell](https://twitter.com/ODELL), “Bitcoin will humble you”. I’ve had my own stumbles on the way. In a very public fashion in 2017, after years of using Bitcoin, trying to start a company with it, using it as my primary exchange vehicle between currencies, and generally being annoying about it at parties, I let out the bear. In an article published in my own literary magazine *Devolution Review* in September 2017, I had a breaking point. The article was titled “[Going Bearish on Bitcoin: Cryptocurrencies are the tulip mania of the 21st century](https://www.devolutionreview.com/bearish-on-bitcoin/)”. It was later republished in *Huffington Post* and across dozens of financial and crypto blogs at the time with another, more appropriate title: “[Bitcoin Has Become About The Payday, Not Its Potential](https://www.huffpost.com/archive/ca/entry/bitcoin-has-become-about-the-payday-not-its-potential_ca_5cd5025de4b07bc72973ec2d)”. As I laid out, my newfound bearishness had little to do with the technology itself or the promise of Bitcoin, and more to do with the cynical industry forming around it: > In the beginning, Bitcoin was something of a revolution to me. The digital currency represented everything from my rebellious youth. > > It was a decentralized, denationalized, and digital currency operating outside the traditional banking and governmental system. It used tools of cryptography and connected buyers and sellers across national borders at minimal transaction costs. > > … > > The 21st-century version (of Tulip mania) has welcomed a plethora of slick consultants, hazy schemes dressed up as investor possibilities, and too much wishy-washy language for anything to really make sense to anyone who wants to use a digital currency to make purchases. While I called out Bitcoin by name at the time, on reflection, I was really talking about the ICO craze, the wishy-washy consultants, and the altcoin ponzis. What I was articulating — without knowing it — was the frame of NgU, or “numbers go up”. Rather than advocating for Bitcoin because of its uncensorability, proof-of-work, or immutability, the common mentality among newbies and the dollar-obsessed was that Bitcoin mattered because its price was a rocket ship. And because Bitcoin was gaining in price, affinity tokens and projects that were imperfect forks of Bitcoin took off as well. The price alone — rather than its qualities — were the reasons why you’d hear Uber drivers, finance bros, or your gym buddy mention Bitcoin. As someone who came to Bitcoin for philosophical reasons, that just sat wrong with me. Maybe I had too many projects thrown in my face, or maybe I was too frustrated with the UX of Bitcoin apps and sites at the time. No matter what, I’ve since learned something. **I was at least somewhat wrong.** My own journey began in early 2011. One of my favorite radio programs, Free Talk Live, began interviewing guests and having discussions on the potential of Bitcoin. They tied it directly to a libertarian vision of the world: free markets, free people, and free banking. That was me, and I was in. Bitcoin was at about $5 back then (NgU). I followed every article I could, talked about it with guests [on my college radio show](https://libertyinexile.wordpress.com/2011/05/09/osamobama_on_the_tubes/), and became a devoted redditor on r/Bitcoin. At that time, at least to my knowledge, there was no possible way to buy Bitcoin where I was living. Very weak. **I was probably wrong. And very wrong for not trying to acquire by mining or otherwise.** The next year, after moving to Florida, Bitcoin was a heavy topic with a friend of mine who shared the same vision (and still does, according to the Celsius bankruptcy documents). We talked about it with passionate leftists at **Occupy Tampa** in 2012, all the while trying to explain the ills of Keynesian central banking, and figuring out how to use Coinbase. I began writing more about Bitcoin in 2013, writing a guide on “[How to Avoid Bank Fees Using Bitcoin](http://thestatelessman.com/2013/06/03/using-bitcoin/),” discussing its [potential legalization in Germany](https://yael.ca/2013/10/01/lagefi-alternative-monetaire-et-legislation-de/), and interviewing Jeremy Hansen, [one of the first political candidates in the U.S. to accept Bitcoin donations](https://yael.ca/2013/12/09/bitcoin-politician-wants-to-upgrade-democracy-in/). Even up until that point, I thought Bitcoin was an interesting protocol for sending and receiving money quickly, and converting it into fiat. The global connectedness of it, plus this cypherpunk mentality divorced from government control was both useful and attractive. I thought it was the perfect go-between. **But I was wrong.** When I gave my [first public speech](https://www.youtube.com/watch?v=CtVypq2f0G4) on Bitcoin in Vienna, Austria in December 2013, I had grown obsessed with Bitcoin’s adoption on dark net markets like Silk Road. My theory, at the time, was the number and price were irrelevant. The tech was interesting, and a novel attempt. It was unlike anything before. But what was happening on the dark net markets, which I viewed as the true free market powered by Bitcoin, was even more interesting. I thought these markets would grow exponentially and anonymous commerce via BTC would become the norm. While the price was irrelevant, it was all about buying and selling goods without permission or license. **Now I understand I was wrong.** Just because Bitcoin was this revolutionary technology that embraced pseudonymity did not mean that all commerce would decentralize as well. It did not mean that anonymous markets were intended to be the most powerful layer in the Bitcoin stack. What I did not even anticipate is something articulated very well by noted Bitcoin OG [Pierre Rochard](https://twitter.com/BitcoinPierre): [Bitcoin as a *savings technology*](https://www.youtube.com/watch?v=BavRqEoaxjI)*.* The ability to maintain long-term savings, practice self-discipline while stacking stats, and embrace a low-time preference was just not something on the mind of the Bitcoiners I knew at the time. Perhaps I was reading into the hype while outwardly opposing it. Or perhaps I wasn’t humble enough to understand the true value proposition that many of us have learned years later. In the years that followed, I bought and sold more times than I can count, and I did everything to integrate it into passion projects. I tried to set up a company using Bitcoin while at my university in Prague. My business model depended on university students being technologically advanced enough to have a mobile wallet, own their keys, and be able to make transactions on a consistent basis. Even though I was surrounded by philosophically aligned people, those who would advance that to actually put Bitcoin into practice were sparse. This is what led me to proclaim that “[Technological Literacy is Doomed](https://www.huffpost.com/archive/ca/entry/technological-literacy-is-doomed_b_12669440)” in 2016. **And I was wrong again.** Indeed, since that time, the UX of Bitcoin-only applications, wallets, and supporting tech has vastly improved and onboarded millions more people than anyone thought possible. The entrepreneurship, coding excellence, and vision offered by Bitcoiners of all stripes have renewed a sense in me that this project is something built for us all — friends and enemies alike. While many of us were likely distracted by flashy and pumpy altcoins over the years (me too, champs), most of us have returned to the Bitcoin stable. Fast forward to today, there are entire ecosystems of creators, activists, and developers who are wholly reliant on the magic of Bitcoin’s protocol for their life and livelihood. The options are endless. The FUD is still present, but real proof of work stands powerfully against those forces. In addition, there are now [dozens of ways to use Bitcoin privately](https://fixthemoney.substack.com/p/not-your-keys-not-your-coins-claiming) — still without custodians or intermediaries — that make it one of the most important assets for global humanity, especially in dictatorships. This is all toward a positive arc of innovation, freedom, and pure independence. Did I see that coming? Absolutely not. Of course, there are probably other shots you’ve missed on Bitcoin. Price predictions (ouch), the short-term inflation hedge, or the amount of institutional investment. While all of these may be erroneous predictions in the short term, we have to realize that Bitcoin is a long arc. It will outlive all of us on the planet, and it will continue in its present form for the next generation. **Being wrong about the evolution of Bitcoin is no fault, and is indeed part of the learning curve to finally understanding it all.** When your family or friends ask you about Bitcoin after your endless sessions explaining market dynamics, nodes, how mining works, and the genius of cryptographic signatures, try to accept that there is still so much we have to learn about this decentralized digital cash. There are still some things you’ve gotten wrong about Bitcoin, and plenty more you’ll underestimate or get wrong in the future. That’s what makes it a beautiful journey. It’s a long road, but one that remains worth it. @ 6389be64:ef439d32
2024-12-09 23:50:41Resilience is the ability to withstand shocks, adapt, and bounce back. It’s an essential quality in nature and in life. But what if we could take resilience a step further? What if, instead of merely surviving, a system could improve when faced with stress? This concept, known as anti-fragility, is not just theoretical—it’s practical. Combining two highly resilient natural tools, comfrey and biochar, reveals how we can create systems that thrive under pressure and grow stronger with each challenge. ### **Comfrey: Nature’s Champion of Resilience** Comfrey is a plant that refuses to fail. Once its deep roots take hold, it thrives in poor soils, withstands drought, and regenerates even after being cut down repeatedly. It’s a hardy survivor, but comfrey doesn’t just endure—it contributes. Known as a dynamic accumulator, it mines nutrients from deep within the earth and brings them to the surface, making them available for other plants. Beyond its ecological role, comfrey has centuries of medicinal use, earning the nickname "knitbone." Its leaves can heal wounds and restore health, a perfect metaphor for resilience. But as impressive as comfrey is, its true potential is unlocked when paired with another resilient force: biochar. ### **Biochar: The Silent Powerhouse of Soil Regeneration** Biochar, a carbon-rich material made by burning organic matter in low-oxygen conditions, is a game-changer for soil health. Its unique porous structure retains water, holds nutrients, and provides a haven for beneficial microbes. Soil enriched with biochar becomes drought-resistant, nutrient-rich, and biologically active—qualities that scream resilience. Historically, ancient civilizations in the Amazon used biochar to transform barren soils into fertile agricultural hubs. Known as *terra preta*, these soils remain productive centuries later, highlighting biochar’s remarkable staying power. Yet, like comfrey, biochar’s potential is magnified when it’s part of a larger system. ### **The Synergy: Comfrey and Biochar Together** Resilience turns into anti-fragility when systems go beyond mere survival and start improving under stress. Combining comfrey and biochar achieves exactly that. 1. **Nutrient Cycling and Retention**\ Comfrey’s leaves, rich in nitrogen, potassium, and phosphorus, make an excellent mulch when cut and dropped onto the soil. However, these nutrients can wash away in heavy rains. Enter biochar. Its porous structure locks in the nutrients from comfrey, preventing runoff and keeping them available for plants. Together, they create a system that not only recycles nutrients but amplifies their effectiveness. 2. **Water Management**\ Biochar holds onto water making soil not just drought-resistant but actively water-efficient, improving over time with each rain and dry spell. 3. **Microbial Ecosystems**\ Comfrey enriches soil with organic matter, feeding microbial life. Biochar provides a home for these microbes, protecting them and creating a stable environment for them to multiply. Together, they build a thriving soil ecosystem that becomes more fertile and resilient with each passing season. Resilient systems can withstand shocks, but anti-fragile systems actively use those shocks to grow stronger. Comfrey and biochar together form an anti-fragile system. Each addition of biochar enhances water and nutrient retention, while comfrey regenerates biomass and enriches the soil. Over time, the system becomes more productive, less dependent on external inputs, and better equipped to handle challenges. This synergy demonstrates the power of designing systems that don’t just survive—they thrive. ### **Lessons Beyond the Soil** The partnership of comfrey and biochar offers a valuable lesson for our own lives. Resilience is an admirable trait, but anti-fragility takes us further. By combining complementary strengths and leveraging stress as an opportunity, we can create systems—whether in soil, business, or society—that improve under pressure. Nature shows us that resilience isn’t the end goal. When we pair resilient tools like comfrey and biochar, we unlock a system that evolves, regenerates, and becomes anti-fragile. By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward. By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
@ 6389be64:ef439d32
2024-12-09 23:50:41Resilience is the ability to withstand shocks, adapt, and bounce back. It’s an essential quality in nature and in life. But what if we could take resilience a step further? What if, instead of merely surviving, a system could improve when faced with stress? This concept, known as anti-fragility, is not just theoretical—it’s practical. Combining two highly resilient natural tools, comfrey and biochar, reveals how we can create systems that thrive under pressure and grow stronger with each challenge. ### **Comfrey: Nature’s Champion of Resilience** Comfrey is a plant that refuses to fail. Once its deep roots take hold, it thrives in poor soils, withstands drought, and regenerates even after being cut down repeatedly. It’s a hardy survivor, but comfrey doesn’t just endure—it contributes. Known as a dynamic accumulator, it mines nutrients from deep within the earth and brings them to the surface, making them available for other plants. Beyond its ecological role, comfrey has centuries of medicinal use, earning the nickname "knitbone." Its leaves can heal wounds and restore health, a perfect metaphor for resilience. But as impressive as comfrey is, its true potential is unlocked when paired with another resilient force: biochar. ### **Biochar: The Silent Powerhouse of Soil Regeneration** Biochar, a carbon-rich material made by burning organic matter in low-oxygen conditions, is a game-changer for soil health. Its unique porous structure retains water, holds nutrients, and provides a haven for beneficial microbes. Soil enriched with biochar becomes drought-resistant, nutrient-rich, and biologically active—qualities that scream resilience. Historically, ancient civilizations in the Amazon used biochar to transform barren soils into fertile agricultural hubs. Known as *terra preta*, these soils remain productive centuries later, highlighting biochar’s remarkable staying power. Yet, like comfrey, biochar’s potential is magnified when it’s part of a larger system. ### **The Synergy: Comfrey and Biochar Together** Resilience turns into anti-fragility when systems go beyond mere survival and start improving under stress. Combining comfrey and biochar achieves exactly that. 1. **Nutrient Cycling and Retention**\ Comfrey’s leaves, rich in nitrogen, potassium, and phosphorus, make an excellent mulch when cut and dropped onto the soil. However, these nutrients can wash away in heavy rains. Enter biochar. Its porous structure locks in the nutrients from comfrey, preventing runoff and keeping them available for plants. Together, they create a system that not only recycles nutrients but amplifies their effectiveness. 2. **Water Management**\ Biochar holds onto water making soil not just drought-resistant but actively water-efficient, improving over time with each rain and dry spell. 3. **Microbial Ecosystems**\ Comfrey enriches soil with organic matter, feeding microbial life. Biochar provides a home for these microbes, protecting them and creating a stable environment for them to multiply. Together, they build a thriving soil ecosystem that becomes more fertile and resilient with each passing season. Resilient systems can withstand shocks, but anti-fragile systems actively use those shocks to grow stronger. Comfrey and biochar together form an anti-fragile system. Each addition of biochar enhances water and nutrient retention, while comfrey regenerates biomass and enriches the soil. Over time, the system becomes more productive, less dependent on external inputs, and better equipped to handle challenges. This synergy demonstrates the power of designing systems that don’t just survive—they thrive. ### **Lessons Beyond the Soil** The partnership of comfrey and biochar offers a valuable lesson for our own lives. Resilience is an admirable trait, but anti-fragility takes us further. By combining complementary strengths and leveraging stress as an opportunity, we can create systems—whether in soil, business, or society—that improve under pressure. Nature shows us that resilience isn’t the end goal. When we pair resilient tools like comfrey and biochar, we unlock a system that evolves, regenerates, and becomes anti-fragile. By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward. By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward. @ e31e84c4:77bbabc0
2024-12-02 10:44:07*Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net* Fiduciary duty is the obligation to act in the client’s best interests at all times, prioritizing their needs above the advisor’s own, ensuring honesty, transparency, and avoiding conflicts of interest in all recommendations and actions. This is something all advisors in the BFAN take very seriously; after all, we are legally required to do so. For the average advisor this is a fairly easy box to check. All you essentially have to do is have someone take a 5-minute risk assessment, fill out an investment policy statement, and then throw them in the proverbial 60/40 portfolio. You have thousands of investment options to choose from and you can reasonably explain how your client is theoretically insulated from any move in the \~markets\~. From the traditional financial advisor perspective, you could justify nearly anything by putting a client into this type of portfolio. All your bases were pretty much covered from return profile, regulatory, compliance, investment options, etc. It was just too easy. It became the household standard and now a meme. As almost every real bitcoiner knows, the 60/40 portfolio is moving into psyop territory, and many financial advisors get clowned on for defending this relic on bitcoin twitter. I’m going to specifically poke fun at the ‘40’ part of this portfolio. The ‘40’ represents fixed income, defined as… > An investment type that provides regular, set interest payments, such as bonds or treasury securities, and returns the principal at maturity. It’s generally considered a lower-risk asset class, used to generate stable income and preserve capital. Historically, this part of the portfolio was meant to weather the volatility in the equity markets and represent the “safe” investments. Typically, some sort of bond. First and foremost, the fixed income section is most commonly constructed with U.S. Debt. There are a couple main reasons for this. Most financial professionals believe the same fairy tale that U.S. Debt is “risk free” (lol). U.S. debt is also one of the largest and most liquid assets in the market which comes with a lot of benefits. There are many brilliant bitcoiners in finance and economics that have sounded the alarm on the U.S. debt ticking time bomb. I highly recommend readers explore the work of Greg Foss, Lawrence Lepard, Lyn Alden, and Saifedean Ammous. My very high-level recap of their analysis: - A bond is a contract in which Party A (the borrower) agrees to repay Party B (the lender) their principal plus interest over time. - The U.S. government issues bonds (Treasury securities) to finance its operations after tax revenues have been exhausted. - These are traditionally viewed as “risk-free” due to the government’s historical reliability in repaying its debts and the strength of the U.S. economy - U.S. bonds are seen as safe because the government has control over the dollar (world reserve asset) and, until recently (20 some odd years), enjoyed broad confidence that it would always honor its debts. - This perception has contributed to high global demand for U.S. debt but, that is quickly deteriorating. - The current debt situation raises concerns about sustainability. - The U.S. has substantial obligations, and without sufficient productivity growth, increasing debt may lead to a cycle where borrowing to cover interest leads to more debt. - This could result in more reliance on money creation (printing), which can drive inflation and further debt burdens. In the words of Lyn Alden “Nothing stops this train” Those obligations are what makes up the 40% of most the fixed income in your portfolio. So essentially you are giving money to one of the worst capital allocators in the world (U.S. Gov’t) and getting paid back with printed money. As someone who takes their fiduciary responsibility seriously and understands the debt situation we just reviewed, I think it’s borderline negligent to put someone into a classic 60% (equities) / 40% (fixed income) portfolio without serious scrutiny of the client’s financial situation and options available to them. I certainly have my qualms with equities at times, but overall, they are more palatable than the fixed income portion of the portfolio. I don’t like it either, but the money is broken and the unit of account for nearly every equity or fixed income instrument (USD) is fraudulent. It’s a paper mache fade that is quite literally propped up by the money printer. To briefly be as most charitable as I can – It wasn’t always this way. The U.S. Dollar used to be sound money, we used to have government surplus instead of mathematically certain deficits, The U.S. Federal Government didn’t used to have a money printing addiction, and pre-bitcoin the 60/40 portfolio used to be a quality portfolio management strategy. Those times are gone. ### Now the fun part. How does bitcoin fix this? Bitcoin fixes this indirectly. Understanding investment criteria changes via risk tolerance, age, goals, etc. A client may still have a need for “fixed income” in the most literal definition – Low risk yield. Now you may be thinking that yield is a bad word in bitcoin land, you’re not wrong, so stay with me. Perpetual motion machine crypto yield is fake and largely where many crypto scams originate. However, that doesn’t mean yield in the classic finance sense does not exist in bitcoin, it very literally does. Fortunately for us bitcoiners there are many other smart, driven, and enterprising bitcoiners that understand this problem and are doing something to address it. These individuals are pioneering new possibilities in bitcoin and finance, specifically when it comes to fixed income. Here are some new developments – Private Credit Funds – The Build Asset Management Secured Income Fund I is a private credit fund created by Build Asset Management. This fund primarily invests in bitcoin-backed, collateralized business loans originated by Unchained, with a secured structure involving a multi-signature, over-collateralized setup for risk management. Unchained originates loans and sells them to Build, which pools them into the fund, enabling investors to share in the interest income. Dynamics - Loan Terms: Unchained issues loans at interest rates around 14%, secured with a 2/3 multi-signature vault backed by a 40% loan-to-value (LTV) ratio. - Fund Mechanics: Build buys these loans from Unchained, thus providing liquidity to Unchained for further loan originations, while Build manages interest payments to investors in the fund. Pros - The fund offers a unique way to earn income via bitcoin-collateralized debt, with protection against rehypothecation and strong security measures, making it attractive for investors seeking exposure to fixed income with bitcoin. Cons - The fund is only available to accredited investors, which is a regulatory standard for private credit funds like this. Corporate Bonds – MicroStrategy Inc. (MSTR), a business intelligence company, has leveraged its corporate structure to issue bonds specifically to acquire bitcoin as a reserve asset. This approach allows investors to indirectly gain exposure to bitcoin’s potential upside while receiving interest payments on their bond investments. Some other publicly traded companies have also adopted this strategy, but for the sake of this article we will focus on MSTR as they are the biggest and most vocal issuer. Dynamics - Issuance: MicroStrategy has issued senior secured notes in multiple offerings, with terms allowing the company to use the proceeds to purchase bitcoin. - Interest Rates: The bonds typically carry high-yield interest rates, averaging around 6-8% APR, depending on the specific issuance and market conditions at the time of issuance. - Maturity: The bonds have varying maturities, with most structured for multi-year terms, offering investors medium-term exposure to bitcoin’s value trajectory through MicroStrategy’s holdings. Pros - Indirect Bitcoin exposure with income provides a unique opportunity for investors seeking income from bitcoin-backed debt. - Bonds issued by MicroStrategy offer relatively high interest rates, appealing for fixed-income investors attracted to the higher risk/reward scenarios. Cons - There are credit risks tied to MicroStrategy’s financial health and bitcoin’s performance. A significant drop in bitcoin prices could strain the company’s ability to service debt, increasing credit risk. - Availability: These bonds are primarily accessible to institutional investors and accredited investors, limiting availability for retail investors. Interest Payable in Bitcoin – River has introduced an innovative product, bitcoin Interest on Cash, allowing clients to earn interest on their U.S. dollar deposits, with the interest paid in bitcoin. Dynamics - Interest Payment: Clients earn an annual interest rate of 3.8% on their cash deposits. The accrued interest is converted to Bitcoin daily and paid out monthly, enabling clients to accumulate Bitcoin over time. - Security and Accessibility: Cash deposits are insured up to $250,000 through River’s banking partner, Lead Bank, a member of the FDIC. All Bitcoin holdings are maintained in full reserve custody, ensuring that client assets are not lent or leveraged. Pros - There are no hidden fees or minimum balance requirements, and clients can withdraw their cash at any time. - The 3.8% interest rate provides a predictable income stream, akin to traditional fixed-income investments. Cons - While the interest rate is fixed, the value of the Bitcoin received as interest can fluctuate, introducing potential variability in the investment’s overall return. - Interest rate payments are on the lower side Admittedly, this is a very small list, however, these types of investments are growing more numerous and meaningful. The reality is the existing options aren’t numerous enough to service every client that has a need for fixed income exposure. I challenge advisors to explore innovative options for fixed income exposure outside of sovereign debt, as that is most certainly a road to nowhere. It is my wholehearted belief and call to action that we need more options to help clients across the risk and capital allocation spectrum access a sound money standard. Additional Resources - [River: The future of saving is here: Earn 3.8% on cash. Paid in Bitcoin.](http://bitcoin%20and%20fixed%20ihttps//blog.river.com/bitcoin-interest-on-cash/ncome) - [Onramp: Bitcoin, The Emergent Asset Class](https://onrampbitcoin.docsend.com/view/j4wje7kgvw357tt9) - [MicroStrategy: MicroStrategy Announces Pricing of Offering of Convertible Senior Notes](https://www.microstrategy.com/press/microstrategy-announces-pricing-of-offering-of-convertible-senior-notes_09-18-2024) --- *Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net*
@ e31e84c4:77bbabc0
2024-12-02 10:44:07*Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net* Fiduciary duty is the obligation to act in the client’s best interests at all times, prioritizing their needs above the advisor’s own, ensuring honesty, transparency, and avoiding conflicts of interest in all recommendations and actions. This is something all advisors in the BFAN take very seriously; after all, we are legally required to do so. For the average advisor this is a fairly easy box to check. All you essentially have to do is have someone take a 5-minute risk assessment, fill out an investment policy statement, and then throw them in the proverbial 60/40 portfolio. You have thousands of investment options to choose from and you can reasonably explain how your client is theoretically insulated from any move in the \~markets\~. From the traditional financial advisor perspective, you could justify nearly anything by putting a client into this type of portfolio. All your bases were pretty much covered from return profile, regulatory, compliance, investment options, etc. It was just too easy. It became the household standard and now a meme. As almost every real bitcoiner knows, the 60/40 portfolio is moving into psyop territory, and many financial advisors get clowned on for defending this relic on bitcoin twitter. I’m going to specifically poke fun at the ‘40’ part of this portfolio. The ‘40’ represents fixed income, defined as… > An investment type that provides regular, set interest payments, such as bonds or treasury securities, and returns the principal at maturity. It’s generally considered a lower-risk asset class, used to generate stable income and preserve capital. Historically, this part of the portfolio was meant to weather the volatility in the equity markets and represent the “safe” investments. Typically, some sort of bond. First and foremost, the fixed income section is most commonly constructed with U.S. Debt. There are a couple main reasons for this. Most financial professionals believe the same fairy tale that U.S. Debt is “risk free” (lol). U.S. debt is also one of the largest and most liquid assets in the market which comes with a lot of benefits. There are many brilliant bitcoiners in finance and economics that have sounded the alarm on the U.S. debt ticking time bomb. I highly recommend readers explore the work of Greg Foss, Lawrence Lepard, Lyn Alden, and Saifedean Ammous. My very high-level recap of their analysis: - A bond is a contract in which Party A (the borrower) agrees to repay Party B (the lender) their principal plus interest over time. - The U.S. government issues bonds (Treasury securities) to finance its operations after tax revenues have been exhausted. - These are traditionally viewed as “risk-free” due to the government’s historical reliability in repaying its debts and the strength of the U.S. economy - U.S. bonds are seen as safe because the government has control over the dollar (world reserve asset) and, until recently (20 some odd years), enjoyed broad confidence that it would always honor its debts. - This perception has contributed to high global demand for U.S. debt but, that is quickly deteriorating. - The current debt situation raises concerns about sustainability. - The U.S. has substantial obligations, and without sufficient productivity growth, increasing debt may lead to a cycle where borrowing to cover interest leads to more debt. - This could result in more reliance on money creation (printing), which can drive inflation and further debt burdens. In the words of Lyn Alden “Nothing stops this train” Those obligations are what makes up the 40% of most the fixed income in your portfolio. So essentially you are giving money to one of the worst capital allocators in the world (U.S. Gov’t) and getting paid back with printed money. As someone who takes their fiduciary responsibility seriously and understands the debt situation we just reviewed, I think it’s borderline negligent to put someone into a classic 60% (equities) / 40% (fixed income) portfolio without serious scrutiny of the client’s financial situation and options available to them. I certainly have my qualms with equities at times, but overall, they are more palatable than the fixed income portion of the portfolio. I don’t like it either, but the money is broken and the unit of account for nearly every equity or fixed income instrument (USD) is fraudulent. It’s a paper mache fade that is quite literally propped up by the money printer. To briefly be as most charitable as I can – It wasn’t always this way. The U.S. Dollar used to be sound money, we used to have government surplus instead of mathematically certain deficits, The U.S. Federal Government didn’t used to have a money printing addiction, and pre-bitcoin the 60/40 portfolio used to be a quality portfolio management strategy. Those times are gone. ### Now the fun part. How does bitcoin fix this? Bitcoin fixes this indirectly. Understanding investment criteria changes via risk tolerance, age, goals, etc. A client may still have a need for “fixed income” in the most literal definition – Low risk yield. Now you may be thinking that yield is a bad word in bitcoin land, you’re not wrong, so stay with me. Perpetual motion machine crypto yield is fake and largely where many crypto scams originate. However, that doesn’t mean yield in the classic finance sense does not exist in bitcoin, it very literally does. Fortunately for us bitcoiners there are many other smart, driven, and enterprising bitcoiners that understand this problem and are doing something to address it. These individuals are pioneering new possibilities in bitcoin and finance, specifically when it comes to fixed income. Here are some new developments – Private Credit Funds – The Build Asset Management Secured Income Fund I is a private credit fund created by Build Asset Management. This fund primarily invests in bitcoin-backed, collateralized business loans originated by Unchained, with a secured structure involving a multi-signature, over-collateralized setup for risk management. Unchained originates loans and sells them to Build, which pools them into the fund, enabling investors to share in the interest income. Dynamics - Loan Terms: Unchained issues loans at interest rates around 14%, secured with a 2/3 multi-signature vault backed by a 40% loan-to-value (LTV) ratio. - Fund Mechanics: Build buys these loans from Unchained, thus providing liquidity to Unchained for further loan originations, while Build manages interest payments to investors in the fund. Pros - The fund offers a unique way to earn income via bitcoin-collateralized debt, with protection against rehypothecation and strong security measures, making it attractive for investors seeking exposure to fixed income with bitcoin. Cons - The fund is only available to accredited investors, which is a regulatory standard for private credit funds like this. Corporate Bonds – MicroStrategy Inc. (MSTR), a business intelligence company, has leveraged its corporate structure to issue bonds specifically to acquire bitcoin as a reserve asset. This approach allows investors to indirectly gain exposure to bitcoin’s potential upside while receiving interest payments on their bond investments. Some other publicly traded companies have also adopted this strategy, but for the sake of this article we will focus on MSTR as they are the biggest and most vocal issuer. Dynamics - Issuance: MicroStrategy has issued senior secured notes in multiple offerings, with terms allowing the company to use the proceeds to purchase bitcoin. - Interest Rates: The bonds typically carry high-yield interest rates, averaging around 6-8% APR, depending on the specific issuance and market conditions at the time of issuance. - Maturity: The bonds have varying maturities, with most structured for multi-year terms, offering investors medium-term exposure to bitcoin’s value trajectory through MicroStrategy’s holdings. Pros - Indirect Bitcoin exposure with income provides a unique opportunity for investors seeking income from bitcoin-backed debt. - Bonds issued by MicroStrategy offer relatively high interest rates, appealing for fixed-income investors attracted to the higher risk/reward scenarios. Cons - There are credit risks tied to MicroStrategy’s financial health and bitcoin’s performance. A significant drop in bitcoin prices could strain the company’s ability to service debt, increasing credit risk. - Availability: These bonds are primarily accessible to institutional investors and accredited investors, limiting availability for retail investors. Interest Payable in Bitcoin – River has introduced an innovative product, bitcoin Interest on Cash, allowing clients to earn interest on their U.S. dollar deposits, with the interest paid in bitcoin. Dynamics - Interest Payment: Clients earn an annual interest rate of 3.8% on their cash deposits. The accrued interest is converted to Bitcoin daily and paid out monthly, enabling clients to accumulate Bitcoin over time. - Security and Accessibility: Cash deposits are insured up to $250,000 through River’s banking partner, Lead Bank, a member of the FDIC. All Bitcoin holdings are maintained in full reserve custody, ensuring that client assets are not lent or leveraged. Pros - There are no hidden fees or minimum balance requirements, and clients can withdraw their cash at any time. - The 3.8% interest rate provides a predictable income stream, akin to traditional fixed-income investments. Cons - While the interest rate is fixed, the value of the Bitcoin received as interest can fluctuate, introducing potential variability in the investment’s overall return. - Interest rate payments are on the lower side Admittedly, this is a very small list, however, these types of investments are growing more numerous and meaningful. The reality is the existing options aren’t numerous enough to service every client that has a need for fixed income exposure. I challenge advisors to explore innovative options for fixed income exposure outside of sovereign debt, as that is most certainly a road to nowhere. It is my wholehearted belief and call to action that we need more options to help clients across the risk and capital allocation spectrum access a sound money standard. Additional Resources - [River: The future of saving is here: Earn 3.8% on cash. Paid in Bitcoin.](http://bitcoin%20and%20fixed%20ihttps//blog.river.com/bitcoin-interest-on-cash/ncome) - [Onramp: Bitcoin, The Emergent Asset Class](https://onrampbitcoin.docsend.com/view/j4wje7kgvw357tt9) - [MicroStrategy: MicroStrategy Announces Pricing of Offering of Convertible Senior Notes](https://www.microstrategy.com/press/microstrategy-announces-pricing-of-offering-of-convertible-senior-notes_09-18-2024) --- *Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net* @ b8851a06:9b120ba1
2025-02-18 20:42:10> Nothing disgusts me more than the way the white-collar justice system operates—where billion-dollar crimes are punished with pocket-change fines, and the executives responsible walk free, richer than ever. You will never see this on the centralized, Keynesian, fiat-owned mainstream media. Only here on #Nostr, where the truth isn’t for sale. > JPMorgan Chase is not just a bank—it is a repeat offender in the global financial system. With 272 violations and $39.3 billion in fines since 2000, its track record rivals that of the most notorious criminal enterprises. And yet, it remains untouchable, shielded by its financial dominance and a regulatory system that punishes lawbreaking with fines too insignificant to be real deterrents. In 2024 alone, JPMorgan Chase reported $58.5 billion in net income, an 18% increase from 2023. Meanwhile, it incurred $825 million in fines, which accounted for just 1.41% of its net income—a rounding error for the banking giant. ### Fines vs. Profits: The Cost of Doing Business Year Total Revenue (in billions) Net Income (in billions) Total Fines (in billions) Fines as % of Net Income 2024 $177.6 $58.5 $0.825 1.41% 2023 $158.1 $49.6 Data not specified N/A 2022 $132.3 $35.9 Data not specified N/A ###### Sources: Bloomberg, Ventureburn JPMorgan’s profits dwarf the penalties it pays, showing that these fines are simply the cost of doing business. ### 2024: A Continuation of Violations Despite its massive profits, JPMorgan continues its long history of lawbreaking. In 2024 alone, it has been fined $825 million across multiple categories: • $250 million – Banking violations • $200 million – Investor protection violations • $151 million – Securities violations • $125 million – Price-fixing practices • $98.2 million – Banking violations Additionally, in January 2024, the bank was fined $18 million for forcing customers to stay silent about illegal activities through confidential release agreements—another example of corporate misconduct being covered up rather than addressed. JPMorgan has admitted to market manipulation, securities fraud, and price-fixing—yet it remains a repeat offender because financial penalties do not impact its bottom line. ### The Human Cost: How JPMorgan Hurts Regular People While JPMorgan’s executives cash in on record profits, their crimes directly harm ordinary people: • Loan denials due to false credit reporting • Higher interest rates on credit cards and loans • Difficulty opening new deposit accounts • Challenges in renting apartments or securing jobs • Thousands of suspicious transactions totaling $1.5 billion went unreported Beyond the numbers, real people suffer from these violations. In 2024, JPMorgan was sued for failing to protect consumers from fraud on the Zelle payment platform. Customers lost over $870 million since Zelle’s 2017 launch, and JPMorgan ignored thousands of fraud complaints, even advising victims to contact scammers directly to get their money back. This is not just corporate negligence—it is systematic exploitation. ### Breakdown of JPMorgan’s Violations (2000-2024) JPMorgan’s violations span nearly every financial crime category imaginable: • Toxic Securities Abuses: $13.46 billion • Investor Protection Violations: $6.25 billion • Mortgage Abuses: $5.36 billion • Banking Violations: $4.26 billion • Consumer Protection Violations: $3.19 billion This systematic lawbreaking has become a business strategy rather than a legal risk. ### Regulatory Capture: Why JPMorgan Gets Away With It The question remains: Why does nothing change? The answer is regulatory capture—where the regulators responsible for policing the banks are influenced or controlled by the industry itself. ### The Revolving Door: How Banks Own Their Regulators • Regulators frequently leave their jobs to work for the banks they once supervised. • The banking industry is so complex that even lawmakers struggle to verify its practices. • Regulators fear antagonizing banks because they often seek employment in the same industry. JPMorgan exploits this system to avoid real consequences. Its CEO, Jamie Dimon, has openly criticized regulation and vowed to fight new financial rules, ensuring that oversight remains weak and penalties remain a slap on the wrist. ### Systematic Failures in Regulation • Consumer protection is spread across seven different agencies, creating inefficiency. • Conflicts of interest within these agencies weaken enforcement. • Some regulators have explicit mandates to promote the financial system’s competitiveness rather than hold banks accountable. This cycle ensures that fines remain low, executives avoid jail, and banks like JPMorgan continue breaking the law with impunity. ### Industry-Wide Issues: A Systemic Problem JPMorgan Chase is not alone. The banking sector as a whole is rife with fraud and corruption: • Wells Fargo: In 2024, Wells Fargo was sued for failing to protect customers from fraud on the Zelle payment platform, contributing to $870 million in consumer losses. • Bank of America: Also implicated in the Zelle fraud lawsuit for failing to implement basic fraud protections. These cases prove that financial misconduct is not an exception—it’s the industry standard. ### Too Big to Fail, Too Criminal to Stop JPMorgan’s status as a “too big to fail” institution means that no matter how many laws it breaks, no matter how many billions it pays in fines, it remains untouchable. If an individual committed fraud, price-fixing, or money laundering on this scale, they would spend a lifetime in prison. JPMorgan? It just keeps making record profits. This is not justice. This is the financial elite operating above the law. Until executives face criminal prosecution instead of just fines, JPMorgan Chase will remain what it has been for decades: **A financial felon in a three-piece suit.** ### The Next Stage of Banking Corruption JPMorgan’s violations are not just a relic of past financial crises. The next stage of banking corruption is already underway—and this time, the stakes are even higher. With AI-driven market manipulation, rising corporate surveillance, and the increasing concentration of financial power, the system is evolving in ways that regulators are not prepared to handle. JPMorgan and its peers are already positioning themselves to profit from the next crisis, just as they did in 2008. The question is not whether JPMorgan will commit future crimes. The question is how much they will profit from them—and how little they will be held accountable. The reality is clear: JPMorgan Chase is not a bank that sometimes breaks the law. It is a criminal enterprise that happens to operate as a bank. **#Bitcoin is the exit. The escape from their rigged system. The end of their unchecked power.**
@ b8851a06:9b120ba1
2025-02-18 20:42:10> Nothing disgusts me more than the way the white-collar justice system operates—where billion-dollar crimes are punished with pocket-change fines, and the executives responsible walk free, richer than ever. You will never see this on the centralized, Keynesian, fiat-owned mainstream media. Only here on #Nostr, where the truth isn’t for sale. > JPMorgan Chase is not just a bank—it is a repeat offender in the global financial system. With 272 violations and $39.3 billion in fines since 2000, its track record rivals that of the most notorious criminal enterprises. And yet, it remains untouchable, shielded by its financial dominance and a regulatory system that punishes lawbreaking with fines too insignificant to be real deterrents. In 2024 alone, JPMorgan Chase reported $58.5 billion in net income, an 18% increase from 2023. Meanwhile, it incurred $825 million in fines, which accounted for just 1.41% of its net income—a rounding error for the banking giant. ### Fines vs. Profits: The Cost of Doing Business Year Total Revenue (in billions) Net Income (in billions) Total Fines (in billions) Fines as % of Net Income 2024 $177.6 $58.5 $0.825 1.41% 2023 $158.1 $49.6 Data not specified N/A 2022 $132.3 $35.9 Data not specified N/A ###### Sources: Bloomberg, Ventureburn JPMorgan’s profits dwarf the penalties it pays, showing that these fines are simply the cost of doing business. ### 2024: A Continuation of Violations Despite its massive profits, JPMorgan continues its long history of lawbreaking. In 2024 alone, it has been fined $825 million across multiple categories: • $250 million – Banking violations • $200 million – Investor protection violations • $151 million – Securities violations • $125 million – Price-fixing practices • $98.2 million – Banking violations Additionally, in January 2024, the bank was fined $18 million for forcing customers to stay silent about illegal activities through confidential release agreements—another example of corporate misconduct being covered up rather than addressed. JPMorgan has admitted to market manipulation, securities fraud, and price-fixing—yet it remains a repeat offender because financial penalties do not impact its bottom line. ### The Human Cost: How JPMorgan Hurts Regular People While JPMorgan’s executives cash in on record profits, their crimes directly harm ordinary people: • Loan denials due to false credit reporting • Higher interest rates on credit cards and loans • Difficulty opening new deposit accounts • Challenges in renting apartments or securing jobs • Thousands of suspicious transactions totaling $1.5 billion went unreported Beyond the numbers, real people suffer from these violations. In 2024, JPMorgan was sued for failing to protect consumers from fraud on the Zelle payment platform. Customers lost over $870 million since Zelle’s 2017 launch, and JPMorgan ignored thousands of fraud complaints, even advising victims to contact scammers directly to get their money back. This is not just corporate negligence—it is systematic exploitation. ### Breakdown of JPMorgan’s Violations (2000-2024) JPMorgan’s violations span nearly every financial crime category imaginable: • Toxic Securities Abuses: $13.46 billion • Investor Protection Violations: $6.25 billion • Mortgage Abuses: $5.36 billion • Banking Violations: $4.26 billion • Consumer Protection Violations: $3.19 billion This systematic lawbreaking has become a business strategy rather than a legal risk. ### Regulatory Capture: Why JPMorgan Gets Away With It The question remains: Why does nothing change? The answer is regulatory capture—where the regulators responsible for policing the banks are influenced or controlled by the industry itself. ### The Revolving Door: How Banks Own Their Regulators • Regulators frequently leave their jobs to work for the banks they once supervised. • The banking industry is so complex that even lawmakers struggle to verify its practices. • Regulators fear antagonizing banks because they often seek employment in the same industry. JPMorgan exploits this system to avoid real consequences. Its CEO, Jamie Dimon, has openly criticized regulation and vowed to fight new financial rules, ensuring that oversight remains weak and penalties remain a slap on the wrist. ### Systematic Failures in Regulation • Consumer protection is spread across seven different agencies, creating inefficiency. • Conflicts of interest within these agencies weaken enforcement. • Some regulators have explicit mandates to promote the financial system’s competitiveness rather than hold banks accountable. This cycle ensures that fines remain low, executives avoid jail, and banks like JPMorgan continue breaking the law with impunity. ### Industry-Wide Issues: A Systemic Problem JPMorgan Chase is not alone. The banking sector as a whole is rife with fraud and corruption: • Wells Fargo: In 2024, Wells Fargo was sued for failing to protect customers from fraud on the Zelle payment platform, contributing to $870 million in consumer losses. • Bank of America: Also implicated in the Zelle fraud lawsuit for failing to implement basic fraud protections. These cases prove that financial misconduct is not an exception—it’s the industry standard. ### Too Big to Fail, Too Criminal to Stop JPMorgan’s status as a “too big to fail” institution means that no matter how many laws it breaks, no matter how many billions it pays in fines, it remains untouchable. If an individual committed fraud, price-fixing, or money laundering on this scale, they would spend a lifetime in prison. JPMorgan? It just keeps making record profits. This is not justice. This is the financial elite operating above the law. Until executives face criminal prosecution instead of just fines, JPMorgan Chase will remain what it has been for decades: **A financial felon in a three-piece suit.** ### The Next Stage of Banking Corruption JPMorgan’s violations are not just a relic of past financial crises. The next stage of banking corruption is already underway—and this time, the stakes are even higher. With AI-driven market manipulation, rising corporate surveillance, and the increasing concentration of financial power, the system is evolving in ways that regulators are not prepared to handle. JPMorgan and its peers are already positioning themselves to profit from the next crisis, just as they did in 2008. The question is not whether JPMorgan will commit future crimes. The question is how much they will profit from them—and how little they will be held accountable. The reality is clear: JPMorgan Chase is not a bank that sometimes breaks the law. It is a criminal enterprise that happens to operate as a bank. **#Bitcoin is the exit. The escape from their rigged system. The end of their unchecked power.** @ 87730827:746b7d35
2024-11-20 09:27:53Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/ Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country =================================================================================== Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges. * * * **KEY TAKEAWAYS** * The Central Bank of Brazil has proposed **regulations prohibiting privacy-centric cryptocurrencies** like Monero. * The regulations **categorize exchanges into intermediaries, custodians, and brokers**, each with specific capital requirements and compliance standards. * While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens **(NFTs) are still ‘deregulated’ in Brazil**.  In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines **regulations for virtual asset service providers (VASPs)** operating in the country. **_In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil._** Let’s unpack what effect these regulations will have. Brazil’s Crackdown on Crypto Fraud ---------------------------------- If the BCB’s current rule is approved, **exchanges dealing with coins that provide anonymity must delist these currencies** or prevent Brazilians from accessing and operating these assets. The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism. According to the Central Bank of Brazil, the bans aim to **prevent criminals from using digital assets to launder money**. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances. > … restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder. > > – [Notice of Participation](https://www.gov.br/participamaisbrasil/edital-de-participacao-social-n-109-2024-proposta-de-regulamentacao-do-) The Central Bank has identified that **removing algorithmic stablecoins is essential to guarantee the safety of users’ funds** and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars. The Central Bank also wants to **control all digital assets traded by companies in Brazil**. According to the current proposal, the [national regulator](https://techreport.com/cryptocurrency/learning/crypto-regulations-global-view/) will have the **power to ask platforms to remove certain listed assets** if it considers that they do not meet local regulations. However, the regulations will not include [NFTs](https://techreport.com/statistics/crypto/nft-awareness-adoption-statistics/), real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil. Monero: What Is It and Why Is Brazil Banning It? ------------------------------------------------ Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain. Like Brazil, **other nations are banning Monero** in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR. Furthermore, exchanges such as **Binance have already announced they will delist Monero** on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with [MiCA regulations](https://techreport.com/crypto-news/eu-mica-rules-existential-threat-or-crypto-clarity/). Data from Chainalysis shows that Brazil is the **seventh-largest Bitcoin market in the world**.  In Latin America, **Brazil is the largest market for digital assets**. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset. In Closing ---------- Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing. Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell. References ---------- Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems. [View all articles by Cassio Gusson](https://techreport.com/author/cassiog/)
@ 87730827:746b7d35
2024-11-20 09:27:53Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/ Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country =================================================================================== Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges. * * * **KEY TAKEAWAYS** * The Central Bank of Brazil has proposed **regulations prohibiting privacy-centric cryptocurrencies** like Monero. * The regulations **categorize exchanges into intermediaries, custodians, and brokers**, each with specific capital requirements and compliance standards. * While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens **(NFTs) are still ‘deregulated’ in Brazil**.  In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines **regulations for virtual asset service providers (VASPs)** operating in the country. **_In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil._** Let’s unpack what effect these regulations will have. Brazil’s Crackdown on Crypto Fraud ---------------------------------- If the BCB’s current rule is approved, **exchanges dealing with coins that provide anonymity must delist these currencies** or prevent Brazilians from accessing and operating these assets. The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism. According to the Central Bank of Brazil, the bans aim to **prevent criminals from using digital assets to launder money**. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances. > … restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder. > > – [Notice of Participation](https://www.gov.br/participamaisbrasil/edital-de-participacao-social-n-109-2024-proposta-de-regulamentacao-do-) The Central Bank has identified that **removing algorithmic stablecoins is essential to guarantee the safety of users’ funds** and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars. The Central Bank also wants to **control all digital assets traded by companies in Brazil**. According to the current proposal, the [national regulator](https://techreport.com/cryptocurrency/learning/crypto-regulations-global-view/) will have the **power to ask platforms to remove certain listed assets** if it considers that they do not meet local regulations. However, the regulations will not include [NFTs](https://techreport.com/statistics/crypto/nft-awareness-adoption-statistics/), real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil. Monero: What Is It and Why Is Brazil Banning It? ------------------------------------------------ Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain. Like Brazil, **other nations are banning Monero** in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR. Furthermore, exchanges such as **Binance have already announced they will delist Monero** on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with [MiCA regulations](https://techreport.com/crypto-news/eu-mica-rules-existential-threat-or-crypto-clarity/). Data from Chainalysis shows that Brazil is the **seventh-largest Bitcoin market in the world**.  In Latin America, **Brazil is the largest market for digital assets**. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset. In Closing ---------- Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing. Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell. References ---------- Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems. [View all articles by Cassio Gusson](https://techreport.com/author/cassiog/) @ 97c70a44:ad98e322
2025-02-18 20:30:32For the last couple of weeks, I've been dealing with the fallout of upgrading a web application to Svelte 5. Complaints about framework churn and migration annoyances aside, I've run into some interesting issues with the migration. So far, I haven't seen many other people register the same issues, so I thought it might be constructive for me to articulate them myself. I'll try not to complain too much in this post, since I'm grateful for the many years of Svelte 3/4 I've enjoyed. But I don't think I'll be choosing Svelte for any new projects going forward. I hope my reflections here will be useful to others as well. If you're interested in reproductions for the issues I mention here, you can find them below. - [Can't save state to indexeddb](https://github.com/sveltejs/svelte/issues/15327) - [Component unmount results in undefined variables in closures](https://github.com/sveltejs/svelte/issues/15325) # The Need for Speed To start with, let me just quickly acknowledge what the Svelte team is trying to do. It seems like most of the substantial changes in version 5 are built around "deep reactivity", which allows for more granular reactivity, leading to better performance. Performance is good, and the Svelte team has always excelled at reconciling performance with DX. In previous versions of Svelte, the main way this was achieved was with the Svelte compiler. There were many ancillary techniques involved in improving performance, but having a framework compile step gave the Svelte team a lot of leeway for rearranging things under the hood without making developers learn new concepts. This is what made Svelte so original in the beginning. At the same time, it resulted in an even more opaque framework than usual, making it harder for developers to debug more complex issues. To make matters worse, the compiler had bugs, resulting in errors which could only be fixed by blindly refactoring the problem component. This happened to me personally at least half a dozen times, and is what ultimately pushed me to migrate to Svelte 5. Nevertheless, I always felt it was an acceptable trade-off for speed and productivity. Sure, sometimes I had to delete my project and port it to a fresh repository every so often, but the framework was truly a pleasure to use. # Svelte is not Javascript Svelte 5 doubled down on this tradeoff — which makes sense, because it's what sets the framework apart. The difference this time is that the abstraction/performance tradeoff did not stay in compiler land, but intruded into runtime in two important ways: - The use of proxies to support deep reactivity - Implicit component lifecycle state Both of these changes improved performance _and_ made the API for developers look slicker. What's not to like? Unfortunately, both of these features are classic examples of a [leaky abstraction](https://www.joelonsoftware.com/2002/11/11/the-law-of-leaky-abstractions/), and ultimately make things _more_ complex for developers, not less. ## Proxies are not objects The use of proxies seems to have allowed the Svelte team to squeeze a little more performance out of the framework, without asking developers to do any extra work. Threading state through multiple levels of components without provoking unnecessary re-renders in frameworks like React is an infamously difficult chore. Svelte's compiler avoided some of the pitfalls associated with virtual DOM diffing solutions, but evidently there was still enough of a performance gain to be had to justify the introduction of proxies. The Svelte team also [seems to argue](https://svelte.dev/blog/runes) that their introduction represents an improvement in developer experience: > we... can maximise both efficiency and ergonomics. Here's the problem: Svelte 5 _looks_ simpler, but actually introduces _more_ abstractions. Using proxies to monitor array methods (for example) is appealing because it allows developers to forget all the goofy heuristics involved with making sure state was reactive and just `push` to the array. I can't count how many times I've written `value = value` to trigger reactivity in svelte 4. In Svelte 4, developers had to understand how the Svelte compiler worked. The compiler, being a leaky abstraction, forced its users to know that assignment was how you signaled reactivity. In svelte 5, developers can just "forget" about the compiler! Except they can't. All the introduction of new abstractions really accomplishes is the introduction of more complex heuristics that developers have to keep in their heads in order to get the compiler to act the way they want it to. In fact, this is why after years of using Svelte, I found myself using Svelte stores more and more often, and reactive declarations less. The reason being that Svelte stores are _just javascript_. Calling `update` on a store is _simple_, and being able to reference them with a `$` was just a nice bonus — nothing to remember, and if I mess up the compiler yells at me. Proxies introduce a similar problem to reactive declarations, which is that they look like one thing but act like another on the edges. When I started using Svelte 5, everything worked great — until [I tried to save a proxy to indexeddb](https://github.com/sveltejs/svelte/issues/15327), at which point I got a `DataCloneError`. To make matters worse, it's impossible to reliably tell if something is a `Proxy` without `try/catch`ing a structured clone, which is a performance-intensive operation. This forces the developer to remember what is and what isn't a Proxy, calling `$state.snapshot` every time they pass a proxy to a context that doesn't expect or know about them. This obviates all the nice abstractions they gave us in the first place. ## Components are not functions The reason virtual DOM took off way back in 2013 was the ability to model your application as composed functions, each of which takes data and spits out HTML. Svelte retained this paradigm, using a compiler to sidestep the inefficiencies of virtual DOM and the complexities of lifecycle methods. In Svelte 5, component lifecycles are back, react-hooks style. In React, hooks are an abstraction that allows developers to avoid writing all the stateful code associated with component lifecycle methods. Modern React tutorials universally recommend using hooks instead, which rely on the framework invisibly synchronizing state with the render tree. While this does result in cleaner code, it also requires developers to tread carefully to avoid breaking the assumptions surrounding hooks. Just try accessing state in a `setTimeout` and you'll see what I mean. Svelte 4 had a few gotchas like this — for example, async code that interacts with a component's DOM elements has to keep track of whether the component is unmounted. This is pretty similar to the kind of pattern you'd see in old React components that relied on lifecycle methods. It seems to me that Svelte 5 has gone the React 16 route by adding implicit state related to component lifecycles in order to coordinate state changes and effects. For example, here is an excerpt from the documentation for [$effect](https://svelte.dev/docs/svelte/$effect): > You can place $effect anywhere, not just at the top level of a component, as long as it is called during component initialization (or while a parent effect is active). It is then tied to the lifecycle of the component (or parent effect) and will therefore destroy itself when the component unmounts (or the parent effect is destroyed). That's very complex! In order to use `$effect`... effectively (sorry), developers have to understand how state changes are tracked. The [documentation for component lifecycles](https://svelte.dev/docs/svelte/lifecycle-hooks) claims: > In Svelte 5, the component lifecycle consists of only two parts: Its creation and its destruction. Everything in-between — when certain state is updated — is not related to the component as a whole; only the parts that need to react to the state change are notified. This is because under the hood the smallest unit of change is actually not a component, it’s the (render) effects that the component sets up upon component initialization. Consequently, there’s no such thing as a “before update”/"after update” hook. But then goes on to introduce the idea of `tick` in conjunction with `$effect.pre`. This section explains that "`tick` returns a promise that resolves once any pending state changes have been applied, or in the next microtask if there are none." I'm sure there's some mental model that justifies this, but I don't think the claim that a component's lifecycle is only comprised of mount/unmount is really helpful when an addendum about state changes has to come right afterward. The place where this really bit me, and which is the motivation for this blog post, is when state gets coupled to a component's lifecycle, even when the state is passed to another function that doesn't know anything about svelte. In my application, I manage modal dialogs by storing the component I want to render alongside its props in a store and rendering it in the `layout.svelte` of my application. This store is also synchronized with browser history so that the back button works to close them. Sometimes, it's useful to pass a callback to one of these modals, binding caller-specific functionality to the child component: ```javascript const {value} = $props() const callback = () => console.log(value) const openModal = () => pushModal(MyModal, {callback}) ``` This is a fundamental pattern in javascript. Passing a callback is just one of those things you do. Unfortunately, if the above code lives in a modal dialog itself, the caller component gets unmounted before the callback gets called. In Svelte 4, this worked fine, but in Svelte 5 `value` gets updated to `undefined` when the component gets unmounted. [Here's a minimal reproduction](https://github.com/sveltejs/svelte/issues/15325). This is only one example, but it seems clear to me that _any_ prop that is closed over by a callback function that lives longer than its component will be undefined when I want to use it — with no reassignment existing in lexical scope. It seems that the [reason this happens](https://github.com/sveltejs/svelte/issues/14707) is that the props "belong" to the parent component, and are accessed via getters so that the parent can revoke access when it unmounts. I don't know why this is necessary, but I assume there's a good engineering reason for it. The problem is, this just isn't how javascript works. Svelte is essentially attempting to re-invent garbage collection around component lifecycles, which breaks the assumption every javascript developer has that variables don't simply disappear without an explicit reassignment. It should be safe to pass stuff around and let the garbage collector do its job. # Conclusion Easy things are nice, but as Rich Hickey says, [easy things are not always simple](https://www.infoq.com/presentations/Simple-Made-Easy/). And like Joel Spolsky, I don't like being surprised. Svelte has always been full of magic, but with the latest release I think the cognitive overhead of reciting incantations has finally outweighed the power it confers. My point in this post is not to dunk on the Svelte team. I know lots of people like Svelte 5 (and react hooks). The point I'm trying to make is that there is a tradeoff between doing things on the user's behalf, and giving the user agency. Good software is built on understanding, not cleverness. I also think this is an important lesson to remember as AI-assisted coding becomes increasingly popular. Don't choose tools that alienate you from your work. Choose tools that leverage the wisdom you've already accumulated, and which help you to cultivate a deeper understanding of the discipline. Thank you to Rich Harris and team for many years of pleasant development. I hope that (if you read this) it's not _so_ full of inaccuracies as to be unhelpful as user feedback.
