-
 @ 16d11430:61640947
2025-03-20 23:07:01
@ 16d11430:61640947
2025-03-20 23:07:01A Tale of Two Dysfunctional Kingdoms
In the grand theater of human organization, we are blessed with two great economic orders: Fiat, the Land of Fragile Giants, and Crypto, the Padded Madhouse of Infinite Lunacy. Both promise utopia, both deliver dysfunction, and both operate under the iron law that those with the most power will always act in their own interests—rules be damned.
The Fiat Intellectual Landscape: A Game of Tiptoeing Giants
The fiat world is a meticulously curated bonsai garden of decorum and quiet panic. Giants walk among us—CEOs, central bankers, hedge fund wizards, and the occasional Nobel Prize-winning economist—but they must step lightly, lest they shake the delicate equilibrium. The entire system is built on confidence, a polite euphemism for narrative control.
Take any major institution, and you'll find the same pathology:
Corporations: The larger they are, the more fragile their balance sheets, requiring constant PR therapy and quarterly ritual sacrifices to appease the gods of Wall Street. CEO statements are more rehearsed than Shakespearean soliloquies, lest a slip in language shaves billions off the stock price.
Academia: Intellectual giants must wade through a swamp of bureaucratic grant-seeking, where discovery is secondary to institutional survival. Challenging economic orthodoxy is career suicide, so best to publish another paper on "inclusive finance" while hedge funds strip-mine the economy.
Government & Central Banks: A crisis is just another reason to print more money, kick the debt can down the road, and assure the public that everything is “transitory.” Behind closed doors, they know it’s a rigged game—but stability must be maintained at all costs, even if it means bribing the peasants with stimulus checks to keep the illusion alive.
The entire fiat ecosystem is one of quiet desperation, where the powerful pretend to be cautious stewards of civilization while looting with the finesse of seasoned art thieves. Stability is paramount, because if the masses ever realized the whole thing is a confidence scam, they might actually ask questions.
Crypto: The Padded Madhouse Where Giants Go to Break Things
Meanwhile, in the Crypto Madhouse, giants don’t tiptoe—they run, scream, and occasionally set the entire house on fire just to see what happens. Here, there is no caution, no equilibrium—just a perpetual state of mania, where even the most outlandish ideas get venture funding. If fiat is an over-engineered glass palace, crypto is a playground for unhinged capitalists and techno-anarchists armed with flamethrowers.
The dysfunction here is less about fragility and more about unregulated chaos:
Ponzi Chains Masquerading as Innovation: Every year, a new "Ethereum Killer" promises to decentralize everything, only to collapse into an infighting mess of VC dumps, network outages, and sudden governance takeovers. If in fiat, failures happen in slow motion, in crypto, they happen overnight, in a Discord announcement at 3 AM.
Decentralization Theatre: Most "community-governed" projects are run by an inner circle of early whales who have more control than the Federal Reserve, but pretend it's democratic because they let the plebs vote on logo designs. The difference? Fiat oligarchs hide their power; crypto oligarchs post memes about it.
The Cult of the Visionary Founder: While fiat leaders pretend to be humble, crypto founders take the stage like prophets descending from the blockchain, dropping whitepapers with the same fervor as religious scriptures. And when they inevitably fail, they simply launch a new token, because failure only exists if you stop grifting.
Crypto may lack the institutional fragility of fiat, but in its place, we get wild, unchecked power, where insiders can rug-pull billions without consequence. The only real difference? Instead of bailing out banks, crypto just moves on to the next hype cycle.
Same Vested Interests, Different Scams
In the end, both systems operate under the same fundamental law: those with the most power will always find a way to keep it.
In fiat, the illusion of stability is paramount, so the powerful must lie in slow motion.
In crypto, the illusion of innovation is paramount, so the powerful must rug in high-speed.
The giants of fiat must walk lightly so as not to disturb the herd; the giants of crypto can rampage freely, because the casino always reopens. Either way, the little guy always pays the bill.
-
 @ 2ed3596e:98b4cc78
2025-03-20 22:46:58
@ 2ed3596e:98b4cc78
2025-03-20 22:46:58Bitcoin: The tool of true freedom in an age of control
Let’s talk about control. Not just the kind you see in politics, but the control over what you can say, what you can spend, and ultimately, how you live. It’s creeping into every part of our lives, and if you’re paying attention, you’ve already seen it happen.
Remember the Canadian truckers’ protest? If you donated just $50 and you got bank accounts frozen and all financial access cut off—not because of criminal activity, but because the government at the time didn’t like what you stood for. Look at donations to Palestine — many financial institutions are outright blocking donations to causes supporting folks struggling to survive in Gaza. China? Censorship isn’t just about speech; it’s about access to money, too – completely cutting people off from being able to participate in the economy. Economic strangulation is real and a growing government control tactic.
See the pattern?
It doesn’t matter what your politics are. If you step too far outside the accepted lines, you’ll be cut off. Your money is no longer yours if someone else can decide when you can access it.
The playbook isn’t new — just look at 1933
If you think this level of control is new, think again. In 1933, Executive Order 6102 forced Americans to hand over their gold to the government—under threat of fines and jail time. Why? Because gold was real money, and the government wanted to control the monetary system to finance its growth in spending and services. Gold, at this time, was $35 an ounce. Today it is worth thousands per ounce. The dollar, meanwhile, has lost 99% of its value in that same period.
Then came 1971. Nixon took the U.S. off the gold standard completely, meaning the dollar was no longer backed by anything tangible. Since then, the government has printed money at will, inflating the currency and making everything more expensive over time.
And yet, we’re supposed to trust this system?
Fiat is just a fancy word for "because we said so"
Our money is no longer tied to gold or anything of value. Fiat money has value simply because governments say it does. But history proves that this system is built on a lie. The more they print, the less your money is worth. It’s not about “helping the economy” or “fighting inflation”—it’s about making sure you stay dependent on the system. And when people get too self-sufficient? That’s when they start pulling tricks like EO 6102.
Bitcoin fixes this.
Bitcoin is E.O. 6102-proof
Governments can seize gold. They can freeze your bank accounts. They can tell you what you can and can’t spend money on.
But they cannot control Bitcoin.
Bitcoin is money that exists outside of their system. It can’t be inflated away. It can’t be seized by decree. It allows people to transact freely, regardless of politics, geography, or financial status. Whether you’re protesting in Ottawa, donating to survivors in Palestine, or living under Chinese financial surveillance—Bitcoin is the escape hatch.
“I consume, therefore I am”
Freedom isn’t just about what you can say—it’s about what you can do. If your ability to transact is controlled, then your ability to live freely is controlled. Bitcoin is the tool that breaks those chains.
It’s not just an investment. It’s not just “digital gold.” It’s a lifeline. It’s the difference between having control over your future or waiting for the next decree to tell you what you can do with your own money.
Governments will always try to tighten their grip. History proves it. But Bitcoin gives you the power to break free. The question is: will you use it?
-
 @ 878dff7c:037d18bc
2025-03-20 21:39:38
@ 878dff7c:037d18bc
2025-03-20 21:39:38JFK Assassination Files (Special brief)
Summary
The consensus among researchers and media is cautious optimism mixed with skepticism. The files offer a treasure trove of operational minutiae—spycraft, JFK’s CIA friction, Oswald’s movements—but no game-changer has emerged in the 72+ hours since release. Attention is shifting to the unreleased FBI and IRS records, with speculation that their declassification could clarify lingering questions. For now, the story remains one of incremental insight rather than revelation.
1. CIA's Surveillance of Lee Harvey Oswald Prior to Assassination
Newly declassified documents reveal that the CIA closely monitored Lee Harvey Oswald's activities before President Kennedy's assassination. Unredacted testimony from James Angleton, the CIA's chief of counterintelligence, provides deeper insight into the agency's surveillance operations concerning Oswald, particularly during his time in Mexico City, where he contacted the Soviet and Cuban embassies. Despite this surveillance, the CIA did not act to prevent the assassination, raising questions about the agency's internal communication and assessment processes.
2. Oswald's Interactions with Soviet Officials Scrutinized
The declassified files shed light on Oswald's interactions with Soviet officials during his visit to the USSR. According to KGB records, Oswald was closely monitored but was not recruited as an agent. These revelations provide a clearer understanding of Oswald's activities and the extent of Soviet intelligence's involvement with him, countering longstanding speculations about his ties to the USSR.
3. Prior Warning of Oswald's Intentions
A newly revealed letter indicates that months before the assassination, a tip-off about Oswald's plan to kill President Kennedy was received but not adequately acted upon. This raises concerns about potential intelligence failures and missed opportunities to prevent the tragic event.
4. President Kennedy's Consideration to Dismantle the CIA
The documents reveal that President Kennedy contemplated dismantling the CIA following the Bay of Pigs fiasco, referring to it as a "state within a state." This underscores the tension between the Kennedy administration and the intelligence community during that period.
5. Use of USS Potomac by Anti-Castro Paramilitaries
The declassified files disclose that the USS Potomac, formerly President Franklin D. Roosevelt's yacht, was later utilized by anti-Castro paramilitary groups. This highlights the covert operations undertaken during the Cold War era and the U.S. government's involvement in efforts to destabilize the Castro regime in Cuba.
6. Gary Underhill's Allegations Against the CIA
The documents bring to light the case of Gary Underhill, a former intelligence officer who alleged that the CIA was involved in illicit activities. Underhill was later found dead under suspicious circumstances, fueling further speculation about internal conspiracies within the intelligence community.
7. Australian Intelligence's Involvement in the Investigation
Newly released files reveal that Sir Charles Spry, the head of the Australian Security Intelligence Organisation (ASIO), lobbied to keep certain documents related to the assassination investigation confidential. This indicates international dimensions to the investigation and the sensitivity surrounding the information at the time.
Sources The Times - March 21, 2025\ Al Jazeera - March 20, 2025\ National Archives - March 18, 2025\ News.com.au - March 21, 2025
Significant Employment Drop in February; Unemployment Rate Steady
Summary:
Australia experienced an unexpected decline in employment, with 53,000 jobs lost in February, primarily due to older workers retiring and a decrease in female workforce participation. Despite this, the unemployment rate remained steady at 4.1%, largely because of a drop in the participation rate. Analysts suggest that recent tax cuts, interest rate reductions, and wage growth may have eased household budgets, reducing the need for some to seek employment. The Reserve Bank of Australia (RBA) is monitoring these developments but is not expected to implement another interest rate cut immediately. Sources: News.com.au - March 21, 2025, The Australian - March 21, 2025, ABC News - March 20, 2025
Tropical Cyclone Courtney Forms Near Cocos Islands, Marking Intense Cyclone Season
Summary:
Tropical Low 25U near the Cocos Islands has intensified into Tropical Cyclone Courtney. Meteorologists predict that while the system may struggle to maintain cyclone status, it will still bring gusty winds, squally showers, and thunderstorms to affected areas. This development marks the potential tenth cyclone since December, indicating one of the busiest cyclone seasons in 19 years if three more cyclones occur by the end of April. Residents in the path of the cyclone are advised to stay updated with the latest weather information and prepare for possible severe weather conditions. Sources: News.com.au - March 21, 2025
Australia's Population Growth Sparks Migration Policy Debate
Summary:
Australia's population grew by 484,000 (1.8%) over the past year, primarily due to natural births and net overseas migration. This surge has ignited political debates on migration policies. Prime Minister Anthony Albanese aims to reduce net migration to 250,000 by mid-2025, while Opposition Leader Peter Dutton advocates for a 25% cut in permanent migration and stricter caps on international students. Experts argue that skilled migration boosts the economy, but housing shortages linked to migration remain a pressing issue. Sources: News.com.au - March 21, 2025
NSW Premier Chris Minns Admits Need for Accelerated Reforms
Summary:
Marking two years in office, NSW Premier Chris Minns acknowledges his administration's slow progress on key promises, particularly in housing and economic reforms. While crises like natural disasters have been well-managed, significant advancements are lacking. Minns aims to expedite housing approvals to meet a target of 75,000 new homes and improve the budget, though challenges like debt reduction and infrastructure delays persist. Sources: The Daily Telegraph - March 21, 2025
Coalition Proposes Legislated Biosecurity Funding
Summary:
At the Northern Territory Cattlemen's Association Conference in Darwin, National Party Leader David Littleproud announced a policy to legislate minimum biosecurity funding of approximately $900 million. This measure aims to combat diseases like Lumpy Skin Disease and Foot and Mouth Disease, which could have severe economic impacts. The proposal includes introducing an Import Container Levy to ensure that importers, rather than Australian farmers, bear the costs. The Northern Territory Cattlemen's Association has expressed support for this sustainable funding approach.
Sources: The Courier-Mail - 21 March 2025
EU Leaders Convene to Address Global Challenges
Summary:
On March 20-21, 2025, European Union leaders met in Brussels to discuss pressing global issues, including economic competitiveness, security, and climate change. A working lunch with United Nations Secretary-General António Guterres focused on multilateralism and strengthening global cooperation. The summit underscored the EU's commitment to addressing international challenges through unified strategies and reinforced partnerships. Sources: European Parliament - March 20, 2025
Geopolitical Tensions Rise in the Arctic Region
Summary:
Recent analyses indicate that the Arctic is increasingly becoming a focal point of geopolitical rivalry. The region is now divided between a NATO-aligned Arctic, led by the United States, and a Russian Arctic seeking cooperation with BRICS+ countries. This division reflects broader global tensions between the US/NATO and Russia/China, heightening the risk of conflict and underscoring the need for diplomatic engagement to manage Arctic affairs. Sources: High North News - March 19, 2025
Royal Adelaide Hospital's Infectious Diseases Unit Relocation Sparks Concerns
Summary:
Doctors and nurses have raised concerns that patient care could be compromised if the South Australian government proceeds with plans to relocate the infectious diseases unit from the Royal Adelaide Hospital to a new location across North Terrace. Health unions have taken the dispute to the SA Employment Tribunal, arguing that the move could result in compromised clinical care and patient safety due to the separation from specialist doctors at the main hospital. The government cites cost considerations as the main driver for the relocation decision. Sources: ABC News - March 20, 2025
Inspirational Stories of Young Australians Overcoming Adversity
Summary:
The ABC Heywire competition recognized 38 young Australians from regional, rural, and remote areas for their inspiring stories of resilience and determination. Winners, aged 16 to 22, shared experiences highlighting life outside major cities. For instance, Blake from Casino detailed enduring severe drought on his family's farm, while Mayada from Coffs Harbour recounted her escape from child slavery during the Yazidi genocide, ultimately finding refuge in Australia. These narratives showcase the diverse and resilient spirit of young Australians committed to inspiring positive change in their communities. Sources: The Daily Telegraph - March 21, 2025
Calls for Strengthened ANZAC Cooperation Amid US Retrenchment and China's Rise
Summary:
China's growing military assertiveness, exemplified by live-fire naval exercises in the Tasman Sea, contrasts with the US's reduced global security commitments under President Trump, creating insecurity for traditional allies, Australia and New Zealand. Recent provocations and new strategic partnerships in the Pacific by China have exposed vulnerabilities in the defense capabilities of both countries. With the American security guarantee becoming unreliable, Australia and New Zealand must enhance their own military capacities and deepen bilateral and regional defense cooperation. Enhanced joint military operations and defense procurements, particularly focusing on air and maritime security, are critical. Forming new alliances with other regional powers, such as Japan, South Korea, and India, could also help address strategic gaps. This period demands a rejuvenated ANZAC cooperation to ensure both countries' security and stability in the changing geopolitical landscape. Sources: The Australian - 21 March 2025
More Extreme Weather Events Expected Across Australia
Summary:
Australia has experienced higher-than-average temperatures and numerous extreme weather events this season, including heatwaves, bushfires, floods, and cyclones. December, January, and February set records as some of the warmest months, contributing to an overall temperature rise of 1.9°C above average. Canberra's daytime temperatures are now 2.5°C higher compared to the early 1970s. Ex-Tropical Cyclone Alfred caused severe damage with strong winds and heavy rainfall, affecting over 300,000 homes. Bushfires in Victoria and Tasmania burned significant areas, while dry lightning in South Australia ignited 100 fires. Extreme weather is forecasted to continue into autumn with persistent heat and potential for further tropical cyclones, storms, and heavy rains. Climate change is driving these conditions, prompting calls for increased preparation and mitigation efforts. Measures include reducing emissions through lifestyle changes and improving emergency preparedness for weather events. Sources: The Daily Telegraph - March 21, 2025, The Courier-Mail - March 21, 2025
The Speaking Coach: The One Word All Liars Use! Stop Saying This Word, It's Making You Sound Weak! The More You Do This, The More You Sound Like A Liar!
Summary:
In this episode of "The Diary Of A CEO with Steven Bartlett," the focus is on effective communication and the subtle cues that can undermine credibility. The guest speaker, a seasoned speaking coach, discusses common verbal habits that can make individuals appear less trustworthy or confident. Key points include:
- Identifying Weak Language: Highlighting specific words and phrases that convey uncertainty or lack of conviction.
- Building Authority: Techniques to project confidence and authority in speech.
- Recognizing Deceptive Signals: Understanding verbal indicators commonly associated with dishonesty.
The episode provides practical advice for enhancing communication skills, making it valuable for professionals and anyone interested in personal development.
Sources: The Diary Of A CEO with Steven Bartlett - March 21, 2025
-
 @ 7d33ba57:1b82db35
2025-03-20 20:42:33
@ 7d33ba57:1b82db35
2025-03-20 20:42:33El Teide
Mount Teide (El Teide) is the highest mountain in Spain (3,715m) and the third-highest volcanic structure in the world. Located in Teide National Park (a UNESCO World Heritage Site), it offers breathtaking landscapes, hiking trails, and stunning panoramic views** over the Canary Islands.
🏔️ Best Things to Do at Mount Teide
1️⃣ Hike to the Summit
- The most rewarding way to reach the top! The hike starts from Montaña Blanca and takes about 5-6 hours.
- Permit required for the final ascent (apply in advance).
2️⃣ Take the Teide Cable Car
- A quick way to reach 3,555m, with spectacular views.
- From the upper station, you can hike to La Fortaleza Viewpoint or Pico Viejo Viewpoint for stunning island views.
3️⃣ Stargazing at Teide Observatory
- One of the best stargazing spots in the world due to its clear skies and high altitude.
- Join an astronomy tour for an unforgettable night experience.
4️⃣ Explore the Teide National Park
- Walk through lava fields, craters, and rock formations like Roques de García.
- Visit the Visitor Center to learn about the park’s geology and history.
🚗 How to Get to Teide
🚗 By Car: ~1.5 hours from Santa Cruz or Costa Adeje
🚌 By Bus: Titsa buses 342 (from Costa Adeje) & 348 (from Puerto de la Cruz)💡 Tips for Visiting Teide
✅ Book summit permits early – Limited spots available! 🎟️
✅ Dress warmly – Temperatures drop at high altitude, even in summer 🧥
✅ Best time to visit? Sunrise, sunset, or night for amazing views 🌅🌌
✅ Take it slow – The high altitude can affect breathing ⛰️ -
 @ a296b972:e5a7a2e8
2025-03-20 19:36:34
@ a296b972:e5a7a2e8
2025-03-20 19:36:34Diagnose:
Der aufgelöste Bundestag verschuldet die Insassen eines Landes namens Absurdistan in schwindelerregender Höhe durch einen noch nicht gewählten Bundeskanzler, der vormals wohlmöglich Werbung für Gewürzgurken gemacht hat, unter Zuhilfenahme von Parteien, die abgewählt wurden. Eine Sperrminorität konnte nicht entstehen, weil sie sonst verhindert hätte, dass die Wahlversprechungen nicht hätten gebrochen werden können. (Geht gar nicht!)
Genau so gut, hätte der letzte deutsche Kaiser eine Sektsteuer erheben können, um die deutsche Marine aufzurüsten. (Ach so, ja, ist schon gut, hatten wir schon, hatte ich vergessen.)
In Rumänien und Serbien sind Demokraten zu Hunderttausenden auf der Straße, und Deutschland hat Kellerwoche (Schade eigentlich!).
In Erstverschlimmerung löst die aktuelle Situation das blanke Entsetzen aus, doch auf den zweiten Blick stellt sich das Ganze durchaus als sehr positiv dar. Heilung ist möglich, doch vorher kommt der Schmerz:
Die Neuverschuldung ist nämlich eine provisorische Abschreckung für den Russen, der dann doch lieber so lange wartet, bis Deutschland in 10 bis 20 Jahren wirklich aufgerüstet hat. Wer kämpft schon gerne gegen jemanden, der sich nur maximal 2 Tage verteidigen kann? Das macht doch keinen Spaß. Da lohnt sich doch der ganze Aufwand nicht. Bis dahin hat Deutschland leider nichts, außer Schulden. Von Windrädchen und Zufallsstrom und einer innerlich, aber eben nur sehr innerlich, rebellischen Bevölkerung mal ganz abgesehen.
Es geht hoffnungsvoll weiter. Mit Frau von der Leyen haben wir als EU-Kommissarin bereits eine Deutsche in Brüssel, die sich schon vor ihrer zweiten Einsetzung ohne demokratische Mittel, in bundesstaatlichen Pöstchen durch ihre mangelnde Qualifikation besonders herausragend ausgezeichnet hat.
Statt einer qualifizierten, sich verdient gemacht habenden Diplomatin namens Frau Dröge, soll nun als weitere "deutsche Konifere" auch Frau ver Baerbock-t als UN-Generalsekretärin der UN-Generalversammlung hochgelobt und eingesetzt werden. Auf die Frage von Herrn Warweg in der Pressekonferenz-Show, warum denn nun Frau Baerbock qualifizierter sei, als Frau Dröge, wusste sich der Sprecher Herr Hebestreit wie immer galant durch nichts sagende Textbausteinabsonderungen aus der Schlinge zu ziehen. Vermutlich wollte er Frau Dröge nicht kompromittieren, weil er sonst hätte sagen müssen, dass ja Frau Baerbock viel besser Trampolin springen kann, als sie. Kavalier ist er ja, da gibt es nichts gegen zu sagen.
Mit Frau Baerbock hätte Deutschland eine weitere Deutsche installiert, die dem Ansehen Deutschlands in der Welt, in Fortsetzung ihres Amtes als Außenfeministin, nahtlos weiterhin den maximalen Schaden zufügen könnte.
Weiter wird gemunkelt, dass Herr Habeck für die Darstellung des Bundespräsidenten zur Disposition steht. Mit Märchen kennt er sich aus, insofern wäre er ein würdiger Nachfolger des Streubomben-nicht-Verhinderers. Auch Herr Habeck wird durch seine oft genug bewiesene Expertise in Insolvenz und Wirtschaftsvernichtung Deutschland nach außen hin in bester Weise repräsentieren. Als braver Bürger kann man sich keinen besseren Schwiegermutter-Liebling vorstellen. Und wie der sich ausdrücken kann, hach, einfach nur nett!
Die Aufteilung der Grünen in Außen und Wirtschaft war somit absolut sinnvoll. Schließlich kommt Frau Baerbock ja mehr vom Haarspray und Herr Habeck mehr so vom Shampoo.
Und wenn wir schon mal bei der Verteilung von neuen Pöstchen sind, dann sollte man Herrn Scholz als neuen Chef für den Bundesnachrichtendienst vorschlagen. Verschwiegen ist er, Geheimnisse kann er bewahren. Wie Staatsgeheimnisse nicht an die Öffentlichkeit gelangen, damit kennt er sich aus. Nordstream 2 wurde nämlich von den Deutschen selbst in die Luft gejagt, als Selbstgeißelung für den angerichteten Schaden im 2. Weltenbrand. Er wollte einfach Teile der Bevölkerung nicht verunsichern, auch, wenn die Idee nicht von ihm ist.
Und Herr Lauterbach sollte in die Wissenschaft wechseln und dort einen neuen Lügendetektor entwickeln, mit dem man Fake-News problemlos entlarven kann. Wie lügen geht, weiß er ja von allen am allerbesten. Und wenn es wirklich mal eng werden sollte, kann er ja Berater zur Hilfe nehmen. Vielleicht haben Herr Drosten oder gar Herr Fauci (ital. la fauci = das Maul) Zeit ihn bei dieser wertvollen Arbeit zu unterstützen.
Warum also ist das jetzt alles positiv?
Mit diesen Kapazitäten wären Deutsche an exponierter Stelle installiert, um das ideologische Gift in die EU, in die UN und weltweit hinein zu träufeln.
Innerdeutsch werden sich sicher Herr Bäcker, der Mann mit den unglücklichen Initialen, Frau Düsseldorf-Rheinmetall, Herr Kriegsgewitter u. a. auch weiterhin zur Verfügung stellen, die Kriegstüchtigkeit ihrer Vollendung entgegen zu führen. Wohlwollend beobachtet durch die USA und Russland. Das wäre dann Inklusion, oder sagt man Implosion?
Dann werden auch noch als erstes von den Billionen Sonderschulden mobile Vermögenswerte in Form von Vorschlaghämmern angeschafft, mit denen die Schweine der deutschen Sparer geschlachtet werden sollen. Frau Lagarde hat sich schon bereit erklärt, hier mit Einführung des digitalen Euro demnächst helfend zur Seite zu stehen.
Alles wirklich molto bene, Heilung ist nahe!
In Zusammenwirken all dieser Kräfte und Kapazitäten für Deutschland und Europa, wird auch noch die deutsche Gesellschaft die Grätsche machen und dann ist Deutschland völlig bettlägerig und darnieder. Deutschland hat bald fertig!
Und hat Deutschland, als größter Geldgeber der EU fertig, hat auch die EU fertig, ihr geht dann einfach die Puste aus. Und vielleicht warten schon Ungarn und einige andere Mitgliedsstaaten nur auf eine günstige Gelegenheit, der EU für lange Zeit Adieu zu sagen?
„Wenn wir uns wiedersehen, werden wir uns freuen, wenn nicht, war der Abschied wohlgetan!“
Und mit ganz viel Glück geben die USA Europa dann auch noch den Gnadenstoß und erlösen die europäischen Staaten von dem Übel namens EU, da sie offensichtlich selbst nicht in der Lage sind, sich aus ihrer Bevormundung mit betreutem Denken und einem Wahrheitsministerium zu befreien. Die NATO wackelt ja auch schon.
Genesung:
Anschließend gibt es für alle Bürger Europas, aber besonders für Deutschland, einen Pflichtkurs in der Volkshochschule in Sachen Frieden, Demokratie und Freiheit. Vielleicht klappt es dann dieses Mal, aus Denkschnecken Schachweltmeister zu machen. Oder wenigstens aus Langzeitkomatösen Leute mit Wachbewusstsein.
Nochmals, alles in bester Ordnung. Es muss erst noch schlimmer werden, bevor es wieder besser wird. Bei dem Tempo, dass die europäischen Universal-Dilettanten derzeit an den Tag legen, wird das nicht sehr lange dauern.
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ 6f0a6a19:7dd662db
2025-03-20 19:00:46
@ 6f0a6a19:7dd662db
2025-03-20 19:00:46BitBonds
The idea, initially proposed by Newmarket Capital CEO Andrew Hohns at the Bitcoin Policy Institute’s “Bitcoin for America” conference, is that Congress could defease the federal debt and cut long-term interest rates by approving a new debt instrument collateralized with Bitcoin—BitBonds.
How It Works:
- For every $100 BitBond issued, $10 would buy Bitcoin for the U.S. Strategic Reserve.
- Bondholders would receive 1% annual interest (lower than traditional Treasuries) and 50% of BTC price appreciation.
A New Bitcoin Standard
At first glance, BitBonds is an innovative way to increase demand for U.S. Treasuries without Federal Reserve intervention while lowering borrowing costs. However, this instrument would signal a radical change in monetary policy.
A 4000-year precedent
Money (as a visual measure of credit) has been and is always socially constructed through a stable exchange ratio.
- Money didn’t appear in ancient Sumer until priests and palace administrators set rates between standard weights of grain and silver on palace-authorized cuneiform tablets.
- In Egypt, money was constructed through economic administrators (related to the king) setting common rates between an abstracted standardized 92 gram copper weight measurement called a Deben and grain.
- Roman and Greek mints fixed ratios and weights between precious metals to establish official coinage and stabilize their value.
- The U.S. established its first currency through a bi-metallic standard, fixing gold and silver rates via the U.S. Mint.
- The modern U.S. monetary system issues its currency on a promise to redeem $100 for $100 + 2% interest.
U.S. government debt became the default monetary exchange rate the moment Nixon suspended gold redemption in 1971. It was the only remaining promised ratio of exchange attached to the US Dollar. Each year, Congress votes to extend this debt-based system by approving the federal budget. And the Federal Reserve then manages the levers of bond prices and yields through open market operations. There is no other federal mechanism for securing universal interest in the dollar, than the interest paid from its debt.
With BitBonds collateralizing 10% of each issuance in Bitcoin, the government would effectively introduce a new promised ratio of exchange to US monetary policy. It would promise to redeem 10 cents of every $1 in this lending program for bitcoin (half for the reserve and half of its appreciated value for the holder). This promise would transition US monetary policy from a pure debt based system to a new implicit exchange rate between Bitcoin and the U.S. dollar.
How BitBonds Would Drive Bitcoin to $10 Million
- First, BitBonds promises unlimited buying pressure on a finite asset. (The government can perpetually issue more BitBonds to acquire Bitcoin.) That, combined with the fact that Treasuries are the world’s primary liquidity engine, would generate unprecedented demand for Bitcoin reserves.
- Second, unlike previous reserve assets like gold, Bitcoin’s indivisibility prevents fractional redemption. This network constraint prevents the government from redeeming less than 1 satoshi (the base unit of Bitcoin) for 10 cents, thereby setting a clear price target for the market. Promising to collateralize 10% of each bond with bitcoin is like priming the pump for max buy pressure, fixing a target price and pulling the trigger.
- Investors would front-run the Treasury’s buying spree with that target in mind and in a matter of time 1 satoshi will equal $0.10 ($10M per BTC).
- At $10M per BTC, Bitcoin’s total valuation would reach $210 trillion—a figure capable of servicing the $189 trillion in global U.S. debt obligations and backing the $21 trillion M2 money supply. This valuation would prime bitcoin to become the world reserve asset backing the world reserve currency (a digital dollar).
- After this transformation, the government would have the precedent to institute a more explicit system of regulating bitcoin and digital dollar redemption. You can learn more about what this system would look like in my thesis for why technocratic government agencies will inevitably use bitcoin to create a cashless digital society: The Anarchist’s Guide to Cashing out of the Matrix.
Why Market Resistance Will Fail
- Selling Bitcoin into a U.S. Treasury buy wall would be a losing trade. A continuous government buyer would absorb any attempt to suppress BTC’s price.
- Foreign governments would be compelled to adopt or lose financial leverage. If the U.S. redefines sovereign debt through Bitcoin, foreign central banks must accumulate Bitcoin or face economic devaluation.
- The Federal Reserve would have no choice but to accommodate Bitcoin-backed Treasuries. If BitBonds reshape U.S. debt issuance, the Fed must either integrate them into monetary policy or risk disrupting Treasury markets.
The short path to a $10 million bitcoin
- The U.S. Treasury launches BitBonds, requiring Bitcoin collateral equal to 10% of each issuance.
- Bitcoin markets recognize that the U.S. government is a continuous net buyer.
- Investors front-run this signal, accelerating Bitcoin accumulation.
- Institutional demand propels BTC to the $10M target, exponentially increasing the value of the SBR.
- Once 1 satoshi = $0.10, the federal government will have a stockpile of bitcoin valued at a cost basis greater than its annual debt obligations.
- Rather than use the stockpile to pay the debt down, the government will find that it needs to enforce a new surveillance-enforced bitcoin redemption policy to maintain a funnel of public bitcoin to the SBR in return for surveillable stablecoins. (read thesis for more)
Bitcoin’s Supply Guarantees a Stable Transition
Unlike gold, Bitcoin’s supply is fixed, transparent, and auditable. Once repricing begins, sovereign wealth funds, pension funds, and financial institutions will be forced to accumulate Bitcoin, play by the new state-issued redemption rules or be left behind.
I'm not sure how long it would take for the market to figure this out, but I’d assume it would be an all-out sprint to $10M BTC once the cat is out of the bag.
-
 @ f240be2b:00c761ba
2025-03-20 17:53:08
@ f240be2b:00c761ba
2025-03-20 17:53:08Warum jetzt ein guter Zeitpunkt sein könnte, sich mit Bitcoin zu beschäftigen
Kennt ihr das? Wenn der Bitcoin-Preis neue Höchststände erreicht, möchte plötzlich jeder einsteigen. Doch sobald die Kurse fallen, überwiegt die Angst. Dabei zeigt die Geschichte: Gerade diese Phasen der Unsicherheit können interessante Zeitpunkte sein, um sich mit dem Thema zu beschäftigen.
Historische Zyklen Bitcoin durchläuft regelmäßige Marktzyklen Nach jedem Tief folgte bisher ein neues Hoch Emotionen spielen eine große Rolle im Markt Psychologie des Marktes Wenn alle euphorisch sind → meist teuer Wenn Unsicherheit herrscht → oft interessante Gelegenheiten Die Masse liegt häufig zum falschen Zeitpunkt richtigRationale Herangehensweise
Statt emotional zu handeln, solltet ihr:
Einen langfristigen Anlagehorizont wählen Regelmäßig kleine Beträge investieren (Cost-Average-Effekt)Hier ein paar Charts die euch helfen sollen und euch mutig werden lassen:
https://www.tradingview.com/chart/BTCUSD/HuGpzZfQ-BITCOIN-Cycle-pattern-completed-Year-end-Target-locked-at-150k/
https://www.tradingview.com/chart/BTCUSD/YVyy9QuU-BITCOIN-Money-Supply-Dollar-and-Bonds-pushing-for-MEGA-RALLY/
https://www.tradingview.com/chart/BTCUSD/pZ0qs5x3-BTCUSD-TSI-shows-that-this-is-the-LAST-BEST-BUY/
https://www.tradingview.com/chart/BTCUSD/x3e7GuLQ-BITCOIN-Is-this-a-Falling-Wedge-bottom-formation/
und jetzt All-In :-)
-
 @ 16f1a010:31b1074b
2025-03-20 15:29:42
@ 16f1a010:31b1074b
2025-03-20 15:29:42What is NSSM?
NSSM (Non-Sucking Service Manager) is a free tool that allows you to install and manage any application as a Windows service. This is particularly useful for applications that don't natively support running as a service, ensuring they start automatically when your system boots and continue running in the background.
Downloading NSSM
- Visit the official NSSM website: https://nssm.cc/
- Download the latest stable release.
- Extract the downloaded ZIP file to a directory of your choice (e.g.,
C:\nssm).
Adding NSSM to Your PATH (Recommended)
Adding NSSM to your system's PATH environment variable allows you to run
nssmcommands from any command prompt window.- Search for "Environment Variables" in the Windows Start menu and select "Edit the system environment variables."

- In the "System Properties" window, click the "Environment Variables..." button.
- In the "System variables" section, find the "Path" variable and click "Edit."
- Click "New" and add the path to the directory where you extracted NSSM (e.g.,
C:\nssm). - Click "OK" on all open windows to save the changes.
- Open a new command prompt window and type
nssm --version. If NSSM is correctly added to your PATH, you should see the version information.
Using NSSM: Installing a Service
- Open a command prompt as administrator.
- Type
nssm install <service_name>and press Enter. Replace<service_name>with the name you want to give to your service. - A GUI will appear, allowing you to configure the service.
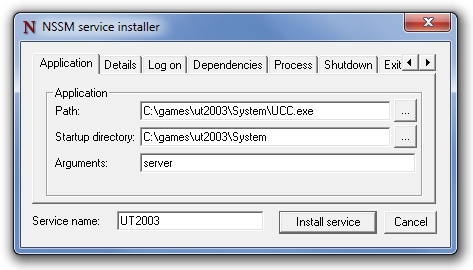
- In the "Path" field, enter the full path to the application's executable.
- In the "Startup directory" field, enter the directory containing the executable.
- Configure any other options as needed, such as "Arguments," "I/O," or "Details."
- Click "Install service."
Example:
bash nssm install MyGrainRelayConclusion
Congratulations, you now have NSSM installed and know the basics of using it to manage windows services. Check my profile for more technical guides on various topics, and stay tuned for more guides.
-
 @ 16f1a010:31b1074b
2025-03-20 14:32:25
@ 16f1a010:31b1074b
2025-03-20 14:32:25grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Introduction
grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Prerequisites
- Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rwwp5xsuryd3knfdr7g
Download Grain
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlPrerequisites: - Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: [Link to MongoDB setup guide].
Download Grain:
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution:
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain:
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files:
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlConfiguration Documentation
You can always find the latest example configs on my site or in the github repo here: config.yml
Config.yml
This
config.ymlfile is where you customize how your Grain relay operates. Each section controls different aspects of the relay's behavior.1.
mongodb(Database Settings)uri: mongodb://localhost:27017/:- This is the connection string for your MongoDB database.
mongodb://localhost:27017/indicates that your MongoDB server is running on the same computer as your Grain relay (localhost) and listening on port 27017 (the default MongoDB port).- If your MongoDB server is on a different machine, you'll need to change
localhostto the server's IP address or hostname. - The trailing
/indicates the root of the mongodb server. You will define the database in the next line.
database: grain:- This specifies the name of the MongoDB database that Grain will use to store Nostr events. Grain will create this database if it doesn't already exist.
- You can name the database whatever you want. If you want to run multiple grain relays, you can and they can have different databases running on the same mongo server.
2.
server(Relay Server Settings)port: :8181:- This sets the port on which your Grain relay will listen for incoming nostr websocket connections and what port the frontend will be available at.
read_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to send data before closing the connection.
write_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to receive data before closing the connection.
idle_timeout: 120 # in seconds:- This is the maximum time (in seconds) that the relay will keep a connection open if there's no activity.
max_connections: 100:- This sets the maximum number of simultaneous client connections that the relay will allow.
max_subscriptions_per_client: 10:- This sets the maximum amount of subscriptions a single client can request from the relay.
3.
resource_limits(System Resource Limits)cpu_cores: 2 # Limit the number of CPU cores the application can use:- This restricts the number of CPU cores that Grain can use. Useful for controlling resource usage on your server.
memory_mb: 1024 # Cap the maximum amount of RAM in MB the application can use:- This limits the maximum amount of RAM (in megabytes) that Grain can use.
heap_size_mb: 512 # Set a limit on the Go garbage collector's heap size in MB:- This sets a limit on the amount of memory that the Go programming language's garbage collector can use.
4.
auth(Authentication Settings)enabled: false # Enable or disable AUTH handling:- If set to
true, this enables authentication handling, requiring clients to authenticate before using the relay.
- If set to
relay_url: "wss://relay.example.com/" # Specify the relay URL:- If authentication is enabled, this is the url that clients will use to authenticate.
5.
UserSync(User Synchronization)user_sync: false:- If set to true, the relay will attempt to sync user data from other relays.
disable_at_startup: true:- If user sync is enabled, this will prevent the sync from starting when the relay starts.
initial_sync_relays: [...]:- A list of other relays to pull user data from.
kinds: []:- A list of event kinds to pull from the other relays. Leaving this empty will pull all event kinds.
limit: 100:- The limit of events to pull from the other relays.
exclude_non_whitelisted: true:- If set to true, only users on the whitelist will have their data synced.
interval: 360:- The interval in minutes that the relay will resync user data.
6.
backup_relay(Backup Relay)enabled: false:- If set to true, the relay will send copies of received events to the backup relay.
url: "wss://some-relay.com":- The url of the backup relay.
7.
event_purge(Event Purging)enabled: false:- If set to
true, the relay will automatically delete old events.
- If set to
keep_interval_hours: 24:- The number of hours to keep events before purging them.
purge_interval_minutes: 240:- How often (in minutes) the purging process runs.
purge_by_category: ...:- Allows you to specify which categories of events (regular, replaceable, addressable, deprecated) to purge.
purge_by_kind_enabled: false:- If set to true, events will be purged based on the kinds listed below.
kinds_to_purge: ...:- A list of event kinds to purge.
exclude_whitelisted: true:- If set to true, events from whitelisted users will not be purged.
8.
event_time_constraints(Event Time Constraints)min_created_at: 1577836800:- The minimum
created_attimestamp (Unix timestamp) that events must have to be accepted by the relay.
- The minimum
max_created_at_string: now+5m:- The maximum created at time that an event can have. This example shows that the max created at time is 5 minutes in the future from the time the event is received.
min_created_at_stringandmax_created_atwork the same way.
9.
rate_limit(Rate Limiting)ws_limit: 100:- The maximum number of WebSocket messages per second that the relay will accept.
ws_burst: 200:- Allows a temporary burst of WebSocket messages.
event_limit: 50:- The maximum number of Nostr events per second that the relay will accept.
event_burst: 100:- Allows a temporary burst of Nostr events.
req_limit: 50:- The limit of http requests per second.
req_burst: 100:- The allowed burst of http requests.
max_event_size: 51200:- The maximum size (in bytes) of a Nostr event that the relay will accept.
kind_size_limits: ...:- Allows you to set size limits for specific event kinds.
category_limits: ...:- Allows you to set rate limits for different event categories (ephemeral, addressable, regular, replaceable).
kind_limits: ...:- Allows you to set rate limits for specific event kinds.
By understanding these settings, you can tailor your Grain Nostr relay to meet your specific needs and resource constraints.
whitelist.yml
The
whitelist.ymlfile is used to control which users, event kinds, and domains are allowed to interact with your Grain relay. Here's a breakdown of the settings:1.
pubkey_whitelist(Public Key Whitelist)enabled: false:- If set to
true, this enables the public key whitelist. Only users whose public keys are listed will be allowed to publish events to your relay.
- If set to
pubkeys::- A list of hexadecimal public keys that are allowed to publish events.
pubkey1andpubkey2are placeholders, you will replace these with actual hexadecimal public keys.
npubs::- A list of npubs that are allowed to publish events.
npub18ls2km9aklhzw9yzqgjfu0anhz2z83hkeknw7sl22ptu8kfs3rjq54am44andnpub2are placeholders, replace them with actual npubs.- npubs are bech32 encoded public keys.
2.
kind_whitelist(Event Kind Whitelist)enabled: false:- If set to
true, this enables the event kind whitelist. Only events with the specified kinds will be allowed.
- If set to
kinds::- A list of event kinds (as strings) that are allowed.
"1"and"2"are example kinds. Replace these with the kinds you want to allow.- Example kinds are 0 for metadata, 1 for short text notes, and 2 for recommend server.
3.
domain_whitelist(Domain Whitelist)enabled: false:- If set to
true, this enables the domain whitelist. This checks the domains .well-known folder for their nostr.json. This file contains a list of pubkeys. They will be considered whitelisted if on this list.
- If set to
domains::- A list of domains that are allowed.
"example.com"and"anotherdomain.com"are example domains. Replace these with the domains you want to allow.
blacklist.yml
The
blacklist.ymlfile allows you to block specific content, users, and words from your Grain relay. Here's a breakdown of the settings:1.
enabled: true- This setting enables the blacklist functionality. If set to
true, the relay will actively block content and users based on the rules defined in this file.
2.
permanent_ban_words:- This section lists words that, if found in an event, will result in a permanent ban for the event's author.
- really bad wordis a placeholder. Replace it with any words you want to permanently block.
3.
temp_ban_words:- This section lists words that, if found in an event, will result in a temporary ban for the event's author.
- crypto,- web3, and- airdropare examples. Replace them with the words you want to temporarily block.
4.
max_temp_bans: 3- This sets the maximum number of temporary bans a user can receive before they are permanently banned.
5.
temp_ban_duration: 3600- This sets the duration of a temporary ban in seconds.
3600seconds equals one hour.
6.
permanent_blacklist_pubkeys:- This section lists hexadecimal public keys that are permanently blocked from using the relay.
- db0c9b8acd6101adb9b281c5321f98f6eebb33c5719d230ed1870997538a9765is an example. Replace it with the public keys you want to block.
7.
permanent_blacklist_npubs:- This section lists npubs that are permanently blocked from using the relay.
- npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtnis an example. Replace it with the npubs you want to block.- npubs are the human readable version of public keys.
8.
mutelist_authors:- This section lists hexadecimal public keys of author of a kind1000 mutelist. Pubkey authors on this mutelist will be considered on the permanent blacklist. This provides a nostr native way to handle the backlist of your relay
- 3fe0ab6cbdb7ee27148202249e3fb3b89423c6f6cda6ef43ea5057c3d93088e4is an example. Replace it with the public keys of authors that have a mutelist you would like to use as a blacklist. Consider using your own.- Important Note: The mutelist Event MUST be stored in this relay for it to be retrieved. This means your relay must have a copy of the authors kind10000 mutelist to consider them for the blacklist.
Running Grain as a Service:
Windows Service:
To run Grain as a Windows service, you can use tools like NSSM (Non-Sucking Service Manager). NSSM allows you to easily install and manage any application as a Windows service.
* For instructions on how to install NSSM, please refer to this article: [Link to NSSM install guide coming soon].-
Open Command Prompt as Administrator:
- Open the Windows Start menu, type "cmd," right-click on "Command Prompt," and select "Run as administrator."
-
Navigate to NSSM Directory:
- Use the
cdcommand to navigate to the directory where you extracted NSSM. For example, if you extracted it toC:\nssm, you would typecd C:\nssmand press Enter.
- Use the
-
Install the Grain Service:
- Run the command
nssm install grain. - A GUI will appear, allowing you to configure the service.
- Run the command
-
Configure Service Details:
- In the "Path" field, enter the full path to your Grain executable (e.g.,
C:\grain\grain_windows_amd64.exe). - In the "Startup directory" field, enter the directory where your Grain executable is located (e.g.,
C:\grain).
- In the "Path" field, enter the full path to your Grain executable (e.g.,
-
Install the Service:
- Click the "Install service" button.
-
Manage the Service:
- You can now manage the Grain service using the Windows Services manager. Open the Start menu, type "services.msc," and press Enter. You can start, stop, pause, or restart the Grain service from there.
Linux Service (systemd):
To run Grain as a Linux service, you can use systemd, the standard service manager for most modern Linux distributions.
-
Create a Systemd Service File:
- Open a text editor with root privileges (e.g.,
sudo nano /etc/systemd/system/grain.service).
- Open a text editor with root privileges (e.g.,
-
Add Service Configuration:
- Add the following content to the
grain.servicefile, replacing the placeholders with your actual paths and user information:
```toml [Unit] Description=Grain Nostr Relay After=network.target
[Service] ExecStart=/path/to/grain_linux_amd64 WorkingDirectory=/path/to/grain/directory Restart=always User=your_user #replace your_user Group=your_group #replace your_group
[Install] WantedBy=multi-user.target ```
- Replace
/path/to/grain/executablewith the full path to your Grain executable. - Replace
/path/to/grain/directorywith the directory containing your Grain executable. - Replace
your_userandyour_groupwith the username and group that will run the Grain service.
- Add the following content to the
-
Reload Systemd:
- Run the command
sudo systemctl daemon-reloadto reload the systemd configuration.
- Run the command
-
Enable the Service:
- Run the command
sudo systemctl enable grain.serviceto enable the service to start automatically on boot.
- Run the command
-
Start the Service:
- Run the command
sudo systemctl start grain.serviceto start the service immediately.
- Run the command
-
Check Service Status:
- Run the command
sudo systemctl status grain.serviceto check the status of the Grain service. This will show you if the service is running and any recent logs. - You can run
sudo journalctl -f -u grain.serviceto watch the logs
- Run the command
More guides are in the works for setting up tailscale to access your relay from anywhere over a private network and for setting up a cloudflare tunnel to your domain to deploy a grain relay accessible on a subdomain of your site eg wss://relay.yourdomain.com
-
 @ 16f1a010:31b1074b
2025-03-20 14:31:19
@ 16f1a010:31b1074b
2025-03-20 14:31:19Introduction
MongoDB is a popular NoSQL document database, meaning it stores data in flexible, JSON-like documents. This makes it highly scalable and adaptable for various applications. This guide will focus on installing the Community Server edition, which is free and open-source.
This article is designed for beginners and those new to MongoDB, providing a clear and concise walkthrough of the installation process. We will cover installation on both Windows and Linux operating systems.
The official MongoDB documentation on the MongoDB website is very informative and you should be able to follow their guides. This article is written to provide a brief overview and a more streamlined installation experience.
Prerequisites
MongoDB Community Server can be installed and run on a wide range of systems. While specific hardware requirements can vary based on your intended use case and the size of your database, here are the general prerequisites:
- Operating System:
- This guide will cover installation on popular versions of Windows and Linux (specifically Ubuntu/Debian). MongoDB also supports other operating systems, which you can find on the official MongoDB website.
- Storage Space:
- You'll need sufficient disk space to store your database files. The amount of space required will depend on the size of your data. It is recommended to have more storage than you think you will initially need.
- RAM:
- While MongoDB can run with minimal RAM, having more RAM will improve performance, especially for larger databases. The amount of RAM needed will depend on the size of your data.
- Basic System Knowledge:
- Familiarity with using the command line or terminal is helpful, especially for Linux installations.
- Basic understanding of file systems and directories.
Essentially, MongoDB is designed to be flexible and can run on most modern systems. As your data grows, you can always scale your hardware accordingly.
Downloading MongoDB Community Server:
To begin, you'll need to download the MongoDB Community Server installation package.
- Visit the official MongoDB download page: https://www.mongodb.com/try/download/community
On the download page, you'll see options to select the following:
- Version: Choose the desired version of MongoDB. It is generally recommended to select the latest stable release.
- Operating System: Select your operating system (Windows or Linux).
- Package: Select the appropriate package type. For Windows, it will typically be
msi. For Linux, you will choose the package type that aligns with your linux distro. For example.debfor Debian/Ubuntu or.rpmfor RedHat/Fedora.
Once you have made your selections, click the "Download" button to download the installer or package.
Installation on Windows:
Running the Installer:
-
Locate the Downloaded Installer:
- Navigate to the directory where you downloaded the MongoDB
.msiinstaller.
- Navigate to the directory where you downloaded the MongoDB
-
Run the Installer:
- Double-click the
.msifile to start the installation wizard.
- Double-click the
-
Welcome Screen:
- Click "Next" on the welcome screen.
-
License Agreement:
- Read the license agreement, check the "I accept the terms in the License Agreement" box, and click "Next."
-
Setup Type:
- Select "Custom" installation. This allows you to choose the installation location and data directory. Click "Next."
-
Installation Location:
- You can change the default installation directory if desired. Click "Next."
-
Service Configuration:
- You can choose to install MongoDB as a service. It is recommended to install as a service.
- You can also change the "Data Directory" location here. It is recommended to change this to a location such as
C:\data\db. If you do not change it here, you will need to create the data directory manually later. - Click "Next."
-
Ready to Install:
- Click "Install" to begin the installation process.
-
Complete Installation:
- Once the installation is complete, click "Finish."
Setting Environment Variables (Optional but Recommended):
Setting the
PATHenvironment variable allows you to run MongoDB commands from any command prompt window without specifying the full path to the executable.-
Open System Properties:
- Search for "Environment Variables" in the Windows Start menu and select "Edit the system environment variables."
-
Environment Variables:
- In the "System Properties" window, click the "Environment Variables..." button.
-
Edit Path Variable:
- In the "System variables" section, find the "Path" variable and click "Edit."
-
Add MongoDB Bin Directory:
- Click "New" and add the path to the MongoDB
bindirectory. This is typicallyC:\Program Files\MongoDB\Server\<version>\bin, replacing<version>with your installed version. - Click "OK" on all open windows to save the changes.
- Click "New" and add the path to the MongoDB
-
Verify Path:
- Open a new command prompt window and type
mongod --version. If MongoDB is installed correctly and thePATHvariable is set, you should see the MongoDB version information.
- Open a new command prompt window and type
Installation on Linux (Ubuntu/Debian):
These instructions are specifically for Debian-based systems like Ubuntu.
Importing the MongoDB Public GPG Key:
-
Open a Terminal:
- Open your terminal application.
-
Import the GPG Key:
- Run the following command to import the MongoDB public GPG key:
bash wget -qO - [https://www.mongodb.org/static/pgp/server-7.0.asc](https://www.mongodb.org/static/pgp/server-7.0.asc) | sudo apt-key add -- This command downloads the GPG key and adds it to your system's trusted keys. This ensures that the packages you download from the MongoDB repository are authentic.
Adding the MongoDB Repository:
-
Add the Repository:
- Run the following command to add the MongoDB repository to your system's sources list:
bash echo "deb [ arch=amd64,arm64 ] [https://repo.mongodb.org/apt/ubuntu](https://repo.mongodb.org/apt/ubuntu) $(lsb_release -cs)/mongodb-org/7.0 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-7.0.list- This command adds the MongoDB repository to your system's package manager sources. The
$(lsb_release -cs)part automatically determines your Ubuntu/Debian version.
-
Update Package List:
- Run the following command to update your package list:
bash sudo apt update- This command refreshes the package list, including the newly added MongoDB repository.
Installing MongoDB:
-
Install MongoDB:
- Run the following command to install the MongoDB Community Server:
bash sudo apt install mongodb-org- This command downloads and installs the MongoDB packages.
After install, linux and windows should both have a system service already setup from the install process. You can check if it's running on linux with
sudo systemctl status mongod. On Windows, you should see the service running as "MongoDB Server" if you open system services on WindowsBasic MongoDB Commands:
After installing and starting MongoDB, you can use the
mongoshell to interact with your database. Here are some basic commands to get you started:Checking MongoDB Version:
First, let's verify that MongoDB is installed correctly by checking its version:
-
Open a Terminal or Command Prompt:
- Open your terminal (Linux/macOS) or command prompt (Windows).
-
Run
mongosh --version:- Type
mongosh --versionand press Enter. - This command will display the installed MongoDB version if it's correctly installed and in your system's PATH.
- Type
Basic MongoDB Shell Commands:
-
Open the
mongoshShell:- Type
mongoshand press Enter. This will open the MongoDB shell, and you'll see a prompt like>.
- Type
-
Show Databases:
- To see a list of all databases on your MongoDB server, type
show dbsand press Enter. - This will display a list of database names.
- To see a list of all databases on your MongoDB server, type
-
Use a Database:
- To switch to a specific database, type
use <database_name>and press Enter. Replace<database_name>with the name of the database you want to use. - Example:
use mydatabase - If the database doesn't exist, MongoDB will create it when you first store data in it.
- To switch to a specific database, type
-
Show Collections:
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
show collectionsand pressing Enter. - Collections are where you store documents (JSON-like data).
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
Example Session:
```bash
mongosh Current Mongosh Log ID: 6563728637951a37887e2730 Connecting to: mongodb://127.0.0.1:27017/?directConnection=true&serverSelectionTimeoutMS=2000&appName=mongosh Using MongoDB: 7.0.3 Using Mongosh: 2.1.1 For mongosh info see: https://docs.mongodb.com/mongodb-shell/
test> show dbs admin 40 KiB config 72 KiB local 40 KiB test> use mydatabase switched to db mydatabase mydatabase> show collections mydatabase> ```
Conclusion
Congratulations! You have successfully installed and started MongoDB Community Server. You've learned how to download, install, and run MongoDB on both Windows and Linux systems, and you've explored some basic commands to interact with your database.
Now, you might want to try an application like grain, a Nostr relay, which utilizes MongoDB as its database. Learn How to Install grain: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rqdpnx56rqv34uyz5g4
Remember, this guide covers the basics. There's much more to explore in the world of MongoDB, including advanced querying, indexing, replication, and sharding. Continue exploring the official MongoDB documentation to deepen your knowledge and unlock the full potential of this powerful database.
- Operating System:
-
 @ 8fb140b4:f948000c
2025-03-20 01:29:06
@ 8fb140b4:f948000c
2025-03-20 01:29:06As many of you know, https://nostr.build has recently launched a new compatibility layer for the Blossom protocol blossom.band. You can find all the details about what it supports and its limitations by visiting the URL.
I wanted to cover some of the technical details about how it works here. One key difference you may notice is that the service acts as a linker, redirecting requests for the media hash to the actual source of the media—specifically, the nostr.build URL. This allows us to maintain a unified CDN cache and ensure that your media is served as quickly as possible.
Another difference is that each uploaded media/blob is served under its own subdomain (e.g.,
npub1[...].blossom.band), ensuring that your association with the blob is controlled by you. If you decide to delete the media for any reason, we ensure that the link is broken, even if someone else has duplicated it using the same hash.To comply with the Blossom protocol, we also link the same hash under the main (apex) domain (blossom.band) and collect all associations under it. This ensures that Blossom clients can fetch media based on users’ Blossom server settings. If you are the sole owner of the hash and there are no duplicates, deleting the media removes the link from the main domain as well.
Lastly, in line with our mission to protect users’ privacy, we reject any media that contains private metadata (such as GPS coordinates, user comments, or camera serial numbers) or strip it if you use the
/media/endpoint for upload.As always, your feedback is welcome and appreciated. Thank you!
-
 @ f1989a96:bcaaf2c1
2025-03-20 14:21:35
@ f1989a96:bcaaf2c1
2025-03-20 14:21:35Good morning, readers!
In Thailand, the government announced a third digital cash handout to “stimulate the economy and drive technological adoption.” This disbursement will allocate 27 billion baht ($800 million) to 2.7 million citizens aged 16-20. Like in previous phases, it will be distributed via a state-controlled “digital wallet” application, which essentially functions as a central bank digital currency (CBDC). This system gives the regime an inside view of Thais’ financial activity and creates a centralized database to monitor, censor, and control.
Meanwhile, in Russia, the central bank has proposed limiting Bitcoin access to only the wealthiest individuals. Under the proposal, only Russians with over $1.2 million in assets or an annual income above $580,000 could buy and sell digital assets — arbitrarily barring everyday Russians (including obviously most journalists and activists) from accessing Bitcoin and the financial independence it grants.
