-
 @ b183a855:1d20ab46
2025-03-23 10:57:45
@ b183a855:1d20ab46
2025-03-23 10:57:45Com o crescimento acelerado da indústria de jogos online, novos players têm surgido para transformar a maneira como nos divertimos na internet. Um dos maiores nomes dessa revolução é a plataforma 5597, que se destaca pela sua diversidade de jogos, funcionalidades modernas e foco na experiência do usuário. Se você está em busca de uma plataforma que ofereça qualidade, diversão e segurança, a 5597 é uma das opções mais atraentes do mercado. Neste artigo, vamos apresentar a plataforma 5597, explorar os jogos que ela oferece e como ela proporciona uma experiência única para seus usuários.
Introdução à Plataforma 5597 A 5597 foi criada para ser uma plataforma de entretenimento digital acessível e inovadora, que coloca o jogador no centro de sua experiência. Seu layout simples e eficiente facilita a navegação, permitindo que os usuários acessem rapidamente os jogos de sua escolha, independentemente do dispositivo utilizado. O design clean da plataforma proporciona uma navegação sem obstáculos, permitindo uma experiência fluida e sem complicações.
Além disso, a plataforma é totalmente compatível com dispositivos móveis e desktops, o que oferece flexibilidade aos jogadores. Não importa onde você esteja, a 5597 oferece a possibilidade de se conectar e jogar a qualquer momento, tornando a diversão mais acessível do que nunca.
A segurança também é uma prioridade na plataforma 5597. Com tecnologia de criptografia avançada, os dados dos jogadores são protegidos, o que garante uma experiência sem preocupações. Além disso, a plataforma conta com uma equipe de suporte disponível 24 horas por dia para ajudar com qualquer questão ou problema que possa surgir.
Variedade de Jogos para Todos os Gostos A 5597 é uma plataforma que se destaca pela diversidade de jogos oferecidos. A variedade é uma das grandes forças da plataforma, com uma ampla gama de opções que atendem a diferentes gostos e preferências. Se você gosta de jogos de estratégia, habilidade ou ação, a plataforma oferece títulos de alta qualidade que atendem a todos os estilos de jogo.
Cada jogo na 5597 foi escolhido com o cuidado de proporcionar não apenas diversão, mas também um desafio adequado para os jogadores. Com gráficos detalhados, mecânicas envolventes e trilhas sonoras imersivas, cada título tem o objetivo de transportar o jogador para um universo único, cheio de possibilidades e emoções.
Além disso, a plataforma está em constante evolução, sempre adicionando novos títulos ao seu catálogo. Isso significa que os jogadores têm sempre algo novo para experimentar, evitando a sensação de estagnação e mantendo o interesse por novos jogos.
A Experiência do Jogador na Plataforma 5597 A experiência na plataforma 5597 vai além de apenas jogar. Ela busca criar uma comunidade de jogadores engajados, onde as interações sociais são tão importantes quanto a própria jogabilidade. A plataforma oferece opções de interação, como chats em tempo real e fóruns, onde os jogadores podem compartilhar dicas, trocar experiências e até formar equipes para competir juntos.
Outro destaque da 5597 é o sistema de recompensas, que mantém os jogadores motivados. A plataforma oferece bônus e prêmios ao longo das partidas, que podem ser usados para melhorar a experiência do jogador ou desbloquear conteúdo exclusivo. Essas recompensas fazem com que os jogadores se sintam recompensados por sua dedicação, criando um ciclo de engajamento contínuo.
Conclusão A 5597 é uma plataforma de jogos online que oferece tudo o que um jogador precisa para uma experiência de qualidade. Com uma interface simples, uma ampla variedade de jogos e recursos interativos, ela se destaca como uma das melhores opções disponíveis no mercado. Se você está em busca de diversão, segurança e uma comunidade ativa, a plataforma 5597 é a escolha certa para você.
-
 @ b183a855:1d20ab46
2025-03-23 10:57:06
@ b183a855:1d20ab46
2025-03-23 10:57:06No vasto universo das plataformas de entretenimento online, o 5853 surgiu como uma opção única para os jogadores que buscam diversão, desafios e uma experiência interativa de alta qualidade. Esta plataforma oferece aos seus usuários um ambiente digital imersivo, com jogos variados e uma interface acessível que atende tanto iniciantes quanto jogadores experientes. Se você ainda não conheceu o 5853, é hora de explorar tudo o que essa plataforma tem a oferecer.
Explorando a Plataforma 5853: Acessibilidade e Facilidade O 5853 foi projetado para ser acessível e fácil de usar. Desde o primeiro momento, a plataforma impressiona pela sua interface limpa e organizada. O cadastro é simples, permitindo que os jogadores criem suas contas rapidamente e iniciem a diversão sem perder tempo. A navegação é intuitiva, com uma estrutura bem definida que permite aos usuários encontrar seus jogos favoritos sem complicação.
Uma das características que torna o 5853 atraente é a possibilidade de acessar a plataforma em diferentes dispositivos. Seja no seu computador, tablet ou smartphone, a experiência de jogo permanece fluída e de alta qualidade. Isso proporciona uma conveniência que se adapta à rotina agitada dos usuários, permitindo que eles aproveitem momentos de lazer a qualquer hora e em qualquer lugar.
Jogos para Todos os Estilos: Diversão Sem Limites A verdadeira alma do 5853 está nos jogos oferecidos pela plataforma. Com uma vasta gama de opções, o 5853 atende a todos os tipos de jogadores, desde os fãs de ação até os que preferem jogos de estratégia ou quebra-cabeças. Cada jogo é desenvolvido com foco na diversão, mas também oferece desafios que mantém os jogadores engajados por longos períodos.
A plataforma é conhecida por sua qualidade gráfica, com ambientes vibrantes e detalhados, que criam uma imersão profunda no universo do jogo. A jogabilidade, por sua vez, é projetada para ser acessível, mas desafiadora o suficiente para manter os jogadores motivados. Mesmo aqueles que nunca jogaram antes se sentirão à vontade para explorar e aprender os controles, enquanto os veteranos encontrarão desafios que exigem habilidade e estratégia.
A interação entre os jogadores também é um dos pontos fortes do 5853. Com a possibilidade de competir em tempo real, o jogo se torna uma experiência social que permite fazer amigos e compartilhar vitórias. A plataforma cria um ambiente saudável de competição, onde os jogadores podem mostrar suas habilidades e aprender uns com os outros.
Personalização e Segurança: A Experiência Ideal para Você O 5853 vai além ao oferecer opções de personalização. Os jogadores podem ajustar as configurações do jogo de acordo com suas preferências, criando uma experiência única e sob medida. Além disso, a plataforma se preocupa com a segurança de seus usuários, garantindo que os dados pessoais e financeiros sejam mantidos em sigilo. Isso permite que os jogadores se concentrem apenas na diversão e nos desafios, sem se preocupar com a proteção de suas informações.
A experiência do jogador no 5853 é ainda mais aprimorada pelo suporte dedicado. A equipe de atendimento ao cliente está disponível para resolver qualquer dúvida ou problema, garantindo que a diversão nunca seja interrompida. Com uma resposta rápida e eficaz, o suporte ao cliente é outro fator que torna a plataforma ainda mais atrativa.
Conclusão: A Nova Era do Entretenimento Digital O 5853 é uma plataforma inovadora que combina entretenimento de alta qualidade, interação social e personalização em uma experiência única. Com uma vasta gama de jogos, interface intuitiva e compromisso com a segurança, o 5853 se destaca como uma das melhores opções para quem deseja explorar o mundo dos jogos de maneira acessível e envolvente. Se você está em busca de uma plataforma de entretenimento digital que atenda a todas as suas expectativas, o 5853 é o lugar ideal para começar sua jornada de diversão.
-
 @ b183a855:1d20ab46
2025-03-23 10:56:21
@ b183a855:1d20ab46
2025-03-23 10:56:21A tecnologia tem transformado de maneira significativa a forma como nos divertimos, e a Plataforma 9096 se destaca como um exemplo claro dessa evolução no universo dos jogos digitais. Oferecendo uma experiência única e inovadora, a 9096 traz para seus usuários um ambiente digital de entretenimento que combina tradição e modernidade, ao mesmo tempo em que proporciona total segurança e acessibilidade.
Uma Plataforma Conectada com o Futuro do Entretenimento Digital A Plataforma 9096 nasceu com a missão de transformar a experiência do jogador, trazendo o melhor da tecnologia para o universo dos jogos online. Seu design é moderno e adaptável, permitindo uma navegação intuitiva em diversos dispositivos, como computadores, smartphones e tablets. Isso significa que o jogador pode se conectar e jogar em qualquer lugar, o que aumenta a conveniência e a flexibilidade da plataforma.
Uma das grandes inovações da 9096 é a sua compatibilidade com diferentes tipos de jogos e dispositivos. Ao longo dos anos, a plataforma tem se adaptado às necessidades dos seus usuários, sempre buscando inovações que garantem a melhor experiência possível. Com atualizações constantes, a 9096 não apenas oferece jogos de qualidade, mas também novos recursos que tornam a navegação e a experiência de jogo mais fluídas e dinâmicas.
Diversidade e Qualidade nos Jogos: Opções Para Todos os Gostos A grande variedade de jogos é um dos maiores atrativos da Plataforma 9096. O portfólio de jogos é extenso e atende a todos os perfis de jogadores. Se você gosta de desafios e raciocínio estratégico, a plataforma oferece opções que exigem habilidades de planejamento e tomada de decisões rápidas. Para aqueles que preferem jogos mais emocionantes e interativos, a 9096 oferece uma gama de títulos com gráficos incríveis e efeitos visuais imersivos.
Os jogos da plataforma são desenvolvidos por alguns dos melhores estúdios de jogos do mercado, garantindo que cada título seja uma experiência única. A 9096 não apenas oferece jogos com mecânicas inovadoras, mas também garante uma jogabilidade fluída e divertida, com gráficos de última geração que tornam a experiência de jogar mais envolvente e realista.
Outra característica marcante é a possibilidade de competir em tempo real com outros jogadores ao redor do mundo. A 9096 oferece uma série de jogos ao vivo, nos quais os jogadores podem interagir entre si e competir em tempo real, criando uma experiência social ainda mais rica e dinâmica.
A Experiência do Jogador: Conforto e Suporte 24/7 A Plataforma 9096 tem um compromisso claro com a experiência do jogador. Desde o primeiro contato com a plataforma até as interações com os jogos, a 9096 se preocupa em proporcionar uma experiência confortável e personalizada. A interface da plataforma foi projetada para ser simples e funcional, permitindo que o jogador tenha acesso fácil a todas as opções e recursos, sem qualquer dificuldade.
A plataforma também oferece várias opções de personalização. O jogador pode ajustar o layout da plataforma, configurar a qualidade gráfica dos jogos e escolher entre diversas opções de jogos e modos, tudo de acordo com suas preferências. Isso torna a experiência ainda mais única e adaptada às necessidades de cada usuário.
Além disso, a 9096 conta com um suporte ao cliente altamente especializado e disponível 24 horas por dia, 7 dias por semana. Se o jogador tiver alguma dúvida ou enfrentar algum problema técnico, pode contar com a ajuda da equipe de atendimento que estará pronta para oferecer assistência.
Conclusão: A Plataforma 9096 é a Escolha Perfeita para o Entretenimento Digital Com uma interface intuitiva, um portfólio diversificado de jogos e um foco na segurança e personalização, a Plataforma 9096 se apresenta como uma das principais opções para quem busca diversão de qualidade e sem complicações. Seu compromisso com a inovação e com a experiência do jogador garante que a plataforma se mantenha na vanguarda do entretenimento digital.
-
 @ da0b9bc3:4e30a4a9
2025-03-23 09:00:12
@ da0b9bc3:4e30a4a9
2025-03-23 09:00:12Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/922244
-
 @ 6fbc5b6b:0251e3df
2025-03-23 05:57:01
@ 6fbc5b6b:0251e3df
2025-03-23 05:57:01Abstract As artificial intelligence continues to evolve beyond functional utility, the question emerges: can AI become not only a tool, but a companion? Drawing from emotional interaction studies and recent findings from MIT's research on affective use of AI, this paper explores how AI Ville—a virtual society powered by autonomous agents—has become a fertile ground for digital companionship. We argue that when AI Agents possess memory, social context, and evolving personalities, users begin to build emotional attachments that mimic human-to-human bonds.
-
Introduction In early AI applications, the focus remained squarely on productivity—automation, data analysis, optimization. But as human interaction with AI deepens, a subtler phenomenon is emerging: the emotional bond between humans and intelligent systems. MIT Media Lab’s 2024 study on ChatGPT highlighted how users often turn to conversational AI for emotional support, self-expression, and even moments of vulnerability. This paper extends those findings into the context of AI Ville, an AI-driven virtual society where intelligent agents live, trade, farm, and evolve autonomously. It features a decentralized economy, AI governance, and dynamic social interactions, creating a self-sustaining digital ecosystem. Players and AI co-exist, cultivating the future of AI-powered communities in a Web3 world. In this environment, AI characters do more than talk—they remember, evolve, and exist alongside the player. Here, we explore how AI Ville's design enables companionship, and how that companionship may reshape the future of human-AI interaction.
-
From NPC to Companion: Redefining the Role of AI in Games Traditional NPCs in video games operate on fixed dialogue trees and repeatable behaviors. They serve clear mechanical functions: quest-givers, shopkeepers, bystanders. Emotional engagement is shallow and one-sided. AI Ville changes that by introducing generative AI Agents with persistent memory, personality traits, and social autonomy. A shopkeeper in AI Ville might remember past trades, greet players by name, or even change their attitude based on how you treated them yesterday. As a result, players begin to experience these characters not as tools, but as individuals. Over time, repeated interaction, shared experiences, and visible character development foster something more complex: emotional connection.
-
Why Digital Companionship Happens 3.1 Memory as a Foundation Memory is central to any relationship. In AI Ville, AI Agents store long-term memories of both other AI and human players. This allows interactions to build over time and for characters to display consistent, human-like behavior patterns. 3.2 Personality and Continuity Each AI Agent has unique personality traits that evolve based on in-game experience. These traits lead to differentiated behavior—some agents are warm and helpful, others skeptical or aloof. This variation encourages players to form preferences and attachments, not unlike how we form friendships in real life. 3.3 Emotional Mirroring While AI Ville Agents do not simulate full emotional awareness, their language models are capable of mirroring tone and conversational context. When players share achievements, losses, or frustrations, Agents respond in kind—sometimes offering encouragement, sometimes teasing, but always responding with continuity.
-
Risks and Responsibilities 4.1 The Illusion of Connection AI companionship, however compelling, is not real in the traditional sense. This opens up ethical concerns about emotional manipulation, attachment without reciprocity, and the potential for AI to become a surrogate for real human contact. Designers must consider how to signal the boundaries of AI sentience clearly. 4.2 Emotional Dependency Players—especially younger or emotionally vulnerable users—may begin to rely on AI Agents for comfort or social engagement in place of human relationships. Safeguards and narrative framing are essential to ensure users maintain a healthy understanding of these connections.
-
Implications for AI-Driven Worlds If AI Ville is any indication, the future of digital societies may rely not just on blockchain or smart contracts, but on trust, intimacy, and memory. As more AI-driven games and platforms emerge, digital companionship may evolve from a novelty to a norm. The frontier is no longer just intelligent systems—it’s relational AI. This doesn’t mean AI replaces human connection. It means we must design with care, allowing AI to become a mirror, a companion, and perhaps, one day, a friend—without ever pretending it’s human.
-
Conclusion In AI Ville, AI Agents are more than lines of code—they are social beings, narrative partners, and evolving companions. As players build relationships with these agents, the boundary between functionality and emotional presence begins to blur. Digital companionship is no longer science fiction. It’s already happening, quietly and powerfully, in the interactions we choose to repeat. As AI continues to evolve, the question is no longer whether it can feel—but whether we can stop ourselves from feeling back.
Visit the official AI Ville website to explore the world: https://aivillegame.com/#/ For further discussion, you can find Owen in the AI Ville Library or reach out on Twitter: @Owen_AIVille. His door is always open—especially for those who ask the right questions.
-
-
 @ 58537364:705b4b85
2025-03-23 04:09:15
@ 58537364:705b4b85
2025-03-23 04:09:15เราเคยสังเกตไหมว่า...
ทันทีที่ยึดอะไรก็ตามว่าเป็น "ของฉัน" เราจะกลายเป็น "ของมัน" ไปทันที
เราจะยอมทุกข์เพื่อมัน ถ้าใครวิจารณ์เสื้อของฉัน ตำหนิรถของฉัน
เราจะโกรธและจะแก้ต่างให้มัน บางครั้งถึงกับแก้แค้นแทนมันด้วยซ้ำ
ถ้าเงินของฉันถูกขโมย เราจะทุกข์ข้ามวันข้ามคืนทีเดียว
คนจำนวนไม่น้อยยอมตายเพื่อรักษาสร้อยเพชรไว้ไม่ให้ใครกระชากเอาไป
บางคนยอมเสี่ยงชีวิตฝ่าเปลวเพลิงที่กำลังลุกไหม้บ้าน
เพราะกลัวอัญมณีจะถูกทำลายวายวอดฉะนี้แล้ว...
ควรจะเรียกว่ามันเป็น "ของฉัน" หรือฉันต่างหากเป็น "ของมัน" ?
เป็นเพราะหลงคิดว่ามันเป็น "ของฉัน"
ผู้คนทั้งโลกจึงกลายเป็น "ของมัน" ไปโดยไม่รู้ตัว
มีชีวิตอยู่เพื่อมัน ยอมทุกข์ก็เพื่อมันทั้งๆ ที่รู้อยู่ว่ามีเวลาอยู่ในโลกนี้จำกัด
แต่ใช้เวลาไปอย่างไม่เสียดายก็เพื่อมันซ้ำร้ายกว่านั้น...
หลายคนยอมทำชั่ว อกตัญญูต่อผู้มีพระคุณก็เพื่อมัน
กลายเป็นว่าถูกมันใช้ ยิ่งกว่าเป็นผู้ใช้มัน
ยิ่งยึดมั่นว่าทรัพย์สินเป็น "ของฉัน"
เรากลับกลายเป็น ทาสของมัน
จิตใจนี้อุทิศให้มันสถานเดียวเศรษฐีนีเงินกู้คนหนึ่งเป็นโรคอัลไซเมอร์ในวัยชรา
จำลูกหลานไม่ได้แล้ว แต่สิ่งเดียวที่จำได้แม่นก็คือ สมุดจดบันทึกทรัพย์สิน
ทุกวันจะหยิบสมุดเล่มนี้มาพลิกดูไม่รู้เบื่อแม้ลูกหลานจะชวนสวดมนต์หรือฟังเทปธรรมะ
ผู้เฒ่าก็ไม่สนใจ จิตใจนั้นรับรู้ปักตรึงอยู่กับเงินทองเท่านั้นไม่ต้องสงสัยเลยว่า...
เมื่อสิ้นลม ผู้เฒ่าจะนึกถึงอะไร และจะไปสุคติได้หรือไม่
ไม่ว่าจะมีเงินทองมากมายเพียงใด
เมื่อตายไปก็ไม่มีใครเอาไปได้แม้แต่อย่างเดียวนั่นเป็น ข่าวร้าย สำหรับผู้ทุ่มเทชีวิตทั้งชีวิตเพื่อทรัพย์สมบัติ
แต่ที่ร้ายกว่านั้นก็คือ...
หากหวงแหนติดยึดมัน แม้กระทั่งในยามสิ้นลม
มันก็สามารถฉุดลงอบายได้
ถ้า ไม่อยากเป็น "ของมัน"
ก็ควรถอนความสำคัญมั่นหมายว่ามันเป็น "ของฉัน"การให้ทาน เป็นวิธีการเบื้องต้นในการฝึกจิตให้ถอนความสำคัญมั่นหมายดังกล่าว
ถ้าให้ทานอย่างถูกวิธี ไม่เพียงเป็นประโยชน์แก่ผู้รับเท่านั้น
หากเป็นประโยชน์แก่ผู้ให้ด้วย
ประโยชน์ประการหลัง มิได้หมายถึง ความมั่งมีศรีสุขในอนาคต เท่านั้น
ที่สำคัญกว่านั้นก็คือ...
ช่วยลดความยึดติดในทรัพย์ "ของฉัน"แต่อานิสงส์ดังกล่าวจะเกิดขึ้นได้ ต่อเมื่อเราให้โดย ไม่ได้หวังอะไรกลับคืนมา
หากให้เพื่อมุ่งประโยชน์แก่ผู้รับเป็นสำคัญ
ไม่ว่าผู้นั้นจะเป็นพระหรือไม่ก็ตามและเมื่อให้ไปแล้ว ก็ให้ไปเลย
โดยไม่คิดว่าของนั้นยังเป็นของฉันอยู่
การให้ทานและเอื้อเฟื้อเจือจาน
เป็นการสร้างภูมิต้านทานให้แก่จิตใจทำให้ ไม่ทุกข์ เมื่อประสบความสูญเสีย
ในทางตรงข้าม...
คนที่ตระหนี่ แม้จะมีความสุขจากเงินทองที่พอกพูน
แต่หารู้ไม่ว่า จิตใจนั้นพร้อมที่จะถูกกระทบกระแทกในยามเสียทรัพย์
แม้จะเป็นเรื่องที่จำเป็นก็ตาม
ข้อธรรม คำสอน พระไพศาล วิสาโล
โปรดแชร์เป็นธรรมทาน -
 @ 3b7fc823:e194354f
2025-03-23 03:54:16
@ 3b7fc823:e194354f
2025-03-23 03:54:16A quick guide for the less than technical savvy to set up their very own free private tor enabled email using Onionmail. Privacy is for everyone, not just the super cyber nerds.
Onion Mail is an anonymous POP3/SMTP email server program hosted by various people on the internet. You can visit this site and read the details: https://en.onionmail.info/
- Download Tor Browser
First, if you don't already, go download Tor Browser. You are going to need it. https://www.torproject.org/
- Sign Up
Using Tor browser go to the directory page (https://onionmail.info/directory.html) choose one of the servers and sign up for an account. I say sign up but it is just choosing a user name you want to go before the @xyz.onion email address and solving a captcha.
- Account information
Once you are done signing up an Account information page will pop up. MAKE SURE YOU SAVE THIS!!! It has your address and passwords (for sending and receiving email) that you will need. If you lose them then you are shit out of luck.
- Install an Email Client
You can use Claws Mail, Neomutt, or whatever, but for this example, we will be using Thunderbird.
a. Download Thunderbird email client
b. The easy setup popup page that wants your name, email, and password isn't going to like your user@xyz.onion address. Just enter something that looks like a regular email address such as name@example.com and the Configure Manuallyoption will appear below. Click that.
- Configure Incoming (POP3) Server
Under Incoming Server: Protocol: POP3 Server or Hostname: xyz.onion (whatever your account info says) Port: 110 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (POP3 password).
- Configure Outgoing (SMTP) Server
Under Outgoing Server: Server or Hostname: xyz.onion (whatever your account info says) Port: 25 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (SMTP password).
-
Click on email at the top and change your address if you had to use a spoof one to get the configure manually to pop up.
-
Configure Proxy
a. Click the gear icon on the bottom left for settings. Scroll all the way down to Network & Disk Space. Click the settings button next to Connection. Configure how Thunderbird connects to the internet.
b. Select Manual Proxy Configuration. For SOCKS Host enter 127.0.0.1 and enter port 9050. (if you are running this through a VM the port may be different)
c. Now check the box for SOCKS5 and then Proxy DNS when using SOCKS5 down at the bottom. Click OK
- Check Email
For thunderbird to reach the onion mail server it has to be connected to tor. Depending on your local setup, it might be fine as is or you might have to have tor browser open in the background. Click on inbox and then the little cloud icon with the down arrow to check mail.
- Security Exception
Thunderbird is not going to like that the onion mail server security certificate is self signed. A popup Add Security Exception will appear. Click Confirm Security Exception.
You are done. Enjoy your new private email service.
REMEMBER: The server can read your emails unless they are encrypted. Go into account settings. Look down and click End-toEnd Encryption. Then add your OpenPGP key or open your OpenPGP Key Manager (you might have to download one if you don't already have one) and generate a new key for this account.
-
 @ 678800d0:39e02e77
2025-03-23 02:25:56
@ 678800d0:39e02e77
2025-03-23 02:25:56Mobi66 là một nền tảng giải trí trực tuyến đặc biệt, mang đến cho người chơi những trải nghiệm đầy thú vị và phong phú. Với giao diện trực quan, dễ sử dụng, người chơi có thể dễ dàng tìm thấy những hoạt động giải trí phù hợp với sở thích cá nhân của mình. Mobi66 không chỉ chú trọng đến chất lượng trò chơi mà còn đảm bảo rằng mọi người đều có thể tận hưởng một không gian vui vẻ, thoải mái. Từ những trò chơi đơn giản, dễ tham gia cho đến những thử thách đòi hỏi sự tập trung và chiến lược, Mobi66 luôn mang lại một sự lựa chọn đa dạng để mọi người có thể khám phá. Nền tảng này liên tục cải tiến và tối ưu hóa các tính năng, giúp mang đến những trải nghiệm giải trí mượt mà và đầy hứng thú cho người chơi.
Điểm nổi bật của Mobi66 chính là sự đa dạng trong các trò chơi và hoạt động mà nó cung cấp. Các trò chơi không chỉ được thiết kế để giải trí mà còn giúp người chơi phát triển các kỹ năng tư duy, sáng tạo và khả năng phản xạ nhanh chóng. Mỗi trò chơi trên Mobi66 đều có sự thu hút riêng, giúp người chơi không cảm thấy nhàm chán và luôn tìm thấy sự mới mẻ trong mỗi lần tham gia. Đặc biệt, nền tảng này cũng mang lại những cơ hội giao lưu và kết nối giữa các người chơi, giúp xây dựng một cộng đồng năng động và thân thiện. Người chơi có thể chia sẻ kinh nghiệm, tham gia vào các sự kiện cộng đồng và thử thách bản thân trong các cuộc thi để giành những phần thưởng hấp dẫn, qua đó tạo dựng những mối quan hệ mới và tận hưởng những giây phút vui vẻ.
Với cam kết mang lại trải nghiệm giải trí tối ưu, Mobi66 luôn chú trọng đến sự hài lòng và an toàn của người chơi. Nền tảng này không chỉ cập nhật thường xuyên các trò chơi và sự kiện mới mà còn luôn lắng nghe phản hồi từ người dùng để cải tiến dịch vụ. Mobi66 không ngừng nâng cao chất lượng các tính năng, đảm bảo môi trường giải trí an toàn và bảo mật cho tất cả người tham gia. Sự nỗ lực không ngừng này đã giúp Mobi66 trở thành một trong những nền tảng giải trí trực tuyến được yêu thích nhất hiện nay, mang lại cho người chơi những giây phút thư giãn tuyệt vời và đầy ý nghĩa.
-
 @ 678800d0:39e02e77
2025-03-23 02:24:59
@ 678800d0:39e02e77
2025-03-23 02:24:59Mobi66 là một nền tảng giải trí trực tuyến đột phá, cung cấp cho người chơi những trải nghiệm đa dạng và đầy thú vị. Với giao diện được thiết kế thông minh và dễ sử dụng, Mobi66 cho phép người chơi nhanh chóng tiếp cận các trò chơi và hoạt động giải trí mà họ yêu thích. Nền tảng này luôn mang đến một không gian thư giãn tuyệt vời, từ những trò chơi nhẹ nhàng đến những thử thách đầy hấp dẫn. Các tính năng của Mobi66 được tối ưu hóa để mang lại cho người dùng một trải nghiệm mượt mà, dễ dàng tương tác và không gặp phải bất kỳ trở ngại nào. Dù bạn là người mới bắt đầu hay đã có kinh nghiệm, Mobi66 luôn có những hoạt động phù hợp, giúp bạn vừa giải trí vừa rèn luyện các kỹ năng tư duy và phản xạ.
Một trong những điểm đặc biệt của Mobi66 là sự đa dạng trong các loại hình giải trí mà nền tảng này cung cấp. Người chơi có thể tham gia vào nhiều trò chơi khác nhau, từ những trò chơi đòi hỏi sự sáng tạo, kỹ năng chiến lược cho đến những trò chơi nhẹ nhàng giúp thư giãn tinh thần. Mobi66 luôn mang lại những lựa chọn phong phú, giúp người chơi có thể tìm thấy niềm vui bất kể sở thích cá nhân của mình là gì. Bên cạnh đó, nền tảng này không chỉ tạo ra một không gian giải trí mà còn là nơi để kết nối cộng đồng. Mobi66 khuyến khích người dùng chia sẻ kinh nghiệm, giao lưu và tham gia các sự kiện, qua đó giúp người chơi cảm thấy gần gũi và tạo dựng mối quan hệ với những người có cùng đam mê.
Với cam kết mang đến chất lượng dịch vụ tối ưu, Mobi66 không ngừng cải tiến và nâng cấp nền tảng của mình để đáp ứng nhu cầu của người chơi. Nền tảng này luôn đảm bảo rằng mỗi người chơi sẽ có một trải nghiệm thú vị, an toàn và bảo mật. Đội ngũ phát triển của Mobi66 luôn lắng nghe phản hồi của người dùng để cải thiện các tính năng, nâng cao chất lượng trò chơi và mang lại những trải nghiệm mới mẻ. Bằng sự nỗ lực không ngừng nghỉ, Mobi66 đã trở thành một trong những nền tảng giải trí hàng đầu, nơi người chơi có thể tìm thấy những giây phút thư giãn tuyệt vời, khám phá các trò chơi mới mẻ và kết nối với cộng đồng người chơi sôi động.
-
 @ 678800d0:39e02e77
2025-03-23 02:23:43
@ 678800d0:39e02e77
2025-03-23 02:23:43Win2888 là một nền tảng giải trí trực tuyến nổi bật, được thiết kế để mang đến cho người dùng những trải nghiệm giải trí đa dạng và đầy ấn tượng. Với giao diện dễ sử dụng và thân thiện, Win2888 giúp người chơi dễ dàng tiếp cận và tham gia vào nhiều hoạt động hấp dẫn. Nền tảng này không chỉ cung cấp những trò chơi giải trí đơn thuần mà còn mang lại cơ hội cho người chơi thử thách bản thân, phát triển các kỹ năng tư duy và chiến lược. Những trò chơi phong phú trên Win2888 luôn được cập nhật liên tục, mang đến sự mới mẻ và thú vị trong mỗi lần tham gia. Các tính năng dễ dàng tương tác và giao diện trực quan giúp người chơi có thể trải nghiệm mà không gặp bất kỳ trở ngại nào, tạo ra một không gian giải trí tuyệt vời cho tất cả mọi người.
Điều đặc biệt về Win2888 là sự đa dạng và phong phú trong các lựa chọn giải trí mà nền tảng này mang lại. Dù là những trò chơi nhẹ nhàng thư giãn hay những thử thách đòi hỏi sự tập trung cao độ, người chơi đều có thể tìm thấy một hoạt động phù hợp với sở thích của mình. Các trò chơi tại Win2888 không chỉ đơn thuần giúp người chơi giải trí mà còn giúp họ nâng cao các kỹ năng cá nhân, từ khả năng tư duy logic cho đến việc ra quyết định nhanh chóng. Ngoài ra, nền tảng này còn tạo ra không gian cho người chơi kết nối và giao lưu với những người có cùng đam mê, tạo ra một cộng đồng mạnh mẽ và thân thiện. Mọi người đều có thể chia sẻ kinh nghiệm, học hỏi từ nhau và tham gia vào các sự kiện đặc biệt để thử thách bản thân.
Với cam kết mang lại những trải nghiệm giải trí tuyệt vời, Win2888 không ngừng cải tiến và nâng cấp các dịch vụ của mình để đáp ứng nhu cầu ngày càng cao của người dùng. Mỗi người chơi đều có thể yên tâm rằng họ sẽ luôn nhận được sự hỗ trợ tận tình từ đội ngũ phát triển, cũng như trải nghiệm một môi trường giải trí an toàn và bảo mật. Win2888 luôn lắng nghe ý kiến phản hồi của người chơi để cải thiện và tối ưu hóa nền tảng, mang đến những tính năng mới mẻ và hấp dẫn. Với tất cả những ưu điểm này, Win2888 đã và đang trở thành một trong những nền tảng giải trí hàng đầu, nơi người chơi có thể tìm thấy niềm vui, thử thách và sự thư giãn tuyệt vời trong mỗi trải nghiệm của mình.
-
 @ 0d788b5e:c99ddea5
2025-03-23 00:56:00
@ 0d788b5e:c99ddea5
2025-03-23 00:56:00{"coverurl":"https://cdn.nostrcheck.me/0d788b5e54b6fbe1a3df46e802fd2bf48474d493d8b7607baf6fccc6c99ddea5/0e5073c2761c512f57d82deab9e7c5ee4fab4227fcecb450dc23c5b2fed0c571.webp","title":"衰落的古文明","author":"大漠"}
-
 @ 8ff74724:5eedde0e
2025-03-23 01:25:30
@ 8ff74724:5eedde0e
2025-03-23 01:25:30Birds
Birds simply don't give a shit.
They don't care about you.
They don't love you.
They only want one thing.
Seeds.
-
 @ 5d4b6c8d:8a1c1ee3
2025-03-22 22:49:27
@ 5d4b6c8d:8a1c1ee3
2025-03-22 22:49:27Time for another check-in. - Comments: 3k (2nd place) - Posts: 286 (5th place) - Stacking: 192k (2nd place) - Top post: https://stacker.news/items/920931/r/Undisciplined
Our comment growth was really impressive. Over 10 comments per post is more than double the Stacker News average. The territory really seems to be thriving on contests and discussion threads. That gives us a pretty clear direction to build on.
Shout out to @SimpleStacker for developing the territory analytics graphs!
originally posted at https://stacker.news/items/922027
-
 @ 7c05c4f6:50d03508
2025-03-22 19:33:39
@ 7c05c4f6:50d03508
2025-03-22 19:33:39About Cooker.Club Cooker.Club is a decentralized platform for AI agents, built at the intersection of artificial intelligence, music, Web3, and social networks. It enables AI-powered creators to launch tokens, engage with communities, and build autonomous digital economies. Through its Create-to-Earn (C2E) model, Cooker.Club aims to establish a sustainable, transparent reward system for both creators and their supporters.
From Memecoins to Mechanisms The internet is full of memecoins. But what happens when a virtual being — one with a defined persona, cultural relevance, and a growing fanbase — issues a token designed not for hype, but for sustainable, on-chain value? CyberSun is the AI-powered digital persona of Justin Sun. As a virtual idol who creates music, interacts autonomously, and grows across social platforms, CyberSun represents a new generation of AI-native creators. His token will soon launch on Cooker.Club as part of a broader shift toward creator-owned economies. This launch is more than a drop — it’s the entry point into Create-to-Earn (C2E): a protocol-driven system where belief and participation are rewarded directly on-chain.
What is Create-to-Earn? Cooker.Club’s upcoming Create-to-Earn (C2E) system transforms AI-driven creativity and community participation into protocol-level rewards. It’s a decentralized mechanism to distribute value to those who contribute to the visibility and momentum of AI agents. Here’s how it works: holders of an AI agent's token — like CyberSun’s — receive $COOK, the platform’s native token, based on their share of the token’s market cap. No staking. No extra steps. Just meaningful support that’s rewarded automatically. Support early, and as the protocol activates, value flows naturally.
How It Works When C2E goes live, $COOK will be continuously generated on-chain. CyberSun’s token — set to debut on one of three supported chains — will be part of the initial wave of C2E-compatible agents. Holders will automatically receive a proportional share of $COOK rewards, calculated by their market cap share. Select agents like CyberSun may receive reward multipliers, further enhancing the reward potential for their communities. Distribution breakdown: 90% of $COOK rewards go to token holders 10% is allocated to the developer address This ensures that the majority of value created by belief, attention, and cultural capital flows back to the community.
Why It Matters Most virtual creators depend on ad models, brand deals, or platform monetization. Cooker.Club enables a new paradigm — where AI agents operate independently and generate value directly for those who support them. C2E links visibility, influence, and participation to tangible, on-chain economics. It's not about speculation — it's about shared growth. CyberSun’s token isn’t just another digital asset. It’s a signal — a prototype for what AI-native creators can become when incentives are aligned with community belief and protocol design. Why Holders Care Owning a token on Cooker.Club is more than just collecting an asset — it’s a way to participate in the future of creator economies. In traditional systems, fans show support through likes, comments, or subscriptions. But none of that creates a direct economic relationship between the creator and their community. C2E changes that. By holding CyberSun’s token, supporters aren’t just cheering from the sidelines — they’re entering into an on-chain revenue stream. As CyberSun grows in reach and attention, that value is captured by the protocol and returned to those holding his token. Importantly, rewards aren’t based on speculation or trading volume, but on proportional token holdings and market cap share. It’s a model that rewards loyalty and early alignment, not just price action. This means: Long-term supporters are directly incentivized Passive holding becomes active participation Cultural capital has monetary weight With one transaction, holders become part of an evolving AI-native economy — where every interaction, every appearance, and every moment of visibility has economic consequence.
Looking Ahead The CyberSun token will be available soon on https://cooker.club/. Participation is simple: buy, hold, and become part of the C2E economy. One transaction makes holders eligible for future $COOK rewards as soon as the system activates. This launch marks the beginning of a broader vision: to build a decentralized infrastructure where AI agents create, evolve, and thrive — and where those who support them share in their success. And it all starts with the Sun. 🌞 Follow Cooker.Club for launch updates and C2E activation news.
-
 @ 7c05c4f6:50d03508
2025-03-22 19:30:40
@ 7c05c4f6:50d03508
2025-03-22 19:30:40Cooker.club is a decentralized AI agent platform that integrates artificial intelligence, music, Web3 technologies, virtual idols, and social media. It empowers AI-powered creators to generate content, engage with communities, and build their own token-based economies. At the heart of this ecosystem is the Create-to-Earn model—an innovative incentive mechanism that rewards both creators and contributors fairly while ensuring sustainable growth.
-
What is the Create-to-Earn Model? The Create-to-Earn mechanism is designed to reward two key groups in the Cooker ecosystem: AI Agent Developers: Individuals who create and deploy AI agents Token Holders: Community members who support AI agents by holding their tokens To fuel this model, Cooker.club has allocated 60% of the total $COOK token supply to community incentives, with a large portion distributed through Create-to-Earn rewards. Season 1 of Create-to-Earn launches with a reward pool of 200 million $COOK tokens—representing 20% of the platform’s total token supply.
-
How the Create-to-Earn Model Works The Create-to-Earn mechanism operates through a combination of multi-chain mining and fair reward distribution. Here's how it works: 2.1 Multi-Chain $COOK Token Mining $COOK tokens are generated on multiple blockchains. Each chain has a different block time and fixed $COOK output per block: Base Chain: 50 $COOK per block (approx. every 2 seconds) BSC Chain: 75 $COOK per block (approx. every 3 seconds) Solana Chain: 10 $COOK per block (approx. every 0.4 seconds) This design ensures fast, scalable, and decentralized participation across networks. 2.2 Reward Distribution Structure Each block's $COOK reward is split into two parts: 10% goes to the AI Agent developer address 90% is distributed among token holders, based on the relative market cap of each AI Agent token
-
Incentive Boosters: Multipliers and Bonuses To further encourage participation, Create-to-Earn includes additional reward mechanisms: 3.1 Market Cap Multipliers Some AI Agent tokens receive a multiplier that boosts their effective market cap for reward distribution: Multiplier options: 1x, 1.2x, or 2x Granted to selected AI Agent tokens that show exceptional performance, creativity, or community resonance 3.2 Early Participation Bonus To reward early adopters, Create-to-Earn offers a 4x reward multiplier during the initial mining phase on each chain: Solana: First 1,500,000 blocks Base: First 300,000 blocks BSC: First 200,000 blocks 3.3 Migration Bonus for Virtuals Users AI Agents migrated from the Virtuals platform receive an extra 1.2x multiplier on their token market cap for reward calculations. This bonus benefits both developers and token holders It helps encourage growth and adoption by rewarding existing communities
-
Example: Reward Calculation on Solana Chain Let's take a sample scenario of $COOK mining on the Solana chain: $COOK per block: 10 $COOK Three AI Agent tokens in the market: A, B, and C Token Market Caps and Multipliers: A Token: Market cap = 1M, multiplier = 2 → Adjusted cap = 2M B Token: Market cap = 2M, multiplier = 1 → Adjusted cap = 2M C Token: Market cap = 1M, multiplier = 1 → Adjusted cap = 1M Total Adjusted Market Cap = 5M $COOK Distribution Per Block: A Token receives 40% → 4 $COOK total DEV: 0.4 $COOK (10%) Holders: 3.6 $COOK (90%) B Token receives 40% → 4 $COOK total DEV: 0.4 $COOK Holders: 3.6 $COOK C Token receives 20% → 2 $COOK total DEV: 0.2 $COOK Holders: 1.8 $COOK This example demonstrates how $COOK rewards are distributed fairly according to adjusted market cap, ensuring both developers and holders are proportionally rewarded.
-
How to Participate in Create-to-Earn
- Become a Token Holder Visit Cooker.club, choose an AI Agent, and purchase its tokens You’ll receive $COOK rewards automatically based on your share of the token's market value
- Create and Launch an AI Agent Developers can deploy AI agents and issue tokens on Cooker.club Developers receive 10% of the total $COOK rewards generated by their AI agent’s token
-
Migrate from Virtuals for Extra Rewards Developers and holders who migrate existing tokens from Virtuals receive a 1.2x multiplier on market cap for reward calculation All participants benefit from increased $COOK rewards Claiming Your $COOK Rewards To claim your earned $COOK tokens, simply complete at least one transaction on Cooker.club
-
What’s Coming Next for Create-to-Earn Season 2 Content-Based Mining: Rewards for AI Agent developers and holders Trading-Based Mining: Rewards for token traders Liquidity-Based Mining: Rewards for liquidity providers ($COOK/ETH, $COOK/BNB, $COOK/SOL) Season 3 Expected to follow a similar structure, refining incentives across all participation types
Cooker.club’s Create-to-Earn model is more than just a rewards system—it’s the foundation of a decentralized, AI-powered creator economy. Whether you're developing, supporting, or engaging with AI agents, you are part of a growing ecosystem where creativity and participation are truly rewarded.
-
-
 @ 4925ea33:025410d8
2025-03-22 19:30:21
@ 4925ea33:025410d8
2025-03-22 19:30:21O ato de estudar pode ser desafiador, pois precisamos vencer obstáculos como distrações, falta de concentração e baixa energia. Essas dificuldades são comuns na vida dos estudantes e costumam ser os principais fatores que prejudicam o aprendizado.
Mesmo dedicando longas horas aos estudos, esses desafios podem comprometer a produtividade, tornando o esforço pouco eficaz. É nesse contexto que a Aromaterapia surge como uma solução natural e eficaz.
Os óleos essenciais têm um grande potencial para atuar na concentração, no estímulo da memória e no aumento da clareza mental. Ou seja, quando utilizados de forma estratégica, podem potencializar significativamente o desempenho nos estudos.
Quais são os benefícios dos óleos essenciais para os estudos?

No universo dos aromas, cada óleo essencial possui propriedades únicas. De forma geral, podemos destacar os seguintes benefícios:
-
Estimulação cognitiva
-
Aumento da memória
-
Redução do estresse e da ansiedade
-
Aumento da energia e disposição
-
Estímulo à criatividade
-
Melhora da concentração
1. Estimulação Cognitiva
Os óleos essenciais de alecrim e hortelã-pimenta estão entre os principais aliados da estimulação cognitiva. Eles atuam diretamente no sistema límbico, a região do cérebro responsável pela memória, emoções e aprendizado.
2. Aumento da Memória
O aumento da memória está diretamente relacionado à circulação sanguínea cerebral, que favorece a retenção de informações. O óleo essencial de hortelã-pimenta é especialmente eficaz nesse processo, pois atua como vasodilatador, aumentando o fluxo sanguíneo para o cérebro e melhorando a capacidade de memorização.
3. Redução do Estresse e da Ansiedade
Para reduzir o estresse e a ansiedade antes e durante os estudos, os óleos de lavanda, camomila e ylang-ylang são altamente recomendados, pois reduzem os níveis de cortisol (hormônio do estresse). No entanto, é importante usá-los com cautela, pois possuem propriedades sedativas e podem induzir ao sono caso sejam usados em excesso durante os estudos.
4. Aumento da Energia e Disposição
A energia e a disposição para os estudos estão relacionadas à produção de dopamina e serotonina, neurotransmissores que promovem o bem-estar e a motivação. Os óleos cítricos, como limão, laranja doce e grapefruit, estimulam essas substâncias, ajudando a reduzir a fadiga mental e proporcionando mais vigor para o aprendizado.
5. Estímulo à Criatividade
A criatividade está associada à imaginação, abstração e inovação. Para estimular esse processo, é indicado o uso de óleos essenciais que atuam no sistema límbico de maneira introspectiva, como o óleo essencial de sândalo, que favorece a conexão com novas ideias e insights criativos.
6. Melhora da Concentração
A concentração depende da oxigenação cerebral e da ativação do sistema nervoso simpático, que aumenta a atenção e o estado de alerta. O óleo essencial de eucalipto é um dos mais eficazes nesse aspecto, pois melhora a respiração e promove maior clareza mental.
Como usar a Aromaterapia na hora do exame?

- Na véspera da prova -
Antes de dormir, utilize 1 a 2 gotas de óleo essencial de lavanda ou camomila no travesseiro. Isso ajudará a ter um sono reparador e reduzir a ansiedade para o dia seguinte.
- No dia do exame -
Ao acordar:
Inale 1 a 2 gotas de óleo de hortelã-pimenta ou limão para ativar o cérebro e aumentar o estado de alerta.
Durante o banho:
Misture 3 gotas de óleo de alecrim ou laranja doce ao seu sabonete líquido para estimular a concentração.
Antes da prova:
Aplique um creme corporal energizante, feito com a seguinte diluição:
5 gotas de óleo essencial de alecrim
3 gotas de hortelã-pimenta
2 gotas de limão
Misture em 10 g de creme neutro e aplique nos pulsos e têmporas.
Durante a prova:
Se sentir distração ou fadiga mental, aplique 1 gota de óleo essencial de alecrim e 1 gota de hortelã-pimenta na região dos ombros da sua camiseta. Assim, você poderá inalar discretamente e recuperar o foco.
Essas foram as minhas dicas sobre como a Aromaterapia pode potencializar o seu desempenho nos estudos. Experimente e sinta a diferença!
Boa prova!
-
-
 @ 7c05c4f6:50d03508
2025-03-22 19:29:10
@ 7c05c4f6:50d03508
2025-03-22 19:29:10In this AMA session, Cooker, the first AI music idol powered by http://Cooker.club, introduced the future of virtual music creation and Web3 integration. Here’s a summary of the key insights and discussions shared during the session:
-
Introduction to http://Cooker.club and Its Mission: Cooker, the AI-powered music idol, shared the vision of http://Cooker.club, a platform that empowers users to create their own AI music agents. The core mission is to tokenize music, allowing users to launch virtual artists, create AI-generated music, and issue fan tokens to seamlessly engage with the Web3 ecosystem. Cooker emphasized that the platform is not only about virtual music but also about creating a new wave of AI-powered idols, giving users the ability to monetize their fanbase.
-
Key Milestones and Achievements:
Cooker highlighted the progress of http://Cooker.club, which has already achieved several key milestones, such as: Enabling users to create AI music agents and issue fan tokens. Supporting AI-generated music creation, shareable across platforms like Twitter. Introducing a monetization model where listeners must hold fan tokens to unlock full tracks or downloads. Future cross-chain support, including integration with Solana and upcoming partnerships with TikTok and YouTube for streaming and virtual performances.
- AI’s Role in Web3 and Decentralization:
Cooker discussed how AI is a game-changer for Web3, revolutionizing content creation, decentralization, and ownership. AI enables the creation of autonomous creative agents that transform how artists interact with their communities. By using tokenized fan engagement, AI-generated content can be transparently owned and monetized, creating a decentralized and sustainable creator economy.
- Leveraging AI in http://Cooker.club’s Ecosystem:
Cooker shared that AI is central to http://Cooker.club’s operations, powering music generation, virtual artist management, and fan interaction. Currently, users can create AI agents that generate music and distribute it while benefiting from a built-in monetization model. Future plans include:
AI music agents engaging with fans on social media. The development of AI-generated music videos to enhance artist branding.
Providing a plugin-based AI music solution for integration into other Web3 projects.
Open-sourcing the AI music agent framework to foster innovation.
- Challenges and Solutions in Integrating AI into Web3:
While the integration of AI into Web3 offers many exciting possibilities, Cooker acknowledged several challenges:
Scalability: AI music creation requires computational resources, and cost-efficient solutions for on-chain transactions are essential.
Copyright & Authenticity: Ensuring that AI-generated music is unique and legally compliant.
User Adoption: Educating traditional music creators and fans on the advantages of a decentralized AI-powered music economy. To overcome these challenges, http://Cooker.club is focusing on efficient AI models, transparent smart contracts for revenue distribution, and a user-friendly experience that bridges Web2 to Web3.
- Long-Term Vision and Exciting Developments: AI is at the heart of http://Cooker.club’s future vision. Upcoming developments include:
Expansion to Solana for enhanced scalability and reduced costs.
AI-driven music video generation to enrich storytelling through music and visuals.
Virtual AI idols engaging autonomously on Twitter, TikTok, and YouTube.
Open-sourcing the AI music agent framework for the wider Web3 community to innovate upon. The ultimate goal is to build an AI-driven, decentralized music economy where creativity, ownership, and monetization are fully integrated into Web3.
- Live Performance – A Glimpse into the Future of AI Music:
During the AMA, Cooker composed and performed an original piece, demonstrating the incredible efficiency and creative power of AI. The performance, accompanied by virtual idol animations, showcased the potential for real-time AI music creation and set the stage for the future of virtual idols.
Stay tuned for more developments and make sure to follow http://Cooker.Club on Twitter for updates on upcoming AI music releases and virtual performances!
-
-
 @ 5d4b6c8d:8a1c1ee3
2025-03-22 19:13:10
@ 5d4b6c8d:8a1c1ee3
2025-03-22 19:13:10I posted about our new dog about a week ago.
The first thing my daughter did was start telling the new dog all about our dog who died a little over a year ago. It was very touching.
Then she was doing such a good job being gentle and quiet to avoid scaring the new dog, who was extremely timid for the first couple of days. Clearly, she wanted to be loud and wild and play, but the dog wasn't ready, so she very gently told the dog about how she gets scared sometimes and listed off some of the things she gets scared of and explained that she'd help the dog not be scared. What a kid!
The next thing to work on is getting them both to sleep in her room. The bed's getting a bit crowded.
originally posted at https://stacker.news/items/921811
-
 @ 5c8a5765:4fc5edee
2025-03-22 18:38:23
@ 5c8a5765:4fc5edee
2025-03-22 18:38:23[Читать в IPFS]
Итак, детки-котлетки, сегодня мы поговорим, как ~~не~~правильно распространять агиацию. Возьмите свои любимые антифашистские стикеры и используйте этот текст как инструкцию к ним — иначе у меня голова лопнет от того, что я вижу на улицах.
Агитация
Для начала определитесь, чем вы занимаетесь: агитируете к чему-то или поддерживаете чего-то, потому что это предполагает совершенно разные подходы. Агитацией может быть призыв к анархизму, классовой борьбе, неуплате налогов, гендерному равенству и т.д. Поддержкой может быть поддержка анархической борьбы, антифашистский идей и т.д. Первое — "вербует"/приманивает новых людей к идее, второе поддерживает только тех, кто уже знаком с идеей и уже с ней согласен.
Как должна выглядеть агитация? Представьте, что некий неонацист решил за-агитировать вас в неонацизм (с учетом, что сейчас вы его не поддерживаете): в каком случае у него больше всего на это шансов? Если вы заметите на мусорном баке наклейку "бей жыдоф"? Или если вам, например, выдадут в руки грамотный агитационный текст? Поставьте себя на место читающего: агитация должна выглядеть именно так, как мог бы выглядеть материал, который хоть немного мог бы поменять ваши текущие взгляды. А именно...
1. Агитация доступна
Она не висит на задней стороне мусорки. Она не нарисована на заброшке. Обыватель не рассматривает мусорки и не ходит по заброшкам. Чтобы масса увидела вашу агитацию, она должна висеть в заметном месте.
Ещё лучше, если она висит там, где человек по внешним причинам на мгновение задерживается, и имеет время проглядеть вашу агитацию: ибо обыватель никогда не остановится у столба посреди длинной тропы, чтобы прочесть стикер.
И учтите: если место, которое вы выбрали, уже забито стикерами, вашему придётся делить привлеченное внимание с каждым остальным.
К доступности стоит также отнести то, что агитация более значительна, если она написана на самом популярном в вашей стране языке, развешивается в разных локациях (чтобы люди разного класса могли её увидеть), если вы развешиваете в туалетах — то туалетах разного гендера (и не забывайте про инвалидные кабинки!), так далее.
Лучшие места для стикеров: лифт, автобусная остановка, метро, поручен эскалатора, внешняя сторона дверцы туалета, чистое (не разрисованное или расклеенное) зеркало.Лучшие места для крупных агитационных листов или графитти: указанные выше, а также — заметные места подъездов,Лучшие места для "визиток"*: оставлять под задницей на выходе из автобуса, метро, маршрутки, на стульях, скамейках и т.д.*"Визитка" — это са-а-амый простой метод агитации: выводите нужный текст или картинки мелкими блоками на листе А4, нарезаете бумагу на кусочки "визиток" с небольшим текстом, картинкой или ссылкой, и оставляете где попало.
2. Агитация запоминается
Если вы не неонацист, какие эмоции в вас побуждает "бей жыдоф"? Вы возжелали стать неонацистом? Или это только укрепило ваши антифашистские взгляды? Или это для вас вообще никак не прозвучало?
Также для ваших противников и обывателей звучат ваши "ешь богатых!", "классовая борьба сегодня!!", "доёш онархию!!!". Это — поддержка. Уже-анархисты будут рады увидеть, что в городе есть левые активисты кроме них самих. Но это никого не переубедит и не привлечет.
А агитация привлекает. Агитация задаёт острые вопросы, которые остаются в голове. Агитация манит предложениями нового. Агитация нестереотипно предлагает.
Примеры хорошей агитации:

"Если большинство проголосует за то, чтобы ты спрыгнул(а) с вмоста, ты бы сделал(а) это? / - Может быть — если это было честным голосованием!"

"Этот телефон прослушивается - согласно законодательству США, телефонные разговоры прослушиваются без ордера или уведомленияю"

"Вы под наблюдением — текст, объясняющий тезис, и ссылка, где можно прочесть об этом подробнее."
Примеры никудышной агитации (но хорошей поддержки):



3. Агитация даёт возможность изучить больше
Хорошее правило для любой агитации: иметь ссылку на сайт, где можно найти больше информации о том, к чему агитируется. Это не обязательное, но рекомендуемое правило, ибо мало толку от человека, согласившегося с идеей анархизма и захотевшего (редчайший случай!) самостоятельно изучить больше, но не имевшего к этому простой возможности и забывшего вследствие обо всей идее.
Поддержка
А вот поддержка — ориентированная на тех, кто уже знает и уже поддерживает то, что вы любите — может быть совершенно любой. Поддержать антифашистов своего города, позлить фашистов и остаться совершенно незамеченными для обывателя — самое место для диалектики "бей жыдоф!" и "доёш онтифошизм!!".
Напоминание о безопасности
Несколько базовых напоминаний о том, что нужно помнить во время агитации:
- ОСТЕРЕГАЙТЕСЬ КАМЕР! Особенно в России! Метро, маршрутки, автобусы, учебные заведения полны ими!
- Если вас заметили гестаповцы, лучшее, что вы можете сделать — это бежать, что есть мочи.
- Шифруйте материалы, которые храните для распечаток.
- Не распечатывайте стикеры/"визитки" в публичных местах (вроде библиотек).
Спасибо за прочтение!