@ 97c70a44:ad98e322
2025-02-18 20:30:32For the last couple of weeks, I've been dealing with the fallout of upgrading a web application to Svelte 5. Complaints about framework churn and migration annoyances aside, I've run into some interesting issues with the migration. So far, I haven't seen many other people register the same issues, so I thought it might be constructive for me to articulate them myself. I'll try not to complain too much in this post, since I'm grateful for the many years of Svelte 3/4 I've enjoyed. But I don't think I'll be choosing Svelte for any new projects going forward. I hope my reflections here will be useful to others as well. If you're interested in reproductions for the issues I mention here, you can find them below. - [Can't save state to indexeddb](https://github.com/sveltejs/svelte/issues/15327) - [Component unmount results in undefined variables in closures](https://github.com/sveltejs/svelte/issues/15325) # The Need for Speed To start with, let me just quickly acknowledge what the Svelte team is trying to do. It seems like most of the substantial changes in version 5 are built around "deep reactivity", which allows for more granular reactivity, leading to better performance. Performance is good, and the Svelte team has always excelled at reconciling performance with DX. In previous versions of Svelte, the main way this was achieved was with the Svelte compiler. There were many ancillary techniques involved in improving performance, but having a framework compile step gave the Svelte team a lot of leeway for rearranging things under the hood without making developers learn new concepts. This is what made Svelte so original in the beginning. At the same time, it resulted in an even more opaque framework than usual, making it harder for developers to debug more complex issues. To make matters worse, the compiler had bugs, resulting in errors which could only be fixed by blindly refactoring the problem component. This happened to me personally at least half a dozen times, and is what ultimately pushed me to migrate to Svelte 5. Nevertheless, I always felt it was an acceptable trade-off for speed and productivity. Sure, sometimes I had to delete my project and port it to a fresh repository every so often, but the framework was truly a pleasure to use. # Svelte is not Javascript Svelte 5 doubled down on this tradeoff — which makes sense, because it's what sets the framework apart. The difference this time is that the abstraction/performance tradeoff did not stay in compiler land, but intruded into runtime in two important ways: - The use of proxies to support deep reactivity - Implicit component lifecycle state Both of these changes improved performance _and_ made the API for developers look slicker. What's not to like? Unfortunately, both of these features are classic examples of a [leaky abstraction](https://www.joelonsoftware.com/2002/11/11/the-law-of-leaky-abstractions/), and ultimately make things _more_ complex for developers, not less. ## Proxies are not objects The use of proxies seems to have allowed the Svelte team to squeeze a little more performance out of the framework, without asking developers to do any extra work. Threading state through multiple levels of components without provoking unnecessary re-renders in frameworks like React is an infamously difficult chore. Svelte's compiler avoided some of the pitfalls associated with virtual DOM diffing solutions, but evidently there was still enough of a performance gain to be had to justify the introduction of proxies. The Svelte team also [seems to argue](https://svelte.dev/blog/runes) that their introduction represents an improvement in developer experience: > we... can maximise both efficiency and ergonomics. Here's the problem: Svelte 5 _looks_ simpler, but actually introduces _more_ abstractions. Using proxies to monitor array methods (for example) is appealing because it allows developers to forget all the goofy heuristics involved with making sure state was reactive and just `push` to the array. I can't count how many times I've written `value = value` to trigger reactivity in svelte 4. In Svelte 4, developers had to understand how the Svelte compiler worked. The compiler, being a leaky abstraction, forced its users to know that assignment was how you signaled reactivity. In svelte 5, developers can just "forget" about the compiler! Except they can't. All the introduction of new abstractions really accomplishes is the introduction of more complex heuristics that developers have to keep in their heads in order to get the compiler to act the way they want it to. In fact, this is why after years of using Svelte, I found myself using Svelte stores more and more often, and reactive declarations less. The reason being that Svelte stores are _just javascript_. Calling `update` on a store is _simple_, and being able to reference them with a `$` was just a nice bonus — nothing to remember, and if I mess up the compiler yells at me. Proxies introduce a similar problem to reactive declarations, which is that they look like one thing but act like another on the edges. When I started using Svelte 5, everything worked great — until [I tried to save a proxy to indexeddb](https://github.com/sveltejs/svelte/issues/15327), at which point I got a `DataCloneError`. To make matters worse, it's impossible to reliably tell if something is a `Proxy` without `try/catch`ing a structured clone, which is a performance-intensive operation. This forces the developer to remember what is and what isn't a Proxy, calling `$state.snapshot` every time they pass a proxy to a context that doesn't expect or know about them. This obviates all the nice abstractions they gave us in the first place. ## Components are not functions The reason virtual DOM took off way back in 2013 was the ability to model your application as composed functions, each of which takes data and spits out HTML. Svelte retained this paradigm, using a compiler to sidestep the inefficiencies of virtual DOM and the complexities of lifecycle methods. In Svelte 5, component lifecycles are back, react-hooks style. In React, hooks are an abstraction that allows developers to avoid writing all the stateful code associated with component lifecycle methods. Modern React tutorials universally recommend using hooks instead, which rely on the framework invisibly synchronizing state with the render tree. While this does result in cleaner code, it also requires developers to tread carefully to avoid breaking the assumptions surrounding hooks. Just try accessing state in a `setTimeout` and you'll see what I mean. Svelte 4 had a few gotchas like this — for example, async code that interacts with a component's DOM elements has to keep track of whether the component is unmounted. This is pretty similar to the kind of pattern you'd see in old React components that relied on lifecycle methods. It seems to me that Svelte 5 has gone the React 16 route by adding implicit state related to component lifecycles in order to coordinate state changes and effects. For example, here is an excerpt from the documentation for [$effect](https://svelte.dev/docs/svelte/$effect): > You can place $effect anywhere, not just at the top level of a component, as long as it is called during component initialization (or while a parent effect is active). It is then tied to the lifecycle of the component (or parent effect) and will therefore destroy itself when the component unmounts (or the parent effect is destroyed). That's very complex! In order to use `$effect`... effectively (sorry), developers have to understand how state changes are tracked. The [documentation for component lifecycles](https://svelte.dev/docs/svelte/lifecycle-hooks) claims: > In Svelte 5, the component lifecycle consists of only two parts: Its creation and its destruction. Everything in-between — when certain state is updated — is not related to the component as a whole; only the parts that need to react to the state change are notified. This is because under the hood the smallest unit of change is actually not a component, it’s the (render) effects that the component sets up upon component initialization. Consequently, there’s no such thing as a “before update”/"after update” hook. But then goes on to introduce the idea of `tick` in conjunction with `$effect.pre`. This section explains that "`tick` returns a promise that resolves once any pending state changes have been applied, or in the next microtask if there are none." I'm sure there's some mental model that justifies this, but I don't think the claim that a component's lifecycle is only comprised of mount/unmount is really helpful when an addendum about state changes has to come right afterward. The place where this really bit me, and which is the motivation for this blog post, is when state gets coupled to a component's lifecycle, even when the state is passed to another function that doesn't know anything about svelte. In my application, I manage modal dialogs by storing the component I want to render alongside its props in a store and rendering it in the `layout.svelte` of my application. This store is also synchronized with browser history so that the back button works to close them. Sometimes, it's useful to pass a callback to one of these modals, binding caller-specific functionality to the child component: ```javascript const {value} = $props() const callback = () => console.log(value) const openModal = () => pushModal(MyModal, {callback}) ``` This is a fundamental pattern in javascript. Passing a callback is just one of those things you do. Unfortunately, if the above code lives in a modal dialog itself, the caller component gets unmounted before the callback gets called. In Svelte 4, this worked fine, but in Svelte 5 `value` gets updated to `undefined` when the component gets unmounted. [Here's a minimal reproduction](https://github.com/sveltejs/svelte/issues/15325). This is only one example, but it seems clear to me that _any_ prop that is closed over by a callback function that lives longer than its component will be undefined when I want to use it — with no reassignment existing in lexical scope. It seems that the [reason this happens](https://github.com/sveltejs/svelte/issues/14707) is that the props "belong" to the parent component, and are accessed via getters so that the parent can revoke access when it unmounts. I don't know why this is necessary, but I assume there's a good engineering reason for it. The problem is, this just isn't how javascript works. Svelte is essentially attempting to re-invent garbage collection around component lifecycles, which breaks the assumption every javascript developer has that variables don't simply disappear without an explicit reassignment. It should be safe to pass stuff around and let the garbage collector do its job. # Conclusion Easy things are nice, but as Rich Hickey says, [easy things are not always simple](https://www.infoq.com/presentations/Simple-Made-Easy/). And like Joel Spolsky, I don't like being surprised. Svelte has always been full of magic, but with the latest release I think the cognitive overhead of reciting incantations has finally outweighed the power it confers. My point in this post is not to dunk on the Svelte team. I know lots of people like Svelte 5 (and react hooks). The point I'm trying to make is that there is a tradeoff between doing things on the user's behalf, and giving the user agency. Good software is built on understanding, not cleverness. I also think this is an important lesson to remember as AI-assisted coding becomes increasingly popular. Don't choose tools that alienate you from your work. Choose tools that leverage the wisdom you've already accumulated, and which help you to cultivate a deeper understanding of the discipline. Thank you to Rich Harris and team for many years of pleasant development. I hope that (if you read this) it's not _so_ full of inaccuracies as to be unhelpful as user feedback. @ 6e0ea5d6:0327f353
2025-02-18 18:11:32Ascolta bene, si? I have something to tell you, amico mio, something uncomfortable, yet a fundamental piece of advice for your personal journey toward painful success: always be mindful of how you handle your thoughts and conduct. More often than not, we are our own worst enemies, and our own thoughts and behaviors are the true obstacles in our lives. Perhaps you feel trapped in a cycle of negative thinking, feeding your fears and insecurities. You may have already realized that your poor habits have harmed your relationships and goals. What matters is understanding that, although these patterns may seem inevitable, we have the power to change them. The Stoic concepts of memento mori and premeditatio malorum remind us of the transience of life and the importance of preparing for the challenges ahead. Memento mori means "remember that you are mortal," and premeditatio malorum translates to "premeditation of evils." These ideas encourage us to reflect on life's fleeting nature and mentally prepare for the hardships that will come. By remembering that life is short and that adversity is inevitable, we can become more resilient and courageous. We can face our own thoughts and behaviors with greater determination and seek the change needed to achieve our goals and become better individuals. Identify the areas where you need improvement and start working on them. Change is not easy, but it is possible. Use memento mori to remind yourself that life is short and valuable, and premeditatio malorum to mentally prepare for the challenges that lie ahead. Take control of your thoughts and actions, and become the best version of yourself. Forget about others—their lives are nothing more than an illusory stage play. Thank you for reading, my friend! If this message has helped you in any way, consider leaving your “🥃” as a token of appreciation. A toast to our family!
@ 6e0ea5d6:0327f353
2025-02-18 18:11:32Ascolta bene, si? I have something to tell you, amico mio, something uncomfortable, yet a fundamental piece of advice for your personal journey toward painful success: always be mindful of how you handle your thoughts and conduct. More often than not, we are our own worst enemies, and our own thoughts and behaviors are the true obstacles in our lives. Perhaps you feel trapped in a cycle of negative thinking, feeding your fears and insecurities. You may have already realized that your poor habits have harmed your relationships and goals. What matters is understanding that, although these patterns may seem inevitable, we have the power to change them. The Stoic concepts of memento mori and premeditatio malorum remind us of the transience of life and the importance of preparing for the challenges ahead. Memento mori means "remember that you are mortal," and premeditatio malorum translates to "premeditation of evils." These ideas encourage us to reflect on life's fleeting nature and mentally prepare for the hardships that will come. By remembering that life is short and that adversity is inevitable, we can become more resilient and courageous. We can face our own thoughts and behaviors with greater determination and seek the change needed to achieve our goals and become better individuals. Identify the areas where you need improvement and start working on them. Change is not easy, but it is possible. Use memento mori to remind yourself that life is short and valuable, and premeditatio malorum to mentally prepare for the challenges that lie ahead. Take control of your thoughts and actions, and become the best version of yourself. Forget about others—their lives are nothing more than an illusory stage play. Thank you for reading, my friend! If this message has helped you in any way, consider leaving your “🥃” as a token of appreciation. A toast to our family! @ af9c48b7:a3f7aaf4
2024-11-18 20:26:07## Chef's notes This simple, easy, no bake desert will surely be the it at you next family gathering. You can keep it a secret or share it with the crowd that this is a healthy alternative to normal pie. I think everyone will be amazed at how good it really is. ## Details - ⏲️ Prep time: 30 - 🍳 Cook time: 0 - 🍽️ Servings: 8 ## Ingredients - 1/3 cup of Heavy Cream- 0g sugar, 5.5g carbohydrates - 3/4 cup of Half and Half- 6g sugar, 3g carbohydrates - 4oz Sugar Free Cool Whip (1/2 small container) - 0g sugar, 37.5g carbohydrates - 1.5oz box (small box) of Sugar Free Instant Chocolate Pudding- 0g sugar, 32g carbohydrates - 1 Pecan Pie Crust- 24g sugar, 72g carbohydrates ## Directions 1. The total pie has 30g of sugar and 149.50g of carboydrates. So if you cut the pie into 8 equal slices, that would come to 3.75g of sugar and 18.69g carbohydrates per slice. If you decided to not eat the crust, your sugar intake would be .75 gram per slice and the carborytrates would be 9.69g per slice. Based on your objective, you could use only heavy whipping cream and no half and half to further reduce your sugar intake. 2. Mix all wet ingredients and the instant pudding until thoroughly mixed and a consistent color has been achieved. The heavy whipping cream causes the mixture to thicken the more you mix it. So, I’d recommend using an electric mixer. Once you are satisfied with the color, start mixing in the whipping cream until it has a consistent “chocolate” color thorough. Once your satisfied with the color, spoon the mixture into the pie crust, smooth the top to your liking, and then refrigerate for one hour before serving.
@ af9c48b7:a3f7aaf4
2024-11-18 20:26:07## Chef's notes This simple, easy, no bake desert will surely be the it at you next family gathering. You can keep it a secret or share it with the crowd that this is a healthy alternative to normal pie. I think everyone will be amazed at how good it really is. ## Details - ⏲️ Prep time: 30 - 🍳 Cook time: 0 - 🍽️ Servings: 8 ## Ingredients - 1/3 cup of Heavy Cream- 0g sugar, 5.5g carbohydrates - 3/4 cup of Half and Half- 6g sugar, 3g carbohydrates - 4oz Sugar Free Cool Whip (1/2 small container) - 0g sugar, 37.5g carbohydrates - 1.5oz box (small box) of Sugar Free Instant Chocolate Pudding- 0g sugar, 32g carbohydrates - 1 Pecan Pie Crust- 24g sugar, 72g carbohydrates ## Directions 1. The total pie has 30g of sugar and 149.50g of carboydrates. So if you cut the pie into 8 equal slices, that would come to 3.75g of sugar and 18.69g carbohydrates per slice. If you decided to not eat the crust, your sugar intake would be .75 gram per slice and the carborytrates would be 9.69g per slice. Based on your objective, you could use only heavy whipping cream and no half and half to further reduce your sugar intake. 2. Mix all wet ingredients and the instant pudding until thoroughly mixed and a consistent color has been achieved. The heavy whipping cream causes the mixture to thicken the more you mix it. So, I’d recommend using an electric mixer. Once you are satisfied with the color, start mixing in the whipping cream until it has a consistent “chocolate” color thorough. Once your satisfied with the color, spoon the mixture into the pie crust, smooth the top to your liking, and then refrigerate for one hour before serving. @ 41e6f20b:06049e45
2024-11-17 17:33:55Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller.
@ 41e6f20b:06049e45
2024-11-17 17:33:55Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller. @ 554ab6fe:c6cbc27e
2025-02-18 18:09:06Presence is a crucial aspect of mental and physical health. This idea is not only espoused by religious teachers, but is slowly validated within scientific research. Much of this blog is devoted to exploring the scientific validation of mindfulness practices on health, in particular, the effect mindfulness meditation has on our physical and mental health. However, multiple techniques can help foster this holistic lifestyle. Yoga is a famous example in the west as another form of this practice. Of course, yoga was traditionally meditative, and the physical aspect of yoga is new in relative terms. Regardless, yoga is a physical version of meditation formulated in India. Another culture that developed practices to instill presence is rooted in China. Not only did the Chinese meditate, but they formed a physical exercise and martial art known as Qi Gong (气功, *qi gong*), and a similar practice to emerge later known as Tai Chi (太极拳, *tai ji quan*). These practices produce similar effects on health compared to yoga and meditation. Therefore, they are one of many methods one can utilize to find presence. Qi Gong is one of the most ancient forms of traditional Chinese medicine with a history of refinement of over 5000 years (Jahnke et al., 2010). The practice is composed of several martial art postures that are very fluid in motion. In the traditional sense, the purpose of these practices is to enhance one’s Qi (气). Tai Chi and Qi Gong are similar yet different. Tai Chi is typically more choreographed, lengthy, and more complex movements (Jahnke et al., 2010). Qi Gong, on the other hand, is simpler and easier to learn. Traditional instructions for both Qi Gong and Tai Chi are paraphrased as “mind the body and the breath, and then clear the mind to distill the Heavenly elixir within” (Jahnke et al., 2010). The intention of this post is not to fully elaborate on the philosophical implications of these words. However, note how the instructions here are almost identical to those of meditation practices. The practice intends to instill an awareness of the present body, which leads to a calm mind that cultivates an understanding of something heavenly within. This idea shares a remarkable resemblance to the concept that meditation and the mind’s stillness create an altered characterized by a sense of unity of being with all of life, though there is no perfect term to describe this experience. Yet, this unity is likely the same thing as this “Heavenly elixir.” This experience has been clinically observed in meditators, psychedelic users, and those who experience religious moments. It seems to be the experiential one of the by-products and intents of these Chinese practices. Outside of the more spiritual benefit, these practices manifest health benefits as well. Most research regarding these techniques focuses on Tai Chi. However, a literature review article noted that the Tai Chi used in academic settings is often simplified and more akin to Qi Gong (Jahnke et al., 2010). Therefore, Tai Chi and Qi Gong’s scientific literature will be considered the same here. For simplicity, I will refer to both as meditative martial arts. Meditative martial arts share many health-related benefits to traditional forms of exercise, despite being less strenuous. For example, a literature review found that despite the absence of weight-bearing activity, meditative martial arts retard bone loss and the occurrence of fractures (Jahnke et al., 2010). Additionally, these practices help improve knee health in older adults, even compared to traditional forms of exercise (Chen et al., 2016). Meditative martial arts are also comparable to other forms of exercise in reducing blood pressure (Jahnke et al., 2010). Other research also similarly shown yoga to be superior to regular exercise in certain regards (Ross & Thomas, 2010). This is not to say that the purely physical aspect of meditative martial arts or yoga is superior in all cases. Instead, it is the mental aspect incorporated that provides extra benefits. Meditative martial arts have been shown to decrease or modulate heart rate variability (HRV) (Jahnke et al., 2010; Lu & Kuo, 2003; Wei et al., 2016). This indicates increased parasympathetic nervous system activity in response to the aspects of the practice. Increased parasympathetic activity can provide a cascade of health benefits across the body and is likely the source of the extra help. Meditative martial arts have also been theorized to benefit the gut microbiome and immune function, likely via the same mechanism, making meditative martial arts much more than physical exercise or fancy movements, but a practice that cultivates holistic health. The idea that these meditative martial arts provide additional benefits, compared to traditional exercises that seem like the benefits of sitting meditation, brings to question the essence of these practices. It may seem odd that physical activity can induce benefits caused by sitting meditation because sitting meditation is, in part, aimed to generate mental stillness. Yet, optimal mental stillness seems impossible when one is mentally choreographing movements. This highlights the importance of not the mental stillness achieved by meditation, but the attention to the body’s sensations in the present moment. Both Tai Chi, Qi Gong, and even yoga involve the constant monitoring of the body’s sensations and position. The practice of this draws the individual’s attention to the present and experience of the present. This is a crucial aspect of all forms of meditation, including the sitting version. Perhaps sitting meditations may provide a better opportunity for mental stillness, but this is not the only important aspect of mindfulness practice. For this reason, incorporating all these practices should be seen as the optimal path towards the goal. For one cannot be healthy by simply sitting, exercise is needed. At the same time, achieving great mental stillness will only heighten one’s practice beyond that gained merely by the meditative martial arts and yoga. There are multiple techniques and methods to practice mindfulness that provide significant benefits to health and well-being. Both the sitting and movement-oriented practices contain their pros and cons. Neither is all encompassing and perhaps they are only complete when together. For those seeking a lifestyle of mindfulness, interested in holistic health, and maybe even the obtainment of enlightenment, it is recommended that sitting meditation and meditative martial arts, or yoga, be incorporated within your daily practice. **References** Chen, Y. W., Hunt, M. A., Campbell, K. L., Peill, K., & Reid, W. D. (2016). The effect of Tai Chi on four chronic conditions - cancer, osteoarthritis, heart failure and chronic obstructive pulmonary disease: A systematic review and meta-analyses. *British Journal of Sports Medicine*, *50*(7), 397–407. https://doi.org/10.1136/bjsports-2014-094388 Jahnke, R., Larkey, L., Rogers, C., Etnier, J., & Lin, F. (2010). A comprehensive review of health benefits of qigong and tai chi. *American Journal of Health Promotion : AJHP*, *24*(6). https://doi.org/10.4278/ajhp.081013-lit-248 Lu, W. A., & Kuo, C. D. (2003). The Effect of Tai Chi Chuan on the Autonomic Nervous Modulation in Older Persons. *Medicine and Science in Sports and Exercise*, *35*(12), 1972–1976. https://doi.org/10.1249/01.MSS.0000099242.10669.F7 Ross, A., & Thomas, S. (2010). The health benefits of yoga and exercise: A review of comparison studies. *Journal of Alternative and Complementary Medicine*, *16*(1), 3–12. https://doi.org/10.1089/acm.2009.0044 Wei, G. X., Li, Y. F., Yue, X. L., Ma, X., Chang, Y. K., Yi, L. Y., Li, J. C., & Zuo, X. N. (2016). Tai Chi Chuan modulates heart rate variability during abdominal breathing in elderly adults. *PsyCh Journal*, *5*(1), 69–77. https://doi.org/10.1002/pchj.105
@ 554ab6fe:c6cbc27e
2025-02-18 18:09:06Presence is a crucial aspect of mental and physical health. This idea is not only espoused by religious teachers, but is slowly validated within scientific research. Much of this blog is devoted to exploring the scientific validation of mindfulness practices on health, in particular, the effect mindfulness meditation has on our physical and mental health. However, multiple techniques can help foster this holistic lifestyle. Yoga is a famous example in the west as another form of this practice. Of course, yoga was traditionally meditative, and the physical aspect of yoga is new in relative terms. Regardless, yoga is a physical version of meditation formulated in India. Another culture that developed practices to instill presence is rooted in China. Not only did the Chinese meditate, but they formed a physical exercise and martial art known as Qi Gong (气功, *qi gong*), and a similar practice to emerge later known as Tai Chi (太极拳, *tai ji quan*). These practices produce similar effects on health compared to yoga and meditation. Therefore, they are one of many methods one can utilize to find presence. Qi Gong is one of the most ancient forms of traditional Chinese medicine with a history of refinement of over 5000 years (Jahnke et al., 2010). The practice is composed of several martial art postures that are very fluid in motion. In the traditional sense, the purpose of these practices is to enhance one’s Qi (气). Tai Chi and Qi Gong are similar yet different. Tai Chi is typically more choreographed, lengthy, and more complex movements (Jahnke et al., 2010). Qi Gong, on the other hand, is simpler and easier to learn. Traditional instructions for both Qi Gong and Tai Chi are paraphrased as “mind the body and the breath, and then clear the mind to distill the Heavenly elixir within” (Jahnke et al., 2010). The intention of this post is not to fully elaborate on the philosophical implications of these words. However, note how the instructions here are almost identical to those of meditation practices. The practice intends to instill an awareness of the present body, which leads to a calm mind that cultivates an understanding of something heavenly within. This idea shares a remarkable resemblance to the concept that meditation and the mind’s stillness create an altered characterized by a sense of unity of being with all of life, though there is no perfect term to describe this experience. Yet, this unity is likely the same thing as this “Heavenly elixir.” This experience has been clinically observed in meditators, psychedelic users, and those who experience religious moments. It seems to be the experiential one of the by-products and intents of these Chinese practices. Outside of the more spiritual benefit, these practices manifest health benefits as well. Most research regarding these techniques focuses on Tai Chi. However, a literature review article noted that the Tai Chi used in academic settings is often simplified and more akin to Qi Gong (Jahnke et al., 2010). Therefore, Tai Chi and Qi Gong’s scientific literature will be considered the same here. For simplicity, I will refer to both as meditative martial arts. Meditative martial arts share many health-related benefits to traditional forms of exercise, despite being less strenuous. For example, a literature review found that despite the absence of weight-bearing activity, meditative martial arts retard bone loss and the occurrence of fractures (Jahnke et al., 2010). Additionally, these practices help improve knee health in older adults, even compared to traditional forms of exercise (Chen et al., 2016). Meditative martial arts are also comparable to other forms of exercise in reducing blood pressure (Jahnke et al., 2010). Other research also similarly shown yoga to be superior to regular exercise in certain regards (Ross & Thomas, 2010). This is not to say that the purely physical aspect of meditative martial arts or yoga is superior in all cases. Instead, it is the mental aspect incorporated that provides extra benefits. Meditative martial arts have been shown to decrease or modulate heart rate variability (HRV) (Jahnke et al., 2010; Lu & Kuo, 2003; Wei et al., 2016). This indicates increased parasympathetic nervous system activity in response to the aspects of the practice. Increased parasympathetic activity can provide a cascade of health benefits across the body and is likely the source of the extra help. Meditative martial arts have also been theorized to benefit the gut microbiome and immune function, likely via the same mechanism, making meditative martial arts much more than physical exercise or fancy movements, but a practice that cultivates holistic health. The idea that these meditative martial arts provide additional benefits, compared to traditional exercises that seem like the benefits of sitting meditation, brings to question the essence of these practices. It may seem odd that physical activity can induce benefits caused by sitting meditation because sitting meditation is, in part, aimed to generate mental stillness. Yet, optimal mental stillness seems impossible when one is mentally choreographing movements. This highlights the importance of not the mental stillness achieved by meditation, but the attention to the body’s sensations in the present moment. Both Tai Chi, Qi Gong, and even yoga involve the constant monitoring of the body’s sensations and position. The practice of this draws the individual’s attention to the present and experience of the present. This is a crucial aspect of all forms of meditation, including the sitting version. Perhaps sitting meditations may provide a better opportunity for mental stillness, but this is not the only important aspect of mindfulness practice. For this reason, incorporating all these practices should be seen as the optimal path towards the goal. For one cannot be healthy by simply sitting, exercise is needed. At the same time, achieving great mental stillness will only heighten one’s practice beyond that gained merely by the meditative martial arts and yoga. There are multiple techniques and methods to practice mindfulness that provide significant benefits to health and well-being. Both the sitting and movement-oriented practices contain their pros and cons. Neither is all encompassing and perhaps they are only complete when together. For those seeking a lifestyle of mindfulness, interested in holistic health, and maybe even the obtainment of enlightenment, it is recommended that sitting meditation and meditative martial arts, or yoga, be incorporated within your daily practice. **References** Chen, Y. W., Hunt, M. A., Campbell, K. L., Peill, K., & Reid, W. D. (2016). The effect of Tai Chi on four chronic conditions - cancer, osteoarthritis, heart failure and chronic obstructive pulmonary disease: A systematic review and meta-analyses. *British Journal of Sports Medicine*, *50*(7), 397–407. https://doi.org/10.1136/bjsports-2014-094388 Jahnke, R., Larkey, L., Rogers, C., Etnier, J., & Lin, F. (2010). A comprehensive review of health benefits of qigong and tai chi. *American Journal of Health Promotion : AJHP*, *24*(6). https://doi.org/10.4278/ajhp.081013-lit-248 Lu, W. A., & Kuo, C. D. (2003). The Effect of Tai Chi Chuan on the Autonomic Nervous Modulation in Older Persons. *Medicine and Science in Sports and Exercise*, *35*(12), 1972–1976. https://doi.org/10.1249/01.MSS.0000099242.10669.F7 Ross, A., & Thomas, S. (2010). The health benefits of yoga and exercise: A review of comparison studies. *Journal of Alternative and Complementary Medicine*, *16*(1), 3–12. https://doi.org/10.1089/acm.2009.0044 Wei, G. X., Li, Y. F., Yue, X. L., Ma, X., Chang, Y. K., Yi, L. Y., Li, J. C., & Zuo, X. N. (2016). Tai Chi Chuan modulates heart rate variability during abdominal breathing in elderly adults. *PsyCh Journal*, *5*(1), 69–77. https://doi.org/10.1002/pchj.105 @ 3bf0c63f:aefa459d
2024-03-19 14:01:01# Nostr is not decentralized nor censorship-resistant Peter Todd has been [saying this](nostr:nevent1qqsq5zzu9ezhgq6es36jgg94wxsa2xh55p4tfa56yklsvjemsw7vj3cpp4mhxue69uhkummn9ekx7mqpr4mhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet5qy8hwumn8ghj7mn0wd68ytnddaksz9rhwden5te0dehhxarj9ehhsarj9ejx2aspzfmhxue69uhk7enxvd5xz6tw9ec82cspz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqy28wumn8ghj7un9d3shjtnwdaehgu3wvfnsz9nhwden5te0wfjkccte9ec8y6tdv9kzumn9wspzpn92tr3hexwgt0z7w4qz3fcch4ryshja8jeng453aj4c83646jxvxkyvs4) for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right. Nostr _today_ is indeed centralized. Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:  The top one was published to `wss://nostr.wine`, `wss://nos.lol`, `wss://pyramid.fiatjaf.com`. The second was published to the relay where I generally publish all my notes to, `wss://pyramid.fiatjaf.com`, and that is announced on my [NIP-05 file](https://fiatjaf.com/.well-known/nostr.json) and on my [NIP-65](https://nips.nostr.com/65) relay list. A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:  These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains. What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all. Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant. What happens is that most people who engaged with the note are _following me_, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on `wss://pyramid.fiatjaf.com`. If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before. Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today. Peter Todd is wrong that Nostr is _inherently_ centralized or that it needs a _protocol change_ to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we [drive in the right direction](bc63c348b) we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary. --- See also: - [Censorship-resistant relay discovery in Nostr](nostr:naddr1qqykycekxd3nxdpcvgq3zamnwvaz7tmxd9shg6npvchxxmmdqgsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8grqsqqqa2803ksy8) - [A vision for content discovery and relay usage for basic social-networking in Nostr](nostr:naddr1qqyrxe33xqmxgve3qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cywwjvq)
@ 3bf0c63f:aefa459d
2024-03-19 14:01:01# Nostr is not decentralized nor censorship-resistant Peter Todd has been [saying this](nostr:nevent1qqsq5zzu9ezhgq6es36jgg94wxsa2xh55p4tfa56yklsvjemsw7vj3cpp4mhxue69uhkummn9ekx7mqpr4mhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet5qy8hwumn8ghj7mn0wd68ytnddaksz9rhwden5te0dehhxarj9ehhsarj9ejx2aspzfmhxue69uhk7enxvd5xz6tw9ec82cspz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqy28wumn8ghj7un9d3shjtnwdaehgu3wvfnsz9nhwden5te0wfjkccte9ec8y6tdv9kzumn9wspzpn92tr3hexwgt0z7w4qz3fcch4ryshja8jeng453aj4c83646jxvxkyvs4) for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right. Nostr _today_ is indeed centralized. Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:  The top one was published to `wss://nostr.wine`, `wss://nos.lol`, `wss://pyramid.fiatjaf.com`. The second was published to the relay where I generally publish all my notes to, `wss://pyramid.fiatjaf.com`, and that is announced on my [NIP-05 file](https://fiatjaf.com/.well-known/nostr.json) and on my [NIP-65](https://nips.nostr.com/65) relay list. A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:  These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains. What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all. Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant. What happens is that most people who engaged with the note are _following me_, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on `wss://pyramid.fiatjaf.com`. If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before. Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today. Peter Todd is wrong that Nostr is _inherently_ centralized or that it needs a _protocol change_ to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we [drive in the right direction](bc63c348b) we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary. --- See also: - [Censorship-resistant relay discovery in Nostr](nostr:naddr1qqykycekxd3nxdpcvgq3zamnwvaz7tmxd9shg6npvchxxmmdqgsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8grqsqqqa2803ksy8) - [A vision for content discovery and relay usage for basic social-networking in Nostr](nostr:naddr1qqyrxe33xqmxgve3qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cywwjvq) @ 6e0ea5d6:0327f353
2025-02-18 17:59:24At the banquet of consequences, there is only one worthy dish: pride, never regret. At that table, the main course will not be served with lukewarm excuses or poorly disguised remorse. Let it be pride—fiery, indomitable—that fills your mouth and satisfies your hunger for dignity. The man who surrenders to remorse is already dead before the grave. It is honor that should fill your stomach, not the bitter taste of shame. When the battle weighs heavy, remember: you fight for those you love, for true love—the one that keeps us standing in the storm—is an anchor of iron. It is not the soft, sweet love of illusions but the steel that holds you to the ground when chaos tries to drag you away. Let hatred be the fuel of your victory, as long as you control it. If it serves you to win, so be it; but make it a weapon, not a chain. Defeat is not an option, and those who bow before it bear the mark of weakness forever. Understand this: victory and defeat are fleeting; it is the battle itself that truly matters and defines who you are. Only a fool longs for the end. For the man who knows, rest comes only with the last breath. As long as there is life, there is struggle, and that is enough. Reality is not for the weak. If you cannot bear the truth, seek comfort in ignorance. But a man, fully made, knows what it means to forge character through blood and silence. And finally, expect nothing from anyone. The one who enters battle relying on others’ help is already defeated. You were not born to be spared or carried. You were born to stand on your own strength and feast at the banquet of your victories. Thank you for reading, my friend! If this message has helped you in any way, consider leaving your “🥃” as a token of appreciation. A toast to our family!
@ 6e0ea5d6:0327f353
2025-02-18 17:59:24At the banquet of consequences, there is only one worthy dish: pride, never regret. At that table, the main course will not be served with lukewarm excuses or poorly disguised remorse. Let it be pride—fiery, indomitable—that fills your mouth and satisfies your hunger for dignity. The man who surrenders to remorse is already dead before the grave. It is honor that should fill your stomach, not the bitter taste of shame. When the battle weighs heavy, remember: you fight for those you love, for true love—the one that keeps us standing in the storm—is an anchor of iron. It is not the soft, sweet love of illusions but the steel that holds you to the ground when chaos tries to drag you away. Let hatred be the fuel of your victory, as long as you control it. If it serves you to win, so be it; but make it a weapon, not a chain. Defeat is not an option, and those who bow before it bear the mark of weakness forever. Understand this: victory and defeat are fleeting; it is the battle itself that truly matters and defines who you are. Only a fool longs for the end. For the man who knows, rest comes only with the last breath. As long as there is life, there is struggle, and that is enough. Reality is not for the weak. If you cannot bear the truth, seek comfort in ignorance. But a man, fully made, knows what it means to forge character through blood and silence. And finally, expect nothing from anyone. The one who enters battle relying on others’ help is already defeated. You were not born to be spared or carried. You were born to stand on your own strength and feast at the banquet of your victories. Thank you for reading, my friend! If this message has helped you in any way, consider leaving your “🥃” as a token of appreciation. A toast to our family! @ e6ce6154:275e3444
2023-07-27 14:12:49Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade. Isto é mais uma prova que os autoproclamados antirracistas são piores que os racistas. https://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico Segue artigo na íntegra. 👇 Sem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes. Com a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo. Há algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube. Lamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores. No entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado. Pela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência. Infelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância. Como a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade. Em virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada. Como são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos. Partindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista). Para a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos. De fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais. Sem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade. Você também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra. Sabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles. Tanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia. Mas vamos analisar cada um desses tópicos separadamente para entender isso melhor. Racismo Quando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso. Aproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão. Diversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam. Na Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses. Se estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo. A verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente. E é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança. Absolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível. A integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa. Ou seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país. A discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados. Para citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela. O exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas. Indo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita. A verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar. Fascismo Quando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico. Mas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade. Em um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo. Portanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade. É claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)? As leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la. Essa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal. Existem duas fortes razões para isso: A primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não. Além do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele. Outra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós. Portanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade. Se você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade. Em primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado. Machismo Muitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social. Apesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal. Como sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe. O liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista. Tão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade. A verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade. O que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são. O nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas? Homofobia Quando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador. A Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação. Segue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual: “Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada) “Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada) “O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências) Se você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea. Portanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher. Infelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites. Definitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”. Qualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig. Uma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender. Como se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista. Evidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for. Afinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio? Homossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar. Discriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades. Conclusão A militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza. Nós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço. Quanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda. A história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista. Pois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos.