In open-source software news, a new tool called Banxaas is making Bitcoin more accessible in West Africa by integrating with local payment providers to facilitate buying and selling Bitcoin using the CFA currency (XOF). This on-and-off ramp could expand financial freedom for human rights activists, dissidents, and everyday citizens.
We end with the latest edition of the HRF x Pubkey Freedom Tech Series, in which HRF’s Zac Guignard sits down with author Jason Maier to discuss how Bitcoin can drive human rights around the world. Together, they examine the shortcomings of today’s financial system and discuss how Bitcoin is aiding people living under authoritarian regimes.
Now, let’s get right to it!
Subscribe Here
GLOBAL NEWS
Thailand | Announces Third Digital Cash Handout to Boost Economy
The government of Thailand announced a third digital cash handout, allocating 27 billion baht ($800 million) to 2.7 million citizens aged 16-20 to “stimulate the economy and drive technological adoption.” Like in previous phases, the regime will distribute the funds through a state-run “digital wallet” application, which would effectively function as a central bank digital currency (CBDC). Past handouts of the CBDC came with strict restrictions: spending was limited to approved vendors within designated areas, purchases were restricted to certain goods, and funds expired after six months. Meanwhile, Prime Minister Paetongtarn Shinawatra called this third handout the first full deployment of the digital wallet system and urged the public to download the official app. This would directly link citizens' financial activity and data to the regime, threaten privacy, and deepen repression in a country with a long history of silencing dissent.
Russia | Central Bank Proposes Restricting Bitcoin Access to Wealthy Only
Russia’s central bank has proposed restricting Bitcoin and cryptocurrency access to only the country’s wealthiest individuals, barring everyday Russians from buying and selling digital assets unless they meet specific income or asset thresholds. Under the proposal, only Russians with over $1.2 million in assets or an annual income above $580,000 could engage with digital assets — effectively putting Bitcoin officially out of reach of most activists and journalists. The central bank claims the measure protects citizens from “volatility and lack of state backing.” But in reality, it likely signals the regime’s fear of Bitcoin’s ability to provide individual financial autonomy. By blocking most Russians from opting out of the state-controlled financial system, the regime is doubling down on financial repression.
India | Advances Digital Rupee CBDC
India’s government is pushing forward with its CBDC, the Digital Rupee, hailing it as a modern payment solution. But as journalist and author Roger Huang puts it, “it looks like a solution searching for a problem to solve.” Beyond the branding, the Digital Rupee enables state control over financial activity. Its programmability allows the government to dictate how, when, and where people spend — restricting transactions to specific merchants, locations, or goods and even imposing expiration dates on money. India’s crackdown on dissent is well-documented, from freezing opposition bank accounts to attempting a Bitcoin ban. Now, the Reserve Bank of India is embedding the CBDC into its digital payment system (UPI), quietly pushing millions into a tightly controlled and surveilled financial system.
Zimbabwe | Financial Regulators Mandate Earnings in ZiG
Zimbabwe’s market regulator is mandating all companies report their earnings in the new ZiG currency despite it losing 96% of its value since its launch last year. This move tightens state control over an already fragile economy, pushing businesses and citizens deeper into an unstable system that has repeatedly wiped out savings through inflation. The ZiG is Zimbabwe’s sixth currency in 15 years, introduced with gold backing to restore confidence in the regime’s ability to manage a currency. Instead, it’s rapidly devaluing, while the US dollar remains the preferred currency for trade and savings — when accessible. For ordinary Zimbabweans, the mandatory use of ZiG for taxes and government services is already a challenge due to its scarcity.
Egypt | Dictator-imposed Reforms Causing Economic Chaos
In the wake of an $8 billion deal with the International Monetary Fund (IMF) last spring, the Egyptian dictatorship has carried out “reforms” that are fueling inflation and making necessities increasingly unaffordable. To meet IMF conditions, Egyptian officials devalued the pound, slashed subsidies, and hiked the cost of fuel and public transportation — driving inflation beyond 20% for months on end. For millions of Egyptians, basic goods are now unaffordable. And the government’s promised minimum wage increase for public workers remains unfulfilled, leaving the public to absorb the price shocks. These undemocratic reforms — never voted on and executed with no way for the public to push back — aimed at securing further financing have only eroded the financial freedom of 114 million Egyptians and pushed the country into greater debt.
China | Facebook Enabling Authoritarian Censorship
A former Meta executive, Sarah Wynn-Williams, has accused Facebook of working “hand in glove” with the Chinese Communist Party (CCP) to censor and surveil content in China. According to Wynn-Williams, Facebook explored building censorship tools that would suppress viral posts until Chinese authorities approved. They even considered sharing user data in exchange for market access to China’s massive user base. Meta denied these claims, saying they fired Wynn-Williams in 2017 for poor performance. Regardless, the revelations highlight the dangers of for-profit, centralized platforms that authoritarian regimes can co-opt. Protocols like nostr (where no single entity moderates content) are more important than ever. Activists and dissidents seeking free communications can get started with nostr here.
BITCOIN AND FREEDOM TECH NEWS
Banxaas | Spend Sats in West Africa
Hundreds of millions of citizens in West Africa still use the CFA franc in an arrangement upheld by more than a dozen authoritarian leaders. Banxaas offers an alternative by bridging Bitcoin with West Africa’s mobile money networks. This allows individuals to buy and sell Bitcoin through local payment providers using the local CFA currency (XOF) and their own Lightning wallet. By integrating with local payment providers, Banxaas serves as a crucial on-and-off-ramp to Bitcoin, bringing the benefits of financial freedom to individuals, nonprofits, and human rights defenders across the region. Watch a demonstration of how Banxaas works here.
Mi Primer Bitcoin | Bitcoin Workbook Translated to Mandarin
Mi Primer Bitcoin, an open-source Bitcoin educational initiative focused on high-school-age students, released a Mandarin translation of its 2025 Bitcoin Diploma. This open-source resource provides mainland Chinese citizens, activists, and dissidents with accessible Bitcoin education at a time when financial freedom is increasingly under threat. With China tightening restrictions on personal wealth and expanding state surveillance of financial activity through the digital yuan CBDC, the diploma offers a useful new resource to learn the alternatives to state-controlled financial systems.
Blitz Wallet | Improves Ecash Functionality for Greater Financial Autonomy
Blitz Wallet, an open-source and self-custodial Bitcoin Lightning, Liquid, and ecash wallet, released an update that improves ecash functionality. Ecash, a Bitcoin-backed digital money system, allows instant and private transactions but requires custodial “mints” to manage tokens. The new update links users’ ecash to their wallet’s seed phrase (the 12-word backup used for Bitcoin recovery), allowing them to restore funds even if their device is lost or stolen. Users can also now transfer ecash between different wallets, increasing flexibility and control over their funds. Improved ecash UX is much-desired for political dissidents who can’t afford for authoritarian regimes to have full oversight over all of their economic activities.
Fedimint | Adds On-chain Support for Everyone
Fedimint, an open-source Bitcoin custody model that lets communities securely manage Bitcoin funds together, released v0.6.0, adding support for on-chain Bitcoin deposits (transactions directly on Bitcoin’s base layer). By offering private and trust-minimized transactions alongside on-chain support, Fedimint makes it easier, especially for nonprofit communities, to self-custody Bitcoin. It provides greater privacy and autonomy versus using fully centralized platforms that are easily subject to the political and regulatory pressure of authoritarian regimes.
Africa Bitcoin Conference | Announces 2025 Conference
The Africa Bitcoin Conference (ABC) announced its fourth edition, set to take place from Dec. 3-5, 2025, in Port Louis, Mauritius. Hosted at the Caudan Art Center, the event will bring together activists, Bitcoin advocates, and freedom tech developers to explore Bitcoin as a pathway to financial freedom. Now the largest Bitcoin gathering in Africa, ABC has established itself as a key platform for discussions on financial inclusion, inflation resistance, and censorship-resistant money — putting tools for financial sovereignty into the hands of those who need them most. HRF is proud to support ABC and, in particular, is proud to help delegates from dozens of authoritarian regimes attend each year. You can learn more about the conference and buy tickets here.
RECOMMENDED CONTENT
HRF x Pubkey — How Bitcoin Brings About Social Change with Jason Maier
In the latest installment of the HRF x Pubkey Freedom Tech Series, HRF Content and Research Associate Zac Guignard sits down with Jason Maier, author of “A Progressive’s Case for Bitcoin,” to share how Bitcoin can spark a meaningful shift in personal liberty worldwide. Jason explains the core monetary properties that make Bitcoin permissionless, censorship-resistant, and a powerful tool for financial freedom. Together, they examine the shortcomings of today’s financial system and discuss how Bitcoin is aiding people living under authoritarian regimes. They talk about how Bitcoin shouldn’t be a political issue and can be useful to anyone, no matter their beliefs. Watch the full conversation here.
Mélancolies de l’Opprimé by Farida Bemba Nabourema
Farida Bemba Nabourema, a renowned Togolese human rights activist, former HRF freedom fellow, and Bitcoin pioneer, announced that her new book “Mélancolies de l’Opprimé” will be released on April 15, 2025. A decade after her first book, “La Pression de l’Oppression,” this deeply personal and reflective work offers hard-earned wisdom for young activists stepping into the struggle against dictatorships and injustice. Nabourema candidly shares the emotional, physical, and psychological toll of resistance and activism while also highlighting the sense of purpose in the pursuit of freedom and human rights. Learn more about the book here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 21335073:a244b1ad
2025-03-20 13:16:22
@ 21335073:a244b1ad
2025-03-20 13:16:22I’d never had the chance to watch Harry Potter on the big screen before. Experiencing the first movie in 3D was nothing short of spectacular. Right from the opening scene with Albus Dumbledore, I was floored—the makeup and costumes were so vivid, it felt like pure magic unfolding before my eyes. It’s clear that real masters of their craft worked behind the scenes, and their artistry shines through. The sets? Absolutely jaw-dropping! The level of detail in Diagon Alley was beyond impressive.
Seeing legends like Alan Rickman as Snape and Maggie Smith as Minerva McGonagall on that massive 3D screen was an unforgettable thrill. The film is packed with phenomenal actors, and it was a joy to catch every tiny eye twitch and subtle nuance of their performances brought to life. It was a mind-blowing experience, and I’d wholeheartedly recommend it to anyone who gets the chance.
Don’t forget to have a little whimsical fun sometimes my friends. 🪄
-
 @ 000002de:c05780a7
2025-03-20 17:07:00
@ 000002de:c05780a7
2025-03-20 17:07:00Its easy to get caught up in media stories and not stop and ask basic questions. One I've had from the start is how widespread are these attacks on the private property have occurred.
If the goal is to hurt Tesla and therefore Musk, then the media stories are the real goal. Not the actual destruction of property. We know from history that many stories get blown out of proportion. I have no doubt that these events are actually happen but I wonder if the number of events has been counted.
originally posted at https://stacker.news/items/919063
-
 @ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53
@ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53MEMORANDUM OF CONVERSATION
SUBJECT: Meeting with Russian President Yeltsin
PARTICIPANTS: - U.S. - President Clinton - Secretary Albright - National Security Advisor Berger - Deputy National Security Advisor Steinberg - Ambassador Sestanovich - Carlos Pascual
- Russia
- Russian President Yeltsin
- Foreign Minister Ivanov
- Kremlin Foreign Policy Advisor Prihodko
- Defense Minister Sergeyev
- Interpreter: Peter Afansenko
- Notetaker: Carlos Pascual
DATE, TIME AND PLACE: November 19, 1999, 10:45 a.m. - 11:40 a.m. Istanbul, Turkey
President Yeltsin: We are in neutral territory here. I welcome you.
The President: Neither of us has a stake here. It's good to see you.
President Yeltsin: Well, Bill, what about those camps here in Turkey that are preparing troops to go into Chechnya? Aren't you in charge of those? I have the details. Minister Ivanov, give me the map. I want to show you where the mercenaries are being trained and then being sent into Chechnya. They are armed to the teeth. (Note: Yeltsin pulls out map of Turkey and circulates it.) Bill, this is your fault. I told Demirel yesterday that I will send the head of the SRV tomorrow and we will show him where the camps are located. These are not state-sanctioned camps. They are sponsored by NGOs and religious organizations. But let me tell you if this were in Russia and there were but one camp, I would throw them all out and put the bandits in the electric chair.
The President: Perhaps Demirel could help you.
President Yeltsin: Well, he ought to. Tomorrow after I get back, I will send the head of the Foreign Intelligence Service here. Bill, did you hurt your leg?
The President: Yes, but it is not bad.
President Yeltsin: When one leg of the President hurts, that is a bad thing.
The President: It lets me know I am alive.
President Yeltsin: I know we are not upset at each other. We were just throwing some jabs. I'm still waiting for you to visit. Bill. I've said to you come to visit in May, then June, then July and then August. Now it's past October and you're still not there.
The President: You're right, Boris, I owe you a visit.
President Yeltsin: Last time I went to the U.S., Bill.
The President: Well, I better set it up. I'll look at the calendar and find a time that's good for you and me.
President Yeltsin: Call me and tell me the month and date. Unless I have another visit, I will do the maximum amount I can to do everything around your schedule. The main things I have are to go to China and India.
The President: Boris, we still have lots to do together.
President Yeltsin: You heard my statement on nuclear arms and on banning nuclear tests. I just signed a law on ratification of a new agreement on the Comprehensive Test Ban Treaty. Isn't that right, Minister Ivanov?
Minister Ivanov: You signed the documents that sent the Comprehensive Test Ban Treaty to the Duma for review.
President Yeltsin: Well, in any case, I still approved it.
The President: Maybe I can get the Congress to agree still. They kept the Treaty even after they rejected it. So perhaps, there is still a chance.
President Yeltsin: Or perhaps it's just the bureaucrats working and they haven't had a chance to send it back to you yet. I'm upset that you signed the law to change the ABM Treaty.
The President: I signed no such law. People in Congress don't like the ABM Treaty. If Congress had its way, they would undermine the treaty. I'm trying to uphold it. But we need a national missile defense to protect against rogue states. We can't have a national missile defense that works without changing the ABM Treaty. But I want to do this cooperatively. I want to persuade you that this is good for both of us. The primary purpose is to protect against terrorists and rogue states. It would be ineffective against Russia. The system we're looking at would operate against just 20 missiles. And, Boris I want to figure out how to share the benefits. For all I know, in twenty years terrorists could have access to nuclear weapons. I know your people don't agree with me, but I'm not trying to overthrow the ABM Treaty. We're still trying to discover what's technically possible with national missile defense, but there are people in America who want to throw over the ABM Treaty. I have made no decisions yet.
President Yeltsin: Bill, Bill. I got your note. It went into all these things in incredible detail. I read it and I was satisfied. I've not yet ceased to believe in you. I ask you one thing. Just give Europe to Russia. The U.S. is not in Europe. Europe should be the business of Europeans. Russia is half European and half Asian.
The President: So you want Asia too?
President Yeltsin: Sure, sure. Bill. Eventually, we will have to agree on all of this.
The President: I don't think the Europeans would like this very much.
President Yeltsin: Not all. But I am a European. I live in Moscow. Moscow is in Europe and I like it. You can take all the other states and provide security to them. I will take Europe and provide them security. Well, not I. Russia will. We will end this conflict in Chechnya. I didn't say all the things I was thinking (in his speech). I listened to you carefully. I took a break just beforehand. Then I listened to you from beginning to end. I can even repeat what you said. Bill, I'm serious. Give Europe to Europe itself. Europe never felt as close to Russia as it does now. We have no difference of opinion with Europe, except maybe on Afganistan and Pakistan—which, by the way, is training Chechens. These are bandits, headhunters and killers. They're raping American women. They're cutting off ears and other parts of their hostages. We're fighting these types of terrorists. Let's not accuse Russia that we are too rough with these kinds of people. There are only two options: kill them or put them on trial. There's no third option, but we can put them on trial, and sentence them to 20-25 years. How many Americans, French, British and Germans have I freed that were there in Chechnya under the OSCE? The Chechen killers don't like the language of the OSCE. Here's my Minister of Defense. Stand up. We have not lost one soldier down there. Tell them.
Minister Sergeyev: We did not lose one soldier in Gudermes.
President Yeltsin: You see, Gudermes was cleansed without one military or civilian killed. We killed 200 bandits. The Minister of Defense is fulfilling the plan as I have said it should be. He's doing this thoughtfully. The soldiers only ask: don't stop the campaign. I promised these guys—I told every soldier, marshal and general—I will bring the campaign to fruition. We have these Chechens under lock and key. We have the key. They can't get in, they can't get out. Except maybe through Georgia; that's Shevardnadze's big mistake. And through Azerbaijan; that's Aliyev's mistake. They're shuttling in under the name of Islam. We're for freedom of religion, but not for fundamentalist Islam. These extremists are against you and against me.
We have the power in Russia to protect all of Europe, including those with missiles. We'll make all the appropriate treaties with China. We're not going to provide nuclear weapons to India. If we give them submarines, it will be only conventional diesel submarines, not nuclear. They would be from the 935 generation. You're going in that direction too. I'm thinking about your proposal—well, what your armed forces are doing—getting rid of fissile materials, particularly plutonium. We should just get rid of it. As soon as it's there, people start thinking of how to make bombs. Look, Russia has the power and intellect to know what to do with Europe. If Ivanov stays here, he will initial the CFE Treaty and I'll sign it under him. But under the OSCE Charter, there is one thing I cannot agree—which is that, based on humanitarian causes, one state can interfere in the affairs of another state.
National Security Advisor Berger: Mr. President, there's nothing in the Charter on one state's interference in the affairs of another.
Secretary Albright: That's right. What the Charter says is that affairs within a state will affect the other states around it.
President Yeltsin: Russia agrees to take out its property and equipment from Georgia in accordance with the new CFE Treaty. I have a statement on this. (looking toward Ivanov) Give it to me. I signed it today. Actually, it was late last night. I like to work late.
The President: Me, too.
President Yeltsin: I know you like to work late, Bill. When you call me, I calculate the time and I tell myself it's 4 a.m. and he's calling me. It lets you cleanse your brain and you feel great. I am not criticizing you, Bill. The President should be encouraged to work hard.
The President: So, we will get an agreement on CFE.
President Yeltsin: Yes.
The President: That's very important, seven years. We've worked on this for a long time.
President Yeltsin: Look, Ivanov has lost the statement in his own bag. He can't find the paper in his own bag. On the Charter, we have to look at it from the beginning. The Charter's ready. However, when states begin to tie in the Charter with the final declaration that has wording unacceptable to us, that's when we'll say no. And responsibility for this will fall fully on the West. (Looking at Ivanov) Give me this thing. It is written on paper. Bill. I am ready to sign it. It is a declaration about what we're talking about.
Secretary Albright: Some states want to record in the declaration your willingness to have an OSCE mission.
President Yeltsin: No, not at all. We will finish this with our own forces. Chechnya is the business of the internal affairs of Russia. We have to decide what to do. After we cleansed Gudermes, the muslim mufti came and asked for help, said I hate Basayev and he should be banned. These are the kinds of leaders we will put forward. I have thought this through carefully.
The President: On the Chechen problem. I have been less critical than others. Even today, I asked the others how they would deal with this if it were their country. This is a political issue. It may be the best thing for you within Russia to tell the Europeans to go to hell. But the best thing for your relations with Europe for the long term is to figure out the policy that you want to have with Europe and to keep that in mind as you deal with Chechnya.
President Yeltsin: (Gets up rapidly) Bill, the meeting is up. We said 20 minutes and it has now been more than 35 minutes.
The President: That's fine. We can say the meeting is over.
President Yeltsin: This meeting has gone on too long. You should come to visit, Bill.
The President: Who will win the election?
President Yeltsin: Putin, of course. He will be the successor to Boris Yeltsin. He's a democrat, and he knows the West.
The President: He's very smart.
President Yeltsin: He's tough. He has an internal ramrod. He's tough internally, and I will do everything possible for him to win—legally, of course. And he will win. You'll do business together. He will continue the Yeltsin line on democracy and economics and widen Russia's contacts. He has the energy and the brains to succeed. Thank you, Bill.
The President: Thank you, Boris. It was good to see you.
End of Conversation
-
 @ a60e79e0:1e0e6813
2025-03-20 12:58:13
@ a60e79e0:1e0e6813
2025-03-20 12:58:13*This is a long form Nostr native version of a post that lives on my Nostr educational website Hello Nostr *
At first glance Nostr might appear quite similar to some of the apps you use every day, such as Twitter, Mastodon, or Facebook, but that couldn't be further from the truth. This post aims to dispel the myth that "Nostr is just a Twitter replacement" and give you a better understanding about the 'what', the 'how' and most importantly, the 'why' of Nostr.
What Is Nostr?
Nostr is a decentralized, open-source protocol designed for censorship-resistant networking and communication on the web. It stands for "Notes and Other Stuff Transmitted by Relays," and it works by allowing users to publish messages (notes) and content in the form of 'other stuff', to a network of servers (relays) that store and distribute the content.
Unlike traditional platforms like Twitter, Ebay or Facebook, Nostr doesn't rely on a central authority; instead, users control their own identities via cryptographic key pairs.
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
Fiatjaf - Nostr Creator
Nostr is not a website or an app you download from a single source — it’s an open protocol, like email or the internet. Think of it as a set of rules that anyone can use to build tools for sharing messages, posts, or other data without needing a centralized middleman like a big tech company.
Nostr was created by a developer named Fiatjaf in 2020, and has since been steadily gaining traction among people who care about privacy, freedom, and censorship resistance.

Why Nostr?
Imagine the scenario, you've been using an online platform for 5 or even 10 years. You've built up thousands of contacts, perhaps built yourself a sizeable reputation, or even rely on the income from the platform to feed your family. Then one day you make a controversial post, sell a certain item or upload a video on a spicy subject to the platform where the owner disagrees with. With the click of a button, your account is removed. All trace of you, your social graph, or even your future income, disappears in an instant.
Read aloud like that is sounds crazy that we'd even entertain using such a platform, right!? Sadly that is the reality in 2025. This is exactly what happens every single day on X, Facebook, Ebay, Paypal, Linkedin, etc.
Looking at the problem through a more social media focused lens, many of us have become slaves to the likes of Instagram, Twitter and TikTok. We use these 'free' apps under the guise of being social with others online. The reality is that we see what those apps want us to see. We've become slaves to the manipulation of complex and opaque algrorithms designed to keep us hooked and try to sell us things.

Unlike traditional platforms, which are often governed by centralized entities wielding significant control over user data, content moderation, and algorithmic influence, Nostr flips the script by prioritizing user sovereignty and resilience. Built on an open-source framework, Nostr allows individuals to control their own data and interact through a network of relays, making it much more difficult for any single authority - be it a corporation, government, or bad actor - to censor or manipulate the flow of information.
- Is a relay refusing to host your notes? Use another or run your own!
- A specific client using an algorithm you don't like, take your identity and social graph elsewhere and choose another!
Take your identity and social graph with you, anywhere any time.
Nostr’s ability to foster authentic, unfiltered conversations while safeguarding user sovereignty has made it a cornerstone for communities seeking alternatives - whether they’re activists, creators, or everyday people tired of being pawns in the data-driven game. It's simple and adaptable design also encourages innovation, inviting developers to build tools and interfaces that keep pushing the boundaries of what the decentralized internet can achieve. In short, Nostr isn’t just a tool; it’s a movement toward a freer, more equitable digital future.

How Does Nostr Work?
Instead of one giant server owned by a single company holding all your posts and messages, Nostr spreads everything across lots of smaller servers called relays. To get started, you download a client, create your account and back up your private key. Your private key is used to secure your account and sign every message you send over the network. This allows anyone you interact with the verify the integrity of the data coming from 'you'.
The Nostr network is essentially a collection of bulletin boards that share a common format
When you write a note, or share some other type of compatible data, your client signs it with your private key, then sends it to one or more relays. Which relays your information is sent to is entirely up to you. These relays share your message with others who want to see it.
For others to see your notes or 'other stuff', they'll need to be able to find you. Typically this is done by using your public key, which looks something like this
npub15c88nc8d44gsp4658dnfu5fahswzzu8gaxm5lkuwjud068swdqfspxssvx. Don't panic though, you don't need to memorize all of your friends public keys, there are more human friendly methods of finding people that we'll come onto later.Once someone is following you, their client will ask all of their connected relays for any data shared by your public key. Their client will receive this data, verify it is signed by your private key and then populate it into their feed.
The “Other Stuff” Explained
Nostr’s name hints at this: Notes and Other Stuff Transmitted by Relays. But what is the “other stuff”? Put simply, it’s all the creative and experimental things people are building on Nostr, beyond simple text based notes. Every action on Nostr is an event - like a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as Nostr Implementation Possibility - NIP. A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client for different purposes.
Here's some content examples of 'Other Stuff':
- Long-Form Content: Think blog posts or articles. NIP-23.
- Private Messaging: Encrypted chats between users. NIP-04.
- Communities: Group chats or forums like Reddit. NIP-72
- Marketplaces: People listing stuff for sale, payable with zaps. NIP-15
- Zaps: Value transfer over the Lightning Network. NIP57
The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around. It’s still early days, so expect the “other stuff” to grow wilder and weirder over time!
Clients vs Relays: What’s the Difference?
Newbies often get tripped up by these two terms, so let’s clearly define them.

Clients
A client is what you use to interact with Nostr. It’s the app or website where you type your posts, read your feed, follow and interact with others. Examples of Nostr clients include:
- Damus (iOS Twitter style client)
- Primal (Cross-platform Twitter style client)
- Amethyst (Android only Twitter style client)
- Habla.News (Web based blog client)
- Olas (Instagram style client)
- 0xchat (Messaging client)
Clients don’t store your data; they just pull it from relays and display it for you. You can switch clients whenever you want, and your account stays the same because it’s tied to your keys, not any single client or app.
Clients are how you use Nostr, and relays are where the data lives. You need both to make the magic happen.
Relays
A relay is a server that stores and shares Nostr data. It’s a little like a post office: you send your note to a relay, and it delivers it to anyone who’s subscribed to see it (like your followers). Relays are run by individuals, groups, or companies who volunteer their computing power. Some are free, some charge a small fee, and you can connect to as many as you like. Most clients will come pre-configured with a list of well-known relays, but you can add or remove any you like.
What Are Zaps?
Zaps are arguably one of Nostr’s coolest features! A zaps is a way to send payments in Bitcoin directly to other users. Imagine liking a post, but instead of just clicking a heart (which you can of course do), you send the poster a few cents worth of Bitcoin to say, “This is awesome!”.
Zaps use Bitcoin's Lightning Network, a faster and cheaper way to move Bitcoin around. To Zap someone, you need a Lightning wallet linked to your Nostr client. Some clients, like Primal, ship with their own custodial wallet to make getting started a breeze. Most clients also allow more advanced users to connect an existing Lightning Wallet to reduce reliance and trust in the client provider.
Zaps are optional but add a fun layer to Nostr. Creators love them because it’s a way to get direct support from fans, with no middleman required.

NIP-05 Identifiers: Your Nostr “Username”
Your nPub, or public key (that long string of letters and numbers) is your 'official' Nostr ID, but it’s not exactly catchy. Enter NIP-05 identifiers, a human-readable and easily sharable way to have people find you. They look like an email address, like
qna@hellonostr.xyz.Here’s how it works:
Most users obtain their NIP-05 ID from a website or service that supports Nostr. Some of these services are free whereas some charge a fee. Some clients, like Primal will set one up for you automatically when you create an account. The email like ID links to your public key, so people can find you more easily. And because these ID's are domain based, there can be no duplicates. qna@hellonostr.xyz can only map to a single public key. The only person that can change that link is the person in control of the domain.
If you control your own domain, you can easily map your Nostr public key to name@my.domain. It’s not mandatory, but it’s super useful for building trust and making your profile recognizable.
Next Steps
So you're bought in. You understand why Nostr is so important and want to get started. Check out our simple onboarding guide here.
Thanks For Reading
Hopefully that moistened your taste buds for more educational Nostr content. This was a basic one, but there will be more focused material coming soon.
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-
 @ 21335073:a244b1ad
2025-03-20 12:24:16
@ 21335073:a244b1ad
2025-03-20 12:24:16Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 7d33ba57:1b82db35
2025-03-20 11:27:54
@ 7d33ba57:1b82db35
2025-03-20 11:27:54Agaete
Agaete is a charming coastal town on the northwest coast of Gran Canaria, known for its stunning cliffs, natural pools, fresh seafood, and rich history. Surrounded by the Agaete Valley, this town offers a mix of nature, culture, and relaxation.
🏛️ Top Things to Do in Agaete
1️⃣ Explore the Agaete Valley (Valle de Agaete)
A lush, green valley famous for its coffee plantations – the only place in Europe where coffee is grown! Take a coffee farm tour and taste local Canarian coffee and wine.
2️⃣ Swim in the Natural Pools of Las Salinas
These volcanic rock pools by the coast provide a unique, sheltered swimming experience with breathtaking ocean views.
3️⃣ Visit Puerto de las Nieves
The picturesque fishing village next to Agaete, where you can enjoy fresh seafood, stroll along the promenade, or catch a ferry to Tenerife.
4️⃣ Hike in Tamadaba Natural Park
Just above Agaete, this stunning nature reserve offers incredible hiking trails with pine forests and breathtaking views of the Atlantic Ocean.
5️⃣ Discover the Necropolis of Maipés
An archaeological site with pre-Hispanic burial mounds dating back over 1,300 years, providing insight into the island’s indigenous history.
🍽️ What to Eat in Agaete
- Pescado fresco – Fresh fish grilled to perfection 🐟
- Cochino negro – A special Canarian black pig dish 🍖
- Queso de flor – Local artisan cheese 🧀
- Agaete coffee & wine – Grown right in the valley ☕🍷
🚗 How to Get to Agaete
🚗 By Car: ~35-40 minutes from Las Palmas
🚌 By Bus: Direct routes from Las Palmas (Lines 103 & 105)💡 Tips for Visiting Agaete
✅ Best time to visit? Year-round, but especially beautiful in spring 🌿
✅ Great for hiking & nature lovers – Bring comfortable shoes 👟
✅ Try local coffee & wine – It’s one of the best-kept secrets of Gran Canaria ☕🍷 -
 @ 20e17dd0:2ae504d7
2025-03-20 10:08:14
@ 20e17dd0:2ae504d7
2025-03-20 10:08:14Prerequisite
Installation
Open a Terminal session and write the following command:
ruby sudo apt install docker.ioYou will be ask permission to install and continueruby yValidation of the installation
To validate the installer, prompt the following command:
ruby docker --versionYou should get:
ruby Docker version 26.1.3, build 26.1.3-0ubuntu1~24.04.1To test if it is running, prompt the following command:
ruby sudo systemctl status dockerYou should get a screen with the docker.service as "running". To get back to command line do CTRL+C
Test Installation
To make sure that everything runs smoothly, write the following command:
ruby sudo docker run hello-worldYou should get a Hello from Docker.You are ready to enjoy pulling docker images!
originally posted at https://stacker.news/items/917064
-
 @ c1e9ab3a:9cb56b43
2025-03-10 21:56:07
@ c1e9ab3a:9cb56b43
2025-03-10 21:56:07Introduction
Throughout human history, the pyramids of Egypt have fascinated scholars, archaeologists, and engineers alike. Traditionally thought of as tombs for pharaohs or religious monuments, alternative theories have speculated that the pyramids may have served advanced technological functions. One such hypothesis suggests that the pyramids acted as large-scale nitrogen fertilizer generators, designed to transform arid desert landscapes into fertile land.
This paper explores the feasibility of such a system by examining how a pyramid could integrate thermal convection, electrolysis, and a self-regulating breeder reactor to sustain nitrogen fixation processes. We will calculate the total power requirements and estimate the longevity of a breeder reactor housed within the structure.
The Pyramid’s Function as a Nitrogen Fertilizer Generator
The hypothesized system involves several key processes:
- Heat and Convection: A fissile material core located in the King's Chamber would generate heat, creating convection currents throughout the pyramid.
- Electrolysis and Hydrogen Production: Water sourced from subterranean channels would undergo electrolysis, splitting into hydrogen and oxygen due to electrical and thermal energy.
- Nitrogen Fixation: The generated hydrogen would react with atmospheric nitrogen (N₂) to produce ammonia (NH₃), a vital component of nitrogen-based fertilizers.
Power Requirements for Continuous Operation
To maintain the pyramid’s core at approximately 450°C, sufficient to drive nitrogen fixation, we estimate a steady-state power requirement of 23.9 gigawatts (GW).
Total Energy Required Over 10,000 Years
Given continuous operation over 10,000 years, the total energy demand can be calculated as:
[ \text{Total time} = 10,000 \times 365.25 \times 24 \times 3600 \text{ seconds} ]
[ \text{Total time} = 3.16 \times 10^{11} \text{ seconds} ]
[ \text{Total energy} = 23.9 \text{ GW} \times 3.16 \times 10^{11} \text{ s} ]
[ \approx 7.55 \times 10^{21} \text{ J} ]
Using a Self-Regulating Breeder Reactor
A breeder reactor could sustain this power requirement by generating more fissile material than it consumes. This reduces the need for frequent refueling.
Pebble Bed Reactor Design
- Self-Regulation: The reactor would use passive cooling and fuel expansion to self-regulate temperature.
- Breeding Process: The reactor would convert thorium-232 into uranium-233, creating a sustainable fuel cycle.
Fissile Material Requirements
Each kilogram of fissile material releases approximately 80 terajoules (TJ) (or 8 × 10^{13} J/kg). Given a 35% efficiency rate, the usable energy per kilogram is:
[ \text{Usable energy per kg} = 8 \times 10^{13} \times 0.35 = 2.8 \times 10^{13} \text{ J/kg} ]
[ \text{Fissile material required} = \frac{7.55 \times 10^{21}}{2.8 \times 10^{13}} ]
[ \approx 2.7 \times 10^{8} \text{ kg} = 270,000 \text{ tons} ]
Impact of a Breeding Ratio
If the reactor operates at a breeding ratio of 1.3, the total fissile material requirement would be reduced to:
[ \frac{270,000}{1.3} \approx 208,000 \text{ tons} ]
Reactor Size and Fuel Replenishment
Assuming a pebble bed reactor housed in the King’s Chamber (~318 cubic meters), the fuel cycle could be sustained with minimal refueling. With a breeding ratio of 1.3, the reactor could theoretically operate for 10,000 years with occasional replenishment of lost material due to inefficiencies.
Managing Scaling in the Steam Generation System
To ensure long-term efficiency, the water supply must be conditioned to prevent mineral scaling. Several strategies could be implemented:
1. Natural Water Softening Using Limestone
- Passing river water through limestone beds could help precipitate out calcium bicarbonate, reducing hardness before entering the steam system.
2. Chemical Additives for Scaling Prevention
- Chelating Agents: Compounds such as citric acid or tannins could be introduced to bind calcium and magnesium ions.
- Phosphate Compounds: These interfere with crystal formation, preventing scale adhesion.
3. Superheating and Pre-Evaporation
- Pre-Evaporation: Water exposed to extreme heat before entering the system would allow minerals to precipitate out before reaching the reactor.
- Superheated Steam: Ensuring only pure vapor enters the steam cycle would prevent mineral buildup.
- Electrolysis of Superheated Steam: Using multi-million volt electrostatic fields to ionize and separate minerals before they enter the steam system.
4. Electrostatic Control for Scaling Mitigation
- The pyramid’s hypothesized high-voltage environment could ionize water molecules, helping to prevent mineral deposits.
Conclusion
If the Great Pyramid were designed as a self-regulating nitrogen fertilizer generator, it would require a continuous 23.9 GW energy supply, which could be met by a breeder reactor housed within its core. With a breeding ratio of 1.3, an initial load of 208,000 tons of fissile material would sustain operations for 10,000 years with minimal refueling.
Additionally, advanced water treatment techniques, including limestone filtration, chemical additives, and electrostatic control, could ensure long-term efficiency by mitigating scaling issues.
While this remains a speculative hypothesis, it presents a fascinating intersection of energy production, water treatment, and environmental engineering as a means to terraform the ancient world.
-
 @ 20e17dd0:2ae504d7
2025-03-20 10:04:35
@ 20e17dd0:2ae504d7
2025-03-20 10:04:35Prerequisite
Installation
Open a Terminal session and write the following command to make sure that Docker is running:
ruby sudo systemctl status dockerYou should get a screen with the docker.service as "running". To get back to command line do CTRL+C
Then, create the volume that Portainer Server will use to store its database:
ruby sudo docker volume create portainer_dataYou are now ready for the on-liner installation:
ruby sudo docker run -d -p 8000:8000 -p 9443:9443 --name portainer --restart=always -v /var/run/docker.sock:/var/run/docker.sock -v portainer_data:/data portainer/portainer-ce:latestTo validate the installer, prompt the following command:
ruby sudo docker psYou should see Portainer's container running.
To access Portainer Server, go to the following adress: https://localhost:9443
Et voila!
-
 @ c1e9ab3a:9cb56b43
2025-03-09 20:13:44
@ c1e9ab3a:9cb56b43
2025-03-09 20:13:44Introduction
Since the mid-1990s, American media has fractured into two distinct and increasingly isolated ecosystems, each with its own Overton window of acceptable discourse. Once upon a time, Americans of different political leanings shared a common set of facts, even if they interpreted them differently. Today, they don’t even agree on what the facts are—or who has the authority to define them.
This divide stems from a deeper philosophical rift in how each side determines truth and legitimacy. The institutional left derives its authority from the expert class—academics, think tanks, scientific consensus, and mainstream media. The populist right, on the other hand, finds its authority in traditional belief systems—religion, historical precedent, and what many call "common sense." As these two moral and epistemological frameworks drift further apart, the result is not just political division but the emergence of two separate cultural nations sharing the same geographic space.
The Battle of Epistemologies: Experts vs. Tradition
The left-leaning camp sees scientific consensus, peer-reviewed research, and institutional expertise as the gold standard of truth. Universities, media organizations, and policy think tanks function as arbiters of knowledge, shaping the moral and political beliefs of those who trust them. From this perspective, governance should be guided by data-driven decisions, often favoring progressive change and bureaucratic administration over democratic populism.
The right-leaning camp is skeptical of these institutions, viewing them as ideologically captured and detached from real-world concerns. Instead, they look to religion, historical wisdom, and traditional social structures as more reliable sources of truth. To them, the "expert class" is not an impartial source of knowledge but a self-reinforcing elite that justifies its own power while dismissing dissenters as uneducated or morally deficient.
This fundamental disagreement over the source of moral and factual authority means that political debates today are rarely about policy alone. They are battles over legitimacy itself. One side sees resistance to climate policies as "anti-science," while the other sees aggressive climate mandates as an elite power grab. One side views traditional gender roles as oppressive, while the other sees rapid changes in gender norms as unnatural and destabilizing. Each group believes the other is not just wrong, but dangerous.
The Consequences of Non-Overlapping Overton Windows
As these worldviews diverge, so do their respective Overton windows—the range of ideas considered acceptable for public discourse. There is little overlap left. What is considered self-evident truth in one camp is often seen as heresy or misinformation in the other. The result is:
- Epistemic Closure – Each side has its own trusted media sources, and cross-exposure is minimal. The left dismisses right-wing media as conspiracy-driven, while the right views mainstream media as corrupt propaganda. Both believe the other is being systematically misled.
- Moralization of Politics – Since truth itself is contested, policy debates become existential battles. Disagreements over issues like immigration, education, or healthcare are no longer just about governance but about moral purity versus moral corruption.
- Cultural and Political Balkanization – Without a shared understanding of reality, compromise becomes impossible. Americans increasingly consume separate news, live in ideologically homogeneous communities, and even speak different political languages.
Conclusion: Two Nations on One Land
A country can survive disagreements, but can it survive when its people no longer share a common source of truth? Historically, such deep societal fractures have led to secession, authoritarianism, or violent conflict. The United States has managed to avoid these extremes so far, but the trendline is clear: as long as each camp continues reinforcing its own epistemology while rejecting the other's as illegitimate, the divide will only grow.
The question is no longer whether America is divided—it is whether these two cultures can continue to coexist under a single political system. Can anything bridge the gap between institutional authority and traditional wisdom? Or are we witnessing the slow but inevitable unraveling of a once-unified nation into two separate moral and epistemic realities?
-
 @ a95c6243:d345522c
2025-03-20 09:59:20
@ a95c6243:d345522c
2025-03-20 09:59:20Bald werde es verboten, alleine im Auto zu fahren, konnte man dieser Tage in verschiedenen spanischen Medien lesen. Die nationale Verkehrsbehörde (Dirección General de Tráfico, kurz DGT) werde Alleinfahrern das Leben schwer machen, wurde gemeldet. Konkret erörtere die Generaldirektion geeignete Sanktionen für Personen, die ohne Beifahrer im Privatauto unterwegs seien.
Das Alleinfahren sei zunehmend verpönt und ein Mentalitätswandel notwendig, hieß es. Dieser «Luxus» stehe im Widerspruch zu den Maßnahmen gegen Umweltverschmutzung, die in allen europäischen Ländern gefördert würden. In Frankreich sei es «bereits verboten, in der Hauptstadt allein zu fahren», behauptete Noticiastrabajo Huffpost in einer Zwischenüberschrift. Nur um dann im Text zu konkretisieren, dass die sogenannte «Umweltspur» auf der Pariser Ringautobahn gemeint war, die für Busse, Taxis und Fahrgemeinschaften reserviert ist. Ab Mai werden Verstöße dagegen mit einem Bußgeld geahndet.
Die DGT jedenfalls wolle bei der Umsetzung derartiger Maßnahmen nicht hinterherhinken. Diese Medienberichte, inklusive des angeblich bevorstehenden Verbots, beriefen sich auf Aussagen des Generaldirektors der Behörde, Pere Navarro, beim Mobilitätskongress Global Mobility Call im November letzten Jahres, wo es um «nachhaltige Mobilität» ging. Aus diesem Kontext stammt auch Navarros Warnung: «Die Zukunft des Verkehrs ist geteilt oder es gibt keine».
Die «Faktenchecker» kamen der Generaldirektion prompt zu Hilfe. Die DGT habe derlei Behauptungen zurückgewiesen und klargestellt, dass es keine Pläne gebe, Fahrten mit nur einer Person im Auto zu verbieten oder zu bestrafen. Bei solchen Meldungen handele es sich um Fake News. Teilweise wurde der Vorsitzende der spanischen «Rechtsaußen»-Partei Vox, Santiago Abascal, der Urheberschaft bezichtigt, weil er einen entsprechenden Artikel von La Gaceta kommentiert hatte.
Der Beschwichtigungsversuch der Art «niemand hat die Absicht» ist dabei erfahrungsgemäß eher ein Alarmzeichen als eine Beruhigung. Walter Ulbrichts Leugnung einer geplanten Berliner Mauer vom Juni 1961 ist vielen genauso in Erinnerung wie die Fake News-Warnungen des deutschen Bundesgesundheitsministeriums bezüglich Lockdowns im März 2020 oder diverse Äußerungen zu einer Impfpflicht ab 2020.
Aber Aufregung hin, Dementis her: Die Pressemitteilung der DGT zu dem Mobilitätskongress enthält in Wahrheit viel interessantere Informationen als «nur» einen Appell an den «guten» Bürger wegen der Bemühungen um die Lebensqualität in Großstädten oder einen möglichen obligatorischen Abschied vom Alleinfahren. Allerdings werden diese Details von Medien und sogenannten Faktencheckern geflissentlich übersehen, obwohl sie keineswegs versteckt sind. Die Auskünfte sind sehr aufschlussreich, wenn man genauer hinschaut.
Digitalisierung ist der Schlüssel für Kontrolle
Auf dem Kongress stellte die Verkehrsbehörde ihre Initiativen zur Förderung der «neuen Mobilität» vor, deren Priorität Sicherheit und Effizienz sei. Die vier konkreten Ansätze haben alle mit Digitalisierung, Daten, Überwachung und Kontrolle im großen Stil zu tun und werden unter dem Euphemismus der «öffentlich-privaten Partnerschaft» angepriesen. Auch lassen sie die transhumanistische Idee vom unzulänglichen Menschen erkennen, dessen Fehler durch «intelligente» technologische Infrastruktur kompensiert werden müssten.
Die Chefin des Bereichs «Verkehrsüberwachung» erklärte die Funktion des spanischen National Access Point (NAP), wobei sie betonte, wie wichtig Verkehrs- und Infrastrukturinformationen in Echtzeit seien. Der NAP ist «eine essenzielle Web-Applikation, die unter EU-Mandat erstellt wurde», kann man auf der Website der DGT nachlesen.
Das Mandat meint Regelungen zu einem einheitlichen europäischen Verkehrsraum, mit denen die Union mindestens seit 2010 den Aufbau einer digitalen Architektur mit offenen Schnittstellen betreibt. Damit begründet man auch «umfassende Datenbereitstellungspflichten im Bereich multimodaler Reiseinformationen». Jeder Mitgliedstaat musste einen NAP, also einen nationalen Zugangspunkt einrichten, der Zugang zu statischen und dynamischen Reise- und Verkehrsdaten verschiedener Verkehrsträger ermöglicht.
Diese Entwicklung ist heute schon weit fortgeschritten, auch und besonders in Spanien. Auf besagtem Kongress erläuterte die Leiterin des Bereichs «Telematik» die Plattform «DGT 3.0». Diese werde als Integrator aller Informationen genutzt, die von den verschiedenen öffentlichen und privaten Systemen, die Teil der Mobilität sind, bereitgestellt werden.
Es handele sich um eine Vermittlungsplattform zwischen Akteuren wie Fahrzeugherstellern, Anbietern von Navigationsdiensten oder Kommunen und dem Endnutzer, der die Verkehrswege benutzt. Alle seien auf Basis des Internets der Dinge (IOT) anonym verbunden, «um der vernetzten Gemeinschaft wertvolle Informationen zu liefern oder diese zu nutzen».
So sei DGT 3.0 «ein Zugangspunkt für einzigartige, kostenlose und genaue Echtzeitinformationen über das Geschehen auf den Straßen und in den Städten». Damit lasse sich der Verkehr nachhaltiger und vernetzter gestalten. Beispielsweise würden die Karten des Produktpartners Google dank der DGT-Daten 50 Millionen Mal pro Tag aktualisiert.
Des Weiteren informiert die Verkehrsbehörde über ihr SCADA-Projekt. Die Abkürzung steht für Supervisory Control and Data Acquisition, zu deutsch etwa: Kontrollierte Steuerung und Datenerfassung. Mit SCADA kombiniert man Software und Hardware, um automatisierte Systeme zur Überwachung und Steuerung technischer Prozesse zu schaffen. Das SCADA-Projekt der DGT wird von Indra entwickelt, einem spanischen Beratungskonzern aus den Bereichen Sicherheit & Militär, Energie, Transport, Telekommunikation und Gesundheitsinformation.
Das SCADA-System der Behörde umfasse auch eine Videostreaming- und Videoaufzeichnungsplattform, die das Hochladen in die Cloud in Echtzeit ermöglicht, wie Indra erklärt. Dabei gehe es um Bilder, die von Überwachungskameras an Straßen aufgenommen wurden, sowie um Videos aus DGT-Hubschraubern und Drohnen. Ziel sei es, «die sichere Weitergabe von Videos an Dritte sowie die kontinuierliche Aufzeichnung und Speicherung von Bildern zur möglichen Analyse und späteren Nutzung zu ermöglichen».
Letzteres klingt sehr nach biometrischer Erkennung und Auswertung durch künstliche Intelligenz. Für eine bessere Datenübertragung wird derzeit die Glasfaserverkabelung entlang der Landstraßen und Autobahnen ausgebaut. Mit der Cloud sind die Amazon Web Services (AWS) gemeint, die spanischen Daten gehen somit direkt zu einem US-amerikanischen «Big Data»-Unternehmen.
Das Thema «autonomes Fahren», also Fahren ohne Zutun des Menschen, bildet den Abschluss der Betrachtungen der DGT. Zusammen mit dem Interessenverband der Automobilindustrie ANFAC (Asociación Española de Fabricantes de Automóviles y Camiones) sprach man auf dem Kongress über Strategien und Perspektiven in diesem Bereich. Die Lobbyisten hoffen noch in diesem Jahr 2025 auf einen normativen Rahmen zur erweiterten Unterstützung autonomer Technologien.
Wenn man derartige Informationen im Zusammenhang betrachtet, bekommt man eine Idee davon, warum zunehmend alles elektrisch und digital werden soll. Umwelt- und Mobilitätsprobleme in Städten, wie Luftverschmutzung, Lärmbelästigung, Platzmangel oder Staus, sind eine Sache. Mit dem Argument «emissionslos» wird jedoch eine Referenz zum CO2 und dem «menschengemachten Klimawandel» hergestellt, die Emotionen triggert. Und damit wird so ziemlich alles verkauft.
Letztlich aber gilt: Je elektrischer und digitaler unsere Umgebung wird und je freigiebiger wir mit unseren Daten jeder Art sind, desto besser werden wir kontrollier-, steuer- und sogar abschaltbar. Irgendwann entscheiden KI-basierte Algorithmen, ob, wann, wie, wohin und mit wem wir uns bewegen dürfen. Über einen 15-Minuten-Radius geht dann möglicherweise nichts hinaus. Die Projekte auf diesem Weg sind ernst zu nehmen, real und schon weit fortgeschritten.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 291c75d9:37f1bfbe
2025-03-08 04:09:59
@ 291c75d9:37f1bfbe
2025-03-08 04:09:59In 1727, a 21-year-old Benjamin Franklin gathered a dozen men in Philadelphia for a bold experiment in intellectual and civic growth. Every Friday night, this group—known as the Junto, from the Spanish juntar ("to join")—met in a tavern or private home to discuss "Morals, Politics, or Natural Philosophy (science)." Far from a casual social club, the Junto was a secret society dedicated to mutual improvement, respectful discourse, and community betterment. What began as a small gathering of tradesmen and thinkers would leave a lasting mark on Franklin’s life and colonial America.
Printers are educated in the belief that when men differ in opinion, both sides ought equally to have the advantage of being heard by the public, and that when Truth and Error have fair play, the former is always an overmatch for the latter. - Benjamin Franklin
The Junto operated under a clear set of rules, detailed by Franklin in his Autobiography:
"The rules that I drew up required that every member, in his turn, should produce one or more queries on any point of Morals, Politics, or Natural Philosophy, to be discuss’d by the company; and once in three months produce and read an essay of his own writing, on any subject he pleased. Our debates were to be under the direction of a president, and to be conducted in the sincere spirit of inquiry after truth, without fondness for dispute, or desire of victory; and, to prevent warmth [heatedness], all expressions of positiveness in opinions, or direct contradiction, were after some time made contraband and prohibited under small pecuniary penalties [monetary fines]."
These guidelines emphasized collaboration over competition. Members were expected to contribute questions or essays, sparking discussions that prioritized truth over ego. To keep debates civil, the group even imposed small fines for overly assertive or contradictory behavior—a practical nudge toward humility and open-mindedness. (Yes, I believe that is an ass tax!)
Rather than admitting new members, Franklin encouraged existing ones to form their own discussion groups. This created a decentralized network of groups ("private relays," as I think of them), echoing the structure of modern platforms like NOSTR—while preserving the Junto’s exclusivity and privacy.
From the beginning, they made it a rule to keep these meetings secret, without applications or admittance of new members. Instead, Franklin encouraged members to form their own groups—in a way acting as private relays of sorts. (I say "private" because they continued to keep the Junto secret, even with these new groups.)
Membership: A Diverse Circle United by Values
The Junto’s twelve founding members came from varied walks of life—printers, surveyors, shoemakers, and clerks—yet shared a commitment to self-improvement. Franklin, though the youngest (around 21 when the group formed), led the Junto with a vision of collective growth. To join, candidates faced a simple vetting process, answering four key questions:
- Have you any particular disrespect for any present members? Answer: I have not.
- Do you sincerely declare that you love mankind in general, of what profession or religion soever? Answer: I do.
- Do you think any person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship? Answer: No.
- Do you love truth for truth’s sake, and will you endeavor impartially to find and receive it yourself and communicate it to others? Answer: Yes.
These criteria reveal the Junto’s core values: respect, tolerance, and an unwavering pursuit of truth. They ensured that members brought not just intellect but also character to the table—placing dialogue as the priority.
One should also note the inspiration from the "Dry Club" of John Locke, William Popple, and Benjamin Furly in the 1690s. They too required affirmation to:
- Whether he loves all men, of what profession or religion soever?
- Whether he thinks no person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship?
- Whether he loves and seeks truth for truth’s sake; and will endeavor impartially to find and receive it himself, and to communicate it to others?
And they agreed: "That no person or opinion be unhandsomely reflected on; but every member behave himself with all the temper, judgment, modesty, and discretion he is master of."
The Discussions: 24 Questions to Spark Insight
Franklin crafted a list of 24 questions to guide the Junto’s conversations, ranging from personal anecdotes to civic concerns. These prompts showcase the group’s intellectual breadth. Here are some of my favorites:
Hath any citizen in your knowledge failed in his business lately, and what have you heard of the cause? Have you lately heard of any citizen’s thriving well, and by what means? Do you know of any fellow citizen who has lately done a worthy action, deserving praise and imitation? Do you think of anything at present in which the Junto may be serviceable to mankind, their country, friends, or themselves? Have you lately observed any defect in the laws of your country, which it would be proper to move the legislature for an amendment? Do you know of any deserving young beginner lately set up, whom it lies in the power of the Junto any way to encourage?
(Read them all here.)
Note the keen attention to success and failure, and the reflection on both. Attention was often placed on the community and individual improvement beyond the members of the group. These questions encouraged members to share knowledge, reflect on virtues and vices, and propose solutions to real-world problems. The result? Discussions that didn’t just end at the tavern door but inspired tangible community improvements.
The Junto’s Legacy: America’s First Lending Library
One of the Junto’s most enduring contributions to Philadelphia—and indeed, to the American colonies—was the creation of the first lending library in 1731. Born from the group’s commitment to mutual improvement and knowledge-sharing, this library became a cornerstone of public education and intellectual life in the community.
The idea for the library emerged naturally from the Junto’s discussions. Members, who came from diverse backgrounds but shared a passion for learning, recognized that their own access to books was often limited and costly—and they referred to them often. To address this, they proposed pooling their personal collections to create a shared resource. This collaborative effort allowed them—and eventually the broader public—to access a wider range of books than any individual could afford alone.
The library operated on a simple yet revolutionary principle: knowledge should be available to all, regardless of wealth or status. By creating a lending system, the Junto democratized access to information, fostering a culture of self-education and curiosity. This was especially significant at a time when books were scarce and formal education was not universally accessible.
The success of the Junto’s library inspired similar initiatives across the colonies, laying the groundwork for the public library system we know today. It also reflected the group’s broader mission: to serve not just its members but the entire community. The library became a symbol of the Junto’s belief in the power of education to uplift individuals and society alike.
With roots extending back to the founding of the Society in 1743, the Library of the American Philosophical Society houses over thirteen million manuscripts, 350,000 volumes and bound periodicals, 250,000 images, and thousands of hours of audiotape. The Library’s holdings make it one of the premier institutions for documenting the history of the American Revolution and Founding, the study of natural history in the 18th and 19th centuries, the study of evolution and genetics, quantum mechanics, and the development of cultural anthropology, among others.
The American Philosophical Society Library continues today. I hope to visit it myself in the future.
Freedom, for Community
Comparing the Junto to Nostr shows how the tools of community and debate evolve with time. Both prove that people crave spaces to connect, share, and grow—whether in a colonial tavern or a digital relay. Yet their differences reveal trade-offs: the Junto’s structure offered depth and focus but capped its reach, while Nostr’s openness promises scale at the cost of order.
In a sense, Nostr feels like the Junto’s modern echo—faster, bigger, and unbound by gates or rules. Franklin might admire its ambition, even if he’d raise an eyebrow at its messiness. For us, the comparison underscores a timeless truth: no matter the medium, the drive to seek truth and build community endures.
The Autobiography of Benjamin Franklin (1771–1790, pub. 1791)
http://www.benjamin-franklin-history.org/junto-club/
Benjamin Franklin, Political, Miscellaneous, and Philosophical Pieces, ed. Benjamin Vaughan (London: 1779), pp. 533–536.
"Rules of a Society" in The Remains of John Locke, Esq. (1714), p. 113
npubpro
-
 @ 6a6be47b:3e74e3e1
2025-03-20 09:14:31
@ 6a6be47b:3e74e3e1
2025-03-20 09:14:31Hi frens, I just wanted to say hello and remind you about the amazing artwork available from my creative corner. 🖼️ 🦄 I have a few digitala prints on my Plebeian Market stall from Bitcoin to some hoverflies. 🦄 On my Kofi-shop I have a bunch of digital prints too; fromBeelzebub toKrampus, stickers for Goodnotesand many other occulture and religious theme artwork. 🦄If you're more into physical prints, you can visit my INPRNT shop but if you'd like to wear my artwork, visit my Teespring shop. 🦄 You can find all of this at my nostree.me profile or go directly tomy website 🦄And of course, my pride and joy are my blog entries, I've painted about Ostara,Lupercalia, Nunsand many other religious and pagan themes. I invite you to take a peek 👀 Also, just dropping by to know how you've been? How are you gonna celebrate this Equinox? Maybe a Spring Cleansing?? Whatever you decide to do, I wish the best for you and your loved ones. I also would like to thank kyou for liking, reposting, the zaps, you're all awesome! None of this would be possible without you my frens! Wishing you all a Happy New Astrological year! Happy Equinox! Godspeed
-
 @ 378562cd:a6fc6773
2025-03-20 14:26:48
@ 378562cd:a6fc6773
2025-03-20 14:26:48When SpongeBob SquarePants first graced television screens in 1999, it quickly became a cultural phenomenon. Its quirky humor, unique animation style, and absurd yet endearing characters captured audiences of all ages. However, beyond its whimsical surface, SpongeBob SquarePants holds surprising ties to real-world marine biology, human behaviors, and even corporate America. Let's take a deep dive into the striking similarities between the show’s universe and real life.