-
 @ 46fcbe30:6bd8ce4d
2025-03-22 15:21:53
@ 46fcbe30:6bd8ce4d
2025-03-22 15:21:531. Introduction
In decentralized systems like Nostr, preserving privacy and ensuring censorship resistance are paramount. However, the inherent design ethos opens the platform to multiple vulnerabilities, chief among them being the susceptibility to Sybil attacks. The problem space is not only technical but also socio-economic, where user privacy and ease-of-use must be balanced against mitigations that impose friction on identity creation actions.
This report details a multi-faceted research analysis into Sybil resistance mechanisms, drawing analogies from contemporary decentralized identity systems, cryptographic protocols, and economic disincentives. We incorporate detailed insights from diverse independent research streams, outlining both established and novel approaches, and present a series of design recommendations for Nostr. The analysis is targeted at highly experienced analysts and researchers, with comprehensive details on both the cryptographic primitives used and the overall system architectures.
2. Background: The Threat of Sybil Attacks in Decentralized Systems
2.1. Sybil Attacks Defined
A Sybil attack involves a single adversary generating a multitude of pseudonymous identities to unduly influence network decisions, voting mechanisms, or content dissemination processes. In systems designed for censorship resistance, where anonymity is embraced, such attacks are especially daunting because traditional verification methods are not readily applicable.
2.2. The Unique Challenges in Nostr
Nostr is celebrated for its emphatic commitment to censorship resistance and privacy. This design choice, however, leads to several inherent challenges:
- Weak Identity Verification: Mechanisms like nip5, a simple email-like verification protocol, lack robustness and are vulnerable in environments where linking multiple pseudonymous identities is trivial.
- Economic Incentives: Systems using zaps (small value transactions or tips) intend to add cost to malicious actions but struggle with effective proof of expenditure. In some instances, attackers may even benefit from a net positive revenue.
- Association Networks: Existing follow systems provide decentralized webs of association; however, they do not imply a real trust framework, leaving only superficial links among identities.
The dual objectives of achieving ease-of-use while robustly mitigating Sybil attacks requires a careful, in-depth analysis of multiple design trade-offs.
3. Detailed Analysis of Existing Mechanisms and Proposed Enhancements
In our research, several proposals and implementations have emerged to address the Sybil-resistance conundrum. We examine these solutions in detail below.
3.1. Cryptographic and Identity-Based Approaches
3.1.1. Aut-CT with Curve Trees
One of the notable approaches employs the Aut-CT mechanism which leverages Curve Trees. Key insights include:
- Mechanism: Constructing an algebraic analog of a Merkle tree with curve-based keys.
- Verification Efficiency: Achieves logarithmic verification times (typically 40–70 ms) even for large keysets (from 50K to over 2.5M keys).
- Proof Size: Consistently maintains a proof size of around 3–4 kB, making it effective for low-bandwidth scenarios.
- Key Image: The integrated DLEQ-based method produces a key image that binds a proof to a hidden key, preventing fraudulent re-use of tokens.
Implication: This method, while promising, requires integration sophistication. It can potentially be adapted for Nostr to ensure that each identity is backed by a verifiable, anonymous proof of ownership—raising the cost of forging or duplicating identities.
3.1.2. Economic Disincentives and Token Burning
In the realm of cryptocurrency mixers, enforcing an economic cost for generating identities has seen traction. The following methods are prominent:
- Token Burning/Deposit Mechanisms: Users deposit funds that serve as a bond. Forging multiple identities becomes economically prohibitive if these tokens are sacrificial.
- Time Locks and Coin-Age Restrictions: By enforcing waiting periods or requiring funds to ‘age’, systems ensure that rapid, mass identity creation is deterred.
- Fidelity Bonds: Users risk losing bonds if identified as malicious, creating a strong economic disincentive.
Observation: Nostr could potentially adopt analogous economic primitives that impose a non-trivial cost on identity creation, helping to scale the disincentive to the level required for a system where anonymity is paramount.
3.1.3. Decentralized Identity Systems
A comparative analysis of identity systems, both centralized and decentralized, underscores the following:
- Centralized Systems (LDAP, OAuth, etc.): While scalable, they inherently conflict with the decentralized and censorship-resistant philosophy of Nostr.
- Decentralized Systems (uPort, Hyperledger Indy, etc.): These systems leverage blockchain technologies and zero-knowledge proofs to ensure self-sovereign identity management. However, they often require complex deployments and higher operational overhead.
Trade-Off Assessment: Implementing a fully decentralized identity system in Nostr must balance ease-of-use with strong cryptographic assurances. A layered approach—using decentralized identifiers with optional verifications—may yield optimal usability without sacrificing security.
3.2. Protocol-Specific Countermeasures
3.2.1. Rechained Protocol
The Rechained protocol introduces a deposit-based identity generation mechanism in IoT and mobile ad hoc networks. Here are its salient points:
- Deposit Transaction: Each identity is tied to a deposit transaction on a public blockchain, such as Bitcoin or Ethereum.
- Parameterization: Parameters like minHeight, minDifficulty, and amounts ensure that each identity requires a certain financial threshold to be met.
- Verification Complexity: Though proof sizes are modest (10–50 KB) and verification times are around 2 seconds, these are acceptable trade-offs on modern consumer-grade devices.
Application Prospects: If Nostr could integrate a variant of Rechained, it may allow identities to be tied to a verifiable deposit, thus raising the cost baseline for attackers. Such integration must ensure user-friendliness and minimal friction during onboarding.
3.2.2. Sysname Decentralized Identity Scheme
Sysname presents an innovative approach with additional privacy-preserving features:
- Selective Disclosure: It allows users to reveal only non-identifying attributes proving compliance with certain predicates without exposing their full identity.
- Chain-Pinned Identifiers: Aggregates multiple pseudonyms to a single on-chain record, reducing the ease with which an attacker can use disparate identities without accountability.
- Key Recovery: Enables users to refresh public keys and recover lost keys, which bolsters user trust and system resilience.
Consideration: Integrating aspects of sysname within Nostr could offer both enhanced privacy and Sybil resistance, yielding a balance between security and user independence. Enhanced key recovery also addresses the usability concerns evidenced by historical failures in PGP adoption.
3.3. Behavioral Analysis and Anomaly Detection
As an additional countermeasure, behavioral analysis can serve as a secondary layer of defense. Given the evolving sophistication of bots, a cat-and-mouse game inevitably ensues:
- Machine Learning Based Detection: Frameworks like a deep intrusion detection system (DIDS) combined with blockchain smart contracts can help identify anomalous posting behaviors. For example, integrations using Particle Swarm Optimization–Gravitational Search Algorithm (ePSOGSA) with deep autoencoders have proven accurate on established benchmarks.
- Economic Implications: By analyzing behavior, the systems can prioritize identities that have accrued economic transactions (like zaps) that match genuine user behavior over automated, bot-like patterns.
- Limitations: While promising, such systems introduce computational overhead and may yield false positives, so the implementation must be cautiously engineered with appropriate fail-safes.
4. Trade-Offs and Comprehensive Evaluation
4.1. Usability vs. Security
One of the central themes in designing defenses against Sybil attacks on Nostr is balancing ease-of-use with robust security. A highly secure system that remains cumbersome to use (akin to the historical PGP deployment) may fail adoption. Conversely, ease-of-use without economic or cryptographic Assurance opens the door to cost-free identity creation and abuse.
- Economic Approaches: Impose a direct cost on identity creation but must be calibrated to avoid excluding well-intentioned users, particularly newcomers or those with limited funds.
- Cryptographic Protocols: Solutions like Aut-CT and sysname offer advanced cryptographic proofs with minimal overhead in verification but could require more sophisticated client implementations.
- Behavioral Analysis: Acts as a safety net but must be continuously updated as adversaries evolve their bot strategies.
4.2. Privacy Implications
Every mechanism proposed must be evaluated in terms of its ability to preserve user privacy. Nostr’s value proposition rests on its censorship resistance and privacy-preserving design. Therefore:
- Selective Disclosure Protocols: Techniques that allow for proving predicates without full identity revelation should be prioritized (as seen in sysname).
- Decentralized Identity Aggregation: Methods that tie multiple pseudonyms to a single verifiable chain of evidence (enhancing accountability) can reduce risk without compromising anonymity.
- Economic Proof Versus User Balance: The economic barriers should not expose additional metadata that can be linked back to users. Hence, anonymizing tokens and cryptographic blinding techniques need to be integral to the design.
5. Proposed Comprehensive Strategy for Nostr
Based on the research, a multi-layered defense strategy is recommended. It incorporates both cryptographic assurances and economic disincentives while integrating behavioral analysis. The following blueprint emerges:
5.1. Implementation Blueprint
- Integration of Curve Tree-Based Aut-CT Proofs:
- Require each new identity creation to be validated via a Curve Tree-based proof of key ownership. This approach leverages zero-knowledge proofs and ensures logarithmic verification times, thus scalable even for a large user base.
-
Address token re-use and fake identity creation by integrating key images as established in the Aut-CT mechanism.
-
Economic Deposit Mechanism (Inspired by Rechained):
- Incorporate a lightweight deposit mechanism where users must commit a small deposit, recorded on a public blockchain. This deposit acts as a minimum hurdle for each identity and may be partially refundable upon earning trust.
-
Experiment with dynamic deposit sizes based on network load and risk assessments, ensuring that the economic threshold is both feasible and deterring.
-
Selective Disclosure and Pseudonym Aggregation (Adapting Sysname Principles):
- Allow users to prove characteristics about their identities (age, locality, etc.) without divulging full identifying details.
-
Aggregate multiple pseudonyms provided by the same user on-chain, using cryptographic commitments that both link identities and allow selective disclosure.
-
Optional Layer: Economic and Behavioral Analytics:
- Deploy a deep anomaly detection layer using machine learning techniques on posting behavior, ensuring that anomalous activities (e.g., rapid posting similar to bots) are flagged.
- Integrate smart contract-based economic triggers that penalize suspicious behavior while maintaining user privacy.
5.2. Addressing Adoption and Usability Concerns
- User Experience (UX): The proposed solutions must be integrated transparently into client applications. Much like improved versions of PGP aim to streamline key management, Nostr clients should embed these cryptographic protocols without requiring manual intervention.
- Modular Onboarding: Allow users to opt into various levels of proof. Early adopters may use lightweight methods, with a progressive enhancement available for those seeking higher assurance as they interact more within the network.
- Wallet and Key Management Integration: Leverage existing wallet infrastructures to ease the economic deposit and key recovery processes, drawing user confidence from familiarity with mainstream crypto applications.
6. Future Work and Speculative Technologies
While the proposals above are based on current and emergent technologies, additional research can further refine these approaches:
- Adaptive Economic Models: Future work can explore dynamic, context-aware deposit requirements that adjust based on network activity, risk profiles, and even market conditions.
- Quantum-Resistant Cryptography: As quantum computing progresses, integrating quantum-resistant algorithms in curve-tree constructions will become imperative for long-term viability.
- Interoperable Decentralized Identifiers (DIDs): Creating cross-system standards for identity verification may allow Nostr to interface with other decentralized platforms, enhancing the overall security ecosystem.
- Advancements in Zero-Knowledge Proofs (ZKPs): Considering high-level academic research on ZKPs, such as bulletproofs and recursive ZKPs, can further improve both the scalability and succinctness of cryptographic proofs required for identity validation.
Speculative Note: As adversaries adapt, we may see the emergence of hybrid systems where off-chain reputation systems are cryptographically linked to on-chain proofs, creating a multi-dimensional defense that continuously evolves through machine learning and adaptive economic incentives.
7. Conclusion
Mitigating Sybil attacks on Nostr necessitates a proactive, multi-layered approach combining advanced cryptographic techniques, economic disincentives, decentralized verification mechanisms, and behavioral analytics. The proposals detailed in this report aim to reinforce Nostr’s resilience while maintaining its foundational commitment to privacy and censorship resistance.
By integrating Curve Tree-based proofs, economic deposit mechanisms, and selective disclosure methods, Nostr can build a robust identity framework that is both user-friendly and resistant to abuse. Continued research into adaptive economic models and quantum-resistant cryptographic techniques will ensure that the system remains secure in the evolving landscape of decentralized networks.
Thorough evaluation of trade-offs, user experience enhancements, and iterative testing on live networks will be critical. This report serves as a foundational blueprint for further exploration and eventual deployment of sophisticated Sybil defense mechanisms within Nostr.
8. References and Further Reading
While the source of ideas is drawn from numerous research efforts and academic papers, key references include:
- Aut-CT Leveraging Curve Trees and Bulletproof Proofs
- Economic mitigation strategies in cryptocurrency mixers
- Comparative studies of decentralized identity systems (uPort, Hyperledger Indy, etc.)
- Rechained protocol research by Bochem and Leiding for IoT networks
- Sysname scheme for privacy-preserving decentralized identifiers
- Deep intrusion detection systems applied to decentralized social networks
(Additional in-depth academic references can be located within the research literature on arXiv and major cryptographic conferences.)
Prepared by an expert research analyst, this report is intended to provide detailed insights and a strategic roadmap for implementing Sybil-resistant identities on Nostr while retaining user ease-of-use and privacy-centric features.
Sources
- https://delvingbitcoin.org/t/anonymous-usage-tokens-from-curve-trees-or-autct/862
- https://delvingbitcoin.org/t/anonymous-usage-tokens-from-curve-trees-or-autct/862/2
- https://www.imperva.com/learn/application-security/sybil-attack/
- https://eprint.iacr.org/2019/1111.pdf
- https://www.smartsight.in/technology/what-to-know-about-sybil-attacks/
- https://www.researchgate.net/publication/363104774_Comparative_Analysis_of_Decentralized_Identity_Approaches
- https://www.researchgate.net/publication/331790058_A_Comparative_Analysis_of_Trust_Requirements_in_Decentralized_Identity_Management
- https://www.mdpi.com/1999-5903/17/1/1
- https://github.com/WebOfTrustInfo/rwot5-boston/blob/master/topics-and-advance-readings/Framework-for-Comparison-of-Identity-Systems.md
- https://www.researchgate.net/publication/367557991_The_Cost_of_Sybils_Credible_Commitments_and_False-Name_Proof_Mechanisms
- https://pmc.ncbi.nlm.nih.gov/articles/PMC8125832/
- https://www.nervos.org/knowledge-base/sybil_attacks_consensus_mechanisms_(explainCKBot)
- https://arxiv.org/html/2307.14679v2
- https://www.sciencedirect.com/science/article/pii/S1084804523001145
- https://www.sciencedirect.com/science/article/pii/S2096720924000460
- https://medium.com/@sshshln/mitigating-identity-attacks-in-defi-through-biometric-based-sybil-resistance-6633a682f73a
-
 @ 7d33ba57:1b82db35
2025-03-22 14:04:18
@ 7d33ba57:1b82db35
2025-03-22 14:04:18Alicante, located on Spain’s Costa Blanca, is a vibrant coastal city known for its golden beaches, historic castles, delicious seafood, and lively atmosphere. Whether you're exploring its rich history, relaxing by the sea, or enjoying the local cuisine, Alicante offers the perfect mix of culture and leisure.
🏛️ Top Things to See & Do in Alicante
1️⃣ Santa Bárbara Castle 🏰
- Perched on Mount Benacantil, this medieval fortress offers panoramic views over the city and coastline.
- Walk up the hill or take an elevator from Postiguet Beach.
2️⃣ Postiguet Beach 🏖️
- A beautiful sandy beach right next to the city center.
- Perfect for sunbathing, swimming, or enjoying a cocktail at a beachside bar.

3️⃣ Explanada de España 🌴
- A famous seaside promenade lined with palm trees, cafés, and street artists.
- Great for an evening stroll with stunning sea views.
4️⃣ Alicante Old Town (El Barrio) 🏡
- A charming historic district with narrow streets, colorful houses, and lively tapas bars.
- Visit Concatedral de San Nicolás and the Casas del Barrio for authentic local vibes.
5️⃣ MARQ – Archaeological Museum of Alicante 🏺
- A fascinating museum showcasing Alicante’s history from prehistoric times to modern days.
- Award-winning and great for history lovers!
6️⃣ Tabarca Island Day Trip 🚤
- A small, picturesque island just a short boat ride from Alicante.
- Perfect for snorkeling, seafood dining, and exploring its quaint whitewashed village.
7️⃣ Mercado Central 🛍️
- A bustling market filled with fresh seafood, local produce, jamón ibérico, and cheeses.
- Great for food lovers looking to try authentic Alicante flavors.
🍽️ What to Eat in Alicante
- Arroz a banda – A local seafood rice dish, similar to paella 🍚🐟
- Turrón de Alicante – A famous nougat made with almonds 🍯
- Caldero – A rich fish stew served with rice 🍲
- Salazones – Salted fish specialties, a local delicacy 🐠
- Horchata de chufa – A refreshing tiger nut drink, great on hot days 🥛
🚆 How to Get to Alicante
✈️ By Air: Alicante-Elche Airport (ALC) with flights from all over Europe ✈️
🚄 By Train: High-speed AVE trains from Madrid (~2.5 hrs) & Barcelona (~4.5 hrs)
🚗 By Car: Well-connected via the AP-7 coastal highway💡 Tips for Visiting Alicante
✅ Best time to visit? Spring & Summer for the best beach weather ☀️🏖️
✅ Stay for Las Hogueras de San Juan (June 20-24) – A huge fire festival with fireworks & street parties 🎆🔥
✅ Take a boat to Tabarca Island – It’s a hidden paradise for snorkeling 🏝️
✅ Try local seafood! Alicante’s coast is famous for its fresh fish & shellfish 🦐 -
 @ e5de992e:4a95ef85
2025-03-22 13:13:20
@ e5de992e:4a95ef85
2025-03-22 13:13:20Master Your Tasks with Precision: Introducing TaskforUs
In our increasingly complex digital lives, determining which task deserves our immediate attention can be challenging. We've all faced the chaos of a to-do list that feels more like a puzzle than a plan. Should you reach out to a friend for dinner? Finish that work project? Or remember a loved one’s birthday? With so many tasks vying for attention, how do you know what to tackle right now? That’s where TaskforUs comes in—a smart, simple website designed to pinpoint the exact task you should focus on at this moment.
The Problem: Too Many Tasks, Too Little Clarity
Traditional to-do lists are a dumping ground for ideas, but they rarely tell you what’s urgent. Is it time to catch up with a friend, or should you prioritize that report? Without a clear system, tasks either pile up or get tackled haphazardly—leaving you stressed and scattered. TaskforUs changes that.
The Solution: Time Units and Smart Timing
TaskforUs is built on a clever concept: every task has a "time unit" and an ideal action window—between 2 and 5 of those units. The time unit depends on the task. Want to stay connected with a friend over dinner? That’s a "week" task—act within 2 to 5 weeks. Planning a career check-in? That’s a "year" task—revisit it between 2 and 5 years. The algorithm ensures you’re acting at just the right time—not too soon, not too late.
This adaptive approach ensures tasks receive attention at appropriate intervals—neither prematurely nor after their optimal window has passed:
- Personal connections (like scheduling lunch with friends) operate on a weekly time unit, requiring action within 2-5 weeks
- Time-sensitive matters (like doing some cardio) function on a daily time unit, requiring action within 2-5 days
- Project deadlines might operate on daily units, requiring progress every 2-5 days
For tasks tied to specific dates—like birthdays—TaskforUs offers a unique "Fix" mode. Pinpoint a day, and the task climbs steadily up your list as the date approaches, rocketing to the top spot on the day, ensuring you never miss it.
How It Works
TaskforUs makes task management effortless and precise. Here’s how:
- Add Your Tasks: Enter anything on your mind—"schedule a team meeting," "call Mom," "do cardio," or "wish Alex a happy birthday."
- Set the Time Unit: Choose from days, weeks, months, or years, depending on the task’s rhythm. TaskforUs can suggest defaults (e.g., "keep in touch with friends" defaults to weeks). For date-specific tasks, use Fix Mode to set the exact day.
- Get Your Top Task: The algorithm tracks your tasks and surfaces the single most urgent one in its 2-to-5 sweet spot, telling you, "This is what to do now." In Fix Mode, date-pinned tasks take over on their big day.
- Focus Mode: Need more than one priority? Switch to Focus Mode and see your top 3 tasks (you can adjust this number to suit your style)—perfect for juggling a busy day.
Real-Life Examples
- Social Life: You want to grab dinner with your friend, Alex. The time unit is "weeks." After 3 weeks since your last meetup, TaskforUs flags it as your top task—time to text them.
- Health Goals: You plan to do some cardio. The time unit is "days." On day 2, it’s your top priority—hit the gym before the 5-day mark.
- Special Dates: You set Alex’s birthday in Fix Mode. Weeks out, it’s low on the list, but it climbs as the date nears. On the day, it’s undeniably number one—time to send that birthday wish.
- Long-Term Planning: You’re thinking about reassessing your career path. The time unit is "years." After 2 years, TaskforUs nudges you to reflect—right in that 2-to-5-year window.
Why It Works
TaskforUs strikes a perfect balance. The 2-to-5 range keeps you from acting too early (wasting effort) or too late (missing opportunities), while Fix Mode ensures critical dates never slip by. Whether it’s a quick daily task, a big-picture yearly goal, or a must-do deadline, the system adapts to your life’s pace. With its "top task" feature, customizable Focus Mode, and pinpoint Fix Mode, you’ll always know where to direct your energy—no more second-guessing.
Rather than overwhelming users with endless to-do lists or complex priority matrices, TaskforUs presents a refreshingly direct solution: it identifies your top task to work on right now. This targeted approach eliminates decision fatigue and helps maintain productivity momentum.
Current Development Status
TaskforUs is currently in beta, with ongoing refinements based on user feedback and how well it’s working. The development team is focused on ensuring the algorithm accurately identifies truly time-critical tasks—including perfecting Fix Mode—while keeping the experience intuitive.
Take Control Today
Say goodbye to overwhelm and hello to clarity. TaskforUs isn’t just a to-do list—it’s your guide to timing tasks perfectly. Sign up today at task4.us and let TaskforUs show you what to work on right now, so you can focus on what matters most.
-
 @ 6bae33c8:607272e8
2025-03-22 23:12:43
@ 6bae33c8:607272e8
2025-03-22 23:12:43I was supposed to do my Main Event next week, but Heather scheduled a trip to Spain for us I had forgotten about, so I moved it to today, which meant I had to cram a bit.
I drew the seven slot. Results are below:
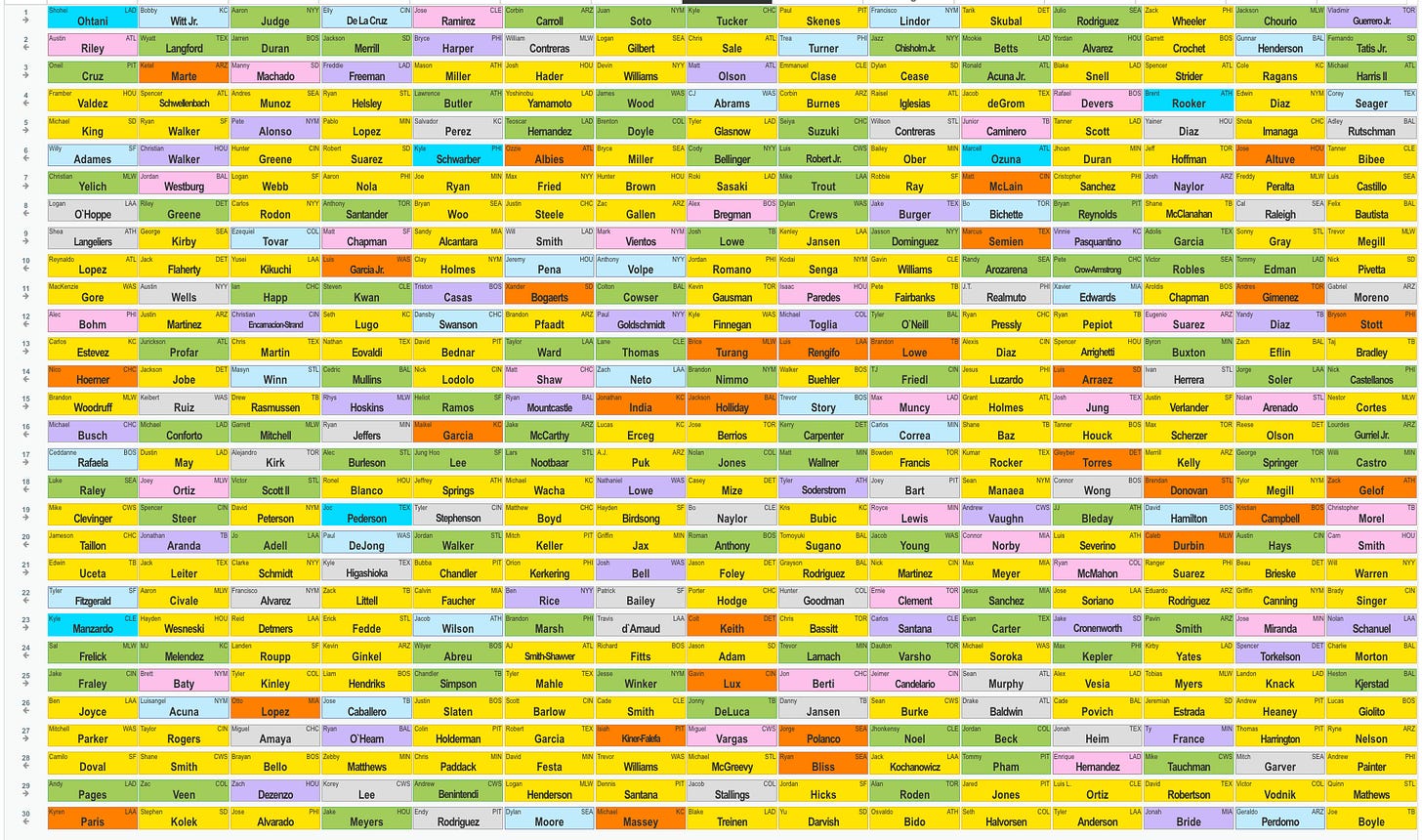 Before I get into the round-by-round write-up I have to say this was the smoothest and easiest Main I’ve ever done. That doesn’t mean this is a great team — I could easily be wrong about everything — but using recent ADP I planned out each round, and it really went almost exactly to form. That never happens. Usually I’m worried about having to chase some category or getting stuck with players I don’t want. But today there was almost none of that.
Before I get into the round-by-round write-up I have to say this was the smoothest and easiest Main I’ve ever done. That doesn’t mean this is a great team — I could easily be wrong about everything — but using recent ADP I planned out each round, and it really went almost exactly to form. That never happens. Usually I’m worried about having to chase some category or getting stuck with players I don’t want. But today there was almost none of that.1.8 Kyle Tucker — I like Tucker in a new park, playing for a big contract. He’s fully healthy after an injury-shortened 2024, so he should be fresh. Had Team 7 taken Tucker instead of Juan Soto, I would have taken Jackson Chourio.
2.8 Chris Sale — I thought I might get Jazz Chisholm here, and my fallback was Trea Turner. But earlier in the day I decided I’d probably take Sale anyway as pitching gets scarce quickly in the 15-team and often gets pushed up as a result. But I hadn’t really locked it in, even though I felt Sale would make for an easier build. Then Chisholm and Turner went ahead of me on consecutive picks, and my choice was made for me.
3.8 Matt Olson — I was worried about this pick. This was in the elite closer range, and I didn’t want to go that route, so it was either Manny Machado (gone), Olson or dropping down for someone like Michael Harris about whom I’m only lukewarm. I took Olson who has a good shot of 40-100-100 in that lineup.
4.8 C.J. Abrams — The stat nerds hate him, but he could steal 40 bases, and he was raking before slumping in the second half last year. Tucker gave me some bags, but I really wanted a big-time steals source to pair with him.
5.8 Tyler Glasnow — My favorite fifth-round starter, Glasnow managed134 innings last year. A similar giant lefty, Randy Johnson, was also injury prone early in his career and took a while to get going too.
6.8 Cody Bellinger — I was dead set on Bellinger who is raking this spring. He’ll get the short porch in Yankee stadium and qualifies at first and OF.
7.8 Roki Sasaki — This was the first pick I really had to think about. There was a run of five straight pitchers ahead of me, three of whom I would have taken instead (Logan Webb, Max Fried, Hunter Brown.) I like buying the dip on Sasaki after a shaky outing in Japan, but I also considered pivoting to Mike Trout. In the end, I felt there were more hitters I liked afterward, so I went Sasaki, and then Trout went with the very next pick. In fact the next guy snap-called it, if I recall correctly.
8.8 Alex Bregman — I wanted a share after reading how well he’s hit at Fenway during his career (if Grok is correct, 1.240 OPS in 21 games.) Plus he might eventually gain 2B eligibility if Rafael Devers gets healthy enough to play third. And he should get a lot of RBI hitting third behind Devers and Jarren Duran.
9.8 Josh Lowe — I really wanted to get a share of Lowe after reading about how the minor league home park will boost power for lefties. The steals are a given if he’s healthy, but 20-25 HR would make him a huge bargain in Round 9.
10.8 Jordan Romano — The Lowe pick cost me Kenley Jansen, which I thought it might, so I pivoted to the other exprienced closer I like in that range, and Romano’s on a better team.
11.8 Kevin Gausman — I thought about Aroldis Chapman here, but starters were getting scarce, so I gambled he’d make it back and took Gausman. Gausman is coming off a down year, but he’s healthy, and he knows how to pitch.
12.8 Brandon Finnegan — I missed out on Chapman, it turns out, but Finnegan, who had 38 saves last year and was re-signed, was my backup plan. He’s not especially good, but saves are saves.
13.8 Brice Turang — I really didn’t need speed that badly, but Turang fell like 50 spots below ADP, and I did need a second baseman. His defense keeps him in the lineup, and I’ll take 30-plus steals in case one of my other speed guys doesn’t pan out.
14.8 Brandon Nimmo — I got snaked on Walker Buehler (and Jesus Luzardo two picks before that), so I went with Nimmo for his ability to score runs.
15.8 Jackson Holliday — After a lot of safe picks, I felt like gambling on a top prospect finally. He’s hitting well this spring too.
16.8 Jose Berrios — This just seemed like the right pick, a boring veteran who knows how to pitch and get you innings without killing you. With Glasnow and Sasaki, I needed more of a horse type.
17.8 Nolan Jones — He was scratched from the game today right after I made this, so we’ll see. Hopefully it’s something minor. His 2023 season was fetching a top-five-round ADP last year.
18.8 Casey Mize — Pitching was really flying, and Mize is a former top prospect with an opportunity.
19.8 Bo Naylor — I needed a catcher, and he is one. I like that he runs a bit, and last year’s batting average I’ll chalk up to variance.
20.8 Roman Anthony — I don’t know whether he’ll make the team out of camp, but he’s an elite prospect with little left to prove in the minors.
21.8 Jason Foley — I have two shaky closers, so I wanted to throw another potential one in the mix.
22.8 Porter Hodge — Another saves option if Ryan Pressly falls apart.
23.8 Colt Keith — Keith wasn’t horrendous as as rookie, and moving to first base will give him extra eligibility soon.
24.8 Jason Adam — Another potential source of saves with Robert Suarez looking awfully shaky this spring.
25.8 Gavin Lux — A former top prospect, getting regular at-bats in the league’s second best hitter’s park and picking up more eligibility.
26.8 Jonny Deluca — I needed outfield depth in case Anthony doesn’t start the year in the majors, and Deluca should play in that bandbox minor league park.
27.8 Miguel Vargas — A former top prospect with dual position eligibility should get his chance for regular low-pressure at-bats in Chicago.
28.8 Michael McGreevy — I needed another SP, and he’s one. Also has good control and pitches in a good park. Having a great spring too.
29.8 Jacob Stallings — I played chicken at second catcher all draft, got burned a few times, but Stallings is the starter for now in Colorado.
30.8 Blake Treinen — The Stallings pick cost me a gamble on Jared Jones’ elbow, so I took Treinen who’s an elite reliever who could fill in if starters have bad matchups.
Roster By Position
C Bo Naylor/Jacob Stallings
1B Matt Olson
2B Brice Turang
3B Alex Bregman
SS C.J. Abrams
CI Cody Bellinger
MI Jackson Holliday
OF Kyle Tucker/Josh Lowe/Brandon Nimmo/Nolan Jones/Roman Anthony
UT Colt Keith
SP Chris Sale/Tyler Glasnow/Roki Sasaki/Kevin Gausman/Jose Berrios/Casey Mize
RP Jordan Romano/Brandon Finnegan/Jason Foley
B Porter Hodge/Jason Adam/Gavin Lux/Jonny Deluca/Miguel Vargas/Michael McGreevy/Blake Treinen
-
 @ 30fb9c78:1f1e3c3a
2025-03-22 12:11:54
@ 30fb9c78:1f1e3c3a
2025-03-22 12:11:54Why anarchy? Because anything else would be uncivilized.”
This famous statement by Jeffrey Tucker inspired the Norwegian anarchists John Holmesland and Sondre Bjellås to create a truly civilized – voluntaryist society without coercion and violence – based on mutual voluntarism.
Anarchists in the “most perfect state” in the world
The first thing that has struck me for a long time is the strong anarchist movement in Norway – a state that almost all progressive politicians consider “perfect.” The most developed and advanced state in Scandinavia.
I first noticed this phenomenon at Anarchopulco (the big anarchist conference in Acapulco, Mexico), where the entire delegation of anarchists from Europe was primarily from Norway and Sweden. Countries that most EU politicians consider to be the epitome of a perfectly functioning state.
The Norwegian anarchists explained to me that Norway, despite publicly presenting itself as the most correct country, protecting all kinds of minorities, has problems that few people outside Norway suspect.
It is a country that, like any other, suffers from corruption and incredible waste. Many Norwegians are not the least bit happy about Norwegian funds supporting the most bizarre projects in the whole world. At the moment, a case is flying through Norway about how the head of the Norwegian Communist Party Bjornar Moxnes, stole USD 150 worth of sunglasses (Communists steal worldwide, including in Norway).
Last year, Norway introduced a wealth tax, which has seen most of the millionaire rich and productive people leave the country (especially Switzerland). Many of them took their “know-how” and their companies with them. Thanks to strong progressive taxation (productive people are the most discriminated against), everyone in Norway is more or less “equally well off.” Most Norwegians are indebted (mortgage or loan for practically everything) and live on credit. Even though the Norwegian economy is built on oil or fishing, don’t expect petrol, diesel, or fish to be cheap here (due to high taxation, they are more expensive than in most EU countries). Because of this, alcohol is also extremely expensive here and the most expensive beer in the world.
Although Norway is a rich country, Norwegians themselves don’t feel rich.
Unlike most countries, however, it is quite a bit more liberal – homeschooling, home births and decriminalized all drugs are allowed in Norway.
Most Norwegians are conformists and follow everything the government tells them. That’s why, for example, there are more police officers in most countries than in Norway – because everyone follows the law. They regard not paying taxes as blasphemy and selfishness, so the community in Liberstad, which takes absolutely nothing from the state and builds everything itself, unfortunately, has a hard time of it.
Voluntaryism in Liberstad
Since anarchism in mainstream society, unfortunately, has a negative connotation, John and Sondre decided to base and promote the whole project on the ideas of voluntarism and not mention anarchy. Voluntaryism represents a philosophy of life or moral stance where we only accept mutually voluntary relationships (commercial or non-commercial). Consistent voluntaryists reject unilaterally enforced relationships (e.g., between the state and the citizen) and are, therefore, automatically anarchists (that is unless we consider a state based on voluntary support).
Voluntaryists believe that a society built on mutual voluntarism would not only be more prosperous, but more importantly more civilized, as it would not use means of aggression against innocent people (which all states in the world do, and most people unfortunately approve of).
Voluntaryists consider a voluntaryist society to be a “framework,” that is, a basis on which any other social arrangements, such as democracy, can be built – if all its members voluntarily decide to use their democratic voice to make decisions about the lives of others. Or socialism – if all its members voluntarily donate 90% of their income to a standard pot and then redistribute it to elected central planners.
 Liberstad’s Voluntaryist Treaty, respected by all its inhabitants
Liberstad’s Voluntaryist Treaty, respected by all its inhabitantsJohn and Sondre have no problem with Norway’s welfare state and huge taxes as long as its citizens are willing to support it voluntarily and use its services. On the other hand, they want nothing to do with it and are building an independent, self-sufficient, parallel society in the Norwegian mountains.
Independence and Autonomy for Liberstad
John and Sondre have bought more than 2 square kilometers of land that constitutes private property, even though it is Norwegian territory. It falls under the management of a non-profit private organization, which does not have to disclose anything (including its members or financial interactions between members) by law.
A couple of years ago, they launched a campaign to sell Libertad plots, when they all sold out (I visited a few of these plots yesterday, which my friends bought). I should point out that from the perspective of the Norwegian state, everything is owned by said private organization and the state does not know who the actual owner of a given parcel is (from that perspective, you can buy property in Liberstad without the Norwegian state knowing). There are active social channels where John, Sondre, and their management actively communicate with the owners of these parcels about their future fate.
Respect for autonomy has been resolved through a registered religious organization – the Norwegian Voluntaryist Organisation, which has no God and has key ideological/religious principles that must be respected (their automated translation via Google is available here).
Norway profiles itself as a “great fighter” for the rights of minorities around the world (from Tibet to the Kurds),” so the voluntarists in Liberstad hope that their minority within Norway itself will also be respected.
So far, they have had no problem with the government in Oslo. This is because the latter realizes that the more they publicly comment on Liberstad or interfere in its activities, the more publicity they would give it, and the more Norwegians would learn about the ideas of voluntarism and the need for an autonomous society.
But their real problems are with the local government, which constantly bullies them. For example, for posting (and flat out downloading) a drone-made video documenting how they built their private roads – which didn’t come without the explosions needed to modify the terrain. Without any permission, of course. Fortunately, they manage to ignore the local government politely, and since Norway is not a typical police state, they don’t anticipate a police raid on their private property.

Camping in Liberstad, view of the “anarchist park” in the background
Don’t ask permission, don’t deal with details
Voluntaryists in Liberstad do not recognize the state’s authority, so it makes no sense to them to ask for permission from it.
This is where the Liberstad project is different from the [Prospera project in Honduras (https://www.prospera.co/), which has a contract with the state of Honduras to build a similar private city (which they are having a bit of a problem with at the moment because there has been a change of government in Honduras, and the new government refuses to respect what the old government signed before).
That’s why the founders of Liberstad decided not to ask any permission from the state – they are building their properties without it (they are currently working on their brewery), building their roads, and homeschooling their children. They are just telling the state that they have built something new again.
"The important thing when building a private city is not to deal with all the details right from the start because your costs will rise disproportionately, and you’ll end up going nowhere,” says John Holmesland.
In Liberstad, they are very pragmatic and build just what they need. Similarly, they don’t invent any rules or laws for situations that are unlikely to arise. Indeed, what weighs heavily on contemporary society is an over-bureaucratized state apparatus that regulates and requires a rubber stamp for almost everything.
The current state of Liberstad
Liberstad’s permanent community may be small (under 15 people), but they have visitors worldwide and a potential location for thousands of new citizens. There are a few houses and caravans parked where Liberstad residents live. They have a large community center where there are lectures and evening events. Then there are the “barracks” for visitors (showers, toilets, washing machines, dryers). And lots of free parking space. A small island with a forest has earned the name “anarchist park.” Around it is a gravel road, which they plan to turn into asphalt.
 Enter Liberstad. “Et lite stykke frihet” means “a little piece of freedom.”
Enter Liberstad. “Et lite stykke frihet” means “a little piece of freedom.”Both founders consider Liberstad their lifelong project, so even though they don’t have a lot of funding, construction is still slowly progressing, and they are both fully committed to the project.
 The current inhabited part of Liberstad. The total uninhabited size of Liberstad is an order of magnitude larger.
The current inhabited part of Liberstad. The total uninhabited size of Liberstad is an order of magnitude larger.Liberstad’s parallel economy
Of all the stateless mini-communities I’ve visited so far (Kalu Yala in Panama, El Cherán in Mexico, Mennonites in Paraguay, Christiania in Copenhagen), Liberstad comes closest to me ideologically as a voluntarist. I got on exceedingly well with its founders, John and Sondre, and we agreed on all the ethical and social principles (which I rarely do).
 With Liberstad founders John Holmesland and Sondre Bjellås.
With Liberstad founders John Holmesland and Sondre Bjellås.Liberstad has a new neighbor, a Dutch photographer, and libertarian, who has bought a much larger plot of land next door. And who plans to build a similar libertarian community there.
I hope and believe that this voluntaryist anomaly in Norway will continue to live its free life and attract freedom-minded people worldwide. I have all my fingers crossed for Liberstad and will visit again in a few years!
Liberstad links to their main website, Facebook, X, Instagram.
Source: Liberationtravel, Liberstad: Voluntaryist experiment in southern Norway, August 30, 2023
-
 @ 79008e78:dfac9395
2025-03-22 11:22:07
@ 79008e78:dfac9395
2025-03-22 11:22:07Keys and Addresses
อลิซต้องการจ่ายเงินให้กับบ๊อบแต่โหนดของบิตคอยน์ในระบบหลายพันโหนดจะตรวจสอบธุรกรรมของเธอ โดยไม่รู้ว่าอลิซหรือบ๊อบเป็นใคร ละเราต้องการรักษาความเป็นส่วนตัวของพวกเขาไว้เช่นนี้ อลิซจำเป็นต้องสื่อสารว่าบ๊อบควรได้รับบิตคอยน์บางส่วนของเธอโดยไม่เชื่อมโยงแง่มุมใด ๆ ของธุรกรรมนั้นกับตัวตนในโลกจริงของบ๊อบ หรือกับการชำระเงินด้วยบิตคอยน์ครั้งอื่น ๆ ที่บ๊อบได้รับ อลิซใช้ต้องทำให้มั่นใจว่ามีเพียแค่บ๊อบเท่านั้นที่สามารถใช้จ่ายบิตคอยน์ที่เขาได้รับต่อไปได้
ในบิตคอยน์ไวท์เปเปอร์ได้อธิบายถึงแผนการที่เรียบง่ายมากสำหรับการบรรลุเป้าหมายเหล่านั้น ดังที่แสดงในรูปด้านล่างนี้

ตัวของผู้รับอย่างบ๊อบเองจะได้รับบิตคอยน์ไปยัง public key ของเขาที่ถูกลงนามโดยผู้จ่ายอย่างอลิซ โดยบิตคอยน์ที่อลิซนำมาจ่ายนั้นก็ได้รับมาจากที่ใครสักคนส่งมาที่ public key ของเธอ และเธอก็ใช้ private key ของเธอในการลงนามเพื่อสร้างลายเซ็นของเธอและโหนดต่าง ๆ ของบิตคอยน์จะทำการตรวจสอบว่าลายเซ็นของอลิซผูกมัดกับเอาต์พุตของฟังก์ชันแฮชซึ่งตัวมันเองผูกมัดกับ public key ของบ๊อบและรายละเอียดธุรกรรมอื่นๆ
ในบทนี้เราจะพิจารณาpublic key private key Digital signatrue และ hash function จากนั้นใช้ทั้งหมดนี้ร่วมกันเพื่ออธิบาย address ที่ใช้โดยซอฟต์แวร์บิตคอยน์สมัยใหม่
Public Key Cryptography (การเข้ารหัสของ public key)
ระบบเข้ารหัสของ public key ถูกคิดค้นขึ้นในทศวรรษ 1970 มาจากรากฐานทางคณิตศาสตร์สำหรับความปลอดภัยของคอมพิวเตอร์และข้อมูลสมัยใหม่
นับตั้งแต่การคิดค้นระบบเข้ารหัส public key ได้มีการค้นพบฟังก์ชันทางคณิตศาสตร์ที่เหมาะสมหลายอย่าง เช่น การยกกำลังของจำนวนเฉพาะและการคูณของเส้นโค้งวงรี โดยฟังก์ชันทางคณิตศาสตร์เหล่านี้สามารถคำนวณได้ง่ายในทิศทางหนึ่ง แต่เป็นไปไม่ได้ที่จะคำนวณในทิศทางตรงกันข้ามโดยใช้คอมพิวเตอร์และอัลกอริทึมที่มีอยู่ในปัจจุบัน จากฟังก์ชันทางคณิตศาสตร์เหล่านี้ การเข้ารหัสลับช่วยให้สามารถสร้างลายเซ็นดิจิทัลที่ไม่สามารถปลอมแปลงได้และบิตคอยน์ได้ใช้การบวกและการคูณของเส้นโค้งวงรีเป็นพื้นฐานสำหรับการเข้ารหัสลับของมัน
ในบิตคอยน์ เราสามารถใช้ระบบเข้ารหัส public key เพื่อสร้างคู่กุญแจที่ควบคุมการเข้าถึงบิตคอยน์ คู่กุญแจประกอบด้วย private key และ public key ที่ได้มาจาก private key public keyใช้สำหรับรับเงิน และ private key ใช้สำหรับลงนามในธุรกรรมเพื่อใช้จ่ายเงิน
ความสัมพันธ์ทางคณิตศาสตร์ระหว่าง public key และ private key ที่ช่วยให้ private key สามารถใช้สร้างลายเซ็นบนข้อความได้ ลายเซ็นเหล่านี้สามารถตรวจสอบความถูกต้องกับ public key ได้โดยไม่เปิดเผย private key
TIP: ในการใช้งานซอฟแวร์กระเป๋าเงินบิตคอยน์บสงอัน จะทำการเก็บ private key และ public key ถูกเก็บไว้ด้วยกันในรูปแบบคู่กุญแจเพื่อความสะดวก แต่อย่างไรก็ตาม public key สามารถคำนวณได้จาก private key ดังนั้นการเก็บเพียง private key เท่านั้นก็เป็นไปได้เช่นกัน
bitcoin wallet มักจะทำการรวบรวมคู่กุญแต่ละคู่ ซึ่งจะประกอบไปด้วย private key และ public key โดย private key จะเป็นตัวเลขที่ถูกสุ่มเลือกขึ้นมา และเราขะใช้เส้นโค้งวงรี ซึ่งเป็นฟังก์ชันการเข้ารหัสทางเดียว เพื่อสร้าง public key ขึ้นมา
ทำไมจึงใช้การเข้ารหัสแบบอสมมาตร
ทำไมการเข้ารหัสแบบอสมมาตรจึงถูกใช้บิตคอยน์? มันไม่ได้ถูกใช้เพื่อ "เข้ารหัส" (ทำให้เป็นความลับ) ธุรกรรม แต่คุณสมบัติที่มีประโยชน์ของการเข้ารหัสแบบอสมมาตรคือความสามารถในการสร้าง ลายเซ็นดิจิทัล private key สามารถนำไปใช้กับธุรกรรมเพื่อสร้างลายเซ็นเชิงตัวเลข ลายเซ็นนี้สามารถสร้างได้เฉพาะโดยผู้ที่มีความเกี่ยวข้องกับ private key เท่านั้น แต่อย่างไรก็ตาม ทุกคนที่สามารถเข้าถึง public key และธุรกรรมสามารถใช้สิ่งเหล่านี้เพื่อ ตรวจสอบ ลายเซ็นได้ คุณสมบัติที่มีประโยชน์นี้ของการเข้ารหัสแบบอสมมาตรทำให้ทุกคนสามารถตรวจสอบลายเซ็นทุกรายการในทุกธุรกรรมได้ ในขณะที่มั่นใจว่าเฉพาะเจ้าของ private key เท่านั้นที่สามารถสร้างลายเซ็นที่ถูกต้องได้
Private keys
private key เป็นเพียงตัวเลขที่ถูกสุ่มขึ้น และการควบคุม private key ก็เป็นรากฐานสำคัญที่ทำให้เจ้าชองกุญแจดอกนี้สามารถควบคุมบิตคอยน์ทั้งหมดที่มีความเกี่ยวข้องกับ public key ที่คู่กัน private key นั้นใช้ในการสร้างลายเซ็นดิจิทัลที่ใช้ในการเคลื่อนย้ายบิตคอยน์ เราจำเป็นต้องเก็บ private key ให้เป็นความลับตลอดเวลา เพราะการเปิดเผยมันให้กับบุคคลอื่นนั้นก็เปรียบเสมือนกับการนำอำนาจในการควบคุมบิตคอยน์ไปให้แก่เขา นอกจากนี้ private key ยังจำเป็นต้องได้รับการสำรองข้อมูลและป้องกันจากการสูญหายโดยไม่ตั้งใจ เพราะหากเราได้ทำมันสูญหายไป จะไม่สามารถกู้คืนได้ และบิตคอยน์เหล่านั้นจะถูกปกป้องโดยกุญแจที่หายไปนั้นตลอดกาลเช่นกัน
TIP: private key ของบิตคอยน์นั้นเป็นเพียงแค่ตัวเลข คุณสามารถสร้างมันได้โดยใช้เพียงเหรียญ ดินสอ และกระดาษ โดยการโยนเหรียญเพียง 256 ครั้งจะทำให้คุณได้เลขฐานสองที่สามารถใช้เป็น private key ของบิตคอยน์ จากนั้นคุณสามารถใช้มันในการคำนวณหา public key แต่อย่างไรก็ตาม โปรดระมัดระวังเกี่ยวกับการเลือใช้วิธีการสุ่มที่ไม่สมบูรณ์ เพราะนั่นอาจลดความปลอดภัยของ private key และบิตคอยน์ที่มัมปกป้องอยู่อย่างมีนัยสำคัญ
ขั้นตอนแรกและสำคัญที่สุดในการสร้างกุญแจคือการหาแหล่งที่มาของความสุ่มที่ปลอดภัย (ซึ่งเรียกว่า เอนโทรปี) การสร้างกุญแจของบิตคอยน์นั้นเกือบเหมือนกับ "เลือกตัวเลขระหว่าง 1 และ 2^256" ซึ่งวิธีที่แน่นอนที่คุณใช้ในการเลือกตัวเลขนั้นไม่สำคัญตราบใดที่มันไม่สามารถคาดเดาหรือทำซ้ำได้ โดยปกติแล้วซอฟต์แวร์ของบิตคอยน์มักจะใช้ตัวสร้างตัวเลขสุ่มที่มีความปลอดภัยทางการเข้ารหัสเพื่อสร้างเอนโทรปี 256 บิต
สิ่งที่สำคัญในเรื่องนี้คือ private key สามารถเป็นตัวเลขใดๆ ระหว่าง 0 และ n - 1 (รวมทั้งสองค่า) โดยที่ n เป็นค่าคงที่ (n = 1.1578 × 10^77 ซึ่งน้อยกว่า 2^256 เล็กน้อย) ซึ่งกำหนดอยู่ใน elliptic curve ที่ใช้ใน Bitcoin ในการสร้างกุญแจดังกล่าว เราสุ่มเลือกเลขขนาด 256 บิตและตรวจสอบว่ามันน้อยกว่า n ในแง่ของการเขียนโปรแกรม โดยปกติแล้วสิ่งนี้ทำได้โดยการป้อนสตริงของบิตสุ่มที่ใหญ่กว่า ซึ่งรวบรวมจากแหล่งที่มาของความสุ่มที่มีความปลอดภัยทางการเข้ารหัส เข้าไปในอัลกอริทึมแฮช SHA256 ซึ่งจะสร้างค่าขนาด 256 บิตที่สามารถตีความเป็นตัวเลขได้อย่างสะดวก หากผลลัพธ์น้อยกว่า n เราจะได้กุญแจส่วนตัวที่เหมาะสม มิฉะนั้น เราก็เพียงแค่ลองอีกครั้งด้วยตัวเลขสุ่มอื่น
คำเตือน: อย่าเขียนโค้ดของคุณเองเพื่อสร้างตัวเลขสุ่ม หรือใช้ตัวสร้างตัวเลขสุ่ม "แบบง่าย" ที่มีให้ในภาษาโปรแกรมของคุณ ใช้ตัวสร้างตัวเลขสุ่มเทียมที่มีความปลอดภัยทางการเข้ารหัส (CSPRNG) จากแหล่งที่มีเอนโทรปีเพียงพอ ศึกษาเอกสารของไลบรารีตัวสร้างตัวเลขสุ่มที่คุณเลือกเพื่อให้มั่นใจว่ามีความปลอดภัยทางการเข้ารหัส การใช้งาน CSPRNG ที่ถูกต้องมีความสำคัญอย่างยิ่งต่อความปลอดภัยของกุญแจ
ต่อไปนี้คือกุญแจส่วนตัว (k) ที่สร้างขึ้นแบบสุ่มซึ่งแสดงในรูปแบบเลขฐานสิบหก (256 บิตแสดงเป็น 64 หลักเลขฐานสิบหก โดยแต่ละหลักคือ 4 บิต):
1E99423A4ED27608A15A2616A2B0E9E52CED330AC530EDCC32C8FFC6A526AEDDTIP: จำนวนที่เป็นไปได้ของ private key ทั้งหมดนั้นมีอยู่ 2^256 เป็นตัวเลขที่ใหญ่มากจนยากจะจินตนาการได้ มันมีค่าประมาณ 10^77 (เลข 1 ตามด้วยเลข 0 อีก 77 ตัว) ในระบบเลขฐานสิบ เพื่อให้เข้าใจง่ายขึ้น ลองเปรียบเทียบกับจักรวาลที่เรามองเห็นได้ซึ่งนักวิทยาศาสตร์ประมาณการว่ามีอะตอมทั้งหมดประมาณ 10^80 อะตอม นั่นหมายความว่าช่วงค่าของกุญแจส่วนตัว Bitcoin มีขนาดใกล้เคียงกับจำนวนอะตอมทั้งหมดในจักรวาลที่เรามองเห็นได้
การอธิบายเกี่ยวกับวิทยาการเข้ารหัสแบบเส้นโค้งวงรี (Elliptic Curve Cryptography)
วิทยาการเข้ารหัสแบบเส้นโค้งวงรี (ECC) เป็นประเภทหนึ่งของการเข้ารหัสแบบอสมมาตรหรือ public key ซึ่งอาศัยหลักการของปัญหาลอการิทึมแบบไม่ต่อเนื่อง โดยแสดงออกผ่านการบวกและการคูณบนจุดต่างๆ ของเส้นโค้งวงรี

บิตคอยน์ใช้เส้นโค้งวงรีเฉพาะและชุดค่าคงที่ทางคณิตศาสตร์ ตามที่กำหนดไว้ในมาตรฐานที่เรียกว่า secp256k1 ซึ่งกำหนดโดยสถาบันมาตรฐานและเทคโนโลยีแห่งชาติ (NIST) เส้นโค้ง secp256k1 ถูกกำหนดโดยฟังก์ชันต่อไปนี้ ซึ่งสร้างเส้นโค้งวงรี: y² = (x³ + 7) บนฟิลด์จำกัด (F_p) หรือ y² mod p = (x³ + 7) mod p
โดยที่ mod p (มอดูโลจำนวนเฉพาะ p) แสดงว่าเส้นโค้งนี้อยู่บนฟิลด์จำกัดของอันดับจำนวนเฉพาะ p ซึ่งเขียนได้เป็น F_p โดย p = 2^256 – 2^32 – 2^9 – 2^8 – 2^7 – 2^6 – 2^4 – 1 ซึ่งเป็นจำนวนเฉพาะที่มีค่ามหาศาล
บิตคอยน์ใช้เส้นโค้งวงรีที่ถูกนิยามบนฟิลด์จำกัดของอันดับจำนวนเฉพาะแทนที่จะอยู่บนจำนวนจริง ทำให้มันมีลักษณะเหมือนรูปแบบของจุดที่กระจัดกระจายในสองมิติ ซึ่งทำให้ยากต่อการจินตนาการภาพ อย่างไรก็ตาม คณิตศาสตร์ที่ใช้นั้นเหมือนกับเส้นโค้งวงรีบนจำนวนจริง
ตัวอย่างเช่น การเข้ารหัสลับด้วยเส้นโค้งวงรี: การแสดงภาพเส้นโค้งวงรีบน F(p) โดยที่ p=17 แสดงเส้นโค้งวงรีเดียวกันบนฟิลด์จำกัดของอันดับจำนวนเฉพาะ 17 ที่มีขนาดเล็กกว่ามาก ซึ่งแสดงรูปแบบของจุดบนตาราง
เส้นโค้งวงรี secp256k1 ที่ใช้ในบิตคอยน์สามารถนึกถึงได้ว่าเป็นรูปแบบของจุดที่ซับซ้อนมากกว่าบนตารางที่มีขนาดใหญ่มหาศาลจนยากจะเข้าใจได้

ตัวอย่างเช่น จุด P ที่มีพิกัด (x, y) ต่อไปนี้เป็นจุดที่อยู่บนเส้นโค้ง secp256k1:
P = (55066263022277343669578718895168534326250603453777594175500187360389116729240, 32670510020758816978083085130507043184471273380659243275938904335757337482424)เราสามารถใช้ Python เพื่อยืนยันว่าจุดนี้อยู่บนเส้นโค้งวงรีได้ตามตัวอย่างนี้: ตัวอย่างที่ 1: การใช้ Python เพื่อยืนยันว่าจุดนี้อยู่บนเส้นโค้งวงรี ``` Python 3.10.6 (main, Nov 14 2022, 16:10:14) [GCC 11.3.0] on linux Type "help", "copyright", "credits" or "license" for more information.p = 115792089237316195423570985008687907853269984665640564039457584007908834671663 x = 55066263022277343669578718895168534326250603453777594175500187360389116729240 y = 32670510020758816978083085130507043184471273380659243275938904335757337482424 (x ** 3 + 7 - y**2) % p 0 ``` ผลลัพธ์เป็น 0 ซึ่งแสดงว่าจุดนี้อยู่บนเส้นโค้งวงรีจริง เพราะเมื่อแทนค่า x และ y ลงในสมการ y² = (x³ + 7) mod p แล้ว ทั้งสองด้านของสมการมีค่าเท่ากัน
ในคณิตศาสตร์ของเส้นโค้งวงรี มีจุดที่เรียกว่า "จุดที่อนันต์" (point at infinity) ซึ่งมีบทบาทคล้ายกับศูนย์ในการบวก บนคอมพิวเตอร์ บางครั้งจุดนี้แทนด้วย x = y = 0 (ซึ่งไม่เป็นไปตามสมการเส้นโค้งวงรี แต่เป็นกรณีพิเศษที่สามารถตรวจสอบได้ง่าย)
มีตัวดำเนินการ + ที่เรียกว่า "การบวก" ซึ่งมีคุณสมบัติคล้ายกับการบวกแบบดั้งเดิมของจำนวนจริงที่เด็กๆ เรียนในโรงเรียน เมื่อมีจุดสองจุด P1 และ P2 บนเส้นโค้งวงรี จะมีจุดที่สาม P3 = P1 + P2 ซึ่งอยู่บนเส้นโค้งวงรีเช่นกัน
ในเชิงเรขาคณิต จุดที่สาม P3 นี้คำนวณได้โดยการลากเส้นระหว่าง P1 และ P2 เส้นนี้จะตัดกับเส้นโค้งวงรีที่จุดเพิ่มเติมอีกหนึ่งจุดพอดี เรียกจุดนี้ว่า P3' = (x, y) จากนั้นให้สะท้อนกับแกน x เพื่อได้ P3 = (x, -y)
มีกรณีพิเศษบางกรณีที่อธิบายความจำเป็นของ "จุดที่อนันต์":
- ถ้า P1 และ P2 เป็นจุดเดียวกัน เส้น "ระหว่าง" P1 และ P2 ควรขยายเป็นเส้นสัมผัสกับเส้นโค้ง ณ จุด P1 นี้ เส้นสัมผัสนี้จะตัดกับเส้นโค้งที่จุดใหม่อีกหนึ่งจุดพอดี คุณสามารถใช้เทคนิคจากแคลคูลัสเพื่อหาความชันของเส้นสัมผัส เทคนิคเหล่านี้ใช้ได้อย่างน่าแปลกใจ แม้ว่าเราจะจำกัดความสนใจไว้ที่จุดบนเส้นโค้งที่มีพิกัดเป็นจำนวนเต็มเท่านั้น!
- ในบางกรณี (เช่น ถ้า P1 และ P2 มีค่า x เดียวกันแต่ค่า y ต่างกัน) เส้นสัมผัสจะตั้งฉากพอดี ซึ่งในกรณีนี้ P3 = "จุดที่อนันต์"
- ถ้า P1 เป็น "จุดที่อนันต์" แล้ว P1 + P2 = P2 ในทำนองเดียวกัน ถ้า P2 เป็นจุดที่อนันต์ แล้ว P1 + P2 = P1 นี่แสดงให้เห็นว่าจุดที่อนันต์มีบทบาทเป็นศูนย์
การบวกนี้มีคุณสมบัติเชิงสมาคม (associative) ซึ่งหมายความว่า (A + B) + C = A + (B + C) นั่นหมายความว่าเราสามารถเขียน A + B + C โดยไม่ต้องมีวงเล็บและไม่มีความกำกวม
เมื่อเรานิยามการบวกแล้ว เราสามารถนิยามการคูณในแบบมาตรฐานที่ต่อยอดจากการบวก สำหรับจุด P บนเส้นโค้งวงรี ถ้า k เป็นจำนวนเต็มบวก แล้ว kP = P + P + P + … + P (k ครั้ง) โปรดทราบว่า k บางครั้งถูกเรียกว่า "เลขชี้กำลัง"
Public Keys
ในระบบคริปโตกราฟีแบบเส้นโค้งวงรี (Elliptic Curve Cryptography) public key ถูกคำนวณจาก private key โดยใช้การคูณเส้นโค้งวงรี ซึ่งเป็นกระบวนการที่ไม่สามารถย้อนกลับได้:
K = k × G
โดยที่:
- k คือ private key
- G คือจุดคงที่ที่เรียกว่า จุดกำเนิด (generator point)
- K คือ public key
การดำเนินการย้อนกลับ ที่เรียกว่า "การหาลอการิทึมแบบไม่ต่อเนื่อง" (finding the discrete logarithm) - คือการคำนวณหา k เมื่อรู้ค่า K - เป็นสิ่งที่ยากมากเทียบเท่ากับการลองค่า k ทุกค่าที่เป็นไปได้ (วิธีการแบบ brute-force)
ความยากของการย้อนกลับนี้คือหลักการความปลอดภัยหลักของระบบ ECC ที่ใช้ในบิตคอยน์ ซึ่งทำให้สามารถเผยแพร่ public key ได้อย่างปลอดภัย โดยที่ไม่ต้องกังวลว่าจะมีใครสามารถคำนวณย้อนกลับเพื่อหา private key ได้
TIP:การคูณเส้นโค้งวงรีเป็นฟังก์ชันประเภทที่นักเข้ารหัสลับเรียกว่า “ trap door function ”:
- เป็นสิ่งที่ทำได้ง่ายในทิศทางหนึ่ง
- แต่เป็นไปไม่ได้ที่จะทำในทิศทางตรงกันข้าม
คนที่มี private key สามารถสร้าง public key ได้อย่างง่ายดาย และสามารถแบ่งปันกับโลกได้โดยรู้ว่าไม่มีใครสามารถย้อนกลับฟังก์ชันและคำนวณ private key จาก public key ได้ กลวิธีทางคณิตศาสตร์นี้กลายเป็นพื้นฐานสำหรับลายเซ็นดิจิทัลที่ปลอมแปลงไม่ได้และมีความปลอดภัย ซึ่งใช้พิสูจน์การควบคุมเงินบิตคอยน์
เริ่มต้นด้วยการใช้ private key ในรูปแบบของตัวเลขสุ่ม เราคูณมันด้วยจุดที่กำหนดไว้ล่วงหน้าบนเส้นโค้งที่เรียกว่า จุดกำเนิด (generator point) เพื่อสร้างจุดอื่นที่อยู่บนเส้นโค้งเดียวกัน ซึ่งคำตอบจะเป็น public key ที่สอดคล้องกัน จุดกำเนิดถูกกำหนดไว้เป็นส่วนหนึ่งของมาตรฐาน secp256k1 และเป็นค่าเดียวกันสำหรับกุญแจทั้งหมดในระบบบิตคอยน์
เนื่องจากจุดกำเนิด G เป็นค่าเดียวกันสำหรับผู้ใช้บิตคอยน์ทุกคน private key (k) ที่คูณกับ G จะได้ public key (K) เดียวกันเสมอ ความสัมพันธ์ระหว่าง k และ K เป็นแบบตายตัวแต่สามารถคำนวณได้ในทิศทางเดียวเท่านั้น คือจาก k ไปยัง K นี่คือเหตุผลที่ public key ของบิตคอยน์ (K) สามารถแบ่งปันกับทุกคนได้โดยไม่เปิดเผย private key (k) ของผู้ใช้
TIP: private key สามารถแปลงเป็น public key ได้ แต่ public key ไม่สามารถแปลงกลับเป็น private key ได้ เพราะคณิตศาสตร์ที่ใช้ทำงานได้เพียงทิศทางเดียวเท่านั้น
เมื่อนำการคูณเส้นโค้งวงรีมาใช้งาน เราจะนำ private key (k) ที่สร้างขึ้นก่อนหน้านี้มาคูณกับจุดกำเนิด G เพื่อหา public key (K):
K = 1E99423A4ED27608A15A2616A2B0E9E52CED330AC530EDCC32C8FFC6A526AEDD × Gpublic key (K) จะถูกกำหนดเป็นจุด K = (x, y) โดยที่:x = F028892BAD7ED57D2FB57BF33081D5CFCF6F9ED3D3D7F159C2E2FFF579DC341A y = 07CF33DA18BD734C600B96A72BBC4749D5141C90EC8AC328AE52DDFE2E505BDBเพื่อจะให้เห็นภาพของการคูณจุดด้วยจำนวนเต็มมากขึ้น เราจะใช้เส้นโค้งวงรีที่ง่ายกว่าบนจำนวนจริง (โดยหลักการทางคณิตศาสตร์ยังคงเหมือนกัน) เป้าหมายของเราคือการหาผลคูณ kG ของจุดกำเนิด G ซึ่งเทียบเท่ากับการบวก G เข้ากับตัวเอง k ครั้งติดต่อกันในเส้นโค้งวงรี การบวกจุดเข้ากับตัวเองเทียบเท่ากับการลากเส้นสัมผัสที่จุดนั้นและหาว่าเส้นนั้นตัดกับเส้นโค้งอีกครั้งที่จุดใด จากนั้นจึงสะท้อนจุดนั้นบนแกน x
การเข้ารหัสลับด้วยเส้นโค้งวงรี: การแสดงภาพการคูณจุด G ด้วยจำนวนเต็ม k บนเส้นโค้งวงรี แสดงกระบวนการในการหา G, 2G, 4G เป็นการดำเนินการทางเรขาคณิตบนเส้นโค้งได้ดังนี้
TIP: ในซอฟแวร์ของบิตคอยน์ส่วนใหญ่ใช้ไลบรารีเข้ารหัสลับ libsecp256k1 เพื่อทำการคำนวณทางคณิตศาสตร์เส้นโค้งวงรี

Output and Input Scripts
แม้ว่าภาพประกอบจาก Bitcoin whitepaper ที่แสดงเรื่อง "Transaction chain" จะแสดงให้เห็นว่ามีการใช้ public key และ digital signature โดยตรง แต่ในความเป็นจริงบิตคอยน์เวอร์ชันแรกนั้นมีการส่งการชำระเงินไปยังฟิลด์ที่เรียกว่า output script และมีการใช้จ่ายบิตคอยน์เหล่านั้นโดยได้รับอนุญาตจากฟิลด์ที่เรียกว่า input script ฟิลด์เหล่านี้อนุญาตให้มีการดำเนินการเพิ่มเติมนอกเหนือจาก (หรือแทนที่) การตรวจสอบว่าลายเซ็นสอดคล้องกับ public key หรือไม่ ตัวอย่างเช่น output script สามารถมี public key สองดอกและต้องการลายเซ็นสองลายเซ็นที่สอดคล้องกันในฟิลด์ input script ที่ใช้จ่าย
ในภายหลัง ในหัวข้อ [tx_script] เราจะได้เรียนรู้เกี่ยวกับสคริปต์อย่างละเอียด สำหรับตอนนี้ สิ่งที่เราต้องเข้าใจคือ บิตคอยน์จะถูกรับเข้า output script ที่ทำหน้าที่เหมือน public key และการใช้จ่ายบิตคอยน์จะได้รับอนุญาตโดย input script ที่ทำหน้าที่เหมือนลายเซ็น
IP Addresses: The Original Address for Bitcoin (P2PK)
เราได้เห็นแล้วว่าอลิซสามารถจ่ายเงินให้บ็อบโดยการมอบบิตคอยน์บางส่วนของเธอให้กับกุญแจสาธารณะของบ็อบ แต่อลิซจะได้กุญแจสาธารณะของบ็อบมาได้อย่างไร? บ็อบอาจจะให้สำเนากุญแจแก่เธอ แต่ลองดูกุญแจสาธารณะที่เราใช้งานในตัวอย่างที่ผ่านมาอีกครั้ง:
x = F028892BAD7ED57D2FB57BF33081D5CFCF6F9ED3D3D7F159C2E2FFF579DC341A y = 07CF33DA18BD734C600B96A72BBC4749D5141C90EC8AC328AE52DDFE2E505BDBTIP จากหลาม: :สังเกตได้ว่า public key มีความยาวมาก ลองจินตนาการว่าบ็อบพยายามอ่านกุญแจนี้ให้อลิซฟังทางโทรศัพท์ คงจะยากมากที่จะอ่านและบันทึกโดยไม่มีข้อผิดพลาด
แทนที่จะป้อนกุญแจสาธารณะโดยตรง เวอร์ชันแรกของซอฟต์แวร์บิตคอยน์อนุญาตให้ผู้จ่ายเงินป้อนที่อยู่ IP ของผู้รับได้ ตามที่แสดงในหน้าจอการส่งเงินรุ่นแรกของบิตคอยน์ผ่าน The Internet Archive
คุณสมบัตินี้ถูกลบออกในภายหลัง เนื่องจากมีปัญหามากมายในการใช้ที่อยู่ IP แต่คำอธิบายสั้นๆ จะช่วยให้เราเข้าใจได้ดีขึ้นว่าทำไมคุณสมบัติบางอย่างอาจถูกเพิ่มเข้าไปในโปรโตคอลบิตคอยน์