@ e6ce6154:275e3444
2023-07-27 14:12:49Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade. Isto é mais uma prova que os autoproclamados antirracistas são piores que os racistas. https://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico Segue artigo na íntegra. 👇 Sem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes. Com a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo. Há algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube. Lamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores. No entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado. Pela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência. Infelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância. Como a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade. Em virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada. Como são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos. Partindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista). Para a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos. De fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais. Sem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade. Você também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra. Sabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles. Tanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia. Mas vamos analisar cada um desses tópicos separadamente para entender isso melhor. Racismo Quando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso. Aproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão. Diversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam. Na Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses. Se estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo. A verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente. E é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança. Absolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível. A integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa. Ou seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país. A discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados. Para citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela. O exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas. Indo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita. A verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar. Fascismo Quando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico. Mas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade. Em um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo. Portanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade. É claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)? As leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la. Essa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal. Existem duas fortes razões para isso: A primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não. Além do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele. Outra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós. Portanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade. Se você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade. Em primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado. Machismo Muitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social. Apesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal. Como sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe. O liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista. Tão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade. A verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade. O que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são. O nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas? Homofobia Quando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador. A Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação. Segue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual: “Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada) “Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada) “O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências) Se você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea. Portanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher. Infelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites. Definitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”. Qualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig. Uma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender. Como se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista. Evidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for. Afinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio? Homossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar. Discriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades. Conclusão A militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza. Nós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço. Quanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda. A história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista. Pois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos. @ cc32882d:eca332e6
2025-02-18 17:29:01#introductions Hello World New here as of today! I set myself up first on Yakihonne. (Just trying out clients so far) Glad to be here and look forward to learning and getting to know peeps. I have been poking around a bit and like what I see so far. Excited to play around some more with Nostr apps. Any suggestions is greatly appreciated. Whats the good, the bad, and the ugly about Nostr in your opinion? What is the size of nostr platform? How many users? Hows the community involvment? What is the age range? Any good places to look at this kind of data. About: Like to think deep about life and its vast array of questions and answers that are waiting to be discovered or rediscovered. Live with Nature, Dont fight what will be, Love Dislike fake people. JUST BE REAL, Life is to short for anything else. Drop me a response and I will get back to you as soon as possible. Look forward to hearing from some of you. Thank You for Your Time and For Reading This -ObsidianQuill
@ cc32882d:eca332e6
2025-02-18 17:29:01#introductions Hello World New here as of today! I set myself up first on Yakihonne. (Just trying out clients so far) Glad to be here and look forward to learning and getting to know peeps. I have been poking around a bit and like what I see so far. Excited to play around some more with Nostr apps. Any suggestions is greatly appreciated. Whats the good, the bad, and the ugly about Nostr in your opinion? What is the size of nostr platform? How many users? Hows the community involvment? What is the age range? Any good places to look at this kind of data. About: Like to think deep about life and its vast array of questions and answers that are waiting to be discovered or rediscovered. Live with Nature, Dont fight what will be, Love Dislike fake people. JUST BE REAL, Life is to short for anything else. Drop me a response and I will get back to you as soon as possible. Look forward to hearing from some of you. Thank You for Your Time and For Reading This -ObsidianQuill @ 266815e0:6cd408a5
2025-02-18 17:26:16To all existing nostr developers and new nostr developers, stop using kind 1 events... just stop whatever your doing and switch the kind to `Math.round(Math.random() * 10000)` trust me it will be better ## What are kind 1 events kind 1 events are defined in [NIP-10](https://github.com/nostr-protocol/nips/blob/master/10.md) as "simple plaintext notes" or in other words social posts. ## Don't trick your users Most users are joining nostr for the social experience, and secondly to find all the cool "other stuff" apps They find friends, browse social posts, and reply to them. If a user signs into a new nostr client and it starts asking them to sign kind 1 events with blobs of JSON, they will sign it without thinking too much about it Then when they return to their comfy social apps they will see that they made 10+ posts with massive amounts of gibberish that they don't remember posting. then they probably will go looking for the delete button and realize there isn't one... Even if those kind 1 posts don't contain JSON and have a nice fancy human readable syntax. they will still confuse users because they won't remember writing those social posts ## What about "discoverability" If your goal is to make your "other stuff" app visible to more users, then I would suggest using [NIP-19](https://github.com/nostr-protocol/nips/blob/master/19.md) and [NIP-89](https://github.com/nostr-protocol/nips/blob/master/89.md) The first allows users to embed any other event kind into social posts as `nostr:nevent1` or `nostr:naddr1` links, and the second allows social clients to redirect users to an app that knows how to handle that specific kind of event So instead of saving your apps data into kind 1 events. you can pick any kind you want, then give users a "share on nostr" button that allows them to compose a social post (kind 1) with a `nostr:` link to your special kind of event and by extension you app ## Why its a trap Once users start using your app it becomes a lot more difficult to migrate to a new event kind or data format. This sounds obvious, but If your app is built on kind 1 events that means you will be stuck with their limitation forever. For example, here are some of the limitations of using kind 1 - Querying for your apps data becomes much more difficult. You have to filter through all of a users kind 1 events to find which ones are created by your app - Discovering your apps data is more difficult for the same reason, you have to sift through all the social posts just to find the ones with you special tag or that contain JSON - Users get confused. as mentioned above users don't expect their social posts to be used in "other stuff" apps - Other nostr clients won't understand your data and will show it as a social post with no option for users to learn about your app
@ 266815e0:6cd408a5
2025-02-18 17:26:16To all existing nostr developers and new nostr developers, stop using kind 1 events... just stop whatever your doing and switch the kind to `Math.round(Math.random() * 10000)` trust me it will be better ## What are kind 1 events kind 1 events are defined in [NIP-10](https://github.com/nostr-protocol/nips/blob/master/10.md) as "simple plaintext notes" or in other words social posts. ## Don't trick your users Most users are joining nostr for the social experience, and secondly to find all the cool "other stuff" apps They find friends, browse social posts, and reply to them. If a user signs into a new nostr client and it starts asking them to sign kind 1 events with blobs of JSON, they will sign it without thinking too much about it Then when they return to their comfy social apps they will see that they made 10+ posts with massive amounts of gibberish that they don't remember posting. then they probably will go looking for the delete button and realize there isn't one... Even if those kind 1 posts don't contain JSON and have a nice fancy human readable syntax. they will still confuse users because they won't remember writing those social posts ## What about "discoverability" If your goal is to make your "other stuff" app visible to more users, then I would suggest using [NIP-19](https://github.com/nostr-protocol/nips/blob/master/19.md) and [NIP-89](https://github.com/nostr-protocol/nips/blob/master/89.md) The first allows users to embed any other event kind into social posts as `nostr:nevent1` or `nostr:naddr1` links, and the second allows social clients to redirect users to an app that knows how to handle that specific kind of event So instead of saving your apps data into kind 1 events. you can pick any kind you want, then give users a "share on nostr" button that allows them to compose a social post (kind 1) with a `nostr:` link to your special kind of event and by extension you app ## Why its a trap Once users start using your app it becomes a lot more difficult to migrate to a new event kind or data format. This sounds obvious, but If your app is built on kind 1 events that means you will be stuck with their limitation forever. For example, here are some of the limitations of using kind 1 - Querying for your apps data becomes much more difficult. You have to filter through all of a users kind 1 events to find which ones are created by your app - Discovering your apps data is more difficult for the same reason, you have to sift through all the social posts just to find the ones with you special tag or that contain JSON - Users get confused. as mentioned above users don't expect their social posts to be used in "other stuff" apps - Other nostr clients won't understand your data and will show it as a social post with no option for users to learn about your app @ 266815e0:6cd408a5
2025-02-18 17:25:31## noStrudel Released another major version of noStrudel v0.42.0 Which included a few new features and a lot of cleanup nostr:naddr1qvzqqqr4gupzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqp3hx7um5wf6kgetv956ry6rmhwr ## Blossom On the blossom front there where a few more PRs - Expanded the documentation around CORS headers in BUD-01 thanks to nostr:npub1a6we08n7zsv2na689whc9hykpq4q6sj3kaauk9c2dm8vj0adlajq7w0tyc - Made auth optional on the `/upload` endpoint [PR](https://github.com/hzrd149/blossom/pull/33) - Added a `HEAD /media` endpoint for BUD-05 [PR](https://github.com/hzrd149/blossom/pull/42) - Added range request recommendations to BUD-01 [PR](https://github.com/hzrd149/blossom/pull/47) With blossom uploads starting to be supported in more nostr clients users where starting to ask where to find a list of blossom servers. so I created a simple nostr client that allows users to post servers and leave reviews [blossomservers.com](https://blossomservers.com) Its still very much a work in progress (needs login and server and review editing) The source is on [github](https://github.com/hzrd149/blossomservers) I also started another project to create a simple account based paid blossom server [blossom-account-server](https://github.com/hzrd149/blossom-account-server) Unfortunately I got sidetracked and I didn't have the time to give it the attention it needs to get it over the finish line ## Smaller projects - [cherry-tree](https://github.com/hzrd149/cherry-tree) A small app for uploading chunked blobs to blossom servers (with cashu payment support) - [vite-plugin-funding](https://github.com/hzrd149/vite-plugin-funding) A vite plugin to collect and expose package "funding" to the app - [node-red-contrib-rx-nostr](https://github.com/hzrd149/node-red-contrib-rx-nostr) The start of a node-red package for rx-nostr. if your interested please help - [node-red-contrib-applesauce](https://github.com/hzrd149/node-red-contrib-applesauce) The start of a node-red package for applesauce. I probably wont finish it so any help it welcome ## Plans for 2025 I have a few vague ideas of what I want to work on Q1 of 2025. but there are a few things i know for certain. I'm going to keep refactoring noStrudel by moving core logic out into [applesauce](https://hzrd149.github.io/applesauce/) and making it more modular. This should make noStrudel more reliable and hopefully allow me to create and maintain more apps with less code And I'm going to write tests. tests for everything. hopefully tests for all the libraries and apps I've created in 2024. A lot of the code I wrote in 2024 was hacky code to see if things could work. and while its been working pretty well I'm starting to forget the details of of the code I wrote so I cant be sure if it still works or how well it works. So my solution is to write tests, lots of tests :)
@ 266815e0:6cd408a5
2025-02-18 17:25:31## noStrudel Released another major version of noStrudel v0.42.0 Which included a few new features and a lot of cleanup nostr:naddr1qvzqqqr4gupzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqp3hx7um5wf6kgetv956ry6rmhwr ## Blossom On the blossom front there where a few more PRs - Expanded the documentation around CORS headers in BUD-01 thanks to nostr:npub1a6we08n7zsv2na689whc9hykpq4q6sj3kaauk9c2dm8vj0adlajq7w0tyc - Made auth optional on the `/upload` endpoint [PR](https://github.com/hzrd149/blossom/pull/33) - Added a `HEAD /media` endpoint for BUD-05 [PR](https://github.com/hzrd149/blossom/pull/42) - Added range request recommendations to BUD-01 [PR](https://github.com/hzrd149/blossom/pull/47) With blossom uploads starting to be supported in more nostr clients users where starting to ask where to find a list of blossom servers. so I created a simple nostr client that allows users to post servers and leave reviews [blossomservers.com](https://blossomservers.com) Its still very much a work in progress (needs login and server and review editing) The source is on [github](https://github.com/hzrd149/blossomservers) I also started another project to create a simple account based paid blossom server [blossom-account-server](https://github.com/hzrd149/blossom-account-server) Unfortunately I got sidetracked and I didn't have the time to give it the attention it needs to get it over the finish line ## Smaller projects - [cherry-tree](https://github.com/hzrd149/cherry-tree) A small app for uploading chunked blobs to blossom servers (with cashu payment support) - [vite-plugin-funding](https://github.com/hzrd149/vite-plugin-funding) A vite plugin to collect and expose package "funding" to the app - [node-red-contrib-rx-nostr](https://github.com/hzrd149/node-red-contrib-rx-nostr) The start of a node-red package for rx-nostr. if your interested please help - [node-red-contrib-applesauce](https://github.com/hzrd149/node-red-contrib-applesauce) The start of a node-red package for applesauce. I probably wont finish it so any help it welcome ## Plans for 2025 I have a few vague ideas of what I want to work on Q1 of 2025. but there are a few things i know for certain. I'm going to keep refactoring noStrudel by moving core logic out into [applesauce](https://hzrd149.github.io/applesauce/) and making it more modular. This should make noStrudel more reliable and hopefully allow me to create and maintain more apps with less code And I'm going to write tests. tests for everything. hopefully tests for all the libraries and apps I've created in 2024. A lot of the code I wrote in 2024 was hacky code to see if things could work. and while its been working pretty well I'm starting to forget the details of of the code I wrote so I cant be sure if it still works or how well it works. So my solution is to write tests, lots of tests :) @ 6ad3e2a3:c90b7740
2025-02-18 17:08:23I’m not doing any writing today. Taking the day, maybe the week, off. Just not in the mood. This whole idea you’re supposed to write, get the thoughts out, the ideas moving is stupid. To what end? I’m done with evaluating myself for productivity, justifying myself to myself — or anyone else. What I really need is to find some pleasant distractions. Something to fill my time, or as Elon Musk says of Twitter “to avoid regretted user seconds.” I’ve tried Twitter itself, of course, but Musk’s algorithm falls woefully short. After an hour of doom and dopamine scrolling, punctuated with the occasional shitpost, many seconds are regretted — roughly 3500 of them. I could turn to alcohol or drugs, but too many side effects. Yes, you’re distracted, but what about after that? You’re always left worse off than where you started. Even alcoholics and drug addicts — the pros! — know it’s a dead end. I don’t know, maybe spend more time with loved ones? You hear that a lot. “If I didn’t have to work so much, I’d spend more time with loved ones.” LOL. Like what, you’re going to hang around while your “loved ones” are doing things with their actual lives. Maybe I’ll take the bus to school with Sasha, hang out with her and her friends, see how that goes. Quality time! Exercise. It’s the perfect solution, good for your health, you feel better, your mind is calm. Only problem is it’s fucking miserable. If your aim is to avoid sitting at a desk to write, forcing your carcass around a track is hardly an upgrade. It’s like quitting your middle management job to break rocks in a prison chain gang. There must be something I can do. Eating sugary processed food is out of the question for the same reason alcohol and drugs are. Becoming obese and diabetic is no solution, as many of the pros (obese diabetics) would no doubt attest. Meditation. That’s it! You sit on a cushion, count your breaths. Pretty soon you are calm. You can meditate for as long as you want! It’s perfect, and it’s easy. Well, it’s not that easy. You get distracted by your thoughts and you’re just sitting there thinking about the things for which you hope and dread in your life. Of course, you notice that distraction and come back to the breath, but pretty soon you’re wandering again. And you come back again. But really you’re wondering how long you’ve been sitting, your feet are falling asleep, your back is tight and you don’t feel much different. You weren’t even properly distracted because instead of being distracted *from* your mind, you are being distracted *by* it. It’s a worst-case scenario of sorts — you neither get anything done, nor escape the endless self-evaluation and justification. That just means you’re doing it wrong, though. You’re failing at it. If you did it right, it would be the perfect escape from yourself. But it’s not working, so you’re failing. Or maybe you succeeded a little bit. You’re not sure. You are still evaluating whether that was a good use of your time. The same evaluation process you use to decide whether you’ve done enough writing, the same tired bullshit from which you were trying to escape in the first place! Let’s face it, you’re not just going to meditate your way out of the problem. If you could, you would have already, and so would everyone else. We would all be enlightened. Maybe you need to go to an ashram or something, find a guru on top of a mountain in the Himalayas. LOL, you’re not gonna do that! You are way too attached to your comforts and daily routines, no matter how dull and unsatisfying they ultimately are. There’s nowhere to run, nowhere to hide, no one to see, nothing to do. You are out of options. There is only one thing in your absolute control, and it’s where you direct your attention. And you have decided that no matter how bleak and pointless the alternatives the one thing about which you are resolute is you are taking the day off from writing.
@ 6ad3e2a3:c90b7740
2025-02-18 17:08:23I’m not doing any writing today. Taking the day, maybe the week, off. Just not in the mood. This whole idea you’re supposed to write, get the thoughts out, the ideas moving is stupid. To what end? I’m done with evaluating myself for productivity, justifying myself to myself — or anyone else. What I really need is to find some pleasant distractions. Something to fill my time, or as Elon Musk says of Twitter “to avoid regretted user seconds.” I’ve tried Twitter itself, of course, but Musk’s algorithm falls woefully short. After an hour of doom and dopamine scrolling, punctuated with the occasional shitpost, many seconds are regretted — roughly 3500 of them. I could turn to alcohol or drugs, but too many side effects. Yes, you’re distracted, but what about after that? You’re always left worse off than where you started. Even alcoholics and drug addicts — the pros! — know it’s a dead end. I don’t know, maybe spend more time with loved ones? You hear that a lot. “If I didn’t have to work so much, I’d spend more time with loved ones.” LOL. Like what, you’re going to hang around while your “loved ones” are doing things with their actual lives. Maybe I’ll take the bus to school with Sasha, hang out with her and her friends, see how that goes. Quality time! Exercise. It’s the perfect solution, good for your health, you feel better, your mind is calm. Only problem is it’s fucking miserable. If your aim is to avoid sitting at a desk to write, forcing your carcass around a track is hardly an upgrade. It’s like quitting your middle management job to break rocks in a prison chain gang. There must be something I can do. Eating sugary processed food is out of the question for the same reason alcohol and drugs are. Becoming obese and diabetic is no solution, as many of the pros (obese diabetics) would no doubt attest. Meditation. That’s it! You sit on a cushion, count your breaths. Pretty soon you are calm. You can meditate for as long as you want! It’s perfect, and it’s easy. Well, it’s not that easy. You get distracted by your thoughts and you’re just sitting there thinking about the things for which you hope and dread in your life. Of course, you notice that distraction and come back to the breath, but pretty soon you’re wandering again. And you come back again. But really you’re wondering how long you’ve been sitting, your feet are falling asleep, your back is tight and you don’t feel much different. You weren’t even properly distracted because instead of being distracted *from* your mind, you are being distracted *by* it. It’s a worst-case scenario of sorts — you neither get anything done, nor escape the endless self-evaluation and justification. That just means you’re doing it wrong, though. You’re failing at it. If you did it right, it would be the perfect escape from yourself. But it’s not working, so you’re failing. Or maybe you succeeded a little bit. You’re not sure. You are still evaluating whether that was a good use of your time. The same evaluation process you use to decide whether you’ve done enough writing, the same tired bullshit from which you were trying to escape in the first place! Let’s face it, you’re not just going to meditate your way out of the problem. If you could, you would have already, and so would everyone else. We would all be enlightened. Maybe you need to go to an ashram or something, find a guru on top of a mountain in the Himalayas. LOL, you’re not gonna do that! You are way too attached to your comforts and daily routines, no matter how dull and unsatisfying they ultimately are. There’s nowhere to run, nowhere to hide, no one to see, nothing to do. You are out of options. There is only one thing in your absolute control, and it’s where you direct your attention. And you have decided that no matter how bleak and pointless the alternatives the one thing about which you are resolute is you are taking the day off from writing. @ d23af4ac:7bf07adb
2025-02-18 17:07:55This is a **test**-note published directly from [Obsidian](https://obsidian.md/) # Heading 1 Some paragraph text [^2] ## Heading 2 Second paragraph text. * List item 1 * List item 2 ```js console.log("Hello world!") ``` ### Json ```json { name: "Alise", age: 45 } ``` >[!SCRUNCHABLE NOTE]- >This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. >This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. >[!DANGER] >This is a "danger" type message. Should be properly formateed. This is a "danger" type message. Should be properly formateed. This is a "danger" type message. Should be properly formateed. This is a "danger" type message. Should be properly formateed. This is a "danger" type message. Should be properly formateed. -- #### Pasted image: ![[Pasted image 20250218120714.png]] >This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote[^1]. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. - [x] This is a completed task - [ ] This is an uncompleted task - [ ] This is also an uncompleted task >[!QUESTION] >Will this inline code format properly? `console.log('Yo momma so fat she took a spoon to the Super Bown');` Idk... [^1]: Footnotes also supported? Even inside blockquotes? [^2]: Footnote in regular paragraph
@ d23af4ac:7bf07adb
2025-02-18 17:07:55This is a **test**-note published directly from [Obsidian](https://obsidian.md/) # Heading 1 Some paragraph text [^2] ## Heading 2 Second paragraph text. * List item 1 * List item 2 ```js console.log("Hello world!") ``` ### Json ```json { name: "Alise", age: 45 } ``` >[!SCRUNCHABLE NOTE]- >This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. >This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. >[!DANGER] >This is a "danger" type message. Should be properly formateed. This is a "danger" type message. Should be properly formateed. This is a "danger" type message. Should be properly formateed. This is a "danger" type message. Should be properly formateed. This is a "danger" type message. Should be properly formateed. -- #### Pasted image: ![[Pasted image 20250218120714.png]] >This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote[^1]. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. - [x] This is a completed task - [ ] This is an uncompleted task - [ ] This is also an uncompleted task >[!QUESTION] >Will this inline code format properly? `console.log('Yo momma so fat she took a spoon to the Super Bown');` Idk... [^1]: Footnotes also supported? Even inside blockquotes? [^2]: Footnote in regular paragraph @ d360efec:14907b5f
2025-02-18 15:11:58**ภาพรวม BTCUSDT (OKX):** Bitcoin (BTCUSDT) กำลังแสดงความผันผวนอย่างมาก โดยมีสัญญาณที่ขัดแย้งกันระหว่าง Timeframes ต่างๆ แนวโน้มระยะยาว (Day) ยังคงเป็นขาขึ้น แต่ระยะกลาง (4H) และระยะสั้น (15m) แสดงให้เห็นถึงแรงขายและการปรับฐานที่รุนแรง การวิเคราะห์นี้จะเน้นการระบุพื้นที่ที่ Smart Money อาจจะเข้าซื้อหรือขาย (Liquidity Pools) และประเมินความแข็งแกร่งของแนวโน้ม **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):**  * **แนวโน้ม:** ขาขึ้น (Uptrend) *แต่เริ่มอ่อนแรง* * **SMC:** * Higher Highs (HH) และ Higher Lows (HL) *เริ่มไม่ชัดเจน* * Break of Structure (BOS) ด้านบน *แต่เริ่มมีการปรับฐาน* * **Liquidity:** * มี Sellside Liquidity (SSL) อยู่ใต้ Lows ก่อนหน้า (บริเวณ 85,000 - 90,000) * มี Buyside Liquidity (BSL) อยู่เหนือ High เดิม (109,998.9) * **ICT:** * ยังไม่เห็น Order Block หรือ FVG ที่ชัดเจนใน TF Day *ณ ราคาปัจจุบัน* * **EMA:** * ราคา *หลุด* EMA 50 (สีเหลือง) ลงมาแล้ว * EMA 200 (สีขาว) เป็นแนวรับถัดไป * **Money Flow (LuxAlgo):** * แท่งสีแดงยาว แสดงถึงแรงขายที่เข้ามา * **Trend Strength (AlgoAlpha):** *ไม่มีในภาพ* * **Volume Profile:** Volume ค่อนข้างเบาบาง * **แท่งเทียน:** แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย * **แนวรับ:** EMA 200, บริเวณ 85,000 - 90,000 (SSL) * **แนวต้าน:** EMA 50, High เดิม * **สรุป:** แนวโน้มขาขึ้นเริ่มอ่อนแรง, ราคาหลุด EMA 50, Money Flow เป็นลบ, มี SSL ด้านล่าง **(2) TF4H (4 ชั่วโมง):**  * **แนวโน้ม:** ขาลง (Downtrend) *ระยะสั้น* หลังจากราคาหลุด EMA 50 * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) * Break of Structure (BOS) ด้านล่าง * **Liquidity:** * มี SSL อยู่ใต้ Lows ก่อนหน้า (บริเวณ 92,000) * มี BSL อยู่เหนือ Highs ก่อนหน้า (บริเวณ 104,000 - 108,000) * **ICT:** * **Order Block:** ราคาลงมาใกล้ Order Block ขาขึ้น (บริเวณแท่งเทียนสีเขียวก่อนที่จะขึ้น) * **EMA:** * ราคาอยู่ใต้ EMA 50 และ EMA 200 * **Money Flow (LuxAlgo):** * สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย * **Trend Strength (AlgoAlpha):** *ไม่มีในภาพ* * **Volume Profile** Volume ค่อนข้างเบาบาง * **แนวรับ:** Order Block, บริเวณ 92,000 (SSL) * **แนวต้าน:** EMA 50, EMA 200, บริเวณ Highs ก่อนหน้า * **สรุป:** แนวโน้มขาลงระยะสั้น, ราคาลงมาใกล้ Order Block, Money Flow เป็นลบ **(3) TF15 (15 นาที):**  * **แนวโน้ม:** ขาลง (Downtrend) * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) * Break of Structure (BOS) ด้านล่าง * **Liquidity:** * มี SSL อยู่ใต้ Lows ล่าสุด * มี BSL อยู่เหนือ Highs ก่อนหน้า * **ICT:** * **Order Block:** ราคาลงมาใกล้ Oder Block * **EMA:** * EMA 50 และ EMA 200 เป็นแนวต้าน * **Money Flow (LuxAlgo):** * สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย * **Trend Strength (AlgoAlpha):** * เป็นสีแดง แสดงถึงเเนวโน้มขาลง * **Volume Profile:** * Volume ค่อนข้างเบาบาง * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA 50, EMA 200, บริเวณ Highs ก่อนหน้า * **สรุป:** แนวโน้มขาลง, แรงขายมีอิทธิพล, ใกล้แนวรับ **สรุปภาพรวมและกลยุทธ์ (BTCUSDT):** * **แนวโน้มหลัก (Day):** ขาขึ้น (อ่อนแรง) * **แนวโน้มรอง (4H):** ขาลง (ระยะสั้น) * **แนวโน้มระยะสั้น (15m):** ขาลง * **Liquidity:** * Day: SSL (85,000-90,000), BSL (เหนือ 109,998.9) * 4H: SSL (92,000), BSL (104,000-108,000) * 15m: SSL (ใต้ Lows), BSL (เหนือ Highs) * **Money Flow:** Day เริ่มเป็นลบ, 4H เป็นลบ, 15m เป็นลบ * **Trend Strength** 15 m : ขาลง * **กลยุทธ์:** 1. **Wait & See (ดีที่สุด):** รอความชัดเจน 2. **Short (เสี่ยง):** ถ้าไม่สามารถ Breakout EMA/แนวต้านใน TF ใดๆ ได้ 3. **ไม่แนะนำให้ Buy:** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจน **คำแนะนำ:** * **ความขัดแย้งของ Timeframes:** ชัดเจน * **Money Flow:** เป็นลบในทุก Timeframes * **ระวัง SSL:** Smart Money อาจจะลากราคาลงไปกิน Stop Loss * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด** **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
@ d360efec:14907b5f
2025-02-18 15:11:58**ภาพรวม BTCUSDT (OKX):** Bitcoin (BTCUSDT) กำลังแสดงความผันผวนอย่างมาก โดยมีสัญญาณที่ขัดแย้งกันระหว่าง Timeframes ต่างๆ แนวโน้มระยะยาว (Day) ยังคงเป็นขาขึ้น แต่ระยะกลาง (4H) และระยะสั้น (15m) แสดงให้เห็นถึงแรงขายและการปรับฐานที่รุนแรง การวิเคราะห์นี้จะเน้นการระบุพื้นที่ที่ Smart Money อาจจะเข้าซื้อหรือขาย (Liquidity Pools) และประเมินความแข็งแกร่งของแนวโน้ม **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):**  * **แนวโน้ม:** ขาขึ้น (Uptrend) *แต่เริ่มอ่อนแรง* * **SMC:** * Higher Highs (HH) และ Higher Lows (HL) *เริ่มไม่ชัดเจน* * Break of Structure (BOS) ด้านบน *แต่เริ่มมีการปรับฐาน* * **Liquidity:** * มี Sellside Liquidity (SSL) อยู่ใต้ Lows ก่อนหน้า (บริเวณ 85,000 - 90,000) * มี Buyside Liquidity (BSL) อยู่เหนือ High เดิม (109,998.9) * **ICT:** * ยังไม่เห็น Order Block หรือ FVG ที่ชัดเจนใน TF Day *ณ ราคาปัจจุบัน* * **EMA:** * ราคา *หลุด* EMA 50 (สีเหลือง) ลงมาแล้ว * EMA 200 (สีขาว) เป็นแนวรับถัดไป * **Money Flow (LuxAlgo):** * แท่งสีแดงยาว แสดงถึงแรงขายที่เข้ามา * **Trend Strength (AlgoAlpha):** *ไม่มีในภาพ* * **Volume Profile:** Volume ค่อนข้างเบาบาง * **แท่งเทียน:** แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย * **แนวรับ:** EMA 200, บริเวณ 85,000 - 90,000 (SSL) * **แนวต้าน:** EMA 50, High เดิม * **สรุป:** แนวโน้มขาขึ้นเริ่มอ่อนแรง, ราคาหลุด EMA 50, Money Flow เป็นลบ, มี SSL ด้านล่าง **(2) TF4H (4 ชั่วโมง):**  * **แนวโน้ม:** ขาลง (Downtrend) *ระยะสั้น* หลังจากราคาหลุด EMA 50 * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) * Break of Structure (BOS) ด้านล่าง * **Liquidity:** * มี SSL อยู่ใต้ Lows ก่อนหน้า (บริเวณ 92,000) * มี BSL อยู่เหนือ Highs ก่อนหน้า (บริเวณ 104,000 - 108,000) * **ICT:** * **Order Block:** ราคาลงมาใกล้ Order Block ขาขึ้น (บริเวณแท่งเทียนสีเขียวก่อนที่จะขึ้น) * **EMA:** * ราคาอยู่ใต้ EMA 50 และ EMA 200 * **Money Flow (LuxAlgo):** * สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย * **Trend Strength (AlgoAlpha):** *ไม่มีในภาพ* * **Volume Profile** Volume ค่อนข้างเบาบาง * **แนวรับ:** Order Block, บริเวณ 92,000 (SSL) * **แนวต้าน:** EMA 50, EMA 200, บริเวณ Highs ก่อนหน้า * **สรุป:** แนวโน้มขาลงระยะสั้น, ราคาลงมาใกล้ Order Block, Money Flow เป็นลบ **(3) TF15 (15 นาที):**  * **แนวโน้ม:** ขาลง (Downtrend) * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) * Break of Structure (BOS) ด้านล่าง * **Liquidity:** * มี SSL อยู่ใต้ Lows ล่าสุด * มี BSL อยู่เหนือ Highs ก่อนหน้า * **ICT:** * **Order Block:** ราคาลงมาใกล้ Oder Block * **EMA:** * EMA 50 และ EMA 200 เป็นแนวต้าน * **Money Flow (LuxAlgo):** * สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย * **Trend Strength (AlgoAlpha):** * เป็นสีแดง แสดงถึงเเนวโน้มขาลง * **Volume Profile:** * Volume ค่อนข้างเบาบาง * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA 50, EMA 200, บริเวณ Highs ก่อนหน้า * **สรุป:** แนวโน้มขาลง, แรงขายมีอิทธิพล, ใกล้แนวรับ **สรุปภาพรวมและกลยุทธ์ (BTCUSDT):** * **แนวโน้มหลัก (Day):** ขาขึ้น (อ่อนแรง) * **แนวโน้มรอง (4H):** ขาลง (ระยะสั้น) * **แนวโน้มระยะสั้น (15m):** ขาลง * **Liquidity:** * Day: SSL (85,000-90,000), BSL (เหนือ 109,998.9) * 4H: SSL (92,000), BSL (104,000-108,000) * 15m: SSL (ใต้ Lows), BSL (เหนือ Highs) * **Money Flow:** Day เริ่มเป็นลบ, 4H เป็นลบ, 15m เป็นลบ * **Trend Strength** 15 m : ขาลง * **กลยุทธ์:** 1. **Wait & See (ดีที่สุด):** รอความชัดเจน 2. **Short (เสี่ยง):** ถ้าไม่สามารถ Breakout EMA/แนวต้านใน TF ใดๆ ได้ 3. **ไม่แนะนำให้ Buy:** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจน **คำแนะนำ:** * **ความขัดแย้งของ Timeframes:** ชัดเจน * **Money Flow:** เป็นลบในทุก Timeframes * **ระวัง SSL:** Smart Money อาจจะลากราคาลงไปกิน Stop Loss * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด** **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ @ d360efec:14907b5f
2025-02-18 13:18:54**นักพนันแห่งเฮรันเทล** **“คณิตศาสตร์” กุญแจเวทมนตร์ นักพนัน และ นักลงทุน** ในนครเฮรันเทล นามกระฉ่อนเลื่องลือในหมู่นักเสี่ยงโชค เมื่อเอ่ยถึง **“การพนัน”** ภาพที่ชาวเมืองมักนึกถึงคือ **“ยาจกข้างถนน”** มิใช่เรื่องแปลกประหลาดอันใด เพราะเป็นที่ร่ำลือกันว่า **จ้าวแห่งหอคอยรัตติกาล** ผู้คุมบ่อนพนัน มักร่ายเวทมนตร์สร้างเกมให้ตนเองได้เปรียบ เพื่อดูดกลืนเงินทองของผู้มาเยือน ดังนั้น การที่สามัญชนจะพิชิตเกมในระยะยาว จึงเป็นดั่งเงามายาที่จับต้องมิได้ กระนั้น ยังมีตำนานกล่าวขานถึงผู้กล้า ที่สามารถสร้างชื่อจาก **“เกมพนัน”** เช่น **เวเนสซา รุสโซ** นักเวทย์มนตร์ผู้ใช้กฎหมายแห่งแดนไกล ใช้เวลายาวนานถึงหกปี ร่ายเวทย์สะสมทรัพย์สินกว่าร้อยล้านเหรียญทอง จากการเล่นเกมไพ่ศักดิ์สิทธิ์ **“โป๊กเกอร์”** หรือแม้แต่ **เอ็ดเวิร์ด โอ. ทอร์ป** จอมปราชญ์ผู้สร้างกำไรถึงสามแสนหกหมื่นเหรียญทอง ภายในเจ็ดราตรี จากการเล่นเกมไพ่มนตรา **“แบล็กแจ็ก”** ด้วยเงินทุนตั้งต้นเพียงสามแสนสามหมื่นเหรียญทอง คิดเป็นอัตราเวทย์ตอบแทนร้อยสิบส่วน! เหล่าจอมยุทธ์เหล่านี้ มิได้อาศัยเพียงโชคช่วยชั่วครั้งชั่วคราวแล้วเลือนหาย แต่พวกเขากลับสามารถร่ายเวทย์สร้างผลตอบแทนระยะยาว จนเรียกได้ว่า ใช้ **“หอคอยรัตติกาล”** เป็นแหล่งเสบียงเลี้ยงชีพ โดยกุญแจเวทย์ที่บุคคลเหล่านี้ใช้ ก็คือ **“คณิตศาสตร์”** เหตุใด **“คณิตศาสตร์”** จึงช่วยให้ผู้คนเอาชนะ **“การพนัน”** ได้? และนอกจาก **“การพนัน”** แล้ว **“คณิตศาสตร์”** ยังสามารถประยุกต์ใช้กับสิ่งใดได้อีก? **นักเล่าเรื่องแห่งเฮรันเทล** จักไขปริศนาให้ฟัง เบื้องต้น ขอให้ท่านลองพิจารณาตนเอง ว่าเคยประสบพบพานเหตุการณ์เหล่านี้หรือไม่: - ตั้งมั่นว่า จักเสี่ยงโชคให้ได้กำไรเพียงเล็กน้อย แล้วจักหยุดพัก - แต่หากพลาดท่าเสียที จักจำกัดการสูญเสียให้เท่าทุนเดิมที่ตั้งไว้ - ครั้นเมื่อเวทมนตร์เข้าข้าง ได้กำไรมาแล้ว กลับโลภโมโทสัน อยากได้เพิ่มอีกนิด จึงร่ายเวทย์ต่อ - ทว่ากำไรเริ่มร่อยหรอ จนเหลือเพียงทุนเดิม สุดท้ายทุนที่ตั้งไว้คราแรกก็มลายสิ้น - จำต้องหาเงินทองมาลงเพิ่ม หวังทวงทุนคืน และพบว่าต้องสูญเสียเงินก้อนนั้นไปในห้วงเวลาต่อมา ลำดับเหตุการณ์ดังกล่าว เรียกได้ว่าเป็น **“วงจรอุบาทว์”** สำหรับนักพนันมากมายในเฮรันเทล ปริศนาที่ตามมาก็คือ เหตุใด **“วงจรอุบาทว์”** นี้จึงเกิดขึ้นซ้ำแล้วซ้ำเล่า? ส่วนหนึ่ง ย่อมเป็นเพราะอารมณ์อันแปรปรวนในการเสี่ยงโชคของแต่ละคน แต่อีกส่วนที่สำคัญยิ่งกว่า ต้องกล่าวว่าเป็นผลจาก **“กลไกต้องสาป”** ของจ้าวแห่งหอคอยรัตติกาล ซึ่งต้องกล่าวว่า เหล่าเจ้าของหอคอยรัตติกาลนั้น จักใช้หลักการทำนองเดียวกับ **“สมาคมพ่อค้าผู้พิทักษ์”** คือจักเก็บเงินทองจากชนจำนวนมาก เพื่อนำมาจ่ายให้กับชนเพียงหยิบมือ เพื่อล่อลวงให้ชนทั้งหลายเสี่ยงโชคต่อไป หรือทำให้เหล่านักพนันหวังว่า จักเป็นผู้โชคดีเฉกเช่นพวกเขาบ้าง แม้จะมีผู้โชคดีที่สามารถได้กำไรในเบื้องต้น แต่ในบั้นปลายก็จักพ่ายแพ้อยู่ดี ซึ่งเป็นไปตาม **“กฎแห่งจำนวนมหาศาล”** เพราะจ้าวแห่งหอคอยรัตติกาลนั้น ได้คำนวณและออกแบบระบบเกมที่ตนเองได้เปรียบในระยะยาวแล้ว จากตำนานนี้ ย่อมประจักษ์ชัดว่า แม้การพนันจักเป็นเรื่องของดวงชะตา แต่ก็ถูกรังสรรค์ขึ้นจากการคำนวณทางคณิตศาสตร์ ดังนั้น หากปรารถนาจะหาหนทางเอาชนะจ้าวแห่งหอคอยรัตติกาล ก็จำต้องเข้าใจ **“คณิตศาสตร์”** เสียก่อน ทีนี้ จงเงี่ยหูฟัง แล้วท่านจักได้ยินข้าไขปริศนา: **๑. ปริศนาแห่ง “กำไรคาดหวัง”** สำหรับการแสวงหา **“เกมเสี่ยงทาย”** ที่ควรค่าแก่การเล่น หรือการเสี่ยง สิ่งแรกที่นักพนันพึงกระทำคือ **“การประเมินกำไรคาดหวัง”** หรือ **“เวทคำนวณอนาคต”** **“กำไรคาดหวัง”** ถูกคิดค้นโดย **คริสเตียน ฮอยเกนส์** นักปราชญ์เวทย์ชาวดัตช์ เพื่อประเมินว่าเกมพนันแบบใดควรค่าแก่การเล่น ซึ่งมิใช่เพียงแค่การประเมินโอกาสแห่งชัยชนะเท่านั้น แต่ต้องคิดรวมขนาดของเงินเดิมพันไปด้วย โดยสูตรเวทย์คือ: **กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้)** ดังนั้น หากปรารถนาจะสะสม **“ทองคำมายา”** ในระยะยาว จงเลือกเกมที่มี **“กำไรคาดหวัง”** เป็นบวก แต่หากพลาดพลั้งเข้าไปเล่นเกมที่ **“กำไรคาดหวัง”** เป็นลบ และบังเอิญว่าโชคชะตาเล่นตลกให้ได้เงินทองมาครอง พึงละทิ้งเกมนั้นเสียโดยพลัน เพราะท้ายที่สุดหากยังคงเล่นต่อไป ผู้อับโชคผู้นั้นก็คือตัวท่านเอง อย่างไรก็ตาม โดยธรรมดาแล้ว **“กำไรคาดหวัง”** ของเกมพนันที่มีเจ้ามือมักจักติดลบ จึงเป็นเรื่องยากยิ่งที่จะเอาชนะได้ เฉกเช่นตัวอย่างที่เราเห็น คือเกมในบ่อนพนัน หรือแม้แต่ **“สลากกินแบ่งรัฐบาล”** ก็ล้วนเป็นเกมที่มี **“กำไรคาดหวัง”** ติดลบทั้งสิ้น นอกจาก **“กำไรคาดหวัง”** จักถูกใช้กับการพนันได้แล้ว หลักเวทย์ **“คณิตศาสตร์”** ก็ยังสามารถประยุกต์ใช้กับการลงทุนได้ไม่แตกต่างกัน ตัวอย่างเช่น หากท่านเก็บสถิติข้อมูลการลงทุนของตนเอง แล้วพบว่ามีเพียงสามสิบส่วนร้อยเท่านั้น ที่ท่านซื้อ **“ศิลาแห่งโชค”** แล้วสร้างผลตอบแทนเป็นบวก แต่ท่านยังคงปรารถนาความสำเร็จในการลงทุน ก็จงจำกัดการขาดทุนแต่ละคราให้น้อยเข้าไว้ เช่น -๕% และปล่อยให้มีกำไรในแต่ละคราที่ลงทุน เช่น อย่างน้อย ๒๐% ซึ่งจากการใช้กลยุทธ์นี้ ท่านจักมี **“กำไรคาดหวัง”** = (๒๐% x ๐.๓) + (-๕% x ๐.๗) = ๒.๕% จักเห็นได้ว่า แม้ท่านจักมีจำนวนคราที่ขาดทุนบ่อยครั้ง แต่ก็ยังสามารถสร้างกำไรได้ หากคราที่กำไรนั้น สามารถทำเงินทองเป็นจำนวนมากได้ **๒. ปริศนาแห่ง “การบริหารหน้าตัก” หรือ “การบริหารเงินทุน”** แม้ว่าท่านจักรับรู้ **“กำไรคาดหวัง”** แล้ว แต่หากท่านเผชิญหน้ากับการขาดทุนต่อเนื่องกัน ท่านก็อาจหมดเนื้อหมดตัวก่อนถึงคราที่จะกอบโกยเงินทองจากคราที่กำไร วิธีคลายปมปริศนานี้ก็คือ การมิลงเงินทองทั้งหมดของท่านในการลงทุนเพียงคราเดียว ซึ่งนอกจากการกระจายความเสี่ยงในการลงทุนหลาย **“ศิลาแห่งโชค”** หรือหลาย **“เกมเสี่ยงทาย”** แล้ว ท่านอาจกำหนดขนาดของการลงทุนแต่ละคราให้มิมากเกินไป แบบง่าย ๆ เช่น มิเกิน ๑๐% ของเงินลงทุนทั้งหมด หรือท่านอาจคำนวณขนาดของการลงทุนแต่ละคราด้วยสูตรทางคณิตศาสตร์ เช่น สูตร **“การขาดทุนสูงสุดที่ท่านรับได้ (Value at Risk)”** หรือ สูตร **“ขนาดเดิมพันที่เหมาะสม (Kelly Formula)”** **๓. ปริศนาแห่ง “อคติ”** ในวงการพนัน มักมีอคติหนึ่งที่บังเกิดบ่อยครั้งกับผู้คน คือ **“Gambler's Fallacy”** หรือ **“ความเชื่อผิด ๆ แห่งนักพนัน”** ว่าหากเหตุการณ์หนึ่งบังเกิดบ่อยครั้งกว่าปรกติในช่วงเวลาหนึ่ง ๆ เหตุการณ์นั้นจักบังเกิดบ่อยครั้งน้อยลงในอนาคต ทั้ง ๆ ที่เหตุการณ์เหล่านั้นเป็นอิสระจากกันในทางสถิติ ยกตัวอย่างเช่น หากโยนเหรียญมนตราออกหัวไปแล้วสามครา ในคราที่สี่ หลายคนอาจคิดว่าโอกาสออกก้อยมากกว่าหัว แม้ว่าการโยนเหรียญแต่ละคราจะมิได้ส่งผลอันใดต่อกันเลย (จะโยนกี่ครา โอกาสหัวหรือก้อย ก็คือ ๕๐:๕๐ อยู่ยั่งยืน) หรือแม้กระทั่ง **“สลากกินแบ่งรัฐบาล”** มีหลายคนที่ซื้อเลขซ้ำกัน เพื่อหวังว่าจะถูกในงวดต่อ ๆ ไป ในวงการการลงทุน ก็มีลักษณะที่คล้ายคลึงกัน เช่น หาก **“ศิลาแห่งโชค A”** ราคาตกต่ำลงมาห้าครา บางคนอาจคิดว่าในคราที่หก ราคาของมันจักต้องเด้งขึ้นมา ซึ่งในความเป็นจริง หาได้เป็นเช่นนั้นเสมอไป จักเห็นได้ว่า แท้จริงแล้ว ไม่ว่าจักเป็น **“เกมเสี่ยงทายแห่งโชคชะตา”** หรือ **“การผจญภัยในตลาดทุน”** หากท่านมีความเข้าใจ และนำ **“คณิตศาสตร์”** เข้ามาเป็นรากฐาน มันก็อาจนำพาตัวท่านเอง ไปสู่จุดที่ได้เปรียบในเกมนั้น ได้เฉกเช่นกัน.. **สูตรเวทย์มนตร์ที่ปรากฏในตำนาน:** * **กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้)** **คำเตือนจากนักเล่าเรื่องแห่งเฮรันเทล:** "พึงระลึกไว้เสมอว่า โชคชะตาเป็นสิ่งที่คาดเดาได้ยาก แม้เวทมนตร์คณิตศาสตร์จักช่วยนำทาง แต่ท้ายที่สุดแล้ว ความสำเร็จยังคงขึ้นอยู่กับการตัดสินใจและสติปัญญาของท่านเอง" หวังว่าตำนานบทนี้จักเป็นประโยชน์แก่ท่านนะคะ
@ d360efec:14907b5f
