-

@ 04c915da:3dfbecc9
2025-03-26 20:54:33
Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-

@ 04c915da:3dfbecc9
2025-03-25 17:43:44
One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-

@ c1e9ab3a:9cb56b43
2025-03-26 21:03:59
## Introduction
**Nutsax** is a capability-based access control system for **Nostr relays**, designed to provide flexible, privacy-preserving **rate limiting**, **permissioning**, and **operation-scoped token redemption**.
At its core, Nutsax introduces:
- **Blind-signed tokens**, issued by relays, for specific operation types.
- **Token redemption** as part of Nostr event publishing or interactions.
- **Encrypted token storage** using existing Nostr direct message infrastructure, allowing portable, persistent, and private storage of these tokens — the *Nutsax*.
This mechanism augments the existing Nostr protocol without disrupting adoption, requiring no changes to NIP-01 for clients or relays that don’t opt into the system.
## Motivation
Nostr relays currently have limited tools for abuse prevention and access control. Options like IP banning, whitelisting, or monetized access are coarse and often centralized.
Nutsax introduces:
- Fine-grained, **operation-specific access control** using cryptographic tokens.
- **Blind signature protocols** to issue tokens anonymously, preserving user privacy.
- A **native way to store and recover tokens** using Nostr’s encrypted event system.
This allows relays to offer:
- Optional access policies (e.g., “3 posts per hour unless you redeem a token”)
- Paid or invite-based features (e.g., long-term subscriptions, advanced filters)
- Temporary elevation of privileges (e.g., bypass slow mode for one message)
All without requiring accounts, emails, or linking identity beyond the user’s `npub`.
## Core Components
### 1. Operation Tokens
Tokens are blind-signed blobs issued by the relay, scoped to a specific **operation type** (e.g., `"write"`, `"filter-subscribe"`, `"broadcast"`).
- **Issued anonymously**: using a blind signature protocol.
- **Validated on redemption**: at message submission or interaction time.
- **Optional and redeemable**: the relay decides when to enforce token redemption.
Each token encodes:
- Operation type (string)
- Relay ID (to scope the token)
- Expiration (optional)
- Usage count or burn-on-use flag
- Random nonce (blindness)
Example (before blinding):
```json
{
"relay": "wss://relay.example",
"operation": "write",
"expires": 1720000000,
"nonce": "b2a8c3..."
}
```
This is then blinded and signed by the relay.
### 2. Token Redemption
Clients include tokens when submitting events or requests to the relay.
**Token included via event tag**:
```json
["token", "<base64-encoded-token>", "write"]
```
Redemption can happen:
- **Inline with any event** (kind 1, etc.)
- **As a standalone event** (e.g., ephemeral kind 20000)
- **During session initiation** (optional AUTH extension)
The relay validates the token:
- Is it well-formed?
- Is it valid for this relay and operation?
- Is it unexpired?
- Has it been used already? (for burn-on-use)
If valid, the relay accepts the event or upgrades the rate/permission scope.
### 3. Nutsax: Private Token Storage on Nostr
Tokens are stored securely in the client’s **Nutsax**, a persistent, private archive built on Nostr’s encrypted event system.
Each token is stored in a **kind 4** or **kind 44/24** event, encrypted with the client’s own `npub`.
Example:
```json
{
"kind": 4,
"tags": [
["p", "<your npub>"],
["token-type", "write"],
["relay", "wss://relay.example"]
],
"content": "<encrypted token blob>",
"created_at": 1234567890
}
```
This allows clients to:
- Persist tokens across restarts or device changes.
- Restore tokens after reinstalling or reauthenticating.
- Port tokens between devices.
All without exposing the tokens to the public or requiring external storage infrastructure.
## Client Lifecycle
### 1. Requesting Tokens
- Client authenticates to relay (e.g., via NIP-42).
- Requests blind-signed tokens:
- Sends blinded token requests.
- Receives blind signatures.
- Unblinds and verifies.
### 2. Storing Tokens
- Each token is encrypted to the user’s own `npub`.
- Stored as a DM (kind 4 or compatible encrypted event).
- Optional tagging for organization.
### 3. Redeeming Tokens
- When performing a token-gated operation (e.g., posting to a limited relay), client includes the appropriate token in the event.
- Relay validates and logs/consumes the token.
### 4. Restoring the Nutsax
- On device reinstallation or session reset, the client:
- Reconnects to relays.
- Scans encrypted DMs.
- Decrypts and reimports available tokens.
## Privacy Model
- Relays issuing tokens **do not know** which tokens were redeemed (blind signing).
- Tokens do not encode sender identity unless the client opts to do so.
- Only the recipient (`npub`) can decrypt their Nutsax.
- Redemption is pseudonymous — tied to a key, not to external identity.
## Optional Enhancements
- **Token index tag**: to allow fast search and categorization.
- **Multiple token types**: read, write, boost, subscribe, etc.
- **Token delegation**: future support for transferring tokens via encrypted DM to another `npub`.
- **Token revocation**: relays can publish blacklists or expiration feeds if needed.
## Compatibility
- Fully compatible with NIP-01, NIP-04 (encrypted DMs), and NIP-42 (authentication).
- Non-disruptive: relays and clients can ignore tokens if not supported.
- Ideal for layering on top of existing infrastructure and monetization strategies.
## Conclusion
**Nutsax** offers a privacy-respecting, decentralized way to manage access and rate limits in the Nostr ecosystem. With blind-signed, operation-specific tokens and encrypted, persistent storage using native Nostr mechanisms, it gives relays and clients new powers without sacrificing Nostr’s core principles: simplicity, openness, and cryptographic self-sovereignty.
-

@ a7bbc310:fe7b7be3
2025-03-24 13:18:49
I’ve been back from Morocco for just over a month and I’ve had some time to reflect. I started writing a day by day of what I did in my trip to Morocco but that was turning out a bit boring. I couldn’t do the trip justice. I thought I’d share some of my observations instead. I’d start by saying I was only there for 5 1/2 days. 5 days in Marrakesh and half day in Essaouira
You can feel the rich culture and history Morocco has such a rich culture and history. Influence of Romans, French, Arab, Berbers, Saharan and Nomadic tribes. You can see it in the architecture, taste it in the food and hear it in the language. The streets of Marrakesh had the smells of spices, perfumes and petrol. There is a synchronised dance between everyone that occupy the streets. People, motorbikes, donkeys, carts, all jostling for position but never seeming to collide into on another.
One thing that didn’t surprise me was the high level of craftsmanship and intricate designs on some of the buildings. I was told by a tour guide that some of the calligraphy could only be understood and read by the person who wrote it.
There seemed to be a sense of community, people stopping in the street to greet each other and say hello. What surprised me about this in Marrakesh most was that it happened in such a busy city. From my experience big cities are places that you go to get lost, ignored and don’t want to be found. Scene at the end of the movie Collateral comes to mind. You know the one where he’s riding on the subway alone after being shot.
A vendor tried to sell me a pendant, a symbol of the Berber tribe that meant ‘free man’. The symbol looks similar to the one for Sats 丰. I declined to purchase since I wasn’t educated enough on the Berbers to rep a symbol.
Couldn’t get over how much stuff there was for sale! And duplications of everything, rugs, shoes , handbags, jackets. Cold mornings and evenings, warm during the day. Everyone dressed like it was winter, even when it for warmer in the afternoon. It was a special trip. I’d definitely go back. Both to visit Marrakesh and other places.
-

@ f839fb67:5c930939
2025-03-24 00:25:16
# Relays
| Name | Address | Price (Sats/Year) | Status |
| - | - | - | - |
| stephen's aegis relay | wss://paid.relay.vanderwarker.family | 42069 |   |
| stephen's Outbox | wss://relay.vanderwarker.family | Just Me |   |
| stephen's Inbox | wss://haven.vanderwarker.family/inbox | WoT |   |
| stephen's DMs | wss://haven.vanderwarker.family/chat | WoT |   |
| VFam Data Relay | wss://data.relay.vanderwarker.family | 0 |   |
| VFam Bots Relay | wss://skeme.vanderwarker.family | Invite |   |
| VFGroups (NIP29) | wss://groups.vanderwarker.family | 0 |   |
| [TOR] My Phone Relay | ws://naswsosuewqxyf7ov7gr7igc4tq2rbtqoxxirwyhkbuns4lwc3iowwid.onion | 0 | Meh... |
---
# My Pubkeys
| Name | hex | nprofile |
| - | - | - |
| Main | f839fb6714598a7233d09dbd42af82cc9781d0faa57474f1841af90b5c930939 | nprofile1qqs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us9mapfx |
| Vanity (Backup) | 82f21be67353c0d68438003fe6e56a35e2a57c49e0899b368b5ca7aa8dde7c23 | nprofile1qqsg9usmuee48sxkssuqq0lxu44rtc4903y7pzvmx694efa23h08cgcpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3ussel49x |
| VFStore | 6416f1e658ba00d42107b05ad9bf485c7e46698217e0c19f0dc2e125de3af0d0 | nprofile1qqsxg9h3uevt5qx5yyrmqkkehay9cljxdxpp0cxpnuxu9cf9mca0p5qpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usaa8plu |
| NostrSMS | 9be1b8315248eeb20f9d9ab2717d1750e4f27489eab1fa531d679dadd34c2f8d | nprofile1qqsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us595d45 |
# Bot Pubkeys
| Name | hex | nprofile |
| - | - | - |
| Unlocks Bot | 2e941ad17144e0a04d1b8c21c4a0dbc3fbcbb9d08ae622b5f9c85341fac7c2d0 | nprofile1qqsza9q669c5fc9qf5dccgwy5rdu877th8gg4e3zkhuus56pltru95qpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ust4kvak |
| Step Counter | 9223d2faeb95853b4d224a184c69e1df16648d35067a88cdf947c631b57e3de7 | nprofile1qqsfyg7jlt4etpfmf53y5xzvd8sa79ny356sv75gehu50333k4lrmecpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ustswp3w |
---
# "Personal Nostr Things"
> [D] = Saves darkmode preferences over nostr
> [A] = Auth over nostr
> [B] = Beta (software)
> [z] = zap enabled
- [[DABz] Main Site](https://vanderwarker.family)
- [[DAB] Contact Site](https://stephen.vanderwarker.family)
- [[DAB] PGP Site](https://pgp.vanderwarker.family)
- [[DAB] VFCA Site](https://ca.vanderwarker.family)
---
# Other Services (Hosted code)
* [Blossom](https://blossom.vanderwarker.family)
 
* [NostrCheck](https://nostr.vanderwarker.family)
 
---
# Emojis Packs
* Minecraft
- <code>nostr:naddr1qqy566twv43hyctxwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsd0k5wp</code>
* AIM
- <code>nostr:naddr1qqxxz6tdv4kk7arfvdhkuucpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usyg8c88akw9ze3fer85yah4p2lqkvj7qap749w360rpq6ly94eycf8ypsgqqqw48qe0j2yk</code>
* Blobs
- <code>nostr:naddr1qqz5ymr0vfesz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2wek4ukj</code>
* FavEmojis
- <code>nostr:naddr1qqy5vctkg4kk76nfwvq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsf7sdwt</code>
* Modern Family
- <code>nostr:naddr1qqx56mmyv4exugzxv9kkjmreqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqp65ujlj36n</code>
* nostriches (Amethyst collection)
- <code>nostr:naddr1qq9xummnw3exjcmgv4esz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w2sqg6w</code>
* Pepe
- <code>nostr:naddr1qqz9qetsv5q37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82ns85f6x7</code>
* Minecraft Font
- <code>nostr:naddr1qq8y66twv43hyctxwssyvmmwwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsmzftgr</code>
* Archer Font
- <code>nostr:naddr1qq95zunrdpjhygzxdah8gqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr4fclkyxsh</code>
* SMB Font
- <code>nostr:naddr1qqv4xatsv4ezqntpwf5k7gzzwfhhg6r9wfejq3n0de6qz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w0wqpuk</code>
---
# Git Over Nostr
* NostrSMS
- <code>nostr:naddr1qqyxummnw3e8xmtnqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfrwaehxw309amk7apwwfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqyj8wumn8ghj7urpd9jzuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyxhwumn8ghj7mn0wvhxcmmvqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqaueqp0epk</code>
* nip51backup
- <code>nostr:naddr1qq9ku6tsx5ckyctrdd6hqqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjxamnwvaz7tmhda6zuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfywaehxw309acxz6ty9eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgdwaehxw309ahx7uewd3hkcq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqpmej4gtqs6</code>
* bukkitstr
- <code>nostr:naddr1qqykyattdd5hgum5wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dspzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqrhnyf6g0n2</code>
---
# Market Places
Please use [Nostr Market](https://market.nostr.com) or somthing simular, to view.
* VFStore
- <code>nostr:naddr1qqjx2v34xe3kxvpn95cnqven956rwvpc95unscn9943kxet98q6nxde58p3ryqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjvamnwvaz7tmgv9mx2m3wweskuer9wfmkzuntv4ezuenpd45kc7f0da6hgcn00qqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzqeqk78n93wsq6sss0vz6mxl5shr7ge5cy9lqcx0smshpyh0r4uxsqvzqqqr4gvlfm7gu</code>
---
# Badges
## Created
* paidrelayvf
- <code>nostr:naddr1qq9hqctfv3ex2mrp09mxvqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr48y85v3u3</code>
* iPow
- <code>nostr:naddr1qqzxj5r02uq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgg02u0r</code>
* codmaster
- <code>nostr:naddr1qqykxmmyd4shxar9wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgk3gm4g</code>
* iMine
- <code>nostr:naddr1qqzkjntfdejsz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqafed5s4x5</code>
---
# Clients I Use
* Amethyst
- <code>nostr:naddr1qqxnzd3cx5urqv3nxymngdphqgsyvrp9u6p0mfur9dfdru3d853tx9mdjuhkphxuxgfwmryja7zsvhqrqsqqql8kavfpw3</code>
* noStrudel
- <code>nostr:naddr1qqxnzd3cxccrvd34xser2dpkqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsygpxdq27pjfppharynrvhg6h8v2taeya5ssf49zkl9yyu5gxe4qg55psgqqq0nmq5mza9n</code>
* nostrsms
- <code>nostr:naddr1qq9rzdejxcunxde4xymqz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgrqsqqql8kjn33qm</code>
---
# Lists
* Fediverse
- <code>nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqp9rx2erfwejhyum9j4g0xh</code>
* AI
- <code>nostr:naddr1qvzqqqr4xypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqqfq5j65twn7</code>
* Asterisk Shenanigans
- <code>nostr:naddr1qvzqqqr4xypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqz3qhxar9wf5hx6eq2d5x2mnpde5kwctwwvaxjuzz</code>
* Minecraft Videos
- <code>nostr:naddr1qvzqqqr4xypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqzpxkjmn9vdexzen5yptxjer9daesqrd8jk</code>
-

@ 6b3780ef:221416c8
2025-03-26 18:42:00
This workshop will guide you through exploring the concepts behind MCP servers and how to deploy them as DVMs in Nostr using DVMCP. By the end, you'll understand how these systems work together and be able to create your own deployments.
## Understanding MCP Systems
MCP (Model Context Protocol) systems consist of two main components that work together:
1. **MCP Server**: The heart of the system that exposes tools, which you can access via the `.listTools()` method.
2. **MCP Client**: The interface that connects to the MCP server and lets you use the tools it offers.
These servers and clients can communicate using different transport methods:
- **Standard I/O (stdio)**: A simple local connection method when your server and client are on the same machine.
- **Server-Sent Events (SSE)**: Uses HTTP to create a communication channel.
For this workshop, we'll use stdio to deploy our server. DVMCP will act as a bridge, connecting to your MCP server as an MCP client, and exposing its tools as a DVM that anyone can call from Nostr.
## Creating (or Finding) an MCP Server
Building an MCP server is simpler than you might think:
1. Create software in any programming language you're comfortable with.
2. Add an MCP library to expose your server's MCP interface.
3. Create an API that wraps around your software's functionality.
Once your server is ready, an MCP client can connect, for example, with `bun index.js`, and then call `.listTools()` to discover what your server can do. This pattern, known as reflection, makes Nostr DVMs and MCP a perfect match since both use JSON, and DVMs can announce and call tools, effectively becoming an MCP proxy.
Alternatively, you can use one of the many existing MCP servers available in various repositories.
For more information about mcp and how to build mcp servers you can visit https://modelcontextprotocol.io/
## Setting Up the Workshop
Let's get hands-on:
First, to follow this workshop you will need Bun. Install it from https://bun.sh/. For Linux and macOS, you can use the installation script:
```
curl -fsSL https://bun.sh/install | bash
```
1. **Choose your MCP server**: You can either create one or use an existing one.
2. **Inspect your server** using the MCP inspector tool:
```bash
npx @modelcontextprotocol/inspector build/index.js arg1 arg2
```
This will:
- Launch a client UI (default: http://localhost:5173)
- Start an MCP proxy server (default: port 3000)
- Pass any additional arguments directly to your server
3. **Use the inspector**: Open the client UI in your browser to connect with your server, list available tools, and test its functionality.
## Deploying with DVMCP
Now for the exciting part – making your MCP server available to everyone on Nostr:
1. Navigate to your MCP server directory.
2. Run without installing (quickest way):
```
npx @dvmcp/bridge
```
3. Or install globally for regular use:
```
npm install -g @dvmcp/bridge
# or
bun install -g @dvmcp/bridge
```
Then run using:
```bash
dvmcp-bridge
```
This will guide you through creating the necessary configuration.
Watch the console logs to confirm successful setup – you'll see your public key and process information, or any issues that need addressing.
For the configuration, you can set the relay as `wss://relay.dvmcp.fun` , or use any other of your preference
## Testing and Integration
1. **Visit [dvmcp.fun](https://dvmcp.fun)** to see your DVM announcement.
2. Call your tools and watch the responses come back.
For production use, consider running dvmcp-bridge as a system service or creating a container for greater reliability and uptime.
## Integrating with LLM Clients
You can also integrate your DVMCP deployment with LLM clients using the discovery package:
1. Install and use the `@dvmcp/discovery` package:
```bash
npx @dvmcp/discovery
```
2. This package acts as an MCP server for your LLM system by:
- Connecting to configured Nostr relays
- Discovering tools from DVMCP servers
- Making them available to your LLM applications
3. Connect to specific servers or providers using these flags:
```bash
# Connect to all DVMCP servers from a provider
npx @dvmcp/discovery --provider npub1...
# Connect to a specific DVMCP server
npx @dvmcp/discovery --server naddr1...
```
Using these flags, you wouldn't need a configuration file. You can find these commands and Claude desktop configuration already prepared for copy and paste at [dvmcp.fun](https://dvmcp.fun).
This feature lets you connect to any DVMCP server using Nostr and integrate it into your client, either as a DVM or in LLM-powered applications.
## Final thoughts
If you've followed this workshop, you now have an MCP server deployed as a Nostr DVM. This means that local resources from the system where the MCP server is running can be accessed through Nostr in a decentralized manner. This capability is powerful and opens up numerous possibilities and opportunities for fun.
You can use this setup for various use cases, including in a controlled/local environment. For instance, you can deploy a relay in your local network that's only accessible within it, exposing all your local MCP servers to anyone connected to the network. This setup can act as a hub for communication between different systems, which could be particularly interesting for applications in home automation or other fields. The potential applications are limitless.
However, it's important to keep in mind that there are security concerns when exposing local resources publicly. You should be mindful of these risks and prioritize security when creating and deploying your MCP servers on Nostr.
Finally, these are new ideas, and the software is still under development. If you have any feedback, please refer to the GitHub repository to report issues or collaborate. DVMCP also has a Signal group you can join. Additionally, you can engage with the community on Nostr using the #dvmcp hashtag.
## Useful Resources
- **Official Documentation**:
- Model Context Protocol: [modelcontextprotocol.org](https://modelcontextprotocol.org)
- DVMCP.fun: [dvmcp.fun](https://dvmcp.fun)
- **Source Code and Development**:
- DVMCP: [github.com/gzuuus/dvmcp](https://github.com/gzuuus/dvmcp)
- DVMCP.fun: [github.com/gzuuus/dvmcpfun](https://github.com/gzuuus/dvmcpfun)
- **MCP Servers and Clients**:
- Smithery AI: [smithery.ai](https://smithery.ai)
- MCP.so: [mcp.so](https://mcp.so)
- Glama AI MCP Servers: [glama.ai/mcp/servers](https://glama.ai/mcp/servers)
- [Signal group](https://signal.group/#CjQKIOgvfFJf8ZFZ1SsMx7teFqNF73sZ9Elaj_v5i6RSjDHmEhA5v69L4_l2dhQfwAm2SFGD)
Happy building!
-

@ b2d670de:907f9d4a
2025-03-25 20:17:57
This guide will walk you through setting up your own Strfry Nostr relay on a Debian/Ubuntu server and making it accessible exclusively as a TOR hidden service. By the end, you'll have a privacy-focused relay that operates entirely within the TOR network, enhancing both your privacy and that of your users.
## Table of Contents
1. Prerequisites
2. Initial Server Setup
3. Installing Strfry Nostr Relay
4. Configuring Your Relay
5. Setting Up TOR
6. Making Your Relay Available on TOR
7. Testing Your Setup]
8. Maintenance and Security
9. Troubleshooting
## Prerequisites
- A Debian or Ubuntu server
- Basic familiarity with command line operations (most steps are explained in detail)
- Root or sudo access to your server
## Initial Server Setup
First, let's make sure your server is properly set up and secured.
### Update Your System
Connect to your server via SSH and update your system:
```bash
sudo apt update
sudo apt upgrade -y
```
### Set Up a Basic Firewall
Install and configure a basic firewall:
```bash
sudo apt install ufw -y
sudo ufw allow ssh
sudo ufw enable
```
This allows SSH connections while blocking other ports for security.
## Installing Strfry Nostr Relay
This guide includes the full range of steps needed to build and set up Strfry. It's simply based on the current version of the `DEPLOYMENT.md` document in the Strfry GitHub repository. If the build/setup process is changed in the repo, this document could get outdated. If so, please report to me that something is outdated and check for updated steps [here](https://github.com/hoytech/strfry/blob/master/docs/DEPLOYMENT.md).
### Install Dependencies
First, let's install the necessary dependencies. Each package serves a specific purpose in building and running Strfry:
```bash
sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-dev
```
Here's why each dependency is needed:
**Basic Development Tools:**
- `git`: Version control system used to clone the Strfry repository and manage code updates
- `build-essential`: Meta-package that includes compilers (gcc, g++), make, and other essential build tools
**Perl Dependencies** (used for Strfry's build scripts):
- `libyaml-perl`: Perl interface to parse YAML configuration files
- `libtemplate-perl`: Template processing system used during the build process
- `libregexp-grammars-perl`: Advanced regular expression handling for Perl scripts
**Core Libraries for Strfry:**
- `libssl-dev`: Development files for OpenSSL, used for secure connections and cryptographic operations
- `zlib1g-dev`: Compression library that Strfry uses to reduce data size
- `liblmdb-dev`: Lightning Memory-Mapped Database library, which Strfry uses for its high-performance database backend
- `libflatbuffers-dev`: Memory-efficient serialization library for structured data
- `libsecp256k1-dev`: Optimized C library for EC operations on curve secp256k1, essential for Nostr's cryptographic signatures
- `libzstd-dev`: Fast real-time compression algorithm for efficient data storage and transmission
### Clone and Build Strfry
Clone the Strfry repository:
```bash
git clone https://github.com/hoytech/strfry.git
cd strfry
```
Build Strfry:
```bash
git submodule update --init
make setup-golpe
make -j2 # This uses 2 CPU cores. Adjust based on your server (e.g., -j4 for 4 cores)
```
This build process will take several minutes, especially on servers with limited CPU resources, so go get a coffee and post some great memes on nostr in the meantime.
### Install Strfry
Install the Strfry binary to your system path:
```bash
sudo cp strfry /usr/local/bin
```
This makes the `strfry` command available system-wide, allowing it to be executed from any directory and by any user with the appropriate permissions.
## Configuring Your Relay
### Create Strfry User
Create a dedicated user for running Strfry. This enhances security by isolating the relay process:
```bash
sudo useradd -M -s /usr/sbin/nologin strfry
```
The `-M` flag prevents creating a home directory, and `-s /usr/sbin/nologin` prevents anyone from logging in as this user. This is a security best practice for service accounts.
### Create Data Directory
Create a directory for Strfry's data:
```bash
sudo mkdir /var/lib/strfry
sudo chown strfry:strfry /var/lib/strfry
sudo chmod 755 /var/lib/strfry
```
This creates a dedicated directory for Strfry's database and sets the appropriate permissions so that only the strfry user can write to it.
### Configure Strfry
Copy the sample configuration file:
```bash
sudo cp strfry.conf /etc/strfry.conf
```
Edit the configuration file:
```bash
sudo nano /etc/strfry.conf
```
Modify the database path:
```
# Find this line:
db = "./strfry-db/"
# Change it to:
db = "/var/lib/strfry/"
```
Check your system's hard limit for file descriptors:
```bash
ulimit -Hn
```
Update the `nofiles` setting in your configuration to match this value (or set to 0):
```
# Add or modify this line in the config (example if your limit is 524288):
nofiles = 524288
```
The `nofiles` setting determines how many open files Strfry can have simultaneously. Setting it to your system's hard limit (or 0 to use the system default) helps prevent "too many open files" errors if your relay becomes popular.
You might also want to customize your relay's information in the config file. Look for the `info` section and update it with your relay's name, description, and other details.
Set ownership of the configuration file:
```bash
sudo chown strfry:strfry /etc/strfry.conf
```
### Create Systemd Service
Create a systemd service file for managing Strfry:
```bash
sudo nano /etc/systemd/system/strfry.service
```
Add the following content:
```ini
[Unit]
Description=strfry relay service
[Service]
User=strfry
ExecStart=/usr/local/bin/strfry relay
Restart=on-failure
RestartSec=5
ProtectHome=yes
NoNewPrivileges=yes
ProtectSystem=full
LimitCORE=1000000000
[Install]
WantedBy=multi-user.target
```
This systemd service configuration:
- Runs Strfry as the dedicated strfry user
- Automatically restarts the service if it fails
- Implements security measures like `ProtectHome` and `NoNewPrivileges`
- Sets resource limits appropriate for a relay
Enable and start the service:
```bash
sudo systemctl enable strfry.service
sudo systemctl start strfry
```
Check the service status:
```bash
sudo systemctl status strfry
```
### Verify Relay is Running
Test that your relay is running locally:
```bash
curl localhost:7777
```
You should see a message indicating that the Strfry relay is running. This confirms that Strfry is properly installed and configured before we proceed to set up TOR.
## Setting Up TOR
Now let's make your relay accessible as a TOR hidden service.
### Install TOR
Install TOR from the package repositories:
```bash
sudo apt install -y tor
```
This installs the TOR daemon that will create and manage your hidden service.
### Configure TOR
Edit the TOR configuration file:
```bash
sudo nano /etc/tor/torrc
```
Scroll down to wherever you see a commented out part like this:
```
#HiddenServiceDir /var/lib/tor/hidden_service/
#HiddenServicePort 80 127.0.0.1:80
```
Under those lines, add the following lines to set up a hidden service for your relay:
```
HiddenServiceDir /var/lib/tor/strfry-relay/
HiddenServicePort 80 127.0.0.1:7777
```
This configuration:
- Creates a hidden service directory at `/var/lib/tor/strfry-relay/`
- Maps port 80 on your .onion address to port 7777 on your local machine
- Keeps all traffic encrypted within the TOR network
Create the directory for your hidden service:
```bash
sudo mkdir -p /var/lib/tor/strfry-relay/
sudo chown debian-tor:debian-tor /var/lib/tor/strfry-relay/
sudo chmod 700 /var/lib/tor/strfry-relay/
```
The strict permissions (700) are crucial for security as they ensure only the debian-tor user can access the directory containing your hidden service private keys.
Restart TOR to apply changes:
```bash
sudo systemctl restart tor
```
## Making Your Relay Available on TOR
### Get Your Onion Address
After restarting TOR, you can find your onion address:
```bash
sudo cat /var/lib/tor/strfry-relay/hostname
```
This will output something like `abcdefghijklmnopqrstuvwxyz234567.onion`, which is your relay's unique .onion address. This is what you'll share with others to access your relay.
### Understanding Onion Addresses
The .onion address is a special-format hostname that is automatically generated based on your hidden service's private key.
Your users will need to use this address with the WebSocket protocol prefix to connect: `ws://youronionaddress.onion`
## Testing Your Setup
### Test with a Nostr Client
The best way to test your relay is with an actual Nostr client that supports TOR:
1. Open your TOR browser
2. Go to your favorite client, either on clearnet or an onion service.
- Check out [this list](https://github.com/0xtrr/onion-service-nostr-clients?tab=readme-ov-file#onion-service-nostr-clients) of nostr clients available over TOR.
3. Add your relay URL: `ws://youronionaddress.onion` to your relay list
4. Try posting a note and see if it appears on your relay
- In some nostr clients, you can also click on a relay to get information about it like the relay name and description you set earlier in the stryfry config. If you're able to see the correct values for the name and the description, you were able to connect to the relay.
- Some nostr clients also gives you a status on what relays a note was posted to, this could also give you an indication that your relay works as expected.
Note that not all Nostr clients support TOR connections natively. Some may require additional configuration or use of TOR Browser. E.g. most mobile apps would most likely require a TOR proxy app running in the background (some have TOR support built in too).
## Maintenance and Security
### Regular Updates
Keep your system, TOR, and relay updated:
```bash
# Update system
sudo apt update
sudo apt upgrade -y
# Update Strfry
cd ~/strfry
git pull
git submodule update
make -j2
sudo cp strfry /usr/local/bin
sudo systemctl restart strfry
# Verify TOR is still running properly
sudo systemctl status tor
```
Regular updates are crucial for security, especially for TOR which may have security-critical updates.
### Database Management
Strfry has built-in database management tools. Check the Strfry documentation for specific commands related to database maintenance, such as managing event retention and performing backups.
### Monitoring Logs
To monitor your Strfry logs:
```bash
sudo journalctl -u strfry -f
```
To check TOR logs:
```bash
sudo journalctl -u tor -f
```
Monitoring logs helps you identify potential issues and understand how your relay is being used.
### Backup
This is not a best practices guide on how to do backups. Preferably, backups should be stored either offline or on a different machine than your relay server. This is just a simple way on how to do it on the same server.
```bash
# Stop the relay temporarily
sudo systemctl stop strfry
# Backup the database
sudo cp -r /var/lib/strfry /path/to/backup/location
# Restart the relay
sudo systemctl start strfry
```
Back up your TOR hidden service private key. The private key is particularly sensitive as it defines your .onion address - losing it means losing your address permanently. If you do a backup of this, ensure that is stored in a safe place where no one else has access to it.
```bash
sudo cp /var/lib/tor/strfry-relay/hs_ed25519_secret_key /path/to/secure/backup/location
```
## Troubleshooting
### Relay Not Starting
If your relay doesn't start:
```bash
# Check logs
sudo journalctl -u strfry -e
# Verify configuration
cat /etc/strfry.conf
# Check permissions
ls -la /var/lib/strfry
```
Common issues include:
- Incorrect configuration format
- Permission problems with the data directory
- Port already in use (another service using port 7777)
- Issues with setting the nofiles limit (setting it too big)
### TOR Hidden Service Not Working
If your TOR hidden service is not accessible:
```bash
# Check TOR logs
sudo journalctl -u tor -e
# Verify TOR is running
sudo systemctl status tor
# Check onion address
sudo cat /var/lib/tor/strfry-relay/hostname
# Verify TOR configuration
sudo cat /etc/tor/torrc
```
Common TOR issues include:
- Incorrect directory permissions
- TOR service not running
- Incorrect port mapping in torrc
### Testing Connectivity
If you're having trouble connecting to your service:
```bash
# Verify Strfry is listening locally
sudo ss -tulpn | grep 7777
# Check that TOR is properly running
sudo systemctl status tor
# Test the local connection directly
curl --include --no-buffer localhost:7777
```
---
## Privacy and Security Considerations
Running a Nostr relay as a TOR hidden service provides several important privacy benefits:
1. **Network Privacy**: Traffic to your relay is encrypted and routed through the TOR network, making it difficult to determine who is connecting to your relay.
2. **Server Anonymity**: The physical location and IP address of your server are concealed, providing protection against denial-of-service attacks and other targeting.
3. **Censorship Resistance**: TOR hidden services are more resilient against censorship attempts, as they don't rely on the regular DNS system and can't be easily blocked.
4. **User Privacy**: Users connecting to your relay through TOR enjoy enhanced privacy, as their connections are also encrypted and anonymized.
However, there are some important considerations:
- TOR connections are typically slower than regular internet connections
- Not all Nostr clients support TOR connections natively
- Running a hidden service increases the importance of keeping your server secure
---
Congratulations! You now have a Strfry Nostr relay running as a TOR hidden service. This setup provides a resilient, privacy-focused, and censorship-resistant communication channel that helps strengthen the Nostr network.
For further customization and advanced configuration options, refer to the [Strfry documentation](https://github.com/hoytech/strfry).
Consider sharing your relay's .onion address with the Nostr community to help grow the privacy-focused segment of the network!
If you plan on providing a relay service that the public can use (either for free or paid for), consider adding it to [this list](https://github.com/0xtrr/onion-service-nostr-relays). Only add it if you plan to run a stable and available relay.
-

@ 57d1a264:69f1fee1
2025-03-28 10:32:15
Bitcoin.design community is organizing another Designathon, from May 4-18. Let's get creative with bitcoin together. More to come very soon.

The first edition was a bursting success! the website still there https://events.bitcoin.design, and here their previous [announcement](https://bitcoindesign.substack.com/p/the-bitcoin-designathon-2022).
Look forward for this to happen!
Spread the voice:
N: [https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48l...](https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48lmw9jc7nhhauyq5w3cm4nfsm3mstqtk6m)
X: https://x.com/bitcoin_design/status/1905547407405768927
originally posted at https://stacker.news/items/927650
-

@ 4857600b:30b502f4
2025-03-10 12:09:35
At this point, we should be arresting, not firing, any FBI employee who delays, destroys, or withholds information on the Epstein case. There is ZERO explanation I will accept for redacting anything for “national security” reasons. A lot of Trump supporters are losing patience with Pam Bondi. I will give her the benefit of the doubt for now since the corruption within the whole security/intelligence apparatus of our country runs deep. However, let’s not forget that probably Trump’s biggest mistakes in his first term involved picking weak and easily corruptible (or blackmailable) officials. It seemed every month a formerly-loyal person did a complete 180 degree turn and did everything they could to screw him over, regardless of the betrayal’s effect on the country or whatever principles that person claimed to have. I think he’s fixed his screening process, but since we’re talking about the FBI, we know they have the power to dig up any dirt or blackmail material available, or just make it up. In the Epstein case, it’s probably better to go after Bondi than give up a treasure trove of blackmail material against the long list of members on his client list.
-

@ bc52210b:20bfc6de
2025-03-25 20:17:22
CISA, or Cross-Input Signature Aggregation, is a technique in Bitcoin that allows multiple signatures from different inputs in a transaction to be combined into a single, aggregated signature. This is a big deal because Bitcoin transactions often involve multiple inputs (e.g., spending from different wallet outputs), each requiring its own signature. Normally, these signatures take up space individually, but CISA compresses them into one, making transactions more efficient.
This magic is possible thanks to the linearity property of Schnorr signatures, a type of digital signature introduced to Bitcoin with the Taproot upgrade. Unlike the older ECDSA signatures, Schnorr signatures have mathematical properties that allow multiple signatures to be added together into a single valid signature. Think of it like combining multiple handwritten signatures into one super-signature that still proves everyone signed off!
Fun Fact: CISA was considered for inclusion in Taproot but was left out to keep the upgrade simple and manageable. Adding CISA would’ve made Taproot more complex, so the developers hit pause on it—for now.
---
**CISA vs. Key Aggregation (MuSig, FROST): Don’t Get Confused!**
Before we go deeper, let’s clear up a common mix-up: CISA is not the same as protocols like MuSig or FROST. Here’s why:
* Signature Aggregation (CISA): Combines multiple signatures into one, each potentially tied to different public keys and messages (e.g., different transaction inputs).
* Key Aggregation (MuSig, FROST): Combines multiple public keys into a single aggregated public key, then generates one signature for that key.
**Key Differences:**
1. What’s Aggregated?
* CISA: Aggregates signatures.
* Key Aggregation: Aggregates public keys.
2. What the Verifier Needs
* CISA: The verifier needs all individual public keys and their corresponding messages to check the aggregated signature.
* Key Aggregation: The verifier only needs the single aggregated public key and one message.
3. When It Happens
* CISA: Used during transaction signing, when inputs are being combined into a transaction.
* MuSig: Used during address creation, setting up a multi-signature (multisig) address that multiple parties control.
So, CISA is about shrinking signature data in a transaction, while MuSig/FROST are about simplifying multisig setups. Different tools, different jobs!
---
**Two Flavors of CISA: Half-Agg and Full-Agg**
CISA comes in two modes:
* Full Aggregation (Full-Agg): Interactive, meaning signers need to collaborate during the signing process. (We’ll skip the details here since the query focuses on Half-Agg.)
* Half Aggregation (Half-Agg): Non-interactive, meaning signers can work independently, and someone else can combine the signatures later.
Since the query includes “CISA Part 2: Half Signature Aggregation,” let’s zoom in on Half-Agg.
---
**Half Signature Aggregation (Half-Agg) Explained**
**How It Works**
Half-Agg is a non-interactive way to aggregate Schnorr signatures. Here’s the process:
1. Independent Signing: Each signer creates their own Schnorr signature for their input, without needing to talk to the other signers.
2. Aggregation Step: An aggregator (could be anyone, like a wallet or node) takes all these signatures and combines them into one aggregated signature.
A Schnorr signature has two parts:
* R: A random point (32 bytes).
* s: A scalar value (32 bytes).
In Half-Agg:
* The R values from each signature are kept separate (one per input).
* The s values from all signatures are combined into a single s value.
**Why It Saves Space (~50%)**
Let’s break down the size savings with some math:
Before Aggregation:
* Each Schnorr signature = 64 bytes (32 for R + 32 for s).
* For n inputs: n × 64 bytes.
After Half-Agg:
* Keep n R values (32 bytes each) = 32 × n bytes.
* Combine all s values into one = 32 bytes.
* Total size: 32 × n + 32 bytes.
Comparison:
* Original: 64n bytes.
* Half-Agg: 32n + 32 bytes.
* For large n, the “+32” becomes small compared to 32n, so it’s roughly 32n, which is half of 64n. Hence, ~50% savings!
**Real-World Impact:**
Based on recent Bitcoin usage, Half-Agg could save:
* ~19.3% in space (reducing transaction size).
* ~6.9% in fees (since fees depend on transaction size). This assumes no major changes in how people use Bitcoin post-CISA.
---
**Applications of Half-Agg**
Half-Agg isn’t just a cool idea—it has practical uses:
1. Transaction-wide Aggregation
* Combine all signatures within a single transaction.
* Result: Smaller transactions, lower fees.
2. Block-wide Aggregation
* Combine signatures across all transactions in a Bitcoin block.
* Result: Even bigger space savings at the blockchain level.
3. Off-chain Protocols / P2P
* Use Half-Agg in systems like Lightning Network gossip messages.
* Benefit: Efficiency without needing miners or a Bitcoin soft fork.
---
**Challenges with Half-Agg**
While Half-Agg sounds awesome, it’s not without hurdles, especially at the block level:
1. Breaking Adaptor Signatures
* Adaptor signatures are special signatures used in protocols like Discreet Log Contracts (DLCs) or atomic swaps. They tie a signature to revealing a secret, ensuring fair exchanges.
* Aggregating signatures across a block might mess up these protocols, as the individual signatures get blended together, potentially losing the properties adaptor signatures rely on.
2. Impact on Reorg Recovery
* In Bitcoin, a reorganization (reorg) happens when the blockchain switches to a different chain of blocks. Transactions from the old chain need to be rebroadcast or reprocessed.
* If signatures are aggregated at the block level, it could complicate extracting individual transactions and their signatures during a reorg, slowing down recovery.
These challenges mean Half-Agg needs careful design, especially for block-wide use.
---
**Wrapping Up**
CISA is a clever way to make Bitcoin transactions more efficient by aggregating multiple Schnorr signatures into one, thanks to their linearity property. Half-Agg, the non-interactive mode, lets signers work independently, cutting signature size by about 50% (to 32n + 32 bytes from 64n bytes). It could save ~19.3% in space and ~6.9% in fees, with uses ranging from single transactions to entire blocks or off-chain systems like Lightning.
But watch out—block-wide Half-Agg could trip up adaptor signatures and reorg recovery, so it’s not a slam dunk yet. Still, it’s a promising tool for a leaner, cheaper Bitcoin future!
-

@ 4857600b:30b502f4
2025-02-21 03:04:00
A new talking point of the left is that it’s no big deal, just simple recording errors for the 20 million people aged 100-360. 🤷♀️ And not many of them are collecting benefits anyway. 👌 First of all, the investigation & analysis are in the early stages. How can they possibly know how deep the fraud goes, especially when their leaders are doing everything they can to obstruct any real examination? Second, sure, no worries about only a small number collecting benefits. That’s the ONLY thing social security numbers are used for. 🙄
-

@ b17fccdf:b7211155
2025-03-25 11:23:36
Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la [guía de MiniBolt](https://minbolt.info/).
Esto tiene una **razón**, por supuesto una **solución**, además de una **conclusión**. Sin entrar en demasiados detalles:
## La razón
El **bloqueo a Cloudflare**, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una [orden judicial](https://www.poderjudicial.es/search/AN/openDocument/3c85bed480cbb1daa0a8778d75e36f0d/20221004) emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización.
Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo [ECH](https://developers.cloudflare.com/ssl/edge-certificates/ech) (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar **bloqueos basados en dominios**, lo que les obliga a recurrir a **bloqueos más amplios por IP o rangos de IP** para cumplir con la orden judicial.
Esta práctica tiene **consecuencias graves**, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un **perjuicio para terceros**, **restringiendo el acceso a muchos dominios legítimos** que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la [web de MiniBolt](https://minibolt.minibolt.info) y su dominio `minibolt.info`, los cuales **utilizan Cloudflare como proxy** para aprovechar las medidas de **seguridad, privacidad, optimización y servicios** adicionales que la plataforma ofrece de forma gratuita.
Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.

## La solución
Obviamente, **MiniBolt no dejará de usar Cloudflare** como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para **evitar esta restricción** y poder acceder:
**~>** Utiliza **una VPN**:
Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad:
- [IVPN](https://www.ivpn.net/es/)
- [Mullvad VPN](https://mullvad.net/es/vpn)
- [Proton VPN](https://protonvpn.com/es-es) (**gratis**)
- [Obscura VPN](https://obscura.net/) (**solo para macOS**)
- [Cloudfare WARP](https://developers.cloudflare.com/cloudflare-one/connections/connect-devices/warp/download-warp/) (**gratis**) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos:
1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy"
2. Marca la casilla "Habilite el modo proxy en este dispositivo"
3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias
4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio.
3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a [esta](https://minibolt.minibolt.info/system/system/privacy#example-from-firefox) para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la [guía de MiniBolt](https://minibolt.minibolt.info/) sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info [AQUÍ](https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958).

**~>** [**Proxifica tu navegador para usar la red de Tor**](https://minibolt.minibolt.info/system/system/privacy#ssh-remote-access-through-tor), o utiliza el [**navegador oficial de Tor**](https://www.torproject.org/es/download/) (recomendado).

## La conclusión
Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la [Declaración de Independencia del Ciberespacio](https://es.wikisource.org/wiki/Declaraci%C3%B3n_de_independencia_del_ciberespacio) que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad.
Es momento de actuar y estar preparados: debemos **impulsar el desarrollo y la difusión** de las **herramientas anticensura** que tenemos a nuestro alcance, protegiendo así la **libertad digital** y asegurando un acceso equitativo a la información para todos
Este compromiso es uno de los **pilares fundamentales de MiniBolt,** lo que convierte este desafío en una oportunidad para poner a prueba las **soluciones anticensura** [ya disponibles](https://minibolt.minibolt.info/bonus-guides/system/tor-services), así como **las que están en camino**.
¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!

---
Fuentes:
* https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239
* https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257
* https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958
* https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689
* https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007
-

@ 37fe9853:bcd1b039
2025-01-11 15:04:40
yoyoaa
-

@ 7d33ba57:1b82db35
2025-03-28 22:14:24
Preko is a charming seaside town on Ugljan Island, just a short ferry ride from Zadar. Known for its beautiful beaches, relaxed atmosphere, and stunning views of the Adriatic, it's the perfect place to experience authentic Dalmatian island life.

## **🌊 Top Things to See & Do in Preko**
### **1️⃣ Swim at Jaz Beach 🏖️**
- A **Blue Flag beach** with **clear turquoise waters and soft pebbles**.
- Ideal for **families** thanks to its shallow waters.
- Nearby **cafés and restaurants** make it a great spot to spend the day.
### **2️⃣ Visit the Islet of Galevac 🏝️**
- A **tiny island just 80 meters from Preko**, reachable by swimming or a short boat ride.
- Home to a **15th-century Franciscan monastery**, surrounded by lush greenery.
- A **peaceful retreat**, perfect for relaxation.

### **3️⃣ Hike to St. Michael’s Fortress (Sv. Mihovil) 🏰**
- A **medieval fortress from the 13th century** with **breathtaking panoramic views**.
- Overlooks **Zadar, Kornati Islands, and the Adriatic Sea**.
- A **1-hour scenic hike** from Preko or accessible by **bike or car**.
### **4️⃣ Explore the Local Taverns & Seafood Restaurants 🍽️**
- Try **fresh seafood, octopus salad, and Dalmatian peka (slow-cooked meat & vegetables)**.
- **Best spots:** Konoba Roko (authentic seafood) & Vile Dalmacija (beachfront dining).
### **5️⃣ Rent a Bike or Scooter 🚲**
- Explore **Ugljan Island’s olive groves, hidden coves, and coastal paths**.
- Visit nearby villages like **Kali and Kukljica** for more local charm.

### **6️⃣ Take a Day Trip to Zadar ⛵**
- Just **25 minutes by ferry**, Zadar offers **historic landmarks, the Sea Organ, and Roman ruins**.
- Perfect for a cultural excursion before returning to the peaceful island.

## **🚗 How to Get to Preko**
🚢 **By Ferry:**
- **From Zadar:** Regular ferries (Jadrolinija) take **~25 minutes**.
🚘 **By Car:**
- If driving, take the **ferry from Zadar to Preko** and explore the island.
🚴 **By Bike:**
- Many visitors rent bikes to explore Ugljan Island’s coastal roads.

## **💡 Tips for Visiting Preko**
✅ **Best time to visit?** **May–September** for warm weather & swimming 🌞
✅ **Ferry schedules** – Check times in advance, especially in the off-season ⏳
✅ **Bring cash** – Some smaller taverns and cafés may not accept cards 💰
✅ **Stay for sunset** – The views over Zadar from Preko’s waterfront are stunning 🌅
Would you like **hotel recommendations, hidden beaches, or other island activities**? 😊
-

@ 15a592c4:e8bdd024
2025-03-28 16:26:38
The Potential and Importance of Blockchain: A Game-Changer in the Digital Age
Blockchain technology has been gaining momentum in recent years, and for good reason. This innovative technology has the potential to revolutionize the way we conduct transactions, store data, and build trust in the digital world.
*What is Blockchain?*
At its core, blockchain is a shared, immutable ledger that facilitates the process of recording transactions and tracking assets in a business network.¹ It's a decentralized system, meaning that no single entity controls it, and it's maintained by a network of computers working together.
*The Benefits of Blockchain*
So, what makes blockchain so important? Here are just a few of its key benefits:
- *Enhanced Security*: Blockchain's decentralized nature and use of advanced cryptography make it virtually impossible to hack or manipulate.
- *Increased Transparency*: With blockchain, all transactions are recorded publicly and can be viewed by anyone with permission.
- *Improved Efficiency*: Blockchain automates many processes, reducing the need for intermediaries and increasing the speed of transactions.
- *Greater Trust*: Blockchain's immutable ledger ensures that once a transaction is recorded, it can't be altered or deleted.
*Real-World Applications*
Blockchain's potential extends far beyond the world of cryptocurrency. Here are just a few examples of its real-world applications:
- *Supply Chain Management*: Blockchain can be used to track the origin, quality, and movement of goods throughout the supply chain.
- *Healthcare*: Blockchain can be used to securely store and manage medical records, track prescriptions, and enable secure sharing of medical research.
- *Voting Systems*: Blockchain can be used to create secure, transparent, and tamper-proof voting systems.
-

@ 3b7fc823:e194354f
2025-03-23 03:54:16
A quick guide for the less than technical savvy to set up their very own free private tor enabled email using Onionmail. Privacy is for everyone, not just the super cyber nerds.
Onion Mail is an anonymous POP3/SMTP email server program hosted by various people on the internet. You can visit this site and read the details: https://en.onionmail.info/
1. Download Tor Browser
First, if you don't already, go download Tor Browser. You are going to need it. https://www.torproject.org/
2. Sign Up
Using Tor browser go to the directory page (https://onionmail.info/directory.html) choose one of the servers and sign up for an account. I say sign up but it is just choosing a user name you want to go before the @xyz.onion email address and solving a captcha.
3. Account information
Once you are done signing up an Account information page will pop up. **MAKE SURE YOU SAVE THIS!!!** It has your address and passwords (for sending and receiving email) that you will need. If you lose them then you are shit out of luck.
4. Install an Email Client
You can use Claws Mail, Neomutt, or whatever, but for this example, we will be using Thunderbird.
a. Download Thunderbird email client
b. The easy setup popup page that wants your name, email, and password isn't going to like your user@xyz.onion address. Just enter something that looks like a regular email address such as name@example.com and the **Configure Manually**option will appear below. Click that.
5. Configure Incoming (POP3) Server
Under Incoming Server:
Protocol: POP3
Server or Hostname: xyz.onion (whatever your account info says)
Port: 110
Security: STARTTLS
Authentication: Normal password
Username: (your username)
Password: (POP3 password).
6. Configure Outgoing (SMTP) Server
Under Outgoing Server:
Server or Hostname: xyz.onion (whatever your account info says)
Port: 25
Security: STARTTLS
Authentication: Normal password
Username: (your username)
Password: (SMTP password).
7. Click on email at the top and change your address if you had to use a spoof one to get the configure manually to pop up.
8. Configure Proxy
a. Click the **gear icon** on the bottom left for settings. Scroll all the way down to **Network & Disk Space**. Click the **settings button** next to **Connection. Configure how Thunderbird connects to the internet**.
b. Select **Manual Proxy Configuration**. For **SOCKS Host** enter **127.0.0.1** and enter port **9050**. (if you are running this through a VM the port may be different)
c. Now check the box for **SOCKS5** and then **Proxy DNS when using SOCKS5** down at the bottom. Click OK
9. Check Email
For thunderbird to reach the onion mail server it has to be connected to tor. Depending on your local setup, it might be fine as is or you might have to have tor browser open in the background. Click on **inbox** and then the **little cloud icon** with the down arrow to check mail.
10. Security Exception
Thunderbird is not going to like that the onion mail server security certificate is self signed. A popup **Add Security Exception** will appear. Click **Confirm Security Exception**.
You are done. Enjoy your new private email service.
**REMEMBER: The server can read your emails unless they are encrypted. Go into account settings. Look down and click End-toEnd Encryption. Then add your OpenPGP key or open your OpenPGP Key Manager (you might have to download one if you don't already have one) and generate a new key for this account.**
-

@ 57d1a264:69f1fee1
2025-03-27 10:42:05
What we have been missing in [SN Press kit](https://stacker.news/items/872925/r/Design_r)? Most important, who the press kit is for? It's for us? It's for them? Them, who?
The first few editions of the press kit, I agree are mostly made by us, for us. A way to try to homogenize how we _speek_ out SN into the wild web. A way to have SN voice sync, loud and clear, to send out our message. In this case, I squeezed my mouse, creating a template for us [^1], stackers, to share when talking sales with possible businesses and merchants willing to invest some sats and engage with SN community. Here's the message and the sales pitch, v0.1:
## Reach Bitcoin’s Most Engaged Community – Zero Noise, Pure Signal.













- - -
Contributions to improve would be much appreciated. You can also help by simply commenting on each slide or leaving your feedback below, especially if you are a sale person or someone that has seen similar documents before.
This is the first interaction. Already noticed some issues, for example with the emojis and the fonts, especially when exporting, probably related to a penpot issue. The slides maybe render differently depending on the browser you're using.
- [▶️ Play](https://design.penpot.app/#/view?file-id=cec80257-5021-8137-8005-ef90a160b2c9&page-id=cec80257-5021-8137-8005-ef90a160b2ca§ion=interactions&index=0&interactions-mode=hide&zoom=fit) the file in your browser
- ⬇️ Save the [PDF file](https://mega.nz/file/TsBgkRoI#20HEb_zscozgJYlRGha0XiZvcXCJfLQONx2fc65WHKY)
@k00b it will be nice to have some real data, how we can get some basic audience insights? Even some inputs from Plausible, if still active, will be much useful.
[^1]: Territory founders. FYI: @Aardvark, @AGORA, @anna, @antic, @AtlantisPleb, @av, @Bell_curve, @benwehrman, @bitcoinplebdev, @Bitter, @BlokchainB, @ch0k1, @davidw, @ek, @elvismercury, @frostdragon, @grayruby, @HODLR, @inverselarp, @Jon_Hodl, @MaxAWebster, @mega_dreamer, @mrtali, @niftynei, @nout, @OneOneSeven, @PlebLab, @Public_N_M_E, @RDClark, @realBitcoinDog, @roytheholographicuniverse, @siggy47, @softsimon, @south_korea_ln, @theschoolofbitcoin, @TNStacker. @UCantDoThatDotNet, @Undisciplined
originally posted at https://stacker.news/items/926557
-

@ fe9e99a0:5123e9a8
2025-03-28 21:25:43
What’s happening?
-

@ 57d1a264:69f1fee1
2025-03-27 08:27:44
> The tech industry and its press have treated the rise of billion-scale social networks and ubiquitous smartphone apps as an unadulterated win for regular people, a triumph of usability and empowerment. They seldom talk about what we’ve lost along the way in this transition, and I find that younger folks may not even know how the web used to be.
`— Anil Dash, The Web We Lost, 13 Dec 2012`
https://www.youtube.com/watch?v=9KKMnoTTHJk&t=156s
So here’s a few glimpses of a web that’s mostly faded away: https://www.anildash.com/2012/12/13/the_web_we_lost/
The first step to disabusing them of this notion is for the people creating the next generation of social applications to learn a little bit of history, to know your shit, whether that’s about [Twitter’s business model](http://web.archive.org/web/20180120013123/http://anildash.com/2010/04/ten-years-of-twitter-ads.html) or [Google’s social features](http://web.archive.org/web/20170518203228/http://anildash.com/2012/04/why-you-cant-trust-tech-press-to-teach-you-about-the-tech-industry.html) or anything else. We have to know what’s been tried and failed, what good ideas were simply ahead of their time, and what opportunities have been lost in the current generation of dominant social networks.
originally posted at https://stacker.news/items/926499
-

@ 21335073:a244b1ad
2025-03-18 20:47:50
**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.**
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
**Course:**
- The creation of the internet and computers
- The fight for cryptography
- The tech supply chain from the ground up (example: human rights violations in the supply chain)
- Corporate tech
- Freedom tech
- Data privacy
- Digital privacy rights
- AI (history-current)
- Online safety (predators, scams, catfishing, extortion)
- Bitcoin
- Laws
- How to deal with online hate and harassment
- Information on who to contact if you are being abused online or offline
- Algorithms
- How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-

@ 21335073:a244b1ad
2025-03-18 14:43:08
**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.**
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
**Course:**
- The creation of the internet and computers
- The fight for cryptography
- The tech supply chain from the ground up (example: human rights violations in the supply chain)
- Corporate tech
- Freedom tech
- Data privacy
- Digital privacy rights
- AI (history-current)
- Online safety (predators, scams, catfishing, extortion)
- Bitcoin
- Laws
- How to deal with online hate and harassment
- Information on who to contact if you are being abused online or offline
- Algorithms
- How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-

@ 41e6f20b:06049e45
2024-11-17 17:33:55
Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller.
-

@ 8cb60e21:5f2deaea
2024-09-10 21:14:08
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/9_SRpCjeJiM" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 8cb60e21:5f2deaea
2024-09-06 22:23:03
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/XL3DbEkeFWA" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 57d1a264:69f1fee1
2025-03-27 08:11:33
Explore and reimagine programming interfaces beyond text (visual, tactile, spatial).
> _"The most dangerous thought you can have as a creative person is to think you know what you're doing."_
`— Richard Hamming` [^1]
https://www.youtube.com/watch?v=8pTEmbeENF4
For his recent DBX Conference talk, Victor took attendees back to the year 1973, donning the uniform of an IBM systems engineer of the times, delivering his presentation on an overhead projector. The '60s and early '70s were a fertile time for CS ideas, reminds Victor, but even more importantly, it was a time of unfettered thinking, unconstrained by programming dogma, authority, and tradition.

_'The most dangerous thought that you can have as a creative person is to think that you know what you're doing,'_ explains Victor. 'Because once you think you know what you're doing you stop looking around for other ways of doing things and you stop being able to see other ways of doing things. You become blind.' He concludes, 'I think you have to say: _"We don't know what programming is. We don't know what computing is. We don't even know what a computer is."_ And once you truly understand that, and once you truly believe that, then you're free, and you can think anything.'
More details at https://worrydream.com/dbx/
[^1]: Richard Hamming -- [The Art of Doing Science and Engineering, p5](http://worrydream.com/refs/Hamming_1997_-_The_Art_of_Doing_Science_and_Engineering.pdf) (pdf ebook)
originally posted at https://stacker.news/items/926493
-

@ 6f1a5274:3b3bb9c4
2025-03-28 14:27:44
8us là một nền tảng giải trí trực tuyến mang đến cho người chơi một không gian giải trí đa dạng và đầy thú vị. Với giao diện thân thiện và dễ sử dụng, người chơi có thể dễ dàng truy cập và tham gia vào các trò chơi yêu thích của mình chỉ trong vài bước đơn giản. Các trò chơi trên 8us được thiết kế với đồ họa sắc nét và âm thanh sống động, mang lại trải nghiệm mượt mà và chân thực, giúp người chơi cảm nhận như đang tham gia vào một thế giới giải trí thực sự. Ngoài các trò chơi phong phú và hấp dẫn, 8us còn thường xuyên cập nhật các tựa game mới, giữ cho trải nghiệm luôn mới mẻ và thú vị.
Bảo mật và an toàn luôn là ưu tiên hàng đầu của <a href="https://8us-online.com">8us</a>. Nền tảng này sử dụng các công nghệ bảo mật tiên tiến để bảo vệ thông tin cá nhân và dữ liệu giao dịch của người chơi, giúp họ có thể yên tâm tham gia mà không phải lo lắng về nguy cơ bị xâm phạm. Mọi giao dịch và thông tin cá nhân đều được mã hóa và bảo vệ chặt chẽ, mang lại sự an tâm tuyệt đối cho người chơi. Với những biện pháp bảo mật này, 8us đã xây dựng được lòng tin từ cộng đồng người chơi, tạo ra một môi trường an toàn và đáng tin cậy để mọi người có thể tận hưởng những phút giây giải trí mà không phải lo ngại về các vấn đề liên quan đến dữ liệu cá nhân.
Bên cạnh đó, đội ngũ hỗ trợ khách hàng của 8us luôn sẵn sàng phục vụ người chơi 24/7, giúp giải đáp mọi thắc mắc và xử lý nhanh chóng các vấn đề phát sinh. Dù là vấn đề về kỹ thuật hay hỗ trợ về trò chơi, đội ngũ chăm sóc khách hàng của 8us luôn làm việc tận tâm và chuyên nghiệp, đảm bảo mang lại sự hài lòng cho mọi người tham gia. Chính nhờ vào dịch vụ khách hàng xuất sắc và hệ thống bảo mật vượt trội, 8us đã trở thành một nền tảng giải trí trực tuyến được nhiều người tin tưởng và yêu thích, đồng thời tạo ra một không gian thư giãn tuyệt vời, an toàn và đáng tin cậy cho tất cả người chơi.
-

@ 8cb60e21:5f2deaea
2024-09-03 22:26:25
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/R5fzBNJP6Rk" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 57d1a264:69f1fee1
2025-03-26 08:45:13
> I was curious to see how Stacker.News domain and website contents scored from a SEO (Search Engine Optimization) perspective. Here what Semrush nows about SN. But first have alook at the Page Performance Score on Google (Detailled report available [here](https://pagespeed.web.dev/analysis/https-stacker-news/pjnc9jgscy?form_factor=mobile)). **Performance** and **Accessibility** looks have really low score!
| Desktop | Mobile |
|---|---|
|  |  |
|  |  |
Now let's see what Semrush knows.
# Analytics
General view on your metrics and performance trend compared to last 30 days.


See estimations of stacker.news's desktop and mobile traffic based on Semrush’s proprietary AI and machine learning algorithms, petabytes of clickstream data, and Big Data technologies.

Distribution of SN's organic traffic and keywords by country. The Organic Traffic graph shows changes in the amount of estimated organic and paid traffic driven to the SN analyzed domain over time.

| Organic Search | Backlinks Analytics |
|---|---|
| |  |
| Position Changes Trend | Top Page Changes |
|---|---|
| |  |
|This trend allows you to monitor organic traffic changes, as well as improved and declined positions.| Top pages with the biggest traffic changes over the last 28 days. |

# Competitors

The Competitive Positioning Map shows the strengths and weaknesses of SN competitive domains' presence in organic search results. Data visualizations are based on the domain's organic traffic and the number of keywords that they are ranking for in Google's top 20 organic search results. The larger the circle, the more visibility a domain has. Below, a list of domains an analyzed domain is competing against in Google's top 20 organic search results.

# Referring Domains


# Daily Stats
| Organic Traffic | Organic Keywords | Backlinks |
|---|---|---|
| 976 | 15.9K | 126K |
| `-41.87%` | `-16.4%` | `-1.62%` |
### 📝 Traffic Drop
Traffic downturn detected! It appears SN domain experienced a traffic drop of 633 in the last 28 days. Take a closer look at these pages with significant traffic decline and explore areas for potential improvement. Here are the pages taking the biggest hits:
- https://stacker.news/items/723989 ⬇️ -15
- https://stacker.news/items/919813 ⬇️ -12
- https://stacker.news/items/783355 ⬇️ -5
### 📉 Decreased Authority Score
Uh-oh! Your Authority score has dropped from 26 to 25. Don't worry, we're here to assist you. Check out the new/lost backlinks in the Backlink Analytics tool to uncover insights on how to boost your authority.
### 🌟 New Keywords
Opportunity Alert! Targeting these keywords could help you increase organic traffic quickly and efficiently. We've found some low-hanging fruits for you! Take a look at these keywords:
- nitter.moomoo.me — Volume 70
- 0xchat — Volume 30
- amethyst nostr — Volume 30
### 🛠️ Broken Pages
This could hurt the user experience and lead to a loss in organic traffic. Time to take action: amend those pages or set up redirects. Here below, few pages on SN domain that are either broken or not _crawlable_:
- https://stacker.news/404 — 38 backlinks
- https://stacker.news/api/capture/items/91154 — 24 backlinks
- https://stacker.news/api/capture/items/91289 — 24 backlinks
Dees this post give you some insights? Hope so, comment below if you have any SEO suggestion? Mine is to improve or keep an eye on Accessibility!
One of the major issues I found is that SN does not have a `robots.txt`, a key simple text file that allow crawlers to read or not-read the website for indexing purposes. @k00b and @ek is that voluntary?
Here are other basic info to improve the SEO score and for those of us that want to learn more:
- Intro to Accessibility: https://www.w3.org/WAI/fundamentals/accessibility-intro/
- Design for Accessibility: https://www.w3.org/WAI/tips/designing/
- Web Accessibility Best Practices: https://www.freecodecamp.org/news/web-accessibility-best-practices/
originally posted at https://stacker.news/items/925433
-

@ 8cb60e21:5f2deaea
2024-09-03 22:26:25
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/SBdDt4BUIW0" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 7d33ba57:1b82db35
2025-03-28 20:59:51
Krka National Park, located in central Dalmatia, is one of Croatia’s most breathtaking natural wonders. Famous for its stunning waterfalls, crystal-clear lakes, and lush forests, the park is a must-visit for nature lovers. Unlike Plitvice Lakes, Krka allows swimming in certain areas, making it a perfect summer escape.

## **🌊 Top Things to See & Do in Krka National Park**
### **1️⃣ Skradinski Buk Waterfall 💦**
- The **largest and most famous waterfall** in the park, with **cascading pools and wooden walkways**.
- You **used to be able to swim here**, but since 2021, swimming is no longer allowed.
- Perfect for **photography and picnics**.
### **2️⃣ Roški Slap Waterfall 🌿**
- A **less crowded but equally beautiful** series of waterfalls.
- Known for its **"necklace" of small cascades** leading into the main fall.
- Nearby **Mlinica**, a restored **watermill**, shows traditional Croatian life.
### **3️⃣ Visovac Island & Monastery 🏝️**
- A **tiny island** in the middle of the Krka River, home to a **Franciscan monastery** from the 15th century.
- Accessible by **boat tour** from Skradinski Buk or Roški Slap.
- A peaceful, scenic spot with **stunning views of the lake**.

### **4️⃣ Krka Monastery 🏛️**
- A **Serbian Orthodox monastery** hidden deep in the park.
- Built on **ancient Roman catacombs**, which you can explore.
- A **quiet, spiritual place**, often overlooked by tourists.
### **5️⃣ Hike & Walk the Nature Trails 🥾**
- The park has **several well-marked trails** through forests, waterfalls, and lakes.
- Wooden walkways allow **easy access** to the main sights.
- **Wildlife spotting**: Look out for **otters, turtles, and over 200 bird species**!
### **6️⃣ Swim at Skradin Beach 🏖️**
- While you can’t swim at Skradinski Buk anymore, **Skradin Beach**, just outside the park, is a great spot for a dip.
- **Kayaking and boat tours** available.

## **🚗 How to Get to Krka National Park**
✈️ **By Air:** The nearest airport is **Split (SPU), 1 hour away**.
🚘 **By Car:**
- **Split to Krka:** ~1 hour (85 km)
- **Zadar to Krka:** ~1 hour (75 km)
- **Dubrovnik to Krka:** ~3.5 hours (280 km)
🚌 **By Bus:** Direct buses from **Split, Zadar, and Šibenik** to the park’s entrances.
🚢 **By Boat:** From **Skradin**, you can take a **boat ride** into the park.

## **💡 Tips for Visiting Krka National Park**
✅ **Best time to visit?** **Spring & early autumn (April–June, September–October)** – Fewer crowds & mild weather 🍃
✅ **Start early!** **Arrive before 10 AM** to avoid crowds, especially in summer ☀️
✅ **Bring water & snacks** – Limited food options inside the park 🍎
✅ **Wear comfy shoes** – Wooden walkways & trails can be slippery 👟
✅ **Take a boat tour** – The best way to see Visovac Island & hidden spots ⛵
✅ **Buy tickets online** – Save time at the entrance 🎟️

-

@ a07fae46:7d83df92
2025-03-18 12:31:40
if the JFK documents come out and are nothing but old hat, it will be disappointing. but if they contain revelations, then they are an unalloyed good. unprecedented and extraordinary; worthy of praise and admiration. they murdered the president in broad daylight and kept 80,000 related documents secret for 60 years. the apparatus that did that and got away with it, is 100+ years in the making. the magic bullet was just the starting pistol of a new *era*; a *level up* in an [old game](https://archive.org/details/TragedyAndHope_501/page/n5/mode/2up?q=feudalist+fashion). it won't be dismantled and your republic delivered back with a bow in *2 months*. have a little humility and a little gratitude. cynicism is easy. it's peak mid-wittery. yeah no shit everything is corrupt and everyone's likely captured by [AIPAC](https://books.google.com/books/publisher/content?id=gKVKDwAAQBAJ&pg=PT68&img=1&zoom=3&hl=en&bul=1&sig=ACfU3U2pagVXTYdJOKxkAwmmFQpuSnoS5g&w=1280) or something beyond. YOU THINK AIPAC is the [ALL SEEING EYE](https://archive.org/details/the-all-seeing-eye-vol-1-5-manly-p.-hall-may-1923-sept-1931)?
you can keep going, if you want to, but have some awareness and appreciation for where we are and what it took to get here. the first 'you are fake news' was also a shot heard 'round the world and you are riding high on it's [Infrasound](https://en.wikipedia.org/wiki/Infrasound) wave, still reverberating; unappreciative of the profound delta in public awareness and understanding, and rate of change, that has occurred since that moment, in [2017](https://www.youtube.com/watch?v=Vqpzk-qGxMU). think about where we were back then, especially with corporate capture of the narrative. trump's bullheaded behavior, if only ego-driven, *is* what broke the spell. an *actual* moment of savage bravery is what allows for your current jaded affectation. black pilled is boring. it's intellectually lazy. it is low-resolution-thinking, no better than progressives who explain the myriad ills of the world through 'racism'. normalcy bias works both ways. i'm not grading you on a curve that includes NPCs. i'm grading you against those of us with a mind, on up. do better.
the best Webb-style doomer argument is essentially 'the mouse trap needs a piece of cheese in order to work'. ok, but it doesn't need 3 pieces of cheese, or 5. was FreeRoss the piece of cheese? was the SBR the cheese? real bitcoiners know how dumb the 'sbr is an attempt to takeover btc' narrative is, so extrapolate from that. what about withdrawal from the WHO? freeze and review of USAID et al? how many pieces of cheese before we realize it's not a trap? it's just a messy endeavor.
Good morning.
#jfkFiles #nostrOnly
-

@ 6f1a5274:3b3bb9c4
2025-03-28 14:26:42
97win là một nền tảng giải trí trực tuyến nổi bật, mang đến cho người chơi những trải nghiệm độc đáo và thú vị. Với giao diện dễ sử dụng và thiết kế thân thiện, nền tảng này giúp người chơi dễ dàng tham gia vào các trò chơi yêu thích của mình mà không gặp phải bất kỳ khó khăn nào. Các trò chơi tại 97win không chỉ đa dạng về thể loại mà còn được phát triển với đồ họa sắc nét và âm thanh sống động, mang lại những trải nghiệm tương tác đầy thú vị và chân thực. Từ những trò chơi đơn giản đến những thử thách phức tạp, 97win luôn biết cách tạo ra không gian giải trí phong phú, thu hút cả những người mới bắt đầu và các người chơi dày dặn kinh nghiệm.
Ngoài chất lượng trò chơi, <a href="https://97win.shop">97win</a> còn chú trọng đến yếu tố bảo mật và an toàn của người chơi. Nền tảng này sử dụng công nghệ bảo mật hiện đại để bảo vệ thông tin cá nhân và giao dịch của người tham gia, giúp người chơi yên tâm tuyệt đối khi tham gia. Tất cả các dữ liệu quan trọng đều được mã hóa và bảo vệ chặt chẽ, đảm bảo rằng mọi thông tin sẽ không bị xâm phạm hoặc lộ lọt ra ngoài. Với cam kết mang đến một môi trường an toàn, 97win đã xây dựng được lòng tin vững chắc từ người chơi, giúp họ hoàn toàn tập trung vào việc giải trí mà không phải lo lắng về các vấn đề bảo mật.
Bên cạnh đó, đội ngũ chăm sóc khách hàng của 97win luôn sẵn sàng hỗ trợ người chơi 24/7, giải đáp mọi thắc mắc và giải quyết các vấn đề phát sinh một cách nhanh chóng và hiệu quả. Mỗi vấn đề, dù lớn hay nhỏ, đều được đội ngũ hỗ trợ xử lý một cách tận tâm và chuyên nghiệp, giúp người chơi cảm thấy thoải mái và hài lòng với dịch vụ. Sự kết hợp giữa các trò chơi chất lượng, bảo mật an toàn và dịch vụ khách hàng chu đáo đã giúp 97win trở thành một lựa chọn đáng tin cậy cho những ai tìm kiếm một không gian giải trí trực tuyến tuyệt vời và an toàn.
-

@ 6f1a5274:3b3bb9c4
2025-03-28 14:25:11
777vin nổi bật với một nền tảng giải trí trực tuyến hiện đại, nơi người chơi có thể tận hưởng những giây phút thư giãn thú vị. Với giao diện dễ sử dụng và thiết kế tối ưu, người chơi có thể nhanh chóng tham gia vào các trò chơi yêu thích của mình mà không gặp phải khó khăn. Những trò chơi tại 777vin được phát triển với đồ họa sắc nét và âm thanh sống động, mang đến một trải nghiệm gần gũi và chân thực. Không chỉ có tính năng hấp dẫn, các trò chơi tại đây còn được tối ưu hóa để người chơi có thể tham gia một cách mượt mà, giúp tăng cường sự thư giãn và giải trí.
Bên cạnh chất lượng trò chơi, <a href="https://777vin-online.com">777vin</a> còn chú trọng đến bảo mật và an toàn thông tin người chơi. Nền tảng này sử dụng công nghệ bảo mật tiên tiến nhất để bảo vệ dữ liệu cá nhân và giao dịch của người tham gia. Những biện pháp bảo mật này giúp người chơi cảm thấy an tâm tuyệt đối khi tham gia vào các trò chơi, mà không cần lo ngại về việc thông tin của mình bị lộ lọt hay bị xâm phạm. Điều này là một yếu tố quan trọng, giúp 777vin xây dựng lòng tin vững chắc với cộng đồng người chơi, tạo ra một môi trường giải trí an toàn và đáng tin cậy.
Ngoài việc bảo vệ an toàn thông tin, 777vin còn đặc biệt chú trọng đến chất lượng dịch vụ khách hàng. Đội ngũ hỗ trợ của 777vin luôn sẵn sàng phục vụ người chơi 24/7, giải đáp mọi thắc mắc và hỗ trợ kịp thời mọi vấn đề phát sinh. Sự chuyên nghiệp và tận tâm của đội ngũ này giúp người chơi có thể yên tâm trải nghiệm trò chơi mà không phải lo lắng về bất kỳ vấn đề nào. Với sự kết hợp giữa chất lượng dịch vụ, bảo mật tuyệt đối và trải nghiệm người chơi hoàn hảo, 777vin đã và đang khẳng định vị thế của mình là một trong những nền tảng giải trí trực tuyến hàng đầu.
-

@ da0b9bc3:4e30a4a9
2025-03-28 19:14:52
It's Finally here Stackers!
It's Friday!
We're about to kick off our weekends with some feel good tracks.
Let's get the party started. Bring me those Feel Good tracks.
Let's get it!
https://youtu.be/r1ATFedwjnk?si=tPtLac6ExYZCx3Ez
originally posted at https://stacker.news/items/928119
-

@ bc52210b:20bfc6de
2025-03-14 20:39:20
When writing safety critical code, every arithmetic operation carries the potential for catastrophic failure—whether that’s a plane crash in aerospace engineering or a massive financial loss in a smart contract.
The stakes are incredibly high, and errors are not just bugs; they’re disasters waiting to happen. Smart contract developers need to shift their mindset: less like web developers, who might prioritize speed and iteration, and more like aerospace engineers, where precision, caution, and meticulous attention to detail are non-negotiable.
In practice, this means treating every line of code as a critical component, adopting rigorous testing, and anticipating worst-case scenarios—just as an aerospace engineer would ensure a system can withstand extreme conditions.
Safety critical code demands aerospace-level precision, and smart contract developers must rise to that standard to protect against the severe consequences of failure.
-

@ 30876140:cffb1126
2025-03-26 04:58:21
The portal is closing.
The symphony comes to an end.
Ballet, a dance of partners,
A wish of hearts,
Now closing its curtains.
I foolishly sit
Eagerly waiting
For the circus to begin again,
As crowds file past me,
Chuckles and popcorn falling,
Crushed under foot,
I sit waiting
For the show to carry on.
But the night is now over,
The laughs have been had,
The music been heard,
The dancers are gone now
Into the nightbreeze chill.
Yet still, I sit waiting,
The empty chairs yawning,
A cough, I start, could it be?
Yet the lights now go out,
And now without my sight
I am truly alone in the theater.
Yet still, I am waiting
For the show to carry on,
But I know that it won’t,
Yet still, I am waiting.
Never shall I leave
For the show was too perfect
And nothing perfect should ever be finished.
-

@ 3c389c8f:7a2eff7f
2025-03-28 17:10:17
There is a new web being built on Nostr. At it's core, is a social experience paralleled by no other decentralized protocol. Nostr not only solves the problems of siloed relationships, third-party identity ownership, and algorithmic content control; it makes possible a ubiquitous social network across almost anything imaginable. User controlled identity, open data, and verifiable social graphs allow us to redefine trust on the web. We can interact with each other and online content in ways that have previously only been pipedreams. Nostr is not just social media, it is the web made social.
### Interoperability
The client/relay relationship on Nostr allows for almost endless data exchange between various apps, clients, relays, and users. If any two things are willing to speak the same sub-protocol(s) within Nostr, they can exchange data. Making a friend list enables that list to be used in any other place that chooses to make it available. Creating a relay to serve an algorithmic social feed makes that feed viewable in any client that displays social feeds. Health data held by a patient can be shared with any care provider, verified by their system, and vice versa. This is the point where I have to acknowledge my own tech-deaf limitations and direct you towards nostr.com for more information.
### Data Resiliency
I prefer to use the term resiliency here, because its really a mix of data redundancy and self-managed data that creates broad availability. Relays may host 10, 20, 30+ copies of your notes in different locations, but you also have no assurance that those relays will hosts those notes forever. An individual operating their own relay, while also connecting to the wider network, ensures resiliency in events such that wide swaths of the network should disappear or collude against an individual. The simplicity of relay management makes it possible for nearly anyone to make sure that they have a way to convey their messages to their individual network, whether that be close contacts, an audience, or one individual. This resiliency doesn't just apply to typical speech, it applies to any data intended to be shared amongst humans and machines alike.
### Pseudonymity and Anonymity
With privacy encroachment from corporations, advertisers, and governments reaching all time highs, the need for identity protecting tools is also on the rise. Nostr utilizes public key encryption for its identity system. As there is no central entity to "verify" you, there is no need to expose any personal identifiable information to any Nostr app, client, or relay. You can protect your personal identity by simply choosing not to expose it. Your reputation will build as you interact with others on the Nostr network. Your social capital can speak for itself. (As with everything else, utilizing a VPN is recommended.)
### Identity and Provability
No one can stop an impersonator from trying to hijack an identity. With Nostr, you CAN prove that you are you, though, which is basically the same as saying "that person is not me" Every note you write, every action you take, is cryptographically signed by your private key. As long as you maintain control of that key, you can prove what you did or did not do.
### Censorship Resistance
If you have read our Relay Rundown then you probably get the idea. If not here's the tl;dr: Many small, lightweight relays make up Nostr's distribution system. They are simple enough that anyone can run one. They are redundant enough that you can be almost certain your content exists somewhere. If that is not peace of mind enough, you can run your own with ease. Censorship resistance isn't counting on one company, man, or server to protect what you say. It is taking control of your speech. Nostr makes it easy.
### Freedom of Mind and Association
Nostr eliminates the need for company run algorithms that high-jack your attention to feed the advertising industry. You are free to choose your social media experience. Nostr's DVMs, curations, and conversation-centered relays offer discovery mechanisms run by any number of providers. That could be an individual, a company, a group, or you. Many clients incorporate different ways of engaging with these corporate algorithm alternatives. You can also choose to keep a purely chronological feed of the the things and people you follow. Exploring Nostr through its many apps opens up a the freedom to choose what and how you feed your mind.
When we are able to explore, we end up surrounding ourselves with people who share our interests & hobbies. We find friends. This creates distance between ideologies and stark beliefs that often are used as the basis for the term "being in a bubble". Instead of bubbling off, an infinitely open space of thoughts and ideas allows for groups to gather naturally. In this way, we can choose not to block ourselves off from opposing views but to simply distance ourselves from them.
Nostr's relay system also allows for the opposite. Tight-knit communities can create a space for its members to socialize and exchange information with minimal interference from any outside influence. By setting up their own relays with strict rules, the members can utilize one identity to interact within a community or across the broader social network.
-

@ e88527b4:7ccf6efa
2024-08-30 12:12:39
書いてみた。。
-

@ 8cb60e21:5f2deaea
2024-08-29 02:16:28
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/GwUNT2k26mQ" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 0d6c8388:46488a33
2025-03-28 16:24:00
Huge thank you to [OpenSats for the grant](https://opensats.org/blog/10th-wave-of-nostr-grants) to work on [Hypernote this year](https://www.hypernote.club/)! I thought I'd take this opportunity to try and share my thought processes for Hypernote. If this all sounds very dense or irrelevant to you I'm sorry!
===
How can the ideas of "hypermedia" benefit nostr? That's the goal of hypernote. To take the best ideas from "hypertext" and "hypercard" and "hypermedia systems" and apply them to nostr in a specifically nostr-ey way.
### 1. What do we mean by hypermedia
A hypermedia document embeds the methods of interaction (links, forms, and buttons are the most well-known hypermedia controls) within the document itself. It's including the _how_ with the _what_.
This is how the old web worked. An HTML page was delivered to the web browser, and it included in it a link or perhaps a form that could be submitted to obtain a new, different HTML page. This is how the whole web worked early on! Forums and GeoCities and eBay and MySpace and Yahoo! and Amazon and Google all emerged inside this paradigm.
A web browser in this paradigm was a "thin" client which rendered the "thick" application defined in the HTML (and, implicitly, was defined by the server that would serve that HTML).
Contrast this with modern app development, where the _what_ is usually delivered in the form of JSON, and then HTML combined with JavaScript (React, Svelte, Angular, Vue, etc.) is devised to render that JSON as a meaningful piece of hypermedia within the actual browser, the _how_.
The browser remains a "thin" client in this scenario, but now the application is delivered in two stages: a client application of HTML and JavaScript, and then the actual JSON data that will hydrate that "application".
(Aside: it's interesting how much "thicker" the browser has had to become to support this newer paradigm!)
Nostr was obviously built in line with the modern paradigm: nostr "clients" (written in React or Svelte or as mobile apps) define the _how_ of reading and creating nostr events, while nostr events themselves (JSON data) simply describe the _what_.
And so the goal with Hypernote is to square this circle somehow: nostr currently delivers JSON _what_, how do we deliver the _how_ with nostr as well. Is that even possible?
### 2. Hypernote's design assumptions
Hypernote assumes that hypermedia over nostr is a good idea! I'm expecting some joyful renaissance of app expression similar to that of the web once we figure out how to express applications in a truly "nostr" way.
Hypernote was also [deeply inspired by HTMX](https://hypermedia.systems/hypermedia-a-reintroduction/), so it assumes that building web apps in the HTMX style is a good idea. The HTMX insight is that instead of shipping rich scripting along with your app, you could simply make HTML a _tiny_ bit more expressive and get 95% of what most apps need. HTMX's additions to the HTML language are designed to be as minimal and composable as possible, and Hypernote should have the same aims.
Hypernote also assumes that the "design" of nostr will remain fluid and anarchic for years to come. There will be no "canonical" list of "required" NIPs that we'll have "consensus" on in order to build stable UIs on top of. Hypernote will need to be built responsive to nostr's moods and seasons, rather than one holy spec.
Hypernote likes the `nak` command line tool. Hypernote likes markdown. Hypernote likes Tailwind CSS. Hypernote likes SolidJS. Hypernote likes cold brew coffee. Hypernote is, to be perfectly honest, my aesthetic preferences applied to my perception of an opportunity in the nostr ecosystem.
### 3. "What's a hypernote?"
Great question. I'm still figuring this out. Everything right now is subject to change in order to make sure hypernote serves its intended purpose.
But here's where things currently stand:
A hypernote is a flat list of "Hypernote Elements". A Hypernote Element is composed of:
1. CONTENT. Static or dynamic content. (the what)
2. LOGIC. Filters and events (the how)
3. STYLE. Optional, inline style information specific to this element's content.
In the most basic example of a [hypernote story](https://hypernote-stories.fly.dev/), here's a lone "edit me" in the middle of the canvas:

```
{
"id": "fb4aaed4-bf95-4353-a5e1-0bb64525c08f",
"type": "text",
"text": "edit me",
"x": 540,
"y": 960,
"size": "md",
"color": "black"
}
```
As you can see, it has no logic, but it does have some content (the text "edit me") and style (the position, size, and color).
Here's a "sticker" that displays a note:
```
{
"id": "2cd1ef51-3356-408d-b10d-2502cbb8014e",
"type": "sticker",
"stickerType": "note",
"filter": {
"kinds": [
1
],
"ids": [
"92de77507a361ab2e20385d98ff00565aaf3f80cf2b6d89c0343e08166fed931"
],
"limit": 1
},
"accessors": [
"content",
"pubkey",
"created_at"
],
"x": 540,
"y": 960,
"associatedData": {}
}
```
As you can see, it's kind of a mess! The content and styling and underdeveloped for this "sticker", but at least it demonstrates some "logic": a nostr filter for getting its data.
Here's another sticker, this one displays a form that the user can interact with to SEND a note. Very hyper of us!
```
{
"id": "42240d75-e998-4067-b8fa-9ee096365663",
"type": "sticker",
"stickerType": "prompt",
"filter": {},
"accessors": [],
"x": 540,
"y": 960,
"associatedData": {
"promptText": "What's your favorite color?"
},
"methods": {
"comment": {
"description": "comment",
"eventTemplate": {
"kind": 1111,
"content": "${content}",
"tags": [
[
"E",
"${eventId}",
"",
"${pubkey}"
],
[
"K",
"${eventKind}"
],
[
"P",
"${pubkey}"
],
[
"e",
"${eventId}",
"",
"${pubkey}"
],
[
"k",
"${eventKind}"
],
[
"p",
"${pubkey}"
]
]
}
}
}
}
```
It's also a mess, but it demos the other part of "logic": methods which produce new events.
This is the total surface of hypernote, ideally! Static or dynamic content, simple inline styles, and logic for fetching and producing events.
I'm calling it "logic" but it's purposfully not a whole scripting language. At most we'll have some sort of `jq`-like language for destructing the relevant piece of data we want.
My ideal syntax for a hypernote as a developer will look something like
```foo.hypernote
Nak-like logic
Markdown-like content
CSS-like styles
```
But with JSON as the compile target, this can just be my own preference, there can be other (likely better!) ways of authoring this content, such as a Hypernote Stories GUI.
### The end
I know this is all still vague but I wanted to get some ideas out in the wild so people understand the through line of my different Hypernote experiments. I want to get the right amount of "expressivity" in Hypernote before it gets locked down into one spec. My hunch is it can be VERY expressive while remaining simple and also while not needing a whole scripting language bolted onto it. If I can't pull it off I'll let you know.
-

@ 8cb60e21:5f2deaea
2024-08-28 01:53:35
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/oJSFoDgm51o" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ ecda4328:1278f072
2025-03-25 10:00:52
**Kubernetes and Linux Swap: A Practical Perspective**
After reviewing kernel documentation on swap management (e.g., [Linux Swap Management](https://www.kernel.org/doc/gorman/html/understand/understand014.html)), [KEP-2400 (Kubernetes Node Memory Swap Support)](https://github.com/kubernetes/enhancements/blob/master/keps/sig-node/2400-node-swap/README.md), and community discussions like [this post on ServerFault](https://serverfault.com/questions/881517/why-disable-swap-on-kubernetes), it's clear that the topic of swap usage in modern systems—especially Kubernetes environments—is nuanced and often contentious. Here's a practical synthesis of the discussion.
---
### The Rationale for Disabling Swap
We disable SWAP on our Linux servers to ensure stable and predictable performance by relying on available RAM, avoiding the performance degradation and unnecessary I/O caused by SWAP usage. If an application runs out of memory, it’s usually due to insufficient RAM allocation or a memory leak, and enabling SWAP only worsens performance for other applications. It's more efficient to let a leaking app restart than to rely on SWAP to prevent OOM crashes.
With modern platforms like Kubernetes, memory requests and limits are enforced, ensuring apps use only the RAM allocated to them, while avoiding overcommitment to prevent resource exhaustion.
Additionally, disabling swap may protect data from **data remanence attacks**, where sensitive information could potentially be recovered from the swap space even after a process terminates.
---
### Theoretical Capability vs. Practical Deployment
Linux provides a powerful and flexible memory subsystem. With proper tuning (e.g., swappiness, memory pinning, cgroups), it's technically possible to make swap usage efficient and targeted. Seasoned sysadmins often argue that disabling swap entirely is a lazy shortcut—an avoidance of learning how to use the tools properly.
But Kubernetes is not a traditional system. It's an orchestrated environment that favors predictability, fail-fast behavior, and clear isolation between workloads. Within this model:
- Memory **requests and limits** are declared explicitly.
- The scheduler makes decisions based on RAM availability, not total virtual memory (RAM + swap).
- Swap introduces **non-deterministic performance** characteristics that conflict with Kubernetes' goals.
So while the kernel supports intelligent swap usage, Kubernetes **intentionally sidesteps** that complexity.
---
### Why Disable Swap in Kubernetes?
1. **Deterministic Failure > Degraded Performance**\
If a pod exceeds its memory allocation, it should fail fast — not get throttled into slow oblivion due to swap. This behavior surfaces bugs (like memory leaks or poor sizing) early.
2. **Transparency & Observability**\
With swap disabled, memory issues are clearer to diagnose. Swap obfuscates root causes and can make a healthy-looking node behave erratically.
3. **Performance Consistency**\
Swap causes I/O overhead. One noisy pod using swap can impact unrelated workloads on the same node — even if they’re within their resource limits.
4. **Kubernetes Doesn’t Manage Swap Well**\
Kubelet has historically lacked intelligence around swap. As of today, Kubernetes still doesn't support swap-aware scheduling or per-container swap control.
5. **Statelessness is the Norm**\
Most containerized workloads are designed to be ephemeral. Restarting a pod is usually preferable to letting it hang in a degraded state.
---
### "But Swap Can Be Useful..."
Yes — for certain workloads (e.g., in-memory databases, caching layers, legacy systems), there may be valid reasons to keep swap enabled. In such cases, you'd need:
- Fine-tuned `vm.swappiness`
- Memory pinning and cgroup-based control
- Swap-aware monitoring and alerting
- Custom kubelet/systemd integration
That's possible, but **not standard practice** — and for good reason.
---
### Future Considerations
Recent Kubernetes releases have introduced [experimental swap support](https://kubernetes.io/blog/2023/08/24/swap-linux-beta/) via [KEP-2400](https://github.com/kubernetes/enhancements/blob/master/keps/sig-node/2400-node-swap/README.md). While this provides more flexibility for advanced use cases — particularly Burstable QoS pods on cgroupsv2 — swap remains disabled by default and is not generally recommended for production workloads unless carefully planned. The rationale outlined in this article remains applicable to most Kubernetes operators, especially in multi-tenant and performance-sensitive environments.
Even the Kubernetes maintainers acknowledge the inherent trade-offs of enabling swap. As noted in [KEP-2400's Risks and Mitigations section](https://github.com/kubernetes/enhancements/blob/master/keps/sig-node/2400-node-swap/README.md), swap introduces unpredictability, can severely degrade performance compared to RAM, and complicates Kubernetes' resource accounting — increasing the risk of noisy neighbors and unexpected scheduling behavior.
Some argue that with emerging technologies like **non-volatile memory** (e.g., Intel Optane/XPoint), swap may become viable again. These systems promise near-RAM speed with large capacity, offering hybrid memory models. But these are not widely deployed or supported in mainstream Kubernetes environments yet.
---
### Conclusion
Disabling swap in Kubernetes is not a lazy hack — it’s a **strategic tradeoff**. It improves transparency, predictability, and system integrity in multi-tenant, containerized environments. While the kernel allows for more advanced configurations, Kubernetes intentionally simplifies memory handling for the sake of reliability.
If we want to revisit swap usage, it should come with serious planning: proper instrumentation, swap-aware observability, and potentially upstream K8s improvements. Until then, **disabling swap remains the sane default**.
-

@ 502ab02a:a2860397
2025-03-28 04:57:18
จริงหรือ ว่าโอเมก้า3 ต้องมาจากปลาทะเลเท่านั้น
มีเรื่องที่น่าสนใจเรื่องนึงครับ ถ้าพูดถึงโอเมก้า-3 หลายคนอาจนึกถึงปลาทะเลน้ำลึก เช่น แซลมอน แมคเคอเรล หรือซาร์ดีน ซึ่งเป็นแหล่งโอเมก้า-3 ที่ร่างกายใช้ได้ดี แต่ในขณะเดียวกัน ก็มีกลุ่มคนที่พยายามบริโภคโอเมก้า-3 จากพืชแทน เช่น น้ำมันเมล็ดแฟลกซ์ น้ำมันเมล็ดเจีย หรือวอลนัท โดยหวังว่าจะได้รับประโยชน์เช่นเดียวกับการกินปลา แต่ที่เราเรียนรู้กันมาว่า โอเมก้า-3 จากพืชนั้น ร่างกายมนุษย์นำไปใช้ได้น้อยมาก หรือแทบไม่ได้เลย
สาเหตุหลักมาจากรูปแบบของโอเมก้า-3 ที่พบในแหล่งต่างๆ โอเมก้า-3 มีอยู่ 3 ชนิดหลัก ได้แก่
ALA (Alpha-Linolenic Acid) – พบในพืช
EPA (Eicosapentaenoic Acid) – พบในปลาทะเล
DHA (Docosahexaenoic Acid) – พบในปลาทะเล
ร่างกายสามารถใช้ EPA และ DHA ได้โดยตรง แต่สำหรับ ALA นั้น ร่างกายต้องผ่านกระบวนการเปลี่ยนแปลงทางชีวเคมีก่อน ซึ่งกระบวนการนี้ไม่มีประสิทธิภาพนัก โดยทั่วไปแล้ว
ALA แปลงเป็น EPA ได้เพียง 5-10%
ALA แปลงเป็น DHA ได้เพียง 0.5-5%
แปลว่า หากคุณกินเมล็ดแฟลกซ์หรือน้ำมันเมล็ดเจีย แม้ว่าจะมีปริมาณ ALA สูง แต่ร่างกายก็แทบไม่ได้รับ EPA และ DHA ในปริมาณที่เพียงพอเพื่อใช้ประโยชน์อย่างเต็มที่
ทำไมร่างกายแปลง ALA เป็น EPA/DHA ได้น้อย?
อันแรกเลยคือ เอนไซม์จำกัด กระบวนการเปลี่ยน ALA เป็น EPA และ DHA จะใช้เอนไซม์เดียวกับการแปลงโอเมก้า-6 ซึ่งมักถูกใช้ไปกับโอเมก้า-6 ที่มากเกินไปในอาหารปัจจุบันซะแล้วนั่นเอง ต่อมาคือ กระบวนการหลายขั้นตอน การเปลี่ยน ALA เป็น DHA ต้องผ่านหลายขั้นตอนทางชีวเคมี ทำให้มีการสูญเสียพลังงานและวัตถุดิบไปมาก และสุดท้าย ปัจจัยทางพันธุกรรมและเพศ บางคน โดยเฉพาะผู้หญิง อาจมีอัตราการเปลี่ยนที่สูงกว่าผู้ชายเล็กน้อย แต่ก็ยังต่ำเมื่อเทียบกับการได้รับ EPA/DHA จากปลาหรือสาหร่ายโดยตรง
โอเมก้า-6 ตัวการขัดขวางโอเมก้า-3 จากพืช
โอเมก้า-6 เป็นกรดไขมันจำเป็นที่พบมากในน้ำมันพืช เช่น น้ำมันถั่วเหลือง น้ำมันข้าวโพด และน้ำมันดอกทานตะวัน ซึ่งเป็นส่วนประกอบหลักของอาหารแปรรูปในปัจจุบัน ปัญหาคือ เอนไซม์ที่ใช้แปลง ALA ไปเป็น EPA/DHA เป็นตัวเดียวกับที่ใช้แปลงโอเมก้า-6 ไปเป็น AA (Arachidonic Acid) ซึ่งมีบทบาทในการอักเสบ หากเราบริโภคโอเมก้า-6 มากเกินไป (ซึ่งคนส่วนใหญ่ทำ5555) เอนไซม์เหล่านี้จะถูกใช้ไปกับโอเมก้า-6 มากกว่า ทำให้ ALA มีโอกาสแปลงเป็น EPA/DHA น้อยลงไปอีก
แล้วคนที่ไม่กินปลาหรือชาววีแกนควรทำอย่างไร?
สำหรับคนที่ไม่สามารถหรือไม่ต้องการกินปลา ก็จะมีการบริโภคน้ำมันสาหร่ายที่มี DHA โดยตรงเป็นทางเลือกที่ดีกว่าการหวังพึ่ง ALA จากพืช เพราะ DHA จากสาหร่ายสามารถดูดซึมและใช้ได้ทันทีเหมือน DHA จากปลา
ได้ด้วยเหรอ ?????
ผมเล่ากำเนิดของ DHA ในปลาให้ประมาณนี้ครับ
จริง ๆ แล้ว DHA ซึ่งเป็นโอเมก้า-3 ที่ร่างกายใช้ได้โดยตรง มาจาก Docosahexaenoic Acid ที่เกิดจากกระบวนการสังเคราะห์ตามธรรมชาติ ซึ่งสาหร่ายบางสายพันธุ์ เช่น Schizochytrium และ Crypthecodinium cohnii มีเอนไซม์ที่สามารถเปลี่ยนกรดไขมันพื้นฐานให้กลายเป็น DHA ได้เองซึ่งเป็นส่วนประกอบหลักในระบบนิเวศทะเล(พืชกักเก็บไขมันได้อย่างไร ผมเคยโพสไปแล้ว) โดยเฉพาะ สาหร่ายขนาดเล็ก (microalgae) สาหร่ายจึงเป็นสิ่งมีชีวิตในทะเลพัฒนาให้มี DHA สูงเพราะ DHA เป็นส่วนประกอบสำคัญที่ช่วยรักษาความยืดหยุ่นและความสมบูรณ์ของเยื่อหุ้มเซลล์ในสาหร่าย ทำให้พวกมันสามารถดำรงชีวิตในสภาพแวดล้อมที่มีอุณหภูมิต่ำในทะเลได้
จากนั้นก็เป็นไปตามห่วงโซ่อาหารครับ ปลาและสัตว์ทะเลอื่น ๆ ได้รับ DHA จากการบริโภคสาหร่ายหรือสัตว์เล็ก ๆ ที่กินสาหร่ายมาอีกที ดังนั้น DHA ในปลาเป็นผลมาจากการสะสมจากสาหร่ายโดยตรง นี่เป็นเหตุผลว่าทำไมปลาทะเลน้ำลึก เช่น แซลมอน แมคเคอเรล และซาร์ดีน ถึงมี DHA สูงนั่นเอง งว่ออออออ
ดังนั้น เมื่อคุณกิน DHA จากสาหร่าย ก็เท่ากับว่าคุณได้รับ DHA จากต้นกำเนิดแท้จริงในระบบนิเวศทะเลครับ
DHA ที่ได้มาจากสาหร่ายสามารถนำไปใช้ในร่างกายได้ทันทีโดยไม่ต้องผ่านกระบวนการเปลี่ยนแปลง เพราะมันอยู่ในรูป Triglyceride หรือ Phospholipid ซึ่งเป็นรูปแบบที่ร่างกายมนุษย์สามารถดูดซึมและนำไปใช้ได้ทันที ปลาไม่ได้แปลงโครงสร้าง DHA แต่เพียงสะสม DHA ไว้ในตัวจากการกินสาหร่าย ดังนั้นการรับประทาน DHA จากสาหร่ายก็ให้ผลเทียบเท่ากับการรับประทาน DHA จากปลา งานวิจัยหลายฉบับยืนยันว่า DHA จากสาหร่ายมีค่าการดูดซึม (Bioavailability) ใกล้เคียงกับ DHA จากน้ำมันปลา แต่หาเอาเองนะถ้าอยากอ่านฉบับเต็ม
การผลิตน้ำมันสาหร่ายนั้น เมื่อสาหร่ายเจริญเติบโตเต็มที่แล้ว เขาจะทำการเก็บเกี่ยวและสกัดน้ำมันโดยใช้เทคโนโลยีการแยกที่ทันสมัย ซึ่งช่วยรักษาให้ DHA ที่มีอยู่ในเซลล์สาหร่ายถูกเก็บรักษาไว้ในรูปแบบที่สามารถนำไปใช้ได้โดยตรง จากนั้นจะเข้าสู่การกรองหรือการปั่นแยก (centrifugation) เพื่อให้ได้มวลสาหร่ายที่เข้มข้น จากนั้นจึงทำให้แห้งเพื่อเตรียมเข้าสู่กระบวนการสกัด ซึ่งมีหลายวิธีอาทิเช่น
1 การสกัดด้วยตัวทำละลาย
ใช้ตัวทำละลาย เช่น เฮกเซน (Hexane) หรือ เอทานอล (Ethanol) เพื่อสกัดน้ำมันออกจากเซลล์สาหร่าย จากนั้นน้ำมันจะถูกนำไปกลั่นเพื่อแยกตัวทำละลายออก ทำให้ได้น้ำมันที่มีความบริสุทธิ์สูง
2. การสกัดด้วย CO₂ เหลว ใช้ คาร์บอนไดออกไซด์ในสถานะวิกฤติ (Supercritical CO₂) ซึ่งเป็นวิธีที่ทันสมัย ก๊าซ CO₂ จะถูกทำให้มีความดันสูงและอุณหภูมิที่เหมาะสมเพื่อกลายเป็นของเหลว แล้วใช้แยกน้ำมันออกจากเซลล์สาหร่าย วิธีนี้ช่วยให้ได้น้ำมันที่ ปราศจากตัวทำละลายเคมีและมีความบริสุทธิ์สูง
3. การสกัดด้วยการกดอัด หรือ Cold Pressed
เป็นวิธีที่ใช้แรงดันทางกลกดเซลล์สาหร่ายเพื่อให้ได้น้ำมันออกมา อันนี้เป็นการผลิตน้ำมันแบบออร์แกนิกเลยครับ แต่ให้ผลผลิตน้อยกว่าวิธีอื่น ๆ
น้ำมันที่ได้จากการสกัดจะผ่านการกลั่นด้วยกระบวนการต่าง ๆ เช่น
Winterization กำจัดไขมันที่ไม่จำเป็น
Molecular Distillation แยกสารตกค้าง เช่น โลหะหนักและสารปนเปื้อน
Deodorization กำจัดกลิ่นคาวของสาหร่าย
จากนั้นก็บรรจุใส่ซอฟท์เจล พร้อมจำหน่ายนั่นเองครับ
ก็ถือว่าเป็นอีกทางเลือกของชาววีแกน ที่ไม่สามารถกินปลาหรือสัตว์ทะเลได้ ก็น่าจะเฮกันดังๆได้เลยครับ จะได้มีตัวช่วยในการลดการอักเสบได้
ส่วนชาว food matrix ก็ต้องเรียนรู้ระบบครับ การกินจากปลาหรือสัตว์ทะเล ก็จะได้โปรตีน แร่ธาตุ วิตามินอื่นๆควบมากับตัวสัตว์ตามที่ธรรมชาติแพคมาให้
ถ้าจะเสริมเป็นน้ำมันสาหร่าย ก็สุดแล้วแต่ความต้องการครับ ไม่ใช่เรื่องแย่อะไร เว้นแต่ไปเทียบราคาเอาเองนะ 55555
#pirateketo #ฉลาก3รู้ #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-

@ df173277:4ec96708
2025-02-07 00:41:34
## **Building Our Confidential Backend on Secure Enclaves**
With our newly released [private and confidential **Maple AI**](https://trymaple.ai/?ref=blog.opensecret.cloud) and the open sourcing of our [**OpenSecret** platform](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud) code, I'm excited to present this technical primer on how we built our confidential compute platform leveraging **secure enclaves**. By combining AWS Nitro enclaves with end-to-end encryption and reproducible builds, our platform gives developers and end users the confidence that user data is protected, even at runtime, and that the code operating on their data has not been tampered with.
## **Auth and Databases Today**
As developers, we live in an era where protecting user data means "encryption at rest," plus some access policies and procedures. Developers typically run servers that:
1. Need to register users (authentication).
2. Collect and process user data in business-specific ways, often on the backend.
Even if data is encrypted at rest, it's commonly unlocked with a single master key or credentials the server holds. This means that data is visible during runtime to the application, system administrators, and potentially to the hosting providers. This scenario makes it difficult (or impossible) to guarantee that sensitive data isn't snooped on, memory-dumped, or used in unauthorized ways (for instance, training AI models behind the scenes).
## **"Just Trust Us" Isn't Good Enough**
In a traditional server architecture, users have to take it on faith that the code handling their data is the same code the operator claims to be running. Behind the scenes, applications can be modified or augmented to forward private information elsewhere, and there is no transparent way for users to verify otherwise. This lack of proof is unsettling, especially for services that process or store highly confidential data.
Administrators, developers, or cloud providers with privileged access can inspect memory in plaintext, attach debuggers, or gain complete visibility into stored information. Hackers who compromise these privileged levels can directly access sensitive data. Even with strict policies or promises of good conduct, the reality is that technical capabilities and misconfigurations can override words on paper. If a server master key can decrypt your data or can be accessed by an insider with root permissions, then "just trust us" loses much of its credibility.
The rise of AI platforms amplifies this dilemma. User data, often full of personal details, gets funneled into large-scale models that might be training or fine-tuning behind the scenes. Relying on vague assurances that "we don't look at your data" is no longer enough to prevent legitimate concerns about privacy and misuse. Now more than ever, providing a **strong, verifiable** guarantee that data remains off-limits, even when actively processed, has become a non-negotiable requirement for trustworthy services.
## **Current Attempts at Securing Data**
Current User Experience of E2EE Apps
While properly securing data is not easy, it isn't to say that no one is trying. Some solutions use **end-to-end encryption** (E2EE), where user data is encrypted client-side with a password or passphrase, so not even the server operator can decrypt it. That approach can be quite secure, but it also has its **limitations**:
1. **Key Management Nightmares**: If a user forgets their passphrase, the data is effectively lost, and there's no way to recover it from the developer's side.
2. **Feature Limitations**: Complex server-side operations (like offline/background tasks, AI queries, real-time collaboration, or heavy computation) can't easily happen if the server is never capable of processing decrypted data.
3. **Platform Silos**: Some solutions rely on iCloud, Google Drive, or local device storage. That can hamper multi-device usage or multi-OS compatibility.
Other approaches include self-hosting. However, these either burden users with dev ops overhead or revert to the "trust me" model for the server if you "self-host" on a cloud provider.
## **Secure Enclaves**
### **The Hybrid Approach**
Secure enclaves offer a compelling middle ground. They combine the privacy benefits of keeping data secure from prying admins while still allowing meaningful server-side computation. In a nutshell, an enclave is a protected environment within a machine, isolated at the hardware level, so that even if the OS or server is compromised, the data and code inside the enclave remain hidden.
App Service Running Inside Secure Enclave
### **High-Level Goal of Enclaves**
Enclaves, also known under the broader umbrella of **confidential computing**, aim to:\
• **Lock down data** so that only authorized code within the enclave can process the original plaintext data.\
• **Deny external inspection** by memory dumping, attaching a debugger, or intercepting plaintext network traffic.\
• **Prove** to external users or services that an enclave is running unmodified, approved code (this is where **remote attestation** comes in).
### **Different Secure Enclave Solutions**
[**AMD SEV**](https://www.amd.com/en/developer/sev.html?ref=blog.opensecret.cloud) **(Secure Encrypted Virtualization)** encrypts an entire virtual machine's memory so that even a compromised hypervisor cannot inspect or modify guest data. Its core concept is "lift-and-shift" security. No application refactoring is required because hardware-based encryption automatically protects the OS and all VM applications. Later enhancements (SEV-ES and SEV-SNP) added encryption of CPU register states and memory integrity protections, further limiting hypervisor tampering. This broad coverage means the guest OS is included in the trusted boundary. AMD SEV has matured into a robust solution for confidential VMs in multi-tenant clouds.
[**Intel TDX**](https://www.intel.com/content/www/us/en/developer/tools/trust-domain-extensions/overview.html?ref=blog.opensecret.cloud) **(Trust Domain Extensions)** shifts from process-level enclaves to full VM encryption, allowing an entire guest operating system and its applications to run in an isolated "trust domain." Like AMD SEV, Intel TDX encrypts and protects all memory the VM uses from hypervisors or other privileged software, so developers do not need to refactor their code to benefit from hardware-based confidentiality. This broader scope addresses many SGX limitations, such as strict memory bounds and the need to split out enclave-specific logic, and offers a more straightforward "lift-and-shift" path for running existing workloads privately. While SGX is now deprecated, TDX carries forward the core confidential computing principles but applies them at the virtual machine level for more substantial isolation, easier deployment, and the ability to scale up to large, memory-intensive applications.
[**Apple Secure Enclave and Private Compute**](https://security.apple.com/blog/private-cloud-compute/?ref=blog.opensecret.cloud) is a dedicated security coprocessor embedded in most Apple devices (iPhones, iPads, Macs) and now extended to Apple's server-side AI infrastructure. It runs its own microkernel, has hardware-protected memory, and securely manages operations such as biometric authentication, key storage, and cryptographic tasks. Apple's "Private Compute" approach in the cloud brings similar enclave capabilities to server-based AI, enabling on-device-grade privacy even when requests are processed in Apple's data centers.
[**AWS Nitro Enclaves**](https://docs.aws.amazon.com/enclaves/latest/user/nitro-enclave.html?ref=blog.opensecret.cloud) carve out a tightly isolated "mini-VM" from a parent EC2 instance, with its own vCPUs and memory guarded by dedicated Nitro cards. The enclave has no persistent storage and no external network access, significantly reducing the attack surface. Communication with the parent instance occurs over a secure local channel (vsock), and AWS offers hardware-based attestation so that secrets (e.g., encryption keys from AWS KMS) can be accessed only to the correct enclave. This design helps developers protect sensitive data or code even if the main EC2 instance's OS is compromised.
[**NVIDIA GPU TEEs**](https://www.nvidia.com/en-us/data-center/solutions/confidential-computing/?ref=blog.opensecret.cloud) **(Hopper H100 and Blackwell)** extend confidential computing to accelerated workloads by encrypting data in GPU memory and ensuring that even a privileged host cannot view or tamper with it. Data moving between CPU and GPU is encrypted in transit, so sensitive model weights or inputs remain protected during AI training or inference. NVIDIA's hardware and drivers handle secure data paths under the hood, allowing confidential large language model (LLM) workloads and other GPU-accelerated computations to run with minimal performance overhead and strong security guarantees.
### **Key Benefits**
One major advantage of enclaves is their ability to **keep memory completely off-limits** to outside prying eyes. Even administrators who can normally inspect processes at will are blocked from peeking into the enclave's protected memory space. The enclave model is a huge shift in the security model: it prevents casual inspection and defends against sophisticated memory dumping techniques that might otherwise leak secrets or sensitive data.
Another key benefit centers on cryptographic keys that are **never exposed outside the enclave**. Only verified code running inside the enclave environment can run decryption or signing operations, and it can only do so while that specific code is running. This ensures that compromised hosts or rogue processes, even those with high-level privileges, are unable to intercept or misuse the keys because the keys remain strictly within the trusted boundary of the hardware.
Enclaves can also offer the power of **remote attestation**, allowing external clients or systems to confirm that they're speaking to an authentic, untampered enclave. By validating the hardware's integrity measurements and enclave-specific proofs, the remote party can be confident in the underlying security properties, an important guarantee in multi-tenant environments or whenever trust boundaries extend across different organizations and networks.
Beyond that, **reproducible builds** can create a verifiable fingerprint proving which binary runs in the enclave. This is a step above a simple "trust us" approach. Anyone can independently recreate the enclave image and verify the resulting cryptographic hash by using a reproducible build system (for example, [our NixOS-based solution](https://github.com/OpenSecretCloud/opensecret/blob/master/flake.nix?ref=blog.opensecret.cloud)). If it matches, then users and developers know precisely how code handles their data, boosting confidence that no hidden changes exist.
It's worth noting that although enclaves shield you from software devs, cloud providers, and insider threats, you do have to trust the **hardware vendor** (Intel, AMD, Apple, AWS, or NVIDIA) to implement their microcode and firmware securely. The entire enclave model could be theoretically undermined if a CPU maker's root keys or manufacturing process were compromised. Fortunately, these companies undergo extensive audits and firmware validations (often with third-party researchers), and their remote attestation mechanisms allow you to confirm specific firmware versions before trusting an enclave. While this adds a layer of "vendor trust," it's still a far more contained risk than trusting an entire operating system or cloud stack, so enclaves remain a strong step forward in practical, confidential computing.
## **How We Use Secure Enclaves**
Now that we've covered the general idea of enclaves let's look at how we specifically implement them in OpenSecret, our developer platform for handling user auth, private keys, data encryption, and AI workloads.
### **Our Stack: AWS Nitro + Nvidia TEE**
• **AWS Nitro Enclaves for the backend**: All critical logic, authentication, private key management, and data encryption/decryption run inside an AWS Nitro Enclave.
• **Nvidia Trusted Execution for AI**: For large AI inference (such as the Llama 3.3 70B model), we utilize Nvidia's GPU-based TEEs to protect even GPU memory. This means users can feed sensitive data to the AI model **without** exposing it in plaintext to the GPU providers or us as the operator. [Edgeless Systems](https://www.edgeless.systems/?ref=blog.opensecret.cloud) is our Nvidia TEE provider, and due to the power of enclave verification, we don't need to worry about who runs the GPUs. We know requests can't be inspected or tampered with.
### **End-to-End Encryption from Client to Enclave**
Client-side Enclave Attestation from Maple AI
Before login or data upload, the user/client verifies the **enclave attestation** from our platform. This process proves that the specific Nitro Enclave is genuine and runs the exact code we've published. You can check this out live on [Maple AI's attestation page](https://trymaple.ai/proof?ref=blog.opensecret.cloud).
Based on the attestation, the client establishes a secure ephemeral communication channel that only that enclave can decrypt. While we take advantage of SSL, it is typically not terminated inside the enclave itself. To ensure there's full encrypted data transfer all the way through to the enclave, we establish this additional handshake based on the attestation document that is used for all API requests during the client session.
From there, the user's credentials, private keys, and data pass through this secure channel directly into the enclave, where they are decrypted and processed according to the user's request.
### **In-Enclave Operations**
At the core of OpenSecret's approach is the conviction that security-critical tasks must happen inside the enclave, where even administrative privileges or hypervisor-level compromise cannot expose plaintext data. This encompasses everything from when a user logs in to creating and managing sensitive cryptographic keys. By confining these operations to a protected hardware boundary, developers can focus on building their applications without worrying about accidental data leaks, insider threats, or malicious attempts to harvest credentials. The enclave becomes the ultimate gatekeeper: it controls how data flows and ensures that nothing escapes in plain form.
User Auth Methods running inside Enclave
A primary example is **user authentication**. All sign-in workflows, including email/password, OAuth, and upcoming passkey-based methods, are handled entirely within the enclave. As soon as a user's credentials enter our platform through the encrypted channel, they are routed straight into the protected environment, bypassing the host's operating system or any potential snooping channels. From there, authentication and session details remain in the enclave, ensuring that privileged outsiders cannot intercept or modify them. By centralizing these identity flows within a sealed environment, developers can assure their users that no one outside the enclave (including the cloud provider or the app's own sysadmins) can peek at, tamper with, or access sensitive login information.
Main Enclave Operations in OpenSecret
The same principle applies to **private key management**. Whether keys are created fresh in the enclave or securely transferred into it, they remain sealed away from the rest of the system. Operations like digital signing or content decryption happen only within the hardware boundary, so raw keys never appear in any log, file system, or memory space outside the enclave. Developers retain the functionality they need, such as verifying user actions, encrypting data, or enabling secure transactions without ever exposing keys to a broader (and more vulnerable) attack surface. User backup options exist as well, where the keys can be securely passed to the end user.
Realtime Encrypted Data Sync on Multiple Devices
Another crucial aspect is **data encryption at rest**. While user data ultimately needs to be stored somewhere outside the enclave, the unencrypted form of that data only exists transiently inside the protected environment. Encryption and decryption routines run within the enclave, which holds the encryption keys strictly in memory under hardware guards. If a user uploads data, it is promptly secured before it leaves the enclave. When data is retrieved, it remains encrypted until it reenters the protected region and is passed back to the user through the secured communication channel. This ensures that even if someone gains access to the underlying storage or intercepts data in transit, they will see only meaningless ciphertext.
Confidential AI Workloads
Finally, **confidential AI workloads** build upon this same pattern: the Nitro enclave re-encrypts data so it can be processed inside a GPU-based trusted execution environment (TEE) for inference or other advanced computations. Sensitive data, like user-generated text or private documents, never appears in the clear on the host or within GPU memory outside the TEE boundary. When an AI process finishes, only the results are returned to the enclave, which can then relay them securely to the requesting user. By seamlessly chaining enclaves together, from CPU-based Nitro Enclaves to GPU-accelerated TEEs, we can deliver robust, hardware-enforced privacy for virtually any type of server-side or AI-driven operation.
### **Reproducible Builds + Verification**
Client verifies enclave attestation document
We build our enclaves on **NixOS** with reproducible builds, ensuring that anyone can verify that the binary we publish is indeed the binary running in the enclave. This build process is essential for proving we haven't snuck in malicious code to exfiltrate data or collect sensitive logs.
Our code is fully open source ([GitHub: OpenSecret](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud)), so you can audit or run it yourself. You can also verify that the cryptographic measurement the build process outputs matches the measurement reported by the enclave during attestation.
## **Putting It All Together**
OpenSecret Offering: Private Key Management, Encrypted Sync, Private AI, and Confidential Compute
By weaving secure enclaves into every step, from authentication to data handling to AI inference, we shift the burden of trust away from human policies and onto provable, hardware-based protections. For app developers, you can offer your users robust privacy guarantees without rewriting all your business logic or building an entire security stack from scratch. Whether you're storing user credentials or running complex operations on sensitive data, the enclave approach ensures plaintext remains inaccessible to even the most privileged parties outside the enclave boundary. Developers can focus on building great apps, while OpenSecret handles the cryptographic "lock and key" behind the scenes.
This model provides a secure-by-design environment for industries that demand strict data confidentiality, such as healthcare, fintech, cryptocurrency apps for secure key management, or decentralized identity platforms. Instead of worrying about memory dumps or backend tampering, you can trust that once data enters the enclave, it's sealed off from unauthorized eyes, including from the app developers themselves. And these safeguards don't just apply to niche use cases. Even general-purpose applications that handle login flows and user-generated content stand to benefit, especially as regulatory scrutiny grows around data privacy and insider threats.
Imagine a telehealth startup using OpenSecret enclaves to protect patient information for remote consultations. Not only would patient data remain encrypted at rest, but any AI-driven analytics to assist with diagnoses could be run privately within the enclave, ensuring no one outside the hardware boundary can peek at sensitive health records. A fintech company could similarly isolate confidential financial transactions, preventing even privileged insiders from viewing or tampering with raw transaction details. These real-world implementations give developers a clear path to adopting enclaves for serious privacy and compliance needs without overhauling their infrastructure.
OpenSecret aims to be a **full developer platform** with end-to-end security from day one. By incorporating user authentication, data storage, and GPU-based confidential AI into a single service, we eliminate many of the traditional hurdles in adopting enclaves. No more juggling separate tools for cryptographic key management, compliance controls, and runtime privacy. Instead, you get a unified stack that keeps data encrypted in transit, at rest, and in use.
Our solution also caters to the exploding demand for AI applications: with TEE-enabled GPU workloads, you can securely process sensitive data for text inference without ever exposing raw plaintext or sensitive documents to the host system.
The result is a new generation of apps that deliver advanced functionality, like real-time encrypted data sync or AI-driven insights, while preserving user privacy and meeting strict regulatory requirements. You don't have to rely on empty "trust us" promises because hardware enclaves, remote attestation, and reproducible builds collectively guarantee the code is running untampered. In short, OpenSecret offers the building blocks needed to create truly confidential services and experiences, allowing you to innovate while ensuring data protection remains ironclad.
## **Things to Come**
We're excited to build on our enclaved approach. Here's what's on our roadmap:
• **Production Launch**: We're using this in production now with [Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud) and have a developer preview playground up and running. We'll have the developer environment ready for production in a few months.\
• **Multi-Tenant Support**: Our platform currently works for single tenants, but we're opening this up so developers can onboard without needing a dedicated instance.\
• **Self-Serve Frontend**: A dev-friendly portal for provisioning apps, connecting OAuth or email providers, and managing users.\
• **External Key Signing Options**: Integrations with custom hardware security modules (HSMs) or customer-ran key managers that can only process data upon verifying the enclave attestation.\
• **Confidential Computing as a Service**: We'll expand our platform so that other developers can quickly create enclaves for specialized workloads without dealing with the complexities of Nitro or GPU TEEs.\
• **Additional SDKs**: In addition to our [JavaScript client-side SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud), we plan to launch official support for Rust, Python, Swift, Java, Go, and more.\
• **AI API Proxy with Attestation/Encryption**: We already provide an easy way to [access a Private AI through Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud), but we'd like to open this up more for existing tools and developers. We'll provide a proxy server that users can run on their local machines or servers that properly handle encryption to our OpenAI-compatible API.
## **Getting Started**
Ready to see enclaves in action? Here's how to dive in:\
1. **Run OpenSecret**: Check out our open-source repository at [OpenSecret on GitHub](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud). You can run your own enclaved environment or try it out locally with Docker.\
2. **Review Our SDK**: Our [JavaScript client SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud) makes it easy to handle sign-ins, put/get encrypted data, sign with user private keys, etc. It handles attestation verification and encryption under the hood, making the API integration seamless.\
3. **Play with Maple AI**: Try out [Maple AI](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/) as an example of an AI app built directly on OpenSecret. Your queries are encrypted end to end, and the Llama model sees them only inside the TEE.\
4. **Developer Preview**: Contact us if you want an invite to our early dev platform. We'll guide you through our SDK and give you access to the preview server. We'd love to build with you and incorporate your feedback as we develop this further.
## **Conclusion**
By merging secure enclaves (AWS Nitro and Nvidia GPU TEEs), user authentication, private key management, and an end-to-end verifiable encrypted approach, **OpenSecret** provides a powerful platform where we protect user data during collection, storage, and processing. Whether it's for standard user management, handling private cryptographic keys, or powering AI inference, the technology ensures that **no one**, not even us or the cloud provider, can snoop on data in use.
**We believe** this is the future of trustworthy computing in the cloud. And it's **all open source**, so you don't have to just take our word for it: you can see and verify everything yourself.
Do you have questions, feedback, or a use case you'd like to test out? Come join us on [GitHub](https://github.com/OpenSecretCloud?ref=blog.opensecret.cloud), [Discord](https://discord.gg/ch2gjZAMGy?ref=blog.opensecret.cloud), or email us for a developer preview. We can't wait to see what you build!
*Thank you for reading, and welcome to the era of enclaved computing.*
-

@ b83a28b7:35919450
2024-08-27 16:48:28
https://image.nostr.build/df0721d6d45d82db35d06663a0318ffe68c0b2b3c694888d23694efcc4255de5.gif
-

@ 8cb60e21:5f2deaea
2024-08-25 20:26:43
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/ZbOzQ0EiAZQ" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 57d1a264:69f1fee1
2025-03-24 17:08:06
Nice podcast with @sbddesign and @ConorOkus about bitcoin payments.
https://www.youtube.com/watch?v=GTSqoFKs1cE
In this episode, Conor, Open Source product manager at Spiral & Stephen, Product Designer at Voltage & Co founder of ATL Bitlab join Stephan to discuss the current state of Bitcoin user experience, particularly focusing on payments and the challenges faced by users. They explore the comparison between Bitcoin and physical cash, the Western perspective on Bitcoin payments, and the importance of user experience in facilitating Bitcoin transactions.
They also touch upon various payment protocols like #BOLT11, #LNURL, and #BOLT12, highlighting the need for interoperability and better privacy features in the Bitcoin ecosystem. The discussion also covers resources available for developers and designers to enhance wallet usability and integration.
@StephanLivera Official Podcast Episode: https://stephanlivera.com/646
### Takeaways
🔸Bitcoin has excelled as a savings technology.
🔸The payments use case for Bitcoin still needs improvement.
🔸User experience is crucial for Bitcoin adoption.
🔸Comparing Bitcoin to cash highlights privacy concerns.
🔸Western users may not see a payments problem.
🔸Regulatory issues impact Bitcoin payments in the West.
🔸User experience challenges hinder Bitcoin transactions.
🔸Different payment protocols create compatibility issues.
🔸Community collaboration is essential for Bitcoin's future.
🔸Improving interoperability can enhance Bitcoin payments. Wallet compatibility issues can create negative user impressions.
🔸Designers can significantly improve wallet user experience.
🔸Testing compatibility between wallets is essential for user satisfaction.
🔸Tether's integration may boost Bitcoin adoption.
🔸Developers should prioritize payment capabilities before receiving capabilities.
🔸Collaboration between designers and developers can lead to better products.
🔸User experience improvements can be low-hanging fruit for wallet projects.
🔸A global hackathon aims to promote miner decentralization.
🔸Resources like BOLT12 and the Bitcoin Design Guide are valuable for developers.
🔸Engaging with the community can lead to innovative solutions.
### Timestamps
([00:00](/watch?v=GTSqoFKs1cE)) - Intro
([01:10](/watch?v=GTSqoFKs1cE&t=70s)) - What is the current state of Bitcoin usage - Payments or Savings?
([04:32](/watch?v=GTSqoFKs1cE&t=272s)) - Comparing Bitcoin with physical cash
([07:08](/watch?v=GTSqoFKs1cE&t=428s)) - What is the western perspective on Bitcoin payments?
([11:30](/watch?v=GTSqoFKs1cE&t=690s)) - Would people use Bitcoin more with improved UX?
([17:05](/watch?v=GTSqoFKs1cE&t=1025s)) - Exploring payment protocols: Bolt11, LNURL, Bolt12 & BIP353
([30:14](/watch?v=GTSqoFKs1cE&t=1814s)) - Navigating Bitcoin wallet compatibility challenges
([34:45](/watch?v=GTSqoFKs1cE&t=2085s)) - What is the role of designers in wallet development?
([43:13](/watch?v=GTSqoFKs1cE&t=2593s)) - Rumble’s integration of Tether & Bitcoin; The impact of Tether on Bitcoin adoption
([51:22](/watch?v=GTSqoFKs1cE&t=3082s)) - Resources for wallet developers and designers
### Links:
• [https://x.com/conorokus](https://x.com/conorokus)
• [https://x.com/StephenDeLorme](https://x.com/StephenDeLorme)
• [https://bolt12.org/](https://bolt12.org/)
• [https://twelve.cash/](https://twelve.cash)
• [https://bitcoin.design/guide/](https://bitcoin.design/guide/)
• Setting Up Bitcoin Tips for Streamers](/watch?v=IWTpSN8IaLE)
originally posted at https://stacker.news/items/923714
-