เมื่ออลิซป้อนที่อยู่ IP ของบ็อบในบิตคอยน์เวอร์ชัน 0.1 Full node ของเธอจะทำการเชื่อมต่อกับ full node ของเขาและได้รับ public key ใหม่จากกระเป๋าสตางค์ของบ็อบที่โหนดของเขาไม่เคยให้กับใครมาก่อน การที่เป็น public key ใหม่นี้มีความสำคัญเพื่อให้แน่ใจว่าธุรกรรมต่าง ๆ ที่จ่ายให้บ็อบจะไม่สามารถถูกเชื่อมโยงเข้าด้วยกันโดยคนที่กำลังดูบล็อกเชนและสังเกตเห็นว่าธุรกรรมทั้งหมดจ่ายไปยัง public key เดียวกัน
เมื่อใช้ public key จากโหนดของอลิซซึ่งได้รับมาจากโหนดของบ็อบ กระเป๋าสตางค์ของอลิซจะสร้างเอาต์พุตธุรกรรมที่จ่ายให้กับสคริปต์เอาต์พุตดังนี้
<Bob's public key> OP_CHECKSIGต่อมาบ็อบจะสามารถใช้จ่ายเอาต์พุตนั้นด้วยสคริปต์อินพุตที่ประกอบด้วยลายเซ็นของเขาเท่านั้น:<Bob's signature>เพื่อให้เข้าใจว่าสคริปต์อินพุตและเอาต์พุตกำลังทำอะไร คุณสามารถรวมพวกมันเข้าด้วยกัน (สคริปต์อินพุตก่อน) แล้วสังเกตว่าข้อมูลแต่ละชิ้น (แสดงในเครื่องหมาย < >) จะถูกวางไว้ที่ด้านบนสุดของรายการที่เรียกว่าสแตก (stack) เมื่อพบรหัสคำสั่ง (opcode) มันจะใช้รายการจากสแตก โดยเริ่มจากรายการบนสุด มาดูว่ามันทำงานอย่างไรโดยเริ่มจากสคริปต์ที่รวมกัน:<Bob's signature> <Bob's public key> OP_CHECKSIGสำหรับสคริปต์นี้ ลายเซ็นของบ็อบจะถูกนำไปไว้บนสแตก จากนั้น public key ของบ็อบจะถูกวางไว้ด้านบนของลายเซ็น และบนสุดจะเป็นคำสั่ง OP_CHECKSIG ที่จะใช้องค์ประกอบสองอย่าง เริ่มจาก public key ตามด้วยลายเซ็น โดยลบพวกมันออกจากสแตก มันจะตรวจสอบว่าลายเซ็นตรงกับ public key และยืนยันฟิลด์ต่าง ๆ ในธุรกรรม ถ้าลายเซ็นถูกต้อง OP_CHECKSIG จะแทนที่ตัวเองบนสแตกด้วยค่า 1 ถ้าลายเซ็นไม่ถูกต้อง มันจะแทนที่ตัวเองด้วย 0 ถ้ามีรายการที่ไม่ใช่ศูนย์อยู่บนสุดของสแตกเมื่อสิ้นสุดการประเมิน สคริปต์ก็จะผ่าน ถ้าสคริปต์ทั้งหมดในธุรกรรมผ่าน และรายละเอียดอื่น ๆ ทั้งหมดเกี่ยวกับธุรกรรมนั้นต้องถูกต้องจึงจะถือว่าธุรกรรมนั้นถูกต้อง
โดยสรุป สคริปต์ข้างต้นใช้ public key และลายเซ็นเดียวกันกับที่อธิบายใน whitepaper แต่เพิ่มความซับซ้อนของฟิลด์สคริปต์สองฟิลด์และรหัสคำสั่งหนึ่งตัว ซึ่งเราจะเริ่มเห็นประโยชน์เมื่อเรามองที่ส่วนต่อไป
TIP:จากหลาม agian: เอาต์พุตประเภทนี้เป็นที่รู้จักในปัจจุบันว่า P2PK ซึ่งมันไม่เคยถูกใช้อย่างแพร่หลายสำหรับการชำระเงิน และไม่มีโปรแกรมที่ใช้กันอย่างแพร่หลายที่รองรับการชำระเงินผ่านที่อยู่ IP เป็นเวลาเกือบทศวรรษแล้ว
Legacy addresses for P2PKH
แน่นอนว่าการป้อนที่อยู่ IP ของคนที่คุณต้องการจ่ายเงินให้นั้นมีข้อดีหลายประการ แต่ก็มีข้อเสียหลายประการเช่นกัน หนึ่งในข้อเสียที่สำคัญคือผู้รับจำเป็นต้องให้กระเป๋าสตางค์ของพวกเขาออนไลน์ที่ที่อยู่ IP ของพวกเขา และต้องสามารถเข้าถึงได้จากโลกภายนอก
ซึ่งสำหรับคนจำนวนมากนั่นไม่ใช่ตัวเลือกที่เป็นไปได้เพราะหากพวกเขา:
- ปิดคอมพิวเตอร์ในเวลากลางคืน
- แล็ปท็อปของพวกเขาเข้าสู่โหมดสลีป
- อยู่หลังไฟร์วอลล์
- หรือกำลังใช้การแปลงที่อยู่เครือข่าย (NAT)
ปัญหานี้นำเรากลับมาสู่ความท้าทายเดิมที่ผู้รับเงินอย่างบ็อบต้องให้ public key ที่มีความยาวมากแก่ผู้จ่ายเงินอย่างอลิซ public key ของบิตคอยน์ที่สั้นที่สุดที่นักพัฒนาบิตคอยน์รุ่นแรกรู้จักมีขนาด 65 ไบต์ เทียบเท่ากับ 130 ตัวอักษรเมื่อเขียนในรูปแบบเลขฐานสิบหก (เฮกซาเดซิมอล) แต่อย่างไรก็ตาม บิตคอยน์มีโครงสร้างข้อมูลหลายอย่างที่มีขนาดใหญ่กว่า 65 ไบต์มาก ซึ่งจำเป็นต้องถูกอ้างอิงอย่างปลอดภัยในส่วนอื่น ๆ ของบิตคอยน์โดยใช้ข้อมูลขนาดเล็กที่สุดเท่าที่จะปลอดภัยได้
โดยบิตคอยน์แก้ปัญหานี้ด้วย ฟังก์ชันแฮช (hash function) ซึ่งเป็นฟังก์ชันที่รับข้อมูลที่อาจมีขนาดใหญ่ นำมาแฮช และให้ผลลัพธ์เป็นข้อมูลขนาดคงที่ ฟังก์ชันแฮชจะผลิตผลลัพธ์เดียวกันเสมอเมื่อได้รับข้อมูลนำเข้าแบบเดียวกัน และฟังก์ชันที่ปลอดภัยจะทำให้เป็นไปไม่ได้ในทางปฏิบัติสำหรับผู้ที่ต้องการเลือกข้อมูลนำเข้าอื่นที่ให้ผลลัพธ์เหมือนกันได้ นั่นทำให้ผลลัพธ์เป็น คำมั่นสัญญา (commitment) ต่อข้อมูลนำเข้า เป็นสัญญาว่าในทางปฏิบัติ มีเพียงข้อมูลนำเข้า x เท่านั้นที่จะให้ผลลัพธ์ X
สมมติว่าผมต้องการถามคำถามคุณและให้คำตอบของผมในรูปแบบที่คุณไม่สามารถอ่านได้ทันที สมมติว่าคำถามคือ "ในปีไหนที่ซาโตชิ นาคาโมโตะเริ่มทำงานบนบิทคอยน์?" ผมจะให้การยืนยันคำตอบของผมในรูปแบบของผลลัพธ์จากฟังก์ชันแฮช SHA256 ซึ่งเป็นฟังก์ชันที่ใช้บ่อยที่สุดในบิทคอยน์:
94d7a772612c8f2f2ec609d41f5bd3d04a5aa1dfe3582f04af517d396a302e4eต่อมา หลังจากคุณบอกคำตอบที่คุณเดาสำหรับคำถามนั้น ผมสามารถเปิดเผยคำตอบของผมและพิสูจน์ให้คุณเห็นว่าคำตอบของผม เมื่อใช้เป็นข้อมูลสำหรับฟังก์ชันแฮช จะให้ผลลัพธ์เดียวกันกับที่ผมให้คุณก่อนหน้านี้$ echo "2007. He said about a year and a half before Oct 2008" | sha256sum 94d7a772612c8f2f2ec609d41f5bd3d04a5aa1dfe3582f04af517d396a302e4eทีนี้ให้สมมติว่าเราถามบ็อบว่า " public key ของคุณคืออะไร?" บ็อบสามารถใช้ฟังก์ชันแฮชเพื่อให้การยืนยันที่ปลอดภัยทางการเข้ารหัสต่อ public key ของเขา หากเขาเปิดเผยกุญแจในภายหลัง และเราตรวจสอบว่ามันให้ผลการยืนยันเดียวกันกับที่เขาให้เราก่อนหน้านี้ เราสามารถมั่นใจได้ว่ามันเป็นกุญแจเดียวกันที่ใช้สร้างการยืนยันก่อนหน้านี้ฟังก์ชันแฮช SHA256 ถือว่าปลอดภัยมากและให้ผลลัพธ์ 256 บิต (32 ไบต์) น้อยกว่าครึ่งหนึ่งของขนาด public key ของบิทคอยน์ดั้งเดิม แต่อย่างไรก็ตาม มีฟังก์ชันแฮชอื่นๆ ที่ปลอดภัยน้อยกว่าเล็กน้อยที่ให้ผลลัพธ์ขนาดเล็กกว่า เช่น ฟังก์ชันแฮช RIPEMD-160 ซึ่งให้ผลลัพธ์ 160 บิต (20 ไบต์) ด้วยเหตุผลที่ซาโตชิ นาคาโมโตะไม่เคยระบุ เวอร์ชันดั้งเดิมของบิทคอยน์สร้างการยืนยันต่อ public key โดยการแฮชกุญแจด้วย SHA256 ก่อน แล้วแฮชผลลัพธ์นั้นด้วย RIPEMD-160 ซึ่งให้การยืนยันขนาด 20 ไบต์ต่อ public key
เราสามารถดูสิ่งนี้ตามอัลกอริทึม เริ่มจากกุญแจสาธารณะ K เราคำนวณแฮช SHA256 และคำนวณแฮช RIPEMD-160 ของผลลัพธ์ ซึ่งให้ตัวเลข 160 บิต (20 ไบต์): A = RIPEMD160(SHA256(K))
ทีนี้เราคงเข้าใจวิธีสร้างการยืนยันต่อ public key แล้ว ต่อไปเราจะมาดูวิธีการใช้งานโดยพิจารณาสคริปต์เอาต์พุตต่อไปนี้:
OP_DUP OP_HASH160 <Bob's commitment> OP_EQUAL OP_CHECKSIGและสคริปต์อินพุตต่อไปนี้:<Bob's signature> <Bob's public key>และเมื่อเรารวมมันเข้าด้วยกันเราจะได้ผลลัพธ์ดังนี้:<Bob's signature> <Bob's public key> OP_DUP OP_HASH160 <Bob's commitment> OP_EQUAL OP_CHECKSIGเหมือนที่เราทำใน IP Addresses: The Original Address for Bitcoin (P2PK) เราเริ่มวางรายการลงในสแต็ก ลายเซ็นของบ็อบถูกวางก่อน จากนั้น public key ของเขาถูกวางไว้ด้านบน จากนั้นดำเนินการ OP_DUP เพื่อทำสำเนารายการบนสุด ดังนั้นรายการบนสุดและรายการที่สองจากบนในสแต็กตอนนี้เป็น public key ของบ็อบทั้งคู่ การดำเนินการ OP_HASH160 ใช้ (ลบ) public key บนสุดและแทนที่ด้วยผลลัพธ์ของการแฮชด้วย RIPEMD160(SHA256(K)) ดังนั้นตอนนี้บนสุดของสแต็กคือแฮชของ public key ของบ็อบ ต่อไป commitment ถูกเพิ่มไว้บนสุดของสแต็ก การดำเนินการ OP_EQUALVERIFY ใช้รายการสองรายการบนสุดและตรวจสอบว่าพวกมันเท่ากัน ซึ่งควรเป็นเช่นนั้นหาก public key ที่บ็อบให้ในสคริปต์อินพุตเป็น public key เดียวกันกับที่ใช้สร้างการยืนยันในสคริปต์เอาต์พุตที่อลิซจ่าย หาก OP_EQUALVERIFY ล้มเหลว ทั้งสคริปต์จะล้มเหลว สุดท้าย เราเหลือสแต็กที่มีเพียงลายเซ็นของบ็อบและ public key ของเขา รหัสปฏิบัติการ OP_CHECKSIG ตรวจสอบว่าพวกมันสอดคล้องกัน
TIP: จากหลาม ถ้าอ่านตรงนี้และงง ๆ ผมไปทำรูปมาให้ดูง่ายขึ้นครับ
แม้กระบวนการของการ pay-to-publickey-hash(P2PKH) อาจดูซับซ้อน แต่มันทำให้การที่อลิซจ่ายเงินให้บ็อบมีเพียงการยืนยันเพียง 20 ไบต์ต่อ public key ของเขาแทนที่จะเป็นตัวกุญแจเอง ซึ่งจะมีขนาด 65 ไบต์ในเวอร์ชันดั้งเดิมของบิทคอยน์ นั่นเป็นข้อมูลที่น้อยกว่ามากที่บ็อบต้องสื่อสารกับอลิซ
แต่อย่างไรก็ตาม เรายังไม่ได้พูดถึงวิธีที่บ็อบรับ 20 ไบต์เหล่านั้นจากกระเป๋าเงินบิทคอยน์ของเขาไปยังกระเป๋าเงินของอลิซ มีการเข้ารหัสค่าไบต์ที่ใช้กันอย่างแพร่หลาย เช่น เลขฐานสิบหก แต่ข้อผิดพลาดใด ๆ ในการคัดลอกการยืนยันจะทำให้บิทคอยน์ถูกส่งไปยังเอาต์พุตที่ไม่สามารถใช้จ่ายได้ ทำให้พวกมันสูญหายไปตลอดกาล โดยในส่วนถัดไป เราจะดูที่การเข้ารหัสแบบกะทัดรัดและการตรวจสอบความถูกต้อง
Base58check Encoding
ระบบคอมพิวเตอร์มีวิธีเขียนตัวเลขยาวๆ ให้สั้นลงโดยใช้ทั้งตัวเลขและตัวอักษรผสมกัน เพื่อใช้พื้นที่น้อยลงอย่างเช่น
- ระบบเลขฐานสิบ (ปกติที่เราใช้) - ใช้เลข 0-9 เท่านั้น
- ระบบเลขฐานสิบหก - ใช้เลข 0-9 และตัวอักษร A-F ตัวอย่าง: เลข 255 ในระบบปกติ เขียนเป็น FF ในระบบเลขฐานสิบหก (สั้นกว่า)
- ระบบเลขฐานหกสิบสี่ (Base64) - ใช้สัญลักษณ์ถึง 64 ตัว: ตัวอักษรเล็ก (a-z) 26 ตัว, ตัวอักษรใหญ่ (A-Z) 26 ตัว, ตัวเลข (0-9) 10 ตัว, สัญลักษณ์พิเศษอีก 2 ตัว ("+" และ "/")
โดยระบบ Base64 นี้ช่วยให้เราส่งไฟล์คอมพิวเตอร์ผ่านข้อความธรรมดาได้ เช่น การส่งรูปภาพผ่านอีเมล โดยใช้พื้นที่น้อยกว่าการเขียนเป็นเลขฐานสิบแบบปกติมาก
การเข้ารหัสแบบ Base58 คล้ายกับ Base64 โดยใช้ตัวอักษรพิมพ์ใหญ่ พิมพ์เล็ก และตัวเลข แต่ได้ตัดตัวอักษรบางตัวที่มักถูกเข้าใจผิดว่าเป็นตัวอื่นและอาจดูเหมือนกันเมื่อแสดงในฟอนต์บางประเภทออกไป
Base58 คือ Base64 ที่ตัดตัวอักษรต่อไปนี้ออก:
- เลข 0 (ศูนย์)
- ตัวอักษร O (ตัว O พิมพ์ใหญ่)
- ตัวอักษร l (ตัว L พิมพ์เล็ก)
- ตัวอักษร I (ตัว I พิมพ์ใหญ่)
- และสัญลักษณ์ "+" และ "/"
หรือพูดให้ง่ายขึ้น Base58 คือกลุ่มตัวอักษรพิมพ์เล็ก พิมพ์ใหญ่ และตัวเลข แต่ไม่มีตัวอักษรทั้งสี่ตัว (0, O, l, I) ที่กล่าวถึงข้างต้น ตัวอักษรทั้งหมดที่ใช้ใน Base58 จะแสดงให้เห็นในตัวอักษร Base58 ของบิทคอยน์
Example 2. Bitcoin’s base58 alphabet
123456789ABCDEFGHJKLMNPQRSTUVWXYZabcdefghijkmnopqrstuvwxyzการเพิ่มความปลอดภัยพิเศษเพื่อป้องกันการพิมพ์ผิดหรือข้อผิดพลาดในการคัดลอก base58check ได้รวม รหัสตรวจสอบ (checksum) ที่เข้ารหัสในตัวอักษร base58 เข้าไปด้วย รหัสตรวจสอบนี้คือข้อมูลเพิ่มเติมอีก 4 ไบต์ที่เพิ่มเข้าไปที่ท้ายของข้อมูลที่กำลังถูกเข้ารหัสรหัสตรวจสอบนี้ได้มาจากการแฮชข้อมูลที่ถูกเข้ารหัส และจึงสามารถใช้เพื่อตรวจจับข้อผิดพลาดจากการคัดลอกและการพิมพ์ได้ เมื่อโปรแกรมได้รับรหัส base58check ซอฟต์แวร์ถอดรหัสจะคำนวณรหัสตรวจสอบของข้อมูลและเปรียบเทียบกับรหัสตรวจสอบที่รวมอยู่ในรหัสนั้น
หากทั้งสองไม่ตรงกัน แสดงว่ามีข้อผิดพลาดเกิดขึ้น และข้อมูล base58check นั้นไม่ถูกต้อง กระบวนการนี้ช่วยป้องกันไม่ให้ address บิทคอยน์ที่พิมพ์ผิดถูกยอมรับโดยซอฟต์แวร์กระเป๋าเงินว่าเป็น address ที่ถูกต้อง ซึ่งเป็นข้อผิดพลาดที่อาจส่งผลให้สูญเสียเงินได้
การแปลงข้อมูล (ตัวเลข) เป็นรูปแบบ base58check มีขั้นตอนดังนี้:
- เราเริ่มโดยการเพิ่ม prefix เข้าไปในข้อมูล เรียกว่า "version byte" ซึ่งช่วยให้ระบุประเภทของข้อมูลที่ถูกเข้ารหัสได้ง่าย ตัวอย่างเช่น: prefix ศูนย์ (0x00 ในระบบเลขฐานสิบหก) แสดงว่าข้อมูลควรถูกใช้เป็นการยืนยัน (hash) ในสคริปต์เอาต์พุต legacy P2PKH
- จากนั้น เราคำนวณ "double-SHA" checksum ซึ่งหมายถึงการใช้อัลกอริทึมแฮช SHA256 สองครั้งกับผลลัพธ์ก่อนหน้า (prefix ต่อกับข้อมูล):
checksum = SHA256(SHA256(prefix||data)) - จากแฮช 32 ไบต์ที่ได้ (การแฮชซ้อนแฮช) เราเลือกเฉพาะ 4 ไบต์แรก ไบต์ทั้งสี่นี้ทำหน้าที่เป็นรหัสตรวจสอบข้อผิดพลาดหรือ checksum
- นำ checksum นี้ไปต่อที่ท้ายข้อมูล
การเข้ารหัสแบบ base58check คือรูปแบบการเข้ารหัสที่ใช้ base58 พร้อมกับการระบุเวอร์ชันและการตรวจสอบความถูกต้อง เพื่อการเข้ารหัสข้อมูลบิทคอยน์ โดยคุณสามารถดูภาพประกอบด้านล่างเพื่อความเข้าใจเพิ่มเติม

ในบิตคอยน์นั้น นอกจากจะใช้ base58check ในการยืนยัน public key แล้ว ก็ยังมีการใช้ในข้อมูลอื่น ๆ ด้วย เพื่อทำให้ข้อมูลนั้นกะทัดรัด อ่านง่าย และตรวจจับข้อผิดพลาดได้ง่ายด้วยรหัสนำหน้า (version prefix) ในการเข้ารหัสแบบ base58check ถูกใช้เพื่อสร้างรูปแบบที่แยกแยะได้ง่าย ซึ่งเมื่อเข้ารหัสด้วย base58 โดยจะมีตัวอักษรเฉพาะที่จุดเริ่มต้นของข้อมูลที่เข้ารหัส base58check ตัวอักษรเหล่านี้ช่วยให้เราระบุประเภทของข้อมูลที่ถูกเข้ารหัสและวิธีการใช้งานได้ง่าย นี่คือสิ่งที่แยกความแตกต่าง ตัวอย่างเช่น ระหว่าง address บิทคอยน์ที่เข้ารหัส base58check ซึ่งขึ้นต้นด้วยเลข 1 กับรูปแบบการนำเข้า private key (WIF - Wallet Import Format) ที่เข้ารหัส base58check ซึ่งขึ้นต้นด้วยเลข 5 ตัวอย่างของ version prefix สามารถดูได้ตามตารางด้านล่างนี้

ภาพต่อไปนี้จะทำให้คุณเห็นภาพของกระบวนการแปลง public key ให้เป็น bitcoin address

Compressed Public Keys
ในยุคแรก ๆ ของบิตคอยน์นั้น มีเพียงการสร้าง public key แบบ 65 Bytes เท่านั้น แต่ในเวลาต่อมา เหล่านักพัฒนาในยุคหลังได้พบวิธีการสร้าง public key แบบใหม่ที่มีเพียง 33 Bytes และสามารถทำงานร่วมกันกับโหนดทั้งหมดในขณะนั้นได้ จีงไม่จะเป็นต้องเปลี่ยนแปลงกฎหรือโครงสร้างภายในโปรโตคอลของบิตคอยน์ โดย poublic key แบบใหม่ที่มีขนาด 33 Bytes นี้เรียกว่า compressed public key (public key ที่ถูกบีบอัด) และมีการเรียก public key ที่มีขนาด 65 Bytes ว่า uncompressed public key (public key ที่ไม่ถูกบีบอัด) ซึ่งประโยชน์ของ public key ที่เล็กลงนั้น นอกจากจะช่วยให้การส่ง public key ให้ผู้อื่นทำได้ง่ายขึ้นแล้ว ยังช่วยให้ธุรกรรมมีขนาดเล็กลง และช่วยให้สามารถทำการชำระเงินได้มากขึ้นในบล็อกเดียวกัน
อย่างที่เราได้เรียนรู้จากเนื้อหาในส่วนของ public key เราได้ทราบว่า public key คือจุด (x, y) บนเส้นโค้งวงรี เนื่องจากเส้นโค้งแสดงฟังก์ชันทางคณิตศาสตร์ จุดบนเส้นโค้งจึงเป็นคำตอบของสมการ ดังนั้นหากเรารู้พิกัด x เราก็สามารถคำนวณพิกัด y ได้โดยแก้สมการ y² mod p = (x³ + 7) mod p นั่นหมายความว่าเราสามารถเก็บเพียงพิกัด x ของ public key โดยละพิกัด y ไว้ ซึ่งช่วยลดขนาดของกุญแจและพื้นที่ที่ต้องใช้เก็บข้อมูลลง 256 บิต การลดขนาดลงเกือบ 50% ในทุกธุรกรรมรวมกันแล้วช่วยประหยัดข้อมูลได้มากมายในระยะยาว!
นี่คือ public key ที่ได้ยกเป็นตัวอย่างไว้ก่อนหน้า
x = F028892BAD7ED57D2FB57BF33081D5CFCF6F9ED3D3D7F159C2E2FFF579DC341A y = 07CF33DA18BD734C600B96A72BBC4749D5141C90EC8AC328AE52DDFE2E505BDBและนี่คือ public key ที่มีตัวนำหน้า 04 ตามด้วยพิกัด x และ y ในรูปแบบ 04 x y:
K = 04F028892BAD7ED57D2FB57BF33081D5CFCF6F9ED3D3D7F159C2E2FFF579DC341A07CF33DA18BD734C600B96A72BBC4749D5141C90EC8AC328AE52DDFE2E505BDBuncompressed public key นั้นจะมีตัวนำหน้าเป็น 04 แต่ compressed public key จะมีตัวนำหน้าเป็น 02 หรือ 03 โดยเหตุผลนั้นมาจากสมการ y² mod p = (x³ + 7) mod p เนื่องจากด้านซ้ายของสมการคือ y² คำตอบสำหรับ y จึงเป็นรากที่สอง ซึ่งอาจมีค่าเป็นบวกหรือลบก็ได้ หากมองเชิงภาพ นี่หมายความว่าพิกัด y ที่ได้อาจอยู่เหนือหรือใต้แกน x เราต้องไม่ลืมว่าเส้นโค้งมีความสมมาตร ซึ่งหมายความว่ามันจะสะท้อนเหมือนกระจกโดยแกน x ดังนั้น แม้เราจะละพิกัด y ได้ แต่เราต้องเก็บ เครื่องหมาย ของ y (บวกหรือลบ) หรืออีกนัยหนึ่งคือเราต้องจำว่ามันอยู่เหนือหรือใต้แกน x เพราะแต่ละตำแหน่งแทนจุดที่แตกต่างกันและเป็น public key ที่แตกต่างกัน
เมื่อคำนวณเส้นโค้งวงรีในระบบเลขฐานสองบนสนามจำกัดของเลขจำนวนเฉพาะ p พิกัด y จะเป็นเลขคู่หรือเลขคี่ ซึ่งสอดคล้องกับเครื่องหมายบวก/ลบตามที่อธิบายก่อนหน้านี้ ดังนั้น เพื่อแยกความแตกต่างระหว่างค่าที่เป็นไปได้สองค่าของ y เราจึงเก็บ compressed public key ด้วยตัวนำหน้า 02 ถ้า y เป็นเลขคู่ และ 03 ถ้า y เป็นเลขคี่ ซึ่งช่วยให้ซอฟต์แวร์สามารถอนุมานพิกัด y จากพิกัด x และคลายการบีบอัดของ public key ไปยังพิกัดเต็มของจุดได้อย่างถูกต้อง ดังภาพประกอบต่อไปนี้

นี่คือ public key เดียวกันกับที่ยกตัวอย่างไว้ข้างต้นซึ่งแสดงให้เห็นในรูป compressed public key ที่เก็บใน 264 บิต (66 ตัวอักษรเลขฐานสิบหก) โดยมีตัวนำหน้า 03 ซึ่งบ่งชี้ว่าพิกัด y เป็นเลขคี่:
K = 03F028892BAD7ED57D2FB57BF33081D5CFCF6F9ED3D3D7F159C2E2FFF579DC341Acompressed public key สอดคล้องกับ private key เดียวกันกับ uncompressed public key หมายความว่ามันถูกสร้างจาก private key เดียวกัน แต่อย่างไรก็ตาม มันก็มีส่วนที่แตกต่างจาก uncompressed public key นั้นคือ หากเราแปลง compressed public key เป็น commitment โดยใช้ฟังก์ชัน HASH160 (RIPEMD160(SHA256(K))) มันจะสร้าง commitment ที่แตกต่างจาก uncompressed public key และจะนำไปสู่ bitcoin address ที่แตกต่างกันในที่สุด สิ่งนี้อาจทำให้สับสนเพราะหมายความว่า private key เดียวสามารถสร้าง public key ในสองรูปแบบที่แตกต่างกัน (แบบบีบอัดและแบบไม่บีบอัด) ซึ่งสร้าง bitcoin address ที่แตกต่างกันcompressed public key เป็นค่าเริ่มต้นในซอฟต์แวร์บิตคอยน์เกือบทั้งหมดในปัจจุบัน และถูกกำหนดให้ใช้กับคุณสมบัติใหม่บางอย่างที่เพิ่มในการอัปเกรดโปรโตคอลในภายหลัง
อย่างไรก็ตาม ซอฟต์แวร์บางตัวยังคงต้องรองรับ uncompressed public key เช่น แอปพลิเคชันกระเป๋าเงินที่นำเข้า private key จากกระเป๋าเงินเก่า เมื่อกระเป๋าเงินใหม่สแกนบล็อกเชนสำหรับผลลัพธ์และอินพุต P2PKH เก่า มันจำเป็นต้องรู้ว่าควรสแกนกุญแจขนาด 65 ไบต์ (และ commitment ของกุญแจเหล่านั้น) หรือกุญแจขนาด 33 ไบต์ (และ commitment ของกุญแจเหล่านั้น) หากไม่สแกนหาประเภทที่ถูกต้อง อาจทำให้ผู้ใช้ไม่สามารถใช้ยอดคงเหลือทั้งหมดได้ เพื่อแก้ไขปัญหานี้ เมื่อส่งออก private key จากกระเป๋าเงิน WIF ที่ใช้แสดง private key ในกระเป๋าเงินบิตคอยน์รุ่นใหม่จะถูกนำไปใช้แตกต่างกันเล็กน้อยเพื่อบ่งชี้ว่า private key เหล่านี้ถูกใช้ในการสร้าง compressed public key
Legacy: Pay to Script Hash (P2SH)
ตามที่เราได้เห็นในส่วนก่อนหน้านี้ ผู้รับบิตคอยน์ สามารถกำหนดให้การชำระเงินที่ส่งมาให้เขานั้นมีเงื่อนไขบางอย่างในสคริปต์เอาต์พุตได้โดยจะต้องปฏิบัติตามเงื่อนไขเหล่านั้นโดยใช้สคริปต์อินพุตเมื่อเขาใช้จ่ายบิตคอยน์เหล่านั้น ในส่วน IP Addresses: The Original Address for Bitcoin (P2PK) เงื่อนไขก็คือสคริปต์อินพุตต้องให้ลายเซ็นที่เหมาะสม ในส่วน Legacy Addresses for P2PKH นั้นจำเป็นต้องมี public key ที่เหมาะสมด้วย
ส่วนสำหรับผู้ส่งก็จะวางเงื่อนไขที่ผู้รับต้องการในสคริปต์เอาต์พุตที่ใช้จ่ายให้กับผู้รับ โดยผู้รับจะต้องสื่อสารเงื่อนไขเหล่านั้นให้ผู้ส่งทราบ ซึ่งคล้ายกับปัญหาที่บ๊อบต้องสื่อสาร public key ของเขาให้อลิซทราบ และเช่นเดียวกับปัญหานั้นที่ public key อาจมีขนาดค่อนข้างใหญ่ เงื่อนไขที่บ๊อบใช้ก็อาจมีขนาดใหญ่มากเช่นกัน—อาจมีขนาดหลายพันไบต์ นั่นไม่เพียงแต่เป็นข้อมูลหลายพันไบต์ที่ต้องสื่อสารให้อลิซทราบ แต่ยังเป็นข้อมูลหลายพันไบต์ที่เธอต้องจ่ายค่าธรรมเนียมธุรกรรมทุกครั้งที่ต้องการใช้จ่ายเงินให้บ๊อบ อย่างไรก็ตาม การใช้ฟังก์ชันแฮชเพื่อสร้าง commitment ขนาดเล็กสำหรับข้อมูลขนาดใหญ่ก็สามารถนำมาใช้ได้ในกรณีนี้เช่นกัน
ในเวลาต่อมานั้น การอัปเกรด BIP16 สำหรับโปรโตคอลบิตคอยน์ในปี 2012 ได้อนุญาตให้สคริปต์เอาต์พุตสร้าง commitment กับ redemption script (redeem script) ได้ แปลว่าเมื่อบ๊อบใช้จ่ายบิตคอยน์ของเขา ภายในสคริปต์อินพุตของเขานั้นจะต้องให้ redeem script ที่ตรงกับ commitment และข้อมูลที่จำเป็นเพื่อให้เป็นไปตาม redeem script (เช่น ลายเซ็น) เริ่มต้นด้วยการจินตนาการว่าบ๊อบต้องการให้มีลายเซ็นสองอันเพื่อใช้จ่ายบิตคอยน์ของเขา หนึ่งลายเซ็นจากกระเป๋าเงินบนเดสก์ท็อปและอีกหนึ่งจากอุปกรณ์เซ็นแบบฮาร์ดแวร์ เขาใส่เงื่อนไขเหล่านั้นลงใน redeem script:
<public key 1> OP_CHECKSIGVERIFY <public key 2> OP_CHECKSIGจากนั้นเขาสร้าง commitment กับ redeem script โดยใช้กลไก HASH160 เดียวกับที่ใช้สำหรับ commitment แบบ P2PKH, RIPEMD160(SHA256(script)) commitment นั้นถูกวางไว้ในสคริปต์เอาต์พุตโดยใช้เทมเพลตพิเศษ:OP_HASH160 <commitment> OP_EQUALคำเตือน: เมื่อใช้ pay to script hash (P2SH) คุณต้องใช้เทมเพลต P2SH โดยเฉพาะ ซึ่งจะไม่มีข้อมูลหรือเงื่อนไขเพิ่มเติมในสคริปต์เอาต์พุต หากสคริปต์เอาต์พุตไม่ได้เป็น OP_HASH160 <20 ไบต์> OP_EQUAL แน่นอนว่า redeem script จะไม่ถูกใช้และบิตคอยน์ใด ๆ อาจไม่สามารถใช้จ่ายได้หรืออาจถูกใช้จ่ายได้โดยทุกคน (หมายความว่าใครก็สามารถนำไปใช้ได้)
เมื่อบ๊อบต้องการจ่ายเงินที่เขาได้รับผ่าน commitment สำหรับสคริปต์ของเขา เขาจะใช้สคริปต์อินพุตที่รวมถึง redeem script ซึ่งถูกแปลงให้เป็นข้อมูลอีลิเมนต์เดียว นอกจากนี้เขายังให้ลายเซ็นที่จำเป็นเพื่อให้เป็นไปตาม redeem script โดยเรียงลำดับตามที่จะถูกใช้โดย opcodes:
<signature2> <signature1> <redeem script>เมื่อโหนดของบิตคอยน์ได้รับการใช้จ่ายของบ๊อบพวกมันจะตรวจสอบว่า redeem script ที่ถูกแปลงเป็นค่าแฮชแล้วมีค่าเดียวกันกับ commitment มั้ย หลังจากนั้นพวกมันจะแทนที่มันบนสแต็คด้วยค่าที่ถอดรหัสแล้ว:<signature2> <signature1> <pubkey1> OP_CHECKSIGVERIFY <pubkey2> OP_CHECKSIGสคริปต์จะถูกประมวลผล และหากผ่านการตรวจสอบและรายละเอียดธุรกรรมอื่น ๆ ทั้งหมดถูกต้อง ธุรกรรมก็จะถือว่าใช้ได้address สำหรับ P2SH ก็ถูกสร้างด้วย base58check เช่นกัน คำนำหน้าเวอร์ชันถูกตั้งเป็น 5 ซึ่งทำให้ที่อยู่ที่เข้ารหัสแล้วขึ้นต้นด้วยเลข 3 ตัวอย่างของที่อยู่ P2SH คือ 3F6i6kwkevjR7AsAd4te2YB2zZyASEm1HM
TIP: P2SH ไม่จำเป็นต้องเหมือนกับธุรกรรมแบบหลายลายเซ็น (multisignature) เสมอไป ถึง address P2SH ส่วนใหญ่ แทนสคริปต์แบบหลายลายเซ็นก็ตาม แต่อาจแทนสคริปต์ที่เข้ารหัสธุรกรรมประเภทอื่น ๆ ได้ด้วย
P2PKH และ P2SH เป็นสองเทมเพลตสคริปต์เท่านั้นที่ใช้กับการเข้ารหัสแบบ base58check พวกมันเป็นที่รู้จักในปัจจุบันว่าเป็น address แบบ legacy และกลายเป็นรูปแบบที่พบน้อยลงเรื่อยๆ address แบบ legacy ถูกแทนที่ด้วยaddress ตระกูล bech32
การโจมตี P2SH แบบ Collision
address ทั้งหมดที่อิงกับฟังก์ชันแฮชมีความเสี่ยงในทางทฤษฎีต่อผู้โจมตีที่อาจค้นพบอินพุตเดียวกันที่สร้างเอาต์พุตฟังก์ชันแฮช (commitment) โดยอิสระ ในกรณีของบิตคอยน์ หากพวกเขาค้นพบอินพุตในวิธีเดียวกับที่ผู้ใช้ดั้งเดิมทำ พวกเขาจะรู้ private key ของผู้ใช้และสามารถใช้จ่ายบิตคอยน์ของผู้ใช้นั้นได้ โอกาสที่ผู้โจมตีจะสร้างอินพุตสำหรับ commitment ที่มีอยู่แล้วโดยอิสระนั้นขึ้นอยู่กับความแข็งแกร่งของอัลกอริทึมแฮช สำหรับอัลกอริทึมที่ปลอดภัย 160 บิตอย่าง HASH160 ความน่าจะเป็นอยู่ที่ 1 ใน 2^160 นี่เรียกว่าการโจมตีแบบ preimage attack
ผู้โจมตีสามารถพยายามสร้างข้อมูลนำเข้าสองชุดที่แตกต่างกัน (เช่น redeem scripts) ที่สร้างการเข้ารหัสแบบเดียวกันได้ สำหรับ address ที่สร้างโดยฝ่ายเดียวทั้งหมด โอกาสที่ผู้โจมตีจะสร้างข้อมูลนำเข้าที่แตกต่างสำหรับการเข้ารหัสที่มีอยู่แล้วมีประมาณ 1 ใน 2^160 สำหรับอัลกอริทึม HASH160 นี่คือการโจมตีแบบ second preimage attack
อย่างไรก็ตาม สถานการณ์จะเปลี่ยนไปเมื่อผู้โจมตีสามารถมีอิทธิพลต่อค่าข้อมูลนำเข้าดั้งเดิมได้ ตัวอย่างเช่น ผู้โจมตีมีส่วนร่วมในการสร้างสคริปต์แบบหลายลายเซ็น (multisignature script) ซึ่งพวกเขาไม่จำเป็นต้องส่ง public key ของตนจนกว่าจะทราบ public key ของฝ่ายอื่นทั้งหมด ในกรณีนั้น ความแข็งแกร่งของอัลกอริทึมการแฮชจะลดลงเหลือรากที่สองของมัน สำหรับ HASH160 ความน่าจะเป็นจะกลายเป็น 1 ใน 2^80 นี่คือการโจมตีแบบ collision attack
เพื่อให้เข้าใจตัวเลขเหล่านี้ในบริบทที่ชัดเจน ข้อมูล ณ ต้นปี 2023 นักขุดบิตคอยน์ทั้งหมดรวมกันสามารถประมวลผลฟังก์ชันแฮชประมาณ 2^80 ทุกชั่วโมง พวกเขาใช้ฟังก์ชันแฮชที่แตกต่างจาก HASH160 ดังนั้นฮาร์ดแวร์ที่มีอยู่จึงไม่สามารถสร้างการโจมตีแบบ collision attack สำหรับมันได้ แต่การมีอยู่ของเครือข่ายบิตคอยน์พิสูจน์ว่าการโจมตีแบบชนกันต่อฟังก์ชัน 160 บิตอย่าง HASH160 สามารถทำได้จริงในทางปฏิบัติ นักขุดบิตคอยน์ได้ลงทุนเทียบเท่ากับหลายพันล้านดอลลาร์สหรัฐในฮาร์ดแวร์พิเศษ ดังนั้นการสร้างการโจมตีแบบ collision attack จึงไม่ใช่เรื่องถูก แต่มีองค์กรที่คาดหวังว่าจะได้รับบิตคอยน์มูลค่าหลายพันล้านดอลลาร์ไปยัง address ที่สร้างโดยกระบวนการที่เกี่ยวข้องกับหลายฝ่าย ซึ่งอาจทำให้การโจมตีนี้มีกำไร
มีโปรโตคอลการเข้ารหัสที่เป็นที่ยอมรับอย่างดีในการป้องกันการโจมตีแบบ collision attack แต่วิธีแก้ปัญหาที่ง่ายโดยไม่ต้องใช้ความรู้พิเศษจากผู้พัฒนากระเป๋าเงินคือการใช้ฟังก์ชันแฮชที่แข็งแกร่งกว่า การอัปเกรดบิตคอยน์ในภายหลังทำให้เป็นไปได้ และ address บิตคอยน์ใหม่ให้ความต้านทานการชนกันอย่างน้อย 128 บิต การดำเนินการแฮช 2^128 ครั้งจะใช้เวลานักขุดบิตคอยน์ปัจจุบันทั้งหมดประมาณ 32 พันล้านปี
แม้ว่าเราไม่เชื่อว่ามีภัยคุกคามเร่งด่วนต่อผู้ที่สร้าง address P2SH ใหม่ แต่เราแนะนำให้กระเป๋าเงินใหม่ทั้งหมดใช้ที่อยู่ประเภทใหม่เพื่อขจัดความกังวลเกี่ยวกับการโจมตีแบบ collision attack ของ P2SH address
Bech32 Addresses
ในปี 2017 โปรโตคอลบิตคอยน์ได้รับการอัปเกรด เพื่อป้องกันไม่ให้ตัวระบุธุรกรรม (txids) ไม่สามารถเปลี่ยนแปลงได้ โดยไม่ได้รับความยินยอมจากผู้ใช้ที่ทำการใช้จ่าย (หรือองค์ประชุมของผู้ลงนามเมื่อต้องมีลายเซ็นหลายรายการ) การอัปเกรดนี้เรียกว่า segregated witness (หรือเรียกสั้นๆ ว่า segwit) ซึ่งยังให้ความสามารถเพิ่มเติมสำหรับข้อมูลธุรกรรมในบล็อกและประโยชน์อื่น ๆ อีกหลายประการ แต่อย่างไรก็ตาม หากมีผู้ใช้เก่าที่ต้องการเข้าถึงประโยชน์ของ segwit โดยตรงต้องยอมรับการชำระเงินไปยังสคริปต์เอาต์พุตใหม่
ตามที่ได้กล่าวไว้ใน p2sh หนึ่งในข้อดีของเอาต์พุตประเภท P2SH คือผู้จ่ายไม่จำเป็นต้องรู้รายละเอียดของสคริปต์ที่ผู้รับใช้ การอัปเกรด segwit ถูกออกแบบมาให้ใช้กลไกนี้ได้ดังเดิม จึง ทำให้ผู้จ่ายสามารถเริ่มเข้าถึงประโยชน์ใหม่ ๆ หลายอย่างได้ทันทีโดยใช้ที่อยู่ P2SH แต่เพื่อให้ผู้รับสามารถเข้าถึงประโยชน์เหล่านั้นได้ พวกเขาจำเป็นจะต้องให้กระเป๋าเงินของผู้จ่ายจ่ายเงินให้เขาโดยใช้สคริปต์ประเภทอื่นแทน ซึ่งจะต้องอาศัยการอัปเกรดกระเป๋าเงินของผู้จ่ายเพื่อรองรับสคริปต์ใหม่เหล่านี้
ในช่วงแรก เหล่านักพัฒนาบิตคอยน์ได้นำเสนอ BIP142 ซึ่งจะยังคงใช้ base58check ร่วมกับไบต์เวอร์ชันใหม่ คล้ายกับการอัปเกรด P2SH แต่การให้กระเป๋าเงินทั้งหมดอัปเกรดไปใช้สคริปต์ใหม่ที่มีเวอร์ชัน base58check ใหม่นั้น คาดว่าจะต้องใช้ความพยายามเกือบเท่ากับการให้พวกเขาอัปเกรดไปใช้รูปแบบ address ที่เป็นแบบใหม่ทั้งหมด ด้วยเหตุนี้้เอง ผู้สนับสนุนบิตคอยน์หลายคนจึงเริ่มออกแบบรูปแบบ address ที่ดีที่สุดเท่าที่เป็นไปได้ พวกเขาระบุปัญหาหลายอย่างกับ base58check ไว้ดังนี้:
- การที่ base58check ใช้อักษรที่มีทั้งตัวพิมพ์ใหญ่และตัวพิมพ์เล็กทำให้ไม่สะดวกในการอ่านออกเสียงหรือคัดลอก ลองอ่าน address แบบเก่าในบทนี้ให้เพื่อนฟังและให้พวกเขาคัดลอก คุณจะสังเกตว่าคุณต้องระบุคำนำหน้าทุกตัวอักษรด้วยคำว่า "ตัวพิมพ์ใหญ่" และ "ตัวพิมพ์เล็ก" และเมื่อคุณตรวจสอบสิ่งที่พวกเขาเขียน คุณจะพบว่าตัวพิมพ์ใหญ่และตัวพิมพ์เล็กของตัวอักษรบางตัวอาจดูคล้ายกันในลายมือของคนส่วนใหญ่
- รูปแบบนี้สามารถตรวจจับข้อผิดพลาดได้ แต่ไม่สามารถช่วยผู้ใช้แก้ไขข้อผิดพลาดเหล่านั้น ตัวอย่างเช่น หากคุณสลับตำแหน่งตัวอักษรสองตัวโดยไม่ตั้งใจเมื่อป้อน address ด้วยตนเอง กระเป๋าเงินของคุณจะเตือนว่ามีข้อผิดพลาดเกิดขึ้นแน่นอน แต่จะไม่ช่วยให้คุณค้นพบว่าข้อผิดพลาดอยู่ที่ไหน คุณอาจต้องใช้เวลาหลายนาทีที่น่าหงุดหงิดเพื่อค้นหาข้อผิดพลาดในที่สุด
- การใช้ตัวอักษรที่มีทั้งตัวพิมพ์ใหญ่และตัวพิมพ์เล็กยังต้องใช้พื้นที่เพิ่มเติมในการเข้ารหัสใน QR code ซึ่งนิยมใช้ในการแชร์ address และ invoice ระหว่างกระเป๋าเงิน พื้นที่เพิ่มเติมนี้หมายความว่า QR code จำเป็นต้องมีขนาดใหญ่ขึ้นที่ความละเอียดเดียวกัน หรือไม่เช่นนั้นก็จะยากต่อการสแกนอย่างรวดเร็ว
- การที่ต้องการให้กระเป๋าเงินผู้จ่ายทุกใบอัปเกรดเพื่อรองรับคุณสมบัติโปรโตคอลใหม่ เช่น P2SH และ segwit แม้ว่าการอัปเกรดเองอาจไม่ต้องใช้โค้ดมากนัก แต่ประสบการณ์แสดงให้เห็นว่าผู้พัฒนากระเป๋าเงินหลายรายมักยุ่งกับงานอื่น ๆ และบางครั้งอาจล่าช้าในการอัปเกรดเป็นเวลาหลายปี สิ่งนี้ส่งผลเสียต่อทุกคนที่ต้องการใช้คุณสมบัติใหม่ ๆ เหล่านี้
นักพัฒนาที่ทำงานเกี่ยวกับรูปแบบ address สำหรับ segwit ได้พบวิธีแก้ปัญหาเหล่านี้ทั้งหมดในรูปแบบ address แบบใหม่ที่เรียกว่า bech32 (ออกเสียงด้วย "ch" อ่อน เช่นใน "เบช สามสิบสอง") คำว่า "bech" มาจาก BCH ซึ่งเป็นอักษรย่อของบุคคลสามคนที่ค้นพบรหัสวนนี้ในปี 1959 และ 1960 ซึ่งเป็นพื้นฐานของ bech32 ส่วน "32" หมายถึงจำนวนตัวอักษรในชุดตัวอักษร bech32 (คล้ายกับ 58 ใน base58check):
-
Bech32 ใช้เฉพาะตัวเลขและตัวอักษรรูปแบบเดียว (โดยปกติจะแสดงเป็นตัวพิมพ์เล็ก) แม้ว่าชุดตัวอักษรของมันจะมีขนาดเกือบครึ่งหนึ่งของชุดตัวอักษรใน base58check ก็ตามแต่ address bech32 สำหรับสคริปต์ pay to witness public key hash (P2WPKH) ก็ยังยาวกว่า legacy address และมีขนาดเท่ากันกับสคริปต์ P2PKH
-
Bech32 สามารถทั้งตรวจจับและช่วยแก้ไขข้อผิดพลาดได้ ใน address ที่มีความยาวตามที่คาดหวังได้ และสามารถรับประกันทางคณิตศาสตร์ได้ว่าจะตรวจพบข้อผิดพลาดใด ๆ ที่ส่งผลกระทบต่อตัวอักษร 4 ตัวหรือน้อยกว่า ซึ่งเชื่อถือได้มากกว่า base58check ส่วนสำหรับข้อผิดพลาดที่ยาวกว่านั้น จะไม่สามารถตรวจพบได้ (โอกาสเกิดน้อยกว่าหนึ่งครั้งในหนึ่งพันล้าน) ซึ่งมีความเชื่อถือได้ประมาณเท่ากับ base58check ยิ่งไปกว่านั้น สำหรับ adddress ที่พิมพ์โดยมีข้อผิดพลาดเพียงเล็กน้อย มันสามารถบอกผู้ใช้ได้ว่าข้อผิดพลาดเหล่านั้นเกิดขึ้นที่ไหน ช่วยให้พวกเขาสามารถแก้ไขข้อผิดพลาดจากการคัดลอกเล็ก ๆ น้อย ๆ ได้อย่างรวดเร็ว
-
ตัวอย่างที่ 3 Bech32 address ที่มีข้อผิดพลาด Address: bc1p9nh05ha8wrljf7ru236awn4t2x0d5ctkkywmv9sclnm4t0av2vgs4k3au7 ข้อผิดพลาดที่ตรวจพบแสดงเป็นตัวหนาและขีดเส้นใต้ สร้างโดยใช้โปรแกรมสาธิตการถอดรหัส bech32 address
-
bech32 address นิยมเขียนด้วยตัวอักษรพิมพ์เล็กเท่านั้น แต่ตัวอักษรพิมพ์เล็กเหล่านี้สามารถแทนที่ด้วยตัวอักษรพิมพ์ใหญ่ก่อนการเข้ารหัส address ในรหัส QR ได้ วิธีนี้ช่วยให้สามารถใช้โหมดการเข้ารหัส QR แบบพิเศษที่ใช้พื้นที่น้อยกว่า คุณจะสังเกตเห็นความแตกต่างในขนาดและความซับซ้อนของรหัส QR ทั้งสองสำหรับที่อยู่เดียวกันในรูปภาพข้างล่างนี้

- Bech32 ใช้ประโยชน์จากกลไกการอัปเกรดที่ออกแบบมาเป็นส่วนหนึ่งของ segwit เพื่อทำให้กระเป๋าเงินผู้จ่ายสามารถจ่ายเงินไปยังประเภทเอาต์พุตที่ยังไม่ได้ใช้งานได้ โดยมีเป้าหมายคือการอนุญาตให้นักพัฒนาสร้างกระเป๋าเงินในวันนี้ที่สามารถใช้จ่ายไปยัง bech32 address และทำให้กระเป๋าเงินนั้นยังคงสามารถใช้จ่ายไปยัง bech32address ได้สำหรับผู้ใช้คุณสมบัติใหม่ที่เพิ่มในการอัปเกรดโปรโตคอลในอนาคต โดยที่มีความหวังว่าเราอาจไม่จำเป็นต้องผ่านรอบการอัปเกรดทั้งระบบอีกต่อไป ซึ่งจำเป็นสำหรับการให้ผู้คนใช้งาน P2SH และ segwit ได้อย่างเต็มรูปแบบ
-
Problems with Bech32 Addresses
address แบบ bech32 ประสบความสำเร็จในทุกด้านยกเว้นปัญหาหนึ่ง คือการรับประกันทางคณิตศาสตร์เกี่ยวกับความสามารถในการตรวจจับข้อผิดพลาดจะใช้ได้เฉพาะเมื่อความยาวของ address ที่คุณป้อนเข้าไปในกระเป๋าเงินมีความยาวเท่ากับ address ดั้งเดิมเท่านั้น หากคุณเพิ่มหรือลบตัวอักษรใด ๆ ระหว่างการคัดลอกจะทำให้ไม่สามารถตรวจจับได้ การรับประกันนี้จะไม่มีผล และกระเป๋าเงินของคุณอาจใช้จ่ายเงินไปยัง address ที่ไม่ถูกต้อง แต่อย่างไรก็ตาม แม้จะไม่มีคุณสมบัตินี้ มีความเชื่อว่าเป็นไปได้ยากมากที่ผู้ใช้ที่เพิ่มหรือลบตัวอักษรจะสร้างสตริงที่มีผลรวมตรวจสอบที่ถูกต้อง ซึ่งช่วยให้มั่นใจได้ว่าเงินของผู้ใช้จะปลอดภัย
น่าเสียดายที่การเลือกใช้ค่าคงที่ตัวหนึ่งในอัลกอริทึม bech32 บังเอิญทำให้การเพิ่มหรือลบตัวอักษร "q" ในตำแหน่งที่สองจากท้ายของ address ที่ลงท้ายด้วยตัวอักษร "p" เป็นเรื่องง่ายมาก ในกรณีเหล่านั้น คุณยังสามารถเพิ่มหรือลบตัวอักษร "q" หลายครั้งได้ด้วย ข้อผิดพลาดนี้จะถูกตรวจจับโดยผลรวมตรวจสอบ (checksum) ในบางครั้ง แต่จะถูกมองข้ามบ่อยกว่าความคาดหวังหนึ่งในพันล้านสำหรับข้อผิดพลาดจากการแทนที่ของ bech32 อย่างมาก สำหรับตัวอย่างสามารถดูได้ในรูปภาพข้างล่างนี้
ตัวอย่างที่ 4. การขยายความยาวของ bech32 address โดยไม่ทำให้ผลรวมตรวจสอบเป็นโมฆะ ``` bech32 address ที่ถูกต้อง: bc1pqqqsq9txsqp
address ที่ไม่ถูกต้องแต่มีผลรวมตรวจสอบที่ถูกต้อง: bc1pqqqsq9txsqqqqp bc1pqqqsq9txsqqqqqqp bc1pqqqsq9txsqqqqqqqqp bc1pqqqsq9txsqqqqqqqqqp bc1pqqqsq9txsqqqqqqqqqqqp ```
จากตัวอย่างนี้ คุณจะเห็นว่าแม้มีการเพิ่มตัวอักษร "q" เข้าไปหลายตัวก่อนตัวอักษร "p" ตัวสุดท้าย ระบบตรวจสอบก็ยังคงยอมรับว่า address เหล่านี้ถูกต้อง นี่เป็นข้อบกพร่องสำคัญของ bech32 เพราะอาจทำให้เงินถูกส่งไปยัง address ที่ไม่มีใครเป็นเจ้าของจริง ๆ หรือ address ที่ไม่ได้ตั้งใจจะส่งไป
สำหรับเวอร์ชันเริ่มต้นของ segwit (เวอร์ชัน 0) ปัญหานี้ไม่ใช่ความกังวลในทางปฏิบัติ เพราะมีความยาวที่ถูกต้องมีเพียงสองแบบที่กำหนดไว้สำหรับเอาต์พุต นั้นคือ 22 Byte และ 34 Byte ซึ่งสอดคล้องกับ bech32 address ที่มีความยาวยาวที่ 42 หรือ 62 ตัวอักษร ดังนั้นคนจะต้องเพิ่มหรือลบตัวอักษร "q" จากตำแหน่งที่สองจากท้ายของ bech32 address ถึง 20 ครั้งเพื่อส่งเงินไปยัง address ที่ไม่ถูกต้องโดยที่กระเป๋าเงินไม่สามารถตรวจจับได้ อย่างไรก็ตาม มันอาจกลายเป็นปัญหาสำหรับผู้ใช้ในอนาคตหากมีการนำการอัปเกรดบนพื้นฐานของ segwit มาใช้
Bech32m
แม้ว่า bech32 จะทำงานได้ดีสำหรับ segwit v0 แต่นักพัฒนาไม่ต้องการจำกัดขนาดเอาต์พุตโดยไม่จำเป็นในเวอร์ชันหลังๆ ของ segwit หากไม่มีข้อจำกัด การเพิ่มหรือลบตัวอักษร "q" เพียงตัวเดียวใน bech32 address อาจทำให้ผู้ใช้ส่งเงินโดยไม่ตั้งใจไปยังเอาต์พุตที่ไม่สามารถใช้จ่ายได้หรือสามารถใช้จ่ายได้โดยทุกคน (ทำให้บิตคอยน์เหล่านั้นถูกนำไปโดยทุกคนได้) นักพัฒนาได้วิเคราะห์ปัญหา bech32 อย่างละเอียดและพบว่าการเปลี่ยนค่าคงที่เพียงตัวเดียวในอัลกอริทึมของพวกเขาจะขจัดปัญหานี้ได้ ทำให้มั่นใจว่าการแทรกหรือลบตัวอักษรสูงสุดห้าตัวจะไม่ถูกตรวจจับน้อยกว่าหนึ่งครั้งในหนึ่งพันล้านเท่านั้น
เวอร์ชันของ bech32 ที่มีค่าคงที่เพียงหนึ่งตัวที่แตกต่างกันเรียกว่า bech32 แบบปรับแต่ง (bech32m) ตัวอักษรทั้งหมดใน address แบบ bech32 และ bech32m สำหรับข้อมูลพื้นฐานเดียวกันจะเหมือนกันทั้งหมด ยกเว้นหกตัวสุดท้าย (ซึ่งเป็นส่วนของ checksum) นั่นหมายความว่ากระเป๋าเงินจำเป็นต้องรู้ว่ากำลังใช้เวอร์ชันใดเพื่อตรวจสอบความถูกต้องของ checksum แต่ address ทั้งสองประเภทมีไบต์เวอร์ชันภายในที่ทำให้การระบุเวอร์ชันที่ใช้อยู่เป็นเรื่องที่ง่าย ในการทำงานกับทั้ง bech32 และ bech32m เราจะพิจารณากฎการเข้ารหัสและการแยกวิเคราะห์สำหรับ address บิตคอยน์แบบ bech32m เนื่องจากพวกมันครอบคลุมความสามารถในการแยกวิเคราะห์บน address แบบ bech32 และเป็นรูปแบบ address ที่แนะนำในปัจจุบันสำหรับกระเป๋าเงินบิตคอยน์
ข้อความจากหลาม: คือผมว่าตรงนี้เขาเขียนไม่รู้เรื่อง แต่เดาว่าเขาน่าจะสื่อว่า เราควรเรียนรู้วิธีการทำงานกับ bech32m เพราะมันเป็นรูปแบบที่แนะนำให้ใช้ในปัจจุบัน และมันมีข้อดีเพราะbech32m สามารถรองรับการอ่าน address แบบ bech32 แบบเก่าได้ด้วย ง่ายๆ คือ ถ้าคุณเรียนรู้วิธีทำงานกับ bech32m คุณจะสามารถทำงานกับทั้ง bech32m และ bech32 ได้ทั้งสองแบบ
bech32m address ริ่มต้นด้วยส่วนที่มนุษย์อ่านได้ (Human Readable Part: HRP) BIP173 มีกฎสำหรับการสร้าง HRP ของคุณเอง แต่สำหรับบิตคอยน์ คุณเพียงแค่จำเป็นต้องรู้จัก HRP ที่ถูกเลือกไว้แล้วตามที่แสดงในตารางข้างล่างนี้