2025-02-18 13:18:54**นักพนันแห่งเฮรันเทล** **“คณิตศาสตร์” กุญแจเวทมนตร์ นักพนัน และ นักลงทุน** ในนครเฮรันเทล นามกระฉ่อนเลื่องลือในหมู่นักเสี่ยงโชค เมื่อเอ่ยถึง **“การพนัน”** ภาพที่ชาวเมืองมักนึกถึงคือ **“ยาจกข้างถนน”** มิใช่เรื่องแปลกประหลาดอันใด เพราะเป็นที่ร่ำลือกันว่า **จ้าวแห่งหอคอยรัตติกาล** ผู้คุมบ่อนพนัน มักร่ายเวทมนตร์สร้างเกมให้ตนเองได้เปรียบ เพื่อดูดกลืนเงินทองของผู้มาเยือน ดังนั้น การที่สามัญชนจะพิชิตเกมในระยะยาว จึงเป็นดั่งเงามายาที่จับต้องมิได้ กระนั้น ยังมีตำนานกล่าวขานถึงผู้กล้า ที่สามารถสร้างชื่อจาก **“เกมพนัน”** เช่น **เวเนสซา รุสโซ** นักเวทย์มนตร์ผู้ใช้กฎหมายแห่งแดนไกล ใช้เวลายาวนานถึงหกปี ร่ายเวทย์สะสมทรัพย์สินกว่าร้อยล้านเหรียญทอง จากการเล่นเกมไพ่ศักดิ์สิทธิ์ **“โป๊กเกอร์”** หรือแม้แต่ **เอ็ดเวิร์ด โอ. ทอร์ป** จอมปราชญ์ผู้สร้างกำไรถึงสามแสนหกหมื่นเหรียญทอง ภายในเจ็ดราตรี จากการเล่นเกมไพ่มนตรา **“แบล็กแจ็ก”** ด้วยเงินทุนตั้งต้นเพียงสามแสนสามหมื่นเหรียญทอง คิดเป็นอัตราเวทย์ตอบแทนร้อยสิบส่วน! เหล่าจอมยุทธ์เหล่านี้ มิได้อาศัยเพียงโชคช่วยชั่วครั้งชั่วคราวแล้วเลือนหาย แต่พวกเขากลับสามารถร่ายเวทย์สร้างผลตอบแทนระยะยาว จนเรียกได้ว่า ใช้ **“หอคอยรัตติกาล”** เป็นแหล่งเสบียงเลี้ยงชีพ โดยกุญแจเวทย์ที่บุคคลเหล่านี้ใช้ ก็คือ **“คณิตศาสตร์”** เหตุใด **“คณิตศาสตร์”** จึงช่วยให้ผู้คนเอาชนะ **“การพนัน”** ได้? และนอกจาก **“การพนัน”** แล้ว **“คณิตศาสตร์”** ยังสามารถประยุกต์ใช้กับสิ่งใดได้อีก? **นักเล่าเรื่องแห่งเฮรันเทล** จักไขปริศนาให้ฟัง เบื้องต้น ขอให้ท่านลองพิจารณาตนเอง ว่าเคยประสบพบพานเหตุการณ์เหล่านี้หรือไม่: - ตั้งมั่นว่า จักเสี่ยงโชคให้ได้กำไรเพียงเล็กน้อย แล้วจักหยุดพัก - แต่หากพลาดท่าเสียที จักจำกัดการสูญเสียให้เท่าทุนเดิมที่ตั้งไว้ - ครั้นเมื่อเวทมนตร์เข้าข้าง ได้กำไรมาแล้ว กลับโลภโมโทสัน อยากได้เพิ่มอีกนิด จึงร่ายเวทย์ต่อ - ทว่ากำไรเริ่มร่อยหรอ จนเหลือเพียงทุนเดิม สุดท้ายทุนที่ตั้งไว้คราแรกก็มลายสิ้น - จำต้องหาเงินทองมาลงเพิ่ม หวังทวงทุนคืน และพบว่าต้องสูญเสียเงินก้อนนั้นไปในห้วงเวลาต่อมา ลำดับเหตุการณ์ดังกล่าว เรียกได้ว่าเป็น **“วงจรอุบาทว์”** สำหรับนักพนันมากมายในเฮรันเทล ปริศนาที่ตามมาก็คือ เหตุใด **“วงจรอุบาทว์”** นี้จึงเกิดขึ้นซ้ำแล้วซ้ำเล่า? ส่วนหนึ่ง ย่อมเป็นเพราะอารมณ์อันแปรปรวนในการเสี่ยงโชคของแต่ละคน แต่อีกส่วนที่สำคัญยิ่งกว่า ต้องกล่าวว่าเป็นผลจาก **“กลไกต้องสาป”** ของจ้าวแห่งหอคอยรัตติกาล ซึ่งต้องกล่าวว่า เหล่าเจ้าของหอคอยรัตติกาลนั้น จักใช้หลักการทำนองเดียวกับ **“สมาคมพ่อค้าผู้พิทักษ์”** คือจักเก็บเงินทองจากชนจำนวนมาก เพื่อนำมาจ่ายให้กับชนเพียงหยิบมือ เพื่อล่อลวงให้ชนทั้งหลายเสี่ยงโชคต่อไป หรือทำให้เหล่านักพนันหวังว่า จักเป็นผู้โชคดีเฉกเช่นพวกเขาบ้าง แม้จะมีผู้โชคดีที่สามารถได้กำไรในเบื้องต้น แต่ในบั้นปลายก็จักพ่ายแพ้อยู่ดี ซึ่งเป็นไปตาม **“กฎแห่งจำนวนมหาศาล”** เพราะจ้าวแห่งหอคอยรัตติกาลนั้น ได้คำนวณและออกแบบระบบเกมที่ตนเองได้เปรียบในระยะยาวแล้ว จากตำนานนี้ ย่อมประจักษ์ชัดว่า แม้การพนันจักเป็นเรื่องของดวงชะตา แต่ก็ถูกรังสรรค์ขึ้นจากการคำนวณทางคณิตศาสตร์ ดังนั้น หากปรารถนาจะหาหนทางเอาชนะจ้าวแห่งหอคอยรัตติกาล ก็จำต้องเข้าใจ **“คณิตศาสตร์”** เสียก่อน ทีนี้ จงเงี่ยหูฟัง แล้วท่านจักได้ยินข้าไขปริศนา: **๑. ปริศนาแห่ง “กำไรคาดหวัง”** สำหรับการแสวงหา **“เกมเสี่ยงทาย”** ที่ควรค่าแก่การเล่น หรือการเสี่ยง สิ่งแรกที่นักพนันพึงกระทำคือ **“การประเมินกำไรคาดหวัง”** หรือ **“เวทคำนวณอนาคต”** **“กำไรคาดหวัง”** ถูกคิดค้นโดย **คริสเตียน ฮอยเกนส์** นักปราชญ์เวทย์ชาวดัตช์ เพื่อประเมินว่าเกมพนันแบบใดควรค่าแก่การเล่น ซึ่งมิใช่เพียงแค่การประเมินโอกาสแห่งชัยชนะเท่านั้น แต่ต้องคิดรวมขนาดของเงินเดิมพันไปด้วย โดยสูตรเวทย์คือ: **กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้)** ดังนั้น หากปรารถนาจะสะสม **“ทองคำมายา”** ในระยะยาว จงเลือกเกมที่มี **“กำไรคาดหวัง”** เป็นบวก แต่หากพลาดพลั้งเข้าไปเล่นเกมที่ **“กำไรคาดหวัง”** เป็นลบ และบังเอิญว่าโชคชะตาเล่นตลกให้ได้เงินทองมาครอง พึงละทิ้งเกมนั้นเสียโดยพลัน เพราะท้ายที่สุดหากยังคงเล่นต่อไป ผู้อับโชคผู้นั้นก็คือตัวท่านเอง อย่างไรก็ตาม โดยธรรมดาแล้ว **“กำไรคาดหวัง”** ของเกมพนันที่มีเจ้ามือมักจักติดลบ จึงเป็นเรื่องยากยิ่งที่จะเอาชนะได้ เฉกเช่นตัวอย่างที่เราเห็น คือเกมในบ่อนพนัน หรือแม้แต่ **“สลากกินแบ่งรัฐบาล”** ก็ล้วนเป็นเกมที่มี **“กำไรคาดหวัง”** ติดลบทั้งสิ้น นอกจาก **“กำไรคาดหวัง”** จักถูกใช้กับการพนันได้แล้ว หลักเวทย์ **“คณิตศาสตร์”** ก็ยังสามารถประยุกต์ใช้กับการลงทุนได้ไม่แตกต่างกัน ตัวอย่างเช่น หากท่านเก็บสถิติข้อมูลการลงทุนของตนเอง แล้วพบว่ามีเพียงสามสิบส่วนร้อยเท่านั้น ที่ท่านซื้อ **“ศิลาแห่งโชค”** แล้วสร้างผลตอบแทนเป็นบวก แต่ท่านยังคงปรารถนาความสำเร็จในการลงทุน ก็จงจำกัดการขาดทุนแต่ละคราให้น้อยเข้าไว้ เช่น -๕% และปล่อยให้มีกำไรในแต่ละคราที่ลงทุน เช่น อย่างน้อย ๒๐% ซึ่งจากการใช้กลยุทธ์นี้ ท่านจักมี **“กำไรคาดหวัง”** = (๒๐% x ๐.๓) + (-๕% x ๐.๗) = ๒.๕% จักเห็นได้ว่า แม้ท่านจักมีจำนวนคราที่ขาดทุนบ่อยครั้ง แต่ก็ยังสามารถสร้างกำไรได้ หากคราที่กำไรนั้น สามารถทำเงินทองเป็นจำนวนมากได้ **๒. ปริศนาแห่ง “การบริหารหน้าตัก” หรือ “การบริหารเงินทุน”** แม้ว่าท่านจักรับรู้ **“กำไรคาดหวัง”** แล้ว แต่หากท่านเผชิญหน้ากับการขาดทุนต่อเนื่องกัน ท่านก็อาจหมดเนื้อหมดตัวก่อนถึงคราที่จะกอบโกยเงินทองจากคราที่กำไร วิธีคลายปมปริศนานี้ก็คือ การมิลงเงินทองทั้งหมดของท่านในการลงทุนเพียงคราเดียว ซึ่งนอกจากการกระจายความเสี่ยงในการลงทุนหลาย **“ศิลาแห่งโชค”** หรือหลาย **“เกมเสี่ยงทาย”** แล้ว ท่านอาจกำหนดขนาดของการลงทุนแต่ละคราให้มิมากเกินไป แบบง่าย ๆ เช่น มิเกิน ๑๐% ของเงินลงทุนทั้งหมด หรือท่านอาจคำนวณขนาดของการลงทุนแต่ละคราด้วยสูตรทางคณิตศาสตร์ เช่น สูตร **“การขาดทุนสูงสุดที่ท่านรับได้ (Value at Risk)”** หรือ สูตร **“ขนาดเดิมพันที่เหมาะสม (Kelly Formula)”** **๓. ปริศนาแห่ง “อคติ”** ในวงการพนัน มักมีอคติหนึ่งที่บังเกิดบ่อยครั้งกับผู้คน คือ **“Gambler's Fallacy”** หรือ **“ความเชื่อผิด ๆ แห่งนักพนัน”** ว่าหากเหตุการณ์หนึ่งบังเกิดบ่อยครั้งกว่าปรกติในช่วงเวลาหนึ่ง ๆ เหตุการณ์นั้นจักบังเกิดบ่อยครั้งน้อยลงในอนาคต ทั้ง ๆ ที่เหตุการณ์เหล่านั้นเป็นอิสระจากกันในทางสถิติ ยกตัวอย่างเช่น หากโยนเหรียญมนตราออกหัวไปแล้วสามครา ในคราที่สี่ หลายคนอาจคิดว่าโอกาสออกก้อยมากกว่าหัว แม้ว่าการโยนเหรียญแต่ละคราจะมิได้ส่งผลอันใดต่อกันเลย (จะโยนกี่ครา โอกาสหัวหรือก้อย ก็คือ ๕๐:๕๐ อยู่ยั่งยืน) หรือแม้กระทั่ง **“สลากกินแบ่งรัฐบาล”** มีหลายคนที่ซื้อเลขซ้ำกัน เพื่อหวังว่าจะถูกในงวดต่อ ๆ ไป ในวงการการลงทุน ก็มีลักษณะที่คล้ายคลึงกัน เช่น หาก **“ศิลาแห่งโชค A”** ราคาตกต่ำลงมาห้าครา บางคนอาจคิดว่าในคราที่หก ราคาของมันจักต้องเด้งขึ้นมา ซึ่งในความเป็นจริง หาได้เป็นเช่นนั้นเสมอไป จักเห็นได้ว่า แท้จริงแล้ว ไม่ว่าจักเป็น **“เกมเสี่ยงทายแห่งโชคชะตา”** หรือ **“การผจญภัยในตลาดทุน”** หากท่านมีความเข้าใจ และนำ **“คณิตศาสตร์”** เข้ามาเป็นรากฐาน มันก็อาจนำพาตัวท่านเอง ไปสู่จุดที่ได้เปรียบในเกมนั้น ได้เฉกเช่นกัน.. **สูตรเวทย์มนตร์ที่ปรากฏในตำนาน:** * **กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้)** **คำเตือนจากนักเล่าเรื่องแห่งเฮรันเทล:** "พึงระลึกไว้เสมอว่า โชคชะตาเป็นสิ่งที่คาดเดาได้ยาก แม้เวทมนตร์คณิตศาสตร์จักช่วยนำทาง แต่ท้ายที่สุดแล้ว ความสำเร็จยังคงขึ้นอยู่กับการตัดสินใจและสติปัญญาของท่านเอง" หวังว่าตำนานบทนี้จักเป็นประโยชน์แก่ท่านนะคะ @ fa805c81:344bed3c
2025-02-18 11:41:15 **" เจอหมีให้แกล้งตาย แต่ถ้าเจอหมีบ่อย ๆ คงเป็นบ้าไปซะก่อน "** มีวันนึง ในยุคดึกดำบรรพ์ เด็กชายซาโตชิผู้รักการเดินป่าเป็นชีวิตจิตใจ แต่วันนี้ต่างออกไปเพราะเขาเห็น หมี ตัวใหญ่ ยืนจังก้าต่อหน้าเขา " เวรกรรมแล้วไง " ไม่ใช่แค่ซาโตชิที่คิดแบบนี้ เป็นผม หรือคุณ ก็คิดแบบนี้กันหมดนั่นแหละ !! *ม่านตาเบิกโพลงขยาย ยับยั้งการหลั่งน้ำลาย หลอดลมขยายตัว หัวใจเต้นรัวสั่น กลั้นปัสสาวะ* "ระบบซิมพาเทติก" ที่ซาโตชิต้องท่องจำในชั้นเรียน เมื่ออยู่ในสถานการ์ณจริงที่ต้อง " สู้หรือหนี " " เกี่ยวข้องกับความเป็นความตาย " ไม่มีความจำเป็นต้องท่องเลย รับรู้เองได้หมดในเวลานั้น ทำยังไงดีนะ ซาโตชิ ...... ไม่ว่าซาโตชิจะทำอย่างไร ไม่ว่าซาโตชิจะทำตามตัวอย่างของระบบซิมพาเทติกที่บอกว่าคนสามารถยกตู้เย็นได้ทั้งที่ไม่เคยยกมาก่อน ถ้าซาโตชิเลือกที่จะ " สู้ " โดยการยกหมีโยนลงหน้าผา !!  หรือซาโตชิเลือกที่จะ " หนี " โดยการสับตีนแตก !!  ในการกระทำสองอย่างนี้ มีบางสิ่งที่เหมือนกัน **" เสียพลังงานอย่างมาก " นี่คือสิ่งที่เหมือนกัน** ระบบซิมพาเทติกคูลดาวน์... หยุดทำงาน ซาโตชิเดินป่าต่ออย่างสบายใจ หรืออาจจะกลับบ้าน ก็แล้วแต่ " อา..มัน**จบ**แล้วสินะ " ซาโตชิพูดขึ้น จากยุคดึกดำบรรพ์ สู่ยุคปัจจุบัน เชื้อสายของซาโตชิ ไม่จำเป็นต้องเข้าป่าไปหาของป่า ไปตลาดนัดก็ได้ ตามกลไกตลาดเสรี ไม่มีความจำเป็นที่ต้องลุ้นว่าจะเจอ หมี อีกต่อไปแล้ว สโคปมาอีกนิดดีกว่าจริง ๆ แล้ว ไม่จำเป็นต้องเป็นหมี หรอกครับ อะไรที่ทำให้สมองเราสื่อว่า สิ่งนี้อันตราย ระบบซิมพาเทติกมันก็ทำงาน... แล้วความอันตรายในยุคปัจจุบันคืออะไร ? หมีในยุคปัจจุบัน....กลายพันธ์เป็นอะไร ???? น่าอนิจจาครับ ที่ Scenario นี้ ดวงมาตกที่เชื้อสายของซาโตชิ กลับกลายเป็น**ครอบครัวมีปัญหาครับ** ( อาจจะเพราะอะไรก็ได้ เอาว่าระบบเงินเฟียต เงินเฟ้อทำให้คนเป็นบ้าแล้วกัน ) เด็กคนนี้โตมาในสภาพที่พ่อแม่ไม่รัก พ่อแม่ทะเลาะกันทุกวัน พ่อกับแม่หย่ากัน พ่อติดเหล้า แม่หนีไปมีสามีใหม่ ทุกครั้งที่พ่อแม่ทะเลาะกัน ทุกครั้งที่พ่อติดเหล้าก็อาละวาด บางครั้งนั่งๆนอนๆทำการบ้านอยู่ดี ๆ พ่อก็เปิดประตูห้องมาในสภาพเมาๆ แล้วชวนทะเลาะ วันที่สงบหายไปไหนนะ วันที่สงบ กลับถูกแทนที่ด้วยความเครียด **ความเครียด ที่กระตุ้นให้ซิมพาเทติกทำงาน...** พวกคุณเห็นความต่างอะไรมั้ยครับ ซาโตชิเจอหมี ซิมพาเทติกทำงาน สู้หรือหนีหมี แล้วจบ แต่กับเด็กคนนี้ ในสภาพครอบครัวที่เลวร้าย ซิมพาเทติกก็ทำงาน **แต่เขาหนีก็ไม่ได้ สู้ก็ไม่ได้นะครับ...** เออเอาละซิ ทำยังไงดีล่ะ ความเครียดเข้ามาทุกวันอย่างคาดเดาไม่ได้ ระบบซิมพาเทติกก็ทำงานแทบทุกวัน 1 ในอวัยวะที่ต้องจัดการกับความเครียดและซิมพาเทติก คือต่อมหมวกไตครับ ต่อมหมวกไตชั้นนอก มีหลายฟังชั่น.. 1 ในนั้นคือการสร้าง Cortisol มาสู้กับความเครียด ต่อมหมวกไตชั้นใน มีหน้าที่คือการสร้างอดรีนาลีน มาเพื่อใช้กับระบบซิมพาเทติก " โอ้ย เมื่อยโว้ยยยยยยย " อันนี่ไม่ใช่คำที่เด็กคนนี้พูดอยู่คนเดียวนะครับ ต่อมหมวกไตก็พูด.... ในเมื่ออวัยวะที่ทำให้เรา Handle กับ Stress ได้ มันเมื่อยแล้ว.. เกิดสิ่งที่เรียกว่า " ต่อมหมวกไตล้า " Stress ที่ไม่สามารถคุมได้ เมื่อนั้นเอง ก็จะเกิดโรคหลายอย่าง 1 ในนั้นคือโรคที่เด็กโตมาในครอบครัวมีปัญหามักจะเป็นกัน " โรคซึมเศร้า " คงไม่ต้องพูดว่าโรคนี้แย่ยังไง คนทุกคนน่าจะเข้าใจดี เพราะงั้นใจความสำคัญที่ผมต้องการบอกคือ หมีไม่จำเป็นต้องเกิดจากครอบครัวก็ได้ครับ แต่หมีคือสภาพแวดล้อมที่เราต้องเจอมันทุกวันอย่างเลี่ยงไม่ได้ เป็นหมีที่เลวร้าย หมีที่สู้ก็ไม่ได้ หนีก็ไม่ได้อีก ได้แต่รอระเบิดเวลาว่าต่อมหมวกไตจะล้าตอนไหน หมีอาจมาในรูปแบบ เจ้านายที่ทำงานขี้วีน เพื่อนสนิทที่ท็อคซิค สามีภรรยาที่คอยพ่นพลังงานลบมาเรื่อย ๆ คุณอาจจะคิดว่า เอ้อ ก็ทนได้แหละ นิดๆหน่อยๆ การขัดแย้งมันไม่ดี เกรงใจเขา ไม่หรอกครับ คุณไม่จำเป็นต้องเอาตัวเองไปอยู่กับพลังงานลบแบบนั้น สงสารต่อมหมวกไตตัวเองบ้าง ถ้ามันจะขัดแย้ง ก็ขัดแย้งให้มันจบไปเลย การหาทางออก หาทางแก้ไขในคสพ. เหมือนซาโตชิที่เลือกจะสู้หรือหนีหมีตั้งแต่ตอนนั้น ความเรื้อรังไม่ใช่ทางออกแน่นอน อย่าเป็นหมีในความสัมพันธ์ของใคร
@ fa805c81:344bed3c
2025-02-18 11:41:15 **" เจอหมีให้แกล้งตาย แต่ถ้าเจอหมีบ่อย ๆ คงเป็นบ้าไปซะก่อน "** มีวันนึง ในยุคดึกดำบรรพ์ เด็กชายซาโตชิผู้รักการเดินป่าเป็นชีวิตจิตใจ แต่วันนี้ต่างออกไปเพราะเขาเห็น หมี ตัวใหญ่ ยืนจังก้าต่อหน้าเขา " เวรกรรมแล้วไง " ไม่ใช่แค่ซาโตชิที่คิดแบบนี้ เป็นผม หรือคุณ ก็คิดแบบนี้กันหมดนั่นแหละ !! *ม่านตาเบิกโพลงขยาย ยับยั้งการหลั่งน้ำลาย หลอดลมขยายตัว หัวใจเต้นรัวสั่น กลั้นปัสสาวะ* "ระบบซิมพาเทติก" ที่ซาโตชิต้องท่องจำในชั้นเรียน เมื่ออยู่ในสถานการ์ณจริงที่ต้อง " สู้หรือหนี " " เกี่ยวข้องกับความเป็นความตาย " ไม่มีความจำเป็นต้องท่องเลย รับรู้เองได้หมดในเวลานั้น ทำยังไงดีนะ ซาโตชิ ...... ไม่ว่าซาโตชิจะทำอย่างไร ไม่ว่าซาโตชิจะทำตามตัวอย่างของระบบซิมพาเทติกที่บอกว่าคนสามารถยกตู้เย็นได้ทั้งที่ไม่เคยยกมาก่อน ถ้าซาโตชิเลือกที่จะ " สู้ " โดยการยกหมีโยนลงหน้าผา !!  หรือซาโตชิเลือกที่จะ " หนี " โดยการสับตีนแตก !!  ในการกระทำสองอย่างนี้ มีบางสิ่งที่เหมือนกัน **" เสียพลังงานอย่างมาก " นี่คือสิ่งที่เหมือนกัน** ระบบซิมพาเทติกคูลดาวน์... หยุดทำงาน ซาโตชิเดินป่าต่ออย่างสบายใจ หรืออาจจะกลับบ้าน ก็แล้วแต่ " อา..มัน**จบ**แล้วสินะ " ซาโตชิพูดขึ้น จากยุคดึกดำบรรพ์ สู่ยุคปัจจุบัน เชื้อสายของซาโตชิ ไม่จำเป็นต้องเข้าป่าไปหาของป่า ไปตลาดนัดก็ได้ ตามกลไกตลาดเสรี ไม่มีความจำเป็นที่ต้องลุ้นว่าจะเจอ หมี อีกต่อไปแล้ว สโคปมาอีกนิดดีกว่าจริง ๆ แล้ว ไม่จำเป็นต้องเป็นหมี หรอกครับ อะไรที่ทำให้สมองเราสื่อว่า สิ่งนี้อันตราย ระบบซิมพาเทติกมันก็ทำงาน... แล้วความอันตรายในยุคปัจจุบันคืออะไร ? หมีในยุคปัจจุบัน....กลายพันธ์เป็นอะไร ???? น่าอนิจจาครับ ที่ Scenario นี้ ดวงมาตกที่เชื้อสายของซาโตชิ กลับกลายเป็น**ครอบครัวมีปัญหาครับ** ( อาจจะเพราะอะไรก็ได้ เอาว่าระบบเงินเฟียต เงินเฟ้อทำให้คนเป็นบ้าแล้วกัน ) เด็กคนนี้โตมาในสภาพที่พ่อแม่ไม่รัก พ่อแม่ทะเลาะกันทุกวัน พ่อกับแม่หย่ากัน พ่อติดเหล้า แม่หนีไปมีสามีใหม่ ทุกครั้งที่พ่อแม่ทะเลาะกัน ทุกครั้งที่พ่อติดเหล้าก็อาละวาด บางครั้งนั่งๆนอนๆทำการบ้านอยู่ดี ๆ พ่อก็เปิดประตูห้องมาในสภาพเมาๆ แล้วชวนทะเลาะ วันที่สงบหายไปไหนนะ วันที่สงบ กลับถูกแทนที่ด้วยความเครียด **ความเครียด ที่กระตุ้นให้ซิมพาเทติกทำงาน...** พวกคุณเห็นความต่างอะไรมั้ยครับ ซาโตชิเจอหมี ซิมพาเทติกทำงาน สู้หรือหนีหมี แล้วจบ แต่กับเด็กคนนี้ ในสภาพครอบครัวที่เลวร้าย ซิมพาเทติกก็ทำงาน **แต่เขาหนีก็ไม่ได้ สู้ก็ไม่ได้นะครับ...** เออเอาละซิ ทำยังไงดีล่ะ ความเครียดเข้ามาทุกวันอย่างคาดเดาไม่ได้ ระบบซิมพาเทติกก็ทำงานแทบทุกวัน 1 ในอวัยวะที่ต้องจัดการกับความเครียดและซิมพาเทติก คือต่อมหมวกไตครับ ต่อมหมวกไตชั้นนอก มีหลายฟังชั่น.. 1 ในนั้นคือการสร้าง Cortisol มาสู้กับความเครียด ต่อมหมวกไตชั้นใน มีหน้าที่คือการสร้างอดรีนาลีน มาเพื่อใช้กับระบบซิมพาเทติก " โอ้ย เมื่อยโว้ยยยยยยย " อันนี่ไม่ใช่คำที่เด็กคนนี้พูดอยู่คนเดียวนะครับ ต่อมหมวกไตก็พูด.... ในเมื่ออวัยวะที่ทำให้เรา Handle กับ Stress ได้ มันเมื่อยแล้ว.. เกิดสิ่งที่เรียกว่า " ต่อมหมวกไตล้า " Stress ที่ไม่สามารถคุมได้ เมื่อนั้นเอง ก็จะเกิดโรคหลายอย่าง 1 ในนั้นคือโรคที่เด็กโตมาในครอบครัวมีปัญหามักจะเป็นกัน " โรคซึมเศร้า " คงไม่ต้องพูดว่าโรคนี้แย่ยังไง คนทุกคนน่าจะเข้าใจดี เพราะงั้นใจความสำคัญที่ผมต้องการบอกคือ หมีไม่จำเป็นต้องเกิดจากครอบครัวก็ได้ครับ แต่หมีคือสภาพแวดล้อมที่เราต้องเจอมันทุกวันอย่างเลี่ยงไม่ได้ เป็นหมีที่เลวร้าย หมีที่สู้ก็ไม่ได้ หนีก็ไม่ได้อีก ได้แต่รอระเบิดเวลาว่าต่อมหมวกไตจะล้าตอนไหน หมีอาจมาในรูปแบบ เจ้านายที่ทำงานขี้วีน เพื่อนสนิทที่ท็อคซิค สามีภรรยาที่คอยพ่นพลังงานลบมาเรื่อย ๆ คุณอาจจะคิดว่า เอ้อ ก็ทนได้แหละ นิดๆหน่อยๆ การขัดแย้งมันไม่ดี เกรงใจเขา ไม่หรอกครับ คุณไม่จำเป็นต้องเอาตัวเองไปอยู่กับพลังงานลบแบบนั้น สงสารต่อมหมวกไตตัวเองบ้าง ถ้ามันจะขัดแย้ง ก็ขัดแย้งให้มันจบไปเลย การหาทางออก หาทางแก้ไขในคสพ. เหมือนซาโตชิที่เลือกจะสู้หรือหนีหมีตั้งแต่ตอนนั้น ความเรื้อรังไม่ใช่ทางออกแน่นอน อย่าเป็นหมีในความสัมพันธ์ของใคร @ 3ca99671:689a4ce4
2025-02-18 09:34:11How to avoid internal pressure and anxiety. Constantly forcing yourself to continue something, doubting its value to anyone other than your ego. And then it starts: "What if I use that framework? Maybe I should switch to another language? No, I’ll master that engine over there, and everything will fall into place." But it doesn’t. You don’t master it, it’s not the right language. In short, you’re stuck. The sense of obligation and the justification of inaction tear you apart. I mean, how is it inaction? Inside, there’s constant work going on, fragments of the future product emerge, but something’s missing… Organization? Publicity? Speaking of publicity, I clearly see that it will only intensify the sense of duty and create additional pressure. Which won’t be a creative energy at all, on the contrary, it’s more likely to lead to despair. You need to be 100 percent confident in the success of what you’re doing, so that without society’s approval of the prototype, you can release the product and not regret a single hour spent on it. Now, that’s belief, that’s love. Alright, this is a draft. So, what exactly is missing? Regarding organization: YES, backlogs and the like are necessary, BUT. Maybe the goals were set incorrectly back when I was working on projects. Because everything turned into organizing inaction. Exactly, organizing with the goal of doing nothing. Here’s another thing: think about the gym, for example. It’s the same with products, you need a hub, a shared space, and it’s easier now. Telegram, Discord, itch.io, GitHub, plenty of info and examples. So, what’s holding me back? Is there something stopping me? Maybe it’s worth finding out how others manage their work. (Here, I contradict myself). Obvious things, but they should be spelled out. And it becomes clear that I can’t handle it alone. I need collaborators. Maybe that’s the secret to ensuring the work continues, huh? If you think about releasing a product as the final point of an expedition. And immediately, the meme about how Hunter was packing his car trunk for the trip to Las Vegas comes to mind. A little lyrical digression: "I had two Unity courses under my belt, ninety hours of Unreal Engine tutorials, three textbooks on procedural world generation, a hard drive half full of unfinished shaders, and a whole universe of tools: pixel-art engines, object destruction plugins, buggy C# scripts, low-poly assets laughing at me... and a liter of espresso, buckets of energy drinks, a box of donut coffee from Steam, a pint of sheer stubbornness, and two dozen tokens of 'unique' in-game helmets. Not that all of this was necessary for an indie project, but once you dive into tech experiments, it’s hard to stop. The only thing driving me crazy was neural networks for enemy AI. There’s no creature in the world more helpless, naive, and predictable than a programmer trying to squeeze machine learning into a platformer about a jumping carrot. And I knew for sure that by morning, we’d be diving into that rabbit hole with rakes in hand." To be continued... P.S: ai translation from russian
@ 3ca99671:689a4ce4
2025-02-18 09:34:11How to avoid internal pressure and anxiety. Constantly forcing yourself to continue something, doubting its value to anyone other than your ego. And then it starts: "What if I use that framework? Maybe I should switch to another language? No, I’ll master that engine over there, and everything will fall into place." But it doesn’t. You don’t master it, it’s not the right language. In short, you’re stuck. The sense of obligation and the justification of inaction tear you apart. I mean, how is it inaction? Inside, there’s constant work going on, fragments of the future product emerge, but something’s missing… Organization? Publicity? Speaking of publicity, I clearly see that it will only intensify the sense of duty and create additional pressure. Which won’t be a creative energy at all, on the contrary, it’s more likely to lead to despair. You need to be 100 percent confident in the success of what you’re doing, so that without society’s approval of the prototype, you can release the product and not regret a single hour spent on it. Now, that’s belief, that’s love. Alright, this is a draft. So, what exactly is missing? Regarding organization: YES, backlogs and the like are necessary, BUT. Maybe the goals were set incorrectly back when I was working on projects. Because everything turned into organizing inaction. Exactly, organizing with the goal of doing nothing. Here’s another thing: think about the gym, for example. It’s the same with products, you need a hub, a shared space, and it’s easier now. Telegram, Discord, itch.io, GitHub, plenty of info and examples. So, what’s holding me back? Is there something stopping me? Maybe it’s worth finding out how others manage their work. (Here, I contradict myself). Obvious things, but they should be spelled out. And it becomes clear that I can’t handle it alone. I need collaborators. Maybe that’s the secret to ensuring the work continues, huh? If you think about releasing a product as the final point of an expedition. And immediately, the meme about how Hunter was packing his car trunk for the trip to Las Vegas comes to mind. A little lyrical digression: "I had two Unity courses under my belt, ninety hours of Unreal Engine tutorials, three textbooks on procedural world generation, a hard drive half full of unfinished shaders, and a whole universe of tools: pixel-art engines, object destruction plugins, buggy C# scripts, low-poly assets laughing at me... and a liter of espresso, buckets of energy drinks, a box of donut coffee from Steam, a pint of sheer stubbornness, and two dozen tokens of 'unique' in-game helmets. Not that all of this was necessary for an indie project, but once you dive into tech experiments, it’s hard to stop. The only thing driving me crazy was neural networks for enemy AI. There’s no creature in the world more helpless, naive, and predictable than a programmer trying to squeeze machine learning into a platformer about a jumping carrot. And I knew for sure that by morning, we’d be diving into that rabbit hole with rakes in hand." To be continued... P.S: ai translation from russian @ e7bc35f8:3ed2a7cf
2025-02-18 09:07:03For those who still trust mainstream narratives about war and foreign intervention, the Douma chemical attack story should serve as a wake-up call. The official version of events—that Syrian government forces carried out a chemical attack on civilians in Douma on April 7, 2018—has been thoroughly dismantled by whistleblowers, independent journalists, and even leaked documents from the Organization for the Prohibition of Chemical Weapons (OPCW). Yet, despite [mounting evidence]( https://thegrayzone.com/2018/03/06/media-propaganda-battle-syria-eastern-ghouta/), mainstream media and Western governments continue to push the debunked narrative, using it to justify military interventions and sustain the illusion of moral authority. This article revisits the Douma deception, breaking down how the false flag operation unfolded and how the truth was systematically suppressed. ### A Timeline of the Manufactured Crisis #### April 7, 2018: The Alleged Chemical Attack On this day, as the Syrian Army engaged terrorist insurgents in Douma, [shocking videos surfaced]( https://youtu.be/sYItxxEO3F8) online showing alleged victims of a chemical attack. Without proper investigation, Western leaders seized on the footage as proof of an [atrocity committed]( https://web.archive.org/web/20200304211152/https://eg.usembassy.gov/united-states-assessment-of-the-assad-regimes-chemical-weapons-use/) by the Assad government. Within 24 hours, then-President Donald Trump tweeted about "Animal Assad" and vowed that Russia and Iran would "pay a big price." This swift response echoed past war propaganda, reminiscent of the lies used to justify the invasion of Iraq.  #### April 14, 2018: The Bombing of Syria Begins Less than a week after the alleged attack, the [United States]( https://youtu.be/w43ok0q5G5A), [France, and Britain launched coordinated missile strikes]( https://www.washingtonpost.com/world/national-security/us-launches-missile-strikes-in-syria/2018/04/13/c68e89d0-3f4a-11e8-974f-aacd97698cef_story.html) on Syrian government targets. Shockingly, these airstrikes were carried out before any independent investigation had even begun. Meanwhile, on the same day, OPCW investigators arrived in Syria to examine the supposed chemical attack site. In a grotesque display of arrogance, the West had already punished Syria for a crime that hadn't been proven. #### April 17, 2018: Doubts Emerge Veteran journalist [Robert Fisk visited Douma]( https://www.independent.co.uk/voices/syria-chemical-attack-gas-douma-robert-fisk-ghouta-damascus-a8307726.html) and interviewed a local doctor who revealed that the victims shown in viral videos had actually died from suffocation—not chemical weapons. The doctor described how panic and dust inhalation in underground shelters had led to casualties, but no traces of nerve agents like **sarin** were found. #### July 6, 2018: OPCW’s Initial Report Undermines the Official Story The OPCW released its [interim findings]( https://www.opcw.org/media-centre/news/2018/07/opcw-issues-fact-finding-mission-reports-chemical-weapons-use-allegations), confirming that: > No organophosphorus nerve agents or their degradation products were detected, either in the environmental samples or in plasma samples from the alleged casualties. And while: > Various chlorinated organic chemicals were found in samples from Locations 2 and 4, along with residues of explosive the report makes no mention of the concentrations or levels of those chemicals. In Addition the "Annex 2" (Open Sources) is blank. In Annex 3 where all chemicals are listed, there is no chemical weapon agent listed. Despite this, Western media and politicians continued to push the idea that Syria had used chemical weapons. #### February–March 2019: Whistleblower Confirms Staged Hospital Footage In a stunning revelation, [BBC producer Riam Dalati]( https://youtu.be/fFLRX5ZiEvo) tweeted that the viral hospital scene—depicting victims being hosed down—had been **staged**. This meant that at least part of the so-called evidence was a fabrication. Shortly after, the OPCW issued its [final report]( https://www.opcw.org/sites/default/files/documents/2019/03/s-1731-2019%28e%29.pdf). While it acknowledged a lack of sarin, > No organophosphorous nerve agents, their degradation products or synthesis impurities were detected [...] it is not currently possible to precisely link the cause of the signs and symptoms to a specific chemical it ambiguously suggested that "a toxic chemical containing reactive chlorine" was likely used. This vague wording allowed Western governments to continue their accusations without hard proof. #### May 2019: Leaked OPCW Report Exposes a Cover-Up A [leaked engineering assessment]( https://web.archive.org/web/20190514174330/http://syriapropagandamedia.org/wp-content/uploads/2019/05/Engineering-assessment-of-two-cylinders-observed-at-the-Douma-incident-27-February-2019-1.pdf) by an OPCW sub-team completely contradicted the official findings. It concluded that the two cylinders found at the scene **were likely manually placed rather than dropped from aircraft**—suggesting [the incident was staged]( https://youtu.be/FU24r2zWVQo). Instead of addressing this bombshell revelation, [OPCW leadership focused]( https://www.opcw.org/sites/default/files/documents/2019/06/Remarks%20of%20the%20Director-General%20Briefing%20for%20States%20Parties%20on%20Syrian%20Arab%20Republic%20Update%20on%20IIT-FFM-SSRC-DAT_1.pdf) on investigating **how the leak happened** rather than the damning content of the report itself. #### October–November 2019: More Whistleblowers Speak Out On October 15th, 2019, the [Courage Foundation]( https://web.archive.org/web/20191024045128/https://couragefound.org/2019/10/opcw-panel-statement/) "convened a panel of concerned individuals from the fields of disarmament, international law, journalism, military operations, medicine and intelligence in Brussels". The whistleblower giving an "extensive presentation, including internal emails, text exchanges and suppressed draft reports..." describes "efforts to exclude some inspectors from the investigation whilst thwarting their attempts to raise legitimate concerns, highlight irregular practices or even to express their differing observations and assessments". The panel "became convinced by the testimony that key information about chemical analyses, toxicology consultations, ballistics studies, and witness testimonies was suppressed, ostensibly to favor a preordained conclusion" and expressed unanimous alarm about "unacceptable practices in the investigation". [Another OPCW whistleblower]( https://www.counterpunch.org/2019/11/15/the-opcw-and-douma-chemical-weapons-watchdog-accused-of-evidence-tampering-by-its-own-inspectors/), referred to as "Alex", a member of this fact finding mission, confirmed that key evidence had been suppressed. He revealed that: "_the signs and symptoms of victims were not consistent with poisoning from chlorine_". Instead of an attack producing multiple fatalities there had been “_a non chemical-related event_”. His findings, which undermined the official narrative, were removed from the final report. At this point, multiple independent voices—including journalists, scientists, and former OPCW officials—had exposed the [Douma deception]( https://wikileaks.org/opcw-douma/#Internal%20OPCW%20E-Mail). But the mainstream media either ignored or actively discredited these revelations. ### How the Media and Government Covered It Up When whistleblowers and [journalists]( https://youtu.be/ojItF6MGL-0) challenged the official story, mainstream outlets worked overtime to discredit them. The propaganda network [Bellingcat]( https://www.bellingcat.com/news/2019/11/25/emails-and-reading-comprehension-opcw-douma-coverage-misses-crucial-facts/) published a weak "debunking" article, which was swiftly dismantled by independent journalist [Caitlin Johnstone]( https://caitlinjohnstone.com/2019/11/27/narrative-managers-faceplant-in-hilarious-opcw-scandal-spin-job/) and veteran columnist [Peter Hitchens]( https://hitchensblog.mailonsunday.co.uk/2019/11/my-response-to-the-bellingcat-attempt-to-spin-away-the-devastating-implications-of-the-opcw-douma-leak-i-have.html). Rather than confronting the facts, the OPCW and its backers dismissed the leaks as unimportant or "[Russian disinformation]( https://www.cbsnews.com/news/opcw-chemical-weapons-watchdog-douma-chlorine-gas-wikileaks-russia-syria-claim-bias-today-2019-11-25/)"—a predictable smear tactic used whenever official narratives collapse. ### Why This Matters The Douma deception is not just an academic debate—it had real-world consequences. The false flag attack was used to justify military aggression against Syria, escalating tensions in the Middle East and prolonging unnecessary suffering. More importantly, it serves as a case study in how governments and media manufacture consent for war. By exposing these propaganda tactics, we can resist manipulation and prevent future conflicts based on lies. The Douma hoax is just one example of how false narratives are weaponized to justify military interventions. The same playbook has been used time and again—from Iraq’s "Weapons of Mass Destruction" to Libya’s "humanitarian intervention." If people learn to recognize propaganda before it leads to war, we can disrupt the cycle of deception. The truth is out there—we just need the courage to face it.
@ e7bc35f8:3ed2a7cf
2025-02-18 09:07:03For those who still trust mainstream narratives about war and foreign intervention, the Douma chemical attack story should serve as a wake-up call. The official version of events—that Syrian government forces carried out a chemical attack on civilians in Douma on April 7, 2018—has been thoroughly dismantled by whistleblowers, independent journalists, and even leaked documents from the Organization for the Prohibition of Chemical Weapons (OPCW). Yet, despite [mounting evidence]( https://thegrayzone.com/2018/03/06/media-propaganda-battle-syria-eastern-ghouta/), mainstream media and Western governments continue to push the debunked narrative, using it to justify military interventions and sustain the illusion of moral authority. This article revisits the Douma deception, breaking down how the false flag operation unfolded and how the truth was systematically suppressed. ### A Timeline of the Manufactured Crisis #### April 7, 2018: The Alleged Chemical Attack On this day, as the Syrian Army engaged terrorist insurgents in Douma, [shocking videos surfaced]( https://youtu.be/sYItxxEO3F8) online showing alleged victims of a chemical attack. Without proper investigation, Western leaders seized on the footage as proof of an [atrocity committed]( https://web.archive.org/web/20200304211152/https://eg.usembassy.gov/united-states-assessment-of-the-assad-regimes-chemical-weapons-use/) by the Assad government. Within 24 hours, then-President Donald Trump tweeted about "Animal Assad" and vowed that Russia and Iran would "pay a big price." This swift response echoed past war propaganda, reminiscent of the lies used to justify the invasion of Iraq.  #### April 14, 2018: The Bombing of Syria Begins Less than a week after the alleged attack, the [United States]( https://youtu.be/w43ok0q5G5A), [France, and Britain launched coordinated missile strikes]( https://www.washingtonpost.com/world/national-security/us-launches-missile-strikes-in-syria/2018/04/13/c68e89d0-3f4a-11e8-974f-aacd97698cef_story.html) on Syrian government targets. Shockingly, these airstrikes were carried out before any independent investigation had even begun. Meanwhile, on the same day, OPCW investigators arrived in Syria to examine the supposed chemical attack site. In a grotesque display of arrogance, the West had already punished Syria for a crime that hadn't been proven. #### April 17, 2018: Doubts Emerge Veteran journalist [Robert Fisk visited Douma]( https://www.independent.co.uk/voices/syria-chemical-attack-gas-douma-robert-fisk-ghouta-damascus-a8307726.html) and interviewed a local doctor who revealed that the victims shown in viral videos had actually died from suffocation—not chemical weapons. The doctor described how panic and dust inhalation in underground shelters had led to casualties, but no traces of nerve agents like **sarin** were found. #### July 6, 2018: OPCW’s Initial Report Undermines the Official Story The OPCW released its [interim findings]( https://www.opcw.org/media-centre/news/2018/07/opcw-issues-fact-finding-mission-reports-chemical-weapons-use-allegations), confirming that: > No organophosphorus nerve agents or their degradation products were detected, either in the environmental samples or in plasma samples from the alleged casualties. And while: > Various chlorinated organic chemicals were found in samples from Locations 2 and 4, along with residues of explosive the report makes no mention of the concentrations or levels of those chemicals. In Addition the "Annex 2" (Open Sources) is blank. In Annex 3 where all chemicals are listed, there is no chemical weapon agent listed. Despite this, Western media and politicians continued to push the idea that Syria had used chemical weapons. #### February–March 2019: Whistleblower Confirms Staged Hospital Footage In a stunning revelation, [BBC producer Riam Dalati]( https://youtu.be/fFLRX5ZiEvo) tweeted that the viral hospital scene—depicting victims being hosed down—had been **staged**. This meant that at least part of the so-called evidence was a fabrication. Shortly after, the OPCW issued its [final report]( https://www.opcw.org/sites/default/files/documents/2019/03/s-1731-2019%28e%29.pdf). While it acknowledged a lack of sarin, > No organophosphorous nerve agents, their degradation products or synthesis impurities were detected [...] it is not currently possible to precisely link the cause of the signs and symptoms to a specific chemical it ambiguously suggested that "a toxic chemical containing reactive chlorine" was likely used. This vague wording allowed Western governments to continue their accusations without hard proof. #### May 2019: Leaked OPCW Report Exposes a Cover-Up A [leaked engineering assessment]( https://web.archive.org/web/20190514174330/http://syriapropagandamedia.org/wp-content/uploads/2019/05/Engineering-assessment-of-two-cylinders-observed-at-the-Douma-incident-27-February-2019-1.pdf) by an OPCW sub-team completely contradicted the official findings. It concluded that the two cylinders found at the scene **were likely manually placed rather than dropped from aircraft**—suggesting [the incident was staged]( https://youtu.be/FU24r2zWVQo). Instead of addressing this bombshell revelation, [OPCW leadership focused]( https://www.opcw.org/sites/default/files/documents/2019/06/Remarks%20of%20the%20Director-General%20Briefing%20for%20States%20Parties%20on%20Syrian%20Arab%20Republic%20Update%20on%20IIT-FFM-SSRC-DAT_1.pdf) on investigating **how the leak happened** rather than the damning content of the report itself. #### October–November 2019: More Whistleblowers Speak Out On October 15th, 2019, the [Courage Foundation]( https://web.archive.org/web/20191024045128/https://couragefound.org/2019/10/opcw-panel-statement/) "convened a panel of concerned individuals from the fields of disarmament, international law, journalism, military operations, medicine and intelligence in Brussels". The whistleblower giving an "extensive presentation, including internal emails, text exchanges and suppressed draft reports..." describes "efforts to exclude some inspectors from the investigation whilst thwarting their attempts to raise legitimate concerns, highlight irregular practices or even to express their differing observations and assessments". The panel "became convinced by the testimony that key information about chemical analyses, toxicology consultations, ballistics studies, and witness testimonies was suppressed, ostensibly to favor a preordained conclusion" and expressed unanimous alarm about "unacceptable practices in the investigation". [Another OPCW whistleblower]( https://www.counterpunch.org/2019/11/15/the-opcw-and-douma-chemical-weapons-watchdog-accused-of-evidence-tampering-by-its-own-inspectors/), referred to as "Alex", a member of this fact finding mission, confirmed that key evidence had been suppressed. He revealed that: "_the signs and symptoms of victims were not consistent with poisoning from chlorine_". Instead of an attack producing multiple fatalities there had been “_a non chemical-related event_”. His findings, which undermined the official narrative, were removed from the final report. At this point, multiple independent voices—including journalists, scientists, and former OPCW officials—had exposed the [Douma deception]( https://wikileaks.org/opcw-douma/#Internal%20OPCW%20E-Mail). But the mainstream media either ignored or actively discredited these revelations. ### How the Media and Government Covered It Up When whistleblowers and [journalists]( https://youtu.be/ojItF6MGL-0) challenged the official story, mainstream outlets worked overtime to discredit them. The propaganda network [Bellingcat]( https://www.bellingcat.com/news/2019/11/25/emails-and-reading-comprehension-opcw-douma-coverage-misses-crucial-facts/) published a weak "debunking" article, which was swiftly dismantled by independent journalist [Caitlin Johnstone]( https://caitlinjohnstone.com/2019/11/27/narrative-managers-faceplant-in-hilarious-opcw-scandal-spin-job/) and veteran columnist [Peter Hitchens]( https://hitchensblog.mailonsunday.co.uk/2019/11/my-response-to-the-bellingcat-attempt-to-spin-away-the-devastating-implications-of-the-opcw-douma-leak-i-have.html). Rather than confronting the facts, the OPCW and its backers dismissed the leaks as unimportant or "[Russian disinformation]( https://www.cbsnews.com/news/opcw-chemical-weapons-watchdog-douma-chlorine-gas-wikileaks-russia-syria-claim-bias-today-2019-11-25/)"—a predictable smear tactic used whenever official narratives collapse. ### Why This Matters The Douma deception is not just an academic debate—it had real-world consequences. The false flag attack was used to justify military aggression against Syria, escalating tensions in the Middle East and prolonging unnecessary suffering. More importantly, it serves as a case study in how governments and media manufacture consent for war. By exposing these propaganda tactics, we can resist manipulation and prevent future conflicts based on lies. The Douma hoax is just one example of how false narratives are weaponized to justify military interventions. The same playbook has been used time and again—from Iraq’s "Weapons of Mass Destruction" to Libya’s "humanitarian intervention." If people learn to recognize propaganda before it leads to war, we can disrupt the cycle of deception. The truth is out there—we just need the courage to face it. @ da0b9bc3:4e30a4a9
2025-02-18 06:25:50Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/889165
@ da0b9bc3:4e30a4a9
2025-02-18 06:25:50Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/889165 @ 88d8c9d1:5b3ac02b
2025-02-18 06:19:24This article was first <a href="https://bitcoinmagazine.com/culture/an-untold-story-of-bitcoin-in-thailand">published</a> on Bitcoin Magazine at Aug 27, 2024. In the rapidly expanding global Bitcoin community, Western biases often dominate the narrative, overlooking diverse stories from around the world. One such story belongs to Didier Somnuke, a small business owner in the heart of Bangkok, a [city](https://www.nationthailand.com/thailand/tourism/40034269) known for welcoming 22.8 million international tourists in 2023, surpassing cities like Paris, London, and New York City. Although Thailand [has](https://www.thestar.com.my/aseanplus/aseanplus-news/2024/08/03/thai-central-bank-unveils-measures-to-tackle-high-household-debt) experienced a massive spike in household debt, reaching 16.37 trillion baht (US$463 billion) or 90.8% of the national GDP, up from less than 14 trillion baht in 2019. [primal.net/p/npub1xzh2kqynr29x6j3ln6x05f26ha0c0ucfr280uzljftlgcthv9r6skqe7dt] aka Didier Somnuke, born in [Yala province](https://en.wikipedia.org/wiki/South_Thailand_insurgency#Human_rights_issues), where geopolitical conflict is a harsh reality. Southern Thailand is [one of the poorest parts of Thailand](https://www.benarnews.org/english/news/thai/south-interviews-09092022123451.html#:~:text=Provinces%20in%20the%20Deep%20South,poverty%20rate%20is%206%20percent.) with a poverty rate of 34% compared to the national average of 6%, according to the World Bank, has been plagued by instability. Since 2004, this turmoil has [claimed](https://thediplomat.com/2023/05/whats-behind-the-growing-number-of-attacks-in-southern-thailand/) over 7,000 lives and injured 13,500 people. As a Thai saying goes, “ทวงสิทธิ์ที่จะมีชีวิตที่ดีกลับคืนมา” (Reclaim the right to a better life), In 2012, Didier left his conflict-ridden hometown for Bangkok, where pursuing higher education was a beacon of hope for a better life. At that time, Bitcoin and financial concepts were distant ideas in Didier's universe. Navigating the vibrant streets of Bangkok, Didier completed his master's degree and joined the workforce, taking up a typical 9-to-5 job. For a domestic migrant, this was a significant achievement. Reflecting on his journey, he recalled his teacher’s words, “When you are old, you have time and money, but you will lack the energy to start a business. If you want to do it, just do it.” With this advice in mind, Didier resigned from his monotonous corporate job after a year and opened a new chapter in his life. Didier borrowed 50,000 THB (approximately 1,500 USD) from his brother to begin a street burger shop. He chose to start a burger business because he believed it was easy to launch with a small investment. Driven by his ambition and inspired by the bustling energy of Bangkok, a city that never sleeps. He spent about a year developing the recipe and began the business in 2015. In the first three to four years, he managed everything on his own as a solo entrepreneur, and his income was lower than the wage he earned in his corporate job. He often wondered if he had made a mistake by quitting his job to start a business that generated less income. However, after five years, everything started to improve. Sales at the shop began to increase, and Didier started hiring employees. He admitted, "I entered the crypto market with greed; all I wanted was to get rich quickly." In 2017, he and his friends pooled their resources to buy three ASIC miners from Bitmain to try mining Bitcoin and altcoins like Litecoin and Dogecoin. They saw a return on their investment within six months. Didier bought his first Bitcoin in early 2017 to purchase those ASIC miners but didn't know how to transfer his Bitcoin, so he ended up using a bank transfer instead. Reflecting on his early experiences, he recalled, "My first Bitcoin were slowly converted to shitcoins during the bull market. I was so lucky. I got a 100% profit almost immediately whenever I bought something." Despite having zero knowledge about cryptocurrency, he gained confidence and became a super shitcoiner, paying very little attention to Bitcoin. In mid-2017, he learned about leverage and trading. His profits skyrocketed due to leverage. Although luck was not always on his side forever, in early 2018, the market crashed, and he lost over 1 million Thai baht (almost 30,000 USD), while his initial capital was just about 100,000 Thai baht (about 3,000 USD). On top of that, he also lost his shitcoins from the mining pool. He had kept all of his shitcoins in the mining pool's custody, and one day, when he checked his account, every shitcoin he owned, worth 10,000 USD were gone. The notice on the mining website, "Hash-to-Coin," stated that if coins were kept with them for more than three months, they would be considered a donation.  He disheartenedly said, "I lost everything." But unlike most people, "I didn't blame Bitcoin. I still see it as the future. I blame myself. I didn't know anything and I did over leverage." He emphasized that despite his heavy financial losses, his girlfriend did not leave him. "My girlfriend was my customer. She regularly came to buy burgers. I met her while I was struggling financially during my early days as an entrepreneur. She supported me and said we could make the money back." Determined to turn his circumstances around, he discovered [Mr. Piriya](https://www.youtube.com/@user-qh7ic9rh3l) on YouTube and started following his live streams about the real Bitcoin education. This marked the moment he began to truly understand what Bitcoin and cryptocurrency are. Enlightened by this unique knowledge, he came to see Bitcoin as a saving technology rather than just a trading tool. Over three years, Didier recovered from his losses and emerged stronger. He got to be friend with Mr. Piriya, and together they founded a company called [Right Shift](https://rightshift.to/) to develop Bitcoin content in Thai language through multiple social media channels, including on Nostr (npub1ejn774qahqmgjsfajawy7634unk88y26yktvwuzp9kfgdeejx9mqdm97a5) with one of the popular hashtag #siamstr. As a team, they translated "The Bitcoin Standard" and "The Fiat Standard" into Thai, both of which became best-selling books in Thailand. They organized the first-ever [Bitcoin Thailand Conference](https://www.youtube.com/watch?v=ihoniIyyHzQ) in 2023 and are now preparing for the next one in September 2024.  Didier now accepts Bitcoin as a payment method in his main burger shop, one of four different franchises. He uses Wallet of Satoshi to process these payments. Within a year of implementing this initiative, he has received over 3 million sats in payments, though he initially expected to see more transactions in Bitcoin. In his marketplace, some neighboring small business owners occasionally ask him about Bitcoin as they notice the large Bitcoin poster in his shop. Although they often lose interest once he explains, according to his several unsuccessful experience. Instead now, he focuses his energy online, where he can make more impact to people who are willing to embrace innovation.  In 2022, approximately [8.4 million](https://www.statista.com/topics/10781/cryptocurrencies-in-thailand/#topicOverview) people in Thailand, accounting for 12% of the country's population, used cryptocurrency. Estimates [suggest](https://www.statista.com/forecasts/1033594/thailand-cryptocurrency-users) that by 2028, this number will rise to about 17.67 million, representing 25% of the population. During our conversation, Didier claimed that there are about 50,000 Bitcoin users in Thailand and speculated that the Thai government might intervene in Bitcoin adoption, potentially mandating the use of KYC wallets because they dislike money systems they can't control. In the worst-case scenario, Didier remains resolute: he will continue advocating for Bitcoin with his friends. "It is not an option," he asserted, "it is the only way to survive."