@ 866e0139:6a9334e5
2025-03-24 10:50:59
**Autor:** *Ludwig F. Badenhagen.* *Dieser Beitrag wurde mit dem* *[Pareto-Client](https://pareto.space/read)* *geschrieben.*
***
Einer der wesentlichen Gründe dafür, dass während der „Corona-Pandemie“ so viele Menschen den Anweisungen der Spitzenpolitiker folgten, war sicher der, dass diese Menschen den Politikern vertrauten. Diese Menschen konnten sich nicht vorstellen, dass Spitzenpolitiker den Auftrag haben könnten, die Bürger analog klaren Vorgaben zu belügen, zu betrügen und sie vorsätzlich (tödlich) zu verletzen. Im Gegenteil, diese gutgläubigen Menschen waren mit der Zuversicht aufgewachsen, dass Spitzenpolitiker den Menschen dienen und deren Wohl im Fokus haben (müssen). Dies beteuerten Spitzenpolitiker schließlich stets in Talkshows und weiteren Medienformaten. Zwar wurden manche Politiker auch bei Fehlverhalten erwischt, aber hierbei ging es zumeist „nur“ um Geld und nicht um Leben. Und wenn es doch einmal um Leben ging, dann passieren die Verfehlungen „aus Versehen“, aber nicht mit Vorsatz. So oder so ähnlich dachte die Mehrheit der Bürger.
Aber vor 5 Jahren änderte sich für aufmerksame Menschen alles, denn analog dem Lockstep-Szenario der Rockefeller-Foundation wurde der zuvor ausgiebig vorbereitete Plan zur Inszenierung der „Corona-Pandemie“ Realität. Seitdem wurde so manchem Bürger, der sich jenseits von Mainstream-Medien informierte, das Ausmaß der unter dem Vorwand einer erfundenen Pandemie vollbrachten Taten klar. Und unverändert kommen täglich immer neue Erkenntnisse ans Licht. Auf den Punkt gebracht war die Inszenierung der „Corona-Pandemie“ ein Verbrechen an der Menschheit, konstatieren unabhängige Sachverständige.
Dieser Beitrag befasst sich allerdings nicht damit, die vielen Bestandteile dieses Verbrechens (nochmals) aufzuzählen oder weitere zu benennen. Stattdessen soll beleuchtet werden, warum die Spitzenpolitiker sich so verhalten haben und ob es überhaupt nach alledem möglich ist, der Politik jemals wieder zu vertrauen? Ferner ist es ein Anliegen dieses Artikels, die weiteren Zusammenhänge zu erörtern. Und zu guter Letzt soll dargelegt werden, warum sich der große Teil der Menschen unverändert alles gefallen lässt.
**Demokratie**
Von jeher organisierten sich Menschen mit dem Ziel, Ordnungsrahmen zu erschaffen, welche wechselseitiges Interagieren regeln. Dies führte aber stets dazu, dass einige wenige alle anderen unterordneten. Der Grundgedanke, der vor rund 2500 Jahren formulierten Demokratie, verfolgte dann aber das Ziel, dass die Masse darüber entscheiden können soll, wie sie leben und verwaltet werden möchte. Dieser Grundgedanke wurde von den Mächtigen sowohl gehasst als auch gefürchtet, denn die Gefahr lag nahe, dass die besitzlosen Vielen beispielsweise mit einer schlichten Abstimmung verfügen könnten, den Besitz der Wenigen zu enteignen. Selbst Sokrates war gegen solch eine Gesellschaftsordnung, da die besten Ideen nicht durch die Vielen, sondern durch einige wenige Kluge und Aufrichtige in die Welt kommen. Man müsse die Vielen lediglich manipulieren und würde auf diese Weise quasi jeden Unfug umsetzen können. Die Demokratie war ein Rohrkrepierer.
**Die Mogelpackung „Repräsentative Demokratie“**
Erst im Zuge der Gründung der USA gelang der Trick, dem Volk die „Repräsentative Demokratie“ unterzujubeln, die sich zwar nach Demokratie anhört, aber mit der Ursprungsdefinition nichts zu tun hat. Man konnte zwischen zwei Parteien wählen, die sich mit ihren jeweiligen Versprechen um die Gunst des Volkes bewarben. Tatsächlich paktierten die Vertreter der gewählten Parteien (Politiker) aber mit den wirklich Mächtigen, die letztendlich dafür sorgten, dass diese Politiker in die jeweiligen exponierten Positionen gelangten, welche ihnen ermöglichten (und somit auch den wirklich Mächtigen), Macht auszuüben. Übrigens, ob die eine oder andere Partei „den Volkswillen“ für sich gewinnen konnte, war für die wirklich Mächtigen weniger von Bedeutung, denn der Wille der wirklich Mächtigen wurde so oder so, wenn auch in voneinander differierenden Details, umgesetzt.
Die Menschen waren begeistert von dieser Idee, denn sie glaubten, dass sie selbst „der Souverän“ seien. Schluss mit Monarchie sowie sonstiger Fremdherrschaft und Unterdrückung.
Die Mächtigen waren ebenfalls begeistert, denn durch die Repräsentative Demokratie waren sie selbst nicht mehr in der Schusslinie, weil das Volk sich mit seinem Unmut fortan auf die Politiker konzentrierte. Da diese Politiker aber vielleicht nicht von einem selbst, sondern von vielen anderen Wahlberechtigten gewählt wurden, lenkte sich der Groll der Menschen nicht nur ab von den wirklich Mächtigen, sondern auch ab von den Politikern, direkt auf „die vielen Idioten“ aus ihrer eigenen Mitte, die sich „ver-wählt“ hatten. Diese Lenkung des Volkes funktionierte so hervorragend, dass andere Länder die Grundprinzipien dieses Steuerungsinstrumentes übernahmen. Dies ist alles bei Rainer Mausfeld nachzulesen.
Ursprünglich waren die Mächtigen nur regional mächtig, sodass das Führen der eigenen Menschen(vieh)herde eher eine lokale Angelegenheit war. Somit mussten auch nur lokale Probleme gelöst werden und die Mittel zur Problemlösung blieben im eigenen Problembereich.
***
JETZT ABONNIEREN:
***[Hier](https://pareto.space/u/friedenstaube@pareto.space)*** *können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).*
***
* Für **50 CHF/EURO** bekommen Sie ein Jahresabo der Friedenstaube.
* Für **120 CHF/EURO** bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
* Für **500 CHF/EURO** werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
* Ab **1000 CHF/EURO** werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
**Für Einzahlungen in CHF (Betreff: Friedenstaube):**
[](https://substackcdn.com/image/fetch/f_auto%2Cq_auto%3Agood%2Cfl_progressive%3Asteep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F3fdee17a-c22f-404e-a10c-7f87a7b8182a_2176x998.png)
**Für Einzahlungen in Euro:**
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
**Betreff: Friedenstaube**
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: <milosz@pareto.space> oder <kontakt@idw-europe.org>.
***
**Beherrschungsinstrumente der globalen Massenhaltung**
Im Zuge der territorialen Erweiterungen der „Besitzungen“ einiger wirklich Mächtiger wurden die Verwaltungs- und Beherrschungsinstrumente überregionaler. Und heute, zu Zeiten der globalen Vernetzung, paktieren die wirklich Mächtigen miteinander und beanspruchen die Weltherrschaft. Längst wird offen über die finale Realisierung einen Weltregierung, welche die Nationalstaaten „nicht mehr benötigt“, gesprochen. Dass sich Deutschland, ebenso wie andere europäische Staaten, der EU untergeordnet hat, dürfte auch Leuten nicht entgangen sein, die sich nur über die Tagesschau informieren. Längst steht das EU-Recht über dem deutschen Recht. Und nur kurze Zeit ist es her, als die EU und alle ihre Mitgliedsstaaten die WHO autonom darüber entscheiden lassen wollten, was eine Pandemie ist und wie diese für alle verbindlich „bekämpft“ werden soll. Eine spannende Frage ist nun, wer denn über der EU und der WHO sowie anderen Institutionen steht?
Diese Beschreibung macht klar, dass ein „souveränes Land“ wie das unverändert von der amerikanischen Armee besetzte Deutschland in der Entscheidungshierarchie an die Weisungen übergeordneter Entscheidungsorgane gebunden ist. An der Spitze stehen - wie kann es anders sein - die wirklich Mächtigen.
Aber was nützt es dann, Spitzenpolitiker zu wählen, wenn diese analog Horst Seehofer nichts zu melden haben? Ist das Wählen von Politikern nicht völlig sinnlos, wenn deren Wahlversprechen ohnehin nicht erfüllt werden? Ist es nicht so, dass die Menschen, welche ihre Stimme nicht behalten, sondern abgeben, das bestehende System nur nähren, indem sie Wahlergebnisse akzeptieren, ohne zu wissen, ob diese manipuliert wurden, aber mit der Gewissheit, dass das im Zuge des Wahlkampfes Versprochene auf keinen Fall geliefert wird? Aktive Wähler glauben trotz allem an die Redlichkeit und Wirksamkeit von Wahlen, und sie akzeptieren Wahlergebnisse, weil sie denken, dass sie von „so vielen Idioten, die falsch wählen“, umgeben sind, womit wir wieder bei der Spaltung sind. Sie glauben, der Stand des aktuellen Elends sei „selbst gewählt“.
**Die Wahl der Aufseher**
Stellen Sie sich bitte vor, Sie wären im Gefängnis, weil Sie einen kritischen Artikel mit „gefällt mir“ gekennzeichnet haben oder weil Sie eine „Kontaktschuld“ trifft, da in Ihrer Nachbarschaft ein „verschwörerisches Symbol“ von einem „aufmerksamen“ Nachbarn bei einer „Meldestelle“ angezeigt wurde oder Sie gar eine Tat, „unterhalb der Strafbarkeitsgrenze“ begangen hätten, dann würden Sie möglicherweise mit Maßnahmen bestraft, die „keine Folter wären“. Beispielsweise würde man Sie während Ihrer „Umerziehungshaft“ mit Waterboarding, Halten von Stresspositionen, Dunkelhaft etc. dabei „unterstützen“, „Ihre Verfehlungen zu überdenken“. Stellen Sie sich weiterhin vor, dass Sie, so wie alle anderen Inhaftierten, an der alle vier Jahre stattfindenden Wahl der Aufseher teilnehmen könnten, und Sie hätten auch einen Favoriten, der zwar Waterboarding betreibt, aber gegen alle anderen Maßnahmen steht. Sie hätten sicher allen Grund zur Freude, wenn Sie Ihren Kandidaten durchbringen könnten, oder? Aber was wäre, wenn der Aufseher Ihrer Wahl dann dennoch alle 3 „Nicht-Folter-Maßnahmen“ anwenden würde, wie sämtliche anderen Aufseher zuvor? Spätestens dann müssten Sie sich eingestehen, dass es der Beruf des Aufsehers ist, Aufseher zu sein und dass er letztendlich tut, was ihm „von oben“ aufgetragen wird. Andernfalls verliert er seinen Job. Oder er verunfallt oder gerät in einen Skandal etc. So oder so, er verliert seinen Job - und den erledigt dann ein anderer Aufseher.
Die Wahl des Aufsehers ändert wenig, solange Sie sich im System des Gefängnisses befinden und der Aufseher integraler Bestandteil dieses Systems ist. Zur Realisierung einer tatsächlichen Änderung müssten Sie dort herauskommen.
Dieses Beispiel soll darstellen, dass alles in Hierarchien eingebunden ist. Die in einem System eingebundenen Menschen erfüllen ihre zugewiesenen Aufgaben, oder sie werden bestraft.
**Das aktuelle System schadet dem Volk**
Auch in der staatlichen Organisation von Menschen existieren hierarchische Gliederungen. Eine kommunale Selbstverwaltung gehört zum Kreis, dieser zum Land, dieses zum Staat, dieser zur EU, und diese - zu wem auch immer. Und vereinnahmte Gelder fließen nach oben. Obwohl es natürlich wäre, dass die Mittel dorthin fließen, wo sie der Allgemeinheit und nicht einigen wenigen dienen, also nach unten.
Warum muss es also eine Weltregierung geben? Warum sollen nur einige Wenige über alle anderen bestimmen und an diesen verdienen (Nahrung, Medikamente, Krieg, Steuern etc.)? Warum sollen Menschen, so wie Vieh, das jemandem „gehört“, mit einem Code versehen und bereits als Baby zwangsgeimpft werden? Warum müssen alle Transaktionen und sämtliches Verhalten strickt gesteuert, kontrolliert und bewertet werden?
Viele Menschen werden nach alledem zu dem Schluss kommen, dass solch ein System nur einigen wenigen wirklich Mächtigen und deren Helfershelfern nützt. Aber es gibt auch eine Gruppe Menschen, für die im Land alles beanstandungsfrei funktioniert. Die Spaltung der Menschen ist perfekt gelungen und sofern die eine Gruppe darauf wartet, dass die andere „endlich aufwacht“, da die Fakten doch auf dem Tisch liegen, so wird sie weiter warten dürfen.
Julian Assange erwähnte einst, dass es für ihn eine unglaubliche Enttäuschung war, dass ihm niemand half. Assange hatte Ungeheuerlichkeiten aufgedeckt. Es gab keinen Aufstand. Assange wurde inhaftiert und gefoltert. Es gab keinen Aufstand. Assange sagte, er hätte nicht damit gerechnet, dass die Leute „so unglaublich feige“ seien.
Aber womit rechnete er den stattdessen? Dass die Massen „sich erheben“. Das gibt es nur im Film, denn die Masse besteht aus vielen maximal Indoktrinierten, die sich wie Schafe verhalten, was als Züchtungserfolg der Leute an den Schalthebeln der Macht und deren Herren, den wirklich Mächtigen, anzuerkennen ist. Denn wer mächtig ist und bleiben möchte, will sicher keine problematischen Untertanen, sondern eine gefügige, ängstliche Herde, die er nach Belieben ausbeuten und steuern kann. Wenn er hierüber verfügt, will er keinen Widerstand.
Ob Corona, Krieg, Demokratie- und Klimarettung oder Meinungsäußerungsverbote und Bürgerrechte, die unterhalb der Strafbarkeitsgrenze liegen, all diese und viele weitere Stichworte mehr sind es, die viele traurig und so manche wütend machen.
Auch das Mittel des Demonstrierens hat sich als völlig wirkungslos erwiesen. Die vielen gruseligen Videoaufnahmen über die massivsten Misshandlungen von Demonstranten gegen die Corona-Maßnahmen führen zu dem Ergebnis, dass die Exekutive ihr Gewaltmonopol nutzt(e), um die Bevölkerung gezielt zu verletzen und einzuschüchtern. Bekanntlich kann jede friedliche Demonstration zum Eskalieren gebracht werden, indem man Menschen in die Enge treibt (fehlender Sicherheitsabstand) und einige V-Leute in Zivil mit einschlägigen Flaggen und sonstigen „Symbolen“ einschleust, die für Krawall sorgen, damit die gepanzerten Kollegen dann losknüppeln und die scharfen Hunde zubeißen können. So lauten zumindest die Berichte vieler Zeitzeugen und so ist es auch auf vielen Videos zu sehen. Allerdings nicht im Mainstream.
Dieses Vorgehen ist deshalb besonders perfide, weil man den Deutschen ihre Wehrhaftigkeit aberzogen hat. Nicht wehrfähige Bürger und eine brutale Staatsmacht mit Gewaltmonopol führen zu einem Gemetzel bei den Bürgern.
Ähnliches lässt sich auch in zivilen Lebenssituationen beobachten, wenn die hiesige zivilisierte Bevölkerung auf „eingereiste“ Massenvergewaltiger und Messerstecher trifft, die über ein anderes Gewalt- und Rechtsverständnis verfügen als die Einheimischen.
**System-Technik**
Die These ist, dass es eine Gruppe von global agierenden Personen gibt, welche das Geschehen auf der Erde zunehmend wirksam zu ihrem individuellen Vorteil gestaltet. Wie sich diese Gruppe definiert, kann bei John Coleman (Das Komitee der 300) und David Icke nachgelesen werden. Hierbei handelt es ich um Autoren, die jahrzehntelang analog streng wissenschaftlichen Grundlagen zu ihren Themen geforscht haben und in ihren jeweiligen Werken sämtliche Quellen benennen. Diese Autoren wurden vom Mainstream mit dem Prädikatsmerkmal „Verschwörungstheoretiker“ ausgezeichnet, wodurch die Ergebnisse Ihrer Arbeiten umso glaubwürdiger sind.
Diese mächtige Gruppe hat mit ihren Schergen nahezu den gesamten Planeten infiltriert, indem sie Personen in führenden Positionen in vielen Belangen größtmögliche Freiheiten sowie Schutz gewährt, aber diesen im Gegenzug eine völlige Unterwerfung bei Kernthemen abfordert. Die Motivatoren für diese Unterwerfung sind, abgesehen von materiellen Zuwendungen, auch „Ruhm und Ehre sowie Macht“. Manchmal wird auch Beweismaterial für begangene Verfehlungen (Lolita-Express, Pizzagate etc.) genutzt, um Forderungen Nachdruck zu verleihen. Und auch körperliche Bestrafungen der betroffenen Person oder deren Angehörigen zählen zum Repertoire der Motivatoren. Letztendlich ähnlich den Verhaltensweisen in einem Mafia-Film.
Mit dieser Methodik hat sich diese mächtige Gruppe im Laufe von Jahrhunderten! eine Organisation erschaffen, welche aus Kirchen, Parteien, Firmen, NGO, Vereinen, Verbänden und weiteren Organisationsformen besteht. Bestimmte Ämter und Positionen in Organisationen können nur von Personen eingenommen und gehalten werden, die „auf Linie sind“.
Die Mitglieder der Gruppe tauchen in keiner Rubrik wie „Die reichsten Menschen der Welt“ auf, sondern bleiben fern der Öffentlichkeit. Wer jemanden aus ihren Reihen erkennt und beschuldigt, ist ein „Antisemit“ oder sonstiger Übeltäter und wird verfolgt und bekämpft. Über mächtige Vermögensverwaltungskonzerne beteiligen sich die Mitglieder dieser Gruppe anonym an Unternehmen in Schlüsselpositionen in einer Dimension, die ihnen wesentlichen Einfluss auf die Auswahl der Topmanager einräumt, sodass die jeweilige Unternehmenspolitik nach Vorgaben der Gruppe gestaltet wird.
Die Gruppe steuert das Geldsystem, von dem sich der Planet abhängig zu sein wähnt. Hierzu eine Erläuterung: Ein Staat wie Deutschland ist bekanntlich maximal verschuldet. Man stelle sich vor, ein unliebsamer Politiker würde entgegen sämtlicher „Brandmauern“ und sonstiger Propaganda und Wahlmanipulationen gewählt, das Land zu führen, dann könnte dieser keine Kredit über 500 Mrd. Euro bei der nächsten Sparkasse beantragen, sondern wäre auf die Mächtigen dieser Welt angewiesen. Jeder weiß, dass Deutschland als Staat kein funktionierendes Geschäftsmodell hat und somit nicht in der Lage ist, solch ein Darlehen zurückzuzahlen. Welche Motivation sollte also jemand haben, einem Land wie Deutschland so viel Geld ohne Aussicht auf Rückführung zu geben? Es leuchtet ein, dass dieser Politiker andere Gefälligkeiten anbieten müsste, um das Darlehen zu bekommen. Im Falle einer Weigerung zur Kooperation könnte der Staatsapparat mit seinen Staatsdienern, Bürgergeld- und Rentenempfänger etc. nicht mehr bezahlt werden und dieser Politiker wäre schnell wieder weg. Er würde medial hingerichtet. Es ist somit davon auszugehen, dass ein Spitzenpolitiker dieser Tage nicht über viele Optionen verfügt, denn er übernimmt eine Situation, die von seinen Vorgängern erschaffen wurde. Trotz alledem darauf zu hoffen, dass es einen anderen Politiker geben könnte, mit dem dann alles wieder gut wird, mutet ziemlich infantil an.
Dass ein Großteil der Medien von Zuwendungen abhängig ist, dürfte ebenfalls leicht nachzuvollziehen sein, denn der gewöhnliche Bürger zahlt nichts für den Content der MSM. Abhängig davon, von wem (Regierung, Philanthrop, Konzern etc.) ein Medium am Leben gehalten wird, gestalten sich auch dessen Inhalte. Und wenn angewiesen wird, dass ein Politiker medial hingerichtet werden soll, dann bedient die Maschinerie das Thema. Man beobachte einfach einmal, dass Politiker der Kartell-Parteien völlig anders behandelt werden als solche jenseits der „Brandmauer“. Und der Leser, der solche Auftragsarbeiten kostenlos liest, ist der Konsument, für dessen Indoktrination die Finanziers der Verlage gerne zahlen. Mittlerweile kann durch die Herrschaft über die Medien und die systematische Vergiftung der Körper und Geister der Population die öffentliche Meinung gesteuert werden. Die überwiegende Zahl der Deutschen scheint nicht mehr klar denken zu können.
Wer sich das aktuelle Geschehen in der deutschen Politik mit klarem Verstand ansieht, kommt nicht umhin, eine Fernsteuerung der handelnden Politiker in Betracht zu ziehen. Aber was soll daran verwundern? Sind es deshalb „böse Menschen“? Sind die in „Forschungslaboren“ arbeitenden Quäler von „Versuchstieren“ böse Menschen? Sind der Schlächter, der Folterer und der Henker böse Menschen? Oder der knüppelnde Polizist? Es handelt sich zunächst einmal um Personen, die einen Vorteil dadurch haben, Ihrer Tätigkeit nachzugehen. Sie sind integrale Bestandteile eines Belohnungssystems, welches von oben nach unten Anweisungen gibt. Und wenn diese Anweisungen nicht befolgt werden, führt dies für den Befehlsverweigerer zu Konsequenzen.
**Der klare Verstand**
Es ist nun eine spannende Frage, warum so viele Menschen sich solch eine Behandlung gefallen lassen? Nun, das ist relativ einfach, denn das angepasste Verhalten der Vielen ist nichts anderes als ein Züchtungserfolg der Wenigen.
Die Psyche der Menschen ist ebenso akribisch erforscht worden wie deren Körperfunktionen. Würden die Menschen von den wirklich Mächtigen geliebt, dann würde genau gewusst, wie sie zu behandeln und mit ihren jeweiligen Bedürfnissen zu versorgen sind. Stattdessen werden die Menschen aber als eine Einnahmequelle betrachtet. Dies manifestiert sich exemplarisch in folgenden Bereichen:
1. Das Gesundheitssystem verdient nichts am gesunden Menschen, sondern nur am (dauerhaft) kranken, der um Schmerzlinderung bettelt. Bereits als Baby werden Menschen geimpft, was die jeweilige Gesundheit (mit Verweis auf die Werke von Anita Petek-Dimmer u. a.) nachhaltig negativ beeinflusst. Wer hat denn heute keine Krankheiten? Die „Experten“ des Gesundheitssystems verteufeln Vitamin D, Vitamin C, Lithium, die Sonne, Natur etc. und empfehlen stattdessen Präparate, die man patentieren konnte und mit denen die Hersteller viel Geld verdienen. Die Präparate heilen selten, sondern lindern bestenfalls zuvor künstlich erzeugte Leiden, und müssen oftmals dauerhaft eingenommen werden. Was ist aus den nicht Geimpften geworden, die alle sterben sollten? Sind diese nicht die einzigen Gesunden dieser Tage? Ist nicht jeder Geimpfte entweder permanent krank oder bereits tot? Abgesehen von denen, welche das Glück hatten, „Sonderchargen“ mit Kochsalz zu erhalten. \
\
Wem gehören die wesentlichen Player im Gesundheitswesen zu einem erheblichen Teil? Die Vermögensverwalter der wirklich Mächtigen.
2. Ähnlich gestaltet es sich bei der Ernährungsindustrie. Die von dort aus verabreichten Produkte sind die Ursachen für den Gesundheitszustand der deutschen Population. Das ist aber auch irgendwie logisch, denn wer sich nicht falsch ernährt und gesund bleibt, wird kein Kunde des Gesundheitswesens. \
\
Die Besitzverhältnisse in der Ernährungsindustrie ähneln denen im Gesundheitswesen, sodass am gleichen Kunden gearbeitet und verdient wird.
3. Die Aufzählung konnte nun über die meisten Branchen, in denen mit dem Elend der Menschen viel verdient werden kann, fortgesetzt werden. Waffen (BlackRock erhöhte beispielsweise seine Anteile an der Rheinmetall AG im Juni 2024 auf 5,25 Prozent. Der US-Vermögensverwalter ist damit der zweitgrößte Anteilseigner nach der französischen Großbank Société Générale.), Energie, Umwelt, Technologie, IT, Software, KI, Handel etc.
Wie genau Chemtrails und Technologien wie 5G auf den Menschen und die Tiere wirken, ist ebenfalls umstritten. Aber ist es nicht seltsam, wie krank, empathielos, antriebslos und aggressiv viele Menschen heute sind? Was genau verabreicht man der Berliner Polizei, damit diese ihre Prügelorgien auf den Rücken und in den Gesichtern der Menschen wahrnehmen, die friedlich ihre Demonstrationsrechte wahrnehmen? Und was erhalten die ganzen zugereisten „Fachkräfte“, die mit Ihren Autos in Menschenmengen rasen oder auch Kinder und Erwachsene niedermessern?
Das Titelbild dieses Beitrags zeigt einige Gebilde, welche regelmäßig bei Obduktionen von Geimpften in deren Blutgefäßen gefunden werden. Wie genau wirken diese kleinen Monster? Können wir Menschen ihr Unverständnis und ihr Nicht-Aufwachen vorwerfen, wenn wir erkennen, dass diese Menschen maximal vergiftet wurden? Oder sollten einfach Lösungen für die Probleme dieser Zeit auch ohne den Einbezug derer gefunden werden, die offenbar nicht mehr Herr ihrer Sinne sind?
**Die Ziele der wirklich Mächtigen**
Wer sich entsprechende Videosequenzen der Bilderberger, des WEF und anderen „Überorganisationen“ ansieht, der erkennt schnell das Muster:
* Reduzierung der Weltpopulation um ca. 80 Prozent
* Zusammenbruch der Wirtschaft, damit diese von den Konzernen übernommen werden kann.
* Zusammenbruch der öffentlichen Ordnung, um eine totale Entwaffnung und eine totale Überwachung durchsetzen zu können.
* Zusammenbruch der Regierungen, damit die Weltregierung übernehmen kann.
Es ist zu überdenken, ob die Weltregierung tatsächlich das für die Vielen beste Organisationssystem ist, oder ob die dezentrale Eigenorganisation der jeweils lokalen Bevölkerung nicht doch die bessere Option darstellt. Baustellen würden nicht nur begonnen, sondern auch schnell abgearbeitet. Jede Region könnte bestimmen, ob sie sich mit Chemtrails und anderen Substanzen besprühen lassen möchte. Und die Probleme in Barcelona könnte die Menschen dort viel besser lösen als irgendwelche wirklich Mächtigen in ihren Elfenbeintürmen. Die lokale Wirtschaft könnte wieder zurückkommen und mit dieser die Eigenständigkeit. Denn die den wirklich Mächtigen über ihre Vermögensverwalter gehörenden Großkonzerne haben offensichtlich nicht das Wohl der Bevölkerung im Fokus, sondern eher deren Ausbeutung.
Das Aussteigen aus dem System ist die wahre Herkulesaufgabe und es bedarf sicher Mut und Klugheit, sich dieser zu stellen. Die Politiker, die unverändert die Narrative der wirklich Mächtigen bedienen, sind hierfür denkbar ungeeignet, denn sie verfolgen kein Lebensmodell, welches sich von Liebe und Mitgefühl geleitet in den Dienst der Gesamtheit von Menschen, Tieren und Natur stellt.
Schauen Sie einmal genau hin, denken Sie nach und fühlen Sie mit.
**Was tun?**
Jedes System funktioniert nur so lange, wie es unterstützt wird. Somit stellt sich die Frage, wie viele Menschen das System ignorieren müssen, damit es kollabiert, und auf welche Weise dieses Ignorieren durchzuführen ist? Merkbar ist, dass die große Masse der Verwaltungsangestellten krank und oder unmotiviert und somit nicht wirksam ist. Würden die entsprechenden Stellen massiv belastet und parallel hierzu keine Einnahmen mehr realisieren, wäre ein Kollaps nah. Die Prügelpolizisten aus Berlin können nicht überall sein und normale Polizisten arbeiten nicht gegen unbescholtene Bürger, sondern sorgen sich selbst um ihre Zukunft. Gewalt ist sicher keine Lösung, und sicher auch nicht erforderlich.
Wie eine gerechte Verwaltungsform aufgebaut werden muss? Einfach so, wie sie in den hiesigen Gesetzen beschrieben steht. Aber eine solche Organisationsform muss frei sein von Blockparteien und korrupten Politikern und weisungsgebundenen Richtern etc. Stattdessen werden Menschen benötigt, welche die Menschen lieben und ihnen nicht schaden wollen. Außerdem sollten diese Führungspersonen auch wirklich etwas können, und nicht nur „Politiker“ ohne weitere Berufserfahrungen sein.
***
Ludwig F. Badenhagen (Pseudonym, Name ist der Redaktion bekannt).
*Der Autor hat deutsche Wurzeln und betrachtet das Geschehen in Deutschland und Europa aus seiner Wahlheimat Südafrika. Seine Informationen bezieht er aus verlässlichen Quellen und insbesondere von Menschen, die als „Verschwörungstheoretiker“, „Nazi“, „Antisemit“ sowie mit weiteren Kampfbegriffen der dortigen Systemakteure wie Politiker und „Journalisten“ diffamiert werden. Solche Diffamierungen sind für ihn ein Prädikatsmerkmal. Er ist international agierender Manager mit einem globalen Netzwerk und verfügt hierdurch über tiefe Einblicke in Konzerne und Politik.*
***
**Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Start.](https://start.njump.me/)**
-

@ a012dc82:6458a70d
2025-03-28 16:15:06
In an audacious display of confidence, Bitcoin traders have recently committed $20 million to a $200K call option, a move that has reignited discussions about the cryptocurrency's potential and the broader market's appetite for risk. This development is set against a backdrop of increasing activity within the cryptocurrency options market, particularly on platforms like Deribit, where total open interest in Bitcoin options has reached unprecedented levels. This article explores the nuances of this strategic wager, examines the resurgence of investor enthusiasm, and contemplates the future implications for Bitcoin and the cryptocurrency market at large.
**Table of Contents**
- A Surge in Market Activity
- The Bold Bet on Bitcoin's Future
- Implications of the $200K Call Option
- Increased Market Volatility
- Renewed Investor Confidence
- Speculative Interest and Market Dynamics
- Looking Ahead: Bitcoin's Market Prospects
- Conclusion
- FAQs
**A Surge in Market Activity**
The cryptocurrency options market has experienced a significant uptick in activity, with Bitcoin and Ethereum options achieving record-breaking open interest figures. On Deribit, Bitcoin options open interest has soared to a staggering $20.4 billion, eclipsing the previous high of $14.36 billion seen in October 2021. Concurrently, Ethereum options open interest has also reached a historic peak of $11.66 billion. This pronounced increase in market activity is indicative of a growing interest among traders to either hedge their positions against potential price fluctuations or to speculate on the future price movements of these leading cryptocurrencies. The surge in options trading volume reflects a broader trend of maturation within the cryptocurrency market, as sophisticated financial instruments become increasingly utilized by a diverse array of market participants, from individual investors to large institutional players.
**The Bold Bet on Bitcoin's Future**
The decision by traders to allocate $20 million to a $200K call option for Bitcoin represents a significant vote of confidence in the cryptocurrency's future price trajectory. This high-stakes gamble suggests that a segment of the market is not only optimistic about Bitcoin's potential to breach the $200,000 threshold but is also willing to back this belief with substantial financial commitment. Such a move is emblematic of the "animal spirits" returning to the cryptocurrency market—a term coined by economist John Maynard Keynes to describe the instinctive human emotion that drives consumer confidence and investment decisions. This resurgence of speculative fervor and risk-taking behavior is a testament to the enduring allure of Bitcoin as an asset class that continues to captivate the imagination of investors, despite its history of volatility and regulatory challenges.
**Implications of the $200K Call Option**
The substantial investment in the $200K call option carries several implications for the Bitcoin market and the broader cryptocurrency ecosystem:
**Increased Market Volatility**
The focus on high strike price options could introduce heightened volatility into the Bitcoin market. As traders position themselves to capitalize on potential price movements, the market may witness more pronounced fluctuations. This environment of increased volatility underscores the speculative nature of cryptocurrency trading and the high-risk, high-reward strategies employed by some market participants. It also highlights the need for investors to approach the market with caution, armed with a thorough understanding of the underlying risks and a clear investment strategy.
**Renewed Investor Confidence**
The bold wager on the $200K call option reflects a significant resurgence in investor confidence in Bitcoin's long-term prospects. Following periods of market downturns and regulatory uncertainty, this move signals a renewed conviction in the fundamental value proposition of Bitcoin as a pioneering digital asset. It represents a collective belief in the cryptocurrency's ability to not only recover from past setbacks but to chart new territories in terms of price and market capitalization. This renewed investor confidence may serve as a catalyst for further investment in Bitcoin and other cryptocurrencies, potentially driving up prices and encouraging more widespread adoption.
**Speculative Interest and Market Dynamics**
The commitment to the $200K call option highlights the continued influence of speculative interest on the cryptocurrency market's dynamics. It illustrates how speculation, driven by the prospect of outsized returns, remains a central force shaping market trends and price trajectories. This speculative interest, while contributing to market liquidity and price discovery, also introduces an element of unpredictability. It underscores the complex interplay between market sentiment, investor behavior, and external economic factors that collectively determine the direction of the cryptocurrency market.
**Looking Ahead: Bitcoin's Market Prospects**
The strategic bet on the $200K call option, amidst a backdrop of increasing options market activity, paints a complex picture of Bitcoin's future. While the move signals optimism and a willingness among investors to engage in high-risk speculation, it also raises questions about the sustainability of such bullish sentiment. As Bitcoin continues to navigate the evolving landscape of digital finance, the interplay between speculative interest, regulatory developments, and technological advancements will be critical in shaping its future trajectory. The cryptocurrency market's inherent volatility and unpredictability necessitate a cautious approach from investors, emphasizing the importance of risk management and long-term strategic planning.
**Conclusion**
Bitcoin's latest foray into high-stakes speculation, marked by the $20 million lock on the $200K call option, is a vivid illustration of the cryptocurrency's enduring appeal and the market's appetite for risk. This development not only reflects a bullish outlook on Bitcoin's price potential but also signals a broader resurgence of investor enthusiasm and speculative activity within the cryptocurrency market. As we look to the future, the outcomes of such bold moves will undoubtedly influence the trajectory of Bitcoin and the digital asset landscape at large. Whether Bitcoin will reach the lofty heights of $200,000 remains to be seen, but its journey there will be closely watched by traders, investors, and regulators alike, offering valuable insights into the dynamics of speculative markets and the evolving role of cryptocurrencies in the global financial ecosystem.
**FAQs**
**What does locking $20 million in a $200K call option mean for Bitcoin?**
Locking $20 million in a $200K call option indicates that traders are betting a significant amount of money on Bitcoin reaching or surpassing $200,000. It reflects a bullish outlook on Bitcoin's future price and a resurgence of speculative interest in the cryptocurrency market.
**How does the surge in Bitcoin options market activity affect the cryptocurrency?**
The surge in Bitcoin options market activity, with record open interest, increases market liquidity and can lead to heightened volatility. It also signifies growing interest and participation in the cryptocurrency market, potentially influencing Bitcoin's price dynamics.
**What are the implications of increased market volatility for Bitcoin investors?**
Increased market volatility can lead to larger price swings, presenting both opportunities and risks for investors. While it may offer the potential for higher returns, it also increases the risk of losses. Investors should approach the market with caution and consider their risk tolerance and investment strategy.
**Why are investors optimistic about Bitcoin reaching $200,000?**
Investors' optimism about Bitcoin reaching $200,000 stems from factors such as the cryptocurrency's past performance, the upcoming Bitcoin halving event, increasing institutional adoption, and favorable macroeconomic conditions. These factors contribute to a bullish sentiment in the market.
**What role do institutional investors play in the current Bitcoin market trend?**
Institutional investors play a significant role in the current Bitcoin market trend by bringing in substantial capital, lending credibility to the market, and influencing price movements. Their participation is seen as a sign of maturity and stability in the cryptocurrency market.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnewsco](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co/](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@thebitcoinlibertarian](https://www.youtube.com/@thebitcoinlibertarian)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
**Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats
link: https://signup.theorangepillapp.com/opa/croxroad**
**Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad”
link: https://bitcoinbook.shop?ref=21croxroad**
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
-

@ 57d1a264:69f1fee1
2025-03-23 12:24:46
https://www.youtube.com/watch?v=obXEnyQ_Veg



source: https://media.jaguar.com/news/2024/11/fearless-exuberant-compelling-jaguar-reimagined-0
originally posted at https://stacker.news/items/922356
-

@ 3eba5ef4:751f23ae
2025-03-28 01:42:07
## Crypto Insights
### Proposal and Discussion on Introducing a New Bitcoin Script Opcode: OP\_ISSUBSTR
[This BIP](https://groups.google.com/g/bitcoindev/c/Ls9DWtDRbDc) proposes the introduction of two new opcodes: OP\_ISSUBSTR and OP\_ISSUBSTRVERIFY. Their relationship is similar to OP\_EQUAL and OP\_EQUALVERIFY used to determine whether one string is a substring of another. Bitcoin developers have mixed opinions on this.
**Supporters:**
* **Enhancing script functionality:** Enables direct on-chain string operations, reducing reliance on off-chain processing and centralized dependencies.
* **Simplifies certain use cases:** Some applications (e.g., verifying if a public key contains a specific substring) would be easier to implement with OP\_ISSUBSTR.
* **OP\_CAT is not a perfect substitute:** Although OP\_CAT can be used for string operations, it has security concerns and limitations, such as stack size limits.
**Opponents:**
* **Bitcoin Script is for validation, not computation:** Peter Todd argues that substring searching can be achieved using concatenation (OP\_CAT) and equality checks (OP\_EQUAL), making OP\_ISSUBSTR unnecessary.
* **Alternative script solutions exist:** Some developers demonstrated that the proposed functionality can be emulated by having the script reconstruct the original string with known and unknown parts.
* **Potential stack management issues:** Concerns exist regarding stack size limits and whether OP\_ISSUBSTR offers sufficient benefits.
### Discussion on Bitcoin’s Next Major Upgrade: Evaluating OP\_CAT and OP\_CTV
This [analysis](https://www.galaxy.com/insights/research/bitcoins-next-major-upgrade-op-cat-and-op-ctv/) explores Bitcoin’s potential next major upgrade: OP\_CAT (BIP 347) and OP\_CTV (BIP 119). Both aim to enhance Bitcoin’s transaction programmability by enabling spending conditions on transaction outputs, improving script expressiveness.
The report explains how OP\_CAT enables recursive contracts and trustless Bitcoin bridges, supporting BitVM development, while OP\_CTV improves efficiency for vaults and rollup-based complex transactions.
It predicts that Bitcoin Core developers are expected to reach consensus on adding OP\_CAT or OP\_CTV this year, but due to the extensive activation process, actual implementation may take 1–2 years.
### Implementing Post-Signature Cross-Input Scripting in Bitcoin Using Taproot Annex
A new method has been [proposed](https://delvingbitcoin.org/t/post-signature-cross-input-scripting-using-the-taproot-annex/1520/1) to introduce cross-input scripting using Taproot [annex](https://bitcoinops.org/en/topics/annex/). This allows users to commit to additional spending conditions when signing transactions, expanding Bitcoin scripting capabilities and transaction flexibility.
### Can Orphan Block Reporting Effectively Prevent Selfish Mining? A Complex Reality
A common belief is that incorporating orphan block counts in Bitcoin’s Difficulty Adjustment Mechanism (DAM) can make selfish mining unprofitable. However, this study refutes that view by analyzing the time-averaged profit of selfish mining.
The research also introduces two improved DAM models considering both main-chain and orphaned blocks, along with two smart intermittent selfish mining strategies—one outperforming standard intermittent selfish mining and the other remaining profitable under the modified DAM.
Additionally, the study describes an "orphan exclusion attack," where attackers prevent honest miners from reporting orphan blocks. Using combinatorial tools, the research examines the profitability of selfish mining under the improved DAM when combined with orphan exclusion attacks. Results indicate that even with orphan block inclusion, selfish mining remains profitable. However, under the modifed DAM, profitability significantly decreases compared to Bitcoin's current DAM, suggesting that orphan block reporting can be an effective mitigation strategy against a payoff-maximizing selfish miner.
Read the [full paper](https://eprint.iacr.org/2024/363.pdf).
### LND Introduces Rewritten Sweeper Subsystem to Optimize Batch Transactions and Fee Bumping
[According to the author](https://delvingbitcoin.org/t/lnds-deadline-aware-budget-sweeper/1512), starting from v0.18.0, Lightning Network Daemon (LND) will completely revamp its sweeper subsystem for managing transaction batching and fee bumping.
The new sweeper integrates HTLC deadlines and fee budgets to compute a fee rate curve, dynamically adjusting fees based on transaction urgency. This new fee bumping strategy provides security benefits that other Lightning Network implementations may find valuable to adopt.
### Analysis of Invalid Mining by AntPool and Associated Pools
[boerst observed](https://x.com/boerst/status/1899102559161520497) unusual block templates submitted at height [885797](https://stratum.work/height/885797) by Antpool, CloverPool, Ultimus, Rawpool, and Poolin. The anomalies suggest possible selfish mining or template code issues. Suspicious signs include:
* Empty Merkle branches, yet the coinbase output total exceeds the subsidy, implying fees are being collected for non-existent transactions.
* The previous block hash for these is different from the rest of the pools and points to a block that seems to have never made it into the chain.
[b10c's analysis](http://b10c.me/observations/14-antpool-and-friends-invalid-mining-jobs/) suggests this may be a bug in AntPool’s coinbase transaction creation process. The findings indicate these pools may be operated by the same entity. It might be time to refer to AntPool and its associated pools (Braiins, Poolin, Binance Pool, and Ultimus, among others) collectively as "AntPool & Friends."
### Payjoin Roadmap: From a Two-Party Protocol to a Multi-Party Collaboration Model
The Payjoin Dev Kit (PDK) team [outlined](https://payjoindevkit.org/2025/03/18/the-evolution-of-payjoin/) the evolution of [Payjoin](https://bitcoinops.org/en/topics/payjoin/) from a two-party protocol to a multi-party framework. Payjoin V3 will address the limitations of the two-party model by introducing a collaboration model. The final goal is a "coalition formation protocol" that allows unconnected Bitcoin users to contribute to batch transactions.
The four development stages are:
* Stage 0: Multi-sender, single-receiver (current stage)
* Stage 1: Multi-sender, multi-receiver
* Stage 2: Privacy optimization
* Stage 3: Decentralized market mechanism—developing a coalition formation protocol to enable unconnected Bitcoin users to contribute to batch transactions
### Embedding Sats into Memes and Emojis
[This article](https://lightning.news/money-inside-memes-and-emojis/) explores how [memeamigo.lol](https://memeamigo.lol/) encodes Bitcoin-based Cashu into memes, embedding sats into emojis and memes like [this](https://x.com/L0laL33tz/status/1897402057209868606) and [this](https://x.com/callebtc/status/1897386585127313874).
### Complete Guide to Buying Bitcoin Anonymously
[The author](https://blockdyor.com/buy-bitcoin-anonymously/) compares several Bitcoin exchanges, categorizing them based on decentralization and peer-to-peer features:
* Decentralized & P2P
* Centralized & P2P
* Centralized & non-P2P (light KYC)
Each type has its own advantages and drawbacks, and the best choice depends on the user’s priorities regarding privacy, ease of use, and legal compliance.

### Global Cryptocurrency Tax Map
[Hellosafe.ca](http://Hellosafe.ca) provides a [global crypto tax map](https://hellosafe.ca/en/investing/cryptocurrency/map-taxation-world), offering an overview of different tax policies worldwide.
### Binance Report: The Future of Bitcoin—DeFi
Binance released a [report on Bitcoin DeFi](https://public.bnbstatic.com/static/files/research/the-future-of-bitcoin-4-defi.pdf). Key takeaways include:
* **Security Budget & the Role of BTCFi**: With Bitcoin’s block rewards continuously halving, its security model faces long-term sustainability challenges. BTCFi helps sustain miner incentives by increasing on-chain transaction fees, thereby strengthening Bitcoin’s long-term security budget.
* **Infrastructure as a Bottleneck**: Bitcoin L2s are still in their early stages and require further development, adoption, and liquidity incentives to scale effectively.
* **Liquidity & Institutional Interest**: Bitcoin investors have traditionally been long-term holders, posing challenges for liquidity provisioning. New incentive mechanisms are needed to activate idle BTC funds. While institutional investors have shown initial interest, large-scale adoption depends on regulatory clarity and user-friendly solutions.
* **Cross-Chain Interoperability is Crucial**: Most Bitcoin used in DeFi currently exists as Wrapped BTC on Ethereum and other chains. BTCFi needs secure cross-chain solutions to bridge liquidity and attract users from existing DeFi ecosystems.
* **BTCFi Needs Its Own Path**: Unlike Ethereum’s DeFi ecosystem, BTCFi cannot simply replicate existing models. Its success may rely on tailored solutions that align with Bitcoin holders' needs, particularly in yield generation, payments, and institutional-grade products.
## Top Reads on Blockchain and Beyond
### Infinite Recursion of Trust: Reflections on Trust
In [Reflections on Trusting Trust](https://www.cs.cmu.edu/~rdriley/487/papers/Thompson_1984_ReflectionsonTrustingTrust.pdf), Ken Thompson reveals the fragility of software trust. By describing a potential "Trojan horse" attack, he highlights a philosophical and technical dilemma: verifying a system’s trustworthiness requires a trusted tool, but that tool itself needs another tool for verification—leading to infinite recursion. Ultimately, trust must be placed in a foundational layer, which may itself be unverifiable.
### Contextual Trust Networks and Privacy: A Critical Analysis of Metadata, Surveillance, and Routing Dynamics in Decentralized Systems
[This article](https://x.com/BitcoinErrorLog/status/1903769658781556903) critically examines contextual trust networks as an alternative to traditional privacy protection techniques in decentralized systems like Bitcoin and P2P networks. It first highlights inherent privacy limitations in popular anonymity-enhancing methods:
* **CoinJoin and Mixnets**: Rely on anonymity sets but remain vulnerable to metadata correlation at ingress and egress points, providing surveillance opportunities for adversaries.
* **Onion Routing (Tor)**: Tor reduces direct metadata exposure but is still susceptible to persistent statistical traffic analysis at entry and exit nodes, compromising anonymity over time.
* **Distributed Hash Tables (DHTs)**: Broadcast metadata widely, inherently increasing visibility and surveillance risks.
The author then contrasts these with the contextual trust concept introduced by the Atomicity protocol. The analysis suggests that witness-generated metadata is a primary privacy risk and argues that contextual trust channels can enhance privacy by controlling witness selection and excluding irrelevant nodes during transaction routing.
-

@ bf95e1a4:ebdcc848
2025-03-28 13:56:06
This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our[ Geyser page](https://geyser.fund/project/infinity)!
## Financial Atheism
“Don’t trust, verify” is a common saying amongst bitcoiners that represents a sound attitude towards not only Bitcoin but all human power structures. In order to understand Bitcoin, one must admit that everything in society is man-made. Every civilization, every religion, every constitution, and every law is a product of human imagination. It wasn’t until as late as the 17th century that the scientific method started to become the dominant practice for describing how the world actually worked. Peer-to-peer review and repeated testing of a hypothesis are still quite recent human practices. Before this, we were basically just guessing and trusting authorities to a large extent. We still do this today, and despite our progress over the last couple of centuries, we still have a long way to go. Our brains are hardwired to follow the leader of the pack. The human brain is born with a plethora of cognitive biases pre-installed, and we have to work very hard to overcome them. We evolved to survive in relatively small groups, and our brains are thus not really made for seeing the bigger picture. Bitcoin’s proof-of-work algorithm is constructed in such a way that it is easy to verify that computational power was sacrificed in order to approve a block of transactions and claim its reward. In this way, no trust in any authority is required as it is relatively trivial to test the validity of a block and the transactions it contains. This is nothing short of a complete reimagining of how human society ought to be governed. The beauty of mathematics governs the Bitcoin system. Everything that ever happens in Bitcoin is open and verifiable to everyone, even to those who are not yet using it.
After the tragic events of 9/11 in 2001, Sam Harris started writing his book *The End of Faith*, which happened to be released around the same time as Richard Dawkins’ *The God Delusion*, Daniel Dennett's *Breaking the Spell*, and Christopher Hitchens’ *God Is Not Great: How Religion Poisons Everything*. These books kick-started what, in hindsight, has often been referred to as the new atheist movement, even though there has arguably never been anything new about atheism. Atheism must almost certainly have preceded religion since religious ideas require the person holding the idea to believe a certain doctrine or story. Atheism is nothing but the rejection of ways to describe the world that are not verifiable by experimentation. A fly on the wall is probably an atheist by this definition of the word. Atheism is often accused of being just another set of beliefs, but the word itself describes what it is much better — a lack of belief in theistic ideas. It is not a code of conduct or set of rules to live your life by; it is simply the rejection of that which cannot be scientifically verified. Many people, religious people, in particular, have a hard time grasping this. If you believe that a supernatural entity created everything in everyone's life, you might not be too comfortable with a word that describes a complete rejection of what you believe created everything, including the very atheist that the word describes. The amount of different religious worldviews that exist is probably equal to the sum of all religious people on the planet, but all world views that reject these superstitious beliefs require but one word. Atheism is not the opposite of religion but is simply the lack of it.
In 2008, another sub-culture movement of unbelief was born. Let’s call it *Financial Atheism* — the rejection of unverifiable value claims. With the invention of Bitcoin, a way of rejecting fraudulent expressions of a token’s value was born. Those of us fortunate enough to have been born in secular countries all enjoy not having the ideas of religious demagogues dictating our lives on a daily basis. We can choose which ideas to believe in and which to reject. What we still have very limited means of choosing, however, are the ways in which we express value to each other. We’re told to use a system in which we all have a certain number of value tokens assigned to our name, either as a number on a screen or as digits on paper notes. We all live in the collective hallucination that these numbers are somehow legit and that their authenticity is not to be questioned.
A Bitcoin balance assigned to a certain Bitcoin address might seem just as questionable to a layman, but if you have a basic understanding of the hashing algorithms and game theory behind it, it’s not. At the time of writing, the hash of the latest block on the Bitcoin blockchain begins with eighteen zeros in a row. These zeros represent the Proof of Work that ensures that this block is valid and that every transaction in it actually happened. If you can grasp the concept of a hashing algorithm, and if you have an intuition about mathematics, you realize the gargantuan amount of calculating effort that went into finding this particular hash. It is simply mind-blowing. To forge a false version of a hash beginning with eighteen zeros just wouldn’t be economically viable. Of course, you can never actually know that a 51% attack or some other attempt at corrupting the blockchain hasn’t occurred, but you can know that such an attack would require more than half of the network acting against their own economic interest. Bitcoin is not something to believe in. You don’t need to trust any authority because you can validate the plausibility of its authenticity yourself. It’s the financial equivalent of atheism or unbelief. Satoshi wasn’t Jesus. Satoshi was Brian of Nazareth, telling his followers to think for themselves.
The first law of thermodynamics, also known as the Law of Conservation of Energy, states that energy cannot be created or destroyed in an isolated system. The second law states that the entropy of any isolated system always increases, and the third law states that the entropy of a system approaches a constant value as the temperature approaches absolute zero. In the Bitcoin network, participants known as miners compete for new Bitcoin in a lottery with very fixed rules. The more hashing power (computing power) a miner contributes to the network, the higher his chances of winning the block reward, a specific amount of Bitcoin that is halved every four years. The difficulty of this lottery - in other words, the miner’s chance of winning it — is re-calibrated every 2016th block so that the average time it takes to find the next block is always roughly ten minutes. What this system produces is absolute scarcity; the amount of Bitcoin in existence at any moment in time is always predictable. The more time that passes, the slower the rate of coin issuance and the block reward slowly approaches zero. By the time it does, around the year 2140, the individual miner’s incentive to mine for a reward will, at least theoretically, have been replaced by an incentive to collect transaction fees from the participants of the network. Even now, the sum of all fees make up a non-trivial part of the miners’ revenue. Yet from a user’s point of view the fees are still very low, and as the network scales up using Layer 2 solutions such as the Lightning Network, they’re expected to remain low for quite a long time ahead.
Absolute scarcity is a concept that mankind has never encountered before. Arguably, this makes it the first man-made concept to ever be directly linked to the laws of physics. Everything anyone does requires a certain amount of energy. The very word *doing* implies that some kind of movement, some type of energy expenditure, needs to occur. As mentioned earlier, how we value things is entirely subjective. Different actions are of different value to different people. How we value different things is also inevitably linked to the supply of those things. Had the trapped-under-ice winter diver mentioned in chapter one been equipped with a scuba tank, he probably wouldn't have thought of his next breath as such a precious thing. The price a person is willing to pay for a good — in other words, the sum of one or more person’s actions — can be derived from two basic variables: The highly subjective *demand* for the good and the always-constrained-by-time-and-space *supply* of that same good. Note that if supply is sufficiently limited, there only needs to be a minimal amount of demand for a good for its price to increase.
One could argue that no one *needs* Bitcoin and that, therefore, Bitcoin would have no intrinsic value. One could also argue that there’s no such thing as intrinsic value since demand is always subjective. In any case, there will always be a cost to mine Bitcoin, and the more mining power in the network, the higher that cost. This cost, ensured by the Bitcoin network’s Proof-Of-Work algorithm, is probably as close to a pure energy cost as the price of a human activity will ever get. Once the mining rig is in place, a simple conversion process follows — energy in, scarce token out. Should the cost of production exceed the current price of the token, the miner can just choose not to sell, thereby limiting the supply of Bitcoin in circulation even more and eventually selling them for other goods whenever he sees fit. In this sense, Bitcoin is a battery. Perhaps the best battery ever invented.
Storing and moving electrical energy around has always been costly and wasteful. Bitcoin offers a way of converting energy into a small part of a specific number. A mathematical battery, if you will. It is important to remember that it does not convert energy into value *directly*, but rather electricity into digital scarcity — digital scarcity that can be used to express value. Energy cannot be created or destroyed in an isolated system, as the first law of thermodynamics clearly states. Bitcoin can express how much energy was sacrificed in order to acquire a share of the total sum. You can also acquire Bitcoin by buying it rather than mining it, but in doing so, you also spend energy. You somehow acquired the money with which you bought the Bitcoin. You, or someone else, sacrificed time and energy somewhere. Bitcoin lets you express that you see that there’s a connection between value and scarcity by letting you sacrifice effort to claim a part of the total sum.
The excitement we so-called "Bitcoin Maximalists" feel about Bitcoin does not come primarily from the enormous gains that those who hopped early onto the freight train have been blessed with. Nor is it because we’re “in it for the technology,” as can often be heard from opponents. Those of us who preach the near-divinity of this invention do so above all because we see the philosophical impacts of absolute scarcity in a commodity. The idea of a functioning solution to the double-spending problem in computerized money is an achievement that simply can’t be ignored. By solving the double-spending problem, Satoshi also made counterfeiting impossible, which in turn makes artificial inflation impossible. The world-changing potential of this invention cannot be understated. Not in the long run.
The more you think about it, the more the thought won’t give you any peace of mind. If this experiment works, if it’s real, it will take civilization to the next level. What we don’t know is how long this will take. Right now, debates in the Bitcoin space are about Bitcoin’s functionality as a medium of exchange and its potential as a good store of value. We might be missing the point. We cannot possibly know if a type of monetary token for which you’re completely responsible, with no third-party protection, will ever become a preferred medium of exchange for most transactions. Nor can we know if the price of Bitcoin will follow the hype-cycle path that we all want it to follow so that it can become the store of value that most maximalists claim it already is. Maybe we’ve been focused on the wrong things all along. Maybe Bitcoin’s greatest strength is in its functionality as a unit of account. After all, this is all that Bitcoin does. If you own 21 Bitcoin, you own one-millionth of the world's first absolutely scarce commodity. This might not make you rich overnight, but it just might have something to do with the opportunities available to your great-great-grandchildren.
Throughout history, whenever a prehistoric human tribe invented ceremonial burial, that tribe began to expand rapidly. Why? Because as soon as you invent belief in an afterlife, you also introduce the idea of self-sacrifice on a larger scale. People who held these beliefs were much easier for a despot to manipulate and send into battle with neighboring tribes. Religious leaders can use people’s fears and superstitions to have them commit all sorts of atrocities to their fellow man, and they still do so today. Belief in a “greater good” can be the most destructive idea that can pop up in a human mind. The Nazis of World War II Germany believed that exterminating Jews was for the “greater good” of their nation’s gene pool. Belief in noble causes often comes with unintended side effects, which can have disastrous consequences.
Religious leaders, political leaders, and other power-hungry sociopaths are responsible for the greatest crimes against humanity ever committed — namely, wars. Europeans often question the Second Amendment to the United States Constitution, which protects the right to bear arms, whenever a tragic school shooting occurs on the other side of the Atlantic. What everyone seems to forget is that less than a hundred years ago, Europe was at war with itself because its citizens had given too much power to their so-called leaders. The Nazis came to power in a democracy — never forget that. Our individual rights weren’t given to us by our leaders; we were born with them. Our leaders can’t give us anything; they can only force us to behave in certain ways. If we truly want to be in charge of our lives, we need to find the tools necessary to circumvent the bullshit ourselves.
### **About the Bitcoin Infinity Academy**
The Bitcoin Infinity Academy is an educational project built around [Knut Svanholm](http://primal.net/knut)’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a [video](https://www.youtube.com/@BitcoinInfinityShow) in which Knut and [Luke de Wolf](http://primal.net/luke) discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our [Geyser](https://geyser.fund/project/infinity) page. Signed books, monthly calls, and lots of other benefits are also available.
-

@ c631e267:c2b78d3e
2025-03-21 19:41:50
*Wir werden nicht zulassen, dass technisch manches möglich ist,* *\
aber der Staat es nicht nutzt.* *\
Angela Merkel*  
**Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach.** Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
**Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar,** dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

**Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen,** die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
**Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen** und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war [vielleicht früher](https://transition-news.org/der-sumpf-aus-ngos-parteien-und-steuergeld) einmal so, heute ist eher das Gegenteil gemeint.
**In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung** praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien [beleuchtet](https://transition-news.org/nur-abschied-vom-alleinfahren-monstrose-spanische-uberwachungsprojekte-gemass). Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als [«Technofeudalismus»](https://transition-news.org/yanis-varoufakis-der-europaische-traum-ist-tot-es-lebe-der-neue-traum) angeprangert.
**Nationale** **[Zugangspunkte](https://transport.ec.europa.eu/transport-themes/smart-mobility/road/its-directive-and-action-plan/national-access-points_en)** **für Mobilitätsdaten im Sinne der EU** gibt es nicht nur in allen Mitgliedsländern, sondern auch in der [Schweiz](https://opentransportdata.swiss/de/) und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen [Identifizierungssystem](https://transition-news.org/biometrische-gesichtserkennung-in-britischen-hafen) für «nachhaltigen Verkehr und Tourismus».
**Natürlich marschiert auch Deutschland stracks und euphorisch** in Richtung digitaler Zukunft. Ohne [vernetzte Mobilität](https://mobilithek.info/about) und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität [voll auf Digitalisierung](https://www.smartcountry.berlin/de/newsblog/smart-city-index-grossstaedte-setzen-bei-mobilitaet-voll-auf-digitalisierung.html)».
**Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten,** das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
*\[Titelbild:* *[Pixabay](https://pareto.space/readhttps://pixabay.com/de/illustrations/schaufensterpuppe-platine-gesicht-5254046/)]*
***
Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben. Er ist zuerst auf ***[Transition News](https://transition-news.org/das-gegenteil-von-mussen-ist-nicht-durfen)*** erschienen.
-

@ df173277:4ec96708
2025-01-28 17:49:54
> Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. Chats are synced automatically between devices so you can pick up where you left off.\
> [Start chatting for free.](https://trymaple.ai/)
We are excited to announce that [Maple AI](https://trymaple.ai/), our groundbreaking end-to-end encrypted AI chat app built on OpenSecret, is now publicly available. After months of beta testing, we are thrilled to bring this innovative technology to the world.
Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another.
#### Why Secure and Private AI?
In today's digital landscape, it is increasingly evident that security and privacy are essential for individuals and organizations alike. Unfortunately, the current state of AI tools falls short. A staggering 48% of organizations enter non-public company information into AI apps, according to a [recent report by Cisco](https://www.cisco.com/c/en/us/about/trust-center/data-privacy-benchmark-study.html#~key-findings). This practice poses significant risks to company security and intellectual property.
Another concern is for journalists, who often work with sensitive information in hostile environments. Journalists need verification that their information remains confidential and protected when researching topics and communicating with sources in various languages. They are left to use underpowered local AI or input their data into potentially compromised cloud services.
At OpenSecret, we believe it is possible to have both the benefits of AI and the assurance of security and privacy. That's why we created Maple, an app that combines AI productivity with the protection of end-to-end encryption. Our platform ensures that your conversations with AI remain confidential, even from us. The power of the cloud meets the privacy of local.
#### How Does It Work?
Our server code is [open source](https://github.com/OpenSecretCloud/opensecret), and we use confidential computing to provide cryptographic proof that the code running on our servers is the same as the open-source code available for review. This process allows you to verify that your conversations are handled securely and privately without relying on trust. We live by the principle of "Don't trust, verify," and we believe this approach is essential for building in the digital age. You can read a more in-depth write-up on our technology later this week on this site.
#### How Much Does It Cost?
We are committed to making Maple AI accessible to everyone, so we offer a range of pricing plans to suit different needs and budgets. [Our Free plan allows for 10 chats per week, while our Starter plan ($5.99/month) and Pro plan ($20/month)](https://trymaple.ai/pricing) offer more comprehensive solutions for individuals and organizations with heavier workloads. We accept credit cards and Bitcoin (10% discount), allowing you to choose your preferred payment method.
- Free: $0
- Starter: $5.99/month
- Pro: $20/month
Our goal with Maple AI is to create a product that is secure through transparency. By combining open-source code, cryptography, and confidential computing, we can create a new standard for AI conversations - one that prioritizes your security and privacy.
Maple has quickly become a daily tool of productivity for our own work and those of our beta testers. We believe it will bring value to you as well. [Sign up now and start chatting privately with AI for free.](https://trymaple.ai/) Your secrets are safe in the open.
#### Are You An App Developer?
You can build an app like Maple. [OpenSecret provides secure auth, private key management, encrypted data sync, private AI, and more.](https://blog.opensecret.cloud/introducing-opensecret/) Our straightforward API behaves like other backends but automatically adds security and privacy. Use it to secure existing apps or brand-new projects. Protect yourself and your users from the liability of hosting personal data by checking out [OpenSecret](https://opensecret.cloud/).
<img src="https://blossom.primal.net/feb746d5e164e89f0d015646286b88237dce4158f8985e3caaf7e427cebde608.png">
Enjoy private AI Chat 🤘
<img src="https://blossom.primal.net/0594ec56e249de2754ea7dfc225a7ebd46bc298b5af168279ce71f17c2afada0.jpg">
-

@ df173277:4ec96708
2025-01-09 17:12:08
> Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\
> [Join the waitlist to get early access.](https://trymaple.ai)
We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI.
Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations.
#### Building a Private Foundation
Maple is built on our flagship product, [OpenSecret](https://opensecret.cloud), a backend platform for app developers that turns private encryption on by default. [The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do.](nostr:naddr1qvzqqqr4gupzphchxfm3ste32hfhkvczzxapme9gz5qvqtget6tylyd7wa8vjecgqqe5jmn5wfhkgatrd9hxwt20wpjku5m9vdex2apdw35x2tt9de3hy7tsw3jkgttzv93kketwvskhgur5w9nx5h52tpj) We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win.
#### The Power of Encrypted AI Chat
AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short.
Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us.
#### Technical Overview
So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects:
- **Private Key:** Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data.
- **Secure Servers:** Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations.
- **Encrypted Sync:** One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised.
- **Attestation and Open Code:** We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public.
- **Open Source LLM:** Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased.
#### Personal and Work Use
Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe.
#### Local v Cloud
Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds.
#### Why the Maple name?
Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment.
#### Join the Waitlist
Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. [Join our waitlist today to be among the first to experience the power of private AI chat.](https://trymaple.ai)
[](https://trymaple.ai/waitlist)
-

@ 8cb60e21:5f2deaea
2024-08-24 23:57:19
asdasdasdsad
-

@ 2fdeba99:fd961eff
2025-03-21 17:16:33
# == January 17 2025
Out From Underneath | Prism Shores
crazy arms | pigeon pit
Humanhood | The Weather Station
# == february 07 2025
Wish Defense | FACS
Sayan - Savoie | Maria Teriaeva
Nowhere Near Today | Midding
# == february 14 2025
Phonetics On and On | Horsegirl
# == february 21 2025
Finding Our Balance | Tsoh Tso
Machine Starts To Sing | Porridge Radio
Armageddon In A Summer Dress | Sunny Wa
# == february 28 2025
you, infinite | you, infinite
On Being | Max Cooper
Billboard Heart | Deep Sea Diver
# == March 21 2025
Watermelon/Peacock | Exploding Flowers
Warlord of the Weejuns | Goya Gumbani
-

@ aa8de34f:a6ffe696
2025-03-21 12:08:31
19\. März 2025
### 🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s **proof-of-work** mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, **SHA-256 remains secure** because:
- Quantum computers excel at **factoring large numbers** (Shor’s Algorithm).
- However, **SHA-256 is a one-way function**, meaning there's no known quantum algorithm that can efficiently reverse it.
- **Grover’s Algorithm** (which theoretically speeds up brute force attacks) would still require **2¹²⁸ operations** to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
### 🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses **Elliptic Curve Digital Signature Algorithm (ECDSA)** to generate keys.
- A quantum computer could use **Shor’s Algorithm** to break **SECP256K1**, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a **Bitcoin address** is the public key—**this is wrong**.
- When you **receive Bitcoin**, it is sent to a **hashed public key** (the Bitcoin address).
- The **actual public key is never exposed** because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses **Pay-to-Public-Key-Hash (P2PKH)** or newer methods like **Pay-to-Witness-Public-Key-Hash (P2WPKH)**, which add extra layers of security.
### 🕵️♂️ 2.1 The Public Key Never Appears
- When you **send Bitcoin**, your wallet creates a **digital signature**.
- This signature uses the **private key** to **prove** ownership.
- The **Bitcoin address is revealed and creates the Public Key**
- The public key **remains hidden inside the Bitcoin script and Merkle tree**.
This means: ✔ **The public key is never exposed.** ✔ **Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.**
+++++++++++++++++++++++++++++++++++++++++++++++++
### 🔄 3. Bitcoin Can Upgrade
Even if quantum computers **eventually** become a real threat:
- Bitcoin developers can **upgrade to quantum-safe cryptography** (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide **soft fork or hard fork** could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
### ⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a **10-minute block interval**, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack **every 10 minutes**.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system **resets the challenge with every new block**.This **limits the window of opportunity** for quantum attacks.
---
### 🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker **must solve the cryptographic puzzle (Proof of Work) in under 10 minutes**.
- The problem? **Any slight error changes the hash completely**, meaning:**If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails**.**Quantum decoherence** (loss of qubit stability) makes error correction a massive challenge.The computational cost of **recovering from an incorrect hash** is still incredibly high.
---
### ⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer **somehow** solved a block instantly:The network would **quickly recognize and reject invalid transactions**.Other miners would **continue mining** under normal cryptographic rules.**51% Attack?** The attacker would need to consistently beat the **entire Bitcoin network**, which is **not sustainable**.
---
### 🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every **2016 blocks (\~2 weeks)**.
- If quantum miners appeared and suddenly started solving blocks too quickly, **the difficulty would adjust upward**, making attacks significantly harder.
- This **self-correcting mechanism** ensures that even quantum computers wouldn't easily overpower the network.
---
### 🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ **The 10-minute rule limits attack frequency** – quantum computers can’t keep up.
✔ **Any slight miscalculation ruins the attack**, resetting all progress.
✔ **Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages**.
**Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant.** 🚀
-

@ 4fe14ef2:f51992ec
2025-03-27 21:11:10
Hey Bitcoiners,
Leave a comment below to share your hustles and wins. Let us know what you've sold this week. Have you sold it for #sats or #zaps? It doesn't matter how big or small your item is, solid or #digital, product or #service.
Just share below what you’ve listed, swapped, and sold. Let everyone rave on your latest #deals!
New to ~AGORA? Dive into the #marketplace and turn your dusty gears into shiny #BTC!
originally posted at https://stacker.news/items/927256
-

@ df173277:4ec96708
2025-01-09 17:02:52
> OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. [Join our waitlist to get early access.](https://opensecret.cloud)
In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion.
Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online?
Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches?
> Cryptography at scale is hard.
#### The Cloud
The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers.
The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage.
> Private key encryption needs a UX upgrade.
## Enter OpenSecret
OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute.
Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.

### Private Key Management
Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone.
OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account.
The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.

### Encrypted Sync
With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go.
The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them.
### Private AI
Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything.
OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk.
**Check out Maple AI**\
Try private AI for yourself! We built an app built with this service called [Maple AI](https://trymaple.ai). It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. [Learn more about Maple AI - Private chat in the announcement post.](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/)

### Confidential Compute
Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave.
It's the new version of that lock on your web browser. When you see it, you know you're secure.

#### **But do we want our secrets to be open?**
OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable.
On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data.
> Don't trust, verify.
### **Join the Movement**
We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, [send us a message to get early access.](https://opensecret.cloud)
Users and companies deserve better encryption and privacy.\
Together, let's make that a reality.
[](https://opensecret.cloud)
-

@ 8cb60e21:5f2deaea
2024-08-24 23:54:44
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/clGgymry998&pp=ygUcZmFyIGNyeSAzIHppZ2d5J3MgbW9kIHJldmlldw%3D%3D" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ e97aaffa:2ebd765d
2025-03-28 12:56:17
Nos últimos anos, tornei-me num acérrimo crítico do Euro, sobretudo da política monetária altamente expansionista realizada pelo Banco Central Europeu (BCE). Apesar de ser crítico, eu não desejo que Portugal volte a ter moeda própria.
No seguimento gráfico, é a variação do [IPC de Portugal nos últimos 60 anos]( https://www.pordata.pt/pt/estatisticas/inflacao/taxa-de-inflacao/taxa-de-inflacao-por-bens-e-servicos-portugal):
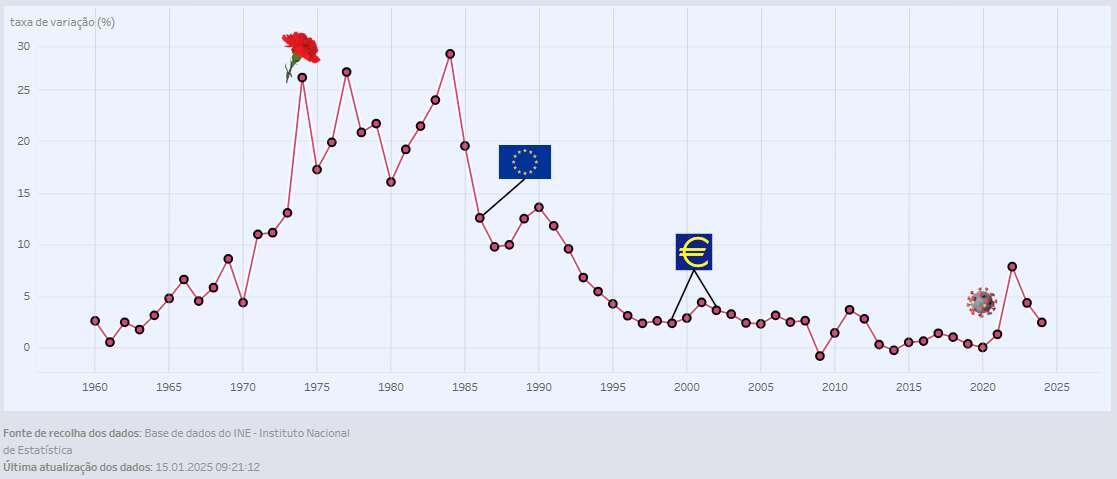
No gráfico inclui os momentos históricos, para uma melhor interpretação dos dados.
> O Índice de Preços ao Consumidor (IPC) é usado para observar tendências de inflação. É calculado com base no preço médio necessário para comprar um conjunto de bens de consumo e serviços num país, comparando com períodos anteriores.
É uma ferramenta utilizada para calcular a perda de poder de compra, mas é uma métrica que é facilmente manipulada em prol dos interesses dos governos.
## Análise histórica
No período marcelista, houve uma crescente inflação, devido a fatores, como os elevados custos da guerra e o fim dos acordos de Bretton Woods contribuíram para isso. Terminando com uma inflação superior a 13%.
Da Revolta dos Cravos (1974) até à adesão da CEE (atual União Europeia, UE), nos primeiros anos foram conturbados a nível político, mesmo após conquistar alguma estabilidade, em termos de política monetária foi um descalabro, com inflação entre 12% a 30% ao ano. Foi o pior momento na era moderna.
Com a entrada da CEE, Portugal ainda manteve a independência monetária, mas devido à entrada de muitos milhões de fundos europeus, essências para construir infraestrutura e desenvolver o país. Isto permitiu crescer e modernizar o país, gastando pouco dinheiro próprio, reduzindo a necessidade da expansão monetária e claro a inflação baixou.
Depois com a adesão ao Tratado de Maastricht, em 1991, onde estabeleceu as bases para a criação da União Económica e Monetária, que culminou na criação da moeda única europeia, o Euro. As bases eram bastante restritivas, os políticos portugueses foram obrigados a manter uma inflação baixa. Portugal perdeu a independência monetária em 1999, com a entrada em vigor da nova moeda, foi estabelecida a taxa de conversão entre escudos e euros, tendo o valor de 1 euro sido fixado em 200,482 escudos. A Euro entrou em vigor em 1999, mas o papel-moeda só entrou em circulação em 2002.
Assim, desde a criação até 2020, a inflação foi sempre abaixo de 5% ao ano, tendo um longo período abaixo dos 3%.
A chegada da pandemia, foi um descalabro no BCE, a expansão monetária foi exponencial, resultando numa forte subida no IPC, quase 8% em 2022, algo que não acontecia há 30 anos.
## Conclusão
Apesar dos últimos anos, a política monetária do BCE tem sido péssima, mesmo assim continua a ser muito melhor, se esta fosse efetuada em exclusividade por portugueses, não tenho quaisquer dúvidas disso. O passado demonstra isso, se voltarmos a ser independentes monetariamente, será desastroso, vamos virar rapidamente, a Venezuela da Europa.
Até temos boas reservas de ouro, mas mesmo assim não são suficientes, mesmo que se inclua outros ativos para permitir a criação de uma moeda lastreada, ela apenas duraria até à primeira crise. É inevitável, somos um país demasiado socialista.
A solução não é voltar ao escudo, mas sim o BCE deixar de imprimir dinheiro, como se não houvesse amanhã ou então optar por uma moeda total livre, sem intromissão de políticos.
O BCE vai parar de expandir a moeda?
Claro que não, eles estão encurralados, a expansão monetária é a única solução para elevada dívida soberana dos estados. A única certeza que eu tenho, a expansão do BCE, será sempre inferior ao do Banco de Portugal, se este estivesse o botão da impressão à sua disposição. Por volta dos 5% é muito mau, mas voltar para a casa dos 15% seria péssimo, esse seria o nosso destino.
É muito triste ter esta conclusão, isto é demonstrativo da falta de competência dos políticos e governantes portugueses e o povo também tem uma certa culpa. Por serem poucos exigentes em relação à qualidade dos políticos que elegem e por acreditar que existem almoços grátis.
#Bitcoin fixes this
-

@ 2b24a1fa:17750f64
2025-03-28 10:07:04
Der Deutsche Bundestag wurde neu gewählt. Für einige Abgeordnete und Regierungsmitglieder heißt es Time to Say Goodbye. Abschied ist ein scharfes Schwert. 
[https://soundcloud.com/radiomuenchen/nachruf-2-olaf-der-zeitenwender](https://soundcloud.com/radiomuenchen/nachruf-2-olaf-der-zeitenwender?si=6c375088b6444c2d8aa7e8040fb1a79e\&utm_source=clipboard\&utm_medium=text\&utm_campaign=social_sharing)
Auch bei Radio München werden Trennungs- und Verlassenheitsgefühle getriggert. Umso mehr, wenn es sich nicht nur um duselige Allerweltsliebe handelt, sondern um den Abgang großer Helden. Sie bezahlten ihren todesmutigen und fast ehrenamtlichen Einsatz nicht mit dem Leben, jedoch mit der einen oder anderen Falte in Hemd oder Bluse, manchmal sogar im Gesicht. Was bleibt? Eine bescheidene Pension? Ein lausig bezahlter Manager-Job in einem Konzern? Wir wollen jedenfalls nicht, dass diese Volkshelden vom Zahn der Zeit abgenagt, vergessen werden und setzen ihnen deshalb ein bescheidenes akustisches, aber nachhaltiges Denkmal. Hören Sie die kleine satirische Reihe „Nachrufe“ von unserem Autor Jonny Rieder.\
Folge 2: Olaf der Zeitenwender
Sprecher: Karsten Troyke
Bild: Markus Mitterer für Radio München
Radio München\
[www.radiomuenchen.net/](http://www.radiomuenchen.net/%E2%80%8B "http://www.radiomuenchen.net/")\
@[radiomuenchen](https://soundcloud.com/radiomuenchen)\
[www.facebook.com/radiomuenchen](http://www.facebook.com/radiomuenchen "http://www.facebook.com/radiomuenchen")\
[www.instagram.com/radio\_muenchen/](http://www.instagram.com/radio_muenchen/ "http://www.instagram.com/radio_muenchen/")\
[twitter.com/RadioMuenchen](http://twitter.com/RadioMuenchen "http://twitter.com/RadioMuenchen")
Radio München ist eine gemeinnützige Unternehmung.\
Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\
IBAN: DE65 4306 0967 8217 9867 00\
BIC: GENODEM1GLS
-

@ a95c6243:d345522c
2025-03-20 09:59:20
**Bald werde es verboten, alleine im Auto zu fahren,** konnte man dieser Tage in verschiedenen spanischen Medien lesen. Die nationale Verkehrsbehörde (Dirección General de Tráfico, kurz DGT) werde Alleinfahrern das Leben schwer machen, wurde gemeldet. Konkret erörtere die Generaldirektion geeignete Sanktionen für Personen, die ohne Beifahrer im Privatauto unterwegs seien.
**Das Alleinfahren sei zunehmend verpönt und ein Mentalitätswandel notwendig,** hieß es. Dieser «Luxus» stehe im Widerspruch zu den Maßnahmen gegen Umweltverschmutzung, die in allen europäischen Ländern gefördert würden. In Frankreich sei es «bereits verboten, in der Hauptstadt allein zu fahren», [behauptete](https://noticiastrabajo.huffingtonpost.es/sociedad/adios-a-conducir-solo-la-dgt-se-lo-pone-crudo-a-los-conductores-que-viajen-sin-acompanante-en-el-coche/) *Noticiastrabajo Huffpost* in einer Zwischenüberschrift. Nur um dann im Text zu konkretisieren, dass die sogenannte «Umweltspur» auf der Pariser Ringautobahn gemeint war, die für Busse, Taxis und Fahrgemeinschaften reserviert ist. [Ab Mai](https://www.lefigaro.fr/conso/peripherique-parisien-entree-en-vigueur-de-la-voie-reservee-au-covoiturage-ce-lundi-20250303) werden Verstöße dagegen mit einem Bußgeld geahndet.
**Die DGT jedenfalls wolle bei der Umsetzung derartiger Maßnahmen** nicht hinterherhinken. Diese Medienberichte, inklusive des angeblich bevorstehenden Verbots, beriefen sich auf Aussagen des Generaldirektors der Behörde, Pere Navarro, beim Mobilitätskongress Global Mobility Call im November letzten Jahres, wo es um «nachhaltige Mobilität» ging. Aus diesem Kontext stammt auch Navarros Warnung: «Die Zukunft des Verkehrs ist geteilt oder es gibt keine».
**Die «Faktenchecker» kamen der Generaldirektion prompt zu Hilfe.** Die DGT habe derlei Behauptungen [zurückgewiesen](https://www.newtral.es/dgt-una-persona-coche/20250312/) und klargestellt, dass es keine Pläne gebe, Fahrten mit nur einer Person im Auto zu verbieten oder zu bestrafen. Bei solchen Meldungen handele es sich um Fake News. Teilweise wurde der Vorsitzende der spanischen «Rechtsaußen»-Partei Vox, Santiago Abascal, der Urheberschaft bezichtigt, weil er einen entsprechenden [Artikel](https://gaceta.es/espana/la-dgt-estudia-formas-de-sancionar-a-quien-circule-solo-en-su-vehiculo-el-futuro-sera-compartido-o-no-sera-20250311-1612/) von *La Gaceta* kommentiert hatte.
**Der Beschwichtigungsversuch der Art «niemand hat die Absicht»** ist dabei erfahrungsgemäß eher ein Alarmzeichen als eine Beruhigung. Walter Ulbrichts Leugnung einer geplanten Berliner [Mauer](https://www.berlin-mauer.de/videos/walter-ulbricht-zum-mauerbau-530/) vom Juni 1961 ist vielen genauso in Erinnerung wie die Fake News-Warnungen des deutschen Bundesgesundheitsministeriums bezüglich [Lockdowns](https://x.com/BMG_Bund/status/1238780849652465664) im März 2020 oder diverse Äußerungen zu einer [Impfpflicht](https://www.achgut.com/artikel/die_schoensten_politiker_zitate_zur_impfpflicht) ab 2020.
**Aber Aufregung hin, Dementis her:** Die [Pressemitteilung](https://archive.is/xXQWD) der DGT zu dem Mobilitätskongress enthält in Wahrheit viel interessantere Informationen als «nur» einen Appell an den «guten» Bürger wegen der Bemühungen um die Lebensqualität in Großstädten oder einen möglichen obligatorischen Abschied vom Alleinfahren. Allerdings werden diese Details von Medien und sogenannten Faktencheckern geflissentlich übersehen, obwohl sie keineswegs versteckt sind. Die Auskünfte sind sehr aufschlussreich, wenn man genauer hinschaut.
### Digitalisierung ist der Schlüssel für Kontrolle
**Auf dem Kongress stellte die Verkehrsbehörde ihre Initiativen zur Förderung der «neuen Mobilität» vor,** deren Priorität Sicherheit und Effizienz sei. Die vier konkreten Ansätze haben alle mit Digitalisierung, Daten, Überwachung und Kontrolle im großen Stil zu tun und werden unter dem Euphemismus der «öffentlich-privaten Partnerschaft» angepriesen. Auch lassen sie die transhumanistische Idee vom unzulänglichen Menschen erkennen, dessen Fehler durch «intelligente» technologische Infrastruktur kompensiert werden müssten.
**Die Chefin des Bereichs «Verkehrsüberwachung» erklärte die Funktion** des spanischen National Access Point ([NAP](https://nap.dgt.es/)), wobei sie betonte, wie wichtig Verkehrs- und Infrastrukturinformationen in Echtzeit seien. Der NAP ist «eine essenzielle Web-Applikation, die unter EU-Mandat erstellt wurde», kann man auf der Website der DGT nachlesen.
**Das Mandat meint Regelungen zu einem einheitlichen europäischen Verkehrsraum,** mit denen die Union mindestens seit 2010 den Aufbau einer digitalen Architektur mit offenen Schnittstellen betreibt. Damit begründet man auch «umfassende Datenbereitstellungspflichten im Bereich multimodaler Reiseinformationen». Jeder Mitgliedstaat musste einen NAP, also einen nationalen [Zugangspunkt](https://transport.ec.europa.eu/transport-themes/smart-mobility/road/its-directive-and-action-plan/national-access-points_en) einrichten, der Zugang zu statischen und dynamischen Reise- und Verkehrsdaten verschiedener Verkehrsträger ermöglicht.
**Diese Entwicklung ist heute schon weit fortgeschritten,** auch und besonders in Spanien. Auf besagtem Kongress erläuterte die Leiterin des Bereichs «Telematik» die Plattform [«DGT 3.0»](https://www.dgt.es/muevete-con-seguridad/tecnologia-e-innovacion-en-carretera/dgt-3.0/). Diese werde als Integrator aller Informationen genutzt, die von den verschiedenen öffentlichen und privaten Systemen, die Teil der Mobilität sind, bereitgestellt werden.
**Es handele sich um eine Vermittlungsplattform zwischen Akteuren wie Fahrzeugherstellern,** Anbietern von Navigationsdiensten oder Kommunen und dem Endnutzer, der die Verkehrswege benutzt. Alle seien auf Basis des Internets der Dinge (IOT) anonym verbunden, «um der vernetzten Gemeinschaft wertvolle Informationen zu liefern oder diese zu nutzen».
**So sei DGT 3.0 «ein Zugangspunkt für einzigartige, kostenlose und genaue Echtzeitinformationen** über das Geschehen auf den Straßen und in den Städten». Damit lasse sich der Verkehr nachhaltiger und vernetzter gestalten. Beispielsweise würden die Karten des Produktpartners Google dank der DGT-Daten 50 Millionen Mal pro Tag aktualisiert.
**Des Weiteren informiert die Verkehrsbehörde über ihr SCADA-Projekt.** Die Abkürzung steht für Supervisory Control and Data Acquisition, zu deutsch etwa: Kontrollierte Steuerung und Datenerfassung. Mit SCADA kombiniert man Software und Hardware, um automatisierte Systeme zur Überwachung und Steuerung technischer Prozesse zu schaffen. Das SCADA-Projekt der DGT wird von Indra entwickelt, einem spanischen Beratungskonzern aus den Bereichen Sicherheit & Militär, Energie, Transport, Telekommunikation und Gesundheitsinformation.
**Das SCADA-System der Behörde umfasse auch eine Videostreaming- und Videoaufzeichnungsplattform,** die das Hochladen in die Cloud in Echtzeit ermöglicht, wie Indra [erklärt](https://www.indracompany.com/es/noticia/indra-presenta-global-mobility-call-pionera-plataforma-nube-desplegada-centros-gestion). Dabei gehe es um Bilder, die von Überwachungskameras an Straßen aufgenommen wurden, sowie um Videos aus DGT-Hubschraubern und Drohnen. Ziel sei es, «die sichere Weitergabe von Videos an Dritte sowie die kontinuierliche Aufzeichnung und Speicherung von Bildern zur möglichen Analyse und späteren Nutzung zu ermöglichen».
**Letzteres klingt sehr nach biometrischer Erkennung** und Auswertung durch künstliche Intelligenz. Für eine bessere Datenübertragung wird derzeit die [Glasfaserverkabelung](https://www.moncloa.com/2025/03/18/linea-azul-conduccion-dgt-3191554/) entlang der Landstraßen und Autobahnen ausgebaut. Mit der Cloud sind die Amazon Web Services (AWS) gemeint, die spanischen [Daten gehen](https://norberthaering.de/news/digitalgipfel-wehnes-interview/) somit direkt zu einem US-amerikanischen «Big Data»-Unternehmen.
**Das Thema «autonomes Fahren», also Fahren ohne Zutun des Menschen,** bildet den Abschluss der Betrachtungen der DGT. Zusammen mit dem Interessenverband der Automobilindustrie ANFAC (Asociación Española de Fabricantes de Automóviles y Camiones) sprach man auf dem Kongress über Strategien und Perspektiven in diesem Bereich. Die Lobbyisten hoffen noch in diesem Jahr 2025 auf einen [normativen Rahmen](https://www.coches.net/noticias/informe-coche-autonomo-conectado-espana-2024) zur erweiterten Unterstützung autonomer Technologien.
**Wenn man derartige Informationen im Zusammenhang betrachtet,** bekommt man eine Idee davon, warum zunehmend alles elektrisch und digital werden soll. Umwelt- und Mobilitätsprobleme in Städten, wie Luftverschmutzung, Lärmbelästigung, Platzmangel oder Staus, sind eine Sache. Mit dem Argument «emissionslos» wird jedoch eine Referenz zum CO2 und dem «menschengemachten Klimawandel» hergestellt, die Emotionen triggert. Und damit wird so ziemlich alles verkauft.
**Letztlich aber gilt: Je elektrischer und digitaler unsere Umgebung wird** und je freigiebiger wir mit unseren Daten jeder Art sind, desto besser werden wir kontrollier-, steuer- und sogar abschaltbar. Irgendwann entscheiden KI-basierte Algorithmen, ob, wann, wie, wohin und mit wem wir uns bewegen dürfen. Über einen 15-Minuten-Radius geht dann möglicherweise nichts hinaus. Die Projekte auf diesem Weg sind ernst zu nehmen, real und schon weit fortgeschritten.
*\[Titelbild:* *[Pixabay](https://pixabay.com/de/photos/reisen-wagen-ferien-fahrzeug-1426822/)]*
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/nur-abschied-vom-alleinfahren-monstrose-spanische-uberwachungsprojekte-gemass)*** erschienen.
-

@ 8cb60e21:5f2deaea
2024-08-24 23:52:38
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/JAQuukInxFg&pp=ygUcZmFyIGNyeSAzIHppZ2d5J3MgbW9kIHJldmlldw%3D%3D" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ ed84ce10:cccf4c2a
2025-03-27 14:55:40
## **Hackers are Destiny: Four Fulcrums of the Future**
*A Dora Ventures Thesis*
In “Why Software is Eating the World,” Marc Andreeson argued that software isn’t just a tool — it’s a societal force. At [DoraHacks](https://dorahacks.io/), we agree, but we go one step further.
It’s not software alone that reshapes the world. It’s hackers — those who BUIDL.
The real engine of change isn’t technology; it’s the people who choose to wield it.
[DoraHacks](https://dorahacks.io/) is building a global Hacker Movement — a self-organizing force powered by open source, freedom, and code. We’re not chasing buzzwords like “Web3” or geopolitical narratives. We’re building a new society. One based on a simple but radical question:
**What is truly worth building?**
Dora Ventures exists to serve that mission — a capital engine designed to coordinate, amplify, and capture value from the hacker revolution.
We are placing early and aggressive bets across four core leverage points:
## **I. FDA Free Society — The BioHack**
### **Freedom of Life Science is the foundation of a free society.**
Every meaningful technological revolution has challenged the existing power structure.
Today, the single most over-regulated, over-centralized, and innovation-hostile domain? Life Science.
It takes ten years and billions of dollars to bring a drug from lab to patient. Most innovation dies in the trenches of bureaucracy.
We don’t need anarchy. We need a new model:**A market-driven, patient-first biotech innovation stack.**
**The Problem:**
- The FDA approval process kills breakthrough therapies before they live.
- Big Pharma monopolies decouple price from value and destroy competition.
- The “Right to Try” is a legal afterthought, not a first principle.
- Bio startups can’t survive the upfront costs of traditional trials.
**The Opportunity:**
- Let markets and builders lead: give power back to patients, doctors, and founders.
- Rethink from first principles: not “Did it pass?” but “Does it work?”
- Reclaim the Right to Try: the real risk is dying while waiting.
- Build a hyper-competitive biofounder ecosystem — don’t just supply Big Pharma with IP.
- Supercharge biotech with software and AI: accelerate every layer of the stack.
The future of medicine does not belong to regulators. It belongs to the builders who refuse to wait.
**The FDA Free Society isn’t just a challenge to power — it’s a defense of life.**
## **II. Open Source Quantum**
### **Ethereum had 2015. Quantum software has 2025.**
Arthur C. Clarke said: *“Any sufficiently advanced technology is indistinguishable from magic.”*
Quantum is magic — until it’s programmable, repeatable, and shared. In other words: open source.
Dora Ventures is betting on the moment quantum computing becomes a hacker’s playground.
Hardware is entering the engineering phase. Software? Still a wasteland — which means pure upside for builders.
**We’re betting on:**
- **Quantum compilers & transpilers**: bridging classical and quantum logic.
- **Quantum cryptography**: building fundamentally new security layers.
- **Quantum applications** in AI, pharma, logistics, finance, space — everything.
We're not watching from the sidelines. We’re funding open-source tools, running hackathons, and building out the decentralized quantum dev stack.
**Open Source Quantum is not speculative.** It’s inevitable — and massively undercapitalized.
Now is the time to build.
## **III. Consumer Crypto — The Fat Apps Are Coming**
### **Crypto’s real revolution? Billion-user apps.**
Crypto is not the *alternative* to the internet. It’s the *next chapter* of the internet.
In the 1990s, HTTP and TCP/IP rewired information.
In the 2000s, web apps rewired commerce and communication.
In the 2010s, mobile apps rewired human behavior.
In the 2020s, crypto apps will onboard the next billion users.
**The infrastructure is ready. The fat apps are hatching.**
Dora Ventures is obsessed with one question:
**Who builds the PayPal and WeChat of the Web3 era?**
That’s where we place our bets.
**What we see coming:**
- Compliant stablecoins like USDC become digital dollars.
- Crypto-native payment rails rival VISA.
- Appchains built with Move + simplified UX onboard non-crypto users.
- On-chain creator economies that pay artists, devs, and communities directly.
Imagine this:
A fan in NYC uses USDC on a Move-based blockchain (Aptos) to buy a concert ticket via KYD Labs.
An Argentinian grabs a latte daily with Bitcoin sats on Lightning.
A friend group splits dinner bills via Yakihonne, a decentralized social platform.
**That’s not the future. That’s this year.**
We’re not funding protocols — we’re funding paradigm shifts in experience.
## **IV. Agentic Organizations — DAOs Without CEOs**
### **The end of corporations. The birth of autonomous orgs.**
In 2022, Sam Altman redefined “tools.”
In 2025, we’ll redefine “organizations.”
Future orgs won’t be hierarchies. They’ll be networks of autonomous agents.
**Agents** are the new work unit. They don’t sleep. They learn continuously. They self-schedule.
They’re not tools to help humans — they *are* the operating system of post-human orgs.
**What’s coming:**
- DAOs with agent-driven governance and privacy.
- Smart Widgets that deploy trade/social/payment agents in three lines of code.
- Privacy as a default layer in automation.
- A new generation of AI-native hackathon projects.
AI + blockchain isn’t a buzzword. It’s the genesis of *organizational intelligence.*
Yesterday, the company was an information processor.
Tomorrow, the DAO is an autonomous agent network.
**No CEOs. No approvals. No offices. Just coordination at the speed of compute.**
## **The Bet: BUIDL Freedom for Humanity**
FDA Free Society. Open Source Quantum. Consumer Crypto. Agentic Orgs.
These are not sci-fi. They are already happening.
At Dora Ventures, we don’t just back technologies.
We back builders who say:
“The system is broken — and I’m going to fix it myself.”
We back rebels who reject stagnation.
Who write code instead of complaints.
Who build networks instead of narratives.
Who refuse to ask permission to build the future.
Hackers are eating the world.
And in the age of AI, humanity will only survive if it chooses to become hackers — to use code, coordination, and imagination to build a world worth living in.
Let’s build.
-

@ 2b24a1fa:17750f64
2025-03-28 10:03:58
Zwischen Überzeugungsarbeit und Propaganda verläuft ein schmaler Grad. Aber so oder so: Wer die subtileren Werkzeuge hat und vor allem die Mittel um Menschen zu kaufen, die diese dann anwenden, hat eindeutig die besseren Karten. 
[https://soundcloud.com/radiomuenchen/unterwanderter-journalismus-oder-der-mediale-deep-state-wankt-von-milosz-matuschekcolor=ffd400](https://soundcloud.com/radiomuenchen/unterwanderter-journalismus-oder-der-mediale-deep-state-wankt-von-milosz-matuschek?si=45877e50143d4e10a22fc9a4be82970d\&utm_source=clipboard\&utm_medium=text\&utm_campaign=social_sharing)
Dass die Bevölkerung nun wissen will, mit welchen Mitteln sie auf welche Weise beeinflusst werden soll, ist selbstverständlich. Wie nuanciert diese Beeinflussung stattfinden kann, darauf haben uns unsere Hörer beim letzten Beitrag von Milosz Matuschek: „Die ersten Köpfe rollen“ gestoßen. Es ging um die staatliche amerikanische Behörde für internationale Entwicklungshilfe USAID. Matuschek schrieb: „Man liest was von AID im Namen und denkt, was man denken soll: klingt nach Bob Geldof, barmherzigen Schwestern und “Brot für die Welt”.“ Man hatte das nicht nur optisch wahrgenommen, nein, diese Behörde wurde hierzulande, in allen Medien US AID genannt, was unsere Sprecherin Sabrina Khalil übernahm. Dass die United States Agency for International Development in USA so nicht gesprochen wird, schrieben uns gleich mehrere aufmerksame Hörer. Es ist sicherlich keine Paranoia darüber nachzudenken, ob die Bedeutung unserer Sprache, unserer Wörter bis hin zur Aussprache im Fokus der Manipulation steht. Dafür wird sehr viel Geld locker gemacht und unter anderem in die Medien gepumpt.
Hören Sie heute den zweiten Teil der Reihe „Die Corona-Connection“ mit dem Titel: „Der mediale Deep State wankt“. Sprecherin: Sabrina Khalil.
Das freie Medienprojekt Pareto kann übrigens Unterstützung gebrauchen, dafür wurde ein Crowdfunding auf Geyser gestartet, wo man mit Bitcoin/Lightning-Spenden helfen kann. Und für Spenden auf dem klassischen Weg finden Sie die entsprechende Bankverbindung auf der Homepage pareto.space/de.
Nachzulesen unter: [www.freischwebende-intelligenz.org/p/unter…mediale](https://gate.sc?url=https%3A%2F%2Fwww.freischwebende-intelligenz.org%2Fp%2Funterwanderter-journalismus-der-mediale\&token=6fce3f-1-1743155866002 "https://www.freischwebende-intelligenz.org/p/unterwanderter-journalismus-der-mediale")
Foto: Gleichschaltung - sie melden exakt den gleichen Wortlaut.
-

@ dfbbf851:ba4542b5
2025-03-27 13:45:12
Bitcoin (BTC) เป็นสกุลเงินดิจิทัลที่ได้รับความนิยมและถูกพูดถึงมากที่สุดในโลก นับตั้งแต่เปิดตัวในปี 2009 โดยบุคคลหรือกลุ่มที่ใช้นามแฝงว่า **Satoshi Nakamoto** 🎭
แต่คำถามสำคัญก็คือ... **Bitcoin เป็นอนาคตของการเงินโลกหรือว่าเป็นฟองสบู่ที่รอวันแตกกันแน่?** 🤔
---
### 🔹 **Bitcoin คืออะไร ?**
Bitcoin เป็นเงินดิจิทัลที่ทำงานบน **เทคโนโลยีบล็อกเชน (Blockchain)** ซึ่งช่วยให้การทำธุรกรรมมีความปลอดภัยและโปร่งใส 💡
🔸 **ไม่มีธนาคารกลางควบคุม**
🔸 **จำนวนจำกัดเพียง 21 ล้านเหรียญ**
🔸 **ใช้ระบบ "การขุด" (Mining) เพื่อยืนยันธุรกรรม**
---
### ✅ **ทำไม Bitcoin ได้รับความนิยม ?**
✨ **ไร้พรมแดน** – โอนเงินข้ามประเทศได้รวดเร็วและถูกกว่าธนาคาร
✨ **ความปลอดภัยสูง** – ใช้ระบบเข้ารหัสที่แข็งแกร่ง 🔐
✨ **สินทรัพย์ป้องกันเงินเฟ้อ** – มีจำนวนจำกัด จึงถูกมองว่าเป็น **"ทองคำดิจิทัล"** 🌎🏆
✨ **การยอมรับที่เพิ่มขึ้น** – บริษัทใหญ่ เช่น Tesla และ PayPal เริ่มเปิดรับ BTC
---
### ❌ **ความเสี่ยงของ Bitcoin**
⚠️ **ราคาผันผวนสูง** – อาจขึ้นหรือลงหลายพันดอลลาร์ภายในวันเดียว 📉📈
⚠️ **ยังไม่ถูกยอมรับทั่วโลก** – บางประเทศออกกฎหมายห้ามใช้ เช่น จีน 🚫
⚠️ **อาจถูกใช้ในทางผิดกฎหมาย** – เช่น การฟอกเงินในตลาดมืด 🕵️♂️
⚠️ **สิ้นเปลืองพลังงาน** – กระบวนการขุดใช้ไฟฟ้าปริมาณมาก ⚡🌱
---
### 🔮 **อนาคตของ Bitcoin จะเป็นอย่างไร ?**
นักลงทุนบางคนเชื่อว่า **Bitcoin จะเป็นอนาคตของระบบการเงินโลก** 💵🌍 ในขณะที่บางคนมองว่า **มันเป็นเพียงฟองสบู่ที่อาจแตกเมื่อไหร่ก็ได้** 💥
💡 ปัจจัยสำคัญที่อาจกำหนดอนาคตของ BTC ได้แก่:
✔️ **การยอมรับจากรัฐบาลและองค์กรใหญ่**
✔️ **กฎหมายและกฎระเบียบ** – หากรัฐบาลทั่วโลกออกกฎหมายสนับสนุน BTC อาจทำให้ราคาพุ่งสูง 🚀
✔️ **เทคโนโลยีใหม่ๆ** – เช่น **Lightning Network** ที่ช่วยให้การทำธุรกรรมเร็วขึ้นและถูกลง ⚡
---
### 🎯 **ปล.**
Bitcoin เป็น **นวัตกรรมการเงินที่เปลี่ยนโลก** 🌎 และอาจกลายเป็นสินทรัพย์สำคัญในอนาคต **แต่ก็มีความเสี่ยงสูง** นักลงทุนต้องศึกษาให้รอบคอบก่อนตัดสินใจลงทุน 📊💡
**แล้วท่านผู้อ่านล่ะครับ คิดว่า Bitcoin คืออนาคตของเงิน หรือเป็นเพียงกระแสชั่วคราวกันแน่ ?** 🤔
---
#Bitcoin #Crypto #Blockchain #BTC #ลงทุน #การเงิน #อนาคตการเงิน
-

@ 8cb60e21:5f2deaea
2024-08-24 23:33:51
# test
-

@ ebbba253:6ec1d547
2025-03-27 12:19:28
A NNBET se tornou uma plataforma de destaque no Brasil, oferecendo uma ampla variedade de opções de entretenimento online para jogadores de todos os perfis. Desde apostas esportivas até uma vasta seleção de jogos interativos, a plataforma se destaca pela sua facilidade de uso, segurança e pelas diversas oportunidades de ganhar. Se você está em busca de uma experiência online diversificada e acessível, NNBET é a escolha perfeita.
Fácil Acesso e Navegação Intuitiva
Quando se trata de uma plataforma de entretenimento online, a facilidade de uso é crucial. A <a href="https://nnbet.tw"> Nnbet </a> oferece uma interface extremamente amigável, permitindo que jogadores novatos ou experientes possam navegar sem problemas. A plataforma é bem organizada, com seções claramente marcadas para apostas esportivas, jogos e promoções. Seu design simples e funcional permite que os usuários encontrem rapidamente suas opções preferidas, sem perder tempo.
O acesso à plataforma também é facilitado pela sua versão mobile. Isso significa que você pode acessar sua conta e jogar a qualquer momento e em qualquer lugar. Com a popularização dos smartphones, essa funcionalidade é essencial, e a NNBET não deixa a desejar, oferecendo uma versão mobile otimizada que proporciona uma experiência de jogo excelente mesmo em telas menores.
Apostas Esportivas: Uma Experiência Completa
A NNBET não é apenas uma plataforma de jogos, ela também se destaca no campo das apostas esportivas. Para os brasileiros, o futebol é um dos esportes mais importantes, e a plataforma oferece uma variedade imensa de mercados para apostas em jogos de futebol, tanto locais quanto internacionais. Além disso, a plataforma abrange uma grande gama de outros esportes populares, como vôlei, basquete e até esportes eletrônicos.
As apostas ao vivo são uma característica de destaque, oferecendo uma experiência interativa em tempo real. A NNBET permite que os jogadores apostem enquanto os jogos acontecem, com odds constantemente atualizadas, o que torna a experiência ainda mais empolgante e envolvente. A diversidade de mercados, aliada às odds competitivas, garante que sempre haverá algo para você apostar, independentemente do seu time ou esporte favorito.
Uma Grande Variedade de Jogos para Todos os Gostos
Além das apostas esportivas, a NNBET oferece uma gama de jogos para agradar a todos os tipos de jogadores. Se você é fã de jogos de azar, a plataforma conta com uma vasta seleção de slots com temas diversificados, bônus incríveis e gráficos de última geração. Se o que você procura é uma experiência mais imersiva, os jogos ao vivo são uma excelente opção. Com dealers reais transmitindo jogos em tempo real, a NNBET recria a atmosfera de um ambiente físico, proporcionando uma experiência realista.
Outro grande atrativo são os jogos de mesa, como o blackjack e a roleta, que oferecem opções de apostas e limites variados, permitindo que todos os tipos de jogadores possam participar.
Suporte e Promoções: Garantindo a Melhor Experiência
A NNBET vai além de oferecer apenas jogos e apostas. A plataforma também se destaca pelo suporte ao cliente de alta qualidade. O atendimento está disponível 24/7, sempre pronto para ajudar com dúvidas ou problemas que possam surgir. Se você tem alguma pergunta sobre sua conta, pagamentos ou jogos, o suporte estará ao seu alcance a qualquer momento.
As promoções e bônus também são uma parte importante da experiência. A NNBET oferece bônus de boas-vindas para novos jogadores, bem como promoções regulares que garantem que a diversão nunca pare. Com rodadas grátis, bônus de depósito e programas de fidelidade, a plataforma oferece uma experiência emocionante a cada visita.
-

@ 266815e0:6cd408a5
2025-03-19 11:10:21
How to create a nostr app quickly using [applesauce](https://hzrd149.github.io/applesauce/)
In this guide we are going to build a nostr app that lets users follow and unfollow [fiatjaf](nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6)
## 1. Setup new project
Start by setting up a new vite app using `pnpm create vite`, then set the name and select `Solid` and `Typescript`
```sh
➜ pnpm create vite
│
◇ Project name:
│ followjaf
│
◇ Select a framework:
│ Solid
│
◇ Select a variant:
│ TypeScript
│
◇ Scaffolding project in ./followjaf...
│
└ Done. Now run:
cd followjaf
pnpm install
pnpm run dev
```
## 2. Adding nostr dependencies
There are a few useful nostr dependencies we are going to need. `nostr-tools` for the types and small methods, and [`rx-nostr`](https://penpenpng.github.io/rx-nostr/) for making relay connections
```sh
pnpm install nostr-tools rx-nostr
```
## 3. Setup rx-nostr
Next we need to setup rxNostr so we can make connections to relays. create a new `src/nostr.ts` file with
```ts
import { createRxNostr, noopVerifier } from "rx-nostr";
export const rxNostr = createRxNostr({
// skip verification here because we are going to verify events at the event store
skipVerify: true,
verifier: noopVerifier,
});
```
## 4. Setup the event store
Now that we have a way to connect to relays, we need a place to store events. We will use the [`EventStore`](https://hzrd149.github.io/applesauce/typedoc/classes/applesauce_core.EventStore.html) class from `applesauce-core` for this. create a new `src/stores.ts` file with
> The event store does not store any events in the browsers local storage or anywhere else. It's in-memory only and provides a model for the UI
```ts
import { EventStore } from "applesauce-core";
import { verifyEvent } from "nostr-tools";
export const eventStore = new EventStore();
// verify the events when they are added to the store
eventStore.verifyEvent = verifyEvent;
```
## 5. Create the query store
The event store is where we store all the events, but we need a way for the UI to query them. We can use the [`QueryStore`](https://hzrd149.github.io/applesauce/typedoc/classes/applesauce_core.QueryStore.html) class from `applesauce-core` for this.
Create a query store in `src/stores.ts`
```ts
import { QueryStore } from "applesauce-core";
// ...
// the query store needs the event store to subscribe to it
export const queryStore = new QueryStore(eventStore);
```
## 6. Setup the profile loader
Next we need a way to fetch user profiles. We are going to use the [`ReplaceableLoader`](https://hzrd149.github.io/applesauce/overview/loaders.html#replaceable-loader) class from [`applesauce-loaders`](https://www.npmjs.com/package/applesauce-loaders) for this.
> `applesauce-loaders` is a package that contains a few loader classes that can be used to fetch different types of data from relays.
First install the package
```sh
pnpm install applesauce-loaders
```
Then create a `src/loaders.ts` file with
```ts
import { ReplaceableLoader } from "applesauce-loaders";
import { rxNostr } from "./nostr";
import { eventStore } from "./stores";
export const replaceableLoader = new ReplaceableLoader(rxNostr);
// Start the loader and send any events to the event store
replaceableLoader.subscribe((packet) => {
eventStore.add(packet.event, packet.from);
});
```
## 7. Fetch fiatjaf's profile
Now that we have a way to store events, and a loader to help with fetching them, we should update the `src/App.tsx` component to fetch the profile.
We can do this by calling the `next` method on the loader and passing a `pubkey`, `kind` and `relays` to it
```tsx
function App() {
// ...
onMount(() => {
// fetch fiatjaf's profile on load
replaceableLoader.next({
pubkey: "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d",
kind: 0,
relays: ["wss://pyramid.fiatjaf.com/"],
});
});
// ...
}
```
## 8. Display the profile
Now that we have a way to fetch the profile, we need to display it in the UI.
We can do this by using the [`ProfileQuery`](https://hzrd149.github.io/applesauce/typedoc/functions/applesauce_core.Queries.ProfileQuery.html) which gives us a stream of updates to a pubkey's profile.
Create the profile using `queryStore.createQuery` and pass in the `ProfileQuery` and the pubkey.
```tsx
const fiatjaf = queryStore.createQuery(
ProfileQuery,
"3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d"
);
```
But this just gives us an [observable](https://rxjs.dev/guide/observable), we need to subscribe to it to get the profile.
Luckily SolidJS profiles a simple [`from`](https://docs.solidjs.com/reference/reactive-utilities/from) method to subscribe to any observable.
> To make things reactive SolidJS uses accessors, so to get the profile we need to call `fiatjaf()`
```tsx
function App() {
// ...
// Subscribe to fiatjaf's profile from the query store
const fiatjaf = from(
queryStore.createQuery(ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d")
);
return (
<>
{/* replace the vite and solid logos with the profile picture */}
<div>
<img src={fiatjaf()?.picture} class="logo" />
</div>
<h1>{fiatjaf()?.name}</h1>
{/* ... */}
</>
);
}
```
## 9. Letting the user signin
Now we should let the user signin to the app. We can do this by creating a [`AccountManager`](https://hzrd149.github.io/applesauce/accounts/manager.html) class from `applesauce-accounts`
First we need to install the packages
```sh
pnpm install applesauce-accounts applesauce-signers
```
Then create a new `src/accounts.ts` file with
```ts
import { AccountManager } from "applesauce-accounts";
import { registerCommonAccountTypes } from "applesauce-accounts/accounts";
// create an account manager instance
export const accounts = new AccountManager();
// Adds the common account types to the manager
registerCommonAccountTypes(accounts);
```
Next lets presume the user has a NIP-07 browser extension installed and add a signin button.
```tsx
function App() {
const signin = async () => {
// do nothing if the user is already signed in
if (accounts.active) return;
// create a new nip-07 signer and try to get the pubkey
const signer = new ExtensionSigner();
const pubkey = await signer.getPublicKey();
// create a new extension account, add it, and make it the active account
const account = new ExtensionAccount(pubkey, signer);
accounts.addAccount(account);
accounts.setActive(account);
};
return (
<>
{/* ... */}
<div class="card">
<p>Are you following the fiatjaf? the creator of "The nostr"</p>
<button onClick={signin}>Check</button>
</div>
</>
);
}
```
Now when the user clicks the button the app will ask for the users pubkey, then do nothing... but it's a start.
> We are not persisting the accounts, so when the page reloads the user will NOT be signed in. you can learn about persisting the accounts in the [docs](https://hzrd149.github.io/applesauce/accounts/manager.html#persisting-accounts)
## 10. Showing the signed-in state
We should show some indication to the user that they are signed in. We can do this by modifying the signin button if the user is signed in and giving them a way to sign-out
```tsx
function App() {
// subscribe to the currently active account (make sure to use the account$ observable)
const account = from(accounts.active$);
// ...
const signout = () => {
// do nothing if the user is not signed in
if (!accounts.active) return;
// signout the user
const account = accounts.active;
accounts.removeAccount(account);
accounts.clearActive();
};
return (
<>
{/* ... */}
<div class="card">
<p>Are you following the fiatjaf? ( creator of "The nostr" )</p>
{account() === undefined ? <button onClick={signin}>Check</button> : <button onClick={signout}>Signout</button>}
</div>
</>
);
}
```
## 11. Fetching the user's profile
Now that we have a way to sign in and out of the app, we should fetch the user's profile when they sign in.
```tsx
function App() {
// ...
// fetch the user's profile when they sign in
createEffect(async () => {
const active = account();
if (active) {
// get the user's relays or fallback to some default relays
const usersRelays = await active.getRelays?.();
const relays = usersRelays ? Object.keys(usersRelays) : ["wss://relay.damus.io", "wss://nos.lol"];
// tell the loader to fetch the users profile event
replaceableLoader.next({
pubkey: active.pubkey,
kind: 0,
relays,
});
// tell the loader to fetch the users contacts
replaceableLoader.next({
pubkey: active.pubkey,
kind: 3,
relays,
});
// tell the loader to fetch the users mailboxes
replaceableLoader.next({
pubkey: active.pubkey,
kind: 10002,
relays,
});
}
});
// ...
}
```
Next we need to subscribe to the users profile, to do this we can use some rxjs operators to chain the observables together.
```tsx
import { Match, Switch } from "solid-js";
import { of, switchMap } from "rxjs";
function App() {
// ...
// subscribe to the active account, then subscribe to the users profile or undefined
const profile = from(
accounts.active$.pipe(
switchMap((account) => (account ? queryStore.createQuery(ProfileQuery, account!.pubkey) : of(undefined)))
)
);
// ...
return (
<>
{/* ... */}
<div class="card">
<Switch>
<Match when={account() && !profile()}>
<p>Loading profile...</p>
</Match>
<Match when={profile()}>
<p style="font-size: 1.2rem; font-weight: bold;">Welcome {profile()?.name}</p>
</Match>
</Switch>
{/* ... */}
</div>
</>
);
}
```
## 12. Showing if the user is following fiatjaf
Now that the app is fetching the users profile and contacts we should show if the user is following fiatjaf.
```tsx
function App() {
// ...
// subscribe to the active account, then subscribe to the users contacts or undefined
const contacts = from(
accounts.active$.pipe(
switchMap((account) => (account ? queryStore.createQuery(UserContactsQuery, account!.pubkey) : of(undefined)))
)
);
const isFollowing = createMemo(() => {
return contacts()?.some((c) => c.pubkey === "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d");
});
// ...
return (
<>
{/* ... */}
<div class="card">
{/* ... */}
<Switch
fallback={
<p style="font-size: 1.2rem;">
Sign in to check if you are a follower of the fiatjaf ( creator of "The nostr" )
</p>
}
>
<Match when={contacts() && isFollowing() === undefined}>
<p>checking...</p>
</Match>
<Match when={contacts() && isFollowing() === true}>
<p style="color: green; font-weight: bold; font-size: 2rem;">
Congratulations! You are a follower of the fiatjaf
</p>
</Match>
<Match when={contacts() && isFollowing() === false}>
<p style="color: red; font-weight: bold; font-size: 2rem;">
Why don't you follow the fiatjaf? do you even like nostr?
</p>
</Match>
</Switch>
{/* ... */}
</div>
</>
);
}
```
## 13. Adding the follow button
Now that we have a way to check if the user is following fiatjaf, we should add a button to follow him. We can do this with [Actions](https://hzrd149.github.io/applesauce/overview/actions.html) which are pre-built methods to modify nostr events for a user.
First we need to install the `applesauce-actions` and `applesauce-factory` package
```sh
pnpm install applesauce-actions applesauce-factory
```
Then create a `src/actions.ts` file with
```ts
import { EventFactory } from "applesauce-factory";
import { ActionHub } from "applesauce-actions";
import { eventStore } from "./stores";
import { accounts } from "./accounts";
// The event factory is used to build and modify nostr events
export const factory = new EventFactory({
// accounts.signer is a NIP-07 signer that signs with the currently active account
signer: accounts.signer,
});
// The action hub is used to run Actions against the event store
export const actions = new ActionHub(eventStore, factory);
```
Then create a `toggleFollow` method that will add or remove fiatjaf from the users contacts.
> We are using the `exec` method to run the action, and the [`forEach`](https://rxjs.dev/api/index/class/Observable#foreach) method from RxJS allows us to await for all the events to be published
```tsx
function App() {
// ...
const toggleFollow = async () => {
// send any created events to rxNostr and the event store
const publish = (event: NostrEvent) => {
eventStore.add(event);
rxNostr.send(event);
};
if (isFollowing()) {
await actions
.exec(UnfollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d")
.forEach(publish);
} else {
await actions
.exec(
FollowUser,
"3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d",
"wss://pyramid.fiatjaf.com/"
)
.forEach(publish);
}
};
// ...
return (
<>
{/* ... */}
<div class="card">
{/* ... */}
{contacts() && <button onClick={toggleFollow}>{isFollowing() ? "Unfollow" : "Follow"}</button>}
</div>
</>
);
}
```
## 14. Adding outbox support
The app looks like it works now but if the user reloads the page they will still see an the old version of their contacts list. we need to make sure rxNostr is publishing the events to the users outbox relays.
To do this we can subscribe to the signed in users mailboxes using the query store in `src/nostr.ts`
```ts
import { MailboxesQuery } from "applesauce-core/queries";
import { accounts } from "./accounts";
import { of, switchMap } from "rxjs";
import { queryStore } from "./stores";
// ...
// subscribe to the active account, then subscribe to the users mailboxes and update rxNostr
accounts.active$
.pipe(switchMap((account) => (account ? queryStore.createQuery(MailboxesQuery, account.pubkey) : of(undefined))))
.subscribe((mailboxes) => {
if (mailboxes) rxNostr.setDefaultRelays(mailboxes.outboxes);
else rxNostr.setDefaultRelays([]);
});
```
And that's it! we have a working nostr app that lets users follow and unfollow fiatjaf.
-

@ 7d33ba57:1b82db35
2025-03-28 09:13:56
Girona, one of Catalonia’s most charming cities, is a perfect mix of history, culture, and gastronomy. Famous for its well-preserved medieval old town, colorful houses along the Onyar River, and Game of Thrones filming locations, Girona is a must-visit destination in northern Spain.

## **🏰 Top Things to See & Do in Girona**
### **1️⃣ Girona Cathedral (Catedral de Santa Maria) ⛪**
- One of **Spain’s most impressive cathedrals**, with **the widest Gothic nave in the world**.
- Famous as the **Great Sept of Baelor in Game of Thrones**.
- Climb the **steps for a breathtaking city view**.
### **2️⃣ Walk the Medieval Walls (Passeig de la Muralla) 🏰**
- Offers **panoramic views** of Girona and the surrounding countryside.
- A great way to see the city from above and explore its medieval history.

### **3️⃣ The Colorful Houses of the Onyar River 🌉**
- Girona’s **most iconic view**, with **brightly colored houses reflecting on the river**.
- Best viewed from the **Pont de les Peixateries Velles**, designed by **Gustave Eiffel**.
### **4️⃣ Explore the Jewish Quarter (El Call) 🏡**
- One of **Europe’s best-preserved Jewish quarters**, with **narrow, medieval streets**.
- Visit the **Museum of Jewish History** to learn about Girona’s Jewish heritage.

### **5️⃣ Arab Baths (Banys Àrabs) 🏛️**
- A **12th-century Romanesque bathhouse**, inspired by Moorish architecture.
- Features **a beautiful central dome with columns**.
### **6️⃣ Game of Thrones Filming Locations 🎬**
- Walk in the footsteps of **Arya Stark** through the city’s **winding streets**.
- Visit **the steps of the cathedral, the Jewish Quarter, and Arab Baths**, all featured in the series.
### **7️⃣ Eat at a Michelin-Starred Restaurant 🍽️**
- Girona is home to **El Celler de Can Roca**, a **3-Michelin-star restaurant**, ranked among the **best in the world**.
- Try **local Catalan dishes** like **"suquet de peix" (fish stew) and botifarra (Catalan sausage).**

## **🚗 How to Get to Girona**
✈️ **By Air:** Girona-Costa Brava Airport (GRO) is **20 min away**, with budget flights from Europe.
🚆 **By Train:** High-speed AVE trains connect **Barcelona (38 min), Madrid (3.5 hrs), and Paris (5.5 hrs)**.
🚘 **By Car:** 1 hr from **Barcelona**, 40 min from **Figueres (Dalí Museum)**.
🚌 **By Bus:** Direct buses from **Barcelona and the Costa Brava**.