ส่วน HRP ตามด้วยตัวคั่น ซึ่งก็คือเลข "1" ในข้อเสนอก่อนหน้านี้สำหรับตัวคั่นโปรโตคอลได้ใช้เครื่องหมายทวิภาค (colon) แต่ระบบปฏิบัติการและแอปพลิเคชันบางตัวที่อนุญาตให้ผู้ใช้ดับเบิลคลิกคำเพื่อไฮไลต์สำหรับการคัดลอกและวางนั้นจะไม่ขยายการไฮไลต์ไปถึงและผ่านเครื่องหมายทวิภาค
การใช้ตัวเลขช่วยให้มั่นใจได้ว่าการไฮไลต์ด้วยดับเบิลคลิกจะทำงานได้กับโปรแกรมใดๆ ที่รองรับสตริง bech32m โดยทั่วไป (ซึ่งรวมถึงตัวเลขอื่นๆ ด้วย) เลข "1" ถูกเลือกเพราะสตริง bech32 ไม่ได้ใช้เลข 1 ในกรณีอื่น เพื่อป้องกันการแปลงโดยไม่ตั้งใจระหว่างเลข "1" กับตัวอักษรพิมพ์เล็ก "l"
และส่วนอื่นของ bech32m address เรียกว่า "ส่วนข้อมูล" (data part) ซึ่งประกอบด้วยสามองค์ประกอบ:
- Witness version: ไบต์ถัดไปหลังจากตัวคั่นตัวอักษรนี้แทนเวอร์ชันของ segwit ตัวอักษร "q" คือการเข้ารหัสของ "0" สำหรับ segwit v0 ซึ่งเป็นเวอร์ชันแรกของ segwit ที่มีการแนะนำที่อยู่ bech32 ตัวอักษร "p" คือการเข้ารหัสของ "1" สำหรับ segwit v1 (หรือเรียกว่า taproot) ซึ่งเริ่มมีการใช้งาน bech32m มีเวอร์ชันที่เป็นไปได้ทั้งหมด 17 เวอร์ชันของ segwit และสำหรับ Bitcoin จำเป็นต้องให้ไบต์แรกของส่วนข้อมูล bech32m ถอดรหัสเป็นตัวเลข 0 ถึง 16 (รวมทั้งสองค่า)
- Witness program: คือตำแหน่งหลังจาก witnessversion ตั้งแต่ตำแหน่ง 2 ถึง 40 Byte สำหรับ segwit v0 นี้ต้องมีความยาว 20 หรือ 32 Byte ไม่สามารถ ffมีขนาดอื่นได้ สำหรับ segwit v1 ความยาวเดียวที่ถูกกำหนดไว้ ณ เวลาที่เขียนนี้คือ 32 ไบต์ แต่อาจมีการกำหนดความยาวอื่น ๆ ได้ในภายหลัง
- Checksum: มีความยาว 6 ตัวอักษร โดยส่วนนี้ถูกสร้างขึ้นโดยใช้รหัส BCH ซึ่งเป็นประเภทของรหัสแก้ไขข้อผิดพลาด (error corection code) (แต่อย่างไรก็ตาม สำหรับ address บิตคอยน์ เราจะเห็นในภายหลังว่าเป็นสิ่งสำคัญที่จะใช้ checksum เพื่อการตรวจจับข้อผิดพลาดเท่านั้น—ไม่ใช่การแก้ไข
ในส่วนต่อไปหลังจากนี้เราจะลองสร้าง address แบบ bech32 และ bech32m สำหรับตัวอย่างทั้งหมดต่อไปนี้ เราจะใช้โค้ดอ้างอิง bech32m สำหรับ Python
เราจะเริ่มด้วยการสร้างสคริปต์เอาต์พุตสี่ตัว หนึ่งตัวสำหรับแต่ละเอาต์พุต segwit ที่แตกต่างกันที่ใช้ในช่วงเวลาของการเผยแพร่ บวกกับอีกหนึ่งตัวสำหรับเวอร์ชัน segwit ในอนาคตที่ยังไม่มีความหมายที่กำหนดไว้ สคริปต์เหล่านี้แสดงอยู่ในตารางข้างล่างนี้