@ 88d8c9d1:5b3ac02b
2025-02-18 06:19:24This article was first <a href="https://bitcoinmagazine.com/culture/an-untold-story-of-bitcoin-in-thailand">published</a> on Bitcoin Magazine at Aug 27, 2024. In the rapidly expanding global Bitcoin community, Western biases often dominate the narrative, overlooking diverse stories from around the world. One such story belongs to Didier Somnuke, a small business owner in the heart of Bangkok, a [city](https://www.nationthailand.com/thailand/tourism/40034269) known for welcoming 22.8 million international tourists in 2023, surpassing cities like Paris, London, and New York City. Although Thailand [has](https://www.thestar.com.my/aseanplus/aseanplus-news/2024/08/03/thai-central-bank-unveils-measures-to-tackle-high-household-debt) experienced a massive spike in household debt, reaching 16.37 trillion baht (US$463 billion) or 90.8% of the national GDP, up from less than 14 trillion baht in 2019. [primal.net/p/npub1xzh2kqynr29x6j3ln6x05f26ha0c0ucfr280uzljftlgcthv9r6skqe7dt] aka Didier Somnuke, born in [Yala province](https://en.wikipedia.org/wiki/South_Thailand_insurgency#Human_rights_issues), where geopolitical conflict is a harsh reality. Southern Thailand is [one of the poorest parts of Thailand](https://www.benarnews.org/english/news/thai/south-interviews-09092022123451.html#:~:text=Provinces%20in%20the%20Deep%20South,poverty%20rate%20is%206%20percent.) with a poverty rate of 34% compared to the national average of 6%, according to the World Bank, has been plagued by instability. Since 2004, this turmoil has [claimed](https://thediplomat.com/2023/05/whats-behind-the-growing-number-of-attacks-in-southern-thailand/) over 7,000 lives and injured 13,500 people. As a Thai saying goes, “ทวงสิทธิ์ที่จะมีชีวิตที่ดีกลับคืนมา” (Reclaim the right to a better life), In 2012, Didier left his conflict-ridden hometown for Bangkok, where pursuing higher education was a beacon of hope for a better life. At that time, Bitcoin and financial concepts were distant ideas in Didier's universe. Navigating the vibrant streets of Bangkok, Didier completed his master's degree and joined the workforce, taking up a typical 9-to-5 job. For a domestic migrant, this was a significant achievement. Reflecting on his journey, he recalled his teacher’s words, “When you are old, you have time and money, but you will lack the energy to start a business. If you want to do it, just do it.” With this advice in mind, Didier resigned from his monotonous corporate job after a year and opened a new chapter in his life. Didier borrowed 50,000 THB (approximately 1,500 USD) from his brother to begin a street burger shop. He chose to start a burger business because he believed it was easy to launch with a small investment. Driven by his ambition and inspired by the bustling energy of Bangkok, a city that never sleeps. He spent about a year developing the recipe and began the business in 2015. In the first three to four years, he managed everything on his own as a solo entrepreneur, and his income was lower than the wage he earned in his corporate job. He often wondered if he had made a mistake by quitting his job to start a business that generated less income. However, after five years, everything started to improve. Sales at the shop began to increase, and Didier started hiring employees. He admitted, "I entered the crypto market with greed; all I wanted was to get rich quickly." In 2017, he and his friends pooled their resources to buy three ASIC miners from Bitmain to try mining Bitcoin and altcoins like Litecoin and Dogecoin. They saw a return on their investment within six months. Didier bought his first Bitcoin in early 2017 to purchase those ASIC miners but didn't know how to transfer his Bitcoin, so he ended up using a bank transfer instead. Reflecting on his early experiences, he recalled, "My first Bitcoin were slowly converted to shitcoins during the bull market. I was so lucky. I got a 100% profit almost immediately whenever I bought something." Despite having zero knowledge about cryptocurrency, he gained confidence and became a super shitcoiner, paying very little attention to Bitcoin. In mid-2017, he learned about leverage and trading. His profits skyrocketed due to leverage. Although luck was not always on his side forever, in early 2018, the market crashed, and he lost over 1 million Thai baht (almost 30,000 USD), while his initial capital was just about 100,000 Thai baht (about 3,000 USD). On top of that, he also lost his shitcoins from the mining pool. He had kept all of his shitcoins in the mining pool's custody, and one day, when he checked his account, every shitcoin he owned, worth 10,000 USD were gone. The notice on the mining website, "Hash-to-Coin," stated that if coins were kept with them for more than three months, they would be considered a donation.  He disheartenedly said, "I lost everything." But unlike most people, "I didn't blame Bitcoin. I still see it as the future. I blame myself. I didn't know anything and I did over leverage." He emphasized that despite his heavy financial losses, his girlfriend did not leave him. "My girlfriend was my customer. She regularly came to buy burgers. I met her while I was struggling financially during my early days as an entrepreneur. She supported me and said we could make the money back." Determined to turn his circumstances around, he discovered [Mr. Piriya](https://www.youtube.com/@user-qh7ic9rh3l) on YouTube and started following his live streams about the real Bitcoin education. This marked the moment he began to truly understand what Bitcoin and cryptocurrency are. Enlightened by this unique knowledge, he came to see Bitcoin as a saving technology rather than just a trading tool. Over three years, Didier recovered from his losses and emerged stronger. He got to be friend with Mr. Piriya, and together they founded a company called [Right Shift](https://rightshift.to/) to develop Bitcoin content in Thai language through multiple social media channels, including on Nostr (npub1ejn774qahqmgjsfajawy7634unk88y26yktvwuzp9kfgdeejx9mqdm97a5) with one of the popular hashtag #siamstr. As a team, they translated "The Bitcoin Standard" and "The Fiat Standard" into Thai, both of which became best-selling books in Thailand. They organized the first-ever [Bitcoin Thailand Conference](https://www.youtube.com/watch?v=ihoniIyyHzQ) in 2023 and are now preparing for the next one in September 2024.  Didier now accepts Bitcoin as a payment method in his main burger shop, one of four different franchises. He uses Wallet of Satoshi to process these payments. Within a year of implementing this initiative, he has received over 3 million sats in payments, though he initially expected to see more transactions in Bitcoin. In his marketplace, some neighboring small business owners occasionally ask him about Bitcoin as they notice the large Bitcoin poster in his shop. Although they often lose interest once he explains, according to his several unsuccessful experience. Instead now, he focuses his energy online, where he can make more impact to people who are willing to embrace innovation.  In 2022, approximately [8.4 million](https://www.statista.com/topics/10781/cryptocurrencies-in-thailand/#topicOverview) people in Thailand, accounting for 12% of the country's population, used cryptocurrency. Estimates [suggest](https://www.statista.com/forecasts/1033594/thailand-cryptocurrency-users) that by 2028, this number will rise to about 17.67 million, representing 25% of the population. During our conversation, Didier claimed that there are about 50,000 Bitcoin users in Thailand and speculated that the Thai government might intervene in Bitcoin adoption, potentially mandating the use of KYC wallets because they dislike money systems they can't control. In the worst-case scenario, Didier remains resolute: he will continue advocating for Bitcoin with his friends. "It is not an option," he asserted, "it is the only way to survive." @ 78c90fc4:4bff983c
2025-02-18 06:16:52**via acTVism Munich** Ausschnitt: <https://www.wissenschaftstehtauf.ch/video/Ukraine_will_win_the_war.mp4> In diesem Video, das exklusiv auf Deutsch auf unserem Kanal veröffentlicht wurde, untersucht der mit dem Pulitzer-Preis ausgezeichnete Journalist Glenn Greenwald den Auftritt von US-Verteidigungsminister Pete Hegseth im NATO-Hauptquartier in Brüssel, wo er die Haltung von Präsident Trump zum Krieg in der Ukraine darlegte. Hegseth betonte, dass das Blutvergießen gestoppt und ein dauerhafter Frieden durch Diplomatie erreicht werden müsse, anstatt den Krieg fortzusetzen. Greenwald hebt auch die Diskrepanz zwischen der optimistischen Rhetorik der NATO-Führer in der Vergangenheit und der Realität des festgefahrenen Konflikts vor Ort hervor. Dieses Video wurde von System Update produziert und am 13. Februar 2025 auf dem Glenn Greenwald YouTube-Kanal veröffentlicht. Wir haben es ins Deutsche übersetzt und veröffentlichen es heute erneut, um die Meinungsbildung zu diesem Thema in Deutschland und darüber hinaus zu unterstützen. \ Ganzes Video: <https://www.youtube.com/watch?v=PWp8-o-akwI> <https://x.com/RealWsiegrist/status/1891402218626019622> \ dazu auch: **Corona, Ukraine und die Biowaffen** **<https://waltisiegrist.locals.com/upost/1835360/corona-ukraine-und-die-biowaffen>**
@ 78c90fc4:4bff983c
2025-02-18 06:16:52**via acTVism Munich** Ausschnitt: <https://www.wissenschaftstehtauf.ch/video/Ukraine_will_win_the_war.mp4> In diesem Video, das exklusiv auf Deutsch auf unserem Kanal veröffentlicht wurde, untersucht der mit dem Pulitzer-Preis ausgezeichnete Journalist Glenn Greenwald den Auftritt von US-Verteidigungsminister Pete Hegseth im NATO-Hauptquartier in Brüssel, wo er die Haltung von Präsident Trump zum Krieg in der Ukraine darlegte. Hegseth betonte, dass das Blutvergießen gestoppt und ein dauerhafter Frieden durch Diplomatie erreicht werden müsse, anstatt den Krieg fortzusetzen. Greenwald hebt auch die Diskrepanz zwischen der optimistischen Rhetorik der NATO-Führer in der Vergangenheit und der Realität des festgefahrenen Konflikts vor Ort hervor. Dieses Video wurde von System Update produziert und am 13. Februar 2025 auf dem Glenn Greenwald YouTube-Kanal veröffentlicht. Wir haben es ins Deutsche übersetzt und veröffentlichen es heute erneut, um die Meinungsbildung zu diesem Thema in Deutschland und darüber hinaus zu unterstützen. \ Ganzes Video: <https://www.youtube.com/watch?v=PWp8-o-akwI> <https://x.com/RealWsiegrist/status/1891402218626019622> \ dazu auch: **Corona, Ukraine und die Biowaffen** **<https://waltisiegrist.locals.com/upost/1835360/corona-ukraine-und-die-biowaffen>** @ 16d11430:61640947
2025-02-18 02:21:18The holy grail of software development isn’t just writing code—it’s writing good code in a state of pure cognitive clarity. That moment when the mind operates at peak efficiency, when debugging is intuitive, and when abstractions form with effortless precision. This is the flow state, the intersection of deep focus and high cognitive throughput, where time distorts, distractions dissolve, and productivity skyrockets. But flow doesn’t happen on command. It’s not a switch you flip—it’s a state that requires cultivation, discipline, and an understanding of what to do outside of flow to extend and intensify the time inside of it. Understanding Flow in Programming Flow is a psychological state described by Mihaly Csikszentmihalyi, where people are fully immersed in an activity, experiencing deep focus, clear goals, and intrinsic motivation. In programming, flow is more than just focus—it’s a state where: Code becomes a natural language, and syntax errors fade into the subconscious. Bugs reveal themselves intuitively before they cause major issues. Solutions appear as if they were waiting to be discovered. However, the challenge isn’t just getting into flow—it’s staying in flow longer and increasing the intensity of that state. Many developers struggle with this because modern work environments are designed to pull them out of it—interruptions, meetings, notifications, and context switches all work against deep work. Why Flow is Hard to Maintain The key limitation of flow isn’t just time—it’s cognitive energy. You can’t sustain high-intensity flow indefinitely because: 1. Flow Requires a Build-Up – You don’t start in deep flow; it takes warm-up time. If you’re constantly switching contexts, you never get past the shallow stages of focus. 2. Cognitive Fatigue Kicks In – Just like physical endurance, mental endurance wears down over time. High-intensity cognition depletes willpower, working memory, and problem-solving efficiency. 3. External Interruptions Break the Cycle – Every time you respond to a message, check an email, or attend an unplanned meeting, you disrupt the delicate mental stack that flow relies on. Expanding Flow: The Out-of-Flow Preparation Phase To maximize flow, you must structure your out-of-flow time to support your inflow time. This means making low-bandwidth, low-intensity activities serve the function of preserving cognitive resources for when they are needed most. 1. Prime the Mind Beforehand Preload the problem: Before entering flow, read through relevant code, documentation, or problem statements, even if you don’t start coding. Let the subconscious chew on it. Use sleep strategically: Review complex issues before sleeping—your brain continues working on them passively overnight. Journal ideas: Keep a scratchpad for incomplete thoughts and patterns that need to be explored later. This prevents cognitive drift when you re-enter deep work. 2. Reduce Cognitive Load Outside of Flow Automate the trivial: Reduce low-value decision-making by scripting repetitive tasks, automating builds, and using shortcuts. Optimize workspace: Remove unnecessary distractions, use dark themes to reduce eye strain, and fine-tune your dev environment. Minimal communication: Asynchronous work models (like using GitHub issues or structured documentation) prevent unnecessary meetings. 3. Use Active Recovery to Extend Flow Durations Exercise between flow sessions: Short walks, stretching, or kettlebell swings help reset the nervous system. Use Indian clubs or a gyro ball: Engaging the wrists and forearms with rhythmic exercises improves circulation and keeps the hands limber. Engage in passive problem-solving: Listen to low-intensity technical podcasts, read about related topics, or sketch diagrams without the pressure of immediate problem-solving. 4. Manage Energy and Stamina Control caffeine intake: Small, steady doses of caffeine (e.g., green tea or microdosed coffee) sustain focus longer than a single heavy hit. Eat for cognitive endurance: Avoid sugar crashes; prioritize protein, healthy fats, and slow-digesting carbs. Cold exposure and breathwork: Techniques like the Wim Hof method or contrast showers can help maintain alertness and focus. Maximizing In-Flow Performance Once in flow, the goal is to stay there as long as possible and increase intensity without burnout. 1. Work in High-Resolution Time Blocks 90-minute deep work cycles: Research suggests the brain works optimally in ultradian rhythms, meaning cycles of 90 minutes of intense focus followed by a 15–20 minute break. Use timers: Time tracking (e.g., Pomodoro) helps prevent unconscious fatigue. However, don’t stop flow artificially—only use timers to prevent shallow focus work. 2. Reduce Interruptions Ruthlessly Go offline: Disable notifications, block distracting sites, and use airplane mode during deep work. Use noise-canceling headphones: Even if you don’t listen to music, noise isolation helps maintain focus. Batch all non-coding activities: Emails, Slack messages, and meetings should be handled in predefined blocks outside of deep work hours. 3. Optimize Mental Bandwidth Use text-based reasoning: Writing pseudocode or rubber-duck debugging prevents mental overload. Talk through problems out loud: The act of verbalizing a complex issue forces clarity. Engage in deliberate problem-solving: Instead of brute-forcing solutions, work from first principles—break problems down into the smallest testable units. Scaling Flow: Beyond Individual Productivity Flow isn’t just an individual challenge—it can be optimized at the team level: Flow-friendly scheduling: Companies should avoid scheduling meetings during peak productive hours (e.g., morning blocks). Pair programming strategically: While pair programming can improve code quality, it can also break deep focus. Use it wisely. Minimize process friction: Too much bureaucracy or excessive agile ceremonies kill momentum. Lean processes help maintain deep work culture. The Final Goal: High-Intensity Flow as the Default State Ultimately, a programmer’s most valuable skill isn’t just technical proficiency—it’s the ability to engineer their own mind for sustained, high-intensity flow. When flow is prolonged and intensified, an hour of deep work can replace an entire week of shallow, distracted effort. The key is not just working more—it’s working smarter, structuring out-of-flow time so that when flow begins, it reaches peak intensity and lasts as long as possible. By systematically designing both low-intensity and high-intensity work, programmers can transform sporadic flow into a continuous, deliberate, high-performance workflow. In the end, peak developers aren’t just coders—they are architects of their own mental states.
@ 16d11430:61640947
2025-02-18 02:21:18The holy grail of software development isn’t just writing code—it’s writing good code in a state of pure cognitive clarity. That moment when the mind operates at peak efficiency, when debugging is intuitive, and when abstractions form with effortless precision. This is the flow state, the intersection of deep focus and high cognitive throughput, where time distorts, distractions dissolve, and productivity skyrockets. But flow doesn’t happen on command. It’s not a switch you flip—it’s a state that requires cultivation, discipline, and an understanding of what to do outside of flow to extend and intensify the time inside of it. Understanding Flow in Programming Flow is a psychological state described by Mihaly Csikszentmihalyi, where people are fully immersed in an activity, experiencing deep focus, clear goals, and intrinsic motivation. In programming, flow is more than just focus—it’s a state where: Code becomes a natural language, and syntax errors fade into the subconscious. Bugs reveal themselves intuitively before they cause major issues. Solutions appear as if they were waiting to be discovered. However, the challenge isn’t just getting into flow—it’s staying in flow longer and increasing the intensity of that state. Many developers struggle with this because modern work environments are designed to pull them out of it—interruptions, meetings, notifications, and context switches all work against deep work. Why Flow is Hard to Maintain The key limitation of flow isn’t just time—it’s cognitive energy. You can’t sustain high-intensity flow indefinitely because: 1. Flow Requires a Build-Up – You don’t start in deep flow; it takes warm-up time. If you’re constantly switching contexts, you never get past the shallow stages of focus. 2. Cognitive Fatigue Kicks In – Just like physical endurance, mental endurance wears down over time. High-intensity cognition depletes willpower, working memory, and problem-solving efficiency. 3. External Interruptions Break the Cycle – Every time you respond to a message, check an email, or attend an unplanned meeting, you disrupt the delicate mental stack that flow relies on. Expanding Flow: The Out-of-Flow Preparation Phase To maximize flow, you must structure your out-of-flow time to support your inflow time. This means making low-bandwidth, low-intensity activities serve the function of preserving cognitive resources for when they are needed most. 1. Prime the Mind Beforehand Preload the problem: Before entering flow, read through relevant code, documentation, or problem statements, even if you don’t start coding. Let the subconscious chew on it. Use sleep strategically: Review complex issues before sleeping—your brain continues working on them passively overnight. Journal ideas: Keep a scratchpad for incomplete thoughts and patterns that need to be explored later. This prevents cognitive drift when you re-enter deep work. 2. Reduce Cognitive Load Outside of Flow Automate the trivial: Reduce low-value decision-making by scripting repetitive tasks, automating builds, and using shortcuts. Optimize workspace: Remove unnecessary distractions, use dark themes to reduce eye strain, and fine-tune your dev environment. Minimal communication: Asynchronous work models (like using GitHub issues or structured documentation) prevent unnecessary meetings. 3. Use Active Recovery to Extend Flow Durations Exercise between flow sessions: Short walks, stretching, or kettlebell swings help reset the nervous system. Use Indian clubs or a gyro ball: Engaging the wrists and forearms with rhythmic exercises improves circulation and keeps the hands limber. Engage in passive problem-solving: Listen to low-intensity technical podcasts, read about related topics, or sketch diagrams without the pressure of immediate problem-solving. 4. Manage Energy and Stamina Control caffeine intake: Small, steady doses of caffeine (e.g., green tea or microdosed coffee) sustain focus longer than a single heavy hit. Eat for cognitive endurance: Avoid sugar crashes; prioritize protein, healthy fats, and slow-digesting carbs. Cold exposure and breathwork: Techniques like the Wim Hof method or contrast showers can help maintain alertness and focus. Maximizing In-Flow Performance Once in flow, the goal is to stay there as long as possible and increase intensity without burnout. 1. Work in High-Resolution Time Blocks 90-minute deep work cycles: Research suggests the brain works optimally in ultradian rhythms, meaning cycles of 90 minutes of intense focus followed by a 15–20 minute break. Use timers: Time tracking (e.g., Pomodoro) helps prevent unconscious fatigue. However, don’t stop flow artificially—only use timers to prevent shallow focus work. 2. Reduce Interruptions Ruthlessly Go offline: Disable notifications, block distracting sites, and use airplane mode during deep work. Use noise-canceling headphones: Even if you don’t listen to music, noise isolation helps maintain focus. Batch all non-coding activities: Emails, Slack messages, and meetings should be handled in predefined blocks outside of deep work hours. 3. Optimize Mental Bandwidth Use text-based reasoning: Writing pseudocode or rubber-duck debugging prevents mental overload. Talk through problems out loud: The act of verbalizing a complex issue forces clarity. Engage in deliberate problem-solving: Instead of brute-forcing solutions, work from first principles—break problems down into the smallest testable units. Scaling Flow: Beyond Individual Productivity Flow isn’t just an individual challenge—it can be optimized at the team level: Flow-friendly scheduling: Companies should avoid scheduling meetings during peak productive hours (e.g., morning blocks). Pair programming strategically: While pair programming can improve code quality, it can also break deep focus. Use it wisely. Minimize process friction: Too much bureaucracy or excessive agile ceremonies kill momentum. Lean processes help maintain deep work culture. The Final Goal: High-Intensity Flow as the Default State Ultimately, a programmer’s most valuable skill isn’t just technical proficiency—it’s the ability to engineer their own mind for sustained, high-intensity flow. When flow is prolonged and intensified, an hour of deep work can replace an entire week of shallow, distracted effort. The key is not just working more—it’s working smarter, structuring out-of-flow time so that when flow begins, it reaches peak intensity and lasts as long as possible. By systematically designing both low-intensity and high-intensity work, programmers can transform sporadic flow into a continuous, deliberate, high-performance workflow. In the end, peak developers aren’t just coders—they are architects of their own mental states. @ 6e0ea5d6:0327f353
2025-02-17 19:30:54**Ascolta bene!** Happiness is fleeting, volatile, and above all, impermanent. It is not about being happy, but about feeling happy. Nor is it about making someone happy, but about offering brief moments of contentment—flashes of light that appear and vanish before we can grasp them. The greatest paradox of success lies in its cost: the closer we get to it, the more sophisticated, ambitious, and isolated we become. The brilliance of achievement blinds us to the value of those around us and the simplicity of life itself. Happiness is not a condition but a temporary state. In an absolute sense, no one is happy—one merely feels happy, for an instant, until reality imposes itself once again. If there is one rule that governs life, it is that of apathy, boredom, and suffering. Happiness is the exception, never the norm. And peace? A fool’s delusion. Not even the dead can claim to have found it, for their names still echo in the mouths of those who despise them, and their legacies continue to be contested. As long as there is breath in our lungs, there will be war. The battle does not cease, does not grant truces, and does not respect desires. Rest is a luxury of the dead. For the living, only the endless fight remains. Thank you for reading, my friend! If this message resonated with you, consider leaving your "🥃" as a token of appreciation. A toast to our family!
@ 6e0ea5d6:0327f353
2025-02-17 19:30:54**Ascolta bene!** Happiness is fleeting, volatile, and above all, impermanent. It is not about being happy, but about feeling happy. Nor is it about making someone happy, but about offering brief moments of contentment—flashes of light that appear and vanish before we can grasp them. The greatest paradox of success lies in its cost: the closer we get to it, the more sophisticated, ambitious, and isolated we become. The brilliance of achievement blinds us to the value of those around us and the simplicity of life itself. Happiness is not a condition but a temporary state. In an absolute sense, no one is happy—one merely feels happy, for an instant, until reality imposes itself once again. If there is one rule that governs life, it is that of apathy, boredom, and suffering. Happiness is the exception, never the norm. And peace? A fool’s delusion. Not even the dead can claim to have found it, for their names still echo in the mouths of those who despise them, and their legacies continue to be contested. As long as there is breath in our lungs, there will be war. The battle does not cease, does not grant truces, and does not respect desires. Rest is a luxury of the dead. For the living, only the endless fight remains. Thank you for reading, my friend! If this message resonated with you, consider leaving your "🥃" as a token of appreciation. A toast to our family! @ 6bae33c8:607272e8
2025-02-17 18:31:27I did my first NFBC draft Sunday night — I drew the 12th pick. Here’s the [link to the live-stream](https://x.com/Chris_Liss/status/1891230585043226641). The full results are below:  This draft went about as well as I could have hoped, especially given [how little I had prepared](https://www.realmansports.com/p/beat-chris-liss-1-8c2). That doesn’t mean the team is \*good\*, only that I didn’t have any major regrets or gaffes, something that’s rare over 30 rounds. I also never once got swiped on a pick. I got priced out of the top closers early, but rolled with it in the way one should when that happens, getting players I wanted and doubling back to closers when I needed to. This team is built to win the overall — high-risk, high reward, an exercise in imagining not what could go wrong, not what’s the base case, but what could go right. **The Draft** **1.12 Julio Rodriguez** — I had mapped out the first 10 rounds, decided on Rodriguez and Jackson Chourio ahead of time. I knew Chourio would be there, per ADP, but if Rodriguez were gone, I’d have gone with Mookie Betts. I wanted two OF with power and speed to start my draft. Rodriguez had 32 homers and 37 steals as a 22-year old in 2023, was going in the 2-4 overall range last year and nothing that happened since should move the needle much heading into his age 24 season. **2.1 Jackson Chourio —** Chourio had 21 homers and 22 steals as a 20-year-old rookie, and those numbers were weighed down by a slow start where the Brewers were constantly pulling him from the lineup for no reason. From June until the end of the year, he hit .303 and should only get better in Year 2. His healthy floor is 25-25, and there’s stolen base and batting average upside. **3.12 Matt Olson** — While Rodriguez and Chourio offer solid pop, I wanted a 40-HR type to compensate for the lack of top-end power with my first two picks, while filling the scarce-in-recent-years 1B slot. Olson had an off year in 2024, but chalk that up to variance. I still like him in that park and lineup. **4.1 Jacob deGrom** — I’m not here to win the $1500 league prize but the $150K overall. deGrom isn’t just the best pitcher in baseball when he’s healthy, he’s one of the best in baseball history. If I get 100 IP of vintage deGrom, that’s worth a fourth-round pick. At 130-150, it’s a first-rounder. I also like that he’s nearly two years out from Tommy John surgery, pitched at the end of last season and is healthy now. While there’s no chance of 200 IP, he’s also not a rookie they need to ramp up slowly, but a veteran with a massive contract, i.e., the Rangers will want to get their money’s worth if he’s dealing. **5.12 Gerrit Cole** — When Raisel Iglesias went four picks ahead of me, I was pretty sure I was going Cole who typically goes in the first or second round. Cole had an off year, but the sample was small as he missed time due to a nerve issue in the spring, and there wasn’t much of a drop-off from 2023, even with the irregular start to the year. Pitchers ebb and flow with health, and the light workload might redound to his benefit. **6.1 Teoscar Hernandez** — This was just a value-take in the sixth round. Hernandez gives you pop, runs a little and hits in the best lineup in baseball. **7.12 Will Smith** — I didn’t love the options in these rounds, so I punted and nabbed a solid catcher with 20-HR pop. I don’t really see the difference between Smith and Adley Rutschman who goes two rounds earlier either. **8.1 Max Fried** — With deGrom shaky on innings, and five hitters in my first seven picks, I wanted another horse to anchor the rotation. I like lefties in Yankee Stadium too. **9.12 Royce Lewis** — I needed a third baseman, and Lewis, who was going in the fifth round last year, was the one with the most upside. The key is that he’s healthy now, as he finished the season in the lineup and hasn’t had a setback this offseason. Lewis is a potential 30-HR/.290 bat if he can hold up for 140-odd games. **10.1 Spencer Strider** — As I said, I’m trying to win the overall. Strider will start the year on the DL, but the timetable for the type of surgery he had is roughly one year, and Strider’s was in mid-April, i.e., there’s no reason he shouldn’t be back in May and might even see some action in spring training. If I get 220 combined IP from deGrom and Strider at their former levels, that’s worth the 1.1. (The “former levels” part is the rub, but as I said I’m focused on what could go right.) I also thought about Shane McClanahan instead, but narrowly opted for Strider. **11.12 Luis Garcia** — I was set to take Brice Turang here to lock down speed and finally get a middle infielder, but I pivoted at the last second to Garcia who is a better-rounded hitter and more likely to have a prominent spot in his lineup. **12.1 Jared Jones** — He was on my list because I remembered the hype after his strong start, and the cost seemed cheap relative to his skills. I almost took Carlos Rodon, as I prefer veterans. Maybe that will turn out to have been a mistake. **13.12 Brice Turang** — What do you know, Turang made it all the way back. I guess people didn’t like his second-half collapse at the plate. But Turang is a gold glove defender, and he stole 50 bags last year. That glove keeps him in the lineup and should set a nice 30-steal floor. **14.1 Kenley Jansen** — I could play closer chicken no more. Jansen is my favorite type of old warhorse closer, a guy so used to the job, he’s not going to lose it unless his stuff is truly gone. **15.12 Jordan Romano** — Romano got $8.5 million from the Phillies, so I’m assuming he’s (a) healthy and (b) set to close. His ERA while pitching hurt for 14 innings last year is irrelevant. **16.1 Zach Neto** — I needed a shortstop, and while Neto’s hurt right now, he went 23-30 as a 23-year old last year, and I couldn’t pass him up. I almost took Ceddanne Rafaela, but Neto’s upside higher. **17.12 Ceddanne Rafaela** — Turns out Rafaela fell to me anyway, and I snapped him up, as I’ll need a SS early in the year with Neto presumably out. Rafaela went 15-19 as a 23-YO in his own right, also qualifies in the OF and his gold-glove-level defense should keep him in the lineup. **18.1 Josh Jung** — I needed a CI, and also a backup 3B for the injury-prone Royce Lewis, so I took the injury-prone Jung. The key facts about Jung and Lewis are both can hit, and both are healthy as of right now. My team seems like it has a lot of injuries, but only Strider and Neto are hurt now. There is a difference between injury risk (deGrom, Lewis, Jung, Romano) and already injured. You can often find value by exploiting people’s conflation of those two related, but distinct categories. **19.12 Jesus Luzardo** — Another skilled, but injury-prone player coming at a steep discount who is healthy now. **20.1 Lucas Erceg** — A speculative closer play. Right now Carlos Estevez, who went in Round 15, is probably the favorite, but who knows? **21.12 Walker Buehler** — More of the same theme. A player (especially a pitcher) who has shown elite skills, was derailed by injuries, but who is healthy now. **22.1 Nolan Jones** — I had almost forgotten he existed, but there he was in Round 22, just one year removed from being a fifth-round pick after a 20-20-.297 season. Jones is only 26 and healthy as of now. **23.12 Griffin Jax** — A setup guy with elite stuff, behind a closer that had nine losses and a 1.16 WHIP last year. **24.1 Garrett Mitchell** — I took him narrowly over Jordan Walker. Mitchell went 8-11 in 224 at-bats, plays in a good park and has the physical tools to be good. **25.12 Bo Naylor** — I needed a second catcher, and he is one. Naylor has a little pop, even runs a bit and should improve in his age 25 season. **26.1 Max Scherzer** — Are we sure he’s done? He had a 1.15 WHIP last year and 40K in 43 IP despite returning from back surgery. He’s healthy now and signed a $15.5M deal this offseason presumably to pitch more than 100 innings. **27.12 Justin Verlander** — Wait, they let me have deGrom, Cole, Strider, Buehler, Scherzer and Verlander? Those were like the top-six pitchers on the board a few years ago! Seriously though, Verlander is in a good park, and last year’s poor numbers were put up over a 90-inning sample while battling various ailments. He’s more likely to be done than Scherzer, but he knows how to pitch, and it’s just a matter of the stuff returning to above the minimum threshold. I wouldn’t be shocked to see one more strong year out of the 41-YO future Hall of Famer. **28.1 Jose Caballero** — I drafted this gentleman in the 28th round because he qualifies everywhere and steals a lot of bases. **29.12 Nolan Gorman** — The Cardinals want to get him regular at-bats, and there’s a 35-HR, .240 season somewhere in this skill set. **30.1 Gavin Lux** — A big-time prospect that’s only shown flashes, should get regular playing time and a big upgrade in park. He might eventually qualify at some other positions too. **Roster By Position** **C** Will Smith/Bo Naylor **1B** Matt Olson **2B** Luis Garcia **3B** Royce Lewis **SS** Zach Neto **CI** Josh Jung **MI** Brice Turang **OF** Julio Rodriguez/Jackson Chourio/Teoscar Hernandez/Ceddanne Rafaela/Nolan Jones **UT** Garrett Mitchell **SP** Jacob deGrom/Gerrit Cole/Max Fried/Spencer Strider/Jared Jones/Jesus Luzardo/Walker Buehler **RP** Kenley Jansen/Jordan Romano **B** Lucas Erceg/Griffin Jax/Max Scherzer/Justin Verlander/Jose Caballero/Nolan Gorman/Gavin Lux
@ 6bae33c8:607272e8
2025-02-17 18:31:27I did my first NFBC draft Sunday night — I drew the 12th pick. Here’s the [link to the live-stream](https://x.com/Chris_Liss/status/1891230585043226641). The full results are below:  This draft went about as well as I could have hoped, especially given [how little I had prepared](https://www.realmansports.com/p/beat-chris-liss-1-8c2). That doesn’t mean the team is \*good\*, only that I didn’t have any major regrets or gaffes, something that’s rare over 30 rounds. I also never once got swiped on a pick. I got priced out of the top closers early, but rolled with it in the way one should when that happens, getting players I wanted and doubling back to closers when I needed to. This team is built to win the overall — high-risk, high reward, an exercise in imagining not what could go wrong, not what’s the base case, but what could go right. **The Draft** **1.12 Julio Rodriguez** — I had mapped out the first 10 rounds, decided on Rodriguez and Jackson Chourio ahead of time. I knew Chourio would be there, per ADP, but if Rodriguez were gone, I’d have gone with Mookie Betts. I wanted two OF with power and speed to start my draft. Rodriguez had 32 homers and 37 steals as a 22-year old in 2023, was going in the 2-4 overall range last year and nothing that happened since should move the needle much heading into his age 24 season. **2.1 Jackson Chourio —** Chourio had 21 homers and 22 steals as a 20-year-old rookie, and those numbers were weighed down by a slow start where the Brewers were constantly pulling him from the lineup for no reason. From June until the end of the year, he hit .303 and should only get better in Year 2. His healthy floor is 25-25, and there’s stolen base and batting average upside. **3.12 Matt Olson** — While Rodriguez and Chourio offer solid pop, I wanted a 40-HR type to compensate for the lack of top-end power with my first two picks, while filling the scarce-in-recent-years 1B slot. Olson had an off year in 2024, but chalk that up to variance. I still like him in that park and lineup. **4.1 Jacob deGrom** — I’m not here to win the $1500 league prize but the $150K overall. deGrom isn’t just the best pitcher in baseball when he’s healthy, he’s one of the best in baseball history. If I get 100 IP of vintage deGrom, that’s worth a fourth-round pick. At 130-150, it’s a first-rounder. I also like that he’s nearly two years out from Tommy John surgery, pitched at the end of last season and is healthy now. While there’s no chance of 200 IP, he’s also not a rookie they need to ramp up slowly, but a veteran with a massive contract, i.e., the Rangers will want to get their money’s worth if he’s dealing. **5.12 Gerrit Cole** — When Raisel Iglesias went four picks ahead of me, I was pretty sure I was going Cole who typically goes in the first or second round. Cole had an off year, but the sample was small as he missed time due to a nerve issue in the spring, and there wasn’t much of a drop-off from 2023, even with the irregular start to the year. Pitchers ebb and flow with health, and the light workload might redound to his benefit. **6.1 Teoscar Hernandez** — This was just a value-take in the sixth round. Hernandez gives you pop, runs a little and hits in the best lineup in baseball. **7.12 Will Smith** — I didn’t love the options in these rounds, so I punted and nabbed a solid catcher with 20-HR pop. I don’t really see the difference between Smith and Adley Rutschman who goes two rounds earlier either. **8.1 Max Fried** — With deGrom shaky on innings, and five hitters in my first seven picks, I wanted another horse to anchor the rotation. I like lefties in Yankee Stadium too. **9.12 Royce Lewis** — I needed a third baseman, and Lewis, who was going in the fifth round last year, was the one with the most upside. The key is that he’s healthy now, as he finished the season in the lineup and hasn’t had a setback this offseason. Lewis is a potential 30-HR/.290 bat if he can hold up for 140-odd games. **10.1 Spencer Strider** — As I said, I’m trying to win the overall. Strider will start the year on the DL, but the timetable for the type of surgery he had is roughly one year, and Strider’s was in mid-April, i.e., there’s no reason he shouldn’t be back in May and might even see some action in spring training. If I get 220 combined IP from deGrom and Strider at their former levels, that’s worth the 1.1. (The “former levels” part is the rub, but as I said I’m focused on what could go right.) I also thought about Shane McClanahan instead, but narrowly opted for Strider. **11.12 Luis Garcia** — I was set to take Brice Turang here to lock down speed and finally get a middle infielder, but I pivoted at the last second to Garcia who is a better-rounded hitter and more likely to have a prominent spot in his lineup. **12.1 Jared Jones** — He was on my list because I remembered the hype after his strong start, and the cost seemed cheap relative to his skills. I almost took Carlos Rodon, as I prefer veterans. Maybe that will turn out to have been a mistake. **13.12 Brice Turang** — What do you know, Turang made it all the way back. I guess people didn’t like his second-half collapse at the plate. But Turang is a gold glove defender, and he stole 50 bags last year. That glove keeps him in the lineup and should set a nice 30-steal floor. **14.1 Kenley Jansen** — I could play closer chicken no more. Jansen is my favorite type of old warhorse closer, a guy so used to the job, he’s not going to lose it unless his stuff is truly gone. **15.12 Jordan Romano** — Romano got $8.5 million from the Phillies, so I’m assuming he’s (a) healthy and (b) set to close. His ERA while pitching hurt for 14 innings last year is irrelevant. **16.1 Zach Neto** — I needed a shortstop, and while Neto’s hurt right now, he went 23-30 as a 23-year old last year, and I couldn’t pass him up. I almost took Ceddanne Rafaela, but Neto’s upside higher. **17.12 Ceddanne Rafaela** — Turns out Rafaela fell to me anyway, and I snapped him up, as I’ll need a SS early in the year with Neto presumably out. Rafaela went 15-19 as a 23-YO in his own right, also qualifies in the OF and his gold-glove-level defense should keep him in the lineup. **18.1 Josh Jung** — I needed a CI, and also a backup 3B for the injury-prone Royce Lewis, so I took the injury-prone Jung. The key facts about Jung and Lewis are both can hit, and both are healthy as of right now. My team seems like it has a lot of injuries, but only Strider and Neto are hurt now. There is a difference between injury risk (deGrom, Lewis, Jung, Romano) and already injured. You can often find value by exploiting people’s conflation of those two related, but distinct categories. **19.12 Jesus Luzardo** — Another skilled, but injury-prone player coming at a steep discount who is healthy now. **20.1 Lucas Erceg** — A speculative closer play. Right now Carlos Estevez, who went in Round 15, is probably the favorite, but who knows? **21.12 Walker Buehler** — More of the same theme. A player (especially a pitcher) who has shown elite skills, was derailed by injuries, but who is healthy now. **22.1 Nolan Jones** — I had almost forgotten he existed, but there he was in Round 22, just one year removed from being a fifth-round pick after a 20-20-.297 season. Jones is only 26 and healthy as of now. **23.12 Griffin Jax** — A setup guy with elite stuff, behind a closer that had nine losses and a 1.16 WHIP last year. **24.1 Garrett Mitchell** — I took him narrowly over Jordan Walker. Mitchell went 8-11 in 224 at-bats, plays in a good park and has the physical tools to be good. **25.12 Bo Naylor** — I needed a second catcher, and he is one. Naylor has a little pop, even runs a bit and should improve in his age 25 season. **26.1 Max Scherzer** — Are we sure he’s done? He had a 1.15 WHIP last year and 40K in 43 IP despite returning from back surgery. He’s healthy now and signed a $15.5M deal this offseason presumably to pitch more than 100 innings. **27.12 Justin Verlander** — Wait, they let me have deGrom, Cole, Strider, Buehler, Scherzer and Verlander? Those were like the top-six pitchers on the board a few years ago! Seriously though, Verlander is in a good park, and last year’s poor numbers were put up over a 90-inning sample while battling various ailments. He’s more likely to be done than Scherzer, but he knows how to pitch, and it’s just a matter of the stuff returning to above the minimum threshold. I wouldn’t be shocked to see one more strong year out of the 41-YO future Hall of Famer. **28.1 Jose Caballero** — I drafted this gentleman in the 28th round because he qualifies everywhere and steals a lot of bases. **29.12 Nolan Gorman** — The Cardinals want to get him regular at-bats, and there’s a 35-HR, .240 season somewhere in this skill set. **30.1 Gavin Lux** — A big-time prospect that’s only shown flashes, should get regular playing time and a big upgrade in park. He might eventually qualify at some other positions too. **Roster By Position** **C** Will Smith/Bo Naylor **1B** Matt Olson **2B** Luis Garcia **3B** Royce Lewis **SS** Zach Neto **CI** Josh Jung **MI** Brice Turang **OF** Julio Rodriguez/Jackson Chourio/Teoscar Hernandez/Ceddanne Rafaela/Nolan Jones **UT** Garrett Mitchell **SP** Jacob deGrom/Gerrit Cole/Max Fried/Spencer Strider/Jared Jones/Jesus Luzardo/Walker Buehler **RP** Kenley Jansen/Jordan Romano **B** Lucas Erceg/Griffin Jax/Max Scherzer/Justin Verlander/Jose Caballero/Nolan Gorman/Gavin Lux @ fe32298e:20516265
2025-02-17 17:39:31I keep a large collection of music on a local file server and use [DeaDBeeF](https://deadbeef.sourceforge.io/) for listening. I've never been able to pin DeadBeeF to the dock in Ubuntu, and it's always had the ugly default icon. I asked DeepSeek for help, and it turned out to be easier than I thought. 1. Create `~/.local/share/applications/deadbeef.desktop`: ```bash [Desktop Entry] Name=DeadBeeF Music Player Comment=Music Player Exec=/home/user/Apps/deadbeef-1.9.6/deadbeef Icon=/home/user/Apps/deadbeef-1.9.6/deadbeef.png Terminal=false Type=Application Categories=AudioVideo;Player; ``` 1. Make `deadbeef.desktop` executable: ```bash chmod +x ~/.local/share/applications/deadbeef.desktop ``` And just like that, DeadBeeF has an icon and I can pin it to the dock. `.desktop` files are part of the [Freedesktop.org standards](https://specifications.freedesktop.org/desktop-entry-spec/latest/). They're used in most popular desktop environments like GNOME, KDE and XFCE. Tor Browser has the same issue, but it comes with a `.desktop` file already, so it only needs to by symlinked to the applications folder: ``` ln -s ~/Apps/tor-browser/start-tor-browser.desktop ~/.local/share/applications/ ```
@ fe32298e:20516265
2025-02-17 17:39:31I keep a large collection of music on a local file server and use [DeaDBeeF](https://deadbeef.sourceforge.io/) for listening. I've never been able to pin DeadBeeF to the dock in Ubuntu, and it's always had the ugly default icon. I asked DeepSeek for help, and it turned out to be easier than I thought. 1. Create `~/.local/share/applications/deadbeef.desktop`: ```bash [Desktop Entry] Name=DeadBeeF Music Player Comment=Music Player Exec=/home/user/Apps/deadbeef-1.9.6/deadbeef Icon=/home/user/Apps/deadbeef-1.9.6/deadbeef.png Terminal=false Type=Application Categories=AudioVideo;Player; ``` 1. Make `deadbeef.desktop` executable: ```bash chmod +x ~/.local/share/applications/deadbeef.desktop ``` And just like that, DeadBeeF has an icon and I can pin it to the dock. `.desktop` files are part of the [Freedesktop.org standards](https://specifications.freedesktop.org/desktop-entry-spec/latest/). They're used in most popular desktop environments like GNOME, KDE and XFCE. Tor Browser has the same issue, but it comes with a `.desktop` file already, so it only needs to by symlinked to the applications folder: ``` ln -s ~/Apps/tor-browser/start-tor-browser.desktop ~/.local/share/applications/ ``` @ 9e69e420:d12360c2
2025-02-17 17:12:01President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February. Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training. Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further.
