-
 @ 16f1a010:31b1074b
2025-02-19 20:57:59
@ 16f1a010:31b1074b
2025-02-19 20:57:59In the rapidly evolving world of Bitcoin, running a Bitcoin node has become more accessible than ever. Platforms like Umbrel, Start9, myNode, and Citadel offer user-friendly interfaces to simplify node management. However, for those serious about maintaining a robust and efficient Lightning node ⚡, relying solely on these platforms may not be the optimal choice.
Let’s delve into why embracing Bitcoin Core and mastering the command-line interface (CLI) can provide a more reliable, sovereign, and empowering experience.
Understanding Node Management Platforms
What Are Umbrel, Start9, myNode, and Citadel?
Umbrel, Start9, myNode, and Citadel are platforms designed to streamline the process of running a Bitcoin node. They offer graphical user interfaces (GUIs) that allow users to manage various applications, including Bitcoin Core and Lightning Network nodes, through a web-based dashboard 🖥️.
These platforms often utilize Docker containers 🐳 to encapsulate applications, providing a modular and isolated environment for each service.

The Appeal of Simplified Node Management
The primary allure of these platforms lies in their simplicity. With minimal command-line interaction, users can deploy a full Bitcoin and Lightning node, along with a suite of additional applications.
✅ Easy one-command installation
✅ Web-based GUI for management
✅ Automatic app updates (but with delays, as we’ll discuss)However, while this convenience is attractive, it comes at a cost.
The Hidden Complexities of Using Node Management Platforms
While the user-friendly nature of these platforms is advantageous, it can also introduce several challenges that may hinder advanced users or those seeking greater control over their nodes.
🚨 Dependency on Maintainers for Updates
One significant concern is the reliance on platform maintainers for updates. Since these platforms manage applications through Docker containers, users must wait for the maintainers to update the container images before they can access new features or security patches.
🔴 Delayed Bitcoin Core updates = potential security risks
🔴 Lightning Network updates are not immediate
🔴 Bugs and vulnerabilities may persist longerInstead of waiting on a third party, why not update Bitcoin Core & LND yourself instantly?
⚙️ Challenges in Customization and Advanced Operations
For users aiming to perform advanced operations, such as:
- Custom backups 📂
- Running specific CLI commands 🖥️
- Optimizing node settings ⚡
…the abstraction layers introduced by these platforms become obstacles.
Navigating through nested directories and issuing commands inside Docker containers makes troubleshooting a nightmare. Instead of a simple
bitcoin-clicommand, you must figure out how to execute it inside the container, adding unnecessary complexity.Increased Backend Complexity
To achieve frontend simplicity, these platforms make the backend more complex.
🚫 Extra layers of abstraction
🚫 Hidden logs and settings
🚫 Harder troubleshootingThe use of multiple Docker containers, custom scripts, and unique file structures can make system maintenance and debugging a pain.
This complication defeats the purpose of “making running a node easy.”
✅ Advantages of Using Bitcoin Core and Command-Line Interface (CLI)
By installing Bitcoin Core directly and using the command-line interface (CLI), you gain several key advantages that make managing a Bitcoin and Lightning node more efficient and empowering.
Direct Control and Immediate Updates
One of the biggest downsides of package manager-based platforms is the reliance on third-party maintainers to release updates. Since Bitcoin Core, Lightning implementations (such as LND, Core Lightning, or Eclair), and other related software evolve rapidly, waiting for platform-specific updates can leave you running outdated or vulnerable versions.
By installing Bitcoin Core directly, you remove this dependency. You can update immediately when new versions are released, ensuring your node benefits from the latest features, security patches, and bug fixes. The same applies to Lightning software—being able to install and update it yourself gives you full autonomy over your node’s performance and security.
🛠 Simplified System Architecture
Platforms like Umbrel and myNode introduce extra complexity by running Bitcoin Core and Lightning inside Docker containers. This means:
- The actual files and configurations are stored inside Docker’s filesystem, making it harder to locate and manage them manually.
- If something breaks, troubleshooting is more difficult due to the added layer of abstraction.
- Running commands requires jumping through Docker shell sessions, adding unnecessary friction to what should be a straightforward process.
Instead, a direct installation of Bitcoin Core, Lightning, and Electrum Server (if needed) results in a cleaner, more understandable system. The software runs natively on your machine, without containerized layers making things more convoluted.
Additionally, setting up your own systemd service files for Bitcoin and Lightning is not as complicated as it seems. Once configured, these services will run automatically on boot, offering the same level of convenience as platforms like Umbrel but without the unnecessary complexity.
Better Lightning Node Management
If you’re running a Lightning Network node, using CLI-based tools provides far more flexibility than relying on a GUI like the ones bundled with node management platforms.
🟢 Custom Backup Strategies – Running Lightning through a GUI-based node manager often means backups are handled in a way that is opaque to the user. With CLI tools, you can easily script automatic backups of your channels, wallets, and configurations.
🟢 Advanced Configuration – Platforms like Umbrel force certain configurations by default, limiting how you can customize your Lightning node. With a direct install, you have full control over: * Channel fees 💰 * Routing policies 📡 * Liquidity management 🔄
🟢 Direct Access to LND, Core Lightning, or Eclair – Instead of issuing commands through a GUI (which is often limited in functionality), you can use: *
lncli(for LND) *lightning-cli(for Core Lightning) …to interact with your node at a deeper level.Enhanced Learning and Engagement
A crucial aspect of running a Bitcoin and Lightning node is understanding how it works.
Using an abstraction layer like Umbrel may get a node running in a few clicks, but it does little to teach users how Bitcoin actually functions.
By setting up Bitcoin Core, Lightning, and related software manually, you will:
✅ Gain practical knowledge of Bitcoin nodes, networking, and system performance.
✅ Learn how to configure and manage RPC commands.
✅ Become less reliant on third-party developers and more confident in troubleshooting.🎯 Running a Bitcoin node is about sovereignty – learn how to control it yourself.
Become more sovereign TODAY
Many guides make this process straightforward K3tan has a fantastic guide on running Bitcoin Core, Electrs, LND and more.
- Ministry of Nodes Guide 2024
- You can find him on nostr
nostr:npub1txwy7guqkrq6ngvtwft7zp70nekcknudagrvrryy2wxnz8ljk2xqz0yt4xEven with the best of guides, if you are running this software,
📖 READ THE DOCUMENTATIONThis is all just software at the end of the day. Most of it is very well documented. Take a moment to actually read through the documentation for yourself when installing. The documentation has step by step guides on setting up the software. Here is a helpful list: * Bitcoin.org Bitcoin Core Linux install instructions * Bitcoin Core Code Repository * Electrs Installation * LND Documentation * LND Code Repository * CLN Documentation * CLN Code Repository
If you have any more resources or links I should add, please comment them . I want to add as much to this article as I can.
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ eac63075:b4988b48
2024-10-20 13:49:55
@ eac63075:b4988b48
2024-10-20 13:49:55Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.
Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.
The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.
Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.
The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
Conclusion of the Technical Debate
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.

Table reference: Patrick Breyer - Chat Control in 23 September 2024
Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.
The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
Conclusion of the Debate
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.
User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
Summary of Consequences
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.
The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.
Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 4ba8e86d:89d32de4
2024-10-01 13:27:38
@ 4ba8e86d:89d32de4
2024-10-01 13:27:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8ff74724:5eedde0e
2025-03-23 01:25:30
@ 8ff74724:5eedde0e
2025-03-23 01:25:30Birds
Birds simply don't give a shit.
They don't care about you.
They don't love you.
They only want one thing.
Seeds.
-
 @ 6bae33c8:607272e8
2025-03-22 23:12:43
@ 6bae33c8:607272e8
2025-03-22 23:12:43I was supposed to do my Main Event next week, but Heather scheduled a trip to Spain for us I had forgotten about, so I moved it to today, which meant I had to cram a bit.
I drew the seven slot. Results are below:
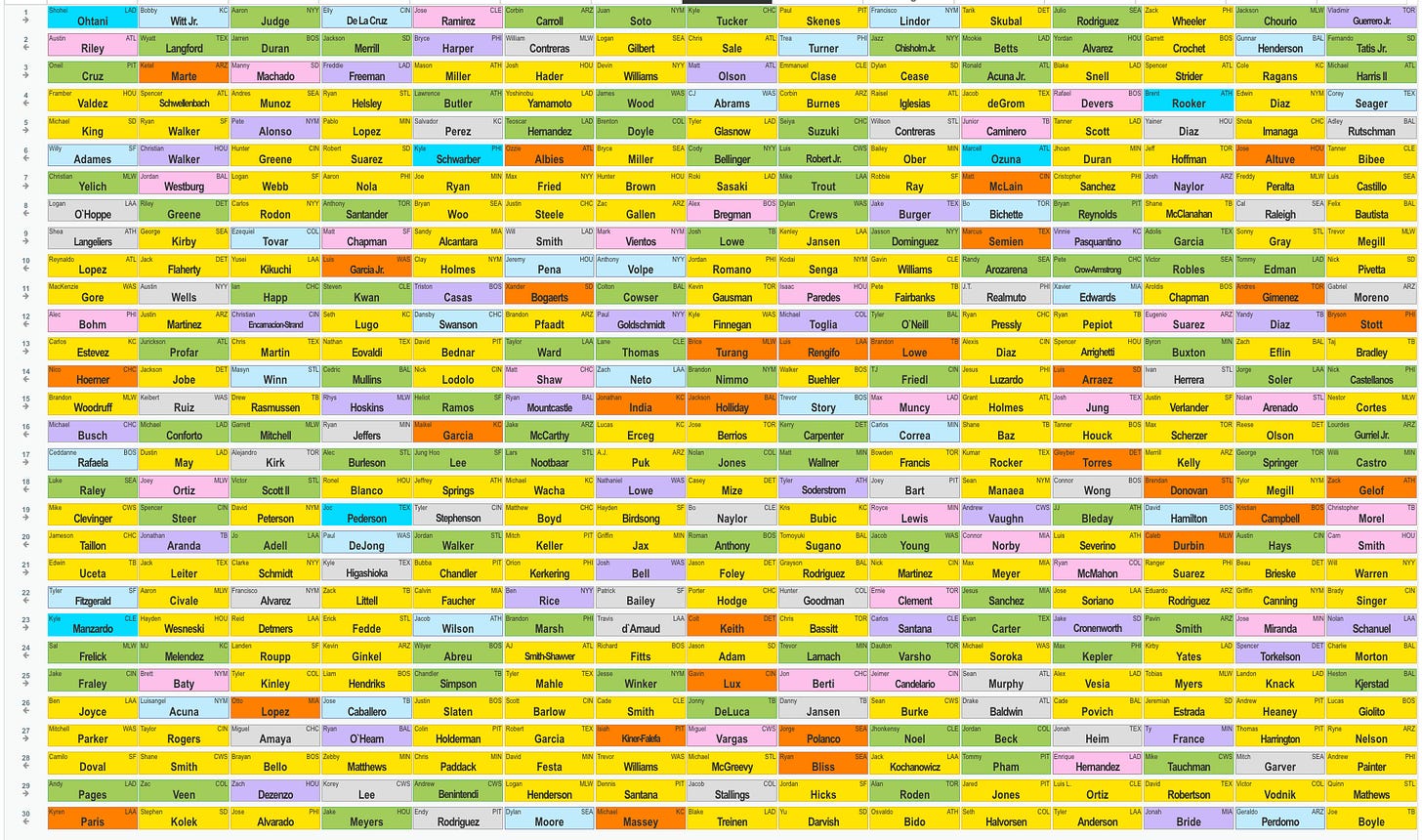 Before I get into the round-by-round write-up I have to say this was the smoothest and easiest Main I’ve ever done. That doesn’t mean this is a great team — I could easily be wrong about everything — but using recent ADP I planned out each round, and it really went almost exactly to form. That never happens. Usually I’m worried about having to chase some category or getting stuck with players I don’t want. But today there was almost none of that.
Before I get into the round-by-round write-up I have to say this was the smoothest and easiest Main I’ve ever done. That doesn’t mean this is a great team — I could easily be wrong about everything — but using recent ADP I planned out each round, and it really went almost exactly to form. That never happens. Usually I’m worried about having to chase some category or getting stuck with players I don’t want. But today there was almost none of that.1.8 Kyle Tucker — I like Tucker in a new park, playing for a big contract. He’s fully healthy after an injury-shortened 2024, so he should be fresh. Had Team 7 taken Tucker instead of Juan Soto, I would have taken Jackson Chourio.
2.8 Chris Sale — I thought I might get Jazz Chisholm here, and my fallback was Trea Turner. But earlier in the day I decided I’d probably take Sale anyway as pitching gets scarce quickly in the 15-team and often gets pushed up as a result. But I hadn’t really locked it in, even though I felt Sale would make for an easier build. Then Chisholm and Turner went ahead of me on consecutive picks, and my choice was made for me.
3.8 Matt Olson — I was worried about this pick. This was in the elite closer range, and I didn’t want to go that route, so it was either Manny Machado (gone), Olson or dropping down for someone like Michael Harris about whom I’m only lukewarm. I took Olson who has a good shot of 40-100-100 in that lineup.
4.8 C.J. Abrams — The stat nerds hate him, but he could steal 40 bases, and he was raking before slumping in the second half last year. Tucker gave me some bags, but I really wanted a big-time steals source to pair with him.
5.8 Tyler Glasnow — My favorite fifth-round starter, Glasnow managed134 innings last year. A similar giant lefty, Randy Johnson, was also injury prone early in his career and took a while to get going too.
6.8 Cody Bellinger — I was dead set on Bellinger who is raking this spring. He’ll get the short porch in Yankee stadium and qualifies at first and OF.
7.8 Roki Sasaki — This was the first pick I really had to think about. There was a run of five straight pitchers ahead of me, three of whom I would have taken instead (Logan Webb, Max Fried, Hunter Brown.) I like buying the dip on Sasaki after a shaky outing in Japan, but I also considered pivoting to Mike Trout. In the end, I felt there were more hitters I liked afterward, so I went Sasaki, and then Trout went with the very next pick. In fact the next guy snap-called it, if I recall correctly.
8.8 Alex Bregman — I wanted a share after reading how well he’s hit at Fenway during his career (if Grok is correct, 1.240 OPS in 21 games.) Plus he might eventually gain 2B eligibility if Rafael Devers gets healthy enough to play third. And he should get a lot of RBI hitting third behind Devers and Jarren Duran.
9.8 Josh Lowe — I really wanted to get a share of Lowe after reading about how the minor league home park will boost power for lefties. The steals are a given if he’s healthy, but 20-25 HR would make him a huge bargain in Round 9.
10.8 Jordan Romano — The Lowe pick cost me Kenley Jansen, which I thought it might, so I pivoted to the other exprienced closer I like in that range, and Romano’s on a better team.
11.8 Kevin Gausman — I thought about Aroldis Chapman here, but starters were getting scarce, so I gambled he’d make it back and took Gausman. Gausman is coming off a down year, but he’s healthy, and he knows how to pitch.
12.8 Brandon Finnegan — I missed out on Chapman, it turns out, but Finnegan, who had 38 saves last year and was re-signed, was my backup plan. He’s not especially good, but saves are saves.
13.8 Brice Turang — I really didn’t need speed that badly, but Turang fell like 50 spots below ADP, and I did need a second baseman. His defense keeps him in the lineup, and I’ll take 30-plus steals in case one of my other speed guys doesn’t pan out.
14.8 Brandon Nimmo — I got snaked on Walker Buehler (and Jesus Luzardo two picks before that), so I went with Nimmo for his ability to score runs.
15.8 Jackson Holliday — After a lot of safe picks, I felt like gambling on a top prospect finally. He’s hitting well this spring too.
16.8 Jose Berrios — This just seemed like the right pick, a boring veteran who knows how to pitch and get you innings without killing you. With Glasnow and Sasaki, I needed more of a horse type.
17.8 Nolan Jones — He was scratched from the game today right after I made this, so we’ll see. Hopefully it’s something minor. His 2023 season was fetching a top-five-round ADP last year.
18.8 Casey Mize — Pitching was really flying, and Mize is a former top prospect with an opportunity.
19.8 Bo Naylor — I needed a catcher, and he is one. I like that he runs a bit, and last year’s batting average I’ll chalk up to variance.
20.8 Roman Anthony — I don’t know whether he’ll make the team out of camp, but he’s an elite prospect with little left to prove in the minors.
21.8 Jason Foley — I have two shaky closers, so I wanted to throw another potential one in the mix.
22.8 Porter Hodge — Another saves option if Ryan Pressly falls apart.
23.8 Colt Keith — Keith wasn’t horrendous as as rookie, and moving to first base will give him extra eligibility soon.
24.8 Jason Adam — Another potential source of saves with Robert Suarez looking awfully shaky this spring.
25.8 Gavin Lux — A former top prospect, getting regular at-bats in the league’s second best hitter’s park and picking up more eligibility.
26.8 Jonny Deluca — I needed outfield depth in case Anthony doesn’t start the year in the majors, and Deluca should play in that bandbox minor league park.
27.8 Miguel Vargas — A former top prospect with dual position eligibility should get his chance for regular low-pressure at-bats in Chicago.
28.8 Michael McGreevy — I needed another SP, and he’s one. Also has good control and pitches in a good park. Having a great spring too.
29.8 Jacob Stallings — I played chicken at second catcher all draft, got burned a few times, but Stallings is the starter for now in Colorado.
30.8 Blake Treinen — The Stallings pick cost me a gamble on Jared Jones’ elbow, so I took Treinen who’s an elite reliever who could fill in if starters have bad matchups.
Roster By Position
C Bo Naylor/Jacob Stallings
1B Matt Olson
2B Brice Turang
3B Alex Bregman
SS C.J. Abrams
CI Cody Bellinger
MI Jackson Holliday
OF Kyle Tucker/Josh Lowe/Brandon Nimmo/Nolan Jones/Roman Anthony
UT Colt Keith
SP Chris Sale/Tyler Glasnow/Roki Sasaki/Kevin Gausman/Jose Berrios/Casey Mize
RP Jordan Romano/Brandon Finnegan/Jason Foley
B Porter Hodge/Jason Adam/Gavin Lux/Jonny Deluca/Miguel Vargas/Michael McGreevy/Blake Treinen
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 4925ea33:025410d8
2025-03-22 19:30:21
@ 4925ea33:025410d8
2025-03-22 19:30:21O ato de estudar pode ser desafiador, pois precisamos vencer obstáculos como distrações, falta de concentração e baixa energia. Essas dificuldades são comuns na vida dos estudantes e costumam ser os principais fatores que prejudicam o aprendizado.
Mesmo dedicando longas horas aos estudos, esses desafios podem comprometer a produtividade, tornando o esforço pouco eficaz. É nesse contexto que a Aromaterapia surge como uma solução natural e eficaz.
Os óleos essenciais têm um grande potencial para atuar na concentração, no estímulo da memória e no aumento da clareza mental. Ou seja, quando utilizados de forma estratégica, podem potencializar significativamente o desempenho nos estudos.
Quais são os benefícios dos óleos essenciais para os estudos?

No universo dos aromas, cada óleo essencial possui propriedades únicas. De forma geral, podemos destacar os seguintes benefícios:
-
Estimulação cognitiva
-
Aumento da memória
-
Redução do estresse e da ansiedade
-
Aumento da energia e disposição
-
Estímulo à criatividade
-
Melhora da concentração
1. Estimulação Cognitiva
Os óleos essenciais de alecrim e hortelã-pimenta estão entre os principais aliados da estimulação cognitiva. Eles atuam diretamente no sistema límbico, a região do cérebro responsável pela memória, emoções e aprendizado.
2. Aumento da Memória
O aumento da memória está diretamente relacionado à circulação sanguínea cerebral, que favorece a retenção de informações. O óleo essencial de hortelã-pimenta é especialmente eficaz nesse processo, pois atua como vasodilatador, aumentando o fluxo sanguíneo para o cérebro e melhorando a capacidade de memorização.
3. Redução do Estresse e da Ansiedade
Para reduzir o estresse e a ansiedade antes e durante os estudos, os óleos de lavanda, camomila e ylang-ylang são altamente recomendados, pois reduzem os níveis de cortisol (hormônio do estresse). No entanto, é importante usá-los com cautela, pois possuem propriedades sedativas e podem induzir ao sono caso sejam usados em excesso durante os estudos.
4. Aumento da Energia e Disposição
A energia e a disposição para os estudos estão relacionadas à produção de dopamina e serotonina, neurotransmissores que promovem o bem-estar e a motivação. Os óleos cítricos, como limão, laranja doce e grapefruit, estimulam essas substâncias, ajudando a reduzir a fadiga mental e proporcionando mais vigor para o aprendizado.
5. Estímulo à Criatividade
A criatividade está associada à imaginação, abstração e inovação. Para estimular esse processo, é indicado o uso de óleos essenciais que atuam no sistema límbico de maneira introspectiva, como o óleo essencial de sândalo, que favorece a conexão com novas ideias e insights criativos.
6. Melhora da Concentração
A concentração depende da oxigenação cerebral e da ativação do sistema nervoso simpático, que aumenta a atenção e o estado de alerta. O óleo essencial de eucalipto é um dos mais eficazes nesse aspecto, pois melhora a respiração e promove maior clareza mental.
Como usar a Aromaterapia na hora do exame?

- Na véspera da prova -
Antes de dormir, utilize 1 a 2 gotas de óleo essencial de lavanda ou camomila no travesseiro. Isso ajudará a ter um sono reparador e reduzir a ansiedade para o dia seguinte.
- No dia do exame -
Ao acordar:
Inale 1 a 2 gotas de óleo de hortelã-pimenta ou limão para ativar o cérebro e aumentar o estado de alerta.
Durante o banho:
Misture 3 gotas de óleo de alecrim ou laranja doce ao seu sabonete líquido para estimular a concentração.
Antes da prova:
Aplique um creme corporal energizante, feito com a seguinte diluição:
5 gotas de óleo essencial de alecrim
3 gotas de hortelã-pimenta
2 gotas de limão
Misture em 10 g de creme neutro e aplique nos pulsos e têmporas.
Durante a prova:
Se sentir distração ou fadiga mental, aplique 1 gota de óleo essencial de alecrim e 1 gota de hortelã-pimenta na região dos ombros da sua camiseta. Assim, você poderá inalar discretamente e recuperar o foco.
Essas foram as minhas dicas sobre como a Aromaterapia pode potencializar o seu desempenho nos estudos. Experimente e sinta a diferença!
Boa prova!
-
-
 @ 5c8a5765:4fc5edee
2025-03-22 18:38:23
@ 5c8a5765:4fc5edee
2025-03-22 18:38:23[Читать в IPFS]
Итак, детки-котлетки, сегодня мы поговорим, как ~~не~~правильно распространять агиацию. Возьмите свои любимые антифашистские стикеры и используйте этот текст как инструкцию к ним — иначе у меня голова лопнет от того, что я вижу на улицах.
Агитация
Для начала определитесь, чем вы занимаетесь: агитируете к чему-то или поддерживаете чего-то, потому что это предполагает совершенно разные подходы. Агитацией может быть призыв к анархизму, классовой борьбе, неуплате налогов, гендерному равенству и т.д. Поддержкой может быть поддержка анархической борьбы, антифашистский идей и т.д. Первое — "вербует"/приманивает новых людей к идее, второе поддерживает только тех, кто уже знаком с идеей и уже с ней согласен.
Как должна выглядеть агитация? Представьте, что некий неонацист решил за-агитировать вас в неонацизм (с учетом, что сейчас вы его не поддерживаете): в каком случае у него больше всего на это шансов? Если вы заметите на мусорном баке наклейку "бей жыдоф"? Или если вам, например, выдадут в руки грамотный агитационный текст? Поставьте себя на место читающего: агитация должна выглядеть именно так, как мог бы выглядеть материал, который хоть немного мог бы поменять ваши текущие взгляды. А именно...
1. Агитация доступна
Она не висит на задней стороне мусорки. Она не нарисована на заброшке. Обыватель не рассматривает мусорки и не ходит по заброшкам. Чтобы масса увидела вашу агитацию, она должна висеть в заметном месте.
Ещё лучше, если она висит там, где человек по внешним причинам на мгновение задерживается, и имеет время проглядеть вашу агитацию: ибо обыватель никогда не остановится у столба посреди длинной тропы, чтобы прочесть стикер.
И учтите: если место, которое вы выбрали, уже забито стикерами, вашему придётся делить привлеченное внимание с каждым остальным.
К доступности стоит также отнести то, что агитация более значительна, если она написана на самом популярном в вашей стране языке, развешивается в разных локациях (чтобы люди разного класса могли её увидеть), если вы развешиваете в туалетах — то туалетах разного гендера (и не забывайте про инвалидные кабинки!), так далее.
Лучшие места для стикеров: лифт, автобусная остановка, метро, поручен эскалатора, внешняя сторона дверцы туалета, чистое (не разрисованное или расклеенное) зеркало.Лучшие места для крупных агитационных листов или графитти: указанные выше, а также — заметные места подъездов,Лучшие места для "визиток"*: оставлять под задницей на выходе из автобуса, метро, маршрутки, на стульях, скамейках и т.д.*"Визитка" — это са-а-амый простой метод агитации: выводите нужный текст или картинки мелкими блоками на листе А4, нарезаете бумагу на кусочки "визиток" с небольшим текстом, картинкой или ссылкой, и оставляете где попало.
2. Агитация запоминается
Если вы не неонацист, какие эмоции в вас побуждает "бей жыдоф"? Вы возжелали стать неонацистом? Или это только укрепило ваши антифашистские взгляды? Или это для вас вообще никак не прозвучало?
Также для ваших противников и обывателей звучат ваши "ешь богатых!", "классовая борьба сегодня!!", "доёш онархию!!!". Это — поддержка. Уже-анархисты будут рады увидеть, что в городе есть левые активисты кроме них самих. Но это никого не переубедит и не привлечет.
А агитация привлекает. Агитация задаёт острые вопросы, которые остаются в голове. Агитация манит предложениями нового. Агитация нестереотипно предлагает.
Примеры хорошей агитации:

"Если большинство проголосует за то, чтобы ты спрыгнул(а) с вмоста, ты бы сделал(а) это? / - Может быть — если это было честным голосованием!"

"Этот телефон прослушивается - согласно законодательству США, телефонные разговоры прослушиваются без ордера или уведомленияю"

"Вы под наблюдением — текст, объясняющий тезис, и ссылка, где можно прочесть об этом подробнее."
Примеры никудышной агитации (но хорошей поддержки):



3. Агитация даёт возможность изучить больше
Хорошее правило для любой агитации: иметь ссылку на сайт, где можно найти больше информации о том, к чему агитируется. Это не обязательное, но рекомендуемое правило, ибо мало толку от человека, согласившегося с идеей анархизма и захотевшего (редчайший случай!) самостоятельно изучить больше, но не имевшего к этому простой возможности и забывшего вследствие обо всей идее.
Поддержка
А вот поддержка — ориентированная на тех, кто уже знает и уже поддерживает то, что вы любите — может быть совершенно любой. Поддержать антифашистов своего города, позлить фашистов и остаться совершенно незамеченными для обывателя — самое место для диалектики "бей жыдоф!" и "доёш онтифошизм!!".
Напоминание о безопасности
Несколько базовых напоминаний о том, что нужно помнить во время агитации:
- ОСТЕРЕГАЙТЕСЬ КАМЕР! Особенно в России! Метро, маршрутки, автобусы, учебные заведения полны ими!
- Если вас заметили гестаповцы, лучшее, что вы можете сделать — это бежать, что есть мочи.
- Шифруйте материалы, которые храните для распечаток.
- Не распечатывайте стикеры/"визитки" в публичных местах (вроде библиотек).
Спасибо за прочтение!

-
 @ e5de992e:4a95ef85
2025-03-22 15:52:25
@ e5de992e:4a95ef85
2025-03-22 15:52:25In a world where our to-do lists seem to grow longer by the minute, figuring out what to tackle next can feel like solving a puzzle with missing pieces. Should you call a friend to catch up? Finish that work project? Or make sure you don’t forget a loved one’s birthday? The overwhelm is real, and traditional task management systems often leave us guessing. That’s where the 2-5 Rule comes in—a groundbreaking concept that powers TaskforUs, a smart, simple website designed to tell you exactly what to work on right now.
What Is the 2-5 Rule?
At its core, the 2-5 Rule is a timing-based approach to task management built on a simple yet powerful idea: every task has a natural rhythm—a “time unit” that dictates how often it should be addressed—and an ideal window for action: between 2 and 5 of those units. The time unit varies depending on the task’s nature:
-
Daily Tasks: (e.g., doing cardio or following up on a quick email)
Time unit: days. Act within 2 to 5 days. -
Weekly Tasks: (e.g., scheduling dinner with a friend)
Time unit: weeks. Act within 2 to 5 weeks. -
Monthly Tasks: (e.g., reviewing your budget)
Time unit: months. Act within 2 to 5 months. -
Yearly Tasks: (e.g., reassessing your career goals)
Time unit: years. Revisit every 2 to 5 years.
The 2-5 Rule ensures you’re neither jumping on tasks too early (wasting energy on something that isn’t urgent) nor leaving them too late (missing opportunities or causing stress). It’s about finding the sweet spot—the perfect moment to act.
For date-specific events like birthdays or anniversaries, TaskforUs introduces a Fix Mode that pins the task to a specific day. As the date approaches, the task climbs your list until it reaches the top on the day itself, ensuring you never miss a critical moment.
The Origins of the 2-5 Rule
The 2-5 Rule was born out of a need to bring structure to the chaos of modern life. Traditional to-do lists are static—they don’t account for the natural ebb and flow of tasks. Urgent tasks get buried under less pressing ones, and long-term goals are often forgotten until it’s too late.
TaskforUs’s creators recognized that timing is as important as priority. They drew inspiration from: - Behavioral Science: Showing that humans thrive on rhythm and consistency. - Project Management Principles: Where tasks are often scheduled based on optimal intervals.
The choice of 2 to 5 units isn’t arbitrary. Research into productivity and habit formation suggests: - Acting too soon (e.g., after just 1 unit) can lead to over-managing. - Waiting too long (beyond 5 units) risks neglect.
The 2-to-5 window strikes a balance—providing enough flexibility while ensuring nothing slips through the cracks. This range also aligns with our natural sense of urgency: after 2 units, a task begins to feel pressing; by 5 units, it risks becoming problematic.
How the 2-5 Rule Works in Practice
Step 1: Define Your Tasks and Time Units
When you add a task to TaskforUs, you assign it a time unit based on its nature: - Example:
- "Schedule dinner with Alex" is a social task (unit: weeks). - "Do cardio" is a health goal (unit: days). - "Reassess my career path" is a long-term goal (unit: years).TaskforUs can suggest defaults based on common patterns, but you can customize the unit to fit your life.
Step 2: Track the 2-5 Window
TaskforUs monitors when you last acted on a task. If it’s been 2 time units, the task enters its “sweet spot” and starts climbing your list. By 5 units, it becomes urgent. - Example:
- If you last met Alex 3 weeks ago, "Schedule dinner with Alex" becomes a top priority. - If it’s been 2 days since your last cardio session, TaskforUs nudges you to hit the gym.Step 3: Handle Fixed Dates with Fix Mode
For tasks tied to specific dates (e.g., birthdays or anniversaries), Fix Mode lets you set an exact date. The task gradually climbs your list as the date nears and becomes the top priority on that day, ensuring you never miss it.
Step 4: Prioritize with Top Task and Focus Mode
- Top Task: TaskforUs surfaces the single most urgent task within the 2-to-5 window.
- Focus Mode: If you prefer to see more, this mode shows your top 3 tasks (or a customizable number), ensuring you’re always focused on what matters most without being overwhelmed by a long list.
The Science Behind the 2-5 Rule
The 2-5 Rule isn’t just a clever idea—it’s grounded in psychology and productivity research:
-
Habit Formation:
Studies (e.g., by Dr. BJ Fogg) show that consistency is key to building routines, yet overdoing it can lead to burnout. The 2-5 window strikes a healthy balance. -
Decision Fatigue:
Research by Dr. Roy Baumeister highlights the mental toll of constant decision-making. By automating prioritization, the 2-5 Rule reduces this burden, freeing up mental energy. -
Zeigarnik Effect:
The Fix Mode leverages the tendency to remember uncompleted tasks, keeping date-specific items front of mind until they’re completed, thereby reducing stress and improving follow-through.
Why You Should Try the 2-5 Rule with TaskforUs
If you’re tired of chaotic to-do lists, missed deadlines, or the nagging feeling of forgetting something important, the 2-5 Rule offers a better way. It works with your natural rhythm, ensuring you focus on what truly matters. TaskforUs brings this concept to life with a user-friendly platform (currently in beta) that: - Eliminates Decision Fatigue: Tells you exactly what to do now. - Balances Urgency and Flexibility: Keeps you in the sweet spot between procrastination and over-management. - Adapts to Your Life’s Rhythm: Customizes time units for daily, weekly, monthly, and yearly tasks. - Ensures You Never Miss Critical Dates: With Fix Mode for date-specific events. - Reduces Stress and Boosts Momentum: By focusing on one Top Task (or a few in Focus Mode).
Real-Life Applications of the 2-5 Rule
-
Social Connections:
Task: “Schedule dinner with Alex”
Time Unit: Weeks
Scenario: If you last met Alex 3 weeks ago, the task becomes your Top Task, prompting you to reconnect. -
Health Goals:
Task: “Do cardio”
Time Unit: Days
Scenario: If it’s been 2 days since your last workout, TaskforUs nudges you to exercise before the 5-day mark. -
Special Dates:
Task: “Wish Alex a happy birthday”
Mode: Fix Mode
Scenario: A month before the birthday, it’s low on your list, but as the date nears, it climbs to the top—ensuring you don’t miss it. -
Long-Term Planning:
Task: “Reassess my career path”
Time Unit: Years
Scenario: If it’s been 2 years since your last review, TaskforUs prompts you to evaluate your goals and progress.
How TaskforUs Brings the 2-5 Rule to Life
TaskforUs is more than just a concept—it’s a practical tool that makes the 2-5 Rule actionable:
-
Top Task:
The algorithm identifies the single most urgent task within your 2-to-5 window. -
Focus Mode:
Displays your top 3 tasks (or a customizable number) to help manage multiple priorities. -
Fix Mode:
Ensures date-specific tasks are prioritized as the due date approaches. -
Smart Defaults:
Suggests time units based on common patterns, while allowing customization to suit your needs. -
Ongoing Refinements:
The TaskforUs team continually improves the algorithm based on user feedback to enhance its accuracy.
Take Control of Your Tasks Today
The 2-5 Rule is more than a productivity hack—it’s a mindset shift. It’s about working smarter, not harder, and timing your tasks to perfection. TaskforUs makes this possible with a simple, intuitive platform designed to help you master your to-do list.
-
-
 @ 46fcbe30:6bd8ce4d
2025-03-22 15:21:53
@ 46fcbe30:6bd8ce4d
2025-03-22 15:21:531. Introduction
In decentralized systems like Nostr, preserving privacy and ensuring censorship resistance are paramount. However, the inherent design ethos opens the platform to multiple vulnerabilities, chief among them being the susceptibility to Sybil attacks. The problem space is not only technical but also socio-economic, where user privacy and ease-of-use must be balanced against mitigations that impose friction on identity creation actions.
This report details a multi-faceted research analysis into Sybil resistance mechanisms, drawing analogies from contemporary decentralized identity systems, cryptographic protocols, and economic disincentives. We incorporate detailed insights from diverse independent research streams, outlining both established and novel approaches, and present a series of design recommendations for Nostr. The analysis is targeted at highly experienced analysts and researchers, with comprehensive details on both the cryptographic primitives used and the overall system architectures.
2. Background: The Threat of Sybil Attacks in Decentralized Systems
2.1. Sybil Attacks Defined
A Sybil attack involves a single adversary generating a multitude of pseudonymous identities to unduly influence network decisions, voting mechanisms, or content dissemination processes. In systems designed for censorship resistance, where anonymity is embraced, such attacks are especially daunting because traditional verification methods are not readily applicable.
2.2. The Unique Challenges in Nostr
Nostr is celebrated for its emphatic commitment to censorship resistance and privacy. This design choice, however, leads to several inherent challenges:
- Weak Identity Verification: Mechanisms like nip5, a simple email-like verification protocol, lack robustness and are vulnerable in environments where linking multiple pseudonymous identities is trivial.
- Economic Incentives: Systems using zaps (small value transactions or tips) intend to add cost to malicious actions but struggle with effective proof of expenditure. In some instances, attackers may even benefit from a net positive revenue.
- Association Networks: Existing follow systems provide decentralized webs of association; however, they do not imply a real trust framework, leaving only superficial links among identities.
The dual objectives of achieving ease-of-use while robustly mitigating Sybil attacks requires a careful, in-depth analysis of multiple design trade-offs.
3. Detailed Analysis of Existing Mechanisms and Proposed Enhancements
In our research, several proposals and implementations have emerged to address the Sybil-resistance conundrum. We examine these solutions in detail below.
3.1. Cryptographic and Identity-Based Approaches
3.1.1. Aut-CT with Curve Trees
One of the notable approaches employs the Aut-CT mechanism which leverages Curve Trees. Key insights include:
- Mechanism: Constructing an algebraic analog of a Merkle tree with curve-based keys.
- Verification Efficiency: Achieves logarithmic verification times (typically 40–70 ms) even for large keysets (from 50K to over 2.5M keys).
- Proof Size: Consistently maintains a proof size of around 3–4 kB, making it effective for low-bandwidth scenarios.
- Key Image: The integrated DLEQ-based method produces a key image that binds a proof to a hidden key, preventing fraudulent re-use of tokens.
Implication: This method, while promising, requires integration sophistication. It can potentially be adapted for Nostr to ensure that each identity is backed by a verifiable, anonymous proof of ownership—raising the cost of forging or duplicating identities.
3.1.2. Economic Disincentives and Token Burning
In the realm of cryptocurrency mixers, enforcing an economic cost for generating identities has seen traction. The following methods are prominent:
- Token Burning/Deposit Mechanisms: Users deposit funds that serve as a bond. Forging multiple identities becomes economically prohibitive if these tokens are sacrificial.
- Time Locks and Coin-Age Restrictions: By enforcing waiting periods or requiring funds to ‘age’, systems ensure that rapid, mass identity creation is deterred.
- Fidelity Bonds: Users risk losing bonds if identified as malicious, creating a strong economic disincentive.
Observation: Nostr could potentially adopt analogous economic primitives that impose a non-trivial cost on identity creation, helping to scale the disincentive to the level required for a system where anonymity is paramount.
3.1.3. Decentralized Identity Systems
A comparative analysis of identity systems, both centralized and decentralized, underscores the following:
- Centralized Systems (LDAP, OAuth, etc.): While scalable, they inherently conflict with the decentralized and censorship-resistant philosophy of Nostr.
- Decentralized Systems (uPort, Hyperledger Indy, etc.): These systems leverage blockchain technologies and zero-knowledge proofs to ensure self-sovereign identity management. However, they often require complex deployments and higher operational overhead.
Trade-Off Assessment: Implementing a fully decentralized identity system in Nostr must balance ease-of-use with strong cryptographic assurances. A layered approach—using decentralized identifiers with optional verifications—may yield optimal usability without sacrificing security.
3.2. Protocol-Specific Countermeasures
3.2.1. Rechained Protocol
The Rechained protocol introduces a deposit-based identity generation mechanism in IoT and mobile ad hoc networks. Here are its salient points:
- Deposit Transaction: Each identity is tied to a deposit transaction on a public blockchain, such as Bitcoin or Ethereum.
- Parameterization: Parameters like minHeight, minDifficulty, and amounts ensure that each identity requires a certain financial threshold to be met.
- Verification Complexity: Though proof sizes are modest (10–50 KB) and verification times are around 2 seconds, these are acceptable trade-offs on modern consumer-grade devices.
Application Prospects: If Nostr could integrate a variant of Rechained, it may allow identities to be tied to a verifiable deposit, thus raising the cost baseline for attackers. Such integration must ensure user-friendliness and minimal friction during onboarding.
3.2.2. Sysname Decentralized Identity Scheme
Sysname presents an innovative approach with additional privacy-preserving features:
- Selective Disclosure: It allows users to reveal only non-identifying attributes proving compliance with certain predicates without exposing their full identity.
- Chain-Pinned Identifiers: Aggregates multiple pseudonyms to a single on-chain record, reducing the ease with which an attacker can use disparate identities without accountability.
- Key Recovery: Enables users to refresh public keys and recover lost keys, which bolsters user trust and system resilience.
Consideration: Integrating aspects of sysname within Nostr could offer both enhanced privacy and Sybil resistance, yielding a balance between security and user independence. Enhanced key recovery also addresses the usability concerns evidenced by historical failures in PGP adoption.
3.3. Behavioral Analysis and Anomaly Detection
As an additional countermeasure, behavioral analysis can serve as a secondary layer of defense. Given the evolving sophistication of bots, a cat-and-mouse game inevitably ensues:
- Machine Learning Based Detection: Frameworks like a deep intrusion detection system (DIDS) combined with blockchain smart contracts can help identify anomalous posting behaviors. For example, integrations using Particle Swarm Optimization–Gravitational Search Algorithm (ePSOGSA) with deep autoencoders have proven accurate on established benchmarks.
- Economic Implications: By analyzing behavior, the systems can prioritize identities that have accrued economic transactions (like zaps) that match genuine user behavior over automated, bot-like patterns.
- Limitations: While promising, such systems introduce computational overhead and may yield false positives, so the implementation must be cautiously engineered with appropriate fail-safes.
4. Trade-Offs and Comprehensive Evaluation
4.1. Usability vs. Security
One of the central themes in designing defenses against Sybil attacks on Nostr is balancing ease-of-use with robust security. A highly secure system that remains cumbersome to use (akin to the historical PGP deployment) may fail adoption. Conversely, ease-of-use without economic or cryptographic Assurance opens the door to cost-free identity creation and abuse.
- Economic Approaches: Impose a direct cost on identity creation but must be calibrated to avoid excluding well-intentioned users, particularly newcomers or those with limited funds.
- Cryptographic Protocols: Solutions like Aut-CT and sysname offer advanced cryptographic proofs with minimal overhead in verification but could require more sophisticated client implementations.
- Behavioral Analysis: Acts as a safety net but must be continuously updated as adversaries evolve their bot strategies.
4.2. Privacy Implications
Every mechanism proposed must be evaluated in terms of its ability to preserve user privacy. Nostr’s value proposition rests on its censorship resistance and privacy-preserving design. Therefore:
- Selective Disclosure Protocols: Techniques that allow for proving predicates without full identity revelation should be prioritized (as seen in sysname).
- Decentralized Identity Aggregation: Methods that tie multiple pseudonyms to a single verifiable chain of evidence (enhancing accountability) can reduce risk without compromising anonymity.
- Economic Proof Versus User Balance: The economic barriers should not expose additional metadata that can be linked back to users. Hence, anonymizing tokens and cryptographic blinding techniques need to be integral to the design.
5. Proposed Comprehensive Strategy for Nostr
Based on the research, a multi-layered defense strategy is recommended. It incorporates both cryptographic assurances and economic disincentives while integrating behavioral analysis. The following blueprint emerges:
5.1. Implementation Blueprint
- Integration of Curve Tree-Based Aut-CT Proofs:
- Require each new identity creation to be validated via a Curve Tree-based proof of key ownership. This approach leverages zero-knowledge proofs and ensures logarithmic verification times, thus scalable even for a large user base.
-
Address token re-use and fake identity creation by integrating key images as established in the Aut-CT mechanism.
-
Economic Deposit Mechanism (Inspired by Rechained):
- Incorporate a lightweight deposit mechanism where users must commit a small deposit, recorded on a public blockchain. This deposit acts as a minimum hurdle for each identity and may be partially refundable upon earning trust.
-
Experiment with dynamic deposit sizes based on network load and risk assessments, ensuring that the economic threshold is both feasible and deterring.
-
Selective Disclosure and Pseudonym Aggregation (Adapting Sysname Principles):
- Allow users to prove characteristics about their identities (age, locality, etc.) without divulging full identifying details.
-
Aggregate multiple pseudonyms provided by the same user on-chain, using cryptographic commitments that both link identities and allow selective disclosure.
-
Optional Layer: Economic and Behavioral Analytics:
- Deploy a deep anomaly detection layer using machine learning techniques on posting behavior, ensuring that anomalous activities (e.g., rapid posting similar to bots) are flagged.
- Integrate smart contract-based economic triggers that penalize suspicious behavior while maintaining user privacy.
5.2. Addressing Adoption and Usability Concerns
- User Experience (UX): The proposed solutions must be integrated transparently into client applications. Much like improved versions of PGP aim to streamline key management, Nostr clients should embed these cryptographic protocols without requiring manual intervention.
- Modular Onboarding: Allow users to opt into various levels of proof. Early adopters may use lightweight methods, with a progressive enhancement available for those seeking higher assurance as they interact more within the network.
- Wallet and Key Management Integration: Leverage existing wallet infrastructures to ease the economic deposit and key recovery processes, drawing user confidence from familiarity with mainstream crypto applications.
6. Future Work and Speculative Technologies
While the proposals above are based on current and emergent technologies, additional research can further refine these approaches:
- Adaptive Economic Models: Future work can explore dynamic, context-aware deposit requirements that adjust based on network activity, risk profiles, and even market conditions.
- Quantum-Resistant Cryptography: As quantum computing progresses, integrating quantum-resistant algorithms in curve-tree constructions will become imperative for long-term viability.
- Interoperable Decentralized Identifiers (DIDs): Creating cross-system standards for identity verification may allow Nostr to interface with other decentralized platforms, enhancing the overall security ecosystem.
- Advancements in Zero-Knowledge Proofs (ZKPs): Considering high-level academic research on ZKPs, such as bulletproofs and recursive ZKPs, can further improve both the scalability and succinctness of cryptographic proofs required for identity validation.
Speculative Note: As adversaries adapt, we may see the emergence of hybrid systems where off-chain reputation systems are cryptographically linked to on-chain proofs, creating a multi-dimensional defense that continuously evolves through machine learning and adaptive economic incentives.
7. Conclusion
Mitigating Sybil attacks on Nostr necessitates a proactive, multi-layered approach combining advanced cryptographic techniques, economic disincentives, decentralized verification mechanisms, and behavioral analytics. The proposals detailed in this report aim to reinforce Nostr’s resilience while maintaining its foundational commitment to privacy and censorship resistance.
By integrating Curve Tree-based proofs, economic deposit mechanisms, and selective disclosure methods, Nostr can build a robust identity framework that is both user-friendly and resistant to abuse. Continued research into adaptive economic models and quantum-resistant cryptographic techniques will ensure that the system remains secure in the evolving landscape of decentralized networks.
Thorough evaluation of trade-offs, user experience enhancements, and iterative testing on live networks will be critical. This report serves as a foundational blueprint for further exploration and eventual deployment of sophisticated Sybil defense mechanisms within Nostr.
8. References and Further Reading
While the source of ideas is drawn from numerous research efforts and academic papers, key references include:
- Aut-CT Leveraging Curve Trees and Bulletproof Proofs
- Economic mitigation strategies in cryptocurrency mixers
- Comparative studies of decentralized identity systems (uPort, Hyperledger Indy, etc.)
- Rechained protocol research by Bochem and Leiding for IoT networks
- Sysname scheme for privacy-preserving decentralized identifiers
- Deep intrusion detection systems applied to decentralized social networks
(Additional in-depth academic references can be located within the research literature on arXiv and major cryptographic conferences.)
Prepared by an expert research analyst, this report is intended to provide detailed insights and a strategic roadmap for implementing Sybil-resistant identities on Nostr while retaining user ease-of-use and privacy-centric features.
Sources
- https://delvingbitcoin.org/t/anonymous-usage-tokens-from-curve-trees-or-autct/862
- https://delvingbitcoin.org/t/anonymous-usage-tokens-from-curve-trees-or-autct/862/2
- https://www.imperva.com/learn/application-security/sybil-attack/
- https://eprint.iacr.org/2019/1111.pdf
- https://www.smartsight.in/technology/what-to-know-about-sybil-attacks/
- https://www.researchgate.net/publication/363104774_Comparative_Analysis_of_Decentralized_Identity_Approaches
- https://www.researchgate.net/publication/331790058_A_Comparative_Analysis_of_Trust_Requirements_in_Decentralized_Identity_Management
- https://www.mdpi.com/1999-5903/17/1/1
- https://github.com/WebOfTrustInfo/rwot5-boston/blob/master/topics-and-advance-readings/Framework-for-Comparison-of-Identity-Systems.md
- https://www.researchgate.net/publication/367557991_The_Cost_of_Sybils_Credible_Commitments_and_False-Name_Proof_Mechanisms
- https://pmc.ncbi.nlm.nih.gov/articles/PMC8125832/
- https://www.nervos.org/knowledge-base/sybil_attacks_consensus_mechanisms_(explainCKBot)
- https://arxiv.org/html/2307.14679v2
- https://www.sciencedirect.com/science/article/pii/S1084804523001145
- https://www.sciencedirect.com/science/article/pii/S2096720924000460
- https://medium.com/@sshshln/mitigating-identity-attacks-in-defi-through-biometric-based-sybil-resistance-6633a682f73a
-
 @ 7d33ba57:1b82db35
2025-03-22 14:04:18
@ 7d33ba57:1b82db35
2025-03-22 14:04:18Alicante, located on Spain’s Costa Blanca, is a vibrant coastal city known for its golden beaches, historic castles, delicious seafood, and lively atmosphere. Whether you're exploring its rich history, relaxing by the sea, or enjoying the local cuisine, Alicante offers the perfect mix of culture and leisure.
🏛️ Top Things to See & Do in Alicante
1️⃣ Santa Bárbara Castle 🏰
- Perched on Mount Benacantil, this medieval fortress offers panoramic views over the city and coastline.
- Walk up the hill or take an elevator from Postiguet Beach.
2️⃣ Postiguet Beach 🏖️
- A beautiful sandy beach right next to the city center.
- Perfect for sunbathing, swimming, or enjoying a cocktail at a beachside bar.