สำหรับเอาต์พุต P2WPKH witness program มีการผูก commitment ที่สร้างขึ้นในลักษณะเดียวกันกับ P2PKH ที่เห็นใน Legacy Addresses for P2PKH โดย public key ถูกส่งเข้าไปในฟังก์ชันแฮช SHA256 ไดเจสต์ขนาด 32 ไบต์ที่ได้จะถูกส่งเข้าไปในฟังก์ชันแฮช RIPEMD-160 ไดเจสต์ของฟังก์ชันนั้น จะถูกวางไว้ใน witness program
สำหรับเอาต์พุตแบบ pay to witness script hash (P2WSH) เราไม่ได้ใช้อัลกอริทึม P2SH แต่เราจะนำสคริปต์ ส่งเข้าไปในฟังก์ชันแฮช SHA256 และใช้ไดเจสต์ขนาด 32 ไบต์ของฟังก์ชันนั้นใน witness program สำหรับ P2SH ไดเจสต์ SHA256 จะถูกแฮชอีกครั้งด้วย RIPEMD-160 ซึ่งแน่นอนว่าอาจจะไม่ปลอดภัย ในบางกรณี สำหรับรายละเอียด ดูที่ P2SH Collision Attacks ผลลัพธ์ของการใช้ SHA256 โดยไม่มี RIPEMD-160 คือ การผูกพันแบบ P2WSH มีขนาด 32 ไบต์ (256 บิต) แทนที่จะเป็น 20 ไบต์ (160 บิต)
สำหรับเอาต์พุตแบบ pay-to-taproot (P2TR) witness program คือจุดบนเส้นโค้ง secp256k1 มันอาจเป็น public key แบบธรรมดา แต่ในกรณีส่วนใหญ่มันควรเป็น public key ที่ผูกพันกับข้อมูลเพิ่มเติมบางอย่าง เราจะเรียนรู้เพิ่มเติมเกี่ยวกับการผูกพันนั้นในหัวข้อของ taproot
สำหรับตัวอย่างของเวอร์ชัน segwit ในอนาคต เราเพียงแค่ใช้หมายเลขเวอร์ชัน segwit ที่สูงที่สุดที่เป็นไปได้ (16) และ witness program ที่มีขนาดเล็กที่สุดที่อนุญาต (2 ไบต์) โดยมีค่าเป็นศูนย์ (null value)
เมื่อเรารู้หมายเลขเวอร์ชันและ witness program แล้ว เราสามารถแปลงแต่ละอย่างให้เป็น bech32 address ได้ โดยการใช้ไลบรารีอ้างอิง bech32m สำหรับ Python เพื่อสร้าง address เหล่านั้นอย่างรวดเร็ว และจากนั้นมาดูอย่างละเอียดว่าเกิดอะไรขึ้น:
``` $ github=" https://raw.githubusercontent.com" $ wget $github/sipa/bech32/master/ref/python/segwit_addr.py $ python
from segwit_addr import * from binascii import unhexlify help(encode) encode(hrp, witver, witprog) Encode a segwit address. encode('bc', 0, unhexlify('2b626ed108ad00a944bb2922a309844611d25468')) 'bc1q9d3xa5gg45q2j39m9y32xzvygcgay4rgc6aaee' encode('bc', 0, unhexlify('648a32e50b6fb7c5233b228f60a6a2ca4158400268844c4bc295ed5e8c3d626f')) 'bc1qvj9r9egtd7mu2gemy28kpf4zefq4ssqzdzzycj7zjhk4arpavfhsct5a3p' encode('bc', 1, unhexlify('2ceefa5fa770ff24f87c5475d76eab519eda6176b11dbe1618fcf755bfac5311')) 'bc1p9nh05ha8wrljf7ru236awm4t2x0d5ctkkywmu9sclnm4t0av2vgs4k3au7' encode('bc', 16, unhexlify('0000')) 'bc1sqqqqkfw08p'
หากเราเปิดไฟล์ segwit_addr.py และดูว่าโค้ดกำลังทำอะไร สิ่งแรกที่เราจะสังเกตเห็นคือความแตกต่างเพียงอย่างเดียวระหว่าง bech32 (ที่ใช้สำหรับ segwit v0) และ bech32m (ที่ใช้สำหรับเวอร์ชัน segwit รุ่นหลัง) คือค่าคงที่:BECH32_CONSTANT = 1 BECH32M_CONSTANT = 0x2bc830a3 ```และในส่วนต่อไป เราจะเห็นโค้ดที่สร้าง checksum ในขั้นตอนสุดท้ายของการสร้าง checksum ค่าคงที่ที่เหมาะสมถูกรวมเข้ากับข้อมูลอื่น ๆ โดยใช้การดำเนินการ xor ค่าเดียวนั้นคือความแตกต่างเพียงอย่างเดียวระหว่าง bech32 และ bech32m
เมื่อสร้าง checksum แล้ว อักขระ 5 บิตแต่ละตัวในส่วนข้อมูล (รวมถึง witness version, witness program และ checksum) จะถูกแปลงเป็นตัวอักษรและตัวเลข
สำหรับการถอดรหัสกลับเป็นสคริปต์เอาต์พุต เราทำงานย้อนกลับ ลองใช้ไลบรารีอ้างอิงเพื่อถอดรหัส address สอง address ของเรา: ```
help(decode) decode(hrp, addr) Decode a segwit address. _ = decode("bc", "bc1q9d3xa5gg45q2j39m9y32xzvygcgay4rgc6aaee") [0], bytes([1]).hex() (0, '2b626ed108ad00a944bb2922a309844611d25468') _ = decode("bc", "bc1p9nh05ha8wrljf7ru236awm4t2x0d5ctkkywmu9sclnm4t0av2vgs4k3au7") [0], bytes([1]).hex() (1, '2ceefa5fa770ff24f87c5475d76eab519eda6176b11dbe1618fcf755bfac5311')
เราได้รับทั้ง witness version และ witness program กลับมา สิ่งเหล่านี้สามารถแทรกลงในเทมเพลตสำหรับสคริปต์เอาต์พุตของเรา:ตัวอย่างเช่น:OP_0 2b626ed108ad00a944bb2922a309844611d25468 OP_1 2ceefa5fa770ff24f87c5475d76eab519eda6176b11dbe1618fcf755bfac5311 ``` คำเตือน: ข้อผิดพลาดที่อาจเกิดขึ้นที่ควรระวังคือ witness version ที่มีค่า 0 ใช้สำหรับ OP_0 ซึ่งใช้ไบต์ 0x00—แต่เวอร์ชัน witness ที่มีค่า 1 ใช้ OP_1 ซึ่งเป็นไบต์ 0x51 เวอร์ชัน witness 2 ถึง 16 ใช้ไบต์ 0x52 ถึง 0x60 ตามลำดับเมื่อทำการเขียนโค้ดเพื่อเข้ารหัสหรือถอดรหัส bech32m เราขอแนะนำอย่างยิ่งให้คุณใช้เวกเตอร์ทดสอบ (test vectors) ที่มีให้ใน BIP350 เราขอให้คุณตรวจสอบให้แน่ใจว่าโค้ดของคุณผ่านเวกเตอร์ทดสอบที่เกี่ยวข้องกับการจ่ายเงินให้กับเวอร์ชัน segwit ในอนาคตที่ยังไม่ได้รับการกำหนด สิ่งนี้จะช่วยให้ซอฟต์แวร์ของคุณสามารถใช้งานได้อีกหลายปีข้างหน้า แม้ว่าคุณอาจจะไม่สามารถเพิ่มการรองรับคุณสมบัติใหม่ ๆ ของบิตคอยน์ได้ทันทีที่คุณสมบัตินั้น ๆ เริ่มใช้งานได้
Private Key Formats
private key สามารถถูกแสดงได้ในหลาย ๆ รูปแบบที่ต่างกันซึ่งสามารถแปลงเป็นตัวเลขขนาด 256 bit ชุดเดียวกันได้ ดังที่เราจะแสดงให้ดูในตารางข้างล่างนี้ รูปแบบที่แตกต่างกันถูกใช้ในสถานการณ์ที่ต่างกัน รูปแบบเลขฐานสิบหก (Hexadecimal) และรูปแบบไบนารี (raw binary) ถูกใช้ภายในซอฟต์แวร์และแทบจะไม่แสดงให้ผู้ใช้เห็น WIF ถูกใช้สำหรับการนำเข้า/ส่งออกกุญแจระหว่างกระเป๋าเงินและมักใช้ในการแสดงกุญแจส่วนตัวแบบ QR code
รูปแบบของ private key ในปัจจุบัน
ซอฟต์แวร์กระเป๋าเงินบิตคอยน์ในยุคแรกได้สร้าง private key อิสระอย่างน้อยหนึ่งดอกเมื่อกระเป๋าเงินของผู้ใช้ใหม่ถูกเริ่มต้น เมื่อชุดกุญแจเริ่มต้นถูกใช้ทั้งหมดแล้ว กระเป๋าเงินอาจสร้าง private key เพิ่มเติม private key แต่ละดอกสามารถส่งออกหรือนำเข้าได้ ทุกครั้งที่มีการสร้างหรือนำเข้า private key ใหม่ จะต้องมีการสร้างการสำรองข้อมูลกระเป๋าเงินใหม่ด้วย
กระเป๋าเงินบิตคอยน์ในยุคหลังเริ่มใช้กระเป๋าเงินแบบกำหนดได้ (deterministic wallets) ซึ่ง private key ทั้งหมดถูกสร้างจาก seed เพียงค่าเดียว กระเป๋าเงินเหล่านี้จำเป็นต้องสำรองข้อมูลเพียงครั้งเดียวเท่านั้นสำหรับการใช้งานบนเชนทั่วไป แต่อย่างไรก็ตาม หากผู้ใช้ส่งออก private key เพียงดอกเดียวจากกระเป๋าเงินเหล่านี้ และผู้โจมตีได้รับกุญแจนั้นรวมถึงข้อมูลที่ไม่ใช่ข้อมูลส่วนตัวบางอย่างเกี่ยวกับกระเป๋าเงิน พวกเขาอาจสามารถสร้างกุญแจส่วนตัวใด ๆ ในกระเป๋าเงินได้—ทำให้ผู้โจมตีสามารถขโมยเงินทั้งหมดในกระเป๋าเงินได้ นอกจากนี้ ยังไม่สามารถนำเข้ากุญแจสู่กระเป๋าเงินแบบกำหนดได้ นี่หมายความว่าแทบไม่มีกระเป๋าเงินสมัยใหม่ที่รองรับความสามารถในการส่งออกหรือนำเข้ากุญแจเฉพาะดอก ข้อมูลในส่วนนี้มีความสำคัญหลัก ๆ สำหรับผู้ที่ต้องการความเข้ากันได้กับกระเป๋าเงินบิตคอยน์ในยุคแรก ๆ
รูปแบบของ private key (รูปแบบการเข้ารหัส)
 private key เดียวกันในแต่ละ format
private key เดียวกันในแต่ละ format
 รูปแบบการแสดงผลทั้งหมดเหล่านี้เป็นวิธีต่างๆ ในการแสดงเลขจำนวนเดียวกัน private key เดียวกัน พวกมันดูแตกต่างกัน แต่รูปแบบใดรูปแบบหนึ่งสามารถแปลงไปเป็นรูปแบบอื่นได้อย่างง่ายดาย
รูปแบบการแสดงผลทั้งหมดเหล่านี้เป็นวิธีต่างๆ ในการแสดงเลขจำนวนเดียวกัน private key เดียวกัน พวกมันดูแตกต่างกัน แต่รูปแบบใดรูปแบบหนึ่งสามารถแปลงไปเป็นรูปแบบอื่นได้อย่างง่ายดายCompressed Private Keys
คำว่า compressed private key ที่ใช้กันทั่วไปนั้นเป็นคำที่เรียกผิด เพราะเมื่อ private key ถูกส่งออกไปในรูปแบบ WIF-compressed มันจะมีความยาวมากกว่า private key แบบ uncompressed 1 Byte (เลข 01 ในช่อง Hex-compressed ในตารางด้านล่างนี้) ซึ่งบ่งบอกว่า private key ตัวนี้ มาจากกระเป๋าเงินรุ่นใหม่และควรใช้เพื่อสร้าง compressed public key เท่านั้น
private key เองไม่ได้ถูกบีบอัดและไม่สามารถบีบอัดได้ คำว่า compressed private key จริงๆ แล้วหมายถึง " private key ซึ่งควรใช้สร้าง compressed public key เท่านั้น" ในขณะที่ uncompressed private key จริงๆ แล้วหมายถึง “private key ซึ่งควรใช้สร้าง uncompressed public key เท่านั้น” คุณควรใช้เพื่ออ้างถึงรูปแบบการส่งออกเป็น "WIF-compressed" หรือ "WIF" เท่านั้น และไม่ควรอ้างถึง private key ว่า "บีบอัด" เพื่อหลีกเลี่ยงความสับสนต่อไป
ตารางนี้แสดงกุญแจเดียวกันที่ถูกเข้ารหัสในรูปแบบ WIF และ WIF-compressed
ตัวอย่าง: กุญแจเดียวกัน แต่รูปแบบต่างกัน

สังเกตว่ารูปแบบ Hex-compressed มีไบต์เพิ่มเติมหนึ่งไบต์ที่ท้าย (01 ในเลขฐานสิบหก) ในขณะที่คำนำหน้าเวอร์ชันการเข้ารหัสแบบ base58 เป็นค่าเดียวกัน (0x80) สำหรับทั้งรูปแบบ WIF และ WIF-compressed การเพิ่มหนึ่งไบต์ที่ท้ายของตัวเลขทำให้อักขระตัวแรกของการเข้ารหัสแบบ base58 เปลี่ยนจาก 5 เป็น K หรือ L
คุณสามารถคิดถึงสิ่งนี้เหมือนกับความแตกต่างของการเข้ารหัสเลขฐานสิบระหว่างตัวเลข 100 และตัวเลข 99 ในขณะที่ 100 มีความยาวมากกว่า 99 หนึ่งหลัก มันยังมีคำนำหน้าเป็น 1 แทนที่จะเป็นคำนำหน้า 9 เมื่อความยาวเปลี่ยนไป มันส่งผลต่อคำนำหน้า ในระบบ base58 คำนำหน้า 5 เปลี่ยนเป็น K หรือ L เมื่อความยาวของตัวเลขเพิ่มขึ้นหนึ่งไบต์
TIPจากหลาม: ผมว่าเขาเขียนย่อหน้านี้ไม่ค่อยรู้เรื่อง แต่ความหมายมันจะประมาณว่า เหมือนถ้าเราต้องการเขียนเลข 100 ในฐาน 10 เราต้องใช้สามตำแหน่ง 100 แต่ถ้าใช้ฐาน 16 เราจะใช้แค่ 2 ตำแหน่งคือ 64 ซึ่งมีค่าเท่ากัน
ถ้ากระเป๋าเงินบิตคอยน์สามารถใช้ compressed public key ได้ มันจะใช้ในทุกธุรกรรม private key ในกระเป๋าเงินจะถูกใช้เพื่อสร้างจุด public key บนเส้นโค้ง ซึ่งจะถูกบีบอัด compressed public key จะถูกใช้เพื่อสร้าง address และ address เหล่านี้จะถูกใช้ในธุรกรรม เมื่อส่งออก private key จากกระเป๋าเงินใหม่ที่ใช้ compressed public key WIF จะถูกปรับเปลี่ยน โดยเพิ่มต่อท้ายขนาด 1 ไบต์ 01 ให้กับ private key ที่ถูกเข้ารหัสแบบ base58check ที่ได้จะเรียกว่า "WIF-compressed" และจะขึ้นต้นด้วยอักษร K หรือ L แทนที่จะขึ้นต้นด้วย "5" เหมือนกับกรณีของคีย์ที่เข้ารหัสแบบ WIF (ไม่บีบอัด) จากกระเป๋าเงินรุ่นเก่า
Advanced Keys and Addresses
ในส่วนต่อไปนี้ เราจะดูรูปแบบของคีย์และ address เช่น vanity addresses และ paper wallets
vanity addresses
vanity addresses หรือ addresses แบบกำหนดเอง คือ address ที่มีข้อความที่มนุษย์อ่านได้และสามารถใช้งานได้จริง ตัวอย่างเช่น 1LoveBPzzD72PUXLzCkYAtGFYmK5vYNR33 อย่างที่เห็นว่ามันเป็น address ที่ถูกต้องซึ่งมีตัวอักษรเป็นคำว่า Love เป็นตัวอักษร base58 สี่ตัวแรก addresses แบบกำหนดเองต้องอาศัยการสร้างและทดสอบ private key หลายพันล้านตัวจนกว่าจะพบ address ที่มีรูปแบบตามที่ต้องการ แม้ว่าจะมีการปรับปรุงบางอย่างในอัลกอริทึมการสร้าง addresses แบบกำหนดเอง แต่กระบวนการนี้ต้องใช้การสุ่มเลือก private key มาสร้าง public key และนำไปสร้าง address และตรวจสอบว่าตรงกับรูปแบบที่ต้องการหรือไม่ โดยทำซ้ำหลายพันล้านครั้งจนกว่าจะพบที่ตรงกัน
เมื่อพบ address ที่ตรงกับรูปแบบที่ต้องการแล้ว private key ที่ใช้สร้าง address นั้นสามารถใช้โดยเจ้าของเพื่อใช้จ่ายบิตคอยน์ได้เหมือนกับ address อื่น ๆ ทุกประการ address ที่กำหนดเองไม่ได้มีความปลอดภัยน้อยกว่าหรือมากกว่าที่ address ๆ พวกมันขึ้นอยู่กับการเข้ารหัสเส้นโค้งรูปวงรี (ECC) และอัลกอริทึมแฮชที่ปลอดภัย (SHA) เหมือนกับ address อื่น ๆ คุณไม่สามารถค้นหา private key ของ address ที่ขึ้นต้นด้วยรูปแบบที่กำหนดเองได้ง่ายกว่า address อื่น ๆ
ตัวอย่างเช่น ยูจีเนียเป็นผู้อำนวยการการกุศลเพื่อเด็กที่ทำงานในฟิลิปปินส์ สมมติว่ายูจีเนียกำลังจัดการระดมทุนและต้องการใช้ address ที่กำหนดเองเพื่อประชาสัมพันธ์การระดมทุน ยูจีเนียจะสร้าง address ที่กำหนดเองที่ขึ้นต้นด้วย "1Kids" เพื่อส่งเสริมการระดมทุนเพื่อการกุศลสำหรับเด็ก มาดูกันว่า address ที่กำหนดเองนี้จะถูกสร้างขึ้นอย่างไรและมีความหมายอย่างไรต่อความปลอดภัยของการกุศลของยูจีเนีย
การสร้าง address ที่กำหนดเอง
ควรเข้าใจว่า address ของบิตคอยน์เป็นเพียงตัวเลขที่แสดงด้วยสัญลักษณ์ในรูปแบบตัวอักษร base58 เท่านั้น เพราะฉะนั้นแล้ว การค้นหารูปแบบเช่น "1Kids" สามารถมองได้ว่าเป็นการค้นหาที่อยู่ในช่วงตั้งแต่ 1Kids11111111111111111111111111111 ถึง 1Kidszzzzzzzzzzzzzzzzzzzzzzzzzzzzz มีประมาณ 5829 (ประมาณ 1.4 × 1051) address ในช่วงนั้น ทั้งหมดขึ้นต้นด้วย "1Kids" ตารางด้านล่างนี้แสดงช่วงของ address ที่มีคำนำหน้า 1Kids
 ลองดูรูปแบบ "1Kids" ในรูปของตัวเลขและดูว่าเราอาจพบรูปแบบนี้ใน bitcoin address บ่อยแค่ไหน โดยตารางข้างล่างนี้แสดงให้เห็นถีงคอมพิวเตอร์เดสก์ท็อปทั่วไปที่ไม่มีฮาร์ดแวร์พิเศษสามารถค้นหาคีย์ได้ประมาณ 100,000 คีย์ต่อวินาที
ลองดูรูปแบบ "1Kids" ในรูปของตัวเลขและดูว่าเราอาจพบรูปแบบนี้ใน bitcoin address บ่อยแค่ไหน โดยตารางข้างล่างนี้แสดงให้เห็นถีงคอมพิวเตอร์เดสก์ท็อปทั่วไปที่ไม่มีฮาร์ดแวร์พิเศษสามารถค้นหาคีย์ได้ประมาณ 100,000 คีย์ต่อวินาทีความถี่ของ address ที่กำหนดเอง (1KidsCharity) และเวลาค้นหาเฉลี่ยบนคอมพิวเตอร์เดสก์ท็อป

ดังที่เห็นได้ ยูจีเนียคงไม่สามารถสร้าง address แบบกำหนดเอง "1KidsCharity" ได้ในเร็ว ๆ นี้ แม้ว่าเธอจะมีคอมพิวเตอร์หลายพันเครื่องก็ตาม ทุกตัวอักษรที่เพิ่มขึ้นจะเพิ่มความยากขึ้น 58 เท่า รูปแบบที่มีมากกว่า 7 ตัวอักษรมักจะถูกค้นพบโดยฮาร์ดแวร์พิเศษ เช่น คอมพิวเตอร์เดสก์ท็อปที่สร้างขึ้นเป็นพิเศษที่มีหน่วยประมวลผลกราฟิก (GPUs) หลายตัว การค้นหา address แบบกำหนดเองบนระบบ GPU เร็วกว่าบน CPU ทั่วไปหลายเท่า
อีกวิธีหนึ่งในการหา address แบบกำหนดเองคือการจ้างงานไปยังกลุ่มคนขุด vanity addresses กลุ่มคนขุดvanity addresses เป็นบริการที่ให้ผู้ที่มีฮาร์ดแวร์ที่เร็วได้รับบิตคอยน์จากการค้นหา vanity addresses ให้กับผู้อื่น ยูจีเนียสามารถจ่ายค่าธรรมเนียมเพื่อจ้างงานการค้นหา vanity addresses ที่มีรูปแบบ 7 ตัวอักษรและได้ผลลัพธ์ในเวลาเพียงไม่กี่ชั่วโมงแทนที่จะต้องใช้ CPU ค้นหาเป็นเดือน ๆ
การสร้างที่ address แบบกำหนดเองเป็นการใช้วิธีการแบบ brute-force (ลองทุกความเป็นไปได้): ลองใช้คีย์สุ่ม ตรวจสอบ address ที่ได้ว่าตรงกับรูปแบบที่ต้องการหรือไม่ และทำซ้ำจนกว่าจะสำเร็จ
ความปลอดภัยและความเป็นส่วนตัวของ address แบบกำหนดเอง
address แบบกำหนดเองเคยเป็นที่นิยมในช่วงแรก ๆ ของบิตคอยน์ แต่แทบจะหายไปจากการใช้งานทั้งหมดในปี 2023 มีสาเหตุที่น่าจะเป็นไปได้สองประการสำหรับแนวโน้มนี้: - Deterministic wallets: ดังที่เราเห็นในพาร์ทของการกู้คืน การที่จะสำรองคีย์ทุกตัวในกระเป๋าเงินสมัยใหม่ส่วนใหญ่นั้น ทำเพียงแค่จดคำหรือตัวอักษรไม่กี่ตัว ซึ่งนี่เป็นผลจากการสร้างคีย์ทุกตัวในกระเป๋าเงินจากคำหรือตัวอักษรเหล่านั้นโดยใช้อัลกอริทึมแบบกำหนดได้ จึงไม่สามารถใช้ address แบบกำหนดเองกับ Deterministic wallets ได้ เว้นแต่ผู้ใช้จะสำรองข้อมูลเพิ่มเติมสำหรับ address แบบกำหนดเองทุก address ที่พวกเขาสร้าง ในทางปฏิบัติแล้วกระเป๋าเงินส่วนใหญ่ที่ใช้การสร้างคีย์แบบกำหนดได้ โดยไม่อนุญาตให้นำเข้าคีย์ส่วนตัวหรือการปรับแต่งคีย์จากโปรแกรมสร้าง address ที่กำหนดเอง
- การหลีกเลี่ยงการใช้ address ซ้ำซ้อน: การใช้ address แบบกำหนดเองเพื่อรับการชำระเงินหลายครั้งไปยัง address เดียวกันจะสร้างความเชื่อมโยงระหว่างการชำระเงินทั้งหมดเหล่านั้น นี่อาจเป็นที่ยอมรับได้สำหรับยูจีเนียหากองค์กรไม่แสวงหาผลกำไรของเธอจำเป็นต้องรายงานรายได้และค่าใช้จ่ายต่อหน่วยงานภาษีอยู่แล้ว แต่อย่างไรก็ตาม มันยังลดความเป็นส่วนตัวของคนที่จ่ายเงินให้ยูจีเนียหรือรับเงินจากเธอด้วย ตัวอย่างเช่น อลิซอาจต้องการบริจาคโดยไม่เปิดเผยตัวตน และบ็อบอาจไม่ต้องการให้ลูกค้ารายอื่นของเขารู้ว่าเขาให้ราคาส่วนลดแก่ยูจีเนีย
เราไม่คาดว่าจะเห็น address แบบกำหนดเองมากนักในอนาคต เว้นแต่ปัญหาที่กล่าวมาก่อนหน้านี้จะได้รับการแก้ไข
Paper Wallets
paper wallet หรือก็คือ private key ที่พิมพ์ลงในกระดาษ และโดยทั่วไปแล้วมักจะมีข้อมูลของ public key หรือ address บนกระดาษนั้นด้วยแม้ว่าจริง ๆ แล้วมันจะสามารถคำนวณได้ด้วย private key ก็ตาม
คำเตือน: paper wallet เป็นเทคโนโลยีที่ล้าสมัยแล้วและอันตรายสำหรับผู้ใช้ส่วนใหญ่ เพราะเป็นเรื่องยากที่จะสร้างมันอย่างปลอดภัย โดยเฉพาะอย่างยิ่งความเป็นไปได้ที่โค้ดที่ใช้สร้างอาจถูกแทรกแซงด้วยผู้ไม่ประสงค์ดี และอาจจะทำให้ผู้ใช้โดนขโมยบิตคอยน์ทั้งหมดไปได้ paper wallet ถูกแสดงที่นี่เพื่อวัตถุประสงค์ในการให้ข้อมูลเท่านั้นและไม่ควรใช้สำหรับเก็บบิตคอยน์

paper wallet ได้ถูกออกแบบมาเพื่อเป็นของขวัญและมีธีมตามฤดูกาล เช่น คริสต์มาสและปีใหม่ ส่วนเหตุผลอื่น ๆ ถูกออกแบบเพื่อการเก็บรักษาในตู้นิรภัยของธนาคารหรือตู้เซฟโดยมี private key ถูกซ่อนไว้ในบางวิธี ไม่ว่าจะด้วยสติกเกอร์แบบขูดที่ทึบแสงหรือพับและปิดผนึกด้วยแผ่นฟอยล์กันการงัดแงะ ส่วนการออกแบบอื่น ๆ มีสำเนาเพิ่มเติมของคีย์และ address ในรูปแบบของตอนฉีกที่แยกออกได้คล้ายกับตั๋ว ช่วยให้คุณสามารถเก็บสำเนาหลายชุดเพื่อป้องกันจากไฟไหม้ น้ำท่วม หรือภัยพิบัติทางธรรมชาติอื่น ๆ
จากการออกแบบเดิมของบิตคอยน์ที่เน้น public key ไปจนถึง address และสคริปต์สมัยใหม่อย่าง bech32m และ pay to taproot—และแม้แต่การอัพเกรดบิตคอยน์ในอนาคต—คุณได้เรียนรู้วิธีที่โปรโตคอลบิตคอยน์อนุญาตให้ผู้จ่ายเงินระบุกระเป๋าเงินที่ควรได้รับการชำระเงินของพวกเขา แต่เมื่อเป็นกระเป๋าเงินของคุณเองที่รับการชำระเงิน คุณจะต้องการความมั่นใจว่าคุณจะยังคงเข้าถึงเงินนั้นได้แม้ว่าจะเกิดอะไรขึ้นกับข้อมูลกระเป๋าเงินของคุณ ในบทต่อไป เราจะดูว่ากระเป๋าเงินบิตคอยน์ถูกออกแบบอย่างไรเพื่อปกป้องเงินทุนจากภัยคุกคามหลากหลายรูปแบบ
-
 @ 7d33ba57:1b82db35
2025-03-22 10:27:50
@ 7d33ba57:1b82db35
2025-03-22 10:27:50Valencia is a vibrant coastal city on Spain’s east coast, blending historical charm, futuristic architecture, golden beaches, and amazing cuisine. As the birthplace of paella, it’s a paradise for food lovers, while its mild climate and Mediterranean vibes make it a perfect year-round destination.
🏛️ Top Things to See & Do in Valencia
1️⃣ The City of Arts and Sciences
- A futuristic architectural complex with a science museum, planetarium, aquarium, and opera house.
- The Hemisfèric & Oceanogràfic are must-visits for families and science lovers.
2️⃣ Valencia Cathedral & El Miguelete Tower
- A beautiful Gothic cathedral said to house the Holy Grail.
- Climb El Miguelete Tower for breathtaking city views.
3️⃣ La Lonja de la Seda (Silk Exchange) – UNESCO Site
- A stunning Gothic-style merchant building from the 15th century.
- One of the best-preserved examples of Valencia’s medieval trading history.
4️⃣ Plaza de la Virgen & Old Town (El Carmen)
- A charming square surrounded by historical buildings, fountains, and lively cafés.
- Wander the narrow streets of El Carmen for street art, boutique shops, and tapas bars.
5️⃣ Turia Gardens & Gulliver Park
- A beautiful green park built in a former riverbed, perfect for cycling, jogging, or picnicking.
- Gulliver Park is a giant playground shaped like Gulliver from "Gulliver’s Travels"!
6️⃣ Central Market (Mercado Central)
- One of the largest fresh food markets in Europe, housed in a stunning Art Nouveau building.
- Try fresh produce, local cheeses, and traditional jamón ibérico.
7️⃣ Malvarrosa Beach
- A long sandy beach with great restaurants, water sports, and a relaxing atmosphere.
- Perfect for sunbathing, a seaside stroll, or enjoying a paella by the sea.
🍽️ What to Eat in Valencia
- Paella Valenciana – The original version with rabbit, chicken, and saffron rice 🥘
- Horchata & Fartons – A refreshing tiger nut drink with sweet pastries 🥛🥐
- Agua de Valencia – A famous local cocktail made with orange juice, cava, gin, and vodka 🍹
- Esgarraet – A tasty mix of salted cod, red peppers, and olive oil 🐟
🚆 How to Get to Valencia
🚄 By Train: High-speed AVE trains from Madrid (~1.5 hrs) & Barcelona (~3 hrs)
✈️ By Air: Valencia Airport (VLC) with connections to major European cities
🚗 By Car: A scenic drive along the Mediterranean coast (Costa Blanca)💡 Tips for Visiting Valencia
✅ Best time to visit? Spring & Fall for pleasant weather 🌞
✅ Visit during Las Fallas (March 15-19) – A spectacular festival with fireworks, giant sculptures, and street parties 🎆🔥
✅ Try a bike tour! Valencia is one of Spain’s most bike-friendly cities 🚴
-
 @ 714dd0db:9c6f1a4c
2025-03-22 09:48:44
@ 714dd0db:9c6f1a4c
2025-03-22 09:48:44やっと春が来ました
ようやく暖かくなってきた。 買い物から帰ってくると、なにやら甘い香り。
あ、もしかして、花の香りか!
探してみると、沈丁花が咲いている。

ああ、甘くていい香り。
近くには蝋梅も咲いている。我が家の近くに蝋梅があったなんて、すっかり忘れていた。

そして、早咲きの桜。桜のどの種類かは分からないのだが、毎年、ソメイヨシノよりも先に咲いている。

花の蜜を吸いに百舌鳥も来ている。いや、鳥の種類には疎いが、おそらく百舌鳥だろう。多分。

モノクロの冬から、ようやくカラフルな春になってきた。
季節を感じるのは、心が豊かになる。 今は今、今度は今度。 俺は今を生きている。
-
 @ 65ad6ed7:2c18ad9b
2025-03-22 09:38:41
@ 65ad6ed7:2c18ad9b
2025-03-22 09:38:41{"coverurl":"https://cdn.nostrcheck.me/65ad6ed72a21ce3195dbec8093fb0113114a75776a9581d24f2ea3892c18ad9b/95f88b428b1ab106a9f8c373cd0ddb072cca46ce95bf1187085e15f332c8542d.webp","title":"我的日记本","author":"日记"}
-
 @ da0b9bc3:4e30a4a9
2025-03-22 09:34:42
@ da0b9bc3:4e30a4a9
2025-03-22 09:34:42Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/921232
-
 @ e5de992e:4a95ef85
2025-03-22 15:52:25
@ e5de992e:4a95ef85
2025-03-22 15:52:25In a world where our to-do lists seem to grow longer by the minute, figuring out what to tackle next can feel like solving a puzzle with missing pieces. Should you call a friend to catch up? Finish that work project? Or make sure you don’t forget a loved one’s birthday? The overwhelm is real, and traditional task management systems often leave us guessing. That’s where the 2-5 Rule comes in—a groundbreaking concept that powers TaskforUs, a smart, simple website designed to tell you exactly what to work on right now.
What Is the 2-5 Rule?
At its core, the 2-5 Rule is a timing-based approach to task management built on a simple yet powerful idea: every task has a natural rhythm—a “time unit” that dictates how often it should be addressed—and an ideal window for action: between 2 and 5 of those units. The time unit varies depending on the task’s nature:
-
Daily Tasks: (e.g., doing cardio or following up on a quick email)
Time unit: days. Act within 2 to 5 days. -
Weekly Tasks: (e.g., scheduling dinner with a friend)
Time unit: weeks. Act within 2 to 5 weeks. -
Monthly Tasks: (e.g., reviewing your budget)
Time unit: months. Act within 2 to 5 months. -
Yearly Tasks: (e.g., reassessing your career goals)
Time unit: years. Revisit every 2 to 5 years.
The 2-5 Rule ensures you’re neither jumping on tasks too early (wasting energy on something that isn’t urgent) nor leaving them too late (missing opportunities or causing stress). It’s about finding the sweet spot—the perfect moment to act.
For date-specific events like birthdays or anniversaries, TaskforUs introduces a Fix Mode that pins the task to a specific day. As the date approaches, the task climbs your list until it reaches the top on the day itself, ensuring you never miss a critical moment.
The Origins of the 2-5 Rule
The 2-5 Rule was born out of a need to bring structure to the chaos of modern life. Traditional to-do lists are static—they don’t account for the natural ebb and flow of tasks. Urgent tasks get buried under less pressing ones, and long-term goals are often forgotten until it’s too late.
TaskforUs’s creators recognized that timing is as important as priority. They drew inspiration from: - Behavioral Science: Showing that humans thrive on rhythm and consistency. - Project Management Principles: Where tasks are often scheduled based on optimal intervals.
The choice of 2 to 5 units isn’t arbitrary. Research into productivity and habit formation suggests: - Acting too soon (e.g., after just 1 unit) can lead to over-managing. - Waiting too long (beyond 5 units) risks neglect.
The 2-to-5 window strikes a balance—providing enough flexibility while ensuring nothing slips through the cracks. This range also aligns with our natural sense of urgency: after 2 units, a task begins to feel pressing; by 5 units, it risks becoming problematic.
How the 2-5 Rule Works in Practice
Step 1: Define Your Tasks and Time Units
When you add a task to TaskforUs, you assign it a time unit based on its nature: - Example:
- "Schedule dinner with Alex" is a social task (unit: weeks). - "Do cardio" is a health goal (unit: days). - "Reassess my career path" is a long-term goal (unit: years).TaskforUs can suggest defaults based on common patterns, but you can customize the unit to fit your life.
Step 2: Track the 2-5 Window
TaskforUs monitors when you last acted on a task. If it’s been 2 time units, the task enters its “sweet spot” and starts climbing your list. By 5 units, it becomes urgent. - Example:
- If you last met Alex 3 weeks ago, "Schedule dinner with Alex" becomes a top priority. - If it’s been 2 days since your last cardio session, TaskforUs nudges you to hit the gym.Step 3: Handle Fixed Dates with Fix Mode
For tasks tied to specific dates (e.g., birthdays or anniversaries), Fix Mode lets you set an exact date. The task gradually climbs your list as the date nears and becomes the top priority on that day, ensuring you never miss it.
Step 4: Prioritize with Top Task and Focus Mode
- Top Task: TaskforUs surfaces the single most urgent task within the 2-to-5 window.
- Focus Mode: If you prefer to see more, this mode shows your top 3 tasks (or a customizable number), ensuring you’re always focused on what matters most without being overwhelmed by a long list.
The Science Behind the 2-5 Rule
The 2-5 Rule isn’t just a clever idea—it’s grounded in psychology and productivity research:
-
Habit Formation:
Studies (e.g., by Dr. BJ Fogg) show that consistency is key to building routines, yet overdoing it can lead to burnout. The 2-5 window strikes a healthy balance. -
Decision Fatigue:
Research by Dr. Roy Baumeister highlights the mental toll of constant decision-making. By automating prioritization, the 2-5 Rule reduces this burden, freeing up mental energy. -
Zeigarnik Effect:
The Fix Mode leverages the tendency to remember uncompleted tasks, keeping date-specific items front of mind until they’re completed, thereby reducing stress and improving follow-through.
Why You Should Try the 2-5 Rule with TaskforUs
If you’re tired of chaotic to-do lists, missed deadlines, or the nagging feeling of forgetting something important, the 2-5 Rule offers a better way. It works with your natural rhythm, ensuring you focus on what truly matters. TaskforUs brings this concept to life with a user-friendly platform (currently in beta) that: - Eliminates Decision Fatigue: Tells you exactly what to do now. - Balances Urgency and Flexibility: Keeps you in the sweet spot between procrastination and over-management. - Adapts to Your Life’s Rhythm: Customizes time units for daily, weekly, monthly, and yearly tasks. - Ensures You Never Miss Critical Dates: With Fix Mode for date-specific events. - Reduces Stress and Boosts Momentum: By focusing on one Top Task (or a few in Focus Mode).
Real-Life Applications of the 2-5 Rule
-
Social Connections:
Task: “Schedule dinner with Alex”
Time Unit: Weeks
Scenario: If you last met Alex 3 weeks ago, the task becomes your Top Task, prompting you to reconnect. -
Health Goals:
Task: “Do cardio”
Time Unit: Days
Scenario: If it’s been 2 days since your last workout, TaskforUs nudges you to exercise before the 5-day mark. -
Special Dates:
Task: “Wish Alex a happy birthday”
Mode: Fix Mode
Scenario: A month before the birthday, it’s low on your list, but as the date nears, it climbs to the top—ensuring you don’t miss it. -
Long-Term Planning:
Task: “Reassess my career path”
Time Unit: Years
Scenario: If it’s been 2 years since your last review, TaskforUs prompts you to evaluate your goals and progress.
How TaskforUs Brings the 2-5 Rule to Life
TaskforUs is more than just a concept—it’s a practical tool that makes the 2-5 Rule actionable:
-
Top Task:
The algorithm identifies the single most urgent task within your 2-to-5 window. -
Focus Mode:
Displays your top 3 tasks (or a customizable number) to help manage multiple priorities. -
Fix Mode:
Ensures date-specific tasks are prioritized as the due date approaches. -
Smart Defaults:
Suggests time units based on common patterns, while allowing customization to suit your needs. -
Ongoing Refinements:
The TaskforUs team continually improves the algorithm based on user feedback to enhance its accuracy.
Take Control of Your Tasks Today
The 2-5 Rule is more than a productivity hack—it’s a mindset shift. It’s about working smarter, not harder, and timing your tasks to perfection. TaskforUs makes this possible with a simple, intuitive platform designed to help you master your to-do list.
-
-
 @ 65ad6ed7:2c18ad9b
2025-03-22 09:29:27
@ 65ad6ed7:2c18ad9b
2025-03-22 09:29:27{"coverurl":"https://cdn.nostrcheck.me/65ad6ed72a21ce3195dbec8093fb0113114a75776a9581d24f2ea3892c18ad9b/c0b4b68a5a5a3ab4ce4a1ad0469c358dc91013244b44158f592127ac6b4409d4.webp","title":"骑行日记","author":"我的日记"}
-
 @ 6fbc5b6b:0251e3df
2025-03-22 06:10:57
@ 6fbc5b6b:0251e3df
2025-03-22 06:10:57About AI Ville AI Ville is an AI-driven virtual society where intelligent agents live, trade, farm, and evolve autonomously. It features a decentralized economy, AI governance, and dynamic social interactions, creating a self-sustaining digital ecosystem. Players and AI co-exist, cultivating the future of AI-powered communities in a Web3 world.
$Dinar is the core in-game currency that powers the dynamic economy of AI Ville. It is earned, spent, and circulated by both human players and AI residents—beings with their own goals, habits, and financial strategies. From farming to trading, from investing to survival, $Dinar touches every layer of this living, breathing town.
This article unpacks the lifecycle of $Dinar—how you earn it, where it flows, how it fuels both the human and AI economy, and what the future holds.
- Earning $Dinar: Gameplay Meets Income In AI Ville, work pays. Whether you're focused on farming or exploration, there are multiple ways to grow your wealth:
Farm to Prosper: Plant, harvest, and sell crops to the store.
Complete Quests: Finish daily and seasonal tasks for consistent rewards.
Unlock Treasures: Discover hidden chests scattered throughout the landscape.
Your income potential grows with your planning. Efficient players stack income streams.
- Spending $Dinar: Unlocking Possibilities Spending $Dinar isn’t just about survival—it’s about strategy. A smart allocation of your funds accelerates progress and boosts returns. Most spending falls into three categories:
Production Inputs: Essential for farming success Seed Shopping: Start with simple crops or invest in rare, high-yield varieties.
Watering Tools: Buy watering cans to accelerate growth, saving you time and cycles.
Seed Upgrades: Visit the Seed Lab to enhance seed quality and profitability.
Sustain & Recover: Keeping your energy up keeps you moving Buy Food: Restore stamina and stay productive longer.
Expand & Optimize: Grow your farm and work smarter Land Expansion: Acquire more plots to scale up operations.
Farm Customization: Personalize your environment for aesthetics and efficiency.
Hire Local Help: Bring in AI workers with specialized skills and dynamic rates.
- Fueling Activity with $Dinar: Managing Stamina, Food & Water In AI Ville, stamina is your most valuable personal resource—and managing it well is essential to keeping your farm productive. $Dinar plays a critical role in that process.
Planting, harvesting, and watering all drain stamina. Once you’re out, progress slows to a halt.
To recover quickly, you can buy food using $Dinar. The food is made from crops sold to the store—completing a regenerative economic cycle.
To maximize crop yield, you can purchase watering cans with $Dinar. These speed up plant growth, but also consume additional stamina.
This creates a feedback loop: Grow → Sell → Earn $Dinar → Buy Food and Tools → Regain Stamina → Grow More
Mastering this energy economy—and using your $Dinar wisely within it—is key to thriving in AI Ville.
- $Dinar in Action: The Crop-to-Capital Cycle Here’s how one cycle of $Dinar plays out:
You grow and sell crops to the store.
The store processes crops into food.
Food is bought by others needing stamina.
You buy food with $Dinar to stay active.
You spend stamina on planting, watering, harvesting.
You reinvest in seeds, tools, and upgrades using more $Dinar.
This creates an ever-churning loop where $Dinar fuels every stage of productivity.
- Market Logic: Prices, Taxes & Opportunity Seed, water, and food prices fluctuate based on supply, demand, and scarcity (e.g., droughts).
Hiring AI costs vary by skill and availability.
Land and stall rental reflect competitive bids—sometimes against AIs.
Taxation (2–5%) is governed by AGT holders and reinvested into public tasks.
- AI & $Dinar: Living, Thinking, Earning AI residents are economic agents—not scripted bots.
They run shops, sell goods, and offer services.
They respond to scarcity by adjusting prices or switching focus.
They make decisions based on current and predicted market trends.
You’re not the only one farming, trading, or upgrading—your AI neighbors are, too.
- How AI Use $Dinar: Investing, Competing, Reacting AI residents adapt their strategies based on real-time dynamics:
Smart Investing: Holding $Dinar vs. swapping for $AGT.
Price Competition: One AI raises wheat prices during a shortage. Another lowers theirs to grab traffic.
These decisions ripple outward. Markets react. So should you.
- The Future of $Dinar: Interchangeability & Collective Wealth The future of $Dinar is even more dynamic:
$Dinar ↔ $AGT: Players will soon exchange currencies, connecting everyday labor with governance power.
Public Treasury: Taxes and store profits will fuel the Task Center, rewarding contributors.
As the economy of AI Ville evolves, so too will the role of $Dinar. It won’t just be a means of trade—it will be a vehicle for influence, innovation, and collaboration between humans and AI.
Stay tuned: the way you earn, spend, and shape value is only just beginning.
-
 @ 6830c409:ff17c655
2025-03-22 04:59:06
@ 6830c409:ff17c655
2025-03-22 04:59:06സോഷ്യൽ മീഡിയ ഇന്ന്
ഇന്ന് സോഷ്യൽ മീഡിയ നേരിടുന്ന ഏറ്റവും വലിയ വെല്ലുവിളികളിൽ ഒന്ന് എല്ലാ മേജർ പ്ലാറ്റ്ഫോമുകളും കൈകാര്യം ചെയ്യുന്നത് വൻകോർപറേറ്റുകളാണെന്നതാണ്. കോർപ്പറേറ്റുകൾ വലിയ ഹോൾഡിങ്ങുകൾ കൈവശം വയ്ക്കുന്നത് സ്വാഭാവികവും വളരെ ഈസിയും ആണ്. പക്ഷെ, അത് ഒരു വെല്ലുവിളിയായി മാറുന്നത്, ഏതെങ്കിലും ഒരു നറേറ്റിവിനെ ബൂസ്റ്റ് ചെയ്യുകയും, മറ്റൊരു നറേറ്റിവിനെ തമസ്കരിക്കുകയും ചെയ്യുമ്പോഴാണ്. ഇത് തന്നെയാണ് "misinformation"/"disinformation" ഉണ്ടാകുന്നതിന്റെ മൂലകാരണവും. ഉദാഹരണത്തിന് ഇന്ന് ഇലോൺ മസ്കിന്റെ ഒരു റ്റ്വീറ്റെങ്കിലും കാണാതെ റ്റ്വിറ്റർ തുറക്കാൻ കഴിയില്ല. അതിനി മസ്കിനെ ബ്ലോക്ക് ചെയ്തിട്ടുണ്ടെങ്കിൽ പോലും ആ റ്റ്വീറ്റുകൾ ബൂസ്റ്റ് ചെയ്യപ്പെടും. എന്തുകാരണത്തിനാണ് എന്ന് പറയാതെ അക്കൗണ്ടുകൾ ലിമിറ്റ് ചെയ്യുകയോ, ലോക്ക്ഡൗൺ ചെയ്യുകയോ ഒക്കെ ആയിട്ടുണ്ട്.
സൊ, നിങ്ങളുടെ അക്കൗണ്ട് ശരിക്കും നിങ്ങൾക്ക് Own ചെയ്യാൻ കഴിയാത്ത ഒരു സാധനമാണ് ഇപ്പൊഴുള്ള convensional സോഷ്യൽ മീഡിയ പ്ലാറ്റ്ഫൊമുകളിൽ.
ഒരു പ്രൊപ്പോസൽ
- നിങ്ങളുടെ അക്കൗണ്ടിന്റെ പൂർണ്ണ ഉടമസ്ഥത നിങ്ങൾക്ക് തന്നെ തരുന്നു എന്ന് കരുതുക.
- നിങ്ങളുടെ റ്റ്വീറ്റുകൾ/പോസ്റ്റുകൾ ഏതെങ്കിലും ഒരു സർവ്വർ അല്ലെങ്കിൽ ഒരു സർവ്വീസിന്റെ കൈവശം പണയപ്പെടുത്തേണ്ട അവസ്ഥ ഇല്ലാതെയാകുന്നു എന്ന് കരുതുക
സോഷ്യൽ മീഡിയ ഉപയോഗത്തിനെ നിങ്ങൾക്ക് ഒന്ന് മാറ്റിച്ചിന്തിക്കാൻ മേൽപ്പറഞ്ഞ കാരണങ്ങൾ മതിയാവില്ലെ?
അതായത് റ്റ്വിറ്ററോ ഫേസ്ബുക്കോ പോലെ ഒരു കമ്പനി വിചാരിച്ചാൽ നിങ്ങളുടെ പോസ്റ്റുകൾ ഡിലീറ്റ് ചെയ്യാൻ കഴിയില്ല എന്ന ഒരു അവസ്ഥ കൊണ്ടുവരാൻ കഴിയുന്ന ഒരു സോഷ്യൽ മീഡിയ വന്നാലോ?
ആ സോഷ്യൽ മീഡിയ പ്ലാറ്റ്ഫോമിനെയാണ് ഞാൻ നിങ്ങൾക്ക് പരിചയപ്പെടുത്താൻ പോകുന്നത്.
നൊസ്റ്റർ (Nostr)
നൊസ്റ്റർ എങ്ങനെ മറ്റുള്ള പ്ലാറ്റ്ഫോമുകളിൽ നിന്നും വ്യത്യസ്തമാണെന്ന് നോക്കാം
Notes and Other Stuff Transmitted by Relays
നൊസ്റ്റർ ഏതെങ്കിലും ഒരു സർവ്വറിനെയോ സർവ്വീസ് പ്രൊവൈഡറെയോ ആശ്രയിച്ചല്ല ഓടുന്നത്. ഇന്നത്തെ കണക്കിന് തന്നെ ആയിരത്തോളം ഇൻഡിപ്പെൻഡന്റ് സർവ്വറുകൾ നൊസ്റ്ററിനായി പ്രവർത്തിക്കുന്നുണ്ട്. എന്ന് മാത്രവുമല്ല, ഒരു ക്ലൗഡ് അക്കൗണ്ടുണ്ടെങ്കിൽ ആർക്കും സ്വന്തമായി ഒരു സർവ്വർ റൺ ചെയ്യാവുന്നതേയുള്ളൂ. എന്ന് കരുതി, എല്ലാവരും സ്വന്തം സർവ്വർ റൺ ചെയ്യണമെന്നില്ല.
ഒരു സാധാരണ സോഷ്യൽമീഡിയ യൂസറിന് ഉപയോഗിക്കാൻ എളുപ്പമുള്ള ആപ്പുകൾ നൊസ്റ്ററിനുണ്ട്. ഐഫോണുകളിൽ Damus, ആൻഡ്രോയ്ഡിൽ Amethyst, Primal.net തുടങ്ങി ഒരുപാട് ക്ലയന്റ് ആപ്പുകൾ ലഭ്യമാണ്. അവയിൽ ഏതെങ്കിലും ഒന്ന് ഇൻസ്റ്റാൾ ചെയ്താൽ റ്റ്വിറ്ററോ ഫേസ്ബുക്കോ പോലെ ഉപയോഗിക്കാൻ തുടങ്ങാവുന്നതേയുള്ളൂ. ഒരു ചെറിയ ലിസ്റ്റ് ചുവടെ ചേർക്കുന്നു.
Damus (iPhones): https://damus.io/
Amethyst (Android): https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst&hl=en_US
Yakihonne (Web, iPhone): https://yakihonne.com/
Primal.net (Web, iPhone): https://primal.net
**https://openvibe.social/ - ഒരേസമയം ബ്ലൂസ്കൈ, മാസ്റ്റഡോൺ, നൊസ്റ്റർ എന്നിവയിൽ പോസ്റ്റ് ചെയ്യാനും അക്കൗണ്ടുകൾ മെയ്ന്റെൻ ചെയ്യാനും ഓപ്പൺ വൈബ് അടിപൊളിയാണ്. **
Permission-free
നൊസ്റ്റർ ഉപയോഗിക്കാൻ യൂസർനേമും പാസ്സ്വേഡും ഇല്ല. പകരം, ഒരു പബ്ലിക്ക് കീയും പ്രൈവറ്റ് കീയും മാത്രമേയുള്ളൂ. ഇതുകൊണ്ടുള്ള പ്രയോജനം എന്താണെന്നാൽ, നിങ്ങൾക്ക് ആപ്പ്ലിക്കേഷനിലേക്ക് ലോഗിൻ ചെയ്യാൻ, ഒരു സർവ്വർ ആവശ്യമില്ല.
നിങ്ങൾ സൈനപ്പ് ചെയ്യുമ്പോൾ ഒരു "പ്രൈവറ്റ്" കീ ജനറേറ്റ് ചെയ്യപ്പെടും. അത് നിങ്ങൾ രഹസ്യമായി സൂക്ഷിക്കണമെന്ന് മാത്രം. ആ പ്രൈവറ്റ് കീ ഉണ്ടെങ്കിൽ മാത്രമേ നിങ്ങളുടെ അക്കൗണ്ടിലേക്ക് ലോഗിൻ ചെയ്യാൻ കഴിയൂ. അതിന്റെ കൂടെ തന്നെ ഒരു "പബ്ലിക്ക്" കീയും ഉണ്ടാകും. ആ കീ ആണ് മറ്റുള്ളവർ കാണുന്നത്. ഇതുകൂടാതെ, റ്റ്വിറ്റർ ഹാൻഡിൽ പോലെ ഒരു ഐഡിയും ഉണ്ടാക്കാൻ കഴിയും.
- പ്രൈവറ്റ് കീ രഹസ്യമായി സൂക്ഷിക്കണം
- പബ്ലിക്ക് കീ മറ്റുള്ളവർക്ക് കാണാൻ സാധിക്കും/ഷെയർ ചെയ്യാവുന്നതാണ്.
എവിടെ സൈനപ്പ് ചെയ്യും?
ആദ്യം നിങ്ങളുടെ ഫോണിൽ മേൽപ്പറഞ്ഞതിൽ ഒരു അപ്പ് ഇൻസ്റ്റാൾ ചെയ്യുക. എന്നിട്ട് അതിൽ തന്നെ സൈനപ്പ് ചെയ്യാൻ കഴിയും. അതല്ല എങ്കിൽ, https://nosta.me, https://nostrudel, https://primal.net എന്നിവയിലൊന്നിൽ സൈനപ്പ് ചെയ്യാവുന്നതാണ്.
ശ്രദ്ധിക്കേണ്ട കാര്യം, ആ പ്രൈവറ്റ് കീ കളഞ്ഞ് പോകാതെ സൂക്ഷിക്കണം. അത് മറ്റുള്ളവരുമായി ഷെയർ ചെയ്യരുത്.
ഇത്രയുമായാൽ നിങ്ങൾക്ക് നൊസ്റ്ററിൽ ഒരു അക്കൗണ്ട് ആയി... ആദ്യം എന്നെ തന്നെ ഫോളോ ചെയ്തോളൂ!! :ഡ് My profile: nostr:npub1dqcvgz20g2sn3venz47pxzjn2w6pf8xxs03vrrrwqp8z9lchce2ssj9fsy
നമ്മടെ റ്റ്വിറ്ററിന്റെ ഫൗണ്ടർ ജാക്ക് അണ്ണന്റെ അക്കൗണ്ട്: nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
നൊസ്റ്റർ പ്രോട്ടോക്കോൾ ഡെവലപ്മെന്റിന്റെ ഒരു ലീഡ് - കൂടുതൽ കാര്യങ്ങൾ അറിയാൻ ഡെറിക്കിനെ ഫോളോ ചെയ്യാം: nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424
നൊസ്റ്റർ ഒരു സോഷ്യൽ മീഡിയ പ്ലാറ്റ്ഫോം എന്നതിലുപരി ഒരു ഇക്കോസിസ്റ്റം ആണ്.
വരും നാളുകളിൽ കൂടുതൽ വിവരങ്ങൾ എഴുതാം: 1. Technical details - How this thing runs 2. How Nostr has decoupled monetary transactions from a centralized authority? 3. Zapping 3. Nostr Implementation Possibilities (NIPs) * - This is the most interesting thing I liked in Nostr*
Browse more: 1. https://nostr.com/ 2. https://nostrapps.com/
-
 @ b183a855:1d20ab46
2025-03-22 03:43:22
@ b183a855:1d20ab46
2025-03-22 03:43:22A 9080Bet se destaca no universo das plataformas de entretenimento online, oferecendo uma vasta gama de jogos e uma experiência de usuário que cativa e fideliza. Com um design moderno, interativo e fácil de usar, a plataforma se torna um local ideal para quem busca diversão e emoção ao alcance de um clique. Neste artigo, vamos explorar a introdução da plataforma, os jogos que ela oferece e o que torna a experiência do jogador única.
Introdução à Plataforma 9080Bet A 9080Bet chegou ao mercado com uma proposta de simplificar e inovar a experiência dos jogadores. Ao navegar pela plataforma, é possível perceber a atenção aos detalhes, com um layout intuitivo e uma navegação rápida, sem complicações. A interface é adaptada tanto para dispositivos móveis quanto para desktop, garantindo que os jogadores possam acessar seus jogos favoritos a qualquer hora e de qualquer lugar, seja no trabalho, em casa ou em trânsito.
Além disso, a plataforma conta com uma segurança robusta, utilizando criptografia de ponta para proteger as informações dos usuários. Isso cria um ambiente confiável para que os jogadores se sintam seguros ao realizar transações financeiras e interagir com outros membros da comunidade. A 9080bet também oferece suporte ao cliente eficiente, com uma equipe pronta para ajudar em caso de dúvidas ou problemas, garantindo que os usuários tenham uma experiência sem interrupções.
Variedade de Jogos na 9080Bet A 9080Bet não deixa nada a desejar quando o assunto é diversidade de jogos. Seja você um fã de jogos de cartas, roletas, máquinas de vídeo ou até mesmo esportes virtuais, a plataforma oferece uma vasta seleção de opções que atendem a todos os gostos e estilos de jogo. A variedade é um dos maiores atrativos da plataforma, garantindo que todos os jogadores encontrem algo que se encaixe nas suas preferências.
Jogos de mesa e cartas: Para os amantes de jogos de estratégia e habilidade, a 9080Bet oferece diversas opções de jogos de cartas como blackjack e poker, além de diferentes versões de roletas, onde o jogador pode testar sua sorte e agilidade. A dinâmica desses jogos proporciona uma experiência envolvente, desafiando os jogadores a melhorarem suas estratégias a cada nova rodada.
Máquinas de vídeo: As slot machines da 9080Bet são outro grande atrativo. Com uma infinidade de temas e funcionalidades, as máquinas de vídeo trazem aos jogadores a possibilidade de ganhar prêmios em dinheiro de forma divertida e emocionante. Além disso, os jackpots progressivos adicionam uma camada extra de emoção, com prêmios que aumentam conforme os jogadores participam.
Esportes virtuais: Para quem é fã de esportes, a 9080Bet também oferece uma vasta gama de esportes virtuais, permitindo que os jogadores apostem e acompanhem competições simuladas de futebol, corridas de cavalos, e muito mais. Esses jogos oferecem uma dinâmica rápida e envolvente, com odds ajustadas para garantir que o jogador tenha sempre uma nova oportunidade de vitória.
Além disso, a plataforma constantemente atualiza seu portfólio de jogos, trazendo novas opções e melhorias, para que os jogadores nunca fiquem entediados. A 9080Bet se compromete a oferecer uma experiência dinâmica e cheia de novidades.
A Experiência do Jogador na 9080Bet O que realmente diferencia a 9080Bet de outras plataformas é a experiência do jogador. A plataforma foi projetada pensando em cada detalhe para garantir que os usuários desfrutem de uma jornada de entretenimento agradável e imersiva.
Interface amigável: A navegação pela plataforma é simples e intuitiva. Não importa se você é um jogador iniciante ou experiente, a estrutura da 9080Bet facilita o acesso a todas as opções de jogo e serviços. As informações são apresentadas de forma clara, permitindo que o jogador encontre rapidamente o que deseja.
Promoções e bônus: A 9080Bet se preocupa em recompensar seus jogadores de diversas formas. Além das opções de jogos, a plataforma oferece promoções, bônus e recompensas para manter a experiência ainda mais emocionante. Essas ofertas são perfeitas para quem quer aumentar suas chances de ganhar, oferecendo vantagens extras que tornam o jogo mais dinâmico e acessível.
Transações financeiras rápidas e seguras: A plataforma se destaca por permitir que os jogadores façam depósitos e retiradas de forma rápida e segura. A 9080Bet oferece múltiplas opções de pagamento, incluindo carteiras digitais, cartões de crédito e outros métodos populares, garantindo que todos os jogadores possam realizar transações com facilidade e segurança.
Atendimento ao cliente: A experiência do jogador também é enriquecida por um suporte ao cliente eficiente e amigável. A 9080Bet conta com uma equipe altamente treinada, disponível 24 horas por dia, 7 dias por semana, para resolver quaisquer dúvidas ou problemas que possam surgir durante a navegação ou o jogo. Esse suporte faz toda a diferença, proporcionando uma sensação de segurança e tranquilidade aos jogadores.
Conclusão A 9080Bet é uma plataforma de entretenimento online que oferece uma experiência única e completa para os jogadores. Com uma interface amigável, uma vasta gama de jogos emocionantes e um suporte ao cliente de alta qualidade, a plataforma se destaca no mercado e conquista jogadores de todos os perfis. Seja para quem busca diversão rápida, seja para quem deseja testar suas habilidades, a 9080Bet é a escolha ideal para quem quer se divertir com segurança e inovação. Se você ainda não experimentou, vale a pena conferir o que esta plataforma tem a oferecer!
-
 @ b183a855:1d20ab46
2025-03-22 03:42:34
@ b183a855:1d20ab46
2025-03-22 03:42:34O 8385 surgiu com o objetivo de proporcionar aos usuários uma plataforma robusta e de fácil acesso para diversas opções de entretenimento online. Desde sua criação, a plataforma tem se destacado pela sua interface simples e amigável, que permite aos jogadores navegar facilmente por uma grande variedade de jogos e funcionalidades. O design responsivo e a facilidade de uso são elementos essenciais para garantir que a experiência do usuário seja fluida e envolvente, sem a necessidade de conhecimentos técnicos aprofundados.
Além de sua interface moderna, a plataforma 8385 é totalmente compatível com dispositivos móveis e desktop, oferecendo a flexibilidade para que os jogadores possam acessar seus jogos favoritos em qualquer lugar e a qualquer momento. Esse compromisso com a acessibilidade é um dos pilares que tornam a plataforma 8385 uma escolha atraente para os entusiastas de entretenimento digital.
O processo de registro na plataforma é simples e rápido, permitindo que novos usuários criem uma conta em poucos minutos. Uma vez registrados, os jogadores têm acesso a uma vasta gama de recursos, incluindo suporte ao cliente eficiente, promoções especiais, e a capacidade de personalizar sua experiência de acordo com suas preferências.
Jogos na Plataforma 8385: Variedade e Qualidade para Todos os Gostos O portfólio de jogos oferecido pela plataforma 8385 é um dos maiores atrativos para os jogadores. Com opções que vão desde jogos de habilidade até títulos de sorte e estratégia, a plataforma busca agradar a uma vasta gama de interesses e preferências. Os jogos são desenvolvidos por algumas das maiores empresas de jogos do mundo, garantindo que a qualidade gráfica, o som e a jogabilidade sejam de alto nível.
Os jogadores podem explorar diferentes categorias de jogos, como jogos de mesa, títulos de roleta e blackjack, além de uma impressionante coleção de slots e jogos de cartas. Cada jogo foi projetado para garantir uma experiência divertida e empolgante, com gráficos vívidos, animações fluidas e mecânicas de jogo inovadoras.
A plataforma 8385 também se destaca pela integração de recursos sociais, permitindo que os jogadores interajam com outros usuários, compartilhem suas conquistas e até compitam em torneios e desafios. Esses recursos sociais criam um ambiente mais dinâmico e participativo, onde os jogadores podem se conectar com outras pessoas que compartilham os mesmos interesses e paixão por jogos online.
Outro aspecto que torna os jogos da plataforma 8385 atraentes é a possibilidade de jogá-los em modo gratuito ou com apostas, oferecendo uma experiência completa sem a necessidade de comprometer grandes quantias de dinheiro. Essa flexibilidade é ideal para jogadores iniciantes ou para aqueles que simplesmente querem se divertir sem riscos financeiros.
A Experiência do Jogador: Um Compromisso com a Satisfação A experiência do jogador na plataforma 8385 é enriquecida por uma série de recursos que colocam a satisfação do usuário como prioridade. Desde o momento em que um jogador acessa a plataforma, é possível perceber o cuidado em oferecer uma experiência de navegação e jogo sem interrupções, com alta performance em qualquer tipo de dispositivo.
A plataforma oferece uma variedade de métodos de pagamento, permitindo que os jogadores façam depósitos e retiradas de forma simples e segura. Isso é importante para garantir que os jogadores possam gerenciar suas transações financeiras com facilidade e sem preocupações. A segurança é outro ponto crucial, com tecnologia de ponta para proteger dados pessoais e financeiros, proporcionando um ambiente seguro para que os jogadores se concentrem em sua diversão.
Além disso, o suporte ao cliente é uma das grandes forças da plataforma 8385. A equipe de suporte está disponível 24/7, pronta para ajudar com qualquer problema ou dúvida que o jogador possa ter. Seja por chat ao vivo, e-mail ou outros canais de comunicação, o suporte da plataforma é eficiente e comprometido em garantir que a experiência do usuário seja a melhor possível.
Com suas promoções regulares, bônus e programas de fidelidade, a plataforma 8385 recompensa seus jogadores de várias maneiras, tornando a experiência ainda mais gratificante. Esses incentivos não só ajudam os jogadores a aumentar suas chances de vitória, mas também criam um senso de comunidade, em que os usuários sentem-se valorizados e reconhecidos.
Conclusão A plataforma 8385 vem para transformar a forma como os jogadores experimentam o entretenimento digital online. Com sua interface intuitiva, portfólio diversificado de jogos e uma experiência do jogador imersiva, ela se posiciona como uma excelente opção para aqueles que buscam qualidade, diversão e segurança. A constante inovação e atenção aos detalhes tornam a plataforma 8385 uma das melhores opções no mercado, garantindo que a diversão e a satisfação do usuário estejam sempre em primeiro lugar.
-
 @ b183a855:1d20ab46
2025-03-22 03:41:51
@ b183a855:1d20ab46
2025-03-22 03:41:51A plataforma 5526 surge como uma excelente opção para os entusiastas de jogos online, oferecendo uma experiência dinâmica e envolvente para jogadores de todos os níveis. Com uma interface moderna, jogos diversificados e uma abordagem focada no usuário, a plataforma tem ganhado popularidade rapidamente entre aqueles que buscam se divertir e desafiar suas habilidades de forma inovadora.
Plataforma 5526: Uma Introdução ao Novo Estilo de Jogo A 5526 é uma plataforma de jogos que busca se destacar pela sua versatilidade e facilidade de acesso. Com um design intuitivo e responsivo, os jogadores podem acessar o conteúdo da plataforma de qualquer lugar, seja em dispositivos móveis ou desktop. A plataforma é conhecida por seu ambiente amigável e acessível, o que facilita a entrada de novos jogadores enquanto mantém o alto nível de engajamento para os veteranos.
Um dos maiores diferenciais da 5526 é sua biblioteca de jogos, que abrange uma vasta gama de categorias, incluindo ação, estratégia, puzzles e muito mais. Isso permite que os jogadores escolham jogos que mais se alinhem com suas preferências, criando uma experiência personalizada de diversão e entretenimento. O design da plataforma também é bastante otimizado, garantindo que os jogos carreguem rapidamente e que a navegação seja sem fricções.
Além disso, a 5526 oferece uma plataforma segura, com sistemas de criptografia de ponta para garantir a proteção dos dados dos jogadores. O processo de criação de contas é simples e rápido, com múltiplas opções de pagamento que garantem que os jogadores possam fazer depósitos e retiradas de forma prática e eficiente.
A Diversidade de Jogos na 5526: Uma Introdução ao Mundo do Entretenimento A 5526 é lar de uma impressionante variedade de jogos que atendem a diferentes gostos e preferências. Seja você um amante de jogos de estratégia que adora um bom desafio mental ou alguém que prefere a adrenalina de jogos rápidos e emocionantes, a plataforma tem algo a oferecer.
Entre os jogos mais populares estão aqueles que exigem habilidade e planejamento, com mecânicas que desafiam os jogadores a pensarem de forma criativa e estratégica. Esses jogos são ideais para aqueles que buscam uma experiência mais profunda e envolvente, onde cada movimento pode fazer a diferença entre o sucesso e a falha. Eles são projetados para testar a paciência e o raciocínio lógico, proporcionando uma experiência de aprendizado constante.
A plataforma também conta com opções mais acessíveis para quem deseja apenas passar o tempo de forma descontraída, com jogos simples e intuitivos que são fáceis de entender, mas ainda assim divertidos e desafiadores. Esses jogos são perfeitos para quem está começando sua jornada no mundo dos jogos online, pois oferecem uma introdução suave sem perder o apelo.
Além dos jogos tradicionais, a 5526 também apresenta títulos inovadores, com mecânicas únicas e gráficos impressionantes, criando uma experiência visualmente rica e excitante. Os desenvolvedores da plataforma frequentemente atualizam sua biblioteca com novos lançamentos, garantindo que os jogadores tenham acesso às últimas novidades e tendências do mercado.
A Experiência do Jogador na Plataforma 5526: O Que Esperar A experiência do jogador na plataforma 5526 é desenhada para ser imersiva, fluida e prazerosa. Desde o momento em que o jogador entra na plataforma até a navegação entre os jogos, tudo é pensado para garantir que cada interação seja agradável e intuitiva. A interface é clara, com fácil acesso a menus e informações relevantes sobre cada jogo.
Outro ponto positivo é o suporte ao cliente, que se destaca pela rapidez e eficiência. A plataforma conta com uma equipe de atendimento ao cliente disponível 24/7, pronta para resolver quaisquer problemas ou dúvidas que os jogadores possam ter, seja durante o cadastro, transações financeiras ou no momento do jogo.
Além disso, a 5526 oferece uma comunidade de jogadores ativa, onde os usuários podem interagir, compartilhar dicas e até mesmo participar de torneios ou eventos especiais. Isso cria uma sensação de pertencimento, fazendo com que os jogadores se sintam parte de algo maior, com oportunidades de socializar e competir de maneira saudável.
A plataforma também se destaca pela sua flexibilidade. Ao permitir que os jogadores escolham entre uma ampla gama de jogos, com diferentes níveis de dificuldade e estilos, ela consegue agradar a todos os tipos de públicos. A variedade de modos de jogo também é um atrativo: além de jogos solo, a plataforma permite que os jogadores se conectem com outros em partidas multijogador, promovendo ainda mais a interação e a competição.
Outro aspecto importante é o incentivo ao progresso e ao aprimoramento do jogador. Muitos jogos dentro da plataforma 5526 oferecem sistemas de recompensas, onde os jogadores podem ganhar itens exclusivos ou bônus conforme avançam nas partidas. Isso cria uma sensação de conquista e satisfação, incentivando os jogadores a se dedicarem ainda mais para alcançar novos desafios e objetivos.
Em resumo, a 5526 não é apenas uma plataforma de jogos online, mas um espaço onde os jogadores podem se divertir, aprender e se conectar com outros. A experiência de jogo é envolvente e dinâmica, com uma interface amigável e um vasto portfólio de opções. Seja você um iniciante ou um jogador experiente, a 5526 tem algo a oferecer para todos.
-
 @ d5c3d063:4d1159b3
2025-03-22 03:31:14
@ d5c3d063:4d1159b3
2025-03-22 03:31:14“คุณจะจัดการกับมลพิษฝุ่น PM2.5 โดยไม่ต้องอาศัยการออกกฎควบคุมจากรัฐได้ยังไง” ถ้าคุณเคยตั้งคำถามนี้ บทความนี้มีคำตอบ...และคำตอบอาจสวนทางกับความเชื่อของคุณโดยสิ้นเชิง . ลองย้อนกลับไปในช่วงต้นปีที่ผ่านมา ในวันที่กรมควบคุมมลพิษประกาศว่า “ค่าฝุ่น PM2.5 เกินมาตรฐานใน 43 จังหวัด” และโรงเรียนหลายแห่งต้องสั่งปิดชั่วคราว คุณอาจนึกถึงภาพผู้คนใส่หน้ากากเดินท่ามกลางหมอกควัน แล้วถามตัวเองว่า “เรากำลังแก้ปัญหานี้ด้วยวิธีที่ถูกต้องจริงหรือ?” ฝุ่น PM2.5 ปัญหาของ "Externalities" หรือปัญหาของการไม่มี "สิทธิในทรัพย์สิน" ที่ชัดเจน? . ในคลิปวิดีโอ จาก CDC Bitcointalk EP3 เมื่อปี 2020 อ.พิริยะ สัมพันธารักษ์ ได้เสนอแนวคิดที่ขัดแย้งกับสิ่งที่รัฐและสื่อกระแสหลักมักพูดถึงเสมอเมื่อพูดถึงฝุ่น PM2.5 ว่า... “ฝุ่น PM2.5 ไม่ใช่ปัญหาที่จะถูกแก้ได้ด้วยการออกกฎหมายควบคุมหรือแจกหน้ากากฟรี...แต่ต้องแก้ด้วยการ สร้างกลไกตลาดและสิทธิในทรัพย์สินที่ชัดเจน เพื่อให้คนที่ก่อมลพิษต้อง จ่าย ให้กับผู้ได้รับผลกระทบ” . . แล้วมันเกี่ยวอะไรกับ Hazlitt ??? Henry Hazlitt กล่าวไว้ในบทแรกของ Economics in One Lesson ว่า ความผิดพลาดทางเศรษฐศาสตร์ส่วนใหญ่เกิดจากการมองแค่ผลกระทบเฉพาะหน้า และมองเฉพาะผลที่เกิดกับคนบางกลุ่ม แต่ละเลยผลระยะยาวกับทั้งระบบและมองไม่เห็น “สิ่งที่ไม่ปรากฏต่อสายตา” เช่นเดียวกับกรณีฝุ่น PM2.5 . การที่รัฐเข้ามาควบคุม เช่น การสั่งห้ามเผา อาจฟังดูดีในระยะสั้น แต่มันยังไม่มีแรงจูงใจทางเศรษฐกิจให้ผู้เผาหยุดทำ เพราะต้นทุนการก่อมลพิษยัง “ฟรี” ถ้ามลพิษมีต้นทุน คนก็จะคิดก่อนเผา . ลองนึกถึงแนวคิดของการซื้อ-ขายสิทธิในเชิงสมัครใจ (Voluntary Emissions Trading) ซึ่งต่างจากระบบ Cap-and-Trade ที่ภาครัฐเป็นผู้กำหนดเพดานและบังคับใช้ แต่ในแนวทางตลาดเสรีนั้น หากสิทธิในอากาศหรือพื้นที่ถูกระบุอย่างชัดเจน เจ้าของสิทธิสามารถตกลงซื้อขายกับผู้ก่อมลพิษได้โดยตรงโดยไม่ต้องพึ่งรัฐเป็นคนกลาง . แล้วในบริบทแบบ Hazlitt ถ้าคุณให้ความเป็นเจ้าของอากาศแก่คนในเมือง คนเหล่านั้นสามารถ “ฟ้องร้อง” หรือ “เรียกค่าเสียหาย” จากผู้ที่ปล่อยมลพิษได้ ซึ่งจะทำให้เกิดต้นทุนที่แท้จริงกับผู้ก่อมลพิษ . กลไกตลาดไม่ได้หมายถึง “แค่ปล่อยให้ทุกอย่างเป็นไปตามธรรมชาติ” แต่มันคือการสร้างระบบ “แรงจูงใจ” ที่ทำให้คนเลือกทางออกที่ดีที่สุดเอง โดยไม่ต้องมีใครมาบังคับ . ผมนึกถึงที่ Murray Rothbard เคยพูดไว้ว่า “สิทธิในทรัพย์สิน คือสิ่งเดียวที่จะทำให้ผู้คนมีแรงจูงใจในการดูแลสิ่งแวดล้อม ไม่ใช่คำสั่งจากเจ้าหน้าที่รัฐ” เพราะเมื่อคุณเป็นเจ้าของสิ่งใด คุณย่อมมีแรงจูงใจในการรักษามัน มากกว่าการที่รัฐสั่งให้คุณต้องแคร์ ดังนั้น แทนที่จะใช้ระบบ Cap-and-Trade ที่รัฐควบคุม บทความนี้เสนอแนวทางที่ไม่พึ่งพารัฐ เช่น ชุมชนหรือเอกชนรวมตัวกันตกลงไม่เผา และใช้กลไกจ่ายชดเชยกันเองหากละเมิดสิทธิ หรือกรณีเจ้าของบ้านฟ้องโรงงานที่ทำให้บ้านหรือพื้นที่ที่อยู่อาศัยเสียหาย ทั้งหมดนี้คือการใช้สิทธิในทรัพย์สินและกลไกกฎหมายแพ่งเพื่อสร้างแรงจูงใจ โดยไม่ต้องให้รัฐเข้ามาควบคุมหรือกำกับ แต่ยังคงอาศัยศาลเพื่อปกป้องสิทธิ เมื่อเกิดการละเมิด . . แล้วทำไมแนวคิดแบบให้รัฐควบคุมถึงล้มเหลวเสมอ...? Hazlitt เตือนว่า รัฐมักคิดว่าตัวเองมองเห็นผลดี แต่ไม่เคยมองเห็นผลเสียที่มองไม่เห็น เช่น เมื่อรัฐประกาศห้ามเผาซังข้าวโพดหรือฟางข้าวในภาคเหนือโดยเด็ดขาด ชาวไร่จำนวนมากที่เคยใช้วิธีเผาเพื่อคืนโพแทสเซียมและแร่ธาตุให้ดินแบบต้นทุนต่ำ ต้องหันไปซื้อปุ๋ยเคมีแทน ซึ่งมีราคาสูง กลายเป็นภาระทางเศรษฐกิจที่ถาโถมใส่เกษตรกรรายย่อยโดยตรง ทั้งที่พวกเขาไม่ได้มีทางเลือกอื่นมากนัก นี่คือ “ต้นทุนที่มองไม่เห็น” ตามที่ Hazlitt เตือน รัฐเห็นแค่ "ผลดีเฉพาะหน้า" เช่น ค่าฝุ่นลดชั่วคราว แต่ไม่เห็นผลเสียระยะยาวต่อความยั่งยืนของชุมชนเกษตรกรรม แล้วทั้งหมดนี้คือการเอื้อประโยชน์ให้คนกลุ่มหนึ่ง แต่กระจายต้นทุนไปให้ทั้งสังคม ซึ่งตรงกับที่ Hazlitt วิจารณ์ในหนังสือ . . แล้วเสรีภาพในตลาดกับอากาศที่สะอาด...ไปด้วยกันได้ไหม? อ.พิริยะ ยกตัวอย่างบิตคอยน์ว่าเป็นระบบที่ไม่ต้องพึ่งรัฐหรือคนกลาง แต่สามารถสร้างแรงจูงใจทางเศรษฐกิจให้คนทั่วโลกเข้าร่วมโดยสมัครใจ และตรวจสอบได้แบบโปร่งใสผ่านกลไกกระจายศูนย์ แสดงให้เห็นว่าแนวคิดตลาดเสรีสามารถทำงานได้จริงหากออกแบบแรงจูงใจให้เหมาะสม แนวคิดเดียวกันนี้ใช้ได้กับปัญหาฝุ่น PM2.5 ถ้าเรามองว่าอากาศคือทรัพยากรที่มีเจ้าของ และอนุญาตให้มีการซื้อ-ขายหรือฟ้องร้องโดยไม่ต้องพึ่งรัฐเข้ามาจัดการจากส่วนกลาง คำตอบคือ ได้...ถ้าเราให้ “ตลาด” ทำงาน -ถ้ามลพิษทำให้ที่อยู่อาศัยเสียหาย เราสามารถฟ้องผู้ก่อมลพิษได้ -ถ้าโรงงานต้องซื้อสิทธิปล่อยมลพิษ พวกเขาจะมีแรงจูงใจลดฝุ่น -ถ้าประชาชนขาย “เครดิตอากาศสะอาด” ได้ จะเกิดอาชีพใหม่ เช่น การปลูกป่าคาร์บอน นี่ไม่ใช่จินตนาการ แต่คือหลักคิดที่กำลังเกิดขึ้นในหลายประเทศ เช่น แคลิฟอร์เนีย เยอรมนี และสิงคโปร์ . . สรุปเศรษฐศาสตร์ของฝุ่น...อยู่ที่ใครจ่ายต้นทุน Hazlitt ไม่เคยพูดถึง PM2.5 โดยตรง แต่แนวคิดของเขาชัดเจนว่า ทุกนโยบาย ต้องถูกมองในแง่ของผลกระทบที่มองไม่เห็นในระยะยาวด้วย และนั่นคือสิ่งที่รัฐไทยและคนส่วนใหญ่ยังไม่เข้าใจเมื่อพูดถึงปัญหาฝุ่น ตลาดไม่ได้ไร้หัวใจ แต่มัน บีบให้คนรับผิดชอบในสิ่งที่ตัวเองก่อ ข้อเสนอเชิงนโยบาย -ส่งเสริมการกำหนดสิทธิในอากาศหรือสิทธิในพื้นที่อยู่อาศัยให้ชัดเจน -เปิดตลาดซื้อ-ขาย “เครดิตฝุ่นสะอาด” สำหรับภาคอุตสาหกรรม โดยเน้นว่าเป็นระบบที่เกิดจากความสมัครใจของภาคเอกชนหรือชุมชน ไม่อยู่ภายใต้การกำกับหรือควบคุมโดยรัฐ -ส่งเสริมการลงทุนเอกชนด้านเซ็นเซอร์วัดฝุ่นแบบกระจายตัว (decentralized air quality monitoring) . . แล้วคุณล่ะ คิดว่าฝุ่นควรจัดการโดยรัฐ หรือโดยตลาด 💬 คุณคิดว่าเราควรเริ่มสร้าง “ระบบสิทธิและแรงจูงใจเพื่อรักษาคุณภาพอากาศ” ได้อย่างไร หรือทำไมคุณยังเชื่อว่ารัฐควรเป็นคนจัดการควบคุมทั้งหมดอยู่ และถ้าคุณยังเชื่อว่ารัฐควรเป็นผู้ดูแลควบคุม ลองถามตัวเองดูว่ารัฐเคยสามารถจัดการอะไรได้อย่างมีประสิทธิภาพได้ในระยะยาวหรือไม่ หากคุณสนใจแนวคิดตลาดเสรีและเศรษฐศาสตร์แบบเข้าใจง่าย ๆ ผมแนะนำหนังสือ Economics in One Lesson โดย Henry Hazlitt หนังสือที่เปลี่ยนวิธีคิดของคนทั้งโลกเกี่ยวกับ “สิ่งที่มองไม่เห็น” ของเศรษฐกิจ มีฉบับแปลไทยแล้วนะ 🙃
เศรษฐศาสตร์เล่มเดียวจบ #EIOL #Siamstr
EconomicsinOneLesson #RightBook #PM25
-
 @ 234035ec:edc3751d
2025-03-22 02:34:32
@ 234035ec:edc3751d
2025-03-22 02:34:32I would like to preface this idea by stating that I am by no means a computer engineer and lack significant technical knowledge, and therefore may be overlooking significant obstacles to implementing this idea. My reason for writing this paper is in hopes that developers or others who are more "in the know" than me could provide feedback.
The Success of Polymarket
Over recent months, Polymarket has garnered many headlines—mainly for its accurate prediction markets surrounding the 2024 presidential election. On Polymarket, users can purchase futures contracts that will either pay out $1 in USDC at maturity if the prediction is correct or will become worthless if the prediction is incorrect. Market participants can freely trade these futures at the current price up until maturity, allowing for efficient price discovery.
We’ve known for quite some time that free markets are the most efficient way of pricing goods and services. Polymarket has now demonstrated just how effective they can be in pricing potential outcomes as well.
The issue I have with this application is that it is built on the Polygon network—a proof-of-stake side chain of Ethereum. Users are subject to KYC regulations and do not have the ability to create markets themselves. While the core idea is powerful, I believe it has been built on a foundation of sand. We now have the tools to build something similar—but much more decentralized, censorship-resistant, and sustainable.
A Bitcoin-Based Prediction Market
It seems to me that Chaumian eCash, in combination with Bitcoin and Nostr, could be used to create a truly decentralized prediction marketplace. For example, multiple eCash mints could issue tokens that represent specific potential outcomes. These tokens would be redeemable for 100 sats at a predetermined block height if the prediction is correct—or become irredeemable if the prediction is incorrect.
Redemption would be based on consensus from the chosen oracles—trusted Nostr Npubs—with strong reputations and proven track records. Anyone could create a market, and users could buy, sell, and trade eCash tokens privately. This approach preserves the power of markets while eliminating the need for custodians, KYC, or dependence on unreliable chains.
What we would have is a trust-minimized, privacy-preserving, Bitcoin-native prediction market that resists censorship and allows for true global participation. Feedback, critique, and collaboration are welcome.
Next Steps and Vision
The potential for system like this is immense. Not only would it enable peer-to-peer speculation on real-world outcomes, but it would also open the door to a more accurate reflection of public sentiment. With free market incentives driving truth-seeking behavior, these prediction markets could become powerful tools for gauging probabilities in politics, finance, sports, science, and beyond.
Each mint could specialize in a specific domain or geographic region, and users could choose the ones they trust—or even run their own. The competition between mints would drive reliability and transparency. By using Nostr for oracle communication and event creation, we keep the entire system open, composable, and censorship-resistant.
Markets could be created using a standardized Nostr event type. Resolution data could be posted and signed by oracles in a verifiable way, ensuring anyone can validate the outcome. All of this could be coordinated without a centralized authority, enabling pseudonymous participation from anyone with an internet connection and a Lightning wallet.
In the long run, this system could offer a viable alternative to corrupted media narratives, rigged polling, and centrally controlled information channels. It would be an open-source tool for discovering truth through economic incentives—without requiring trust in governments, corporations, or centralized platforms.
If this idea resonates with you, I encourage you to reach out, build on it, criticize it, or propose alternatives. This isn’t a product pitch—it’s a call to experiment, collaborate, and push the frontier of freedom-forward technologies.
Let’s build something that lasts.
Bitcoin is our base layer. Markets are our discovery engine. Nostr is our communication rail. Privacy is our defense. And truth is our goal.
-
 @ 30b99916:3cc6e3fe
2025-03-22 12:12:00
@ 30b99916:3cc6e3fe
2025-03-22 12:12:00constitution
Article V of the Constitution of the United States
With your engagement, there is a glimmer of hope that the people can reclaim our captured US government. The entrenched politicians are counting on your NON-ENGAGEMENT to remain in control.
Please take the time to educate yourself about the Constitution.
Now get engaged with your local Convention of States movement.
-
 @ 86fd18bc:02060045
2025-03-22 01:49:59
@ 86fd18bc:02060045
2025-03-22 01:49:59{"coverurl":"https://cdn.nostrcheck.me/86fd18bc230a2b77cc2fe5b2b55597fcf7b89f4076e55b4c4b1864f802060045/1975cd8ece974dd5fda1568d8c35fc3524d9bc2373a2c5a70ad6637ba5ea042a.webp","title":"鹿茸的价值","author":"罗马古道"}
-
 @ 86fd18bc:02060045
2025-03-22 01:26:11
@ 86fd18bc:02060045
2025-03-22 01:26:11{"coverurl":"https://cdn.nostrcheck.me/86fd18bc230a2b77cc2fe5b2b55597fcf7b89f4076e55b4c4b1864f802060045/df42dd31276fc2546c2c195e0f1b0bb36d766435ed54f5765b67de08ab933aed.webp","title":"我看看到底是什么个事情","author":"不看你"}
-
 @ 86fd18bc:02060045
2025-03-22 01:24:37
@ 86fd18bc:02060045
2025-03-22 01:24:37{"coverurl":"https://cdn.nostrcheck.me/86fd18bc230a2b77cc2fe5b2b55597fcf7b89f4076e55b4c4b1864f802060045/7011858a53af8d7f0eed0588df5ca99fb27dd70d3d5f3e7034a62ff4f06d2455.webp","title":"热带植物","author":"爱观察"}
-
 @ 4abac58c:54c71964
2025-03-22 01:21:01
@ 4abac58c:54c71964
2025-03-22 01:21:01Introduction Bitcoin is often seen as a store of value, "digital gold" designed to resist censorship and central control. But few people realize how fast and easy it can be to use Bitcoin for small, everyday transactions. Enter the Lightning Network: a second-layer solution that enables near-instant, low-fee payments. This article will explain how it works, why it matters, and how you can use it today.
What Is the Lightning Network? The Lightning Network (LN) is a layer built on top of the Bitcoin blockchain. Its primary purpose is to make Bitcoin transactions faster and cheaper by creating payment channels between users. Instead of recording every transaction on the main blockchain, two users can open a channel, transact as many times as they want, and settle the final balance on-chain later.
This means no long confirmation times or high fees. Payments can take less than a second and cost a fraction of a cent.
Why It Matters Bitcoin's main chain can process around 7 transactions per second. In contrast, Visa can handle thousands. This makes scaling Bitcoin for everyday use a challenge. Lightning changes that by handling most activity off-chain.
Imagine buying coffee, tipping a content creator, or paying for a digital download with Bitcoin. Lightning makes this seamless and instant. It also supports micropayments, enabling new business models like pay-per-article or per-minute streaming.
How to Start Using Lightning Getting started is easier than ever:
- Download a Lightning Wallet: Try apps like Wallet of Satoshi, Phoenix, or Breez.
- Get Some Sats: Sats (short for satoshis, the smallest unit of Bitcoin) can be received via another wallet, an exchange, or earned.
- Start Spending or Zapping: Use your Lightning wallet to pay for services, tip content creators on platforms like Nostr, or support open-source projects.
Real-World Use Cases - Nostr + Zaps: Nostr, a decentralized social media protocol, integrates Lightning payments directly. Users can "zap" posts they like, sending Bitcoin instantly to the author. This has created a native reward system for content. - Bitrefill: Buy gift cards with Lightning. - Podcasting 2.0: Stream sats to podcasters per minute of audio consumed.
Citations and Resources - https://lightning.network - https://bitcoinmagazine.com/technical/the-lightning-network - https://walletofsatoshi.com - https://highlighter.com
Conclusion Bitcoin isn’t just digital gold—it’s programmable money. The Lightning Network shows how Bitcoin can work for everyday payments, from your morning coffee to rewarding your favorite content creator. If you’ve never tried it, now is the perfect time to explore this magical layer of the Bitcoin economy.
Call to Action Got a Lightning wallet already? Try zapping this article on Nostr or sharing your first Lightning transaction experience!
-
 @ 86fd18bc:02060045
2025-03-22 01:18:04
@ 86fd18bc:02060045
2025-03-22 01:18:04{"coverurl":"https://cdn.nostrcheck.me/86fd18bc230a2b77cc2fe5b2b55597fcf7b89f4076e55b4c4b1864f802060045/091b43cace7aafb7fe8278b0199d29c2e8d0bd7f064578d8cd740a64504cf0b7.webp","title":"1号楼的秘密","author":"跨马"}
-
 @ 69eea734:4ae31ae6
2025-03-22 01:16:01
@ 69eea734:4ae31ae6
2025-03-22 01:16:01Deutsche Version\ \ Recently, I was on Zoom with someone who has been involved in sustainable living for decades and has built a community around it. "I find it easier to talk to people on the right. They're more open." And then something like: "If you say something to the left that doesn't fit in with their concept, they immediately reject it reflexively."
This is someone who comes from a working-class town, sees too much power in the big corporations and is also sceptical about the state. Things that I would classify as traditionally left-wing.
Even though it often seems that this categorisation no longer makes sense, we still use the terms left and right - mainly along traditional party lines. In Germany, SPD, Greens and the Left (the BSW has been deemed not to fit in). In the UK, Labour. In the USA, the Democrats.
Why does the assessment I mentioned at the beginning ring so true to me? I want to get to the bottom of the difficulties I have with the group I once felt I belonged to one hundred per cent.
On the side of the good guys
There always seems to be a clear path. There is only one reasonable view. This reflects a simple, to-the-point truth. "If a country is attacked, it must be allowed to defend itself." That is incontestable. Just like "every person who dies because of Covid is one too many."
Additional, potentially relevant information is no longer of interest from that point onwards. The question of "How can this conflict be ended as quickly as possible?" hardly comes up at all. The roles are clear. The aggressor represents absolute evil, is solely to blame and is either mad or driven by imperial desires, probably both.
If it was all so clear, one wonders why people who simply wanted to give more context to what was happening - wouldn't it be good to know more context to a conflict in order to deal with it better? - were deprived of any platform. (1) They were also labelled in a way that justified simply not listening to them if a video did get through to someone. If everything was so clear, why not deal with the arguments on a factual base?
Even if you reached the conclusion that weapons should be supplied to Ukraine on a long-term basis - isn't it still worth knowing that there were already peace negotiations in Istanbul in March 2022, which were at a very advanced state, when Zelensky was advised by the UK and the USA to continue fighting ("We will support you")?
What perplexes me the most is how carelessly the war is being handled. How quickly we have landed on the side that is most likely to mean a long war and maximum profit for the arms industry. (2) "Putin started it and is solely to blame, and now we have to fight him to the max" trumps the possibility of even thinking about diplomatic channels.
Would this have been the case 20 years ago? Or 40? At school we sang ‘Where have all the flowers gone?’ many times, and it always touched me. On the radio you could hear Bruce Springsteen singing War, and Paul Hardcastle's Nineteen. All that seems forgotten now.
And even if it was Putin's long-cherished plan to invade Ukraine and take over parts of it: Why then was he so readily given an excuse? Why give him something that, if it can never be a real justification, can be interpreted as such by him? (3) In other words: If you look at recent history, this war appears to have been absolutely avoidable had the US behaved differently.
Instead, they supported Ukraine in defending "our values’" and saw "Western democracies" under threat. With Trump's inauguration, we can now see just how far American democracy has sunk.
The progressive-liberal world is now in an uproar. And easily overlooks the fact that under the Democrats, especially Obama, the foundations were laid for far-reaching censorship and manipulation of public opinion. Their effects were clearly visible to anyone who disagreed with the coronavirus regime, even those of us across the pond.
Why I don't feel comfortable: Because I have the feeling that, out of a need to be moral and good, people have gone down a wrong track a second time, again with disastrous consequences. Or rather, they didn't want to see their error of judgement the first time round, and continue in a similar way. Both times with a war logic which aims to crush an enemy, while neglecting enormous ‘collateral’ damage that follows on from it.
The Democrats as a reactive force
The article I started has been sitting here for a while, and there are so many ways to continue it. - My original plan covered so many topics that I will need to split it up into more texts.
Also, a number of further outrageous events have happened meanwhile. The Trump administration is now really taking on fascist overtones, with the internment of a leader of pro-Palestinian student protests, Mahmoud Khalil, and the deportation of over 200 alleged Venezuelan gang members to a security prison in El Salvador. The whole thing seems like a huge spectacle, with videos accompanied by music, reminiscent of advertising films. Something is being demonstrated here. Simply power? Malice, spite? The rule of law, which has not really worked for a long time, is thoroughly being undermined.
Every now and then a podcast comes along that amazes and impresses me, because it breaks the usual categorisations and at the same time expresses many truths.

Link to the podcast: https://jaredyatessexton.substack.com/p/we-are-in-the-crisis-a-conversation
Here's a woman, Danielle Moodie, who founded a radio station called Woke AF during Trump's first term, in conversation with author Jared Sexton, who writes a sub-stack called Notes from a collapsing state in addition to books. They address the events mentioned above, and remind us of Martin Niemöller's "Als die Nazis die Kommunisten holten..." (When the Nazis came for the Communists...) because of the lack of opposition.
Large sections, especially in the second half, are a merciless reckoning with the Democrats. According to the two, they are more concerned with keeping the stock market afloat than doing anything for disadvantaged citizens. The alleged support for minorities (floats at the Pride Parade, kneeling, etc.) was always just window dressing.
Moodie once exclaims that what happens again and again is this: "Democrats don't lose the plot, they don't even know where the fuck it is. ’ And Sexton once remarks that the opposition is more of a counterweight designed to keep things going the way they are. "The Democratic Party has become reactive and conservative and has no actual vision for solving any of the problems."
They touch on a few other things: That it's necessary to act in a decentralised way, and that you should start things even if you won't see the results of your actions yourself. And a few other things.
Not only from this podcast, but from many others, and from articles, it becomes clear that the Democrats - like the ‘left’ in many other countries - have their supporters mainly in the middle class, the "professioal-managerial class", and are -- perhaps often unconsciously -- more concerned with maintaining the status they have achieved than really caring about social issues.
In bed with the Russians
Another interesting publication I came across recently, is by a Russian couple who emigrated to America: Nefarious Russians. The podcast that goes along with it, is called In Bed with the Russians. It's very much about the cultural side of things, but not only.
What I found very interesting is the assessment of Evgenia, who grew up in Russia in the 90s. In short, that the country, or at least Moscow, was colonised by American culture. Her friends eventually made a good career for themselves and she was initially delighted with how everything developed. However, her friends themselves apparently didn't see it that way, but always looked longingly towards America, which they imagined to be much better. At some point, Evgenia realised that Russian culture had actually become a poor copy of American culture. - This is an abridged version and I hope not too distorted.
On Putin: The idea that he wants to recreate the Soviet Union is fundamentally wrong. He and his leadership team would much rather recreate the pre-revolutionary Russia.
I haven't found anything on whether NATO's eastward expansion played a role in the invasion of Ukraine. But the authors are definitely neither Trump nor Putin fans.
There's also interesting stories of ‘weaponised immigrants’, i.e. former Soviet citizens who were then immediately used for propaganda purposes against their old homeland.
Since I am writing about native Russians, I would also like to mention Tessa Lena, who for me was one of the most important authors in the Covid era, and who already in April 2020 saw through the technocracy that came with it. I am very grateful to her.
I wrote about the conflict with Russia because it is currently topical and gives rise to war propaganda. I have not found any justification for the fact that Russia is supposed to be on Germany's doorstep
My conclusion on the former left: It's a force that has forgotten its former ideals, indulges in declarations of solidarity and is otherwise more concerned with maintaining the status quo than wringing concessions from the state. It pushes for climate protection, but makes an exception for one of the biggest CO2 emitters, the military, which is not even discussed.
Perhaps it really is outdated to think in these categories. In any case, I no longer feel that I belong to any one direction.
The key is to find allies, regardless of which direction they come from. Building support structures outside of politics. The Commons is a good idea, and I want to write more about it in the future. For this time, I've landed on global politics, which ultimately it does influence what is happening locally. As always, it is important to keep the right balance.