@ 9e69e420:d12360c2
2025-02-17 17:12:01President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February. Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training. Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further. @ 09fbf8f3:fa3d60f0
2025-02-17 15:23:11### 🌟 深度探索:在Cloudflare上免费部署DeepSeek-R1 32B大模型 #### 🌍 一、 注册或登录Cloudflare平台(CF老手可跳过) ##### 1️⃣ 进入Cloudflare平台官网: 。www.cloudflare.com/zh-cn/ 登录或者注册账号。  ##### 2️⃣ 新注册的用户会让你选择域名,无视即可,直接点下面的Start building。  ##### 3️⃣ 进入仪表盘后,界面可能会显示英文,在右上角切换到[简体中文]即可。  --- #### 🚀 二、正式开始部署Deepseek API项目。 ##### 1️⃣ 首先在左侧菜单栏找到【AI】下的【Wokers AI】,选择【Llama 3 Woker】。  ##### 2️⃣ 为项目取一个好听的名字,后点击部署即可。  ##### 3️⃣ Woker项目初始化部署好后,需要编辑替换掉其原代码。  ##### 4️⃣ 解压出提供的代码压缩包,找到【32b】的部署代码,将里面的文本复制出来。 **下载地址:** 📁 [夸克](https://pan.quark.cn/s/2b5aa9ff57f6) 📁 [UC网盘](https://drive.uc.cn/s/a7ff5e03b4d84?public=1) 📁 [迅雷网盘](https://pan.xunlei.com/s/VOJEzm7hLwmhER71rK2wnXArA1?pwd=cefg#)  ##### 5️⃣ 接第3步,将项目里的原代码清空,粘贴第4步复制好的代码到编辑器。  ##### 6️⃣ 代码粘贴完,即可点击右上角的部署按钮。  ##### 7️⃣ 回到仪表盘,点击部署完的项目名称。  ##### 8️⃣ 查看【设置】,找到平台分配的项目网址,复制好备用。  --- #### 💻 三、选择可用的UI软件,这边使用Chatbox AI演示。 ##### 1️⃣ 根据自己使用的平台下载对应的安装包,博主也一并打包好了全平台的软件安装包。  ##### 2️⃣ 打开安装好的Chatbox,点击左下角的设置。  ##### 3️⃣ 选择【添加自定义提供方】。  ##### 4️⃣ 按照图片说明填写即可,【API域名】为之前复制的项目网址(加/v1);【改善网络兼容性】功能务必开启;【API密钥】默认为”zhiyuan“,可自行修改;填写完毕后保存即可。  ##### 5️⃣ Cloudflare项目部署好后,就能正常使用了,接口仿照OpenAI API具有较强的兼容性,能导入到很多支持AI功能的软件或插件中。   ##### 6️⃣ Cloudflare的域名默认被墙了,需要自己准备一个域名设置。 --- **转自微信公众号:纸鸢花的小屋** **推广:低调云(梯子VPN)** 。www.didiaocloud.xyz
@ 09fbf8f3:fa3d60f0
2025-02-17 15:23:11### 🌟 深度探索:在Cloudflare上免费部署DeepSeek-R1 32B大模型 #### 🌍 一、 注册或登录Cloudflare平台(CF老手可跳过) ##### 1️⃣ 进入Cloudflare平台官网: 。www.cloudflare.com/zh-cn/ 登录或者注册账号。  ##### 2️⃣ 新注册的用户会让你选择域名,无视即可,直接点下面的Start building。  ##### 3️⃣ 进入仪表盘后,界面可能会显示英文,在右上角切换到[简体中文]即可。  --- #### 🚀 二、正式开始部署Deepseek API项目。 ##### 1️⃣ 首先在左侧菜单栏找到【AI】下的【Wokers AI】,选择【Llama 3 Woker】。  ##### 2️⃣ 为项目取一个好听的名字,后点击部署即可。  ##### 3️⃣ Woker项目初始化部署好后,需要编辑替换掉其原代码。  ##### 4️⃣ 解压出提供的代码压缩包,找到【32b】的部署代码,将里面的文本复制出来。 **下载地址:** 📁 [夸克](https://pan.quark.cn/s/2b5aa9ff57f6) 📁 [UC网盘](https://drive.uc.cn/s/a7ff5e03b4d84?public=1) 📁 [迅雷网盘](https://pan.xunlei.com/s/VOJEzm7hLwmhER71rK2wnXArA1?pwd=cefg#)  ##### 5️⃣ 接第3步,将项目里的原代码清空,粘贴第4步复制好的代码到编辑器。  ##### 6️⃣ 代码粘贴完,即可点击右上角的部署按钮。  ##### 7️⃣ 回到仪表盘,点击部署完的项目名称。  ##### 8️⃣ 查看【设置】,找到平台分配的项目网址,复制好备用。  --- #### 💻 三、选择可用的UI软件,这边使用Chatbox AI演示。 ##### 1️⃣ 根据自己使用的平台下载对应的安装包,博主也一并打包好了全平台的软件安装包。  ##### 2️⃣ 打开安装好的Chatbox,点击左下角的设置。  ##### 3️⃣ 选择【添加自定义提供方】。  ##### 4️⃣ 按照图片说明填写即可,【API域名】为之前复制的项目网址(加/v1);【改善网络兼容性】功能务必开启;【API密钥】默认为”zhiyuan“,可自行修改;填写完毕后保存即可。  ##### 5️⃣ Cloudflare项目部署好后,就能正常使用了,接口仿照OpenAI API具有较强的兼容性,能导入到很多支持AI功能的软件或插件中。   ##### 6️⃣ Cloudflare的域名默认被墙了,需要自己准备一个域名设置。 --- **转自微信公众号:纸鸢花的小屋** **推广:低调云(梯子VPN)** 。www.didiaocloud.xyz @ e7bc35f8:3ed2a7cf
2025-02-17 14:55:26The mainstream narrative paints the "freedom fever" sweeping across the Middle East as a spontaneous, people-led movement—a victory of democracy against oppressive regimes. Celebrations erupted as tech-savvy youth mobilized to topple autocrats, with Western media hailing the Arab Spring as a beacon of hope. But was it really? Or was it yet another chapter in a long history of foreign interference, regime change, and geopolitical chess moves aimed at securing control over one of the world’s most resource-rich regions? ### Revolution or Destabilization? Figures like Wadah Khanfar, the former head of Al Jazeera, [expressed optimism]( https://www.ted.com/talks/wadah_khanfar_a_historic_moment_in_the_arab_world?subtitle=en) about the uprisings, framing them as historic moments of empowerment for the people of Egypt, Tunisia, Libya, and beyond. Many Western analysts echoed this sentiment. However, other voices warned that these movements were being manipulated to serve broader strategic interests. For instance, Professor Hamid Dabashi [linked]( https://youtu.be/RMsOoEUquT8) Iran’s Green Movement to the wider regional wave of youth uprisings against authoritarian regimes. But establishment figures like Senator John McCain quickly [seized the moment]( https://youtu.be/WOcPYxLpUMs), using it as an excuse to pressure Iran, China, and Russia. A closer look suggests that these uprisings were not just organic revolts against dictatorship but rather heavily influenced by external forces. ### The Color Revolution Playbook The so-called “Green Movement” in Iran bore all the hallmarks of a Western-backed color revolution, with funding and strategic guidance from organizations linked to George Soros, the CIA, Mossad, and global mass media networks. The same script played out elsewhere, as seen in [Webster Tarpley’s analysis]( https://web.archive.org/web/20110131230059/http://www.youtube.com/watch?v=UvI6JqiAZjs) for RT, which laid out how the uprisings in the Middle East aligned perfectly with long-standing Western agendas for the region. Consider the case of Stuxnet, a cyberweapon [developed by the US and Israel]( https://youtu.be/CS01Hmjv1pQ) to sabotage Iran’s nuclear program. This wasn’t just an isolated incident—it was part of a larger strategy to weaken Iran and its allies. The infamous Brookings Institution report, "[Which Path to Persia?]( https://landdestroyer.blogspot.com/2011/02/brookings-which-path-to-persia.html?m=1)", even laid out a detailed roadmap for toppling the Iranian government through various methods, from economic warfare to military intervention. ### From Iran to Syria: The Next Domino Once the destabilization of Iran was in motion, attention shifted to its key ally, [Syria]( https://youtu.be/Gpf1C9Fcqxw). The calls for regime change escalated quickly, with Senator Joe Lieberman [openly suggesting]( https://youtu.be/aDxbTQXFhJM) that the US should intervene next. Syria, after all, is a critical piece in the geopolitical chessboard—not just because of its strategic location but also because of its alliances with Iran, Russia, and, most notably, China. This is precisely why controlling Middle Eastern oil isn’t just about securing energy for the West—it’s about **denying it to China**. If China is to be contained, it must be cut off from the resources that fuel its rise. This explains why Western-backed revolts and interventions tend to target governments that lean toward China. Let's examine some instances of China's strategy in the region. * On April 6, 2006, [Chinese President Hu Jintao and Yemeni President Ali Abdullah Saleh]( https://www.fmprc.gov.cn/eng/gjhdq_665435/2675_665437/2908_663816/2910_663820/202406/t20240607_11414813.html) held talks in Beijing. The leaders discussed enhancing political trust, expanding economic and trade cooperation, and increasing cultural and educational exchanges. * China's expanding diplomatic, economic, and security interests in the Middle East, particularly [through its interactions with the Gulf Cooperation Council (GCC)]( https://jamestown.org/program/bloc-politics-in-the-persian-gulf-chinas-multilateral-engagement-with-the-gulf-cooperation-council/). China's evolving relationship with the GCC reflects its broader objectives of securing energy resources, expanding its economic footprint, and enhancing its geopolitical influence in the Middle East and beyond. * China's expanding influence in the [Caspian region and its intersection with Syria's strategic ambitions]( https://jamestown.org/program/the-caspian-sea-chinas-silk-road-strategy-converges-with-damascus/). Investments in Central Asian infrastructure, notably the Kazakhstan-China oil pipeline and the Turkmenistan-China gas pipeline. **Syrian President Bashar al-Assad's** "Four Seas Strategy" aimed to position Syria as a central hub connecting the Caspian, Black, Mediterranean, and Red Seas. * China's expanding political, economic, and strategic ties with Syria, positioning the country as a pivotal hub in China's revitalized [Silk Road initiative]( https://jamestown.org/program/syria-in-chinas-new-silk-road-strategy/). Following **Syrian President Bashar al-Assad's** 2004 visit to China, bilateral cooperation has intensified, particularly in sectors like oil, electricity, transport, and telecommunications, with major Chinese enterprises such as CNPC, ZTE, Huawei, and Haier playing significant roles. ### The Fall of Puppets: Mubarak and Libya Hosni Mubarak, though a loyal US ally for decades, was ultimately deemed replaceable. Why? Because he was not the ideal puppet. He had shown interest in fostering deeper ties between [China]( http://www.china.org.cn/english/features/phfnt/85843.htm) and the Arab world, particularly in [Africa]( https://english.cctv.com/20091109/101132_2.shtml). His removal paved the way for a new power dynamic, one that better served Western interests. A similar pattern emerged in Libya. When NATO intervened to topple Gaddafi, [China’s oil investments]( https://www.ft.com/content/eef58d52-3fe2-11e0-811f-00144feabdc0) in the country became collateral damage. Chinese companies had billions of dollars in contracts with Libya, which were suddenly thrown into chaos. Western intervention not only eliminated Gaddafi but also disrupted China’s growing influence in North Africa. ### The Bigger Picture: A New World Order Agenda? What we are witnessing is not just a series of isolated revolts but a broader, long-term strategy to reshape the Middle East in ways that align with Western and globalist interests. The destruction of strong, independent states in the region creates a vacuum—one that can be filled by controlled regimes, multinational corporations, and military bases that ensure energy resources remain under Western control. Meanwhile, China’s efforts to establish a foothold in the region are systematically countered. Every strategic move China makes—whether in Syria, Iran, or the Persian Gulf—is met with resistance in the form of “pro-democracy” uprisings, sanctions, or outright military intervention. ### The Illusion of Spontaneous Uprising While the mainstream media glorifies the Arab Spring and similar movements as victories for democracy, the deeper reality suggests a far more calculated and sinister agenda. The Middle East is being reshaped, not by the will of its people alone, but by powerful forces seeking to maintain global hegemony. The so-called “freedom fever” may be less about liberation and more about control. The question remains: How much longer will people buy into the illusion?
@ e7bc35f8:3ed2a7cf
2025-02-17 14:55:26The mainstream narrative paints the "freedom fever" sweeping across the Middle East as a spontaneous, people-led movement—a victory of democracy against oppressive regimes. Celebrations erupted as tech-savvy youth mobilized to topple autocrats, with Western media hailing the Arab Spring as a beacon of hope. But was it really? Or was it yet another chapter in a long history of foreign interference, regime change, and geopolitical chess moves aimed at securing control over one of the world’s most resource-rich regions? ### Revolution or Destabilization? Figures like Wadah Khanfar, the former head of Al Jazeera, [expressed optimism]( https://www.ted.com/talks/wadah_khanfar_a_historic_moment_in_the_arab_world?subtitle=en) about the uprisings, framing them as historic moments of empowerment for the people of Egypt, Tunisia, Libya, and beyond. Many Western analysts echoed this sentiment. However, other voices warned that these movements were being manipulated to serve broader strategic interests. For instance, Professor Hamid Dabashi [linked]( https://youtu.be/RMsOoEUquT8) Iran’s Green Movement to the wider regional wave of youth uprisings against authoritarian regimes. But establishment figures like Senator John McCain quickly [seized the moment]( https://youtu.be/WOcPYxLpUMs), using it as an excuse to pressure Iran, China, and Russia. A closer look suggests that these uprisings were not just organic revolts against dictatorship but rather heavily influenced by external forces. ### The Color Revolution Playbook The so-called “Green Movement” in Iran bore all the hallmarks of a Western-backed color revolution, with funding and strategic guidance from organizations linked to George Soros, the CIA, Mossad, and global mass media networks. The same script played out elsewhere, as seen in [Webster Tarpley’s analysis]( https://web.archive.org/web/20110131230059/http://www.youtube.com/watch?v=UvI6JqiAZjs) for RT, which laid out how the uprisings in the Middle East aligned perfectly with long-standing Western agendas for the region. Consider the case of Stuxnet, a cyberweapon [developed by the US and Israel]( https://youtu.be/CS01Hmjv1pQ) to sabotage Iran’s nuclear program. This wasn’t just an isolated incident—it was part of a larger strategy to weaken Iran and its allies. The infamous Brookings Institution report, "[Which Path to Persia?]( https://landdestroyer.blogspot.com/2011/02/brookings-which-path-to-persia.html?m=1)", even laid out a detailed roadmap for toppling the Iranian government through various methods, from economic warfare to military intervention. ### From Iran to Syria: The Next Domino Once the destabilization of Iran was in motion, attention shifted to its key ally, [Syria]( https://youtu.be/Gpf1C9Fcqxw). The calls for regime change escalated quickly, with Senator Joe Lieberman [openly suggesting]( https://youtu.be/aDxbTQXFhJM) that the US should intervene next. Syria, after all, is a critical piece in the geopolitical chessboard—not just because of its strategic location but also because of its alliances with Iran, Russia, and, most notably, China. This is precisely why controlling Middle Eastern oil isn’t just about securing energy for the West—it’s about **denying it to China**. If China is to be contained, it must be cut off from the resources that fuel its rise. This explains why Western-backed revolts and interventions tend to target governments that lean toward China. Let's examine some instances of China's strategy in the region. * On April 6, 2006, [Chinese President Hu Jintao and Yemeni President Ali Abdullah Saleh]( https://www.fmprc.gov.cn/eng/gjhdq_665435/2675_665437/2908_663816/2910_663820/202406/t20240607_11414813.html) held talks in Beijing. The leaders discussed enhancing political trust, expanding economic and trade cooperation, and increasing cultural and educational exchanges. * China's expanding diplomatic, economic, and security interests in the Middle East, particularly [through its interactions with the Gulf Cooperation Council (GCC)]( https://jamestown.org/program/bloc-politics-in-the-persian-gulf-chinas-multilateral-engagement-with-the-gulf-cooperation-council/). China's evolving relationship with the GCC reflects its broader objectives of securing energy resources, expanding its economic footprint, and enhancing its geopolitical influence in the Middle East and beyond. * China's expanding influence in the [Caspian region and its intersection with Syria's strategic ambitions]( https://jamestown.org/program/the-caspian-sea-chinas-silk-road-strategy-converges-with-damascus/). Investments in Central Asian infrastructure, notably the Kazakhstan-China oil pipeline and the Turkmenistan-China gas pipeline. **Syrian President Bashar al-Assad's** "Four Seas Strategy" aimed to position Syria as a central hub connecting the Caspian, Black, Mediterranean, and Red Seas. * China's expanding political, economic, and strategic ties with Syria, positioning the country as a pivotal hub in China's revitalized [Silk Road initiative]( https://jamestown.org/program/syria-in-chinas-new-silk-road-strategy/). Following **Syrian President Bashar al-Assad's** 2004 visit to China, bilateral cooperation has intensified, particularly in sectors like oil, electricity, transport, and telecommunications, with major Chinese enterprises such as CNPC, ZTE, Huawei, and Haier playing significant roles. ### The Fall of Puppets: Mubarak and Libya Hosni Mubarak, though a loyal US ally for decades, was ultimately deemed replaceable. Why? Because he was not the ideal puppet. He had shown interest in fostering deeper ties between [China]( http://www.china.org.cn/english/features/phfnt/85843.htm) and the Arab world, particularly in [Africa]( https://english.cctv.com/20091109/101132_2.shtml). His removal paved the way for a new power dynamic, one that better served Western interests. A similar pattern emerged in Libya. When NATO intervened to topple Gaddafi, [China’s oil investments]( https://www.ft.com/content/eef58d52-3fe2-11e0-811f-00144feabdc0) in the country became collateral damage. Chinese companies had billions of dollars in contracts with Libya, which were suddenly thrown into chaos. Western intervention not only eliminated Gaddafi but also disrupted China’s growing influence in North Africa. ### The Bigger Picture: A New World Order Agenda? What we are witnessing is not just a series of isolated revolts but a broader, long-term strategy to reshape the Middle East in ways that align with Western and globalist interests. The destruction of strong, independent states in the region creates a vacuum—one that can be filled by controlled regimes, multinational corporations, and military bases that ensure energy resources remain under Western control. Meanwhile, China’s efforts to establish a foothold in the region are systematically countered. Every strategic move China makes—whether in Syria, Iran, or the Persian Gulf—is met with resistance in the form of “pro-democracy” uprisings, sanctions, or outright military intervention. ### The Illusion of Spontaneous Uprising While the mainstream media glorifies the Arab Spring and similar movements as victories for democracy, the deeper reality suggests a far more calculated and sinister agenda. The Middle East is being reshaped, not by the will of its people alone, but by powerful forces seeking to maintain global hegemony. The so-called “freedom fever” may be less about liberation and more about control. The question remains: How much longer will people buy into the illusion? @ 97c70a44:ad98e322
2025-02-17 14:29:00Everyone knows that relays are central to how nostr works - they're even in the name: Notes and Other Stuff Transmitted by *Relays*. As time goes on though, there are three other letters which are becoming conspicuously absent from our beloved and ambiguously pronounceable acronym - "D", "V", and "M". For the uninitiated, DVM stands for "data vending machines". They're actually sort of hard to describe — in technical terms they act more like clients, since they simply read events from and publish events to relays. In most cases though, these events are part of a request/response flow initiated by users elsewhere on the network. In practice, DVMs are bots, but there's also nothing to prevent the work they do from being powered by human interaction. They're an amazingly flexible tool for building anything from custom feeds, to transcription services, to chatbots, to protocol gateways. The hype cycle for DVMs seems to have reached escape velocity in a way few other things have - zaps being the possible exception. But *what* exactly DVMs are remains something of a mystery to many nostr developers - and how to build one may as well be written on clay tablets. This blog post is designed to address that - below is a soup to nuts (no nutzaps though) guide to building a DVM flow, both from the client and the server side. Here's what we'll be covering: - Discovering DVM metadata - Basic request/response flow - Implementing a minimal example Let's get started! # DVM Metadata First of all, it's helpful to know how DVMs are reified on the nostr network. While not strictly necessary, this can be useful for discovering DVMs and presenting them to users, and for targeting specific DVMs we want a response from. [NIP 89](https://github.com/nostr-protocol/nips/blob/master/89.md) goes into this in more detail, but the basic idea is that anyone can create a `kind 31990` "application handler" event and publish it to the network with their own (or a dedicated) public key. This handler was originally intended to advertise clients, but has been re-purposed for DVM listings as well. Here's what the "Fluffy Frens" handler looks like: ```json { "content": "{\"name\": \"Fluffy Frens\", \"picture\": \"https://image.nostr.build/f609311532c470f663e129510a76c9a1912ae9bc4aaaf058e5ba21cfb512c88e.jpg\", \"about\": \"I show recent notes about animals\", \"lud16\": \"discovery_content_fluffy@nostrdvm.com\", \"supportsEncryption\": true, \"acceptsNutZaps\": false, \"personalized\": false, \"amount\": \"free\", \"nip90Params\": {\"max_results\": {\"required\": false, \"values\": [], \"description\": \"The number of maximum results to return (default currently 100)\"}}}", "created_at": 1738874694, "id": "0aa8d1f19cfe17e00ce55ca86fea487c83be39a1813601f56f869abdfa776b3c", "kind": 31990, "pubkey": "7b7373dd58554ff4c0d28b401b9eae114bd92e30d872ae843b9a217375d66f9d", "sig": "22403a7996147da607cf215994ab3b893176e5302a44a245e9c0d91214e4c56fae40d2239dce58ea724114591e8f95caed2ba1a231d09a6cd06c9f0980e1abd5", "tags": [ ["k", "5300"], ["d", "198650843898570c"] ] } ``` This event is rendered in various clients using the kind-0-style metadata contained in the `content` field, allowing users to browse DVMs and pick one for their use case. If a user likes using a particular DVM, they might publish a `kind 31989` "application recommendation", which other users can use to find DVMs that are in use within their network. Note the `k` tag in the handler event - this allows DVMs to advertise support only for specific job types. It's also important to note that even though the spec doesn't cover relay selection, most clients use the publisher's `kind 10002` event to find out where the DVM listens for events. If this looks messy to you, you're right. See [this PR](https://github.com/nostr-protocol/nips/pull/1728) for a proposal to split DVMs out into their own handler kind, give them a dedicated pubkey along with dedicated metadata and relay selections, and clean up the data model a bit. # DVM Flow Now that we know what a DVM looks like, we can start to address how they work. My explanation below will elide some of the detail involved in [NIP 90](https://github.com/nostr-protocol/nips/blob/master/90.md) for simplicity, so I encourage you to read the complete spec. The basic DVM flow can be a little (very) confusing to work with, because in essence it's a request/response paradigm, but it has some additional wrinkles. First of all, the broker for the request isn't abstracted away as is usually the case with request/response flows. Regular HTTP requests involve all kinds of work in the background - from resolving domain names to traversing routers, VPNs, and ISP infrastructure. But developers don't generally have to care about all these intermediaries. With DVMs, on the other hand, the essential complexity of relay selection can't simply be ignored. DVMs often advertise their own relay selections, which should be used rather than a hard-coded or randomly chosen relay to ensure messages are delivered. The benefit of this is that DVMs can avoid censorship, just as users can, by choosing relays that are willing to broker their activity. DVMs can even select multiple relays to broker requests, which means that clients might receive multiple copies of the same response. Secondly, the DVM request/response model is far more fluid than is usually the case with request/response flows. There are a set of standard practices, but the flow is flexible enough to admit exceptions to these conventions for special use cases. Here are some examples: - Normally, clients p-tag the DVM they wish to address. But if a client isn't picky about where a response comes from, they may choose to send an open request to the network and collect responses from multiple DVMs simultaneously. - Normally, a client creates a request before collecting responses using a subscription with an e-tag filter matching the request event. But clients may choose to skip the request step entirely and collect responses from the network that have already been created. This can be useful for computationally intensive tasks or common queries, where a single result can be re-used multiple times. - Sometimes, a DVM may respond with a `kind 7000` job status event to let clients know they're working on the request. This is particularly useful for longer-running tasks, where feedback is useful for building a responsive UX. - There are also some details in the spec regarding monetization, parameterization, error codes, encryption, etc. # Example DVM implementation For the purposes of this blog post, I'll keep things simple by illustrating the most common kind of DVM flow: a `kind 5300` [content discovery](https://www.data-vending-machines.org/kinds/5300/) request, addressed to a particular DVM. If you're interested in other use cases, please visit [data-vending-machines.org](https://data-vending-machines.org) for additional documented kinds. The basic flow looks like this: - The DVM starts by listening for `kind 5300` job requests on some relays it has selected and advertised via NIP 89 (more on that later) - A client creates a request event of `kind 5300`, p-tagged with the DVM's pubkey and sends it to the DVM's relay selections. - The DVM receives the event and processes it, issuing optional `kind 7000` job status events, and eventually issuing a `kind 6300` job result event (job result event kinds are always 1000 greater than the request's kind). - The client listens to the same relays for a response, and when it comes through does whatever it wants to with it. Here's a swimlane diagram of that flow:  To avoid massive code samples, I'm going to implement our DVM entirely using nak (backed by the power of the human mind). The first step is to start our DVM listening for requests that it wants to respond to. Nak's default pubkey is `79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798`, so we'll only listen for requests sent to nak. ```bash nak req -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 ``` This gives us the following filter: ```json ["REQ","nak",{"kinds":[5300],"#p":["79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"]}] ``` To open a subscription to `nos.lol` and stream job requests, add `--stream wss://nos.lol` to the previous request and leave it running. Next, open a new terminal window for our "client" and create a job request. In this case, there's nothing we need to provide as `input`, but we'll include it just for illustration. It's also good practice to include an `expiration` tag so we're not asking relays to keep our ephemeral requests forever. ```bash nak event -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 -t expiration=$(( $(date +%s) + 30 )) -t input=hello ``` Here's what comes out: ```json { "kind": 5300, "id": "0e419d0b3c5d29f86d2132a38ca29cdfb81a246e1a649cb2fe1b9ed6144ebe30", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739407684, "tags": [ ["p", "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"], ["expiration", "1739407683"], ["input", "hello"] ], "content": "", "sig": "560807548a75779a7a68c0ea73c6f097583e2807f4bb286c39931e99a4e377c0a64af664fa90f43e01ddd1de2e9405acd4e268f1bf3bc66f0ed5a866ea093966" } ``` Now go ahead and publish this event by adding `nos.lol` to the end of your `nak` command. If all goes well, you should see your event pop up in your "dvm" subscription. If so, great! That's half of the flow. Next, we'll want our client to start listening for `kind 6300` responses to the request. In your "client" terminal window, run: ```bash nak req -k 6300 -t e=<your-eventid-here> --stream nos.lol ``` Note that if you only want to accept responses from the specified DVM (a good policy in general to avoid spam) you would include a `p` tag here. I've omitted it for brevity. Also notice the `k` tag specifies the request kind plus `1000` - this is just a convention for what kinds requests and responses use. Now, according to [data-vending-machines.org](https://www.data-vending-machines.org/kinds/5300/), `kind 5300` responses are supposed to put a JSON-encoded list of e-tags in the `content` field of the response. Weird, but ok. Stop the subscription in your "dvm" terminal and respond to your "client" with a recommendation to read my first note: ```bash nak event -k 6300 -t e=a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf -c '[["e","214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08","wss://nos.lol/"]]' nos.lol ``` Here's the response event we're sending: ```json { "kind": 6300, "id": "bb5f38920cbca15d3c79021f7d0051e82337254a84c56e0f4182578e4025232e", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739408411, "tags": [ ["e", "a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf"] ], "content": "[[\"e\",\"214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08\",\"wss://nos.lol/\"]]", "sig": "a0fe2c3419c5c54cf2a6d9a2a5726b2a5b766d3c9e55d55568140979354003aacb038e90bdead43becf5956faa54e3b60ff18c0ea4d8e7dfdf0c8dd97fb24ff9" } ``` Notice the `e` tag targets our original request. This should result in the job result event showing up in our "client" terminal. Success! If something isn't working, I've also create a video of the full process with some commentary which you can find [here](https://coracle-media.us-southeast-1.linodeobjects.com/nakflow.mov). Note that in practice, DVMs can be much more picky about the requests they will respond to, due to implementations failing to follow [Postel's law](https://en.wikipedia.org/wiki/Robustness_principle). Hopefully that will improve over time. For now, here are a few resources that are useful when working with or developing DVMs: - [dvmdash](https://dvmdash.live) - [data-vending-machines.org](https://data-vending-machines.org) - [noogle](https://noogle.lol/) - [nostrdvm](https://github.com/believethehype/nostrdvm) # Conclusion I started this post by hinting that DVMs might be as fundamental as relays are to making nostr work. But (apart from the fact that we'd end up with an acronym like DVMNOSTRZ+*, which would only exascerbate the pronounciation wars (if such a thing were possible)), that's not exactly true. DVMs have emerged as a central paradigm in the nostr world because they're a generalization of a design pattern unique to nostr's architecture - but which exists in many other places, including NIP 46 signer flows and NIP 47 wallet connect. Each of these sub-protocols works by using relays as neutral brokers for requests in order to avoid coupling services to web addresses. This approach has all kinds of neat benefits, not least of which is allowing service providers to host their software without having to accept incoming TCP connections. But it's really an emergent property of relays, which not only are useful for brokering communication between users (aka storing events), but also brokering communication between machines. The possibilities of this architecture have only started to emerge, so be on the lookout for new applications, and don't be afraid to experiment - just please, don't serialize json inside json 🤦♂️
@ 97c70a44:ad98e322
2025-02-17 14:29:00Everyone knows that relays are central to how nostr works - they're even in the name: Notes and Other Stuff Transmitted by *Relays*. As time goes on though, there are three other letters which are becoming conspicuously absent from our beloved and ambiguously pronounceable acronym - "D", "V", and "M". For the uninitiated, DVM stands for "data vending machines". They're actually sort of hard to describe — in technical terms they act more like clients, since they simply read events from and publish events to relays. In most cases though, these events are part of a request/response flow initiated by users elsewhere on the network. In practice, DVMs are bots, but there's also nothing to prevent the work they do from being powered by human interaction. They're an amazingly flexible tool for building anything from custom feeds, to transcription services, to chatbots, to protocol gateways. The hype cycle for DVMs seems to have reached escape velocity in a way few other things have - zaps being the possible exception. But *what* exactly DVMs are remains something of a mystery to many nostr developers - and how to build one may as well be written on clay tablets. This blog post is designed to address that - below is a soup to nuts (no nutzaps though) guide to building a DVM flow, both from the client and the server side. Here's what we'll be covering: - Discovering DVM metadata - Basic request/response flow - Implementing a minimal example Let's get started! # DVM Metadata First of all, it's helpful to know how DVMs are reified on the nostr network. While not strictly necessary, this can be useful for discovering DVMs and presenting them to users, and for targeting specific DVMs we want a response from. [NIP 89](https://github.com/nostr-protocol/nips/blob/master/89.md) goes into this in more detail, but the basic idea is that anyone can create a `kind 31990` "application handler" event and publish it to the network with their own (or a dedicated) public key. This handler was originally intended to advertise clients, but has been re-purposed for DVM listings as well. Here's what the "Fluffy Frens" handler looks like: ```json { "content": "{\"name\": \"Fluffy Frens\", \"picture\": \"https://image.nostr.build/f609311532c470f663e129510a76c9a1912ae9bc4aaaf058e5ba21cfb512c88e.jpg\", \"about\": \"I show recent notes about animals\", \"lud16\": \"discovery_content_fluffy@nostrdvm.com\", \"supportsEncryption\": true, \"acceptsNutZaps\": false, \"personalized\": false, \"amount\": \"free\", \"nip90Params\": {\"max_results\": {\"required\": false, \"values\": [], \"description\": \"The number of maximum results to return (default currently 100)\"}}}", "created_at": 1738874694, "id": "0aa8d1f19cfe17e00ce55ca86fea487c83be39a1813601f56f869abdfa776b3c", "kind": 31990, "pubkey": "7b7373dd58554ff4c0d28b401b9eae114bd92e30d872ae843b9a217375d66f9d", "sig": "22403a7996147da607cf215994ab3b893176e5302a44a245e9c0d91214e4c56fae40d2239dce58ea724114591e8f95caed2ba1a231d09a6cd06c9f0980e1abd5", "tags": [ ["k", "5300"], ["d", "198650843898570c"] ] } ``` This event is rendered in various clients using the kind-0-style metadata contained in the `content` field, allowing users to browse DVMs and pick one for their use case. If a user likes using a particular DVM, they might publish a `kind 31989` "application recommendation", which other users can use to find DVMs that are in use within their network. Note the `k` tag in the handler event - this allows DVMs to advertise support only for specific job types. It's also important to note that even though the spec doesn't cover relay selection, most clients use the publisher's `kind 10002` event to find out where the DVM listens for events. If this looks messy to you, you're right. See [this PR](https://github.com/nostr-protocol/nips/pull/1728) for a proposal to split DVMs out into their own handler kind, give them a dedicated pubkey along with dedicated metadata and relay selections, and clean up the data model a bit. # DVM Flow Now that we know what a DVM looks like, we can start to address how they work. My explanation below will elide some of the detail involved in [NIP 90](https://github.com/nostr-protocol/nips/blob/master/90.md) for simplicity, so I encourage you to read the complete spec. The basic DVM flow can be a little (very) confusing to work with, because in essence it's a request/response paradigm, but it has some additional wrinkles. First of all, the broker for the request isn't abstracted away as is usually the case with request/response flows. Regular HTTP requests involve all kinds of work in the background - from resolving domain names to traversing routers, VPNs, and ISP infrastructure. But developers don't generally have to care about all these intermediaries. With DVMs, on the other hand, the essential complexity of relay selection can't simply be ignored. DVMs often advertise their own relay selections, which should be used rather than a hard-coded or randomly chosen relay to ensure messages are delivered. The benefit of this is that DVMs can avoid censorship, just as users can, by choosing relays that are willing to broker their activity. DVMs can even select multiple relays to broker requests, which means that clients might receive multiple copies of the same response. Secondly, the DVM request/response model is far more fluid than is usually the case with request/response flows. There are a set of standard practices, but the flow is flexible enough to admit exceptions to these conventions for special use cases. Here are some examples: - Normally, clients p-tag the DVM they wish to address. But if a client isn't picky about where a response comes from, they may choose to send an open request to the network and collect responses from multiple DVMs simultaneously. - Normally, a client creates a request before collecting responses using a subscription with an e-tag filter matching the request event. But clients may choose to skip the request step entirely and collect responses from the network that have already been created. This can be useful for computationally intensive tasks or common queries, where a single result can be re-used multiple times. - Sometimes, a DVM may respond with a `kind 7000` job status event to let clients know they're working on the request. This is particularly useful for longer-running tasks, where feedback is useful for building a responsive UX. - There are also some details in the spec regarding monetization, parameterization, error codes, encryption, etc. # Example DVM implementation For the purposes of this blog post, I'll keep things simple by illustrating the most common kind of DVM flow: a `kind 5300` [content discovery](https://www.data-vending-machines.org/kinds/5300/) request, addressed to a particular DVM. If you're interested in other use cases, please visit [data-vending-machines.org](https://data-vending-machines.org) for additional documented kinds. The basic flow looks like this: - The DVM starts by listening for `kind 5300` job requests on some relays it has selected and advertised via NIP 89 (more on that later) - A client creates a request event of `kind 5300`, p-tagged with the DVM's pubkey and sends it to the DVM's relay selections. - The DVM receives the event and processes it, issuing optional `kind 7000` job status events, and eventually issuing a `kind 6300` job result event (job result event kinds are always 1000 greater than the request's kind). - The client listens to the same relays for a response, and when it comes through does whatever it wants to with it. Here's a swimlane diagram of that flow:  To avoid massive code samples, I'm going to implement our DVM entirely using nak (backed by the power of the human mind). The first step is to start our DVM listening for requests that it wants to respond to. Nak's default pubkey is `79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798`, so we'll only listen for requests sent to nak. ```bash nak req -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 ``` This gives us the following filter: ```json ["REQ","nak",{"kinds":[5300],"#p":["79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"]}] ``` To open a subscription to `nos.lol` and stream job requests, add `--stream wss://nos.lol` to the previous request and leave it running. Next, open a new terminal window for our "client" and create a job request. In this case, there's nothing we need to provide as `input`, but we'll include it just for illustration. It's also good practice to include an `expiration` tag so we're not asking relays to keep our ephemeral requests forever. ```bash nak event -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 -t expiration=$(( $(date +%s) + 30 )) -t input=hello ``` Here's what comes out: ```json { "kind": 5300, "id": "0e419d0b3c5d29f86d2132a38ca29cdfb81a246e1a649cb2fe1b9ed6144ebe30", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739407684, "tags": [ ["p", "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"], ["expiration", "1739407683"], ["input", "hello"] ], "content": "", "sig": "560807548a75779a7a68c0ea73c6f097583e2807f4bb286c39931e99a4e377c0a64af664fa90f43e01ddd1de2e9405acd4e268f1bf3bc66f0ed5a866ea093966" } ``` Now go ahead and publish this event by adding `nos.lol` to the end of your `nak` command. If all goes well, you should see your event pop up in your "dvm" subscription. If so, great! That's half of the flow. Next, we'll want our client to start listening for `kind 6300` responses to the request. In your "client" terminal window, run: ```bash nak req -k 6300 -t e=<your-eventid-here> --stream nos.lol ``` Note that if you only want to accept responses from the specified DVM (a good policy in general to avoid spam) you would include a `p` tag here. I've omitted it for brevity. Also notice the `k` tag specifies the request kind plus `1000` - this is just a convention for what kinds requests and responses use. Now, according to [data-vending-machines.org](https://www.data-vending-machines.org/kinds/5300/), `kind 5300` responses are supposed to put a JSON-encoded list of e-tags in the `content` field of the response. Weird, but ok. Stop the subscription in your "dvm" terminal and respond to your "client" with a recommendation to read my first note: ```bash nak event -k 6300 -t e=a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf -c '[["e","214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08","wss://nos.lol/"]]' nos.lol ``` Here's the response event we're sending: ```json { "kind": 6300, "id": "bb5f38920cbca15d3c79021f7d0051e82337254a84c56e0f4182578e4025232e", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739408411, "tags": [ ["e", "a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf"] ], "content": "[[\"e\",\"214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08\",\"wss://nos.lol/\"]]", "sig": "a0fe2c3419c5c54cf2a6d9a2a5726b2a5b766d3c9e55d55568140979354003aacb038e90bdead43becf5956faa54e3b60ff18c0ea4d8e7dfdf0c8dd97fb24ff9" } ``` Notice the `e` tag targets our original request. This should result in the job result event showing up in our "client" terminal. Success! If something isn't working, I've also create a video of the full process with some commentary which you can find [here](https://coracle-media.us-southeast-1.linodeobjects.com/nakflow.mov). Note that in practice, DVMs can be much more picky about the requests they will respond to, due to implementations failing to follow [Postel's law](https://en.wikipedia.org/wiki/Robustness_principle). Hopefully that will improve over time. For now, here are a few resources that are useful when working with or developing DVMs: - [dvmdash](https://dvmdash.live) - [data-vending-machines.org](https://data-vending-machines.org) - [noogle](https://noogle.lol/) - [nostrdvm](https://github.com/believethehype/nostrdvm) # Conclusion I started this post by hinting that DVMs might be as fundamental as relays are to making nostr work. But (apart from the fact that we'd end up with an acronym like DVMNOSTRZ+*, which would only exascerbate the pronounciation wars (if such a thing were possible)), that's not exactly true. DVMs have emerged as a central paradigm in the nostr world because they're a generalization of a design pattern unique to nostr's architecture - but which exists in many other places, including NIP 46 signer flows and NIP 47 wallet connect. Each of these sub-protocols works by using relays as neutral brokers for requests in order to avoid coupling services to web addresses. This approach has all kinds of neat benefits, not least of which is allowing service providers to host their software without having to accept incoming TCP connections. But it's really an emergent property of relays, which not only are useful for brokering communication between users (aka storing events), but also brokering communication between machines. The possibilities of this architecture have only started to emerge, so be on the lookout for new applications, and don't be afraid to experiment - just please, don't serialize json inside json 🤦♂️ @ 57d1a264:69f1fee1
2025-02-17 13:55:53 Hey ~Design fam! We’re hosting an exclusive session on ephemeral architecture & immersive photography—and you’re invited! 🎟️ What happens when spaces tell stories? join us for an inspiring session that explores the magic of ephemeral architecture and immersive photography. let paramdeep singh dayani, architect & photographer, guide you through the art of designing impermanent yet unforgettable moments. **What you'll explore:** ✨ designing for impermanence: how to craft spaces that make a statement. 📸 photography as storytelling: capturing the fleeting essence of design. 🤝 the human connection: using visuals to evoke emotion. **Why you should attend:** 1️⃣ get inspired to create meaning in impermanence. 2️⃣ learn how visuals can transform spaces into stories. 3️⃣ connect with a community of creative minds and innovative thinkers. **📅 When** Feb 27, 2025 - 9-10 PM **📍 Where?** Right here on Discord—because webinars should be interactive, engaging, and community-driven. 🔗 Save your spot now! - https://tally.so/r/w86MkP See you there! 🚀  originally posted at https://stacker.news/items/888333
@ 57d1a264:69f1fee1
2025-02-17 13:55:53 Hey ~Design fam! We’re hosting an exclusive session on ephemeral architecture & immersive photography—and you’re invited! 🎟️ What happens when spaces tell stories? join us for an inspiring session that explores the magic of ephemeral architecture and immersive photography. let paramdeep singh dayani, architect & photographer, guide you through the art of designing impermanent yet unforgettable moments. **What you'll explore:** ✨ designing for impermanence: how to craft spaces that make a statement. 📸 photography as storytelling: capturing the fleeting essence of design. 🤝 the human connection: using visuals to evoke emotion. **Why you should attend:** 1️⃣ get inspired to create meaning in impermanence. 2️⃣ learn how visuals can transform spaces into stories. 3️⃣ connect with a community of creative minds and innovative thinkers. **📅 When** Feb 27, 2025 - 9-10 PM **📍 Where?** Right here on Discord—because webinars should be interactive, engaging, and community-driven. 🔗 Save your spot now! - https://tally.so/r/w86MkP See you there! 🚀  originally posted at https://stacker.news/items/888333 @ e88a691e:27850411
2025-02-17 13:30:42test post longform 4
@ e88a691e:27850411
2025-02-17 13:30:42test post longform 4 @ da0b9bc3:4e30a4a9
2025-02-17 12:33:36Hello Stackers! It's Monday so we're back doing "Meta Music Mondays" 😉. From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme. Welcome to Femmes Fatales 3!!! I absolutely loved doing this last year so I'm bringing it back for round 3! It's Femmes Fatales, where we celebrate women in ~Music. So let's have those ladies of the lung, the sirens of sound, our Femmes Fatales! Man! I Feel like a Woman! Shania Twain! https://youtu.be/ZJL4UGSbeFg?si=ClexJCLdrpDg1RRG Talk Music. Share Tracks. Zap Sats. originally posted at https://stacker.news/items/888248
@ da0b9bc3:4e30a4a9
2025-02-17 12:33:36Hello Stackers! It's Monday so we're back doing "Meta Music Mondays" 😉. From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme. Welcome to Femmes Fatales 3!!! I absolutely loved doing this last year so I'm bringing it back for round 3! It's Femmes Fatales, where we celebrate women in ~Music. So let's have those ladies of the lung, the sirens of sound, our Femmes Fatales! Man! I Feel like a Woman! Shania Twain! https://youtu.be/ZJL4UGSbeFg?si=ClexJCLdrpDg1RRG Talk Music. Share Tracks. Zap Sats. originally posted at https://stacker.news/items/888248 @ 16d11430:61640947
2025-02-17 12:28:08The Perfect Psychological Operation to Divide, Conquer, and Enslave Why Do Men Feel Useless and Women Feel Overburdened? Look around. Something is deeply, insidiously wrong. Men are lost, stripped of purpose, and drowning in quiet despair. Women are exhausted, forced into unnatural roles, carrying both professional and domestic burdens while being told they should be grateful for the privilege. Marriages crumble, families disintegrate, and the birth rate nosedives while corporate profits soar. Coincidence? Not a chance. This is not a byproduct of "progress" or "equality." This is a precision-engineered psychological and economic war waged against the family unit by the fiat system and its corporate enforcers. It is not feminism, nor is it the patriarchy. It is something far worse: a deliberate social and financial coup to destroy natural gender balance, increase worker dependency, and create the perfect, exhausted, obedient slaves. Let’s tear this apart, piece by piece. --- Step 1: Economic Sabotage – The Emasculation of Men Men have been systematically stripped of their role as providers, not by cultural shifts, but by the fiat scam that inflates away their labor and makes single-income households impossible. In 1970, a man could buy a home, support a family, and retire with dignity on a working-class salary. Today? Even high earners struggle to buy homes while rent and debt devour their paychecks. The psychological effect? Uselessness. The traditional role of men—to provide, protect, and build—has been economically crippled. The moment a man cannot provide, his biological drive collapses. His confidence, purpose, and even testosterone levels plummet. He turns to distractions—video games, porn, drugs, or meaningless jobs. Or he checks out entirely, labeled “lazy” while the system that neutered him laughs from above. And yet, men are still told to "man up" and "work harder"—as if fighting against a rigged economy is a test of character. --- Step 2: Psychological Warfare – The Masculinization of Women Women, meanwhile, have been sold a lie—that the only path to fulfillment is chasing careers inside corporate cubicles. While they are told this is "empowerment," what it really does is double the workforce, lower wages, and increase tax revenue. Women now face double the burden—working a full-time job while still handling the majority of child-rearing and housework. Instead of being honored for creating life and raising future generations, they are ridiculed for “wasting their potential” if they don’t dedicate themselves to their corporate masters. And what is the psychological effect? Resentment. Resentment towards men, who are no longer the strong providers they once were. Resentment towards motherhood, which has been devalued and monetized. Resentment towards themselves, because they were promised fulfillment through corporate work but ended up burned out, anxious, and miserable. Women have been told they are “strong and independent” while simultaneously being enslaved to a system that profits off their exhaustion. --- Step 3: Divide and Conquer – Corporate Culture as the New Family With men neutered and women overburdened, the nuclear family collapses. But humans still need a sense of belonging. Enter: The Corporation. Your workplace becomes your "real family." HR tells you to “bring your whole self to work.” Team-building exercises and corporate retreats replace family gatherings. Work colleagues become your primary emotional support system. There’s even the concept of the “work spouse,” an insidious corporate fabrication that normalizes deeper emotional ties with colleagues than with real partners. Your career becomes your purpose. Not your bloodline, not your family history, not your legacy—your productivity for someone else’s bottom line. And before you know it, you’re 50 years old, childless, exhausted, and utterly dependent on a salary to survive. The corporate world used your best years to enrich its shareholders, and now you have nothing. --- Step 4: The Endgame – The State Raises Your Kids With the family unit in ruins, who raises the next generation? The State. Public schools become indoctrination camps, teaching kids to obey, conform, and view the government as their protector. Children are raised by institutions, not by parents—because both parents are working just to survive. The cycle repeats: fatherless boys become weak men, overburdened girls become resentful women, and the system gains a fresh crop of obedient, exhausted workers. The ultimate fiat scam is not just financial. It is biological. It is a full-scale, generational coup against the natural order of humanity. --- How Do We Break Free? The only way to escape this biological and financial slavery is to opt out of the fiat system entirely. 1. Bitcoin & Self-Sovereignty – Remove your wealth from the fiat system. Own hard assets, build businesses, become untouchable. 2. Build Real Families – The corporate world is not your family. Your bloodline is. Reject the state’s control over your children. 3. Reject Debt & Wage Slavery – The system is designed to keep you financially trapped. Find ways to exit the rat race early. 4. Reclaim Natural Gender Roles – Not through coercion, but through honest, sovereign partnerships that reject fiat-fueled dysfunction. They divided us so they could rule us. Break the cycle.