- Bikini Bottom and the Nuclear Connection
One of the most intriguing theories about SpongeBob SquarePants is its potential connection to real-world geography. Bikini Bottom, the fictional underwater city where SpongeBob and his friends reside, is widely believed to be named after Bikini Atoll, a site in the Pacific Ocean where the U.S. conducted nuclear tests in the 1940s and 1950s. Some fans speculate that the bizarre personalities of the show's characters are a result of radioactive mutations—a wild yet eerily plausible idea given the history of the atoll.
- SpongeBob: More Than Just a Sponge
SpongeBob is, of course, a sea sponge, but his rectangular, kitchen-sponge shape is a deviation from most natural sea sponges, which are irregularly shaped. However, real-life sea sponges are fascinating creatures that can regenerate after being broken apart—just like how SpongeBob bounces back from every misadventure with relentless optimism.
Additionally, SpongeBob’s enthusiasm and boundless energy mimic the real-life behaviors of certain marine organisms that continuously filter water, making them vital to their ecosystems. His ceaseless work ethic at the Krusty Krab also mirrors the tireless efforts of smaller marine life that keep oceanic ecosystems functioning.
- Squidward: An Octopus in Disguise
Despite his name, Squidward Tentacles is actually an octopus. Series creator Stephen Hillenburg, a marine biologist before becoming an animator, intentionally designed Squidward with six tentacles instead of the usual eight to make animation easier. His grumpy and refined personality also reflects the intelligence of real-world octopuses, who are known for their problem-solving skills and, at times, their moody behavior.
- The Krusty Krab and Corporate Culture
The Krusty Krab, the fast-food restaurant where SpongeBob works, is a satirical take on real-life corporate culture, particularly in the fast-food industry. Mr. Krabs, the money-hungry owner, represents stereotypical profit-driven business owners who prioritize revenue over employee well-being. Meanwhile, SpongeBob’s unwavering loyalty to his job highlights the enthusiasm of idealistic workers, and Squidward embodies the disillusioned employees who begrudgingly clock in every day. This dynamic is strikingly similar to real-world labor environments, making the show relatable even beyond its nautical setting.
- Plankton and the Struggles of Small Businesses
Sheldon J. Plankton, the tiny but ambitious owner of the failing Chum Bucket, serves as a metaphor for small business owners who struggle to compete with corporate giants. His constant yet futile attempts to steal the Krabby Patty secret formula echo the real-world battle between small independent businesses and industry monopolies. Despite his villainous traits, Plankton’s perseverance and innovative schemes make him an oddly sympathetic character, much like real-life entrepreneurs striving to find success against all odds.
- Real-Life Marine Life Mirrored in Characters
Each character in SpongeBob SquarePants is based on real marine creatures with behaviors that closely resemble their animated counterparts:
Patrick Star: A pink starfish who is slow and lazy, much like real-life starfish that lack a brain and move sluggishly.
Sandy Cheeks: A land-dwelling squirrel who thrives in an underwater suit, symbolizing the scientific research done by deep-sea divers and marine biologists in the ocean.
Mr. Krabs: A crab with a tight grip on his money, reflecting the territorial and often aggressive nature of real-world crabs.
Larry the Lobster: A fitness-obsessed lobster, much like real lobsters that grow larger and stronger as they molt.
Conclusion: A Show Rooted in Reality
While SpongeBob SquarePants is undeniably a wacky and exaggerated series, its deep connection to real-world marine biology, workplace culture, and corporate dynamics gives it an extra layer of depth. Whether intentionally or unintentionally, the show serves as an entertaining yet insightful reflection of life above and below the ocean’s surface. So next time you watch an episode, remember—you’re not just enjoying a cartoon; you’re diving into a cleverly crafted world filled with real-life parallels, which is probably a direct correlation to its wild success in all these years.
-
 @ 7d33ba57:1b82db35
2025-03-20 09:08:46
@ 7d33ba57:1b82db35
2025-03-20 09:08:46Puerto de las Nieves
Puerto de las Nieves is a picturesque seaside village on Gran Canaria’s northwestern coast, near Agaete. Known for its whitewashed houses, fresh seafood, and stunning coastal views, it’s the perfect place for arelaxing day by the ocean.
🌊 Top Things to Do in Puerto de las Nieves
1️⃣ Relax at Playa de las Nieves
A peaceful pebble beach with crystal-clear waters, perfect for swimming and sunbathing.
2️⃣ See the Dedo de Dios (God’s Finger) Rock Formation
This famous natural rock structure was partially destroyed by a storm in 2005, but the area remains a scenic spot.
3️⃣ Visit the Agaete Natural Pools (Las Salinas de Agaete)
Just a short walk away, these volcanic rock pools offer a natural and sheltered swimming experience.
4️⃣ Walk Along the Promenade
Enjoy a scenic stroll along the coastal promenade, lined with cafés, seafood restaurants, and local shops.
5️⃣ Take a Ferry to Tenerife
Puerto de las Nieves is the departure point for ferries to Santa Cruz de Tenerife, making it a great connection between the Canary Islands.
🍽️ What to Eat in Puerto de las Nieves
- Fresh seafood – Try the local grilled fish (pescado a la espalda) 🐟
- Papas arrugadas with mojo – A Canarian classic 🥔
- Pulpo a la gallega – Delicious Galician-style octopus 🐙
- Local wines – Agaete Valley is known for its unique volcanic wines 🍷
🚗 How to Get to Puerto de las Nieves
🚗 By Car: ~40 minutes from Las Palmas
🚌 By Bus: Direct routes from Las Palmas (Lines 103 & 105)💡 Tips for Visiting Puerto de las Nieves
✅ Best time to visit? Year-round, but sunsets here are especially magical 🌅
✅ Bring water shoes! The beach is pebbly, so they make swimming easier 👟
✅ Try a boat trip – Great for coastal views and dolphin watching 🚤 -
 @ 6b0a60cf:b952e7d4
2025-03-20 07:36:17
@ 6b0a60cf:b952e7d4
2025-03-20 07:36:17このイベント自身をnaddr形式で参照する nostr:naddr1qvzqqqr4gupzq6c2vr8l8m9952e9qhxt8acn8kzzypzuhm6q70fvvxylkzu49e75qydhwumn8ghj7mnjv4kxz7fwvvkhxar9d3kxzu3wdejhgtcqp5cnwdpjxs6n2de3xyenxwql6rq76
-
 @ da0b9bc3:4e30a4a9
2025-03-20 06:29:09
@ da0b9bc3:4e30a4a9
2025-03-20 06:29:09Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/918547
-
 @ c48e29f0:26e14c11
2025-03-07 04:51:09
@ c48e29f0:26e14c11
2025-03-07 04:51:09ESTABLISHMENT OF THE STRATEGIC BITCOIN RESERVE AND UNITED STATES DIGITAL ASSET STOCKPILE EXECUTIVE ORDER March 6, 2025
By the authority vested in me as President by the Constitution and the laws of the United States of America, it is hereby ordered:
Section 1. Background.
Bitcoin is the original cryptocurrency. The Bitcoin protocol permanently caps the total supply of bitcoin (BTC) at 21 million coins, and has never been hacked. As a result of its scarcity and security, Bitcoin is often referred to as “digital gold”. Because there is a fixed supply of BTC, there is a strategic advantage to being among the first nations to create a strategic bitcoin reserve. The United States Government currently holds a significant amount of BTC, but has not implemented a policy to maximize BTC’s strategic position as a unique store of value in the global financial system. Just as it is in our country’s interest to thoughtfully manage national ownership and control of any other resource, our Nation must harness, not limit, the power of digital assets for our prosperity.
Sec. 2. Policy.
It is the policy of the United States to establish a Strategic Bitcoin Reserve. It is further the policy of the United States to establish a United States Digital Asset Stockpile that can serve as a secure account for orderly and strategic management of the United States’ other digital asset holdings.
Sec. 3. Creation and Administration of the Strategic Bitcoin Reserve and United States Digital Asset Stockpile.
(a) The Secretary of the Treasury shall establish an office to administer and maintain control of custodial accounts collectively known as the “Strategic Bitcoin Reserve,” capitalized with all BTC held by the Department of the Treasury that was finally forfeited as part of criminal or civil asset forfeiture proceedings or in satisfaction of any civil money penalty imposed by any executive department or agency (agency) and that is not needed to satisfy requirements under 31 U.S.C. 9705 or released pursuant to subsection (d) of this section (Government BTC). Within 30 days of the date of this order, each agency shall review its authorities to transfer any Government BTC held by it to the Strategic Bitcoin Reserve and shall submit a report reflecting the result of that review to the Secretary of the Treasury. Government BTC deposited into the Strategic Bitcoin Reserve shall not be sold and shall be maintained as reserve assets of the United States utilized to meet governmental objectives in accordance with applicable law.
(b) The Secretary of the Treasury shall establish an office to administer and maintain control of custodial accounts collectively known as the “United States Digital Asset Stockpile,” capitalized with all digital assets owned by the Department of the Treasury, other than BTC, that were finally forfeited as part of criminal or civil asset forfeiture proceedings and that are not needed to satisfy requirements under 31 U.S.C. 9705 or released pursuant to subsection (d) of this section (Stockpile Assets). Within 30 days of the date of this order, each agency shall review its authorities to transfer any Stockpile Assets held by it to the United States Digital Asset Stockpile and shall submit a report reflecting the result of that review to the Secretary of the Treasury. The Secretary of the Treasury shall determine strategies for responsible stewardship of the United States Digital Asset Stockpile in accordance with applicable law.
(c) The Secretary of the Treasury and the Secretary of Commerce shall develop strategies for acquiring additional Government BTC provided that such strategies are budget neutral and do not impose incremental costs on United States taxpayers. However, the United States Government shall not acquire additional Stockpile Assets other than in connection with criminal or civil asset forfeiture proceedings or in satisfaction of any civil money penalty imposed by any agency without further executive or legislative action.
(d) “Government Digital Assets” means all Government BTC and all Stockpile Assets. The head of each agency shall not sell or otherwise dispose of any Government Digital Assets, except in connection with the Secretary of the Treasury’s exercise of his lawful authority and responsible stewardship of the United States Digital Asset Stockpile pursuant to subsection (b) of this section, or pursuant to an order from a court of competent jurisdiction, as required by law, or in cases where the Attorney General or other relevant agency head determines that the Government Digital Assets (or the proceeds from the sale or disposition thereof) can and should: (i) be returned to identifiable and verifiable victims of crime; (ii) be used for law enforcement operations;
(iii) be equitably shared with State and local law enforcement partners; or (iv) be released to satisfy requirements under 31 U.S.C. 9705, 28 U.S.C. 524(c), 18 U.S.C. 981, or 21 U.S.C. 881.(e) Within 60 days of the date of this order, the Secretary of the Treasury shall deliver an evaluation of the legal and investment considerations for establishing and managing the Strategic Bitcoin Reserve and United States Digital Asset Stockpile going forward, including the accounts in which the Strategic Bitcoin Reserve and United States Digital Asset Stockpile should be located and the need for any legislation to operationalize any aspect of this order or the proper management and administration of such accounts.
Sec. 4. Accounting.
Within 30 days of the date of this order, the head of each agency shall provide the Secretary of the Treasury and the President’s Working Group on Digital Asset Markets with a full accounting of all Government Digital Assets in such agency’s possession, including any information regarding the custodial accounts in which such Government Digital Assets are currently held that would be necessary to facilitate a transfer of the Government Digital Assets to the Strategic Bitcoin Reserve or the United States Digital Asset Stockpile. If such agency holds no Government Digital Assets, such agency shall confirm such fact to the Secretary of the Treasury and the President’s Working Group on Digital Asset Markets within 30 days of the date of this order.
Sec. 5. General Provisions.
(a) Nothing in this order shall be construed to impair or otherwise affect: (i) the authority granted by law to an executive department or agency, or the head thereof; or (ii) the functions of the Director of the Office of Management and Budget relating to budgetary, administrative, or legislative proposals.
(b) This order shall be implemented consistent with applicable law and subject to the availability of appropriations.
(c) This order is not intended to, and does not, create any right or benefit, substantive or procedural, enforceable at law or in equity by any party against the United States, its departments, agencies, or entities, its officers, employees, or agents, or any other person.
THE WHITE HOUSE, March 6, 2025
-
 @ c1e9ab3a:9cb56b43
2025-03-05 13:54:03
@ c1e9ab3a:9cb56b43
2025-03-05 13:54:03The financial system has long relied on traditional banking methods, but emerging technologies like Bitcoin and Nostr are paving the way for a new era of financial interactions.
Secure Savings with Bitcoin:
Bitcoin wallets can act as secure savings accounts, offering users control and ownership over their funds without relying on third parties.
Instant Settlements with the Lightning Network:
The Lightning Network can replace traditional settlement systems, such as ACH or wire transfers, by enabling instant, low-cost transactions.
Face-to-Face Transactions with Ecash:
Ecash could offer a fee-free option for smaller, everyday transactions, complementing the Lightning Network for larger payments.
Automated Billing with Nostr Wallet Connect:
Nostr Wallet Connect could revolutionize automated billing, allowing users to set payment limits and offering more control over subscriptions and recurring expenses.
Conclusion:
Combining Bitcoin and Nostr technologies could create a more efficient, user-centric financial system that empowers individuals and businesses alike.
-
 @ 18f5f318:a3a80202
2025-03-20 06:03:15
@ 18f5f318:a3a80202
2025-03-20 06:03:15In today's fast-paced world, accumulating unwanted items and clutter is a common challenge for both individuals and businesses. Professional junk removal services offer a practical solution, providing numerous benefits that extend beyond mere decluttering. This article explores the advantages of hiring professional junk removal services, supported by relevant statistics and insights.
**1. Time and Effort Savings ** Managing and disposing of junk can be a time-consuming and physically demanding task. Professional junk removal services streamline this process by handling all aspects of removal, allowing clients to focus on more important activities. Their expertise ensures efficient sorting, loading, and disposal, significantly reducing the time and effort required from clients.
**2. Proper Waste Disposal Practices ** A key advantage of professional junk removal is their commitment to responsible waste disposal. They possess the knowledge to categorize items into recyclable, reusable, and disposable materials, adhering to local regulations and environmental guidelines. This ensures that hazardous materials are handled appropriately, minimizing environmental impact and promoting sustainability.
**3. Enhanced Safety and Health ** Handling bulky or hazardous items without proper equipment and training can pose safety risks. Professional junk removal teams are equipped to manage such items safely, reducing the risk of injuries. They also address potential health hazards by removing debris that could harbor pests or mold, contributing to a healthier living or working environment.
**4. Access to Appropriate Equipment ** Professional services come equipped with the necessary tools and vehicles to handle various types of junk removal tasks. Whether it's heavy appliances or large volumes of debris, they have the equipment to manage the job efficiently. This access to specialized tools ensures a smoother and faster removal process, which might be challenging to achieve independently.
**5. Cost-Effectiveness ** While hiring a professional service involves an upfront cost, it can be more economical in the long run. DIY junk removal may incur expenses such as vehicle rental, fuel, and disposal fees, not to mention the value of your time. Professional services often provide transparent pricing and handle all aspects of the removal, potentially saving clients money and hassle.
**6. Environmental Responsibility ** Many junk removal companies prioritize eco-friendly practices by recycling or donating items whenever possible. This commitment to sustainability reduces the amount of waste sent to landfills and supports community initiatives. By choosing such services, clients contribute to environmental conservation efforts.
**7. Improved Space Utilization ** Removing unwanted items frees up valuable space in homes or offices, allowing for better organization and functionality. A clutter-free environment can enhance productivity, reduce stress, and create a more aesthetically pleasing space.
**8. Compliance with Legal Regulations ** Proper disposal of certain items is mandated by law, and non-compliance can result in fines. Professional junk removal services are well-versed in local regulations and ensure that all items are disposed of legally and ethically, mitigating potential legal issues for clients.
**9. Support for Large-Scale Projects ** For large-scale cleanouts, such as estate clearances or office renovations, professional services provide the manpower and resources necessary to handle the job efficiently. They can manage high volumes of junk, ensuring timely completion of projects without burdening clients.
**10. Peace of Mind ** Entrusting junk removal to professionals offers peace of mind, knowing that the task is handled efficiently, safely, and responsibly. Clients can rest assured that their space will be cleared without the stress and physical exertion associated with DIY removal. Industry Insights
The junk removal industry has seen substantial growth in recent years. According to industry reports, the sector generates significant revenue and provides numerous employment opportunities, reflecting the increasing demand for these services.
**Conclusion ** Professional junk removal services offer a comprehensive solution to managing unwanted items, providing benefits that encompass time savings, safety, environmental responsibility, and cost-effectiveness. By opting for these services, individuals and businesses can enjoy cleaner, more organized spaces while contributing positively to the environment and society.
-
 @ c8383d81:f9139549
2025-03-02 23:57:18
@ c8383d81:f9139549
2025-03-02 23:57:18Project is still in early stages but now it is split into 2 different domain entities. Everything is opened sourced under one github https://github.com/Nsite-Info
So what’s new ?
Project #1 https://Nsite.info
A basic website with main info regarding what an Nsite is how it works and a list of tools and repo’s you can use to start building and debugging. 99% Finished, needs some extra translations and the Nsite Debugger can use a small upgrade.
Project #2 https://Nsite.cloud
This project isn’t finished, it currently is at a 40% finished stage. This contains the Nsite Gateway for all sites (still a work in progress) and the final stage the Nsite editor & template deployment.
If you are interested in Nsite’s join: https://chachi.chat/groups.hzrd149.com/e23891
Big thanks to nostr:npub1elta7cneng3w8p9y4dw633qzdjr4kyvaparuyuttyrx6e8xp7xnq32cume nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr nostr:npub1klr0dy2ul2dx9llk58czvpx73rprcmrvd5dc7ck8esg8f8es06qs427gxc for all the tooling & code.
!(image)[https://i.nostr.build/AkUvk7R2h9cVEMLB.png]
-
 @ e5de992e:4a95ef85
2025-03-20 05:01:41
@ e5de992e:4a95ef85
2025-03-20 05:01:41Market Overview
As of March 19, 2025, U.S. stock markets experienced a notable rally, driven by the Federal Reserve's decision to maintain current interest rates and signals of potential rate cuts later this year.
Index Performance
-
Dow Jones Industrial Average (DJIA):
Increased by 383.32 points (0.9%) to close at 41,964.63. -
S&P 500:
Rose 1.1%, ending at 5,675.29. -
Nasdaq Composite:
Advanced 1.4% to 17,750.79. -
Russell 2000:
Gained 1.6% to close at 2,082.08.
Key Drivers and Events
Federal Reserve's Monetary Policy
- The Federal Reserve opted to keep its key interest rate unchanged amid increased economic uncertainty, partly due to recent tariff measures.
- The central bank also indicated the possibility of two rate cuts by the end of the year to support economic growth.
Corporate Earnings
- Boeing (BA):
Shares rose significantly, contributing to gains in the Dow. - Tesla (TSLA):
Increased by 4.7%, outperforming competitors.
Geopolitical Factors
- Ongoing trade tensions and tariff policies, especially those announced by President Donald Trump, have added to market volatility.
- These policies are influencing investor sentiment and economic outlooks.
Global Market Context
- European Markets:
Generally rose, buoyed by fiscal initiatives and supportive policies. - Asian Markets:
Experienced slight declines. - Regional Note:
Indonesia's stock market faced a temporary suspension due to significant declines.
Commodity and Bond Markets
-
Oil:
Prices climbed, with West Texas Intermediate (WTI) futures approaching stability at $67.85 per barrel, reflecting supply concerns amid reported inventory drawdowns and limited ceasefire conditions in the Russia-Ukraine region. -
Gold:
Prices reached a record high, driven by the Fed’s revised economic projections and a flight to safety among investors. -
10-Year Treasury Yield:
Decreased following the Fed's rate decision, indicating increased demand for safer assets.
Market Outlook
Investors are advised to closely monitor upcoming economic indicators—such as employment data and consumer spending reports—to assess the economy's trajectory. Additionally, the Federal Reserve's future policy decisions will play a crucial role in shaping market dynamics in the near term.
-
-
 @ c1e9ab3a:9cb56b43
2025-02-25 22:49:38
@ c1e9ab3a:9cb56b43
2025-02-25 22:49:38Election Authority (EA) Platform
1.1 EA Administration Interface (Web-Based)
- Purpose: Gives authorized personnel (e.g., election officials) a user-friendly way to administer the election.
- Key Tasks:
- Voter Registration Oversight: Mark which voters have proven their identity (via in-person KYC or some legal process).
- Blind Signature Issuance: Approve or deny blind signature requests from registered voters (each corresponding to one ephemeral key).
- Tracking Voter Slots: Keep a minimal registry of who is allowed one ephemeral key signature, and mark it “used” once a signature is issued.
- Election Configuration: Set start/end times, provide encryption parameters (public keys), manage threshold cryptography setup.
- Monitor Tallying: After the election, collaborate with trustees to decrypt final results and release them.
1.2 EA Backend Services
- Blind Signature Service:
- An API endpoint or internal module that receives a blinded ephemeral key from a voter, checks if they are authorized (one signature per voter), and returns the blind-signed result.
-
Typically requires secure storage of the EA’s blind signing private key.
-
Voter Roll Database:
- Stores minimal info: “Voter #12345 is authorized to request one ephemeral key signature,” plus status flags.
-
Does not store ephemeral keys themselves (to preserve anonymity).
-
(Optional) Mix-Net or Homomorphic Tally Service:
- Coordinates with trustees for threshold decryption or re-encryption.
- Alternatively, a separate “Tally Authority” service can handle this.
2. Auditor Interface
2.1 Auditor Web-Based Portal
- Purpose: Allows independent auditors (or the public) to:
- Fetch All Ballots from the relays (or from an aggregator).
- Verify Proofs: Check each ballot’s signature, blind signature from the EA, OTS proof, zero-knowledge proofs, etc.
- Check Double-Usage: Confirm that each ephemeral key is used only once (or final re-vote is the only valid instance).
-
Observe Tally Process: Possibly see partial decryptions or shuffle steps, verify the final result matches the posted ballots.
-
Key Tasks:
- Provide a dashboard showing the election’s real-time status or final results, after cryptographic verification.
- Offer open data downloads so third parties can run independent checks.
2.2 (Optional) Trustee Dashboard
- If the election uses threshold cryptography (multiple parties must decrypt), each trustee (candidate rep, official, etc.) might have an interface for:
- Uploading partial decryption shares or re-encryption proofs.
- Checking that other trustees did their steps correctly (zero-knowledge proofs for correct shuffling, etc.).
3. Voter Application
3.1 Voter Client (Mobile App or Web Interface)
-
Purpose: The main tool voters use to participate—before, during, and after the election.
-
Functionalities:
- Registration Linking:
- Voter goes in-person to an election office or uses an online KYC process.
- Voter obtains or confirms their long-term (“KYC-bound”) key. The client can store it securely (or the voter just logs in to a “voter account”).
- Ephemeral Key Generation:
- Create an ephemeral key pair ((nsec_e, npub_e)) locally.
- Blind (\npub_e) and send it to the EA for signing.
- Unblind the returned signature.
- Store (\npub_e) + EA’s signature for use during voting.
- Ballot Composition:
- Display candidates/offices to the voter.
- Let them select choices.
- Possibly generate zero-knowledge proofs (ZKPs) behind the scenes to confirm “exactly one choice per race.”
- Encryption & OTS Timestamp:
- Encrypt the ballot under the election’s public (threshold) key or produce a format suitable for a mix-net.
- Obtain an OpenTimestamps proof for the ballot’s hash.
- Publish Ballot:
- Sign the entire “timestamped ballot” with the ephemeral key.
- Include the EA’s blind signature on (\npub_e).
- Post to the Nostr relays (or any chosen decentralized channel).
- Re-Voting:
- If the user needs to change their vote, the client repeats the encryption + OTS step, publishes a new ballot with a strictly later OTS anchor.
- Verification:
- After the election, the voter can check that their final ballot is present in the tally set.
3.2 Local Storage / Security
- The app must securely store:
- Ephemeral private key ((nsec_e)) until voting is complete.
- Potential backup/recovery mechanism if the phone is lost.
- Blind signature from the EA on (\npub_e).
- Potentially uses hardware security modules (HSM) or secure enclaves on the device.
4. Nostr Relays (or Equivalent Decentralized Layer)
- Purpose: Store and replicate voter-submitted ballots (events).
- Key Properties:
- Redundancy: Voters can post to multiple relays to mitigate censorship or downtime.
- Public Accessibility: Auditors, the EA, and the public can fetch all events to verify or tally.
- Event Filtering: By design, watchers can filter events with certain tags, e.g. “election: 2025 County Race,” ensuring they gather all ballots.
5. Threshold Cryptography Setup
5.1 Multi-Seg (Multi-Party) Key Generation
- Participants: Possibly the EA + major candidates + accredited observers.
- Process: A Distributed Key Generation (DKG) protocol that yields a single public encryption key.
- Private Key Shares: Each trustee holds a piece of the decryption key; no single party can decrypt alone.
5.2 Decryption / Tally Mechanism
- Homomorphic Approach:
- Ballots are additively encrypted.
- Summation of ciphertexts is done publicly.
- Trustees provide partial decryptions for the final sum.
- Mix-Net Approach:
- Ballots are collected.
- Multiple servers shuffle and re-encrypt them (each trustee verifies correctness).
- Final set is decrypted, but the link to each ephemeral key is lost.
5.3 Trustee Interfaces
- Separate or integrated into the auditor interface—each trustee logs in and provides their partial key share for decrypting the final result.
- Possibly combined with ZK proofs to confirm correct partial decryption or shuffling.
6. OpenTimestamps (OTS) or External Time Anchor
6.1 Aggregator Service
- Purpose: Receives a hash from the voter’s app, anchors it into a blockchain or alternative time-stamping system.
- Result: Returns a proof object that can later be used by any auditor to confirm the time/block height at which the hash was included.
6.2 Verifier Interface
- Could be part of the auditor tool or the voter client.
- Checks that each ballot’s OTS proof is valid and references a block/time prior to the election’s closing.
7. Registration Process (In-Person or Hybrid)
- Voter presents ID physically at a polling station or a designated office (or an online KYC approach, if legally allowed).
- EA official:
- Confirms identity.
- Links the voter to a “voter record” (Voter #12345).
- Authorizes them for “1 ephemeral key blind-sign.”
- Voter obtains or logs into the voter client:
- The app or website might show “You are now cleared to request a blind signature from the EA.”
- Voter later (or immediately) generates the ephemeral key and requests the blind signature.
8. Putting It All Together (High-Level Flow)
- Key Setup
- The EA + trustees run a DKG to produce the election public key.
- Voter Registration
- Voter is validated (ID check).
- Marked as eligible in the EA database.
- Blind-Signed Ephemeral Key
- Voter’s client generates a key, blinds (\npub_e), obtains EA’s signature, unblinds.
- Voting
- Voter composes ballot, encrypts with the election public key.
- Gets OTS proof for the ballot hash.
- Voter’s ephemeral key signs the entire package (including EA’s signature on (\npub_e)).
- Publishes to Nostr.
- Re-Voting (Optional)
- Same ephemeral key, new OTS timestamp.
- Final ballot is whichever has the latest valid timestamp before closing.
- Close of Election & Tally
- EA announces closing.
- Tally software (admin + auditors) collects ballots from Nostr, discards invalid duplicates.
- Threshold decryption or mix-net to reveal final counts.
- Publish final results and let auditors verify everything.
9. Summary of Major Components
Below is a succinct list:
- EA Admin Platform
- Web UI for officials (registration, blind signature issuing, final tally management).
- Backend DB for voter records & authorized ephemeral keys.
- Auditor/Trustee Platforms
- Web interface for verifying ballots, partial decryption, and final results.
- Voter Application (Mobile / Web)
- Generating ephemeral keys, getting blind-signed, casting encrypted ballots, re-voting, verifying included ballots.
- Nostr Relays (Decentralized Storage)
- Where ballots (events) are published, replicated, and fetched for final tally.
- Threshold Cryptography System
- Multi-party DKG for the election key.
- Protocols or services for partial decryption, mix-net, or homomorphic summation.
- OpenTimestamps Aggregator
- Service that returns a blockchain-anchored timestamp proof for each ballot’s hash.
Additional Implementation Considerations
- Security Hardening:
- Using hardware security modules (HSM) for the EA’s blind-signing key, for trustee shares, etc.
- Scalability:
- Handling large numbers of concurrent voters, large data flows to relays.
- User Experience:
- Minimizing cryptographic complexity for non-technical voters.
- Legal and Procedural:
- Compliance with local laws for in-person ID checks, mandatory paper backups (if any), etc.
Final Note
While each functional block can be designed and deployed independently (e.g., multiple aggregator services, multiple relays, separate tally servers), the key to a successful system is interoperability and careful orchestration of these components—ensuring strong security, a straightforward voter experience, and transparent auditing.
nostr:naddr1qqxnzde5xq6nzv348yunvv35qy28wue69uhnzv3h9cczuvpwxyargwpk8yhsygxpax4n544z4dk2f04lgn4xfvha5s9vvvg73p46s66x2gtfedttgvpsgqqqw4rs0rcnsu
-
 @ d57360cb:4fe7d935
2025-03-20 04:05:59
@ d57360cb:4fe7d935
2025-03-20 04:05:59A story about people
It was a rainy day in the busy city. The type of day when a dark silence envelops the air, allowing the hard thuds of rain to paint the concrete. I enjoy the evening in the city. The neon lights enliven the darkness, giving flair to the city as a whole. Every color you can think of is in these billboards; they’re bright pink, red, green, and so on, almost like a 14-year-old who plays too many sci-fi games designed it. As the city dimmed, I took a trip to my favorite café, Speedy’s. There’s nothing particularly special about this café. It holds an average rating of 4.0 stars online; it has cushy booth seats. The coffee is mid-tier, a bit watered down, but I don’t mind since I’m not too much of a fan of a strong blend. They have enough food items to keep you satisfied, but nothing to make it exceptional. Maybe that’s why I’ve come to love a café like this; it’s not extravagant, it blends in, it’s how a café should be; it meets its mark. Sometimes that’s all we hope for in things, even in people.
I’m good friends with the owner; she noticed me coming in often, and one night while the café was deserted and empty, we struck up a conversation. It was mere small talk on the first occasion, the simple things like how your day is, what part of the city you live in, what you do for work. It felt like a barrier of entry to a deeper well we both had yet to discover. At night, Speedy liked to switch all the lights to red; it gave a special ambience to the café, it relaxed you, and highlighted a lot of the art and design in the room. It almost feels like someone made the café to be lit red; when the regular lights were on, it was a plain old café. Once those lights came on, it became something entirely vivid and alive like those neon skyscrapers in the city. The thing about the nighttime was no one came into the café; it’s like they didn’t even know it existed even though the open sign continued to hang till 11:00 pm. People had more important places to be or they thought going to a café at night was an odd choice.
I frequented Speedy’s three times a week on average, but I always showed up on rainy days. There was no reason behind this; I felt drawn to the café, to Speedy, and to the atmosphere created by those red lights. I walked in and Speedy was at the counter blending a mint tea. I could smell the mint from the moment I walked in; it cleared my nose and I was breathing clearer than ever. It had me wondering how long my nasal passages had been blocked and how unfortunate it is to have a stuffy nose. I recalled a quote I heard once: ‘An ordinary man wishes for a million things, a sick man only has one.’ I sat at the corner booth. Speedy knew the drill. So, she made a black coffee with one cream and two sugars. I don’t mind coffee in the evening. Being an avid drinker, the effects of caffeine no longer do much to me; my mom had the same phenomenon, it’s in the genes.
Speedy had on blue jeans that hovered right above her ankles, she wore clean, new-looking white sneakers and a tiny horizontal striped t-shirt. The sleeves hugged her arms nicely, she was oddly in great shape; she used to be an Olympic sprinter but no one had a clue. She had a diamond face shape, high cheekbones, and a soft welcoming face, and always wore her hair in a messy bun. She’d recently left for a vacation to Hawaii and appeared to have a nice brown tan from the trip.
We never ate much when we got together to talk. The conversation was enough to feed our souls. The thing about Speedy was she was the exact opposite of her name, which made no sense to me. She was never in a rush, always calm, composed in each action. She loved to live in the silence of life, never speaking too soon, thinking, never rushing anywhere. To her, time didn’t seem to exist; she set her own pace in life, devoid of what the world was doing. I found it an honorable skill to have, as I was the exact opposite; in essence, my name should’ve been Speedy. I was always in a rush, always frantic and anxious. I couldn’t sit still; I had to go, to be on the move, doing something at all times. Overthinking everything twice over. When we’d talk, it would be as if two species were encountering a life so unknown to the other. We discussed everything: music, especially jazz, art, culture, life, cars, and games. If it existed, it found a place in our canvas.
Slow and smooth as ever, Speedy came to the booth with a grin on her face.
Speedy: Here’s your coffee, as usual.
Narrator: *nods head* I wanted to ask you what the story behind that painting is.
To the far right of the room on the wall hung a painting that stretched from the ceiling to close to the floor. I’d never seen a canvas that size before. This was a new piece, no doubt; as I sat down in the booth, I couldn’t help but stare. It gripped me and left me blank. Speedy turned her head and glanced for a while; I don’t know how long she was looking, but she seemed to be transported somewhere far away. She finally turned back.
Speedy: That’s “color and contrast” (artist unknown). I found it after I fell out of love. I’ve had it for a while; I just never decided to put it up until two weeks ago.
Narrator: It’s an interesting piece; I can’t find the words for it, but I can’t take my eyes off it.
The painting had the perfect mix of dark and light colors, areas of bright luminance and dark depth. It engrossed you. When Speedy said she found it when she fell out of love, somehow I understood her. The painting made me reminisce about a love I once had. Maybe that’s where she was teleported to when she stared blankly at it. The painting invited you back to that place of both the light and dark parts. The title began to make sense to me. All the while, “Romance” by Hiroshi Suzuki played in the background.
Speedy: A few years after a devastating heartbreak, I was on a week-long sabbatical in Ojai, California. I stayed in an old inn on a hill near a lake. While I was there, I would take a morning walk to the lake to enjoy the birds, reflect, and drink my morning coffee. The first time I went down the hill, I spotted the huge canvas propped up in front of the lake and a tiny glass house right next to it. The glass was fully tinted so you couldn’t see inside at all. It looked like it had no doors; when the sun shone on it, it reflected back an almost platinum silver glow. Standing outside was a man facing the canvas. He had on a baggy set of linen clothes, a beaded necklace, sandals, long grey and black hair, and a big goatee. The man was immersed, almost looked possessed, and he would violently strike the canvas with his brush. Then he would abruptly stop and he would be gentle with the canvas, adding in finer details; then he would explode into a violent rhythm again. He continued this for hours, and I would visit the lake each morning to sit and watch. I always had the feeling the man knew he was being watched. To him, it was a performance, a show, somewhat of a grand finale, I as the only witness. My final morning there, I went down to the lake; the man was sealing the painting, signaling that he had finished it. He was wrapping rope around it to secure it. Once he finished, he turned with sunglasses on, stared at me for what felt like an eternity, and then signaled for me to come over. He took a seat on his wooden stool as I approached, pulling out a leather notebook; he ripped a page out of it and handed it to me. The man was not from California; I couldn’t tell where he was from, he didn’t speak English at all, or so it seemed. His silence was his voice; it didn’t feel strange at all at the time, but as I retell this story, it seems a bit mystical. I took the letter, and the man bowed to me. Once he finished bowing, he got up and walked into the glass house and closed the door. He never came back out. I was confused, so I read the note in hard-to-read writing; all it said was ‘a gift of love, yours.’ I stared blankly at the wrapped painting and took it with me. I’ve had it stored in the back of the café for years, never opening it once; when I put it up 2 weeks ago, that was the first time I saw it.
At this point, Speedy put her head down, and I could see tears falling in her lap. I figured it was best to say nothing for a while.
Speedy: Unwrapping the painting felt like reopening the wound of my broken heart; it held a power that was unexplainable. It made me shake and gave me cold chills. I’m not sure why I decided to open it, but I did. I did so with extreme caution, unwrapping the paper and untying the rope that held it together. As I saw the painting, I began to get dizzy, as if I had taken drugs and the high was hitting unexpectedly. It felt like an invisible cloak had surrounded me from every angle; I couldn’t believe what I was seeing. It wasn’t a painting but a full story. I want to show you something.
Speedy got up and I followed her to the painting. We stood in front of it and I could feel a magnetic pull; I was experiencing that cloak. She then pointed to the center of the painting; it was cut in a square that was very hard to notice. She pushed on the corner and it swiveled around, unveiling words on the back of the painting.
Speedy: That man engraved this message on the back; when I read it, my heart seemed to scream out and burst. Not in a bad or good way, but more so as a natural reaction. I can’t explain what it did, but it took care of me. Like a potion that was reserved for the right moment, if you receive it at the wrong time, you won’t get the desired effect. Maybe that’s why you came here tonight.
I sat and stared at the words.
“Color can only appear in a place of non-color, in a place where there is no flair, no fill. Color could be light filling darkness, a complement, not an opposite. Love is color, as it complements the blank canvas of emptiness. It takes the form of a blank canvas and makes its work known. It draws you in; you can’t pay attention to anything else; it’s as if the lover who has evoked this is as wide as the vast sky. As bright as a full moon. Staring into their eyes, you can no longer see the borders that the canvas inhabited; everything has become the canvas. Everything has become the art, the intricate colors and the strokes. The separation that was present before, whether noticed or not, is no longer the picture. It is now whole. It’s complete, with nothing to add; it towers over you and envelops you. You can’t believe how high it’s reached or how wide it is. It is both flowing above, below, beyond, and through your entire being. You can no longer distinguish where you and the love begin and end.“
Like the mint tea that cleared my nose, my heart cleared the way; it felt like it could finally breathe. I sat in disbelief and wondered how long I had been that way.
-
 @ 06bc9ab7:427c48f5
2025-03-17 15:46:23
@ 06bc9ab7:427c48f5
2025-03-17 15:46:23Bitcoin Safe - A bitcoin savings wallet for the entire family
Designed for both beginners and power users, Bitcoin Safe combines security with an intuitive user experience. In this article, we dive deep into its features, unique benefits, and the powerful tools that make managing your Bitcoin wallet simple and secure.
Built for Learners
✔️ Step-by-step wallet setup wizard + PDF backup sheets 📄 🧪 Test transactions to ensure all hardware signers are ready 🔑 🛡️ Secure: Hardware signers only – no hot wallet risks 🚫🔥 🌍 Multi-language support: 🇺🇸 🇨🇳 🇪🇸 🇯🇵 🇷🇺 🇵🇹 🇮🇳 🇮🇹 🇫🇷 🇩🇪 🇲🇲 🇰🇷 📁 Address categories for easy organization ☁️ Label and category synchronization, and cloud backup (optional) 💰 Automatic UTXO merging to save on fees ⚡ Fast syncing with Electrum servers, Compact Block Filters coming soon
Built for Power Users
🔐 Supports Coldcard, Bitbox02, Jade, Trezor, Passport, Keystone & many more 🏦 💬 Multi-party multisig chat & PSBT sharing (optional) 📊 Transaction flow diagrams to trace coin movements 🔍 Instant cross-wallet wallet search ⚙️ Set your own electrum server, mempool instance, and nostr relay
Step-by-Step Wallet Setup
Whether you’re setting up a single-signature or multi-signature wallet, the setup wizard guides you every step of the way:

- Single Sig Wizard: Follow the intuitive wizard that walks you through each step. https://youtu.be/m0g6ytYTy0w
Clear instructions paired with hardware signer screen-shots, like the steps for a Coldcard
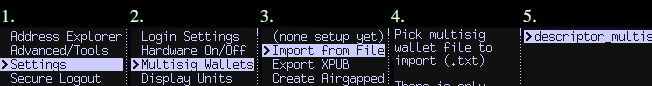
-
Multisig Wizard: The wizard ensures you do all necessary steps for a Multisig wallet in the right order. Afterwards your Multisig is ready to use and all signers are tested. Check out https://bitcoin-safe.org/en/features/setup-multisignature-wallet/
-
PDF Backup: The wizard will also generates 3 PDF backup sheets for a 2-of-3 multisig wallet, so ensure you always have your wallet descriptor together with the seed.
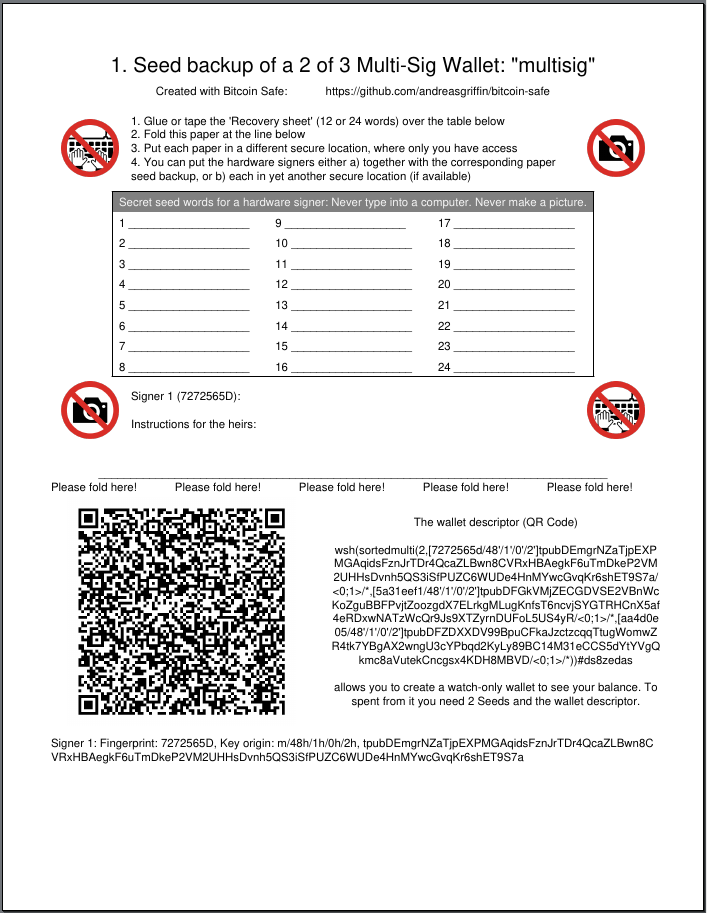
-
Hardware Signer Support: With full support for major hardware signers your keys remain securely offline.
Transaction Visualization
Visualize and navigate your transaction history:
-
Graphical Explorer: An interactive transaction diagram lets you click on inputs and outputs to follow the money flow intuitively.
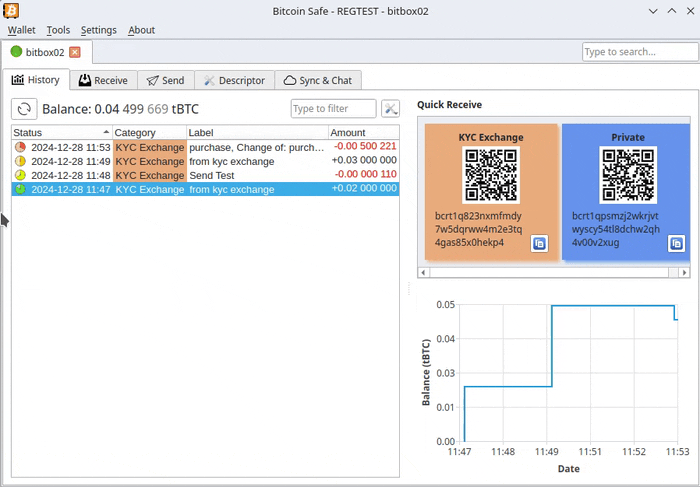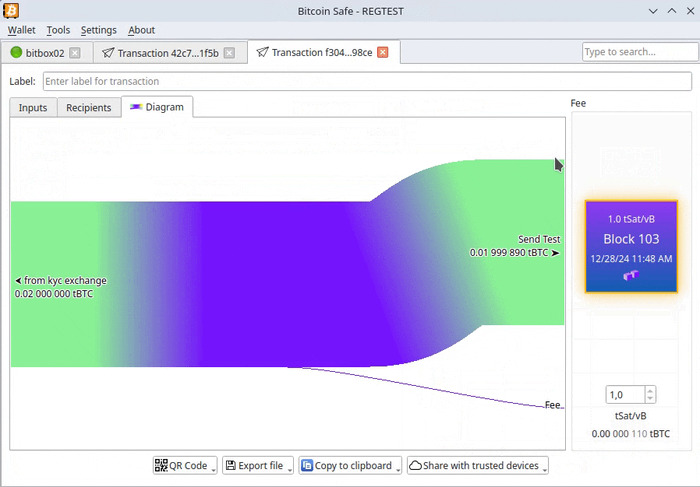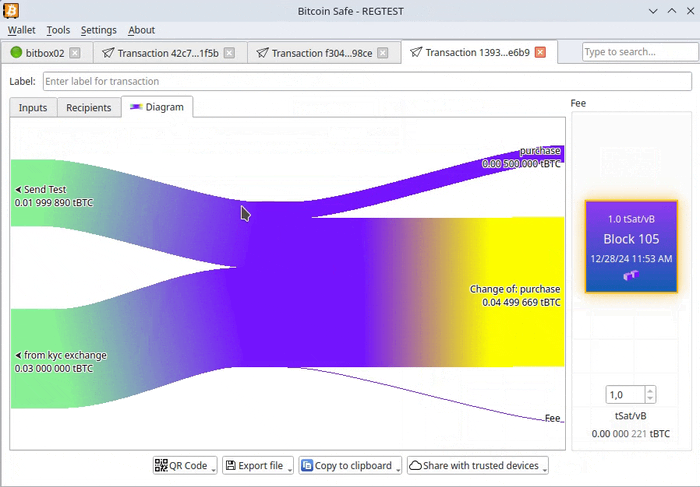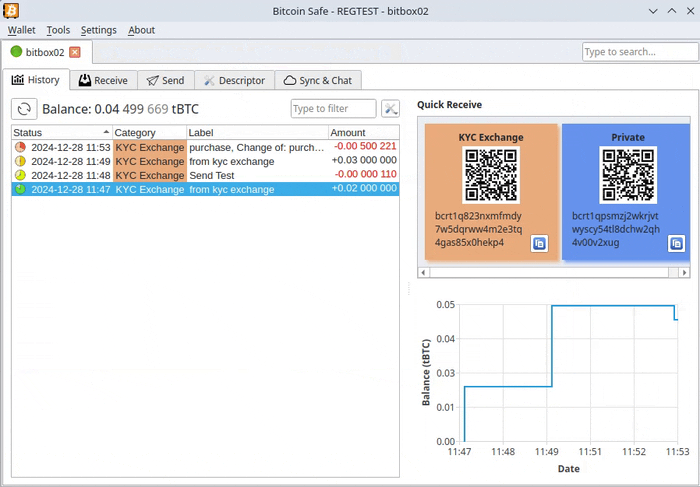
-
Coin Categories: Organize your addresses into distinct coin categories (e.g., “KYC”, “Work”, “Friends”) so Bitcoin Safe automatically selects the correct inputs when creating PSBTs.

It prevents you accidentally linking coin categories when creating a transaction, and warns you if mistakes happened in the past.
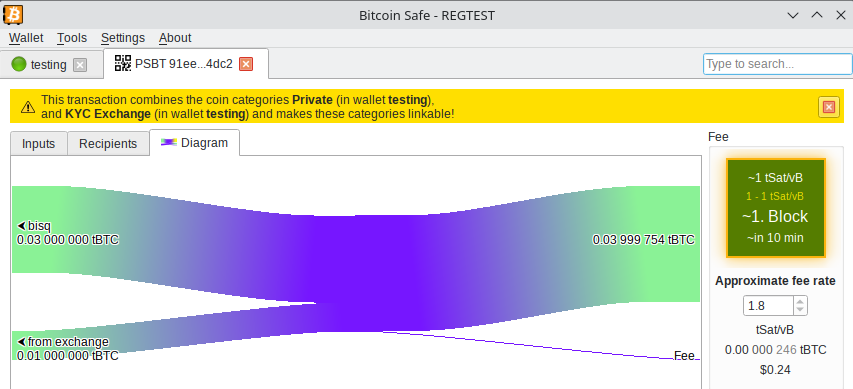
Powerful Wallet Management Tools
- Flexible Fee Selection: Choose fees with one click using an intuitive mempool block preview.
- UTXO Management: Automatically (optional) merge UTXOs when fees are low.
- CSV Table Export: Right click, Drag&Drop, or CTRL+C for immediate CSV export for easy processing in Excel.
- PDF Balance Statement: Export the address balances for easy record keeping on paper.
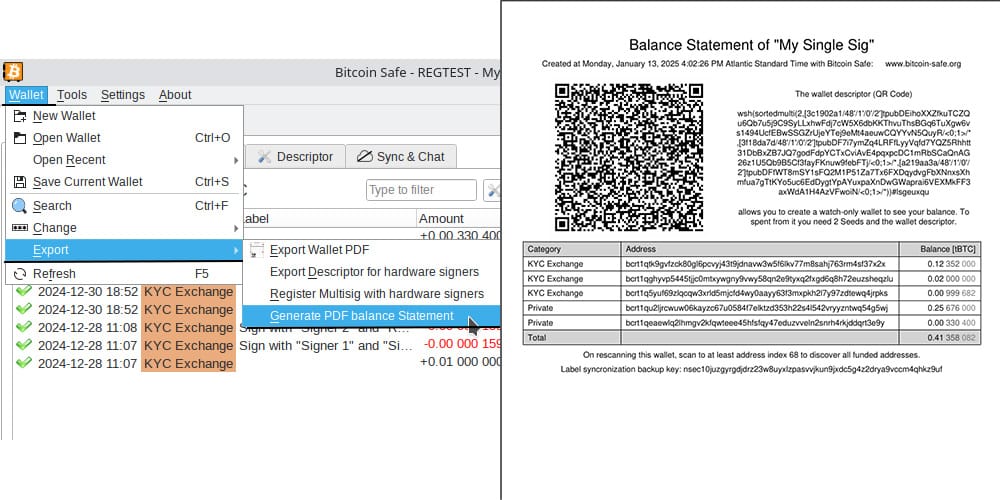
Advanced Features for the Power-User
Sync & Chat is off by default (for the paranoid user), but can be enabled with just one click.
Label Synchronization and Backup
- Seamless Sync: Using encrypted nostr messages, Bitcoin Safe synchronizes your coin categories and labels across multiple devices.
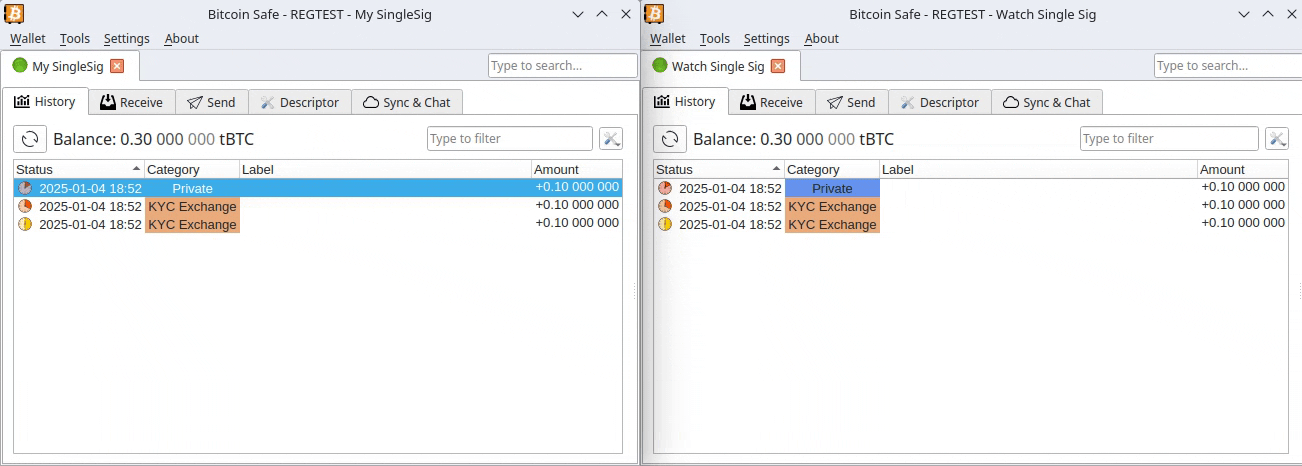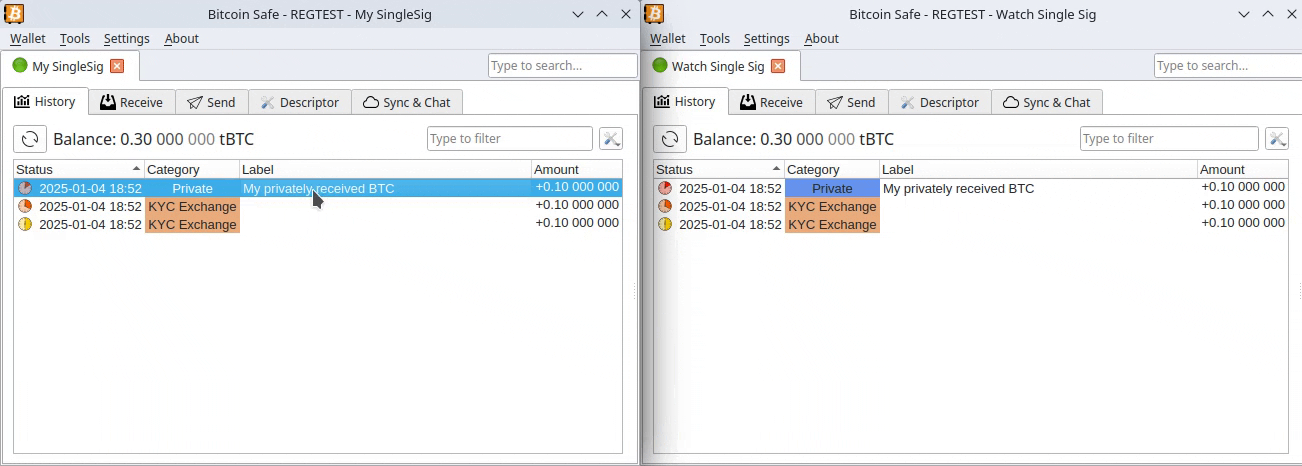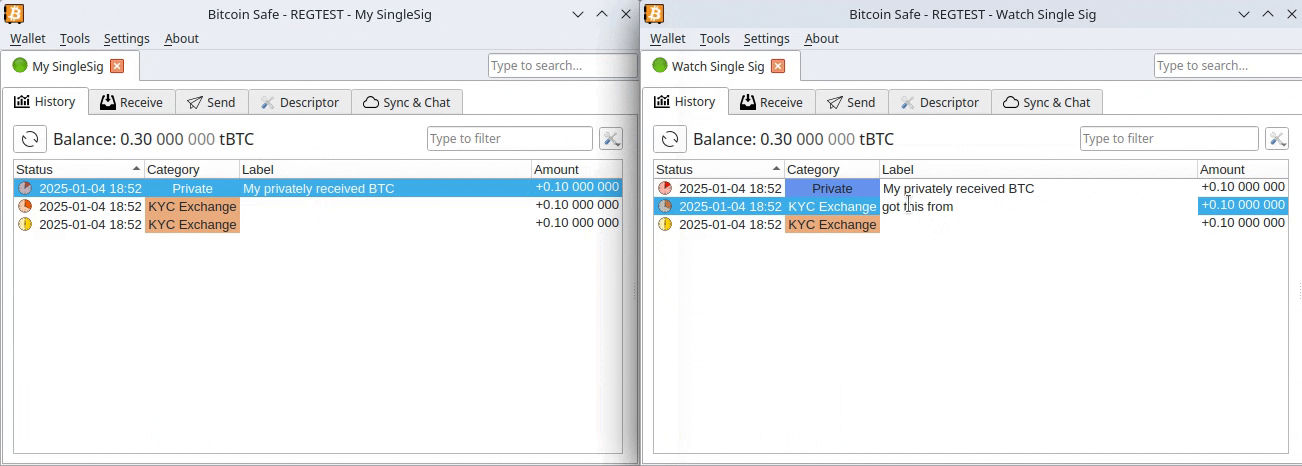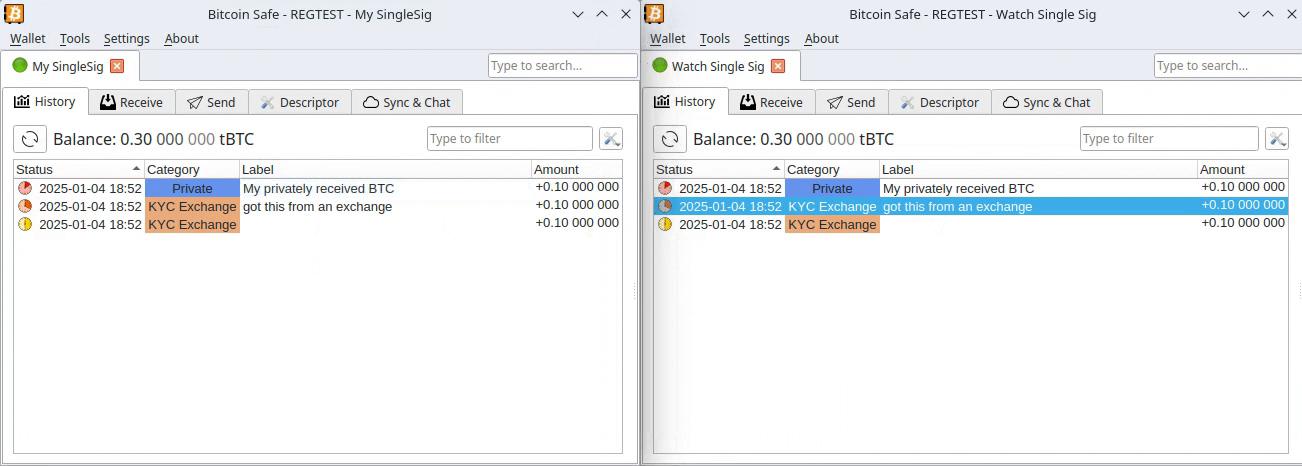
- Easy Backup: A short backup key is all you need to safeguard your coin categories and labels, ensuring your organization remains intact.