3️⃣ Explanada de España 🌴
- A famous seaside promenade lined with palm trees, cafés, and street artists.
- Great for an evening stroll with stunning sea views.
4️⃣ Alicante Old Town (El Barrio) 🏡
- A charming historic district with narrow streets, colorful houses, and lively tapas bars.
- Visit Concatedral de San Nicolás and the Casas del Barrio for authentic local vibes.
5️⃣ MARQ – Archaeological Museum of Alicante 🏺
- A fascinating museum showcasing Alicante’s history from prehistoric times to modern days.
- Award-winning and great for history lovers!
6️⃣ Tabarca Island Day Trip 🚤
- A small, picturesque island just a short boat ride from Alicante.
- Perfect for snorkeling, seafood dining, and exploring its quaint whitewashed village.
7️⃣ Mercado Central 🛍️
- A bustling market filled with fresh seafood, local produce, jamón ibérico, and cheeses.
- Great for food lovers looking to try authentic Alicante flavors.
🍽️ What to Eat in Alicante
- Arroz a banda – A local seafood rice dish, similar to paella 🍚🐟
- Turrón de Alicante – A famous nougat made with almonds 🍯
- Caldero – A rich fish stew served with rice 🍲
- Salazones – Salted fish specialties, a local delicacy 🐠
- Horchata de chufa – A refreshing tiger nut drink, great on hot days 🥛
🚆 How to Get to Alicante
✈️ By Air: Alicante-Elche Airport (ALC) with flights from all over Europe ✈️
🚄 By Train: High-speed AVE trains from Madrid (~2.5 hrs) & Barcelona (~4.5 hrs)
🚗 By Car: Well-connected via the AP-7 coastal highway💡 Tips for Visiting Alicante
✅ Best time to visit? Spring & Summer for the best beach weather ☀️🏖️
✅ Stay for Las Hogueras de San Juan (June 20-24) – A huge fire festival with fireworks & street parties 🎆🔥
✅ Take a boat to Tabarca Island – It’s a hidden paradise for snorkeling 🏝️
✅ Try local seafood! Alicante’s coast is famous for its fresh fish & shellfish 🦐 -
 @ e5de992e:4a95ef85
2025-03-22 13:13:20
@ e5de992e:4a95ef85
2025-03-22 13:13:20Master Your Tasks with Precision: Introducing TaskforUs
In our increasingly complex digital lives, determining which task deserves our immediate attention can be challenging. We've all faced the chaos of a to-do list that feels more like a puzzle than a plan. Should you reach out to a friend for dinner? Finish that work project? Or remember a loved one’s birthday? With so many tasks vying for attention, how do you know what to tackle right now? That’s where TaskforUs comes in—a smart, simple website designed to pinpoint the exact task you should focus on at this moment.
The Problem: Too Many Tasks, Too Little Clarity
Traditional to-do lists are a dumping ground for ideas, but they rarely tell you what’s urgent. Is it time to catch up with a friend, or should you prioritize that report? Without a clear system, tasks either pile up or get tackled haphazardly—leaving you stressed and scattered. TaskforUs changes that.
The Solution: Time Units and Smart Timing
TaskforUs is built on a clever concept: every task has a "time unit" and an ideal action window—between 2 and 5 of those units. The time unit depends on the task. Want to stay connected with a friend over dinner? That’s a "week" task—act within 2 to 5 weeks. Planning a career check-in? That’s a "year" task—revisit it between 2 and 5 years. The algorithm ensures you’re acting at just the right time—not too soon, not too late.
This adaptive approach ensures tasks receive attention at appropriate intervals—neither prematurely nor after their optimal window has passed:
- Personal connections (like scheduling lunch with friends) operate on a weekly time unit, requiring action within 2-5 weeks
- Time-sensitive matters (like doing some cardio) function on a daily time unit, requiring action within 2-5 days
- Project deadlines might operate on daily units, requiring progress every 2-5 days
For tasks tied to specific dates—like birthdays—TaskforUs offers a unique "Fix" mode. Pinpoint a day, and the task climbs steadily up your list as the date approaches, rocketing to the top spot on the day, ensuring you never miss it.
How It Works
TaskforUs makes task management effortless and precise. Here’s how:
- Add Your Tasks: Enter anything on your mind—"schedule a team meeting," "call Mom," "do cardio," or "wish Alex a happy birthday."
- Set the Time Unit: Choose from days, weeks, months, or years, depending on the task’s rhythm. TaskforUs can suggest defaults (e.g., "keep in touch with friends" defaults to weeks). For date-specific tasks, use Fix Mode to set the exact day.
- Get Your Top Task: The algorithm tracks your tasks and surfaces the single most urgent one in its 2-to-5 sweet spot, telling you, "This is what to do now." In Fix Mode, date-pinned tasks take over on their big day.
- Focus Mode: Need more than one priority? Switch to Focus Mode and see your top 3 tasks (you can adjust this number to suit your style)—perfect for juggling a busy day.
Real-Life Examples
- Social Life: You want to grab dinner with your friend, Alex. The time unit is "weeks." After 3 weeks since your last meetup, TaskforUs flags it as your top task—time to text them.
- Health Goals: You plan to do some cardio. The time unit is "days." On day 2, it’s your top priority—hit the gym before the 5-day mark.
- Special Dates: You set Alex’s birthday in Fix Mode. Weeks out, it’s low on the list, but it climbs as the date nears. On the day, it’s undeniably number one—time to send that birthday wish.
- Long-Term Planning: You’re thinking about reassessing your career path. The time unit is "years." After 2 years, TaskforUs nudges you to reflect—right in that 2-to-5-year window.
Why It Works
TaskforUs strikes a perfect balance. The 2-to-5 range keeps you from acting too early (wasting effort) or too late (missing opportunities), while Fix Mode ensures critical dates never slip by. Whether it’s a quick daily task, a big-picture yearly goal, or a must-do deadline, the system adapts to your life’s pace. With its "top task" feature, customizable Focus Mode, and pinpoint Fix Mode, you’ll always know where to direct your energy—no more second-guessing.
Rather than overwhelming users with endless to-do lists or complex priority matrices, TaskforUs presents a refreshingly direct solution: it identifies your top task to work on right now. This targeted approach eliminates decision fatigue and helps maintain productivity momentum.
Current Development Status
TaskforUs is currently in beta, with ongoing refinements based on user feedback and how well it’s working. The development team is focused on ensuring the algorithm accurately identifies truly time-critical tasks—including perfecting Fix Mode—while keeping the experience intuitive.
Take Control Today
Say goodbye to overwhelm and hello to clarity. TaskforUs isn’t just a to-do list—it’s your guide to timing tasks perfectly. Sign up today at task4.us and let TaskforUs show you what to work on right now, so you can focus on what matters most.
-
 @ 30b99916:3cc6e3fe
2025-03-22 12:12:00
@ 30b99916:3cc6e3fe
2025-03-22 12:12:00constitution
Article V of the Constitution of the United States
With your engagement, there is a glimmer of hope that the people can reclaim our captured US government. The entrenched politicians are counting on your NON-ENGAGEMENT to remain in control.
Please take the time to educate yourself about the Constitution.
Now get engaged with your local Convention of States movement.
-
 @ 30fb9c78:1f1e3c3a
2025-03-22 12:11:54
@ 30fb9c78:1f1e3c3a
2025-03-22 12:11:54Why anarchy? Because anything else would be uncivilized.”
This famous statement by Jeffrey Tucker inspired the Norwegian anarchists John Holmesland and Sondre Bjellås to create a truly civilized – voluntaryist society without coercion and violence – based on mutual voluntarism.
Anarchists in the “most perfect state” in the world
The first thing that has struck me for a long time is the strong anarchist movement in Norway – a state that almost all progressive politicians consider “perfect.” The most developed and advanced state in Scandinavia.
I first noticed this phenomenon at Anarchopulco (the big anarchist conference in Acapulco, Mexico), where the entire delegation of anarchists from Europe was primarily from Norway and Sweden. Countries that most EU politicians consider to be the epitome of a perfectly functioning state.
The Norwegian anarchists explained to me that Norway, despite publicly presenting itself as the most correct country, protecting all kinds of minorities, has problems that few people outside Norway suspect.
It is a country that, like any other, suffers from corruption and incredible waste. Many Norwegians are not the least bit happy about Norwegian funds supporting the most bizarre projects in the whole world. At the moment, a case is flying through Norway about how the head of the Norwegian Communist Party Bjornar Moxnes, stole USD 150 worth of sunglasses (Communists steal worldwide, including in Norway).
Last year, Norway introduced a wealth tax, which has seen most of the millionaire rich and productive people leave the country (especially Switzerland). Many of them took their “know-how” and their companies with them. Thanks to strong progressive taxation (productive people are the most discriminated against), everyone in Norway is more or less “equally well off.” Most Norwegians are indebted (mortgage or loan for practically everything) and live on credit. Even though the Norwegian economy is built on oil or fishing, don’t expect petrol, diesel, or fish to be cheap here (due to high taxation, they are more expensive than in most EU countries). Because of this, alcohol is also extremely expensive here and the most expensive beer in the world.
Although Norway is a rich country, Norwegians themselves don’t feel rich.
Unlike most countries, however, it is quite a bit more liberal – homeschooling, home births and decriminalized all drugs are allowed in Norway.
Most Norwegians are conformists and follow everything the government tells them. That’s why, for example, there are more police officers in most countries than in Norway – because everyone follows the law. They regard not paying taxes as blasphemy and selfishness, so the community in Liberstad, which takes absolutely nothing from the state and builds everything itself, unfortunately, has a hard time of it.
Voluntaryism in Liberstad
Since anarchism in mainstream society, unfortunately, has a negative connotation, John and Sondre decided to base and promote the whole project on the ideas of voluntarism and not mention anarchy. Voluntaryism represents a philosophy of life or moral stance where we only accept mutually voluntary relationships (commercial or non-commercial). Consistent voluntaryists reject unilaterally enforced relationships (e.g., between the state and the citizen) and are, therefore, automatically anarchists (that is unless we consider a state based on voluntary support).
Voluntaryists believe that a society built on mutual voluntarism would not only be more prosperous, but more importantly more civilized, as it would not use means of aggression against innocent people (which all states in the world do, and most people unfortunately approve of).
Voluntaryists consider a voluntaryist society to be a “framework,” that is, a basis on which any other social arrangements, such as democracy, can be built – if all its members voluntarily decide to use their democratic voice to make decisions about the lives of others. Or socialism – if all its members voluntarily donate 90% of their income to a standard pot and then redistribute it to elected central planners.
 Liberstad’s Voluntaryist Treaty, respected by all its inhabitants
Liberstad’s Voluntaryist Treaty, respected by all its inhabitantsJohn and Sondre have no problem with Norway’s welfare state and huge taxes as long as its citizens are willing to support it voluntarily and use its services. On the other hand, they want nothing to do with it and are building an independent, self-sufficient, parallel society in the Norwegian mountains.
Independence and Autonomy for Liberstad
John and Sondre have bought more than 2 square kilometers of land that constitutes private property, even though it is Norwegian territory. It falls under the management of a non-profit private organization, which does not have to disclose anything (including its members or financial interactions between members) by law.
A couple of years ago, they launched a campaign to sell Libertad plots, when they all sold out (I visited a few of these plots yesterday, which my friends bought). I should point out that from the perspective of the Norwegian state, everything is owned by said private organization and the state does not know who the actual owner of a given parcel is (from that perspective, you can buy property in Liberstad without the Norwegian state knowing). There are active social channels where John, Sondre, and their management actively communicate with the owners of these parcels about their future fate.
Respect for autonomy has been resolved through a registered religious organization – the Norwegian Voluntaryist Organisation, which has no God and has key ideological/religious principles that must be respected (their automated translation via Google is available here).
Norway profiles itself as a “great fighter” for the rights of minorities around the world (from Tibet to the Kurds),” so the voluntarists in Liberstad hope that their minority within Norway itself will also be respected.
So far, they have had no problem with the government in Oslo. This is because the latter realizes that the more they publicly comment on Liberstad or interfere in its activities, the more publicity they would give it, and the more Norwegians would learn about the ideas of voluntarism and the need for an autonomous society.
But their real problems are with the local government, which constantly bullies them. For example, for posting (and flat out downloading) a drone-made video documenting how they built their private roads – which didn’t come without the explosions needed to modify the terrain. Without any permission, of course. Fortunately, they manage to ignore the local government politely, and since Norway is not a typical police state, they don’t anticipate a police raid on their private property.

Camping in Liberstad, view of the “anarchist park” in the background
Don’t ask permission, don’t deal with details
Voluntaryists in Liberstad do not recognize the state’s authority, so it makes no sense to them to ask for permission from it.
This is where the Liberstad project is different from the [Prospera project in Honduras (https://www.prospera.co/), which has a contract with the state of Honduras to build a similar private city (which they are having a bit of a problem with at the moment because there has been a change of government in Honduras, and the new government refuses to respect what the old government signed before).
That’s why the founders of Liberstad decided not to ask any permission from the state – they are building their properties without it (they are currently working on their brewery), building their roads, and homeschooling their children. They are just telling the state that they have built something new again.
"The important thing when building a private city is not to deal with all the details right from the start because your costs will rise disproportionately, and you’ll end up going nowhere,” says John Holmesland.
In Liberstad, they are very pragmatic and build just what they need. Similarly, they don’t invent any rules or laws for situations that are unlikely to arise. Indeed, what weighs heavily on contemporary society is an over-bureaucratized state apparatus that regulates and requires a rubber stamp for almost everything.
The current state of Liberstad
Liberstad’s permanent community may be small (under 15 people), but they have visitors worldwide and a potential location for thousands of new citizens. There are a few houses and caravans parked where Liberstad residents live. They have a large community center where there are lectures and evening events. Then there are the “barracks” for visitors (showers, toilets, washing machines, dryers). And lots of free parking space. A small island with a forest has earned the name “anarchist park.” Around it is a gravel road, which they plan to turn into asphalt.
 Enter Liberstad. “Et lite stykke frihet” means “a little piece of freedom.”
Enter Liberstad. “Et lite stykke frihet” means “a little piece of freedom.”Both founders consider Liberstad their lifelong project, so even though they don’t have a lot of funding, construction is still slowly progressing, and they are both fully committed to the project.
 The current inhabited part of Liberstad. The total uninhabited size of Liberstad is an order of magnitude larger.
The current inhabited part of Liberstad. The total uninhabited size of Liberstad is an order of magnitude larger.Liberstad’s parallel economy
Of all the stateless mini-communities I’ve visited so far (Kalu Yala in Panama, El Cherán in Mexico, Mennonites in Paraguay, Christiania in Copenhagen), Liberstad comes closest to me ideologically as a voluntarist. I got on exceedingly well with its founders, John and Sondre, and we agreed on all the ethical and social principles (which I rarely do).
 With Liberstad founders John Holmesland and Sondre Bjellås.
With Liberstad founders John Holmesland and Sondre Bjellås.Liberstad has a new neighbor, a Dutch photographer, and libertarian, who has bought a much larger plot of land next door. And who plans to build a similar libertarian community there.
I hope and believe that this voluntaryist anomaly in Norway will continue to live its free life and attract freedom-minded people worldwide. I have all my fingers crossed for Liberstad and will visit again in a few years!
Liberstad links to their main website, Facebook, X, Instagram.
Source: Liberationtravel, Liberstad: Voluntaryist experiment in southern Norway, August 30, 2023
-
 @ 7d33ba57:1b82db35
2025-03-22 10:27:50
@ 7d33ba57:1b82db35
2025-03-22 10:27:50Valencia is a vibrant coastal city on Spain’s east coast, blending historical charm, futuristic architecture, golden beaches, and amazing cuisine. As the birthplace of paella, it’s a paradise for food lovers, while its mild climate and Mediterranean vibes make it a perfect year-round destination.
🏛️ Top Things to See & Do in Valencia
1️⃣ The City of Arts and Sciences
- A futuristic architectural complex with a science museum, planetarium, aquarium, and opera house.
- The Hemisfèric & Oceanogràfic are must-visits for families and science lovers.
2️⃣ Valencia Cathedral & El Miguelete Tower
- A beautiful Gothic cathedral said to house the Holy Grail.
- Climb El Miguelete Tower for breathtaking city views.
3️⃣ La Lonja de la Seda (Silk Exchange) – UNESCO Site
- A stunning Gothic-style merchant building from the 15th century.
- One of the best-preserved examples of Valencia’s medieval trading history.
4️⃣ Plaza de la Virgen & Old Town (El Carmen)
- A charming square surrounded by historical buildings, fountains, and lively cafés.
- Wander the narrow streets of El Carmen for street art, boutique shops, and tapas bars.
5️⃣ Turia Gardens & Gulliver Park
- A beautiful green park built in a former riverbed, perfect for cycling, jogging, or picnicking.
- Gulliver Park is a giant playground shaped like Gulliver from "Gulliver’s Travels"!
6️⃣ Central Market (Mercado Central)
- One of the largest fresh food markets in Europe, housed in a stunning Art Nouveau building.
- Try fresh produce, local cheeses, and traditional jamón ibérico.
7️⃣ Malvarrosa Beach
- A long sandy beach with great restaurants, water sports, and a relaxing atmosphere.
- Perfect for sunbathing, a seaside stroll, or enjoying a paella by the sea.
🍽️ What to Eat in Valencia
- Paella Valenciana – The original version with rabbit, chicken, and saffron rice 🥘
- Horchata & Fartons – A refreshing tiger nut drink with sweet pastries 🥛🥐
- Agua de Valencia – A famous local cocktail made with orange juice, cava, gin, and vodka 🍹
- Esgarraet – A tasty mix of salted cod, red peppers, and olive oil 🐟
🚆 How to Get to Valencia
🚄 By Train: High-speed AVE trains from Madrid (~1.5 hrs) & Barcelona (~3 hrs)
✈️ By Air: Valencia Airport (VLC) with connections to major European cities
🚗 By Car: A scenic drive along the Mediterranean coast (Costa Blanca)💡 Tips for Visiting Valencia
✅ Best time to visit? Spring & Fall for pleasant weather 🌞
✅ Visit during Las Fallas (March 15-19) – A spectacular festival with fireworks, giant sculptures, and street parties 🎆🔥
✅ Try a bike tour! Valencia is one of Spain’s most bike-friendly cities 🚴
-
 @ 714dd0db:9c6f1a4c
2025-03-22 09:48:44
@ 714dd0db:9c6f1a4c
2025-03-22 09:48:44やっと春が来ました
ようやく暖かくなってきた。 買い物から帰ってくると、なにやら甘い香り。
あ、もしかして、花の香りか!
探してみると、沈丁花が咲いている。

ああ、甘くていい香り。
近くには蝋梅も咲いている。我が家の近くに蝋梅があったなんて、すっかり忘れていた。

そして、早咲きの桜。桜のどの種類かは分からないのだが、毎年、ソメイヨシノよりも先に咲いている。

花の蜜を吸いに百舌鳥も来ている。いや、鳥の種類には疎いが、おそらく百舌鳥だろう。多分。

モノクロの冬から、ようやくカラフルな春になってきた。
季節を感じるのは、心が豊かになる。 今は今、今度は今度。 俺は今を生きている。
-
 @ da0b9bc3:4e30a4a9
2025-03-22 09:34:42
@ da0b9bc3:4e30a4a9
2025-03-22 09:34:42Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/921232
-
 @ 6830c409:ff17c655
2025-03-22 04:59:06
@ 6830c409:ff17c655
2025-03-22 04:59:06സോഷ്യൽ മീഡിയ ഇന്ന്
ഇന്ന് സോഷ്യൽ മീഡിയ നേരിടുന്ന ഏറ്റവും വലിയ വെല്ലുവിളികളിൽ ഒന്ന് എല്ലാ മേജർ പ്ലാറ്റ്ഫോമുകളും കൈകാര്യം ചെയ്യുന്നത് വൻകോർപറേറ്റുകളാണെന്നതാണ്. കോർപ്പറേറ്റുകൾ വലിയ ഹോൾഡിങ്ങുകൾ കൈവശം വയ്ക്കുന്നത് സ്വാഭാവികവും വളരെ ഈസിയും ആണ്. പക്ഷെ, അത് ഒരു വെല്ലുവിളിയായി മാറുന്നത്, ഏതെങ്കിലും ഒരു നറേറ്റിവിനെ ബൂസ്റ്റ് ചെയ്യുകയും, മറ്റൊരു നറേറ്റിവിനെ തമസ്കരിക്കുകയും ചെയ്യുമ്പോഴാണ്. ഇത് തന്നെയാണ് "misinformation"/"disinformation" ഉണ്ടാകുന്നതിന്റെ മൂലകാരണവും. ഉദാഹരണത്തിന് ഇന്ന് ഇലോൺ മസ്കിന്റെ ഒരു റ്റ്വീറ്റെങ്കിലും കാണാതെ റ്റ്വിറ്റർ തുറക്കാൻ കഴിയില്ല. അതിനി മസ്കിനെ ബ്ലോക്ക് ചെയ്തിട്ടുണ്ടെങ്കിൽ പോലും ആ റ്റ്വീറ്റുകൾ ബൂസ്റ്റ് ചെയ്യപ്പെടും. എന്തുകാരണത്തിനാണ് എന്ന് പറയാതെ അക്കൗണ്ടുകൾ ലിമിറ്റ് ചെയ്യുകയോ, ലോക്ക്ഡൗൺ ചെയ്യുകയോ ഒക്കെ ആയിട്ടുണ്ട്.
സൊ, നിങ്ങളുടെ അക്കൗണ്ട് ശരിക്കും നിങ്ങൾക്ക് Own ചെയ്യാൻ കഴിയാത്ത ഒരു സാധനമാണ് ഇപ്പൊഴുള്ള convensional സോഷ്യൽ മീഡിയ പ്ലാറ്റ്ഫൊമുകളിൽ.
ഒരു പ്രൊപ്പോസൽ
- നിങ്ങളുടെ അക്കൗണ്ടിന്റെ പൂർണ്ണ ഉടമസ്ഥത നിങ്ങൾക്ക് തന്നെ തരുന്നു എന്ന് കരുതുക.
- നിങ്ങളുടെ റ്റ്വീറ്റുകൾ/പോസ്റ്റുകൾ ഏതെങ്കിലും ഒരു സർവ്വർ അല്ലെങ്കിൽ ഒരു സർവ്വീസിന്റെ കൈവശം പണയപ്പെടുത്തേണ്ട അവസ്ഥ ഇല്ലാതെയാകുന്നു എന്ന് കരുതുക
സോഷ്യൽ മീഡിയ ഉപയോഗത്തിനെ നിങ്ങൾക്ക് ഒന്ന് മാറ്റിച്ചിന്തിക്കാൻ മേൽപ്പറഞ്ഞ കാരണങ്ങൾ മതിയാവില്ലെ?
അതായത് റ്റ്വിറ്ററോ ഫേസ്ബുക്കോ പോലെ ഒരു കമ്പനി വിചാരിച്ചാൽ നിങ്ങളുടെ പോസ്റ്റുകൾ ഡിലീറ്റ് ചെയ്യാൻ കഴിയില്ല എന്ന ഒരു അവസ്ഥ കൊണ്ടുവരാൻ കഴിയുന്ന ഒരു സോഷ്യൽ മീഡിയ വന്നാലോ?
ആ സോഷ്യൽ മീഡിയ പ്ലാറ്റ്ഫോമിനെയാണ് ഞാൻ നിങ്ങൾക്ക് പരിചയപ്പെടുത്താൻ പോകുന്നത്.
നൊസ്റ്റർ (Nostr)
നൊസ്റ്റർ എങ്ങനെ മറ്റുള്ള പ്ലാറ്റ്ഫോമുകളിൽ നിന്നും വ്യത്യസ്തമാണെന്ന് നോക്കാം
Notes and Other Stuff Transmitted by Relays
നൊസ്റ്റർ ഏതെങ്കിലും ഒരു സർവ്വറിനെയോ സർവ്വീസ് പ്രൊവൈഡറെയോ ആശ്രയിച്ചല്ല ഓടുന്നത്. ഇന്നത്തെ കണക്കിന് തന്നെ ആയിരത്തോളം ഇൻഡിപ്പെൻഡന്റ് സർവ്വറുകൾ നൊസ്റ്ററിനായി പ്രവർത്തിക്കുന്നുണ്ട്. എന്ന് മാത്രവുമല്ല, ഒരു ക്ലൗഡ് അക്കൗണ്ടുണ്ടെങ്കിൽ ആർക്കും സ്വന്തമായി ഒരു സർവ്വർ റൺ ചെയ്യാവുന്നതേയുള്ളൂ. എന്ന് കരുതി, എല്ലാവരും സ്വന്തം സർവ്വർ റൺ ചെയ്യണമെന്നില്ല.
ഒരു സാധാരണ സോഷ്യൽമീഡിയ യൂസറിന് ഉപയോഗിക്കാൻ എളുപ്പമുള്ള ആപ്പുകൾ നൊസ്റ്ററിനുണ്ട്. ഐഫോണുകളിൽ Damus, ആൻഡ്രോയ്ഡിൽ Amethyst, Primal.net തുടങ്ങി ഒരുപാട് ക്ലയന്റ് ആപ്പുകൾ ലഭ്യമാണ്. അവയിൽ ഏതെങ്കിലും ഒന്ന് ഇൻസ്റ്റാൾ ചെയ്താൽ റ്റ്വിറ്ററോ ഫേസ്ബുക്കോ പോലെ ഉപയോഗിക്കാൻ തുടങ്ങാവുന്നതേയുള്ളൂ. ഒരു ചെറിയ ലിസ്റ്റ് ചുവടെ ചേർക്കുന്നു.
Damus (iPhones): https://damus.io/
Amethyst (Android): https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst&hl=en_US
Yakihonne (Web, iPhone): https://yakihonne.com/
Primal.net (Web, iPhone): https://primal.net
**https://openvibe.social/ - ഒരേസമയം ബ്ലൂസ്കൈ, മാസ്റ്റഡോൺ, നൊസ്റ്റർ എന്നിവയിൽ പോസ്റ്റ് ചെയ്യാനും അക്കൗണ്ടുകൾ മെയ്ന്റെൻ ചെയ്യാനും ഓപ്പൺ വൈബ് അടിപൊളിയാണ്. **
Permission-free
നൊസ്റ്റർ ഉപയോഗിക്കാൻ യൂസർനേമും പാസ്സ്വേഡും ഇല്ല. പകരം, ഒരു പബ്ലിക്ക് കീയും പ്രൈവറ്റ് കീയും മാത്രമേയുള്ളൂ. ഇതുകൊണ്ടുള്ള പ്രയോജനം എന്താണെന്നാൽ, നിങ്ങൾക്ക് ആപ്പ്ലിക്കേഷനിലേക്ക് ലോഗിൻ ചെയ്യാൻ, ഒരു സർവ്വർ ആവശ്യമില്ല.
നിങ്ങൾ സൈനപ്പ് ചെയ്യുമ്പോൾ ഒരു "പ്രൈവറ്റ്" കീ ജനറേറ്റ് ചെയ്യപ്പെടും. അത് നിങ്ങൾ രഹസ്യമായി സൂക്ഷിക്കണമെന്ന് മാത്രം. ആ പ്രൈവറ്റ് കീ ഉണ്ടെങ്കിൽ മാത്രമേ നിങ്ങളുടെ അക്കൗണ്ടിലേക്ക് ലോഗിൻ ചെയ്യാൻ കഴിയൂ. അതിന്റെ കൂടെ തന്നെ ഒരു "പബ്ലിക്ക്" കീയും ഉണ്ടാകും. ആ കീ ആണ് മറ്റുള്ളവർ കാണുന്നത്. ഇതുകൂടാതെ, റ്റ്വിറ്റർ ഹാൻഡിൽ പോലെ ഒരു ഐഡിയും ഉണ്ടാക്കാൻ കഴിയും.
- പ്രൈവറ്റ് കീ രഹസ്യമായി സൂക്ഷിക്കണം
- പബ്ലിക്ക് കീ മറ്റുള്ളവർക്ക് കാണാൻ സാധിക്കും/ഷെയർ ചെയ്യാവുന്നതാണ്.
എവിടെ സൈനപ്പ് ചെയ്യും?
ആദ്യം നിങ്ങളുടെ ഫോണിൽ മേൽപ്പറഞ്ഞതിൽ ഒരു അപ്പ് ഇൻസ്റ്റാൾ ചെയ്യുക. എന്നിട്ട് അതിൽ തന്നെ സൈനപ്പ് ചെയ്യാൻ കഴിയും. അതല്ല എങ്കിൽ, https://nosta.me, https://nostrudel, https://primal.net എന്നിവയിലൊന്നിൽ സൈനപ്പ് ചെയ്യാവുന്നതാണ്.
ശ്രദ്ധിക്കേണ്ട കാര്യം, ആ പ്രൈവറ്റ് കീ കളഞ്ഞ് പോകാതെ സൂക്ഷിക്കണം. അത് മറ്റുള്ളവരുമായി ഷെയർ ചെയ്യരുത്.
ഇത്രയുമായാൽ നിങ്ങൾക്ക് നൊസ്റ്ററിൽ ഒരു അക്കൗണ്ട് ആയി... ആദ്യം എന്നെ തന്നെ ഫോളോ ചെയ്തോളൂ!! :ഡ് My profile: nostr:npub1dqcvgz20g2sn3venz47pxzjn2w6pf8xxs03vrrrwqp8z9lchce2ssj9fsy
നമ്മടെ റ്റ്വിറ്ററിന്റെ ഫൗണ്ടർ ജാക്ക് അണ്ണന്റെ അക്കൗണ്ട്: nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
നൊസ്റ്റർ പ്രോട്ടോക്കോൾ ഡെവലപ്മെന്റിന്റെ ഒരു ലീഡ് - കൂടുതൽ കാര്യങ്ങൾ അറിയാൻ ഡെറിക്കിനെ ഫോളോ ചെയ്യാം: nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424
നൊസ്റ്റർ ഒരു സോഷ്യൽ മീഡിയ പ്ലാറ്റ്ഫോം എന്നതിലുപരി ഒരു ഇക്കോസിസ്റ്റം ആണ്.
വരും നാളുകളിൽ കൂടുതൽ വിവരങ്ങൾ എഴുതാം: 1. Technical details - How this thing runs 2. How Nostr has decoupled monetary transactions from a centralized authority? 3. Zapping 3. Nostr Implementation Possibilities (NIPs) * - This is the most interesting thing I liked in Nostr*
Browse more: 1. https://nostr.com/ 2. https://nostrapps.com/
-
 @ 234035ec:edc3751d
2025-03-22 02:34:32
@ 234035ec:edc3751d
2025-03-22 02:34:32I would like to preface this idea by stating that I am by no means a computer engineer and lack significant technical knowledge, and therefore may be overlooking significant obstacles to implementing this idea. My reason for writing this paper is in hopes that developers or others who are more "in the know" than me could provide feedback.
The Success of Polymarket
Over recent months, Polymarket has garnered many headlines—mainly for its accurate prediction markets surrounding the 2024 presidential election. On Polymarket, users can purchase futures contracts that will either pay out $1 in USDC at maturity if the prediction is correct or will become worthless if the prediction is incorrect. Market participants can freely trade these futures at the current price up until maturity, allowing for efficient price discovery.
We’ve known for quite some time that free markets are the most efficient way of pricing goods and services. Polymarket has now demonstrated just how effective they can be in pricing potential outcomes as well.
The issue I have with this application is that it is built on the Polygon network—a proof-of-stake side chain of Ethereum. Users are subject to KYC regulations and do not have the ability to create markets themselves. While the core idea is powerful, I believe it has been built on a foundation of sand. We now have the tools to build something similar—but much more decentralized, censorship-resistant, and sustainable.
A Bitcoin-Based Prediction Market
It seems to me that Chaumian eCash, in combination with Bitcoin and Nostr, could be used to create a truly decentralized prediction marketplace. For example, multiple eCash mints could issue tokens that represent specific potential outcomes. These tokens would be redeemable for 100 sats at a predetermined block height if the prediction is correct—or become irredeemable if the prediction is incorrect.
Redemption would be based on consensus from the chosen oracles—trusted Nostr Npubs—with strong reputations and proven track records. Anyone could create a market, and users could buy, sell, and trade eCash tokens privately. This approach preserves the power of markets while eliminating the need for custodians, KYC, or dependence on unreliable chains.
What we would have is a trust-minimized, privacy-preserving, Bitcoin-native prediction market that resists censorship and allows for true global participation. Feedback, critique, and collaboration are welcome.
Next Steps and Vision
The potential for system like this is immense. Not only would it enable peer-to-peer speculation on real-world outcomes, but it would also open the door to a more accurate reflection of public sentiment. With free market incentives driving truth-seeking behavior, these prediction markets could become powerful tools for gauging probabilities in politics, finance, sports, science, and beyond.
Each mint could specialize in a specific domain or geographic region, and users could choose the ones they trust—or even run their own. The competition between mints would drive reliability and transparency. By using Nostr for oracle communication and event creation, we keep the entire system open, composable, and censorship-resistant.
Markets could be created using a standardized Nostr event type. Resolution data could be posted and signed by oracles in a verifiable way, ensuring anyone can validate the outcome. All of this could be coordinated without a centralized authority, enabling pseudonymous participation from anyone with an internet connection and a Lightning wallet.
In the long run, this system could offer a viable alternative to corrupted media narratives, rigged polling, and centrally controlled information channels. It would be an open-source tool for discovering truth through economic incentives—without requiring trust in governments, corporations, or centralized platforms.
If this idea resonates with you, I encourage you to reach out, build on it, criticize it, or propose alternatives. This isn’t a product pitch—it’s a call to experiment, collaborate, and push the frontier of freedom-forward technologies.
Let’s build something that lasts.
Bitcoin is our base layer. Markets are our discovery engine. Nostr is our communication rail. Privacy is our defense. And truth is our goal.
-
 @ 4abac58c:54c71964
2025-03-22 01:21:01
@ 4abac58c:54c71964
2025-03-22 01:21:01Introduction Bitcoin is often seen as a store of value, "digital gold" designed to resist censorship and central control. But few people realize how fast and easy it can be to use Bitcoin for small, everyday transactions. Enter the Lightning Network: a second-layer solution that enables near-instant, low-fee payments. This article will explain how it works, why it matters, and how you can use it today.
What Is the Lightning Network? The Lightning Network (LN) is a layer built on top of the Bitcoin blockchain. Its primary purpose is to make Bitcoin transactions faster and cheaper by creating payment channels between users. Instead of recording every transaction on the main blockchain, two users can open a channel, transact as many times as they want, and settle the final balance on-chain later.
This means no long confirmation times or high fees. Payments can take less than a second and cost a fraction of a cent.
Why It Matters Bitcoin's main chain can process around 7 transactions per second. In contrast, Visa can handle thousands. This makes scaling Bitcoin for everyday use a challenge. Lightning changes that by handling most activity off-chain.
Imagine buying coffee, tipping a content creator, or paying for a digital download with Bitcoin. Lightning makes this seamless and instant. It also supports micropayments, enabling new business models like pay-per-article or per-minute streaming.
How to Start Using Lightning Getting started is easier than ever:
- Download a Lightning Wallet: Try apps like Wallet of Satoshi, Phoenix, or Breez.
- Get Some Sats: Sats (short for satoshis, the smallest unit of Bitcoin) can be received via another wallet, an exchange, or earned.
- Start Spending or Zapping: Use your Lightning wallet to pay for services, tip content creators on platforms like Nostr, or support open-source projects.
Real-World Use Cases - Nostr + Zaps: Nostr, a decentralized social media protocol, integrates Lightning payments directly. Users can "zap" posts they like, sending Bitcoin instantly to the author. This has created a native reward system for content. - Bitrefill: Buy gift cards with Lightning. - Podcasting 2.0: Stream sats to podcasters per minute of audio consumed.
Citations and Resources - https://lightning.network - https://bitcoinmagazine.com/technical/the-lightning-network - https://walletofsatoshi.com - https://highlighter.com
Conclusion Bitcoin isn’t just digital gold—it’s programmable money. The Lightning Network shows how Bitcoin can work for everyday payments, from your morning coffee to rewarding your favorite content creator. If you’ve never tried it, now is the perfect time to explore this magical layer of the Bitcoin economy.
Call to Action Got a Lightning wallet already? Try zapping this article on Nostr or sharing your first Lightning transaction experience!
-
 @ 2dd9250b:6e928072
2025-03-22 00:22:40
@ 2dd9250b:6e928072
2025-03-22 00:22:40Vi recentemente um post onde a pessoa diz que aquele final do filme O Doutrinador (2019) não faz sentido porque mesmo o protagonista explodindo o Palácio dos Três Poderes, não acaba com a corrupção no Brasil.
Progressistas não sabem ler e não conseguem interpretar textos corretamente. O final de Doutrinador não tem a ver com isso, tem a ver com a relação entre o Herói e a sua Cidade.
Nas histórias em quadrinhos há uma ligação entre a cidade e o Super-Herói. Gotham City por exemplo, cria o Batman. Isso é mostrado em The Batman (2022) e em Batman: Cavaleiro das Trevas, quando aquele garoto no final, diz para o Batman não fugir, porque ele queria ver o Batman de novo. E o Comissário Gordon diz que o "Batman é o que a cidade de Gotham precisa."
Batman: Cavaleiro das Trevas Ressurge mostra a cidade de Gotham sendo tomada pela corrupção e pela ideologia do Bane. A Cidade vai definhando em imoralidade e o Bruce, ao olhar da prisão a cidade sendo destruída, decide que o Batman precisa voltar porque se Gotham for destruída, o Batman é destruído junto. E isso o da forças para consegue fugir daquele poço e voltar para salvar Gotham.
Isso também é mostrado em Demolidor. Na série Demolidor o Matt Murdock sempre fala que precisa defender a cidade Cozinha do Inferno; que o Fisk não vai dominar a cidade e fazer o que ele quiser nela. Inclusive na terceira temporada isso fica mais evidente na luta final na mansão do Fisk, onde Matt grita que agora a cidade toda vai saber o que ele fez; a cidade vai ver o mal que ele é para Hell's Kitchen, porque a gente sabe que o Fisk fez de tudo para a imagem do Demolidor entrar e descrédito perante os cidadãos, então o que acontece no final do filme O Doutrinador não significa que ele está acabando com a corrupção quando explode o Congresso, ele está praticamente interrompendo o ciclo do sistema, colocando uma falha em sua engrenagem.
Quando você ouve falar de Brasília, você pensa na corrupção dos políticos, onde a farra acontece,, onde corruptos desviam dinheiro arrecadado dos impostos, impostos estes que são centralizados na União. Então quando você ouve falarem de Brasília, sempre pensa que o pessoal que mora lá, mora junto com tudo de podre que acontece no Brasil.
Logo quando o Doutrinador explode tudo ali, ele está basicamente destruindo o mecanismo que suja Brasília. Ele está fazendo isso naquela cidade. Porque o símbolo da cidade é justamente esse, a farsa de que naquele lugar o povo será ouvido e a justiça será feita. Ele está destruindo a ideologia de que o Estado nos protege, nos dá segurança, saúde e educação. Porque na verdade o Estado só existe para privilegiar os políticos, funcionários públicos de auto escalão, suas famílias e amigos. Enquanto que o povo sofre para sustentar a elite política. O protagonista Miguel entendeu isso quando a filha dele morreu na fila do SUS.
-
 @ 30fb9c78:1f1e3c3a
2025-03-22 00:18:06
@ 30fb9c78:1f1e3c3a
2025-03-22 00:18:06It’s easy to identify the presence of something, but it’s much harder to identify the absence of something. If your boyfriend brings you flowers, that’s awfully nice. If he never brings you flowers, it might take you a while to notice. Maybe you do eventually notice, but you decide to cope. You tell yourself you don’t care about getting flowers. Maybe you take it a step further: “Actually, flowers are really basic and lame. Only basic girls like flowers. I’m a cool girl and cool girls don’t care about getting flowers.”
If this goes on for long enough—even if you are genuinely presented with flowers at some point—you will see them as a kind of joke. Flowers are now a bit. It sounds so trivial, I know, but if you dull your “receptors for flowers” for years on end, you will eventually fail to see the beauty of the gesture.
Entering the void
I’m deeply troubled by the fact that I see this happening at a massive scale, all around us. Except the problem is not a lack of bouquets, of course. It’s a lack of meaning.
Life has gotten very chaotic incredibly quickly. It has become increasingly difficult to parse anything from the static. People started coping with this lack of meaning through a kind of ironic detachment (which is very much still around), but it has matured into a pervasive cultural apathy, a permeating numbness. This isn’t nihilism per se. (Even nihilists have a sincere belief system; they just sincerely believe that life is meaningless.) What we’re dealing with is worse than nihilism. People are checking out of life in their 20s and 30s without reaching any profound conclusions about the point of it all.