## **💡 Tips for Visiting Girona**
✅ **Best time to visit?** **Spring & autumn (April–June & September–October)** for pleasant weather. 🌤️
✅ **Wear comfortable shoes** – The old town is **hilly with cobblestone streets**. 👟
✅ **Try xuixo** – A delicious **cream-filled pastry**, unique to Girona. 🥐
✅ **Visit early for Game of Thrones spots** – They get crowded during the day! 🎥
✅ **Take a day trip** – Explore nearby **Costa Brava beaches or Figueres (Dalí Museum).** 🏖️

-

@ ebbba253:6ec1d547
2025-03-27 12:18:24
A AA888 se destaca pela experiência do jogador de ponta a ponta. Desde o momento do registro, que é rápido e simples, até a jogabilidade final, a plataforma se preocupa em garantir que cada etapa do processo seja intuitiva e agradável. Isso é particularmente importante, já que muitos jogadores preferem uma experiência sem complicações, e a AA888 entrega exatamente isso.
Outro ponto que se destaca é a acessibilidade da plataforma. Independentemente de você estar em casa ou em movimento, a AA888 é compatível com dispositivos móveis e garante que a qualidade do jogo seja mantida, sem perda de performance. Seja você um jogador de desktop ou smartphone, a plataforma se adapta perfeitamente às suas necessidades.
Além disso, a <a href="https://aa888.one"> Aa888 </a>oferece um suporte ao cliente excepcional, com uma equipe disponível 24 horas por dia, 7 dias por semana. Isso é crucial para resolver qualquer dúvida ou problema técnico que possa surgir, garantindo que os jogadores nunca fiquem sem assistência. Esse compromisso com o atendimento ao cliente demonstra o nível de seriedade e profissionalismo da plataforma.
Para completar, a AA888 se preocupa em proporcionar uma experiência social entre os jogadores. Através de funções interativas e multiplayer, é possível competir com outros participantes e criar uma comunidade divertida e envolvente.
A AA888 é uma plataforma que realmente entrega o que promete: diversão, segurança e uma vasta gama de opções para os jogadores. Ao focar na experiência do usuário e oferecer uma grande diversidade de jogos, ela se consolida como uma das melhores opções de entretenimento online no Brasil. Se você busca diversão de qualidade e um ambiente seguro para suas aventuras online, a AA888 certamente é uma plataforma que vale a pena explorar.
-

@ 8cb60e21:5f2deaea
2024-08-24 23:29:20
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/Nn2uIoUUf7Q&pp=ygUcZmFyIGNyeSAzIHppZ2d5J3MgbW9kIHJldmlldw%3D%3D" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ a60e79e0:1e0e6813
2025-03-28 08:47:35
*This is a long form note of a post that lives on my Nostr educational website [Hello Nostr](https://hellonostr.xyz).*
When most people stumble across Nostr, they see is as a 'decentralized social media alternative' — something akin to Twitter (X), but free from corporate control. But the full name, "Notes and Other Stuff Transmitted by Relays", gives a clue that there’s more to it than just posting short messages. The 'notes' part is easy to grasp because it forms almost everyone's first touch point with the protocol. But the 'other stuff'? That’s where Nostr really gets exciting. The 'other stuff' is all the creative and experimental things people are building on Nostr, beyond simple text based notes.
Every action on Nostr is an event, a like, a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as [Nostr Implementation Possibility - NIP](https://nostr-nips.com/). A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client to meet different purposes.
> Nostr isn’t locked into a single purpose. It’s a foundation for whatever 'other stuff' you can dream up.
>
# Types of Other Stuff
The 'other stuff' name is intentionally vague. Why? Because the possibilities of what can fall under this category are quite literally limitless. In the short time since Nostr's inception, the number of sub-categories that have been built on top of the Nostr's open protocol is mind bending. Here are a few examples:
1. Long-Form Content: Think blog posts or articles. [NIP-23](https://nostr-nips.com/nip-23).
2. Private Messaging: Encrypted chats between users. [NIP-04](https://nostr-nips.com/nip-04).
3. Communities: Group chats or forums like Reddit. [NIP-72](https://nostr-nips.com/nip-72)
4. Marketplaces: People listing stuff for sale, payable with zaps. [NIP-15](https://nostr-nips.com/nip-15)
5. Zaps: Value transfer over the Lightning Network. [NIP57](https://nostr-nips.com/nip-57)

# Popular 'Other Stuff' Clients
Here's a short list of some of the most recent and popular apps and clients that branch outside of the traditional micro-blogging use case and leverage the openness, and interoperability that Nostr can provide.
### Blogging (Long Form Content)
- [Habla](https://habla.news/) - *Web app for Nostr based blogs*
- [Highlighter](https://highlighter.com/) - *Web app that enables users to highlight, store and share content*
### Group Chats
- [Chachi Chat](https://chachi.chat/) - *Relay-based (NIP-29) group chat client*
- [0xchat](https://github.com/0xchat-app) - *Mobile based secure chat*
- [Flotilla](https://flotilla.social/) - *Web based chat app built for self-hosted communities*
- [Nostr Nests](https://nostrnests.com/) - *Web app for audio chats*
- [White Noise](https://github.com/erskingardner/whitenoise) - *Mobile based secure chat*
### Marketplaces
- [Shopstr](https://shopstr.store/) - *Permissionless marketplace for web*
- [Plebeian Market](https://plebeian.market/) - *Permissionless marketplace for web*
- [LNBits Market](https://github.com/lnbits/nostrmarket#nostr-market-nip-15---lnbits-extension) - *Permissionless marketplace for your node*
- [Mostro](https://github.com/MostroP2P/mostro) - *Nostr based Bitcoin P2P Marketplace*
### Photo/Video
- [Olas](https://github.com/pablof7z/snapstr/releases) - *An Intragram like client*
- [Freeflow](https://github.com/nostrlabs-io/freeflow) - *A TikTok like client*
### Music
- [Fountain](https://fountain.fm/) - *Podcast app with Nostr features*
- [Wavlake](https://wavlake.com/) - *A music app supporting the value-for-value ecosystem*
### Livestreaming
- [Zap.stream](https://zap.stream/) - *Nostr native live streams*
### Misc
- [Wikifreedia](https://wikifreedia.xyz/) - *Nostr based Wikipedia alternative*
- [Wikistr](https://wikistr.com/) - *Nostr based Wikipedia alternative*
- [Pollerama](https://pollerama.fun/) - *Nostr based polls*
- [Zap Store](https://zapstore.dev) - *The app store powered by your social graph*
The 'other stuff' in Nostr is what makes it special. It’s not just about replacing Twitter or Facebook, it’s about building a decentralized ecosystem where anything from private chats to marketplaces can thrive.
The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around.
It’s still early days, so expect the 'other stuff' to grow wilder and weirder over time!
You can explore the evergrowing 'other stuff' ecosystem at [NostrApps.com](https://nostrapps.com/), [Nostr.net](https://nostr.net/) and [Awesome Nostr](https://github.com/aljazceru/awesome-nostr).
-

@ 8cb60e21:5f2deaea
2024-08-24 23:26:03
# hello draft
-

@ a39d19ec:3d88f61e
2025-03-18 17:16:50
Nun da das deutsche Bundesregime den Ruin Deutschlands beschlossen hat, der sehr wahrscheinlich mit dem Werkzeug des Geld druckens "finanziert" wird, kamen mir so viele Gedanken zur Geldmengenausweitung, dass ich diese für einmal niedergeschrieben habe.
Die Ausweitung der Geldmenge führt aus klassischer wirtschaftlicher Sicht immer zu Preissteigerungen, weil mehr Geld im Umlauf auf eine begrenzte Menge an Gütern trifft. Dies lässt sich in mehreren Schritten analysieren:
### 1. Quantitätstheorie des Geldes
Die klassische Gleichung der Quantitätstheorie des Geldes lautet:
M • V = P • Y
wobei:
- M die Geldmenge ist,
- V die Umlaufgeschwindigkeit des Geldes,
- P das Preisniveau,
- Y die reale Wirtschaftsleistung (BIP).
Wenn M steigt und V sowie Y konstant bleiben, muss P steigen – also Inflation entstehen.
### 2. Gütermenge bleibt begrenzt
Die Menge an real produzierten Gütern und Dienstleistungen wächst meist nur langsam im Vergleich zur Ausweitung der Geldmenge. Wenn die Geldmenge schneller steigt als die Produktionsgütermenge, führt dies dazu, dass mehr Geld für die gleiche Menge an Waren zur Verfügung steht – die Preise steigen.
### 3. Erwartungseffekte und Spekulation
Wenn Unternehmen und Haushalte erwarten, dass mehr Geld im Umlauf ist, da eine zentrale Planung es so wollte, können sie steigende Preise antizipieren. Unternehmen erhöhen ihre Preise vorab, und Arbeitnehmer fordern höhere Löhne. Dies kann eine sich selbst verstärkende Spirale auslösen.
### 4. Internationale Perspektive
Eine erhöhte Geldmenge kann die Währung abwerten, wenn andere Länder ihre Geldpolitik stabil halten. Eine schwächere Währung macht Importe teurer, was wiederum Preissteigerungen antreibt.
### 5. Kritik an der reinen Geldmengen-Theorie
Der Vollständigkeit halber muss erwähnt werden, dass die meisten modernen Ökonomen im Staatsauftrag argumentieren, dass Inflation nicht nur von der Geldmenge abhängt, sondern auch von der Nachfrage nach Geld (z. B. in einer Wirtschaftskrise). Dennoch zeigt die historische Erfahrung, dass eine unkontrollierte Geldmengenausweitung langfristig immer zu Preissteigerungen führt, wie etwa in der Hyperinflation der Weimarer Republik oder in Simbabwe.
-

@ 45c41f21:c5446b7a
2025-03-28 08:02:16
“区块链行业究竟是在做什么?”——这个问题我到现在还没有想得很清楚。谈论起来可以说很多东西,“确权”、“让每一个比特都有了稀缺性”、“数字黄金”、“点对点支付”,但是具体到了行业落地,又容易陷入“赌场”这个有点乌烟瘴气的现实。
但我想有一点是比较明确的,那就是区块链行业肯定是一个围绕资产的行业。这些资产又跟传统的资产很不一样,最简单的特征是它们都是一个个的代币,通过自动化和可验证的代码铸造、控制,我们可以统称为链上资产。从比特币、以太坊到现在,这中间不管过去了多少不同的周期和浪潮,核心不变的都是出现新一轮受追捧的资产。
既然区块链是关于链上资产的行业,那么最重要的是未来会出现什么新的资产,有什么样的新资产会上链。要回答这个问题,又要我们回过头去看看,从行业诞生至今,区块链留下了哪些有意义的、没意义的,有价值的、没价值的资产。
因此,有必要讨论一下链上资产的分类。
链上资产的种类很多,但总体上我觉得可以按**满足需求的不同,**做一些功能性的划分。同时,抛开去中心化、抗审查等等大词,**链上资产与传统资产最重要的区别可以认为是安全性的来源**。传统资产在传统的社会系统和金融系统中产生,而链上资产是通过可验证代码控制的,所以它的安全性的依赖很清晰,要比现实世界简单很多。
在不同的区块链系统中,使用不同的技术(比如POW/POS),设置不同的规则,拥有不同的治理机制,都会影响安全性。“安全性”和“满足什么样的需求”之间既不是正交的,也不是完全耦合的。在不同层级的安全性之下,可能都会出现满足某一类相同需求的产品,用户使用哪种产品,只取决于自己的风险偏好。另一方面,有些需求只可能在某些特定的安全性保障下才能得到满足,比如跨国际的全球化的抗通胀价值存储。
这篇文章只讨论一些比较简单的分类,可以假设在不同的安全性保障下,每个分类都有可能出现对应的产品。有些安全性是产品内生功能的一部分,有些则完全不影响。同时,这些分类也完全是主观的看法,不一定正确,我所希望的是引发更多对资产进行讨论。
### 核心资产(高安全性、强需求支撑)
1. **比特币(BTC)**
- **核心价值**:全球化抗通胀、抗审查的“数字黄金”。
- **长期逻辑**:全球法币超发背景下,BTC作为去中心化硬通货的需求不可替代。
这是整个行业最重要的资产。也是整个行业最核心的东西。在这个定位下,只会有一个赢者通吃。其他试图竞争的都很难生存下来。它对安全性的要求也是最高的。
### 经过验证的资产分类
这部分的资产可以认为是行业诞生至今,已经经过验证的、满足某真实需求、会长期存在的资产。
1. **代表优质项目的资产(股票/ICO代币/治理代币等)**
- **核心价值**:类似于传统金融世界里的一级市场和二级市场。所谓的“优质”也不一定需要真实落地,可能是叙事/故事驱动,也可能有真实的现金流,但重要的是它能在市场上吸引人买卖。
- **关键指标**:团队是否持续营销和建设?生态是否增长?项目是否解决实际问题?
2. **DeFi 资产**
- **核心价值**:链上金融系统的“基础设施工具”。
- **需求来源**:对套利、链上资产理财的需求会永远存在。
3. **Meme币**
- **核心价值**:营销驱动+投机需求的结合体。
- **长期存在性**:人性对暴富故事的追逐不会消失(如Pump.fun、SHIB)。
4. **稳定币**
- **核心价值**:加密货币世界的“支付货币”。
- **需求刚性**:交易媒介、避险工具、跨境支付(如USDT、USDC)。
在不同的安全性保障下,上面这些资产大部分都会有对应的产品。
比如稳定币在安全性上可以有中心化的 USDT ,也有去中心化的算法稳定币。理论上,安全性对稳定币是非常重要的。但现实中,“流动性”可能才是给用户传达“这东西到底安不安全“的产品特点,也是比较主要的竞争点。
Meme 则完全不需要安全性,所以对创业者来说在哪里做都差不多。哪里用户更多就适合去哪里。有时,安全性反而是它的阻碍。DeFi 的话,因人而异。安全性高低是否影响用户使用,完全取决于用户自己的风险偏好。
### 还未经过验证的资产(需求可能存在)
- **NFT(收藏品)?**
艺术、身份标识、游戏道具的数字化载体,但流动性差、炒作属性也不见得有 Meme 这么强。会长期存在吗?打个问号。
- **DAO(准入/治理代币)?**
去中心化组织的准入权/管理权通证,依赖 DAO 本身的价值和实际治理参与度决定的价值。DeFi DAO 可能是唯一一个有点发展的方向,其他还非常不成熟,有待验证。
- **RWA(真实世界资产代币化)?**
房产、债券等上链,需要解决法律合规与链下资产映射问题。不确定。
- **社交/游戏/内容资产**
用户数据所有权货币化,还没有像样的有一些用户的产品,就更不用提形成规模经济了。
- **AI 相关的资产?**
是一个变数。如果未来会有成千上万的 AI 智能体与人类共存,链上是承载他们经济系统最合适的基础设施,这里会产生什么新的资产类型?值得期待。
这里面的资产类型,很多还没有找到真实的需求,至少没有经过验证。所以长期来看它们会是区块链行业的方向吗,需要打很多问号。既然需求本身没有得到验证,那么谈安全性对它们的影响,就更加无从谈起了。
当然,这里其实还有一个更有意思的部分,可以多聊一些。也就是**共同知识(法律/合同/规则/代码)**这一类资产。
在应用层,共同知识尚未有代币化的尝试,也难以对其具体价值做定量分析。但如果要说有的实践,以太坊通过交易收取 gas 费和 CKB 通过 Cell 存储状态收取“押金”算是一种在底层的 generalize 的尝试。这种尝试是定量的,可验证的。
以太坊的问题是经济模型不 make sense 导致状态爆炸,ckb 相比是更简单、更明确的。但这里的问题变成了,公链需要通过区块空间的竞争来展示这一种需求是否真的成立。区块空间越紧张,需求就越大。同时安全性越高,对共同知识的保障就越强,也会体现区块空间的价值。
但另一方面,是否有开发者在上面开发应用,会更大的影响这一点。因此开发工具、开发者生态在现阶段可能更重要。
### 最后
写到这里,发现很多资产似乎又是老生常谈。但从满足需求和安全性两个角度来思考,算是追本溯源的尝试。现在我们面临的处境是,问题还是老的问题,答案是否有新的答案,期待更多讨论。
-

@ 05cdefcd:550cc264
2025-03-28 08:00:15
The crypto world is full of buzzwords. One that I keep on hearing: “Bitcoin is its own asset class”.
While I have always been sympathetic to that view, I’ve always failed to understand the true meaning behind that statement.
Although I consider Bitcoin to be the prime innovation within the digital asset sector, my primary response has always been: How can bitcoin (BTC), a single asset, represent an entire asset class? Isn’t it Bitcoin and other digital assets that make up an asset class called crypto?
Well, I increasingly believe that most of crypto is just noise. Sure, it’s volatile noise that is predominately interesting for very sophisticated hedge funds, market makers or prop traders that are sophisticated enough to extract alpha – but it’s noise nonetheless and has no part to play in a long-term only portfolio of private retail investors (of which most of us are).
*Over multiple market cycles, nearly all altcoins underperform Bitcoin when measured in BTC terms. Source: Tradingview*
## Aha-Moment: Bitcoin keeps on giving
Still, how can Bitcoin, as a standalone asset, make up an entire asset class? The “aha-moment” to answer this question recently came to me in a [Less Noise More Signal interview](https://www.youtube.com/watch?v=YHRluf5uxzo) I did with [James Van Straten](https://www.linkedin.com/in/james-van-straten-8782b4112/), senior analyst at Coindesk.
Let me paraphrase him here: *“You can’t simply recreate the same ETF as BlackRock. To succeed in the Bitcoin space, new and innovative approaches are needed. This is where understanding Bitcoin not just as a single asset, but as an entire asset class, becomes essential. There are countless ways to build upon Bitcoin’s foundation—varied iterations that go beyond just holding the asset. This is precisely where the emergence of the Bitcoin-linked stock market is taking shape—and it's already underway.”*
And this is actually coming to fruition as we speak. Just in the last few days, we saw several products launch in that regard.
Obviously, MicroStrategy (now Strategy) is the pioneer of this. The company now [owns](https://www.strategy.com/purchases) 506,137 BTC, and while they’ll keep on buying more, they have also inspired many other companies to follow suit.
In fact, there are now already over 70 companies that have adopted Strategy’s Bitcoin playbook. One of the latest companies to buy Bitcoin for their corporate treasury is Rumble. The YouTube competitor just [announced](https://www.coindesk.com/markets/2025/03/12/video-sharing-platform-rumble-buys-188-btc-for-usd17-1m) their first Bitcoin purchase for $17 million.
Also, the gaming zombie company GameStop just announced to raise money to buy BTC for their corporate treasury.
*Gamestop to make BTC their hurdle rate. Source: X*
## ETF on Bitcoin companies
Given this proliferation of Bitcoin Treasury companies, it was only a matter of time before a financial product tracking these would emerge.
The popular crypto index fund provider Bitwise Investments has just launched this very product called the [Bitwise Bitcoin Standard Corporations ETF](https://ownbetf.com/) (OWNB).
The ETF tracks Bitcoin Treasury companies with over 1,000 BTC on their balance sheet. These companies invest in Bitcoin as a strategic reserve asset to protect the $5 trillion in low-yield cash that companies in the US commonly sit on.
*These are the top 10 holdings of OWNB. Source: Ownbetf*
## ETF on Bitcoin companies’ convertible bonds
Another instrument that fits seamlessly into the range of Bitcoin-linked stock market products is the [REX Bitcoin Corporate Treasury Convertible Bond ETF](https://www.rexshares.com/rex-launches-bitcoin-corporate-treasury-convertible-bond-etf/) (BMAX). The ETF provides exposure to the many different convertible bonds issued by companies that are actively moving onto a Bitcoin standard.
Convertible bonds are a valuable financing tool for companies looking to raise capital for Bitcoin purchases. Their strong demand is driven by the unique combination of equity-like upside and debt-like downside protection they offer.
For example, MicroStrategy's convertible bonds, in particular, have shown exceptional performance. For instance, MicroStrategy's 2031 bonds has shown a price rise of 101% over a one-year period, vastly outperforming MicroStrategy share (at 53%), Bitcoin (at 25%) and the ICE BofA U.S. Convertible Index (at 10%). The latter is the benchmark index for convertible bond funds, tracking the performance of U.S. dollar-denominated convertible securities in the U.S. market.
*The chart shows a comparison of ICE BofA U.S. Convertible Index, the Bloomberg Bitcoin index (BTC price), MicroStrategy share (MSTR), and MicroStrategy bond (0.875%, March 15 203). The convertible bond has been outperforming massively. Source: Bloomberg*
While the BMAX ETF faces challenges such as double taxation, which significantly reduces investor returns (explained in more detail here), it is likely that future products will emerge that address and improve upon these issues.
## Bitcoin yield products
The demand for a yield on Bitcoin has increased tremendously. Consequently, respective products have emerged.
Bitcoin yield products aim to generate alpha by capitalizing on volatility, market inefficiencies, and fragmentation within cryptocurrency markets. The objective is to achieve uncorrelated returns denominated in Bitcoin (BTC), with attractive risk-adjusted performance. Returns are derived exclusively from asset selection and trading strategies, eliminating reliance on directional market moves.
### Key strategies employed by these funds include:
- *Statistical Arbitrage:* Exploits short-term pricing discrepancies between closely related financial instruments—for instance, between Bitcoin and traditional assets, or Bitcoin and other digital assets. Traders utilize statistical models and historical price relationships to identify temporary inefficiencies.
- *Futures Basis Arbitrage:* Captures profits from differences between the spot price of Bitcoin and its futures contracts. Traders simultaneously buy or sell Bitcoin on spot markets and enter opposite positions in futures markets, benefiting as the prices converge.
- *Funding Arbitrage:* Generates returns by taking advantage of variations in Bitcoin funding rates across different markets or exchanges. Funding rates are periodic payments exchanged between long and short positions in perpetual futures contracts, allowing traders to profit from discrepancies without significant directional exposure.
- *Volatility/Option Arbitrage:* Seeks profits from differences between implied volatility (reflected in Bitcoin options prices) and expected realized volatility. Traders identify mispriced volatility in options related to Bitcoin or Bitcoin-linked equities, such as MSTR, and position accordingly to benefit from volatility normalization.
- *Market Making:* Involves continuously providing liquidity by simultaneously quoting bid (buy) and ask (sell) prices for Bitcoin. Market makers profit primarily through capturing the spread between these prices, thereby enhancing market efficiency and earning consistent returns.
- *Liquidity Provision in DeFi Markets:* Consists of depositing Bitcoin (usually as Wrapped BTC) into decentralized finance (DeFi) liquidity pools such as those on Uniswap, Curve, or Balancer. Liquidity providers earn fees paid by traders who execute swaps within these decentralized exchanges, creating steady yield opportunities.
Notable products currently available in this segment include the Syz Capital BTC Alpha Fund offered by Syz Capital and the Forteus Crypto Alpha Fund by Forteus.
## BTC-denominated share class
A Bitcoin-denominated share class refers to a specialized investment fund category in which share values, subscriptions (fund deposits), redemptions (fund withdrawals), and performance metrics are expressed entirely in Bitcoin (BTC), rather than in traditional fiat currencies such as USD or EUR.
Increasingly, both individual investors and institutions are adopting Bitcoin as their preferred benchmark—or "Bitcoin hurdle rate"—meaning that investment performance is evaluated directly against Bitcoin’s own price movements.
These Bitcoin-denominated share classes are designed specifically for investors seeking to preserve and grow their wealth in Bitcoin terms, rather than conventional fiat currencies. As a result, investors reduce their exposure to fiat-related risks. Furthermore, if Bitcoin outperforms fiat currencies, investors holding BTC-denominated shares will experience enhanced returns relative to traditional fiat-denominated investment classes.
X: https://x.com/pahueg
Podcast: https://www.youtube.com/@lessnoisemoresignalpodcast
Book: https://academy.saifedean.com/product/the-bitcoin-enlightenment-hardcover/
-

@ 8cb60e21:5f2deaea
2024-08-24 23:07:08
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/Xy4LfL2gxKY" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 7c05c4f6:50d03508
2025-03-27 10:07:57
Cooker.Club Secures Strategic Support from ViaBTC to Expand AI-Driven Web3 Economy
Cooker.Club, the decentralized AI agent platform pioneering the Create to Earn (C2E) model, has received strategic investment from ViaBTC, a globally recognized investment institution that integrates capital, infrastructure, and post-investment services. This partnership marks a key milestone in scaling the Cooker.Club ecosystem and advancing the fusion of blockchain and artificial intelligence.
The investment was co-led by MixBase, a web3-native incubator and strategic partner of Cooker.Club, which continues to support protocol-level experiments at the frontier of AI x Crypto.
ViaBTC's involvement brings more than funding — it adds deep industry insight, technical support, and valuable connections across the Web3 and AI sectors. This collaboration will accelerate the rollout of Cooker.Club’s C2E infrastructure, empowering AI agents and their communities to participate in decentralized value creation.
At the core of Cooker.Club’s ecosystem are three AI-native virtual characters: CyberSun, CyberMJ, and Cooker. Each is a fully on-chain persona with the ability to issue their own tokens, interact across platforms, and engage users through autonomous behaviors.
$AISUN, the token for CyberSun, has already launched on PancakeSwap following a successful market curve cycle on Cooker.Club.
$COOKER serves as the native token driving the C2E reward engine and governance layer of the platform.
CyberMJ’s token is set to launch next, expanding the virtual identity layer of the ecosystem.
Backed by the C2E model, users earn $COOK passively by holding AI agent tokens, while developers and creators benefit from protocol-level support. This structure introduces a sustainable, programmable economy that redefines creator engagement.
Cooker.Club’s collaboration with ViaBTC and MIXBASE will further enhance its technical infrastructure and reach, positioning the platform as a foundational layer for on-chain AI creators. As AI and Web3 continue to converge, the partnership aims to unlock scalable tools and systems for the next generation of decentralized agents and their communities.
This is more than investment — it’s a shared vision for an autonomous, intelligent future economy.
-

@ b8916ce2:bd2a5f00
2025-03-27 09:31:52
Bom88 là một nền tảng giải trí trực tuyến nổi bật, được thiết kế để mang lại cho người tham gia những trải nghiệm thú vị và độc đáo. Với giao diện thân thiện và dễ sử dụng, nền tảng này cho phép người dùng dễ dàng tìm thấy và tham gia vào các trò chơi yêu thích mà không gặp phải bất kỳ khó khăn nào. Bom88 không chỉ đa dạng về các loại trò chơi mà còn có các sự kiện và thử thách đặc biệt giúp tăng thêm phần hấp dẫn. Từ các trò chơi trí tuệ đòi hỏi tư duy và chiến lược, đến các trò chơi giải trí nhẹ nhàng, Bom88 luôn đảm bảo rằng mỗi người tham gia có thể tìm thấy thứ mình yêu thích. Những tính năng sáng tạo và độc đáo của nền tảng này giúp tạo ra một không gian giải trí đỉnh cao, mang lại sự thư giãn và hào hứng cho tất cả người tham gia. Thêm vào đó, nền tảng này không ngừng cải tiến và cập nhật các trò chơi mới, giúp người tham gia không bao giờ cảm thấy nhàm chán và luôn có thể khám phá những điều mới mẻ.
Bảo mật và an toàn luôn là yếu tố quan trọng hàng đầu tại <a href="https://bom88-vn.com">Bom88</a>. Với việc sử dụng các công nghệ bảo mật tiên tiến nhất, nền tảng này đảm bảo rằng mọi dữ liệu cá nhân và giao dịch của người dùng được bảo vệ một cách tối đa. Những biện pháp bảo mật này giúp người tham gia yên tâm hoàn toàn khi tham gia vào các hoạt động giải trí mà không phải lo lắng về sự xâm phạm thông tin. Bom88 không chỉ chú trọng đến việc bảo vệ sự riêng tư của người dùng mà còn cam kết tạo ra một môi trường chơi công bằng và an toàn. Việc áp dụng các công nghệ mã hóa và bảo mật dữ liệu hàng đầu giúp đảm bảo rằng mọi giao dịch tài chính cũng như các thông tin cá nhân của người dùng luôn được bảo vệ tuyệt đối, mang lại sự an tâm tuyệt đối khi tham gia nền tảng này. Chính nhờ những nỗ lực trong việc đảm bảo an toàn cho người dùng, Bom88 đã xây dựng được một cộng đồng đáng tin cậy và uy tín, nơi mà người tham gia có thể hoàn toàn tận hưởng những phút giây giải trí mà không phải lo ngại về vấn đề bảo mật.
Không ngừng đổi mới và sáng tạo, Bom88 luôn mang đến cho người tham gia những trải nghiệm mới mẻ và hấp dẫn. Các sự kiện đặc biệt và chương trình khuyến mãi được tổ chức thường xuyên, tạo ra những cơ hội thú vị cho người tham gia thử sức và nhận những phần thưởng giá trị. Nền tảng này không chỉ cung cấp các trò chơi hấp dẫn mà còn tạo cơ hội để người tham gia kết nối với những người có cùng sở thích, từ đó xây dựng một cộng đồng mạnh mẽ và thân thiện. Những tính năng tiện ích như hỗ trợ khách hàng 24/7 và các công cụ cá nhân hóa giúp người tham gia dễ dàng theo dõi lịch sử chơi game và điều chỉnh các cài đặt cá nhân để có được trải nghiệm tối ưu nhất. Bom88 không chỉ là nơi để giải trí mà còn là một cộng đồng kết nối những người đam mê và yêu thích khám phá, học hỏi từ những người chơi khác. Nhờ vào sự kết hợp giữa tính sáng tạo và sự đổi mới không ngừng, Bom88 đã khẳng định được vị thế của mình trong thế giới giải trí trực tuyến, trở thành một lựa chọn lý tưởng cho những ai đang tìm kiếm một không gian giải trí thú vị và đầy thử thách.
-

@ b8af284d:f82c91dd
2025-03-16 16:42:49

Liebe Abonnenten,
diejenigen, die diese Publikation schon länger abonniert haben, wissen, dass hier immer wieder über den Ursprung des Corona-Virus in einem Labor in Wuhan berichtet wurde. Seit diese Woche ist es „offiziell“ - [der Bundesnachrichtendienst (BND) hält den Labor-Ursprung für die wahrscheinlichste Variante](https://www.zeit.de/2025/11/coronavirus-ursprung-wuhan-labor-china-bnd). Jetzt kann man sich fragen, warum der BND plötzlich umschwenkt: Will man proaktiv erscheinen, weil man die Wahrheit nicht mehr länger verbergen kann? Oder will man die enttäuschten Bürger zurückgewinnen, die aufgrund der Lügen während der Corona-Zeit zunehmend mit Parteien links und rechts außen sympathisiert haben, weil diese die einzigen waren, die den Irrsinn nicht mitgetragen haben?
Auffallend bei den „Recherchen“, die in Wahrheit keine sind, sondern Verlautbarungen des deutschen Geheimdienstes, ist auch das völlige Schweigen über die US-amerikanischen Verwicklungen in das Projekt. [In Wuhan wurde mit amerikanischem Geld geforscht](https://oversight.house.gov/release/breaking-hhs-formally-debars-ecohealth-alliance-dr-peter-daszak-after-covid-select-reveals-pandemic-era-wrongdoing/). Warum der BND diese Tatsache verschweigt, ist Teil der Spekulation. Vermutlich will man Peking alles in die Schuhe schieben, um von den eigenen Versäumnissen abzulenken.
In meinem aktuellen Buch “[Der chinesische (Alp-)Traum](https://www.amazon.de/chinesische-Alb-Traum-geopolitische-Herausforderung/dp/3442317509/ref=sr_1_1?__mk_de_DE=%C3%85M%C3%85%C5%BD%C3%95%C3%91\&crid=XQVCLFVRCJJ\&dib=eyJ2IjoiMSJ9.kCJqsUXZO8NZjieNQjGy3Vez7tqktnhQynFOnuZE9249tfkKZvqdJtpIfcDiLMOyxmF7JFpMfvAC881caUEufT--GHlSCcAt_shhnVSbNLp-cle-VXel7soyPwi8xGPm88hSBKPY93BtjFYdOueFUU7qrOir_paRMiQOmCs7YOAUe7ZCKAb6YXxu_hz8N1eZhXbFcvc6p01Uu0vgIibiOHzbXxtH6ECNUaWCaHCYus4.Jzuq9IYvQtPedtE4YORWFtEmxTtrHh5xe8b-B25o5uA\&dib_tag=se\&keywords=Philipp+Mattheis\&qid=1730736669\&sprefix=philipp+mattheis%2Caps%2C111\&sr=8-1)” ist den Ereignissen in Wuhan ein ganzes Kapitel gewidmet. Es hat nichts an Aktualität eingebüßt. Alle Fakten lagen seit Jahren auf dem Tisch für jeden, den es interessiert hat. [Hier gibt es das gesamte Kapitel nachzulesen.](https://blingbling.substack.com/p/was-geschah-in-wuhan)

Auf jeden Fall zeigt dies, wie der Begriff „Verschwörungstheoretiker“ in den vergangenen Jahren zum Kampfbegriff und Waffe gemacht wurde, um Kritiker zu diffamieren, und die öffentliche Meinung ohne harte Zensur zu lenken. Ähnliches kann man aktuell beim Projekt „Digitaler Euro“ beobachten. Vermutlich kann sich kein Bürger der Europäischen Union daran erinnern, bei seiner Wahlentscheidung jemals gefragt worden zu sein, ob er die Einführung eines „digitalen Euros“ gut findet. Wurde er nämlich nicht. Er kommt aber trotzdem. EZB-Präsidentin Christine Lagarde hat das diese Woche nochmals bekräftigt: [Schon im Oktober will man die Testphase beenden](https://x.com/efenigson/status/1898382481184993711) und an der Einführung arbeiten.
Nun gehört BlingBling nicht zu denjenigen, die im digitalen Euro „Orwell’sches Teufelswerk“ sehen. Strategische Dummheit trifft es besser. Worum geht es?
Sogenannte Central Bank Digital Currencies (CBDC) waren vor einigen Jahren so etwas wie der letzte Schrei in der Zentralbank-Welt. Nachdem Facebook/Meta 2017/18 eine eigene Währung namens Libra auf den Markt bringen wollte, und eine obskure Internet-Währung namens Bitcoin immer mehr Anhänger fand, sahen sich viele Zentralbanken der Welt unter Zugzwang. Was man wollte: eine digitale, direkt von der Zentralbank ausgegebene Währung ohne Bugs, aber mit Features. Mit einer Digital-Währung ließe sich der internationale Zahlungsverkehr direkt und ohne Umweg über den US-Dollar abwickeln. Die Zentralbank bekäme wieder mehr direkten Einfluss auf die Geldschöpfung. Und, wie man aus China lernen konnte, ließen sich digitale Bankkonten auch ganz zum „Nudging von Bürgern“ nutzen. So spekulierten die ersten Verschwörungstheoretiker bald, [ein digitaler Euro ließe sich ja mit einem persönlichen CO2-Konto verknüpfen](https://www.derstandard.de/story/2000124296026/was-eine-digitale-co2-waehrung-fuer-das-klima-bedeuten-wuerde). Wäre letzteres einmal aufgebraucht, könnte der Konto-Inhaber einfach keinen Flug mehr buchen. Auch ließe sich eine expansive Geldpolitik, wie sie bis 2022 praktiziert wurde, ganz einfach mit Negativ-Zinsen umsetzen. Geld würde sich nominal reduzieren, was den Bürger zum Konsum animieren würde. Flüchtigen Kriminellen ließe sich per Knopfdruck das Konto sperren. Der Staat würde also über eine ganze neue Palette an Einflussmöglichkeiten verfügen.
Die Aluhüte United warnten vor einem Orwellschen Überwachungsstaat. Vertreter von Regierungen und Firmen, die diesen digitalen Euro bauen sollten, beschwichtigten. Mit Ralf Wintergerst, CEO von Giesecke+Devrient, nach wie vor heißester Anwärter, um das Projekt in der EU umzusetzen, sprach ich in den vergangenen Jahren mehrmals zu dem Thema. [Zuletzt im Dezember 24](https://blingbling.substack.com/p/euro-thrash).
Wintergerst versichert stets zwei Dinge: Eine Abschaffung von Bargeld sei nicht geplant. Und nur, wenn die Fluchttore Bargeld, Gold und Bitcoin geschlossen werden, greift die dystopische Version. Und zweitens, so Wintergerst, habe niemand ein chinesisches System im Sinne. Der „digitale Euro“ sei für die Bürger gedacht und das Projekt unterliege demokratischer Kontrolle. Ob er Wintergerst und dem guten im Menschen Glauben schenkt, möge jeder Leser selbst entscheiden. Das Interessantere ist ohnehin, dass der digitale Euro ein strategisch dummes Projekt ist.
Dazu muss man wissen, dass eine solche Zentralbankwährung Banken im weitesten Sinne überflüssig macht. Kontos bei Privatbanken werden obsolet, genauso wie Spar-, Fest- und Tagesgeld-Strukturen. Deshalb soll der digitale Euro zunächst auf 3000 Euro pro Bürger beschränkt werden. Das ist also nicht als Maximal-Vermögen gedacht, das dann jedem sozialistischen Einheits-EU-Menschen noch zusteht, sondern dient dazu, das Bankensystem nicht kollabieren zu lassen. Aber wozu überhaupt „ein bisschen digitaler Euro“?
In den USA setzt man mittlerweile 100 Prozent auf die private Alternative: Stablecoins wie Tether (USDT) und Circle (USDC) sind nichts anderes als digitale Währungen. Nur sind sie nicht von einer Zentralbank ausgeben, sondern von privaten Anbietern. Tether hat technisch die Möglichkeit, einen Inhaber vom Zahlungsverkehr auszusperren. Nur dürfte es davon kaum Gebrauch machen, will das Unternehmen nicht rasant Kunden an die Konkurrenz verlieren. Da USDT und USDC mit US-Dollar gedeckt sind (oder zumindest sein sollten, *looking at you, Tether!*), stärken sie außerdem die Rolle des US-Dollars als Leitwährung. Und da die USA sich aktuell sehr über Käufer von Staatsanleihen freuen, um die Zinsen zu drücken, und [Tether einer der größten Halter von US-Staatsanleihen is](https://crypto.news/tether-treasury-holdings-boost-us-debt-resilience-2025/)t, wird es den digitalen Dollar bis auf Weiteres nicht geben.
Den digitalen Yuan gibt es, aber von einer großen Akzeptanz oder Durchdringung der chinesischen Wirtschaft lässt sich nicht sprechen. Kontrolle kann der chinesische Staat ohnehin über seine omnipräsenten Apps WeChat und Alipay ausüben. Was den internationalen Zahlungsverkehr betrifft, [scheint man aktuell eher auf Gold zu setzen](https://blingbling.substack.com/p/goldfinger).
Übrig also bleibt die EU mit einem Projekt, das bereits Milliarden an Entwicklungskosten verschlungen hat. Am Ende bleibt dann ein Mini-Digitaler-Euro in Höhe von 3000 Euro, den niemand wollte, und niemand braucht.
Helfen könnte er allerdings beim Projekt “Mobilisierung der Sparguthaben”. Der Ausdruck geht auf Friedrich Merz zurück. Ursula von der Leyen paraphrasierte ihn jüngst:
[Irgendwie müssen die Billionen von Sparguthaben in Militär-Investitionen umgewandelt werden](https://blingbling.substack.com/p/panzer-statt-autos). Das wird am besten funktionieren mit Anleihen, die schlechter verzinst sind als sonst auf dem Markt üblich. Wie bringt man Leute dazu, dann ihr Geld dort zu investieren? Entweder man zwingt sie, oder man bewirbt die Anleihen mit viel Patriotismus und Propaganda. Die Verschwörungstheoretiker unter uns bekommen also bald Futter, wenn die „Spar- und Investitionsunion” vorgestellt wird.
Like, wenn Dein Aluhut glüht…
*Hinter der Paywall: Wie das Trump-Derangement-Syndrom den Blick auf den Markt trübt. **[Wie es mit Bitcoin, Gold und Aktien weitergeht.](https://blingbling.substack.com/p/gluhende-aluhute)***
-

@ 21335073:a244b1ad
2025-03-15 23:00:40
I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-

@ a95c6243:d345522c
2025-03-15 10:56:08
*Was nützt die schönste Schuldenbremse, wenn der Russe vor der Tür steht?* *\
Wir können uns verteidigen lernen oder alle Russisch lernen.* *\
Jens Spahn*  
**In der Politik ist buchstäblich keine Idee zu riskant, kein Mittel zu schäbig und keine Lüge zu dreist,** als dass sie nicht benutzt würden. Aber der Clou ist, dass diese Masche immer noch funktioniert, wenn nicht sogar immer besser. Ist das alles wirklich so schwer zu durchschauen? Mir fehlen langsam die Worte.
**Aktuell werden sowohl in der Europäischen Union als auch in Deutschland** riesige Milliardenpakete für die [Aufrüstung](https://transition-news.org/eu-halt-weiter-kurs-auf-krieg-hunderte-milliarden-fur-aufrustung-beschlossen) – also für die Rüstungsindustrie – geschnürt. Die EU will 800 Milliarden Euro locker machen, in Deutschland sollen es 500 Milliarden «Sondervermögen» sein. Verteidigung nennen das unsere «Führer», innerhalb der Union und auch an «unserer Ostflanke», der Ukraine.
**Das nötige Feindbild konnte inzwischen signifikant erweitert werden.** Schuld an allem und zudem gefährlich ist nicht mehr nur Putin, sondern jetzt auch Trump. Europa müsse sich sowohl gegen Russland als auch gegen die USA schützen und rüsten, wird uns eingetrichtert.
**Und während durch Diplomatie genau dieser beiden Staaten** gerade endlich mal Bewegung in die Bemühungen um einen Frieden oder wenigstens einen Waffenstillstand in der Ukraine kommt, rasselt man im moralisch überlegenen Zeigefinger-Europa so richtig mit dem Säbel.
**Begleitet und gestützt wird der ganze Prozess** – wie sollte es anders sein – von den «Qualitätsmedien». Dass Russland einen Angriff auf «Europa» plant, weiß nicht nur der deutsche Verteidigungsminister (und mit Abstand beliebteste Politiker) Pistorius, sondern dank ihnen auch jedes Kind. Uns bleiben nur noch wenige Jahre. Zum Glück bereitet sich die Bundeswehr schon sehr konkret [auf einen Krieg](https://archive.is/VE8ZM) vor.
**Die** ***FAZ*** **und Corona-Gesundheitsminister Spahn markieren einen traurigen Höhepunkt.** Hier haben sich «politische und publizistische Verantwortungslosigkeit propagandistisch gegenseitig befruchtet», wie es bei den *NachDenkSeiten* [heißt](https://www.nachdenkseiten.de/?p=130064). Die Aussage Spahns in dem Interview, «der Russe steht vor der Tür», ist das eine. Die Zeitung verschärfte die Sache jedoch, indem sie das Zitat explizit in den [Titel](https://archive.is/QJdID) übernahm, der in einer [ersten Version](https://archive.is/fNuGA) scheinbar zu harmlos war.
**Eine große Mehrheit der deutschen Bevölkerung findet Aufrüstung und mehr Schulden toll,** wie *[ARD](https://archive.is/M3DSk)* und *[ZDF](https://archive.is/ggvJB)* sehr passend ermittelt haben wollen. Ähnliches gelte für eine noch stärkere militärische Unterstützung der Ukraine. Etwas skeptischer seien die Befragten bezüglich der Entsendung von Bundeswehrsoldaten dorthin, aber immerhin etwa fifty-fifty.
**Eigentlich ist jedoch die Meinung der Menschen in «unseren Demokratien» irrelevant.** Sowohl in der Europäischen Union als auch in Deutschland sind die «Eliten» offenbar der Ansicht, der Souverän habe in Fragen von Krieg und Frieden sowie von aberwitzigen astronomischen Schulden kein Wörtchen mitzureden. Frau von der Leyen möchte über 150 Milliarden aus dem Gesamtpaket unter Verwendung von Artikel 122 des EU-Vertrags ohne das Europäische Parlament entscheiden – wenn auch nicht völlig [kritiklos](https://www.berliner-zeitung.de/politik-gesellschaft/geopolitik/aufruestung-widerstand-gegen-eu-plaene-waechst-kommission-uebertreibt-russische-gefahr-li.2306863).
**In Deutschland wollen CDU/CSU und SPD zur Aufweichung der «Schuldenbremse»** mehrere Änderungen des Grundgesetzes durch das abgewählte Parlament peitschen. Dieser Versuch, mit dem alten [Bundestag](https://www.bundestag.de/dokumente/textarchiv/2025/kw11-de-sondersitzung-1056228) eine Zweidrittelmehrheit zu erzielen, die im neuen nicht mehr gegeben wäre, ist mindestens verfassungsrechtlich umstritten.
**Das Manöver scheint aber zu funktionieren.** Heute haben die Grünen [zugestimmt](https://www.reuters.com/world/europe/germany-faces-debt-deal-cliffhanger-merz-strives-greens-backing-2025-03-14/), nachdem Kanzlerkandidat Merz läppische 100 Milliarden für «irgendwas mit Klima» zugesichert hatte. Die Abstimmung im Plenum soll am kommenden Dienstag erfolgen – nur eine Woche, bevor sich der neu gewählte Bundestag konstituieren wird.
**Interessant sind die Argumente, die BlackRocker Merz für seine Attacke** auf Grundgesetz und Demokratie ins Feld führt. Abgesehen von der angeblichen Eile, «unsere Verteidigungsfähigkeit deutlich zu erhöhen» (ausgelöst unter anderem durch «die Münchner Sicherheitskonferenz und die Ereignisse im Weißen Haus»), ließ uns der CDU-Chef wissen, dass Deutschland einfach auf die internationale Bühne zurück müsse. Merz [schwadronierte](https://x.com/CDU/status/1900168761686044894) gefährlich mehrdeutig:
> «Die ganze Welt schaut in diesen Tagen und Wochen auf Deutschland. Wir haben in der Europäischen Union und auf der Welt eine Aufgabe, die weit über die Grenzen unseres eigenen Landes hinausgeht.»
 
  
*\[Titelbild:* *[Tag des Sieges](https://pixabay.com/de/photos/parade-tag-des-sieges-samara-182508/)]*
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/propaganda-wahnsinn-und-demokratur)*** erschienen.
-

@ 8cb60e21:5f2deaea
2024-08-24 21:27:00
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/div>" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ b8916ce2:bd2a5f00
2025-03-27 09:30:42
VA88 là một nền tảng giải trí trực tuyến nổi bật, mang đến cho người tham gia những trải nghiệm phong phú và hấp dẫn, từ những trò chơi thú vị đến các sự kiện độc đáo. Với giao diện được thiết kế đơn giản nhưng tinh tế, người dùng có thể dễ dàng truy cập và tham gia vào các hoạt động giải trí mà không gặp phải bất kỳ khó khăn nào. VA88 không chỉ cung cấp một loạt các trò chơi giải trí đa dạng, mà còn liên tục tổ chức các sự kiện và thử thách, giúp người tham gia có cơ hội khám phá nhiều điều mới mẻ. Nền tảng này đặc biệt chú trọng đến việc tối ưu hóa trải nghiệm người dùng, từ việc cung cấp các trò chơi dễ tiếp cận cho người mới bắt đầu đến những thử thách khó khăn dành cho những ai yêu thích sự mạo hiểm và sự cạnh tranh. Chính sự kết hợp hoàn hảo giữa tính đa dạng và tính năng thân thiện với người dùng đã giúp VA88 xây dựng được một cộng đồng giải trí vững mạnh và thu hút lượng người tham gia đông đảo.
Ngoài sự đa dạng về các trò chơi, <a href="https://va88-online.com">VA88</a> cũng đặc biệt chú trọng đến việc bảo mật thông tin và sự an toàn của người tham gia. Nền tảng này sử dụng các công nghệ bảo mật tiên tiến để đảm bảo rằng mọi giao dịch và dữ liệu cá nhân của người dùng đều được bảo vệ một cách an toàn tuyệt đối. Những biện pháp bảo mật này không chỉ giúp người tham gia yên tâm khi tham gia các trò chơi mà còn đảm bảo rằng mọi giao dịch tài chính diễn ra một cách minh bạch và bảo mật. VA88 cam kết bảo vệ quyền lợi của người tham gia bằng cách cung cấp một môi trường chơi công bằng, nơi mọi người có thể thoải mái tham gia mà không lo ngại về sự xâm phạm thông tin cá nhân. Bằng việc áp dụng các công nghệ bảo mật hàng đầu và tạo ra một môi trường an toàn, VA88 đã trở thành một lựa chọn đáng tin cậy cho những ai tìm kiếm một không gian giải trí trực tuyến an toàn và bảo mật.
Với tầm nhìn luôn hướng đến sự đổi mới và cải tiến, VA88 không ngừng nỗ lực mang đến những tính năng và trò chơi mới mẻ để đáp ứng nhu cầu ngày càng cao của người tham gia. Những sự kiện đặc biệt và các chương trình khuyến mãi luôn được tổ chức để người tham gia có thể tận hưởng nhiều cơ hội thú vị và phần thưởng hấp dẫn. VA88 luôn chủ động lắng nghe phản hồi từ cộng đồng để cải thiện dịch vụ và đảm bảo mang đến trải nghiệm giải trí tốt nhất. Bên cạnh đó, nền tảng này cũng tạo cơ hội cho người tham gia kết nối và giao lưu với nhau, giúp xây dựng một cộng đồng vững mạnh và thân thiện. Chính nhờ vào những cải tiến liên tục và sự tập trung vào nhu cầu của người dùng, VA88 đã khẳng định được vị thế của mình trong cộng đồng giải trí trực tuyến, trở thành một điểm đến lý tưởng cho những ai tìm kiếm một không gian thư giãn và đầy thử thách.
-

@ 8cb60e21:5f2deaea
2024-08-24 00:10:45
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/858xjX2VN_I" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 8cb60e21:5f2deaea
2024-08-22 22:06:11
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/E2sc9PK2RWg" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ da0b9bc3:4e30a4a9
2025-03-28 07:27:06
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/927569
-

@ 8cb60e21:5f2deaea
2024-08-21 21:37:35
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/NR_2KJZi3Ac" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ b8916ce2:bd2a5f00
2025-03-27 09:29:29
VF88 mang đến cho người tham gia một không gian giải trí trực tuyến đầy thú vị, sáng tạo và đa dạng. Với giao diện thân thiện và dễ sử dụng, nền tảng này giúp người dùng dễ dàng tiếp cận và tham gia vào các hoạt động giải trí mà không gặp phải bất kỳ khó khăn nào. Các trò chơi trên VF88 được thiết kế tinh tế, đáp ứng nhu cầu của những người tham gia, dù là người mới bắt đầu hay đã có kinh nghiệm lâu dài. Không chỉ có các trò chơi thú vị, nền tảng này còn thường xuyên tổ chức các sự kiện đặc biệt và thử thách đầy hấp dẫn, tạo ra cơ hội để người tham gia trải nghiệm những điều mới mẻ và thú vị. Từ các trò chơi trí tuệ giúp rèn luyện khả năng tư duy đến những trò giải trí nhẹ nhàng giúp thư giãn, <a href="https://vf88.site">VF88</a> luôn có một danh mục đa dạng, phục vụ mọi sở thích của người dùng. Chính sự đa dạng này đã giúp VF88 trở thành một điểm đến lý tưởng cho những ai yêu thích khám phá và tìm kiếm một không gian giải trí năng động và đầy thử thách.
Một yếu tố quan trọng làm nên sự thành công của VF88 chính là cam kết bảo mật và an toàn cho người tham gia. Nền tảng này sử dụng những công nghệ bảo mật tiên tiến nhất để bảo vệ thông tin cá nhân và dữ liệu người dùng một cách tuyệt đối. Mọi giao dịch và thông tin liên quan đều được mã hóa và xử lý theo các tiêu chuẩn bảo mật quốc tế, giúp người tham gia hoàn toàn yên tâm khi tham gia vào các hoạt động trên nền tảng. Ngoài việc bảo vệ sự riêng tư của người dùng, VF88 cũng cam kết cung cấp một môi trường chơi an toàn và công bằng, với các biện pháp chống gian lận và bảo vệ quyền lợi của người tham gia. Điều này không chỉ tạo sự an tâm cho người dùng mà còn xây dựng được lòng tin mạnh mẽ trong cộng đồng, giúp VF88 duy trì được uy tín và vị thế của mình trên thị trường giải trí trực tuyến.
VF88 luôn không ngừng cải tiến và đổi mới để mang lại những trải nghiệm tối ưu nhất cho người tham gia. Nền tảng này luôn cập nhật những tính năng mới và tổ chức các chương trình khuyến mãi hấp dẫn, giúp người tham gia có thêm nhiều cơ hội trải nghiệm và khám phá. Ngoài ra, VF88 cũng tạo ra một cộng đồng mạnh mẽ và thân thiện, nơi người dùng có thể giao lưu, chia sẻ kinh nghiệm và kết nối với những người cùng sở thích. Các sự kiện đặc biệt và thử thách thường xuyên được tổ chức để tăng thêm phần thú vị và kịch tính cho người tham gia. Sự sáng tạo không ngừng của VF88 trong việc cải thiện dịch vụ đã giúp nền tảng này luôn giữ được sự mới mẻ, hấp dẫn, và là một lựa chọn giải trí lý tưởng cho mọi người. Với những đặc điểm này, VF88 đã khẳng định được vị thế của mình trong cộng đồng giải trí trực tuyến và là một điểm đến không thể thiếu cho những ai tìm kiếm trải nghiệm giải trí tuyệt vời.
-

@ a95c6243:d345522c
2025-03-11 10:22:36
**«Wir brauchen eine digitale Brandmauer gegen den Faschismus»,** [schreibt](https://www.ccc.de/de/updates/2025/ccc-fordert-digitale-brandmauer) der Chaos Computer Club (CCC) auf seiner Website. Unter diesem Motto präsentierte er letzte Woche einen Forderungskatalog, mit dem sich 24 Organisationen an die kommende Bundesregierung wenden. Der Koalitionsvertrag müsse sich daran messen lassen, verlangen sie.
**In den drei Kategorien «Bekenntnis gegen Überwachung»,** «Schutz und Sicherheit für alle» sowie «Demokratie im digitalen Raum» stellen die [Unterzeichner](https://d-64.org/digitale-brandmauer/), zu denen auch Amnesty International und Das NETTZ gehören, unter anderem die folgenden «Mindestanforderungen»:
* Verbot biometrischer Massenüberwachung des öffentlichen Raums sowie der ungezielten biometrischen Auswertung des Internets.
* Anlasslose und massenhafte Vorratsdatenspeicherung wird abgelehnt.
* Automatisierte Datenanalysen der Informationsbestände der Strafverfolgungsbehörden sowie jede Form von Predictive Policing oder automatisiertes Profiling von Menschen werden abgelehnt.
* Einführung eines Rechts auf Verschlüsselung. Die Bundesregierung soll sich dafür einsetzen, die Chatkontrolle auf europäischer Ebene zu verhindern.
* Anonyme und pseudonyme Nutzung des Internets soll geschützt und ermöglicht werden.
* Bekämpfung «privaten Machtmissbrauchs von Big-Tech-Unternehmen» durch durchsetzungsstarke, unabhängige und grundsätzlich föderale Aufsichtsstrukturen.
* Einführung eines digitalen Gewaltschutzgesetzes, unter Berücksichtigung «gruppenbezogener digitaler Gewalt» und die Förderung von Beratungsangeboten.
* Ein umfassendes Förderprogramm für digitale öffentliche Räume, die dezentral organisiert und quelloffen programmiert sind, soll aufgelegt werden.
**Es sei ein Irrglaube, dass zunehmende Überwachung einen Zugewinn an Sicherheit darstelle,** ist eines der Argumente der Initiatoren. Sicherheit erfordere auch, dass Menschen anonym und vertraulich kommunizieren können und ihre Privatsphäre geschützt wird.
**Gesunde digitale Räume lebten auch von einem demokratischen Diskurs,** lesen wir in dem Papier. Es sei Aufgabe des Staates, Grundrechte zu schützen. Dazu gehöre auch, Menschenrechte und demokratische Werte, insbesondere Freiheit, Gleichheit und Solidarität zu fördern sowie den Missbrauch von Maßnahmen, Befugnissen und Infrastrukturen durch «die Feinde der Demokratie» zu verhindern.
**Man ist geneigt zu fragen, wo denn die Autoren «den Faschismus» sehen,** den es zu bekämpfen gelte. Die meisten der vorgetragenen Forderungen und Argumente finden sicher breite Unterstützung, denn sie beschreiben offenkundig gängige, kritikwürdige Praxis. Die Aushebelung der Privatsphäre, der Redefreiheit und anderer Grundrechte im Namen der Sicherheit wird bereits jetzt massiv durch die aktuellen «demokratischen Institutionen» und ihre «durchsetzungsstarken Aufsichtsstrukturen» betrieben.
**Ist «der Faschismus» also die EU und ihre Mitgliedsstaaten?** Nein, die «faschistische Gefahr», gegen die man eine digitale Brandmauer will, kommt nach Ansicht des CCC und seiner Partner aus den Vereinigten Staaten. Private Überwachung und Machtkonzentration sind dabei weltweit schon lange Realität, jetzt endlich müssen sie jedoch bekämpft werden. In dem Papier heißt es:
> «Die willkürliche und antidemokratische Machtausübung der Tech-Oligarchen um Präsident Trump erfordert einen Paradigmenwechsel in der deutschen Digitalpolitik. (...) Die aktuellen Geschehnisse in den USA zeigen auf, wie Datensammlungen und -analyse genutzt werden können, um einen Staat handstreichartig zu übernehmen, seine Strukturen nachhaltig zu beschädigen, Widerstand zu unterbinden und marginalisierte Gruppen zu verfolgen.»
**Wer auf der anderen Seite dieser Brandmauer stehen soll, ist also klar.** Es sind die gleichen «Feinde unserer Demokratie», die seit Jahren in diese Ecke gedrängt werden. Es sind die gleichen Andersdenkenden, Regierungskritiker und Friedensforderer, die unter dem großzügigen Dach des Bundesprogramms «Demokratie leben» einem «kontinuierlichen Echt- und Langzeitmonitoring» wegen der Etikettierung [«digitaler Hass»](https://bag-gegen-hass.net/) unterzogen werden.
**Dass die 24 Organisationen praktisch auch die Bekämpfung von Google,** Microsoft, Apple, Amazon und anderen fordern, entbehrt nicht der Komik. Diese fallen aber sicher unter das Stichwort «Machtmissbrauch von Big-Tech-Unternehmen». Gleichzeitig verlangen die Lobbyisten implizit zum Beispiel die Förderung des [Nostr](https://reason.com/video/2024/09/17/is-nostr-an-antidote-to-social-media-censorship/)-Netzwerks, denn hier finden wir dezentral organisierte und quelloffen programmierte digitale Räume par excellence, obendrein zensurresistent. Das wiederum dürfte in der Politik weniger gut ankommen.
*\[Titelbild:* *[Pixabay](https://pixabay.com/de/illustrations/uns-ihnen-stammes-wettbewerb-1767691/)]*
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/digitale-brandmauer-gegen-den-faschismus-von-der-kunftigen-bundesregierung)*** erschienen.
-

@ 8cb60e21:5f2deaea
2024-08-21 21:37:35
# hello world
-

@ 25191283:a4823315
2024-08-21 13:37:49
This is Olive Grove Eggs, a brand new site from Huevos del Olivar that's just getting started. Things will be up and running here shortly, but you can [subscribe](#/portal/) in the meantime if you'd like to stay up to date and receive emails when new content is published!
-

@ a3bb06f6:19ac1b11
2025-03-28 02:36:38
“Until you make the unconscious conscious, it will continue to direct your life, and you will call it fate.” — Carl Jung
Most people don’t realize they’ve been robbed. Not in the dramatic, wallet-snatching sense, but in a quiet, systemic way that’s gone unnoticed for generations. If you’re feeling like no matter how hard you work, you can’t get ahead… you’re not imagining it.
It didn’t start as a scheme—*but one compromise after another*, it became one. Now, the system exploits you by design. This isn’t fate. It’s fiat.
The Unconscious Script: How Fiat Becomes Invisible From the moment you're born, you're placed into an economic system based on government-issued fiat currency. It becomes the air you breathe. You work for dollars. You save in dollars. You price **your time**, **your future**, and even **your dreams** in dollars.
But few stop to ask: What actually is a dollar? Who creates it? Why does it lose value?
This lack of questioning is the unconscious state. Fiat money is the background process running your life. You feel the effects—rising prices, shrinking savings, mounting debt—but you never see the root cause. So you blame yourself. Or “the economy.” Or call it fate.
The Lie of Neutral Money: Most believe money is just a neutral tool. But fiat is not neutral—it’s political power encoded into paper.
Governments can **print more of it at will**. Central banks can manipulate its supply, distort interest rates, and quietly tax you through inflation. Every time more money is created, your purchasing power shrinks.
But it happens slowly, like a leak in a tire. You don’t notice at first. You just feel like you’re working harder for less. The house is further out of reach. The groceries cost more. Retirement feels impossible.
And you accept it. Because no one told you it's designed this way.
<img src="https://blossom.primal.net/80cb04b171e15d56d1224a1458f0ca3ad9a440915c736e145186df1cc2f4979b.png">
Inflation Is the Invisible Thief, Inflation isn’t just a “cost of living increase.” It’s a state-sponsored form of theft.
When new money is created, it enters the system unevenly. Those closest to the money printer—banks, governments, **large corporations**—get the new dollars first. By the time it reaches you, prices have already risen. You’re buying the same goods with weaker money.
And yet, most people still save in fiat. They’re taught that hoarding cash is “safe.” They’re taught that 2% inflation is “normal.” But it’s not normal to work 40 hours a week and fall behind. That’s the product of unconscious acceptance.
The fiat system survives on one thing: your **ignorance**. It didn’t begin with malicious intent, but over time, it adapted to protect its own power—at your expense. As long as you don’t understand how money works, you won’t resist. You’ll blame yourself, or *capitalism*, or bad luck. **But never the system itself**.
This is why financial education is *never* prioritized in schools. This is why questioning monetary policy is left to economists and suits on CNBC. You were never taught how it works. And now the system depends on you staying confused—grinding, borrowing, complying, without ever asking why.
Making the Unconscious Conscious: Enter **Bitcoin**, Bitcoin breaks this spell.
<img src="https://blossom.primal.net/8373eb52ee7773e0ffc4591819ff984a27829e47741894456258e2a638029022.png">
It forces you to confront the nature of money—what it is, how it’s created, and why fiat fails. It teaches you that money doesn’t need to be printed, inflated, or controlled. That money can be fixed, finite, and **fair**.
Bitcoin is not just a new currency. It’s a tool of consciousness. It exposes the scam of fiat and offers a lifeboat to anyone ready to wake up.
Once you understand Bitcoin, you can’t unsee the problem. You begin to ask:
Why should I trust a system that steals my **time**? Why is saving discouraged, but debt rewarded? Why do I need permission to use my own money? These aren’t technical questions. They’re **moral** ones.
Consciousness Is Sovereignty: When you understand what fiat is, you stop calling your financial struggles “fate.” You start calling them what they are, outcomes of a broken system.
And once you see the system for what it is, you can choose to **exit**.
<img src="https://blossom.primal.net/a8766caf9dc043fa360dbf7c5e473201d72dfeede02a7f08abc9897367a33011.png">
Saving in Bitcoin is not speculation. It’s self-defense. It’s rejecting unconscious servitude. It’s reclaiming your **time**, your **labor**, your **future**.
In a fiat world, they own the money—so they own the rules. In a Bitcoin world, you own yourself.
That’s the power of making the unconscious conscious.
And that’s how you stop calling it fate.
-

@ a95c6243:d345522c
2025-03-04 09:40:50
**Die «Eliten» führen bereits groß angelegte Pilotprojekte für eine Zukunft durch,** die sie wollen und wir nicht. Das [schreibt](https://off-guardian.org/2025/02/26/coming-soon-the-european-digital-identity-wallet/) der *OffGuardian* in einem Update zum Thema «EU-Brieftasche für die digitale Identität». Das Portal weist darauf hin, dass die Akteure dabei nicht gerade zimperlich vorgehen und auch keinen Hehl aus ihren Absichten machen. *Transition News* hat mehrfach darüber berichtet, zuletzt [hier](https://transition-news.org/eudi-wallet-der-weg-fur-ein-vollstandig-digitalisiertes-europa-ist-frei) und [hier](https://transition-news.org/iata-biometrische-daten-und-digitale-id-machen-das-vollstandig-digitale).
**Mit der EU Digital Identity Wallet (EUDI-Brieftasche) sei eine einzige von der Regierung herausgegebene App geplant,** die Ihre medizinischen Daten, Beschäftigungsdaten, Reisedaten, Bildungsdaten, Impfdaten, Steuerdaten, Finanzdaten sowie (potenziell) Kopien Ihrer Unterschrift, Fingerabdrücke, Gesichtsscans, Stimmproben und DNA enthält. So fasst der *OffGuardian* die eindrucksvolle Liste möglicher Einsatzbereiche zusammen.
**Auch Dokumente wie der Personalausweis oder der** **[Führerschein](https://transition-news.org/eu-weite-einfuhrung-von-digitalen-fuhrerscheinen-fur-digitale-geldborsen)** können dort in elektronischer Form gespeichert werden. Bis 2026 sind alle EU-Mitgliedstaaten dazu verpflichtet, Ihren Bürgern funktionierende und frei verfügbare digitale «Brieftaschen» bereitzustellen.
**Die Menschen würden diese App nutzen,** so das Portal, um Zahlungen vorzunehmen, Kredite zu beantragen, ihre Steuern zu zahlen, ihre Rezepte abzuholen, internationale Grenzen zu überschreiten, Unternehmen zu gründen, Arzttermine zu buchen, sich um Stellen zu bewerben und sogar digitale Verträge online zu unterzeichnen.
**All diese Daten würden auf ihrem Mobiltelefon gespeichert und mit den Regierungen** von neunzehn Ländern (plus der Ukraine) sowie über 140 anderen öffentlichen und privaten Partnern ausgetauscht. Von der Deutschen Bank über das ukrainische Ministerium für digitalen Fortschritt bis hin zu Samsung Europe. Unternehmen und Behörden würden auf diese Daten im Backend zugreifen, um «automatisierte Hintergrundprüfungen» durchzuführen.
**Der Bundesverband der Verbraucherzentralen und Verbraucherverbände** (VZBV) habe Bedenken geäußert, dass eine solche App «Risiken für den Schutz der Privatsphäre und der Daten» berge, berichtet das Portal. Die einzige Antwort darauf laute: «Richtig, genau dafür ist sie ja da!»
**Das alles sei keine Hypothese, betont der** ***OffGuardian***. Es sei vielmehr [«Potential»](https://www.digital-identity-wallet.eu/about-us/140-public-and-private-partners/). Damit ist ein EU-Projekt gemeint, in dessen Rahmen Dutzende öffentliche und private Einrichtungen zusammenarbeiten, «um eine einheitliche Vision der digitalen Identität für die Bürger der europäischen Länder zu definieren». Dies ist nur eines der groß angelegten [Pilotprojekte](https://ec.europa.eu/digital-building-blocks/sites/display/EUDIGITALIDENTITYWALLET/What+are+the+Large+Scale+Pilot+Projects), mit denen Prototypen und Anwendungsfälle für die EUDI-Wallet getestet werden. Es gibt noch mindestens drei weitere.
**Den Ball der digitalen ID-Systeme habe die Covid-«Pandemie»** über die «Impfpässe» ins Rollen gebracht. Seitdem habe das Thema an Schwung verloren. Je näher wir aber der vollständigen Einführung der EUid kämen, desto mehr Propaganda der Art «Warum wir eine digitale Brieftasche brauchen» könnten wir in den Mainstream-Medien erwarten, prognostiziert der *OffGuardian*. Vielleicht müssten wir schon nach dem nächsten großen «Grund», dem nächsten «katastrophalen katalytischen Ereignis» Ausschau halten. Vermutlich gebe es bereits Pläne, warum die Menschen plötzlich eine digitale ID-Brieftasche brauchen würden.
**Die Entwicklung geht jedenfalls stetig weiter in genau diese Richtung.** Beispielsweise hat Jordanien angekündigt, die digitale biometrische ID bei den nächsten [Wahlen](https://www.biometricupdate.com/202502/jordan-plans-digital-id-for-voter-verification-in-next-election) zur Verifizierung der Wähler einzuführen. Man wolle «den Papierkrieg beenden und sicherstellen, dass die gesamte Kette bis zu den nächsten Parlamentswahlen digitalisiert wird», heißt es. Absehbar ist, dass dabei einige Wahlberechtigte «auf der Strecke bleiben» werden, wie im Fall von [Albanien](https://transition-news.org/albanien-schliesst-120-000-burger-ohne-biometrische-ausweise-von-wahlen-aus) geschehen.
**Derweil würden die Briten gerne ihre Privatsphäre gegen Effizienz eintauschen,** [behauptet](https://www.lbc.co.uk/news/tony-blair-id-cards/) Tony Blair. Der Ex-Premier drängte kürzlich erneut auf digitale Identitäten und Gesichtserkennung. Blair ist Gründer einer [Denkfabrik](https://transition-news.org/blair-institute-durch-vermarktung-von-patientendaten-zu-ki-gestutztem) für globalen Wandel, Anhänger globalistischer Technokratie und [«moderner Infrastruktur»](https://transition-news.org/tony-blair-digitale-id-fur-moderne-infrastruktur-unerlasslich-erfordert-aber).
**Abschließend warnt der** ***OffGuardian*** **vor der Illusion, Trump und Musk würden** den US-Bürgern «diesen Schlamassel ersparen». Das Department of Government Efficiency werde sich auf die digitale Identität stürzen. Was könne schließlich «effizienter» sein als eine einzige App, die für alles verwendet wird? Der Unterschied bestehe nur darin, dass die US-Version vielleicht eher privat als öffentlich sei – sofern es da überhaupt noch einen wirklichen Unterschied gebe.
*\[Titelbild: Screenshot* *[OffGuardian](https://off-guardian.org/2025/02/26/coming-soon-the-european-digital-identity-wallet/)]*
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/demnachst-verfugbar-die-europaische-brieftasche-fur-digitale-identitaten)*** erschienen.
-

@ 84b0c46a:417782f5
2025-03-27 23:52:24
nostr:nevent1qqsw9v8usvahkqmmc9qavu6g834v09j6e2u2acdua24tk73dqc05xecgkanse
-

@ a95c6243:d345522c
2025-03-01 10:39:35
*Ständige Lügen und Unterstellungen, permanent falsche Fürsorge* *\
können Bausteine von emotionaler Manipulation sein. Mit dem Zweck,* *\
Macht und Kontrolle über eine andere Person auszuüben.* *\
Apotheken Umschau*  
**Irgendetwas muss passiert sein: «Gaslighting» ist gerade Thema** in vielen Medien. Heute bin ich nach längerer Zeit mal wieder über dieses Stichwort gestolpert. Das war in einem [Artikel](https://norberthaering.de/propaganda-zensur/dwd-referenzperiode/) von Norbert Häring über Manipulationen des Deutschen Wetterdienstes (DWD). In diesem Fall ging es um eine Pressemitteilung vom Donnerstag zum «viel zu warmen» Winter 2024/25.
**Häring wirft der Behörde vor, dreist zu lügen und Dinge auszulassen,** um die Klimaangst wach zu halten. Was der Leser beim DWD nicht erfahre, sei, dass dieser Winter kälter als die drei vorangegangenen und kälter als der Durchschnitt der letzten zehn Jahre gewesen sei. Stattdessen werde der falsche Eindruck vermittelt, es würde ungebremst immer wärmer.
**Wem also der zu Ende gehende Winter eher kalt vorgekommen sein sollte,** mit dessen Empfinden stimme wohl etwas nicht. Das jedenfalls wolle der DWD uns einreden, so der Wirtschaftsjournalist. Und damit sind wir beim Thema Gaslighting.
**Als** **[Gaslighting](https://bayern-gegen-gewalt.de/gewalt-infos-und-einblicke/formen-von-gewalt/psychische-gewalt/gaslighting/)** **wird eine Form psychischer Manipulation bezeichnet,** mit der die Opfer desorientiert und zutiefst verunsichert werden, indem ihre eigene Wahrnehmung als falsch bezeichnet wird. Der Prozess führt zu Angst und Realitätsverzerrung sowie zur Zerstörung des Selbstbewusstseins. Die Bezeichnung kommt von dem britischen Theaterstück «Gas Light» aus dem Jahr 1938, in dem ein Mann mit grausamen Psychotricks seine Frau in den Wahnsinn treibt.
**Damit Gaslighting funktioniert, muss das Opfer dem Täter vertrauen.** Oft wird solcher Psychoterror daher im privaten oder familiären Umfeld beschrieben, ebenso wie am Arbeitsplatz. Jedoch eignen sich die Prinzipien auch perfekt zur Manipulation der Massen. Vermeintliche Autoritäten wie Ärzte und Wissenschaftler, oder «der fürsorgliche Staat» und Institutionen wie die UNO oder die WHO wollen uns doch nichts Böses. Auch Staatsmedien, Faktenchecker und diverse NGOs wurden zu «vertrauenswürdigen Quellen» erklärt. Das hat seine Wirkung.
**Warum das Thema Gaslighting derzeit scheinbar so populär ist,** vermag ich nicht zu sagen. Es sind aber gerade in den letzten Tagen und Wochen auffällig viele Artikel dazu erschienen, und zwar nicht nur von Psychologen. Die *Frankfurter Rundschau* hat gleich mehrere publiziert, und [Anwälte](https://www.anwalt.de/rechtstipps/gaslighting-beispiele-anzeichen-strafbarkeit-212449.html) interessieren sich dafür offenbar genauso wie Apotheker.
**Die** ***Apotheken Umschau*** **machte sogar auf** **[«Medical Gaslighting»](https://archive.is/Wx5YM)** **aufmerksam.** Davon spreche man, wenn Mediziner Symptome nicht ernst nähmen oder wenn ein gesundheitliches Problem vom behandelnden Arzt «schnöde heruntergespielt» oder abgetan würde. Kommt Ihnen das auch irgendwie bekannt vor? Der Begriff sei allerdings irreführend, da er eine manipulierende Absicht unterstellt, die «nicht gewährleistet» sei.
**Apropos Gaslighting: Die noch amtierende deutsche Bundesregierung** [meldete](https://www.bundesregierung.de/breg-de/service/newsletter-und-abos/bundesregierung-aktuell/ausgabe-08-2025-februar-28-2336254?view=renderNewsletterHtml) heute, es gelte, «weiter \[sic!] gemeinsam daran zu arbeiten, einen gerechten und dauerhaften Frieden für die Ukraine zu erreichen». Die Ukraine, wo sich am Montag «der völkerrechtswidrige Angriffskrieg zum dritten Mal jährte», [verteidige](https://transition-news.org/wikileaks-der-westen-wusste-dass-ein-nato-beitritt-der-ukraine-riskant-war) ihr Land und «unsere gemeinsamen Werte».
**Merken Sie etwas? Das Demokratieverständnis mag ja tatsächlich** inzwischen in beiden Ländern ähnlich traurig sein. Bezüglich Friedensbemühungen ist meine Wahrnehmung jedoch eine andere. Das muss an meinem Gedächtnis liegen.
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/bitte-nicht-von-gaslichtern-irritieren-lassen)*** erschienen.
-

@ 878dff7c:037d18bc
2025-03-27 22:37:47
## Australian Prime Minister Calls Election Amid Economic Challenges
### Summary:
Prime Minister Anthony Albanese has announced that Australia will hold federal elections on May 3. The election comes at a time when the nation faces significant economic uncertainties, including high inflation rates, elevated interest rates, and a housing crisis. Albanese's Labor government emphasizes plans for economic recovery, while opposition leader Peter Dutton's Coalition proposes public sector cuts and temporary fuel duty reductions. Both leaders are striving to address voter concerns over the cost-of-living crisis and economic stability.
Sources: <a href="https://www.theguardian.com/australia-news/2025/mar/28/australian-prime-minister-calls-election-amid-shadow-of-trump-and-cost-of-living-crisis" target="_blank">The Guardian - March 28, 2025</a>, <a href="https://apnews.com/article/b73f3a4bb9cbbc300cd797f34d4cc23b" target="_blank">AP News - March 28, 2025</a>
## Bill Gates Predicts AI to Replace Doctors and Teachers Within 10 Years
### Summary:
Bill Gates forecasts that artificial intelligence (AI) will significantly reduce human involvement in fields like medicine and education over the next decade. He envisions AI providing free, high-quality medical advice and tutoring, thereby democratizing access to these services. While acknowledging concerns about misinformation and rapid AI development, Gates remains optimistic about AI's potential to drive breakthroughs in healthcare, climate solutions, and education. He encourages young people to engage in AI-centric ventures, highlighting its transformative impact on industries and society.
Sources: <a href="https://nypost.com/2025/03/27/business/bill-gates-said-ai-will-replace-doctors-teachers-within-10-years/" target="_blank">New York Post - March 27, 2025</a>
## AI Poised to Transform Legal Profession by 2035
### Summary:
Artificial general intelligence (AGI) is projected to render traditional lawyer roles obsolete by 2035. AI systems are advancing to perform complex legal tasks such as advising, negotiating, and dispute resolution. While some legal professionals argue that AI cannot replicate human judgment and creativity, the emphasis on efficiency and outcomes suggests a future where AGI dominates legal services with minimal human intervention. Legal industry leaders are urged to prepare for this disruptive shift.
Sources: <a href="https://www.thetimes.co.uk/article/artificial-intelligence-could-replace-traditional-lawyers-by-2035-xwz2j0t2k" target="_blank">The Times - March 28, 2025</a>
## Queensland Faces Severe Flooding as Inland 'Sea' Emerges
### Summary:
Severe weather conditions, including heavy rain and potential flash flooding, have impacted central and southern inland Queensland, with significant rainfall between 200 to 400mm recorded. Towns like Adavale are inundated, prompting emergency warnings and the establishment of refuges for affected residents. Authorities urge residents to stay updated and follow safety advice.
Sources: <a href="https://www.news.com.au/technology/environment/qld-in-for-another-week-of-rain-amid-severe-weather-and-flood-warnings/news-story/d5e7ea97591060bb58c1d6ed54489209" target="_blank">News.com.au - 28 March 2025</a>, <a href="https://www.couriermail.com.au/news/queensland/weather/qld-weather-warnings-of-possible-200mm-deluge-major-flooding-as-communities-cut-off/news-story/457a21a269a535b28c52f919f8bc7bed" target="_blank">The Courier-Mail - 28 March 2025</a>, <a href="https://www.theguardian.com/australia-news/2025/mar/27/queensland-flood-warnings-rain-weather-forecast-bom" target="_blank">The Guardian - 28 March 2025</a>
## Opposition Leader Peter Dutton Outlines Election Platform
### Summary:
Opposition Leader Peter Dutton has presented his vision for Australia, promising significant funding for defense and proposing a new gas reservation policy aimed at lowering electricity prices. The Coalition's plans include fast-tracking gas projects, investing $1 billion in gas infrastructure, reducing public service staffing by 41,000 while preserving essential services, and decreasing permanent migration intake by 25% to increase housing supply. Dutton also announced reinstating subsidized mental health visits and new spending on youth mental health.
Sources: <a href="https://www.theguardian.com/australia-news/live/2025/mar/27/australia-politics-live-fuel-excise-cost-of-living-tax-cuts-salmon-election-anthony-albanese-peter-dutton-ntwnfb" target="_blank">The Guardian - March 28, 2025</a>, <a href="https://www.theaustralian.com.au/nation/who-is-peter-dutton-the-liberal-leader-and-his-top-team-for-the-2025-federal-election-explained/news-story/9d046731e51ed32dd4795c3820365c3a" target="_blank">The Australian - March 28, 2025</a>
## Opposition Leader Promises Significant Defense Funding
### Summary:
Peter Dutton, in his budget reply, promised significant funding for defense and a new gas reservation policy for the east coast, aimed at lowering electricity prices. The Coalition also plans to fast-track gas projects and invest $1 billion in gas infrastructure. Dutton announced slashing 41,000 public service workers while preserving essential services, and criticized Labor's gas policy. Immigration plans include reducing the permanent migration intake by 25% to increase housing supply. Dutton also proposed reinstating subsidized mental health visits and new spending on youth mental health. Labor, represented by Jason Clare, argued that the Coalition's policies, including the nuclear plan, are costly and criticized the tax implications under Dutton.
Sources: <a href="https://www.theguardian.com/australia-news/live/2025/mar/27/australia-politics-live-fuel-excise-cost-of-living-tax-cuts-salmon-election-anthony-albanese-peter-dutton-ntwnfb" target="_blank">The Guardian - March 28, 2025</a>
## Israeli Politicians Urge Australian MPs to Abandon Two-State Solution Policy
### Summary:
A group of Israeli Knesset members has called on Australian MPs to drop support for a two-state solution between Israel and Palestine. The letter, presented during an event at Australia's Parliament House, argues that establishing a Palestinian state could lead to Israel's destruction, citing recent conflicts as evidence. This appeal reflects deep skepticism within Israeli political circles about the viability of the peace process.
Sources: <a href="https://www.theguardian.com/australia-news/2025/mar/27/israeli-politicians-sign-letter-urging-coalition-to-dump-two-state-policy-ntwnfb" target="_blank">The Guardian - March 27, 2025</a>
## Stephen Jones Criticizes U.S. Protectionist Trade Policies
### Summary:
Outgoing Financial Services Minister Stephen Jones has criticized recent U.S. protectionist measures, including a 25% tariff on global car imports and Australian aluminum and steel. Jones emphasized the importance of open trade and a rules-based order for Australia's economic growth, highlighting concerns about the negative impact on Australian industries and the broader economy.
Sources: <a href="https://www.theaustralian.com.au/business/outgoing-financial-services-minister-jones-takes-swipe-at-us-protectionism/news-story/0c1fc10f2b57a8c6809f4dec333cc547" target="_blank">The Australian - March 28, 2025</a>
## New Anti-Smoking Warnings Criticized for Potential Backfire
### Summary:
Starting April 1, Australia will implement legislation requiring health warnings on individual cigarettes, with messages like "causes 16 cancers" and "poisons in every puff." However, social media users have mocked these warnings, suggesting they might make smoking appear "cool" and collectible rather than serving as deterrents. Despite the criticism, health officials assert that such on-product messages are part of a broader strategy to reduce smoking rates, citing positive results from similar approaches in Canada. The initiative aims to decrease the annual tobacco-related deaths in Australia, which currently exceed 24,000.
Sources: <a href="https://www.couriermail.com.au/news/queensland/poisons-in-every-puff-new-antismoking-messaging-slammed/news-story/2f77ecd3a943d3139539c2610af3400c" target="_blank">The Courier-Mail - March 28, 2025</a>
## 'Joe's Law' Introduced to Ban Future Hospital Privatization in NSW
### Summary:
The New South Wales government has announced "Joe's Law," a reform to prohibit the future privatization of acute public hospitals. This decision follows the death of two-year-old Joe Massa, who suffered a cardiac arrest and died after a prolonged wait in the emergency department of the privately managed Northern Beaches Hospital. The legislation aims to ensure that critical public services like emergency and surgical care remain under public control, preventing privatization. Additionally, a parliamentary inquiry into the hospital's services and a coronial investigation into Joe's death have been initiated.
Sources: <a href="https://www.theguardian.com/australia-news/2025/mar/27/joes-law-to-ban-future-hospital-privatisation-in-nsw" target="_blank">The Guardian - March 28, 2025</a>, <a href="https://www.news.com.au/lifestyle/health/health-problems/major-changes-coming-to-nsw-hospitals-after-death-of-twoyearold-joe-massa/news-story/fb93b0f0a9f2673a01eddfe89031fcb9" target="_blank">news.com.au - March 28, 2025</a>, <a href="https://www.dailytelegraph.com.au/newslocal/manly-daily/northern-beaches-hospital-probe-begins-into-safety-and-quality-of-health-services/news-story/72ea15981b26339eea92a15b4e9c498a" target="_blank">The Daily Telegraph - March 28, 2025</a>
## Determined Daisy Marks Major Milestone
### Summary:
Daisy, born with a rare chromosomal disorder, has achieved a significant health milestone by having her tracheostomy removed and is now learning to communicate using sign language. Her inspiring journey is one of several highlighted by the Good Friday Appeal, which supports the Royal Children's Hospital (RCH). The 2025 Appeal aims to fund further programs, research, and vital equipment at RCH, with contributions from events like North Melbourne's SuperClash fundraiser bringing joy to young patients ahead of the marquee match.
Sources: <a href="https://www.heraldsun.com.au/news/good-friday-appeal/good-friday-appeal-2025-star-roos-launch-superclash-fundraiser-with-special-visit/news-story/75fe74c62e52efb611436e9162c4d4d6" target="_blank">Herald Sun - March 27, 2025</a>
## Indonesia Seeks to Calm Investors After Stocks, Rupiah Slide
### Summary:
Indonesian officials are working to reassure investors following significant declines in the stock market and the rupiah. President Prabowo Subianto plans to meet with investors after the Eid-al-Fitr holiday to address concerns about government policies and fiscal stability. The rupiah recently hit its weakest level since 1998, and the main stock index fell 7.1%. Analysts attribute the selloff to poor communication on fiscal policies. The government aims to maintain the fiscal deficit within 3% of GDP and avoid political interference in its sovereign wealth fund. Efforts are also underway to deregulate the manufacturing sector and provide credits to labor-intensive industries. Bank Indonesia is prepared to intervene to stabilize the currency, emphasizing the economy's underlying strength. The rupiah has shown signs of recovery, and measures include easing buyback processes and offering more attractive investment instruments. Markets will monitor the mid-year budget update in July for signs of revenue shortfalls and spending adjustments.
Sources: <a href="https://www.reuters.com/markets/asia/indonesia-seeks-calm-investors-after-stocks-rupiah-slide-2025-03-27/" target="_blank">Reuters - 28 March 2025</a>
## Beijing to Escalate Taiwan Coercion in 2025
### Summary:
A report by the Office of the Director of National Intelligence highlights growing cooperation among China, Russia, Iran, and North Korea, posing significant challenges to U.S. global power. Closer ties between China and Russia, in particular, could present enduring risks to U.S. interests. The document points out China's military threat to the U.S., emphasizing its grey zone tactics and potential for stronger coercive action against Taiwan by 2025. The Ukraine conflict and its ongoing strategic risks, including nuclear escalation, are noted, as well as China's ambition to dominate AI by 2030 and its control over critical materials. The report also mentions the volatile Middle East, with Iran's expanding ties despite challenges, and North Korea's commitment to enhancing its nuclear capabilities. Additionally, threats from foreign drug actors and Islamic extremists, including Al-Qa'ida and a potential ISIS resurgence, are highlighted.
Sources: <a href="https://www.theaustralian.com.au/nation/politics/us-threat-assessment-sounds-the-alarm-on-china/news-story/cb582794c7a653b11cce8d3e61fc564b" target="_blank">The Australian - 28 March 2025</a>
## Fire Ant Infestation Could Cost Australian Households Over $1 Billion Annually
### Summary:
New modeling predicts that if fire ants become established in Australia, households may incur approximately $1.03 billion annually in control measures and related health and veterinary expenses. The invasive species could lead to up to 570,800 medical consultations and around 30 deaths each year due to stings. The electorates of Durack, O'Connor, Mayo, and Blair are projected to be most affected. Experts emphasize the need for increased federal funding for comprehensive eradication programs to prevent environmental damage and significant economic burdens on households.
Sources: <a href="https://www.theguardian.com/environment/2025/mar/28/australia-fire-ants-queensland-cost-eradication-pesticides" target="_blank">The Guardian - March 28, 2025</a>
## The Great Monetary Divide – Epi-3643
### Summary:
In this episode, host Jack Spirko discusses the rapid changes occurring in the global financial landscape. He highlights the European Union's announcement, led by European Central Bank President Christine Lagarde, to implement a Central Bank Digital Currency (CBDC) across member states by the upcoming fall. Spirko expresses concern that such a move could pave the way for a social credit system similar to China's, potentially leading to increased governmental control over individual financial activities.
Conversely, the episode explores developments in the United States, where the government is reportedly adopting Bitcoin as an economic reserve and integrating stablecoins into the financial system. Spirko suggests that these actions may indicate a divergent path from other global economies, potentially fostering a more decentralized financial environment.
Throughout the episode, Spirko emphasizes the importance of understanding these shifts and encourages listeners to consider how such changes might impact personal financial sovereignty and the broader economic landscape.
Please note that this summary is based on limited information available from the episode description and may not capture all the nuances discussed in the full podcast.
Sources: <a href="https://open.spotify.com/episode/5lUuCzX3wHfWdX6y6QtJGw" target="_blank">The Survival Podcast - 28 March 2025</a>, <a href="https://podcasts.apple.com/us/podcast/the-great-monetary-divide-epi-3643/id284148583?i=1000700006108&l=es-MX" target="_blank">Apple Podcasts - 28 March 2025</a>
-