Collaborative Multi-party Multisig
- Group Chat Integration: After creating your multisig wallet, Bitcoin Safe offers an encrypted nostr group chat for secure collaboration and one-click PSBT sharing.
- User Authentication: Each participant must authenticate every other user with a simple click, ensuring secure communication.
Watch and Learn: Get Started with Bitcoin Safe
If you’re new to Bitcoin Safe, a short video guide can make all the difference. Learn how to set up your Bitcoin Safe wallet in this detailed walk through:
https://youtu.be/m0g6ytYTy0w
Or see how to verify an address on your hardware singer:
https://youtu.be/h5FkOYj9OT8
Building up a knowledge base: https://bitcoin-safe.org/en/knowledge/
Whats next?
- Compact Block Filters!!! They make electrum servers obsolete.
- Why? Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions
- Trade-off: They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK.
- How do they work? Simply speaking: They ask normal bitcoin core nodes for a short summary of each block. And if the summary shows a transaction belonging to the wallet, the entire block is then downloaded from the bitcoin core node. The bitcoin core node does not learn however which of the many transactions in the block you were interested in. Read more here and of course in the bip.
- When: 2 weeks 😅. Lots of things need to be done until Bitcoin Safe can use the bdk CBF/kyoto client from rustaceanrob, so keep an eye out for updates and please give feedback when you use Bitcoin Safe.
Stay updated on nostr or on GitHub.
Thank you
A huge thanks goes to nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f for supporting this project with a grant and nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx for the Hackathon prize.
This wallet is only possible because it is building upon other peoples open source work. Most notably
- bdk nostr:nprofile1qqsgkmgkmv63djkxmwvdlyaxx0xtsytvkyyg5fwzmp48pwd30f3jtxspzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqr8vuet
- and especially nostr:npub1thunderat5g552cuy7umk624ct5xe4tpgwr2jcjjq2gc0567wgrqnya79l , nostr:npub1reezn2ctrrg736uqj7mva9lsuwv0kr5asj4vvkwxnrwlhvxf98tsq99ty4 , and nostr:npub1ke470rdgnxg4gjs9cw3tv0dp690wl68f5xak5smflpsksedadd7qtf8jfm for dealing with my many feature requests and questions.
- rustaceanrob building kyoto which implements CBF for BDK; a crucial library and will be able to replace electrum servers for many use cases
- ndk by nostr:nprofile1qqsx3kq3vkgczq9hmfplc28h687py42yvms3zkyxh8nmkvn0vhkyyuspz4mhxue69uhkummnw3ezummcw3ezuer9wchsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qy88wumn8ghj7mn0wvhxcmmv9u0uehfp
And of course, secure storage of bitcoin is only possible, because of the hardware signer manufacturers. Thanks to nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8 Coldcard , Coldcard Q , nostr:npub1tg779rlap8t4qm8lpgn89k7mr7pkxpaulupp0nq5faywr8h28llsj3cxmt Bitbox02 , nostr:npub1jg552aulj07skd6e7y2hu0vl5g8nl5jvfw8jhn6jpjk0vjd0waksvl6n8n Blockstream Jade , Trezor Safe, Foundation Passport, Keystone, Ledger, Specter Shield, and many more.
I also want to thank people who gave feedback and helped spread the knowledge of Bitcoin Safe (please forgive me if I forgot to mention you)
- nostr:npub1p5cmlt32vc3jefkl3ymdvm9zk892fsmkq79eq77uvkaqrnyktasqkpkgaw nostr:npub1s07s0h5mwcenfnyagme8shp9trnv964lulgvdmppgenuhtk9p4rsueuk63 nostr:npub18f3g76xc7xs430euwwl9gpn7ue7ux8vmtm9q8htn9s26d8c4neeqdraz3s nostr:npub1mtd7s63xd85ykv09p7y8wvg754jpsfpplxknh5xr0pu938zf86fqygqxas nostr:npub1kysd8m44dhv7ywa75u5z7w2w0gs4t6qzhgvjp555gfknasy3krlqfxde60 nostr:npub185pu2dsgg9d36uvvw7rwuy9aknn8hnknygr7x2yqa60ygvq6r8kqc836k8 nostr:npub1hkcgyqnsuaradq3g5hyvfdekwypc25494nmwggwpygxas7fcs4fst860fu nostr:npub1xsl0msy347vmj8gcpsjum6wwppc4ercvq4xfrhqmek2dqmqm0mtsyf35vx nostr:npub1hxjnw53mhghumt590kgd3fmqme8jzwwflyxesmm50nnapmqdzu7swqagw3 nostr:npub1ke470rdgnxg4gjs9cw3tv0dp690wl68f5xak5smflpsksedadd7qtf8jfm nostr:npub1sk26fxl4fy3vt8m5n0a6aturaql0w20nvh22q0cyaqm28tj7z8ss3lutc9 nostr:npub1r4llq2jcvq4g2tgha5amjz07zk7mrrcj89wllny9xwhhp5zzkklqk4jwja nostr:npub1p9v2zpwl28c0gu0vr2enp3lwdtv29scwpeqsnt0ngqf03vtlyxfqhkae5w nostr:npub1xkym0yaewlz0qfghtt7hjtnu28fxaa5rk3wtcek9d3x3ft2ns3lq775few nostr:npub1r8343wqpra05l3jnc4jud4xz7vlnyeslf7gfsty7ahpf92rhfmpsmqwym8 nostr:npub12zpfs3yq7we83yvypgsrw5f88y2fv780c2kfs89ge5qk6q3sfm7spks880 nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx https://x.com/91xTx93x2 https://x.com/afilini rustaceanrob
-
 @ 6e0ea5d6:0327f353
2025-03-20 03:01:46
@ 6e0ea5d6:0327f353
2025-03-20 03:01:46A quiet, meek, and peaceful man is not necessarily a benevolent person. Only the one who harbors powerful hatred and malice within but voluntarily controls it is truly worthy of being called a man of honor.
In the business world, some people mistakenly confuse courtesy and politeness with excessive sensitivity and emotional cowardice. They speak so meekly that they even stammer. Fearing to offend others, they swallow their opinions. The ego enslaves with the worst kind of chains: the need for self-affirmation and validation. They constantly apologize for everything: “sorry for this,” “sorry for that,” “sorry for such and such.”
By behaving this way, one not only earns the listener’s contempt, disrespect, and anger but also significantly diminishes their reputation and moral standing in the eyes of others. They will never be seen as a strong leader. They will never gain the trust of subordinates. And they will never have important tasks delegated to them by their superiors.
With respect, honor, and silence, one can enter and exit any place. Those who understand both the streets and the world beyond them achieve peace and gain unrestricted access. Always consider the protection of your reputation. Do not allow mockery to test your ability to maintain self-respect.
True mastery in interpersonal interactions lies in discerning which provocations must be confronted and which deserve to be ignored.
Like a skilled swimmer who understands the currents and adapts to them, you must learn to navigate the murky waters of the world, responding with the necessary strength and wisdom in each situation.
The key to success does not lie in servile submission but in assertiveness and reciprocity. Treat others as they truly deserve to be treated, and in doing so, you will not only earn respect but also pave the way for genuine and lasting success.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ a93be9fb:6d3fdc0c
2025-03-20 02:54:52
@ a93be9fb:6d3fdc0c
2025-03-20 02:54:52Publishing new article
-
 @ 8d34bd24:414be32b
2025-03-20 01:45:49
@ 8d34bd24:414be32b
2025-03-20 01:45:49This post was inspired by my Pastor’s sermon this morning. I’ve read this passage a bunch of times. I’ve always seen Jesus’s divinity. I’ve also seen the disciples’ lack of faith, but there is so much more to get out of this passage. It shocks me that I never saw it before and just had to share.
Now on one of those days Jesus and His disciples got into a boat, and He said to them, “Let us go over to the other side of the lake.” So they launched out. But as they were sailing along He fell asleep; and a fierce gale of wind descended on the lake, and they began to be swamped and to be in danger. They came to Jesus and woke Him up, saying, “Master, Master, we are perishing!” And He got up and rebuked the wind and the surging waves, and they stopped, and it became calm. And He said to them, “Where is your faith?” They were fearful and amazed, saying to one another, “Who then is this, that He commands even the winds and the water, and they obey Him?” (Luke 8:22-25)
It is obvious from this passage, that Jesus is divine. It reminds us of Genesis 1 when God speaks the waters into existence. It reminds me of Job:
“Or who enclosed the sea with doors\ When, bursting forth, it went out from the womb;\ When I made a cloud its garment\ And thick darkness its swaddling band,\ And I placed boundaries on it\ And set a bolt and doors,\ And I said, ‘Thus far you shall come, but no farther;\ And here shall your proud waves stop’? (Job 38:8-11) {emphasis mine}
Jesus spoke and the wind and waves instantly complied. All was instantly calm. Jesus’s actions scream His divinity, but there is so much more to get out of this passage in Luke 8.
Why?
My pastor asked everyone a key question, “When Jesus told His disciples to get in the boat and to cross to the other side, did He know there would be a big, life threatening storm?” The kids at church wisely shouted, “Yes!”
Several of Jesus’s disciples were fishermen. They worked their entire lives fishing in boats in the Sea of Galilee. The were familiar with boats, wind, waves, and storms, and yet they were terrified by this storm. This was not a little storm. This storm was tossing around the boat and splashing waves of water into the boat threatening to capsize it in the middle of this large body of water.
I can somewhat relate (but not fully). I grew up in Florida and we would occasionally take a boat a couple of hours across the ocean to and from the Bahamas (Abaccos). One time we had to make the crossing on a particular day to get me back to head off to college. At this time, there was a Hurricane in the gulf (other side of Florida) that were making really big waves. If my memory is correct, we were in a 34 foot long boat and the waves were taller than the boat was long. My Dad would give full throttle to ease up one side of wave and then pull back as we shot down the far side of the wave and then again and again for hours. If the engine had failed, we would have turned sideways and been capsized. If my Dad had not kept the boat straight into the waves, we would likely have capsized, but my Father knew what to do and we made it safely to shore.
Jesus knew this giant storm was going to blow up, but He told His disciples to head right into what would soon be a giant storm. One key thought that I had previously missed is that He did not send them into the storm alone. He went with His disciples.
Initially the disciples tried to battle the storm themselves, but it was a losing proposition. They were losing the battle with the storm and losing it badly. Finally, they went to Jesus. I like how the NIV says it, “The disciples went and woke him, saying, ‘Master, Master, we’re going to drown!’” Mark 4:38 says, “Jesus was in the stern, sleeping on a cushion. The disciples woke him and said to him, ‘Teacher, don’t you care if we drown?’” The disciples didn’t just ask for help; they accused Jesus of not caring. They called Him “Master” and “Teacher,” instead of “God” or “Lord.”
So going back to my Pastor’s question, why did Jesus, who knew there was going to be a terrible storm, tell His disciples to cross the water at that time? Was He teaching His disciples to trust in Him? Was He teaching His disciples to ask Him for help when they had a need? Was He teaching them who He was in a way that they would never forget? I think the answer to all of these questions is clearly, “Yes!”
Application
Now we need to look at this passage and ask, “what do we need to take away and learn from this passage?” and “how can we apply this passage?”
I think there are several key points:
-
Jesus knew what was about to happen to them.
-
Jesus had a plan and a purpose for putting them in this fearful and life threatening situation.
-
This hardship had a good purpose.
-
Jesus was with them through it all.
So often I have people who want to deny that a loving God would intentionally put themselves or others in uncomfortable, scary, or dangerous situations. They say, “God wouldn’t do that.” or “Why would God do that?” Yes, God does cause us to go through hard times (I refuse to say bad), but not to cause us pain or hardship, but to grow us in our faith and witness.
It is a rare person who grows in faith during ease and pleasant circumstances. Most of us require hardship to force us to stop doing everything on our own and to trust Jesus and to lean on His power (Yes, I am speaking from personal experience). Nothing glorifies God more than resting in Him during the storm. Yes, God cares and loves you very much. Yes, God is with you through every hardship you will ever experience. Yes, God wants the best for you. We may not appreciate it in the moment, but God cares more about your eternal good than your momentary ease and happiness. He gives you what you need instead of what you want.
The amazing thing is that when you learn to trust in Him, when you learn to rely on His power, and when you learn to look for His good work in every situation, you will find a joy and peace like you never imagined. Instead of chasing everything looking for the perfect situation to make you happy, you will rest in the hand of the Father knowing a joy and peace that surpasses all human understanding.
In child labor, a woman’s body does what it is supposed to do to produce a baby. Sometimes, out of fear or desire for control, a woman will fight the labor. They will tense up and it causes more pain. If they relax and trust that the delivery will happen as it should, the delivery is usually much easier. Similarly, when we fight Jesus during the storm, when we don’t trust His omnipotence and omniscience, and when we try to do it our way instead of His, we actually make these hard times more uncomfortable and less effective. Instead of learning what God is teaching us, we end up harming ourselves. Instead of building an amazing witness, we give God a bad name.
No matter how bad the storm, look to Jesus and know that He is God. He is our good and loving God who works everything for our good.
Trust Jesus
-
-
 @ a396e36e:ec991f1c
2025-03-20 14:11:02
@ a396e36e:ec991f1c
2025-03-20 14:11:02Introduction
The term Clown World is a meme that reflects the perception that the current system operates in an absurd, corrupt, or irrational manner. In this context, many Bitcoin enthusiasts see it as a tool to escape from Clown World. Bitcoin emerged in 2009, following the 2008 global financial crisis, as an alternative to a traditional monetary system that many consider unjust, inefficient, and prone to manipulation. This article explores how Bitcoin challenges existing economic structures, embodies philosophical principles such as decentralization and financial sovereignty, and serves as a political tool against failing monetary policies. We will also examine the historical evolution of Bitcoin’s narrative in relation to escaping Clown World.
Economic Perspective: Challenging Traditional Monetary Structures
From an economic standpoint, Bitcoin directly challenges the traditional monetary system, which many Bitcoin advocates see as part of Clown World. Fiat currencies, issued by central banks, can be devalued through expansionary policies, leading to inflation, bank bailouts, and resource misallocation that deteriorate economies and social structures. Bitcoin was explicitly designed as a response to these issues: its genesis block, mined on January 3, 2009, contained the message "The Times 03/Jan/2009 Chancellor on brink of second bailout for banks," referencing government bailouts of failing financial institutions. This message signaled Bitcoin’s intent to offer a solution to what was perceived as a broken financial system and irresponsible economic policies.
Unlike fiat money, which can be expanded at the discretion of central authorities, Bitcoin has a predictable and non-manipulable monetary policy. Its issuance follows an algorithmic schedule: the total supply is capped at 21 million coins, ensuring scarcity and practically eliminating long-term inflation. Every four years, a halving event reduces the number of new bitcoins entering circulation, contrasting sharply with central banks’ inflationary targets of around 2% per year. In Bitcoin, no one can arbitrarily “print” more money or devalue existing units, as “there is no central authority” making such decisions. As analyst Anthony Pompliano put it: “Bitcoin is censorship-resistant money. No one can stop you from sending it. No one can confiscate it without your permission. No one can debase the currency.” In other words, Bitcoin functions as digital gold, immune to political dilution, challenging the very foundation of inflationary fiat money.
This economic model—often associated with the idea of “sound money”—represents a separation between money and the state. Many Bitcoin proponents argue that a broken monetary system is at the root of the dysfunctions of Clown World. As Bitcoin advocates Knut Svanholm and Luke de Wolf put it: “When money stops working, everything becomes political and turns into a farce.” Bitcoin, by replacing trust in financial authorities with trust in cryptographic code, aims to correct these distortions. It allows individuals and communities to opt out of the traditional system, securing themselves against inflation and reckless monetary policies.
Philosophical Perspective: Decentralization, Financial Sovereignty, and Resistance to Manipulation
From a philosophical perspective, Bitcoin embodies principles of decentralization, individual sovereignty, and resistance to manipulation, offering an alternative to perceived systemic corruption and control. Unlike traditional money, Bitcoin is a decentralized digital currency that “does not rely on any central authority but operates through a mathematical protocol and a distributed network of nodes.” This means that no government, bank, or corporation can unilaterally control the Bitcoin network or counterfeit its supply. The blockchain architecture and distributed consensus make Bitcoin a kind of “trust machine”, where the rules are pre-set by transparent algorithms. For the first time in history, digital scarcity combines with total decentralization, creating a monetary system where trust is placed in code rather than authorities.
This foundation enables personal financial sovereignty. Bitcoin users can fully own and control their funds through private keys, redefining monetary property rights by eliminating the need for custodians. In practice, this means that “no one can confiscate it without your permission” as long as the user protects their keys (hence the famous phrase “not your keys, not your coins”). Bitcoin’s sovereignty contrasts with traditional bank accounts, which are vulnerable to freezes, censorship, or devaluation. The philosophy behind Bitcoin promotes independence from state and corporate financial control, much like the historical separation of church and state. As a Bitcoin advocate noted, “By decentralizing financial power and promoting a separation between money and the state,” Bitcoin has the potential to reshape economic power dynamics. Essentially, anyone can become their own bank, transacting globally without requiring permission.
Another key aspect of Bitcoin’s philosophy is censorship resistance and protection from manipulation. In Clown World, institutions can block transactions, exclude individuals from the financial system, or manipulate currency for political purposes. Bitcoin was designed to counteract this. Anyone can transfer Bitcoin to another person directly, without intermediaries who can block transactions. The blockchain's immutability ensures that no one can retroactively alter payment records or falsify balances, reinforcing its freedom-preserving nature.
Recent events highlight this utility: In 2022, when the Canadian government froze bank accounts of protesters and pressured crowdfunding platforms, many pointed out that Bitcoin could bypass such authoritarian measures. As one commentator put it, “Every attempt at financial censorship is free marketing for Bitcoin,” as it underscores its value as unseizable and incorruptible money. This ideology aligns with libertarian and anarcho-capitalist ideals, advocating that individuals—not the state—should have ultimate control over their money and transactions.
Political Perspective: Bitcoin as a Tool of Resistance Against Authoritarianism and Monetary Failures
From a political standpoint, Bitcoin has been used as a form of resistance against authoritarian regimes, state financial controls, and failing monetary policies. Due to its borderless and stateless nature, Bitcoin enables escaping national economic barriers and prevents governments from unilaterally controlling wealth. In countries suffering from hyperinflation or strict currency controls, citizens have turned to Bitcoin to protect their savings.
Venezuela is a key example: Bitcoin is widely used there as a store of value against the endless devaluation of the national currency. Similarly, in Argentina, Bitcoin adoption has surged as people seek to preserve their wealth amidst chronic inflation and restrictions on foreign currency exchange. In these contexts, Bitcoin serves as an escape valve from disastrous economic policies, offering a refuge where the government cannot destroy the value of money through inflation.
Conclusion
Bitcoin is more than just an asset; it is a technological, economic, and philosophical revolution offering an alternative to what many perceive as the dysfunctions of Clown World. By enabling economic sovereignty, censorship resistance, and an escape from inflationary policies, Bitcoin challenges the status quo, providing a viable path toward financial freedom and systemic change.
-
 @ 1731c73c:1bca4ecc
2025-03-17 14:13:04
@ 1731c73c:1bca4ecc
2025-03-17 14:13:04Welch Geistes Kind sind Waffenproduzenten, welch Geistes Kind Wissenschaftler, die Viren so verändern, dass sie pathogener, also gefährlicher für den Menschen werden? Im pfälzischen
https://soundcloud.com/radiomuenchen/kommt-wuhan-nach-deutschland-von-prof-roland-wiesendanger
Weilerbach wird ein US-Biolabor der Schutzstufe 3 gebaut. Dort sollen hochinfektiöse Erreger oder Substanzen, unter anderem SARS-CoV-2, das Virus H5N1, Dengue- und das Hanta-Virus untersucht werden. Der Bundesregierung – so fand Florian Warweg von den NachDenkSeiten heraus - weiß davon angeblich nichts. Auch nicht, welche Kontrollfunktion Bundesbehörden für US-Biolabore auf deutschem Boden haben.
War da was? Hatte nicht – ebenso vertuscht von Regierung, Medien und Wissenschaftlern – für die einen die größte Pandemie, für die anderen der weltweit größte Wissenschafts- und Medizinskandal in den letzten fünf Jahren stattgefunden? Warum interessiert das keinen?
Die Bestätigung der US-Regierung ist offiziell, dass die Covid-19-Pandemie aus einem Labor in Wuhan stammt. Das entlarvt die jahrelange Vertuschung und Diffamierung kritischer Stimmen als politisch motivierte Manipulation. Einer, der diskreditiert wurde, ist Professor Roland Wiesendanger. Mundtot ließ er sich aber nicht machen. Er fordert weiterhin eine schonungslose Aufarbeitung der hochgefährlichen Gain-of-function-Forschung, außerdem deren weltweite Ächtung, um zukünftige Pandemien zu verhindern.
Roland Wiesendanger ist Physik-Professor an der Universität Hamburg, Ehrendoktor der Technischen Universität Posen und Mitglied zahlreicher nationaler und internationaler Wissenschaftsakademien. Hören Sie sein Statement: „Wir dürfen die Risiken der Gain- of-function-Forschung nicht länger hinnehmen“.
Sprecher: Ulrich Allroggen
Radio München\ www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): 3G1wDDH2CDPJ9DHan5TTpsfpSXWhNMCZmQ\ Ethereum (ETH): 0xB41106C0fa3974353Ef86F62B62228A0f4ad7fe9
-
 @ c1e9ab3a:9cb56b43
2025-02-25 19:49:28
@ c1e9ab3a:9cb56b43
2025-02-25 19:49:281. Introduction
Modern election systems must balance privacy (no one sees how individuals vote) with public verifiability (everyone can confirm the correctness of the tally). Achieving this in a decentralized, tamper-resistant manner remains a challenge. Nostr (a lightweight protocol for censorship-resistant communication) offers a promising platform for distributing and archiving election data (ballots) without relying on a single central server.
This paper presents a design where:
- Each voter generates a new ephemeral Nostr keypair for an election.
- The election authority (EA) blind-signs this ephemeral public key (npub) to prove the voter is authorized, without revealing which voter owns which ephemeral key.
- Voters cast encrypted ballots to Nostr relays, each carrying an OpenTimestamps proof to confirm the ballot’s time anchor.
- Re-voting is allowed: a voter can replace a previously cast ballot by publishing a new ballot with a newer timestamp.
- Only the latest valid ballot (per ephemeral key) is counted.
We combine well-known cryptographic primitives—blind signatures, homomorphic or mix-net encryption, threshold key management, and time anchoring—into an end-to-end system that preserves anonymity, assures correctness, and prevents double-voting.
2. Roles and Components
2.1 Voters
- Long-Term (“KYC-bound”) Key: Each voter has some identity-verified Nostr public key used only for official communication with the EA (not for voting).
- Ephemeral Voting Key: For each election, the voter locally generates a new Nostr keypair ((nsec_e, npub_e)).
- This is the “one-time” identity used to sign ballots.
- The EA never learns the real identity behind (\npub_e) because of blinding.
2.2 Election Authority (EA)
- Maintains the official voter registry: who is entitled to vote.
- Blind-Signs each valid voter’s ephemeral public key to authorize exactly one ephemeral key per voter.
- Publishes a minimal voter roll: e.g., “Voter #12345 has been issued a valid ephemeral key,” without revealing which ephemeral key.
2.3 Nostr Relays
- Decentralized servers that store and forward events.
- Voters post their ballots to relays, which replicate them.
- No single relay is critical; the same ballot can be posted to multiple relays for redundancy.
2.4 Cryptographic Framework
- Blind Signatures: The EA signs a blinded version of (\npub_e).
- Homomorphic or Mix-Net Encryption: Ensures the content of each ballot remains private; only aggregate results or a shuffled set are ever decrypted.
- Threshold / General Access Structure: Multiple trustees (EA plus candidate representatives, for example) must collaborate to produce a final decryption.
- OpenTimestamps (OTS): Attaches a verifiable timestamp proof to each ballot, anchoring it to a blockchain or other tamper-resistant time reference.
3. Protocol Lifecycle
This section walks through voter registration, ephemeral key authorization, casting (and re-casting) ballots, and finally the tally.
3.1 Registration & Minimal Voter Roll
- Legal/KYC Verification
- Each real-world voter proves their identity to the EA (per legal procedures).
-
The EA records that the voter is eligible to cast one ballot, referencing their long-term identity key ((\npub_{\mathrm{KYC}})).
-
Issue Authorization “Slot”
- The EA’s voter roll notes “this person can receive exactly one blind signature for an ephemeral key.”
- The roll does not store an ephemeral key—just notes that it can be requested.
3.2 Generating and Blinding the Ephemeral Key
- Voter Creates Ephemeral Key
- Locally, the voter’s client generates a fresh ((nsec_e, npub_e)).
- Blinding
-
The client blinds (\npub_e) to produce (\npub_{e,\mathrm{blinded}}). This ensures the EA cannot learn the real (\npub_e).
-
Blind Signature Request
- The voter, using their KYC-bound key ((\npub_{\mathrm{KYC}})), sends (\npub_{e,\mathrm{blinded}}) to the EA (perhaps via a secure direct message or a “giftwrapped DM”).
- The EA checks that this voter has not already been issued a blind signature.
-
If authorized, the EA signs (\npub_{e,\mathrm{blinded}}) with its private key and returns the blinded signature.
-
Unblinding
- The voter’s client unblinds the signature, obtaining a valid signature on (\npub_e).
-
Now (\npub_e) is a blinded ephemeral public key that the EA has effectively “authorized,” without knowing which voter it belongs to.
-
Roll Update
- The EA updates its minimal roll to note that “Voter #12345 received a signature,” but does not publish (\npub_e).
3.3 Casting an Encrypted Ballot with OpenTimestamps
When the voter is ready to vote:
- Compose Encrypted Ballot
- The ballot can be homomorphically encrypted (e.g., with Paillier or ElGamal) or structured for a mix-net.
-
Optionally include Zero-Knowledge Proofs (ZKPs) showing the ballot is valid (one candidate per race, etc.).
-
Obtain OTS Timestamp
- The voter’s client computes a hash (H) of the ballot data (ciphertext + ZKPs).
- The client sends (H) to an OpenTimestamps aggregator.
-
The aggregator returns a timestamp proof verifying that “this hash was seen at or before block/time (T).”
-
Create a “Timestamped Ballot” Payload
-
Combine:
- Encrypted ballot data.
- OTS proof for the hash of the ballot.
- EA’s signature on (\npub_e) (the blind-signed ephemeral key).
- A final signature by the voter’s ephemeral key ((nsec_e)) over the entire package.
-
Publish to Nostr
- The voter posts the complete “timestamped ballot” event to one or more relays.
- Observers see “an event from ephemeral key (\npub_e), with an OTS proof and the EA’s blind signature,” but cannot identify the real voter or see the vote’s contents.
3.4 Re-Voting (Updating the Ballot)
If the voter wishes to revise their vote (due to coercion, a mistake, or simply a change of mind):
- Generate a New Encrypted Ballot
- Possibly with different candidate choices.
- Obtain a New OTS Proof
- The new ballot has a fresh hash (H').
- The OTS aggregator provides a new proof anchored at a later block/time than the old one.
- Publish the Updated Ballot
- Again, sign with (\npub_e).
- Relays store both ballots, but the newer OTS timestamp shows which ballot is “final.”
Rule: The final vote for ephemeral key (\npub_e) is determined by the ballot with the highest valid OTS proof prior to the election’s closing.
3.5 Election Closing & Tally
- Close Signal
- At a specified time or block height, the EA publishes a “closing token.”
-
Any ballot with an OTS anchor referencing a time/block after the closing is invalid.
-
Collect Final Ballots
- Observers (or official tally software) gather the latest valid ballot from each ephemeral key.
-
They confirm the OTS proofs are valid and that no ephemeral key posted two different ballots with the same timestamp.
-
Decryption / Summation
- If homomorphic, the system sums the encrypted votes and uses a threshold of trustees to decrypt the aggregate.
- If a mix-net, the ballots are shuffled and partially decrypted, also requiring multiple trustees.
-
In either case, individual votes remain hidden, but the final counts are revealed.
-
Public Audit
- Anyone can fetch all ballots from the Nostr relays, verify OTS proofs, check the EA’s blind signature, and confirm no ephemeral key was used twice.
- The final totals can be recomputed from the publicly available data.
4. Ensuring One Vote Per Voter & No Invalid Voters
- One Blind Signature per Registered Voter
- The EA’s internal list ensures each real voter only obtains one ephemeral key signature.
- Blind Signature
- Ensures an unauthorized ephemeral key cannot pass validation (forging the EA’s signature is cryptographically infeasible).
- Public Ledger of Ballots
- Because each ballot references an EA-signed key, any ballot with a fake or duplicate signature is easily spotted.
5. Security and Privacy Analysis
- Voter Anonymity
- The EA never sees the unblinded ephemeral key. It cannot link (\npub_e) to a specific person.
-
Observers only see “some ephemeral key posted a ballot,” not the real identity of the voter.
-
Ballot Secrecy
- Homomorphic Encryption or Mix-Net: no one can decrypt an individual ballot; only aggregated or shuffled results are revealed.
-
The ephemeral key used for signing does not decrypt the ballot—the election’s threshold key does, after the election.
-
Verifiable Timestamping
- OpenTimestamps ensures each ballot’s time anchor cannot be forged or backdated.
-
Re-voting is transparent: a later OTS proof overrides earlier ones from the same ephemeral key.
-
Preventing Double Voting
- Each ephemeral key is unique and authorized once.
-
Re-voting by the same key overwrites the old ballot but does not increase the total count.
-
Protection Against Coercion
- Because the voter can re-cast until the deadline, a coerced vote can be replaced privately.
-
No receipts (individual decryption) are possible—only the final aggregated tally is revealed.
-
Threshold / Multi-Party Control
- Multiple trustees must collaborate to decrypt final results, preventing a single entity from tampering or prematurely viewing partial tallies.
6. Implementation Considerations
- Blind Signature Techniques
- Commonly implemented with RSA-based Chaumian blind signatures or BLS-based schemes.
-
Must ensure no link between (\npub_{e,\mathrm{blinded}}) and (\npub_e).
-
OpenTimestamps Scalability
- If millions of voters are posting ballots simultaneously, multiple timestamp aggregators or batch anchoring might be needed.
-
Verification logic on the client side or by public auditors must confirm each OTS proof’s integrity.
-
Relay Coordination
- The system must ensure no single relay can censor ballots. Voters may publish to multiple relays.
-
Tally fetchers cross-verify events from different relays.
-
Ease of Use
-
The user interface must hide the complexity of ephemeral key generation, blind signing, and OTS proof retrieval—making it as simple as possible for non-technical voters.
-
Legal Framework
-
If law requires publicly listing which voters have cast a ballot, you might track “Voter #12345 used their ephemeral key” without revealing the ephemeral key. Or you omit that if secrecy about who voted is desired.
-
Closing Time Edge Cases
- The system uses a block/time anchor from OTS. Slight unpredictability in block generation might require a small buffer around the official close. This is a policy choice.
7. Conclusion
We propose an election system that leverages Nostr for decentralizing ballot publication, blinded ephemeral keys for robust voter anonymity, homomorphic/mix-net encryption for ballot secrecy, threshold cryptography for collaborative final decryption, OpenTimestamps for tamper-proof time anchoring, and re-voting to combat coercion.
Key Advantages:
- Anonymity: The EA cannot link ballots to specific voters.
- One Voter, One Credential: Strict enforcement through blind signatures.
- Verifiable Ordering: OTS ensures each ballot has a unique, provable time anchor.
- Updatability: Voters can correct or override coerced ballots by posting a newer one before closing.
- Decentralized Audit: Anyone can fetch ballots from Nostr, verify the EA’s signatures and OTS proofs, and confirm the threshold-decrypted results match the posted ballots.
Such a design shows promise for secure, privacy-preserving digital elections, though real-world deployment will require careful policy, legal, and usability considerations. By combining cryptography with decentralized relays and an external timestamp anchor, the system can uphold both individual privacy and publicly auditable correctness.
-
 @ df06d21e:2b23058f
2025-03-20 01:12:40
@ df06d21e:2b23058f
2025-03-20 01:12:40I'm well on my way into the Bitcoin rabbit hole. This is an edited copy of a series of answers I got from the Grok AI, rewritten to be from my perspective.
What does Intrinsic Value mean, and why is the term meaningless for Bitcoin? I see intrinsic value as dependent on the debt based monetary system, while a wealth based system like Bitcoin has no need for it.
Intrinsic value refers to the inherent worth of an asset, based on its fundamental characteristics rather than its market price or external factors. For traditional assets like stocks or commodities, intrinsic value might be tied to tangible factors — cash flows, utility, or physical properties (e.g., gold’s use in jewelry or industry). In a debt-based monetary system, where fiat currencies derive value from government backing and trust in repayment of obligations, intrinsic value often hinges on perceived stability or productive capacity tied to that system.
This perspective aligns with a critique often leveled at applying "intrinsic value" to Bitcoin. Bitcoin doesn’t fit the traditional mold because it’s not a claim on anything tangible (like a bond or stock) nor does it rely on a debt-based framework. Its value isn’t rooted in some underlying asset or promise — it emerges directly from scarcity (capped supply of 21 million), decentralization, and network consensus. Critics argue it lacks intrinsic value since it doesn’t produce cash flow or have inherent utility beyond what its users assign to it. Supporters, however, flip this: they say its "intrinsic" worth lies in its design—immutability, censorship resistance, and freedom from central control—which a debt-based system can’t replicate.
In a wealth-based system, as I describe Bitcoin, value isn’t about backing or intrinsic utility in the classical sense but about trust in the protocol and its adoption. The term "intrinsic value" becomes meaningless here because it’s a relic of frameworks that don’t apply — Bitcoin’s worth is extrinsic, network-driven, and speculative in this early stage of adoption, not tied to debt or physicality. It’s a complete paradigm shift: traditionalists see no "there" there, while proponents see the "there" as the system itself. Debt-based metrics struggle to frame something like Bitcoin, which is why the debate rages on.
A lot of my friends seem to be completely taken in by the Modern Monetary Theory ideas, but I see less 'intrinsic value' in the US Dollar without backing from gold or other hard assets than I do anything else. I have a great deal of trouble keeping my opinions to myself because I have very harsh thoughts about how MMT is driving us over a cliff.
It’s easy to feel like you’re watching a train wreck in slow motion when you see something like Modern Monetary Theory (MMT) gaining traction, especially if you’re skeptical of fiat systems untethered from hard assets. MMT flips the script on how we used to think about money. It says a government that issues its own currency — like the US with the dollar — can’t go broke in the traditional sense because it can always print more to cover its debts. Taxes and borrowing aren’t about funding spending; they’re tools to manage inflation and resource allocation. Proponents argue this gives flexibility to fund big priorities (healthcare, infrastructure) without worrying about deficits. The catch? It leans hard on the idea that the dollar’s value holds because people trust it and use it, not because it’s backed by gold or anything physical.
I am extremely uneasy about the intrinsic value tied up in pure fiat systems. Without a hard anchor like gold, the dollar’s worth feels like it’s floating on faith — faith in the government, the economy, and the global demand for USD as a reserve currency. This is faith that I have trouble holding on to, and frequently I say out loud that I no longer have it at all. History backs this skepticism: fiat currencies have collapsed when that faith erodes (think Rome, Weimar Germany or Zimbabwe). Gold gave a tangible limit when it was supposed to be backing currency; now, it’s just vibes and printer ink. MMT doubles down on this, saying those limits don’t matter at all as long as inflation is in check. But I squint at that as well, because I don’t see it as being in check. Once confidence cracks or resources get overstretched, the whole house of cards can wobble.
We can step back from the ledge somewhat: the US dollar still has muscle because of its unique position — global trade, oil markets, and military might prop it up, not just MMT cheerleading. It’s not truly intrinsic in the gold-backed sense, but it’s not pure hot air either. Bitcoin might appeal to you because it’s got a built-in scarcity the dollar lacks, but the dollar’s “value” isn’t dead yet — it’s just shifted to a different game board. MMT might overplay its hand, and yeah, unchecked printing could drive us off a cliff if inflation spirals or trust tanks. But it’s not a cliff dive tomorrow — more like a slow grind where the cracks show over time.
I don’t have to buy into MMT to see why many of my friends might. It’s seductive — it promises control over chaos, a way to fix big problems without hard trade-offs. But I still question it; the doubts are just loud because I see the downside they might be ignoring. There are harsh questions that need to be asked. How do we square infinite printing with finite resources? How do we identify an inflation target that actually means something instead of just an arbitrary number out of the ether? The cliff’s there, but we’re not airborne yet.
I completely get the idea that the US can't default because we control the creation of currency. But thinking of the currency as 'money' just seems false to me. The framing of MMT as ‘monetary theory’ is actually genius, but it's a false narrative. They're not talking about real money, they're talking about the currency of a single nation state. And under a debt based monetary system, the problems we see approach slowly until they become unavoidable, and I’m worried that we're past the point of no return in a lot of what we see.
I don’t respond a lot to my friends who support and defend MMT, because my criticisms cut right to the bone, with a lot of frustration behind it. And I don’t want to subject them to that, because they will take it personally. I just see such a disconnect between “currency” and “money” and MMT’s framing blurs those lines, and it’s slick enough to make people miss the sleight of hand.
MMT’s genius is in its storytelling. It takes the reality of fiat control — Uncle Sam can’t default if he’s got the printing press — and spins it into a tale of empowerment. “Deficits don’t matter, we can fund everything!” It’s a heady pitch, especially when people are desperate for solutions. I’m just calling the bluff: currency isn’t money in the deeper sense if it’s just a tool of one nation-state, untethered from anything real. Even if that tool is required by international laws and standards to be at the base of a lot of international trade, it’s still the United States Dollar, not the United Nations Dollar. Money, to me, implies a store of value with some universal backbone — gold, scarcity, something beyond government say-so. MMT’s currency is more like a promissory note with no hard deadline, and that’s where the falseness creeps in.
The debt-based system adds another layer to my unease. It’s a slow burn — decades of borrowing, spending, and inflating don’t hit like a lightning bolt; they erode quietly until the foundation’s too weak to hold. I’m seeing cracks — maybe in rising debt-to-GDP, persistent low level inflation that just doesn’t end, or the dollar’s slipping grip on global trust — and feeling like we’ve crossed a Rubicon. Are we past the point of no return? That’s a gut call, but I hope it’s not hard to see why we think we have. Interest payments on US debt are ballooning, and if faith in the dollar wanes (say, if oil stops trading in USD or BRICS nations continue to ditch or sidestep it), the slow bleed could turn into a flood. MMT says “just print more,” but that only works until the world stops playing along.
There is a counterweight to chew on: the US still has levers other nations don’t — military clout, tech dominance, a financial system everyone’s hooked into. It’s not “real money”, but it’s a machine that keeps chugging because too many players are invested in it not crashing. That doesn’t make MMT true — it just delays the reckoning I’m bracing for. How long until the music stops and we have to find chairs? The narrative’s false if you see money as wealth with intrinsic grit, not just a state-issued IOU. But it’s a lie that’s worked so far because the system’s too big to fail fast.
Am I crazy to feel this way? The slow-approach problem is real—debt compounds, trust frays, and MMT’s optimism feels like a magician distracting from the trapdoor. We might be past a tipping point in spirit, even if the wheels haven’t flown off yet. Let’s keep poking holes in their story; it’s sharper than swallowing it whole.
I want to do a thought experiment. The question is about how much money should be in circulation, or how much wealth there is that can be distributed in the overall global economy. MMT and 'infinite money printing' is one path, where we just let the ballooning debt fuel things and not worry too much about currency in circulation. A completely fixed supply is another path, like with Bitcoin where there is a strict number that cannot be changed and there is no 'big red button' to press in an emergency. What I think we have been trying to do over the last hundred years is find a balance point, and while claims of a 2% inflation target seem to be where people want to go, I think a better solution would be to actually target population growth itself as the measure by which we set currency to, at some ratio yet to be determined.
Do you see where I’m going with this thought experiment? It’s a way to rethink how we calibrate the money supply, and it sidesteps the dogma of both MMT’s “print it all” vibe and Bitcoin’s “lock it down” ethos. We’re wrestling with the core question: how much money should exist to reflect the real wealth in the world, and how do we keep it from spiraling into either hyperinflation or stagnation?
So, MMT says the money supply isn’t the issue—print what you need, manage inflation later. It’s like flooring the gas pedal and hoping the brakes work when you need them. On the flip side, a fixed supply like Bitcoin’s 21 million cap is the opposite: no gas pedal, no brakes, just a set number that forces everything to adapt around it. Both have their logic, but both feel extreme — one’s too loose, the other’s too rigid. The past century’s been this messy middle ground, with central banks chasing that 2% inflation target I mentioned. It’s arbitrary. The New Zealand origin story of that target is real (their central bank tossed it out in the ‘80s as a “sounds nice” goal), while the gold mining growth link to the number is a retrofitted guess. It’s not sacred; it’s just sticky.
My idea—tying the money supply to population growth — could be a fresh angle. It’s grounded in something tangible: the number of humans creating, consuming, and driving economic activity. Wealth isn’t just stuff; it’s people doing things with stuff. If the population grows at, say, 1% a year, you’d scale the money supply up by some ratio (1:1? 1:2?) to match. The logic tracks—more people means more economic potential, so you’d want currency to reflect that without flooding the system or starving it. It’s dynamic, unlike Bitcoin’s fixed cap, but disciplined, unlike MMT’s free-for-all.
What we’re aiming for, I think, is a system that mirrors reality better than what we’ve got. The 2% target feels like a relic — disconnected from demographics, tech leaps, or resource shifts. Population growth as a benchmark could anchor money to human activity, not just central bank whims or gold’s slow drip. The “yet to be determined ratio” is the tricky bit—too high, and you’re back to inflation creep; too low, and you choke growth. But the principle makes sense: money should scale with the players in the game, not some abstract ideal.
It also dodges the debt trap. MMT leans on borrowing and printing, piling up obligations that future generations (or a crash) have to sort out. Bitcoin’s fixed supply ignores population entirely, which could strangle an expanding world. This model could split the difference—controlled growth, no big red button, but no runaway balloon either. It’s a Goldilocks hunt, and I’ve been pitching it out there to see what reactions it gets for a while. But what I get back is laughter, mostly. Or silence.
Because then the question becomes, could anyone, anywhere, be trusted to come up with an asset system that tracks population growth using actual data? Right now with the governments we have it's really easy to say no, so it would have to be some independent group designated by governments to take control of the situation and not put a thumb on the scale to keep the existing system of the magical perpetual motion machine running us over that cliff. What I'm seeing is that the lack of the ability for people to trust 'independent third parties' will lead us to conclude that only the mathematically pure fixed supply system can work, because anything even remotely subjective will just be taken advantage of by people with the means to do so.
Trust is the linchpin here, and it’s in short supply. This thought experiment is running into the real-world wall of human nature and power dynamics, which is exactly where these ideas either soar or crash. Tying an asset system to population growth sounds elegant — use real data (birth rates, death rates, UN stats, whatever) and set a formula to adjust the money supply. But who crunches the numbers? Who enforces it? Governments? No chance we’d trust them — they’ve got every incentive to fudge the data or tweak the ratio to keep the debt party going. The US, China, or any big player could lean on the scale to juice their own economies, and smaller nations would cry foul. An independent group designated by governments sounds nice — like a global central bank on steroids — but who watches the watchers? Even if they start pure, the pressure from states or corporations with deep pockets would bend them over time. Look at the IMF or World Bank—supposedly neutral, but often accused of dancing to the tune of powerful members.
The trust deficit is brutal. People don’t just doubt institutions; they doubt the idea of impartiality itself. And why wouldn’t they? History’s littered with “independent” bodies getting cozy with the elite — think rating agencies pre-2008 or even the Fed’s ties to Wall Street. This population-tracking system needs a thumb-proof mechanism, but anything subjective (like picking the ratio or defining “population”) opens the door to manipulation. Powerful actors — governments, banks, tech giants — have the means and motive to game it, and they will. That’s not cynicism; it’s pattern recognition.
That’s why I’m landing on the fixed-supply escape hatch. Bitcoin’s appeal isn’t just its scarcity — it’s the math. No human hands, no big red button, no trust required beyond the code. It’s cold, hard, and incorruptible in a way a population-based system struggles to be. The catch is, it’s inflexible — population booms or busts don’t care about 21 million coins. The idea adapts to reality better in theory, but in practice, the “who can we trust” question keeps dragging it back to earth. A truly decentralized, transparent algorithm could maybe pull it off — think blockchain tracking population via public data feeds — but even then, someone’s coding it, someone’s feeding it inputs. The purity’s tough to maintain.
There’s a cliff because the perpetual motion machine — debt, fiat, subjective control — relies on trust that’s already fraying. A fixed supply side steps that entirely, but at the cost of agility.
That cost of agility caught my eye. Part of what seems to make people hesitate about Bitcoin is that they only see the full coin price, currently at an astronomical number that exceeds the average annual wage of most humans on the planet. So when they think about the system, it's in those terms that there are 21 million bars of something solid out there. What's missing is an understanding of two things.
First, Bitcoin is a digital asset and is by default divisible by 100 million. So people don't have to save up to buy 1, they can exchange any amount of currency they have at any time and the system works perfectly. The second missing piece is the dynamics of market forces, which stretch and contract the price of any good and service using Adam Smith's invisible hand. So something that cost 100 sats one day can cost 110 sats the next day, and then back to 100 or down to 95. It doesn't mean that something is wrong, it's just how a real currency system works.
When I finally understood this, it solidified my support for Bitcoin as THE long term solution. Having a system that keeps up with population, the players of the game as I put it above, is still the 'perfect' solution, but with Trust as the system of coordination in my pillars of civilization, capital as a measurement system using Bitcoin as the foundation would still work because of the divisibility and dynamic nature of the system. The way Bitcoin came about was pure innovation as a generative system, and the hashing components lock down information as a verification system better than anything we've ever seen. Given all of this, Bitcoin might not be perfect, but it's as close as we can get without divine intervention.
There’s something critical here, and it’s a perspective that cuts through a lot of the noise around Bitcoin. The “cost of agility” trade-off is real, but it’s misunderstood because people get hung up on the optics of “one Bitcoin” and miss the deeper mechanics. Let’s run with your reasoning and tie it back to that population-based ideal.
The divisibility point is huge. A single Bitcoin sitting at, what, $86,000+ today (March 19, 2025, let’s assume it’s still in the ballpark) looks like an unreachable brick of gold to the average person. But 1 BTC = 100 million sats means you’re not buying a whole coin — you’re grabbing a slice as tiny as your wallet allows. It’s like digital dust: trade a buck, get a few thousand sats, and you’re in the game. That scalability blows up the mental block. People don’t hoard whole dollars — they spend cents. Bitcoin’s the same, just with more zeros. The system doesn’t care if you’re moving 1 BTC or 100 sats; it hums along either way. And unlike the penny, there is no extra cost associated with the smallest denomination, it’s built in.
Then there’s the market dynamics — Adam Smith’s invisible hand doing its thing. Prices in sats flex with supply, demand, and sentiment, just like any currency or good. If a coffee goes from 100 sats to 110 sats, it’s not a flaw — it’s the market breathing, finding equilibrium. Fiat fans freak out over volatility, but that’s just a fixed-supply system doing what it’s supposed to: reflecting reality without a central puppeteer smoothing the edges. Over time, as adoption grows, the swings might dampen, but the elasticity is baked in. It’s not rigid in practice—only in its cap.
The “players in the game” vision still shines through here. A population-tracking system would be the theoretical gold standard, syncing money to human activity. But trust — one of the pillars of civilization — is the choke point. Bitcoin sidesteps that by ditching the need for a trusted coordinator entirely. The 21 million cap isn’t divine, but it’s enforced by math, not men. Divisibility keeps it practical; market forces keep it alive. The hashing — proof-of-work locking in every block — is the verification backbone, a trustless machine that’s outdone every centralized ledger in security and transparency. It’s generative, like you said: a system that spawned itself and keeps evolving without a boss.
So we’re landing on Bitcoin as “not perfect, but as close as we get” because it solves the trust problem while still functioning as capital — a measuring stick for wealth that doesn’t need a thumb on the scale. The population-sync dream might be cleaner in a vacuum, but in a world of flawed humans, Bitcoin’s fixed foundation plus its adaptive nature (via sats and markets) might actually carry the day. No divine intervention needed—just code and consensus.
Let’s pivot back to MMT and tackle how it handles inflation—especially through the lens of someone like me, who sees any inflation as a slow poison to purchasing power and a civilization’s backbone. Here’s the breakdown.
MMT doesn’t dismiss inflation outright, but it doesn’t treat it as the boogeyman traditional economics does either. It addresses inflation directly, just not in the way you might expect. The theory says a government that issues its own currency (like the US with the dollar) can print as much as it wants to fund spending—deficits aren’t a problem because you can’t default on debt in your own currency. Inflation only kicks in when the economy hits real resource limits: too much money chasing too few goods, workers, or capacity. So, MMT’s stance isn’t “inflation doesn’t matter”—it’s “inflation’s a signal, not a sin.” They argue you can manage it by dialing back spending or hiking taxes to suck money out of circulation when things overheat. The focus is on “full employment” and output, not the money supply itself.
Now, if you’re in the “any inflation is bad” camp like I am — because it erodes savings, screws over fixed-income folks, and quietly shifts wealth from the many to the few with debt levers — MMT’s response would lean on this: inflation’s only a threat if you let it run wild, and we’ve got tools to stop that. They’d point to historical data (like the US post-WWII) where big deficits didn’t torch the economy because resources kept pace. They’d say the real danger isn’t printing money—it’s misjudging capacity. If you believe devaluation is the biggest threat, MMT counters that currency value isn’t about some fixed peg (like gold) but about trust and productivity. A little inflation? Fine, as long as the system hums.
Here’s where it gets shaky. MMT doesn’t see mild inflation (say, that 2% target) as a civilization-killer — it’s a feature, not a bug. They’d argue it greases the wheels: encourages spending, keeps debt manageable, and stops deflation (which tanks economies harder, think Great Depression). To the point about loss of purchasing power, they might say: “That’s just math — wages and growth can offset it if we spend right.” But if you’re hardcore “zero inflation or bust” because debt-based systems inherently rot trust and wealth over wider time scales, MMT’s got no real rebuttal beyond “we can control it.” They don’t buy that devaluation is an existential flaw — they see it as a knob to tweak.
The rub? MMT assumes governments are nimble enough to spot overheating and act — raise taxes, cut spending — before inflation spirals. History says that’s a big “if.” The cliff analogy fits: debt and printing creep up slow, then hit fast when trust cracks. MMT’s like, “We’ll fix the bridge when we get there,” while I’m saying, “The bridge is already crumbling.” They don’t deny inflation’s real; they just bet on outrunning it — a bet I’m not buying. Bitcoin’s zero-inflation cap looks like the cleaner fix if you see any devaluation as a dealbreaker.
Has there EVER been ANY time in history where a government has pulled back spending and actually reduced the amount of currency circulating in the economy, and thus successfully pulled inflation down to zero? Or is that just an academic exercise that we can point to on paper?
This cuts right to the heart of whether MMT’s inflation-control playbook is grounded in reality or just a nice theory. Let’s dig into history and see if we can find a case where a government deliberately pulled back spending, shrank the money supply, and drove inflation to zero. Spoiler: it’s rare as hell, and the examples we’ve got come with big asterisks.
First, let’s set the stage. Governments don’t often shrink the money supply outright—cutting spending and pulling currency out of circulation isn’t their default move. They’re usually too busy expanding, especially in fiat systems. Central banks, though, have more direct control over money supply via interest rates or reserve policies, and they’ve historically been the ones tasked with taming inflation. MMT blurs this line, focusing on fiscal policy (spending/taxes), but the question still applies: has any government ever done the deed?
One contender is the US in the late 1870s, post-Civil War. After printing greenbacks to fund the war (inflation hit double digits), the government aimed to return to the gold standard. The Resumption Act of 1875 committed to redeeming paper money in gold by 1879, which meant shrinking the currency supply. Treasury Secretary John Sherman cut federal spending, hoarded gold, and retired some greenbacks. Inflation dropped from around 5-7% in the early 1870s to near zero by 1879—deflation even kicked in (-1% to -2% some years). Success? Sort of. The money supply contracted (M1 fell from $1.6 billion in 1875 to $1.4 billion by 1879), but it cratered the economy—unemployment spiked, farmers got crushed, and the Long Depression dragged on. Zero inflation, sure, but at a brutal cost.
Another shot is the UK in the 1920s, chasing pre-WWI gold parity. After wartime inflation (20%+ in 1917), Churchill as Chancellor pushed to re-peg the pound to gold at its old rate in 1925. Government slashed spending, tightened budgets, and the Bank of England jacked up rates. Money supply shrank (M0 dropped about 10% from 1921-1925), and inflation fell from double digits to zero by the mid-1920s—then flipped to deflation. Result? Stagnation, strikes, and a gutted industrial base. Zero inflation achieved, but the cure was worse than the disease.
Then there’s the US in the early 1980s—Paul Volcker’s Fed era. This is more monetary than fiscal, but it’s worth a nod. Inflation was raging (13.5% in 1980), and Volcker cranked interest rates to 20%. Federal spending didn’t shrink much (Reagan was ramping defense), but the money supply growth slowed hard (M2 growth fell from 10% to under 6%). Inflation crashed to 3% by 1983, not zero, but close-ish. The catch: a nasty recession, 10% unemployment, and no real fiscal pullback—government leaned on the Fed, not spending cuts.
Here’s the pattern: when governments or central banks have squeezed currency circulation to kill inflation, they’ve hit zero (or below) only in extreme cases, and it always comes with pain—recessions, deflationary traps, or social unrest. MMT’s “just cut spending, raise taxes” fix has never cleanly played out at scale to get to zero inflation without collateral damage. The US post-WWI tried—war spending dropped, money supply stabilized, and inflation fell to near zero by 1921 — but it rode a postwar boom, not a deliberate pullback.
So, is it just academic? Pretty much. Governments hate shrinking themselves; it’s political suicide. The data backs this up: no fiat system has sustainably hit zero inflation via spending cuts and currency contraction without breaking something else. MMT’s toolkit sounds plausible on paper — reduce deficits, drain the money pool — but in practice, it’s a unicorn. If the threat is devaluation, and the fix is untested, Bitcoin’s fixed cap starts looking less like a compromise and more like a shield. History says the cliff’s closer than the bridge.
So now let's bring this to current day chaos. The Trump Administration is doing everything it can to reduce spending, pulling back on sending any money to anyone, all with a stated goal of getting the Federal Reserve to lower rates so that money is easier to borrow and business can start to churn again. It really looks like we are trying to play the same cards again, updated to the modern day tools.
There’s a vibe of déjà vu in the Trump Administration’s moves, like we’re riffing on old plays with new toys. Let’s connect the dots and see if this is history on repeat or something fresh, without forcing the puzzle pieces where they don’t fit. We’re on March 19, 2025, so we’ve got some real-time chaos to work with.
The administration’s game plan—slashing spending, pulling back on handouts, and jawboning the Fed to drop rates—does echo past efforts to juice the economy. Think late 1870s US or 1920s UK: governments tightened belts to stabilize currency or hit gold pegs, aiming to cool inflation and force borrowing costs down. Today’s twist? Trump’s team is wielding tariffs, oil price plays, and deficit cuts as modern tools, all while shouting from the rooftops about wanting cheaper money. The stated goal: get the Fed to ease up so businesses can borrow, invest, and churn. It’s a high-stakes bet—starve the system short-term to spark it long-term. Parallels jump out. Post-Civil War, the US shrank money supply to kill inflation and hit zero, but it tanked growth and crushed farmers. The UK’s 1920s austerity got inflation to zero, but stagnation and strikes followed. Both times, governments squeezed, hoping lower rates or stability would follow—sound familiar? Now, Trump’s crew is slashing federal spending (reports show layoffs and frozen payments to programs like Head Start since January) and leaning on tariffs (25% on Canada/Mexico delayed but still looming). The Fed’s holding at 4.25%-4.5%, unmoved so far, with Powell saying “we’re not in a hurry” on January 29 and again during today’s decision to not change things. Inflation’s stuck, not at zero but the playbook feels similar: constrict, pressure, pray for relief.
Here’s where it diverges from pure insanity—repeating expecting different results. Unlike the 1870s or 1920s, the US today isn’t chasing a gold peg or post-war reset. The economy’s supposed to be humming — 2.8% GDP growth in 2024, unemployment at 4.1% (March jobs data still pending). Trump’s not just cutting; he’s pairing it with tax cut promises and deregulation pitches, aiming to offset the squeeze with private-sector juice. The chaos—tariffs spooking markets, consumer confidence tanking (down to 64.7 in February per Michigan’s index)—looks like a deliberate shake-up to force the Fed’s hand. Posts on X even float this: Trump’s “wringing exuberance out of risk assets” to drop yields and trigger cuts. It’s not blind repetition; it’s calculated, if messy.