“People are so worn down," my friend told me on a recent phone call. She’s right: there’s a real lack of palpable ambition and vitality these days, a stunning lack of life force in the world. Another friend told me that “this has been going on for so long that people wouldn’t know meaning if it walked up and bit them in the ass.” It’s true—so many of the things that once gave the average person’s life real meaning are now treated with sarcasm and contempt: college is a waste of money, work is a waste of your life, getting married is just a piece of paper, having kids is a nightmare, family is a burden, hobbies are merely quaint, earnestly expressing yourself is cringe, leaving the house is exhausting, religion is for idiots, the list goes on. If you allow yourself to internalize this perspective, eventually everything becomes a dumb joke.
A quick aside before we get into it: it’s taken me a long time to write this piece. This is partly because this whole phenomenon is, in a way, its own kind of absence. It’s been hard for me to identify what is going on and what is missing. I’ve had my own cycles of coping with it. I’ve been telling myself that I don’t care about people not caring. But obviously I do. So here goes.
A culture of chaos
The cultural forces that spawned this collective response have been quietly working their way into everything for decades—probably since the 1970s if I had to stick a pin in it. It reached new heights in the 1990s, but it took off exponentially since the mass adoption of the internet, social media, and the pandemic. We boiling frogs started to feel the water get really hot around 2015, I think, and it’s only gotten hotter and hotter since.
We’re so saturated in this environment that people are not only numbing out, they’re kind of making a spectacle of it: from TikTok’s “quiet quitting” trend to Vetements entire “ironic” aesthetic. You know it’s bad when the corporations get on board. The detachment is so widespread that most companies don’t even have the genuine confidence to market their own products. Everything is delivered with a wink from one eye and an eye-roll from the other. We live in a mud puddle of memes, ironic hot takes, and self-conscious self-reference. David Foster Wallace called it exactly thirty years ago, in the summer of 1993:
“[…] The harvest has been dark: the forms of our best rebellious art have become mere gestures, schticks, not only sterile but perversely enslaving. How can even the idea of rebellion against corporate culture stay meaningful when Chrysler Inc. advertises trucks by invoking “The Dodge Rebellion”?
David Foster Wallace, E Unibus Pluram: Television and U.S. Fiction (The Review of Contemporary Fiction, link to full pdf)
Rest in Peace David Foster Wallace, you would have loved Barbie. We swim in a wretched sea of meaningless mush, and when you have to trudge through nothing but slop all day, every day, it gets harder and harder to not numb out. I really cannot emphasize it enough: there’s so much and it just keeps coming. There’s lots to do. There’s lots to buy. The “content” never ends. Baby Gronk rizzed up Livvy! Wait—you’ve never had vegan tacos there?! Haley Bieber got a manicure! You should get an Apple Watch!
Meaningless distractions, all.
Thanks to the internet and our insatiably consumerist culture, it is finally possible to distract yourself for every waking minute of your life and barely even notice you’re doing it. When you mix all colors of paint together, you get black. Everything quickly becomes nothing.
What else? Well, there’s the ubiquity of pornography which has zapped everyone of their sex drive. It’s been said many times before: everything is sexy and no one is horny. Social media and the fear of cancel culture got together to create the most utterly dull popular culture and celebrity elite to ever exist. It stands for nothing, it risks nothing, so there’s nothing to engage with. Culture is just kind of “there,” and no one really cares about it.
An unfortunate by-product of this is that there’s also very little to which we can aspire. Life is not a meritocracy, and the void at the top has allowed for figures like Andrew Tate to be taken seriously by both fans and critics alike. The blame is always being shifted around. Men think women are the problem. Women think men are the problem. The boomers think it’s the millennials. The millennials think it’s the boomers. It’s social media. No it’s the pandemic. No it’s [your pet theory here].
Death and loneliness abound. Everyone is constantly joking about killing themselves while Canada rolls out a “humane” service to do just that (MAID). People are struggling: most people simply cannot cope without substances like marijuana, alcohol, drugs, and SSRIs. People are lonely: they have fewer friends and live far from their families. Dating seems impossible. Men and women in the prime of their lives are struggling to meet even one potential partner who shares their values and vision for a relationship. Oh, and our phones—Gen Z averages an unfathomable 9 hours of screen time per day—have ruined our attention spans to the point where we can no longer read a book, let alone sit quietly with nothing but our thoughts. If you’re an intelligent, hardworking person, odds are the job you’ll have out of college, and for the next 40-50 years, will involve 10+ hours a day of staring at a laptop screen in a state of heightened stress.
To top it all off, we can’t have meaningful conversations about any of this stuff because everyone runs their thoughts through their own kind of personal HR filter. People are self-reporting their thought crimes to themselves. I’m literally doing that right now. I’m sure I’ve theoretically “offended” all sorts of people in the last paragraph alone. Catherine, when you talked about the jobs you forgot to say that it mainly applies to privileged folks! Well, you got me there. The point stands: things are trending down. Something is deeply wrong. We all know it. We all feel it.
We think ironic detachment will protect us
The picture is bleak. It’s so sad it’s difficult to comprehend. How do you protect yourself in such a world?
You simply don’t allow yourself to experience it.
Think back to the flower metaphor. This is where we don’t receive flowers, but we cope. Same thing here. We look around the world, struggle to see the meaning in its chaos, and unconsciously tell ourselves that finding meaning isn’t that important. If I can’t pursue my own fulfillment, at least I can pursue my own pleasure. This is a somewhat reasonable reaction to the present circumstances. It feels straightforward enough—it’s binary, measurable, and everyone else is doing it. This is how the numbness starts.
And perhaps this route is even better—maybe even cool. Being ironically detached from life is endlessly glamorized in our culture. There’s a certain status in pretending nothing affects you and you don’t care. Cue photo montage of a strung-out Kate Moss staring listlessly into the middle distance.
Taking the ironic detachment route is also easy. It’s easy to laugh at other people, mock them, throw your head back, be a critic. Standing for nothing has the obvious appeal of making you impossible to pin down. There’s something very chic about smoking a cigarette outside a bar and being all like whatever. You’re playing a game of hide-and-seek with life, and you’re hiding. It’s thrilling to find a good place to hide, to have people seeking you. But in our drug-fueled debauchery, our coy, sarcastic conversations, and perhaps most of all in our fleeting, romantic encounters, we should heed the words of British psychoanalyst Donald Winnicott:
“It is a joy to be hidden, and a disaster not to be found.”
It is a disaster not to be found, a total disaster to not be able to connect with others because we were too preoccupied with ourselves. The whole reason for ironic detachment is to build a protective wall between oneself and the world. We think we’re building a wall, but we’re really hollowing ourselves out from the inside. Eventually, without really noticing it, there will be nothing left for the wall to defend. There will be no one to find.
It’s not hard to see where the pervasive numbness comes in from here, as a sort of sinister phase two. The opposite of love is not hate, but apathy. I hope it’s obvious why this is a problem, but maybe you’re still thinking so what. To put it succinctly: when you take an ironic, negative, or numb attitude to everything, you are by definition not on the line for solutions, and when you stop looking for solutions, you lose all agency and will in your life.
Possible antidotes
We can’t keep going down the path we’re on, but we also can’t go back. Don’t worry, I’m not going to give full-throated endorsement for Post-Post-Irony, or David-Foster-Wallacian New Sincerity, as he does in the essay I quoted earlier (though I do think cringe sincerity is preferable to total apathy). We’re too far gone from the early 90s. We can’t put the internet back in the box or log off forever. Too much of our lives is irrevocably online, we’re all too self-aware, and a saccharine glaze of sincerity is too affected to feel real. Besides, we’ve all been cornered by the guy at the bar with a well-worn paperback in his pocket who locks eyes with you and whispers, “But how are you, really?” as if it’s a profound question. I would hate to subject anyone to such an encounter.
Rather than jump to sincerity, I’d like to start with basic honesty. It would be great if we started just telling the truth—to ourselves and each other. The truth is good. (I mean the truth, by the way. Not “our truth.” The truth, the real truth, does not have to market itself as “authentic,” like an influencer does, it simply is.) In other words: stop hiding and start seeking. Stop hiding from the sad truths and start seeking the transcendent truths that will address the sadness. When we flip the game of hide-and-seek, we can stop worrying about someone finding us, and start seeking the truth in the world, in others, and in ourselves.
With honesty as the foundation, I would advocate next for embracing reality—our real lives, right now—and not clinging to an abstract idea of how our lives should be. In other words: everything that we see exclusively online does not really matter. The broader culture’s idea of “a perfect life” changes every couple years. Measuring the distance between our real lives and some ever-changing, impossible ideal will do nothing but break our spirit. Besides, I have never met a person who has a dream life in reality. And reality—the truth—is what counts.
This doesn’t mean we shouldn’t strive. Things are never so fundamentally broken that we cannot move just a bit closer towards our goals and try again and again to live up to our values. Goals and values are good to have. The bigger and more transcendent the better, I say.
Once we figure out all that stuff—the big goals, the transcendent values—we should take responsibility for them. Standing for something is hard because what you’re implicitly saying is, “I don’t necessarily stand for all those other things over there.” This is a risk. People will not always agree with you. By saying “I believe in God,” for example, you’re also saying “I am not an atheist.” Atheists might think you’re stupid. (This begs the question, “And?”) We should take responsibility for our beliefs, but be prepared to calmly and rationally explain them. Criticize the world all you want, but do the hard work of building something better to take its place.
In this process, the process of seeking and telling the truth, having values and goals, and taking a stand for something, we’re bound to fail, to fall short, and to make mistakes. This is also hard. Our culture simultaneously demands both perfection and apology, but is notoriously unforgiving. Everyone needs a little forgiveness from time to time. We need to remember that it is okay to make mistakes if we try to remedy them. It’s also okay to be seen trying. Don’t take the easy route, which is always harder and more costly in the end. To shock yourself out of a numb state, to restore your life force and vitality, you will need to work hard and to submit to something bigger than your own desires.
I started with flowers, so I’d like to end with them, too. We all know that life does not hand out bouquets. Flowers do not just appear in the world. The same is true for a life of meaning. Both are grown, over time, from the tiniest seeds. You have to cultivate meaning in your life. You need to do the hard work of tilling the soil and nurturing the seeds. No one can do it for you. Grow your own flowers and give them away to everyone you meet. You’re right: the earth is not very fertile, people are not always grateful, flowers eventually die. But do you still see the point of it all? Do you see the beauty of the gesture?
Source: Catherine Shannon, Everyone is numbing out, July 27, 2023
-
 @ d34e832d:383f78d0
2025-03-21 20:31:24
@ d34e832d:383f78d0
2025-03-21 20:31:24Introduction
Unlike other cetaceans that rely on whistles and songs, sperm whales primarily use echolocation and patterned click sequences to convey information. This paper explores the structure, function, and implications of their vocal communication, particularly in relation to their social behaviors and cognitive abilities.
1. The Nature of Sperm Whale Vocalizations
Sperm whales produce three primary types of clicks:
- Echolocation clicks for navigation and hunting.
- Regular clicks used in deep diving.
- Codas, which are rhythmic sequences exchanged between individuals, believed to function in social bonding and identification.Each whale possesses a monumental sound-producing organ, the spermaceti organ, which allows for the production of powerful sounds that can travel long distances. The structure of these clicks suggests a level of vocal learning and adaptation, as different populations exhibit distinct coda repertoires.
2. Cultural and Regional Variation in Codas
Research indicates that different sperm whale clans have unique dialects, much like human languages. These dialects are not genetically inherited but culturally transmitted, meaning whales learn their communication styles from social interactions rather than instinct alone. Studies conducted in the Caribbean and the Pacific have revealed that whales in different regions have distinct coda patterns, with some being universal and others specific to certain clans.
3. Social Organization and Communication
Sperm whales are matrilineal and live in stable social units composed of mothers, calves, and juveniles, while males often lead solitary lives. Communication plays a critical role in maintaining social bonds within these groups.
- Codas serve as an acoustic signature that helps individuals recognize each other.
- More complex codas may function in coordinating group movements or teaching young whales.
- Some researchers hypothesize that codas convey emotional states, much like tone of voice in human speech.4. Theories on Whale Intelligence and Language-Like Communication
The complexity of sperm whale vocalization raises profound questions about their cognitive abilities.
- Some researchers argue that sperm whale communication exhibits combinatorial properties, meaning that codas might function in ways similar to human phonemes, allowing for an extensive range of meanings.
- Studies using AI and machine learning have attempted to decode potential syntax patterns, but a full understanding of their language remains elusive.5. Conservation Implications and the Need for Further Research
Understanding sperm whale communication is essential for conservation efforts. Noise pollution from shipping, sonar, and industrial activities can interfere with whale vocalizations, potentially disrupting social structures and navigation. Future research must focus on long-term coda tracking, cross-species comparisons, and experimental approaches to deciphering their meaning.
Consider
Sperm whale vocal communication represents one of the most intriguing areas of marine mammal research. Their ability to transmit learned vocalizations across generations suggests a high degree of cultural complexity. Although we have yet to fully decode their language, the study of sperm whale codas offers critical insights into non-human intelligence, social structures, and the evolution of communication in the animal kingdom.
-
 @ 7bc05901:8c26d22b
2025-03-21 19:47:15
@ 7bc05901:8c26d22b
2025-03-21 19:47:15Decentralization is a beautiful return volley to the censorship regimes that have ruled American social media, but the decentralization piece isn't the biggest impact Nostr is having on me. The empowerment and encouragement to start building are what overwhelms. Since I began sending zaps just a few weeks ago, every idea I have had for an app over the last decade is organically re-emerging as executable Nostr apps.
The rise of AI alongside Nostr's invention/discovery is serendipitous for someone who doesn't have the coding experience to develop an app from scratch like myself. It is also a great moment for apps that had a social feature -- which was essentially every app. "Connect it using Facebook" was such a non-starter for me. I live in a small town where Facebook is a gossip cesspool. There are intriguing communities there, sure, but the overwhelming dread that overcomes me when I open that app doesn't justify digging for the socially-delightful gems. Further, any app that integrates with facebook is or becomes a variation on an already existing feature that META has engineered into their platform -- they want, they need your eyeballs. On their site.
Nostr makes no such demands. It doesn't care which site is being used to access the protocol, and what features exist on that site. It is available to help, secure a user's identity, and doesn't make many demands in return.
My friend and local farmer Ryan and I have discussed an app for years, built it and rebuilt it using different tools, but we ultimately got distracted by more pressing and less complicated projects. I think a huge barrier to execute it was the sense that it would be impossible to achieve any network effects, plus the thought of managing the social side was overwhelming. It required us to need really powerful tools, and to maintain a lot of data that we didn't really want to hold onto. It was essentially an app for local food producers and consumers. With Nostr at play, we could build something like this and simultaneously onboard our local community to the Nostr protocol while also providing a lightweight solution to managing the complicated part of an online marketplace. The lightning payments come as an added bonus.
We are tracking the use of another app which is sweeping through local food producers, which is only in its beta phase, and restarting our build of a marketplace that is worth building and encourages a sustainable local food supply, this time with a protocol that reduces 90 percent of the annoying part of that build, and doesn't require anyone spend time on Zuckerberg's playground.
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ 6a6be47b:3e74e3e1
2025-03-21 18:45:32
@ 6a6be47b:3e74e3e1
2025-03-21 18:45:32Hey frens! Today, I spent a big chunk of the morning painting with watercolors. This is only the second time I've completed a piece using this technique in a long while. It feels like coming back home after a vacation: you enjoyed the time away and relaxed, but when you're lucky enough to have a safe space to call home, there's really nothing like it. 🖼️
🎨 That's exactly how I feel about painting with watercolors again. I'm really excited to share what I've been working on with you soon. In the meantime, I've got a new blog post up about Ostara and the Spring Equinox. ⭐️Today, I just feel so blessed and excited about the future. I'm simply soaking up the moment, I guess. I hope you're feeling the same way too! Today, I also whipped up some mini veggie quiches chef's kiss.
 🧑🍳 I wanted to spice things up a bit in the kitchen as well!
🪄I just wanted to share a little bit from my day and express how grateful I am. What did you get up to today? I'd love to hear more about it!
🧑🍳 I wanted to spice things up a bit in the kitchen as well!
🪄I just wanted to share a little bit from my day and express how grateful I am. What did you get up to today? I'd love to hear more about it! -
 @ 6bae33c8:607272e8
2025-03-21 18:23:28
@ 6bae33c8:607272e8
2025-03-21 18:23:28I put Beat Chris Liss 3 in quotes because technically this was not a Beat Chris Liss league — I just bought it at the last minute to get an extra league. In any event, I drew the seventh spot, and here are the results:
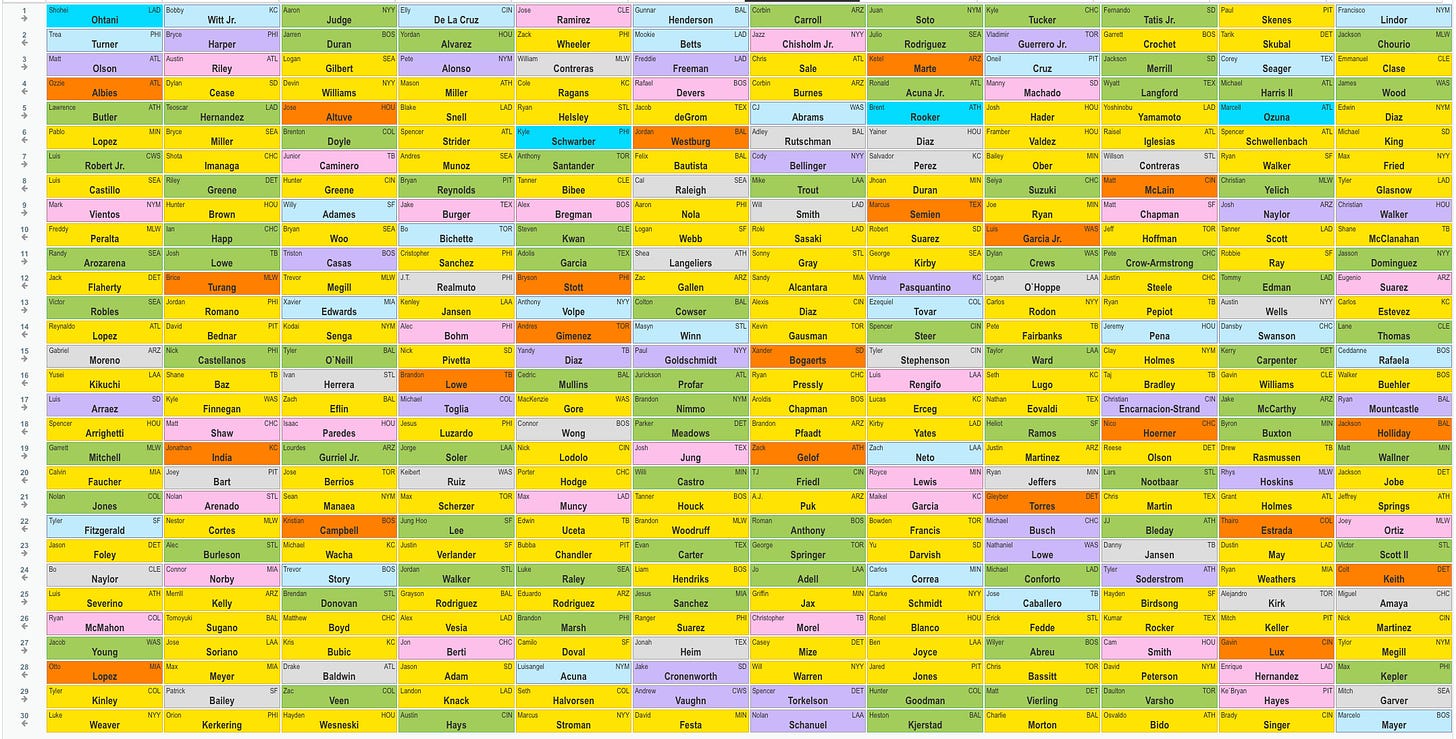
1.7 Corbin Carroll — He’s been hitting home runs this spring, a signal his shoulder is healthy. You know he’ll run, and given how he performed at the end of last year, I’d expect the batting average to bounce back too.
2.8 Jazz Chisholm — I want to see what he can do with a full year in Yankee Stadium. He’s a health risk, but he was a 20-20-ish player in Miami with only 100 games in 2023. It’s also nice that he qualifies at 3B and OF. I considered Mookie Betts, who slipped, but I’m concerned about severe weight loss from an illness undermining the first half of his season.
3.7 Chris Sale — He’s a Hall of Fame level pitcher with his health and form back. Remember when Justin Verlander faded in his 30s and then got it back together? I expect a few good years from Sale before he declines again.
4.8 Corbin Burnes — I don’t really even like Burnes, but he slipped a full round past ADP, and I value-took.
5.7 C.J. Abrams — I love this pick, probably my favorite of the draft. Abrams is a 20-30 player despite attitude issues. What if he matures and gets it together at age 24?
6.8 Adley Rustchman — I didn’t see anything I liked, and I was light on power. One way to get a leg up power-wise is to draft elite catchers.
7.7 Cody Bellinger — I like him with Yankee Stadium’s short porch, a few steals from a first-base-eligible player and also outfield eligibility.
8.8 Mike Trout — I had enough pitching and speed, but I needed some power, and Trout still has as much as anyone if he could ever play 100-plus games. He’s healthy now at least.
9.7 Will Smith — A second top catcher to pair with Rutschman. I was light on power through five rounds, but my next four picks were 20-plus HR catchers, Bellinger in Yankee Stadium and Trout.
10.8 Roki Sasaki — He slipped a couple rounds after a rough outing in Japan, but he was still throwing 100 with nasty movement. Another value-take.
11.7 Sonny Gray — A favorite old warhorse in a good pitcher’s park. I really wanted Sandy Alcantara, but Gray’s ADP was higher, so I thought there was a better chance to get Alcantara on the way back.
12.8 Sandy Alcantara — Turns out I thought right. I love Alcantara, who was going in the third round a couple years ago, now that he’s healthy and throwing 100 mph again.
13.7 Alexis Diaz — Taking Alcantara cost me my two go-to closers, Kenley Jansen and Jordan Romano, both of whom went earlier than usual, so I pivoted to Diaz. I thought this was a mistake at first — Diaz has been bad this spring, and he wasn’t even good last year, either, but he’s the closer until further notice, and a couple spring outings shouldn’t move the needle that much.
14.8 Kevin Gausman — Another old warhorse, coming off a down year, possibly due to injury. His velocity has been back up this spring too.
15.7 Xander Bogaerts — Another ADP value-take. Bogaerts had double digit homers and steals in 111 games last year and is a good bet to hit for a decent average.
16.8 Ryan Pressly — Another shaky closer, Pressly had three walks in an inning against the Dodgers, but he’s probably not losing the job over one ugly but scoreless outing.
17.7 Aroldis Chapman — Named the Red Sox closer, Chapman is probably the best of the three I drafted thus far. His ADP was lower because he was only given the role a couple days ago. Chapman perfectly fits the old warhorse mold I like too.
18.8 Brandon Pfaadt — I didn’t really need another starter, but he was the best player left on the board, and you always run out of pitching.
19.7 Zack Gelof — He strikes out a ton, but he went 17-25 last year in 138 games as a rookie, and now he gets to play in a minor-league band box. Lawrence Butler went 22-18 and is going in the fifth round!
20.8 T.J. Friedl — I was light on OF, and Friedl is one. He has a little pop, runs and is expected to lead off for the Reds in the best non-Coors hitting park in baseball.
21.7 A.J. Puk — I was still a little light in saves, and Puk is in the running for the Arizona job.
22.8 Roman Anthony — I don’t know if he’ll break camp with the Red Sox, but he was the remaining player I would have felt worst getting snaked on. He doesn’t have much left to prove in the minors.
23.7 George Springer — He went 20-20 in 2023 and 19-16 last year. He could be done, but at 35 he’s not ancient.
24.8 Jo Adell — I needed to fill in the outfield, and Adell should play, run and hit for power. The strikeouts and batting average risk are bad, but he’s still young enough to improve.
25.7 Griffin Jax — He’s a top reliever, next in line for saves and closer Jhoan Duran isn’t very good.
26.8 Christopher Morel — I needed a corner and Morel is one. (If I needed a mushroom, this would also hold.) He hit .196 last year, but he has good pop and should play OF for the Rays in a small minor-league park.
27.6 Casey Mize — The former No. 1 overall pick has looked good this spring, and he’s completely healthy.
28.6 Will Warren — Warren should get a shot in the Yankees rotation, given the injuries to Gerrit Cole and Luis Gil.
29.6 Spencer Torkelson — Another former No. 1 overall pick for the Tigers, Torkelson hit 31 homers in 2023 and should get another shot this year given his strong spring.
30.6 Nolan Schanuel — I just wanted an extra corner with regular playing time heading into the year. He runs a little and had 13 HR, but in a full season of at-bats.
Roster By Position:
C Adley Rustchman/Will Smith
1B Cody Bellinger
2B Xander Bogaerts
3B Jazz Chisholm
SS C.J. Abrams
CI Christopher Morel
MI Zack Gelof
OF Corbin Carroll/Mike Trout/T.J. Friedl/Roman Anthony/George Springer
UT Jo Adell
SP Chris Sale/Corbin Burnes/Roki Sasaki/Sonny Gray/Sandy Alcantara/Kevin Gausman
RP Alexis Diaz/Ryan Pressly/Aroldis Chapman
B Brandon Pfaadt/A.J. Puk/Griffin Jax/Casey Mize/Will Warren/Spencer Torkelson/Nolan Schanuel
-
 @ 6ad3e2a3:c90b7740
2025-03-21 18:21:50
@ 6ad3e2a3:c90b7740
2025-03-21 18:21:50There are two ways things happen in this world: top-down and bottom-up. Top-down is via authoritarian edict, i.e. fascism, no matter how benign-seeming. It is the government imposing a tax, incentivizing a behavior, creating a new law. Bottom-up is the organic process of people doing what interests them voluntarily, what benefits them, what they decide is best individually.
There is but one legitimate role for top-down and that is in creating good conditions for bottom up. The US Constitution is fascism in that it forces you to adhere to its edicts as the supreme law of the land. But it’s also an effective boundary creating the necessary conditions for free markets, free expression, creativity and prosperity.
All governments are fascistic in that they use force to achieve their agendas. But the best ones use only the minimum necessary force to create conditions for bottom-up prosperity. There is no other kind of prosperity.
. . .
Governments aren’t the only entities that are fascistic. Schools, corporations, institutions and individuals, almost invariably, are too. Yes, I am a fascist and very likely so are you. Don’t believe me? Do you have a voice inside your head telling you what you must get done today, evaluating your progress as a person, critiquing and coercing you into doing things that are “good” for you and avoiding ones that are “bad”? If so, you are fascist.
Why not just trust yourself to make the right choices? Why all the nudging, coaxing, coaching, evaluating and gamifying? Who is this voice, what gives it the authority, the requisite wisdom to manage your affairs? Haven’t all your shortcomings, disappointments and general dissatisfactions taken place despite its ever-presence? What makes you think you are better off for having had this in-house micromanagement?
. . .
The top-down edicts that rule our lives are by and large unnecessarily oppressive. Yes, we should create some good top-down conditions for bottom up organic thriving like buying healthy food, getting fresh air, not consuming excessive amounts of alcohol or drugs, but the moment to moment hall-monitoring, the voice that requires you to achieve something or justify your existence? That’s fascism.
. . .
The mind is a powerful tool when it comes to planning, doing math or following a recipe, but if it can’t be turned off, if it’s not just optimizing your path from A to B, but optimizing YOU, that’s fascism.
. . .
I think about the problem of human governance through this lens. I imagine everyone charged with power over a polity has an agenda, and that agenda, insofar as it requires force to achieve, is fascistic. They want it to go this way rather than that way, and some people don’t agree. The quality of leadership then is the extent to which that force is used to preserve the bottom-up freedom of the individual to pursue his interests without undue interference, either from authorities themselves or other individuals who would unduly disrupt him.
The Constitution is an excellent guideline for this, and I surely won’t be able to come up with a better one in this Substack. It’s why I support Trump’s efforts to trim the top-down public sector and return productivity to the bottom-up private one, why I support deportation of adjudicated criminals who are here illegally, but oppose removing people with green cards or on valid student visas for protesting via constitutionally protected speech.
I don’t root for politicians like they play for my favorite sports team. I root for the freedom of the individual, the possibility of a largely bottom-up society wherein prosperity is possible. And I do this while knowing it will never happen exactly the way I would like, so long as I am bound by the fascism coming from inside the house.
-
 @ bf95e1a4:ebdcc848
2025-03-21 17:03:01
@ bf95e1a4:ebdcc848
2025-03-21 17:03:01This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
Preface
At the time of writing, it is New Year’s Day, and 2019 has just begun. For once, I have a resolution to live up to: I’ve promised myself to write a page per day every day this year until I have something real to publish. In June 2018, I published my first book, Three Minute Reads on Bitcoin — A Year of Thoughts. The book consisted of articles I had published online from May 2017 up to that point. This time it’s different. Instead of a mere collection of articles, I intend to write a “proper” book. A book that explains why Bitcoin is the most important invention of our lives.
I didn’t choose Bitcoin; it chose me. I had been trying to figure out how the world worked under the hood all my life, and then this simple idea of absolute scarcity popped up. It had a profound impact on how I view human interaction. Because of my curious nature, I instantly fell deep into the rabbit hole. I decided to educate myself on how this mysterious technology worked, and that got me into Austrian economics, which expressed very clearly what I had always suspected — that you really can't create value out of thin air.
In this book, I will try to explain every aspect of what makes this technology so special, what sets it apart from the abundant shameless copies of it, what’s wrong with our current system, and what the future might look like. In just two days from the time of writing these words, we’ll celebrate the ten-year anniversary of the Genesis Block when the Bitcoin blockchain came into being. That block contained a message, a newspaper headline that read: “03/Jan/2009 Chancellor on brink of second bailout for banks”. No one knows why Bitcoin’s mysterious creator, Satoshi Nakamoto, chose to include this in the Genesis Block. There is also some debate on whether the Genesis Block was actually mined on the 3rd of January since the next block wasn’t mined until six days later. Somehow, Satoshi managed to stay hidden and weave several layers of mystique into the fabric of Bitcoin from the very beginning, which is part of what makes its conception so immaculate. This book aims to strip Bitcoin of its shady cloak and illuminate its true nature. After all, the only thing any person can do about Bitcoin now is to study it.
Foreword
My journey down the Bitcoin rabbit hole has provided me with a newfound clarity of how our world should be perceived. In the same way that getting married and having my first child were beautiful life-changing events, discovering Bitcoin was a new chapter in my life. I can easily divide my life into two distinct periods: before and after Bitcoin.
Before discovering Bitcoin, life was perplexing. For years, even dating back to my school days, I had an innate sense that something was amiss in the world. Although I wasn’t a good student by any means, it was obvious back then that many aspects of life simply didn’t add up.
One thing that I was sure of was that money was corrupt. However, it took me a while to realize that money itself is fundamentally corrupt. Furthermore, what is typically taught and accepted as money by society is a perversion of what money should be. These are the first steps of understanding Bitcoin, which require you to admit that you have been fooled and lied to all your life. The hard lessons of hard money.
The way I see it, the revelation about the true nature of money is akin to a bracing cold shower that wakes you up to reality. Emerging from that cold shower is an incredibly liberating and invigorating sensation. Unfortunately, many individuals are not motivated enough to take that crucial step into the chilly waters. Instead, they will later experience an ice-cold bucket of water being dumped on their head unexpectedly whilst naked on a cold winter’s day.
The year 2020 was a watershed moment in my journey towards truth, and it was Bitcoin that served as my guide. As the world grappled with an unprecedented black swan event in March of that year, every asset, including bitcoin, took a severe hit. However, what followed in the subsequent months was the largest money-printing expedition in history. A tsunami of stimulus was pumped into the markets. The outcome was a K-shaped recovery. Small, honest brick-and-mortar businesses continued to suffer while many of the largest conglomerates not only rebounded but reached all-time highs. This ludicrous, short-sighted plan, known as quantitative easing, resulted in the most pronounced example of the Cantillon effect in human history, a fact that should have served as a wake-up call for anyone who was not already suspicious of the events surrounding the global financial crisis of 2008.
Since entering my post-bitcoin life, I’ve experienced a newfound coherence. The transition was not exactly instant, instead it has been a continuous process of discovering bitcoin over and over again, and I owe many of these enlightening moments to Knut Svanholm’s writing, for which I’m grateful.
While Knut’s books do not serve as a technical guide for Bitcoin, they provide a deep and philosophical introduction to a new era of money; the separation of money and state. The end of fiat money.
The creation of fiat money, a practice that emerged with the rise of central banking, has been the source of significant damage to human civilisation. Central banking, championed by Keynesianism, has granted immense power to centralized entities, allowing them to dictate fiscal policies and control the creation of money for billions of people. The very idea of a single entity wielding such vast authority and determining the economic fate of entire populations is utter madness. The state monopolizes money because it allows them to print money rather than having to directly tax people (but it still doesn’t stop them). Printing money is more easy, subtle and lucrative than direct taxation. And this continual erosion of purchasing power can be readily associated with the evident decline and deterioration of modern society.
At the heart of the issue is the importance of individual property rights. The money that individuals earn and save is their property, not the state’s. The state’s duty (should there be a need for it to exist) is to safeguard private property, not to continually debase or confiscate it. A centralized power that constantly devalues your hard-earned money and time by printing money is both morally and ethically wrong. Every individual has the right to turn their hard work into savings that they can rely on for the future.
In Bitcoin: Sovereignty through Mathematics, Knut not only delves into the fundamental principles underlying Bitcoin’s creation but also presents the groundbreaking concept of absolute scarcity. Bitcoin’s limited supply of 21 million and the impossibility of creating more due to its protocol creates a condition of absolute scarcity, a first in human history. Absolute scarcity, coupled with Knut’s poetic description of Bitcoin’s creation as "an immaculate conception," emphasizes its unique and revolutionary nature. The term "immaculate conception" highlights the fact that Bitcoin’s creation was not based on any pre-existing financial system but rather emerged from a set of mathematical principles that ensure its security and scarcity. The conditions that gave birth to Bitcoin will never be replicated, which further cements Bitcoin’s status as a one-of-a-kind element that will revolutionize the way we view and use money. Absolute scarcity aligns with the Austrian school of economics’ views on money, which argue that sound money should be scarce, durable, and difficult to counterfeit. Bitcoin ticks all the boxes for sound money, laying the ground for a genuine foundation to end the era of so-called cheap or easy money.
In the follow-up to this book, Bitcoin: Independence Reimagined1, Knut presents us, using plain logic and reasoning, the primitive constraints of the current fiat system and status quo governance. These structures, which we have so readily accepted, are gradually stripping us of our freedoms. By highlighting these shortcomings, he urges us to critically examine them and envision a future where we exercise greater autonomy over our lives, both financially and socially. Bitcoin’s simple and secure existence stands in contrast to the coercive and interventionist nature of the fiat system. Bitcoin is sincere; it neither favors nor opposes us. Bitcoin simply exists. Coming to terms with this truth is both humbling and liberating.
Knut’s writing, with its clear and elegant style, offers insightful guidance for those interested in exploring the deeper implications of Bitcoin beyond its function as a mere currency, recognizing it as a truly transformative breakthrough. A breakthrough that provides us with hope, a viable solution to reverse the degeneracy and decadence plaguing humanity.
Prince Philip of Serbia, 21st February 2023
Footnotes:
1. This foreword was originally written for a combined volume containing both Bitcoin: Sovereignty Through Mathematics and Bitcoin: Independence Reimagined.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ c239c0f9:fa4a5015
2025-03-21 15:51:57
@ c239c0f9:fa4a5015
2025-03-21 15:51:57Block:#888777- March 2025The Monthly Thunderbolt Dispatch On Bitcoin layers two innovations, aggregating the Best posts about the ~Lightning Network and others Bitcoin L2 solution- Exclusively on Stacker.News
It's again that time of the month, time to catch up with the latest features and trends that are shaping the future of Bitcoin. Each issue covers the latest trends and greatest advancements dictating the future of Bitcoin adoption—the very first and most commented insights from around the SN world. In every issue arrives expert analysis, in-depth interview, and breaking news of the most significant advancements in the Bitcoin layer two solutions.
Subscribe and make sure you don’t miss anything about the ~Lightning Revolution!
Now let's focus on the top five items for each category, an electrifying selection that hope you'll be able to read before next edition.
Happy Zapping!
Top ~Lightning posts
Most zapranked posts this month:
-
Underrated privacy tools on Lightning by @DarthCoin 4750 sats \ 21 comments \ 10 Mar on
~lightning -
ngx_l402: L402 Authentication for Nginx with LNURL, LND & NWC Support by @dhananjay 3602 sats \ 11 comments \ 11 Mar on
~lightning -
LNBϟG discusses fees and routing node management by @C_Otto 908 sats \ 3 comments \ 15 Mar on
~lightning -
New Release: Breez SDK - Nodeless 0.7.1 by @_ds 264 sats \ 1 comment \ 19 Feb on
~lightning -
Alby Hub Lightning Channel Stats the first 6 months by @k00b 376 sats \ 8 comments \ 27 Feb on
~lightning
Top posts by comments
This month we replaced the top posts by sats with these most commented posts (excluding those already listed above):
-
Cowbold Beta available for Testing: The best P2P Bitcoin alternativ to SplitWise by @supratic 699 sats \ 24 comments \ 1 Mar on
~lightning -
Nwc alternative to coinos, testing by @dingding541 150 sats \ 22 comments \ 17 Mar on
~lightning -
Payments below dust limit not trustless by @BallLightning 2141 sats \ 18 comments \ 11 Mar on
~lightning -
Question of trust regarding LSPs by @Fiatrevelation 385 sats \ 18 comments \ 14 Mar on
~lightning -
Question For CLN Start9 Users? by @siggy47 617 sats \ 15 comments \ 4 Mar on
~lightning
Top ~Lightning Boosts
Check them all here.
-
Try out the Ark protocol on signet by @nwoodfine 2083 sats \ 30k boost \ 12 comments \ 19 Mar on
~lightning -
Amboss CEO On Growth Of The Lightning Network, Tether (USDT) On Lightning by @Jestopher_BTC 577 sats \ 20k boost \ 10 comments \ 19 Feb on
~lightning -
Building Self Custody Lightning in 2025 by @k00b 2293 sats \ 10k boost \ 8 comments \ 23 Jan on
~lightning
Top Lightning posts outside ~Lightning
This month best posts about the Lightning Network outside ~Lightning territory:
-
SN is a badass use case for noncustodial lightning by @Fiatrevelation 1998 sats \ 15 comments \ 19 Feb on
~meta -
Alby Hub: Improving the Self-Custodial Lightning Experience by @teemupleb 4642 sats \ 8 comments \ 8 Mar on
~meta -
SN is a badass use case for noncustodial lightning by @Fiatrevelation 1834 sats \ 13 comments \ 20 Feb on
~meta -
Bitcoin Users... and especially Lightning users live in a Total Bubble (sofar) by @028559d218 1304 sats \ 24 comments \ 8 Mar on
~bitcoin -
🚀 New Geocaching Meets Lightning App ⚡ by @questforsats 4518 sats \ 170k boost \ 86 comments \ 20 Feb on
~builders
Forever top ~Lightning posts
La crème de la crème... check them all here. Plenty of new entries this month too at #1, #2, #4 and #5! This means old posts get still zaps... well done zappers 💪
-
👨🚀 We're releasing 𝗔𝗟𝗕𝗬 𝗚𝗢 - the easiest lightning mobile wallet by @Alby 29.2k sats \ 41 comments \ 25 Sep 2024 on
~lightning -
Building Self Custody Lightning in 2025 by @k00b 2303 sats \ 8 comments \ 22 Jan on
~lightning -
Lightning Wallets: Self-Custody Despite Poor Network - Apps Tested in Zimbabwe by @anita 72.8k sats \ 39 comments \ 28 Jan 2024 on
~lightning -
How to Attach Your self-hosted LNbits wallet to SEND/RECEIVE sats to/from SN by @supratic 1765 sats \ 18 comments \ 23 Sep 2024 on
~lightning -
A Way to Use Stacker News to improve your Zap Receiving by @bzzzt 1652 sats \ 22 comments \ 15 Jul 2024 on
~lightning
Forever top Lightning posts outside ~Lightning
Lot of changes here, but probably due to the recent relevance search and unbusting search functionality changes:
-
Rethinking Lightning by @benthecarman with 51.6k sats \ 137 comments \ 6 Jan 2024 on
~bitcoin -
Lightning Everywhere by @TonyGiorgio with 12k sats \ 27 comments \ 24 Jul 2023 on
~bitcoin -
Lightning is dead, long live the Lightning! by @supertestnet and zaps forwarded to @anita (50%) @k00b (50%) 6321 sats \ 28 comments \ @tolot 27 Oct 2023 on
~bitcoin -
Lightning Is Doomed by @Rsync25 2450 sats \ 15 comments \ 27 Nov 2023 on
~bitcoin -
We Need More Apps with Lightning, Not More Lightning Apps by @kr 5030 sats \ 22 comments \ @kr 12 May 2023 on
~bitcoin
-
-
 @ 2fb77d26:c47a6ee1
2025-03-21 15:49:40
@ 2fb77d26:c47a6ee1
2025-03-21 15:49:40»Pershing II« – das war eines der ersten englischen Wörter, das mir als Kind geläufig war. Es handelt sich um die Typenbezeichnung einer US-Mittelstreckenrakete, einer nuklearen Boden-Boden-Rakete, die mit einem thermonuklearen Sprengkopf vom Typ W85 ausgestattet war, eine Reichweite von etwa 1.800 km hatte und somit von Süddeutschland aus Ziele im westlichen Russland binnen fünf Minuten erreichen konnte. Es war Anfang der 1980er Jahre. Die Zeit des Kalten Krieges. Eine Bezeichnung, die George Orwell mit seinem Essay »You and the Atomic Bomb« (Du und die Atombombe) im Jahre 1945 geprägt hatte. Die Fronten waren verhärtet.
Die westdeutsche Friedensbewegung protestierte lautstark gegen die Stationierung von Atomsprengköpfen auf heimischem Boden. Nachdem die im NATO-Doppelbeschluss vom 12. Dezember 1979 vereinbarten Abrüstungsverhandlungen zwischen den Atommächten jedoch erfolglos geblieben waren, entschied der Deutsche Bundestag am 22. November 1983, der Stationierung von US-Atomwaffen im Lande zuzustimmen. Diese war 1985 abgeschlossen und ganze 120 Exemplare der todbringenden Massenvernichtungswaffe in der Bundesrepublik verteilt worden. Außer Deutschland tat kein Land den USA diesen Gefallen.
Ich hatte die militärische Artikelbezeichnung »Pershing II« im Radio aufgeschnappt, welcher zu Hause fast durchgehend in Betrieb war, und später ein paar Bilder der Raketen in den Abendnachrichten gesehen. Noch gab es nur ARD, ZDF und das Regionalprogramm. Dementsprechend rar waren visuelle Informationen. Und aufgrund meiner frühen Begeisterung für Fluggeräte aller Art, zeichnete ich daraufhin ständig Raketen. Da ich außerdem bereits in diesem zarten Alter von fünf oder sechs Jahren extrem von Musik angetan war und durchweg versuchte, englische Songtexte, zum Beispiel von den Beatles, dem Klang der Stimmen folgend nachzusingen, übte auch der fremd klingende Begriff »Pershing II« eine gewisse Faszination auf mich aus.
Was mir meine Eltern diesbezüglich sagten oder erklärten, kann ich leider nicht mehr erinnern – als erklärte Pazifisten nahmen sie die latente Gefahr eines Nuklearkrieges aber sicher nicht mit der spielerisch-kindlichen Leichtigkeit, die ich im Umgang mit gemalten oder gebastelten Raketen an den Tag legte. Das Thema nukleare Kriegsführung beherrschte die Nachrichten dieser Zeit und erzeugte Angst. Denn Militärstrategen sprachen Anfang der 1980er Jahre allen Ernstes davon, dass der Atomkrieg zwischenzeitlich präziser und somit auch führbarer geworden sei. Damals wie heute – absoluter Irrsinn.
Neben der Berlin-Blockade 1948/1949 und der Kuba-Krise, war die Auseinandersetzung um die Stationierung von Mittelstreckenraketen in Westeuropa von 1979 bis 1983 also eine der drei kritischsten Phasen des Kalten Krieges.
Nie war die Welt einem fatalen wie letalen nuklearen Schlagabtausch der Supermächte näher als zu diesen drei Zeitpunkten in der Geschichte. Bis heute, so scheint es.
Denn die stetig eskalierende Ukraine-Krise rückt dieses vergessen geglaubte Horror-Szenario wieder in den Fokus der Öffentlichkeit. Polit-Darsteller wie der Maoist und China-Fan Robert Habeck äußern dieser Tage dummdreist, keine Angst vor einem Dritten Weltkrieg zu haben. Sogenannte Sicherheitsexperten erklären im ZDF, dass man sich vor Putins Bomben nicht fürchten solle, obwohl man in Mainz permanent Angst schürt und schon am 5. Mai 2022 titelt, »Moskau simuliert Atomangriff in Kaliningrad«.
Der »Beobachter Gesundheit« gibt Tipps dazu, wie man die Panik vor einem Atomkrieg mental in den Griff bekommen kann, während das deutsche BBK (Bundesamt für Bevölkerungsschutz und Katastrophenhilfe) der Bevölkerung bereits empfiehlt, im Zuge der Ukraine-Krise Notvorräte anzulegen und Marschgepäck bereitzuhalten. Auf der Webseite »wikiHow« findet sich ein sehr umfassender, bebilderter Ratgeber mit dem Titel »Einen Atomkrieg überleben«. Beim Lesen der zahlreichen, mutmaßlich nur bedingt hilfreichen Tipps zur Meisterung der nuklearen Apokalypse dürfte jedem normalen Menschen etwas mulmig werden.
Hofberichterstatter Ruprecht Polenz lässt sich beim Propaganda-Multiplikator ZEIT ONLINE am 30. April 2022 dennoch zu der wagemutigen Formulierung verleiten, »wer einen Atomkrieg verhindern will, darf Putin nicht gewinnen lassen«. Solch ein Statement ist nicht nur falsch und realitätsfremd, sondern zeugt gleichsam von der bewussten Negierung von Faktenlage und historischen Hintergründen zur Ukraine-Krise. Dabei könnte man es durchaus besser wissen.
Die RAND-Corporation, ein im Jahre 1948 gegründeter, einflussreicher Think Tank der US-Hegemonie, veröffentlichte zum Beispiel schon im Jahr 2019 ein vielsagendes, 354 Seiten umfassendes Strategiepapier unter der Überschrift »Overextending and Unbalancing Russia«. Frei übersetzt: Eine Strategie, um Russland überzustrapazieren und aus dem Gleichgewicht zu bringen – ökonomisch, militärisch und gesellschaftlich – mit dem singulären Ziel, die geopolitische Dominanz der Vereinigten Staaten zu bewahren. Ein durchdachtes Drehbuch zur finalen Erniedrigung und Bezwingung des ewigen Klassenfeindes sowie dem Erhalt der unipolaren Weltordnung, der Pax Americana.
Der Ansatz der RAND-Corporation: Die Osterweiterung der NATO forcieren, das Ansehen Russlands in der Welt zerstören, kostenintensives, nukleares Wettrüsten, die Ukraine bewaffnen, um einen militärischen Stellvertreterkonflikt mit Putin zu provozieren, um die ehemalige Sowjetunion anschließend mittels internationaler Sanktionen – legitimiert durch den brodelnden Krieg – finanziell in die Knie zu zwingen.
Verblüffend, wie sehr doch die im RAND-Strategiepapier aufgezeigte Vorgehensweise den aktuellen Geschehnissen an den Außengrenzen des Riesenreiches gleicht. Fast macht es den Anschein, als folgten die Geostrategen in Washington den Empfehlungen ihrer kostspieligen Think Tanks. Dies ließ sich auch im Zuge der Corona-Krise beobachten, die im Ablauf fraglos dem von der Rockefeller-Stiftung erarbeiteten Pandemie-Szenario »Lock Step« glich, wie Journalist Norbert Häring bereits am 28. Mai 2020 ausführlich berichtet.
Was das totalitäre Krisen-Drehbuch der RAND-Corporation nicht detailliert behandelt, sind die akuten Risiken einer potenziellen nuklearen Eskalation. Denn es endet mit dem möglichen Aufkeimen eines militärischen Konflikts und schließt schlicht mit dem Hinweis:
»Auch wenn die US-Armee nicht direkt an der Operation beteiligt ist, wird sie eine Schlüsselrolle bei der Abmilderung der Folgen spielen. Wie bereits erwähnt, bergen alle Maßnahmen, die der Schwächung Russlands dienen, einiges an Risiko. Infolgedessen werden das Abschreckungspotential sowie die operativen Fähigkeiten des US-Militärs in Europa gestärkt werden müssen. Es besteht die Möglichkeit, dass die Spannungen mit Russland zu einem Konflikt eskalieren.«
Die USA betrachten den Einsatz von Atomwaffen dabei offensichtlich als probates Mittel. Warum sonst modernisieren die Amerikaner seit Jahren ihr Arsenal und geben Milliarden US-Dollar dafür aus? Das macht eigentlich nur Sinn, wenn man plant, diese Waffen irgendwann einzusetzen. Der »Plot« für die Events nach dem Aufflammen einer militärischen Auseinandersetzung mit Russland ist vermutlich Verschlusssache und liegt nur Eingeweihten im Weißen Haus, Pentagon, CIA-Hauptquartier sowie den Verbündeten in EU und NATO-Hauptquartier vor.
Das ist bedauerlich. Denn ein Einblick in die aktuellen militärischen Planspiele und strategischen Szenarien der NATO-Hegemonie wäre hilfreich, um zu verstehen, ob die Arroganz des Westens tatsächlich einen Punkt erreicht hat, an dem man einen Atomkrieg in Kauf nehmen würde, um Russland und China auf ihre Plätze zu verweisen und im globalen Club der Technokraten am Kopfende zu sitzen. Um einen Konflikt der Systeme – Kapitalismus, Sozialismus, Kommunismus – handelt es sich nämlich nicht, auch wenn Medien dies gerne so darstellen, sondern um Machtkämpfe innerhalb der internationalen Oligarchie. Die drei Machtblöcke kämpfen um Vorherrschaft in der totalitären Weltordnung der nahen Zukunft.
Die Frage ist nur: Tun sie dies einvernehmlich – oder handelt es sich an Russlands Grenzen um ernsthafte, kriegerische Auseinandersetzungen, die in letzter Konsequenz militärisch entschieden werden müssen? Das RAND-Strategiepapier scheint davon auszugehen, dass Wirtschafts- und Informationskrieg, begleitet von NATO-Drohgebärden, ausreichen, um das Rennen zu Gunsten des Wertewestens zu entscheiden. Es gilt zu hoffen, dass diese Interpretation des Schriftstücks zutrifft. Ansonsten läuft die moderne Zivilisation Gefahr, sich in die Steinzeit zurückzubomben. Wie das aussieht, zeigt eindrücklich der Film »The Day After« (Der Tag danach) aus dem Jahre 1983.
Der zwei Stunden lange Streifen von Regisseur Nicholas Meyer ist bildgewaltig, beängstigend, ernüchternd und deprimierend. Er zeigt nicht nur, wie binnen weniger Tage aus einem Kalten Krieg ein Atomkrieg wird, sondern auch, was dessen schreckliche Folgen sind. Schon ein kurzer, etwas mehr als acht Minuten langer Zusammenschnitt macht klar, dass man ein absoluter Narr sein muss, um keine Angst vor thermonuklearen Angriffen zu haben.
Im Film gibt der US-Oberbefehlshaber nach der Zerstörung des NATO-Hauptquartiers den Befehl zum Atomschlag. Das entsprechende NATO-Protokoll wird aktiviert und die Raketensilos einsatzbereit gemacht. Das Drehbuch lässt offen, wer den Erstschlag führt. Klar ist, dass sobald die Sprengköpfe des Westens unterwegs sind, Russland einen Gegenangriff mit 300 Interkontinentalraketen auslöst und die Vereinigten Staaten in die Steinzeit bombt.
Überall im Land der unbegrenzten Möglichkeiten steigen feurige Atompilze in den Himmel. Metropolen werden in Sekunden ausradiert, Lebewesen, Pflanzen und Gebäude verdampfen in Feuersbrünsten um den Einschlagsort, ganze Landstriche werden vom Erdboden getilgt – und schon in den ersten Minuten nach Explosion der Nuklearsprengköpfe sterben weite Teile der Bevölkerung. 90 Millionen innerhalb weniger Stunden, wie eine Simulation mit dem etwas unheimlichen Titel »Plan A« der Princeton-Universität von 2019 berechnet hat.
Der eigentliche Horror beginnt allerdings erst. Denn die schlimmsten Szenen des Films sind jene, die den Zustand der Welt zwei Wochen nach den Atomschlägen zeigen. Im Land herrscht Anomie. Chaos und Zerstörung, wohin man schaut. Vorindustrielle Zustände. Die Städte sind unbewohnbar und die Überlebenden leiden an Strahlenkrankheit. Haare und Zähne fallen aus. Bei manchen binnen weniger Stunden oder Tage, bei anderen dauert es Wochen. Ein grausamer Tod auf Raten. Alles stirbt, siecht dahin. In den Ruinen entstehen Flüchtlingslager. Seuchen brechen aus. Militärkommandos erschießen willkürlich Menschen. Recht, Gerichte und Prozesse gibt es nicht mehr. Und um zu überleben, bewaffnen sich schlussendlich auch die Zivilisten und töten sich gegenseitig. Absolute Barbarei.
»The Day After« erklärt nicht, wer diesen Krieg gewinnt, nennt keinen Sieger. Vermutlich, weil Regisseur Nicholas Meyer schmerzlich bewusst war, dass es bei einem ausgewachsenen Atomkrieg keine Gewinner geben kann.
Er bedeutet das Ende der modernen Zivilisation. Nicht umsonst hat Albert Einstein früh vor militärischem Missbrauch entsprechender wissenschaftlicher Erkenntnisse gewarnt. So lässt der Streifen aus Zeiten das kalten Krieges auch das Ende offen. Kein Hollywood-Finale. Kein Happy End. Die beklemmenden Gefühle bleiben. Weder Will Smith noch James Bond tauchen auf, um die Welt in letzter Minute doch noch zu retten. Sie ist kaputt. Tot. Eine nuklear verseuchte Wüste. Kein Hoffnungsschimmer am Horizont.
Wer das Pech hatte, die Erstschläge zu überleben, stirbt langsam, aber sicher – und vor allem qualvoll.
Vielleicht sollten Spitzenpolitiker, Dogmatiker, Propagandisten und Kriegshetzer von heute sich diesen Film einmal in Ruhe anschauen, bevor sie leichtfertig derartige Optionen in Betracht ziehen. Ich habe »The Day After« nur ein einziges Mal in meinem Leben gesehen – wenige Monate, nachdem ich den Begriff »Pershing II« das erste Mal als kleines Kind im Radio hörte und meine Eltern neugierig fragte, was es damit auf sich hat – das war ausreichend. Die Eindrücke wirken bis heute. Ich bin mir auch mehr als dreißig Jahre später immer noch der unverrückbaren, indiskutablen Tatsache bewusst, dass es niemals zu einem Atomkrieg kommen darf. Jeder, der diesen Film gesehen, wird das unterschreiben.
Ich jedenfalls werde nie vergessen, wie ich eines nachts heimlich im dunklen Wohnzimmer der heimischen Dachwohnung ganz nahe vor dem Fernseher saß. Eigentlich durfte ich nur ein paar Mal in der Woche ausgewählte Kindersendungen anschauen. Aber meine Eltern schliefen bereits. Es muss circa 23:00 Uhr gewesen sein, denn nach den Spätfilmen war damals in der Regel Sendeschluss. Und das was war meist gegen eins oder halb zwei.
Just als ich den kleinen Röhrenfernseher anschaltete, begann »im Ersten« der bis heute in mir nachhallende Spielfilm. Der Tag danach. Zunächst begeistert von den vielen Raketen und irgendwie noch fasziniert von den mir bis dato unbekannten, riesigen Explosionen, die Atombomben auslösen, blieb ich gebannt sitzen. Wie versteinert. Bis zur Schlussszene, in der sich eine Handvoll strahlenverseuchter, zerrissener, verrottender Menschen, die kaum noch Haare auf dem Kopf haben und aussehen wie Zombies, in den staubigen Ruinen einer leeren Großstadt kraftlos in den Armen liegen und hilflos schluchzen. Die Kamera zieht auf. Dann Schwarzblende – und eine letzte, dünne, einsam flehende Stimme im Äther:
»Hello, is anybody there? Anybody at all?« (Hallo, ist da jemand? Irgendjemand?)
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32
@ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32For our first edition of #Nostrversity, we'll be diving into Nostr Wallet Connect, or #NWC; a handy means of connecting a #Lightning wallet to your favorite #Nostr app that quickly became the standard and is now an essential part of onboarding to Nostr for any new user who wants to experience the magic of zaps. Yet NWC enables so much more than just one-tap-zapping, as we will see when we look a little closer at how it works under the hood.
Lightning History on Nostr
Back in the wild-west days of Nostr, before nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s invented zaps, Bitcoin psychopaths were already sending sats to one another over Nostr. However, the way we had to do it back then was by going into our Lightning wallet, selecting "receive," inputting an amount we wanted, and copy/pasting an invoice from the wallet into our Nostr note, then hope someone was willing to pay it. And the payment side was just as cumbersome, requiring manually copying the invoice from your Nostr client, pasting it into a Lightning wallet so you could see how much the other user wanted, and then deciding if you were even willing to send it.
It didn't take long before Nostr clients, particularly on mobile, started rendering Lightning invoices in a convenient format that showed the invoice amount and a "Pay" button, that would prompt the user to open a Lightning wallet. This took out a decent amount of friction for the sender, but it was still just as big a hassle for the receiver.
Then zaps came along, and soon everyone had the ability to send sats to any other user when they found value in the content they posted. At least, any other user that added their Lightning address to their profile and whose Lightning wallet provider supported sending a "paid" receipt to a Nostr relay. Receiver friction had been virtually eliminated and the sats began to flow. Nostr also became the de facto directory for Bitcoiner payment addresses. If you heard nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a say something brilliant on a podcast, you could just look her up on any Nostr client with zaps and send some sats her way as a thank you.
Enter the zapathon, a community event with one purpose: break nostr:npub1hcwcj72tlyk7thtyc8nq763vwrq5p2avnyeyrrlwxrzuvdl7j3usj4h9rq by zapping each other so much it was effectively a DDOS attack. Sure, it was a stress test on other wallets too, but most users were on Wallet of Satoshi because it was the easiest way to get a Lightning address with a mobile wallet.
It was a ton of fun flinging sats around as fast as your fingers would let you! However, a new friction point was soon discovered from trying to zap so frequently. Every time you tapped the zap icon in your Nostr client, you had to wait for your wallet to open and present the invoice to approve payment, then switch back to your Nostr client to zap the next note. Not a big deal when you only send a zap occasionally, but when trying to zap every note in your feed, it adds a significant amount of time and extra clicks. In fact, this small amount of friction, whether you realize it or not, often acts as just enough of a barrier to zapping that you will choose not to zap a post you found some value in, just because of the extra 5 seconds it takes to load into your wallet app, approve the payment, and switch back to your Nostr client.
Wouldn't it be amazing if we could have one-tap-zaps?
I can't recall if there were any other methods by which this was achieved, but the method that caught on was developed and released into the wild by nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm, who called it Nostr Wallet Connect. At that time (March of 2023), Alby was a custodial Lightning wallet for your web browser, and while you could connect your own node to it using LNDHub, most people just stuck with their custodial option since it came with a Lightning address. Nostr Wallet Connect was, at that time, a way to connect your Alby wallet to a Nostr client.
I am not certain which client was the first to support NWC, but I know that #Amethyst was pretty early on, and it was an instant success. Users could get a "connection string" from Alby, paste it into Amethyst, and zap with a single tap of their finger. Just like zaps themselves had eliminated the friction for receiving payments via Lightning for anyone with a Lightning address, Nostr Wallet Connect had eliminated the friction for sending payments. No more wasted seconds switching back and forth between Nostr client and wallet app, just tap and zap sent, tap again and another zap gone.
Of course, this meant that it was all too easy to send way more sats out of your wallet than you intended. This was solved by the ability to set budgets, so your wallet would cut you off once you reached the max amount you had set for yourself.
Because Alby had made Nostr Wallet Connect open source and part of the Nostr protocol, it didn't take long before more and more clients started adding support for it. Users demanded it and wouldn't shut up about it until it was added. Other wallet providers also saw the value of including it. Now it is simply expected, and any wallet that doesn't include it won't attract Nostr users.
Notably, Wallet of Satoshi went from being the most popular wallet among Nostr users to being a rare and quaint throwback to a bygone era, because they never integrated NWC and they pulled away from serving anyone in the U.S. out of fear of regulation under the Biden administration.
So we arrive at the state of Lightning on Nostr today, with Lightning addresses in our profiles for receiving zaps, and Nostr Wallet Connect for sending, and hard pressed to find Nostr clients that don't support both.
So... How does it work?
All of that history is great, but you're here to learn how this technology works. What is happening behind the scenes when you tap that little ⚡️ icon and sats seem to magically leave your Lightning wallet and show up on your screen as a zap underneath the latest nostr:npub1lrnvvs6z78s9yjqxxr38uyqkmn34lsaxznnqgd877j4z2qej3j5s09qnw5 meme, without you having to fiddle around with any Lightning invoices at all?
It's really quite simple, in the end. Your wallet communicating with your Nostr client using a Nostr relay in the middle, the same way you communicate with other Nostr users by saving notes to a relay that they can retrieve them from.
First, your Nostr client has to know how to "tag" your wallet, and on which relay to send it notes. This is why you need to get a "connection string" from your wallet to paste into your Nostr client. This string has all the information that is needed for your Nostr client to know how to communicate with your wallet, and for your wallet to be sure that the payment requests are authorized by you.
Let's take a look at an example connection string:
nostr+walletconnect://b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4?relay=wss%3A%2F%2Frelay.damus.io&secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cLooks like a bunch of gobbledygook, right? We'll break down each of its parts and see what it does.
nostr+walletconnect://This portion just defines the type of information that follows it. Because the string starts with this marker, any software reading it will know that what follows is information on how to communicate with a Lightning wallet, so long as it has been programmed to recognize it.
b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4This section is just a public key, the same as an npub. In fact, it can be readily converted to an npub if you want using nostr:npub1zdr58j526qsrkdjhcg9xs60xfutqeey2ucugms04efnlx3spnmns2eqha9's key converter. It's a nostr identity just like yours or mine, but you won't find any GM posts or catstr pictures in its note history. It's only posting special note types used by NWC. This public key belongs to your Lightning wallet, and just like you can have multiple npubs for each of your alter egos, your wallet creates a separate public key to use with each new app you want to connect it to. Or at least it should. The Nostr client you use will tag your wallet in notes it creates by using this public key.
relay=wss%3A%2F%2Frelay.damus.ioThis section is probably easily recognizable. It's the same as typing
relay=wss://relay.damus.io, except that it has to use%3A%2F%2Fin place of://. This tells your Nostr client which relay it needs to use to communicate with your wallet. Hopefully your wallet uses a relay with high up-time, because one of the major ways for NWC to fail is if the relay is down. You also can't use just any relay. It has to accept the note kinds used by NWC, which is why wallets don't typically let their users choose the relay that will be used. You also can't just modify the connection string to use a relay you prefer, even if you know it allows NWC note kinds. This is because it will result in your Nostr client sending requests to your wallet on that relay, but your wallet is not reading from that relay, so it will never receive the requests.secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cThis is just a Nostr private key. It's an nsec, but in hex format. Your wallet is giving your Nostr client a private key that it must use to sign all of the requests it sends to your wallet. No request signed by any other private key will be answered by your wallet. Your wallet will generate a separate private key for each connection string, allowing you as the user to revoke those connections individually, or set a separate budget for each connection.
When you tap the ⚡️ icon in your Nostr client, it obtains a Lightning invoice from the user's wallet you are trying to zap using their Lightning address. It then creates a note tagging your wallet's public key and requesting payment of that Lightning invoice, signing the note with the private key your wallet generated for it, and writing that note to the specified Nostr relay. Your wallet is constantly checking that relay for new notes and when it sees the payment request signed by an authorized private key, it pays the invoice, so long as it is within the budget you set, and sends out a payment receipt stating it has been paid so your client can light up the zap indicator to show that it was successful. All of this from a single tap of your finger in Amethyst.
More than Zaps
Now that we know the basics of how NWC works, it doesn't take much extrapolation to realize that this communication between wallet and Nostr client could be used for much more than just payment requests. A client could ask for your wallet's balance information, or transaction history, or ask for a lightning invoice. In fact, why does it have to be a Nostr client making those requests at all? Why not a mobile wallet app, or browser extension?
One of the major pieces of friction felt by those who run Lightning nodes is the difficulty of connecting to them remotely in a secure way. nostr:npub1aghreq2dpz3h3799hrawev5gf5zc2kt4ch9ykhp9utt0jd3gdu2qtlmhct and nostr:npub126ntw5mnermmj0znhjhgdk8lh2af72sm8qfzq48umdlnhaj9kuns3le9ll allow for connecting via Tor by default, but that can be painfully slow and unreliable. Anyone who has set up a connection to their node via LND Rest over Tor to their nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5 wallet can attest to the frustration of opening their wallet and waiting several seconds for the interface to load, only to receive a timeout notice.
Nostr Wallet Connect has eliminated this issue thanks to Alby Hub and Alby Go. Just create a new connection in Alby Hub, give it a budget, and scan the QR code with Alby Go and you have a fully-functional, mobile Lightning wallet connected to your node at home that loads extremely quickly and reliably, so long as the Nostr relay in-between is up and running.
Now, you may be concerned that the information being passed back and forth on this Nostr relay is incredibly sensitive financial information, especially if balance and transaction history is involved. However, this is not a concern because the content of the notes is fully encrypted. The relay owner, or anyone else with access to read data on that relay, has no idea what information is contained in the messages being sent between wallet provider and Nostr client, or Lightning node and mobile wallet. And because neither npub being used by your wallet provider or your Nostr client is the same as your npub, there is nothing tying the messages to you.
As a result, NWC is quickly becoming an integral piece of Lightning infrastructure, even if those making use of it have no interest in joining Nostr at all.
The Future of NWC
To wrap this up, I'd like to point the reader to recent developments with Nostr Wallet Connect, and other use-cases we could very well see in the near future.
First, NWC may not just be for Lightning. nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 recently revealed that he has a working prototype of on-chain payments via NWC.
nostr:nevent1qvzqqqqqqypzpckv7l8jqspl8u4y54dn9rcduwlrs4v2040nxce0m2h0cunvrj8tqyw8wumn8ghj7un9d3shjtnzd96xxmmfdecxzunt9e3k7mf0qyfhwumn8ghj7am0wsh82arcduhx7mn99uq32amnwvaz7tmjv4kxz7fww468smewdahx2tcqyzswntflhlvuea2uf3035r94azm32frnskk5qp2evj43x6nz6kt9zd7j485
We are already seeing it used with eCash wallets like nostr:npub1kvaln6tm0re4d99q9e4ma788wpvnw0jzkz595cljtfgwhldd75xsj9tkzv. There is no reason we shouldn't expect to see it used with all forms of Bitcoin payments. This could lead to an explosion of available wallet applications for all platforms, since they will simply be an interface for communicating with your node or wallet provider.
NWC can also be used for subscriptions, as alluded to in nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8's note above. Before you protest about what an awful monetization model subscriptions are, I generally agree. That said, subscriptions where the user remains in control the entire time, and can unilaterally cancel the subscription at any time, without having to jump through hoops and give explanations about why they no longer want to use the service, is a massive improvement over the current status quo. Remember, NWC allows the user to set a budget for each connection. This means your subscription can't incrementally increase its monthly fee on you. Not without you willingly going into your wallet settings and adjusting the monthly budget, at any rate.
Last one before we close this out: NWC can be used for streaming services where you pay only for what you use, and give yourself a budget. Instead of paying a monthly subscription to Netflix, you could pay per minute that you watch. Previously this could only be done by topping up a wallet controlled by the service itself, the way nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5's wallet worked with streaming sats for Podcasting 2.0. But now NWC is coming to Fountain, and users can bring their own wallet that they control.
The future of NWC is bright, and it extends well beyond zapping memes on Nostr. It's going to open up a world of possibilities for how we can use our sats to stream media, make reoccurring donations, use micro-payments to rent compute, and so much more. I don't know about you, but I am here for it!
-
 @ a012dc82:6458a70d
2025-03-21 15:42:13
@ a012dc82:6458a70d
2025-03-21 15:42:13In the ever-evolving landscape of finance and investment, Bitcoin has emerged as a pivotal player, challenging traditional notions of wealth and assets. Often likened to "digital gold," Bitcoin's unique properties have led some to view it in an even more nuanced light—as "digital pearls." This article delves into how Bitcoin is redefining wealth in the digital age, drawing parallels with historical assets and exploring its impact on modern investment strategies. The comparison to digital pearls is not merely poetic but serves as a metaphor for the transformation of value from physical to digital realms. This shift is not just technological but cultural, reflecting changing attitudes towards what constitutes real wealth in our increasingly digital world.
The digital age has brought about a profound transformation in how we perceive and interact with value. Traditional assets like real estate and precious metals have been joined by a new class of digital assets, from cryptocurrencies to NFTs, reshaping the landscape of investment and wealth. This shift is not merely about the assets themselves but represents a broader change in societal values and economic structures. The rise of digital assets challenges the monopoly of physical assets as the sole bearers of value, suggesting a future where wealth is as much about information and digital ownership as it is about tangible possessions.
Table of Contents
-
The Evolution of Value: From Tangible to Digital
-
Bitcoin: The Digital Pearls of the 21st Century
-
Redefining Wealth and Investment
-
The Future of Digital Wealth
-
Conclusion
-
FAQs
The Evolution of Value: From Tangible to Digital
Historically, the concept of wealth has been tied to tangible assets: land, gold, and precious stones. These assets were prized for their scarcity, durability, and, in many cases, their beauty. However, the digital age has ushered in a new era of value, one where intangible assets like data, software, and digital currencies have become just as, if not more, valuable than their physical counterparts. This transition from tangible to intangible assets marks a significant shift in the global economy, reflecting changes in how we work, live, and interact with the world around us. The value is increasingly found not in physical objects but in the data and digital experiences they enable.
Bitcoin, since its inception in 2009, has epitomized this shift. Created as a decentralized digital currency, it offers a new form of wealth that is secure, transferable, and free from the control of any government or institution. Its blockchain technology ensures transparency and immutability, making it a trustworthy digital asset. This revolutionary approach to currency and wealth has not only challenged traditional financial systems but also redefined what constitutes value in the 21st century. Bitcoin represents a paradigm shift, moving us away from centralized financial systems and towards a more democratized form of wealth.
Bitcoin: The Digital Pearls of the 21st Century
Just as pearls were once a symbol of wealth and status, Bitcoin has emerged as a modern equivalent in the digital realm. The comparison extends beyond mere value; it reflects a shift in what society considers precious. Pearls, formed in the depths of the ocean, were valued for their rarity and beauty. Similarly, Bitcoin, 'mined' through complex computational processes, holds value due to its finite supply and the energy invested in its creation. This digital creation process, known as mining, parallels the natural formation of pearls, adding a layer of intrigue and value to Bitcoin's narrative.
The story of Maisie Plant and her pearl necklace, traded for a New York mansion, illustrates the fluid nature of value. Just as the perceived worth of pearls has fluctuated over time, Bitcoin's value is also subject to change. However, its digital nature and global accessibility mark a departure from traditional assets, offering a new form of wealth that transcends physical boundaries. This story not only highlights the changing nature of value but also serves as a reminder of the subjective and evolving nature of what society deems valuable.
Redefining Wealth and Investment
Bitcoin's rise challenges conventional investment wisdom. Traditional portfolios, heavy on stocks, bonds, and real estate, are being reevaluated as investors seek to diversify with digital assets. Bitcoin's volatility, while often cited as a risk, also presents opportunities for significant returns, drawing parallels with early investments in tech giants like Amazon and Google. This shift towards digital assets represents a broader change in investment strategies, reflecting a new era of wealth where digital assets play a central role.
Moreover, Bitcoin's decentralized nature offers a hedge against inflation and economic instability. In countries facing currency devaluation or financial crisis, it has become a means of preserving wealth, akin to how gold has been used historically. This aspect of Bitcoin highlights its potential not just as an investment but as a tool for economic empowerment and stability. The ability to store and transfer wealth independently of traditional financial systems is a powerful feature, particularly in regions where those systems are unreliable or inaccessible.
The Future of Digital Wealth
As we move further into the digital age, the definition of wealth continues to evolve. Bitcoin, and the broader category of cryptocurrencies, are at the forefront of this shift. They challenge individuals and institutions to rethink what constitutes an asset and how value is assigned and preserved. This evolution is not without its challenges and controversies, but it also offers unprecedented opportunities for innovation and growth.
The integration of Bitcoin into mainstream finance, through ETFs, futures, and other investment vehicles, signifies a growing acceptance of digital currencies as a legitimate form of wealth. However, as with all investments, there are risks and uncertainties. The regulatory landscape, technological advancements, and market dynamics will all play a role in shaping the future of Bitcoin and digital wealth. This future is not just about Bitcoin itself but about the broader implications of a world where digital assets are as common and valued as traditional ones.
Conclusion
Bitcoin's comparison to "digital pearls" offers a compelling framework for understanding its place in the modern economy. Just as the value of pearls once reflected societal trends and desires, so too does Bitcoin capture the zeitgeist of the digital age—a symbol of a new era of wealth that is decentralized, digital, and diverse. As we navigate this new landscape, the story of Bitcoin is far from over; it continues to challenge, redefine, and inspire the future of finance. The journey of Bitcoin from an obscure digital currency to a new form of digital wealth mirrors the broader transformation of the economy and society in the digital age.
FAQs
Why is Bitcoin compared to gold or pearls? Bitcoin is often compared to gold because it shares characteristics such as scarcity, durability, and being a store of value. The comparison to pearls, however, emphasizes its unique, evolving status as a coveted asset, reflecting shifts in societal values and the concept of wealth.
How does Bitcoin work? Bitcoin transactions are verified by network participants (miners) and recorded in blocks on the blockchain. Users can send and receive bitcoins using digital wallets. The supply of Bitcoin is capped at 21 million, ensuring its scarcity.
Is Bitcoin a good investment? Bitcoin's value can be highly volatile, making it a risky investment. However, some view it as a hedge against inflation and a potential part of a diversified investment portfolio. As with any investment, it's important to do thorough research and consider your financial situation and risk tolerance.
Can Bitcoin be converted into real money? Yes, Bitcoin can be exchanged for traditional currencies through online exchanges, peer-to-peer platforms, and some retail locations. The exchange rate varies based on market conditions.
Is Bitcoin legal? The legality of Bitcoin varies by country. Some countries have embraced it, while others have imposed restrictions or outright bans. It's important to check the regulations in your specific location.
What is the future of Bitcoin? The future of Bitcoin is uncertain and subject to various factors, including technological developments, regulatory changes, and market dynamics. It continues to gain acceptance and has sparked a global conversation about the nature of money and the future of financial systems.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 43bb87e2:12cc9cb8
2025-03-21 15:06:52
@ 43bb87e2:12cc9cb8
2025-03-21 15:06:52There was once a little girl that got into some expensive golden wrapping paper, and her father got upset. In his anger, he yelled at his little daughter for wrecking the expensive wrapping paper. The daughter then decided to use the ripped and wrecked wrapping paper to wrap a gift for someone. Again, the father let his anger take over and got mad at the little girl for using the ripped paper for the gift wrapping. The next morning, the little girl presented the tattered, golden wrapped box to her father and said this is for you, Dad. He opened the wrapped box and saw that the box was empty inside. The dad again got angry and told his daughter that when you give a gift to someone, there is supposed to be something inside of it. The little girl, in tears, looked up at her father and said, but it is full daddy. I blew kisses into it until it was completely full. The father then broke down and started crying. He dropped to his knees and put his arms around his precious and innocent daughter. He desperately apologized to her for his anger and continued to ask for her forgiveness. A short while after this, his daughter was taken from this earth because of an accident. The father kept the golden wrapped box next to him for the rest of his life to remind him of the love he had from his daughter.
Nothing else matters in this world or even comes close to the unconditional love that our children and family have for us.
With life being so busy, don’t you dare forget, what really matters in this world. And you be sure to take care of your loved ones, family, and friends.
For we do not know when the last day we will be on this earth.
CHERISH EVERY MOMENT AND LOVE WITH ALL YOUR HEART!
DO NOT LET ANGER RULE OVER YOU.
TELL EVERYONE IN YOUR LIFE,
THAT YOU LOVE THEM!
TELL THEM TODAY!
DO IT NOW!
LOVE YOU ALL, BE BLESSED!
-
 @ da0b9bc3:4e30a4a9
2025-03-21 13:58:11
@ da0b9bc3:4e30a4a9
2025-03-21 13:58:11It's Finally here Stackers!
It's Friday!
We're about to kick off our weekends with some feel good tracks.
Let's get the party started. Bring me those Feel Good tracks.
Let's get it!
This song never doesn't put me in a good mood.
https://youtu.be/fnwZeLdLPdQ?si=ZlbiGSp2r6DtMx6P
originally posted at https://stacker.news/items/920041
-
 @ 46fcbe30:6bd8ce4d
2025-03-21 13:57:11
@ 46fcbe30:6bd8ce4d
2025-03-21 13:57:11Table of Contents
- Introduction
- Overview of the Nostr Ecosystem
- Current Use Cases and Quantitative Metrics
- User Adoption Metrics
- Network Resilience and Decentralization
- Operational Challenges and Scalability
- Replication Overhead and Bandwidth Issues
- Relay Downtime and Financial Sustainability
- Market Disruption and Sentiment
- Disrupting Twitter and Centralized Social Platforms
- Impact on Decentralized Social Media and Censorship Resistance
- Future Trends and 5-Year Outlook
- Innovative Protocol Developments
- Quantitative Forecasting and Diffusion Modeling
- Networking and Integration with Emerging Technologies
- Conclusions and Strategic Recommendations
1. Introduction
The Nostr ecosystem has emerged as a powerful decentralized alternative to traditional social media networks, particularly as a potential disruptor of Twitter and other centralized—and even existing decentralized—social media platforms. Developed using a protocol based on cryptographic key pairs and a multi-relay system, Nostr is unique in its provision of censorship resistance and user sovereignty. In this report, we provide a detailed analysis of the current state, scalability challenges, and market disruption potential of Nostr, followed by speculative insights on its trajectory over the next five years.
2. Overview of the Nostr Ecosystem
Launched in 2022, Nostr (Notes and Other Stuff Transmitted by Relays) has rapidly gained traction as an open and decentralized social network. Some of the core features include:
- Decentralized Communication: Relying on independent relays across multiple countries and autonomous systems, Nostr offers an architecture that ensures posts are not stored on a single centralized server.
- Censorship Resistance: With cryptographic authentication and a decentralized relay structure, content censorship becomes significantly more difficult than in traditional networks.
- User Sovereignty: Empowering users with cryptographic key pairs allows for enhanced privacy and data ownership.
- Wide Geographic Distribution: The ecosystem spreads over 44 countries and 151 autonomous systems, underscoring its global reach.
Notable endorsements from figures such as Jack Dorsey, Edward Snowden, Vitalik Buterin, and Sen. Cynthia Lummis have bolstered its reputation as an experimental yet promising alternative to centralized social platforms.
3. Current Use Cases and Quantitative Metrics
User Adoption Metrics
- User Base: In just two years, the Nostr network has attracted over 4 million users, a significant figure given its nascent stage and decentralized nature.
- Content Generation: With over 60 million posts, the volume of content mirrors the rapid adoption and active usage seen in more centralized models.
- Post Replication: Empirical measurements indicate that there are 17.8 million text notes among these posts, replicated on an average of 34.6 relays per post. This level of replication underlines robust resilience and availability even if significant portions of the network experience downtime.
Network Resilience and Decentralization
- Global Distribution: Nostr’s decentralized network ensures high availability with >90% post accessibility even under simulated network failures (e.g., removal of key relays or autonomous systems).
- Robustness: The dispersion across 712 relays illustrates that decentralization is not only a design choice but also a working reality, which contributes to the network’s reliability.
4. Operational Challenges and Scalability
While the Nostr ecosystem demonstrates significant promise, it faces noteworthy operational challenges.
Replication Overhead and Bandwidth Issues
- Excessive Redundancy: Detailed studies have shown that nearly 98.2% of retrieval traffic is redundant. In practice, this equates to an estimated 144 TiB of unnecessary bandwidth consumption.
- Optimization Proposals: To mitigate these inefficiencies, there's a proposal to limit post replications from 34.6 relays to between 10 and 20 relays per post. This could reduce redundant data copies by between 380 million to 480 million instances, potentially lowering operational costs and improving bandwidth utilization.
- Scaling Concerns: With a projected network load of 10 million events per day (or approximately 2 TB annually), the throughput requirement of ~115 TPS is putting a strain on the current architecture. This has led to debates on whether solutions like the current outbox mechanism are sufficient or if further fundamental redesigns and emergent moderation systems are needed.
Relay Downtime and Financial Sustainability
- Relay Stability: Data indicates roughly 20% of relays suffer from significant downtime (exceeding 40% operational time), and 132 relays have been classified as 'dead'. This is a concern for maintaining network integrity.
- Economic Model Challenges: With 95% of free-to-use relays unable to cover operational costs due to minimal zap-based income, there is an urgent need for innovative monetization or community funding models to ensure long-term sustainability.
5. Market Disruption and Sentiment
Nostr is positioned as both a disruptor to traditional centralized social platforms—most notably Twitter—and a catalyst for change within decentralized social media.
Disrupting Twitter and Centralized Platforms
- User Shift: While Twitter remains the most well-known platform, the high-profile endorsements and robust user base of Nostr indicate that there is both market intrigue and a gradual shift among early adopters. Disruption here is measured not only in user numbers but also in the paradigm shift towards decentralized content distribution.
- Market Penetration: Current metrics (4 million users, 60 million posts) suggest that Nostr is challenging Twitter's centralized model insofar as it appeals to users prioritizing censorship resistance, data sovereignty, and resiliency against centralized failures. However, mainstream adoption on par with Twitter is still not realized, and there remains a gap in user experience and feature richness.
Impact on Decentralized Social Media and Censorship Resistance
- Complementary Integrations: As decentralized social media ecosystems continue to mature, integration between Nostr and other censorship-resistant platforms is increasingly likely. This can include interoperability protocols, shared identity management systems, and cross-platform content replication.
- Comparative Advantage: Nostr's network design offers unique advantages over other decentralized social media, particularly in its straightforward, relay-based communication protocol. This positions Nostr to potentially serve as an underpinning technology for a broader decoherent ecosystem of social networks.
- Sentiment Toward Scalability Innovations: Discussions around scaling Nostr often focus on the balance between ensuring redundancy (for resilience) and reducing overhead (for efficiency). The sentiment is one of cautious optimism: while outbox solutions offer a stopgap, many experts advocate for more fundamental architectural redesigns in the long-term.
6. Future Trends and 5-Year Outlook
Looking forward, the evolution of Nostr will likely be shaped by several interrelated trends and emerging technical innovations.
Innovative Protocol Developments
- Decentralized Identity and Reputation Mechanisms: The next phase may see the introduction of distributed reputation systems and rating mechanisms that aid in spam management and improve trustworthiness without compromising decentralization.
- Optimistic Replication and Selective Mirroring: Innovations such as selective content mirroring and event pruning will be key in managing bandwidth and storage demands while remaining true to the decentralized philosophy.
Quantitative Forecasting and Diffusion Modeling
- Forecast Models: By integrating modified Bass diffusion models and learning curve effects, predictions suggest that Nostr can potentially spur significant market disruption within five years. Recent studies indicate that forecasting models in disruptive technology fields have reached accuracies of up to 82% for demand projections.
- Hybrid Quantitative Techniques: Leveraging methods like LDA2Vec and patent citation network analysis, combined with multi-criteria decision-making models (as seen in extended UTAUT approaches), will be crucial for accurately estimating future adoption and cost efficiencies.
- Metrics to Monitor: Future research should focus on user growth rates, relay uptime percentages, cost reductions achieved through replication optimizations, and overall sentiment analysis using advanced deep learning architectures that overcome traditional pitfalls (e.g., sarcasm and multipolarity in text data).
Networking and Integration with Emerging Technologies
- Integration with Other Decentralized Platforms: One promising avenue is exploring cross-platform interoperability with other decentralized and blockchain-based social networks, which could lead to a more cohesive ecosystem. This would not only enhance user experience but also enable shared security and moderation frameworks.
- Next-Generation Relays: The deployment of relays that are more resilient through redundancy optimization and financial sustainability models (perhaps incorporating micro-transaction revenue models or community-driven funding) is another critical area. Such improvements could mitigate the issues of relay downtime and excessive network overhead.
- Contrarian Approaches: A contrarian perspective suggests that instead of building on current frameworks, a radical overhaul of the network architecture might be considered, potentially by leveraging novel distributed ledger technologies or leveraging a hybrid centralized-decentralized model during the transition phase to ensure smoother scaling.
7. Conclusions and Strategic Recommendations
The Nostr ecosystem represents a significant stride toward decentralized, censorship-resistant social media. While its current market adoption and technical design offer a robust alternative to centralized platforms like Twitter, several challenges must be addressed for sustained growth and disruption:
-
Optimization of Data Replication: Reducing redundant data transfers without compromising resilience is essential. Limiting the replication factor and exploring optimistic retrieval mechanisms could provide a balance between availability and efficiency.
-
Relay Stability and Sustainability: With nearly 20% of relays experiencing significant downtime, innovative financial and technical models (such as micro-payments and community funding) should be deployed to enhance the operational reliability of network nodes.
-
Enhanced Moderation and Reputation Systems: Emerging strategies for decentralized content moderation and reputation management could reduce spam and improve content quality while preserving the open nature of the network.
-
Interoperability with Other Decentralized Platforms: Fostering integration with other emerging systems could accelerate market disruption across the broader spectrum of social media.
-
Future-Proofing Through Quantitative Forecasting: Continual adoption of cutting-edge forecasting models and machine learning techniques to measure sentiment and track network metrics is imperative for proactive evolution.
-
Exploring Contrarian Innovations: In addition to incremental changes, it is important not to discount radically new architectures that may emerge from ongoing research in distributed systems and blockchain technologies.
Final Outlook
In the coming five years, Nostr has the potential to disrupt not only Twitter but also the broader landscape of both centralized and decentralized social media. Although the current architecture presents significant scaling challenges, proactive investments in replication optimization, relay stability, and cross-platform integration will likely propel the network into a more mature phase of adoption. The ecosystem will benefit from a dual approach that combines both evolutionary improvements and revolutionary changes, ensuring that it remains robust while meeting the demands of a growing, globally distributed user base.
Appendices
Appendix A: Data and Metrics Summary
- User Base: ~4 million
- Post Volume: >60 million posts
- Average Relay Replication: ~34.6 replicas per post
- Geographical Distribution: 44 countries, 151 autonomous systems
- Bandwidth Waste: ~144 TiB due to redundancy
- Network Load: 10 million events/day (~2TB/year)
- Throughput Requirement: ~115 TPS
Appendix B: Key Technical Proposals
- Replication Control: Limit copies to 10–20 relays for optimal efficiency.
- Selective Mirroring: Implement event pruning and selective content mirroring.
- Decentralized Reputation Systems: Develop distributed rating mechanisms to enhance distributed moderation.
Appendix C: Forecasting and Quantitative Methods
- Diffusion Modeling: Modified Bass models with multi-market dynamics.
- Hybrid Quantitative Techniques: Integration of machine learning (CNN-LSTM, LDA2Vec) with multi‐criteria decision models.
Recommendations for Further Research
- Investigate the comparative performance of alternative replication strategies in decentralized networks.
- Explore funding models that can sustain relay operations without compromising neutrality or decentralization.
- Conduct long-term sentiment analysis using advanced neural architectures to understand evolving user attitudes.
- Evaluate the prospective benefits of radical design overhauls versus incremental enhancements in ensuring network scalability.
This report is intended for expert analysts and researchers in decentralized network systems and social media disruption. It synthesizes current empirical findings with speculative insights to inform future strategies and academic inquiry.
Sources
- https://www.voltage.cloud/blog/exploring-6-use-cases-of-nostr-beyond-messaging
- https://arxiv.org/abs/2402.05709
- https://arxiv.org/html/2402.05709v1
- https://papers.ssrn.com/sol3/Delivery.cfm/5146515.pdf?abstractid=5146515&mirid=1
- https://matchnode.com/blog-and-podcasts/mastering-paid-social-media-advertising-a-comprehensive-guide/
- https://blockworks.co/news/jack-dorsey-app-to-disrupt-twitter
- https://www.securities.io/nostr-a-better-twitter/
- https://medium.com/@jasminedevv/battle-of-the-decentralized-twitter-alternatives-c9f51114614a
- https://www.murrayrudd.pro/nostrs-relay-revolution-scaling-decentralized-networks-for-growth/
- https://github.com/nostr-protocol/nips/issues/75
- https://news.ycombinator.com/item?id=42758579
- https://www.toptal.com/deep-learning/4-sentiment-analysis-accuracy-traps
- https://www.researchgate.net/publication/3076742_Forecasting_the_Market_Diffusion_of_Disruptive_and_Discontinuous_Innovation
- https://www.globenewswire.com/news-release/2025/03/17/3043701/0/en/United-States-Online-Household-Furniture-Market-Report-2025-2029-Analysis-of-Price-Sensitivity-Lifecycle-Customer-Purchase-Basket-Adoption-Rates-and-Purchase-Criteria.html
- https://northeast.newschannelnebraska.com/story/52583550/laser-welding-market-growth-industrial-adoption-rate
- https://www.sciencedirect.com/science/article/am/pii/S2405896323014453
- https://www.marketsandmarkets.com/Market-Reports/industry-5-market-35376359.html
-
 @ 8671a6e5:f88194d1
2025-03-21 13:38:50
@ 8671a6e5:f88194d1
2025-03-21 13:38:50As old people tend to say:\ \ *nasal voice* “Back in my day…” … Bitcoin was this wild, beautiful thing, new. It was something technical that came alive before our very eyes after running a node (just a .exe running on a windows machine in my case).\ Even when you started to painstakingly mined bitcoin on a GPU, in a pool, you felt like growing a network of like minded people, or at least people who thought there was something there. Even if we couldn’t comprehend what it all would lead to (or what fiat value it could reach).\ Then came the first paper wallets, the first good software wallets and attempts at hardware wallets, the first buzz of owning your own value — it was motivating and rewarding. The look on the face of other people you explained bitcoin to, when they’ve seen their first transaction pop up after validation. Awesome.\ \ Back then, it wasn’t about fiat gains or slick marketing campaigns; it was about a distributed network “generating” numbers, keeping a distribute ledger “in synchronization”, at the same time it was a middle finger to the system, representing freedom to transact in value we valued ourselves because of the underlying network of people, nodes and miners.\ \ It was this sort of secret handshake between tech minded people, anti-globalists, anarchists, nerds and rebels who saw the fiat scam for what it was.\ Orange-pilling wasn’t even a term; it was just what you did.\ You'd walk people through the setup of bitcoin core, and the white paper, told them why central banks are a trick that functions as a legalized Ponzi scheme and you showed them bitcoin’s workings without middlemen.\ You played around with bitcoin, person to person, no bullshit, no subscriptions, no suits, no posing like a big shot, no referral links.\ Those were the fun times — pre-Saylor, pre-nation-state hype, pre-every Laura, Luigi, and self-proclaimed “OG” thinking they’re going to conquer the world.\ I miss that.
But times change.
\ The good ol' days are dead
It’s not the first instance in our lifetime that we see things pop-up, being invented, and where some good new idea becomes a reality and then that very good idea becomes an institution (there’s an obscure 1990s movie reference for you).\ We live and learn, just like the first technical people setting up their own point of presence internet servers, we all have to learn how to grow and adapt.
Early Bitcoiners didn’t have referral links or corporate sponsors — they had a mission, and the spirit came from within themselves and from the math and tech they’ve seen at work in practice. And yes, educating about it was important, as was looking for ways to improve bitcoin (the early years weren't exactly main-stream material for example).
From that learning yourself about Bitcoin and feeling the need to share and convince others around you, came the need to talk and learn together with others.
You’d talk your buddy into installing a wallet over a coffee, maybe show your uncle how to buy a few bitcoin, and it felt like planting seeds for something real.
Even if they didn’t get it—“So this number goes from my address to your address?”—you kept explaining and showing.
Then the suits rolled in. Bigger companies wer started, like Blockstream, Trezor, Coinbase and Binance.
Wall Street, Saylor with his infinite buy tweets, El Salvador and its volcano bonds, the US ETF approval — and the game changed, everyone heard about it one way or another. That’s damned important! You’re NOT the bringer of news.\ \ Suddenly, it wasn’t grassroots anymore; it was headlines, hype and game-theory. As predicted by so many in the space.\ Fine, whatever, it's progress or something else, but we as bitcoiners need to adapt to that reality.\ Some adaptations will also cause us to put energy elsewhere than before.\ What worked in 2012 or 2016, might not work anymore after 2024.\ ”We bitcoiners route around problems.” Right?
You didn’t need new people to create an account, or be part of a ‘squad’ or team, you certainly didn’t need them to sell merchandise. You just showed them bitcoin’s inner workings.\ \ Bitcoin was the marketing, the engine, the product and the goal. Bitcoin was the core. Just like digital communication was the core of the earliest internet enthusiasts. The magic of sending a text into the network, and through clever routing, someone thousands of miles away could read it almost immediately, that was the magic, the core.
Sending value with bitcoin has that same magical way, immutable, uncensored, unconfiscatable, with proven digital scarcity and forced honesty.
Nowadays we have so-called orange-pillers.\ They’re trying to spread those values. Or so they should..
They didn’t get the memo on Bitcoin becoming more commonly known apparently, and if they did, their lust for dopamine has long replaced that with their urge to get people to install a lightning wallet. It’s sometimes rather disturbing to see this Orange Pill’ing play out.
They’re out there, like they’re stuck in 2013. But they’re usually not from 2013 at all, more like class of 2020’ish. Not that it matters, they’re still living in the illusion that there are people out there that didn’t hear of bitcoin and that THEY and THEY alone can save these poor souls.\ After 2018 it’s safe to say that that’s not the case.\ I’ll repeat that for the die-hard orange-piller: they do not need you to hear about bitcoin.
These Orange Pillers have another kind of magic happen:
While they’re winning over new souls into bitcoin, one barber, taxi driver and babysitter at a time, they get the small electric charge in their brain that tells them their wealth, their (and their holding's) value will go up somehow. They’re also desperate to make some kind of connection with other bitcoiners, and while they lack that connection, they try to find (or make) new bitcoiners around them.\ This approach might have worked in the past, but things are different now. You’re usually talking to people who you try to convince of something they’ve already rejected (often harshly rejected) or never will care about .\ Most people, do not give a damn about inflation or how that came to be. Certainly when they’re doing their job.\ \ It’s like someone shoving the book of a cult under your nose and trying to convince you it’s going to save your life. You’re not open to it, neither are most of the Orange pill targets to your bitcoin gospel.\ Orange Pillers don’t see how the very people they try to convince today weren’t “in it” for a variety of (good for them) reasons. Unlike in the old days, where people’s natural state was “not heard of bitcoin”; since it was new, and people genuinely didn’t learn about it or read into it.\ That’s however, not the case today. That taxi driver? He heard about bitcoin. Be sure.
Such new people today, are almost non-existing, they either bought some long ago, got rekt trading shitcoins and stayed away.\ That, or they found it all a bit too “iffy” (thank you mainstream media) and will politely hold back from not yelling to your face, “I don’t care about that Bitcoin stuff!”.\ They know it’s some form of money or value, they know it exists. Which makes orange pillers the bringers of old news to the bottom of the barral.\ They might get a “hit” now and then of course. But even then, your impact is neglectable in a world that rewards cowardice and short term greed. You’re too late. You don’t scale. And it doesn’t matter.
Since 2020, it has shifted from genuinely introducing people to bitcoin to just "spreading it for the sake of spreading it."\ It looks more and more like an old lion, pacing back and forth in a cramped cage at an old ZOO, restless and frustrated.\ There’s just empty repetition.
The mental breakdown of orange-pilling
\ Let’s look a little further into the act of orange pilling.\ \ It's not like a 1990s hacker type showing a brand new Hayes -compatible modem to his buddy and trying to get a connection going to a local Point of Presence to get internet access.\ \ It’s more like showing your holiday pictures to an uninterested family member. All to get the dopamine hit, the ‘aha moment’ out of someone is now your own ‘aha got someone new’ moment. Like an addict looking for that next high.\ \ You want them to get the app, get some sats and feel the same feeling you have. While they’re worrying about cleaning a table for example, or getting your bill.\ \ This “badge of honor” of Orange Pilling someone is that little shot of dopamine many people need (especially in group) to feel validated.\ The real feeling has everything to do with social conformity1 and the involved brain areas that get stimulus shots and increased activity.2\ \ Above that, for the sake of the mental reward, some people go further down the social boundaries. That’s why orange pilling, often comes across as pushy, unnatural and/or annoying.\ It’s because it’s basically an activity with all the neuro stimulus of an addiction, or done as an ego boost.
Math based
On top of all of that. If you do the math on it the whole action becomes even more ludicrous.\ \ The math in the early days of bitcoin was simple: there was exponential expansion of the number of bitcoiners.\ Purely for bitcoin, the growth in numbers is still going strong, but the percentage has now naturally been flattened out because of media coverage, scams that trick people into other stuff and the close to impossible way to scale the onboarding from a person to person level to larger scales (there are apps doing a good job however, but even then it spread under former bitcoin users or people already in the know on some level, like former shitcoiners).\ \ So even at the rate of trying to orange-pill let’s say 10 people per week (many bitcoiners don’t even tàlk to 10 people a week, let alone convince them to use bitcoin).\ \ When hypothetically 50% of these people (not unusual with word of mouth recommendations) actually install the app you recommended, and we take also a high percentage of 10% actually do a regular buy of bitcoin after installing any of these apps (Strike or Blink or any other).\ \ Given that hypothetical high rate of 10 people a day plus the conversion rate, it would take approximately 200 weeks, close to four years (pun intended) to reach 2000 people as a critical mass that actually installed and used the bitcoin app.\ \ If these 2000 people all buy for about 1000$ worth of bitcoin each, they’ll be good for about 2 million dollars in bitcoin buys over a four year period.\ Even if you take very, very optimistic statistics this, you’ll get a close to zero impact, safe for the occasional big shot you might encounter and converts into a mini-Saylor, or the occasional person you might have saved a few thousand dollars (because they all keep thinking in fiat terms anyway).\ \ But on the other side, people with +100 million dollars to spend will surely have advisors and in-house knowledge, to not having to to rely on your sorry ass explaining bitcoin or installing Wallet of Satoshi on their phone or something.\ \ That’s all peanuts. It’s futile. And you’re fighting an honorable battle from 11 years ago.
### \ Why
I can't grasp why so many people keep doing this the way they do.
Orange-pilling mostly works when the price is going up anyway, unfortunately.
However, when BTC’s up 15% in a week, everyone’s a genius and your coworker suddenly can be all ears about “sound money” and future price gains.
When it’s crashing or flat? Good luck, nobody cares among the normies, unless the “orange-pillee” (the target) has their own ulterior motives for listening (like getting someone to at least give them some attention in any form).
And by the way, to come back to these taxi drivers you try to convince… many taxi drivers already had their share of die hard bitcoiners in their car, and got the explanation. Some of them even act like total noobs probably to get some sats out of your orange pilling wallet. They’re good at playing dumb, trust me.\ \ Do you really think a taxi driver in let’s say Lugano, Amsterdam or Prague didn’t already know bitcoin before you tried to convince him to accept it? You’re not the first. At all.
Most of all, you interact with people while they’re doing their job. You’re actually interfering with their work. When a waiter in a fully booked restaurant has to halt his word and listen to you explaining how to install a lightning wallet on their old iphone that’s almost out of battery, you’re losing anyway.\ They might listen, they might even be pestered to the point they’ll install the damned app. And what do you win or achieve?\ A sparkle in your brain that says “you’re such a cool bitcoiner”?\ Then… after what’s usually a painful few minutes going through a horrible counter-intuitive interface, you get them 5000 sats or whatever over to them.
Oh and adding things like “Hey man, keep these sats for at least 4 years, it will go up in price” is just rotten as well. Just give the people a decent tip and leave. You’re not doing anyone a favor.
When the moment’s there ànd some people are clearly open to it, thèn you might add some info. Point them to an easy to use non KYC app (if there is such a thing).\ But even then, just letting someone know you want to pay in bitcoin, should be enough, WHISPER bitcoin.\ They don’t need your pushy sales pitch on top of the daily struggles they face in hospitality and retail jobs.\ \ The squads
An example,... I saw this crew, let’s name them the “Re-play” squad, they’re all wearing blue hats and have a few flyers with them from a marketing company which managed to put them to some good use at a very low expense rate.
This image is still stuck in my head, some random European country during late summer time — local Bitcoiners, along with some counterparts from other countries. The real “we’re the future” types.
Sitting on the floor at a Bitcoin party, rolling “funny cigarettes” passing a lighter, chatting and laughing about how they orange-pilled some dude in a bar.
 “Yeah, man, I showed him how to set up a Lightning wallet in a few minutes, he’s in!”. Then taking a big puff.\
Except here’s the punchline: the guy wasn’t “in” he was probably just some horny schmuck trying to get into the pants of a woman Bitcoiner in the group, who’d flashed her … QR code at him.
“Yeah, man, I showed him how to set up a Lightning wallet in a few minutes, he’s in!”. Then taking a big puff.\
Except here’s the punchline: the guy wasn’t “in” he was probably just some horny schmuck trying to get into the pants of a woman Bitcoiner in the group, who’d flashed her … QR code at him.They’re all proud, they’re all high, they all belong to a group now … and they’re convinced they’re conquering the world one wallet at a time (they don’t do the math on that, neither should they,… ignorance is bliss).
Doing good for bitcoin has been transcended into an egotrip, and the short-lived kick in the orbitofrontal cortex3 for “doing something”, it’s the filling of a lingering emptiness.\ \ The same people move around like they’re an anthill, reminiscent of the hippie communes, until they’ve returned to their misery at home, knee deep in sorrows of the fiat world. As is the orange pilled person by they way, who’s life won’t be helped by a few sats and yet a new app on their phone. An app they’ll hardly use, unless they start to bond with the other bitcoiners in the area.
These people you target already have had all chances in the world to learn about bitcoin but are too far gone to care.\ Podcasts, books, family members that are into bitcoin, or whatever blog or online service… even the biggest shitcoin casino’s only have rather decent guides and basic explanations. There are excellent educational apps like yzer.io4 as well as the excellent lopp.net5 website by Jameson Lopp.
Convincing people one-by-one doesn’t work anymore—it’s inefficient and outdated since the price surges, media coverage, and ETF launches. Even if some are open to it, it’s a futile, unscalable solution of dread, working indirectly for the benefit of the Wall street types or some shitcoin casinos (where most “new coiners” end up).
Orange pillers, also never can “read the room”. The crew in a busy restaurant or bar isn’t waiting for any explanation about UTXOs or custodians from you!
Even if you'll hit machine-like numbers of onboarding twenty people a day (By then, you’ll need to avoid being labeled the local bitcoin village fool in your community) and assume they're all pure bitcoiners afterwards.\ Which won’t happen either as any incentive of the orange pilled people is clearly nòt long-term thinking; otherwise they would have onboarded you some 8 years ago!\ \ People are extremely lazy, and the general public usually has an attention span of about 8 seconds at best6.\ Back in the early days, you could sit people down and show another tech person for hours on end how to work with bitcoin, now more than a decade later, you have about 5 to 60 seconds tops. (most lightning wallet’s onboarding sequence easily takes 2 tot 5 minutes)
To further convince yourself how pointless Orange Pilling is today: go out and watch people on a public transport vehicle: they scroll and swipe through TikTok and Instagram. You’ll notice they’re swipe-apes, there’s no substance or reliable source of bitcoin buying power there, no bitcoin innovation will come from them, and no philosophical insights will ever be ignited in their buy-the-next-cool-sneakers-now brain. They’re not a target audience. They’re the all singing and all dancing crap of the world. They’re not convinced, Inconvincible and inconvertible.
Meanwhile, no substantial steps have been made for bitcoin, even if you get them to install that app you so desperately want them to have. Neither can you expect the no-coiners or pre-coiners (god I hate that word, it sounds kinky somehow) to do anything for bitcoin, as the gap between them and the actual positive impact they could have is too wide.\ It costs time, studying and experimenting. While these people excel at thing like: shopping, watching dime-a-dozen garbage series on Netflix, watching social media posts that don’t challenge them, and eating take-out food while score some drugs.\ \ So… to conclude the story about that dude in the bar which was so carefully orange pilled by our “Re play” squad members, he probably traded his sats for a beer by now (although that demands some form of effort in finding a recipient that has beer and wants to trade it for sats, which is unlikely) , more likely he forgot about the app altogether or he’s trading shitcoins to “make more money as greed that sets in. And he probably got that woman’s telephone number, to “talk about those bitcoins” later on at his crappy rental apartment right above a shoarma restaurant.\ \ The phrase “everyone’s a scammer” includes people who pretend to care about bitcoin just to get something out of it. Even a complete newbie or shitcoin fan will fake interest in bitcoin to seem legit. I’ve watched it happen.
Orange-pilling: the good, the bad, and the ugly
\ So onboarding devolved into this whole subculture of failure, and started to manifest itself over time as a empty motion, a series of must-do things.\ \ The Pavlovian response whenever someone is a walking opportunity for accepting bitcoin (certainly in any bar, restaurant or hotel), results in the foaming at the mouth to get them onboarded on some app or wallet.\ It’s so pointless I actually feel ashamed when I’m in a group that starts to hawk and push their lightning wallets onto unsuspecting people who just want to do their job.\ (and Lightning Wallets are so crappy to onboard people with, it’s mind numbingly stupid)\ \ To my amazement, there are actually a lot of bitcoin holders, or people that claim to be into bitcoin (especially in a bull market) who still pester random people with this kind of behavior.\ \ Some of these are trying to get them to click a referral link from a venture capital firm, in return for a few bucks (incentives these days are needed to get the groundswell going apparently), or worse even, make them install some non-custodial wallet and run into the brick wall of initial on-chain setup fees and then run away like a complete loser because they’re too cheap to fork that initial on-chain fee out for the people they’ve tried to onboard. “Yeah, like, you can buy these 100.000 sats online later if you like and thèn you can have this wallet, but at least it’s not custodial eh.. uh … My buddies are over there, I’ll see you later”.\ \ When you start to observe these people in the wild, it’s like watching a gaze of raccoons going through some neighborhood’s trash cans at night (without the playful conviction).\ Fascinating, if you’re into low-budget wildlife documentaries.
 Gaze of raccoons looking for a QR code
Gaze of raccoons looking for a QR codeIF you still want to onboard someone, point them to the right info at the right time (when thèy ask you).\ I call it “Bitcoin whispering”. #BitcoinWhispering
### \ \ Let’s quickly look at the three sort of Orange Pillers:
The pushy ideologists: The most annoying of the bunch, but at the same time the ones who mean really well. I sometimes feel sorry for them.\ No one’s safe from them. Hairdresser? “You should accept Bitcoin, man.” Bartender? “Credit cards are no goog, why not use Lightning?” Taxi driver? “Ever heard of Lightning? I can tip you in Bitcoin, man.” They’re not educating; they’re feeding their ego and their need to spread the word.
The referral grifters: More damaging to Bitcoin than shitcoiners in my opinion. They don’t care about Bitcoin’s properties; it’s just a slot machine for them. And if they understand, their short term greed and social circle dependency makes them go for spreading the word of a middleman company.\ “Sign up with my link, bro, stack those sats!”\ Their goal? A kickback and the next pat on the back from their miserable squad members.
The show-offs: The worst. They don’t know anything themselves but love the spotlight. “Yeah, I got my barber stacking sats!” Yet when it’s time to actually help onboard a business, they’re nowhere to be found. All talk, no substance. They achieve a small social circle of noob bitcoiners surrounding them, with most of them going through the shitcoin-phase shortly after or swapping off-the book gains. They’re not good for bitcoin and usually don’t stay that long anyway.\ \ The world doesn’t need your savior complex.
After the second half of 2024 if someone wanted in, they’ll find a way. And if they ask a Bitcoiner for help? Sure, we’ll point them in the right direction — most of us will help when asked (gladly so).\ But this idea that you, oh mighty orange-piller, need to swoop in and “save” people is more about you than about bitcoin.
Create a good, nice, safe (protected from scams!) environment or way to get people to the info and the other way around.\ Be there when people can ask questions, lead by example, make it work and show it. If an app is easy to use, makes sense and has no friction, then people will come. If you’re pestering people and hounding them into liking something that’s so far removed from their reality (fiat-world), they’ll be scared away and not return.
### \ Conclusion
Although I miss the old days, I also realize they ain’t coming back — when orange-pilling was just sharing a crazy new idea with someone who was open to it.
The Orange pilling space is now too keen for a large part to shove their bitcoin app in someone’s face, be it in dollars, a few sats or a discount on their next transaction fee at some multi level marketing middleman.\ This onboarding is also strangely in parallel with what shitcoiners or the most vile fiat companies do, OP’ers are too desperate for relevance so they often don’t look at the value proposition of bitcoin anymore. Filling their void got the upper hand.\ Their shot of feelgood moments needs to be filled.\ While there’s close to no impact to gain anymore on one-one-one convincing.\ The lesson to save in bitcoin, is usually lost on the people anyway, which was the last reason left to do it.\ \ Be there when people ask for help on bitcoin, build stuff, but stop the aggressive orange-pilling, it serves no purpose anymore other than your dopamine hit and a token feeling for “doing something”, and it’s a sad addiction.
Therefore in 2025, orange-pilling has become of a full-blown mental issue.
by AVB
if you like my writings : tip here
\ Footnotes:
https://journal.psych.ac.cn/xlkxjz/EN/Y2015/V23/I11/1956
https://www.frontiersin.org/journals/behavioral-neuroscience/articles/10.3389/fnbeh.2019.00160/full
https://en.wikipedia.org/wiki/Orbitofrontal_cortex
https://yzer.io/
https://lopp.net
https://theweek.com/health-and-wellness/1025836/tiktok-brain-and-attention-spans
Share
TopLatest
-
 @ 8ff74724:5eedde0e
2025-03-21 13:38:45
@ 8ff74724:5eedde0e
2025-03-21 13:38:45And another.
-
 @ 8ff74724:5eedde0e
2025-03-21 13:33:32
@ 8ff74724:5eedde0e
2025-03-21 13:33:32This is a test.
Of a flycat article.
-Satoshi
-
 @ 58537364:705b4b85
2025-03-21 12:37:28
@ 58537364:705b4b85
2025-03-21 12:37:28เสียงตะโกนของ “อิทัปปัจจยตา”
ทุกอย่างตะโกนคำว่า “อิทัปปัจจยตา” อยู่ตลอดเวลา
“ท่านทั้งหลายนั่งอยู่ที่นี่ แต่ไม่ได้ยินเสียงตะโกนที่ดังลั่นไปหมดของธรรมชาติว่า ‘อิทัปปัจจยตา’ เสียงตะโกนของอิทัปปัจจยตา คือการร้องบอกร้องตะโกนว่า ‘เพราะมีสิ่งนี้เป็นปัจจัย สิ่งนี้จึงเกิดขึ้น’ หมายความว่า ท่านต้องดูลงไปที่ทุกสิ่งที่อยู่รอบตัวเราในเวลานี้ว่า ทุกสิ่งกำลังเป็นอิทัปปัจจยตา หรือเป็นไปตาม ‘กฎอิทัปปัจจยตา’”
ต้นไม้ต้นนี้มีความเป็นไปตามกฎอิทัปปัจจยตา ไม่มีอะไรมาต้านทานได้ ถ้าเราเข้าใจข้อเท็จจริงที่กำลังเป็นอยู่กับต้นไม้ เราจะเหมือนได้ยินมันตะโกนบอกว่า “อิทัปปัจจยตา” ไม่มีอะไรมากไปกว่านั้น มันเพียงบอกว่า “เมื่อมีสิ่งนี้เป็นปัจจัย สิ่งนี้จึงเกิดขึ้น”
ต้นไม้ไม่ได้หยุดเพียงเท่านั้น มันมีการเปลี่ยนแปลงเกิดขึ้นเรื่อยๆ ใบไม้ทุกใบก็บอกอย่างนั้น คงเป็นเสียงที่ดังเหลือประมาณว่า ใบไม้ทุกใบร้องตะโกนว่า “อิทัปปัจจยตา”
ผู้มีปัญญาและเข้าใจหัวใจของพระพุทธศาสนา จะไปนั่งอยู่ที่ไหนก็ได้ยินเสียงตะโกนว่า “อิทัปปัจจยตา” สนั่นหวั่นไหวไปหมด นี่พูดถึงแค่ต้นไม้ต้นเดียว ถ้าเป็นต้นไม้จำนวนมากก็เป็นเช่นเดียวกัน
เมื่อมองไปที่ก้อนหิน ก้อนหินก็เป็นเช่นเดียวกัน อนุภาคของมันเปลี่ยนแปลงอยู่ตลอดเวลา ก้อนหินที่เราเห็นอาจเกิดขึ้นมาเมื่อหลายพันล้านปีมาแล้ว จนมันแตกสลายและถูกทำให้มาอยู่ตรงนี้ มันจึงกล่าวว่า “อิทัปปัจจยตา” เพราะมีสิ่งนี้เป็นปัจจัย ฉันจึงมานั่งอยู่ที่นี่
ทุกอย่างตะโกนคำว่า “อิทัปปัจจยตา” ตลอดเวลา
- ต้นไม้ เม็ดกรวด เม็ดทราย มด แมลง สัตว์ต่างๆ รวมถึงมนุษย์เอง
- แม้แต่ร่างกายของเราเองก็ตะโกนบอกถึงอิทัปปัจจยตา
แม้เราจะเคยได้ยินคำว่า “อนิจจัง ทุกขัง อนัตตา” อาการของสิ่งเหล่านี้ยิ่งสะท้อนถึงอิทัปปัจจยตาอย่างชัดเจน
ดังนั้น เราต้องทำความเข้าใจจนซึมซาบอยู่ในใจ จนรู้สึกว่าไม่ว่าเราจะมองไปทางไหน ก็เห็นถึงภาวะของ อิทัปปัจจยตา ได้ยินเสียงของมัน หรือแม้แต่สัมผัสผ่านการดมกลิ่นและลิ้มรส
เมื่อเข้าใจสิ่งนี้ จะสามารถเรียกผู้นั้นว่า ‘เป็นพุทธบริษัทผู้เห็นธรรม’
สามารถเห็นกิเลสและทุกข์ แล้วป้องกันหรือกำจัดกิเลสและทุกข์ให้น้อยลงไปได้มากทีเดียว— พุทธทาสภิกขุ
(จากหนังสือธรรมบรรยาย “อิทัปปัจจยตา” หน้า 131–133)
อิทัปปัจจยตา: กฎอันเฉียบขาดตลอดจักรวาล
https://image.nostr.build/abc776213ec6371da681aa5766390f67e1ae97dc1d7157774e02eb93d1f21f56.jpg
“อิทัปปัจจยตา” เป็นกฎของธรรมชาติที่ไม่อาจเปลี่ยนแปลง
คำว่า “อิทัปปัจจยตา” อาจเป็นคำที่ไม่คุ้นหู แต่ขอให้สนใจ เพราะมันเป็นกฎของธรรมชาติที่แน่นอนตลอดจักรวาลและอนันตกาล
- สิ่งนี้เกิดขึ้น เพราะมีเหตุปัจจัยนี้
- สิ่งนี้มี เพราะสิ่งนี้มี
- ดวงอาทิตย์ ดวงจันทร์ ดวงดาว ทุกอย่างล้วนเกิดขึ้นตามกฎของ “อิทัปปัจจยตา”
เมื่อทำสิ่งนี้ มันต้องเกิดสิ่งนั้นขึ้น
เมื่อทำสิ่งนี้ มันต้องเกิดทุกข์ขึ้น
เมื่อทำสิ่งนี้ มันต้องเกิดความดับทุกข์ขึ้นนี่คือปรมัตถธรรมอันสูงสุด ไม่มีสัตว์ ไม่มีบุคคล ไม่มีพระเจ้าที่เป็นตัวตน
มีเพียง กฎอิทัปปัจจยตา ที่เป็นกฎของธรรมชาติอันเฉียบขาดพระพุทธเจ้าตรัสรู้ ก็คือ ตรัสรู้เรื่อง “อิทัปปัจจยตา”
เรามักเรียกกันว่า “ปฏิจจสมุปบาท” ซึ่งหมายถึงเฉพาะเรื่องทุกข์ของสิ่งมีชีวิต แต่ “อิทัปปัจจยตา” กว้างขวางกว่านั้น ทุกสิ่งไม่ว่าจะมีชีวิตหรือไม่มีชีวิตล้วนตกอยู่ใต้อำนาจของกฎนี้
กฎของอิทัปปัจจยตาไม่ใช่ฝ่ายบวกหรือฝ่ายลบ
- ไม่ใช่ Positive
- ไม่ใช่ Negative
- เป็น “สายกลาง” ของมันเองคนเราต่างหากที่ไปบัญญัติว่า “นี่คือสุข นี่คือทุกข์ นี่คือแพ้ นี่คือชนะ”
แต่แท้จริงแล้ว ทุกอย่างเป็นไปตามอิทัปปัจจยตาความเข้าใจในปรมัตถธรรมต้องไปให้ถึงจุดนี้
- จนไม่มีสัตว์ ไม่มีบุคคล
- ไม่ใช่สัตว์ ไม่ใช่บุคคล
- แต่ก็ไม่ใช่ว่าไม่มีอะไรเลย และก็ไม่ได้มีสิ่งใดที่ตายตัว
ทุกอย่างเป็นเพียง กระแสของการเปลี่ยนแปลงและปรุงแต่ง
เมื่อเข้าใจถึงจุดนี้ จึงจะรู้อย่างที่พระพุทธเจ้าท่านรู้ และดับทุกข์ได้
นี่คือสิ่งสูงสุดที่ต้องเคารพ คือ กฎของ “อิทัปปัจจยตา”— พุทธทาสภิกขุ
(จากธรรมบรรยายประจำวันเสาร์ ภาคอาสาฬหบูชา ชุด “ฟ้าสางระหว่าง 50 ปีที่มีสวนโมกข์” ครั้งที่ 19 เมื่อวันที่ 13 สิงหาคม 2526 ณ ศาลามหานาวา สวนโมกขพลาราม จากหนังสือ “ธรรมานุภาพ”) -
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ c88809a0:a46266e2
2025-03-21 11:00:01
@ c88809a0:a46266e2
2025-03-21 11:00:01Introduction
UX Research is currently being conducted on the needs of activists. There is still much to learn in this area and we are at just the very beginning. These observations and learnings will change over time. Activists are championing freedom all over the world and if we build communication and financial tools for them that solve real problems which they are facing we will enable them to continue to do the valuable work they are doing.
We want to understand their needs, their problems and their fears, so that when we build solutions we ensure that it is fulfilling the primary goals of the person using it.
Fundamentally this is with the ethos of putting the humans at the center of everything we build.
The below is written for you the builders. And for you the activists.
We hope this information empowers you and that it will initiate an open dialogue between activists and builders. Where knowledge is open and transparent to everyone. Where you feel free to ask questions. Where you feel empowered. Where we all continue to collborativley build freedom technology.
Background
The below data was collected by conducting an in person workshop with a group of activists and Nostr developers. During this workshop we used the Jobs to be Done framework to uncover the UX needs of activists. This workshop involved approximately 20 people. 11 of which were activists or individuals who are activists as well as builders.
This write-up covers 3 main areas:
Observations: What have we observed?
a. 5 Areas of communication
What are the 5 main areas in which activists are communicating?
b. Fears
What are the main fears of activists when using a product?
c. Jobs to be done
What are the main jobs that activists expect the product to perform when they are using it.
Learnings: What can we learn based on the observations?
Observations