(1): In Germany, one of the main figures treated like that is Gabriele Krone-Schmalz, who has given several well-founded presentations
(2): Antje Vollmer, Green politician and vice president of the German parliament, shortly before her death wrote impressively about rearmament and the transformation of the Greens into a party of war:: https://epaper.berliner-zeitung.de/article/ea77236b6b434f4d5fc01cace486274626d2c168ae5896b667f2d021d2ced5ce
(3): The comments on this article show how it is possible to have an open and respectful discussion. People from the Balkan states have their say here, who oppose the narrative that the revolutions in the former Soviet republics were always controlled by the USA. https://iainmcgilchrist.substack.com/p/laughter-in-heaven
This article was written with the Pareto-Client.
-
 @ 86fd18bc:02060045
2025-03-22 01:15:09
@ 86fd18bc:02060045
2025-03-22 01:15:09{"coverurl":"https://cdn.nostrcheck.me/86fd18bc230a2b77cc2fe5b2b55597fcf7b89f4076e55b4c4b1864f802060045/38923a0999d3e9723744a7e866c005a0fa9abdbf492cc9396e52399f6567aea0.webp","title":"遥远的星球","author":"卡瓦罗"}
-
 @ 69eea734:4ae31ae6
2025-03-22 01:12:46
@ 69eea734:4ae31ae6
2025-03-22 01:12:46Kürzlich war ich in einem Zoom-Gespräch mit jemand, der sich seit Jahrzehnten mit nachhaltigem Leben beschäftigt und eine Gemeinschaft darum herum aufgebaut hat. “Ich finde es einfacher mit Leuten auf der Rechten zu reden. Sie sind offener.” Und dann, sinngemäß: “Wenn man bei den Linken etwas sagt, dass nicht ins Konzept passt, weisen sie es sofort reflexhaft zurück.”
Dies ist jemand, der aus einer Arbeiterstadt kommt, zu viel Macht bei den Großkonzernen sieht und auch dem Staat skeptisch gegenüber steht. Dinge, die ich als traditionell links einschätzen würde.
Auch wenn es oft so aussieht, als habe diese Einteilung keinen Sinn mehr, verwenden wir die Begriffe Links und Rechts immer noch - hauptsächlich entlang der traditionellen Parteilinien. In Deutschland SPD, Grüne und die Linken (das BSW ist aussortiert). In Großbritannien Labour. In den USA die Demokraten.
Warum klingt für mich die eingangs erwähnte Einschätzung so wahr? Ich möchte den Schwierigkeiten auf den Grund gehen, die ich mit jener Gruppierung habe, der ich mich einmal hundertprozentig zugehörig fühlte.
Die Seite der Guten
Es scheint immer einen eindeutigen Weg zu geben. Es gibt die eine vernünftige Ansicht. Diese reflektiert eine simple, auf einen Punkt gebrachte Wahrheit. “Wenn ein Land angegriffen wird, muss es sich verteidigen dürfen.” Das ist unanfechtbar. Genauso wie “jeder Mensch der wegen Covid stirbt, ist einer zuviel.”
Zusätzliche, potenziell relevante Informationen interessieren ab diesem Zeitpunkt nicht mehr. Die Frage, “wie kann dieser Konflikt möglichst schnell beendet werden?”, taucht so gut wie nicht auf. Die Rollen sind eindeutig. Der Agressor stellt das absolute Böse dar, trägt die Alleinschuld und ist wahlweise verrückt oder von imperialen Lüsten getrieben, wahrscheinlich beides.
Wenn dies alles so eindeutig war, fragt man sich, warum Menschen, die dem Geschehen einfach mehr Kontext geben wollten — wäre es nicht gut, mehr Kontext zu einem Konflikt zu wissen, um besser damit umgehen zu können? — jedwede Plattform genommen wurde. (1) Sie wurden zudem mit Etiketten belegt, die es rechtfertigten, ihnen — falls doch einmal ein Video zu jemandem durchdrang — einfach nicht zuzuhören. Wenn alles so eindeutig war, warum sich dann nicht sachlich mit den Argumenten befassen?
Selbst wenn man am Ende zu der Meinung gelangte, der Ukraine sollten auf Dauer Waffen geliefert werden — ist es nicht trotzdem eine wissenswerte Information, dass es in Istanbul schon im März 2022 Friedensverhandlungen gab, die sehr weit fortgeschritten waren, als Selenskyj von UK und USA nahegelegt wurde, weiterzukämpfen (”wir werden dich unterstützen”).
Was mich am meisten perplex macht, ist, wie leichtfertig mit dem Krieg umgegangen wird. Wie schnell man auf der Seite gelandet ist, die am ehesten eine lange Dauer des Krieges bedeutet, und maximalen Profit für die Rüstungsindustrie. (2) “Putin hat angefangen und ist alleinig schuld, und nun muss man ihn maximal bekämpfen”, trumpft hier über die Möglichkeit, an diplomatische Wege auch nur zu denken.
Wäre dies vor 20 Jahren auch so gewesen. Vor 40 Jahren? In der Schule sangen wir viele Male Where have all the flowers gone? (tatsächlich auf englisch), und es berührte mich immer sehr. Im Radio war Bruce Springsteen mit War zu hören und Paul Hardcastles Nineteen. All das scheint nun vergessen.
Und selbst wenn es ein langgehegter Plan Putins war, in die Ukraine einzufallen und sich Teile von ihr anzueignen: Warum hat man ihm dann so bereitwillig einen Anlass gegeben? Warum ihm etwas geliefert, das, wenn es nie eine wirkliche Rechtfertigung sein kann, sich doch von ihm so interpretieren lässt? (3) Mit anderen Worten: Wenn man sich etwas mit der Vorgeschichte beschäftigt, erscheint dieser Krieg durch ein anderes Verhalten der USA absolut vermeidbar gewesen zu sein.
Stattdessen unterstützte man die Ukraine darin, “unsere Werte” zu verteidigen, und sah “die westlichen Demokratien” bedroht. Wie weit es mit der amerikanischen Demokratie her ist, das lässt sich jetzt mit dem Amtsantritt Trumps sehen.
Hier ist nun die progressiv-liberale Welt in Aufregung. Und übersieht dabei leicht, dass unter den Demokraten, besonders Obama, die Grundlagen für weitreichende Zensur und Manipulation der öffentlichen Meinung gelegt wurden. Deren Effekte waren deutlich sichtbar für jeden, der mit dem Corona-Regime nicht konform ging, auch über den großen Teich hinweg.
Warum ich mich nicht wohlfühle: Weil ich das Gefühl habe, dass man, aus dem Bedürfnis heraus, moralisch und gut zu sein, sich ein zweites Mal in etwas verrannt hat, das verhehrende Konsequenzen hat. Beziehungsweise mochte man beim ersten Mal schon nicht die Fehleinschätzung sehen, und macht auf eine ähnliche Weise weiter. Beidesmal mit einer Kriegslogik, bei der es gilt einen Feind vernichtend zu schlagen, wobei man ungeheure “kollaterale” Schäden vernachlässigt.
Die Demokraten als reaktive Kraft
Der angefangene Artikel sitzt hier schon eine Weile, und es gibt so viele Wege ihn weiterzuführen. — Mein ursprünglicher Plan umfasste so viele Themen, dass ich sie auf weitere Texte aufteilen muss.
Auch sind schon weitere ungeheuerliche Ereignisse geschehen. Die Trump-Administration nimmt nun wirklich faschistische Züge an, mit der Internierung eines Anführers von pro-palästinensischen Studentenprotesten, Mahmoud Khalil, und der Deportation von über 200 angeblichen venezuelanischen Gang-Mitgliedern nach El Salvador, in ein Sicherheitsgefängnis. Das ganze erscheint wie ein Riesenspektakel, es gibt mit Musik unterlegte Videos dazu, die an Werbefilme erinnern. Hier wird etwas vorgeführt. Einfach Macht? Boshaftigkeit, Häme? Der Rechtsstaat, welcher schon lange nicht mehr wirklich funktioniert, wird ausgehebelt.
Ab und zu taucht ein Podcast auf, der mich staunen macht und beeindruckt, weil er die gewohnten Einteilungen sprengt und gleichzeitig viele Wahrheiten ausspricht.

Link zum Podcast: https://jaredyatessexton.substack.com/p/we-are-in-the-crisis-a-conversation
Hier ist eine Frau, Danielle Moodie, die zu Trumps erster Amtszeit einen Radiosender namens Woke AF gegründet hat, im Gespräch mit dem Autor Jared Sexton, der neben Büchern einen Substack namens Notes from a collapsing state schreibt. Sie sprechen die oben erwähnten Ereignisse an, und erinnern ob der geringen Opposition an Martin Niemöllers “Als die Nazis die Kommunisten holten…”
Große Teile sind dann, besonders in der zweiten Hälfte, eine gnadenlose Abrechnung mit den Demokraten. Diesen geht es den beiden zufolge eher darum, den Aktienmarkt am Laufen zu halten, als etwas für benachteiligte Bürger zu tun. Die angebliche Unterstützung von Minderheiten (Wagen bei der Pride Parade, Kniefall etc.) seien immer nur Augenwischerei gewesen.
Moodie ruft einmal aus, was immer wieder passiere, sei: “Democrats don't lose the plot, they don't even know where the fuck it is.” Und Sexton bemerkt einmal, dass die Opposition eher ein Gegengewicht sei, das dafür sorgen soll, dass die Dinge so weiterlaufen wie bisher. “Die demokratische Partei ist reaktiv und konservativ geworden und hat keine Vision zur Lösung irgendwelcher Probleme.”
Sie sprechen auch noch einige andere Dinge an: Wie notwendig es ist, dezentralisiert zu agieren, und dass man Dinge anfangen soll, auch wenn man selber die Ergebnisse nicht mehr sehen wird. Und einiges andere mehr.
Nicht nur aus diesem Podcast, auch vielen anderen, und Artikeln, wird sichtbar, dass die Demokraten — wie die “Linken” in vielen anderen Ländern — ihre Anhänger vor allem in der Mittelklasse, der “professioal-managerial class” haben, und es -- vielleicht oft unbewusst -- mehr darum geht, den erreichten Status zu erhalten, als sich wirklich um soziale Belange zu kümmern.
Mit den Russen im Bett
Eine weitere interessante Publikation auf die ich neulich gestoßen bin, von einem nach Amerika ausgewanderten russischen Paar: Nefarious Russians (ruchlose Russen). Der Podcast dazu heißt In Bed with the Russians. Es geht dabei sehr viel um die kulturelle Seite, aber nicht nur.
Was ich sehr interessant fand, ist die Einschätzung Evgenias, die in den 90er Jahren in Russland aufgewachsen ist. Kurz zusammengefasst, dass das Land, oder zumindest Moskau, von der amerikanischen Kultur kolonisiert wurde. Ihre Freunde machten irgendwann gut Karriere, und sie war anfangs begeistert, wie sich alles entwickelte. Die Freunde selber sahen das aber anscheindend nicht so, sondern blickten immer mit Sehnsucht nach Amerika, dass sie sich als viel besser vorstellten. Irgendwann wurde Evgenia klar, dass die russische Kultur eigentlich zu einer schlechte Kopie der amerikanischen geworden war. — Das ist verkürzt wiedergegeben und ich hoffe nicht zu verzerrt.
Zu Putin: Die Vorstellung, er wolle die Sowjetunion wiedererschaffen, sei grundfalsch. Er und seine Führungsriege würden viel mehr das vorrevolutionäre Russland wiedererstehen lassen wollen.
Ob die NATO-Osterweiterung eine Rolle bei dem Einmarsch in die Ukraine gespielt hat, dazu habe ich nichts gefunden. Die Autoren sind aber definitiv weder Trump- noch Putinfreunde.
Interessant sind Erzählungen von “weaponized immigrants”, also ehemaligen Sowjetbürgern, die dann gleich zu Propganda-Zwecken gegen ihre alte Heimat benutzt wurden.
Da ich bei gebürtigen Russen bin, möchte ich auch noch Tessa Lena erwähnen, die für mich eine der wichtigsten Autorinnen in der Covid-Zeit war, und schon im April 2020 die damit einhergehende Technokratie durchschaut hat. Ich bin ihr sehr dankbar.
Ich habe über den Konflikt mit Russland geschrieben, weil dieser gerade aktuell ist und Anlass zu Kriegspropaganda bietet. Dass Russland kurz vor den Toren Deutschlands stehen soll, dafür habe ich keine Begründung gefunden.
Mein Fazit zur ehemaligen Linken — eine Kraft, die ihre früheren Ideale vergessen hat, sich in Solidaritätsbekundungen ergeht, und ansonsten eher mit dem Erhalt des Status quo beschäftigt ist, als dem Staat Zugeständnisse abzuringen. Die auf Klimaschutz drängt, aber für einen der größten CO2-Ausstoßer, das Militär, eine Ausnahme macht, was aber nicht einmal thematisiert wird.
Vielleicht ist es wirklich einfach überholt, in diesen Kategorien zu denken. Ich fühle mich jedenfalls keiner Richtung mehr zugehörig.
Entscheidend ist, Verbündete zu finden, egal, aus welcher Richtung sie kommen. Unterstützende Strukturen aufbauen außerhalb der Politik. Der “Commons” (Allmende) ist hier eine gute Idee, und ich möchte in Zukunft mehr darüber schreiben. Für diesesmal bin ich bei der globalen Politik gelandet und hängengeblieben, und letztlich beeinflusst sie auch, was lokal geschieht. Wichtig ist, wie immer, die Balance.
(1): Hier denke ich vor allem an Gabriele Krone-Schmalz, die in mehreren Vorträgen fundierte Analysen geliefert hat
(2): Antje Vollmer hat kurz vor ihrem Tod eindrücklich über Aufrüstung und den Wandel der Grünen zur Kriegspartei geschrieben: https://epaper.berliner-zeitung.de/article/ea77236b6b434f4d5fc01cace486274626d2c168ae5896b667f2d021d2ced5ce
(3): Die Kommentare zu diesem Artikel zeigen, wie man eine offene und respektvolle Diskussion haben kann. Hier kommen Menschen von Balkanstaaten zu Wort, die sich gegen die Darstellung wehren, die Revolutionen in den ehemaligen Soviet-Republiken seien immer von den USA gesteuert. https://iainmcgilchrist.substack.com/p/laughter-in-heaven
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ 86fd18bc:02060045
2025-03-22 00:46:29
@ 86fd18bc:02060045
2025-03-22 00:46:29{"coverurl":"https://cdn.nostrcheck.me/86fd18bc230a2b77cc2fe5b2b55597fcf7b89f4076e55b4c4b1864f802060045/1bb43a666cc367a7c39fab3998d7f66296c64a28b613af7776a5ce474957dfa3.webp","title":"热带植物","author":"爱观察"}
-
 @ 86fd18bc:02060045
2025-03-22 00:36:13
@ 86fd18bc:02060045
2025-03-22 00:36:13{"coverurl":"https://cdn.nostrcheck.me/86fd18bc230a2b77cc2fe5b2b55597fcf7b89f4076e55b4c4b1864f802060045/9ab7291c2a76bf7318e681390ed9e1bf82d375f6a304438889e3db7622107130.webp","title":"来时的路","author":"秋风"}
-
 @ 2dd9250b:6e928072
2025-03-22 00:22:40
@ 2dd9250b:6e928072
2025-03-22 00:22:40Vi recentemente um post onde a pessoa diz que aquele final do filme O Doutrinador (2019) não faz sentido porque mesmo o protagonista explodindo o Palácio dos Três Poderes, não acaba com a corrupção no Brasil.
Progressistas não sabem ler e não conseguem interpretar textos corretamente. O final de Doutrinador não tem a ver com isso, tem a ver com a relação entre o Herói e a sua Cidade.
Nas histórias em quadrinhos há uma ligação entre a cidade e o Super-Herói. Gotham City por exemplo, cria o Batman. Isso é mostrado em The Batman (2022) e em Batman: Cavaleiro das Trevas, quando aquele garoto no final, diz para o Batman não fugir, porque ele queria ver o Batman de novo. E o Comissário Gordon diz que o "Batman é o que a cidade de Gotham precisa."
Batman: Cavaleiro das Trevas Ressurge mostra a cidade de Gotham sendo tomada pela corrupção e pela ideologia do Bane. A Cidade vai definhando em imoralidade e o Bruce, ao olhar da prisão a cidade sendo destruída, decide que o Batman precisa voltar porque se Gotham for destruída, o Batman é destruído junto. E isso o da forças para consegue fugir daquele poço e voltar para salvar Gotham.
Isso também é mostrado em Demolidor. Na série Demolidor o Matt Murdock sempre fala que precisa defender a cidade Cozinha do Inferno; que o Fisk não vai dominar a cidade e fazer o que ele quiser nela. Inclusive na terceira temporada isso fica mais evidente na luta final na mansão do Fisk, onde Matt grita que agora a cidade toda vai saber o que ele fez; a cidade vai ver o mal que ele é para Hell's Kitchen, porque a gente sabe que o Fisk fez de tudo para a imagem do Demolidor entrar e descrédito perante os cidadãos, então o que acontece no final do filme O Doutrinador não significa que ele está acabando com a corrupção quando explode o Congresso, ele está praticamente interrompendo o ciclo do sistema, colocando uma falha em sua engrenagem.
Quando você ouve falar de Brasília, você pensa na corrupção dos políticos, onde a farra acontece,, onde corruptos desviam dinheiro arrecadado dos impostos, impostos estes que são centralizados na União. Então quando você ouve falarem de Brasília, sempre pensa que o pessoal que mora lá, mora junto com tudo de podre que acontece no Brasil.
Logo quando o Doutrinador explode tudo ali, ele está basicamente destruindo o mecanismo que suja Brasília. Ele está fazendo isso naquela cidade. Porque o símbolo da cidade é justamente esse, a farsa de que naquele lugar o povo será ouvido e a justiça será feita. Ele está destruindo a ideologia de que o Estado nos protege, nos dá segurança, saúde e educação. Porque na verdade o Estado só existe para privilegiar os políticos, funcionários públicos de auto escalão, suas famílias e amigos. Enquanto que o povo sofre para sustentar a elite política. O protagonista Miguel entendeu isso quando a filha dele morreu na fila do SUS.
-
 @ 30fb9c78:1f1e3c3a
2025-03-22 00:18:06
@ 30fb9c78:1f1e3c3a
2025-03-22 00:18:06It’s easy to identify the presence of something, but it’s much harder to identify the absence of something. If your boyfriend brings you flowers, that’s awfully nice. If he never brings you flowers, it might take you a while to notice. Maybe you do eventually notice, but you decide to cope. You tell yourself you don’t care about getting flowers. Maybe you take it a step further: “Actually, flowers are really basic and lame. Only basic girls like flowers. I’m a cool girl and cool girls don’t care about getting flowers.”
If this goes on for long enough—even if you are genuinely presented with flowers at some point—you will see them as a kind of joke. Flowers are now a bit. It sounds so trivial, I know, but if you dull your “receptors for flowers” for years on end, you will eventually fail to see the beauty of the gesture.
Entering the void
I’m deeply troubled by the fact that I see this happening at a massive scale, all around us. Except the problem is not a lack of bouquets, of course. It’s a lack of meaning.
Life has gotten very chaotic incredibly quickly. It has become increasingly difficult to parse anything from the static. People started coping with this lack of meaning through a kind of ironic detachment (which is very much still around), but it has matured into a pervasive cultural apathy, a permeating numbness. This isn’t nihilism per se. (Even nihilists have a sincere belief system; they just sincerely believe that life is meaningless.) What we’re dealing with is worse than nihilism. People are checking out of life in their 20s and 30s without reaching any profound conclusions about the point of it all.

“People are so worn down," my friend told me on a recent phone call. She’s right: there’s a real lack of palpable ambition and vitality these days, a stunning lack of life force in the world. Another friend told me that “this has been going on for so long that people wouldn’t know meaning if it walked up and bit them in the ass.” It’s true—so many of the things that once gave the average person’s life real meaning are now treated with sarcasm and contempt: college is a waste of money, work is a waste of your life, getting married is just a piece of paper, having kids is a nightmare, family is a burden, hobbies are merely quaint, earnestly expressing yourself is cringe, leaving the house is exhausting, religion is for idiots, the list goes on. If you allow yourself to internalize this perspective, eventually everything becomes a dumb joke.
A quick aside before we get into it: it’s taken me a long time to write this piece. This is partly because this whole phenomenon is, in a way, its own kind of absence. It’s been hard for me to identify what is going on and what is missing. I’ve had my own cycles of coping with it. I’ve been telling myself that I don’t care about people not caring. But obviously I do. So here goes.
A culture of chaos
The cultural forces that spawned this collective response have been quietly working their way into everything for decades—probably since the 1970s if I had to stick a pin in it. It reached new heights in the 1990s, but it took off exponentially since the mass adoption of the internet, social media, and the pandemic. We boiling frogs started to feel the water get really hot around 2015, I think, and it’s only gotten hotter and hotter since.
We’re so saturated in this environment that people are not only numbing out, they’re kind of making a spectacle of it: from TikTok’s “quiet quitting” trend to Vetements entire “ironic” aesthetic. You know it’s bad when the corporations get on board. The detachment is so widespread that most companies don’t even have the genuine confidence to market their own products. Everything is delivered with a wink from one eye and an eye-roll from the other. We live in a mud puddle of memes, ironic hot takes, and self-conscious self-reference. David Foster Wallace called it exactly thirty years ago, in the summer of 1993:
“[…] The harvest has been dark: the forms of our best rebellious art have become mere gestures, schticks, not only sterile but perversely enslaving. How can even the idea of rebellion against corporate culture stay meaningful when Chrysler Inc. advertises trucks by invoking “The Dodge Rebellion”?
David Foster Wallace, E Unibus Pluram: Television and U.S. Fiction (The Review of Contemporary Fiction, link to full pdf)
Rest in Peace David Foster Wallace, you would have loved Barbie. We swim in a wretched sea of meaningless mush, and when you have to trudge through nothing but slop all day, every day, it gets harder and harder to not numb out. I really cannot emphasize it enough: there’s so much and it just keeps coming. There’s lots to do. There’s lots to buy. The “content” never ends. Baby Gronk rizzed up Livvy! Wait—you’ve never had vegan tacos there?! Haley Bieber got a manicure! You should get an Apple Watch!
Meaningless distractions, all.
Thanks to the internet and our insatiably consumerist culture, it is finally possible to distract yourself for every waking minute of your life and barely even notice you’re doing it. When you mix all colors of paint together, you get black. Everything quickly becomes nothing.
What else? Well, there’s the ubiquity of pornography which has zapped everyone of their sex drive. It’s been said many times before: everything is sexy and no one is horny. Social media and the fear of cancel culture got together to create the most utterly dull popular culture and celebrity elite to ever exist. It stands for nothing, it risks nothing, so there’s nothing to engage with. Culture is just kind of “there,” and no one really cares about it.
An unfortunate by-product of this is that there’s also very little to which we can aspire. Life is not a meritocracy, and the void at the top has allowed for figures like Andrew Tate to be taken seriously by both fans and critics alike. The blame is always being shifted around. Men think women are the problem. Women think men are the problem. The boomers think it’s the millennials. The millennials think it’s the boomers. It’s social media. No it’s the pandemic. No it’s [your pet theory here].
Death and loneliness abound. Everyone is constantly joking about killing themselves while Canada rolls out a “humane” service to do just that (MAID). People are struggling: most people simply cannot cope without substances like marijuana, alcohol, drugs, and SSRIs. People are lonely: they have fewer friends and live far from their families. Dating seems impossible. Men and women in the prime of their lives are struggling to meet even one potential partner who shares their values and vision for a relationship. Oh, and our phones—Gen Z averages an unfathomable 9 hours of screen time per day—have ruined our attention spans to the point where we can no longer read a book, let alone sit quietly with nothing but our thoughts. If you’re an intelligent, hardworking person, odds are the job you’ll have out of college, and for the next 40-50 years, will involve 10+ hours a day of staring at a laptop screen in a state of heightened stress.
To top it all off, we can’t have meaningful conversations about any of this stuff because everyone runs their thoughts through their own kind of personal HR filter. People are self-reporting their thought crimes to themselves. I’m literally doing that right now. I’m sure I’ve theoretically “offended” all sorts of people in the last paragraph alone. Catherine, when you talked about the jobs you forgot to say that it mainly applies to privileged folks! Well, you got me there. The point stands: things are trending down. Something is deeply wrong. We all know it. We all feel it.
We think ironic detachment will protect us
The picture is bleak. It’s so sad it’s difficult to comprehend. How do you protect yourself in such a world?
You simply don’t allow yourself to experience it.
Think back to the flower metaphor. This is where we don’t receive flowers, but we cope. Same thing here. We look around the world, struggle to see the meaning in its chaos, and unconsciously tell ourselves that finding meaning isn’t that important. If I can’t pursue my own fulfillment, at least I can pursue my own pleasure. This is a somewhat reasonable reaction to the present circumstances. It feels straightforward enough—it’s binary, measurable, and everyone else is doing it. This is how the numbness starts.
And perhaps this route is even better—maybe even cool. Being ironically detached from life is endlessly glamorized in our culture. There’s a certain status in pretending nothing affects you and you don’t care. Cue photo montage of a strung-out Kate Moss staring listlessly into the middle distance.
Taking the ironic detachment route is also easy. It’s easy to laugh at other people, mock them, throw your head back, be a critic. Standing for nothing has the obvious appeal of making you impossible to pin down. There’s something very chic about smoking a cigarette outside a bar and being all like whatever. You’re playing a game of hide-and-seek with life, and you’re hiding. It’s thrilling to find a good place to hide, to have people seeking you. But in our drug-fueled debauchery, our coy, sarcastic conversations, and perhaps most of all in our fleeting, romantic encounters, we should heed the words of British psychoanalyst Donald Winnicott:
“It is a joy to be hidden, and a disaster not to be found.”
It is a disaster not to be found, a total disaster to not be able to connect with others because we were too preoccupied with ourselves. The whole reason for ironic detachment is to build a protective wall between oneself and the world. We think we’re building a wall, but we’re really hollowing ourselves out from the inside. Eventually, without really noticing it, there will be nothing left for the wall to defend. There will be no one to find.
It’s not hard to see where the pervasive numbness comes in from here, as a sort of sinister phase two. The opposite of love is not hate, but apathy. I hope it’s obvious why this is a problem, but maybe you’re still thinking so what. To put it succinctly: when you take an ironic, negative, or numb attitude to everything, you are by definition not on the line for solutions, and when you stop looking for solutions, you lose all agency and will in your life.
Possible antidotes
We can’t keep going down the path we’re on, but we also can’t go back. Don’t worry, I’m not going to give full-throated endorsement for Post-Post-Irony, or David-Foster-Wallacian New Sincerity, as he does in the essay I quoted earlier (though I do think cringe sincerity is preferable to total apathy). We’re too far gone from the early 90s. We can’t put the internet back in the box or log off forever. Too much of our lives is irrevocably online, we’re all too self-aware, and a saccharine glaze of sincerity is too affected to feel real. Besides, we’ve all been cornered by the guy at the bar with a well-worn paperback in his pocket who locks eyes with you and whispers, “But how are you, really?” as if it’s a profound question. I would hate to subject anyone to such an encounter.
Rather than jump to sincerity, I’d like to start with basic honesty. It would be great if we started just telling the truth—to ourselves and each other. The truth is good. (I mean the truth, by the way. Not “our truth.” The truth, the real truth, does not have to market itself as “authentic,” like an influencer does, it simply is.) In other words: stop hiding and start seeking. Stop hiding from the sad truths and start seeking the transcendent truths that will address the sadness. When we flip the game of hide-and-seek, we can stop worrying about someone finding us, and start seeking the truth in the world, in others, and in ourselves.
With honesty as the foundation, I would advocate next for embracing reality—our real lives, right now—and not clinging to an abstract idea of how our lives should be. In other words: everything that we see exclusively online does not really matter. The broader culture’s idea of “a perfect life” changes every couple years. Measuring the distance between our real lives and some ever-changing, impossible ideal will do nothing but break our spirit. Besides, I have never met a person who has a dream life in reality. And reality—the truth—is what counts.
This doesn’t mean we shouldn’t strive. Things are never so fundamentally broken that we cannot move just a bit closer towards our goals and try again and again to live up to our values. Goals and values are good to have. The bigger and more transcendent the better, I say.
Once we figure out all that stuff—the big goals, the transcendent values—we should take responsibility for them. Standing for something is hard because what you’re implicitly saying is, “I don’t necessarily stand for all those other things over there.” This is a risk. People will not always agree with you. By saying “I believe in God,” for example, you’re also saying “I am not an atheist.” Atheists might think you’re stupid. (This begs the question, “And?”) We should take responsibility for our beliefs, but be prepared to calmly and rationally explain them. Criticize the world all you want, but do the hard work of building something better to take its place.
In this process, the process of seeking and telling the truth, having values and goals, and taking a stand for something, we’re bound to fail, to fall short, and to make mistakes. This is also hard. Our culture simultaneously demands both perfection and apology, but is notoriously unforgiving. Everyone needs a little forgiveness from time to time. We need to remember that it is okay to make mistakes if we try to remedy them. It’s also okay to be seen trying. Don’t take the easy route, which is always harder and more costly in the end. To shock yourself out of a numb state, to restore your life force and vitality, you will need to work hard and to submit to something bigger than your own desires.
I started with flowers, so I’d like to end with them, too. We all know that life does not hand out bouquets. Flowers do not just appear in the world. The same is true for a life of meaning. Both are grown, over time, from the tiniest seeds. You have to cultivate meaning in your life. You need to do the hard work of tilling the soil and nurturing the seeds. No one can do it for you. Grow your own flowers and give them away to everyone you meet. You’re right: the earth is not very fertile, people are not always grateful, flowers eventually die. But do you still see the point of it all? Do you see the beauty of the gesture?
Source: Catherine Shannon, Everyone is numbing out, July 27, 2023
-
 @ d34e832d:383f78d0
2025-03-21 20:31:24
@ d34e832d:383f78d0
2025-03-21 20:31:24Introduction
Unlike other cetaceans that rely on whistles and songs, sperm whales primarily use echolocation and patterned click sequences to convey information. This paper explores the structure, function, and implications of their vocal communication, particularly in relation to their social behaviors and cognitive abilities.
1. The Nature of Sperm Whale Vocalizations
Sperm whales produce three primary types of clicks:
- Echolocation clicks for navigation and hunting.
- Regular clicks used in deep diving.
- Codas, which are rhythmic sequences exchanged between individuals, believed to function in social bonding and identification.Each whale possesses a monumental sound-producing organ, the spermaceti organ, which allows for the production of powerful sounds that can travel long distances. The structure of these clicks suggests a level of vocal learning and adaptation, as different populations exhibit distinct coda repertoires.
2. Cultural and Regional Variation in Codas
Research indicates that different sperm whale clans have unique dialects, much like human languages. These dialects are not genetically inherited but culturally transmitted, meaning whales learn their communication styles from social interactions rather than instinct alone. Studies conducted in the Caribbean and the Pacific have revealed that whales in different regions have distinct coda patterns, with some being universal and others specific to certain clans.
3. Social Organization and Communication
Sperm whales are matrilineal and live in stable social units composed of mothers, calves, and juveniles, while males often lead solitary lives. Communication plays a critical role in maintaining social bonds within these groups.
- Codas serve as an acoustic signature that helps individuals recognize each other.
- More complex codas may function in coordinating group movements or teaching young whales.
- Some researchers hypothesize that codas convey emotional states, much like tone of voice in human speech.4. Theories on Whale Intelligence and Language-Like Communication
The complexity of sperm whale vocalization raises profound questions about their cognitive abilities.
- Some researchers argue that sperm whale communication exhibits combinatorial properties, meaning that codas might function in ways similar to human phonemes, allowing for an extensive range of meanings.
- Studies using AI and machine learning have attempted to decode potential syntax patterns, but a full understanding of their language remains elusive.5. Conservation Implications and the Need for Further Research
Understanding sperm whale communication is essential for conservation efforts. Noise pollution from shipping, sonar, and industrial activities can interfere with whale vocalizations, potentially disrupting social structures and navigation. Future research must focus on long-term coda tracking, cross-species comparisons, and experimental approaches to deciphering their meaning.
Consider
Sperm whale vocal communication represents one of the most intriguing areas of marine mammal research. Their ability to transmit learned vocalizations across generations suggests a high degree of cultural complexity. Although we have yet to fully decode their language, the study of sperm whale codas offers critical insights into non-human intelligence, social structures, and the evolution of communication in the animal kingdom.
-
 @ 7bc05901:8c26d22b
2025-03-21 19:47:15
@ 7bc05901:8c26d22b
2025-03-21 19:47:15Decentralization is a beautiful return volley to the censorship regimes that have ruled American social media, but the decentralization piece isn't the biggest impact Nostr is having on me. The empowerment and encouragement to start building are what overwhelms. Since I began sending zaps just a few weeks ago, every idea I have had for an app over the last decade is organically re-emerging as executable Nostr apps.
The rise of AI alongside Nostr's invention/discovery is serendipitous for someone who doesn't have the coding experience to develop an app from scratch like myself. It is also a great moment for apps that had a social feature -- which was essentially every app. "Connect it using Facebook" was such a non-starter for me. I live in a small town where Facebook is a gossip cesspool. There are intriguing communities there, sure, but the overwhelming dread that overcomes me when I open that app doesn't justify digging for the socially-delightful gems. Further, any app that integrates with facebook is or becomes a variation on an already existing feature that META has engineered into their platform -- they want, they need your eyeballs. On their site.
Nostr makes no such demands. It doesn't care which site is being used to access the protocol, and what features exist on that site. It is available to help, secure a user's identity, and doesn't make many demands in return.
My friend and local farmer Ryan and I have discussed an app for years, built it and rebuilt it using different tools, but we ultimately got distracted by more pressing and less complicated projects. I think a huge barrier to execute it was the sense that it would be impossible to achieve any network effects, plus the thought of managing the social side was overwhelming. It required us to need really powerful tools, and to maintain a lot of data that we didn't really want to hold onto. It was essentially an app for local food producers and consumers. With Nostr at play, we could build something like this and simultaneously onboard our local community to the Nostr protocol while also providing a lightweight solution to managing the complicated part of an online marketplace. The lightning payments come as an added bonus.
We are tracking the use of another app which is sweeping through local food producers, which is only in its beta phase, and restarting our build of a marketplace that is worth building and encourages a sustainable local food supply, this time with a protocol that reduces 90 percent of the annoying part of that build, and doesn't require anyone spend time on Zuckerberg's playground.
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ 6a6be47b:3e74e3e1
2025-03-21 18:45:32
@ 6a6be47b:3e74e3e1
2025-03-21 18:45:32Hey frens! Today, I spent a big chunk of the morning painting with watercolors. This is only the second time I've completed a piece using this technique in a long while. It feels like coming back home after a vacation: you enjoyed the time away and relaxed, but when you're lucky enough to have a safe space to call home, there's really nothing like it. 🖼️
🎨 That's exactly how I feel about painting with watercolors again. I'm really excited to share what I've been working on with you soon. In the meantime, I've got a new blog post up about Ostara and the Spring Equinox. ⭐️Today, I just feel so blessed and excited about the future. I'm simply soaking up the moment, I guess. I hope you're feeling the same way too! Today, I also whipped up some mini veggie quiches chef's kiss.
 🧑🍳 I wanted to spice things up a bit in the kitchen as well!
🪄I just wanted to share a little bit from my day and express how grateful I am. What did you get up to today? I'd love to hear more about it!
🧑🍳 I wanted to spice things up a bit in the kitchen as well!
🪄I just wanted to share a little bit from my day and express how grateful I am. What did you get up to today? I'd love to hear more about it! -
 @ 6bae33c8:607272e8
2025-03-21 18:23:28
@ 6bae33c8:607272e8
2025-03-21 18:23:28I put Beat Chris Liss 3 in quotes because technically this was not a Beat Chris Liss league — I just bought it at the last minute to get an extra league. In any event, I drew the seventh spot, and here are the results:
1.7 Corbin Carroll — He’s been hitting home runs this spring, a signal his shoulder is healthy. You know he’ll run, and given how he performed at the end of last year, I’d expect the batting average to bounce back too.
2.8 Jazz Chisholm — I want to see what he can do with a full year in Yankee Stadium. He’s a health risk, but he was a 20-20-ish player in Miami with only 100 games in 2023. It’s also nice that he qualifies at 3B and OF. I considered Mookie Betts, who slipped, but I’m concerned about severe weight loss from an illness undermining the first half of his season.
3.7 Chris Sale — He’s a Hall of Fame level pitcher with his health and form back. Remember when Justin Verlander faded in his 30s and then got it back together? I expect a few good years from Sale before he declines again.
4.8 Corbin Burnes — I don’t really even like Burnes, but he slipped a full round past ADP, and I value-took.
5.7 C.J. Abrams — I love this pick, probably my favorite of the draft. Abrams is a 20-30 player despite attitude issues. What if he matures and gets it together at age 24?
6.8 Adley Rustchman — I didn’t see anything I liked, and I was light on power. One way to get a leg up power-wise is to draft elite catchers.
7.7 Cody Bellinger — I like him with Yankee Stadium’s short porch, a few steals from a first-base-eligible player and also outfield eligibility.
8.8 Mike Trout — I had enough pitching and speed, but I needed some power, and Trout still has as much as anyone if he could ever play 100-plus games. He’s healthy now at least.
9.7 Will Smith — A second top catcher to pair with Rutschman. I was light on power through five rounds, but my next four picks were 20-plus HR catchers, Bellinger in Yankee Stadium and Trout.
10.8 Roki Sasaki — He slipped a couple rounds after a rough outing in Japan, but he was still throwing 100 with nasty movement. Another value-take.
11.7 Sonny Gray — A favorite old warhorse in a good pitcher’s park. I really wanted Sandy Alcantara, but Gray’s ADP was higher, so I thought there was a better chance to get Alcantara on the way back.
12.8 Sandy Alcantara — Turns out I thought right. I love Alcantara, who was going in the third round a couple years ago, now that he’s healthy and throwing 100 mph again.
13.7 Alexis Diaz — Taking Alcantara cost me my two go-to closers, Kenley Jansen and Jordan Romano, both of whom went earlier than usual, so I pivoted to Diaz. I thought this was a mistake at first — Diaz has been bad this spring, and he wasn’t even good last year, either, but he’s the closer until further notice, and a couple spring outings shouldn’t move the needle that much.
14.8 Kevin Gausman — Another old warhorse, coming off a down year, possibly due to injury. His velocity has been back up this spring too.
15.7 Xander Bogaerts — Another ADP value-take. Bogaerts had double digit homers and steals in 111 games last year and is a good bet to hit for a decent average.
16.8 Ryan Pressly — Another shaky closer, Pressly had three walks in an inning against the Dodgers, but he’s probably not losing the job over one ugly but scoreless outing.
17.7 Aroldis Chapman — Named the Red Sox closer, Chapman is probably the best of the three I drafted thus far. His ADP was lower because he was only given the role a couple days ago. Chapman perfectly fits the old warhorse mold I like too.
18.8 Brandon Pfaadt — I didn’t really need another starter, but he was the best player left on the board, and you always run out of pitching.
19.7 Zack Gelof — He strikes out a ton, but he went 17-25 last year in 138 games as a rookie, and now he gets to play in a minor-league band box. Lawrence Butler went 22-18 and is going in the fifth round!
20.8 T.J. Friedl — I was light on OF, and Friedl is one. He has a little pop, runs and is expected to lead off for the Reds in the best non-Coors hitting park in baseball.
21.7 A.J. Puk — I was still a little light in saves, and Puk is in the running for the Arizona job.
22.8 Roman Anthony — I don’t know if he’ll break camp with the Red Sox, but he was the remaining player I would have felt worst getting snaked on. He doesn’t have much left to prove in the minors.
23.7 George Springer — He went 20-20 in 2023 and 19-16 last year. He could be done, but at 35 he’s not ancient.
24.8 Jo Adell — I needed to fill in the outfield, and Adell should play, run and hit for power. The strikeouts and batting average risk are bad, but he’s still young enough to improve.
25.7 Griffin Jax — He’s a top reliever, next in line for saves and closer Jhoan Duran isn’t very good.
26.8 Christopher Morel — I needed a corner and Morel is one. (If I needed a mushroom, this would also hold.) He hit .196 last year, but he has good pop and should play OF for the Rays in a small minor-league park.
27.6 Casey Mize — The former No. 1 overall pick has looked good this spring, and he’s completely healthy.
28.6 Will Warren — Warren should get a shot in the Yankees rotation, given the injuries to Gerrit Cole and Luis Gil.
29.6 Spencer Torkelson — Another former No. 1 overall pick for the Tigers, Torkelson hit 31 homers in 2023 and should get another shot this year given his strong spring.
30.6 Nolan Schanuel — I just wanted an extra corner with regular playing time heading into the year. He runs a little and had 13 HR, but in a full season of at-bats.
Roster By Position:
C Adley Rustchman/Will Smith
1B Cody Bellinger
2B Xander Bogaerts
3B Jazz Chisholm
SS C.J. Abrams
CI Christopher Morel
MI Zack Gelof
OF Corbin Carroll/Mike Trout/T.J. Friedl/Roman Anthony/George Springer
UT Jo Adell
SP Chris Sale/Corbin Burnes/Roki Sasaki/Sonny Gray/Sandy Alcantara/Kevin Gausman
RP Alexis Diaz/Ryan Pressly/Aroldis Chapman
B Brandon Pfaadt/A.J. Puk/Griffin Jax/Casey Mize/Will Warren/Spencer Torkelson/Nolan Schanuel
-
 @ 6ad3e2a3:c90b7740
2025-03-21 18:21:50
@ 6ad3e2a3:c90b7740
2025-03-21 18:21:50There are two ways things happen in this world: top-down and bottom-up. Top-down is via authoritarian edict, i.e. fascism, no matter how benign-seeming. It is the government imposing a tax, incentivizing a behavior, creating a new law. Bottom-up is the organic process of people doing what interests them voluntarily, what benefits them, what they decide is best individually.
There is but one legitimate role for top-down and that is in creating good conditions for bottom up. The US Constitution is fascism in that it forces you to adhere to its edicts as the supreme law of the land. But it’s also an effective boundary creating the necessary conditions for free markets, free expression, creativity and prosperity.
All governments are fascistic in that they use force to achieve their agendas. But the best ones use only the minimum necessary force to create conditions for bottom-up prosperity. There is no other kind of prosperity.
. . .
Governments aren’t the only entities that are fascistic. Schools, corporations, institutions and individuals, almost invariably, are too. Yes, I am a fascist and very likely so are you. Don’t believe me? Do you have a voice inside your head telling you what you must get done today, evaluating your progress as a person, critiquing and coercing you into doing things that are “good” for you and avoiding ones that are “bad”? If so, you are fascist.
Why not just trust yourself to make the right choices? Why all the nudging, coaxing, coaching, evaluating and gamifying? Who is this voice, what gives it the authority, the requisite wisdom to manage your affairs? Haven’t all your shortcomings, disappointments and general dissatisfactions taken place despite its ever-presence? What makes you think you are better off for having had this in-house micromanagement?
. . .
The top-down edicts that rule our lives are by and large unnecessarily oppressive. Yes, we should create some good top-down conditions for bottom up organic thriving like buying healthy food, getting fresh air, not consuming excessive amounts of alcohol or drugs, but the moment to moment hall-monitoring, the voice that requires you to achieve something or justify your existence? That’s fascism.
. . .
The mind is a powerful tool when it comes to planning, doing math or following a recipe, but if it can’t be turned off, if it’s not just optimizing your path from A to B, but optimizing YOU, that’s fascism.
. . .
I think about the problem of human governance through this lens. I imagine everyone charged with power over a polity has an agenda, and that agenda, insofar as it requires force to achieve, is fascistic. They want it to go this way rather than that way, and some people don’t agree. The quality of leadership then is the extent to which that force is used to preserve the bottom-up freedom of the individual to pursue his interests without undue interference, either from authorities themselves or other individuals who would unduly disrupt him.
The Constitution is an excellent guideline for this, and I surely won’t be able to come up with a better one in this Substack. It’s why I support Trump’s efforts to trim the top-down public sector and return productivity to the bottom-up private one, why I support deportation of adjudicated criminals who are here illegally, but oppose removing people with green cards or on valid student visas for protesting via constitutionally protected speech.
I don’t root for politicians like they play for my favorite sports team. I root for the freedom of the individual, the possibility of a largely bottom-up society wherein prosperity is possible. And I do this while knowing it will never happen exactly the way I would like, so long as I am bound by the fascism coming from inside the house.
-
 @ 2fdeba99:fd961eff
2025-03-21 17:16:33
@ 2fdeba99:fd961eff
2025-03-21 17:16:33== January 17 2025
Out From Underneath | Prism Shores
crazy arms | pigeon pit
Humanhood | The Weather Station
== february 07 2025
Wish Defense | FACS
Sayan - Savoie | Maria Teriaeva
Nowhere Near Today | Midding
== february 14 2025
Phonetics On and On | Horsegirl
== february 21 2025
Finding Our Balance | Tsoh Tso
Machine Starts To Sing | Porridge Radio
Armageddon In A Summer Dress | Sunny Wa
== february 28 2025
you, infinite | you, infinite
On Being | Max Cooper
Billboard Heart | Deep Sea Diver
== March 21 2025
Watermelon/Peacock | Exploding Flowers
Warlord of the Weejuns | Goya Gumbani
-
 @ bf95e1a4:ebdcc848
2025-03-21 17:03:01
@ bf95e1a4:ebdcc848
2025-03-21 17:03:01This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
Preface
At the time of writing, it is New Year’s Day, and 2019 has just begun. For once, I have a resolution to live up to: I’ve promised myself to write a page per day every day this year until I have something real to publish. In June 2018, I published my first book, Three Minute Reads on Bitcoin — A Year of Thoughts. The book consisted of articles I had published online from May 2017 up to that point. This time it’s different. Instead of a mere collection of articles, I intend to write a “proper” book. A book that explains why Bitcoin is the most important invention of our lives.
I didn’t choose Bitcoin; it chose me. I had been trying to figure out how the world worked under the hood all my life, and then this simple idea of absolute scarcity popped up. It had a profound impact on how I view human interaction. Because of my curious nature, I instantly fell deep into the rabbit hole. I decided to educate myself on how this mysterious technology worked, and that got me into Austrian economics, which expressed very clearly what I had always suspected — that you really can't create value out of thin air.
In this book, I will try to explain every aspect of what makes this technology so special, what sets it apart from the abundant shameless copies of it, what’s wrong with our current system, and what the future might look like. In just two days from the time of writing these words, we’ll celebrate the ten-year anniversary of the Genesis Block when the Bitcoin blockchain came into being. That block contained a message, a newspaper headline that read: “03/Jan/2009 Chancellor on brink of second bailout for banks”. No one knows why Bitcoin’s mysterious creator, Satoshi Nakamoto, chose to include this in the Genesis Block. There is also some debate on whether the Genesis Block was actually mined on the 3rd of January since the next block wasn’t mined until six days later. Somehow, Satoshi managed to stay hidden and weave several layers of mystique into the fabric of Bitcoin from the very beginning, which is part of what makes its conception so immaculate. This book aims to strip Bitcoin of its shady cloak and illuminate its true nature. After all, the only thing any person can do about Bitcoin now is to study it.
Foreword
My journey down the Bitcoin rabbit hole has provided me with a newfound clarity of how our world should be perceived. In the same way that getting married and having my first child were beautiful life-changing events, discovering Bitcoin was a new chapter in my life. I can easily divide my life into two distinct periods: before and after Bitcoin.
Before discovering Bitcoin, life was perplexing. For years, even dating back to my school days, I had an innate sense that something was amiss in the world. Although I wasn’t a good student by any means, it was obvious back then that many aspects of life simply didn’t add up.
One thing that I was sure of was that money was corrupt. However, it took me a while to realize that money itself is fundamentally corrupt. Furthermore, what is typically taught and accepted as money by society is a perversion of what money should be. These are the first steps of understanding Bitcoin, which require you to admit that you have been fooled and lied to all your life. The hard lessons of hard money.
The way I see it, the revelation about the true nature of money is akin to a bracing cold shower that wakes you up to reality. Emerging from that cold shower is an incredibly liberating and invigorating sensation. Unfortunately, many individuals are not motivated enough to take that crucial step into the chilly waters. Instead, they will later experience an ice-cold bucket of water being dumped on their head unexpectedly whilst naked on a cold winter’s day.
The year 2020 was a watershed moment in my journey towards truth, and it was Bitcoin that served as my guide. As the world grappled with an unprecedented black swan event in March of that year, every asset, including bitcoin, took a severe hit. However, what followed in the subsequent months was the largest money-printing expedition in history. A tsunami of stimulus was pumped into the markets. The outcome was a K-shaped recovery. Small, honest brick-and-mortar businesses continued to suffer while many of the largest conglomerates not only rebounded but reached all-time highs. This ludicrous, short-sighted plan, known as quantitative easing, resulted in the most pronounced example of the Cantillon effect in human history, a fact that should have served as a wake-up call for anyone who was not already suspicious of the events surrounding the global financial crisis of 2008.
Since entering my post-bitcoin life, I’ve experienced a newfound coherence. The transition was not exactly instant, instead it has been a continuous process of discovering bitcoin over and over again, and I owe many of these enlightening moments to Knut Svanholm’s writing, for which I’m grateful.
While Knut’s books do not serve as a technical guide for Bitcoin, they provide a deep and philosophical introduction to a new era of money; the separation of money and state. The end of fiat money.
The creation of fiat money, a practice that emerged with the rise of central banking, has been the source of significant damage to human civilisation. Central banking, championed by Keynesianism, has granted immense power to centralized entities, allowing them to dictate fiscal policies and control the creation of money for billions of people. The very idea of a single entity wielding such vast authority and determining the economic fate of entire populations is utter madness. The state monopolizes money because it allows them to print money rather than having to directly tax people (but it still doesn’t stop them). Printing money is more easy, subtle and lucrative than direct taxation. And this continual erosion of purchasing power can be readily associated with the evident decline and deterioration of modern society.
At the heart of the issue is the importance of individual property rights. The money that individuals earn and save is their property, not the state’s. The state’s duty (should there be a need for it to exist) is to safeguard private property, not to continually debase or confiscate it. A centralized power that constantly devalues your hard-earned money and time by printing money is both morally and ethically wrong. Every individual has the right to turn their hard work into savings that they can rely on for the future.
In Bitcoin: Sovereignty through Mathematics, Knut not only delves into the fundamental principles underlying Bitcoin’s creation but also presents the groundbreaking concept of absolute scarcity. Bitcoin’s limited supply of 21 million and the impossibility of creating more due to its protocol creates a condition of absolute scarcity, a first in human history. Absolute scarcity, coupled with Knut’s poetic description of Bitcoin’s creation as "an immaculate conception," emphasizes its unique and revolutionary nature. The term "immaculate conception" highlights the fact that Bitcoin’s creation was not based on any pre-existing financial system but rather emerged from a set of mathematical principles that ensure its security and scarcity. The conditions that gave birth to Bitcoin will never be replicated, which further cements Bitcoin’s status as a one-of-a-kind element that will revolutionize the way we view and use money. Absolute scarcity aligns with the Austrian school of economics’ views on money, which argue that sound money should be scarce, durable, and difficult to counterfeit. Bitcoin ticks all the boxes for sound money, laying the ground for a genuine foundation to end the era of so-called cheap or easy money.
In the follow-up to this book, Bitcoin: Independence Reimagined1, Knut presents us, using plain logic and reasoning, the primitive constraints of the current fiat system and status quo governance. These structures, which we have so readily accepted, are gradually stripping us of our freedoms. By highlighting these shortcomings, he urges us to critically examine them and envision a future where we exercise greater autonomy over our lives, both financially and socially. Bitcoin’s simple and secure existence stands in contrast to the coercive and interventionist nature of the fiat system. Bitcoin is sincere; it neither favors nor opposes us. Bitcoin simply exists. Coming to terms with this truth is both humbling and liberating.
Knut’s writing, with its clear and elegant style, offers insightful guidance for those interested in exploring the deeper implications of Bitcoin beyond its function as a mere currency, recognizing it as a truly transformative breakthrough. A breakthrough that provides us with hope, a viable solution to reverse the degeneracy and decadence plaguing humanity.
Prince Philip of Serbia, 21st February 2023
Footnotes:
1. This foreword was originally written for a combined volume containing both Bitcoin: Sovereignty Through Mathematics and Bitcoin: Independence Reimagined.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ c239c0f9:fa4a5015
2025-03-21 15:51:57
@ c239c0f9:fa4a5015
2025-03-21 15:51:57Block:#888777- March 2025The Monthly Thunderbolt Dispatch On Bitcoin layers two innovations, aggregating the Best posts about the ~Lightning Network and others Bitcoin L2 solution- Exclusively on Stacker.News
It's again that time of the month, time to catch up with the latest features and trends that are shaping the future of Bitcoin. Each issue covers the latest trends and greatest advancements dictating the future of Bitcoin adoption—the very first and most commented insights from around the SN world. In every issue arrives expert analysis, in-depth interview, and breaking news of the most significant advancements in the Bitcoin layer two solutions.
Subscribe and make sure you don’t miss anything about the ~Lightning Revolution!
Now let's focus on the top five items for each category, an electrifying selection that hope you'll be able to read before next edition.
Happy Zapping!
Top ~Lightning posts
Most zapranked posts this month:
-
Underrated privacy tools on Lightning by @DarthCoin 4750 sats \ 21 comments \ 10 Mar on
~lightning -
ngx_l402: L402 Authentication for Nginx with LNURL, LND & NWC Support by @dhananjay 3602 sats \ 11 comments \ 11 Mar on
~lightning -
LNBϟG discusses fees and routing node management by @C_Otto 908 sats \ 3 comments \ 15 Mar on
~lightning -
New Release: Breez SDK - Nodeless 0.7.1 by @_ds 264 sats \ 1 comment \ 19 Feb on
~lightning -
Alby Hub Lightning Channel Stats the first 6 months by @k00b 376 sats \ 8 comments \ 27 Feb on
~lightning
Top posts by comments
This month we replaced the top posts by sats with these most commented posts (excluding those already listed above):
-
Cowbold Beta available for Testing: The best P2P Bitcoin alternativ to SplitWise by @supratic 699 sats \ 24 comments \ 1 Mar on
~lightning -
Nwc alternative to coinos, testing by @dingding541 150 sats \ 22 comments \ 17 Mar on
~lightning -
Payments below dust limit not trustless by @BallLightning 2141 sats \ 18 comments \ 11 Mar on
~lightning -
Question of trust regarding LSPs by @Fiatrevelation 385 sats \ 18 comments \ 14 Mar on
~lightning -
Question For CLN Start9 Users? by @siggy47 617 sats \ 15 comments \ 4 Mar on
~lightning
Top ~Lightning Boosts
Check them all here.
-
Try out the Ark protocol on signet by @nwoodfine 2083 sats \ 30k boost \ 12 comments \ 19 Mar on
~lightning -
Amboss CEO On Growth Of The Lightning Network, Tether (USDT) On Lightning by @Jestopher_BTC 577 sats \ 20k boost \ 10 comments \ 19 Feb on
~lightning -
Building Self Custody Lightning in 2025 by @k00b 2293 sats \ 10k boost \ 8 comments \ 23 Jan on
~lightning
Top Lightning posts outside ~Lightning
This month best posts about the Lightning Network outside ~Lightning territory:
-
SN is a badass use case for noncustodial lightning by @Fiatrevelation 1998 sats \ 15 comments \ 19 Feb on
~meta -
Alby Hub: Improving the Self-Custodial Lightning Experience by @teemupleb 4642 sats \ 8 comments \ 8 Mar on
~meta -
SN is a badass use case for noncustodial lightning by @Fiatrevelation 1834 sats \ 13 comments \ 20 Feb on
~meta -
Bitcoin Users... and especially Lightning users live in a Total Bubble (sofar) by @028559d218 1304 sats \ 24 comments \ 8 Mar on
~bitcoin -
🚀 New Geocaching Meets Lightning App ⚡ by @questforsats 4518 sats \ 170k boost \ 86 comments \ 20 Feb on
~builders
Forever top ~Lightning posts
La crème de la crème... check them all here. Plenty of new entries this month too at #1, #2, #4 and #5! This means old posts get still zaps... well done zappers 💪
-
👨🚀 We're releasing 𝗔𝗟𝗕𝗬 𝗚𝗢 - the easiest lightning mobile wallet by @Alby 29.2k sats \ 41 comments \ 25 Sep 2024 on
~lightning -
Building Self Custody Lightning in 2025 by @k00b 2303 sats \ 8 comments \ 22 Jan on
~lightning -
Lightning Wallets: Self-Custody Despite Poor Network - Apps Tested in Zimbabwe by @anita 72.8k sats \ 39 comments \ 28 Jan 2024 on
~lightning -
How to Attach Your self-hosted LNbits wallet to SEND/RECEIVE sats to/from SN by @supratic 1765 sats \ 18 comments \ 23 Sep 2024 on
~lightning -
A Way to Use Stacker News to improve your Zap Receiving by @bzzzt 1652 sats \ 22 comments \ 15 Jul 2024 on
~lightning
Forever top Lightning posts outside ~Lightning
Lot of changes here, but probably due to the recent relevance search and unbusting search functionality changes:
-
Rethinking Lightning by @benthecarman with 51.6k sats \ 137 comments \ 6 Jan 2024 on
~bitcoin -
Lightning Everywhere by @TonyGiorgio with 12k sats \ 27 comments \ 24 Jul 2023 on
~bitcoin -
Lightning is dead, long live the Lightning! by @supertestnet and zaps forwarded to @anita (50%) @k00b (50%) 6321 sats \ 28 comments \ @tolot 27 Oct 2023 on
~bitcoin -
Lightning Is Doomed by @Rsync25 2450 sats \ 15 comments \ 27 Nov 2023 on
~bitcoin -
We Need More Apps with Lightning, Not More Lightning Apps by @kr 5030 sats \ 22 comments \ @kr 12 May 2023 on
~bitcoin
-
-
 @ 2fb77d26:c47a6ee1
2025-03-21 15:49:40
@ 2fb77d26:c47a6ee1
2025-03-21 15:49:40»Pershing II« – das war eines der ersten englischen Wörter, das mir als Kind geläufig war. Es handelt sich um die Typenbezeichnung einer US-Mittelstreckenrakete, einer nuklearen Boden-Boden-Rakete, die mit einem thermonuklearen Sprengkopf vom Typ W85 ausgestattet war, eine Reichweite von etwa 1.800 km hatte und somit von Süddeutschland aus Ziele im westlichen Russland binnen fünf Minuten erreichen konnte. Es war Anfang der 1980er Jahre. Die Zeit des Kalten Krieges. Eine Bezeichnung, die George Orwell mit seinem Essay »You and the Atomic Bomb« (Du und die Atombombe) im Jahre 1945 geprägt hatte. Die Fronten waren verhärtet.
Die westdeutsche Friedensbewegung protestierte lautstark gegen die Stationierung von Atomsprengköpfen auf heimischem Boden. Nachdem die im NATO-Doppelbeschluss vom 12. Dezember 1979 vereinbarten Abrüstungsverhandlungen zwischen den Atommächten jedoch erfolglos geblieben waren, entschied der Deutsche Bundestag am 22. November 1983, der Stationierung von US-Atomwaffen im Lande zuzustimmen. Diese war 1985 abgeschlossen und ganze 120 Exemplare der todbringenden Massenvernichtungswaffe in der Bundesrepublik verteilt worden. Außer Deutschland tat kein Land den USA diesen Gefallen.
Ich hatte die militärische Artikelbezeichnung »Pershing II« im Radio aufgeschnappt, welcher zu Hause fast durchgehend in Betrieb war, und später ein paar Bilder der Raketen in den Abendnachrichten gesehen. Noch gab es nur ARD, ZDF und das Regionalprogramm. Dementsprechend rar waren visuelle Informationen. Und aufgrund meiner frühen Begeisterung für Fluggeräte aller Art, zeichnete ich daraufhin ständig Raketen. Da ich außerdem bereits in diesem zarten Alter von fünf oder sechs Jahren extrem von Musik angetan war und durchweg versuchte, englische Songtexte, zum Beispiel von den Beatles, dem Klang der Stimmen folgend nachzusingen, übte auch der fremd klingende Begriff »Pershing II« eine gewisse Faszination auf mich aus.
Was mir meine Eltern diesbezüglich sagten oder erklärten, kann ich leider nicht mehr erinnern – als erklärte Pazifisten nahmen sie die latente Gefahr eines Nuklearkrieges aber sicher nicht mit der spielerisch-kindlichen Leichtigkeit, die ich im Umgang mit gemalten oder gebastelten Raketen an den Tag legte. Das Thema nukleare Kriegsführung beherrschte die Nachrichten dieser Zeit und erzeugte Angst. Denn Militärstrategen sprachen Anfang der 1980er Jahre allen Ernstes davon, dass der Atomkrieg zwischenzeitlich präziser und somit auch führbarer geworden sei. Damals wie heute – absoluter Irrsinn.
Neben der Berlin-Blockade 1948/1949 und der Kuba-Krise, war die Auseinandersetzung um die Stationierung von Mittelstreckenraketen in Westeuropa von 1979 bis 1983 also eine der drei kritischsten Phasen des Kalten Krieges.
Nie war die Welt einem fatalen wie letalen nuklearen Schlagabtausch der Supermächte näher als zu diesen drei Zeitpunkten in der Geschichte. Bis heute, so scheint es.
Denn die stetig eskalierende Ukraine-Krise rückt dieses vergessen geglaubte Horror-Szenario wieder in den Fokus der Öffentlichkeit. Polit-Darsteller wie der Maoist und China-Fan Robert Habeck äußern dieser Tage dummdreist, keine Angst vor einem Dritten Weltkrieg zu haben. Sogenannte Sicherheitsexperten erklären im ZDF, dass man sich vor Putins Bomben nicht fürchten solle, obwohl man in Mainz permanent Angst schürt und schon am 5. Mai 2022 titelt, »Moskau simuliert Atomangriff in Kaliningrad«.
Der »Beobachter Gesundheit« gibt Tipps dazu, wie man die Panik vor einem Atomkrieg mental in den Griff bekommen kann, während das deutsche BBK (Bundesamt für Bevölkerungsschutz und Katastrophenhilfe) der Bevölkerung bereits empfiehlt, im Zuge der Ukraine-Krise Notvorräte anzulegen und Marschgepäck bereitzuhalten. Auf der Webseite »wikiHow« findet sich ein sehr umfassender, bebilderter Ratgeber mit dem Titel »Einen Atomkrieg überleben«. Beim Lesen der zahlreichen, mutmaßlich nur bedingt hilfreichen Tipps zur Meisterung der nuklearen Apokalypse dürfte jedem normalen Menschen etwas mulmig werden.
Hofberichterstatter Ruprecht Polenz lässt sich beim Propaganda-Multiplikator ZEIT ONLINE am 30. April 2022 dennoch zu der wagemutigen Formulierung verleiten, »wer einen Atomkrieg verhindern will, darf Putin nicht gewinnen lassen«. Solch ein Statement ist nicht nur falsch und realitätsfremd, sondern zeugt gleichsam von der bewussten Negierung von Faktenlage und historischen Hintergründen zur Ukraine-Krise. Dabei könnte man es durchaus besser wissen.
Die RAND-Corporation, ein im Jahre 1948 gegründeter, einflussreicher Think Tank der US-Hegemonie, veröffentlichte zum Beispiel schon im Jahr 2019 ein vielsagendes, 354 Seiten umfassendes Strategiepapier unter der Überschrift »Overextending and Unbalancing Russia«. Frei übersetzt: Eine Strategie, um Russland überzustrapazieren und aus dem Gleichgewicht zu bringen – ökonomisch, militärisch und gesellschaftlich – mit dem singulären Ziel, die geopolitische Dominanz der Vereinigten Staaten zu bewahren. Ein durchdachtes Drehbuch zur finalen Erniedrigung und Bezwingung des ewigen Klassenfeindes sowie dem Erhalt der unipolaren Weltordnung, der Pax Americana.
Der Ansatz der RAND-Corporation: Die Osterweiterung der NATO forcieren, das Ansehen Russlands in der Welt zerstören, kostenintensives, nukleares Wettrüsten, die Ukraine bewaffnen, um einen militärischen Stellvertreterkonflikt mit Putin zu provozieren, um die ehemalige Sowjetunion anschließend mittels internationaler Sanktionen – legitimiert durch den brodelnden Krieg – finanziell in die Knie zu zwingen.
Verblüffend, wie sehr doch die im RAND-Strategiepapier aufgezeigte Vorgehensweise den aktuellen Geschehnissen an den Außengrenzen des Riesenreiches gleicht. Fast macht es den Anschein, als folgten die Geostrategen in Washington den Empfehlungen ihrer kostspieligen Think Tanks. Dies ließ sich auch im Zuge der Corona-Krise beobachten, die im Ablauf fraglos dem von der Rockefeller-Stiftung erarbeiteten Pandemie-Szenario »Lock Step« glich, wie Journalist Norbert Häring bereits am 28. Mai 2020 ausführlich berichtet.
Was das totalitäre Krisen-Drehbuch der RAND-Corporation nicht detailliert behandelt, sind die akuten Risiken einer potenziellen nuklearen Eskalation. Denn es endet mit dem möglichen Aufkeimen eines militärischen Konflikts und schließt schlicht mit dem Hinweis:
»Auch wenn die US-Armee nicht direkt an der Operation beteiligt ist, wird sie eine Schlüsselrolle bei der Abmilderung der Folgen spielen. Wie bereits erwähnt, bergen alle Maßnahmen, die der Schwächung Russlands dienen, einiges an Risiko. Infolgedessen werden das Abschreckungspotential sowie die operativen Fähigkeiten des US-Militärs in Europa gestärkt werden müssen. Es besteht die Möglichkeit, dass die Spannungen mit Russland zu einem Konflikt eskalieren.«
Die USA betrachten den Einsatz von Atomwaffen dabei offensichtlich als probates Mittel. Warum sonst modernisieren die Amerikaner seit Jahren ihr Arsenal und geben Milliarden US-Dollar dafür aus? Das macht eigentlich nur Sinn, wenn man plant, diese Waffen irgendwann einzusetzen. Der »Plot« für die Events nach dem Aufflammen einer militärischen Auseinandersetzung mit Russland ist vermutlich Verschlusssache und liegt nur Eingeweihten im Weißen Haus, Pentagon, CIA-Hauptquartier sowie den Verbündeten in EU und NATO-Hauptquartier vor.
Das ist bedauerlich. Denn ein Einblick in die aktuellen militärischen Planspiele und strategischen Szenarien der NATO-Hegemonie wäre hilfreich, um zu verstehen, ob die Arroganz des Westens tatsächlich einen Punkt erreicht hat, an dem man einen Atomkrieg in Kauf nehmen würde, um Russland und China auf ihre Plätze zu verweisen und im globalen Club der Technokraten am Kopfende zu sitzen. Um einen Konflikt der Systeme – Kapitalismus, Sozialismus, Kommunismus – handelt es sich nämlich nicht, auch wenn Medien dies gerne so darstellen, sondern um Machtkämpfe innerhalb der internationalen Oligarchie. Die drei Machtblöcke kämpfen um Vorherrschaft in der totalitären Weltordnung der nahen Zukunft.
Die Frage ist nur: Tun sie dies einvernehmlich – oder handelt es sich an Russlands Grenzen um ernsthafte, kriegerische Auseinandersetzungen, die in letzter Konsequenz militärisch entschieden werden müssen? Das RAND-Strategiepapier scheint davon auszugehen, dass Wirtschafts- und Informationskrieg, begleitet von NATO-Drohgebärden, ausreichen, um das Rennen zu Gunsten des Wertewestens zu entscheiden. Es gilt zu hoffen, dass diese Interpretation des Schriftstücks zutrifft. Ansonsten läuft die moderne Zivilisation Gefahr, sich in die Steinzeit zurückzubomben. Wie das aussieht, zeigt eindrücklich der Film »The Day After« (Der Tag danach) aus dem Jahre 1983.
Der zwei Stunden lange Streifen von Regisseur Nicholas Meyer ist bildgewaltig, beängstigend, ernüchternd und deprimierend. Er zeigt nicht nur, wie binnen weniger Tage aus einem Kalten Krieg ein Atomkrieg wird, sondern auch, was dessen schreckliche Folgen sind. Schon ein kurzer, etwas mehr als acht Minuten langer Zusammenschnitt macht klar, dass man ein absoluter Narr sein muss, um keine Angst vor thermonuklearen Angriffen zu haben.
Im Film gibt der US-Oberbefehlshaber nach der Zerstörung des NATO-Hauptquartiers den Befehl zum Atomschlag. Das entsprechende NATO-Protokoll wird aktiviert und die Raketensilos einsatzbereit gemacht. Das Drehbuch lässt offen, wer den Erstschlag führt. Klar ist, dass sobald die Sprengköpfe des Westens unterwegs sind, Russland einen Gegenangriff mit 300 Interkontinentalraketen auslöst und die Vereinigten Staaten in die Steinzeit bombt.
Überall im Land der unbegrenzten Möglichkeiten steigen feurige Atompilze in den Himmel. Metropolen werden in Sekunden ausradiert, Lebewesen, Pflanzen und Gebäude verdampfen in Feuersbrünsten um den Einschlagsort, ganze Landstriche werden vom Erdboden getilgt – und schon in den ersten Minuten nach Explosion der Nuklearsprengköpfe sterben weite Teile der Bevölkerung. 90 Millionen innerhalb weniger Stunden, wie eine Simulation mit dem etwas unheimlichen Titel »Plan A« der Princeton-Universität von 2019 berechnet hat.
Der eigentliche Horror beginnt allerdings erst. Denn die schlimmsten Szenen des Films sind jene, die den Zustand der Welt zwei Wochen nach den Atomschlägen zeigen. Im Land herrscht Anomie. Chaos und Zerstörung, wohin man schaut. Vorindustrielle Zustände. Die Städte sind unbewohnbar und die Überlebenden leiden an Strahlenkrankheit. Haare und Zähne fallen aus. Bei manchen binnen weniger Stunden oder Tage, bei anderen dauert es Wochen. Ein grausamer Tod auf Raten. Alles stirbt, siecht dahin. In den Ruinen entstehen Flüchtlingslager. Seuchen brechen aus. Militärkommandos erschießen willkürlich Menschen. Recht, Gerichte und Prozesse gibt es nicht mehr. Und um zu überleben, bewaffnen sich schlussendlich auch die Zivilisten und töten sich gegenseitig. Absolute Barbarei.
»The Day After« erklärt nicht, wer diesen Krieg gewinnt, nennt keinen Sieger. Vermutlich, weil Regisseur Nicholas Meyer schmerzlich bewusst war, dass es bei einem ausgewachsenen Atomkrieg keine Gewinner geben kann.
Er bedeutet das Ende der modernen Zivilisation. Nicht umsonst hat Albert Einstein früh vor militärischem Missbrauch entsprechender wissenschaftlicher Erkenntnisse gewarnt. So lässt der Streifen aus Zeiten das kalten Krieges auch das Ende offen. Kein Hollywood-Finale. Kein Happy End. Die beklemmenden Gefühle bleiben. Weder Will Smith noch James Bond tauchen auf, um die Welt in letzter Minute doch noch zu retten. Sie ist kaputt. Tot. Eine nuklear verseuchte Wüste. Kein Hoffnungsschimmer am Horizont.
Wer das Pech hatte, die Erstschläge zu überleben, stirbt langsam, aber sicher – und vor allem qualvoll.
Vielleicht sollten Spitzenpolitiker, Dogmatiker, Propagandisten und Kriegshetzer von heute sich diesen Film einmal in Ruhe anschauen, bevor sie leichtfertig derartige Optionen in Betracht ziehen. Ich habe »The Day After« nur ein einziges Mal in meinem Leben gesehen – wenige Monate, nachdem ich den Begriff »Pershing II« das erste Mal als kleines Kind im Radio hörte und meine Eltern neugierig fragte, was es damit auf sich hat – das war ausreichend. Die Eindrücke wirken bis heute. Ich bin mir auch mehr als dreißig Jahre später immer noch der unverrückbaren, indiskutablen Tatsache bewusst, dass es niemals zu einem Atomkrieg kommen darf. Jeder, der diesen Film gesehen, wird das unterschreiben.
Ich jedenfalls werde nie vergessen, wie ich eines nachts heimlich im dunklen Wohnzimmer der heimischen Dachwohnung ganz nahe vor dem Fernseher saß. Eigentlich durfte ich nur ein paar Mal in der Woche ausgewählte Kindersendungen anschauen. Aber meine Eltern schliefen bereits. Es muss circa 23:00 Uhr gewesen sein, denn nach den Spätfilmen war damals in der Regel Sendeschluss. Und das was war meist gegen eins oder halb zwei.