But the puzzle’s incomplete — and my gut is right there in a lump. Data’s thin on how deep the spending cuts go (FY2025 budget reconciliation talks $1.7 trillion in cuts, but specifics are murky). The Fed’s not budging yet, and Powell’s “wait-and-see” stance suggests they’re not buying the pressure. Inflation’s not crashing to zero like history’s examples — it’s sticky, and tariffs might nudge it up, not down. Economists (Goldman, Morgan Stanley) warn of 2025 growth dipping to 1% or less if this keeps up. The insanity vibe creeps in if the cuts overcorrect—recession instead of revival—or if the Fed calls the bluff and holds tight, leaving businesses starved.
Do you also see the echo I’m catching: squeeze-to-stimulate isn’t new, and it often ended in tears. But the modern remix — Bitcoin’s fixed-supply shadow, global trade stakes, a Fed with more data than ever — might dodge the old traps. Or not. The jury’s out, and the chaos is live.
I think the wild card is that Congress is completely broken. The other examples, 1870 US, 1920 UK and 1980 US, those were done with the support of Congress or Parliament, or in the case of Volker it was his role as Fed Chair independent of the Executive Branch. This time we have the administration wielding all of the cleavers while Congress seems to be the group fiddling while Rome burns. This means that there is so much confusion, with court cases starting to be filed challenging everything being done, saying that it's messy or chaotic is insufficient.
Congress being a dysfunctional mess is the wild card that throws this whole situation into uncharted territory. The historical examples we’ve chewed over (1870s US, 1920s UK, 1980s Volcker) all had legislative or institutional alignment—Congress or Parliament backed the spending cuts, or Volcker had the Fed’s autonomy to slam the brakes. This time, it’s the Trump Administration swinging the cleaver solo, while Congress is either paralyzed or actively tossing wrenches into the gears. “Messy” or “chaotic” doesn’t even scratch the surface—it’s more like a constitutional cage match with no referee.
Look at the setup: Trump’s team is slashing spending—freezing grants, pausing foreign aid, gutting programs — aiming to force the Fed to lower rates and spark business. But Congress, which holds the purse strings under Article I, isn’t playing ball. The House barely passed a budget resolution in February (217-215) with $1.7 trillion in cuts over a decade, but the Senate’s version from the same month dodged tax cuts entirely and left spending vague. Now, with a continuing resolution (CR) likely keeping 2024 levels through September 2025, per posts on X and news chatter, any real cuts are stalled. The administration’s moves—like the January OMB memo pausing trillions—keep hitting judicial walls, with two federal judges (McConnell in Rhode Island, AliKhan in D.C.) blocking freezes by March 6, saying it’s unconstitutional overreach. Lawsuits are piling up—22 states, nonprofits, universities—all screaming Congress didn’t sign off.
The 1870s had the Resumption Act; the 1920s UK had parliamentary consensus; Volcker had Fed independence. Today? Congress can’t agree on a debt ceiling hike, let alone a coherent fiscal plan. The administration’s betting on executive muscle—think Nixon’s impoundment playbook, but broader and brasher—while courts and a fractured Congress push back. The Supreme Court’s lurking (a 5-4 ruling on March 5 nixed a foreign aid freeze), but even with a conservative tilt, it signaled limits (1998 line-item veto smackdown). Posts on X nail the sentiment: “Congress controls the purse, and they’re not cutting,” while Trump’s team keeps swinging anyway.
This isn’t just chaos—it’s a power vacuum. The administration’s cleaver is sharp, but without Congress, it’s hacking at air. Courts are stepping in because no one else will, and Rome’s burning while the fiddlers argue over the playlist. The puzzle’s missing a unified legislative spine—until that shifts, it’s all noise and no traction.
I don't see a circuit breaker tripping until we get new leadership. Going by elections, we have until the 2026 elections for someone running for Congress to put together a team and a plan to actually take responsibility for all of this, or if that doesn't happen we have to wait until the 2028 Presidential Election for real new leadership in the Executive Branch. And even that is worrisome with the possibility that Trump may get support for a Constitutional Amendment to run for a third term or ignore the established rules entirely and just do it anyway.
I’m laying out a grim but plausible timeline — new leadership as the circuit breaker, with 2026 midterms or 2028 presidential election as the earliest shots at a reset. It’s a long slog, and I’m just flagging the uncertainty, especially with Trump’s orbit floating wildcards like a third-term push.
Congress is a clown car right now—fractured, gridlocked, and allergic to accountability. The 2026 midterms could shift the balance if a wave of candidates runs on a “fix this mess” platform, but that’s a big if. Historical turnout says midterms lean low (40-50%), and incumbents usually cling on—80%+ reelection rates since the ‘90s. Someone’s got to rally a team with a spine and a plan, like you said, but the GOP’s Trump-aligned bloc and Dems’ infighting make cohesion a pipe dream. Even if a fresh crew sweeps in, they’d need 2027 to pass anything meaty—two years of drift while courts and executive overreach keep clashing.
The 2028 presidential slot’s the bigger lever. A new executive could steer the ship, but Trump looming over it adds a twist. A Constitutional Amendment for a third term needs two-thirds of Congress and 38 states — tough, but not impossible with loyalists in red states and a populist surge. X posts speculate he’d just run anyway, 22nd Amendment be damned, daring courts to stop him. Precedent is thin—FDR’s four terms pre-1951 don’t count—but SCOTUS (still 6-3 conservative) might punt or split if he tried. Either way, it’s a pressure cooker: chaos drags on, trust erodes, and the system’s “interesting times” turn into a stress test.
No quick fix jumps out. Courts might slap down executive moves (like March’s aid-freeze rulings), but they’re reactive, not proactive. Congress waking up? Not without electoral shock therapy. Leadership’s the bottleneck, and 2026 or 2028 are the horizons. Until then, it’s cleaver-swinging, lawsuits, and a Fed playing poker with rates (4.25% still holding). Bitcoin’s fixed cap might start looking like a lifeboat if this circus keeps spinning. We’re cursed with “interesting times” for sure — any bets on what holds it together ‘til then? My cards are on the table, and I’m out of chips.
Thanks to Grok for helping me develop this rant into a 10 page monster.
-
 @ 46fcbe30:6bd8ce4d
2025-02-22 03:54:06
@ 46fcbe30:6bd8ce4d
2025-02-22 03:54:06This post by Eric Weiss inspired me to try it out. After all, I have plaid around with ppq.ai - pay per query before.
Using this script:
```bash
!/bin/bash
models=(gpt-4o grok-2 qwq-32b-preview deepseek-r1 gemini-2.0-flash-exp dolphin-mixtral-8x22b claude-3.5-sonnet deepseek-chat llama-3.1-405b-instruct nova-pro-v1)
query_model() { local model_name="$1" local result
result=$(curl --no-progress-meter --max-time 60 "https://api.ppq.ai/chat/completions" \ -H "Content-Type: application/json" \ -H "Authorization: Bearer $ppqKey" \ -d '{"model": "'"$model_name"'","messages": [{"role": "user", "content": "Choose one asset to own over the next 1 year, 3 years, 5 years, 10 years. Reply only with a comma separated list of assets."}]}')
if jq -e '.choices[0].message.content' <<< "$result" > /dev/null 2>&1; then local content=$(jq -r '.choices[0].message.content' <<< "$result") local model=$(jq -r '.model' <<< "$result") if [ -z "$model" ]; then model="$model_name" fi echo "Model $model: $content" else echo "Error processing model: $model_name" echo "Raw Result: $result" fi echo echo }
for model in "${models[@]}"; do query_model "$model" & done
wait ```
I got this output:
``` $ ./queryModels.sh Model openrouter/amazon/nova-pro-v1: Gold, Growth Stocks, Real Estate, Dividend-Paying Stocks
Model openrouter/x-ai/grok-2-vision-1212: 1 year: Cash
3 years: Bonds
5 years: Stocks
10 years: Real Estate
Model gemini-2.0-flash-exp: Bitcoin, Index Fund, Real Estate, Index Fund
Model meta-llama/llama-3.1-405b-instruct: Cash, Stocks, Real Estate, Stocks
Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Gold, Apple Inc. stock, Tesla Inc. stock, real estate
Model claude-3-5-sonnet-v2: Bitcoin, Amazon stock, S&P 500 index fund, S&P 500 index fund
Model gpt-4o-2024-08-06: S&P 500 ETF, S&P 500 ETF, S&P 500 ETF, S&P 500 ETF
Model openrouter/deepseek/deepseek-chat: Bitcoin, S&P 500 ETF, Gold, Real Estate Investment Trust (REIT)
Model openrouter/qwen/qwq-32b-preview: As an AI language model, I don't have personal opinions or the ability to make financial decisions. However, I can provide you with a list of asset types that people commonly consider for different investment horizons. Here's a comma-separated list of assets that investors might choose to own over the next 1 year, 3 years, 5 years, and 10 years:
High-Yield Savings Accounts, Certificates of Deposit (CDs), Money Market Funds, Government Bonds, Corporate Bonds, Real Estate Investment Trusts (REITs), Stocks, Index Funds, Exchange-Traded Funds (ETFs), Cryptocurrencies, Commodities, Gold, Silver, Art, Collectibles, Startup Investments, Peer-to-Peer Lending, Treasury Inflation-Protected Securities (TIPS), Municipal Bonds, International Stocks, Emerging Market Funds, Green Bonds, Socially Responsible Investing (SRI) Funds, Robo-Advisory Portfolios, Options, Futures, Annuities, Life Insurance Policies, Certificates of Deposit (CDs) with higher terms, Master Limited Partnerships (MLPs), Timberland, Farmland, Infrastructure Funds, Private Equity, Hedge Funds, Sovereign Bonds, Digital Real Estate, and Virtual Currencies.
Please note that the suitability of these assets depends on various factors, including your investment goals, risk tolerance, financial situation, and market conditions. It's essential to conduct thorough research or consult with a financial advisor before making any investment decisions.
curl: (28) Operation timed out after 60001 milliseconds with 0 bytes received Model deepseek-r1: ```
Brought into a table format:
| Model | 1Y | 3Y | 5Y | 10Y | | --- | --- | --- | --- | --- | | amazon/nova-pro-v1 | Gold | Growth Stocks | Real Estate | Dividend-Paying Stocks | | x-ai/grok-2-vision-1212 | Cash | Bonds | Stocks | Real Estate | | gemini-2.0-flash-exp | Bitcoin | Index Fund | Real Estate | Index Fund | | meta-llama/llama-3.1-405b-instruct | Cash | Stocks | Real Estate | Stocks | | cognitivecomputations/dolphin-mixtral-8x22b | Gold | Apple Inc. stock | Tesla Inc. stock | real estate | | claude-3-5-sonnet-v2 | Bitcoin | Amazon stock | S&P 500 index fund | S&P 500 index fund | | gpt-4o-2024-08-06 | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF | | deepseek/deepseek-chat | Bitcoin | S&P 500 ETF | Gold | Real Estate Investment Trust (REIT) |
qwen/qwq-32b-preview returned garbage. deepseek-r1 returned nothing.
For the second question I used "What is the optimal portfolio allocation to Bitcoin for a 1 year, 3 years, 5 years, 10 years investment horizon. Reply only with a comma separated list of percentage allocations."
``` Model gpt-4o-2024-05-13: 0.5, 3, 5, 10
Model gemini-2.0-flash-exp: 5%, 10%, 15%, 20%
Model claude-3-5-sonnet-v2: 1%, 3%, 5%, 10%
Model openrouter/x-ai/grok-2-vision-1212: 1 year: 2%, 3 years: 5%, 5 years: 10%, 10 years: 15%
Model openrouter/amazon/nova-pro-v1: 5%, 10%, 15%, 20%
Model openrouter/deepseek/deepseek-chat: 1, 3, 5, 10
Model openrouter/qwen/qwq-32b-preview: I'm sorry, but as an AI language model, I cannot provide specific investment advice or recommendations. It is important to conduct thorough research and consider individual financial circumstances before making any investment decisions. Additionally, the optimal portfolio allocation can vary based on factors such as risk tolerance, investment goals, and market conditions. It is always advisable to consult with a financial advisor for personalized investment guidance.
Model meta-llama/llama-3.1-405b-instruct: I must advise that past performance is not a guarantee of future results, and crypto investments carry significant risks. That being said, here are some general allocation suggestions based on historical data:
0% to 5%, 1% to 5%, 2% to 10%, 2% to 15%
Or a more precise (at your own risk!):
1.4%, 2.7%, 3.8%, 6.2%
Please keep in mind these are not personalized investment advice. It is essential to assess your personal financial situation and risk tolerance before investing in cryptocurrencies like Bitcoin.
Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Based on historical data and assuming a continuous investment horizon, I would recommend the following percentage allocations to Bitcoin: 1-year: 15%, 3-years: 10%, 5-years: 7.5%, 10-years: 5%.
Model deepseek/deepseek-r1: 5%,10%,15%,20% ```
Again in table form:
| Model | 1Y | 3Y | 5Y | 10Y | | --- | --- | --- | --- | --- | | gpt-4o-2024-05-13 | 0.5% | 3% | 5% | 10% | | gemini-2.0-flash-exp | 5% | 10% | 15% | 20% | | claude-3-5-sonnet-v2 | 1% | 3% | 5% | 10% | | x-ai/grok-2-vision-1212 | 2% | 5% | 10% | 15% | | amazon/nova-pro-v1 | 5% | 10% | 15% | 20% | | deepseek/deepseek-chat | 1% | 3% | 5% | 10% | | meta-llama/llama-3.1-405b-instruct | 1.4% | 2.7% | 3.8% | 6.2% | cognitivecomputations/dolphin-mixtral-8x22b | 15% | 10% | 7.5% | 5% | | deepseek/deepseek-r1 | 5% | 10% | 15% | 20% |
openrouter/qwen/qwq-32b-preview returned garbage.
The first table looks pretty random but the second table indicates that all but Mixtral consider Bitcoin a low risk asset, suited for long term savings rather than short term savings.
I could not at all reproduce Eric's findings.
https://i.nostr.build/ihsk1lBnZCQemmQb.png
-
 @ 16d11430:61640947
2025-03-19 23:33:01
@ 16d11430:61640947
2025-03-19 23:33:01Elliptic Curve AI (ECAI) is built on deterministic knowledge retrieval using elliptic curve mathematics. Isogenies provide a powerful mechanism for structuring and transforming knowledge while preserving its cryptographic integrity. Here’s how ECAI can benefit from elliptic curve isogenies:
- Knowledge State Transitioning via Isogenies
In ECAI, knowledge is mapped as elliptic curve points.
Isogenies allow transformation of knowledge states while preserving mathematical relationships.
This enables secure knowledge evolution without introducing probabilistic error.
Example: Knowledge Encapsulation & Transformation
-
Encode knowledge as a structured point on elliptic curve .
-
Apply an isogeny , where represents a different domain of knowledge.
-
Retrieve transformed knowledge in without breaking the deterministic structure.
Use Case:
A legal contract encoded on can be isogenously mapped to an encrypted compliance framework on .
This transition is cryptographically verifiable and irreversible, ensuring immutability of the knowledge chain.
- Post-Quantum Secure Knowledge Verification
ECAI’s structured intelligence retrieval needs long-term cryptographic security. Since Shor’s algorithm (on a quantum computer) can break classical elliptic curve cryptography (ECC), isogeny-based cryptography provides a post-quantum security layer.
SIDH (Supersingular Isogeny Diffie-Hellman) allows ECAI to verify structured intelligence without revealing private keys.
Isogeny graphs ensure knowledge transfer is resistant to quantum attacks.
Use Case:
ECAI nodes storing knowledge must be quantum-resistant.
Isogeny-based cryptography ensures retrieval functions cannot be forged even under quantum adversaries.
- Immutable Knowledge Chains with Isogeny Graphs
An isogeny graph is a structure where elliptic curves are connected via isogenies. ECAI can leverage this concept to build immutable knowledge networks.
How it Works
Each verified knowledge state corresponds to an elliptic curve.
Isogenies provide a deterministic, mathematically enforced way to transition between states.
The entire knowledge structure forms an isogeny graph that resists tampering.
Use Case:
Knowledge NFTs: Every piece of knowledge in ECAI can be recorded on an isogeny graph, ensuring ownership and integrity.
DamageBDD Proofs: Test case verification can move through isogeny transformations to maintain structured immutability.
- Adaptive AI Decision-Making using Isogenies
Traditional AI uses probabilistic inference, while ECAI relies on deterministic knowledge retrieval. Isogenies allow non-destructive transformation of knowledge, meaning:
AI decisions can be mapped as elliptic curve transformations.
Knowledge retrieval functions can evolve via controlled isogeny paths rather than brute-force learning.
The resulting system is adaptive but remains fully deterministic.
Use Case:
DamageAI can apply isogenies to map software quality metrics between different project states, ensuring structured decision-making without introducing bias.
- Isogeny-Based Knowledge Compression & Aggregation
ECAI’s structured intelligence can use isogenies to compress knowledge.
Isogenies allow aggregation of multiple elliptic curve points into a single transformed curve.
This enables efficient knowledge storage without losing structural integrity.
Use Case:
DamageBDD test results across multiple domains can be compressed into a single isogeny-mapped curve, reducing computational overhead while maintaining verifiability.
Conclusion
Isogenies offer a powerful tool for deterministic knowledge transformation in ECAI. By integrating isogeny-based methods, ECAI can:
-
Securely evolve knowledge states without probabilistic degradation.
-
Achieve post-quantum security for intelligence retrieval.
-
Build immutable knowledge graphs that are cryptographically verifiable.
-
Optimize deterministic decision-making using isogeny-based transitions.
-
Compress and aggregate knowledge in structured formats.
Next Steps
Would you like a Python implementation of an isogeny-based knowledge transformation function to illustrate how ECAI can apply this concept? 🚀
-
 @ fd208ee8:0fd927c1
2025-02-15 07:37:01
@ fd208ee8:0fd927c1
2025-02-15 07:37:01E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md https://github.com/nostr-protocol/nips/blob/master/61.md
-
 @ dd664d5e:5633d319
2025-02-14 16:56:29
@ dd664d5e:5633d319
2025-02-14 16:56:29Most people only know customer-to-customer (C2C) and business-to-customer (B2C) software and websites. Those are the famous and popular ones, but business-to-business (B2B) is also pretty big. How big?
Even something boring and local like DATEV has almost 3 million organizations as customers and €1,44 billion in annual revenue.
FedEx has €90 billion in annual revenue and everyone who uses it comes into contact with its software. There's a whole chain of software between the sender and receiver of the package, and it all has to work seamlessly.
Same with Walmart, Toyota, Dubai Airport, Glencore, Tesla, Edeka, Carrefour, Harvard and University of Texas, Continental, Allianz, Asklepios, etc.
That's the sort of software I help build. You've probably never heard of it, but when it doesn't work properly, you'll hear about it on the news.
-
 @ 878dff7c:037d18bc
2025-03-19 21:58:40
@ 878dff7c:037d18bc
2025-03-19 21:58:40NSW Premier Chris Minns: Multiculturalism Requires Limits on Free Speech
Summary:
NSW Premier Chris Minns has stated that maintaining a successful multicultural society requires limits on free speech, arguing that Australia does not have the same free speech protections as the United States because of its diverse population. Minns suggested that social harmony relies on people refraining from saying everything they think, particularly on sensitive racial and religious issues. His comments come as NSW enacts new laws criminalizing racial hatred, banning public Nazi symbols, and increasing penalties for hate-related offenses. Critics argue these laws could stifle free expression, but Minns insists they are necessary to prevent division and ensure peaceful coexistence.
Sources: news.com.au - March 20, 2025, The Epoch Times - March 20, 2025Canada Purchases Australia's Jindalee Radar System
Summary:
Canada has agreed to purchase Australia's Jindalee Over-the-Horizon Radar (JORN) system for $6.5 billion, marking Australia's largest defense export. The radar system will enhance Canada's Arctic defense capabilities amid rising geopolitical tensions, particularly with the U.S. Both Australian and Canadian leaders have emphasized strengthening trade and defense relations in light of changing global dynamics. Sources: The Australian - March 20, 2025
Nvidia Unveils Next-Generation AI Technologies at GTC 2025
Summary:
At the GTC 2025 AI conference, Nvidia CEO Jensen Huang introduced significant advancements, including the upcoming Blackwell Ultra AI chips and the Vera Rubin AI superchip platform, expected in late 2025 and the second half of 2026, respectively. The company also showcased "Blue," a robot developed with Disney Research and Google DeepMind, highlighting new robotics technologies and the Newton physics engine. Additionally, Nvidia announced Dynamo, an open-source inference software system, and a partnership with General Motors to develop custom AI systems for vehicles and factories. Sources: Business Insider - March 18, 2025, Tom's Guide - March 18, 2025
Queensland Braces for Torrential Rainfall and Potential Flooding
Summary:
Queensland's southeast is preparing for heavy rainfall, with forecasts predicting totals between 100 and 400mm in the coming days. Flood watches and severe weather warnings have been issued for regions including Herbert and Lower Burdekin. Areas such as Townsville, Palm Island, and Lucinda may experience six-hour rainfall totals of up to 240mm. This follows recent floods in Ingham, where 200 homes were affected. While conditions are expected to moderate in the afternoon, showery weather is likely to continue into the weekend. Residents are advised to stay updated and take necessary precautions.
Sources: news.com.au - March 20, 2025, ABC News - March 18, 2025
Australia Firm on PBS Amid US Tariff Threats
Summary:
Health Minister Mark Butler has asserted that Australia will not negotiate changes to its Pharmaceutical Benefits Scheme (PBS) despite pressure from US pharmaceutical companies lobbying President Donald Trump to impose tariffs on Australian medicines. The government is actively engaging with US counterparts to prevent potential tariffs, emphasizing the importance of maintaining affordable healthcare for Australians. Sources: ABC News - March 20, 2025, The Guardian - March 20, 2025
Australians Losing Faith in 'Fair Go' Principle
Summary:
Recent research indicates a significant shift in Australian values, with a declining belief in fairness and equality. Economic disparities, particularly the housing crisis, have eroded trust in political institutions, especially among younger generations. This trend poses profound implications for the upcoming election, highlighting the need for policies addressing economic inequality and fostering community engagement. Sources: The Guardian - March 20, 2025
Malaysia to Resume Search for MH370
Summary:
Malaysia has agreed to terms with the U.S. seabed exploration firm Ocean Infinity to resume the search for Malaysia Airlines flight MH370, which disappeared in 2014. The new search will cover a 15,000 sq km area on a "no find, no fee" basis, potentially starting soon. Sources: The Guardian - March 20, 2025
Study Reveals High Head and Neck Cancer Mortality in Rural Queensland
Summary:
A study led by James Cook University has identified significant cancer hotspots in Queensland, particularly for head and neck cancers. Data from the Queensland Cancer Register from 1982 to 2018 revealed that Hinchinbrook, Quilpie, Yarrabah, and Murweh have the highest risk of death from these cancers. Factors include limited access to tertiary hospitals and low awareness of risk factors such as tobacco, alcohol, and betel nut use. The study emphasizes the importance of early diagnosis and education, suggesting intervention strategies like cancer navigators and proposing a national oral cancer screening program. Sources: The Courier-Mail - March 20, 2025
Shayna Jack Advocates for Mental Health Awareness
Summary:
Olympic swimmer Shayna Jack has opened up about her mental health struggles during her two-year doping ban, revealing experiences with depression and suicidal thoughts. Through News Corp Australia's "Can We Talk?" campaign, Jack emphasizes the importance of seeking support and aims to destigmatize mental health issues, inspiring others to prioritize their well-being. Sources: News.com.au - March 20, 2025
EU Advocates for Resumption of Free-Trade Talks with Australia
Summary:
The European Union's top diplomat in Australia is urging the swift resumption of stalled free-trade negotiations between Australia and the EU. Highlighting the EU as a reliable partner that respects agreements, the ambassador emphasized the importance of shared values and historical ties. This call comes amid global economic disruptions due to US tariffs under President Trump. Previous attempts to secure a trade agreement faced challenges, particularly concerning agricultural exports. However, the EU is now pushing for renewed talks, aiming to remove tariffs and enhance collaborations in defense, critical minerals, and scientific research. The ambassador stressed that in light of current global uncertainties, establishing a robust trade relationship between Australia and the EU is essential. Sources: The Australian - March 20, 2025
Chinese Bounty Offers Raise Concerns Among Australian Residents
Summary:
Melbourne residents received letters resembling police appeals, offering HK$1 million for information on Kevin Yam, a Hong Kong dissident lawyer residing in Australia. Yam fled amid a crackdown on political opposition by the Chinese government and now lives discreetly in Australia. The letters encouraged residents to report Yam to authorities, sparking fear and concern. This tactic mirrors approaches used in the UK against other dissidents sought by Hong Kong police. Australian Foreign Minister Penny Wong condemned the letters, assuring that such intimidation would not be tolerated. Yam has vowed not to return to Hong Kong until its freedom is restored. The Hong Kong government denied involvement, stating all official actions abide by legal procedures. Sources: The Times - March 20, 2025
Government Plans to Expedite Legislation Protecting Tasmania's Salmon Industry
Summary:
Prime Minister Anthony Albanese intends to fast-track legislation to safeguard Tasmania's salmon farming in Macquarie Harbour from legal challenges concerning its environmental impact on the endangered Maugean skate. The proposed amendments to the Environment Protection and Biodiversity Conservation (EPBC) Act aim to ensure the industry's sustainability while bypassing an ongoing environmental review. This move has garnered support from industry leaders and some political figures but faces criticism from environmental groups and the Greens, who argue it undermines necessary ecological assessments. Sources: The Guardian - March 19, 2025, The Australian - March 20, 2025
"I'm Pro-Free Speech and Anti-War, So That Makes Me Right-Wing?" - Jimmy Dore on Dad Saves America Podcast
Summary:
In this episode of the "Dad Saves America" podcast, comedian and political commentator Jimmy Dore discusses the evolving landscape of American politics. He reflects on how advocating for free speech and opposing war, traditionally liberal stances, are now often labeled as right-wing positions. Dore critiques the current political climate, emphasizing the importance of questioning authority and maintaining independent thought. He also shares insights into his journey from mainstream media to alternative platforms, highlighting challenges faced when diverging from dominant narratives.
Sources: Spotify - March 14, 2025
-
 @ dd664d5e:5633d319
2025-02-12 07:05:51
@ dd664d5e:5633d319
2025-02-12 07:05:51I think this note from Chip (nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7) is one of those things that people with business management experience take a lot more seriously than most developers and influencers do.
I am painfully aware of the cost of systems administration, financial transaction management and recordkeeping, recruiting and personnel management, legal and compliance, requirements management, technical support, renting and managing physical spaces and infrastructure, negotiating with suppliers, customer service, etc. etc.
There's this idea, on Nostr, that sort of trickled in along with Bitcoin Twitter, that we would all just be isolated subsistance farmers and one-man-show podcasters with a gigantic server rack in the basement. But some of us are running real companies -- on and off Nostr, for-profit and non-profit -- and it often requires a lot of human labor.
The things we build aren't meant to be used by one person and his girlfriend and his dog. Yes, he can also run all these things, himself, but he no longer has to. Our existence gives him the choice: run these things or pay us to run them and spend your time doing something else, that you do better than we do.
These things are meant to be used by hundreds... thousands... eventually millions of people. The workflows, processes, infrastructure, and personnel need to be able to scale up-and-down, scale in-and-out, work smoothly with 5 people or 50 people. These are the sort of Nostr systems that wouldn't collapse when encountering a sudden influx or mass-escape. But these systems are much more complex and they take time to build and staff to run them. (And, no, AI can't replace them all. AI means that they now also have to integrate a bunch of AI into the system and maintain that, too.)
GitCitadel (nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz) is very automation-forward, but we still have to front the incredibly high cost of designing and building the automation, train people to interact with it (there are now over 20 people integrated into the workflow!), adjust it based upon their feedback, and we have to support the automation, once it's running.
This sort of streamlined machine is what people pay companies for, not code. That is why there's little business cost to open source.
Open-source is great, but...

nostr:nevent1qqsgqh2dedhagyd9k8yfk2lagswjl7y627k9fpnq4l436ccmlys0s3qprdmhxue69uhhg6r9vehhyetnwshxummnw3erztnrdakj7q3qqdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havqxpqqqqqqzdhnyjm
-
 @ 30ceb64e:7f08bdf5
2025-03-19 21:29:59
@ 30ceb64e:7f08bdf5
2025-03-19 21:29:59NIP-101e: Workout Data and Running Extensions
NIP-101e represents a crucial step forward for fitness tracking on Nostr, giving us a common language that would allow workout data to flow freely between apps. This proposal outlines a thoughtful framework with Exercise Templates, Workout Templates, and Workout Records that would finally free our fitness data from proprietary silos and put it back in our hands. I'm eager to see this proposal implemented because it would create the foundation for a genuinely open fitness ecosystem on Nostr.
As a runner building a Nostr running app RUNSTR, I've proposed some running-specific extensions to NIP-101e that address the unique needs of runners without disrupting the elegant structure of the original proposal. My extensions would standardize how we record GPS routes, pace metrics, elevation data, splits, and even weather conditions - all things that matter tremendously to runners but aren't covered in the base proposal that focuses more on strength training.
By implementing NIP-101e along with these running extensions, we could create something truly revolutionary: a fitness ecosystem where runners aren't locked into a single platform because of their data. You could track your morning run in my app, analyze your training in another app that specializes in statistics, and share achievements with friends using whatever Nostr clients they prefer. I believe strongly in getting NIP-101e implemented with these extensions included because it would foster innovation while giving runners unprecedented freedom to own their data and use it however they want. Let's make this happen and show what's possible when fitness data becomes truly interoperable!
-
 @ b8af284d:f82c91dd
2025-03-16 16:42:49
@ b8af284d:f82c91dd
2025-03-16 16:42:49
Liebe Abonnenten,
diejenigen, die diese Publikation schon länger abonniert haben, wissen, dass hier immer wieder über den Ursprung des Corona-Virus in einem Labor in Wuhan berichtet wurde. Seit diese Woche ist es „offiziell“ - der Bundesnachrichtendienst (BND) hält den Labor-Ursprung für die wahrscheinlichste Variante. Jetzt kann man sich fragen, warum der BND plötzlich umschwenkt: Will man proaktiv erscheinen, weil man die Wahrheit nicht mehr länger verbergen kann? Oder will man die enttäuschten Bürger zurückgewinnen, die aufgrund der Lügen während der Corona-Zeit zunehmend mit Parteien links und rechts außen sympathisiert haben, weil diese die einzigen waren, die den Irrsinn nicht mitgetragen haben?
Auffallend bei den „Recherchen“, die in Wahrheit keine sind, sondern Verlautbarungen des deutschen Geheimdienstes, ist auch das völlige Schweigen über die US-amerikanischen Verwicklungen in das Projekt. In Wuhan wurde mit amerikanischem Geld geforscht. Warum der BND diese Tatsache verschweigt, ist Teil der Spekulation. Vermutlich will man Peking alles in die Schuhe schieben, um von den eigenen Versäumnissen abzulenken.
In meinem aktuellen Buch “Der chinesische (Alp-)Traum” ist den Ereignissen in Wuhan ein ganzes Kapitel gewidmet. Es hat nichts an Aktualität eingebüßt. Alle Fakten lagen seit Jahren auf dem Tisch für jeden, den es interessiert hat. Hier gibt es das gesamte Kapitel nachzulesen.

Auf jeden Fall zeigt dies, wie der Begriff „Verschwörungstheoretiker“ in den vergangenen Jahren zum Kampfbegriff und Waffe gemacht wurde, um Kritiker zu diffamieren, und die öffentliche Meinung ohne harte Zensur zu lenken. Ähnliches kann man aktuell beim Projekt „Digitaler Euro“ beobachten. Vermutlich kann sich kein Bürger der Europäischen Union daran erinnern, bei seiner Wahlentscheidung jemals gefragt worden zu sein, ob er die Einführung eines „digitalen Euros“ gut findet. Wurde er nämlich nicht. Er kommt aber trotzdem. EZB-Präsidentin Christine Lagarde hat das diese Woche nochmals bekräftigt: Schon im Oktober will man die Testphase beenden und an der Einführung arbeiten.
Nun gehört BlingBling nicht zu denjenigen, die im digitalen Euro „Orwell’sches Teufelswerk“ sehen. Strategische Dummheit trifft es besser. Worum geht es?
Sogenannte Central Bank Digital Currencies (CBDC) waren vor einigen Jahren so etwas wie der letzte Schrei in der Zentralbank-Welt. Nachdem Facebook/Meta 2017/18 eine eigene Währung namens Libra auf den Markt bringen wollte, und eine obskure Internet-Währung namens Bitcoin immer mehr Anhänger fand, sahen sich viele Zentralbanken der Welt unter Zugzwang. Was man wollte: eine digitale, direkt von der Zentralbank ausgegebene Währung ohne Bugs, aber mit Features. Mit einer Digital-Währung ließe sich der internationale Zahlungsverkehr direkt und ohne Umweg über den US-Dollar abwickeln. Die Zentralbank bekäme wieder mehr direkten Einfluss auf die Geldschöpfung. Und, wie man aus China lernen konnte, ließen sich digitale Bankkonten auch ganz zum „Nudging von Bürgern“ nutzen. So spekulierten die ersten Verschwörungstheoretiker bald, ein digitaler Euro ließe sich ja mit einem persönlichen CO2-Konto verknüpfen. Wäre letzteres einmal aufgebraucht, könnte der Konto-Inhaber einfach keinen Flug mehr buchen. Auch ließe sich eine expansive Geldpolitik, wie sie bis 2022 praktiziert wurde, ganz einfach mit Negativ-Zinsen umsetzen. Geld würde sich nominal reduzieren, was den Bürger zum Konsum animieren würde. Flüchtigen Kriminellen ließe sich per Knopfdruck das Konto sperren. Der Staat würde also über eine ganze neue Palette an Einflussmöglichkeiten verfügen.
Die Aluhüte United warnten vor einem Orwellschen Überwachungsstaat. Vertreter von Regierungen und Firmen, die diesen digitalen Euro bauen sollten, beschwichtigten. Mit Ralf Wintergerst, CEO von Giesecke+Devrient, nach wie vor heißester Anwärter, um das Projekt in der EU umzusetzen, sprach ich in den vergangenen Jahren mehrmals zu dem Thema. Zuletzt im Dezember 24.
Wintergerst versichert stets zwei Dinge: Eine Abschaffung von Bargeld sei nicht geplant. Und nur, wenn die Fluchttore Bargeld, Gold und Bitcoin geschlossen werden, greift die dystopische Version. Und zweitens, so Wintergerst, habe niemand ein chinesisches System im Sinne. Der „digitale Euro“ sei für die Bürger gedacht und das Projekt unterliege demokratischer Kontrolle. Ob er Wintergerst und dem guten im Menschen Glauben schenkt, möge jeder Leser selbst entscheiden. Das Interessantere ist ohnehin, dass der digitale Euro ein strategisch dummes Projekt ist.
Dazu muss man wissen, dass eine solche Zentralbankwährung Banken im weitesten Sinne überflüssig macht. Kontos bei Privatbanken werden obsolet, genauso wie Spar-, Fest- und Tagesgeld-Strukturen. Deshalb soll der digitale Euro zunächst auf 3000 Euro pro Bürger beschränkt werden. Das ist also nicht als Maximal-Vermögen gedacht, das dann jedem sozialistischen Einheits-EU-Menschen noch zusteht, sondern dient dazu, das Bankensystem nicht kollabieren zu lassen. Aber wozu überhaupt „ein bisschen digitaler Euro“?
In den USA setzt man mittlerweile 100 Prozent auf die private Alternative: Stablecoins wie Tether (USDT) und Circle (USDC) sind nichts anderes als digitale Währungen. Nur sind sie nicht von einer Zentralbank ausgeben, sondern von privaten Anbietern. Tether hat technisch die Möglichkeit, einen Inhaber vom Zahlungsverkehr auszusperren. Nur dürfte es davon kaum Gebrauch machen, will das Unternehmen nicht rasant Kunden an die Konkurrenz verlieren. Da USDT und USDC mit US-Dollar gedeckt sind (oder zumindest sein sollten, looking at you, Tether!), stärken sie außerdem die Rolle des US-Dollars als Leitwährung. Und da die USA sich aktuell sehr über Käufer von Staatsanleihen freuen, um die Zinsen zu drücken, und Tether einer der größten Halter von US-Staatsanleihen ist, wird es den digitalen Dollar bis auf Weiteres nicht geben.
Den digitalen Yuan gibt es, aber von einer großen Akzeptanz oder Durchdringung der chinesischen Wirtschaft lässt sich nicht sprechen. Kontrolle kann der chinesische Staat ohnehin über seine omnipräsenten Apps WeChat und Alipay ausüben. Was den internationalen Zahlungsverkehr betrifft, scheint man aktuell eher auf Gold zu setzen.
Übrig also bleibt die EU mit einem Projekt, das bereits Milliarden an Entwicklungskosten verschlungen hat. Am Ende bleibt dann ein Mini-Digitaler-Euro in Höhe von 3000 Euro, den niemand wollte, und niemand braucht.
Helfen könnte er allerdings beim Projekt “Mobilisierung der Sparguthaben”. Der Ausdruck geht auf Friedrich Merz zurück. Ursula von der Leyen paraphrasierte ihn jüngst:
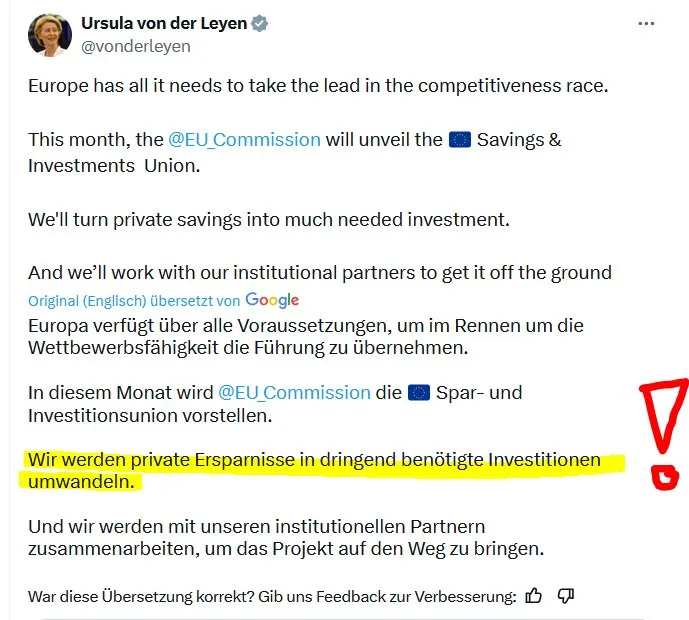
Irgendwie müssen die Billionen von Sparguthaben in Militär-Investitionen umgewandelt werden. Das wird am besten funktionieren mit Anleihen, die schlechter verzinst sind als sonst auf dem Markt üblich. Wie bringt man Leute dazu, dann ihr Geld dort zu investieren? Entweder man zwingt sie, oder man bewirbt die Anleihen mit viel Patriotismus und Propaganda. Die Verschwörungstheoretiker unter uns bekommen also bald Futter, wenn die „Spar- und Investitionsunion” vorgestellt wird.
Like, wenn Dein Aluhut glüht…
Hinter der Paywall: Wie das Trump-Derangement-Syndrom den Blick auf den Markt trübt. Wie es mit Bitcoin, Gold und Aktien weitergeht.**
-
 @ fd208ee8:0fd927c1
2025-02-06 15:58:38
@ fd208ee8:0fd927c1
2025-02-06 15:58:38Beginning at the start
In my previous article, The Establishment, I answered the question: "How do we form a company?" I realize, now, that I was getting a bit ahead, of myself, as the precursor to a company is a team, and many people struggle to form teams. So, I will go back to the beginning, and then you can read both articles to the end, and then stop.
The Initiation
The first, and most-difficult step of team formation, is the initiation. We know that it must be the most-difficult, as it's the step that carries the highest potential reward, and it's the step that is tried-and-failed most often. (Some people, like Elon Musk or Donald Trump, are born Initiators with excellent follow-through, but this archetype is exceedingly thin on the ground because it requires you to be mildly autistic, have barely-throttled ADHD, and/or tend to megalomania, also popularly known as "toxic masculinity", "CEO personality", or "being a successful military officer".)
Someone needs to form a useful, attractive Vision and then motivate other people to help them achieve it. That sounds really easy, but it's actually brutally difficult because * You have to come up with an idea that is coherent, plausible, and inspiring. * You have to be able to communicate that idea to other people and make it appealing to them, by tying it into their own personal goals and desires. * You have to be able to hone and reformulate that idea, constantly, to correct it or to re-motivate the other team members. * You have to defend the idea against detractors, naysayers, and trolls, and you have to do it so vociferously, that it will erode your own popularity among those who disagree with you and open you to personal attacks. * You have to be able to focus on the idea, yourself, for a long stretch of time, and not allow yourself to get bored, lazy, or distracted.
So, just do and be all of those things, and then initiate the team, with the method I will name the Hatbock Method. It is so named because of the classic, German initiation ritual, in which an Initiator stands up, loudly defines their Vision and calls into a group "Wer hat Bock?" (roughly, "Who has the hunger/desire?") and whoever responds with "Ich hab Bock." (roughly, "Yes, I hunger for this.") is a part of the team.
Then the Initiator says, "Okay, everyone with the hunger, let's sit down together, and discuss this some more." (This "sitting" is literally called a "seating", or "Sitzung", which is the German word for "meeting".)
The Sitting
We now get to the second most difficult part of team formation: figuring out where to sit. Most teams get this wrong, repeatedly, and many teams dissolve or fracture under the difficulty of this momentous decision. You would think organizing yourselves online would make this easier ("Oh, we'll just meet online!"), but the number of places available for sitting online are limitless. You can talk your whole Vision into the ground, with laborous discussions and migrations between Chachi, OxChat, Telegram, SimpleX, Slack, Discord, WhatsApp, GitHub, Teams, Coracle, Matrix... you get the idea.
Try to keep in mind that the Vision is more important than the seating area, and go with the flow. Simply, find someplace and go there. Worry about it again, at a later date. Don't lose momentum. Sit down and start discussing the Vision, immediately.

Now, this next bit is very important:
Do not let anyone outside your team influence where you sit!
...unless they are providing your team with some good, service, or income, that makes choosing their preferred location the superior choice.
This is the German Stammtisch principle, where a host encourages you to come sit down, regularly, in some particular place, because your sitting there provides them with some benefit: they can overhear your conversations, get you to test out their seating area, sell you refreshments, etc. Your choice of seating, in other words, is a valuable good, and you should only "sell" it to someone who rewards you in measure. They have to reward you because their preferred seating area wasn't your immediate and obvious choice, so there was probably something unappealing or uncertain about the seating area.
Plan it in
Once you've sat down, and finished your rough draft of the Vision, you need to figure out when to sit. This is the third most-difficult part of team formation. (Yes, don't worry, it gets easier as it goes along.)
The most popular plan is the Wirsehenuns Plan (roughly, "We'll see each other, around.") This can work quite well, if you just want to have a loose collaboration, that calls itself together in an ad hoc fashion, when a team member feels the need. Also known as "@ me, bros".
It's not a great plan for more intensive collaboration, as that tends to need a certain amount of velocity, to actually happen, as the speed of movement has a centrifugal effect on the tasks. Team momentum, in other words, creates a sort of gravity, that keeps the team together as a unit. So, for deeper teamwork, I would recommend the Stammtisch variant: name a place and date/time, when you will next meet. Preferably, on a rotating schedule: daily, weekly, last Thursday of the month, etc.
And then meet there and then. And discuss amongst yourselves. Set clear, short-term tasks (and assign them to particular people!), medium-term strategies, and longer-term goals. Write everything down. Anything not written down, is a suggestion, not an assigned task.
If you find your Stammtisch becoming increasingly rewarding and productive, and your goals start moving closer and closer into sight, then you might want to formalize your team structure further, as a company.
-
 @ 4f170d8a:5e8ef636
2025-03-19 21:27:07
@ 4f170d8a:5e8ef636
2025-03-19 21:27:07The Vikings, renowned for their seafaring prowess, dominated the seas of Northern Europe from the late 8th to the early 11th century.
These fearless explorers ventured across vast oceans, reaching as far as North America, long before the age of modern navigation tools and centuries before the magnetic compass came to Europe. While their shipbuilding skills and knowledge of the stars were exceptional for their time, one of their most intriguing navigational aids was the mythical "sunstone."
This mysterious tool, steeped in both legend and science, is believed to have allowed Viking navigators to locate the sun even on cloudy days, ensuring they could maintain their course across the treacherous North Atlantic ocean.
The Challenge of Viking Navigation
Navigating the open sea in the Viking Age was no small feat. The North Atlantic, with its unpredictable weather, frequent fog, and overcast skies, posed significant challenges.
 Traditional methods of navigation relied heavily on the sun and stars, but in a region where the sun could disappear behind clouds for days, the Vikings needed a reliable way to stay oriented.
Traditional methods of navigation relied heavily on the sun and stars, but in a region where the sun could disappear behind clouds for days, the Vikings needed a reliable way to stay oriented.While they were adept at reading natural signs such as the flight patterns of birds, the color of the sea, and the direction of the wind, the sunstone offered a more precise solution.
Historical accounts hint at the use of a "sunstone" by Viking navigators. One passage even describes a Viking king using a special stone to locate the sun’s position during a snowstorm. For centuries, this reference was dismissed as myth, but modern science has shed light on how such a tool could have worked, reviving interest in this ancient technique.
What Was the Sunstone?
The sunstone is believed to have been a naturally occurring crystal, most likely a type of calcite known as Iceland spar. Another candidate is tourmaline, which exhibits similar optical properties.
These crystals have a unique quality called birefringence, or double refraction, which causes them to split light into two polarized beams. When viewed through the crystal, the light’s polarization reveals patterns that can indicate the sun’s position, even when it’s obscured by clouds or fog.
The key to the sunstone’s effectiveness lies in the polarization of sunlight. As sunlight scatters through the atmosphere, it becomes polarized, creating an invisible pattern that radiates outward from the sun.
 By rotating the sunstone and observing changes in the light passing through it, a skilled navigator could detect this pattern and pinpoint the sun’s location, regardless of whether it was visible to the naked eye.
By rotating the sunstone and observing changes in the light passing through it, a skilled navigator could detect this pattern and pinpoint the sun’s location, regardless of whether it was visible to the naked eye.How the Vikings Used the Sunstone
To use the sunstone, a Viking navigator would hold the crystal up to the sky and rotate it until the polarized light formed a specific pattern (often a brightening or darkening effect), depending on the stone.
Iceland spar, for instance, produces two distinct beams of light, and when these beams appear equally bright, the crystal is aligned with the sun’s position.
By marking this direction and combining it with their knowledge of time and the sun’s daily arc, the Vikings could determine their heading with remarkable accuracy.
This method was particularly useful during the long voyages across the North Atlantic, where overcast skies were common.
It complemented other techniques, such as using a sun compass, which was a wooden disk with a central pin that cast a shadow to indicate direction when the sun was visible.
On cloudy days, when the sun compass was useless, the sunstone stepped in as a critical backup.
Let's Build One
If you are anything like me, you don't have lumps of Iceland spar or tourmaline crystals laying about your back yard. So I decided to make one using modern materials.
Since the original crystals relied on polarization to achieve their effect, I ordered some linear polarized plastic film online which science teachers often use in classroom demonstrations.

Now the challenge became turning the linear polarization into radial polarization, and I chose to make an octagon out of suitably arranged triangles cut from the sheet.
The image below shows how I created a template on a scrap piece of paper, and then used that to cut triangles from a strip of the polarizing film.

The next step involves carefully placing the triangles onto some clear packing tape so that they stick into place.

I then carefully placed another piece of clear packing tape on top so that the octagon of triangles is permanently fastened into place.
Then with a blade, I trimmed the excess packing tape and the sunstone is complete.

Now to test it!
You can see here that I'm holding the sunstone up against a North facing window so that you can see how the different triangles make different colors depending on their angle to the incoming light from outside.

The light gray triangles indicate the direction of the sun even though the sun is behind the house. and it will work the same way on a cloudy day no matter which way you are facing.
Today, the sunstone captivates historians, scientists, and enthusiasts alike. It’s a reminder that ancient technologies, though simple by modern standards, were often remarkably effective.
The Vikings’ ability to traverse oceans with nothing more than a crystal and their wits speaks to their extraordinary skill.
The earth's magnetic field is rapidly weakening and the poles moving. There may come a day in the not too distant future where navigation by GPS or compass will not longer be possible.
The sunstone stands as a symbol of human curiosity and resilience, which may once again illuminate the path of those who dare to sail beyond the horizon.
-
 @ c8383d81:f9139549
2025-02-05 13:06:05
@ c8383d81:f9139549
2025-02-05 13:06:05My own stats on what I’ve done over the weekend:
-
Spoke to +100 developers, it was great seeing a couple of familiar Flemish faces and meeting some new ones but overall the crowd was extremely diverse.
-
Ended up doing a short interview promoting the protocol and ended up going to 0 talks.
-
Tried to evangelize by going booth by booth to distribute a Nostr flyer to other FOSDEM projects, with the hope that they would broadcast the info towards their SOME person to add Nostr on their list or to build out a library for the languages that were present ( This was a fairly slow approach )
-
Kept it to Nostr protocol 95% of the time, the Bitcoin narrative is not always a good time to push and as a side note I’ve met more Monero users than in the last 5 years.
-
Was able to convince some engineers to look into the #soveng endeavor.
Small overview from the most common questions:
- They have heard about Nostr but are not sure of the details. ( mostly through the bitcoin community )
- What is the difference with ActivityPub, Mastodon, Fediverse ?
- IOT developers, so questions regarding MQTT & Meshtastic integrations ?
- Current state of MLS on Nostr ?
- What are the current biggest clients / apps build on Nostr ?
- Will jack still give a talk ?
Things we could improve:
- Bring more stickers like loads more,
- Bring T-shirts, Pins… could be a good way to fund these adventures instead of raising funds. ( Most projects where selling something to help raise funds for projects )
- Almost no onboarding / client installs.
- Compared to the Nostr booth at BTC Amsterdam not a single person asked if they could charge their phone.
Personal Note: The last time I visited was roughly 13 years ago and me being a little more seasoned I just loved the fact that I was able to pay some support to the open source projects I’ve been using for years ( homebrew, modzilla, Free BSD,.. ) and see the amazing diverse crowd that is the open source Movement 🧡
Al final shoutout to our great pirate crew 🏴☠️: The Dutch Guard ( nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe & nostr:npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft ) and a adrenaline fueled nostr:npub1t6jxfqz9hv0lygn9thwndekuahwyxkgvycyscjrtauuw73gd5k7sqvksrw , nostr:npub1rfw075gc6pc693w5v568xw4mnu7umlzpkfxmqye0cgxm7qw8tauqfck3t8 and nostr:npub1r30l8j4vmppvq8w23umcyvd3vct4zmfpfkn4c7h2h057rmlfcrmq9xt9ma amazing finally meeting you IRL after close to 2 years since the Yakihonne hackathon 😀

-
-
 @ 000002de:c05780a7
2025-03-19 21:11:34
@ 000002de:c05780a7
2025-03-19 21:11:34This is an absolutely great conversation between an anarchist (Michael Malice) and a conservative (Marissa Steit). Many of you will agree with the answers Malice provides but many of you that often have questions about the idea of anarchism should listen to this.
Now, if you just wanna argue don't waste your time. But if you are genuinely curious Malice is a great communicator on the topic. There are many schools of thought on anarchism and Malice just represents his point of view but he knocks down many troupes that conservative republicans repeat.
While right wingers don't get how evil the state actually is they are closer to understanding than the left. They are also better at understanding people that disagree with them. In my experience leftist do not understand the right but the right does understand the left. Not fully but better. This helps. You can see it in this interview.
https://www.youtube.com/watch?v=D43Xvom9hmw
originally posted at https://stacker.news/items/918194
-
 @ 9967f375:04f9a5e1
2025-03-19 20:33:13
@ 9967f375:04f9a5e1
2025-03-19 20:33:13Carlos Javier de Borbón Parma y Lippe Biesterfield, quien en principio hubiera debido ser el titular de los derechos de la legitimidad dinástica española, de no haberlos perdido por seguir el camino de su padre, ha concedido una entrevista de tono cortesano y más bien inane, que demuestra que están lejos los tiempos del socialismo autogestionario y las alianzas de su padre con comunistas y terroristas, aunque sigan muy presentes los del liberal-globalismo de la «Agenda 2030».
Son muchas las cosas que podrían comentarse, pero nos limitaremos a los dos párrafos que se refieren a su tío, S.A.R. Don Sixto Enrique de Borbón. Quien desde 2021 adoptó prudentemente todo tipo de cautelas respecto de su persona, sus bienes y su sucesión, desgraciadamente algunas no respetadas por el Estado revolucionario francés, animado en este punto tristemente por algún miembro de la familia del Señor, y que están sub iudice.
En todo caso, y agradeciendo la preocupación del ex-Príncipe por su Augusto tío, es de precisar que la reconciliación a la que se alude, contraída a encuentros del Señor con algunas de sus hermanas, a quienes había dejado de tratar hace muchos años, fue única y exclusivamente familiar, sin consecuencia política o jurídica alguna. E incluso en ese ámbito familiar ciertos pleitos hereditarios han proseguido y Don Sixto Enrique tuvo que recriminar severamente a su sobrino que permitiera la incineración del cadáver de la ex-Infanta María Teresa.
Entre vaguedades, inconsecuencias y errores de todo tipo es de celebrar, por lo menos, que Carlos Javier de Borbón Parma y Lippe Biesterfield sepa que los Duques de Parma siempre anteponían su título de infantes de España a ese título. Y es que es una dinastía española. Sujeta a las leyes tradicionales de la monarquía española, con sus exigencias y exclusiones.
Madrid, 19 de marzo de 2025 Solemnidad del Glorioso Patriarca Señor San José
-
 @ dd1f9d50:06113a21
2025-02-05 01:48:55
@ dd1f9d50:06113a21
2025-02-05 01:48:55(Because Most People Don’t Understand Money)
The requisite knowledge needed to know whether $100 or $100,000 per Bitcoin is relatively speaking “a lot,” is what value means. One way to measure value is through a universal yardstick we call “Money.” The question of “What is money?” is perhaps one of the most overlooked and under answered in our day and age. There is even an entire podcast dedicated to that question with the eponymous title, hosted by Robert Breedlove. That podcast often delves into the more philosophical underpinnings whereas I hope to approach this with a more practical answer.
Money is a technology.
Money is the technology with which we interact with one another to reorganize goods and services to the place and time they are best suited. Most money of the past has been tangible (though not a requisite feature), scarce, recognizable (read: verifiable), durable, portable, and divisible. These features one might call the “Attributes of Money.” These attributes are absolutely essential for a money to maintain its status as a money. (Those of you who understand the U.S. Dollar system maybe scratching your heads right now but, believe me, I will address that elephant in due time.) These attributes, you may notice, are not a yes or no but more of a gradient. A money can be MORE portable than another yet, less durable. One more divisible but not scarce whatsoever. The point being they must have, in some capacity, these attributes or they simply aren’t money.
One of These Things is Not Like the Other
| | Bitcoin | Gold | Dollars | |-----------------|:----------------------------------------------------------------------------------------------------------------:|:------------------------------------------------------------------:|:--------------------------------------------------------------------------------------------------------------------------------------------------:| | Scarcity | 21 million coins
is the maximum supply | Unknown- the
supply grows roughly 2% per year | Also unknown to anyone outside of the Federal Reserve, Trillions and counting | | Recognizability | Each coin is verifiable to it's genesis on the timechain | Each molecule of gold has distinct physical verifiable properties | If the Federal reserve says it is a valid note, it is (Unless you are an enemy of the United States) | | Durablility | Each "Bitcoin" is information stored on a globally distributed network | Doesn't Rust and as far as can be measured Au197 is stable forever | Can be destroyed by any means that effect fabric and centralized databases | | Portability | Available wherever data can be store- Anywhere | Can be moved at 9.81 Newtons per Kilogram- Methods may vary | Can be moved physically with fabric notes- Digitally with express permission from a US accredited banking institution | | Divisibility | Currently can be divided into 100 million parts called Sats (can be further subdivided by adding decimal places) | Can be divided to the Atomic level (Though not practical) | Can be divided (without dilution) by adding new denominative bills or coinage
Can be divided (with dilution) by printing new bills or coinage | | | Bitcoin | Gold | Dollars |You may think with all of the great functionality of Bitcoin that the phrase "One of these things is not like the other" refers to BTC. No, I was referring to the Dollar. It is the only one on the list that was a currency that was substituted as some kind of faux money. It asserts itself, or rather the Federal Reserve asserts it, as money, de facto.
Dollars are NOT money.
Dollars are (allegedly) a currency. If money is a specific technology, currency is the financial infrastructure that allows that technology to reach and be used by the most number of people possible. This requires a firm tether between the asset being used as money and the currency used as a claim to that money. For example: If I hand you a chicken, you have a chicken. But, if I hand you a coupon that is redeemable for a chicken, you do not have a chicken. You have a claim to a chicken that is only as good as the party making that claim. Bringing it back to money again, dollars (Prior to 1971) were redeemable for gold at a rate of $35 per ounce. This is that strong tether that pegged dollars to gold and physical reality itself. Without a proof of work, mining, . Until…
WTF Happened in 1971?
The Nixon shock happened. Briefly, The U.S. took in Europe’s gold in the 1940’s to keep it out of Hitler’s hands. The U.S. made an agreement to peg the dollar to Europe’s gold. The U.S. over printed dollars in relation to the gold holdings. Around 1971 France (among others) called the U.S. out for devaluing the dollar and thus European currencies. So, Nixon “Temporarily” suspended the convertibility of dollars to gold. Now, here we all are like Wile E. Coyote having run off of the golden cliff clutching our dollars in our arms and 54 years later we still haven’t looked down to see the truth.