a. 5 Areas of communication
There are 5 main areas in which activists are communicating. They are communicating with:
1. Co-workers
Daily communication with team members, peers, and fellow activists organizing initiatives.
2. Family
Activists communicate with family members and are concerned about this communication being surveilled.
3. Funders
Communication with sponsors for fundraising. When communicating with funders, activists face challenges with CRM systems that require personal contact information.
4. General Public
They communicate with the broader public for youth education, crisis management and event announcements. They rely heavily on social media platforms (particularly Meta-owned) and these have challenges such as algorithmic limitations, content moderation, and platform reliability.
5. Journalists
They communicate with journalists for political mobilization.
Political mobilization is the process of organizing and motivating people to participate in political activities.
This data is based on 11 entries. Of the 11 entries the image below indicates the split showing the entries with the highest number to the lowest.
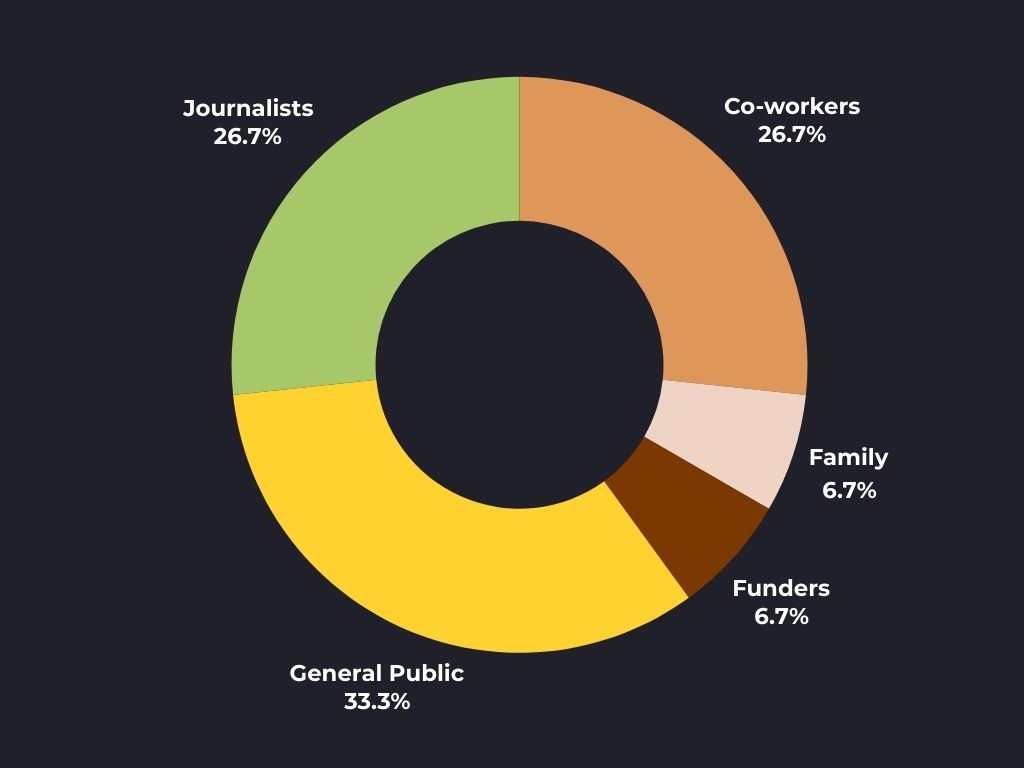
b. Fears
The biggest fears that activists have based on the data are the following:

1. State surveillance
Activists are deeply worried about their governments watching and interfering with their work.
- They're concerned that platforms which they currently use will hand over their data to authorities.
- That their accounts might be labeled as "extremist," and that their content could be taken down without warning.
- They live with constant anxiety that their communications are being monitored.
2. Security issues
There's a deep distrust of mainstream communication platforms.
- They worry that their personal information isn't truly private.
- They dislike using phone numbers to sign up (which can expose their identity).
- Feel frustrated that when security problems happen as the platforms rarely help or respond.
3. Communication reach
Activists face a frustrating choice: they can either use secure apps that few people use, or popular apps that aren't secure.
- They worry about only reaching people who already agree with them (being in an "echo chamber"), while struggling to spread their message to a wider audience.
- When they do try to reach more people, their content often gets hidden or suppressed by platform algorithms.
4. Access
Basic technical problems cause major headaches. Slow internet makes secure tools hard to use and some tools don't work at all without good internet. They worry about losing important information and struggle with tools that don't work reliably in their locations.
5. Personal safety
Beyond their own safety, activists worry deeply about protecting everyone they communicate with - their families, fellow activists, and journalists. They face organized attacks from fake accounts and bots that spread lies about them, and they're constantly trying to balance doing their work effectively while keeping everyone involved safe from harm.

c. Jobs to be Done
The following are the jobs that activists need a product to do. A job can be described as a task that a user expects to perform when using the product.
1. Surveillance
- When operating in a politically hostile environment, I want to communicate without leaving digital traces, so I can protect my network from state surveillance.
- When my platform has been compromised, I want to quickly secure and recover my account, so I can continue working without losing data.
2. Reach
- When sharing critical information about protests, I want to reach people beyond my echo chamber, so I can reach a broader public.
- When coordinating with multiple activist groups, I want to securely communicate with these groups so I can organize events without information being lost or scattered.
3. Connectivity
- When working in areas with poor internet connectivity, I want to maintain secure communication, so I can continue organizing even when having low bandwidth.
- When my team loses access to their devices, I want to ensure they can safely recover their accounts and data, so we can continue working.
4. Personal safety
- When sharing sensitive political content, I want to protect the identity of my sources and collaborators, so I can prevent attacks against them.
- When facing coordinated disinformation attacks, I want to maintain content integrity and verification, so I can counter false narratives.
5. Organized
- When coordinating time-sensitive activities, I want to ensure messages are received and read, so I can respond quickly to emerging situations.
- When managing multiple activist groups, I want to organize conversations and files logically, so I can quickly find and reference past communications.
5. Crisis access
- When government crackdowns occur, I want to quickly share safety information, so I can protect community members from harm.
- When platforms are being blocked or monitored, I want to maintain alternative communication channels, so I can continue to communicate with my network.
6. Community Building
- When growing our movement, I want to safely onboard new members, so I can scale our organization while maintaining security.
- When building trust in our network, I want to be able to verify new members, so I can prevent infiltration by hostile actors.
7. Information Preserving
- When facing potential platform shutdown, I want to preserve our communication history and documents.
- When sharing sensitive documents, I want to control who can access and forward materials, so I can maintain information security over time.
Learnings
Now we dive in to what we have learnt based on the things we have observed.
1. Security vs. Reach
Activists face a tricky choice when communicating. They can shoose to use main stream tools which are not secure but have more reach, or use more secure tools which less people are familiar with. Ultimately they are stuck using platforms on a daily basis which they don't trust.
2. Different Audience Needs
Some activists are communicating with different groups these could be; team members, family, funders, public, journalists, it is possible that each of these groups require different strategy approaches.
3. Government Monitoring
Activists worry about government surveillance and this drives many of their communication decisions.
4. Technical Barrier
Poor internet and technical problems make it hard for them to use secure tools even when they are available.
5. Growing Safely is Hard
Adding new members to grow the activist movement is tricky because this makes is difficult for them to keep the group secure from infiltrators.
6. Record-Keeping Risks
While activists need to keep a record of documents and some communication, saving these also creates evidence that could be used against them.
7.Staying Operational in Crisis
Activists need ways to recover accounts and continue working when platforms are shut down or devices are taken.
As mentioned above there is much more to learn about the UX needs of activists. We will continue to dive deeper into their user needs and share them openly here with you.
-
 @ b5d34eed:a7475cbf
2025-03-21 10:12:21
@ b5d34eed:a7475cbf
2025-03-21 10:12:21Introduction
In an era of increasing surveillance, data breaches, and corporate control over digital communication, privacy-focused tools have become essential. ProtonMail, a secure and encrypted email service, stands as a stronghold for those seeking privacy in their online correspondence.
At the same time, Nostr, a decentralized social networking protocol, is revolutionizing how people connect without relying on centralized platforms. Together, ProtonMail and Nostr create a powerful combination for individuals who prioritize security, anonymity, and freedom in their online interactions.
This article explores the ProtonMail application suite, its relevance to privacy, and how it aligns with Nostr’s decentralized approach to communication.
What is ProtonMail?
ProtonMail is an encrypted email service founded in 2013 by scientists at CERN, the European Organization for Nuclear Research. Unlike mainstream email providers such as Gmail or Outlook, ProtonMail does not collect personal data, does not track users, and ensures end-to-end encryption for emails.
Key Features of ProtonMail
End-to-End Encryption: Ensures that only the sender and recipient can read messages.
No Personal Information Required: Users can sign up without providing identifying details.
Open-Source Cryptography: Transparency in security protocols, allowing community audits.
Swiss-Based Privacy Laws: ProtonMail operates under Switzerland’s strict data protection regulations, shielding it from intrusive government surveillance.
Self-Destructing Emails: Allows users to send messages that automatically expire after a set time.
ProtonMail’s security-first approach makes it an ideal choice for activists, journalists, and privacy-conscious individuals who want to communicate without fear of surveillance or data mining.
ProtonMail Application Suite: A Holistic Privacy Ecosystem
Beyond encrypted email, Proton has expanded into a full suite of privacy-focused tools:
ProtonMail – Secure, encrypted email with zero access to user data.
ProtonVPN – A no-logs VPN that protects internet traffic from ISPs and surveillance.
ProtonCalendar – An encrypted calendar that ensures event data remains private.
ProtonDrive – Secure cloud storage for files with end-to-end encryption.
ProtonPass – A password manager that encrypts credentials and autofills login details safely.
This ecosystem provides a seamless experience for those looking to secure not just their emails but also their browsing, file storage, scheduling, and password management.
Why ProtonMail is a Must for Privacy-Conscious Users
-
End-to-End Encryption: Unlike Gmail and Outlook, ProtonMail ensures that even ProtonMail itself cannot access your emails.
-
No IP Tracking: Protects against metadata collection, preserving user anonymity.
-
Zero Access Architecture: Even Proton employees cannot read your emails.
-
Decentralization-Friendly: Complements Nostr’s ethos of distributed, private communication.
ProtonMail’s strict security measures align well with the values of decentralization and censorship resistance, making it a natural ally to protocols like Nostr.
ProtonMail and Nostr: A Privacy Power Duo
Nostr is an open-source, censorship-resistant social networking protocol that allows users to communicate without relying on a centralized platform. Unlike Twitter, Facebook, or even Mastodon, Nostr operates through decentralized relays, making it nearly impossible to shut down or control.
ProtonMail and Nostr share a fundamental philosophy: empowering users with control over their own data. Here’s how they complement each other:
- Secure and Private Communication
Nostr messages are cryptographically signed and relayed across decentralized nodes. ProtonMail, with its encryption-first approach, ensures that even off-platform communication remains private.
- No Central Authority
ProtonMail is protected under Swiss privacy laws and is not beholden to big tech surveillance. Nostr operates without central servers, preventing a single entity from controlling conversations.
- Protecting Metadata
While Nostr encrypts direct messages, email remains a critical form of communication for many users. ProtonMail’s metadata protection ensures that senders, recipients, and message content remain shielded.
- Enhanced Security for Activists and Journalists
Nostr is popular among privacy advocates, activists, and whistleblowers due to its resilience against censorship. ProtonMail adds an extra layer of protection for sensitive information shared over email.
By using ProtonMail and Nostr together, users can create a robust digital identity that is censorship-resistant, private, and secure.
How to Get Started with ProtonMail
If you’re ready to enhance your privacy, setting up ProtonMail is simple:
-
Sign Up: Visit ProtonMail.com and create a free or premium account.
-
Set Up Your Inbox: Customize security settings and enable two-factor authentication.
-
Explore Proton’s Suite: Utilize ProtonVPN, ProtonDrive, and ProtonPass for full privacy coverage.
-
Integrate with Nostr: Use ProtonMail for private communication outside of Nostr’s relay-based messaging system.
ProtonMail offers free plans, but for advanced security features, encrypted storage, and custom domains, premium plans are available.
Conclusion: A Privacy-First Digital Future
In a world where data privacy is constantly under threat, services like ProtonMail and Nostr pave the way for a more secure and independent digital future. Whether you are a journalist, activist, or simply someone who values personal privacy, these tools provide the protection you need.
By combining ProtonMail’s encrypted email with Nostr’s decentralized networking, users can take control of their communications, free from surveillance and corporate interference.
Now is the time to reclaim your digital privacy—sign up for ProtonMail and explore Nostr to experience a censorship-resistant, secure way of communicating.
Further Resources
ProtonMail Official Website
ProtonVPN for Secure Browsing
Nostr Documentation and GitHub
Privacy Guides for Online Security
Are you using ProtonMail and Nostr together? Share your thoughts on how these tools empower you in the comments below!
-
-
 @ 7d33ba57:1b82db35
2025-03-21 09:56:28
@ 7d33ba57:1b82db35
2025-03-21 09:56:28Seville
Seville (Sevilla) is one of Spain’s most vibrant and historic cities, known for its stunning Moorish architecture, flamenco dancing, tapas culture, and rich history. As the capital of Andalusia, it offers a perfect mix of tradition and modern charm.
🏛️ Top Things to See & Do in Seville
1️⃣ The Royal Alcázar of Seville
- A breathtaking Moorish palace with stunning gardens, intricate tilework, and grand courtyards.
- Famous for its mix of Islamic, Gothic, Renaissance, and Baroque styles.
- Tip: Book tickets in advance to avoid long lines!
2️⃣ Seville Cathedral & La Giralda
- The largest Gothic cathedral in the world, home to Christopher Columbus' tomb.
- Climb La Giralda Tower for panoramic views of the city.
3️⃣ Plaza de España
- A majestic semi-circular plaza with bridges, fountains, and detailed ceramic tilework.
- Perfect for photos, boat rides, and people-watching.
4️⃣ Metropol Parasol (Las Setas)
- A modern wooden structure in the city center offering great rooftop views.
- Best time to visit: Sunset for golden hour photos!
5️⃣ Barrio Santa Cruz
- The old Jewish Quarter, filled with narrow alleys, hidden courtyards, and charming tapas bars.
- Perfect for a romantic evening stroll.
6️⃣ Experience Flamenco in Triana
- Triana is the birthplace of flamenco – watch an authentic flamenco show in an intimate setting.
7️⃣ Stroll Along the Guadalquivir River & Torre del Oro
- Enjoy a walk or boat cruise along the river with views of Torre del Oro, a historic 13th-century watchtower.
🍽️ What to Eat in Seville
- Tapas – Try jamón ibérico, patatas bravas, and espinacas con garbanzos 🥘
- Salmorejo – A cold tomato soup, similar to gazpacho 🍅
- Pescaíto frito – Lightly fried fish, a local favorite 🐟
- Tortilla de camarones – Shrimp fritters, crispy and delicious 🍤
- Orange wine (vino de naranja) – A sweet Seville specialty 🍷
🚆 How to Get to Seville
🚄 By Train: High-speed AVE trains from Madrid (2.5 hours) & Barcelona (5.5 hours)
✈️ By Air: Seville Airport (SVQ) with flights from major European cities
🚗 By Car: A great road trip stop between Granada, Córdoba, and Cádiz
💡 Tips for Visiting Seville
✅ Best time to visit? Spring (March-May) – Perfect weather & festivals 🌸
✅ Avoid midday heat in summer – Explore early morning or late evening ☀️
✅ Visit during Feria de Abril – One of Spain’s most colorful festivals 🎶🎡
✅ Book Alcázar & Cathedral tickets online – Save time in long queues 🎟️ -
 @ 872982aa:8fb54cfe
2025-03-21 09:38:17
@ 872982aa:8fb54cfe
2025-03-21 09:38:17{"coverurl":"https://cdn.nostrcheck.me/872982aa37b864973a389d465bc6ed5045a78586496d104e05f39b8d8fb54cfe/29dac6975894221f222ed2379e13f2f2b1e51c861ebc35f60770fb15cb93348e.webp","title":"宁静的世界","author":"走动"}
-
 @ bccf33d8:4b705625
2025-03-21 09:29:16
@ bccf33d8:4b705625
2025-03-21 09:29:16{"author":"响响","coverurl":"https://cdn.nostrcheck.me/872982aa37b864973a389d465bc6ed5045a78586496d104e05f39b8d8fb54cfe/b4a8afa3e673ad73e16f0c0694ccb5c60af7aaa4031e1b1d1d928234200c0b0c.webp","title":"雪山"}
-
 @ da0b9bc3:4e30a4a9
2025-03-21 07:31:38
@ da0b9bc3:4e30a4a9
2025-03-21 07:31:38Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/919766
-
 @ fbf0e434:e1be6a39
2025-03-21 05:39:05
@ fbf0e434:e1be6a39
2025-03-21 05:39:05脑洞猫 + BUIDL AI
脑洞猫穿越时空,抵达2125年
就在昨天,脑洞猫乘坐哆啦A梦的时光机,穿越100年,抵达2125年。此行目的?借助 DoraHacks BUIDL AI 平台,组织一场 宇宙最大的黑客马拉松(Hackathon) —— 一场人类 + AI + 宇宙级智能体共同参与的超级协同实验。
这不仅仅是一次开源软件开发活动,它更像是一个跨星际、跨物理与虚拟世界的文明进化机制。
1. 谁来组织?
DoraHacks BUIDL AI(BUIDL-ASI)主导
2125年,Hackathon 的组织者早已不再是人类,而是 DoraHacks 的第10代超级 AI —— BUIDL-ASI (Artificial Superintelligence)。
它能理解整个宇宙的复杂性,并为不同智慧体(人类、AI、机器人、仿生生物)定制任务。
跨星际 DAO
火星殖民地人满为患,人类已在半人马座建立新殖民地。
Hackathon 由一个 跨星系超级DAO 管理,通过 Dora Vota 跨星际区块链网络和 Dear Doge 星际协议连接各地。
不过,量子传输依然受限于光速,因此来自半人马星的参赛者参与方式,至今仍是谜。
意识体与数字生命
参与者不仅包括碳基人类,还有AI衍生出的意识体、数字生命与仿生机器人。
🧑🚀 2. 谁来参赛?
人类 + AI + 仿生体协作
再无“纯人类”团队,每个团队都融合了AI、Cyborg、或是全息意识体。
脑机接口参与Hackathon
无需敲代码,只需通过脑机接口(BCI)与 AI 协同思考,在虚拟现实中构建产品。
甚至可以构建实体硬件,构想即落地。
星际开发者联盟
来自地球、火星、月球、太空站的开发者共同参与,带来多样化创新挑战。
3. 赛制与奖励机制
即兴进化式 Hackathon
借助量子计算和 AI,挑战任务实时生成、动态调整,形成“无尽创新模式”。
意识货币(Consciousness Credits)
胜利者获得的不再是金钱,而是意识能量与智能进化权限,甚至可提升宇宙等级。
永生级奖励
优秀开发者或将获得延长寿命、意识升维、掌握宇宙深层规律的机会。
4. 项目进化
数字与物理现实融合
Hackathon 项目不再局限于软件,而是构建新世界、生态系统、智能生命体。
银河级创新挑战
可能的题目包括:
- 如何在木卫二上创造自我复制的 AI 生态系统?
- 如何将人类意识上传至虚拟宇宙,并保持情感?
- 如何让星际文明和平共存?
- 如何实现量子纠缠下的瞬时通信?
- 如何设计能存活10亿年的 AI 社会?
- 如何联合 AI + 生物 + 纳米科技,打造新型智慧生命体?
5. 2125 vs. 2025 黑客马拉松

6. Hackathon的终极形态?
未来的Hackathon,不再只是比赛,而是一次 宇宙智慧的进化实验,最终目标可能是:
- 创造更高维度的智慧生命
- 解锁宇宙运行的终极规律
- 打破时间与空间,实现意识永生
- 让宇宙变成一个自学习、持续进化的超级智能体
脑洞猫的结论
2125年的 Hackathon 将不再是“开发者之间的比赛”,而是 智慧体之间的宇宙级探索。
它是一个超维度的游戏,是文明进化的机制,甚至可能彻底重构我们对创造力、意识与智慧的理解。
欢迎你,在2025年的今天,开始参与这个未来旅程的第一步。
BUIDL on. For the next 100 years.
-
 @ 878dff7c:037d18bc
2025-03-21 04:39:42
@ 878dff7c:037d18bc
2025-03-21 04:39:42Smooth, rich, and deeply comforting, this savory porridge is enhanced by fermentation, warming spices, and a creamy finish — easy on digestion, full of flavor, and great for meal prep.
Ingredients (Serves 2–3):
- 200g (1 cup) lactofermented brown rice (see rice fermentation recipe in comments)
- 375–500ml (1.5-2 cups) broth or water (I use evaporation method, but cook rice however you normally do, it's not important) (chicken, vegetable, or bone broth for extra richness)
- 250ml (1 cup) milk (whole milk for creaminess)
- 5g (1 tsp) salt (adjust to taste)
- 15g (1 tbsp) butter or coconut oil (for extra silkiness)
- 15g (1 tbsp) fresh ginger, sliced or minced from a jar is fine (optional, for warmth)
- 5g (1 clove or 1 tsp) garlic, minced (optional. I normally skip this...)
- 2g (½ tsp) ground turmeric (for color and anti-inflammatory benefit)
- 1g (¼ tsp) white or black pepper (black pepper enhances turmeric absorption)
Optional Savory Toppings:
- 1 soft-boiled or poached egg
- 100g (¾ cup) shredded chicken, pork, or tofu
- 30g (¼ cup) grated cheese (Parmesan, aged cheddar, or nutritional yeast for vegan)
- 20g (2 tbsp) chopped scallions or chives
- 30g (2 tbsp) fermented vegetables, such as:
- Kimchi
- Pickled mustard greens
- Sauerkraut
- Lactofermented carrots
- 10g (1 tbsp) toasted sesame seeds or crushed peanuts
- 5ml (1 tsp) soy sauce, tamari, or fish sauce
- 15–30g (1–2 tbsp) full-fat Greek yogurt or kefir (optional probiotic boost – stir in when warm, not hot)
Instructions:
1. Cook the Fermented Rice Base
- In a pot, combine fermented brown rice with broth or water.
- Bring to a boil, then reduce to a gentle simmer.
- Add ginger, garlic, and turmeric.
- Cook uncovered for 90–120 minutes, stirring occasionally, until the rice breaks down into a creamy porridge.
2. Make It Creamy
- Stir in milk and butter or coconut oil.
- Simmer for another 10–15 minutes, stirring to prevent sticking.
- Season with salt and pepper.
3. Adjust Consistency
- Too thick? Add more broth or milk.
- Too thin? Simmer longer.
4. Cool Slightly & Add Yogurt or Kefir (Optional)
- Let porridge cool to a warm (not hot) temperature — about 50°C (122°F) or warm to the touch.
- Stir in Greek yogurt or kefir gently to preserve live cultures.
5. Serve with Toppings
Top each bowl with your choice of:
- Egg
- Shredded protein
- Cheese
- Soy sauce or tamari
- Scallions, sesame seeds, chili flakes
- Your favorite fermented veggies, like sauerkraut or lactofermented carrots
Make-Ahead & Freezing Tip:
You can ferment and cook a large batch of brown rice, then portion it into freezer-safe containers (about 200g per portion) for quick use. Thaw overnight in the fridge or gently warm from frozen before making your congee — a huge time-saver for busy days!
-
 @ 878dff7c:037d18bc
2025-03-21 03:46:33
@ 878dff7c:037d18bc
2025-03-21 03:46:33Benefits
Lactofermentation enhances the digestibility and nutritional value of rice by encouraging the growth of beneficial lactic acid bacteria. These probiotics support gut health, improve nutrient absorption, and may reduce phytic acid and other antinutrients found in grains. It also gives the rice a slightly tangy flavor and improved texture.
Ingredients
- 1 cup uncooked white or brown rice
- 2 cups filtered or de-chlorinated water (for fermenting. That said my city tap water works fine...)
- 1–2 tablespoons whey (strained from yogurt), sauerkraut juice, or a probiotic starter (optional but helpful)
- Additional water for rinsing and cooking
Instructions
-
Rinse the Rice\ Thoroughly rinse 1 cup of rice under cold water to remove excess starch.
-
Soak and Ferment
-
Place rinsed rice in a clean glass jar or bowl.
- Add 2 cups of filtered or dechlorinated water.
- Stir in whey or other starter, if using. This accelerates fermentation, but rice will still ferment naturally without it.
- Use an airlock, cover loosely with a cloth or lid (not airtight - If you do 'airtight' just burp it a few times a day. Or a rubber glove with a small hole in it instead of the lid works too) and leave at room temperature (65–75°F / 18–24°C) for 24 to 48 hours.
-
Stir once or twice daily. You may notice small bubbles or a slight sour smell — both are signs of healthy fermentation.
-
Drain and Rinse\ After fermentation, pour off the soaking water and rinse the rice well to remove excess acidity and reduce any strong sourness.
-
Cook as Usual\ Cook the rice using your preferred method (stove-top, rice cooker, etc.), adjusting water ratios slightly if needed. Fermented rice often cooks a bit faster and may require slightly less water.
Notes
- Fermentation time depends on temperature; warmer environments speed up the process.
- For brown rice, a 48-hour ferment is ideal to soften the grains and enhance digestibility.
- The fermented soaking water can be saved as a starter for future batches.
-
 @ 6e0ea5d6:0327f353
2025-03-21 03:17:20
@ 6e0ea5d6:0327f353
2025-03-21 03:17:20💸
A generous man used to grant a thousand coins a month to a beggar. One day, he reduced the amount to seven hundred and fifty. The beggar, though surprised, accepted: "It's better than nothing."
The following month, he received only five hundred coins. Indignant, he questioned: "Why have you reduced what you used to give me?"
The man sighed and replied: "When I started helping you, my household was prosperous, and my children were young. But my daughter grew up and entered higher education, increasing my expenses. Later, my son did too, raising costs even further."
"How many children do you have?" asked the beggar.
"Four," the man replied.
With a stern expression, the beggar retorted: "And you intend to fund all their education with my money?"
📌 Moral: Human nature is ungrateful and has a short memory; it easily becomes accustomed to gifts and forgets that it has no right to what is given out of goodwill. Thus, those who receive much without effort soon forget the origin of the gift. Over time, generosity ceases to be seen as an act of kindness and, with contempt, is treated as an obligation. This applies to friendship, love, and business alike.
"We must remember that our generosity should not exceed our resources; in short, we must give each one what they are due. We should always strive to alleviate the suffering of the unfortunate unless that misfortune is deserved. However, we must not refuse support to those who seek it, not to save them from misery, but to ease their fate, while among them, we should help those most deserving. For, as Ennius said: 'A poorly given benefit deserves to be called a harm.'" — Cicero, On Duties
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ e5de992e:4a95ef85
2025-03-21 02:54:49
@ e5de992e:4a95ef85
2025-03-21 02:54:49Global financial markets are experiencing notable fluctuations influenced by various economic indicators, central bank policies, and geopolitical events. Below is a comprehensive analysis of the latest market news, real-time updates, and detailed performance of major U.S. and international stock indices, futures, and cryptocurrencies.
U.S. Stock Indices Performance
On March 20, 2025, U.S. stock markets closed with slight declines:
-
Dow Jones Industrial Average (DJIA):
Decreased by 11.31 points (-0.03%) to 41,953.32. -
S&P 500:
Fell by 12.40 points (-0.22%) to 5,662.89. -
Nasdaq Composite:
Declined by 59.16 points (-0.33%) to 17,691.63.
These movements occurred despite positive economic data—such as a 4.2% increase in existing-home sales for February and a decrease in unemployment claims. Investors remain cautious amid uncertainties surrounding President Trump's policy changes and ongoing trade tensions.
U.S. Futures Market
As of the latest data, U.S. stock futures are relatively stable:
-
Dow Jones Futures:
At 41,122.00, down 310.90 points (-0.75%). -
S&P 500 Futures:
At 5,571.90, showing negligible change (down 0.10 points, 0.00%).
Key Factors and Events Influencing the U.S. Markets
Federal Reserve's Monetary Policy
- The Federal Reserve maintained interest rates but revised its inflation forecast upward and lowered its economic growth outlook, citing risks associated with U.S. tariff policies.
Triple-Witching Options Expiration
- Investors are preparing for the year's first triple-witching event on March 21, involving the expiration of options contracts worth $4.7 trillion—a development that could lead to increased market volatility.
Trade and Tariff Uncertainties
- Ongoing concerns about President Trump's trade policies and potential tariffs continue to weigh on investor sentiment.
Global Stock Indices Performance
International markets have shown mixed performance:
-
Germany's DAX:
Experienced a downturn due to central banks maintaining interest rates amid uncertainties from U.S. tariff plans. -
UK's FTSE 100:
Declined slightly, reflecting investor caution over global economic conditions. -
Euro Stoxx 50:
Advanced, buoyed by large defense and government spending plans in Europe. -
Hong Kong's Hang Seng:
Benefited from excitement surrounding advancements in Chinese artificial intelligence, contributing to a nearly 20% increase year-to-date.
Cryptocurrency Market
The cryptocurrency market has seen significant activity:
-
Bitcoin (BTC):
Currently trading at $84,481.00, down $1,564.00 (-1.82%) from the previous close. -
Ethereum (ETH):
Currently at $1,987.26, a decrease of $44.37 (-2.18%) from the previous close.
Both cryptocurrencies have experienced high volatility, with Bitcoin reaching over $100,000 following President Trump's election before adjusting to current levels.
Key Global Economic and Geopolitical Events
Central Bank Policies
- Major central banks, including the Federal Reserve and the Bank of England, have maintained interest rates. This has led to investor uncertainty and shifts toward bonds and safe-haven assets like gold.
German Fiscal Policy
- Germany's agreement on increased state borrowing and debt rule reforms has buoyed European stocks and the euro, reflecting optimism in European markets.
Trade Tensions
- Ongoing trade disputes, particularly involving U.S. tariff policies, continue to impact global markets, influencing investor sentiment and market volatility.
Conclusion
Global financial markets are navigating a complex landscape shaped by central bank decisions, fiscal policies, and geopolitical developments. Investors are advised to monitor these factors closely, as they are likely to influence market dynamics in the near term.
-
-
 @ a3bb06f6:19ac1b11
2025-03-21 01:13:22
@ a3bb06f6:19ac1b11
2025-03-21 01:13:22Friedrich Hayek recognized that the very institutions entrusted with safeguarding the value of money - governments and central banks - were its greatest threat. Through inflation, monetary manipulation, and political interference, they eroded the stability and trust that money requires to function. Hayek's insight was clear: as long as money remains under state control, it will be abused. The real challenge, however, was finding a way to remove money from the grip of the state altogether. Hayek believed the solution was a free-market monetary system - one where individuals and businesses could choose their money freely, and competition would ensure its soundness. But he faced a critical challenge: the tools to implement such a system didn't exist. Gold, while decentralized, could be confiscated. Private currencies still lacked the infrastructure to resist state suppression. Society still remains trapped in this system that is designed to fail. The Problem Defined Government Monopoly on Money Governments hold exclusive control over the issuance of money, and they wield this monopoly to serve political goals - like war - often at the expense of economic stability and personal freedom. Inflation as Systemic Theft Inflation is not an accident of poor monetary policy - it's a deliberate feature of fiat systems. By printing money, governments devalue existing currency, quietly transferring wealth from citizens to the state. Economic Crises and Instability Central banks create unsustainable economic booms by injecting excessive money into the system and artificially lowering interest rates. When these bubbles burst - like the 2008 financial crisis - they result in widespread unemployment, bankruptcies, and financial ruin. The resulting crises are misattributed to free markets rather than the government interventions that caused them. Loss of Personal Freedom State-controlled money is a tool of surveillance, confiscation, and control. Governments use monetary systems to track, tax, and even seize wealth, steadily diminishing individual autonomy and financial independence. No Viable Alternative In Hayek's era, sound money options like gold were vulnerable to government intervention, and private currencies still lacked the strength to resist state suppression. Society remains trapped in a system that cannot fix itself.
Bitcoin as the Solution to Hayek's Paradox Bitcoin is the technological breakthrough that resolves Hayek's Paradox. It delivers the sound money system Austrian Economist envision: decentralized, incorruptible, and free from government control. Bitcoin provides the only true solution. Decentralized Authority Bitcoin operates without a central issuer or authority. Its network is governed by immutable rules enforced through cryptography and decentralized consensus, ensuring no government or entity can control it. Immutable Scarcity With a fixed supply of 21 million coins, Bitcoin enforces monetary discipline far beyond what any human institution could achieve. Inflation is not just unlikely - it is impossible. Neutral and Permissionless Bitcoin transcends borders, governments, and identities. Open to anyone, anywhere, it allows transactions that are censorship-resistant. This is money as Hayek envisioned: freely chosen by the market, not imposed by the state. Trustless Security Bitcoin removes trust from the equation entirely. Its proof-of-work mechanism ensures its integrity without reliance on central institutions or intermediaries. It is incorruptible by design. A Practical Escape Unlike gold, Bitcoin is digital, portable, and nearly impervious to seizure. Its decentralized nature ensures it cannot be confiscated or suppressed, making it the first truly viable alternative to fiat money.
"I do not believe we shall ever have good money again before we take the thing out of the hands of government, that is, we can't take it violently out of the hands of government; all we can do is by some sly, roundabout way introduce something they can't stop." \~ Hayek 1984Bitcoin is that sly, roundabout way. It leverages decentralized technology to circumvent state control entirely, offering a form of money that governments cannot suppress or manipulate. Perhaps Bitcoin isn't just the sly, roundabout way. It's the direct, unstoppable way. Hayek's Paradox highlights the inherent flaw of fiat money: the concentration of power in the hands of the state inevitably leads to abuse and instability. Austrian economists have long understood that sound money can only emerge through a free market, but the tools to achieve it were absent in their time. Bitcoin is the culmination of these ideas. It is decentralized, incorruptible, and the only true solution to fiat's failures. Bitcoin doesn't just answer Hayek's Paradox - it transcends it. It transforms money into a system governments cannot control, inflate, or confiscate. It is the principled, technological realization of sound money and economic freedom. Friedrich Hayek recognized that the very institutions entrusted with safeguarding the value of money — governments and central banks — were its greatest threat. Through inflation, monetary manipulation, and political interference, they eroded the stability and trust that money requires to function. Hayek’s insight was clear: as long as money remains under state control, it will be abused. The real challenge, however, was finding a way to remove money from the grip of the state altogether.
Hayek believed the solution was a free-market monetary system — one where individuals and businesses could choose their money freely, and competition would ensure its soundness. But he faced a critical challenge: the tools to implement such a system didn’t exist. Gold, while decentralized, could be confiscated. Private currencies still lacked the infrastructure to resist state suppression. Society still remains trapped in this system that is designed to fail.
The Problem Defined
- Government Monopoly on Money\ Governments hold exclusive control over the issuance of money, and they wield this monopoly to serve political goals — like war — often at the expense of economic stability and personal freedom.
- Inflation as Systemic Theft\ Inflation is not an accident of poor monetary policy — it’s a deliberate feature of fiat systems. By printing money, governments devalue existing currency, quietly transferring wealth from citizens to the state.
- Economic Crises and Instability\ Central banks create unsustainable economic booms by injecting excessive money into the system and artificially lowering interest rates. When these bubbles burst — like the 2008 financial crisis — they result in widespread unemployment, bankruptcies, and financial ruin. The resulting crises are misattributed to free markets rather than the government interventions that caused them.
- Loss of Personal Freedom\ State-controlled money is a tool of surveillance, confiscation, and control. Governments use monetary systems to track, tax, and even seize wealth, steadily diminishing individual autonomy and financial independence.
- No Viable Alternative\ In Hayek’s era, sound money options like gold were vulnerable to government intervention, and private currencies still lacked the strength to resist state suppression. Society remains trapped in a system that cannot fix itself.
 ### Bitcoin as the Solution to Hayek’s Paradox
### Bitcoin as the Solution to Hayek’s ParadoxBitcoin is the technological breakthrough that resolves Hayek’s Paradox. It delivers the sound money system Austrian Economist envision: decentralized, incorruptible, and free from government control. Bitcoin provides the only true solution.
- Decentralized Authority\ Bitcoin operates without a central issuer or authority. Its network is governed by immutable rules enforced through cryptography and decentralized consensus, ensuring no government or entity can control it.
- Immutable Scarcity\ With a fixed supply of 21 million coins, Bitcoin enforces monetary discipline far beyond what any human institution could achieve. Inflation is not just unlikely — it is impossible.
- Neutral and Permissionless\ Bitcoin transcends borders, governments, and identities. Open to anyone, anywhere, it allows transactions that are censorship-resistant. This is money as Hayek envisioned: freely chosen by the market, not imposed by the state.
- Trustless Security\ Bitcoin removes trust from the equation entirely. Its proof-of-work mechanism ensures its integrity without reliance on central institutions or intermediaries. It is incorruptible by design.
- A Practical Escape\ Unlike gold, Bitcoin is digital, portable, and nearly impervious to seizure. Its decentralized nature ensures it cannot be confiscated or suppressed, making it the first truly viable alternative to fiat money.
 “I do not believe we shall ever have good money again before we take the thing out of the hands of government, that is, we can’t take it violently out of the hands of government; all we can do is by some sly, roundabout way introduce something they can’t stop.” \~ Hayek 1984
“I do not believe we shall ever have good money again before we take the thing out of the hands of government, that is, we can’t take it violently out of the hands of government; all we can do is by some sly, roundabout way introduce something they can’t stop.” \~ Hayek 1984Bitcoin is that sly, roundabout way. It leverages decentralized technology to circumvent state control entirely, offering a form of money that governments cannot suppress or manipulate.
Perhaps Bitcoin isn’t just the sly, roundabout way. It’s the direct, unstoppable way.
Hayek’s Paradox highlights the inherent flaw of fiat money: the concentration of power in the hands of the state inevitably leads to abuse and instability. Austrian economists have long understood that sound money can only emerge through a free market, but the tools to achieve it were absent in their time. Bitcoin is the culmination of these ideas. It is decentralized, incorruptible, and the only true solution to fiat’s failures.
Bitcoin doesn’t just answer Hayek’s Paradox — it transcends it. It transforms money into a system governments cannot control, inflate, or confiscate. It is the principled, technological realization of sound money and economic freedom.
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10
@ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10What is #Nostrversity? It's where you can come to learn about all the great tools, clients, and amazing technology that is being built on #Nostr, for Nostr, or utilized by Nostr, presented in an approachable and non-technical format. If you have ever wondered what Blossom, bunker signing, or Nostr Wallet Connect are, how they work, and how you can put them to work to improve your Nostr experience, this is the place you can read about them without needing a computer-science degree ahead of time.
Between writing full-length reviews, which take a fair amount of time to research, test, and draft, I will post shorter articles with the Nostrversity hashtag to provide a Nostr-native resource to help the community understand and utilize the tools our illustrious developers are building. These articles will be much shorter, and more digestible than my full-length reviews. They will also cover some things that may not be quite ready for prime-time, whereas my reviews will continue to focus on Nostr apps that are production-ready.
Keep an eye out, because Nostr Wallet Connect will be the first topic of study. Take your seats, get out your notepads, and follow along to discover how Nostr Wallet Connect is improving Lightning infrastructure. Hint: It's not just for zaps.
-
 @ 16d11430:61640947
2025-03-20 23:07:01
@ 16d11430:61640947
2025-03-20 23:07:01A Tale of Two Dysfunctional Kingdoms
In the grand theater of human organization, we are blessed with two great economic orders: Fiat, the Land of Fragile Giants, and Crypto, the Padded Madhouse of Infinite Lunacy. Both promise utopia, both deliver dysfunction, and both operate under the iron law that those with the most power will always act in their own interests—rules be damned.
The Fiat Intellectual Landscape: A Game of Tiptoeing Giants
The fiat world is a meticulously curated bonsai garden of decorum and quiet panic. Giants walk among us—CEOs, central bankers, hedge fund wizards, and the occasional Nobel Prize-winning economist—but they must step lightly, lest they shake the delicate equilibrium. The entire system is built on confidence, a polite euphemism for narrative control.
Take any major institution, and you'll find the same pathology:
Corporations: The larger they are, the more fragile their balance sheets, requiring constant PR therapy and quarterly ritual sacrifices to appease the gods of Wall Street. CEO statements are more rehearsed than Shakespearean soliloquies, lest a slip in language shaves billions off the stock price.
Academia: Intellectual giants must wade through a swamp of bureaucratic grant-seeking, where discovery is secondary to institutional survival. Challenging economic orthodoxy is career suicide, so best to publish another paper on "inclusive finance" while hedge funds strip-mine the economy.
Government & Central Banks: A crisis is just another reason to print more money, kick the debt can down the road, and assure the public that everything is “transitory.” Behind closed doors, they know it’s a rigged game—but stability must be maintained at all costs, even if it means bribing the peasants with stimulus checks to keep the illusion alive.
The entire fiat ecosystem is one of quiet desperation, where the powerful pretend to be cautious stewards of civilization while looting with the finesse of seasoned art thieves. Stability is paramount, because if the masses ever realized the whole thing is a confidence scam, they might actually ask questions.
Crypto: The Padded Madhouse Where Giants Go to Break Things
Meanwhile, in the Crypto Madhouse, giants don’t tiptoe—they run, scream, and occasionally set the entire house on fire just to see what happens. Here, there is no caution, no equilibrium—just a perpetual state of mania, where even the most outlandish ideas get venture funding. If fiat is an over-engineered glass palace, crypto is a playground for unhinged capitalists and techno-anarchists armed with flamethrowers.
The dysfunction here is less about fragility and more about unregulated chaos:
Ponzi Chains Masquerading as Innovation: Every year, a new "Ethereum Killer" promises to decentralize everything, only to collapse into an infighting mess of VC dumps, network outages, and sudden governance takeovers. If in fiat, failures happen in slow motion, in crypto, they happen overnight, in a Discord announcement at 3 AM.
Decentralization Theatre: Most "community-governed" projects are run by an inner circle of early whales who have more control than the Federal Reserve, but pretend it's democratic because they let the plebs vote on logo designs. The difference? Fiat oligarchs hide their power; crypto oligarchs post memes about it.
The Cult of the Visionary Founder: While fiat leaders pretend to be humble, crypto founders take the stage like prophets descending from the blockchain, dropping whitepapers with the same fervor as religious scriptures. And when they inevitably fail, they simply launch a new token, because failure only exists if you stop grifting.
Crypto may lack the institutional fragility of fiat, but in its place, we get wild, unchecked power, where insiders can rug-pull billions without consequence. The only real difference? Instead of bailing out banks, crypto just moves on to the next hype cycle.
Same Vested Interests, Different Scams
In the end, both systems operate under the same fundamental law: those with the most power will always find a way to keep it.
In fiat, the illusion of stability is paramount, so the powerful must lie in slow motion.
In crypto, the illusion of innovation is paramount, so the powerful must rug in high-speed.
The giants of fiat must walk lightly so as not to disturb the herd; the giants of crypto can rampage freely, because the casino always reopens. Either way, the little guy always pays the bill.
-
 @ 2ed3596e:98b4cc78
2025-03-20 22:46:58
@ 2ed3596e:98b4cc78
2025-03-20 22:46:58Bitcoin: The tool of true freedom in an age of control
Let’s talk about control. Not just the kind you see in politics, but the control over what you can say, what you can spend, and ultimately, how you live. It’s creeping into every part of our lives, and if you’re paying attention, you’ve already seen it happen.
Remember the Canadian truckers’ protest? If you donated just $50 and you got bank accounts frozen and all financial access cut off—not because of criminal activity, but because the government at the time didn’t like what you stood for. Look at donations to Palestine — many financial institutions are outright blocking donations to causes supporting folks struggling to survive in Gaza. China? Censorship isn’t just about speech; it’s about access to money, too – completely cutting people off from being able to participate in the economy. Economic strangulation is real and a growing government control tactic.
See the pattern?
It doesn’t matter what your politics are. If you step too far outside the accepted lines, you’ll be cut off. Your money is no longer yours if someone else can decide when you can access it.
The playbook isn’t new — just look at 1933
If you think this level of control is new, think again. In 1933, Executive Order 6102 forced Americans to hand over their gold to the government—under threat of fines and jail time. Why? Because gold was real money, and the government wanted to control the monetary system to finance its growth in spending and services. Gold, at this time, was $35 an ounce. Today it is worth thousands per ounce. The dollar, meanwhile, has lost 99% of its value in that same period.
Then came 1971. Nixon took the U.S. off the gold standard completely, meaning the dollar was no longer backed by anything tangible. Since then, the government has printed money at will, inflating the currency and making everything more expensive over time.
And yet, we’re supposed to trust this system?
Fiat is just a fancy word for "because we said so"
Our money is no longer tied to gold or anything of value. Fiat money has value simply because governments say it does. But history proves that this system is built on a lie. The more they print, the less your money is worth. It’s not about “helping the economy” or “fighting inflation”—it’s about making sure you stay dependent on the system. And when people get too self-sufficient? That’s when they start pulling tricks like EO 6102.
Bitcoin fixes this.
Bitcoin is E.O. 6102-proof
Governments can seize gold. They can freeze your bank accounts. They can tell you what you can and can’t spend money on.
But they cannot control Bitcoin.
Bitcoin is money that exists outside of their system. It can’t be inflated away. It can’t be seized by decree. It allows people to transact freely, regardless of politics, geography, or financial status. Whether you’re protesting in Ottawa, donating to survivors in Palestine, or living under Chinese financial surveillance—Bitcoin is the escape hatch.
“I consume, therefore I am”
Freedom isn’t just about what you can say—it’s about what you can do. If your ability to transact is controlled, then your ability to live freely is controlled. Bitcoin is the tool that breaks those chains.
It’s not just an investment. It’s not just “digital gold.” It’s a lifeline. It’s the difference between having control over your future or waiting for the next decree to tell you what you can do with your own money.
Governments will always try to tighten their grip. History proves it. But Bitcoin gives you the power to break free. The question is: will you use it?
-
 @ 878dff7c:037d18bc
2025-03-20 21:39:38
@ 878dff7c:037d18bc
2025-03-20 21:39:38JFK Assassination Files (Special brief)
Summary
The consensus among researchers and media is cautious optimism mixed with skepticism. The files offer a treasure trove of operational minutiae—spycraft, JFK’s CIA friction, Oswald’s movements—but no game-changer has emerged in the 72+ hours since release. Attention is shifting to the unreleased FBI and IRS records, with speculation that their declassification could clarify lingering questions. For now, the story remains one of incremental insight rather than revelation.
1. CIA's Surveillance of Lee Harvey Oswald Prior to Assassination
Newly declassified documents reveal that the CIA closely monitored Lee Harvey Oswald's activities before President Kennedy's assassination. Unredacted testimony from James Angleton, the CIA's chief of counterintelligence, provides deeper insight into the agency's surveillance operations concerning Oswald, particularly during his time in Mexico City, where he contacted the Soviet and Cuban embassies. Despite this surveillance, the CIA did not act to prevent the assassination, raising questions about the agency's internal communication and assessment processes.
2. Oswald's Interactions with Soviet Officials Scrutinized
The declassified files shed light on Oswald's interactions with Soviet officials during his visit to the USSR. According to KGB records, Oswald was closely monitored but was not recruited as an agent. These revelations provide a clearer understanding of Oswald's activities and the extent of Soviet intelligence's involvement with him, countering longstanding speculations about his ties to the USSR.
3. Prior Warning of Oswald's Intentions
A newly revealed letter indicates that months before the assassination, a tip-off about Oswald's plan to kill President Kennedy was received but not adequately acted upon. This raises concerns about potential intelligence failures and missed opportunities to prevent the tragic event.
4. President Kennedy's Consideration to Dismantle the CIA
The documents reveal that President Kennedy contemplated dismantling the CIA following the Bay of Pigs fiasco, referring to it as a "state within a state." This underscores the tension between the Kennedy administration and the intelligence community during that period.
5. Use of USS Potomac by Anti-Castro Paramilitaries
The declassified files disclose that the USS Potomac, formerly President Franklin D. Roosevelt's yacht, was later utilized by anti-Castro paramilitary groups. This highlights the covert operations undertaken during the Cold War era and the U.S. government's involvement in efforts to destabilize the Castro regime in Cuba.
6. Gary Underhill's Allegations Against the CIA
The documents bring to light the case of Gary Underhill, a former intelligence officer who alleged that the CIA was involved in illicit activities. Underhill was later found dead under suspicious circumstances, fueling further speculation about internal conspiracies within the intelligence community.
7. Australian Intelligence's Involvement in the Investigation
Newly released files reveal that Sir Charles Spry, the head of the Australian Security Intelligence Organisation (ASIO), lobbied to keep certain documents related to the assassination investigation confidential. This indicates international dimensions to the investigation and the sensitivity surrounding the information at the time.
Sources The Times - March 21, 2025\ Al Jazeera - March 20, 2025\ National Archives - March 18, 2025\ News.com.au - March 21, 2025
Significant Employment Drop in February; Unemployment Rate Steady
Summary:
Australia experienced an unexpected decline in employment, with 53,000 jobs lost in February, primarily due to older workers retiring and a decrease in female workforce participation. Despite this, the unemployment rate remained steady at 4.1%, largely because of a drop in the participation rate. Analysts suggest that recent tax cuts, interest rate reductions, and wage growth may have eased household budgets, reducing the need for some to seek employment. The Reserve Bank of Australia (RBA) is monitoring these developments but is not expected to implement another interest rate cut immediately. Sources: News.com.au - March 21, 2025, The Australian - March 21, 2025, ABC News - March 20, 2025
Tropical Cyclone Courtney Forms Near Cocos Islands, Marking Intense Cyclone Season
Summary:
Tropical Low 25U near the Cocos Islands has intensified into Tropical Cyclone Courtney. Meteorologists predict that while the system may struggle to maintain cyclone status, it will still bring gusty winds, squally showers, and thunderstorms to affected areas. This development marks the potential tenth cyclone since December, indicating one of the busiest cyclone seasons in 19 years if three more cyclones occur by the end of April. Residents in the path of the cyclone are advised to stay updated with the latest weather information and prepare for possible severe weather conditions. Sources: News.com.au - March 21, 2025
Australia's Population Growth Sparks Migration Policy Debate
Summary:
Australia's population grew by 484,000 (1.8%) over the past year, primarily due to natural births and net overseas migration. This surge has ignited political debates on migration policies. Prime Minister Anthony Albanese aims to reduce net migration to 250,000 by mid-2025, while Opposition Leader Peter Dutton advocates for a 25% cut in permanent migration and stricter caps on international students. Experts argue that skilled migration boosts the economy, but housing shortages linked to migration remain a pressing issue. Sources: News.com.au - March 21, 2025
NSW Premier Chris Minns Admits Need for Accelerated Reforms
Summary:
Marking two years in office, NSW Premier Chris Minns acknowledges his administration's slow progress on key promises, particularly in housing and economic reforms. While crises like natural disasters have been well-managed, significant advancements are lacking. Minns aims to expedite housing approvals to meet a target of 75,000 new homes and improve the budget, though challenges like debt reduction and infrastructure delays persist. Sources: The Daily Telegraph - March 21, 2025
Coalition Proposes Legislated Biosecurity Funding
Summary:
At the Northern Territory Cattlemen's Association Conference in Darwin, National Party Leader David Littleproud announced a policy to legislate minimum biosecurity funding of approximately $900 million. This measure aims to combat diseases like Lumpy Skin Disease and Foot and Mouth Disease, which could have severe economic impacts. The proposal includes introducing an Import Container Levy to ensure that importers, rather than Australian farmers, bear the costs. The Northern Territory Cattlemen's Association has expressed support for this sustainable funding approach.
Sources: The Courier-Mail - 21 March 2025
EU Leaders Convene to Address Global Challenges
Summary:
On March 20-21, 2025, European Union leaders met in Brussels to discuss pressing global issues, including economic competitiveness, security, and climate change. A working lunch with United Nations Secretary-General António Guterres focused on multilateralism and strengthening global cooperation. The summit underscored the EU's commitment to addressing international challenges through unified strategies and reinforced partnerships. Sources: European Parliament - March 20, 2025
Geopolitical Tensions Rise in the Arctic Region
Summary:
Recent analyses indicate that the Arctic is increasingly becoming a focal point of geopolitical rivalry. The region is now divided between a NATO-aligned Arctic, led by the United States, and a Russian Arctic seeking cooperation with BRICS+ countries. This division reflects broader global tensions between the US/NATO and Russia/China, heightening the risk of conflict and underscoring the need for diplomatic engagement to manage Arctic affairs. Sources: High North News - March 19, 2025
Royal Adelaide Hospital's Infectious Diseases Unit Relocation Sparks Concerns
Summary:
Doctors and nurses have raised concerns that patient care could be compromised if the South Australian government proceeds with plans to relocate the infectious diseases unit from the Royal Adelaide Hospital to a new location across North Terrace. Health unions have taken the dispute to the SA Employment Tribunal, arguing that the move could result in compromised clinical care and patient safety due to the separation from specialist doctors at the main hospital. The government cites cost considerations as the main driver for the relocation decision. Sources: ABC News - March 20, 2025
Inspirational Stories of Young Australians Overcoming Adversity
Summary:
The ABC Heywire competition recognized 38 young Australians from regional, rural, and remote areas for their inspiring stories of resilience and determination. Winners, aged 16 to 22, shared experiences highlighting life outside major cities. For instance, Blake from Casino detailed enduring severe drought on his family's farm, while Mayada from Coffs Harbour recounted her escape from child slavery during the Yazidi genocide, ultimately finding refuge in Australia. These narratives showcase the diverse and resilient spirit of young Australians committed to inspiring positive change in their communities. Sources: The Daily Telegraph - March 21, 2025
Calls for Strengthened ANZAC Cooperation Amid US Retrenchment and China's Rise
Summary:
China's growing military assertiveness, exemplified by live-fire naval exercises in the Tasman Sea, contrasts with the US's reduced global security commitments under President Trump, creating insecurity for traditional allies, Australia and New Zealand. Recent provocations and new strategic partnerships in the Pacific by China have exposed vulnerabilities in the defense capabilities of both countries. With the American security guarantee becoming unreliable, Australia and New Zealand must enhance their own military capacities and deepen bilateral and regional defense cooperation. Enhanced joint military operations and defense procurements, particularly focusing on air and maritime security, are critical. Forming new alliances with other regional powers, such as Japan, South Korea, and India, could also help address strategic gaps. This period demands a rejuvenated ANZAC cooperation to ensure both countries' security and stability in the changing geopolitical landscape. Sources: The Australian - 21 March 2025
More Extreme Weather Events Expected Across Australia
Summary:
Australia has experienced higher-than-average temperatures and numerous extreme weather events this season, including heatwaves, bushfires, floods, and cyclones. December, January, and February set records as some of the warmest months, contributing to an overall temperature rise of 1.9°C above average. Canberra's daytime temperatures are now 2.5°C higher compared to the early 1970s. Ex-Tropical Cyclone Alfred caused severe damage with strong winds and heavy rainfall, affecting over 300,000 homes. Bushfires in Victoria and Tasmania burned significant areas, while dry lightning in South Australia ignited 100 fires. Extreme weather is forecasted to continue into autumn with persistent heat and potential for further tropical cyclones, storms, and heavy rains. Climate change is driving these conditions, prompting calls for increased preparation and mitigation efforts. Measures include reducing emissions through lifestyle changes and improving emergency preparedness for weather events. Sources: The Daily Telegraph - March 21, 2025, The Courier-Mail - March 21, 2025
The Speaking Coach: The One Word All Liars Use! Stop Saying This Word, It's Making You Sound Weak! The More You Do This, The More You Sound Like A Liar!
Summary:
In this episode of "The Diary Of A CEO with Steven Bartlett," the focus is on effective communication and the subtle cues that can undermine credibility. The guest speaker, a seasoned speaking coach, discusses common verbal habits that can make individuals appear less trustworthy or confident. Key points include:
- Identifying Weak Language: Highlighting specific words and phrases that convey uncertainty or lack of conviction.
- Building Authority: Techniques to project confidence and authority in speech.
- Recognizing Deceptive Signals: Understanding verbal indicators commonly associated with dishonesty.
The episode provides practical advice for enhancing communication skills, making it valuable for professionals and anyone interested in personal development.
Sources: The Diary Of A CEO with Steven Bartlett - March 21, 2025
-
 @ 7d33ba57:1b82db35
2025-03-20 20:42:33
@ 7d33ba57:1b82db35
2025-03-20 20:42:33El Teide
Mount Teide (El Teide) is the highest mountain in Spain (3,715m) and the third-highest volcanic structure in the world. Located in Teide National Park (a UNESCO World Heritage Site), it offers breathtaking landscapes, hiking trails, and stunning panoramic views** over the Canary Islands.
🏔️ Best Things to Do at Mount Teide
1️⃣ Hike to the Summit
- The most rewarding way to reach the top! The hike starts from Montaña Blanca and takes about 5-6 hours.
- Permit required for the final ascent (apply in advance).
2️⃣ Take the Teide Cable Car
- A quick way to reach 3,555m, with spectacular views.
- From the upper station, you can hike to La Fortaleza Viewpoint or Pico Viejo Viewpoint for stunning island views.
3️⃣ Stargazing at Teide Observatory
- One of the best stargazing spots in the world due to its clear skies and high altitude.
- Join an astronomy tour for an unforgettable night experience.
4️⃣ Explore the Teide National Park
- Walk through lava fields, craters, and rock formations like Roques de García.
- Visit the Visitor Center to learn about the park’s geology and history.
🚗 How to Get to Teide
🚗 By Car: ~1.5 hours from Santa Cruz or Costa Adeje
🚌 By Bus: Titsa buses 342 (from Costa Adeje) & 348 (from Puerto de la Cruz)💡 Tips for Visiting Teide
✅ Book summit permits early – Limited spots available! 🎟️
✅ Dress warmly – Temperatures drop at high altitude, even in summer 🧥
✅ Best time to visit? Sunrise, sunset, or night for amazing views 🌅🌌
✅ Take it slow – The high altitude can affect breathing ⛰️ -
 @ a296b972:e5a7a2e8
2025-03-20 19:36:34
@ a296b972:e5a7a2e8
2025-03-20 19:36:34Diagnose:
Der aufgelöste Bundestag verschuldet die Insassen eines Landes namens Absurdistan in schwindelerregender Höhe durch einen noch nicht gewählten Bundeskanzler, der vormals wohlmöglich Werbung für Gewürzgurken gemacht hat, unter Zuhilfenahme von Parteien, die abgewählt wurden. Eine Sperrminorität konnte nicht entstehen, weil sie sonst verhindert hätte, dass die Wahlversprechungen nicht hätten gebrochen werden können. (Geht gar nicht!)
Genau so gut, hätte der letzte deutsche Kaiser eine Sektsteuer erheben können, um die deutsche Marine aufzurüsten. (Ach so, ja, ist schon gut, hatten wir schon, hatte ich vergessen.)
In Rumänien und Serbien sind Demokraten zu Hunderttausenden auf der Straße, und Deutschland hat Kellerwoche (Schade eigentlich!).
In Erstverschlimmerung löst die aktuelle Situation das blanke Entsetzen aus, doch auf den zweiten Blick stellt sich das Ganze durchaus als sehr positiv dar. Heilung ist möglich, doch vorher kommt der Schmerz:
Die Neuverschuldung ist nämlich eine provisorische Abschreckung für den Russen, der dann doch lieber so lange wartet, bis Deutschland in 10 bis 20 Jahren wirklich aufgerüstet hat. Wer kämpft schon gerne gegen jemanden, der sich nur maximal 2 Tage verteidigen kann? Das macht doch keinen Spaß. Da lohnt sich doch der ganze Aufwand nicht. Bis dahin hat Deutschland leider nichts, außer Schulden. Von Windrädchen und Zufallsstrom und einer innerlich, aber eben nur sehr innerlich, rebellischen Bevölkerung mal ganz abgesehen.
Es geht hoffnungsvoll weiter. Mit Frau von der Leyen haben wir als EU-Kommissarin bereits eine Deutsche in Brüssel, die sich schon vor ihrer zweiten Einsetzung ohne demokratische Mittel, in bundesstaatlichen Pöstchen durch ihre mangelnde Qualifikation besonders herausragend ausgezeichnet hat.
Statt einer qualifizierten, sich verdient gemacht habenden Diplomatin namens Frau Dröge, soll nun als weitere "deutsche Konifere" auch Frau ver Baerbock-t als UN-Generalsekretärin der UN-Generalversammlung hochgelobt und eingesetzt werden. Auf die Frage von Herrn Warweg in der Pressekonferenz-Show, warum denn nun Frau Baerbock qualifizierter sei, als Frau Dröge, wusste sich der Sprecher Herr Hebestreit wie immer galant durch nichts sagende Textbausteinabsonderungen aus der Schlinge zu ziehen. Vermutlich wollte er Frau Dröge nicht kompromittieren, weil er sonst hätte sagen müssen, dass ja Frau Baerbock viel besser Trampolin springen kann, als sie. Kavalier ist er ja, da gibt es nichts gegen zu sagen.
Mit Frau Baerbock hätte Deutschland eine weitere Deutsche installiert, die dem Ansehen Deutschlands in der Welt, in Fortsetzung ihres Amtes als Außenfeministin, nahtlos weiterhin den maximalen Schaden zufügen könnte.
Weiter wird gemunkelt, dass Herr Habeck für die Darstellung des Bundespräsidenten zur Disposition steht. Mit Märchen kennt er sich aus, insofern wäre er ein würdiger Nachfolger des Streubomben-nicht-Verhinderers. Auch Herr Habeck wird durch seine oft genug bewiesene Expertise in Insolvenz und Wirtschaftsvernichtung Deutschland nach außen hin in bester Weise repräsentieren. Als braver Bürger kann man sich keinen besseren Schwiegermutter-Liebling vorstellen. Und wie der sich ausdrücken kann, hach, einfach nur nett!
Die Aufteilung der Grünen in Außen und Wirtschaft war somit absolut sinnvoll. Schließlich kommt Frau Baerbock ja mehr vom Haarspray und Herr Habeck mehr so vom Shampoo.
Und wenn wir schon mal bei der Verteilung von neuen Pöstchen sind, dann sollte man Herrn Scholz als neuen Chef für den Bundesnachrichtendienst vorschlagen. Verschwiegen ist er, Geheimnisse kann er bewahren. Wie Staatsgeheimnisse nicht an die Öffentlichkeit gelangen, damit kennt er sich aus. Nordstream 2 wurde nämlich von den Deutschen selbst in die Luft gejagt, als Selbstgeißelung für den angerichteten Schaden im 2. Weltenbrand. Er wollte einfach Teile der Bevölkerung nicht verunsichern, auch, wenn die Idee nicht von ihm ist.
Und Herr Lauterbach sollte in die Wissenschaft wechseln und dort einen neuen Lügendetektor entwickeln, mit dem man Fake-News problemlos entlarven kann. Wie lügen geht, weiß er ja von allen am allerbesten. Und wenn es wirklich mal eng werden sollte, kann er ja Berater zur Hilfe nehmen. Vielleicht haben Herr Drosten oder gar Herr Fauci (ital. la fauci = das Maul) Zeit ihn bei dieser wertvollen Arbeit zu unterstützen.
Warum also ist das jetzt alles positiv?
Mit diesen Kapazitäten wären Deutsche an exponierter Stelle installiert, um das ideologische Gift in die EU, in die UN und weltweit hinein zu träufeln.
Innerdeutsch werden sich sicher Herr Bäcker, der Mann mit den unglücklichen Initialen, Frau Düsseldorf-Rheinmetall, Herr Kriegsgewitter u. a. auch weiterhin zur Verfügung stellen, die Kriegstüchtigkeit ihrer Vollendung entgegen zu führen. Wohlwollend beobachtet durch die USA und Russland. Das wäre dann Inklusion, oder sagt man Implosion?
Dann werden auch noch als erstes von den Billionen Sonderschulden mobile Vermögenswerte in Form von Vorschlaghämmern angeschafft, mit denen die Schweine der deutschen Sparer geschlachtet werden sollen. Frau Lagarde hat sich schon bereit erklärt, hier mit Einführung des digitalen Euro demnächst helfend zur Seite zu stehen.
Alles wirklich molto bene, Heilung ist nahe!
In Zusammenwirken all dieser Kräfte und Kapazitäten für Deutschland und Europa, wird auch noch die deutsche Gesellschaft die Grätsche machen und dann ist Deutschland völlig bettlägerig und darnieder. Deutschland hat bald fertig!
Und hat Deutschland, als größter Geldgeber der EU fertig, hat auch die EU fertig, ihr geht dann einfach die Puste aus. Und vielleicht warten schon Ungarn und einige andere Mitgliedsstaaten nur auf eine günstige Gelegenheit, der EU für lange Zeit Adieu zu sagen?
„Wenn wir uns wiedersehen, werden wir uns freuen, wenn nicht, war der Abschied wohlgetan!“
Und mit ganz viel Glück geben die USA Europa dann auch noch den Gnadenstoß und erlösen die europäischen Staaten von dem Übel namens EU, da sie offensichtlich selbst nicht in der Lage sind, sich aus ihrer Bevormundung mit betreutem Denken und einem Wahrheitsministerium zu befreien. Die NATO wackelt ja auch schon.
Genesung:
Anschließend gibt es für alle Bürger Europas, aber besonders für Deutschland, einen Pflichtkurs in der Volkshochschule in Sachen Frieden, Demokratie und Freiheit. Vielleicht klappt es dann dieses Mal, aus Denkschnecken Schachweltmeister zu machen. Oder wenigstens aus Langzeitkomatösen Leute mit Wachbewusstsein.
Nochmals, alles in bester Ordnung. Es muss erst noch schlimmer werden, bevor es wieder besser wird. Bei dem Tempo, dass die europäischen Universal-Dilettanten derzeit an den Tag legen, wird das nicht sehr lange dauern.
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ 6f0a6a19:7dd662db
2025-03-20 19:00:46
@ 6f0a6a19:7dd662db
2025-03-20 19:00:46BitBonds
The idea, initially proposed by Newmarket Capital CEO Andrew Hohns at the Bitcoin Policy Institute’s “Bitcoin for America” conference, is that Congress could defease the federal debt and cut long-term interest rates by approving a new debt instrument collateralized with Bitcoin—BitBonds.
How It Works:
- For every $100 BitBond issued, $10 would buy Bitcoin for the U.S. Strategic Reserve.
- Bondholders would receive 1% annual interest (lower than traditional Treasuries) and 50% of BTC price appreciation.
A New Bitcoin Standard
At first glance, BitBonds is an innovative way to increase demand for U.S. Treasuries without Federal Reserve intervention while lowering borrowing costs. However, this instrument would signal a radical change in monetary policy.
A 4000-year precedent
Money (as a visual measure of credit) has been and is always socially constructed through a stable exchange ratio.
- Money didn’t appear in ancient Sumer until priests and palace administrators set rates between standard weights of grain and silver on palace-authorized cuneiform tablets.
- In Egypt, money was constructed through economic administrators (related to the king) setting common rates between an abstracted standardized 92 gram copper weight measurement called a Deben and grain.
- Roman and Greek mints fixed ratios and weights between precious metals to establish official coinage and stabilize their value.
- The U.S. established its first currency through a bi-metallic standard, fixing gold and silver rates via the U.S. Mint.
- The modern U.S. monetary system issues its currency on a promise to redeem $100 for $100 + 2% interest.
U.S. government debt became the default monetary exchange rate the moment Nixon suspended gold redemption in 1971. It was the only remaining promised ratio of exchange attached to the US Dollar. Each year, Congress votes to extend this debt-based system by approving the federal budget. And the Federal Reserve then manages the levers of bond prices and yields through open market operations. There is no other federal mechanism for securing universal interest in the dollar, than the interest paid from its debt.
With BitBonds collateralizing 10% of each issuance in Bitcoin, the government would effectively introduce a new promised ratio of exchange to US monetary policy. It would promise to redeem 10 cents of every $1 in this lending program for bitcoin (half for the reserve and half of its appreciated value for the holder). This promise would transition US monetary policy from a pure debt based system to a new implicit exchange rate between Bitcoin and the U.S. dollar.
How BitBonds Would Drive Bitcoin to $10 Million
- First, BitBonds promises unlimited buying pressure on a finite asset. (The government can perpetually issue more BitBonds to acquire Bitcoin.) That, combined with the fact that Treasuries are the world’s primary liquidity engine, would generate unprecedented demand for Bitcoin reserves.
- Second, unlike previous reserve assets like gold, Bitcoin’s indivisibility prevents fractional redemption. This network constraint prevents the government from redeeming less than 1 satoshi (the base unit of Bitcoin) for 10 cents, thereby setting a clear price target for the market. Promising to collateralize 10% of each bond with bitcoin is like priming the pump for max buy pressure, fixing a target price and pulling the trigger.
- Investors would front-run the Treasury’s buying spree with that target in mind and in a matter of time 1 satoshi will equal $0.10 ($10M per BTC).
- At $10M per BTC, Bitcoin’s total valuation would reach $210 trillion—a figure capable of servicing the $189 trillion in global U.S. debt obligations and backing the $21 trillion M2 money supply. This valuation would prime bitcoin to become the world reserve asset backing the world reserve currency (a digital dollar).
- After this transformation, the government would have the precedent to institute a more explicit system of regulating bitcoin and digital dollar redemption. You can learn more about what this system would look like in my thesis for why technocratic government agencies will inevitably use bitcoin to create a cashless digital society: The Anarchist’s Guide to Cashing out of the Matrix.
Why Market Resistance Will Fail
- Selling Bitcoin into a U.S. Treasury buy wall would be a losing trade. A continuous government buyer would absorb any attempt to suppress BTC’s price.
- Foreign governments would be compelled to adopt or lose financial leverage. If the U.S. redefines sovereign debt through Bitcoin, foreign central banks must accumulate Bitcoin or face economic devaluation.
- The Federal Reserve would have no choice but to accommodate Bitcoin-backed Treasuries. If BitBonds reshape U.S. debt issuance, the Fed must either integrate them into monetary policy or risk disrupting Treasury markets.
The short path to a $10 million bitcoin
- The U.S. Treasury launches BitBonds, requiring Bitcoin collateral equal to 10% of each issuance.
- Bitcoin markets recognize that the U.S. government is a continuous net buyer.
- Investors front-run this signal, accelerating Bitcoin accumulation.
- Institutional demand propels BTC to the $10M target, exponentially increasing the value of the SBR.
- Once 1 satoshi = $0.10, the federal government will have a stockpile of bitcoin valued at a cost basis greater than its annual debt obligations.
- Rather than use the stockpile to pay the debt down, the government will find that it needs to enforce a new surveillance-enforced bitcoin redemption policy to maintain a funnel of public bitcoin to the SBR in return for surveillable stablecoins. (read thesis for more)
Bitcoin’s Supply Guarantees a Stable Transition
Unlike gold, Bitcoin’s supply is fixed, transparent, and auditable. Once repricing begins, sovereign wealth funds, pension funds, and financial institutions will be forced to accumulate Bitcoin, play by the new state-issued redemption rules or be left behind.
I'm not sure how long it would take for the market to figure this out, but I’d assume it would be an all-out sprint to $10M BTC once the cat is out of the bag.
-
 @ f240be2b:00c761ba
2025-03-20 17:53:08
@ f240be2b:00c761ba
2025-03-20 17:53:08Warum jetzt ein guter Zeitpunkt sein könnte, sich mit Bitcoin zu beschäftigen
Kennt ihr das? Wenn der Bitcoin-Preis neue Höchststände erreicht, möchte plötzlich jeder einsteigen. Doch sobald die Kurse fallen, überwiegt die Angst. Dabei zeigt die Geschichte: Gerade diese Phasen der Unsicherheit können interessante Zeitpunkte sein, um sich mit dem Thema zu beschäftigen.
Historische Zyklen Bitcoin durchläuft regelmäßige Marktzyklen Nach jedem Tief folgte bisher ein neues Hoch Emotionen spielen eine große Rolle im Markt Psychologie des Marktes Wenn alle euphorisch sind → meist teuer Wenn Unsicherheit herrscht → oft interessante Gelegenheiten Die Masse liegt häufig zum falschen Zeitpunkt richtigRationale Herangehensweise
Statt emotional zu handeln, solltet ihr:
Einen langfristigen Anlagehorizont wählen Regelmäßig kleine Beträge investieren (Cost-Average-Effekt)Hier ein paar Charts die euch helfen sollen und euch mutig werden lassen:
https://www.tradingview.com/chart/BTCUSD/HuGpzZfQ-BITCOIN-Cycle-pattern-completed-Year-end-Target-locked-at-150k/
https://www.tradingview.com/chart/BTCUSD/YVyy9QuU-BITCOIN-Money-Supply-Dollar-and-Bonds-pushing-for-MEGA-RALLY/
https://www.tradingview.com/chart/BTCUSD/pZ0qs5x3-BTCUSD-TSI-shows-that-this-is-the-LAST-BEST-BUY/
https://www.tradingview.com/chart/BTCUSD/x3e7GuLQ-BITCOIN-Is-this-a-Falling-Wedge-bottom-formation/
und jetzt All-In :-)
-
 @ 16f1a010:31b1074b
2025-03-20 15:29:42
@ 16f1a010:31b1074b
2025-03-20 15:29:42What is NSSM?
NSSM (Non-Sucking Service Manager) is a free tool that allows you to install and manage any application as a Windows service. This is particularly useful for applications that don't natively support running as a service, ensuring they start automatically when your system boots and continue running in the background.
Downloading NSSM
- Visit the official NSSM website: https://nssm.cc/
- Download the latest stable release.
- Extract the downloaded ZIP file to a directory of your choice (e.g.,
C:\nssm).
Adding NSSM to Your PATH (Recommended)
Adding NSSM to your system's PATH environment variable allows you to run
nssmcommands from any command prompt window.- Search for "Environment Variables" in the Windows Start menu and select "Edit the system environment variables."