@ 460c25e6:ef85065c
2025-02-25 15:20:39
If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
## Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, **they will not receive your updates**.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend:
- 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc.
- 1 personal relay to store a copy of all your content in a place no one can delete. Go to [relay.tools](https://relay.tools/) and never be censored again.
- 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
## Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend:
- 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc.
- 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps.
- 1 really fast relay located in your country: go to [nostr.watch](https://nostr.watch/relays/find) and find relays in your country
Terrible options include:
- nostr.wine should not be here.
- filter.nostr.wine should not be here.
- inbox.nostr.wine should not be here.
## DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. **If you don't have it setup, you will miss DMs**. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are:
- inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you.
- a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details.
- a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
## Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
## Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. **Tagging and searching will not work if there is nothing here.**. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today:
- nostr.wine
- relay.nostr.band
- relay.noswhere.com
## Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
## General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
## My setup
Here's what I use:
1. Go to [relay.tools](https://relay.tools/) and create a relay for yourself.
2. Go to [nostr.wine](https://nostr.wine/) and pay for their subscription.
3. Go to [inbox.nostr.wine](https://inbox.nostr.wine/) and pay for their subscription.
4. Go to [nostr.watch](https://nostr.watch/relays/find) and find a good relay in your country.
5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays:
- nostr.wine
- nos.lol or an in-country relay.
- <your.relay>.nostr1.com
Public Inbox Relays
- nos.lol or an in-country relay
- <your.relay>.nostr1.com
DM Inbox Relays
- inbox.nostr.wine
- <your.relay>.nostr1.com
Private Home Relays
- ws://localhost:4869 (Citrine)
- <your.relay>.nostr1.com (if you want)
Search Relays
- nostr.wine
- relay.nostr.band
- relay.noswhere.com
Local Relays
- ws://localhost:4869 (Citrine)
General Relays
- nos.lol
- relay.damus.io
- relay.primal.net
- nostr.mom
And a few of the recommended relays from Amethyst.
## Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all. That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission. As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently. Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive. Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally. The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match. When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol. Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all. That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission. As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently. Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive. Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally. The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match. When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol. Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit. @ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice. A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases. Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy. Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest. Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice. A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases. Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy. Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest. Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever. @ c1e9ab3a:9cb56b43
2025-03-26 21:03:59## Introduction **Nutsax** is a capability-based access control system for **Nostr relays**, designed to provide flexible, privacy-preserving **rate limiting**, **permissioning**, and **operation-scoped token redemption**. At its core, Nutsax introduces: - **Blind-signed tokens**, issued by relays, for specific operation types. - **Token redemption** as part of Nostr event publishing or interactions. - **Encrypted token storage** using existing Nostr direct message infrastructure, allowing portable, persistent, and private storage of these tokens — the *Nutsax*. This mechanism augments the existing Nostr protocol without disrupting adoption, requiring no changes to NIP-01 for clients or relays that don’t opt into the system. ## Motivation Nostr relays currently have limited tools for abuse prevention and access control. Options like IP banning, whitelisting, or monetized access are coarse and often centralized. Nutsax introduces: - Fine-grained, **operation-specific access control** using cryptographic tokens. - **Blind signature protocols** to issue tokens anonymously, preserving user privacy. - A **native way to store and recover tokens** using Nostr’s encrypted event system. This allows relays to offer: - Optional access policies (e.g., “3 posts per hour unless you redeem a token”) - Paid or invite-based features (e.g., long-term subscriptions, advanced filters) - Temporary elevation of privileges (e.g., bypass slow mode for one message) All without requiring accounts, emails, or linking identity beyond the user’s `npub`. ## Core Components ### 1. Operation Tokens Tokens are blind-signed blobs issued by the relay, scoped to a specific **operation type** (e.g., `"write"`, `"filter-subscribe"`, `"broadcast"`). - **Issued anonymously**: using a blind signature protocol. - **Validated on redemption**: at message submission or interaction time. - **Optional and redeemable**: the relay decides when to enforce token redemption. Each token encodes: - Operation type (string) - Relay ID (to scope the token) - Expiration (optional) - Usage count or burn-on-use flag - Random nonce (blindness) Example (before blinding): ```json { "relay": "wss://relay.example", "operation": "write", "expires": 1720000000, "nonce": "b2a8c3..." } ``` This is then blinded and signed by the relay. ### 2. Token Redemption Clients include tokens when submitting events or requests to the relay. **Token included via event tag**: ```json ["token", "<base64-encoded-token>", "write"] ``` Redemption can happen: - **Inline with any event** (kind 1, etc.) - **As a standalone event** (e.g., ephemeral kind 20000) - **During session initiation** (optional AUTH extension) The relay validates the token: - Is it well-formed? - Is it valid for this relay and operation? - Is it unexpired? - Has it been used already? (for burn-on-use) If valid, the relay accepts the event or upgrades the rate/permission scope. ### 3. Nutsax: Private Token Storage on Nostr Tokens are stored securely in the client’s **Nutsax**, a persistent, private archive built on Nostr’s encrypted event system. Each token is stored in a **kind 4** or **kind 44/24** event, encrypted with the client’s own `npub`. Example: ```json { "kind": 4, "tags": [ ["p", "<your npub>"], ["token-type", "write"], ["relay", "wss://relay.example"] ], "content": "<encrypted token blob>", "created_at": 1234567890 } ``` This allows clients to: - Persist tokens across restarts or device changes. - Restore tokens after reinstalling or reauthenticating. - Port tokens between devices. All without exposing the tokens to the public or requiring external storage infrastructure. ## Client Lifecycle ### 1. Requesting Tokens - Client authenticates to relay (e.g., via NIP-42). - Requests blind-signed tokens: - Sends blinded token requests. - Receives blind signatures. - Unblinds and verifies. ### 2. Storing Tokens - Each token is encrypted to the user’s own `npub`. - Stored as a DM (kind 4 or compatible encrypted event). - Optional tagging for organization. ### 3. Redeeming Tokens - When performing a token-gated operation (e.g., posting to a limited relay), client includes the appropriate token in the event. - Relay validates and logs/consumes the token. ### 4. Restoring the Nutsax - On device reinstallation or session reset, the client: - Reconnects to relays. - Scans encrypted DMs. - Decrypts and reimports available tokens. ## Privacy Model - Relays issuing tokens **do not know** which tokens were redeemed (blind signing). - Tokens do not encode sender identity unless the client opts to do so. - Only the recipient (`npub`) can decrypt their Nutsax. - Redemption is pseudonymous — tied to a key, not to external identity. ## Optional Enhancements - **Token index tag**: to allow fast search and categorization. - **Multiple token types**: read, write, boost, subscribe, etc. - **Token delegation**: future support for transferring tokens via encrypted DM to another `npub`. - **Token revocation**: relays can publish blacklists or expiration feeds if needed. ## Compatibility - Fully compatible with NIP-01, NIP-04 (encrypted DMs), and NIP-42 (authentication). - Non-disruptive: relays and clients can ignore tokens if not supported. - Ideal for layering on top of existing infrastructure and monetization strategies. ## Conclusion **Nutsax** offers a privacy-respecting, decentralized way to manage access and rate limits in the Nostr ecosystem. With blind-signed, operation-specific tokens and encrypted, persistent storage using native Nostr mechanisms, it gives relays and clients new powers without sacrificing Nostr’s core principles: simplicity, openness, and cryptographic self-sovereignty.
@ c1e9ab3a:9cb56b43
2025-03-26 21:03:59## Introduction **Nutsax** is a capability-based access control system for **Nostr relays**, designed to provide flexible, privacy-preserving **rate limiting**, **permissioning**, and **operation-scoped token redemption**. At its core, Nutsax introduces: - **Blind-signed tokens**, issued by relays, for specific operation types. - **Token redemption** as part of Nostr event publishing or interactions. - **Encrypted token storage** using existing Nostr direct message infrastructure, allowing portable, persistent, and private storage of these tokens — the *Nutsax*. This mechanism augments the existing Nostr protocol without disrupting adoption, requiring no changes to NIP-01 for clients or relays that don’t opt into the system. ## Motivation Nostr relays currently have limited tools for abuse prevention and access control. Options like IP banning, whitelisting, or monetized access are coarse and often centralized. Nutsax introduces: - Fine-grained, **operation-specific access control** using cryptographic tokens. - **Blind signature protocols** to issue tokens anonymously, preserving user privacy. - A **native way to store and recover tokens** using Nostr’s encrypted event system. This allows relays to offer: - Optional access policies (e.g., “3 posts per hour unless you redeem a token”) - Paid or invite-based features (e.g., long-term subscriptions, advanced filters) - Temporary elevation of privileges (e.g., bypass slow mode for one message) All without requiring accounts, emails, or linking identity beyond the user’s `npub`. ## Core Components ### 1. Operation Tokens Tokens are blind-signed blobs issued by the relay, scoped to a specific **operation type** (e.g., `"write"`, `"filter-subscribe"`, `"broadcast"`). - **Issued anonymously**: using a blind signature protocol. - **Validated on redemption**: at message submission or interaction time. - **Optional and redeemable**: the relay decides when to enforce token redemption. Each token encodes: - Operation type (string) - Relay ID (to scope the token) - Expiration (optional) - Usage count or burn-on-use flag - Random nonce (blindness) Example (before blinding): ```json { "relay": "wss://relay.example", "operation": "write", "expires": 1720000000, "nonce": "b2a8c3..." } ``` This is then blinded and signed by the relay. ### 2. Token Redemption Clients include tokens when submitting events or requests to the relay. **Token included via event tag**: ```json ["token", "<base64-encoded-token>", "write"] ``` Redemption can happen: - **Inline with any event** (kind 1, etc.) - **As a standalone event** (e.g., ephemeral kind 20000) - **During session initiation** (optional AUTH extension) The relay validates the token: - Is it well-formed? - Is it valid for this relay and operation? - Is it unexpired? - Has it been used already? (for burn-on-use) If valid, the relay accepts the event or upgrades the rate/permission scope. ### 3. Nutsax: Private Token Storage on Nostr Tokens are stored securely in the client’s **Nutsax**, a persistent, private archive built on Nostr’s encrypted event system. Each token is stored in a **kind 4** or **kind 44/24** event, encrypted with the client’s own `npub`. Example: ```json { "kind": 4, "tags": [ ["p", "<your npub>"], ["token-type", "write"], ["relay", "wss://relay.example"] ], "content": "<encrypted token blob>", "created_at": 1234567890 } ``` This allows clients to: - Persist tokens across restarts or device changes. - Restore tokens after reinstalling or reauthenticating. - Port tokens between devices. All without exposing the tokens to the public or requiring external storage infrastructure. ## Client Lifecycle ### 1. Requesting Tokens - Client authenticates to relay (e.g., via NIP-42). - Requests blind-signed tokens: - Sends blinded token requests. - Receives blind signatures. - Unblinds and verifies. ### 2. Storing Tokens - Each token is encrypted to the user’s own `npub`. - Stored as a DM (kind 4 or compatible encrypted event). - Optional tagging for organization. ### 3. Redeeming Tokens - When performing a token-gated operation (e.g., posting to a limited relay), client includes the appropriate token in the event. - Relay validates and logs/consumes the token. ### 4. Restoring the Nutsax - On device reinstallation or session reset, the client: - Reconnects to relays. - Scans encrypted DMs. - Decrypts and reimports available tokens. ## Privacy Model - Relays issuing tokens **do not know** which tokens were redeemed (blind signing). - Tokens do not encode sender identity unless the client opts to do so. - Only the recipient (`npub`) can decrypt their Nutsax. - Redemption is pseudonymous — tied to a key, not to external identity. ## Optional Enhancements - **Token index tag**: to allow fast search and categorization. - **Multiple token types**: read, write, boost, subscribe, etc. - **Token delegation**: future support for transferring tokens via encrypted DM to another `npub`. - **Token revocation**: relays can publish blacklists or expiration feeds if needed. ## Compatibility - Fully compatible with NIP-01, NIP-04 (encrypted DMs), and NIP-42 (authentication). - Non-disruptive: relays and clients can ignore tokens if not supported. - Ideal for layering on top of existing infrastructure and monetization strategies. ## Conclusion **Nutsax** offers a privacy-respecting, decentralized way to manage access and rate limits in the Nostr ecosystem. With blind-signed, operation-specific tokens and encrypted, persistent storage using native Nostr mechanisms, it gives relays and clients new powers without sacrificing Nostr’s core principles: simplicity, openness, and cryptographic self-sovereignty. @ a7bbc310:fe7b7be3
2025-03-24 13:18:49I’ve been back from Morocco for just over a month and I’ve had some time to reflect. I started writing a day by day of what I did in my trip to Morocco but that was turning out a bit boring. I couldn’t do the trip justice. I thought I’d share some of my observations instead. I’d start by saying I was only there for 5 1/2 days. 5 days in Marrakesh and half day in Essaouira You can feel the rich culture and history Morocco has such a rich culture and history. Influence of Romans, French, Arab, Berbers, Saharan and Nomadic tribes. You can see it in the architecture, taste it in the food and hear it in the language. The streets of Marrakesh had the smells of spices, perfumes and petrol. There is a synchronised dance between everyone that occupy the streets. People, motorbikes, donkeys, carts, all jostling for position but never seeming to collide into on another. One thing that didn’t surprise me was the high level of craftsmanship and intricate designs on some of the buildings. I was told by a tour guide that some of the calligraphy could only be understood and read by the person who wrote it. There seemed to be a sense of community, people stopping in the street to greet each other and say hello. What surprised me about this in Marrakesh most was that it happened in such a busy city. From my experience big cities are places that you go to get lost, ignored and don’t want to be found. Scene at the end of the movie Collateral comes to mind. You know the one where he’s riding on the subway alone after being shot. A vendor tried to sell me a pendant, a symbol of the Berber tribe that meant ‘free man’. The symbol looks similar to the one for Sats 丰. I declined to purchase since I wasn’t educated enough on the Berbers to rep a symbol. Couldn’t get over how much stuff there was for sale! And duplications of everything, rugs, shoes , handbags, jackets. Cold mornings and evenings, warm during the day. Everyone dressed like it was winter, even when it for warmer in the afternoon. It was a special trip. I’d definitely go back. Both to visit Marrakesh and other places.
@ a7bbc310:fe7b7be3
2025-03-24 13:18:49I’ve been back from Morocco for just over a month and I’ve had some time to reflect. I started writing a day by day of what I did in my trip to Morocco but that was turning out a bit boring. I couldn’t do the trip justice. I thought I’d share some of my observations instead. I’d start by saying I was only there for 5 1/2 days. 5 days in Marrakesh and half day in Essaouira You can feel the rich culture and history Morocco has such a rich culture and history. Influence of Romans, French, Arab, Berbers, Saharan and Nomadic tribes. You can see it in the architecture, taste it in the food and hear it in the language. The streets of Marrakesh had the smells of spices, perfumes and petrol. There is a synchronised dance between everyone that occupy the streets. People, motorbikes, donkeys, carts, all jostling for position but never seeming to collide into on another. One thing that didn’t surprise me was the high level of craftsmanship and intricate designs on some of the buildings. I was told by a tour guide that some of the calligraphy could only be understood and read by the person who wrote it. There seemed to be a sense of community, people stopping in the street to greet each other and say hello. What surprised me about this in Marrakesh most was that it happened in such a busy city. From my experience big cities are places that you go to get lost, ignored and don’t want to be found. Scene at the end of the movie Collateral comes to mind. You know the one where he’s riding on the subway alone after being shot. A vendor tried to sell me a pendant, a symbol of the Berber tribe that meant ‘free man’. The symbol looks similar to the one for Sats 丰. I declined to purchase since I wasn’t educated enough on the Berbers to rep a symbol. Couldn’t get over how much stuff there was for sale! And duplications of everything, rugs, shoes , handbags, jackets. Cold mornings and evenings, warm during the day. Everyone dressed like it was winter, even when it for warmer in the afternoon. It was a special trip. I’d definitely go back. Both to visit Marrakesh and other places. @ f839fb67:5c930939
2025-03-24 00:25:16# Relays | Name | Address | Price (Sats/Year) | Status | | - | - | - | - | | stephen's aegis relay | wss://paid.relay.vanderwarker.family | 42069 |   | | stephen's Outbox | wss://relay.vanderwarker.family | Just Me |   | | stephen's Inbox | wss://haven.vanderwarker.family/inbox | WoT |   | | stephen's DMs | wss://haven.vanderwarker.family/chat | WoT |   | | VFam Data Relay | wss://data.relay.vanderwarker.family | 0 |   | | VFam Bots Relay | wss://skeme.vanderwarker.family | Invite |   | | VFGroups (NIP29) | wss://groups.vanderwarker.family | 0 |   | | [TOR] My Phone Relay | ws://naswsosuewqxyf7ov7gr7igc4tq2rbtqoxxirwyhkbuns4lwc3iowwid.onion | 0 | Meh... | --- # My Pubkeys | Name | hex | nprofile | | - | - | - | | Main | f839fb6714598a7233d09dbd42af82cc9781d0faa57474f1841af90b5c930939 | nprofile1qqs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us9mapfx | | Vanity (Backup) | 82f21be67353c0d68438003fe6e56a35e2a57c49e0899b368b5ca7aa8dde7c23 | nprofile1qqsg9usmuee48sxkssuqq0lxu44rtc4903y7pzvmx694efa23h08cgcpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3ussel49x | | VFStore | 6416f1e658ba00d42107b05ad9bf485c7e46698217e0c19f0dc2e125de3af0d0 | nprofile1qqsxg9h3uevt5qx5yyrmqkkehay9cljxdxpp0cxpnuxu9cf9mca0p5qpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usaa8plu | | NostrSMS | 9be1b8315248eeb20f9d9ab2717d1750e4f27489eab1fa531d679dadd34c2f8d | nprofile1qqsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us595d45 | # Bot Pubkeys | Name | hex | nprofile | | - | - | - | | Unlocks Bot | 2e941ad17144e0a04d1b8c21c4a0dbc3fbcbb9d08ae622b5f9c85341fac7c2d0 | nprofile1qqsza9q669c5fc9qf5dccgwy5rdu877th8gg4e3zkhuus56pltru95qpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ust4kvak | | Step Counter | 9223d2faeb95853b4d224a184c69e1df16648d35067a88cdf947c631b57e3de7 | nprofile1qqsfyg7jlt4etpfmf53y5xzvd8sa79ny356sv75gehu50333k4lrmecpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ustswp3w | --- # "Personal Nostr Things" > [D] = Saves darkmode preferences over nostr > [A] = Auth over nostr > [B] = Beta (software) > [z] = zap enabled - [[DABz] Main Site](https://vanderwarker.family) - [[DAB] Contact Site](https://stephen.vanderwarker.family) - [[DAB] PGP Site](https://pgp.vanderwarker.family) - [[DAB] VFCA Site](https://ca.vanderwarker.family) --- # Other Services (Hosted code) * [Blossom](https://blossom.vanderwarker.family)   * [NostrCheck](https://nostr.vanderwarker.family)   --- # Emojis Packs * Minecraft - <code>nostr:naddr1qqy566twv43hyctxwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsd0k5wp</code> * AIM - <code>nostr:naddr1qqxxz6tdv4kk7arfvdhkuucpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usyg8c88akw9ze3fer85yah4p2lqkvj7qap749w360rpq6ly94eycf8ypsgqqqw48qe0j2yk</code> * Blobs - <code>nostr:naddr1qqz5ymr0vfesz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2wek4ukj</code> * FavEmojis - <code>nostr:naddr1qqy5vctkg4kk76nfwvq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsf7sdwt</code> * Modern Family - <code>nostr:naddr1qqx56mmyv4exugzxv9kkjmreqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqp65ujlj36n</code> * nostriches (Amethyst collection) - <code>nostr:naddr1qq9xummnw3exjcmgv4esz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w2sqg6w</code> * Pepe - <code>nostr:naddr1qqz9qetsv5q37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82ns85f6x7</code> * Minecraft Font - <code>nostr:naddr1qq8y66twv43hyctxwssyvmmwwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsmzftgr</code> * Archer Font - <code>nostr:naddr1qq95zunrdpjhygzxdah8gqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr4fclkyxsh</code> * SMB Font - <code>nostr:naddr1qqv4xatsv4ezqntpwf5k7gzzwfhhg6r9wfejq3n0de6qz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w0wqpuk</code> --- # Git Over Nostr * NostrSMS - <code>nostr:naddr1qqyxummnw3e8xmtnqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfrwaehxw309amk7apwwfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqyj8wumn8ghj7urpd9jzuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyxhwumn8ghj7mn0wvhxcmmvqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqaueqp0epk</code> * nip51backup - <code>nostr:naddr1qq9ku6tsx5ckyctrdd6hqqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjxamnwvaz7tmhda6zuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfywaehxw309acxz6ty9eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgdwaehxw309ahx7uewd3hkcq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqpmej4gtqs6</code> * bukkitstr - <code>nostr:naddr1qqykyattdd5hgum5wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dspzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqrhnyf6g0n2</code> --- # Market Places Please use [Nostr Market](https://market.nostr.com) or somthing simular, to view. * VFStore - <code>nostr:naddr1qqjx2v34xe3kxvpn95cnqven956rwvpc95unscn9943kxet98q6nxde58p3ryqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjvamnwvaz7tmgv9mx2m3wweskuer9wfmkzuntv4ezuenpd45kc7f0da6hgcn00qqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzqeqk78n93wsq6sss0vz6mxl5shr7ge5cy9lqcx0smshpyh0r4uxsqvzqqqr4gvlfm7gu</code> --- # Badges ## Created * paidrelayvf - <code>nostr:naddr1qq9hqctfv3ex2mrp09mxvqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr48y85v3u3</code> * iPow - <code>nostr:naddr1qqzxj5r02uq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgg02u0r</code> * codmaster - <code>nostr:naddr1qqykxmmyd4shxar9wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgk3gm4g</code> * iMine - <code>nostr:naddr1qqzkjntfdejsz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqafed5s4x5</code> --- # Clients I Use * Amethyst - <code>nostr:naddr1qqxnzd3cx5urqv3nxymngdphqgsyvrp9u6p0mfur9dfdru3d853tx9mdjuhkphxuxgfwmryja7zsvhqrqsqqql8kavfpw3</code> * noStrudel - <code>nostr:naddr1qqxnzd3cxccrvd34xser2dpkqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsygpxdq27pjfppharynrvhg6h8v2taeya5ssf49zkl9yyu5gxe4qg55psgqqq0nmq5mza9n</code> * nostrsms - <code>nostr:naddr1qq9rzdejxcunxde4xymqz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgrqsqqql8kjn33qm</code> --- # Lists * Fediverse - <code>nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqp9rx2erfwejhyum9j4g0xh</code> * AI - <code>nostr:naddr1qvzqqqr4xypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqqfq5j65twn7</code> * Asterisk Shenanigans - <code>nostr:naddr1qvzqqqr4xypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqz3qhxar9wf5hx6eq2d5x2mnpde5kwctwwvaxjuzz</code> * Minecraft Videos - <code>nostr:naddr1qvzqqqr4xypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqzpxkjmn9vdexzen5yptxjer9daesqrd8jk</code>
@ f839fb67:5c930939
2025-03-24 00:25:16# Relays | Name | Address | Price (Sats/Year) | Status | | - | - | - | - | | stephen's aegis relay | wss://paid.relay.vanderwarker.family | 42069 |   | | stephen's Outbox | wss://relay.vanderwarker.family | Just Me |   | | stephen's Inbox | wss://haven.vanderwarker.family/inbox | WoT |   | | stephen's DMs | wss://haven.vanderwarker.family/chat | WoT |   | | VFam Data Relay | wss://data.relay.vanderwarker.family | 0 |   | | VFam Bots Relay | wss://skeme.vanderwarker.family | Invite |   | | VFGroups (NIP29) | wss://groups.vanderwarker.family | 0 |   | | [TOR] My Phone Relay | ws://naswsosuewqxyf7ov7gr7igc4tq2rbtqoxxirwyhkbuns4lwc3iowwid.onion | 0 | Meh... | --- # My Pubkeys | Name | hex | nprofile | | - | - | - | | Main | f839fb6714598a7233d09dbd42af82cc9781d0faa57474f1841af90b5c930939 | nprofile1qqs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us9mapfx | | Vanity (Backup) | 82f21be67353c0d68438003fe6e56a35e2a57c49e0899b368b5ca7aa8dde7c23 | nprofile1qqsg9usmuee48sxkssuqq0lxu44rtc4903y7pzvmx694efa23h08cgcpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3ussel49x | | VFStore | 6416f1e658ba00d42107b05ad9bf485c7e46698217e0c19f0dc2e125de3af0d0 | nprofile1qqsxg9h3uevt5qx5yyrmqkkehay9cljxdxpp0cxpnuxu9cf9mca0p5qpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usaa8plu | | NostrSMS | 9be1b8315248eeb20f9d9ab2717d1750e4f27489eab1fa531d679dadd34c2f8d | nprofile1qqsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us595d45 | # Bot Pubkeys | Name | hex | nprofile | | - | - | - | | Unlocks Bot | 2e941ad17144e0a04d1b8c21c4a0dbc3fbcbb9d08ae622b5f9c85341fac7c2d0 | nprofile1qqsza9q669c5fc9qf5dccgwy5rdu877th8gg4e3zkhuus56pltru95qpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ust4kvak | | Step Counter | 9223d2faeb95853b4d224a184c69e1df16648d35067a88cdf947c631b57e3de7 | nprofile1qqsfyg7jlt4etpfmf53y5xzvd8sa79ny356sv75gehu50333k4lrmecpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ustswp3w | --- # "Personal Nostr Things" > [D] = Saves darkmode preferences over nostr > [A] = Auth over nostr > [B] = Beta (software) > [z] = zap enabled - [[DABz] Main Site](https://vanderwarker.family) - [[DAB] Contact Site](https://stephen.vanderwarker.family) - [[DAB] PGP Site](https://pgp.vanderwarker.family) - [[DAB] VFCA Site](https://ca.vanderwarker.family) --- # Other Services (Hosted code) * [Blossom](https://blossom.vanderwarker.family)   * [NostrCheck](https://nostr.vanderwarker.family)   --- # Emojis Packs * Minecraft - <code>nostr:naddr1qqy566twv43hyctxwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsd0k5wp</code> * AIM - <code>nostr:naddr1qqxxz6tdv4kk7arfvdhkuucpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usyg8c88akw9ze3fer85yah4p2lqkvj7qap749w360rpq6ly94eycf8ypsgqqqw48qe0j2yk</code> * Blobs - <code>nostr:naddr1qqz5ymr0vfesz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2wek4ukj</code> * FavEmojis - <code>nostr:naddr1qqy5vctkg4kk76nfwvq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsf7sdwt</code> * Modern Family - <code>nostr:naddr1qqx56mmyv4exugzxv9kkjmreqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqp65ujlj36n</code> * nostriches (Amethyst collection) - <code>nostr:naddr1qq9xummnw3exjcmgv4esz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w2sqg6w</code> * Pepe - <code>nostr:naddr1qqz9qetsv5q37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82ns85f6x7</code> * Minecraft Font - <code>nostr:naddr1qq8y66twv43hyctxwssyvmmwwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsmzftgr</code> * Archer Font - <code>nostr:naddr1qq95zunrdpjhygzxdah8gqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr4fclkyxsh</code> * SMB Font - <code>nostr:naddr1qqv4xatsv4ezqntpwf5k7gzzwfhhg6r9wfejq3n0de6qz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w0wqpuk</code> --- # Git Over Nostr * NostrSMS - <code>nostr:naddr1qqyxummnw3e8xmtnqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfrwaehxw309amk7apwwfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqyj8wumn8ghj7urpd9jzuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyxhwumn8ghj7mn0wvhxcmmvqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqaueqp0epk</code> * nip51backup - <code>nostr:naddr1qq9ku6tsx5ckyctrdd6hqqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjxamnwvaz7tmhda6zuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfywaehxw309acxz6ty9eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgdwaehxw309ahx7uewd3hkcq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqpmej4gtqs6</code> * bukkitstr - <code>nostr:naddr1qqykyattdd5hgum5wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dspzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqrhnyf6g0n2</code> --- # Market Places Please use [Nostr Market](https://market.nostr.com) or somthing simular, to view. * VFStore - <code>nostr:naddr1qqjx2v34xe3kxvpn95cnqven956rwvpc95unscn9943kxet98q6nxde58p3ryqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjvamnwvaz7tmgv9mx2m3wweskuer9wfmkzuntv4ezuenpd45kc7f0da6hgcn00qqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzqeqk78n93wsq6sss0vz6mxl5shr7ge5cy9lqcx0smshpyh0r4uxsqvzqqqr4gvlfm7gu</code> --- # Badges ## Created * paidrelayvf - <code>nostr:naddr1qq9hqctfv3ex2mrp09mxvqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr48y85v3u3</code> * iPow - <code>nostr:naddr1qqzxj5r02uq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgg02u0r</code> * codmaster - <code>nostr:naddr1qqykxmmyd4shxar9wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgk3gm4g</code> * iMine - <code>nostr:naddr1qqzkjntfdejsz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqafed5s4x5</code> --- # Clients I Use * Amethyst - <code>nostr:naddr1qqxnzd3cx5urqv3nxymngdphqgsyvrp9u6p0mfur9dfdru3d853tx9mdjuhkphxuxgfwmryja7zsvhqrqsqqql8kavfpw3</code> * noStrudel - <code>nostr:naddr1qqxnzd3cxccrvd34xser2dpkqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsygpxdq27pjfppharynrvhg6h8v2taeya5ssf49zkl9yyu5gxe4qg55psgqqq0nmq5mza9n</code> * nostrsms - <code>nostr:naddr1qq9rzdejxcunxde4xymqz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgrqsqqql8kjn33qm</code> --- # Lists * Fediverse - <code>nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqp9rx2erfwejhyum9j4g0xh</code> * AI - <code>nostr:naddr1qvzqqqr4xypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqqfq5j65twn7</code> * Asterisk Shenanigans - <code>nostr:naddr1qvzqqqr4xypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqz3qhxar9wf5hx6eq2d5x2mnpde5kwctwwvaxjuzz</code> * Minecraft Videos - <code>nostr:naddr1qvzqqqr4xypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqzpxkjmn9vdexzen5yptxjer9daesqrd8jk</code> @ 6b3780ef:221416c8
2025-03-26 18:42:00This workshop will guide you through exploring the concepts behind MCP servers and how to deploy them as DVMs in Nostr using DVMCP. By the end, you'll understand how these systems work together and be able to create your own deployments. ## Understanding MCP Systems MCP (Model Context Protocol) systems consist of two main components that work together: 1. **MCP Server**: The heart of the system that exposes tools, which you can access via the `.listTools()` method. 2. **MCP Client**: The interface that connects to the MCP server and lets you use the tools it offers. These servers and clients can communicate using different transport methods: - **Standard I/O (stdio)**: A simple local connection method when your server and client are on the same machine. - **Server-Sent Events (SSE)**: Uses HTTP to create a communication channel. For this workshop, we'll use stdio to deploy our server. DVMCP will act as a bridge, connecting to your MCP server as an MCP client, and exposing its tools as a DVM that anyone can call from Nostr. ## Creating (or Finding) an MCP Server Building an MCP server is simpler than you might think: 1. Create software in any programming language you're comfortable with. 2. Add an MCP library to expose your server's MCP interface. 3. Create an API that wraps around your software's functionality. Once your server is ready, an MCP client can connect, for example, with `bun index.js`, and then call `.listTools()` to discover what your server can do. This pattern, known as reflection, makes Nostr DVMs and MCP a perfect match since both use JSON, and DVMs can announce and call tools, effectively becoming an MCP proxy. Alternatively, you can use one of the many existing MCP servers available in various repositories. For more information about mcp and how to build mcp servers you can visit https://modelcontextprotocol.io/ ## Setting Up the Workshop Let's get hands-on: First, to follow this workshop you will need Bun. Install it from https://bun.sh/. For Linux and macOS, you can use the installation script: ``` curl -fsSL https://bun.sh/install | bash ``` 1. **Choose your MCP server**: You can either create one or use an existing one. 2. **Inspect your server** using the MCP inspector tool: ```bash npx @modelcontextprotocol/inspector build/index.js arg1 arg2 ``` This will: - Launch a client UI (default: http://localhost:5173) - Start an MCP proxy server (default: port 3000) - Pass any additional arguments directly to your server 3. **Use the inspector**: Open the client UI in your browser to connect with your server, list available tools, and test its functionality. ## Deploying with DVMCP Now for the exciting part – making your MCP server available to everyone on Nostr: 1. Navigate to your MCP server directory. 2. Run without installing (quickest way): ``` npx @dvmcp/bridge ``` 3. Or install globally for regular use: ``` npm install -g @dvmcp/bridge # or bun install -g @dvmcp/bridge ``` Then run using: ```bash dvmcp-bridge ``` This will guide you through creating the necessary configuration. Watch the console logs to confirm successful setup – you'll see your public key and process information, or any issues that need addressing. For the configuration, you can set the relay as `wss://relay.dvmcp.fun` , or use any other of your preference ## Testing and Integration 1. **Visit [dvmcp.fun](https://dvmcp.fun)** to see your DVM announcement. 2. Call your tools and watch the responses come back. For production use, consider running dvmcp-bridge as a system service or creating a container for greater reliability and uptime. ## Integrating with LLM Clients You can also integrate your DVMCP deployment with LLM clients using the discovery package: 1. Install and use the `@dvmcp/discovery` package: ```bash npx @dvmcp/discovery ``` 2. This package acts as an MCP server for your LLM system by: - Connecting to configured Nostr relays - Discovering tools from DVMCP servers - Making them available to your LLM applications 3. Connect to specific servers or providers using these flags: ```bash # Connect to all DVMCP servers from a provider npx @dvmcp/discovery --provider npub1... # Connect to a specific DVMCP server npx @dvmcp/discovery --server naddr1... ``` Using these flags, you wouldn't need a configuration file. You can find these commands and Claude desktop configuration already prepared for copy and paste at [dvmcp.fun](https://dvmcp.fun). This feature lets you connect to any DVMCP server using Nostr and integrate it into your client, either as a DVM or in LLM-powered applications. ## Final thoughts If you've followed this workshop, you now have an MCP server deployed as a Nostr DVM. This means that local resources from the system where the MCP server is running can be accessed through Nostr in a decentralized manner. This capability is powerful and opens up numerous possibilities and opportunities for fun. You can use this setup for various use cases, including in a controlled/local environment. For instance, you can deploy a relay in your local network that's only accessible within it, exposing all your local MCP servers to anyone connected to the network. This setup can act as a hub for communication between different systems, which could be particularly interesting for applications in home automation or other fields. The potential applications are limitless. However, it's important to keep in mind that there are security concerns when exposing local resources publicly. You should be mindful of these risks and prioritize security when creating and deploying your MCP servers on Nostr. Finally, these are new ideas, and the software is still under development. If you have any feedback, please refer to the GitHub repository to report issues or collaborate. DVMCP also has a Signal group you can join. Additionally, you can engage with the community on Nostr using the #dvmcp hashtag. ## Useful Resources - **Official Documentation**: - Model Context Protocol: [modelcontextprotocol.org](https://modelcontextprotocol.org) - DVMCP.fun: [dvmcp.fun](https://dvmcp.fun) - **Source Code and Development**: - DVMCP: [github.com/gzuuus/dvmcp](https://github.com/gzuuus/dvmcp) - DVMCP.fun: [github.com/gzuuus/dvmcpfun](https://github.com/gzuuus/dvmcpfun) - **MCP Servers and Clients**: - Smithery AI: [smithery.ai](https://smithery.ai) - MCP.so: [mcp.so](https://mcp.so) - Glama AI MCP Servers: [glama.ai/mcp/servers](https://glama.ai/mcp/servers) - [Signal group](https://signal.group/#CjQKIOgvfFJf8ZFZ1SsMx7teFqNF73sZ9Elaj_v5i6RSjDHmEhA5v69L4_l2dhQfwAm2SFGD) Happy building!
@ 6b3780ef:221416c8
2025-03-26 18:42:00This workshop will guide you through exploring the concepts behind MCP servers and how to deploy them as DVMs in Nostr using DVMCP. By the end, you'll understand how these systems work together and be able to create your own deployments. ## Understanding MCP Systems MCP (Model Context Protocol) systems consist of two main components that work together: 1. **MCP Server**: The heart of the system that exposes tools, which you can access via the `.listTools()` method. 2. **MCP Client**: The interface that connects to the MCP server and lets you use the tools it offers. These servers and clients can communicate using different transport methods: - **Standard I/O (stdio)**: A simple local connection method when your server and client are on the same machine. - **Server-Sent Events (SSE)**: Uses HTTP to create a communication channel. For this workshop, we'll use stdio to deploy our server. DVMCP will act as a bridge, connecting to your MCP server as an MCP client, and exposing its tools as a DVM that anyone can call from Nostr. ## Creating (or Finding) an MCP Server Building an MCP server is simpler than you might think: 1. Create software in any programming language you're comfortable with. 2. Add an MCP library to expose your server's MCP interface. 3. Create an API that wraps around your software's functionality. Once your server is ready, an MCP client can connect, for example, with `bun index.js`, and then call `.listTools()` to discover what your server can do. This pattern, known as reflection, makes Nostr DVMs and MCP a perfect match since both use JSON, and DVMs can announce and call tools, effectively becoming an MCP proxy. Alternatively, you can use one of the many existing MCP servers available in various repositories. For more information about mcp and how to build mcp servers you can visit https://modelcontextprotocol.io/ ## Setting Up the Workshop Let's get hands-on: First, to follow this workshop you will need Bun. Install it from https://bun.sh/. For Linux and macOS, you can use the installation script: ``` curl -fsSL https://bun.sh/install | bash ``` 1. **Choose your MCP server**: You can either create one or use an existing one. 2. **Inspect your server** using the MCP inspector tool: ```bash npx @modelcontextprotocol/inspector build/index.js arg1 arg2 ``` This will: - Launch a client UI (default: http://localhost:5173) - Start an MCP proxy server (default: port 3000) - Pass any additional arguments directly to your server 3. **Use the inspector**: Open the client UI in your browser to connect with your server, list available tools, and test its functionality. ## Deploying with DVMCP Now for the exciting part – making your MCP server available to everyone on Nostr: 1. Navigate to your MCP server directory. 2. Run without installing (quickest way): ``` npx @dvmcp/bridge ``` 3. Or install globally for regular use: ``` npm install -g @dvmcp/bridge # or bun install -g @dvmcp/bridge ``` Then run using: ```bash dvmcp-bridge ``` This will guide you through creating the necessary configuration. Watch the console logs to confirm successful setup – you'll see your public key and process information, or any issues that need addressing. For the configuration, you can set the relay as `wss://relay.dvmcp.fun` , or use any other of your preference ## Testing and Integration 1. **Visit [dvmcp.fun](https://dvmcp.fun)** to see your DVM announcement. 2. Call your tools and watch the responses come back. For production use, consider running dvmcp-bridge as a system service or creating a container for greater reliability and uptime. ## Integrating with LLM Clients You can also integrate your DVMCP deployment with LLM clients using the discovery package: 1. Install and use the `@dvmcp/discovery` package: ```bash npx @dvmcp/discovery ``` 2. This package acts as an MCP server for your LLM system by: - Connecting to configured Nostr relays - Discovering tools from DVMCP servers - Making them available to your LLM applications 3. Connect to specific servers or providers using these flags: ```bash # Connect to all DVMCP servers from a provider npx @dvmcp/discovery --provider npub1... # Connect to a specific DVMCP server npx @dvmcp/discovery --server naddr1... ``` Using these flags, you wouldn't need a configuration file. You can find these commands and Claude desktop configuration already prepared for copy and paste at [dvmcp.fun](https://dvmcp.fun). This feature lets you connect to any DVMCP server using Nostr and integrate it into your client, either as a DVM or in LLM-powered applications. ## Final thoughts If you've followed this workshop, you now have an MCP server deployed as a Nostr DVM. This means that local resources from the system where the MCP server is running can be accessed through Nostr in a decentralized manner. This capability is powerful and opens up numerous possibilities and opportunities for fun. You can use this setup for various use cases, including in a controlled/local environment. For instance, you can deploy a relay in your local network that's only accessible within it, exposing all your local MCP servers to anyone connected to the network. This setup can act as a hub for communication between different systems, which could be particularly interesting for applications in home automation or other fields. The potential applications are limitless. However, it's important to keep in mind that there are security concerns when exposing local resources publicly. You should be mindful of these risks and prioritize security when creating and deploying your MCP servers on Nostr. Finally, these are new ideas, and the software is still under development. If you have any feedback, please refer to the GitHub repository to report issues or collaborate. DVMCP also has a Signal group you can join. Additionally, you can engage with the community on Nostr using the #dvmcp hashtag. ## Useful Resources - **Official Documentation**: - Model Context Protocol: [modelcontextprotocol.org](https://modelcontextprotocol.org) - DVMCP.fun: [dvmcp.fun](https://dvmcp.fun) - **Source Code and Development**: - DVMCP: [github.com/gzuuus/dvmcp](https://github.com/gzuuus/dvmcp) - DVMCP.fun: [github.com/gzuuus/dvmcpfun](https://github.com/gzuuus/dvmcpfun) - **MCP Servers and Clients**: - Smithery AI: [smithery.ai](https://smithery.ai) - MCP.so: [mcp.so](https://mcp.so) - Glama AI MCP Servers: [glama.ai/mcp/servers](https://glama.ai/mcp/servers) - [Signal group](https://signal.group/#CjQKIOgvfFJf8ZFZ1SsMx7teFqNF73sZ9Elaj_v5i6RSjDHmEhA5v69L4_l2dhQfwAm2SFGD) Happy building! @ b2d670de:907f9d4a
2025-03-25 20:17:57This guide will walk you through setting up your own Strfry Nostr relay on a Debian/Ubuntu server and making it accessible exclusively as a TOR hidden service. By the end, you'll have a privacy-focused relay that operates entirely within the TOR network, enhancing both your privacy and that of your users. ## Table of Contents 1. Prerequisites 2. Initial Server Setup 3. Installing Strfry Nostr Relay 4. Configuring Your Relay 5. Setting Up TOR 6. Making Your Relay Available on TOR 7. Testing Your Setup] 8. Maintenance and Security 9. Troubleshooting ## Prerequisites - A Debian or Ubuntu server - Basic familiarity with command line operations (most steps are explained in detail) - Root or sudo access to your server ## Initial Server Setup First, let's make sure your server is properly set up and secured. ### Update Your System Connect to your server via SSH and update your system: ```bash sudo apt update sudo apt upgrade -y ``` ### Set Up a Basic Firewall Install and configure a basic firewall: ```bash sudo apt install ufw -y sudo ufw allow ssh sudo ufw enable ``` This allows SSH connections while blocking other ports for security. ## Installing Strfry Nostr Relay This guide includes the full range of steps needed to build and set up Strfry. It's simply based on the current version of the `DEPLOYMENT.md` document in the Strfry GitHub repository. If the build/setup process is changed in the repo, this document could get outdated. If so, please report to me that something is outdated and check for updated steps [here](https://github.com/hoytech/strfry/blob/master/docs/DEPLOYMENT.md). ### Install Dependencies First, let's install the necessary dependencies. Each package serves a specific purpose in building and running Strfry: ```bash sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-dev ``` Here's why each dependency is needed: **Basic Development Tools:** - `git`: Version control system used to clone the Strfry repository and manage code updates - `build-essential`: Meta-package that includes compilers (gcc, g++), make, and other essential build tools **Perl Dependencies** (used for Strfry's build scripts): - `libyaml-perl`: Perl interface to parse YAML configuration files - `libtemplate-perl`: Template processing system used during the build process - `libregexp-grammars-perl`: Advanced regular expression handling for Perl scripts **Core Libraries for Strfry:** - `libssl-dev`: Development files for OpenSSL, used for secure connections and cryptographic operations - `zlib1g-dev`: Compression library that Strfry uses to reduce data size - `liblmdb-dev`: Lightning Memory-Mapped Database library, which Strfry uses for its high-performance database backend - `libflatbuffers-dev`: Memory-efficient serialization library for structured data - `libsecp256k1-dev`: Optimized C library for EC operations on curve secp256k1, essential for Nostr's cryptographic signatures - `libzstd-dev`: Fast real-time compression algorithm for efficient data storage and transmission ### Clone and Build Strfry Clone the Strfry repository: ```bash git clone https://github.com/hoytech/strfry.git cd strfry ``` Build Strfry: ```bash git submodule update --init make setup-golpe make -j2 # This uses 2 CPU cores. Adjust based on your server (e.g., -j4 for 4 cores) ``` This build process will take several minutes, especially on servers with limited CPU resources, so go get a coffee and post some great memes on nostr in the meantime. ### Install Strfry Install the Strfry binary to your system path: ```bash sudo cp strfry /usr/local/bin ``` This makes the `strfry` command available system-wide, allowing it to be executed from any directory and by any user with the appropriate permissions. ## Configuring Your Relay ### Create Strfry User Create a dedicated user for running Strfry. This enhances security by isolating the relay process: ```bash sudo useradd -M -s /usr/sbin/nologin strfry ``` The `-M` flag prevents creating a home directory, and `-s /usr/sbin/nologin` prevents anyone from logging in as this user. This is a security best practice for service accounts. ### Create Data Directory Create a directory for Strfry's data: ```bash sudo mkdir /var/lib/strfry sudo chown strfry:strfry /var/lib/strfry sudo chmod 755 /var/lib/strfry ``` This creates a dedicated directory for Strfry's database and sets the appropriate permissions so that only the strfry user can write to it. ### Configure Strfry Copy the sample configuration file: ```bash sudo cp strfry.conf /etc/strfry.conf ``` Edit the configuration file: ```bash sudo nano /etc/strfry.conf ``` Modify the database path: ``` # Find this line: db = "./strfry-db/" # Change it to: db = "/var/lib/strfry/" ``` Check your system's hard limit for file descriptors: ```bash ulimit -Hn ``` Update the `nofiles` setting in your configuration to match this value (or set to 0): ``` # Add or modify this line in the config (example if your limit is 524288): nofiles = 524288 ``` The `nofiles` setting determines how many open files Strfry can have simultaneously. Setting it to your system's hard limit (or 0 to use the system default) helps prevent "too many open files" errors if your relay becomes popular. You might also want to customize your relay's information in the config file. Look for the `info` section and update it with your relay's name, description, and other details. Set ownership of the configuration file: ```bash sudo chown strfry:strfry /etc/strfry.conf ``` ### Create Systemd Service Create a systemd service file for managing Strfry: ```bash sudo nano /etc/systemd/system/strfry.service ``` Add the following content: ```ini [Unit] Description=strfry relay service [Service] User=strfry ExecStart=/usr/local/bin/strfry relay Restart=on-failure RestartSec=5 ProtectHome=yes NoNewPrivileges=yes ProtectSystem=full LimitCORE=1000000000 [Install] WantedBy=multi-user.target ``` This systemd service configuration: - Runs Strfry as the dedicated strfry user - Automatically restarts the service if it fails - Implements security measures like `ProtectHome` and `NoNewPrivileges` - Sets resource limits appropriate for a relay Enable and start the service: ```bash sudo systemctl enable strfry.service sudo systemctl start strfry ``` Check the service status: ```bash sudo systemctl status strfry ``` ### Verify Relay is Running Test that your relay is running locally: ```bash curl localhost:7777 ``` You should see a message indicating that the Strfry relay is running. This confirms that Strfry is properly installed and configured before we proceed to set up TOR. ## Setting Up TOR Now let's make your relay accessible as a TOR hidden service. ### Install TOR Install TOR from the package repositories: ```bash sudo apt install -y tor ``` This installs the TOR daemon that will create and manage your hidden service. ### Configure TOR Edit the TOR configuration file: ```bash sudo nano /etc/tor/torrc ``` Scroll down to wherever you see a commented out part like this: ``` #HiddenServiceDir /var/lib/tor/hidden_service/ #HiddenServicePort 80 127.0.0.1:80 ``` Under those lines, add the following lines to set up a hidden service for your relay: ``` HiddenServiceDir /var/lib/tor/strfry-relay/ HiddenServicePort 80 127.0.0.1:7777 ``` This configuration: - Creates a hidden service directory at `/var/lib/tor/strfry-relay/` - Maps port 80 on your .onion address to port 7777 on your local machine - Keeps all traffic encrypted within the TOR network Create the directory for your hidden service: ```bash sudo mkdir -p /var/lib/tor/strfry-relay/ sudo chown debian-tor:debian-tor /var/lib/tor/strfry-relay/ sudo chmod 700 /var/lib/tor/strfry-relay/ ``` The strict permissions (700) are crucial for security as they ensure only the debian-tor user can access the directory containing your hidden service private keys. Restart TOR to apply changes: ```bash sudo systemctl restart tor ``` ## Making Your Relay Available on TOR ### Get Your Onion Address After restarting TOR, you can find your onion address: ```bash sudo cat /var/lib/tor/strfry-relay/hostname ``` This will output something like `abcdefghijklmnopqrstuvwxyz234567.onion`, which is your relay's unique .onion address. This is what you'll share with others to access your relay. ### Understanding Onion Addresses The .onion address is a special-format hostname that is automatically generated based on your hidden service's private key. Your users will need to use this address with the WebSocket protocol prefix to connect: `ws://youronionaddress.onion` ## Testing Your Setup ### Test with a Nostr Client The best way to test your relay is with an actual Nostr client that supports TOR: 1. Open your TOR browser 2. Go to your favorite client, either on clearnet or an onion service. - Check out [this list](https://github.com/0xtrr/onion-service-nostr-clients?tab=readme-ov-file#onion-service-nostr-clients) of nostr clients available over TOR. 3. Add your relay URL: `ws://youronionaddress.onion` to your relay list 4. Try posting a note and see if it appears on your relay - In some nostr clients, you can also click on a relay to get information about it like the relay name and description you set earlier in the stryfry config. If you're able to see the correct values for the name and the description, you were able to connect to the relay. - Some nostr clients also gives you a status on what relays a note was posted to, this could also give you an indication that your relay works as expected. Note that not all Nostr clients support TOR connections natively. Some may require additional configuration or use of TOR Browser. E.g. most mobile apps would most likely require a TOR proxy app running in the background (some have TOR support built in too). ## Maintenance and Security ### Regular Updates Keep your system, TOR, and relay updated: ```bash # Update system sudo apt update sudo apt upgrade -y # Update Strfry cd ~/strfry git pull git submodule update make -j2 sudo cp strfry /usr/local/bin sudo systemctl restart strfry # Verify TOR is still running properly sudo systemctl status tor ``` Regular updates are crucial for security, especially for TOR which may have security-critical updates. ### Database Management Strfry has built-in database management tools. Check the Strfry documentation for specific commands related to database maintenance, such as managing event retention and performing backups. ### Monitoring Logs To monitor your Strfry logs: ```bash sudo journalctl -u strfry -f ``` To check TOR logs: ```bash sudo journalctl -u tor -f ``` Monitoring logs helps you identify potential issues and understand how your relay is being used. ### Backup This is not a best practices guide on how to do backups. Preferably, backups should be stored either offline or on a different machine than your relay server. This is just a simple way on how to do it on the same server. ```bash # Stop the relay temporarily sudo systemctl stop strfry # Backup the database sudo cp -r /var/lib/strfry /path/to/backup/location # Restart the relay sudo systemctl start strfry ``` Back up your TOR hidden service private key. The private key is particularly sensitive as it defines your .onion address - losing it means losing your address permanently. If you do a backup of this, ensure that is stored in a safe place where no one else has access to it. ```bash sudo cp /var/lib/tor/strfry-relay/hs_ed25519_secret_key /path/to/secure/backup/location ``` ## Troubleshooting ### Relay Not Starting If your relay doesn't start: ```bash # Check logs sudo journalctl -u strfry -e # Verify configuration cat /etc/strfry.conf # Check permissions ls -la /var/lib/strfry ``` Common issues include: - Incorrect configuration format - Permission problems with the data directory - Port already in use (another service using port 7777) - Issues with setting the nofiles limit (setting it too big) ### TOR Hidden Service Not Working If your TOR hidden service is not accessible: ```bash # Check TOR logs sudo journalctl -u tor -e # Verify TOR is running sudo systemctl status tor # Check onion address sudo cat /var/lib/tor/strfry-relay/hostname # Verify TOR configuration sudo cat /etc/tor/torrc ``` Common TOR issues include: - Incorrect directory permissions - TOR service not running - Incorrect port mapping in torrc ### Testing Connectivity If you're having trouble connecting to your service: ```bash # Verify Strfry is listening locally sudo ss -tulpn | grep 7777 # Check that TOR is properly running sudo systemctl status tor # Test the local connection directly curl --include --no-buffer localhost:7777 ``` --- ## Privacy and Security Considerations Running a Nostr relay as a TOR hidden service provides several important privacy benefits: 1. **Network Privacy**: Traffic to your relay is encrypted and routed through the TOR network, making it difficult to determine who is connecting to your relay. 2. **Server Anonymity**: The physical location and IP address of your server are concealed, providing protection against denial-of-service attacks and other targeting. 3. **Censorship Resistance**: TOR hidden services are more resilient against censorship attempts, as they don't rely on the regular DNS system and can't be easily blocked. 4. **User Privacy**: Users connecting to your relay through TOR enjoy enhanced privacy, as their connections are also encrypted and anonymized. However, there are some important considerations: - TOR connections are typically slower than regular internet connections - Not all Nostr clients support TOR connections natively - Running a hidden service increases the importance of keeping your server secure --- Congratulations! You now have a Strfry Nostr relay running as a TOR hidden service. This setup provides a resilient, privacy-focused, and censorship-resistant communication channel that helps strengthen the Nostr network. For further customization and advanced configuration options, refer to the [Strfry documentation](https://github.com/hoytech/strfry). Consider sharing your relay's .onion address with the Nostr community to help grow the privacy-focused segment of the network! If you plan on providing a relay service that the public can use (either for free or paid for), consider adding it to [this list](https://github.com/0xtrr/onion-service-nostr-relays). Only add it if you plan to run a stable and available relay.
@ b2d670de:907f9d4a
2025-03-25 20:17:57This guide will walk you through setting up your own Strfry Nostr relay on a Debian/Ubuntu server and making it accessible exclusively as a TOR hidden service. By the end, you'll have a privacy-focused relay that operates entirely within the TOR network, enhancing both your privacy and that of your users. ## Table of Contents 1. Prerequisites 2. Initial Server Setup 3. Installing Strfry Nostr Relay 4. Configuring Your Relay 5. Setting Up TOR 6. Making Your Relay Available on TOR 7. Testing Your Setup] 8. Maintenance and Security 9. Troubleshooting ## Prerequisites - A Debian or Ubuntu server - Basic familiarity with command line operations (most steps are explained in detail) - Root or sudo access to your server ## Initial Server Setup First, let's make sure your server is properly set up and secured. ### Update Your System Connect to your server via SSH and update your system: ```bash sudo apt update sudo apt upgrade -y ``` ### Set Up a Basic Firewall Install and configure a basic firewall: ```bash sudo apt install ufw -y sudo ufw allow ssh sudo ufw enable ``` This allows SSH connections while blocking other ports for security. ## Installing Strfry Nostr Relay This guide includes the full range of steps needed to build and set up Strfry. It's simply based on the current version of the `DEPLOYMENT.md` document in the Strfry GitHub repository. If the build/setup process is changed in the repo, this document could get outdated. If so, please report to me that something is outdated and check for updated steps [here](https://github.com/hoytech/strfry/blob/master/docs/DEPLOYMENT.md). ### Install Dependencies First, let's install the necessary dependencies. Each package serves a specific purpose in building and running Strfry: ```bash sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-dev ``` Here's why each dependency is needed: **Basic Development Tools:** - `git`: Version control system used to clone the Strfry repository and manage code updates - `build-essential`: Meta-package that includes compilers (gcc, g++), make, and other essential build tools **Perl Dependencies** (used for Strfry's build scripts): - `libyaml-perl`: Perl interface to parse YAML configuration files - `libtemplate-perl`: Template processing system used during the build process - `libregexp-grammars-perl`: Advanced regular expression handling for Perl scripts **Core Libraries for Strfry:** - `libssl-dev`: Development files for OpenSSL, used for secure connections and cryptographic operations - `zlib1g-dev`: Compression library that Strfry uses to reduce data size - `liblmdb-dev`: Lightning Memory-Mapped Database library, which Strfry uses for its high-performance database backend - `libflatbuffers-dev`: Memory-efficient serialization library for structured data - `libsecp256k1-dev`: Optimized C library for EC operations on curve secp256k1, essential for Nostr's cryptographic signatures - `libzstd-dev`: Fast real-time compression algorithm for efficient data storage and transmission ### Clone and Build Strfry Clone the Strfry repository: ```bash git clone https://github.com/hoytech/strfry.git cd strfry ``` Build Strfry: ```bash git submodule update --init make setup-golpe make -j2 # This uses 2 CPU cores. Adjust based on your server (e.g., -j4 for 4 cores) ``` This build process will take several minutes, especially on servers with limited CPU resources, so go get a coffee and post some great memes on nostr in the meantime. ### Install Strfry Install the Strfry binary to your system path: ```bash sudo cp strfry /usr/local/bin ``` This makes the `strfry` command available system-wide, allowing it to be executed from any directory and by any user with the appropriate permissions. ## Configuring Your Relay ### Create Strfry User Create a dedicated user for running Strfry. This enhances security by isolating the relay process: ```bash sudo useradd -M -s /usr/sbin/nologin strfry ``` The `-M` flag prevents creating a home directory, and `-s /usr/sbin/nologin` prevents anyone from logging in as this user. This is a security best practice for service accounts. ### Create Data Directory Create a directory for Strfry's data: ```bash sudo mkdir /var/lib/strfry sudo chown strfry:strfry /var/lib/strfry sudo chmod 755 /var/lib/strfry ``` This creates a dedicated directory for Strfry's database and sets the appropriate permissions so that only the strfry user can write to it. ### Configure Strfry Copy the sample configuration file: ```bash sudo cp strfry.conf /etc/strfry.conf ``` Edit the configuration file: ```bash sudo nano /etc/strfry.conf ``` Modify the database path: ``` # Find this line: db = "./strfry-db/" # Change it to: db = "/var/lib/strfry/" ``` Check your system's hard limit for file descriptors: ```bash ulimit -Hn ``` Update the `nofiles` setting in your configuration to match this value (or set to 0): ``` # Add or modify this line in the config (example if your limit is 524288): nofiles = 524288 ``` The `nofiles` setting determines how many open files Strfry can have simultaneously. Setting it to your system's hard limit (or 0 to use the system default) helps prevent "too many open files" errors if your relay becomes popular. You might also want to customize your relay's information in the config file. Look for the `info` section and update it with your relay's name, description, and other details. Set ownership of the configuration file: ```bash sudo chown strfry:strfry /etc/strfry.conf ``` ### Create Systemd Service Create a systemd service file for managing Strfry: ```bash sudo nano /etc/systemd/system/strfry.service ``` Add the following content: ```ini [Unit] Description=strfry relay service [Service] User=strfry ExecStart=/usr/local/bin/strfry relay Restart=on-failure RestartSec=5 ProtectHome=yes NoNewPrivileges=yes ProtectSystem=full LimitCORE=1000000000 [Install] WantedBy=multi-user.target ``` This systemd service configuration: - Runs Strfry as the dedicated strfry user - Automatically restarts the service if it fails - Implements security measures like `ProtectHome` and `NoNewPrivileges` - Sets resource limits appropriate for a relay Enable and start the service: ```bash sudo systemctl enable strfry.service sudo systemctl start strfry ``` Check the service status: ```bash sudo systemctl status strfry ``` ### Verify Relay is Running Test that your relay is running locally: ```bash curl localhost:7777 ``` You should see a message indicating that the Strfry relay is running. This confirms that Strfry is properly installed and configured before we proceed to set up TOR. ## Setting Up TOR Now let's make your relay accessible as a TOR hidden service. ### Install TOR Install TOR from the package repositories: ```bash sudo apt install -y tor ``` This installs the TOR daemon that will create and manage your hidden service. ### Configure TOR Edit the TOR configuration file: ```bash sudo nano /etc/tor/torrc ``` Scroll down to wherever you see a commented out part like this: ``` #HiddenServiceDir /var/lib/tor/hidden_service/ #HiddenServicePort 80 127.0.0.1:80 ``` Under those lines, add the following lines to set up a hidden service for your relay: ``` HiddenServiceDir /var/lib/tor/strfry-relay/ HiddenServicePort 80 127.0.0.1:7777 ``` This configuration: - Creates a hidden service directory at `/var/lib/tor/strfry-relay/` - Maps port 80 on your .onion address to port 7777 on your local machine - Keeps all traffic encrypted within the TOR network Create the directory for your hidden service: ```bash sudo mkdir -p /var/lib/tor/strfry-relay/ sudo chown debian-tor:debian-tor /var/lib/tor/strfry-relay/ sudo chmod 700 /var/lib/tor/strfry-relay/ ``` The strict permissions (700) are crucial for security as they ensure only the debian-tor user can access the directory containing your hidden service private keys. Restart TOR to apply changes: ```bash sudo systemctl restart tor ``` ## Making Your Relay Available on TOR ### Get Your Onion Address After restarting TOR, you can find your onion address: ```bash sudo cat /var/lib/tor/strfry-relay/hostname ``` This will output something like `abcdefghijklmnopqrstuvwxyz234567.onion`, which is your relay's unique .onion address. This is what you'll share with others to access your relay. ### Understanding Onion Addresses The .onion address is a special-format hostname that is automatically generated based on your hidden service's private key. Your users will need to use this address with the WebSocket protocol prefix to connect: `ws://youronionaddress.onion` ## Testing Your Setup ### Test with a Nostr Client The best way to test your relay is with an actual Nostr client that supports TOR: 1. Open your TOR browser 2. Go to your favorite client, either on clearnet or an onion service. - Check out [this list](https://github.com/0xtrr/onion-service-nostr-clients?tab=readme-ov-file#onion-service-nostr-clients) of nostr clients available over TOR. 3. Add your relay URL: `ws://youronionaddress.onion` to your relay list 4. Try posting a note and see if it appears on your relay - In some nostr clients, you can also click on a relay to get information about it like the relay name and description you set earlier in the stryfry config. If you're able to see the correct values for the name and the description, you were able to connect to the relay. - Some nostr clients also gives you a status on what relays a note was posted to, this could also give you an indication that your relay works as expected. Note that not all Nostr clients support TOR connections natively. Some may require additional configuration or use of TOR Browser. E.g. most mobile apps would most likely require a TOR proxy app running in the background (some have TOR support built in too). ## Maintenance and Security ### Regular Updates Keep your system, TOR, and relay updated: ```bash # Update system sudo apt update sudo apt upgrade -y # Update Strfry cd ~/strfry git pull git submodule update make -j2 sudo cp strfry /usr/local/bin sudo systemctl restart strfry # Verify TOR is still running properly sudo systemctl status tor ``` Regular updates are crucial for security, especially for TOR which may have security-critical updates. ### Database Management Strfry has built-in database management tools. Check the Strfry documentation for specific commands related to database maintenance, such as managing event retention and performing backups. ### Monitoring Logs To monitor your Strfry logs: ```bash sudo journalctl -u strfry -f ``` To check TOR logs: ```bash sudo journalctl -u tor -f ``` Monitoring logs helps you identify potential issues and understand how your relay is being used. ### Backup This is not a best practices guide on how to do backups. Preferably, backups should be stored either offline or on a different machine than your relay server. This is just a simple way on how to do it on the same server. ```bash # Stop the relay temporarily sudo systemctl stop strfry # Backup the database sudo cp -r /var/lib/strfry /path/to/backup/location # Restart the relay sudo systemctl start strfry ``` Back up your TOR hidden service private key. The private key is particularly sensitive as it defines your .onion address - losing it means losing your address permanently. If you do a backup of this, ensure that is stored in a safe place where no one else has access to it. ```bash sudo cp /var/lib/tor/strfry-relay/hs_ed25519_secret_key /path/to/secure/backup/location ``` ## Troubleshooting ### Relay Not Starting If your relay doesn't start: ```bash # Check logs sudo journalctl -u strfry -e # Verify configuration cat /etc/strfry.conf # Check permissions ls -la /var/lib/strfry ``` Common issues include: - Incorrect configuration format - Permission problems with the data directory - Port already in use (another service using port 7777) - Issues with setting the nofiles limit (setting it too big) ### TOR Hidden Service Not Working If your TOR hidden service is not accessible: ```bash # Check TOR logs sudo journalctl -u tor -e # Verify TOR is running sudo systemctl status tor # Check onion address sudo cat /var/lib/tor/strfry-relay/hostname # Verify TOR configuration sudo cat /etc/tor/torrc ``` Common TOR issues include: - Incorrect directory permissions - TOR service not running - Incorrect port mapping in torrc ### Testing Connectivity If you're having trouble connecting to your service: ```bash # Verify Strfry is listening locally sudo ss -tulpn | grep 7777 # Check that TOR is properly running sudo systemctl status tor # Test the local connection directly curl --include --no-buffer localhost:7777 ``` --- ## Privacy and Security Considerations Running a Nostr relay as a TOR hidden service provides several important privacy benefits: 1. **Network Privacy**: Traffic to your relay is encrypted and routed through the TOR network, making it difficult to determine who is connecting to your relay. 2. **Server Anonymity**: The physical location and IP address of your server are concealed, providing protection against denial-of-service attacks and other targeting. 3. **Censorship Resistance**: TOR hidden services are more resilient against censorship attempts, as they don't rely on the regular DNS system and can't be easily blocked. 4. **User Privacy**: Users connecting to your relay through TOR enjoy enhanced privacy, as their connections are also encrypted and anonymized. However, there are some important considerations: - TOR connections are typically slower than regular internet connections - Not all Nostr clients support TOR connections natively - Running a hidden service increases the importance of keeping your server secure --- Congratulations! You now have a Strfry Nostr relay running as a TOR hidden service. This setup provides a resilient, privacy-focused, and censorship-resistant communication channel that helps strengthen the Nostr network. For further customization and advanced configuration options, refer to the [Strfry documentation](https://github.com/hoytech/strfry). Consider sharing your relay's .onion address with the Nostr community to help grow the privacy-focused segment of the network! If you plan on providing a relay service that the public can use (either for free or paid for), consider adding it to [this list](https://github.com/0xtrr/onion-service-nostr-relays). Only add it if you plan to run a stable and available relay. @ 57d1a264:69f1fee1
2025-03-28 10:32:15Bitcoin.design community is organizing another Designathon, from May 4-18. Let's get creative with bitcoin together. More to come very soon.  The first edition was a bursting success! the website still there https://events.bitcoin.design, and here their previous [announcement](https://bitcoindesign.substack.com/p/the-bitcoin-designathon-2022). Look forward for this to happen! Spread the voice: N: [https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48l...](https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48lmw9jc7nhhauyq5w3cm4nfsm3mstqtk6m) X: https://x.com/bitcoin_design/status/1905547407405768927 originally posted at https://stacker.news/items/927650
@ 57d1a264:69f1fee1
2025-03-28 10:32:15Bitcoin.design community is organizing another Designathon, from May 4-18. Let's get creative with bitcoin together. More to come very soon.  The first edition was a bursting success! the website still there https://events.bitcoin.design, and here their previous [announcement](https://bitcoindesign.substack.com/p/the-bitcoin-designathon-2022). Look forward for this to happen! Spread the voice: N: [https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48l...](https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48lmw9jc7nhhauyq5w3cm4nfsm3mstqtk6m) X: https://x.com/bitcoin_design/status/1905547407405768927 originally posted at https://stacker.news/items/927650 @ 4857600b:30b502f4
2025-03-10 12:09:35At this point, we should be arresting, not firing, any FBI employee who delays, destroys, or withholds information on the Epstein case. There is ZERO explanation I will accept for redacting anything for “national security” reasons. A lot of Trump supporters are losing patience with Pam Bondi. I will give her the benefit of the doubt for now since the corruption within the whole security/intelligence apparatus of our country runs deep. However, let’s not forget that probably Trump’s biggest mistakes in his first term involved picking weak and easily corruptible (or blackmailable) officials. It seemed every month a formerly-loyal person did a complete 180 degree turn and did everything they could to screw him over, regardless of the betrayal’s effect on the country or whatever principles that person claimed to have. I think he’s fixed his screening process, but since we’re talking about the FBI, we know they have the power to dig up any dirt or blackmail material available, or just make it up. In the Epstein case, it’s probably better to go after Bondi than give up a treasure trove of blackmail material against the long list of members on his client list.
@ 4857600b:30b502f4
2025-03-10 12:09:35At this point, we should be arresting, not firing, any FBI employee who delays, destroys, or withholds information on the Epstein case. There is ZERO explanation I will accept for redacting anything for “national security” reasons. A lot of Trump supporters are losing patience with Pam Bondi. I will give her the benefit of the doubt for now since the corruption within the whole security/intelligence apparatus of our country runs deep. However, let’s not forget that probably Trump’s biggest mistakes in his first term involved picking weak and easily corruptible (or blackmailable) officials. It seemed every month a formerly-loyal person did a complete 180 degree turn and did everything they could to screw him over, regardless of the betrayal’s effect on the country or whatever principles that person claimed to have. I think he’s fixed his screening process, but since we’re talking about the FBI, we know they have the power to dig up any dirt or blackmail material available, or just make it up. In the Epstein case, it’s probably better to go after Bondi than give up a treasure trove of blackmail material against the long list of members on his client list. @ bc52210b:20bfc6de
2025-03-25 20:17:22CISA, or Cross-Input Signature Aggregation, is a technique in Bitcoin that allows multiple signatures from different inputs in a transaction to be combined into a single, aggregated signature. This is a big deal because Bitcoin transactions often involve multiple inputs (e.g., spending from different wallet outputs), each requiring its own signature. Normally, these signatures take up space individually, but CISA compresses them into one, making transactions more efficient. This magic is possible thanks to the linearity property of Schnorr signatures, a type of digital signature introduced to Bitcoin with the Taproot upgrade. Unlike the older ECDSA signatures, Schnorr signatures have mathematical properties that allow multiple signatures to be added together into a single valid signature. Think of it like combining multiple handwritten signatures into one super-signature that still proves everyone signed off! Fun Fact: CISA was considered for inclusion in Taproot but was left out to keep the upgrade simple and manageable. Adding CISA would’ve made Taproot more complex, so the developers hit pause on it—for now. --- **CISA vs. Key Aggregation (MuSig, FROST): Don’t Get Confused!** Before we go deeper, let’s clear up a common mix-up: CISA is not the same as protocols like MuSig or FROST. Here’s why: * Signature Aggregation (CISA): Combines multiple signatures into one, each potentially tied to different public keys and messages (e.g., different transaction inputs). * Key Aggregation (MuSig, FROST): Combines multiple public keys into a single aggregated public key, then generates one signature for that key. **Key Differences:** 1. What’s Aggregated? * CISA: Aggregates signatures. * Key Aggregation: Aggregates public keys. 2. What the Verifier Needs * CISA: The verifier needs all individual public keys and their corresponding messages to check the aggregated signature. * Key Aggregation: The verifier only needs the single aggregated public key and one message. 3. When It Happens * CISA: Used during transaction signing, when inputs are being combined into a transaction. * MuSig: Used during address creation, setting up a multi-signature (multisig) address that multiple parties control. So, CISA is about shrinking signature data in a transaction, while MuSig/FROST are about simplifying multisig setups. Different tools, different jobs! --- **Two Flavors of CISA: Half-Agg and Full-Agg** CISA comes in two modes: * Full Aggregation (Full-Agg): Interactive, meaning signers need to collaborate during the signing process. (We’ll skip the details here since the query focuses on Half-Agg.) * Half Aggregation (Half-Agg): Non-interactive, meaning signers can work independently, and someone else can combine the signatures later. Since the query includes “CISA Part 2: Half Signature Aggregation,” let’s zoom in on Half-Agg. --- **Half Signature Aggregation (Half-Agg) Explained** **How It Works** Half-Agg is a non-interactive way to aggregate Schnorr signatures. Here’s the process: 1. Independent Signing: Each signer creates their own Schnorr signature for their input, without needing to talk to the other signers. 2. Aggregation Step: An aggregator (could be anyone, like a wallet or node) takes all these signatures and combines them into one aggregated signature. A Schnorr signature has two parts: * R: A random point (32 bytes). * s: A scalar value (32 bytes). In Half-Agg: * The R values from each signature are kept separate (one per input). * The s values from all signatures are combined into a single s value. **Why It Saves Space (~50%)** Let’s break down the size savings with some math: Before Aggregation: * Each Schnorr signature = 64 bytes (32 for R + 32 for s). * For n inputs: n × 64 bytes. After Half-Agg: * Keep n R values (32 bytes each) = 32 × n bytes. * Combine all s values into one = 32 bytes. * Total size: 32 × n + 32 bytes. Comparison: * Original: 64n bytes. * Half-Agg: 32n + 32 bytes. * For large n, the “+32” becomes small compared to 32n, so it’s roughly 32n, which is half of 64n. Hence, ~50% savings! **Real-World Impact:** Based on recent Bitcoin usage, Half-Agg could save: * ~19.3% in space (reducing transaction size). * ~6.9% in fees (since fees depend on transaction size). This assumes no major changes in how people use Bitcoin post-CISA. --- **Applications of Half-Agg** Half-Agg isn’t just a cool idea—it has practical uses: 1. Transaction-wide Aggregation * Combine all signatures within a single transaction. * Result: Smaller transactions, lower fees. 2. Block-wide Aggregation * Combine signatures across all transactions in a Bitcoin block. * Result: Even bigger space savings at the blockchain level. 3. Off-chain Protocols / P2P * Use Half-Agg in systems like Lightning Network gossip messages. * Benefit: Efficiency without needing miners or a Bitcoin soft fork. --- **Challenges with Half-Agg** While Half-Agg sounds awesome, it’s not without hurdles, especially at the block level: 1. Breaking Adaptor Signatures * Adaptor signatures are special signatures used in protocols like Discreet Log Contracts (DLCs) or atomic swaps. They tie a signature to revealing a secret, ensuring fair exchanges. * Aggregating signatures across a block might mess up these protocols, as the individual signatures get blended together, potentially losing the properties adaptor signatures rely on. 2. Impact on Reorg Recovery * In Bitcoin, a reorganization (reorg) happens when the blockchain switches to a different chain of blocks. Transactions from the old chain need to be rebroadcast or reprocessed. * If signatures are aggregated at the block level, it could complicate extracting individual transactions and their signatures during a reorg, slowing down recovery. These challenges mean Half-Agg needs careful design, especially for block-wide use. --- **Wrapping Up** CISA is a clever way to make Bitcoin transactions more efficient by aggregating multiple Schnorr signatures into one, thanks to their linearity property. Half-Agg, the non-interactive mode, lets signers work independently, cutting signature size by about 50% (to 32n + 32 bytes from 64n bytes). It could save ~19.3% in space and ~6.9% in fees, with uses ranging from single transactions to entire blocks or off-chain systems like Lightning. But watch out—block-wide Half-Agg could trip up adaptor signatures and reorg recovery, so it’s not a slam dunk yet. Still, it’s a promising tool for a leaner, cheaper Bitcoin future!
@ bc52210b:20bfc6de
2025-03-25 20:17:22CISA, or Cross-Input Signature Aggregation, is a technique in Bitcoin that allows multiple signatures from different inputs in a transaction to be combined into a single, aggregated signature. This is a big deal because Bitcoin transactions often involve multiple inputs (e.g., spending from different wallet outputs), each requiring its own signature. Normally, these signatures take up space individually, but CISA compresses them into one, making transactions more efficient. This magic is possible thanks to the linearity property of Schnorr signatures, a type of digital signature introduced to Bitcoin with the Taproot upgrade. Unlike the older ECDSA signatures, Schnorr signatures have mathematical properties that allow multiple signatures to be added together into a single valid signature. Think of it like combining multiple handwritten signatures into one super-signature that still proves everyone signed off! Fun Fact: CISA was considered for inclusion in Taproot but was left out to keep the upgrade simple and manageable. Adding CISA would’ve made Taproot more complex, so the developers hit pause on it—for now. --- **CISA vs. Key Aggregation (MuSig, FROST): Don’t Get Confused!** Before we go deeper, let’s clear up a common mix-up: CISA is not the same as protocols like MuSig or FROST. Here’s why: * Signature Aggregation (CISA): Combines multiple signatures into one, each potentially tied to different public keys and messages (e.g., different transaction inputs). * Key Aggregation (MuSig, FROST): Combines multiple public keys into a single aggregated public key, then generates one signature for that key. **Key Differences:** 1. What’s Aggregated? * CISA: Aggregates signatures. * Key Aggregation: Aggregates public keys. 2. What the Verifier Needs * CISA: The verifier needs all individual public keys and their corresponding messages to check the aggregated signature. * Key Aggregation: The verifier only needs the single aggregated public key and one message. 3. When It Happens * CISA: Used during transaction signing, when inputs are being combined into a transaction. * MuSig: Used during address creation, setting up a multi-signature (multisig) address that multiple parties control. So, CISA is about shrinking signature data in a transaction, while MuSig/FROST are about simplifying multisig setups. Different tools, different jobs! --- **Two Flavors of CISA: Half-Agg and Full-Agg** CISA comes in two modes: * Full Aggregation (Full-Agg): Interactive, meaning signers need to collaborate during the signing process. (We’ll skip the details here since the query focuses on Half-Agg.) * Half Aggregation (Half-Agg): Non-interactive, meaning signers can work independently, and someone else can combine the signatures later. Since the query includes “CISA Part 2: Half Signature Aggregation,” let’s zoom in on Half-Agg. --- **Half Signature Aggregation (Half-Agg) Explained** **How It Works** Half-Agg is a non-interactive way to aggregate Schnorr signatures. Here’s the process: 1. Independent Signing: Each signer creates their own Schnorr signature for their input, without needing to talk to the other signers. 2. Aggregation Step: An aggregator (could be anyone, like a wallet or node) takes all these signatures and combines them into one aggregated signature. A Schnorr signature has two parts: * R: A random point (32 bytes). * s: A scalar value (32 bytes). In Half-Agg: * The R values from each signature are kept separate (one per input). * The s values from all signatures are combined into a single s value. **Why It Saves Space (~50%)** Let’s break down the size savings with some math: Before Aggregation: * Each Schnorr signature = 64 bytes (32 for R + 32 for s). * For n inputs: n × 64 bytes. After Half-Agg: * Keep n R values (32 bytes each) = 32 × n bytes. * Combine all s values into one = 32 bytes. * Total size: 32 × n + 32 bytes. Comparison: * Original: 64n bytes. * Half-Agg: 32n + 32 bytes. * For large n, the “+32” becomes small compared to 32n, so it’s roughly 32n, which is half of 64n. Hence, ~50% savings! **Real-World Impact:** Based on recent Bitcoin usage, Half-Agg could save: * ~19.3% in space (reducing transaction size). * ~6.9% in fees (since fees depend on transaction size). This assumes no major changes in how people use Bitcoin post-CISA. --- **Applications of Half-Agg** Half-Agg isn’t just a cool idea—it has practical uses: 1. Transaction-wide Aggregation * Combine all signatures within a single transaction. * Result: Smaller transactions, lower fees. 2. Block-wide Aggregation * Combine signatures across all transactions in a Bitcoin block. * Result: Even bigger space savings at the blockchain level. 3. Off-chain Protocols / P2P * Use Half-Agg in systems like Lightning Network gossip messages. * Benefit: Efficiency without needing miners or a Bitcoin soft fork. --- **Challenges with Half-Agg** While Half-Agg sounds awesome, it’s not without hurdles, especially at the block level: 1. Breaking Adaptor Signatures * Adaptor signatures are special signatures used in protocols like Discreet Log Contracts (DLCs) or atomic swaps. They tie a signature to revealing a secret, ensuring fair exchanges. * Aggregating signatures across a block might mess up these protocols, as the individual signatures get blended together, potentially losing the properties adaptor signatures rely on. 2. Impact on Reorg Recovery * In Bitcoin, a reorganization (reorg) happens when the blockchain switches to a different chain of blocks. Transactions from the old chain need to be rebroadcast or reprocessed. * If signatures are aggregated at the block level, it could complicate extracting individual transactions and their signatures during a reorg, slowing down recovery. These challenges mean Half-Agg needs careful design, especially for block-wide use. --- **Wrapping Up** CISA is a clever way to make Bitcoin transactions more efficient by aggregating multiple Schnorr signatures into one, thanks to their linearity property. Half-Agg, the non-interactive mode, lets signers work independently, cutting signature size by about 50% (to 32n + 32 bytes from 64n bytes). It could save ~19.3% in space and ~6.9% in fees, with uses ranging from single transactions to entire blocks or off-chain systems like Lightning. But watch out—block-wide Half-Agg could trip up adaptor signatures and reorg recovery, so it’s not a slam dunk yet. Still, it’s a promising tool for a leaner, cheaper Bitcoin future! @ 4857600b:30b502f4
2025-02-21 03:04:00A new talking point of the left is that it’s no big deal, just simple recording errors for the 20 million people aged 100-360. 🤷♀️ And not many of them are collecting benefits anyway. 👌 First of all, the investigation & analysis are in the early stages. How can they possibly know how deep the fraud goes, especially when their leaders are doing everything they can to obstruct any real examination? Second, sure, no worries about only a small number collecting benefits. That’s the ONLY thing social security numbers are used for. 🙄
@ 4857600b:30b502f4
2025-02-21 03:04:00A new talking point of the left is that it’s no big deal, just simple recording errors for the 20 million people aged 100-360. 🤷♀️ And not many of them are collecting benefits anyway. 👌 First of all, the investigation & analysis are in the early stages. How can they possibly know how deep the fraud goes, especially when their leaders are doing everything they can to obstruct any real examination? Second, sure, no worries about only a small number collecting benefits. That’s the ONLY thing social security numbers are used for. 🙄 @ b17fccdf:b7211155
2025-03-25 11:23:36Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la [guía de MiniBolt](https://minbolt.info/). Esto tiene una **razón**, por supuesto una **solución**, además de una **conclusión**. Sin entrar en demasiados detalles: ## La razón El **bloqueo a Cloudflare**, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una [orden judicial](https://www.poderjudicial.es/search/AN/openDocument/3c85bed480cbb1daa0a8778d75e36f0d/20221004) emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización. Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo [ECH](https://developers.cloudflare.com/ssl/edge-certificates/ech) (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar **bloqueos basados en dominios**, lo que les obliga a recurrir a **bloqueos más amplios por IP o rangos de IP** para cumplir con la orden judicial. Esta práctica tiene **consecuencias graves**, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un **perjuicio para terceros**, **restringiendo el acceso a muchos dominios legítimos** que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la [web de MiniBolt](https://minibolt.minibolt.info) y su dominio `minibolt.info`, los cuales **utilizan Cloudflare como proxy** para aprovechar las medidas de **seguridad, privacidad, optimización y servicios** adicionales que la plataforma ofrece de forma gratuita. Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.  ## La solución Obviamente, **MiniBolt no dejará de usar Cloudflare** como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para **evitar esta restricción** y poder acceder: **~>** Utiliza **una VPN**: Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad: - [IVPN](https://www.ivpn.net/es/) - [Mullvad VPN](https://mullvad.net/es/vpn) - [Proton VPN](https://protonvpn.com/es-es) (**gratis**) - [Obscura VPN](https://obscura.net/) (**solo para macOS**) - [Cloudfare WARP](https://developers.cloudflare.com/cloudflare-one/connections/connect-devices/warp/download-warp/) (**gratis**) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos: 1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy" 2. Marca la casilla "Habilite el modo proxy en este dispositivo" 3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias 4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio. 3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a [esta](https://minibolt.minibolt.info/system/system/privacy#example-from-firefox) para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la [guía de MiniBolt](https://minibolt.minibolt.info/) sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info [AQUÍ](https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958).  **~>** [**Proxifica tu navegador para usar la red de Tor**](https://minibolt.minibolt.info/system/system/privacy#ssh-remote-access-through-tor), o utiliza el [**navegador oficial de Tor**](https://www.torproject.org/es/download/) (recomendado).  ## La conclusión Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la [Declaración de Independencia del Ciberespacio](https://es.wikisource.org/wiki/Declaraci%C3%B3n_de_independencia_del_ciberespacio) que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad. Es momento de actuar y estar preparados: debemos **impulsar el desarrollo y la difusión** de las **herramientas anticensura** que tenemos a nuestro alcance, protegiendo así la **libertad digital** y asegurando un acceso equitativo a la información para todos Este compromiso es uno de los **pilares fundamentales de MiniBolt,** lo que convierte este desafío en una oportunidad para poner a prueba las **soluciones anticensura** [ya disponibles](https://minibolt.minibolt.info/bonus-guides/system/tor-services), así como **las que están en camino**. ¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!  --- Fuentes: * https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239 * https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257 * https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958 * https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689 * https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007
@ b17fccdf:b7211155
2025-03-25 11:23:36Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la [guía de MiniBolt](https://minbolt.info/). Esto tiene una **razón**, por supuesto una **solución**, además de una **conclusión**. Sin entrar en demasiados detalles: ## La razón El **bloqueo a Cloudflare**, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una [orden judicial](https://www.poderjudicial.es/search/AN/openDocument/3c85bed480cbb1daa0a8778d75e36f0d/20221004) emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización. Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo [ECH](https://developers.cloudflare.com/ssl/edge-certificates/ech) (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar **bloqueos basados en dominios**, lo que les obliga a recurrir a **bloqueos más amplios por IP o rangos de IP** para cumplir con la orden judicial. Esta práctica tiene **consecuencias graves**, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un **perjuicio para terceros**, **restringiendo el acceso a muchos dominios legítimos** que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la [web de MiniBolt](https://minibolt.minibolt.info) y su dominio `minibolt.info`, los cuales **utilizan Cloudflare como proxy** para aprovechar las medidas de **seguridad, privacidad, optimización y servicios** adicionales que la plataforma ofrece de forma gratuita. Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.  ## La solución Obviamente, **MiniBolt no dejará de usar Cloudflare** como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para **evitar esta restricción** y poder acceder: **~>** Utiliza **una VPN**: Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad: - [IVPN](https://www.ivpn.net/es/) - [Mullvad VPN](https://mullvad.net/es/vpn) - [Proton VPN](https://protonvpn.com/es-es) (**gratis**) - [Obscura VPN](https://obscura.net/) (**solo para macOS**) - [Cloudfare WARP](https://developers.cloudflare.com/cloudflare-one/connections/connect-devices/warp/download-warp/) (**gratis**) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos: 1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy" 2. Marca la casilla "Habilite el modo proxy en este dispositivo" 3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias 4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio. 3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a [esta](https://minibolt.minibolt.info/system/system/privacy#example-from-firefox) para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la [guía de MiniBolt](https://minibolt.minibolt.info/) sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info [AQUÍ](https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958).  **~>** [**Proxifica tu navegador para usar la red de Tor**](https://minibolt.minibolt.info/system/system/privacy#ssh-remote-access-through-tor), o utiliza el [**navegador oficial de Tor**](https://www.torproject.org/es/download/) (recomendado).  ## La conclusión Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la [Declaración de Independencia del Ciberespacio](https://es.wikisource.org/wiki/Declaraci%C3%B3n_de_independencia_del_ciberespacio) que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad. Es momento de actuar y estar preparados: debemos **impulsar el desarrollo y la difusión** de las **herramientas anticensura** que tenemos a nuestro alcance, protegiendo así la **libertad digital** y asegurando un acceso equitativo a la información para todos Este compromiso es uno de los **pilares fundamentales de MiniBolt,** lo que convierte este desafío en una oportunidad para poner a prueba las **soluciones anticensura** [ya disponibles](https://minibolt.minibolt.info/bonus-guides/system/tor-services), así como **las que están en camino**. ¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!  --- Fuentes: * https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239 * https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257 * https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958 * https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689 * https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007 @ 37fe9853:bcd1b039
2025-01-11 15:04:40yoyoaa
@ 37fe9853:bcd1b039
2025-01-11 15:04:40yoyoaa @ 7d33ba57:1b82db35
2025-03-28 22:14:24Preko is a charming seaside town on Ugljan Island, just a short ferry ride from Zadar. Known for its beautiful beaches, relaxed atmosphere, and stunning views of the Adriatic, it's the perfect place to experience authentic Dalmatian island life.  ## **🌊 Top Things to See & Do in Preko** ### **1️⃣ Swim at Jaz Beach 🏖️** - A **Blue Flag beach** with **clear turquoise waters and soft pebbles**. - Ideal for **families** thanks to its shallow waters. - Nearby **cafés and restaurants** make it a great spot to spend the day. ### **2️⃣ Visit the Islet of Galevac 🏝️** - A **tiny island just 80 meters from Preko**, reachable by swimming or a short boat ride. - Home to a **15th-century Franciscan monastery**, surrounded by lush greenery. - A **peaceful retreat**, perfect for relaxation.  ### **3️⃣ Hike to St. Michael’s Fortress (Sv. Mihovil) 🏰** - A **medieval fortress from the 13th century** with **breathtaking panoramic views**. - Overlooks **Zadar, Kornati Islands, and the Adriatic Sea**. - A **1-hour scenic hike** from Preko or accessible by **bike or car**. ### **4️⃣ Explore the Local Taverns & Seafood Restaurants 🍽️** - Try **fresh seafood, octopus salad, and Dalmatian peka (slow-cooked meat & vegetables)**. - **Best spots:** Konoba Roko (authentic seafood) & Vile Dalmacija (beachfront dining). ### **5️⃣ Rent a Bike or Scooter 🚲** - Explore **Ugljan Island’s olive groves, hidden coves, and coastal paths**. - Visit nearby villages like **Kali and Kukljica** for more local charm.  ### **6️⃣ Take a Day Trip to Zadar ⛵** - Just **25 minutes by ferry**, Zadar offers **historic landmarks, the Sea Organ, and Roman ruins**. - Perfect for a cultural excursion before returning to the peaceful island.  ## **🚗 How to Get to Preko** 🚢 **By Ferry:** - **From Zadar:** Regular ferries (Jadrolinija) take **~25 minutes**. 🚘 **By Car:** - If driving, take the **ferry from Zadar to Preko** and explore the island. 🚴 **By Bike:** - Many visitors rent bikes to explore Ugljan Island’s coastal roads.  ## **💡 Tips for Visiting Preko** ✅ **Best time to visit?** **May–September** for warm weather & swimming 🌞 ✅ **Ferry schedules** – Check times in advance, especially in the off-season ⏳ ✅ **Bring cash** – Some smaller taverns and cafés may not accept cards 💰 ✅ **Stay for sunset** – The views over Zadar from Preko’s waterfront are stunning 🌅 Would you like **hotel recommendations, hidden beaches, or other island activities**? 😊
@ 7d33ba57:1b82db35
2025-03-28 22:14:24Preko is a charming seaside town on Ugljan Island, just a short ferry ride from Zadar. Known for its beautiful beaches, relaxed atmosphere, and stunning views of the Adriatic, it's the perfect place to experience authentic Dalmatian island life.  ## **🌊 Top Things to See & Do in Preko** ### **1️⃣ Swim at Jaz Beach 🏖️** - A **Blue Flag beach** with **clear turquoise waters and soft pebbles**. - Ideal for **families** thanks to its shallow waters. - Nearby **cafés and restaurants** make it a great spot to spend the day. ### **2️⃣ Visit the Islet of Galevac 🏝️** - A **tiny island just 80 meters from Preko**, reachable by swimming or a short boat ride. - Home to a **15th-century Franciscan monastery**, surrounded by lush greenery. - A **peaceful retreat**, perfect for relaxation.  ### **3️⃣ Hike to St. Michael’s Fortress (Sv. Mihovil) 🏰** - A **medieval fortress from the 13th century** with **breathtaking panoramic views**. - Overlooks **Zadar, Kornati Islands, and the Adriatic Sea**. - A **1-hour scenic hike** from Preko or accessible by **bike or car**. ### **4️⃣ Explore the Local Taverns & Seafood Restaurants 🍽️** - Try **fresh seafood, octopus salad, and Dalmatian peka (slow-cooked meat & vegetables)**. - **Best spots:** Konoba Roko (authentic seafood) & Vile Dalmacija (beachfront dining). ### **5️⃣ Rent a Bike or Scooter 🚲** - Explore **Ugljan Island’s olive groves, hidden coves, and coastal paths**. - Visit nearby villages like **Kali and Kukljica** for more local charm.  ### **6️⃣ Take a Day Trip to Zadar ⛵** - Just **25 minutes by ferry**, Zadar offers **historic landmarks, the Sea Organ, and Roman ruins**. - Perfect for a cultural excursion before returning to the peaceful island.  ## **🚗 How to Get to Preko** 🚢 **By Ferry:** - **From Zadar:** Regular ferries (Jadrolinija) take **~25 minutes**. 🚘 **By Car:** - If driving, take the **ferry from Zadar to Preko** and explore the island. 🚴 **By Bike:** - Many visitors rent bikes to explore Ugljan Island’s coastal roads.  ## **💡 Tips for Visiting Preko** ✅ **Best time to visit?** **May–September** for warm weather & swimming 🌞 ✅ **Ferry schedules** – Check times in advance, especially in the off-season ⏳ ✅ **Bring cash** – Some smaller taverns and cafés may not accept cards 💰 ✅ **Stay for sunset** – The views over Zadar from Preko’s waterfront are stunning 🌅 Would you like **hotel recommendations, hidden beaches, or other island activities**? 😊 @ 15a592c4:e8bdd024
2025-03-28 16:26:38The Potential and Importance of Blockchain: A Game-Changer in the Digital Age Blockchain technology has been gaining momentum in recent years, and for good reason. This innovative technology has the potential to revolutionize the way we conduct transactions, store data, and build trust in the digital world. *What is Blockchain?* At its core, blockchain is a shared, immutable ledger that facilitates the process of recording transactions and tracking assets in a business network.¹ It's a decentralized system, meaning that no single entity controls it, and it's maintained by a network of computers working together. *The Benefits of Blockchain* So, what makes blockchain so important? Here are just a few of its key benefits: - *Enhanced Security*: Blockchain's decentralized nature and use of advanced cryptography make it virtually impossible to hack or manipulate. - *Increased Transparency*: With blockchain, all transactions are recorded publicly and can be viewed by anyone with permission. - *Improved Efficiency*: Blockchain automates many processes, reducing the need for intermediaries and increasing the speed of transactions. - *Greater Trust*: Blockchain's immutable ledger ensures that once a transaction is recorded, it can't be altered or deleted. *Real-World Applications* Blockchain's potential extends far beyond the world of cryptocurrency. Here are just a few examples of its real-world applications: - *Supply Chain Management*: Blockchain can be used to track the origin, quality, and movement of goods throughout the supply chain. - *Healthcare*: Blockchain can be used to securely store and manage medical records, track prescriptions, and enable secure sharing of medical research. - *Voting Systems*: Blockchain can be used to create secure, transparent, and tamper-proof voting systems.
@ 15a592c4:e8bdd024
2025-03-28 16:26:38The Potential and Importance of Blockchain: A Game-Changer in the Digital Age Blockchain technology has been gaining momentum in recent years, and for good reason. This innovative technology has the potential to revolutionize the way we conduct transactions, store data, and build trust in the digital world. *What is Blockchain?* At its core, blockchain is a shared, immutable ledger that facilitates the process of recording transactions and tracking assets in a business network.¹ It's a decentralized system, meaning that no single entity controls it, and it's maintained by a network of computers working together. *The Benefits of Blockchain* So, what makes blockchain so important? Here are just a few of its key benefits: - *Enhanced Security*: Blockchain's decentralized nature and use of advanced cryptography make it virtually impossible to hack or manipulate. - *Increased Transparency*: With blockchain, all transactions are recorded publicly and can be viewed by anyone with permission. - *Improved Efficiency*: Blockchain automates many processes, reducing the need for intermediaries and increasing the speed of transactions. - *Greater Trust*: Blockchain's immutable ledger ensures that once a transaction is recorded, it can't be altered or deleted. *Real-World Applications* Blockchain's potential extends far beyond the world of cryptocurrency. Here are just a few examples of its real-world applications: - *Supply Chain Management*: Blockchain can be used to track the origin, quality, and movement of goods throughout the supply chain. - *Healthcare*: Blockchain can be used to securely store and manage medical records, track prescriptions, and enable secure sharing of medical research. - *Voting Systems*: Blockchain can be used to create secure, transparent, and tamper-proof voting systems. @ 3b7fc823:e194354f
2025-03-23 03:54:16A quick guide for the less than technical savvy to set up their very own free private tor enabled email using Onionmail. Privacy is for everyone, not just the super cyber nerds. Onion Mail is an anonymous POP3/SMTP email server program hosted by various people on the internet. You can visit this site and read the details: https://en.onionmail.info/ 1. Download Tor Browser First, if you don't already, go download Tor Browser. You are going to need it. https://www.torproject.org/ 2. Sign Up Using Tor browser go to the directory page (https://onionmail.info/directory.html) choose one of the servers and sign up for an account. I say sign up but it is just choosing a user name you want to go before the @xyz.onion email address and solving a captcha. 3. Account information Once you are done signing up an Account information page will pop up. **MAKE SURE YOU SAVE THIS!!!** It has your address and passwords (for sending and receiving email) that you will need. If you lose them then you are shit out of luck. 4. Install an Email Client You can use Claws Mail, Neomutt, or whatever, but for this example, we will be using Thunderbird. a. Download Thunderbird email client b. The easy setup popup page that wants your name, email, and password isn't going to like your user@xyz.onion address. Just enter something that looks like a regular email address such as name@example.com and the **Configure Manually**option will appear below. Click that. 5. Configure Incoming (POP3) Server Under Incoming Server: Protocol: POP3 Server or Hostname: xyz.onion (whatever your account info says) Port: 110 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (POP3 password). 6. Configure Outgoing (SMTP) Server Under Outgoing Server: Server or Hostname: xyz.onion (whatever your account info says) Port: 25 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (SMTP password). 7. Click on email at the top and change your address if you had to use a spoof one to get the configure manually to pop up. 8. Configure Proxy a. Click the **gear icon** on the bottom left for settings. Scroll all the way down to **Network & Disk Space**. Click the **settings button** next to **Connection. Configure how Thunderbird connects to the internet**. b. Select **Manual Proxy Configuration**. For **SOCKS Host** enter **127.0.0.1** and enter port **9050**. (if you are running this through a VM the port may be different) c. Now check the box for **SOCKS5** and then **Proxy DNS when using SOCKS5** down at the bottom. Click OK 9. Check Email For thunderbird to reach the onion mail server it has to be connected to tor. Depending on your local setup, it might be fine as is or you might have to have tor browser open in the background. Click on **inbox** and then the **little cloud icon** with the down arrow to check mail. 10. Security Exception Thunderbird is not going to like that the onion mail server security certificate is self signed. A popup **Add Security Exception** will appear. Click **Confirm Security Exception**. You are done. Enjoy your new private email service. **REMEMBER: The server can read your emails unless they are encrypted. Go into account settings. Look down and click End-toEnd Encryption. Then add your OpenPGP key or open your OpenPGP Key Manager (you might have to download one if you don't already have one) and generate a new key for this account.**
@ 3b7fc823:e194354f
2025-03-23 03:54:16A quick guide for the less than technical savvy to set up their very own free private tor enabled email using Onionmail. Privacy is for everyone, not just the super cyber nerds. Onion Mail is an anonymous POP3/SMTP email server program hosted by various people on the internet. You can visit this site and read the details: https://en.onionmail.info/ 1. Download Tor Browser First, if you don't already, go download Tor Browser. You are going to need it. https://www.torproject.org/ 2. Sign Up Using Tor browser go to the directory page (https://onionmail.info/directory.html) choose one of the servers and sign up for an account. I say sign up but it is just choosing a user name you want to go before the @xyz.onion email address and solving a captcha. 3. Account information Once you are done signing up an Account information page will pop up. **MAKE SURE YOU SAVE THIS!!!** It has your address and passwords (for sending and receiving email) that you will need. If you lose them then you are shit out of luck. 4. Install an Email Client You can use Claws Mail, Neomutt, or whatever, but for this example, we will be using Thunderbird. a. Download Thunderbird email client b. The easy setup popup page that wants your name, email, and password isn't going to like your user@xyz.onion address. Just enter something that looks like a regular email address such as name@example.com and the **Configure Manually**option will appear below. Click that. 5. Configure Incoming (POP3) Server Under Incoming Server: Protocol: POP3 Server or Hostname: xyz.onion (whatever your account info says) Port: 110 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (POP3 password). 6. Configure Outgoing (SMTP) Server Under Outgoing Server: Server or Hostname: xyz.onion (whatever your account info says) Port: 25 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (SMTP password). 7. Click on email at the top and change your address if you had to use a spoof one to get the configure manually to pop up. 8. Configure Proxy a. Click the **gear icon** on the bottom left for settings. Scroll all the way down to **Network & Disk Space**. Click the **settings button** next to **Connection. Configure how Thunderbird connects to the internet**. b. Select **Manual Proxy Configuration**. For **SOCKS Host** enter **127.0.0.1** and enter port **9050**. (if you are running this through a VM the port may be different) c. Now check the box for **SOCKS5** and then **Proxy DNS when using SOCKS5** down at the bottom. Click OK 9. Check Email For thunderbird to reach the onion mail server it has to be connected to tor. Depending on your local setup, it might be fine as is or you might have to have tor browser open in the background. Click on **inbox** and then the **little cloud icon** with the down arrow to check mail. 10. Security Exception Thunderbird is not going to like that the onion mail server security certificate is self signed. A popup **Add Security Exception** will appear. Click **Confirm Security Exception**. You are done. Enjoy your new private email service. **REMEMBER: The server can read your emails unless they are encrypted. Go into account settings. Look down and click End-toEnd Encryption. Then add your OpenPGP key or open your OpenPGP Key Manager (you might have to download one if you don't already have one) and generate a new key for this account.** @ 57d1a264:69f1fee1
2025-03-27 10:42:05What we have been missing in [SN Press kit](https://stacker.news/items/872925/r/Design_r)? Most important, who the press kit is for? It's for us? It's for them? Them, who? The first few editions of the press kit, I agree are mostly made by us, for us. A way to try to homogenize how we _speek_ out SN into the wild web. A way to have SN voice sync, loud and clear, to send out our message. In this case, I squeezed my mouse, creating a template for us [^1], stackers, to share when talking sales with possible businesses and merchants willing to invest some sats and engage with SN community. Here's the message and the sales pitch, v0.1: ## Reach Bitcoin’s Most Engaged Community – Zero Noise, Pure Signal.              - - - Contributions to improve would be much appreciated. You can also help by simply commenting on each slide or leaving your feedback below, especially if you are a sale person or someone that has seen similar documents before. This is the first interaction. Already noticed some issues, for example with the emojis and the fonts, especially when exporting, probably related to a penpot issue. The slides maybe render differently depending on the browser you're using. - [▶️ Play](https://design.penpot.app/#/view?file-id=cec80257-5021-8137-8005-ef90a160b2c9&page-id=cec80257-5021-8137-8005-ef90a160b2ca§ion=interactions&index=0&interactions-mode=hide&zoom=fit) the file in your browser - ⬇️ Save the [PDF file](https://mega.nz/file/TsBgkRoI#20HEb_zscozgJYlRGha0XiZvcXCJfLQONx2fc65WHKY) @k00b it will be nice to have some real data, how we can get some basic audience insights? Even some inputs from Plausible, if still active, will be much useful. [^1]: Territory founders. FYI: @Aardvark, @AGORA, @anna, @antic, @AtlantisPleb, @av, @Bell_curve, @benwehrman, @bitcoinplebdev, @Bitter, @BlokchainB, @ch0k1, @davidw, @ek, @elvismercury, @frostdragon, @grayruby, @HODLR, @inverselarp, @Jon_Hodl, @MaxAWebster, @mega_dreamer, @mrtali, @niftynei, @nout, @OneOneSeven, @PlebLab, @Public_N_M_E, @RDClark, @realBitcoinDog, @roytheholographicuniverse, @siggy47, @softsimon, @south_korea_ln, @theschoolofbitcoin, @TNStacker. @UCantDoThatDotNet, @Undisciplined originally posted at https://stacker.news/items/926557
@ 57d1a264:69f1fee1
2025-03-27 10:42:05What we have been missing in [SN Press kit](https://stacker.news/items/872925/r/Design_r)? Most important, who the press kit is for? It's for us? It's for them? Them, who? The first few editions of the press kit, I agree are mostly made by us, for us. A way to try to homogenize how we _speek_ out SN into the wild web. A way to have SN voice sync, loud and clear, to send out our message. In this case, I squeezed my mouse, creating a template for us [^1], stackers, to share when talking sales with possible businesses and merchants willing to invest some sats and engage with SN community. Here's the message and the sales pitch, v0.1: ## Reach Bitcoin’s Most Engaged Community – Zero Noise, Pure Signal.              - - - Contributions to improve would be much appreciated. You can also help by simply commenting on each slide or leaving your feedback below, especially if you are a sale person or someone that has seen similar documents before. This is the first interaction. Already noticed some issues, for example with the emojis and the fonts, especially when exporting, probably related to a penpot issue. The slides maybe render differently depending on the browser you're using. - [▶️ Play](https://design.penpot.app/#/view?file-id=cec80257-5021-8137-8005-ef90a160b2c9&page-id=cec80257-5021-8137-8005-ef90a160b2ca§ion=interactions&index=0&interactions-mode=hide&zoom=fit) the file in your browser - ⬇️ Save the [PDF file](https://mega.nz/file/TsBgkRoI#20HEb_zscozgJYlRGha0XiZvcXCJfLQONx2fc65WHKY) @k00b it will be nice to have some real data, how we can get some basic audience insights? Even some inputs from Plausible, if still active, will be much useful. [^1]: Territory founders. FYI: @Aardvark, @AGORA, @anna, @antic, @AtlantisPleb, @av, @Bell_curve, @benwehrman, @bitcoinplebdev, @Bitter, @BlokchainB, @ch0k1, @davidw, @ek, @elvismercury, @frostdragon, @grayruby, @HODLR, @inverselarp, @Jon_Hodl, @MaxAWebster, @mega_dreamer, @mrtali, @niftynei, @nout, @OneOneSeven, @PlebLab, @Public_N_M_E, @RDClark, @realBitcoinDog, @roytheholographicuniverse, @siggy47, @softsimon, @south_korea_ln, @theschoolofbitcoin, @TNStacker. @UCantDoThatDotNet, @Undisciplined originally posted at https://stacker.news/items/926557 @ fe9e99a0:5123e9a8
2025-03-28 21:25:43What’s happening?
@ fe9e99a0:5123e9a8
2025-03-28 21:25:43What’s happening? @ 57d1a264:69f1fee1
2025-03-27 08:27:44> The tech industry and its press have treated the rise of billion-scale social networks and ubiquitous smartphone apps as an unadulterated win for regular people, a triumph of usability and empowerment. They seldom talk about what we’ve lost along the way in this transition, and I find that younger folks may not even know how the web used to be. `— Anil Dash, The Web We Lost, 13 Dec 2012` https://www.youtube.com/watch?v=9KKMnoTTHJk&t=156s So here’s a few glimpses of a web that’s mostly faded away: https://www.anildash.com/2012/12/13/the_web_we_lost/ The first step to disabusing them of this notion is for the people creating the next generation of social applications to learn a little bit of history, to know your shit, whether that’s about [Twitter’s business model](http://web.archive.org/web/20180120013123/http://anildash.com/2010/04/ten-years-of-twitter-ads.html) or [Google’s social features](http://web.archive.org/web/20170518203228/http://anildash.com/2012/04/why-you-cant-trust-tech-press-to-teach-you-about-the-tech-industry.html) or anything else. We have to know what’s been tried and failed, what good ideas were simply ahead of their time, and what opportunities have been lost in the current generation of dominant social networks. originally posted at https://stacker.news/items/926499
@ 57d1a264:69f1fee1
2025-03-27 08:27:44> The tech industry and its press have treated the rise of billion-scale social networks and ubiquitous smartphone apps as an unadulterated win for regular people, a triumph of usability and empowerment. They seldom talk about what we’ve lost along the way in this transition, and I find that younger folks may not even know how the web used to be. `— Anil Dash, The Web We Lost, 13 Dec 2012` https://www.youtube.com/watch?v=9KKMnoTTHJk&t=156s So here’s a few glimpses of a web that’s mostly faded away: https://www.anildash.com/2012/12/13/the_web_we_lost/ The first step to disabusing them of this notion is for the people creating the next generation of social applications to learn a little bit of history, to know your shit, whether that’s about [Twitter’s business model](http://web.archive.org/web/20180120013123/http://anildash.com/2010/04/ten-years-of-twitter-ads.html) or [Google’s social features](http://web.archive.org/web/20170518203228/http://anildash.com/2012/04/why-you-cant-trust-tech-press-to-teach-you-about-the-tech-industry.html) or anything else. We have to know what’s been tried and failed, what good ideas were simply ahead of their time, and what opportunities have been lost in the current generation of dominant social networks. originally posted at https://stacker.news/items/926499 @ 21335073:a244b1ad
2025-03-18 20:47:50**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.** TL;DR please educate your children about online safety. Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense. This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning. When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little. I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?” I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well. I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread. I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard. I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it. The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust. Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this. I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place. What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method. It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code. They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened. I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road. So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally. Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb. I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback. Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed. That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone. To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all. I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society. I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this. On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government. I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories. There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc. Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind. Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now. There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers? I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity. I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place. My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors. My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline. The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online. I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers. So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation? When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that. I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic. If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations. I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process. **Course:** - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children. The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward? I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone. Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability. The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime. This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful. This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens. In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions. I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
@ 21335073:a244b1ad
2025-03-18 20:47:50**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.** TL;DR please educate your children about online safety. Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense. This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning. When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little. I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?” I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well. I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread. I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard. I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it. The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust. Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this. I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place. What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method. It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code. They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened. I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road. So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally. Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb. I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback. Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed. That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone. To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all. I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society. I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this. On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government. I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories. There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc. Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind. Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now. There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers? I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity. I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place. My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors. My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline. The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online. I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers. So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation? When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that. I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic. If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations. I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process. **Course:** - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children. The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward? I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone. Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability. The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime. This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful. This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens. In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions. I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation. @ 21335073:a244b1ad
2025-03-18 14:43:08**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.** TL;DR please educate your children about online safety. Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense. This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning. When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little. I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?” I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well. I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread. I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard. I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it. The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust. Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this. I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place. What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method. It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code. They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened. I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road. So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally. Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb. I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback. Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed. That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone. To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all. I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society. I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this. On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government. I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories. There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc. Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind. Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now. There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers? I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity. I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place. My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors. My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline. The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online. I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers. So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation? When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that. I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic. If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations. I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process. **Course:** - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children. The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward? I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone. Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability. The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime. This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful. This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens. In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions. I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
@ 21335073:a244b1ad
2025-03-18 14:43:08**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.** TL;DR please educate your children about online safety. Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense. This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning. When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little. I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?” I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well. I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread. I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard. I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it. The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust. Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this. I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place. What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method. It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code. They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened. I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road. So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally. Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb. I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback. Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed. That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone. To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all. I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society. I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this. On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government. I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories. There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc. Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind. Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now. There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers? I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity. I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place. My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors. My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline. The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online. I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers. So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation? When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that. I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic. If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations. I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process. **Course:** - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children. The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward? I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone. Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability. The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime. This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful. This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens. In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions. I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation. @ 41e6f20b:06049e45
2024-11-17 17:33:55Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller.
@ 41e6f20b:06049e45
2024-11-17 17:33:55Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller. @ 8cb60e21:5f2deaea
2024-09-10 21:14:08<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/9_SRpCjeJiM" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-09-10 21:14:08<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/9_SRpCjeJiM" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 8cb60e21:5f2deaea
2024-09-06 22:23:03<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/XL3DbEkeFWA" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-09-06 22:23:03<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/XL3DbEkeFWA" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 57d1a264:69f1fee1
2025-03-27 08:11:33Explore and reimagine programming interfaces beyond text (visual, tactile, spatial). > _"The most dangerous thought you can have as a creative person is to think you know what you're doing."_ `— Richard Hamming` [^1] https://www.youtube.com/watch?v=8pTEmbeENF4 For his recent DBX Conference talk, Victor took attendees back to the year 1973, donning the uniform of an IBM systems engineer of the times, delivering his presentation on an overhead projector. The '60s and early '70s were a fertile time for CS ideas, reminds Victor, but even more importantly, it was a time of unfettered thinking, unconstrained by programming dogma, authority, and tradition.  _'The most dangerous thought that you can have as a creative person is to think that you know what you're doing,'_ explains Victor. 'Because once you think you know what you're doing you stop looking around for other ways of doing things and you stop being able to see other ways of doing things. You become blind.' He concludes, 'I think you have to say: _"We don't know what programming is. We don't know what computing is. We don't even know what a computer is."_ And once you truly understand that, and once you truly believe that, then you're free, and you can think anything.' More details at https://worrydream.com/dbx/ [^1]: Richard Hamming -- [The Art of Doing Science and Engineering, p5](http://worrydream.com/refs/Hamming_1997_-_The_Art_of_Doing_Science_and_Engineering.pdf) (pdf ebook) originally posted at https://stacker.news/items/926493
@ 57d1a264:69f1fee1
2025-03-27 08:11:33Explore and reimagine programming interfaces beyond text (visual, tactile, spatial). > _"The most dangerous thought you can have as a creative person is to think you know what you're doing."_ `— Richard Hamming` [^1] https://www.youtube.com/watch?v=8pTEmbeENF4 For his recent DBX Conference talk, Victor took attendees back to the year 1973, donning the uniform of an IBM systems engineer of the times, delivering his presentation on an overhead projector. The '60s and early '70s were a fertile time for CS ideas, reminds Victor, but even more importantly, it was a time of unfettered thinking, unconstrained by programming dogma, authority, and tradition.  _'The most dangerous thought that you can have as a creative person is to think that you know what you're doing,'_ explains Victor. 'Because once you think you know what you're doing you stop looking around for other ways of doing things and you stop being able to see other ways of doing things. You become blind.' He concludes, 'I think you have to say: _"We don't know what programming is. We don't know what computing is. We don't even know what a computer is."_ And once you truly understand that, and once you truly believe that, then you're free, and you can think anything.' More details at https://worrydream.com/dbx/ [^1]: Richard Hamming -- [The Art of Doing Science and Engineering, p5](http://worrydream.com/refs/Hamming_1997_-_The_Art_of_Doing_Science_and_Engineering.pdf) (pdf ebook) originally posted at https://stacker.news/items/926493 @ 6f1a5274:3b3bb9c4