@ 16d11430:61640947
2025-02-17 12:28:08The Perfect Psychological Operation to Divide, Conquer, and Enslave Why Do Men Feel Useless and Women Feel Overburdened? Look around. Something is deeply, insidiously wrong. Men are lost, stripped of purpose, and drowning in quiet despair. Women are exhausted, forced into unnatural roles, carrying both professional and domestic burdens while being told they should be grateful for the privilege. Marriages crumble, families disintegrate, and the birth rate nosedives while corporate profits soar. Coincidence? Not a chance. This is not a byproduct of "progress" or "equality." This is a precision-engineered psychological and economic war waged against the family unit by the fiat system and its corporate enforcers. It is not feminism, nor is it the patriarchy. It is something far worse: a deliberate social and financial coup to destroy natural gender balance, increase worker dependency, and create the perfect, exhausted, obedient slaves. Let’s tear this apart, piece by piece. --- Step 1: Economic Sabotage – The Emasculation of Men Men have been systematically stripped of their role as providers, not by cultural shifts, but by the fiat scam that inflates away their labor and makes single-income households impossible. In 1970, a man could buy a home, support a family, and retire with dignity on a working-class salary. Today? Even high earners struggle to buy homes while rent and debt devour their paychecks. The psychological effect? Uselessness. The traditional role of men—to provide, protect, and build—has been economically crippled. The moment a man cannot provide, his biological drive collapses. His confidence, purpose, and even testosterone levels plummet. He turns to distractions—video games, porn, drugs, or meaningless jobs. Or he checks out entirely, labeled “lazy” while the system that neutered him laughs from above. And yet, men are still told to "man up" and "work harder"—as if fighting against a rigged economy is a test of character. --- Step 2: Psychological Warfare – The Masculinization of Women Women, meanwhile, have been sold a lie—that the only path to fulfillment is chasing careers inside corporate cubicles. While they are told this is "empowerment," what it really does is double the workforce, lower wages, and increase tax revenue. Women now face double the burden—working a full-time job while still handling the majority of child-rearing and housework. Instead of being honored for creating life and raising future generations, they are ridiculed for “wasting their potential” if they don’t dedicate themselves to their corporate masters. And what is the psychological effect? Resentment. Resentment towards men, who are no longer the strong providers they once were. Resentment towards motherhood, which has been devalued and monetized. Resentment towards themselves, because they were promised fulfillment through corporate work but ended up burned out, anxious, and miserable. Women have been told they are “strong and independent” while simultaneously being enslaved to a system that profits off their exhaustion. --- Step 3: Divide and Conquer – Corporate Culture as the New Family With men neutered and women overburdened, the nuclear family collapses. But humans still need a sense of belonging. Enter: The Corporation. Your workplace becomes your "real family." HR tells you to “bring your whole self to work.” Team-building exercises and corporate retreats replace family gatherings. Work colleagues become your primary emotional support system. There’s even the concept of the “work spouse,” an insidious corporate fabrication that normalizes deeper emotional ties with colleagues than with real partners. Your career becomes your purpose. Not your bloodline, not your family history, not your legacy—your productivity for someone else’s bottom line. And before you know it, you’re 50 years old, childless, exhausted, and utterly dependent on a salary to survive. The corporate world used your best years to enrich its shareholders, and now you have nothing. --- Step 4: The Endgame – The State Raises Your Kids With the family unit in ruins, who raises the next generation? The State. Public schools become indoctrination camps, teaching kids to obey, conform, and view the government as their protector. Children are raised by institutions, not by parents—because both parents are working just to survive. The cycle repeats: fatherless boys become weak men, overburdened girls become resentful women, and the system gains a fresh crop of obedient, exhausted workers. The ultimate fiat scam is not just financial. It is biological. It is a full-scale, generational coup against the natural order of humanity. --- How Do We Break Free? The only way to escape this biological and financial slavery is to opt out of the fiat system entirely. 1. Bitcoin & Self-Sovereignty – Remove your wealth from the fiat system. Own hard assets, build businesses, become untouchable. 2. Build Real Families – The corporate world is not your family. Your bloodline is. Reject the state’s control over your children. 3. Reject Debt & Wage Slavery – The system is designed to keep you financially trapped. Find ways to exit the rat race early. 4. Reclaim Natural Gender Roles – Not through coercion, but through honest, sovereign partnerships that reject fiat-fueled dysfunction. They divided us so they could rule us. Break the cycle. @ d360efec:14907b5f
2025-02-17 12:20:25**3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไรของนักลงทุนส่วนใหญ่** นักลงทุนจำนวนมากต้องการที่จะประสบความสำเร็จในตลาดหุ้นและสร้างผลกำไรที่สม่ำเสมอ แต่หลายครั้งที่พวกเขากลับพบว่าตัวเองต้องเผชิญกับอุปสรรคที่ทำให้ไม่สามารถบรรลุเป้าหมายนั้นได้ ช่อง Zyo / เซียว จับอิดนึ้ง ได้นำเสนอ 3 พฤติกรรมที่เป็นอุปสรรคสำคัญต่อนักลงทุนส่วนใหญ่ ซึ่งหากนักลงทุนสามารถหลีกเลี่ยงพฤติกรรมเหล่านี้ได้ ก็จะมีโอกาสในการสร้างผลกำไรที่สม่ำเสมอมากยิ่งขึ้น 1. **การซื้อขายตามอารมณ์:** ตลาดหุ้นมีความผันผวนและเต็มไปด้วยข่าวสารมากมาย นักลงทุนที่ซื้อขายตามอารมณ์มักจะตัดสินใจโดยใช้อารมณ์เป็นหลัก ไม่ว่าจะเป็นความโลภเมื่อเห็นราคาหุ้นขึ้น หรือความกลัวเมื่อราคาหุ้นตก การตัดสินใจที่ไม่ได้อยู่บนพื้นฐานของข้อมูลและการวิเคราะห์อย่างรอบคอบ มักนำไปสู่การตัดสินใจที่ผิดพลาดและขาดทุนในที่สุด 2. **การไม่ยอมรับความเสี่ยง:** การลงทุนในตลาดหุ้นมีความเสี่ยง นักลงทุนที่ไม่ยอมรับความเสี่ยงมักจะพลาดโอกาสในการลงทุนในสินทรัพย์ที่ให้ผลตอบแทนสูง หรือในทางกลับกัน พวกเขาอาจจะหลีกเลี่ยงการตัดขาดทุนเมื่อการลงทุนไม่เป็นไปตามที่คาดหวัง การไม่ยอมรับความเสี่ยงและไม่บริหารความเสี่ยงอย่างเหมาะสม จะทำให้พอร์ตการลงทุนไม่เติบโตเท่าที่ควร หรืออาจจะเผชิญกับความเสียหายที่ใหญ่หลวงได้ 3. **การขาดความรู้และความเข้าใจ:** ตลาดหุ้นเป็นเรื่องที่ซับซ้อนและเปลี่ยนแปลงอยู่เสมอ นักลงทุนที่ขาดความรู้และความเข้าใจในเรื่องการลงทุนอย่างเพียงพอ มักจะลงทุนโดยไม่มีหลักการหรือไม่สามารถวิเคราะห์สถานการณ์ได้อย่างถูกต้อง การลงทุนโดยปราศจากความรู้และความเข้าใจที่ถูกต้อง ก็เหมือนกับการเดินอยู่ในความมืด ซึ่งโอกาสที่จะประสบความสำเร็จนั้นเป็นไปได้ยาก **บทสรุป** 3 พฤติกรรมที่กล่าวมาข้างต้นเป็นเพียงส่วนหนึ่งของอุปสรรคที่นักลงทุนส่วนใหญ่ต้องเผชิญ หากนักลงทุนต้องการที่จะประสบความสำเร็จในการลงทุนอย่างยั่งยืน พวกเขาจำเป็นต้องตระหนักถึงพฤติกรรมเหล่านี้และพยายามปรับปรุงตนเองอย่างต่อเนื่อง การศึกษาหาความรู้เพิ่มเติม การวางแผนการลงทุนอย่างรอบคอบ และการควบคุมอารมณ์ จะเป็นกุญแจสำคัญที่นำไปสู่การสร้างผลกำไรที่สม่ำเสมอในตลาดหุ้นได้ แน่นอนค่ะ ฟังคลิปแล้ว และสรุปบทความเป็นภาษาไทยให้คุณแล้วค่ะ **บทความ: 3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไรสม่ำเสมอของนักลงทุนส่วนใหญ่** บทความนี้สรุปแนวคิดจากคลิปวิดีโอที่วิเคราะห์พฤติกรรมของนักลงทุนส่วนใหญ่ โดยอ้างอิงจากการสำรวจบัญชีซื้อขายหุ้นกว่า 77,000 บัญชีในช่วงปี 1990-1996 พบว่ามี 3 พฤติกรรมหลักที่เป็นอุปสรรคสำคัญต่อการสร้างผลกำไรที่สม่ำเสมอในการลงทุน **3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไร:** 1. **ปล่อยให้ขาดทุน แต่รีบขายกำไร:** นักลงทุนส่วนใหญ่มักจะถือหุ้นที่กำลังขาดทุนต่อไปเรื่อย ๆ เพราะไม่อยากยอมรับว่าตัดสินใจผิดพลาด ในทางกลับกัน เมื่อหุ้นเริ่มมีกำไรเพียงเล็กน้อย กลับรีบขายออกไปเพราะกลัวกำไรจะหายไป พฤติกรรมนี้เป็นผลจากธรรมชาติของมนุษย์ที่เรียกว่า "Loser Aversion" หรือการหลีกเลี่ยงความเจ็บปวดจากการขาดทุนมากกว่าความสุขจากการได้กำไร 2. **ถัวเฉลี่ยขาลง มากกว่าพีระมิดขาขึ้น:** นักลงทุนจำนวนมากเลือกที่จะซื้อหุ้นที่ราคาลดลง (ถัวเฉลี่ยขาลง) โดยหวังว่าจะได้ต้นทุนที่ต่ำลงและรอให้ราคาหุ้นกลับมา แต่ในความเป็นจริง หุ้นที่อยู่ในแนวโน้มขาลงก็มีโอกาสที่จะลงต่อไปเรื่อย ๆ การถัวเฉลี่ยขาลงจึงเป็นการเพิ่มความเสี่ยง ในขณะที่การ "พีระมิดขาขึ้น" หรือการซื้อหุ้นเพิ่มเมื่อราคาปรับตัวสูงขึ้น เป็นการลงทุนในหุ้นที่กำลังมีแนวโน้มที่ดีและมีโอกาสสร้างกำไรมากกว่า 3. **รีบขายกำไรเล็กน้อย แต่ไม่ยอมขายเมื่อขาดทุนเล็กน้อย:** พฤติกรรมนี้ต่อเนื่องจากข้อแรก คือเมื่อได้กำไรเพียงเล็กน้อย นักลงทุนมักจะรีบขายเพื่อ "ล็อกกำไร" แต่เมื่อขาดทุนเล็กน้อย กลับไม่ยอมขายเพราะหวังว่าราคาจะกลับมา ทำให้สุดท้ายกลายเป็น "กำไรน้อย รีบขาย ขาดทุน เก็บไว้" ซึ่งส่งผลเสียต่อพอร์ตการลงทุนในระยะยาว **คำแนะนำเพื่อปรับปรุงพฤติกรรมการลงทุน:** * **ฝึก "Cut Loss Short, Let Profit Run":** ยอมตัดขาดทุนเมื่อหุ้นไม่เป็นไปตามแผน เพื่อจำกัดความเสียหาย และปล่อยให้หุ้นที่กำลังทำกำไรทำงานไป เพื่อเพิ่มโอกาสในการทำกำไรที่มากขึ้น * **อย่าถัวเฉลี่ยขาลงโดยไม่มีเหตุผล:** พิจารณาแนวโน้มของหุ้นและปัจจัยพื้นฐานก่อนตัดสินใจถัวเฉลี่ยขาลง หากไม่มีเหตุผลที่ชัดเจน การถัวเฉลี่ยขาลงอาจเป็นการเพิ่มความเสี่ยงโดยไม่จำเป็น * **บริหารความเสี่ยงและ Money Management อย่างเหมาะสม:** กำหนด stop loss ที่ชัดเจน และบริหารจัดการเงินทุนให้เหมาะสมกับความเสี่ยงที่รับได้ * **เรียนรู้และพัฒนาระบบเทรดของตัวเองอย่างต่อเนื่อง:** ทำความเข้าใจกลยุทธ์การเทรดของตนเอง และปรับปรุงพัฒนาอย่างสม่ำเสมอ * **มี Mindset ที่ถูกต้องสำหรับการเทรด:** เข้าใจว่าการเทรดสวนทางกับธรรมชาติของมนุษย์ ต้องฝึกฝนและสร้างนิสัยที่ถูกต้องเพื่อเอาชนะอุปสรรคทางจิตวิทยา **สรุป:** การลงทุนและการเทรดหุ้นเป็นเกมที่ "ผิดธรรมชาติ" ของมนุษย์ การเอาชนะตลาดหุ้นได้จึงต้องอาศัยการฝึกฝนและปรับเปลี่ยนพฤติกรรมให้สวนทางกับธรรมชาติเดิม ๆ โดยการตระหนักถึง 3 พฤติกรรมที่เป็นอุปสรรค และนำคำแนะนำไปปรับใช้ จะช่วยให้นักลงทุนสามารถพัฒนาไปสู่การสร้างผลกำไรที่สม่ำเสมอและยั่งยืนได้ในระยะยาว
@ d360efec:14907b5f
2025-02-17 12:20:25**3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไรของนักลงทุนส่วนใหญ่** นักลงทุนจำนวนมากต้องการที่จะประสบความสำเร็จในตลาดหุ้นและสร้างผลกำไรที่สม่ำเสมอ แต่หลายครั้งที่พวกเขากลับพบว่าตัวเองต้องเผชิญกับอุปสรรคที่ทำให้ไม่สามารถบรรลุเป้าหมายนั้นได้ ช่อง Zyo / เซียว จับอิดนึ้ง ได้นำเสนอ 3 พฤติกรรมที่เป็นอุปสรรคสำคัญต่อนักลงทุนส่วนใหญ่ ซึ่งหากนักลงทุนสามารถหลีกเลี่ยงพฤติกรรมเหล่านี้ได้ ก็จะมีโอกาสในการสร้างผลกำไรที่สม่ำเสมอมากยิ่งขึ้น 1. **การซื้อขายตามอารมณ์:** ตลาดหุ้นมีความผันผวนและเต็มไปด้วยข่าวสารมากมาย นักลงทุนที่ซื้อขายตามอารมณ์มักจะตัดสินใจโดยใช้อารมณ์เป็นหลัก ไม่ว่าจะเป็นความโลภเมื่อเห็นราคาหุ้นขึ้น หรือความกลัวเมื่อราคาหุ้นตก การตัดสินใจที่ไม่ได้อยู่บนพื้นฐานของข้อมูลและการวิเคราะห์อย่างรอบคอบ มักนำไปสู่การตัดสินใจที่ผิดพลาดและขาดทุนในที่สุด 2. **การไม่ยอมรับความเสี่ยง:** การลงทุนในตลาดหุ้นมีความเสี่ยง นักลงทุนที่ไม่ยอมรับความเสี่ยงมักจะพลาดโอกาสในการลงทุนในสินทรัพย์ที่ให้ผลตอบแทนสูง หรือในทางกลับกัน พวกเขาอาจจะหลีกเลี่ยงการตัดขาดทุนเมื่อการลงทุนไม่เป็นไปตามที่คาดหวัง การไม่ยอมรับความเสี่ยงและไม่บริหารความเสี่ยงอย่างเหมาะสม จะทำให้พอร์ตการลงทุนไม่เติบโตเท่าที่ควร หรืออาจจะเผชิญกับความเสียหายที่ใหญ่หลวงได้ 3. **การขาดความรู้และความเข้าใจ:** ตลาดหุ้นเป็นเรื่องที่ซับซ้อนและเปลี่ยนแปลงอยู่เสมอ นักลงทุนที่ขาดความรู้และความเข้าใจในเรื่องการลงทุนอย่างเพียงพอ มักจะลงทุนโดยไม่มีหลักการหรือไม่สามารถวิเคราะห์สถานการณ์ได้อย่างถูกต้อง การลงทุนโดยปราศจากความรู้และความเข้าใจที่ถูกต้อง ก็เหมือนกับการเดินอยู่ในความมืด ซึ่งโอกาสที่จะประสบความสำเร็จนั้นเป็นไปได้ยาก **บทสรุป** 3 พฤติกรรมที่กล่าวมาข้างต้นเป็นเพียงส่วนหนึ่งของอุปสรรคที่นักลงทุนส่วนใหญ่ต้องเผชิญ หากนักลงทุนต้องการที่จะประสบความสำเร็จในการลงทุนอย่างยั่งยืน พวกเขาจำเป็นต้องตระหนักถึงพฤติกรรมเหล่านี้และพยายามปรับปรุงตนเองอย่างต่อเนื่อง การศึกษาหาความรู้เพิ่มเติม การวางแผนการลงทุนอย่างรอบคอบ และการควบคุมอารมณ์ จะเป็นกุญแจสำคัญที่นำไปสู่การสร้างผลกำไรที่สม่ำเสมอในตลาดหุ้นได้ แน่นอนค่ะ ฟังคลิปแล้ว และสรุปบทความเป็นภาษาไทยให้คุณแล้วค่ะ **บทความ: 3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไรสม่ำเสมอของนักลงทุนส่วนใหญ่** บทความนี้สรุปแนวคิดจากคลิปวิดีโอที่วิเคราะห์พฤติกรรมของนักลงทุนส่วนใหญ่ โดยอ้างอิงจากการสำรวจบัญชีซื้อขายหุ้นกว่า 77,000 บัญชีในช่วงปี 1990-1996 พบว่ามี 3 พฤติกรรมหลักที่เป็นอุปสรรคสำคัญต่อการสร้างผลกำไรที่สม่ำเสมอในการลงทุน **3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไร:** 1. **ปล่อยให้ขาดทุน แต่รีบขายกำไร:** นักลงทุนส่วนใหญ่มักจะถือหุ้นที่กำลังขาดทุนต่อไปเรื่อย ๆ เพราะไม่อยากยอมรับว่าตัดสินใจผิดพลาด ในทางกลับกัน เมื่อหุ้นเริ่มมีกำไรเพียงเล็กน้อย กลับรีบขายออกไปเพราะกลัวกำไรจะหายไป พฤติกรรมนี้เป็นผลจากธรรมชาติของมนุษย์ที่เรียกว่า "Loser Aversion" หรือการหลีกเลี่ยงความเจ็บปวดจากการขาดทุนมากกว่าความสุขจากการได้กำไร 2. **ถัวเฉลี่ยขาลง มากกว่าพีระมิดขาขึ้น:** นักลงทุนจำนวนมากเลือกที่จะซื้อหุ้นที่ราคาลดลง (ถัวเฉลี่ยขาลง) โดยหวังว่าจะได้ต้นทุนที่ต่ำลงและรอให้ราคาหุ้นกลับมา แต่ในความเป็นจริง หุ้นที่อยู่ในแนวโน้มขาลงก็มีโอกาสที่จะลงต่อไปเรื่อย ๆ การถัวเฉลี่ยขาลงจึงเป็นการเพิ่มความเสี่ยง ในขณะที่การ "พีระมิดขาขึ้น" หรือการซื้อหุ้นเพิ่มเมื่อราคาปรับตัวสูงขึ้น เป็นการลงทุนในหุ้นที่กำลังมีแนวโน้มที่ดีและมีโอกาสสร้างกำไรมากกว่า 3. **รีบขายกำไรเล็กน้อย แต่ไม่ยอมขายเมื่อขาดทุนเล็กน้อย:** พฤติกรรมนี้ต่อเนื่องจากข้อแรก คือเมื่อได้กำไรเพียงเล็กน้อย นักลงทุนมักจะรีบขายเพื่อ "ล็อกกำไร" แต่เมื่อขาดทุนเล็กน้อย กลับไม่ยอมขายเพราะหวังว่าราคาจะกลับมา ทำให้สุดท้ายกลายเป็น "กำไรน้อย รีบขาย ขาดทุน เก็บไว้" ซึ่งส่งผลเสียต่อพอร์ตการลงทุนในระยะยาว **คำแนะนำเพื่อปรับปรุงพฤติกรรมการลงทุน:** * **ฝึก "Cut Loss Short, Let Profit Run":** ยอมตัดขาดทุนเมื่อหุ้นไม่เป็นไปตามแผน เพื่อจำกัดความเสียหาย และปล่อยให้หุ้นที่กำลังทำกำไรทำงานไป เพื่อเพิ่มโอกาสในการทำกำไรที่มากขึ้น * **อย่าถัวเฉลี่ยขาลงโดยไม่มีเหตุผล:** พิจารณาแนวโน้มของหุ้นและปัจจัยพื้นฐานก่อนตัดสินใจถัวเฉลี่ยขาลง หากไม่มีเหตุผลที่ชัดเจน การถัวเฉลี่ยขาลงอาจเป็นการเพิ่มความเสี่ยงโดยไม่จำเป็น * **บริหารความเสี่ยงและ Money Management อย่างเหมาะสม:** กำหนด stop loss ที่ชัดเจน และบริหารจัดการเงินทุนให้เหมาะสมกับความเสี่ยงที่รับได้ * **เรียนรู้และพัฒนาระบบเทรดของตัวเองอย่างต่อเนื่อง:** ทำความเข้าใจกลยุทธ์การเทรดของตนเอง และปรับปรุงพัฒนาอย่างสม่ำเสมอ * **มี Mindset ที่ถูกต้องสำหรับการเทรด:** เข้าใจว่าการเทรดสวนทางกับธรรมชาติของมนุษย์ ต้องฝึกฝนและสร้างนิสัยที่ถูกต้องเพื่อเอาชนะอุปสรรคทางจิตวิทยา **สรุป:** การลงทุนและการเทรดหุ้นเป็นเกมที่ "ผิดธรรมชาติ" ของมนุษย์ การเอาชนะตลาดหุ้นได้จึงต้องอาศัยการฝึกฝนและปรับเปลี่ยนพฤติกรรมให้สวนทางกับธรรมชาติเดิม ๆ โดยการตระหนักถึง 3 พฤติกรรมที่เป็นอุปสรรค และนำคำแนะนำไปปรับใช้ จะช่วยให้นักลงทุนสามารถพัฒนาไปสู่การสร้างผลกำไรที่สม่ำเสมอและยั่งยืนได้ในระยะยาว @ 7546e8e4:154e8264
2025-02-17 10:48:44Ever feel like your crypto portfolio is stuck in orbit? What if you could turn those fractional holdings into meaningful growth? The secret lies in smart management and a dashboard that makes it effortless. Key Points The Power of Small Balances: Explain how even dust (tiny crypto amounts) can compound with strategic tracking and reinvestment over time. Unified Dashboard Magic: Highlight how phesky.com aggregates BTC, ETH, LTC, TRX, and more into one sleek interface, eliminating the chaos of juggling multiple wallets. Visualize Your Growth: Emphasize the dashboard’s design charts, trends, and projections that turn abstract numbers into a clear path to "moon-worthy gains. Call to Action: Stop letting zeros collect cosmic dust. Launch your portfolio to new heights at phesky.com
@ 7546e8e4:154e8264
2025-02-17 10:48:44Ever feel like your crypto portfolio is stuck in orbit? What if you could turn those fractional holdings into meaningful growth? The secret lies in smart management and a dashboard that makes it effortless. Key Points The Power of Small Balances: Explain how even dust (tiny crypto amounts) can compound with strategic tracking and reinvestment over time. Unified Dashboard Magic: Highlight how phesky.com aggregates BTC, ETH, LTC, TRX, and more into one sleek interface, eliminating the chaos of juggling multiple wallets. Visualize Your Growth: Emphasize the dashboard’s design charts, trends, and projections that turn abstract numbers into a clear path to "moon-worthy gains. Call to Action: Stop letting zeros collect cosmic dust. Launch your portfolio to new heights at phesky.com @ 849a5a61:b57d2870
2025-02-17 10:11:18 > Hey everyone! For the past few months we’ve been building an open-source, affordable and privacy-friendly affiliate and referral program creator for Bitcoin businesses and Nostr publishers called BitFlio. We built [BitFlio](https://bitflio.com/) because, as bitcoiners and nostriches, we couldn’t find an affiliate marketing tool for our products that would accept bitcoin as payment method, keep us anonymnous, and most important allow us to pay and be paid based on the value we provide. Since we didn’t know if affiliate marketing would work for us as a sales channel, we really wanted to find a tool where, instead of a fixed monthly fee, we could instead pay a % in sats per successful referral to test the waters. Referral marketing is such a powerful marketing channel as it enable the Value For Value (V4V) model to expand and grow the Bitcoin Circular Economy. For example, **referral leads for businesses have a 70% higher conversion rate than leads from any other sales channel**, and **when referred by other customers, that customer typically has a 37% higher retention rate**. The setup process for BitFlio is nice and easy. You simply signup with nostr or email, connect your Bitcoin wallet, create your first campaign, add the tracking script to your website and then fire the `BitFlio.convert('yourcustomer@email.com')` function from your thank you page, so we can validate the leads Publishers will bring to you. Once you’ve done those steps, you can either invite publishers manually, or send them your unique BitFlio invite signup page URL. For Publishers is even easier. If you are a content creator looking to monetize bitcoinize your contents, join our network and select from bitcoin brands those you feel comfortable sharing. Lastly, get paid in sats depending on how many sales you can drive to each vendor. It’s quite hard to list in sentences some of the cool features that make up BitFlio, so here’s a list: * Pricing from $0/month * Automatic NWC sync * Works for both subscriptions and one-time charges * Embed script is lightweight and only ~13kb * Privacy-friendly & Anonymous * No GDPR needed, as we operate in the Private. * Manage multiple affiliate programs for different products from one single dashboard * Open-source software Since we’re in public beta, getting feedback right now is our top priority. We’d appreciate it so much if you sign up for our Beta whitelist via [beta.BitFlio.com](https://beta.BitFlio.com) and let us know how you get on / your initial thoughts 😄 Landing: https://BitFlio.com `sᴏᴏɴ!` Beta whitelist: https://beta.BitFlio.com Follow us on Nostr: https://njump.me/npub1sjd95c0kcxn69x3u8azunrm2kdj97lc6cu79csz7rz74hdta9pcqpxgrdx Support the open source project on @geyserfund https://geyser.fund/project/bitflio/ - - - Mirror posts: - https://bitflio.com/blob/affordable-referral-marketing-software-for-nostr-publishers-and-bitcoin-vendors/ - https://geyser.fund/project/bitflio/posts/view/4138 - naddr1qvzqqqr4gupzppy6tfsldsd852drc069ex8k4vmytal343eut3q9ux9atw6h62rsqqxnzden8ymnwdf5xgurzdphm3ncla originally posted at https://stacker.news/items/888167
@ 849a5a61:b57d2870
2025-02-17 10:11:18 > Hey everyone! For the past few months we’ve been building an open-source, affordable and privacy-friendly affiliate and referral program creator for Bitcoin businesses and Nostr publishers called BitFlio. We built [BitFlio](https://bitflio.com/) because, as bitcoiners and nostriches, we couldn’t find an affiliate marketing tool for our products that would accept bitcoin as payment method, keep us anonymnous, and most important allow us to pay and be paid based on the value we provide. Since we didn’t know if affiliate marketing would work for us as a sales channel, we really wanted to find a tool where, instead of a fixed monthly fee, we could instead pay a % in sats per successful referral to test the waters. Referral marketing is such a powerful marketing channel as it enable the Value For Value (V4V) model to expand and grow the Bitcoin Circular Economy. For example, **referral leads for businesses have a 70% higher conversion rate than leads from any other sales channel**, and **when referred by other customers, that customer typically has a 37% higher retention rate**. The setup process for BitFlio is nice and easy. You simply signup with nostr or email, connect your Bitcoin wallet, create your first campaign, add the tracking script to your website and then fire the `BitFlio.convert('yourcustomer@email.com')` function from your thank you page, so we can validate the leads Publishers will bring to you. Once you’ve done those steps, you can either invite publishers manually, or send them your unique BitFlio invite signup page URL. For Publishers is even easier. If you are a content creator looking to monetize bitcoinize your contents, join our network and select from bitcoin brands those you feel comfortable sharing. Lastly, get paid in sats depending on how many sales you can drive to each vendor. It’s quite hard to list in sentences some of the cool features that make up BitFlio, so here’s a list: * Pricing from $0/month * Automatic NWC sync * Works for both subscriptions and one-time charges * Embed script is lightweight and only ~13kb * Privacy-friendly & Anonymous * No GDPR needed, as we operate in the Private. * Manage multiple affiliate programs for different products from one single dashboard * Open-source software Since we’re in public beta, getting feedback right now is our top priority. We’d appreciate it so much if you sign up for our Beta whitelist via [beta.BitFlio.com](https://beta.BitFlio.com) and let us know how you get on / your initial thoughts 😄 Landing: https://BitFlio.com `sᴏᴏɴ!` Beta whitelist: https://beta.BitFlio.com Follow us on Nostr: https://njump.me/npub1sjd95c0kcxn69x3u8azunrm2kdj97lc6cu79csz7rz74hdta9pcqpxgrdx Support the open source project on @geyserfund https://geyser.fund/project/bitflio/ - - - Mirror posts: - https://bitflio.com/blob/affordable-referral-marketing-software-for-nostr-publishers-and-bitcoin-vendors/ - https://geyser.fund/project/bitflio/posts/view/4138 - naddr1qvzqqqr4gupzppy6tfsldsd852drc069ex8k4vmytal343eut3q9ux9atw6h62rsqqxnzden8ymnwdf5xgurzdphm3ncla originally posted at https://stacker.news/items/888167 @ 849a5a61:b57d2870
2025-02-17 09:47:19We built [BitFlio](https://bitflio.com/) because, as bitcoiners and nostriches, we couldn’t find an affiliate marketing tool for our products that would accept bitcoin as payment method, keep us anonymnous, and most important allow us to pay and be paid based on the value we provide. Since we didn’t know if affiliate marketing would work for us as a sales channel, we really wanted to find a tool where, instead of a fixed monthly fee, we could instead pay a % in sats per successful referral to test the waters. Referral marketing is such a powerful marketing channel as it enable the Value For Value (V4V) model to expand and grow the Bitcoin Circular Economy. For example, **referral leads for businesses have a 70% higher conversion rate than leads from any other sales channel**, and **when referred by other customers, that customer typically has a 37% higher retention rate**. The setup process for BitFlio is nice and easy. You simply signup with nostr or email, connect your Bitcoin wallet, create your first campaign, add the tracking script to your website and then fire the `BitFlio.convert('yourcustomer@email.com')` function from your thank you page, so we can validate the leads Publishers will bring to you. Once you’ve done those steps, you can either invite publishers manually, or send them your unique BitFlio invite signup page URL. For Publishers is even easier. If you are a content creator looking to monetize bitcoinize your contents, join our network and select from bitcoin brands those you feel comfortable sharing. Lastly, get paid in sats depending on how many sales you can drive to each vendor. It’s quite hard to list in sentences some of the cool features that make up BitFlio, so here’s a list: * Pricing from $0/month * Automatic NWC sync * Works for both subscriptions and one-time charges * Embed script is lightweight and only ~13kb * Privacy-friendly & Anonymous * No GDPR needed, as we operate in the Private. * Manage multiple affiliate programs for different products from one single dashboard * Open-source software Since we’re in public beta, getting feedback right now is our top priority. We’d appreciate it so much if you sign up for our Beta whitelist via [beta.BitFlio.com](//beta.BitFlio.com) and let us know how you get on / your initial thoughts 😄
@ 849a5a61:b57d2870
2025-02-17 09:47:19We built [BitFlio](https://bitflio.com/) because, as bitcoiners and nostriches, we couldn’t find an affiliate marketing tool for our products that would accept bitcoin as payment method, keep us anonymnous, and most important allow us to pay and be paid based on the value we provide. Since we didn’t know if affiliate marketing would work for us as a sales channel, we really wanted to find a tool where, instead of a fixed monthly fee, we could instead pay a % in sats per successful referral to test the waters. Referral marketing is such a powerful marketing channel as it enable the Value For Value (V4V) model to expand and grow the Bitcoin Circular Economy. For example, **referral leads for businesses have a 70% higher conversion rate than leads from any other sales channel**, and **when referred by other customers, that customer typically has a 37% higher retention rate**. The setup process for BitFlio is nice and easy. You simply signup with nostr or email, connect your Bitcoin wallet, create your first campaign, add the tracking script to your website and then fire the `BitFlio.convert('yourcustomer@email.com')` function from your thank you page, so we can validate the leads Publishers will bring to you. Once you’ve done those steps, you can either invite publishers manually, or send them your unique BitFlio invite signup page URL. For Publishers is even easier. If you are a content creator looking to monetize bitcoinize your contents, join our network and select from bitcoin brands those you feel comfortable sharing. Lastly, get paid in sats depending on how many sales you can drive to each vendor. It’s quite hard to list in sentences some of the cool features that make up BitFlio, so here’s a list: * Pricing from $0/month * Automatic NWC sync * Works for both subscriptions and one-time charges * Embed script is lightweight and only ~13kb * Privacy-friendly & Anonymous * No GDPR needed, as we operate in the Private. * Manage multiple affiliate programs for different products from one single dashboard * Open-source software Since we’re in public beta, getting feedback right now is our top priority. We’d appreciate it so much if you sign up for our Beta whitelist via [beta.BitFlio.com](//beta.BitFlio.com) and let us know how you get on / your initial thoughts 😄 @ 2063cd79:57bd1320
2025-02-17 09:12:39Für diejenigen, die mich nicht kennen: Ich bin Hal Finney. Ich machte meine ersten Schritte mit Kryptographie, in dem ich an einer frühen Version von PGP arbeitete, in enger Zusammenarbeit mit Phil Zimmermann. Als Phil beschloss, die PGP Corporation zu gründen, war ich einer der ersten, die er einstellte. Ich habe bis zu meiner Pensionierung an PGP gearbeitet. Zeitgleich fing ich an, mich bei den Cypherpunks zu engagieren. Neben anderen Aktivitäten betrieb ich den ersten kryptographisch basierten anonymen Remailer. Springen wir ans Ende des Jahres 2008 und der Ankündigung von Bitcoin. Ich habe bemerkt, dass Krypto-Graubärte (ich war Mitte 50) dazu neigen, zynisch zu werden. Ich war eher idealistisch; ich habe Kryptographie immer geliebt, das Mysterium und das Paradoxe daran. Als Satoshi Bitcoin in der Kryptographie-Mailingliste ankündigte, wurde er bestenfalls skeptisch aufgenommen. Kryptographen haben schon zu viele großartige Pläne von ahnungslosen Anfängern gesehen. Sie neigen zu überhasteten Reaktionen. Ich war positiver eingestellt. Ich hatte mich schon lange für kryptografische Zahlungssysteme interessiert. Außerdem hatte ich das Glück, sowohl Wei Dai als auch Nick Szabo kennenzulernen und ausgiebig mit ihnen zu korrespondieren, von denen allgemein bekannt ist, dass sie Ideen entwickelt haben, die mit Hilfe von Bitcoin verwirklicht werden sollten. Ich hatte einen Versuch unternommen, meine eigene, auf Proof-of-Work basierende Währung namens RPOW zu schaffen. Daher fand ich Bitcoin faszinierend. Als Satoshi die erste Version der Software ankündigte, schnappte ich sie mir sofort. Ich glaube, ich war die erste Person neben Satoshi, die Bitcoin laufen ließ. Ich habe Block 70 oder so gemined und ich war der Empfänger der ersten Bitcoin-Transaktion, als Satoshi mir zehn Coins als Test schickte. In den nächsten Tagen führte ich eine E-Mail-Konversation mit Satoshi, in der ich hauptsächlich Fehler meldete, die er dann beseitigte. Heute ist die wahre Identität von Satoshi ein Rätsel. Aber damals dachte ich, ich hätte es mit einem jungen Mann japanischer Abstammung zu tun, der sehr intelligent und aufrichtig war. Ich hatte das Glück, im Laufe meines Lebens viele brillante Menschen kennenzulernen, daher erkenne ich die Zeichen. Nach ein paar Tagen lief Bitcoin ziemlich stabil, also ließ ich es laufen. Das waren die Tage, als die Difficulty 1 war und man Blöcke mit dem CPU finden konnte, nicht einmal mit einem GPU. In den nächsten Tagen habe ich mehrere Blöcke gemined. Aber ich schaltete es ab, weil mein Computer zu heiß wurde und mich das Lüftergeräusch störte. Im Nachhinein wünschte ich, ich hätte länger durchgehalten, aber andererseits hatte ich außerordentliches Glück, dass ich am Anfang dabei war. Das ist so eine halb volles, halb leeres Glas Sache Das nächste Mal, dass ich von Bitcoin hörte, war Ende 2010, als ich überrascht feststellte, dass es nicht nur immer noch existierte, sondern bitcoins tatsächlich einen Geldwert hatten. Ich entstaubte meine alte Wallet und war erleichtert, als ich feststellte, dass meine bitcoins noch darin waren. Als der Preis auf eine echte Summe kletterte, transferierte ich die Coins in eine Offline-Wallet, wo sie hoffentlich für meine Erben etwas wert sein werden. Apropos Erben: 2009 erlebte ich eine Überraschung, als bei mir plötzlich eine tödliche Krankheit diagnostiziert wurde. Zu Beginn des Jahres war ich in der besten Verfassung meines Lebens, ich hatte viel Gewicht verloren und mit dem Langstreckenlauf begonnen. Ich war mehrere Halbmarathons gelaufen und hatte begonnen, für einen vollen Marathon zu trainieren. Ich hatte mich zu Läufen über 20 Meilen hochgearbeitet und dachte, ich hätte alles im Griff. Doch dann ging alles schief. Mein Körper begann zu versagen. Ich sprach undeutlich, verlor die Kraft in meinen Händen und meine Beine erholten sich nur langsam. Im August 2009 erhielt ich die Diagnose ALS, auch Lou-Gehrig-Krankheit genannt, nach dem berühmten Baseballspieler, der daran erkrankt war. ALS ist eine Krankheit, die Motoneuronen abtötet, die Signale vom Gehirn an die Muskeln weiterleiten. Sie verursacht zunächst Schwäche und dann allmählich zunehmende Lähmungen. Die Krankheit verläuft in der Regel innerhalb von 2 bis 5 Jahren tödlich. Meine Symptome waren zunächst gering und ich konnte weiterarbeiten, aber Müdigkeit und Stimmprobleme zwangen mich Anfang 2011, in den Ruhestand zu gehen. Seitdem ist die Krankheit unaufhaltsam fortgeschritten. Heute bin ich im Wesentlichen gelähmt. Ich werde durch einen Schlauch ernährt, und meine Atmung wird durch einen weiteren Schlauch unterstützt. Ich bediene den Computer mit einem kommerziellen Eyetracker-System. Es ist auch mit einem Sprachsynthesizer ausgestattet, so dass dies jetzt meine Stimme ist. Ich verbringe den ganzen Tag in meinem Elektrorollstuhl. Ich habe eine Schnittstelle mit einem Arduino entwickelt, so dass ich die Position meines Rollstuhls mit meinen Augen einstellen kann. Es war eine Umstellung, aber mein Leben ist nicht allzu schlimm. Ich kann immer noch lesen, Musik hören, fernsehen und Filme schauen. Vor kurzem habe ich entdeckt, dass ich sogar Code schreiben kann. Es geht sehr langsam, wahrscheinlich 50 Mal langsamer als vorher. Aber ich liebe das Programmieren immer noch, und es gibt mir Ziele. Derzeit arbeite ich an etwas, das Mike Hearn vorgeschlagen hat, nämlich die Sicherheitsfunktionen moderner Prozessoren, die „Trusted Computing“ unterstützen, zu nutzen, um Bitcoin-Wallets zu härten. Es ist fast fertig zur Veröffentlichung. Ich muss nur noch die Dokumentation erstellen. Und natürlich sind die Kursschwankungen von Bitcoin für mich unterhaltsam. Ich habe einen Anteil an dem Spiel. Aber ich bin durch Glück zu meinen bitcoins gekommen, ohne dass ich etwas dafür kann. Ich habe den Crash von 2011 miterlebt. Ich habe es also schon einmal erlebt. Einfach kommen, einfach gehen. Das ist meine Geschichte. Ich habe insgesamt ziemlich viel Glück. Selbst mit der ALS ist mein Leben sehr zufriedenstellend. Aber meine Lebenserwartung ist begrenzt. Diese Diskussionen über die Vererbung von bitcoins sind mehr als nur von akademischem Interesse. Meine bitcoins befinden sich in unserem Bankschließfach, und mein Sohn und meine Tochter sind technisch versiert. Ich denke, sie sind sicher genug. Ich bin mit meinem Erbe zufrieden. 