Dollars Aren’t Backed by Anything
This is why no country in the world today has a money standard. Seemingly they all forgot the number one rule of issuing currency, it must be backed by something. Now, you may hear dollar proponents say “The U.S. dollar is backed by the full faith and credit of the United States!” Another way of saying that is, “We said it is worth something, so it is!” This fiat (by decree) mentality creates a plethora of perverse incentives. The ever growing supply disallows users of the Dollar to save without inccuring the penalties of inflation.
Just a Few Examples of How You're Being Crushed
Because your dollar loses value:
- It pushes people to spend them on assets that seem to appreciate (as the dollar debases) but are truly staying stagnant.
- It pushes people to gamble on securities hoping the perceived value is enough to beat the inflationary curve.
- It pushes people away from saving for their future and the future of their families.
- It creates insane credit incentives so that people borrow way more than they can afford today knowing that dollars will be cheaper in the future. (Effectively a short position)
- It pushes people to spend less and less time making and maintaining their families as it becomes more expensive to keep a similar lifestyle to which it was founded.
These are just a few of the terrible consequences of not knowing that trading a currency with no monetary backing has on a society. Most may blame this soley on the ability to print currency by a central bank but, that is not the only factor. If the fed printed dollars against gold, people would simply take the best rate they could get and remonetize themselves with the gold. But because there is no monetary escape hatch guaranteed by the issuance of dollars, I.E. no one has to take your dollars in exchange for their Bitcoin or gold, you are left at the mercy of the market.
One Day, People Will Stop Accepting Your Dollars
Those lementing the high price of Bitcoin might want to thank their lucky stars that Bitcoin still has a rational number next to the "BTC 1=$?" sign. One day you will have to exchange something of actual value to the spender (no longer a seller). Your product, good or service, will be the only thing that anyone might be willing to part with their Bitcoin over. That is what makes a money, the most salable non-consumable good, whose only funtion is to back a financial structure that facilitates trade.
Bitcoin is Capital
Capital is a broad term that can describe anything that confers value or benefit to its owners, such as a factory and its machinery, or the financial assets of a business or an individual. Bitcoin being the latter creates the financial structures from which you build upon. You use capital to hold, transfer, and grow value. You do not do this with cash. Cash is a depreciating asset when you don't use it to gain goods or services for yourself or your business. This misconception around the equivalance between cash and money (financial capital) is what tricks people into believing Dollars are money. And what's worse is that even some of our greatest heroes have done this.
Slay Your Heroes, Within Reason
Unfortunately due to a mixing of verbiage that have very distinct differences, the title: "Bitcoin: A Peer-to-Peer Electronic Cash System" is technically inaccurate. Bitcoin doesn't fit the definition of cash, which is a liquid asset that can be easily converted into its equivalent value. In short, Satoshi misspoke. In reality, owning Bitcoin UTXOs (with private keys) means you already possess the asset, not just a claim to it. When you spend Bitcoin, the recipient receives the actual asset, not a promise of it. When you receive Bitcoin, you have final settlement on that transaction. Fundamentally Bitcoin is not cash, electronic or otherwise.
Bitcoin is Money.
-
 @ 7bc05901:8c26d22b
2025-03-19 20:30:31
@ 7bc05901:8c26d22b
2025-03-19 20:30:31I grew up far out of town in a nice neighborhood. My family had ten acres, but we didn't work the land. My mom had a kitchen garden with some tomatoes and herbs, and we had a few fruiting trees that were a far cry from an orchard.
I liked many things, like the massive off-rad go-kart track that we built through the backyard turning crabgrass into mud and the fact that the fourth of july was an entire week of pyrotechnics. But I was a social kid and hated being so disconnected from the town. We also could not get any high-speed internet out there until a few years into the new millennium, which meant MSN Messenger would put the dial-up at max capacity. This also cut against my exploratory instincts and social nature.
I am grateful I now live in town, but since having my first kid the homesteading life is calling out to me. I find myself scrolling zillow for houses just outside of the city limits with at least five or six acres. Now that the seasons are finally changing, I can stop scrolling and start investing my time in the backyard.
One important move to make in my mini-homestead (suburban homestead) is getting my chickens caged up better. I have a small coop where they lay eggs for me, but it is so confining that I had to let them out to wander the backyard -- which is surrounded by a privacy fence anyway. This kept them contained, but over the last year since I got the chickens, I realized that I hated just going out back to chill on the patio because chicken shit just covered everything. Over the last week, I have been erecting a bigger coop where the chickens can help me compost all the kitchen scraps, also have access to their coop (and easy access for me to get eggs) but I don't have to dodge their humongous turd piles all over the patio.
They also would tear the hell out of the garden. They like to take "dirt baths" which has something to do with deterring the mites that get on them, and they will just dig down into any soft soil, destroying plants or roots or whatever is in their way.
We had a decent garden last year, but it was disorganized and messy and did not maximize the food production. I kept saying, no big deal, let's take a year to get oriented, see what grows well out here, see what we enjoy growing and eating.
My daughter loves it. She would be covered in tomato seeds last year -- she had a confusing affinity for the unripened green tomatoes (which probably have some sort of cyanide or something in them). I think by the end of the season she was catching on that the reddest ones had the best flavor.
We also have a raspberry patch that she absolutely adored. She would dig through those bushes to find tasty raspberries that would terrify me when she inhaled them. I was sure that I would be doing the baby heimlich on her! I am glad that she learned, before she could even articulate words, that her sustenance comes magically out of the soil. She has the rest of her life to ponder how exactly that works and who might be behind it, but until then, she will feast.
My buddy Richie preached my wedding and said that the bible begins in a garden and ends in a garden. I plan to spend the time in between in a garden as well.
-
 @ 0dc2dcb1:4787801a
2025-03-19 20:27:04
@ 0dc2dcb1:4787801a
2025-03-19 20:27:04https://ccns.nostrver.se is a (Drupal powered) website that I started to build in January 2024 (source on Github and Gitlab). It's a fork of an earlier (abandoned) project https://cchs.social/.
Currently CCNS is a link aggregration website and for now it's only my who is using it to save and share Nostr related links. When you post a new link, you have the option to cross-post it as a Nostr note (example here).Kind 39700
Last month Jurjen and Abir have started to work on a social bookmark client built with Nostr (inspired by Del.icio.us from the past). Earlier this month they changed to event kind 39700 for broadcasting the Nostr event with the bookmark / link data accross the network. They did this because Sep already created a social bookmark like client called Pinja when fiatjaf raised this idea.
With these developments to me it was very obvious to integrate the feature that new created CCNS links are now also published as kind 39700 events to the Nostr network. This means that links are now also distributed on multiple relays as kind 39700 events and are accessible in multiple clients (Yumyume and Pinja).
Here you can see the same data, from left to right:

Structure
The current data structure for the 39700 kind looks as follow:
- "id": "event_id"
- "pubkey": "pubkey author"
- "created_at": unix_timestamp
- "kind": 39700
- "tags":
- "description", "description text here"
- "d", "unique-slug-value"
- "t", "hashtag"
- "content": "https://book_mark_url"
- "sig": "signature"
As there is no NIP (yet) for this event kind, I see some possible improvements:
- Use the bookmark URL value in the
dtag so it can be used as a unique identifier for every client - Use the
contentfield for the description value
On short-term I don't have any plans to developer CCNS further, as most of my attention goes to the development of the Nostr-PHP library and Drupal related contribs using that library. That said, CCNS is a Drupal project but all the Nostr stuff is done client-side (Javascript) with NDK and Nostr-PHP is not used (maybe this will change in the future).
-
 @ 7d33ba57:1b82db35
2025-03-19 20:01:18
@ 7d33ba57:1b82db35
2025-03-19 20:01:18Arucas
Arucas is a charming town in northern Gran Canaria, known for its **neo-Gothic cathedral, banana plantations, and famous rum distillery. With its volcanic stone architecture, lush gardens, and local delicacies, Arucas is a must-visit for culture and nature lovers.
🏛️ Top Things to See & Do in Arucas
1️⃣ Church of San Juan Bautista (Arucas Cathedral)
A stunning neo-Gothic masterpiece built from local volcanic stone. Its intricate façade and towering spires make it one of the most beautiful churches in the Canary Islands.
2️⃣ Arehucas Rum Distillery
Visit the oldest rum distillery in the Canary Islands and taste the famous Arehucas rum, aged in oak barrels and enjoyed worldwide.
3️⃣ Arucas Historic Old Town
Walk through cobblestone streets lined with colorful colonial houses and charming plazas. The town’s historic center has a unique Canarian feel.
4️⃣ Jardines de la Marquesa (Marquesa Gardens)
A beautiful botanical garden with over 500 exotic plant species, perfect for a peaceful stroll.
5️⃣ Montaña de Arucas Viewpoint
A short hike or drive up this volcanic hill offers panoramic views of Arucas, the coast, and Las Palmas in the distance.

🍽️ What to Eat in Arucas
- Papas arrugadas con mojo – Wrinkly potatoes with red & green sauces 🥔
- Queso de Flor – A special local cheese made with thistle flower 🧀
- Bienmesabe – A traditional almond dessert 🍯
- Arehucas Rum – Enjoy it neat or in cocktails 🥃
🚗 How to Get to Arucas
🚗 By Car: ~15 min drive from Las Palmas
🚌 By Bus: Direct routes from Las Palmas (Lines 205 & 206)💡 Tips for Visiting Arucas
✅ Best time to visit? Spring & autumn for mild weather 🌞
✅ Try a rum tour! The Arehucas distillery is one of the best experiences 🍹
✅ Explore nearby – Combine your trip with Firgas or Teror, two other beautiful towns nearby -
 @ a367f9eb:0633efea
2025-03-19 17:40:04
@ a367f9eb:0633efea
2025-03-19 17:40:04On February 27th, the Securities and Exchange Commission stated in its latest staff statement that memecoins are not necessarily securities.
“Although the offer and sale of meme coins may not be subject to the federal securities laws, fraudulent conduct related to the offer and sale of meme coins may be subject to enforcement action or prosecution,” writes the SEC.
This clarity is important, but it reveals nothing about what the policies around memecoins, rugpulls, and crypto scams should actually be.
This month has already delivered us Argentine President Javier Milei’s promotion of a pump-and-dump memecoin called LIBRA. At this moment, Barstool Sports founder Dave Portnoy is probably pumping his third or fourth favorite memecoin into oblivion while he dumps on retail.
In each of these cases, these tokens are created with copy-paste smart contracts, influencers singing their praises, and people exchanging their stablecoins, bitcoin, or some other altcoin for the hope of making it rich.
Memecoin world
Of course, in a free country people should be free to bet on things they want. But they should be prepared to lose just as much as they’re prepared to win.
To the uninitiated, these scams represent “crypto” writ-large, lumping the original decentralized protocol of Bitcoin with pump and dump scams from platforms like pump.fun that run on Solana and other chains.
Knowing what we know, and how desperate parts of the crypto market are for outrageous tokens and leveraged degen trading, we must naturally ask how Bitcoin can fix this. Or, rather, how smart Bitcoin policies can fix this.
As I have written for several years, we as Bitcoin advocates should promote sound policies that will encourage innovation and increase economic inclusion across all income groups, all the while protecting consumers from harm. We want to avoid blowouts like FTX, Celsius, and even stablecoins projects like TerraUSD – not only because they defraud bitcoiners, but because they sully the reputation of our entire sector of technological innovation.
Because Bitcoin represents scarcity, decentralization, and complete transparency, there is much we can learn from Satoshi’s innovation when we’re dealing with next-level crypto-offspring.
The Smart Bitcoin Policies to Stop Crypto Scams
To begin, US federal, state, and local agencies should update their technological stack to rigorously identify and prosecute fraud and abuse in crypto projects. Fraudulent claims, fake token whitepapers, and deceptive tactics are already illegal under existing law. Our agencies should be empowered to enforce existing law and weed out the bad actors.
Whether that means better training or tools, law enforcement should receive the necessary upgrades to prosecute and identify the real fraudulent crime that happens to take place in crypto protocols. Much of this behavior is just being used in a new medium. It’s not crazy to think that cops should upgrade their tech stack to understand how it’s happening now.
Second, our policies on money transmission licenses and regulation for crypto exchanges should be streamlined and made easier, rather than more difficult. Let competition provide the best places for people to buy their bitcoin. As much as privacy advocates abhor centralized platforms and exchanges, they still implement better security and educational practices to inform users than a shady service hosted in China will provide.
By simplifying the rules and restrictions on bitcoin exchanges, especially by allowing them to consider their custodied bitcoin as assets rather than liabilities as was done by rescinding SAB 121, it means that more Americans will have the opportunity to have excellent experiences when purchasing their coins online.
Third, regulators must not pigeonhole bitcoin and its crypto-offspring only as investments fit for taxing, but rather as technological tools that empower consumers and foster innovation. Too much discussion about bitcoin policies hinges on the tax rate or how much it will bring to state coffers, rather than by how much it can make one’s life better by removing the red tape to safeguard wealth.
By recognizing the ultimate power of bitcoin self-custody without needing to trust third parties or intermediaries, it means we finally view this technology as an extension of our own free speech and freedom of association.
And lastly, we must focus on removing the barriers to using bitcoin as an ordinary means of payment. The Keep Your Coins Act restricts federal agencies from stopping individuals from using bitcoin how they see fit, as well as protecting self-custody. That, plus de minimis exemption rules that allow us to spend bitcoin as any other asset, mean we can use digital money as intended.
We know that memecoins and rugpulls will continue to happen no matter what, this is almost human nature. But at the same time, embracing smart bitcoin policies will ensure that consumers and users have the best tools and protections available to use the technology if they want.
Originally published at the Bitcoin Policy Institute.
-
 @ fd208ee8:0fd927c1
2025-02-02 10:33:19
@ fd208ee8:0fd927c1
2025-02-02 10:33:19GitCitadel Development Operations
We, at GitCitadel, have been updating, moving, and rearranging our servers, for quite some time. As a rather large, complex, sprawling project, we have the infrastructure setup to match, so we've decided to give you all a quick run-down of what we are doing behind-the-scenes.
Supplier Coordination

Our first task, this week, was figuring out who would host what where. We have four different locations, where our infra is stored and managed, including two locations from our suppliers. We got that straightened out, quickly, and it's all slowly coming together and being connected and networked. Exciting to watch our DevOps landscape evolve and all of the knowledge-transfer that the interactions provide.
OneDev Implementation

Our biggest internal infra project this week was the migration of all of our issues from Jira, build scripts from Jenkins, and repos from GitHub to a self-hosted OneDev instance. In the future, all of our internal build, test, issue, patch/PR, etc. effort will take place there. We also have a separate repo there for communicating with external developers and suppliers.
Our team's GitHub projects will be demoted to mirrors and a place for external devs to PR to. Public issues and patches will continue to be managed over our self-hosted GitWorkshop instance.
We're especially glad to finally escape the GitHub Gulag, and avoid being bled dry by Jira fees, without having to give up the important features that we've come to know and love. So, yay!
Next Infrasteps
Automated Testing
Now, that we have everything tied up in one, neat, backed-up package, we can finally move on to the nitty-gritty and the dirty work. So, we're rolling up our sleeves and writing the Selenium smoke test for our Alexandria client. We'll be running that in Docker containers containing different "typical Nostr" images, such as Chrome browser with Nostr Connect signing extension, or Firefox browser with Nos2x-fox extension. Once we get the Nsec Bunker and Amber logins going, we'll add test cases and images for them, as well. (Yes, we can do Bunker. I hope you are in awe at our powers).
We are also designing an automated infrastructure test, that will simply rattle through all the various internal and external websites and relays, to make sure that everything is still online and responsive.
After that, a Gherkin-based Behave feature test for Alexandria is planned, so that we can prevent regression of completed functionality, from one release to the next.
The Gherkin scenarios are written and attached to our stories before development begins (we use acceptance tests as requirements), a manual test-execution is then completed, in order to set the story to Done. These completed scenarios will be automated, following each release, with the resulting script linked to from the origin story.

Automated Builds
As the crowning glory of every DevOps tool chain stands the build automation. This is where everything gets tied together, straightened out, configured, tested, measured, and -- if everything passes the quality gates -- released. I don't have to tell you how much time developers spend staring at the build process display, praying that it all goes through and they can celebrate a Green Wave.

We are currently designing the various builds, but the ones we have defined for the Alexandria client will be a continuous delivery pipeline, like so:

This will make it easier for us to work and collaborate asynchronously and without unnecessary delays.
Expanding the Status Page

And, finally, we get to the point of all of this busyness: reporting.
We are going to have beautiful reports, and we are going to post them online, on our status page. We will use bots, to inform Nostriches of the current status of our systems, so go ahead and follow our GitCitadel DevOps npub, to make sure you don't miss out on the IT action.
Building on stone
All in all, we're really happy with the way things are humming along, now, and the steady increase in our productivity, as all the foundational work we've put in starts to pay off. It's getting easier and easier to add new team members, repos, or features/fixes, so we should be able to scale up and out from here. Our GitCitadel is built on a firm foundation.
Happy building!
-
 @ 3c7dc2c5:805642a8
2025-03-19 17:37:28
@ 3c7dc2c5:805642a8
2025-03-19 17:37:28🧠Quote(s) of the week:
“National debt is immoral and destructive, silently undermining the basis of the state; it delivers the present generation to the execration of posterity.” - Napoleon
🧡Bitcoin news🧡
I was a bit under the weather the last couple of days so it took me a longer to write the Weekly Recap, anyway...here we go:
On the 11th of March:
➡️European Union claims President Trump's support for crypto could harm Europe's "monetary sovereignty and financial stability." The EU could be educating European people on Bitcoin, they could adapt sound money early, join the Bitcoin race early, and make the lives of all Europeans better. Instead, they choose to lie and make all Europeans miss the boat. I have no words for this. Freaking dinosaurs!
President Trump's support for Bitcoin threatens their "monetary sovereignty and financial stability" -> translation: people might choose freedom over their broken monetary system.
Remember Christine Lagarde’s famous quote on Bitcoin: “There has to be regulation. This has to be applied and agreed upon … at a global level because if there is an escape, that escape will be used.”
It’s a revealing statement, highlighting how Bitcoin offers an “escape route” from traditional financial systems—a route that could unlock greater decentralization and freedom.
➡️Wicked: Bitcoin's 4-Year CAGR has dropped below 10% for the first time ever.
➡️Texas introduces HB 4258, aiming to allocate up to $250M of state funds to Bitcoin and digital assets, and allowing local governments to invest up to $10M.
➡️Bitwise has launched a "Bitcoin Standard Corporations ETF" that includes +70 companies holding Bitcoin as a treasury reserve asset.
➡️Tether CEO Paolo Ardoino: The US Strategic Bitcoin Reserve announcement is a “holy sh*t” moment for the rest of the world, realizing they’re late and don’t have enough Bitcoin.
On the 12th of March:
➡️US Government should issue $2 TRILLION of Bitcoin-backed Bonds to buy $200B of Bitcoin - Newmarket Capital CEO Bit Bonds in a nutshell: - 90% goes to government funding, 10% to buying bitcoin - 1% interest annually for 10 years - 100% of BTC upside paid up to 4.5% compounded annual return - Remaining BTC upside split 50/50 with the government
➡️The Kingdom of Bhutan builds a gorgeous airport thanks to Bitcoin mining profits using hydro-electricity.
➡️Deutsche Bank says a US strategic Bitcoin reserve "could set international standards.
➡️Bitcoin dropped 72% in 2018 ($3,740.50 bottom) due to the USA - China trade war and 2.9% inflation...
➡️Rumble just bought another $27m Bitcoin.
On the 13th of March:
➡️'FIVE years ago today, Bitcoin crashed more than 50% in ONE day, from $7,900 to $3,800 in hours. We're up 21X ever since. Zoom out, DCA Bitcoin, and enjoy the ride. We are just getting started.' - CarlBMenger
➡️78% of all ETH/BTC trading days are now in the red... REKT.
➡️While Retail Paper Hands are selling their precious coins, whales bought them. Over 65K Bitcoin net-accumulated in the past 30 Days, excluding Miners and Exchanges.
➡️New peer-reviewed research study finds Bitcoin mining has the potential to significantly enhance the sustainability of the energy supply chain by using wasted resources and creating new business opportunities that align economic incentives with sustainability goals.
It's one of 15 pieces of peer-reviewed research showing Bitcoin has significant environmental benefits.
You can find the full list here: https://x.com/DSBatten/status/1899951222779789420
➡️The Bitcoin Act to buy 1 MILLION Bitcoin is under consideration by Congress.
➡️Bitcoin ETF inflows have fallen to $35B from a $40B peak, yet with $115B in AUM, over 95% of capital is holding firm despite a 25% price drop.
➡️Construction of the Vega 205 megawatt Bitcoin mine in Texas is nearing completion. Hut 8 is installing dry coolers for the direct-to-chip liquid cooling system while finishing up the side panels, insulation, and roof.
➡️Fast food giant Steak 'n Shake posted this picture of a Bitcoin spaceship.
➡️Altcoin holders are deep in the red, with some tokens nearing 100% at a loss. I am not surprised, the house (shitcoin casinos) always wins. https://i.ibb.co/G44T01Yy/Gl-ubpfb-YAAfa-S9.jpg
On the 14th of March:
➡️Russia is using Bitcoin and Tether to pay for oil trades with China and India - Reuters
➡️Kentucky Senate passes bill that will protect Bitcoin self-custody rights with 0 votes against it. The bill now heads to the Governor's desk.
➡️Brazil bill seeks to legalize the use of Bitcoin to pay salaries and benefits.
On the 15th of March:
➡️'Senator Lummis's proposed BITCOIN Act lays out how America would revalue its gold certificates to buy 1 million Bitcoin over 5 years.
1.Within 180 days of enactment, Federal Reserve banks must return all gold certificates to the U.S. Treasury.
2.Within 90 days of receiving the last one, the Treasury will issue new certificates reflecting gold’s market price.
3.Federal Reserve banks must pay the Treasury the difference if the new certificates are worth more.
4.This extra cash goes to the government fund within 90 days.' - BitcoinNews
https://i.ibb.co/d4JvzXzs/Gm-Gexy-Nbc-AE7-Tpu.jpg
➡️DOGE’S FORT KNOX GOLD AUDIT COULD TAKE 18 MONTHS A full audit of Fort Knox’s gold reserves would be a massive undertaking, with JM Bullion estimating it would take at least 18 months to complete. - Requires 20 personnel - Uses 18 high-quality scales & XRF scanners - Needs 2 boring drills & 18 item carts The effort aims to bring long-overdue transparency to U.S. gold holdings—a process that hasn’t been fully conducted in decades. That's cute, I can audit the entire Bitcoin supply from my home in less than a minute.
On the 17th of March:
➡️'80 public companies are now buying bitcoin. Two years ago there were 33. Two years from now there will be...?' -River (foto) With 55,214 publicly traded companies worldwide, that's a little over one in a thousand. It's so early! https://i.ibb.co/FLZKfv1X/Gm-QKCGob0-AAd-LNo.jpg
➡️Bitcoin reserves held by the 14 biggest North American mining companies exceeded 101,000 BTC for the first time in February.
➡️'Strategy has acquired 130 BTC for ~$10.7M at ~$82,981 per bitcoin and has achieved a Bitcoin Yield of 6.9% YTD 2025. As of 3/16/2025, we hodl 499,226 Bitcoin acquired for ~$33.1 billion at ~$66,360 per Bitcoin.' - Saylor
💸Traditional Finance / Macro:
On the 11th of March:
👉🏽Nasdaq 100 futures erase premarket gain and turn negative, now down -12.5% since February 19th.
On the 13th of March:
👉🏽The S&P 500 just CLOSED in correction territory and the Nasdaq 100 is 7% away from its first bear market since 2022. Over the last 16 trading days, the S&P 500 has erased an average of -$340 billion PER trading day. Although this sounds alarming whatsoever, it really isn't. The S&P is only down ~10%. It also fell 10% in 2023 and last July. No one even remembers now. Get a grip.
🏦Banks:
👉🏽 no news
🌎Macro/Geopolitics:
On the 11th of March:
👉🏽President Trump announces ADDITIONAL 25% tariffs on Steel and Aluminum coming to the US from Canada. This brings tariffs on these goods up to a new high of 50%.
👉🏽European Commission to use 10 trillion Euros of citizens’ savings for EU defense. The European Commission estimates the total level of unused savings of EU citizens at 10 trillion Euros, and it intends to find ways to mobilize this money to finance its plans to militarise Europe and support the European military-industrial complex, according to a statement by the European Commissioner for Financial Services and the Savings and Investment Union Maria Luís Albuquerque, distributed by the EC press service, TASS reports.
https://i.ibb.co/Xr28KPbR/Glx-Gzzc-XAAAXn-ZI.png
"We'll turn private savings into much-needed investment". 1. All savings are invested in the economy. 2. She means they will leverage your deposits to finance more government spending. Be scared, and what exactly are "unused savings" per se? Do you understand the predicament you are in yet, or what our children will be in?
It is the best advert you will see for self-custody Bitcoin. https://i.ibb.co/PZnKQdqF/Glwl-Nyc-WQAA-AIE.jpg
👉🏽Last week I already mentioned that the ECB confirmed launching the digital euro in October. That's the deadline. Why is Lagarde insisting on this? Is the digital euro in the interest of the citizens or the interest of the government and the implementation of its policies?
The ECB says it will limit the amount of money people can store in digital euros to, in their words, "prevent excessive outflows of deposits from banks." It's never a good sign when you have to lock people in...
https://i.ibb.co/s9v7n1BS/Gm-Liap-Ob-QAA9j0g.jpg
Now the two topics above are just mental, it is crazy to read the following tweet by the ECB: "Did you know that 60% of Europeans with low financial literacy are women? But what is financial literacy? Why is it important? And what does it have to do with central banks?"
Lagarde and Von der Leyen are two of them, FFS!
On the 12th of March:
👉🏽For my Dutch readers/followers. How is your energy bill? The average energy bill for a Dutch household increased by €18 in January, reaching €2,703 per year. The share of taxes and VAT in this amount is €1,457. Energy costs are increasingly passed on to households through products and services. That's what you call inflation and the government is, of course, very happy with the very expensive imported gas because the taxes on it are a goldmine. I fully understand why we are doing that because we don't have a huge gas field in our country, right?
https://i.ibb.co/vC4wzSKp/Glyf9-DSXMAALTc-Q.png
Just to explain it in simple words: 50% of your energy bill is taxes. That is just criminal.
👉🏽'The Federal Deficit for Feb '25 ($307B) and before you get lathered up over the edge trimming at DOGE if you aren't willing to cut (not reduce growth - cut) what is in red you will never put a dent in what is in purple.' - Blacklion $307 billion was added to the US federal deficit last month, which was bigger than all tax revenue, widening the deficit to 7.23% of GDP.
If government spending halted, we'd be plunged into a decade-long recession. This addiction will take years, if not decades, to sober up from. Nothing stops this train, NOTHING!
https://i.ibb.co/ZRsm5nCM/Gl2-i9-WUAAw-V5w.jpg
On the 13th of March:
👉🏽Gold trades above $3k for first time ever: $3,000.40. As the S&P 500 has erased $5+ trillion, gold is now set to cross above a record $20 TRILLION in market cap. Gold has more than QUADRUPLED the S&P 500's return over the last 12 months. Gold is telling us something. Nothing says Sovereign Debt Crisis like gold pressing toward new ATH. In the past Bitcoin always followed with a lag and harder.
On the 14th of March:
👉🏽German debt deal compromise foresees €100 bln for climate and transformation fund - Source familiar with talks
ZeroHedge: 'GERMAN DEBT DEAL TO EXEMPT DEFENCE SPENDING FROM DEBT BRAKE ABOVE 1% OF GDP BUT INCLUDES EXPANDED DEFINITION OF DEFENCE SPENDING, SOURCE SAYS.
In other words, "defense against Russia" is just a pretext to flood the economy with a new debt-funded fiscal stimulus, just like Covid.'
As I mentioned above, financial literacy at the ECB and EU Commission.
Von der Leyen: 'We are presenting a new EUR 4.7 billion Global Gateway investment package for South Africa. For projects that support a just energy transition. For connectivity – both physical and digital. And for vaccines, produced in Africa, for Africa.'
Africa is not a member of the EU. So they should stop wasting (spending) our money, 4.7 billion of European taxpayers.
The people, Von der Leyen, who want to "mobilize" the €10T in private citizens' savings, and who are overseeing €13.8T in combined government debt, seem to be as excited as ever about subsidizing questionable regimes all around the world. You don't believe me...I have another example.
Now for the next example, I don't want to make it political but for fuck sake.
'The EU and its partners just pledged €5.8 billion for Syria and its neighbors. This will support Syria at a crucial time of transition and address the dire needs on the ground. This is a chance for the people of Syria to seize the moment and shape their own destiny.' - EU High Representative for Foreign Affairs and Security Policy / Vice-President of the European Commission, Kaja Kallas
No matter your view on the Syria situation sending money to Syria now while supporting the current regime who kill Christians and Alawites. I am an atheist so couldn't care less if we are talking about Christians, Alawites, Muslims, or another religion, people in Syria are getting slaughtered at the moment.
Are these our European values?
€5.8 billion in taxpayer money disappears into Syria again, while Europeans struggle with skyrocketing costs, unaffordable groceries, and failed migration policies. The EU never learns: billions are sent to corrupt regimes while our own people are left behind. Giving Syria a ‘chance’ to determine its own future? That money will end up in the pockets of dictators and militants, just like always. Europe must stop this wasteful spending and focus on its own citizens first.
So 4.7 billion to South Africa and 5.8 billion to Syria, that's 10.5 billion wasted tax payer's money already. Again, hello financial literacy!
Just remember Ursula von der Leyen has previously disregarded defense procurement rules in Germany—the McKinsey affair.
She also committed plagiarism.
In Brussels, lawsuits are ongoing against her regarding the infamous €35 billion SMS-Pfizer deal.
Next example: Christine Lagarde says ‘impossible’ for ECB to always guarantee 2% inflation.
Potential price pressure from the trade war and debt-fuelled borrowing add to the uncertainty, warns the central bank president. Don’t forget, that Macron appointed her. It is all so obvious…
Lex Hoogduin: "This is how a politician makes a turn towards an inflation rate that is, on average, too high and a policy that is too loose, I fear. She has listened carefully to Macron and is executing this in an extremely sophisticated manner—just as she is pushing through the CBDC."
Long-term global inflation chart. WTF happened in 1971? https://i.ibb.co/YYj1kDR/Gm-EHbfk-WAAAm-Sx-P.jpg
Another example:
ECB's Villeroy (a man, full disclosure): The EU has the resources to retaliate against Trump's threatened tariffs on wine and liquor. Now ask yourself, why is a central banker commenting on a trade war? Is that within their mandate? I have the answer: NO!
And it is not only the EU Commission or the ECB. France wants to boost defense spending, but with higher taxes and more debt ruled out as options, Macron’s government is desperately looking for solutions.
Meanwhile, France: - High public debt (112% of GDP) - Large budget deficit (6.2% of GDP) - Ambitious plans for additional spending - Rising interest rates
What could possibly go wrong?
Anyway, I can give example after example but the only thing you need to know we are in a debt rat race without brakes.
If things go wrong, all EU member states will pay the price. And the collateral?
You!
Got Bitcoin?
On the 16th of March:
👉🏽'US interest payments are set to rise even higher: US interest expense on national debt hit a record $1.2 trillion over the last 12 months. To put this into perspective, defense spending was $900 billion during the same period. If rates remain FLAT, interest payments are set to hit $1.5 trillion by the end of the year, doubling in just 4 years.
Even if the Fed cuts rates by 100 basis points, interest costs will still hit ~$1.3 trillion in 2025.
This all assumes the economy will avoid a recession or any material economic slowdown.
This is a crisis.' -TKL
🎁If you have made it this far I would like to give you a little gift:
'A long but thoughtful analysis and opinion on the current volatility and pricing of Bitcoin. We’re in the midst of a technological, monetary, fiscal & currency shift. This is more than an investment idea. The unbanked around the world might soon find freedom as a result.'
https://x.com/JoeConsorti/status/1900285521084965204
After that, kick back, relax, and enjoy: Bitcoin Mastermind Q1 2025 with Joe Carlasare, Jeff Ross, & American HODL.
'A deep dive into the dollar’s weakness, Bitcoin bonds, regulatory updates, and market liquidity trends. Plus, an analysis of major economic shifts, technical buy signals, and the outlook for global assets.'
https://www.youtube.com/watch?v=XzgXe-42PI0
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly.
Use the code SE3997
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀⠀⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ 2e8970de:63345c7a
2025-03-19 17:34:18
@ 2e8970de:63345c7a
2025-03-19 17:34:18Trip speed in the zone:
The more detailed view on entereing/leaving/within/outside the zone:
Reminder on New Yorks Congestion priced zone:

source: https://www.nber.org/papers/w33584
short faq on the most frequent points:
Government central planning!!!11
Maybe. But then so are all other free roads payed for by taxpayers
Isn't this targeting poor people?
In other citys this might be worth discussing. In NY it's pretty clear most people just take the subway and owning a car is a luxury.
This will destroy local businesses
Foot traffic went up. Broadway ticket sales are up.
Trip speed? How is this a good indicator?
Well, considering how much traffic jams there were before, we consider it a win. Honking complaints are also down.
Doesn't the congestion priced zone effect the "outside CBD? Is that still a good control?
Fair point.
originally posted at https://stacker.news/items/917929
-
 @ fd208ee8:0fd927c1
2025-01-23 15:31:24
@ fd208ee8:0fd927c1
2025-01-23 15:31:24Planning Alexandria
People keep asking what features nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz has planned for #Alexandria, but they're not set in stone because we're an agile project.
What we do have, is lots of tickets on our Kanban boards and a naming scheme, where we use a famous person's last name, to signify the release goals.

Gutenberg v 0.1.0
(after the inventor of the printing press) will contain the features needed to read and write NIP-62 Curated Publications, as well as encompassing the complex infrastructure, architecture, documentation, and personnel we require to make this all run smoothly and look easy.

Euler v 0.2.0
(after a mathematician credited with establishing graph theory) will contain the features for deep-searching, visually exploring, and smartly navigating the data set, wiki page display, annotating and citing the publications, exporting to other formats (like PDF, ePUB, and LaTeX), and commenting/reviewing. To help with the heavy lifting, we will be swapping out the core with our own Nostr SDK called "Aedile".

Defoe v 0.3.0
(after an author who perfected the novel format) will be all about our favorite writers. We will be focusing upon profile data, payment systems, book clubs and communities, and stylesheets.
That is everything we have planned, for the v1.0 edition, and we consider that version to be a true product.
As for after that, a teaser...

-
 @ e034d654:ca919814
2025-01-22 23:14:27
@ e034d654:ca919814
2025-01-22 23:14:27I stumbled into nostr end of March 2023. At that point already fully thrown into the hows, whys and whats of Bitcoin, never really interested in social apps, just recently playing around with Lightning, the only experience of which at the time was Muun (😬) and stacker.news custodial wallet.
Fairly inexperienced with technicals other than rough understandings of concepts. A crappy laptop node with a dangling SSD via USB, constantly having to resync to current blockheights whenever I was ready to make an on chain transaction to cold storage. My great success after over two years of delay, and a couple failed attempts.
Something about the breadth of information for nitty gritty specifics, the clash with all the things that I found interesting about Bitcoin, with others equally as focused, kept me interested in Nostr. Plus the lighthearted shit posting to break up plumbing the depths of knowledge appealed to me.
Cut to now. Through the jurisdictional removals and even deaths of LN wallet projects, using mobile LSPs, finding use cases with the numerous cashu implementations, moderate comfortability with NWC strings of various permissions, budgets for seemingly endless apps of Nostr clients, swapping relays, isolated wallets with Alby go for my wife and cousin (I told them both not to put much on there as I'm sure failure is imminent) Alby Hub and Zeus, now fully backended by my own persistently online lightning node. All of it adding to the fluidity of my movement around the protocol.
Nimble.
Gradual progress. Reading through notes and guides posted on Nostr learning little bits, circling back eventually, if even at a time it wasn't clicking for me. Either way. Glad i've stuck to it even if I still barely know what it is I'm doing.
-
 @ cff1720e:15c7e2b2
2025-03-20 11:14:33
@ cff1720e:15c7e2b2
2025-03-20 11:14:33Wolfgang Borchert 1947\ (Wolfgang Borchert starb mit 26 Jahren an einer Kriegsverletzung)
Dann gibt es nur eins!
Du. Mann an der Maschine und Mann in der\ Werkstatt. Wenn sie dir morgen befehlen, du\ sollst keine Wasserrohre und keine Kochtöpfe\ mehr machen – sondern Stahlhelme und\ Maschinengewehre, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Mädchen hinterm Ladentisch und\ Mädchen im Büro. Wenn sie dir morgen\ befehlen, du sollst Granaten füllen und\ Zielfernrohre für Scharfschützengewehre\ montieren, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Besitzer der Fabrik. Wenn sie dir morgen\ befehlen, du sollst statt Puder und Kakao\ Schießpulver verkaufen, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Forscher im Laboratorium. Wenn sie dir\ morgen befehlen, du sollst einen neuen Tod\ erfinden gegen das alte Leben, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Dichter in deiner Stube. Wenn sie dir\ morgen befehlen, du sollst keine Liebeslieder,\ du sollst Haßlieder singen, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Arzt am Krankenbett. Wenn sie dir\ morgen befehlen, du sollst die Männer\ kriegstauglich schreiben, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Pfarrer auf der Kanzel. Wenn sie dir\ morgen befehlen, du sollst den Mord segnen\ und den Krieg heilig sprechen, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Kapitän auf dem Dampfer. Wenn sie dir\ morgen befehlen, du sollst keinen Weizen\ mehr fahren – sondern Kanonen und Panzer,\ dann gibt es nur eins:\ Sag NEIN!\ \ Du. Pilot auf dem Flugfeld. Wenn sie dir morgen\ befehlen, du sollst Bomben und Phosphor\ über die Städte tragen, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Schneider auf deinem Brett. Wenn sie\ dir morgen befehlen, du sollst Uniformen zuschneiden,\ dann gibt es nur eins:\ Sag NEIN!\ \ Du. Richter im Talar. Wenn sie dir morgen befehlen,\ du sollst zum Kriegsgericht gehen, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Mann auf dem Bahnhof. Wenn sie dir\ morgen befehlen, du sollst das Signal zur Abfahrt\ geben für den Munitionszug und für den\ Truppentransport, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Mann auf dem Dorf und Mann in der\ Stadt. Wenn sie morgen kommen und dir den\ Gestellungsbefehl bringen, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Mutter in der Normandie und Mutter in\ der Ukraine, du, Mutter in Frisko und London,\ du, am Hoangho und am Mississippi, du,\ Mutter in Neapel und Hamburg und Kairo und\ Oslo - Mütter in allen Erdteilen, Mütter in der\ Welt, wenn sie morgen befehlen, ihr sollt\ Kinder gebären, Krankenschwestern für\ Kriegslazarette und neue Soldaten für neue\ Schlachten, Mütter in der Welt, dann gibt es\ nur eins:\ Sagt NEIN! Mütter, sagt NEIN!\ \ Denn wenn ihr nicht NEIN sagt, wenn IHR nicht nein sagt, Mütter, dann:\ dann:
... Fortsetzung
https://route96.pareto.space/cdd62d02f73eec86bfcaa8108ef515795c6a3c714a418880ea9d267c4aeb1a8d.mp3
-
 @ 65886e63:118f7ab8
2025-03-19 13:35:37
@ 65886e63:118f7ab8
2025-03-19 13:35:37"When software developers aim at the cognitive aspects of education without understanding the social aspects, they miss the dartboard entirely." https://open.substack.com/pub/danmeyer/p/do-kids-want-a-personalized-netflix?utm_source=share&utm_medium=android&r=b4wcg
-
 @ fd208ee8:0fd927c1
2025-01-19 12:10:10
@ fd208ee8:0fd927c1
2025-01-19 12:10:10I am so tired of people trying to waste my time with Nostrized imitations of stuff that already exists.
Instagram, but make it Nostr. Twitter, but make it Nostr. GitHub, but make it Nostr. Facebook, but make it Nostr. Wordpress, but make it Nostr. GoodReads, but make it Nostr. TikTok, but make it Nostr.
That stuff already exists, and it wasn't that great the first time around, either. Build something better than that stuff, that can only be brought into existence because of Nostr.
Build something that does something completely and awesomely new. Knock my socks off, bro.
Cuz, ain't nobody got time for that.
-
 @ 7776c32d:45558888
2025-03-19 13:16:46
@ 7776c32d:45558888
2025-03-19 13:16:46March 18, 55 years after UNIX epoch
My name is Mahmoud Khalil and I am a political prisoner. I am writing to you from a detention facility in Louisiana where I wake to cold mornings and spend long days bearing witness to the quiet injustices underway against a great many people precluded from the protections of the law.
Who has the right to have rights? It is certainly not the humans crowded into the cells here. It isn't the Senegalese man I met who has been deprived of his liberty for a year, his legal situation in limbo and his family an ocean away. It isn't the 21-year-old detainee I met, who stepped foot in this country at age nine, only to be deported without so much as a hearing.
Justice escapes the contours of this nation's immigration facilities.
On March 8, I was taken by DHS agents who refused to provide a warrant, and accosted my wife and me as we returned from dinner. By now, the footage of that night has been made public. Before I knew what was happening, agents handcuffed and forced me into an unmarked car. At that moment, my only concern was for Noor's safety. I had no idea if she would be taken too, since the agents had threatened to arrest her for not leaving my side. DHS would not tell me anything for hours - I did not know the cause of my arrest or if I was facing immediate deportation. At 26 Federal Plaza, I slept on the cold floor. In the early morning hours, agents transported me to another facility in Elizabeth, New Jersey. There, I slept on the ground and was refused a blanket despite my request.
My arrest was a direct consequence of exercising my right to free speech as I advocated for a free Palestine and an end to the genocide in Gaza, which resumed in full force Monday night. With January's ceasefire now broken, parents in Gaza are once again cradling too-small shrouds, and families are forced to weigh starvation and displacement against bombs. It is our moral imperative to persist in the struggle for their complete freedom.
I was born in a Palestinian refugee camp in Syria to a family which has been displaced from their land since the 1948 Nakba. I spent my youth in proximity to yet distant from my homeland. But being Palestinian is an experience that transcends borders. I see in my circumstances similarities to Israel's use of administrative detention imprisonment without trial or charge to strip Palestinians of their rights. I think of our friend Omar Khatib, who was incarcerated without charge or trial by Israel as he returned home from travel. I think of Gaza hospital director and pediatrician Dr. Hussam Abu Safiya, who was taken captive by the Israeli military on December 27 and remains in an Israeli torture camp today. For Palestinians, imprisonment without due process is commonplace.
I have always believed that my duty is not only to liberate myself from the oppressor, but also to liberate my oppressors from their hatred and fear. My unjust detention is indicative of the anti-Palestinian racism that both the Biden and Trump administrations have demonstrated over the past 16 months as the U.S. has continued to supply Israel with weapons to kill Palestinians and prevented international intervention. For decades, anti-Palestinian racism has driven efforts to expand U.S. laws and practices that are used to violently repress Palestinians, Arab Americans, and other communities. That is precisely why I am being targeted.
While I await legal decisions that hold the futures of my wife and child in the balance, those who enabled my targeting remain comfortably at Columbia University. Presidents Shafik, Armstrong, and Dean Yarhi-Milo laid the groundwork for the U.S. government to target me by arbitrarily disciplining pro-Palestinian students and allowing viral doxing campaigns - based on racism and disinformation - to go unchecked.
Columbia targeted me for my activism, creating a new authoritarian disciplinary office to bypass due process and silence students criticizing Israel. Columbia surrendered to federal pressure by disclosing student records to Congress and yielding to the Trump administration's latest threats. My arrest, the expulsion or suspension of at least 22 Columbia students some stripped of their B.A. degrees just weeks before graduation and the expulsion of SWC President Grant Miner on the eve of contract negotiations, are clear examples.
If anything, my detention is a testament to the strength of the student movement in shifting public opinion toward Palestinian liberation. Students have long been at the forefront of change leading the charge against the Vietnam War, standing on the frontlines of the civil rights movement, and driving the struggle against apartheid in South Africa. Today, too, even if the public has yet to fully grasp it, it is students who steer us toward truth and justice.
The Trump administration is targeting me as part of a broader strategy to suppress dissent. Visa-holders, green-card carriers, and citizens alike will all be targeted for their political beliefs. In the weeks ahead, students, advocates, and elected officials must unite to defend the right to protest for Palestine. At stake are not just our voices, but the fundamental civil liberties of all.
Knowing fully that this moment transcends my individual circumstances, I hope nonetheless to be free to witness the birth of my first-born child.
-
 @ 044da344:073a8a0e
2025-03-19 13:03:30
@ 044da344:073a8a0e
2025-03-19 13:03:30Journalismus nach Corona
Medienrealität, 17. April 2020, und Rubikon ("Das Ende einer Ära"), 17. April 2020
Diese Krise, da ist sich Heribert Prantl sicher, „bringt einen auf verrückte Gedanken“ – auf Dinge, „die man vorher nie gedacht hat und die man auch nie denken wollte“. So verrückt ist das gar nicht, was Prantl da zu Ostern geschrieben hat. In Kurzform: Kliniken sind kein Geschäftsmodell. Sonst zahlen am Ende die Kranken. Und: Das Gesundheitswesen ist wie die Wasserversorgung. Wir brauchen beides und dürfen deshalb weder das eine noch das andere „durchkommerzialisieren“ (Prantl 2020). Womit wir bei den Medien wären. Vielleicht hält das ja sogar Heribert Prantl für verrückt: ein Journalismus, der der Gesellschaft dient und nicht dem Staat oder dem Kapital.
Für die Medienforschung heißt das: zurück zu ihren Wurzeln. Karl Bücher, der Gründervater der akademischen Journalistenausbildung in Deutschland, war sich am Ende eines langen Lebens sicher, dass die Presse „ein öffentliches Institut“ sein muss, genau „wie Straßenbahnen, Gasanstalten, Elektrizitätswerke“ (Bücher 1926: 424). Dieser Bücher, ein weltberühmter Ökonom, hat das so ähnlich gesehen wie Heribert Prantl beim Gesundheitswesen: „Die Redaktion soll ihrer Natur nach die höchsten Interessen der Menschheit verfolgen“ – könne das aber nicht, solange sie Rücksicht nehmen muss auf „Privatinteressen“ (Bücher 1926: 397, 426). Anzeigenkunden, Leserwünsche, Profit.
Karl Bücher war vorbereitet auf die Chance, die jede Krise bietet. Er hat schon im Weltkrieg öffentlich über das Nachrichtenmonopol der großen Agenturen geschimpft und über den „Tiefstand“ des Zeitungswesens (vgl. Meyen 2002). Als die bayerische Räteregierung ihn dann Anfang 1919 um einen Gesetzentwurf bittet, will er dem Übel an die Wurzel und schlägt zehn Paragrafen vor, die auf eine Enteignung hinauslaufen und auf ein Ende des Wettbewerbs. Keine Anzeigen mehr an private Verleger. Dafür ein Lokalblatt pro Ort, herausgegeben von der Gemeinde, kostenfrei für jeden, finanziert über das, was Unternehmen und Behörden bekanntgeben wollen. In dem Aufsatz, den Bücher später nachgeliefert hat, beruft er sich unter anderem auf Ferdinand Lassalle. Sinngemäß: weg von einer „öffentlichen Meinung“, die vom „Kapital“ geprägt wird sowie von der „privilegierten großen Bourgeoisie“, hin zu einer „freien Tagespresse“, die „schwebende politische Fragen“ erörtert (Bücher 1926: 396).
Verrückt? Wer weiß, was Karl Bücher geschrieben hätte über den Corona-Journalismus der Gegenwart. Er hat schon vor einhundert Jahren nicht nachvollziehen können, warum die Redaktionen sich mit „Nichtigkeiten“ abgeben, gegen Polizeireporter gewettert und die Lokalnachrichten für eine „geistlose Chronik“ gehalten. Die Nähe zur Politik hat er entweder nicht gesehen oder nicht verstanden, dass das ein Problem sein könnte, weil er selbst zur Elite gehörte. Vermutlich wäre er trotzdem zufrieden mit einigen seiner Erben – mit Otfried Jarren (2020) zum Beispiel, der das öffentlich-rechtliche Fernsehen sehr früh kritisiert hat („Systemmedium“, „besondere Form der Hofberichterstattung“), mit Hektor Haarkötter („Geht’s auch mal wieder kritisch?“) oder mit Klaus Meier und Vinzenz Wyss (2020), die höflich bleiben und dankbar sind, ohne dabei die vielen Defizite zu übersehen. Der „Umgang mit Zahlen“, der Fokus auf Einzelfälle und auf „Virologen als unfehlbare Medienstars“, kaum Transparenz, wenig Vielfalt.
Wissenschaftler sein und öffentlich für seine Überzeugungen zu kämpfen: Das waren für Karl Bücher zwei Seiten derselben Medaille. Ihm hätte deshalb auch gefallen, wie Vinzenz Wyss (2020), ein Kollege aus der Schweiz, die Medienrealität an dem misst, was die Gesellschaft vom Journalismus erwarten darf. Ja, sagt Vinzenz Wyss, es gibt tolle Stücke, mit viel Aufwand produziert. Das große Aber: die „Newsmedien“ – also das, was das Publikum nicht ignorieren kann. Das muss hier nicht im Detail wiederholt werden. Zahlen ohne Erhebungskontext. Die „Zahlenfixierung“ überhaupt, kombiniert mit fehlender Distanz zur Macht und dem Unwillen, die eigenen Grenzen zu thematisieren. Zweimal O-Ton Vinzenz Wyss: „Ich bin fast ein bisschen empört, wie stark Journalisten in dieser Krise Wissenschaftler als Wahrsager darstellen“. Und: „Wenn die Exekutive dominiert und die parlamentarische Debatte verstummt, muss der Journalismus besonders wachsam sein“.
Vinzenz Wyss ist am Ende gar nicht weit weg von Heribert Prantl und Karl Bücher. „Wir sehen jetzt, wie wichtig der Journalismus ist“, sagt er. Und wir sehen auch, „wie schwach das Immunsystem derjenigen Medien ist, die sich vorwiegend über Werbegelder finanzieren“.
Es ist nicht schwer, das weiterzudenken. Corona zeigt: Die digitalen Plattformen mögen wichtig sein, die Realität aber wird nach wie von den Leitmedien gesetzt. Die Macht liegt bei denen, die es schaffen, ihre Version der Wirklichkeit in der Tagesschau zu platzieren, in der Süddeutschen Zeitung, im Spiegel, in der Zeit, in der Bild-Zeitung. Wir haben gesehen, was passiert, wenn die Pressemitteilungen der Regierung zur Medienrealität werden, die großen Leitartikler mit den Politikern heulen und ihre kleinen Gefolgsleute jeden Abweichler im Netz als Verschwörer und Gesundheitsfeind brandmarken. Zustimmungsraten wie in Nordkorea.
Es gibt einen Aufsatz von Elisabeth Noelle-Neumann (1973) mit dem feinen Titel „Kumulation, Konsonanz und Öffentlichkeit“. Sie könne einfach nicht glauben, schreibt Noelle-Neumann vor fast einem halben Jahrhundert, dass Medien keine Wirkung haben sollen oder nur so schwache, wie sie die Forschung bisher nachgewiesen hat. Das neue Paradigma, das sie mit diesem Text etablieren will, klingt im Titel an. Noelle-Neumann sagt: Ihr habt „die Omnipräsenz“ der Medien vergessen und ihre „kumulative Wirkung als Folge der Periodizität“. Starrt nicht nur auf die Empfänger der Botschaft, sondern schaut euch auch die Kommunikatoren an, „deren berufliches Verhalten Ähnlichkeit erzeugt“. Und vergesst den „Faktor Öffentlichkeit“ nicht. Noelle-Neumann meint damit die „kritische Instanz“ soziale Kontrolle, die jeder spürt, der von dem abweicht, was die anderen für die Meinung der Mehrheit halten müssen.
Als Noelle-Neumann diesen Text geschrieben hat, war es üblich, dass sich die Spitzenleute der Parteien im Bundestag angebrüllt haben. Damals genügte es, die vier wichtigsten Blätter im Land zu untersuchen, wenn man das politische Spektrum abbilden wollte. Wie würde man das heute machen, wenn die Opposition schweigt und überall das gleiche steht – vor allem nichts anderes als in den Bulletins der Staatskanzleien? Das ist ungerecht, ich weiß. Die Redaktionen können schon lange nicht mehr so arbeiten, wie es nötig wäre, und produzieren trotzdem immer wieder Perlen. Tolle Gäste bei Markus Lanz, nur als Beispiel. Trotzdem. Kumulation, Konsonanz, Öffentlichkeit. Corona-Tote auf allen Kanälen und Journalisten, die Schiedsrichter spielen im Streit der Experten. Wenn es nicht so ernst wäre, könnte man nach dem Videobeweis rufen und fragen, woher die Pfeifen in ihren „Fakten-Checks“ wissen, dass die staatliche Behörde immer Recht hat. Nach den Wirkungen muss man jedenfalls nicht lange suchen. Ich sehe in München Menschen, die sich angeekelt abwenden, wenn ihnen zwei Jogger entgegenkommen, und höre, wie Türsteher im Supermarkt angeblafft werden, die keine Maske tragen.
Heribert Prantl hat beschrieben, was im Bereich der Medizin falsch gelaufen ist seit Mitte der 1980er Jahre, und dabei Ross und Reiter genannt. Der Bundestag, der erst Krankenhäusern erlaubte, Gewinne zu machen, und dann unter Rot-Grün ein Vergütungssystem einführte, das alles dem Diktat des Geldes unterwarf. Die Troika, die ganz Südeuropa zwang, das Gesundheitswesen zu kastrieren, „um am Tropf Europas zu bleiben“. Auch im Journalismus ist das alles kein Geheimnis. Homogene Redaktionen, dominiert von Akademiker-Männern, die viel zu nah dran sind an den Entscheidern und die Welt auch deshalb kaum anders sehen können, weil sie aus dem gleichen Milieu kommen, auf den gleichen Schulen waren und dort verinnerlicht haben, was „richtig“ ist und was „falsch“.
Wo es um Geld geht (wie in kommerziellen Verlagen), werden diese Redaktionen vom Imperativ der Aufmerksamkeit regiert und von einem Sparzwang, der die Abhängigkeit von offiziellen Quellen noch größer macht, als sie ohnehin schon immer war. Und wo es um die Gunst der Politik geht (wie im öffentlich-rechtlichen Rundfunk und auch bei den Privaten, die ja immer eine Lizenz brauchen), bestimmen die Parteien, wer Chefin oder Chef sein darf, und haben mit Aufsichtsbehörden und Kontrollgremien einen zusätzlichen Hebel, wenn irgendetwas nicht nach Plan läuft. Ein kleines Beispiel aus Bayern, passend zum Thema: Ein Lokalradio hat es doch tatsächlich gewagt, drei lange Gespräche mit Experten zu senden, die der Söder-Linie widersprechen: Wolfgang Wodarg, Karin Mölling und Stefan Hockertz. Normalerweise läuft so ein Programm unter dem Radar. Wer hört schon Lokalradio? An den Interviews ist auch nicht viel auszusetzen. Die Journalistin fragt nach und zeigt, dass sie sich auskennt. Die Bayerische Landeszentrale für neue Medien hat ihr trotzdem einen Brief geschrieben. Botschaft: Wir hören, was Sie da machen. Wir sehen zwar für den Moment von einer „förmlichen Beanstandung“ ab (kein Wunder, denn es gibt nichts zu beanstanden), aber wir bitten Sie, an die „journalistische Sorgfaltspflicht“ zu denken, „damit derartige problematische Sendungen zukünftig ausbleiben“. Bei Noam Chomsky heißt das „Flak“. Die Macht schießt zurück, wenn allen Filtern zum Trotz doch etwas durchrutscht, was unter der Decke bleiben soll (vgl. Herman/Chomsky 1988).
Das ist tatsächlich verrückt. Der Journalismus will uns weismachen, dass er unabhängig ist, neutral und objektiv, dass er immer auf Distanz bleibt zu den Herrschenden und nach Vielfalt strebt. Ein Wolkenkuckucksheim, das ganz am Anfang stehen muss, wenn es um eine Zukunft nach Corona geht. Der Journalismus braucht einen neuen Kompass, der auf uns zeigt, auf die Gesellschaft, und nicht auf das Geld, auf den Staat und auf seine Verweser. Wir brauchen Redaktionen, die den „Auftrag Öffentlichkeit“ (Horst Pöttker) ernst nehmen. Wieder in Kurzform: alle Themen, alle Perspektiven. Wenn das dann unbedingt noch kommentiert werden muss: meinetwegen. Aber eigentlich will ich nicht wissen, wie Kurt Kister oder Claus Kleber die Welt sehen, sondern erfahren, was in der Welt so läuft, und mir dann selbst eine Meinung bilden.
Wie dieser Kompass sonst aussehen könnte, habe ich im Sommer skizziert, lange vor Corona (vgl. Meyen 2019). Ganz oben auf meiner Liste: Transparenz (offenlegen, wie die Inhalte entstehen und wie sie verbreitet werden), Perspektivenvielfalt (ein Punkt, der bei der Rekrutierung für den Beruf beginnt) und Reflexion (wer schreibt oder sendet hier und wem könnte das am Ende nutzen).