2025-03-28 14:27:448us là một nền tảng giải trí trực tuyến mang đến cho người chơi một không gian giải trí đa dạng và đầy thú vị. Với giao diện thân thiện và dễ sử dụng, người chơi có thể dễ dàng truy cập và tham gia vào các trò chơi yêu thích của mình chỉ trong vài bước đơn giản. Các trò chơi trên 8us được thiết kế với đồ họa sắc nét và âm thanh sống động, mang lại trải nghiệm mượt mà và chân thực, giúp người chơi cảm nhận như đang tham gia vào một thế giới giải trí thực sự. Ngoài các trò chơi phong phú và hấp dẫn, 8us còn thường xuyên cập nhật các tựa game mới, giữ cho trải nghiệm luôn mới mẻ và thú vị. Bảo mật và an toàn luôn là ưu tiên hàng đầu của <a href="https://8us-online.com">8us</a>. Nền tảng này sử dụng các công nghệ bảo mật tiên tiến để bảo vệ thông tin cá nhân và dữ liệu giao dịch của người chơi, giúp họ có thể yên tâm tham gia mà không phải lo lắng về nguy cơ bị xâm phạm. Mọi giao dịch và thông tin cá nhân đều được mã hóa và bảo vệ chặt chẽ, mang lại sự an tâm tuyệt đối cho người chơi. Với những biện pháp bảo mật này, 8us đã xây dựng được lòng tin từ cộng đồng người chơi, tạo ra một môi trường an toàn và đáng tin cậy để mọi người có thể tận hưởng những phút giây giải trí mà không phải lo ngại về các vấn đề liên quan đến dữ liệu cá nhân. Bên cạnh đó, đội ngũ hỗ trợ khách hàng của 8us luôn sẵn sàng phục vụ người chơi 24/7, giúp giải đáp mọi thắc mắc và xử lý nhanh chóng các vấn đề phát sinh. Dù là vấn đề về kỹ thuật hay hỗ trợ về trò chơi, đội ngũ chăm sóc khách hàng của 8us luôn làm việc tận tâm và chuyên nghiệp, đảm bảo mang lại sự hài lòng cho mọi người tham gia. Chính nhờ vào dịch vụ khách hàng xuất sắc và hệ thống bảo mật vượt trội, 8us đã trở thành một nền tảng giải trí trực tuyến được nhiều người tin tưởng và yêu thích, đồng thời tạo ra một không gian thư giãn tuyệt vời, an toàn và đáng tin cậy cho tất cả người chơi.
@ 6f1a5274:3b3bb9c4
2025-03-28 14:27:448us là một nền tảng giải trí trực tuyến mang đến cho người chơi một không gian giải trí đa dạng và đầy thú vị. Với giao diện thân thiện và dễ sử dụng, người chơi có thể dễ dàng truy cập và tham gia vào các trò chơi yêu thích của mình chỉ trong vài bước đơn giản. Các trò chơi trên 8us được thiết kế với đồ họa sắc nét và âm thanh sống động, mang lại trải nghiệm mượt mà và chân thực, giúp người chơi cảm nhận như đang tham gia vào một thế giới giải trí thực sự. Ngoài các trò chơi phong phú và hấp dẫn, 8us còn thường xuyên cập nhật các tựa game mới, giữ cho trải nghiệm luôn mới mẻ và thú vị. Bảo mật và an toàn luôn là ưu tiên hàng đầu của <a href="https://8us-online.com">8us</a>. Nền tảng này sử dụng các công nghệ bảo mật tiên tiến để bảo vệ thông tin cá nhân và dữ liệu giao dịch của người chơi, giúp họ có thể yên tâm tham gia mà không phải lo lắng về nguy cơ bị xâm phạm. Mọi giao dịch và thông tin cá nhân đều được mã hóa và bảo vệ chặt chẽ, mang lại sự an tâm tuyệt đối cho người chơi. Với những biện pháp bảo mật này, 8us đã xây dựng được lòng tin từ cộng đồng người chơi, tạo ra một môi trường an toàn và đáng tin cậy để mọi người có thể tận hưởng những phút giây giải trí mà không phải lo ngại về các vấn đề liên quan đến dữ liệu cá nhân. Bên cạnh đó, đội ngũ hỗ trợ khách hàng của 8us luôn sẵn sàng phục vụ người chơi 24/7, giúp giải đáp mọi thắc mắc và xử lý nhanh chóng các vấn đề phát sinh. Dù là vấn đề về kỹ thuật hay hỗ trợ về trò chơi, đội ngũ chăm sóc khách hàng của 8us luôn làm việc tận tâm và chuyên nghiệp, đảm bảo mang lại sự hài lòng cho mọi người tham gia. Chính nhờ vào dịch vụ khách hàng xuất sắc và hệ thống bảo mật vượt trội, 8us đã trở thành một nền tảng giải trí trực tuyến được nhiều người tin tưởng và yêu thích, đồng thời tạo ra một không gian thư giãn tuyệt vời, an toàn và đáng tin cậy cho tất cả người chơi. @ 8cb60e21:5f2deaea
2024-09-03 22:26:25<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/R5fzBNJP6Rk" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-09-03 22:26:25<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/R5fzBNJP6Rk" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 57d1a264:69f1fee1
2025-03-26 08:45:13> I was curious to see how Stacker.News domain and website contents scored from a SEO (Search Engine Optimization) perspective. Here what Semrush nows about SN. But first have alook at the Page Performance Score on Google (Detailled report available [here](https://pagespeed.web.dev/analysis/https-stacker-news/pjnc9jgscy?form_factor=mobile)). **Performance** and **Accessibility** looks have really low score! | Desktop | Mobile | |---|---| |  |  | |  |  | Now let's see what Semrush knows. # Analytics General view on your metrics and performance trend compared to last 30 days.   See estimations of stacker.news's desktop and mobile traffic based on Semrush’s proprietary AI and machine learning algorithms, petabytes of clickstream data, and Big Data technologies.  Distribution of SN's organic traffic and keywords by country. The Organic Traffic graph shows changes in the amount of estimated organic and paid traffic driven to the SN analyzed domain over time.  | Organic Search | Backlinks Analytics | |---|---| | |  | | Position Changes Trend | Top Page Changes | |---|---| | |  | |This trend allows you to monitor organic traffic changes, as well as improved and declined positions.| Top pages with the biggest traffic changes over the last 28 days. |  # Competitors  The Competitive Positioning Map shows the strengths and weaknesses of SN competitive domains' presence in organic search results. Data visualizations are based on the domain's organic traffic and the number of keywords that they are ranking for in Google's top 20 organic search results. The larger the circle, the more visibility a domain has. Below, a list of domains an analyzed domain is competing against in Google's top 20 organic search results.  # Referring Domains   # Daily Stats | Organic Traffic | Organic Keywords | Backlinks | |---|---|---| | 976 | 15.9K | 126K | | `-41.87%` | `-16.4%` | `-1.62%` | ### 📝 Traffic Drop Traffic downturn detected! It appears SN domain experienced a traffic drop of 633 in the last 28 days. Take a closer look at these pages with significant traffic decline and explore areas for potential improvement. Here are the pages taking the biggest hits: - https://stacker.news/items/723989 ⬇️ -15 - https://stacker.news/items/919813 ⬇️ -12 - https://stacker.news/items/783355 ⬇️ -5 ### 📉 Decreased Authority Score Uh-oh! Your Authority score has dropped from 26 to 25. Don't worry, we're here to assist you. Check out the new/lost backlinks in the Backlink Analytics tool to uncover insights on how to boost your authority. ### 🌟 New Keywords Opportunity Alert! Targeting these keywords could help you increase organic traffic quickly and efficiently. We've found some low-hanging fruits for you! Take a look at these keywords: - nitter.moomoo.me — Volume 70 - 0xchat — Volume 30 - amethyst nostr — Volume 30 ### 🛠️ Broken Pages This could hurt the user experience and lead to a loss in organic traffic. Time to take action: amend those pages or set up redirects. Here below, few pages on SN domain that are either broken or not _crawlable_: - https://stacker.news/404 — 38 backlinks - https://stacker.news/api/capture/items/91154 — 24 backlinks - https://stacker.news/api/capture/items/91289 — 24 backlinks Dees this post give you some insights? Hope so, comment below if you have any SEO suggestion? Mine is to improve or keep an eye on Accessibility! One of the major issues I found is that SN does not have a `robots.txt`, a key simple text file that allow crawlers to read or not-read the website for indexing purposes. @k00b and @ek is that voluntary? Here are other basic info to improve the SEO score and for those of us that want to learn more: - Intro to Accessibility: https://www.w3.org/WAI/fundamentals/accessibility-intro/ - Design for Accessibility: https://www.w3.org/WAI/tips/designing/ - Web Accessibility Best Practices: https://www.freecodecamp.org/news/web-accessibility-best-practices/ originally posted at https://stacker.news/items/925433
@ 57d1a264:69f1fee1
2025-03-26 08:45:13> I was curious to see how Stacker.News domain and website contents scored from a SEO (Search Engine Optimization) perspective. Here what Semrush nows about SN. But first have alook at the Page Performance Score on Google (Detailled report available [here](https://pagespeed.web.dev/analysis/https-stacker-news/pjnc9jgscy?form_factor=mobile)). **Performance** and **Accessibility** looks have really low score! | Desktop | Mobile | |---|---| |  |  | |  |  | Now let's see what Semrush knows. # Analytics General view on your metrics and performance trend compared to last 30 days.   See estimations of stacker.news's desktop and mobile traffic based on Semrush’s proprietary AI and machine learning algorithms, petabytes of clickstream data, and Big Data technologies.  Distribution of SN's organic traffic and keywords by country. The Organic Traffic graph shows changes in the amount of estimated organic and paid traffic driven to the SN analyzed domain over time.  | Organic Search | Backlinks Analytics | |---|---| | |  | | Position Changes Trend | Top Page Changes | |---|---| | |  | |This trend allows you to monitor organic traffic changes, as well as improved and declined positions.| Top pages with the biggest traffic changes over the last 28 days. |  # Competitors  The Competitive Positioning Map shows the strengths and weaknesses of SN competitive domains' presence in organic search results. Data visualizations are based on the domain's organic traffic and the number of keywords that they are ranking for in Google's top 20 organic search results. The larger the circle, the more visibility a domain has. Below, a list of domains an analyzed domain is competing against in Google's top 20 organic search results.  # Referring Domains   # Daily Stats | Organic Traffic | Organic Keywords | Backlinks | |---|---|---| | 976 | 15.9K | 126K | | `-41.87%` | `-16.4%` | `-1.62%` | ### 📝 Traffic Drop Traffic downturn detected! It appears SN domain experienced a traffic drop of 633 in the last 28 days. Take a closer look at these pages with significant traffic decline and explore areas for potential improvement. Here are the pages taking the biggest hits: - https://stacker.news/items/723989 ⬇️ -15 - https://stacker.news/items/919813 ⬇️ -12 - https://stacker.news/items/783355 ⬇️ -5 ### 📉 Decreased Authority Score Uh-oh! Your Authority score has dropped from 26 to 25. Don't worry, we're here to assist you. Check out the new/lost backlinks in the Backlink Analytics tool to uncover insights on how to boost your authority. ### 🌟 New Keywords Opportunity Alert! Targeting these keywords could help you increase organic traffic quickly and efficiently. We've found some low-hanging fruits for you! Take a look at these keywords: - nitter.moomoo.me — Volume 70 - 0xchat — Volume 30 - amethyst nostr — Volume 30 ### 🛠️ Broken Pages This could hurt the user experience and lead to a loss in organic traffic. Time to take action: amend those pages or set up redirects. Here below, few pages on SN domain that are either broken or not _crawlable_: - https://stacker.news/404 — 38 backlinks - https://stacker.news/api/capture/items/91154 — 24 backlinks - https://stacker.news/api/capture/items/91289 — 24 backlinks Dees this post give you some insights? Hope so, comment below if you have any SEO suggestion? Mine is to improve or keep an eye on Accessibility! One of the major issues I found is that SN does not have a `robots.txt`, a key simple text file that allow crawlers to read or not-read the website for indexing purposes. @k00b and @ek is that voluntary? Here are other basic info to improve the SEO score and for those of us that want to learn more: - Intro to Accessibility: https://www.w3.org/WAI/fundamentals/accessibility-intro/ - Design for Accessibility: https://www.w3.org/WAI/tips/designing/ - Web Accessibility Best Practices: https://www.freecodecamp.org/news/web-accessibility-best-practices/ originally posted at https://stacker.news/items/925433 @ 8cb60e21:5f2deaea
2024-09-03 22:26:25<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/SBdDt4BUIW0" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-09-03 22:26:25<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/SBdDt4BUIW0" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 7d33ba57:1b82db35
2025-03-28 20:59:51Krka National Park, located in central Dalmatia, is one of Croatia’s most breathtaking natural wonders. Famous for its stunning waterfalls, crystal-clear lakes, and lush forests, the park is a must-visit for nature lovers. Unlike Plitvice Lakes, Krka allows swimming in certain areas, making it a perfect summer escape.  ## **🌊 Top Things to See & Do in Krka National Park** ### **1️⃣ Skradinski Buk Waterfall 💦** - The **largest and most famous waterfall** in the park, with **cascading pools and wooden walkways**. - You **used to be able to swim here**, but since 2021, swimming is no longer allowed. - Perfect for **photography and picnics**. ### **2️⃣ Roški Slap Waterfall 🌿** - A **less crowded but equally beautiful** series of waterfalls. - Known for its **"necklace" of small cascades** leading into the main fall. - Nearby **Mlinica**, a restored **watermill**, shows traditional Croatian life. ### **3️⃣ Visovac Island & Monastery 🏝️** - A **tiny island** in the middle of the Krka River, home to a **Franciscan monastery** from the 15th century. - Accessible by **boat tour** from Skradinski Buk or Roški Slap. - A peaceful, scenic spot with **stunning views of the lake**.  ### **4️⃣ Krka Monastery 🏛️** - A **Serbian Orthodox monastery** hidden deep in the park. - Built on **ancient Roman catacombs**, which you can explore. - A **quiet, spiritual place**, often overlooked by tourists. ### **5️⃣ Hike & Walk the Nature Trails 🥾** - The park has **several well-marked trails** through forests, waterfalls, and lakes. - Wooden walkways allow **easy access** to the main sights. - **Wildlife spotting**: Look out for **otters, turtles, and over 200 bird species**! ### **6️⃣ Swim at Skradin Beach 🏖️** - While you can’t swim at Skradinski Buk anymore, **Skradin Beach**, just outside the park, is a great spot for a dip. - **Kayaking and boat tours** available.  ## **🚗 How to Get to Krka National Park** ✈️ **By Air:** The nearest airport is **Split (SPU), 1 hour away**. 🚘 **By Car:** - **Split to Krka:** ~1 hour (85 km) - **Zadar to Krka:** ~1 hour (75 km) - **Dubrovnik to Krka:** ~3.5 hours (280 km) 🚌 **By Bus:** Direct buses from **Split, Zadar, and Šibenik** to the park’s entrances. 🚢 **By Boat:** From **Skradin**, you can take a **boat ride** into the park.  ## **💡 Tips for Visiting Krka National Park** ✅ **Best time to visit?** **Spring & early autumn (April–June, September–October)** – Fewer crowds & mild weather 🍃 ✅ **Start early!** **Arrive before 10 AM** to avoid crowds, especially in summer ☀️ ✅ **Bring water & snacks** – Limited food options inside the park 🍎 ✅ **Wear comfy shoes** – Wooden walkways & trails can be slippery 👟 ✅ **Take a boat tour** – The best way to see Visovac Island & hidden spots ⛵ ✅ **Buy tickets online** – Save time at the entrance 🎟️ 
@ 7d33ba57:1b82db35
2025-03-28 20:59:51Krka National Park, located in central Dalmatia, is one of Croatia’s most breathtaking natural wonders. Famous for its stunning waterfalls, crystal-clear lakes, and lush forests, the park is a must-visit for nature lovers. Unlike Plitvice Lakes, Krka allows swimming in certain areas, making it a perfect summer escape.  ## **🌊 Top Things to See & Do in Krka National Park** ### **1️⃣ Skradinski Buk Waterfall 💦** - The **largest and most famous waterfall** in the park, with **cascading pools and wooden walkways**. - You **used to be able to swim here**, but since 2021, swimming is no longer allowed. - Perfect for **photography and picnics**. ### **2️⃣ Roški Slap Waterfall 🌿** - A **less crowded but equally beautiful** series of waterfalls. - Known for its **"necklace" of small cascades** leading into the main fall. - Nearby **Mlinica**, a restored **watermill**, shows traditional Croatian life. ### **3️⃣ Visovac Island & Monastery 🏝️** - A **tiny island** in the middle of the Krka River, home to a **Franciscan monastery** from the 15th century. - Accessible by **boat tour** from Skradinski Buk or Roški Slap. - A peaceful, scenic spot with **stunning views of the lake**.  ### **4️⃣ Krka Monastery 🏛️** - A **Serbian Orthodox monastery** hidden deep in the park. - Built on **ancient Roman catacombs**, which you can explore. - A **quiet, spiritual place**, often overlooked by tourists. ### **5️⃣ Hike & Walk the Nature Trails 🥾** - The park has **several well-marked trails** through forests, waterfalls, and lakes. - Wooden walkways allow **easy access** to the main sights. - **Wildlife spotting**: Look out for **otters, turtles, and over 200 bird species**! ### **6️⃣ Swim at Skradin Beach 🏖️** - While you can’t swim at Skradinski Buk anymore, **Skradin Beach**, just outside the park, is a great spot for a dip. - **Kayaking and boat tours** available.  ## **🚗 How to Get to Krka National Park** ✈️ **By Air:** The nearest airport is **Split (SPU), 1 hour away**. 🚘 **By Car:** - **Split to Krka:** ~1 hour (85 km) - **Zadar to Krka:** ~1 hour (75 km) - **Dubrovnik to Krka:** ~3.5 hours (280 km) 🚌 **By Bus:** Direct buses from **Split, Zadar, and Šibenik** to the park’s entrances. 🚢 **By Boat:** From **Skradin**, you can take a **boat ride** into the park.  ## **💡 Tips for Visiting Krka National Park** ✅ **Best time to visit?** **Spring & early autumn (April–June, September–October)** – Fewer crowds & mild weather 🍃 ✅ **Start early!** **Arrive before 10 AM** to avoid crowds, especially in summer ☀️ ✅ **Bring water & snacks** – Limited food options inside the park 🍎 ✅ **Wear comfy shoes** – Wooden walkways & trails can be slippery 👟 ✅ **Take a boat tour** – The best way to see Visovac Island & hidden spots ⛵ ✅ **Buy tickets online** – Save time at the entrance 🎟️  @ a07fae46:7d83df92
2025-03-18 12:31:40if the JFK documents come out and are nothing but old hat, it will be disappointing. but if they contain revelations, then they are an unalloyed good. unprecedented and extraordinary; worthy of praise and admiration. they murdered the president in broad daylight and kept 80,000 related documents secret for 60 years. the apparatus that did that and got away with it, is 100+ years in the making. the magic bullet was just the starting pistol of a new *era*; a *level up* in an [old game](https://archive.org/details/TragedyAndHope_501/page/n5/mode/2up?q=feudalist+fashion). it won't be dismantled and your republic delivered back with a bow in *2 months*. have a little humility and a little gratitude. cynicism is easy. it's peak mid-wittery. yeah no shit everything is corrupt and everyone's likely captured by [AIPAC](https://books.google.com/books/publisher/content?id=gKVKDwAAQBAJ&pg=PT68&img=1&zoom=3&hl=en&bul=1&sig=ACfU3U2pagVXTYdJOKxkAwmmFQpuSnoS5g&w=1280) or something beyond. YOU THINK AIPAC is the [ALL SEEING EYE](https://archive.org/details/the-all-seeing-eye-vol-1-5-manly-p.-hall-may-1923-sept-1931)? you can keep going, if you want to, but have some awareness and appreciation for where we are and what it took to get here. the first 'you are fake news' was also a shot heard 'round the world and you are riding high on it's [Infrasound](https://en.wikipedia.org/wiki/Infrasound) wave, still reverberating; unappreciative of the profound delta in public awareness and understanding, and rate of change, that has occurred since that moment, in [2017](https://www.youtube.com/watch?v=Vqpzk-qGxMU). think about where we were back then, especially with corporate capture of the narrative. trump's bullheaded behavior, if only ego-driven, *is* what broke the spell. an *actual* moment of savage bravery is what allows for your current jaded affectation. black pilled is boring. it's intellectually lazy. it is low-resolution-thinking, no better than progressives who explain the myriad ills of the world through 'racism'. normalcy bias works both ways. i'm not grading you on a curve that includes NPCs. i'm grading you against those of us with a mind, on up. do better. the best Webb-style doomer argument is essentially 'the mouse trap needs a piece of cheese in order to work'. ok, but it doesn't need 3 pieces of cheese, or 5. was FreeRoss the piece of cheese? was the SBR the cheese? real bitcoiners know how dumb the 'sbr is an attempt to takeover btc' narrative is, so extrapolate from that. what about withdrawal from the WHO? freeze and review of USAID et al? how many pieces of cheese before we realize it's not a trap? it's just a messy endeavor. Good morning. #jfkFiles #nostrOnly
@ a07fae46:7d83df92
2025-03-18 12:31:40if the JFK documents come out and are nothing but old hat, it will be disappointing. but if they contain revelations, then they are an unalloyed good. unprecedented and extraordinary; worthy of praise and admiration. they murdered the president in broad daylight and kept 80,000 related documents secret for 60 years. the apparatus that did that and got away with it, is 100+ years in the making. the magic bullet was just the starting pistol of a new *era*; a *level up* in an [old game](https://archive.org/details/TragedyAndHope_501/page/n5/mode/2up?q=feudalist+fashion). it won't be dismantled and your republic delivered back with a bow in *2 months*. have a little humility and a little gratitude. cynicism is easy. it's peak mid-wittery. yeah no shit everything is corrupt and everyone's likely captured by [AIPAC](https://books.google.com/books/publisher/content?id=gKVKDwAAQBAJ&pg=PT68&img=1&zoom=3&hl=en&bul=1&sig=ACfU3U2pagVXTYdJOKxkAwmmFQpuSnoS5g&w=1280) or something beyond. YOU THINK AIPAC is the [ALL SEEING EYE](https://archive.org/details/the-all-seeing-eye-vol-1-5-manly-p.-hall-may-1923-sept-1931)? you can keep going, if you want to, but have some awareness and appreciation for where we are and what it took to get here. the first 'you are fake news' was also a shot heard 'round the world and you are riding high on it's [Infrasound](https://en.wikipedia.org/wiki/Infrasound) wave, still reverberating; unappreciative of the profound delta in public awareness and understanding, and rate of change, that has occurred since that moment, in [2017](https://www.youtube.com/watch?v=Vqpzk-qGxMU). think about where we were back then, especially with corporate capture of the narrative. trump's bullheaded behavior, if only ego-driven, *is* what broke the spell. an *actual* moment of savage bravery is what allows for your current jaded affectation. black pilled is boring. it's intellectually lazy. it is low-resolution-thinking, no better than progressives who explain the myriad ills of the world through 'racism'. normalcy bias works both ways. i'm not grading you on a curve that includes NPCs. i'm grading you against those of us with a mind, on up. do better. the best Webb-style doomer argument is essentially 'the mouse trap needs a piece of cheese in order to work'. ok, but it doesn't need 3 pieces of cheese, or 5. was FreeRoss the piece of cheese? was the SBR the cheese? real bitcoiners know how dumb the 'sbr is an attempt to takeover btc' narrative is, so extrapolate from that. what about withdrawal from the WHO? freeze and review of USAID et al? how many pieces of cheese before we realize it's not a trap? it's just a messy endeavor. Good morning. #jfkFiles #nostrOnly @ 6f1a5274:3b3bb9c4
2025-03-28 14:26:4297win là một nền tảng giải trí trực tuyến nổi bật, mang đến cho người chơi những trải nghiệm độc đáo và thú vị. Với giao diện dễ sử dụng và thiết kế thân thiện, nền tảng này giúp người chơi dễ dàng tham gia vào các trò chơi yêu thích của mình mà không gặp phải bất kỳ khó khăn nào. Các trò chơi tại 97win không chỉ đa dạng về thể loại mà còn được phát triển với đồ họa sắc nét và âm thanh sống động, mang lại những trải nghiệm tương tác đầy thú vị và chân thực. Từ những trò chơi đơn giản đến những thử thách phức tạp, 97win luôn biết cách tạo ra không gian giải trí phong phú, thu hút cả những người mới bắt đầu và các người chơi dày dặn kinh nghiệm. Ngoài chất lượng trò chơi, <a href="https://97win.shop">97win</a> còn chú trọng đến yếu tố bảo mật và an toàn của người chơi. Nền tảng này sử dụng công nghệ bảo mật hiện đại để bảo vệ thông tin cá nhân và giao dịch của người tham gia, giúp người chơi yên tâm tuyệt đối khi tham gia. Tất cả các dữ liệu quan trọng đều được mã hóa và bảo vệ chặt chẽ, đảm bảo rằng mọi thông tin sẽ không bị xâm phạm hoặc lộ lọt ra ngoài. Với cam kết mang đến một môi trường an toàn, 97win đã xây dựng được lòng tin vững chắc từ người chơi, giúp họ hoàn toàn tập trung vào việc giải trí mà không phải lo lắng về các vấn đề bảo mật. Bên cạnh đó, đội ngũ chăm sóc khách hàng của 97win luôn sẵn sàng hỗ trợ người chơi 24/7, giải đáp mọi thắc mắc và giải quyết các vấn đề phát sinh một cách nhanh chóng và hiệu quả. Mỗi vấn đề, dù lớn hay nhỏ, đều được đội ngũ hỗ trợ xử lý một cách tận tâm và chuyên nghiệp, giúp người chơi cảm thấy thoải mái và hài lòng với dịch vụ. Sự kết hợp giữa các trò chơi chất lượng, bảo mật an toàn và dịch vụ khách hàng chu đáo đã giúp 97win trở thành một lựa chọn đáng tin cậy cho những ai tìm kiếm một không gian giải trí trực tuyến tuyệt vời và an toàn.
@ 6f1a5274:3b3bb9c4
2025-03-28 14:26:4297win là một nền tảng giải trí trực tuyến nổi bật, mang đến cho người chơi những trải nghiệm độc đáo và thú vị. Với giao diện dễ sử dụng và thiết kế thân thiện, nền tảng này giúp người chơi dễ dàng tham gia vào các trò chơi yêu thích của mình mà không gặp phải bất kỳ khó khăn nào. Các trò chơi tại 97win không chỉ đa dạng về thể loại mà còn được phát triển với đồ họa sắc nét và âm thanh sống động, mang lại những trải nghiệm tương tác đầy thú vị và chân thực. Từ những trò chơi đơn giản đến những thử thách phức tạp, 97win luôn biết cách tạo ra không gian giải trí phong phú, thu hút cả những người mới bắt đầu và các người chơi dày dặn kinh nghiệm. Ngoài chất lượng trò chơi, <a href="https://97win.shop">97win</a> còn chú trọng đến yếu tố bảo mật và an toàn của người chơi. Nền tảng này sử dụng công nghệ bảo mật hiện đại để bảo vệ thông tin cá nhân và giao dịch của người tham gia, giúp người chơi yên tâm tuyệt đối khi tham gia. Tất cả các dữ liệu quan trọng đều được mã hóa và bảo vệ chặt chẽ, đảm bảo rằng mọi thông tin sẽ không bị xâm phạm hoặc lộ lọt ra ngoài. Với cam kết mang đến một môi trường an toàn, 97win đã xây dựng được lòng tin vững chắc từ người chơi, giúp họ hoàn toàn tập trung vào việc giải trí mà không phải lo lắng về các vấn đề bảo mật. Bên cạnh đó, đội ngũ chăm sóc khách hàng của 97win luôn sẵn sàng hỗ trợ người chơi 24/7, giải đáp mọi thắc mắc và giải quyết các vấn đề phát sinh một cách nhanh chóng và hiệu quả. Mỗi vấn đề, dù lớn hay nhỏ, đều được đội ngũ hỗ trợ xử lý một cách tận tâm và chuyên nghiệp, giúp người chơi cảm thấy thoải mái và hài lòng với dịch vụ. Sự kết hợp giữa các trò chơi chất lượng, bảo mật an toàn và dịch vụ khách hàng chu đáo đã giúp 97win trở thành một lựa chọn đáng tin cậy cho những ai tìm kiếm một không gian giải trí trực tuyến tuyệt vời và an toàn. @ 6f1a5274:3b3bb9c4
2025-03-28 14:25:11777vin nổi bật với một nền tảng giải trí trực tuyến hiện đại, nơi người chơi có thể tận hưởng những giây phút thư giãn thú vị. Với giao diện dễ sử dụng và thiết kế tối ưu, người chơi có thể nhanh chóng tham gia vào các trò chơi yêu thích của mình mà không gặp phải khó khăn. Những trò chơi tại 777vin được phát triển với đồ họa sắc nét và âm thanh sống động, mang đến một trải nghiệm gần gũi và chân thực. Không chỉ có tính năng hấp dẫn, các trò chơi tại đây còn được tối ưu hóa để người chơi có thể tham gia một cách mượt mà, giúp tăng cường sự thư giãn và giải trí. Bên cạnh chất lượng trò chơi, <a href="https://777vin-online.com">777vin</a> còn chú trọng đến bảo mật và an toàn thông tin người chơi. Nền tảng này sử dụng công nghệ bảo mật tiên tiến nhất để bảo vệ dữ liệu cá nhân và giao dịch của người tham gia. Những biện pháp bảo mật này giúp người chơi cảm thấy an tâm tuyệt đối khi tham gia vào các trò chơi, mà không cần lo ngại về việc thông tin của mình bị lộ lọt hay bị xâm phạm. Điều này là một yếu tố quan trọng, giúp 777vin xây dựng lòng tin vững chắc với cộng đồng người chơi, tạo ra một môi trường giải trí an toàn và đáng tin cậy. Ngoài việc bảo vệ an toàn thông tin, 777vin còn đặc biệt chú trọng đến chất lượng dịch vụ khách hàng. Đội ngũ hỗ trợ của 777vin luôn sẵn sàng phục vụ người chơi 24/7, giải đáp mọi thắc mắc và hỗ trợ kịp thời mọi vấn đề phát sinh. Sự chuyên nghiệp và tận tâm của đội ngũ này giúp người chơi có thể yên tâm trải nghiệm trò chơi mà không phải lo lắng về bất kỳ vấn đề nào. Với sự kết hợp giữa chất lượng dịch vụ, bảo mật tuyệt đối và trải nghiệm người chơi hoàn hảo, 777vin đã và đang khẳng định vị thế của mình là một trong những nền tảng giải trí trực tuyến hàng đầu.
@ 6f1a5274:3b3bb9c4
2025-03-28 14:25:11777vin nổi bật với một nền tảng giải trí trực tuyến hiện đại, nơi người chơi có thể tận hưởng những giây phút thư giãn thú vị. Với giao diện dễ sử dụng và thiết kế tối ưu, người chơi có thể nhanh chóng tham gia vào các trò chơi yêu thích của mình mà không gặp phải khó khăn. Những trò chơi tại 777vin được phát triển với đồ họa sắc nét và âm thanh sống động, mang đến một trải nghiệm gần gũi và chân thực. Không chỉ có tính năng hấp dẫn, các trò chơi tại đây còn được tối ưu hóa để người chơi có thể tham gia một cách mượt mà, giúp tăng cường sự thư giãn và giải trí. Bên cạnh chất lượng trò chơi, <a href="https://777vin-online.com">777vin</a> còn chú trọng đến bảo mật và an toàn thông tin người chơi. Nền tảng này sử dụng công nghệ bảo mật tiên tiến nhất để bảo vệ dữ liệu cá nhân và giao dịch của người tham gia. Những biện pháp bảo mật này giúp người chơi cảm thấy an tâm tuyệt đối khi tham gia vào các trò chơi, mà không cần lo ngại về việc thông tin của mình bị lộ lọt hay bị xâm phạm. Điều này là một yếu tố quan trọng, giúp 777vin xây dựng lòng tin vững chắc với cộng đồng người chơi, tạo ra một môi trường giải trí an toàn và đáng tin cậy. Ngoài việc bảo vệ an toàn thông tin, 777vin còn đặc biệt chú trọng đến chất lượng dịch vụ khách hàng. Đội ngũ hỗ trợ của 777vin luôn sẵn sàng phục vụ người chơi 24/7, giải đáp mọi thắc mắc và hỗ trợ kịp thời mọi vấn đề phát sinh. Sự chuyên nghiệp và tận tâm của đội ngũ này giúp người chơi có thể yên tâm trải nghiệm trò chơi mà không phải lo lắng về bất kỳ vấn đề nào. Với sự kết hợp giữa chất lượng dịch vụ, bảo mật tuyệt đối và trải nghiệm người chơi hoàn hảo, 777vin đã và đang khẳng định vị thế của mình là một trong những nền tảng giải trí trực tuyến hàng đầu. @ da0b9bc3:4e30a4a9
2025-03-28 19:14:52It's Finally here Stackers! It's Friday! We're about to kick off our weekends with some feel good tracks. Let's get the party started. Bring me those Feel Good tracks. Let's get it! https://youtu.be/r1ATFedwjnk?si=tPtLac6ExYZCx3Ez originally posted at https://stacker.news/items/928119
@ da0b9bc3:4e30a4a9
2025-03-28 19:14:52It's Finally here Stackers! It's Friday! We're about to kick off our weekends with some feel good tracks. Let's get the party started. Bring me those Feel Good tracks. Let's get it! https://youtu.be/r1ATFedwjnk?si=tPtLac6ExYZCx3Ez originally posted at https://stacker.news/items/928119 @ bc52210b:20bfc6de
2025-03-14 20:39:20When writing safety critical code, every arithmetic operation carries the potential for catastrophic failure—whether that’s a plane crash in aerospace engineering or a massive financial loss in a smart contract. The stakes are incredibly high, and errors are not just bugs; they’re disasters waiting to happen. Smart contract developers need to shift their mindset: less like web developers, who might prioritize speed and iteration, and more like aerospace engineers, where precision, caution, and meticulous attention to detail are non-negotiable. In practice, this means treating every line of code as a critical component, adopting rigorous testing, and anticipating worst-case scenarios—just as an aerospace engineer would ensure a system can withstand extreme conditions. Safety critical code demands aerospace-level precision, and smart contract developers must rise to that standard to protect against the severe consequences of failure.
@ bc52210b:20bfc6de
2025-03-14 20:39:20When writing safety critical code, every arithmetic operation carries the potential for catastrophic failure—whether that’s a plane crash in aerospace engineering or a massive financial loss in a smart contract. The stakes are incredibly high, and errors are not just bugs; they’re disasters waiting to happen. Smart contract developers need to shift their mindset: less like web developers, who might prioritize speed and iteration, and more like aerospace engineers, where precision, caution, and meticulous attention to detail are non-negotiable. In practice, this means treating every line of code as a critical component, adopting rigorous testing, and anticipating worst-case scenarios—just as an aerospace engineer would ensure a system can withstand extreme conditions. Safety critical code demands aerospace-level precision, and smart contract developers must rise to that standard to protect against the severe consequences of failure. @ 30876140:cffb1126
2025-03-26 04:58:21The portal is closing. The symphony comes to an end. Ballet, a dance of partners, A wish of hearts, Now closing its curtains. I foolishly sit Eagerly waiting For the circus to begin again, As crowds file past me, Chuckles and popcorn falling, Crushed under foot, I sit waiting For the show to carry on. But the night is now over, The laughs have been had, The music been heard, The dancers are gone now Into the nightbreeze chill. Yet still, I sit waiting, The empty chairs yawning, A cough, I start, could it be? Yet the lights now go out, And now without my sight I am truly alone in the theater. Yet still, I am waiting For the show to carry on, But I know that it won’t, Yet still, I am waiting. Never shall I leave For the show was too perfect And nothing perfect should ever be finished.
@ 30876140:cffb1126
2025-03-26 04:58:21The portal is closing. The symphony comes to an end. Ballet, a dance of partners, A wish of hearts, Now closing its curtains. I foolishly sit Eagerly waiting For the circus to begin again, As crowds file past me, Chuckles and popcorn falling, Crushed under foot, I sit waiting For the show to carry on. But the night is now over, The laughs have been had, The music been heard, The dancers are gone now Into the nightbreeze chill. Yet still, I sit waiting, The empty chairs yawning, A cough, I start, could it be? Yet the lights now go out, And now without my sight I am truly alone in the theater. Yet still, I am waiting For the show to carry on, But I know that it won’t, Yet still, I am waiting. Never shall I leave For the show was too perfect And nothing perfect should ever be finished. @ 3c389c8f:7a2eff7f
2025-03-28 17:10:17There is a new web being built on Nostr. At it's core, is a social experience paralleled by no other decentralized protocol. Nostr not only solves the problems of siloed relationships, third-party identity ownership, and algorithmic content control; it makes possible a ubiquitous social network across almost anything imaginable. User controlled identity, open data, and verifiable social graphs allow us to redefine trust on the web. We can interact with each other and online content in ways that have previously only been pipedreams. Nostr is not just social media, it is the web made social. ### Interoperability The client/relay relationship on Nostr allows for almost endless data exchange between various apps, clients, relays, and users. If any two things are willing to speak the same sub-protocol(s) within Nostr, they can exchange data. Making a friend list enables that list to be used in any other place that chooses to make it available. Creating a relay to serve an algorithmic social feed makes that feed viewable in any client that displays social feeds. Health data held by a patient can be shared with any care provider, verified by their system, and vice versa. This is the point where I have to acknowledge my own tech-deaf limitations and direct you towards nostr.com for more information. ### Data Resiliency I prefer to use the term resiliency here, because its really a mix of data redundancy and self-managed data that creates broad availability. Relays may host 10, 20, 30+ copies of your notes in different locations, but you also have no assurance that those relays will hosts those notes forever. An individual operating their own relay, while also connecting to the wider network, ensures resiliency in events such that wide swaths of the network should disappear or collude against an individual. The simplicity of relay management makes it possible for nearly anyone to make sure that they have a way to convey their messages to their individual network, whether that be close contacts, an audience, or one individual. This resiliency doesn't just apply to typical speech, it applies to any data intended to be shared amongst humans and machines alike. ### Pseudonymity and Anonymity With privacy encroachment from corporations, advertisers, and governments reaching all time highs, the need for identity protecting tools is also on the rise. Nostr utilizes public key encryption for its identity system. As there is no central entity to "verify" you, there is no need to expose any personal identifiable information to any Nostr app, client, or relay. You can protect your personal identity by simply choosing not to expose it. Your reputation will build as you interact with others on the Nostr network. Your social capital can speak for itself. (As with everything else, utilizing a VPN is recommended.) ### Identity and Provability No one can stop an impersonator from trying to hijack an identity. With Nostr, you CAN prove that you are you, though, which is basically the same as saying "that person is not me" Every note you write, every action you take, is cryptographically signed by your private key. As long as you maintain control of that key, you can prove what you did or did not do. ### Censorship Resistance If you have read our Relay Rundown then you probably get the idea. If not here's the tl;dr: Many small, lightweight relays make up Nostr's distribution system. They are simple enough that anyone can run one. They are redundant enough that you can be almost certain your content exists somewhere. If that is not peace of mind enough, you can run your own with ease. Censorship resistance isn't counting on one company, man, or server to protect what you say. It is taking control of your speech. Nostr makes it easy. ### Freedom of Mind and Association Nostr eliminates the need for company run algorithms that high-jack your attention to feed the advertising industry. You are free to choose your social media experience. Nostr's DVMs, curations, and conversation-centered relays offer discovery mechanisms run by any number of providers. That could be an individual, a company, a group, or you. Many clients incorporate different ways of engaging with these corporate algorithm alternatives. You can also choose to keep a purely chronological feed of the the things and people you follow. Exploring Nostr through its many apps opens up a the freedom to choose what and how you feed your mind. When we are able to explore, we end up surrounding ourselves with people who share our interests & hobbies. We find friends. This creates distance between ideologies and stark beliefs that often are used as the basis for the term "being in a bubble". Instead of bubbling off, an infinitely open space of thoughts and ideas allows for groups to gather naturally. In this way, we can choose not to block ourselves off from opposing views but to simply distance ourselves from them. Nostr's relay system also allows for the opposite. Tight-knit communities can create a space for its members to socialize and exchange information with minimal interference from any outside influence. By setting up their own relays with strict rules, the members can utilize one identity to interact within a community or across the broader social network.
@ 3c389c8f:7a2eff7f
2025-03-28 17:10:17There is a new web being built on Nostr. At it's core, is a social experience paralleled by no other decentralized protocol. Nostr not only solves the problems of siloed relationships, third-party identity ownership, and algorithmic content control; it makes possible a ubiquitous social network across almost anything imaginable. User controlled identity, open data, and verifiable social graphs allow us to redefine trust on the web. We can interact with each other and online content in ways that have previously only been pipedreams. Nostr is not just social media, it is the web made social. ### Interoperability The client/relay relationship on Nostr allows for almost endless data exchange between various apps, clients, relays, and users. If any two things are willing to speak the same sub-protocol(s) within Nostr, they can exchange data. Making a friend list enables that list to be used in any other place that chooses to make it available. Creating a relay to serve an algorithmic social feed makes that feed viewable in any client that displays social feeds. Health data held by a patient can be shared with any care provider, verified by their system, and vice versa. This is the point where I have to acknowledge my own tech-deaf limitations and direct you towards nostr.com for more information. ### Data Resiliency I prefer to use the term resiliency here, because its really a mix of data redundancy and self-managed data that creates broad availability. Relays may host 10, 20, 30+ copies of your notes in different locations, but you also have no assurance that those relays will hosts those notes forever. An individual operating their own relay, while also connecting to the wider network, ensures resiliency in events such that wide swaths of the network should disappear or collude against an individual. The simplicity of relay management makes it possible for nearly anyone to make sure that they have a way to convey their messages to their individual network, whether that be close contacts, an audience, or one individual. This resiliency doesn't just apply to typical speech, it applies to any data intended to be shared amongst humans and machines alike. ### Pseudonymity and Anonymity With privacy encroachment from corporations, advertisers, and governments reaching all time highs, the need for identity protecting tools is also on the rise. Nostr utilizes public key encryption for its identity system. As there is no central entity to "verify" you, there is no need to expose any personal identifiable information to any Nostr app, client, or relay. You can protect your personal identity by simply choosing not to expose it. Your reputation will build as you interact with others on the Nostr network. Your social capital can speak for itself. (As with everything else, utilizing a VPN is recommended.) ### Identity and Provability No one can stop an impersonator from trying to hijack an identity. With Nostr, you CAN prove that you are you, though, which is basically the same as saying "that person is not me" Every note you write, every action you take, is cryptographically signed by your private key. As long as you maintain control of that key, you can prove what you did or did not do. ### Censorship Resistance If you have read our Relay Rundown then you probably get the idea. If not here's the tl;dr: Many small, lightweight relays make up Nostr's distribution system. They are simple enough that anyone can run one. They are redundant enough that you can be almost certain your content exists somewhere. If that is not peace of mind enough, you can run your own with ease. Censorship resistance isn't counting on one company, man, or server to protect what you say. It is taking control of your speech. Nostr makes it easy. ### Freedom of Mind and Association Nostr eliminates the need for company run algorithms that high-jack your attention to feed the advertising industry. You are free to choose your social media experience. Nostr's DVMs, curations, and conversation-centered relays offer discovery mechanisms run by any number of providers. That could be an individual, a company, a group, or you. Many clients incorporate different ways of engaging with these corporate algorithm alternatives. You can also choose to keep a purely chronological feed of the the things and people you follow. Exploring Nostr through its many apps opens up a the freedom to choose what and how you feed your mind. When we are able to explore, we end up surrounding ourselves with people who share our interests & hobbies. We find friends. This creates distance between ideologies and stark beliefs that often are used as the basis for the term "being in a bubble". Instead of bubbling off, an infinitely open space of thoughts and ideas allows for groups to gather naturally. In this way, we can choose not to block ourselves off from opposing views but to simply distance ourselves from them. Nostr's relay system also allows for the opposite. Tight-knit communities can create a space for its members to socialize and exchange information with minimal interference from any outside influence. By setting up their own relays with strict rules, the members can utilize one identity to interact within a community or across the broader social network. @ e88527b4:7ccf6efa
2024-08-30 12:12:39書いてみた。。
@ e88527b4:7ccf6efa
2024-08-30 12:12:39書いてみた。。 @ 8cb60e21:5f2deaea
2024-08-29 02:16:28<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/GwUNT2k26mQ" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-08-29 02:16:28<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/GwUNT2k26mQ" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 0d6c8388:46488a33
2025-03-28 16:24:00Huge thank you to [OpenSats for the grant](https://opensats.org/blog/10th-wave-of-nostr-grants) to work on [Hypernote this year](https://www.hypernote.club/)! I thought I'd take this opportunity to try and share my thought processes for Hypernote. If this all sounds very dense or irrelevant to you I'm sorry! === How can the ideas of "hypermedia" benefit nostr? That's the goal of hypernote. To take the best ideas from "hypertext" and "hypercard" and "hypermedia systems" and apply them to nostr in a specifically nostr-ey way. ### 1. What do we mean by hypermedia A hypermedia document embeds the methods of interaction (links, forms, and buttons are the most well-known hypermedia controls) within the document itself. It's including the _how_ with the _what_. This is how the old web worked. An HTML page was delivered to the web browser, and it included in it a link or perhaps a form that could be submitted to obtain a new, different HTML page. This is how the whole web worked early on! Forums and GeoCities and eBay and MySpace and Yahoo! and Amazon and Google all emerged inside this paradigm. A web browser in this paradigm was a "thin" client which rendered the "thick" application defined in the HTML (and, implicitly, was defined by the server that would serve that HTML). Contrast this with modern app development, where the _what_ is usually delivered in the form of JSON, and then HTML combined with JavaScript (React, Svelte, Angular, Vue, etc.) is devised to render that JSON as a meaningful piece of hypermedia within the actual browser, the _how_. The browser remains a "thin" client in this scenario, but now the application is delivered in two stages: a client application of HTML and JavaScript, and then the actual JSON data that will hydrate that "application". (Aside: it's interesting how much "thicker" the browser has had to become to support this newer paradigm!) Nostr was obviously built in line with the modern paradigm: nostr "clients" (written in React or Svelte or as mobile apps) define the _how_ of reading and creating nostr events, while nostr events themselves (JSON data) simply describe the _what_. And so the goal with Hypernote is to square this circle somehow: nostr currently delivers JSON _what_, how do we deliver the _how_ with nostr as well. Is that even possible? ### 2. Hypernote's design assumptions Hypernote assumes that hypermedia over nostr is a good idea! I'm expecting some joyful renaissance of app expression similar to that of the web once we figure out how to express applications in a truly "nostr" way. Hypernote was also [deeply inspired by HTMX](https://hypermedia.systems/hypermedia-a-reintroduction/), so it assumes that building web apps in the HTMX style is a good idea. The HTMX insight is that instead of shipping rich scripting along with your app, you could simply make HTML a _tiny_ bit more expressive and get 95% of what most apps need. HTMX's additions to the HTML language are designed to be as minimal and composable as possible, and Hypernote should have the same aims. Hypernote also assumes that the "design" of nostr will remain fluid and anarchic for years to come. There will be no "canonical" list of "required" NIPs that we'll have "consensus" on in order to build stable UIs on top of. Hypernote will need to be built responsive to nostr's moods and seasons, rather than one holy spec. Hypernote likes the `nak` command line tool. Hypernote likes markdown. Hypernote likes Tailwind CSS. Hypernote likes SolidJS. Hypernote likes cold brew coffee. Hypernote is, to be perfectly honest, my aesthetic preferences applied to my perception of an opportunity in the nostr ecosystem. ### 3. "What's a hypernote?" Great question. I'm still figuring this out. Everything right now is subject to change in order to make sure hypernote serves its intended purpose. But here's where things currently stand: A hypernote is a flat list of "Hypernote Elements". A Hypernote Element is composed of: 1. CONTENT. Static or dynamic content. (the what) 2. LOGIC. Filters and events (the how) 3. STYLE. Optional, inline style information specific to this element's content. In the most basic example of a [hypernote story](https://hypernote-stories.fly.dev/), here's a lone "edit me" in the middle of the canvas:  ``` { "id": "fb4aaed4-bf95-4353-a5e1-0bb64525c08f", "type": "text", "text": "edit me", "x": 540, "y": 960, "size": "md", "color": "black" } ``` As you can see, it has no logic, but it does have some content (the text "edit me") and style (the position, size, and color). Here's a "sticker" that displays a note: ``` { "id": "2cd1ef51-3356-408d-b10d-2502cbb8014e", "type": "sticker", "stickerType": "note", "filter": { "kinds": [ 1 ], "ids": [ "92de77507a361ab2e20385d98ff00565aaf3f80cf2b6d89c0343e08166fed931" ], "limit": 1 }, "accessors": [ "content", "pubkey", "created_at" ], "x": 540, "y": 960, "associatedData": {} } ``` As you can see, it's kind of a mess! The content and styling and underdeveloped for this "sticker", but at least it demonstrates some "logic": a nostr filter for getting its data. Here's another sticker, this one displays a form that the user can interact with to SEND a note. Very hyper of us! ``` { "id": "42240d75-e998-4067-b8fa-9ee096365663", "type": "sticker", "stickerType": "prompt", "filter": {}, "accessors": [], "x": 540, "y": 960, "associatedData": { "promptText": "What's your favorite color?" }, "methods": { "comment": { "description": "comment", "eventTemplate": { "kind": 1111, "content": "${content}", "tags": [ [ "E", "${eventId}", "", "${pubkey}" ], [ "K", "${eventKind}" ], [ "P", "${pubkey}" ], [ "e", "${eventId}", "", "${pubkey}" ], [ "k", "${eventKind}" ], [ "p", "${pubkey}" ] ] } } } } ``` It's also a mess, but it demos the other part of "logic": methods which produce new events. This is the total surface of hypernote, ideally! Static or dynamic content, simple inline styles, and logic for fetching and producing events. I'm calling it "logic" but it's purposfully not a whole scripting language. At most we'll have some sort of `jq`-like language for destructing the relevant piece of data we want. My ideal syntax for a hypernote as a developer will look something like ```foo.hypernote Nak-like logic Markdown-like content CSS-like styles ``` But with JSON as the compile target, this can just be my own preference, there can be other (likely better!) ways of authoring this content, such as a Hypernote Stories GUI. ### The end I know this is all still vague but I wanted to get some ideas out in the wild so people understand the through line of my different Hypernote experiments. I want to get the right amount of "expressivity" in Hypernote before it gets locked down into one spec. My hunch is it can be VERY expressive while remaining simple and also while not needing a whole scripting language bolted onto it. If I can't pull it off I'll let you know.
@ 0d6c8388:46488a33
2025-03-28 16:24:00Huge thank you to [OpenSats for the grant](https://opensats.org/blog/10th-wave-of-nostr-grants) to work on [Hypernote this year](https://www.hypernote.club/)! I thought I'd take this opportunity to try and share my thought processes for Hypernote. If this all sounds very dense or irrelevant to you I'm sorry! === How can the ideas of "hypermedia" benefit nostr? That's the goal of hypernote. To take the best ideas from "hypertext" and "hypercard" and "hypermedia systems" and apply them to nostr in a specifically nostr-ey way. ### 1. What do we mean by hypermedia A hypermedia document embeds the methods of interaction (links, forms, and buttons are the most well-known hypermedia controls) within the document itself. It's including the _how_ with the _what_. This is how the old web worked. An HTML page was delivered to the web browser, and it included in it a link or perhaps a form that could be submitted to obtain a new, different HTML page. This is how the whole web worked early on! Forums and GeoCities and eBay and MySpace and Yahoo! and Amazon and Google all emerged inside this paradigm. A web browser in this paradigm was a "thin" client which rendered the "thick" application defined in the HTML (and, implicitly, was defined by the server that would serve that HTML). Contrast this with modern app development, where the _what_ is usually delivered in the form of JSON, and then HTML combined with JavaScript (React, Svelte, Angular, Vue, etc.) is devised to render that JSON as a meaningful piece of hypermedia within the actual browser, the _how_. The browser remains a "thin" client in this scenario, but now the application is delivered in two stages: a client application of HTML and JavaScript, and then the actual JSON data that will hydrate that "application". (Aside: it's interesting how much "thicker" the browser has had to become to support this newer paradigm!) Nostr was obviously built in line with the modern paradigm: nostr "clients" (written in React or Svelte or as mobile apps) define the _how_ of reading and creating nostr events, while nostr events themselves (JSON data) simply describe the _what_. And so the goal with Hypernote is to square this circle somehow: nostr currently delivers JSON _what_, how do we deliver the _how_ with nostr as well. Is that even possible? ### 2. Hypernote's design assumptions Hypernote assumes that hypermedia over nostr is a good idea! I'm expecting some joyful renaissance of app expression similar to that of the web once we figure out how to express applications in a truly "nostr" way. Hypernote was also [deeply inspired by HTMX](https://hypermedia.systems/hypermedia-a-reintroduction/), so it assumes that building web apps in the HTMX style is a good idea. The HTMX insight is that instead of shipping rich scripting along with your app, you could simply make HTML a _tiny_ bit more expressive and get 95% of what most apps need. HTMX's additions to the HTML language are designed to be as minimal and composable as possible, and Hypernote should have the same aims. Hypernote also assumes that the "design" of nostr will remain fluid and anarchic for years to come. There will be no "canonical" list of "required" NIPs that we'll have "consensus" on in order to build stable UIs on top of. Hypernote will need to be built responsive to nostr's moods and seasons, rather than one holy spec. Hypernote likes the `nak` command line tool. Hypernote likes markdown. Hypernote likes Tailwind CSS. Hypernote likes SolidJS. Hypernote likes cold brew coffee. Hypernote is, to be perfectly honest, my aesthetic preferences applied to my perception of an opportunity in the nostr ecosystem. ### 3. "What's a hypernote?" Great question. I'm still figuring this out. Everything right now is subject to change in order to make sure hypernote serves its intended purpose. But here's where things currently stand: A hypernote is a flat list of "Hypernote Elements". A Hypernote Element is composed of: 1. CONTENT. Static or dynamic content. (the what) 2. LOGIC. Filters and events (the how) 3. STYLE. Optional, inline style information specific to this element's content. In the most basic example of a [hypernote story](https://hypernote-stories.fly.dev/), here's a lone "edit me" in the middle of the canvas:  ``` { "id": "fb4aaed4-bf95-4353-a5e1-0bb64525c08f", "type": "text", "text": "edit me", "x": 540, "y": 960, "size": "md", "color": "black" } ``` As you can see, it has no logic, but it does have some content (the text "edit me") and style (the position, size, and color). Here's a "sticker" that displays a note: ``` { "id": "2cd1ef51-3356-408d-b10d-2502cbb8014e", "type": "sticker", "stickerType": "note", "filter": { "kinds": [ 1 ], "ids": [ "92de77507a361ab2e20385d98ff00565aaf3f80cf2b6d89c0343e08166fed931" ], "limit": 1 }, "accessors": [ "content", "pubkey", "created_at" ], "x": 540, "y": 960, "associatedData": {} } ``` As you can see, it's kind of a mess! The content and styling and underdeveloped for this "sticker", but at least it demonstrates some "logic": a nostr filter for getting its data. Here's another sticker, this one displays a form that the user can interact with to SEND a note. Very hyper of us! ``` { "id": "42240d75-e998-4067-b8fa-9ee096365663", "type": "sticker", "stickerType": "prompt", "filter": {}, "accessors": [], "x": 540, "y": 960, "associatedData": { "promptText": "What's your favorite color?" }, "methods": { "comment": { "description": "comment", "eventTemplate": { "kind": 1111, "content": "${content}", "tags": [ [ "E", "${eventId}", "", "${pubkey}" ], [ "K", "${eventKind}" ], [ "P", "${pubkey}" ], [ "e", "${eventId}", "", "${pubkey}" ], [ "k", "${eventKind}" ], [ "p", "${pubkey}" ] ] } } } } ``` It's also a mess, but it demos the other part of "logic": methods which produce new events. This is the total surface of hypernote, ideally! Static or dynamic content, simple inline styles, and logic for fetching and producing events. I'm calling it "logic" but it's purposfully not a whole scripting language. At most we'll have some sort of `jq`-like language for destructing the relevant piece of data we want. My ideal syntax for a hypernote as a developer will look something like ```foo.hypernote Nak-like logic Markdown-like content CSS-like styles ``` But with JSON as the compile target, this can just be my own preference, there can be other (likely better!) ways of authoring this content, such as a Hypernote Stories GUI. ### The end I know this is all still vague but I wanted to get some ideas out in the wild so people understand the through line of my different Hypernote experiments. I want to get the right amount of "expressivity" in Hypernote before it gets locked down into one spec. My hunch is it can be VERY expressive while remaining simple and also while not needing a whole scripting language bolted onto it. If I can't pull it off I'll let you know. @ 8cb60e21:5f2deaea
2024-08-28 01:53:35<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/oJSFoDgm51o" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-08-28 01:53:35<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/oJSFoDgm51o" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ ecda4328:1278f072
2025-03-25 10:00:52**Kubernetes and Linux Swap: A Practical Perspective** After reviewing kernel documentation on swap management (e.g., [Linux Swap Management](https://www.kernel.org/doc/gorman/html/understand/understand014.html)), [KEP-2400 (Kubernetes Node Memory Swap Support)](https://github.com/kubernetes/enhancements/blob/master/keps/sig-node/2400-node-swap/README.md), and community discussions like [this post on ServerFault](https://serverfault.com/questions/881517/why-disable-swap-on-kubernetes), it's clear that the topic of swap usage in modern systems—especially Kubernetes environments—is nuanced and often contentious. Here's a practical synthesis of the discussion. --- ### The Rationale for Disabling Swap We disable SWAP on our Linux servers to ensure stable and predictable performance by relying on available RAM, avoiding the performance degradation and unnecessary I/O caused by SWAP usage. If an application runs out of memory, it’s usually due to insufficient RAM allocation or a memory leak, and enabling SWAP only worsens performance for other applications. It's more efficient to let a leaking app restart than to rely on SWAP to prevent OOM crashes. With modern platforms like Kubernetes, memory requests and limits are enforced, ensuring apps use only the RAM allocated to them, while avoiding overcommitment to prevent resource exhaustion. Additionally, disabling swap may protect data from **data remanence attacks**, where sensitive information could potentially be recovered from the swap space even after a process terminates. --- ### Theoretical Capability vs. Practical Deployment Linux provides a powerful and flexible memory subsystem. With proper tuning (e.g., swappiness, memory pinning, cgroups), it's technically possible to make swap usage efficient and targeted. Seasoned sysadmins often argue that disabling swap entirely is a lazy shortcut—an avoidance of learning how to use the tools properly. But Kubernetes is not a traditional system. It's an orchestrated environment that favors predictability, fail-fast behavior, and clear isolation between workloads. Within this model: - Memory **requests and limits** are declared explicitly. - The scheduler makes decisions based on RAM availability, not total virtual memory (RAM + swap). - Swap introduces **non-deterministic performance** characteristics that conflict with Kubernetes' goals. So while the kernel supports intelligent swap usage, Kubernetes **intentionally sidesteps** that complexity. --- ### Why Disable Swap in Kubernetes? 1. **Deterministic Failure > Degraded Performance**\ If a pod exceeds its memory allocation, it should fail fast — not get throttled into slow oblivion due to swap. This behavior surfaces bugs (like memory leaks or poor sizing) early. 2. **Transparency & Observability**\ With swap disabled, memory issues are clearer to diagnose. Swap obfuscates root causes and can make a healthy-looking node behave erratically. 3. **Performance Consistency**\ Swap causes I/O overhead. One noisy pod using swap can impact unrelated workloads on the same node — even if they’re within their resource limits. 4. **Kubernetes Doesn’t Manage Swap Well**\ Kubelet has historically lacked intelligence around swap. As of today, Kubernetes still doesn't support swap-aware scheduling or per-container swap control. 5. **Statelessness is the Norm**\ Most containerized workloads are designed to be ephemeral. Restarting a pod is usually preferable to letting it hang in a degraded state. --- ### "But Swap Can Be Useful..." Yes — for certain workloads (e.g., in-memory databases, caching layers, legacy systems), there may be valid reasons to keep swap enabled. In such cases, you'd need: - Fine-tuned `vm.swappiness` - Memory pinning and cgroup-based control - Swap-aware monitoring and alerting - Custom kubelet/systemd integration That's possible, but **not standard practice** — and for good reason. --- ### Future Considerations Recent Kubernetes releases have introduced [experimental swap support](https://kubernetes.io/blog/2023/08/24/swap-linux-beta/) via [KEP-2400](https://github.com/kubernetes/enhancements/blob/master/keps/sig-node/2400-node-swap/README.md). While this provides more flexibility for advanced use cases — particularly Burstable QoS pods on cgroupsv2 — swap remains disabled by default and is not generally recommended for production workloads unless carefully planned. The rationale outlined in this article remains applicable to most Kubernetes operators, especially in multi-tenant and performance-sensitive environments. Even the Kubernetes maintainers acknowledge the inherent trade-offs of enabling swap. As noted in [KEP-2400's Risks and Mitigations section](https://github.com/kubernetes/enhancements/blob/master/keps/sig-node/2400-node-swap/README.md), swap introduces unpredictability, can severely degrade performance compared to RAM, and complicates Kubernetes' resource accounting — increasing the risk of noisy neighbors and unexpected scheduling behavior. Some argue that with emerging technologies like **non-volatile memory** (e.g., Intel Optane/XPoint), swap may become viable again. These systems promise near-RAM speed with large capacity, offering hybrid memory models. But these are not widely deployed or supported in mainstream Kubernetes environments yet. --- ### Conclusion Disabling swap in Kubernetes is not a lazy hack — it’s a **strategic tradeoff**. It improves transparency, predictability, and system integrity in multi-tenant, containerized environments. While the kernel allows for more advanced configurations, Kubernetes intentionally simplifies memory handling for the sake of reliability. If we want to revisit swap usage, it should come with serious planning: proper instrumentation, swap-aware observability, and potentially upstream K8s improvements. Until then, **disabling swap remains the sane default**.
@ ecda4328:1278f072
2025-03-25 10:00:52**Kubernetes and Linux Swap: A Practical Perspective** After reviewing kernel documentation on swap management (e.g., [Linux Swap Management](https://www.kernel.org/doc/gorman/html/understand/understand014.html)), [KEP-2400 (Kubernetes Node Memory Swap Support)](https://github.com/kubernetes/enhancements/blob/master/keps/sig-node/2400-node-swap/README.md), and community discussions like [this post on ServerFault](https://serverfault.com/questions/881517/why-disable-swap-on-kubernetes), it's clear that the topic of swap usage in modern systems—especially Kubernetes environments—is nuanced and often contentious. Here's a practical synthesis of the discussion. --- ### The Rationale for Disabling Swap We disable SWAP on our Linux servers to ensure stable and predictable performance by relying on available RAM, avoiding the performance degradation and unnecessary I/O caused by SWAP usage. If an application runs out of memory, it’s usually due to insufficient RAM allocation or a memory leak, and enabling SWAP only worsens performance for other applications. It's more efficient to let a leaking app restart than to rely on SWAP to prevent OOM crashes. With modern platforms like Kubernetes, memory requests and limits are enforced, ensuring apps use only the RAM allocated to them, while avoiding overcommitment to prevent resource exhaustion. Additionally, disabling swap may protect data from **data remanence attacks**, where sensitive information could potentially be recovered from the swap space even after a process terminates. --- ### Theoretical Capability vs. Practical Deployment Linux provides a powerful and flexible memory subsystem. With proper tuning (e.g., swappiness, memory pinning, cgroups), it's technically possible to make swap usage efficient and targeted. Seasoned sysadmins often argue that disabling swap entirely is a lazy shortcut—an avoidance of learning how to use the tools properly. But Kubernetes is not a traditional system. It's an orchestrated environment that favors predictability, fail-fast behavior, and clear isolation between workloads. Within this model: - Memory **requests and limits** are declared explicitly. - The scheduler makes decisions based on RAM availability, not total virtual memory (RAM + swap). - Swap introduces **non-deterministic performance** characteristics that conflict with Kubernetes' goals. So while the kernel supports intelligent swap usage, Kubernetes **intentionally sidesteps** that complexity. --- ### Why Disable Swap in Kubernetes? 1. **Deterministic Failure > Degraded Performance**\ If a pod exceeds its memory allocation, it should fail fast — not get throttled into slow oblivion due to swap. This behavior surfaces bugs (like memory leaks or poor sizing) early. 2. **Transparency & Observability**\ With swap disabled, memory issues are clearer to diagnose. Swap obfuscates root causes and can make a healthy-looking node behave erratically. 3. **Performance Consistency**\ Swap causes I/O overhead. One noisy pod using swap can impact unrelated workloads on the same node — even if they’re within their resource limits. 4. **Kubernetes Doesn’t Manage Swap Well**\ Kubelet has historically lacked intelligence around swap. As of today, Kubernetes still doesn't support swap-aware scheduling or per-container swap control. 5. **Statelessness is the Norm**\ Most containerized workloads are designed to be ephemeral. Restarting a pod is usually preferable to letting it hang in a degraded state. --- ### "But Swap Can Be Useful..." Yes — for certain workloads (e.g., in-memory databases, caching layers, legacy systems), there may be valid reasons to keep swap enabled. In such cases, you'd need: - Fine-tuned `vm.swappiness` - Memory pinning and cgroup-based control - Swap-aware monitoring and alerting - Custom kubelet/systemd integration That's possible, but **not standard practice** — and for good reason. --- ### Future Considerations Recent Kubernetes releases have introduced [experimental swap support](https://kubernetes.io/blog/2023/08/24/swap-linux-beta/) via [KEP-2400](https://github.com/kubernetes/enhancements/blob/master/keps/sig-node/2400-node-swap/README.md). While this provides more flexibility for advanced use cases — particularly Burstable QoS pods on cgroupsv2 — swap remains disabled by default and is not generally recommended for production workloads unless carefully planned. The rationale outlined in this article remains applicable to most Kubernetes operators, especially in multi-tenant and performance-sensitive environments. Even the Kubernetes maintainers acknowledge the inherent trade-offs of enabling swap. As noted in [KEP-2400's Risks and Mitigations section](https://github.com/kubernetes/enhancements/blob/master/keps/sig-node/2400-node-swap/README.md), swap introduces unpredictability, can severely degrade performance compared to RAM, and complicates Kubernetes' resource accounting — increasing the risk of noisy neighbors and unexpected scheduling behavior. Some argue that with emerging technologies like **non-volatile memory** (e.g., Intel Optane/XPoint), swap may become viable again. These systems promise near-RAM speed with large capacity, offering hybrid memory models. But these are not widely deployed or supported in mainstream Kubernetes environments yet. --- ### Conclusion Disabling swap in Kubernetes is not a lazy hack — it’s a **strategic tradeoff**. It improves transparency, predictability, and system integrity in multi-tenant, containerized environments. While the kernel allows for more advanced configurations, Kubernetes intentionally simplifies memory handling for the sake of reliability. If we want to revisit swap usage, it should come with serious planning: proper instrumentation, swap-aware observability, and potentially upstream K8s improvements. Until then, **disabling swap remains the sane default**. @ 502ab02a:a2860397
2025-03-28 04:57:18จริงหรือ ว่าโอเมก้า3 ต้องมาจากปลาทะเลเท่านั้น มีเรื่องที่น่าสนใจเรื่องนึงครับ ถ้าพูดถึงโอเมก้า-3 หลายคนอาจนึกถึงปลาทะเลน้ำลึก เช่น แซลมอน แมคเคอเรล หรือซาร์ดีน ซึ่งเป็นแหล่งโอเมก้า-3 ที่ร่างกายใช้ได้ดี แต่ในขณะเดียวกัน ก็มีกลุ่มคนที่พยายามบริโภคโอเมก้า-3 จากพืชแทน เช่น น้ำมันเมล็ดแฟลกซ์ น้ำมันเมล็ดเจีย หรือวอลนัท โดยหวังว่าจะได้รับประโยชน์เช่นเดียวกับการกินปลา แต่ที่เราเรียนรู้กันมาว่า โอเมก้า-3 จากพืชนั้น ร่างกายมนุษย์นำไปใช้ได้น้อยมาก หรือแทบไม่ได้เลย สาเหตุหลักมาจากรูปแบบของโอเมก้า-3 ที่พบในแหล่งต่างๆ โอเมก้า-3 มีอยู่ 3 ชนิดหลัก ได้แก่ ALA (Alpha-Linolenic Acid) – พบในพืช EPA (Eicosapentaenoic Acid) – พบในปลาทะเล DHA (Docosahexaenoic Acid) – พบในปลาทะเล ร่างกายสามารถใช้ EPA และ DHA ได้โดยตรง แต่สำหรับ ALA นั้น ร่างกายต้องผ่านกระบวนการเปลี่ยนแปลงทางชีวเคมีก่อน ซึ่งกระบวนการนี้ไม่มีประสิทธิภาพนัก โดยทั่วไปแล้ว ALA แปลงเป็น EPA ได้เพียง 5-10% ALA แปลงเป็น DHA ได้เพียง 0.5-5% แปลว่า หากคุณกินเมล็ดแฟลกซ์หรือน้ำมันเมล็ดเจีย แม้ว่าจะมีปริมาณ ALA สูง แต่ร่างกายก็แทบไม่ได้รับ EPA และ DHA ในปริมาณที่เพียงพอเพื่อใช้ประโยชน์อย่างเต็มที่ ทำไมร่างกายแปลง ALA เป็น EPA/DHA ได้น้อย? อันแรกเลยคือ เอนไซม์จำกัด กระบวนการเปลี่ยน ALA เป็น EPA และ DHA จะใช้เอนไซม์เดียวกับการแปลงโอเมก้า-6 ซึ่งมักถูกใช้ไปกับโอเมก้า-6 ที่มากเกินไปในอาหารปัจจุบันซะแล้วนั่นเอง ต่อมาคือ กระบวนการหลายขั้นตอน การเปลี่ยน ALA เป็น DHA ต้องผ่านหลายขั้นตอนทางชีวเคมี ทำให้มีการสูญเสียพลังงานและวัตถุดิบไปมาก และสุดท้าย ปัจจัยทางพันธุกรรมและเพศ บางคน โดยเฉพาะผู้หญิง อาจมีอัตราการเปลี่ยนที่สูงกว่าผู้ชายเล็กน้อย แต่ก็ยังต่ำเมื่อเทียบกับการได้รับ EPA/DHA จากปลาหรือสาหร่ายโดยตรง โอเมก้า-6 ตัวการขัดขวางโอเมก้า-3 จากพืช โอเมก้า-6 เป็นกรดไขมันจำเป็นที่พบมากในน้ำมันพืช เช่น น้ำมันถั่วเหลือง น้ำมันข้าวโพด และน้ำมันดอกทานตะวัน ซึ่งเป็นส่วนประกอบหลักของอาหารแปรรูปในปัจจุบัน ปัญหาคือ เอนไซม์ที่ใช้แปลง ALA ไปเป็น EPA/DHA เป็นตัวเดียวกับที่ใช้แปลงโอเมก้า-6 ไปเป็น AA (Arachidonic Acid) ซึ่งมีบทบาทในการอักเสบ หากเราบริโภคโอเมก้า-6 มากเกินไป (ซึ่งคนส่วนใหญ่ทำ5555) เอนไซม์เหล่านี้จะถูกใช้ไปกับโอเมก้า-6 มากกว่า ทำให้ ALA มีโอกาสแปลงเป็น EPA/DHA น้อยลงไปอีก แล้วคนที่ไม่กินปลาหรือชาววีแกนควรทำอย่างไร? สำหรับคนที่ไม่สามารถหรือไม่ต้องการกินปลา ก็จะมีการบริโภคน้ำมันสาหร่ายที่มี DHA โดยตรงเป็นทางเลือกที่ดีกว่าการหวังพึ่ง ALA จากพืช เพราะ DHA จากสาหร่ายสามารถดูดซึมและใช้ได้ทันทีเหมือน DHA จากปลา ได้ด้วยเหรอ ????? ผมเล่ากำเนิดของ DHA ในปลาให้ประมาณนี้ครับ จริง ๆ แล้ว DHA ซึ่งเป็นโอเมก้า-3 ที่ร่างกายใช้ได้โดยตรง มาจาก Docosahexaenoic Acid ที่เกิดจากกระบวนการสังเคราะห์ตามธรรมชาติ ซึ่งสาหร่ายบางสายพันธุ์ เช่น Schizochytrium และ Crypthecodinium cohnii มีเอนไซม์ที่สามารถเปลี่ยนกรดไขมันพื้นฐานให้กลายเป็น DHA ได้เองซึ่งเป็นส่วนประกอบหลักในระบบนิเวศทะเล(พืชกักเก็บไขมันได้อย่างไร ผมเคยโพสไปแล้ว) โดยเฉพาะ สาหร่ายขนาดเล็ก (microalgae) สาหร่ายจึงเป็นสิ่งมีชีวิตในทะเลพัฒนาให้มี DHA สูงเพราะ DHA เป็นส่วนประกอบสำคัญที่ช่วยรักษาความยืดหยุ่นและความสมบูรณ์ของเยื่อหุ้มเซลล์ในสาหร่าย ทำให้พวกมันสามารถดำรงชีวิตในสภาพแวดล้อมที่มีอุณหภูมิต่ำในทะเลได้ จากนั้นก็เป็นไปตามห่วงโซ่อาหารครับ ปลาและสัตว์ทะเลอื่น ๆ ได้รับ DHA จากการบริโภคสาหร่ายหรือสัตว์เล็ก ๆ ที่กินสาหร่ายมาอีกที ดังนั้น DHA ในปลาเป็นผลมาจากการสะสมจากสาหร่ายโดยตรง นี่เป็นเหตุผลว่าทำไมปลาทะเลน้ำลึก เช่น แซลมอน แมคเคอเรล และซาร์ดีน ถึงมี DHA สูงนั่นเอง งว่ออออออ ดังนั้น เมื่อคุณกิน DHA จากสาหร่าย ก็เท่ากับว่าคุณได้รับ DHA จากต้นกำเนิดแท้จริงในระบบนิเวศทะเลครับ DHA ที่ได้มาจากสาหร่ายสามารถนำไปใช้ในร่างกายได้ทันทีโดยไม่ต้องผ่านกระบวนการเปลี่ยนแปลง เพราะมันอยู่ในรูป Triglyceride หรือ Phospholipid ซึ่งเป็นรูปแบบที่ร่างกายมนุษย์สามารถดูดซึมและนำไปใช้ได้ทันที ปลาไม่ได้แปลงโครงสร้าง DHA แต่เพียงสะสม DHA ไว้ในตัวจากการกินสาหร่าย ดังนั้นการรับประทาน DHA จากสาหร่ายก็ให้ผลเทียบเท่ากับการรับประทาน DHA จากปลา งานวิจัยหลายฉบับยืนยันว่า DHA จากสาหร่ายมีค่าการดูดซึม (Bioavailability) ใกล้เคียงกับ DHA จากน้ำมันปลา แต่หาเอาเองนะถ้าอยากอ่านฉบับเต็ม การผลิตน้ำมันสาหร่ายนั้น เมื่อสาหร่ายเจริญเติบโตเต็มที่แล้ว เขาจะทำการเก็บเกี่ยวและสกัดน้ำมันโดยใช้เทคโนโลยีการแยกที่ทันสมัย ซึ่งช่วยรักษาให้ DHA ที่มีอยู่ในเซลล์สาหร่ายถูกเก็บรักษาไว้ในรูปแบบที่สามารถนำไปใช้ได้โดยตรง จากนั้นจะเข้าสู่การกรองหรือการปั่นแยก (centrifugation) เพื่อให้ได้มวลสาหร่ายที่เข้มข้น จากนั้นจึงทำให้แห้งเพื่อเตรียมเข้าสู่กระบวนการสกัด ซึ่งมีหลายวิธีอาทิเช่น 1 การสกัดด้วยตัวทำละลาย ใช้ตัวทำละลาย เช่น เฮกเซน (Hexane) หรือ เอทานอล (Ethanol) เพื่อสกัดน้ำมันออกจากเซลล์สาหร่าย จากนั้นน้ำมันจะถูกนำไปกลั่นเพื่อแยกตัวทำละลายออก ทำให้ได้น้ำมันที่มีความบริสุทธิ์สูง 2. การสกัดด้วย CO₂ เหลว ใช้ คาร์บอนไดออกไซด์ในสถานะวิกฤติ (Supercritical CO₂) ซึ่งเป็นวิธีที่ทันสมัย ก๊าซ CO₂ จะถูกทำให้มีความดันสูงและอุณหภูมิที่เหมาะสมเพื่อกลายเป็นของเหลว แล้วใช้แยกน้ำมันออกจากเซลล์สาหร่าย วิธีนี้ช่วยให้ได้น้ำมันที่ ปราศจากตัวทำละลายเคมีและมีความบริสุทธิ์สูง 3. การสกัดด้วยการกดอัด หรือ Cold Pressed เป็นวิธีที่ใช้แรงดันทางกลกดเซลล์สาหร่ายเพื่อให้ได้น้ำมันออกมา อันนี้เป็นการผลิตน้ำมันแบบออร์แกนิกเลยครับ แต่ให้ผลผลิตน้อยกว่าวิธีอื่น ๆ น้ำมันที่ได้จากการสกัดจะผ่านการกลั่นด้วยกระบวนการต่าง ๆ เช่น Winterization กำจัดไขมันที่ไม่จำเป็น Molecular Distillation แยกสารตกค้าง เช่น โลหะหนักและสารปนเปื้อน Deodorization กำจัดกลิ่นคาวของสาหร่าย จากนั้นก็บรรจุใส่ซอฟท์เจล พร้อมจำหน่ายนั่นเองครับ ก็ถือว่าเป็นอีกทางเลือกของชาววีแกน ที่ไม่สามารถกินปลาหรือสัตว์ทะเลได้ ก็น่าจะเฮกันดังๆได้เลยครับ จะได้มีตัวช่วยในการลดการอักเสบได้ ส่วนชาว food matrix ก็ต้องเรียนรู้ระบบครับ การกินจากปลาหรือสัตว์ทะเล ก็จะได้โปรตีน แร่ธาตุ วิตามินอื่นๆควบมากับตัวสัตว์ตามที่ธรรมชาติแพคมาให้ ถ้าจะเสริมเป็นน้ำมันสาหร่าย ก็สุดแล้วแต่ความต้องการครับ ไม่ใช่เรื่องแย่อะไร เว้นแต่ไปเทียบราคาเอาเองนะ 55555 #pirateketo #ฉลาก3รู้ #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
@ 502ab02a:a2860397
2025-03-28 04:57:18จริงหรือ ว่าโอเมก้า3 ต้องมาจากปลาทะเลเท่านั้น มีเรื่องที่น่าสนใจเรื่องนึงครับ ถ้าพูดถึงโอเมก้า-3 หลายคนอาจนึกถึงปลาทะเลน้ำลึก เช่น แซลมอน แมคเคอเรล หรือซาร์ดีน ซึ่งเป็นแหล่งโอเมก้า-3 ที่ร่างกายใช้ได้ดี แต่ในขณะเดียวกัน ก็มีกลุ่มคนที่พยายามบริโภคโอเมก้า-3 จากพืชแทน เช่น น้ำมันเมล็ดแฟลกซ์ น้ำมันเมล็ดเจีย หรือวอลนัท โดยหวังว่าจะได้รับประโยชน์เช่นเดียวกับการกินปลา แต่ที่เราเรียนรู้กันมาว่า โอเมก้า-3 จากพืชนั้น ร่างกายมนุษย์นำไปใช้ได้น้อยมาก หรือแทบไม่ได้เลย สาเหตุหลักมาจากรูปแบบของโอเมก้า-3 ที่พบในแหล่งต่างๆ โอเมก้า-3 มีอยู่ 3 ชนิดหลัก ได้แก่ ALA (Alpha-Linolenic Acid) – พบในพืช EPA (Eicosapentaenoic Acid) – พบในปลาทะเล DHA (Docosahexaenoic Acid) – พบในปลาทะเล ร่างกายสามารถใช้ EPA และ DHA ได้โดยตรง แต่สำหรับ ALA นั้น ร่างกายต้องผ่านกระบวนการเปลี่ยนแปลงทางชีวเคมีก่อน ซึ่งกระบวนการนี้ไม่มีประสิทธิภาพนัก โดยทั่วไปแล้ว ALA แปลงเป็น EPA ได้เพียง 5-10% ALA แปลงเป็น DHA ได้เพียง 0.5-5% แปลว่า หากคุณกินเมล็ดแฟลกซ์หรือน้ำมันเมล็ดเจีย แม้ว่าจะมีปริมาณ ALA สูง แต่ร่างกายก็แทบไม่ได้รับ EPA และ DHA ในปริมาณที่เพียงพอเพื่อใช้ประโยชน์อย่างเต็มที่ ทำไมร่างกายแปลง ALA เป็น EPA/DHA ได้น้อย? อันแรกเลยคือ เอนไซม์จำกัด กระบวนการเปลี่ยน ALA เป็น EPA และ DHA จะใช้เอนไซม์เดียวกับการแปลงโอเมก้า-6 ซึ่งมักถูกใช้ไปกับโอเมก้า-6 ที่มากเกินไปในอาหารปัจจุบันซะแล้วนั่นเอง ต่อมาคือ กระบวนการหลายขั้นตอน การเปลี่ยน ALA เป็น DHA ต้องผ่านหลายขั้นตอนทางชีวเคมี ทำให้มีการสูญเสียพลังงานและวัตถุดิบไปมาก และสุดท้าย ปัจจัยทางพันธุกรรมและเพศ บางคน โดยเฉพาะผู้หญิง อาจมีอัตราการเปลี่ยนที่สูงกว่าผู้ชายเล็กน้อย แต่ก็ยังต่ำเมื่อเทียบกับการได้รับ EPA/DHA จากปลาหรือสาหร่ายโดยตรง โอเมก้า-6 ตัวการขัดขวางโอเมก้า-3 จากพืช โอเมก้า-6 เป็นกรดไขมันจำเป็นที่พบมากในน้ำมันพืช เช่น น้ำมันถั่วเหลือง น้ำมันข้าวโพด และน้ำมันดอกทานตะวัน ซึ่งเป็นส่วนประกอบหลักของอาหารแปรรูปในปัจจุบัน ปัญหาคือ เอนไซม์ที่ใช้แปลง ALA ไปเป็น EPA/DHA เป็นตัวเดียวกับที่ใช้แปลงโอเมก้า-6 ไปเป็น AA (Arachidonic Acid) ซึ่งมีบทบาทในการอักเสบ หากเราบริโภคโอเมก้า-6 มากเกินไป (ซึ่งคนส่วนใหญ่ทำ5555) เอนไซม์เหล่านี้จะถูกใช้ไปกับโอเมก้า-6 มากกว่า ทำให้ ALA มีโอกาสแปลงเป็น EPA/DHA น้อยลงไปอีก แล้วคนที่ไม่กินปลาหรือชาววีแกนควรทำอย่างไร? สำหรับคนที่ไม่สามารถหรือไม่ต้องการกินปลา ก็จะมีการบริโภคน้ำมันสาหร่ายที่มี DHA โดยตรงเป็นทางเลือกที่ดีกว่าการหวังพึ่ง ALA จากพืช เพราะ DHA จากสาหร่ายสามารถดูดซึมและใช้ได้ทันทีเหมือน DHA จากปลา ได้ด้วยเหรอ ????? ผมเล่ากำเนิดของ DHA ในปลาให้ประมาณนี้ครับ จริง ๆ แล้ว DHA ซึ่งเป็นโอเมก้า-3 ที่ร่างกายใช้ได้โดยตรง มาจาก Docosahexaenoic Acid ที่เกิดจากกระบวนการสังเคราะห์ตามธรรมชาติ ซึ่งสาหร่ายบางสายพันธุ์ เช่น Schizochytrium และ Crypthecodinium cohnii มีเอนไซม์ที่สามารถเปลี่ยนกรดไขมันพื้นฐานให้กลายเป็น DHA ได้เองซึ่งเป็นส่วนประกอบหลักในระบบนิเวศทะเล(พืชกักเก็บไขมันได้อย่างไร ผมเคยโพสไปแล้ว) โดยเฉพาะ สาหร่ายขนาดเล็ก (microalgae) สาหร่ายจึงเป็นสิ่งมีชีวิตในทะเลพัฒนาให้มี DHA สูงเพราะ DHA เป็นส่วนประกอบสำคัญที่ช่วยรักษาความยืดหยุ่นและความสมบูรณ์ของเยื่อหุ้มเซลล์ในสาหร่าย ทำให้พวกมันสามารถดำรงชีวิตในสภาพแวดล้อมที่มีอุณหภูมิต่ำในทะเลได้ จากนั้นก็เป็นไปตามห่วงโซ่อาหารครับ ปลาและสัตว์ทะเลอื่น ๆ ได้รับ DHA จากการบริโภคสาหร่ายหรือสัตว์เล็ก ๆ ที่กินสาหร่ายมาอีกที ดังนั้น DHA ในปลาเป็นผลมาจากการสะสมจากสาหร่ายโดยตรง นี่เป็นเหตุผลว่าทำไมปลาทะเลน้ำลึก เช่น แซลมอน แมคเคอเรล และซาร์ดีน ถึงมี DHA สูงนั่นเอง งว่ออออออ ดังนั้น เมื่อคุณกิน DHA จากสาหร่าย ก็เท่ากับว่าคุณได้รับ DHA จากต้นกำเนิดแท้จริงในระบบนิเวศทะเลครับ DHA ที่ได้มาจากสาหร่ายสามารถนำไปใช้ในร่างกายได้ทันทีโดยไม่ต้องผ่านกระบวนการเปลี่ยนแปลง เพราะมันอยู่ในรูป Triglyceride หรือ Phospholipid ซึ่งเป็นรูปแบบที่ร่างกายมนุษย์สามารถดูดซึมและนำไปใช้ได้ทันที ปลาไม่ได้แปลงโครงสร้าง DHA แต่เพียงสะสม DHA ไว้ในตัวจากการกินสาหร่าย ดังนั้นการรับประทาน DHA จากสาหร่ายก็ให้ผลเทียบเท่ากับการรับประทาน DHA จากปลา งานวิจัยหลายฉบับยืนยันว่า DHA จากสาหร่ายมีค่าการดูดซึม (Bioavailability) ใกล้เคียงกับ DHA จากน้ำมันปลา แต่หาเอาเองนะถ้าอยากอ่านฉบับเต็ม การผลิตน้ำมันสาหร่ายนั้น เมื่อสาหร่ายเจริญเติบโตเต็มที่แล้ว เขาจะทำการเก็บเกี่ยวและสกัดน้ำมันโดยใช้เทคโนโลยีการแยกที่ทันสมัย ซึ่งช่วยรักษาให้ DHA ที่มีอยู่ในเซลล์สาหร่ายถูกเก็บรักษาไว้ในรูปแบบที่สามารถนำไปใช้ได้โดยตรง จากนั้นจะเข้าสู่การกรองหรือการปั่นแยก (centrifugation) เพื่อให้ได้มวลสาหร่ายที่เข้มข้น จากนั้นจึงทำให้แห้งเพื่อเตรียมเข้าสู่กระบวนการสกัด ซึ่งมีหลายวิธีอาทิเช่น 1 การสกัดด้วยตัวทำละลาย ใช้ตัวทำละลาย เช่น เฮกเซน (Hexane) หรือ เอทานอล (Ethanol) เพื่อสกัดน้ำมันออกจากเซลล์สาหร่าย จากนั้นน้ำมันจะถูกนำไปกลั่นเพื่อแยกตัวทำละลายออก ทำให้ได้น้ำมันที่มีความบริสุทธิ์สูง 2. การสกัดด้วย CO₂ เหลว ใช้ คาร์บอนไดออกไซด์ในสถานะวิกฤติ (Supercritical CO₂) ซึ่งเป็นวิธีที่ทันสมัย ก๊าซ CO₂ จะถูกทำให้มีความดันสูงและอุณหภูมิที่เหมาะสมเพื่อกลายเป็นของเหลว แล้วใช้แยกน้ำมันออกจากเซลล์สาหร่าย วิธีนี้ช่วยให้ได้น้ำมันที่ ปราศจากตัวทำละลายเคมีและมีความบริสุทธิ์สูง 3. การสกัดด้วยการกดอัด หรือ Cold Pressed เป็นวิธีที่ใช้แรงดันทางกลกดเซลล์สาหร่ายเพื่อให้ได้น้ำมันออกมา อันนี้เป็นการผลิตน้ำมันแบบออร์แกนิกเลยครับ แต่ให้ผลผลิตน้อยกว่าวิธีอื่น ๆ น้ำมันที่ได้จากการสกัดจะผ่านการกลั่นด้วยกระบวนการต่าง ๆ เช่น Winterization กำจัดไขมันที่ไม่จำเป็น Molecular Distillation แยกสารตกค้าง เช่น โลหะหนักและสารปนเปื้อน Deodorization กำจัดกลิ่นคาวของสาหร่าย จากนั้นก็บรรจุใส่ซอฟท์เจล พร้อมจำหน่ายนั่นเองครับ ก็ถือว่าเป็นอีกทางเลือกของชาววีแกน ที่ไม่สามารถกินปลาหรือสัตว์ทะเลได้ ก็น่าจะเฮกันดังๆได้เลยครับ จะได้มีตัวช่วยในการลดการอักเสบได้ ส่วนชาว food matrix ก็ต้องเรียนรู้ระบบครับ การกินจากปลาหรือสัตว์ทะเล ก็จะได้โปรตีน แร่ธาตุ วิตามินอื่นๆควบมากับตัวสัตว์ตามที่ธรรมชาติแพคมาให้ ถ้าจะเสริมเป็นน้ำมันสาหร่าย ก็สุดแล้วแต่ความต้องการครับ ไม่ใช่เรื่องแย่อะไร เว้นแต่ไปเทียบราคาเอาเองนะ 55555 #pirateketo #ฉลาก3รู้ #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr @ df173277:4ec96708
2025-02-07 00:41:34## **Building Our Confidential Backend on Secure Enclaves** With our newly released [private and confidential **Maple AI**](https://trymaple.ai/?ref=blog.opensecret.cloud) and the open sourcing of our [**OpenSecret** platform](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud) code, I'm excited to present this technical primer on how we built our confidential compute platform leveraging **secure enclaves**. By combining AWS Nitro enclaves with end-to-end encryption and reproducible builds, our platform gives developers and end users the confidence that user data is protected, even at runtime, and that the code operating on their data has not been tampered with. ## **Auth and Databases Today** As developers, we live in an era where protecting user data means "encryption at rest," plus some access policies and procedures. Developers typically run servers that: 1. Need to register users (authentication). 2. Collect and process user data in business-specific ways, often on the backend. Even if data is encrypted at rest, it's commonly unlocked with a single master key or credentials the server holds. This means that data is visible during runtime to the application, system administrators, and potentially to the hosting providers. This scenario makes it difficult (or impossible) to guarantee that sensitive data isn't snooped on, memory-dumped, or used in unauthorized ways (for instance, training AI models behind the scenes). ## **"Just Trust Us" Isn't Good Enough** In a traditional server architecture, users have to take it on faith that the code handling their data is the same code the operator claims to be running. Behind the scenes, applications can be modified or augmented to forward private information elsewhere, and there is no transparent way for users to verify otherwise. This lack of proof is unsettling, especially for services that process or store highly confidential data. Administrators, developers, or cloud providers with privileged access can inspect memory in plaintext, attach debuggers, or gain complete visibility into stored information. Hackers who compromise these privileged levels can directly access sensitive data. Even with strict policies or promises of good conduct, the reality is that technical capabilities and misconfigurations can override words on paper. If a server master key can decrypt your data or can be accessed by an insider with root permissions, then "just trust us" loses much of its credibility. The rise of AI platforms amplifies this dilemma. User data, often full of personal details, gets funneled into large-scale models that might be training or fine-tuning behind the scenes. Relying on vague assurances that "we don't look at your data" is no longer enough to prevent legitimate concerns about privacy and misuse. Now more than ever, providing a **strong, verifiable** guarantee that data remains off-limits, even when actively processed, has become a non-negotiable requirement for trustworthy services. ## **Current Attempts at Securing Data** Current User Experience of E2EE Apps While properly securing data is not easy, it isn't to say that no one is trying. Some solutions use **end-to-end encryption** (E2EE), where user data is encrypted client-side with a password or passphrase, so not even the server operator can decrypt it. That approach can be quite secure, but it also has its **limitations**: 1. **Key Management Nightmares**: If a user forgets their passphrase, the data is effectively lost, and there's no way to recover it from the developer's side. 2. **Feature Limitations**: Complex server-side operations (like offline/background tasks, AI queries, real-time collaboration, or heavy computation) can't easily happen if the server is never capable of processing decrypted data. 3. **Platform Silos**: Some solutions rely on iCloud, Google Drive, or local device storage. That can hamper multi-device usage or multi-OS compatibility. Other approaches include self-hosting. However, these either burden users with dev ops overhead or revert to the "trust me" model for the server if you "self-host" on a cloud provider. ## **Secure Enclaves** ### **The Hybrid Approach** Secure enclaves offer a compelling middle ground. They combine the privacy benefits of keeping data secure from prying admins while still allowing meaningful server-side computation. In a nutshell, an enclave is a protected environment within a machine, isolated at the hardware level, so that even if the OS or server is compromised, the data and code inside the enclave remain hidden. App Service Running Inside Secure Enclave ### **High-Level Goal of Enclaves** Enclaves, also known under the broader umbrella of **confidential computing**, aim to:\ • **Lock down data** so that only authorized code within the enclave can process the original plaintext data.\ • **Deny external inspection** by memory dumping, attaching a debugger, or intercepting plaintext network traffic.\ • **Prove** to external users or services that an enclave is running unmodified, approved code (this is where **remote attestation** comes in). ### **Different Secure Enclave Solutions** [**AMD SEV**](https://www.amd.com/en/developer/sev.html?ref=blog.opensecret.cloud) **(Secure Encrypted Virtualization)** encrypts an entire virtual machine's memory so that even a compromised hypervisor cannot inspect or modify guest data. Its core concept is "lift-and-shift" security. No application refactoring is required because hardware-based encryption automatically protects the OS and all VM applications. Later enhancements (SEV-ES and SEV-SNP) added encryption of CPU register states and memory integrity protections, further limiting hypervisor tampering. This broad coverage means the guest OS is included in the trusted boundary. AMD SEV has matured into a robust solution for confidential VMs in multi-tenant clouds. [**Intel TDX**](https://www.intel.com/content/www/us/en/developer/tools/trust-domain-extensions/overview.html?ref=blog.opensecret.cloud) **(Trust Domain Extensions)** shifts from process-level enclaves to full VM encryption, allowing an entire guest operating system and its applications to run in an isolated "trust domain." Like AMD SEV, Intel TDX encrypts and protects all memory the VM uses from hypervisors or other privileged software, so developers do not need to refactor their code to benefit from hardware-based confidentiality. This broader scope addresses many SGX limitations, such as strict memory bounds and the need to split out enclave-specific logic, and offers a more straightforward "lift-and-shift" path for running existing workloads privately. While SGX is now deprecated, TDX carries forward the core confidential computing principles but applies them at the virtual machine level for more substantial isolation, easier deployment, and the ability to scale up to large, memory-intensive applications. [**Apple Secure Enclave and Private Compute**](https://security.apple.com/blog/private-cloud-compute/?ref=blog.opensecret.cloud) is a dedicated security coprocessor embedded in most Apple devices (iPhones, iPads, Macs) and now extended to Apple's server-side AI infrastructure. It runs its own microkernel, has hardware-protected memory, and securely manages operations such as biometric authentication, key storage, and cryptographic tasks. Apple's "Private Compute" approach in the cloud brings similar enclave capabilities to server-based AI, enabling on-device-grade privacy even when requests are processed in Apple's data centers. [**AWS Nitro Enclaves**](https://docs.aws.amazon.com/enclaves/latest/user/nitro-enclave.html?ref=blog.opensecret.cloud) carve out a tightly isolated "mini-VM" from a parent EC2 instance, with its own vCPUs and memory guarded by dedicated Nitro cards. The enclave has no persistent storage and no external network access, significantly reducing the attack surface. Communication with the parent instance occurs over a secure local channel (vsock), and AWS offers hardware-based attestation so that secrets (e.g., encryption keys from AWS KMS) can be accessed only to the correct enclave. This design helps developers protect sensitive data or code even if the main EC2 instance's OS is compromised. [**NVIDIA GPU TEEs**](https://www.nvidia.com/en-us/data-center/solutions/confidential-computing/?ref=blog.opensecret.cloud) **(Hopper H100 and Blackwell)** extend confidential computing to accelerated workloads by encrypting data in GPU memory and ensuring that even a privileged host cannot view or tamper with it. Data moving between CPU and GPU is encrypted in transit, so sensitive model weights or inputs remain protected during AI training or inference. NVIDIA's hardware and drivers handle secure data paths under the hood, allowing confidential large language model (LLM) workloads and other GPU-accelerated computations to run with minimal performance overhead and strong security guarantees. ### **Key Benefits** One major advantage of enclaves is their ability to **keep memory completely off-limits** to outside prying eyes. Even administrators who can normally inspect processes at will are blocked from peeking into the enclave's protected memory space. The enclave model is a huge shift in the security model: it prevents casual inspection and defends against sophisticated memory dumping techniques that might otherwise leak secrets or sensitive data. Another key benefit centers on cryptographic keys that are **never exposed outside the enclave**. Only verified code running inside the enclave environment can run decryption or signing operations, and it can only do so while that specific code is running. This ensures that compromised hosts or rogue processes, even those with high-level privileges, are unable to intercept or misuse the keys because the keys remain strictly within the trusted boundary of the hardware. Enclaves can also offer the power of **remote attestation**, allowing external clients or systems to confirm that they're speaking to an authentic, untampered enclave. By validating the hardware's integrity measurements and enclave-specific proofs, the remote party can be confident in the underlying security properties, an important guarantee in multi-tenant environments or whenever trust boundaries extend across different organizations and networks. Beyond that, **reproducible builds** can create a verifiable fingerprint proving which binary runs in the enclave. This is a step above a simple "trust us" approach. Anyone can independently recreate the enclave image and verify the resulting cryptographic hash by using a reproducible build system (for example, [our NixOS-based solution](https://github.com/OpenSecretCloud/opensecret/blob/master/flake.nix?ref=blog.opensecret.cloud)). If it matches, then users and developers know precisely how code handles their data, boosting confidence that no hidden changes exist. It's worth noting that although enclaves shield you from software devs, cloud providers, and insider threats, you do have to trust the **hardware vendor** (Intel, AMD, Apple, AWS, or NVIDIA) to implement their microcode and firmware securely. The entire enclave model could be theoretically undermined if a CPU maker's root keys or manufacturing process were compromised. Fortunately, these companies undergo extensive audits and firmware validations (often with third-party researchers), and their remote attestation mechanisms allow you to confirm specific firmware versions before trusting an enclave. While this adds a layer of "vendor trust," it's still a far more contained risk than trusting an entire operating system or cloud stack, so enclaves remain a strong step forward in practical, confidential computing. ## **How We Use Secure Enclaves** Now that we've covered the general idea of enclaves let's look at how we specifically implement them in OpenSecret, our developer platform for handling user auth, private keys, data encryption, and AI workloads. ### **Our Stack: AWS Nitro + Nvidia TEE** • **AWS Nitro Enclaves for the backend**: All critical logic, authentication, private key management, and data encryption/decryption run inside an AWS Nitro Enclave. • **Nvidia Trusted Execution for AI**: For large AI inference (such as the Llama 3.3 70B model), we utilize Nvidia's GPU-based TEEs to protect even GPU memory. This means users can feed sensitive data to the AI model **without** exposing it in plaintext to the GPU providers or us as the operator. [Edgeless Systems](https://www.edgeless.systems/?ref=blog.opensecret.cloud) is our Nvidia TEE provider, and due to the power of enclave verification, we don't need to worry about who runs the GPUs. We know requests can't be inspected or tampered with. ### **End-to-End Encryption from Client to Enclave** Client-side Enclave Attestation from Maple AI Before login or data upload, the user/client verifies the **enclave attestation** from our platform. This process proves that the specific Nitro Enclave is genuine and runs the exact code we've published. You can check this out live on [Maple AI's attestation page](https://trymaple.ai/proof?ref=blog.opensecret.cloud). Based on the attestation, the client establishes a secure ephemeral communication channel that only that enclave can decrypt. While we take advantage of SSL, it is typically not terminated inside the enclave itself. To ensure there's full encrypted data transfer all the way through to the enclave, we establish this additional handshake based on the attestation document that is used for all API requests during the client session. From there, the user's credentials, private keys, and data pass through this secure channel directly into the enclave, where they are decrypted and processed according to the user's request. ### **In-Enclave Operations** At the core of OpenSecret's approach is the conviction that security-critical tasks must happen inside the enclave, where even administrative privileges or hypervisor-level compromise cannot expose plaintext data. This encompasses everything from when a user logs in to creating and managing sensitive cryptographic keys. By confining these operations to a protected hardware boundary, developers can focus on building their applications without worrying about accidental data leaks, insider threats, or malicious attempts to harvest credentials. The enclave becomes the ultimate gatekeeper: it controls how data flows and ensures that nothing escapes in plain form. User Auth Methods running inside Enclave A primary example is **user authentication**. All sign-in workflows, including email/password, OAuth, and upcoming passkey-based methods, are handled entirely within the enclave. As soon as a user's credentials enter our platform through the encrypted channel, they are routed straight into the protected environment, bypassing the host's operating system or any potential snooping channels. From there, authentication and session details remain in the enclave, ensuring that privileged outsiders cannot intercept or modify them. By centralizing these identity flows within a sealed environment, developers can assure their users that no one outside the enclave (including the cloud provider or the app's own sysadmins) can peek at, tamper with, or access sensitive login information. Main Enclave Operations in OpenSecret The same principle applies to **private key management**. Whether keys are created fresh in the enclave or securely transferred into it, they remain sealed away from the rest of the system. Operations like digital signing or content decryption happen only within the hardware boundary, so raw keys never appear in any log, file system, or memory space outside the enclave. Developers retain the functionality they need, such as verifying user actions, encrypting data, or enabling secure transactions without ever exposing keys to a broader (and more vulnerable) attack surface. User backup options exist as well, where the keys can be securely passed to the end user. Realtime Encrypted Data Sync on Multiple Devices Another crucial aspect is **data encryption at rest**. While user data ultimately needs to be stored somewhere outside the enclave, the unencrypted form of that data only exists transiently inside the protected environment. Encryption and decryption routines run within the enclave, which holds the encryption keys strictly in memory under hardware guards. If a user uploads data, it is promptly secured before it leaves the enclave. When data is retrieved, it remains encrypted until it reenters the protected region and is passed back to the user through the secured communication channel. This ensures that even if someone gains access to the underlying storage or intercepts data in transit, they will see only meaningless ciphertext. Confidential AI Workloads Finally, **confidential AI workloads** build upon this same pattern: the Nitro enclave re-encrypts data so it can be processed inside a GPU-based trusted execution environment (TEE) for inference or other advanced computations. Sensitive data, like user-generated text or private documents, never appears in the clear on the host or within GPU memory outside the TEE boundary. When an AI process finishes, only the results are returned to the enclave, which can then relay them securely to the requesting user. By seamlessly chaining enclaves together, from CPU-based Nitro Enclaves to GPU-accelerated TEEs, we can deliver robust, hardware-enforced privacy for virtually any type of server-side or AI-driven operation. ### **Reproducible Builds + Verification** Client verifies enclave attestation document We build our enclaves on **NixOS** with reproducible builds, ensuring that anyone can verify that the binary we publish is indeed the binary running in the enclave. This build process is essential for proving we haven't snuck in malicious code to exfiltrate data or collect sensitive logs. Our code is fully open source ([GitHub: OpenSecret](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud)), so you can audit or run it yourself. You can also verify that the cryptographic measurement the build process outputs matches the measurement reported by the enclave during attestation. ## **Putting It All Together** OpenSecret Offering: Private Key Management, Encrypted Sync, Private AI, and Confidential Compute By weaving secure enclaves into every step, from authentication to data handling to AI inference, we shift the burden of trust away from human policies and onto provable, hardware-based protections. For app developers, you can offer your users robust privacy guarantees without rewriting all your business logic or building an entire security stack from scratch. Whether you're storing user credentials or running complex operations on sensitive data, the enclave approach ensures plaintext remains inaccessible to even the most privileged parties outside the enclave boundary. Developers can focus on building great apps, while OpenSecret handles the cryptographic "lock and key" behind the scenes. This model provides a secure-by-design environment for industries that demand strict data confidentiality, such as healthcare, fintech, cryptocurrency apps for secure key management, or decentralized identity platforms. Instead of worrying about memory dumps or backend tampering, you can trust that once data enters the enclave, it's sealed off from unauthorized eyes, including from the app developers themselves. And these safeguards don't just apply to niche use cases. Even general-purpose applications that handle login flows and user-generated content stand to benefit, especially as regulatory scrutiny grows around data privacy and insider threats. Imagine a telehealth startup using OpenSecret enclaves to protect patient information for remote consultations. Not only would patient data remain encrypted at rest, but any AI-driven analytics to assist with diagnoses could be run privately within the enclave, ensuring no one outside the hardware boundary can peek at sensitive health records. A fintech company could similarly isolate confidential financial transactions, preventing even privileged insiders from viewing or tampering with raw transaction details. These real-world implementations give developers a clear path to adopting enclaves for serious privacy and compliance needs without overhauling their infrastructure. OpenSecret aims to be a **full developer platform** with end-to-end security from day one. By incorporating user authentication, data storage, and GPU-based confidential AI into a single service, we eliminate many of the traditional hurdles in adopting enclaves. No more juggling separate tools for cryptographic key management, compliance controls, and runtime privacy. Instead, you get a unified stack that keeps data encrypted in transit, at rest, and in use. Our solution also caters to the exploding demand for AI applications: with TEE-enabled GPU workloads, you can securely process sensitive data for text inference without ever exposing raw plaintext or sensitive documents to the host system. The result is a new generation of apps that deliver advanced functionality, like real-time encrypted data sync or AI-driven insights, while preserving user privacy and meeting strict regulatory requirements. You don't have to rely on empty "trust us" promises because hardware enclaves, remote attestation, and reproducible builds collectively guarantee the code is running untampered. In short, OpenSecret offers the building blocks needed to create truly confidential services and experiences, allowing you to innovate while ensuring data protection remains ironclad. ## **Things to Come** We're excited to build on our enclaved approach. Here's what's on our roadmap: • **Production Launch**: We're using this in production now with [Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud) and have a developer preview playground up and running. We'll have the developer environment ready for production in a few months.\ • **Multi-Tenant Support**: Our platform currently works for single tenants, but we're opening this up so developers can onboard without needing a dedicated instance.\ • **Self-Serve Frontend**: A dev-friendly portal for provisioning apps, connecting OAuth or email providers, and managing users.\ • **External Key Signing Options**: Integrations with custom hardware security modules (HSMs) or customer-ran key managers that can only process data upon verifying the enclave attestation.\ • **Confidential Computing as a Service**: We'll expand our platform so that other developers can quickly create enclaves for specialized workloads without dealing with the complexities of Nitro or GPU TEEs.\ • **Additional SDKs**: In addition to our [JavaScript client-side SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud), we plan to launch official support for Rust, Python, Swift, Java, Go, and more.\ • **AI API Proxy with Attestation/Encryption**: We already provide an easy way to [access a Private AI through Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud), but we'd like to open this up more for existing tools and developers. We'll provide a proxy server that users can run on their local machines or servers that properly handle encryption to our OpenAI-compatible API. ## **Getting Started** Ready to see enclaves in action? Here's how to dive in:\ 1. **Run OpenSecret**: Check out our open-source repository at [OpenSecret on GitHub](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud). You can run your own enclaved environment or try it out locally with Docker.\ 2. **Review Our SDK**: Our [JavaScript client SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud) makes it easy to handle sign-ins, put/get encrypted data, sign with user private keys, etc. It handles attestation verification and encryption under the hood, making the API integration seamless.\ 3. **Play with Maple AI**: Try out [Maple AI](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/) as an example of an AI app built directly on OpenSecret. Your queries are encrypted end to end, and the Llama model sees them only inside the TEE.\ 4. **Developer Preview**: Contact us if you want an invite to our early dev platform. We'll guide you through our SDK and give you access to the preview server. We'd love to build with you and incorporate your feedback as we develop this further. ## **Conclusion** By merging secure enclaves (AWS Nitro and Nvidia GPU TEEs), user authentication, private key management, and an end-to-end verifiable encrypted approach, **OpenSecret** provides a powerful platform where we protect user data during collection, storage, and processing. Whether it's for standard user management, handling private cryptographic keys, or powering AI inference, the technology ensures that **no one**, not even us or the cloud provider, can snoop on data in use. **We believe** this is the future of trustworthy computing in the cloud. And it's **all open source**, so you don't have to just take our word for it: you can see and verify everything yourself. Do you have questions, feedback, or a use case you'd like to test out? Come join us on [GitHub](https://github.com/OpenSecretCloud?ref=blog.opensecret.cloud), [Discord](https://discord.gg/ch2gjZAMGy?ref=blog.opensecret.cloud), or email us for a developer preview. We can't wait to see what you build! *Thank you for reading, and welcome to the era of enclaved computing.*
@ df173277:4ec96708
2025-02-07 00:41:34## **Building Our Confidential Backend on Secure Enclaves** With our newly released [private and confidential **Maple AI**](https://trymaple.ai/?ref=blog.opensecret.cloud) and the open sourcing of our [**OpenSecret** platform](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud) code, I'm excited to present this technical primer on how we built our confidential compute platform leveraging **secure enclaves**. By combining AWS Nitro enclaves with end-to-end encryption and reproducible builds, our platform gives developers and end users the confidence that user data is protected, even at runtime, and that the code operating on their data has not been tampered with. ## **Auth and Databases Today** As developers, we live in an era where protecting user data means "encryption at rest," plus some access policies and procedures. Developers typically run servers that: 1. Need to register users (authentication). 2. Collect and process user data in business-specific ways, often on the backend. Even if data is encrypted at rest, it's commonly unlocked with a single master key or credentials the server holds. This means that data is visible during runtime to the application, system administrators, and potentially to the hosting providers. This scenario makes it difficult (or impossible) to guarantee that sensitive data isn't snooped on, memory-dumped, or used in unauthorized ways (for instance, training AI models behind the scenes). ## **"Just Trust Us" Isn't Good Enough** In a traditional server architecture, users have to take it on faith that the code handling their data is the same code the operator claims to be running. Behind the scenes, applications can be modified or augmented to forward private information elsewhere, and there is no transparent way for users to verify otherwise. This lack of proof is unsettling, especially for services that process or store highly confidential data. Administrators, developers, or cloud providers with privileged access can inspect memory in plaintext, attach debuggers, or gain complete visibility into stored information. Hackers who compromise these privileged levels can directly access sensitive data. Even with strict policies or promises of good conduct, the reality is that technical capabilities and misconfigurations can override words on paper. If a server master key can decrypt your data or can be accessed by an insider with root permissions, then "just trust us" loses much of its credibility. The rise of AI platforms amplifies this dilemma. User data, often full of personal details, gets funneled into large-scale models that might be training or fine-tuning behind the scenes. Relying on vague assurances that "we don't look at your data" is no longer enough to prevent legitimate concerns about privacy and misuse. Now more than ever, providing a **strong, verifiable** guarantee that data remains off-limits, even when actively processed, has become a non-negotiable requirement for trustworthy services. ## **Current Attempts at Securing Data** Current User Experience of E2EE Apps While properly securing data is not easy, it isn't to say that no one is trying. Some solutions use **end-to-end encryption** (E2EE), where user data is encrypted client-side with a password or passphrase, so not even the server operator can decrypt it. That approach can be quite secure, but it also has its **limitations**: 1. **Key Management Nightmares**: If a user forgets their passphrase, the data is effectively lost, and there's no way to recover it from the developer's side. 2. **Feature Limitations**: Complex server-side operations (like offline/background tasks, AI queries, real-time collaboration, or heavy computation) can't easily happen if the server is never capable of processing decrypted data. 3. **Platform Silos**: Some solutions rely on iCloud, Google Drive, or local device storage. That can hamper multi-device usage or multi-OS compatibility. Other approaches include self-hosting. However, these either burden users with dev ops overhead or revert to the "trust me" model for the server if you "self-host" on a cloud provider. ## **Secure Enclaves** ### **The Hybrid Approach** Secure enclaves offer a compelling middle ground. They combine the privacy benefits of keeping data secure from prying admins while still allowing meaningful server-side computation. In a nutshell, an enclave is a protected environment within a machine, isolated at the hardware level, so that even if the OS or server is compromised, the data and code inside the enclave remain hidden. App Service Running Inside Secure Enclave ### **High-Level Goal of Enclaves** Enclaves, also known under the broader umbrella of **confidential computing**, aim to:\ • **Lock down data** so that only authorized code within the enclave can process the original plaintext data.\ • **Deny external inspection** by memory dumping, attaching a debugger, or intercepting plaintext network traffic.\ • **Prove** to external users or services that an enclave is running unmodified, approved code (this is where **remote attestation** comes in). ### **Different Secure Enclave Solutions** [**AMD SEV**](https://www.amd.com/en/developer/sev.html?ref=blog.opensecret.cloud) **(Secure Encrypted Virtualization)** encrypts an entire virtual machine's memory so that even a compromised hypervisor cannot inspect or modify guest data. Its core concept is "lift-and-shift" security. No application refactoring is required because hardware-based encryption automatically protects the OS and all VM applications. Later enhancements (SEV-ES and SEV-SNP) added encryption of CPU register states and memory integrity protections, further limiting hypervisor tampering. This broad coverage means the guest OS is included in the trusted boundary. AMD SEV has matured into a robust solution for confidential VMs in multi-tenant clouds. [**Intel TDX**](https://www.intel.com/content/www/us/en/developer/tools/trust-domain-extensions/overview.html?ref=blog.opensecret.cloud) **(Trust Domain Extensions)** shifts from process-level enclaves to full VM encryption, allowing an entire guest operating system and its applications to run in an isolated "trust domain." Like AMD SEV, Intel TDX encrypts and protects all memory the VM uses from hypervisors or other privileged software, so developers do not need to refactor their code to benefit from hardware-based confidentiality. This broader scope addresses many SGX limitations, such as strict memory bounds and the need to split out enclave-specific logic, and offers a more straightforward "lift-and-shift" path for running existing workloads privately. While SGX is now deprecated, TDX carries forward the core confidential computing principles but applies them at the virtual machine level for more substantial isolation, easier deployment, and the ability to scale up to large, memory-intensive applications. [**Apple Secure Enclave and Private Compute**](https://security.apple.com/blog/private-cloud-compute/?ref=blog.opensecret.cloud) is a dedicated security coprocessor embedded in most Apple devices (iPhones, iPads, Macs) and now extended to Apple's server-side AI infrastructure. It runs its own microkernel, has hardware-protected memory, and securely manages operations such as biometric authentication, key storage, and cryptographic tasks. Apple's "Private Compute" approach in the cloud brings similar enclave capabilities to server-based AI, enabling on-device-grade privacy even when requests are processed in Apple's data centers. [**AWS Nitro Enclaves**](https://docs.aws.amazon.com/enclaves/latest/user/nitro-enclave.html?ref=blog.opensecret.cloud) carve out a tightly isolated "mini-VM" from a parent EC2 instance, with its own vCPUs and memory guarded by dedicated Nitro cards. The enclave has no persistent storage and no external network access, significantly reducing the attack surface. Communication with the parent instance occurs over a secure local channel (vsock), and AWS offers hardware-based attestation so that secrets (e.g., encryption keys from AWS KMS) can be accessed only to the correct enclave. This design helps developers protect sensitive data or code even if the main EC2 instance's OS is compromised. [**NVIDIA GPU TEEs**](https://www.nvidia.com/en-us/data-center/solutions/confidential-computing/?ref=blog.opensecret.cloud) **(Hopper H100 and Blackwell)** extend confidential computing to accelerated workloads by encrypting data in GPU memory and ensuring that even a privileged host cannot view or tamper with it. Data moving between CPU and GPU is encrypted in transit, so sensitive model weights or inputs remain protected during AI training or inference. NVIDIA's hardware and drivers handle secure data paths under the hood, allowing confidential large language model (LLM) workloads and other GPU-accelerated computations to run with minimal performance overhead and strong security guarantees. ### **Key Benefits** One major advantage of enclaves is their ability to **keep memory completely off-limits** to outside prying eyes. Even administrators who can normally inspect processes at will are blocked from peeking into the enclave's protected memory space. The enclave model is a huge shift in the security model: it prevents casual inspection and defends against sophisticated memory dumping techniques that might otherwise leak secrets or sensitive data. Another key benefit centers on cryptographic keys that are **never exposed outside the enclave**. Only verified code running inside the enclave environment can run decryption or signing operations, and it can only do so while that specific code is running. This ensures that compromised hosts or rogue processes, even those with high-level privileges, are unable to intercept or misuse the keys because the keys remain strictly within the trusted boundary of the hardware. Enclaves can also offer the power of **remote attestation**, allowing external clients or systems to confirm that they're speaking to an authentic, untampered enclave. By validating the hardware's integrity measurements and enclave-specific proofs, the remote party can be confident in the underlying security properties, an important guarantee in multi-tenant environments or whenever trust boundaries extend across different organizations and networks. Beyond that, **reproducible builds** can create a verifiable fingerprint proving which binary runs in the enclave. This is a step above a simple "trust us" approach. Anyone can independently recreate the enclave image and verify the resulting cryptographic hash by using a reproducible build system (for example, [our NixOS-based solution](https://github.com/OpenSecretCloud/opensecret/blob/master/flake.nix?ref=blog.opensecret.cloud)). If it matches, then users and developers know precisely how code handles their data, boosting confidence that no hidden changes exist. It's worth noting that although enclaves shield you from software devs, cloud providers, and insider threats, you do have to trust the **hardware vendor** (Intel, AMD, Apple, AWS, or NVIDIA) to implement their microcode and firmware securely. The entire enclave model could be theoretically undermined if a CPU maker's root keys or manufacturing process were compromised. Fortunately, these companies undergo extensive audits and firmware validations (often with third-party researchers), and their remote attestation mechanisms allow you to confirm specific firmware versions before trusting an enclave. While this adds a layer of "vendor trust," it's still a far more contained risk than trusting an entire operating system or cloud stack, so enclaves remain a strong step forward in practical, confidential computing. ## **How We Use Secure Enclaves** Now that we've covered the general idea of enclaves let's look at how we specifically implement them in OpenSecret, our developer platform for handling user auth, private keys, data encryption, and AI workloads. ### **Our Stack: AWS Nitro + Nvidia TEE** • **AWS Nitro Enclaves for the backend**: All critical logic, authentication, private key management, and data encryption/decryption run inside an AWS Nitro Enclave. • **Nvidia Trusted Execution for AI**: For large AI inference (such as the Llama 3.3 70B model), we utilize Nvidia's GPU-based TEEs to protect even GPU memory. This means users can feed sensitive data to the AI model **without** exposing it in plaintext to the GPU providers or us as the operator. [Edgeless Systems](https://www.edgeless.systems/?ref=blog.opensecret.cloud) is our Nvidia TEE provider, and due to the power of enclave verification, we don't need to worry about who runs the GPUs. We know requests can't be inspected or tampered with. ### **End-to-End Encryption from Client to Enclave** Client-side Enclave Attestation from Maple AI Before login or data upload, the user/client verifies the **enclave attestation** from our platform. This process proves that the specific Nitro Enclave is genuine and runs the exact code we've published. You can check this out live on [Maple AI's attestation page](https://trymaple.ai/proof?ref=blog.opensecret.cloud). Based on the attestation, the client establishes a secure ephemeral communication channel that only that enclave can decrypt. While we take advantage of SSL, it is typically not terminated inside the enclave itself. To ensure there's full encrypted data transfer all the way through to the enclave, we establish this additional handshake based on the attestation document that is used for all API requests during the client session. From there, the user's credentials, private keys, and data pass through this secure channel directly into the enclave, where they are decrypted and processed according to the user's request. ### **In-Enclave Operations** At the core of OpenSecret's approach is the conviction that security-critical tasks must happen inside the enclave, where even administrative privileges or hypervisor-level compromise cannot expose plaintext data. This encompasses everything from when a user logs in to creating and managing sensitive cryptographic keys. By confining these operations to a protected hardware boundary, developers can focus on building their applications without worrying about accidental data leaks, insider threats, or malicious attempts to harvest credentials. The enclave becomes the ultimate gatekeeper: it controls how data flows and ensures that nothing escapes in plain form. User Auth Methods running inside Enclave A primary example is **user authentication**. All sign-in workflows, including email/password, OAuth, and upcoming passkey-based methods, are handled entirely within the enclave. As soon as a user's credentials enter our platform through the encrypted channel, they are routed straight into the protected environment, bypassing the host's operating system or any potential snooping channels. From there, authentication and session details remain in the enclave, ensuring that privileged outsiders cannot intercept or modify them. By centralizing these identity flows within a sealed environment, developers can assure their users that no one outside the enclave (including the cloud provider or the app's own sysadmins) can peek at, tamper with, or access sensitive login information. Main Enclave Operations in OpenSecret The same principle applies to **private key management**. Whether keys are created fresh in the enclave or securely transferred into it, they remain sealed away from the rest of the system. Operations like digital signing or content decryption happen only within the hardware boundary, so raw keys never appear in any log, file system, or memory space outside the enclave. Developers retain the functionality they need, such as verifying user actions, encrypting data, or enabling secure transactions without ever exposing keys to a broader (and more vulnerable) attack surface. User backup options exist as well, where the keys can be securely passed to the end user. Realtime Encrypted Data Sync on Multiple Devices Another crucial aspect is **data encryption at rest**. While user data ultimately needs to be stored somewhere outside the enclave, the unencrypted form of that data only exists transiently inside the protected environment. Encryption and decryption routines run within the enclave, which holds the encryption keys strictly in memory under hardware guards. If a user uploads data, it is promptly secured before it leaves the enclave. When data is retrieved, it remains encrypted until it reenters the protected region and is passed back to the user through the secured communication channel. This ensures that even if someone gains access to the underlying storage or intercepts data in transit, they will see only meaningless ciphertext. Confidential AI Workloads Finally, **confidential AI workloads** build upon this same pattern: the Nitro enclave re-encrypts data so it can be processed inside a GPU-based trusted execution environment (TEE) for inference or other advanced computations. Sensitive data, like user-generated text or private documents, never appears in the clear on the host or within GPU memory outside the TEE boundary. When an AI process finishes, only the results are returned to the enclave, which can then relay them securely to the requesting user. By seamlessly chaining enclaves together, from CPU-based Nitro Enclaves to GPU-accelerated TEEs, we can deliver robust, hardware-enforced privacy for virtually any type of server-side or AI-driven operation. ### **Reproducible Builds + Verification** Client verifies enclave attestation document We build our enclaves on **NixOS** with reproducible builds, ensuring that anyone can verify that the binary we publish is indeed the binary running in the enclave. This build process is essential for proving we haven't snuck in malicious code to exfiltrate data or collect sensitive logs. Our code is fully open source ([GitHub: OpenSecret](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud)), so you can audit or run it yourself. You can also verify that the cryptographic measurement the build process outputs matches the measurement reported by the enclave during attestation. ## **Putting It All Together** OpenSecret Offering: Private Key Management, Encrypted Sync, Private AI, and Confidential Compute By weaving secure enclaves into every step, from authentication to data handling to AI inference, we shift the burden of trust away from human policies and onto provable, hardware-based protections. For app developers, you can offer your users robust privacy guarantees without rewriting all your business logic or building an entire security stack from scratch. Whether you're storing user credentials or running complex operations on sensitive data, the enclave approach ensures plaintext remains inaccessible to even the most privileged parties outside the enclave boundary. Developers can focus on building great apps, while OpenSecret handles the cryptographic "lock and key" behind the scenes. This model provides a secure-by-design environment for industries that demand strict data confidentiality, such as healthcare, fintech, cryptocurrency apps for secure key management, or decentralized identity platforms. Instead of worrying about memory dumps or backend tampering, you can trust that once data enters the enclave, it's sealed off from unauthorized eyes, including from the app developers themselves. And these safeguards don't just apply to niche use cases. Even general-purpose applications that handle login flows and user-generated content stand to benefit, especially as regulatory scrutiny grows around data privacy and insider threats. Imagine a telehealth startup using OpenSecret enclaves to protect patient information for remote consultations. Not only would patient data remain encrypted at rest, but any AI-driven analytics to assist with diagnoses could be run privately within the enclave, ensuring no one outside the hardware boundary can peek at sensitive health records. A fintech company could similarly isolate confidential financial transactions, preventing even privileged insiders from viewing or tampering with raw transaction details. These real-world implementations give developers a clear path to adopting enclaves for serious privacy and compliance needs without overhauling their infrastructure. OpenSecret aims to be a **full developer platform** with end-to-end security from day one. By incorporating user authentication, data storage, and GPU-based confidential AI into a single service, we eliminate many of the traditional hurdles in adopting enclaves. No more juggling separate tools for cryptographic key management, compliance controls, and runtime privacy. Instead, you get a unified stack that keeps data encrypted in transit, at rest, and in use. Our solution also caters to the exploding demand for AI applications: with TEE-enabled GPU workloads, you can securely process sensitive data for text inference without ever exposing raw plaintext or sensitive documents to the host system. The result is a new generation of apps that deliver advanced functionality, like real-time encrypted data sync or AI-driven insights, while preserving user privacy and meeting strict regulatory requirements. You don't have to rely on empty "trust us" promises because hardware enclaves, remote attestation, and reproducible builds collectively guarantee the code is running untampered. In short, OpenSecret offers the building blocks needed to create truly confidential services and experiences, allowing you to innovate while ensuring data protection remains ironclad. ## **Things to Come** We're excited to build on our enclaved approach. Here's what's on our roadmap: • **Production Launch**: We're using this in production now with [Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud) and have a developer preview playground up and running. We'll have the developer environment ready for production in a few months.\ • **Multi-Tenant Support**: Our platform currently works for single tenants, but we're opening this up so developers can onboard without needing a dedicated instance.\ • **Self-Serve Frontend**: A dev-friendly portal for provisioning apps, connecting OAuth or email providers, and managing users.\ • **External Key Signing Options**: Integrations with custom hardware security modules (HSMs) or customer-ran key managers that can only process data upon verifying the enclave attestation.\ • **Confidential Computing as a Service**: We'll expand our platform so that other developers can quickly create enclaves for specialized workloads without dealing with the complexities of Nitro or GPU TEEs.\ • **Additional SDKs**: In addition to our [JavaScript client-side SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud), we plan to launch official support for Rust, Python, Swift, Java, Go, and more.\ • **AI API Proxy with Attestation/Encryption**: We already provide an easy way to [access a Private AI through Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud), but we'd like to open this up more for existing tools and developers. We'll provide a proxy server that users can run on their local machines or servers that properly handle encryption to our OpenAI-compatible API. ## **Getting Started** Ready to see enclaves in action? Here's how to dive in:\ 1. **Run OpenSecret**: Check out our open-source repository at [OpenSecret on GitHub](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud). You can run your own enclaved environment or try it out locally with Docker.\ 2. **Review Our SDK**: Our [JavaScript client SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud) makes it easy to handle sign-ins, put/get encrypted data, sign with user private keys, etc. It handles attestation verification and encryption under the hood, making the API integration seamless.\ 3. **Play with Maple AI**: Try out [Maple AI](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/) as an example of an AI app built directly on OpenSecret. Your queries are encrypted end to end, and the Llama model sees them only inside the TEE.\ 4. **Developer Preview**: Contact us if you want an invite to our early dev platform. We'll guide you through our SDK and give you access to the preview server. We'd love to build with you and incorporate your feedback as we develop this further. ## **Conclusion** By merging secure enclaves (AWS Nitro and Nvidia GPU TEEs), user authentication, private key management, and an end-to-end verifiable encrypted approach, **OpenSecret** provides a powerful platform where we protect user data during collection, storage, and processing. Whether it's for standard user management, handling private cryptographic keys, or powering AI inference, the technology ensures that **no one**, not even us or the cloud provider, can snoop on data in use. **We believe** this is the future of trustworthy computing in the cloud. And it's **all open source**, so you don't have to just take our word for it: you can see and verify everything yourself. Do you have questions, feedback, or a use case you'd like to test out? Come join us on [GitHub](https://github.com/OpenSecretCloud?ref=blog.opensecret.cloud), [Discord](https://discord.gg/ch2gjZAMGy?ref=blog.opensecret.cloud), or email us for a developer preview. We can't wait to see what you build! *Thank you for reading, and welcome to the era of enclaved computing.* @ b83a28b7:35919450
2024-08-27 16:48:28https://image.nostr.build/df0721d6d45d82db35d06663a0318ffe68c0b2b3c694888d23694efcc4255de5.gif
@ b83a28b7:35919450
2024-08-27 16:48:28https://image.nostr.build/df0721d6d45d82db35d06663a0318ffe68c0b2b3c694888d23694efcc4255de5.gif @ 8cb60e21:5f2deaea
2024-08-25 20:26:43<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/ZbOzQ0EiAZQ" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-08-25 20:26:43<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/ZbOzQ0EiAZQ" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 57d1a264:69f1fee1
2025-03-24 17:08:06Nice podcast with @sbddesign and @ConorOkus about bitcoin payments. https://www.youtube.com/watch?v=GTSqoFKs1cE In this episode, Conor, Open Source product manager at Spiral & Stephen, Product Designer at Voltage & Co founder of ATL Bitlab join Stephan to discuss the current state of Bitcoin user experience, particularly focusing on payments and the challenges faced by users. They explore the comparison between Bitcoin and physical cash, the Western perspective on Bitcoin payments, and the importance of user experience in facilitating Bitcoin transactions. They also touch upon various payment protocols like #BOLT11, #LNURL, and #BOLT12, highlighting the need for interoperability and better privacy features in the Bitcoin ecosystem. The discussion also covers resources available for developers and designers to enhance wallet usability and integration. @StephanLivera Official Podcast Episode: https://stephanlivera.com/646 ### Takeaways 🔸Bitcoin has excelled as a savings technology. 🔸The payments use case for Bitcoin still needs improvement. 🔸User experience is crucial for Bitcoin adoption. 🔸Comparing Bitcoin to cash highlights privacy concerns. 🔸Western users may not see a payments problem. 🔸Regulatory issues impact Bitcoin payments in the West. 🔸User experience challenges hinder Bitcoin transactions. 🔸Different payment protocols create compatibility issues. 🔸Community collaboration is essential for Bitcoin's future. 🔸Improving interoperability can enhance Bitcoin payments. Wallet compatibility issues can create negative user impressions. 🔸Designers can significantly improve wallet user experience. 🔸Testing compatibility between wallets is essential for user satisfaction. 🔸Tether's integration may boost Bitcoin adoption. 🔸Developers should prioritize payment capabilities before receiving capabilities. 🔸Collaboration between designers and developers can lead to better products. 🔸User experience improvements can be low-hanging fruit for wallet projects. 🔸A global hackathon aims to promote miner decentralization. 🔸Resources like BOLT12 and the Bitcoin Design Guide are valuable for developers. 🔸Engaging with the community can lead to innovative solutions. ### Timestamps ([00:00](/watch?v=GTSqoFKs1cE)) - Intro ([01:10](/watch?v=GTSqoFKs1cE&t=70s)) - What is the current state of Bitcoin usage - Payments or Savings? ([04:32](/watch?v=GTSqoFKs1cE&t=272s)) - Comparing Bitcoin with physical cash ([07:08](/watch?v=GTSqoFKs1cE&t=428s)) - What is the western perspective on Bitcoin payments? ([11:30](/watch?v=GTSqoFKs1cE&t=690s)) - Would people use Bitcoin more with improved UX? ([17:05](/watch?v=GTSqoFKs1cE&t=1025s)) - Exploring payment protocols: Bolt11, LNURL, Bolt12 & BIP353 ([30:14](/watch?v=GTSqoFKs1cE&t=1814s)) - Navigating Bitcoin wallet compatibility challenges ([34:45](/watch?v=GTSqoFKs1cE&t=2085s)) - What is the role of designers in wallet development? ([43:13](/watch?v=GTSqoFKs1cE&t=2593s)) - Rumble’s integration of Tether & Bitcoin; The impact of Tether on Bitcoin adoption ([51:22](/watch?v=GTSqoFKs1cE&t=3082s)) - Resources for wallet developers and designers ### Links: • [https://x.com/conorokus](https://x.com/conorokus) • [https://x.com/StephenDeLorme](https://x.com/StephenDeLorme) • [https://bolt12.org/](https://bolt12.org/) • [https://twelve.cash/](https://twelve.cash) • [https://bitcoin.design/guide/](https://bitcoin.design/guide/) • Setting Up Bitcoin Tips for Streamers](/watch?v=IWTpSN8IaLE) originally posted at https://stacker.news/items/923714
@ 57d1a264:69f1fee1
2025-03-24 17:08:06Nice podcast with @sbddesign and @ConorOkus about bitcoin payments. https://www.youtube.com/watch?v=GTSqoFKs1cE In this episode, Conor, Open Source product manager at Spiral & Stephen, Product Designer at Voltage & Co founder of ATL Bitlab join Stephan to discuss the current state of Bitcoin user experience, particularly focusing on payments and the challenges faced by users. They explore the comparison between Bitcoin and physical cash, the Western perspective on Bitcoin payments, and the importance of user experience in facilitating Bitcoin transactions. They also touch upon various payment protocols like #BOLT11, #LNURL, and #BOLT12, highlighting the need for interoperability and better privacy features in the Bitcoin ecosystem. The discussion also covers resources available for developers and designers to enhance wallet usability and integration. @StephanLivera Official Podcast Episode: https://stephanlivera.com/646 ### Takeaways 🔸Bitcoin has excelled as a savings technology. 🔸The payments use case for Bitcoin still needs improvement. 🔸User experience is crucial for Bitcoin adoption. 🔸Comparing Bitcoin to cash highlights privacy concerns. 🔸Western users may not see a payments problem. 🔸Regulatory issues impact Bitcoin payments in the West. 🔸User experience challenges hinder Bitcoin transactions. 🔸Different payment protocols create compatibility issues. 🔸Community collaboration is essential for Bitcoin's future. 🔸Improving interoperability can enhance Bitcoin payments. Wallet compatibility issues can create negative user impressions. 🔸Designers can significantly improve wallet user experience. 🔸Testing compatibility between wallets is essential for user satisfaction. 🔸Tether's integration may boost Bitcoin adoption. 🔸Developers should prioritize payment capabilities before receiving capabilities. 🔸Collaboration between designers and developers can lead to better products. 🔸User experience improvements can be low-hanging fruit for wallet projects. 🔸A global hackathon aims to promote miner decentralization. 🔸Resources like BOLT12 and the Bitcoin Design Guide are valuable for developers. 🔸Engaging with the community can lead to innovative solutions. ### Timestamps ([00:00](/watch?v=GTSqoFKs1cE)) - Intro ([01:10](/watch?v=GTSqoFKs1cE&t=70s)) - What is the current state of Bitcoin usage - Payments or Savings? ([04:32](/watch?v=GTSqoFKs1cE&t=272s)) - Comparing Bitcoin with physical cash ([07:08](/watch?v=GTSqoFKs1cE&t=428s)) - What is the western perspective on Bitcoin payments? ([11:30](/watch?v=GTSqoFKs1cE&t=690s)) - Would people use Bitcoin more with improved UX? ([17:05](/watch?v=GTSqoFKs1cE&t=1025s)) - Exploring payment protocols: Bolt11, LNURL, Bolt12 & BIP353 ([30:14](/watch?v=GTSqoFKs1cE&t=1814s)) - Navigating Bitcoin wallet compatibility challenges ([34:45](/watch?v=GTSqoFKs1cE&t=2085s)) - What is the role of designers in wallet development? ([43:13](/watch?v=GTSqoFKs1cE&t=2593s)) - Rumble’s integration of Tether & Bitcoin; The impact of Tether on Bitcoin adoption ([51:22](/watch?v=GTSqoFKs1cE&t=3082s)) - Resources for wallet developers and designers ### Links: • [https://x.com/conorokus](https://x.com/conorokus) • [https://x.com/StephenDeLorme](https://x.com/StephenDeLorme) • [https://bolt12.org/](https://bolt12.org/) • [https://twelve.cash/](https://twelve.cash) • [https://bitcoin.design/guide/](https://bitcoin.design/guide/) • Setting Up Bitcoin Tips for Streamers](/watch?v=IWTpSN8IaLE) originally posted at https://stacker.news/items/923714 @ 866e0139:6a9334e5