Just als ich den kleinen Röhrenfernseher anschaltete, begann »im Ersten« der bis heute in mir nachhallende Spielfilm. Der Tag danach. Zunächst begeistert von den vielen Raketen und irgendwie noch fasziniert von den mir bis dato unbekannten, riesigen Explosionen, die Atombomben auslösen, blieb ich gebannt sitzen. Wie versteinert. Bis zur Schlussszene, in der sich eine Handvoll strahlenverseuchter, zerrissener, verrottender Menschen, die kaum noch Haare auf dem Kopf haben und aussehen wie Zombies, in den staubigen Ruinen einer leeren Großstadt kraftlos in den Armen liegen und hilflos schluchzen. Die Kamera zieht auf. Dann Schwarzblende – und eine letzte, dünne, einsam flehende Stimme im Äther:
»Hello, is anybody there? Anybody at all?« (Hallo, ist da jemand? Irgendjemand?)
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32
@ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32For our first edition of #Nostrversity, we'll be diving into Nostr Wallet Connect, or #NWC; a handy means of connecting a #Lightning wallet to your favorite #Nostr app that quickly became the standard and is now an essential part of onboarding to Nostr for any new user who wants to experience the magic of zaps. Yet NWC enables so much more than just one-tap-zapping, as we will see when we look a little closer at how it works under the hood.
Lightning History on Nostr
Back in the wild-west days of Nostr, before nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s invented zaps, Bitcoin psychopaths were already sending sats to one another over Nostr. However, the way we had to do it back then was by going into our Lightning wallet, selecting "receive," inputting an amount we wanted, and copy/pasting an invoice from the wallet into our Nostr note, then hope someone was willing to pay it. And the payment side was just as cumbersome, requiring manually copying the invoice from your Nostr client, pasting it into a Lightning wallet so you could see how much the other user wanted, and then deciding if you were even willing to send it.
It didn't take long before Nostr clients, particularly on mobile, started rendering Lightning invoices in a convenient format that showed the invoice amount and a "Pay" button, that would prompt the user to open a Lightning wallet. This took out a decent amount of friction for the sender, but it was still just as big a hassle for the receiver.
Then zaps came along, and soon everyone had the ability to send sats to any other user when they found value in the content they posted. At least, any other user that added their Lightning address to their profile and whose Lightning wallet provider supported sending a "paid" receipt to a Nostr relay. Receiver friction had been virtually eliminated and the sats began to flow. Nostr also became the de facto directory for Bitcoiner payment addresses. If you heard nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a say something brilliant on a podcast, you could just look her up on any Nostr client with zaps and send some sats her way as a thank you.
Enter the zapathon, a community event with one purpose: break nostr:npub1hcwcj72tlyk7thtyc8nq763vwrq5p2avnyeyrrlwxrzuvdl7j3usj4h9rq by zapping each other so much it was effectively a DDOS attack. Sure, it was a stress test on other wallets too, but most users were on Wallet of Satoshi because it was the easiest way to get a Lightning address with a mobile wallet.
It was a ton of fun flinging sats around as fast as your fingers would let you! However, a new friction point was soon discovered from trying to zap so frequently. Every time you tapped the zap icon in your Nostr client, you had to wait for your wallet to open and present the invoice to approve payment, then switch back to your Nostr client to zap the next note. Not a big deal when you only send a zap occasionally, but when trying to zap every note in your feed, it adds a significant amount of time and extra clicks. In fact, this small amount of friction, whether you realize it or not, often acts as just enough of a barrier to zapping that you will choose not to zap a post you found some value in, just because of the extra 5 seconds it takes to load into your wallet app, approve the payment, and switch back to your Nostr client.
Wouldn't it be amazing if we could have one-tap-zaps?
I can't recall if there were any other methods by which this was achieved, but the method that caught on was developed and released into the wild by nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm, who called it Nostr Wallet Connect. At that time (March of 2023), Alby was a custodial Lightning wallet for your web browser, and while you could connect your own node to it using LNDHub, most people just stuck with their custodial option since it came with a Lightning address. Nostr Wallet Connect was, at that time, a way to connect your Alby wallet to a Nostr client.
I am not certain which client was the first to support NWC, but I know that #Amethyst was pretty early on, and it was an instant success. Users could get a "connection string" from Alby, paste it into Amethyst, and zap with a single tap of their finger. Just like zaps themselves had eliminated the friction for receiving payments via Lightning for anyone with a Lightning address, Nostr Wallet Connect had eliminated the friction for sending payments. No more wasted seconds switching back and forth between Nostr client and wallet app, just tap and zap sent, tap again and another zap gone.
Of course, this meant that it was all too easy to send way more sats out of your wallet than you intended. This was solved by the ability to set budgets, so your wallet would cut you off once you reached the max amount you had set for yourself.
Because Alby had made Nostr Wallet Connect open source and part of the Nostr protocol, it didn't take long before more and more clients started adding support for it. Users demanded it and wouldn't shut up about it until it was added. Other wallet providers also saw the value of including it. Now it is simply expected, and any wallet that doesn't include it won't attract Nostr users.
Notably, Wallet of Satoshi went from being the most popular wallet among Nostr users to being a rare and quaint throwback to a bygone era, because they never integrated NWC and they pulled away from serving anyone in the U.S. out of fear of regulation under the Biden administration.
So we arrive at the state of Lightning on Nostr today, with Lightning addresses in our profiles for receiving zaps, and Nostr Wallet Connect for sending, and hard pressed to find Nostr clients that don't support both.
So... How does it work?
All of that history is great, but you're here to learn how this technology works. What is happening behind the scenes when you tap that little ⚡️ icon and sats seem to magically leave your Lightning wallet and show up on your screen as a zap underneath the latest nostr:npub1lrnvvs6z78s9yjqxxr38uyqkmn34lsaxznnqgd877j4z2qej3j5s09qnw5 meme, without you having to fiddle around with any Lightning invoices at all?
It's really quite simple, in the end. Your wallet communicating with your Nostr client using a Nostr relay in the middle, the same way you communicate with other Nostr users by saving notes to a relay that they can retrieve them from.
First, your Nostr client has to know how to "tag" your wallet, and on which relay to send it notes. This is why you need to get a "connection string" from your wallet to paste into your Nostr client. This string has all the information that is needed for your Nostr client to know how to communicate with your wallet, and for your wallet to be sure that the payment requests are authorized by you.
Let's take a look at an example connection string:
nostr+walletconnect://b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4?relay=wss%3A%2F%2Frelay.damus.io&secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cLooks like a bunch of gobbledygook, right? We'll break down each of its parts and see what it does.
nostr+walletconnect://This portion just defines the type of information that follows it. Because the string starts with this marker, any software reading it will know that what follows is information on how to communicate with a Lightning wallet, so long as it has been programmed to recognize it.
b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4This section is just a public key, the same as an npub. In fact, it can be readily converted to an npub if you want using nostr:npub1zdr58j526qsrkdjhcg9xs60xfutqeey2ucugms04efnlx3spnmns2eqha9's key converter. It's a nostr identity just like yours or mine, but you won't find any GM posts or catstr pictures in its note history. It's only posting special note types used by NWC. This public key belongs to your Lightning wallet, and just like you can have multiple npubs for each of your alter egos, your wallet creates a separate public key to use with each new app you want to connect it to. Or at least it should. The Nostr client you use will tag your wallet in notes it creates by using this public key.
relay=wss%3A%2F%2Frelay.damus.ioThis section is probably easily recognizable. It's the same as typing
relay=wss://relay.damus.io, except that it has to use%3A%2F%2Fin place of://. This tells your Nostr client which relay it needs to use to communicate with your wallet. Hopefully your wallet uses a relay with high up-time, because one of the major ways for NWC to fail is if the relay is down. You also can't use just any relay. It has to accept the note kinds used by NWC, which is why wallets don't typically let their users choose the relay that will be used. You also can't just modify the connection string to use a relay you prefer, even if you know it allows NWC note kinds. This is because it will result in your Nostr client sending requests to your wallet on that relay, but your wallet is not reading from that relay, so it will never receive the requests.secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cThis is just a Nostr private key. It's an nsec, but in hex format. Your wallet is giving your Nostr client a private key that it must use to sign all of the requests it sends to your wallet. No request signed by any other private key will be answered by your wallet. Your wallet will generate a separate private key for each connection string, allowing you as the user to revoke those connections individually, or set a separate budget for each connection.
When you tap the ⚡️ icon in your Nostr client, it obtains a Lightning invoice from the user's wallet you are trying to zap using their Lightning address. It then creates a note tagging your wallet's public key and requesting payment of that Lightning invoice, signing the note with the private key your wallet generated for it, and writing that note to the specified Nostr relay. Your wallet is constantly checking that relay for new notes and when it sees the payment request signed by an authorized private key, it pays the invoice, so long as it is within the budget you set, and sends out a payment receipt stating it has been paid so your client can light up the zap indicator to show that it was successful. All of this from a single tap of your finger in Amethyst.
More than Zaps
Now that we know the basics of how NWC works, it doesn't take much extrapolation to realize that this communication between wallet and Nostr client could be used for much more than just payment requests. A client could ask for your wallet's balance information, or transaction history, or ask for a lightning invoice. In fact, why does it have to be a Nostr client making those requests at all? Why not a mobile wallet app, or browser extension?
One of the major pieces of friction felt by those who run Lightning nodes is the difficulty of connecting to them remotely in a secure way. nostr:npub1aghreq2dpz3h3799hrawev5gf5zc2kt4ch9ykhp9utt0jd3gdu2qtlmhct and nostr:npub126ntw5mnermmj0znhjhgdk8lh2af72sm8qfzq48umdlnhaj9kuns3le9ll allow for connecting via Tor by default, but that can be painfully slow and unreliable. Anyone who has set up a connection to their node via LND Rest over Tor to their nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5 wallet can attest to the frustration of opening their wallet and waiting several seconds for the interface to load, only to receive a timeout notice.
Nostr Wallet Connect has eliminated this issue thanks to Alby Hub and Alby Go. Just create a new connection in Alby Hub, give it a budget, and scan the QR code with Alby Go and you have a fully-functional, mobile Lightning wallet connected to your node at home that loads extremely quickly and reliably, so long as the Nostr relay in-between is up and running.
Now, you may be concerned that the information being passed back and forth on this Nostr relay is incredibly sensitive financial information, especially if balance and transaction history is involved. However, this is not a concern because the content of the notes is fully encrypted. The relay owner, or anyone else with access to read data on that relay, has no idea what information is contained in the messages being sent between wallet provider and Nostr client, or Lightning node and mobile wallet. And because neither npub being used by your wallet provider or your Nostr client is the same as your npub, there is nothing tying the messages to you.
As a result, NWC is quickly becoming an integral piece of Lightning infrastructure, even if those making use of it have no interest in joining Nostr at all.
The Future of NWC
To wrap this up, I'd like to point the reader to recent developments with Nostr Wallet Connect, and other use-cases we could very well see in the near future.
First, NWC may not just be for Lightning. nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 recently revealed that he has a working prototype of on-chain payments via NWC.
nostr:nevent1qvzqqqqqqypzpckv7l8jqspl8u4y54dn9rcduwlrs4v2040nxce0m2h0cunvrj8tqyw8wumn8ghj7un9d3shjtnzd96xxmmfdecxzunt9e3k7mf0qyfhwumn8ghj7am0wsh82arcduhx7mn99uq32amnwvaz7tmjv4kxz7fww468smewdahx2tcqyzswntflhlvuea2uf3035r94azm32frnskk5qp2evj43x6nz6kt9zd7j485
We are already seeing it used with eCash wallets like nostr:npub1kvaln6tm0re4d99q9e4ma788wpvnw0jzkz595cljtfgwhldd75xsj9tkzv. There is no reason we shouldn't expect to see it used with all forms of Bitcoin payments. This could lead to an explosion of available wallet applications for all platforms, since they will simply be an interface for communicating with your node or wallet provider.
NWC can also be used for subscriptions, as alluded to in nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8's note above. Before you protest about what an awful monetization model subscriptions are, I generally agree. That said, subscriptions where the user remains in control the entire time, and can unilaterally cancel the subscription at any time, without having to jump through hoops and give explanations about why they no longer want to use the service, is a massive improvement over the current status quo. Remember, NWC allows the user to set a budget for each connection. This means your subscription can't incrementally increase its monthly fee on you. Not without you willingly going into your wallet settings and adjusting the monthly budget, at any rate.
Last one before we close this out: NWC can be used for streaming services where you pay only for what you use, and give yourself a budget. Instead of paying a monthly subscription to Netflix, you could pay per minute that you watch. Previously this could only be done by topping up a wallet controlled by the service itself, the way nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5's wallet worked with streaming sats for Podcasting 2.0. But now NWC is coming to Fountain, and users can bring their own wallet that they control.
The future of NWC is bright, and it extends well beyond zapping memes on Nostr. It's going to open up a world of possibilities for how we can use our sats to stream media, make reoccurring donations, use micro-payments to rent compute, and so much more. I don't know about you, but I am here for it!
-
 @ a012dc82:6458a70d
2025-03-21 15:42:13
@ a012dc82:6458a70d
2025-03-21 15:42:13In the ever-evolving landscape of finance and investment, Bitcoin has emerged as a pivotal player, challenging traditional notions of wealth and assets. Often likened to "digital gold," Bitcoin's unique properties have led some to view it in an even more nuanced light—as "digital pearls." This article delves into how Bitcoin is redefining wealth in the digital age, drawing parallels with historical assets and exploring its impact on modern investment strategies. The comparison to digital pearls is not merely poetic but serves as a metaphor for the transformation of value from physical to digital realms. This shift is not just technological but cultural, reflecting changing attitudes towards what constitutes real wealth in our increasingly digital world.
The digital age has brought about a profound transformation in how we perceive and interact with value. Traditional assets like real estate and precious metals have been joined by a new class of digital assets, from cryptocurrencies to NFTs, reshaping the landscape of investment and wealth. This shift is not merely about the assets themselves but represents a broader change in societal values and economic structures. The rise of digital assets challenges the monopoly of physical assets as the sole bearers of value, suggesting a future where wealth is as much about information and digital ownership as it is about tangible possessions.
Table of Contents
-
The Evolution of Value: From Tangible to Digital
-
Bitcoin: The Digital Pearls of the 21st Century
-
Redefining Wealth and Investment
-
The Future of Digital Wealth
-
Conclusion
-
FAQs
The Evolution of Value: From Tangible to Digital
Historically, the concept of wealth has been tied to tangible assets: land, gold, and precious stones. These assets were prized for their scarcity, durability, and, in many cases, their beauty. However, the digital age has ushered in a new era of value, one where intangible assets like data, software, and digital currencies have become just as, if not more, valuable than their physical counterparts. This transition from tangible to intangible assets marks a significant shift in the global economy, reflecting changes in how we work, live, and interact with the world around us. The value is increasingly found not in physical objects but in the data and digital experiences they enable.
Bitcoin, since its inception in 2009, has epitomized this shift. Created as a decentralized digital currency, it offers a new form of wealth that is secure, transferable, and free from the control of any government or institution. Its blockchain technology ensures transparency and immutability, making it a trustworthy digital asset. This revolutionary approach to currency and wealth has not only challenged traditional financial systems but also redefined what constitutes value in the 21st century. Bitcoin represents a paradigm shift, moving us away from centralized financial systems and towards a more democratized form of wealth.
Bitcoin: The Digital Pearls of the 21st Century
Just as pearls were once a symbol of wealth and status, Bitcoin has emerged as a modern equivalent in the digital realm. The comparison extends beyond mere value; it reflects a shift in what society considers precious. Pearls, formed in the depths of the ocean, were valued for their rarity and beauty. Similarly, Bitcoin, 'mined' through complex computational processes, holds value due to its finite supply and the energy invested in its creation. This digital creation process, known as mining, parallels the natural formation of pearls, adding a layer of intrigue and value to Bitcoin's narrative.
The story of Maisie Plant and her pearl necklace, traded for a New York mansion, illustrates the fluid nature of value. Just as the perceived worth of pearls has fluctuated over time, Bitcoin's value is also subject to change. However, its digital nature and global accessibility mark a departure from traditional assets, offering a new form of wealth that transcends physical boundaries. This story not only highlights the changing nature of value but also serves as a reminder of the subjective and evolving nature of what society deems valuable.
Redefining Wealth and Investment
Bitcoin's rise challenges conventional investment wisdom. Traditional portfolios, heavy on stocks, bonds, and real estate, are being reevaluated as investors seek to diversify with digital assets. Bitcoin's volatility, while often cited as a risk, also presents opportunities for significant returns, drawing parallels with early investments in tech giants like Amazon and Google. This shift towards digital assets represents a broader change in investment strategies, reflecting a new era of wealth where digital assets play a central role.
Moreover, Bitcoin's decentralized nature offers a hedge against inflation and economic instability. In countries facing currency devaluation or financial crisis, it has become a means of preserving wealth, akin to how gold has been used historically. This aspect of Bitcoin highlights its potential not just as an investment but as a tool for economic empowerment and stability. The ability to store and transfer wealth independently of traditional financial systems is a powerful feature, particularly in regions where those systems are unreliable or inaccessible.
The Future of Digital Wealth
As we move further into the digital age, the definition of wealth continues to evolve. Bitcoin, and the broader category of cryptocurrencies, are at the forefront of this shift. They challenge individuals and institutions to rethink what constitutes an asset and how value is assigned and preserved. This evolution is not without its challenges and controversies, but it also offers unprecedented opportunities for innovation and growth.
The integration of Bitcoin into mainstream finance, through ETFs, futures, and other investment vehicles, signifies a growing acceptance of digital currencies as a legitimate form of wealth. However, as with all investments, there are risks and uncertainties. The regulatory landscape, technological advancements, and market dynamics will all play a role in shaping the future of Bitcoin and digital wealth. This future is not just about Bitcoin itself but about the broader implications of a world where digital assets are as common and valued as traditional ones.
Conclusion
Bitcoin's comparison to "digital pearls" offers a compelling framework for understanding its place in the modern economy. Just as the value of pearls once reflected societal trends and desires, so too does Bitcoin capture the zeitgeist of the digital age—a symbol of a new era of wealth that is decentralized, digital, and diverse. As we navigate this new landscape, the story of Bitcoin is far from over; it continues to challenge, redefine, and inspire the future of finance. The journey of Bitcoin from an obscure digital currency to a new form of digital wealth mirrors the broader transformation of the economy and society in the digital age.
FAQs
Why is Bitcoin compared to gold or pearls? Bitcoin is often compared to gold because it shares characteristics such as scarcity, durability, and being a store of value. The comparison to pearls, however, emphasizes its unique, evolving status as a coveted asset, reflecting shifts in societal values and the concept of wealth.
How does Bitcoin work? Bitcoin transactions are verified by network participants (miners) and recorded in blocks on the blockchain. Users can send and receive bitcoins using digital wallets. The supply of Bitcoin is capped at 21 million, ensuring its scarcity.
Is Bitcoin a good investment? Bitcoin's value can be highly volatile, making it a risky investment. However, some view it as a hedge against inflation and a potential part of a diversified investment portfolio. As with any investment, it's important to do thorough research and consider your financial situation and risk tolerance.
Can Bitcoin be converted into real money? Yes, Bitcoin can be exchanged for traditional currencies through online exchanges, peer-to-peer platforms, and some retail locations. The exchange rate varies based on market conditions.
Is Bitcoin legal? The legality of Bitcoin varies by country. Some countries have embraced it, while others have imposed restrictions or outright bans. It's important to check the regulations in your specific location.
What is the future of Bitcoin? The future of Bitcoin is uncertain and subject to various factors, including technological developments, regulatory changes, and market dynamics. It continues to gain acceptance and has sparked a global conversation about the nature of money and the future of financial systems.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ cc601241:181cd0d2
2025-03-21 15:11:09
@ cc601241:181cd0d2
2025-03-21 15:11:09
- Money doesn't grow on trees
- There is no such thing as a free lunch
- Energy cannot be created or destroyed
What if I told you these are three different ways of saying the exact same thing?
If you recognize that money is a unit of account, a medium of exchange, and a store of value, then it's only natural to accept that money at its most abstract formulation is simply information:
"Money is information. It is information we collect about the cost of things. We use it to quantify the world around us. To allow us to figure out what our things are worth in relation to other things. The soundness of a money measures its reliability in storing value over time. Sound money is reliable; you can count on it having a certain value today and in the future. Sound money allows us to determine the proper price of goods and services. Unsound money makes it difficult to figure out what anything should cost. Sound money accurately stores information about the cost of things. Sound money is a sensible store of information."
So long as fiat money can be printed ad infintum to bankroll the military industrial complex, why would we consider the US dollar to be accurate information? Why would we be surprised to see the negative externalities of dark money, regulatory capture, institutional usury, systemic seigniorage, and pervasive rent-seeking happening everywhere? Why wouldn't we start questioning the ripple effects of the Cantillon effect? Why wouldn't the rest of the world's economic actors that operate downstream of the dollar supply not live in constant fear, uncertainty, and doubt? If not resentment, cynicism, and desperation?
"Infinite money creates a scarcity mindset in almost everyone. Most people observe the rising cost of living and experience the feeling of fear or even panic. Fear of the unknown, fear of the future. Uncertainty about making ends meet. Leaky money promotes hoarding, individualism, and fast food culture, where everything is built as quickly and cheaply as possible."
If money is no longer a reliable measure of value but simply a means of control and extraction, how can humanity collaborate or organize or build together? How can we incentivize cooperation? How can we coincide our wants? How can we hope at all?
"Money is a medium of communication. It is one of the most common ways we communicate. Money is a sense-making apparatus. In the broken money world, a subtle distortion becomes ingrained in the foundational layer of sense-making, leading to a systemic corruption of all communication within the system."
Enter a pseudonymous, Good Samaritan, white hat coder: Satoshi Nakamoto.
A cypherpunk who asked a very simple question...

What if there was a money that was not backed by the Federal Reserve or 11 aircraft carriers and 5,000 nuclear warheads and the monopoly of violence? What if that money was backed not by physical scarcity (gold) or political scarcity (fiat) but by mathematical scarcity (blockchain aka timechain)? What if that money operated on principles like "rules without rulers" and "don't trust, verify?" What if we finally had an Occam's razor for economics?

What if that money were backed by the currency of the universe itself: energy?
"Bitcoin's immaculate conception presents the possibility that it has always existed. The genesis block could be viewed merely as the first time we started recording Bitcoin. Knut Svanholm has discussed the idea that Bitcoin might be an element with an atomic weight of zero and that the discovery of Bitcoin is better described as the discovery of our ability to observe this element.
For an element to have an atomic weight of zero, it must be void of protons or neutrons, possessing only electrons. Element zero is purely information. If element zero had always existed prior to our ability to measure it, that means it would have existed back to the time of Lao Tzu. If true, it means there could be undiscovered methods for gauging that information. The understanding of how to observe element zero might not be a binary event.
The interesting thing about observing element zero is that the process requires energy. Producing element zero requires a predictable amount of energy. Interacting with element zero requires energy. By spending Bitcoin, we capture a measurement of the value of the thing we spent it on, priced in energy; because element zero requires energy to produce, we can almost think of pricing other things in Bitcoin as pricing the energy spent in creating them. Element zero transfers energy."
All economy is just the transformation of energy into value. If one accept this definition of economics, then Bitcoin is the purest conversation of energy into value. This would explain why the world is seeing an emergent first principle emerge known as the Joule Paradox:
"Energy sets the value of bitcoin and bitcoin sets the value of energy."

Therefore, Bitcoin is the only money that obeys the laws of thermodynamics.
If we have a transparent public ledger of information backed by energy, we could safely call this document the most objective database in the entire world because energy is the only thing in the entire universe that no one can fake.
That's the power of triple entry bookkeeping. No one can cook the books anymore.

Once humanity is able to guarantee the separation of Money and State, suddenly everyone has a way to protect their own time and energy without having to trust a third party. We are no longer slaves to "absolute power corrupts absolutely". We are no longer beholden to the powers that be. Humanity finally has an incorruptible, immutable, unconfiscatable, permissionless, borderless, open source money available to all.
In a world of manipulated markets, self-sovereignty starts with sound money.
Believe it or not, the thesis of The Dao of Bitcoin: Towards a Cosmology of Energy Money (by Scott Dedels—which I have been quoting throughout this article) states that Bitcoin is "perfect money" (or "daomoney" as he coins it) for the following reason:
Bitcoin = time = money = energy = Bitcoin
There is nothing more valuable than protecting your time & energy. But no one can force you to believe that. Self-sovereignty is a game of consent. The first act of financial freedom is to choose it. The deeper into the Bitcoin rabbithole you go, the sooner you'll have the unmistakable epiphany:
Bitcoin is a strange game where the only winning move is to play.
Bitcoin is just money without the Bullshit. No CEO, no country, no committee, no corporation, no cartel, no council, no conglomerate, no counter-party, no church, no cult of personality. Just pure P2P energy transfer. That's the beauty of freedom money. That's the reason for energy money. That's the answer to the game theory.
With absolute mathematical scarcity, individuals can finally afford an abundance mindset.
For the sovereign individual, all you have to do is nothing but HODL.
That's financial wu wei.
That's energy money that aligns with the universe & vibes with the Dao.

-
 @ 43bb87e2:12cc9cb8
2025-03-21 15:06:52
@ 43bb87e2:12cc9cb8
2025-03-21 15:06:52There was once a little girl that got into some expensive golden wrapping paper, and her father got upset. In his anger, he yelled at his little daughter for wrecking the expensive wrapping paper. The daughter then decided to use the ripped and wrecked wrapping paper to wrap a gift for someone. Again, the father let his anger take over and got mad at the little girl for using the ripped paper for the gift wrapping. The next morning, the little girl presented the tattered, golden wrapped box to her father and said this is for you, Dad. He opened the wrapped box and saw that the box was empty inside. The dad again got angry and told his daughter that when you give a gift to someone, there is supposed to be something inside of it. The little girl, in tears, looked up at her father and said, but it is full daddy. I blew kisses into it until it was completely full. The father then broke down and started crying. He dropped to his knees and put his arms around his precious and innocent daughter. He desperately apologized to her for his anger and continued to ask for her forgiveness. A short while after this, his daughter was taken from this earth because of an accident. The father kept the golden wrapped box next to him for the rest of his life to remind him of the love he had from his daughter.
Nothing else matters in this world or even comes close to the unconditional love that our children and family have for us.
With life being so busy, don’t you dare forget, what really matters in this world. And you be sure to take care of your loved ones, family, and friends.
For we do not know when the last day we will be on this earth.
CHERISH EVERY MOMENT AND LOVE WITH ALL YOUR HEART!
DO NOT LET ANGER RULE OVER YOU.
TELL EVERYONE IN YOUR LIFE,
THAT YOU LOVE THEM!
TELL THEM TODAY!
DO IT NOW!
LOVE YOU ALL, BE BLESSED!
-
 @ da0b9bc3:4e30a4a9
2025-03-21 13:58:11
@ da0b9bc3:4e30a4a9
2025-03-21 13:58:11It's Finally here Stackers!
It's Friday!
We're about to kick off our weekends with some feel good tracks.
Let's get the party started. Bring me those Feel Good tracks.
Let's get it!
This song never doesn't put me in a good mood.
https://youtu.be/fnwZeLdLPdQ?si=ZlbiGSp2r6DtMx6P
originally posted at https://stacker.news/items/920041
-
 @ 46fcbe30:6bd8ce4d
2025-03-21 13:57:11
@ 46fcbe30:6bd8ce4d
2025-03-21 13:57:11Table of Contents
- Introduction
- Overview of the Nostr Ecosystem
- Current Use Cases and Quantitative Metrics
- User Adoption Metrics
- Network Resilience and Decentralization
- Operational Challenges and Scalability
- Replication Overhead and Bandwidth Issues
- Relay Downtime and Financial Sustainability
- Market Disruption and Sentiment
- Disrupting Twitter and Centralized Social Platforms
- Impact on Decentralized Social Media and Censorship Resistance
- Future Trends and 5-Year Outlook
- Innovative Protocol Developments
- Quantitative Forecasting and Diffusion Modeling
- Networking and Integration with Emerging Technologies
- Conclusions and Strategic Recommendations
1. Introduction
The Nostr ecosystem has emerged as a powerful decentralized alternative to traditional social media networks, particularly as a potential disruptor of Twitter and other centralized—and even existing decentralized—social media platforms. Developed using a protocol based on cryptographic key pairs and a multi-relay system, Nostr is unique in its provision of censorship resistance and user sovereignty. In this report, we provide a detailed analysis of the current state, scalability challenges, and market disruption potential of Nostr, followed by speculative insights on its trajectory over the next five years.
2. Overview of the Nostr Ecosystem
Launched in 2022, Nostr (Notes and Other Stuff Transmitted by Relays) has rapidly gained traction as an open and decentralized social network. Some of the core features include:
- Decentralized Communication: Relying on independent relays across multiple countries and autonomous systems, Nostr offers an architecture that ensures posts are not stored on a single centralized server.
- Censorship Resistance: With cryptographic authentication and a decentralized relay structure, content censorship becomes significantly more difficult than in traditional networks.
- User Sovereignty: Empowering users with cryptographic key pairs allows for enhanced privacy and data ownership.
- Wide Geographic Distribution: The ecosystem spreads over 44 countries and 151 autonomous systems, underscoring its global reach.
Notable endorsements from figures such as Jack Dorsey, Edward Snowden, Vitalik Buterin, and Sen. Cynthia Lummis have bolstered its reputation as an experimental yet promising alternative to centralized social platforms.
3. Current Use Cases and Quantitative Metrics
User Adoption Metrics
- User Base: In just two years, the Nostr network has attracted over 4 million users, a significant figure given its nascent stage and decentralized nature.
- Content Generation: With over 60 million posts, the volume of content mirrors the rapid adoption and active usage seen in more centralized models.
- Post Replication: Empirical measurements indicate that there are 17.8 million text notes among these posts, replicated on an average of 34.6 relays per post. This level of replication underlines robust resilience and availability even if significant portions of the network experience downtime.
Network Resilience and Decentralization
- Global Distribution: Nostr’s decentralized network ensures high availability with >90% post accessibility even under simulated network failures (e.g., removal of key relays or autonomous systems).
- Robustness: The dispersion across 712 relays illustrates that decentralization is not only a design choice but also a working reality, which contributes to the network’s reliability.
4. Operational Challenges and Scalability
While the Nostr ecosystem demonstrates significant promise, it faces noteworthy operational challenges.
Replication Overhead and Bandwidth Issues
- Excessive Redundancy: Detailed studies have shown that nearly 98.2% of retrieval traffic is redundant. In practice, this equates to an estimated 144 TiB of unnecessary bandwidth consumption.
- Optimization Proposals: To mitigate these inefficiencies, there's a proposal to limit post replications from 34.6 relays to between 10 and 20 relays per post. This could reduce redundant data copies by between 380 million to 480 million instances, potentially lowering operational costs and improving bandwidth utilization.
- Scaling Concerns: With a projected network load of 10 million events per day (or approximately 2 TB annually), the throughput requirement of ~115 TPS is putting a strain on the current architecture. This has led to debates on whether solutions like the current outbox mechanism are sufficient or if further fundamental redesigns and emergent moderation systems are needed.
Relay Downtime and Financial Sustainability
- Relay Stability: Data indicates roughly 20% of relays suffer from significant downtime (exceeding 40% operational time), and 132 relays have been classified as 'dead'. This is a concern for maintaining network integrity.
- Economic Model Challenges: With 95% of free-to-use relays unable to cover operational costs due to minimal zap-based income, there is an urgent need for innovative monetization or community funding models to ensure long-term sustainability.
5. Market Disruption and Sentiment
Nostr is positioned as both a disruptor to traditional centralized social platforms—most notably Twitter—and a catalyst for change within decentralized social media.
Disrupting Twitter and Centralized Platforms
- User Shift: While Twitter remains the most well-known platform, the high-profile endorsements and robust user base of Nostr indicate that there is both market intrigue and a gradual shift among early adopters. Disruption here is measured not only in user numbers but also in the paradigm shift towards decentralized content distribution.
- Market Penetration: Current metrics (4 million users, 60 million posts) suggest that Nostr is challenging Twitter's centralized model insofar as it appeals to users prioritizing censorship resistance, data sovereignty, and resiliency against centralized failures. However, mainstream adoption on par with Twitter is still not realized, and there remains a gap in user experience and feature richness.
Impact on Decentralized Social Media and Censorship Resistance
- Complementary Integrations: As decentralized social media ecosystems continue to mature, integration between Nostr and other censorship-resistant platforms is increasingly likely. This can include interoperability protocols, shared identity management systems, and cross-platform content replication.
- Comparative Advantage: Nostr's network design offers unique advantages over other decentralized social media, particularly in its straightforward, relay-based communication protocol. This positions Nostr to potentially serve as an underpinning technology for a broader decoherent ecosystem of social networks.
- Sentiment Toward Scalability Innovations: Discussions around scaling Nostr often focus on the balance between ensuring redundancy (for resilience) and reducing overhead (for efficiency). The sentiment is one of cautious optimism: while outbox solutions offer a stopgap, many experts advocate for more fundamental architectural redesigns in the long-term.
6. Future Trends and 5-Year Outlook
Looking forward, the evolution of Nostr will likely be shaped by several interrelated trends and emerging technical innovations.
Innovative Protocol Developments
- Decentralized Identity and Reputation Mechanisms: The next phase may see the introduction of distributed reputation systems and rating mechanisms that aid in spam management and improve trustworthiness without compromising decentralization.
- Optimistic Replication and Selective Mirroring: Innovations such as selective content mirroring and event pruning will be key in managing bandwidth and storage demands while remaining true to the decentralized philosophy.
Quantitative Forecasting and Diffusion Modeling
- Forecast Models: By integrating modified Bass diffusion models and learning curve effects, predictions suggest that Nostr can potentially spur significant market disruption within five years. Recent studies indicate that forecasting models in disruptive technology fields have reached accuracies of up to 82% for demand projections.
- Hybrid Quantitative Techniques: Leveraging methods like LDA2Vec and patent citation network analysis, combined with multi-criteria decision-making models (as seen in extended UTAUT approaches), will be crucial for accurately estimating future adoption and cost efficiencies.
- Metrics to Monitor: Future research should focus on user growth rates, relay uptime percentages, cost reductions achieved through replication optimizations, and overall sentiment analysis using advanced deep learning architectures that overcome traditional pitfalls (e.g., sarcasm and multipolarity in text data).
Networking and Integration with Emerging Technologies
- Integration with Other Decentralized Platforms: One promising avenue is exploring cross-platform interoperability with other decentralized and blockchain-based social networks, which could lead to a more cohesive ecosystem. This would not only enhance user experience but also enable shared security and moderation frameworks.
- Next-Generation Relays: The deployment of relays that are more resilient through redundancy optimization and financial sustainability models (perhaps incorporating micro-transaction revenue models or community-driven funding) is another critical area. Such improvements could mitigate the issues of relay downtime and excessive network overhead.
- Contrarian Approaches: A contrarian perspective suggests that instead of building on current frameworks, a radical overhaul of the network architecture might be considered, potentially by leveraging novel distributed ledger technologies or leveraging a hybrid centralized-decentralized model during the transition phase to ensure smoother scaling.
7. Conclusions and Strategic Recommendations
The Nostr ecosystem represents a significant stride toward decentralized, censorship-resistant social media. While its current market adoption and technical design offer a robust alternative to centralized platforms like Twitter, several challenges must be addressed for sustained growth and disruption:
-
Optimization of Data Replication: Reducing redundant data transfers without compromising resilience is essential. Limiting the replication factor and exploring optimistic retrieval mechanisms could provide a balance between availability and efficiency.
-
Relay Stability and Sustainability: With nearly 20% of relays experiencing significant downtime, innovative financial and technical models (such as micro-payments and community funding) should be deployed to enhance the operational reliability of network nodes.
-
Enhanced Moderation and Reputation Systems: Emerging strategies for decentralized content moderation and reputation management could reduce spam and improve content quality while preserving the open nature of the network.
-
Interoperability with Other Decentralized Platforms: Fostering integration with other emerging systems could accelerate market disruption across the broader spectrum of social media.
-
Future-Proofing Through Quantitative Forecasting: Continual adoption of cutting-edge forecasting models and machine learning techniques to measure sentiment and track network metrics is imperative for proactive evolution.
-
Exploring Contrarian Innovations: In addition to incremental changes, it is important not to discount radically new architectures that may emerge from ongoing research in distributed systems and blockchain technologies.
Final Outlook
In the coming five years, Nostr has the potential to disrupt not only Twitter but also the broader landscape of both centralized and decentralized social media. Although the current architecture presents significant scaling challenges, proactive investments in replication optimization, relay stability, and cross-platform integration will likely propel the network into a more mature phase of adoption. The ecosystem will benefit from a dual approach that combines both evolutionary improvements and revolutionary changes, ensuring that it remains robust while meeting the demands of a growing, globally distributed user base.
Appendices
Appendix A: Data and Metrics Summary
- User Base: ~4 million
- Post Volume: >60 million posts
- Average Relay Replication: ~34.6 replicas per post
- Geographical Distribution: 44 countries, 151 autonomous systems
- Bandwidth Waste: ~144 TiB due to redundancy
- Network Load: 10 million events/day (~2TB/year)
- Throughput Requirement: ~115 TPS
Appendix B: Key Technical Proposals
- Replication Control: Limit copies to 10–20 relays for optimal efficiency.
- Selective Mirroring: Implement event pruning and selective content mirroring.
- Decentralized Reputation Systems: Develop distributed rating mechanisms to enhance distributed moderation.
Appendix C: Forecasting and Quantitative Methods
- Diffusion Modeling: Modified Bass models with multi-market dynamics.
- Hybrid Quantitative Techniques: Integration of machine learning (CNN-LSTM, LDA2Vec) with multi‐criteria decision models.
Recommendations for Further Research
- Investigate the comparative performance of alternative replication strategies in decentralized networks.
- Explore funding models that can sustain relay operations without compromising neutrality or decentralization.
- Conduct long-term sentiment analysis using advanced neural architectures to understand evolving user attitudes.
- Evaluate the prospective benefits of radical design overhauls versus incremental enhancements in ensuring network scalability.
This report is intended for expert analysts and researchers in decentralized network systems and social media disruption. It synthesizes current empirical findings with speculative insights to inform future strategies and academic inquiry.
Sources
- https://www.voltage.cloud/blog/exploring-6-use-cases-of-nostr-beyond-messaging
- https://arxiv.org/abs/2402.05709
- https://arxiv.org/html/2402.05709v1
- https://papers.ssrn.com/sol3/Delivery.cfm/5146515.pdf?abstractid=5146515&mirid=1
- https://matchnode.com/blog-and-podcasts/mastering-paid-social-media-advertising-a-comprehensive-guide/
- https://blockworks.co/news/jack-dorsey-app-to-disrupt-twitter
- https://www.securities.io/nostr-a-better-twitter/
- https://medium.com/@jasminedevv/battle-of-the-decentralized-twitter-alternatives-c9f51114614a
- https://www.murrayrudd.pro/nostrs-relay-revolution-scaling-decentralized-networks-for-growth/
- https://github.com/nostr-protocol/nips/issues/75
- https://news.ycombinator.com/item?id=42758579
- https://www.toptal.com/deep-learning/4-sentiment-analysis-accuracy-traps
- https://www.researchgate.net/publication/3076742_Forecasting_the_Market_Diffusion_of_Disruptive_and_Discontinuous_Innovation
- https://www.globenewswire.com/news-release/2025/03/17/3043701/0/en/United-States-Online-Household-Furniture-Market-Report-2025-2029-Analysis-of-Price-Sensitivity-Lifecycle-Customer-Purchase-Basket-Adoption-Rates-and-Purchase-Criteria.html
- https://northeast.newschannelnebraska.com/story/52583550/laser-welding-market-growth-industrial-adoption-rate
- https://www.sciencedirect.com/science/article/am/pii/S2405896323014453
- https://www.marketsandmarkets.com/Market-Reports/industry-5-market-35376359.html
-
 @ 8671a6e5:f88194d1
2025-03-21 13:38:50
@ 8671a6e5:f88194d1
2025-03-21 13:38:50As old people tend to say:\ \ *nasal voice* “Back in my day…” … Bitcoin was this wild, beautiful thing, new. It was something technical that came alive before our very eyes after running a node (just a .exe running on a windows machine in my case).\ Even when you started to painstakingly mined bitcoin on a GPU, in a pool, you felt like growing a network of like minded people, or at least people who thought there was something there. Even if we couldn’t comprehend what it all would lead to (or what fiat value it could reach).\ Then came the first paper wallets, the first good software wallets and attempts at hardware wallets, the first buzz of owning your own value — it was motivating and rewarding. The look on the face of other people you explained bitcoin to, when they’ve seen their first transaction pop up after validation. Awesome.\ \ Back then, it wasn’t about fiat gains or slick marketing campaigns; it was about a distributed network “generating” numbers, keeping a distribute ledger “in synchronization”, at the same time it was a middle finger to the system, representing freedom to transact in value we valued ourselves because of the underlying network of people, nodes and miners.\ \ It was this sort of secret handshake between tech minded people, anti-globalists, anarchists, nerds and rebels who saw the fiat scam for what it was.\ Orange-pilling wasn’t even a term; it was just what you did.\ You'd walk people through the setup of bitcoin core, and the white paper, told them why central banks are a trick that functions as a legalized Ponzi scheme and you showed them bitcoin’s workings without middlemen.\ You played around with bitcoin, person to person, no bullshit, no subscriptions, no suits, no posing like a big shot, no referral links.\ Those were the fun times — pre-Saylor, pre-nation-state hype, pre-every Laura, Luigi, and self-proclaimed “OG” thinking they’re going to conquer the world.\ I miss that.
But times change.
\ The good ol' days are dead
It’s not the first instance in our lifetime that we see things pop-up, being invented, and where some good new idea becomes a reality and then that very good idea becomes an institution (there’s an obscure 1990s movie reference for you).\ We live and learn, just like the first technical people setting up their own point of presence internet servers, we all have to learn how to grow and adapt.
Early Bitcoiners didn’t have referral links or corporate sponsors — they had a mission, and the spirit came from within themselves and from the math and tech they’ve seen at work in practice. And yes, educating about it was important, as was looking for ways to improve bitcoin (the early years weren't exactly main-stream material for example).
From that learning yourself about Bitcoin and feeling the need to share and convince others around you, came the need to talk and learn together with others.
You’d talk your buddy into installing a wallet over a coffee, maybe show your uncle how to buy a few bitcoin, and it felt like planting seeds for something real.
Even if they didn’t get it—“So this number goes from my address to your address?”—you kept explaining and showing.
Then the suits rolled in. Bigger companies wer started, like Blockstream, Trezor, Coinbase and Binance.
Wall Street, Saylor with his infinite buy tweets, El Salvador and its volcano bonds, the US ETF approval — and the game changed, everyone heard about it one way or another. That’s damned important! You’re NOT the bringer of news.\ \ Suddenly, it wasn’t grassroots anymore; it was headlines, hype and game-theory. As predicted by so many in the space.\ Fine, whatever, it's progress or something else, but we as bitcoiners need to adapt to that reality.\ Some adaptations will also cause us to put energy elsewhere than before.\ What worked in 2012 or 2016, might not work anymore after 2024.\ ”We bitcoiners route around problems.” Right?
You didn’t need new people to create an account, or be part of a ‘squad’ or team, you certainly didn’t need them to sell merchandise. You just showed them bitcoin’s inner workings.\ \ Bitcoin was the marketing, the engine, the product and the goal. Bitcoin was the core. Just like digital communication was the core of the earliest internet enthusiasts. The magic of sending a text into the network, and through clever routing, someone thousands of miles away could read it almost immediately, that was the magic, the core.
Sending value with bitcoin has that same magical way, immutable, uncensored, unconfiscatable, with proven digital scarcity and forced honesty.
Nowadays we have so-called orange-pillers.\ They’re trying to spread those values. Or so they should..
They didn’t get the memo on Bitcoin becoming more commonly known apparently, and if they did, their lust for dopamine has long replaced that with their urge to get people to install a lightning wallet. It’s sometimes rather disturbing to see this Orange Pill’ing play out.
They’re out there, like they’re stuck in 2013. But they’re usually not from 2013 at all, more like class of 2020’ish. Not that it matters, they’re still living in the illusion that there are people out there that didn’t hear of bitcoin and that THEY and THEY alone can save these poor souls.\ After 2018 it’s safe to say that that’s not the case.\ I’ll repeat that for the die-hard orange-piller: they do not need you to hear about bitcoin.
These Orange Pillers have another kind of magic happen:
While they’re winning over new souls into bitcoin, one barber, taxi driver and babysitter at a time, they get the small electric charge in their brain that tells them their wealth, their (and their holding's) value will go up somehow. They’re also desperate to make some kind of connection with other bitcoiners, and while they lack that connection, they try to find (or make) new bitcoiners around them.\ This approach might have worked in the past, but things are different now. You’re usually talking to people who you try to convince of something they’ve already rejected (often harshly rejected) or never will care about .\ Most people, do not give a damn about inflation or how that came to be. Certainly when they’re doing their job.\ \ It’s like someone shoving the book of a cult under your nose and trying to convince you it’s going to save your life. You’re not open to it, neither are most of the Orange pill targets to your bitcoin gospel.\ Orange Pillers don’t see how the very people they try to convince today weren’t “in it” for a variety of (good for them) reasons. Unlike in the old days, where people’s natural state was “not heard of bitcoin”; since it was new, and people genuinely didn’t learn about it or read into it.\ That’s however, not the case today. That taxi driver? He heard about bitcoin. Be sure.
Such new people today, are almost non-existing, they either bought some long ago, got rekt trading shitcoins and stayed away.\ That, or they found it all a bit too “iffy” (thank you mainstream media) and will politely hold back from not yelling to your face, “I don’t care about that Bitcoin stuff!”.\ They know it’s some form of money or value, they know it exists. Which makes orange pillers the bringers of old news to the bottom of the barral.\ They might get a “hit” now and then of course. But even then, your impact is neglectable in a world that rewards cowardice and short term greed. You’re too late. You don’t scale. And it doesn’t matter.
Since 2020, it has shifted from genuinely introducing people to bitcoin to just "spreading it for the sake of spreading it."\ It looks more and more like an old lion, pacing back and forth in a cramped cage at an old ZOO, restless and frustrated.\ There’s just empty repetition.
The mental breakdown of orange-pilling
\ Let’s look a little further into the act of orange pilling.\ \ It's not like a 1990s hacker type showing a brand new Hayes -compatible modem to his buddy and trying to get a connection going to a local Point of Presence to get internet access.\ \ It’s more like showing your holiday pictures to an uninterested family member. All to get the dopamine hit, the ‘aha moment’ out of someone is now your own ‘aha got someone new’ moment. Like an addict looking for that next high.\ \ You want them to get the app, get some sats and feel the same feeling you have. While they’re worrying about cleaning a table for example, or getting your bill.\ \ This “badge of honor” of Orange Pilling someone is that little shot of dopamine many people need (especially in group) to feel validated.\ The real feeling has everything to do with social conformity1 and the involved brain areas that get stimulus shots and increased activity.2\ \ Above that, for the sake of the mental reward, some people go further down the social boundaries. That’s why orange pilling, often comes across as pushy, unnatural and/or annoying.\ It’s because it’s basically an activity with all the neuro stimulus of an addiction, or done as an ego boost.
Math based
On top of all of that. If you do the math on it the whole action becomes even more ludicrous.\ \ The math in the early days of bitcoin was simple: there was exponential expansion of the number of bitcoiners.\ Purely for bitcoin, the growth in numbers is still going strong, but the percentage has now naturally been flattened out because of media coverage, scams that trick people into other stuff and the close to impossible way to scale the onboarding from a person to person level to larger scales (there are apps doing a good job however, but even then it spread under former bitcoin users or people already in the know on some level, like former shitcoiners).\ \ So even at the rate of trying to orange-pill let’s say 10 people per week (many bitcoiners don’t even tàlk to 10 people a week, let alone convince them to use bitcoin).\ \ When hypothetically 50% of these people (not unusual with word of mouth recommendations) actually install the app you recommended, and we take also a high percentage of 10% actually do a regular buy of bitcoin after installing any of these apps (Strike or Blink or any other).\ \ Given that hypothetical high rate of 10 people a day plus the conversion rate, it would take approximately 200 weeks, close to four years (pun intended) to reach 2000 people as a critical mass that actually installed and used the bitcoin app.\ \ If these 2000 people all buy for about 1000$ worth of bitcoin each, they’ll be good for about 2 million dollars in bitcoin buys over a four year period.\ Even if you take very, very optimistic statistics this, you’ll get a close to zero impact, safe for the occasional big shot you might encounter and converts into a mini-Saylor, or the occasional person you might have saved a few thousand dollars (because they all keep thinking in fiat terms anyway).\ \ But on the other side, people with +100 million dollars to spend will surely have advisors and in-house knowledge, to not having to to rely on your sorry ass explaining bitcoin or installing Wallet of Satoshi on their phone or something.\ \ That’s all peanuts. It’s futile. And you’re fighting an honorable battle from 11 years ago.
### \ Why
I can't grasp why so many people keep doing this the way they do.
Orange-pilling mostly works when the price is going up anyway, unfortunately.
However, when BTC’s up 15% in a week, everyone’s a genius and your coworker suddenly can be all ears about “sound money” and future price gains.
When it’s crashing or flat? Good luck, nobody cares among the normies, unless the “orange-pillee” (the target) has their own ulterior motives for listening (like getting someone to at least give them some attention in any form).
And by the way, to come back to these taxi drivers you try to convince… many taxi drivers already had their share of die hard bitcoiners in their car, and got the explanation. Some of them even act like total noobs probably to get some sats out of your orange pilling wallet. They’re good at playing dumb, trust me.\ \ Do you really think a taxi driver in let’s say Lugano, Amsterdam or Prague didn’t already know bitcoin before you tried to convince him to accept it? You’re not the first. At all.
Most of all, you interact with people while they’re doing their job. You’re actually interfering with their work. When a waiter in a fully booked restaurant has to halt his word and listen to you explaining how to install a lightning wallet on their old iphone that’s almost out of battery, you’re losing anyway.\ They might listen, they might even be pestered to the point they’ll install the damned app. And what do you win or achieve?\ A sparkle in your brain that says “you’re such a cool bitcoiner”?\ Then… after what’s usually a painful few minutes going through a horrible counter-intuitive interface, you get them 5000 sats or whatever over to them.
Oh and adding things like “Hey man, keep these sats for at least 4 years, it will go up in price” is just rotten as well. Just give the people a decent tip and leave. You’re not doing anyone a favor.
When the moment’s there ànd some people are clearly open to it, thèn you might add some info. Point them to an easy to use non KYC app (if there is such a thing).\ But even then, just letting someone know you want to pay in bitcoin, should be enough, WHISPER bitcoin.\ They don’t need your pushy sales pitch on top of the daily struggles they face in hospitality and retail jobs.\ \ The squads
An example,... I saw this crew, let’s name them the “Re-play” squad, they’re all wearing blue hats and have a few flyers with them from a marketing company which managed to put them to some good use at a very low expense rate.
This image is still stuck in my head, some random European country during late summer time — local Bitcoiners, along with some counterparts from other countries. The real “we’re the future” types.
Sitting on the floor at a Bitcoin party, rolling “funny cigarettes” passing a lighter, chatting and laughing about how they orange-pilled some dude in a bar.
 “Yeah, man, I showed him how to set up a Lightning wallet in a few minutes, he’s in!”. Then taking a big puff.\
Except here’s the punchline: the guy wasn’t “in” he was probably just some horny schmuck trying to get into the pants of a woman Bitcoiner in the group, who’d flashed her … QR code at him.
“Yeah, man, I showed him how to set up a Lightning wallet in a few minutes, he’s in!”. Then taking a big puff.\
Except here’s the punchline: the guy wasn’t “in” he was probably just some horny schmuck trying to get into the pants of a woman Bitcoiner in the group, who’d flashed her … QR code at him.They’re all proud, they’re all high, they all belong to a group now … and they’re convinced they’re conquering the world one wallet at a time (they don’t do the math on that, neither should they,… ignorance is bliss).
Doing good for bitcoin has been transcended into an egotrip, and the short-lived kick in the orbitofrontal cortex3 for “doing something”, it’s the filling of a lingering emptiness.\ \ The same people move around like they’re an anthill, reminiscent of the hippie communes, until they’ve returned to their misery at home, knee deep in sorrows of the fiat world. As is the orange pilled person by they way, who’s life won’t be helped by a few sats and yet a new app on their phone. An app they’ll hardly use, unless they start to bond with the other bitcoiners in the area.
These people you target already have had all chances in the world to learn about bitcoin but are too far gone to care.\ Podcasts, books, family members that are into bitcoin, or whatever blog or online service… even the biggest shitcoin casino’s only have rather decent guides and basic explanations. There are excellent educational apps like yzer.io4 as well as the excellent lopp.net5 website by Jameson Lopp.
Convincing people one-by-one doesn’t work anymore—it’s inefficient and outdated since the price surges, media coverage, and ETF launches. Even if some are open to it, it’s a futile, unscalable solution of dread, working indirectly for the benefit of the Wall street types or some shitcoin casinos (where most “new coiners” end up).
Orange pillers, also never can “read the room”. The crew in a busy restaurant or bar isn’t waiting for any explanation about UTXOs or custodians from you!
Even if you'll hit machine-like numbers of onboarding twenty people a day (By then, you’ll need to avoid being labeled the local bitcoin village fool in your community) and assume they're all pure bitcoiners afterwards.\ Which won’t happen either as any incentive of the orange pilled people is clearly nòt long-term thinking; otherwise they would have onboarded you some 8 years ago!\ \ People are extremely lazy, and the general public usually has an attention span of about 8 seconds at best6.\ Back in the early days, you could sit people down and show another tech person for hours on end how to work with bitcoin, now more than a decade later, you have about 5 to 60 seconds tops. (most lightning wallet’s onboarding sequence easily takes 2 tot 5 minutes)
To further convince yourself how pointless Orange Pilling is today: go out and watch people on a public transport vehicle: they scroll and swipe through TikTok and Instagram. You’ll notice they’re swipe-apes, there’s no substance or reliable source of bitcoin buying power there, no bitcoin innovation will come from them, and no philosophical insights will ever be ignited in their buy-the-next-cool-sneakers-now brain. They’re not a target audience. They’re the all singing and all dancing crap of the world. They’re not convinced, Inconvincible and inconvertible.
Meanwhile, no substantial steps have been made for bitcoin, even if you get them to install that app you so desperately want them to have. Neither can you expect the no-coiners or pre-coiners (god I hate that word, it sounds kinky somehow) to do anything for bitcoin, as the gap between them and the actual positive impact they could have is too wide.\ It costs time, studying and experimenting. While these people excel at thing like: shopping, watching dime-a-dozen garbage series on Netflix, watching social media posts that don’t challenge them, and eating take-out food while score some drugs.\ \ So… to conclude the story about that dude in the bar which was so carefully orange pilled by our “Re play” squad members, he probably traded his sats for a beer by now (although that demands some form of effort in finding a recipient that has beer and wants to trade it for sats, which is unlikely) , more likely he forgot about the app altogether or he’s trading shitcoins to “make more money as greed that sets in. And he probably got that woman’s telephone number, to “talk about those bitcoins” later on at his crappy rental apartment right above a shoarma restaurant.\ \ The phrase “everyone’s a scammer” includes people who pretend to care about bitcoin just to get something out of it. Even a complete newbie or shitcoin fan will fake interest in bitcoin to seem legit. I’ve watched it happen.
Orange-pilling: the good, the bad, and the ugly
\ So onboarding devolved into this whole subculture of failure, and started to manifest itself over time as a empty motion, a series of must-do things.\ \ The Pavlovian response whenever someone is a walking opportunity for accepting bitcoin (certainly in any bar, restaurant or hotel), results in the foaming at the mouth to get them onboarded on some app or wallet.\ It’s so pointless I actually feel ashamed when I’m in a group that starts to hawk and push their lightning wallets onto unsuspecting people who just want to do their job.\ (and Lightning Wallets are so crappy to onboard people with, it’s mind numbingly stupid)\ \ To my amazement, there are actually a lot of bitcoin holders, or people that claim to be into bitcoin (especially in a bull market) who still pester random people with this kind of behavior.\ \ Some of these are trying to get them to click a referral link from a venture capital firm, in return for a few bucks (incentives these days are needed to get the groundswell going apparently), or worse even, make them install some non-custodial wallet and run into the brick wall of initial on-chain setup fees and then run away like a complete loser because they’re too cheap to fork that initial on-chain fee out for the people they’ve tried to onboard. “Yeah, like, you can buy these 100.000 sats online later if you like and thèn you can have this wallet, but at least it’s not custodial eh.. uh … My buddies are over there, I’ll see you later”.\ \ When you start to observe these people in the wild, it’s like watching a gaze of raccoons going through some neighborhood’s trash cans at night (without the playful conviction).\ Fascinating, if you’re into low-budget wildlife documentaries.
 Gaze of raccoons looking for a QR code
Gaze of raccoons looking for a QR codeIF you still want to onboard someone, point them to the right info at the right time (when thèy ask you).\ I call it “Bitcoin whispering”. #BitcoinWhispering
### \ \ Let’s quickly look at the three sort of Orange Pillers:
The pushy ideologists: The most annoying of the bunch, but at the same time the ones who mean really well. I sometimes feel sorry for them.\ No one’s safe from them. Hairdresser? “You should accept Bitcoin, man.” Bartender? “Credit cards are no goog, why not use Lightning?” Taxi driver? “Ever heard of Lightning? I can tip you in Bitcoin, man.” They’re not educating; they’re feeding their ego and their need to spread the word.
The referral grifters: More damaging to Bitcoin than shitcoiners in my opinion. They don’t care about Bitcoin’s properties; it’s just a slot machine for them. And if they understand, their short term greed and social circle dependency makes them go for spreading the word of a middleman company.\ “Sign up with my link, bro, stack those sats!”\ Their goal? A kickback and the next pat on the back from their miserable squad members.
The show-offs: The worst. They don’t know anything themselves but love the spotlight. “Yeah, I got my barber stacking sats!” Yet when it’s time to actually help onboard a business, they’re nowhere to be found. All talk, no substance. They achieve a small social circle of noob bitcoiners surrounding them, with most of them going through the shitcoin-phase shortly after or swapping off-the book gains. They’re not good for bitcoin and usually don’t stay that long anyway.\ \ The world doesn’t need your savior complex.
After the second half of 2024 if someone wanted in, they’ll find a way. And if they ask a Bitcoiner for help? Sure, we’ll point them in the right direction — most of us will help when asked (gladly so).\ But this idea that you, oh mighty orange-piller, need to swoop in and “save” people is more about you than about bitcoin.
Create a good, nice, safe (protected from scams!) environment or way to get people to the info and the other way around.\ Be there when people can ask questions, lead by example, make it work and show it. If an app is easy to use, makes sense and has no friction, then people will come. If you’re pestering people and hounding them into liking something that’s so far removed from their reality (fiat-world), they’ll be scared away and not return.
### \ Conclusion
Although I miss the old days, I also realize they ain’t coming back — when orange-pilling was just sharing a crazy new idea with someone who was open to it.
The Orange pilling space is now too keen for a large part to shove their bitcoin app in someone’s face, be it in dollars, a few sats or a discount on their next transaction fee at some multi level marketing middleman.\ This onboarding is also strangely in parallel with what shitcoiners or the most vile fiat companies do, OP’ers are too desperate for relevance so they often don’t look at the value proposition of bitcoin anymore. Filling their void got the upper hand.\ Their shot of feelgood moments needs to be filled.\ While there’s close to no impact to gain anymore on one-one-one convincing.\ The lesson to save in bitcoin, is usually lost on the people anyway, which was the last reason left to do it.\ \ Be there when people ask for help on bitcoin, build stuff, but stop the aggressive orange-pilling, it serves no purpose anymore other than your dopamine hit and a token feeling for “doing something”, and it’s a sad addiction.
Therefore in 2025, orange-pilling has become of a full-blown mental issue.
by AVB
if you like my writings : tip here
\ Footnotes:
https://journal.psych.ac.cn/xlkxjz/EN/Y2015/V23/I11/1956
https://www.frontiersin.org/journals/behavioral-neuroscience/articles/10.3389/fnbeh.2019.00160/full
https://en.wikipedia.org/wiki/Orbitofrontal_cortex
https://yzer.io/
https://lopp.net
https://theweek.com/health-and-wellness/1025836/tiktok-brain-and-attention-spans
Share
TopLatest
-
 @ 5d4b6c8d:8a1c1ee3
2025-03-21 13:20:20
@ 5d4b6c8d:8a1c1ee3
2025-03-21 13:20:20It's March Madness and @grayruby finally caved on my proposed contest design. We'll see if it's as great as I thought or as dumb as he thought. What are we expecting from this tournament?
Professional basketball is in its pre-postseason lull, as most teams either don't need to win many more games or don't want to. Is there a fix and why is it less communism?
The MLB season has kicked off and the Dodgers are heavy favorites already. Our MLB survivor pool is going to start soon (weren't we going to do something with fantasy baseball?). Plus, baseball realignment.
We're still on Ovi Watch as the NHL season comes to a close.
And, of course, the NFL Draft is coming up. Is the picture getting any clearer about where the top prospects are going?
Also, whatever stackers want us to cover.
originally posted at https://stacker.news/items/919995
-
 @ 8ff74724:5eedde0e
2025-03-21 13:18:58
@ 8ff74724:5eedde0e
2025-03-21 13:18:58This is a test blog post.
blog ... blog ... blog
-
 @ 58537364:705b4b85
2025-03-21 12:37:28
@ 58537364:705b4b85
2025-03-21 12:37:28เสียงตะโกนของ “อิทัปปัจจยตา”
ทุกอย่างตะโกนคำว่า “อิทัปปัจจยตา” อยู่ตลอดเวลา
“ท่านทั้งหลายนั่งอยู่ที่นี่ แต่ไม่ได้ยินเสียงตะโกนที่ดังลั่นไปหมดของธรรมชาติว่า ‘อิทัปปัจจยตา’ เสียงตะโกนของอิทัปปัจจยตา คือการร้องบอกร้องตะโกนว่า ‘เพราะมีสิ่งนี้เป็นปัจจัย สิ่งนี้จึงเกิดขึ้น’ หมายความว่า ท่านต้องดูลงไปที่ทุกสิ่งที่อยู่รอบตัวเราในเวลานี้ว่า ทุกสิ่งกำลังเป็นอิทัปปัจจยตา หรือเป็นไปตาม ‘กฎอิทัปปัจจยตา’”
ต้นไม้ต้นนี้มีความเป็นไปตามกฎอิทัปปัจจยตา ไม่มีอะไรมาต้านทานได้ ถ้าเราเข้าใจข้อเท็จจริงที่กำลังเป็นอยู่กับต้นไม้ เราจะเหมือนได้ยินมันตะโกนบอกว่า “อิทัปปัจจยตา” ไม่มีอะไรมากไปกว่านั้น มันเพียงบอกว่า “เมื่อมีสิ่งนี้เป็นปัจจัย สิ่งนี้จึงเกิดขึ้น”