- In the "System Properties" window, click the "Environment Variables..." button.
- In the "System variables" section, find the "Path" variable and click "Edit."
- Click "New" and add the path to the directory where you extracted NSSM (e.g.,
C:\nssm). - Click "OK" on all open windows to save the changes.
- Open a new command prompt window and type
nssm --version. If NSSM is correctly added to your PATH, you should see the version information.
Using NSSM: Installing a Service
- Open a command prompt as administrator.
- Type
nssm install <service_name>and press Enter. Replace<service_name>with the name you want to give to your service. - A GUI will appear, allowing you to configure the service.
- In the "Path" field, enter the full path to the application's executable.
- In the "Startup directory" field, enter the directory containing the executable.
- Configure any other options as needed, such as "Arguments," "I/O," or "Details."
- Click "Install service."
Example:
bash nssm install MyGrainRelayConclusion
Congratulations, you now have NSSM installed and know the basics of using it to manage windows services. Check my profile for more technical guides on various topics, and stay tuned for more guides.
-
 @ 16f1a010:31b1074b
2025-03-20 14:32:25
@ 16f1a010:31b1074b
2025-03-20 14:32:25grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Introduction
grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Prerequisites
- Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rwwp5xsuryd3knfdr7g
Download Grain
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlPrerequisites: - Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: [Link to MongoDB setup guide].
Download Grain:
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution:
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain:
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files:
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlConfiguration Documentation
You can always find the latest example configs on my site or in the github repo here: config.yml
Config.yml
This
config.ymlfile is where you customize how your Grain relay operates. Each section controls different aspects of the relay's behavior.1.
mongodb(Database Settings)uri: mongodb://localhost:27017/:- This is the connection string for your MongoDB database.
mongodb://localhost:27017/indicates that your MongoDB server is running on the same computer as your Grain relay (localhost) and listening on port 27017 (the default MongoDB port).- If your MongoDB server is on a different machine, you'll need to change
localhostto the server's IP address or hostname. - The trailing
/indicates the root of the mongodb server. You will define the database in the next line.
database: grain:- This specifies the name of the MongoDB database that Grain will use to store Nostr events. Grain will create this database if it doesn't already exist.
- You can name the database whatever you want. If you want to run multiple grain relays, you can and they can have different databases running on the same mongo server.
2.
server(Relay Server Settings)port: :8181:- This sets the port on which your Grain relay will listen for incoming nostr websocket connections and what port the frontend will be available at.
read_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to send data before closing the connection.
write_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to receive data before closing the connection.
idle_timeout: 120 # in seconds:- This is the maximum time (in seconds) that the relay will keep a connection open if there's no activity.
max_connections: 100:- This sets the maximum number of simultaneous client connections that the relay will allow.
max_subscriptions_per_client: 10:- This sets the maximum amount of subscriptions a single client can request from the relay.
3.
resource_limits(System Resource Limits)cpu_cores: 2 # Limit the number of CPU cores the application can use:- This restricts the number of CPU cores that Grain can use. Useful for controlling resource usage on your server.
memory_mb: 1024 # Cap the maximum amount of RAM in MB the application can use:- This limits the maximum amount of RAM (in megabytes) that Grain can use.
heap_size_mb: 512 # Set a limit on the Go garbage collector's heap size in MB:- This sets a limit on the amount of memory that the Go programming language's garbage collector can use.
4.
auth(Authentication Settings)enabled: false # Enable or disable AUTH handling:- If set to
true, this enables authentication handling, requiring clients to authenticate before using the relay.
- If set to
relay_url: "wss://relay.example.com/" # Specify the relay URL:- If authentication is enabled, this is the url that clients will use to authenticate.
5.
UserSync(User Synchronization)user_sync: false:- If set to true, the relay will attempt to sync user data from other relays.
disable_at_startup: true:- If user sync is enabled, this will prevent the sync from starting when the relay starts.
initial_sync_relays: [...]:- A list of other relays to pull user data from.
kinds: []:- A list of event kinds to pull from the other relays. Leaving this empty will pull all event kinds.
limit: 100:- The limit of events to pull from the other relays.
exclude_non_whitelisted: true:- If set to true, only users on the whitelist will have their data synced.
interval: 360:- The interval in minutes that the relay will resync user data.
6.
backup_relay(Backup Relay)enabled: false:- If set to true, the relay will send copies of received events to the backup relay.
url: "wss://some-relay.com":- The url of the backup relay.
7.
event_purge(Event Purging)enabled: false:- If set to
true, the relay will automatically delete old events.
- If set to
keep_interval_hours: 24:- The number of hours to keep events before purging them.
purge_interval_minutes: 240:- How often (in minutes) the purging process runs.
purge_by_category: ...:- Allows you to specify which categories of events (regular, replaceable, addressable, deprecated) to purge.
purge_by_kind_enabled: false:- If set to true, events will be purged based on the kinds listed below.
kinds_to_purge: ...:- A list of event kinds to purge.
exclude_whitelisted: true:- If set to true, events from whitelisted users will not be purged.
8.
event_time_constraints(Event Time Constraints)min_created_at: 1577836800:- The minimum
created_attimestamp (Unix timestamp) that events must have to be accepted by the relay.
- The minimum
max_created_at_string: now+5m:- The maximum created at time that an event can have. This example shows that the max created at time is 5 minutes in the future from the time the event is received.
min_created_at_stringandmax_created_atwork the same way.
9.
rate_limit(Rate Limiting)ws_limit: 100:- The maximum number of WebSocket messages per second that the relay will accept.
ws_burst: 200:- Allows a temporary burst of WebSocket messages.
event_limit: 50:- The maximum number of Nostr events per second that the relay will accept.
event_burst: 100:- Allows a temporary burst of Nostr events.
req_limit: 50:- The limit of http requests per second.
req_burst: 100:- The allowed burst of http requests.
max_event_size: 51200:- The maximum size (in bytes) of a Nostr event that the relay will accept.
kind_size_limits: ...:- Allows you to set size limits for specific event kinds.
category_limits: ...:- Allows you to set rate limits for different event categories (ephemeral, addressable, regular, replaceable).
kind_limits: ...:- Allows you to set rate limits for specific event kinds.
By understanding these settings, you can tailor your Grain Nostr relay to meet your specific needs and resource constraints.
whitelist.yml
The
whitelist.ymlfile is used to control which users, event kinds, and domains are allowed to interact with your Grain relay. Here's a breakdown of the settings:1.
pubkey_whitelist(Public Key Whitelist)enabled: false:- If set to
true, this enables the public key whitelist. Only users whose public keys are listed will be allowed to publish events to your relay.
- If set to
pubkeys::- A list of hexadecimal public keys that are allowed to publish events.
pubkey1andpubkey2are placeholders, you will replace these with actual hexadecimal public keys.
npubs::- A list of npubs that are allowed to publish events.
npub18ls2km9aklhzw9yzqgjfu0anhz2z83hkeknw7sl22ptu8kfs3rjq54am44andnpub2are placeholders, replace them with actual npubs.- npubs are bech32 encoded public keys.
2.
kind_whitelist(Event Kind Whitelist)enabled: false:- If set to
true, this enables the event kind whitelist. Only events with the specified kinds will be allowed.
- If set to
kinds::- A list of event kinds (as strings) that are allowed.
"1"and"2"are example kinds. Replace these with the kinds you want to allow.- Example kinds are 0 for metadata, 1 for short text notes, and 2 for recommend server.
3.
domain_whitelist(Domain Whitelist)enabled: false:- If set to
true, this enables the domain whitelist. This checks the domains .well-known folder for their nostr.json. This file contains a list of pubkeys. They will be considered whitelisted if on this list.
- If set to
domains::- A list of domains that are allowed.
"example.com"and"anotherdomain.com"are example domains. Replace these with the domains you want to allow.
blacklist.yml
The
blacklist.ymlfile allows you to block specific content, users, and words from your Grain relay. Here's a breakdown of the settings:1.
enabled: true- This setting enables the blacklist functionality. If set to
true, the relay will actively block content and users based on the rules defined in this file.
2.
permanent_ban_words:- This section lists words that, if found in an event, will result in a permanent ban for the event's author.
- really bad wordis a placeholder. Replace it with any words you want to permanently block.
3.
temp_ban_words:- This section lists words that, if found in an event, will result in a temporary ban for the event's author.
- crypto,- web3, and- airdropare examples. Replace them with the words you want to temporarily block.
4.
max_temp_bans: 3- This sets the maximum number of temporary bans a user can receive before they are permanently banned.
5.
temp_ban_duration: 3600- This sets the duration of a temporary ban in seconds.
3600seconds equals one hour.
6.
permanent_blacklist_pubkeys:- This section lists hexadecimal public keys that are permanently blocked from using the relay.
- db0c9b8acd6101adb9b281c5321f98f6eebb33c5719d230ed1870997538a9765is an example. Replace it with the public keys you want to block.
7.
permanent_blacklist_npubs:- This section lists npubs that are permanently blocked from using the relay.
- npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtnis an example. Replace it with the npubs you want to block.- npubs are the human readable version of public keys.
8.
mutelist_authors:- This section lists hexadecimal public keys of author of a kind1000 mutelist. Pubkey authors on this mutelist will be considered on the permanent blacklist. This provides a nostr native way to handle the backlist of your relay
- 3fe0ab6cbdb7ee27148202249e3fb3b89423c6f6cda6ef43ea5057c3d93088e4is an example. Replace it with the public keys of authors that have a mutelist you would like to use as a blacklist. Consider using your own.- Important Note: The mutelist Event MUST be stored in this relay for it to be retrieved. This means your relay must have a copy of the authors kind10000 mutelist to consider them for the blacklist.
Running Grain as a Service:
Windows Service:
To run Grain as a Windows service, you can use tools like NSSM (Non-Sucking Service Manager). NSSM allows you to easily install and manage any application as a Windows service.
* For instructions on how to install NSSM, please refer to this article: [Link to NSSM install guide coming soon].-
Open Command Prompt as Administrator:
- Open the Windows Start menu, type "cmd," right-click on "Command Prompt," and select "Run as administrator."
-
Navigate to NSSM Directory:
- Use the
cdcommand to navigate to the directory where you extracted NSSM. For example, if you extracted it toC:\nssm, you would typecd C:\nssmand press Enter.
- Use the
-
Install the Grain Service:
- Run the command
nssm install grain. - A GUI will appear, allowing you to configure the service.
- Run the command
-
Configure Service Details:
- In the "Path" field, enter the full path to your Grain executable (e.g.,
C:\grain\grain_windows_amd64.exe). - In the "Startup directory" field, enter the directory where your Grain executable is located (e.g.,
C:\grain).
- In the "Path" field, enter the full path to your Grain executable (e.g.,
-
Install the Service:
- Click the "Install service" button.
-
Manage the Service:
- You can now manage the Grain service using the Windows Services manager. Open the Start menu, type "services.msc," and press Enter. You can start, stop, pause, or restart the Grain service from there.
Linux Service (systemd):
To run Grain as a Linux service, you can use systemd, the standard service manager for most modern Linux distributions.
-
Create a Systemd Service File:
- Open a text editor with root privileges (e.g.,
sudo nano /etc/systemd/system/grain.service).
- Open a text editor with root privileges (e.g.,
-
Add Service Configuration:
- Add the following content to the
grain.servicefile, replacing the placeholders with your actual paths and user information:
```toml [Unit] Description=Grain Nostr Relay After=network.target
[Service] ExecStart=/path/to/grain_linux_amd64 WorkingDirectory=/path/to/grain/directory Restart=always User=your_user #replace your_user Group=your_group #replace your_group
[Install] WantedBy=multi-user.target ```
- Replace
/path/to/grain/executablewith the full path to your Grain executable. - Replace
/path/to/grain/directorywith the directory containing your Grain executable. - Replace
your_userandyour_groupwith the username and group that will run the Grain service.
- Add the following content to the
-
Reload Systemd:
- Run the command
sudo systemctl daemon-reloadto reload the systemd configuration.
- Run the command
-
Enable the Service:
- Run the command
sudo systemctl enable grain.serviceto enable the service to start automatically on boot.
- Run the command
-
Start the Service:
- Run the command
sudo systemctl start grain.serviceto start the service immediately.
- Run the command
-
Check Service Status:
- Run the command
sudo systemctl status grain.serviceto check the status of the Grain service. This will show you if the service is running and any recent logs. - You can run
sudo journalctl -f -u grain.serviceto watch the logs
- Run the command
More guides are in the works for setting up tailscale to access your relay from anywhere over a private network and for setting up a cloudflare tunnel to your domain to deploy a grain relay accessible on a subdomain of your site eg wss://relay.yourdomain.com
-
 @ 16f1a010:31b1074b
2025-03-20 14:31:19
@ 16f1a010:31b1074b
2025-03-20 14:31:19Introduction
MongoDB is a popular NoSQL document database, meaning it stores data in flexible, JSON-like documents. This makes it highly scalable and adaptable for various applications. This guide will focus on installing the Community Server edition, which is free and open-source.
This article is designed for beginners and those new to MongoDB, providing a clear and concise walkthrough of the installation process. We will cover installation on both Windows and Linux operating systems.
The official MongoDB documentation on the MongoDB website is very informative and you should be able to follow their guides. This article is written to provide a brief overview and a more streamlined installation experience.
Prerequisites
MongoDB Community Server can be installed and run on a wide range of systems. While specific hardware requirements can vary based on your intended use case and the size of your database, here are the general prerequisites:
- Operating System:
- This guide will cover installation on popular versions of Windows and Linux (specifically Ubuntu/Debian). MongoDB also supports other operating systems, which you can find on the official MongoDB website.
- Storage Space:
- You'll need sufficient disk space to store your database files. The amount of space required will depend on the size of your data. It is recommended to have more storage than you think you will initially need.
- RAM:
- While MongoDB can run with minimal RAM, having more RAM will improve performance, especially for larger databases. The amount of RAM needed will depend on the size of your data.
- Basic System Knowledge:
- Familiarity with using the command line or terminal is helpful, especially for Linux installations.
- Basic understanding of file systems and directories.
Essentially, MongoDB is designed to be flexible and can run on most modern systems. As your data grows, you can always scale your hardware accordingly.
Downloading MongoDB Community Server:
To begin, you'll need to download the MongoDB Community Server installation package.
- Visit the official MongoDB download page: https://www.mongodb.com/try/download/community
On the download page, you'll see options to select the following:
- Version: Choose the desired version of MongoDB. It is generally recommended to select the latest stable release.
- Operating System: Select your operating system (Windows or Linux).
- Package: Select the appropriate package type. For Windows, it will typically be
msi. For Linux, you will choose the package type that aligns with your linux distro. For example.debfor Debian/Ubuntu or.rpmfor RedHat/Fedora.
Once you have made your selections, click the "Download" button to download the installer or package.
Installation on Windows:
Running the Installer:
-
Locate the Downloaded Installer:
- Navigate to the directory where you downloaded the MongoDB
.msiinstaller.
- Navigate to the directory where you downloaded the MongoDB
-
Run the Installer:
- Double-click the
.msifile to start the installation wizard.
- Double-click the
-
Welcome Screen:
- Click "Next" on the welcome screen.
-
License Agreement:
- Read the license agreement, check the "I accept the terms in the License Agreement" box, and click "Next."
-
Setup Type:
- Select "Custom" installation. This allows you to choose the installation location and data directory. Click "Next."
-
Installation Location:
- You can change the default installation directory if desired. Click "Next."
-
Service Configuration:
- You can choose to install MongoDB as a service. It is recommended to install as a service.
- You can also change the "Data Directory" location here. It is recommended to change this to a location such as
C:\data\db. If you do not change it here, you will need to create the data directory manually later. - Click "Next."
-
Ready to Install:
- Click "Install" to begin the installation process.
-
Complete Installation:
- Once the installation is complete, click "Finish."
Setting Environment Variables (Optional but Recommended):
Setting the
PATHenvironment variable allows you to run MongoDB commands from any command prompt window without specifying the full path to the executable.-
Open System Properties:
- Search for "Environment Variables" in the Windows Start menu and select "Edit the system environment variables."
-
Environment Variables:
- In the "System Properties" window, click the "Environment Variables..." button.
-
Edit Path Variable:
- In the "System variables" section, find the "Path" variable and click "Edit."
-
Add MongoDB Bin Directory:
- Click "New" and add the path to the MongoDB
bindirectory. This is typicallyC:\Program Files\MongoDB\Server\<version>\bin, replacing<version>with your installed version. - Click "OK" on all open windows to save the changes.
- Click "New" and add the path to the MongoDB
-
Verify Path:
- Open a new command prompt window and type
mongod --version. If MongoDB is installed correctly and thePATHvariable is set, you should see the MongoDB version information.
- Open a new command prompt window and type
Installation on Linux (Ubuntu/Debian):
These instructions are specifically for Debian-based systems like Ubuntu.
Importing the MongoDB Public GPG Key:
-
Open a Terminal:
- Open your terminal application.
-
Import the GPG Key:
- Run the following command to import the MongoDB public GPG key:
bash wget -qO - [https://www.mongodb.org/static/pgp/server-7.0.asc](https://www.mongodb.org/static/pgp/server-7.0.asc) | sudo apt-key add -- This command downloads the GPG key and adds it to your system's trusted keys. This ensures that the packages you download from the MongoDB repository are authentic.
Adding the MongoDB Repository:
-
Add the Repository:
- Run the following command to add the MongoDB repository to your system's sources list:
bash echo "deb [ arch=amd64,arm64 ] [https://repo.mongodb.org/apt/ubuntu](https://repo.mongodb.org/apt/ubuntu) $(lsb_release -cs)/mongodb-org/7.0 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-7.0.list- This command adds the MongoDB repository to your system's package manager sources. The
$(lsb_release -cs)part automatically determines your Ubuntu/Debian version.
-
Update Package List:
- Run the following command to update your package list:
bash sudo apt update- This command refreshes the package list, including the newly added MongoDB repository.
Installing MongoDB:
-
Install MongoDB:
- Run the following command to install the MongoDB Community Server:
bash sudo apt install mongodb-org- This command downloads and installs the MongoDB packages.
After install, linux and windows should both have a system service already setup from the install process. You can check if it's running on linux with
sudo systemctl status mongod. On Windows, you should see the service running as "MongoDB Server" if you open system services on WindowsBasic MongoDB Commands:
After installing and starting MongoDB, you can use the
mongoshell to interact with your database. Here are some basic commands to get you started:Checking MongoDB Version:
First, let's verify that MongoDB is installed correctly by checking its version:
-
Open a Terminal or Command Prompt:
- Open your terminal (Linux/macOS) or command prompt (Windows).
-
Run
mongosh --version:- Type
mongosh --versionand press Enter. - This command will display the installed MongoDB version if it's correctly installed and in your system's PATH.
- Type
Basic MongoDB Shell Commands:
-
Open the
mongoshShell:- Type
mongoshand press Enter. This will open the MongoDB shell, and you'll see a prompt like>.
- Type
-
Show Databases:
- To see a list of all databases on your MongoDB server, type
show dbsand press Enter. - This will display a list of database names.
- To see a list of all databases on your MongoDB server, type
-
Use a Database:
- To switch to a specific database, type
use <database_name>and press Enter. Replace<database_name>with the name of the database you want to use. - Example:
use mydatabase - If the database doesn't exist, MongoDB will create it when you first store data in it.
- To switch to a specific database, type
-
Show Collections:
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
show collectionsand pressing Enter. - Collections are where you store documents (JSON-like data).
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
Example Session:
```bash
mongosh Current Mongosh Log ID: 6563728637951a37887e2730 Connecting to: mongodb://127.0.0.1:27017/?directConnection=true&serverSelectionTimeoutMS=2000&appName=mongosh Using MongoDB: 7.0.3 Using Mongosh: 2.1.1 For mongosh info see: https://docs.mongodb.com/mongodb-shell/
test> show dbs admin 40 KiB config 72 KiB local 40 KiB test> use mydatabase switched to db mydatabase mydatabase> show collections mydatabase> ```
Conclusion
Congratulations! You have successfully installed and started MongoDB Community Server. You've learned how to download, install, and run MongoDB on both Windows and Linux systems, and you've explored some basic commands to interact with your database.
Now, you might want to try an application like grain, a Nostr relay, which utilizes MongoDB as its database. Learn How to Install grain: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rqdpnx56rqv34uyz5g4
Remember, this guide covers the basics. There's much more to explore in the world of MongoDB, including advanced querying, indexing, replication, and sharding. Continue exploring the official MongoDB documentation to deepen your knowledge and unlock the full potential of this powerful database.
- Operating System:
-
 @ f1989a96:bcaaf2c1
2025-03-20 14:21:35
@ f1989a96:bcaaf2c1
2025-03-20 14:21:35Good morning, readers!
In Thailand, the government announced a third digital cash handout to “stimulate the economy and drive technological adoption.” This disbursement will allocate 27 billion baht ($800 million) to 2.7 million citizens aged 16-20. Like in previous phases, it will be distributed via a state-controlled “digital wallet” application, which essentially functions as a central bank digital currency (CBDC). This system gives the regime an inside view of Thais’ financial activity and creates a centralized database to monitor, censor, and control.
Meanwhile, in Russia, the central bank has proposed limiting Bitcoin access to only the wealthiest individuals. Under the proposal, only Russians with over $1.2 million in assets or an annual income above $580,000 could buy and sell digital assets — arbitrarily barring everyday Russians (including obviously most journalists and activists) from accessing Bitcoin and the financial independence it grants.
In open-source software news, a new tool called Banxaas is making Bitcoin more accessible in West Africa by integrating with local payment providers to facilitate buying and selling Bitcoin using the CFA currency (XOF). This on-and-off ramp could expand financial freedom for human rights activists, dissidents, and everyday citizens.
We end with the latest edition of the HRF x Pubkey Freedom Tech Series, in which HRF’s Zac Guignard sits down with author Jason Maier to discuss how Bitcoin can drive human rights around the world. Together, they examine the shortcomings of today’s financial system and discuss how Bitcoin is aiding people living under authoritarian regimes.
Now, let’s get right to it!
Subscribe Here
GLOBAL NEWS
Thailand | Announces Third Digital Cash Handout to Boost Economy
The government of Thailand announced a third digital cash handout, allocating 27 billion baht ($800 million) to 2.7 million citizens aged 16-20 to “stimulate the economy and drive technological adoption.” Like in previous phases, the regime will distribute the funds through a state-run “digital wallet” application, which would effectively function as a central bank digital currency (CBDC). Past handouts of the CBDC came with strict restrictions: spending was limited to approved vendors within designated areas, purchases were restricted to certain goods, and funds expired after six months. Meanwhile, Prime Minister Paetongtarn Shinawatra called this third handout the first full deployment of the digital wallet system and urged the public to download the official app. This would directly link citizens' financial activity and data to the regime, threaten privacy, and deepen repression in a country with a long history of silencing dissent.
Russia | Central Bank Proposes Restricting Bitcoin Access to Wealthy Only
Russia’s central bank has proposed restricting Bitcoin and cryptocurrency access to only the country’s wealthiest individuals, barring everyday Russians from buying and selling digital assets unless they meet specific income or asset thresholds. Under the proposal, only Russians with over $1.2 million in assets or an annual income above $580,000 could engage with digital assets — effectively putting Bitcoin officially out of reach of most activists and journalists. The central bank claims the measure protects citizens from “volatility and lack of state backing.” But in reality, it likely signals the regime’s fear of Bitcoin’s ability to provide individual financial autonomy. By blocking most Russians from opting out of the state-controlled financial system, the regime is doubling down on financial repression.
India | Advances Digital Rupee CBDC
India’s government is pushing forward with its CBDC, the Digital Rupee, hailing it as a modern payment solution. But as journalist and author Roger Huang puts it, “it looks like a solution searching for a problem to solve.” Beyond the branding, the Digital Rupee enables state control over financial activity. Its programmability allows the government to dictate how, when, and where people spend — restricting transactions to specific merchants, locations, or goods and even imposing expiration dates on money. India’s crackdown on dissent is well-documented, from freezing opposition bank accounts to attempting a Bitcoin ban. Now, the Reserve Bank of India is embedding the CBDC into its digital payment system (UPI), quietly pushing millions into a tightly controlled and surveilled financial system.
Zimbabwe | Financial Regulators Mandate Earnings in ZiG
Zimbabwe’s market regulator is mandating all companies report their earnings in the new ZiG currency despite it losing 96% of its value since its launch last year. This move tightens state control over an already fragile economy, pushing businesses and citizens deeper into an unstable system that has repeatedly wiped out savings through inflation. The ZiG is Zimbabwe’s sixth currency in 15 years, introduced with gold backing to restore confidence in the regime’s ability to manage a currency. Instead, it’s rapidly devaluing, while the US dollar remains the preferred currency for trade and savings — when accessible. For ordinary Zimbabweans, the mandatory use of ZiG for taxes and government services is already a challenge due to its scarcity.
Egypt | Dictator-imposed Reforms Causing Economic Chaos
In the wake of an $8 billion deal with the International Monetary Fund (IMF) last spring, the Egyptian dictatorship has carried out “reforms” that are fueling inflation and making necessities increasingly unaffordable. To meet IMF conditions, Egyptian officials devalued the pound, slashed subsidies, and hiked the cost of fuel and public transportation — driving inflation beyond 20% for months on end. For millions of Egyptians, basic goods are now unaffordable. And the government’s promised minimum wage increase for public workers remains unfulfilled, leaving the public to absorb the price shocks. These undemocratic reforms — never voted on and executed with no way for the public to push back — aimed at securing further financing have only eroded the financial freedom of 114 million Egyptians and pushed the country into greater debt.
China | Facebook Enabling Authoritarian Censorship
A former Meta executive, Sarah Wynn-Williams, has accused Facebook of working “hand in glove” with the Chinese Communist Party (CCP) to censor and surveil content in China. According to Wynn-Williams, Facebook explored building censorship tools that would suppress viral posts until Chinese authorities approved. They even considered sharing user data in exchange for market access to China’s massive user base. Meta denied these claims, saying they fired Wynn-Williams in 2017 for poor performance. Regardless, the revelations highlight the dangers of for-profit, centralized platforms that authoritarian regimes can co-opt. Protocols like nostr (where no single entity moderates content) are more important than ever. Activists and dissidents seeking free communications can get started with nostr here.
BITCOIN AND FREEDOM TECH NEWS
Banxaas | Spend Sats in West Africa
Hundreds of millions of citizens in West Africa still use the CFA franc in an arrangement upheld by more than a dozen authoritarian leaders. Banxaas offers an alternative by bridging Bitcoin with West Africa’s mobile money networks. This allows individuals to buy and sell Bitcoin through local payment providers using the local CFA currency (XOF) and their own Lightning wallet. By integrating with local payment providers, Banxaas serves as a crucial on-and-off-ramp to Bitcoin, bringing the benefits of financial freedom to individuals, nonprofits, and human rights defenders across the region. Watch a demonstration of how Banxaas works here.
Mi Primer Bitcoin | Bitcoin Workbook Translated to Mandarin
Mi Primer Bitcoin, an open-source Bitcoin educational initiative focused on high-school-age students, released a Mandarin translation of its 2025 Bitcoin Diploma. This open-source resource provides mainland Chinese citizens, activists, and dissidents with accessible Bitcoin education at a time when financial freedom is increasingly under threat. With China tightening restrictions on personal wealth and expanding state surveillance of financial activity through the digital yuan CBDC, the diploma offers a useful new resource to learn the alternatives to state-controlled financial systems.
Blitz Wallet | Improves Ecash Functionality for Greater Financial Autonomy
Blitz Wallet, an open-source and self-custodial Bitcoin Lightning, Liquid, and ecash wallet, released an update that improves ecash functionality. Ecash, a Bitcoin-backed digital money system, allows instant and private transactions but requires custodial “mints” to manage tokens. The new update links users’ ecash to their wallet’s seed phrase (the 12-word backup used for Bitcoin recovery), allowing them to restore funds even if their device is lost or stolen. Users can also now transfer ecash between different wallets, increasing flexibility and control over their funds. Improved ecash UX is much-desired for political dissidents who can’t afford for authoritarian regimes to have full oversight over all of their economic activities.
Fedimint | Adds On-chain Support for Everyone
Fedimint, an open-source Bitcoin custody model that lets communities securely manage Bitcoin funds together, released v0.6.0, adding support for on-chain Bitcoin deposits (transactions directly on Bitcoin’s base layer). By offering private and trust-minimized transactions alongside on-chain support, Fedimint makes it easier, especially for nonprofit communities, to self-custody Bitcoin. It provides greater privacy and autonomy versus using fully centralized platforms that are easily subject to the political and regulatory pressure of authoritarian regimes.
Africa Bitcoin Conference | Announces 2025 Conference
The Africa Bitcoin Conference (ABC) announced its fourth edition, set to take place from Dec. 3-5, 2025, in Port Louis, Mauritius. Hosted at the Caudan Art Center, the event will bring together activists, Bitcoin advocates, and freedom tech developers to explore Bitcoin as a pathway to financial freedom. Now the largest Bitcoin gathering in Africa, ABC has established itself as a key platform for discussions on financial inclusion, inflation resistance, and censorship-resistant money — putting tools for financial sovereignty into the hands of those who need them most. HRF is proud to support ABC and, in particular, is proud to help delegates from dozens of authoritarian regimes attend each year. You can learn more about the conference and buy tickets here.
RECOMMENDED CONTENT
HRF x Pubkey — How Bitcoin Brings About Social Change with Jason Maier
In the latest installment of the HRF x Pubkey Freedom Tech Series, HRF Content and Research Associate Zac Guignard sits down with Jason Maier, author of “A Progressive’s Case for Bitcoin,” to share how Bitcoin can spark a meaningful shift in personal liberty worldwide. Jason explains the core monetary properties that make Bitcoin permissionless, censorship-resistant, and a powerful tool for financial freedom. Together, they examine the shortcomings of today’s financial system and discuss how Bitcoin is aiding people living under authoritarian regimes. They talk about how Bitcoin shouldn’t be a political issue and can be useful to anyone, no matter their beliefs. Watch the full conversation here.
Mélancolies de l’Opprimé by Farida Bemba Nabourema
Farida Bemba Nabourema, a renowned Togolese human rights activist, former HRF freedom fellow, and Bitcoin pioneer, announced that her new book “Mélancolies de l’Opprimé” will be released on April 15, 2025. A decade after her first book, “La Pression de l’Oppression,” this deeply personal and reflective work offers hard-earned wisdom for young activists stepping into the struggle against dictatorships and injustice. Nabourema candidly shares the emotional, physical, and psychological toll of resistance and activism while also highlighting the sense of purpose in the pursuit of freedom and human rights. Learn more about the book here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 58537364:705b4b85
2025-03-20 14:03:27
@ 58537364:705b4b85
2025-03-20 14:03:27“สุขเวทนา” ที่แท้ก็คือ “มายา”
เป็นเหมือนลูกคลื่นลูกหนึ่ง
ที่เกิดขึ้นเพราะน้ำถูกลมพัด
เดี๋ยวมันก็แตกกระจายไป
หากต้องการจะมีชีวิตอย่างเกษมแล้ว
ก็ต้องอาศัยความรู้เรื่อง อนิจจัง ทุกขัง อนัตตา ให้สมบูรณ์
มันจะต่อต้านกันได้กับอารมณ์ คือ รูป เสียง กลิ่น รส สัมผัส ที่มากระทบ
ไม่ให้ไปหลงรัก หรือหลงเกลียดเรื่องวุ่นวายมีอยู่ ๒ อย่างเท่านั้น
- ไปหลงรัก อย่างหนึ่ง
- ไปหลงเกลียด อย่างหนึ่ง
ซึ่งเป็นเหตุให้หัวเราะและต้องร้องไห้
ถ้าใครมองเห็นว่า หัวเราะก็กระหืดกระหอบ มันเหนื่อยเหมือนกัน
ร้องไห้ก็กระหืดกระหอบ เหมือนกัน
สู้อยู่เฉย ๆ ดีกว่า อย่าต้องหัวเราะ อย่าต้องร้องไห้
นี่แหละ! มันเป็นความเกษมเราอย่าได้ตกไปเป็นทาสของอารมณ์
จนไปหัวเราะหรือร้องไห้ตามที่อารมณ์มายั่ว
เราเป็นอิสระแก่ตัว หยุดอยู่ หรือเกษมอยู่อย่างนี้ดีกว่า
ใช้ อนิจจัง ทุกขัง อนัตตา เป็นเครื่องมือกำกับชีวิต
- รูป เสียง กลิ่น รส สัมผัส เป็น มายา เป็น illusion
- "ตัวกู-ของกู" ก็เป็น illusion
- เพราะ "ตัวกู-ของกู" มันเกิดมาจากอารมณ์
- "ตัวกู-ของกู" เป็นมายา อารมณ์ทั้งหลายก็เป็นมายา
เห็นได้ด้วยหลัก อนิจจัง ทุกขัง อนัตตา
...ความทุกข์ก็ไม่เกิด
เราจะตัดลัดมองไปดูสิ่งที่เป็น “สุขเวทนา”
สุขเวทนา คือ ความสุขสนุกสนาน เอร็ดอร่อย
ที่เป็นสุขนั้นเรียกว่า “สุขเวทนา”แต่สุขเวทนา เป็นมายา
เพราะมันเป็นเหมือนลูกคลื่นที่เกิดขึ้นเป็นคราว ๆ
ไม่ใช่ตัวจริงอะไรที่พูดดังนี้ก็เพราะว่า
ในบรรดาสิ่งทั้งปวงในโลกทั้งหมดทุกโลก
ไม่ว่าโลกไหน มันมีค่าอยู่ก็ตรงที่ให้เกิดสุขเวทนาลองคิดดูให้ดีว่า...
- ท่านศึกษาเล่าเรียนทำไม?
- ท่านประกอบอาชีพ หน้าที่การงานทำไม?
- ท่านสะสมทรัพย์สมบัติ เกียรติยศ ชื่อเสียง พวกพ้องบริวารทำไม?มันก็เพื่อสุขเวทนาอย่างเดียว
เพราะฉะนั้น แปลว่า อะไร ๆ มันก็มารวมจุดอยู่ที่สุขเวทนาหมดฉะนั้น ถ้าเรามีความรู้ในเรื่องนี้
จัดการกับเรื่องนี้ให้ถูกต้องเพียงเรื่องเดียวเท่านั้น
ทุกเรื่องมันถูกหมดเพราะฉะนั้น จึงต้องดูสุขเวทนาให้ถูกต้องตามที่เป็นจริงว่า
มันก็เป็น “มายา” ชนิดหนึ่งเราจะต้องจัดการให้สมกันกับที่มันเป็นมายา
ไม่ใช่ว่า จะต้องไปตั้งข้อรังเกียจ เกลียดชังมัน
อย่างนั้นมันยิ่ง บ้าบอที่สุดถ้าเข้าไปหลงรัก หลงเป็นทาสมัน
ก็เป็นเรื่อง บ้าบอที่สุดแต่ว่าไปจัดการกับมันอย่างไรให้ถูกต้อง
นั้นแหละเป็นธรรมะ
เป็น ลูกศิษย์ของพระพุทธเจ้า
ที่จะเอาชนะความทุกข์ได้ และไม่ต้องเป็น โรคทางวิญญาณ
สุขเวทนา ที่แท้ก็คือ มายา
มันก็ต้องทำโดยวิธีที่พิจารณาให้เห็นว่า
“สุขเวทนา” นี้ ที่แท้ก็คือ “มายา”เป็นเหมือน ลูกคลื่นลูกหนึ่ง
ที่เกิดขึ้นเพราะ น้ำถูกลมพัดหมายความว่า
เมื่อ รูป เสียง กลิ่น รส ฯ เข้ามา
แล้ว ความโง่ คือ อวิชชา โมหะ ออกรับ
กระทบกันแล้วเป็นคลื่นกล่าวคือ สุขเวทนาเกิดขึ้นมา
แต่ เดี๋ยวมันก็แตกกระจายไป
ถ้ามองเห็นอย่างนี้แล้ว
เราก็ไม่เป็นทาสของสุขเวทนา
เราสามารถ ควบคุม จะจัด จะทำกับมันได้
ในวิธีที่ ไม่เป็นทุกข์- ตัวเองก็ไม่เป็นทุกข์
- ครอบครัวก็ไม่เป็นทุกข์
- เพื่อนบ้านก็ไม่เป็นทุกข์
- คนทั้งโลกก็ไม่พลอยเป็นทุกข์
เพราะมีเราเป็นมูลเหตุ
ถ้าทุกคนเป็นอย่างนี้
โลกนี้ก็มีสันติภาพถาวร
เป็นความสุขที่แท้จริงและถาวรนี่คือ อานิสงส์ของการหายโรคโดยวิธีต่าง ๆ กัน
ไม่เป็นโรค “ตัวกู” ไม่เป็นโรค “ของกู”
พุทธทาสภิกขุ
ที่มา : คำบรรยายชุด “แก่นพุทธศาสน์”
ปีพุทธศักราช ๒๕๐๔
ครั้งที่ ๑
หัวข้อเรื่อง “ใจความทั้งหมดของพระพุทธศาสนา”
ณ ศิริราชพยาบาล มหาวิทยาลัยมหิดล
เมื่อวันที่ ๑๗ ธันวาคม ๒๕๐๔ -
 @ 21335073:a244b1ad
2025-03-20 13:16:22
@ 21335073:a244b1ad
2025-03-20 13:16:22I’d never had the chance to watch Harry Potter on the big screen before. Experiencing the first movie in 3D was nothing short of spectacular. Right from the opening scene with Albus Dumbledore, I was floored—the makeup and costumes were so vivid, it felt like pure magic unfolding before my eyes. It’s clear that real masters of their craft worked behind the scenes, and their artistry shines through. The sets? Absolutely jaw-dropping! The level of detail in Diagon Alley was beyond impressive.
Seeing legends like Alan Rickman as Snape and Maggie Smith as Minerva McGonagall on that massive 3D screen was an unforgettable thrill. The film is packed with phenomenal actors, and it was a joy to catch every tiny eye twitch and subtle nuance of their performances brought to life. It was a mind-blowing experience, and I’d wholeheartedly recommend it to anyone who gets the chance.
Don’t forget to have a little whimsical fun sometimes my friends. 🪄
-
 @ a60e79e0:1e0e6813
2025-03-20 12:58:13
@ a60e79e0:1e0e6813
2025-03-20 12:58:13*This is a long form Nostr native version of a post that lives on my Nostr educational website Hello Nostr *
At first glance Nostr might appear quite similar to some of the apps you use every day, such as Twitter, Mastodon, or Facebook, but that couldn't be further from the truth. This post aims to dispel the myth that "Nostr is just a Twitter replacement" and give you a better understanding about the 'what', the 'how' and most importantly, the 'why' of Nostr.
What Is Nostr?
Nostr is a decentralized, open-source protocol designed for censorship-resistant networking and communication on the web. It stands for "Notes and Other Stuff Transmitted by Relays," and it works by allowing users to publish messages (notes) and content in the form of 'other stuff', to a network of servers (relays) that store and distribute the content.
Unlike traditional platforms like Twitter, Ebay or Facebook, Nostr doesn't rely on a central authority; instead, users control their own identities via cryptographic key pairs.
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
Fiatjaf - Nostr Creator
Nostr is not a website or an app you download from a single source — it’s an open protocol, like email or the internet. Think of it as a set of rules that anyone can use to build tools for sharing messages, posts, or other data without needing a centralized middleman like a big tech company.
Nostr was created by a developer named Fiatjaf in 2020, and has since been steadily gaining traction among people who care about privacy, freedom, and censorship resistance.