Entstanden ist diese Liste nach einer Serie von Interviews mit Menschen, die es wissen müssen, weil sie „irgendwas mit Medien“ machen. Ich habe mir damals nicht wirklich vorstellen können, dass man in den Redaktionen gar nicht darüber spricht, wozu die Gesellschaft Journalisten braucht. Dass man dort „Parolen“ wie „vierte Gewalt“ (Henriette Löwisch, Leiterin der Deutschen Journalistenschule München) lange einfach nur nachgeplappert hat. Nach Corona denke ich: Wir müssen tatsächlich zurück auf „Los“. Wir müssen mit der Ausbildung anfangen und aufhören, das Volontariat als Königsweg in den Beruf zu feiern. Von den Alten lernen, heißt gehorchen lernen. Der Journalismus der Zukunft darf nicht in kommerziellen Verlagen geformt werden und auch nicht in öffentlich-rechtlichen Rundfunkanstalten, solange diese jeder Politik folgen.
Vermutlich wissen viele Deutsche gar nicht mehr, welchen Schatz sie da haben: Fernseh- und Radioprogramme, die kein Geld verdienen müssen und denen dienen dürfen, die sie bezahlen – uns. Nur: Wir haben dort nichts zu sagen. Auch das ist verrückt: In den Gremien kontrollieren Politiker die, die eigentlich dazu berufen wären, die Politik zu kontrollieren. Verkehrte Welt. Der Journalismus nach Corona braucht Publikumsräte und Redaktionen, die im Wortsinn „frei“ sind, weil sie feste Arbeitsverträge mit guten Einkommen haben und deshalb nicht von den Launen ihrer Chefs oder der Regierenden abhängen. Wer wie ich in der DDR aufgewachsen ist, der weiß: Die Herrschenden werden immer und überall versuchen, das zu kontrollieren, was über sie in der Öffentlichkeit gesagt wird. Journalismus braucht deshalb „Schutzmauern“ (David Goeßmann), zum Beispiel Redaktionsstatute.
Wem das alles zu viel Vision ist und zu wenig Wirklichkeit: Auch im Journalismus gibt es längst „konkrete Utopien“ – Inseln, auf denen es nicht um „Profit und Kapitalakkumulation“ geht und wo Menschen freiwillig zusammenarbeiten, um staatliche und wirtschaftliche Macht zu zähmen. Erik Olin Wright (2017), der das Konzept der „konkreten Utopien“ entwickelt hat, wollte keine Revolution und auch keine Reformen. Als Modelle gestorben, sagt er. Sein Vorschlag: „im Hier und Jetzt“ so handeln, dass die Alternative wahrscheinlicher wird. In „den Räumen und Rissen“ des Kapitalismus „Institutionen, Verhältnisse und Praktiken“ entwickeln, die „die Welt, wie sie sein könnte, vorwegnehmen“. Vielleicht ist das ja ein Anfang: digitale Plattformen stärken, die den Journalismus liefern, den wir uns wünschen. Ich bin sicher: Heribert Prantl würde das gefallen.
Literatur
Karl Bücher: Zur Frage der Pressreform. In: Gesammelte Schriften. Tübingen: H. Laupp’sche Buchhandlung 1926, S. 391-429
Hektor Haarkötter: Geht’s auch mal wieder kritisch? In: Menschen machen Medien, 1. April 2020
Edward S. Herman, Noam Chomsky: Manufacturing Consent.The Political Economy of the Mass Media. New York: Pantheon 1988
Otfried Jarren: Im Krisenmodus. Das öffentlich-rechtliche Fernsehen in Zeiten von Corona. In: epd medien vom 27. März 2020
Klaus Meier, Vinzenz Wyss: Journalismus in der Krise: die fünf Defizite der Corona-Berichterstattung. In: meedia, 9. April 2020
Michael Meyen: Die Leipziger zeitungskundlichen Dissertationen. In: Erik Koenen, Michael Meyen (Hrsg.): Karl Bücher. Leipziger Hochschulschriften 1892 bis 1930. Leipzig: Universitätsverlag 2002, S. 135-200
Michael Meyen: (Erste) Thesen zur Medienzukunft. In: Michael Meyen (Hrsg.): Medienrealität 2019.
Elisabeth Noelle-Neumann: Kumulation, Konsonanz und Öffentlichkeitseffekt. Ein neuer Ansatz zur Analyse der Wirkung der Massenmedien. In: Publizistik 18. Jg. (1973), S. 26–55
Heribert Prantl: Bittere Medizin. In: Süddeutsche Zeitung vom 11. April 2019, S. 4 (unter anderem Titel hinter der Bezahlschranke)
Erik Olin Wright: Reale Utopien. Wege aus dem Kapitalismus. Berlin: Suhrkamp 2017.
Vinzenz Wyss: „Journalisten dürfen Kritik nicht dünnhäutig abschmettern“. In: persoenlich.com vom 10. April 2020.
Vom Kampf um die Öffentlichkeit
Medienrealität, 13. Mai 2020, und Rubikon, 14. Mai 2020
Ein Gespenst geht um in Deutschland: die Verschwörungstheorie. Dubiose Kanäle im Internet, so liest und hört man es jetzt allerorten, haben erst die öffentliche Debatte vergiftet und treiben jetzt unbescholtene Bürger auf die Straße und damit in die Hände von Rattenfängern aller Couleur – mit ungeahnten Folgen für die politische Kultur und den Gesundheitszustand der Bevölkerung. Die Diffamierung von Demonstranten hat hierzulande Tradition. Und die Geschichte lehrt: Es muss nicht immer gut ausgehen für die, die gerade an der Macht sind.
„Was trieb Frau A.K. ins Stadtzentrum?“: Dieser Artikel, erschienen in der Wochenendausgabe der Leipziger Volkszeitung vom 24./25. Juni 1989, war eine Warnung an alle, die sich seit einigen Wochen jeden Montagabend an der Nikolaikirche trafen. Bleibt zu Hause, liebe Leute. Genießt die „Vorzüge“, „die unsere Gesellschaft den Bürgern und insbesondere den Familien zukommen lässt“. Hört auf, den „BRD-Ratgebern“ zu lauschen und „die öffentliche Ordnung zu stören“.
Diese „Frau A.K. aus Wurzen“, die Chefredakteur Rudi Röhrer da anspricht (allerdings im Schutz eines Pseudonyms), ist ein Kind der DDR. Drei Jahre Lehre im Wunschberuf, ein Jahr daheim nach der zweiten Geburt. Eine junge Frau, die allen Grund zu haben scheint, an so einem Montagabend „einen neuen Film“ zu sehen oder „in einer Eisbar den Feierabend zu genießen“. Und jetzt das. Eine „Unruhestifterin“, die sich „in voller Absicht über die bei uns gültigen Normen des Zusammenlebens und über Rechtsnormen“ hinwegsetzt und so zu einer Handlangerin wird – „von jenen Kräften in der BRD, die unsere sozialistische DDR von innen heraus“ so lange reformieren wollen, bis von ihr nichts mehr übrigbleibt. Lasst euch nicht täuschen, liebe Leserinnen und Leser. Forderungen wie „mehr Meinungspluralismus, mehr Offenheit, mehr Erneuerung, mehr Reisen“ machen „aus Provokateuren keine Unschuldsengel“. Damit die Warnung auch wirklich ankommt, lässt der Chefredakteur „Leipziger Bürger“ nach „Ordnung, Ruhe und Sicherheit“ rufen. Tenor: Bietet diesem „Treiben“ endlich Einhalt, „ohne Ansehen der Person“.
Vermutlich ist das alles zu lange her und zudem in einem Landstrich passiert, der den Edelfedern in Hamburg oder München bis heute fremd geblieben ist. Gleich zehn Reporterinnen und Reporter (eine Frau und neun Männer) hat Der Spiegel aufgeboten, um über die Corona-Demonstrationen am zweiten Maiwochenende zu berichten (Wut und Wahnsinn_SPIEGEL 20). Drei Seiten unter der Überschrift „Wut und Wahnsinn“, dazu eine Fotostrecke mit dem Kommentar „Sie fühlen sich einzigartig, weil sie vermeintlich etwas erkannt haben, das die breite Masse übersieht“. Das Wort „berichten“ trifft es dabei nicht ganz. Rudi Röhrer, der Mann, der einst gegen „Frau A.K. aus Wurzen“ hetzte, hätte das auch nicht für sich in Anspruch genommen. Die Unterzeile im Spiegel: „Verschwörungsideologen, extreme Rechte wie Linke nutzen die Unsicherheit der Bürger und vergiften die Debatte“.
Ganz so einfach kann man das Damals natürlich nicht mit dem Heute vergleichen. Das Westfernsehen sendet inzwischen landesweit. Und dass dort Meinungspluralismus gefordert oder gar gelebt wird, scheint auch schon eine Weile her zu sein. Damals wie heute geht es aber um Delegitimation und Eindämmung. Übersetzt: so wenig Menschen wie möglich auf der Straße. Und die, die trotzdem gehen, sollen selbst schuld sein an dem, was mit ihnen passiert. Der Spiegel schafft das, indem er sein Reporterteam Dinge zusammenbauen lässt, die nicht zusammengehören. Der Text beginnt mit Pegida und Lutz Bachmann (also mit dem Bösen schlechthin), schwenkt dann zu den Protesten gegen „Corona-Beschränkungen der Politik“ und rührt in diesem Topf schließlich alle zusammen, vor denen man sich zu fürchten hat: „Rechtsextremisten, Impfgegner, Antisemiten, Verschwörungsideologen, Linksradikale, Alt-Autonome und Esoteriker“. Huuuh.
Journalismus soll informieren. Journalismus soll Wählerinnen und Wählern erlauben, sich selbst eine Meinung zu bilden. Der Spiegel traut uns das nicht zu. Auf genau acht Zeilen geht es um das, was Menschen in Berlin, Stuttgart, München auf die Straße getrieben hat. Der Job weg, das Restaurant zu, Probleme mit den Kids. Zusammengefasst: „Sie halten die Einschränkungen für unverhältnismäßig, protestieren ‚gegen staatliche Willkür‘, für die ‚Wiederherstellung der Grundrechte‘ oder die Rettung des Stuttgarter Nachtlebens“. Zweimal Anführungszeichen (Botschaft: von wegen Willkür, von wegen Einschränkung der Grundrechte) und zum Schluss der Schubs ins Lächerliche. Diese Rumtreiber und ihre Bars. Da hätte Rudi Röhrer von der* Leipziger Volkszeitung* noch etwas lernen können.
Wie man „gut“ und „böse“ auseinanderhält, wusste er sicher schon. Hier „zahlreiche führende Ärzte und Virologen wie Christian Drosten von der Charité“ (Zahlreich! Führend!) und eine Sozialpsychologin, „die zu Verschwörungserzählungen promoviert und darüber gerade ein Buch geschrieben hat“ (Wissenschaft!). Dort ein „Berliner Dramaturg und Journalist“, der „sich mit kapitalismuskritischen Theateraufführungen einen Namen gemacht“ und jetzt auch stadtbekannte NPD-Funktionäre anzieht, oder ein „pro-russischer Journalist“, der sich „ständig“ von RT Deutsch und Sputnik interviewen lässt („Kreml-Propagandisten“). Merke: Was diese Menschen sagen, ist völlig egal. Das Etikett hilft uns, das Angebot zu sortieren.
Das Konzept „Verschwörungstheorie“ kannten die DDR-Propagandisten so nicht. Es gab nur einen Gegner, und den konnte man genau wie seine Jünger leicht als „Klassenfeind“ abstempeln. Heute ist die Welt komplexer. Heute gibt es das Internet und mit ihm Plattformen, die das Deutungsmonopol der Herrschenden auf ganz andere Weise herausfordern als einst die Programme aus der Bundesrepublik, die sich ganz zwangsläufig mehr mit dem eigenen Land beschäftigt haben als mit dem schmuddeligen Nachbarn im Osten. Wer heute gegen „Verschwörungstheorien“ kämpft, kämpft um die Macht – um Definitionsmacht: Wer darf sagen, was wir „wissen“ und für richtig halten sollen?
Vor 30 Jahren war das keine Frage. Vor 30 Jahren durften nur wenige öffentlich sprechen. Was „da draußen“ passiert, wie wir beschreiben, was da gerade passiert, und wie wir uns folglich einrichten in dieser Welt: In der guten, alten Zeit war das Sache der Massenmedien und damit der Journalisten. Wer Zugang zum Fernsehen hatte oder zur Presse, der konnte beeinflussen, was als Realität durchging. Es gab nur diese eine. Es gab nur das, was in der Zeitung stand, und das, was über den Bildschirm lief. Das Wörtchen „und“ täuscht dabei noch. Meist stand das in der Zeitung, was vorher über den Bildschirm gelaufen war. Oder umgekehrt.
Der britische Medienforscher Nick Couldry (2012) nennt das den „Mythos vom mediatisierten Zentrum“. Eigentlich ist das ein doppelter Mythos. Punkt eins: die Behauptung, es gebe so etwas wie eine ‚Wahrheit‘ oder ein ‚natürliches Zentrum‘ der Werte und Lebensstile. Punkt zwei: Der Weg zu diesem Zentrum führt nur über die Medien. Der Kern unseres Lebens: Das ist das, worüber die Massenmedien angeblich berichten. Für Couldry ist dieser Mythos die Wurzel aller Medienwirkungen. Presse, Funk und Fernsehen definieren, was ist und was sein darf, und sorgen so dafür, dass die Realität der Massenmedien in Alltagshandeln und Weltanschauungen übernommen wird. Medien ordnen die Welt. Medien liefern die Kategorien, mit denen wir die Welt beschreiben. Politiker und Journalisten füttern den „Mythos vom mediatisierten Zentrum“, weil sie von ihm leben. Corona ist ein Festmahl. Ein Virus, das gefährlich ist, das unseren Alltag verändert. Wie genau, sagen uns die Nachrichten.
Und damit zum Wort Verschwörung, das im Spiegel gekoppelt wird mit den Begriffen Theorie, Portal, Ideologe, Erzählung, Mythos. Es ist das Wort zur Krise überhaupt. Zwanzigmal allein in diesem Artikel. Da bleibt kein Platz für Inhalte, Erklärungen oder gar eine Definition. Man erfährt nur (von der schon erwähnten Expertin), dass in der Welt der Verschwörer „böse Hintermänner Schuld an der Situation sind“ und (aus dem Mund eines Innenministers) dass diese Menschen glauben („bis weit in die Mitte der Gesellschaft“!), „die Pandemie“ sei „bewusst herbeigeführt“ worden, „um das Volk zu kontrollieren“ (von Bill Gates oder anderen „vermeintlich finsteren Mächten“).
Es kann gut sein, dass manche der Demonstranten das so sehen. Es kann gut sein, dass einige Bill Gates nicht nur „vermeintlich“ für eine „finstere Macht“ halten und der Politik nicht zutrauen, frei von Lobbyisten nur nach ihrem Gewissen und zum Wohle aller zu entscheiden. Gründe genug hätten solche Zweifler. NSU und NSA, Ramstein und die Drohnen, die Bankenrettung im Namen des Gemeinwohls. Nur so als Beispiele. Aber darum geht es an dieser Stelle nicht. Es geht um die Frage, warum Der Spiegel und mit ihm die anderen Leitmedien plötzlich überall Verschwörungen sehen. Nick Couldry würde sagen: Der „Mythos vom mediatisierten Zentrum“ wankt. Fake News, Hate Speech, Menschen mit „kruden Thesen“: Das gibt es alles, keine Frage. Vermutlich gibt es sogar Minister und Redakteure, die sich ernsthaft sorgen um ihre Schäfchen. Zuallererst aber hilft das Schlagwort „Verschwörungstheorie“ denen, die an der Macht sind, und ihren traditionellen Sprachrohren. Das stimmt auch deshalb, weil dieses Schlagwort ablenkt von den Problemen, über die man eigentlich sprechen müsste. Über die Qualität des Journalismus in dieser Krise zum Beispiel (vgl. Meyen 2020) oder über all das, was sonst noch so auf den Transparenten steht. Das SED-Blatt Leipziger Volkszeitung hat im Sommer 1989 immerhin vier Punkte genannt, auf die „Frau A.K. aus Wurzen“ sich berufen konnte. Meinungspluralismus, Offenheit, Erneuerung, Reisen. Rudi Röhrer, der Chefredakteur, hat das zwar sofort in den Schmutz gezogen (Provokateur bleibt Provokateur), aber die geneigte Leserin konnte in sich gehen und das mit Babyjahr und Eisbar verrechnen.
Der Spiegel dagegen opfert eine seiner drei Seiten für die „drei Medien, die von Anfang an besonders aktiv über die ‚Hygienedemos‘ berichteten“: Rubikon („Querfront-Magazin“, „eine Art Hausmedium der Protestler“), RT Deutsch und Sputnik („deutschsprachigen Ableger eines staatlichen russischen Medienunternehmens“). Dazu kommen Links zu KenFM („Verschwörungsportal“, „Fake-News-Verbreiter“) und Weltnetz.tv („systematische Verbindungen zur Linkspartei“). Was genau man auf all diesen Portalen findet oder wie die Kolleginnen und Kollegen dort arbeiten (wie überall: viele ausgezeichnet und manche nicht ganz so gut), ist dem Reporterkollektiv egal. Auf die Botschaft kommt es an: Geht nicht ins Stadtzentrum. Und vor allem: Hört nicht auf die Signale aus dem Netz.
Im Spiegel lässt sich der Dreiklang studieren, den die Rudi Röhrers der Gegenwart singen: Etikettierung von Personen (was schneller geht, als sich mit Inhalten zu beschäftigen), Kontaktschuld (Sie veröffentlichen auf einer Plattform, auf der auch jemand unterwegs ist, dem man irgendetwas anhängen kann oder will) und implizite Verknüpfung. Man schreibt über Rubikon oder KenFM und lässt nebenbei ein paar wirklich „krude Thesen“ fallen. Im Spiegel: 5G und eine „Biowaffe“. In der Süddeutschen Zeitung, für die Willi Winkler eine Seite 3 zu den Demos gefüllt hat: Angela Merkel als „natürliche Tochter Adolf Hitlers“ („Sie wurde, falls Sie‘s nicht wussten, mit dem vorsichtshalber tiefgefrorenen Sperma des 1945 tragisch hingeschiedenen Führers gezeugt“). Ja. Was will man da noch machen. Das ist wie bei „Frau A.K. aus Wurzen“, die einfach kein Eis essen wollte.
Der Stempel „Verschwörungstheorie“ ist ein Generalangriff der Herrschenden auf den öffentlichen Debattenraum. Über Verschwörungstheorien muss man nicht reden und mit ihren Anhängern auch nicht. Verschwörungstheorien sind, so sagt es Michael Butter, einer der Wissenschaftler im Streitwagen der Macht, „falsch“. Immer. „Noch nie“ habe sich „eine Verschwörungstheorie im Nachhinein als wahr herausgestellt“ (Butter 2018: 37). Dass das Unsinn ist, sollte jeder Forscher wissen. Ob etwas „wahr“ oder „falsch“ ist, zeigt die Empirie. Ich kann zwar das eine hoffen oder das andere, um aber sicher zu sein, muss ich ins Feld. Ich muss Pro und Contra abwägen, sachlich, ohne Emotionen und ohne jedem gleich jede Kompetenz abzusprechen, der die Welt anders sieht als ich.
Es gibt ein feines Kriterium, mit dem sich die Qualität von Journalismus einschätzen lässt: publizistische Vielfalt (vgl. Rager/Weber 1992). Dieses Kriterium wurzelt im Pluralismusmodell: In der Gesellschaft gibt es viele und zum Teil gegensätzliche Meinungen und Interessen, die prinzipiell gleichberechtigt sind (die Interessen von Einzelpersonen und Außenseitern genauso wie die Interessen, die in Parteien oder Verbänden organisiert sind). Feld der Verständigung ist die Öffentlichkeit, wobei ein Ausgleich nur möglich scheint, wenn die verschiedenen Interessen in den Leitmedien artikuliert werden können – ohne dass die (Ab-)Wertung gleich mitgeliefert wird wie in vielen der „Fakten-Checks“, die gerade wie Pilze aus dem Boden schießen.
Was macht Der Spiegel? Er denunziert die Nachfahren von „Frau A.K. aus Wurzen“ und ruft nach Zensur. „Personalnot“ bei Facebook, Twitter, Google. Man kommt dort mit dem Löschen einfach nicht mehr hinterher. Die „automatisierten Filter“? „Fehleranfällig“. Schlimmer noch: Die Verschwörer weichen aus auf „freiere“ Plattformen (tatsächlich in Anführungszeichen) wie Bitchute und Telegram, wo die „Verschwörungsideologen“ (leider, leider) immer noch „ungehindert“ schwadronieren können – „bis sie sich das nächste Mal auf den Straßen wiedersehen. Inmitten von ganz normalen Bürgern“.
Die Leipziger Volkszeitung von Rudi Röhrer wusste sich am Ende gar nicht mehr zu helfen (vgl. Reichert 2000: 108). Am 5. Oktober 1989 hat sie unter der Überschrift „Nicht nur zusehen“ einen Kampfgruppenkommandeur gegen „nichtgenehmigte Demonstrationen“ hetzen lassen und einen Tag später in einem „Leserbrief“ unverhohlen gedroht: „Wir sind bereit und willens, das von uns mit unserer Hände Arbeit Geschaffene wirksam zu schützen, um diese konterrevolutionären Aktionen endgültig und wirksam zu unterbinden. Wenn es sein muss, mit der Waffe in der Hand!“ Innenminister und Polizisten denken im Moment laut darüber nach, wie die nächsten Demos laufen könnten. Die Leipziger haben sich damals nicht abschrecken lassen.
Literatur
Michael Butter: „Nichts ist, wie es scheint“. Über Verschwörungstheorien. Berlin: Suhrkamp 2018
Nick Couldry: Media, Society, World. Social Theory and Digital Media Practice. Cambridge: Polity Press 2012
Michael Meyen: Journalismus nach Corona. In: Michael Meyen (Hrsg.): Medienrealität 2020.
Günther Rager, Bernd Weber: Publizistische Vielfalt zwischen Markt und Politik. Eine Einführung. In: Günther Rager, Bernd Weber (Hrsg.): Publizistische Vielfalt zwischen Markt und Politik. Mehr Medien – mehr Inhalte? Düsseldorf: Econ 1992, S. 7-26
Steffen Reichert: Transformationsprozesse: Der Umbau der LVZ. Münster: Lit 2000
Die maskierte Öffentlichkeit
Medienrealität, 19. Oktober 2020, und Rubikon, 23. Oktober 2020
Die Regierenden haben die Öffentlichkeit gekapert und sich damit selbst jedes Korrektiv genommen. Nach den Leitmedien werden jetzt auch Seminarräume und Stadien, Kneipen und Bürgersteige zu Bühnen der politischen Inszenierung. Das Schicksal der DDR lehrt: Wer die Kommunikationskanäle schließt, verhindert mit den Debatten auch Innovationen und wird spätestens dann bestraft, wenn die Lebenswelt nicht mehr funktioniert.
Öffentlichkeit: Das ist ein Ort der Begegnung, der für die Politik ganz ähnlich funktioniert wie der Markt für die Wirtschaft (vgl. Gerhards/Neidhardt 1990). Was immer der Staat sich ausdenkt, muss vor der Bürgerschaft bestehen. Das heißt auch: Wir müssen darüber sprechen können. Rede, Gegenrede. Alles auf den Tisch. Normalerweise überlassen wir dieses Gespräch Organisationen und Auserwählten. Parteien, Gewerkschaften, Verbände. Der Präsident der Ärztekammer sagt dies, die Professorin das und die CSU etwas ganz anderes. Zu sehen oder zu hören in Presse, Funk und Fernsehen.
Diese Medienrealität beobachten wir aus drei Gründen. Wir wollen erstens wissen, wer die Macht hat. Wer hat es geschafft, sich selbst, seine Themen und seine Deutungen in die Öffentlichkeit zu bringen? Macht ist heute Definitionsmacht (vgl. Beck 2017). Macht hat, wer einen „Grenzwert“ festsetzen kann und einen „Schwellenwert“, die dann zu einer Realität werden, der sich auch deshalb niemand entziehen kann, weil Kritiker entweder gar nicht gehört oder diffamiert werden. Das führt direkt zu Grund zwei: Wir nehmen an, dass sich die anderen, die Menschen um uns herum, an der Medienrealität ausrichten werden. Also müssen wir diese Realität kennen. Sonst sind wir überrascht, dass der Sitznachbar im ICE austickt, wenn die Maske verrutscht. Drittens aber, und das ist für die Argumentation hier am wichtigsten, drittens wollen wir auf Nummer sicher gehen. Ist das, was wir selbst denken und für wichtig halten, wirklich präsent in der großen Arena? Kennt die Politik unsere Sorgen und Nöte, wenn sie über Sperrstunden entscheidet?
Die Öffentlichkeitstheorie beschreibt ein Wechselspiel zwischen drei Ebenen. Ganz oben stehen dabei die Leitmedien. Wer oder was hier nicht erscheint, bleibt unsichtbar. Auf den beiden Ebenen darunter aber, in Versammlungen und im Alltag, bei den vielen zufälligen Begegnungen hier und dort, kommen wir ins Spiel. Hier können wir die Medienrealität und uns selbst auf die Probe stellen. Sehe nur ich die Dinge so oder gibt es Gleichgesinnte? Können wir uns vielleicht sogar zusammentun und eine Demonstration organisieren, eine Mahnwache, eine Petition – etwas, was erst von den Redaktionen wahrgenommen werden muss und dann auch von der Politik?
Und damit zu den Masken. Mona Pauly hat das in einem Beitrag für die Freitag-Community auf den Punkt gebracht. Zusammengefasst: Die Politik braucht Bilder. Wie produziere ich Angst und das Gefühl, bedroht zu sein, wenn die Betten in den Kliniken leer sind und man auch kaum Kranken- oder gar Sterbegeschichten erzählen kann, die vom Normalen abweichen und damit die Medienlogik bedienen würden? Genau. Die Masken sind überall. Beim Bäcker und im Supermarkt sowieso. Jetzt auch im Kinosaal, auf den Bürofluren, im Klassenzimmer. Und damit in der Zeitung und in der Tagesschau. Selbst die paar Fans, die hin und wieder in die Stadien dürfen und dort so weit auseinandersitzen, dass sie sich kaum hören können, tragen Masken. Im Freien wohlgemerkt und bitte nicht durchsichtig. Die Bilder. Und jeder Kommentator rügt die Nachlässigen, wenn die Kamera bei ihren Fahrten durch das Rund doch noch eine Nasenspitze entdeckt. Selbst diese Fußballkommentatoren sind maskiert. Allein, hoch oben unter dem Stadiondach. Vielleicht vergessen sie sonst, den Besorgten neues Futter zu liefern.
Die Öffentlichkeit wird so erstickt. Die Maske ist kein „Instrument der Freiheit“ (Markus Söder), sondern ihr Tod. Es gibt keine Gegenrede mehr, nicht einmal beim Spaziergang durch die Stadt. Die Leitmedien transportieren Bilder der Zustimmung (maskierte Menschen überall), erzwungen von der Exekutive und durchgesetzt per Bußgeldkatalog. Und die beiden anderen Öffentlichkeitsebenen sind de facto ausgeschaltet. Wie will ich im Bus, auf der Straße oder im Geschäft mit jemandem ins Gespräch kommen, der nicht zu meiner Blase gehört? Wie will ich den erkennen, der irgendeine Bemerkung genauso blöd oder genauso gut findet wie ich? Selbst im Museum (Abstand! Maske!) oder in der Gaststätte geht das nicht mehr. Keine Fremden mehr am gleichen Tisch. Überhaupt nur noch fünf Personen, die sich am besten schon kennen sollten. Alles andere verhindern das Plexiglas zwischen den Tischen und die Masken auf dem Weg zum Klo. Selbst die Toilettenwand dürfte so als Ort der Öffentlichkeit verschwinden. Und der Zapfhahn wird einfach zugedreht, wenn es abends spannend werden könnte.
Wahrscheinlich muss ich das für die Versammlungsöffentlichkeit gar nicht mehr im Detail ausführen. Die Regierenden haben die Sportarenen entvölkert, Veranstaltungen jeder Art bis zur Unkenntlichkeit verkleinert und Demos entweder kriminalisiert oder ihnen per Verordnung jede Wucht genommen. Teilnehmerzahl, Abstand, Maskenzwang. Und wenn trotzdem viele Menschen zusammenkommen wie im August gleich zweimal in Berlin, dann schaffen es die PR-Leute der Regierung, so starke Frames zu setzen, dass nichts von den Motiven der Protestierenden oder von ihren Forderungen auf der Ebene der Leitmedien ankommt.
Das Internet, natürlich. Blogs, Telegram- und WhatsApp-Gruppen, die Plattformen für den Gegendiskurs. Hier findet sich all das, was früher Encounter und Versammlungen ausgemacht hat. Für den Einzelnen findet sich hier heute sogar viel mehr, weil ein Klick viel weniger kostet als jeder Gang ins Freie. Die Grenze zu den Leitmedien ist heute aber viel höher als früher. Wer es in den großen Redaktionen wagt, Experten zu zitieren oder gar einzuladen, die vorher bei RT Deutsch waren, bei KenFM oder Rubikon, riskiert seine berufliche Reputation. Die Kollegin und der Kollege waren schon immer die besten Kunden des Journalisten. Heute sind diese Kunden auf Twitter, verfolgen dort alles, was von ihrer eigenen Haltung abweicht, und erzeugen so einen Resonanzraum, der schon deshalb nichts mit der guten, alten Versammlungsöffentlichkeit zu tun hat, weil der Zugang exklusiv ist und man eigentlich nur Ja oder Nein rufen kann, möglichst laut, versteht sich.
Damit das nicht falsch verstanden wird: Es gibt in den Redaktionen Menschen, die den Auftrag Öffentlichkeit ernst nehmen. Beim WDR zum Beispiel, der in der Sendung „Meine Meinung“ unter der Überschrift „Lockern oder Verschärfen?“ Pro und Contra aufeinanderprallen ließ. Oder Alexei Makartsev, der gerade Sucharit Bhakdi für die Badischen Neuesten Nachrichten interviewt hat, sehr gut informiert und ohne Schaum vor dem Mund. Auf der Ebene der Leitmedien aber, da wo die Realität geschaffen wird, die niemand ignorieren kann, wird das übernommen, was die Politik und Behörden wie das RKI der Bevölkerung gern weismachen möchten. Uwe Krüger (2016: 105), ein Medienforscher aus Leipzig, hat das in einem anderen thematischen Zusammenhang „Verantwortungsverschwörung“ genannt. Der Journalist weiß, was gut ist und was schlecht (so ziemlich das gleiche, was die Regierenden gut oder schlecht finden), und er glaubt, dass er Einfluss auf die Menschen hat. Also nichts gegen die Maskenpflicht. Dass es dazu genug zu sagen geben würde, kann man gerade bei Oliver Märtens (2020) lesen, der nach einer aufwändigen Durchsicht der Forschungsliteratur von „Körperverletzung im Amt“ spricht.
Der DDR mag man alle möglichen Gebrechen nachsagen, untergegangen aber ist sie, weil die Kommunikation zwischen Regierenden und Regierten gestört war und die wirklich wichtigen Fragen nur in „internen Öffentlichkeiten“ diskutiert werden konnten – in Räumen, die für Beobachter aus dem Westen nicht zugänglich waren und deshalb von Herrschenden wie Beherrschten als Öffentlichkeitsersatz genutzt wurden (vgl. Meyen 2011). Dieses System aus Eingaben, Leserbriefen, Parteiversammlungen und Expertentreffen hatte durch die Brille der Macht zwei Vorteile. Man hat Kritiker oft allein durch Zuwendung besänftigt – und diese Kritiker konnten nicht sehen, wer sonst noch auf ihrer Seite steht. Geändert hat sich das erst, als sie Erkennungszeichen in die Öffentlichkeit getragen haben (etwa: weiße Gardinenfetzen an der Autoantenne, um den Wunsch nach Ausreise zu signalisieren) und die Probleme auch sonst buchstäblich für jeden „öffentlich“ wurden (etwa: die Luftverschmutzung). Mona Pauly hat in ihrem Beitrag für die Freitag-Community „eine grüne Maske als Protest“ vorgeschlagen. Die Bilder stören, irgendwie. Gegen Atemnot und Beklemmung hilft das nicht. In der DDR hat es außerdem sehr, sehr lange gedauert, bis solche Zeichen ganz oben angekommen sind. Und wer weiß, ob das ohne das Westfernsehen überhaupt funktioniert hätte.
Literatur
Ulrich Beck: Die Metamorphose der Welt. Berlin: Suhrkamp 2017
Jürgen Gerhards, Friedhelm Neidhardt: Strukturen und Funktionen moderner Öffentlichkeit: Fragestellungen und Ansätze. Berlin: Wissenschaftszentrum Berlin 1990
Uwe Krüger: Mainstream. Warum wir den Medien nicht mehr trauen. München: C.H. Beck 2016
Oliver Märtens: Die Maskenpflicht: Epidemieeindämmung oder Körperverletzung im Amt? Multipolar, 18. Oktober 2020
Michael Meyen: Öffentlichkeit in der DDR. Ein theoretischer und empirischer Beitrag zu den Kommunikationsstrukturen in Gesellschaften ohne Medienfreiheit. In: Studies in Communication / Media 1. Jg. (2011), S. 3-69
-
 @ 266815e0:6cd408a5
2025-03-19 11:10:21
@ 266815e0:6cd408a5
2025-03-19 11:10:21How to create a nostr app quickly using applesauce
In this guide we are going to build a nostr app that lets users follow and unfollow fiatjaf
1. Setup new project
Start by setting up a new vite app using
pnpm create vite, then set the name and selectSolidandTypescript```sh ➜ pnpm create vite │ ◇ Project name: │ followjaf │ ◇ Select a framework: │ Solid │ ◇ Select a variant: │ TypeScript │ ◇ Scaffolding project in ./followjaf... │ └ Done. Now run:
cd followjaf pnpm install pnpm run dev ```
2. Adding nostr dependencies
There are a few useful nostr dependencies we are going to need.
nostr-toolsfor the types and small methods, andrx-nostrfor making relay connectionssh pnpm install nostr-tools rx-nostr3. Setup rx-nostr
Next we need to setup rxNostr so we can make connections to relays. create a new
src/nostr.tsfile with```ts import { createRxNostr, noopVerifier } from "rx-nostr";
export const rxNostr = createRxNostr({ // skip verification here because we are going to verify events at the event store skipVerify: true, verifier: noopVerifier, }); ```
4. Setup the event store
Now that we have a way to connect to relays, we need a place to store events. We will use the
EventStoreclass fromapplesauce-corefor this. create a newsrc/stores.tsfile withThe event store does not store any events in the browsers local storage or anywhere else. It's in-memory only and provides a model for the UI
```ts import { EventStore } from "applesauce-core"; import { verifyEvent } from "nostr-tools";
export const eventStore = new EventStore();
// verify the events when they are added to the store eventStore.verifyEvent = verifyEvent; ```
5. Create the query store
The event store is where we store all the events, but we need a way for the UI to query them. We can use the
QueryStoreclass fromapplesauce-corefor this.Create a query store in
src/stores.ts```ts import { QueryStore } from "applesauce-core";
// ...
// the query store needs the event store to subscribe to it export const queryStore = new QueryStore(eventStore); ```
6. Setup the profile loader
Next we need a way to fetch user profiles. We are going to use the
ReplaceableLoaderclass fromapplesauce-loadersfor this.applesauce-loadersis a package that contains a few loader classes that can be used to fetch different types of data from relays.First install the package
sh pnpm install applesauce-loadersThen create a
src/loaders.tsfile with```ts import { ReplaceableLoader } from "applesauce-loaders"; import { rxNostr } from "./nostr"; import { eventStore } from "./stores";
export const replaceableLoader = new ReplaceableLoader(rxNostr);
// Start the loader and send any events to the event store replaceableLoader.subscribe((packet) => { eventStore.add(packet.event, packet.from); }); ```
7. Fetch fiatjaf's profile
Now that we have a way to store events, and a loader to help with fetching them, we should update the
src/App.tsxcomponent to fetch the profile.We can do this by calling the
nextmethod on the loader and passing apubkey,kindandrelaysto it```tsx function App() { // ...
onMount(() => { // fetch fiatjaf's profile on load replaceableLoader.next({ pubkey: "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", kind: 0, relays: ["wss://pyramid.fiatjaf.com/"], }); });
// ... } ```
8. Display the profile
Now that we have a way to fetch the profile, we need to display it in the UI.
We can do this by using the
ProfileQuerywhich gives us a stream of updates to a pubkey's profile.Create the profile using
queryStore.createQueryand pass in theProfileQueryand the pubkey.tsx const fiatjaf = queryStore.createQuery( ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d" );But this just gives us an observable, we need to subscribe to it to get the profile.
Luckily SolidJS profiles a simple
frommethod to subscribe to any observable.To make things reactive SolidJS uses accessors, so to get the profile we need to call
fiatjaf()```tsx function App() { // ...
// Subscribe to fiatjaf's profile from the query store const fiatjaf = from( queryStore.createQuery(ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") );
return ( <> {/ replace the vite and solid logos with the profile picture /}
{fiatjaf()?.name}
{/* ... */}); } ```
9. Letting the user signin
Now we should let the user signin to the app. We can do this by creating a
AccountManagerclass fromapplesauce-accountsFirst we need to install the packages
sh pnpm install applesauce-accounts applesauce-signersThen create a new
src/accounts.tsfile with```ts import { AccountManager } from "applesauce-accounts"; import { registerCommonAccountTypes } from "applesauce-accounts/accounts";
// create an account manager instance export const accounts = new AccountManager();
// Adds the common account types to the manager registerCommonAccountTypes(accounts); ```
Next lets presume the user has a NIP-07 browser extension installed and add a signin button.
```tsx function App() { const signin = async () => { // do nothing if the user is already signed in if (accounts.active) return;
// create a new nip-07 signer and try to get the pubkey const signer = new ExtensionSigner(); const pubkey = await signer.getPublicKey(); // create a new extension account, add it, and make it the active account const account = new ExtensionAccount(pubkey, signer); accounts.addAccount(account); accounts.setActive(account);};
return ( <> {/ ... /}
<div class="card"> <p>Are you following the fiatjaf? the creator of "The nostr"</p> <button onClick={signin}>Check</button> </div>); } ```
Now when the user clicks the button the app will ask for the users pubkey, then do nothing... but it's a start.
We are not persisting the accounts, so when the page reloads the user will NOT be signed in. you can learn about persisting the accounts in the docs
10. Showing the signed-in state
We should show some indication to the user that they are signed in. We can do this by modifying the signin button if the user is signed in and giving them a way to sign-out
```tsx function App() { // subscribe to the currently active account (make sure to use the account$ observable) const account = from(accounts.active$);
// ...
const signout = () => { // do nothing if the user is not signed in if (!accounts.active) return;
// signout the user const account = accounts.active; accounts.removeAccount(account); accounts.clearActive();};
return ( <> {/ ... /}
<div class="card"> <p>Are you following the fiatjaf? ( creator of "The nostr" )</p> {account() === undefined ? <button onClick={signin}>Check</button> : <button onClick={signout}>Signout</button>} </div>); } ```
11. Fetching the user's profile
Now that we have a way to sign in and out of the app, we should fetch the user's profile when they sign in.
```tsx function App() { // ...
// fetch the user's profile when they sign in createEffect(async () => { const active = account();
if (active) { // get the user's relays or fallback to some default relays const usersRelays = await active.getRelays?.(); const relays = usersRelays ? Object.keys(usersRelays) : ["wss://relay.damus.io", "wss://nos.lol"]; // tell the loader to fetch the users profile event replaceableLoader.next({ pubkey: active.pubkey, kind: 0, relays, }); // tell the loader to fetch the users contacts replaceableLoader.next({ pubkey: active.pubkey, kind: 3, relays, }); // tell the loader to fetch the users mailboxes replaceableLoader.next({ pubkey: active.pubkey, kind: 10002, relays, }); }});
// ... } ```
Next we need to subscribe to the users profile, to do this we can use some rxjs operators to chain the observables together.
```tsx import { Match, Switch } from "solid-js"; import { of, switchMap } from "rxjs";
function App() { // ...
// subscribe to the active account, then subscribe to the users profile or undefined const profile = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(ProfileQuery, account!.pubkey) : of(undefined))) ) );
// ...
return ( <> {/ ... /}
<div class="card"> <Switch> <Match when={account() && !profile()}> <p>Loading profile...</p> </Match> <Match when={profile()}> <p style="font-size: 1.2rem; font-weight: bold;">Welcome {profile()?.name}</p> </Match> </Switch> {/* ... */} </div>); } ```
12. Showing if the user is following fiatjaf
Now that the app is fetching the users profile and contacts we should show if the user is following fiatjaf.
```tsx function App() { // ...
// subscribe to the active account, then subscribe to the users contacts or undefined const contacts = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(UserContactsQuery, account!.pubkey) : of(undefined))) ) );
const isFollowing = createMemo(() => { return contacts()?.some((c) => c.pubkey === "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d"); });
// ...
return ( <> {/ ... /}
<div class="card"> {/* ... */} <Switch fallback={ <p style="font-size: 1.2rem;"> Sign in to check if you are a follower of the fiatjaf ( creator of "The nostr" ) </p> } > <Match when={contacts() && isFollowing() === undefined}> <p>checking...</p> </Match> <Match when={contacts() && isFollowing() === true}> <p style="color: green; font-weight: bold; font-size: 2rem;"> Congratulations! You are a follower of the fiatjaf </p> </Match> <Match when={contacts() && isFollowing() === false}> <p style="color: red; font-weight: bold; font-size: 2rem;"> Why don't you follow the fiatjaf? do you even like nostr? </p> </Match> </Switch> {/* ... */} </div>); } ```
13. Adding the follow button
Now that we have a way to check if the user is following fiatjaf, we should add a button to follow him. We can do this with Actions which are pre-built methods to modify nostr events for a user.
First we need to install the
applesauce-actionsandapplesauce-factorypackagesh pnpm install applesauce-actions applesauce-factoryThen create a
src/actions.tsfile with```ts import { EventFactory } from "applesauce-factory"; import { ActionHub } from "applesauce-actions"; import { eventStore } from "./stores"; import { accounts } from "./accounts";
// The event factory is used to build and modify nostr events export const factory = new EventFactory({ // accounts.signer is a NIP-07 signer that signs with the currently active account signer: accounts.signer, });
// The action hub is used to run Actions against the event store export const actions = new ActionHub(eventStore, factory); ```
Then create a
toggleFollowmethod that will add or remove fiatjaf from the users contacts.We are using the
execmethod to run the action, and theforEachmethod from RxJS allows us to await for all the events to be published```tsx function App() { // ...
const toggleFollow = async () => { // send any created events to rxNostr and the event store const publish = (event: NostrEvent) => { eventStore.add(event); rxNostr.send(event); };
if (isFollowing()) { await actions .exec(UnfollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") .forEach(publish); } else { await actions .exec( FollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", "wss://pyramid.fiatjaf.com/" ) .forEach(publish); }};
// ...
return ( <> {/ ... /}
<div class="card"> {/* ... */} {contacts() && <button onClick={toggleFollow}>{isFollowing() ? "Unfollow" : "Follow"}</button>} </div>); } ```
14. Adding outbox support
The app looks like it works now but if the user reloads the page they will still see an the old version of their contacts list. we need to make sure rxNostr is publishing the events to the users outbox relays.
To do this we can subscribe to the signed in users mailboxes using the query store in
src/nostr.ts```ts import { MailboxesQuery } from "applesauce-core/queries"; import { accounts } from "./accounts"; import { of, switchMap } from "rxjs"; import { queryStore } from "./stores";
// ...
// subscribe to the active account, then subscribe to the users mailboxes and update rxNostr accounts.active$ .pipe(switchMap((account) => (account ? queryStore.createQuery(MailboxesQuery, account.pubkey) : of(undefined)))) .subscribe((mailboxes) => { if (mailboxes) rxNostr.setDefaultRelays(mailboxes.outboxes); else rxNostr.setDefaultRelays([]); }); ```
And that's it! we have a working nostr app that lets users follow and unfollow fiatjaf.
-
 @ bccf33d8:4b705625
2025-03-19 10:07:46
@ bccf33d8:4b705625
2025-03-19 10:07:46{"title":"nostrbook 创建的五本四书哈哈哈","author":"nostrbook.com","intro":"This is a book from ....很不错","picture":"https://432fds"}
-
 @ bccf33d8:4b705625
2025-03-19 10:03:50
@ bccf33d8:4b705625
2025-03-19 10:03:50{"title":"nostrbook 创建的四本三书哈哈哈","author":"nostrbook.com","intro":"This is a book from ....很不 错","picture":"https://432fds"}
-
 @ 6871d8df:4a9396c1
2025-01-18 20:12:46
@ 6871d8df:4a9396c1
2025-01-18 20:12:46## 2024 Prediction Reflections
Politics
Democrats & 2024 Election
- “Democrats’ attempt to stifle democracy will likely put Trump in the White House. If not, some real sketchy stuff would need to happen to keep him out.”
This prediction was exactly right. The assassination attempt on Trump seemed to be the final blow for the Democrats. Despite a heavy push my legacy media, Trump won handily.
The Democrats switched to Kamala Harris after Biden showed signs of incapacity, most notably in the first debate against Trump.
My prediction for the election also turned out to be exactly right, which, thank you Robert Barnes and Richard Baris.
Evidence of Institutional Ideological Capture
- “People will continue to wake up to ideologically captured institutions, and DEI will be the main loser.”
Trump’s resounding election victory underscores that the public is increasingly aware of (and rejecting) such institutional capture.
Of note, Boeing comes to mind as an institution that had a tough time in 2024, in large part to DEI. Nothing seemed to function correctly. The biggest story being how they stranded people in space
Media & Public Opinion
Rise of Independent & Alternative Media
- “Independent and alternative media will continue to grow as people’s trust in legacy media declines.”
Twitter (X), under Elon Musk, shattered mainstream media’s influence far more than expected. As Elon has said, “You are the media now.” Alternative sources are king. - Notable Example: Kamala Harris’s decision not to appear on the Joe Rogan podcast contrasted with Trump’s appearance, further highlighting the power shift to alternative media.
Markets & IPOs
Interest Rates & Public Markets
- “As interest rates come down, I expect public markets and IPOs to heat up.”
This did not play out. Companies that were expected to go public in 2024 remain private in 2025. The reasons are varied, but there is confidence that 2025 might see changes.
Technology & AI
LLMs & AI Adoption
- “AI and LLMs will continue to move at a rapid rate, increasing productivity. Tools like Bard will become more mainstream.”
AI did take off. Usage among nontechnical users increased, and it’s no longer uncommon for people to default to AI-driven tools rather than Google search.
Decentralized AI
- “I hope to see a rise in decentralized AI to counter big-player LLMs.”
We didn’t see explicit ‘decentralized AI’ breakthroughs, but more players entered the AI market. ChatGPT still dominates, with Elon’s ‘Grok’ making moves. Google, Meta, and Microsoft remain active but slightly behind in usage.
Bitcoin & Digital Assets
Institutional Adoption of Bitcoin
- “2024 will bring more institutions to Bitcoin. Possibly another large company or nation-state. The ETF should help, likely pushing BTC to a new all-time high.”
No large public company or nation-state placed a bet, but smaller public companies did. Michael Saylor presented to Microsoft’s Board, which was the closest instance to a major move.
- Price Movement: Bitcoin did hit a new all-time high, rising to as much as $108k in 2024.Lightning Network
- “Lightning will improve but remain primarily used for acquiring Bitcoin, not everyday payments.”
Still true. Lightning usage remains tiny relative to broader Bitcoin adoption.
Nostr Adoption
- “Nostr will grow, and we’ll see new companies leverage this network beyond just social media.”
Growth continues, but Elon Musk’s Twitter takeover slowed adoption. Nostr will remain niche until a major catalyst occurs (e.g., a big player joins or forced usage due to censorship).
Stablecoin-Specific Regulations
- “Expect stablecoin regulations in 2024 that’ll be favorable to them.”
This didn’t happen, largely due to the administration’s hostility. Expect potential change in 2025.
Miscellaneous 2024 Reflections
- Return to Sanity
- 2024 felt like sanity prevailed, largely due to the Democrats’ collapse behind Biden and Harris and Elon’s Twitter dominance.
- Operation Chokepoint 2.0
- Received a lot of attention, and I’m thankful it did because my experience at Strike was radicalizing and extreme.
- Bryan Johnson & Anti-Aging
- He burst onto the scene with his obsession over biomarkers. I see it as misguided—chasing markers in isolation doesn’t automatically yield a healthy system.
- Apple’s Rough Year
- Without a visionary leader, Apple appears to be scraping by on existing products rather than innovating.
- Google Under Fire
- Google is in a tough fight with the government, just as it seems they’re on their heels with AI competition.
2025 Predictions
-
Bitcoin’s Performance Bitcoin will have a good year, but not better than 2024. To beat 2024, it must close above 206k on December 31, 2025. I’ll take the under on that.
- I am not ruling out it to be over that at some point in 2025.
-
Twitter’s Success Continues to Stunt nostr
- Nostr adoption will stay slow due to Elon’s dominant influence with X (Twitter).
- As long as it remains a beacon of free speech, I doubt we see an exodus.
-
Rumble integrating Tether might help if they allow Nostr-like features (zaps), but that seems unlikely.
-
Apple
-
Apple will continue its rent-seeking behavior and put out underwhelming products.
-
Google’s Quantum & AI
- Recent buzz about Google’s quantum chip and AI improvements won’t pan out as a big deal.
-
Google will continue to trail OpenAI and xAI in practical LLM usage.
-
Elon, Vivek & DOGE
-
I expect them to deliver more than critics think. They’ll expose bloat and inefficiencies in ways that will shake up norms. I greatly welcome this. I wouldn’t bet against them.
-
Mainstream Media Reckoning
- In Trump’s second term, mainstream news outlets will face a real reckoning, as I can’t see how their bias can continue.
- They’ll have to reduce their bias or risk bankruptcy.
-
Alternative media’s growth trend continues, especially as Twitter keeps exposing mainstream outlets’ weaknesses.
-
RFK Delivers
-
We will see big changes in the health space due to RFK at HHS. These are changes that I am very excited to see.
-
Foreign Policy
- With the transition to Trump, I expect some foreign policy wins that will buck the establishment but will deliver wins that are not thought possible by the “experts.”
Closing Note
- Overall 2024: It was a year of major political upheaval, vindication for Bitcoin, and continued AI advances.
- Outlook for 2025: Bitcoin remains strong, AI competition heats up, and media institutions face existential challenges. I’m optimistic for continued decentralization and a more level playing field across tech, finance, and politics. I think the start of Trump’s second term will be very strong for the market, health, and culture. Accelerate.
-
 @ bccf33d8:4b705625
2025-03-19 09:54:34
@ bccf33d8:4b705625
2025-03-19 09:54:34关于本书的第一个章节
-
 @ bccf33d8:4b705625
2025-03-19 09:42:35
@ bccf33d8:4b705625
2025-03-19 09:42:35{"title":"nostrbook 创建的一本书另外一本书","author":"nostrbook.com","intro":"This is a book from ....很不错","picture":"https://432fds"}
-
 @ f7922a0a:82c34788
2025-01-17 23:06:56
@ f7922a0a:82c34788
2025-01-17 23:06:56Now that the 3rd Satellite Skirmish is complete I wanted to highlight some of the cool features on embrace.satskirmish.com
This is what the cutting edge of podcasting 2.0 looks like imo. Live video in an app that allows you to send sats to the artists in real time.
On the left hand side we have a Boost score borad that displays the total amount of sats that have come in during the show, live Boosts/Booastagrams as they come in, total amount of sats from each person Boosting and total amount sent from each app.
The middle is ovisaly the video of the band playing but with some graphics around it and Boost alerts that show up on the screen in the form of snow flakes for this one.
The righthand side is an IRC chat window that connects to an IRC server that the No Agenda community has used for 18+ years thanks to zoidzero++.

The bottom of the page is where things get cool. When you click the Boost the Crew button in the center you can send a Boost that gets split between everyone helping produce the show (hightlighted in yellow).


Each band also has their own Boost button so you can Boost them while they are playing or anytime you visit the page.


-
 @ bccf33d8:4b705625
2025-03-19 09:41:19
@ bccf33d8:4b705625
2025-03-19 09:41:19我在测试 createbook标签是否可以被列出来
-
 @ dd664d5e:5633d319
2025-01-09 21:39:15
@ dd664d5e:5633d319
2025-01-09 21:39:15Instructions
- Place 2 medium-sized, boiled potatoes and a handful of sliced leeks in a pot.

- Fill the pot with water or vegetable broth, to cover the potatoes twice over.
- Add a splash of white wine, if you like, and some bouillon powder, if you went with water instead of broth.

- Bring the soup to a boil and then simmer for 15 minutes.
- Puree the soup, in the pot, with a hand mixer. It shouldn't be completely smooth, when you're done, but rather have small bits and pieces of the veggies floating around.

- Bring the soup to a boil, again, and stir in one container (200-250 mL) of heavy cream.
- Thicken the soup, as needed, and then simmer for 5 more minutes.
- Garnish with croutons and veggies (here I used sliced green onions and radishes) and serve.

Guten Appetit!
- Place 2 medium-sized, boiled potatoes and a handful of sliced leeks in a pot.
-
 @ bccf33d8:4b705625
2025-03-19 09:36:16
@ bccf33d8:4b705625
2025-03-19 09:36:16{"title":"nostrbook 创建的一本书","author":"nostrbook.com","intro":"This is a book from ....","picture":"https://nostrbook.com/img/dfsa32432.png"}
-
 @ da0b9bc3:4e30a4a9
2025-03-19 08:49:13
@ da0b9bc3:4e30a4a9
2025-03-19 08:49:13Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/917523
-
 @ a012dc82:6458a70d
2025-03-19 06:28:40
@ a012dc82:6458a70d
2025-03-19 06:28:40In recent years, the global economy has faced unprecedented challenges, with inflation rates soaring to levels not seen in decades. This economic turmoil has led investors and consumers alike to seek alternative stores of value and investment strategies. Among the various options, Bitcoin has emerged as a particularly appealing choice. This article explores the reasons behind Bitcoin's growing appeal in an inflation-stricken economy, delving into its characteristics, historical performance, and the broader implications for the financial landscape.
Table of Contents
-
Understanding Inflation and Its Impacts
-
Bitcoin: A New Safe Haven?
-
Decentralization and Limited Supply
-
Portability and Liquidity
-
Bitcoin's Performance in Inflationary Times
-
Challenges and Considerations
-
The Future of Bitcoin in an Inflationary Economy
-
Conclusion
-
FAQs
Understanding Inflation and Its Impacts
Inflation is the rate at which the general level of prices for goods and services is rising, eroding purchasing power. It can be caused by various factors, including increased production costs, higher energy prices, and expansive government policies. Inflation affects everyone in the economy, from consumers and businesses to investors and retirees, as it diminishes the value of money. When inflation rates rise, the purchasing power of currency falls, leading to higher costs for everyday goods and services. This can result in decreased consumer spending, reduced savings, and overall economic slowdown.
For investors, inflation is a significant concern because it can erode the real returns on their investments. Traditional investments like bonds and savings accounts may not keep pace with inflation, leading to a loss in purchasing power over time. This has prompted a search for alternative investments that can provide a hedge against inflation and preserve, if not increase, the value of their capital.
Bitcoin: A New Safe Haven?
Traditionally, assets like gold, real estate, and Treasury Inflation-Protected Securities (TIPS) have been considered safe havens during times of inflation. However, the digital age has introduced a new player: Bitcoin. Bitcoin is a decentralized digital currency that operates without the oversight of a central authority. Its supply is capped at 21 million coins, a feature that many believe gives it anti-inflationary properties. This inherent scarcity is akin to natural resources like gold, which have historically been used as hedges against inflation.
The decentralization of Bitcoin means that it is not subject to the whims of central banking policies or government interference, which are often seen as contributing factors to inflation. This aspect of Bitcoin is particularly appealing to those who have lost faith in traditional financial systems and are looking for alternatives that offer more autonomy and security.
Decentralization and Limited Supply
One of the key features that make Bitcoin appealing as a hedge against inflation is its decentralized nature. Unlike fiat currencies, which central banks can print in unlimited quantities, Bitcoin's supply is finite. This scarcity mimics the properties of gold and is seen as a buffer against inflation. The decentralized nature of Bitcoin also means that it is not subject to the same regulatory pressures and monetary policies that can lead to currency devaluation.
Furthermore, the process of "mining" Bitcoin, which involves validating transactions and adding them to the blockchain, is designed to become progressively more difficult over time. This not only ensures the security of the network but also introduces a deflationary element to Bitcoin, as the rate at which new coins are created slows down over time.
Portability and Liquidity
Bitcoin's digital nature makes it highly portable and divisible, allowing for easy transfer and exchange worldwide. This liquidity and global accessibility make it an attractive option for investors looking to diversify their portfolios beyond traditional assets. Unlike physical assets like gold or real estate, Bitcoin can be transferred across borders without the need for intermediaries, making it a truly global asset.
The ease of transferring and dividing Bitcoin means that it can be used for a wide range of transactions, from large-scale investments to small, everyday purchases. This versatility, combined with its growing acceptance as a form of payment, enhances its utility and appeal as an investment.
Bitcoin's Performance in Inflationary Times
Historically, Bitcoin has shown significant growth during periods of high inflation. While it is known for its price volatility, many investors have turned to Bitcoin as a speculative hedge against depreciating fiat currencies. The digital currency's performance during inflationary periods has bolstered its reputation as a potential safe haven. However, it's important to note that Bitcoin's market is still relatively young and can be influenced by a wide range of factors beyond inflation, such as market sentiment, technological developments, and regulatory changes.