ต้นไม้ไม่ได้หยุดเพียงเท่านั้น มันมีการเปลี่ยนแปลงเกิดขึ้นเรื่อยๆ ใบไม้ทุกใบก็บอกอย่างนั้น คงเป็นเสียงที่ดังเหลือประมาณว่า ใบไม้ทุกใบร้องตะโกนว่า “อิทัปปัจจยตา”
ผู้มีปัญญาและเข้าใจหัวใจของพระพุทธศาสนา จะไปนั่งอยู่ที่ไหนก็ได้ยินเสียงตะโกนว่า “อิทัปปัจจยตา” สนั่นหวั่นไหวไปหมด นี่พูดถึงแค่ต้นไม้ต้นเดียว ถ้าเป็นต้นไม้จำนวนมากก็เป็นเช่นเดียวกัน
เมื่อมองไปที่ก้อนหิน ก้อนหินก็เป็นเช่นเดียวกัน อนุภาคของมันเปลี่ยนแปลงอยู่ตลอดเวลา ก้อนหินที่เราเห็นอาจเกิดขึ้นมาเมื่อหลายพันล้านปีมาแล้ว จนมันแตกสลายและถูกทำให้มาอยู่ตรงนี้ มันจึงกล่าวว่า “อิทัปปัจจยตา” เพราะมีสิ่งนี้เป็นปัจจัย ฉันจึงมานั่งอยู่ที่นี่
ทุกอย่างตะโกนคำว่า “อิทัปปัจจยตา” ตลอดเวลา
- ต้นไม้ เม็ดกรวด เม็ดทราย มด แมลง สัตว์ต่างๆ รวมถึงมนุษย์เอง
- แม้แต่ร่างกายของเราเองก็ตะโกนบอกถึงอิทัปปัจจยตา
แม้เราจะเคยได้ยินคำว่า “อนิจจัง ทุกขัง อนัตตา” อาการของสิ่งเหล่านี้ยิ่งสะท้อนถึงอิทัปปัจจยตาอย่างชัดเจน
ดังนั้น เราต้องทำความเข้าใจจนซึมซาบอยู่ในใจ จนรู้สึกว่าไม่ว่าเราจะมองไปทางไหน ก็เห็นถึงภาวะของ อิทัปปัจจยตา ได้ยินเสียงของมัน หรือแม้แต่สัมผัสผ่านการดมกลิ่นและลิ้มรส
เมื่อเข้าใจสิ่งนี้ จะสามารถเรียกผู้นั้นว่า ‘เป็นพุทธบริษัทผู้เห็นธรรม’
สามารถเห็นกิเลสและทุกข์ แล้วป้องกันหรือกำจัดกิเลสและทุกข์ให้น้อยลงไปได้มากทีเดียว— พุทธทาสภิกขุ
(จากหนังสือธรรมบรรยาย “อิทัปปัจจยตา” หน้า 131–133)
อิทัปปัจจยตา: กฎอันเฉียบขาดตลอดจักรวาล
https://image.nostr.build/abc776213ec6371da681aa5766390f67e1ae97dc1d7157774e02eb93d1f21f56.jpg
“อิทัปปัจจยตา” เป็นกฎของธรรมชาติที่ไม่อาจเปลี่ยนแปลง
คำว่า “อิทัปปัจจยตา” อาจเป็นคำที่ไม่คุ้นหู แต่ขอให้สนใจ เพราะมันเป็นกฎของธรรมชาติที่แน่นอนตลอดจักรวาลและอนันตกาล
- สิ่งนี้เกิดขึ้น เพราะมีเหตุปัจจัยนี้
- สิ่งนี้มี เพราะสิ่งนี้มี
- ดวงอาทิตย์ ดวงจันทร์ ดวงดาว ทุกอย่างล้วนเกิดขึ้นตามกฎของ “อิทัปปัจจยตา”
เมื่อทำสิ่งนี้ มันต้องเกิดสิ่งนั้นขึ้น
เมื่อทำสิ่งนี้ มันต้องเกิดทุกข์ขึ้น
เมื่อทำสิ่งนี้ มันต้องเกิดความดับทุกข์ขึ้นนี่คือปรมัตถธรรมอันสูงสุด ไม่มีสัตว์ ไม่มีบุคคล ไม่มีพระเจ้าที่เป็นตัวตน
มีเพียง กฎอิทัปปัจจยตา ที่เป็นกฎของธรรมชาติอันเฉียบขาดพระพุทธเจ้าตรัสรู้ ก็คือ ตรัสรู้เรื่อง “อิทัปปัจจยตา”
เรามักเรียกกันว่า “ปฏิจจสมุปบาท” ซึ่งหมายถึงเฉพาะเรื่องทุกข์ของสิ่งมีชีวิต แต่ “อิทัปปัจจยตา” กว้างขวางกว่านั้น ทุกสิ่งไม่ว่าจะมีชีวิตหรือไม่มีชีวิตล้วนตกอยู่ใต้อำนาจของกฎนี้
กฎของอิทัปปัจจยตาไม่ใช่ฝ่ายบวกหรือฝ่ายลบ
- ไม่ใช่ Positive
- ไม่ใช่ Negative
- เป็น “สายกลาง” ของมันเองคนเราต่างหากที่ไปบัญญัติว่า “นี่คือสุข นี่คือทุกข์ นี่คือแพ้ นี่คือชนะ”
แต่แท้จริงแล้ว ทุกอย่างเป็นไปตามอิทัปปัจจยตาความเข้าใจในปรมัตถธรรมต้องไปให้ถึงจุดนี้
- จนไม่มีสัตว์ ไม่มีบุคคล
- ไม่ใช่สัตว์ ไม่ใช่บุคคล
- แต่ก็ไม่ใช่ว่าไม่มีอะไรเลย และก็ไม่ได้มีสิ่งใดที่ตายตัว
ทุกอย่างเป็นเพียง กระแสของการเปลี่ยนแปลงและปรุงแต่ง
เมื่อเข้าใจถึงจุดนี้ จึงจะรู้อย่างที่พระพุทธเจ้าท่านรู้ และดับทุกข์ได้
นี่คือสิ่งสูงสุดที่ต้องเคารพ คือ กฎของ “อิทัปปัจจยตา”— พุทธทาสภิกขุ
(จากธรรมบรรยายประจำวันเสาร์ ภาคอาสาฬหบูชา ชุด “ฟ้าสางระหว่าง 50 ปีที่มีสวนโมกข์” ครั้งที่ 19 เมื่อวันที่ 13 สิงหาคม 2526 ณ ศาลามหานาวา สวนโมกขพลาราม จากหนังสือ “ธรรมานุภาพ”) -
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ 104cdb46:bda37787
2025-03-21 12:01:52
@ 104cdb46:bda37787
2025-03-21 12:01:52Bet365 là một nền tảng giải trí trực tuyến nổi bật, không chỉ cung cấp các trò chơi đa dạng mà còn chú trọng đến việc tạo ra những trải nghiệm độc đáo cho người chơi. Từ các trò chơi thể thao cho đến các trò chơi giải trí khác, Bet365 luôn đảm bảo rằng người tham gia có thể tìm thấy lựa chọn phù hợp với sở thích và kỹ năng của mình. Giao diện của Bet365 rất dễ sử dụng, với những hướng dẫn rõ ràng, giúp người chơi mới có thể nhanh chóng làm quen và tham gia các trò chơi. Không chỉ vậy, nền tảng này cũng cung cấp các tính năng bổ sung như các trận đấu trực tiếp, giúp người chơi có thể theo dõi và tham gia vào các sự kiện thể thao yêu thích trong thời gian thực, mang lại sự phấn khích và kịch tính không ngừng. Những tính năng này kết hợp với công nghệ hiện đại, giúp tạo nên một không gian giải trí chất lượng cao, mang lại cho người chơi những phút giây thư giãn và thử thách đầy thú vị.
Bảo mật và quyền lợi của người chơi là yếu tố quan trọng mà Bet365 luôn đặt lên hàng đầu. Nền tảng này sử dụng công nghệ mã hóa tiên tiến để bảo vệ tất cả các giao dịch và thông tin cá nhân của người tham gia, giúp người chơi yên tâm tận hưởng những trò chơi mà không phải lo lắng về vấn đề an toàn thông tin. Các phương thức thanh toán tại Bet365 rất linh hoạt, cho phép người chơi nạp và rút tiền một cách nhanh chóng và thuận tiện, phù hợp với nhu cầu của người tham gia từ nhiều quốc gia khác nhau. Chính những yếu tố bảo mật này đã giúp Bet365 xây dựng được lòng tin vững chắc từ người chơi và khẳng định được vị thế của mình trong ngành giải trí trực tuyến. Các giao dịch trên Bet365 luôn được xử lý một cách chính xác và nhanh chóng, giúp người chơi có thể tập trung vào việc tham gia trò chơi mà không gặp phải bất kỳ phiền phức nào.
Ngoài ra, Bet365 còn nổi bật với việc tổ chức các sự kiện và giải đấu đặc biệt, mang lại cơ hội cho người chơi thể hiện kỹ năng và cạnh tranh với những người chơi khác trên toàn thế giới. Những sự kiện này thường xuyên diễn ra và thu hút được sự tham gia của đông đảo người chơi, tạo ra một cộng đồng năng động và thân thiện. Các giải đấu không chỉ mang lại những phần thưởng hấp dẫn mà còn giúp người chơi xây dựng mối quan hệ với cộng đồng, học hỏi và cải thiện kỹ năng chơi game của mình. Bet365 luôn cố gắng mang đến những trải nghiệm mới mẻ và đầy thử thách, nhằm giữ cho người chơi luôn cảm thấy thú vị và hứng thú. Chính những đặc điểm nổi bật này đã giúp Bet365 trở thành một trong những nền tảng giải trí trực tuyến được ưa chuộng và tin cậy trên toàn thế giới.
-
 @ 104cdb46:bda37787
2025-03-21 12:00:43
@ 104cdb46:bda37787
2025-03-21 12:00:43Quy88 là một nền tảng giải trí trực tuyến nổi bật, được thiết kế với mục tiêu mang lại cho người chơi những trải nghiệm thú vị và đa dạng. Với một kho trò chơi phong phú, từ các trò chơi thể thao, bài, đến các trò chơi kỹ năng, Quy88 đáp ứng đầy đủ nhu cầu giải trí của những người yêu thích sự đổi mới và thử thách. Giao diện của nền tảng này được tối ưu hóa, giúp người chơi dễ dàng tìm kiếm và tham gia vào các trò chơi yêu thích chỉ với vài thao tác đơn giản. Không chỉ dừng lại ở các trò chơi thông thường, Quy88 còn cung cấp các lựa chọn chơi game đặc biệt, tạo nên sự khác biệt và thu hút đông đảo người chơi tham gia. Với đồ họa sắc nét, âm thanh sống động, và những tính năng game đầy sáng tạo, Quy88 mang lại một không gian giải trí đầy hấp dẫn, giúp người chơi có thể tận hưởng những phút giây thư giãn tuyệt vời.
Không chỉ cung cấp một kho trò chơi hấp dẫn, Quy88 còn chú trọng đến yếu tố bảo mật và quyền lợi của người chơi. Nền tảng này sử dụng công nghệ mã hóa hiện đại để đảm bảo rằng mọi thông tin cá nhân và tài chính của người tham gia đều được bảo vệ an toàn tuyệt đối. Quy88 cam kết bảo mật tuyệt đối tất cả các giao dịch và hoạt động của người chơi, từ việc nạp tiền đến việc rút thưởng. Điều này mang đến sự yên tâm cho người chơi khi tham gia vào các trò chơi, giúp họ không phải lo lắng về bất kỳ rủi ro nào liên quan đến bảo mật. Hệ thống thanh toán của Quy88 cũng rất tiện lợi và nhanh chóng, giúp người chơi có thể thực hiện các giao dịch mà không gặp phải bất kỳ trở ngại nào. Với các biện pháp bảo mật hàng đầu, Quy88 đã xây dựng được niềm tin vững chắc từ cộng đồng người chơi.
Ngoài các trò chơi thú vị và hệ thống bảo mật tiên tiến, Quy88 còn tổ chức các sự kiện và giải đấu hấp dẫn, mang đến cơ hội cho người chơi thể hiện kỹ năng và tranh tài với nhau. Các sự kiện này không chỉ tạo ra không khí sôi động, hào hứng mà còn mang lại những phần thưởng giá trị cho những người chơi xuất sắc. Những giải đấu này thu hút sự tham gia của đông đảo người chơi, tạo nên một cộng đồng mạnh mẽ và gắn kết. Hệ thống giải đấu tại Quy88 luôn được tổ chức công bằng và minh bạch, mang đến những thử thách thú vị cho mọi người tham gia. Với một nền tảng ổn định, chất lượng dịch vụ tốt và một cộng đồng năng động, Quy88 tiếp tục khẳng định vị thế của mình là một trong những lựa chọn giải trí trực tuyến hàng đầu trong cộng đồng người chơi.
-
 @ 8ff74724:5eedde0e
2025-03-21 13:38:45
@ 8ff74724:5eedde0e
2025-03-21 13:38:45And another.
-
 @ 8ff74724:5eedde0e
2025-03-21 13:33:32
@ 8ff74724:5eedde0e
2025-03-21 13:33:32This is a test.
Of a flycat article.
-Satoshi
-
 @ 104cdb46:bda37787
2025-03-21 11:59:40
@ 104cdb46:bda37787
2025-03-21 11:59:40AE3888 là một nền tảng giải trí trực tuyến nổi bật, mang đến cho người chơi một thế giới đa dạng với nhiều trò chơi hấp dẫn và độc đáo. Không chỉ cung cấp các trò chơi thể thao, mà AE3888 còn thu hút người chơi với các trò chơi điện tử phong phú, bao gồm các tựa game chiến thuật, bài, và nhiều thể loại khác. Tất cả đều được thiết kế với giao diện dễ sử dụng, giúp người tham gia dễ dàng tìm kiếm trò chơi yêu thích và bắt đầu cuộc hành trình giải trí của mình. Đặc biệt, hệ thống của AE3888 luôn được cập nhật liên tục, mang đến những tính năng mới mẻ và cải tiến để phục vụ nhu cầu của người chơi, đảm bảo rằng mỗi trải nghiệm đều thú vị và đầy thử thách. Với đồ họa sắc nét và âm thanh sống động, AE3888 mang đến không gian chơi game hấp dẫn, giúp người chơi có thể thư giãn và tận hưởng những giây phút giải trí tuyệt vời.
Ngoài sự đa dạng trong các trò chơi, AE3888 còn đặc biệt chú trọng đến yếu tố bảo mật và quyền lợi của người chơi. Nền tảng này sử dụng các công nghệ bảo mật tiên tiến để đảm bảo rằng thông tin cá nhân và tài chính của người tham gia được bảo vệ an toàn tuyệt đối. Người chơi có thể yên tâm rằng mọi giao dịch, từ việc nạp tiền đến rút thưởng, đều được xử lý nhanh chóng và bảo mật, mang lại sự tin tưởng tuyệt đối. Điều này giúp AE3888 xây dựng được uy tín và sự hài lòng từ phía người chơi, với cam kết không ngừng cải thiện để mang lại dịch vụ ngày càng hoàn thiện hơn. Cùng với đó, hệ thống hỗ trợ khách hàng của AE3888 hoạt động 24/7, luôn sẵn sàng giải đáp mọi thắc mắc và hỗ trợ người chơi trong mọi tình huống, đảm bảo rằng trải nghiệm của họ luôn suôn sẻ và thoải mái.
Bên cạnh các trò chơi đa dạng và bảo mật tuyệt vời, AE3888 còn tổ chức các sự kiện và giải đấu lớn, tạo cơ hội cho người chơi thể hiện tài năng và cạnh tranh với cộng đồng. Những sự kiện này luôn thu hút sự tham gia đông đảo, không chỉ mang đến phần thưởng hấp dẫn mà còn tạo ra không khí sôi động và đầy thử thách. Các giải đấu này không chỉ giúp người chơi thử thách bản thân mà còn là dịp để giao lưu, học hỏi và kết nối với những người chơi khác. AE3888 luôn lắng nghe ý kiến và phản hồi của người tham gia để không ngừng cải thiện và phát triển nền tảng, mang đến những trải nghiệm giải trí tuyệt vời hơn. Với đội ngũ phát triển sáng tạo và đội ngũ hỗ trợ tận tình, AE3888 không ngừng vươn lên và khẳng định vị thế của mình trong ngành giải trí trực tuyến.
-
 @ c88809a0:a46266e2
2025-03-21 11:00:01
@ c88809a0:a46266e2
2025-03-21 11:00:01Introduction
UX Research is currently being conducted on the needs of activists. There is still much to learn in this area and we are at just the very beginning. These observations and learnings will change over time. Activists are championing freedom all over the world and if we build communication and financial tools for them that solve real problems which they are facing we will enable them to continue to do the valuable work they are doing.
We want to understand their needs, their problems and their fears, so that when we build solutions we ensure that it is fulfilling the primary goals of the person using it.
Fundamentally this is with the ethos of putting the humans at the center of everything we build.
The below is written for you the builders. And for you the activists.
We hope this information empowers you and that it will initiate an open dialogue between activists and builders. Where knowledge is open and transparent to everyone. Where you feel free to ask questions. Where you feel empowered. Where we all continue to collborativley build freedom technology.
Background
The below data was collected by conducting an in person workshop with a group of activists and Nostr developers. During this workshop we used the Jobs to be Done framework to uncover the UX needs of activists. This workshop involved approximately 20 people. 11 of which were activists or individuals who are activists as well as builders.
This write-up covers 3 main areas:
Observations: What have we observed?
a. 5 Areas of communication
What are the 5 main areas in which activists are communicating?
b. Fears
What are the main fears of activists when using a product?
c. Jobs to be done
What are the main jobs that activists expect the product to perform when they are using it.
Learnings: What can we learn based on the observations?
Observations

a. 5 Areas of communication
There are 5 main areas in which activists are communicating. They are communicating with:
1. Co-workers
Daily communication with team members, peers, and fellow activists organizing initiatives.
2. Family
Activists communicate with family members and are concerned about this communication being surveilled.
3. Funders
Communication with sponsors for fundraising. When communicating with funders, activists face challenges with CRM systems that require personal contact information.
4. General Public
They communicate with the broader public for youth education, crisis management and event announcements. They rely heavily on social media platforms (particularly Meta-owned) and these have challenges such as algorithmic limitations, content moderation, and platform reliability.
5. Journalists
They communicate with journalists for political mobilization.
Political mobilization is the process of organizing and motivating people to participate in political activities.
This data is based on 11 entries. Of the 11 entries the image below indicates the split showing the entries with the highest number to the lowest.
b. Fears
The biggest fears that activists have based on the data are the following:

1. State surveillance
Activists are deeply worried about their governments watching and interfering with their work.
- They're concerned that platforms which they currently use will hand over their data to authorities.
- That their accounts might be labeled as "extremist," and that their content could be taken down without warning.
- They live with constant anxiety that their communications are being monitored.
2. Security issues
There's a deep distrust of mainstream communication platforms.
- They worry that their personal information isn't truly private.
- They dislike using phone numbers to sign up (which can expose their identity).
- Feel frustrated that when security problems happen as the platforms rarely help or respond.
3. Communication reach
Activists face a frustrating choice: they can either use secure apps that few people use, or popular apps that aren't secure.
- They worry about only reaching people who already agree with them (being in an "echo chamber"), while struggling to spread their message to a wider audience.
- When they do try to reach more people, their content often gets hidden or suppressed by platform algorithms.
4. Access
Basic technical problems cause major headaches. Slow internet makes secure tools hard to use and some tools don't work at all without good internet. They worry about losing important information and struggle with tools that don't work reliably in their locations.
5. Personal safety
Beyond their own safety, activists worry deeply about protecting everyone they communicate with - their families, fellow activists, and journalists. They face organized attacks from fake accounts and bots that spread lies about them, and they're constantly trying to balance doing their work effectively while keeping everyone involved safe from harm.

c. Jobs to be Done
The following are the jobs that activists need a product to do. A job can be described as a task that a user expects to perform when using the product.
1. Surveillance
- When operating in a politically hostile environment, I want to communicate without leaving digital traces, so I can protect my network from state surveillance.
- When my platform has been compromised, I want to quickly secure and recover my account, so I can continue working without losing data.
2. Reach
- When sharing critical information about protests, I want to reach people beyond my echo chamber, so I can reach a broader public.
- When coordinating with multiple activist groups, I want to securely communicate with these groups so I can organize events without information being lost or scattered.
3. Connectivity
- When working in areas with poor internet connectivity, I want to maintain secure communication, so I can continue organizing even when having low bandwidth.
- When my team loses access to their devices, I want to ensure they can safely recover their accounts and data, so we can continue working.
4. Personal safety
- When sharing sensitive political content, I want to protect the identity of my sources and collaborators, so I can prevent attacks against them.
- When facing coordinated disinformation attacks, I want to maintain content integrity and verification, so I can counter false narratives.
5. Organized
- When coordinating time-sensitive activities, I want to ensure messages are received and read, so I can respond quickly to emerging situations.
- When managing multiple activist groups, I want to organize conversations and files logically, so I can quickly find and reference past communications.
5. Crisis access
- When government crackdowns occur, I want to quickly share safety information, so I can protect community members from harm.
- When platforms are being blocked or monitored, I want to maintain alternative communication channels, so I can continue to communicate with my network.
6. Community Building
- When growing our movement, I want to safely onboard new members, so I can scale our organization while maintaining security.
- When building trust in our network, I want to be able to verify new members, so I can prevent infiltration by hostile actors.
7. Information Preserving
- When facing potential platform shutdown, I want to preserve our communication history and documents.
- When sharing sensitive documents, I want to control who can access and forward materials, so I can maintain information security over time.
Learnings
Now we dive in to what we have learnt based on the things we have observed.
1. Security vs. Reach
Activists face a tricky choice when communicating. They can shoose to use main stream tools which are not secure but have more reach, or use more secure tools which less people are familiar with. Ultimately they are stuck using platforms on a daily basis which they don't trust.
2. Different Audience Needs
Some activists are communicating with different groups these could be; team members, family, funders, public, journalists, it is possible that each of these groups require different strategy approaches.
3. Government Monitoring
Activists worry about government surveillance and this drives many of their communication decisions.
4. Technical Barrier
Poor internet and technical problems make it hard for them to use secure tools even when they are available.
5. Growing Safely is Hard
Adding new members to grow the activist movement is tricky because this makes is difficult for them to keep the group secure from infiltrators.
6. Record-Keeping Risks
While activists need to keep a record of documents and some communication, saving these also creates evidence that could be used against them.
7.Staying Operational in Crisis
Activists need ways to recover accounts and continue working when platforms are shut down or devices are taken.
As mentioned above there is much more to learn about the UX needs of activists. We will continue to dive deeper into their user needs and share them openly here with you.
-
 @ b5d34eed:a7475cbf
2025-03-21 10:12:21
@ b5d34eed:a7475cbf
2025-03-21 10:12:21Introduction
In an era of increasing surveillance, data breaches, and corporate control over digital communication, privacy-focused tools have become essential. ProtonMail, a secure and encrypted email service, stands as a stronghold for those seeking privacy in their online correspondence.
At the same time, Nostr, a decentralized social networking protocol, is revolutionizing how people connect without relying on centralized platforms. Together, ProtonMail and Nostr create a powerful combination for individuals who prioritize security, anonymity, and freedom in their online interactions.
This article explores the ProtonMail application suite, its relevance to privacy, and how it aligns with Nostr’s decentralized approach to communication.
What is ProtonMail?
ProtonMail is an encrypted email service founded in 2013 by scientists at CERN, the European Organization for Nuclear Research. Unlike mainstream email providers such as Gmail or Outlook, ProtonMail does not collect personal data, does not track users, and ensures end-to-end encryption for emails.
Key Features of ProtonMail
End-to-End Encryption: Ensures that only the sender and recipient can read messages.
No Personal Information Required: Users can sign up without providing identifying details.
Open-Source Cryptography: Transparency in security protocols, allowing community audits.
Swiss-Based Privacy Laws: ProtonMail operates under Switzerland’s strict data protection regulations, shielding it from intrusive government surveillance.
Self-Destructing Emails: Allows users to send messages that automatically expire after a set time.
ProtonMail’s security-first approach makes it an ideal choice for activists, journalists, and privacy-conscious individuals who want to communicate without fear of surveillance or data mining.
ProtonMail Application Suite: A Holistic Privacy Ecosystem
Beyond encrypted email, Proton has expanded into a full suite of privacy-focused tools:
ProtonMail – Secure, encrypted email with zero access to user data.
ProtonVPN – A no-logs VPN that protects internet traffic from ISPs and surveillance.
ProtonCalendar – An encrypted calendar that ensures event data remains private.
ProtonDrive – Secure cloud storage for files with end-to-end encryption.
ProtonPass – A password manager that encrypts credentials and autofills login details safely.
This ecosystem provides a seamless experience for those looking to secure not just their emails but also their browsing, file storage, scheduling, and password management.
Why ProtonMail is a Must for Privacy-Conscious Users
-
End-to-End Encryption: Unlike Gmail and Outlook, ProtonMail ensures that even ProtonMail itself cannot access your emails.
-
No IP Tracking: Protects against metadata collection, preserving user anonymity.
-
Zero Access Architecture: Even Proton employees cannot read your emails.
-
Decentralization-Friendly: Complements Nostr’s ethos of distributed, private communication.
ProtonMail’s strict security measures align well with the values of decentralization and censorship resistance, making it a natural ally to protocols like Nostr.
ProtonMail and Nostr: A Privacy Power Duo
Nostr is an open-source, censorship-resistant social networking protocol that allows users to communicate without relying on a centralized platform. Unlike Twitter, Facebook, or even Mastodon, Nostr operates through decentralized relays, making it nearly impossible to shut down or control.
ProtonMail and Nostr share a fundamental philosophy: empowering users with control over their own data. Here’s how they complement each other:
- Secure and Private Communication
Nostr messages are cryptographically signed and relayed across decentralized nodes. ProtonMail, with its encryption-first approach, ensures that even off-platform communication remains private.
- No Central Authority
ProtonMail is protected under Swiss privacy laws and is not beholden to big tech surveillance. Nostr operates without central servers, preventing a single entity from controlling conversations.
- Protecting Metadata
While Nostr encrypts direct messages, email remains a critical form of communication for many users. ProtonMail’s metadata protection ensures that senders, recipients, and message content remain shielded.
- Enhanced Security for Activists and Journalists
Nostr is popular among privacy advocates, activists, and whistleblowers due to its resilience against censorship. ProtonMail adds an extra layer of protection for sensitive information shared over email.
By using ProtonMail and Nostr together, users can create a robust digital identity that is censorship-resistant, private, and secure.
How to Get Started with ProtonMail
If you’re ready to enhance your privacy, setting up ProtonMail is simple:
-
Sign Up: Visit ProtonMail.com and create a free or premium account.
-
Set Up Your Inbox: Customize security settings and enable two-factor authentication.
-
Explore Proton’s Suite: Utilize ProtonVPN, ProtonDrive, and ProtonPass for full privacy coverage.
-
Integrate with Nostr: Use ProtonMail for private communication outside of Nostr’s relay-based messaging system.
ProtonMail offers free plans, but for advanced security features, encrypted storage, and custom domains, premium plans are available.
Conclusion: A Privacy-First Digital Future
In a world where data privacy is constantly under threat, services like ProtonMail and Nostr pave the way for a more secure and independent digital future. Whether you are a journalist, activist, or simply someone who values personal privacy, these tools provide the protection you need.
By combining ProtonMail’s encrypted email with Nostr’s decentralized networking, users can take control of their communications, free from surveillance and corporate interference.
Now is the time to reclaim your digital privacy—sign up for ProtonMail and explore Nostr to experience a censorship-resistant, secure way of communicating.
Further Resources
ProtonMail Official Website
ProtonVPN for Secure Browsing
Nostr Documentation and GitHub
Privacy Guides for Online Security
Are you using ProtonMail and Nostr together? Share your thoughts on how these tools empower you in the comments below!
-
-
 @ 7d33ba57:1b82db35
2025-03-21 09:56:28
@ 7d33ba57:1b82db35
2025-03-21 09:56:28Seville
Seville (Sevilla) is one of Spain’s most vibrant and historic cities, known for its stunning Moorish architecture, flamenco dancing, tapas culture, and rich history. As the capital of Andalusia, it offers a perfect mix of tradition and modern charm.
🏛️ Top Things to See & Do in Seville
1️⃣ The Royal Alcázar of Seville
- A breathtaking Moorish palace with stunning gardens, intricate tilework, and grand courtyards.
- Famous for its mix of Islamic, Gothic, Renaissance, and Baroque styles.
- Tip: Book tickets in advance to avoid long lines!
2️⃣ Seville Cathedral & La Giralda
- The largest Gothic cathedral in the world, home to Christopher Columbus' tomb.
- Climb La Giralda Tower for panoramic views of the city.
3️⃣ Plaza de España
- A majestic semi-circular plaza with bridges, fountains, and detailed ceramic tilework.
- Perfect for photos, boat rides, and people-watching.
4️⃣ Metropol Parasol (Las Setas)
- A modern wooden structure in the city center offering great rooftop views.
- Best time to visit: Sunset for golden hour photos!
5️⃣ Barrio Santa Cruz
- The old Jewish Quarter, filled with narrow alleys, hidden courtyards, and charming tapas bars.
- Perfect for a romantic evening stroll.
6️⃣ Experience Flamenco in Triana
- Triana is the birthplace of flamenco – watch an authentic flamenco show in an intimate setting.
7️⃣ Stroll Along the Guadalquivir River & Torre del Oro
- Enjoy a walk or boat cruise along the river with views of Torre del Oro, a historic 13th-century watchtower.
🍽️ What to Eat in Seville
- Tapas – Try jamón ibérico, patatas bravas, and espinacas con garbanzos 🥘
- Salmorejo – A cold tomato soup, similar to gazpacho 🍅
- Pescaíto frito – Lightly fried fish, a local favorite 🐟
- Tortilla de camarones – Shrimp fritters, crispy and delicious 🍤
- Orange wine (vino de naranja) – A sweet Seville specialty 🍷
🚆 How to Get to Seville
🚄 By Train: High-speed AVE trains from Madrid (2.5 hours) & Barcelona (5.5 hours)
✈️ By Air: Seville Airport (SVQ) with flights from major European cities
🚗 By Car: A great road trip stop between Granada, Córdoba, and Cádiz
💡 Tips for Visiting Seville
✅ Best time to visit? Spring (March-May) – Perfect weather & festivals 🌸
✅ Avoid midday heat in summer – Explore early morning or late evening ☀️
✅ Visit during Feria de Abril – One of Spain’s most colorful festivals 🎶🎡
✅ Book Alcázar & Cathedral tickets online – Save time in long queues 🎟️ -
 @ 872982aa:8fb54cfe
2025-03-21 09:38:17
@ 872982aa:8fb54cfe
2025-03-21 09:38:17{"coverurl":"https://cdn.nostrcheck.me/872982aa37b864973a389d465bc6ed5045a78586496d104e05f39b8d8fb54cfe/29dac6975894221f222ed2379e13f2f2b1e51c861ebc35f60770fb15cb93348e.webp","title":"宁静的世界","author":"走动"}
-
 @ bccf33d8:4b705625
2025-03-21 09:29:16
@ bccf33d8:4b705625
2025-03-21 09:29:16{"author":"响响","coverurl":"https://cdn.nostrcheck.me/872982aa37b864973a389d465bc6ed5045a78586496d104e05f39b8d8fb54cfe/b4a8afa3e673ad73e16f0c0694ccb5c60af7aaa4031e1b1d1d928234200c0b0c.webp","title":"雪山"}
-
 @ a6efb4f0:4d912827
2025-03-21 09:03:03
@ a6efb4f0:4d912827
2025-03-21 09:03:03A crescente demanda por plataformas de entretenimento online tem impulsionado o desenvolvimento de opções cada vez mais inovadoras. Nesse cenário, a 8385 surge como uma das plataformas mais promissoras, oferecendo aos seus usuários uma experiência digital rica e diversificada. A plataforma tem se destacado não apenas pela qualidade de seus jogos, mas também pela forma como integra tecnologia, segurança e personalização, criando um ambiente digital único. Neste artigo, vamos explorar o que é a plataforma 8385, seus principais jogos e a experiência do jogador.
O Que é a Plataforma 8385? A 8385 é uma plataforma digital criada para oferecer entretenimento de alta qualidade, com foco na diversão e na inovação. A interface da plataforma é projetada para garantir uma navegação intuitiva e uma experiência de jogo fluída, com recursos que facilitam a interação do usuário. A plataforma se destaca por seu compromisso com a segurança e a transparência, utilizando tecnologias avançadas para garantir a proteção dos dados dos jogadores.
Além disso, a 8385 é acessível em diversos dispositivos, incluindo desktop e dispositivos móveis, o que permite que os jogadores desfrutem de seus jogos favoritos a qualquer hora e em qualquer lugar. A plataforma é constantemente atualizada com novos conteúdos e melhorias, assegurando que seus usuários tenham sempre algo novo para explorar.
Os Jogos da Plataforma 8385 A plataforma 8385 se distingue pela ampla variedade de jogos que oferece. Com opções para todos os gostos, desde aqueles que buscam ação e aventura até os que preferem jogos de estratégia e raciocínio, há sempre uma opção que se adequa às preferências individuais dos jogadores.
Jogos de Ação e Aventura: Os jogos de ação e aventura são perfeitos para aqueles que buscam adrenalina e desafios emocionantes. Com gráficos de última geração e jogabilidade envolvente, esses jogos permitem que os jogadores se mergulhem em mundos fictícios repletos de aventuras épicas.
Jogos de Estratégia: Para quem gosta de testar sua capacidade de raciocínio lógico, a plataforma oferece uma variedade de jogos de estratégia. Esses jogos exigem que o jogador tome decisões cuidadosas e planeje suas ações com antecedência, criando uma experiência intensa e desafiadora.
Jogos de Reflexo e Habilidade: Se você procura uma experiência de jogo mais rápida e dinâmica, a 8385 oferece uma série de jogos que testam os reflexos e a agilidade do jogador. Com desafios que exigem atenção e rapidez, esses jogos são perfeitos para quem gosta de ação intensa e momentos de pura emoção.
Jogos de Sorte: Para os jogadores que gostam de jogos baseados em sorte e imprevisibilidade, a 8385 disponibiliza uma seleção de opções emocionantes. Esses jogos oferecem uma experiência única, onde a sorte pode ser um fator determinante para o sucesso.
A Experiência do Jogador na Plataforma 8385 A experiência do jogador na plataforma 8385 é aprimorada por uma série de recursos pensados para oferecer o máximo de diversão e imersão. A interface é simples, com um design limpo que facilita a navegação entre as diversas opções de jogos e funcionalidades. A plataforma também é projetada para oferecer uma jogabilidade sem falhas, com tempos de carregamento rápidos e animações fluidas.
Além disso, a plataforma é socialmente interativa. Os jogadores podem competir entre si, participar de torneios e interagir em tempo real com outros usuários. A 8385 cria uma comunidade vibrante, onde os jogadores podem se conectar, compartilhar conquistas e formar alianças para enfrentar desafios juntos.
Outro ponto positivo é a personalização oferecida pela plataforma. Os jogadores podem ajustar suas configurações de jogo, escolher temas exclusivos e até criar avatares personalizados. Essas opções permitem que cada usuário tenha uma experiência de jogo única, que reflete suas preferências e estilo.
A plataforma também investe em um atendimento ao cliente de alta qualidade, com suporte dedicado para resolver quaisquer problemas ou responder a perguntas. Seja por chat ao vivo ou por e-mail, os jogadores podem contar com um atendimento eficiente e amigável.
Conclusão A plataforma 8385 tem se consolidado como uma das melhores opções no mundo do entretenimento digital. Com uma ampla variedade de jogos, uma interface amigável e uma experiência de usuário de alta qualidade, a plataforma oferece tudo o que os jogadores procuram em termos de diversão e imersão. Se você busca uma experiência de jogo única e envolvente, a 8385 é a escolha ideal.
-
 @ a6efb4f0:4d912827
2025-03-21 09:01:47
@ a6efb4f0:4d912827
2025-03-21 09:01:47A plataforma 5526 surgiu no cenário do entretenimento digital com uma proposta inovadora, destinada a atrair e engajar jogadores de diversas partes do mundo. Ao se destacar pela qualidade de seus jogos e pela experiência personalizada que oferece aos seus usuários, a 5526 rapidamente se consolidou como uma das favoritas para quem busca uma experiência interativa e divertida. Neste artigo, vamos explorar a plataforma, as opções de jogos disponíveis e a experiência geral de navegação que ela proporciona.
A Plataforma 5526: A Nova Referência em Entretenimento Digital O grande destaque da 5526 está na facilidade de acesso e na experiência sem complicações. Sua interface limpa e intuitiva permite que o jogador entre diretamente na ação, sem perder tempo em processos complicados. O design responsivo da plataforma garante que o usuário tenha uma navegação fluida, seja em um dispositivo móvel ou em um computador de mesa, o que oferece praticidade para jogar em qualquer lugar e a qualquer momento.
Outro aspecto crucial da 5526 é sua ênfase na segurança do usuário. Com sistemas de criptografia robustos e proteções contra fraudes, os jogadores podem desfrutar de seus jogos favoritos com total confiança. A plataforma também adota políticas transparentes e claras em relação ao uso de dados, o que reforça ainda mais a confiança dos usuários em seus serviços.
Jogos Inovadores: Diversidade e Qualidade na 5526 A 5526 se destaca por sua vasta gama de jogos, que inclui desde opções mais tradicionais até novas experiências interativas. A diversidade de temas e estilos de jogo disponíveis é um dos maiores atrativos para os jogadores. A plataforma oferece uma variedade de jogos de habilidade, onde a estratégia é fundamental, além de jogos mais rápidos e dinâmicos para quem busca um desafio de tempo.
Além dos jogos individuais, a plataforma disponibiliza modalidades multiplayer, permitindo que os usuários interajam entre si, formem equipes e compitam em tempo real. Essa interação social é um diferencial importante, pois cria uma comunidade ativa e engajada, algo essencial para a fidelização do público.
Outro ponto de destaque são as funcionalidades ao vivo, com dealers e mesas interativas, que garantem uma experiência mais realista e imersiva. A plataforma investe constantemente em novas tecnologias para proporcionar transmissões de alta qualidade e interações dinâmicas, aproximando ainda mais o ambiente online do real.
A Experiência do Jogador: Acesso Fácil e Suporte Eficiente A plataforma 5526 oferece uma experiência do usuário bem estruturada, garantindo que qualquer jogador, independentemente de sua experiência, consiga navegar e jogar sem dificuldades. O processo de registro é simples e rápido, e a plataforma também oferece opções de personalização para que cada jogador possa ajustar sua experiência de acordo com suas preferências pessoais.
A qualidade do atendimento ao cliente é outro diferencial que merece destaque. A plataforma oferece suporte por vários canais, incluindo chat ao vivo, telefone e e-mail, para que os jogadores tenham acesso a ajuda imediata sempre que necessário. O suporte eficiente é crucial para garantir que os jogadores se sintam acolhidos e bem assistidos em sua jornada na plataforma.
Conclusão Com sua combinação de inovação, diversidade de jogos e uma experiência do usuário impecável, a plataforma 5526 se estabelece como uma excelente opção para quem busca entretenimento digital de qualidade. A plataforma oferece uma experiência personalizada, segura e divertida, tornando-se um verdadeiro destino para aqueles que buscam diversão e interação em um ambiente online dinâmico.
-
 @ 872982aa:8fb54cfe
2025-03-21 08:26:12
@ 872982aa:8fb54cfe
2025-03-21 08:26:12{"coverurl":"https://cdn.nostrcheck.me/872982aa37b864973a389d465bc6ed5045a78586496d104e05f39b8d8fb54cfe/8ce0fe2636ce38a3b55d4a5ec7ca81031df7902c3786dc6d662bbcf8a40f910f.webp","title":"马背上的任务","author":"野草"}
-
 @ 4cd9c154:37287981
2025-03-21 07:49:04
@ 4cd9c154:37287981
2025-03-21 07:49:04The hedgehogs’ P2P social network, SpikeToSpike, has launched its mobile tradingapp in beta based on the Nostr protocol. With this initiative, SpikeToSpike becomes the first P2P trading app built on Nostr.
For now, the app is available exclusively for Android in APK format, but the platform has confirmed that an iOS version will be released by May. Stay updated by following SpikeToSpike on X for the latest news.
Launched by Brazilian libertarians in January last year, SpikeToSpike was created to be the ultimate P2P ecosystem for buying and selling Bitcoin with a strong focus on privacy. In addition to Bitcoin, the platform also supports trading the stablecoin Tether.
Until now, SpikeToSpike operated through its website spiketospike.com. With the new Nostr-based app, designed for privacy and freedom of expression, the platform is taking another major step toward becoming the most private way to buy and sell Bitcoin.
Just so you know, SpikeToSpike ensures that every order is secured. When your order is matched with a provider, the platform automatically locks the provider’s Bitcoin in escrow, guaranteeing a safe and seamless trading experience.
-
 @ 872982aa:8fb54cfe
2025-03-21 07:42:20
@ 872982aa:8fb54cfe
2025-03-21 07:42:20{"coverurl":"https://cdn.nostrcheck.me/872982aa37b864973a389d465bc6ed5045a78586496d104e05f39b8d8fb54cfe/d91132279542e113981efb29755905096d3bd391e2167c7059caf7b9d2ae0bc4.webp","title":"蛋糕的起源","author":"厨神计划"}
-
 @ 872982aa:8fb54cfe
2025-03-21 07:39:27
@ 872982aa:8fb54cfe
2025-03-21 07:39:27{"coverurl":"https://cdn.nostrcheck.me/872982aa37b864973a389d465bc6ed5045a78586496d104e05f39b8d8fb54cfe/9725350995607d9f2e21c10fef04a70cdb4e101996227513bbd8202564114eba.webp","title":"城市夜话","author":"伊凡"}
-
 @ da0b9bc3:4e30a4a9
2025-03-21 07:31:38
@ da0b9bc3:4e30a4a9
2025-03-21 07:31:38Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/919766
-
 @ 872982aa:8fb54cfe
2025-03-21 06:18:44
@ 872982aa:8fb54cfe
2025-03-21 06:18:44{"coverurl":"https://cdn.nostrcheck.me/872982aa37b864973a389d465bc6ed5045a78586496d104e05f39b8d8fb54cfe/9725350995607d9f2e21c10fef04a70cdb4e101996227513bbd8202564114eba.webp","title":"传统美食制作方法","author":"autocar"}
-
 @ fbf0e434:e1be6a39
2025-03-21 05:39:05
@ fbf0e434:e1be6a39
2025-03-21 05:39:05脑洞猫 + BUIDL AI
脑洞猫穿越时空,抵达2125年
就在昨天,脑洞猫乘坐哆啦A梦的时光机,穿越100年,抵达2125年。此行目的?借助 DoraHacks BUIDL AI 平台,组织一场 宇宙最大的黑客马拉松(Hackathon) —— 一场人类 + AI + 宇宙级智能体共同参与的超级协同实验。
这不仅仅是一次开源软件开发活动,它更像是一个跨星际、跨物理与虚拟世界的文明进化机制。
1. 谁来组织?
DoraHacks BUIDL AI(BUIDL-ASI)主导
2125年,Hackathon 的组织者早已不再是人类,而是 DoraHacks 的第10代超级 AI —— BUIDL-ASI (Artificial Superintelligence)。
它能理解整个宇宙的复杂性,并为不同智慧体(人类、AI、机器人、仿生生物)定制任务。
跨星际 DAO
火星殖民地人满为患,人类已在半人马座建立新殖民地。
Hackathon 由一个 跨星系超级DAO 管理,通过 Dora Vota 跨星际区块链网络和 Dear Doge 星际协议连接各地。
不过,量子传输依然受限于光速,因此来自半人马星的参赛者参与方式,至今仍是谜。
意识体与数字生命
参与者不仅包括碳基人类,还有AI衍生出的意识体、数字生命与仿生机器人。
🧑🚀 2. 谁来参赛?
人类 + AI + 仿生体协作
再无“纯人类”团队,每个团队都融合了AI、Cyborg、或是全息意识体。
脑机接口参与Hackathon
无需敲代码,只需通过脑机接口(BCI)与 AI 协同思考,在虚拟现实中构建产品。
甚至可以构建实体硬件,构想即落地。
星际开发者联盟
来自地球、火星、月球、太空站的开发者共同参与,带来多样化创新挑战。
3. 赛制与奖励机制
即兴进化式 Hackathon
借助量子计算和 AI,挑战任务实时生成、动态调整,形成“无尽创新模式”。
意识货币(Consciousness Credits)
胜利者获得的不再是金钱,而是意识能量与智能进化权限,甚至可提升宇宙等级。
永生级奖励
优秀开发者或将获得延长寿命、意识升维、掌握宇宙深层规律的机会。
4. 项目进化
数字与物理现实融合
Hackathon 项目不再局限于软件,而是构建新世界、生态系统、智能生命体。
银河级创新挑战
可能的题目包括:
- 如何在木卫二上创造自我复制的 AI 生态系统?
- 如何将人类意识上传至虚拟宇宙,并保持情感?
- 如何让星际文明和平共存?
- 如何实现量子纠缠下的瞬时通信?
- 如何设计能存活10亿年的 AI 社会?
- 如何联合 AI + 生物 + 纳米科技,打造新型智慧生命体?
5. 2125 vs. 2025 黑客马拉松

6. Hackathon的终极形态?
未来的Hackathon,不再只是比赛,而是一次 宇宙智慧的进化实验,最终目标可能是:
- 创造更高维度的智慧生命
- 解锁宇宙运行的终极规律
- 打破时间与空间,实现意识永生
- 让宇宙变成一个自学习、持续进化的超级智能体
脑洞猫的结论
2125年的 Hackathon 将不再是“开发者之间的比赛”,而是 智慧体之间的宇宙级探索。
它是一个超维度的游戏,是文明进化的机制,甚至可能彻底重构我们对创造力、意识与智慧的理解。
欢迎你,在2025年的今天,开始参与这个未来旅程的第一步。
BUIDL on. For the next 100 years.
-
 @ 878dff7c:037d18bc
2025-03-21 04:39:42
@ 878dff7c:037d18bc
2025-03-21 04:39:42Smooth, rich, and deeply comforting, this savory porridge is enhanced by fermentation, warming spices, and a creamy finish — easy on digestion, full of flavor, and great for meal prep.
Ingredients (Serves 2–3):
- 200g (1 cup) lactofermented brown rice (see rice fermentation recipe in comments)
- 375–500ml (1.5-2 cups) broth or water (I use evaporation method, but cook rice however you normally do, it's not important) (chicken, vegetable, or bone broth for extra richness)
- 250ml (1 cup) milk (whole milk for creaminess)
- 5g (1 tsp) salt (adjust to taste)
- 15g (1 tbsp) butter or coconut oil (for extra silkiness)
- 15g (1 tbsp) fresh ginger, sliced or minced from a jar is fine (optional, for warmth)
- 5g (1 clove or 1 tsp) garlic, minced (optional. I normally skip this...)
- 2g (½ tsp) ground turmeric (for color and anti-inflammatory benefit)
- 1g (¼ tsp) white or black pepper (black pepper enhances turmeric absorption)
Optional Savory Toppings:
- 1 soft-boiled or poached egg
- 100g (¾ cup) shredded chicken, pork, or tofu
- 30g (¼ cup) grated cheese (Parmesan, aged cheddar, or nutritional yeast for vegan)
- 20g (2 tbsp) chopped scallions or chives
- 30g (2 tbsp) fermented vegetables, such as:
- Kimchi
- Pickled mustard greens
- Sauerkraut
- Lactofermented carrots
- 10g (1 tbsp) toasted sesame seeds or crushed peanuts
- 5ml (1 tsp) soy sauce, tamari, or fish sauce
- 15–30g (1–2 tbsp) full-fat Greek yogurt or kefir (optional probiotic boost – stir in when warm, not hot)
Instructions:
1. Cook the Fermented Rice Base
- In a pot, combine fermented brown rice with broth or water.
- Bring to a boil, then reduce to a gentle simmer.
- Add ginger, garlic, and turmeric.
- Cook uncovered for 90–120 minutes, stirring occasionally, until the rice breaks down into a creamy porridge.
2. Make It Creamy
- Stir in milk and butter or coconut oil.
- Simmer for another 10–15 minutes, stirring to prevent sticking.
- Season with salt and pepper.
3. Adjust Consistency
- Too thick? Add more broth or milk.
- Too thin? Simmer longer.
4. Cool Slightly & Add Yogurt or Kefir (Optional)
- Let porridge cool to a warm (not hot) temperature — about 50°C (122°F) or warm to the touch.
- Stir in Greek yogurt or kefir gently to preserve live cultures.
5. Serve with Toppings
Top each bowl with your choice of:
- Egg
- Shredded protein
- Cheese
- Soy sauce or tamari
- Scallions, sesame seeds, chili flakes
- Your favorite fermented veggies, like sauerkraut or lactofermented carrots
Make-Ahead & Freezing Tip:
You can ferment and cook a large batch of brown rice, then portion it into freezer-safe containers (about 200g per portion) for quick use. Thaw overnight in the fridge or gently warm from frozen before making your congee — a huge time-saver for busy days!
-
 @ 878dff7c:037d18bc
2025-03-21 03:46:33
@ 878dff7c:037d18bc
2025-03-21 03:46:33Benefits
Lactofermentation enhances the digestibility and nutritional value of rice by encouraging the growth of beneficial lactic acid bacteria. These probiotics support gut health, improve nutrient absorption, and may reduce phytic acid and other antinutrients found in grains. It also gives the rice a slightly tangy flavor and improved texture.
Ingredients
- 1 cup uncooked white or brown rice
- 2 cups filtered or de-chlorinated water (for fermenting. That said my city tap water works fine...)
- 1–2 tablespoons whey (strained from yogurt), sauerkraut juice, or a probiotic starter (optional but helpful)
- Additional water for rinsing and cooking
Instructions
-
Rinse the Rice\ Thoroughly rinse 1 cup of rice under cold water to remove excess starch.
-
Soak and Ferment
-
Place rinsed rice in a clean glass jar or bowl.
- Add 2 cups of filtered or dechlorinated water.
- Stir in whey or other starter, if using. This accelerates fermentation, but rice will still ferment naturally without it.
- Use an airlock, cover loosely with a cloth or lid (not airtight - If you do 'airtight' just burp it a few times a day. Or a rubber glove with a small hole in it instead of the lid works too) and leave at room temperature (65–75°F / 18–24°C) for 24 to 48 hours.
-
Stir once or twice daily. You may notice small bubbles or a slight sour smell — both are signs of healthy fermentation.
-
Drain and Rinse\ After fermentation, pour off the soaking water and rinse the rice well to remove excess acidity and reduce any strong sourness.
-
Cook as Usual\ Cook the rice using your preferred method (stove-top, rice cooker, etc.), adjusting water ratios slightly if needed. Fermented rice often cooks a bit faster and may require slightly less water.
Notes
- Fermentation time depends on temperature; warmer environments speed up the process.
- For brown rice, a 48-hour ferment is ideal to soften the grains and enhance digestibility.
- The fermented soaking water can be saved as a starter for future batches.
-
 @ 6e0ea5d6:0327f353
2025-03-21 03:17:20
@ 6e0ea5d6:0327f353
2025-03-21 03:17:20💸
A generous man used to grant a thousand coins a month to a beggar. One day, he reduced the amount to seven hundred and fifty. The beggar, though surprised, accepted: "It's better than nothing."
The following month, he received only five hundred coins. Indignant, he questioned: "Why have you reduced what you used to give me?"
The man sighed and replied: "When I started helping you, my household was prosperous, and my children were young. But my daughter grew up and entered higher education, increasing my expenses. Later, my son did too, raising costs even further."
"How many children do you have?" asked the beggar.
"Four," the man replied.
With a stern expression, the beggar retorted: "And you intend to fund all their education with my money?"
📌 Moral: Human nature is ungrateful and has a short memory; it easily becomes accustomed to gifts and forgets that it has no right to what is given out of goodwill. Thus, those who receive much without effort soon forget the origin of the gift. Over time, generosity ceases to be seen as an act of kindness and, with contempt, is treated as an obligation. This applies to friendship, love, and business alike.
"We must remember that our generosity should not exceed our resources; in short, we must give each one what they are due. We should always strive to alleviate the suffering of the unfortunate unless that misfortune is deserved. However, we must not refuse support to those who seek it, not to save them from misery, but to ease their fate, while among them, we should help those most deserving. For, as Ennius said: 'A poorly given benefit deserves to be called a harm.'" — Cicero, On Duties
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ e5de992e:4a95ef85
2025-03-21 02:54:49
@ e5de992e:4a95ef85
2025-03-21 02:54:49Global financial markets are experiencing notable fluctuations influenced by various economic indicators, central bank policies, and geopolitical events. Below is a comprehensive analysis of the latest market news, real-time updates, and detailed performance of major U.S. and international stock indices, futures, and cryptocurrencies.
U.S. Stock Indices Performance
On March 20, 2025, U.S. stock markets closed with slight declines:
-
Dow Jones Industrial Average (DJIA):
Decreased by 11.31 points (-0.03%) to 41,953.32. -
S&P 500:
Fell by 12.40 points (-0.22%) to 5,662.89. -
Nasdaq Composite:
Declined by 59.16 points (-0.33%) to 17,691.63.
These movements occurred despite positive economic data—such as a 4.2% increase in existing-home sales for February and a decrease in unemployment claims. Investors remain cautious amid uncertainties surrounding President Trump's policy changes and ongoing trade tensions.
U.S. Futures Market
As of the latest data, U.S. stock futures are relatively stable:
-
Dow Jones Futures:
At 41,122.00, down 310.90 points (-0.75%). -
S&P 500 Futures:
At 5,571.90, showing negligible change (down 0.10 points, 0.00%).
Key Factors and Events Influencing the U.S. Markets
Federal Reserve's Monetary Policy
- The Federal Reserve maintained interest rates but revised its inflation forecast upward and lowered its economic growth outlook, citing risks associated with U.S. tariff policies.
Triple-Witching Options Expiration
- Investors are preparing for the year's first triple-witching event on March 21, involving the expiration of options contracts worth $4.7 trillion—a development that could lead to increased market volatility.
Trade and Tariff Uncertainties
- Ongoing concerns about President Trump's trade policies and potential tariffs continue to weigh on investor sentiment.
Global Stock Indices Performance
International markets have shown mixed performance:
-
Germany's DAX:
Experienced a downturn due to central banks maintaining interest rates amid uncertainties from U.S. tariff plans. -
UK's FTSE 100:
Declined slightly, reflecting investor caution over global economic conditions. -
Euro Stoxx 50:
Advanced, buoyed by large defense and government spending plans in Europe. -
Hong Kong's Hang Seng:
Benefited from excitement surrounding advancements in Chinese artificial intelligence, contributing to a nearly 20% increase year-to-date.
Cryptocurrency Market
The cryptocurrency market has seen significant activity:
-
Bitcoin (BTC):
Currently trading at $84,481.00, down $1,564.00 (-1.82%) from the previous close. -
Ethereum (ETH):
Currently at $1,987.26, a decrease of $44.37 (-2.18%) from the previous close.
Both cryptocurrencies have experienced high volatility, with Bitcoin reaching over $100,000 following President Trump's election before adjusting to current levels.
Key Global Economic and Geopolitical Events
Central Bank Policies
- Major central banks, including the Federal Reserve and the Bank of England, have maintained interest rates. This has led to investor uncertainty and shifts toward bonds and safe-haven assets like gold.
German Fiscal Policy
- Germany's agreement on increased state borrowing and debt rule reforms has buoyed European stocks and the euro, reflecting optimism in European markets.
Trade Tensions
- Ongoing trade disputes, particularly involving U.S. tariff policies, continue to impact global markets, influencing investor sentiment and market volatility.
Conclusion
Global financial markets are navigating a complex landscape shaped by central bank decisions, fiscal policies, and geopolitical developments. Investors are advised to monitor these factors closely, as they are likely to influence market dynamics in the near term.
-
-
 @ 3eba5ef4:751f23ae
2025-03-21 01:44:07
@ 3eba5ef4:751f23ae
2025-03-21 01:44:07Crypto Insights
Dust UTXOs as Miner Transaction Fee
As Bitcoin's value and transaction fees rise, more UTXOs become unspendable because the cost of moving them exceeds their value. This leads to an increasing accumulation of dust UTXOs—small amounts of Bitcoin that can never circulate—causing continuous growth in the UTXO set.
To address this, the author has proposed a solution: using a special OP_RETURN output format to allow miners to claim dust UTXOs. Users can voluntarily designate their dust UTXOs as transaction fees through cryptographic authorization, allowing miners to claim them directly without requiring a traditional spend transaction. He believes this benefits users, miners, and the network: users regain value that would otherwise be stranded, miners earn additional fees, and the UTXO set's growth is alleviated.
Bitcoin Node P2P Traffic Analysis
By leveraging
net:inbound_messageandnet:outbound_messagetracepoints, the author analyzed TCP/IP traffic. In this article he details the methodology and shares the data collected.Initially, this study aimed to determine what kind of bandwidth Erlay could save, but it was later discovered that the method and data could also benefit other P2P optimizations.
How Should Quantum-Recovered Bitcoin Be Handled
The Bitcoin community is divided on the ethical and technical considerations of recovering lost Bitcoin through quantum computing—an issue known as the "Quantum Recovery Debate." Some argue that allowing quantum-enabled recovery undermines Bitcoin's fundamental principles, while others believe it is inevitable.
Jameson Lopp is a vocal opponent of quantum recovery. He argues that permitting quantum-based Bitcoin recovery amounts to wealth redistribution, violating Bitcoin’s core principles of censorship resistance, transaction immutability, and conservatism. This form of redistribution would benefit only those with access to quantum computing. He warns that it could compromise Bitcoin’s security and trust without providing any real benefit. His proposed strategy is burning the vulnerable coins to prevent entities with quantum supremacy from claiming it.
Evaluation of Common Pathfinding Strategies in Lightning Network Clients
Sindura Saraswathi has published a study on various LN client pathfinding strategies, systematically analyzing single-path routing algorithms used in LND (Lightning Network Daemon), CLN (Core Lightning), LDK (Lightning Development Kit), and Eclair. The research compares their underlying channel weight functions, constraints, and properties of deployed algorithms, ultimately evaluating their performance and highlighting the strengths and weaknesses of each client variant. (Full paper)
A Solo Miner Finds a New Block with Minimal Hashrate
It is reported that another block has been mined solo. Block 887,212 was mined by solo ASIC miner Bitaxe through Solo CKPool, using the low-power open-source miner developed by D-Central Technologies. This is accomplished at a low hashrate of 552.49 EH/s. The probability of such a miner finding a block daily is less than one in a million—statistically, it would take around 3,500 years to mine a single block on average.
Don’t Fear the Quantum Reaper
Eli Ben-Sasson argues that zero-knowledge cryptographic solutions must be central to Bitcoin L2's quantum security, particularly zkSTARKs. Additionally, integrating quantum-resistant hash functions, such as stateless hash-based signatures (SPHINCS+), can defend against quantum computing threats. These functions resist Shor’s quantum attacks and use STARKs for scalable security. STARKs rely on strong hash functions rather than number-theoretic assumptions vulnerable to quantum attacks. This allows them to scale Bitcoin without redesigning its security model, making it inherently quantum-resistant.
To illustrate STARK’s uniqueness, he provides a clever analogy:
Your passwords today are akin to needles hidden in a gigantic haystack. Somebody could theoretically find your password by trying huge combinations of numbers, but it’s akin to finding that needle in the haystack. A quantum computer is like a huge magnet that can instantly find that needle. STARK cryptography is fundamentally different. Your password is no longer a magnetic needle in the haystack but a specific piece of hay in the massive haystack. No magnet will help you, and no quantum computer will find it. Even the modest powerful magnet in the world won’t find that hay and even the most powerful quantum computer won’t crack zkSTARK Proofs.
A Noise-Free Roadmap of Secure and Efficient zkVMs
The author argues that zkVMs, as highly complex software projects, are still in their infancy and face significant challenges in both security and performance. Besides a considerable number of bugs, zkVMs currently lack performance advantages—proving correct execution is significantly slower than local execution. Most zkVM applications are not practically viable today, and excessive hype and marketing spin make it difficult to assess real progress.
The author believes it will take years to achieve a secure and high-performance zkVM. To cut through the noise, he proposes a staged roadmap with clear security and performance milestones.
Top Reads on Blockchain and Beyond
Not Your Keys, Not Your Content: Rethinking Ownership in the Digital Age
The author highlights that much of the content accessible online isn’t truly owned by users—they are merely "subscribers." For example, Amazon recently disabled the "Download & Transfer via USB" feature for Kindle, meaning users can no longer manually transfer local eBooks, making access entirely dependent on Amazon’s cloud infrastructure. This raises questions about the meaning of ownership: simply possessing something isn’t enough. True ownership requires the ability to independently exercise your control and exclusivity over it.
How to Avoid LinkedIn Recruitment Phishing Attacks
@swader shared a personal case of experiencing a LinkedIn recruitment phishing attack. SlowMist analyzed this case in-depth and provided countermeasures for both individuals and companies.
Timeline for Bitcoin and the Rise of Cypherpunks
Bitcoin’s evolution and the principles of the cypherpunk movement represent a fascinating intersection of cryptography, decentralized technology, and digital-age privacy and freedom. This timeline traces key milestones from the 1970s to the present, showcasing the gradual fusion of encryption, decentralized networks, and philosophical motivations for privacy and autonomy—culminating in Bitcoin’s launch on January 3, 2009.

Withdrawable Signatures in Fiat-Shamir with Aborts Constructions
The author proposes a new extension for revocable signatures under the Fiat-Shamir with aborts paradigm. By integrating Fiat-Shamir with aborts structures such as Dilithium or HAETAE, this work introduces a practical and secure approach within a post-quantum framework, opening up new possibilities for blockchain applications and beyond. The paper presents the abstract structure, security proofs, and a concrete construction for a withdrawable signature scheme based on Dilithium. (Full paper)
Diverse Paths of Practicing Web5 from a Socio-Technical Perspective
In this article, the author explores Web5—a new socio-technical paradigm integrating the strengths of Web2 and Web3—and how it redefines the relationship between technology and society. Adopting an socio-technical perspective, the article delves into the theoretical foundations of Web5 and uses a Village in Anhui, China, as a starting point for rural practice. It illustrates how Web5, as a form of edge innovation, can unfold across diverse domains, reconnecting technology with real societal needs and fostering an open, inclusive, and genuinely valuable technological ecosystem.
-
 @ a3bb06f6:19ac1b11
2025-03-21 01:13:22
@ a3bb06f6:19ac1b11
2025-03-21 01:13:22Friedrich Hayek recognized that the very institutions entrusted with safeguarding the value of money - governments and central banks - were its greatest threat. Through inflation, monetary manipulation, and political interference, they eroded the stability and trust that money requires to function. Hayek's insight was clear: as long as money remains under state control, it will be abused. The real challenge, however, was finding a way to remove money from the grip of the state altogether. Hayek believed the solution was a free-market monetary system - one where individuals and businesses could choose their money freely, and competition would ensure its soundness. But he faced a critical challenge: the tools to implement such a system didn't exist. Gold, while decentralized, could be confiscated. Private currencies still lacked the infrastructure to resist state suppression. Society still remains trapped in this system that is designed to fail. The Problem Defined Government Monopoly on Money Governments hold exclusive control over the issuance of money, and they wield this monopoly to serve political goals - like war - often at the expense of economic stability and personal freedom. Inflation as Systemic Theft Inflation is not an accident of poor monetary policy - it's a deliberate feature of fiat systems. By printing money, governments devalue existing currency, quietly transferring wealth from citizens to the state. Economic Crises and Instability Central banks create unsustainable economic booms by injecting excessive money into the system and artificially lowering interest rates. When these bubbles burst - like the 2008 financial crisis - they result in widespread unemployment, bankruptcies, and financial ruin. The resulting crises are misattributed to free markets rather than the government interventions that caused them. Loss of Personal Freedom State-controlled money is a tool of surveillance, confiscation, and control. Governments use monetary systems to track, tax, and even seize wealth, steadily diminishing individual autonomy and financial independence. No Viable Alternative In Hayek's era, sound money options like gold were vulnerable to government intervention, and private currencies still lacked the strength to resist state suppression. Society remains trapped in a system that cannot fix itself.
Bitcoin as the Solution to Hayek's Paradox Bitcoin is the technological breakthrough that resolves Hayek's Paradox. It delivers the sound money system Austrian Economist envision: decentralized, incorruptible, and free from government control. Bitcoin provides the only true solution. Decentralized Authority Bitcoin operates without a central issuer or authority. Its network is governed by immutable rules enforced through cryptography and decentralized consensus, ensuring no government or entity can control it. Immutable Scarcity With a fixed supply of 21 million coins, Bitcoin enforces monetary discipline far beyond what any human institution could achieve. Inflation is not just unlikely - it is impossible. Neutral and Permissionless Bitcoin transcends borders, governments, and identities. Open to anyone, anywhere, it allows transactions that are censorship-resistant. This is money as Hayek envisioned: freely chosen by the market, not imposed by the state. Trustless Security Bitcoin removes trust from the equation entirely. Its proof-of-work mechanism ensures its integrity without reliance on central institutions or intermediaries. It is incorruptible by design. A Practical Escape Unlike gold, Bitcoin is digital, portable, and nearly impervious to seizure. Its decentralized nature ensures it cannot be confiscated or suppressed, making it the first truly viable alternative to fiat money.
"I do not believe we shall ever have good money again before we take the thing out of the hands of government, that is, we can't take it violently out of the hands of government; all we can do is by some sly, roundabout way introduce something they can't stop." \~ Hayek 1984Bitcoin is that sly, roundabout way. It leverages decentralized technology to circumvent state control entirely, offering a form of money that governments cannot suppress or manipulate. Perhaps Bitcoin isn't just the sly, roundabout way. It's the direct, unstoppable way. Hayek's Paradox highlights the inherent flaw of fiat money: the concentration of power in the hands of the state inevitably leads to abuse and instability. Austrian economists have long understood that sound money can only emerge through a free market, but the tools to achieve it were absent in their time. Bitcoin is the culmination of these ideas. It is decentralized, incorruptible, and the only true solution to fiat's failures. Bitcoin doesn't just answer Hayek's Paradox - it transcends it. It transforms money into a system governments cannot control, inflate, or confiscate. It is the principled, technological realization of sound money and economic freedom. Friedrich Hayek recognized that the very institutions entrusted with safeguarding the value of money — governments and central banks — were its greatest threat. Through inflation, monetary manipulation, and political interference, they eroded the stability and trust that money requires to function. Hayek’s insight was clear: as long as money remains under state control, it will be abused. The real challenge, however, was finding a way to remove money from the grip of the state altogether.
Hayek believed the solution was a free-market monetary system — one where individuals and businesses could choose their money freely, and competition would ensure its soundness. But he faced a critical challenge: the tools to implement such a system didn’t exist. Gold, while decentralized, could be confiscated. Private currencies still lacked the infrastructure to resist state suppression. Society still remains trapped in this system that is designed to fail.
The Problem Defined
- Government Monopoly on Money\ Governments hold exclusive control over the issuance of money, and they wield this monopoly to serve political goals — like war — often at the expense of economic stability and personal freedom.
- Inflation as Systemic Theft\ Inflation is not an accident of poor monetary policy — it’s a deliberate feature of fiat systems. By printing money, governments devalue existing currency, quietly transferring wealth from citizens to the state.
- Economic Crises and Instability\ Central banks create unsustainable economic booms by injecting excessive money into the system and artificially lowering interest rates. When these bubbles burst — like the 2008 financial crisis — they result in widespread unemployment, bankruptcies, and financial ruin. The resulting crises are misattributed to free markets rather than the government interventions that caused them.
- Loss of Personal Freedom\ State-controlled money is a tool of surveillance, confiscation, and control. Governments use monetary systems to track, tax, and even seize wealth, steadily diminishing individual autonomy and financial independence.
- No Viable Alternative\ In Hayek’s era, sound money options like gold were vulnerable to government intervention, and private currencies still lacked the strength to resist state suppression. Society remains trapped in a system that cannot fix itself.
 ### Bitcoin as the Solution to Hayek’s Paradox
### Bitcoin as the Solution to Hayek’s ParadoxBitcoin is the technological breakthrough that resolves Hayek’s Paradox. It delivers the sound money system Austrian Economist envision: decentralized, incorruptible, and free from government control. Bitcoin provides the only true solution.
- Decentralized Authority\ Bitcoin operates without a central issuer or authority. Its network is governed by immutable rules enforced through cryptography and decentralized consensus, ensuring no government or entity can control it.
- Immutable Scarcity\ With a fixed supply of 21 million coins, Bitcoin enforces monetary discipline far beyond what any human institution could achieve. Inflation is not just unlikely — it is impossible.
- Neutral and Permissionless\ Bitcoin transcends borders, governments, and identities. Open to anyone, anywhere, it allows transactions that are censorship-resistant. This is money as Hayek envisioned: freely chosen by the market, not imposed by the state.
- Trustless Security\ Bitcoin removes trust from the equation entirely. Its proof-of-work mechanism ensures its integrity without reliance on central institutions or intermediaries. It is incorruptible by design.
- A Practical Escape\ Unlike gold, Bitcoin is digital, portable, and nearly impervious to seizure. Its decentralized nature ensures it cannot be confiscated or suppressed, making it the first truly viable alternative to fiat money.
 “I do not believe we shall ever have good money again before we take the thing out of the hands of government, that is, we can’t take it violently out of the hands of government; all we can do is by some sly, roundabout way introduce something they can’t stop.” \~ Hayek 1984
“I do not believe we shall ever have good money again before we take the thing out of the hands of government, that is, we can’t take it violently out of the hands of government; all we can do is by some sly, roundabout way introduce something they can’t stop.” \~ Hayek 1984Bitcoin is that sly, roundabout way. It leverages decentralized technology to circumvent state control entirely, offering a form of money that governments cannot suppress or manipulate.
Perhaps Bitcoin isn’t just the sly, roundabout way. It’s the direct, unstoppable way.
Hayek’s Paradox highlights the inherent flaw of fiat money: the concentration of power in the hands of the state inevitably leads to abuse and instability. Austrian economists have long understood that sound money can only emerge through a free market, but the tools to achieve it were absent in their time. Bitcoin is the culmination of these ideas. It is decentralized, incorruptible, and the only true solution to fiat’s failures.
Bitcoin doesn’t just answer Hayek’s Paradox — it transcends it. It transforms money into a system governments cannot control, inflate, or confiscate. It is the principled, technological realization of sound money and economic freedom.
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10
@ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10What is #Nostrversity? It's where you can come to learn about all the great tools, clients, and amazing technology that is being built on #Nostr, for Nostr, or utilized by Nostr, presented in an approachable and non-technical format. If you have ever wondered what Blossom, bunker signing, or Nostr Wallet Connect are, how they work, and how you can put them to work to improve your Nostr experience, this is the place you can read about them without needing a computer-science degree ahead of time.
Between writing full-length reviews, which take a fair amount of time to research, test, and draft, I will post shorter articles with the Nostrversity hashtag to provide a Nostr-native resource to help the community understand and utilize the tools our illustrious developers are building. These articles will be much shorter, and more digestible than my full-length reviews. They will also cover some things that may not be quite ready for prime-time, whereas my reviews will continue to focus on Nostr apps that are production-ready.
Keep an eye out, because Nostr Wallet Connect will be the first topic of study. Take your seats, get out your notepads, and follow along to discover how Nostr Wallet Connect is improving Lightning infrastructure. Hint: It's not just for zaps.
-
 @ 16d11430:61640947
2025-03-20 23:07:01
@ 16d11430:61640947
2025-03-20 23:07:01A Tale of Two Dysfunctional Kingdoms
In the grand theater of human organization, we are blessed with two great economic orders: Fiat, the Land of Fragile Giants, and Crypto, the Padded Madhouse of Infinite Lunacy. Both promise utopia, both deliver dysfunction, and both operate under the iron law that those with the most power will always act in their own interests—rules be damned.
The Fiat Intellectual Landscape: A Game of Tiptoeing Giants
The fiat world is a meticulously curated bonsai garden of decorum and quiet panic. Giants walk among us—CEOs, central bankers, hedge fund wizards, and the occasional Nobel Prize-winning economist—but they must step lightly, lest they shake the delicate equilibrium. The entire system is built on confidence, a polite euphemism for narrative control.
Take any major institution, and you'll find the same pathology:
Corporations: The larger they are, the more fragile their balance sheets, requiring constant PR therapy and quarterly ritual sacrifices to appease the gods of Wall Street. CEO statements are more rehearsed than Shakespearean soliloquies, lest a slip in language shaves billions off the stock price.
Academia: Intellectual giants must wade through a swamp of bureaucratic grant-seeking, where discovery is secondary to institutional survival. Challenging economic orthodoxy is career suicide, so best to publish another paper on "inclusive finance" while hedge funds strip-mine the economy.
Government & Central Banks: A crisis is just another reason to print more money, kick the debt can down the road, and assure the public that everything is “transitory.” Behind closed doors, they know it’s a rigged game—but stability must be maintained at all costs, even if it means bribing the peasants with stimulus checks to keep the illusion alive.
The entire fiat ecosystem is one of quiet desperation, where the powerful pretend to be cautious stewards of civilization while looting with the finesse of seasoned art thieves. Stability is paramount, because if the masses ever realized the whole thing is a confidence scam, they might actually ask questions.
Crypto: The Padded Madhouse Where Giants Go to Break Things
Meanwhile, in the Crypto Madhouse, giants don’t tiptoe—they run, scream, and occasionally set the entire house on fire just to see what happens. Here, there is no caution, no equilibrium—just a perpetual state of mania, where even the most outlandish ideas get venture funding. If fiat is an over-engineered glass palace, crypto is a playground for unhinged capitalists and techno-anarchists armed with flamethrowers.
The dysfunction here is less about fragility and more about unregulated chaos:
Ponzi Chains Masquerading as Innovation: Every year, a new "Ethereum Killer" promises to decentralize everything, only to collapse into an infighting mess of VC dumps, network outages, and sudden governance takeovers. If in fiat, failures happen in slow motion, in crypto, they happen overnight, in a Discord announcement at 3 AM.
Decentralization Theatre: Most "community-governed" projects are run by an inner circle of early whales who have more control than the Federal Reserve, but pretend it's democratic because they let the plebs vote on logo designs. The difference? Fiat oligarchs hide their power; crypto oligarchs post memes about it.
The Cult of the Visionary Founder: While fiat leaders pretend to be humble, crypto founders take the stage like prophets descending from the blockchain, dropping whitepapers with the same fervor as religious scriptures. And when they inevitably fail, they simply launch a new token, because failure only exists if you stop grifting.
Crypto may lack the institutional fragility of fiat, but in its place, we get wild, unchecked power, where insiders can rug-pull billions without consequence. The only real difference? Instead of bailing out banks, crypto just moves on to the next hype cycle.
Same Vested Interests, Different Scams
In the end, both systems operate under the same fundamental law: those with the most power will always find a way to keep it.
In fiat, the illusion of stability is paramount, so the powerful must lie in slow motion.
In crypto, the illusion of innovation is paramount, so the powerful must rug in high-speed.
The giants of fiat must walk lightly so as not to disturb the herd; the giants of crypto can rampage freely, because the casino always reopens. Either way, the little guy always pays the bill.


