2025-03-24 10:50:59**Autor:** *Ludwig F. Badenhagen.* *Dieser Beitrag wurde mit dem* *[Pareto-Client](https://pareto.space/read)* *geschrieben.* *** Einer der wesentlichen Gründe dafür, dass während der „Corona-Pandemie“ so viele Menschen den Anweisungen der Spitzenpolitiker folgten, war sicher der, dass diese Menschen den Politikern vertrauten. Diese Menschen konnten sich nicht vorstellen, dass Spitzenpolitiker den Auftrag haben könnten, die Bürger analog klaren Vorgaben zu belügen, zu betrügen und sie vorsätzlich (tödlich) zu verletzen. Im Gegenteil, diese gutgläubigen Menschen waren mit der Zuversicht aufgewachsen, dass Spitzenpolitiker den Menschen dienen und deren Wohl im Fokus haben (müssen). Dies beteuerten Spitzenpolitiker schließlich stets in Talkshows und weiteren Medienformaten. Zwar wurden manche Politiker auch bei Fehlverhalten erwischt, aber hierbei ging es zumeist „nur“ um Geld und nicht um Leben. Und wenn es doch einmal um Leben ging, dann passieren die Verfehlungen „aus Versehen“, aber nicht mit Vorsatz. So oder so ähnlich dachte die Mehrheit der Bürger. Aber vor 5 Jahren änderte sich für aufmerksame Menschen alles, denn analog dem Lockstep-Szenario der Rockefeller-Foundation wurde der zuvor ausgiebig vorbereitete Plan zur Inszenierung der „Corona-Pandemie“ Realität. Seitdem wurde so manchem Bürger, der sich jenseits von Mainstream-Medien informierte, das Ausmaß der unter dem Vorwand einer erfundenen Pandemie vollbrachten Taten klar. Und unverändert kommen täglich immer neue Erkenntnisse ans Licht. Auf den Punkt gebracht war die Inszenierung der „Corona-Pandemie“ ein Verbrechen an der Menschheit, konstatieren unabhängige Sachverständige. Dieser Beitrag befasst sich allerdings nicht damit, die vielen Bestandteile dieses Verbrechens (nochmals) aufzuzählen oder weitere zu benennen. Stattdessen soll beleuchtet werden, warum die Spitzenpolitiker sich so verhalten haben und ob es überhaupt nach alledem möglich ist, der Politik jemals wieder zu vertrauen? Ferner ist es ein Anliegen dieses Artikels, die weiteren Zusammenhänge zu erörtern. Und zu guter Letzt soll dargelegt werden, warum sich der große Teil der Menschen unverändert alles gefallen lässt. **Demokratie** Von jeher organisierten sich Menschen mit dem Ziel, Ordnungsrahmen zu erschaffen, welche wechselseitiges Interagieren regeln. Dies führte aber stets dazu, dass einige wenige alle anderen unterordneten. Der Grundgedanke, der vor rund 2500 Jahren formulierten Demokratie, verfolgte dann aber das Ziel, dass die Masse darüber entscheiden können soll, wie sie leben und verwaltet werden möchte. Dieser Grundgedanke wurde von den Mächtigen sowohl gehasst als auch gefürchtet, denn die Gefahr lag nahe, dass die besitzlosen Vielen beispielsweise mit einer schlichten Abstimmung verfügen könnten, den Besitz der Wenigen zu enteignen. Selbst Sokrates war gegen solch eine Gesellschaftsordnung, da die besten Ideen nicht durch die Vielen, sondern durch einige wenige Kluge und Aufrichtige in die Welt kommen. Man müsse die Vielen lediglich manipulieren und würde auf diese Weise quasi jeden Unfug umsetzen können. Die Demokratie war ein Rohrkrepierer. **Die Mogelpackung „Repräsentative Demokratie“** Erst im Zuge der Gründung der USA gelang der Trick, dem Volk die „Repräsentative Demokratie“ unterzujubeln, die sich zwar nach Demokratie anhört, aber mit der Ursprungsdefinition nichts zu tun hat. Man konnte zwischen zwei Parteien wählen, die sich mit ihren jeweiligen Versprechen um die Gunst des Volkes bewarben. Tatsächlich paktierten die Vertreter der gewählten Parteien (Politiker) aber mit den wirklich Mächtigen, die letztendlich dafür sorgten, dass diese Politiker in die jeweiligen exponierten Positionen gelangten, welche ihnen ermöglichten (und somit auch den wirklich Mächtigen), Macht auszuüben. Übrigens, ob die eine oder andere Partei „den Volkswillen“ für sich gewinnen konnte, war für die wirklich Mächtigen weniger von Bedeutung, denn der Wille der wirklich Mächtigen wurde so oder so, wenn auch in voneinander differierenden Details, umgesetzt. Die Menschen waren begeistert von dieser Idee, denn sie glaubten, dass sie selbst „der Souverän“ seien. Schluss mit Monarchie sowie sonstiger Fremdherrschaft und Unterdrückung. Die Mächtigen waren ebenfalls begeistert, denn durch die Repräsentative Demokratie waren sie selbst nicht mehr in der Schusslinie, weil das Volk sich mit seinem Unmut fortan auf die Politiker konzentrierte. Da diese Politiker aber vielleicht nicht von einem selbst, sondern von vielen anderen Wahlberechtigten gewählt wurden, lenkte sich der Groll der Menschen nicht nur ab von den wirklich Mächtigen, sondern auch ab von den Politikern, direkt auf „die vielen Idioten“ aus ihrer eigenen Mitte, die sich „ver-wählt“ hatten. Diese Lenkung des Volkes funktionierte so hervorragend, dass andere Länder die Grundprinzipien dieses Steuerungsinstrumentes übernahmen. Dies ist alles bei Rainer Mausfeld nachzulesen. Ursprünglich waren die Mächtigen nur regional mächtig, sodass das Führen der eigenen Menschen(vieh)herde eher eine lokale Angelegenheit war. Somit mussten auch nur lokale Probleme gelöst werden und die Mittel zur Problemlösung blieben im eigenen Problembereich. *** JETZT ABONNIEREN: ***[Hier](https://pareto.space/u/friedenstaube@pareto.space)*** *können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).* *** * Für **50 CHF/EURO** bekommen Sie ein Jahresabo der Friedenstaube. * Für **120 CHF/EURO** bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube. * Für **500 CHF/EURO** werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube. * Ab **1000 CHF/EURO** werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie). **Für Einzahlungen in CHF (Betreff: Friedenstaube):** [](https://substackcdn.com/image/fetch/f_auto%2Cq_auto%3Agood%2Cfl_progressive%3Asteep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F3fdee17a-c22f-404e-a10c-7f87a7b8182a_2176x998.png) **Für Einzahlungen in Euro:** Milosz Matuschek IBAN DE 53710520500000814137 BYLADEM1TST Sparkasse Traunstein-Trostberg **Betreff: Friedenstaube** Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: <milosz@pareto.space> oder <kontakt@idw-europe.org>. *** **Beherrschungsinstrumente der globalen Massenhaltung** Im Zuge der territorialen Erweiterungen der „Besitzungen“ einiger wirklich Mächtiger wurden die Verwaltungs- und Beherrschungsinstrumente überregionaler. Und heute, zu Zeiten der globalen Vernetzung, paktieren die wirklich Mächtigen miteinander und beanspruchen die Weltherrschaft. Längst wird offen über die finale Realisierung einen Weltregierung, welche die Nationalstaaten „nicht mehr benötigt“, gesprochen. Dass sich Deutschland, ebenso wie andere europäische Staaten, der EU untergeordnet hat, dürfte auch Leuten nicht entgangen sein, die sich nur über die Tagesschau informieren. Längst steht das EU-Recht über dem deutschen Recht. Und nur kurze Zeit ist es her, als die EU und alle ihre Mitgliedsstaaten die WHO autonom darüber entscheiden lassen wollten, was eine Pandemie ist und wie diese für alle verbindlich „bekämpft“ werden soll. Eine spannende Frage ist nun, wer denn über der EU und der WHO sowie anderen Institutionen steht? Diese Beschreibung macht klar, dass ein „souveränes Land“ wie das unverändert von der amerikanischen Armee besetzte Deutschland in der Entscheidungshierarchie an die Weisungen übergeordneter Entscheidungsorgane gebunden ist. An der Spitze stehen - wie kann es anders sein - die wirklich Mächtigen. Aber was nützt es dann, Spitzenpolitiker zu wählen, wenn diese analog Horst Seehofer nichts zu melden haben? Ist das Wählen von Politikern nicht völlig sinnlos, wenn deren Wahlversprechen ohnehin nicht erfüllt werden? Ist es nicht so, dass die Menschen, welche ihre Stimme nicht behalten, sondern abgeben, das bestehende System nur nähren, indem sie Wahlergebnisse akzeptieren, ohne zu wissen, ob diese manipuliert wurden, aber mit der Gewissheit, dass das im Zuge des Wahlkampfes Versprochene auf keinen Fall geliefert wird? Aktive Wähler glauben trotz allem an die Redlichkeit und Wirksamkeit von Wahlen, und sie akzeptieren Wahlergebnisse, weil sie denken, dass sie von „so vielen Idioten, die falsch wählen“, umgeben sind, womit wir wieder bei der Spaltung sind. Sie glauben, der Stand des aktuellen Elends sei „selbst gewählt“. **Die Wahl der Aufseher** Stellen Sie sich bitte vor, Sie wären im Gefängnis, weil Sie einen kritischen Artikel mit „gefällt mir“ gekennzeichnet haben oder weil Sie eine „Kontaktschuld“ trifft, da in Ihrer Nachbarschaft ein „verschwörerisches Symbol“ von einem „aufmerksamen“ Nachbarn bei einer „Meldestelle“ angezeigt wurde oder Sie gar eine Tat, „unterhalb der Strafbarkeitsgrenze“ begangen hätten, dann würden Sie möglicherweise mit Maßnahmen bestraft, die „keine Folter wären“. Beispielsweise würde man Sie während Ihrer „Umerziehungshaft“ mit Waterboarding, Halten von Stresspositionen, Dunkelhaft etc. dabei „unterstützen“, „Ihre Verfehlungen zu überdenken“. Stellen Sie sich weiterhin vor, dass Sie, so wie alle anderen Inhaftierten, an der alle vier Jahre stattfindenden Wahl der Aufseher teilnehmen könnten, und Sie hätten auch einen Favoriten, der zwar Waterboarding betreibt, aber gegen alle anderen Maßnahmen steht. Sie hätten sicher allen Grund zur Freude, wenn Sie Ihren Kandidaten durchbringen könnten, oder? Aber was wäre, wenn der Aufseher Ihrer Wahl dann dennoch alle 3 „Nicht-Folter-Maßnahmen“ anwenden würde, wie sämtliche anderen Aufseher zuvor? Spätestens dann müssten Sie sich eingestehen, dass es der Beruf des Aufsehers ist, Aufseher zu sein und dass er letztendlich tut, was ihm „von oben“ aufgetragen wird. Andernfalls verliert er seinen Job. Oder er verunfallt oder gerät in einen Skandal etc. So oder so, er verliert seinen Job - und den erledigt dann ein anderer Aufseher. Die Wahl des Aufsehers ändert wenig, solange Sie sich im System des Gefängnisses befinden und der Aufseher integraler Bestandteil dieses Systems ist. Zur Realisierung einer tatsächlichen Änderung müssten Sie dort herauskommen. Dieses Beispiel soll darstellen, dass alles in Hierarchien eingebunden ist. Die in einem System eingebundenen Menschen erfüllen ihre zugewiesenen Aufgaben, oder sie werden bestraft. **Das aktuelle System schadet dem Volk** Auch in der staatlichen Organisation von Menschen existieren hierarchische Gliederungen. Eine kommunale Selbstverwaltung gehört zum Kreis, dieser zum Land, dieses zum Staat, dieser zur EU, und diese - zu wem auch immer. Und vereinnahmte Gelder fließen nach oben. Obwohl es natürlich wäre, dass die Mittel dorthin fließen, wo sie der Allgemeinheit und nicht einigen wenigen dienen, also nach unten. Warum muss es also eine Weltregierung geben? Warum sollen nur einige Wenige über alle anderen bestimmen und an diesen verdienen (Nahrung, Medikamente, Krieg, Steuern etc.)? Warum sollen Menschen, so wie Vieh, das jemandem „gehört“, mit einem Code versehen und bereits als Baby zwangsgeimpft werden? Warum müssen alle Transaktionen und sämtliches Verhalten strickt gesteuert, kontrolliert und bewertet werden? Viele Menschen werden nach alledem zu dem Schluss kommen, dass solch ein System nur einigen wenigen wirklich Mächtigen und deren Helfershelfern nützt. Aber es gibt auch eine Gruppe Menschen, für die im Land alles beanstandungsfrei funktioniert. Die Spaltung der Menschen ist perfekt gelungen und sofern die eine Gruppe darauf wartet, dass die andere „endlich aufwacht“, da die Fakten doch auf dem Tisch liegen, so wird sie weiter warten dürfen. Julian Assange erwähnte einst, dass es für ihn eine unglaubliche Enttäuschung war, dass ihm niemand half. Assange hatte Ungeheuerlichkeiten aufgedeckt. Es gab keinen Aufstand. Assange wurde inhaftiert und gefoltert. Es gab keinen Aufstand. Assange sagte, er hätte nicht damit gerechnet, dass die Leute „so unglaublich feige“ seien. Aber womit rechnete er den stattdessen? Dass die Massen „sich erheben“. Das gibt es nur im Film, denn die Masse besteht aus vielen maximal Indoktrinierten, die sich wie Schafe verhalten, was als Züchtungserfolg der Leute an den Schalthebeln der Macht und deren Herren, den wirklich Mächtigen, anzuerkennen ist. Denn wer mächtig ist und bleiben möchte, will sicher keine problematischen Untertanen, sondern eine gefügige, ängstliche Herde, die er nach Belieben ausbeuten und steuern kann. Wenn er hierüber verfügt, will er keinen Widerstand. Ob Corona, Krieg, Demokratie- und Klimarettung oder Meinungsäußerungsverbote und Bürgerrechte, die unterhalb der Strafbarkeitsgrenze liegen, all diese und viele weitere Stichworte mehr sind es, die viele traurig und so manche wütend machen. Auch das Mittel des Demonstrierens hat sich als völlig wirkungslos erwiesen. Die vielen gruseligen Videoaufnahmen über die massivsten Misshandlungen von Demonstranten gegen die Corona-Maßnahmen führen zu dem Ergebnis, dass die Exekutive ihr Gewaltmonopol nutzt(e), um die Bevölkerung gezielt zu verletzen und einzuschüchtern. Bekanntlich kann jede friedliche Demonstration zum Eskalieren gebracht werden, indem man Menschen in die Enge treibt (fehlender Sicherheitsabstand) und einige V-Leute in Zivil mit einschlägigen Flaggen und sonstigen „Symbolen“ einschleust, die für Krawall sorgen, damit die gepanzerten Kollegen dann losknüppeln und die scharfen Hunde zubeißen können. So lauten zumindest die Berichte vieler Zeitzeugen und so ist es auch auf vielen Videos zu sehen. Allerdings nicht im Mainstream. Dieses Vorgehen ist deshalb besonders perfide, weil man den Deutschen ihre Wehrhaftigkeit aberzogen hat. Nicht wehrfähige Bürger und eine brutale Staatsmacht mit Gewaltmonopol führen zu einem Gemetzel bei den Bürgern. Ähnliches lässt sich auch in zivilen Lebenssituationen beobachten, wenn die hiesige zivilisierte Bevölkerung auf „eingereiste“ Massenvergewaltiger und Messerstecher trifft, die über ein anderes Gewalt- und Rechtsverständnis verfügen als die Einheimischen. **System-Technik** Die These ist, dass es eine Gruppe von global agierenden Personen gibt, welche das Geschehen auf der Erde zunehmend wirksam zu ihrem individuellen Vorteil gestaltet. Wie sich diese Gruppe definiert, kann bei John Coleman (Das Komitee der 300) und David Icke nachgelesen werden. Hierbei handelt es ich um Autoren, die jahrzehntelang analog streng wissenschaftlichen Grundlagen zu ihren Themen geforscht haben und in ihren jeweiligen Werken sämtliche Quellen benennen. Diese Autoren wurden vom Mainstream mit dem Prädikatsmerkmal „Verschwörungstheoretiker“ ausgezeichnet, wodurch die Ergebnisse Ihrer Arbeiten umso glaubwürdiger sind. Diese mächtige Gruppe hat mit ihren Schergen nahezu den gesamten Planeten infiltriert, indem sie Personen in führenden Positionen in vielen Belangen größtmögliche Freiheiten sowie Schutz gewährt, aber diesen im Gegenzug eine völlige Unterwerfung bei Kernthemen abfordert. Die Motivatoren für diese Unterwerfung sind, abgesehen von materiellen Zuwendungen, auch „Ruhm und Ehre sowie Macht“. Manchmal wird auch Beweismaterial für begangene Verfehlungen (Lolita-Express, Pizzagate etc.) genutzt, um Forderungen Nachdruck zu verleihen. Und auch körperliche Bestrafungen der betroffenen Person oder deren Angehörigen zählen zum Repertoire der Motivatoren. Letztendlich ähnlich den Verhaltensweisen in einem Mafia-Film. Mit dieser Methodik hat sich diese mächtige Gruppe im Laufe von Jahrhunderten! eine Organisation erschaffen, welche aus Kirchen, Parteien, Firmen, NGO, Vereinen, Verbänden und weiteren Organisationsformen besteht. Bestimmte Ämter und Positionen in Organisationen können nur von Personen eingenommen und gehalten werden, die „auf Linie sind“. Die Mitglieder der Gruppe tauchen in keiner Rubrik wie „Die reichsten Menschen der Welt“ auf, sondern bleiben fern der Öffentlichkeit. Wer jemanden aus ihren Reihen erkennt und beschuldigt, ist ein „Antisemit“ oder sonstiger Übeltäter und wird verfolgt und bekämpft. Über mächtige Vermögensverwaltungskonzerne beteiligen sich die Mitglieder dieser Gruppe anonym an Unternehmen in Schlüsselpositionen in einer Dimension, die ihnen wesentlichen Einfluss auf die Auswahl der Topmanager einräumt, sodass die jeweilige Unternehmenspolitik nach Vorgaben der Gruppe gestaltet wird. Die Gruppe steuert das Geldsystem, von dem sich der Planet abhängig zu sein wähnt. Hierzu eine Erläuterung: Ein Staat wie Deutschland ist bekanntlich maximal verschuldet. Man stelle sich vor, ein unliebsamer Politiker würde entgegen sämtlicher „Brandmauern“ und sonstiger Propaganda und Wahlmanipulationen gewählt, das Land zu führen, dann könnte dieser keine Kredit über 500 Mrd. Euro bei der nächsten Sparkasse beantragen, sondern wäre auf die Mächtigen dieser Welt angewiesen. Jeder weiß, dass Deutschland als Staat kein funktionierendes Geschäftsmodell hat und somit nicht in der Lage ist, solch ein Darlehen zurückzuzahlen. Welche Motivation sollte also jemand haben, einem Land wie Deutschland so viel Geld ohne Aussicht auf Rückführung zu geben? Es leuchtet ein, dass dieser Politiker andere Gefälligkeiten anbieten müsste, um das Darlehen zu bekommen. Im Falle einer Weigerung zur Kooperation könnte der Staatsapparat mit seinen Staatsdienern, Bürgergeld- und Rentenempfänger etc. nicht mehr bezahlt werden und dieser Politiker wäre schnell wieder weg. Er würde medial hingerichtet. Es ist somit davon auszugehen, dass ein Spitzenpolitiker dieser Tage nicht über viele Optionen verfügt, denn er übernimmt eine Situation, die von seinen Vorgängern erschaffen wurde. Trotz alledem darauf zu hoffen, dass es einen anderen Politiker geben könnte, mit dem dann alles wieder gut wird, mutet ziemlich infantil an. Dass ein Großteil der Medien von Zuwendungen abhängig ist, dürfte ebenfalls leicht nachzuvollziehen sein, denn der gewöhnliche Bürger zahlt nichts für den Content der MSM. Abhängig davon, von wem (Regierung, Philanthrop, Konzern etc.) ein Medium am Leben gehalten wird, gestalten sich auch dessen Inhalte. Und wenn angewiesen wird, dass ein Politiker medial hingerichtet werden soll, dann bedient die Maschinerie das Thema. Man beobachte einfach einmal, dass Politiker der Kartell-Parteien völlig anders behandelt werden als solche jenseits der „Brandmauer“. Und der Leser, der solche Auftragsarbeiten kostenlos liest, ist der Konsument, für dessen Indoktrination die Finanziers der Verlage gerne zahlen. Mittlerweile kann durch die Herrschaft über die Medien und die systematische Vergiftung der Körper und Geister der Population die öffentliche Meinung gesteuert werden. Die überwiegende Zahl der Deutschen scheint nicht mehr klar denken zu können. Wer sich das aktuelle Geschehen in der deutschen Politik mit klarem Verstand ansieht, kommt nicht umhin, eine Fernsteuerung der handelnden Politiker in Betracht zu ziehen. Aber was soll daran verwundern? Sind es deshalb „böse Menschen“? Sind die in „Forschungslaboren“ arbeitenden Quäler von „Versuchstieren“ böse Menschen? Sind der Schlächter, der Folterer und der Henker böse Menschen? Oder der knüppelnde Polizist? Es handelt sich zunächst einmal um Personen, die einen Vorteil dadurch haben, Ihrer Tätigkeit nachzugehen. Sie sind integrale Bestandteile eines Belohnungssystems, welches von oben nach unten Anweisungen gibt. Und wenn diese Anweisungen nicht befolgt werden, führt dies für den Befehlsverweigerer zu Konsequenzen. **Der klare Verstand** Es ist nun eine spannende Frage, warum so viele Menschen sich solch eine Behandlung gefallen lassen? Nun, das ist relativ einfach, denn das angepasste Verhalten der Vielen ist nichts anderes als ein Züchtungserfolg der Wenigen. Die Psyche der Menschen ist ebenso akribisch erforscht worden wie deren Körperfunktionen. Würden die Menschen von den wirklich Mächtigen geliebt, dann würde genau gewusst, wie sie zu behandeln und mit ihren jeweiligen Bedürfnissen zu versorgen sind. Stattdessen werden die Menschen aber als eine Einnahmequelle betrachtet. Dies manifestiert sich exemplarisch in folgenden Bereichen: 1. Das Gesundheitssystem verdient nichts am gesunden Menschen, sondern nur am (dauerhaft) kranken, der um Schmerzlinderung bettelt. Bereits als Baby werden Menschen geimpft, was die jeweilige Gesundheit (mit Verweis auf die Werke von Anita Petek-Dimmer u. a.) nachhaltig negativ beeinflusst. Wer hat denn heute keine Krankheiten? Die „Experten“ des Gesundheitssystems verteufeln Vitamin D, Vitamin C, Lithium, die Sonne, Natur etc. und empfehlen stattdessen Präparate, die man patentieren konnte und mit denen die Hersteller viel Geld verdienen. Die Präparate heilen selten, sondern lindern bestenfalls zuvor künstlich erzeugte Leiden, und müssen oftmals dauerhaft eingenommen werden. Was ist aus den nicht Geimpften geworden, die alle sterben sollten? Sind diese nicht die einzigen Gesunden dieser Tage? Ist nicht jeder Geimpfte entweder permanent krank oder bereits tot? Abgesehen von denen, welche das Glück hatten, „Sonderchargen“ mit Kochsalz zu erhalten. \ \ Wem gehören die wesentlichen Player im Gesundheitswesen zu einem erheblichen Teil? Die Vermögensverwalter der wirklich Mächtigen. 2. Ähnlich gestaltet es sich bei der Ernährungsindustrie. Die von dort aus verabreichten Produkte sind die Ursachen für den Gesundheitszustand der deutschen Population. Das ist aber auch irgendwie logisch, denn wer sich nicht falsch ernährt und gesund bleibt, wird kein Kunde des Gesundheitswesens. \ \ Die Besitzverhältnisse in der Ernährungsindustrie ähneln denen im Gesundheitswesen, sodass am gleichen Kunden gearbeitet und verdient wird. 3. Die Aufzählung konnte nun über die meisten Branchen, in denen mit dem Elend der Menschen viel verdient werden kann, fortgesetzt werden. Waffen (BlackRock erhöhte beispielsweise seine Anteile an der Rheinmetall AG im Juni 2024 auf 5,25 Prozent. Der US-Vermögensverwalter ist damit der zweitgrößte Anteilseigner nach der französischen Großbank Société Générale.), Energie, Umwelt, Technologie, IT, Software, KI, Handel etc. Wie genau Chemtrails und Technologien wie 5G auf den Menschen und die Tiere wirken, ist ebenfalls umstritten. Aber ist es nicht seltsam, wie krank, empathielos, antriebslos und aggressiv viele Menschen heute sind? Was genau verabreicht man der Berliner Polizei, damit diese ihre Prügelorgien auf den Rücken und in den Gesichtern der Menschen wahrnehmen, die friedlich ihre Demonstrationsrechte wahrnehmen? Und was erhalten die ganzen zugereisten „Fachkräfte“, die mit Ihren Autos in Menschenmengen rasen oder auch Kinder und Erwachsene niedermessern? Das Titelbild dieses Beitrags zeigt einige Gebilde, welche regelmäßig bei Obduktionen von Geimpften in deren Blutgefäßen gefunden werden. Wie genau wirken diese kleinen Monster? Können wir Menschen ihr Unverständnis und ihr Nicht-Aufwachen vorwerfen, wenn wir erkennen, dass diese Menschen maximal vergiftet wurden? Oder sollten einfach Lösungen für die Probleme dieser Zeit auch ohne den Einbezug derer gefunden werden, die offenbar nicht mehr Herr ihrer Sinne sind? **Die Ziele der wirklich Mächtigen** Wer sich entsprechende Videosequenzen der Bilderberger, des WEF und anderen „Überorganisationen“ ansieht, der erkennt schnell das Muster: * Reduzierung der Weltpopulation um ca. 80 Prozent * Zusammenbruch der Wirtschaft, damit diese von den Konzernen übernommen werden kann. * Zusammenbruch der öffentlichen Ordnung, um eine totale Entwaffnung und eine totale Überwachung durchsetzen zu können. * Zusammenbruch der Regierungen, damit die Weltregierung übernehmen kann. Es ist zu überdenken, ob die Weltregierung tatsächlich das für die Vielen beste Organisationssystem ist, oder ob die dezentrale Eigenorganisation der jeweils lokalen Bevölkerung nicht doch die bessere Option darstellt. Baustellen würden nicht nur begonnen, sondern auch schnell abgearbeitet. Jede Region könnte bestimmen, ob sie sich mit Chemtrails und anderen Substanzen besprühen lassen möchte. Und die Probleme in Barcelona könnte die Menschen dort viel besser lösen als irgendwelche wirklich Mächtigen in ihren Elfenbeintürmen. Die lokale Wirtschaft könnte wieder zurückkommen und mit dieser die Eigenständigkeit. Denn die den wirklich Mächtigen über ihre Vermögensverwalter gehörenden Großkonzerne haben offensichtlich nicht das Wohl der Bevölkerung im Fokus, sondern eher deren Ausbeutung. Das Aussteigen aus dem System ist die wahre Herkulesaufgabe und es bedarf sicher Mut und Klugheit, sich dieser zu stellen. Die Politiker, die unverändert die Narrative der wirklich Mächtigen bedienen, sind hierfür denkbar ungeeignet, denn sie verfolgen kein Lebensmodell, welches sich von Liebe und Mitgefühl geleitet in den Dienst der Gesamtheit von Menschen, Tieren und Natur stellt. Schauen Sie einmal genau hin, denken Sie nach und fühlen Sie mit. **Was tun?** Jedes System funktioniert nur so lange, wie es unterstützt wird. Somit stellt sich die Frage, wie viele Menschen das System ignorieren müssen, damit es kollabiert, und auf welche Weise dieses Ignorieren durchzuführen ist? Merkbar ist, dass die große Masse der Verwaltungsangestellten krank und oder unmotiviert und somit nicht wirksam ist. Würden die entsprechenden Stellen massiv belastet und parallel hierzu keine Einnahmen mehr realisieren, wäre ein Kollaps nah. Die Prügelpolizisten aus Berlin können nicht überall sein und normale Polizisten arbeiten nicht gegen unbescholtene Bürger, sondern sorgen sich selbst um ihre Zukunft. Gewalt ist sicher keine Lösung, und sicher auch nicht erforderlich. Wie eine gerechte Verwaltungsform aufgebaut werden muss? Einfach so, wie sie in den hiesigen Gesetzen beschrieben steht. Aber eine solche Organisationsform muss frei sein von Blockparteien und korrupten Politikern und weisungsgebundenen Richtern etc. Stattdessen werden Menschen benötigt, welche die Menschen lieben und ihnen nicht schaden wollen. Außerdem sollten diese Führungspersonen auch wirklich etwas können, und nicht nur „Politiker“ ohne weitere Berufserfahrungen sein. *** Ludwig F. Badenhagen (Pseudonym, Name ist der Redaktion bekannt). *Der Autor hat deutsche Wurzeln und betrachtet das Geschehen in Deutschland und Europa aus seiner Wahlheimat Südafrika. Seine Informationen bezieht er aus verlässlichen Quellen und insbesondere von Menschen, die als „Verschwörungstheoretiker“, „Nazi“, „Antisemit“ sowie mit weiteren Kampfbegriffen der dortigen Systemakteure wie Politiker und „Journalisten“ diffamiert werden. Solche Diffamierungen sind für ihn ein Prädikatsmerkmal. Er ist international agierender Manager mit einem globalen Netzwerk und verfügt hierdurch über tiefe Einblicke in Konzerne und Politik.* *** **Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Start.](https://start.njump.me/)**
@ 866e0139:6a9334e5
2025-03-24 10:50:59**Autor:** *Ludwig F. Badenhagen.* *Dieser Beitrag wurde mit dem* *[Pareto-Client](https://pareto.space/read)* *geschrieben.* *** Einer der wesentlichen Gründe dafür, dass während der „Corona-Pandemie“ so viele Menschen den Anweisungen der Spitzenpolitiker folgten, war sicher der, dass diese Menschen den Politikern vertrauten. Diese Menschen konnten sich nicht vorstellen, dass Spitzenpolitiker den Auftrag haben könnten, die Bürger analog klaren Vorgaben zu belügen, zu betrügen und sie vorsätzlich (tödlich) zu verletzen. Im Gegenteil, diese gutgläubigen Menschen waren mit der Zuversicht aufgewachsen, dass Spitzenpolitiker den Menschen dienen und deren Wohl im Fokus haben (müssen). Dies beteuerten Spitzenpolitiker schließlich stets in Talkshows und weiteren Medienformaten. Zwar wurden manche Politiker auch bei Fehlverhalten erwischt, aber hierbei ging es zumeist „nur“ um Geld und nicht um Leben. Und wenn es doch einmal um Leben ging, dann passieren die Verfehlungen „aus Versehen“, aber nicht mit Vorsatz. So oder so ähnlich dachte die Mehrheit der Bürger. Aber vor 5 Jahren änderte sich für aufmerksame Menschen alles, denn analog dem Lockstep-Szenario der Rockefeller-Foundation wurde der zuvor ausgiebig vorbereitete Plan zur Inszenierung der „Corona-Pandemie“ Realität. Seitdem wurde so manchem Bürger, der sich jenseits von Mainstream-Medien informierte, das Ausmaß der unter dem Vorwand einer erfundenen Pandemie vollbrachten Taten klar. Und unverändert kommen täglich immer neue Erkenntnisse ans Licht. Auf den Punkt gebracht war die Inszenierung der „Corona-Pandemie“ ein Verbrechen an der Menschheit, konstatieren unabhängige Sachverständige. Dieser Beitrag befasst sich allerdings nicht damit, die vielen Bestandteile dieses Verbrechens (nochmals) aufzuzählen oder weitere zu benennen. Stattdessen soll beleuchtet werden, warum die Spitzenpolitiker sich so verhalten haben und ob es überhaupt nach alledem möglich ist, der Politik jemals wieder zu vertrauen? Ferner ist es ein Anliegen dieses Artikels, die weiteren Zusammenhänge zu erörtern. Und zu guter Letzt soll dargelegt werden, warum sich der große Teil der Menschen unverändert alles gefallen lässt. **Demokratie** Von jeher organisierten sich Menschen mit dem Ziel, Ordnungsrahmen zu erschaffen, welche wechselseitiges Interagieren regeln. Dies führte aber stets dazu, dass einige wenige alle anderen unterordneten. Der Grundgedanke, der vor rund 2500 Jahren formulierten Demokratie, verfolgte dann aber das Ziel, dass die Masse darüber entscheiden können soll, wie sie leben und verwaltet werden möchte. Dieser Grundgedanke wurde von den Mächtigen sowohl gehasst als auch gefürchtet, denn die Gefahr lag nahe, dass die besitzlosen Vielen beispielsweise mit einer schlichten Abstimmung verfügen könnten, den Besitz der Wenigen zu enteignen. Selbst Sokrates war gegen solch eine Gesellschaftsordnung, da die besten Ideen nicht durch die Vielen, sondern durch einige wenige Kluge und Aufrichtige in die Welt kommen. Man müsse die Vielen lediglich manipulieren und würde auf diese Weise quasi jeden Unfug umsetzen können. Die Demokratie war ein Rohrkrepierer. **Die Mogelpackung „Repräsentative Demokratie“** Erst im Zuge der Gründung der USA gelang der Trick, dem Volk die „Repräsentative Demokratie“ unterzujubeln, die sich zwar nach Demokratie anhört, aber mit der Ursprungsdefinition nichts zu tun hat. Man konnte zwischen zwei Parteien wählen, die sich mit ihren jeweiligen Versprechen um die Gunst des Volkes bewarben. Tatsächlich paktierten die Vertreter der gewählten Parteien (Politiker) aber mit den wirklich Mächtigen, die letztendlich dafür sorgten, dass diese Politiker in die jeweiligen exponierten Positionen gelangten, welche ihnen ermöglichten (und somit auch den wirklich Mächtigen), Macht auszuüben. Übrigens, ob die eine oder andere Partei „den Volkswillen“ für sich gewinnen konnte, war für die wirklich Mächtigen weniger von Bedeutung, denn der Wille der wirklich Mächtigen wurde so oder so, wenn auch in voneinander differierenden Details, umgesetzt. Die Menschen waren begeistert von dieser Idee, denn sie glaubten, dass sie selbst „der Souverän“ seien. Schluss mit Monarchie sowie sonstiger Fremdherrschaft und Unterdrückung. Die Mächtigen waren ebenfalls begeistert, denn durch die Repräsentative Demokratie waren sie selbst nicht mehr in der Schusslinie, weil das Volk sich mit seinem Unmut fortan auf die Politiker konzentrierte. Da diese Politiker aber vielleicht nicht von einem selbst, sondern von vielen anderen Wahlberechtigten gewählt wurden, lenkte sich der Groll der Menschen nicht nur ab von den wirklich Mächtigen, sondern auch ab von den Politikern, direkt auf „die vielen Idioten“ aus ihrer eigenen Mitte, die sich „ver-wählt“ hatten. Diese Lenkung des Volkes funktionierte so hervorragend, dass andere Länder die Grundprinzipien dieses Steuerungsinstrumentes übernahmen. Dies ist alles bei Rainer Mausfeld nachzulesen. Ursprünglich waren die Mächtigen nur regional mächtig, sodass das Führen der eigenen Menschen(vieh)herde eher eine lokale Angelegenheit war. Somit mussten auch nur lokale Probleme gelöst werden und die Mittel zur Problemlösung blieben im eigenen Problembereich. *** JETZT ABONNIEREN: ***[Hier](https://pareto.space/u/friedenstaube@pareto.space)*** *können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).* *** * Für **50 CHF/EURO** bekommen Sie ein Jahresabo der Friedenstaube. * Für **120 CHF/EURO** bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube. * Für **500 CHF/EURO** werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube. * Ab **1000 CHF/EURO** werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie). **Für Einzahlungen in CHF (Betreff: Friedenstaube):** [](https://substackcdn.com/image/fetch/f_auto%2Cq_auto%3Agood%2Cfl_progressive%3Asteep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F3fdee17a-c22f-404e-a10c-7f87a7b8182a_2176x998.png) **Für Einzahlungen in Euro:** Milosz Matuschek IBAN DE 53710520500000814137 BYLADEM1TST Sparkasse Traunstein-Trostberg **Betreff: Friedenstaube** Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: <milosz@pareto.space> oder <kontakt@idw-europe.org>. *** **Beherrschungsinstrumente der globalen Massenhaltung** Im Zuge der territorialen Erweiterungen der „Besitzungen“ einiger wirklich Mächtiger wurden die Verwaltungs- und Beherrschungsinstrumente überregionaler. Und heute, zu Zeiten der globalen Vernetzung, paktieren die wirklich Mächtigen miteinander und beanspruchen die Weltherrschaft. Längst wird offen über die finale Realisierung einen Weltregierung, welche die Nationalstaaten „nicht mehr benötigt“, gesprochen. Dass sich Deutschland, ebenso wie andere europäische Staaten, der EU untergeordnet hat, dürfte auch Leuten nicht entgangen sein, die sich nur über die Tagesschau informieren. Längst steht das EU-Recht über dem deutschen Recht. Und nur kurze Zeit ist es her, als die EU und alle ihre Mitgliedsstaaten die WHO autonom darüber entscheiden lassen wollten, was eine Pandemie ist und wie diese für alle verbindlich „bekämpft“ werden soll. Eine spannende Frage ist nun, wer denn über der EU und der WHO sowie anderen Institutionen steht? Diese Beschreibung macht klar, dass ein „souveränes Land“ wie das unverändert von der amerikanischen Armee besetzte Deutschland in der Entscheidungshierarchie an die Weisungen übergeordneter Entscheidungsorgane gebunden ist. An der Spitze stehen - wie kann es anders sein - die wirklich Mächtigen. Aber was nützt es dann, Spitzenpolitiker zu wählen, wenn diese analog Horst Seehofer nichts zu melden haben? Ist das Wählen von Politikern nicht völlig sinnlos, wenn deren Wahlversprechen ohnehin nicht erfüllt werden? Ist es nicht so, dass die Menschen, welche ihre Stimme nicht behalten, sondern abgeben, das bestehende System nur nähren, indem sie Wahlergebnisse akzeptieren, ohne zu wissen, ob diese manipuliert wurden, aber mit der Gewissheit, dass das im Zuge des Wahlkampfes Versprochene auf keinen Fall geliefert wird? Aktive Wähler glauben trotz allem an die Redlichkeit und Wirksamkeit von Wahlen, und sie akzeptieren Wahlergebnisse, weil sie denken, dass sie von „so vielen Idioten, die falsch wählen“, umgeben sind, womit wir wieder bei der Spaltung sind. Sie glauben, der Stand des aktuellen Elends sei „selbst gewählt“. **Die Wahl der Aufseher** Stellen Sie sich bitte vor, Sie wären im Gefängnis, weil Sie einen kritischen Artikel mit „gefällt mir“ gekennzeichnet haben oder weil Sie eine „Kontaktschuld“ trifft, da in Ihrer Nachbarschaft ein „verschwörerisches Symbol“ von einem „aufmerksamen“ Nachbarn bei einer „Meldestelle“ angezeigt wurde oder Sie gar eine Tat, „unterhalb der Strafbarkeitsgrenze“ begangen hätten, dann würden Sie möglicherweise mit Maßnahmen bestraft, die „keine Folter wären“. Beispielsweise würde man Sie während Ihrer „Umerziehungshaft“ mit Waterboarding, Halten von Stresspositionen, Dunkelhaft etc. dabei „unterstützen“, „Ihre Verfehlungen zu überdenken“. Stellen Sie sich weiterhin vor, dass Sie, so wie alle anderen Inhaftierten, an der alle vier Jahre stattfindenden Wahl der Aufseher teilnehmen könnten, und Sie hätten auch einen Favoriten, der zwar Waterboarding betreibt, aber gegen alle anderen Maßnahmen steht. Sie hätten sicher allen Grund zur Freude, wenn Sie Ihren Kandidaten durchbringen könnten, oder? Aber was wäre, wenn der Aufseher Ihrer Wahl dann dennoch alle 3 „Nicht-Folter-Maßnahmen“ anwenden würde, wie sämtliche anderen Aufseher zuvor? Spätestens dann müssten Sie sich eingestehen, dass es der Beruf des Aufsehers ist, Aufseher zu sein und dass er letztendlich tut, was ihm „von oben“ aufgetragen wird. Andernfalls verliert er seinen Job. Oder er verunfallt oder gerät in einen Skandal etc. So oder so, er verliert seinen Job - und den erledigt dann ein anderer Aufseher. Die Wahl des Aufsehers ändert wenig, solange Sie sich im System des Gefängnisses befinden und der Aufseher integraler Bestandteil dieses Systems ist. Zur Realisierung einer tatsächlichen Änderung müssten Sie dort herauskommen. Dieses Beispiel soll darstellen, dass alles in Hierarchien eingebunden ist. Die in einem System eingebundenen Menschen erfüllen ihre zugewiesenen Aufgaben, oder sie werden bestraft. **Das aktuelle System schadet dem Volk** Auch in der staatlichen Organisation von Menschen existieren hierarchische Gliederungen. Eine kommunale Selbstverwaltung gehört zum Kreis, dieser zum Land, dieses zum Staat, dieser zur EU, und diese - zu wem auch immer. Und vereinnahmte Gelder fließen nach oben. Obwohl es natürlich wäre, dass die Mittel dorthin fließen, wo sie der Allgemeinheit und nicht einigen wenigen dienen, also nach unten. Warum muss es also eine Weltregierung geben? Warum sollen nur einige Wenige über alle anderen bestimmen und an diesen verdienen (Nahrung, Medikamente, Krieg, Steuern etc.)? Warum sollen Menschen, so wie Vieh, das jemandem „gehört“, mit einem Code versehen und bereits als Baby zwangsgeimpft werden? Warum müssen alle Transaktionen und sämtliches Verhalten strickt gesteuert, kontrolliert und bewertet werden? Viele Menschen werden nach alledem zu dem Schluss kommen, dass solch ein System nur einigen wenigen wirklich Mächtigen und deren Helfershelfern nützt. Aber es gibt auch eine Gruppe Menschen, für die im Land alles beanstandungsfrei funktioniert. Die Spaltung der Menschen ist perfekt gelungen und sofern die eine Gruppe darauf wartet, dass die andere „endlich aufwacht“, da die Fakten doch auf dem Tisch liegen, so wird sie weiter warten dürfen. Julian Assange erwähnte einst, dass es für ihn eine unglaubliche Enttäuschung war, dass ihm niemand half. Assange hatte Ungeheuerlichkeiten aufgedeckt. Es gab keinen Aufstand. Assange wurde inhaftiert und gefoltert. Es gab keinen Aufstand. Assange sagte, er hätte nicht damit gerechnet, dass die Leute „so unglaublich feige“ seien. Aber womit rechnete er den stattdessen? Dass die Massen „sich erheben“. Das gibt es nur im Film, denn die Masse besteht aus vielen maximal Indoktrinierten, die sich wie Schafe verhalten, was als Züchtungserfolg der Leute an den Schalthebeln der Macht und deren Herren, den wirklich Mächtigen, anzuerkennen ist. Denn wer mächtig ist und bleiben möchte, will sicher keine problematischen Untertanen, sondern eine gefügige, ängstliche Herde, die er nach Belieben ausbeuten und steuern kann. Wenn er hierüber verfügt, will er keinen Widerstand. Ob Corona, Krieg, Demokratie- und Klimarettung oder Meinungsäußerungsverbote und Bürgerrechte, die unterhalb der Strafbarkeitsgrenze liegen, all diese und viele weitere Stichworte mehr sind es, die viele traurig und so manche wütend machen. Auch das Mittel des Demonstrierens hat sich als völlig wirkungslos erwiesen. Die vielen gruseligen Videoaufnahmen über die massivsten Misshandlungen von Demonstranten gegen die Corona-Maßnahmen führen zu dem Ergebnis, dass die Exekutive ihr Gewaltmonopol nutzt(e), um die Bevölkerung gezielt zu verletzen und einzuschüchtern. Bekanntlich kann jede friedliche Demonstration zum Eskalieren gebracht werden, indem man Menschen in die Enge treibt (fehlender Sicherheitsabstand) und einige V-Leute in Zivil mit einschlägigen Flaggen und sonstigen „Symbolen“ einschleust, die für Krawall sorgen, damit die gepanzerten Kollegen dann losknüppeln und die scharfen Hunde zubeißen können. So lauten zumindest die Berichte vieler Zeitzeugen und so ist es auch auf vielen Videos zu sehen. Allerdings nicht im Mainstream. Dieses Vorgehen ist deshalb besonders perfide, weil man den Deutschen ihre Wehrhaftigkeit aberzogen hat. Nicht wehrfähige Bürger und eine brutale Staatsmacht mit Gewaltmonopol führen zu einem Gemetzel bei den Bürgern. Ähnliches lässt sich auch in zivilen Lebenssituationen beobachten, wenn die hiesige zivilisierte Bevölkerung auf „eingereiste“ Massenvergewaltiger und Messerstecher trifft, die über ein anderes Gewalt- und Rechtsverständnis verfügen als die Einheimischen. **System-Technik** Die These ist, dass es eine Gruppe von global agierenden Personen gibt, welche das Geschehen auf der Erde zunehmend wirksam zu ihrem individuellen Vorteil gestaltet. Wie sich diese Gruppe definiert, kann bei John Coleman (Das Komitee der 300) und David Icke nachgelesen werden. Hierbei handelt es ich um Autoren, die jahrzehntelang analog streng wissenschaftlichen Grundlagen zu ihren Themen geforscht haben und in ihren jeweiligen Werken sämtliche Quellen benennen. Diese Autoren wurden vom Mainstream mit dem Prädikatsmerkmal „Verschwörungstheoretiker“ ausgezeichnet, wodurch die Ergebnisse Ihrer Arbeiten umso glaubwürdiger sind. Diese mächtige Gruppe hat mit ihren Schergen nahezu den gesamten Planeten infiltriert, indem sie Personen in führenden Positionen in vielen Belangen größtmögliche Freiheiten sowie Schutz gewährt, aber diesen im Gegenzug eine völlige Unterwerfung bei Kernthemen abfordert. Die Motivatoren für diese Unterwerfung sind, abgesehen von materiellen Zuwendungen, auch „Ruhm und Ehre sowie Macht“. Manchmal wird auch Beweismaterial für begangene Verfehlungen (Lolita-Express, Pizzagate etc.) genutzt, um Forderungen Nachdruck zu verleihen. Und auch körperliche Bestrafungen der betroffenen Person oder deren Angehörigen zählen zum Repertoire der Motivatoren. Letztendlich ähnlich den Verhaltensweisen in einem Mafia-Film. Mit dieser Methodik hat sich diese mächtige Gruppe im Laufe von Jahrhunderten! eine Organisation erschaffen, welche aus Kirchen, Parteien, Firmen, NGO, Vereinen, Verbänden und weiteren Organisationsformen besteht. Bestimmte Ämter und Positionen in Organisationen können nur von Personen eingenommen und gehalten werden, die „auf Linie sind“. Die Mitglieder der Gruppe tauchen in keiner Rubrik wie „Die reichsten Menschen der Welt“ auf, sondern bleiben fern der Öffentlichkeit. Wer jemanden aus ihren Reihen erkennt und beschuldigt, ist ein „Antisemit“ oder sonstiger Übeltäter und wird verfolgt und bekämpft. Über mächtige Vermögensverwaltungskonzerne beteiligen sich die Mitglieder dieser Gruppe anonym an Unternehmen in Schlüsselpositionen in einer Dimension, die ihnen wesentlichen Einfluss auf die Auswahl der Topmanager einräumt, sodass die jeweilige Unternehmenspolitik nach Vorgaben der Gruppe gestaltet wird. Die Gruppe steuert das Geldsystem, von dem sich der Planet abhängig zu sein wähnt. Hierzu eine Erläuterung: Ein Staat wie Deutschland ist bekanntlich maximal verschuldet. Man stelle sich vor, ein unliebsamer Politiker würde entgegen sämtlicher „Brandmauern“ und sonstiger Propaganda und Wahlmanipulationen gewählt, das Land zu führen, dann könnte dieser keine Kredit über 500 Mrd. Euro bei der nächsten Sparkasse beantragen, sondern wäre auf die Mächtigen dieser Welt angewiesen. Jeder weiß, dass Deutschland als Staat kein funktionierendes Geschäftsmodell hat und somit nicht in der Lage ist, solch ein Darlehen zurückzuzahlen. Welche Motivation sollte also jemand haben, einem Land wie Deutschland so viel Geld ohne Aussicht auf Rückführung zu geben? Es leuchtet ein, dass dieser Politiker andere Gefälligkeiten anbieten müsste, um das Darlehen zu bekommen. Im Falle einer Weigerung zur Kooperation könnte der Staatsapparat mit seinen Staatsdienern, Bürgergeld- und Rentenempfänger etc. nicht mehr bezahlt werden und dieser Politiker wäre schnell wieder weg. Er würde medial hingerichtet. Es ist somit davon auszugehen, dass ein Spitzenpolitiker dieser Tage nicht über viele Optionen verfügt, denn er übernimmt eine Situation, die von seinen Vorgängern erschaffen wurde. Trotz alledem darauf zu hoffen, dass es einen anderen Politiker geben könnte, mit dem dann alles wieder gut wird, mutet ziemlich infantil an. Dass ein Großteil der Medien von Zuwendungen abhängig ist, dürfte ebenfalls leicht nachzuvollziehen sein, denn der gewöhnliche Bürger zahlt nichts für den Content der MSM. Abhängig davon, von wem (Regierung, Philanthrop, Konzern etc.) ein Medium am Leben gehalten wird, gestalten sich auch dessen Inhalte. Und wenn angewiesen wird, dass ein Politiker medial hingerichtet werden soll, dann bedient die Maschinerie das Thema. Man beobachte einfach einmal, dass Politiker der Kartell-Parteien völlig anders behandelt werden als solche jenseits der „Brandmauer“. Und der Leser, der solche Auftragsarbeiten kostenlos liest, ist der Konsument, für dessen Indoktrination die Finanziers der Verlage gerne zahlen. Mittlerweile kann durch die Herrschaft über die Medien und die systematische Vergiftung der Körper und Geister der Population die öffentliche Meinung gesteuert werden. Die überwiegende Zahl der Deutschen scheint nicht mehr klar denken zu können. Wer sich das aktuelle Geschehen in der deutschen Politik mit klarem Verstand ansieht, kommt nicht umhin, eine Fernsteuerung der handelnden Politiker in Betracht zu ziehen. Aber was soll daran verwundern? Sind es deshalb „böse Menschen“? Sind die in „Forschungslaboren“ arbeitenden Quäler von „Versuchstieren“ böse Menschen? Sind der Schlächter, der Folterer und der Henker böse Menschen? Oder der knüppelnde Polizist? Es handelt sich zunächst einmal um Personen, die einen Vorteil dadurch haben, Ihrer Tätigkeit nachzugehen. Sie sind integrale Bestandteile eines Belohnungssystems, welches von oben nach unten Anweisungen gibt. Und wenn diese Anweisungen nicht befolgt werden, führt dies für den Befehlsverweigerer zu Konsequenzen. **Der klare Verstand** Es ist nun eine spannende Frage, warum so viele Menschen sich solch eine Behandlung gefallen lassen? Nun, das ist relativ einfach, denn das angepasste Verhalten der Vielen ist nichts anderes als ein Züchtungserfolg der Wenigen. Die Psyche der Menschen ist ebenso akribisch erforscht worden wie deren Körperfunktionen. Würden die Menschen von den wirklich Mächtigen geliebt, dann würde genau gewusst, wie sie zu behandeln und mit ihren jeweiligen Bedürfnissen zu versorgen sind. Stattdessen werden die Menschen aber als eine Einnahmequelle betrachtet. Dies manifestiert sich exemplarisch in folgenden Bereichen: 1. Das Gesundheitssystem verdient nichts am gesunden Menschen, sondern nur am (dauerhaft) kranken, der um Schmerzlinderung bettelt. Bereits als Baby werden Menschen geimpft, was die jeweilige Gesundheit (mit Verweis auf die Werke von Anita Petek-Dimmer u. a.) nachhaltig negativ beeinflusst. Wer hat denn heute keine Krankheiten? Die „Experten“ des Gesundheitssystems verteufeln Vitamin D, Vitamin C, Lithium, die Sonne, Natur etc. und empfehlen stattdessen Präparate, die man patentieren konnte und mit denen die Hersteller viel Geld verdienen. Die Präparate heilen selten, sondern lindern bestenfalls zuvor künstlich erzeugte Leiden, und müssen oftmals dauerhaft eingenommen werden. Was ist aus den nicht Geimpften geworden, die alle sterben sollten? Sind diese nicht die einzigen Gesunden dieser Tage? Ist nicht jeder Geimpfte entweder permanent krank oder bereits tot? Abgesehen von denen, welche das Glück hatten, „Sonderchargen“ mit Kochsalz zu erhalten. \ \ Wem gehören die wesentlichen Player im Gesundheitswesen zu einem erheblichen Teil? Die Vermögensverwalter der wirklich Mächtigen. 2. Ähnlich gestaltet es sich bei der Ernährungsindustrie. Die von dort aus verabreichten Produkte sind die Ursachen für den Gesundheitszustand der deutschen Population. Das ist aber auch irgendwie logisch, denn wer sich nicht falsch ernährt und gesund bleibt, wird kein Kunde des Gesundheitswesens. \ \ Die Besitzverhältnisse in der Ernährungsindustrie ähneln denen im Gesundheitswesen, sodass am gleichen Kunden gearbeitet und verdient wird. 3. Die Aufzählung konnte nun über die meisten Branchen, in denen mit dem Elend der Menschen viel verdient werden kann, fortgesetzt werden. Waffen (BlackRock erhöhte beispielsweise seine Anteile an der Rheinmetall AG im Juni 2024 auf 5,25 Prozent. Der US-Vermögensverwalter ist damit der zweitgrößte Anteilseigner nach der französischen Großbank Société Générale.), Energie, Umwelt, Technologie, IT, Software, KI, Handel etc. Wie genau Chemtrails und Technologien wie 5G auf den Menschen und die Tiere wirken, ist ebenfalls umstritten. Aber ist es nicht seltsam, wie krank, empathielos, antriebslos und aggressiv viele Menschen heute sind? Was genau verabreicht man der Berliner Polizei, damit diese ihre Prügelorgien auf den Rücken und in den Gesichtern der Menschen wahrnehmen, die friedlich ihre Demonstrationsrechte wahrnehmen? Und was erhalten die ganzen zugereisten „Fachkräfte“, die mit Ihren Autos in Menschenmengen rasen oder auch Kinder und Erwachsene niedermessern? Das Titelbild dieses Beitrags zeigt einige Gebilde, welche regelmäßig bei Obduktionen von Geimpften in deren Blutgefäßen gefunden werden. Wie genau wirken diese kleinen Monster? Können wir Menschen ihr Unverständnis und ihr Nicht-Aufwachen vorwerfen, wenn wir erkennen, dass diese Menschen maximal vergiftet wurden? Oder sollten einfach Lösungen für die Probleme dieser Zeit auch ohne den Einbezug derer gefunden werden, die offenbar nicht mehr Herr ihrer Sinne sind? **Die Ziele der wirklich Mächtigen** Wer sich entsprechende Videosequenzen der Bilderberger, des WEF und anderen „Überorganisationen“ ansieht, der erkennt schnell das Muster: * Reduzierung der Weltpopulation um ca. 80 Prozent * Zusammenbruch der Wirtschaft, damit diese von den Konzernen übernommen werden kann. * Zusammenbruch der öffentlichen Ordnung, um eine totale Entwaffnung und eine totale Überwachung durchsetzen zu können. * Zusammenbruch der Regierungen, damit die Weltregierung übernehmen kann. Es ist zu überdenken, ob die Weltregierung tatsächlich das für die Vielen beste Organisationssystem ist, oder ob die dezentrale Eigenorganisation der jeweils lokalen Bevölkerung nicht doch die bessere Option darstellt. Baustellen würden nicht nur begonnen, sondern auch schnell abgearbeitet. Jede Region könnte bestimmen, ob sie sich mit Chemtrails und anderen Substanzen besprühen lassen möchte. Und die Probleme in Barcelona könnte die Menschen dort viel besser lösen als irgendwelche wirklich Mächtigen in ihren Elfenbeintürmen. Die lokale Wirtschaft könnte wieder zurückkommen und mit dieser die Eigenständigkeit. Denn die den wirklich Mächtigen über ihre Vermögensverwalter gehörenden Großkonzerne haben offensichtlich nicht das Wohl der Bevölkerung im Fokus, sondern eher deren Ausbeutung. Das Aussteigen aus dem System ist die wahre Herkulesaufgabe und es bedarf sicher Mut und Klugheit, sich dieser zu stellen. Die Politiker, die unverändert die Narrative der wirklich Mächtigen bedienen, sind hierfür denkbar ungeeignet, denn sie verfolgen kein Lebensmodell, welches sich von Liebe und Mitgefühl geleitet in den Dienst der Gesamtheit von Menschen, Tieren und Natur stellt. Schauen Sie einmal genau hin, denken Sie nach und fühlen Sie mit. **Was tun?** Jedes System funktioniert nur so lange, wie es unterstützt wird. Somit stellt sich die Frage, wie viele Menschen das System ignorieren müssen, damit es kollabiert, und auf welche Weise dieses Ignorieren durchzuführen ist? Merkbar ist, dass die große Masse der Verwaltungsangestellten krank und oder unmotiviert und somit nicht wirksam ist. Würden die entsprechenden Stellen massiv belastet und parallel hierzu keine Einnahmen mehr realisieren, wäre ein Kollaps nah. Die Prügelpolizisten aus Berlin können nicht überall sein und normale Polizisten arbeiten nicht gegen unbescholtene Bürger, sondern sorgen sich selbst um ihre Zukunft. Gewalt ist sicher keine Lösung, und sicher auch nicht erforderlich. Wie eine gerechte Verwaltungsform aufgebaut werden muss? Einfach so, wie sie in den hiesigen Gesetzen beschrieben steht. Aber eine solche Organisationsform muss frei sein von Blockparteien und korrupten Politikern und weisungsgebundenen Richtern etc. Stattdessen werden Menschen benötigt, welche die Menschen lieben und ihnen nicht schaden wollen. Außerdem sollten diese Führungspersonen auch wirklich etwas können, und nicht nur „Politiker“ ohne weitere Berufserfahrungen sein. *** Ludwig F. Badenhagen (Pseudonym, Name ist der Redaktion bekannt). *Der Autor hat deutsche Wurzeln und betrachtet das Geschehen in Deutschland und Europa aus seiner Wahlheimat Südafrika. Seine Informationen bezieht er aus verlässlichen Quellen und insbesondere von Menschen, die als „Verschwörungstheoretiker“, „Nazi“, „Antisemit“ sowie mit weiteren Kampfbegriffen der dortigen Systemakteure wie Politiker und „Journalisten“ diffamiert werden. Solche Diffamierungen sind für ihn ein Prädikatsmerkmal. Er ist international agierender Manager mit einem globalen Netzwerk und verfügt hierdurch über tiefe Einblicke in Konzerne und Politik.* *** **Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Start.](https://start.njump.me/)** @ a012dc82:6458a70d
2025-03-28 16:15:06In an audacious display of confidence, Bitcoin traders have recently committed $20 million to a $200K call option, a move that has reignited discussions about the cryptocurrency's potential and the broader market's appetite for risk. This development is set against a backdrop of increasing activity within the cryptocurrency options market, particularly on platforms like Deribit, where total open interest in Bitcoin options has reached unprecedented levels. This article explores the nuances of this strategic wager, examines the resurgence of investor enthusiasm, and contemplates the future implications for Bitcoin and the cryptocurrency market at large. **Table of Contents** - A Surge in Market Activity - The Bold Bet on Bitcoin's Future - Implications of the $200K Call Option - Increased Market Volatility - Renewed Investor Confidence - Speculative Interest and Market Dynamics - Looking Ahead: Bitcoin's Market Prospects - Conclusion - FAQs **A Surge in Market Activity** The cryptocurrency options market has experienced a significant uptick in activity, with Bitcoin and Ethereum options achieving record-breaking open interest figures. On Deribit, Bitcoin options open interest has soared to a staggering $20.4 billion, eclipsing the previous high of $14.36 billion seen in October 2021. Concurrently, Ethereum options open interest has also reached a historic peak of $11.66 billion. This pronounced increase in market activity is indicative of a growing interest among traders to either hedge their positions against potential price fluctuations or to speculate on the future price movements of these leading cryptocurrencies. The surge in options trading volume reflects a broader trend of maturation within the cryptocurrency market, as sophisticated financial instruments become increasingly utilized by a diverse array of market participants, from individual investors to large institutional players. **The Bold Bet on Bitcoin's Future** The decision by traders to allocate $20 million to a $200K call option for Bitcoin represents a significant vote of confidence in the cryptocurrency's future price trajectory. This high-stakes gamble suggests that a segment of the market is not only optimistic about Bitcoin's potential to breach the $200,000 threshold but is also willing to back this belief with substantial financial commitment. Such a move is emblematic of the "animal spirits" returning to the cryptocurrency market—a term coined by economist John Maynard Keynes to describe the instinctive human emotion that drives consumer confidence and investment decisions. This resurgence of speculative fervor and risk-taking behavior is a testament to the enduring allure of Bitcoin as an asset class that continues to captivate the imagination of investors, despite its history of volatility and regulatory challenges. **Implications of the $200K Call Option** The substantial investment in the $200K call option carries several implications for the Bitcoin market and the broader cryptocurrency ecosystem: **Increased Market Volatility** The focus on high strike price options could introduce heightened volatility into the Bitcoin market. As traders position themselves to capitalize on potential price movements, the market may witness more pronounced fluctuations. This environment of increased volatility underscores the speculative nature of cryptocurrency trading and the high-risk, high-reward strategies employed by some market participants. It also highlights the need for investors to approach the market with caution, armed with a thorough understanding of the underlying risks and a clear investment strategy. **Renewed Investor Confidence** The bold wager on the $200K call option reflects a significant resurgence in investor confidence in Bitcoin's long-term prospects. Following periods of market downturns and regulatory uncertainty, this move signals a renewed conviction in the fundamental value proposition of Bitcoin as a pioneering digital asset. It represents a collective belief in the cryptocurrency's ability to not only recover from past setbacks but to chart new territories in terms of price and market capitalization. This renewed investor confidence may serve as a catalyst for further investment in Bitcoin and other cryptocurrencies, potentially driving up prices and encouraging more widespread adoption. **Speculative Interest and Market Dynamics** The commitment to the $200K call option highlights the continued influence of speculative interest on the cryptocurrency market's dynamics. It illustrates how speculation, driven by the prospect of outsized returns, remains a central force shaping market trends and price trajectories. This speculative interest, while contributing to market liquidity and price discovery, also introduces an element of unpredictability. It underscores the complex interplay between market sentiment, investor behavior, and external economic factors that collectively determine the direction of the cryptocurrency market. **Looking Ahead: Bitcoin's Market Prospects** The strategic bet on the $200K call option, amidst a backdrop of increasing options market activity, paints a complex picture of Bitcoin's future. While the move signals optimism and a willingness among investors to engage in high-risk speculation, it also raises questions about the sustainability of such bullish sentiment. As Bitcoin continues to navigate the evolving landscape of digital finance, the interplay between speculative interest, regulatory developments, and technological advancements will be critical in shaping its future trajectory. The cryptocurrency market's inherent volatility and unpredictability necessitate a cautious approach from investors, emphasizing the importance of risk management and long-term strategic planning. **Conclusion** Bitcoin's latest foray into high-stakes speculation, marked by the $20 million lock on the $200K call option, is a vivid illustration of the cryptocurrency's enduring appeal and the market's appetite for risk. This development not only reflects a bullish outlook on Bitcoin's price potential but also signals a broader resurgence of investor enthusiasm and speculative activity within the cryptocurrency market. As we look to the future, the outcomes of such bold moves will undoubtedly influence the trajectory of Bitcoin and the digital asset landscape at large. Whether Bitcoin will reach the lofty heights of $200,000 remains to be seen, but its journey there will be closely watched by traders, investors, and regulators alike, offering valuable insights into the dynamics of speculative markets and the evolving role of cryptocurrencies in the global financial ecosystem. **FAQs** **What does locking $20 million in a $200K call option mean for Bitcoin?** Locking $20 million in a $200K call option indicates that traders are betting a significant amount of money on Bitcoin reaching or surpassing $200,000. It reflects a bullish outlook on Bitcoin's future price and a resurgence of speculative interest in the cryptocurrency market. **How does the surge in Bitcoin options market activity affect the cryptocurrency?** The surge in Bitcoin options market activity, with record open interest, increases market liquidity and can lead to heightened volatility. It also signifies growing interest and participation in the cryptocurrency market, potentially influencing Bitcoin's price dynamics. **What are the implications of increased market volatility for Bitcoin investors?** Increased market volatility can lead to larger price swings, presenting both opportunities and risks for investors. While it may offer the potential for higher returns, it also increases the risk of losses. Investors should approach the market with caution and consider their risk tolerance and investment strategy. **Why are investors optimistic about Bitcoin reaching $200,000?** Investors' optimism about Bitcoin reaching $200,000 stems from factors such as the cryptocurrency's past performance, the upcoming Bitcoin halving event, increasing institutional adoption, and favorable macroeconomic conditions. These factors contribute to a bullish sentiment in the market. **What role do institutional investors play in the current Bitcoin market trend?** Institutional investors play a significant role in the current Bitcoin market trend by bringing in substantial capital, lending credibility to the market, and influencing price movements. Their participation is seen as a sign of maturity and stability in the cryptocurrency market. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnewsco](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co/](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@thebitcoinlibertarian](https://www.youtube.com/@thebitcoinlibertarian)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** **Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad** **Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
@ a012dc82:6458a70d
2025-03-28 16:15:06In an audacious display of confidence, Bitcoin traders have recently committed $20 million to a $200K call option, a move that has reignited discussions about the cryptocurrency's potential and the broader market's appetite for risk. This development is set against a backdrop of increasing activity within the cryptocurrency options market, particularly on platforms like Deribit, where total open interest in Bitcoin options has reached unprecedented levels. This article explores the nuances of this strategic wager, examines the resurgence of investor enthusiasm, and contemplates the future implications for Bitcoin and the cryptocurrency market at large. **Table of Contents** - A Surge in Market Activity - The Bold Bet on Bitcoin's Future - Implications of the $200K Call Option - Increased Market Volatility - Renewed Investor Confidence - Speculative Interest and Market Dynamics - Looking Ahead: Bitcoin's Market Prospects - Conclusion - FAQs **A Surge in Market Activity** The cryptocurrency options market has experienced a significant uptick in activity, with Bitcoin and Ethereum options achieving record-breaking open interest figures. On Deribit, Bitcoin options open interest has soared to a staggering $20.4 billion, eclipsing the previous high of $14.36 billion seen in October 2021. Concurrently, Ethereum options open interest has also reached a historic peak of $11.66 billion. This pronounced increase in market activity is indicative of a growing interest among traders to either hedge their positions against potential price fluctuations or to speculate on the future price movements of these leading cryptocurrencies. The surge in options trading volume reflects a broader trend of maturation within the cryptocurrency market, as sophisticated financial instruments become increasingly utilized by a diverse array of market participants, from individual investors to large institutional players. **The Bold Bet on Bitcoin's Future** The decision by traders to allocate $20 million to a $200K call option for Bitcoin represents a significant vote of confidence in the cryptocurrency's future price trajectory. This high-stakes gamble suggests that a segment of the market is not only optimistic about Bitcoin's potential to breach the $200,000 threshold but is also willing to back this belief with substantial financial commitment. Such a move is emblematic of the "animal spirits" returning to the cryptocurrency market—a term coined by economist John Maynard Keynes to describe the instinctive human emotion that drives consumer confidence and investment decisions. This resurgence of speculative fervor and risk-taking behavior is a testament to the enduring allure of Bitcoin as an asset class that continues to captivate the imagination of investors, despite its history of volatility and regulatory challenges. **Implications of the $200K Call Option** The substantial investment in the $200K call option carries several implications for the Bitcoin market and the broader cryptocurrency ecosystem: **Increased Market Volatility** The focus on high strike price options could introduce heightened volatility into the Bitcoin market. As traders position themselves to capitalize on potential price movements, the market may witness more pronounced fluctuations. This environment of increased volatility underscores the speculative nature of cryptocurrency trading and the high-risk, high-reward strategies employed by some market participants. It also highlights the need for investors to approach the market with caution, armed with a thorough understanding of the underlying risks and a clear investment strategy. **Renewed Investor Confidence** The bold wager on the $200K call option reflects a significant resurgence in investor confidence in Bitcoin's long-term prospects. Following periods of market downturns and regulatory uncertainty, this move signals a renewed conviction in the fundamental value proposition of Bitcoin as a pioneering digital asset. It represents a collective belief in the cryptocurrency's ability to not only recover from past setbacks but to chart new territories in terms of price and market capitalization. This renewed investor confidence may serve as a catalyst for further investment in Bitcoin and other cryptocurrencies, potentially driving up prices and encouraging more widespread adoption. **Speculative Interest and Market Dynamics** The commitment to the $200K call option highlights the continued influence of speculative interest on the cryptocurrency market's dynamics. It illustrates how speculation, driven by the prospect of outsized returns, remains a central force shaping market trends and price trajectories. This speculative interest, while contributing to market liquidity and price discovery, also introduces an element of unpredictability. It underscores the complex interplay between market sentiment, investor behavior, and external economic factors that collectively determine the direction of the cryptocurrency market. **Looking Ahead: Bitcoin's Market Prospects** The strategic bet on the $200K call option, amidst a backdrop of increasing options market activity, paints a complex picture of Bitcoin's future. While the move signals optimism and a willingness among investors to engage in high-risk speculation, it also raises questions about the sustainability of such bullish sentiment. As Bitcoin continues to navigate the evolving landscape of digital finance, the interplay between speculative interest, regulatory developments, and technological advancements will be critical in shaping its future trajectory. The cryptocurrency market's inherent volatility and unpredictability necessitate a cautious approach from investors, emphasizing the importance of risk management and long-term strategic planning. **Conclusion** Bitcoin's latest foray into high-stakes speculation, marked by the $20 million lock on the $200K call option, is a vivid illustration of the cryptocurrency's enduring appeal and the market's appetite for risk. This development not only reflects a bullish outlook on Bitcoin's price potential but also signals a broader resurgence of investor enthusiasm and speculative activity within the cryptocurrency market. As we look to the future, the outcomes of such bold moves will undoubtedly influence the trajectory of Bitcoin and the digital asset landscape at large. Whether Bitcoin will reach the lofty heights of $200,000 remains to be seen, but its journey there will be closely watched by traders, investors, and regulators alike, offering valuable insights into the dynamics of speculative markets and the evolving role of cryptocurrencies in the global financial ecosystem. **FAQs** **What does locking $20 million in a $200K call option mean for Bitcoin?** Locking $20 million in a $200K call option indicates that traders are betting a significant amount of money on Bitcoin reaching or surpassing $200,000. It reflects a bullish outlook on Bitcoin's future price and a resurgence of speculative interest in the cryptocurrency market. **How does the surge in Bitcoin options market activity affect the cryptocurrency?** The surge in Bitcoin options market activity, with record open interest, increases market liquidity and can lead to heightened volatility. It also signifies growing interest and participation in the cryptocurrency market, potentially influencing Bitcoin's price dynamics. **What are the implications of increased market volatility for Bitcoin investors?** Increased market volatility can lead to larger price swings, presenting both opportunities and risks for investors. While it may offer the potential for higher returns, it also increases the risk of losses. Investors should approach the market with caution and consider their risk tolerance and investment strategy. **Why are investors optimistic about Bitcoin reaching $200,000?** Investors' optimism about Bitcoin reaching $200,000 stems from factors such as the cryptocurrency's past performance, the upcoming Bitcoin halving event, increasing institutional adoption, and favorable macroeconomic conditions. These factors contribute to a bullish sentiment in the market. **What role do institutional investors play in the current Bitcoin market trend?** Institutional investors play a significant role in the current Bitcoin market trend by bringing in substantial capital, lending credibility to the market, and influencing price movements. Their participation is seen as a sign of maturity and stability in the cryptocurrency market. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnewsco](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co/](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@thebitcoinlibertarian](https://www.youtube.com/@thebitcoinlibertarian)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** **Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad** **Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.* @ 57d1a264:69f1fee1
2025-03-23 12:24:46https://www.youtube.com/watch?v=obXEnyQ_Veg    source: https://media.jaguar.com/news/2024/11/fearless-exuberant-compelling-jaguar-reimagined-0 originally posted at https://stacker.news/items/922356
@ 57d1a264:69f1fee1
2025-03-23 12:24:46https://www.youtube.com/watch?v=obXEnyQ_Veg    source: https://media.jaguar.com/news/2024/11/fearless-exuberant-compelling-jaguar-reimagined-0 originally posted at https://stacker.news/items/922356 @ 3eba5ef4:751f23ae
2025-03-28 01:42:07## Crypto Insights ### Proposal and Discussion on Introducing a New Bitcoin Script Opcode: OP\_ISSUBSTR [This BIP](https://groups.google.com/g/bitcoindev/c/Ls9DWtDRbDc) proposes the introduction of two new opcodes: OP\_ISSUBSTR and OP\_ISSUBSTRVERIFY. Their relationship is similar to OP\_EQUAL and OP\_EQUALVERIFY used to determine whether one string is a substring of another. Bitcoin developers have mixed opinions on this. **Supporters:** * **Enhancing script functionality:** Enables direct on-chain string operations, reducing reliance on off-chain processing and centralized dependencies. * **Simplifies certain use cases:** Some applications (e.g., verifying if a public key contains a specific substring) would be easier to implement with OP\_ISSUBSTR. * **OP\_CAT is not a perfect substitute:** Although OP\_CAT can be used for string operations, it has security concerns and limitations, such as stack size limits. **Opponents:** * **Bitcoin Script is for validation, not computation:** Peter Todd argues that substring searching can be achieved using concatenation (OP\_CAT) and equality checks (OP\_EQUAL), making OP\_ISSUBSTR unnecessary. * **Alternative script solutions exist:** Some developers demonstrated that the proposed functionality can be emulated by having the script reconstruct the original string with known and unknown parts. * **Potential stack management issues:** Concerns exist regarding stack size limits and whether OP\_ISSUBSTR offers sufficient benefits. ### Discussion on Bitcoin’s Next Major Upgrade: Evaluating OP\_CAT and OP\_CTV This [analysis](https://www.galaxy.com/insights/research/bitcoins-next-major-upgrade-op-cat-and-op-ctv/) explores Bitcoin’s potential next major upgrade: OP\_CAT (BIP 347) and OP\_CTV (BIP 119). Both aim to enhance Bitcoin’s transaction programmability by enabling spending conditions on transaction outputs, improving script expressiveness. The report explains how OP\_CAT enables recursive contracts and trustless Bitcoin bridges, supporting BitVM development, while OP\_CTV improves efficiency for vaults and rollup-based complex transactions. It predicts that Bitcoin Core developers are expected to reach consensus on adding OP\_CAT or OP\_CTV this year, but due to the extensive activation process, actual implementation may take 1–2 years. ### Implementing Post-Signature Cross-Input Scripting in Bitcoin Using Taproot Annex A new method has been [proposed](https://delvingbitcoin.org/t/post-signature-cross-input-scripting-using-the-taproot-annex/1520/1) to introduce cross-input scripting using Taproot [annex](https://bitcoinops.org/en/topics/annex/). This allows users to commit to additional spending conditions when signing transactions, expanding Bitcoin scripting capabilities and transaction flexibility. ### Can Orphan Block Reporting Effectively Prevent Selfish Mining? A Complex Reality A common belief is that incorporating orphan block counts in Bitcoin’s Difficulty Adjustment Mechanism (DAM) can make selfish mining unprofitable. However, this study refutes that view by analyzing the time-averaged profit of selfish mining. The research also introduces two improved DAM models considering both main-chain and orphaned blocks, along with two smart intermittent selfish mining strategies—one outperforming standard intermittent selfish mining and the other remaining profitable under the modified DAM. Additionally, the study describes an "orphan exclusion attack," where attackers prevent honest miners from reporting orphan blocks. Using combinatorial tools, the research examines the profitability of selfish mining under the improved DAM when combined with orphan exclusion attacks. Results indicate that even with orphan block inclusion, selfish mining remains profitable. However, under the modifed DAM, profitability significantly decreases compared to Bitcoin's current DAM, suggesting that orphan block reporting can be an effective mitigation strategy against a payoff-maximizing selfish miner. Read the [full paper](https://eprint.iacr.org/2024/363.pdf). ### LND Introduces Rewritten Sweeper Subsystem to Optimize Batch Transactions and Fee Bumping [According to the author](https://delvingbitcoin.org/t/lnds-deadline-aware-budget-sweeper/1512), starting from v0.18.0, Lightning Network Daemon (LND) will completely revamp its sweeper subsystem for managing transaction batching and fee bumping. The new sweeper integrates HTLC deadlines and fee budgets to compute a fee rate curve, dynamically adjusting fees based on transaction urgency. This new fee bumping strategy provides security benefits that other Lightning Network implementations may find valuable to adopt. ### Analysis of Invalid Mining by AntPool and Associated Pools [boerst observed](https://x.com/boerst/status/1899102559161520497) unusual block templates submitted at height [885797](https://stratum.work/height/885797) by Antpool, CloverPool, Ultimus, Rawpool, and Poolin. The anomalies suggest possible selfish mining or template code issues. Suspicious signs include: * Empty Merkle branches, yet the coinbase output total exceeds the subsidy, implying fees are being collected for non-existent transactions. * The previous block hash for these is different from the rest of the pools and points to a block that seems to have never made it into the chain. [b10c's analysis](http://b10c.me/observations/14-antpool-and-friends-invalid-mining-jobs/) suggests this may be a bug in AntPool’s coinbase transaction creation process. The findings indicate these pools may be operated by the same entity. It might be time to refer to AntPool and its associated pools (Braiins, Poolin, Binance Pool, and Ultimus, among others) collectively as "AntPool & Friends." ### Payjoin Roadmap: From a Two-Party Protocol to a Multi-Party Collaboration Model The Payjoin Dev Kit (PDK) team [outlined](https://payjoindevkit.org/2025/03/18/the-evolution-of-payjoin/) the evolution of [Payjoin](https://bitcoinops.org/en/topics/payjoin/) from a two-party protocol to a multi-party framework. Payjoin V3 will address the limitations of the two-party model by introducing a collaboration model. The final goal is a "coalition formation protocol" that allows unconnected Bitcoin users to contribute to batch transactions. The four development stages are: * Stage 0: Multi-sender, single-receiver (current stage) * Stage 1: Multi-sender, multi-receiver * Stage 2: Privacy optimization * Stage 3: Decentralized market mechanism—developing a coalition formation protocol to enable unconnected Bitcoin users to contribute to batch transactions ### Embedding Sats into Memes and Emojis [This article](https://lightning.news/money-inside-memes-and-emojis/) explores how [memeamigo.lol](https://memeamigo.lol/) encodes Bitcoin-based Cashu into memes, embedding sats into emojis and memes like [this](https://x.com/L0laL33tz/status/1897402057209868606) and [this](https://x.com/callebtc/status/1897386585127313874). ### Complete Guide to Buying Bitcoin Anonymously [The author](https://blockdyor.com/buy-bitcoin-anonymously/) compares several Bitcoin exchanges, categorizing them based on decentralization and peer-to-peer features: * Decentralized & P2P * Centralized & P2P * Centralized & non-P2P (light KYC) Each type has its own advantages and drawbacks, and the best choice depends on the user’s priorities regarding privacy, ease of use, and legal compliance.  ### Global Cryptocurrency Tax Map [Hellosafe.ca](http://Hellosafe.ca) provides a [global crypto tax map](https://hellosafe.ca/en/investing/cryptocurrency/map-taxation-world), offering an overview of different tax policies worldwide. ### Binance Report: The Future of Bitcoin—DeFi Binance released a [report on Bitcoin DeFi](https://public.bnbstatic.com/static/files/research/the-future-of-bitcoin-4-defi.pdf). Key takeaways include: * **Security Budget & the Role of BTCFi**: With Bitcoin’s block rewards continuously halving, its security model faces long-term sustainability challenges. BTCFi helps sustain miner incentives by increasing on-chain transaction fees, thereby strengthening Bitcoin’s long-term security budget. * **Infrastructure as a Bottleneck**: Bitcoin L2s are still in their early stages and require further development, adoption, and liquidity incentives to scale effectively. * **Liquidity & Institutional Interest**: Bitcoin investors have traditionally been long-term holders, posing challenges for liquidity provisioning. New incentive mechanisms are needed to activate idle BTC funds. While institutional investors have shown initial interest, large-scale adoption depends on regulatory clarity and user-friendly solutions. * **Cross-Chain Interoperability is Crucial**: Most Bitcoin used in DeFi currently exists as Wrapped BTC on Ethereum and other chains. BTCFi needs secure cross-chain solutions to bridge liquidity and attract users from existing DeFi ecosystems. * **BTCFi Needs Its Own Path**: Unlike Ethereum’s DeFi ecosystem, BTCFi cannot simply replicate existing models. Its success may rely on tailored solutions that align with Bitcoin holders' needs, particularly in yield generation, payments, and institutional-grade products. ## Top Reads on Blockchain and Beyond ### Infinite Recursion of Trust: Reflections on Trust In [Reflections on Trusting Trust](https://www.cs.cmu.edu/~rdriley/487/papers/Thompson_1984_ReflectionsonTrustingTrust.pdf), Ken Thompson reveals the fragility of software trust. By describing a potential "Trojan horse" attack, he highlights a philosophical and technical dilemma: verifying a system’s trustworthiness requires a trusted tool, but that tool itself needs another tool for verification—leading to infinite recursion. Ultimately, trust must be placed in a foundational layer, which may itself be unverifiable. ### Contextual Trust Networks and Privacy: A Critical Analysis of Metadata, Surveillance, and Routing Dynamics in Decentralized Systems [This article](https://x.com/BitcoinErrorLog/status/1903769658781556903) critically examines contextual trust networks as an alternative to traditional privacy protection techniques in decentralized systems like Bitcoin and P2P networks. It first highlights inherent privacy limitations in popular anonymity-enhancing methods: * **CoinJoin and Mixnets**: Rely on anonymity sets but remain vulnerable to metadata correlation at ingress and egress points, providing surveillance opportunities for adversaries. * **Onion Routing (Tor)**: Tor reduces direct metadata exposure but is still susceptible to persistent statistical traffic analysis at entry and exit nodes, compromising anonymity over time. * **Distributed Hash Tables (DHTs)**: Broadcast metadata widely, inherently increasing visibility and surveillance risks. The author then contrasts these with the contextual trust concept introduced by the Atomicity protocol. The analysis suggests that witness-generated metadata is a primary privacy risk and argues that contextual trust channels can enhance privacy by controlling witness selection and excluding irrelevant nodes during transaction routing.
@ 3eba5ef4:751f23ae
2025-03-28 01:42:07## Crypto Insights ### Proposal and Discussion on Introducing a New Bitcoin Script Opcode: OP\_ISSUBSTR [This BIP](https://groups.google.com/g/bitcoindev/c/Ls9DWtDRbDc) proposes the introduction of two new opcodes: OP\_ISSUBSTR and OP\_ISSUBSTRVERIFY. Their relationship is similar to OP\_EQUAL and OP\_EQUALVERIFY used to determine whether one string is a substring of another. Bitcoin developers have mixed opinions on this. **Supporters:** * **Enhancing script functionality:** Enables direct on-chain string operations, reducing reliance on off-chain processing and centralized dependencies. * **Simplifies certain use cases:** Some applications (e.g., verifying if a public key contains a specific substring) would be easier to implement with OP\_ISSUBSTR. * **OP\_CAT is not a perfect substitute:** Although OP\_CAT can be used for string operations, it has security concerns and limitations, such as stack size limits. **Opponents:** * **Bitcoin Script is for validation, not computation:** Peter Todd argues that substring searching can be achieved using concatenation (OP\_CAT) and equality checks (OP\_EQUAL), making OP\_ISSUBSTR unnecessary. * **Alternative script solutions exist:** Some developers demonstrated that the proposed functionality can be emulated by having the script reconstruct the original string with known and unknown parts. * **Potential stack management issues:** Concerns exist regarding stack size limits and whether OP\_ISSUBSTR offers sufficient benefits. ### Discussion on Bitcoin’s Next Major Upgrade: Evaluating OP\_CAT and OP\_CTV This [analysis](https://www.galaxy.com/insights/research/bitcoins-next-major-upgrade-op-cat-and-op-ctv/) explores Bitcoin’s potential next major upgrade: OP\_CAT (BIP 347) and OP\_CTV (BIP 119). Both aim to enhance Bitcoin’s transaction programmability by enabling spending conditions on transaction outputs, improving script expressiveness. The report explains how OP\_CAT enables recursive contracts and trustless Bitcoin bridges, supporting BitVM development, while OP\_CTV improves efficiency for vaults and rollup-based complex transactions. It predicts that Bitcoin Core developers are expected to reach consensus on adding OP\_CAT or OP\_CTV this year, but due to the extensive activation process, actual implementation may take 1–2 years. ### Implementing Post-Signature Cross-Input Scripting in Bitcoin Using Taproot Annex A new method has been [proposed](https://delvingbitcoin.org/t/post-signature-cross-input-scripting-using-the-taproot-annex/1520/1) to introduce cross-input scripting using Taproot [annex](https://bitcoinops.org/en/topics/annex/). This allows users to commit to additional spending conditions when signing transactions, expanding Bitcoin scripting capabilities and transaction flexibility. ### Can Orphan Block Reporting Effectively Prevent Selfish Mining? A Complex Reality A common belief is that incorporating orphan block counts in Bitcoin’s Difficulty Adjustment Mechanism (DAM) can make selfish mining unprofitable. However, this study refutes that view by analyzing the time-averaged profit of selfish mining. The research also introduces two improved DAM models considering both main-chain and orphaned blocks, along with two smart intermittent selfish mining strategies—one outperforming standard intermittent selfish mining and the other remaining profitable under the modified DAM. Additionally, the study describes an "orphan exclusion attack," where attackers prevent honest miners from reporting orphan blocks. Using combinatorial tools, the research examines the profitability of selfish mining under the improved DAM when combined with orphan exclusion attacks. Results indicate that even with orphan block inclusion, selfish mining remains profitable. However, under the modifed DAM, profitability significantly decreases compared to Bitcoin's current DAM, suggesting that orphan block reporting can be an effective mitigation strategy against a payoff-maximizing selfish miner. Read the [full paper](https://eprint.iacr.org/2024/363.pdf). ### LND Introduces Rewritten Sweeper Subsystem to Optimize Batch Transactions and Fee Bumping [According to the author](https://delvingbitcoin.org/t/lnds-deadline-aware-budget-sweeper/1512), starting from v0.18.0, Lightning Network Daemon (LND) will completely revamp its sweeper subsystem for managing transaction batching and fee bumping. The new sweeper integrates HTLC deadlines and fee budgets to compute a fee rate curve, dynamically adjusting fees based on transaction urgency. This new fee bumping strategy provides security benefits that other Lightning Network implementations may find valuable to adopt. ### Analysis of Invalid Mining by AntPool and Associated Pools [boerst observed](https://x.com/boerst/status/1899102559161520497) unusual block templates submitted at height [885797](https://stratum.work/height/885797) by Antpool, CloverPool, Ultimus, Rawpool, and Poolin. The anomalies suggest possible selfish mining or template code issues. Suspicious signs include: * Empty Merkle branches, yet the coinbase output total exceeds the subsidy, implying fees are being collected for non-existent transactions. * The previous block hash for these is different from the rest of the pools and points to a block that seems to have never made it into the chain. [b10c's analysis](http://b10c.me/observations/14-antpool-and-friends-invalid-mining-jobs/) suggests this may be a bug in AntPool’s coinbase transaction creation process. The findings indicate these pools may be operated by the same entity. It might be time to refer to AntPool and its associated pools (Braiins, Poolin, Binance Pool, and Ultimus, among others) collectively as "AntPool & Friends." ### Payjoin Roadmap: From a Two-Party Protocol to a Multi-Party Collaboration Model The Payjoin Dev Kit (PDK) team [outlined](https://payjoindevkit.org/2025/03/18/the-evolution-of-payjoin/) the evolution of [Payjoin](https://bitcoinops.org/en/topics/payjoin/) from a two-party protocol to a multi-party framework. Payjoin V3 will address the limitations of the two-party model by introducing a collaboration model. The final goal is a "coalition formation protocol" that allows unconnected Bitcoin users to contribute to batch transactions. The four development stages are: * Stage 0: Multi-sender, single-receiver (current stage) * Stage 1: Multi-sender, multi-receiver * Stage 2: Privacy optimization * Stage 3: Decentralized market mechanism—developing a coalition formation protocol to enable unconnected Bitcoin users to contribute to batch transactions ### Embedding Sats into Memes and Emojis [This article](https://lightning.news/money-inside-memes-and-emojis/) explores how [memeamigo.lol](https://memeamigo.lol/) encodes Bitcoin-based Cashu into memes, embedding sats into emojis and memes like [this](https://x.com/L0laL33tz/status/1897402057209868606) and [this](https://x.com/callebtc/status/1897386585127313874). ### Complete Guide to Buying Bitcoin Anonymously [The author](https://blockdyor.com/buy-bitcoin-anonymously/) compares several Bitcoin exchanges, categorizing them based on decentralization and peer-to-peer features: * Decentralized & P2P * Centralized & P2P * Centralized & non-P2P (light KYC) Each type has its own advantages and drawbacks, and the best choice depends on the user’s priorities regarding privacy, ease of use, and legal compliance.  ### Global Cryptocurrency Tax Map [Hellosafe.ca](http://Hellosafe.ca) provides a [global crypto tax map](https://hellosafe.ca/en/investing/cryptocurrency/map-taxation-world), offering an overview of different tax policies worldwide. ### Binance Report: The Future of Bitcoin—DeFi Binance released a [report on Bitcoin DeFi](https://public.bnbstatic.com/static/files/research/the-future-of-bitcoin-4-defi.pdf). Key takeaways include: * **Security Budget & the Role of BTCFi**: With Bitcoin’s block rewards continuously halving, its security model faces long-term sustainability challenges. BTCFi helps sustain miner incentives by increasing on-chain transaction fees, thereby strengthening Bitcoin’s long-term security budget. * **Infrastructure as a Bottleneck**: Bitcoin L2s are still in their early stages and require further development, adoption, and liquidity incentives to scale effectively. * **Liquidity & Institutional Interest**: Bitcoin investors have traditionally been long-term holders, posing challenges for liquidity provisioning. New incentive mechanisms are needed to activate idle BTC funds. While institutional investors have shown initial interest, large-scale adoption depends on regulatory clarity and user-friendly solutions. * **Cross-Chain Interoperability is Crucial**: Most Bitcoin used in DeFi currently exists as Wrapped BTC on Ethereum and other chains. BTCFi needs secure cross-chain solutions to bridge liquidity and attract users from existing DeFi ecosystems. * **BTCFi Needs Its Own Path**: Unlike Ethereum’s DeFi ecosystem, BTCFi cannot simply replicate existing models. Its success may rely on tailored solutions that align with Bitcoin holders' needs, particularly in yield generation, payments, and institutional-grade products. ## Top Reads on Blockchain and Beyond ### Infinite Recursion of Trust: Reflections on Trust In [Reflections on Trusting Trust](https://www.cs.cmu.edu/~rdriley/487/papers/Thompson_1984_ReflectionsonTrustingTrust.pdf), Ken Thompson reveals the fragility of software trust. By describing a potential "Trojan horse" attack, he highlights a philosophical and technical dilemma: verifying a system’s trustworthiness requires a trusted tool, but that tool itself needs another tool for verification—leading to infinite recursion. Ultimately, trust must be placed in a foundational layer, which may itself be unverifiable. ### Contextual Trust Networks and Privacy: A Critical Analysis of Metadata, Surveillance, and Routing Dynamics in Decentralized Systems [This article](https://x.com/BitcoinErrorLog/status/1903769658781556903) critically examines contextual trust networks as an alternative to traditional privacy protection techniques in decentralized systems like Bitcoin and P2P networks. It first highlights inherent privacy limitations in popular anonymity-enhancing methods: * **CoinJoin and Mixnets**: Rely on anonymity sets but remain vulnerable to metadata correlation at ingress and egress points, providing surveillance opportunities for adversaries. * **Onion Routing (Tor)**: Tor reduces direct metadata exposure but is still susceptible to persistent statistical traffic analysis at entry and exit nodes, compromising anonymity over time. * **Distributed Hash Tables (DHTs)**: Broadcast metadata widely, inherently increasing visibility and surveillance risks. The author then contrasts these with the contextual trust concept introduced by the Atomicity protocol. The analysis suggests that witness-generated metadata is a primary privacy risk and argues that contextual trust channels can enhance privacy by controlling witness selection and excluding irrelevant nodes during transaction routing. @ bf95e1a4:ebdcc848
2025-03-28 13:56:06This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our[ Geyser page](https://geyser.fund/project/infinity)! ## Financial Atheism “Don’t trust, verify” is a common saying amongst bitcoiners that represents a sound attitude towards not only Bitcoin but all human power structures. In order to understand Bitcoin, one must admit that everything in society is man-made. Every civilization, every religion, every constitution, and every law is a product of human imagination. It wasn’t until as late as the 17th century that the scientific method started to become the dominant practice for describing how the world actually worked. Peer-to-peer review and repeated testing of a hypothesis are still quite recent human practices. Before this, we were basically just guessing and trusting authorities to a large extent. We still do this today, and despite our progress over the last couple of centuries, we still have a long way to go. Our brains are hardwired to follow the leader of the pack. The human brain is born with a plethora of cognitive biases pre-installed, and we have to work very hard to overcome them. We evolved to survive in relatively small groups, and our brains are thus not really made for seeing the bigger picture. Bitcoin’s proof-of-work algorithm is constructed in such a way that it is easy to verify that computational power was sacrificed in order to approve a block of transactions and claim its reward. In this way, no trust in any authority is required as it is relatively trivial to test the validity of a block and the transactions it contains. This is nothing short of a complete reimagining of how human society ought to be governed. The beauty of mathematics governs the Bitcoin system. Everything that ever happens in Bitcoin is open and verifiable to everyone, even to those who are not yet using it. After the tragic events of 9/11 in 2001, Sam Harris started writing his book *The End of Faith*, which happened to be released around the same time as Richard Dawkins’ *The God Delusion*, Daniel Dennett's *Breaking the Spell*, and Christopher Hitchens’ *God Is Not Great: How Religion Poisons Everything*. These books kick-started what, in hindsight, has often been referred to as the new atheist movement, even though there has arguably never been anything new about atheism. Atheism must almost certainly have preceded religion since religious ideas require the person holding the idea to believe a certain doctrine or story. Atheism is nothing but the rejection of ways to describe the world that are not verifiable by experimentation. A fly on the wall is probably an atheist by this definition of the word. Atheism is often accused of being just another set of beliefs, but the word itself describes what it is much better — a lack of belief in theistic ideas. It is not a code of conduct or set of rules to live your life by; it is simply the rejection of that which cannot be scientifically verified. Many people, religious people, in particular, have a hard time grasping this. If you believe that a supernatural entity created everything in everyone's life, you might not be too comfortable with a word that describes a complete rejection of what you believe created everything, including the very atheist that the word describes. The amount of different religious worldviews that exist is probably equal to the sum of all religious people on the planet, but all world views that reject these superstitious beliefs require but one word. Atheism is not the opposite of religion but is simply the lack of it. In 2008, another sub-culture movement of unbelief was born. Let’s call it *Financial Atheism* — the rejection of unverifiable value claims. With the invention of Bitcoin, a way of rejecting fraudulent expressions of a token’s value was born. Those of us fortunate enough to have been born in secular countries all enjoy not having the ideas of religious demagogues dictating our lives on a daily basis. We can choose which ideas to believe in and which to reject. What we still have very limited means of choosing, however, are the ways in which we express value to each other. We’re told to use a system in which we all have a certain number of value tokens assigned to our name, either as a number on a screen or as digits on paper notes. We all live in the collective hallucination that these numbers are somehow legit and that their authenticity is not to be questioned. A Bitcoin balance assigned to a certain Bitcoin address might seem just as questionable to a layman, but if you have a basic understanding of the hashing algorithms and game theory behind it, it’s not. At the time of writing, the hash of the latest block on the Bitcoin blockchain begins with eighteen zeros in a row. These zeros represent the Proof of Work that ensures that this block is valid and that every transaction in it actually happened. If you can grasp the concept of a hashing algorithm, and if you have an intuition about mathematics, you realize the gargantuan amount of calculating effort that went into finding this particular hash. It is simply mind-blowing. To forge a false version of a hash beginning with eighteen zeros just wouldn’t be economically viable. Of course, you can never actually know that a 51% attack or some other attempt at corrupting the blockchain hasn’t occurred, but you can know that such an attack would require more than half of the network acting against their own economic interest. Bitcoin is not something to believe in. You don’t need to trust any authority because you can validate the plausibility of its authenticity yourself. It’s the financial equivalent of atheism or unbelief. Satoshi wasn’t Jesus. Satoshi was Brian of Nazareth, telling his followers to think for themselves. The first law of thermodynamics, also known as the Law of Conservation of Energy, states that energy cannot be created or destroyed in an isolated system. The second law states that the entropy of any isolated system always increases, and the third law states that the entropy of a system approaches a constant value as the temperature approaches absolute zero. In the Bitcoin network, participants known as miners compete for new Bitcoin in a lottery with very fixed rules. The more hashing power (computing power) a miner contributes to the network, the higher his chances of winning the block reward, a specific amount of Bitcoin that is halved every four years. The difficulty of this lottery - in other words, the miner’s chance of winning it — is re-calibrated every 2016th block so that the average time it takes to find the next block is always roughly ten minutes. What this system produces is absolute scarcity; the amount of Bitcoin in existence at any moment in time is always predictable. The more time that passes, the slower the rate of coin issuance and the block reward slowly approaches zero. By the time it does, around the year 2140, the individual miner’s incentive to mine for a reward will, at least theoretically, have been replaced by an incentive to collect transaction fees from the participants of the network. Even now, the sum of all fees make up a non-trivial part of the miners’ revenue. Yet from a user’s point of view the fees are still very low, and as the network scales up using Layer 2 solutions such as the Lightning Network, they’re expected to remain low for quite a long time ahead. Absolute scarcity is a concept that mankind has never encountered before. Arguably, this makes it the first man-made concept to ever be directly linked to the laws of physics. Everything anyone does requires a certain amount of energy. The very word *doing* implies that some kind of movement, some type of energy expenditure, needs to occur. As mentioned earlier, how we value things is entirely subjective. Different actions are of different value to different people. How we value different things is also inevitably linked to the supply of those things. Had the trapped-under-ice winter diver mentioned in chapter one been equipped with a scuba tank, he probably wouldn't have thought of his next breath as such a precious thing. The price a person is willing to pay for a good — in other words, the sum of one or more person’s actions — can be derived from two basic variables: The highly subjective *demand* for the good and the always-constrained-by-time-and-space *supply* of that same good. Note that if supply is sufficiently limited, there only needs to be a minimal amount of demand for a good for its price to increase. One could argue that no one *needs* Bitcoin and that, therefore, Bitcoin would have no intrinsic value. One could also argue that there’s no such thing as intrinsic value since demand is always subjective. In any case, there will always be a cost to mine Bitcoin, and the more mining power in the network, the higher that cost. This cost, ensured by the Bitcoin network’s Proof-Of-Work algorithm, is probably as close to a pure energy cost as the price of a human activity will ever get. Once the mining rig is in place, a simple conversion process follows — energy in, scarce token out. Should the cost of production exceed the current price of the token, the miner can just choose not to sell, thereby limiting the supply of Bitcoin in circulation even more and eventually selling them for other goods whenever he sees fit. In this sense, Bitcoin is a battery. Perhaps the best battery ever invented. Storing and moving electrical energy around has always been costly and wasteful. Bitcoin offers a way of converting energy into a small part of a specific number. A mathematical battery, if you will. It is important to remember that it does not convert energy into value *directly*, but rather electricity into digital scarcity — digital scarcity that can be used to express value. Energy cannot be created or destroyed in an isolated system, as the first law of thermodynamics clearly states. Bitcoin can express how much energy was sacrificed in order to acquire a share of the total sum. You can also acquire Bitcoin by buying it rather than mining it, but in doing so, you also spend energy. You somehow acquired the money with which you bought the Bitcoin. You, or someone else, sacrificed time and energy somewhere. Bitcoin lets you express that you see that there’s a connection between value and scarcity by letting you sacrifice effort to claim a part of the total sum. The excitement we so-called "Bitcoin Maximalists" feel about Bitcoin does not come primarily from the enormous gains that those who hopped early onto the freight train have been blessed with. Nor is it because we’re “in it for the technology,” as can often be heard from opponents. Those of us who preach the near-divinity of this invention do so above all because we see the philosophical impacts of absolute scarcity in a commodity. The idea of a functioning solution to the double-spending problem in computerized money is an achievement that simply can’t be ignored. By solving the double-spending problem, Satoshi also made counterfeiting impossible, which in turn makes artificial inflation impossible. The world-changing potential of this invention cannot be understated. Not in the long run. The more you think about it, the more the thought won’t give you any peace of mind. If this experiment works, if it’s real, it will take civilization to the next level. What we don’t know is how long this will take. Right now, debates in the Bitcoin space are about Bitcoin’s functionality as a medium of exchange and its potential as a good store of value. We might be missing the point. We cannot possibly know if a type of monetary token for which you’re completely responsible, with no third-party protection, will ever become a preferred medium of exchange for most transactions. Nor can we know if the price of Bitcoin will follow the hype-cycle path that we all want it to follow so that it can become the store of value that most maximalists claim it already is. Maybe we’ve been focused on the wrong things all along. Maybe Bitcoin’s greatest strength is in its functionality as a unit of account. After all, this is all that Bitcoin does. If you own 21 Bitcoin, you own one-millionth of the world's first absolutely scarce commodity. This might not make you rich overnight, but it just might have something to do with the opportunities available to your great-great-grandchildren. Throughout history, whenever a prehistoric human tribe invented ceremonial burial, that tribe began to expand rapidly. Why? Because as soon as you invent belief in an afterlife, you also introduce the idea of self-sacrifice on a larger scale. People who held these beliefs were much easier for a despot to manipulate and send into battle with neighboring tribes. Religious leaders can use people’s fears and superstitions to have them commit all sorts of atrocities to their fellow man, and they still do so today. Belief in a “greater good” can be the most destructive idea that can pop up in a human mind. The Nazis of World War II Germany believed that exterminating Jews was for the “greater good” of their nation’s gene pool. Belief in noble causes often comes with unintended side effects, which can have disastrous consequences. Religious leaders, political leaders, and other power-hungry sociopaths are responsible for the greatest crimes against humanity ever committed — namely, wars. Europeans often question the Second Amendment to the United States Constitution, which protects the right to bear arms, whenever a tragic school shooting occurs on the other side of the Atlantic. What everyone seems to forget is that less than a hundred years ago, Europe was at war with itself because its citizens had given too much power to their so-called leaders. The Nazis came to power in a democracy — never forget that. Our individual rights weren’t given to us by our leaders; we were born with them. Our leaders can’t give us anything; they can only force us to behave in certain ways. If we truly want to be in charge of our lives, we need to find the tools necessary to circumvent the bullshit ourselves. ### **About the Bitcoin Infinity Academy** The Bitcoin Infinity Academy is an educational project built around [Knut Svanholm](http://primal.net/knut)’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a [video](https://www.youtube.com/@BitcoinInfinityShow) in which Knut and [Luke de Wolf](http://primal.net/luke) discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our [Geyser](https://geyser.fund/project/infinity) page. Signed books, monthly calls, and lots of other benefits are also available.
@ bf95e1a4:ebdcc848
2025-03-28 13:56:06This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our[ Geyser page](https://geyser.fund/project/infinity)! ## Financial Atheism “Don’t trust, verify” is a common saying amongst bitcoiners that represents a sound attitude towards not only Bitcoin but all human power structures. In order to understand Bitcoin, one must admit that everything in society is man-made. Every civilization, every religion, every constitution, and every law is a product of human imagination. It wasn’t until as late as the 17th century that the scientific method started to become the dominant practice for describing how the world actually worked. Peer-to-peer review and repeated testing of a hypothesis are still quite recent human practices. Before this, we were basically just guessing and trusting authorities to a large extent. We still do this today, and despite our progress over the last couple of centuries, we still have a long way to go. Our brains are hardwired to follow the leader of the pack. The human brain is born with a plethora of cognitive biases pre-installed, and we have to work very hard to overcome them. We evolved to survive in relatively small groups, and our brains are thus not really made for seeing the bigger picture. Bitcoin’s proof-of-work algorithm is constructed in such a way that it is easy to verify that computational power was sacrificed in order to approve a block of transactions and claim its reward. In this way, no trust in any authority is required as it is relatively trivial to test the validity of a block and the transactions it contains. This is nothing short of a complete reimagining of how human society ought to be governed. The beauty of mathematics governs the Bitcoin system. Everything that ever happens in Bitcoin is open and verifiable to everyone, even to those who are not yet using it. After the tragic events of 9/11 in 2001, Sam Harris started writing his book *The End of Faith*, which happened to be released around the same time as Richard Dawkins’ *The God Delusion*, Daniel Dennett's *Breaking the Spell*, and Christopher Hitchens’ *God Is Not Great: How Religion Poisons Everything*. These books kick-started what, in hindsight, has often been referred to as the new atheist movement, even though there has arguably never been anything new about atheism. Atheism must almost certainly have preceded religion since religious ideas require the person holding the idea to believe a certain doctrine or story. Atheism is nothing but the rejection of ways to describe the world that are not verifiable by experimentation. A fly on the wall is probably an atheist by this definition of the word. Atheism is often accused of being just another set of beliefs, but the word itself describes what it is much better — a lack of belief in theistic ideas. It is not a code of conduct or set of rules to live your life by; it is simply the rejection of that which cannot be scientifically verified. Many people, religious people, in particular, have a hard time grasping this. If you believe that a supernatural entity created everything in everyone's life, you might not be too comfortable with a word that describes a complete rejection of what you believe created everything, including the very atheist that the word describes. The amount of different religious worldviews that exist is probably equal to the sum of all religious people on the planet, but all world views that reject these superstitious beliefs require but one word. Atheism is not the opposite of religion but is simply the lack of it. In 2008, another sub-culture movement of unbelief was born. Let’s call it *Financial Atheism* — the rejection of unverifiable value claims. With the invention of Bitcoin, a way of rejecting fraudulent expressions of a token’s value was born. Those of us fortunate enough to have been born in secular countries all enjoy not having the ideas of religious demagogues dictating our lives on a daily basis. We can choose which ideas to believe in and which to reject. What we still have very limited means of choosing, however, are the ways in which we express value to each other. We’re told to use a system in which we all have a certain number of value tokens assigned to our name, either as a number on a screen or as digits on paper notes. We all live in the collective hallucination that these numbers are somehow legit and that their authenticity is not to be questioned. A Bitcoin balance assigned to a certain Bitcoin address might seem just as questionable to a layman, but if you have a basic understanding of the hashing algorithms and game theory behind it, it’s not. At the time of writing, the hash of the latest block on the Bitcoin blockchain begins with eighteen zeros in a row. These zeros represent the Proof of Work that ensures that this block is valid and that every transaction in it actually happened. If you can grasp the concept of a hashing algorithm, and if you have an intuition about mathematics, you realize the gargantuan amount of calculating effort that went into finding this particular hash. It is simply mind-blowing. To forge a false version of a hash beginning with eighteen zeros just wouldn’t be economically viable. Of course, you can never actually know that a 51% attack or some other attempt at corrupting the blockchain hasn’t occurred, but you can know that such an attack would require more than half of the network acting against their own economic interest. Bitcoin is not something to believe in. You don’t need to trust any authority because you can validate the plausibility of its authenticity yourself. It’s the financial equivalent of atheism or unbelief. Satoshi wasn’t Jesus. Satoshi was Brian of Nazareth, telling his followers to think for themselves. The first law of thermodynamics, also known as the Law of Conservation of Energy, states that energy cannot be created or destroyed in an isolated system. The second law states that the entropy of any isolated system always increases, and the third law states that the entropy of a system approaches a constant value as the temperature approaches absolute zero. In the Bitcoin network, participants known as miners compete for new Bitcoin in a lottery with very fixed rules. The more hashing power (computing power) a miner contributes to the network, the higher his chances of winning the block reward, a specific amount of Bitcoin that is halved every four years. The difficulty of this lottery - in other words, the miner’s chance of winning it — is re-calibrated every 2016th block so that the average time it takes to find the next block is always roughly ten minutes. What this system produces is absolute scarcity; the amount of Bitcoin in existence at any moment in time is always predictable. The more time that passes, the slower the rate of coin issuance and the block reward slowly approaches zero. By the time it does, around the year 2140, the individual miner’s incentive to mine for a reward will, at least theoretically, have been replaced by an incentive to collect transaction fees from the participants of the network. Even now, the sum of all fees make up a non-trivial part of the miners’ revenue. Yet from a user’s point of view the fees are still very low, and as the network scales up using Layer 2 solutions such as the Lightning Network, they’re expected to remain low for quite a long time ahead. Absolute scarcity is a concept that mankind has never encountered before. Arguably, this makes it the first man-made concept to ever be directly linked to the laws of physics. Everything anyone does requires a certain amount of energy. The very word *doing* implies that some kind of movement, some type of energy expenditure, needs to occur. As mentioned earlier, how we value things is entirely subjective. Different actions are of different value to different people. How we value different things is also inevitably linked to the supply of those things. Had the trapped-under-ice winter diver mentioned in chapter one been equipped with a scuba tank, he probably wouldn't have thought of his next breath as such a precious thing. The price a person is willing to pay for a good — in other words, the sum of one or more person’s actions — can be derived from two basic variables: The highly subjective *demand* for the good and the always-constrained-by-time-and-space *supply* of that same good. Note that if supply is sufficiently limited, there only needs to be a minimal amount of demand for a good for its price to increase. One could argue that no one *needs* Bitcoin and that, therefore, Bitcoin would have no intrinsic value. One could also argue that there’s no such thing as intrinsic value since demand is always subjective. In any case, there will always be a cost to mine Bitcoin, and the more mining power in the network, the higher that cost. This cost, ensured by the Bitcoin network’s Proof-Of-Work algorithm, is probably as close to a pure energy cost as the price of a human activity will ever get. Once the mining rig is in place, a simple conversion process follows — energy in, scarce token out. Should the cost of production exceed the current price of the token, the miner can just choose not to sell, thereby limiting the supply of Bitcoin in circulation even more and eventually selling them for other goods whenever he sees fit. In this sense, Bitcoin is a battery. Perhaps the best battery ever invented. Storing and moving electrical energy around has always been costly and wasteful. Bitcoin offers a way of converting energy into a small part of a specific number. A mathematical battery, if you will. It is important to remember that it does not convert energy into value *directly*, but rather electricity into digital scarcity — digital scarcity that can be used to express value. Energy cannot be created or destroyed in an isolated system, as the first law of thermodynamics clearly states. Bitcoin can express how much energy was sacrificed in order to acquire a share of the total sum. You can also acquire Bitcoin by buying it rather than mining it, but in doing so, you also spend energy. You somehow acquired the money with which you bought the Bitcoin. You, or someone else, sacrificed time and energy somewhere. Bitcoin lets you express that you see that there’s a connection between value and scarcity by letting you sacrifice effort to claim a part of the total sum. The excitement we so-called "Bitcoin Maximalists" feel about Bitcoin does not come primarily from the enormous gains that those who hopped early onto the freight train have been blessed with. Nor is it because we’re “in it for the technology,” as can often be heard from opponents. Those of us who preach the near-divinity of this invention do so above all because we see the philosophical impacts of absolute scarcity in a commodity. The idea of a functioning solution to the double-spending problem in computerized money is an achievement that simply can’t be ignored. By solving the double-spending problem, Satoshi also made counterfeiting impossible, which in turn makes artificial inflation impossible. The world-changing potential of this invention cannot be understated. Not in the long run. The more you think about it, the more the thought won’t give you any peace of mind. If this experiment works, if it’s real, it will take civilization to the next level. What we don’t know is how long this will take. Right now, debates in the Bitcoin space are about Bitcoin’s functionality as a medium of exchange and its potential as a good store of value. We might be missing the point. We cannot possibly know if a type of monetary token for which you’re completely responsible, with no third-party protection, will ever become a preferred medium of exchange for most transactions. Nor can we know if the price of Bitcoin will follow the hype-cycle path that we all want it to follow so that it can become the store of value that most maximalists claim it already is. Maybe we’ve been focused on the wrong things all along. Maybe Bitcoin’s greatest strength is in its functionality as a unit of account. After all, this is all that Bitcoin does. If you own 21 Bitcoin, you own one-millionth of the world's first absolutely scarce commodity. This might not make you rich overnight, but it just might have something to do with the opportunities available to your great-great-grandchildren. Throughout history, whenever a prehistoric human tribe invented ceremonial burial, that tribe began to expand rapidly. Why? Because as soon as you invent belief in an afterlife, you also introduce the idea of self-sacrifice on a larger scale. People who held these beliefs were much easier for a despot to manipulate and send into battle with neighboring tribes. Religious leaders can use people’s fears and superstitions to have them commit all sorts of atrocities to their fellow man, and they still do so today. Belief in a “greater good” can be the most destructive idea that can pop up in a human mind. The Nazis of World War II Germany believed that exterminating Jews was for the “greater good” of their nation’s gene pool. Belief in noble causes often comes with unintended side effects, which can have disastrous consequences. Religious leaders, political leaders, and other power-hungry sociopaths are responsible for the greatest crimes against humanity ever committed — namely, wars. Europeans often question the Second Amendment to the United States Constitution, which protects the right to bear arms, whenever a tragic school shooting occurs on the other side of the Atlantic. What everyone seems to forget is that less than a hundred years ago, Europe was at war with itself because its citizens had given too much power to their so-called leaders. The Nazis came to power in a democracy — never forget that. Our individual rights weren’t given to us by our leaders; we were born with them. Our leaders can’t give us anything; they can only force us to behave in certain ways. If we truly want to be in charge of our lives, we need to find the tools necessary to circumvent the bullshit ourselves. ### **About the Bitcoin Infinity Academy** The Bitcoin Infinity Academy is an educational project built around [Knut Svanholm](http://primal.net/knut)’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a [video](https://www.youtube.com/@BitcoinInfinityShow) in which Knut and [Luke de Wolf](http://primal.net/luke) discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our [Geyser](https://geyser.fund/project/infinity) page. Signed books, monthly calls, and lots of other benefits are also available. @ c631e267:c2b78d3e
2025-03-21 19:41:50*Wir werden nicht zulassen, dass technisch manches möglich ist,* *\ aber der Staat es nicht nutzt.* *\ Angela Merkel*   **Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach.** Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides. **Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar,** dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.  **Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen,** die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch. **Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen** und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war [vielleicht früher](https://transition-news.org/der-sumpf-aus-ngos-parteien-und-steuergeld) einmal so, heute ist eher das Gegenteil gemeint. **In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung** praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien [beleuchtet](https://transition-news.org/nur-abschied-vom-alleinfahren-monstrose-spanische-uberwachungsprojekte-gemass). Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als [«Technofeudalismus»](https://transition-news.org/yanis-varoufakis-der-europaische-traum-ist-tot-es-lebe-der-neue-traum) angeprangert. **Nationale** **[Zugangspunkte](https://transport.ec.europa.eu/transport-themes/smart-mobility/road/its-directive-and-action-plan/national-access-points_en)** **für Mobilitätsdaten im Sinne der EU** gibt es nicht nur in allen Mitgliedsländern, sondern auch in der [Schweiz](https://opentransportdata.swiss/de/) und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen [Identifizierungssystem](https://transition-news.org/biometrische-gesichtserkennung-in-britischen-hafen) für «nachhaltigen Verkehr und Tourismus». **Natürlich marschiert auch Deutschland stracks und euphorisch** in Richtung digitaler Zukunft. Ohne [vernetzte Mobilität](https://mobilithek.info/about) und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität [voll auf Digitalisierung](https://www.smartcountry.berlin/de/newsblog/smart-city-index-grossstaedte-setzen-bei-mobilitaet-voll-auf-digitalisierung.html)». **Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten,** das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten. *\[Titelbild:* *[Pixabay](https://pareto.space/readhttps://pixabay.com/de/illustrations/schaufensterpuppe-platine-gesicht-5254046/)]* *** Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben. Er ist zuerst auf ***[Transition News](https://transition-news.org/das-gegenteil-von-mussen-ist-nicht-durfen)*** erschienen.
@ c631e267:c2b78d3e
2025-03-21 19:41:50*Wir werden nicht zulassen, dass technisch manches möglich ist,* *\ aber der Staat es nicht nutzt.* *\ Angela Merkel*   **Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach.** Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides. **Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar,** dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.  **Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen,** die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch. **Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen** und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war [vielleicht früher](https://transition-news.org/der-sumpf-aus-ngos-parteien-und-steuergeld) einmal so, heute ist eher das Gegenteil gemeint. **In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung** praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien [beleuchtet](https://transition-news.org/nur-abschied-vom-alleinfahren-monstrose-spanische-uberwachungsprojekte-gemass). Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als [«Technofeudalismus»](https://transition-news.org/yanis-varoufakis-der-europaische-traum-ist-tot-es-lebe-der-neue-traum) angeprangert. **Nationale** **[Zugangspunkte](https://transport.ec.europa.eu/transport-themes/smart-mobility/road/its-directive-and-action-plan/national-access-points_en)** **für Mobilitätsdaten im Sinne der EU** gibt es nicht nur in allen Mitgliedsländern, sondern auch in der [Schweiz](https://opentransportdata.swiss/de/) und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen [Identifizierungssystem](https://transition-news.org/biometrische-gesichtserkennung-in-britischen-hafen) für «nachhaltigen Verkehr und Tourismus». **Natürlich marschiert auch Deutschland stracks und euphorisch** in Richtung digitaler Zukunft. Ohne [vernetzte Mobilität](https://mobilithek.info/about) und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität [voll auf Digitalisierung](https://www.smartcountry.berlin/de/newsblog/smart-city-index-grossstaedte-setzen-bei-mobilitaet-voll-auf-digitalisierung.html)». **Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten,** das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten. *\[Titelbild:* *[Pixabay](https://pareto.space/readhttps://pixabay.com/de/illustrations/schaufensterpuppe-platine-gesicht-5254046/)]* *** Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben. Er ist zuerst auf ***[Transition News](https://transition-news.org/das-gegenteil-von-mussen-ist-nicht-durfen)*** erschienen. @ df173277:4ec96708
2025-01-28 17:49:54> Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. Chats are synced automatically between devices so you can pick up where you left off.\ > [Start chatting for free.](https://trymaple.ai/) We are excited to announce that [Maple AI](https://trymaple.ai/), our groundbreaking end-to-end encrypted AI chat app built on OpenSecret, is now publicly available. After months of beta testing, we are thrilled to bring this innovative technology to the world. Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another. #### Why Secure and Private AI? In today's digital landscape, it is increasingly evident that security and privacy are essential for individuals and organizations alike. Unfortunately, the current state of AI tools falls short. A staggering 48% of organizations enter non-public company information into AI apps, according to a [recent report by Cisco](https://www.cisco.com/c/en/us/about/trust-center/data-privacy-benchmark-study.html#~key-findings). This practice poses significant risks to company security and intellectual property. Another concern is for journalists, who often work with sensitive information in hostile environments. Journalists need verification that their information remains confidential and protected when researching topics and communicating with sources in various languages. They are left to use underpowered local AI or input their data into potentially compromised cloud services. At OpenSecret, we believe it is possible to have both the benefits of AI and the assurance of security and privacy. That's why we created Maple, an app that combines AI productivity with the protection of end-to-end encryption. Our platform ensures that your conversations with AI remain confidential, even from us. The power of the cloud meets the privacy of local. #### How Does It Work? Our server code is [open source](https://github.com/OpenSecretCloud/opensecret), and we use confidential computing to provide cryptographic proof that the code running on our servers is the same as the open-source code available for review. This process allows you to verify that your conversations are handled securely and privately without relying on trust. We live by the principle of "Don't trust, verify," and we believe this approach is essential for building in the digital age. You can read a more in-depth write-up on our technology later this week on this site. #### How Much Does It Cost? We are committed to making Maple AI accessible to everyone, so we offer a range of pricing plans to suit different needs and budgets. [Our Free plan allows for 10 chats per week, while our Starter plan ($5.99/month) and Pro plan ($20/month)](https://trymaple.ai/pricing) offer more comprehensive solutions for individuals and organizations with heavier workloads. We accept credit cards and Bitcoin (10% discount), allowing you to choose your preferred payment method. - Free: $0 - Starter: $5.99/month - Pro: $20/month Our goal with Maple AI is to create a product that is secure through transparency. By combining open-source code, cryptography, and confidential computing, we can create a new standard for AI conversations - one that prioritizes your security and privacy. Maple has quickly become a daily tool of productivity for our own work and those of our beta testers. We believe it will bring value to you as well. [Sign up now and start chatting privately with AI for free.](https://trymaple.ai/) Your secrets are safe in the open. #### Are You An App Developer? You can build an app like Maple. [OpenSecret provides secure auth, private key management, encrypted data sync, private AI, and more.](https://blog.opensecret.cloud/introducing-opensecret/) Our straightforward API behaves like other backends but automatically adds security and privacy. Use it to secure existing apps or brand-new projects. Protect yourself and your users from the liability of hosting personal data by checking out [OpenSecret](https://opensecret.cloud/). <img src="https://blossom.primal.net/feb746d5e164e89f0d015646286b88237dce4158f8985e3caaf7e427cebde608.png"> Enjoy private AI Chat 🤘 <img src="https://blossom.primal.net/0594ec56e249de2754ea7dfc225a7ebd46bc298b5af168279ce71f17c2afada0.jpg">
@ df173277:4ec96708
2025-01-28 17:49:54> Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. Chats are synced automatically between devices so you can pick up where you left off.\ > [Start chatting for free.](https://trymaple.ai/) We are excited to announce that [Maple AI](https://trymaple.ai/), our groundbreaking end-to-end encrypted AI chat app built on OpenSecret, is now publicly available. After months of beta testing, we are thrilled to bring this innovative technology to the world. Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another. #### Why Secure and Private AI? In today's digital landscape, it is increasingly evident that security and privacy are essential for individuals and organizations alike. Unfortunately, the current state of AI tools falls short. A staggering 48% of organizations enter non-public company information into AI apps, according to a [recent report by Cisco](https://www.cisco.com/c/en/us/about/trust-center/data-privacy-benchmark-study.html#~key-findings). This practice poses significant risks to company security and intellectual property. Another concern is for journalists, who often work with sensitive information in hostile environments. Journalists need verification that their information remains confidential and protected when researching topics and communicating with sources in various languages. They are left to use underpowered local AI or input their data into potentially compromised cloud services. At OpenSecret, we believe it is possible to have both the benefits of AI and the assurance of security and privacy. That's why we created Maple, an app that combines AI productivity with the protection of end-to-end encryption. Our platform ensures that your conversations with AI remain confidential, even from us. The power of the cloud meets the privacy of local. #### How Does It Work? Our server code is [open source](https://github.com/OpenSecretCloud/opensecret), and we use confidential computing to provide cryptographic proof that the code running on our servers is the same as the open-source code available for review. This process allows you to verify that your conversations are handled securely and privately without relying on trust. We live by the principle of "Don't trust, verify," and we believe this approach is essential for building in the digital age. You can read a more in-depth write-up on our technology later this week on this site. #### How Much Does It Cost? We are committed to making Maple AI accessible to everyone, so we offer a range of pricing plans to suit different needs and budgets. [Our Free plan allows for 10 chats per week, while our Starter plan ($5.99/month) and Pro plan ($20/month)](https://trymaple.ai/pricing) offer more comprehensive solutions for individuals and organizations with heavier workloads. We accept credit cards and Bitcoin (10% discount), allowing you to choose your preferred payment method. - Free: $0 - Starter: $5.99/month - Pro: $20/month Our goal with Maple AI is to create a product that is secure through transparency. By combining open-source code, cryptography, and confidential computing, we can create a new standard for AI conversations - one that prioritizes your security and privacy. Maple has quickly become a daily tool of productivity for our own work and those of our beta testers. We believe it will bring value to you as well. [Sign up now and start chatting privately with AI for free.](https://trymaple.ai/) Your secrets are safe in the open. #### Are You An App Developer? You can build an app like Maple. [OpenSecret provides secure auth, private key management, encrypted data sync, private AI, and more.](https://blog.opensecret.cloud/introducing-opensecret/) Our straightforward API behaves like other backends but automatically adds security and privacy. Use it to secure existing apps or brand-new projects. Protect yourself and your users from the liability of hosting personal data by checking out [OpenSecret](https://opensecret.cloud/). <img src="https://blossom.primal.net/feb746d5e164e89f0d015646286b88237dce4158f8985e3caaf7e427cebde608.png"> Enjoy private AI Chat 🤘 <img src="https://blossom.primal.net/0594ec56e249de2754ea7dfc225a7ebd46bc298b5af168279ce71f17c2afada0.jpg"> @ df173277:4ec96708
2025-01-09 17:12:08> Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\ > [Join the waitlist to get early access.](https://trymaple.ai) We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI. Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations. #### Building a Private Foundation Maple is built on our flagship product, [OpenSecret](https://opensecret.cloud), a backend platform for app developers that turns private encryption on by default. [The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do.](nostr:naddr1qvzqqqr4gupzphchxfm3ste32hfhkvczzxapme9gz5qvqtget6tylyd7wa8vjecgqqe5jmn5wfhkgatrd9hxwt20wpjku5m9vdex2apdw35x2tt9de3hy7tsw3jkgttzv93kketwvskhgur5w9nx5h52tpj) We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win. #### The Power of Encrypted AI Chat AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short. Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us. #### Technical Overview So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects: - **Private Key:** Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data. - **Secure Servers:** Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations. - **Encrypted Sync:** One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised. - **Attestation and Open Code:** We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public. - **Open Source LLM:** Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased. #### Personal and Work Use Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe. #### Local v Cloud Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds. #### Why the Maple name? Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment. #### Join the Waitlist Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. [Join our waitlist today to be among the first to experience the power of private AI chat.](https://trymaple.ai) [](https://trymaple.ai/waitlist)
@ df173277:4ec96708