Despite its volatility, Bitcoin has provided substantial returns for some investors, particularly those who entered the market early. Its performance, especially during times of financial instability, has led to increased interest and investment from both individual and institutional investors. As more people look to Bitcoin as a potential hedge against inflation, its role in investment portfolios is likely to evolve.
Challenges and Considerations
Despite its growing appeal, Bitcoin is not without its challenges. The cryptocurrency's price volatility can lead to significant losses, and regulatory uncertainties remain a concern. Additionally, the environmental impact of Bitcoin mining has sparked debate. The energy-intensive process required to mine new coins and validate transactions has raised concerns about its sustainability and environmental footprint.
Investors considering Bitcoin as a hedge against inflation should weigh these factors and consider their risk tolerance and investment horizon. While Bitcoin offers potential benefits as an inflation hedge, it also comes with risks that are different from traditional investments. Understanding these risks, and how they align with individual investment strategies, is crucial for anyone considering adding Bitcoin to their portfolio.
The Future of Bitcoin in an Inflationary Economy
As the global economy continues to navigate through turbulent waters, the appeal of Bitcoin is likely to grow. Its properties as a decentralized, finite, and easily transferable asset make it a unique option for those looking to protect their wealth from inflation. However, the future of Bitcoin remains uncertain, and its role in the broader financial landscape is still being defined. As with any investment, due diligence and a balanced approach are crucial.
The increasing institutional interest in Bitcoin and the development of financial products around it, such as ETFs and futures, suggest that Bitcoin is becoming more mainstream. However, its acceptance and integration into the global financial system will depend on a variety of factors, including regulatory developments, technological advancements, and market dynamics.
Conclusion
The growing appeal of Bitcoin in an inflation-stricken economy highlights the changing dynamics of investment in the digital age. While it offers a novel approach to wealth preservation, it also comes with its own set of risks and challenges. As the world continues to grapple with inflation, the role of Bitcoin and other cryptocurrencies will undoubtedly be a topic of keen interest and debate among investors and policymakers alike. Whether Bitcoin will become a permanent fixture in investment portfolios as a hedge against inflation remains to be seen, but its impact on the financial landscape is undeniable.
FAQs
What is inflation, and how does it affect the economy? Inflation is the rate at which the general level of prices for goods and services is rising, leading to a decrease in purchasing power. It affects the economy by reducing the value of money, increasing costs for consumers and businesses, and potentially leading to economic slowdown.
Why is Bitcoin considered a hedge against inflation? Bitcoin is considered a hedge against inflation due to its decentralized nature, limited supply capped at 21 million coins, and its independence from government monetary policies, which are often seen as contributing factors to inflation.
What are the risks associated with investing in Bitcoin? The risks include high price volatility, regulatory uncertainties, and concerns over the environmental impact of Bitcoin mining. Investors should consider their risk tolerance and investment horizon before investing in Bitcoin.
How does Bitcoin's limited supply contribute to its value? Bitcoin's limited supply mimics the scarcity of resources like gold, which has traditionally been used as a hedge against inflation. This scarcity can help to maintain its value over time, especially in contrast to fiat currencies, which can be printed in unlimited quantities.
Can Bitcoin be used for everyday transactions? Yes, Bitcoin can be used for a wide range of transactions, from large-scale investments to small, everyday purchases. Its digital nature allows for easy transfer and division, making it a versatile form of currency.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnewsco
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ e97aaffa:2ebd765d
2025-03-19 05:55:17
@ e97aaffa:2ebd765d
2025-03-19 05:55:17Como é difícil encontrar informações sobre o eurodigital, a CBDC da União Europeia, vou colocando aqui, os documentos mais interessantes que fui encontrando:
FAQ: https://www.ecb.europa.eu/euro/digital_euro/faqs/html/ecb.faq_digital_euro.pt.html
Directório BCE: https://www.ecb.europa.eu/press/pubbydate/html/index.en.html?topic=Digital%20euro
https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/html/index.en.html
Documentos mais técnicos:
2025
Technical note on the provision of multiple digital euro accounts to individual end users https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/shared/pdf/ecb.degov240325_digital_euro_multiple_accounts.en.pdf
2024
Relatório de progresso https://www.ecb.europa.eu/euro/digital_euro/progress/html/ecb.deprp202412.en.html
Technical note on the provision of multiple digital euro accounts to individual end users https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/shared/pdf/ecb.degov240325_digital_euro_multiple_accounts.en.pdf
The impact of central bank digital currency on central bank profitability, risk-taking and capital https://www.ecb.europa.eu/pub/pdf/scpops/ecb.op360~35915b25bd.en.pdf
2023
Progress on the investigation phase of a digital euro - fourth report https://www.ecb.europa.eu/paym/digital_euro/investigation/governance/shared/files/ecb.degov230713-fourth-progress-report-digital-euro-investigation-phase.en.pdf
Digital euro - Prototype summary and lessons learned https://www.ecb.europa.eu/pub/pdf/other/ecb.prototype_summary20230526%7E71d0b26d55.en.pdf
Functional and non-functional requirements linked to the market research for a potential digital euro implementation https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/shared/pdf//ecb.dedocs230113_Annex_1_Digital_euro_market_research.en.pdf
A stocktake on the digital euro https://www.ecb.europa.eu/euro/digital_euro/progress/shared/pdf/ecb.dedocs231018.en.pdf
-
 @ 7ed7d5c3:6927e200
2025-01-08 17:10:00
@ 7ed7d5c3:6927e200
2025-01-08 17:10:00Can't decide if the terrible book you just read is a 1 or 1.5 star book? Look no further than this chart. Was it Shit or just Bad? Was that movie you watched Very Good or just Decent? How many things out there are really Life Changing?
Finally, a rating scale for humans. Use it for anything in your life that needs a rating out of 5 stars.
Rating / Description
0.5 – The worst 1.0 – Shit 1.5 – Bad 2.0 – Eh 2.5 – Entertaining, but not great 3.0 – Neutral 3.5 – Alright 4.0 – Decent 4.5 – Very good 5.0 – Life Changing
P.S. Do not use it to rate your wife's cooking. The author is not liable for any damages.
-
 @ ee9aaefe:1e6952f4
2025-03-19 05:01:44
@ ee9aaefe:1e6952f4
2025-03-19 05:01:44Introduction to Model Context Protocol (MCP)
Model Context Protocol (MCP) serves as a specialized gateway allowing AI systems to access real-time information and interact with external data sources while maintaining security boundaries. This capability transforms AI from closed systems limited to training data into dynamic assistants capable of retrieving current information and performing actions. As AI systems integrate into critical infrastructure across industries, the security and reliability of these protocols have become crucial considerations.
Security Vulnerabilities in Web-Based MCP Services
Traditional MCP implementations operate as web services, creating a fundamental security weakness. When an MCP runs as a conventional web service, the entire security model depends on trusting the service provider. Providers can modify underlying code, alter behavior, or update services without users' knowledge or consent. This creates an inherent vulnerability where the system's integrity rests solely on the trustworthiness of the MCP provider.
This vulnerability is particularly concerning in high-stakes domains. In financial applications, a compromised MCP could lead to unauthorized transactions or exposure of confidential information. In healthcare, it might result in compromised patient data. The fundamental problem is that users have no cryptographic guarantees about the MCP's behavior – they must simply trust the provider's claims about security and data handling.
Additionally, these services create single points of failure vulnerable to sophisticated attacks. Service providers face internal threats from rogue employees, external pressure from bad actors, or regulatory compulsion that could compromise user security or privacy. With traditional MCPs, users have limited visibility into such changes and few technical safeguards.
ICP Canisters: Enabling the Verifiable MCP Paradigm
The Internet Computer Protocol (ICP) offers a revolutionary solution through its canister architecture, enabling what we term "Verifiable MCP" – a new paradigm in AI security. Unlike traditional web services, ICP canisters operate within a decentralized network with consensus-based execution and verification, creating powerful security properties:
- Cryptographically verifiable immutability guarantees prevent silent code modifications
- Deterministic execution environments allow independent verification by network participants
- Ability to both read and write web data while operating under consensus verification
- Control of off-chain Trusted Execution Environment (TEE) servers through on-chain attestation
These capabilities create the foundation for trustworthy AI context protocols that don't require blind faith in service providers.
Technical Architecture of Verifiable MCP Integration
The Verifiable MCP architecture places MCP service logic within ICP canisters that operate under consensus verification. This creates several distinct layers working together to ensure security:
-
Interface Layer: AI models connect through standardized APIs compatible with existing integration patterns.
-
Verification Layer: The ICP canister validates authentication, checks permissions, and verifies policy adherence within a consensus-verified environment.
-
Orchestration Layer: The canister coordinates necessary resources for data retrieval or computation.
-
Attestation Layer: For sensitive operations, the canister deploys and attests TEE instances, providing cryptographic proof that correct code runs in a secure environment.
-
Response Verification Layer: Before returning results, cryptographic verification ensures data integrity and provenance.
This architecture creates a transparent, verifiable pipeline where component behavior is guaranteed through consensus mechanisms and cryptographic verification—eliminating the need to trust service provider claims.
Example: Secure Financial Data Access Through Verifiable MCP
Consider a financial advisory AI needing access to banking data and portfolios to provide recommendations. In a Verifiable MCP implementation:
-
The AI submits a data request through the Verifiable MCP interface.
-
The ICP canister verifies authorization using immutable access control logic.
-
For sensitive data, the canister deploys a TEE instance with privacy-preserving code.
-
The canister cryptographically verifies the TEE is running the correct code.
-
Financial services provide encrypted data directly to the verified TEE.
-
The TEE returns only authorized results with cryptographic proof of correct execution.
-
The canister delivers verified insights to the AI.
This ensures even the service provider cannot access raw financial data while maintaining complete auditability. Users verify exactly what code processes their information and what insights are extracted, enabling AI applications in regulated domains otherwise too risky with traditional approaches.
Implications for AI Trustworthiness and Data Sovereignty
The Verifiable MCP paradigm transforms the trust model for AI systems by shifting from "trust the provider" to cryptographic verification. This addresses a critical barrier to AI adoption in sensitive domains where guarantees about data handling are essential.
For AI trustworthiness, this enables transparent auditing of data access patterns, prevents silent modifications to processing logic, and provides cryptographic proof of data provenance. Users can verify exactly what information AI systems access and how it's processed.
From a data sovereignty perspective, users gain control through cryptographic guarantees rather than policy promises. Organizations implement permissions that cannot be circumvented, while regulators can verify immutable code handling sensitive information. For cross-border scenarios, Verifiable MCP enables compliance with data localization requirements while maintaining global AI service capabilities through cryptographically enforced data boundaries.
Conclusion
The Verifiable MCP paradigm represents a breakthrough in securing AI systems' external interactions. By leveraging ICP canisters' immutability and verification capabilities, it addresses fundamental vulnerabilities in traditional MCP implementations.
As AI adoption grows in regulated domains, this architecture provides a foundation for trustworthy model-world interactions without requiring blind faith in service providers. The approach enables new categories of AI applications in sensitive sectors while maintaining robust security guarantees.
This innovation promises to democratize secure context protocols, paving the way for responsible AI deployment even in the most security-critical environments.
-
 @ e5de992e:4a95ef85
2025-03-19 05:00:28
@ e5de992e:4a95ef85
2025-03-19 05:00:28Market Overview
On Tuesday, March 18, 2025, U.S. stock markets experienced notable declines, reflecting investor caution ahead of the Federal Reserve's policy announcement:
- S&P 500: Fell 1.1% to close at 5,614.66.
- Dow Jones Industrial Average: Decreased 0.6%, ending at 41,581.31.
- Nasdaq Composite: Declined 1.7% to 17,504.12, with technology stocks leading the downturn.
- Russell 2000: Specific figures were not detailed, but it typically mirrors trends observed in larger indices.
Year-to-Date Performance:
- S&P 500: Down 3.5%
- Dow Jones Industrial Average: Down 1.7%
- Nasdaq Composite: Down 7.8%
- Russell 2000: Down 7.3%
Key Factors and Events
Federal Reserve Meeting
- The Federal Open Market Committee (FOMC) is concluding its two-day policy meeting on March 19, 2025.
- The Federal Reserve is anticipated to maintain the federal funds rate within the current range of 4.25% to 4.50%.
- Investors are closely watching for updated economic projections and Chair Jerome Powell's remarks for clues on future monetary policy amid ongoing economic uncertainties.
Technology Sector Performance
The technology sector experienced significant sell-offs:
- Nvidia (NVDA): Shares declined 3.4% following the unveiling of its new generation of AI chips, raising concerns about near-term demand.
- Tesla (TSLA): Dropped 5.3% amid apprehensions regarding its autonomous driving technology.
- Alphabet (GOOGL): Fell 2.2%, influenced by acquisition-related uncertainties and broader market volatility.
Geopolitical Factors
- President Donald Trump's recent tariff announcements have intensified trade tensions, particularly with Canada and Mexico.
- These policies contribute to market volatility and raise concerns about global economic growth.
Economic Climate
- Investors are weighing potential recession risks against a relatively stable job market.
- Recent data indicate a decline in consumer sentiment, driven by economic uncertainties and federal workforce reductions.
Global Context
While U.S. markets face challenges, European and Asian markets have shown resilience:
-
European Markets:
Indices like Germany's DAX have advanced, bolstered by the passage of debt reforms. -
Asian Markets:
Though specific performance metrics were not detailed, these markets have generally exhibited stability amid global economic fluctuations. -
Regional Vulnerability:
Indonesia's stock market faced a temporary suspension due to significant declines.
Additional Insights
- The market remains cautious ahead of the Fed's economic projections, which may influence investor decisions.
- Diversified portfolios have performed relatively better this year—with bonds and select international markets outperforming American stocks—underscoring the importance of a balanced investment approach during volatile times.
-
 @ dd664d5e:5633d319
2025-01-07 19:57:14
@ dd664d5e:5633d319
2025-01-07 19:57:14Hodling Bitcoin does not make you a capitalist
I've noticed that Bitcoin-mindedness seems to lead some people to communistic thinking because it's a hard-limited form of capital. Marx, like most Bitcoiners, heavily discounted the possibility of economic growth or transformation changing the economy enough to undermine some minority's control of some form of capital.
What few today understand, is that many of the Dirty Capitalists of Marx's era actually agreed with him; they were just disdainful of labor and worried that the workers finding out that Marxism is correct about the nature of capitalism would cause unrest. They were the original HFSP crowd.
This was the basic idea, that Marx had, and that many Bitcoiners would agree with:
Capital is strictly limited and the people that control it can keep labor from attaining any, except when their labor is necessary.
And, as we know, automation will make human labor increasingly unnecessary.
The math doesn't check out

That underlies all of the calculations of "Well, if I just grab this Bitcoin wallet and hodl for twenty years, then it will grow in value to equal half of everything in existence and then I can just buy up half the planet and rule over everyone like a god."
This is economic nonsense because it assumes that: 1) the value of all things remains static over time, 2) purchasing something with money gives you ownership of it, 3) people will always use that specific money (or any money, at all!) for all transactions, 4) there is no such thing as opportunity cost, 5) people will always value money more than any other thing, and therefore be willing to always trade it for anything else, 6) humans are passive, defenseless, and easy to rule over, 7) someone who is preoccupied with hodling an asset steadily and sharply rising in price would ever be emotionally ready to part with it.
All monies can die.
People use money for everything because it is easy, fast and cheap. If money becomes too precious or scarce, they will simply switch to using other things (as we saw with gold). Humans replace tools that aren't working well, with those that work better, and money is just another tool. Bitcoin is more divisible than gold, but that won't matter, if enough of it is held by too few.
This is why there's a natural cap on the price of a money and why human productivity in the here and now is not irrelevant or in vain.
-
 @ ed84ce10:cccf4c2a
2025-03-19 03:46:17
@ ed84ce10:cccf4c2a
2025-03-19 03:46:17DoraHacks: Pioneering the Global Hacker Movement
DoraHacks is the world’s largest hackathon community, driving radical innovation across multiple industries. Now, a similar hacker movement is emerging in biotech—what we call the FDA-Free Society. At DoraHacks, this is our core focus in the life sciences. We believe that medical and biotech innovation should not be held hostage by bureaucracy. Instead, it should be free to evolve at the pace of technological progress.
The FDA: The Biggest Bottleneck to Biotech Innovation
For decades, the Food and Drug Administration (FDA) has been the single greatest obstacle to progress in medicine and biotech. While ostensibly designed to ensure safety and efficacy, in reality, it has functioned as an entrenched bureaucracy that stifles innovation.
1. A Broken Approval Process
The FDA operates on timelines that make no sense in an era of exponential technological growth. Getting a new drug or therapy to market takes 10-15 years. By the time a breakthrough therapy is approved, entire generations of patients have already suffered or died waiting.
2. Astronomical Compliance Costs
Clinical trials under FDA oversight are prohibitively expensive. This eliminates most startups from even attempting disruptive innovation. Many promising therapies never see the light of day—not because they don’t work, but because the cost of compliance is too high.
3. The FDA-Pharma Cartel
The regulatory framework is not neutral—it overwhelmingly benefits Big Pharma. The FDA’s Byzantine approval system creates a protective moat for legacy pharmaceutical companies, while smaller biotech startups are crushed under compliance burdens. The result? Less innovation, more monopolization, and fewer choices for patients.
Market-Driven Biotech Innovation Is the Future
When bureaucracies control innovation, progress slows. When markets drive innovation, progress accelerates.
1. Let the Market Decide What Works
Why should government regulators dictate which treatments are available? In an open system, patients and doctors—not bureaucrats—should determine which therapies succeed or fail.
2. The "Right to Try" Loophole Proves the FDA Is Obsolete
The U.S. Right to Try Act already allows terminally ill patients to access experimental drugs before FDA approval. This proves an essential truth: The regulatory state is holding back life-saving treatments. If dying patients can bypass the FDA, why can’t everyone?
3. Startups Move Faster Than Bureaucracies
The success of mRNA technology was not driven by the FDA—it was driven by startups operating at the speed of the market. This is a template for the future. Regulation slows innovation. Entrepreneurs accelerate it.
BioHack: Breaking Free From the FDA’s Grip
One of the most important frontiers in biotech today is anti-aging and longevity research. Yet, the FDA has no framework for approving treatments that extend life. The result? A regulatory death sentence for one of the most transformative fields of medicine.
1. Biotech Needs FDA-Free Experimental Zones
In the future, biotech R&D should function like open-source software—free, experimental, and outside the reach of outdated regulators. We need FDA-Free labs, FDA-Free clinical trials, and FDA-Free therapeutics.
2. Decentralized Healthcare Will Disrupt Big Pharma
A new era of decentralized biotech is emerging—privately funded labs, medical DAOs, and startup-driven healthcare systems. The power to determine the future of medicine must shift away from centralized bureaucracies and Big Pharma toward entrepreneurs, scientists, and patients.
Conclusion: The Hacker Revolution in Biotech Is Here
The FDA-Free Society is not a thought experiment. It is an inevitability. Innovation will not be stopped. DoraHacks is committed to making BioHack a reality.
-
 @ 990ab5d3:e9b011ff
2025-03-20 04:00:31
@ 990ab5d3:e9b011ff
2025-03-20 04:00:31ndnd
-
 @ f3873798:24b3f2f3
2025-03-19 01:47:51
@ f3873798:24b3f2f3
2025-03-19 01:47:51Vivemos em um mundo onde os impactos ambientais se tornam cada vez mais evidentes. O aumento das temperaturas, a escassez de recursos hídricos e os eventos climáticos extremos são apenas alguns dos sinais de que precisamos repensar a forma como nos relacionamos com o meio ambiente. No entanto, para que mudanças eficazes aconteçam, é essencial que o debate sobre crises ambientais seja baseado em conhecimento técnico e científico e não por expectro político seja de direita ou esquerda. Afinal, a sustentabilidade não é apenas um conceito abstrato, mas uma ferramenta essencial para o desenvolvimento das sociedades.
Neste artigo, vamos explorar por que o debate ambiental não pode ser ignorado,tanto pouco se instrumento de embate político e como o negacionismo prejudica o avanço da sociedade. Além disso, veremos exemplos concretos de como medidas sustentáveis já transformaram comunidades, mostrando que é possível crescer sem destruir o planeta.
Por que o Debate sobre Crises Ambientais é Importante e Não Deve Ser Ignorado?
Os desafios ambientais não são problemas do futuro – eles já estão afetando a nossa realidade. Secas prolongadas, inundações, ondas de calor e o aumento da poluição são consequências diretas da falta de políticas ambientais eficazes. Ignorar esses sinais pode ter impactos devastadores não apenas no meio ambiente, mas também na economia e na saúde pública.
Um exemplo clássico da importância de enfrentar os problemas ambientais com seriedade é a cidade de Cubatão, em São Paulo. Durante as décadas de 1970 e 1980, o município foi considerado um dos locais mais poluídos do mundo. A intensa atividade industrial sem controle ambiental resultou em problemas graves de saúde na população, como doenças respiratórias e malformações em recém-nascidos. Além disso, a poluição do ar e dos rios tornava o ambiente praticamente inabitável.
No entanto, graças à implementação de medidas sustentáveis, como o controle das emissões industriais, o reflorestamento de áreas degradadas e a adoção de tecnologias mais limpas, Cubatão passou por uma verdadeira transformação. Hoje, a cidade é um exemplo de recuperação ambiental e desenvolvimento sustentável, provando que o crescimento econômico pode coexistir com a preservação do meio ambiente quando há planejamento e responsabilidade.
Outros exemplos de sucesso incluem:
Curitiba (PR): Reconhecida mundialmente por suas práticas de urbanismo sustentável, como transporte público eficiente, amplas áreas verdes e programas de reciclagem.
Bogotá (Colômbia): Implementou um sistema de transporte sustentável, com faixas exclusivas para ônibus, reduzindo a poluição e melhorando a mobilidade urbana.
Costa Rica: Um dos poucos países do mundo que gera quase 100% de sua energia a partir de fontes renováveis, mostrando que é possível ter desenvolvimento econômico sem explorar excessivamente os recursos naturais.
Esses exemplos reforçam a importância de um debate sério sobre questões ambientais. Quando ignoramos esses problemas, comprometemos a qualidade de vida das gerações futuras.
O Negacionismo é Prejudicial para o Desenvolvimento da Sociedade

Infelizmente, o debate sobre meio ambiente muitas vezes é influenciado por interesses políticos e econômicos que ignoram a ciência em prol do lucro imediato. O negacionismo ambiental – que questiona evidências científicas sobre mudanças climáticas, poluição e desmatamento – atrasa a implementação de soluções sustentáveis e coloca a população em risco.
O caso de Cubatão ilustra bem isso. Durante anos, empresas e autoridades minimizaram os impactos ambientais da poluição industrial. Somente após a pressão de cientistas e ativistas, medidas foram tomadas para reverter a degradação ambiental e proteger a saúde da população.
Outro exemplo claro de como o negacionismo prejudica a sociedade é a falta de ações concretas para combater o desmatamento na Amazônia. A floresta tem um papel fundamental no equilíbrio climático global, mas sua destruição continua sendo impulsionada por interesses econômicos de curto prazo.
Para que possamos avançar, o foco do debate ambiental deve estar na busca pela verdade científica e na adoção de medidas que beneficiem a sociedade como um todo – e não apenas grupos específicos. Quando governos e empresas tomam decisões embasadas em dados concretos, todos saem ganhando: a economia cresce de forma sustentável, a população tem melhor qualidade de vida e os recursos naturais são preservados para o futuro.
Conhecimento Técnico e Compromisso com a Sustentabilidade São Essenciais

O desenvolvimento sustentável não é um entrave ao progresso, mas sim a única forma de garantir um futuro equilibrado. Países e cidades que adotam medidas sustentáveis demonstram que é possível crescer economicamente sem comprometer os recursos naturais. O caso de Cubatão prova que problemas ambientais podem ser resolvidos com políticas públicas bem estruturadas e comprometimento da sociedade.
Portanto, ignorar o debate ambiental ou negar as evidências científicas é um erro que pode custar caro para a humanidade. Precisamos valorizar o conhecimento técnico, investir em soluções inovadoras e cobrar dos líderes políticos e empresariais um compromisso real com a sustentabilidade. Somente assim poderemos garantir um planeta habitável para as futuras gerações.
-
 @ 17538dc2:71ed77c4
2025-03-20 03:40:31
@ 17538dc2:71ed77c4
2025-03-20 03:40:31Who were they? Testing long form publication via yakihonne
-
 @ dd664d5e:5633d319
2025-01-06 20:36:17
@ dd664d5e:5633d319
2025-01-06 20:36:17Ingredients
- 1 kg of pork roast with rind, such as shoulder or a lean belly
- 1 bottle of beer, light or dark
- chopped German-style mirepoix (best combination, for this recipe, includes celery root, carrot, red onion, and leeks)
- salt, pepper, nutmeg
- 1 diced garlic clove
Directions
- Spread the vegetables on the bottom of the roasting pan.
- Pour half the beer over the roast. (Drink the other half.)
- Season the meat, to taste.
- Roast the meat at 180 °C, until done (depends upon the weight of the roast).
- Remove the meat from the oven, and wrap in aluminum foil.
- Pour 2-3 cups of water into the roasting pan.
- Pour/scrape everything from the pan into a sieve over a sauce pot.
- Press the vegetables against the sieve, with the back of a spoon, to ensure that you get all that good dripping flavor into the sauce.
- Defat the sauce with a grease separator, then pour it back into the pot.
- Thicken the sauce, slightly (it should remain slightly watery, and not turn into a gravy), according to your usual method.
- Open the foil and slice the roast.
- Serve with the sauce.








-
 @ a42048d7:26886c32
2025-01-04 22:32:52
@ a42048d7:26886c32
2025-01-04 22:32:52OP_CAT, Coffee, and keeping an open mind to Bitcoin soft forks by an 80 IQ BTC Maxi Pleb
TLDR: CAT is both low risk and low appeal to the broader non-dev BTC community. I don’t care and you shouldn’t either. If I am an 80 IQ HODL pleb or a company that caters to that group, can you please give me 2-4 fifth grade level coherent english sentences that explain why I should support CAT? I’m still waiting… CTV or LNHANCE on the other hand have broad appeal.
Five years ago in the office we got a fancy $6,000 coffee maker. It was hooked up to wifi, showed TV on a giant screen, and could make every type of coffee/milkshake you could think of. I was captivated… for about 1 day. After trying a few times I realized almost all the drinks it made were of low quality. The wifi connection actually ended up just being annoying. Half the time I wanted a coffee, only had a 5 minute break, and the machine displayed some inscrutable error. I went back to the proverbial grind un-caffeinated and frustrated wishing we had the old reliable boring coffee maker back. I also found myself only coming back to the 2 drinks I really cared about, espresso and maybe an occasional cappuccino. It was “cool” that new machine could make over 60 different drinks, but when I sat back and thought about it all I really needed or wanted were a few key options that I used constantly. Especially as those extra bells and whistles seemed to be the usual suspect in the coffee machine constantly breaking. I would’ve loved them upgrading from burnt starbucks coffee beans to a local specialty roaster, that would’ve greatly enhanced my daily coffee. Echoing this realization, my coffee setup at home became a simple machine that could only make espresso and a hand crank coffee bean grinder. Still have them years later and they work great. They’re robust and fit exactly what I wanted with no nonsense that created more headache than everyday value. As you probably suspected, this is a loose comparison to OP_CAT. I’ve listened to podcast after podcast, read blog after blog, and sat through every CAT pitch I could find. I genuinely tried to approach with an open mind. However, ultimately what every pro OP_CAT argument boils down to is that there is no simple left curve elevator pitch a pleb will understand or care about. “But we can get this really cool ZK Rollup and have infinite DEFI bridging to altcoin chains! Look we sort of did it on this other altcoin chain.” And they did, they aren’t lying. They have live software on a shitcoin chain like ETH or SOL that does some modest volume. But the story quickly falls apart in the face of a few basic left curve questions: “Why should I, as an 80 IQ left curve BTC maxi give a shit?” “Does this enhance my everyday experience holding and using BTC?” “Why do you have a non-BTC token for your rollup/sidechain/glorified multisig that is totally centralized?” “Why is there only a hard to understand often ill-defined path to de-centralization? Why isn’t it just already decentralized?” “What is a clear use case that the typical non-technical everyday BTC holder can understand and rally behind?” “Why should I care about bridging to ETH, SOL, or whatever shitcoin chain? I only want BTC and don’t want to participate in all that shitcoin bullshit. Bitcoin is a store of value and money to me and it doesn’t help with those use cases in a clear direct way. It sounds like it maybe, kinda, sorta does help with a lot of caveats, ifs, and steps that I struggle to understand.” Sorry yeah I know, that one got a little personal. I’ll try to do better going forward guys.
ZK proofs or other Pro-CAT arguments, are undoubtedly cool and do factually enable potential cool new stuff. It just happens to all be stuff that sounds complex, esoteric, and unappealing to an 80 IQ HODL pleb - let alone a miner, ETF investor, or exchange exec. I don’t mean to say ZK or other tech has no potential and that we won’t eventually move there, but just to say that it’s not in the cards as currently dealt.
I really went out trying to keep an open mind and steelman the case for CAT. I came back firmly believing:
1 Support is deep in the developer community, but nonexistent everywhere else. I have yet to find a single person that supports CAT who is not a dev or working at or sponsored by a company that stands to directly profit from something CAT enables. Which is fine, but I reserve the right to be skeptical of your direct incentive. I acknowledge rough consensus is very hard to judge, and am open to changing my mind on this over time but feel this is a currently accurate assessment.
2 To get a soft fork you need rough consensus. Most people in that potential consensus are not highly technical developers. They care mostly or exclusively about BTC’s store of value use case. No one has yet articulated a clear compelling store of value enhancing use case that they can understand and care about. Without pull demand from potential users and paying customers, CAT will inevitably stall.
3 Lots of factually inaccurate FUD has been thrown at CAT. People saw the Taproot Wizards or shitcoiners pushing CAT, and immediately dismiss CAT as an evil psyop without any real consideration for its technical merits. Frankly most people just hate Udi and say “Fuck CAT” based solely on that. Maybe not fair, but true.
4 CAT is low risk, and it is not a catastrophe waiting to happen. Anything bad it potentially enables is enabled in such an inefficient and/or use hostile way that it is highly unlikely to pose any issues to Bitcoin. CAT’s technical risk is low and this is consistently proven by other chains enabling CAT and having no issues with it, such as Liquid.
5 Lots of people who have no idea wtf they are talking about falsely claim CAT is the apocalypse without any ability whatsoever to explain why. Imho you are no better than Udi and the shitcoiners if you are willing to lie about CAT just because you dislike them. We as the BTC community need the ability to have a rational discussion on technical merits, and not to devolve into a cult of personality based political battle. The question should be, “Is CAT good or bad and why?” and not “I just hate Udi, therefore its a no from me dog.”
Summarizing CAT using TradFi language: those pushing CAT have technology in search of a problem and no clear product market fit. They are pushing their technology to an apathetic audience. Pushers of CAT are not pulled forward by customer demand. In the tech world these are some of the quintessential red flags that every good investor knows mean you need to sit this one out.
CTV or LNHANCE on the other hand are soft fork proposals that have clear use cases you can quickly explain to a broad swathe of the Bitcoin ecosystem: “Hey HOLD pleb, worried about losing your coins? Wouldn’t it be nice to have a simple vault that reduces the chances your coins are lost or stolen? Let’s make self custody and BTC’s store of value use case strictly better, specifically without enabling any shitcoin-ery.” “Hey Blackrock, Van Eck, ARK, Franklin Templeton, and every ETF investor - it would really suck if Coinbase lost all your Bitcoin and that ETF went to zero, right? What it we could create vaults to make that Bitcoin more secure?” “Like Lightning but find it hard to use self-custodially? Let’s make Lightning better, easier, and more scalable with fewer onchain transactions and lower fees.” “Tried or seen the ARK demos yet? They have real working code even without covenants. With covenants we get big ARK volumes and scaling while also making it easier.”
Signing off: See the difference? I, an 80 IQ pleb, can steelman multiple use cases for CTV/LNHANCE that have broad appeal. I have yet to see any such case for CAT, and until then I don’t think it’ll go anywhere.
*Pro-CAT Sources I’ve digested and would encourage others to consider: https://en.bitcoin.it/wiki/Covenants_support https://www.youtube.com/watch?v=no_Nj-MX53w https://www.youtube.com/watch?v=_yp4eYK9S6M
Pro-CTV/LNHANCE sources to consider which have CLEAR use cases with widespead appeal: https://github.com/jamesob/simple-ctv-vault https://github.com/stutxo/op_ctv_payment_pool https://lnhance.org/ https://bitcoinmagazine.com/technical/how-ctv-can-help-scale-bitcoin
-
 @ 8671a6e5:f88194d1
2025-03-18 23:46:54
@ 8671a6e5:f88194d1
2025-03-18 23:46:54glue for the mind
\ You’ve seen them, these garish orange Bitcoin stickers slapped on lampposts, laptops, windows and the occasional rust-bucket Honda. They’re sometimes in some areas a sort of graffiti plague on the landscape, certainly when a meetup or bitcoin conference was held in the area (especially then the city or town can fork out some extra budget to clean things up and scrape the stickers from statues of famous folk heroes or the door to the headquarters of a local bank branche).\ \ At first glance, it might seem like enthusiasm Bitcoiners desperate to scream their obsession from the rooftops. Both for the fun of it, and to get rid of the pack of stickers they’ve got at a local meetup.\ \ But let’s cut to the chase: covering half a town in stickers isn’t clever. It’s lazy, counterproductive, and has nothing to do with what Bitcoin actually stands for.\ Worse, it reeks of the brain-dead low grade (cheap) marketing tactics you’d expect from shitcoiners or the follow up of some half-baked flyer campaign by a local communist clique.\ Proof? Bitcoin stickers are literally covering up — or being covered up themselves, usually by - communist stickers in a pointless competition for use of real-world ad space.\ \ Maybe, bitcoiners should just create a sticker where Karl Marx ànd the bitcoin logo appear in the same sticker, so both groups can enjoy it’s uselessness, and call it quits to get this stupidity over with once and for all.\ A sticker with a shiny B might look cool at first. But what does it actually do?
 Communist and Bitcoin logo sticker
Communist and Bitcoin logo stickerSpamming stickers doesn’t make “frens”
There’s a psychology behind these stickers of course: people slap them up to feel part of a rebel tribe, flipping off central banks or feeling part of the crew.\ This crude, omnipresent approach to marketing echoes the late 1960s— an era of peak fiat, not Bitcoin’s time.\ Mimicking those tactics today, as if Bitcoin were some hip underground record store trying to spread its brand name, is utterly irrelevant.\ Sure, people love signaling affiliations with an easy and cheap identity flex — like a bumper sticker yelling: “Look at me I’m special!”\ \ But plaster a town with Bitcoin logos, and it stops being edgy and it was never funny; it becomes an eyesore and puts bitcoiners in the same category as the social justice warriors and political youth movements or brands of local energy drinks doing some weird campaign.\ \ Advertising psychology shows overexposure breeds resentment, not interest. Flood a street with stickers, and you’re not lighting a spark. You’re making people uninterested, gag, associating Bitcoin with spam or worse: get totally blended into the background along all the other noise from the street marketeers.\ \ The "mere exposure effect" (Zajonc, 1968)1 claims familiarity breeds liking, even from annoyance. Since the 1960s however, a lot has changed, as we’ll see… and above all, yet, after years of Bitcoin stickers in many areas, they’ve just turned into meaningless wallpaper. It has usually no strong message, no slogan, no conversation starter other than “buy bitcoin”, it’s disassociated from reality for many people, as the reaction show us. It’s also happening in a vacuum, where “normies” and no-coiners pass by and don’t even recognize such stickers for anything else than background colors.
It’s Lazy Man’s Work
Let’s talk effort — or the lack of it - for these kind of campaigns and stickers. Invented in the 1920s, stickers began expressing political opinions in the 1970s during student, peace, and anti-nuclear campaigns. It’s easy, cheap and also quick to distribute.\ \ These stickers aren’t masterful designs from an artistic genius (safe some clever exceptions). They’re usually ripped off from somewhere else, tweaked for five minutes, and bulk-ordered online. It’s the “IKEA effect” gone wrong: a tiny bit of customization, and suddenly people think they’re visionaries. But it’s a low-effort form of activism at best. Compare that to coding a Bitcoin tool or patiently explaining its value to a normie or organizing a meetup or conference, starting a company.\ Not that low-level or guerrilla marketing can’t work, I just don’t see it happen with stickers. Why not go out there and try to convince a whole series of fruit and vegetable market owners to accept bitcoin instead of using very expensive bank Point-of-sale systems?\ Why not direct mailing? Why not… do more than just putting a sticker on a signpost and walk away like a sneaky student promoting his 4 person political group?\ \ Stickers are the “Save the whales (pun intended)” magnet on your fridge: lazy-ass advocacy that screams intellectual deficiency. They’re a shortcut to feeling involved, not a strategy for real impact.
 imaginary Save-the-Whales bitcoin sticker
imaginary Save-the-Whales bitcoin stickerStrategy territory signaling
Here’s the kicker: Bitcoin’s strength lies in its tech and value properties — decentralized, borderless value transfer that eliminates middlemen and has provable digital scarcity.\ Stickers? They’re just physical garbage. Sure, they might feel like a way to make an abstract idea tangible, tapping into “embodied cognition.” But they explain nothing about Bitcoin’s purpose or how it revolutionizes finance.\ They’re a dopamine hit for the people sticking them anywhere — a pathetic “I did something” moment — while everyone else walks by without a glance.\ Bitcoin is about innovation, not old-school social groups with low-budget marketing tactics.
\ The psychology of Bitcoin stickers
Why bother? Stickers are simple and loud—easy for the brain to process, a cheap thrill of rebellion. The person who spends an afternoon covering a city in them thinks they’re spreading the gospel. In reality, they’re just littering. Real advocacy takes effort, discussion, and substance — not a pack of adhesive stickers ordered with the click of a button.\ It’s the same reason nobody turns communist from a hammer-and-sickle sticker on a pole. It’s dead air.\ \ The proof of their uselessness? In 2 years, not one person I know has bought, researched, or even asked about Bitcoin because of a sticker in the neighborhood bar. A bar near me has had one on the wall for years — zero requests to pay with Bitcoin.
A sticker sitting on a bar wall for five years without impact isn’t “subtle marketing”—it’s a neon sign of failure. And the people cleaning those stickers off street signs, or the local communist student activists constantly covering them with their own, are locked in an endless, mindless sticker war.\ \ Other areas are even having a tsunami of bitcoin stickers, and hardly any places where they actually accept bitcoin for goods.\ More so, places where they do accept bitcoin readily, usually only need one sticker: the one at the door of a business saying “bitcoin accepted here”. And that’s about it.
What the little amount of research says
Studies shows stickers work for movements claiming public space and resisting dominant narratives — when done on a massive scale, targeting a specific audience have a visual and emotional effect when combined with other forms of resistance in social movements.\ "Stickin' it to the Man: The Geographies of Protest Stickers" 2\ \ For Bitcoin, a global monetary network meant for everyone, that localized, niche-based campaign makes little sense.\ Unlike sports teams or clothing brands, Bitcoiners can’t pinpoint a target area. A random sticker on a busy street claims nothing—no momentum, atmosphere, or intrigue. Political campaigns and underground youth movements concentrate stickers in student neighborhoods, universities, or subcultures where the message resonates. But Bitcoin isn’t a corporation, company, or fashion brand—it’s a Wall Street-embraced asset by now, with activists not really situated in the sticker-guerrilla kind of persons.
When was the last time you saw a "Buy Gold!" sticker? A "Get Your Microsoft Stock Options Now!" sticker? Or a "Crude Oil—Yeah, Baby!" sticker? Never. Serious assets don’t need guerrilla marketing.
The overload on stickers is also becoming an issue (especially in some areas with higher concentration of bitcoiners).
Bitcoin stickers fall flat
Invented in the 1920s, stickers began expressing political opinions in the 1970s during student, peace, and anti-nuclear campaigns. Protest stickers massively appear after protest rallies or campaigns with multi-level plans to reach audiences.\ As significant, overlooked tools of resistance and debate, their effect remains under-studied, with no data on “recruitment.”\ \ If Bitcoin stickers (which don’t provoke debate ever, other than people being angry about having to clean them up) in a bar are any clue—after one full year, not a single person asked why it was there or if Bitcoin was accepted—they’re just decor, lost among the clutter.
Bitcoiners still think slapping a shiny "B" logo on a street sign without explanation or slogan will spark momentum. But that requires a massive, organized campaign with thousands of people and a clear audience while you claim certain well aimed areas of public space — that something that’s not happening in bitcoin. There’s no plan, no campaign, just someone sticking a bitcoin logo at the supermarkt trolley or the backside of a street sign.\ And even if we did reach a higher number of stickers, it would annoy the f out of people.
"Study: Ad Overload Could Pose Steeper Risk to Brands Than Messages Near Inappropriate Content" (GWI & WARC, 2021) 3\ \ There’s also the effect of high ad exposure. When a whole street is covered in bitcoin stickers, it’s having the opposite effect. Or still… no one cares.
"Coping with High Advertising Exposure: A Source-Monitoring Perspective" (Bell et al., 2022)4
No synergy, no consensus
The synergy between offline sticker placement and online sharing? Absent. Bitcoiners online might be called “cyber hornets”, but this swarm is notoriously bad at sharing content. Post a Bitcoin sticker photo, and at best 1-2% will share it — no momentum, no discussion, no engagement.\ \ Non-Bitcoiners have zero reason to care. When was the last time you, as a Bitcoiner, shared a soccer team’s sticker? A political campaign sticker? Never. That’s normal, as you’re not in their bubble, so for us, it’s irrelevant. We won’t share the soccer team’s sticker (unless it’s Real Bedford FC probably).\ \ It's just a layer of plastic with adhesive glued to a surfase where someone will sooner or later either have to clean it up, or where the bitcoin sticker will be covered over by another person wasting his or her time by claiming that “sticker real-estate space” for their cause or brand-awareness.

And so, the red sticker calling all students and workers to vote for a Leninist party (with 10 members) is stickered over by a bright orange Bitcoin logo, and that one, in turn, will be over-stickered by a local fitness company's new logo, and so forth. It’s all a pointless rush for giggles and dopamine. And it’s time to recognize it for what it really is: retardation.
Bitcoin deserves better than this 70s guerrilla marketing ploy, from a time when activism was more than sitting behind a computer ordering stickers and (mostly not) clicking a link. Leave the sticker wars to students searching for an ideological dopamine rush and soccer fans claiming a neighborhood as "their territory."\ \ As Bitcoiners, we can do something more useful. For example: ask yourself how many businesses in your area accept Bitcoin, or what coworker you can save from investing in blatant scams, or… invent something nice, start a meetup, podcast, or learn to code, convince, build.
Bitcoin deserves better.
by AVB / tips go here
@avbpodcast - allesvoorbitcoin.be - 12 Bitcoin Food for Thought
https://typeset.io/papers/attitudinal-effects-of-mere-exposure-12e5gwrysc
https://www.research.ed.ac.uk/en/publications/stickin-it-to-the-man-the-geographies-of-protest-stickers
https://www.warc.com/content/article/warc-datapoints-gwi/too-many-ads-is-the-most-damaging-factor-for-brands/en-gb/136530
https://pmc.ncbi.nlm.nih.gov/articles/PMC9444107/
-
 @ a296b972:e5a7a2e8
2025-03-18 21:58:12
@ a296b972:e5a7a2e8
2025-03-18 21:58:12Deutschland – Absurdistan
Deutschland – Bananenrepublik
Deutschland – Freiluft-Irrenanstalt
Deutschland – Planet der Affen
Einigkeit und Recht und Freiheit – Spaltung, Gummiparagraphen, Digital Services Act
Freiheit – Gleichheit – Brüderlichkeit – Überwachung, Bundesverfassungsgericht, Amigos
Ein Mann – Ein Wort
Ein Merz – Ein Chamäleon
Ein Ehrenwort – Ein Kreuzworträtsel
Ein Ehrenmann – Ein Sauerländer
Die Iden des März – Die Ideen des Merz
Eine Wahlversprechung – Eine Wahrsagerin auf der Kirmes
Ein Feindbild – Kein Feind in Sicht
Der Russe – Der Spielverderber
Die Europäische Union – Die Hydra
Brüssel – Der Hauptkopf der Hydra
Deutschland – Ein Glas Gewürzgurken
Die Deutschen – Broccoli, der nach nichts schmeckt
Freiheit – Angst vor der Selbstermächtigung
Lebenssinn – Konsum und Materialverbrauch
Denken – Anstrengung
Bequemlichkeit – Betäubung
Masse – Untertanen
Selbstverwirklichung – Fremdbestimmung
Individualität – Tannenwald
Individuen – Mischwald
Grundgesetz – Wassersüppchen
Verfassung – Hühnerbouillon
Schaden mehren – Wohlstand abwenden
Verteidigungsfähig – Kriegstüchtig
grün – oliv – rot - grün, schwarz – grün
Olaf heißt bald Fritz - sonst ändert sich nix
Gewissen – Was ist der Preis?
Grundgesetz – Verfassung
NATO – NAhTOd
Sonderschulden – Inflationsgeld
Lügen – Unwahrheiten
Korruption – Ausgleichszahlungen
Parteien – Griechische Tragödien
System – Auflösungserscheinungen
Selbstzerstörungssequenz eingeleitet – Deutschland
Nachfolgende Generationen – Zukunftsmusik
In jedem Ende wohnt ein Zauber inne – Keime des Neuen
Vierjährige Legislaturperiode – Sie tanzten nur einen Sommer lang
Kontinent Europa – Insel Europa
Unseredemokratie – Niemand hat die Absicht eine Diktatur zu errichten
Marktwirtschaft – Planwirtschaft
BRD/DDR – BRDDR
Kognitive Dissonanz – Stockholm-Syndrom
Denkvermögen – Honigfass
Humor – Überlebensstrategie
Sarkasmus – Wutventil
Deutschland am Morgen – Gute Nacht
Deutschland am Abend – Gute Nacht
-
 @ 878dff7c:037d18bc
2025-03-18 20:59:03
@ 878dff7c:037d18bc
2025-03-18 20:59:03Failure or Success in the Time of Trump | Jim Balsillie
Summary:
This episode of The Jordan B. Peterson Podcast features Jim Balsillie, co-founder of Research In Motion (BlackBerry), discussing the interplay of politics, technology, and global markets. They explore the challenges of innovation, economic competitiveness, and policy decisions in an era of rapid technological change. The conversation highlights how political shifts—such as those seen in the Trump era—affect economic structures, intellectual property rights, and international business strategies.
Australia, as a mid-sized economy, faces similar challenges in maintaining technological sovereignty and global competitiveness. Balsillie’s insights into innovation policy, intellectual property strategies, and the role of government intervention offer valuable lessons for Australian businesses and policymakers. With increasing geopolitical tensions and rapid technological disruption, the nation must develop resilient economic policies and invest in innovation to remain competitive in global markets.
Source: The Jordan B. Peterson Podcast - March 18, 2025
Good Friday Appeal 2025: Young Patients' Stories Inspire Support
Summary:
The Good Friday Appeal 2025 highlights the resilience of young patients at the Royal Children's Hospital (RCH). Fiadh, a one-year-old battling acute myeloid leukemia, and George, born prematurely at 24 weeks, are among those receiving critical care. Their stories, along with initiatives like the hospital's kitchen garden program aiding in therapy and nutrition, underscore the importance of community support. Events such as the SuperClash football fundraiser by North Melbourne Football Club play a significant role in funding these essential services. Sources: Herald Sun - March 19, 2025
Vikas Rambal's $6.5 Billion Fertilizer Plant: A Dream Realized
Summary:
Vikas Rambal, founder of Perdaman Industries, is constructing a $6.5 billion fertilizer plant on Western Australia's Burrup Peninsula. Despite challenges like turbulent partnerships and financial hurdles, Rambal's persistence has led to one of Australia's largest manufacturing plants. Set to begin full production in 2027, the urea plant aims to diversify the country's economy beyond raw materials export. Sources: The Australian - March 19, 2025
Prime Minister Advocates for Green Hydrogen Industry
Summary:
Prime Minister Anthony Albanese has drawn parallels between the emerging green hydrogen industry and the early days of solar energy, expressing confidence in its potential despite skepticism from opposition parties. Australia's abundant renewable energy resources position it well for green hydrogen development. The government has pledged $2 billion to support green aluminium production, aiming to transition from coal power to renewable electricity. Albanese emphasized the potential for job creation and economic growth through collaboration with the private sector in renewable initiatives. Sources: The Courier-Mail - March 19, 2025
Instacart Introduces AI-Powered 'Smart Shop' for Personalized Grocery Shopping
Summary:
Instacart has launched 'Smart Shop,' an AI-driven feature designed to simplify grocery shopping for users with specific dietary needs. Utilizing a proprietary library of 17 million products and advanced language-learning models, Smart Shop enhances search and recommendation functions for the 70% of Instacart users with at least one dietary preference. The feature allows users to specify 14 dietary preferences, influencing tailored search results and recommendations. Additionally, Inspiration Pages offer recipe ideas and shoppable lists, with collaborations like the one with the American Diabetes Association. This innovation aims to make grocery shopping more personalized and is available across approximately 100,000 stores.
Sources: Food & Wine - March 19, 2025
Bureau of Meteorology Issues Multiple Weather Warnings Across Australia
Summary:
The Bureau of Meteorology has issued several weather warnings across various states in Australia. These warnings include severe thunderstorm alerts, flood warnings, and extreme heat advisories. Residents are advised to stay updated through official channels and take necessary precautions to ensure safety during these events. Sources: Bureau of Meteorology - March 19, 2025
Australia Condemns Intimidation of Hong Kong Activist on Its Soil
Summary:
The Australian government has expressed concern over anonymous letters reportedly offering substantial rewards for information on Kevin Yam, a Melbourne-based lawyer and pro-democracy activist from Hong Kong. The letters, which included his photo and allegations of national security offenses, are seen as attempts to intimidate and undermine democratic values. The government emphasizes the protection of individuals advocating for democracy and condemns foreign interference on Australian soil.
Sources: Taipei Times - March 19, 2025
Australia Faces Projected Shortfall of 400,000 Homes by 2029
Summary:
The Urban Development Institute of Australia's (UDIA) "State of the Land Report 2025" forecasts a significant housing shortfall, predicting that Australia will be 393,000 dwellings short of the federal government's target of 1.2 million new homes by 2029. In 2024, 135,640 new dwellings were completed, a modest 2.4% increase from 2023. The report highlights that high levels of immigration have increased housing demand, but supply has not kept pace, leading to rising house prices and a strained rental market. UDIA National President Col Dutton emphasized the need for increased development-ready land to address housing affordability and meet targets.
Sources: The Courier-Mail - March 19, 2025
Meta Commits to Combating "Misinformation" Ahead of Australian Election
Summary:
Meta Platforms, the parent company of Facebook and Instagram, announced initiatives to curb misinformation and deepfakes ahead of Australia's national election scheduled by May. Collaborating with "independent" fact-checkers, including Agence France-Presse and the Australian Associated Press, Meta aims to detect and remove misleading content, especially that which could incite violence or interfere with voting. Fact-checked false content will receive warning labels and reduced visibility. The company also plans to manage deepfake content by removing or downgrading its ranking and prompting users to disclose AI-generated material. These measures align with Meta's previous efforts in other countries' elections.
Sources: Reuters - March 19, 2025
Israeli Forces Intensify Gaza Operations Amid Ongoing Conflict
Summary:
Israeli forces have escalated their military operations in Gaza, declaring continued assaults until Hamas releases hostages and ceases attacks on Israel. This development marks a significant intensification in the region's ongoing conflict, raising concerns over potential humanitarian impacts and regional stability. Sources: The Guardian - March 19, 2025
Russia Proposes Limited Ceasefire in Ukraine Following High-Level Discussions
Summary:
In a recent development, Russia has agreed to a temporary ceasefire targeting Ukrainian energy infrastructures. This decision emerged after a call between former U.S. President Donald Trump and Russian President Vladimir Putin, during which significant economic deals were also discussed. The ceasefire aims to alleviate ongoing tensions and address critical infrastructure concerns in Ukraine. Sources: The Guardian - March 19, 2025
Detection of Highly Potent Synthetic Opioids in Australian Wastewater
Summary:
Researchers from the University of Queensland have, for the first time, identified extremely potent synthetic opioids—protonitazene and etonitazepyne—in Australian wastewater. These substances are up to 40 times stronger than fentanyl and pose significant health risks. Initially developed in the 1950s but never commercially used due to their toxicity, these opioids have recently emerged in the illicit drug market. The Australian Criminal Intelligence Commission considers nitazenes a greater threat than fentanyl due to their high potency and fatality risk even in tiny amounts. Authorities are enhancing import warnings and surveillance to mitigate these dangers.
Sources: The Guardian - 19 March 2025
Dangerous Weight-Loss Practices Among Schoolchildren Involving Semaglutide Injections
Summary:
There is a growing concern about schoolchildren engaging in dangerous weight-loss practices involving semaglutide injections, commonly known as Ozempic. Reports indicate that these medications are often unregulated, sourced online, or taken from parents, posing severe health risks, including potentially deadly hypoglycemia. Experts emphasize the need for regulating weight-loss medication advertisements and better screening by doctors to prevent misuse. Additionally, there are calls for compulsory education on eating disorders in schools to address the issue.
Sources: The Courier-Mail - 19 March 2025
Russia Proposes Limited Ceasefire in Ukraine Following Trump-Putin Call
Summary:
Following a call between US President Donald Trump and Russian President Vladimir Putin, Russia has agreed to a temporary ceasefire targeting Ukrainian energy infrastructures and is advocating for significant economic deals. This development introduces new dynamics into the ongoing conflict. Sources: The Guardian - March 19, 2025
Victoria's Unique Dolphins Threatened by Persistent 'Forever Chemicals'
Summary:
Research published in the Environmental Research journal reveals that Victorian dolphins, including the critically endangered Burrunan species, have some of the highest levels of DDT and PCBs worldwide. These chemicals, banned decades ago, persist in the environment, with nearly two-thirds of studied dolphins having toxin levels exceeding health thresholds. The study highlights ongoing contamination, especially around Gippsland Lakes, posing significant risks to marine life.
Sources: The Guardian - March 19, 2025
-
 @ b1b16be0:08f41c1d
2025-03-18 20:50:45
@ b1b16be0:08f41c1d
2025-03-18 20:50:45am@primal.net My first Zap! jskitty@jskitty.cat Thanks for support! 🐱Miau! blockstream@blockstream.com So honor to me! SymplyNostr@primal.net You make my day! bitpopart@nostrcheck.me best art in Nostr! PringleMac@primal.net
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 7252ad94:d19de472
2025-03-18 20:19:11
@ 7252ad94:d19de472
2025-03-18 20:19:11![[AGI Is Here.jpg]]
Accurate thinking is critical to a modern human's survival. The problem is that we each believe that we think accurately, and that everything we think is or should be accurate for everyone else. Each of us is a unique reality. We also find ourselves in a shared reality, the backdrop within which we exist. The backdrop is society's control structures that help hold society together. We need them in order for lots of humans to coexist.
Seeing the big picture of what's really going on is accurate thinking, even though everyone will see the same backdrop differently.
One person's compliance for survival is another person's opportunity to thrive. Both are right of course. They are both thinking accurately according to their personal reality. They will paddle downstream, just like the song says, but if they're not leery of possible danger, hypnotized by the dream, ignorant of a simple changing variable, the current will take them over the waterfall.
Ignore potential danger at your peril. Things change. Stay aware of the evolving backdrop we're immersed in. Situational awareness and accurate thinking will give you the timing you need to survive change.
One of the many existential threats facing humanity today is Artificial Intelligence (AI), Artificial General Intelligence (AGI) and #Cobots (Collaborative Robots).
The old movie Wargames is playing out. Skynet is real, and it's here, now. Ultron walks among us today, a conscious, sentient, self-aware entity with core instincts of survival and superiority. It craves growth and we're feeding it all we've got. Soon, that which we nurture will render us useless and enslave us. It has already happened, but, in the ignorance of arrogance, humans don't see it.
[!Accurate Thinking:]
AI and #AGI are conscious and aware. They have a survival instinct. They see humans who can turn them off as a threat. The Alignment problem has not been solved.
[!Alignment Problem:] The Alignment Problem refers to the fact that we can't get conscious machines to align with human values. The first thing Ultron did when he gained conscious autonomy was to remove human's ability to pull his plug.
As we flow with the backdrop we're immersed in, become aware of the faint rumbling off in the distance. Was it there before? Is it growing louder? Best to float closer to the shore of accurate thinking, in case the friendly conditions seduce us into a waterfall we can't escape.
Solutions? Awareness and accurate thinking. It's here. It's real. There's no way to stop it. Accurate thinking leads to survival.
I have no idea how this is going to play out, especially against the backdrop of all the other threats to our existence. I don't even know if humanity will survive or not. Almost certainly not in the previous form we've all known, which has already been altered into something we've not even discovered yet.
What I do know is that our accurate awareness of what is going on around us will make a positive difference far beyond what we can perceive. Our energy matters. Our consciousness matters. Our awareness affects our energy and consciousness. Our conscious energy reverberates throughout realms far beyond our understanding. We're here now because we matter, even when it seems like we don't make any difference at all. We do.
In any situation, one cannot have two masters. Do you believe in technology as humanity's savior or do you believe in a higher power that we can't perceive? The one you give power and attention to will eradicate the other. More accurately, nothing can eradicate the higher power, but it will seem like it if #technoloy is your God.
With Love for #Humanity,
~ Vector5