Why Nostr?
Imagine the scenario, you've been using an online platform for 5 or even 10 years. You've built up thousands of contacts, perhaps built yourself a sizeable reputation, or even rely on the income from the platform to feed your family. Then one day you make a controversial post, sell a certain item or upload a video on a spicy subject to the platform where the owner disagrees with. With the click of a button, your account is removed. All trace of you, your social graph, or even your future income, disappears in an instant.
Read aloud like that is sounds crazy that we'd even entertain using such a platform, right!? Sadly that is the reality in 2025. This is exactly what happens every single day on X, Facebook, Ebay, Paypal, Linkedin, etc.
Looking at the problem through a more social media focused lens, many of us have become slaves to the likes of Instagram, Twitter and TikTok. We use these 'free' apps under the guise of being social with others online. The reality is that we see what those apps want us to see. We've become slaves to the manipulation of complex and opaque algrorithms designed to keep us hooked and try to sell us things.

Unlike traditional platforms, which are often governed by centralized entities wielding significant control over user data, content moderation, and algorithmic influence, Nostr flips the script by prioritizing user sovereignty and resilience. Built on an open-source framework, Nostr allows individuals to control their own data and interact through a network of relays, making it much more difficult for any single authority - be it a corporation, government, or bad actor - to censor or manipulate the flow of information.
- Is a relay refusing to host your notes? Use another or run your own!
- A specific client using an algorithm you don't like, take your identity and social graph elsewhere and choose another!
Take your identity and social graph with you, anywhere any time.
Nostr’s ability to foster authentic, unfiltered conversations while safeguarding user sovereignty has made it a cornerstone for communities seeking alternatives - whether they’re activists, creators, or everyday people tired of being pawns in the data-driven game. It's simple and adaptable design also encourages innovation, inviting developers to build tools and interfaces that keep pushing the boundaries of what the decentralized internet can achieve. In short, Nostr isn’t just a tool; it’s a movement toward a freer, more equitable digital future.

How Does Nostr Work?
Instead of one giant server owned by a single company holding all your posts and messages, Nostr spreads everything across lots of smaller servers called relays. To get started, you download a client, create your account and back up your private key. Your private key is used to secure your account and sign every message you send over the network. This allows anyone you interact with the verify the integrity of the data coming from 'you'.
The Nostr network is essentially a collection of bulletin boards that share a common format
When you write a note, or share some other type of compatible data, your client signs it with your private key, then sends it to one or more relays. Which relays your information is sent to is entirely up to you. These relays share your message with others who want to see it.
For others to see your notes or 'other stuff', they'll need to be able to find you. Typically this is done by using your public key, which looks something like this
npub15c88nc8d44gsp4658dnfu5fahswzzu8gaxm5lkuwjud068swdqfspxssvx. Don't panic though, you don't need to memorize all of your friends public keys, there are more human friendly methods of finding people that we'll come onto later.Once someone is following you, their client will ask all of their connected relays for any data shared by your public key. Their client will receive this data, verify it is signed by your private key and then populate it into their feed.
The “Other Stuff” Explained
Nostr’s name hints at this: Notes and Other Stuff Transmitted by Relays. But what is the “other stuff”? Put simply, it’s all the creative and experimental things people are building on Nostr, beyond simple text based notes. Every action on Nostr is an event - like a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as Nostr Implementation Possibility - NIP. A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client for different purposes.
Here's some content examples of 'Other Stuff':
- Long-Form Content: Think blog posts or articles. NIP-23.
- Private Messaging: Encrypted chats between users. NIP-04.
- Communities: Group chats or forums like Reddit. NIP-72
- Marketplaces: People listing stuff for sale, payable with zaps. NIP-15
- Zaps: Value transfer over the Lightning Network. NIP57
The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around. It’s still early days, so expect the “other stuff” to grow wilder and weirder over time!
Clients vs Relays: What’s the Difference?
Newbies often get tripped up by these two terms, so let’s clearly define them.

Clients
A client is what you use to interact with Nostr. It’s the app or website where you type your posts, read your feed, follow and interact with others. Examples of Nostr clients include:
- Damus (iOS Twitter style client)
- Primal (Cross-platform Twitter style client)
- Amethyst (Android only Twitter style client)
- Habla.News (Web based blog client)
- Olas (Instagram style client)
- 0xchat (Messaging client)
Clients don’t store your data; they just pull it from relays and display it for you. You can switch clients whenever you want, and your account stays the same because it’s tied to your keys, not any single client or app.
Clients are how you use Nostr, and relays are where the data lives. You need both to make the magic happen.
Relays
A relay is a server that stores and shares Nostr data. It’s a little like a post office: you send your note to a relay, and it delivers it to anyone who’s subscribed to see it (like your followers). Relays are run by individuals, groups, or companies who volunteer their computing power. Some are free, some charge a small fee, and you can connect to as many as you like. Most clients will come pre-configured with a list of well-known relays, but you can add or remove any you like.
What Are Zaps?
Zaps are arguably one of Nostr’s coolest features! A zaps is a way to send payments in Bitcoin directly to other users. Imagine liking a post, but instead of just clicking a heart (which you can of course do), you send the poster a few cents worth of Bitcoin to say, “This is awesome!”.
Zaps use Bitcoin's Lightning Network, a faster and cheaper way to move Bitcoin around. To Zap someone, you need a Lightning wallet linked to your Nostr client. Some clients, like Primal, ship with their own custodial wallet to make getting started a breeze. Most clients also allow more advanced users to connect an existing Lightning Wallet to reduce reliance and trust in the client provider.
Zaps are optional but add a fun layer to Nostr. Creators love them because it’s a way to get direct support from fans, with no middleman required.