2025-01-09 17:12:08> Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\ > [Join the waitlist to get early access.](https://trymaple.ai) We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI. Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations. #### Building a Private Foundation Maple is built on our flagship product, [OpenSecret](https://opensecret.cloud), a backend platform for app developers that turns private encryption on by default. [The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do.](nostr:naddr1qvzqqqr4gupzphchxfm3ste32hfhkvczzxapme9gz5qvqtget6tylyd7wa8vjecgqqe5jmn5wfhkgatrd9hxwt20wpjku5m9vdex2apdw35x2tt9de3hy7tsw3jkgttzv93kketwvskhgur5w9nx5h52tpj) We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win. #### The Power of Encrypted AI Chat AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short. Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us. #### Technical Overview So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects: - **Private Key:** Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data. - **Secure Servers:** Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations. - **Encrypted Sync:** One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised. - **Attestation and Open Code:** We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public. - **Open Source LLM:** Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased. #### Personal and Work Use Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe. #### Local v Cloud Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds. #### Why the Maple name? Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment. #### Join the Waitlist Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. [Join our waitlist today to be among the first to experience the power of private AI chat.](https://trymaple.ai) [](https://trymaple.ai/waitlist) @ 8cb60e21:5f2deaea
2024-08-24 23:57:19asdasdasdsad
@ 8cb60e21:5f2deaea
2024-08-24 23:57:19asdasdasdsad @ 2fdeba99:fd961eff
2025-03-21 17:16:33# == January 17 2025 Out From Underneath | Prism Shores crazy arms | pigeon pit Humanhood | The Weather Station # == february 07 2025 Wish Defense | FACS Sayan - Savoie | Maria Teriaeva Nowhere Near Today | Midding # == february 14 2025 Phonetics On and On | Horsegirl # == february 21 2025 Finding Our Balance | Tsoh Tso Machine Starts To Sing | Porridge Radio Armageddon In A Summer Dress | Sunny Wa # == february 28 2025 you, infinite | you, infinite On Being | Max Cooper Billboard Heart | Deep Sea Diver # == March 21 2025 Watermelon/Peacock | Exploding Flowers Warlord of the Weejuns | Goya Gumbani
@ 2fdeba99:fd961eff
2025-03-21 17:16:33# == January 17 2025 Out From Underneath | Prism Shores crazy arms | pigeon pit Humanhood | The Weather Station # == february 07 2025 Wish Defense | FACS Sayan - Savoie | Maria Teriaeva Nowhere Near Today | Midding # == february 14 2025 Phonetics On and On | Horsegirl # == february 21 2025 Finding Our Balance | Tsoh Tso Machine Starts To Sing | Porridge Radio Armageddon In A Summer Dress | Sunny Wa # == february 28 2025 you, infinite | you, infinite On Being | Max Cooper Billboard Heart | Deep Sea Diver # == March 21 2025 Watermelon/Peacock | Exploding Flowers Warlord of the Weejuns | Goya Gumbani @ aa8de34f:a6ffe696
2025-03-21 12:08:3119\. März 2025 ### 🔐 1. SHA-256 is Quantum-Resistant Bitcoin’s **proof-of-work** mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, **SHA-256 remains secure** because: - Quantum computers excel at **factoring large numbers** (Shor’s Algorithm). - However, **SHA-256 is a one-way function**, meaning there's no known quantum algorithm that can efficiently reverse it. - **Grover’s Algorithm** (which theoretically speeds up brute force attacks) would still require **2¹²⁸ operations** to break SHA-256 – far beyond practical reach. ++++++++++++++++++++++++++++++++++++++++++++++++++ ### 🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses Bitcoin uses **Elliptic Curve Digital Signature Algorithm (ECDSA)** to generate keys. - A quantum computer could use **Shor’s Algorithm** to break **SECP256K1**, the curve Bitcoin uses. - If you never reuse addresses, it is an additional security element - 🔑 1. Bitcoin Addresses Are NOT Public Keys Many people assume a **Bitcoin address** is the public key—**this is wrong**. - When you **receive Bitcoin**, it is sent to a **hashed public key** (the Bitcoin address). - The **actual public key is never exposed** because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend - Bitcoin uses **Pay-to-Public-Key-Hash (P2PKH)** or newer methods like **Pay-to-Witness-Public-Key-Hash (P2WPKH)**, which add extra layers of security. ### 🕵️♂️ 2.1 The Public Key Never Appears - When you **send Bitcoin**, your wallet creates a **digital signature**. - This signature uses the **private key** to **prove** ownership. - The **Bitcoin address is revealed and creates the Public Key** - The public key **remains hidden inside the Bitcoin script and Merkle tree**. This means: ✔ **The public key is never exposed.** ✔ **Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.** +++++++++++++++++++++++++++++++++++++++++++++++++ ### 🔄 3. Bitcoin Can Upgrade Even if quantum computers **eventually** become a real threat: - Bitcoin developers can **upgrade to quantum-safe cryptography** (e.g., lattice-based cryptography or post-quantum signatures like Dilithium). - Bitcoin’s decentralized nature ensures a network-wide **soft fork or hard fork** could transition to quantum-resistant keys. ++++++++++++++++++++++++++++++++++++++++++++++++++ ### ⏳ 4. The 10-Minute Block Rule as a Security Feature - Bitcoin’s network operates on a **10-minute block interval**, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack **every 10 minutes**.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system **resets the challenge with every new block**.This **limits the window of opportunity** for quantum attacks. --- ### 🎯 5. Quantum Attack Needs to Solve a Block in Real-Time - A quantum attacker **must solve the cryptographic puzzle (Proof of Work) in under 10 minutes**. - The problem? **Any slight error changes the hash completely**, meaning:**If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails**.**Quantum decoherence** (loss of qubit stability) makes error correction a massive challenge.The computational cost of **recovering from an incorrect hash** is still incredibly high. --- ### ⚡ 6. Network Resilience – Even if a Block Is Hacked - Even if a quantum computer **somehow** solved a block instantly:The network would **quickly recognize and reject invalid transactions**.Other miners would **continue mining** under normal cryptographic rules.**51% Attack?** The attacker would need to consistently beat the **entire Bitcoin network**, which is **not sustainable**. --- ### 🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats - Bitcoin adjusts mining difficulty every **2016 blocks (\~2 weeks)**. - If quantum miners appeared and suddenly started solving blocks too quickly, **the difficulty would adjust upward**, making attacks significantly harder. - This **self-correcting mechanism** ensures that even quantum computers wouldn't easily overpower the network. --- ### 🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin ✔ **The 10-minute rule limits attack frequency** – quantum computers can’t keep up. ✔ **Any slight miscalculation ruins the attack**, resetting all progress. ✔ **Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages**. **Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant.** 🚀
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119\. März 2025 ### 🔐 1. SHA-256 is Quantum-Resistant Bitcoin’s **proof-of-work** mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, **SHA-256 remains secure** because: - Quantum computers excel at **factoring large numbers** (Shor’s Algorithm). - However, **SHA-256 is a one-way function**, meaning there's no known quantum algorithm that can efficiently reverse it. - **Grover’s Algorithm** (which theoretically speeds up brute force attacks) would still require **2¹²⁸ operations** to break SHA-256 – far beyond practical reach. ++++++++++++++++++++++++++++++++++++++++++++++++++ ### 🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses Bitcoin uses **Elliptic Curve Digital Signature Algorithm (ECDSA)** to generate keys. - A quantum computer could use **Shor’s Algorithm** to break **SECP256K1**, the curve Bitcoin uses. - If you never reuse addresses, it is an additional security element - 🔑 1. Bitcoin Addresses Are NOT Public Keys Many people assume a **Bitcoin address** is the public key—**this is wrong**. - When you **receive Bitcoin**, it is sent to a **hashed public key** (the Bitcoin address). - The **actual public key is never exposed** because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend - Bitcoin uses **Pay-to-Public-Key-Hash (P2PKH)** or newer methods like **Pay-to-Witness-Public-Key-Hash (P2WPKH)**, which add extra layers of security. ### 🕵️♂️ 2.1 The Public Key Never Appears - When you **send Bitcoin**, your wallet creates a **digital signature**. - This signature uses the **private key** to **prove** ownership. - The **Bitcoin address is revealed and creates the Public Key** - The public key **remains hidden inside the Bitcoin script and Merkle tree**. This means: ✔ **The public key is never exposed.** ✔ **Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.** +++++++++++++++++++++++++++++++++++++++++++++++++ ### 🔄 3. Bitcoin Can Upgrade Even if quantum computers **eventually** become a real threat: - Bitcoin developers can **upgrade to quantum-safe cryptography** (e.g., lattice-based cryptography or post-quantum signatures like Dilithium). - Bitcoin’s decentralized nature ensures a network-wide **soft fork or hard fork** could transition to quantum-resistant keys. ++++++++++++++++++++++++++++++++++++++++++++++++++ ### ⏳ 4. The 10-Minute Block Rule as a Security Feature - Bitcoin’s network operates on a **10-minute block interval**, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack **every 10 minutes**.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system **resets the challenge with every new block**.This **limits the window of opportunity** for quantum attacks. --- ### 🎯 5. Quantum Attack Needs to Solve a Block in Real-Time - A quantum attacker **must solve the cryptographic puzzle (Proof of Work) in under 10 minutes**. - The problem? **Any slight error changes the hash completely**, meaning:**If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails**.**Quantum decoherence** (loss of qubit stability) makes error correction a massive challenge.The computational cost of **recovering from an incorrect hash** is still incredibly high. --- ### ⚡ 6. Network Resilience – Even if a Block Is Hacked - Even if a quantum computer **somehow** solved a block instantly:The network would **quickly recognize and reject invalid transactions**.Other miners would **continue mining** under normal cryptographic rules.**51% Attack?** The attacker would need to consistently beat the **entire Bitcoin network**, which is **not sustainable**. --- ### 🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats - Bitcoin adjusts mining difficulty every **2016 blocks (\~2 weeks)**. - If quantum miners appeared and suddenly started solving blocks too quickly, **the difficulty would adjust upward**, making attacks significantly harder. - This **self-correcting mechanism** ensures that even quantum computers wouldn't easily overpower the network. --- ### 🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin ✔ **The 10-minute rule limits attack frequency** – quantum computers can’t keep up. ✔ **Any slight miscalculation ruins the attack**, resetting all progress. ✔ **Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages**. **Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant.** 🚀 @ 4fe14ef2:f51992ec
2025-03-27 21:11:10Hey Bitcoiners, Leave a comment below to share your hustles and wins. Let us know what you've sold this week. Have you sold it for #sats or #zaps? It doesn't matter how big or small your item is, solid or #digital, product or #service. Just share below what you’ve listed, swapped, and sold. Let everyone rave on your latest #deals! New to ~AGORA? Dive into the #marketplace and turn your dusty gears into shiny #BTC! originally posted at https://stacker.news/items/927256
@ 4fe14ef2:f51992ec
2025-03-27 21:11:10Hey Bitcoiners, Leave a comment below to share your hustles and wins. Let us know what you've sold this week. Have you sold it for #sats or #zaps? It doesn't matter how big or small your item is, solid or #digital, product or #service. Just share below what you’ve listed, swapped, and sold. Let everyone rave on your latest #deals! New to ~AGORA? Dive into the #marketplace and turn your dusty gears into shiny #BTC! originally posted at https://stacker.news/items/927256 @ df173277:4ec96708
2025-01-09 17:02:52> OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. [Join our waitlist to get early access.](https://opensecret.cloud) In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion. Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online? Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches? > Cryptography at scale is hard. #### The Cloud The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers. The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage. > Private key encryption needs a UX upgrade. ## Enter OpenSecret OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute. Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.  ### Private Key Management Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone. OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account. The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.  ### Encrypted Sync With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go. The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them. ### Private AI Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything. OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk. **Check out Maple AI**\ Try private AI for yourself! We built an app built with this service called [Maple AI](https://trymaple.ai). It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. [Learn more about Maple AI - Private chat in the announcement post.](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/)  ### Confidential Compute Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave. It's the new version of that lock on your web browser. When you see it, you know you're secure.  #### **But do we want our secrets to be open?** OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable. On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data. > Don't trust, verify. ### **Join the Movement** We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, [send us a message to get early access.](https://opensecret.cloud) Users and companies deserve better encryption and privacy.\ Together, let's make that a reality. [](https://opensecret.cloud)
@ df173277:4ec96708
2025-01-09 17:02:52> OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. [Join our waitlist to get early access.](https://opensecret.cloud) In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion. Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online? Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches? > Cryptography at scale is hard. #### The Cloud The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers. The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage. > Private key encryption needs a UX upgrade. ## Enter OpenSecret OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute. Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.  ### Private Key Management Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone. OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account. The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.  ### Encrypted Sync With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go. The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them. ### Private AI Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything. OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk. **Check out Maple AI**\ Try private AI for yourself! We built an app built with this service called [Maple AI](https://trymaple.ai). It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. [Learn more about Maple AI - Private chat in the announcement post.](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/)  ### Confidential Compute Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave. It's the new version of that lock on your web browser. When you see it, you know you're secure.  #### **But do we want our secrets to be open?** OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable. On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data. > Don't trust, verify. ### **Join the Movement** We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, [send us a message to get early access.](https://opensecret.cloud) Users and companies deserve better encryption and privacy.\ Together, let's make that a reality. [](https://opensecret.cloud) @ 8cb60e21:5f2deaea
2024-08-24 23:54:44<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/clGgymry998&pp=ygUcZmFyIGNyeSAzIHppZ2d5J3MgbW9kIHJldmlldw%3D%3D" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-08-24 23:54:44<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/clGgymry998&pp=ygUcZmFyIGNyeSAzIHppZ2d5J3MgbW9kIHJldmlldw%3D%3D" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ e97aaffa:2ebd765d
2025-03-28 12:56:17Nos últimos anos, tornei-me num acérrimo crítico do Euro, sobretudo da política monetária altamente expansionista realizada pelo Banco Central Europeu (BCE). Apesar de ser crítico, eu não desejo que Portugal volte a ter moeda própria. No seguimento gráfico, é a variação do [IPC de Portugal nos últimos 60 anos]( https://www.pordata.pt/pt/estatisticas/inflacao/taxa-de-inflacao/taxa-de-inflacao-por-bens-e-servicos-portugal):  No gráfico inclui os momentos históricos, para uma melhor interpretação dos dados. > O Índice de Preços ao Consumidor (IPC) é usado para observar tendências de inflação. É calculado com base no preço médio necessário para comprar um conjunto de bens de consumo e serviços num país, comparando com períodos anteriores. É uma ferramenta utilizada para calcular a perda de poder de compra, mas é uma métrica que é facilmente manipulada em prol dos interesses dos governos. ## Análise histórica No período marcelista, houve uma crescente inflação, devido a fatores, como os elevados custos da guerra e o fim dos acordos de Bretton Woods contribuíram para isso. Terminando com uma inflação superior a 13%. Da Revolta dos Cravos (1974) até à adesão da CEE (atual União Europeia, UE), nos primeiros anos foram conturbados a nível político, mesmo após conquistar alguma estabilidade, em termos de política monetária foi um descalabro, com inflação entre 12% a 30% ao ano. Foi o pior momento na era moderna. Com a entrada da CEE, Portugal ainda manteve a independência monetária, mas devido à entrada de muitos milhões de fundos europeus, essências para construir infraestrutura e desenvolver o país. Isto permitiu crescer e modernizar o país, gastando pouco dinheiro próprio, reduzindo a necessidade da expansão monetária e claro a inflação baixou. Depois com a adesão ao Tratado de Maastricht, em 1991, onde estabeleceu as bases para a criação da União Económica e Monetária, que culminou na criação da moeda única europeia, o Euro. As bases eram bastante restritivas, os políticos portugueses foram obrigados a manter uma inflação baixa. Portugal perdeu a independência monetária em 1999, com a entrada em vigor da nova moeda, foi estabelecida a taxa de conversão entre escudos e euros, tendo o valor de 1 euro sido fixado em 200,482 escudos. A Euro entrou em vigor em 1999, mas o papel-moeda só entrou em circulação em 2002. Assim, desde a criação até 2020, a inflação foi sempre abaixo de 5% ao ano, tendo um longo período abaixo dos 3%. A chegada da pandemia, foi um descalabro no BCE, a expansão monetária foi exponencial, resultando numa forte subida no IPC, quase 8% em 2022, algo que não acontecia há 30 anos. ## Conclusão Apesar dos últimos anos, a política monetária do BCE tem sido péssima, mesmo assim continua a ser muito melhor, se esta fosse efetuada em exclusividade por portugueses, não tenho quaisquer dúvidas disso. O passado demonstra isso, se voltarmos a ser independentes monetariamente, será desastroso, vamos virar rapidamente, a Venezuela da Europa. Até temos boas reservas de ouro, mas mesmo assim não são suficientes, mesmo que se inclua outros ativos para permitir a criação de uma moeda lastreada, ela apenas duraria até à primeira crise. É inevitável, somos um país demasiado socialista. A solução não é voltar ao escudo, mas sim o BCE deixar de imprimir dinheiro, como se não houvesse amanhã ou então optar por uma moeda total livre, sem intromissão de políticos. O BCE vai parar de expandir a moeda? Claro que não, eles estão encurralados, a expansão monetária é a única solução para elevada dívida soberana dos estados. A única certeza que eu tenho, a expansão do BCE, será sempre inferior ao do Banco de Portugal, se este estivesse o botão da impressão à sua disposição. Por volta dos 5% é muito mau, mas voltar para a casa dos 15% seria péssimo, esse seria o nosso destino. É muito triste ter esta conclusão, isto é demonstrativo da falta de competência dos políticos e governantes portugueses e o povo também tem uma certa culpa. Por serem poucos exigentes em relação à qualidade dos políticos que elegem e por acreditar que existem almoços grátis. #Bitcoin fixes this
@ e97aaffa:2ebd765d
2025-03-28 12:56:17Nos últimos anos, tornei-me num acérrimo crítico do Euro, sobretudo da política monetária altamente expansionista realizada pelo Banco Central Europeu (BCE). Apesar de ser crítico, eu não desejo que Portugal volte a ter moeda própria. No seguimento gráfico, é a variação do [IPC de Portugal nos últimos 60 anos]( https://www.pordata.pt/pt/estatisticas/inflacao/taxa-de-inflacao/taxa-de-inflacao-por-bens-e-servicos-portugal):  No gráfico inclui os momentos históricos, para uma melhor interpretação dos dados. > O Índice de Preços ao Consumidor (IPC) é usado para observar tendências de inflação. É calculado com base no preço médio necessário para comprar um conjunto de bens de consumo e serviços num país, comparando com períodos anteriores. É uma ferramenta utilizada para calcular a perda de poder de compra, mas é uma métrica que é facilmente manipulada em prol dos interesses dos governos. ## Análise histórica No período marcelista, houve uma crescente inflação, devido a fatores, como os elevados custos da guerra e o fim dos acordos de Bretton Woods contribuíram para isso. Terminando com uma inflação superior a 13%. Da Revolta dos Cravos (1974) até à adesão da CEE (atual União Europeia, UE), nos primeiros anos foram conturbados a nível político, mesmo após conquistar alguma estabilidade, em termos de política monetária foi um descalabro, com inflação entre 12% a 30% ao ano. Foi o pior momento na era moderna. Com a entrada da CEE, Portugal ainda manteve a independência monetária, mas devido à entrada de muitos milhões de fundos europeus, essências para construir infraestrutura e desenvolver o país. Isto permitiu crescer e modernizar o país, gastando pouco dinheiro próprio, reduzindo a necessidade da expansão monetária e claro a inflação baixou. Depois com a adesão ao Tratado de Maastricht, em 1991, onde estabeleceu as bases para a criação da União Económica e Monetária, que culminou na criação da moeda única europeia, o Euro. As bases eram bastante restritivas, os políticos portugueses foram obrigados a manter uma inflação baixa. Portugal perdeu a independência monetária em 1999, com a entrada em vigor da nova moeda, foi estabelecida a taxa de conversão entre escudos e euros, tendo o valor de 1 euro sido fixado em 200,482 escudos. A Euro entrou em vigor em 1999, mas o papel-moeda só entrou em circulação em 2002. Assim, desde a criação até 2020, a inflação foi sempre abaixo de 5% ao ano, tendo um longo período abaixo dos 3%. A chegada da pandemia, foi um descalabro no BCE, a expansão monetária foi exponencial, resultando numa forte subida no IPC, quase 8% em 2022, algo que não acontecia há 30 anos. ## Conclusão Apesar dos últimos anos, a política monetária do BCE tem sido péssima, mesmo assim continua a ser muito melhor, se esta fosse efetuada em exclusividade por portugueses, não tenho quaisquer dúvidas disso. O passado demonstra isso, se voltarmos a ser independentes monetariamente, será desastroso, vamos virar rapidamente, a Venezuela da Europa. Até temos boas reservas de ouro, mas mesmo assim não são suficientes, mesmo que se inclua outros ativos para permitir a criação de uma moeda lastreada, ela apenas duraria até à primeira crise. É inevitável, somos um país demasiado socialista. A solução não é voltar ao escudo, mas sim o BCE deixar de imprimir dinheiro, como se não houvesse amanhã ou então optar por uma moeda total livre, sem intromissão de políticos. O BCE vai parar de expandir a moeda? Claro que não, eles estão encurralados, a expansão monetária é a única solução para elevada dívida soberana dos estados. A única certeza que eu tenho, a expansão do BCE, será sempre inferior ao do Banco de Portugal, se este estivesse o botão da impressão à sua disposição. Por volta dos 5% é muito mau, mas voltar para a casa dos 15% seria péssimo, esse seria o nosso destino. É muito triste ter esta conclusão, isto é demonstrativo da falta de competência dos políticos e governantes portugueses e o povo também tem uma certa culpa. Por serem poucos exigentes em relação à qualidade dos políticos que elegem e por acreditar que existem almoços grátis. #Bitcoin fixes this @ 2b24a1fa:17750f64
2025-03-28 10:07:04Der Deutsche Bundestag wurde neu gewählt. Für einige Abgeordnete und Regierungsmitglieder heißt es Time to Say Goodbye. Abschied ist ein scharfes Schwert.  [https://soundcloud.com/radiomuenchen/nachruf-2-olaf-der-zeitenwender](https://soundcloud.com/radiomuenchen/nachruf-2-olaf-der-zeitenwender?si=6c375088b6444c2d8aa7e8040fb1a79e\&utm_source=clipboard\&utm_medium=text\&utm_campaign=social_sharing) Auch bei Radio München werden Trennungs- und Verlassenheitsgefühle getriggert. Umso mehr, wenn es sich nicht nur um duselige Allerweltsliebe handelt, sondern um den Abgang großer Helden. Sie bezahlten ihren todesmutigen und fast ehrenamtlichen Einsatz nicht mit dem Leben, jedoch mit der einen oder anderen Falte in Hemd oder Bluse, manchmal sogar im Gesicht. Was bleibt? Eine bescheidene Pension? Ein lausig bezahlter Manager-Job in einem Konzern? Wir wollen jedenfalls nicht, dass diese Volkshelden vom Zahn der Zeit abgenagt, vergessen werden und setzen ihnen deshalb ein bescheidenes akustisches, aber nachhaltiges Denkmal. Hören Sie die kleine satirische Reihe „Nachrufe“ von unserem Autor Jonny Rieder.\ Folge 2: Olaf der Zeitenwender Sprecher: Karsten Troyke Bild: Markus Mitterer für Radio München Radio München\ [www.radiomuenchen.net/](http://www.radiomuenchen.net/%E2%80%8B "http://www.radiomuenchen.net/")\ @[radiomuenchen](https://soundcloud.com/radiomuenchen)\ [www.facebook.com/radiomuenchen](http://www.facebook.com/radiomuenchen "http://www.facebook.com/radiomuenchen")\ [www.instagram.com/radio\_muenchen/](http://www.instagram.com/radio_muenchen/ "http://www.instagram.com/radio_muenchen/")\ [twitter.com/RadioMuenchen](http://twitter.com/RadioMuenchen "http://twitter.com/RadioMuenchen") Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen. GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS
@ 2b24a1fa:17750f64
2025-03-28 10:07:04Der Deutsche Bundestag wurde neu gewählt. Für einige Abgeordnete und Regierungsmitglieder heißt es Time to Say Goodbye. Abschied ist ein scharfes Schwert.  [https://soundcloud.com/radiomuenchen/nachruf-2-olaf-der-zeitenwender](https://soundcloud.com/radiomuenchen/nachruf-2-olaf-der-zeitenwender?si=6c375088b6444c2d8aa7e8040fb1a79e\&utm_source=clipboard\&utm_medium=text\&utm_campaign=social_sharing) Auch bei Radio München werden Trennungs- und Verlassenheitsgefühle getriggert. Umso mehr, wenn es sich nicht nur um duselige Allerweltsliebe handelt, sondern um den Abgang großer Helden. Sie bezahlten ihren todesmutigen und fast ehrenamtlichen Einsatz nicht mit dem Leben, jedoch mit der einen oder anderen Falte in Hemd oder Bluse, manchmal sogar im Gesicht. Was bleibt? Eine bescheidene Pension? Ein lausig bezahlter Manager-Job in einem Konzern? Wir wollen jedenfalls nicht, dass diese Volkshelden vom Zahn der Zeit abgenagt, vergessen werden und setzen ihnen deshalb ein bescheidenes akustisches, aber nachhaltiges Denkmal. Hören Sie die kleine satirische Reihe „Nachrufe“ von unserem Autor Jonny Rieder.\ Folge 2: Olaf der Zeitenwender Sprecher: Karsten Troyke Bild: Markus Mitterer für Radio München Radio München\ [www.radiomuenchen.net/](http://www.radiomuenchen.net/%E2%80%8B "http://www.radiomuenchen.net/")\ @[radiomuenchen](https://soundcloud.com/radiomuenchen)\ [www.facebook.com/radiomuenchen](http://www.facebook.com/radiomuenchen "http://www.facebook.com/radiomuenchen")\ [www.instagram.com/radio\_muenchen/](http://www.instagram.com/radio_muenchen/ "http://www.instagram.com/radio_muenchen/")\ [twitter.com/RadioMuenchen](http://twitter.com/RadioMuenchen "http://twitter.com/RadioMuenchen") Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen. GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS @ a95c6243:d345522c
2025-03-20 09:59:20**Bald werde es verboten, alleine im Auto zu fahren,** konnte man dieser Tage in verschiedenen spanischen Medien lesen. Die nationale Verkehrsbehörde (Dirección General de Tráfico, kurz DGT) werde Alleinfahrern das Leben schwer machen, wurde gemeldet. Konkret erörtere die Generaldirektion geeignete Sanktionen für Personen, die ohne Beifahrer im Privatauto unterwegs seien. **Das Alleinfahren sei zunehmend verpönt und ein Mentalitätswandel notwendig,** hieß es. Dieser «Luxus» stehe im Widerspruch zu den Maßnahmen gegen Umweltverschmutzung, die in allen europäischen Ländern gefördert würden. In Frankreich sei es «bereits verboten, in der Hauptstadt allein zu fahren», [behauptete](https://noticiastrabajo.huffingtonpost.es/sociedad/adios-a-conducir-solo-la-dgt-se-lo-pone-crudo-a-los-conductores-que-viajen-sin-acompanante-en-el-coche/) *Noticiastrabajo Huffpost* in einer Zwischenüberschrift. Nur um dann im Text zu konkretisieren, dass die sogenannte «Umweltspur» auf der Pariser Ringautobahn gemeint war, die für Busse, Taxis und Fahrgemeinschaften reserviert ist. [Ab Mai](https://www.lefigaro.fr/conso/peripherique-parisien-entree-en-vigueur-de-la-voie-reservee-au-covoiturage-ce-lundi-20250303) werden Verstöße dagegen mit einem Bußgeld geahndet. **Die DGT jedenfalls wolle bei der Umsetzung derartiger Maßnahmen** nicht hinterherhinken. Diese Medienberichte, inklusive des angeblich bevorstehenden Verbots, beriefen sich auf Aussagen des Generaldirektors der Behörde, Pere Navarro, beim Mobilitätskongress Global Mobility Call im November letzten Jahres, wo es um «nachhaltige Mobilität» ging. Aus diesem Kontext stammt auch Navarros Warnung: «Die Zukunft des Verkehrs ist geteilt oder es gibt keine». **Die «Faktenchecker» kamen der Generaldirektion prompt zu Hilfe.** Die DGT habe derlei Behauptungen [zurückgewiesen](https://www.newtral.es/dgt-una-persona-coche/20250312/) und klargestellt, dass es keine Pläne gebe, Fahrten mit nur einer Person im Auto zu verbieten oder zu bestrafen. Bei solchen Meldungen handele es sich um Fake News. Teilweise wurde der Vorsitzende der spanischen «Rechtsaußen»-Partei Vox, Santiago Abascal, der Urheberschaft bezichtigt, weil er einen entsprechenden [Artikel](https://gaceta.es/espana/la-dgt-estudia-formas-de-sancionar-a-quien-circule-solo-en-su-vehiculo-el-futuro-sera-compartido-o-no-sera-20250311-1612/) von *La Gaceta* kommentiert hatte. **Der Beschwichtigungsversuch der Art «niemand hat die Absicht»** ist dabei erfahrungsgemäß eher ein Alarmzeichen als eine Beruhigung. Walter Ulbrichts Leugnung einer geplanten Berliner [Mauer](https://www.berlin-mauer.de/videos/walter-ulbricht-zum-mauerbau-530/) vom Juni 1961 ist vielen genauso in Erinnerung wie die Fake News-Warnungen des deutschen Bundesgesundheitsministeriums bezüglich [Lockdowns](https://x.com/BMG_Bund/status/1238780849652465664) im März 2020 oder diverse Äußerungen zu einer [Impfpflicht](https://www.achgut.com/artikel/die_schoensten_politiker_zitate_zur_impfpflicht) ab 2020. **Aber Aufregung hin, Dementis her:** Die [Pressemitteilung](https://archive.is/xXQWD) der DGT zu dem Mobilitätskongress enthält in Wahrheit viel interessantere Informationen als «nur» einen Appell an den «guten» Bürger wegen der Bemühungen um die Lebensqualität in Großstädten oder einen möglichen obligatorischen Abschied vom Alleinfahren. Allerdings werden diese Details von Medien und sogenannten Faktencheckern geflissentlich übersehen, obwohl sie keineswegs versteckt sind. Die Auskünfte sind sehr aufschlussreich, wenn man genauer hinschaut. ### Digitalisierung ist der Schlüssel für Kontrolle **Auf dem Kongress stellte die Verkehrsbehörde ihre Initiativen zur Förderung der «neuen Mobilität» vor,** deren Priorität Sicherheit und Effizienz sei. Die vier konkreten Ansätze haben alle mit Digitalisierung, Daten, Überwachung und Kontrolle im großen Stil zu tun und werden unter dem Euphemismus der «öffentlich-privaten Partnerschaft» angepriesen. Auch lassen sie die transhumanistische Idee vom unzulänglichen Menschen erkennen, dessen Fehler durch «intelligente» technologische Infrastruktur kompensiert werden müssten. **Die Chefin des Bereichs «Verkehrsüberwachung» erklärte die Funktion** des spanischen National Access Point ([NAP](https://nap.dgt.es/)), wobei sie betonte, wie wichtig Verkehrs- und Infrastrukturinformationen in Echtzeit seien. Der NAP ist «eine essenzielle Web-Applikation, die unter EU-Mandat erstellt wurde», kann man auf der Website der DGT nachlesen. **Das Mandat meint Regelungen zu einem einheitlichen europäischen Verkehrsraum,** mit denen die Union mindestens seit 2010 den Aufbau einer digitalen Architektur mit offenen Schnittstellen betreibt. Damit begründet man auch «umfassende Datenbereitstellungspflichten im Bereich multimodaler Reiseinformationen». Jeder Mitgliedstaat musste einen NAP, also einen nationalen [Zugangspunkt](https://transport.ec.europa.eu/transport-themes/smart-mobility/road/its-directive-and-action-plan/national-access-points_en) einrichten, der Zugang zu statischen und dynamischen Reise- und Verkehrsdaten verschiedener Verkehrsträger ermöglicht. **Diese Entwicklung ist heute schon weit fortgeschritten,** auch und besonders in Spanien. Auf besagtem Kongress erläuterte die Leiterin des Bereichs «Telematik» die Plattform [«DGT 3.0»](https://www.dgt.es/muevete-con-seguridad/tecnologia-e-innovacion-en-carretera/dgt-3.0/). Diese werde als Integrator aller Informationen genutzt, die von den verschiedenen öffentlichen und privaten Systemen, die Teil der Mobilität sind, bereitgestellt werden. **Es handele sich um eine Vermittlungsplattform zwischen Akteuren wie Fahrzeugherstellern,** Anbietern von Navigationsdiensten oder Kommunen und dem Endnutzer, der die Verkehrswege benutzt. Alle seien auf Basis des Internets der Dinge (IOT) anonym verbunden, «um der vernetzten Gemeinschaft wertvolle Informationen zu liefern oder diese zu nutzen». **So sei DGT 3.0 «ein Zugangspunkt für einzigartige, kostenlose und genaue Echtzeitinformationen** über das Geschehen auf den Straßen und in den Städten». Damit lasse sich der Verkehr nachhaltiger und vernetzter gestalten. Beispielsweise würden die Karten des Produktpartners Google dank der DGT-Daten 50 Millionen Mal pro Tag aktualisiert. **Des Weiteren informiert die Verkehrsbehörde über ihr SCADA-Projekt.** Die Abkürzung steht für Supervisory Control and Data Acquisition, zu deutsch etwa: Kontrollierte Steuerung und Datenerfassung. Mit SCADA kombiniert man Software und Hardware, um automatisierte Systeme zur Überwachung und Steuerung technischer Prozesse zu schaffen. Das SCADA-Projekt der DGT wird von Indra entwickelt, einem spanischen Beratungskonzern aus den Bereichen Sicherheit & Militär, Energie, Transport, Telekommunikation und Gesundheitsinformation. **Das SCADA-System der Behörde umfasse auch eine Videostreaming- und Videoaufzeichnungsplattform,** die das Hochladen in die Cloud in Echtzeit ermöglicht, wie Indra [erklärt](https://www.indracompany.com/es/noticia/indra-presenta-global-mobility-call-pionera-plataforma-nube-desplegada-centros-gestion). Dabei gehe es um Bilder, die von Überwachungskameras an Straßen aufgenommen wurden, sowie um Videos aus DGT-Hubschraubern und Drohnen. Ziel sei es, «die sichere Weitergabe von Videos an Dritte sowie die kontinuierliche Aufzeichnung und Speicherung von Bildern zur möglichen Analyse und späteren Nutzung zu ermöglichen». **Letzteres klingt sehr nach biometrischer Erkennung** und Auswertung durch künstliche Intelligenz. Für eine bessere Datenübertragung wird derzeit die [Glasfaserverkabelung](https://www.moncloa.com/2025/03/18/linea-azul-conduccion-dgt-3191554/) entlang der Landstraßen und Autobahnen ausgebaut. Mit der Cloud sind die Amazon Web Services (AWS) gemeint, die spanischen [Daten gehen](https://norberthaering.de/news/digitalgipfel-wehnes-interview/) somit direkt zu einem US-amerikanischen «Big Data»-Unternehmen. **Das Thema «autonomes Fahren», also Fahren ohne Zutun des Menschen,** bildet den Abschluss der Betrachtungen der DGT. Zusammen mit dem Interessenverband der Automobilindustrie ANFAC (Asociación Española de Fabricantes de Automóviles y Camiones) sprach man auf dem Kongress über Strategien und Perspektiven in diesem Bereich. Die Lobbyisten hoffen noch in diesem Jahr 2025 auf einen [normativen Rahmen](https://www.coches.net/noticias/informe-coche-autonomo-conectado-espana-2024) zur erweiterten Unterstützung autonomer Technologien. **Wenn man derartige Informationen im Zusammenhang betrachtet,** bekommt man eine Idee davon, warum zunehmend alles elektrisch und digital werden soll. Umwelt- und Mobilitätsprobleme in Städten, wie Luftverschmutzung, Lärmbelästigung, Platzmangel oder Staus, sind eine Sache. Mit dem Argument «emissionslos» wird jedoch eine Referenz zum CO2 und dem «menschengemachten Klimawandel» hergestellt, die Emotionen triggert. Und damit wird so ziemlich alles verkauft. **Letztlich aber gilt: Je elektrischer und digitaler unsere Umgebung wird** und je freigiebiger wir mit unseren Daten jeder Art sind, desto besser werden wir kontrollier-, steuer- und sogar abschaltbar. Irgendwann entscheiden KI-basierte Algorithmen, ob, wann, wie, wohin und mit wem wir uns bewegen dürfen. Über einen 15-Minuten-Radius geht dann möglicherweise nichts hinaus. Die Projekte auf diesem Weg sind ernst zu nehmen, real und schon weit fortgeschritten. *\[Titelbild:* *[Pixabay](https://pixabay.com/de/photos/reisen-wagen-ferien-fahrzeug-1426822/)]* *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/nur-abschied-vom-alleinfahren-monstrose-spanische-uberwachungsprojekte-gemass)*** erschienen.
@ a95c6243:d345522c
2025-03-20 09:59:20**Bald werde es verboten, alleine im Auto zu fahren,** konnte man dieser Tage in verschiedenen spanischen Medien lesen. Die nationale Verkehrsbehörde (Dirección General de Tráfico, kurz DGT) werde Alleinfahrern das Leben schwer machen, wurde gemeldet. Konkret erörtere die Generaldirektion geeignete Sanktionen für Personen, die ohne Beifahrer im Privatauto unterwegs seien. **Das Alleinfahren sei zunehmend verpönt und ein Mentalitätswandel notwendig,** hieß es. Dieser «Luxus» stehe im Widerspruch zu den Maßnahmen gegen Umweltverschmutzung, die in allen europäischen Ländern gefördert würden. In Frankreich sei es «bereits verboten, in der Hauptstadt allein zu fahren», [behauptete](https://noticiastrabajo.huffingtonpost.es/sociedad/adios-a-conducir-solo-la-dgt-se-lo-pone-crudo-a-los-conductores-que-viajen-sin-acompanante-en-el-coche/) *Noticiastrabajo Huffpost* in einer Zwischenüberschrift. Nur um dann im Text zu konkretisieren, dass die sogenannte «Umweltspur» auf der Pariser Ringautobahn gemeint war, die für Busse, Taxis und Fahrgemeinschaften reserviert ist. [Ab Mai](https://www.lefigaro.fr/conso/peripherique-parisien-entree-en-vigueur-de-la-voie-reservee-au-covoiturage-ce-lundi-20250303) werden Verstöße dagegen mit einem Bußgeld geahndet. **Die DGT jedenfalls wolle bei der Umsetzung derartiger Maßnahmen** nicht hinterherhinken. Diese Medienberichte, inklusive des angeblich bevorstehenden Verbots, beriefen sich auf Aussagen des Generaldirektors der Behörde, Pere Navarro, beim Mobilitätskongress Global Mobility Call im November letzten Jahres, wo es um «nachhaltige Mobilität» ging. Aus diesem Kontext stammt auch Navarros Warnung: «Die Zukunft des Verkehrs ist geteilt oder es gibt keine». **Die «Faktenchecker» kamen der Generaldirektion prompt zu Hilfe.** Die DGT habe derlei Behauptungen [zurückgewiesen](https://www.newtral.es/dgt-una-persona-coche/20250312/) und klargestellt, dass es keine Pläne gebe, Fahrten mit nur einer Person im Auto zu verbieten oder zu bestrafen. Bei solchen Meldungen handele es sich um Fake News. Teilweise wurde der Vorsitzende der spanischen «Rechtsaußen»-Partei Vox, Santiago Abascal, der Urheberschaft bezichtigt, weil er einen entsprechenden [Artikel](https://gaceta.es/espana/la-dgt-estudia-formas-de-sancionar-a-quien-circule-solo-en-su-vehiculo-el-futuro-sera-compartido-o-no-sera-20250311-1612/) von *La Gaceta* kommentiert hatte. **Der Beschwichtigungsversuch der Art «niemand hat die Absicht»** ist dabei erfahrungsgemäß eher ein Alarmzeichen als eine Beruhigung. Walter Ulbrichts Leugnung einer geplanten Berliner [Mauer](https://www.berlin-mauer.de/videos/walter-ulbricht-zum-mauerbau-530/) vom Juni 1961 ist vielen genauso in Erinnerung wie die Fake News-Warnungen des deutschen Bundesgesundheitsministeriums bezüglich [Lockdowns](https://x.com/BMG_Bund/status/1238780849652465664) im März 2020 oder diverse Äußerungen zu einer [Impfpflicht](https://www.achgut.com/artikel/die_schoensten_politiker_zitate_zur_impfpflicht) ab 2020. **Aber Aufregung hin, Dementis her:** Die [Pressemitteilung](https://archive.is/xXQWD) der DGT zu dem Mobilitätskongress enthält in Wahrheit viel interessantere Informationen als «nur» einen Appell an den «guten» Bürger wegen der Bemühungen um die Lebensqualität in Großstädten oder einen möglichen obligatorischen Abschied vom Alleinfahren. Allerdings werden diese Details von Medien und sogenannten Faktencheckern geflissentlich übersehen, obwohl sie keineswegs versteckt sind. Die Auskünfte sind sehr aufschlussreich, wenn man genauer hinschaut. ### Digitalisierung ist der Schlüssel für Kontrolle **Auf dem Kongress stellte die Verkehrsbehörde ihre Initiativen zur Förderung der «neuen Mobilität» vor,** deren Priorität Sicherheit und Effizienz sei. Die vier konkreten Ansätze haben alle mit Digitalisierung, Daten, Überwachung und Kontrolle im großen Stil zu tun und werden unter dem Euphemismus der «öffentlich-privaten Partnerschaft» angepriesen. Auch lassen sie die transhumanistische Idee vom unzulänglichen Menschen erkennen, dessen Fehler durch «intelligente» technologische Infrastruktur kompensiert werden müssten. **Die Chefin des Bereichs «Verkehrsüberwachung» erklärte die Funktion** des spanischen National Access Point ([NAP](https://nap.dgt.es/)), wobei sie betonte, wie wichtig Verkehrs- und Infrastrukturinformationen in Echtzeit seien. Der NAP ist «eine essenzielle Web-Applikation, die unter EU-Mandat erstellt wurde», kann man auf der Website der DGT nachlesen. **Das Mandat meint Regelungen zu einem einheitlichen europäischen Verkehrsraum,** mit denen die Union mindestens seit 2010 den Aufbau einer digitalen Architektur mit offenen Schnittstellen betreibt. Damit begründet man auch «umfassende Datenbereitstellungspflichten im Bereich multimodaler Reiseinformationen». Jeder Mitgliedstaat musste einen NAP, also einen nationalen [Zugangspunkt](https://transport.ec.europa.eu/transport-themes/smart-mobility/road/its-directive-and-action-plan/national-access-points_en) einrichten, der Zugang zu statischen und dynamischen Reise- und Verkehrsdaten verschiedener Verkehrsträger ermöglicht. **Diese Entwicklung ist heute schon weit fortgeschritten,** auch und besonders in Spanien. Auf besagtem Kongress erläuterte die Leiterin des Bereichs «Telematik» die Plattform [«DGT 3.0»](https://www.dgt.es/muevete-con-seguridad/tecnologia-e-innovacion-en-carretera/dgt-3.0/). Diese werde als Integrator aller Informationen genutzt, die von den verschiedenen öffentlichen und privaten Systemen, die Teil der Mobilität sind, bereitgestellt werden. **Es handele sich um eine Vermittlungsplattform zwischen Akteuren wie Fahrzeugherstellern,** Anbietern von Navigationsdiensten oder Kommunen und dem Endnutzer, der die Verkehrswege benutzt. Alle seien auf Basis des Internets der Dinge (IOT) anonym verbunden, «um der vernetzten Gemeinschaft wertvolle Informationen zu liefern oder diese zu nutzen». **So sei DGT 3.0 «ein Zugangspunkt für einzigartige, kostenlose und genaue Echtzeitinformationen** über das Geschehen auf den Straßen und in den Städten». Damit lasse sich der Verkehr nachhaltiger und vernetzter gestalten. Beispielsweise würden die Karten des Produktpartners Google dank der DGT-Daten 50 Millionen Mal pro Tag aktualisiert. **Des Weiteren informiert die Verkehrsbehörde über ihr SCADA-Projekt.** Die Abkürzung steht für Supervisory Control and Data Acquisition, zu deutsch etwa: Kontrollierte Steuerung und Datenerfassung. Mit SCADA kombiniert man Software und Hardware, um automatisierte Systeme zur Überwachung und Steuerung technischer Prozesse zu schaffen. Das SCADA-Projekt der DGT wird von Indra entwickelt, einem spanischen Beratungskonzern aus den Bereichen Sicherheit & Militär, Energie, Transport, Telekommunikation und Gesundheitsinformation. **Das SCADA-System der Behörde umfasse auch eine Videostreaming- und Videoaufzeichnungsplattform,** die das Hochladen in die Cloud in Echtzeit ermöglicht, wie Indra [erklärt](https://www.indracompany.com/es/noticia/indra-presenta-global-mobility-call-pionera-plataforma-nube-desplegada-centros-gestion). Dabei gehe es um Bilder, die von Überwachungskameras an Straßen aufgenommen wurden, sowie um Videos aus DGT-Hubschraubern und Drohnen. Ziel sei es, «die sichere Weitergabe von Videos an Dritte sowie die kontinuierliche Aufzeichnung und Speicherung von Bildern zur möglichen Analyse und späteren Nutzung zu ermöglichen». **Letzteres klingt sehr nach biometrischer Erkennung** und Auswertung durch künstliche Intelligenz. Für eine bessere Datenübertragung wird derzeit die [Glasfaserverkabelung](https://www.moncloa.com/2025/03/18/linea-azul-conduccion-dgt-3191554/) entlang der Landstraßen und Autobahnen ausgebaut. Mit der Cloud sind die Amazon Web Services (AWS) gemeint, die spanischen [Daten gehen](https://norberthaering.de/news/digitalgipfel-wehnes-interview/) somit direkt zu einem US-amerikanischen «Big Data»-Unternehmen. **Das Thema «autonomes Fahren», also Fahren ohne Zutun des Menschen,** bildet den Abschluss der Betrachtungen der DGT. Zusammen mit dem Interessenverband der Automobilindustrie ANFAC (Asociación Española de Fabricantes de Automóviles y Camiones) sprach man auf dem Kongress über Strategien und Perspektiven in diesem Bereich. Die Lobbyisten hoffen noch in diesem Jahr 2025 auf einen [normativen Rahmen](https://www.coches.net/noticias/informe-coche-autonomo-conectado-espana-2024) zur erweiterten Unterstützung autonomer Technologien. **Wenn man derartige Informationen im Zusammenhang betrachtet,** bekommt man eine Idee davon, warum zunehmend alles elektrisch und digital werden soll. Umwelt- und Mobilitätsprobleme in Städten, wie Luftverschmutzung, Lärmbelästigung, Platzmangel oder Staus, sind eine Sache. Mit dem Argument «emissionslos» wird jedoch eine Referenz zum CO2 und dem «menschengemachten Klimawandel» hergestellt, die Emotionen triggert. Und damit wird so ziemlich alles verkauft. **Letztlich aber gilt: Je elektrischer und digitaler unsere Umgebung wird** und je freigiebiger wir mit unseren Daten jeder Art sind, desto besser werden wir kontrollier-, steuer- und sogar abschaltbar. Irgendwann entscheiden KI-basierte Algorithmen, ob, wann, wie, wohin und mit wem wir uns bewegen dürfen. Über einen 15-Minuten-Radius geht dann möglicherweise nichts hinaus. Die Projekte auf diesem Weg sind ernst zu nehmen, real und schon weit fortgeschritten. *\[Titelbild:* *[Pixabay](https://pixabay.com/de/photos/reisen-wagen-ferien-fahrzeug-1426822/)]* *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/nur-abschied-vom-alleinfahren-monstrose-spanische-uberwachungsprojekte-gemass)*** erschienen. @ 8cb60e21:5f2deaea
2024-08-24 23:52:38<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/JAQuukInxFg&pp=ygUcZmFyIGNyeSAzIHppZ2d5J3MgbW9kIHJldmlldw%3D%3D" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-08-24 23:52:38<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/JAQuukInxFg&pp=ygUcZmFyIGNyeSAzIHppZ2d5J3MgbW9kIHJldmlldw%3D%3D" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ ed84ce10:cccf4c2a
2025-03-27 14:55:40## **Hackers are Destiny: Four Fulcrums of the Future** *A Dora Ventures Thesis* In “Why Software is Eating the World,” Marc Andreeson argued that software isn’t just a tool — it’s a societal force. At [DoraHacks](https://dorahacks.io/), we agree, but we go one step further. It’s not software alone that reshapes the world. It’s hackers — those who BUIDL. The real engine of change isn’t technology; it’s the people who choose to wield it. [DoraHacks](https://dorahacks.io/) is building a global Hacker Movement — a self-organizing force powered by open source, freedom, and code. We’re not chasing buzzwords like “Web3” or geopolitical narratives. We’re building a new society. One based on a simple but radical question: **What is truly worth building?** Dora Ventures exists to serve that mission — a capital engine designed to coordinate, amplify, and capture value from the hacker revolution. We are placing early and aggressive bets across four core leverage points: ## **I. FDA Free Society — The BioHack** ### **Freedom of Life Science is the foundation of a free society.** Every meaningful technological revolution has challenged the existing power structure. Today, the single most over-regulated, over-centralized, and innovation-hostile domain? Life Science. It takes ten years and billions of dollars to bring a drug from lab to patient. Most innovation dies in the trenches of bureaucracy. We don’t need anarchy. We need a new model:**A market-driven, patient-first biotech innovation stack.** **The Problem:** - The FDA approval process kills breakthrough therapies before they live. - Big Pharma monopolies decouple price from value and destroy competition. - The “Right to Try” is a legal afterthought, not a first principle. - Bio startups can’t survive the upfront costs of traditional trials. **The Opportunity:** - Let markets and builders lead: give power back to patients, doctors, and founders. - Rethink from first principles: not “Did it pass?” but “Does it work?” - Reclaim the Right to Try: the real risk is dying while waiting. - Build a hyper-competitive biofounder ecosystem — don’t just supply Big Pharma with IP. - Supercharge biotech with software and AI: accelerate every layer of the stack. The future of medicine does not belong to regulators. It belongs to the builders who refuse to wait. **The FDA Free Society isn’t just a challenge to power — it’s a defense of life.** ## **II. Open Source Quantum** ### **Ethereum had 2015. Quantum software has 2025.** Arthur C. Clarke said: *“Any sufficiently advanced technology is indistinguishable from magic.”* Quantum is magic — until it’s programmable, repeatable, and shared. In other words: open source. Dora Ventures is betting on the moment quantum computing becomes a hacker’s playground. Hardware is entering the engineering phase. Software? Still a wasteland — which means pure upside for builders. **We’re betting on:** - **Quantum compilers & transpilers**: bridging classical and quantum logic. - **Quantum cryptography**: building fundamentally new security layers. - **Quantum applications** in AI, pharma, logistics, finance, space — everything. We're not watching from the sidelines. We’re funding open-source tools, running hackathons, and building out the decentralized quantum dev stack. **Open Source Quantum is not speculative.** It’s inevitable — and massively undercapitalized. Now is the time to build. ## **III. Consumer Crypto — The Fat Apps Are Coming** ### **Crypto’s real revolution? Billion-user apps.** Crypto is not the *alternative* to the internet. It’s the *next chapter* of the internet. In the 1990s, HTTP and TCP/IP rewired information. In the 2000s, web apps rewired commerce and communication. In the 2010s, mobile apps rewired human behavior. In the 2020s, crypto apps will onboard the next billion users. **The infrastructure is ready. The fat apps are hatching.** Dora Ventures is obsessed with one question: **Who builds the PayPal and WeChat of the Web3 era?** That’s where we place our bets. **What we see coming:** - Compliant stablecoins like USDC become digital dollars. - Crypto-native payment rails rival VISA. - Appchains built with Move + simplified UX onboard non-crypto users. - On-chain creator economies that pay artists, devs, and communities directly. Imagine this: A fan in NYC uses USDC on a Move-based blockchain (Aptos) to buy a concert ticket via KYD Labs. An Argentinian grabs a latte daily with Bitcoin sats on Lightning. A friend group splits dinner bills via Yakihonne, a decentralized social platform. **That’s not the future. That’s this year.** We’re not funding protocols — we’re funding paradigm shifts in experience. ## **IV. Agentic Organizations — DAOs Without CEOs** ### **The end of corporations. The birth of autonomous orgs.** In 2022, Sam Altman redefined “tools.” In 2025, we’ll redefine “organizations.” Future orgs won’t be hierarchies. They’ll be networks of autonomous agents. **Agents** are the new work unit. They don’t sleep. They learn continuously. They self-schedule. They’re not tools to help humans — they *are* the operating system of post-human orgs. **What’s coming:** - DAOs with agent-driven governance and privacy. - Smart Widgets that deploy trade/social/payment agents in three lines of code. - Privacy as a default layer in automation. - A new generation of AI-native hackathon projects. AI + blockchain isn’t a buzzword. It’s the genesis of *organizational intelligence.* Yesterday, the company was an information processor. Tomorrow, the DAO is an autonomous agent network. **No CEOs. No approvals. No offices. Just coordination at the speed of compute.** ## **The Bet: BUIDL Freedom for Humanity** FDA Free Society. Open Source Quantum. Consumer Crypto. Agentic Orgs. These are not sci-fi. They are already happening. At Dora Ventures, we don’t just back technologies. We back builders who say: “The system is broken — and I’m going to fix it myself.” We back rebels who reject stagnation. Who write code instead of complaints. Who build networks instead of narratives. Who refuse to ask permission to build the future. Hackers are eating the world. And in the age of AI, humanity will only survive if it chooses to become hackers — to use code, coordination, and imagination to build a world worth living in. Let’s build.
@ ed84ce10:cccf4c2a
2025-03-27 14:55:40## **Hackers are Destiny: Four Fulcrums of the Future** *A Dora Ventures Thesis* In “Why Software is Eating the World,” Marc Andreeson argued that software isn’t just a tool — it’s a societal force. At [DoraHacks](https://dorahacks.io/), we agree, but we go one step further. It’s not software alone that reshapes the world. It’s hackers — those who BUIDL. The real engine of change isn’t technology; it’s the people who choose to wield it. [DoraHacks](https://dorahacks.io/) is building a global Hacker Movement — a self-organizing force powered by open source, freedom, and code. We’re not chasing buzzwords like “Web3” or geopolitical narratives. We’re building a new society. One based on a simple but radical question: **What is truly worth building?** Dora Ventures exists to serve that mission — a capital engine designed to coordinate, amplify, and capture value from the hacker revolution. We are placing early and aggressive bets across four core leverage points: ## **I. FDA Free Society — The BioHack** ### **Freedom of Life Science is the foundation of a free society.** Every meaningful technological revolution has challenged the existing power structure. Today, the single most over-regulated, over-centralized, and innovation-hostile domain? Life Science. It takes ten years and billions of dollars to bring a drug from lab to patient. Most innovation dies in the trenches of bureaucracy. We don’t need anarchy. We need a new model:**A market-driven, patient-first biotech innovation stack.** **The Problem:** - The FDA approval process kills breakthrough therapies before they live. - Big Pharma monopolies decouple price from value and destroy competition. - The “Right to Try” is a legal afterthought, not a first principle. - Bio startups can’t survive the upfront costs of traditional trials. **The Opportunity:** - Let markets and builders lead: give power back to patients, doctors, and founders. - Rethink from first principles: not “Did it pass?” but “Does it work?” - Reclaim the Right to Try: the real risk is dying while waiting. - Build a hyper-competitive biofounder ecosystem — don’t just supply Big Pharma with IP. - Supercharge biotech with software and AI: accelerate every layer of the stack. The future of medicine does not belong to regulators. It belongs to the builders who refuse to wait. **The FDA Free Society isn’t just a challenge to power — it’s a defense of life.** ## **II. Open Source Quantum** ### **Ethereum had 2015. Quantum software has 2025.** Arthur C. Clarke said: *“Any sufficiently advanced technology is indistinguishable from magic.”* Quantum is magic — until it’s programmable, repeatable, and shared. In other words: open source. Dora Ventures is betting on the moment quantum computing becomes a hacker’s playground. Hardware is entering the engineering phase. Software? Still a wasteland — which means pure upside for builders. **We’re betting on:** - **Quantum compilers & transpilers**: bridging classical and quantum logic. - **Quantum cryptography**: building fundamentally new security layers. - **Quantum applications** in AI, pharma, logistics, finance, space — everything. We're not watching from the sidelines. We’re funding open-source tools, running hackathons, and building out the decentralized quantum dev stack. **Open Source Quantum is not speculative.** It’s inevitable — and massively undercapitalized. Now is the time to build. ## **III. Consumer Crypto — The Fat Apps Are Coming** ### **Crypto’s real revolution? Billion-user apps.** Crypto is not the *alternative* to the internet. It’s the *next chapter* of the internet. In the 1990s, HTTP and TCP/IP rewired information. In the 2000s, web apps rewired commerce and communication. In the 2010s, mobile apps rewired human behavior. In the 2020s, crypto apps will onboard the next billion users. **The infrastructure is ready. The fat apps are hatching.** Dora Ventures is obsessed with one question: **Who builds the PayPal and WeChat of the Web3 era?** That’s where we place our bets. **What we see coming:** - Compliant stablecoins like USDC become digital dollars. - Crypto-native payment rails rival VISA. - Appchains built with Move + simplified UX onboard non-crypto users. - On-chain creator economies that pay artists, devs, and communities directly. Imagine this: A fan in NYC uses USDC on a Move-based blockchain (Aptos) to buy a concert ticket via KYD Labs. An Argentinian grabs a latte daily with Bitcoin sats on Lightning. A friend group splits dinner bills via Yakihonne, a decentralized social platform. **That’s not the future. That’s this year.** We’re not funding protocols — we’re funding paradigm shifts in experience. ## **IV. Agentic Organizations — DAOs Without CEOs** ### **The end of corporations. The birth of autonomous orgs.** In 2022, Sam Altman redefined “tools.” In 2025, we’ll redefine “organizations.” Future orgs won’t be hierarchies. They’ll be networks of autonomous agents. **Agents** are the new work unit. They don’t sleep. They learn continuously. They self-schedule. They’re not tools to help humans — they *are* the operating system of post-human orgs. **What’s coming:** - DAOs with agent-driven governance and privacy. - Smart Widgets that deploy trade/social/payment agents in three lines of code. - Privacy as a default layer in automation. - A new generation of AI-native hackathon projects. AI + blockchain isn’t a buzzword. It’s the genesis of *organizational intelligence.* Yesterday, the company was an information processor. Tomorrow, the DAO is an autonomous agent network. **No CEOs. No approvals. No offices. Just coordination at the speed of compute.** ## **The Bet: BUIDL Freedom for Humanity** FDA Free Society. Open Source Quantum. Consumer Crypto. Agentic Orgs. These are not sci-fi. They are already happening. At Dora Ventures, we don’t just back technologies. We back builders who say: “The system is broken — and I’m going to fix it myself.” We back rebels who reject stagnation. Who write code instead of complaints. Who build networks instead of narratives. Who refuse to ask permission to build the future. Hackers are eating the world. And in the age of AI, humanity will only survive if it chooses to become hackers — to use code, coordination, and imagination to build a world worth living in. Let’s build. @ 2b24a1fa:17750f64
2025-03-28 10:03:58Zwischen Überzeugungsarbeit und Propaganda verläuft ein schmaler Grad. Aber so oder so: Wer die subtileren Werkzeuge hat und vor allem die Mittel um Menschen zu kaufen, die diese dann anwenden, hat eindeutig die besseren Karten.  [https://soundcloud.com/radiomuenchen/unterwanderter-journalismus-oder-der-mediale-deep-state-wankt-von-milosz-matuschekcolor=ffd400](https://soundcloud.com/radiomuenchen/unterwanderter-journalismus-oder-der-mediale-deep-state-wankt-von-milosz-matuschek?si=45877e50143d4e10a22fc9a4be82970d\&utm_source=clipboard\&utm_medium=text\&utm_campaign=social_sharing) Dass die Bevölkerung nun wissen will, mit welchen Mitteln sie auf welche Weise beeinflusst werden soll, ist selbstverständlich. Wie nuanciert diese Beeinflussung stattfinden kann, darauf haben uns unsere Hörer beim letzten Beitrag von Milosz Matuschek: „Die ersten Köpfe rollen“ gestoßen. Es ging um die staatliche amerikanische Behörde für internationale Entwicklungshilfe USAID. Matuschek schrieb: „Man liest was von AID im Namen und denkt, was man denken soll: klingt nach Bob Geldof, barmherzigen Schwestern und “Brot für die Welt”.“ Man hatte das nicht nur optisch wahrgenommen, nein, diese Behörde wurde hierzulande, in allen Medien US AID genannt, was unsere Sprecherin Sabrina Khalil übernahm. Dass die United States Agency for International Development in USA so nicht gesprochen wird, schrieben uns gleich mehrere aufmerksame Hörer. Es ist sicherlich keine Paranoia darüber nachzudenken, ob die Bedeutung unserer Sprache, unserer Wörter bis hin zur Aussprache im Fokus der Manipulation steht. Dafür wird sehr viel Geld locker gemacht und unter anderem in die Medien gepumpt. Hören Sie heute den zweiten Teil der Reihe „Die Corona-Connection“ mit dem Titel: „Der mediale Deep State wankt“. Sprecherin: Sabrina Khalil. Das freie Medienprojekt Pareto kann übrigens Unterstützung gebrauchen, dafür wurde ein Crowdfunding auf Geyser gestartet, wo man mit Bitcoin/Lightning-Spenden helfen kann. Und für Spenden auf dem klassischen Weg finden Sie die entsprechende Bankverbindung auf der Homepage pareto.space/de. Nachzulesen unter: [www.freischwebende-intelligenz.org/p/unter…mediale](https://gate.sc?url=https%3A%2F%2Fwww.freischwebende-intelligenz.org%2Fp%2Funterwanderter-journalismus-der-mediale\&token=6fce3f-1-1743155866002 "https://www.freischwebende-intelligenz.org/p/unterwanderter-journalismus-der-mediale") Foto: Gleichschaltung - sie melden exakt den gleichen Wortlaut.
@ 2b24a1fa:17750f64
2025-03-28 10:03:58Zwischen Überzeugungsarbeit und Propaganda verläuft ein schmaler Grad. Aber so oder so: Wer die subtileren Werkzeuge hat und vor allem die Mittel um Menschen zu kaufen, die diese dann anwenden, hat eindeutig die besseren Karten.  [https://soundcloud.com/radiomuenchen/unterwanderter-journalismus-oder-der-mediale-deep-state-wankt-von-milosz-matuschekcolor=ffd400](https://soundcloud.com/radiomuenchen/unterwanderter-journalismus-oder-der-mediale-deep-state-wankt-von-milosz-matuschek?si=45877e50143d4e10a22fc9a4be82970d\&utm_source=clipboard\&utm_medium=text\&utm_campaign=social_sharing) Dass die Bevölkerung nun wissen will, mit welchen Mitteln sie auf welche Weise beeinflusst werden soll, ist selbstverständlich. Wie nuanciert diese Beeinflussung stattfinden kann, darauf haben uns unsere Hörer beim letzten Beitrag von Milosz Matuschek: „Die ersten Köpfe rollen“ gestoßen. Es ging um die staatliche amerikanische Behörde für internationale Entwicklungshilfe USAID. Matuschek schrieb: „Man liest was von AID im Namen und denkt, was man denken soll: klingt nach Bob Geldof, barmherzigen Schwestern und “Brot für die Welt”.“ Man hatte das nicht nur optisch wahrgenommen, nein, diese Behörde wurde hierzulande, in allen Medien US AID genannt, was unsere Sprecherin Sabrina Khalil übernahm. Dass die United States Agency for International Development in USA so nicht gesprochen wird, schrieben uns gleich mehrere aufmerksame Hörer. Es ist sicherlich keine Paranoia darüber nachzudenken, ob die Bedeutung unserer Sprache, unserer Wörter bis hin zur Aussprache im Fokus der Manipulation steht. Dafür wird sehr viel Geld locker gemacht und unter anderem in die Medien gepumpt. Hören Sie heute den zweiten Teil der Reihe „Die Corona-Connection“ mit dem Titel: „Der mediale Deep State wankt“. Sprecherin: Sabrina Khalil. Das freie Medienprojekt Pareto kann übrigens Unterstützung gebrauchen, dafür wurde ein Crowdfunding auf Geyser gestartet, wo man mit Bitcoin/Lightning-Spenden helfen kann. Und für Spenden auf dem klassischen Weg finden Sie die entsprechende Bankverbindung auf der Homepage pareto.space/de. Nachzulesen unter: [www.freischwebende-intelligenz.org/p/unter…mediale](https://gate.sc?url=https%3A%2F%2Fwww.freischwebende-intelligenz.org%2Fp%2Funterwanderter-journalismus-der-mediale\&token=6fce3f-1-1743155866002 "https://www.freischwebende-intelligenz.org/p/unterwanderter-journalismus-der-mediale") Foto: Gleichschaltung - sie melden exakt den gleichen Wortlaut. @ dfbbf851:ba4542b5
2025-03-27 13:45:12Bitcoin (BTC) เป็นสกุลเงินดิจิทัลที่ได้รับความนิยมและถูกพูดถึงมากที่สุดในโลก นับตั้งแต่เปิดตัวในปี 2009 โดยบุคคลหรือกลุ่มที่ใช้นามแฝงว่า **Satoshi Nakamoto** 🎭 แต่คำถามสำคัญก็คือ... **Bitcoin เป็นอนาคตของการเงินโลกหรือว่าเป็นฟองสบู่ที่รอวันแตกกันแน่?** 🤔 --- ### 🔹 **Bitcoin คืออะไร ?** Bitcoin เป็นเงินดิจิทัลที่ทำงานบน **เทคโนโลยีบล็อกเชน (Blockchain)** ซึ่งช่วยให้การทำธุรกรรมมีความปลอดภัยและโปร่งใส 💡 🔸 **ไม่มีธนาคารกลางควบคุม** 🔸 **จำนวนจำกัดเพียง 21 ล้านเหรียญ** 🔸 **ใช้ระบบ "การขุด" (Mining) เพื่อยืนยันธุรกรรม** --- ### ✅ **ทำไม Bitcoin ได้รับความนิยม ?** ✨ **ไร้พรมแดน** – โอนเงินข้ามประเทศได้รวดเร็วและถูกกว่าธนาคาร ✨ **ความปลอดภัยสูง** – ใช้ระบบเข้ารหัสที่แข็งแกร่ง 🔐 ✨ **สินทรัพย์ป้องกันเงินเฟ้อ** – มีจำนวนจำกัด จึงถูกมองว่าเป็น **"ทองคำดิจิทัล"** 🌎🏆 ✨ **การยอมรับที่เพิ่มขึ้น** – บริษัทใหญ่ เช่น Tesla และ PayPal เริ่มเปิดรับ BTC --- ### ❌ **ความเสี่ยงของ Bitcoin** ⚠️ **ราคาผันผวนสูง** – อาจขึ้นหรือลงหลายพันดอลลาร์ภายในวันเดียว 📉📈 ⚠️ **ยังไม่ถูกยอมรับทั่วโลก** – บางประเทศออกกฎหมายห้ามใช้ เช่น จีน 🚫 ⚠️ **อาจถูกใช้ในทางผิดกฎหมาย** – เช่น การฟอกเงินในตลาดมืด 🕵️♂️ ⚠️ **สิ้นเปลืองพลังงาน** – กระบวนการขุดใช้ไฟฟ้าปริมาณมาก ⚡🌱 --- ### 🔮 **อนาคตของ Bitcoin จะเป็นอย่างไร ?** นักลงทุนบางคนเชื่อว่า **Bitcoin จะเป็นอนาคตของระบบการเงินโลก** 💵🌍 ในขณะที่บางคนมองว่า **มันเป็นเพียงฟองสบู่ที่อาจแตกเมื่อไหร่ก็ได้** 💥 💡 ปัจจัยสำคัญที่อาจกำหนดอนาคตของ BTC ได้แก่: ✔️ **การยอมรับจากรัฐบาลและองค์กรใหญ่** ✔️ **กฎหมายและกฎระเบียบ** – หากรัฐบาลทั่วโลกออกกฎหมายสนับสนุน BTC อาจทำให้ราคาพุ่งสูง 🚀 ✔️ **เทคโนโลยีใหม่ๆ** – เช่น **Lightning Network** ที่ช่วยให้การทำธุรกรรมเร็วขึ้นและถูกลง ⚡ --- ### 🎯 **ปล.** Bitcoin เป็น **นวัตกรรมการเงินที่เปลี่ยนโลก** 🌎 และอาจกลายเป็นสินทรัพย์สำคัญในอนาคต **แต่ก็มีความเสี่ยงสูง** นักลงทุนต้องศึกษาให้รอบคอบก่อนตัดสินใจลงทุน 📊💡 **แล้วท่านผู้อ่านล่ะครับ คิดว่า Bitcoin คืออนาคตของเงิน หรือเป็นเพียงกระแสชั่วคราวกันแน่ ?** 🤔 --- #Bitcoin #Crypto #Blockchain #BTC #ลงทุน #การเงิน #อนาคตการเงิน
@ dfbbf851:ba4542b5
2025-03-27 13:45:12Bitcoin (BTC) เป็นสกุลเงินดิจิทัลที่ได้รับความนิยมและถูกพูดถึงมากที่สุดในโลก นับตั้งแต่เปิดตัวในปี 2009 โดยบุคคลหรือกลุ่มที่ใช้นามแฝงว่า **Satoshi Nakamoto** 🎭 แต่คำถามสำคัญก็คือ... **Bitcoin เป็นอนาคตของการเงินโลกหรือว่าเป็นฟองสบู่ที่รอวันแตกกันแน่?** 🤔 --- ### 🔹 **Bitcoin คืออะไร ?** Bitcoin เป็นเงินดิจิทัลที่ทำงานบน **เทคโนโลยีบล็อกเชน (Blockchain)** ซึ่งช่วยให้การทำธุรกรรมมีความปลอดภัยและโปร่งใส 💡 🔸 **ไม่มีธนาคารกลางควบคุม** 🔸 **จำนวนจำกัดเพียง 21 ล้านเหรียญ** 🔸 **ใช้ระบบ "การขุด" (Mining) เพื่อยืนยันธุรกรรม** --- ### ✅ **ทำไม Bitcoin ได้รับความนิยม ?** ✨ **ไร้พรมแดน** – โอนเงินข้ามประเทศได้รวดเร็วและถูกกว่าธนาคาร ✨ **ความปลอดภัยสูง** – ใช้ระบบเข้ารหัสที่แข็งแกร่ง 🔐 ✨ **สินทรัพย์ป้องกันเงินเฟ้อ** – มีจำนวนจำกัด จึงถูกมองว่าเป็น **"ทองคำดิจิทัล"** 🌎🏆 ✨ **การยอมรับที่เพิ่มขึ้น** – บริษัทใหญ่ เช่น Tesla และ PayPal เริ่มเปิดรับ BTC --- ### ❌ **ความเสี่ยงของ Bitcoin** ⚠️ **ราคาผันผวนสูง** – อาจขึ้นหรือลงหลายพันดอลลาร์ภายในวันเดียว 📉📈 ⚠️ **ยังไม่ถูกยอมรับทั่วโลก** – บางประเทศออกกฎหมายห้ามใช้ เช่น จีน 🚫 ⚠️ **อาจถูกใช้ในทางผิดกฎหมาย** – เช่น การฟอกเงินในตลาดมืด 🕵️♂️ ⚠️ **สิ้นเปลืองพลังงาน** – กระบวนการขุดใช้ไฟฟ้าปริมาณมาก ⚡🌱 --- ### 🔮 **อนาคตของ Bitcoin จะเป็นอย่างไร ?** นักลงทุนบางคนเชื่อว่า **Bitcoin จะเป็นอนาคตของระบบการเงินโลก** 💵🌍 ในขณะที่บางคนมองว่า **มันเป็นเพียงฟองสบู่ที่อาจแตกเมื่อไหร่ก็ได้** 💥 💡 ปัจจัยสำคัญที่อาจกำหนดอนาคตของ BTC ได้แก่: ✔️ **การยอมรับจากรัฐบาลและองค์กรใหญ่** ✔️ **กฎหมายและกฎระเบียบ** – หากรัฐบาลทั่วโลกออกกฎหมายสนับสนุน BTC อาจทำให้ราคาพุ่งสูง 🚀 ✔️ **เทคโนโลยีใหม่ๆ** – เช่น **Lightning Network** ที่ช่วยให้การทำธุรกรรมเร็วขึ้นและถูกลง ⚡ --- ### 🎯 **ปล.** Bitcoin เป็น **นวัตกรรมการเงินที่เปลี่ยนโลก** 🌎 และอาจกลายเป็นสินทรัพย์สำคัญในอนาคต **แต่ก็มีความเสี่ยงสูง** นักลงทุนต้องศึกษาให้รอบคอบก่อนตัดสินใจลงทุน 📊💡 **แล้วท่านผู้อ่านล่ะครับ คิดว่า Bitcoin คืออนาคตของเงิน หรือเป็นเพียงกระแสชั่วคราวกันแน่ ?** 🤔 --- #Bitcoin #Crypto #Blockchain #BTC #ลงทุน #การเงิน #อนาคตการเงิน @ 8cb60e21:5f2deaea
2024-08-24 23:33:51# test
@ 8cb60e21:5f2deaea
2024-08-24 23:33:51# test @ ebbba253:6ec1d547
2025-03-27 12:19:28A NNBET se tornou uma plataforma de destaque no Brasil, oferecendo uma ampla variedade de opções de entretenimento online para jogadores de todos os perfis. Desde apostas esportivas até uma vasta seleção de jogos interativos, a plataforma se destaca pela sua facilidade de uso, segurança e pelas diversas oportunidades de ganhar. Se você está em busca de uma experiência online diversificada e acessível, NNBET é a escolha perfeita. Fácil Acesso e Navegação Intuitiva Quando se trata de uma plataforma de entretenimento online, a facilidade de uso é crucial. A <a href="https://nnbet.tw"> Nnbet </a> oferece uma interface extremamente amigável, permitindo que jogadores novatos ou experientes possam navegar sem problemas. A plataforma é bem organizada, com seções claramente marcadas para apostas esportivas, jogos e promoções. Seu design simples e funcional permite que os usuários encontrem rapidamente suas opções preferidas, sem perder tempo. O acesso à plataforma também é facilitado pela sua versão mobile. Isso significa que você pode acessar sua conta e jogar a qualquer momento e em qualquer lugar. Com a popularização dos smartphones, essa funcionalidade é essencial, e a NNBET não deixa a desejar, oferecendo uma versão mobile otimizada que proporciona uma experiência de jogo excelente mesmo em telas menores. Apostas Esportivas: Uma Experiência Completa A NNBET não é apenas uma plataforma de jogos, ela também se destaca no campo das apostas esportivas. Para os brasileiros, o futebol é um dos esportes mais importantes, e a plataforma oferece uma variedade imensa de mercados para apostas em jogos de futebol, tanto locais quanto internacionais. Além disso, a plataforma abrange uma grande gama de outros esportes populares, como vôlei, basquete e até esportes eletrônicos. As apostas ao vivo são uma característica de destaque, oferecendo uma experiência interativa em tempo real. A NNBET permite que os jogadores apostem enquanto os jogos acontecem, com odds constantemente atualizadas, o que torna a experiência ainda mais empolgante e envolvente. A diversidade de mercados, aliada às odds competitivas, garante que sempre haverá algo para você apostar, independentemente do seu time ou esporte favorito. Uma Grande Variedade de Jogos para Todos os Gostos Além das apostas esportivas, a NNBET oferece uma gama de jogos para agradar a todos os tipos de jogadores. Se você é fã de jogos de azar, a plataforma conta com uma vasta seleção de slots com temas diversificados, bônus incríveis e gráficos de última geração. Se o que você procura é uma experiência mais imersiva, os jogos ao vivo são uma excelente opção. Com dealers reais transmitindo jogos em tempo real, a NNBET recria a atmosfera de um ambiente físico, proporcionando uma experiência realista. Outro grande atrativo são os jogos de mesa, como o blackjack e a roleta, que oferecem opções de apostas e limites variados, permitindo que todos os tipos de jogadores possam participar. Suporte e Promoções: Garantindo a Melhor Experiência A NNBET vai além de oferecer apenas jogos e apostas. A plataforma também se destaca pelo suporte ao cliente de alta qualidade. O atendimento está disponível 24/7, sempre pronto para ajudar com dúvidas ou problemas que possam surgir. Se você tem alguma pergunta sobre sua conta, pagamentos ou jogos, o suporte estará ao seu alcance a qualquer momento. As promoções e bônus também são uma parte importante da experiência. A NNBET oferece bônus de boas-vindas para novos jogadores, bem como promoções regulares que garantem que a diversão nunca pare. Com rodadas grátis, bônus de depósito e programas de fidelidade, a plataforma oferece uma experiência emocionante a cada visita.
@ ebbba253:6ec1d547
2025-03-27 12:19:28A NNBET se tornou uma plataforma de destaque no Brasil, oferecendo uma ampla variedade de opções de entretenimento online para jogadores de todos os perfis. Desde apostas esportivas até uma vasta seleção de jogos interativos, a plataforma se destaca pela sua facilidade de uso, segurança e pelas diversas oportunidades de ganhar. Se você está em busca de uma experiência online diversificada e acessível, NNBET é a escolha perfeita. Fácil Acesso e Navegação Intuitiva Quando se trata de uma plataforma de entretenimento online, a facilidade de uso é crucial. A <a href="https://nnbet.tw"> Nnbet </a> oferece uma interface extremamente amigável, permitindo que jogadores novatos ou experientes possam navegar sem problemas. A plataforma é bem organizada, com seções claramente marcadas para apostas esportivas, jogos e promoções. Seu design simples e funcional permite que os usuários encontrem rapidamente suas opções preferidas, sem perder tempo. O acesso à plataforma também é facilitado pela sua versão mobile. Isso significa que você pode acessar sua conta e jogar a qualquer momento e em qualquer lugar. Com a popularização dos smartphones, essa funcionalidade é essencial, e a NNBET não deixa a desejar, oferecendo uma versão mobile otimizada que proporciona uma experiência de jogo excelente mesmo em telas menores. Apostas Esportivas: Uma Experiência Completa A NNBET não é apenas uma plataforma de jogos, ela também se destaca no campo das apostas esportivas. Para os brasileiros, o futebol é um dos esportes mais importantes, e a plataforma oferece uma variedade imensa de mercados para apostas em jogos de futebol, tanto locais quanto internacionais. Além disso, a plataforma abrange uma grande gama de outros esportes populares, como vôlei, basquete e até esportes eletrônicos. As apostas ao vivo são uma característica de destaque, oferecendo uma experiência interativa em tempo real. A NNBET permite que os jogadores apostem enquanto os jogos acontecem, com odds constantemente atualizadas, o que torna a experiência ainda mais empolgante e envolvente. A diversidade de mercados, aliada às odds competitivas, garante que sempre haverá algo para você apostar, independentemente do seu time ou esporte favorito. Uma Grande Variedade de Jogos para Todos os Gostos Além das apostas esportivas, a NNBET oferece uma gama de jogos para agradar a todos os tipos de jogadores. Se você é fã de jogos de azar, a plataforma conta com uma vasta seleção de slots com temas diversificados, bônus incríveis e gráficos de última geração. Se o que você procura é uma experiência mais imersiva, os jogos ao vivo são uma excelente opção. Com dealers reais transmitindo jogos em tempo real, a NNBET recria a atmosfera de um ambiente físico, proporcionando uma experiência realista. Outro grande atrativo são os jogos de mesa, como o blackjack e a roleta, que oferecem opções de apostas e limites variados, permitindo que todos os tipos de jogadores possam participar. Suporte e Promoções: Garantindo a Melhor Experiência A NNBET vai além de oferecer apenas jogos e apostas. A plataforma também se destaca pelo suporte ao cliente de alta qualidade. O atendimento está disponível 24/7, sempre pronto para ajudar com dúvidas ou problemas que possam surgir. Se você tem alguma pergunta sobre sua conta, pagamentos ou jogos, o suporte estará ao seu alcance a qualquer momento. As promoções e bônus também são uma parte importante da experiência. A NNBET oferece bônus de boas-vindas para novos jogadores, bem como promoções regulares que garantem que a diversão nunca pare. Com rodadas grátis, bônus de depósito e programas de fidelidade, a plataforma oferece uma experiência emocionante a cada visita. @ 266815e0:6cd408a5
2025-03-19 11:10:21How to create a nostr app quickly using [applesauce](https://hzrd149.github.io/applesauce/) In this guide we are going to build a nostr app that lets users follow and unfollow [fiatjaf](nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6) ## 1. Setup new project Start by setting up a new vite app using `pnpm create vite`, then set the name and select `Solid` and `Typescript` ```sh ➜ pnpm create vite │ ◇ Project name: │ followjaf │ ◇ Select a framework: │ Solid │ ◇ Select a variant: │ TypeScript │ ◇ Scaffolding project in ./followjaf... │ └ Done. Now run: cd followjaf pnpm install pnpm run dev ``` ## 2. Adding nostr dependencies There are a few useful nostr dependencies we are going to need. `nostr-tools` for the types and small methods, and [`rx-nostr`](https://penpenpng.github.io/rx-nostr/) for making relay connections ```sh pnpm install nostr-tools rx-nostr ``` ## 3. Setup rx-nostr Next we need to setup rxNostr so we can make connections to relays. create a new `src/nostr.ts` file with ```ts import { createRxNostr, noopVerifier } from "rx-nostr"; export const rxNostr = createRxNostr({ // skip verification here because we are going to verify events at the event store skipVerify: true, verifier: noopVerifier, }); ``` ## 4. Setup the event store Now that we have a way to connect to relays, we need a place to store events. We will use the [`EventStore`](https://hzrd149.github.io/applesauce/typedoc/classes/applesauce_core.EventStore.html) class from `applesauce-core` for this. create a new `src/stores.ts` file with > The event store does not store any events in the browsers local storage or anywhere else. It's in-memory only and provides a model for the UI ```ts import { EventStore } from "applesauce-core"; import { verifyEvent } from "nostr-tools"; export const eventStore = new EventStore(); // verify the events when they are added to the store eventStore.verifyEvent = verifyEvent; ``` ## 5. Create the query store The event store is where we store all the events, but we need a way for the UI to query them. We can use the [`QueryStore`](https://hzrd149.github.io/applesauce/typedoc/classes/applesauce_core.QueryStore.html) class from `applesauce-core` for this. Create a query store in `src/stores.ts` ```ts import { QueryStore } from "applesauce-core"; // ... // the query store needs the event store to subscribe to it export const queryStore = new QueryStore(eventStore); ``` ## 6. Setup the profile loader Next we need a way to fetch user profiles. We are going to use the [`ReplaceableLoader`](https://hzrd149.github.io/applesauce/overview/loaders.html#replaceable-loader) class from [`applesauce-loaders`](https://www.npmjs.com/package/applesauce-loaders) for this. > `applesauce-loaders` is a package that contains a few loader classes that can be used to fetch different types of data from relays. First install the package ```sh pnpm install applesauce-loaders ``` Then create a `src/loaders.ts` file with ```ts import { ReplaceableLoader } from "applesauce-loaders"; import { rxNostr } from "./nostr"; import { eventStore } from "./stores"; export const replaceableLoader = new ReplaceableLoader(rxNostr); // Start the loader and send any events to the event store replaceableLoader.subscribe((packet) => { eventStore.add(packet.event, packet.from); }); ``` ## 7. Fetch fiatjaf's profile Now that we have a way to store events, and a loader to help with fetching them, we should update the `src/App.tsx` component to fetch the profile. We can do this by calling the `next` method on the loader and passing a `pubkey`, `kind` and `relays` to it ```tsx function App() { // ... onMount(() => { // fetch fiatjaf's profile on load replaceableLoader.next({ pubkey: "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", kind: 0, relays: ["wss://pyramid.fiatjaf.com/"], }); }); // ... } ``` ## 8. Display the profile Now that we have a way to fetch the profile, we need to display it in the UI. We can do this by using the [`ProfileQuery`](https://hzrd149.github.io/applesauce/typedoc/functions/applesauce_core.Queries.ProfileQuery.html) which gives us a stream of updates to a pubkey's profile. Create the profile using `queryStore.createQuery` and pass in the `ProfileQuery` and the pubkey. ```tsx const fiatjaf = queryStore.createQuery( ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d" ); ``` But this just gives us an [observable](https://rxjs.dev/guide/observable), we need to subscribe to it to get the profile. Luckily SolidJS profiles a simple [`from`](https://docs.solidjs.com/reference/reactive-utilities/from) method to subscribe to any observable. > To make things reactive SolidJS uses accessors, so to get the profile we need to call `fiatjaf()` ```tsx function App() { // ... // Subscribe to fiatjaf's profile from the query store const fiatjaf = from( queryStore.createQuery(ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") ); return ( <> {/* replace the vite and solid logos with the profile picture */} <div> <img src={fiatjaf()?.picture} class="logo" /> </div> <h1>{fiatjaf()?.name}</h1> {/* ... */} </> ); } ``` ## 9. Letting the user signin Now we should let the user signin to the app. We can do this by creating a [`AccountManager`](https://hzrd149.github.io/applesauce/accounts/manager.html) class from `applesauce-accounts` First we need to install the packages ```sh pnpm install applesauce-accounts applesauce-signers ``` Then create a new `src/accounts.ts` file with ```ts import { AccountManager } from "applesauce-accounts"; import { registerCommonAccountTypes } from "applesauce-accounts/accounts"; // create an account manager instance export const accounts = new AccountManager(); // Adds the common account types to the manager registerCommonAccountTypes(accounts); ``` Next lets presume the user has a NIP-07 browser extension installed and add a signin button. ```tsx function App() { const signin = async () => { // do nothing if the user is already signed in if (accounts.active) return; // create a new nip-07 signer and try to get the pubkey const signer = new ExtensionSigner(); const pubkey = await signer.getPublicKey(); // create a new extension account, add it, and make it the active account const account = new ExtensionAccount(pubkey, signer); accounts.addAccount(account); accounts.setActive(account); }; return ( <> {/* ... */} <div class="card"> <p>Are you following the fiatjaf? the creator of "The nostr"</p> <button onClick={signin}>Check</button> </div> </> ); } ``` Now when the user clicks the button the app will ask for the users pubkey, then do nothing... but it's a start. > We are not persisting the accounts, so when the page reloads the user will NOT be signed in. you can learn about persisting the accounts in the [docs](https://hzrd149.github.io/applesauce/accounts/manager.html#persisting-accounts) ## 10. Showing the signed-in state We should show some indication to the user that they are signed in. We can do this by modifying the signin button if the user is signed in and giving them a way to sign-out ```tsx function App() { // subscribe to the currently active account (make sure to use the account$ observable) const account = from(accounts.active$); // ... const signout = () => { // do nothing if the user is not signed in if (!accounts.active) return; // signout the user const account = accounts.active; accounts.removeAccount(account); accounts.clearActive(); }; return ( <> {/* ... */} <div class="card"> <p>Are you following the fiatjaf? ( creator of "The nostr" )</p> {account() === undefined ? <button onClick={signin}>Check</button> : <button onClick={signout}>Signout</button>} </div> </> ); } ``` ## 11. Fetching the user's profile Now that we have a way to sign in and out of the app, we should fetch the user's profile when they sign in. ```tsx function App() { // ... // fetch the user's profile when they sign in createEffect(async () => { const active = account(); if (active) { // get the user's relays or fallback to some default relays const usersRelays = await active.getRelays?.(); const relays = usersRelays ? Object.keys(usersRelays) : ["wss://relay.damus.io", "wss://nos.lol"]; // tell the loader to fetch the users profile event replaceableLoader.next({ pubkey: active.pubkey, kind: 0, relays, }); // tell the loader to fetch the users contacts replaceableLoader.next({ pubkey: active.pubkey, kind: 3, relays, }); // tell the loader to fetch the users mailboxes replaceableLoader.next({ pubkey: active.pubkey, kind: 10002, relays, }); } }); // ... } ``` Next we need to subscribe to the users profile, to do this we can use some rxjs operators to chain the observables together. ```tsx import { Match, Switch } from "solid-js"; import { of, switchMap } from "rxjs"; function App() { // ... // subscribe to the active account, then subscribe to the users profile or undefined const profile = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(ProfileQuery, account!.pubkey) : of(undefined))) ) ); // ... return ( <> {/* ... */} <div class="card"> <Switch> <Match when={account() && !profile()}> <p>Loading profile...</p> </Match> <Match when={profile()}> <p style="font-size: 1.2rem; font-weight: bold;">Welcome {profile()?.name}</p> </Match> </Switch> {/* ... */} </div> </> ); } ``` ## 12. Showing if the user is following fiatjaf Now that the app is fetching the users profile and contacts we should show if the user is following fiatjaf. ```tsx function App() { // ... // subscribe to the active account, then subscribe to the users contacts or undefined const contacts = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(UserContactsQuery, account!.pubkey) : of(undefined))) ) ); const isFollowing = createMemo(() => { return contacts()?.some((c) => c.pubkey === "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d"); }); // ... return ( <> {/* ... */} <div class="card"> {/* ... */} <Switch fallback={ <p style="font-size: 1.2rem;"> Sign in to check if you are a follower of the fiatjaf ( creator of "The nostr" ) </p> } > <Match when={contacts() && isFollowing() === undefined}> <p>checking...</p> </Match> <Match when={contacts() && isFollowing() === true}> <p style="color: green; font-weight: bold; font-size: 2rem;"> Congratulations! You are a follower of the fiatjaf </p> </Match> <Match when={contacts() && isFollowing() === false}> <p style="color: red; font-weight: bold; font-size: 2rem;"> Why don't you follow the fiatjaf? do you even like nostr? </p> </Match> </Switch> {/* ... */} </div> </> ); } ``` ## 13. Adding the follow button Now that we have a way to check if the user is following fiatjaf, we should add a button to follow him. We can do this with [Actions](https://hzrd149.github.io/applesauce/overview/actions.html) which are pre-built methods to modify nostr events for a user. First we need to install the `applesauce-actions` and `applesauce-factory` package ```sh pnpm install applesauce-actions applesauce-factory ``` Then create a `src/actions.ts` file with ```ts import { EventFactory } from "applesauce-factory"; import { ActionHub } from "applesauce-actions"; import { eventStore } from "./stores"; import { accounts } from "./accounts"; // The event factory is used to build and modify nostr events export const factory = new EventFactory({ // accounts.signer is a NIP-07 signer that signs with the currently active account signer: accounts.signer, }); // The action hub is used to run Actions against the event store export const actions = new ActionHub(eventStore, factory); ``` Then create a `toggleFollow` method that will add or remove fiatjaf from the users contacts. > We are using the `exec` method to run the action, and the [`forEach`](https://rxjs.dev/api/index/class/Observable#foreach) method from RxJS allows us to await for all the events to be published ```tsx function App() { // ... const toggleFollow = async () => { // send any created events to rxNostr and the event store const publish = (event: NostrEvent) => { eventStore.add(event); rxNostr.send(event); }; if (isFollowing()) { await actions .exec(UnfollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") .forEach(publish); } else { await actions .exec( FollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", "wss://pyramid.fiatjaf.com/" ) .forEach(publish); } }; // ... return ( <> {/* ... */} <div class="card"> {/* ... */} {contacts() && <button onClick={toggleFollow}>{isFollowing() ? "Unfollow" : "Follow"}</button>} </div> </> ); } ``` ## 14. Adding outbox support The app looks like it works now but if the user reloads the page they will still see an the old version of their contacts list. we need to make sure rxNostr is publishing the events to the users outbox relays. To do this we can subscribe to the signed in users mailboxes using the query store in `src/nostr.ts` ```ts import { MailboxesQuery } from "applesauce-core/queries"; import { accounts } from "./accounts"; import { of, switchMap } from "rxjs"; import { queryStore } from "./stores"; // ... // subscribe to the active account, then subscribe to the users mailboxes and update rxNostr accounts.active$ .pipe(switchMap((account) => (account ? queryStore.createQuery(MailboxesQuery, account.pubkey) : of(undefined)))) .subscribe((mailboxes) => { if (mailboxes) rxNostr.setDefaultRelays(mailboxes.outboxes); else rxNostr.setDefaultRelays([]); }); ``` And that's it! we have a working nostr app that lets users follow and unfollow fiatjaf.
@ 266815e0:6cd408a5
2025-03-19 11:10:21How to create a nostr app quickly using [applesauce](https://hzrd149.github.io/applesauce/) In this guide we are going to build a nostr app that lets users follow and unfollow [fiatjaf](nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6) ## 1. Setup new project Start by setting up a new vite app using `pnpm create vite`, then set the name and select `Solid` and `Typescript` ```sh ➜ pnpm create vite │ ◇ Project name: │ followjaf │ ◇ Select a framework: │ Solid │ ◇ Select a variant: │ TypeScript │ ◇ Scaffolding project in ./followjaf... │ └ Done. Now run: cd followjaf pnpm install pnpm run dev ``` ## 2. Adding nostr dependencies There are a few useful nostr dependencies we are going to need. `nostr-tools` for the types and small methods, and [`rx-nostr`](https://penpenpng.github.io/rx-nostr/) for making relay connections ```sh pnpm install nostr-tools rx-nostr ``` ## 3. Setup rx-nostr Next we need to setup rxNostr so we can make connections to relays. create a new `src/nostr.ts` file with ```ts import { createRxNostr, noopVerifier } from "rx-nostr"; export const rxNostr = createRxNostr({ // skip verification here because we are going to verify events at the event store skipVerify: true, verifier: noopVerifier, }); ``` ## 4. Setup the event store Now that we have a way to connect to relays, we need a place to store events. We will use the [`EventStore`](https://hzrd149.github.io/applesauce/typedoc/classes/applesauce_core.EventStore.html) class from `applesauce-core` for this. create a new `src/stores.ts` file with > The event store does not store any events in the browsers local storage or anywhere else. It's in-memory only and provides a model for the UI ```ts import { EventStore } from "applesauce-core"; import { verifyEvent } from "nostr-tools"; export const eventStore = new EventStore(); // verify the events when they are added to the store eventStore.verifyEvent = verifyEvent; ``` ## 5. Create the query store The event store is where we store all the events, but we need a way for the UI to query them. We can use the [`QueryStore`](https://hzrd149.github.io/applesauce/typedoc/classes/applesauce_core.QueryStore.html) class from `applesauce-core` for this. Create a query store in `src/stores.ts` ```ts import { QueryStore } from "applesauce-core"; // ... // the query store needs the event store to subscribe to it export const queryStore = new QueryStore(eventStore); ``` ## 6. Setup the profile loader Next we need a way to fetch user profiles. We are going to use the [`ReplaceableLoader`](https://hzrd149.github.io/applesauce/overview/loaders.html#replaceable-loader) class from [`applesauce-loaders`](https://www.npmjs.com/package/applesauce-loaders) for this. > `applesauce-loaders` is a package that contains a few loader classes that can be used to fetch different types of data from relays. First install the package ```sh pnpm install applesauce-loaders ``` Then create a `src/loaders.ts` file with ```ts import { ReplaceableLoader } from "applesauce-loaders"; import { rxNostr } from "./nostr"; import { eventStore } from "./stores"; export const replaceableLoader = new ReplaceableLoader(rxNostr); // Start the loader and send any events to the event store replaceableLoader.subscribe((packet) => { eventStore.add(packet.event, packet.from); }); ``` ## 7. Fetch fiatjaf's profile Now that we have a way to store events, and a loader to help with fetching them, we should update the `src/App.tsx` component to fetch the profile. We can do this by calling the `next` method on the loader and passing a `pubkey`, `kind` and `relays` to it ```tsx function App() { // ... onMount(() => { // fetch fiatjaf's profile on load replaceableLoader.next({ pubkey: "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", kind: 0, relays: ["wss://pyramid.fiatjaf.com/"], }); }); // ... } ``` ## 8. Display the profile Now that we have a way to fetch the profile, we need to display it in the UI. We can do this by using the [`ProfileQuery`](https://hzrd149.github.io/applesauce/typedoc/functions/applesauce_core.Queries.ProfileQuery.html) which gives us a stream of updates to a pubkey's profile. Create the profile using `queryStore.createQuery` and pass in the `ProfileQuery` and the pubkey. ```tsx const fiatjaf = queryStore.createQuery( ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d" ); ``` But this just gives us an [observable](https://rxjs.dev/guide/observable), we need to subscribe to it to get the profile. Luckily SolidJS profiles a simple [`from`](https://docs.solidjs.com/reference/reactive-utilities/from) method to subscribe to any observable. > To make things reactive SolidJS uses accessors, so to get the profile we need to call `fiatjaf()` ```tsx function App() { // ... // Subscribe to fiatjaf's profile from the query store const fiatjaf = from( queryStore.createQuery(ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") ); return ( <> {/* replace the vite and solid logos with the profile picture */} <div> <img src={fiatjaf()?.picture} class="logo" /> </div> <h1>{fiatjaf()?.name}</h1> {/* ... */} </> ); } ``` ## 9. Letting the user signin Now we should let the user signin to the app. We can do this by creating a [`AccountManager`](https://hzrd149.github.io/applesauce/accounts/manager.html) class from `applesauce-accounts` First we need to install the packages ```sh pnpm install applesauce-accounts applesauce-signers ``` Then create a new `src/accounts.ts` file with ```ts import { AccountManager } from "applesauce-accounts"; import { registerCommonAccountTypes } from "applesauce-accounts/accounts"; // create an account manager instance export const accounts = new AccountManager(); // Adds the common account types to the manager registerCommonAccountTypes(accounts); ``` Next lets presume the user has a NIP-07 browser extension installed and add a signin button. ```tsx function App() { const signin = async () => { // do nothing if the user is already signed in if (accounts.active) return; // create a new nip-07 signer and try to get the pubkey const signer = new ExtensionSigner(); const pubkey = await signer.getPublicKey(); // create a new extension account, add it, and make it the active account const account = new ExtensionAccount(pubkey, signer); accounts.addAccount(account); accounts.setActive(account); }; return ( <> {/* ... */} <div class="card"> <p>Are you following the fiatjaf? the creator of "The nostr"</p> <button onClick={signin}>Check</button> </div> </> ); } ``` Now when the user clicks the button the app will ask for the users pubkey, then do nothing... but it's a start. > We are not persisting the accounts, so when the page reloads the user will NOT be signed in. you can learn about persisting the accounts in the [docs](https://hzrd149.github.io/applesauce/accounts/manager.html#persisting-accounts) ## 10. Showing the signed-in state We should show some indication to the user that they are signed in. We can do this by modifying the signin button if the user is signed in and giving them a way to sign-out ```tsx function App() { // subscribe to the currently active account (make sure to use the account$ observable) const account = from(accounts.active$); // ... const signout = () => { // do nothing if the user is not signed in if (!accounts.active) return; // signout the user const account = accounts.active; accounts.removeAccount(account); accounts.clearActive(); }; return ( <> {/* ... */} <div class="card"> <p>Are you following the fiatjaf? ( creator of "The nostr" )</p> {account() === undefined ? <button onClick={signin}>Check</button> : <button onClick={signout}>Signout</button>} </div> </> ); } ``` ## 11. Fetching the user's profile Now that we have a way to sign in and out of the app, we should fetch the user's profile when they sign in. ```tsx function App() { // ... // fetch the user's profile when they sign in createEffect(async () => { const active = account(); if (active) { // get the user's relays or fallback to some default relays const usersRelays = await active.getRelays?.(); const relays = usersRelays ? Object.keys(usersRelays) : ["wss://relay.damus.io", "wss://nos.lol"]; // tell the loader to fetch the users profile event replaceableLoader.next({ pubkey: active.pubkey, kind: 0, relays, }); // tell the loader to fetch the users contacts replaceableLoader.next({ pubkey: active.pubkey, kind: 3, relays, }); // tell the loader to fetch the users mailboxes replaceableLoader.next({ pubkey: active.pubkey, kind: 10002, relays, }); } }); // ... } ``` Next we need to subscribe to the users profile, to do this we can use some rxjs operators to chain the observables together. ```tsx import { Match, Switch } from "solid-js"; import { of, switchMap } from "rxjs"; function App() { // ... // subscribe to the active account, then subscribe to the users profile or undefined const profile = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(ProfileQuery, account!.pubkey) : of(undefined))) ) ); // ... return ( <> {/* ... */} <div class="card"> <Switch> <Match when={account() && !profile()}> <p>Loading profile...</p> </Match> <Match when={profile()}> <p style="font-size: 1.2rem; font-weight: bold;">Welcome {profile()?.name}</p> </Match> </Switch> {/* ... */} </div> </> ); } ``` ## 12. Showing if the user is following fiatjaf Now that the app is fetching the users profile and contacts we should show if the user is following fiatjaf. ```tsx function App() { // ... // subscribe to the active account, then subscribe to the users contacts or undefined const contacts = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(UserContactsQuery, account!.pubkey) : of(undefined))) ) ); const isFollowing = createMemo(() => { return contacts()?.some((c) => c.pubkey === "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d"); }); // ... return ( <> {/* ... */} <div class="card"> {/* ... */} <Switch fallback={ <p style="font-size: 1.2rem;"> Sign in to check if you are a follower of the fiatjaf ( creator of "The nostr" ) </p> } > <Match when={contacts() && isFollowing() === undefined}> <p>checking...</p> </Match> <Match when={contacts() && isFollowing() === true}> <p style="color: green; font-weight: bold; font-size: 2rem;"> Congratulations! You are a follower of the fiatjaf </p> </Match> <Match when={contacts() && isFollowing() === false}> <p style="color: red; font-weight: bold; font-size: 2rem;"> Why don't you follow the fiatjaf? do you even like nostr? </p> </Match> </Switch> {/* ... */} </div> </> ); } ``` ## 13. Adding the follow button Now that we have a way to check if the user is following fiatjaf, we should add a button to follow him. We can do this with [Actions](https://hzrd149.github.io/applesauce/overview/actions.html) which are pre-built methods to modify nostr events for a user. First we need to install the `applesauce-actions` and `applesauce-factory` package ```sh pnpm install applesauce-actions applesauce-factory ``` Then create a `src/actions.ts` file with ```ts import { EventFactory } from "applesauce-factory"; import { ActionHub } from "applesauce-actions"; import { eventStore } from "./stores"; import { accounts } from "./accounts"; // The event factory is used to build and modify nostr events export const factory = new EventFactory({ // accounts.signer is a NIP-07 signer that signs with the currently active account signer: accounts.signer, }); // The action hub is used to run Actions against the event store export const actions = new ActionHub(eventStore, factory); ``` Then create a `toggleFollow` method that will add or remove fiatjaf from the users contacts. > We are using the `exec` method to run the action, and the [`forEach`](https://rxjs.dev/api/index/class/Observable#foreach) method from RxJS allows us to await for all the events to be published ```tsx function App() { // ... const toggleFollow = async () => { // send any created events to rxNostr and the event store const publish = (event: NostrEvent) => { eventStore.add(event); rxNostr.send(event); }; if (isFollowing()) { await actions .exec(UnfollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") .forEach(publish); } else { await actions .exec( FollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", "wss://pyramid.fiatjaf.com/" ) .forEach(publish); } }; // ... return ( <> {/* ... */} <div class="card"> {/* ... */} {contacts() && <button onClick={toggleFollow}>{isFollowing() ? "Unfollow" : "Follow"}</button>} </div> </> ); } ``` ## 14. Adding outbox support The app looks like it works now but if the user reloads the page they will still see an the old version of their contacts list. we need to make sure rxNostr is publishing the events to the users outbox relays. To do this we can subscribe to the signed in users mailboxes using the query store in `src/nostr.ts` ```ts import { MailboxesQuery } from "applesauce-core/queries"; import { accounts } from "./accounts"; import { of, switchMap } from "rxjs"; import { queryStore } from "./stores"; // ... // subscribe to the active account, then subscribe to the users mailboxes and update rxNostr accounts.active$ .pipe(switchMap((account) => (account ? queryStore.createQuery(MailboxesQuery, account.pubkey) : of(undefined)))) .subscribe((mailboxes) => { if (mailboxes) rxNostr.setDefaultRelays(mailboxes.outboxes); else rxNostr.setDefaultRelays([]); }); ``` And that's it! we have a working nostr app that lets users follow and unfollow fiatjaf. @ 7d33ba57:1b82db35
2025-03-28 09:13:56Girona, one of Catalonia’s most charming cities, is a perfect mix of history, culture, and gastronomy. Famous for its well-preserved medieval old town, colorful houses along the Onyar River, and Game of Thrones filming locations, Girona is a must-visit destination in northern Spain.  ## **🏰 Top Things to See & Do in Girona** ### **1️⃣ Girona Cathedral (Catedral de Santa Maria) ⛪** - One of **Spain’s most impressive cathedrals**, with **the widest Gothic nave in the world**. - Famous as the **Great Sept of Baelor in Game of Thrones**. - Climb the **steps for a breathtaking city view**. ### **2️⃣ Walk the Medieval Walls (Passeig de la Muralla) 🏰** - Offers **panoramic views** of Girona and the surrounding countryside. - A great way to see the city from above and explore its medieval history.  ### **3️⃣ The Colorful Houses of the Onyar River 🌉** - Girona’s **most iconic view**, with **brightly colored houses reflecting on the river**. - Best viewed from the **Pont de les Peixateries Velles**, designed by **Gustave Eiffel**. ### **4️⃣ Explore the Jewish Quarter (El Call) 🏡** - One of **Europe’s best-preserved Jewish quarters**, with **narrow, medieval streets**. - Visit the **Museum of Jewish History** to learn about Girona’s Jewish heritage.  ### **5️⃣ Arab Baths (Banys Àrabs) 🏛️** - A **12th-century Romanesque bathhouse**, inspired by Moorish architecture. - Features **a beautiful central dome with columns**. ### **6️⃣ Game of Thrones Filming Locations 🎬** - Walk in the footsteps of **Arya Stark** through the city’s **winding streets**. - Visit **the steps of the cathedral, the Jewish Quarter, and Arab Baths**, all featured in the series. ### **7️⃣ Eat at a Michelin-Starred Restaurant 🍽️** - Girona is home to **El Celler de Can Roca**, a **3-Michelin-star restaurant**, ranked among the **best in the world**. - Try **local Catalan dishes** like **"suquet de peix" (fish stew) and botifarra (Catalan sausage).**  ## **🚗 How to Get to Girona** ✈️ **By Air:** Girona-Costa Brava Airport (GRO) is **20 min away**, with budget flights from Europe. 🚆 **By Train:** High-speed AVE trains connect **Barcelona (38 min), Madrid (3.5 hrs), and Paris (5.5 hrs)**. 🚘 **By Car:** 1 hr from **Barcelona**, 40 min from **Figueres (Dalí Museum)**. 🚌 **By Bus:** Direct buses from **Barcelona and the Costa Brava**.  ## **💡 Tips for Visiting Girona** ✅ **Best time to visit?** **Spring & autumn (April–June & September–October)** for pleasant weather. 🌤️ ✅ **Wear comfortable shoes** – The old town is **hilly with cobblestone streets**. 👟 ✅ **Try xuixo** – A delicious **cream-filled pastry**, unique to Girona. 🥐 ✅ **Visit early for Game of Thrones spots** – They get crowded during the day! 🎥 ✅ **Take a day trip** – Explore nearby **Costa Brava beaches or Figueres (Dalí Museum).** 🏖️ 
@ 7d33ba57:1b82db35
2025-03-28 09:13:56Girona, one of Catalonia’s most charming cities, is a perfect mix of history, culture, and gastronomy. Famous for its well-preserved medieval old town, colorful houses along the Onyar River, and Game of Thrones filming locations, Girona is a must-visit destination in northern Spain.  ## **🏰 Top Things to See & Do in Girona** ### **1️⃣ Girona Cathedral (Catedral de Santa Maria) ⛪** - One of **Spain’s most impressive cathedrals**, with **the widest Gothic nave in the world**. - Famous as the **Great Sept of Baelor in Game of Thrones**. - Climb the **steps for a breathtaking city view**. ### **2️⃣ Walk the Medieval Walls (Passeig de la Muralla) 🏰** - Offers **panoramic views** of Girona and the surrounding countryside. - A great way to see the city from above and explore its medieval history.  ### **3️⃣ The Colorful Houses of the Onyar River 🌉** - Girona’s **most iconic view**, with **brightly colored houses reflecting on the river**. - Best viewed from the **Pont de les Peixateries Velles**, designed by **Gustave Eiffel**. ### **4️⃣ Explore the Jewish Quarter (El Call) 🏡** - One of **Europe’s best-preserved Jewish quarters**, with **narrow, medieval streets**. - Visit the **Museum of Jewish History** to learn about Girona’s Jewish heritage.  ### **5️⃣ Arab Baths (Banys Àrabs) 🏛️** - A **12th-century Romanesque bathhouse**, inspired by Moorish architecture. - Features **a beautiful central dome with columns**. ### **6️⃣ Game of Thrones Filming Locations 🎬** - Walk in the footsteps of **Arya Stark** through the city’s **winding streets**. - Visit **the steps of the cathedral, the Jewish Quarter, and Arab Baths**, all featured in the series. ### **7️⃣ Eat at a Michelin-Starred Restaurant 🍽️** - Girona is home to **El Celler de Can Roca**, a **3-Michelin-star restaurant**, ranked among the **best in the world**. - Try **local Catalan dishes** like **"suquet de peix" (fish stew) and botifarra (Catalan sausage).**  ## **🚗 How to Get to Girona** ✈️ **By Air:** Girona-Costa Brava Airport (GRO) is **20 min away**, with budget flights from Europe. 🚆 **By Train:** High-speed AVE trains connect **Barcelona (38 min), Madrid (3.5 hrs), and Paris (5.5 hrs)**. 🚘 **By Car:** 1 hr from **Barcelona**, 40 min from **Figueres (Dalí Museum)**. 🚌 **By Bus:** Direct buses from **Barcelona and the Costa Brava**.  ## **💡 Tips for Visiting Girona** ✅ **Best time to visit?** **Spring & autumn (April–June & September–October)** for pleasant weather. 🌤️ ✅ **Wear comfortable shoes** – The old town is **hilly with cobblestone streets**. 👟 ✅ **Try xuixo** – A delicious **cream-filled pastry**, unique to Girona. 🥐 ✅ **Visit early for Game of Thrones spots** – They get crowded during the day! 🎥 ✅ **Take a day trip** – Explore nearby **Costa Brava beaches or Figueres (Dalí Museum).** 🏖️  @ ebbba253:6ec1d547
2025-03-27 12:18:24A AA888 se destaca pela experiência do jogador de ponta a ponta. Desde o momento do registro, que é rápido e simples, até a jogabilidade final, a plataforma se preocupa em garantir que cada etapa do processo seja intuitiva e agradável. Isso é particularmente importante, já que muitos jogadores preferem uma experiência sem complicações, e a AA888 entrega exatamente isso. Outro ponto que se destaca é a acessibilidade da plataforma. Independentemente de você estar em casa ou em movimento, a AA888 é compatível com dispositivos móveis e garante que a qualidade do jogo seja mantida, sem perda de performance. Seja você um jogador de desktop ou smartphone, a plataforma se adapta perfeitamente às suas necessidades. Além disso, a <a href="https://aa888.one"> Aa888 </a>oferece um suporte ao cliente excepcional, com uma equipe disponível 24 horas por dia, 7 dias por semana. Isso é crucial para resolver qualquer dúvida ou problema técnico que possa surgir, garantindo que os jogadores nunca fiquem sem assistência. Esse compromisso com o atendimento ao cliente demonstra o nível de seriedade e profissionalismo da plataforma. Para completar, a AA888 se preocupa em proporcionar uma experiência social entre os jogadores. Através de funções interativas e multiplayer, é possível competir com outros participantes e criar uma comunidade divertida e envolvente. A AA888 é uma plataforma que realmente entrega o que promete: diversão, segurança e uma vasta gama de opções para os jogadores. Ao focar na experiência do usuário e oferecer uma grande diversidade de jogos, ela se consolida como uma das melhores opções de entretenimento online no Brasil. Se você busca diversão de qualidade e um ambiente seguro para suas aventuras online, a AA888 certamente é uma plataforma que vale a pena explorar.
@ ebbba253:6ec1d547
2025-03-27 12:18:24A AA888 se destaca pela experiência do jogador de ponta a ponta. Desde o momento do registro, que é rápido e simples, até a jogabilidade final, a plataforma se preocupa em garantir que cada etapa do processo seja intuitiva e agradável. Isso é particularmente importante, já que muitos jogadores preferem uma experiência sem complicações, e a AA888 entrega exatamente isso. Outro ponto que se destaca é a acessibilidade da plataforma. Independentemente de você estar em casa ou em movimento, a AA888 é compatível com dispositivos móveis e garante que a qualidade do jogo seja mantida, sem perda de performance. Seja você um jogador de desktop ou smartphone, a plataforma se adapta perfeitamente às suas necessidades. Além disso, a <a href="https://aa888.one"> Aa888 </a>oferece um suporte ao cliente excepcional, com uma equipe disponível 24 horas por dia, 7 dias por semana. Isso é crucial para resolver qualquer dúvida ou problema técnico que possa surgir, garantindo que os jogadores nunca fiquem sem assistência. Esse compromisso com o atendimento ao cliente demonstra o nível de seriedade e profissionalismo da plataforma. Para completar, a AA888 se preocupa em proporcionar uma experiência social entre os jogadores. Através de funções interativas e multiplayer, é possível competir com outros participantes e criar uma comunidade divertida e envolvente. A AA888 é uma plataforma que realmente entrega o que promete: diversão, segurança e uma vasta gama de opções para os jogadores. Ao focar na experiência do usuário e oferecer uma grande diversidade de jogos, ela se consolida como uma das melhores opções de entretenimento online no Brasil. Se você busca diversão de qualidade e um ambiente seguro para suas aventuras online, a AA888 certamente é uma plataforma que vale a pena explorar. @ 8cb60e21:5f2deaea
2024-08-24 23:29:20<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/Nn2uIoUUf7Q&pp=ygUcZmFyIGNyeSAzIHppZ2d5J3MgbW9kIHJldmlldw%3D%3D" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-08-24 23:29:20<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/Nn2uIoUUf7Q&pp=ygUcZmFyIGNyeSAzIHppZ2d5J3MgbW9kIHJldmlldw%3D%3D" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ a60e79e0:1e0e6813
2025-03-28 08:47:35*This is a long form note of a post that lives on my Nostr educational website [Hello Nostr](https://hellonostr.xyz).* When most people stumble across Nostr, they see is as a 'decentralized social media alternative' — something akin to Twitter (X), but free from corporate control. But the full name, "Notes and Other Stuff Transmitted by Relays", gives a clue that there’s more to it than just posting short messages. The 'notes' part is easy to grasp because it forms almost everyone's first touch point with the protocol. But the 'other stuff'? That’s where Nostr really gets exciting. The 'other stuff' is all the creative and experimental things people are building on Nostr, beyond simple text based notes. Every action on Nostr is an event, a like, a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as [Nostr Implementation Possibility - NIP](https://nostr-nips.com/). A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client to meet different purposes. > Nostr isn’t locked into a single purpose. It’s a foundation for whatever 'other stuff' you can dream up. > # Types of Other Stuff The 'other stuff' name is intentionally vague. Why? Because the possibilities of what can fall under this category are quite literally limitless. In the short time since Nostr's inception, the number of sub-categories that have been built on top of the Nostr's open protocol is mind bending. Here are a few examples: 1. Long-Form Content: Think blog posts or articles. [NIP-23](https://nostr-nips.com/nip-23). 2. Private Messaging: Encrypted chats between users. [NIP-04](https://nostr-nips.com/nip-04). 3. Communities: Group chats or forums like Reddit. [NIP-72](https://nostr-nips.com/nip-72) 4. Marketplaces: People listing stuff for sale, payable with zaps. [NIP-15](https://nostr-nips.com/nip-15) 5. Zaps: Value transfer over the Lightning Network. [NIP57](https://nostr-nips.com/nip-57)  # Popular 'Other Stuff' Clients Here's a short list of some of the most recent and popular apps and clients that branch outside of the traditional micro-blogging use case and leverage the openness, and interoperability that Nostr can provide. ### Blogging (Long Form Content) - [Habla](https://habla.news/) - *Web app for Nostr based blogs* - [Highlighter](https://highlighter.com/) - *Web app that enables users to highlight, store and share content* ### Group Chats - [Chachi Chat](https://chachi.chat/) - *Relay-based (NIP-29) group chat client* - [0xchat](https://github.com/0xchat-app) - *Mobile based secure chat* - [Flotilla](https://flotilla.social/) - *Web based chat app built for self-hosted communities* - [Nostr Nests](https://nostrnests.com/) - *Web app for audio chats* - [White Noise](https://github.com/erskingardner/whitenoise) - *Mobile based secure chat*  ### Marketplaces - [Shopstr](https://shopstr.store/) - *Permissionless marketplace for web* - [Plebeian Market](https://plebeian.market/) - *Permissionless marketplace for web* - [LNBits Market](https://github.com/lnbits/nostrmarket#nostr-market-nip-15---lnbits-extension) - *Permissionless marketplace for your node* - [Mostro](https://github.com/MostroP2P/mostro) - *Nostr based Bitcoin P2P Marketplace* ### Photo/Video - [Olas](https://github.com/pablof7z/snapstr/releases) - *An Intragram like client* - [Freeflow](https://github.com/nostrlabs-io/freeflow) - *A TikTok like client* ### Music - [Fountain](https://fountain.fm/) - *Podcast app with Nostr features* - [Wavlake](https://wavlake.com/) - *A music app supporting the value-for-value ecosystem*  ### Livestreaming - [Zap.stream](https://zap.stream/) - *Nostr native live streams* ### Misc - [Wikifreedia](https://wikifreedia.xyz/) - *Nostr based Wikipedia alternative* - [Wikistr](https://wikistr.com/) - *Nostr based Wikipedia alternative* - [Pollerama](https://pollerama.fun/) - *Nostr based polls* - [Zap Store](https://zapstore.dev) - *The app store powered by your social graph*  The 'other stuff' in Nostr is what makes it special. It’s not just about replacing Twitter or Facebook, it’s about building a decentralized ecosystem where anything from private chats to marketplaces can thrive. The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around. It’s still early days, so expect the 'other stuff' to grow wilder and weirder over time! You can explore the evergrowing 'other stuff' ecosystem at [NostrApps.com](https://nostrapps.com/), [Nostr.net](https://nostr.net/) and [Awesome Nostr](https://github.com/aljazceru/awesome-nostr).
@ a60e79e0:1e0e6813
2025-03-28 08:47:35*This is a long form note of a post that lives on my Nostr educational website [Hello Nostr](https://hellonostr.xyz).* When most people stumble across Nostr, they see is as a 'decentralized social media alternative' — something akin to Twitter (X), but free from corporate control. But the full name, "Notes and Other Stuff Transmitted by Relays", gives a clue that there’s more to it than just posting short messages. The 'notes' part is easy to grasp because it forms almost everyone's first touch point with the protocol. But the 'other stuff'? That’s where Nostr really gets exciting. The 'other stuff' is all the creative and experimental things people are building on Nostr, beyond simple text based notes. Every action on Nostr is an event, a like, a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as [Nostr Implementation Possibility - NIP](https://nostr-nips.com/). A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client to meet different purposes. > Nostr isn’t locked into a single purpose. It’s a foundation for whatever 'other stuff' you can dream up. > # Types of Other Stuff The 'other stuff' name is intentionally vague. Why? Because the possibilities of what can fall under this category are quite literally limitless. In the short time since Nostr's inception, the number of sub-categories that have been built on top of the Nostr's open protocol is mind bending. Here are a few examples: 1. Long-Form Content: Think blog posts or articles. [NIP-23](https://nostr-nips.com/nip-23). 2. Private Messaging: Encrypted chats between users. [NIP-04](https://nostr-nips.com/nip-04). 3. Communities: Group chats or forums like Reddit. [NIP-72](https://nostr-nips.com/nip-72) 4. Marketplaces: People listing stuff for sale, payable with zaps. [NIP-15](https://nostr-nips.com/nip-15) 5. Zaps: Value transfer over the Lightning Network. [NIP57](https://nostr-nips.com/nip-57)  # Popular 'Other Stuff' Clients Here's a short list of some of the most recent and popular apps and clients that branch outside of the traditional micro-blogging use case and leverage the openness, and interoperability that Nostr can provide. ### Blogging (Long Form Content) - [Habla](https://habla.news/) - *Web app for Nostr based blogs* - [Highlighter](https://highlighter.com/) - *Web app that enables users to highlight, store and share content* ### Group Chats - [Chachi Chat](https://chachi.chat/) - *Relay-based (NIP-29) group chat client* - [0xchat](https://github.com/0xchat-app) - *Mobile based secure chat* - [Flotilla](https://flotilla.social/) - *Web based chat app built for self-hosted communities* - [Nostr Nests](https://nostrnests.com/) - *Web app for audio chats* - [White Noise](https://github.com/erskingardner/whitenoise) - *Mobile based secure chat*  ### Marketplaces - [Shopstr](https://shopstr.store/) - *Permissionless marketplace for web* - [Plebeian Market](https://plebeian.market/) - *Permissionless marketplace for web* - [LNBits Market](https://github.com/lnbits/nostrmarket#nostr-market-nip-15---lnbits-extension) - *Permissionless marketplace for your node* - [Mostro](https://github.com/MostroP2P/mostro) - *Nostr based Bitcoin P2P Marketplace* ### Photo/Video - [Olas](https://github.com/pablof7z/snapstr/releases) - *An Intragram like client* - [Freeflow](https://github.com/nostrlabs-io/freeflow) - *A TikTok like client* ### Music - [Fountain](https://fountain.fm/) - *Podcast app with Nostr features* - [Wavlake](https://wavlake.com/) - *A music app supporting the value-for-value ecosystem*  ### Livestreaming - [Zap.stream](https://zap.stream/) - *Nostr native live streams* ### Misc - [Wikifreedia](https://wikifreedia.xyz/) - *Nostr based Wikipedia alternative* - [Wikistr](https://wikistr.com/) - *Nostr based Wikipedia alternative* - [Pollerama](https://pollerama.fun/) - *Nostr based polls* - [Zap Store](https://zapstore.dev) - *The app store powered by your social graph*  The 'other stuff' in Nostr is what makes it special. It’s not just about replacing Twitter or Facebook, it’s about building a decentralized ecosystem where anything from private chats to marketplaces can thrive. The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around. It’s still early days, so expect the 'other stuff' to grow wilder and weirder over time! You can explore the evergrowing 'other stuff' ecosystem at [NostrApps.com](https://nostrapps.com/), [Nostr.net](https://nostr.net/) and [Awesome Nostr](https://github.com/aljazceru/awesome-nostr). @ 8cb60e21:5f2deaea
2024-08-24 23:26:03# hello draft
@ 8cb60e21:5f2deaea
2024-08-24 23:26:03# hello draft @ a39d19ec:3d88f61e
2025-03-18 17:16:50Nun da das deutsche Bundesregime den Ruin Deutschlands beschlossen hat, der sehr wahrscheinlich mit dem Werkzeug des Geld druckens "finanziert" wird, kamen mir so viele Gedanken zur Geldmengenausweitung, dass ich diese für einmal niedergeschrieben habe. Die Ausweitung der Geldmenge führt aus klassischer wirtschaftlicher Sicht immer zu Preissteigerungen, weil mehr Geld im Umlauf auf eine begrenzte Menge an Gütern trifft. Dies lässt sich in mehreren Schritten analysieren: ### 1. Quantitätstheorie des Geldes Die klassische Gleichung der Quantitätstheorie des Geldes lautet: M • V = P • Y wobei: - M die Geldmenge ist, - V die Umlaufgeschwindigkeit des Geldes, - P das Preisniveau, - Y die reale Wirtschaftsleistung (BIP). Wenn M steigt und V sowie Y konstant bleiben, muss P steigen – also Inflation entstehen. ### 2. Gütermenge bleibt begrenzt Die Menge an real produzierten Gütern und Dienstleistungen wächst meist nur langsam im Vergleich zur Ausweitung der Geldmenge. Wenn die Geldmenge schneller steigt als die Produktionsgütermenge, führt dies dazu, dass mehr Geld für die gleiche Menge an Waren zur Verfügung steht – die Preise steigen. ### 3. Erwartungseffekte und Spekulation Wenn Unternehmen und Haushalte erwarten, dass mehr Geld im Umlauf ist, da eine zentrale Planung es so wollte, können sie steigende Preise antizipieren. Unternehmen erhöhen ihre Preise vorab, und Arbeitnehmer fordern höhere Löhne. Dies kann eine sich selbst verstärkende Spirale auslösen. ### 4. Internationale Perspektive Eine erhöhte Geldmenge kann die Währung abwerten, wenn andere Länder ihre Geldpolitik stabil halten. Eine schwächere Währung macht Importe teurer, was wiederum Preissteigerungen antreibt. ### 5. Kritik an der reinen Geldmengen-Theorie Der Vollständigkeit halber muss erwähnt werden, dass die meisten modernen Ökonomen im Staatsauftrag argumentieren, dass Inflation nicht nur von der Geldmenge abhängt, sondern auch von der Nachfrage nach Geld (z. B. in einer Wirtschaftskrise). Dennoch zeigt die historische Erfahrung, dass eine unkontrollierte Geldmengenausweitung langfristig immer zu Preissteigerungen führt, wie etwa in der Hyperinflation der Weimarer Republik oder in Simbabwe.
@ a39d19ec:3d88f61e
2025-03-18 17:16:50Nun da das deutsche Bundesregime den Ruin Deutschlands beschlossen hat, der sehr wahrscheinlich mit dem Werkzeug des Geld druckens "finanziert" wird, kamen mir so viele Gedanken zur Geldmengenausweitung, dass ich diese für einmal niedergeschrieben habe. Die Ausweitung der Geldmenge führt aus klassischer wirtschaftlicher Sicht immer zu Preissteigerungen, weil mehr Geld im Umlauf auf eine begrenzte Menge an Gütern trifft. Dies lässt sich in mehreren Schritten analysieren: ### 1. Quantitätstheorie des Geldes Die klassische Gleichung der Quantitätstheorie des Geldes lautet: M • V = P • Y wobei: - M die Geldmenge ist, - V die Umlaufgeschwindigkeit des Geldes, - P das Preisniveau, - Y die reale Wirtschaftsleistung (BIP). Wenn M steigt und V sowie Y konstant bleiben, muss P steigen – also Inflation entstehen. ### 2. Gütermenge bleibt begrenzt Die Menge an real produzierten Gütern und Dienstleistungen wächst meist nur langsam im Vergleich zur Ausweitung der Geldmenge. Wenn die Geldmenge schneller steigt als die Produktionsgütermenge, führt dies dazu, dass mehr Geld für die gleiche Menge an Waren zur Verfügung steht – die Preise steigen. ### 3. Erwartungseffekte und Spekulation Wenn Unternehmen und Haushalte erwarten, dass mehr Geld im Umlauf ist, da eine zentrale Planung es so wollte, können sie steigende Preise antizipieren. Unternehmen erhöhen ihre Preise vorab, und Arbeitnehmer fordern höhere Löhne. Dies kann eine sich selbst verstärkende Spirale auslösen. ### 4. Internationale Perspektive Eine erhöhte Geldmenge kann die Währung abwerten, wenn andere Länder ihre Geldpolitik stabil halten. Eine schwächere Währung macht Importe teurer, was wiederum Preissteigerungen antreibt. ### 5. Kritik an der reinen Geldmengen-Theorie Der Vollständigkeit halber muss erwähnt werden, dass die meisten modernen Ökonomen im Staatsauftrag argumentieren, dass Inflation nicht nur von der Geldmenge abhängt, sondern auch von der Nachfrage nach Geld (z. B. in einer Wirtschaftskrise). Dennoch zeigt die historische Erfahrung, dass eine unkontrollierte Geldmengenausweitung langfristig immer zu Preissteigerungen führt, wie etwa in der Hyperinflation der Weimarer Republik oder in Simbabwe. @ 45c41f21:c5446b7a
2025-03-28 08:02:16“区块链行业究竟是在做什么?”——这个问题我到现在还没有想得很清楚。谈论起来可以说很多东西,“确权”、“让每一个比特都有了稀缺性”、“数字黄金”、“点对点支付”,但是具体到了行业落地,又容易陷入“赌场”这个有点乌烟瘴气的现实。 但我想有一点是比较明确的,那就是区块链行业肯定是一个围绕资产的行业。这些资产又跟传统的资产很不一样,最简单的特征是它们都是一个个的代币,通过自动化和可验证的代码铸造、控制,我们可以统称为链上资产。从比特币、以太坊到现在,这中间不管过去了多少不同的周期和浪潮,核心不变的都是出现新一轮受追捧的资产。 既然区块链是关于链上资产的行业,那么最重要的是未来会出现什么新的资产,有什么样的新资产会上链。要回答这个问题,又要我们回过头去看看,从行业诞生至今,区块链留下了哪些有意义的、没意义的,有价值的、没价值的资产。 因此,有必要讨论一下链上资产的分类。 链上资产的种类很多,但总体上我觉得可以按**满足需求的不同,**做一些功能性的划分。同时,抛开去中心化、抗审查等等大词,**链上资产与传统资产最重要的区别可以认为是安全性的来源**。传统资产在传统的社会系统和金融系统中产生,而链上资产是通过可验证代码控制的,所以它的安全性的依赖很清晰,要比现实世界简单很多。 在不同的区块链系统中,使用不同的技术(比如POW/POS),设置不同的规则,拥有不同的治理机制,都会影响安全性。“安全性”和“满足什么样的需求”之间既不是正交的,也不是完全耦合的。在不同层级的安全性之下,可能都会出现满足某一类相同需求的产品,用户使用哪种产品,只取决于自己的风险偏好。另一方面,有些需求只可能在某些特定的安全性保障下才能得到满足,比如跨国际的全球化的抗通胀价值存储。 这篇文章只讨论一些比较简单的分类,可以假设在不同的安全性保障下,每个分类都有可能出现对应的产品。有些安全性是产品内生功能的一部分,有些则完全不影响。同时,这些分类也完全是主观的看法,不一定正确,我所希望的是引发更多对资产进行讨论。 ### 核心资产(高安全性、强需求支撑) 1. **比特币(BTC)** - **核心价值**:全球化抗通胀、抗审查的“数字黄金”。 - **长期逻辑**:全球法币超发背景下,BTC作为去中心化硬通货的需求不可替代。 这是整个行业最重要的资产。也是整个行业最核心的东西。在这个定位下,只会有一个赢者通吃。其他试图竞争的都很难生存下来。它对安全性的要求也是最高的。 ### 经过验证的资产分类 这部分的资产可以认为是行业诞生至今,已经经过验证的、满足某真实需求、会长期存在的资产。 1. **代表优质项目的资产(股票/ICO代币/治理代币等)** - **核心价值**:类似于传统金融世界里的一级市场和二级市场。所谓的“优质”也不一定需要真实落地,可能是叙事/故事驱动,也可能有真实的现金流,但重要的是它能在市场上吸引人买卖。 - **关键指标**:团队是否持续营销和建设?生态是否增长?项目是否解决实际问题? 2. **DeFi 资产** - **核心价值**:链上金融系统的“基础设施工具”。 - **需求来源**:对套利、链上资产理财的需求会永远存在。 3. **Meme币** - **核心价值**:营销驱动+投机需求的结合体。 - **长期存在性**:人性对暴富故事的追逐不会消失(如Pump.fun、SHIB)。 4. **稳定币** - **核心价值**:加密货币世界的“支付货币”。 - **需求刚性**:交易媒介、避险工具、跨境支付(如USDT、USDC)。 在不同的安全性保障下,上面这些资产大部分都会有对应的产品。 比如稳定币在安全性上可以有中心化的 USDT ,也有去中心化的算法稳定币。理论上,安全性对稳定币是非常重要的。但现实中,“流动性”可能才是给用户传达“这东西到底安不安全“的产品特点,也是比较主要的竞争点。 Meme 则完全不需要安全性,所以对创业者来说在哪里做都差不多。哪里用户更多就适合去哪里。有时,安全性反而是它的阻碍。DeFi 的话,因人而异。安全性高低是否影响用户使用,完全取决于用户自己的风险偏好。 ### 还未经过验证的资产(需求可能存在) - **NFT(收藏品)?** 艺术、身份标识、游戏道具的数字化载体,但流动性差、炒作属性也不见得有 Meme 这么强。会长期存在吗?打个问号。 - **DAO(准入/治理代币)?** 去中心化组织的准入权/管理权通证,依赖 DAO 本身的价值和实际治理参与度决定的价值。DeFi DAO 可能是唯一一个有点发展的方向,其他还非常不成熟,有待验证。 - **RWA(真实世界资产代币化)?** 房产、债券等上链,需要解决法律合规与链下资产映射问题。不确定。 - **社交/游戏/内容资产** 用户数据所有权货币化,还没有像样的有一些用户的产品,就更不用提形成规模经济了。 - **AI 相关的资产?** 是一个变数。如果未来会有成千上万的 AI 智能体与人类共存,链上是承载他们经济系统最合适的基础设施,这里会产生什么新的资产类型?值得期待。 这里面的资产类型,很多还没有找到真实的需求,至少没有经过验证。所以长期来看它们会是区块链行业的方向吗,需要打很多问号。既然需求本身没有得到验证,那么谈安全性对它们的影响,就更加无从谈起了。 当然,这里其实还有一个更有意思的部分,可以多聊一些。也就是**共同知识(法律/合同/规则/代码)**这一类资产。 在应用层,共同知识尚未有代币化的尝试,也难以对其具体价值做定量分析。但如果要说有的实践,以太坊通过交易收取 gas 费和 CKB 通过 Cell 存储状态收取“押金”算是一种在底层的 generalize 的尝试。这种尝试是定量的,可验证的。 以太坊的问题是经济模型不 make sense 导致状态爆炸,ckb 相比是更简单、更明确的。但这里的问题变成了,公链需要通过区块空间的竞争来展示这一种需求是否真的成立。区块空间越紧张,需求就越大。同时安全性越高,对共同知识的保障就越强,也会体现区块空间的价值。 但另一方面,是否有开发者在上面开发应用,会更大的影响这一点。因此开发工具、开发者生态在现阶段可能更重要。 ### 最后 写到这里,发现很多资产似乎又是老生常谈。但从满足需求和安全性两个角度来思考,算是追本溯源的尝试。现在我们面临的处境是,问题还是老的问题,答案是否有新的答案,期待更多讨论。
@ 45c41f21:c5446b7a
2025-03-28 08:02:16“区块链行业究竟是在做什么?”——这个问题我到现在还没有想得很清楚。谈论起来可以说很多东西,“确权”、“让每一个比特都有了稀缺性”、“数字黄金”、“点对点支付”,但是具体到了行业落地,又容易陷入“赌场”这个有点乌烟瘴气的现实。 但我想有一点是比较明确的,那就是区块链行业肯定是一个围绕资产的行业。这些资产又跟传统的资产很不一样,最简单的特征是它们都是一个个的代币,通过自动化和可验证的代码铸造、控制,我们可以统称为链上资产。从比特币、以太坊到现在,这中间不管过去了多少不同的周期和浪潮,核心不变的都是出现新一轮受追捧的资产。 既然区块链是关于链上资产的行业,那么最重要的是未来会出现什么新的资产,有什么样的新资产会上链。要回答这个问题,又要我们回过头去看看,从行业诞生至今,区块链留下了哪些有意义的、没意义的,有价值的、没价值的资产。 因此,有必要讨论一下链上资产的分类。 链上资产的种类很多,但总体上我觉得可以按**满足需求的不同,**做一些功能性的划分。同时,抛开去中心化、抗审查等等大词,**链上资产与传统资产最重要的区别可以认为是安全性的来源**。传统资产在传统的社会系统和金融系统中产生,而链上资产是通过可验证代码控制的,所以它的安全性的依赖很清晰,要比现实世界简单很多。 在不同的区块链系统中,使用不同的技术(比如POW/POS),设置不同的规则,拥有不同的治理机制,都会影响安全性。“安全性”和“满足什么样的需求”之间既不是正交的,也不是完全耦合的。在不同层级的安全性之下,可能都会出现满足某一类相同需求的产品,用户使用哪种产品,只取决于自己的风险偏好。另一方面,有些需求只可能在某些特定的安全性保障下才能得到满足,比如跨国际的全球化的抗通胀价值存储。 这篇文章只讨论一些比较简单的分类,可以假设在不同的安全性保障下,每个分类都有可能出现对应的产品。有些安全性是产品内生功能的一部分,有些则完全不影响。同时,这些分类也完全是主观的看法,不一定正确,我所希望的是引发更多对资产进行讨论。 ### 核心资产(高安全性、强需求支撑) 1. **比特币(BTC)** - **核心价值**:全球化抗通胀、抗审查的“数字黄金”。 - **长期逻辑**:全球法币超发背景下,BTC作为去中心化硬通货的需求不可替代。 这是整个行业最重要的资产。也是整个行业最核心的东西。在这个定位下,只会有一个赢者通吃。其他试图竞争的都很难生存下来。它对安全性的要求也是最高的。 ### 经过验证的资产分类 这部分的资产可以认为是行业诞生至今,已经经过验证的、满足某真实需求、会长期存在的资产。 1. **代表优质项目的资产(股票/ICO代币/治理代币等)** - **核心价值**:类似于传统金融世界里的一级市场和二级市场。所谓的“优质”也不一定需要真实落地,可能是叙事/故事驱动,也可能有真实的现金流,但重要的是它能在市场上吸引人买卖。 - **关键指标**:团队是否持续营销和建设?生态是否增长?项目是否解决实际问题? 2. **DeFi 资产** - **核心价值**:链上金融系统的“基础设施工具”。 - **需求来源**:对套利、链上资产理财的需求会永远存在。 3. **Meme币** - **核心价值**:营销驱动+投机需求的结合体。 - **长期存在性**:人性对暴富故事的追逐不会消失(如Pump.fun、SHIB)。 4. **稳定币** - **核心价值**:加密货币世界的“支付货币”。 - **需求刚性**:交易媒介、避险工具、跨境支付(如USDT、USDC)。 在不同的安全性保障下,上面这些资产大部分都会有对应的产品。 比如稳定币在安全性上可以有中心化的 USDT ,也有去中心化的算法稳定币。理论上,安全性对稳定币是非常重要的。但现实中,“流动性”可能才是给用户传达“这东西到底安不安全“的产品特点,也是比较主要的竞争点。 Meme 则完全不需要安全性,所以对创业者来说在哪里做都差不多。哪里用户更多就适合去哪里。有时,安全性反而是它的阻碍。DeFi 的话,因人而异。安全性高低是否影响用户使用,完全取决于用户自己的风险偏好。 ### 还未经过验证的资产(需求可能存在) - **NFT(收藏品)?** 艺术、身份标识、游戏道具的数字化载体,但流动性差、炒作属性也不见得有 Meme 这么强。会长期存在吗?打个问号。 - **DAO(准入/治理代币)?** 去中心化组织的准入权/管理权通证,依赖 DAO 本身的价值和实际治理参与度决定的价值。DeFi DAO 可能是唯一一个有点发展的方向,其他还非常不成熟,有待验证。 - **RWA(真实世界资产代币化)?** 房产、债券等上链,需要解决法律合规与链下资产映射问题。不确定。 - **社交/游戏/内容资产** 用户数据所有权货币化,还没有像样的有一些用户的产品,就更不用提形成规模经济了。 - **AI 相关的资产?** 是一个变数。如果未来会有成千上万的 AI 智能体与人类共存,链上是承载他们经济系统最合适的基础设施,这里会产生什么新的资产类型?值得期待。 这里面的资产类型,很多还没有找到真实的需求,至少没有经过验证。所以长期来看它们会是区块链行业的方向吗,需要打很多问号。既然需求本身没有得到验证,那么谈安全性对它们的影响,就更加无从谈起了。 当然,这里其实还有一个更有意思的部分,可以多聊一些。也就是**共同知识(法律/合同/规则/代码)**这一类资产。 在应用层,共同知识尚未有代币化的尝试,也难以对其具体价值做定量分析。但如果要说有的实践,以太坊通过交易收取 gas 费和 CKB 通过 Cell 存储状态收取“押金”算是一种在底层的 generalize 的尝试。这种尝试是定量的,可验证的。 以太坊的问题是经济模型不 make sense 导致状态爆炸,ckb 相比是更简单、更明确的。但这里的问题变成了,公链需要通过区块空间的竞争来展示这一种需求是否真的成立。区块空间越紧张,需求就越大。同时安全性越高,对共同知识的保障就越强,也会体现区块空间的价值。 但另一方面,是否有开发者在上面开发应用,会更大的影响这一点。因此开发工具、开发者生态在现阶段可能更重要。 ### 最后 写到这里,发现很多资产似乎又是老生常谈。但从满足需求和安全性两个角度来思考,算是追本溯源的尝试。现在我们面临的处境是,问题还是老的问题,答案是否有新的答案,期待更多讨论。 @ 05cdefcd:550cc264
2025-03-28 08:00:15The crypto world is full of buzzwords. One that I keep on hearing: “Bitcoin is its own asset class”. While I have always been sympathetic to that view, I’ve always failed to understand the true meaning behind that statement. Although I consider Bitcoin to be the prime innovation within the digital asset sector, my primary response has always been: How can bitcoin (BTC), a single asset, represent an entire asset class? Isn’t it Bitcoin and other digital assets that make up an asset class called crypto? Well, I increasingly believe that most of crypto is just noise. Sure, it’s volatile noise that is predominately interesting for very sophisticated hedge funds, market makers or prop traders that are sophisticated enough to extract alpha – but it’s noise nonetheless and has no part to play in a long-term only portfolio of private retail investors (of which most of us are). *Over multiple market cycles, nearly all altcoins underperform Bitcoin when measured in BTC terms. Source: Tradingview* ## Aha-Moment: Bitcoin keeps on giving Still, how can Bitcoin, as a standalone asset, make up an entire asset class? The “aha-moment” to answer this question recently came to me in a [Less Noise More Signal interview](https://www.youtube.com/watch?v=YHRluf5uxzo) I did with [James Van Straten](https://www.linkedin.com/in/james-van-straten-8782b4112/), senior analyst at Coindesk. Let me paraphrase him here: *“You can’t simply recreate the same ETF as BlackRock. To succeed in the Bitcoin space, new and innovative approaches are needed. This is where understanding Bitcoin not just as a single asset, but as an entire asset class, becomes essential. There are countless ways to build upon Bitcoin’s foundation—varied iterations that go beyond just holding the asset. This is precisely where the emergence of the Bitcoin-linked stock market is taking shape—and it's already underway.”* And this is actually coming to fruition as we speak. Just in the last few days, we saw several products launch in that regard. Obviously, MicroStrategy (now Strategy) is the pioneer of this. The company now [owns](https://www.strategy.com/purchases) 506,137 BTC, and while they’ll keep on buying more, they have also inspired many other companies to follow suit. In fact, there are now already over 70 companies that have adopted Strategy’s Bitcoin playbook. One of the latest companies to buy Bitcoin for their corporate treasury is Rumble. The YouTube competitor just [announced](https://www.coindesk.com/markets/2025/03/12/video-sharing-platform-rumble-buys-188-btc-for-usd17-1m) their first Bitcoin purchase for $17 million. Also, the gaming zombie company GameStop just announced to raise money to buy BTC for their corporate treasury. *Gamestop to make BTC their hurdle rate. Source: X* ## ETF on Bitcoin companies Given this proliferation of Bitcoin Treasury companies, it was only a matter of time before a financial product tracking these would emerge. The popular crypto index fund provider Bitwise Investments has just launched this very product called the [Bitwise Bitcoin Standard Corporations ETF](https://ownbetf.com/) (OWNB). The ETF tracks Bitcoin Treasury companies with over 1,000 BTC on their balance sheet. These companies invest in Bitcoin as a strategic reserve asset to protect the $5 trillion in low-yield cash that companies in the US commonly sit on. *These are the top 10 holdings of OWNB. Source: Ownbetf* ## ETF on Bitcoin companies’ convertible bonds Another instrument that fits seamlessly into the range of Bitcoin-linked stock market products is the [REX Bitcoin Corporate Treasury Convertible Bond ETF](https://www.rexshares.com/rex-launches-bitcoin-corporate-treasury-convertible-bond-etf/) (BMAX). The ETF provides exposure to the many different convertible bonds issued by companies that are actively moving onto a Bitcoin standard. Convertible bonds are a valuable financing tool for companies looking to raise capital for Bitcoin purchases. Their strong demand is driven by the unique combination of equity-like upside and debt-like downside protection they offer. For example, MicroStrategy's convertible bonds, in particular, have shown exceptional performance. For instance, MicroStrategy's 2031 bonds has shown a price rise of 101% over a one-year period, vastly outperforming MicroStrategy share (at 53%), Bitcoin (at 25%) and the ICE BofA U.S. Convertible Index (at 10%). The latter is the benchmark index for convertible bond funds, tracking the performance of U.S. dollar-denominated convertible securities in the U.S. market. *The chart shows a comparison of ICE BofA U.S. Convertible Index, the Bloomberg Bitcoin index (BTC price), MicroStrategy share (MSTR), and MicroStrategy bond (0.875%, March 15 203). The convertible bond has been outperforming massively. Source: Bloomberg* While the BMAX ETF faces challenges such as double taxation, which significantly reduces investor returns (explained in more detail here), it is likely that future products will emerge that address and improve upon these issues. ## Bitcoin yield products The demand for a yield on Bitcoin has increased tremendously. Consequently, respective products have emerged. Bitcoin yield products aim to generate alpha by capitalizing on volatility, market inefficiencies, and fragmentation within cryptocurrency markets. The objective is to achieve uncorrelated returns denominated in Bitcoin (BTC), with attractive risk-adjusted performance. Returns are derived exclusively from asset selection and trading strategies, eliminating reliance on directional market moves. ### Key strategies employed by these funds include: - *Statistical Arbitrage:* Exploits short-term pricing discrepancies between closely related financial instruments—for instance, between Bitcoin and traditional assets, or Bitcoin and other digital assets. Traders utilize statistical models and historical price relationships to identify temporary inefficiencies. - *Futures Basis Arbitrage:* Captures profits from differences between the spot price of Bitcoin and its futures contracts. Traders simultaneously buy or sell Bitcoin on spot markets and enter opposite positions in futures markets, benefiting as the prices converge. - *Funding Arbitrage:* Generates returns by taking advantage of variations in Bitcoin funding rates across different markets or exchanges. Funding rates are periodic payments exchanged between long and short positions in perpetual futures contracts, allowing traders to profit from discrepancies without significant directional exposure. - *Volatility/Option Arbitrage:* Seeks profits from differences between implied volatility (reflected in Bitcoin options prices) and expected realized volatility. Traders identify mispriced volatility in options related to Bitcoin or Bitcoin-linked equities, such as MSTR, and position accordingly to benefit from volatility normalization. - *Market Making:* Involves continuously providing liquidity by simultaneously quoting bid (buy) and ask (sell) prices for Bitcoin. Market makers profit primarily through capturing the spread between these prices, thereby enhancing market efficiency and earning consistent returns. - *Liquidity Provision in DeFi Markets:* Consists of depositing Bitcoin (usually as Wrapped BTC) into decentralized finance (DeFi) liquidity pools such as those on Uniswap, Curve, or Balancer. Liquidity providers earn fees paid by traders who execute swaps within these decentralized exchanges, creating steady yield opportunities. Notable products currently available in this segment include the Syz Capital BTC Alpha Fund offered by Syz Capital and the Forteus Crypto Alpha Fund by Forteus. ## BTC-denominated share class A Bitcoin-denominated share class refers to a specialized investment fund category in which share values, subscriptions (fund deposits), redemptions (fund withdrawals), and performance metrics are expressed entirely in Bitcoin (BTC), rather than in traditional fiat currencies such as USD or EUR. Increasingly, both individual investors and institutions are adopting Bitcoin as their preferred benchmark—or "Bitcoin hurdle rate"—meaning that investment performance is evaluated directly against Bitcoin’s own price movements. These Bitcoin-denominated share classes are designed specifically for investors seeking to preserve and grow their wealth in Bitcoin terms, rather than conventional fiat currencies. As a result, investors reduce their exposure to fiat-related risks. Furthermore, if Bitcoin outperforms fiat currencies, investors holding BTC-denominated shares will experience enhanced returns relative to traditional fiat-denominated investment classes. X: https://x.com/pahueg Podcast: https://www.youtube.com/@lessnoisemoresignalpodcast Book: https://academy.saifedean.com/product/the-bitcoin-enlightenment-hardcover/