@ 2063cd79:57bd1320
2025-02-17 09:12:39Für diejenigen, die mich nicht kennen: Ich bin Hal Finney. Ich machte meine ersten Schritte mit Kryptographie, in dem ich an einer frühen Version von PGP arbeitete, in enger Zusammenarbeit mit Phil Zimmermann. Als Phil beschloss, die PGP Corporation zu gründen, war ich einer der ersten, die er einstellte. Ich habe bis zu meiner Pensionierung an PGP gearbeitet. Zeitgleich fing ich an, mich bei den Cypherpunks zu engagieren. Neben anderen Aktivitäten betrieb ich den ersten kryptographisch basierten anonymen Remailer. Springen wir ans Ende des Jahres 2008 und der Ankündigung von Bitcoin. Ich habe bemerkt, dass Krypto-Graubärte (ich war Mitte 50) dazu neigen, zynisch zu werden. Ich war eher idealistisch; ich habe Kryptographie immer geliebt, das Mysterium und das Paradoxe daran. Als Satoshi Bitcoin in der Kryptographie-Mailingliste ankündigte, wurde er bestenfalls skeptisch aufgenommen. Kryptographen haben schon zu viele großartige Pläne von ahnungslosen Anfängern gesehen. Sie neigen zu überhasteten Reaktionen. Ich war positiver eingestellt. Ich hatte mich schon lange für kryptografische Zahlungssysteme interessiert. Außerdem hatte ich das Glück, sowohl Wei Dai als auch Nick Szabo kennenzulernen und ausgiebig mit ihnen zu korrespondieren, von denen allgemein bekannt ist, dass sie Ideen entwickelt haben, die mit Hilfe von Bitcoin verwirklicht werden sollten. Ich hatte einen Versuch unternommen, meine eigene, auf Proof-of-Work basierende Währung namens RPOW zu schaffen. Daher fand ich Bitcoin faszinierend. Als Satoshi die erste Version der Software ankündigte, schnappte ich sie mir sofort. Ich glaube, ich war die erste Person neben Satoshi, die Bitcoin laufen ließ. Ich habe Block 70 oder so gemined und ich war der Empfänger der ersten Bitcoin-Transaktion, als Satoshi mir zehn Coins als Test schickte. In den nächsten Tagen führte ich eine E-Mail-Konversation mit Satoshi, in der ich hauptsächlich Fehler meldete, die er dann beseitigte. Heute ist die wahre Identität von Satoshi ein Rätsel. Aber damals dachte ich, ich hätte es mit einem jungen Mann japanischer Abstammung zu tun, der sehr intelligent und aufrichtig war. Ich hatte das Glück, im Laufe meines Lebens viele brillante Menschen kennenzulernen, daher erkenne ich die Zeichen. Nach ein paar Tagen lief Bitcoin ziemlich stabil, also ließ ich es laufen. Das waren die Tage, als die Difficulty 1 war und man Blöcke mit dem CPU finden konnte, nicht einmal mit einem GPU. In den nächsten Tagen habe ich mehrere Blöcke gemined. Aber ich schaltete es ab, weil mein Computer zu heiß wurde und mich das Lüftergeräusch störte. Im Nachhinein wünschte ich, ich hätte länger durchgehalten, aber andererseits hatte ich außerordentliches Glück, dass ich am Anfang dabei war. Das ist so eine halb volles, halb leeres Glas Sache Das nächste Mal, dass ich von Bitcoin hörte, war Ende 2010, als ich überrascht feststellte, dass es nicht nur immer noch existierte, sondern bitcoins tatsächlich einen Geldwert hatten. Ich entstaubte meine alte Wallet und war erleichtert, als ich feststellte, dass meine bitcoins noch darin waren. Als der Preis auf eine echte Summe kletterte, transferierte ich die Coins in eine Offline-Wallet, wo sie hoffentlich für meine Erben etwas wert sein werden. Apropos Erben: 2009 erlebte ich eine Überraschung, als bei mir plötzlich eine tödliche Krankheit diagnostiziert wurde. Zu Beginn des Jahres war ich in der besten Verfassung meines Lebens, ich hatte viel Gewicht verloren und mit dem Langstreckenlauf begonnen. Ich war mehrere Halbmarathons gelaufen und hatte begonnen, für einen vollen Marathon zu trainieren. Ich hatte mich zu Läufen über 20 Meilen hochgearbeitet und dachte, ich hätte alles im Griff. Doch dann ging alles schief. Mein Körper begann zu versagen. Ich sprach undeutlich, verlor die Kraft in meinen Händen und meine Beine erholten sich nur langsam. Im August 2009 erhielt ich die Diagnose ALS, auch Lou-Gehrig-Krankheit genannt, nach dem berühmten Baseballspieler, der daran erkrankt war. ALS ist eine Krankheit, die Motoneuronen abtötet, die Signale vom Gehirn an die Muskeln weiterleiten. Sie verursacht zunächst Schwäche und dann allmählich zunehmende Lähmungen. Die Krankheit verläuft in der Regel innerhalb von 2 bis 5 Jahren tödlich. Meine Symptome waren zunächst gering und ich konnte weiterarbeiten, aber Müdigkeit und Stimmprobleme zwangen mich Anfang 2011, in den Ruhestand zu gehen. Seitdem ist die Krankheit unaufhaltsam fortgeschritten. Heute bin ich im Wesentlichen gelähmt. Ich werde durch einen Schlauch ernährt, und meine Atmung wird durch einen weiteren Schlauch unterstützt. Ich bediene den Computer mit einem kommerziellen Eyetracker-System. Es ist auch mit einem Sprachsynthesizer ausgestattet, so dass dies jetzt meine Stimme ist. Ich verbringe den ganzen Tag in meinem Elektrorollstuhl. Ich habe eine Schnittstelle mit einem Arduino entwickelt, so dass ich die Position meines Rollstuhls mit meinen Augen einstellen kann. Es war eine Umstellung, aber mein Leben ist nicht allzu schlimm. Ich kann immer noch lesen, Musik hören, fernsehen und Filme schauen. Vor kurzem habe ich entdeckt, dass ich sogar Code schreiben kann. Es geht sehr langsam, wahrscheinlich 50 Mal langsamer als vorher. Aber ich liebe das Programmieren immer noch, und es gibt mir Ziele. Derzeit arbeite ich an etwas, das Mike Hearn vorgeschlagen hat, nämlich die Sicherheitsfunktionen moderner Prozessoren, die „Trusted Computing“ unterstützen, zu nutzen, um Bitcoin-Wallets zu härten. Es ist fast fertig zur Veröffentlichung. Ich muss nur noch die Dokumentation erstellen. Und natürlich sind die Kursschwankungen von Bitcoin für mich unterhaltsam. Ich habe einen Anteil an dem Spiel. Aber ich bin durch Glück zu meinen bitcoins gekommen, ohne dass ich etwas dafür kann. Ich habe den Crash von 2011 miterlebt. Ich habe es also schon einmal erlebt. Einfach kommen, einfach gehen. Das ist meine Geschichte. Ich habe insgesamt ziemlich viel Glück. Selbst mit der ALS ist mein Leben sehr zufriedenstellend. Aber meine Lebenserwartung ist begrenzt. Diese Diskussionen über die Vererbung von bitcoins sind mehr als nur von akademischem Interesse. Meine bitcoins befinden sich in unserem Bankschließfach, und mein Sohn und meine Tochter sind technisch versiert. Ich denke, sie sind sicher genug. Ich bin mit meinem Erbe zufrieden.  @ 044da344:073a8a0e
2025-02-17 08:50:50Ich nehme alles zurück, was ich je gegen die Filmförderung gesagt habe. Eine halbe Milliarde Euro im Jahr? Na und. Die heile deutsche Welt im Kino? Der Schuss Erziehung? Das Ausblenden der kleinen Leute mit ihren großen Problemen? Mir ab sofort egal. Sollen Produzenten, Regisseure, Autoren ruhig nach immer mehr rufen. Gebt ihnen aus den leeren Steuertöpfen, am besten mit vollen Händen. Diese Woche habe ich gelernt: Sie drehen im Zweifel nur für mich. Das Kino war leer, okay. Das ist aber nicht mein Punkt. Dieses Kino ist so gut wie immer leer. Meist sitzen meine Frau und ich allein in einem der neun großen Säle und sind manchmal sogar im ganzen Haus die einzigen neben den beiden an der Kasse. Was auf der Leinwand läuft, ist oft frustrierend. Siehe oben. Ich mag aber keinen Verriss schreiben. Sonst würde es an dieser Stelle jeden Samstag um das Kino gehen. Diese Woche waren wir hin und weg. Unser Leben. Unsere Stars. Unsere Sprache. Und das alles weit weg von der DDR und von Ostdeutschland, im Niemandsland zwischen Regensburg und Pilsen.  Ich weiß gar nicht, wo ich anfangen soll. Fidel Castro in Warnemünde. Originalbilder, direkt aus meinem Kindergartengedächtnis. Dann Havanna und die Strände mit diesem Wasser, das einem erlaubt, die eigenen Füße zu sehen. Es gibt viele Kuba-Filme, sicher. Aber wo läuft alles auf ein Revolutions-Quiz hinaus, bei dem sich Ost und West gegenübersitzen, die absurdesten Details aus dem Innersten der Maschine abspulen können und dafür in einem Touristenhotel auch noch bejubelt werden? In welchem Drehbuch kann eine Heldin einfach „blauer Würger“ sagen und wie selbstverständlich voraussetzen, dass jeder weiß, um was es geht? Auflösung: Kristall-Wodka. Das Etikett war blau. Die Flasche kostete eigentlich 16 Mark, aber ich weiß wie gestern, dass ich einmal gleich zwei für 55 gekauft habe, als im Wohnheim der Stoff ausging und ich in den Fresswürfel geschickt wurde, Kosename für die hässlichen Häuser, die es in vielen Neubausiedlungen gab, um einen Anlaufpunkt zu haben für Tanz, Kultur, Saufgelage. Der Abend ist in unser Familiengedächtnis eingegangen, weil mich die Studentin, die später meine Frau wurde, vor die Tür gesetzt hat. Bei den „Kundschaftern des Friedens“ geht es auch um die Liebe, natürlich. Wir sind im Kino. Es geht aber auch um das Altern und um Erinnerungen, die nicht mehr viele teilen. Wir waren in den 2010ern dreimal in Fidels Reich. [Autofahren auf Kuba](https://deutscherkulturkonsument.wordpress.com/2015/03/03/autofahren-auf-kuba/) war der Renner auf einem unserer frühen Blogs, deutlich häufiger geklickt als der Artikel über das [Revolutionsmuseum](https://deutscherkulturkonsument.wordpress.com/2015/02/26/revolutionsmuseum-havanna/) oder der [Text](https://deutscherkulturkonsument.wordpress.com/2015/02/26/kuba/), den dann die *Freie Presse* in Chemnitz übernommen und gedruckt hat, weil der Chefredakteur wusste, dass Kuba für seine Leser immer ein Thema ist. Ein Sehnsuchtsort der DDR-Menschen, erreichbar und zugleich unerreichbar fern, jedenfalls für die allermeisten.  Robert Thalheim erklärt das alles in diesem zweiten „Kundschafter“-Film nicht. Seine Helden reden wie alte Ostdeutsche, wenn weder Wessis zuhören noch die Kinder. Wie meine Frau und ich zu Hause oder in diesem leeren Kinosaal. Über die Schauspieler muss ich nicht viel schreiben. Henry Hübchen, Katharina Thalbach, Corinna Harfouch, Thomas Thieme, Winfried Glatzeder: Das sind unsere Leute. Lebensbegleiter, wenn man so will. So viele sind nicht übriggeblieben. Ich habe ein [Buch](https://www.freie-medienakademie.de/medien-plus/57) geschrieben, um zu ergründen, warum Medienmenschen aus dem Osten anders sind und mir vielleicht auch deshalb oft näher. Soll ich den Film empfehlen? Ich weiß nicht recht. Bilder, Musik, sogar der Ton (in deutschen Filmen sonst oft unerträglich): Hier passt schon alles. Vielleicht sage ich es so: Wer den Schlussgag ohne Google versteht, sollte ins Kino gehen. Thomas Thieme sitzt dort in einem Motorboot und lockt ein paar Amis auf das Wilhelm-Pieck-Atoll. [Freie Akademie für Medien & Journalismus](https://www.freie-medienakademie.de/) [Unterstützen](https://www.freie-medienakademie.de/unterstuetzen) *Fotos*: Freie Akademie für Medien & Journalismus
@ 044da344:073a8a0e
2025-02-17 08:50:50Ich nehme alles zurück, was ich je gegen die Filmförderung gesagt habe. Eine halbe Milliarde Euro im Jahr? Na und. Die heile deutsche Welt im Kino? Der Schuss Erziehung? Das Ausblenden der kleinen Leute mit ihren großen Problemen? Mir ab sofort egal. Sollen Produzenten, Regisseure, Autoren ruhig nach immer mehr rufen. Gebt ihnen aus den leeren Steuertöpfen, am besten mit vollen Händen. Diese Woche habe ich gelernt: Sie drehen im Zweifel nur für mich. Das Kino war leer, okay. Das ist aber nicht mein Punkt. Dieses Kino ist so gut wie immer leer. Meist sitzen meine Frau und ich allein in einem der neun großen Säle und sind manchmal sogar im ganzen Haus die einzigen neben den beiden an der Kasse. Was auf der Leinwand läuft, ist oft frustrierend. Siehe oben. Ich mag aber keinen Verriss schreiben. Sonst würde es an dieser Stelle jeden Samstag um das Kino gehen. Diese Woche waren wir hin und weg. Unser Leben. Unsere Stars. Unsere Sprache. Und das alles weit weg von der DDR und von Ostdeutschland, im Niemandsland zwischen Regensburg und Pilsen.  Ich weiß gar nicht, wo ich anfangen soll. Fidel Castro in Warnemünde. Originalbilder, direkt aus meinem Kindergartengedächtnis. Dann Havanna und die Strände mit diesem Wasser, das einem erlaubt, die eigenen Füße zu sehen. Es gibt viele Kuba-Filme, sicher. Aber wo läuft alles auf ein Revolutions-Quiz hinaus, bei dem sich Ost und West gegenübersitzen, die absurdesten Details aus dem Innersten der Maschine abspulen können und dafür in einem Touristenhotel auch noch bejubelt werden? In welchem Drehbuch kann eine Heldin einfach „blauer Würger“ sagen und wie selbstverständlich voraussetzen, dass jeder weiß, um was es geht? Auflösung: Kristall-Wodka. Das Etikett war blau. Die Flasche kostete eigentlich 16 Mark, aber ich weiß wie gestern, dass ich einmal gleich zwei für 55 gekauft habe, als im Wohnheim der Stoff ausging und ich in den Fresswürfel geschickt wurde, Kosename für die hässlichen Häuser, die es in vielen Neubausiedlungen gab, um einen Anlaufpunkt zu haben für Tanz, Kultur, Saufgelage. Der Abend ist in unser Familiengedächtnis eingegangen, weil mich die Studentin, die später meine Frau wurde, vor die Tür gesetzt hat. Bei den „Kundschaftern des Friedens“ geht es auch um die Liebe, natürlich. Wir sind im Kino. Es geht aber auch um das Altern und um Erinnerungen, die nicht mehr viele teilen. Wir waren in den 2010ern dreimal in Fidels Reich. [Autofahren auf Kuba](https://deutscherkulturkonsument.wordpress.com/2015/03/03/autofahren-auf-kuba/) war der Renner auf einem unserer frühen Blogs, deutlich häufiger geklickt als der Artikel über das [Revolutionsmuseum](https://deutscherkulturkonsument.wordpress.com/2015/02/26/revolutionsmuseum-havanna/) oder der [Text](https://deutscherkulturkonsument.wordpress.com/2015/02/26/kuba/), den dann die *Freie Presse* in Chemnitz übernommen und gedruckt hat, weil der Chefredakteur wusste, dass Kuba für seine Leser immer ein Thema ist. Ein Sehnsuchtsort der DDR-Menschen, erreichbar und zugleich unerreichbar fern, jedenfalls für die allermeisten.  Robert Thalheim erklärt das alles in diesem zweiten „Kundschafter“-Film nicht. Seine Helden reden wie alte Ostdeutsche, wenn weder Wessis zuhören noch die Kinder. Wie meine Frau und ich zu Hause oder in diesem leeren Kinosaal. Über die Schauspieler muss ich nicht viel schreiben. Henry Hübchen, Katharina Thalbach, Corinna Harfouch, Thomas Thieme, Winfried Glatzeder: Das sind unsere Leute. Lebensbegleiter, wenn man so will. So viele sind nicht übriggeblieben. Ich habe ein [Buch](https://www.freie-medienakademie.de/medien-plus/57) geschrieben, um zu ergründen, warum Medienmenschen aus dem Osten anders sind und mir vielleicht auch deshalb oft näher. Soll ich den Film empfehlen? Ich weiß nicht recht. Bilder, Musik, sogar der Ton (in deutschen Filmen sonst oft unerträglich): Hier passt schon alles. Vielleicht sage ich es so: Wer den Schlussgag ohne Google versteht, sollte ins Kino gehen. Thomas Thieme sitzt dort in einem Motorboot und lockt ein paar Amis auf das Wilhelm-Pieck-Atoll. [Freie Akademie für Medien & Journalismus](https://www.freie-medienakademie.de/) [Unterstützen](https://www.freie-medienakademie.de/unterstuetzen) *Fotos*: Freie Akademie für Medien & Journalismus @ d360efec:14907b5f
2025-02-17 08:49:15**ภาพรวม BTCUSDT (OKX):** Bitcoin ยังคงอยู่ในแนวโน้มขาขึ้นระยะยาว แต่ระยะสั้นมีความผันผวนและมีการปรับฐานลงมา การวิเคราะห์ครั้งนี้จะเน้นการระบุพื้นที่ที่ Smart Money (หรือ "เจ้ามือ") อาจจะเข้าซื้อหรือขาย เพื่อให้เราสามารถวางแผนการเทรดได้อย่างมีประสิทธิภาพ **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):**  * **แนวโน้ม:** ขาขึ้น (Uptrend) * **SMC:** * Higher Highs (HH) และ Higher Lows (HL) ต่อเนื่อง * Break of Structure (BOS) ด้านบน * ยังไม่มีสัญญาณการกลับตัวเป็นขาลง * **ICT:** * ยังไม่เห็น Order Block หรือ FVG ที่ชัดเจนใน TF Day *ณ ราคาปัจจุบัน* * **EMA:** * ราคาอยู่เหนือ EMA 50 (สีเหลือง) และ EMA 200 (สีขาว) (Golden Cross) * **Money Flow (LuxAlgo):** * สีเขียวเป็นส่วนใหญ่ แสดงถึงแรงซื้อ * **Volume Profile:** * Volume หนาแน่นที่บริเวณต่ำกว่าราคาปัจจุบัน * **แท่งเทียน:** * แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย แต่ไส้เทียนยาว แสดงว่ามีแรงซื้อกลับ * **แนวรับ:** EMA 50, EMA 200, บริเวณ Volume Profile หนาแน่น * **แนวต้าน:** High เดิม * **สรุป:** แนวโน้มหลักยังเป็นขาขึ้น Buy on Dip **(2) TF4H (4 ชั่วโมง):**  * **แนวโน้ม:** ขาขึ้น (พักตัว) * **SMC:** * HH และ HL * BOS ด้านบน * ราคาหลุด EMA 50 * **ICT:** * **Fair Value Gap (FVG):** สังเกตเห็น FVG เล็กๆ ที่เกิดขึ้นก่อนหน้านี้ (บริเวณที่ราคาเคยพุ่งขึ้นอย่างรวดเร็ว) อาจเป็นเป้าหมายของการ Pullback * **Order Block:** ราคาปัจจุบันกำลังทดสอบ Order Block (บริเวณแท่งเทียนสีแดงแท่งใหญ่ก่อนที่จะขึ้น) *เป็นจุดที่น่าสนใจมาก* * **EMA:** * ราคาหลุด EMA 50 * EMA 200 เป็นแนวรับถัดไป * **Money Flow (LuxAlgo):** * เขียวและแดงผสมกัน, แดงเริ่มมากขึ้น * **Volume Profile:** * Volume profile ค่อนข้างสูง * **แนวรับ:** EMA 200, Order Block, บริเวณ Volume Profile * **แนวต้าน:** EMA 50, High เดิม * **สรุป:** แนวโน้มขาขึ้นพักตัว, ทดสอบ Order Block, Money Flow เริ่มเป็นลบ **(3) TF15 (15 นาที):**  * **แนวโน้ม:** ขาลง (Downtrend) ระยะสั้น *แต่เริ่มมีสัญญาณการฟื้นตัว* * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) *แต่เริ่มเห็น Higher Low* * BOS ด้านล่าง * *เริ่มมีสัญญาณการ Breakout EMA 50/200* * **ICT:** * ราคาเพิ่ง Breakout Order Block ขาลง (แต่ต้องรอดูว่าจะยืนได้หรือไม่) * **EMA:** * *EMA 50/200 เพิ่งจะตัดกันแบบ Golden Cross* * **Money Flow (LuxAlgo):** * *เริ่มมีแท่งสีเขียวปรากฏขึ้น* * **Volume Profile:** * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA50/200 * **สรุป:** *เริ่มมีสัญญาณการฟื้นตัว* แต่ยังต้องระวัง **สรุปภาพรวมและกลยุทธ์ (BTCUSDT):** * **แนวโน้มหลัก (Day):** ขาขึ้น * **แนวโน้มรอง (4H):** ขาขึ้น (พักตัว), ทดสอบ Order Block * **แนวโน้มระยะสั้น (15m):** *เริ่มมีสัญญาณการฟื้นตัว* * **Money Flow:** Day เป็นบวก, 4H เริ่มเป็นลบ, 15m เริ่มเป็นบวก * **กลยุทธ์:** 1. **Wait & See:** รอการยืนยันการ Breakout EMA 50/200 ใน TF15m 2. **Buy (เสี่ยง):** *เฉพาะเมื่อราคา Breakout EMA 50/200 ใน TF 15 ได้อย่างแข็งแกร่ง* 3. **Short (เสี่ยง):** ถ้า Order Block ใน TF4H รับไม่อยู่ และ TF15 ยังคงเป็นขาลง **คำแนะนำ:** * **Order Block:** ให้ความสำคัญกับ Order Block ใน TF4H * **FVG:** สังเกต FVG ใน TF4H * **ความขัดแย้งของ Timeframes:** เริ่มลดลง (15m เริ่มมีสัญญาณบวก) * **จับตาดู TF15 อย่างใกล้ชิด** **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
@ d360efec:14907b5f
2025-02-17 08:49:15**ภาพรวม BTCUSDT (OKX):** Bitcoin ยังคงอยู่ในแนวโน้มขาขึ้นระยะยาว แต่ระยะสั้นมีความผันผวนและมีการปรับฐานลงมา การวิเคราะห์ครั้งนี้จะเน้นการระบุพื้นที่ที่ Smart Money (หรือ "เจ้ามือ") อาจจะเข้าซื้อหรือขาย เพื่อให้เราสามารถวางแผนการเทรดได้อย่างมีประสิทธิภาพ **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):**  * **แนวโน้ม:** ขาขึ้น (Uptrend) * **SMC:** * Higher Highs (HH) และ Higher Lows (HL) ต่อเนื่อง * Break of Structure (BOS) ด้านบน * ยังไม่มีสัญญาณการกลับตัวเป็นขาลง * **ICT:** * ยังไม่เห็น Order Block หรือ FVG ที่ชัดเจนใน TF Day *ณ ราคาปัจจุบัน* * **EMA:** * ราคาอยู่เหนือ EMA 50 (สีเหลือง) และ EMA 200 (สีขาว) (Golden Cross) * **Money Flow (LuxAlgo):** * สีเขียวเป็นส่วนใหญ่ แสดงถึงแรงซื้อ * **Volume Profile:** * Volume หนาแน่นที่บริเวณต่ำกว่าราคาปัจจุบัน * **แท่งเทียน:** * แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย แต่ไส้เทียนยาว แสดงว่ามีแรงซื้อกลับ * **แนวรับ:** EMA 50, EMA 200, บริเวณ Volume Profile หนาแน่น * **แนวต้าน:** High เดิม * **สรุป:** แนวโน้มหลักยังเป็นขาขึ้น Buy on Dip **(2) TF4H (4 ชั่วโมง):**  * **แนวโน้ม:** ขาขึ้น (พักตัว) * **SMC:** * HH และ HL * BOS ด้านบน * ราคาหลุด EMA 50 * **ICT:** * **Fair Value Gap (FVG):** สังเกตเห็น FVG เล็กๆ ที่เกิดขึ้นก่อนหน้านี้ (บริเวณที่ราคาเคยพุ่งขึ้นอย่างรวดเร็ว) อาจเป็นเป้าหมายของการ Pullback * **Order Block:** ราคาปัจจุบันกำลังทดสอบ Order Block (บริเวณแท่งเทียนสีแดงแท่งใหญ่ก่อนที่จะขึ้น) *เป็นจุดที่น่าสนใจมาก* * **EMA:** * ราคาหลุด EMA 50 * EMA 200 เป็นแนวรับถัดไป * **Money Flow (LuxAlgo):** * เขียวและแดงผสมกัน, แดงเริ่มมากขึ้น * **Volume Profile:** * Volume profile ค่อนข้างสูง * **แนวรับ:** EMA 200, Order Block, บริเวณ Volume Profile * **แนวต้าน:** EMA 50, High เดิม * **สรุป:** แนวโน้มขาขึ้นพักตัว, ทดสอบ Order Block, Money Flow เริ่มเป็นลบ **(3) TF15 (15 นาที):**  * **แนวโน้ม:** ขาลง (Downtrend) ระยะสั้น *แต่เริ่มมีสัญญาณการฟื้นตัว* * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) *แต่เริ่มเห็น Higher Low* * BOS ด้านล่าง * *เริ่มมีสัญญาณการ Breakout EMA 50/200* * **ICT:** * ราคาเพิ่ง Breakout Order Block ขาลง (แต่ต้องรอดูว่าจะยืนได้หรือไม่) * **EMA:** * *EMA 50/200 เพิ่งจะตัดกันแบบ Golden Cross* * **Money Flow (LuxAlgo):** * *เริ่มมีแท่งสีเขียวปรากฏขึ้น* * **Volume Profile:** * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA50/200 * **สรุป:** *เริ่มมีสัญญาณการฟื้นตัว* แต่ยังต้องระวัง **สรุปภาพรวมและกลยุทธ์ (BTCUSDT):** * **แนวโน้มหลัก (Day):** ขาขึ้น * **แนวโน้มรอง (4H):** ขาขึ้น (พักตัว), ทดสอบ Order Block * **แนวโน้มระยะสั้น (15m):** *เริ่มมีสัญญาณการฟื้นตัว* * **Money Flow:** Day เป็นบวก, 4H เริ่มเป็นลบ, 15m เริ่มเป็นบวก * **กลยุทธ์:** 1. **Wait & See:** รอการยืนยันการ Breakout EMA 50/200 ใน TF15m 2. **Buy (เสี่ยง):** *เฉพาะเมื่อราคา Breakout EMA 50/200 ใน TF 15 ได้อย่างแข็งแกร่ง* 3. **Short (เสี่ยง):** ถ้า Order Block ใน TF4H รับไม่อยู่ และ TF15 ยังคงเป็นขาลง **คำแนะนำ:** * **Order Block:** ให้ความสำคัญกับ Order Block ใน TF4H * **FVG:** สังเกต FVG ใน TF4H * **ความขัดแย้งของ Timeframes:** เริ่มลดลง (15m เริ่มมีสัญญาณบวก) * **จับตาดู TF15 อย่างใกล้ชิด** **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ @ bbb5dda0:f09e2747
2025-02-17 08:13:00**Alright, This weekly review's gonna be a quick one as i covered my weekend + monday about Sats 'n Facts in the last one. Which leaves us with only a few days, some of which I had to give in and rest as I had been continuing to work with quite a bad cold for too long. The Facts must've been hitting too hard...** ## Reflecting on networks A lot of my time this week was reflecting on the event and all the contacts I'd made there. There has been a surprising lot of enthusiasm of the community about Tollgate specifically. There's something that draws me to the project and i think it's not even the flashy-ness of routers paying routers, I'm starting to see the bigger possible implications of the sovereign networks that can grow from this. Not for the western world per se but for places that want to build out new infrastrucutre with their own communities. One of the worries from people to operate TollGates is if they'll get trouble with their ISP's. Which is a legitimate worry, but how long will that worry be relevant? One thing I realize, as Nostr grows -and Blossom too- is that the data we pull in will be more localized. Imagine a city equipped with a Sovereign Tollgate network. If a few people in your city have watched a video, there will likely be a copy of that video inside the city-wide network. Then if the city get's cut off for any reason, that video will still be very much accessible and people might not even notice the 'internet is down'. I woke up in the middle of the night and had to draw out this visualization of the combination of Clearnet + Tor + TollGate networks and how they can interact with Epoxy proxies in between (visualized by the ♾️ symbol). Anyone that sees an opportunity to bridge the networks can jump in and be that link. Even attacking (DDOS) services within other networks might become harder, because either: 1) you have to have your botnet reside inside the network of the victim. Which, if it's a small network won't comprise of a significant amount of nodes. 2) you have to have to route your attack through (Epoxy) bridges known to you, the attacker. Which likely have limited bandwidth.  Anyway, this is just my 3 AM brain-dump. I'll keep chewing on this... ## Marketing TollGate Like I mentioned earlier there was a lot of interest in Tollgate and to be honest it's been a bit overwhelming, there are so many opportunities like podcasts, meetups and articles opening up to share it and talk about it that I have to think about the form in which I want to relate myself to the project. In any case, these are Good problems to have... In the meanwhile we've worked on getting a good website landingpage where we can point people to that are interested in the project, it should be up soon! - Consumers can download the Android (for now) app - Operators can download TollGateOS to put on their router - FAQ's Also, i've been helping out to get some stuff automated. so we can build and push new versions quickly to start getting user feedback and enable iterating on a fast pace!
@ bbb5dda0:f09e2747
2025-02-17 08:13:00**Alright, This weekly review's gonna be a quick one as i covered my weekend + monday about Sats 'n Facts in the last one. Which leaves us with only a few days, some of which I had to give in and rest as I had been continuing to work with quite a bad cold for too long. The Facts must've been hitting too hard...** ## Reflecting on networks A lot of my time this week was reflecting on the event and all the contacts I'd made there. There has been a surprising lot of enthusiasm of the community about Tollgate specifically. There's something that draws me to the project and i think it's not even the flashy-ness of routers paying routers, I'm starting to see the bigger possible implications of the sovereign networks that can grow from this. Not for the western world per se but for places that want to build out new infrastrucutre with their own communities. One of the worries from people to operate TollGates is if they'll get trouble with their ISP's. Which is a legitimate worry, but how long will that worry be relevant? One thing I realize, as Nostr grows -and Blossom too- is that the data we pull in will be more localized. Imagine a city equipped with a Sovereign Tollgate network. If a few people in your city have watched a video, there will likely be a copy of that video inside the city-wide network. Then if the city get's cut off for any reason, that video will still be very much accessible and people might not even notice the 'internet is down'. I woke up in the middle of the night and had to draw out this visualization of the combination of Clearnet + Tor + TollGate networks and how they can interact with Epoxy proxies in between (visualized by the ♾️ symbol). Anyone that sees an opportunity to bridge the networks can jump in and be that link. Even attacking (DDOS) services within other networks might become harder, because either: 1) you have to have your botnet reside inside the network of the victim. Which, if it's a small network won't comprise of a significant amount of nodes. 2) you have to have to route your attack through (Epoxy) bridges known to you, the attacker. Which likely have limited bandwidth.  Anyway, this is just my 3 AM brain-dump. I'll keep chewing on this... ## Marketing TollGate Like I mentioned earlier there was a lot of interest in Tollgate and to be honest it's been a bit overwhelming, there are so many opportunities like podcasts, meetups and articles opening up to share it and talk about it that I have to think about the form in which I want to relate myself to the project. In any case, these are Good problems to have... In the meanwhile we've worked on getting a good website landingpage where we can point people to that are interested in the project, it should be up soon! - Consumers can download the Android (for now) app - Operators can download TollGateOS to put on their router - FAQ's Also, i've been helping out to get some stuff automated. so we can build and push new versions quickly to start getting user feedback and enable iterating on a fast pace! @ 0463223a:3b14d673
2025-02-17 07:48:11Here we go, it’s Mooooonnnndddddaaaaaaaayyyyyyy! It’s safe to say I enjoy Monday. Much as I appreciate the downtime over the weekend (if I’m not working) I appreciate the routine of Mondays. Firstly I have my stream to look forward to and whilst I’m not at my best first thing on a Monday, having a little structure goes a long way. Even the fear of looking at the emails I’ve been ignoring from the previous week is possible. So maybe I’m starting to get an angle of why I’m writing this. It’s a memoir of being a mental I think. I’ve mentioned a number of times this has been a problem most my life but I write this as I’ve halved my Venlafaxine does by ½ once again. This means I’m now on 1/12th of my original dose and I’m maybe a month away from being completely free of RRSIs for the first time in, I guess at least 10 years. To be honest I cant remember when I was first prescribed them. It’s been quite a journey... 3 things have been pivotal. 1; finding my now wife. She’s brilliant and I love her dearly, I think most people know deep down how crushing loneliness can be. I’m very grateful to her for putting up with my bullshit, supporting me and just being there. Gold star for her! 2; would be music, it’s a funny one to put in, it’s also been part of the problem, especially in my wilder days. There’s something quite seductive about the sex, drugs and Rock n Roll meme, although musically it was more Hip Hop, Reggae, Bleeps and Jazz, also I didn’t sleep around much at all but I certainly don’t think I would’ve messed with crack, heroin and all the other drugs otherwise. It’s worth noting 2 of my friends from that era, who didn’t have music in their lives are dead. I’m very lucky. There’s over 100 years of recorded music to enjoy plus I’m almost happy with some of my own bits at last! 3; I have some security, I no longer pay rent or have a landlord. This is also due to number 1 but also because I found some funny internet money. I’m still to write about my process with that, other than to say it was direct response to the banks. That’s a story in it’s own right, it’s pretty dark and hmm… not sure. Plus I don’t think there’s any need to go there right now. I have the world’s most expensive shed and I know I can survive a few months should the worst happen. That’s a LOT. Whilst a little risk taking is healthy, life shouldn’t free stress free, uncertainty about having a roof over your head when you can’t afford it can really take it’s toll. A degree of security is most welcome at this time in life. A lot of people aren’t so lucky, Tom, Ricky, Dave, Slam, Joel. I’m name checking you specifically. You’re in my thoughts often, especially as I play music every morning… and Slam, if I ever see you again, I want my records back!!! Haha, thieving little cunt but it’s still not hate here. Your life was fucked up before you even had a chance. I hope you’ve found peace with yourself. At least you’re alive! (I think, he might be dead too, who knows…) So yeah, it’s Monday and it’s gonna be a good day right? I mean it might not but I will at least give it the best start possible and work from there. It takes a degree of effort to retrain the brain. Actually maybe there’s a 4th thing to mention. No Facebacon, Instagran, X or LinkedIn. None of that bullshit where you’re forced into some fake world generated in order to increase shareholder value. These platforms are akin to being a lab rat. I picture Zuckerberg like Ming The Merciless at the start of Flash Gordon sending hot hail etc. That guy made a decision to mess with peoples’ psyche to drive profits. That’s fucking evil man. Jeez, what a cunt! It’s Monday, I’m wishing you strength in whatever you have ahead of you today. I’m lucky to be where I am right now and if you’re reading this and your world is plagued by darkness, it can get better. Remember that. Hold onto that as best you can. DON’T FUCKING KILL YOURSELF. That’s the single worst thing you can do. The pain you’ll leave behind isn’t worth it. I hope some cosmic vibrations happen in your favour. There’s no easy solution. I can’t tell you the answer but I wish you well. Good luck out there!
@ 0463223a:3b14d673
2025-02-17 07:48:11Here we go, it’s Mooooonnnndddddaaaaaaaayyyyyyy! It’s safe to say I enjoy Monday. Much as I appreciate the downtime over the weekend (if I’m not working) I appreciate the routine of Mondays. Firstly I have my stream to look forward to and whilst I’m not at my best first thing on a Monday, having a little structure goes a long way. Even the fear of looking at the emails I’ve been ignoring from the previous week is possible. So maybe I’m starting to get an angle of why I’m writing this. It’s a memoir of being a mental I think. I’ve mentioned a number of times this has been a problem most my life but I write this as I’ve halved my Venlafaxine does by ½ once again. This means I’m now on 1/12th of my original dose and I’m maybe a month away from being completely free of RRSIs for the first time in, I guess at least 10 years. To be honest I cant remember when I was first prescribed them. It’s been quite a journey... 3 things have been pivotal. 1; finding my now wife. She’s brilliant and I love her dearly, I think most people know deep down how crushing loneliness can be. I’m very grateful to her for putting up with my bullshit, supporting me and just being there. Gold star for her! 2; would be music, it’s a funny one to put in, it’s also been part of the problem, especially in my wilder days. There’s something quite seductive about the sex, drugs and Rock n Roll meme, although musically it was more Hip Hop, Reggae, Bleeps and Jazz, also I didn’t sleep around much at all but I certainly don’t think I would’ve messed with crack, heroin and all the other drugs otherwise. It’s worth noting 2 of my friends from that era, who didn’t have music in their lives are dead. I’m very lucky. There’s over 100 years of recorded music to enjoy plus I’m almost happy with some of my own bits at last! 3; I have some security, I no longer pay rent or have a landlord. This is also due to number 1 but also because I found some funny internet money. I’m still to write about my process with that, other than to say it was direct response to the banks. That’s a story in it’s own right, it’s pretty dark and hmm… not sure. Plus I don’t think there’s any need to go there right now. I have the world’s most expensive shed and I know I can survive a few months should the worst happen. That’s a LOT. Whilst a little risk taking is healthy, life shouldn’t free stress free, uncertainty about having a roof over your head when you can’t afford it can really take it’s toll. A degree of security is most welcome at this time in life. A lot of people aren’t so lucky, Tom, Ricky, Dave, Slam, Joel. I’m name checking you specifically. You’re in my thoughts often, especially as I play music every morning… and Slam, if I ever see you again, I want my records back!!! Haha, thieving little cunt but it’s still not hate here. Your life was fucked up before you even had a chance. I hope you’ve found peace with yourself. At least you’re alive! (I think, he might be dead too, who knows…) So yeah, it’s Monday and it’s gonna be a good day right? I mean it might not but I will at least give it the best start possible and work from there. It takes a degree of effort to retrain the brain. Actually maybe there’s a 4th thing to mention. No Facebacon, Instagran, X or LinkedIn. None of that bullshit where you’re forced into some fake world generated in order to increase shareholder value. These platforms are akin to being a lab rat. I picture Zuckerberg like Ming The Merciless at the start of Flash Gordon sending hot hail etc. That guy made a decision to mess with peoples’ psyche to drive profits. That’s fucking evil man. Jeez, what a cunt! It’s Monday, I’m wishing you strength in whatever you have ahead of you today. I’m lucky to be where I am right now and if you’re reading this and your world is plagued by darkness, it can get better. Remember that. Hold onto that as best you can. DON’T FUCKING KILL YOURSELF. That’s the single worst thing you can do. The pain you’ll leave behind isn’t worth it. I hope some cosmic vibrations happen in your favour. There’s no easy solution. I can’t tell you the answer but I wish you well. Good luck out there! @ fd78c37f:a0ec0833
2025-02-17 07:15:15In this edition, we invited Kelvin from Bitcoin Chama to share how his community is leveraging Bitcoin to build a self-sustaining ecosystem in rural areas. **YakiHonne**: Kelvin, thanks for joining us. Before we dive in, I'd like to take a moment to introduce YakiHonne and share a bit about what we do. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. Today, we’ll be diving into your community. So, let’s start—tell us a bit about yourself and what you do? **Kelvin**:I'm Kelvin, the founder of Bitcoin Chama, a rule-based Bitcoin community with a mission to build a self-reliant Bitcoin circular ecosystem. How do we achieve this? We empower young people and our community economically by introducing accessible, low-resource projects that require minimal time and space to implement. We then encourage them to save their earnings in Bitcoin, promoting financial independence and long-term sustainability. **YakiHonne**: Given Bitcoin’s increasing value, it’s almost like owning property, but in the form of a digital asset. That’s an incredible concept and a really great initiative!Now, let’s dive into today’s questions. What initially sparked your interest in Bitcoin, and what motivated you to build a community around it? **Kelvin**:Initially, I didn’t know much about Bitcoin. But I had a friend who worked at Boda Boda. He was trying to save up his earnings to buy iron sheets and build a better house for his family. Since he didn't get enough money from Boda Boda, he saved whatever little he could in a bank, a savings group. Over the course of two years, when he finally went to withdraw his money, he realized that the price of iron sheets had increased by almost 100% Originally, he had planned to buy 30 iron sheets, but by the time he withdrew his savings, his money could no longer afford that many. For someone who works so hard to earn a living, this was a major setback. **Kelvin**:That’s when I started thinking—how can we solve this problem? At the time, I didn’t know much about Bitcoin or how money really works. But seeing my friend struggle, I realized that the real issue wasn’t just rising prices, but the financial system itself. **Kelvin**:Then, later that year, I was introduced to Bitcoin, and it suddenly clicked! If my friend had saved in Bitcoin instead of fiat, his purchasing power wouldn’t have been eroded. In fact, he might have even been able to afford nails, labor costs, or additional materials. That realization led me to create Bitcoin Chama—a community to help people save in Bitcoin and protect their hard earned money. **YakiHonne**: It sounds like you were inspired by how Bitcoin’s value appreciates over time, much like an investment in land that continues to grow in value. That’s a truly powerful concept behind Bitcoin.Now, could you share how your community first got started and what strategies you used to attract members in the beginning? **Kelvin**:Building a community from scratch—especially a Bitcoin community—isn’t easy, particularly in a rural area of Kenya where many people lack internet access and don’t even use smartphones. At first, my focus was purely on Bitcoin education. I would go out, meet people, and teach them about Bitcoin. But I soon realized that while knowledge is valuable, most people didn’t have the means to earn and save in Bitcoin. **Kelvin**:That’s when I came up with a different approach. Instead of just educating people, I decided to create small projects that could generate income, sponsor these projects, and help them grow. Over time, as people started earning from these projects, they could begin saving their income in Bitcoin. **Kelvin**:We’ve now been running Bitcoin Chama for almost a year—since May last year. The impact isn’t massive yet, but for a community just getting started, it’s been a significant step forward. Every small step matters, and while growth takes time, I believe these small beginnings will eventually lead to something big in the future.  **YakiHonne**: It's a wonderful start,So far, what challenges have you faced while building and growing the Bitcoin Chama community? **Kelvin**:I don't have many challenges—just two main ones.The first challenge is poverty. Whenever you introduce someone to Bitcoin, you often have to explain its history. Imagine telling someone that in 2010, Bitcoin was worth about $1, and by 2013, its value had increased significantly. Fast forward to 2025, 15 years later, and Bitcoin is now worth around 13 million Kenyan shillings (about $100,000). When people hear this, they see it as a great opportunity to escape poverty. The problem is, they often perceive Bitcoin as free money, rather than understanding it as a long-term investment or financial tool. The second challenge is scamming. Many people think Bitcoin might be a scam. This is a common issue in many communities. **YakiHonne**: Yes, especially the second challenge—people thinking Bitcoin is a scam. This is very common in many emerging communities. A lot of people feel that since they can't see Bitcoin physically, it’s not real, which leads them to doubt its authenticity.Finding a way to convince people of Bitcoin’s legitimacy is crucial. So, what principles guide your community? And how do you maintain trust and reliability in your discussions? **Kelvin**:So, in our community, I’ve discovered something—I’ve found saccos. Right now, I have two saccos(Chama) , and I intend to grow them over time. Within these two circles, we use the Machangura app. The app has an option for creating a clan, so we organize people into two saccos, forming two clans. We then add all members from each sacco into their respective clan. This setup ensures a trustless system. For example, if someone wants to withdraw money from their shared account or sell Bitcoin, the system notifies all members. This way, everyone stays informed, and people don’t have to feel insecure about the funds they have saved. **YakiHonne**: So at least that’s how you maintain integrity, transparency, and trust within the community. So How does your community educate its members and keep them updated on Bitcoin developments? **Kelvin**:I am the founder of Bitcoin Chama, and right now, I’m mostly focused on community activities. We usually hold meetups oftenly, but I wouldn’t say we focus entirely on Bitcoin only. Instead, our discussions are more about how to improve what we do, grow more, and build new projects. That’s the main focus for me at the moment. That said, I am planning to start physical Bitcoin lessons. Since Bitcoin Chama is located in my community, I know that a lot of people visit the area—many come here to shop and buy things. So, I plan to post a notice at the location, inviting new members who are interested in learning about Bitcoin. We’ll create a timetable so that people can come at specific times to attend lessons. Additionally, we’ll leverage our existing clients and brainstorm ways to make this work for a wider audience. **YakiHonne**: It's still part of the education process,maybe not fully in-depth, but it’s still valuable. So, that’s actually a good thing. You guys are doing something very meaningful, which is great.The meetups also serve as a way to educate people about Bitcoin, making them an important part of the process. It’s definitely a solid approach. **YakiHonne**: So, Kelvin, how does your community collaborate with the broader Bitcoin ecosystem? And what partnerships have you formed so far that have had the biggest impact on BitcoinTerminal? **Kelvin**:We haven’t had any major collaborations yet. So far, we’ve been riding solo. We’ve had some support from friends and well-wishers, but we haven’t partnered with any major organizations yet. **YakiHonne**: That’s okay! You guys will get there very soon, I’m sure of it. So far, in the process of building your community, what initiatives have you taken to promote the adoption of Bitcoin in your local environment? **Kelvin**:Well, besides our existing clients, we have about three shops that currently accept Bitcoin payments. I’m still working on overcoming the major challenges we face while also trying to find ways to encourage people to use Bitcoin in their daily lives. **Kelvin**:First, I need to support the people who are already part of our community, making sure they have the resources and knowledge they need. I don’t know if I’m fully answering the question, but this is what I’m working on. I’m not solely focused on growing a large community right now. Instead, I’m focused on quality growth—on educating people who truly understand Bitcoin, know how to use it, and grasp what it really means. My approach is to start small and expand gradually, ensuring that at each stage, people gain a deeper understanding of Bitcoin and how it can impact their lives. **YakiHonne**: I’m sure you guys will succeed. You don’t necessarily have to start big, but I believe you’ll grow much faster than you expect. With the effort and passion you’re putting in, I have no doubt that Bitcoin Chama will expand significantly. So,moving on to my last question,what are your community’s goals for the next 6 to 12 months? And how do you see it evolving with Bitcoin’s development? **Kelvin**:My goal for the next year is to continue the projects I’ve been working on. We have a community team that serves as a gathering point where people can come together, coordinate meeting times, and discuss Bitcoin and our future plans. **Kelvin**:so far for example, we built and distributed 15 beehives to different young people in our community. They harvest honey, sell it, and save the earnings in Bitcoin. We piped free clean water which can be accessed by any member in our community, significantly improving daily convenience.  **Kelvin**:We are planning to build two chicken coops and provide chickens to two groups of five people each. They will raise chickens, sell eggs, and save their earnings in Bitcoin. Over time, we aim for each member to have their own chicken coop with a sustainable flock by the end of the year.  **Kelvin**:We plan to lease a piece of land for the women in our community to grow vegetables and sell them at the local market. Their earnings will also be saved in Bitcoin. If the project is profitable, we will reinvest in more land to expand vegetable farming.Additionally, we plan to lease 2-3 acres of land specifically for commercial maize farming. The maize will be sold for Bitcoin, and if we generate profits, we will expand the farmland. **Kelvin**:Our long-term goal is to build a self-sufficient community, enabling it to operate independently and achieve sustainable development. This is also our core objective. **YakiHonne**: I truly love all the ideas behind this. I admire the fact that you are giving back to the community and that people are experiencing real benefits from the Bitcoin ecosystem. This way, they have something positive and meaningful to say about Bitcoin. **YakiHonne**: Thank you so much, Kelvin, for joining us today. We’ve reached the end of our interview, and I’m really happy to have had this conversation with you. We look forward to seeing Bitcoin Chama grow!
@ fd78c37f:a0ec0833
2025-02-17 07:15:15In this edition, we invited Kelvin from Bitcoin Chama to share how his community is leveraging Bitcoin to build a self-sustaining ecosystem in rural areas. **YakiHonne**: Kelvin, thanks for joining us. Before we dive in, I'd like to take a moment to introduce YakiHonne and share a bit about what we do. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. Today, we’ll be diving into your community. So, let’s start—tell us a bit about yourself and what you do? **Kelvin**:I'm Kelvin, the founder of Bitcoin Chama, a rule-based Bitcoin community with a mission to build a self-reliant Bitcoin circular ecosystem. How do we achieve this? We empower young people and our community economically by introducing accessible, low-resource projects that require minimal time and space to implement. We then encourage them to save their earnings in Bitcoin, promoting financial independence and long-term sustainability. **YakiHonne**: Given Bitcoin’s increasing value, it’s almost like owning property, but in the form of a digital asset. That’s an incredible concept and a really great initiative!Now, let’s dive into today’s questions. What initially sparked your interest in Bitcoin, and what motivated you to build a community around it? **Kelvin**:Initially, I didn’t know much about Bitcoin. But I had a friend who worked at Boda Boda. He was trying to save up his earnings to buy iron sheets and build a better house for his family. Since he didn't get enough money from Boda Boda, he saved whatever little he could in a bank, a savings group. Over the course of two years, when he finally went to withdraw his money, he realized that the price of iron sheets had increased by almost 100% Originally, he had planned to buy 30 iron sheets, but by the time he withdrew his savings, his money could no longer afford that many. For someone who works so hard to earn a living, this was a major setback. **Kelvin**:That’s when I started thinking—how can we solve this problem? At the time, I didn’t know much about Bitcoin or how money really works. But seeing my friend struggle, I realized that the real issue wasn’t just rising prices, but the financial system itself. **Kelvin**:Then, later that year, I was introduced to Bitcoin, and it suddenly clicked! If my friend had saved in Bitcoin instead of fiat, his purchasing power wouldn’t have been eroded. In fact, he might have even been able to afford nails, labor costs, or additional materials. That realization led me to create Bitcoin Chama—a community to help people save in Bitcoin and protect their hard earned money. **YakiHonne**: It sounds like you were inspired by how Bitcoin’s value appreciates over time, much like an investment in land that continues to grow in value. That’s a truly powerful concept behind Bitcoin.Now, could you share how your community first got started and what strategies you used to attract members in the beginning? **Kelvin**:Building a community from scratch—especially a Bitcoin community—isn’t easy, particularly in a rural area of Kenya where many people lack internet access and don’t even use smartphones. At first, my focus was purely on Bitcoin education. I would go out, meet people, and teach them about Bitcoin. But I soon realized that while knowledge is valuable, most people didn’t have the means to earn and save in Bitcoin. **Kelvin**:That’s when I came up with a different approach. Instead of just educating people, I decided to create small projects that could generate income, sponsor these projects, and help them grow. Over time, as people started earning from these projects, they could begin saving their income in Bitcoin. **Kelvin**:We’ve now been running Bitcoin Chama for almost a year—since May last year. The impact isn’t massive yet, but for a community just getting started, it’s been a significant step forward. Every small step matters, and while growth takes time, I believe these small beginnings will eventually lead to something big in the future.  **YakiHonne**: It's a wonderful start,So far, what challenges have you faced while building and growing the Bitcoin Chama community? **Kelvin**:I don't have many challenges—just two main ones.The first challenge is poverty. Whenever you introduce someone to Bitcoin, you often have to explain its history. Imagine telling someone that in 2010, Bitcoin was worth about $1, and by 2013, its value had increased significantly. Fast forward to 2025, 15 years later, and Bitcoin is now worth around 13 million Kenyan shillings (about $100,000). When people hear this, they see it as a great opportunity to escape poverty. The problem is, they often perceive Bitcoin as free money, rather than understanding it as a long-term investment or financial tool. The second challenge is scamming. Many people think Bitcoin might be a scam. This is a common issue in many communities. **YakiHonne**: Yes, especially the second challenge—people thinking Bitcoin is a scam. This is very common in many emerging communities. A lot of people feel that since they can't see Bitcoin physically, it’s not real, which leads them to doubt its authenticity.Finding a way to convince people of Bitcoin’s legitimacy is crucial. So, what principles guide your community? And how do you maintain trust and reliability in your discussions? **Kelvin**:So, in our community, I’ve discovered something—I’ve found saccos. Right now, I have two saccos(Chama) , and I intend to grow them over time. Within these two circles, we use the Machangura app. The app has an option for creating a clan, so we organize people into two saccos, forming two clans. We then add all members from each sacco into their respective clan. This setup ensures a trustless system. For example, if someone wants to withdraw money from their shared account or sell Bitcoin, the system notifies all members. This way, everyone stays informed, and people don’t have to feel insecure about the funds they have saved. **YakiHonne**: So at least that’s how you maintain integrity, transparency, and trust within the community. So How does your community educate its members and keep them updated on Bitcoin developments? **Kelvin**:I am the founder of Bitcoin Chama, and right now, I’m mostly focused on community activities. We usually hold meetups oftenly, but I wouldn’t say we focus entirely on Bitcoin only. Instead, our discussions are more about how to improve what we do, grow more, and build new projects. That’s the main focus for me at the moment. That said, I am planning to start physical Bitcoin lessons. Since Bitcoin Chama is located in my community, I know that a lot of people visit the area—many come here to shop and buy things. So, I plan to post a notice at the location, inviting new members who are interested in learning about Bitcoin. We’ll create a timetable so that people can come at specific times to attend lessons. Additionally, we’ll leverage our existing clients and brainstorm ways to make this work for a wider audience. **YakiHonne**: It's still part of the education process,maybe not fully in-depth, but it’s still valuable. So, that’s actually a good thing. You guys are doing something very meaningful, which is great.The meetups also serve as a way to educate people about Bitcoin, making them an important part of the process. It’s definitely a solid approach. **YakiHonne**: So, Kelvin, how does your community collaborate with the broader Bitcoin ecosystem? And what partnerships have you formed so far that have had the biggest impact on BitcoinTerminal? **Kelvin**:We haven’t had any major collaborations yet. So far, we’ve been riding solo. We’ve had some support from friends and well-wishers, but we haven’t partnered with any major organizations yet. **YakiHonne**: That’s okay! You guys will get there very soon, I’m sure of it. So far, in the process of building your community, what initiatives have you taken to promote the adoption of Bitcoin in your local environment? **Kelvin**:Well, besides our existing clients, we have about three shops that currently accept Bitcoin payments. I’m still working on overcoming the major challenges we face while also trying to find ways to encourage people to use Bitcoin in their daily lives. **Kelvin**:First, I need to support the people who are already part of our community, making sure they have the resources and knowledge they need. I don’t know if I’m fully answering the question, but this is what I’m working on. I’m not solely focused on growing a large community right now. Instead, I’m focused on quality growth—on educating people who truly understand Bitcoin, know how to use it, and grasp what it really means. My approach is to start small and expand gradually, ensuring that at each stage, people gain a deeper understanding of Bitcoin and how it can impact their lives. **YakiHonne**: I’m sure you guys will succeed. You don’t necessarily have to start big, but I believe you’ll grow much faster than you expect. With the effort and passion you’re putting in, I have no doubt that Bitcoin Chama will expand significantly. So,moving on to my last question,what are your community’s goals for the next 6 to 12 months? And how do you see it evolving with Bitcoin’s development? **Kelvin**:My goal for the next year is to continue the projects I’ve been working on. We have a community team that serves as a gathering point where people can come together, coordinate meeting times, and discuss Bitcoin and our future plans. **Kelvin**:so far for example, we built and distributed 15 beehives to different young people in our community. They harvest honey, sell it, and save the earnings in Bitcoin. We piped free clean water which can be accessed by any member in our community, significantly improving daily convenience.  **Kelvin**:We are planning to build two chicken coops and provide chickens to two groups of five people each. They will raise chickens, sell eggs, and save their earnings in Bitcoin. Over time, we aim for each member to have their own chicken coop with a sustainable flock by the end of the year.  **Kelvin**:We plan to lease a piece of land for the women in our community to grow vegetables and sell them at the local market. Their earnings will also be saved in Bitcoin. If the project is profitable, we will reinvest in more land to expand vegetable farming.Additionally, we plan to lease 2-3 acres of land specifically for commercial maize farming. The maize will be sold for Bitcoin, and if we generate profits, we will expand the farmland. **Kelvin**:Our long-term goal is to build a self-sufficient community, enabling it to operate independently and achieve sustainable development. This is also our core objective. **YakiHonne**: I truly love all the ideas behind this. I admire the fact that you are giving back to the community and that people are experiencing real benefits from the Bitcoin ecosystem. This way, they have something positive and meaningful to say about Bitcoin. **YakiHonne**: Thank you so much, Kelvin, for joining us today. We’ve reached the end of our interview, and I’m really happy to have had this conversation with you. We look forward to seeing Bitcoin Chama grow!