NIP-05 Identifiers: Your Nostr “Username”
Your nPub, or public key (that long string of letters and numbers) is your 'official' Nostr ID, but it’s not exactly catchy. Enter NIP-05 identifiers, a human-readable and easily sharable way to have people find you. They look like an email address, like
qna@hellonostr.xyz.Here’s how it works:
Most users obtain their NIP-05 ID from a website or service that supports Nostr. Some of these services are free whereas some charge a fee. Some clients, like Primal will set one up for you automatically when you create an account. The email like ID links to your public key, so people can find you more easily. And because these ID's are domain based, there can be no duplicates. qna@hellonostr.xyz can only map to a single public key. The only person that can change that link is the person in control of the domain.
If you control your own domain, you can easily map your Nostr public key to name@my.domain. It’s not mandatory, but it’s super useful for building trust and making your profile recognizable.
Next Steps
So you're bought in. You understand why Nostr is so important and want to get started. Check out our simple onboarding guide here.
Thanks For Reading
Hopefully that moistened your taste buds for more educational Nostr content. This was a basic one, but there will be more focused material coming soon.
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-
 @ 21335073:a244b1ad
2025-03-20 12:24:16
@ 21335073:a244b1ad
2025-03-20 12:24:16Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 7d33ba57:1b82db35
2025-03-20 11:27:54
@ 7d33ba57:1b82db35
2025-03-20 11:27:54Agaete
Agaete is a charming coastal town on the northwest coast of Gran Canaria, known for its stunning cliffs, natural pools, fresh seafood, and rich history. Surrounded by the Agaete Valley, this town offers a mix of nature, culture, and relaxation.
🏛️ Top Things to Do in Agaete
1️⃣ Explore the Agaete Valley (Valle de Agaete)
A lush, green valley famous for its coffee plantations – the only place in Europe where coffee is grown! Take a coffee farm tour and taste local Canarian coffee and wine.
2️⃣ Swim in the Natural Pools of Las Salinas
These volcanic rock pools by the coast provide a unique, sheltered swimming experience with breathtaking ocean views.
3️⃣ Visit Puerto de las Nieves
The picturesque fishing village next to Agaete, where you can enjoy fresh seafood, stroll along the promenade, or catch a ferry to Tenerife.
4️⃣ Hike in Tamadaba Natural Park
Just above Agaete, this stunning nature reserve offers incredible hiking trails with pine forests and breathtaking views of the Atlantic Ocean.
5️⃣ Discover the Necropolis of Maipés
An archaeological site with pre-Hispanic burial mounds dating back over 1,300 years, providing insight into the island’s indigenous history.
🍽️ What to Eat in Agaete
- Pescado fresco – Fresh fish grilled to perfection 🐟
- Cochino negro – A special Canarian black pig dish 🍖
- Queso de flor – Local artisan cheese 🧀
- Agaete coffee & wine – Grown right in the valley ☕🍷
🚗 How to Get to Agaete
🚗 By Car: ~35-40 minutes from Las Palmas
🚌 By Bus: Direct routes from Las Palmas (Lines 103 & 105)💡 Tips for Visiting Agaete
✅ Best time to visit? Year-round, but especially beautiful in spring 🌿
✅ Great for hiking & nature lovers – Bring comfortable shoes 👟
✅ Try local coffee & wine – It’s one of the best-kept secrets of Gran Canaria ☕🍷 -
 @ 20e17dd0:2ae504d7
2025-03-20 10:08:14
@ 20e17dd0:2ae504d7
2025-03-20 10:08:14Prerequisite
Installation
Open a Terminal session and write the following command:
ruby sudo apt install docker.ioYou will be ask permission to install and continueruby yValidation of the installation
To validate the installer, prompt the following command:
ruby docker --versionYou should get:
ruby Docker version 26.1.3, build 26.1.3-0ubuntu1~24.04.1To test if it is running, prompt the following command:
ruby sudo systemctl status dockerYou should get a screen with the docker.service as "running". To get back to command line do CTRL+C
Test Installation
To make sure that everything runs smoothly, write the following command:
ruby sudo docker run hello-worldYou should get a Hello from Docker.You are ready to enjoy pulling docker images!
originally posted at https://stacker.news/items/917064
-
 @ 20e17dd0:2ae504d7
2025-03-20 10:04:35
@ 20e17dd0:2ae504d7
2025-03-20 10:04:35Prerequisite
Installation
Open a Terminal session and write the following command to make sure that Docker is running:
ruby sudo systemctl status dockerYou should get a screen with the docker.service as "running". To get back to command line do CTRL+C
Then, create the volume that Portainer Server will use to store its database:
ruby sudo docker volume create portainer_dataYou are now ready for the on-liner installation:
ruby sudo docker run -d -p 8000:8000 -p 9443:9443 --name portainer --restart=always -v /var/run/docker.sock:/var/run/docker.sock -v portainer_data:/data portainer/portainer-ce:latestTo validate the installer, prompt the following command:
ruby sudo docker psYou should see Portainer's container running.
To access Portainer Server, go to the following adress: https://localhost:9443
Et voila!
-
 @ a95c6243:d345522c
2025-03-20 09:59:20
@ a95c6243:d345522c
2025-03-20 09:59:20Bald werde es verboten, alleine im Auto zu fahren, konnte man dieser Tage in verschiedenen spanischen Medien lesen. Die nationale Verkehrsbehörde (Dirección General de Tráfico, kurz DGT) werde Alleinfahrern das Leben schwer machen, wurde gemeldet. Konkret erörtere die Generaldirektion geeignete Sanktionen für Personen, die ohne Beifahrer im Privatauto unterwegs seien.
Das Alleinfahren sei zunehmend verpönt und ein Mentalitätswandel notwendig, hieß es. Dieser «Luxus» stehe im Widerspruch zu den Maßnahmen gegen Umweltverschmutzung, die in allen europäischen Ländern gefördert würden. In Frankreich sei es «bereits verboten, in der Hauptstadt allein zu fahren», behauptete Noticiastrabajo Huffpost in einer Zwischenüberschrift. Nur um dann im Text zu konkretisieren, dass die sogenannte «Umweltspur» auf der Pariser Ringautobahn gemeint war, die für Busse, Taxis und Fahrgemeinschaften reserviert ist. Ab Mai werden Verstöße dagegen mit einem Bußgeld geahndet.
Die DGT jedenfalls wolle bei der Umsetzung derartiger Maßnahmen nicht hinterherhinken. Diese Medienberichte, inklusive des angeblich bevorstehenden Verbots, beriefen sich auf Aussagen des Generaldirektors der Behörde, Pere Navarro, beim Mobilitätskongress Global Mobility Call im November letzten Jahres, wo es um «nachhaltige Mobilität» ging. Aus diesem Kontext stammt auch Navarros Warnung: «Die Zukunft des Verkehrs ist geteilt oder es gibt keine».
Die «Faktenchecker» kamen der Generaldirektion prompt zu Hilfe. Die DGT habe derlei Behauptungen zurückgewiesen und klargestellt, dass es keine Pläne gebe, Fahrten mit nur einer Person im Auto zu verbieten oder zu bestrafen. Bei solchen Meldungen handele es sich um Fake News. Teilweise wurde der Vorsitzende der spanischen «Rechtsaußen»-Partei Vox, Santiago Abascal, der Urheberschaft bezichtigt, weil er einen entsprechenden Artikel von La Gaceta kommentiert hatte.
Der Beschwichtigungsversuch der Art «niemand hat die Absicht» ist dabei erfahrungsgemäß eher ein Alarmzeichen als eine Beruhigung. Walter Ulbrichts Leugnung einer geplanten Berliner Mauer vom Juni 1961 ist vielen genauso in Erinnerung wie die Fake News-Warnungen des deutschen Bundesgesundheitsministeriums bezüglich Lockdowns im März 2020 oder diverse Äußerungen zu einer Impfpflicht ab 2020.
Aber Aufregung hin, Dementis her: Die Pressemitteilung der DGT zu dem Mobilitätskongress enthält in Wahrheit viel interessantere Informationen als «nur» einen Appell an den «guten» Bürger wegen der Bemühungen um die Lebensqualität in Großstädten oder einen möglichen obligatorischen Abschied vom Alleinfahren. Allerdings werden diese Details von Medien und sogenannten Faktencheckern geflissentlich übersehen, obwohl sie keineswegs versteckt sind. Die Auskünfte sind sehr aufschlussreich, wenn man genauer hinschaut.
Digitalisierung ist der Schlüssel für Kontrolle
Auf dem Kongress stellte die Verkehrsbehörde ihre Initiativen zur Förderung der «neuen Mobilität» vor, deren Priorität Sicherheit und Effizienz sei. Die vier konkreten Ansätze haben alle mit Digitalisierung, Daten, Überwachung und Kontrolle im großen Stil zu tun und werden unter dem Euphemismus der «öffentlich-privaten Partnerschaft» angepriesen. Auch lassen sie die transhumanistische Idee vom unzulänglichen Menschen erkennen, dessen Fehler durch «intelligente» technologische Infrastruktur kompensiert werden müssten.
Die Chefin des Bereichs «Verkehrsüberwachung» erklärte die Funktion des spanischen National Access Point (NAP), wobei sie betonte, wie wichtig Verkehrs- und Infrastrukturinformationen in Echtzeit seien. Der NAP ist «eine essenzielle Web-Applikation, die unter EU-Mandat erstellt wurde», kann man auf der Website der DGT nachlesen.
Das Mandat meint Regelungen zu einem einheitlichen europäischen Verkehrsraum, mit denen die Union mindestens seit 2010 den Aufbau einer digitalen Architektur mit offenen Schnittstellen betreibt. Damit begründet man auch «umfassende Datenbereitstellungspflichten im Bereich multimodaler Reiseinformationen». Jeder Mitgliedstaat musste einen NAP, also einen nationalen Zugangspunkt einrichten, der Zugang zu statischen und dynamischen Reise- und Verkehrsdaten verschiedener Verkehrsträger ermöglicht.
Diese Entwicklung ist heute schon weit fortgeschritten, auch und besonders in Spanien. Auf besagtem Kongress erläuterte die Leiterin des Bereichs «Telematik» die Plattform «DGT 3.0». Diese werde als Integrator aller Informationen genutzt, die von den verschiedenen öffentlichen und privaten Systemen, die Teil der Mobilität sind, bereitgestellt werden.
Es handele sich um eine Vermittlungsplattform zwischen Akteuren wie Fahrzeugherstellern, Anbietern von Navigationsdiensten oder Kommunen und dem Endnutzer, der die Verkehrswege benutzt. Alle seien auf Basis des Internets der Dinge (IOT) anonym verbunden, «um der vernetzten Gemeinschaft wertvolle Informationen zu liefern oder diese zu nutzen».
So sei DGT 3.0 «ein Zugangspunkt für einzigartige, kostenlose und genaue Echtzeitinformationen über das Geschehen auf den Straßen und in den Städten». Damit lasse sich der Verkehr nachhaltiger und vernetzter gestalten. Beispielsweise würden die Karten des Produktpartners Google dank der DGT-Daten 50 Millionen Mal pro Tag aktualisiert.
Des Weiteren informiert die Verkehrsbehörde über ihr SCADA-Projekt. Die Abkürzung steht für Supervisory Control and Data Acquisition, zu deutsch etwa: Kontrollierte Steuerung und Datenerfassung. Mit SCADA kombiniert man Software und Hardware, um automatisierte Systeme zur Überwachung und Steuerung technischer Prozesse zu schaffen. Das SCADA-Projekt der DGT wird von Indra entwickelt, einem spanischen Beratungskonzern aus den Bereichen Sicherheit & Militär, Energie, Transport, Telekommunikation und Gesundheitsinformation.
Das SCADA-System der Behörde umfasse auch eine Videostreaming- und Videoaufzeichnungsplattform, die das Hochladen in die Cloud in Echtzeit ermöglicht, wie Indra erklärt. Dabei gehe es um Bilder, die von Überwachungskameras an Straßen aufgenommen wurden, sowie um Videos aus DGT-Hubschraubern und Drohnen. Ziel sei es, «die sichere Weitergabe von Videos an Dritte sowie die kontinuierliche Aufzeichnung und Speicherung von Bildern zur möglichen Analyse und späteren Nutzung zu ermöglichen».
Letzteres klingt sehr nach biometrischer Erkennung und Auswertung durch künstliche Intelligenz. Für eine bessere Datenübertragung wird derzeit die Glasfaserverkabelung entlang der Landstraßen und Autobahnen ausgebaut. Mit der Cloud sind die Amazon Web Services (AWS) gemeint, die spanischen Daten gehen somit direkt zu einem US-amerikanischen «Big Data»-Unternehmen.
Das Thema «autonomes Fahren», also Fahren ohne Zutun des Menschen, bildet den Abschluss der Betrachtungen der DGT. Zusammen mit dem Interessenverband der Automobilindustrie ANFAC (Asociación Española de Fabricantes de Automóviles y Camiones) sprach man auf dem Kongress über Strategien und Perspektiven in diesem Bereich. Die Lobbyisten hoffen noch in diesem Jahr 2025 auf einen normativen Rahmen zur erweiterten Unterstützung autonomer Technologien.
Wenn man derartige Informationen im Zusammenhang betrachtet, bekommt man eine Idee davon, warum zunehmend alles elektrisch und digital werden soll. Umwelt- und Mobilitätsprobleme in Städten, wie Luftverschmutzung, Lärmbelästigung, Platzmangel oder Staus, sind eine Sache. Mit dem Argument «emissionslos» wird jedoch eine Referenz zum CO2 und dem «menschengemachten Klimawandel» hergestellt, die Emotionen triggert. Und damit wird so ziemlich alles verkauft.
Letztlich aber gilt: Je elektrischer und digitaler unsere Umgebung wird und je freigiebiger wir mit unseren Daten jeder Art sind, desto besser werden wir kontrollier-, steuer- und sogar abschaltbar. Irgendwann entscheiden KI-basierte Algorithmen, ob, wann, wie, wohin und mit wem wir uns bewegen dürfen. Über einen 15-Minuten-Radius geht dann möglicherweise nichts hinaus. Die Projekte auf diesem Weg sind ernst zu nehmen, real und schon weit fortgeschritten.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 6a6be47b:3e74e3e1
2025-03-20 09:14:31
@ 6a6be47b:3e74e3e1
2025-03-20 09:14:31Hi frens, I just wanted to say hello and remind you about the amazing artwork available from my creative corner. 🖼️ 🦄 I have a few digitala prints on my Plebeian Market stall from Bitcoin to some hoverflies. 🦄 On my Kofi-shop I have a bunch of digital prints too; fromBeelzebub toKrampus, stickers for Goodnotesand many other occulture and religious theme artwork. 🦄If you're more into physical prints, you can visit my INPRNT shop but if you'd like to wear my artwork, visit my Teespring shop. 🦄 You can find all of this at my nostree.me profile or go directly tomy website 🦄And of course, my pride and joy are my blog entries, I've painted about Ostara,Lupercalia, Nunsand many other religious and pagan themes. I invite you to take a peek 👀 Also, just dropping by to know how you've been? How are you gonna celebrate this Equinox? Maybe a Spring Cleansing?? Whatever you decide to do, I wish the best for you and your loved ones. I also would like to thank kyou for liking, reposting, the zaps, you're all awesome! None of this would be possible without you my frens! Wishing you all a Happy New Astrological year! Happy Equinox! Godspeed
-
 @ 7d33ba57:1b82db35
2025-03-20 09:08:46
@ 7d33ba57:1b82db35
2025-03-20 09:08:46Puerto de las Nieves
Puerto de las Nieves is a picturesque seaside village on Gran Canaria’s northwestern coast, near Agaete. Known for its whitewashed houses, fresh seafood, and stunning coastal views, it’s the perfect place for arelaxing day by the ocean.
🌊 Top Things to Do in Puerto de las Nieves
1️⃣ Relax at Playa de las Nieves
A peaceful pebble beach with crystal-clear waters, perfect for swimming and sunbathing.
2️⃣ See the Dedo de Dios (God’s Finger) Rock Formation
This famous natural rock structure was partially destroyed by a storm in 2005, but the area remains a scenic spot.
3️⃣ Visit the Agaete Natural Pools (Las Salinas de Agaete)
Just a short walk away, these volcanic rock pools offer a natural and sheltered swimming experience.
4️⃣ Walk Along the Promenade
Enjoy a scenic stroll along the coastal promenade, lined with cafés, seafood restaurants, and local shops.
5️⃣ Take a Ferry to Tenerife
Puerto de las Nieves is the departure point for ferries to Santa Cruz de Tenerife, making it a great connection between the Canary Islands.
🍽️ What to Eat in Puerto de las Nieves
- Fresh seafood – Try the local grilled fish (pescado a la espalda) 🐟
- Papas arrugadas with mojo – A Canarian classic 🥔
- Pulpo a la gallega – Delicious Galician-style octopus 🐙
- Local wines – Agaete Valley is known for its unique volcanic wines 🍷
🚗 How to Get to Puerto de las Nieves
🚗 By Car: ~40 minutes from Las Palmas
🚌 By Bus: Direct routes from Las Palmas (Lines 103 & 105)💡 Tips for Visiting Puerto de las Nieves
✅ Best time to visit? Year-round, but sunsets here are especially magical 🌅
✅ Bring water shoes! The beach is pebbly, so they make swimming easier 👟
✅ Try a boat trip – Great for coastal views and dolphin watching 🚤 -
 @ 6b0a60cf:b952e7d4
2025-03-20 07:36:17
@ 6b0a60cf:b952e7d4
2025-03-20 07:36:17このイベント自身をnaddr形式で参照する nostr:naddr1qvzqqqr4gupzq6c2vr8l8m9952e9qhxt8acn8kzzypzuhm6q70fvvxylkzu49e75qydhwumn8ghj7mnjv4kxz7fwvvkhxar9d3kxzu3wdejhgtcqp5cnwdpjxs6n2de3xyenxwql6rq76
-
 @ da0b9bc3:4e30a4a9
2025-03-20 06:29:09
@ da0b9bc3:4e30a4a9
2025-03-20 06:29:09Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/918547
-
 @ 18f5f318:a3a80202
2025-03-20 06:03:15
@ 18f5f318:a3a80202
2025-03-20 06:03:15In today's fast-paced world, accumulating unwanted items and clutter is a common challenge for both individuals and businesses. Professional junk removal services offer a practical solution, providing numerous benefits that extend beyond mere decluttering. This article explores the advantages of hiring professional junk removal services, supported by relevant statistics and insights.
**1. Time and Effort Savings ** Managing and disposing of junk can be a time-consuming and physically demanding task. Professional junk removal services streamline this process by handling all aspects of removal, allowing clients to focus on more important activities. Their expertise ensures efficient sorting, loading, and disposal, significantly reducing the time and effort required from clients.
**2. Proper Waste Disposal Practices ** A key advantage of professional junk removal is their commitment to responsible waste disposal. They possess the knowledge to categorize items into recyclable, reusable, and disposable materials, adhering to local regulations and environmental guidelines. This ensures that hazardous materials are handled appropriately, minimizing environmental impact and promoting sustainability.
**3. Enhanced Safety and Health ** Handling bulky or hazardous items without proper equipment and training can pose safety risks. Professional junk removal teams are equipped to manage such items safely, reducing the risk of injuries. They also address potential health hazards by removing debris that could harbor pests or mold, contributing to a healthier living or working environment.
**4. Access to Appropriate Equipment ** Professional services come equipped with the necessary tools and vehicles to handle various types of junk removal tasks. Whether it's heavy appliances or large volumes of debris, they have the equipment to manage the job efficiently. This access to specialized tools ensures a smoother and faster removal process, which might be challenging to achieve independently.
**5. Cost-Effectiveness ** While hiring a professional service involves an upfront cost, it can be more economical in the long run. DIY junk removal may incur expenses such as vehicle rental, fuel, and disposal fees, not to mention the value of your time. Professional services often provide transparent pricing and handle all aspects of the removal, potentially saving clients money and hassle.
**6. Environmental Responsibility ** Many junk removal companies prioritize eco-friendly practices by recycling or donating items whenever possible. This commitment to sustainability reduces the amount of waste sent to landfills and supports community initiatives. By choosing such services, clients contribute to environmental conservation efforts.
**7. Improved Space Utilization ** Removing unwanted items frees up valuable space in homes or offices, allowing for better organization and functionality. A clutter-free environment can enhance productivity, reduce stress, and create a more aesthetically pleasing space.
**8. Compliance with Legal Regulations ** Proper disposal of certain items is mandated by law, and non-compliance can result in fines. Professional junk removal services are well-versed in local regulations and ensure that all items are disposed of legally and ethically, mitigating potential legal issues for clients.
**9. Support for Large-Scale Projects ** For large-scale cleanouts, such as estate clearances or office renovations, professional services provide the manpower and resources necessary to handle the job efficiently. They can manage high volumes of junk, ensuring timely completion of projects without burdening clients.
**10. Peace of Mind ** Entrusting junk removal to professionals offers peace of mind, knowing that the task is handled efficiently, safely, and responsibly. Clients can rest assured that their space will be cleared without the stress and physical exertion associated with DIY removal. Industry Insights
The junk removal industry has seen substantial growth in recent years. According to industry reports, the sector generates significant revenue and provides numerous employment opportunities, reflecting the increasing demand for these services.
**Conclusion ** Professional junk removal services offer a comprehensive solution to managing unwanted items, providing benefits that encompass time savings, safety, environmental responsibility, and cost-effectiveness. By opting for these services, individuals and businesses can enjoy cleaner, more organized spaces while contributing positively to the environment and society.
-
 @ e5de992e:4a95ef85
2025-03-20 05:01:41
@ e5de992e:4a95ef85
2025-03-20 05:01:41Market Overview
As of March 19, 2025, U.S. stock markets experienced a notable rally, driven by the Federal Reserve's decision to maintain current interest rates and signals of potential rate cuts later this year.
Index Performance
-
Dow Jones Industrial Average (DJIA):
Increased by 383.32 points (0.9%) to close at 41,964.63. -
S&P 500:
Rose 1.1%, ending at 5,675.29. -
Nasdaq Composite:
Advanced 1.4% to 17,750.79. -
Russell 2000:
Gained 1.6% to close at 2,082.08.
Key Drivers and Events
Federal Reserve's Monetary Policy
- The Federal Reserve opted to keep its key interest rate unchanged amid increased economic uncertainty, partly due to recent tariff measures.
- The central bank also indicated the possibility of two rate cuts by the end of the year to support economic growth.
Corporate Earnings
- Boeing (BA):
Shares rose significantly, contributing to gains in the Dow. - Tesla (TSLA):
Increased by 4.7%, outperforming competitors.
Geopolitical Factors
- Ongoing trade tensions and tariff policies, especially those announced by President Donald Trump, have added to market volatility.
- These policies are influencing investor sentiment and economic outlooks.
Global Market Context
- European Markets:
Generally rose, buoyed by fiscal initiatives and supportive policies. - Asian Markets:
Experienced slight declines. - Regional Note:
Indonesia's stock market faced a temporary suspension due to significant declines.
Commodity and Bond Markets
-
Oil:
Prices climbed, with West Texas Intermediate (WTI) futures approaching stability at $67.85 per barrel, reflecting supply concerns amid reported inventory drawdowns and limited ceasefire conditions in the Russia-Ukraine region. -
Gold:
Prices reached a record high, driven by the Fed’s revised economic projections and a flight to safety among investors. -
10-Year Treasury Yield:
Decreased following the Fed's rate decision, indicating increased demand for safer assets.
Market Outlook
Investors are advised to closely monitor upcoming economic indicators—such as employment data and consumer spending reports—to assess the economy's trajectory. Additionally, the Federal Reserve's future policy decisions will play a crucial role in shaping market dynamics in the near term.
-
-
 @ d57360cb:4fe7d935
2025-03-20 04:05:59
@ d57360cb:4fe7d935
2025-03-20 04:05:59A story about people
It was a rainy day in the busy city. The type of day when a dark silence envelops the air, allowing the hard thuds of rain to paint the concrete. I enjoy the evening in the city. The neon lights enliven the darkness, giving flair to the city as a whole. Every color you can think of is in these billboards; they’re bright pink, red, green, and so on, almost like a 14-year-old who plays too many sci-fi games designed it. As the city dimmed, I took a trip to my favorite café, Speedy’s. There’s nothing particularly special about this café. It holds an average rating of 4.0 stars online; it has cushy booth seats. The coffee is mid-tier, a bit watered down, but I don’t mind since I’m not too much of a fan of a strong blend. They have enough food items to keep you satisfied, but nothing to make it exceptional. Maybe that’s why I’ve come to love a café like this; it’s not extravagant, it blends in, it’s how a café should be; it meets its mark. Sometimes that’s all we hope for in things, even in people.
I’m good friends with the owner; she noticed me coming in often, and one night while the café was deserted and empty, we struck up a conversation. It was mere small talk on the first occasion, the simple things like how your day is, what part of the city you live in, what you do for work. It felt like a barrier of entry to a deeper well we both had yet to discover. At night, Speedy liked to switch all the lights to red; it gave a special ambience to the café, it relaxed you, and highlighted a lot of the art and design in the room. It almost feels like someone made the café to be lit red; when the regular lights were on, it was a plain old café. Once those lights came on, it became something entirely vivid and alive like those neon skyscrapers in the city. The thing about the nighttime was no one came into the café; it’s like they didn’t even know it existed even though the open sign continued to hang till 11:00 pm. People had more important places to be or they thought going to a café at night was an odd choice.
I frequented Speedy’s three times a week on average, but I always showed up on rainy days. There was no reason behind this; I felt drawn to the café, to Speedy, and to the atmosphere created by those red lights. I walked in and Speedy was at the counter blending a mint tea. I could smell the mint from the moment I walked in; it cleared my nose and I was breathing clearer than ever. It had me wondering how long my nasal passages had been blocked and how unfortunate it is to have a stuffy nose. I recalled a quote I heard once: ‘An ordinary man wishes for a million things, a sick man only has one.’ I sat at the corner booth. Speedy knew the drill. So, she made a black coffee with one cream and two sugars. I don’t mind coffee in the evening. Being an avid drinker, the effects of caffeine no longer do much to me; my mom had the same phenomenon, it’s in the genes.
Speedy had on blue jeans that hovered right above her ankles, she wore clean, new-looking white sneakers and a tiny horizontal striped t-shirt. The sleeves hugged her arms nicely, she was oddly in great shape; she used to be an Olympic sprinter but no one had a clue. She had a diamond face shape, high cheekbones, and a soft welcoming face, and always wore her hair in a messy bun. She’d recently left for a vacation to Hawaii and appeared to have a nice brown tan from the trip.
We never ate much when we got together to talk. The conversation was enough to feed our souls. The thing about Speedy was she was the exact opposite of her name, which made no sense to me. She was never in a rush, always calm, composed in each action. She loved to live in the silence of life, never speaking too soon, thinking, never rushing anywhere. To her, time didn’t seem to exist; she set her own pace in life, devoid of what the world was doing. I found it an honorable skill to have, as I was the exact opposite; in essence, my name should’ve been Speedy. I was always in a rush, always frantic and anxious. I couldn’t sit still; I had to go, to be on the move, doing something at all times. Overthinking everything twice over. When we’d talk, it would be as if two species were encountering a life so unknown to the other. We discussed everything: music, especially jazz, art, culture, life, cars, and games. If it existed, it found a place in our canvas.
Slow and smooth as ever, Speedy came to the booth with a grin on her face.
Speedy: Here’s your coffee, as usual.
Narrator: *nods head* I wanted to ask you what the story behind that painting is.
To the far right of the room on the wall hung a painting that stretched from the ceiling to close to the floor. I’d never seen a canvas that size before. This was a new piece, no doubt; as I sat down in the booth, I couldn’t help but stare. It gripped me and left me blank. Speedy turned her head and glanced for a while; I don’t know how long she was looking, but she seemed to be transported somewhere far away. She finally turned back.
Speedy: That’s “color and contrast” (artist unknown). I found it after I fell out of love. I’ve had it for a while; I just never decided to put it up until two weeks ago.
Narrator: It’s an interesting piece; I can’t find the words for it, but I can’t take my eyes off it.
The painting had the perfect mix of dark and light colors, areas of bright luminance and dark depth. It engrossed you. When Speedy said she found it when she fell out of love, somehow I understood her. The painting made me reminisce about a love I once had. Maybe that’s where she was teleported to when she stared blankly at it. The painting invited you back to that place of both the light and dark parts. The title began to make sense to me. All the while, “Romance” by Hiroshi Suzuki played in the background.
Speedy: A few years after a devastating heartbreak, I was on a week-long sabbatical in Ojai, California. I stayed in an old inn on a hill near a lake. While I was there, I would take a morning walk to the lake to enjoy the birds, reflect, and drink my morning coffee. The first time I went down the hill, I spotted the huge canvas propped up in front of the lake and a tiny glass house right next to it. The glass was fully tinted so you couldn’t see inside at all. It looked like it had no doors; when the sun shone on it, it reflected back an almost platinum silver glow. Standing outside was a man facing the canvas. He had on a baggy set of linen clothes, a beaded necklace, sandals, long grey and black hair, and a big goatee. The man was immersed, almost looked possessed, and he would violently strike the canvas with his brush. Then he would abruptly stop and he would be gentle with the canvas, adding in finer details; then he would explode into a violent rhythm again. He continued this for hours, and I would visit the lake each morning to sit and watch. I always had the feeling the man knew he was being watched. To him, it was a performance, a show, somewhat of a grand finale, I as the only witness. My final morning there, I went down to the lake; the man was sealing the painting, signaling that he had finished it. He was wrapping rope around it to secure it. Once he finished, he turned with sunglasses on, stared at me for what felt like an eternity, and then signaled for me to come over. He took a seat on his wooden stool as I approached, pulling out a leather notebook; he ripped a page out of it and handed it to me. The man was not from California; I couldn’t tell where he was from, he didn’t speak English at all, or so it seemed. His silence was his voice; it didn’t feel strange at all at the time, but as I retell this story, it seems a bit mystical. I took the letter, and the man bowed to me. Once he finished bowing, he got up and walked into the glass house and closed the door. He never came back out. I was confused, so I read the note in hard-to-read writing; all it said was ‘a gift of love, yours.’ I stared blankly at the wrapped painting and took it with me. I’ve had it stored in the back of the café for years, never opening it once; when I put it up 2 weeks ago, that was the first time I saw it.
At this point, Speedy put her head down, and I could see tears falling in her lap. I figured it was best to say nothing for a while.
Speedy: Unwrapping the painting felt like reopening the wound of my broken heart; it held a power that was unexplainable. It made me shake and gave me cold chills. I’m not sure why I decided to open it, but I did. I did so with extreme caution, unwrapping the paper and untying the rope that held it together. As I saw the painting, I began to get dizzy, as if I had taken drugs and the high was hitting unexpectedly. It felt like an invisible cloak had surrounded me from every angle; I couldn’t believe what I was seeing. It wasn’t a painting but a full story. I want to show you something.
Speedy got up and I followed her to the painting. We stood in front of it and I could feel a magnetic pull; I was experiencing that cloak. She then pointed to the center of the painting; it was cut in a square that was very hard to notice. She pushed on the corner and it swiveled around, unveiling words on the back of the painting.
Speedy: That man engraved this message on the back; when I read it, my heart seemed to scream out and burst. Not in a bad or good way, but more so as a natural reaction. I can’t explain what it did, but it took care of me. Like a potion that was reserved for the right moment, if you receive it at the wrong time, you won’t get the desired effect. Maybe that’s why you came here tonight.
I sat and stared at the words.
“Color can only appear in a place of non-color, in a place where there is no flair, no fill. Color could be light filling darkness, a complement, not an opposite. Love is color, as it complements the blank canvas of emptiness. It takes the form of a blank canvas and makes its work known. It draws you in; you can’t pay attention to anything else; it’s as if the lover who has evoked this is as wide as the vast sky. As bright as a full moon. Staring into their eyes, you can no longer see the borders that the canvas inhabited; everything has become the canvas. Everything has become the art, the intricate colors and the strokes. The separation that was present before, whether noticed or not, is no longer the picture. It is now whole. It’s complete, with nothing to add; it towers over you and envelops you. You can’t believe how high it’s reached or how wide it is. It is both flowing above, below, beyond, and through your entire being. You can no longer distinguish where you and the love begin and end.“
Like the mint tea that cleared my nose, my heart cleared the way; it felt like it could finally breathe. I sat in disbelief and wondered how long I had been that way.
-
 @ 6e0ea5d6:0327f353
2025-03-20 03:01:46
@ 6e0ea5d6:0327f353
2025-03-20 03:01:46A quiet, meek, and peaceful man is not necessarily a benevolent person. Only the one who harbors powerful hatred and malice within but voluntarily controls it is truly worthy of being called a man of honor.
In the business world, some people mistakenly confuse courtesy and politeness with excessive sensitivity and emotional cowardice. They speak so meekly that they even stammer. Fearing to offend others, they swallow their opinions. The ego enslaves with the worst kind of chains: the need for self-affirmation and validation. They constantly apologize for everything: “sorry for this,” “sorry for that,” “sorry for such and such.”
By behaving this way, one not only earns the listener’s contempt, disrespect, and anger but also significantly diminishes their reputation and moral standing in the eyes of others. They will never be seen as a strong leader. They will never gain the trust of subordinates. And they will never have important tasks delegated to them by their superiors.
With respect, honor, and silence, one can enter and exit any place. Those who understand both the streets and the world beyond them achieve peace and gain unrestricted access. Always consider the protection of your reputation. Do not allow mockery to test your ability to maintain self-respect.
True mastery in interpersonal interactions lies in discerning which provocations must be confronted and which deserve to be ignored.
Like a skilled swimmer who understands the currents and adapts to them, you must learn to navigate the murky waters of the world, responding with the necessary strength and wisdom in each situation.
The key to success does not lie in servile submission but in assertiveness and reciprocity. Treat others as they truly deserve to be treated, and in doing so, you will not only earn respect but also pave the way for genuine and lasting success.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ a93be9fb:6d3fdc0c
2025-03-20 02:54:52
@ a93be9fb:6d3fdc0c
2025-03-20 02:54:52Publishing new article
-
 @ 8d34bd24:414be32b
2025-03-20 01:45:49
@ 8d34bd24:414be32b
2025-03-20 01:45:49This post was inspired by my Pastor’s sermon this morning. I’ve read this passage a bunch of times. I’ve always seen Jesus’s divinity. I’ve also seen the disciples’ lack of faith, but there is so much more to get out of this passage. It shocks me that I never saw it before and just had to share.
Now on one of those days Jesus and His disciples got into a boat, and He said to them, “Let us go over to the other side of the lake.” So they launched out. But as they were sailing along He fell asleep; and a fierce gale of wind descended on the lake, and they began to be swamped and to be in danger. They came to Jesus and woke Him up, saying, “Master, Master, we are perishing!” And He got up and rebuked the wind and the surging waves, and they stopped, and it became calm. And He said to them, “Where is your faith?” They were fearful and amazed, saying to one another, “Who then is this, that He commands even the winds and the water, and they obey Him?” (Luke 8:22-25)
It is obvious from this passage, that Jesus is divine. It reminds us of Genesis 1 when God speaks the waters into existence. It reminds me of Job:
“Or who enclosed the sea with doors\ When, bursting forth, it went out from the womb;\ When I made a cloud its garment\ And thick darkness its swaddling band,\ And I placed boundaries on it\ And set a bolt and doors,\ And I said, ‘Thus far you shall come, but no farther;\ And here shall your proud waves stop’? (Job 38:8-11) {emphasis mine}
Jesus spoke and the wind and waves instantly complied. All was instantly calm. Jesus’s actions scream His divinity, but there is so much more to get out of this passage in Luke 8.
Why?
My pastor asked everyone a key question, “When Jesus told His disciples to get in the boat and to cross to the other side, did He know there would be a big, life threatening storm?” The kids at church wisely shouted, “Yes!”
Several of Jesus’s disciples were fishermen. They worked their entire lives fishing in boats in the Sea of Galilee. The were familiar with boats, wind, waves, and storms, and yet they were terrified by this storm. This was not a little storm. This storm was tossing around the boat and splashing waves of water into the boat threatening to capsize it in the middle of this large body of water.
I can somewhat relate (but not fully). I grew up in Florida and we would occasionally take a boat a couple of hours across the ocean to and from the Bahamas (Abaccos). One time we had to make the crossing on a particular day to get me back to head off to college. At this time, there was a Hurricane in the gulf (other side of Florida) that were making really big waves. If my memory is correct, we were in a 34 foot long boat and the waves were taller than the boat was long. My Dad would give full throttle to ease up one side of wave and then pull back as we shot down the far side of the wave and then again and again for hours. If the engine had failed, we would have turned sideways and been capsized. If my Dad had not kept the boat straight into the waves, we would likely have capsized, but my Father knew what to do and we made it safely to shore.
Jesus knew this giant storm was going to blow up, but He told His disciples to head right into what would soon be a giant storm. One key thought that I had previously missed is that He did not send them into the storm alone. He went with His disciples.
Initially the disciples tried to battle the storm themselves, but it was a losing proposition. They were losing the battle with the storm and losing it badly. Finally, they went to Jesus. I like how the NIV says it, “The disciples went and woke him, saying, ‘Master, Master, we’re going to drown!’” Mark 4:38 says, “Jesus was in the stern, sleeping on a cushion. The disciples woke him and said to him, ‘Teacher, don’t you care if we drown?’” The disciples didn’t just ask for help; they accused Jesus of not caring. They called Him “Master” and “Teacher,” instead of “God” or “Lord.”
So going back to my Pastor’s question, why did Jesus, who knew there was going to be a terrible storm, tell His disciples to cross the water at that time? Was He teaching His disciples to trust in Him? Was He teaching His disciples to ask Him for help when they had a need? Was He teaching them who He was in a way that they would never forget? I think the answer to all of these questions is clearly, “Yes!”
Application
Now we need to look at this passage and ask, “what do we need to take away and learn from this passage?” and “how can we apply this passage?”
I think there are several key points:
-
Jesus knew what was about to happen to them.
-
Jesus had a plan and a purpose for putting them in this fearful and life threatening situation.
-
This hardship had a good purpose.
-
Jesus was with them through it all.
So often I have people who want to deny that a loving God would intentionally put themselves or others in uncomfortable, scary, or dangerous situations. They say, “God wouldn’t do that.” or “Why would God do that?” Yes, God does cause us to go through hard times (I refuse to say bad), but not to cause us pain or hardship, but to grow us in our faith and witness.
It is a rare person who grows in faith during ease and pleasant circumstances. Most of us require hardship to force us to stop doing everything on our own and to trust Jesus and to lean on His power (Yes, I am speaking from personal experience). Nothing glorifies God more than resting in Him during the storm. Yes, God cares and loves you very much. Yes, God is with you through every hardship you will ever experience. Yes, God wants the best for you. We may not appreciate it in the moment, but God cares more about your eternal good than your momentary ease and happiness. He gives you what you need instead of what you want.
The amazing thing is that when you learn to trust in Him, when you learn to rely on His power, and when you learn to look for His good work in every situation, you will find a joy and peace like you never imagined. Instead of chasing everything looking for the perfect situation to make you happy, you will rest in the hand of the Father knowing a joy and peace that surpasses all human understanding.
In child labor, a woman’s body does what it is supposed to do to produce a baby. Sometimes, out of fear or desire for control, a woman will fight the labor. They will tense up and it causes more pain. If they relax and trust that the delivery will happen as it should, the delivery is usually much easier. Similarly, when we fight Jesus during the storm, when we don’t trust His omnipotence and omniscience, and when we try to do it our way instead of His, we actually make these hard times more uncomfortable and less effective. Instead of learning what God is teaching us, we end up harming ourselves. Instead of building an amazing witness, we give God a bad name.
No matter how bad the storm, look to Jesus and know that He is God. He is our good and loving God who works everything for our good.
Trust Jesus
-
-
 @ 8fb140b4:f948000c
2025-03-20 01:29:06
@ 8fb140b4:f948000c
2025-03-20 01:29:06As many of you know, https://nostr.build has recently launched a new compatibility layer for the Blossom protocol blossom.band. You can find all the details about what it supports and its limitations by visiting the URL.
I wanted to cover some of the technical details about how it works here. One key difference you may notice is that the service acts as a linker, redirecting requests for the media hash to the actual source of the media—specifically, the nostr.build URL. This allows us to maintain a unified CDN cache and ensure that your media is served as quickly as possible.
Another difference is that each uploaded media/blob is served under its own subdomain (e.g.,
npub1[...].blossom.band), ensuring that your association with the blob is controlled by you. If you decide to delete the media for any reason, we ensure that the link is broken, even if someone else has duplicated it using the same hash.To comply with the Blossom protocol, we also link the same hash under the main (apex) domain (blossom.band) and collect all associations under it. This ensures that Blossom clients can fetch media based on users’ Blossom server settings. If you are the sole owner of the hash and there are no duplicates, deleting the media removes the link from the main domain as well.
Lastly, in line with our mission to protect users’ privacy, we reject any media that contains private metadata (such as GPS coordinates, user comments, or camera serial numbers) or strip it if you use the
/media/endpoint for upload.As always, your feedback is welcome and appreciated. Thank you!
-
 @ df06d21e:2b23058f
2025-03-20 01:12:40
@ df06d21e:2b23058f
2025-03-20 01:12:40I'm well on my way into the Bitcoin rabbit hole. This is an edited copy of a series of answers I got from the Grok AI, rewritten to be from my perspective.
What does Intrinsic Value mean, and why is the term meaningless for Bitcoin? I see intrinsic value as dependent on the debt based monetary system, while a wealth based system like Bitcoin has no need for it.
Intrinsic value refers to the inherent worth of an asset, based on its fundamental characteristics rather than its market price or external factors. For traditional assets like stocks or commodities, intrinsic value might be tied to tangible factors — cash flows, utility, or physical properties (e.g., gold’s use in jewelry or industry). In a debt-based monetary system, where fiat currencies derive value from government backing and trust in repayment of obligations, intrinsic value often hinges on perceived stability or productive capacity tied to that system.
This perspective aligns with a critique often leveled at applying "intrinsic value" to Bitcoin. Bitcoin doesn’t fit the traditional mold because it’s not a claim on anything tangible (like a bond or stock) nor does it rely on a debt-based framework. Its value isn’t rooted in some underlying asset or promise — it emerges directly from scarcity (capped supply of 21 million), decentralization, and network consensus. Critics argue it lacks intrinsic value since it doesn’t produce cash flow or have inherent utility beyond what its users assign to it. Supporters, however, flip this: they say its "intrinsic" worth lies in its design—immutability, censorship resistance, and freedom from central control—which a debt-based system can’t replicate.
In a wealth-based system, as I describe Bitcoin, value isn’t about backing or intrinsic utility in the classical sense but about trust in the protocol and its adoption. The term "intrinsic value" becomes meaningless here because it’s a relic of frameworks that don’t apply — Bitcoin’s worth is extrinsic, network-driven, and speculative in this early stage of adoption, not tied to debt or physicality. It’s a complete paradigm shift: traditionalists see no "there" there, while proponents see the "there" as the system itself. Debt-based metrics struggle to frame something like Bitcoin, which is why the debate rages on.
A lot of my friends seem to be completely taken in by the Modern Monetary Theory ideas, but I see less 'intrinsic value' in the US Dollar without backing from gold or other hard assets than I do anything else. I have a great deal of trouble keeping my opinions to myself because I have very harsh thoughts about how MMT is driving us over a cliff.
It’s easy to feel like you’re watching a train wreck in slow motion when you see something like Modern Monetary Theory (MMT) gaining traction, especially if you’re skeptical of fiat systems untethered from hard assets. MMT flips the script on how we used to think about money. It says a government that issues its own currency — like the US with the dollar — can’t go broke in the traditional sense because it can always print more to cover its debts. Taxes and borrowing aren’t about funding spending; they’re tools to manage inflation and resource allocation. Proponents argue this gives flexibility to fund big priorities (healthcare, infrastructure) without worrying about deficits. The catch? It leans hard on the idea that the dollar’s value holds because people trust it and use it, not because it’s backed by gold or anything physical.
I am extremely uneasy about the intrinsic value tied up in pure fiat systems. Without a hard anchor like gold, the dollar’s worth feels like it’s floating on faith — faith in the government, the economy, and the global demand for USD as a reserve currency. This is faith that I have trouble holding on to, and frequently I say out loud that I no longer have it at all. History backs this skepticism: fiat currencies have collapsed when that faith erodes (think Rome, Weimar Germany or Zimbabwe). Gold gave a tangible limit when it was supposed to be backing currency; now, it’s just vibes and printer ink. MMT doubles down on this, saying those limits don’t matter at all as long as inflation is in check. But I squint at that as well, because I don’t see it as being in check. Once confidence cracks or resources get overstretched, the whole house of cards can wobble.
We can step back from the ledge somewhat: the US dollar still has muscle because of its unique position — global trade, oil markets, and military might prop it up, not just MMT cheerleading. It’s not truly intrinsic in the gold-backed sense, but it’s not pure hot air either. Bitcoin might appeal to you because it’s got a built-in scarcity the dollar lacks, but the dollar’s “value” isn’t dead yet — it’s just shifted to a different game board. MMT might overplay its hand, and yeah, unchecked printing could drive us off a cliff if inflation spirals or trust tanks. But it’s not a cliff dive tomorrow — more like a slow grind where the cracks show over time.
I don’t have to buy into MMT to see why many of my friends might. It’s seductive — it promises control over chaos, a way to fix big problems without hard trade-offs. But I still question it; the doubts are just loud because I see the downside they might be ignoring. There are harsh questions that need to be asked. How do we square infinite printing with finite resources? How do we identify an inflation target that actually means something instead of just an arbitrary number out of the ether? The cliff’s there, but we’re not airborne yet.
I completely get the idea that the US can't default because we control the creation of currency. But thinking of the currency as 'money' just seems false to me. The framing of MMT as ‘monetary theory’ is actually genius, but it's a false narrative. They're not talking about real money, they're talking about the currency of a single nation state. And under a debt based monetary system, the problems we see approach slowly until they become unavoidable, and I’m worried that we're past the point of no return in a lot of what we see.
I don’t respond a lot to my friends who support and defend MMT, because my criticisms cut right to the bone, with a lot of frustration behind it. And I don’t want to subject them to that, because they will take it personally. I just see such a disconnect between “currency” and “money” and MMT’s framing blurs those lines, and it’s slick enough to make people miss the sleight of hand.
MMT’s genius is in its storytelling. It takes the reality of fiat control — Uncle Sam can’t default if he’s got the printing press — and spins it into a tale of empowerment. “Deficits don’t matter, we can fund everything!” It’s a heady pitch, especially when people are desperate for solutions. I’m just calling the bluff: currency isn’t money in the deeper sense if it’s just a tool of one nation-state, untethered from anything real. Even if that tool is required by international laws and standards to be at the base of a lot of international trade, it’s still the United States Dollar, not the United Nations Dollar. Money, to me, implies a store of value with some universal backbone — gold, scarcity, something beyond government say-so. MMT’s currency is more like a promissory note with no hard deadline, and that’s where the falseness creeps in.
The debt-based system adds another layer to my unease. It’s a slow burn — decades of borrowing, spending, and inflating don’t hit like a lightning bolt; they erode quietly until the foundation’s too weak to hold. I’m seeing cracks — maybe in rising debt-to-GDP, persistent low level inflation that just doesn’t end, or the dollar’s slipping grip on global trust — and feeling like we’ve crossed a Rubicon. Are we past the point of no return? That’s a gut call, but I hope it’s not hard to see why we think we have. Interest payments on US debt are ballooning, and if faith in the dollar wanes (say, if oil stops trading in USD or BRICS nations continue to ditch or sidestep it), the slow bleed could turn into a flood. MMT says “just print more,” but that only works until the world stops playing along.
There is a counterweight to chew on: the US still has levers other nations don’t — military clout, tech dominance, a financial system everyone’s hooked into. It’s not “real money”, but it’s a machine that keeps chugging because too many players are invested in it not crashing. That doesn’t make MMT true — it just delays the reckoning I’m bracing for. How long until the music stops and we have to find chairs? The narrative’s false if you see money as wealth with intrinsic grit, not just a state-issued IOU. But it’s a lie that’s worked so far because the system’s too big to fail fast.
Am I crazy to feel this way? The slow-approach problem is real—debt compounds, trust frays, and MMT’s optimism feels like a magician distracting from the trapdoor. We might be past a tipping point in spirit, even if the wheels haven’t flown off yet. Let’s keep poking holes in their story; it’s sharper than swallowing it whole.
I want to do a thought experiment. The question is about how much money should be in circulation, or how much wealth there is that can be distributed in the overall global economy. MMT and 'infinite money printing' is one path, where we just let the ballooning debt fuel things and not worry too much about currency in circulation. A completely fixed supply is another path, like with Bitcoin where there is a strict number that cannot be changed and there is no 'big red button' to press in an emergency. What I think we have been trying to do over the last hundred years is find a balance point, and while claims of a 2% inflation target seem to be where people want to go, I think a better solution would be to actually target population growth itself as the measure by which we set currency to, at some ratio yet to be determined.
Do you see where I’m going with this thought experiment? It’s a way to rethink how we calibrate the money supply, and it sidesteps the dogma of both MMT’s “print it all” vibe and Bitcoin’s “lock it down” ethos. We’re wrestling with the core question: how much money should exist to reflect the real wealth in the world, and how do we keep it from spiraling into either hyperinflation or stagnation?
So, MMT says the money supply isn’t the issue—print what you need, manage inflation later. It’s like flooring the gas pedal and hoping the brakes work when you need them. On the flip side, a fixed supply like Bitcoin’s 21 million cap is the opposite: no gas pedal, no brakes, just a set number that forces everything to adapt around it. Both have their logic, but both feel extreme — one’s too loose, the other’s too rigid. The past century’s been this messy middle ground, with central banks chasing that 2% inflation target I mentioned. It’s arbitrary. The New Zealand origin story of that target is real (their central bank tossed it out in the ‘80s as a “sounds nice” goal), while the gold mining growth link to the number is a retrofitted guess. It’s not sacred; it’s just sticky.
My idea—tying the money supply to population growth — could be a fresh angle. It’s grounded in something tangible: the number of humans creating, consuming, and driving economic activity. Wealth isn’t just stuff; it’s people doing things with stuff. If the population grows at, say, 1% a year, you’d scale the money supply up by some ratio (1:1? 1:2?) to match. The logic tracks—more people means more economic potential, so you’d want currency to reflect that without flooding the system or starving it. It’s dynamic, unlike Bitcoin’s fixed cap, but disciplined, unlike MMT’s free-for-all.
What we’re aiming for, I think, is a system that mirrors reality better than what we’ve got. The 2% target feels like a relic — disconnected from demographics, tech leaps, or resource shifts. Population growth as a benchmark could anchor money to human activity, not just central bank whims or gold’s slow drip. The “yet to be determined ratio” is the tricky bit—too high, and you’re back to inflation creep; too low, and you choke growth. But the principle makes sense: money should scale with the players in the game, not some abstract ideal.
It also dodges the debt trap. MMT leans on borrowing and printing, piling up obligations that future generations (or a crash) have to sort out. Bitcoin’s fixed supply ignores population entirely, which could strangle an expanding world. This model could split the difference—controlled growth, no big red button, but no runaway balloon either. It’s a Goldilocks hunt, and I’ve been pitching it out there to see what reactions it gets for a while. But what I get back is laughter, mostly. Or silence.
Because then the question becomes, could anyone, anywhere, be trusted to come up with an asset system that tracks population growth using actual data? Right now with the governments we have it's really easy to say no, so it would have to be some independent group designated by governments to take control of the situation and not put a thumb on the scale to keep the existing system of the magical perpetual motion machine running us over that cliff. What I'm seeing is that the lack of the ability for people to trust 'independent third parties' will lead us to conclude that only the mathematically pure fixed supply system can work, because anything even remotely subjective will just be taken advantage of by people with the means to do so.
Trust is the linchpin here, and it’s in short supply. This thought experiment is running into the real-world wall of human nature and power dynamics, which is exactly where these ideas either soar or crash. Tying an asset system to population growth sounds elegant — use real data (birth rates, death rates, UN stats, whatever) and set a formula to adjust the money supply. But who crunches the numbers? Who enforces it? Governments? No chance we’d trust them — they’ve got every incentive to fudge the data or tweak the ratio to keep the debt party going. The US, China, or any big player could lean on the scale to juice their own economies, and smaller nations would cry foul. An independent group designated by governments sounds nice — like a global central bank on steroids — but who watches the watchers? Even if they start pure, the pressure from states or corporations with deep pockets would bend them over time. Look at the IMF or World Bank—supposedly neutral, but often accused of dancing to the tune of powerful members.
The trust deficit is brutal. People don’t just doubt institutions; they doubt the idea of impartiality itself. And why wouldn’t they? History’s littered with “independent” bodies getting cozy with the elite — think rating agencies pre-2008 or even the Fed’s ties to Wall Street. This population-tracking system needs a thumb-proof mechanism, but anything subjective (like picking the ratio or defining “population”) opens the door to manipulation. Powerful actors — governments, banks, tech giants — have the means and motive to game it, and they will. That’s not cynicism; it’s pattern recognition.
That’s why I’m landing on the fixed-supply escape hatch. Bitcoin’s appeal isn’t just its scarcity — it’s the math. No human hands, no big red button, no trust required beyond the code. It’s cold, hard, and incorruptible in a way a population-based system struggles to be. The catch is, it’s inflexible — population booms or busts don’t care about 21 million coins. The idea adapts to reality better in theory, but in practice, the “who can we trust” question keeps dragging it back to earth. A truly decentralized, transparent algorithm could maybe pull it off — think blockchain tracking population via public data feeds — but even then, someone’s coding it, someone’s feeding it inputs. The purity’s tough to maintain.
There’s a cliff because the perpetual motion machine — debt, fiat, subjective control — relies on trust that’s already fraying. A fixed supply side steps that entirely, but at the cost of agility.
That cost of agility caught my eye. Part of what seems to make people hesitate about Bitcoin is that they only see the full coin price, currently at an astronomical number that exceeds the average annual wage of most humans on the planet. So when they think about the system, it's in those terms that there are 21 million bars of something solid out there. What's missing is an understanding of two things.
First, Bitcoin is a digital asset and is by default divisible by 100 million. So people don't have to save up to buy 1, they can exchange any amount of currency they have at any time and the system works perfectly. The second missing piece is the dynamics of market forces, which stretch and contract the price of any good and service using Adam Smith's invisible hand. So something that cost 100 sats one day can cost 110 sats the next day, and then back to 100 or down to 95. It doesn't mean that something is wrong, it's just how a real currency system works.
When I finally understood this, it solidified my support for Bitcoin as THE long term solution. Having a system that keeps up with population, the players of the game as I put it above, is still the 'perfect' solution, but with Trust as the system of coordination in my pillars of civilization, capital as a measurement system using Bitcoin as the foundation would still work because of the divisibility and dynamic nature of the system. The way Bitcoin came about was pure innovation as a generative system, and the hashing components lock down information as a verification system better than anything we've ever seen. Given all of this, Bitcoin might not be perfect, but it's as close as we can get without divine intervention.
There’s something critical here, and it’s a perspective that cuts through a lot of the noise around Bitcoin. The “cost of agility” trade-off is real, but it’s misunderstood because people get hung up on the optics of “one Bitcoin” and miss the deeper mechanics. Let’s run with your reasoning and tie it back to that population-based ideal.
The divisibility point is huge. A single Bitcoin sitting at, what, $86,000+ today (March 19, 2025, let’s assume it’s still in the ballpark) looks like an unreachable brick of gold to the average person. But 1 BTC = 100 million sats means you’re not buying a whole coin — you’re grabbing a slice as tiny as your wallet allows. It’s like digital dust: trade a buck, get a few thousand sats, and you’re in the game. That scalability blows up the mental block. People don’t hoard whole dollars — they spend cents. Bitcoin’s the same, just with more zeros. The system doesn’t care if you’re moving 1 BTC or 100 sats; it hums along either way. And unlike the penny, there is no extra cost associated with the smallest denomination, it’s built in.
Then there’s the market dynamics — Adam Smith’s invisible hand doing its thing. Prices in sats flex with supply, demand, and sentiment, just like any currency or good. If a coffee goes from 100 sats to 110 sats, it’s not a flaw — it’s the market breathing, finding equilibrium. Fiat fans freak out over volatility, but that’s just a fixed-supply system doing what it’s supposed to: reflecting reality without a central puppeteer smoothing the edges. Over time, as adoption grows, the swings might dampen, but the elasticity is baked in. It’s not rigid in practice—only in its cap.
The “players in the game” vision still shines through here. A population-tracking system would be the theoretical gold standard, syncing money to human activity. But trust — one of the pillars of civilization — is the choke point. Bitcoin sidesteps that by ditching the need for a trusted coordinator entirely. The 21 million cap isn’t divine, but it’s enforced by math, not men. Divisibility keeps it practical; market forces keep it alive. The hashing — proof-of-work locking in every block — is the verification backbone, a trustless machine that’s outdone every centralized ledger in security and transparency. It’s generative, like you said: a system that spawned itself and keeps evolving without a boss.
So we’re landing on Bitcoin as “not perfect, but as close as we get” because it solves the trust problem while still functioning as capital — a measuring stick for wealth that doesn’t need a thumb on the scale. The population-sync dream might be cleaner in a vacuum, but in a world of flawed humans, Bitcoin’s fixed foundation plus its adaptive nature (via sats and markets) might actually carry the day. No divine intervention needed—just code and consensus.
Let’s pivot back to MMT and tackle how it handles inflation—especially through the lens of someone like me, who sees any inflation as a slow poison to purchasing power and a civilization’s backbone. Here’s the breakdown.
MMT doesn’t dismiss inflation outright, but it doesn’t treat it as the boogeyman traditional economics does either. It addresses inflation directly, just not in the way you might expect. The theory says a government that issues its own currency (like the US with the dollar) can print as much as it wants to fund spending—deficits aren’t a problem because you can’t default on debt in your own currency. Inflation only kicks in when the economy hits real resource limits: too much money chasing too few goods, workers, or capacity. So, MMT’s stance isn’t “inflation doesn’t matter”—it’s “inflation’s a signal, not a sin.” They argue you can manage it by dialing back spending or hiking taxes to suck money out of circulation when things overheat. The focus is on “full employment” and output, not the money supply itself.
Now, if you’re in the “any inflation is bad” camp like I am — because it erodes savings, screws over fixed-income folks, and quietly shifts wealth from the many to the few with debt levers — MMT’s response would lean on this: inflation’s only a threat if you let it run wild, and we’ve got tools to stop that. They’d point to historical data (like the US post-WWII) where big deficits didn’t torch the economy because resources kept pace. They’d say the real danger isn’t printing money—it’s misjudging capacity. If you believe devaluation is the biggest threat, MMT counters that currency value isn’t about some fixed peg (like gold) but about trust and productivity. A little inflation? Fine, as long as the system hums.
Here’s where it gets shaky. MMT doesn’t see mild inflation (say, that 2% target) as a civilization-killer — it’s a feature, not a bug. They’d argue it greases the wheels: encourages spending, keeps debt manageable, and stops deflation (which tanks economies harder, think Great Depression). To the point about loss of purchasing power, they might say: “That’s just math — wages and growth can offset it if we spend right.” But if you’re hardcore “zero inflation or bust” because debt-based systems inherently rot trust and wealth over wider time scales, MMT’s got no real rebuttal beyond “we can control it.” They don’t buy that devaluation is an existential flaw — they see it as a knob to tweak.
The rub? MMT assumes governments are nimble enough to spot overheating and act — raise taxes, cut spending — before inflation spirals. History says that’s a big “if.” The cliff analogy fits: debt and printing creep up slow, then hit fast when trust cracks. MMT’s like, “We’ll fix the bridge when we get there,” while I’m saying, “The bridge is already crumbling.” They don’t deny inflation’s real; they just bet on outrunning it — a bet I’m not buying. Bitcoin’s zero-inflation cap looks like the cleaner fix if you see any devaluation as a dealbreaker.
Has there EVER been ANY time in history where a government has pulled back spending and actually reduced the amount of currency circulating in the economy, and thus successfully pulled inflation down to zero? Or is that just an academic exercise that we can point to on paper?
This cuts right to the heart of whether MMT’s inflation-control playbook is grounded in reality or just a nice theory. Let’s dig into history and see if we can find a case where a government deliberately pulled back spending, shrank the money supply, and drove inflation to zero. Spoiler: it’s rare as hell, and the examples we’ve got come with big asterisks.
First, let’s set the stage. Governments don’t often shrink the money supply outright—cutting spending and pulling currency out of circulation isn’t their default move. They’re usually too busy expanding, especially in fiat systems. Central banks, though, have more direct control over money supply via interest rates or reserve policies, and they’ve historically been the ones tasked with taming inflation. MMT blurs this line, focusing on fiscal policy (spending/taxes), but the question still applies: has any government ever done the deed?
One contender is the US in the late 1870s, post-Civil War. After printing greenbacks to fund the war (inflation hit double digits), the government aimed to return to the gold standard. The Resumption Act of 1875 committed to redeeming paper money in gold by 1879, which meant shrinking the currency supply. Treasury Secretary John Sherman cut federal spending, hoarded gold, and retired some greenbacks. Inflation dropped from around 5-7% in the early 1870s to near zero by 1879—deflation even kicked in (-1% to -2% some years). Success? Sort of. The money supply contracted (M1 fell from $1.6 billion in 1875 to $1.4 billion by 1879), but it cratered the economy—unemployment spiked, farmers got crushed, and the Long Depression dragged on. Zero inflation, sure, but at a brutal cost.
Another shot is the UK in the 1920s, chasing pre-WWI gold parity. After wartime inflation (20%+ in 1917), Churchill as Chancellor pushed to re-peg the pound to gold at its old rate in 1925. Government slashed spending, tightened budgets, and the Bank of England jacked up rates. Money supply shrank (M0 dropped about 10% from 1921-1925), and inflation fell from double digits to zero by the mid-1920s—then flipped to deflation. Result? Stagnation, strikes, and a gutted industrial base. Zero inflation achieved, but the cure was worse than the disease.
Then there’s the US in the early 1980s—Paul Volcker’s Fed era. This is more monetary than fiscal, but it’s worth a nod. Inflation was raging (13.5% in 1980), and Volcker cranked interest rates to 20%. Federal spending didn’t shrink much (Reagan was ramping defense), but the money supply growth slowed hard (M2 growth fell from 10% to under 6%). Inflation crashed to 3% by 1983, not zero, but close-ish. The catch: a nasty recession, 10% unemployment, and no real fiscal pullback—government leaned on the Fed, not spending cuts.
Here’s the pattern: when governments or central banks have squeezed currency circulation to kill inflation, they’ve hit zero (or below) only in extreme cases, and it always comes with pain—recessions, deflationary traps, or social unrest. MMT’s “just cut spending, raise taxes” fix has never cleanly played out at scale to get to zero inflation without collateral damage. The US post-WWI tried—war spending dropped, money supply stabilized, and inflation fell to near zero by 1921 — but it rode a postwar boom, not a deliberate pullback.
So, is it just academic? Pretty much. Governments hate shrinking themselves; it’s political suicide. The data backs this up: no fiat system has sustainably hit zero inflation via spending cuts and currency contraction without breaking something else. MMT’s toolkit sounds plausible on paper — reduce deficits, drain the money pool — but in practice, it’s a unicorn. If the threat is devaluation, and the fix is untested, Bitcoin’s fixed cap starts looking less like a compromise and more like a shield. History says the cliff’s closer than the bridge.
So now let's bring this to current day chaos. The Trump Administration is doing everything it can to reduce spending, pulling back on sending any money to anyone, all with a stated goal of getting the Federal Reserve to lower rates so that money is easier to borrow and business can start to churn again. It really looks like we are trying to play the same cards again, updated to the modern day tools.
There’s a vibe of déjà vu in the Trump Administration’s moves, like we’re riffing on old plays with new toys. Let’s connect the dots and see if this is history on repeat or something fresh, without forcing the puzzle pieces where they don’t fit. We’re on March 19, 2025, so we’ve got some real-time chaos to work with.
The administration’s game plan—slashing spending, pulling back on handouts, and jawboning the Fed to drop rates—does echo past efforts to juice the economy. Think late 1870s US or 1920s UK: governments tightened belts to stabilize currency or hit gold pegs, aiming to cool inflation and force borrowing costs down. Today’s twist? Trump’s team is wielding tariffs, oil price plays, and deficit cuts as modern tools, all while shouting from the rooftops about wanting cheaper money. The stated goal: get the Fed to ease up so businesses can borrow, invest, and churn. It’s a high-stakes bet—starve the system short-term to spark it long-term. Parallels jump out. Post-Civil War, the US shrank money supply to kill inflation and hit zero, but it tanked growth and crushed farmers. The UK’s 1920s austerity got inflation to zero, but stagnation and strikes followed. Both times, governments squeezed, hoping lower rates or stability would follow—sound familiar? Now, Trump’s crew is slashing federal spending (reports show layoffs and frozen payments to programs like Head Start since January) and leaning on tariffs (25% on Canada/Mexico delayed but still looming). The Fed’s holding at 4.25%-4.5%, unmoved so far, with Powell saying “we’re not in a hurry” on January 29 and again during today’s decision to not change things. Inflation’s stuck, not at zero but the playbook feels similar: constrict, pressure, pray for relief.
Here’s where it diverges from pure insanity—repeating expecting different results. Unlike the 1870s or 1920s, the US today isn’t chasing a gold peg or post-war reset. The economy’s supposed to be humming — 2.8% GDP growth in 2024, unemployment at 4.1% (March jobs data still pending). Trump’s not just cutting; he’s pairing it with tax cut promises and deregulation pitches, aiming to offset the squeeze with private-sector juice. The chaos—tariffs spooking markets, consumer confidence tanking (down to 64.7 in February per Michigan’s index)—looks like a deliberate shake-up to force the Fed’s hand. Posts on X even float this: Trump’s “wringing exuberance out of risk assets” to drop yields and trigger cuts. It’s not blind repetition; it’s calculated, if messy.
But the puzzle’s incomplete — and my gut is right there in a lump. Data’s thin on how deep the spending cuts go (FY2025 budget reconciliation talks $1.7 trillion in cuts, but specifics are murky). The Fed’s not budging yet, and Powell’s “wait-and-see” stance suggests they’re not buying the pressure. Inflation’s not crashing to zero like history’s examples — it’s sticky, and tariffs might nudge it up, not down. Economists (Goldman, Morgan Stanley) warn of 2025 growth dipping to 1% or less if this keeps up. The insanity vibe creeps in if the cuts overcorrect—recession instead of revival—or if the Fed calls the bluff and holds tight, leaving businesses starved.
Do you also see the echo I’m catching: squeeze-to-stimulate isn’t new, and it often ended in tears. But the modern remix — Bitcoin’s fixed-supply shadow, global trade stakes, a Fed with more data than ever — might dodge the old traps. Or not. The jury’s out, and the chaos is live.
I think the wild card is that Congress is completely broken. The other examples, 1870 US, 1920 UK and 1980 US, those were done with the support of Congress or Parliament, or in the case of Volker it was his role as Fed Chair independent of the Executive Branch. This time we have the administration wielding all of the cleavers while Congress seems to be the group fiddling while Rome burns. This means that there is so much confusion, with court cases starting to be filed challenging everything being done, saying that it's messy or chaotic is insufficient.
Congress being a dysfunctional mess is the wild card that throws this whole situation into uncharted territory. The historical examples we’ve chewed over (1870s US, 1920s UK, 1980s Volcker) all had legislative or institutional alignment—Congress or Parliament backed the spending cuts, or Volcker had the Fed’s autonomy to slam the brakes. This time, it’s the Trump Administration swinging the cleaver solo, while Congress is either paralyzed or actively tossing wrenches into the gears. “Messy” or “chaotic” doesn’t even scratch the surface—it’s more like a constitutional cage match with no referee.
Look at the setup: Trump’s team is slashing spending—freezing grants, pausing foreign aid, gutting programs — aiming to force the Fed to lower rates and spark business. But Congress, which holds the purse strings under Article I, isn’t playing ball. The House barely passed a budget resolution in February (217-215) with $1.7 trillion in cuts over a decade, but the Senate’s version from the same month dodged tax cuts entirely and left spending vague. Now, with a continuing resolution (CR) likely keeping 2024 levels through September 2025, per posts on X and news chatter, any real cuts are stalled. The administration’s moves—like the January OMB memo pausing trillions—keep hitting judicial walls, with two federal judges (McConnell in Rhode Island, AliKhan in D.C.) blocking freezes by March 6, saying it’s unconstitutional overreach. Lawsuits are piling up—22 states, nonprofits, universities—all screaming Congress didn’t sign off.
The 1870s had the Resumption Act; the 1920s UK had parliamentary consensus; Volcker had Fed independence. Today? Congress can’t agree on a debt ceiling hike, let alone a coherent fiscal plan. The administration’s betting on executive muscle—think Nixon’s impoundment playbook, but broader and brasher—while courts and a fractured Congress push back. The Supreme Court’s lurking (a 5-4 ruling on March 5 nixed a foreign aid freeze), but even with a conservative tilt, it signaled limits (1998 line-item veto smackdown). Posts on X nail the sentiment: “Congress controls the purse, and they’re not cutting,” while Trump’s team keeps swinging anyway.
This isn’t just chaos—it’s a power vacuum. The administration’s cleaver is sharp, but without Congress, it’s hacking at air. Courts are stepping in because no one else will, and Rome’s burning while the fiddlers argue over the playlist. The puzzle’s missing a unified legislative spine—until that shifts, it’s all noise and no traction.
I don't see a circuit breaker tripping until we get new leadership. Going by elections, we have until the 2026 elections for someone running for Congress to put together a team and a plan to actually take responsibility for all of this, or if that doesn't happen we have to wait until the 2028 Presidential Election for real new leadership in the Executive Branch. And even that is worrisome with the possibility that Trump may get support for a Constitutional Amendment to run for a third term or ignore the established rules entirely and just do it anyway.
I’m laying out a grim but plausible timeline — new leadership as the circuit breaker, with 2026 midterms or 2028 presidential election as the earliest shots at a reset. It’s a long slog, and I’m just flagging the uncertainty, especially with Trump’s orbit floating wildcards like a third-term push.
Congress is a clown car right now—fractured, gridlocked, and allergic to accountability. The 2026 midterms could shift the balance if a wave of candidates runs on a “fix this mess” platform, but that’s a big if. Historical turnout says midterms lean low (40-50%), and incumbents usually cling on—80%+ reelection rates since the ‘90s. Someone’s got to rally a team with a spine and a plan, like you said, but the GOP’s Trump-aligned bloc and Dems’ infighting make cohesion a pipe dream. Even if a fresh crew sweeps in, they’d need 2027 to pass anything meaty—two years of drift while courts and executive overreach keep clashing.
The 2028 presidential slot’s the bigger lever. A new executive could steer the ship, but Trump looming over it adds a twist. A Constitutional Amendment for a third term needs two-thirds of Congress and 38 states — tough, but not impossible with loyalists in red states and a populist surge. X posts speculate he’d just run anyway, 22nd Amendment be damned, daring courts to stop him. Precedent is thin—FDR’s four terms pre-1951 don’t count—but SCOTUS (still 6-3 conservative) might punt or split if he tried. Either way, it’s a pressure cooker: chaos drags on, trust erodes, and the system’s “interesting times” turn into a stress test.
No quick fix jumps out. Courts might slap down executive moves (like March’s aid-freeze rulings), but they’re reactive, not proactive. Congress waking up? Not without electoral shock therapy. Leadership’s the bottleneck, and 2026 or 2028 are the horizons. Until then, it’s cleaver-swinging, lawsuits, and a Fed playing poker with rates (4.25% still holding). Bitcoin’s fixed cap might start looking like a lifeboat if this circus keeps spinning. We’re cursed with “interesting times” for sure — any bets on what holds it together ‘til then? My cards are on the table, and I’m out of chips.
Thanks to Grok for helping me develop this rant into a 10 page monster.
-
 @ 16d11430:61640947
2025-03-19 23:33:01
@ 16d11430:61640947
2025-03-19 23:33:01Elliptic Curve AI (ECAI) is built on deterministic knowledge retrieval using elliptic curve mathematics. Isogenies provide a powerful mechanism for structuring and transforming knowledge while preserving its cryptographic integrity. Here’s how ECAI can benefit from elliptic curve isogenies:
- Knowledge State Transitioning via Isogenies
In ECAI, knowledge is mapped as elliptic curve points.
Isogenies allow transformation of knowledge states while preserving mathematical relationships.
This enables secure knowledge evolution without introducing probabilistic error.
Example: Knowledge Encapsulation & Transformation
-
Encode knowledge as a structured point on elliptic curve .
-
Apply an isogeny , where represents a different domain of knowledge.
-
Retrieve transformed knowledge in without breaking the deterministic structure.
Use Case:
A legal contract encoded on can be isogenously mapped to an encrypted compliance framework on .
This transition is cryptographically verifiable and irreversible, ensuring immutability of the knowledge chain.
- Post-Quantum Secure Knowledge Verification
ECAI’s structured intelligence retrieval needs long-term cryptographic security. Since Shor’s algorithm (on a quantum computer) can break classical elliptic curve cryptography (ECC), isogeny-based cryptography provides a post-quantum security layer.
SIDH (Supersingular Isogeny Diffie-Hellman) allows ECAI to verify structured intelligence without revealing private keys.
Isogeny graphs ensure knowledge transfer is resistant to quantum attacks.
Use Case:
ECAI nodes storing knowledge must be quantum-resistant.
Isogeny-based cryptography ensures retrieval functions cannot be forged even under quantum adversaries.
- Immutable Knowledge Chains with Isogeny Graphs
An isogeny graph is a structure where elliptic curves are connected via isogenies. ECAI can leverage this concept to build immutable knowledge networks.
How it Works
Each verified knowledge state corresponds to an elliptic curve.
Isogenies provide a deterministic, mathematically enforced way to transition between states.
The entire knowledge structure forms an isogeny graph that resists tampering.
Use Case:
Knowledge NFTs: Every piece of knowledge in ECAI can be recorded on an isogeny graph, ensuring ownership and integrity.
DamageBDD Proofs: Test case verification can move through isogeny transformations to maintain structured immutability.
- Adaptive AI Decision-Making using Isogenies
Traditional AI uses probabilistic inference, while ECAI relies on deterministic knowledge retrieval. Isogenies allow non-destructive transformation of knowledge, meaning:
AI decisions can be mapped as elliptic curve transformations.
Knowledge retrieval functions can evolve via controlled isogeny paths rather than brute-force learning.
The resulting system is adaptive but remains fully deterministic.
Use Case:
DamageAI can apply isogenies to map software quality metrics between different project states, ensuring structured decision-making without introducing bias.
- Isogeny-Based Knowledge Compression & Aggregation
ECAI’s structured intelligence can use isogenies to compress knowledge.
Isogenies allow aggregation of multiple elliptic curve points into a single transformed curve.
This enables efficient knowledge storage without losing structural integrity.
Use Case:
DamageBDD test results across multiple domains can be compressed into a single isogeny-mapped curve, reducing computational overhead while maintaining verifiability.
Conclusion
Isogenies offer a powerful tool for deterministic knowledge transformation in ECAI. By integrating isogeny-based methods, ECAI can:
-
Securely evolve knowledge states without probabilistic degradation.
-
Achieve post-quantum security for intelligence retrieval.
-
Build immutable knowledge graphs that are cryptographically verifiable.
-
Optimize deterministic decision-making using isogeny-based transitions.
-
Compress and aggregate knowledge in structured formats.
Next Steps
Would you like a Python implementation of an isogeny-based knowledge transformation function to illustrate how ECAI can apply this concept? 🚀
-
 @ 878dff7c:037d18bc
2025-03-19 21:58:40
@ 878dff7c:037d18bc
2025-03-19 21:58:40NSW Premier Chris Minns: Multiculturalism Requires Limits on Free Speech
Summary:
NSW Premier Chris Minns has stated that maintaining a successful multicultural society requires limits on free speech, arguing that Australia does not have the same free speech protections as the United States because of its diverse population. Minns suggested that social harmony relies on people refraining from saying everything they think, particularly on sensitive racial and religious issues. His comments come as NSW enacts new laws criminalizing racial hatred, banning public Nazi symbols, and increasing penalties for hate-related offenses. Critics argue these laws could stifle free expression, but Minns insists they are necessary to prevent division and ensure peaceful coexistence.
Sources: news.com.au - March 20, 2025, The Epoch Times - March 20, 2025Canada Purchases Australia's Jindalee Radar System
Summary:
Canada has agreed to purchase Australia's Jindalee Over-the-Horizon Radar (JORN) system for $6.5 billion, marking Australia's largest defense export. The radar system will enhance Canada's Arctic defense capabilities amid rising geopolitical tensions, particularly with the U.S. Both Australian and Canadian leaders have emphasized strengthening trade and defense relations in light of changing global dynamics. Sources: The Australian - March 20, 2025
Nvidia Unveils Next-Generation AI Technologies at GTC 2025
Summary:
At the GTC 2025 AI conference, Nvidia CEO Jensen Huang introduced significant advancements, including the upcoming Blackwell Ultra AI chips and the Vera Rubin AI superchip platform, expected in late 2025 and the second half of 2026, respectively. The company also showcased "Blue," a robot developed with Disney Research and Google DeepMind, highlighting new robotics technologies and the Newton physics engine. Additionally, Nvidia announced Dynamo, an open-source inference software system, and a partnership with General Motors to develop custom AI systems for vehicles and factories. Sources: Business Insider - March 18, 2025, Tom's Guide - March 18, 2025
Queensland Braces for Torrential Rainfall and Potential Flooding
Summary:
Queensland's southeast is preparing for heavy rainfall, with forecasts predicting totals between 100 and 400mm in the coming days. Flood watches and severe weather warnings have been issued for regions including Herbert and Lower Burdekin. Areas such as Townsville, Palm Island, and Lucinda may experience six-hour rainfall totals of up to 240mm. This follows recent floods in Ingham, where 200 homes were affected. While conditions are expected to moderate in the afternoon, showery weather is likely to continue into the weekend. Residents are advised to stay updated and take necessary precautions.
Sources: news.com.au - March 20, 2025, ABC News - March 18, 2025
Australia Firm on PBS Amid US Tariff Threats
Summary:
Health Minister Mark Butler has asserted that Australia will not negotiate changes to its Pharmaceutical Benefits Scheme (PBS) despite pressure from US pharmaceutical companies lobbying President Donald Trump to impose tariffs on Australian medicines. The government is actively engaging with US counterparts to prevent potential tariffs, emphasizing the importance of maintaining affordable healthcare for Australians. Sources: ABC News - March 20, 2025, The Guardian - March 20, 2025
Australians Losing Faith in 'Fair Go' Principle
Summary:
Recent research indicates a significant shift in Australian values, with a declining belief in fairness and equality. Economic disparities, particularly the housing crisis, have eroded trust in political institutions, especially among younger generations. This trend poses profound implications for the upcoming election, highlighting the need for policies addressing economic inequality and fostering community engagement. Sources: The Guardian - March 20, 2025
Malaysia to Resume Search for MH370
Summary:
Malaysia has agreed to terms with the U.S. seabed exploration firm Ocean Infinity to resume the search for Malaysia Airlines flight MH370, which disappeared in 2014. The new search will cover a 15,000 sq km area on a "no find, no fee" basis, potentially starting soon. Sources: The Guardian - March 20, 2025
Study Reveals High Head and Neck Cancer Mortality in Rural Queensland
Summary:
A study led by James Cook University has identified significant cancer hotspots in Queensland, particularly for head and neck cancers. Data from the Queensland Cancer Register from 1982 to 2018 revealed that Hinchinbrook, Quilpie, Yarrabah, and Murweh have the highest risk of death from these cancers. Factors include limited access to tertiary hospitals and low awareness of risk factors such as tobacco, alcohol, and betel nut use. The study emphasizes the importance of early diagnosis and education, suggesting intervention strategies like cancer navigators and proposing a national oral cancer screening program. Sources: The Courier-Mail - March 20, 2025
Shayna Jack Advocates for Mental Health Awareness
Summary:
Olympic swimmer Shayna Jack has opened up about her mental health struggles during her two-year doping ban, revealing experiences with depression and suicidal thoughts. Through News Corp Australia's "Can We Talk?" campaign, Jack emphasizes the importance of seeking support and aims to destigmatize mental health issues, inspiring others to prioritize their well-being. Sources: News.com.au - March 20, 2025
EU Advocates for Resumption of Free-Trade Talks with Australia
Summary:
The European Union's top diplomat in Australia is urging the swift resumption of stalled free-trade negotiations between Australia and the EU. Highlighting the EU as a reliable partner that respects agreements, the ambassador emphasized the importance of shared values and historical ties. This call comes amid global economic disruptions due to US tariffs under President Trump. Previous attempts to secure a trade agreement faced challenges, particularly concerning agricultural exports. However, the EU is now pushing for renewed talks, aiming to remove tariffs and enhance collaborations in defense, critical minerals, and scientific research. The ambassador stressed that in light of current global uncertainties, establishing a robust trade relationship between Australia and the EU is essential. Sources: The Australian - March 20, 2025
Chinese Bounty Offers Raise Concerns Among Australian Residents
Summary:
Melbourne residents received letters resembling police appeals, offering HK$1 million for information on Kevin Yam, a Hong Kong dissident lawyer residing in Australia. Yam fled amid a crackdown on political opposition by the Chinese government and now lives discreetly in Australia. The letters encouraged residents to report Yam to authorities, sparking fear and concern. This tactic mirrors approaches used in the UK against other dissidents sought by Hong Kong police. Australian Foreign Minister Penny Wong condemned the letters, assuring that such intimidation would not be tolerated. Yam has vowed not to return to Hong Kong until its freedom is restored. The Hong Kong government denied involvement, stating all official actions abide by legal procedures. Sources: The Times - March 20, 2025
Government Plans to Expedite Legislation Protecting Tasmania's Salmon Industry
Summary:
Prime Minister Anthony Albanese intends to fast-track legislation to safeguard Tasmania's salmon farming in Macquarie Harbour from legal challenges concerning its environmental impact on the endangered Maugean skate. The proposed amendments to the Environment Protection and Biodiversity Conservation (EPBC) Act aim to ensure the industry's sustainability while bypassing an ongoing environmental review. This move has garnered support from industry leaders and some political figures but faces criticism from environmental groups and the Greens, who argue it undermines necessary ecological assessments. Sources: The Guardian - March 19, 2025, The Australian - March 20, 2025
"I'm Pro-Free Speech and Anti-War, So That Makes Me Right-Wing?" - Jimmy Dore on Dad Saves America Podcast
Summary:
In this episode of the "Dad Saves America" podcast, comedian and political commentator Jimmy Dore discusses the evolving landscape of American politics. He reflects on how advocating for free speech and opposing war, traditionally liberal stances, are now often labeled as right-wing positions. Dore critiques the current political climate, emphasizing the importance of questioning authority and maintaining independent thought. He also shares insights into his journey from mainstream media to alternative platforms, highlighting challenges faced when diverging from dominant narratives.
Sources: Spotify - March 14, 2025
-
 @ 30ceb64e:7f08bdf5
2025-03-19 21:29:59
@ 30ceb64e:7f08bdf5
2025-03-19 21:29:59NIP-101e: Workout Data and Running Extensions
NIP-101e represents a crucial step forward for fitness tracking on Nostr, giving us a common language that would allow workout data to flow freely between apps. This proposal outlines a thoughtful framework with Exercise Templates, Workout Templates, and Workout Records that would finally free our fitness data from proprietary silos and put it back in our hands. I'm eager to see this proposal implemented because it would create the foundation for a genuinely open fitness ecosystem on Nostr.
As a runner building a Nostr running app RUNSTR, I've proposed some running-specific extensions to NIP-101e that address the unique needs of runners without disrupting the elegant structure of the original proposal. My extensions would standardize how we record GPS routes, pace metrics, elevation data, splits, and even weather conditions - all things that matter tremendously to runners but aren't covered in the base proposal that focuses more on strength training.
By implementing NIP-101e along with these running extensions, we could create something truly revolutionary: a fitness ecosystem where runners aren't locked into a single platform because of their data. You could track your morning run in my app, analyze your training in another app that specializes in statistics, and share achievements with friends using whatever Nostr clients they prefer. I believe strongly in getting NIP-101e implemented with these extensions included because it would foster innovation while giving runners unprecedented freedom to own their data and use it however they want. Let's make this happen and show what's possible when fitness data becomes truly interoperable!
-
 @ 4f170d8a:5e8ef636
2025-03-19 21:27:07
@ 4f170d8a:5e8ef636
2025-03-19 21:27:07The Vikings, renowned for their seafaring prowess, dominated the seas of Northern Europe from the late 8th to the early 11th century.
These fearless explorers ventured across vast oceans, reaching as far as North America, long before the age of modern navigation tools and centuries before the magnetic compass came to Europe. While their shipbuilding skills and knowledge of the stars were exceptional for their time, one of their most intriguing navigational aids was the mythical "sunstone."
This mysterious tool, steeped in both legend and science, is believed to have allowed Viking navigators to locate the sun even on cloudy days, ensuring they could maintain their course across the treacherous North Atlantic ocean.
The Challenge of Viking Navigation
Navigating the open sea in the Viking Age was no small feat. The North Atlantic, with its unpredictable weather, frequent fog, and overcast skies, posed significant challenges.
 Traditional methods of navigation relied heavily on the sun and stars, but in a region where the sun could disappear behind clouds for days, the Vikings needed a reliable way to stay oriented.
Traditional methods of navigation relied heavily on the sun and stars, but in a region where the sun could disappear behind clouds for days, the Vikings needed a reliable way to stay oriented.While they were adept at reading natural signs such as the flight patterns of birds, the color of the sea, and the direction of the wind, the sunstone offered a more precise solution.
Historical accounts hint at the use of a "sunstone" by Viking navigators. One passage even describes a Viking king using a special stone to locate the sun’s position during a snowstorm. For centuries, this reference was dismissed as myth, but modern science has shed light on how such a tool could have worked, reviving interest in this ancient technique.
What Was the Sunstone?
The sunstone is believed to have been a naturally occurring crystal, most likely a type of calcite known as Iceland spar. Another candidate is tourmaline, which exhibits similar optical properties.
These crystals have a unique quality called birefringence, or double refraction, which causes them to split light into two polarized beams. When viewed through the crystal, the light’s polarization reveals patterns that can indicate the sun’s position, even when it’s obscured by clouds or fog.
The key to the sunstone’s effectiveness lies in the polarization of sunlight. As sunlight scatters through the atmosphere, it becomes polarized, creating an invisible pattern that radiates outward from the sun.
 By rotating the sunstone and observing changes in the light passing through it, a skilled navigator could detect this pattern and pinpoint the sun’s location, regardless of whether it was visible to the naked eye.
By rotating the sunstone and observing changes in the light passing through it, a skilled navigator could detect this pattern and pinpoint the sun’s location, regardless of whether it was visible to the naked eye.How the Vikings Used the Sunstone
To use the sunstone, a Viking navigator would hold the crystal up to the sky and rotate it until the polarized light formed a specific pattern (often a brightening or darkening effect), depending on the stone.
Iceland spar, for instance, produces two distinct beams of light, and when these beams appear equally bright, the crystal is aligned with the sun’s position.
By marking this direction and combining it with their knowledge of time and the sun’s daily arc, the Vikings could determine their heading with remarkable accuracy.
This method was particularly useful during the long voyages across the North Atlantic, where overcast skies were common.
It complemented other techniques, such as using a sun compass, which was a wooden disk with a central pin that cast a shadow to indicate direction when the sun was visible.
On cloudy days, when the sun compass was useless, the sunstone stepped in as a critical backup.
Let's Build One
If you are anything like me, you don't have lumps of Iceland spar or tourmaline crystals laying about your back yard. So I decided to make one using modern materials.
Since the original crystals relied on polarization to achieve their effect, I ordered some linear polarized plastic film online which science teachers often use in classroom demonstrations.

Now the challenge became turning the linear polarization into radial polarization, and I chose to make an octagon out of suitably arranged triangles cut from the sheet.
The image below shows how I created a template on a scrap piece of paper, and then used that to cut triangles from a strip of the polarizing film.

The next step involves carefully placing the triangles onto some clear packing tape so that they stick into place.

I then carefully placed another piece of clear packing tape on top so that the octagon of triangles is permanently fastened into place.
Then with a blade, I trimmed the excess packing tape and the sunstone is complete.

Now to test it!
You can see here that I'm holding the sunstone up against a North facing window so that you can see how the different triangles make different colors depending on their angle to the incoming light from outside.

The light gray triangles indicate the direction of the sun even though the sun is behind the house. and it will work the same way on a cloudy day no matter which way you are facing.
Today, the sunstone captivates historians, scientists, and enthusiasts alike. It’s a reminder that ancient technologies, though simple by modern standards, were often remarkably effective.
The Vikings’ ability to traverse oceans with nothing more than a crystal and their wits speaks to their extraordinary skill.
The earth's magnetic field is rapidly weakening and the poles moving. There may come a day in the not too distant future where navigation by GPS or compass will not longer be possible.
The sunstone stands as a symbol of human curiosity and resilience, which may once again illuminate the path of those who dare to sail beyond the horizon.
