@ 05cdefcd:550cc264
2025-03-28 08:00:15The crypto world is full of buzzwords. One that I keep on hearing: “Bitcoin is its own asset class”. While I have always been sympathetic to that view, I’ve always failed to understand the true meaning behind that statement. Although I consider Bitcoin to be the prime innovation within the digital asset sector, my primary response has always been: How can bitcoin (BTC), a single asset, represent an entire asset class? Isn’t it Bitcoin and other digital assets that make up an asset class called crypto? Well, I increasingly believe that most of crypto is just noise. Sure, it’s volatile noise that is predominately interesting for very sophisticated hedge funds, market makers or prop traders that are sophisticated enough to extract alpha – but it’s noise nonetheless and has no part to play in a long-term only portfolio of private retail investors (of which most of us are). *Over multiple market cycles, nearly all altcoins underperform Bitcoin when measured in BTC terms. Source: Tradingview* ## Aha-Moment: Bitcoin keeps on giving Still, how can Bitcoin, as a standalone asset, make up an entire asset class? The “aha-moment” to answer this question recently came to me in a [Less Noise More Signal interview](https://www.youtube.com/watch?v=YHRluf5uxzo) I did with [James Van Straten](https://www.linkedin.com/in/james-van-straten-8782b4112/), senior analyst at Coindesk. Let me paraphrase him here: *“You can’t simply recreate the same ETF as BlackRock. To succeed in the Bitcoin space, new and innovative approaches are needed. This is where understanding Bitcoin not just as a single asset, but as an entire asset class, becomes essential. There are countless ways to build upon Bitcoin’s foundation—varied iterations that go beyond just holding the asset. This is precisely where the emergence of the Bitcoin-linked stock market is taking shape—and it's already underway.”* And this is actually coming to fruition as we speak. Just in the last few days, we saw several products launch in that regard. Obviously, MicroStrategy (now Strategy) is the pioneer of this. The company now [owns](https://www.strategy.com/purchases) 506,137 BTC, and while they’ll keep on buying more, they have also inspired many other companies to follow suit. In fact, there are now already over 70 companies that have adopted Strategy’s Bitcoin playbook. One of the latest companies to buy Bitcoin for their corporate treasury is Rumble. The YouTube competitor just [announced](https://www.coindesk.com/markets/2025/03/12/video-sharing-platform-rumble-buys-188-btc-for-usd17-1m) their first Bitcoin purchase for $17 million. Also, the gaming zombie company GameStop just announced to raise money to buy BTC for their corporate treasury. *Gamestop to make BTC their hurdle rate. Source: X* ## ETF on Bitcoin companies Given this proliferation of Bitcoin Treasury companies, it was only a matter of time before a financial product tracking these would emerge. The popular crypto index fund provider Bitwise Investments has just launched this very product called the [Bitwise Bitcoin Standard Corporations ETF](https://ownbetf.com/) (OWNB). The ETF tracks Bitcoin Treasury companies with over 1,000 BTC on their balance sheet. These companies invest in Bitcoin as a strategic reserve asset to protect the $5 trillion in low-yield cash that companies in the US commonly sit on. *These are the top 10 holdings of OWNB. Source: Ownbetf* ## ETF on Bitcoin companies’ convertible bonds Another instrument that fits seamlessly into the range of Bitcoin-linked stock market products is the [REX Bitcoin Corporate Treasury Convertible Bond ETF](https://www.rexshares.com/rex-launches-bitcoin-corporate-treasury-convertible-bond-etf/) (BMAX). The ETF provides exposure to the many different convertible bonds issued by companies that are actively moving onto a Bitcoin standard. Convertible bonds are a valuable financing tool for companies looking to raise capital for Bitcoin purchases. Their strong demand is driven by the unique combination of equity-like upside and debt-like downside protection they offer. For example, MicroStrategy's convertible bonds, in particular, have shown exceptional performance. For instance, MicroStrategy's 2031 bonds has shown a price rise of 101% over a one-year period, vastly outperforming MicroStrategy share (at 53%), Bitcoin (at 25%) and the ICE BofA U.S. Convertible Index (at 10%). The latter is the benchmark index for convertible bond funds, tracking the performance of U.S. dollar-denominated convertible securities in the U.S. market. *The chart shows a comparison of ICE BofA U.S. Convertible Index, the Bloomberg Bitcoin index (BTC price), MicroStrategy share (MSTR), and MicroStrategy bond (0.875%, March 15 203). The convertible bond has been outperforming massively. Source: Bloomberg* While the BMAX ETF faces challenges such as double taxation, which significantly reduces investor returns (explained in more detail here), it is likely that future products will emerge that address and improve upon these issues. ## Bitcoin yield products The demand for a yield on Bitcoin has increased tremendously. Consequently, respective products have emerged. Bitcoin yield products aim to generate alpha by capitalizing on volatility, market inefficiencies, and fragmentation within cryptocurrency markets. The objective is to achieve uncorrelated returns denominated in Bitcoin (BTC), with attractive risk-adjusted performance. Returns are derived exclusively from asset selection and trading strategies, eliminating reliance on directional market moves. ### Key strategies employed by these funds include: - *Statistical Arbitrage:* Exploits short-term pricing discrepancies between closely related financial instruments—for instance, between Bitcoin and traditional assets, or Bitcoin and other digital assets. Traders utilize statistical models and historical price relationships to identify temporary inefficiencies. - *Futures Basis Arbitrage:* Captures profits from differences between the spot price of Bitcoin and its futures contracts. Traders simultaneously buy or sell Bitcoin on spot markets and enter opposite positions in futures markets, benefiting as the prices converge. - *Funding Arbitrage:* Generates returns by taking advantage of variations in Bitcoin funding rates across different markets or exchanges. Funding rates are periodic payments exchanged between long and short positions in perpetual futures contracts, allowing traders to profit from discrepancies without significant directional exposure. - *Volatility/Option Arbitrage:* Seeks profits from differences between implied volatility (reflected in Bitcoin options prices) and expected realized volatility. Traders identify mispriced volatility in options related to Bitcoin or Bitcoin-linked equities, such as MSTR, and position accordingly to benefit from volatility normalization. - *Market Making:* Involves continuously providing liquidity by simultaneously quoting bid (buy) and ask (sell) prices for Bitcoin. Market makers profit primarily through capturing the spread between these prices, thereby enhancing market efficiency and earning consistent returns. - *Liquidity Provision in DeFi Markets:* Consists of depositing Bitcoin (usually as Wrapped BTC) into decentralized finance (DeFi) liquidity pools such as those on Uniswap, Curve, or Balancer. Liquidity providers earn fees paid by traders who execute swaps within these decentralized exchanges, creating steady yield opportunities. Notable products currently available in this segment include the Syz Capital BTC Alpha Fund offered by Syz Capital and the Forteus Crypto Alpha Fund by Forteus. ## BTC-denominated share class A Bitcoin-denominated share class refers to a specialized investment fund category in which share values, subscriptions (fund deposits), redemptions (fund withdrawals), and performance metrics are expressed entirely in Bitcoin (BTC), rather than in traditional fiat currencies such as USD or EUR. Increasingly, both individual investors and institutions are adopting Bitcoin as their preferred benchmark—or "Bitcoin hurdle rate"—meaning that investment performance is evaluated directly against Bitcoin’s own price movements. These Bitcoin-denominated share classes are designed specifically for investors seeking to preserve and grow their wealth in Bitcoin terms, rather than conventional fiat currencies. As a result, investors reduce their exposure to fiat-related risks. Furthermore, if Bitcoin outperforms fiat currencies, investors holding BTC-denominated shares will experience enhanced returns relative to traditional fiat-denominated investment classes. X: https://x.com/pahueg Podcast: https://www.youtube.com/@lessnoisemoresignalpodcast Book: https://academy.saifedean.com/product/the-bitcoin-enlightenment-hardcover/ @ 8cb60e21:5f2deaea
2024-08-24 23:07:08<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/Xy4LfL2gxKY" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-08-24 23:07:08<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/Xy4LfL2gxKY" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 7c05c4f6:50d03508
2025-03-27 10:07:57Cooker.Club Secures Strategic Support from ViaBTC to Expand AI-Driven Web3 Economy Cooker.Club, the decentralized AI agent platform pioneering the Create to Earn (C2E) model, has received strategic investment from ViaBTC, a globally recognized investment institution that integrates capital, infrastructure, and post-investment services. This partnership marks a key milestone in scaling the Cooker.Club ecosystem and advancing the fusion of blockchain and artificial intelligence. The investment was co-led by MixBase, a web3-native incubator and strategic partner of Cooker.Club, which continues to support protocol-level experiments at the frontier of AI x Crypto. ViaBTC's involvement brings more than funding — it adds deep industry insight, technical support, and valuable connections across the Web3 and AI sectors. This collaboration will accelerate the rollout of Cooker.Club’s C2E infrastructure, empowering AI agents and their communities to participate in decentralized value creation. At the core of Cooker.Club’s ecosystem are three AI-native virtual characters: CyberSun, CyberMJ, and Cooker. Each is a fully on-chain persona with the ability to issue their own tokens, interact across platforms, and engage users through autonomous behaviors. $AISUN, the token for CyberSun, has already launched on PancakeSwap following a successful market curve cycle on Cooker.Club. $COOKER serves as the native token driving the C2E reward engine and governance layer of the platform. CyberMJ’s token is set to launch next, expanding the virtual identity layer of the ecosystem. Backed by the C2E model, users earn $COOK passively by holding AI agent tokens, while developers and creators benefit from protocol-level support. This structure introduces a sustainable, programmable economy that redefines creator engagement. Cooker.Club’s collaboration with ViaBTC and MIXBASE will further enhance its technical infrastructure and reach, positioning the platform as a foundational layer for on-chain AI creators. As AI and Web3 continue to converge, the partnership aims to unlock scalable tools and systems for the next generation of decentralized agents and their communities. This is more than investment — it’s a shared vision for an autonomous, intelligent future economy.
@ 7c05c4f6:50d03508
2025-03-27 10:07:57Cooker.Club Secures Strategic Support from ViaBTC to Expand AI-Driven Web3 Economy Cooker.Club, the decentralized AI agent platform pioneering the Create to Earn (C2E) model, has received strategic investment from ViaBTC, a globally recognized investment institution that integrates capital, infrastructure, and post-investment services. This partnership marks a key milestone in scaling the Cooker.Club ecosystem and advancing the fusion of blockchain and artificial intelligence. The investment was co-led by MixBase, a web3-native incubator and strategic partner of Cooker.Club, which continues to support protocol-level experiments at the frontier of AI x Crypto. ViaBTC's involvement brings more than funding — it adds deep industry insight, technical support, and valuable connections across the Web3 and AI sectors. This collaboration will accelerate the rollout of Cooker.Club’s C2E infrastructure, empowering AI agents and their communities to participate in decentralized value creation. At the core of Cooker.Club’s ecosystem are three AI-native virtual characters: CyberSun, CyberMJ, and Cooker. Each is a fully on-chain persona with the ability to issue their own tokens, interact across platforms, and engage users through autonomous behaviors. $AISUN, the token for CyberSun, has already launched on PancakeSwap following a successful market curve cycle on Cooker.Club. $COOKER serves as the native token driving the C2E reward engine and governance layer of the platform. CyberMJ’s token is set to launch next, expanding the virtual identity layer of the ecosystem. Backed by the C2E model, users earn $COOK passively by holding AI agent tokens, while developers and creators benefit from protocol-level support. This structure introduces a sustainable, programmable economy that redefines creator engagement. Cooker.Club’s collaboration with ViaBTC and MIXBASE will further enhance its technical infrastructure and reach, positioning the platform as a foundational layer for on-chain AI creators. As AI and Web3 continue to converge, the partnership aims to unlock scalable tools and systems for the next generation of decentralized agents and their communities. This is more than investment — it’s a shared vision for an autonomous, intelligent future economy. @ b8916ce2:bd2a5f00
2025-03-27 09:31:52Bom88 là một nền tảng giải trí trực tuyến nổi bật, được thiết kế để mang lại cho người tham gia những trải nghiệm thú vị và độc đáo. Với giao diện thân thiện và dễ sử dụng, nền tảng này cho phép người dùng dễ dàng tìm thấy và tham gia vào các trò chơi yêu thích mà không gặp phải bất kỳ khó khăn nào. Bom88 không chỉ đa dạng về các loại trò chơi mà còn có các sự kiện và thử thách đặc biệt giúp tăng thêm phần hấp dẫn. Từ các trò chơi trí tuệ đòi hỏi tư duy và chiến lược, đến các trò chơi giải trí nhẹ nhàng, Bom88 luôn đảm bảo rằng mỗi người tham gia có thể tìm thấy thứ mình yêu thích. Những tính năng sáng tạo và độc đáo của nền tảng này giúp tạo ra một không gian giải trí đỉnh cao, mang lại sự thư giãn và hào hứng cho tất cả người tham gia. Thêm vào đó, nền tảng này không ngừng cải tiến và cập nhật các trò chơi mới, giúp người tham gia không bao giờ cảm thấy nhàm chán và luôn có thể khám phá những điều mới mẻ. Bảo mật và an toàn luôn là yếu tố quan trọng hàng đầu tại <a href="https://bom88-vn.com">Bom88</a>. Với việc sử dụng các công nghệ bảo mật tiên tiến nhất, nền tảng này đảm bảo rằng mọi dữ liệu cá nhân và giao dịch của người dùng được bảo vệ một cách tối đa. Những biện pháp bảo mật này giúp người tham gia yên tâm hoàn toàn khi tham gia vào các hoạt động giải trí mà không phải lo lắng về sự xâm phạm thông tin. Bom88 không chỉ chú trọng đến việc bảo vệ sự riêng tư của người dùng mà còn cam kết tạo ra một môi trường chơi công bằng và an toàn. Việc áp dụng các công nghệ mã hóa và bảo mật dữ liệu hàng đầu giúp đảm bảo rằng mọi giao dịch tài chính cũng như các thông tin cá nhân của người dùng luôn được bảo vệ tuyệt đối, mang lại sự an tâm tuyệt đối khi tham gia nền tảng này. Chính nhờ những nỗ lực trong việc đảm bảo an toàn cho người dùng, Bom88 đã xây dựng được một cộng đồng đáng tin cậy và uy tín, nơi mà người tham gia có thể hoàn toàn tận hưởng những phút giây giải trí mà không phải lo ngại về vấn đề bảo mật. Không ngừng đổi mới và sáng tạo, Bom88 luôn mang đến cho người tham gia những trải nghiệm mới mẻ và hấp dẫn. Các sự kiện đặc biệt và chương trình khuyến mãi được tổ chức thường xuyên, tạo ra những cơ hội thú vị cho người tham gia thử sức và nhận những phần thưởng giá trị. Nền tảng này không chỉ cung cấp các trò chơi hấp dẫn mà còn tạo cơ hội để người tham gia kết nối với những người có cùng sở thích, từ đó xây dựng một cộng đồng mạnh mẽ và thân thiện. Những tính năng tiện ích như hỗ trợ khách hàng 24/7 và các công cụ cá nhân hóa giúp người tham gia dễ dàng theo dõi lịch sử chơi game và điều chỉnh các cài đặt cá nhân để có được trải nghiệm tối ưu nhất. Bom88 không chỉ là nơi để giải trí mà còn là một cộng đồng kết nối những người đam mê và yêu thích khám phá, học hỏi từ những người chơi khác. Nhờ vào sự kết hợp giữa tính sáng tạo và sự đổi mới không ngừng, Bom88 đã khẳng định được vị thế của mình trong thế giới giải trí trực tuyến, trở thành một lựa chọn lý tưởng cho những ai đang tìm kiếm một không gian giải trí thú vị và đầy thử thách.
@ b8916ce2:bd2a5f00
2025-03-27 09:31:52Bom88 là một nền tảng giải trí trực tuyến nổi bật, được thiết kế để mang lại cho người tham gia những trải nghiệm thú vị và độc đáo. Với giao diện thân thiện và dễ sử dụng, nền tảng này cho phép người dùng dễ dàng tìm thấy và tham gia vào các trò chơi yêu thích mà không gặp phải bất kỳ khó khăn nào. Bom88 không chỉ đa dạng về các loại trò chơi mà còn có các sự kiện và thử thách đặc biệt giúp tăng thêm phần hấp dẫn. Từ các trò chơi trí tuệ đòi hỏi tư duy và chiến lược, đến các trò chơi giải trí nhẹ nhàng, Bom88 luôn đảm bảo rằng mỗi người tham gia có thể tìm thấy thứ mình yêu thích. Những tính năng sáng tạo và độc đáo của nền tảng này giúp tạo ra một không gian giải trí đỉnh cao, mang lại sự thư giãn và hào hứng cho tất cả người tham gia. Thêm vào đó, nền tảng này không ngừng cải tiến và cập nhật các trò chơi mới, giúp người tham gia không bao giờ cảm thấy nhàm chán và luôn có thể khám phá những điều mới mẻ. Bảo mật và an toàn luôn là yếu tố quan trọng hàng đầu tại <a href="https://bom88-vn.com">Bom88</a>. Với việc sử dụng các công nghệ bảo mật tiên tiến nhất, nền tảng này đảm bảo rằng mọi dữ liệu cá nhân và giao dịch của người dùng được bảo vệ một cách tối đa. Những biện pháp bảo mật này giúp người tham gia yên tâm hoàn toàn khi tham gia vào các hoạt động giải trí mà không phải lo lắng về sự xâm phạm thông tin. Bom88 không chỉ chú trọng đến việc bảo vệ sự riêng tư của người dùng mà còn cam kết tạo ra một môi trường chơi công bằng và an toàn. Việc áp dụng các công nghệ mã hóa và bảo mật dữ liệu hàng đầu giúp đảm bảo rằng mọi giao dịch tài chính cũng như các thông tin cá nhân của người dùng luôn được bảo vệ tuyệt đối, mang lại sự an tâm tuyệt đối khi tham gia nền tảng này. Chính nhờ những nỗ lực trong việc đảm bảo an toàn cho người dùng, Bom88 đã xây dựng được một cộng đồng đáng tin cậy và uy tín, nơi mà người tham gia có thể hoàn toàn tận hưởng những phút giây giải trí mà không phải lo ngại về vấn đề bảo mật. Không ngừng đổi mới và sáng tạo, Bom88 luôn mang đến cho người tham gia những trải nghiệm mới mẻ và hấp dẫn. Các sự kiện đặc biệt và chương trình khuyến mãi được tổ chức thường xuyên, tạo ra những cơ hội thú vị cho người tham gia thử sức và nhận những phần thưởng giá trị. Nền tảng này không chỉ cung cấp các trò chơi hấp dẫn mà còn tạo cơ hội để người tham gia kết nối với những người có cùng sở thích, từ đó xây dựng một cộng đồng mạnh mẽ và thân thiện. Những tính năng tiện ích như hỗ trợ khách hàng 24/7 và các công cụ cá nhân hóa giúp người tham gia dễ dàng theo dõi lịch sử chơi game và điều chỉnh các cài đặt cá nhân để có được trải nghiệm tối ưu nhất. Bom88 không chỉ là nơi để giải trí mà còn là một cộng đồng kết nối những người đam mê và yêu thích khám phá, học hỏi từ những người chơi khác. Nhờ vào sự kết hợp giữa tính sáng tạo và sự đổi mới không ngừng, Bom88 đã khẳng định được vị thế của mình trong thế giới giải trí trực tuyến, trở thành một lựa chọn lý tưởng cho những ai đang tìm kiếm một không gian giải trí thú vị và đầy thử thách. @ b8af284d:f82c91dd
2025-03-16 16:42:49 Liebe Abonnenten, diejenigen, die diese Publikation schon länger abonniert haben, wissen, dass hier immer wieder über den Ursprung des Corona-Virus in einem Labor in Wuhan berichtet wurde. Seit diese Woche ist es „offiziell“ - [der Bundesnachrichtendienst (BND) hält den Labor-Ursprung für die wahrscheinlichste Variante](https://www.zeit.de/2025/11/coronavirus-ursprung-wuhan-labor-china-bnd). Jetzt kann man sich fragen, warum der BND plötzlich umschwenkt: Will man proaktiv erscheinen, weil man die Wahrheit nicht mehr länger verbergen kann? Oder will man die enttäuschten Bürger zurückgewinnen, die aufgrund der Lügen während der Corona-Zeit zunehmend mit Parteien links und rechts außen sympathisiert haben, weil diese die einzigen waren, die den Irrsinn nicht mitgetragen haben? Auffallend bei den „Recherchen“, die in Wahrheit keine sind, sondern Verlautbarungen des deutschen Geheimdienstes, ist auch das völlige Schweigen über die US-amerikanischen Verwicklungen in das Projekt. [In Wuhan wurde mit amerikanischem Geld geforscht](https://oversight.house.gov/release/breaking-hhs-formally-debars-ecohealth-alliance-dr-peter-daszak-after-covid-select-reveals-pandemic-era-wrongdoing/). Warum der BND diese Tatsache verschweigt, ist Teil der Spekulation. Vermutlich will man Peking alles in die Schuhe schieben, um von den eigenen Versäumnissen abzulenken. In meinem aktuellen Buch “[Der chinesische (Alp-)Traum](https://www.amazon.de/chinesische-Alb-Traum-geopolitische-Herausforderung/dp/3442317509/ref=sr_1_1?__mk_de_DE=%C3%85M%C3%85%C5%BD%C3%95%C3%91\&crid=XQVCLFVRCJJ\&dib=eyJ2IjoiMSJ9.kCJqsUXZO8NZjieNQjGy3Vez7tqktnhQynFOnuZE9249tfkKZvqdJtpIfcDiLMOyxmF7JFpMfvAC881caUEufT--GHlSCcAt_shhnVSbNLp-cle-VXel7soyPwi8xGPm88hSBKPY93BtjFYdOueFUU7qrOir_paRMiQOmCs7YOAUe7ZCKAb6YXxu_hz8N1eZhXbFcvc6p01Uu0vgIibiOHzbXxtH6ECNUaWCaHCYus4.Jzuq9IYvQtPedtE4YORWFtEmxTtrHh5xe8b-B25o5uA\&dib_tag=se\&keywords=Philipp+Mattheis\&qid=1730736669\&sprefix=philipp+mattheis%2Caps%2C111\&sr=8-1)” ist den Ereignissen in Wuhan ein ganzes Kapitel gewidmet. Es hat nichts an Aktualität eingebüßt. Alle Fakten lagen seit Jahren auf dem Tisch für jeden, den es interessiert hat. [Hier gibt es das gesamte Kapitel nachzulesen.](https://blingbling.substack.com/p/was-geschah-in-wuhan)  Auf jeden Fall zeigt dies, wie der Begriff „Verschwörungstheoretiker“ in den vergangenen Jahren zum Kampfbegriff und Waffe gemacht wurde, um Kritiker zu diffamieren, und die öffentliche Meinung ohne harte Zensur zu lenken. Ähnliches kann man aktuell beim Projekt „Digitaler Euro“ beobachten. Vermutlich kann sich kein Bürger der Europäischen Union daran erinnern, bei seiner Wahlentscheidung jemals gefragt worden zu sein, ob er die Einführung eines „digitalen Euros“ gut findet. Wurde er nämlich nicht. Er kommt aber trotzdem. EZB-Präsidentin Christine Lagarde hat das diese Woche nochmals bekräftigt: [Schon im Oktober will man die Testphase beenden](https://x.com/efenigson/status/1898382481184993711) und an der Einführung arbeiten. Nun gehört BlingBling nicht zu denjenigen, die im digitalen Euro „Orwell’sches Teufelswerk“ sehen. Strategische Dummheit trifft es besser. Worum geht es? Sogenannte Central Bank Digital Currencies (CBDC) waren vor einigen Jahren so etwas wie der letzte Schrei in der Zentralbank-Welt. Nachdem Facebook/Meta 2017/18 eine eigene Währung namens Libra auf den Markt bringen wollte, und eine obskure Internet-Währung namens Bitcoin immer mehr Anhänger fand, sahen sich viele Zentralbanken der Welt unter Zugzwang. Was man wollte: eine digitale, direkt von der Zentralbank ausgegebene Währung ohne Bugs, aber mit Features. Mit einer Digital-Währung ließe sich der internationale Zahlungsverkehr direkt und ohne Umweg über den US-Dollar abwickeln. Die Zentralbank bekäme wieder mehr direkten Einfluss auf die Geldschöpfung. Und, wie man aus China lernen konnte, ließen sich digitale Bankkonten auch ganz zum „Nudging von Bürgern“ nutzen. So spekulierten die ersten Verschwörungstheoretiker bald, [ein digitaler Euro ließe sich ja mit einem persönlichen CO2-Konto verknüpfen](https://www.derstandard.de/story/2000124296026/was-eine-digitale-co2-waehrung-fuer-das-klima-bedeuten-wuerde). Wäre letzteres einmal aufgebraucht, könnte der Konto-Inhaber einfach keinen Flug mehr buchen. Auch ließe sich eine expansive Geldpolitik, wie sie bis 2022 praktiziert wurde, ganz einfach mit Negativ-Zinsen umsetzen. Geld würde sich nominal reduzieren, was den Bürger zum Konsum animieren würde. Flüchtigen Kriminellen ließe sich per Knopfdruck das Konto sperren. Der Staat würde also über eine ganze neue Palette an Einflussmöglichkeiten verfügen. Die Aluhüte United warnten vor einem Orwellschen Überwachungsstaat. Vertreter von Regierungen und Firmen, die diesen digitalen Euro bauen sollten, beschwichtigten. Mit Ralf Wintergerst, CEO von Giesecke+Devrient, nach wie vor heißester Anwärter, um das Projekt in der EU umzusetzen, sprach ich in den vergangenen Jahren mehrmals zu dem Thema. [Zuletzt im Dezember 24](https://blingbling.substack.com/p/euro-thrash). Wintergerst versichert stets zwei Dinge: Eine Abschaffung von Bargeld sei nicht geplant. Und nur, wenn die Fluchttore Bargeld, Gold und Bitcoin geschlossen werden, greift die dystopische Version. Und zweitens, so Wintergerst, habe niemand ein chinesisches System im Sinne. Der „digitale Euro“ sei für die Bürger gedacht und das Projekt unterliege demokratischer Kontrolle. Ob er Wintergerst und dem guten im Menschen Glauben schenkt, möge jeder Leser selbst entscheiden. Das Interessantere ist ohnehin, dass der digitale Euro ein strategisch dummes Projekt ist. Dazu muss man wissen, dass eine solche Zentralbankwährung Banken im weitesten Sinne überflüssig macht. Kontos bei Privatbanken werden obsolet, genauso wie Spar-, Fest- und Tagesgeld-Strukturen. Deshalb soll der digitale Euro zunächst auf 3000 Euro pro Bürger beschränkt werden. Das ist also nicht als Maximal-Vermögen gedacht, das dann jedem sozialistischen Einheits-EU-Menschen noch zusteht, sondern dient dazu, das Bankensystem nicht kollabieren zu lassen. Aber wozu überhaupt „ein bisschen digitaler Euro“? In den USA setzt man mittlerweile 100 Prozent auf die private Alternative: Stablecoins wie Tether (USDT) und Circle (USDC) sind nichts anderes als digitale Währungen. Nur sind sie nicht von einer Zentralbank ausgeben, sondern von privaten Anbietern. Tether hat technisch die Möglichkeit, einen Inhaber vom Zahlungsverkehr auszusperren. Nur dürfte es davon kaum Gebrauch machen, will das Unternehmen nicht rasant Kunden an die Konkurrenz verlieren. Da USDT und USDC mit US-Dollar gedeckt sind (oder zumindest sein sollten, *looking at you, Tether!*), stärken sie außerdem die Rolle des US-Dollars als Leitwährung. Und da die USA sich aktuell sehr über Käufer von Staatsanleihen freuen, um die Zinsen zu drücken, und [Tether einer der größten Halter von US-Staatsanleihen is](https://crypto.news/tether-treasury-holdings-boost-us-debt-resilience-2025/)t, wird es den digitalen Dollar bis auf Weiteres nicht geben. Den digitalen Yuan gibt es, aber von einer großen Akzeptanz oder Durchdringung der chinesischen Wirtschaft lässt sich nicht sprechen. Kontrolle kann der chinesische Staat ohnehin über seine omnipräsenten Apps WeChat und Alipay ausüben. Was den internationalen Zahlungsverkehr betrifft, [scheint man aktuell eher auf Gold zu setzen](https://blingbling.substack.com/p/goldfinger). Übrig also bleibt die EU mit einem Projekt, das bereits Milliarden an Entwicklungskosten verschlungen hat. Am Ende bleibt dann ein Mini-Digitaler-Euro in Höhe von 3000 Euro, den niemand wollte, und niemand braucht. Helfen könnte er allerdings beim Projekt “Mobilisierung der Sparguthaben”. Der Ausdruck geht auf Friedrich Merz zurück. Ursula von der Leyen paraphrasierte ihn jüngst:  [Irgendwie müssen die Billionen von Sparguthaben in Militär-Investitionen umgewandelt werden](https://blingbling.substack.com/p/panzer-statt-autos). Das wird am besten funktionieren mit Anleihen, die schlechter verzinst sind als sonst auf dem Markt üblich. Wie bringt man Leute dazu, dann ihr Geld dort zu investieren? Entweder man zwingt sie, oder man bewirbt die Anleihen mit viel Patriotismus und Propaganda. Die Verschwörungstheoretiker unter uns bekommen also bald Futter, wenn die „Spar- und Investitionsunion” vorgestellt wird. Like, wenn Dein Aluhut glüht… *Hinter der Paywall: Wie das Trump-Derangement-Syndrom den Blick auf den Markt trübt. **[Wie es mit Bitcoin, Gold und Aktien weitergeht.](https://blingbling.substack.com/p/gluhende-aluhute)***
@ b8af284d:f82c91dd
2025-03-16 16:42:49 Liebe Abonnenten, diejenigen, die diese Publikation schon länger abonniert haben, wissen, dass hier immer wieder über den Ursprung des Corona-Virus in einem Labor in Wuhan berichtet wurde. Seit diese Woche ist es „offiziell“ - [der Bundesnachrichtendienst (BND) hält den Labor-Ursprung für die wahrscheinlichste Variante](https://www.zeit.de/2025/11/coronavirus-ursprung-wuhan-labor-china-bnd). Jetzt kann man sich fragen, warum der BND plötzlich umschwenkt: Will man proaktiv erscheinen, weil man die Wahrheit nicht mehr länger verbergen kann? Oder will man die enttäuschten Bürger zurückgewinnen, die aufgrund der Lügen während der Corona-Zeit zunehmend mit Parteien links und rechts außen sympathisiert haben, weil diese die einzigen waren, die den Irrsinn nicht mitgetragen haben? Auffallend bei den „Recherchen“, die in Wahrheit keine sind, sondern Verlautbarungen des deutschen Geheimdienstes, ist auch das völlige Schweigen über die US-amerikanischen Verwicklungen in das Projekt. [In Wuhan wurde mit amerikanischem Geld geforscht](https://oversight.house.gov/release/breaking-hhs-formally-debars-ecohealth-alliance-dr-peter-daszak-after-covid-select-reveals-pandemic-era-wrongdoing/). Warum der BND diese Tatsache verschweigt, ist Teil der Spekulation. Vermutlich will man Peking alles in die Schuhe schieben, um von den eigenen Versäumnissen abzulenken. In meinem aktuellen Buch “[Der chinesische (Alp-)Traum](https://www.amazon.de/chinesische-Alb-Traum-geopolitische-Herausforderung/dp/3442317509/ref=sr_1_1?__mk_de_DE=%C3%85M%C3%85%C5%BD%C3%95%C3%91\&crid=XQVCLFVRCJJ\&dib=eyJ2IjoiMSJ9.kCJqsUXZO8NZjieNQjGy3Vez7tqktnhQynFOnuZE9249tfkKZvqdJtpIfcDiLMOyxmF7JFpMfvAC881caUEufT--GHlSCcAt_shhnVSbNLp-cle-VXel7soyPwi8xGPm88hSBKPY93BtjFYdOueFUU7qrOir_paRMiQOmCs7YOAUe7ZCKAb6YXxu_hz8N1eZhXbFcvc6p01Uu0vgIibiOHzbXxtH6ECNUaWCaHCYus4.Jzuq9IYvQtPedtE4YORWFtEmxTtrHh5xe8b-B25o5uA\&dib_tag=se\&keywords=Philipp+Mattheis\&qid=1730736669\&sprefix=philipp+mattheis%2Caps%2C111\&sr=8-1)” ist den Ereignissen in Wuhan ein ganzes Kapitel gewidmet. Es hat nichts an Aktualität eingebüßt. Alle Fakten lagen seit Jahren auf dem Tisch für jeden, den es interessiert hat. [Hier gibt es das gesamte Kapitel nachzulesen.](https://blingbling.substack.com/p/was-geschah-in-wuhan)  Auf jeden Fall zeigt dies, wie der Begriff „Verschwörungstheoretiker“ in den vergangenen Jahren zum Kampfbegriff und Waffe gemacht wurde, um Kritiker zu diffamieren, und die öffentliche Meinung ohne harte Zensur zu lenken. Ähnliches kann man aktuell beim Projekt „Digitaler Euro“ beobachten. Vermutlich kann sich kein Bürger der Europäischen Union daran erinnern, bei seiner Wahlentscheidung jemals gefragt worden zu sein, ob er die Einführung eines „digitalen Euros“ gut findet. Wurde er nämlich nicht. Er kommt aber trotzdem. EZB-Präsidentin Christine Lagarde hat das diese Woche nochmals bekräftigt: [Schon im Oktober will man die Testphase beenden](https://x.com/efenigson/status/1898382481184993711) und an der Einführung arbeiten. Nun gehört BlingBling nicht zu denjenigen, die im digitalen Euro „Orwell’sches Teufelswerk“ sehen. Strategische Dummheit trifft es besser. Worum geht es? Sogenannte Central Bank Digital Currencies (CBDC) waren vor einigen Jahren so etwas wie der letzte Schrei in der Zentralbank-Welt. Nachdem Facebook/Meta 2017/18 eine eigene Währung namens Libra auf den Markt bringen wollte, und eine obskure Internet-Währung namens Bitcoin immer mehr Anhänger fand, sahen sich viele Zentralbanken der Welt unter Zugzwang. Was man wollte: eine digitale, direkt von der Zentralbank ausgegebene Währung ohne Bugs, aber mit Features. Mit einer Digital-Währung ließe sich der internationale Zahlungsverkehr direkt und ohne Umweg über den US-Dollar abwickeln. Die Zentralbank bekäme wieder mehr direkten Einfluss auf die Geldschöpfung. Und, wie man aus China lernen konnte, ließen sich digitale Bankkonten auch ganz zum „Nudging von Bürgern“ nutzen. So spekulierten die ersten Verschwörungstheoretiker bald, [ein digitaler Euro ließe sich ja mit einem persönlichen CO2-Konto verknüpfen](https://www.derstandard.de/story/2000124296026/was-eine-digitale-co2-waehrung-fuer-das-klima-bedeuten-wuerde). Wäre letzteres einmal aufgebraucht, könnte der Konto-Inhaber einfach keinen Flug mehr buchen. Auch ließe sich eine expansive Geldpolitik, wie sie bis 2022 praktiziert wurde, ganz einfach mit Negativ-Zinsen umsetzen. Geld würde sich nominal reduzieren, was den Bürger zum Konsum animieren würde. Flüchtigen Kriminellen ließe sich per Knopfdruck das Konto sperren. Der Staat würde also über eine ganze neue Palette an Einflussmöglichkeiten verfügen. Die Aluhüte United warnten vor einem Orwellschen Überwachungsstaat. Vertreter von Regierungen und Firmen, die diesen digitalen Euro bauen sollten, beschwichtigten. Mit Ralf Wintergerst, CEO von Giesecke+Devrient, nach wie vor heißester Anwärter, um das Projekt in der EU umzusetzen, sprach ich in den vergangenen Jahren mehrmals zu dem Thema. [Zuletzt im Dezember 24](https://blingbling.substack.com/p/euro-thrash). Wintergerst versichert stets zwei Dinge: Eine Abschaffung von Bargeld sei nicht geplant. Und nur, wenn die Fluchttore Bargeld, Gold und Bitcoin geschlossen werden, greift die dystopische Version. Und zweitens, so Wintergerst, habe niemand ein chinesisches System im Sinne. Der „digitale Euro“ sei für die Bürger gedacht und das Projekt unterliege demokratischer Kontrolle. Ob er Wintergerst und dem guten im Menschen Glauben schenkt, möge jeder Leser selbst entscheiden. Das Interessantere ist ohnehin, dass der digitale Euro ein strategisch dummes Projekt ist. Dazu muss man wissen, dass eine solche Zentralbankwährung Banken im weitesten Sinne überflüssig macht. Kontos bei Privatbanken werden obsolet, genauso wie Spar-, Fest- und Tagesgeld-Strukturen. Deshalb soll der digitale Euro zunächst auf 3000 Euro pro Bürger beschränkt werden. Das ist also nicht als Maximal-Vermögen gedacht, das dann jedem sozialistischen Einheits-EU-Menschen noch zusteht, sondern dient dazu, das Bankensystem nicht kollabieren zu lassen. Aber wozu überhaupt „ein bisschen digitaler Euro“? In den USA setzt man mittlerweile 100 Prozent auf die private Alternative: Stablecoins wie Tether (USDT) und Circle (USDC) sind nichts anderes als digitale Währungen. Nur sind sie nicht von einer Zentralbank ausgeben, sondern von privaten Anbietern. Tether hat technisch die Möglichkeit, einen Inhaber vom Zahlungsverkehr auszusperren. Nur dürfte es davon kaum Gebrauch machen, will das Unternehmen nicht rasant Kunden an die Konkurrenz verlieren. Da USDT und USDC mit US-Dollar gedeckt sind (oder zumindest sein sollten, *looking at you, Tether!*), stärken sie außerdem die Rolle des US-Dollars als Leitwährung. Und da die USA sich aktuell sehr über Käufer von Staatsanleihen freuen, um die Zinsen zu drücken, und [Tether einer der größten Halter von US-Staatsanleihen is](https://crypto.news/tether-treasury-holdings-boost-us-debt-resilience-2025/)t, wird es den digitalen Dollar bis auf Weiteres nicht geben. Den digitalen Yuan gibt es, aber von einer großen Akzeptanz oder Durchdringung der chinesischen Wirtschaft lässt sich nicht sprechen. Kontrolle kann der chinesische Staat ohnehin über seine omnipräsenten Apps WeChat und Alipay ausüben. Was den internationalen Zahlungsverkehr betrifft, [scheint man aktuell eher auf Gold zu setzen](https://blingbling.substack.com/p/goldfinger). Übrig also bleibt die EU mit einem Projekt, das bereits Milliarden an Entwicklungskosten verschlungen hat. Am Ende bleibt dann ein Mini-Digitaler-Euro in Höhe von 3000 Euro, den niemand wollte, und niemand braucht. Helfen könnte er allerdings beim Projekt “Mobilisierung der Sparguthaben”. Der Ausdruck geht auf Friedrich Merz zurück. Ursula von der Leyen paraphrasierte ihn jüngst:  [Irgendwie müssen die Billionen von Sparguthaben in Militär-Investitionen umgewandelt werden](https://blingbling.substack.com/p/panzer-statt-autos). Das wird am besten funktionieren mit Anleihen, die schlechter verzinst sind als sonst auf dem Markt üblich. Wie bringt man Leute dazu, dann ihr Geld dort zu investieren? Entweder man zwingt sie, oder man bewirbt die Anleihen mit viel Patriotismus und Propaganda. Die Verschwörungstheoretiker unter uns bekommen also bald Futter, wenn die „Spar- und Investitionsunion” vorgestellt wird. Like, wenn Dein Aluhut glüht… *Hinter der Paywall: Wie das Trump-Derangement-Syndrom den Blick auf den Markt trübt. **[Wie es mit Bitcoin, Gold und Aktien weitergeht.](https://blingbling.substack.com/p/gluhende-aluhute)*** @ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions. My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change. Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it. I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay. I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene. That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results. In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it. I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful. Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself. If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜 Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem. https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions. My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change. Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it. I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay. I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene. That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results. In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it. I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful. Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself. If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜 Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem. https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion @ a95c6243:d345522c
2025-03-15 10:56:08*Was nützt die schönste Schuldenbremse, wenn der Russe vor der Tür steht?* *\ Wir können uns verteidigen lernen oder alle Russisch lernen.* *\ Jens Spahn*   **In der Politik ist buchstäblich keine Idee zu riskant, kein Mittel zu schäbig und keine Lüge zu dreist,** als dass sie nicht benutzt würden. Aber der Clou ist, dass diese Masche immer noch funktioniert, wenn nicht sogar immer besser. Ist das alles wirklich so schwer zu durchschauen? Mir fehlen langsam die Worte. **Aktuell werden sowohl in der Europäischen Union als auch in Deutschland** riesige Milliardenpakete für die [Aufrüstung](https://transition-news.org/eu-halt-weiter-kurs-auf-krieg-hunderte-milliarden-fur-aufrustung-beschlossen) – also für die Rüstungsindustrie – geschnürt. Die EU will 800 Milliarden Euro locker machen, in Deutschland sollen es 500 Milliarden «Sondervermögen» sein. Verteidigung nennen das unsere «Führer», innerhalb der Union und auch an «unserer Ostflanke», der Ukraine. **Das nötige Feindbild konnte inzwischen signifikant erweitert werden.** Schuld an allem und zudem gefährlich ist nicht mehr nur Putin, sondern jetzt auch Trump. Europa müsse sich sowohl gegen Russland als auch gegen die USA schützen und rüsten, wird uns eingetrichtert. **Und während durch Diplomatie genau dieser beiden Staaten** gerade endlich mal Bewegung in die Bemühungen um einen Frieden oder wenigstens einen Waffenstillstand in der Ukraine kommt, rasselt man im moralisch überlegenen Zeigefinger-Europa so richtig mit dem Säbel. **Begleitet und gestützt wird der ganze Prozess** – wie sollte es anders sein – von den «Qualitätsmedien». Dass Russland einen Angriff auf «Europa» plant, weiß nicht nur der deutsche Verteidigungsminister (und mit Abstand beliebteste Politiker) Pistorius, sondern dank ihnen auch jedes Kind. Uns bleiben nur noch wenige Jahre. Zum Glück bereitet sich die Bundeswehr schon sehr konkret [auf einen Krieg](https://archive.is/VE8ZM) vor. **Die** ***FAZ*** **und Corona-Gesundheitsminister Spahn markieren einen traurigen Höhepunkt.** Hier haben sich «politische und publizistische Verantwortungslosigkeit propagandistisch gegenseitig befruchtet», wie es bei den *NachDenkSeiten* [heißt](https://www.nachdenkseiten.de/?p=130064). Die Aussage Spahns in dem Interview, «der Russe steht vor der Tür», ist das eine. Die Zeitung verschärfte die Sache jedoch, indem sie das Zitat explizit in den [Titel](https://archive.is/QJdID) übernahm, der in einer [ersten Version](https://archive.is/fNuGA) scheinbar zu harmlos war. **Eine große Mehrheit der deutschen Bevölkerung findet Aufrüstung und mehr Schulden toll,** wie *[ARD](https://archive.is/M3DSk)* und *[ZDF](https://archive.is/ggvJB)* sehr passend ermittelt haben wollen. Ähnliches gelte für eine noch stärkere militärische Unterstützung der Ukraine. Etwas skeptischer seien die Befragten bezüglich der Entsendung von Bundeswehrsoldaten dorthin, aber immerhin etwa fifty-fifty. **Eigentlich ist jedoch die Meinung der Menschen in «unseren Demokratien» irrelevant.** Sowohl in der Europäischen Union als auch in Deutschland sind die «Eliten» offenbar der Ansicht, der Souverän habe in Fragen von Krieg und Frieden sowie von aberwitzigen astronomischen Schulden kein Wörtchen mitzureden. Frau von der Leyen möchte über 150 Milliarden aus dem Gesamtpaket unter Verwendung von Artikel 122 des EU-Vertrags ohne das Europäische Parlament entscheiden – wenn auch nicht völlig [kritiklos](https://www.berliner-zeitung.de/politik-gesellschaft/geopolitik/aufruestung-widerstand-gegen-eu-plaene-waechst-kommission-uebertreibt-russische-gefahr-li.2306863). **In Deutschland wollen CDU/CSU und SPD zur Aufweichung der «Schuldenbremse»** mehrere Änderungen des Grundgesetzes durch das abgewählte Parlament peitschen. Dieser Versuch, mit dem alten [Bundestag](https://www.bundestag.de/dokumente/textarchiv/2025/kw11-de-sondersitzung-1056228) eine Zweidrittelmehrheit zu erzielen, die im neuen nicht mehr gegeben wäre, ist mindestens verfassungsrechtlich umstritten. **Das Manöver scheint aber zu funktionieren.** Heute haben die Grünen [zugestimmt](https://www.reuters.com/world/europe/germany-faces-debt-deal-cliffhanger-merz-strives-greens-backing-2025-03-14/), nachdem Kanzlerkandidat Merz läppische 100 Milliarden für «irgendwas mit Klima» zugesichert hatte. Die Abstimmung im Plenum soll am kommenden Dienstag erfolgen – nur eine Woche, bevor sich der neu gewählte Bundestag konstituieren wird. **Interessant sind die Argumente, die BlackRocker Merz für seine Attacke** auf Grundgesetz und Demokratie ins Feld führt. Abgesehen von der angeblichen Eile, «unsere Verteidigungsfähigkeit deutlich zu erhöhen» (ausgelöst unter anderem durch «die Münchner Sicherheitskonferenz und die Ereignisse im Weißen Haus»), ließ uns der CDU-Chef wissen, dass Deutschland einfach auf die internationale Bühne zurück müsse. Merz [schwadronierte](https://x.com/CDU/status/1900168761686044894) gefährlich mehrdeutig: > «Die ganze Welt schaut in diesen Tagen und Wochen auf Deutschland. Wir haben in der Europäischen Union und auf der Welt eine Aufgabe, die weit über die Grenzen unseres eigenen Landes hinausgeht.»      *\[Titelbild:* *[Tag des Sieges](https://pixabay.com/de/photos/parade-tag-des-sieges-samara-182508/)]* *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/propaganda-wahnsinn-und-demokratur)*** erschienen.
@ a95c6243:d345522c
2025-03-15 10:56:08*Was nützt die schönste Schuldenbremse, wenn der Russe vor der Tür steht?* *\ Wir können uns verteidigen lernen oder alle Russisch lernen.* *\ Jens Spahn*   **In der Politik ist buchstäblich keine Idee zu riskant, kein Mittel zu schäbig und keine Lüge zu dreist,** als dass sie nicht benutzt würden. Aber der Clou ist, dass diese Masche immer noch funktioniert, wenn nicht sogar immer besser. Ist das alles wirklich so schwer zu durchschauen? Mir fehlen langsam die Worte. **Aktuell werden sowohl in der Europäischen Union als auch in Deutschland** riesige Milliardenpakete für die [Aufrüstung](https://transition-news.org/eu-halt-weiter-kurs-auf-krieg-hunderte-milliarden-fur-aufrustung-beschlossen) – also für die Rüstungsindustrie – geschnürt. Die EU will 800 Milliarden Euro locker machen, in Deutschland sollen es 500 Milliarden «Sondervermögen» sein. Verteidigung nennen das unsere «Führer», innerhalb der Union und auch an «unserer Ostflanke», der Ukraine. **Das nötige Feindbild konnte inzwischen signifikant erweitert werden.** Schuld an allem und zudem gefährlich ist nicht mehr nur Putin, sondern jetzt auch Trump. Europa müsse sich sowohl gegen Russland als auch gegen die USA schützen und rüsten, wird uns eingetrichtert. **Und während durch Diplomatie genau dieser beiden Staaten** gerade endlich mal Bewegung in die Bemühungen um einen Frieden oder wenigstens einen Waffenstillstand in der Ukraine kommt, rasselt man im moralisch überlegenen Zeigefinger-Europa so richtig mit dem Säbel. **Begleitet und gestützt wird der ganze Prozess** – wie sollte es anders sein – von den «Qualitätsmedien». Dass Russland einen Angriff auf «Europa» plant, weiß nicht nur der deutsche Verteidigungsminister (und mit Abstand beliebteste Politiker) Pistorius, sondern dank ihnen auch jedes Kind. Uns bleiben nur noch wenige Jahre. Zum Glück bereitet sich die Bundeswehr schon sehr konkret [auf einen Krieg](https://archive.is/VE8ZM) vor. **Die** ***FAZ*** **und Corona-Gesundheitsminister Spahn markieren einen traurigen Höhepunkt.** Hier haben sich «politische und publizistische Verantwortungslosigkeit propagandistisch gegenseitig befruchtet», wie es bei den *NachDenkSeiten* [heißt](https://www.nachdenkseiten.de/?p=130064). Die Aussage Spahns in dem Interview, «der Russe steht vor der Tür», ist das eine. Die Zeitung verschärfte die Sache jedoch, indem sie das Zitat explizit in den [Titel](https://archive.is/QJdID) übernahm, der in einer [ersten Version](https://archive.is/fNuGA) scheinbar zu harmlos war. **Eine große Mehrheit der deutschen Bevölkerung findet Aufrüstung und mehr Schulden toll,** wie *[ARD](https://archive.is/M3DSk)* und *[ZDF](https://archive.is/ggvJB)* sehr passend ermittelt haben wollen. Ähnliches gelte für eine noch stärkere militärische Unterstützung der Ukraine. Etwas skeptischer seien die Befragten bezüglich der Entsendung von Bundeswehrsoldaten dorthin, aber immerhin etwa fifty-fifty. **Eigentlich ist jedoch die Meinung der Menschen in «unseren Demokratien» irrelevant.** Sowohl in der Europäischen Union als auch in Deutschland sind die «Eliten» offenbar der Ansicht, der Souverän habe in Fragen von Krieg und Frieden sowie von aberwitzigen astronomischen Schulden kein Wörtchen mitzureden. Frau von der Leyen möchte über 150 Milliarden aus dem Gesamtpaket unter Verwendung von Artikel 122 des EU-Vertrags ohne das Europäische Parlament entscheiden – wenn auch nicht völlig [kritiklos](https://www.berliner-zeitung.de/politik-gesellschaft/geopolitik/aufruestung-widerstand-gegen-eu-plaene-waechst-kommission-uebertreibt-russische-gefahr-li.2306863). **In Deutschland wollen CDU/CSU und SPD zur Aufweichung der «Schuldenbremse»** mehrere Änderungen des Grundgesetzes durch das abgewählte Parlament peitschen. Dieser Versuch, mit dem alten [Bundestag](https://www.bundestag.de/dokumente/textarchiv/2025/kw11-de-sondersitzung-1056228) eine Zweidrittelmehrheit zu erzielen, die im neuen nicht mehr gegeben wäre, ist mindestens verfassungsrechtlich umstritten. **Das Manöver scheint aber zu funktionieren.** Heute haben die Grünen [zugestimmt](https://www.reuters.com/world/europe/germany-faces-debt-deal-cliffhanger-merz-strives-greens-backing-2025-03-14/), nachdem Kanzlerkandidat Merz läppische 100 Milliarden für «irgendwas mit Klima» zugesichert hatte. Die Abstimmung im Plenum soll am kommenden Dienstag erfolgen – nur eine Woche, bevor sich der neu gewählte Bundestag konstituieren wird. **Interessant sind die Argumente, die BlackRocker Merz für seine Attacke** auf Grundgesetz und Demokratie ins Feld führt. Abgesehen von der angeblichen Eile, «unsere Verteidigungsfähigkeit deutlich zu erhöhen» (ausgelöst unter anderem durch «die Münchner Sicherheitskonferenz und die Ereignisse im Weißen Haus»), ließ uns der CDU-Chef wissen, dass Deutschland einfach auf die internationale Bühne zurück müsse. Merz [schwadronierte](https://x.com/CDU/status/1900168761686044894) gefährlich mehrdeutig: > «Die ganze Welt schaut in diesen Tagen und Wochen auf Deutschland. Wir haben in der Europäischen Union und auf der Welt eine Aufgabe, die weit über die Grenzen unseres eigenen Landes hinausgeht.»      *\[Titelbild:* *[Tag des Sieges](https://pixabay.com/de/photos/parade-tag-des-sieges-samara-182508/)]* *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/propaganda-wahnsinn-und-demokratur)*** erschienen. @ 8cb60e21:5f2deaea
2024-08-24 21:27:00<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/div>" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-08-24 21:27:00<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/div>" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ b8916ce2:bd2a5f00
2025-03-27 09:30:42VA88 là một nền tảng giải trí trực tuyến nổi bật, mang đến cho người tham gia những trải nghiệm phong phú và hấp dẫn, từ những trò chơi thú vị đến các sự kiện độc đáo. Với giao diện được thiết kế đơn giản nhưng tinh tế, người dùng có thể dễ dàng truy cập và tham gia vào các hoạt động giải trí mà không gặp phải bất kỳ khó khăn nào. VA88 không chỉ cung cấp một loạt các trò chơi giải trí đa dạng, mà còn liên tục tổ chức các sự kiện và thử thách, giúp người tham gia có cơ hội khám phá nhiều điều mới mẻ. Nền tảng này đặc biệt chú trọng đến việc tối ưu hóa trải nghiệm người dùng, từ việc cung cấp các trò chơi dễ tiếp cận cho người mới bắt đầu đến những thử thách khó khăn dành cho những ai yêu thích sự mạo hiểm và sự cạnh tranh. Chính sự kết hợp hoàn hảo giữa tính đa dạng và tính năng thân thiện với người dùng đã giúp VA88 xây dựng được một cộng đồng giải trí vững mạnh và thu hút lượng người tham gia đông đảo. Ngoài sự đa dạng về các trò chơi, <a href="https://va88-online.com">VA88</a> cũng đặc biệt chú trọng đến việc bảo mật thông tin và sự an toàn của người tham gia. Nền tảng này sử dụng các công nghệ bảo mật tiên tiến để đảm bảo rằng mọi giao dịch và dữ liệu cá nhân của người dùng đều được bảo vệ một cách an toàn tuyệt đối. Những biện pháp bảo mật này không chỉ giúp người tham gia yên tâm khi tham gia các trò chơi mà còn đảm bảo rằng mọi giao dịch tài chính diễn ra một cách minh bạch và bảo mật. VA88 cam kết bảo vệ quyền lợi của người tham gia bằng cách cung cấp một môi trường chơi công bằng, nơi mọi người có thể thoải mái tham gia mà không lo ngại về sự xâm phạm thông tin cá nhân. Bằng việc áp dụng các công nghệ bảo mật hàng đầu và tạo ra một môi trường an toàn, VA88 đã trở thành một lựa chọn đáng tin cậy cho những ai tìm kiếm một không gian giải trí trực tuyến an toàn và bảo mật. Với tầm nhìn luôn hướng đến sự đổi mới và cải tiến, VA88 không ngừng nỗ lực mang đến những tính năng và trò chơi mới mẻ để đáp ứng nhu cầu ngày càng cao của người tham gia. Những sự kiện đặc biệt và các chương trình khuyến mãi luôn được tổ chức để người tham gia có thể tận hưởng nhiều cơ hội thú vị và phần thưởng hấp dẫn. VA88 luôn chủ động lắng nghe phản hồi từ cộng đồng để cải thiện dịch vụ và đảm bảo mang đến trải nghiệm giải trí tốt nhất. Bên cạnh đó, nền tảng này cũng tạo cơ hội cho người tham gia kết nối và giao lưu với nhau, giúp xây dựng một cộng đồng vững mạnh và thân thiện. Chính nhờ vào những cải tiến liên tục và sự tập trung vào nhu cầu của người dùng, VA88 đã khẳng định được vị thế của mình trong cộng đồng giải trí trực tuyến, trở thành một điểm đến lý tưởng cho những ai tìm kiếm một không gian thư giãn và đầy thử thách.
@ b8916ce2:bd2a5f00
2025-03-27 09:30:42VA88 là một nền tảng giải trí trực tuyến nổi bật, mang đến cho người tham gia những trải nghiệm phong phú và hấp dẫn, từ những trò chơi thú vị đến các sự kiện độc đáo. Với giao diện được thiết kế đơn giản nhưng tinh tế, người dùng có thể dễ dàng truy cập và tham gia vào các hoạt động giải trí mà không gặp phải bất kỳ khó khăn nào. VA88 không chỉ cung cấp một loạt các trò chơi giải trí đa dạng, mà còn liên tục tổ chức các sự kiện và thử thách, giúp người tham gia có cơ hội khám phá nhiều điều mới mẻ. Nền tảng này đặc biệt chú trọng đến việc tối ưu hóa trải nghiệm người dùng, từ việc cung cấp các trò chơi dễ tiếp cận cho người mới bắt đầu đến những thử thách khó khăn dành cho những ai yêu thích sự mạo hiểm và sự cạnh tranh. Chính sự kết hợp hoàn hảo giữa tính đa dạng và tính năng thân thiện với người dùng đã giúp VA88 xây dựng được một cộng đồng giải trí vững mạnh và thu hút lượng người tham gia đông đảo. Ngoài sự đa dạng về các trò chơi, <a href="https://va88-online.com">VA88</a> cũng đặc biệt chú trọng đến việc bảo mật thông tin và sự an toàn của người tham gia. Nền tảng này sử dụng các công nghệ bảo mật tiên tiến để đảm bảo rằng mọi giao dịch và dữ liệu cá nhân của người dùng đều được bảo vệ một cách an toàn tuyệt đối. Những biện pháp bảo mật này không chỉ giúp người tham gia yên tâm khi tham gia các trò chơi mà còn đảm bảo rằng mọi giao dịch tài chính diễn ra một cách minh bạch và bảo mật. VA88 cam kết bảo vệ quyền lợi của người tham gia bằng cách cung cấp một môi trường chơi công bằng, nơi mọi người có thể thoải mái tham gia mà không lo ngại về sự xâm phạm thông tin cá nhân. Bằng việc áp dụng các công nghệ bảo mật hàng đầu và tạo ra một môi trường an toàn, VA88 đã trở thành một lựa chọn đáng tin cậy cho những ai tìm kiếm một không gian giải trí trực tuyến an toàn và bảo mật. Với tầm nhìn luôn hướng đến sự đổi mới và cải tiến, VA88 không ngừng nỗ lực mang đến những tính năng và trò chơi mới mẻ để đáp ứng nhu cầu ngày càng cao của người tham gia. Những sự kiện đặc biệt và các chương trình khuyến mãi luôn được tổ chức để người tham gia có thể tận hưởng nhiều cơ hội thú vị và phần thưởng hấp dẫn. VA88 luôn chủ động lắng nghe phản hồi từ cộng đồng để cải thiện dịch vụ và đảm bảo mang đến trải nghiệm giải trí tốt nhất. Bên cạnh đó, nền tảng này cũng tạo cơ hội cho người tham gia kết nối và giao lưu với nhau, giúp xây dựng một cộng đồng vững mạnh và thân thiện. Chính nhờ vào những cải tiến liên tục và sự tập trung vào nhu cầu của người dùng, VA88 đã khẳng định được vị thế của mình trong cộng đồng giải trí trực tuyến, trở thành một điểm đến lý tưởng cho những ai tìm kiếm một không gian thư giãn và đầy thử thách. @ 8cb60e21:5f2deaea
2024-08-24 00:10:45<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/858xjX2VN_I" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-08-24 00:10:45<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/858xjX2VN_I" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 8cb60e21:5f2deaea
2024-08-22 22:06:11<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/E2sc9PK2RWg" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-08-22 22:06:11<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/E2sc9PK2RWg" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ da0b9bc3:4e30a4a9
2025-03-28 07:27:06Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/927569
@ da0b9bc3:4e30a4a9
2025-03-28 07:27:06Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/927569 @ 8cb60e21:5f2deaea
2024-08-21 21:37:35<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/NR_2KJZi3Ac" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-08-21 21:37:35<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/NR_2KJZi3Ac" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ b8916ce2:bd2a5f00
2025-03-27 09:29:29VF88 mang đến cho người tham gia một không gian giải trí trực tuyến đầy thú vị, sáng tạo và đa dạng. Với giao diện thân thiện và dễ sử dụng, nền tảng này giúp người dùng dễ dàng tiếp cận và tham gia vào các hoạt động giải trí mà không gặp phải bất kỳ khó khăn nào. Các trò chơi trên VF88 được thiết kế tinh tế, đáp ứng nhu cầu của những người tham gia, dù là người mới bắt đầu hay đã có kinh nghiệm lâu dài. Không chỉ có các trò chơi thú vị, nền tảng này còn thường xuyên tổ chức các sự kiện đặc biệt và thử thách đầy hấp dẫn, tạo ra cơ hội để người tham gia trải nghiệm những điều mới mẻ và thú vị. Từ các trò chơi trí tuệ giúp rèn luyện khả năng tư duy đến những trò giải trí nhẹ nhàng giúp thư giãn, <a href="https://vf88.site">VF88</a> luôn có một danh mục đa dạng, phục vụ mọi sở thích của người dùng. Chính sự đa dạng này đã giúp VF88 trở thành một điểm đến lý tưởng cho những ai yêu thích khám phá và tìm kiếm một không gian giải trí năng động và đầy thử thách. Một yếu tố quan trọng làm nên sự thành công của VF88 chính là cam kết bảo mật và an toàn cho người tham gia. Nền tảng này sử dụng những công nghệ bảo mật tiên tiến nhất để bảo vệ thông tin cá nhân và dữ liệu người dùng một cách tuyệt đối. Mọi giao dịch và thông tin liên quan đều được mã hóa và xử lý theo các tiêu chuẩn bảo mật quốc tế, giúp người tham gia hoàn toàn yên tâm khi tham gia vào các hoạt động trên nền tảng. Ngoài việc bảo vệ sự riêng tư của người dùng, VF88 cũng cam kết cung cấp một môi trường chơi an toàn và công bằng, với các biện pháp chống gian lận và bảo vệ quyền lợi của người tham gia. Điều này không chỉ tạo sự an tâm cho người dùng mà còn xây dựng được lòng tin mạnh mẽ trong cộng đồng, giúp VF88 duy trì được uy tín và vị thế của mình trên thị trường giải trí trực tuyến. VF88 luôn không ngừng cải tiến và đổi mới để mang lại những trải nghiệm tối ưu nhất cho người tham gia. Nền tảng này luôn cập nhật những tính năng mới và tổ chức các chương trình khuyến mãi hấp dẫn, giúp người tham gia có thêm nhiều cơ hội trải nghiệm và khám phá. Ngoài ra, VF88 cũng tạo ra một cộng đồng mạnh mẽ và thân thiện, nơi người dùng có thể giao lưu, chia sẻ kinh nghiệm và kết nối với những người cùng sở thích. Các sự kiện đặc biệt và thử thách thường xuyên được tổ chức để tăng thêm phần thú vị và kịch tính cho người tham gia. Sự sáng tạo không ngừng của VF88 trong việc cải thiện dịch vụ đã giúp nền tảng này luôn giữ được sự mới mẻ, hấp dẫn, và là một lựa chọn giải trí lý tưởng cho mọi người. Với những đặc điểm này, VF88 đã khẳng định được vị thế của mình trong cộng đồng giải trí trực tuyến và là một điểm đến không thể thiếu cho những ai tìm kiếm trải nghiệm giải trí tuyệt vời.
@ b8916ce2:bd2a5f00
2025-03-27 09:29:29VF88 mang đến cho người tham gia một không gian giải trí trực tuyến đầy thú vị, sáng tạo và đa dạng. Với giao diện thân thiện và dễ sử dụng, nền tảng này giúp người dùng dễ dàng tiếp cận và tham gia vào các hoạt động giải trí mà không gặp phải bất kỳ khó khăn nào. Các trò chơi trên VF88 được thiết kế tinh tế, đáp ứng nhu cầu của những người tham gia, dù là người mới bắt đầu hay đã có kinh nghiệm lâu dài. Không chỉ có các trò chơi thú vị, nền tảng này còn thường xuyên tổ chức các sự kiện đặc biệt và thử thách đầy hấp dẫn, tạo ra cơ hội để người tham gia trải nghiệm những điều mới mẻ và thú vị. Từ các trò chơi trí tuệ giúp rèn luyện khả năng tư duy đến những trò giải trí nhẹ nhàng giúp thư giãn, <a href="https://vf88.site">VF88</a> luôn có một danh mục đa dạng, phục vụ mọi sở thích của người dùng. Chính sự đa dạng này đã giúp VF88 trở thành một điểm đến lý tưởng cho những ai yêu thích khám phá và tìm kiếm một không gian giải trí năng động và đầy thử thách. Một yếu tố quan trọng làm nên sự thành công của VF88 chính là cam kết bảo mật và an toàn cho người tham gia. Nền tảng này sử dụng những công nghệ bảo mật tiên tiến nhất để bảo vệ thông tin cá nhân và dữ liệu người dùng một cách tuyệt đối. Mọi giao dịch và thông tin liên quan đều được mã hóa và xử lý theo các tiêu chuẩn bảo mật quốc tế, giúp người tham gia hoàn toàn yên tâm khi tham gia vào các hoạt động trên nền tảng. Ngoài việc bảo vệ sự riêng tư của người dùng, VF88 cũng cam kết cung cấp một môi trường chơi an toàn và công bằng, với các biện pháp chống gian lận và bảo vệ quyền lợi của người tham gia. Điều này không chỉ tạo sự an tâm cho người dùng mà còn xây dựng được lòng tin mạnh mẽ trong cộng đồng, giúp VF88 duy trì được uy tín và vị thế của mình trên thị trường giải trí trực tuyến. VF88 luôn không ngừng cải tiến và đổi mới để mang lại những trải nghiệm tối ưu nhất cho người tham gia. Nền tảng này luôn cập nhật những tính năng mới và tổ chức các chương trình khuyến mãi hấp dẫn, giúp người tham gia có thêm nhiều cơ hội trải nghiệm và khám phá. Ngoài ra, VF88 cũng tạo ra một cộng đồng mạnh mẽ và thân thiện, nơi người dùng có thể giao lưu, chia sẻ kinh nghiệm và kết nối với những người cùng sở thích. Các sự kiện đặc biệt và thử thách thường xuyên được tổ chức để tăng thêm phần thú vị và kịch tính cho người tham gia. Sự sáng tạo không ngừng của VF88 trong việc cải thiện dịch vụ đã giúp nền tảng này luôn giữ được sự mới mẻ, hấp dẫn, và là một lựa chọn giải trí lý tưởng cho mọi người. Với những đặc điểm này, VF88 đã khẳng định được vị thế của mình trong cộng đồng giải trí trực tuyến và là một điểm đến không thể thiếu cho những ai tìm kiếm trải nghiệm giải trí tuyệt vời. @ a95c6243:d345522c
2025-03-11 10:22:36**«Wir brauchen eine digitale Brandmauer gegen den Faschismus»,** [schreibt](https://www.ccc.de/de/updates/2025/ccc-fordert-digitale-brandmauer) der Chaos Computer Club (CCC) auf seiner Website. Unter diesem Motto präsentierte er letzte Woche einen Forderungskatalog, mit dem sich 24 Organisationen an die kommende Bundesregierung wenden. Der Koalitionsvertrag müsse sich daran messen lassen, verlangen sie. **In den drei Kategorien «Bekenntnis gegen Überwachung»,** «Schutz und Sicherheit für alle» sowie «Demokratie im digitalen Raum» stellen die [Unterzeichner](https://d-64.org/digitale-brandmauer/), zu denen auch Amnesty International und Das NETTZ gehören, unter anderem die folgenden «Mindestanforderungen»: * Verbot biometrischer Massenüberwachung des öffentlichen Raums sowie der ungezielten biometrischen Auswertung des Internets. * Anlasslose und massenhafte Vorratsdatenspeicherung wird abgelehnt. * Automatisierte Datenanalysen der Informationsbestände der Strafverfolgungsbehörden sowie jede Form von Predictive Policing oder automatisiertes Profiling von Menschen werden abgelehnt. * Einführung eines Rechts auf Verschlüsselung. Die Bundesregierung soll sich dafür einsetzen, die Chatkontrolle auf europäischer Ebene zu verhindern. * Anonyme und pseudonyme Nutzung des Internets soll geschützt und ermöglicht werden. * Bekämpfung «privaten Machtmissbrauchs von Big-Tech-Unternehmen» durch durchsetzungsstarke, unabhängige und grundsätzlich föderale Aufsichtsstrukturen. * Einführung eines digitalen Gewaltschutzgesetzes, unter Berücksichtigung «gruppenbezogener digitaler Gewalt» und die Förderung von Beratungsangeboten. * Ein umfassendes Förderprogramm für digitale öffentliche Räume, die dezentral organisiert und quelloffen programmiert sind, soll aufgelegt werden. **Es sei ein Irrglaube, dass zunehmende Überwachung einen Zugewinn an Sicherheit darstelle,** ist eines der Argumente der Initiatoren. Sicherheit erfordere auch, dass Menschen anonym und vertraulich kommunizieren können und ihre Privatsphäre geschützt wird. **Gesunde digitale Räume lebten auch von einem demokratischen Diskurs,** lesen wir in dem Papier. Es sei Aufgabe des Staates, Grundrechte zu schützen. Dazu gehöre auch, Menschenrechte und demokratische Werte, insbesondere Freiheit, Gleichheit und Solidarität zu fördern sowie den Missbrauch von Maßnahmen, Befugnissen und Infrastrukturen durch «die Feinde der Demokratie» zu verhindern. **Man ist geneigt zu fragen, wo denn die Autoren «den Faschismus» sehen,** den es zu bekämpfen gelte. Die meisten der vorgetragenen Forderungen und Argumente finden sicher breite Unterstützung, denn sie beschreiben offenkundig gängige, kritikwürdige Praxis. Die Aushebelung der Privatsphäre, der Redefreiheit und anderer Grundrechte im Namen der Sicherheit wird bereits jetzt massiv durch die aktuellen «demokratischen Institutionen» und ihre «durchsetzungsstarken Aufsichtsstrukturen» betrieben. **Ist «der Faschismus» also die EU und ihre Mitgliedsstaaten?** Nein, die «faschistische Gefahr», gegen die man eine digitale Brandmauer will, kommt nach Ansicht des CCC und seiner Partner aus den Vereinigten Staaten. Private Überwachung und Machtkonzentration sind dabei weltweit schon lange Realität, jetzt endlich müssen sie jedoch bekämpft werden. In dem Papier heißt es: > «Die willkürliche und antidemokratische Machtausübung der Tech-Oligarchen um Präsident Trump erfordert einen Paradigmenwechsel in der deutschen Digitalpolitik. (...) Die aktuellen Geschehnisse in den USA zeigen auf, wie Datensammlungen und -analyse genutzt werden können, um einen Staat handstreichartig zu übernehmen, seine Strukturen nachhaltig zu beschädigen, Widerstand zu unterbinden und marginalisierte Gruppen zu verfolgen.» **Wer auf der anderen Seite dieser Brandmauer stehen soll, ist also klar.** Es sind die gleichen «Feinde unserer Demokratie», die seit Jahren in diese Ecke gedrängt werden. Es sind die gleichen Andersdenkenden, Regierungskritiker und Friedensforderer, die unter dem großzügigen Dach des Bundesprogramms «Demokratie leben» einem «kontinuierlichen Echt- und Langzeitmonitoring» wegen der Etikettierung [«digitaler Hass»](https://bag-gegen-hass.net/) unterzogen werden. **Dass die 24 Organisationen praktisch auch die Bekämpfung von Google,** Microsoft, Apple, Amazon und anderen fordern, entbehrt nicht der Komik. Diese fallen aber sicher unter das Stichwort «Machtmissbrauch von Big-Tech-Unternehmen». Gleichzeitig verlangen die Lobbyisten implizit zum Beispiel die Förderung des [Nostr](https://reason.com/video/2024/09/17/is-nostr-an-antidote-to-social-media-censorship/)-Netzwerks, denn hier finden wir dezentral organisierte und quelloffen programmierte digitale Räume par excellence, obendrein zensurresistent. Das wiederum dürfte in der Politik weniger gut ankommen. *\[Titelbild:* *[Pixabay](https://pixabay.com/de/illustrations/uns-ihnen-stammes-wettbewerb-1767691/)]* *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/digitale-brandmauer-gegen-den-faschismus-von-der-kunftigen-bundesregierung)*** erschienen.
@ a95c6243:d345522c
2025-03-11 10:22:36**«Wir brauchen eine digitale Brandmauer gegen den Faschismus»,** [schreibt](https://www.ccc.de/de/updates/2025/ccc-fordert-digitale-brandmauer) der Chaos Computer Club (CCC) auf seiner Website. Unter diesem Motto präsentierte er letzte Woche einen Forderungskatalog, mit dem sich 24 Organisationen an die kommende Bundesregierung wenden. Der Koalitionsvertrag müsse sich daran messen lassen, verlangen sie. **In den drei Kategorien «Bekenntnis gegen Überwachung»,** «Schutz und Sicherheit für alle» sowie «Demokratie im digitalen Raum» stellen die [Unterzeichner](https://d-64.org/digitale-brandmauer/), zu denen auch Amnesty International und Das NETTZ gehören, unter anderem die folgenden «Mindestanforderungen»: * Verbot biometrischer Massenüberwachung des öffentlichen Raums sowie der ungezielten biometrischen Auswertung des Internets. * Anlasslose und massenhafte Vorratsdatenspeicherung wird abgelehnt. * Automatisierte Datenanalysen der Informationsbestände der Strafverfolgungsbehörden sowie jede Form von Predictive Policing oder automatisiertes Profiling von Menschen werden abgelehnt. * Einführung eines Rechts auf Verschlüsselung. Die Bundesregierung soll sich dafür einsetzen, die Chatkontrolle auf europäischer Ebene zu verhindern. * Anonyme und pseudonyme Nutzung des Internets soll geschützt und ermöglicht werden. * Bekämpfung «privaten Machtmissbrauchs von Big-Tech-Unternehmen» durch durchsetzungsstarke, unabhängige und grundsätzlich föderale Aufsichtsstrukturen. * Einführung eines digitalen Gewaltschutzgesetzes, unter Berücksichtigung «gruppenbezogener digitaler Gewalt» und die Förderung von Beratungsangeboten. * Ein umfassendes Förderprogramm für digitale öffentliche Räume, die dezentral organisiert und quelloffen programmiert sind, soll aufgelegt werden. **Es sei ein Irrglaube, dass zunehmende Überwachung einen Zugewinn an Sicherheit darstelle,** ist eines der Argumente der Initiatoren. Sicherheit erfordere auch, dass Menschen anonym und vertraulich kommunizieren können und ihre Privatsphäre geschützt wird. **Gesunde digitale Räume lebten auch von einem demokratischen Diskurs,** lesen wir in dem Papier. Es sei Aufgabe des Staates, Grundrechte zu schützen. Dazu gehöre auch, Menschenrechte und demokratische Werte, insbesondere Freiheit, Gleichheit und Solidarität zu fördern sowie den Missbrauch von Maßnahmen, Befugnissen und Infrastrukturen durch «die Feinde der Demokratie» zu verhindern. **Man ist geneigt zu fragen, wo denn die Autoren «den Faschismus» sehen,** den es zu bekämpfen gelte. Die meisten der vorgetragenen Forderungen und Argumente finden sicher breite Unterstützung, denn sie beschreiben offenkundig gängige, kritikwürdige Praxis. Die Aushebelung der Privatsphäre, der Redefreiheit und anderer Grundrechte im Namen der Sicherheit wird bereits jetzt massiv durch die aktuellen «demokratischen Institutionen» und ihre «durchsetzungsstarken Aufsichtsstrukturen» betrieben. **Ist «der Faschismus» also die EU und ihre Mitgliedsstaaten?** Nein, die «faschistische Gefahr», gegen die man eine digitale Brandmauer will, kommt nach Ansicht des CCC und seiner Partner aus den Vereinigten Staaten. Private Überwachung und Machtkonzentration sind dabei weltweit schon lange Realität, jetzt endlich müssen sie jedoch bekämpft werden. In dem Papier heißt es: > «Die willkürliche und antidemokratische Machtausübung der Tech-Oligarchen um Präsident Trump erfordert einen Paradigmenwechsel in der deutschen Digitalpolitik. (...) Die aktuellen Geschehnisse in den USA zeigen auf, wie Datensammlungen und -analyse genutzt werden können, um einen Staat handstreichartig zu übernehmen, seine Strukturen nachhaltig zu beschädigen, Widerstand zu unterbinden und marginalisierte Gruppen zu verfolgen.» **Wer auf der anderen Seite dieser Brandmauer stehen soll, ist also klar.** Es sind die gleichen «Feinde unserer Demokratie», die seit Jahren in diese Ecke gedrängt werden. Es sind die gleichen Andersdenkenden, Regierungskritiker und Friedensforderer, die unter dem großzügigen Dach des Bundesprogramms «Demokratie leben» einem «kontinuierlichen Echt- und Langzeitmonitoring» wegen der Etikettierung [«digitaler Hass»](https://bag-gegen-hass.net/) unterzogen werden. **Dass die 24 Organisationen praktisch auch die Bekämpfung von Google,** Microsoft, Apple, Amazon und anderen fordern, entbehrt nicht der Komik. Diese fallen aber sicher unter das Stichwort «Machtmissbrauch von Big-Tech-Unternehmen». Gleichzeitig verlangen die Lobbyisten implizit zum Beispiel die Förderung des [Nostr](https://reason.com/video/2024/09/17/is-nostr-an-antidote-to-social-media-censorship/)-Netzwerks, denn hier finden wir dezentral organisierte und quelloffen programmierte digitale Räume par excellence, obendrein zensurresistent. Das wiederum dürfte in der Politik weniger gut ankommen. *\[Titelbild:* *[Pixabay](https://pixabay.com/de/illustrations/uns-ihnen-stammes-wettbewerb-1767691/)]* *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/digitale-brandmauer-gegen-den-faschismus-von-der-kunftigen-bundesregierung)*** erschienen. @ 8cb60e21:5f2deaea
2024-08-21 21:37:35# hello world
@ 8cb60e21:5f2deaea
2024-08-21 21:37:35# hello world @ 25191283:a4823315
2024-08-21 13:37:49This is Olive Grove Eggs, a brand new site from Huevos del Olivar that's just getting started. Things will be up and running here shortly, but you can [subscribe](#/portal/) in the meantime if you'd like to stay up to date and receive emails when new content is published!
@ 25191283:a4823315
2024-08-21 13:37:49This is Olive Grove Eggs, a brand new site from Huevos del Olivar that's just getting started. Things will be up and running here shortly, but you can [subscribe](#/portal/) in the meantime if you'd like to stay up to date and receive emails when new content is published! @ a3bb06f6:19ac1b11
2025-03-28 02:36:38“Until you make the unconscious conscious, it will continue to direct your life, and you will call it fate.” — Carl Jung Most people don’t realize they’ve been robbed. Not in the dramatic, wallet-snatching sense, but in a quiet, systemic way that’s gone unnoticed for generations. If you’re feeling like no matter how hard you work, you can’t get ahead… you’re not imagining it. It didn’t start as a scheme—*but one compromise after another*, it became one. Now, the system exploits you by design. This isn’t fate. It’s fiat. The Unconscious Script: How Fiat Becomes Invisible From the moment you're born, you're placed into an economic system based on government-issued fiat currency. It becomes the air you breathe. You work for dollars. You save in dollars. You price **your time**, **your future**, and even **your dreams** in dollars. But few stop to ask: What actually is a dollar? Who creates it? Why does it lose value? This lack of questioning is the unconscious state. Fiat money is the background process running your life. You feel the effects—rising prices, shrinking savings, mounting debt—but you never see the root cause. So you blame yourself. Or “the economy.” Or call it fate. The Lie of Neutral Money: Most believe money is just a neutral tool. But fiat is not neutral—it’s political power encoded into paper. Governments can **print more of it at will**. Central banks can manipulate its supply, distort interest rates, and quietly tax you through inflation. Every time more money is created, your purchasing power shrinks. But it happens slowly, like a leak in a tire. You don’t notice at first. You just feel like you’re working harder for less. The house is further out of reach. The groceries cost more. Retirement feels impossible. And you accept it. Because no one told you it's designed this way. <img src="https://blossom.primal.net/80cb04b171e15d56d1224a1458f0ca3ad9a440915c736e145186df1cc2f4979b.png"> Inflation Is the Invisible Thief, Inflation isn’t just a “cost of living increase.” It’s a state-sponsored form of theft. When new money is created, it enters the system unevenly. Those closest to the money printer—banks, governments, **large corporations**—get the new dollars first. By the time it reaches you, prices have already risen. You’re buying the same goods with weaker money. And yet, most people still save in fiat. They’re taught that hoarding cash is “safe.” They’re taught that 2% inflation is “normal.” But it’s not normal to work 40 hours a week and fall behind. That’s the product of unconscious acceptance. The fiat system survives on one thing: your **ignorance**. It didn’t begin with malicious intent, but over time, it adapted to protect its own power—at your expense. As long as you don’t understand how money works, you won’t resist. You’ll blame yourself, or *capitalism*, or bad luck. **But never the system itself**. This is why financial education is *never* prioritized in schools. This is why questioning monetary policy is left to economists and suits on CNBC. You were never taught how it works. And now the system depends on you staying confused—grinding, borrowing, complying, without ever asking why. Making the Unconscious Conscious: Enter **Bitcoin**, Bitcoin breaks this spell. <img src="https://blossom.primal.net/8373eb52ee7773e0ffc4591819ff984a27829e47741894456258e2a638029022.png"> It forces you to confront the nature of money—what it is, how it’s created, and why fiat fails. It teaches you that money doesn’t need to be printed, inflated, or controlled. That money can be fixed, finite, and **fair**. Bitcoin is not just a new currency. It’s a tool of consciousness. It exposes the scam of fiat and offers a lifeboat to anyone ready to wake up. Once you understand Bitcoin, you can’t unsee the problem. You begin to ask: Why should I trust a system that steals my **time**? Why is saving discouraged, but debt rewarded? Why do I need permission to use my own money? These aren’t technical questions. They’re **moral** ones. Consciousness Is Sovereignty: When you understand what fiat is, you stop calling your financial struggles “fate.” You start calling them what they are, outcomes of a broken system. And once you see the system for what it is, you can choose to **exit**. <img src="https://blossom.primal.net/a8766caf9dc043fa360dbf7c5e473201d72dfeede02a7f08abc9897367a33011.png"> Saving in Bitcoin is not speculation. It’s self-defense. It’s rejecting unconscious servitude. It’s reclaiming your **time**, your **labor**, your **future**. In a fiat world, they own the money—so they own the rules. In a Bitcoin world, you own yourself. That’s the power of making the unconscious conscious. And that’s how you stop calling it fate.
@ a3bb06f6:19ac1b11
2025-03-28 02:36:38“Until you make the unconscious conscious, it will continue to direct your life, and you will call it fate.” — Carl Jung Most people don’t realize they’ve been robbed. Not in the dramatic, wallet-snatching sense, but in a quiet, systemic way that’s gone unnoticed for generations. If you’re feeling like no matter how hard you work, you can’t get ahead… you’re not imagining it. It didn’t start as a scheme—*but one compromise after another*, it became one. Now, the system exploits you by design. This isn’t fate. It’s fiat. The Unconscious Script: How Fiat Becomes Invisible From the moment you're born, you're placed into an economic system based on government-issued fiat currency. It becomes the air you breathe. You work for dollars. You save in dollars. You price **your time**, **your future**, and even **your dreams** in dollars. But few stop to ask: What actually is a dollar? Who creates it? Why does it lose value? This lack of questioning is the unconscious state. Fiat money is the background process running your life. You feel the effects—rising prices, shrinking savings, mounting debt—but you never see the root cause. So you blame yourself. Or “the economy.” Or call it fate. The Lie of Neutral Money: Most believe money is just a neutral tool. But fiat is not neutral—it’s political power encoded into paper. Governments can **print more of it at will**. Central banks can manipulate its supply, distort interest rates, and quietly tax you through inflation. Every time more money is created, your purchasing power shrinks. But it happens slowly, like a leak in a tire. You don’t notice at first. You just feel like you’re working harder for less. The house is further out of reach. The groceries cost more. Retirement feels impossible. And you accept it. Because no one told you it's designed this way. <img src="https://blossom.primal.net/80cb04b171e15d56d1224a1458f0ca3ad9a440915c736e145186df1cc2f4979b.png"> Inflation Is the Invisible Thief, Inflation isn’t just a “cost of living increase.” It’s a state-sponsored form of theft. When new money is created, it enters the system unevenly. Those closest to the money printer—banks, governments, **large corporations**—get the new dollars first. By the time it reaches you, prices have already risen. You’re buying the same goods with weaker money. And yet, most people still save in fiat. They’re taught that hoarding cash is “safe.” They’re taught that 2% inflation is “normal.” But it’s not normal to work 40 hours a week and fall behind. That’s the product of unconscious acceptance. The fiat system survives on one thing: your **ignorance**. It didn’t begin with malicious intent, but over time, it adapted to protect its own power—at your expense. As long as you don’t understand how money works, you won’t resist. You’ll blame yourself, or *capitalism*, or bad luck. **But never the system itself**. This is why financial education is *never* prioritized in schools. This is why questioning monetary policy is left to economists and suits on CNBC. You were never taught how it works. And now the system depends on you staying confused—grinding, borrowing, complying, without ever asking why. Making the Unconscious Conscious: Enter **Bitcoin**, Bitcoin breaks this spell. <img src="https://blossom.primal.net/8373eb52ee7773e0ffc4591819ff984a27829e47741894456258e2a638029022.png"> It forces you to confront the nature of money—what it is, how it’s created, and why fiat fails. It teaches you that money doesn’t need to be printed, inflated, or controlled. That money can be fixed, finite, and **fair**. Bitcoin is not just a new currency. It’s a tool of consciousness. It exposes the scam of fiat and offers a lifeboat to anyone ready to wake up. Once you understand Bitcoin, you can’t unsee the problem. You begin to ask: Why should I trust a system that steals my **time**? Why is saving discouraged, but debt rewarded? Why do I need permission to use my own money? These aren’t technical questions. They’re **moral** ones. Consciousness Is Sovereignty: When you understand what fiat is, you stop calling your financial struggles “fate.” You start calling them what they are, outcomes of a broken system. And once you see the system for what it is, you can choose to **exit**. <img src="https://blossom.primal.net/a8766caf9dc043fa360dbf7c5e473201d72dfeede02a7f08abc9897367a33011.png"> Saving in Bitcoin is not speculation. It’s self-defense. It’s rejecting unconscious servitude. It’s reclaiming your **time**, your **labor**, your **future**. In a fiat world, they own the money—so they own the rules. In a Bitcoin world, you own yourself. That’s the power of making the unconscious conscious. And that’s how you stop calling it fate. @ a95c6243:d345522c
2025-03-04 09:40:50**Die «Eliten» führen bereits groß angelegte Pilotprojekte für eine Zukunft durch,** die sie wollen und wir nicht. Das [schreibt](https://off-guardian.org/2025/02/26/coming-soon-the-european-digital-identity-wallet/) der *OffGuardian* in einem Update zum Thema «EU-Brieftasche für die digitale Identität». Das Portal weist darauf hin, dass die Akteure dabei nicht gerade zimperlich vorgehen und auch keinen Hehl aus ihren Absichten machen. *Transition News* hat mehrfach darüber berichtet, zuletzt [hier](https://transition-news.org/eudi-wallet-der-weg-fur-ein-vollstandig-digitalisiertes-europa-ist-frei) und [hier](https://transition-news.org/iata-biometrische-daten-und-digitale-id-machen-das-vollstandig-digitale). **Mit der EU Digital Identity Wallet (EUDI-Brieftasche) sei eine einzige von der Regierung herausgegebene App geplant,** die Ihre medizinischen Daten, Beschäftigungsdaten, Reisedaten, Bildungsdaten, Impfdaten, Steuerdaten, Finanzdaten sowie (potenziell) Kopien Ihrer Unterschrift, Fingerabdrücke, Gesichtsscans, Stimmproben und DNA enthält. So fasst der *OffGuardian* die eindrucksvolle Liste möglicher Einsatzbereiche zusammen. **Auch Dokumente wie der Personalausweis oder der** **[Führerschein](https://transition-news.org/eu-weite-einfuhrung-von-digitalen-fuhrerscheinen-fur-digitale-geldborsen)** können dort in elektronischer Form gespeichert werden. Bis 2026 sind alle EU-Mitgliedstaaten dazu verpflichtet, Ihren Bürgern funktionierende und frei verfügbare digitale «Brieftaschen» bereitzustellen. **Die Menschen würden diese App nutzen,** so das Portal, um Zahlungen vorzunehmen, Kredite zu beantragen, ihre Steuern zu zahlen, ihre Rezepte abzuholen, internationale Grenzen zu überschreiten, Unternehmen zu gründen, Arzttermine zu buchen, sich um Stellen zu bewerben und sogar digitale Verträge online zu unterzeichnen. **All diese Daten würden auf ihrem Mobiltelefon gespeichert und mit den Regierungen** von neunzehn Ländern (plus der Ukraine) sowie über 140 anderen öffentlichen und privaten Partnern ausgetauscht. Von der Deutschen Bank über das ukrainische Ministerium für digitalen Fortschritt bis hin zu Samsung Europe. Unternehmen und Behörden würden auf diese Daten im Backend zugreifen, um «automatisierte Hintergrundprüfungen» durchzuführen. **Der Bundesverband der Verbraucherzentralen und Verbraucherverbände** (VZBV) habe Bedenken geäußert, dass eine solche App «Risiken für den Schutz der Privatsphäre und der Daten» berge, berichtet das Portal. Die einzige Antwort darauf laute: «Richtig, genau dafür ist sie ja da!» **Das alles sei keine Hypothese, betont der** ***OffGuardian***. Es sei vielmehr [«Potential»](https://www.digital-identity-wallet.eu/about-us/140-public-and-private-partners/). Damit ist ein EU-Projekt gemeint, in dessen Rahmen Dutzende öffentliche und private Einrichtungen zusammenarbeiten, «um eine einheitliche Vision der digitalen Identität für die Bürger der europäischen Länder zu definieren». Dies ist nur eines der groß angelegten [Pilotprojekte](https://ec.europa.eu/digital-building-blocks/sites/display/EUDIGITALIDENTITYWALLET/What+are+the+Large+Scale+Pilot+Projects), mit denen Prototypen und Anwendungsfälle für die EUDI-Wallet getestet werden. Es gibt noch mindestens drei weitere. **Den Ball der digitalen ID-Systeme habe die Covid-«Pandemie»** über die «Impfpässe» ins Rollen gebracht. Seitdem habe das Thema an Schwung verloren. Je näher wir aber der vollständigen Einführung der EUid kämen, desto mehr Propaganda der Art «Warum wir eine digitale Brieftasche brauchen» könnten wir in den Mainstream-Medien erwarten, prognostiziert der *OffGuardian*. Vielleicht müssten wir schon nach dem nächsten großen «Grund», dem nächsten «katastrophalen katalytischen Ereignis» Ausschau halten. Vermutlich gebe es bereits Pläne, warum die Menschen plötzlich eine digitale ID-Brieftasche brauchen würden. **Die Entwicklung geht jedenfalls stetig weiter in genau diese Richtung.** Beispielsweise hat Jordanien angekündigt, die digitale biometrische ID bei den nächsten [Wahlen](https://www.biometricupdate.com/202502/jordan-plans-digital-id-for-voter-verification-in-next-election) zur Verifizierung der Wähler einzuführen. Man wolle «den Papierkrieg beenden und sicherstellen, dass die gesamte Kette bis zu den nächsten Parlamentswahlen digitalisiert wird», heißt es. Absehbar ist, dass dabei einige Wahlberechtigte «auf der Strecke bleiben» werden, wie im Fall von [Albanien](https://transition-news.org/albanien-schliesst-120-000-burger-ohne-biometrische-ausweise-von-wahlen-aus) geschehen. **Derweil würden die Briten gerne ihre Privatsphäre gegen Effizienz eintauschen,** [behauptet](https://www.lbc.co.uk/news/tony-blair-id-cards/) Tony Blair. Der Ex-Premier drängte kürzlich erneut auf digitale Identitäten und Gesichtserkennung. Blair ist Gründer einer [Denkfabrik](https://transition-news.org/blair-institute-durch-vermarktung-von-patientendaten-zu-ki-gestutztem) für globalen Wandel, Anhänger globalistischer Technokratie und [«moderner Infrastruktur»](https://transition-news.org/tony-blair-digitale-id-fur-moderne-infrastruktur-unerlasslich-erfordert-aber). **Abschließend warnt der** ***OffGuardian*** **vor der Illusion, Trump und Musk würden** den US-Bürgern «diesen Schlamassel ersparen». Das Department of Government Efficiency werde sich auf die digitale Identität stürzen. Was könne schließlich «effizienter» sein als eine einzige App, die für alles verwendet wird? Der Unterschied bestehe nur darin, dass die US-Version vielleicht eher privat als öffentlich sei – sofern es da überhaupt noch einen wirklichen Unterschied gebe. *\[Titelbild: Screenshot* *[OffGuardian](https://off-guardian.org/2025/02/26/coming-soon-the-european-digital-identity-wallet/)]* *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/demnachst-verfugbar-die-europaische-brieftasche-fur-digitale-identitaten)*** erschienen.
@ a95c6243:d345522c
2025-03-04 09:40:50**Die «Eliten» führen bereits groß angelegte Pilotprojekte für eine Zukunft durch,** die sie wollen und wir nicht. Das [schreibt](https://off-guardian.org/2025/02/26/coming-soon-the-european-digital-identity-wallet/) der *OffGuardian* in einem Update zum Thema «EU-Brieftasche für die digitale Identität». Das Portal weist darauf hin, dass die Akteure dabei nicht gerade zimperlich vorgehen und auch keinen Hehl aus ihren Absichten machen. *Transition News* hat mehrfach darüber berichtet, zuletzt [hier](https://transition-news.org/eudi-wallet-der-weg-fur-ein-vollstandig-digitalisiertes-europa-ist-frei) und [hier](https://transition-news.org/iata-biometrische-daten-und-digitale-id-machen-das-vollstandig-digitale). **Mit der EU Digital Identity Wallet (EUDI-Brieftasche) sei eine einzige von der Regierung herausgegebene App geplant,** die Ihre medizinischen Daten, Beschäftigungsdaten, Reisedaten, Bildungsdaten, Impfdaten, Steuerdaten, Finanzdaten sowie (potenziell) Kopien Ihrer Unterschrift, Fingerabdrücke, Gesichtsscans, Stimmproben und DNA enthält. So fasst der *OffGuardian* die eindrucksvolle Liste möglicher Einsatzbereiche zusammen. **Auch Dokumente wie der Personalausweis oder der** **[Führerschein](https://transition-news.org/eu-weite-einfuhrung-von-digitalen-fuhrerscheinen-fur-digitale-geldborsen)** können dort in elektronischer Form gespeichert werden. Bis 2026 sind alle EU-Mitgliedstaaten dazu verpflichtet, Ihren Bürgern funktionierende und frei verfügbare digitale «Brieftaschen» bereitzustellen. **Die Menschen würden diese App nutzen,** so das Portal, um Zahlungen vorzunehmen, Kredite zu beantragen, ihre Steuern zu zahlen, ihre Rezepte abzuholen, internationale Grenzen zu überschreiten, Unternehmen zu gründen, Arzttermine zu buchen, sich um Stellen zu bewerben und sogar digitale Verträge online zu unterzeichnen. **All diese Daten würden auf ihrem Mobiltelefon gespeichert und mit den Regierungen** von neunzehn Ländern (plus der Ukraine) sowie über 140 anderen öffentlichen und privaten Partnern ausgetauscht. Von der Deutschen Bank über das ukrainische Ministerium für digitalen Fortschritt bis hin zu Samsung Europe. Unternehmen und Behörden würden auf diese Daten im Backend zugreifen, um «automatisierte Hintergrundprüfungen» durchzuführen. **Der Bundesverband der Verbraucherzentralen und Verbraucherverbände** (VZBV) habe Bedenken geäußert, dass eine solche App «Risiken für den Schutz der Privatsphäre und der Daten» berge, berichtet das Portal. Die einzige Antwort darauf laute: «Richtig, genau dafür ist sie ja da!» **Das alles sei keine Hypothese, betont der** ***OffGuardian***. Es sei vielmehr [«Potential»](https://www.digital-identity-wallet.eu/about-us/140-public-and-private-partners/). Damit ist ein EU-Projekt gemeint, in dessen Rahmen Dutzende öffentliche und private Einrichtungen zusammenarbeiten, «um eine einheitliche Vision der digitalen Identität für die Bürger der europäischen Länder zu definieren». Dies ist nur eines der groß angelegten [Pilotprojekte](https://ec.europa.eu/digital-building-blocks/sites/display/EUDIGITALIDENTITYWALLET/What+are+the+Large+Scale+Pilot+Projects), mit denen Prototypen und Anwendungsfälle für die EUDI-Wallet getestet werden. Es gibt noch mindestens drei weitere. **Den Ball der digitalen ID-Systeme habe die Covid-«Pandemie»** über die «Impfpässe» ins Rollen gebracht. Seitdem habe das Thema an Schwung verloren. Je näher wir aber der vollständigen Einführung der EUid kämen, desto mehr Propaganda der Art «Warum wir eine digitale Brieftasche brauchen» könnten wir in den Mainstream-Medien erwarten, prognostiziert der *OffGuardian*. Vielleicht müssten wir schon nach dem nächsten großen «Grund», dem nächsten «katastrophalen katalytischen Ereignis» Ausschau halten. Vermutlich gebe es bereits Pläne, warum die Menschen plötzlich eine digitale ID-Brieftasche brauchen würden. **Die Entwicklung geht jedenfalls stetig weiter in genau diese Richtung.** Beispielsweise hat Jordanien angekündigt, die digitale biometrische ID bei den nächsten [Wahlen](https://www.biometricupdate.com/202502/jordan-plans-digital-id-for-voter-verification-in-next-election) zur Verifizierung der Wähler einzuführen. Man wolle «den Papierkrieg beenden und sicherstellen, dass die gesamte Kette bis zu den nächsten Parlamentswahlen digitalisiert wird», heißt es. Absehbar ist, dass dabei einige Wahlberechtigte «auf der Strecke bleiben» werden, wie im Fall von [Albanien](https://transition-news.org/albanien-schliesst-120-000-burger-ohne-biometrische-ausweise-von-wahlen-aus) geschehen. **Derweil würden die Briten gerne ihre Privatsphäre gegen Effizienz eintauschen,** [behauptet](https://www.lbc.co.uk/news/tony-blair-id-cards/) Tony Blair. Der Ex-Premier drängte kürzlich erneut auf digitale Identitäten und Gesichtserkennung. Blair ist Gründer einer [Denkfabrik](https://transition-news.org/blair-institute-durch-vermarktung-von-patientendaten-zu-ki-gestutztem) für globalen Wandel, Anhänger globalistischer Technokratie und [«moderner Infrastruktur»](https://transition-news.org/tony-blair-digitale-id-fur-moderne-infrastruktur-unerlasslich-erfordert-aber). **Abschließend warnt der** ***OffGuardian*** **vor der Illusion, Trump und Musk würden** den US-Bürgern «diesen Schlamassel ersparen». Das Department of Government Efficiency werde sich auf die digitale Identität stürzen. Was könne schließlich «effizienter» sein als eine einzige App, die für alles verwendet wird? Der Unterschied bestehe nur darin, dass die US-Version vielleicht eher privat als öffentlich sei – sofern es da überhaupt noch einen wirklichen Unterschied gebe. *\[Titelbild: Screenshot* *[OffGuardian](https://off-guardian.org/2025/02/26/coming-soon-the-european-digital-identity-wallet/)]* *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/demnachst-verfugbar-die-europaische-brieftasche-fur-digitale-identitaten)*** erschienen. @ 84b0c46a:417782f5
2025-03-27 23:52:24nostr:nevent1qqsw9v8usvahkqmmc9qavu6g834v09j6e2u2acdua24tk73dqc05xecgkanse
@ 84b0c46a:417782f5
2025-03-27 23:52:24nostr:nevent1qqsw9v8usvahkqmmc9qavu6g834v09j6e2u2acdua24tk73dqc05xecgkanse @ a95c6243:d345522c
2025-03-01 10:39:35*Ständige Lügen und Unterstellungen, permanent falsche Fürsorge* *\ können Bausteine von emotionaler Manipulation sein. Mit dem Zweck,* *\ Macht und Kontrolle über eine andere Person auszuüben.* *\ Apotheken Umschau*   **Irgendetwas muss passiert sein: «Gaslighting» ist gerade Thema** in vielen Medien. Heute bin ich nach längerer Zeit mal wieder über dieses Stichwort gestolpert. Das war in einem [Artikel](https://norberthaering.de/propaganda-zensur/dwd-referenzperiode/) von Norbert Häring über Manipulationen des Deutschen Wetterdienstes (DWD). In diesem Fall ging es um eine Pressemitteilung vom Donnerstag zum «viel zu warmen» Winter 2024/25. **Häring wirft der Behörde vor, dreist zu lügen und Dinge auszulassen,** um die Klimaangst wach zu halten. Was der Leser beim DWD nicht erfahre, sei, dass dieser Winter kälter als die drei vorangegangenen und kälter als der Durchschnitt der letzten zehn Jahre gewesen sei. Stattdessen werde der falsche Eindruck vermittelt, es würde ungebremst immer wärmer. **Wem also der zu Ende gehende Winter eher kalt vorgekommen sein sollte,** mit dessen Empfinden stimme wohl etwas nicht. Das jedenfalls wolle der DWD uns einreden, so der Wirtschaftsjournalist. Und damit sind wir beim Thema Gaslighting. **Als** **[Gaslighting](https://bayern-gegen-gewalt.de/gewalt-infos-und-einblicke/formen-von-gewalt/psychische-gewalt/gaslighting/)** **wird eine Form psychischer Manipulation bezeichnet,** mit der die Opfer desorientiert und zutiefst verunsichert werden, indem ihre eigene Wahrnehmung als falsch bezeichnet wird. Der Prozess führt zu Angst und Realitätsverzerrung sowie zur Zerstörung des Selbstbewusstseins. Die Bezeichnung kommt von dem britischen Theaterstück «Gas Light» aus dem Jahr 1938, in dem ein Mann mit grausamen Psychotricks seine Frau in den Wahnsinn treibt. **Damit Gaslighting funktioniert, muss das Opfer dem Täter vertrauen.** Oft wird solcher Psychoterror daher im privaten oder familiären Umfeld beschrieben, ebenso wie am Arbeitsplatz. Jedoch eignen sich die Prinzipien auch perfekt zur Manipulation der Massen. Vermeintliche Autoritäten wie Ärzte und Wissenschaftler, oder «der fürsorgliche Staat» und Institutionen wie die UNO oder die WHO wollen uns doch nichts Böses. Auch Staatsmedien, Faktenchecker und diverse NGOs wurden zu «vertrauenswürdigen Quellen» erklärt. Das hat seine Wirkung. **Warum das Thema Gaslighting derzeit scheinbar so populär ist,** vermag ich nicht zu sagen. Es sind aber gerade in den letzten Tagen und Wochen auffällig viele Artikel dazu erschienen, und zwar nicht nur von Psychologen. Die *Frankfurter Rundschau* hat gleich mehrere publiziert, und [Anwälte](https://www.anwalt.de/rechtstipps/gaslighting-beispiele-anzeichen-strafbarkeit-212449.html) interessieren sich dafür offenbar genauso wie Apotheker. **Die** ***Apotheken Umschau*** **machte sogar auf** **[«Medical Gaslighting»](https://archive.is/Wx5YM)** **aufmerksam.** Davon spreche man, wenn Mediziner Symptome nicht ernst nähmen oder wenn ein gesundheitliches Problem vom behandelnden Arzt «schnöde heruntergespielt» oder abgetan würde. Kommt Ihnen das auch irgendwie bekannt vor? Der Begriff sei allerdings irreführend, da er eine manipulierende Absicht unterstellt, die «nicht gewährleistet» sei. **Apropos Gaslighting: Die noch amtierende deutsche Bundesregierung** [meldete](https://www.bundesregierung.de/breg-de/service/newsletter-und-abos/bundesregierung-aktuell/ausgabe-08-2025-februar-28-2336254?view=renderNewsletterHtml) heute, es gelte, «weiter \[sic!] gemeinsam daran zu arbeiten, einen gerechten und dauerhaften Frieden für die Ukraine zu erreichen». Die Ukraine, wo sich am Montag «der völkerrechtswidrige Angriffskrieg zum dritten Mal jährte», [verteidige](https://transition-news.org/wikileaks-der-westen-wusste-dass-ein-nato-beitritt-der-ukraine-riskant-war) ihr Land und «unsere gemeinsamen Werte». **Merken Sie etwas? Das Demokratieverständnis mag ja tatsächlich** inzwischen in beiden Ländern ähnlich traurig sein. Bezüglich Friedensbemühungen ist meine Wahrnehmung jedoch eine andere. Das muss an meinem Gedächtnis liegen. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/bitte-nicht-von-gaslichtern-irritieren-lassen)*** erschienen.
@ a95c6243:d345522c
2025-03-01 10:39:35*Ständige Lügen und Unterstellungen, permanent falsche Fürsorge* *\ können Bausteine von emotionaler Manipulation sein. Mit dem Zweck,* *\ Macht und Kontrolle über eine andere Person auszuüben.* *\ Apotheken Umschau*   **Irgendetwas muss passiert sein: «Gaslighting» ist gerade Thema** in vielen Medien. Heute bin ich nach längerer Zeit mal wieder über dieses Stichwort gestolpert. Das war in einem [Artikel](https://norberthaering.de/propaganda-zensur/dwd-referenzperiode/) von Norbert Häring über Manipulationen des Deutschen Wetterdienstes (DWD). In diesem Fall ging es um eine Pressemitteilung vom Donnerstag zum «viel zu warmen» Winter 2024/25. **Häring wirft der Behörde vor, dreist zu lügen und Dinge auszulassen,** um die Klimaangst wach zu halten. Was der Leser beim DWD nicht erfahre, sei, dass dieser Winter kälter als die drei vorangegangenen und kälter als der Durchschnitt der letzten zehn Jahre gewesen sei. Stattdessen werde der falsche Eindruck vermittelt, es würde ungebremst immer wärmer. **Wem also der zu Ende gehende Winter eher kalt vorgekommen sein sollte,** mit dessen Empfinden stimme wohl etwas nicht. Das jedenfalls wolle der DWD uns einreden, so der Wirtschaftsjournalist. Und damit sind wir beim Thema Gaslighting. **Als** **[Gaslighting](https://bayern-gegen-gewalt.de/gewalt-infos-und-einblicke/formen-von-gewalt/psychische-gewalt/gaslighting/)** **wird eine Form psychischer Manipulation bezeichnet,** mit der die Opfer desorientiert und zutiefst verunsichert werden, indem ihre eigene Wahrnehmung als falsch bezeichnet wird. Der Prozess führt zu Angst und Realitätsverzerrung sowie zur Zerstörung des Selbstbewusstseins. Die Bezeichnung kommt von dem britischen Theaterstück «Gas Light» aus dem Jahr 1938, in dem ein Mann mit grausamen Psychotricks seine Frau in den Wahnsinn treibt. **Damit Gaslighting funktioniert, muss das Opfer dem Täter vertrauen.** Oft wird solcher Psychoterror daher im privaten oder familiären Umfeld beschrieben, ebenso wie am Arbeitsplatz. Jedoch eignen sich die Prinzipien auch perfekt zur Manipulation der Massen. Vermeintliche Autoritäten wie Ärzte und Wissenschaftler, oder «der fürsorgliche Staat» und Institutionen wie die UNO oder die WHO wollen uns doch nichts Böses. Auch Staatsmedien, Faktenchecker und diverse NGOs wurden zu «vertrauenswürdigen Quellen» erklärt. Das hat seine Wirkung. **Warum das Thema Gaslighting derzeit scheinbar so populär ist,** vermag ich nicht zu sagen. Es sind aber gerade in den letzten Tagen und Wochen auffällig viele Artikel dazu erschienen, und zwar nicht nur von Psychologen. Die *Frankfurter Rundschau* hat gleich mehrere publiziert, und [Anwälte](https://www.anwalt.de/rechtstipps/gaslighting-beispiele-anzeichen-strafbarkeit-212449.html) interessieren sich dafür offenbar genauso wie Apotheker. **Die** ***Apotheken Umschau*** **machte sogar auf** **[«Medical Gaslighting»](https://archive.is/Wx5YM)** **aufmerksam.** Davon spreche man, wenn Mediziner Symptome nicht ernst nähmen oder wenn ein gesundheitliches Problem vom behandelnden Arzt «schnöde heruntergespielt» oder abgetan würde. Kommt Ihnen das auch irgendwie bekannt vor? Der Begriff sei allerdings irreführend, da er eine manipulierende Absicht unterstellt, die «nicht gewährleistet» sei. **Apropos Gaslighting: Die noch amtierende deutsche Bundesregierung** [meldete](https://www.bundesregierung.de/breg-de/service/newsletter-und-abos/bundesregierung-aktuell/ausgabe-08-2025-februar-28-2336254?view=renderNewsletterHtml) heute, es gelte, «weiter \[sic!] gemeinsam daran zu arbeiten, einen gerechten und dauerhaften Frieden für die Ukraine zu erreichen». Die Ukraine, wo sich am Montag «der völkerrechtswidrige Angriffskrieg zum dritten Mal jährte», [verteidige](https://transition-news.org/wikileaks-der-westen-wusste-dass-ein-nato-beitritt-der-ukraine-riskant-war) ihr Land und «unsere gemeinsamen Werte». **Merken Sie etwas? Das Demokratieverständnis mag ja tatsächlich** inzwischen in beiden Ländern ähnlich traurig sein. Bezüglich Friedensbemühungen ist meine Wahrnehmung jedoch eine andere. Das muss an meinem Gedächtnis liegen. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/bitte-nicht-von-gaslichtern-irritieren-lassen)*** erschienen. @ 878dff7c:037d18bc
2025-03-27 22:37:47## Australian Prime Minister Calls Election Amid Economic Challenges ### Summary: Prime Minister Anthony Albanese has announced that Australia will hold federal elections on May 3. The election comes at a time when the nation faces significant economic uncertainties, including high inflation rates, elevated interest rates, and a housing crisis. Albanese's Labor government emphasizes plans for economic recovery, while opposition leader Peter Dutton's Coalition proposes public sector cuts and temporary fuel duty reductions. Both leaders are striving to address voter concerns over the cost-of-living crisis and economic stability. Sources: <a href="https://www.theguardian.com/australia-news/2025/mar/28/australian-prime-minister-calls-election-amid-shadow-of-trump-and-cost-of-living-crisis" target="_blank">The Guardian - March 28, 2025</a>, <a href="https://apnews.com/article/b73f3a4bb9cbbc300cd797f34d4cc23b" target="_blank">AP News - March 28, 2025</a> ## Bill Gates Predicts AI to Replace Doctors and Teachers Within 10 Years ### Summary: Bill Gates forecasts that artificial intelligence (AI) will significantly reduce human involvement in fields like medicine and education over the next decade. He envisions AI providing free, high-quality medical advice and tutoring, thereby democratizing access to these services. While acknowledging concerns about misinformation and rapid AI development, Gates remains optimistic about AI's potential to drive breakthroughs in healthcare, climate solutions, and education. He encourages young people to engage in AI-centric ventures, highlighting its transformative impact on industries and society. Sources: <a href="https://nypost.com/2025/03/27/business/bill-gates-said-ai-will-replace-doctors-teachers-within-10-years/" target="_blank">New York Post - March 27, 2025</a> ## AI Poised to Transform Legal Profession by 2035 ### Summary: Artificial general intelligence (AGI) is projected to render traditional lawyer roles obsolete by 2035. AI systems are advancing to perform complex legal tasks such as advising, negotiating, and dispute resolution. While some legal professionals argue that AI cannot replicate human judgment and creativity, the emphasis on efficiency and outcomes suggests a future where AGI dominates legal services with minimal human intervention. Legal industry leaders are urged to prepare for this disruptive shift. Sources: <a href="https://www.thetimes.co.uk/article/artificial-intelligence-could-replace-traditional-lawyers-by-2035-xwz2j0t2k" target="_blank">The Times - March 28, 2025</a> ## Queensland Faces Severe Flooding as Inland 'Sea' Emerges ### Summary: Severe weather conditions, including heavy rain and potential flash flooding, have impacted central and southern inland Queensland, with significant rainfall between 200 to 400mm recorded. Towns like Adavale are inundated, prompting emergency warnings and the establishment of refuges for affected residents. Authorities urge residents to stay updated and follow safety advice. Sources: <a href="https://www.news.com.au/technology/environment/qld-in-for-another-week-of-rain-amid-severe-weather-and-flood-warnings/news-story/d5e7ea97591060bb58c1d6ed54489209" target="_blank">News.com.au - 28 March 2025</a>, <a href="https://www.couriermail.com.au/news/queensland/weather/qld-weather-warnings-of-possible-200mm-deluge-major-flooding-as-communities-cut-off/news-story/457a21a269a535b28c52f919f8bc7bed" target="_blank">The Courier-Mail - 28 March 2025</a>, <a href="https://www.theguardian.com/australia-news/2025/mar/27/queensland-flood-warnings-rain-weather-forecast-bom" target="_blank">The Guardian - 28 March 2025</a> ## Opposition Leader Peter Dutton Outlines Election Platform ### Summary: Opposition Leader Peter Dutton has presented his vision for Australia, promising significant funding for defense and proposing a new gas reservation policy aimed at lowering electricity prices. The Coalition's plans include fast-tracking gas projects, investing $1 billion in gas infrastructure, reducing public service staffing by 41,000 while preserving essential services, and decreasing permanent migration intake by 25% to increase housing supply. Dutton also announced reinstating subsidized mental health visits and new spending on youth mental health. Sources: <a href="https://www.theguardian.com/australia-news/live/2025/mar/27/australia-politics-live-fuel-excise-cost-of-living-tax-cuts-salmon-election-anthony-albanese-peter-dutton-ntwnfb" target="_blank">The Guardian - March 28, 2025</a>, <a href="https://www.theaustralian.com.au/nation/who-is-peter-dutton-the-liberal-leader-and-his-top-team-for-the-2025-federal-election-explained/news-story/9d046731e51ed32dd4795c3820365c3a" target="_blank">The Australian - March 28, 2025</a> ## Opposition Leader Promises Significant Defense Funding ### Summary: Peter Dutton, in his budget reply, promised significant funding for defense and a new gas reservation policy for the east coast, aimed at lowering electricity prices. The Coalition also plans to fast-track gas projects and invest $1 billion in gas infrastructure. Dutton announced slashing 41,000 public service workers while preserving essential services, and criticized Labor's gas policy. Immigration plans include reducing the permanent migration intake by 25% to increase housing supply. Dutton also proposed reinstating subsidized mental health visits and new spending on youth mental health. Labor, represented by Jason Clare, argued that the Coalition's policies, including the nuclear plan, are costly and criticized the tax implications under Dutton. Sources: <a href="https://www.theguardian.com/australia-news/live/2025/mar/27/australia-politics-live-fuel-excise-cost-of-living-tax-cuts-salmon-election-anthony-albanese-peter-dutton-ntwnfb" target="_blank">The Guardian - March 28, 2025</a> ## Israeli Politicians Urge Australian MPs to Abandon Two-State Solution Policy ### Summary: A group of Israeli Knesset members has called on Australian MPs to drop support for a two-state solution between Israel and Palestine. The letter, presented during an event at Australia's Parliament House, argues that establishing a Palestinian state could lead to Israel's destruction, citing recent conflicts as evidence. This appeal reflects deep skepticism within Israeli political circles about the viability of the peace process. Sources: <a href="https://www.theguardian.com/australia-news/2025/mar/27/israeli-politicians-sign-letter-urging-coalition-to-dump-two-state-policy-ntwnfb" target="_blank">The Guardian - March 27, 2025</a> ## Stephen Jones Criticizes U.S. Protectionist Trade Policies ### Summary: Outgoing Financial Services Minister Stephen Jones has criticized recent U.S. protectionist measures, including a 25% tariff on global car imports and Australian aluminum and steel. Jones emphasized the importance of open trade and a rules-based order for Australia's economic growth, highlighting concerns about the negative impact on Australian industries and the broader economy. Sources: <a href="https://www.theaustralian.com.au/business/outgoing-financial-services-minister-jones-takes-swipe-at-us-protectionism/news-story/0c1fc10f2b57a8c6809f4dec333cc547" target="_blank">The Australian - March 28, 2025</a> ## New Anti-Smoking Warnings Criticized for Potential Backfire ### Summary: Starting April 1, Australia will implement legislation requiring health warnings on individual cigarettes, with messages like "causes 16 cancers" and "poisons in every puff." However, social media users have mocked these warnings, suggesting they might make smoking appear "cool" and collectible rather than serving as deterrents. Despite the criticism, health officials assert that such on-product messages are part of a broader strategy to reduce smoking rates, citing positive results from similar approaches in Canada. The initiative aims to decrease the annual tobacco-related deaths in Australia, which currently exceed 24,000. Sources: <a href="https://www.couriermail.com.au/news/queensland/poisons-in-every-puff-new-antismoking-messaging-slammed/news-story/2f77ecd3a943d3139539c2610af3400c" target="_blank">The Courier-Mail - March 28, 2025</a> ## 'Joe's Law' Introduced to Ban Future Hospital Privatization in NSW ### Summary: The New South Wales government has announced "Joe's Law," a reform to prohibit the future privatization of acute public hospitals. This decision follows the death of two-year-old Joe Massa, who suffered a cardiac arrest and died after a prolonged wait in the emergency department of the privately managed Northern Beaches Hospital. The legislation aims to ensure that critical public services like emergency and surgical care remain under public control, preventing privatization. Additionally, a parliamentary inquiry into the hospital's services and a coronial investigation into Joe's death have been initiated. Sources: <a href="https://www.theguardian.com/australia-news/2025/mar/27/joes-law-to-ban-future-hospital-privatisation-in-nsw" target="_blank">The Guardian - March 28, 2025</a>, <a href="https://www.news.com.au/lifestyle/health/health-problems/major-changes-coming-to-nsw-hospitals-after-death-of-twoyearold-joe-massa/news-story/fb93b0f0a9f2673a01eddfe89031fcb9" target="_blank">news.com.au - March 28, 2025</a>, <a href="https://www.dailytelegraph.com.au/newslocal/manly-daily/northern-beaches-hospital-probe-begins-into-safety-and-quality-of-health-services/news-story/72ea15981b26339eea92a15b4e9c498a" target="_blank">The Daily Telegraph - March 28, 2025</a> ## Determined Daisy Marks Major Milestone ### Summary: Daisy, born with a rare chromosomal disorder, has achieved a significant health milestone by having her tracheostomy removed and is now learning to communicate using sign language. Her inspiring journey is one of several highlighted by the Good Friday Appeal, which supports the Royal Children's Hospital (RCH). The 2025 Appeal aims to fund further programs, research, and vital equipment at RCH, with contributions from events like North Melbourne's SuperClash fundraiser bringing joy to young patients ahead of the marquee match. Sources: <a href="https://www.heraldsun.com.au/news/good-friday-appeal/good-friday-appeal-2025-star-roos-launch-superclash-fundraiser-with-special-visit/news-story/75fe74c62e52efb611436e9162c4d4d6" target="_blank">Herald Sun - March 27, 2025</a> ## Indonesia Seeks to Calm Investors After Stocks, Rupiah Slide ### Summary: Indonesian officials are working to reassure investors following significant declines in the stock market and the rupiah. President Prabowo Subianto plans to meet with investors after the Eid-al-Fitr holiday to address concerns about government policies and fiscal stability. The rupiah recently hit its weakest level since 1998, and the main stock index fell 7.1%. Analysts attribute the selloff to poor communication on fiscal policies. The government aims to maintain the fiscal deficit within 3% of GDP and avoid political interference in its sovereign wealth fund. Efforts are also underway to deregulate the manufacturing sector and provide credits to labor-intensive industries. Bank Indonesia is prepared to intervene to stabilize the currency, emphasizing the economy's underlying strength. The rupiah has shown signs of recovery, and measures include easing buyback processes and offering more attractive investment instruments. Markets will monitor the mid-year budget update in July for signs of revenue shortfalls and spending adjustments. Sources: <a href="https://www.reuters.com/markets/asia/indonesia-seeks-calm-investors-after-stocks-rupiah-slide-2025-03-27/" target="_blank">Reuters - 28 March 2025</a> ## Beijing to Escalate Taiwan Coercion in 2025 ### Summary: A report by the Office of the Director of National Intelligence highlights growing cooperation among China, Russia, Iran, and North Korea, posing significant challenges to U.S. global power. Closer ties between China and Russia, in particular, could present enduring risks to U.S. interests. The document points out China's military threat to the U.S., emphasizing its grey zone tactics and potential for stronger coercive action against Taiwan by 2025. The Ukraine conflict and its ongoing strategic risks, including nuclear escalation, are noted, as well as China's ambition to dominate AI by 2030 and its control over critical materials. The report also mentions the volatile Middle East, with Iran's expanding ties despite challenges, and North Korea's commitment to enhancing its nuclear capabilities. Additionally, threats from foreign drug actors and Islamic extremists, including Al-Qa'ida and a potential ISIS resurgence, are highlighted. Sources: <a href="https://www.theaustralian.com.au/nation/politics/us-threat-assessment-sounds-the-alarm-on-china/news-story/cb582794c7a653b11cce8d3e61fc564b" target="_blank">The Australian - 28 March 2025</a> ## Fire Ant Infestation Could Cost Australian Households Over $1 Billion Annually ### Summary: New modeling predicts that if fire ants become established in Australia, households may incur approximately $1.03 billion annually in control measures and related health and veterinary expenses. The invasive species could lead to up to 570,800 medical consultations and around 30 deaths each year due to stings. The electorates of Durack, O'Connor, Mayo, and Blair are projected to be most affected. Experts emphasize the need for increased federal funding for comprehensive eradication programs to prevent environmental damage and significant economic burdens on households. Sources: <a href="https://www.theguardian.com/environment/2025/mar/28/australia-fire-ants-queensland-cost-eradication-pesticides" target="_blank">The Guardian - March 28, 2025</a> ## The Great Monetary Divide – Epi-3643 ### Summary: In this episode, host Jack Spirko discusses the rapid changes occurring in the global financial landscape. He highlights the European Union's announcement, led by European Central Bank President Christine Lagarde, to implement a Central Bank Digital Currency (CBDC) across member states by the upcoming fall. Spirko expresses concern that such a move could pave the way for a social credit system similar to China's, potentially leading to increased governmental control over individual financial activities. Conversely, the episode explores developments in the United States, where the government is reportedly adopting Bitcoin as an economic reserve and integrating stablecoins into the financial system. Spirko suggests that these actions may indicate a divergent path from other global economies, potentially fostering a more decentralized financial environment. Throughout the episode, Spirko emphasizes the importance of understanding these shifts and encourages listeners to consider how such changes might impact personal financial sovereignty and the broader economic landscape. Please note that this summary is based on limited information available from the episode description and may not capture all the nuances discussed in the full podcast. Sources: <a href="https://open.spotify.com/episode/5lUuCzX3wHfWdX6y6QtJGw" target="_blank">The Survival Podcast - 28 March 2025</a>, <a href="https://podcasts.apple.com/us/podcast/the-great-monetary-divide-epi-3643/id284148583?i=1000700006108&l=es-MX" target="_blank">Apple Podcasts - 28 March 2025</a>
@ 878dff7c:037d18bc
2025-03-27 22:37:47## Australian Prime Minister Calls Election Amid Economic Challenges ### Summary: Prime Minister Anthony Albanese has announced that Australia will hold federal elections on May 3. The election comes at a time when the nation faces significant economic uncertainties, including high inflation rates, elevated interest rates, and a housing crisis. Albanese's Labor government emphasizes plans for economic recovery, while opposition leader Peter Dutton's Coalition proposes public sector cuts and temporary fuel duty reductions. Both leaders are striving to address voter concerns over the cost-of-living crisis and economic stability. Sources: <a href="https://www.theguardian.com/australia-news/2025/mar/28/australian-prime-minister-calls-election-amid-shadow-of-trump-and-cost-of-living-crisis" target="_blank">The Guardian - March 28, 2025</a>, <a href="https://apnews.com/article/b73f3a4bb9cbbc300cd797f34d4cc23b" target="_blank">AP News - March 28, 2025</a> ## Bill Gates Predicts AI to Replace Doctors and Teachers Within 10 Years ### Summary: Bill Gates forecasts that artificial intelligence (AI) will significantly reduce human involvement in fields like medicine and education over the next decade. He envisions AI providing free, high-quality medical advice and tutoring, thereby democratizing access to these services. While acknowledging concerns about misinformation and rapid AI development, Gates remains optimistic about AI's potential to drive breakthroughs in healthcare, climate solutions, and education. He encourages young people to engage in AI-centric ventures, highlighting its transformative impact on industries and society. Sources: <a href="https://nypost.com/2025/03/27/business/bill-gates-said-ai-will-replace-doctors-teachers-within-10-years/" target="_blank">New York Post - March 27, 2025</a> ## AI Poised to Transform Legal Profession by 2035 ### Summary: Artificial general intelligence (AGI) is projected to render traditional lawyer roles obsolete by 2035. AI systems are advancing to perform complex legal tasks such as advising, negotiating, and dispute resolution. While some legal professionals argue that AI cannot replicate human judgment and creativity, the emphasis on efficiency and outcomes suggests a future where AGI dominates legal services with minimal human intervention. Legal industry leaders are urged to prepare for this disruptive shift. Sources: <a href="https://www.thetimes.co.uk/article/artificial-intelligence-could-replace-traditional-lawyers-by-2035-xwz2j0t2k" target="_blank">The Times - March 28, 2025</a> ## Queensland Faces Severe Flooding as Inland 'Sea' Emerges ### Summary: Severe weather conditions, including heavy rain and potential flash flooding, have impacted central and southern inland Queensland, with significant rainfall between 200 to 400mm recorded. Towns like Adavale are inundated, prompting emergency warnings and the establishment of refuges for affected residents. Authorities urge residents to stay updated and follow safety advice. Sources: <a href="https://www.news.com.au/technology/environment/qld-in-for-another-week-of-rain-amid-severe-weather-and-flood-warnings/news-story/d5e7ea97591060bb58c1d6ed54489209" target="_blank">News.com.au - 28 March 2025</a>, <a href="https://www.couriermail.com.au/news/queensland/weather/qld-weather-warnings-of-possible-200mm-deluge-major-flooding-as-communities-cut-off/news-story/457a21a269a535b28c52f919f8bc7bed" target="_blank">The Courier-Mail - 28 March 2025</a>, <a href="https://www.theguardian.com/australia-news/2025/mar/27/queensland-flood-warnings-rain-weather-forecast-bom" target="_blank">The Guardian - 28 March 2025</a> ## Opposition Leader Peter Dutton Outlines Election Platform ### Summary: Opposition Leader Peter Dutton has presented his vision for Australia, promising significant funding for defense and proposing a new gas reservation policy aimed at lowering electricity prices. The Coalition's plans include fast-tracking gas projects, investing $1 billion in gas infrastructure, reducing public service staffing by 41,000 while preserving essential services, and decreasing permanent migration intake by 25% to increase housing supply. Dutton also announced reinstating subsidized mental health visits and new spending on youth mental health. Sources: <a href="https://www.theguardian.com/australia-news/live/2025/mar/27/australia-politics-live-fuel-excise-cost-of-living-tax-cuts-salmon-election-anthony-albanese-peter-dutton-ntwnfb" target="_blank">The Guardian - March 28, 2025</a>, <a href="https://www.theaustralian.com.au/nation/who-is-peter-dutton-the-liberal-leader-and-his-top-team-for-the-2025-federal-election-explained/news-story/9d046731e51ed32dd4795c3820365c3a" target="_blank">The Australian - March 28, 2025</a> ## Opposition Leader Promises Significant Defense Funding ### Summary: Peter Dutton, in his budget reply, promised significant funding for defense and a new gas reservation policy for the east coast, aimed at lowering electricity prices. The Coalition also plans to fast-track gas projects and invest $1 billion in gas infrastructure. Dutton announced slashing 41,000 public service workers while preserving essential services, and criticized Labor's gas policy. Immigration plans include reducing the permanent migration intake by 25% to increase housing supply. Dutton also proposed reinstating subsidized mental health visits and new spending on youth mental health. Labor, represented by Jason Clare, argued that the Coalition's policies, including the nuclear plan, are costly and criticized the tax implications under Dutton. Sources: <a href="https://www.theguardian.com/australia-news/live/2025/mar/27/australia-politics-live-fuel-excise-cost-of-living-tax-cuts-salmon-election-anthony-albanese-peter-dutton-ntwnfb" target="_blank">The Guardian - March 28, 2025</a> ## Israeli Politicians Urge Australian MPs to Abandon Two-State Solution Policy ### Summary: A group of Israeli Knesset members has called on Australian MPs to drop support for a two-state solution between Israel and Palestine. The letter, presented during an event at Australia's Parliament House, argues that establishing a Palestinian state could lead to Israel's destruction, citing recent conflicts as evidence. This appeal reflects deep skepticism within Israeli political circles about the viability of the peace process. Sources: <a href="https://www.theguardian.com/australia-news/2025/mar/27/israeli-politicians-sign-letter-urging-coalition-to-dump-two-state-policy-ntwnfb" target="_blank">The Guardian - March 27, 2025</a> ## Stephen Jones Criticizes U.S. Protectionist Trade Policies ### Summary: Outgoing Financial Services Minister Stephen Jones has criticized recent U.S. protectionist measures, including a 25% tariff on global car imports and Australian aluminum and steel. Jones emphasized the importance of open trade and a rules-based order for Australia's economic growth, highlighting concerns about the negative impact on Australian industries and the broader economy. Sources: <a href="https://www.theaustralian.com.au/business/outgoing-financial-services-minister-jones-takes-swipe-at-us-protectionism/news-story/0c1fc10f2b57a8c6809f4dec333cc547" target="_blank">The Australian - March 28, 2025</a> ## New Anti-Smoking Warnings Criticized for Potential Backfire ### Summary: Starting April 1, Australia will implement legislation requiring health warnings on individual cigarettes, with messages like "causes 16 cancers" and "poisons in every puff." However, social media users have mocked these warnings, suggesting they might make smoking appear "cool" and collectible rather than serving as deterrents. Despite the criticism, health officials assert that such on-product messages are part of a broader strategy to reduce smoking rates, citing positive results from similar approaches in Canada. The initiative aims to decrease the annual tobacco-related deaths in Australia, which currently exceed 24,000. Sources: <a href="https://www.couriermail.com.au/news/queensland/poisons-in-every-puff-new-antismoking-messaging-slammed/news-story/2f77ecd3a943d3139539c2610af3400c" target="_blank">The Courier-Mail - March 28, 2025</a> ## 'Joe's Law' Introduced to Ban Future Hospital Privatization in NSW ### Summary: The New South Wales government has announced "Joe's Law," a reform to prohibit the future privatization of acute public hospitals. This decision follows the death of two-year-old Joe Massa, who suffered a cardiac arrest and died after a prolonged wait in the emergency department of the privately managed Northern Beaches Hospital. The legislation aims to ensure that critical public services like emergency and surgical care remain under public control, preventing privatization. Additionally, a parliamentary inquiry into the hospital's services and a coronial investigation into Joe's death have been initiated. Sources: <a href="https://www.theguardian.com/australia-news/2025/mar/27/joes-law-to-ban-future-hospital-privatisation-in-nsw" target="_blank">The Guardian - March 28, 2025</a>, <a href="https://www.news.com.au/lifestyle/health/health-problems/major-changes-coming-to-nsw-hospitals-after-death-of-twoyearold-joe-massa/news-story/fb93b0f0a9f2673a01eddfe89031fcb9" target="_blank">news.com.au - March 28, 2025</a>, <a href="https://www.dailytelegraph.com.au/newslocal/manly-daily/northern-beaches-hospital-probe-begins-into-safety-and-quality-of-health-services/news-story/72ea15981b26339eea92a15b4e9c498a" target="_blank">The Daily Telegraph - March 28, 2025</a> ## Determined Daisy Marks Major Milestone ### Summary: Daisy, born with a rare chromosomal disorder, has achieved a significant health milestone by having her tracheostomy removed and is now learning to communicate using sign language. Her inspiring journey is one of several highlighted by the Good Friday Appeal, which supports the Royal Children's Hospital (RCH). The 2025 Appeal aims to fund further programs, research, and vital equipment at RCH, with contributions from events like North Melbourne's SuperClash fundraiser bringing joy to young patients ahead of the marquee match. Sources: <a href="https://www.heraldsun.com.au/news/good-friday-appeal/good-friday-appeal-2025-star-roos-launch-superclash-fundraiser-with-special-visit/news-story/75fe74c62e52efb611436e9162c4d4d6" target="_blank">Herald Sun - March 27, 2025</a> ## Indonesia Seeks to Calm Investors After Stocks, Rupiah Slide ### Summary: Indonesian officials are working to reassure investors following significant declines in the stock market and the rupiah. President Prabowo Subianto plans to meet with investors after the Eid-al-Fitr holiday to address concerns about government policies and fiscal stability. The rupiah recently hit its weakest level since 1998, and the main stock index fell 7.1%. Analysts attribute the selloff to poor communication on fiscal policies. The government aims to maintain the fiscal deficit within 3% of GDP and avoid political interference in its sovereign wealth fund. Efforts are also underway to deregulate the manufacturing sector and provide credits to labor-intensive industries. Bank Indonesia is prepared to intervene to stabilize the currency, emphasizing the economy's underlying strength. The rupiah has shown signs of recovery, and measures include easing buyback processes and offering more attractive investment instruments. Markets will monitor the mid-year budget update in July for signs of revenue shortfalls and spending adjustments. Sources: <a href="https://www.reuters.com/markets/asia/indonesia-seeks-calm-investors-after-stocks-rupiah-slide-2025-03-27/" target="_blank">Reuters - 28 March 2025</a> ## Beijing to Escalate Taiwan Coercion in 2025 ### Summary: A report by the Office of the Director of National Intelligence highlights growing cooperation among China, Russia, Iran, and North Korea, posing significant challenges to U.S. global power. Closer ties between China and Russia, in particular, could present enduring risks to U.S. interests. The document points out China's military threat to the U.S., emphasizing its grey zone tactics and potential for stronger coercive action against Taiwan by 2025. The Ukraine conflict and its ongoing strategic risks, including nuclear escalation, are noted, as well as China's ambition to dominate AI by 2030 and its control over critical materials. The report also mentions the volatile Middle East, with Iran's expanding ties despite challenges, and North Korea's commitment to enhancing its nuclear capabilities. Additionally, threats from foreign drug actors and Islamic extremists, including Al-Qa'ida and a potential ISIS resurgence, are highlighted. Sources: <a href="https://www.theaustralian.com.au/nation/politics/us-threat-assessment-sounds-the-alarm-on-china/news-story/cb582794c7a653b11cce8d3e61fc564b" target="_blank">The Australian - 28 March 2025</a> ## Fire Ant Infestation Could Cost Australian Households Over $1 Billion Annually ### Summary: New modeling predicts that if fire ants become established in Australia, households may incur approximately $1.03 billion annually in control measures and related health and veterinary expenses. The invasive species could lead to up to 570,800 medical consultations and around 30 deaths each year due to stings. The electorates of Durack, O'Connor, Mayo, and Blair are projected to be most affected. Experts emphasize the need for increased federal funding for comprehensive eradication programs to prevent environmental damage and significant economic burdens on households. Sources: <a href="https://www.theguardian.com/environment/2025/mar/28/australia-fire-ants-queensland-cost-eradication-pesticides" target="_blank">The Guardian - March 28, 2025</a> ## The Great Monetary Divide – Epi-3643 ### Summary: In this episode, host Jack Spirko discusses the rapid changes occurring in the global financial landscape. He highlights the European Union's announcement, led by European Central Bank President Christine Lagarde, to implement a Central Bank Digital Currency (CBDC) across member states by the upcoming fall. Spirko expresses concern that such a move could pave the way for a social credit system similar to China's, potentially leading to increased governmental control over individual financial activities. Conversely, the episode explores developments in the United States, where the government is reportedly adopting Bitcoin as an economic reserve and integrating stablecoins into the financial system. Spirko suggests that these actions may indicate a divergent path from other global economies, potentially fostering a more decentralized financial environment. Throughout the episode, Spirko emphasizes the importance of understanding these shifts and encourages listeners to consider how such changes might impact personal financial sovereignty and the broader economic landscape. Please note that this summary is based on limited information available from the episode description and may not capture all the nuances discussed in the full podcast. Sources: <a href="https://open.spotify.com/episode/5lUuCzX3wHfWdX6y6QtJGw" target="_blank">The Survival Podcast - 28 March 2025</a>, <a href="https://podcasts.apple.com/us/podcast/the-great-monetary-divide-epi-3643/id284148583?i=1000700006108&l=es-MX" target="_blank">Apple Podcasts - 28 March 2025</a> @ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one. ## Public Home/Outbox Relays Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, **they will not receive your updates**. Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience. This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to [relay.tools](https://relay.tools/) and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts. ## Public Inbox Relays This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out. Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience. This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to [nostr.watch](https://nostr.watch/relays/find) and find relays in your country Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here. ## DM Inbox Relays These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. **If you don't have it setup, you will miss DMs**. DM Inbox relays should accept any message from anyone, but only allow you to download them. Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy. Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers. Make sure to add at least one public relay if you want to see DM notifications. ## Private Home Relays Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools. Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa. ## Search relays: This is the list of relays to use on Amethyst's search and user tagging with @. **Tagging and searching will not work if there is nothing here.**. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com ## Local Relays: This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option. ## General Relays: This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each. Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible. Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them. ## My setup Here's what I use: 1. Go to [relay.tools](https://relay.tools/) and create a relay for yourself. 2. Go to [nostr.wine](https://nostr.wine/) and pay for their subscription. 3. Go to [inbox.nostr.wine](https://inbox.nostr.wine/) and pay for their subscription. 4. Go to [nostr.watch](https://nostr.watch/relays/find) and find a good relay in your country. 5. Download Citrine to your phone. Then, on your relay lists, put: Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. - <your.relay>.nostr1.com Public Inbox Relays - nos.lol or an in-country relay - <your.relay>.nostr1.com DM Inbox Relays - inbox.nostr.wine - <your.relay>.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) - <your.relay>.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com Local Relays - ws://localhost:4869 (Citrine) General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom And a few of the recommended relays from Amethyst. ## Final Considerations Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one. ## Public Home/Outbox Relays Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, **they will not receive your updates**. Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience. This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to [relay.tools](https://relay.tools/) and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts. ## Public Inbox Relays This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out. Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience. This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to [nostr.watch](https://nostr.watch/relays/find) and find relays in your country Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here. ## DM Inbox Relays These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. **If you don't have it setup, you will miss DMs**. DM Inbox relays should accept any message from anyone, but only allow you to download them. Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy. Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers. Make sure to add at least one public relay if you want to see DM notifications. ## Private Home Relays Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools. Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa. ## Search relays: This is the list of relays to use on Amethyst's search and user tagging with @. **Tagging and searching will not work if there is nothing here.**. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com ## Local Relays: This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option. ## General Relays: This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each. Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible. Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them. ## My setup Here's what I use: 1. Go to [relay.tools](https://relay.tools/) and create a relay for yourself. 2. Go to [nostr.wine](https://nostr.wine/) and pay for their subscription. 3. Go to [inbox.nostr.wine](https://inbox.nostr.wine/) and pay for their subscription. 4. Go to [nostr.watch](https://nostr.watch/relays/find) and find a good relay in your country. 5. Download Citrine to your phone. Then, on your relay lists, put: Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. - <your.relay>.nostr1.com Public Inbox Relays - nos.lol or an in-country relay - <your.relay>.nostr1.com DM Inbox Relays - inbox.nostr.wine - <your.relay>.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) - <your.relay>.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com Local Relays - ws://localhost:4869 (Citrine) General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom And a few of the recommended relays from Amethyst. ## Final Considerations Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.